Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
447 results about "Cyber Space" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
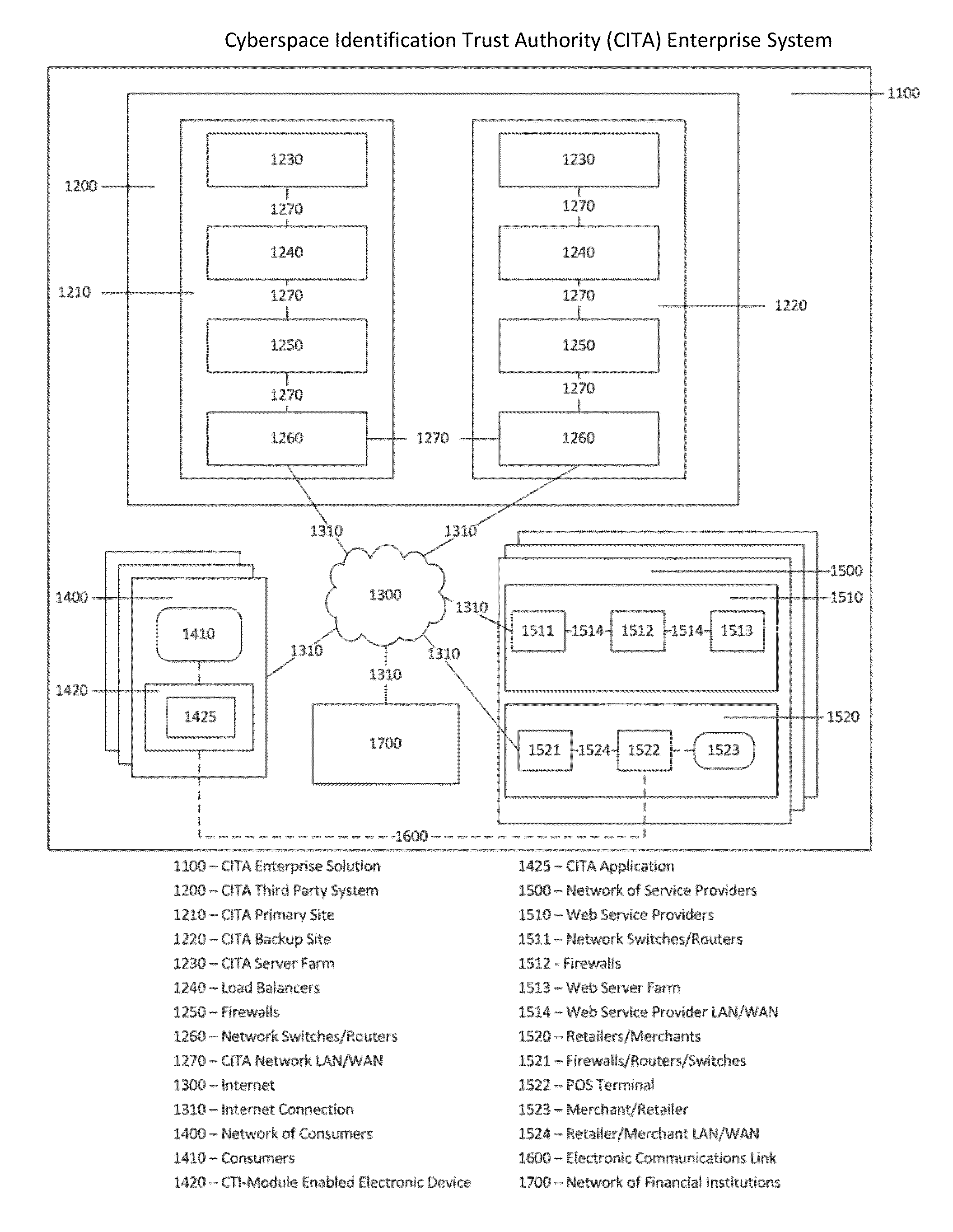
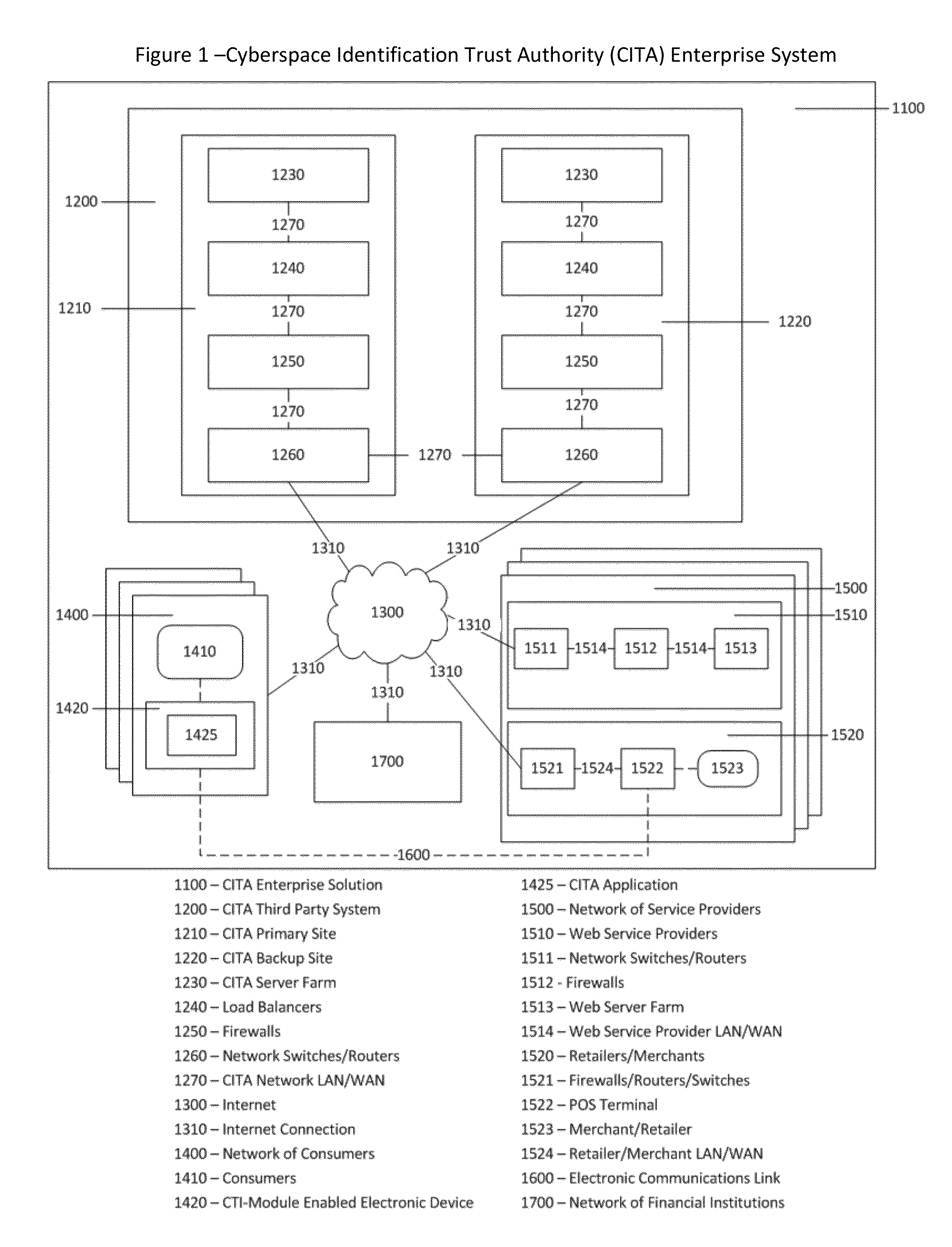
Cyberspace Identification Trust Authority (CITA) System and Method
InactiveUS20130226813A1Eliminate chanceSecure transmissionFinanceProtocol authorisationTrusted authorityPayment
When two parties of a cyberspace transaction register their identity attributes under a CITA system each party is assigned a unique, encrypted and digitally signed identity token. When the consuming party seeks access too, or payment for, cyberspace services, the providing party submits their identity token to the consuming party. The consuming party creates a request token, containing both the consumers' and the providers' identity tokens, and the transaction related information, to the CITA system. The CITA system validates the identity tokens and either creates a payment confirmation token by processing the payment request, or creates an access confirmation token by dynamically defining the minimal consumer identity attributes required to gain access to the provider's service. The confirmation token is encrypted and digitally signed and returned to the consumer, and then forwarded to the provider to complete the transaction without either party openly exchanging personal identity attributes.
Owner:VOLTZ ROBERT MATTHEW
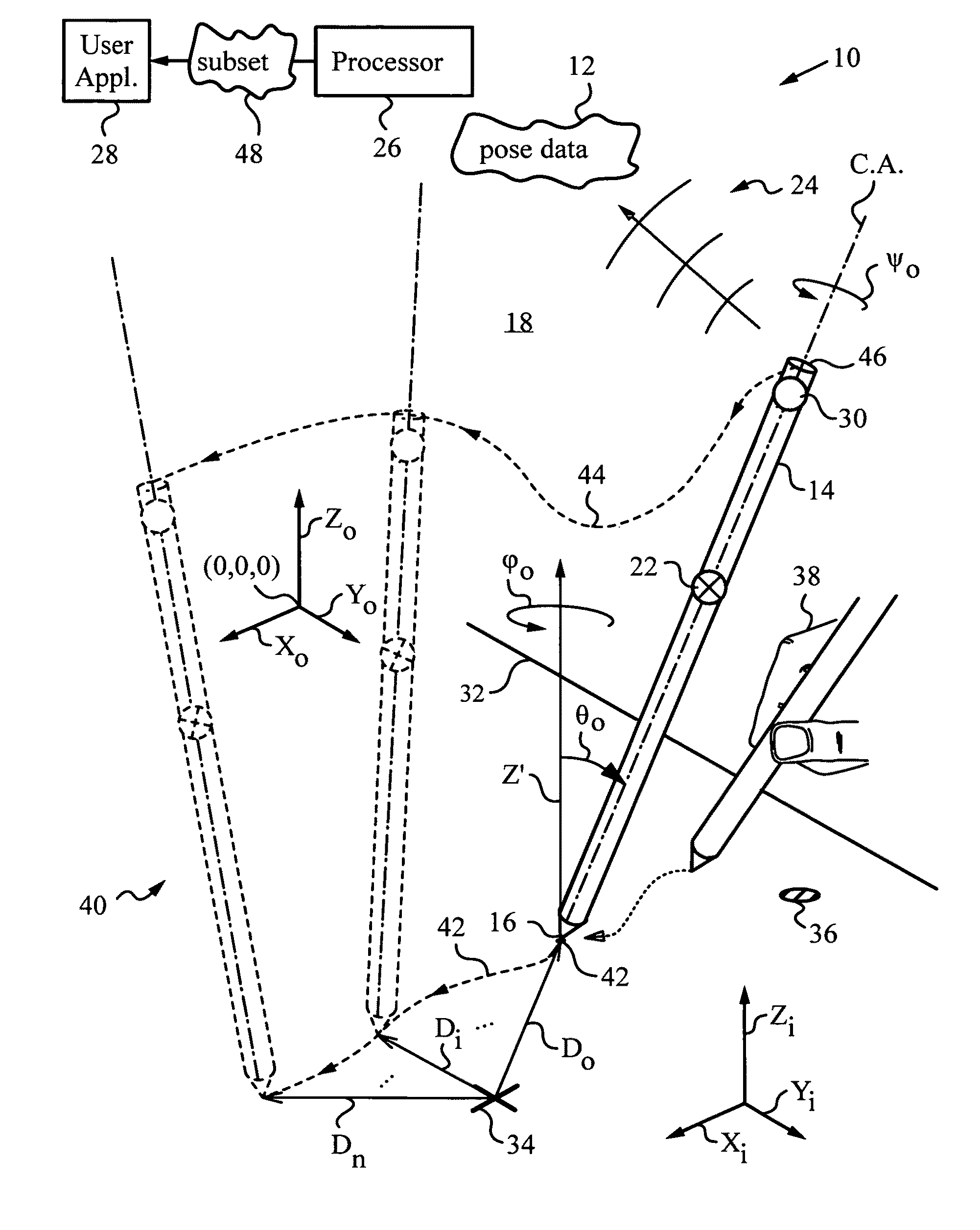
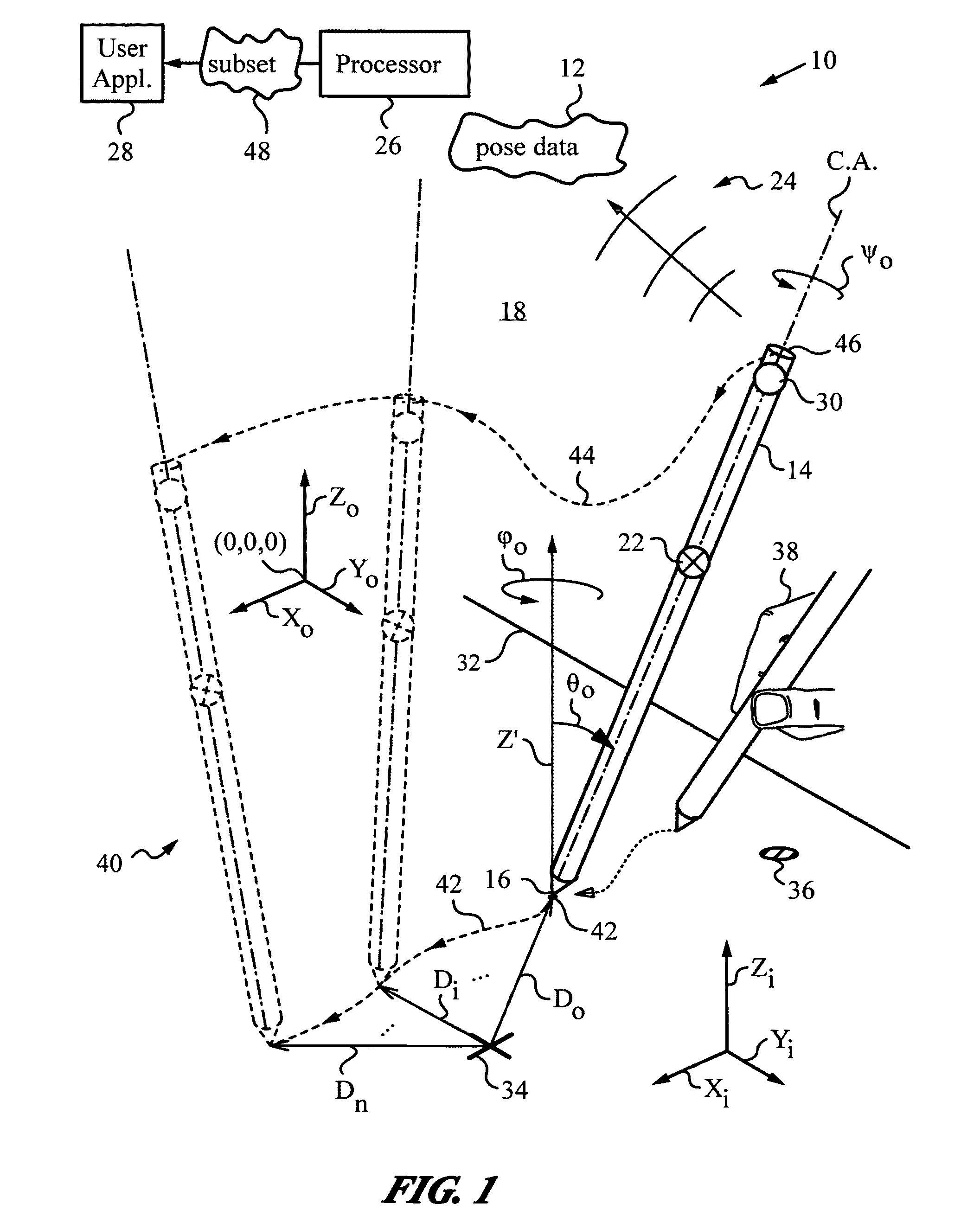
Computer interface employing a manipulated object with absolute pose detection component and a display
ActiveUS7961909B2Input/output for user-computer interactionImage enhancementPhotovoltaic detectorsRemote control
A system that has a remote control, e.g., a wand, equipped with a relative motion sensor that outputs data indicative of a change in position of the wand. The system also has one or more light sources and a photodetector that detects their light and outputs data indicative of the detected light. The system uses one or more controllers to determine the absolute position of the wand based on the data output by the relative motion sensor and by the photodetector. The data enables determination of the absolute pose of the wand, which includes the absolute position of a reference point chosen on the wand and the absolute orientation of the wand. To properly express the absolute parameters of position and / or orientation of the wand a reference location is chosen with respect to which the calculations are performed. The system is coupled to a display that shows an image defined by a first and second orthogonal axes such as two axes belonging to world coordinates (Xo,Yo,Zo). The one or more controllers are configured to generate signals that are a function of the absolute position of the wand in or along a third axis for rendering the display. To simplify the mapping of a real three-dimensional environment in which the wand is operated to the cyberspace of the application that the system is running, the third axis is preferably the third Cartesian coordinate axis of world coordinates (Xo,Yo,Zo).
Owner:ELECTRONICS SCRIPTING PRODS
Collaborative team crawling:Large scale information gathering over the internet
InactiveUS6182085B1Reduce processing overheadEfficient accessDrawing from basic elementsData processing applicationsTree (data structure)Workload
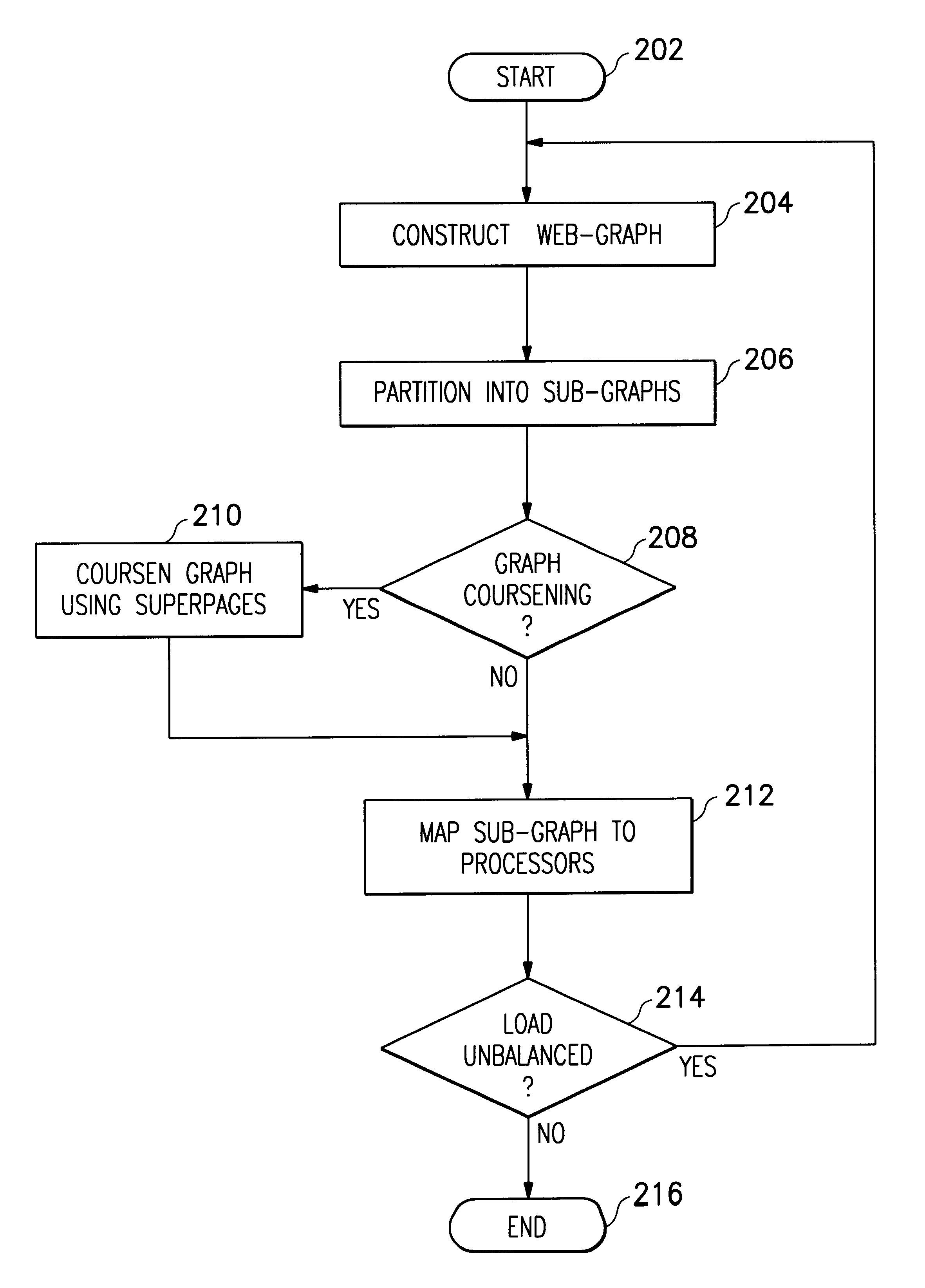
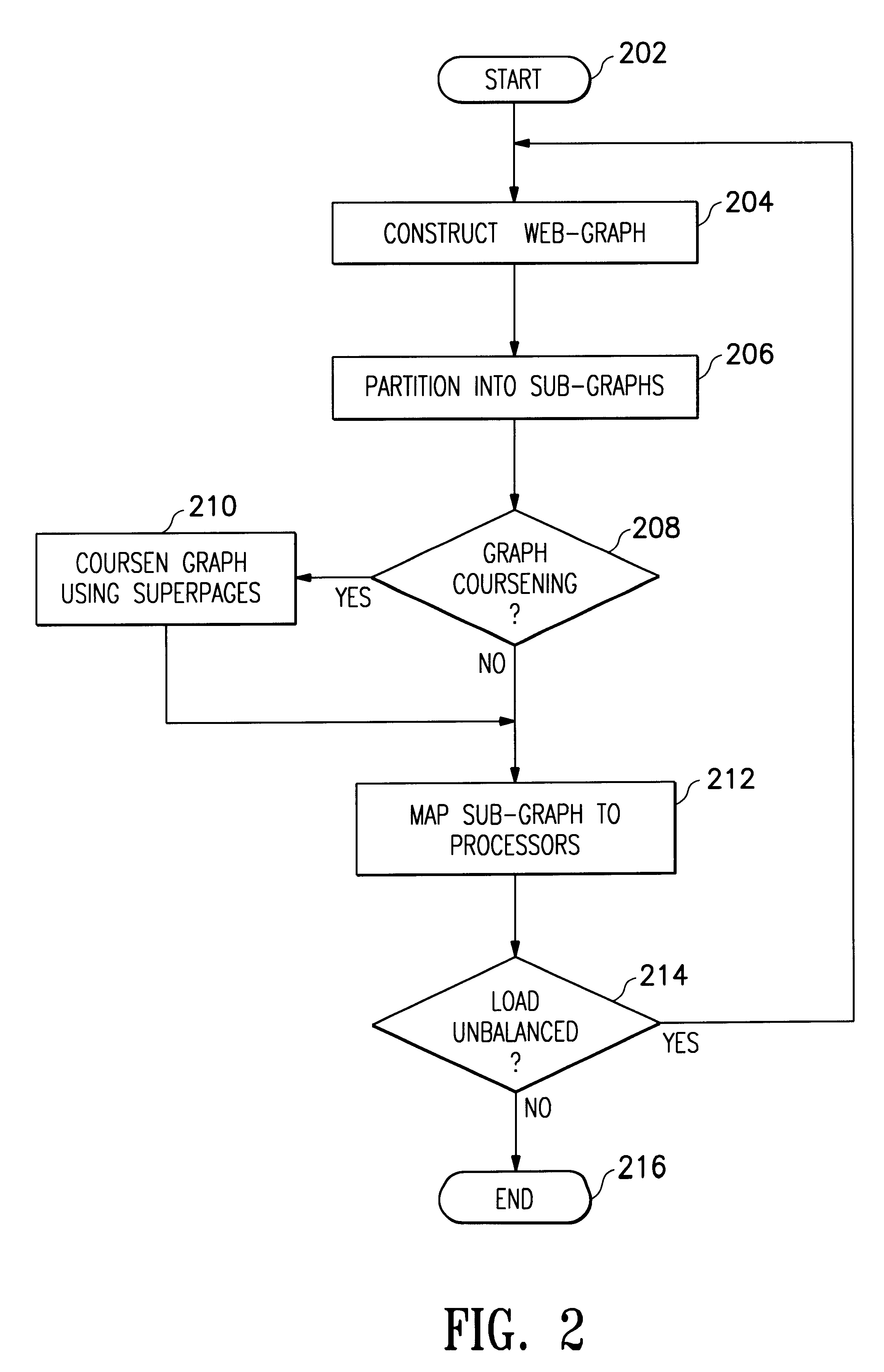
A distributed collection of web-crawlers to gather information over a large portion of the cyberspace. These crawlers share the overall crawling through a cyberspace partition scheme. They also collaborate with each other through load balancing to maximally utilize the computing resources of each of the crawlers. The invention takes advantage of the hierarchical nature of the cyberspace namespace and uses the syntactic components of the URL structure as the main vehicle for dividing and assigning crawling workload to individual crawler. The partition scheme is completely distributed in which each crawler makes the partitioning decision based on its own crawling status and a globally replicated partition tree data structure.
