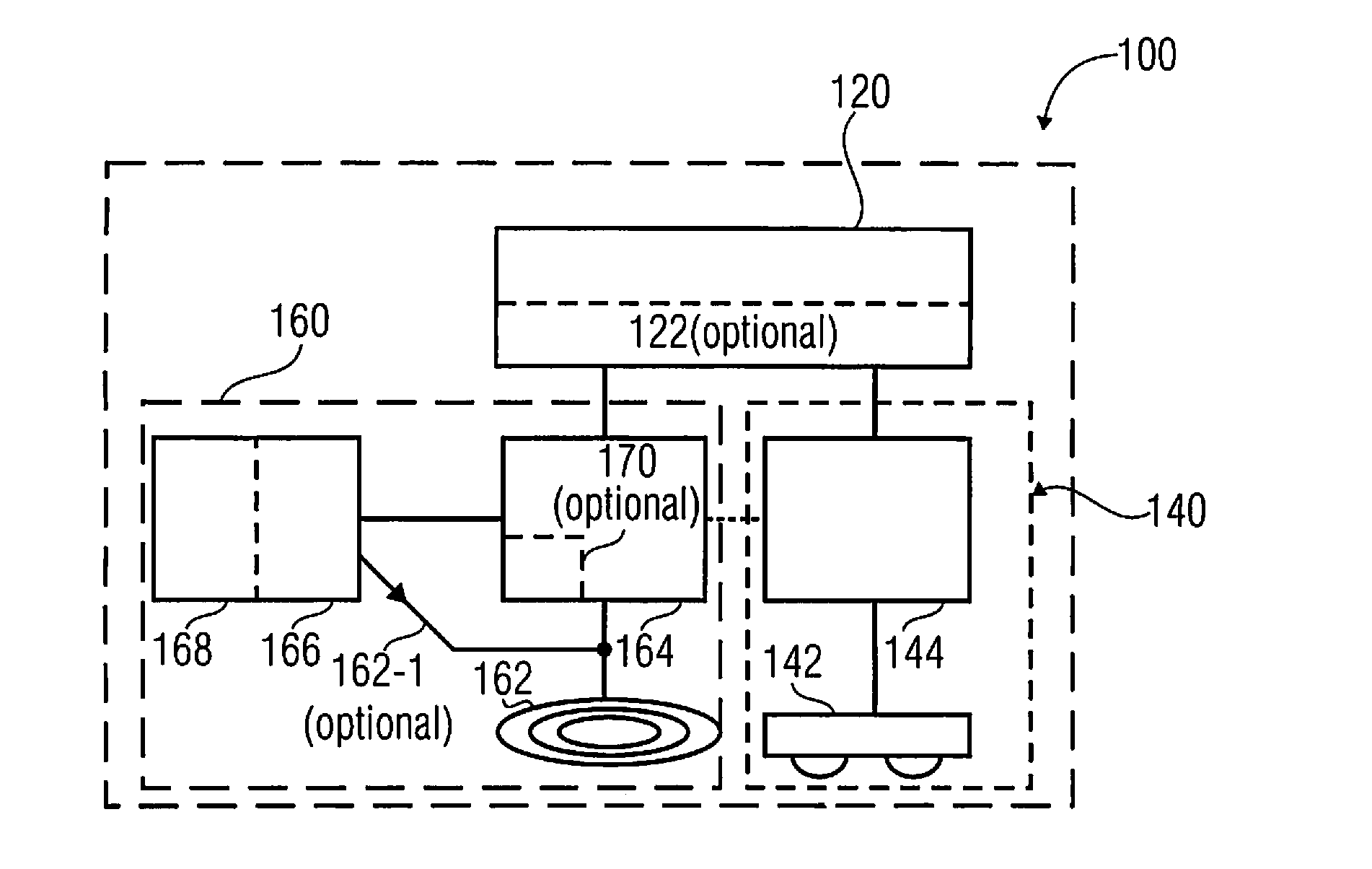
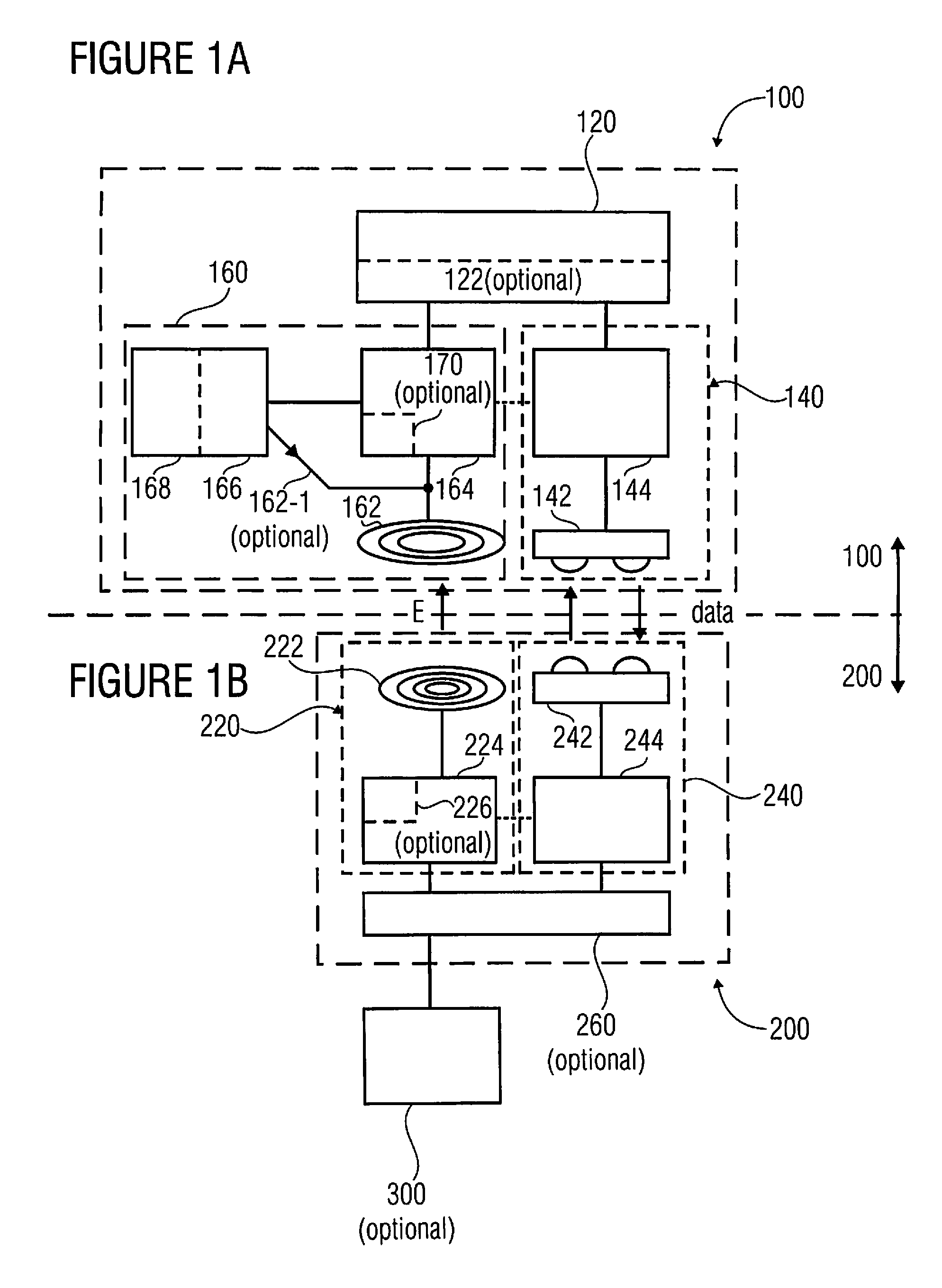
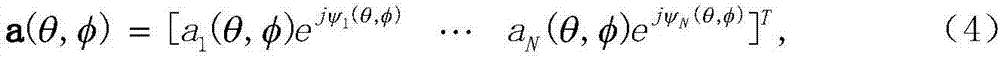Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1306results about How to "Guaranteed availability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
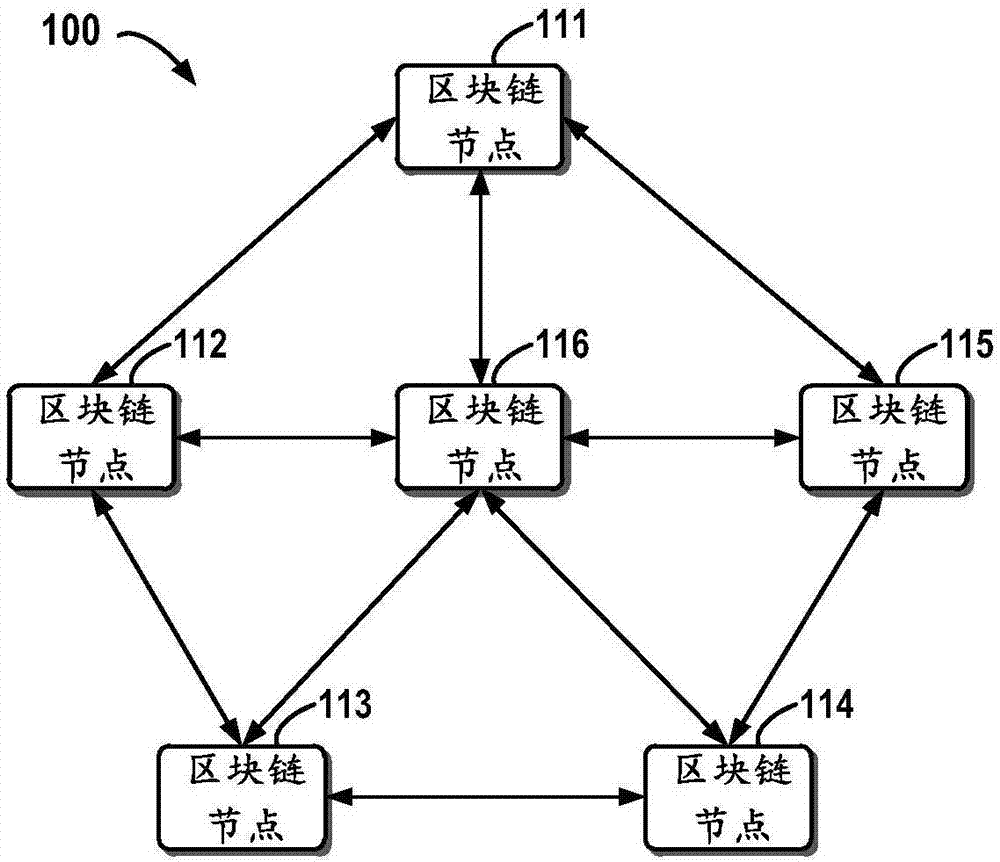
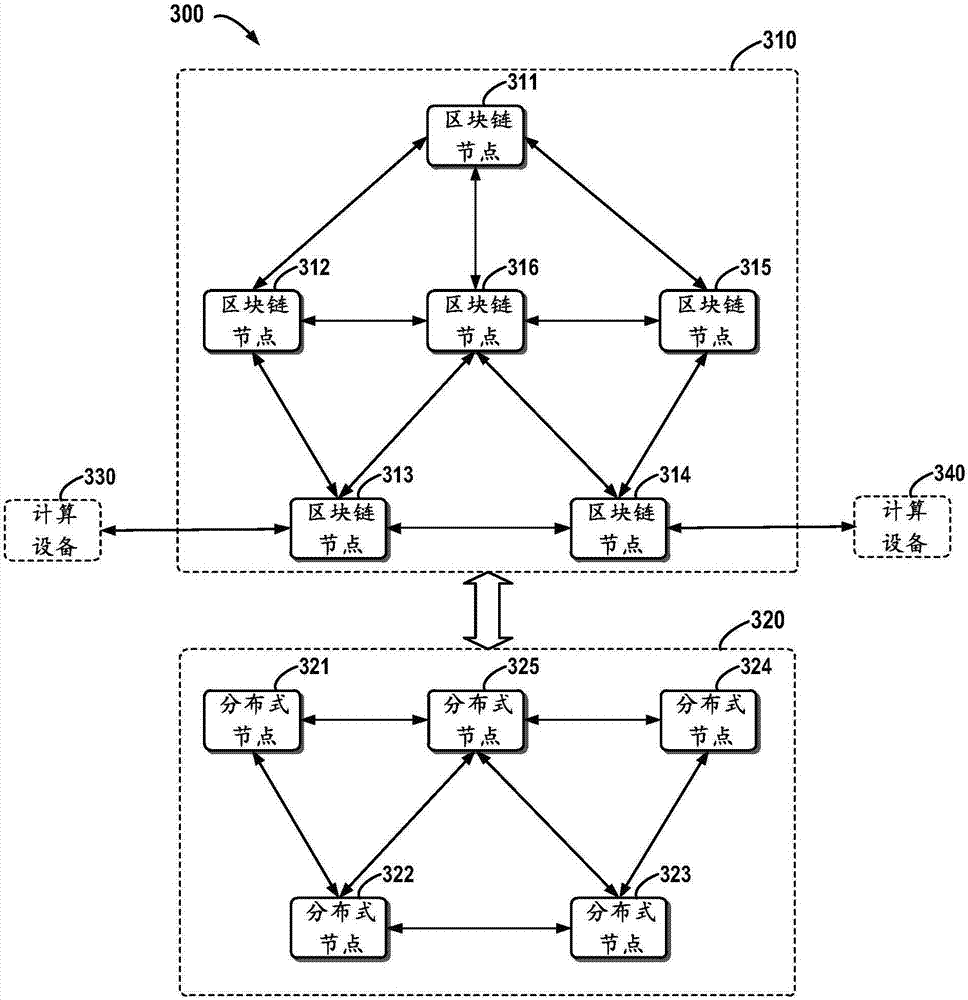
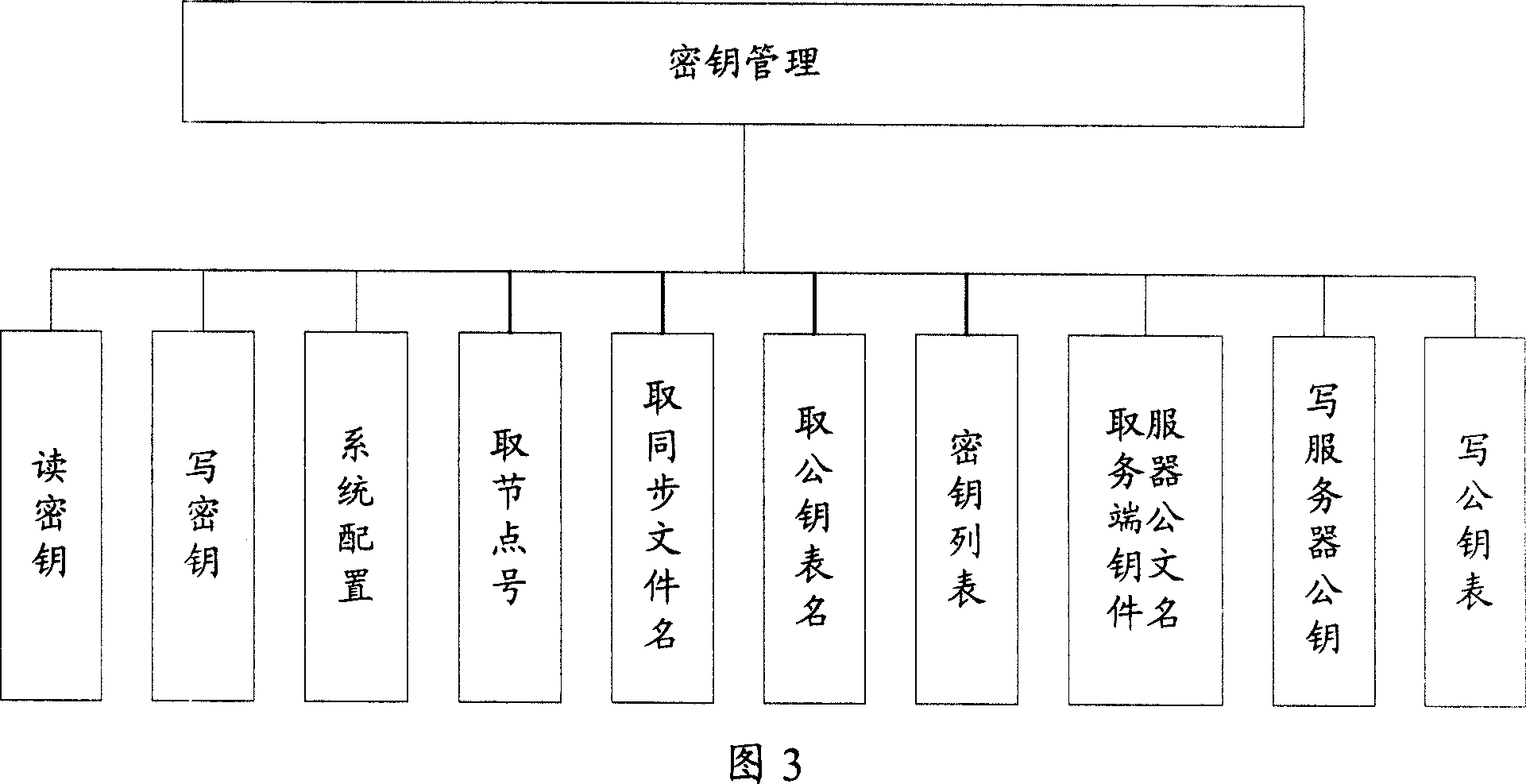
Block chain-based distributed storage
InactiveCN107273410ASolve the problem of limited node capacityAchieve tamper resistanceFile access structuresSpecial data processing applicationsTamper resistanceDistributed File System
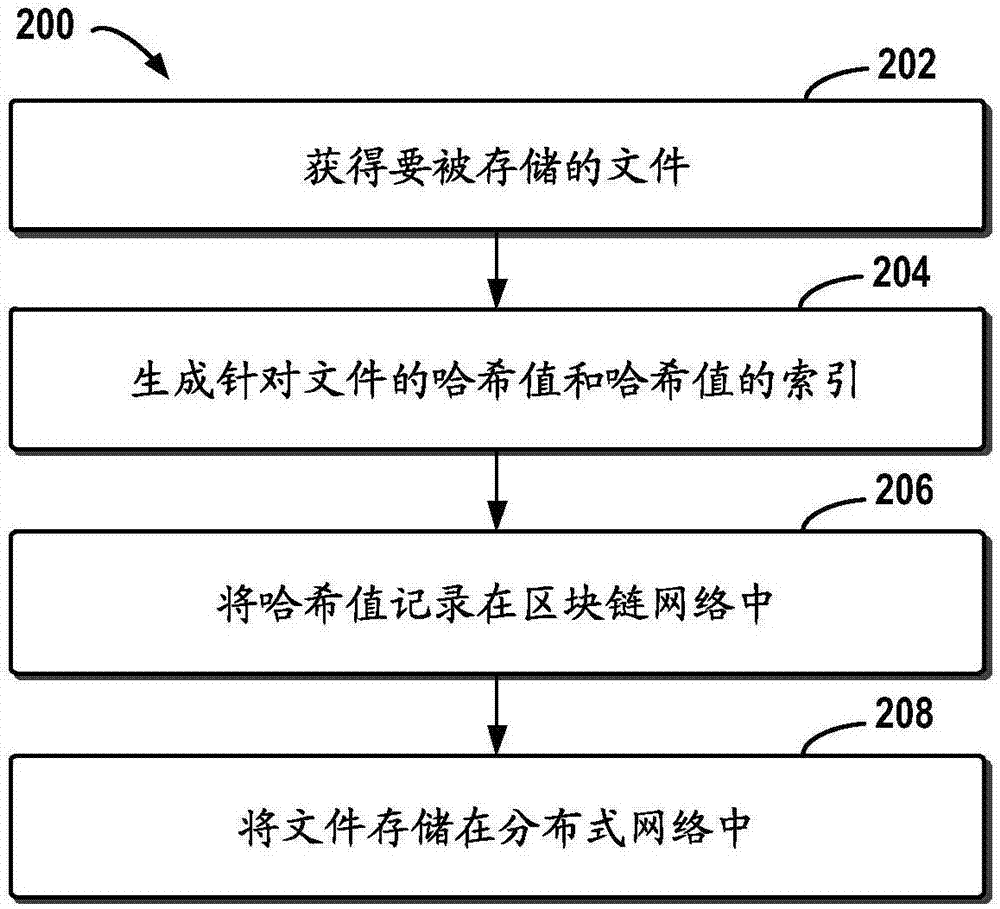
The embodiment of the disclosure relates to block chain-based distributed storage, and discloses a block chain-based distributed storage method. The method includes: obtaining a file which needs to be stored, and generating a hash value and an index of the hash value for the file. The method also includes: recording the hash value in a block chain network, and storing the file in a distributed network, wherein the file is located on the basis of the hash value in the distributed network. Therefore, according to the embodiment of the disclosure, tampering proofing and the distributed storage of the file can be realized through combining a block chain and a distributed file system, thus the problem of the limited capacity of block chain nodes is solved, and the authenticity and the availability of the stored file are effectively guaranteed.
