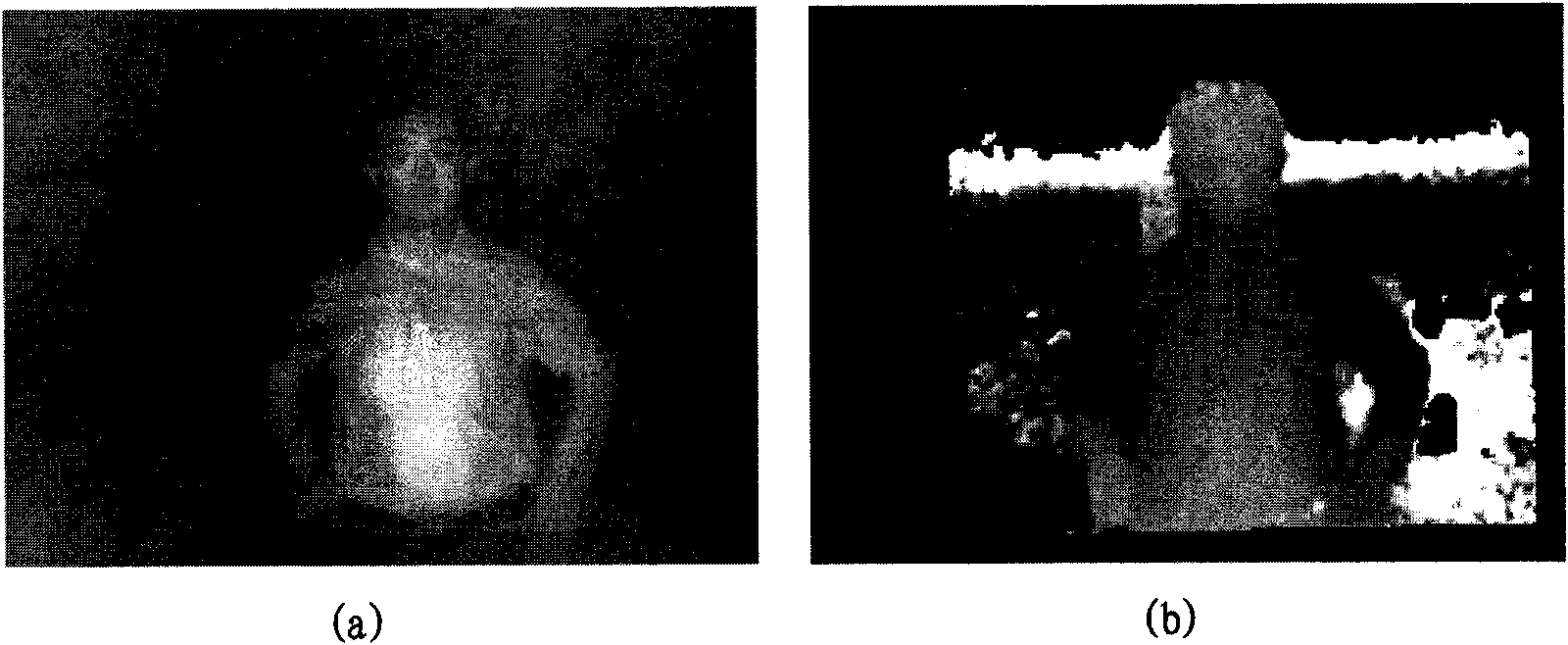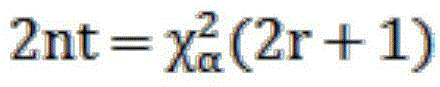Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
363results about How to "Accurate verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
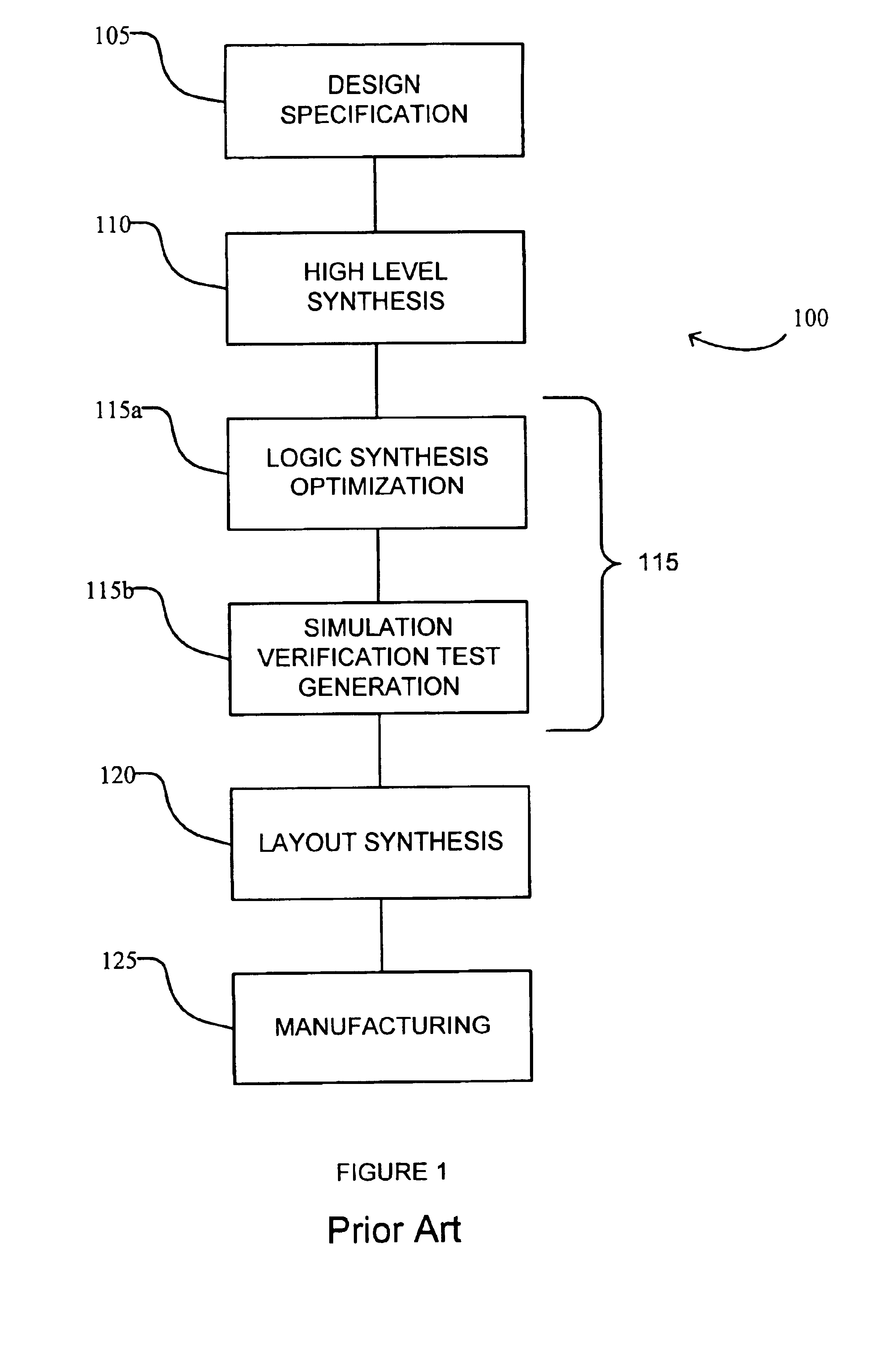
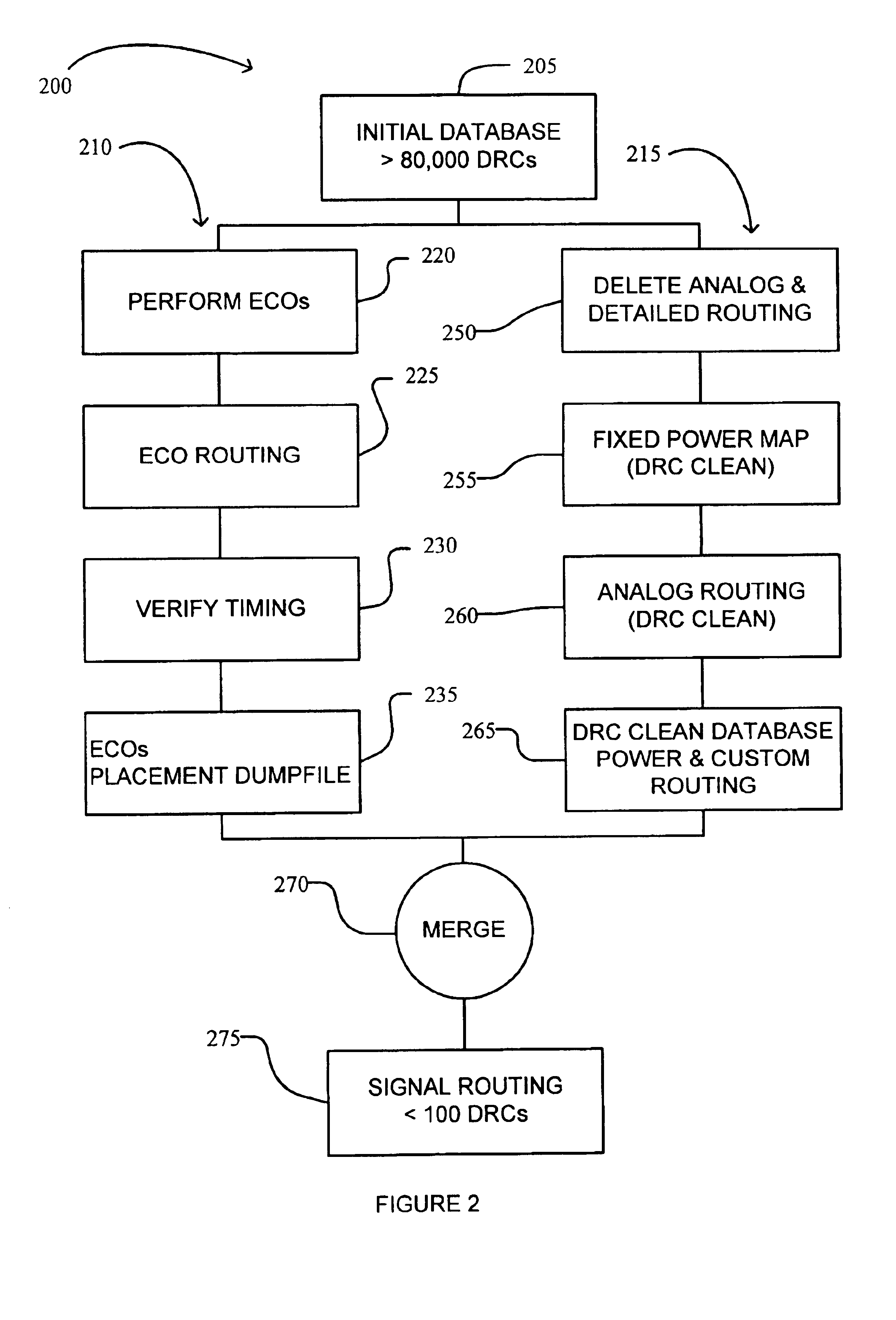
Split and merge design flow concept for fast turnaround time of circuit layout design
ActiveUS6898770B2Increase turnaround timeAccurate verificationComputer aided designSoftware simulation/interpretation/emulationSufficient timeTurnaround time
A method and system is disclosed to improve the turnaround time to provide adequate time to meet project schedules in the event that adjustments or modifications to the design are necessary. A method for improving a turnaround time for design verification of a process database representing a semiconductor design includes the steps of (a) deriving a timing database and a (DNE) database from the process database; (b) performing, using the timing database, one or more design changes and one or more timing verifications and corrections to generate a modified timing database; (c) initiating, using the process database, physical validation of the semiconductor design prior to completion of step (b) to generate a modified DNE database; (d) merging the modified timing database with the modified DNE database to form a modified process database; and (e) performing, using the modified process database, one or more design verification checks of the semiconductor design.
Owner:BELL SEMICON LLC
Automated cortical mapping
InactiveUS20050182456A1Quickly and accurately obtaining a functional map of an area of the brainReduce adverse effectsHead electrodesElectromyographyClosed loopEngineering
A method for cortical mapping includes utilizing subdural electrodes as selectable stimulus points in a closed loop system of cortical mapping based on electromyographic detection events. A system for cortical mapping includes a plurality of subdural electrodes formed as a grid, a cortical stimulator for stimulating individual pairs of the plurality of subdural electrodes, and an electromyograph for detecting reaction to the stimulating. The system may include a controller structured for associating the reaction with one of the individual pairs of the plurality of subdural electrodes. The system and method allow quick and accurate functional mapping of an area of the brain, automatic mapping, and essentially realtime feedback for a probe localization process. Use of the system and method provides intraoperative functional localization while reducing a possibility of adverse effects to the patient.
Owner:ZIOBRO JOHN F +1
Automated pass-through surgical instrument tray reader
ActiveUS7644016B2Reduce processing costsEfficient collectionElectric signal transmission systemsSurgical furnitureData terminalEngineering
An apparatus and method for interrogating and automatically identifying a radio-frequency tagged surgical instrument tray and its contents of RFID-tagged surgical instruments are disclosed. The surgical instrument tray and its contents come into contact with an RF signal transmitted by the RFID reader, and as a result, the RFID tags affixed on the instrument tray and the surgical instruments respond by transmitting back to the RFID reader data pertaining to the history of the surgical instruments. A data terminal, which is connected to the RFID reader, may contain data pertaining to the radio frequency tagged surgical instruments during packaging, and during the return of the surgical instrument trays to the packager, identifies the surgical instruments.
Owner:WARSAW ORTHOPEDIC INC
Automated pass-through surgical instrument tray reader
ActiveUS20060043177A1Cost reductionReduce processing costsElectric signal transmission systemsSurgical furnitureRadio frequencyInstrument tray
An apparatus and method for interrogating and automatically identifying a radio-frequency tagged surgical instrument tray and its contents of RFID-tagged surgical instruments are disclosed. The surgical instrument tray and its contents come into contact with an RF signal transmitted by the RFID reader, and as a result, the RFID tags affixed on the instrument tray and the surgical instruments respond by transmitting back to the RFID reader data pertaining to the history of the surgical instruments. A data terminal, which is connected to the RFID reader, may contain data pertaining to the radio frequency tagged surgical instruments during packaging, and during the return of the surgical instrument trays to the packager, identifies the surgical instruments.
Owner:WARSAW ORTHOPEDIC INC
Methods and Systems for Measuring and Verifying Additives for Use in a Dialysis Machine
ActiveUS20110054378A1Reasonable portabilityAccurate measurementDialysis systemsMedical devicesGraphicsGraphical user interface
The present application discloses a portable dialysis system for conducting a dialysis treatment. The portable dialysis system has a controller unit that includes a display, a scale, a bar code reader, and a memory storing a plurality of programmatic instructions. Upon execution, the instructions generate a first graphical user interface, a second graphical user interface, and a third graphical user interface for presentation on the display. The first graphical user interface displays each additive required for use in the dialysis treatment. The second graphical user interface prompts a user to submit additives to scanning using the bar code scanner. The third graphical user interface prompts a user to submit additives to measurement using the scale.
Owner:FRESENIUS MEDICAL CARE HLDG INC
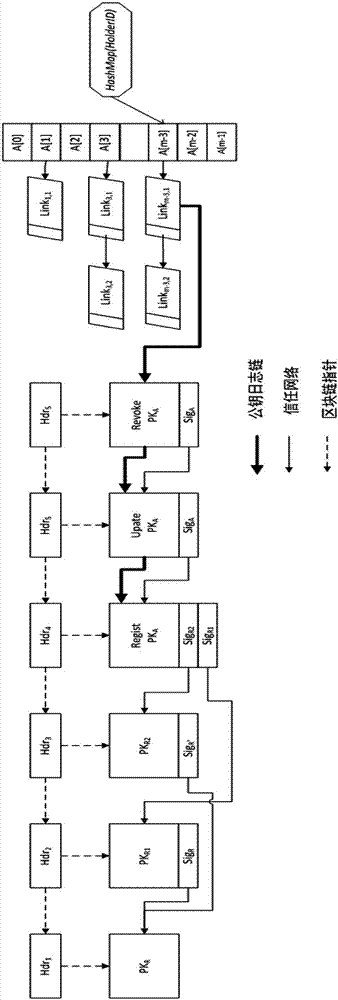
Decentralized public key management method and system based on trusted network
ActiveCN107070644AEfficient verificationEfficient queryKey distribution for secure communicationStructure of Management InformationUser identifier
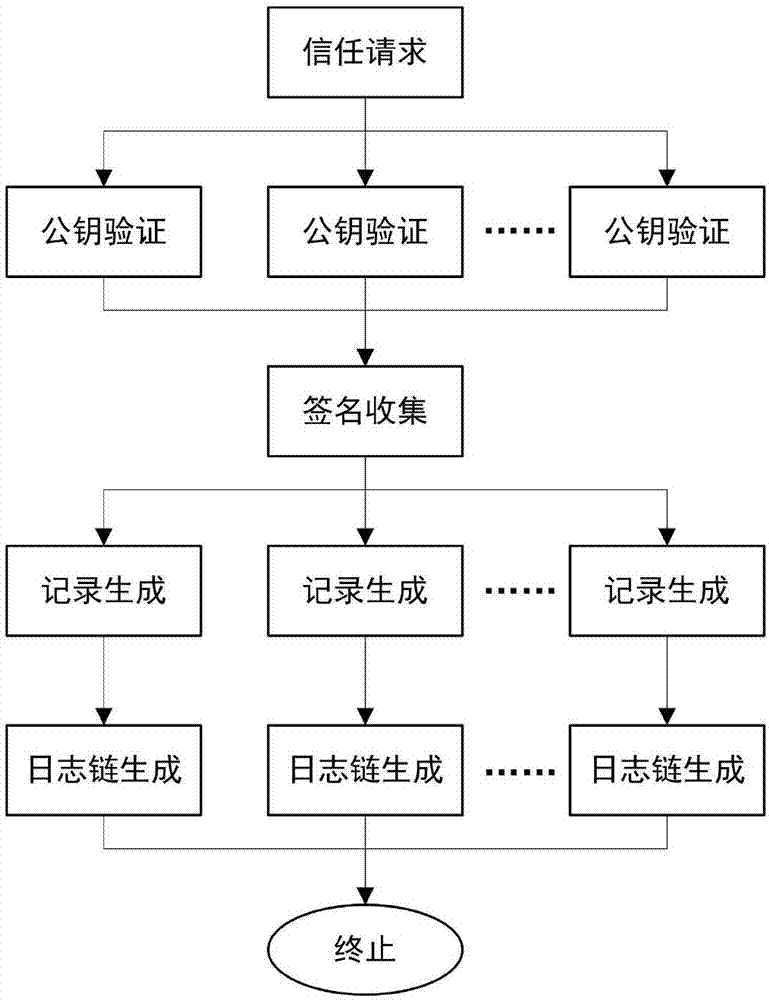
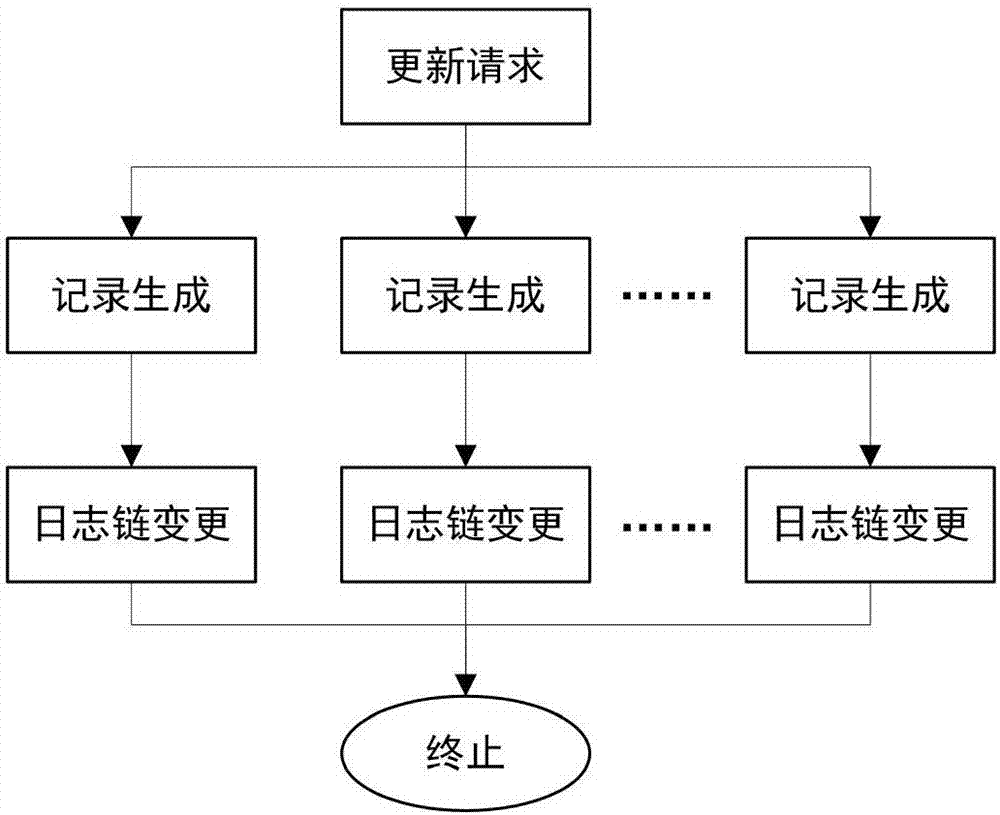
The invention mainly belongs to the technical field of information security, and specifically relates to a novel decentralized public key management method and a trusted model. The method is constructed on distributed data network platforms such as a block chain and P2P (Peer to Peer) in order to ensure that all nodes in the platforms can participate in maintenance of whole-life-cycle management of public keys of users, and the changes of the public keys of the users in various states in a life cycle are recorded in a bill form. Through the method, public keys passing verification can be recorded and added into a consistent public key storage structure of a platform to be saved; a public key log chain is generated for all public key records of the same user according to a time sequence, and an authentication chain and a trusted network are formed on the basis of a referrer signature; and efficient search of the public keys can be realized on the basis of user identifiers. Through adoption of the method, the public keys of the users can be issued and acquired conveniently and accurately, and the effectiveness, correctness, consistency and non-fraudulence of acquired public keys are ensured. The method can be taken as an infrastructure supporting authentication, encryption, integrity and accountability services.