Owner:IBM CORP
System and method for a cyber intelligence hub
InactiveUS20160119365A1Advanced analyticalWeb data retrievalVisual data miningWeb crawlerCyber Space
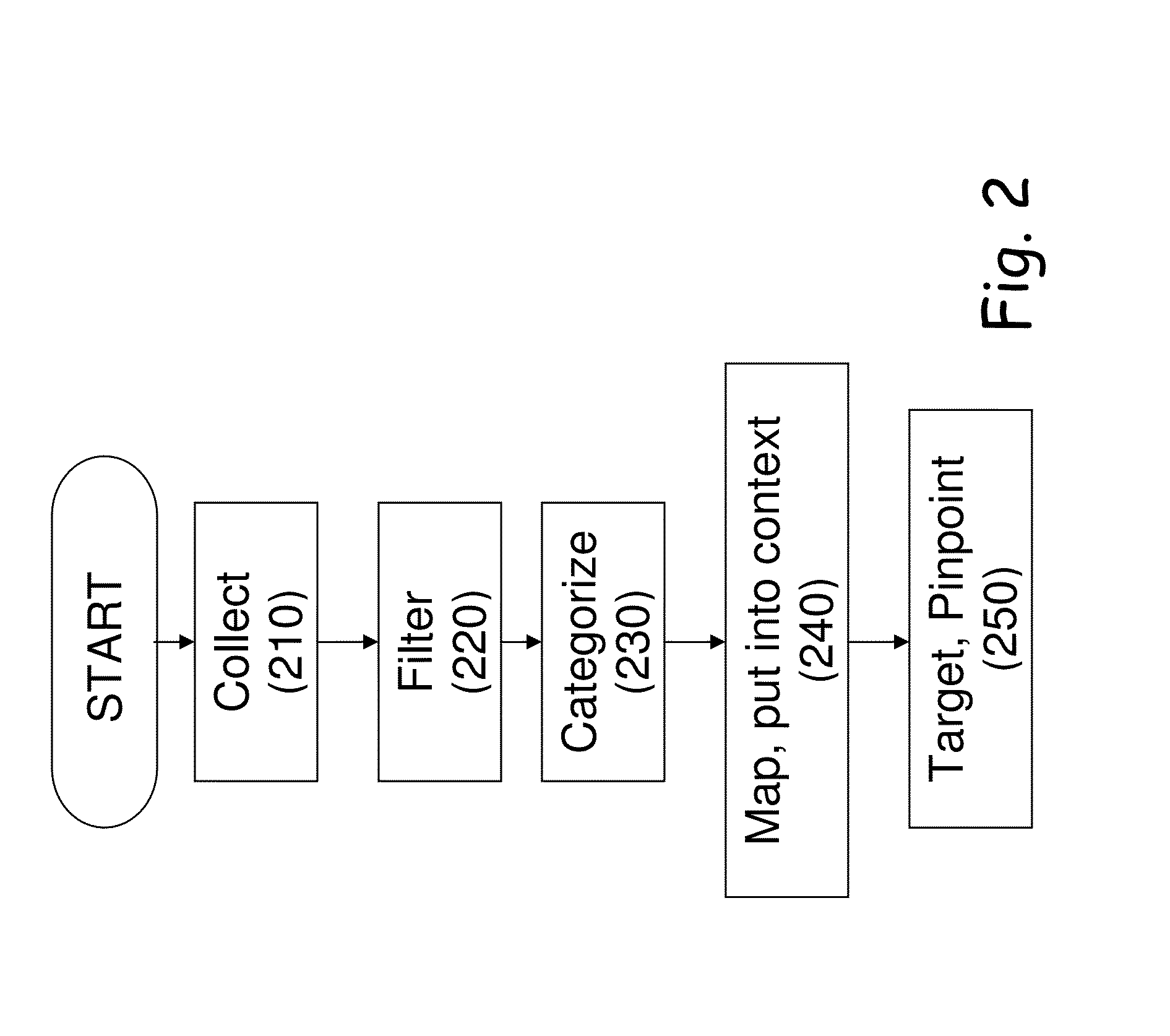
A method for defining and forming a cyber intelligence channel communicating with consumers is facing cyber threats in real time. The method includes collecting information, such that web crawlers and scrapers. The method also includes filtering the collected information, by filtering mechanisms founded on advanced algorithms. The method goes on to categorize the information into groups based on their unique characteristics, collecting capabilities and input and output constraints. The method further includes mapping the information and putting it into context and targeting and pinpointing the information, such that the data collected in the data intelligence collection unit is gathered through innovative technologies that enable automated and massive, yet targeted collection of the data that exists in the cyber space.
Owner:COMSEC CONSULTING
Real-time collaborative commerce in a multiple browser environment
A technique is disclosed for facilitating electronic commerce and / or information exchange. The technique of the present invention enables a content provider to create a web space which can surface large amounts of product data into one single view. In addition, the display and layout of the web space may be dynamically customized. Further, if desired, customer specific data may be overlaid on product catalog data. In this way, customers are able to quickly grasp the extent of the virtual store and access products of interest by drilling-down on any single region of the store. Additionally, customer behavior patterns and activities may be tracked in real-time. This information may be used to enable a on-line merchant to respond appropriately, in real-time, in order to facilitate sales of merchandise to current on-line shoppers.
Owner:URBANPIXEL
System and method to create a collaborative web-based multimedia contextual dialogue
InactiveUS20120260195A1Multimedia data browsing/visualisationMultiple digital computer combinationsGraphicsWhiteboard
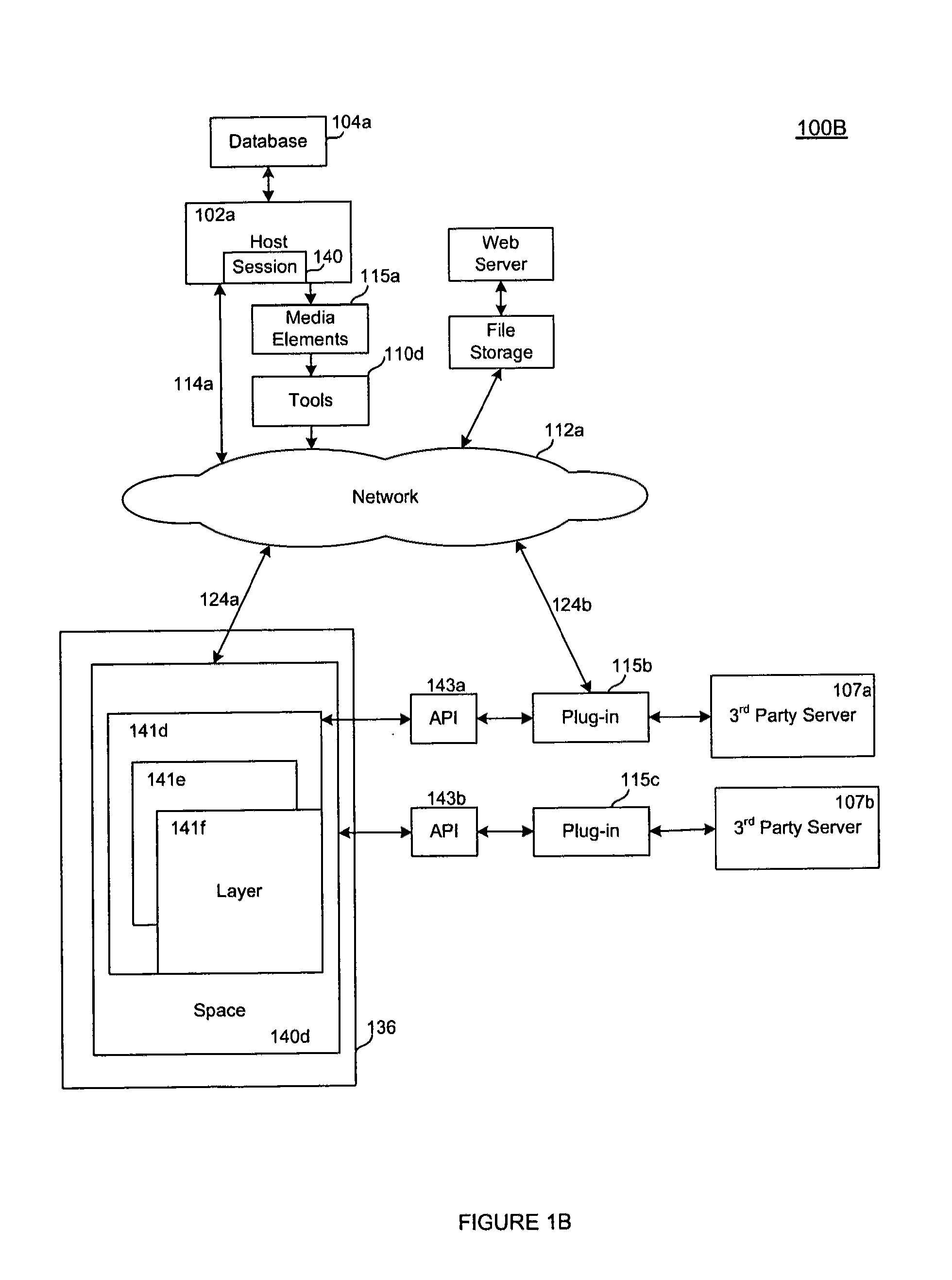
The present invention relates a method and system for collaborating in a shared network space comprising logging in from the one or more user machines to the shared space in a network from a user application to a host, wherein the shared space is created by interaction of executable codes in the host and the user application and the shared space is described by a session attribute list; loading a media application with tools into a one or more user machines; inputting graphical content; and displaying the content by other user machines in the shared space synchronously or asynchronously including anchoring a sidebar panel to a region of a browser; creating one or more user messages in the sidebar panel; displaying graphical content on a whiteboard; highlighting points of interest within the graphical content; and associating said user messages to the points of interest by one or more lines.
Owner:SIMULAT
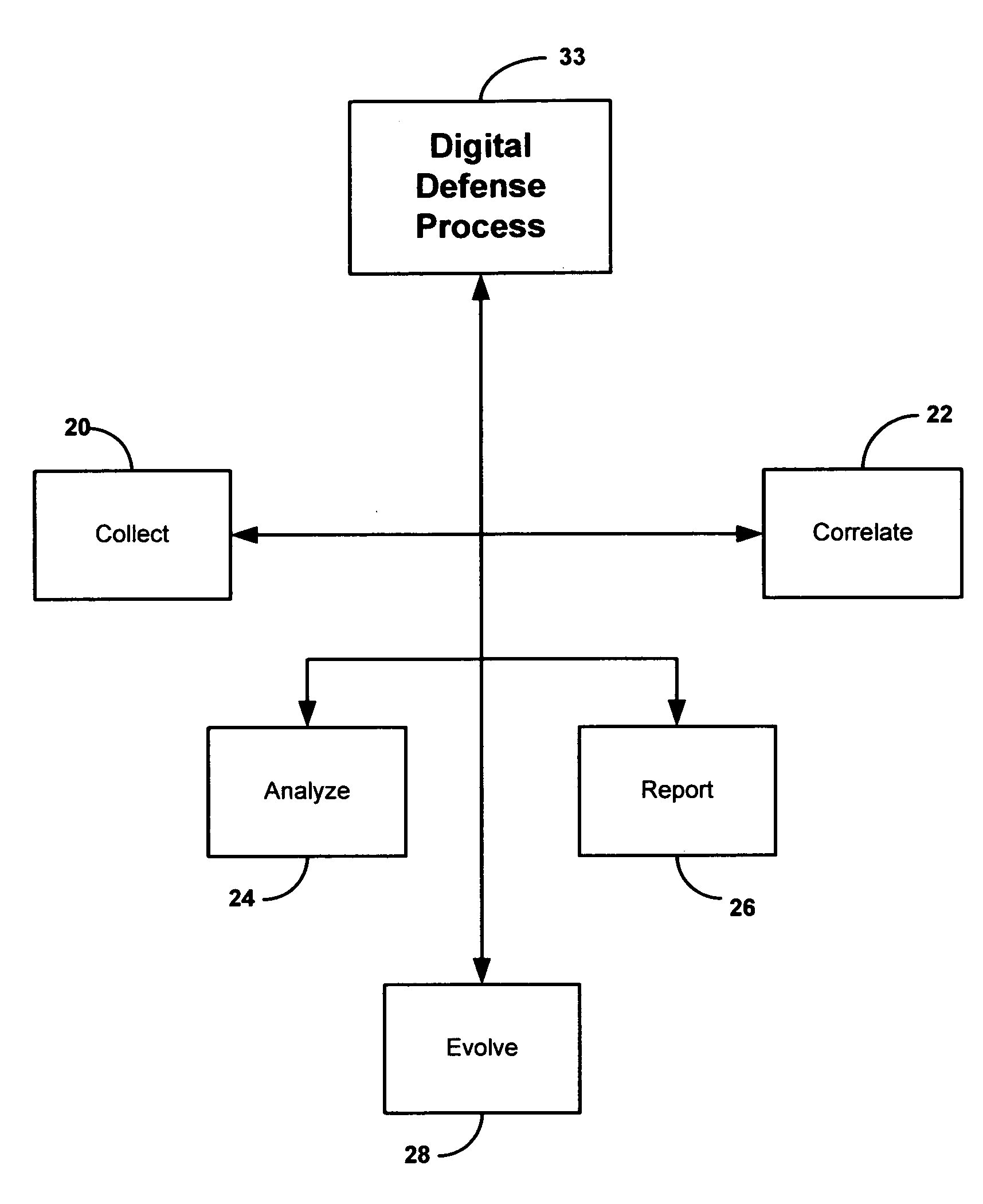
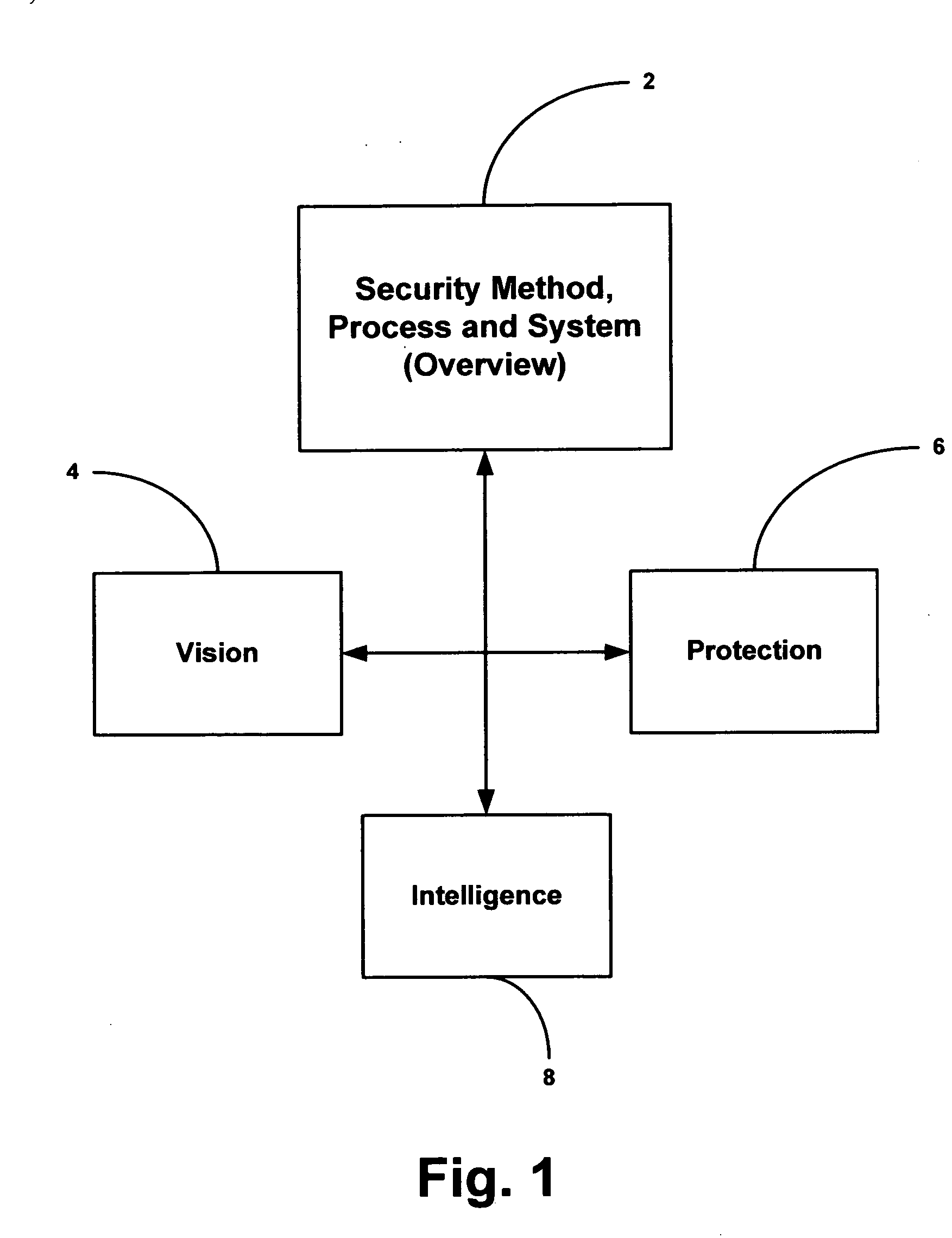
Security system and method including individual applications
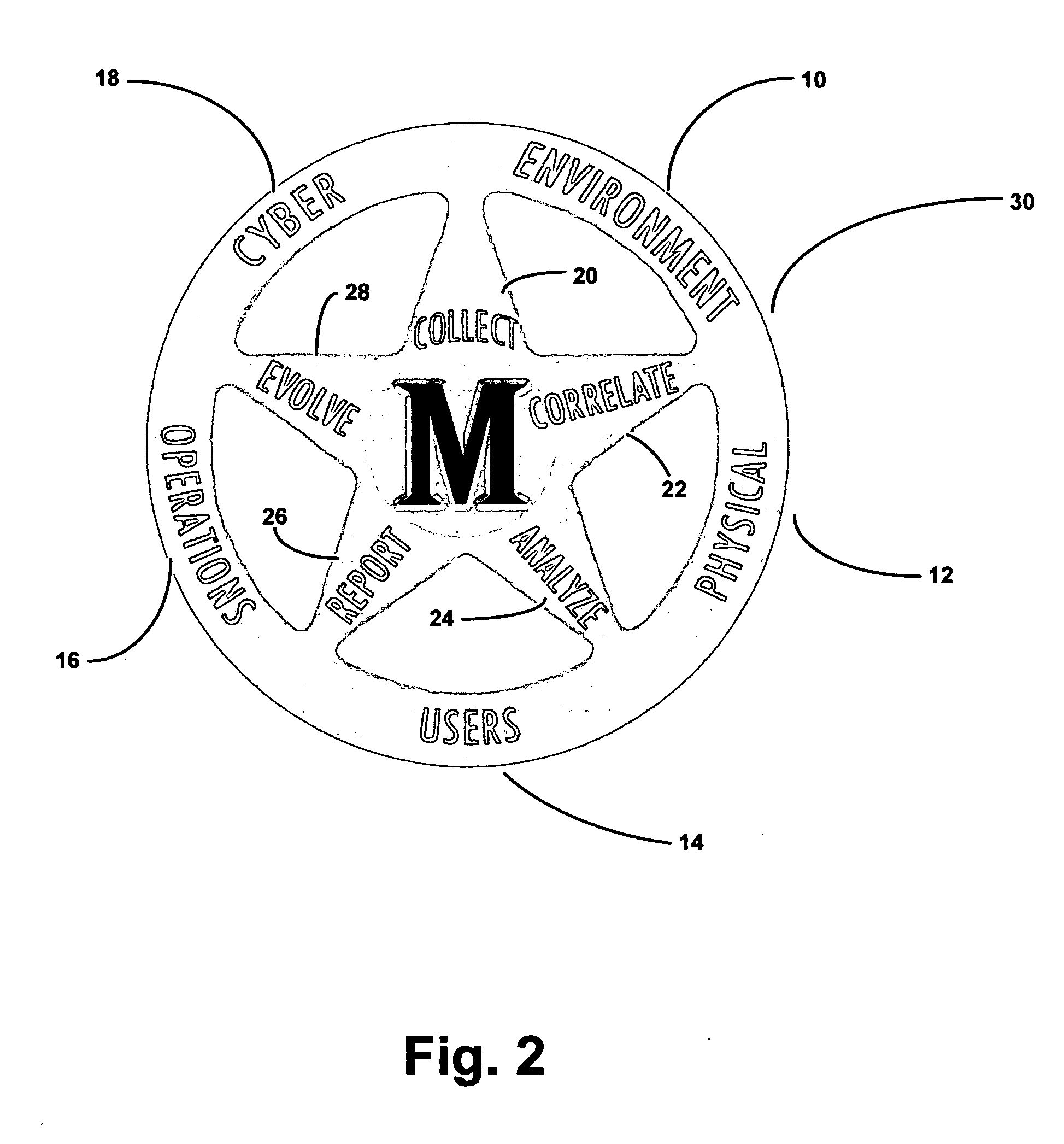
InactiveUS20070180522A1Great advantageReduce downtimeMemory loss protectionUser identity/authority verificationEnvironmental issueAnalysis data
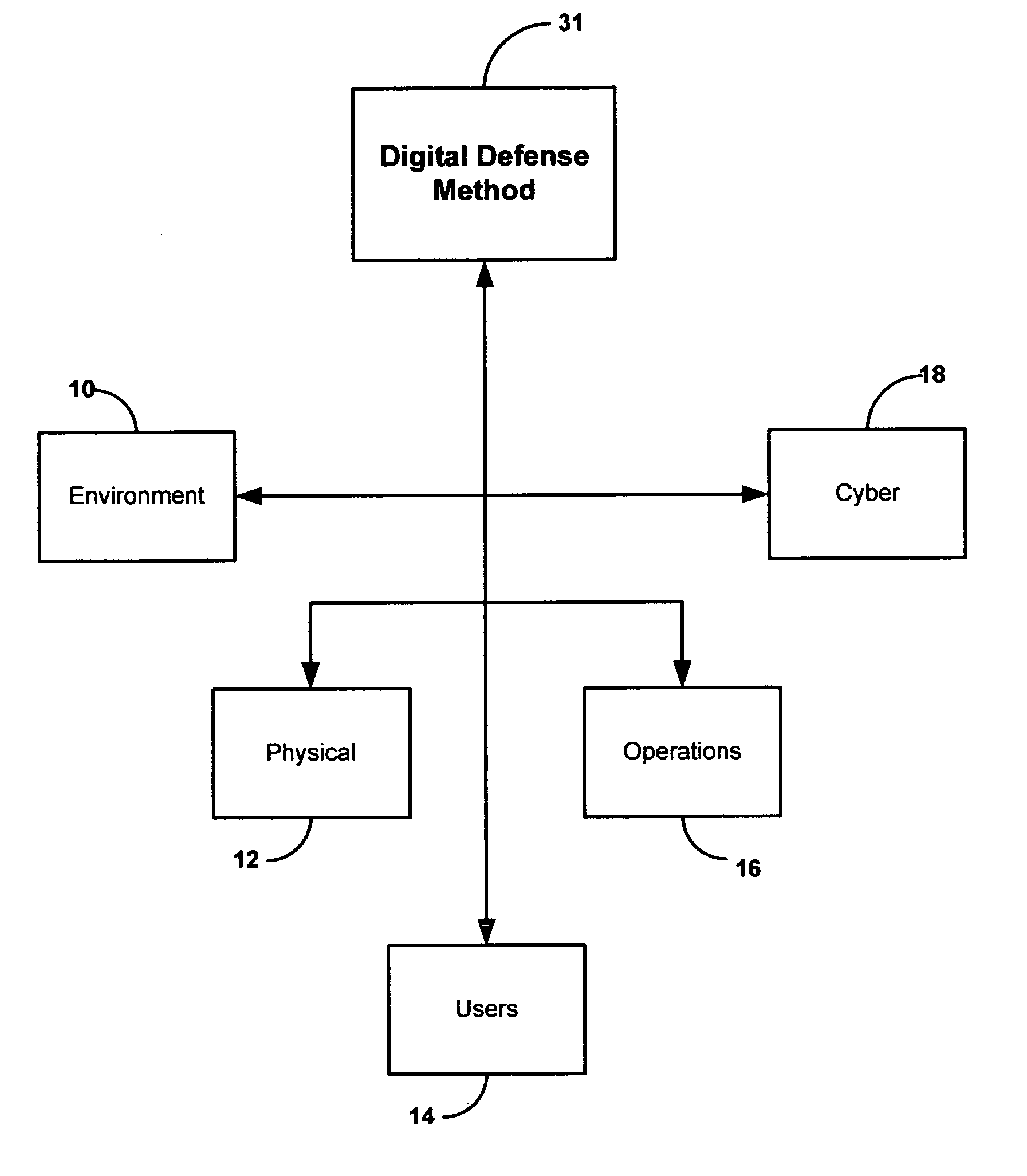
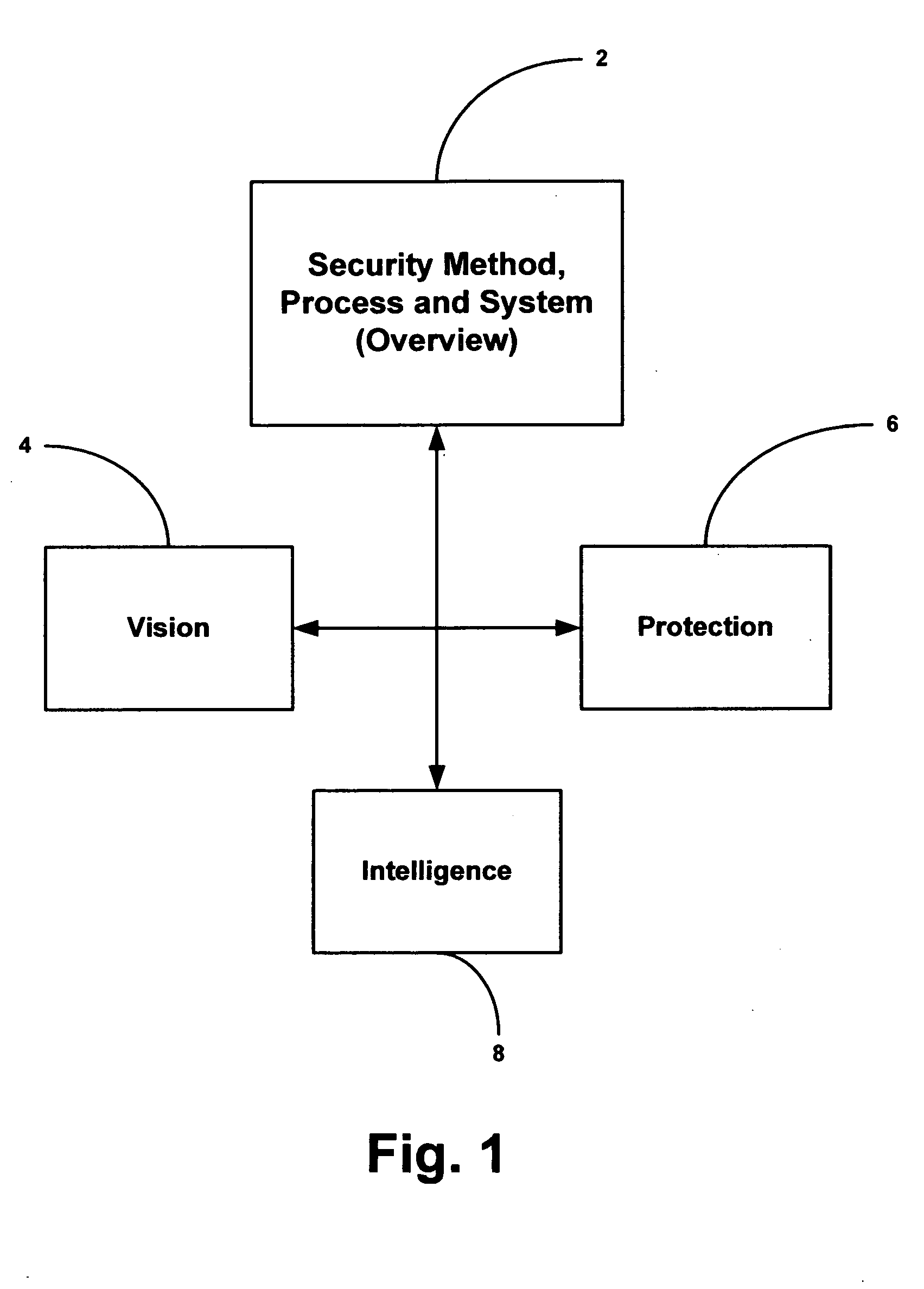
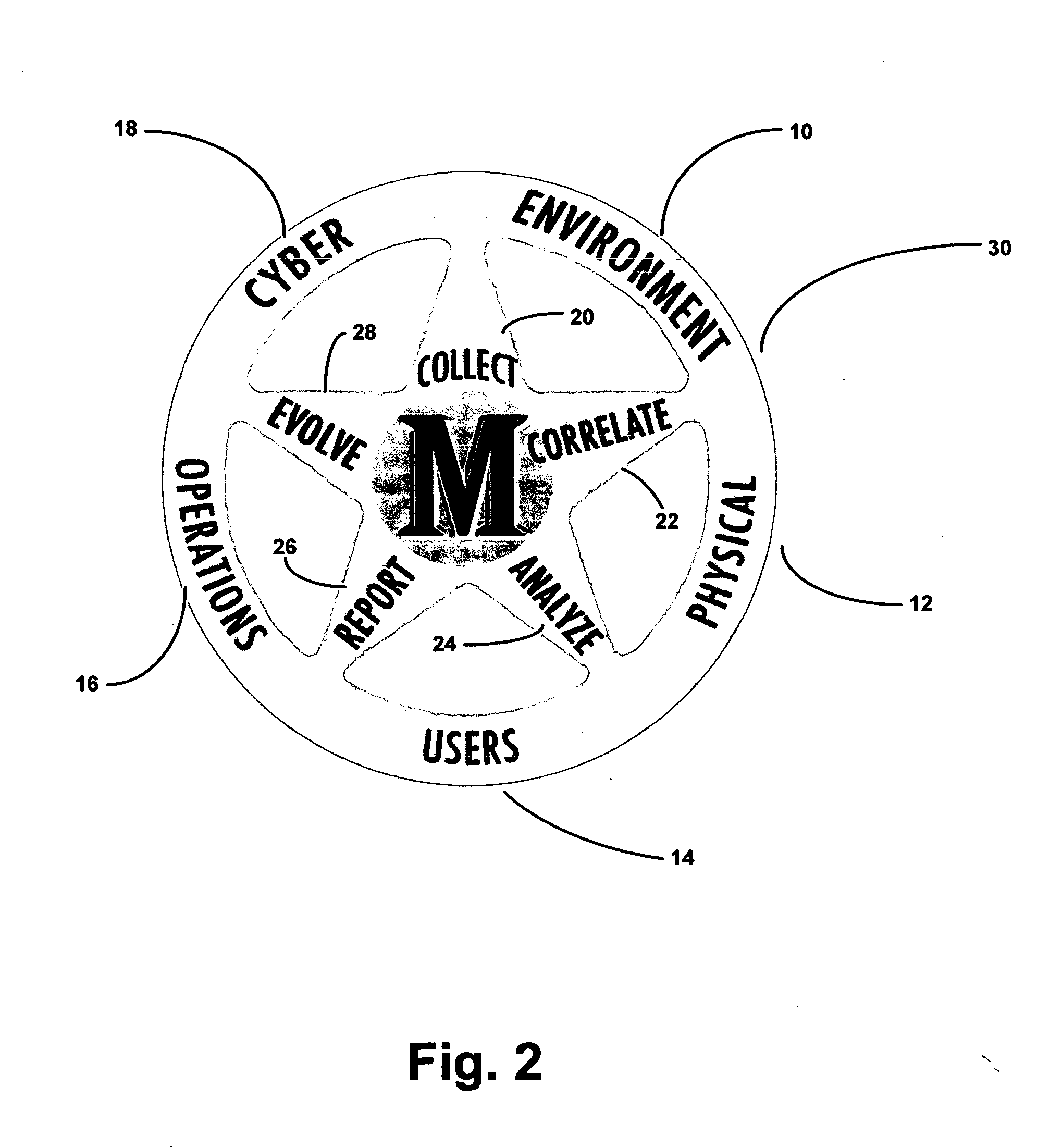
A method and system for providing security to organizations having data and information, involving a vision specific to the organization by gathering information and determining current and future plans and needs, a scenario for protection from invasive activities including cyber-space and physical invasion, and intelligence to assist in determining protection. Also included are present and needed environmental concerns and threats, present and needed physical components, present and needed education and training for end users with access to the information, operations by examination, monitoring and detailing present and needed processes, and cyber presence including one or more computers, functions, locations, configurations, and trust relationships. Also considered are the importance of proprietary information, off-site back-ups, access-level restrictions to data, log books and preventions to minimize down-time of systems due to maintenance or attack. Also involved are collecting data, correlating the data, analyzing the data, providing reports, and evolving the method based upon information gathered. A number of different application are also provided.