Owner:SHANGHAI DIANRONG INFORMATION TECH CO LTD
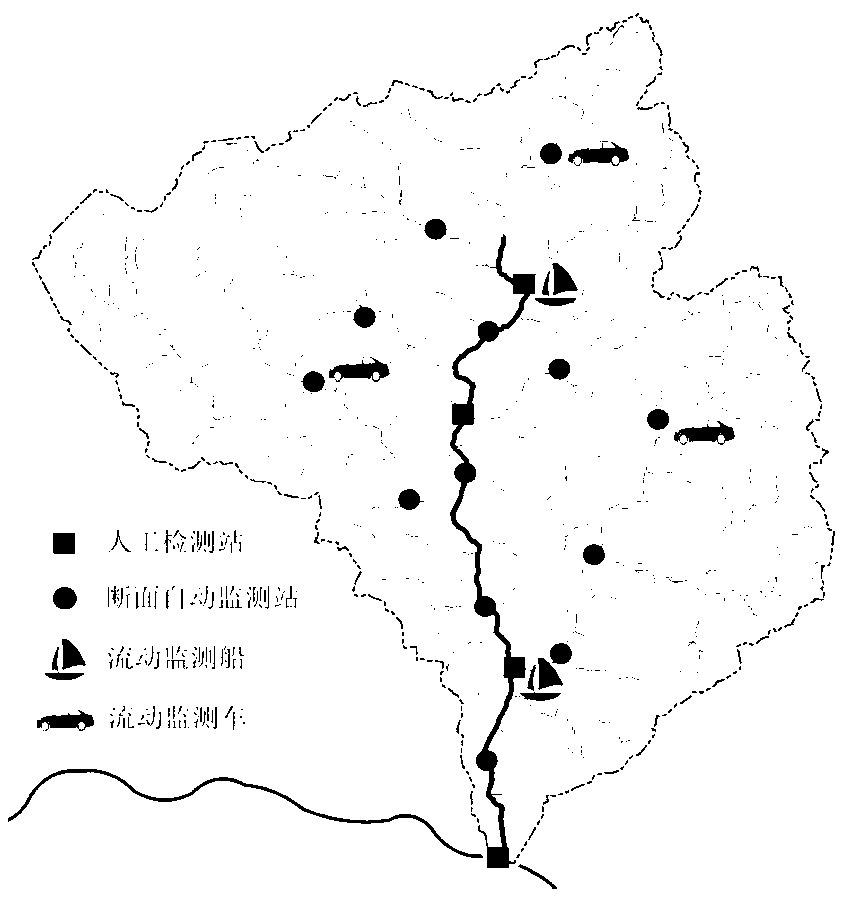
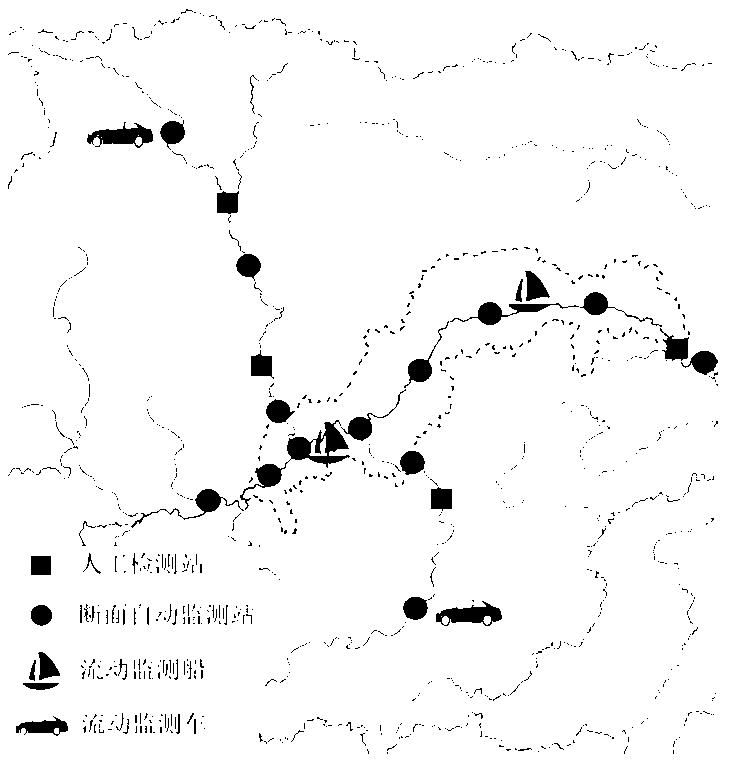
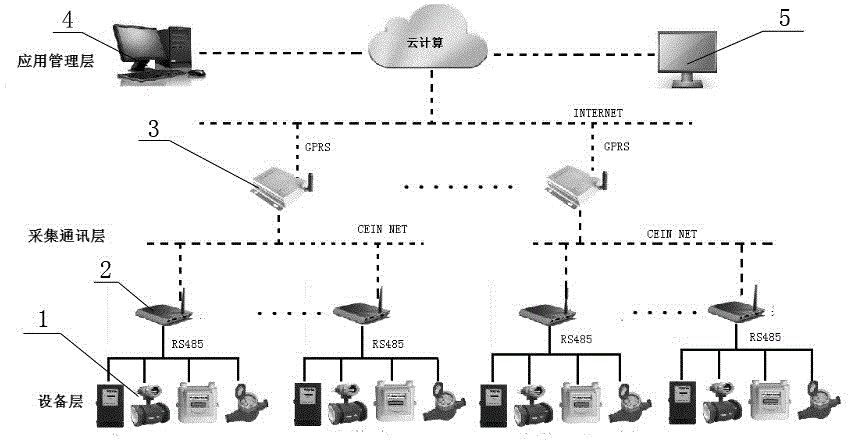
System and method for monitoring hydrology and water quality of river basin under influence of water projects based on Internet of Things
ActiveCN103175513AReal-timeAchieving processing powerChemical analysis using titrationOpen water surveyHydrometryWater quality
The invention provides a method for monitoring hydrology and water quality of a river basin under influence of water projects based on Internet of Things. According to the method, various fixed and flowing sensors are additionally mounted so as to obtain real-time hydrology and water quality data of important water areas, in combination with a video technology, monitoring on a spot environment is achieved, the monitoring information is transmitted through the Internet of Things, intelligent prediction for hydrology and water quality of the river basin is carried out through a neural network, and finally, critical applications, such as current situation assessment, tendency estimation, implementation effect estimation and extreme event handling, are achieved through an expert system. The method provided by the invention can provide real-time, reliable and complete hydrology and water quality information for the river basin under influence of water projects, and can achieve cross-regional and multi-machine type integrated remote protection for the river basin.
Owner:CHINA THREE GORGES CORPORATION
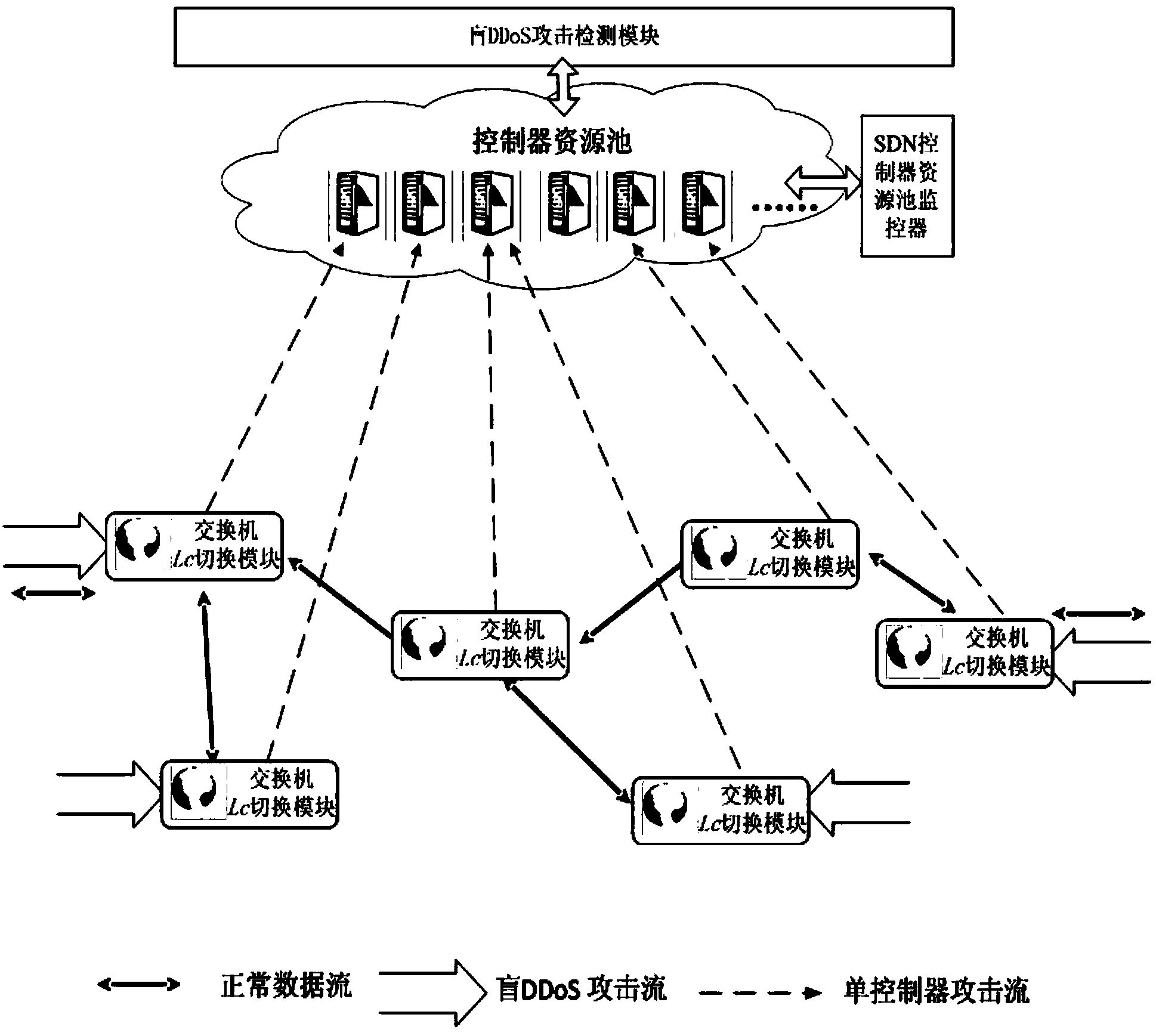
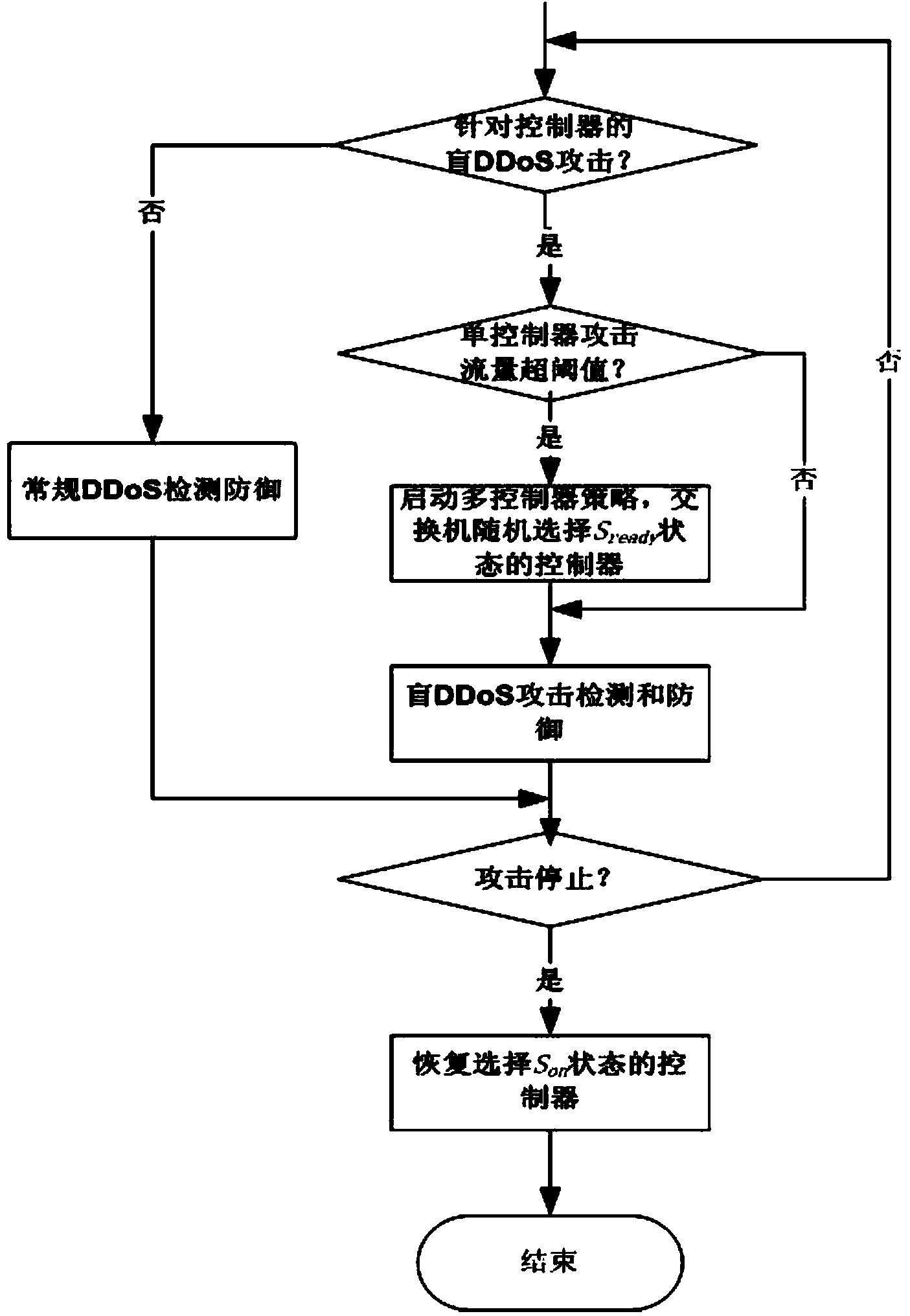
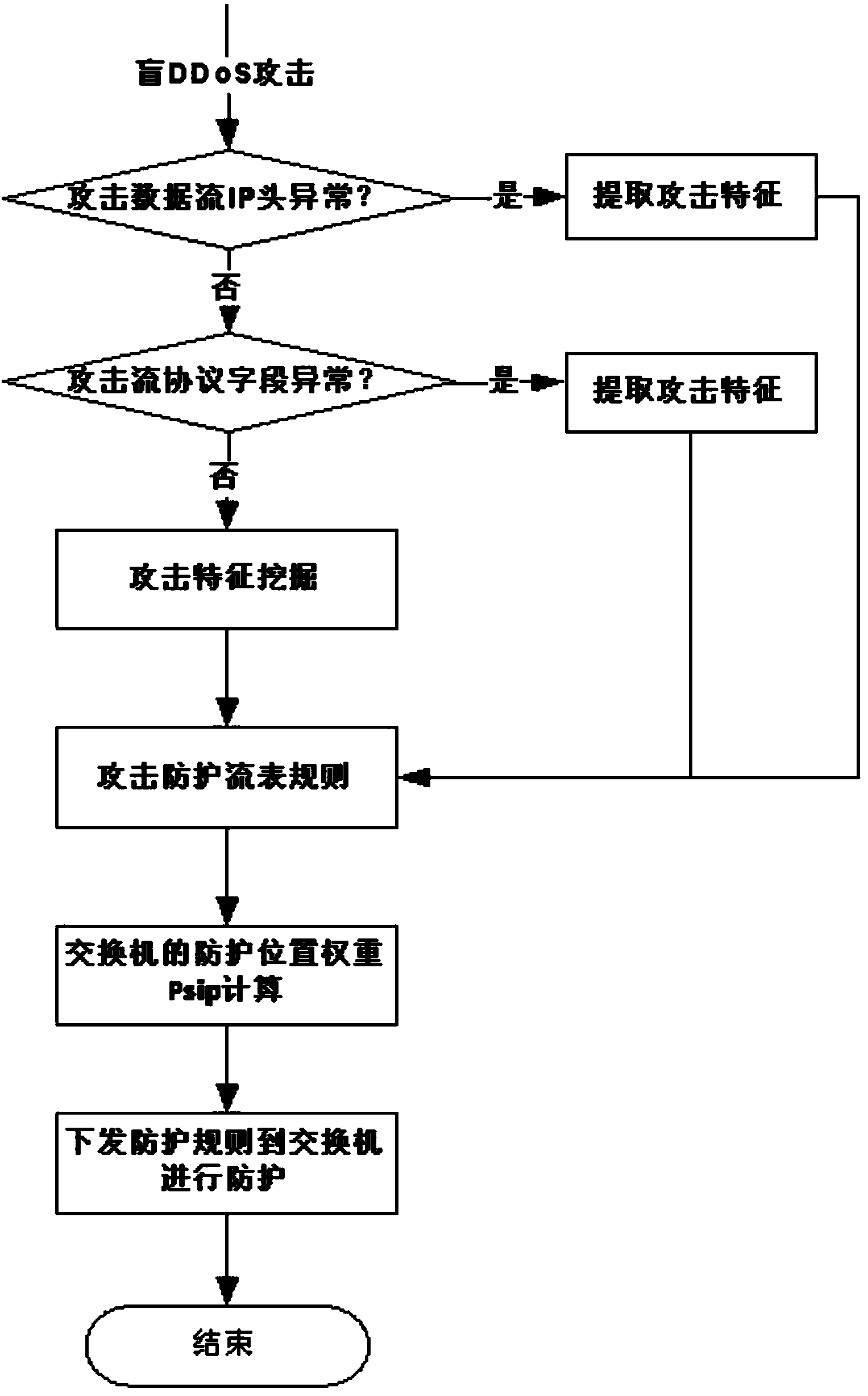
Method and system for preventing blind DDoS attacks on SDN controllers
The invention relates to a method and system for preventing blind DDoS attacks on SDN controllers. The system comprises an SDN controller resource pool monitor, a controller list dynamic switching module deployed on an SDN switch and an attack detection application module, and the attack detection application module and the controllers carry out data interaction through data interfaces. The SDN controller resource pool monitor is used for maintaining the establishment of a plurality of physical machine and / or virtual machine controllers, data synchronism, IP address distribution and state lists