Owner:UNIV OF SCI & TECH BEIJING
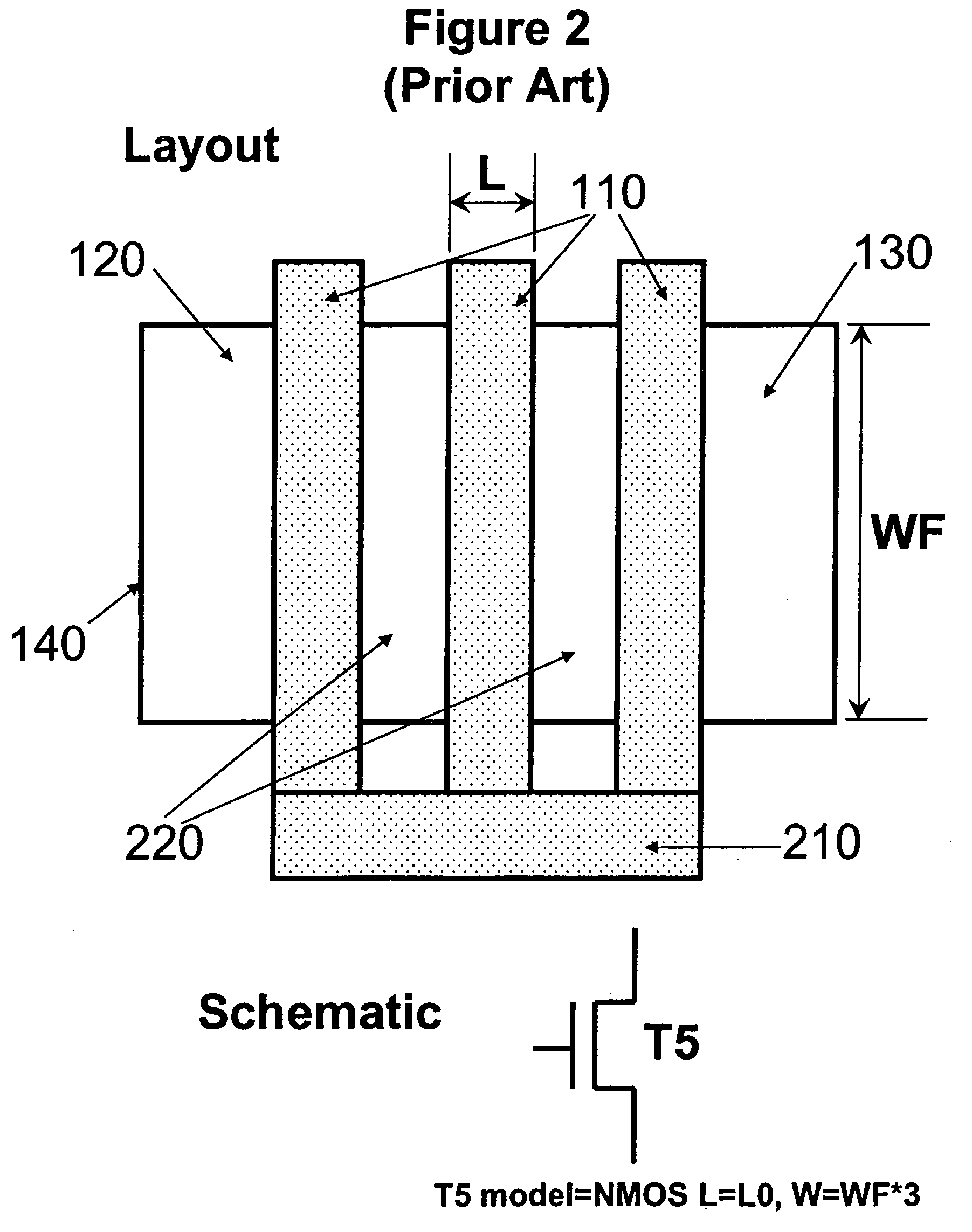
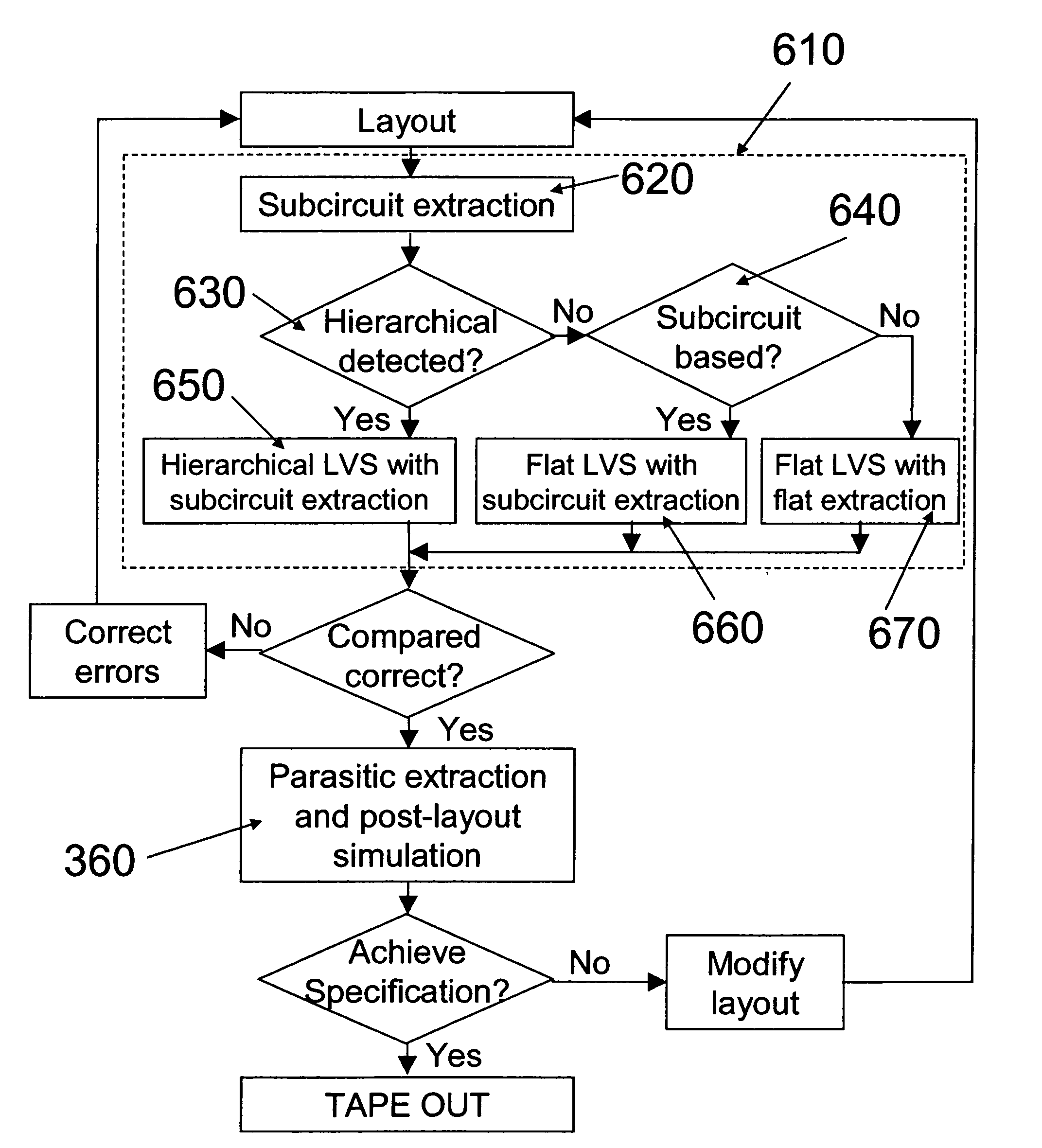
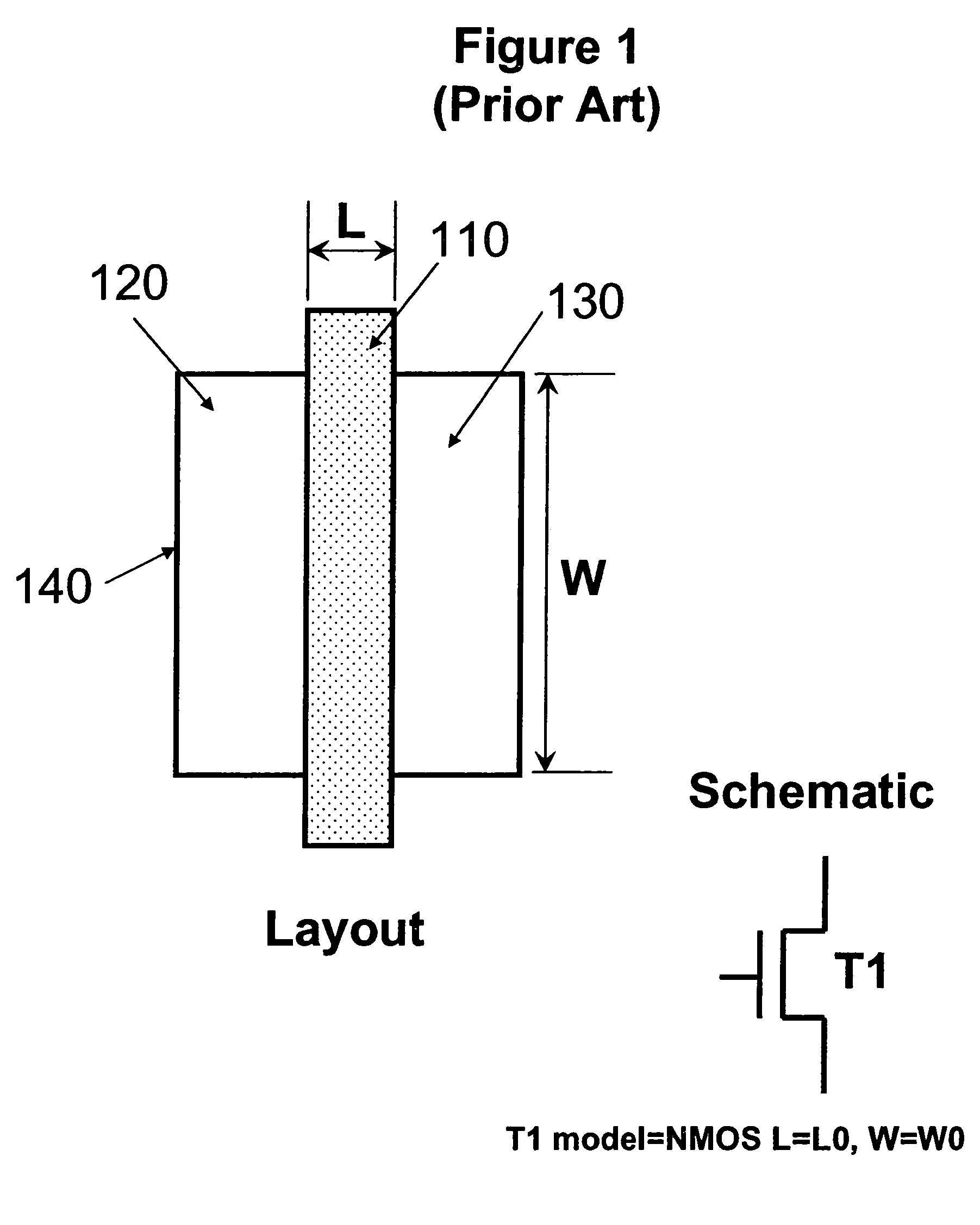
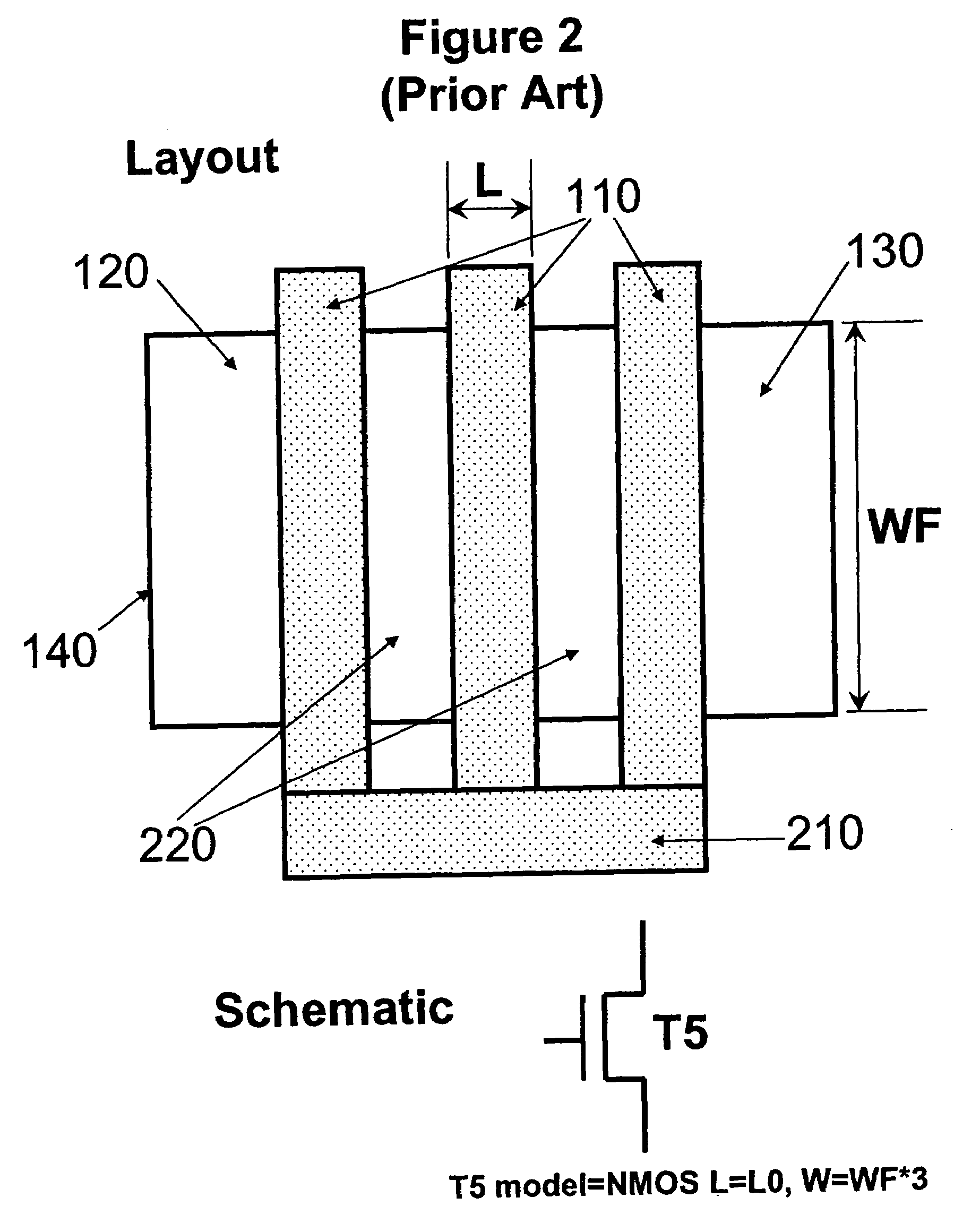
Method of checking the layout versus the schematic of multi-fingered MOS transistor layouts using a sub-circuit based extraction
InactiveUS20050216873A1Improve trustEasy to identifyCAD circuit designSoftware simulation/interpretation/emulationDevice PropertiesComputer architecture
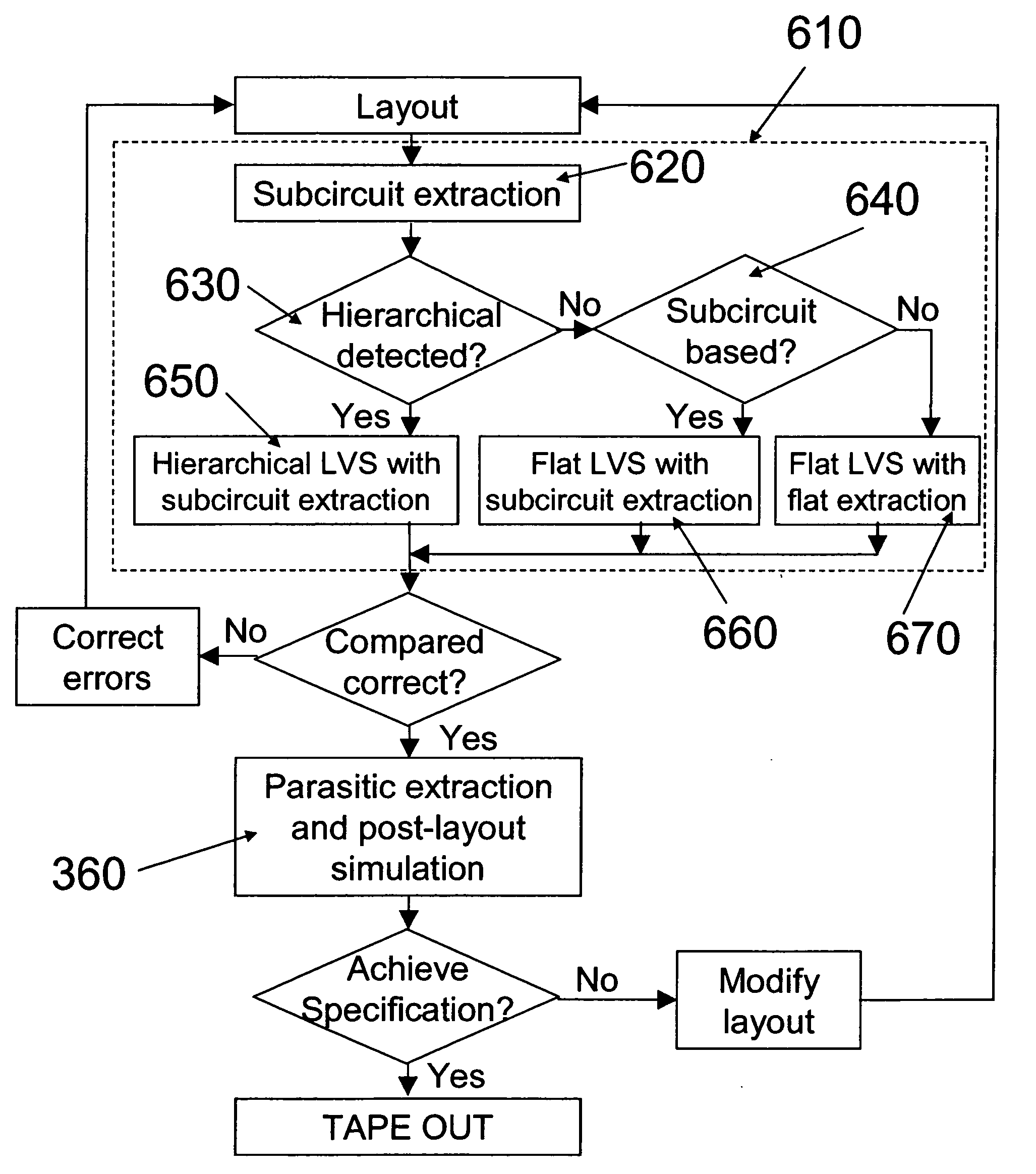
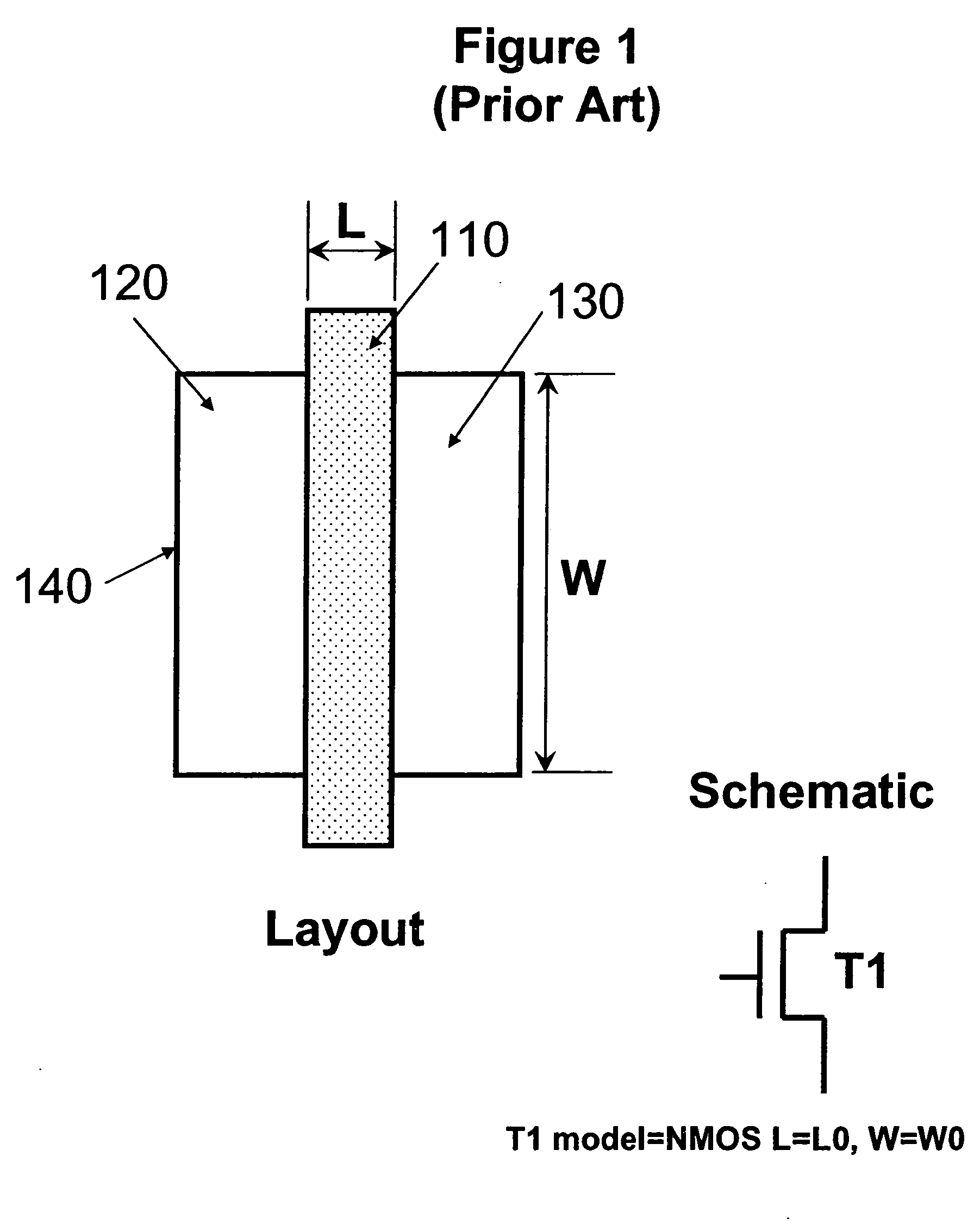
A sub-circuit based extraction method which extracts a multi-finger MOS transistor directly as a sub-circuit is described. By adding three marking layers, the method provides the layout extracted netlist with a complete list of device geometric parameters corresponding to the device properties as presented in the sub-circuit model based schematic netlist. By performing a layout-versus-schematic comparison based on all geometric parameters extracted, the layout checking is performed in a complete and accurate way where each device parameter is checked against the corresponding design schematic. This complete and accurate geometric parameter comparison enhances the confidence level of the layout physical verification.
Owner:IBM CORP
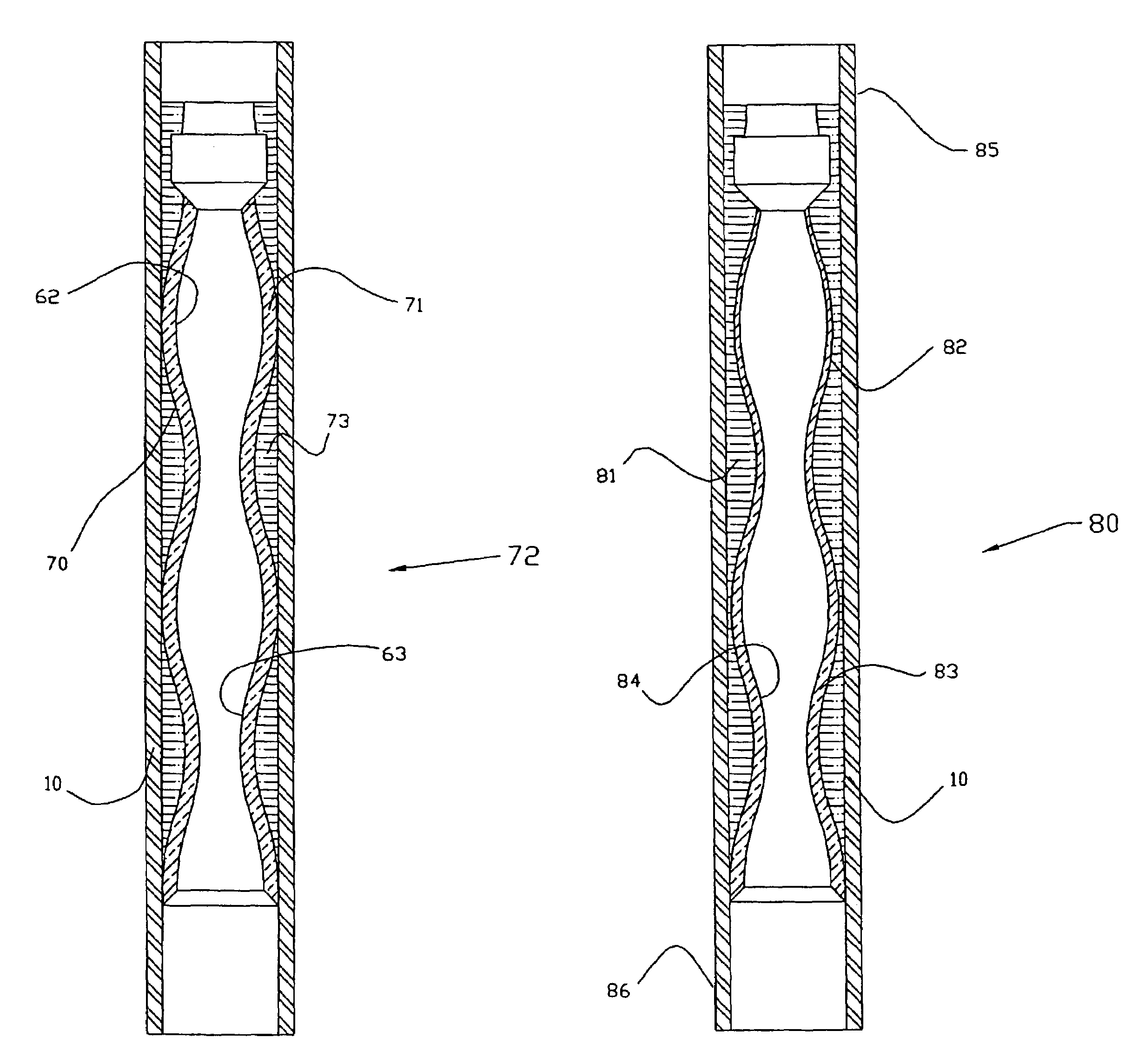
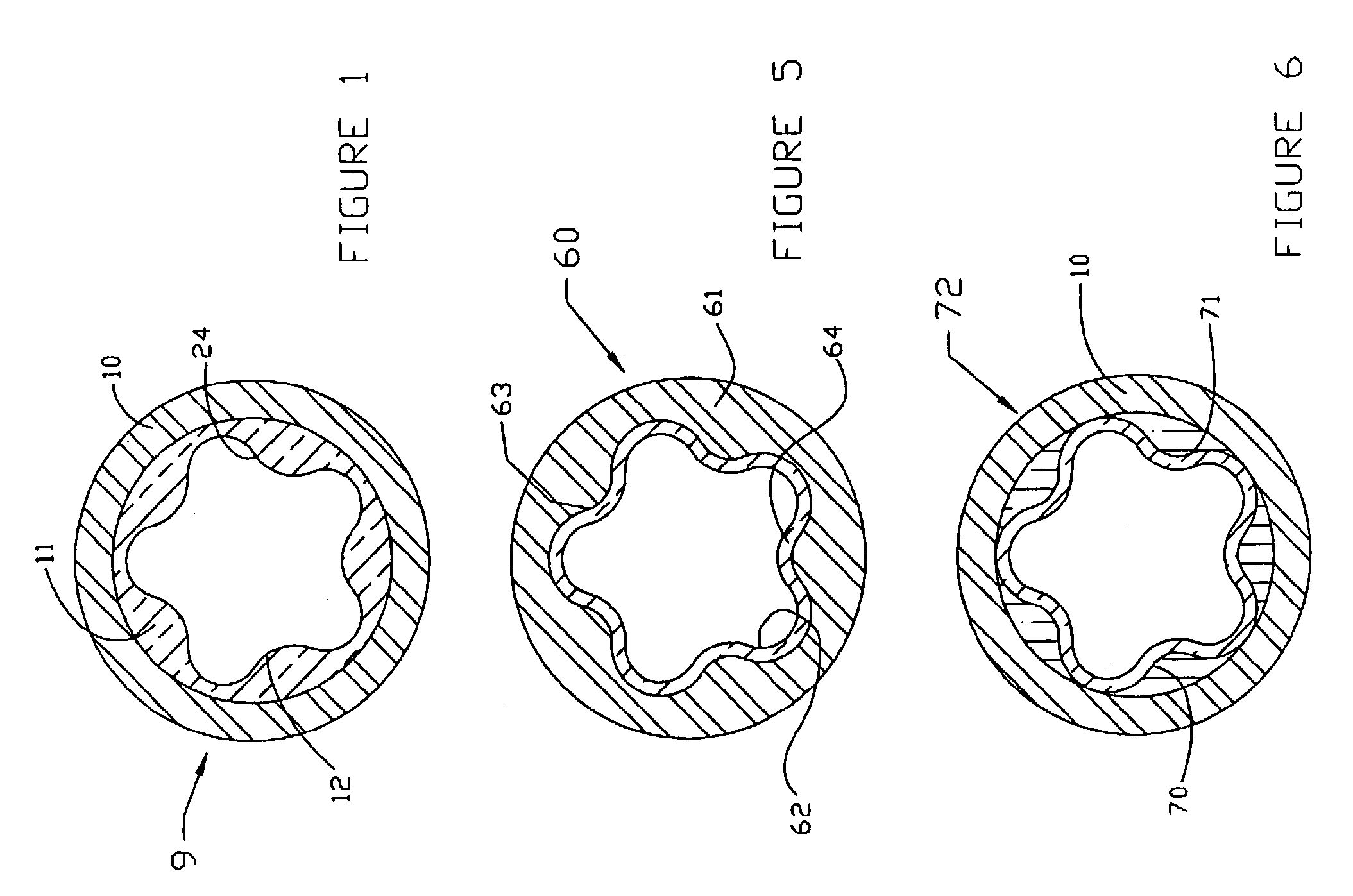
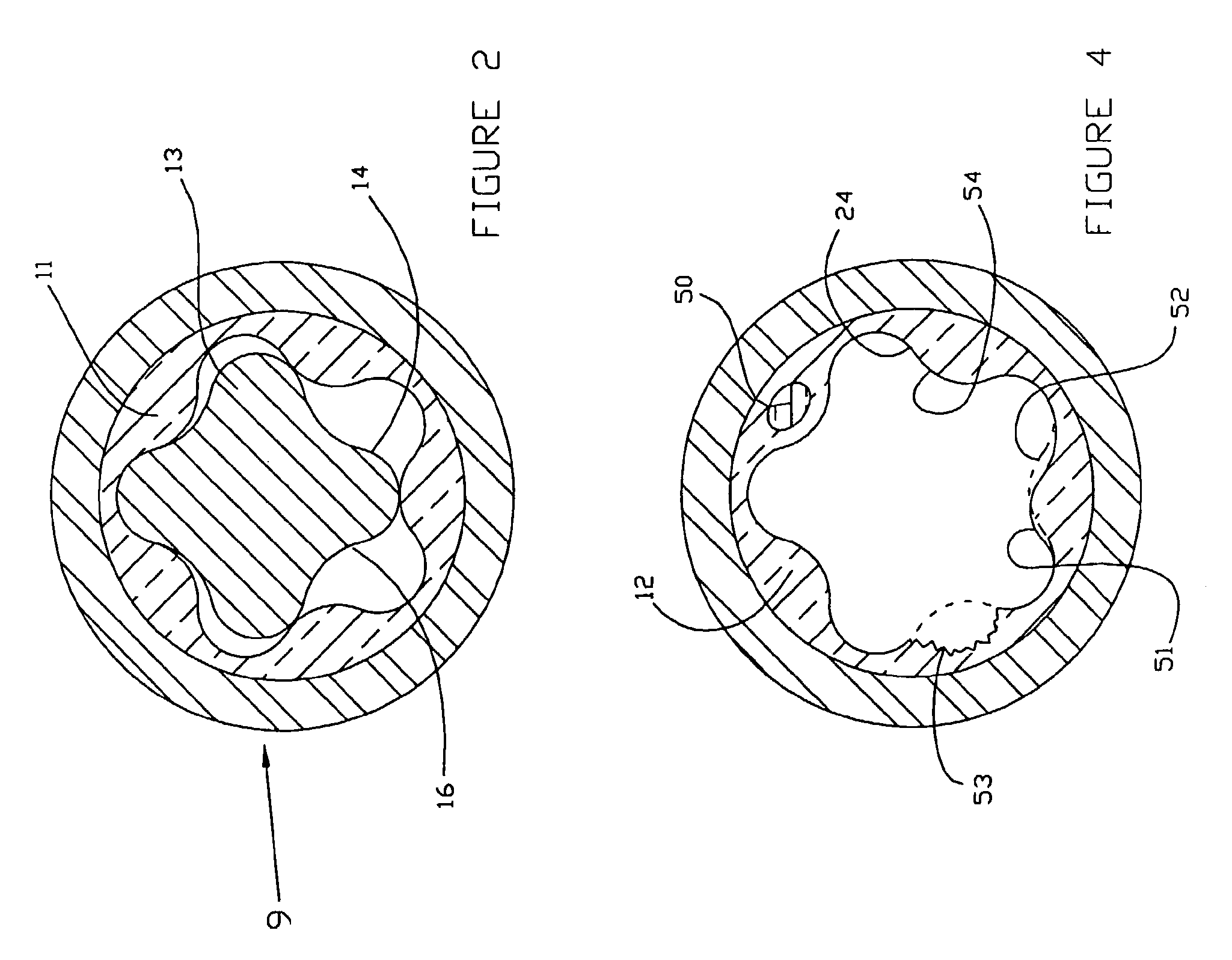
Progressive cavity pump/motor
InactiveUS6881045B2Accurate verificationOscillating piston enginesEngine of intermeshing engagement typeEngineeringDrill bit
A progressive cavity pump or motor, particularly suitable for hydrocarbon recovery operations, includes a rotor 20 and a stator 10. Fluid pressure in cavities between the stator and the rotor create torque which rotates the bit. An interior surface of the stator is rigidly secured to the outer housing of the pump stator and defines an interior profile. A substantially uniform thickness elastomeric layer 62 is supported on the outer housing. The pump rotor has an exterior profile which corresponds with the interior profile of the elastomeric layer.