Owner:BAGNALL ROBERT J
Underground space high-precision positioning method based on laser scanning and sequence encoded graphics
InactiveCN102053249AMeet the application requirements of fast and high-precision positioningPhotogrammetry/videogrammetryElectromagnetic wave reradiationLaser scanningEngineering
The invention discloses an underground space high-precision positioning method based on laser scanning and sequence encoded graphics. Aiming at the rapid high-precision positioning, orientation, altitude determination and navigation of moving targets in a GPS signal-free underground well of a mine, the method can make the breakthrough in key directions from the design, decoding and optimized layout of the encoded graphics, the economical and rapid acquisition of a fine and accurate road network-a three-dimensional well network space model consisting of underground tunnels of mine, a high-precision positioning algorithm of the moving targets in well restraint spaces (precise resolving of position, direction, altitude parameters), a three-dimensional well network space matching algorithm, athree-dimensional navigation technology to a final navigation platform and terminal control system, and the like, thus key technologies for underground rapid high-precision positioning and navigationas well as software and hardware systems are formed to eventually achieve the leaping-development of a underground unmanned mining technology for the mine in our country. Besides, the method disclosed in the invention can also meet the application demands of large urban underground space, deep and long traffic tunnel, large grotto, large building interior, large overpass and subway space on the rapid high-precision positioning and navigation of the moving targets, thereby pushing forward the development of the underground space positioning technology in our country.
Owner:吴立新 +1
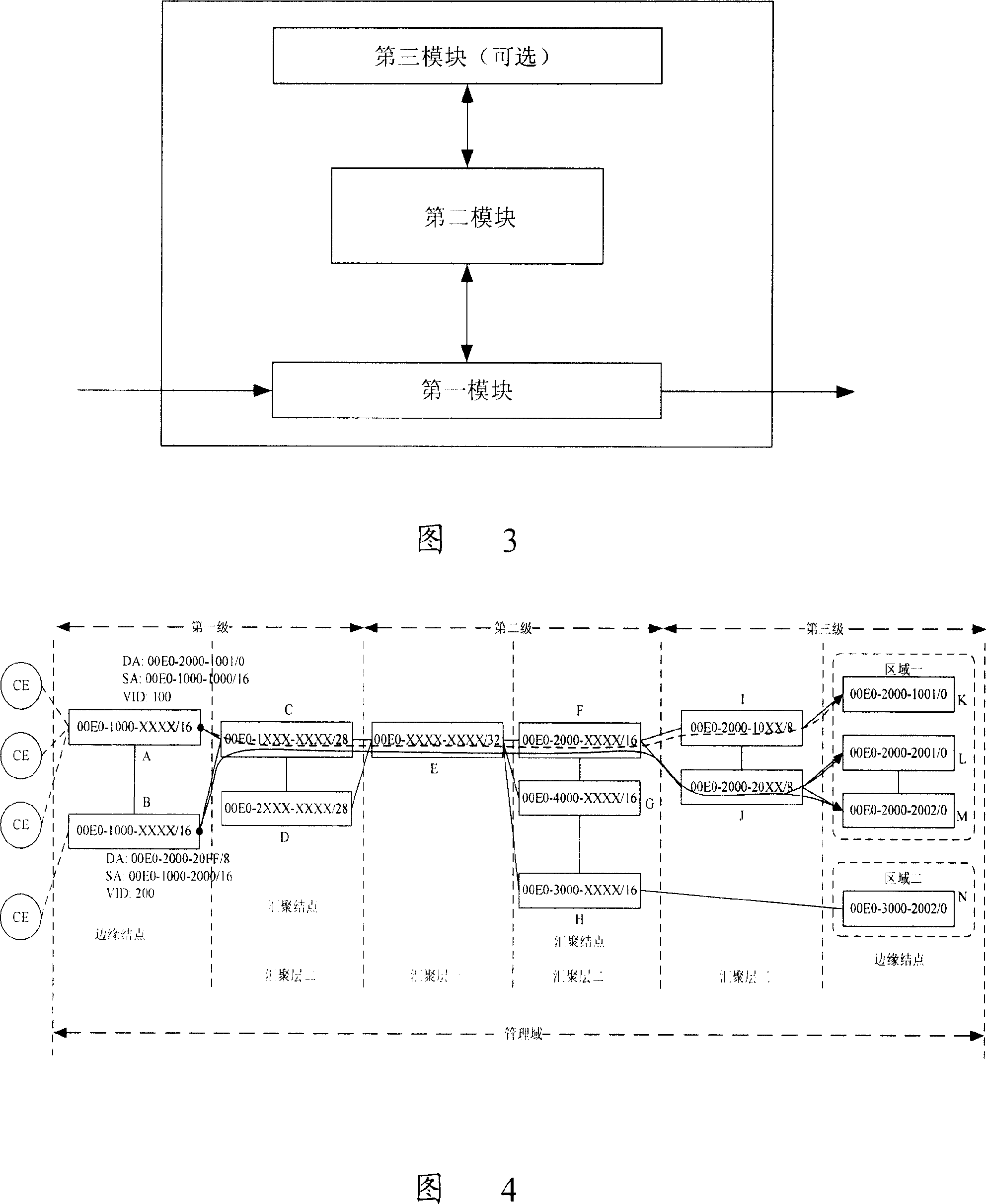
Data forwarding method for layer 2 network and network and node devices
ActiveCN101127696AFast convergenceSupport connectionData switching by path configurationMAC addressBroadcasting
The utility model discloses a data rely method, a network and a node device in a two-layer network, which sets an management field in a network, and uniformly deploys virtual MAC addresses for the node devices in the management field according to a predetermined convergence principle, and imports identifying information used for marking the virtual MAC address field which the node device belongs to, for the virtual MAC address; when the network transmits data, a marginal node device encapsulates the received data with a virtual MAC address, and transmits the data to a destination node device according to a virtual MAC address forwarding table which is deployed with virtual MAC addresses. The utility model has the advantages that making the quantity of ESP reaching a destination device not be limited by the quantity of VID of the distributive PBT, extending the quantity of ESP reaching a destination device, truly realizing a tag capacity of 260 in a limited cyberspace, the connection of P2MP and MP2MP, and supporting a multicasting connection and a broadcasting connection.
Owner:HUAWEI TECH CO LTD
Security system and method
InactiveUS20070180525A1Provide securityAvoid and minimize down-timeMemory loss protectionError detection/correctionEnvironmental issueAnalysis data
A method and system for providing security to organizations having data and information, involving a vision specific to the organization by gathering information and determining current and future plans and needs, a scenario for protection from invasive activities including cyber-space and physical invasion, and intelligence to assist in determining protection. Also included are present and needed environmental concerns and threats, present and needed physical components, present and needed education and training for end users with access to the information, operations by examination, monitoring and detailing present and needed processes, and cyber presence including one or more computers, functions, locations, configurations, and trust relationships. Also considered are the importance of proprietary information, off-site back-ups, access-level restrictions to data, log books and preventions to minimize down-time of systems due to maintenance or attack. Also involved are collecting data, correlating the data, analyzing the data, providing reports, and evolving the method based upon information gathered.