to be issued to the switch. The attack detection application module detects the communication data streams of the controllers and the switch in an SDN network, and when blind DDoS attack streams on the controllers are detected, the SDN controller resource pool monitor dynamically adjusts the number of the controllers according to attack flow generated when the blind DDoS attacks occur. The method can dynamically adjust the number of the controllers, the blind DDoS attacks on the controllers can be effectively prevented, and the usability of the SDN network is guaranteed.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
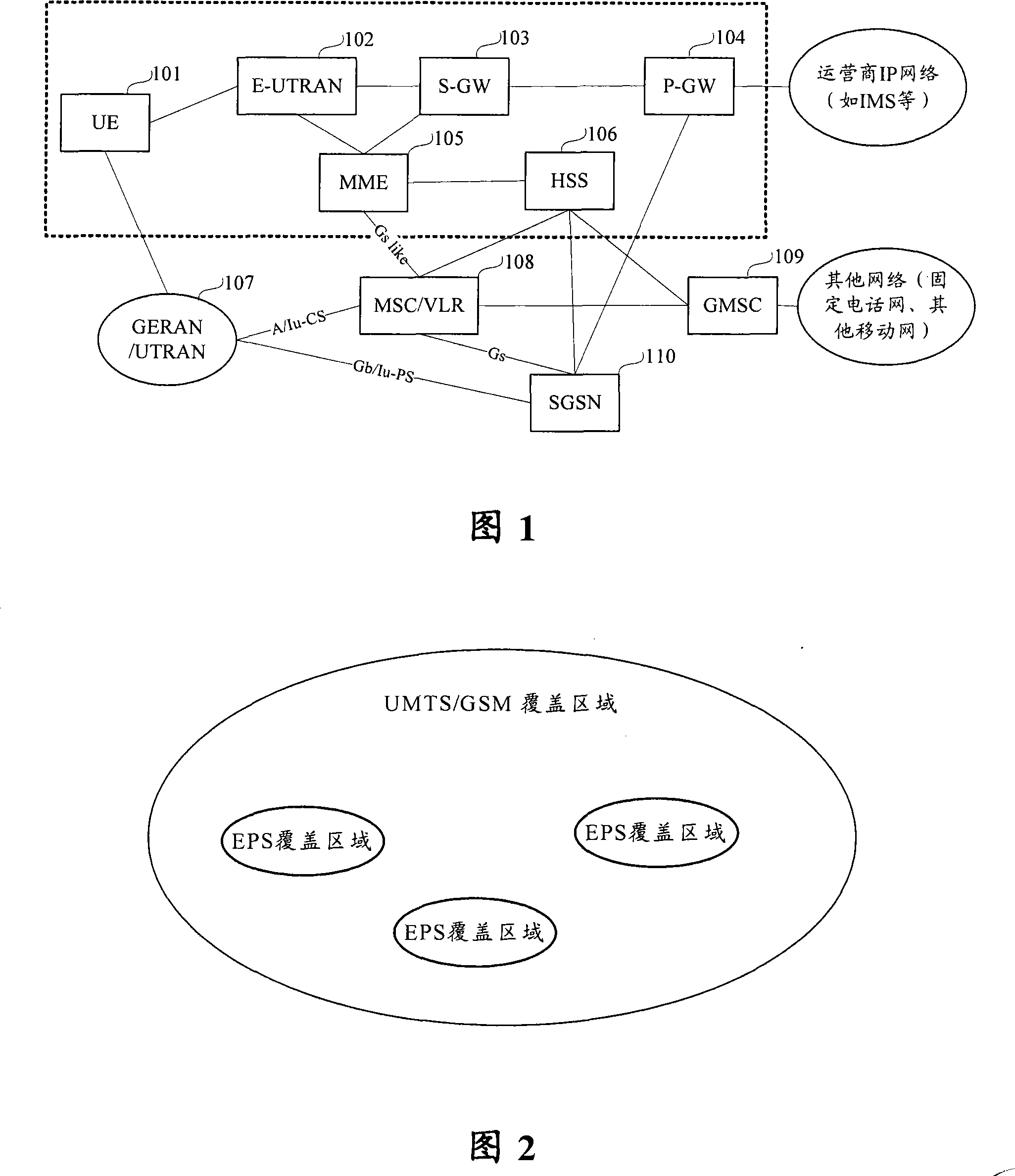
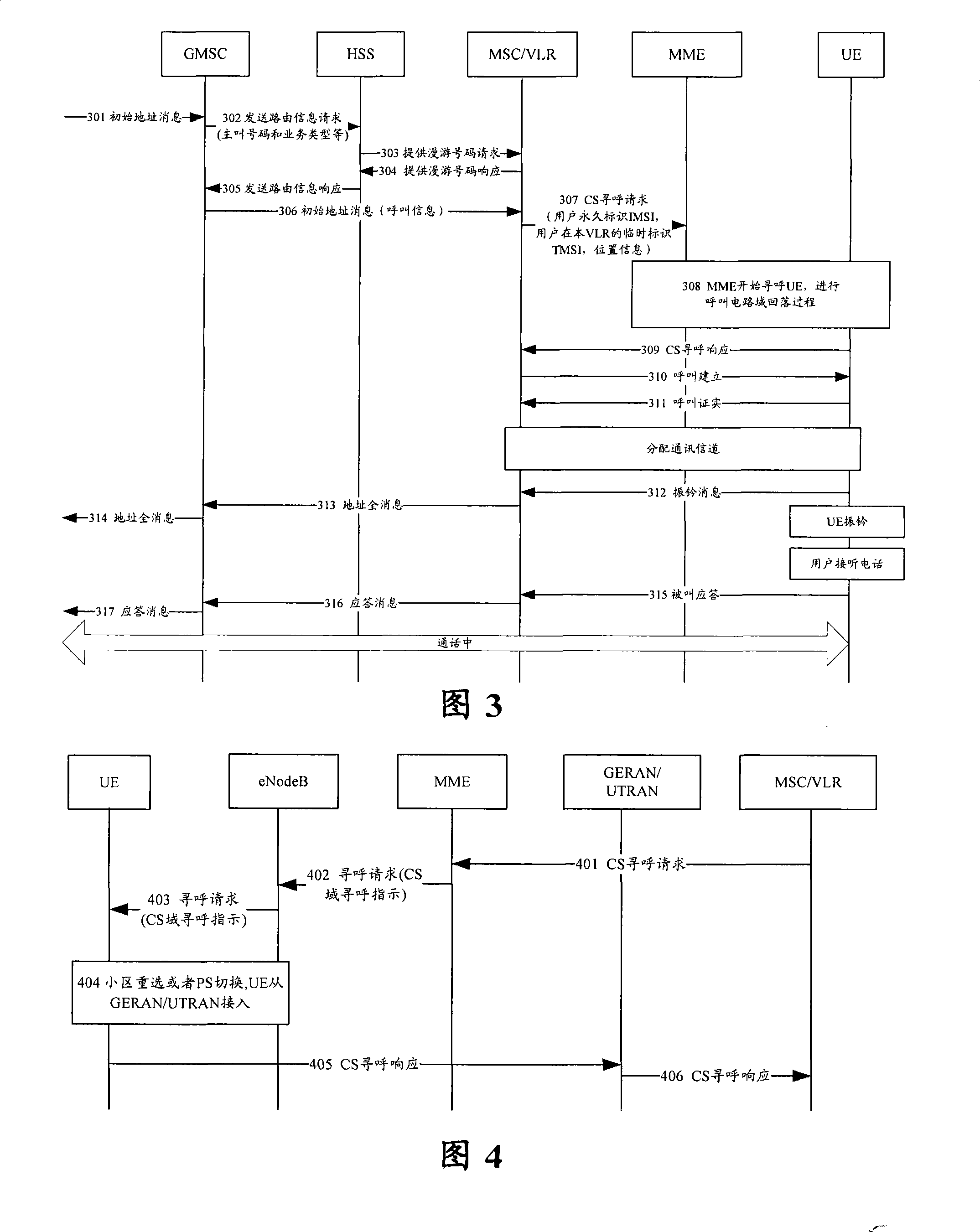
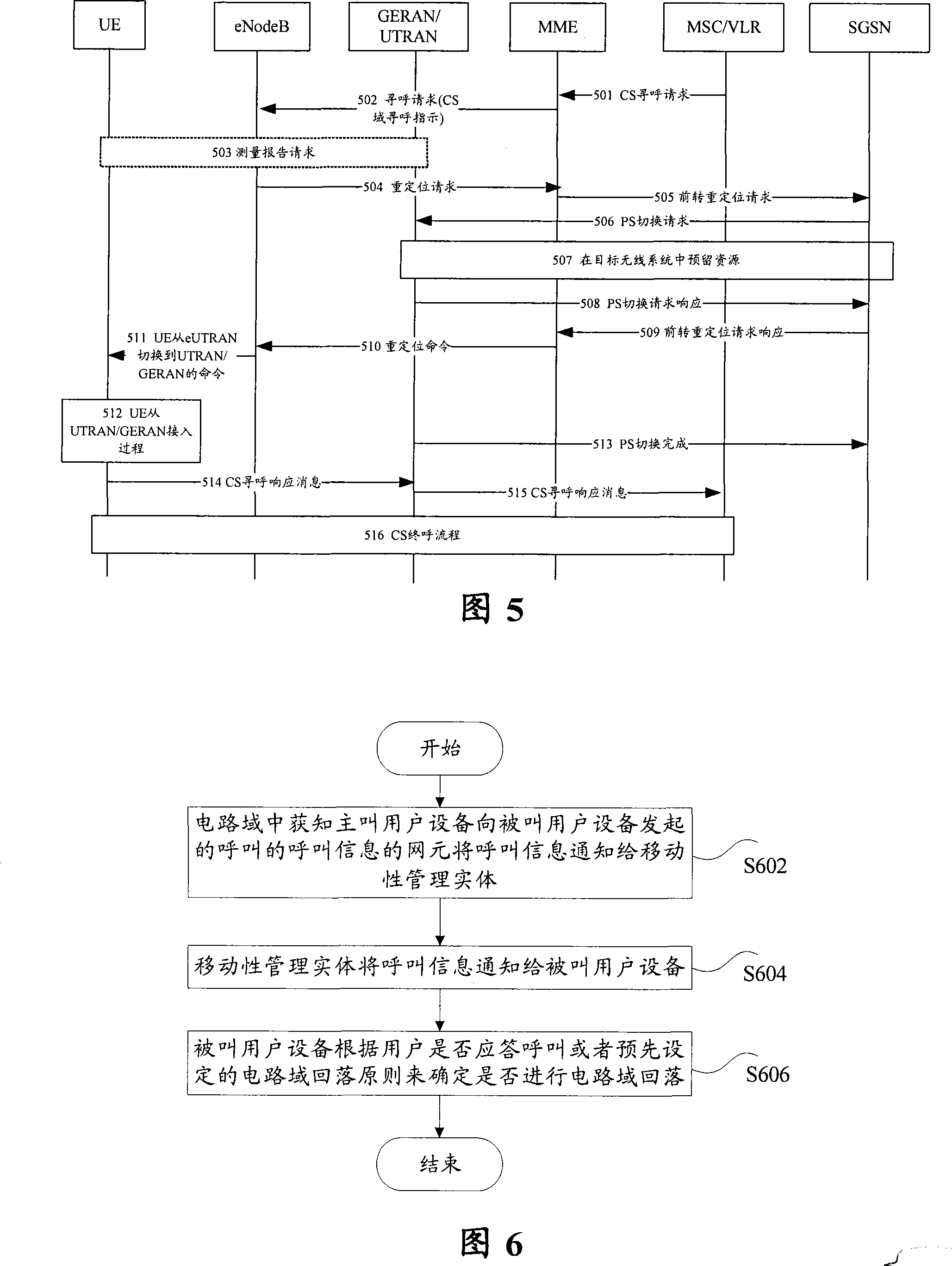
Control method, system and device for circuit field fall-back
ActiveCN101222765AImprove satisfactionGuaranteed availabilityConnection managementRadio/inductive link selection arrangementsUsabilityNetwork service
Owner:ZTE CORP
Automatic pomelo peel-flesh separating device and method
The invention discloses an automatic pomelo peel-flesh separating device and an automatic pomelo peel-flesh separating method. The method comprises the following steps: first, clamping and placing a pomelo on a fixing needle which is in the center of a working bench by cooperatively controlling a vertical electric push rod and an unfolding electric push rod, and operating a peeling mechanical claw; then, measuring the size of the profile of the pomelo by utilizing a laser distance sensor, performing data analysis processing on the data of the profile size of the pomelo and determining subsequent actions by a power supply and a control cabinet, and respectively cutting off the top cover of the pomelo and dividing the peel of the pomelo into eight pieces equally by cooperatively controlling the actions of an upper horizontal stepping motor, a lower horizontal stepping motor and a vertical stepping motor, and utilizing a top removal cutting knife and a peel scratching hobbing knife; finally, cooperatively controlling the vertical electric push rod and the unfolding electric push rod to move, and enabling the peeling mechanical claw to move along the trajectory in the peel of the pomelo to peel the peel of the pomelo, clamp the flesh of the pomelo and separate the flesh from the peel. According to the device and the method, the pomelo can be charged and discharged automatically; after the top of the pomelo is removed and the peel is scratched, all pieces of the peel are peeled precisely simultaneously without hurting the flesh.