Owner:ROBBINS & MYERS ENERGY SYST
Validation and verification apparatus and method
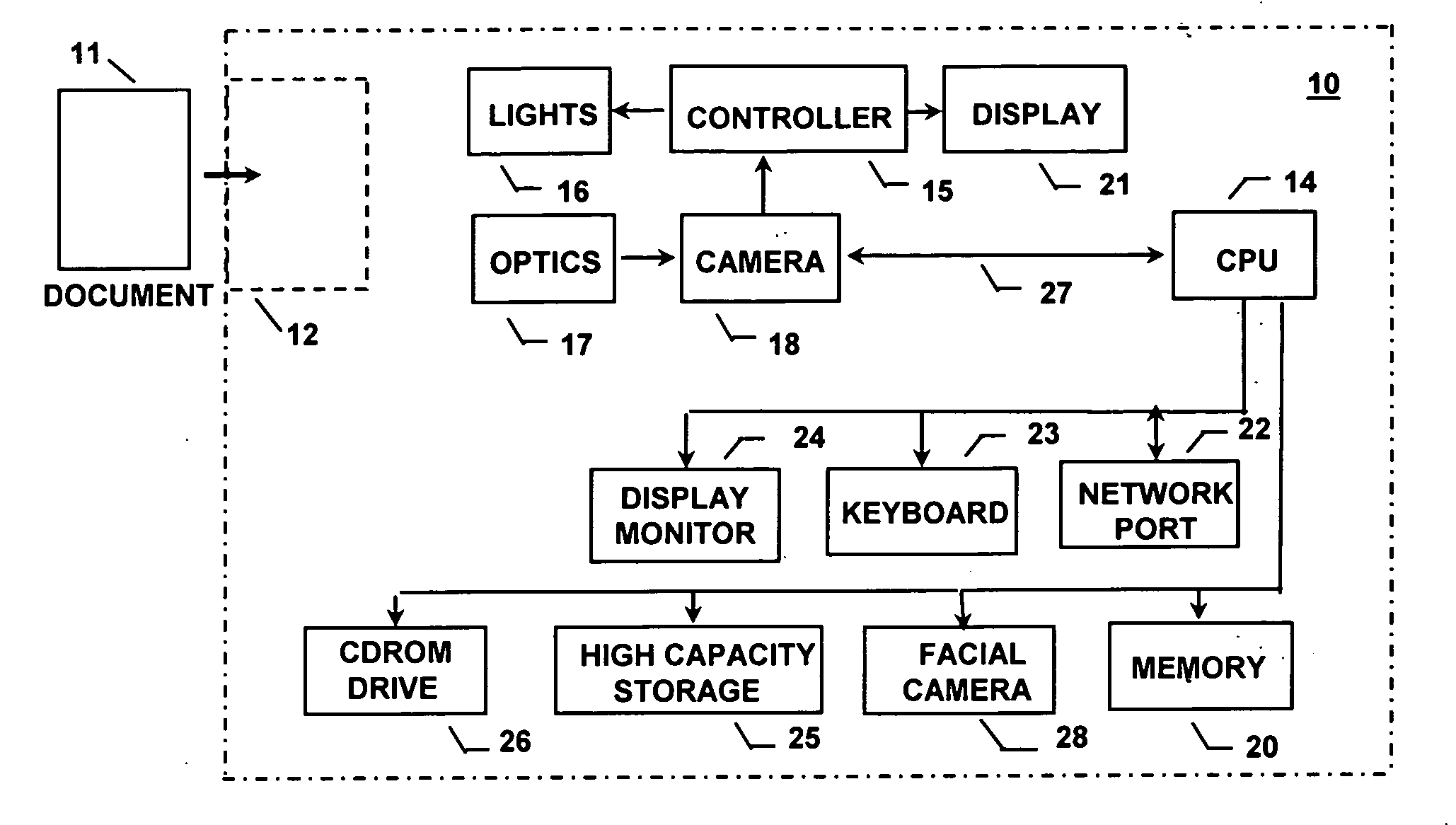
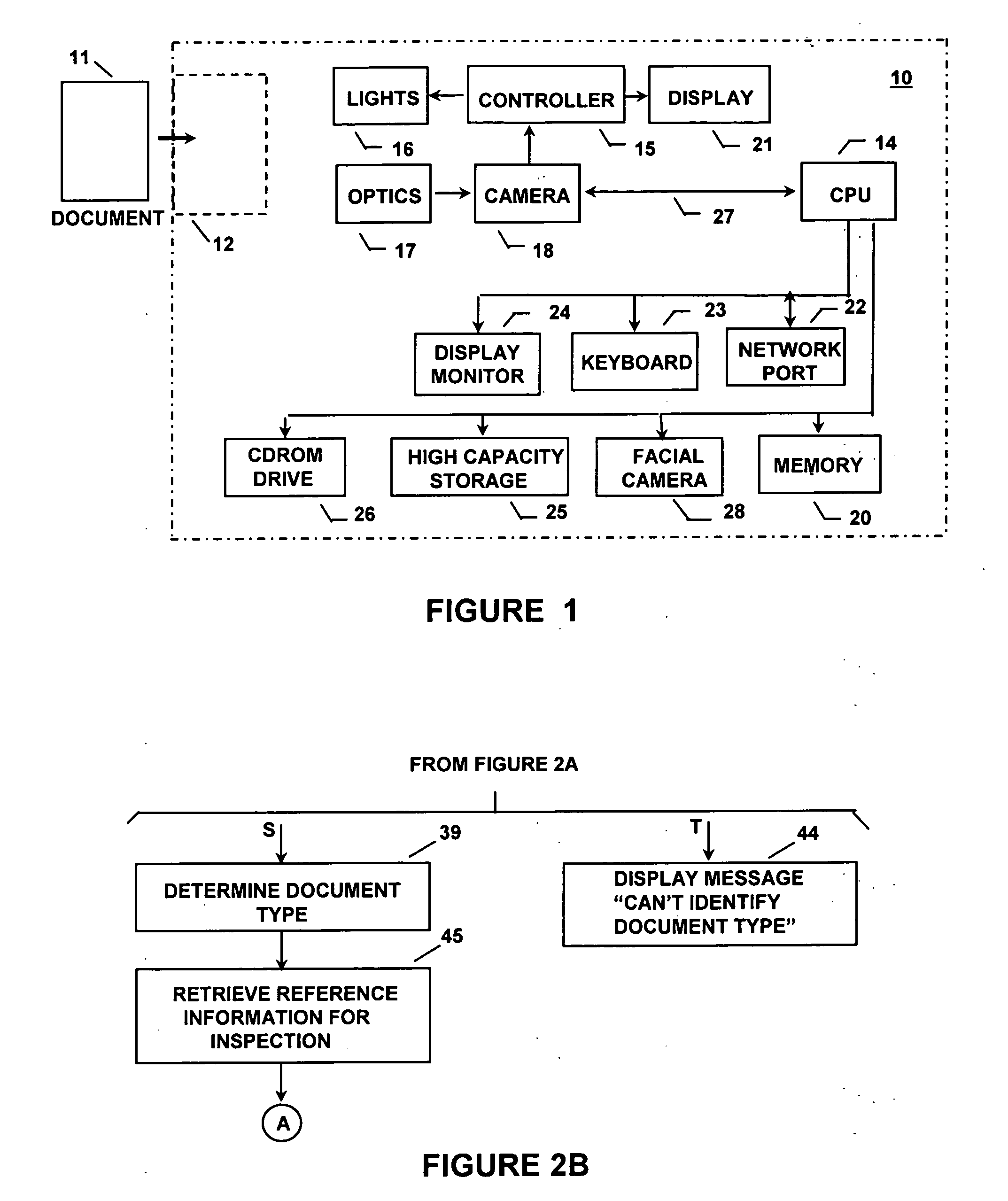
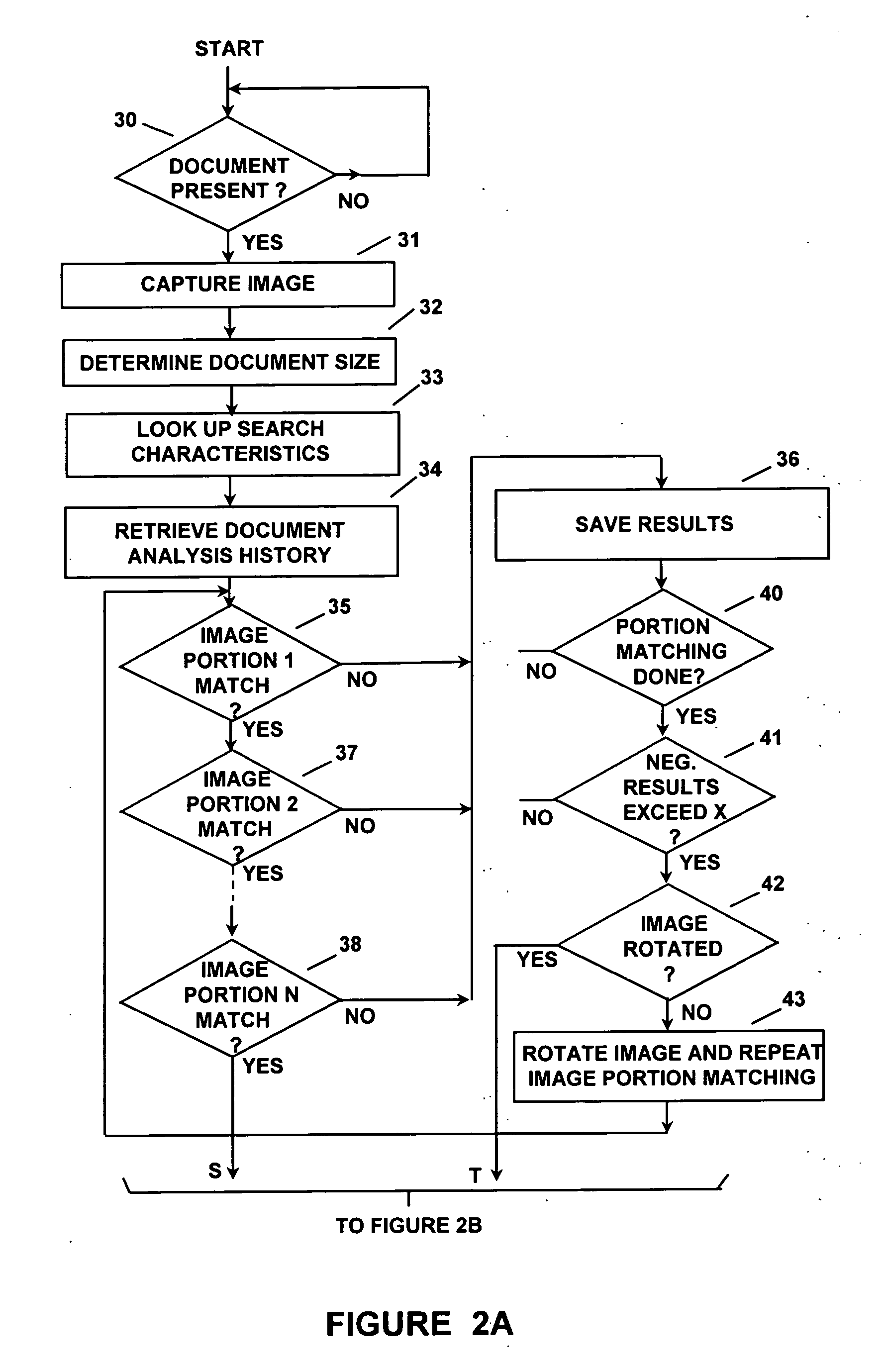
InactiveUS7110573B2Accurate verificationProcessing speedPaper-money testing devicesCharacter and pattern recognitionDocument preparationBiometrics
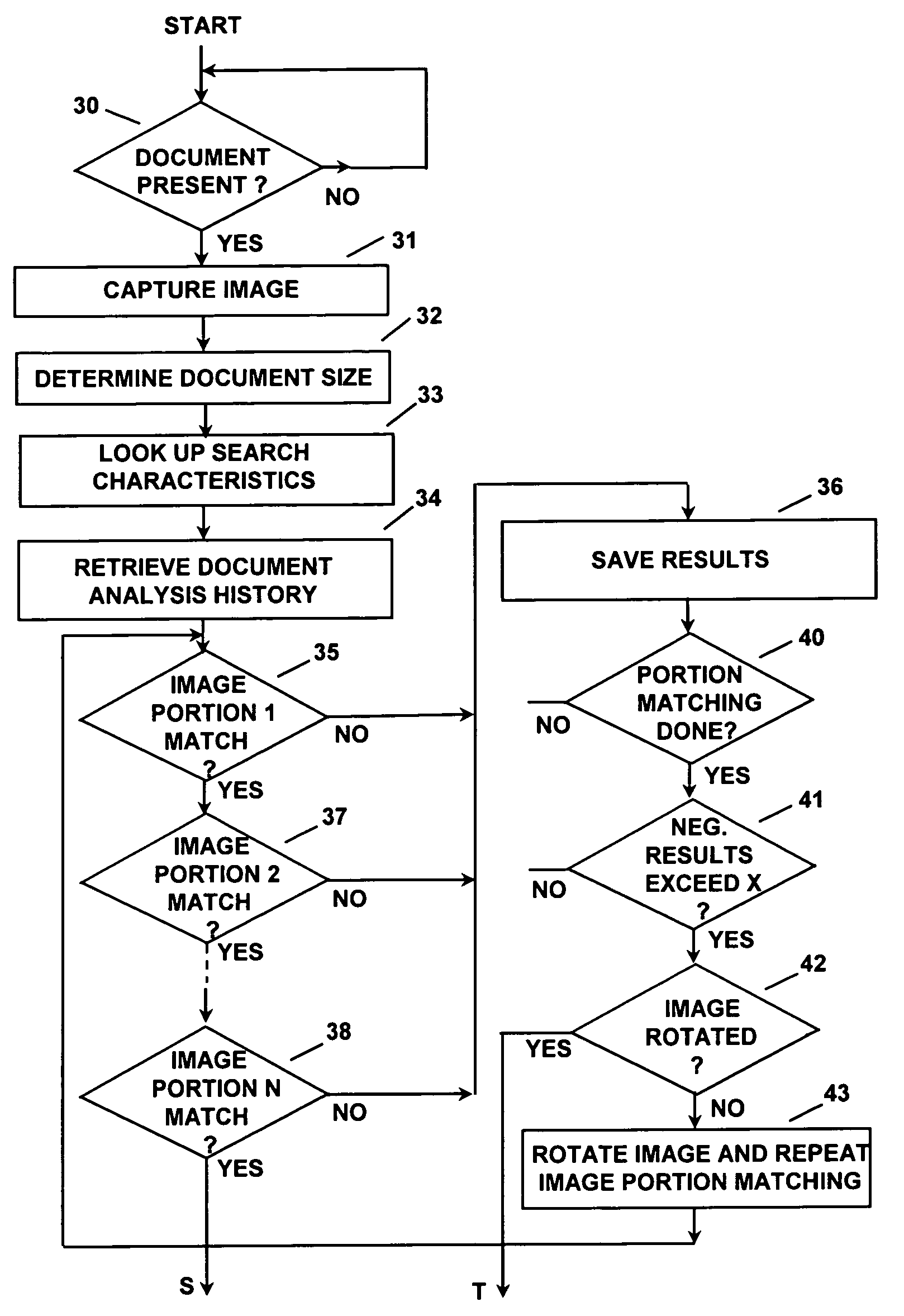
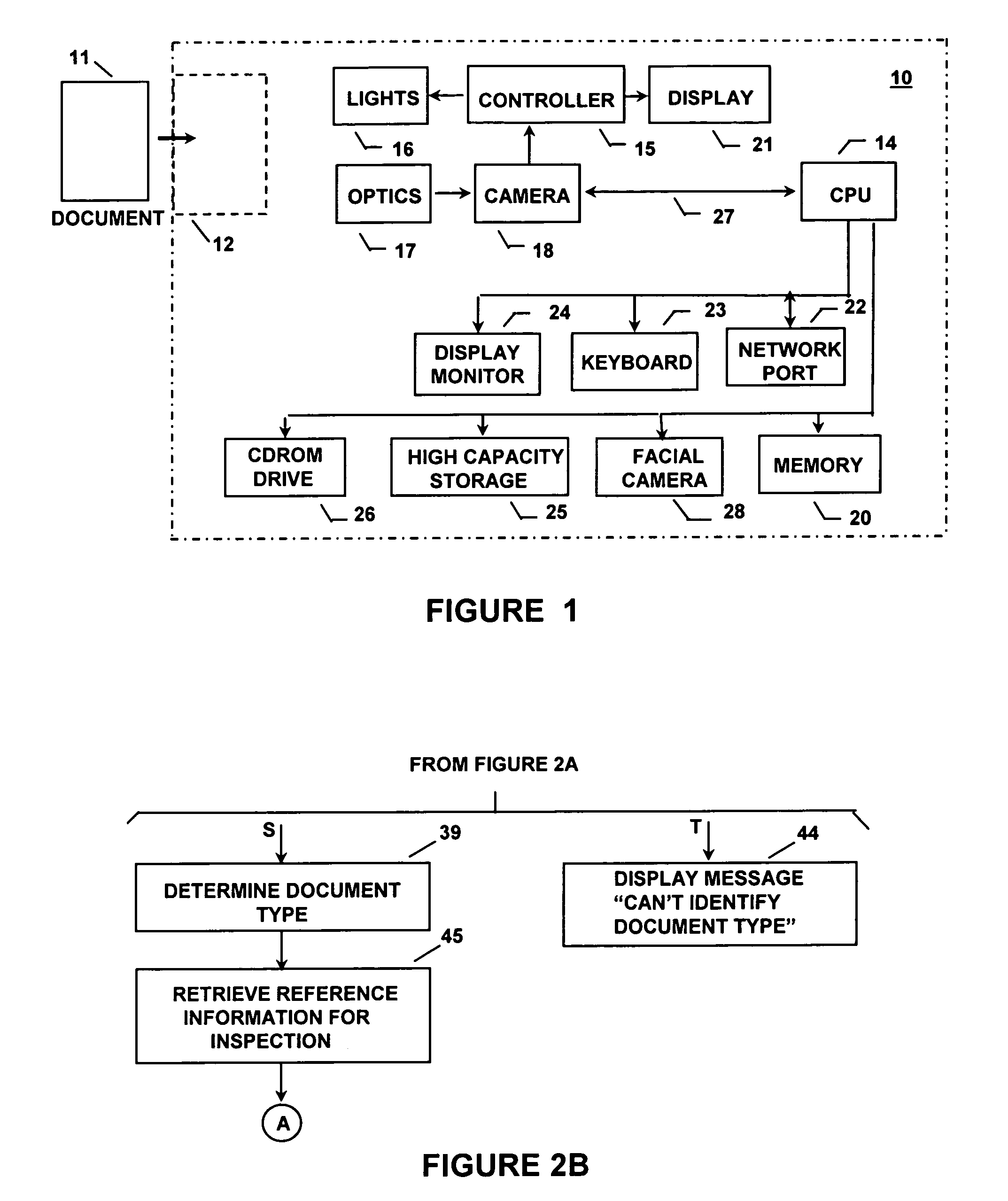
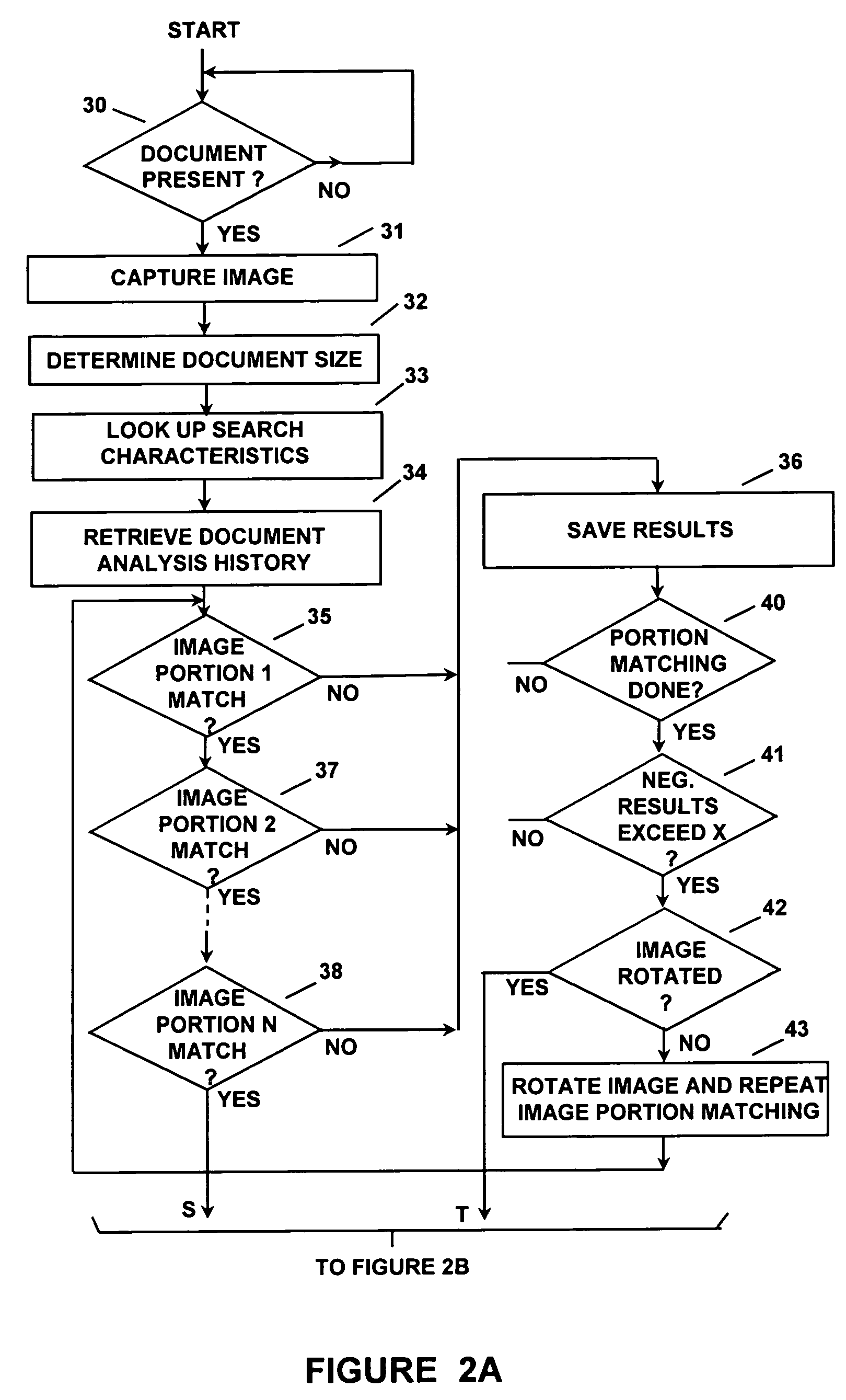
Apparatus and a method are disclosed for automatically identifying and validating a document, for validating the identity of a bearer of a document, for verifying that the bearer has authorization to participate in an activity represented by the document, and for comparing information on the document against information databases to determine if there are known concerns about the document or its bearer. A document type is narrowed by initially determining the size of the document, and is then identified from amongst a group of documents by looking for colors or other characteristics at specific locations on the document only until the document is identified. The order in which document locations are looked at is dependent upon a history of the types of documents that have been identified. An identified document is verified by first looking up reference information about the document type and using that information to read specific contents and check only specific security and other features utilized on the document. The contents of a document are checked against a database to verify its contents, and other databases are checked for stolen documents, known valid documents, and prohibited travel or entry. Biometrics in databases, on documents and directly from the document bearer are compared to verify the bearer.
Owner:ACUANT
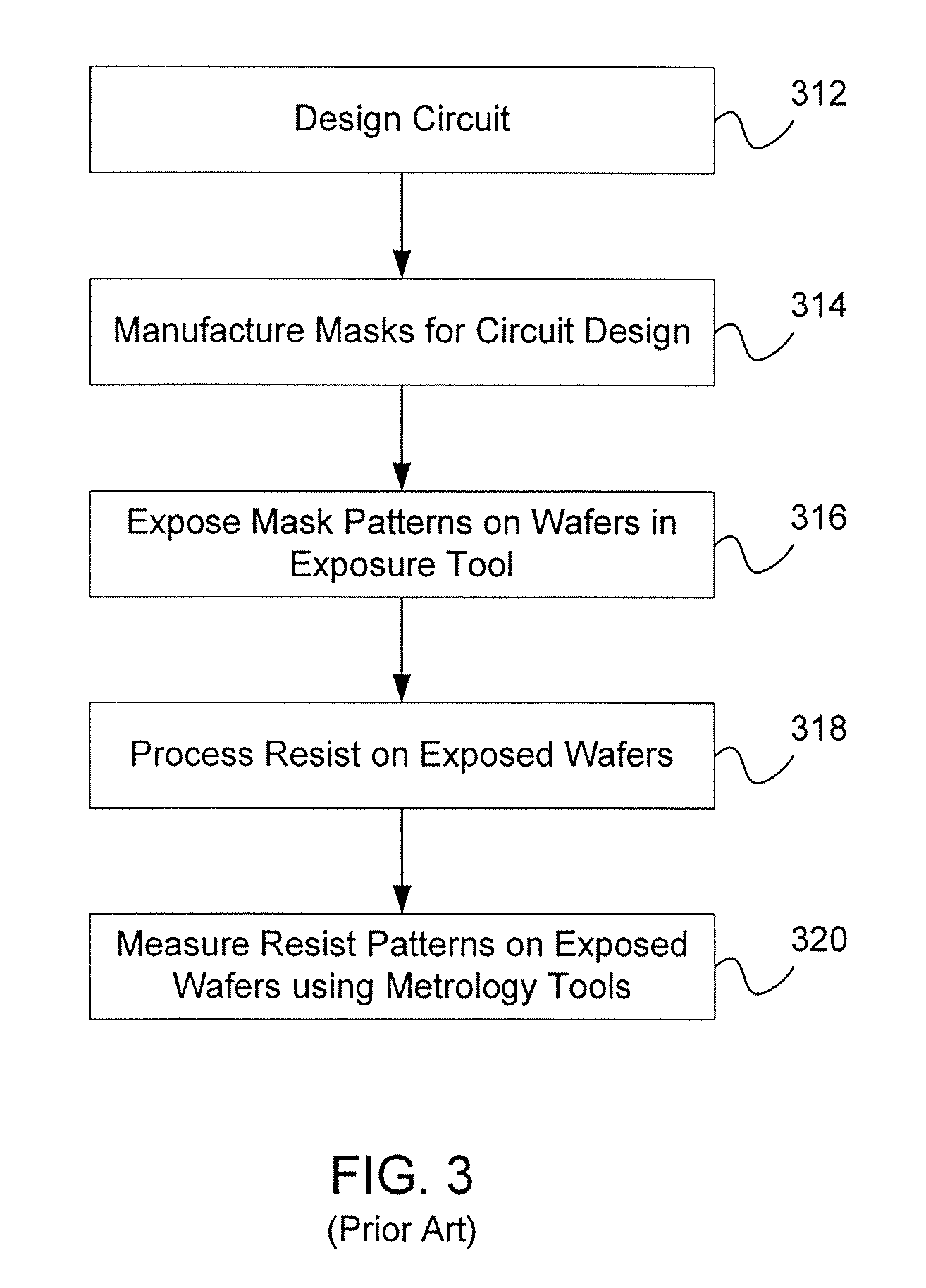
Method for lithography model calibration
ActiveUS7488933B2More accurate and separable optical and resist modelsImprove predictabilityPhotomechanical apparatusCalibration apparatusLithography processWafer fabrication
A method for separately calibrating an optical model and a resist model of lithography process using information derived from in-situ aerial image measurements to improve the calibration of both the optical model and the resist model components of the lithography simulation model. Aerial images produced by an exposure tool are measured using an image sensor array loaded into the exposure tool. Multiple embodiments of measuring aerial image information and using the measured aerial image information to calibrate the optical model and the resist model are disclosed. The method of the invention creates more accurate and separable optical and resist models, leading to better predictability of the pattern transfer process from mask to wafer, more accurate verification of circuit patterns and how they will actually print in production, and more accurate model-based process control in the wafer fabrication facility.