Owner:BAGNALL ROBERT J
Cyberspace Trusted Identity (CTI) Module
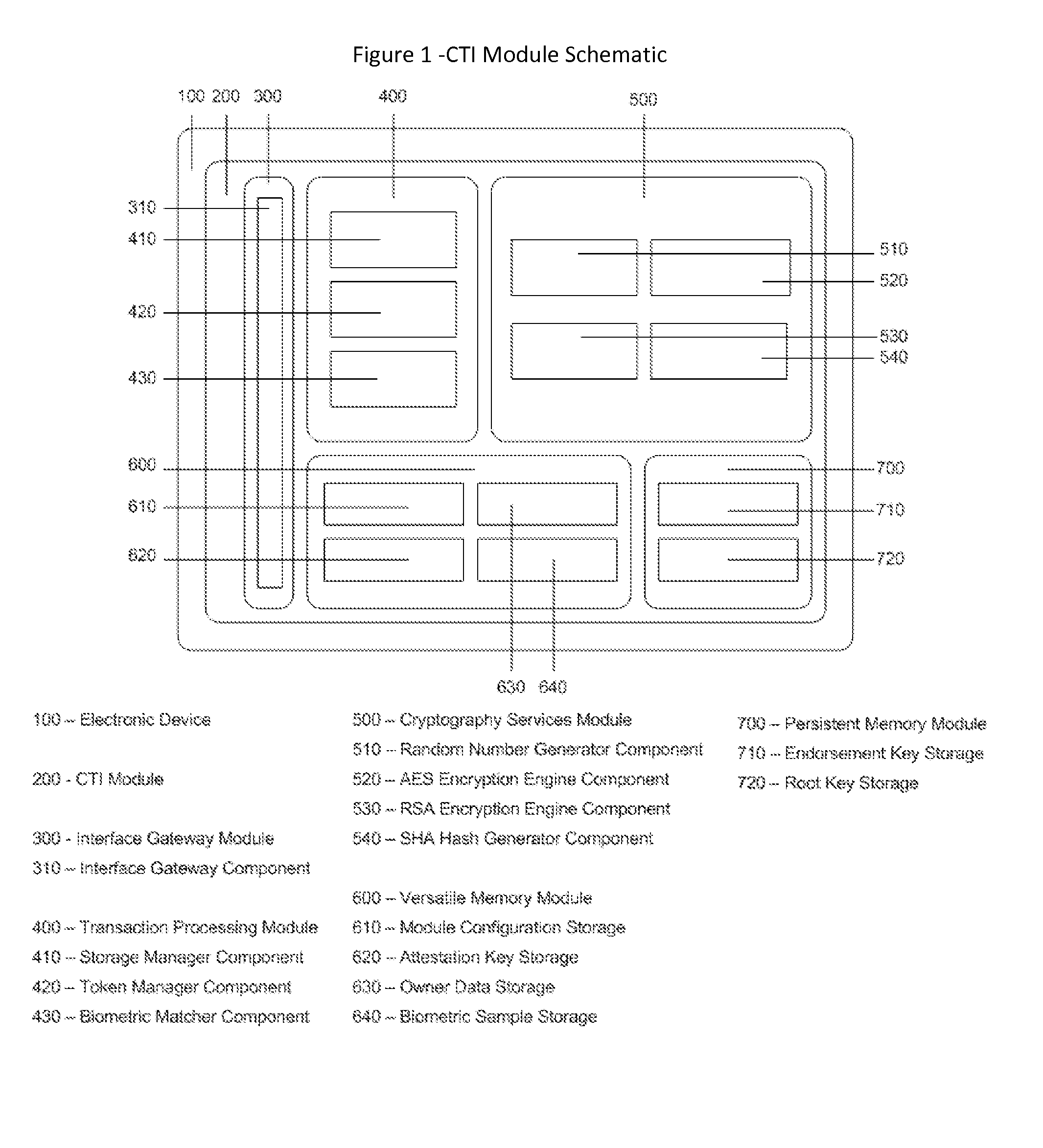
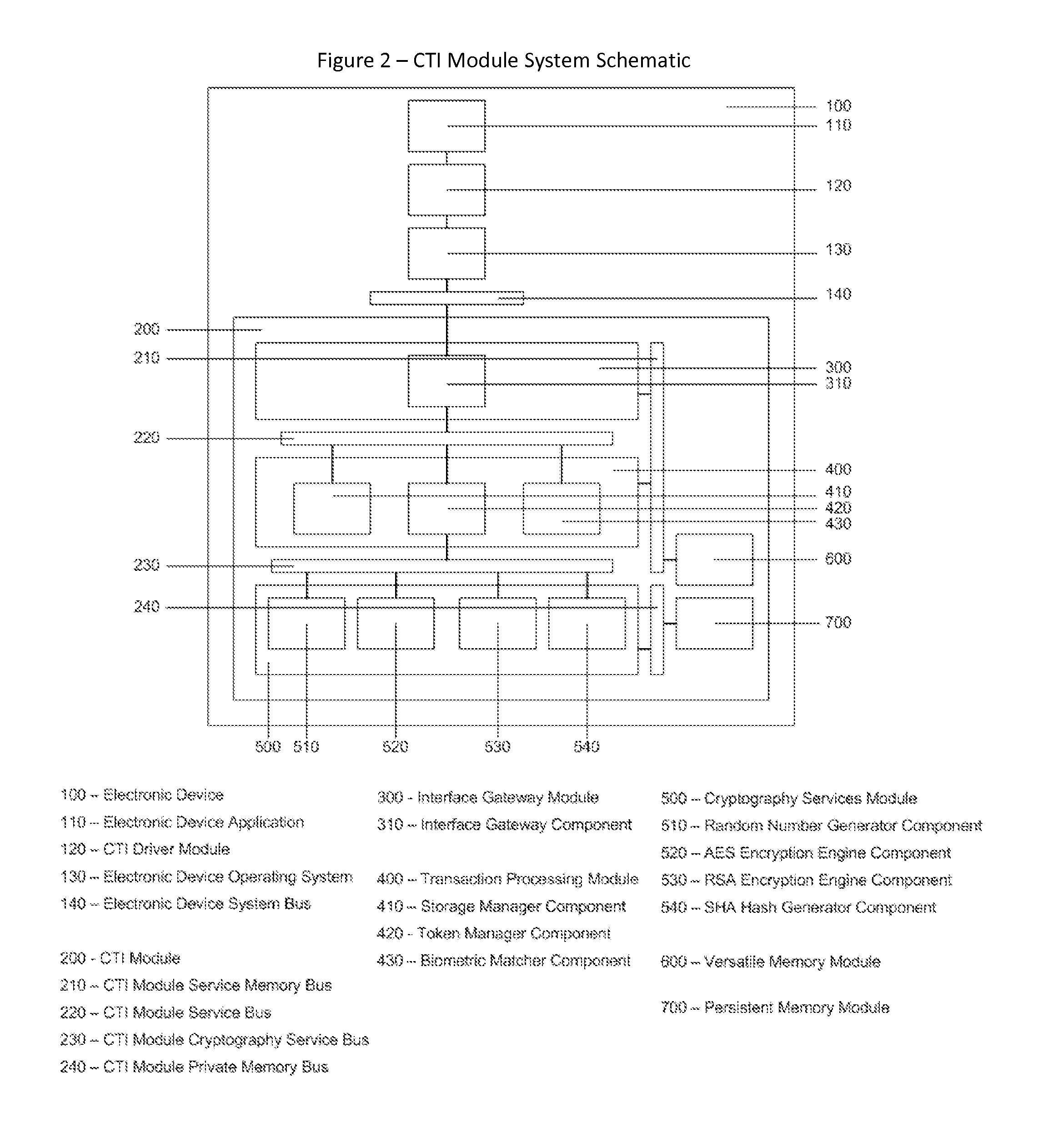
InactiveUS20130219481A1Eliminate needIncrease storage capacityDigital data processing detailsMultiple digital computer combinationsTrusted authorityDigital identity
The Cyberspace Trusted Identity (CTI) module provides secure storage of a cyberspace user's personal identity information and a security infrastructure to guarantee the integrity and privacy of a cyberspace transaction. When the owner of an electronic device registers their biometric samples on the CTI module the module becomes locked and the information stored on the module can only be accessed when the device owner provides a live biometric sample, which matches the registered biometric sample. When the CTI Module is registered under a trusted third party system; a Cyberspace Identification Trust Authority (CITA) system, the module provides a secure mechanism for storing a cyberspace user's digital identity tokens and for conducting safe and reliable cyberspace transactions between two cyberspace users. The CTI Module eliminates the need to carry man-made identity tokens, or the need to remember and / or openly exchange personal identity information, when conducting a cyberspace transaction.
Owner:VOLTZ ROBERT MATTHEW
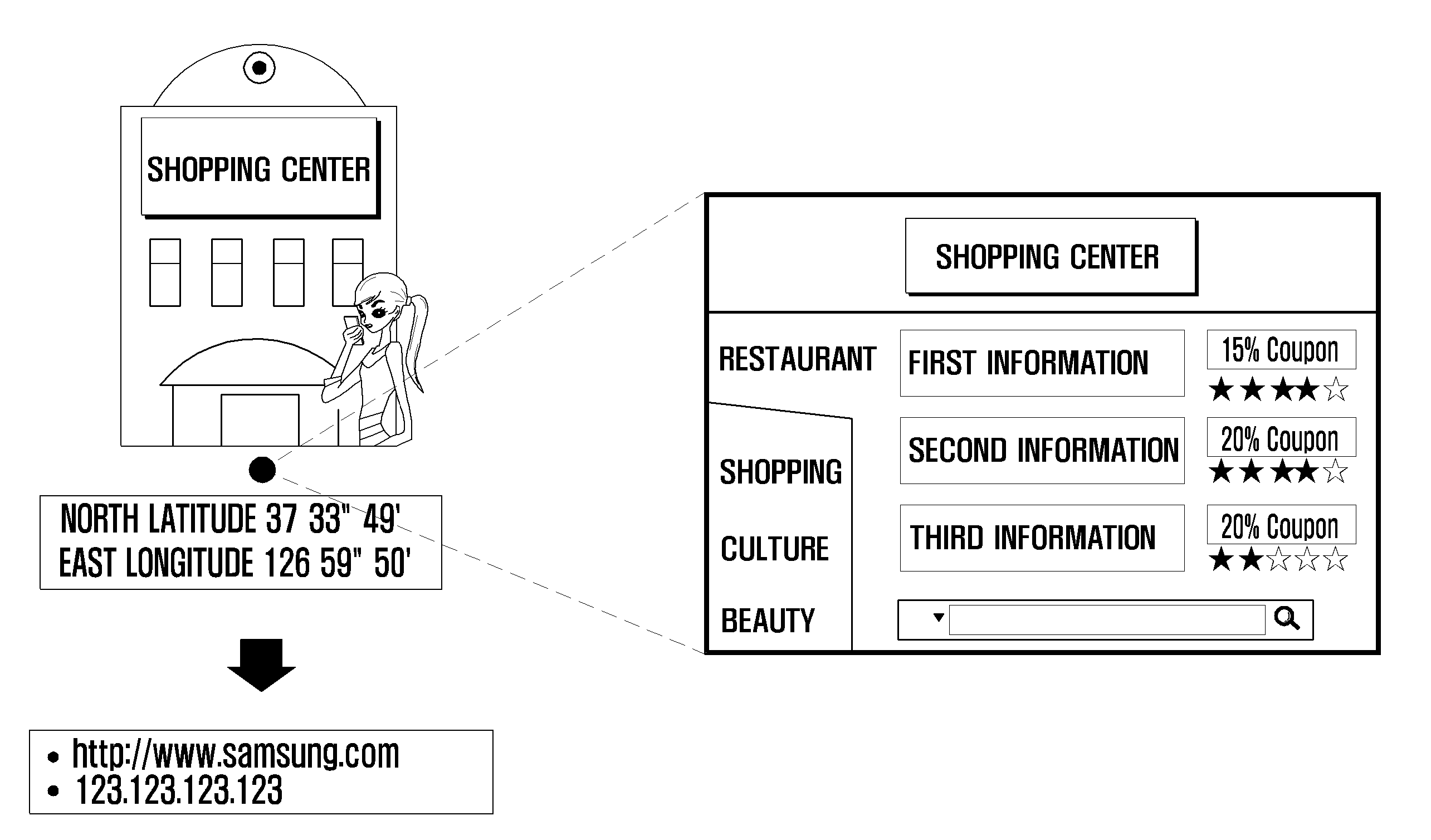
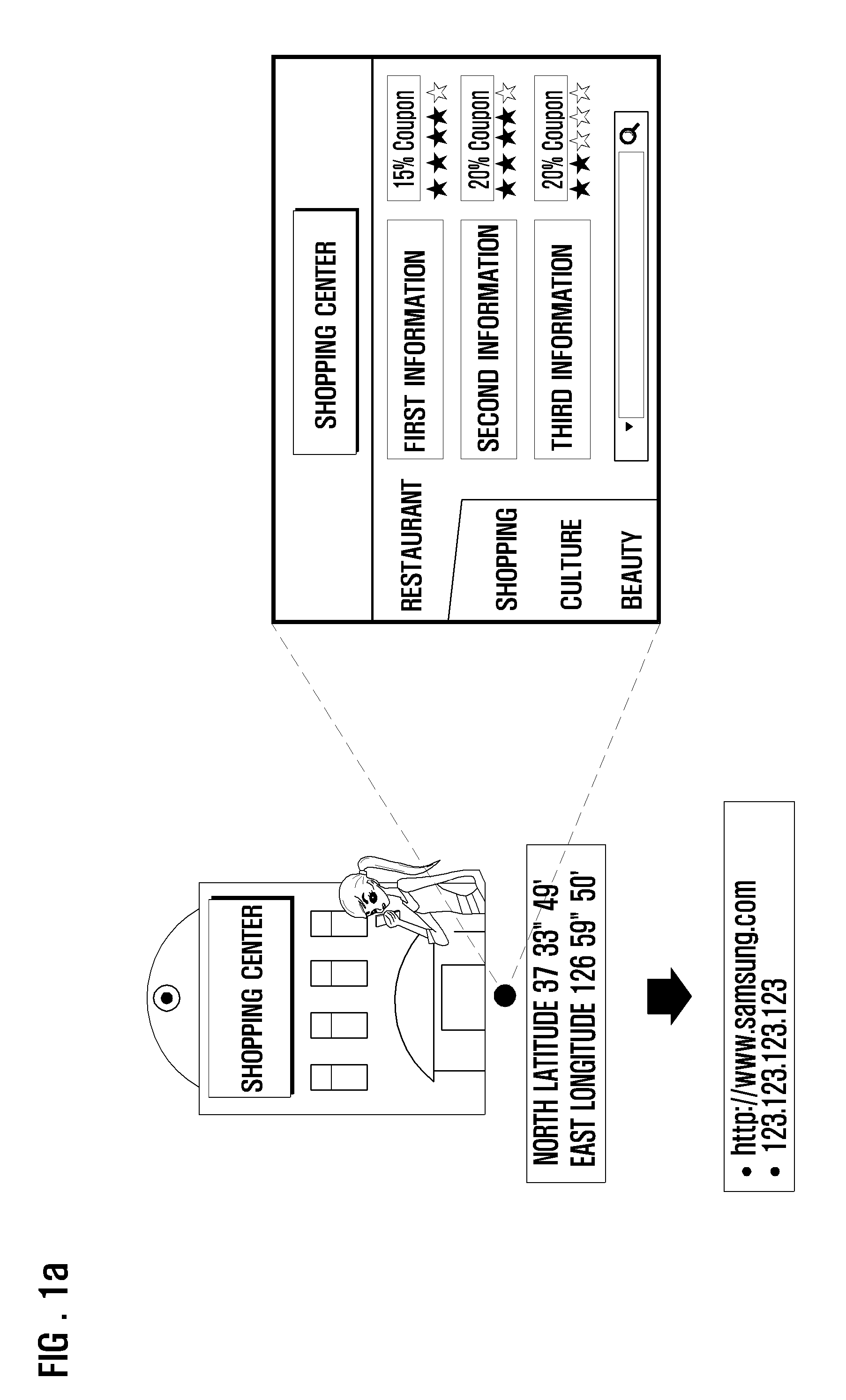
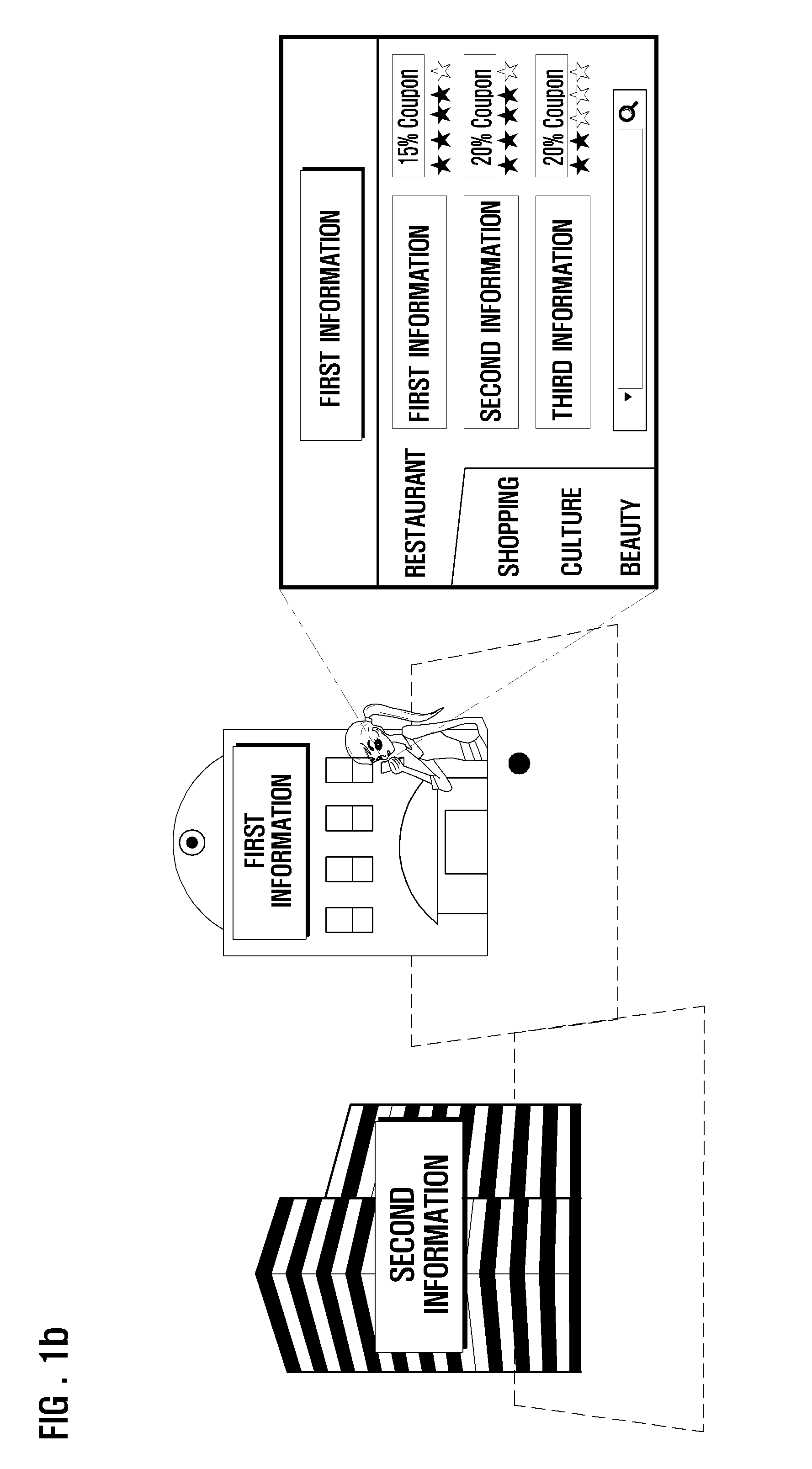
Location-based information service method and mobile terminal therefor
InactiveUS20090197620A1Automatic accessRoad vehicles traffic controlInformation formatIp addressService provision
Owner:SAMSUNG ELECTRONICS CO LTD
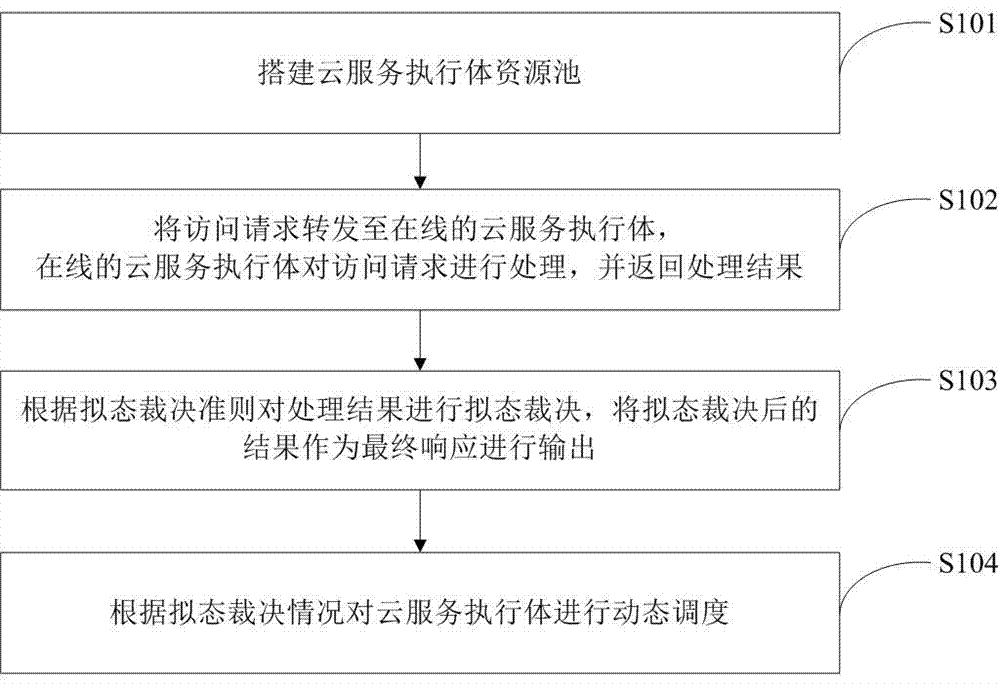
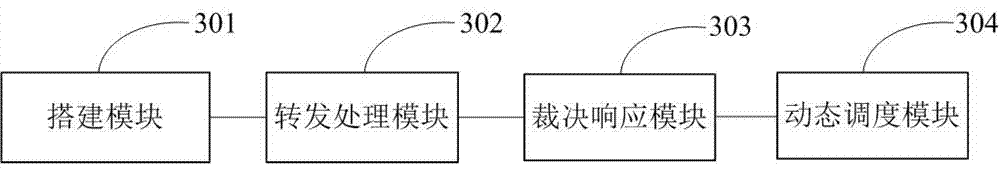
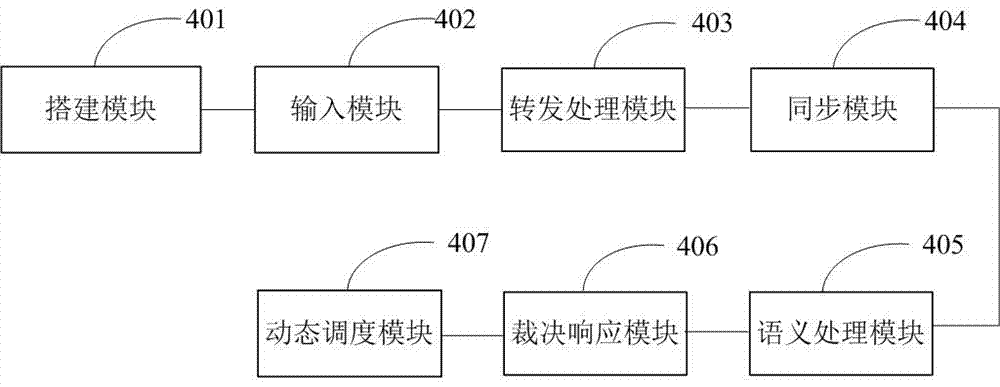
Secure cloud service construction method and device based on mimic defense
InactiveCN107454082AGuaranteed to provide the correctEnhanced endogenous securityTransmissionResource poolGuideline
The invention belongs to the technical field of network space security, and especially relates to a secure cloud service construction method and device based on mimic defense. The secure cloud service construction method based on mimic defense includes the following steps: a cloud service executor resource pool is built; an access request is forwarded to online cloud service executors, and the online cloud service executors process the access request and return processing results; the processing results are decided in a mimic way according to the mimic decision criterion, and the results after mimic decision are output as final response; and the cloud service executors are scheduled dynamically according to the mimic decision condition. A secure cloud service construction device based on mimic defense includes a building module, a forwarding and processing module, a decision response module, and a dynamic scheduling module. The invention provides a secure cloud service construction method and device based on mimic defense in order to solve security problems brought by the dependence on a single cloud service, to improve the reliability and security of cloud services, and to ensure correct response to an access request.