Owner:JIANGSU UNIV
System and method for liquid air production power storage and power release
InactiveUS20090293502A1Reduce maintenance costsEliminate needSolidificationLiquefactionStored energyElectricity
Systems and methods for releasing and replacing stored energy comprise capturing inlet air from the ambient environment so the inlet air flows in a first general direction. Released liquid air flows in a second general direction, the second general direction being substantially opposite to the first general direction. The released liquid air is pumped to pressure, and the released liquid air and inlet air flow past each other such that heat exchange occurs. The inlet air warms the released liquid air such that the released liquid air is substantially vaporized, and the released liquid air cools the inlet air. Moisture and carbon dioxide are removed from the inlet air, and the inlet air is compressed and cooled such that the inlet air is substantially liquefied. The substantially liquefied air replaces a portion of the released liquid air; and the substantially vaporized released liquid air is combusted with fuel to produce electricity.
Owner:EXPANSION ENERGY
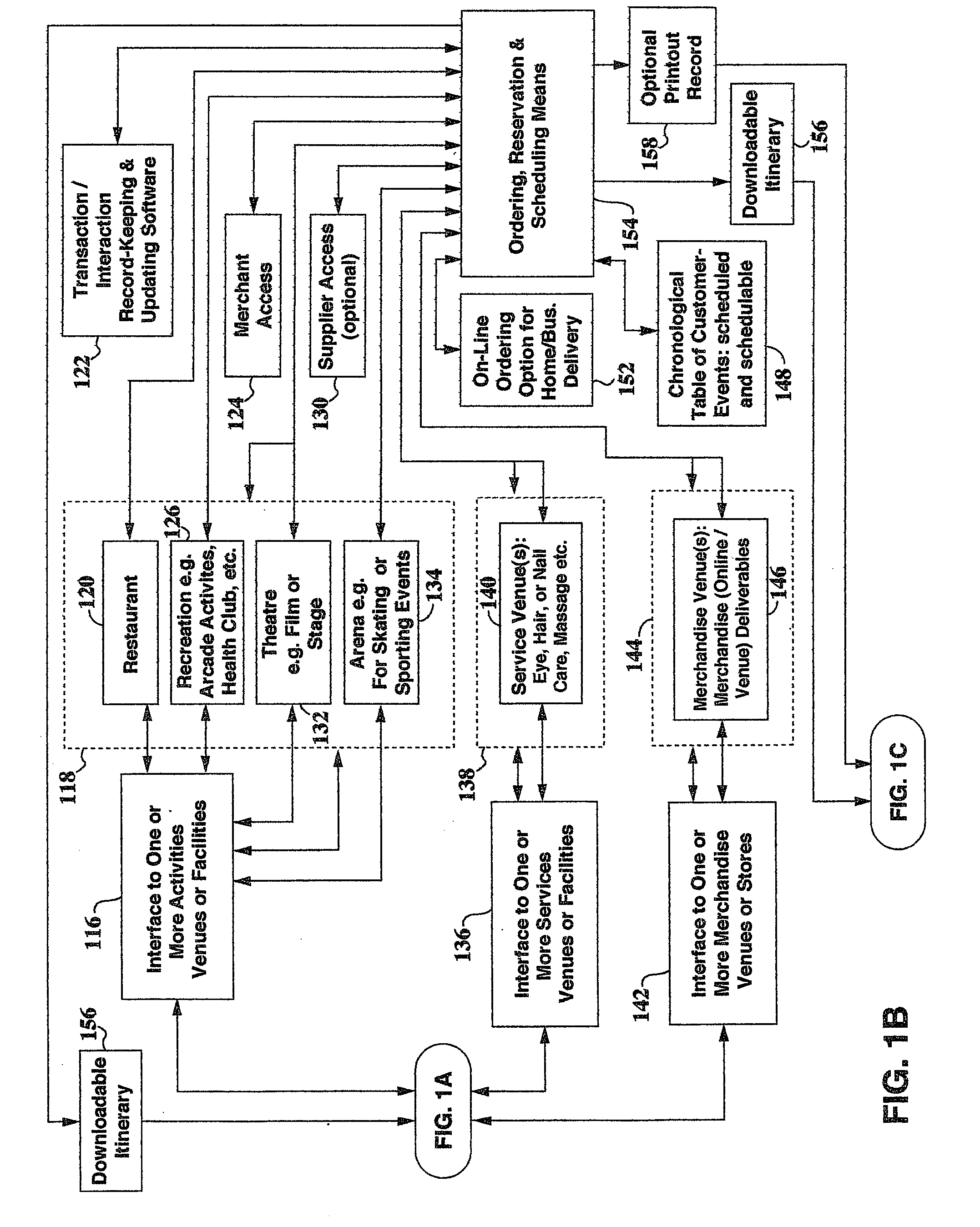
System for expediting procurement of deliverables from expedited service areas
ActiveUS20090048878A1Optimize traffic flowImprove experienceInstruments for road network navigationDigital data processing detailsDeliverableOperations management
A system for expediting procurement of one or more deliverables by a customer of one or more expedited service areas including one or more designated expedited service areas, the designated expedited service areas associated with, and located at, adjacent to, or in the vicinity of, one or more venues, and the venues providing one or more venue-available deliverables. At least some of the designated expedited service areas include a distinct physical location that scheduled-customers visit separate from non-scheduled customers configured to provide procurance of venue-available deliverables more quickly to scheduled-customers.