Owner:ASML NETHERLANDS BV
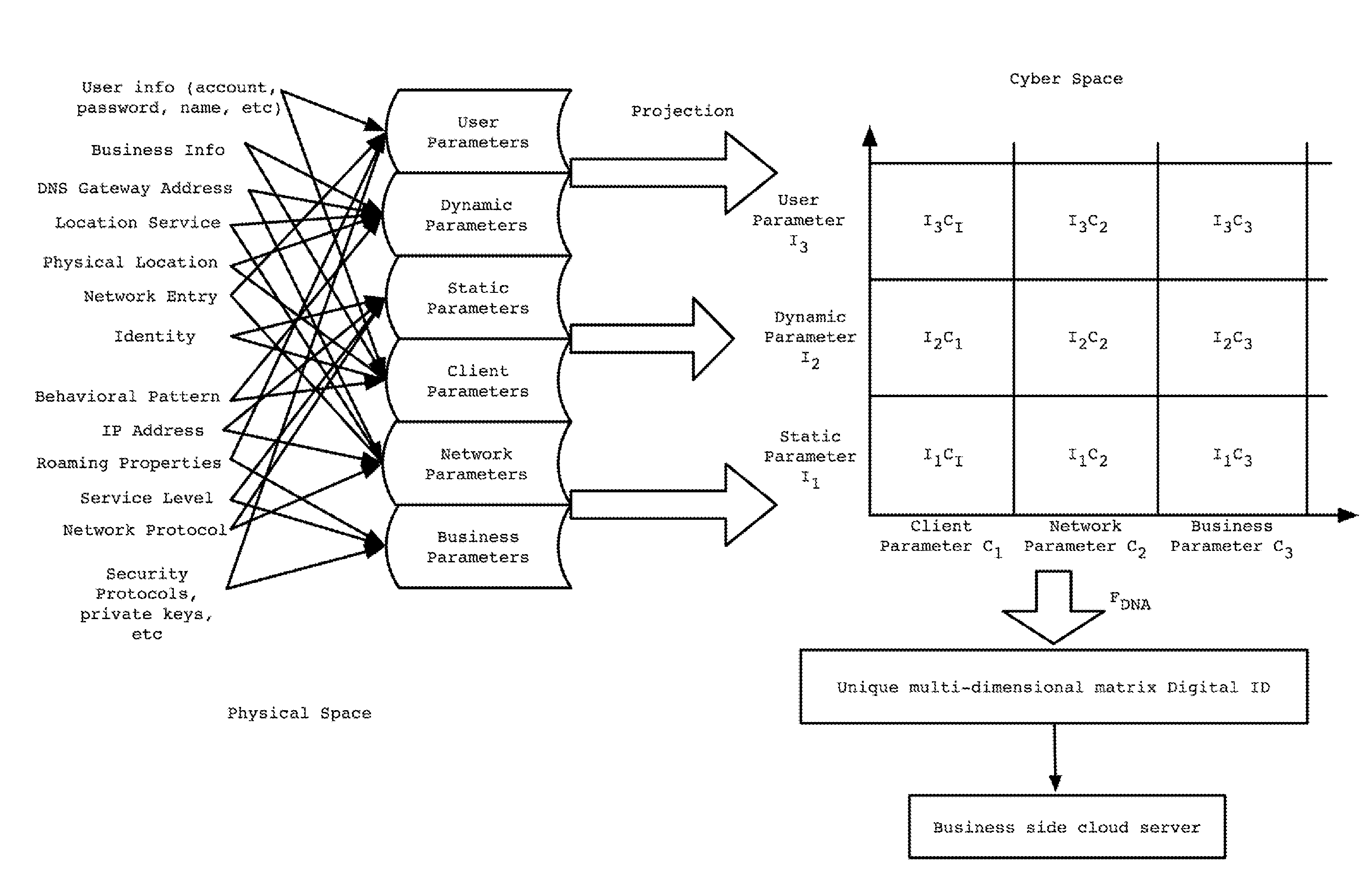
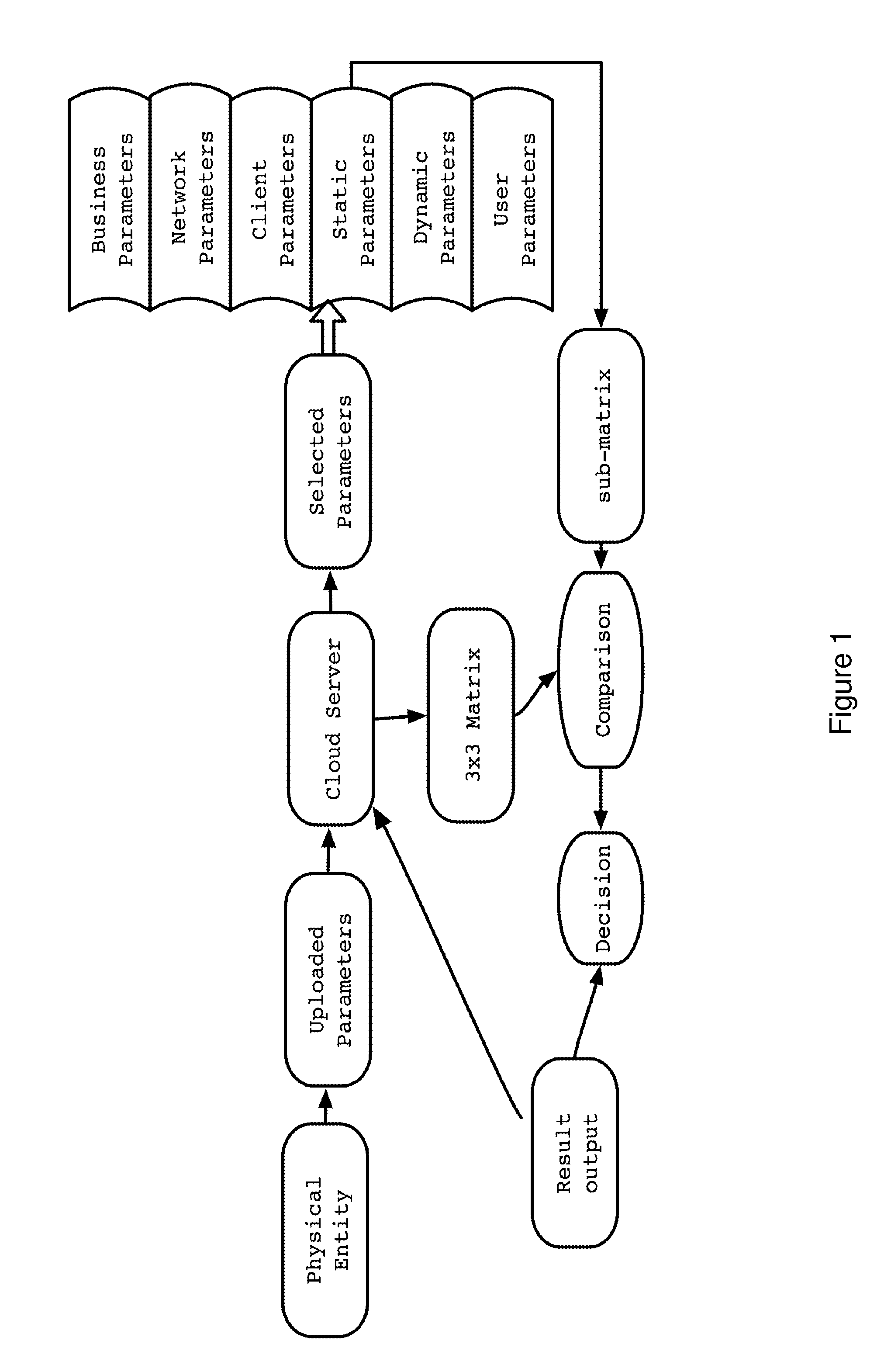
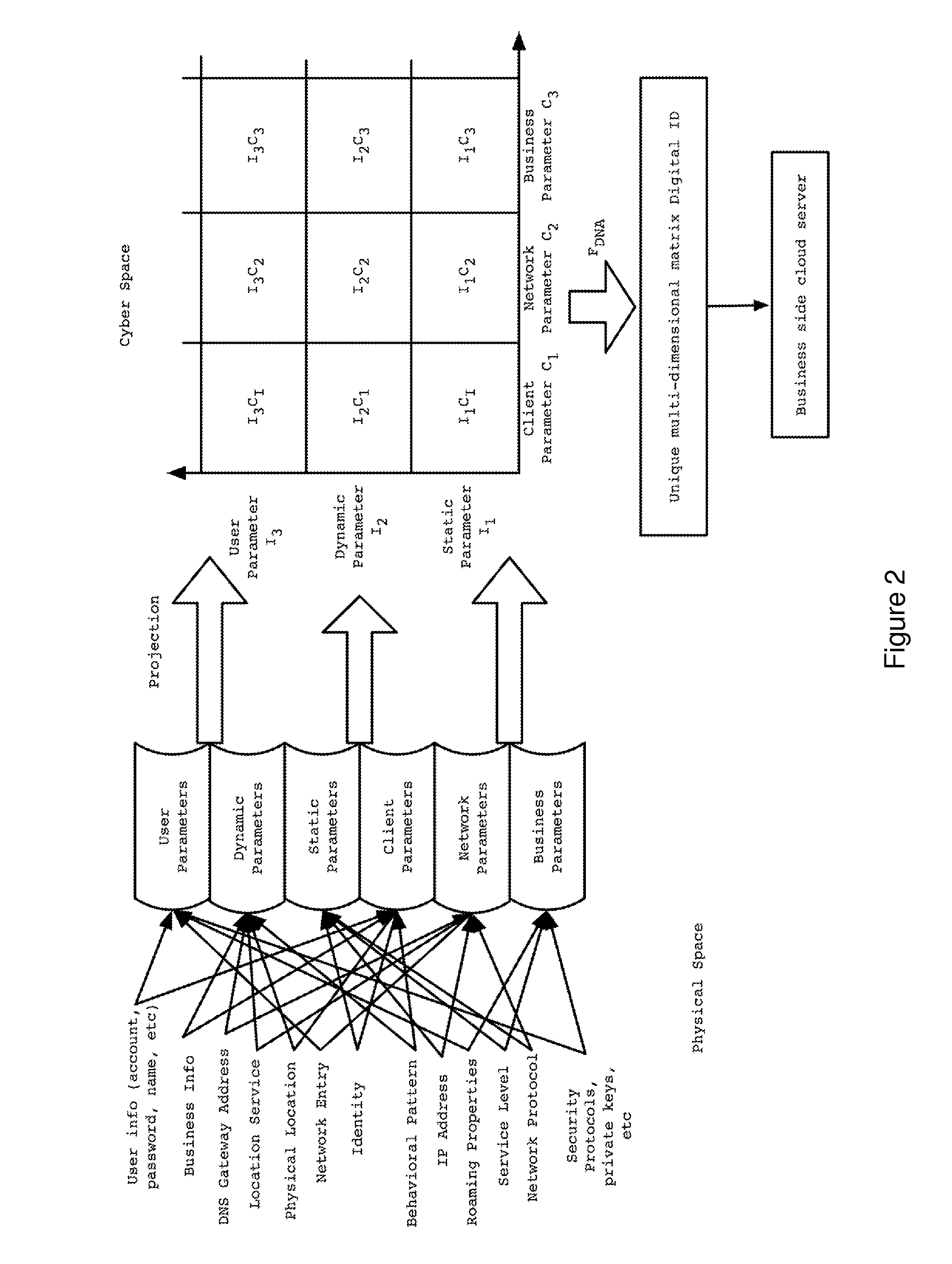
Cyber gene identification technology based on entity features in cyber space
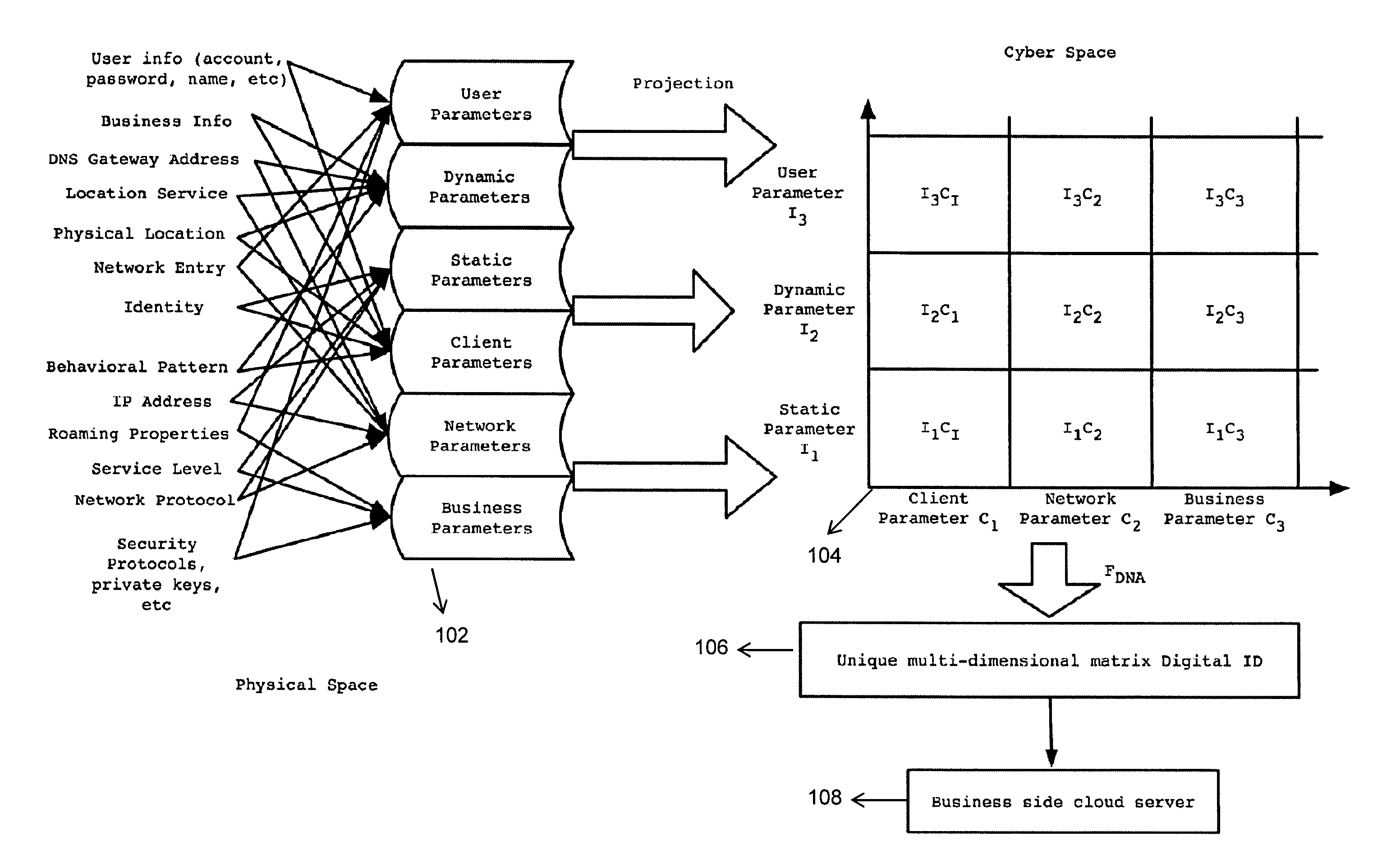
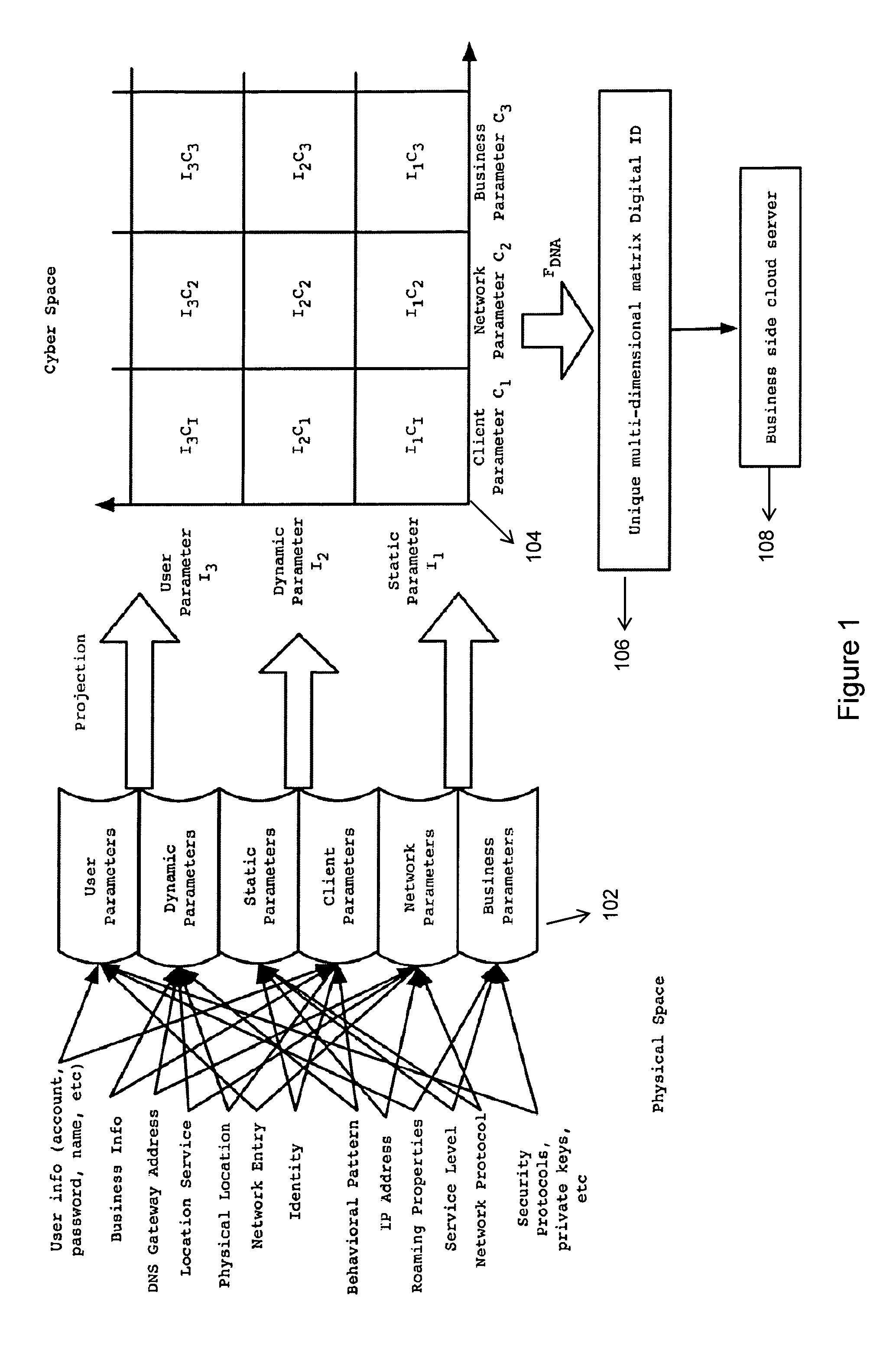
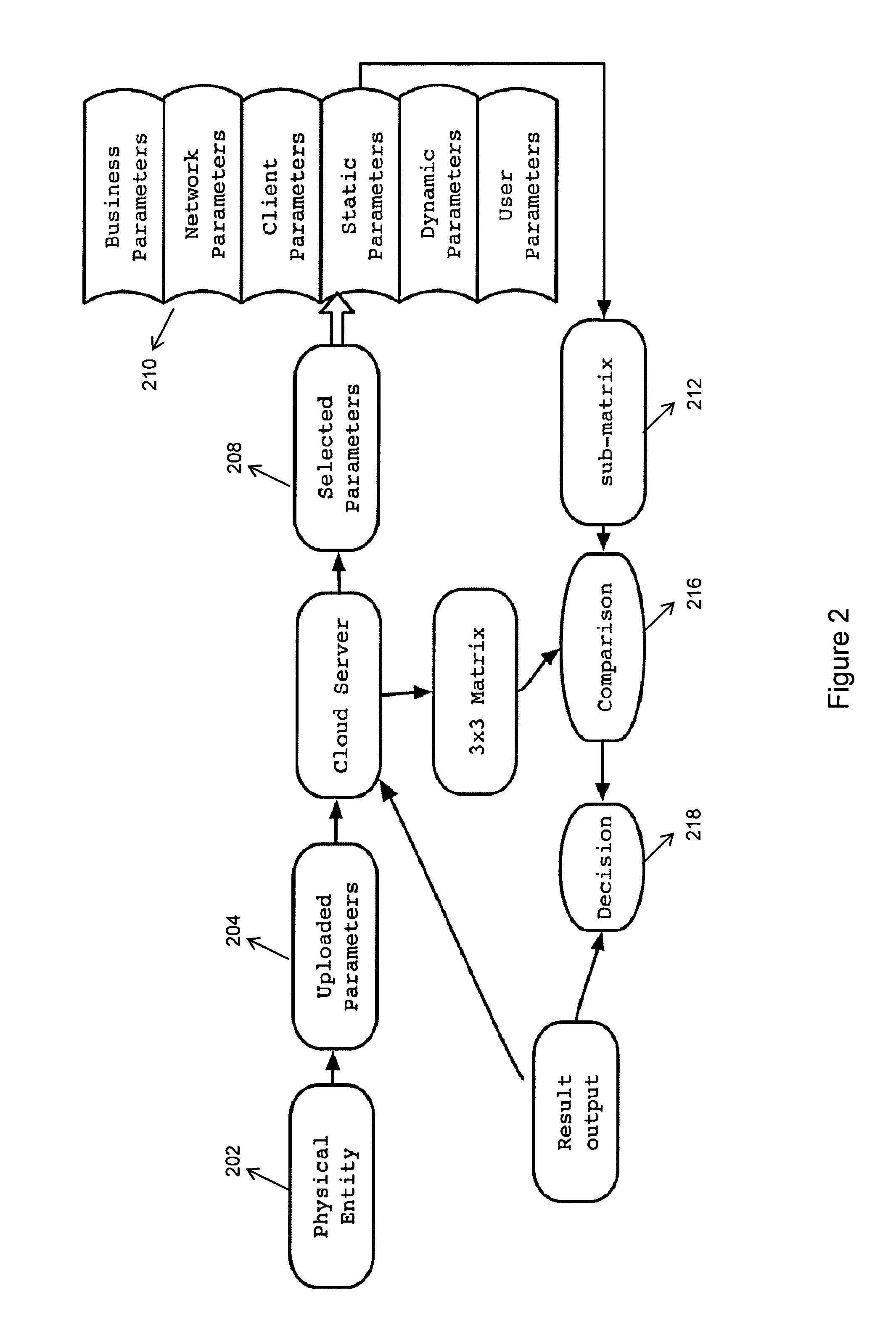
ActiveUS20110302640A1Accurate verificationDigital data processing detailsMultiple digital computer combinationsInternet privacyStandardization
A new identification (ID) technology comprising unified and standardized object identification within Cyber Space is disclosed based upon intrinsic properties of the entity to be identified. This Cyber Gene ID (or Cyber ID) technology extracts intrinsic information from either the physical users or their cyberspace counterparts, and such information is categorized into client parameters, dynamic parameters, static parameters, cloud parameters, connection parameters and user parameters.
Owner:JIANGSU DIGITAL DNA TECH CO LTD
Validation and verification apparatus and method
InactiveUS20050229010A1Accurate verificationProcessing speedPaper-money testing devicesCharacter and pattern recognitionDocument preparationBiometrics
Apparatus and a method are disclosed for automatically identifying and validating a document, for validating the identity of a bearer of a document, for verifying that the bearer has authorization to participate in an activity represented by the document, and for comparing information on the document against information databases to determine if there are known concerns about the document or its bearer. A document type is narrowed by initially determining the size of the document, and is then identified from amongst a group of documents by looking for colors or other characteristics at specific locations on the document only until the document is identified. The order in which document locations are looked at is dependent upon a history of the types of documents that have been identified. An identified document is verified by first looking up reference information about the document type and using that information to read specific contents and check only specific security and other features utilized on the document. The contents of a document are checked against a database to verify its contents, and other databases are checked for stolen documents, known valid documents, and prohibited travel or entry. Biometrics in databases, on documents and directly from the document bearer are compared to verify the bearer.
Owner:ACUANT
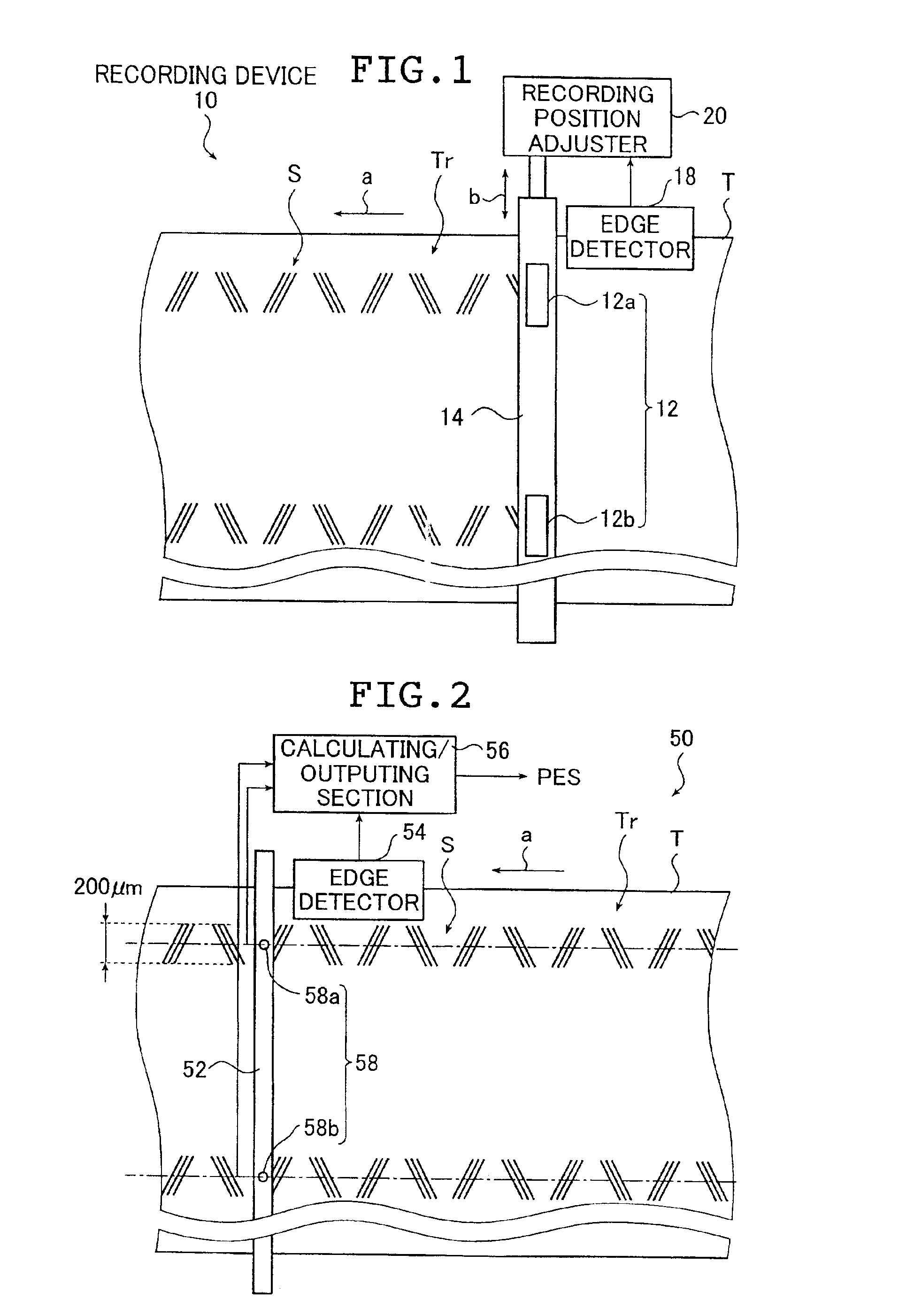
Servo signal recording device and servo signal verifying device using edge detection
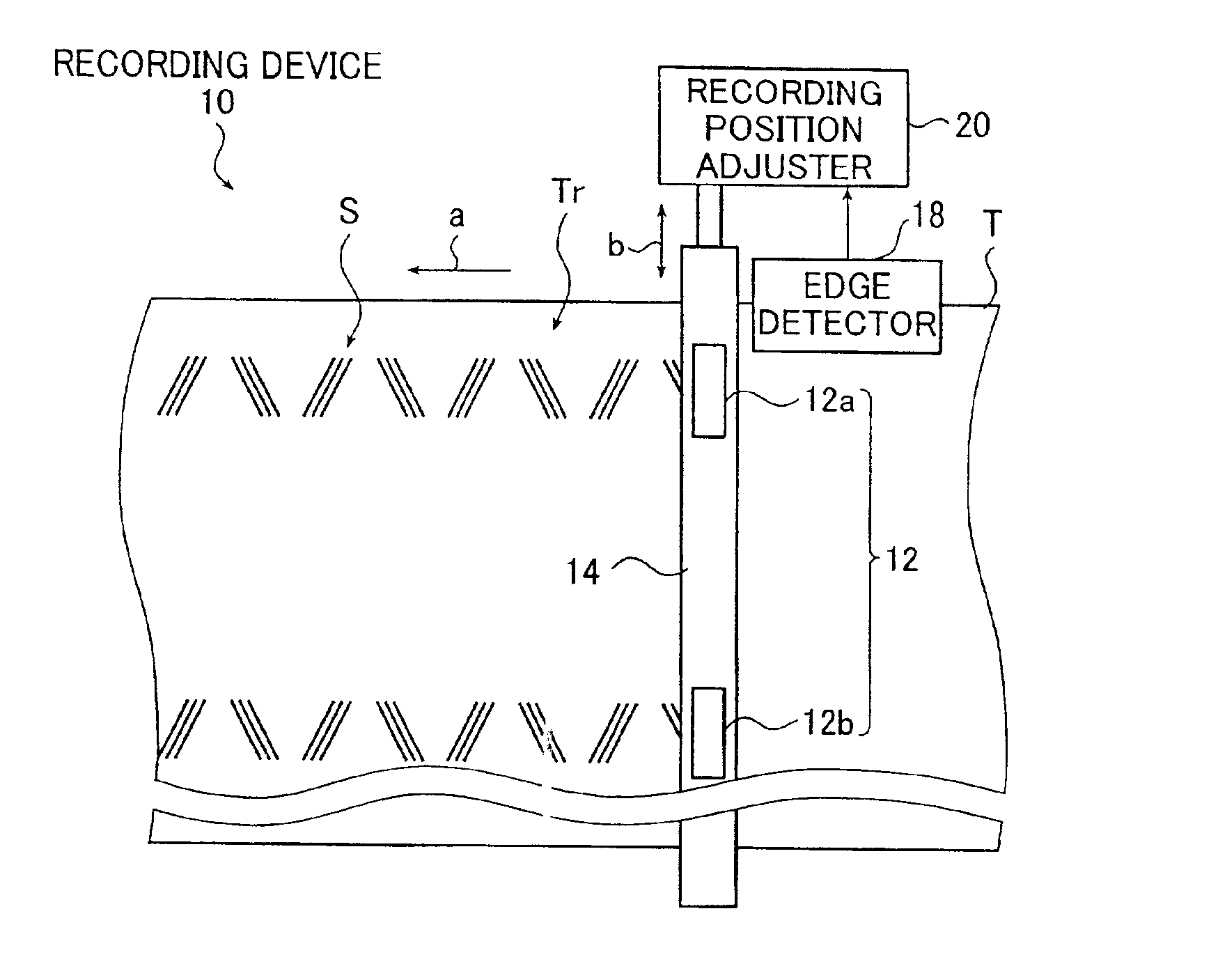
InactiveUS6865050B2Accurate verificationAppropriately evaluatedTrack finding/aligningAlignment for track following on tapesMagnetic tapeControl theory
The servo signal recording device records a servo signal onto a magnetic tape. The device includes a transporting unit for transporting the magnetic tape along its lengthwise direction, a recording unit for recording the servo signal onto the transported magnetic tape, a detecting unit for detecting an edge of the magnetic tape at a time when the servo signal is recorded and an adjusting unit for adjusting a recording position of the servo signal along a crosswise direction of the magnetic tape in accordance with a detection result of the edge of the magnetic tape by the detecting unit. The servo signal verifying device verifies a servo signal recorded onto a magnetic tape. The device includes a reproducing unit for reproducing the servo signal, a detecting unit for detecting an edge of the magnetic tape at a time when the reproducing unit reproduces the servo signal and a calculating unit for calculating a verification result of the servo signal recorded onto the magnetic tape using a reproduction result of the servo signal and a detection result of the edge.