Owner:THE PLA INFORMATION ENG UNIV
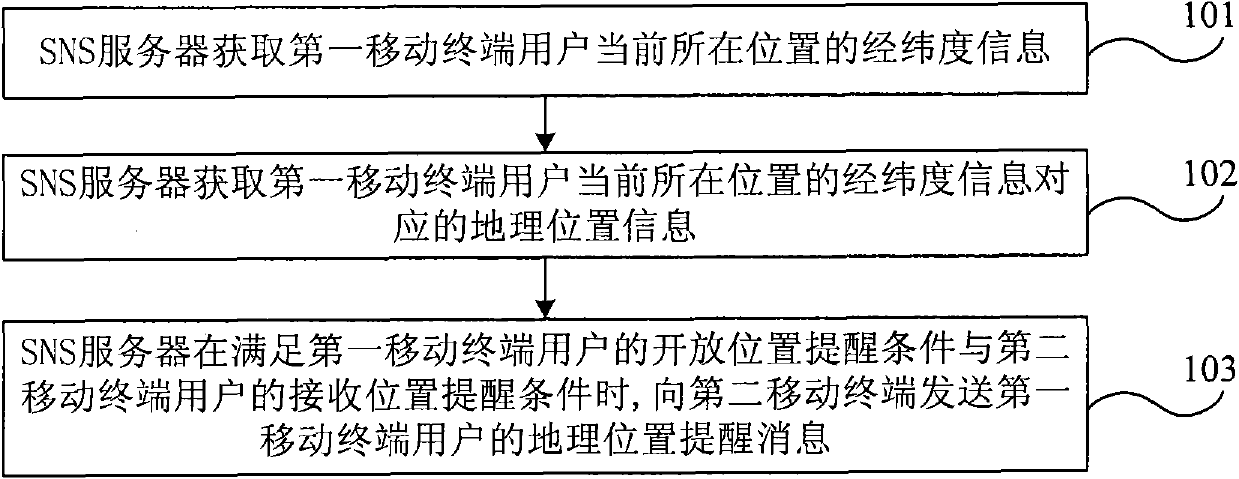
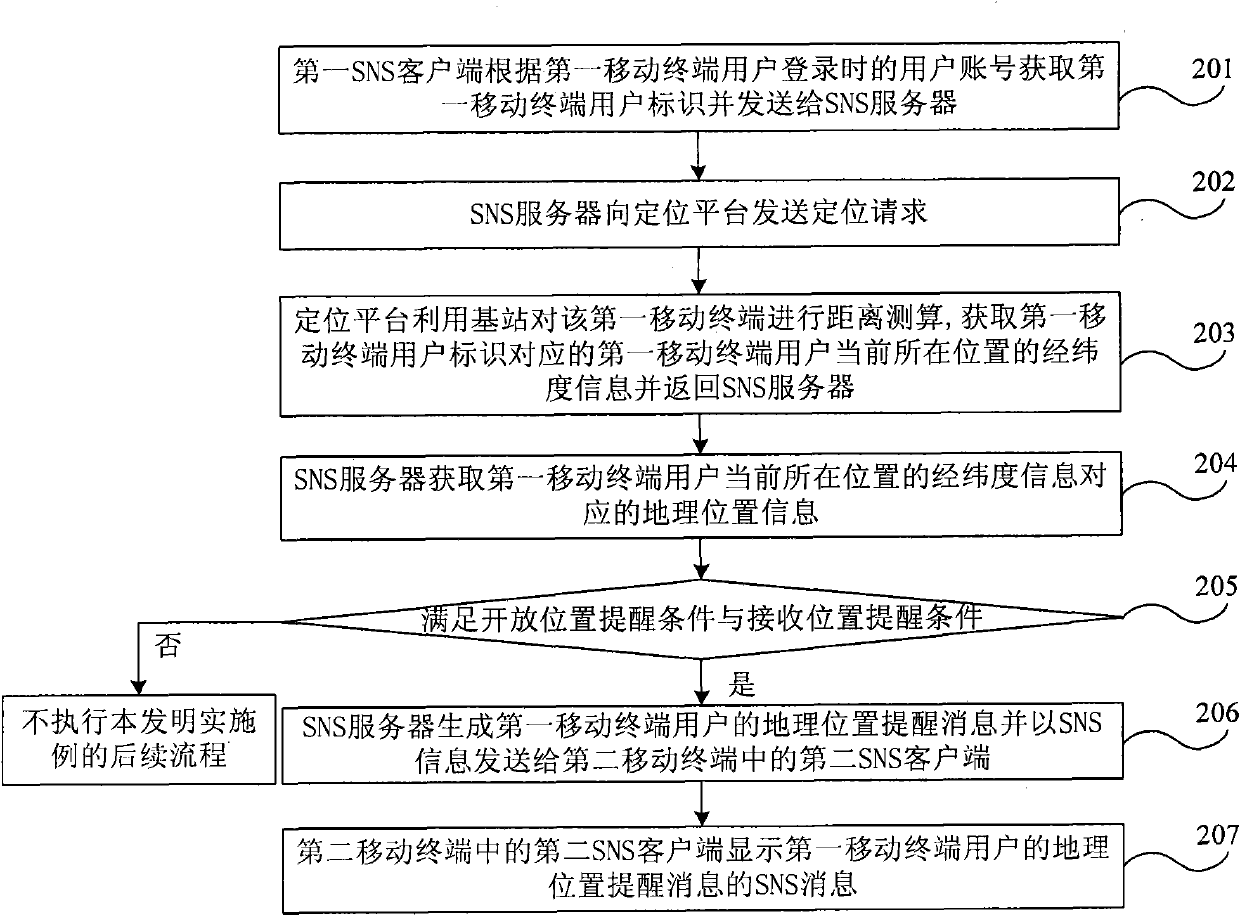
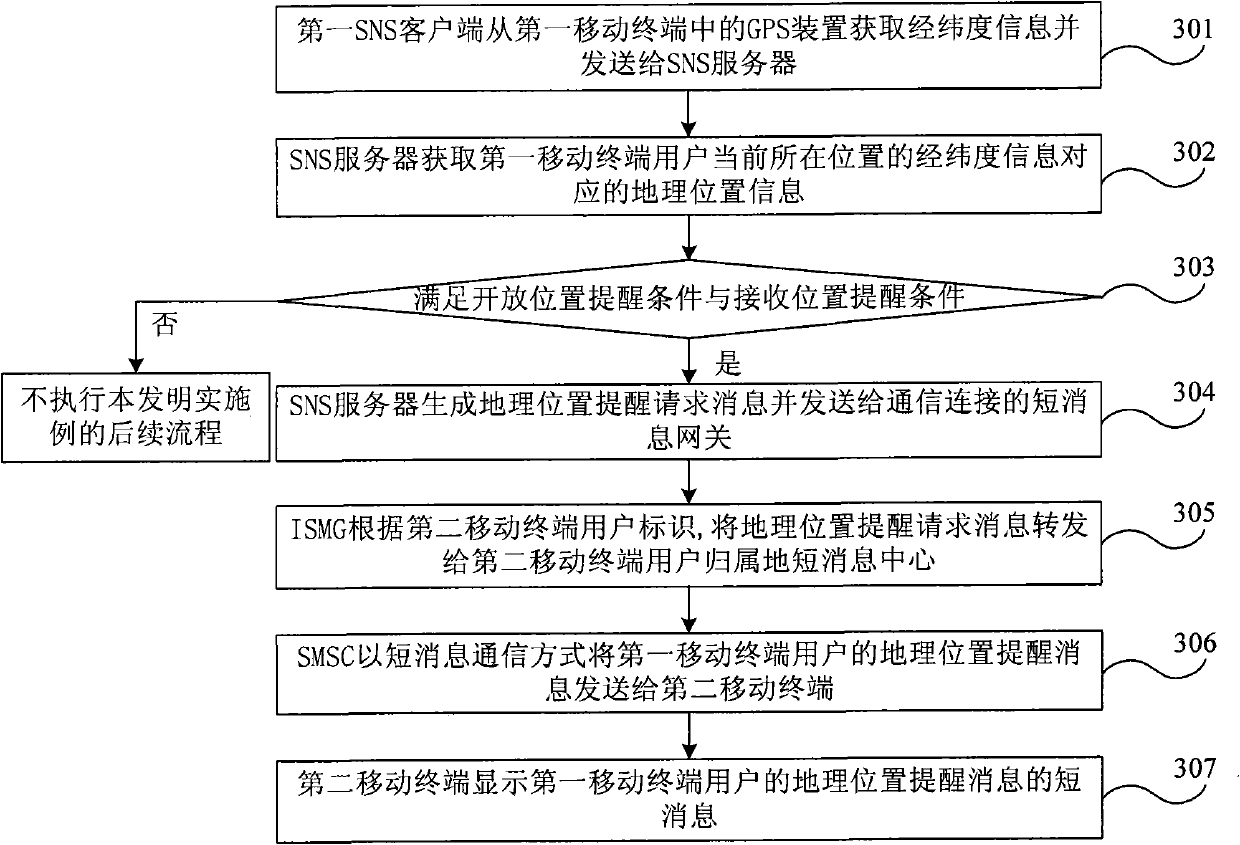
Method and system for giving prompt for indicating user positions in social network service network system
ActiveCN101997917AEnhance the sense of real distanceRich new social experienceMessaging/mailboxes/announcementsLocation information based serviceReal-time computingGeolocation
The invention discloses a method and a system for giving prompt for indicating user positions in a social network service network system. The method for giving a prompt for the user positions in the social network service network system comprises the following steps that: a social network service SNS server acquires longitude and latitude information of the current position of a first mobile terminal user, and a first mobile terminal has a first SNS client; the SNS server acquires geographic position information corresponding to the longitude and latitude information; and when meeting the reminding condition of an opening position of the first mobile terminal user and the reminding condition of a receiving position of a second mobile terminal user, the SNS server sends geographic positionreminding information of the first mobile terminal user to a second mobile terminal. In the embodiment of the invention, when one user enters network space of the other user in the SNS network system, the other user is reminded in time, so that the communication between the two users can be performed in time.
Owner:CHINA TELECOM CORP LTD
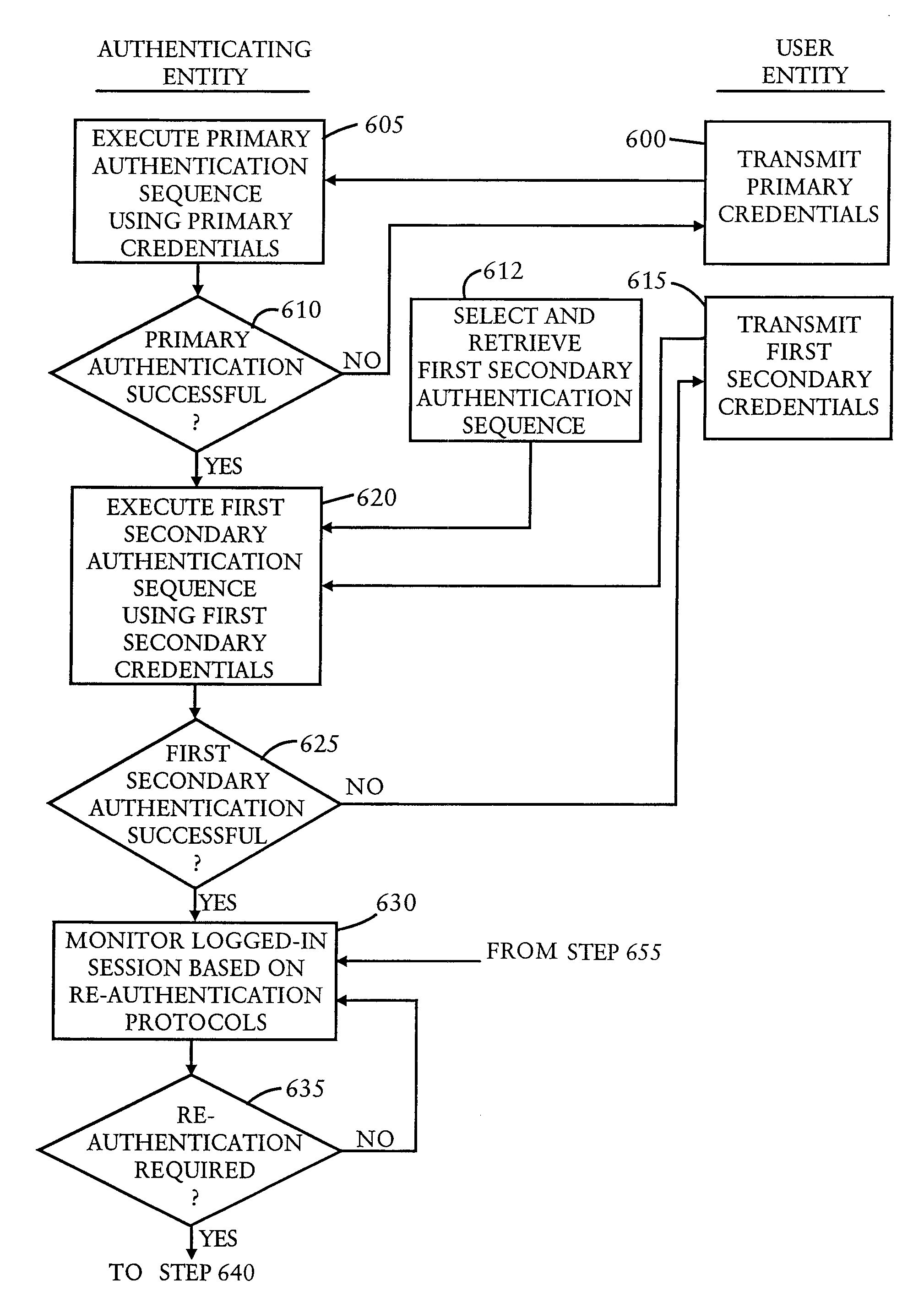
Flexible and adjustable authentication in cyberspace
ActiveUS7886346B2Digital data processing detailsMultiple digital computer combinationsCyber SpaceAuthentication
To authenticate a user of a communications network, credentials from the user are centrally receiving. An authentication sequence is retrieved from a plurality of retrievable authentication sequences, and the retrieved authentication sequence is performed to authenticate the user based on the received credentials.
Owner:VMWARE INC
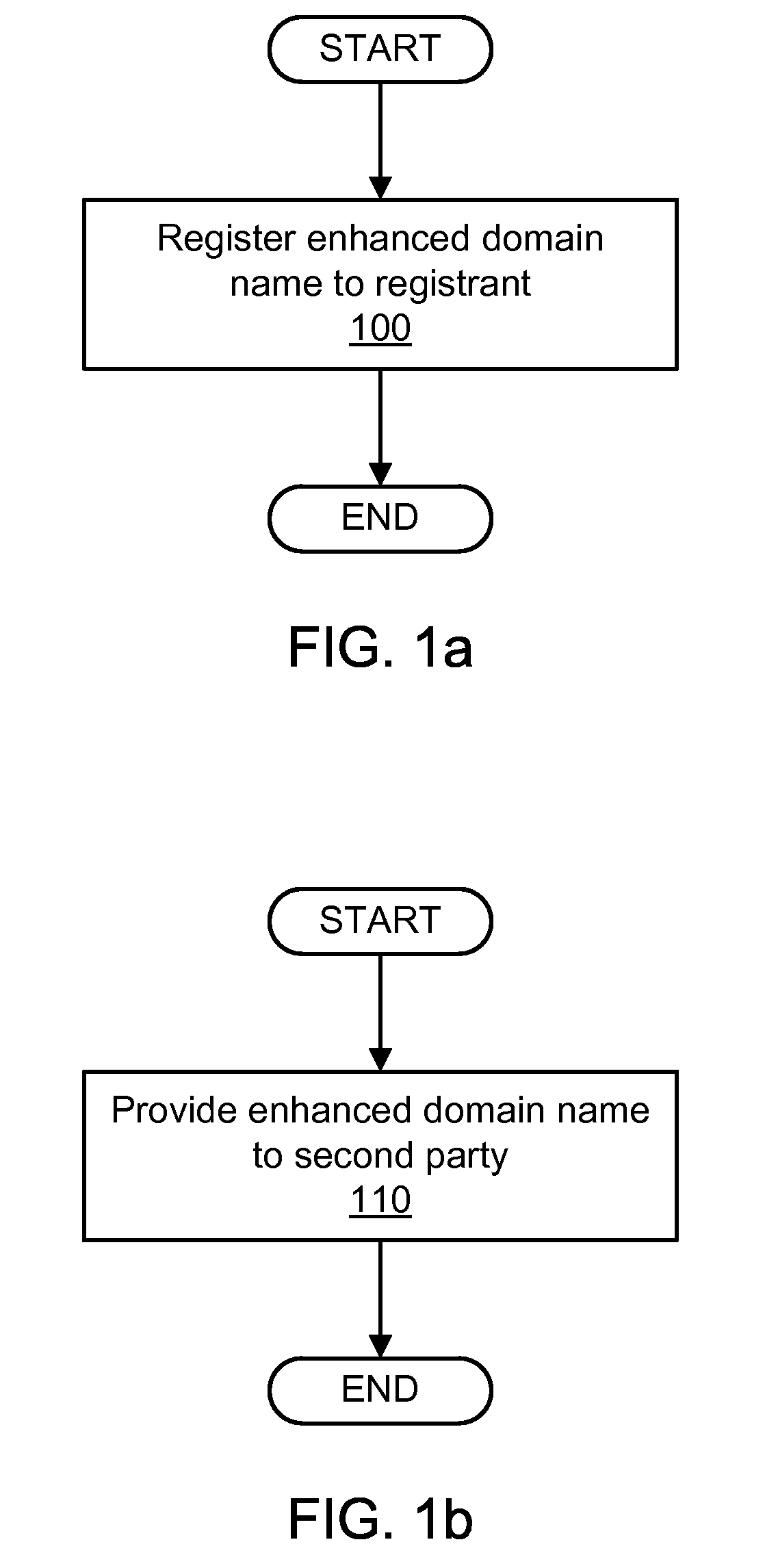
Enhanced domain name generation and registration
ActiveUS8301743B2Function increaseMultiple digital computer combinationsTransmissionDomain nameWeb space
Methods of the present inventions allow for generating and providing an enhanced domain name. An exemplary method may comprise providing an enhanced domain to a second party. The enhanced domain may comprise a domain name, a web space automatically enabled and associated with the domain name, and at least one application automatically enabled and associated with the domain name.
Owner:GO DADDY OPERATING
System and method of a knowledge management and networking environment
Systems and methods of a knowledge management networking are disclosed here. In one aspect, embodiments of the present disclosure include a method, which may be implemented on a system, of hosting a web-space having a plurality of objects, the plurality of objects to include one or more of, representations of a set of users, a set of web-items, and a set of nets; wherein a net of the set of nets is a subset of the web-space comprising a sub-plurality of the plurality of objects. One embodiment can include, tracking an explicit relationship between a first set of at least two objects of the set of objects; the explicit relationship to be pre-determined by a user of the set of users, identifying an implicit relationship between a second set of at least two objects of the set of objects; the implicit relationship to be identified based on a semantic relationship between the at least two objects, and determining a default set of privacy rules governing access between the at least two objects based on one or more of the identified explicit relationship and the implicit relationship.
Owner:FIVER LLC
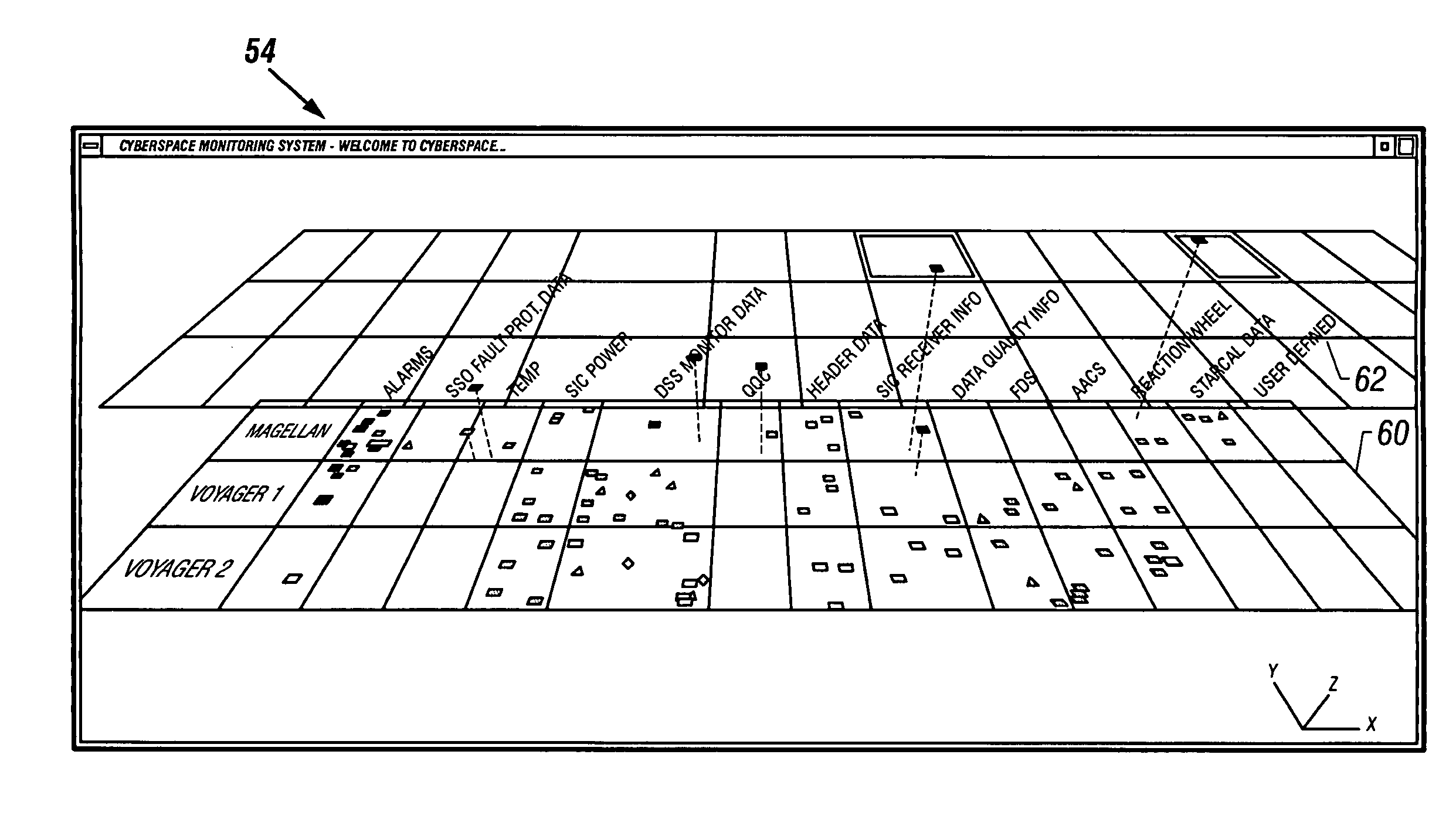
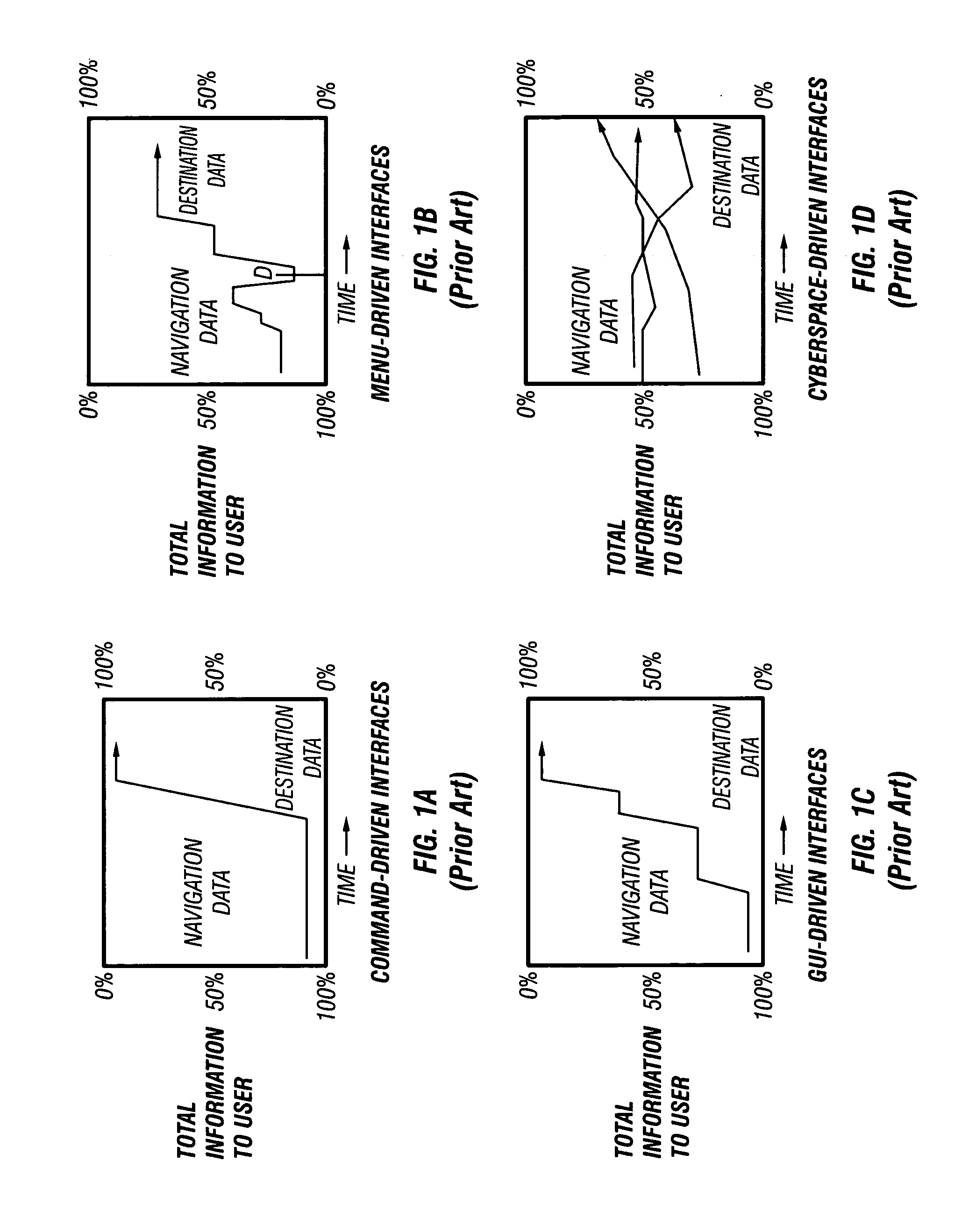
Monitoring and analysis of data in cyberspace
Information from monitored systems is displayed in three dimensional cyberspace representations defining a virtual universe having three dimensions. Fixed and dynamic data parameter outputs from the monitored systems are visually represented as graphic objects that are positioned in the virtual universe based on relationships to the system and to the data parameter categories. Attributes and values of the data parameters are indicated by manipulating properties of the graphic object such as position, color, shape, and motion.