Owner:EXPEDITED DUAL COMMERCE LLC
Methods, devices and systems for establishing end-to-end secure connections and for securely communicating data packets
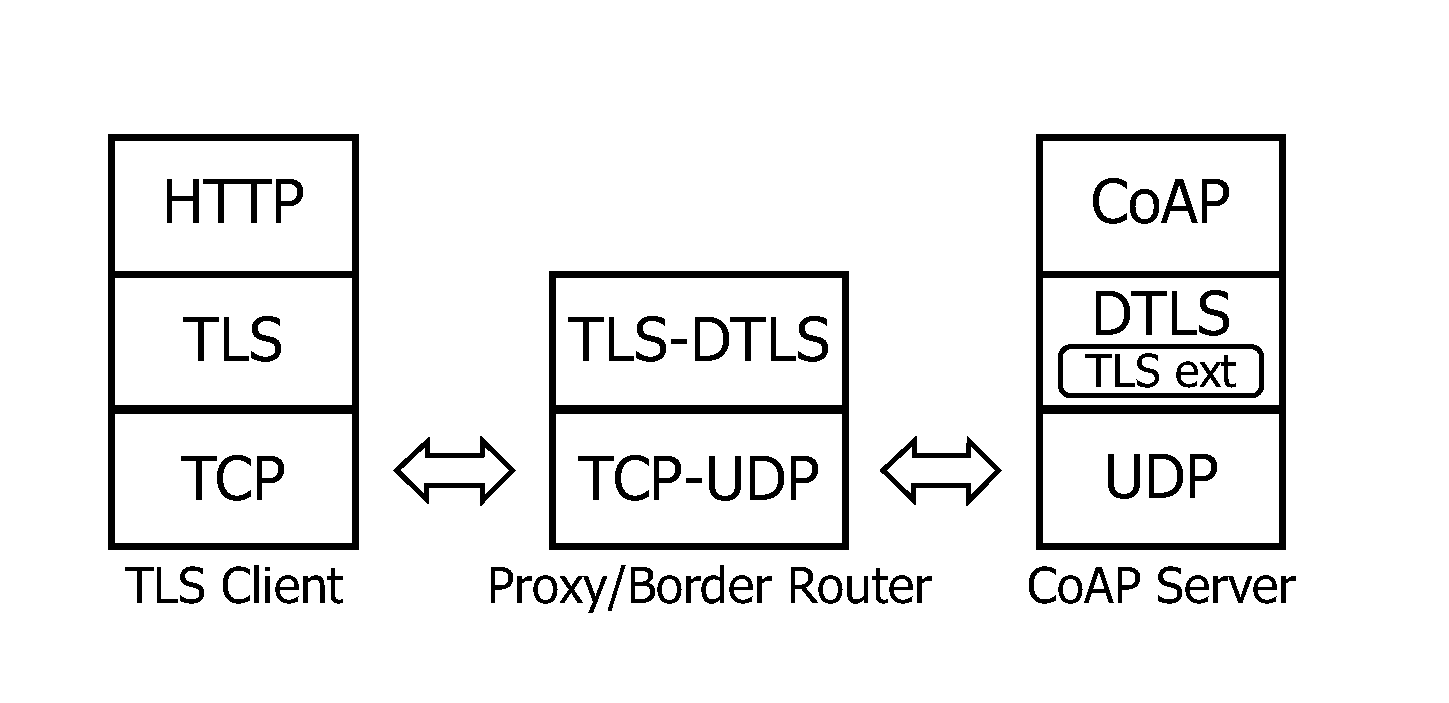
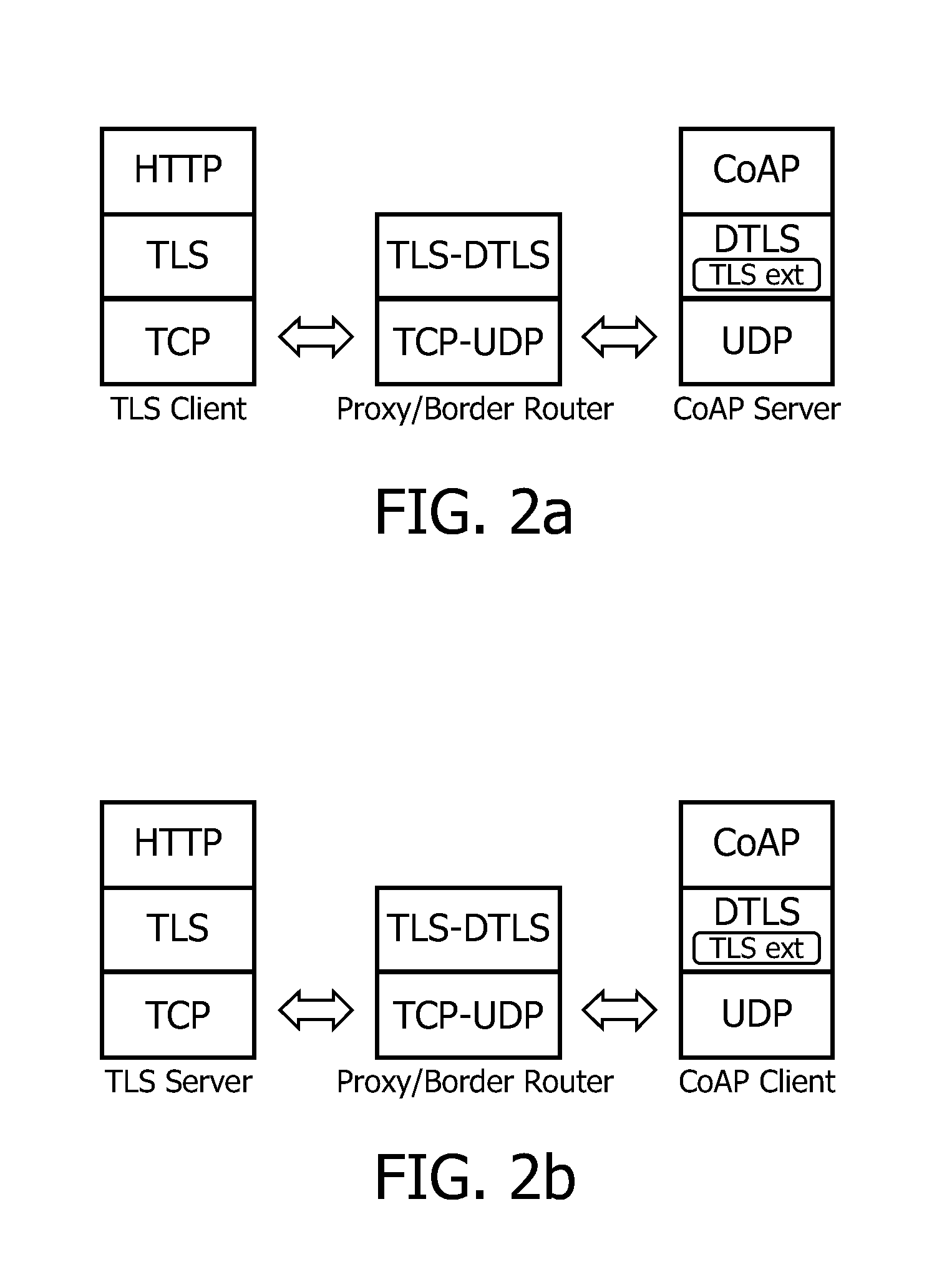
ActiveUS20140143855A1Guaranteed availabilityImprove efficiencyMultiple digital computer combinationsProgram controlEnd to end securityCommunications system
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
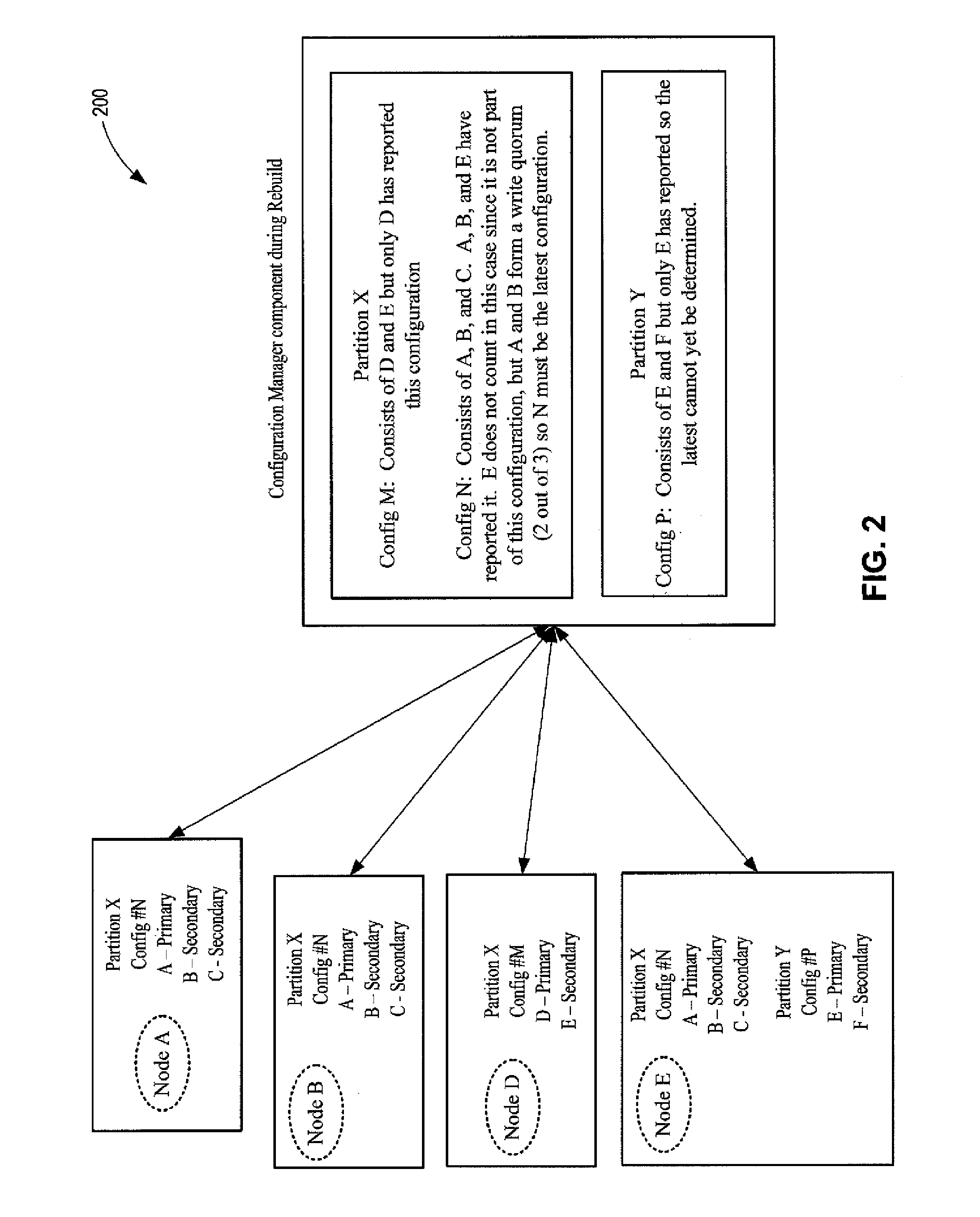
Quorum based transactionally consistent membership management in distributed storage systems
ActiveUS20100106813A1Improve usabilityGuaranteed availabilityDigital computer detailsDatabase distribution/replicationHybrid storage systemDistributed computing
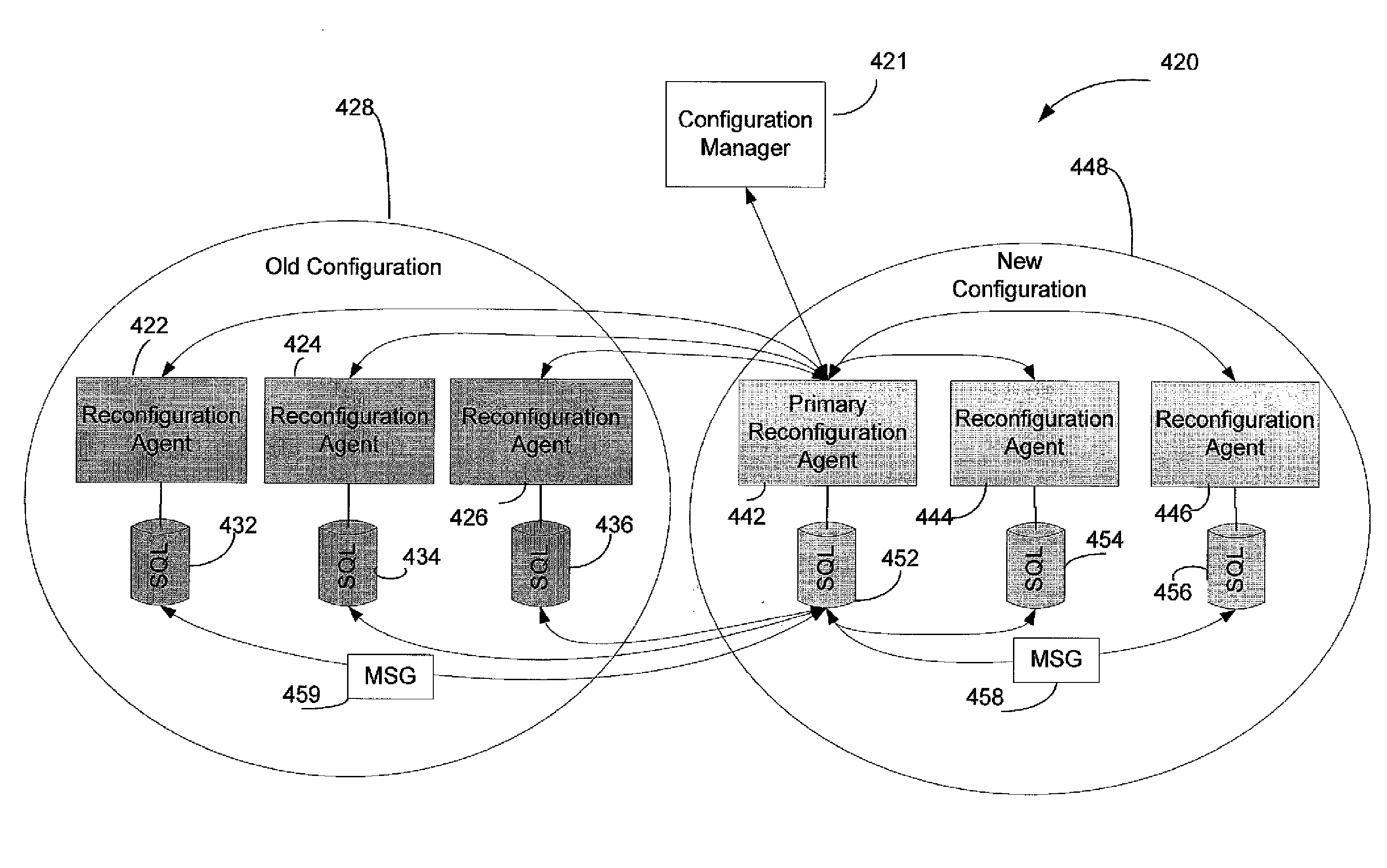
Systems and methods that restore a failed reconfiguration of nodes in a distributed environment. By analyzing reports from read / write quorums of nodes associated with a configuration, automatic recovery for data partitions can be facilitated. Moreover, a configuration manager component tracks current configurations for replication units and determines whether a reconfiguration is required (e.g., due to node failures, node recovery, replica additions / deletions, replica moves, or replica role changes, and the like.) Reconfigurations of data activated as being replicated from an old configuration to being replicated on a new configuration may be performed in a transactionally consistent manner based on dynamic quorums associated with the new configuration and the old configuration.