Owner:FUJIFILM CORP +1
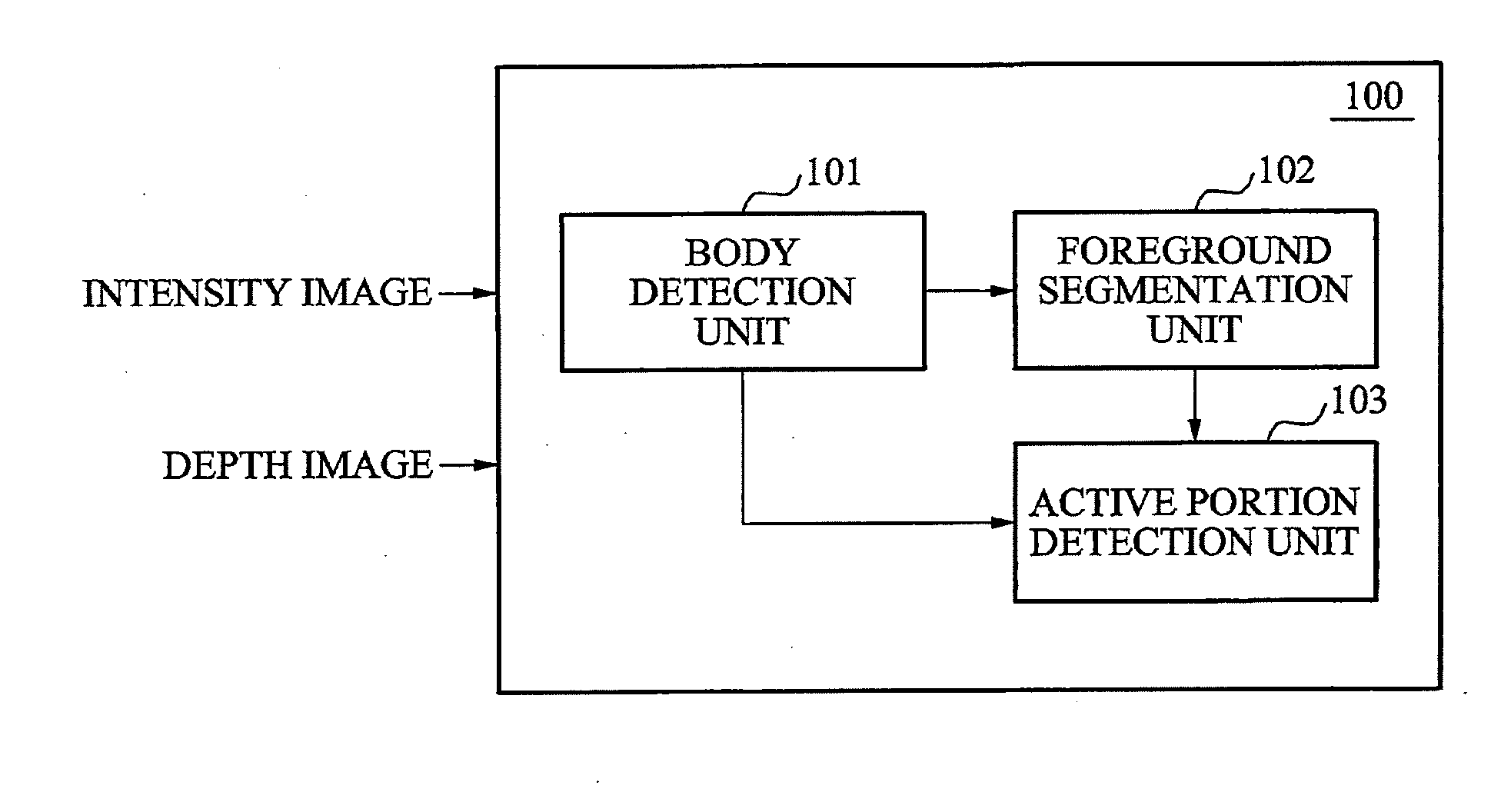
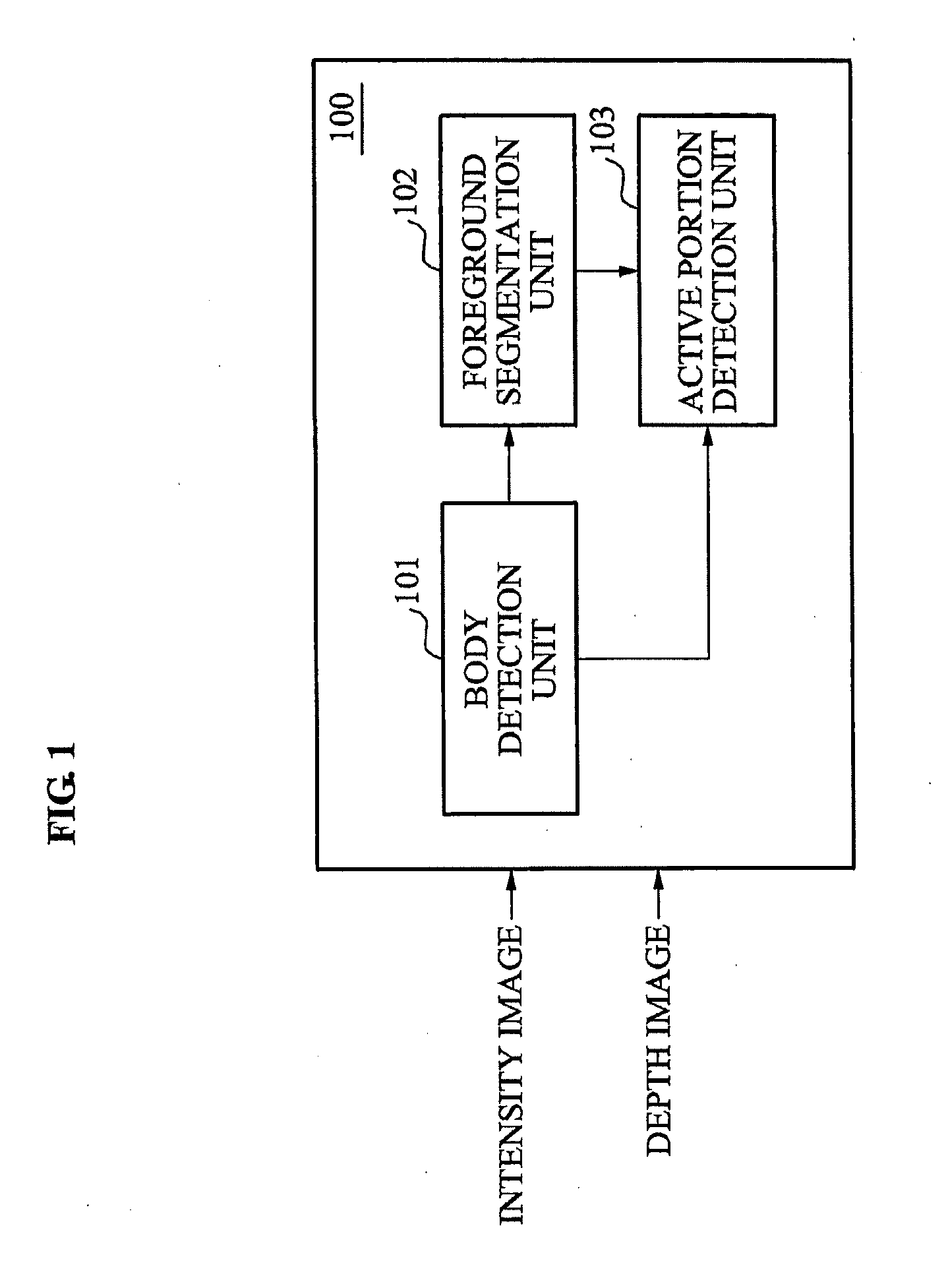
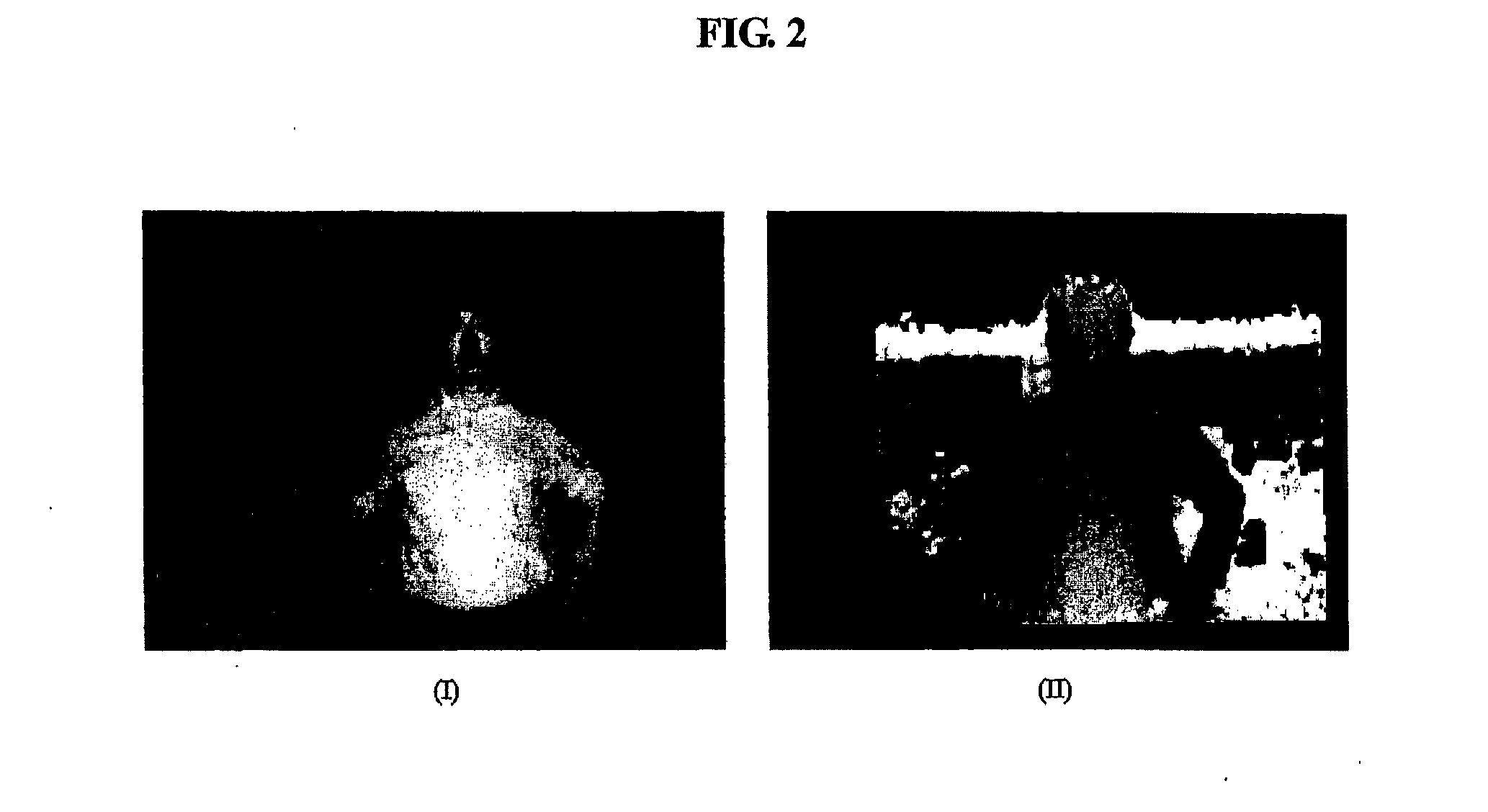
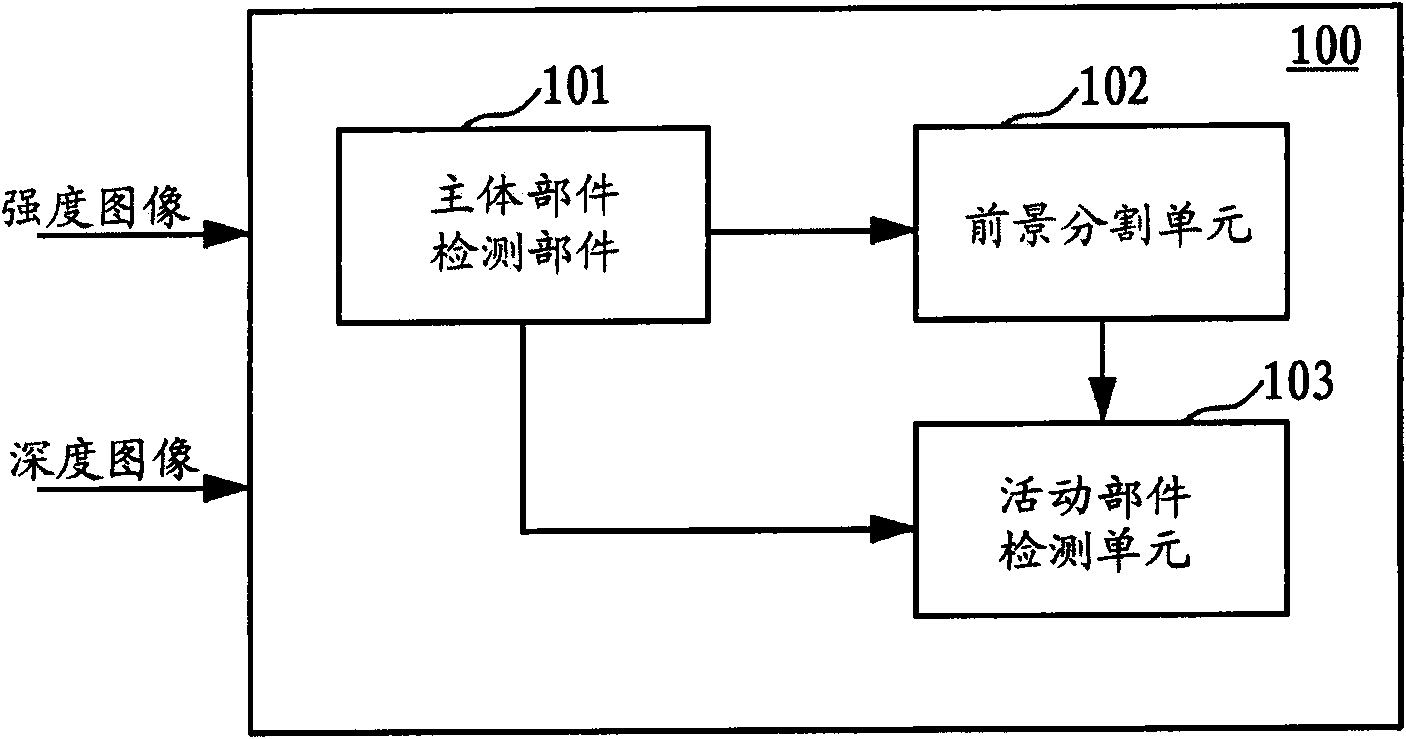
Target analysis apparatus, method and computer-readable medium
InactiveUS20110044506A1Improve target analysis performanceAccurate segmentationImage enhancementImage analysisTarget analysisComputer vision
Provided is a target analysis apparatus, method and computer-readable medium based on a depth image and an intensity image of a target is provided. The target analysis apparatus may include a body detection unit to detect a body of the target from the intensity image of the target, a foreground segmentation unit to calculate an intensity threshold value in accordance with intensity values from the detected body, to transform the intensity image into a binary image using the intensity threshold value, and to mask the depth image of the target using the binary image as a mask to thereby obtain a masked depth image, and an active portion detection unit to detect an active portion of the body of the target from the masked depth image.
Owner:SAMSUNG ELECTRONICS CO LTD
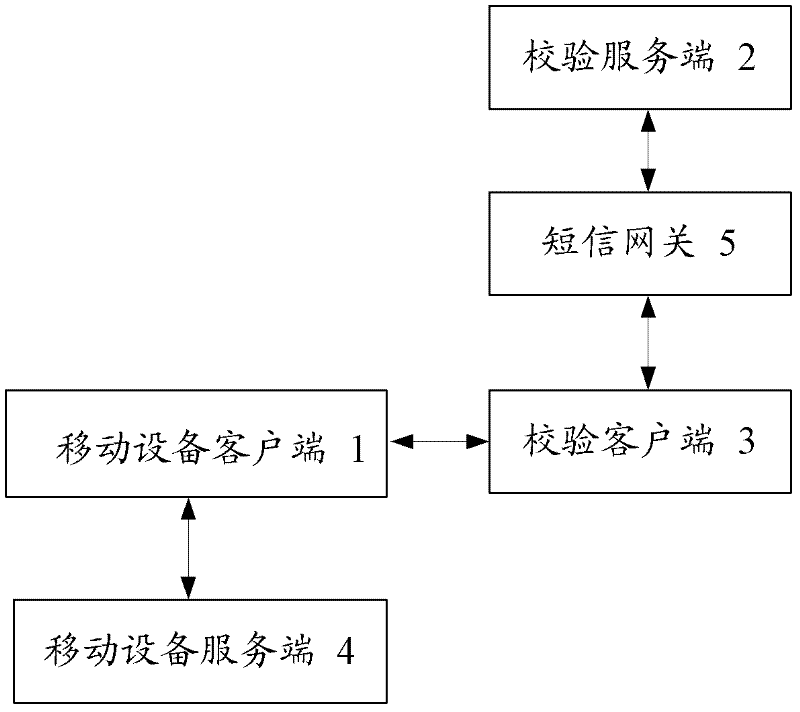
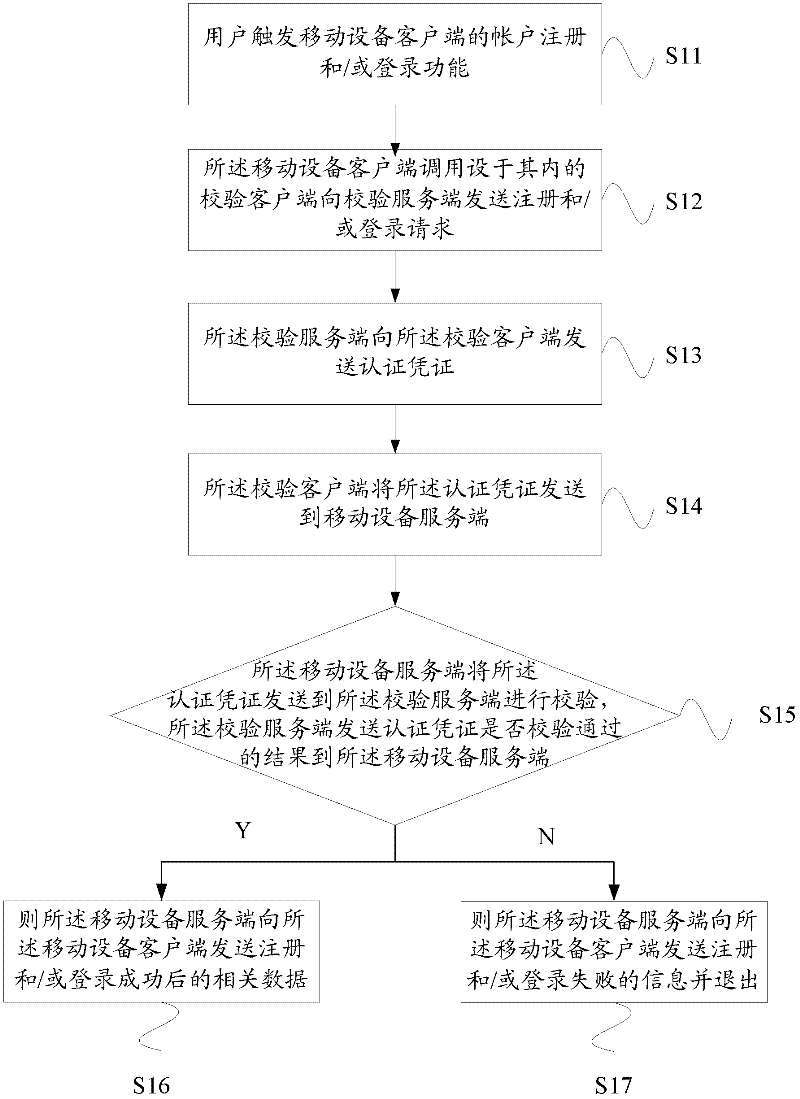
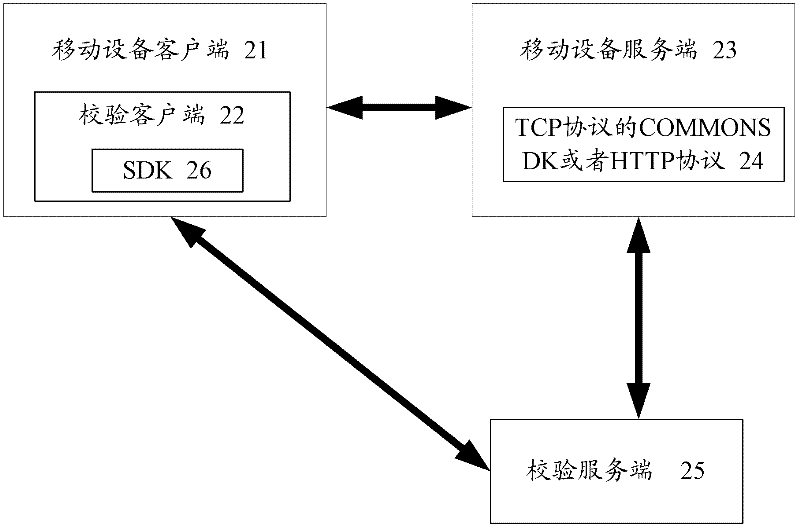
One-key registration and login verification method and system used in mobile equipment
ActiveCN102447696AImprove experienceReduce the amount of developmentTransmissionSecurity arrangementAuthentication
The invention relates to a one-key registration and login verification method and a system used in mobile equipment. The method comprises the following steps: a user triggers an account registration and / or login function of a client side of the mobile equipment; the client side of the mobile equipment calls a verification client side arranged in the client side to send a registration and / or login request to a verification server side; the verification server side sends an authentication credential to the verification client side; the verification client side sends the authentication credential to a server side of the mobile equipment; the server side of the mobile equipment sends the authentication credential to the verification server side for verification, and the verification server side sends the result whether the authentication credential passes verification to the server side of the mobile equipment; and if the authentication credential passes verification, the server side of the mobile equipment sends relevant data after successful registration and / or login to the client side of the mobile equipment. By adopting the one-key registration and login verification method and system used in the mobile equipment, quick account registration and login for the mobile equipment can be simply and safely realized.