Owner:CALIFORNIA INST OF TECH
Spatial information cluster cache pre-fetching method for network spatial information service system
ActiveCN102355490AHigh Prefetch AccuracyIn line with intensive access rulesTransmissionCache serverParallel computing
The invention discloses a spatial information cluster cache pre-fetching method for a network spatial information service system. Combined with the long-term epidemic characteristics and short-term epidemic characteristics of tile access, the method comprises the following steps of: establishing a tile transition probability estimation method and establishing a basic Markov model according to theglobal property of tile access and based on the long-term epidemic characteristics of tile access conforming to the Zipf distribution rule; based on the space-time local change of the tile access mode, predicting the tile with large follow-up state access transition probability by use of the basic Markov model, wherein the tile is used as a cache object; and finally uniformly distributing the cache objects into the cluster cache server according to the access transition probability of the pre-fetched tile. In the method, the global property of the tile access mode as well as the space-time local change of the tile access mode are taken into consideration so that the cache pre-fetching object is relatively stable and can adapt to the access distribution change; and thus, the hit rate is relatively high, the cache replacement frequency can be reduced, and the stability and service efficiency of the cluster cache system are improved.
Owner:WUHAN UNIV
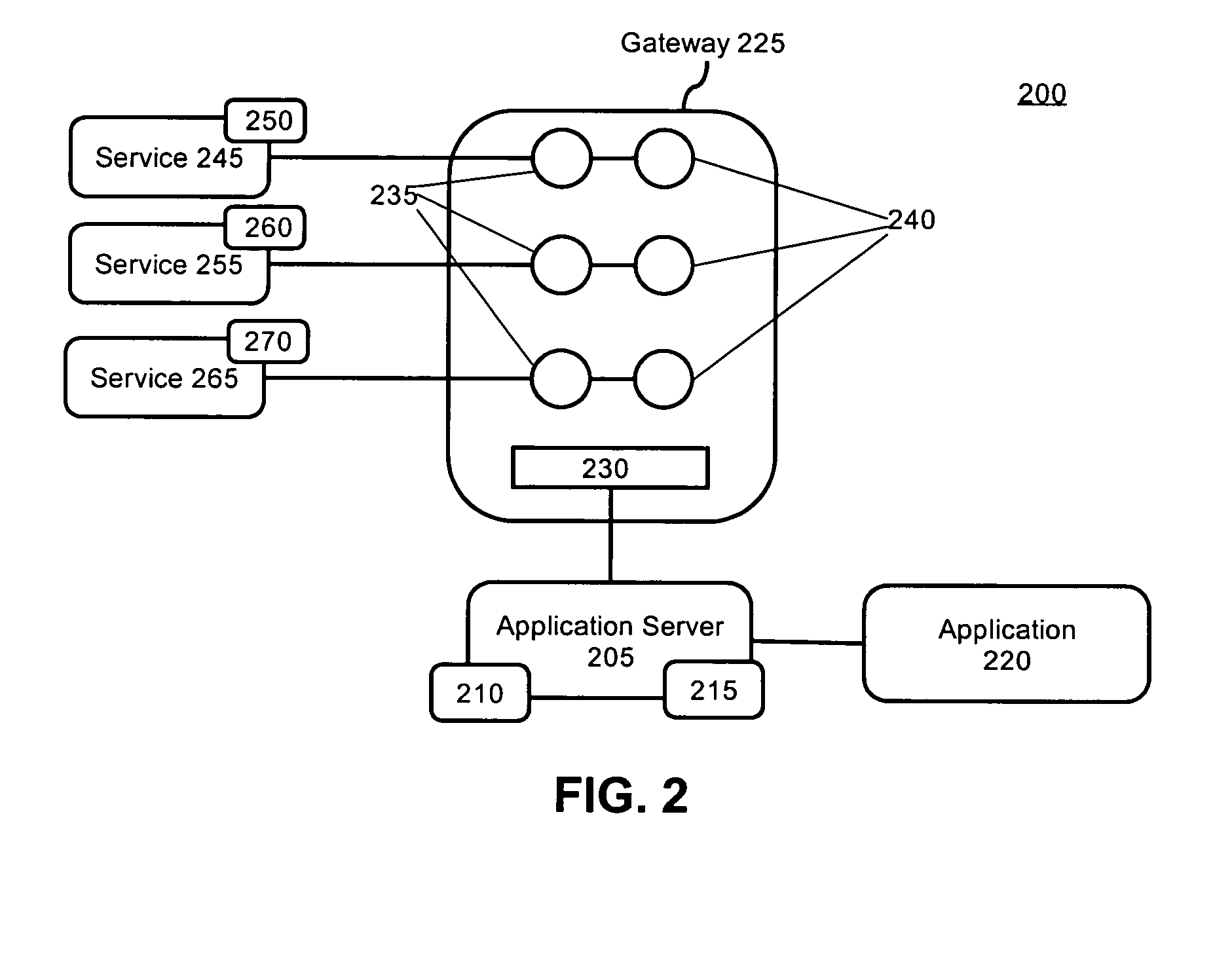
Providing web services from a service environment with a gateway
ActiveUS20050114437A1Multiple digital computer combinationsNetwork connectionsApplication serverWeb service
A method for providing Web services can include the step of registering a Web service with a service provider. The Web service can be installed within a service environment. A request for the Web service can be sent by a service user to an application server disposed within an application environment. The network space of the application environment can be different from the network space of the service environment. The application server can access the requested Web service using a gateway, such as a Parlay gateway. Once the Web service is accessed by the application server, service data for the Web service can be transported between the application server and the service user.
Owner:ACER INC
Honeypot defense method and system based on mimicry defense, equipment and medium
The invention discloses a honeypot defense method and system based on mimicry defense, equipment and a medium, which are applied to the technical field of network security. A virtualization managementsubsystem comprises a mirror image management module, a honeypot management module, a virtual network management module and a control scheduler which are connected in sequence, the mirror image management module constructs a mimicry honeypot mirror image through a KVM virtual machine mirror image technology, a plurality of virtual high-interaction honeypots and a mimicry honeypot system are obtained, and the honeypots are mimicry honeypots; the honeypot management module manages the honeypots and monitors the state of the honeypots; the virtual network management module controls the honeypotsystem to perform data access and network communication; and a control scheduler dynamically switches the mimicry honeypots and the network according to the output judgment result of the mimicry honeypots. According to the invention, mimicry defense is combined with the honeypot system, so that the security and controllability of network space security defense are improved.
Owner:PURPLE MOUNTAIN LAB +1
Cyber gene identification technology based on entity features in cyber space
ActiveUS8832808B2Accurate verificationDigital data processing detailsUnauthorized memory use protectionInternet privacyCyber Space
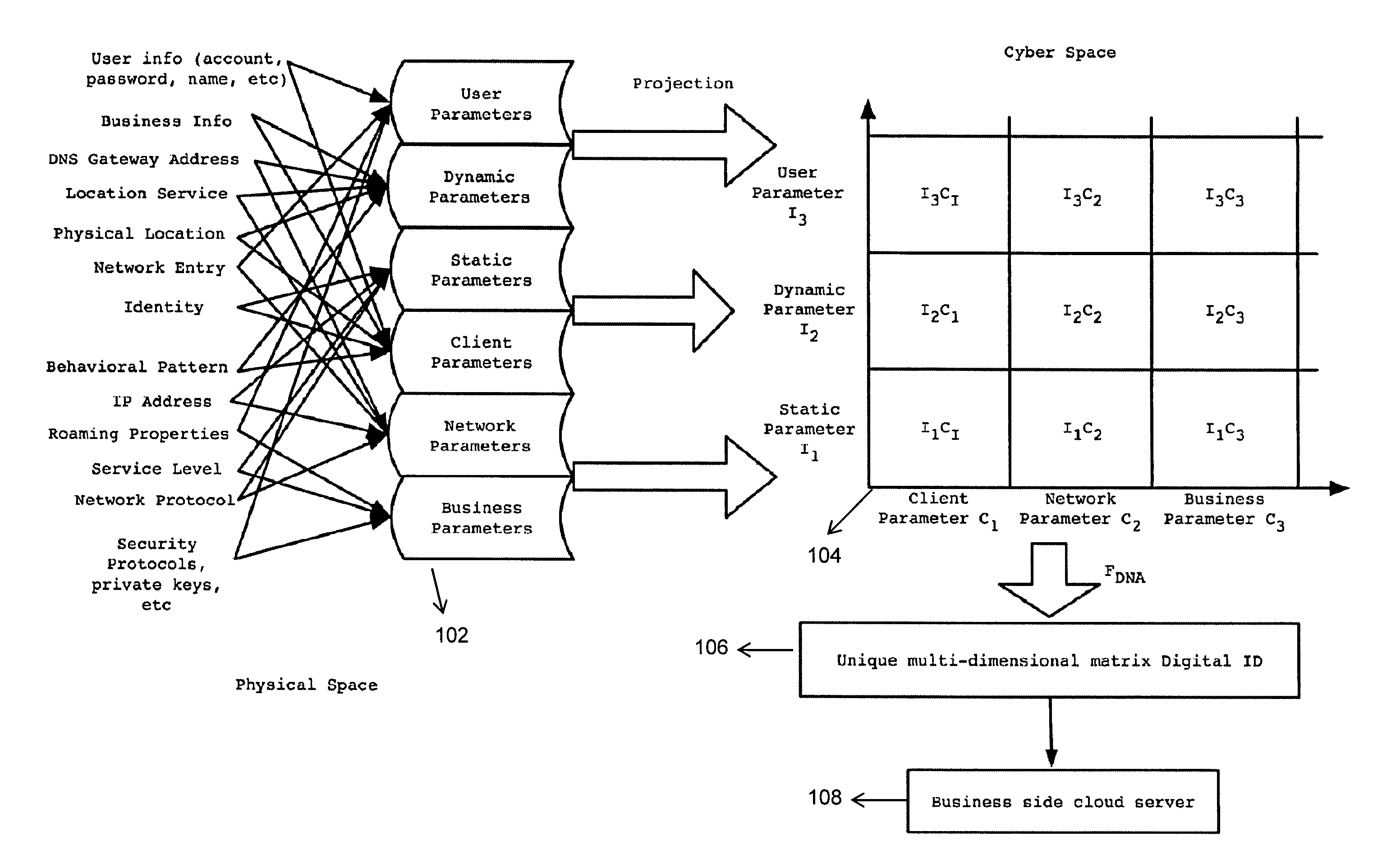
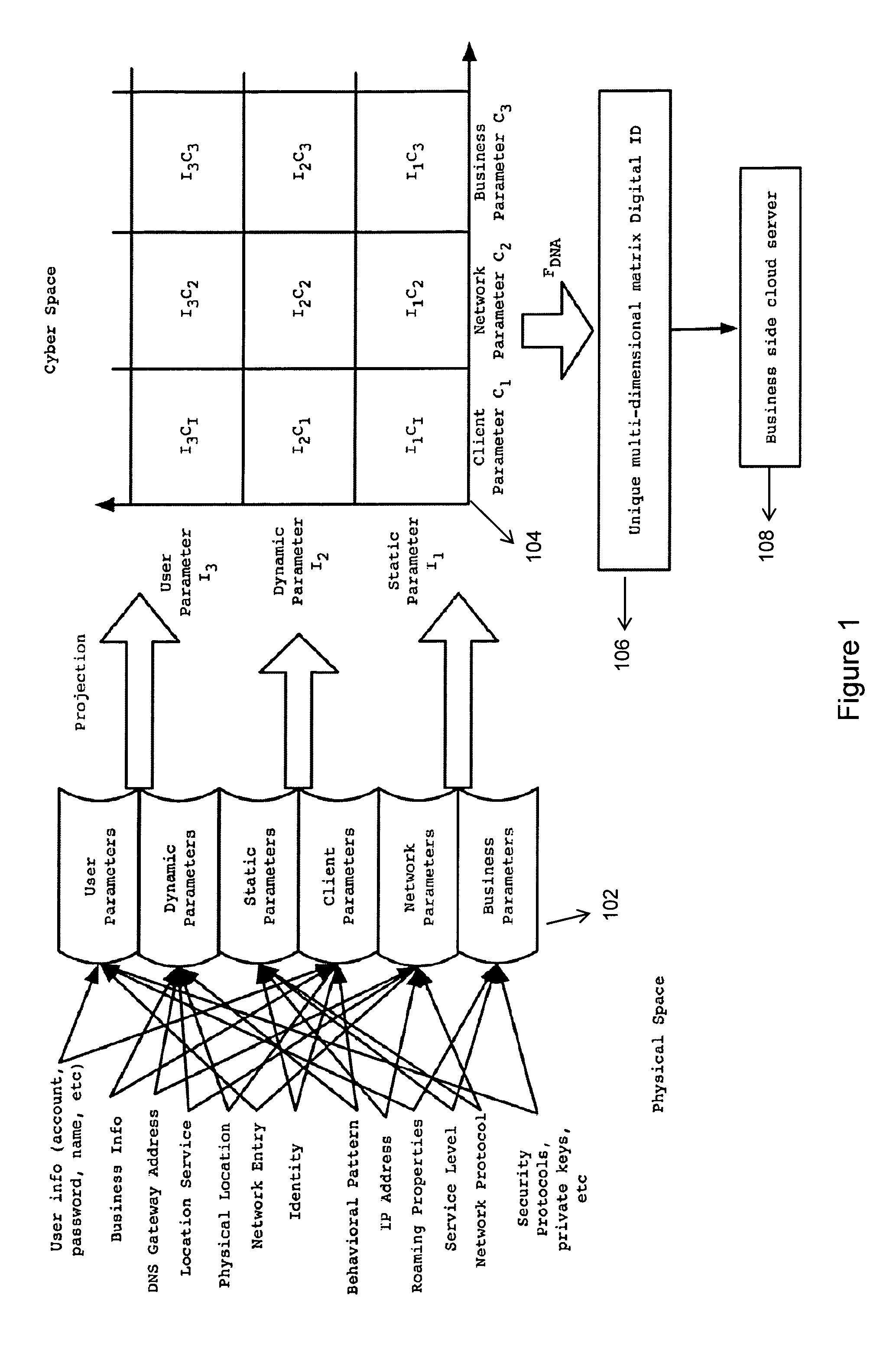
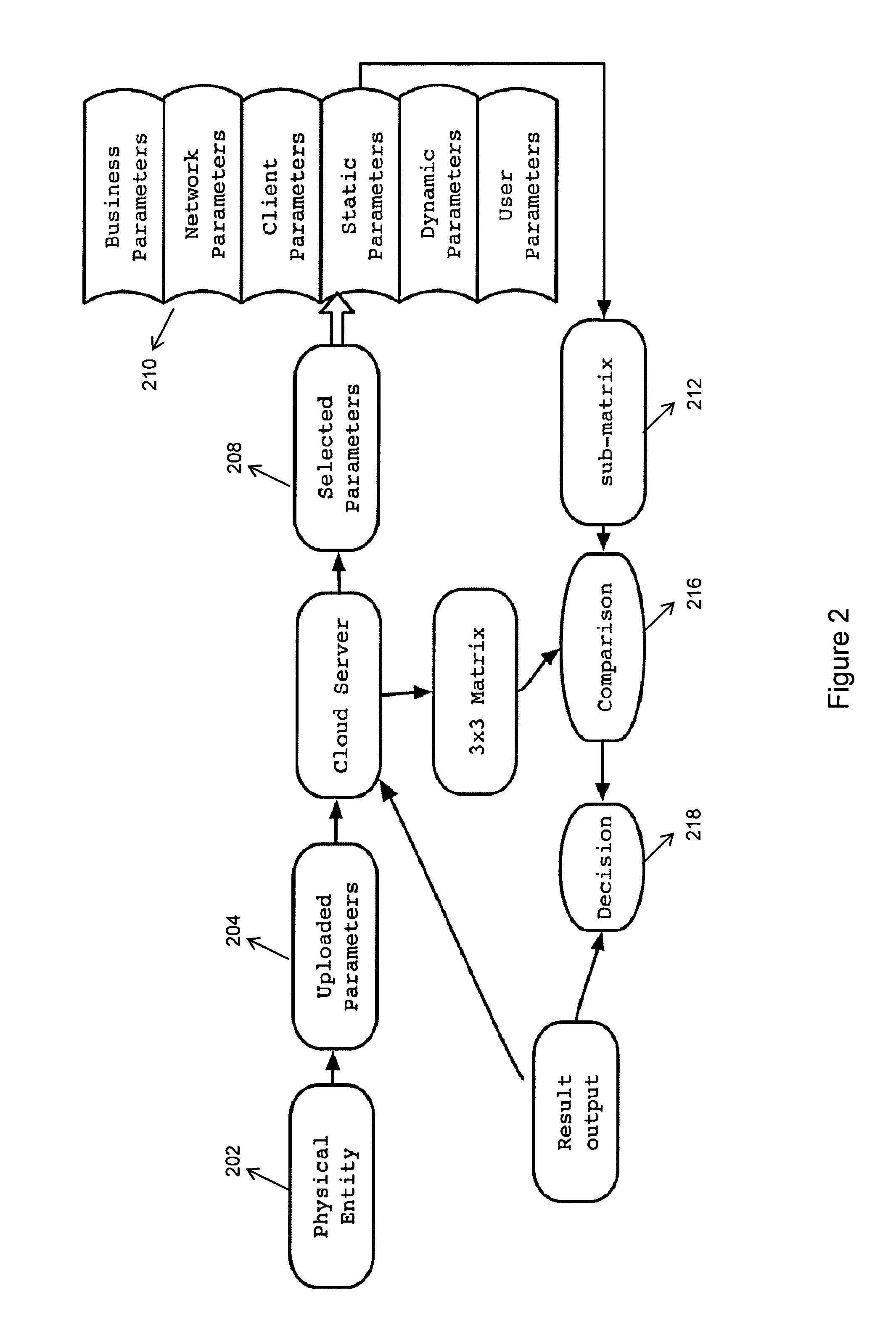
A new identification (ID) technology comprising unified and standardized object identification within Cyber Space is disclosed based upon intrinsic properties of the entity to be identified. This Cyber Gene ID (or Cyber ID) technology extracts intrinsic information from either the physical users or their cyberspace counterparts, and such information is categorized into client parameters, dynamic parameters, static parameters, cloud parameters, connection parameters and user parameters.