Owner:MICROSOFT TECH LICENSING LLC
N+1 failover and resynchronization of data storage appliances
InactiveUS20110060940A1Without impairing performanceGuaranteed availabilityRedundant hardware error correctionFailoverFull data
Reciprocal data storage protection is combined with “N+1” hardware provisioning and on-demand resynchronization to guarantee full data availability without impairing performance. Pairs of nodes are identified that act as backups for each other, where each node stores a secondary copy of data allocated to its reciprocal, paired node. A single extra node is brought online to take over the role of a failed node and assumes the role of the primary node it replaced.
Owner:TAYLOR TRACY M +2
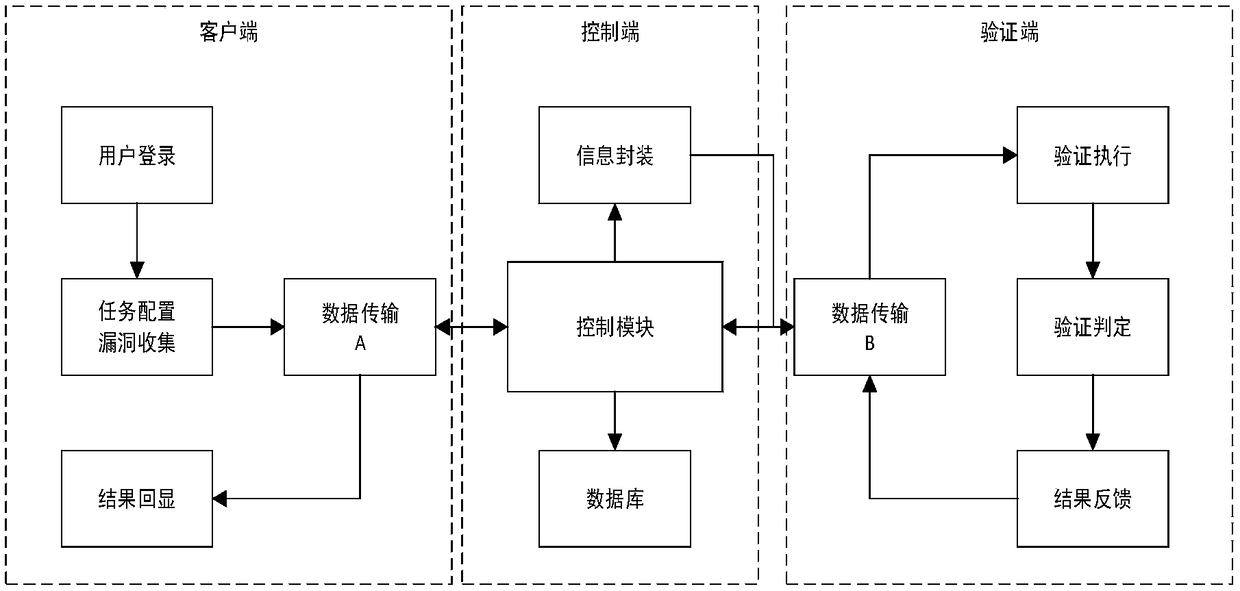
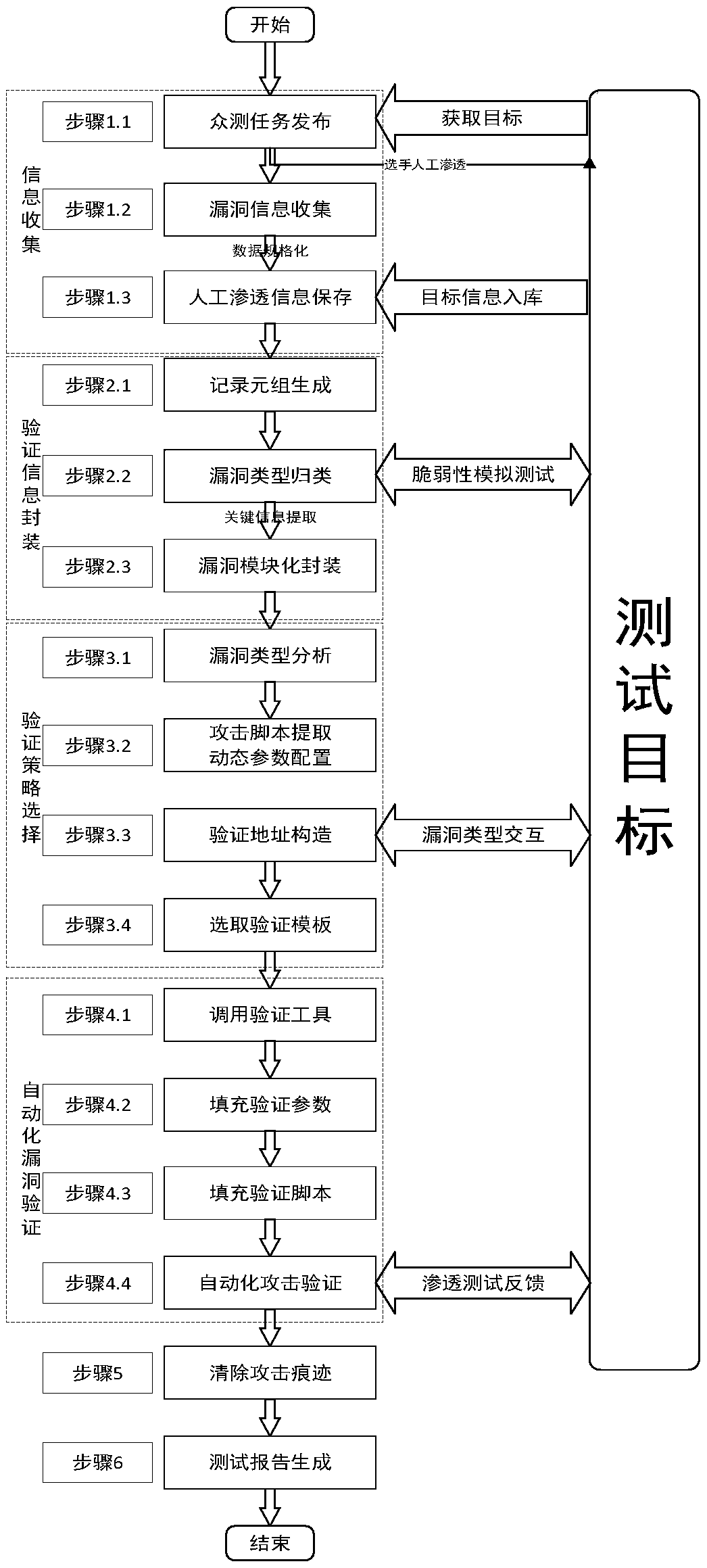
A security vulnerability automatic verification system based on a crowd test platform
ActiveCN109325351AGuaranteed accuracyGuaranteed availabilitySoftware testing/debuggingPlatform integrity maintainanceModularityField data
The invention discloses a security vulnerability automatic verification system based on a crowd testing platform. The system executes the following steps of 1, collecting the verification information;2, implementing the authentication information encapsulation, classifying all kinds of vulnerabilities collected by security vulnerability automatic verification system according to their types, extracting the key information from vulnerability detection results for each type of vulnerabilities, taking the key information as the necessary field data to submit the vulnerabilities, collecting the required data according to the fields, and packaging the data in a unified interface modularly; 3, searching for an authentication strategy, and selecting an appropriate attack script template and a vulnerability utilization tool according to suspicious vulnerability identification and type information; 4, carrying out automatic vulnerability verification; 5, clearing the verification trace; 6, generating a scanning report.
Owner:CHINA INFOMRAITON CONSULTING & DESIGNING INST CO LTD
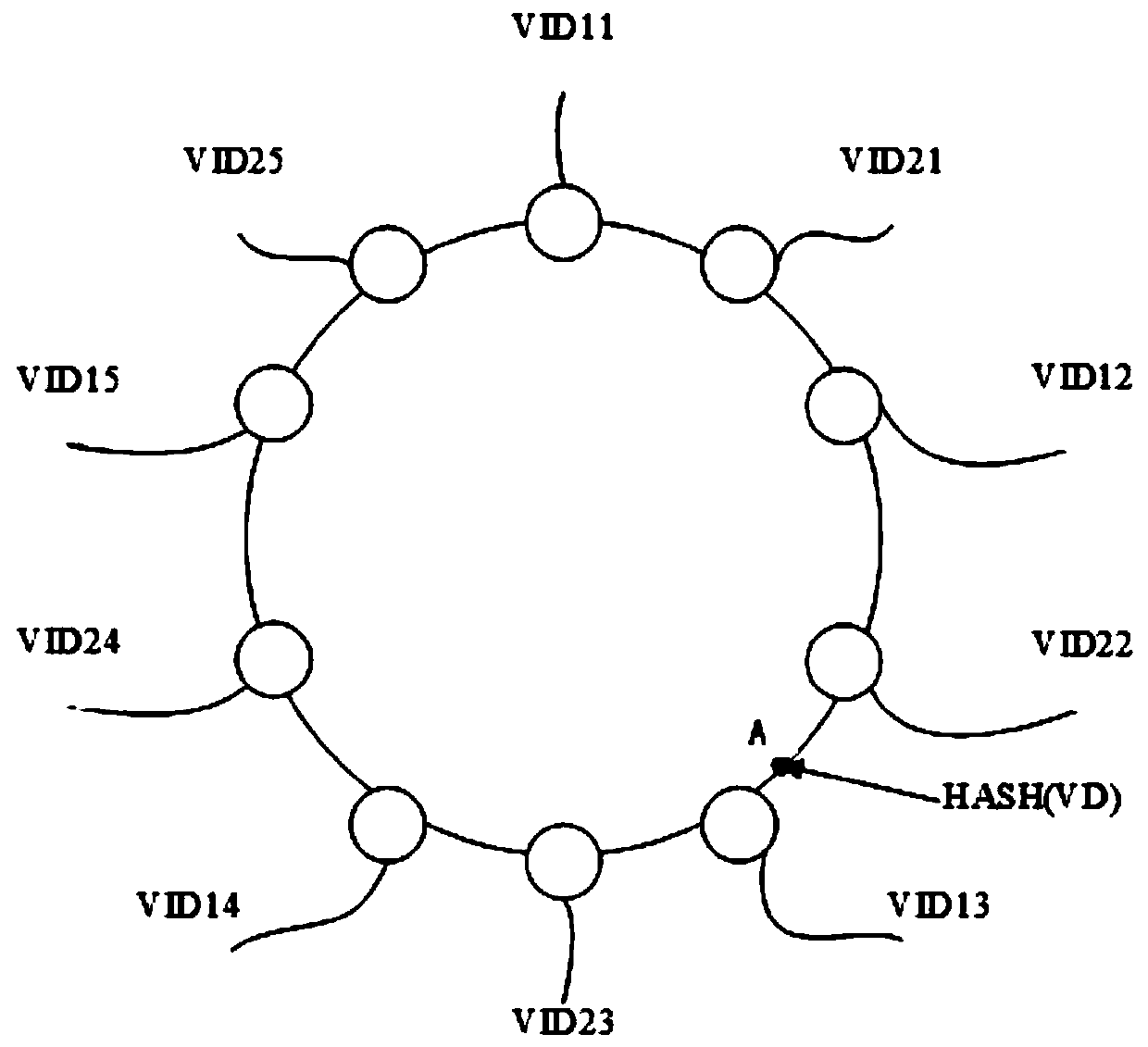
Distributed data storage method and system based on multilayer consistent hashing
ActiveCN110169040AAvoid inconsistenciesImprove fault toleranceError detection/correctionFile access structuresState variationConsistent hashing
A distributed data storage method and system based on multilayer consistent hashing are provided. The system includes a plurality of storage nodes for providing data storage and redundancy protection;a plurality of management nodes for maintaining storage node attributes and virtual groups-storage node mapping information; a plurality of monitoring nodes for maintaining storage node state and processing state changes such as storage node addition, deletion, and failure; and one or more clients that provide storage system access points for applications or users. Storage nodes are organized ina tree structure, with each storage node in each layer of the tree being assigned with multiple identities and a hash space maintaining consisteny hash space. Instead of sharing a hash space between all storage nodes, multiple hash spaces in the storage node architecture tree that are consistent across each layer. The system guarantees the reliability and availability of the stored procedure and avoids the problem of load imbalance when accessing the system.