Owner:SHENGQU INFORMATION TECH SHANGHAI
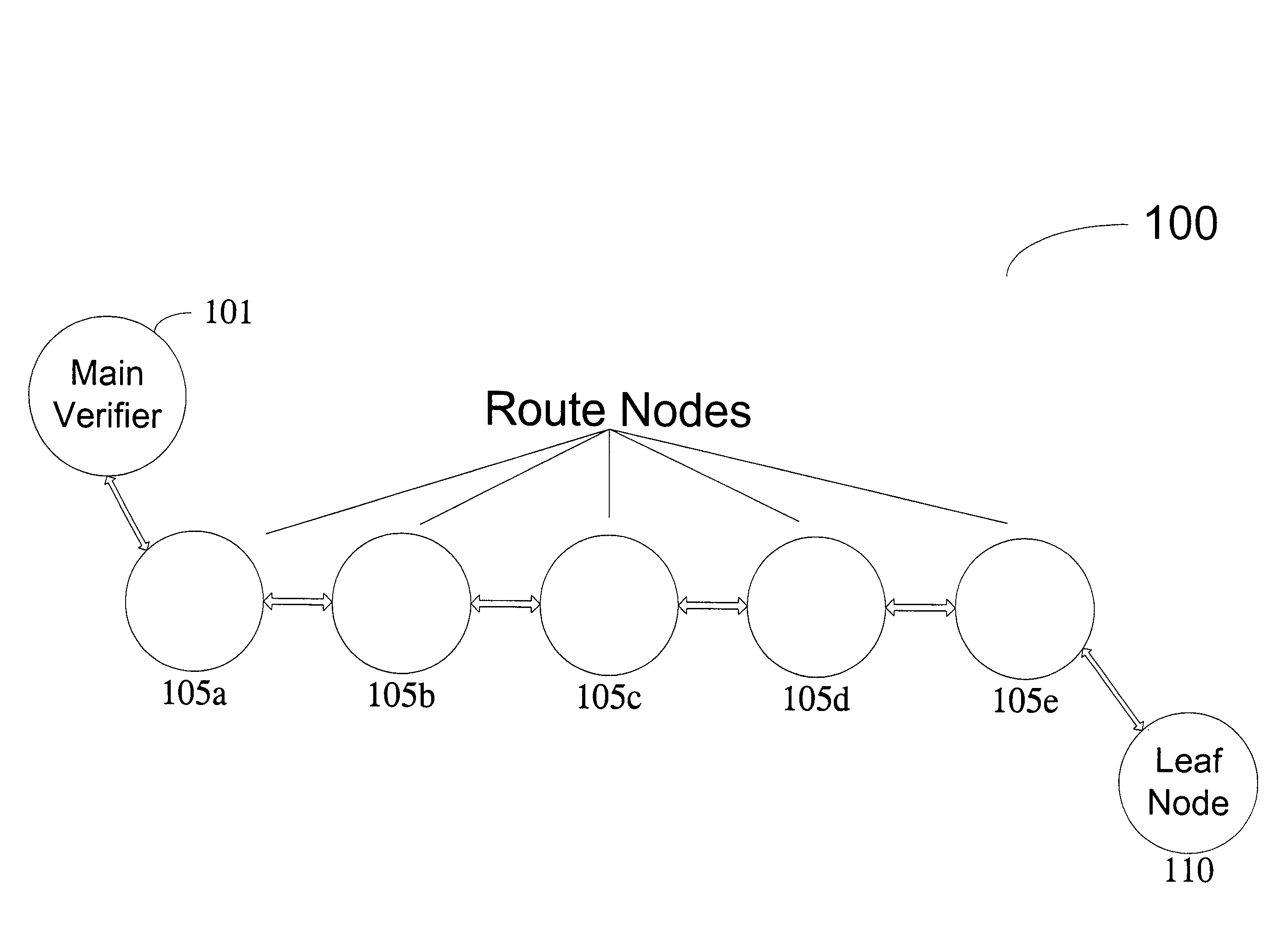
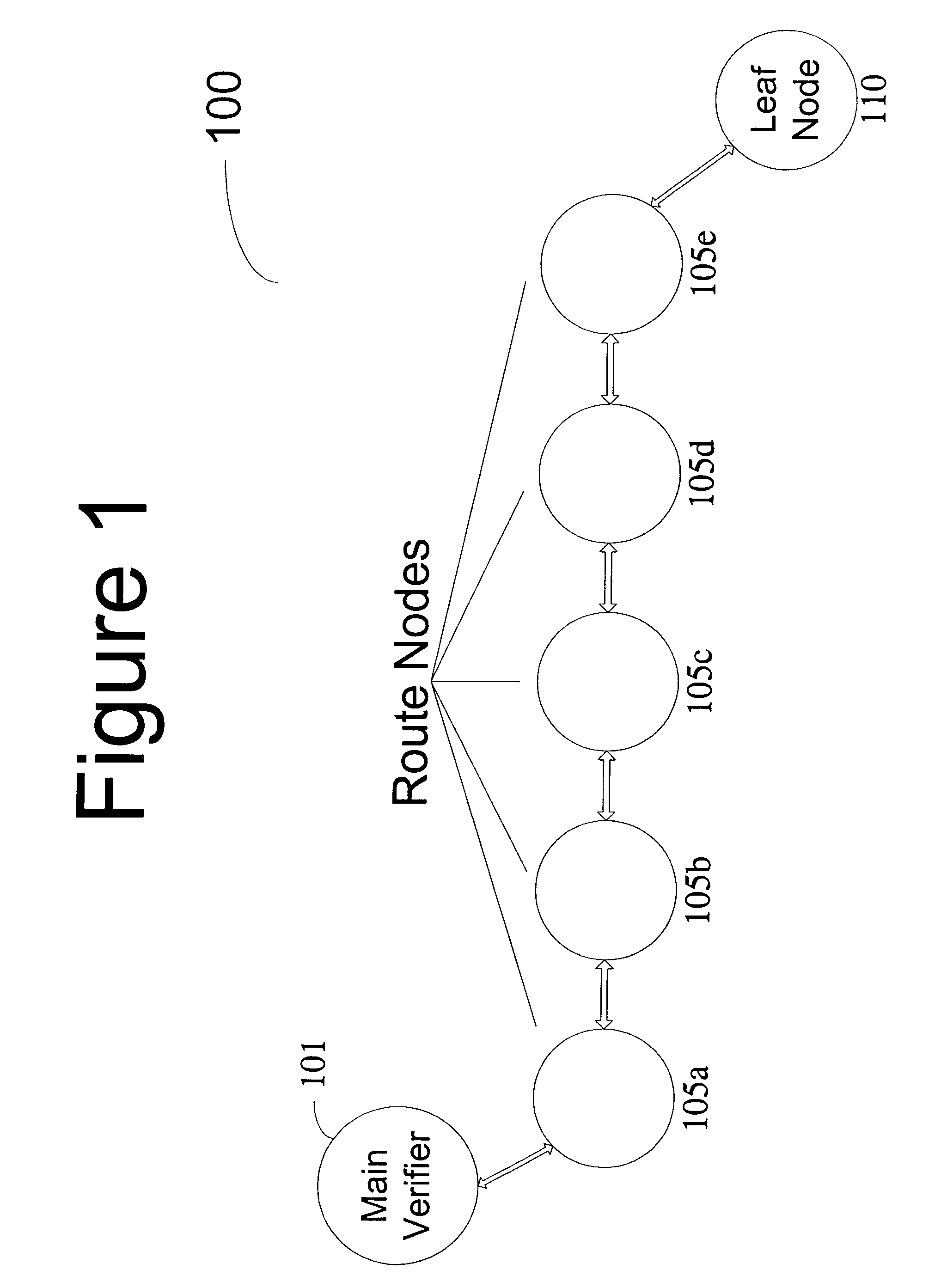
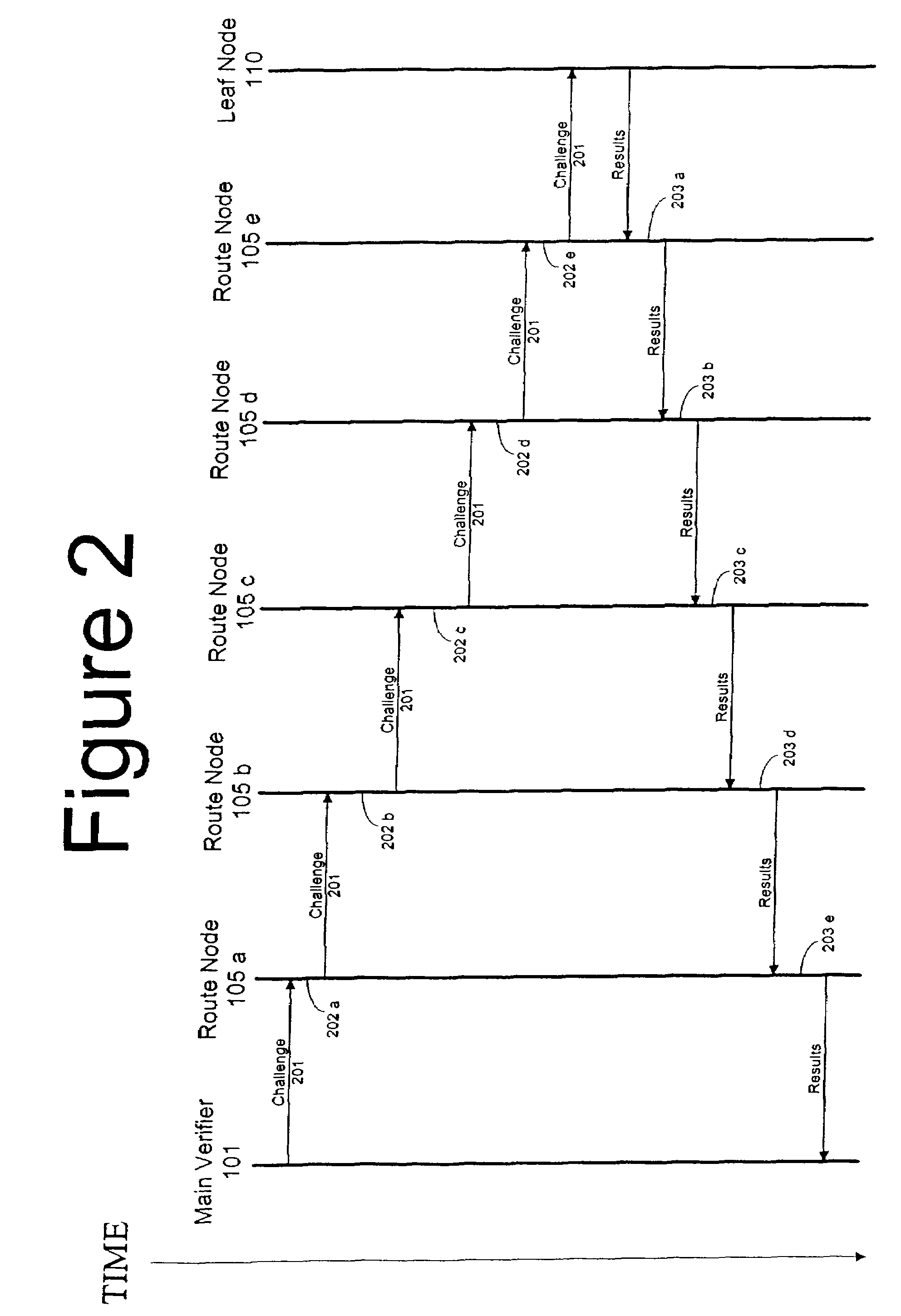
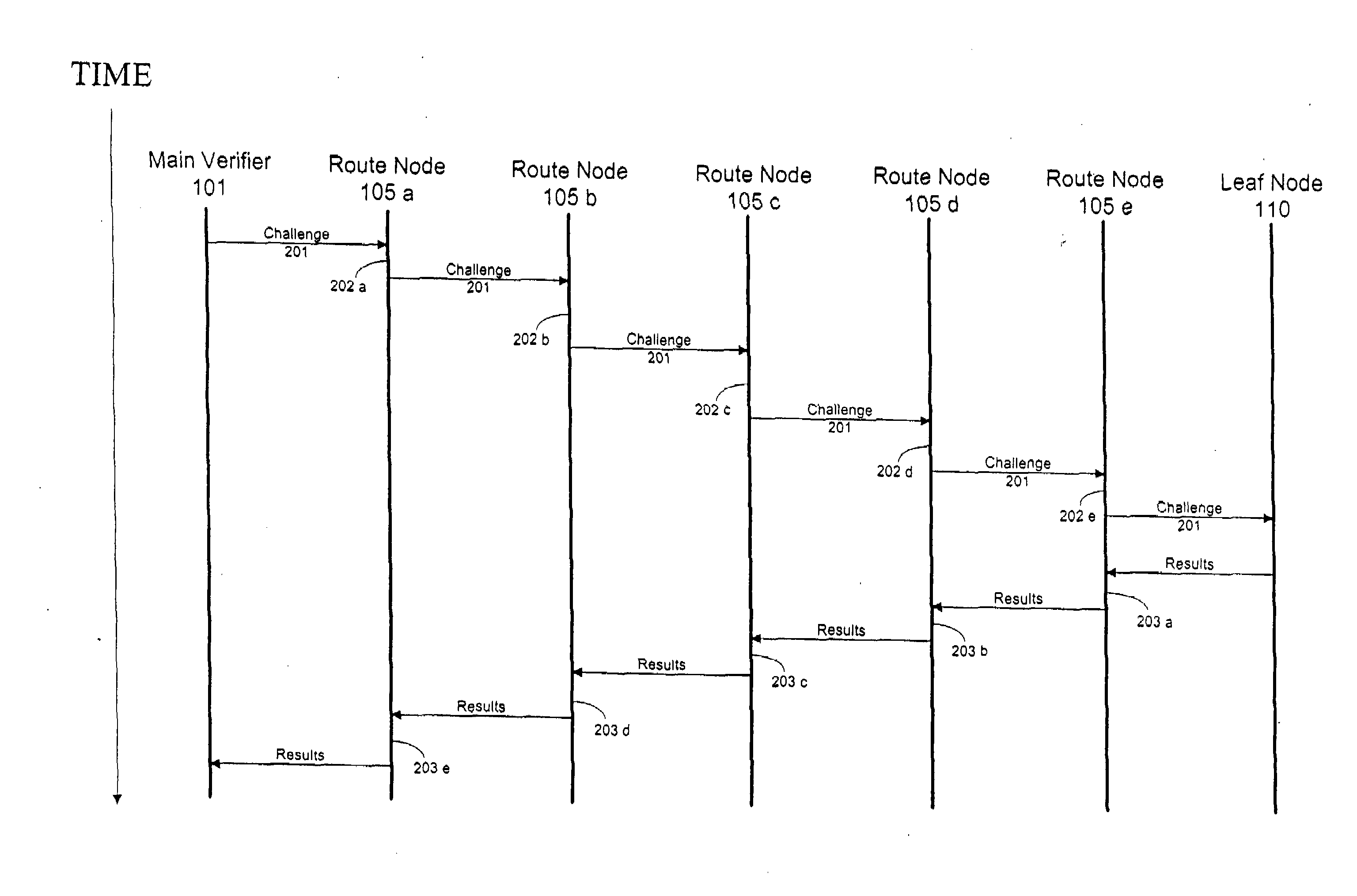
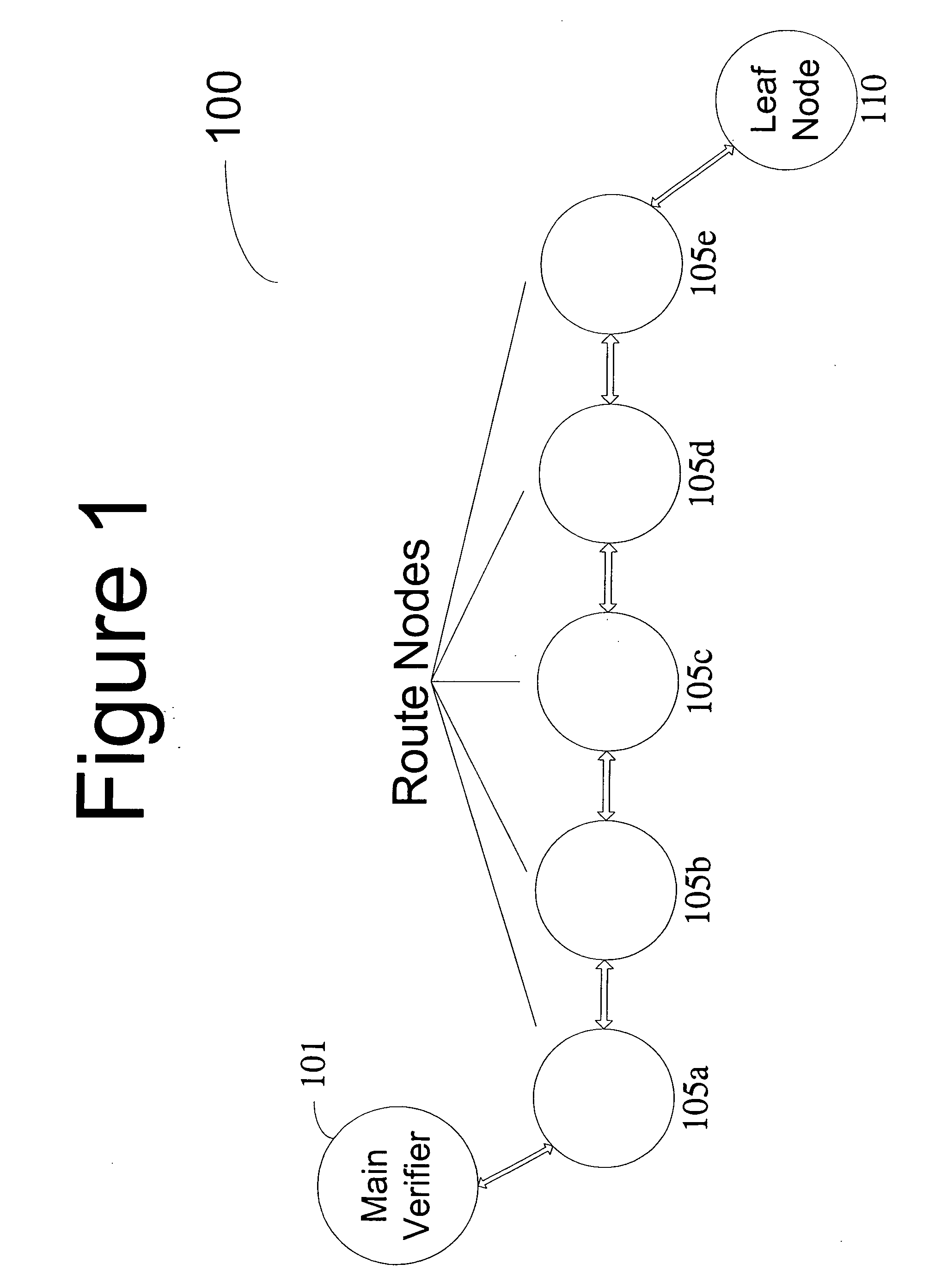
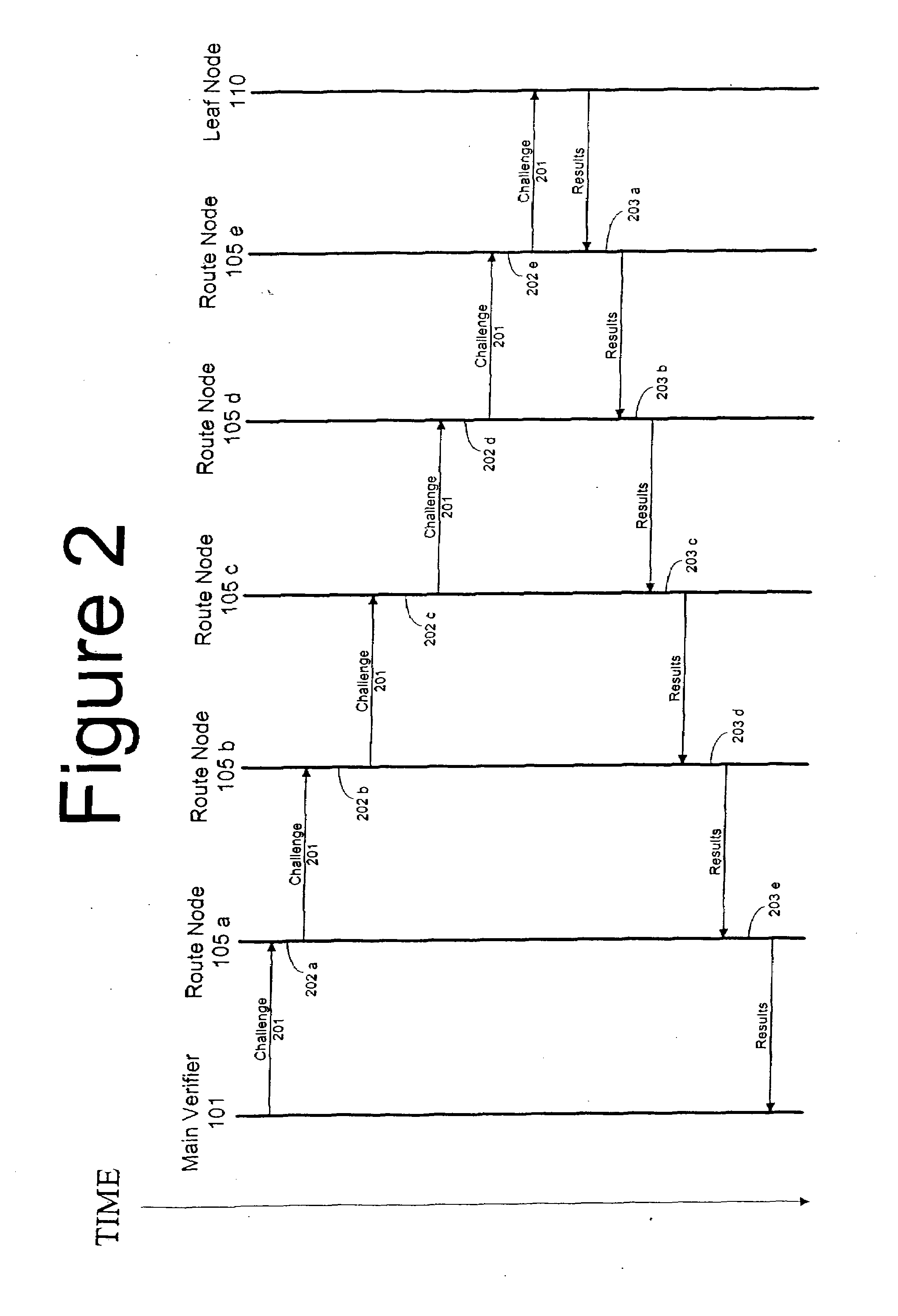
Method and computer product to increase accuracy of time-based software verification for sensor networks
InactiveUS7877596B2Accurate verificationMinimum time delayUser identity/authority verificationMultiple digital computer combinationsLine sensorMinimum time
A recursive verification protocol to reduce the time variance due to delays in the network by putting the subject node at most one hop from the verifier node provides for an efficient manner to test wireless sensor nodes. Since the software signatures are time based, recursive testing will give a much cleaner signal for positive verification of the software running on any one node in the sensor network. In this protocol, the main verifier checks its neighbor, who in turn checks its neighbor, and continuing this process until all nodes have been verified. This ensures minimum time delays for the software verification. Should a node fail the test, the software verification downstream is halted until an alternative path (one not including the failed node) is found. Utilizing techniques well known in the art, having a node tested twice, or not at all, can be avoided.
Owner:HONEYWELL INT INC
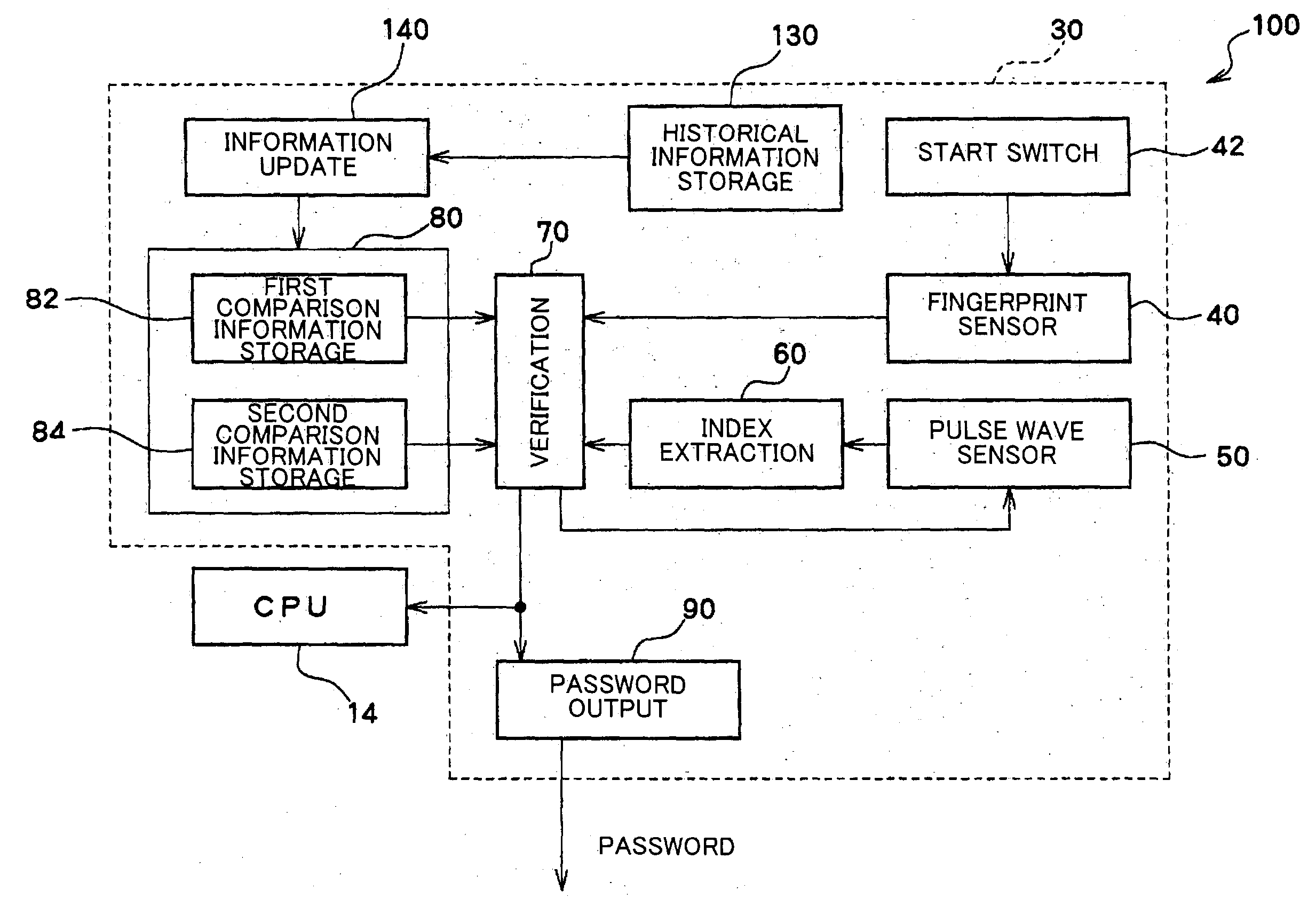
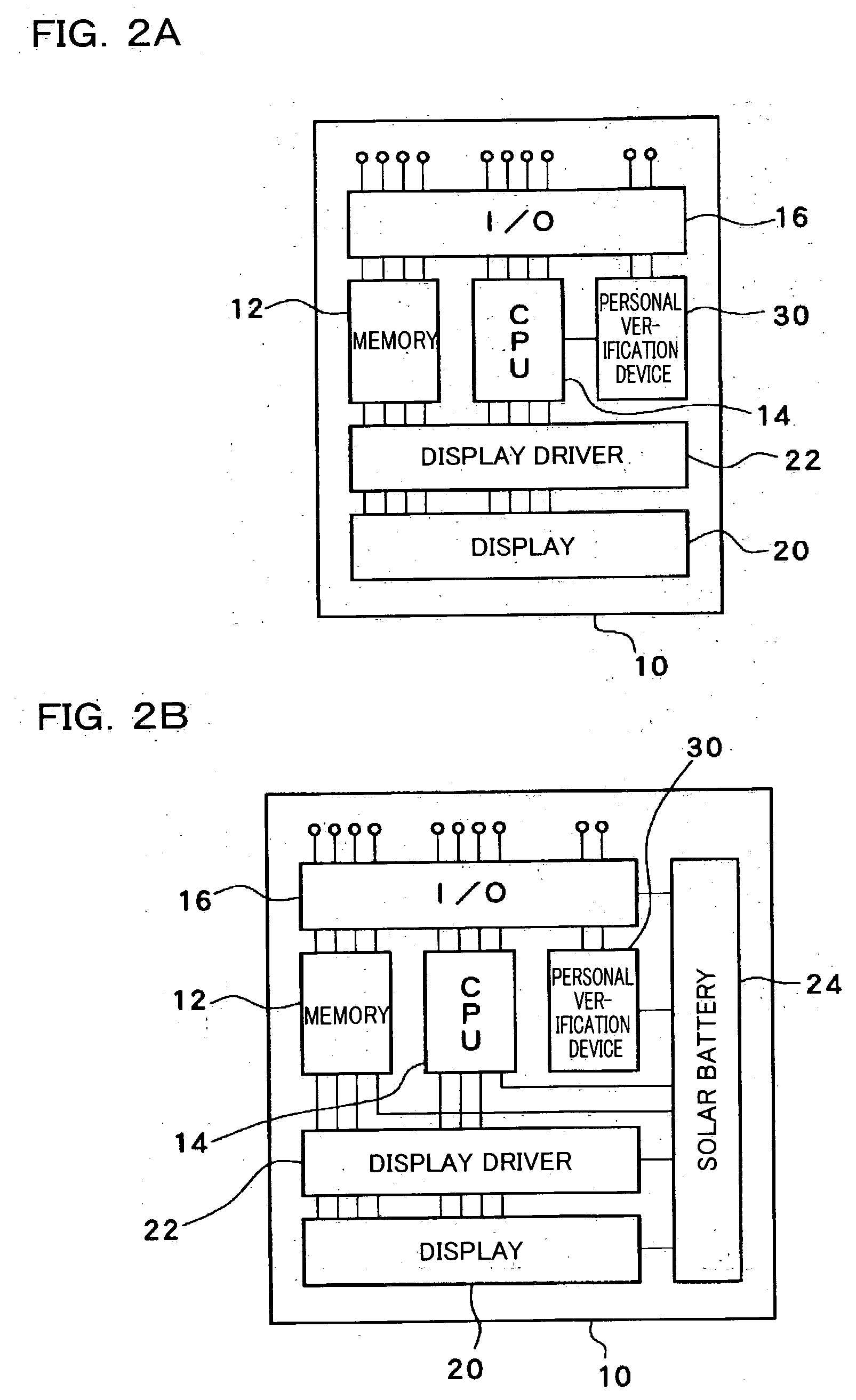
Personal verification device, card-type information storage medium, and information processing system using the same
ActiveUS20050053264A1Highly accurateDifficult to verifyPerson identificationComputer security arrangementsFingerprintInformation handling system
A personal verification device includes a fingerprint sensor which detects a fingerprint of an operator, and a pulse wave sensor which detects a pulse wave of the operator. An index extraction section processes the pulse wave detected by the pulse wave sensor and extracts at least one index. First reference information which is compared with a fingerprint is stored in a first reference information storage section. Second reference information which is compared with the at least one index is stored in a second reference information storage section. A verification section outputs a signal indicating that the operator is true when it is determined that the operator is a registered person based on the result of comparison between the fingerprint and the first reference information, and it is determined that the operator is alive based on the result of comparison between the at least one index and the second reference information.
Owner:138 EAST LCD ADVANCEMENTS LTD
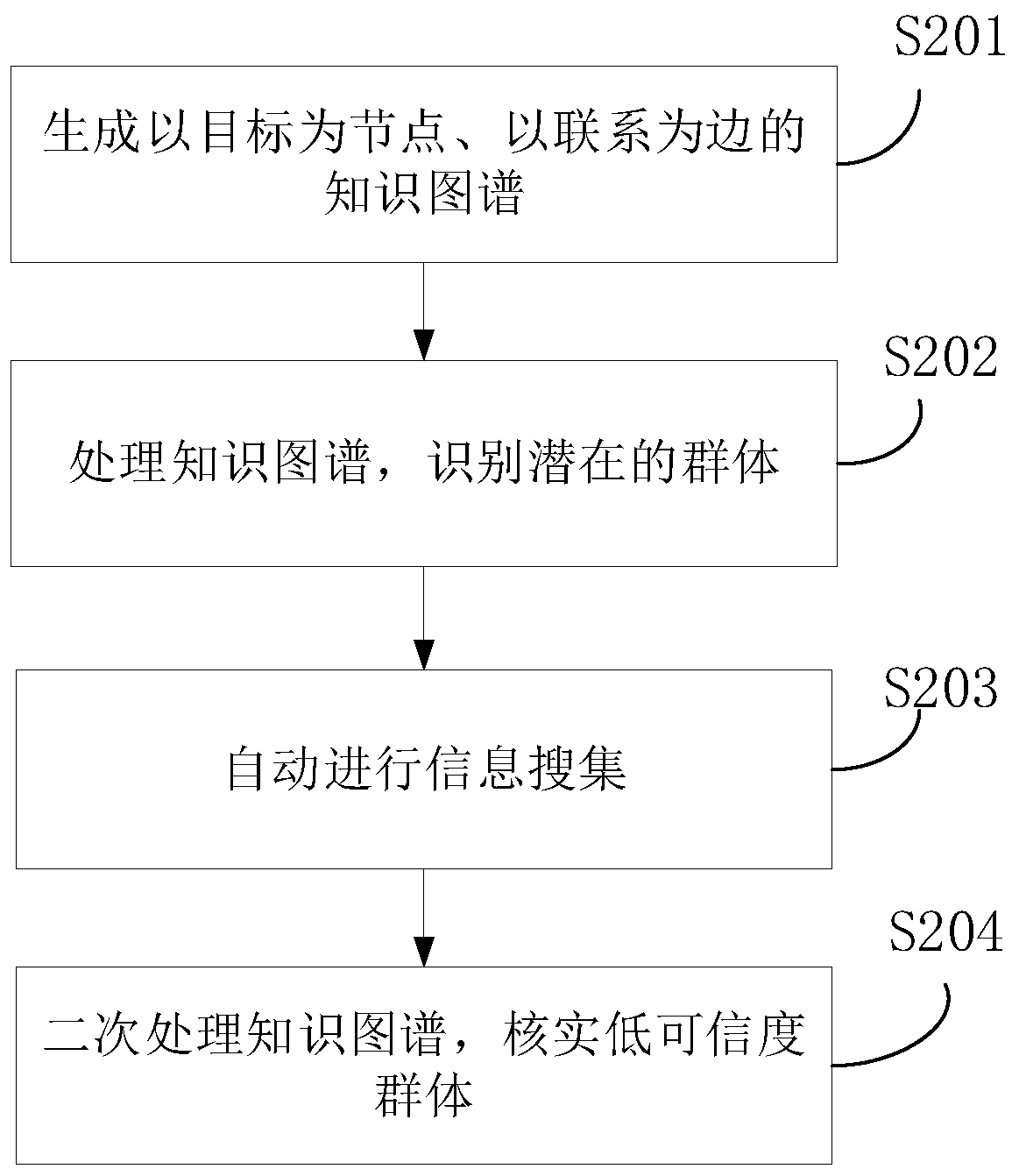
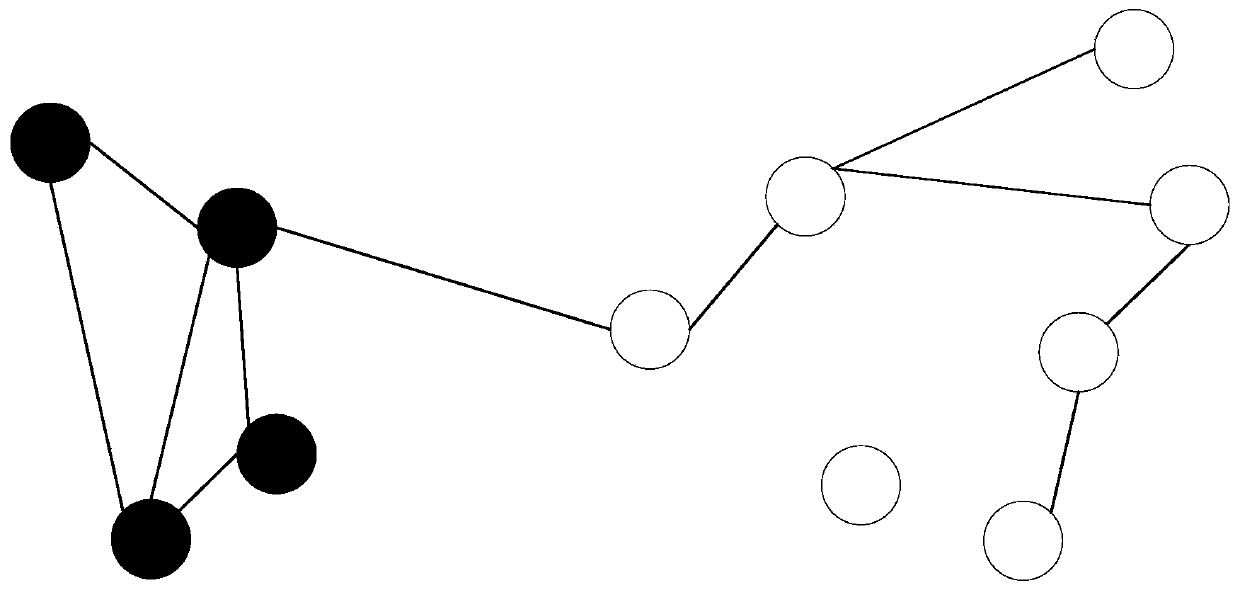
Recognition method and device based on knowledge graph, electronic device and storage medium
InactiveCN110110093AReduce false positive rateAccurate identificationMachine learningSpecial data processing applicationsTheoretical computer scienceData source
The embodiment of the invention discloses a recognition method and device based on a knowledge graph, an electronic device and a storage medium. The method comprises: obtaining a plurality of targetsand first information related to behaviors of the targets from a plurality of heterogeneous data sources through intelligent processing, establishing a knowledge graph with the targets as nodes and connection between the targets as edges, and the nodes and the edges being provided with at least one attribute; processing the knowledge graph according to the risk degree in the at least one attribute, and automatically identifying at least one potential low-credibility group; automatically sending an information collection message to the related nodes of the potential low-credibility group through at least one communication channel; and receiving second information fed back by the information collection message, intelligently processing the second information, updating the knowledge graph, and confirming and marking the verified low-credibility group.