Owner:JIANGSU DIGITAL DNA TECH CO LTD
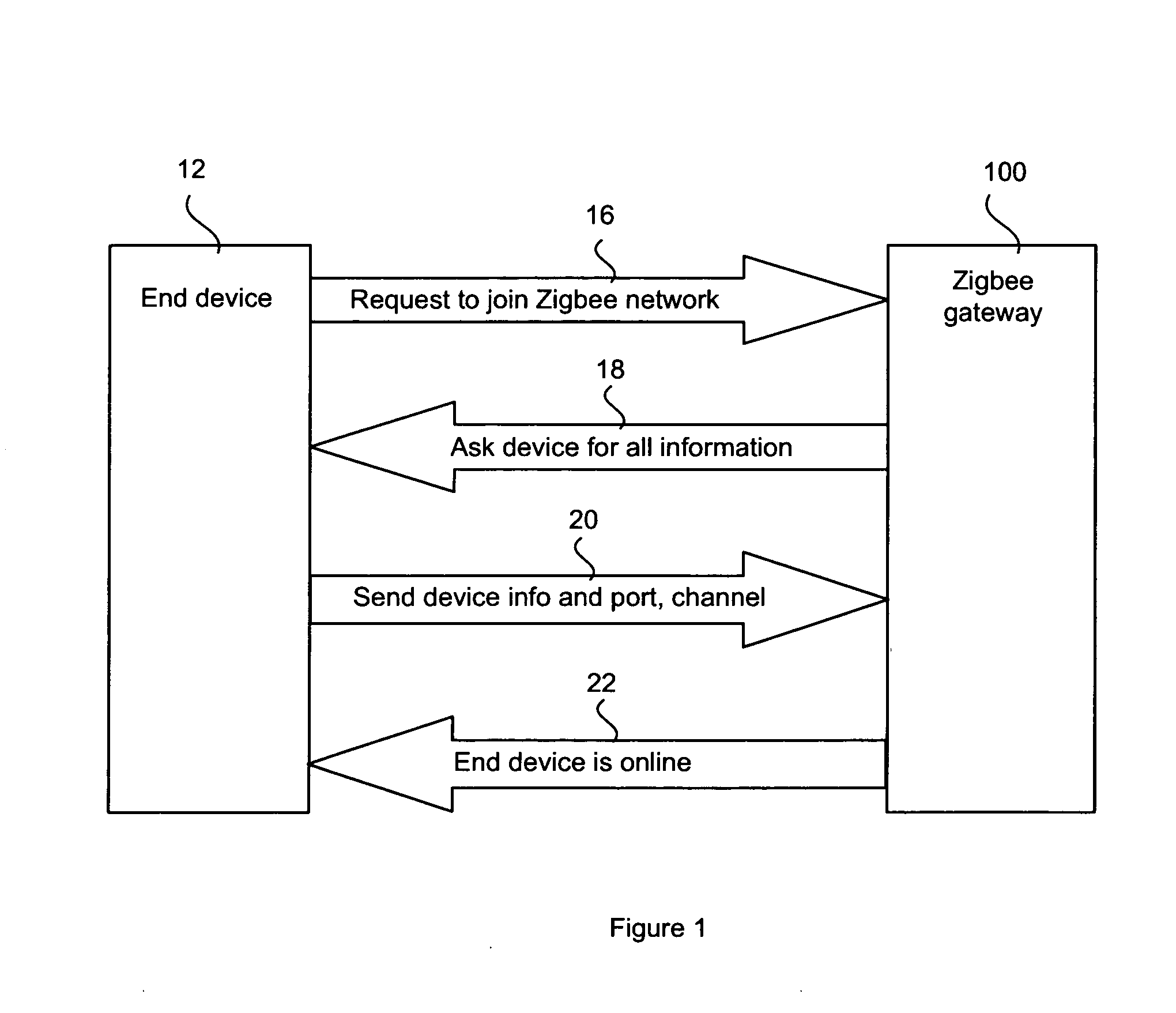
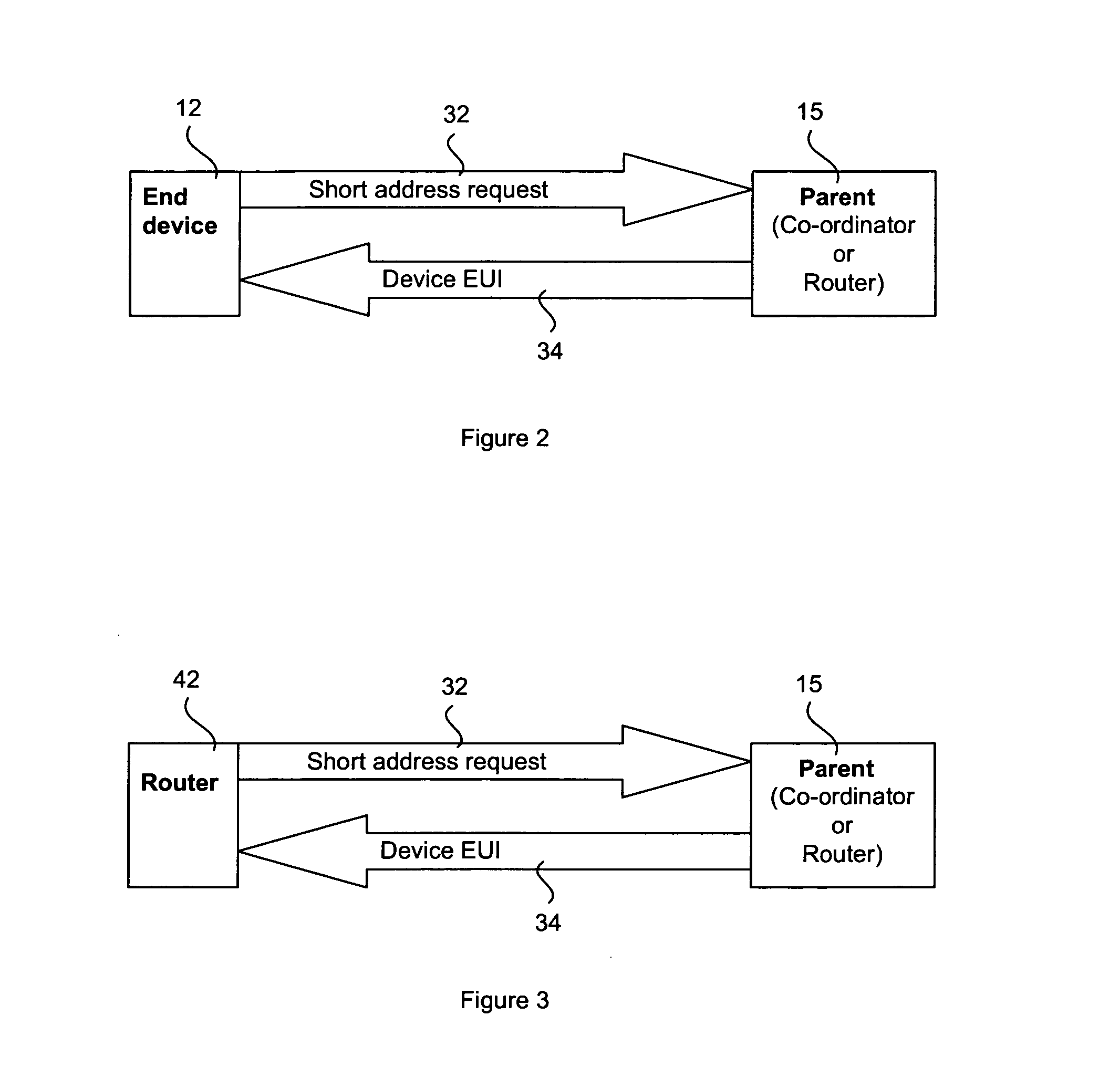
Device roaming on a zigbee network
InactiveUS20090094349A1Function increaseEnergy efficient ICTError prevention/detection by using return channelTerminal equipmentRanking
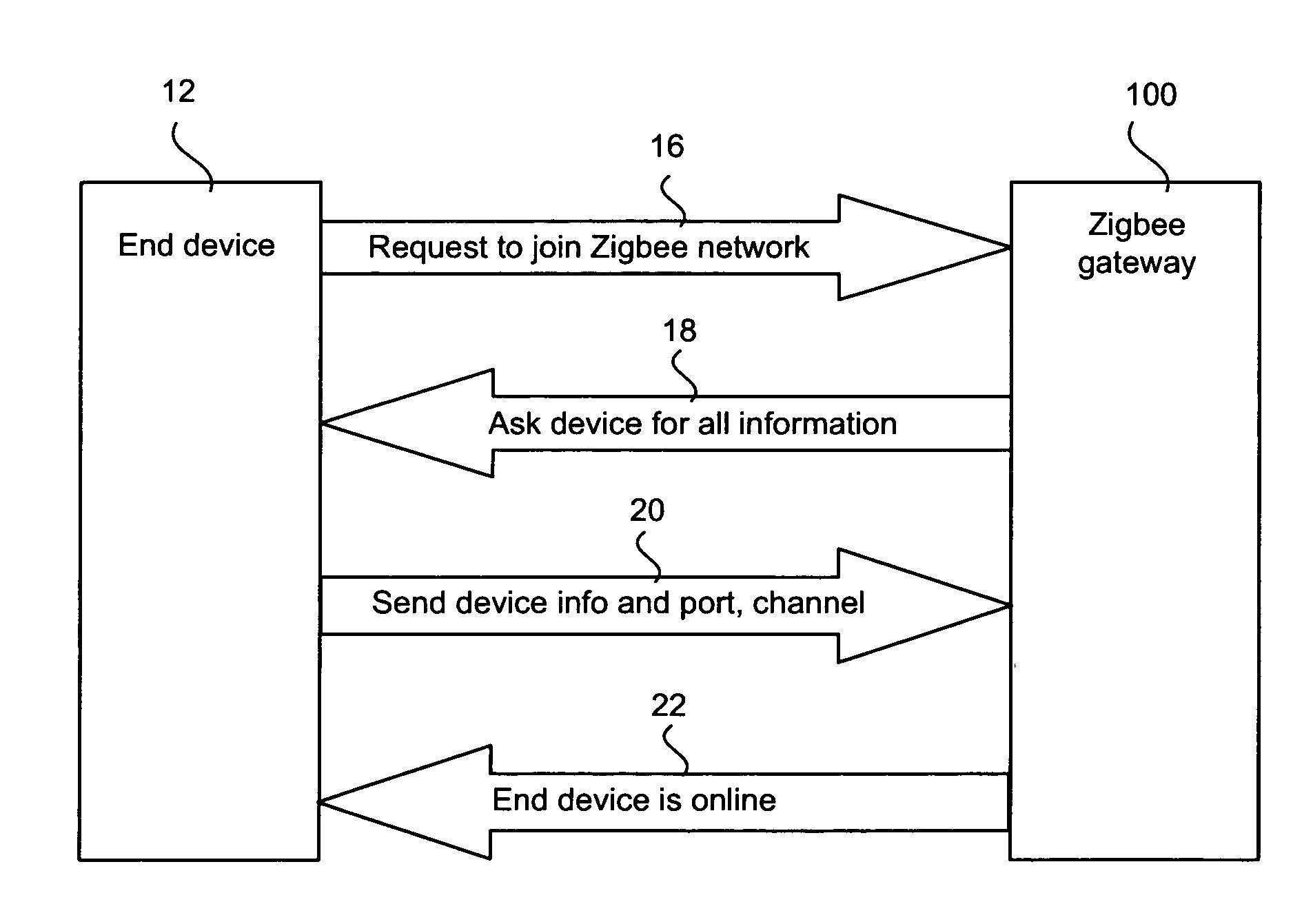
An end device in a Zigbee network space is configured to roam between available Zigbee networks. When the end device determines that a quality of a current connection has fallen below a minimum threshold, the end device evaluates the network space for available networks. The end device stores a list of Zigbee networks that it is authorized to join and joins the most preferred Zigbee network, as determined by, for example, a signal strength or a stored network ranking.
Owner:AMX LLC
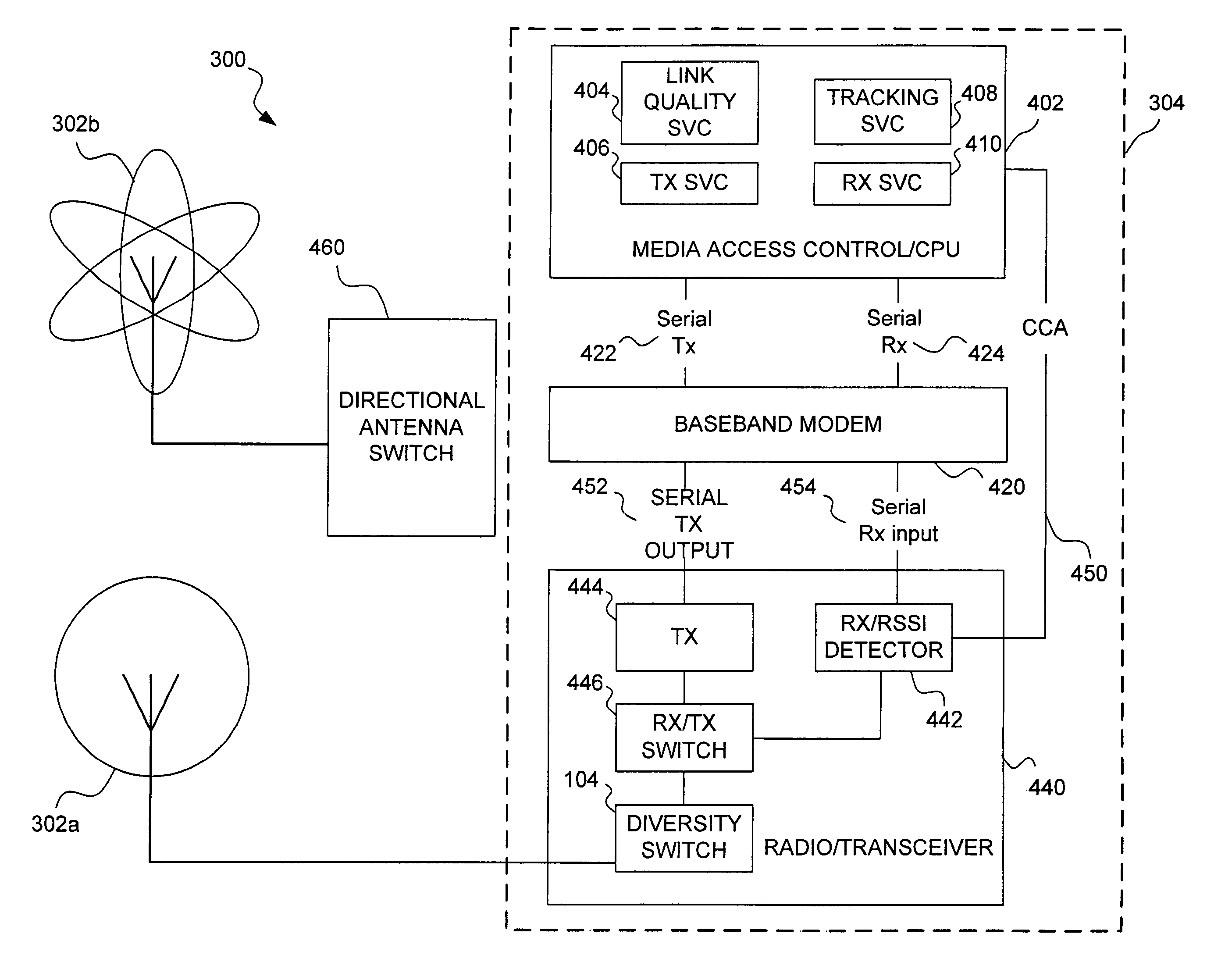
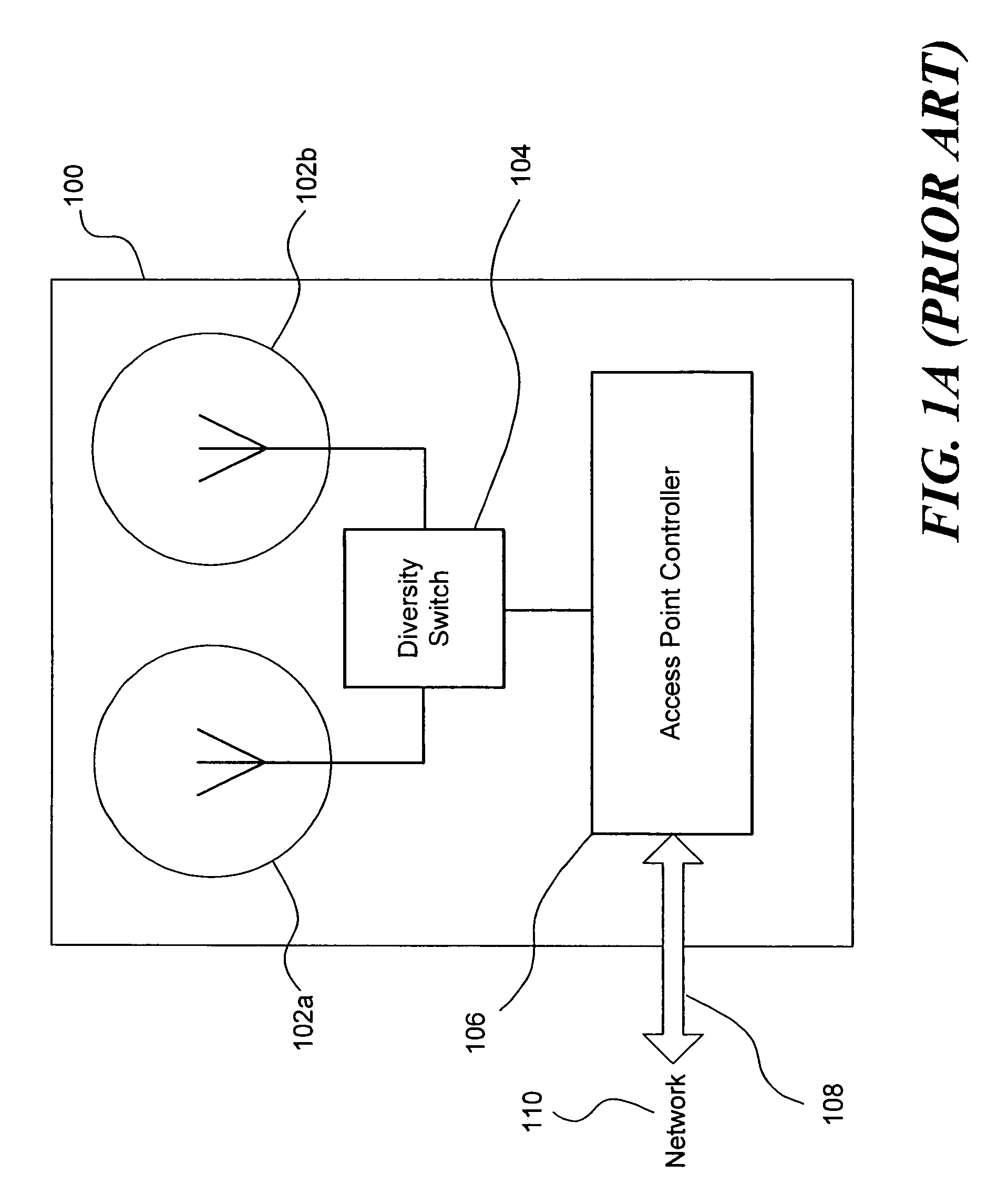
Multi-access system and method using multi-sectored antenna
InactiveUS7359679B2High gainFacilitate communicationDiversity/multi-antenna systemsTransmission noise suppressionOmnidirectional antennaLow data rate
A wireless access point is equipped with both an omnidirectional antenna and a directable antenna that can be selectively directed to any of a plurality of directional spaces overlapping the network space served by the omnidirectional antenna. The directable antenna is directed to an optimal directional space for a client when the access point is communicating with the client at a high data rate. The access point can intermittently exchange information with other clients using the omnidirectional antenna. The omnidirectional antenna enables broadcast signals to be transmitted to any client in the entire network space, but at a lower data rate. A preferred data rate and an optimal client directional space are re-determined periodically or as necessary based on parameters such as the data rate, signal strength, and rate of success in communicating data.
Owner:MICROSOFT TECH LICENSING LLC
Quay berth-based intelligent supervision method and system
InactiveCN102831787ARealize intelligent analysis and alarmMarine craft traffic controlDynamic monitoringInformation networks
The invention discloses a quay berth-based intelligent supervision method and system. The method comprises the following steps of: establishing a cyber space covering the south China Sea and inland river channel by combining the public security information network and the frontier inspection intranet based on the existing GPS (Global Positioning System), AIS (Automatic Identification System) and GSM (Global System for Mobile Communications) wireless transmission positioning technology; and performing dynamic strict supervision on the state of the track, speed, leaning, anchorage and the like of the ship in the cyber space by use of an independently developed dynamic supervision application platform. Through the invention, each state of the ship in the whole navigation life cycle is accurately mastered by use of the ship whole-course dynamic monitoring technology, and the whole course of real-time tracking management is performed on the ship navigation condition according to laws.
Owner:广东省公安边防总队 +1
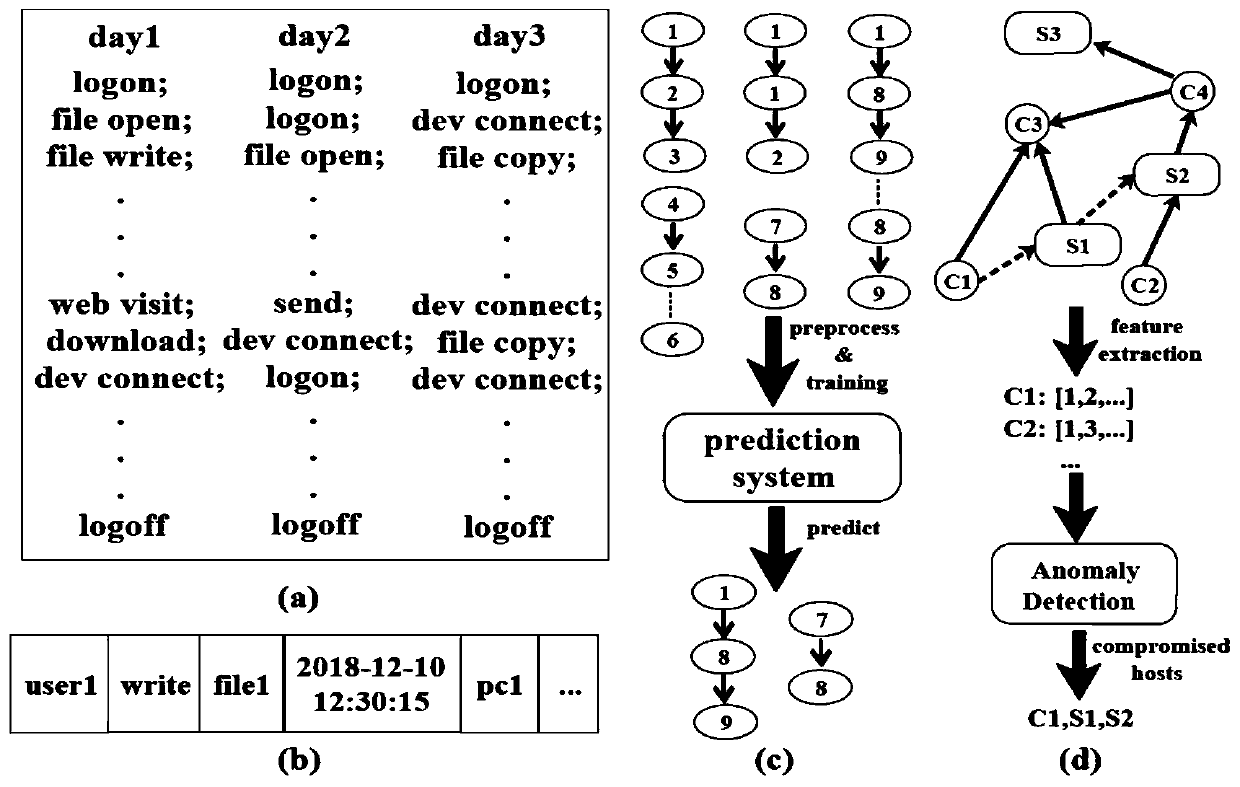
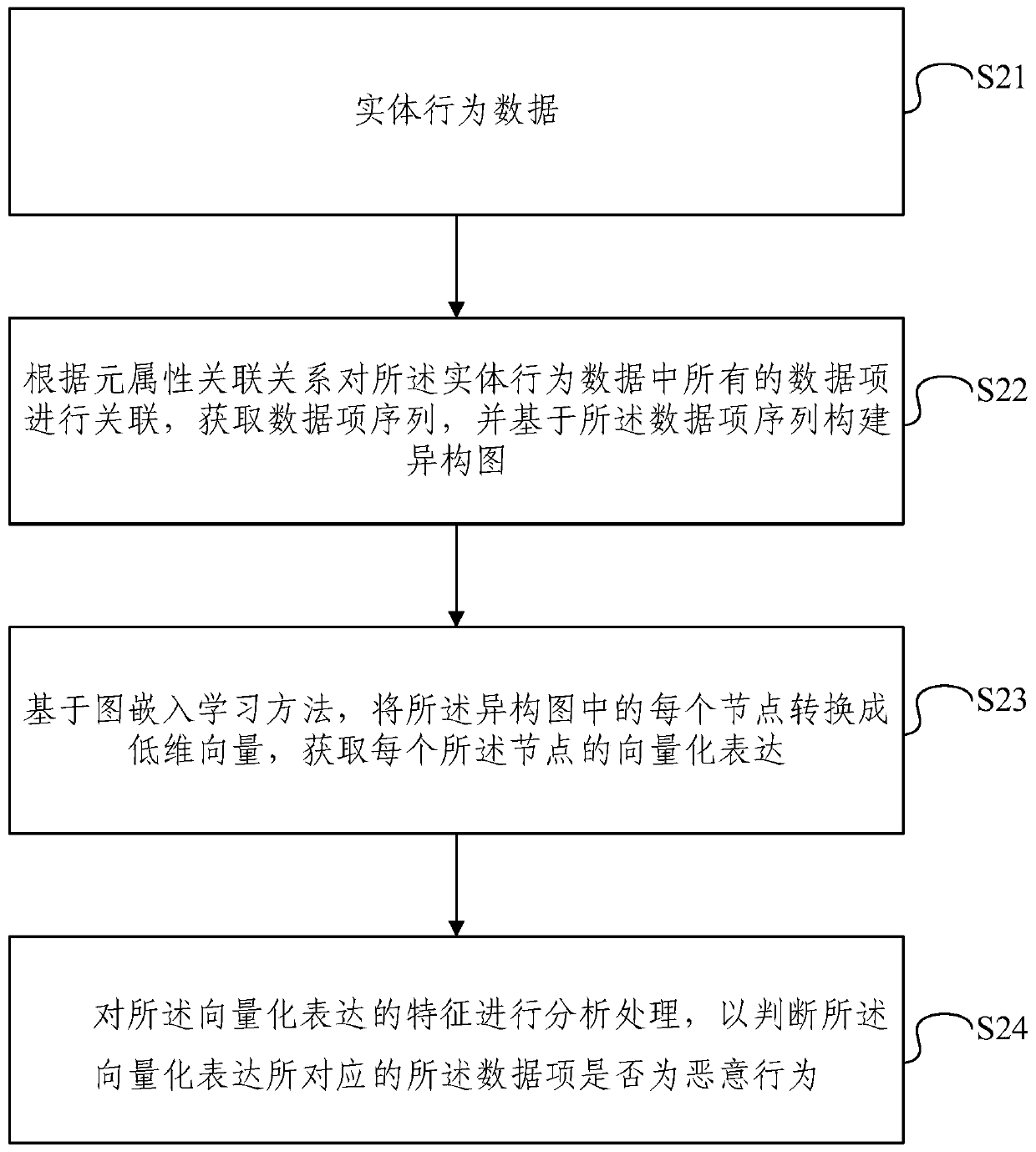
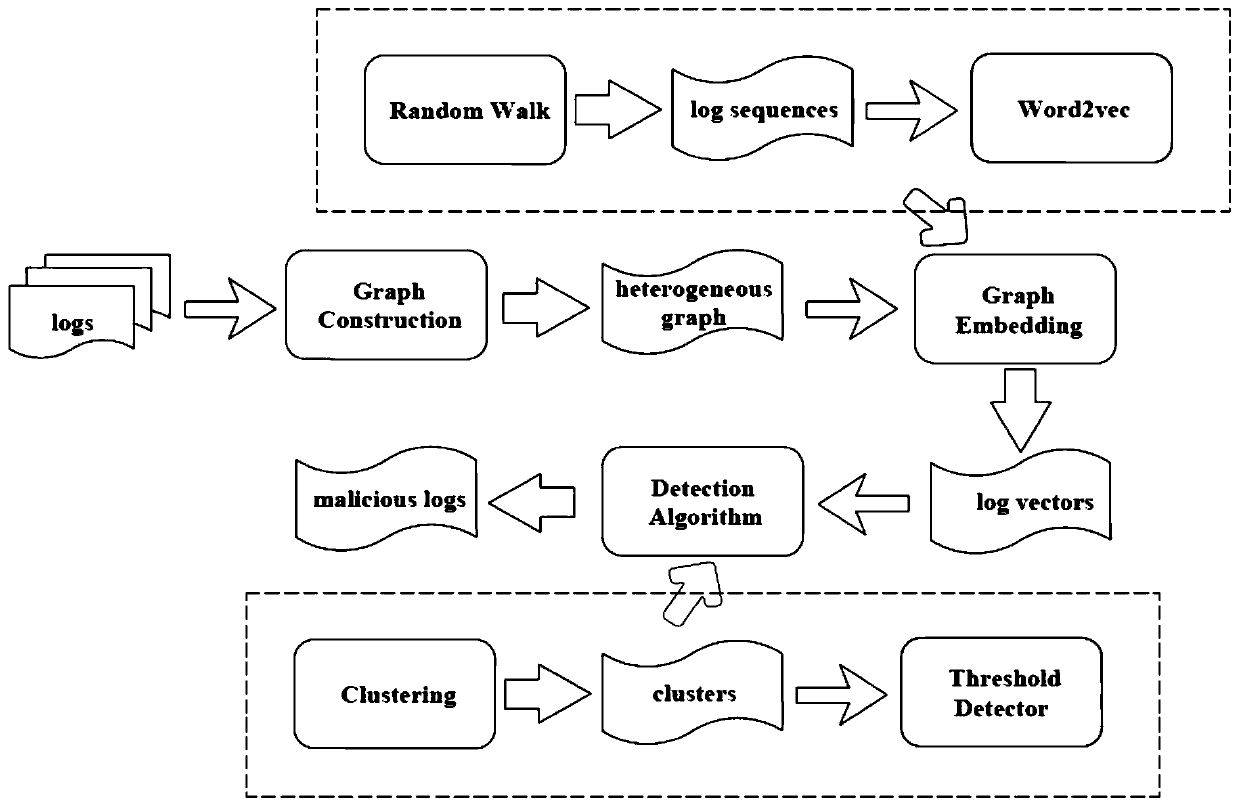
Network space security threat detection method and system based on heterogeneous graph embedding
ActiveCN110958220AHigh precisionEasy to detectCharacter and pattern recognitionTransmissionTheoretical computer scienceLabeled data
The embodiment of the invention provides a heterogeneous graph embedding-based network space security threat detection method and system. The method comprises the steps of obtaining entity behavior data; associating all data items in the entity behavior data according to the meta-attribute association relationship to obtain a data item sequence, and constructing a heterogeneous graph based on thedata item sequence; converting each node in the heterogeneous graph into a low-dimensional vector based on a graph embedding learning method, and obtaining vectorized expression of each node; and analyzing and processing the features of the vectorized expression to judge whether the data item corresponding to the vectorized expression is a malicious behavior or not. According to the embodiment, the heterogeneous graph for threat detection is established, entity behavior data items are simplified and represented in a vectorized mode, data item level threat detection for network space security is provided, later manual correction is not needed, labeled data items serve as training samples, and the detection precision and the detection feasibility are effectively improved.