Owner:简链科技(广东)有限公司
Method and computer product to increase accuracy of time-based software verification for sensor networks
InactiveUS20070271452A1Reduce time varianceAccurate verificationUser identity/authority verificationMultiple digital computer combinationsLine sensorMinimum time
A recursive verification protocol to reduce the time variance due to delays in the network by putting the subject node at most one hop from the verifier node provides for an efficient manner to test wireless sensor nodes. Since the software signatures are time based, recursive testing will give a much cleaner signal for positive verification of the software running on any one node in the sensor network. In this protocol, the main verifier checks its neighbor, who in turn checks its neighbor, and continuing this process until all nodes have been verified. This ensures minimum time delays for the software verification. Should a node fail the test, the software verification downstream is halted until an alternative path (one not including the failed node) is found. Utilizing techniques well known in the art, having a node tested twice, or not at all, can be avoided.
Owner:HONEYWELL INT INC
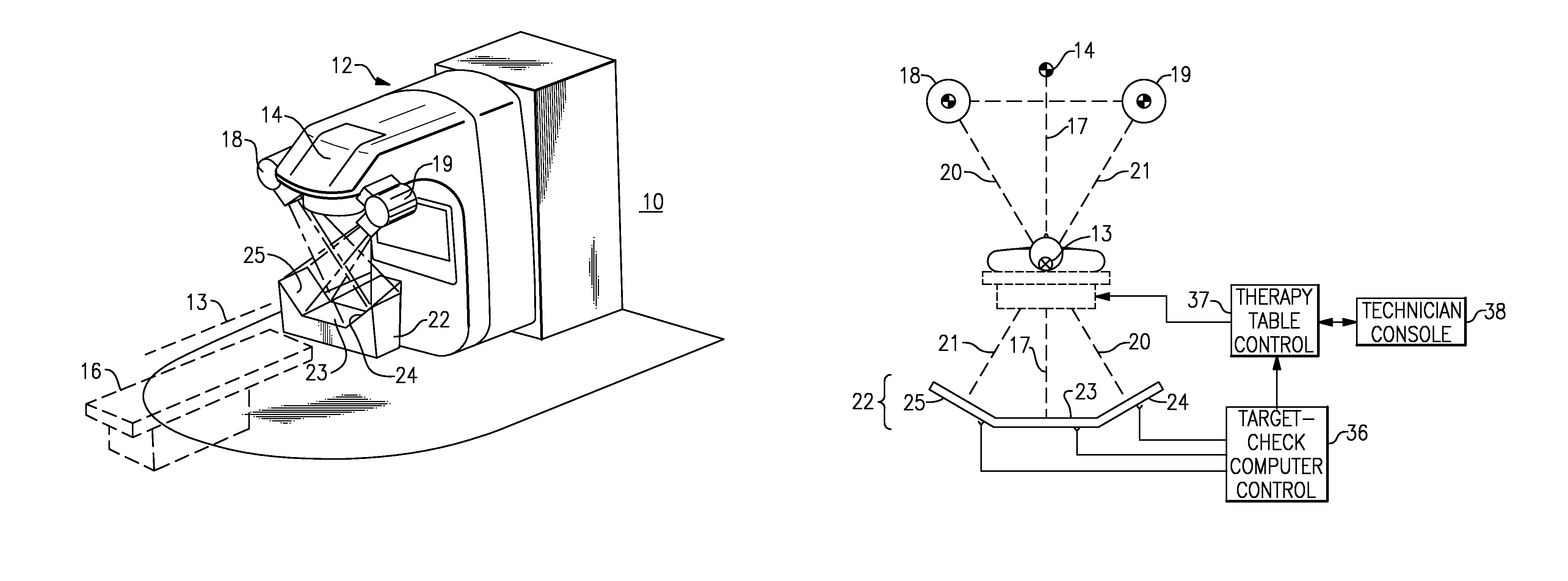
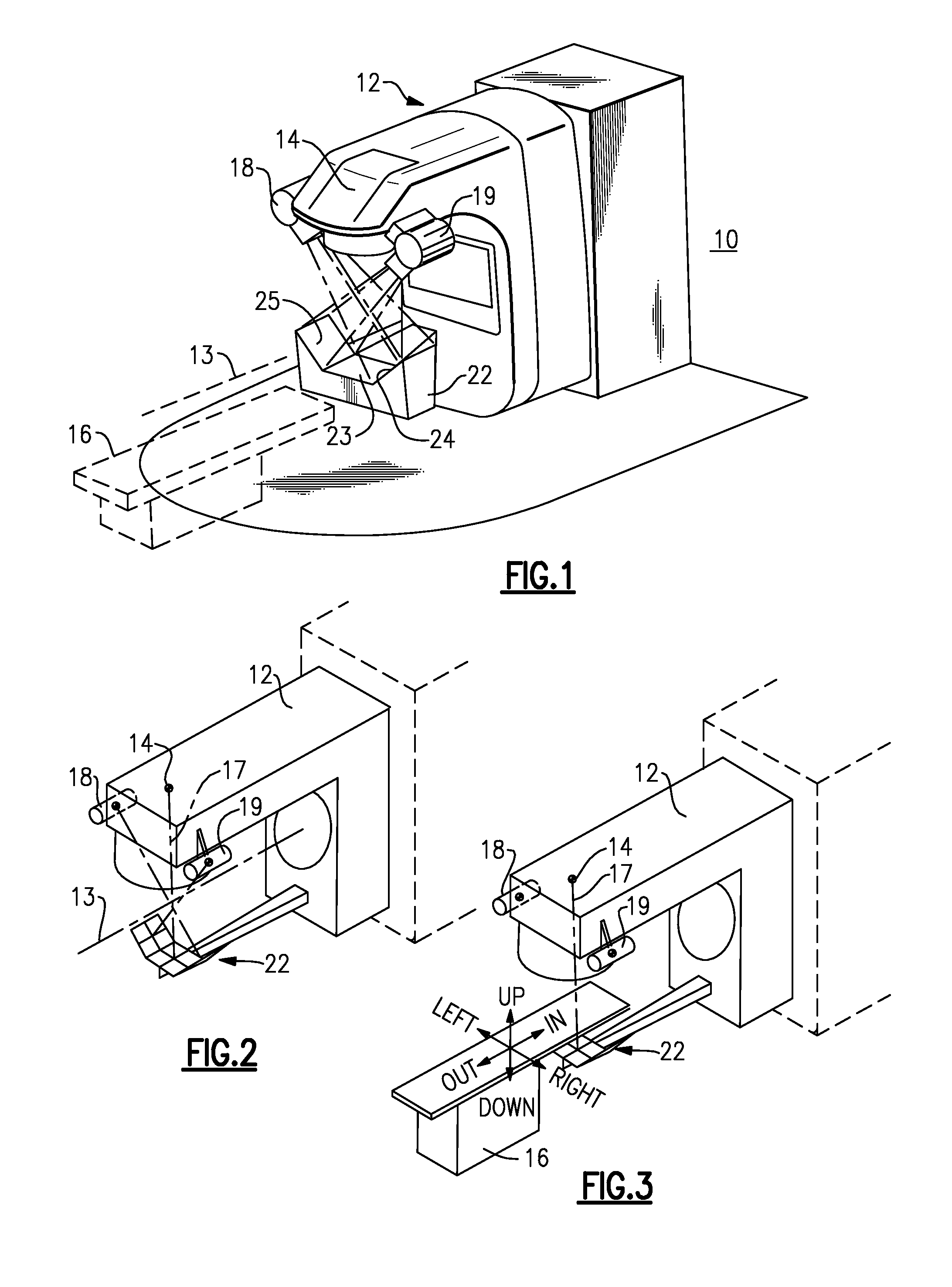
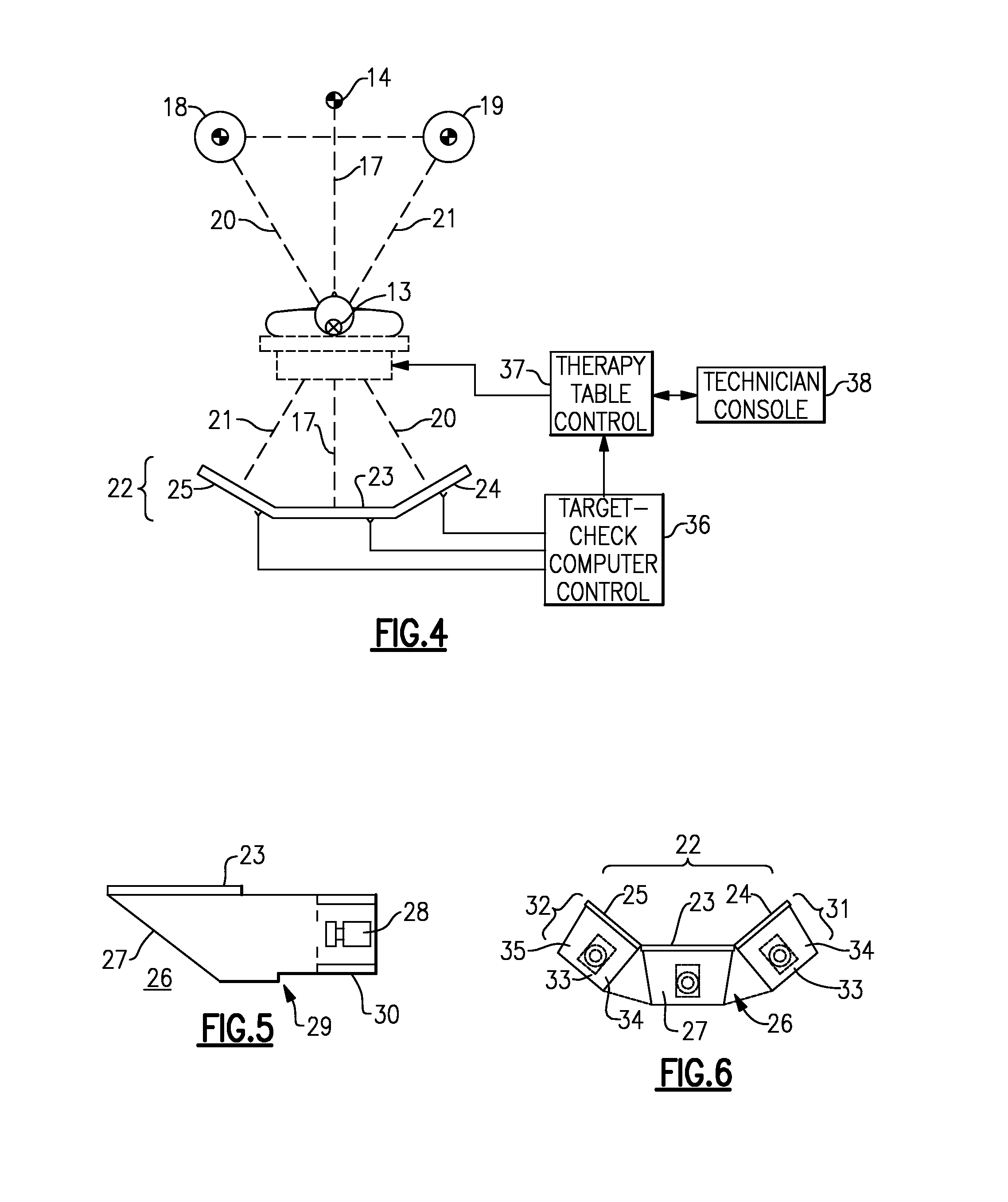
Radiation therapy machine with triple KV/MV imaging
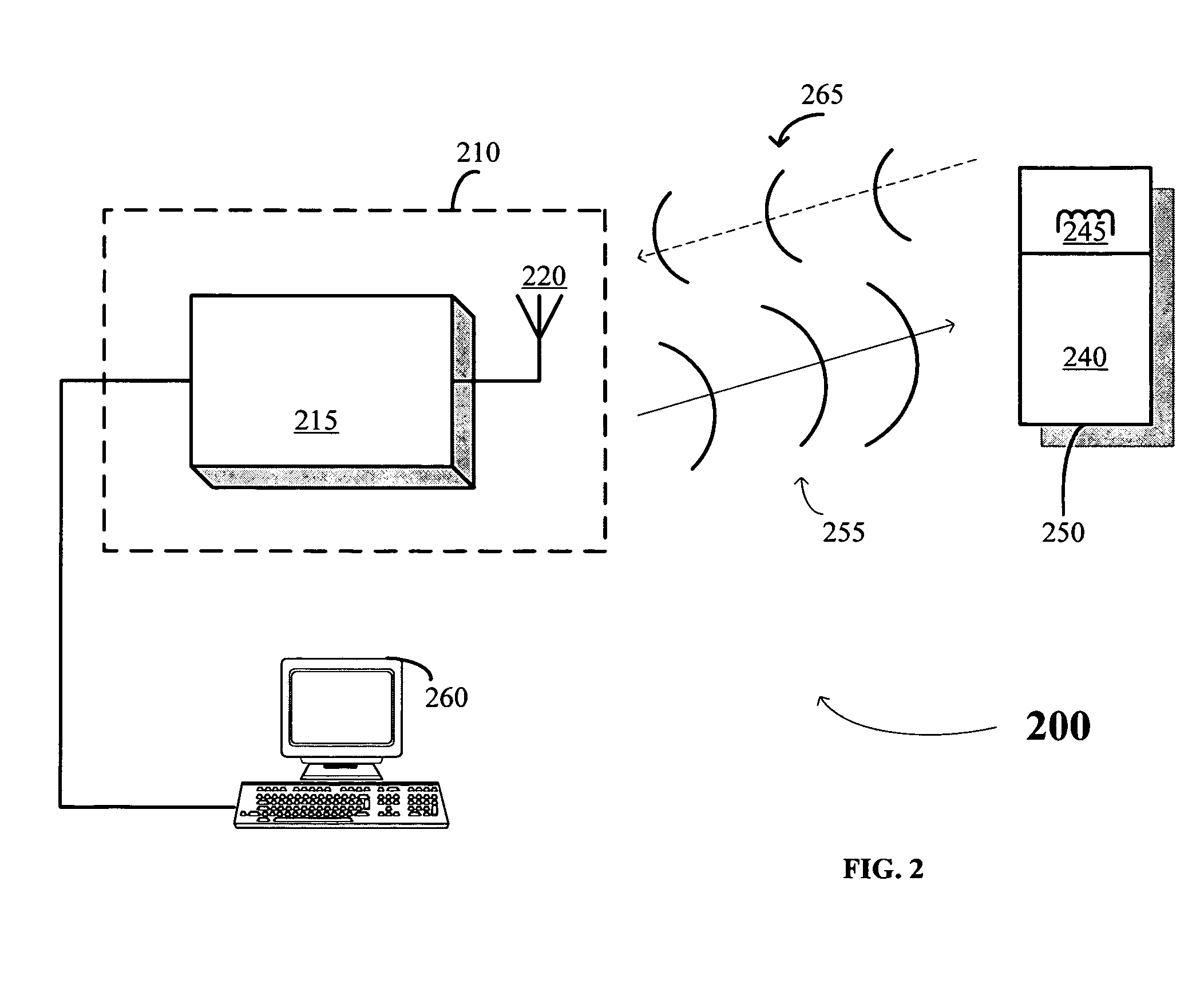
InactiveUS7502443B1Precise positioningHigh-quality imageRadiation beam directing meansX-ray/gamma-ray/particle-irradiation therapyImage detectorMedical physics
A triple imager arrangement is mounted onto a linear accelerator, providing pre- or post-treatment images of a patient, for verification and monitoring of patient position. Left and right diagnostic radiation sources mounted onto the treatment head. The triple imager arrangement is mounted on the gantry counterweight, with a portal imager and left and right diagnostic image detectors. Image-forming plates of the portal imager and the diagnostic imagers are positioned perpendicular to the therapy beam central axis, and perpendicular to the central axes of the diagnostic sources. The image forming plates are the same given distance X from the respective source. The resulting image information can be used in conjunction with an assistance module for assisting the linear accelerator therapist in accurate adjustment of the patient position.
Owner:CABLON MEDICAL +1
Method of checking the layout versus the schematic of multi-fingered MOS transistor layouts using a sub-circuit based extraction
InactiveUS7139990B2Improve trustEasy to identifyCAD circuit designSoftware simulation/interpretation/emulationComputer architectureDevice Properties
A sub-circuit based extraction method which extracts a multi-finger MOS transistor directly as a sub-circuit is described. By adding three marking layers, the method provides the layout extracted netlist with a complete list of device geometric parameters corresponding to the device properties as presented in the sub-circuit model based schematic netlist. By performing a layout-versus-schematic comparison based on all geometric parameters extracted, the layout checking is performed in a complete and accurate way where each device parameter is checked against the corresponding design schematic. This complete and accurate geometric parameter comparison enhances the confidence level of the layout physical verification.
Owner:IBM CORP
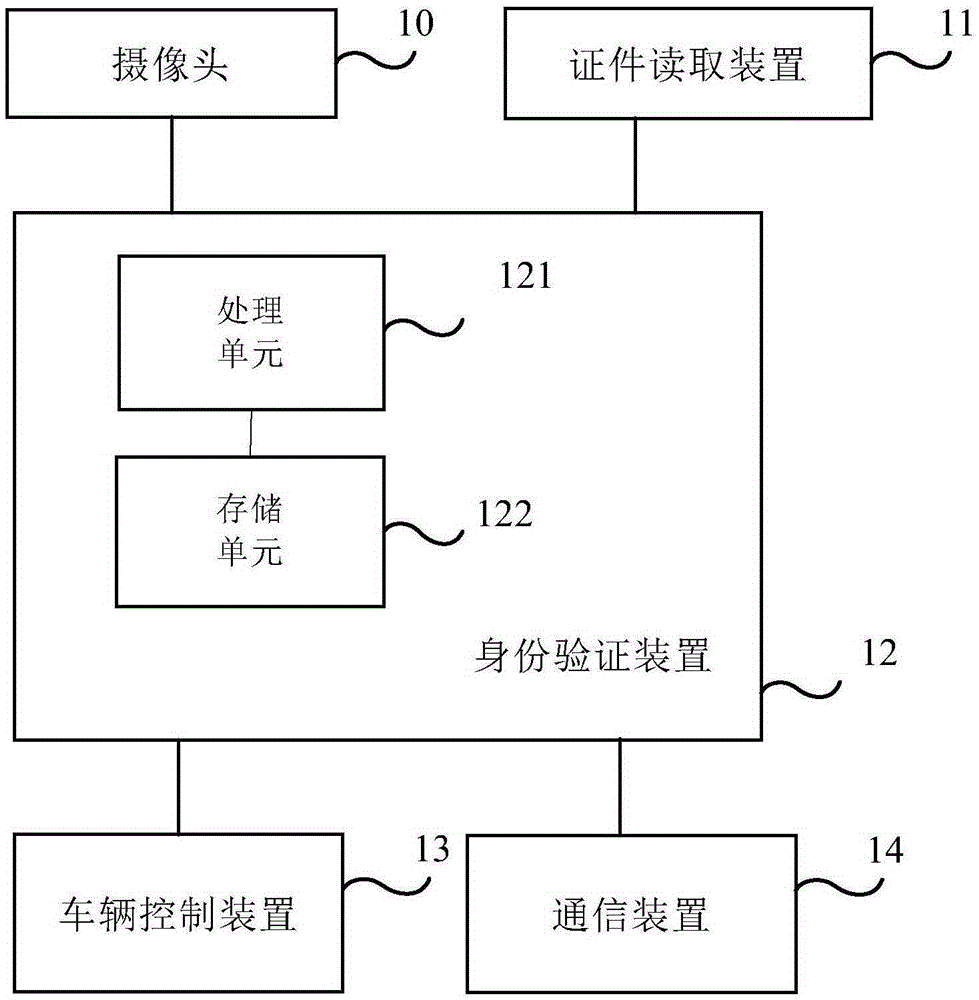
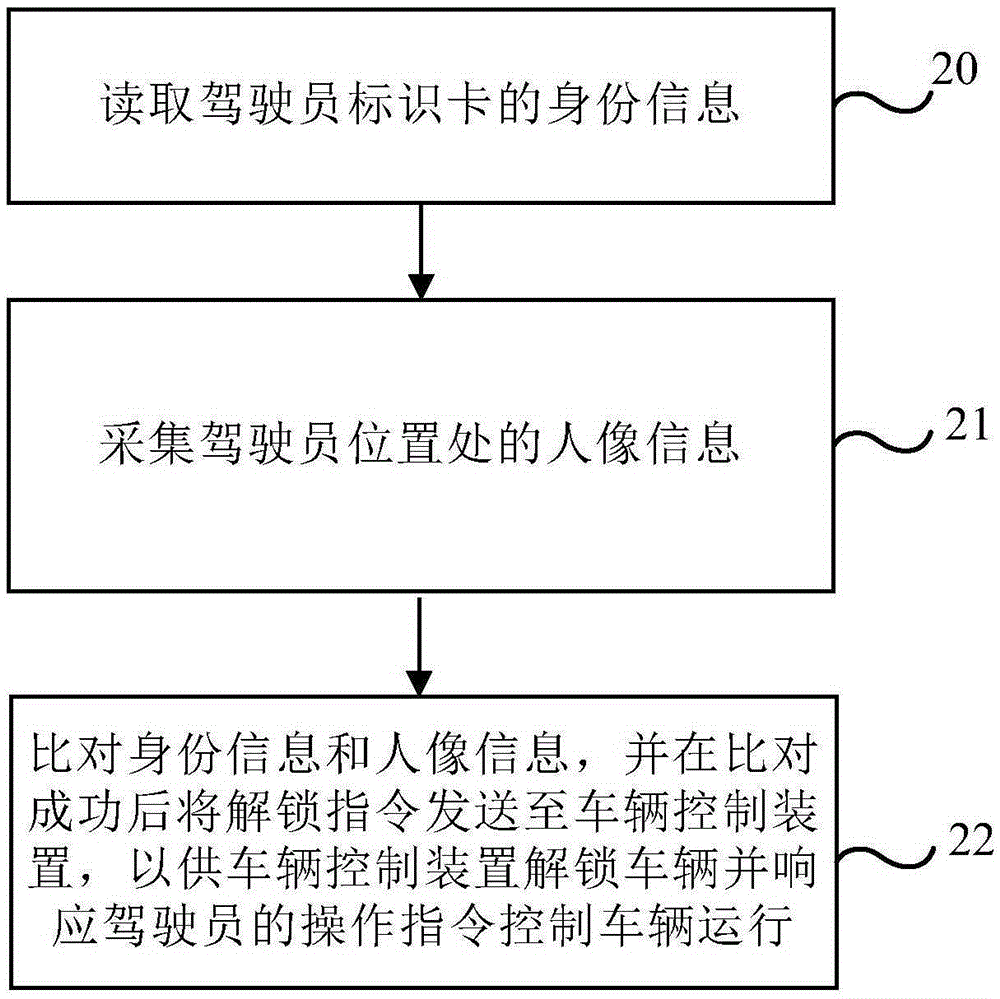
Driver identity verification system and method
InactiveCN105320863AAccurate verificationEnsure safetyDigital data authenticationElectricityVerification system
Embodiments of the present invention disclose a driver identity verification system and method, and can overcome the defect that an existing vehicle management technology cannot accurately and timely verify the identity of a driver and determine whether the driver is the vehicle owner or a legally authorizer. The system comprises: a document reading apparatus which is electrically connected to an identity verification apparatus and is used for reading identity information of a driver by a driver identification card inserted into the document reading apparatus and transmitting the identity information to the identity verification apparatus; a camera which is arranged in a cockpit of a vehicle, is electrically connected to the identity verification apparatus and is used for acquiring personal image information at the position of the driver according to an instruction of the identity verification apparatus and transmitting the personal image information to the identity verification apparatus; and the identity verification apparatus which is electrically connected to a vehicle control apparatus and is used for comparing the identity information with the personal image information and sending an unlocking instruction to the vehicle control apparatus when the comparison is successful, so that the vehicle control apparatus unlocks the vehicle and responds to an operation instruction of the driver to control the vehicle operation.
Owner:宝鸡市公安局交通警察支队
Automated Pass-Through Surgical Instrument Tray Reader
ActiveUS20100108761A1Reduce processing costsEfficient collectionElectric signal transmission systemsSurgical furnitureData terminalEngineering
An apparatus and method for interrogating and automatically identifying a radio-frequency tagged surgical instrument tray and its contents of RFID-tagged surgical instruments are disclosed. The surgical instrument tray and its contents come into contact with an RF signal transmitted by the RFID reader, and as a result, the RFID tags affixed on the instrument tray and the surgical instruments respond by transmitting back to the RFID reader data pertaining to the history of the surgical instruments. A data terminal, which is connected to the RFID reader, may contain data pertaining to the radio frequency tagged surgical instruments during packaging, and during the return of the surgical instrument trays to the packager, identifies the surgical instruments.
Owner:WARSAW ORTHOPEDIC INC
Article in-out tracking system and method based on RFID
ActiveCN101021894AImprove reading success rateAutomatic verificationSensing record carriersLogisticsWork patternAuthentication
This invention provides an in / out tracking system and a method based on RFID goods including RFID labels, a reader, a working state control unit, reader antennas and a back end data process unit, in which, the working state control unit is connected with the reader to control the working state of the reader, the RFID label is composed of multiple RFID labels and antennas of which are set in angle solving the problem that labels adhered on metals can't be read and improve the limit of reading angles between antennas of labels and readers. This invention also applies a double verification method to carry out double verification to multiple identity verification cards, and the control unit will convert the system from the standby mode to activation working mode only when the verification is successful.
Owner:THE HONG KONG POLYTECHNIC UNIV
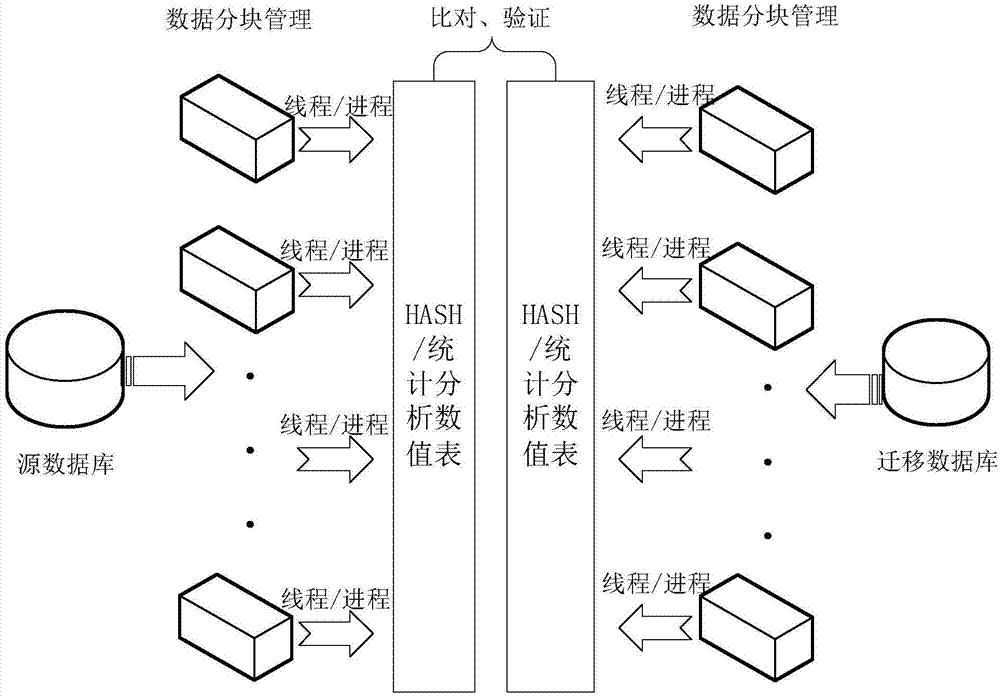
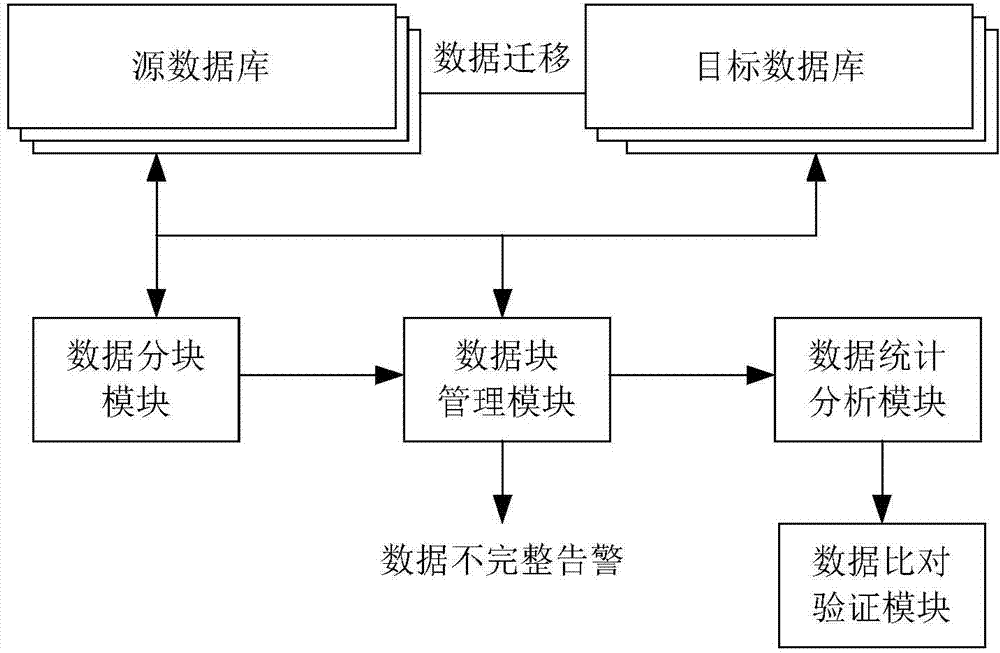
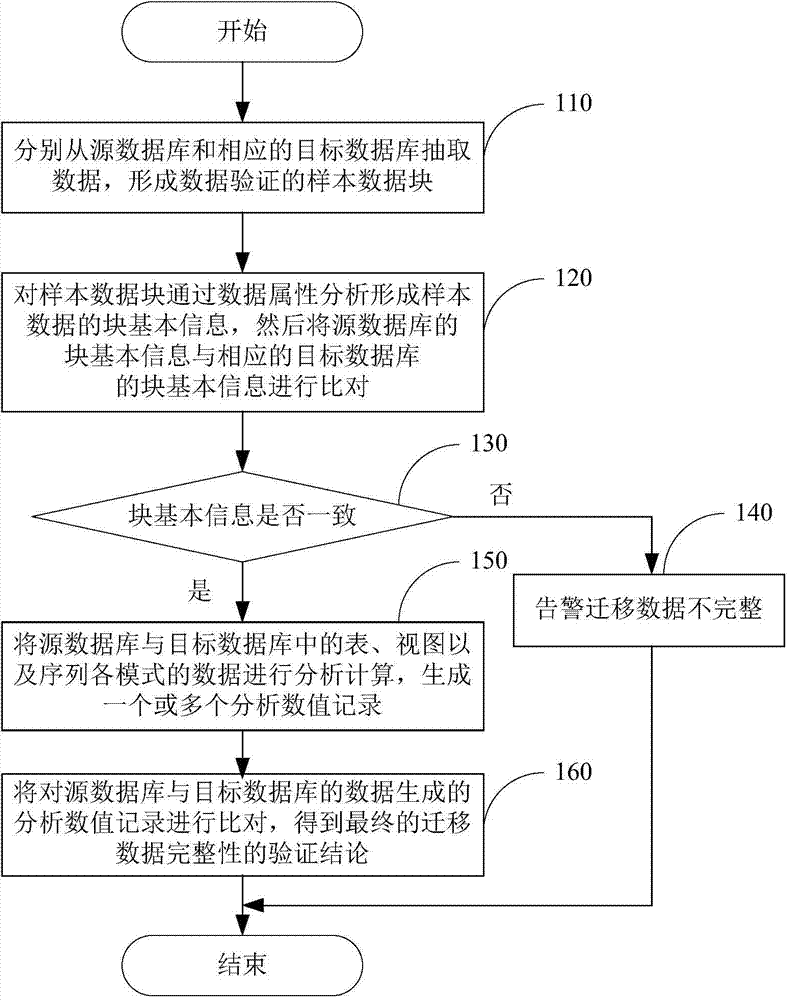
Database migration data verification method and system
ActiveCN104504122AReduce loadEfficient verificationSpecial data processing applicationsData integritySource Data Verification
The invention discloses a database migration data verification method and system. The system comprises various source databases and target databases. The method comprises that a data segmentation module extracts data from the source databases and the corresponding target databases to form sample data blocks of data verification. A data block management module performs data attributive analysis on the sample data blocks to form sample data block basic information and compares the block basic information of the source databases with corresponding target database basic information to obtain the conclusion of the integrity of migration data. By means of the method and the system, the block basic information obtained through sample extraction by the source databases and the target databases is compared to verify the database migration data, and accordingly, the loads of former comparison of a large number of data are reduced greatly.
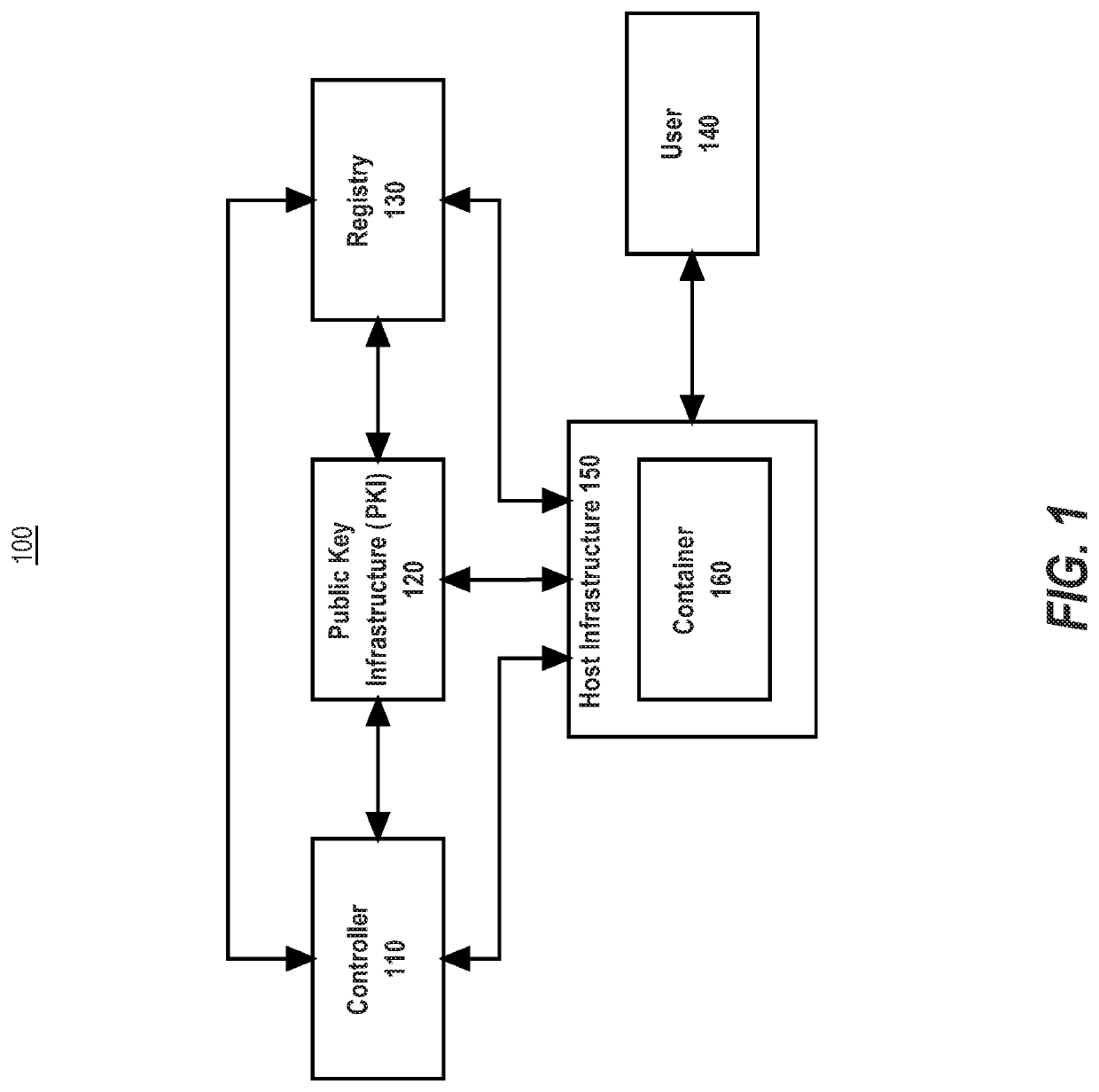
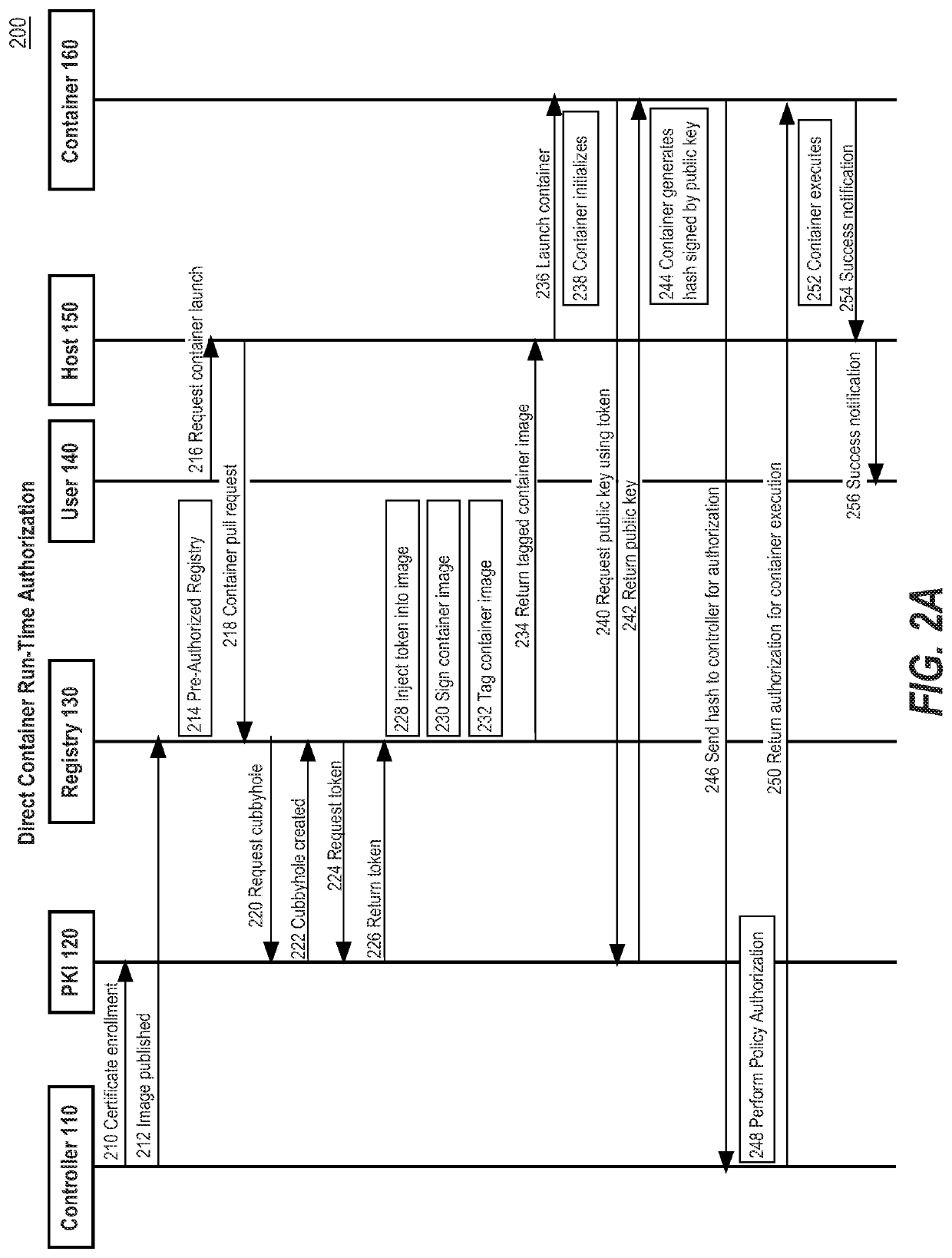
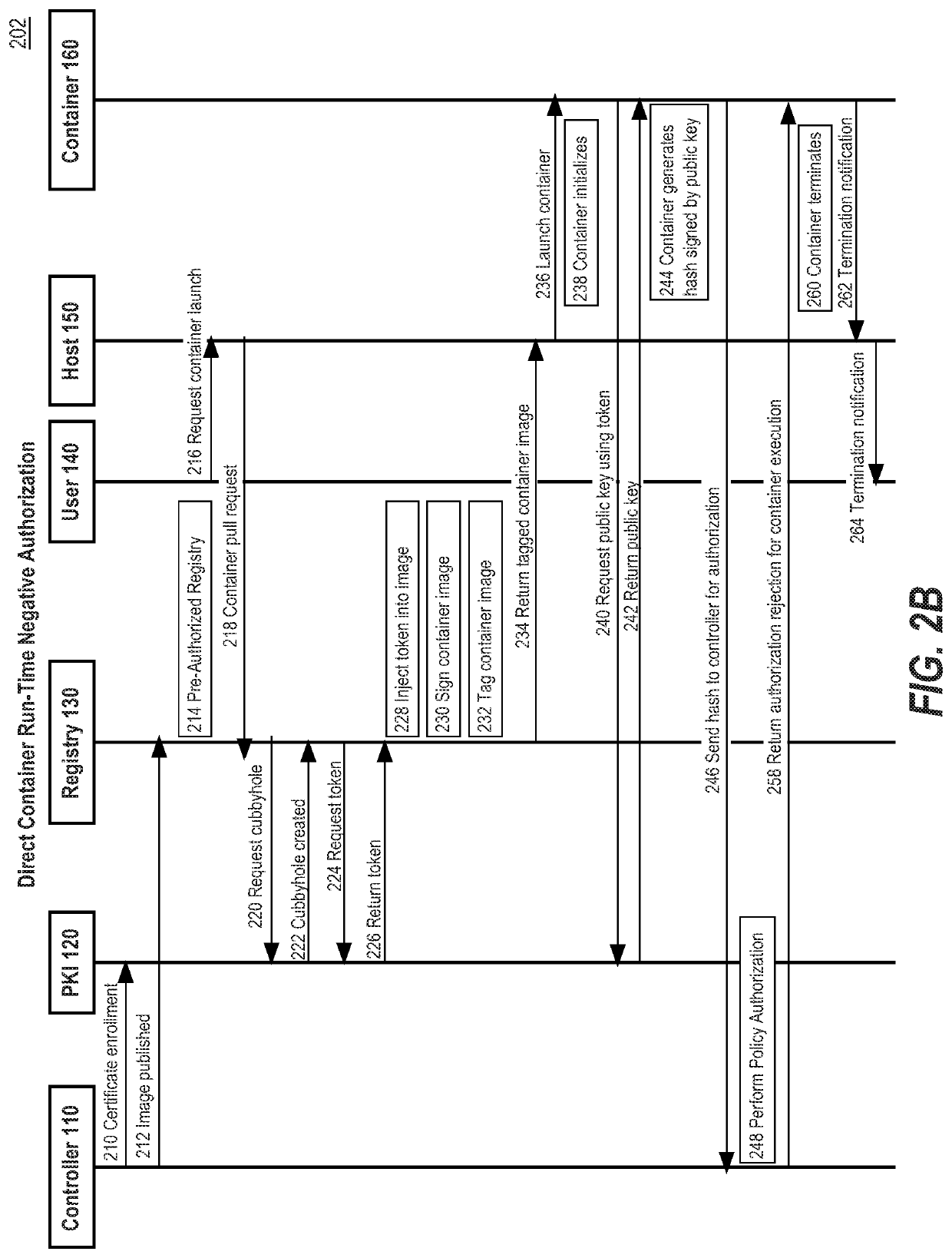
Container authorization policies for network trust
ActiveUS20200021615A1Accurate trackingAccurate verificationKey distribution for secure communicationUser identity/authority verificationBusiness enterpriseEngineering
The container deployment system of the present disclosure provides systems and processes to perform authorization of each unique container instance by the enterprise organization that published the container image and requested the container instance. A controller may be programmed or configured to apply one or more authorization policies to determine if a container instance should be executed or not. The authorization policies may include rules that restrict the number of containers running, cost consideration for executing a container, violations of time constraints for the execution of a container image, and violations of location constraints for execution of a container image, among other variations.
Owner:CISCO TECH INC
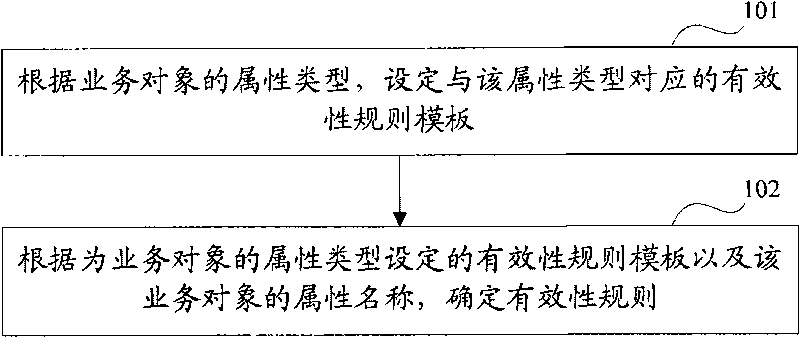
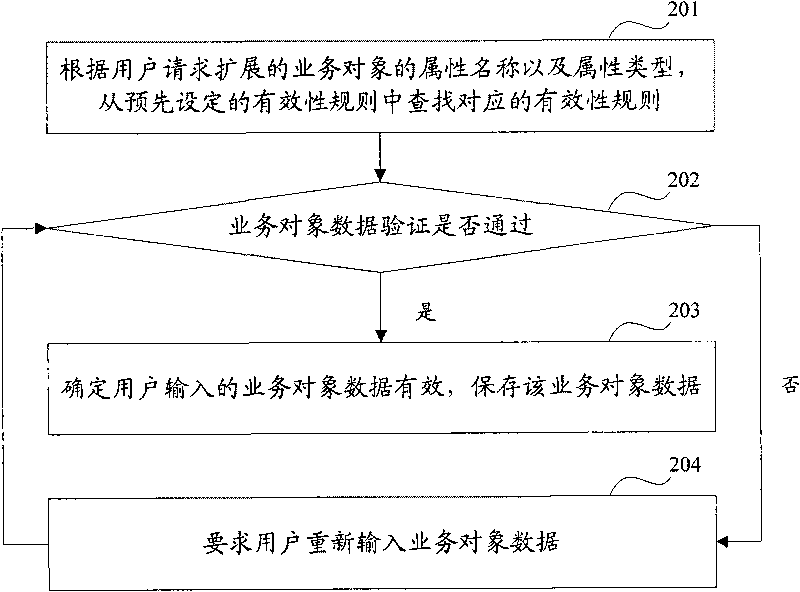
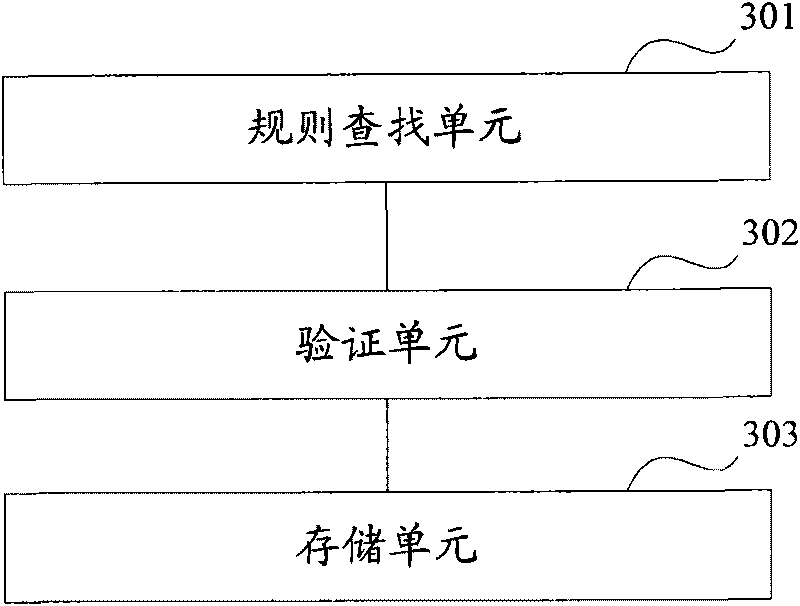
Method and device for verifying service data object
InactiveCN101727466AImprove accuracyImprove usabilitySpecial data processing applicationsUser inputValidation methods
The invention discloses a method and a device for verifying a service data object for solving the problem of low accuracy of effectiveness verification for the service data object in the conventional technology. The invention adopts a main technical scheme that: the method for verifying the service data object comprises the following steps: searching an effectiveness rule corresponding to an attribute name and an attribute type in a preset effectiveness rule according to the attribute name and attribute type of a service object extended by a user request; verifying the service data object input by a user according to the found effectiveness rule; and when the service data object passes the verification, saving the service data object. Through the technical scheme, the effectiveness and the availability of the service data object input by the user are improved, and the efficiency of effectiveness verification of the service data object is improved.
Owner:PEKING UNIV FOUNDER GRP CO LTD +1
Target analysis method and device based on intensity image and range image
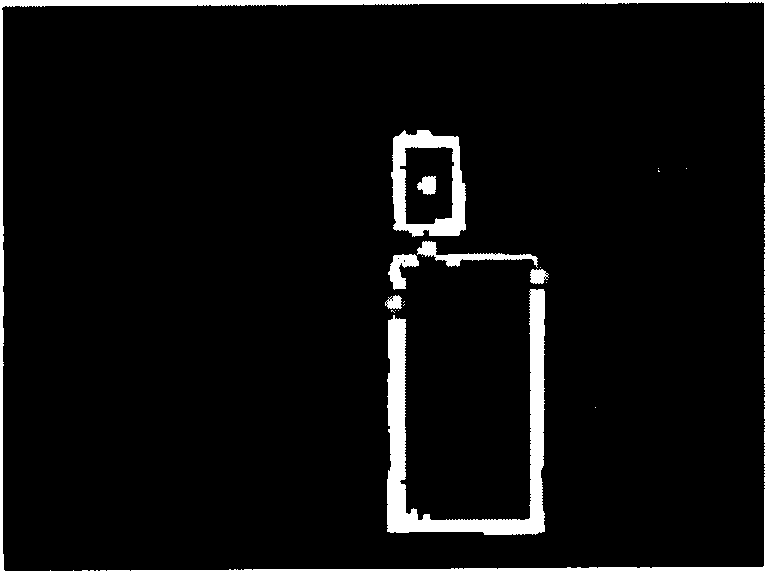
InactiveCN101996401AAccurate verificationNarrow down the search spaceImage enhancementImage analysisTarget analysisComputer vision
The invention provides a target analysis method and device based on intensity image and range image. The device comprises a main part detecting unit, a foreground segmentation unit and a moving part detecting unit, wherein the main part detecting unit detects the main part of a target from the intensity image of the target; the foreground segmentation unit calculates the intensity threshold on the basis of the intensity value of the detected main part, uses the intensity threshold to convert the intensity image to a binary image and uses the binary image to mask the range image to obtain a mask range image; and the moving part detecting unit detects the moving part of the target from the mask range image.
Owner:SAMSUNG ELECTRONICS CO LTD +1
Cyber gene identification technology based on entity features in cyber space
ActiveUS8832808B2Accurate verificationDigital data processing detailsUnauthorized memory use protectionInternet privacyCyber Space
A new identification (ID) technology comprising unified and standardized object identification within Cyber Space is disclosed based upon intrinsic properties of the entity to be identified. This Cyber Gene ID (or Cyber ID) technology extracts intrinsic information from either the physical users or their cyberspace counterparts, and such information is categorized into client parameters, dynamic parameters, static parameters, cloud parameters, connection parameters and user parameters.
Owner:JIANGSU DIGITAL DNA TECH CO LTD
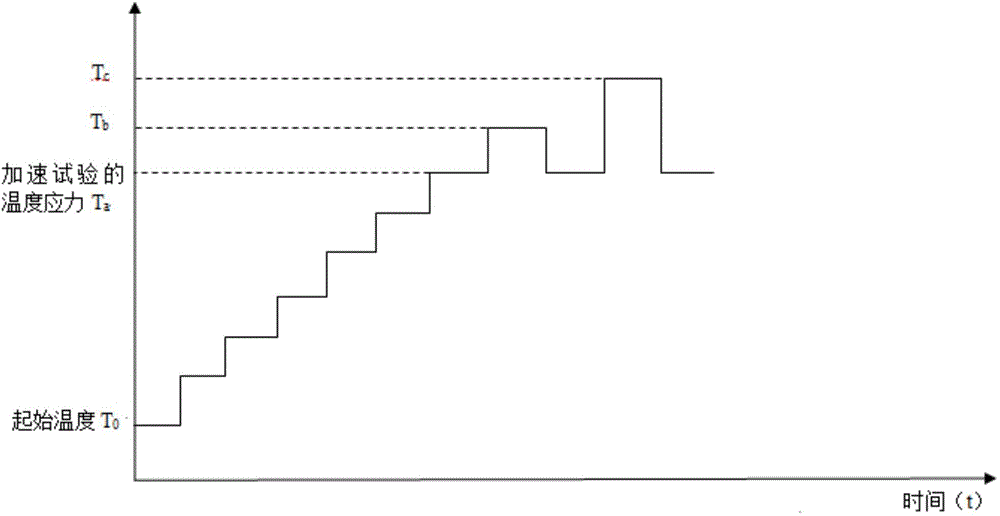
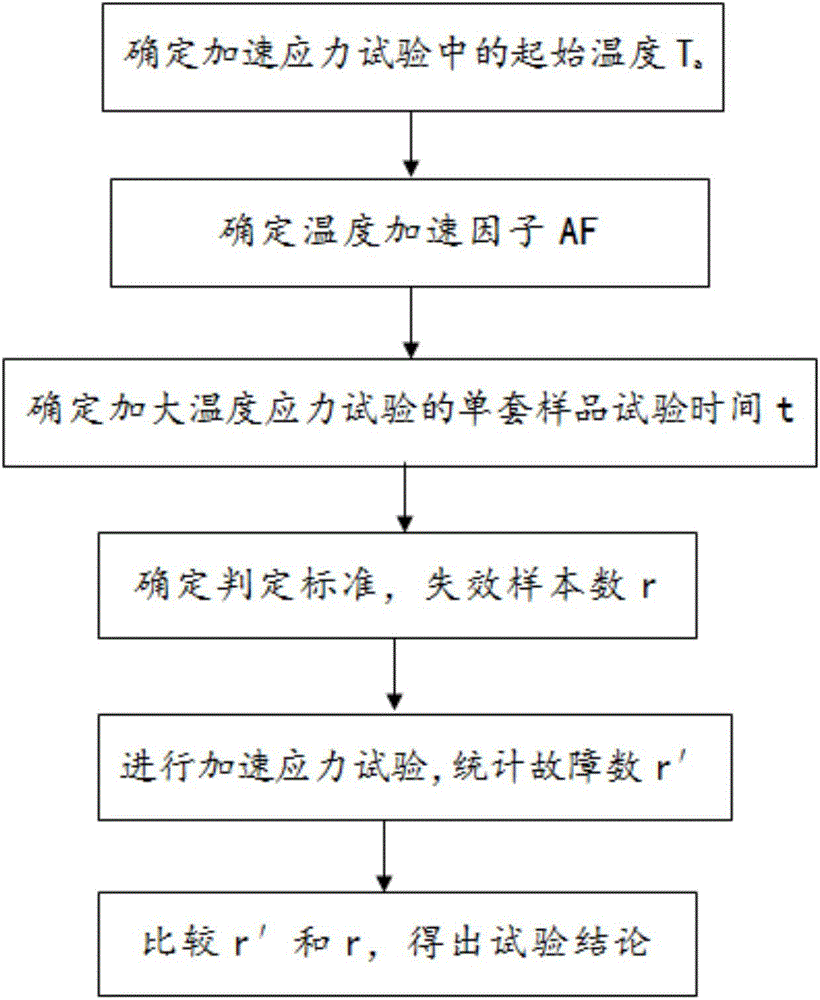
Method for verifying product reliability through temperature-stress-increased accelerated lift test
InactiveCN104459408ARealize reliability verificationReduce spendingElectrical testingTemperature stressSingle sample
The invention provides a method for verifying the product reliability through a temperature-stress-increased accelerated lift test. The method includes the steps that the initial temperature in a temperature-stress-increased test is firstly determined, then temperature accelerated factors and single-sample testing time of the temperature-stress-increased test are determined, the number of efficacy losing samples is further calculated, a temperature-stress-increased reliability verification test is finally carried out, the number of faults of the samples is counted, the number of the faults is compared with the number of the efficacy losing samples, and the test can be completed. By means of the method, under the condition that a fault mode and a fault mechanism are not changed, the testing time can be shortened, the test expenditure and the manpower expenditure can be saved, and the practical level of the mean time between faults of products can be accurately verified.
Owner:NO 20 RES INST OF CHINA ELECTRONICS TECH GRP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com