Owner:INST OF INFORMATION ENG CAS
Implement method of power control cognition MAC protocol based on time division multiple access (TDMA)
InactiveCN101651969AReduce the probability of collisionAchieve protectionNetwork traffic/resource managementNetwork topologiesFrequency spectrumCode division multiple access
The invention discloses an implement method of power control cognition MAC protocol based on time division multiple access (TDMA). The method comprises the following steps: adopting strict time slot division, finishing time slot allocation among node pairs by a three-way handshake manner, namely, reserving application, reserving confirmation and deciding sending; realizing collision-free transmission in node communication process; and introducing a power control mechanism to improve the reuse rate of cyber space. The method can eliminate problems of multiple channels hiding a send terminal, multiple channels hiding a receiving terminal and multiple channels exposing terminals, and can dramatically decrease the impact on network performance brought by the problem of multiple channels hidingthe send terminal. The simulation result indicates, compared with dynamic spectrum access MAC (DSA-MAC) protocol, the invention can effectively enhance network throughput and decrease access time delay with the increment of network business volume.
Owner:XI AN JIAOTONG UNIV
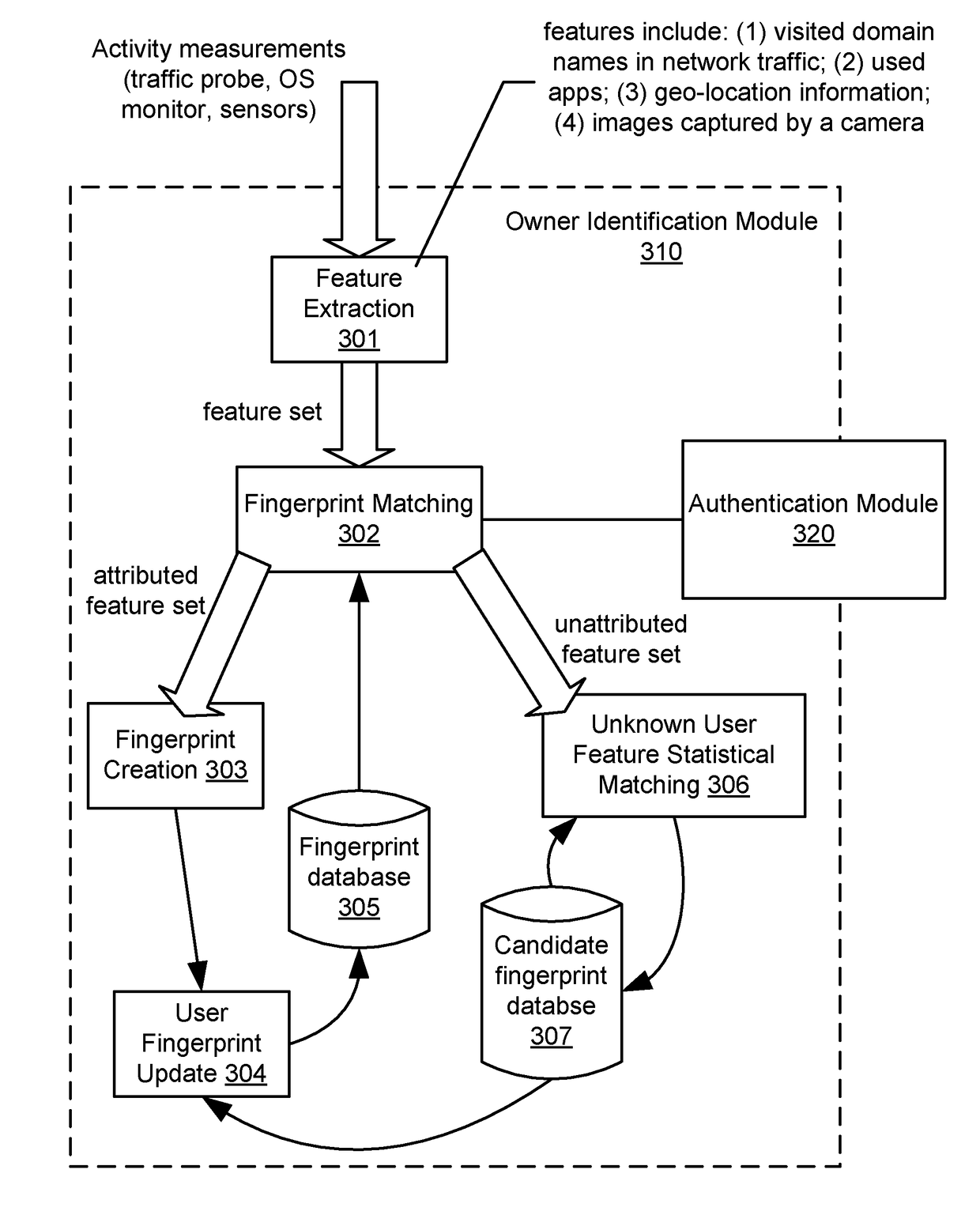
Cross identification of users in cyber space and physical world
A method for using a user device. The method includes obtaining, during a fingerprint learning phase, a historical portion of user activity data associated with user activity of a user using the user device, analyzing, by a computer processor of the user device, the historical portion to generate a fingerprint of the user, wherein the fingerprint represents characteristics of the user activity, obtaining, during a fingerprint matching phase subsequent to the fingerprint learning phase, an ongoing portion of the user activity data, analyzing, by the computer processor and based on the fingerprint, the ongoing portion to determine a match, wherein the match is determined at a time point within the fingerprint matching phase, and unlocking, by the computer processor and in response to determining the match, a locked data item for access, therein the locked data item is stored on the user device. The locked data item is associated to the user owning, assigned to, or normally and legitimately using the user device. In one embodiment, once unlocked the data item can be used to authenticate the user associated to it, i.e., the user owning, assigned to, or normally and legitimately using the user device on which the data item is stored.
Owner:THE BOEING CO
PEKS (public-key encryption with keyword search) method for lattice-based cloud stored cyphertext data under standard model
ActiveCN106789044AReaction securityResist attackKey distribution for secure communicationUser identity/authority verificationTechnical standardModular exponentiation
The invention belongs to the technical field of cyberspace security and particularly relates to a PEKS (public-key encryption with keyword search) method for lattice-based cloud stored cyphertext data under standard model. The method of the invention has no need for a random oracle so that the security of the designed PEKS method can more truly reflected; a designed cryptographic algorithm is based on assumption of LWE (learning with errors) hard problems, quantum computer attacks can be resisted effectively. The method of the invention has a need for specifying a unique cloud server to perform testing and return corresponding search results, so that no malicious servers are able to execute search test operation, and malicious server attacks are partly avoided accordingly. In addition, the algorithm can ensure that cyphertext is undistinguishable. Furthermore, in keyword cyphertext generation phase, the method of the invention needs no computing of high-overhead modular exponentiation and bilinear pairing operation, but the computing of finite linear algebraic operation, and accordingly is highly worthy of practical application in post-quantum communication environments.
Owner:SOUTHWEST PETROLEUM UNIV
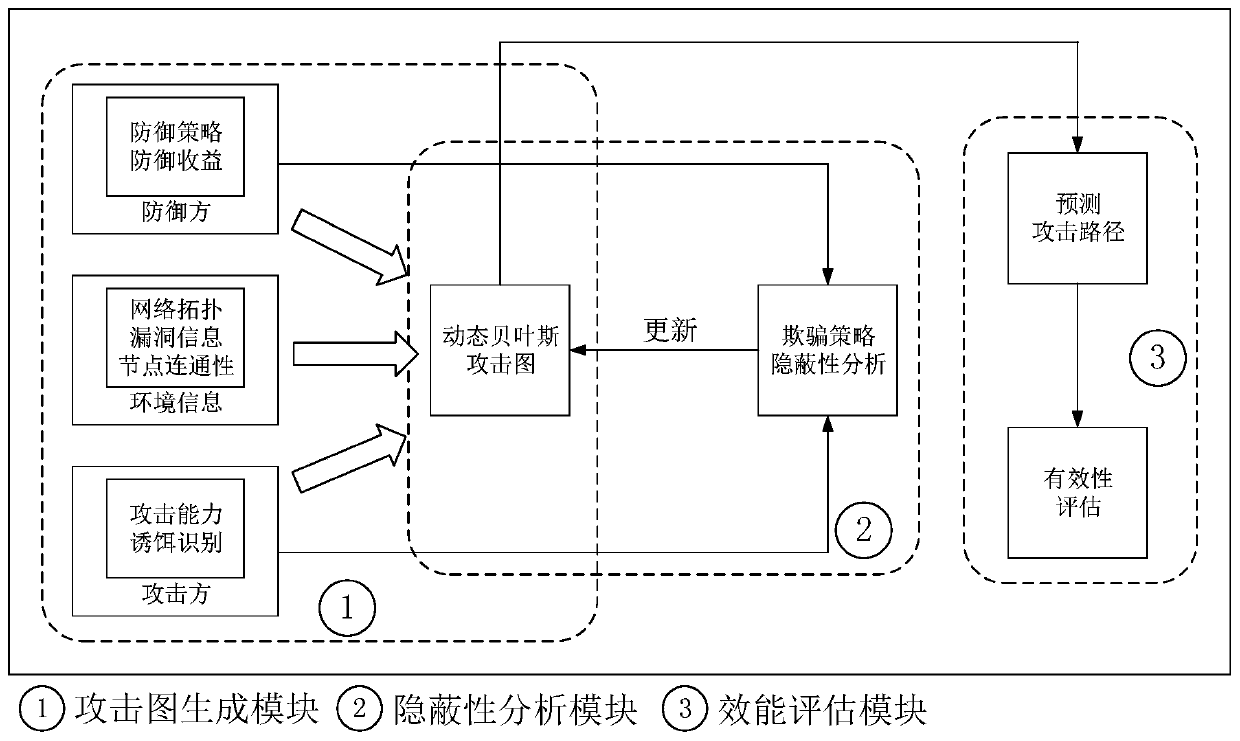
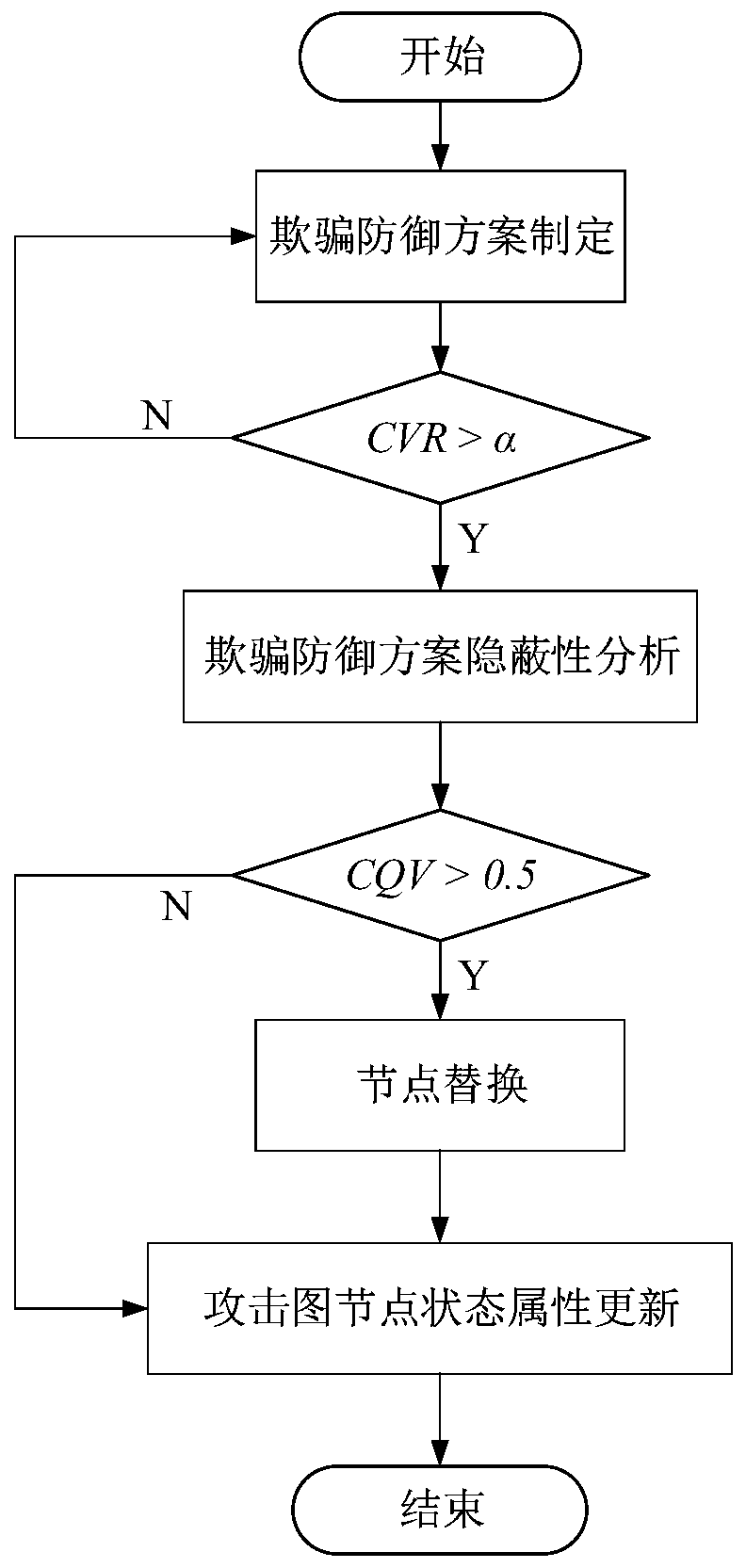
Network spoofing performance evaluation method based on dynamic Bayesian attack graph
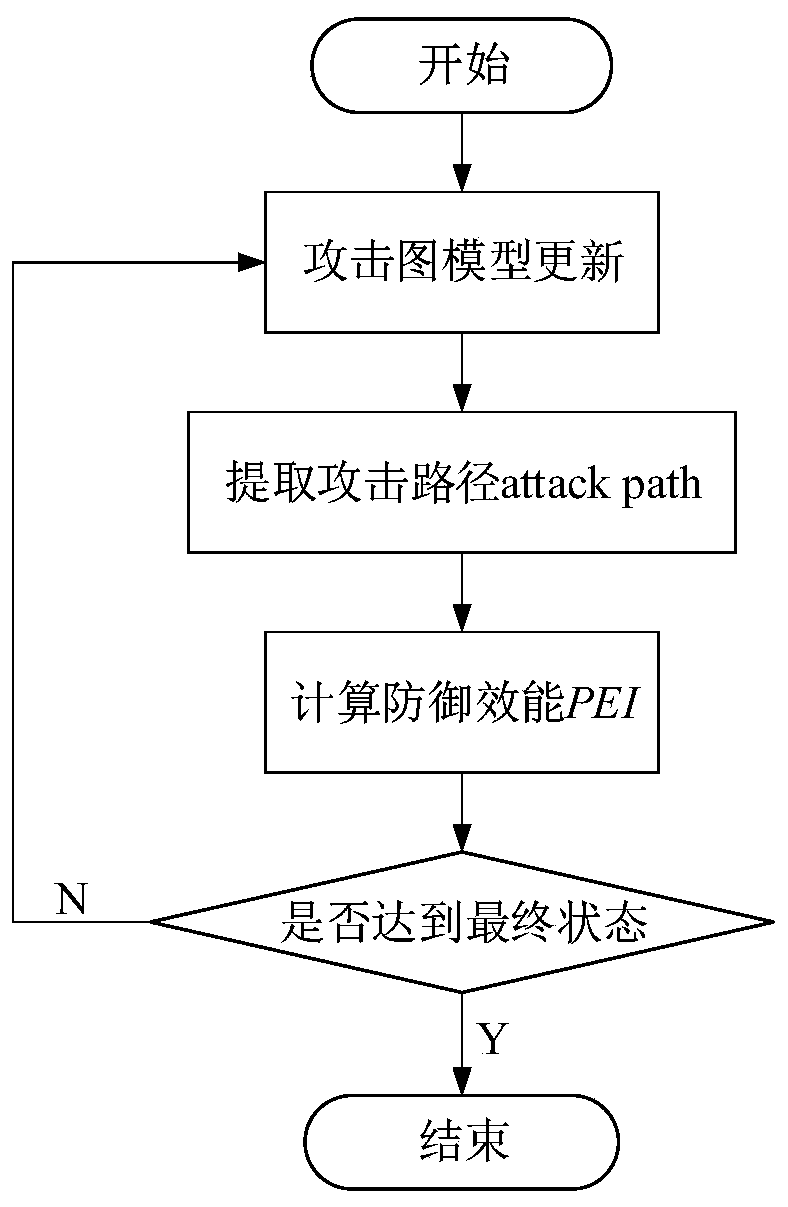
ActiveCN111371758AGuaranteed availabilityDefense Effectiveness Efficiently AssessedMathematical modelsTransmissionAttackTheoretical computer science
The invention discloses a network spoofing defense efficiency evaluation method based on a dynamic Bayesian attack graph, and belongs to the field of network space security. The method comprises the following steps: speculating attacker ability by analyzing vulnerability elements in a current network, and constructing a dynamic Bayesian attack graph model; aiming at the defense characteristics ofnetwork spoofing and counterfeiting real assets, the consistency of real nodes and bait nodes in the aspects of network characteristics, equipment fingerprints, file attributes and the like is comprehensively compared, so that a spoofing scheme is subjected to concealment analysis, and whether a defense strategy can achieve an expected effect or not is judged; and updating the attack graph model according to the analysis result and the attack and defense confrontation information, and giving a quantitative index to evaluate the effectiveness of deception defense. The method can be integrated on a server serving as a control center, other nodes in the network do not need to be modified, and the method has good applicability.
Owner:SOUTHEAST UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com