Owner:HERE DATA TECH
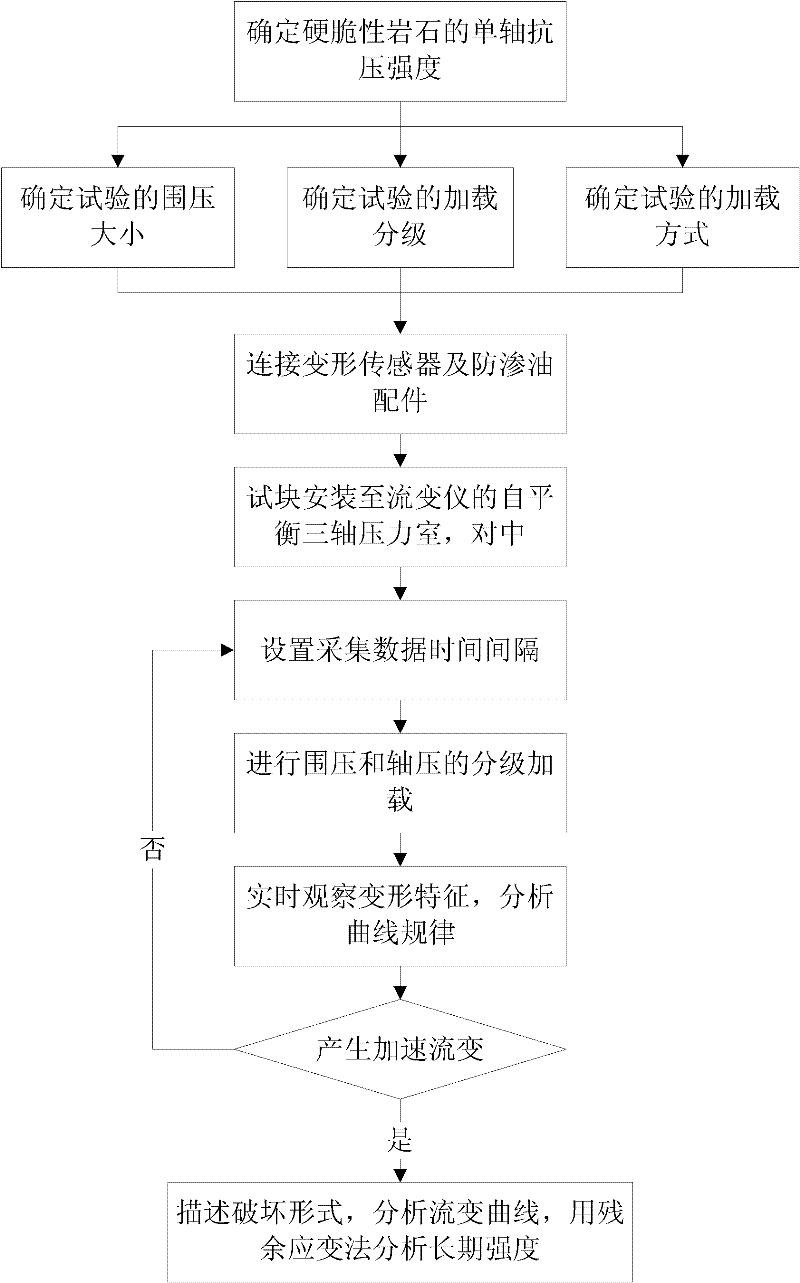
Triaxial rheological test process and method for hard and crisp rock
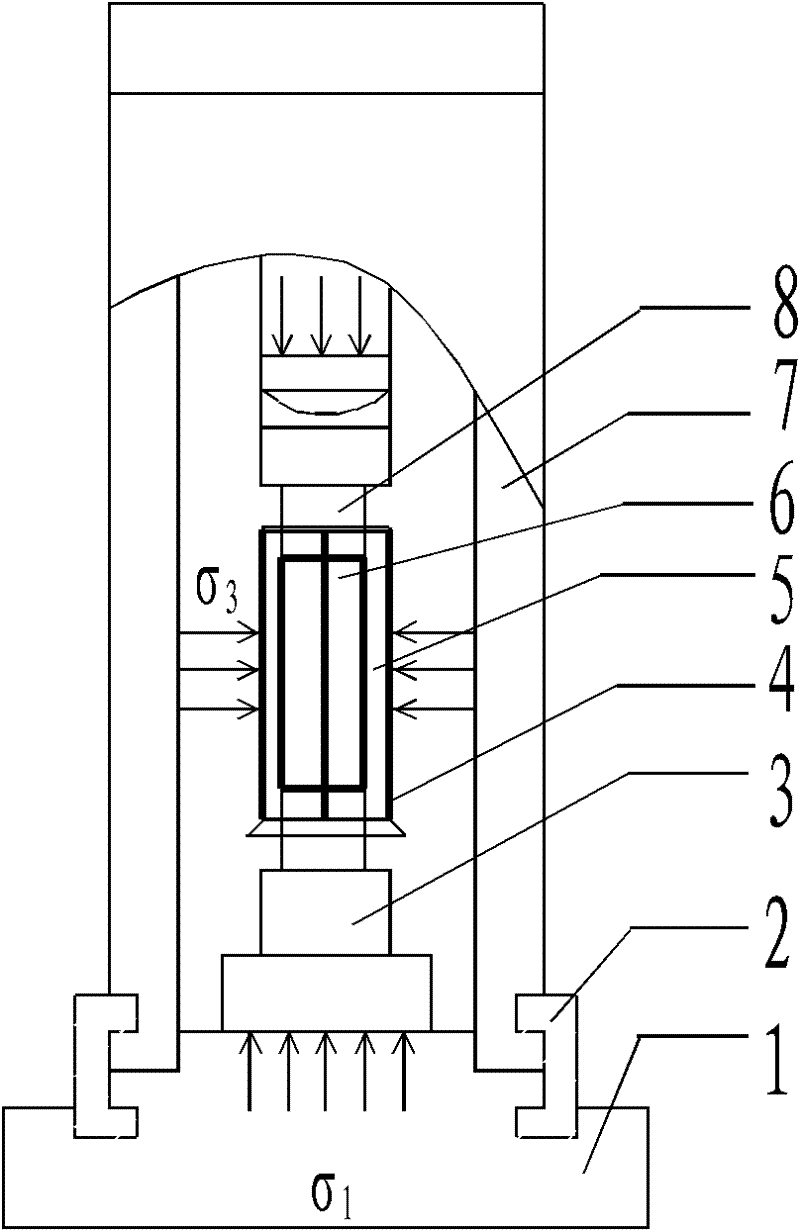
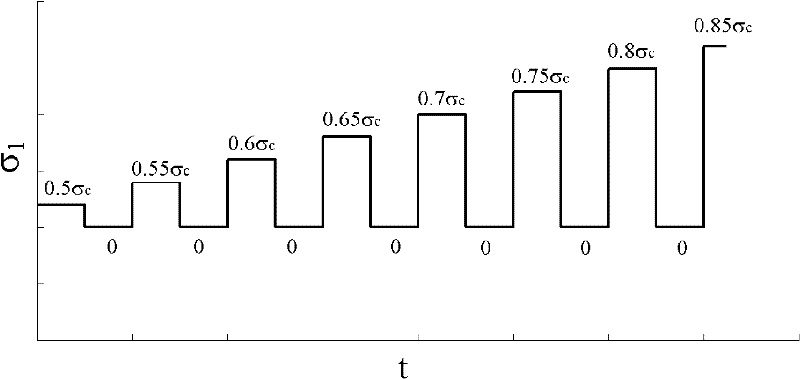
InactiveCN102128741AAvoid mutationsReduce axial output levelStrength propertiesHeat-shrinkable sleeveSteel tube
The invention relates to a triaxial rheological test process and method for a hard and crisp rock. The method comprises the following steps of: 1, determining an instantaneous triaxial compressive strength of the hard and crisp rock and loading by adopting a triaxial rheological mode; 2, determining the size of a confining pressure of a test and test loading grades and adopting a loading mode of circularly loading and unloading; 3, sealing a rock sample by using a heat-shrinkable sleeve and a stainless steel tube hoop so as to prevent oil from leaking; 4, applying the confining pressure to a set value, applying a first stage of axial load after the confining pressure is stable, and reasonably setting a time interval of recording data; 5, after the deformation is stable, continuously applying axial stresses in a grading mode until the test is completed; and 6, determining the long-term strength of the rock by adopting a residual strain method. In the invention, a reasonable value of the confining pressure is provided so as to furthest avoid deformation mutation caused by local fracture of the rock; the test loading grades are reasonably determined so as to not only obtain a threshold value of the creep stress of the rock, but also obtain an accelerated creep curve; and the scheme of determining the long-term strength of the hard and crisp rock by using the residual strain method of the loading and unloading rheological test is provided.
Owner:SHANDONG UNIV
Verification method and system for adoptability of electronic data evidence
InactiveCN103593618AGuaranteed availabilityProof of integrityDigital data protectionDigital data authenticationGeographic siteTimestamp
The invention relates to a verification method and system for adoptability of electronic data evidence. The method includes: authenticating a forensics subject and a system user, embedding authentication results and data such as digital digest, timestamp and geographic location into a QR code through a QR code generating program, displaying the results and data in a generated authentication report, comparing the information recognized through the QR code to corresponding information collected by data verification during authentication to determine whether the information is consistent to the corresponding information or not; if yes, determining that identity of the forensics subject is correct and that the electronic data evidence remains not tampered; if not, determining that identity of the forensics subject is not correct or that the electronic data evidence remains tampered. The completeness of the electronic data evidence is proved by extracting the digital digest from the electronic data evidence; legality of the forensics subject is guaranteed through authentication and verification over the forensics subject; adoptability of the electronic data evidence is guaranteed in terms of both time and space by adding the timestamp and geographic location data information.
Owner:BEIJING REALDATA SCI & TECH
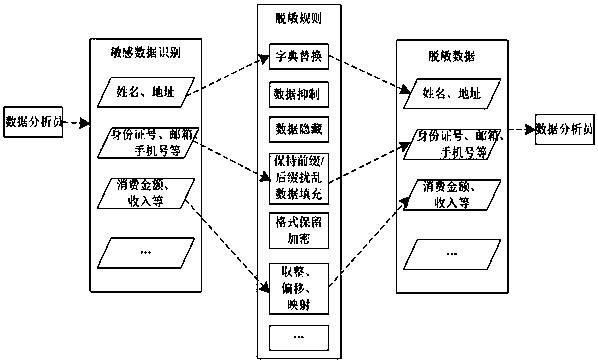
Data desensitization method based on authority
InactiveCN108418676AGuaranteed availabilityImprove access efficiencyEncryption apparatus with shift registers/memoriesInternet privacyOriginal data
The invention relates to a data desensitization method based on an authority. The method comprises the following steps of 1, performing sensitive data recognition on original data, and building desensitization rules for the sensitive data; 2, defining a corresponding strategy between authorities and the desensitization rules: according to the access authority of a user, controlling access authorities of sensitive information, privacy information and secret information, and according to requirements of the different authorities on the sensitive data, making desensitization strategies corresponding to the authorities; 3, positioning desensitization data: positioning and recognizing desensitization data according to features of the sensitive data during a process of accessing the informationin the original data; and 4, dynamically generating the sensitive data: when the original data is output for displaying, desensitizing and outputting the data according to the desensitization strategycorresponding to the access authority of the user.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
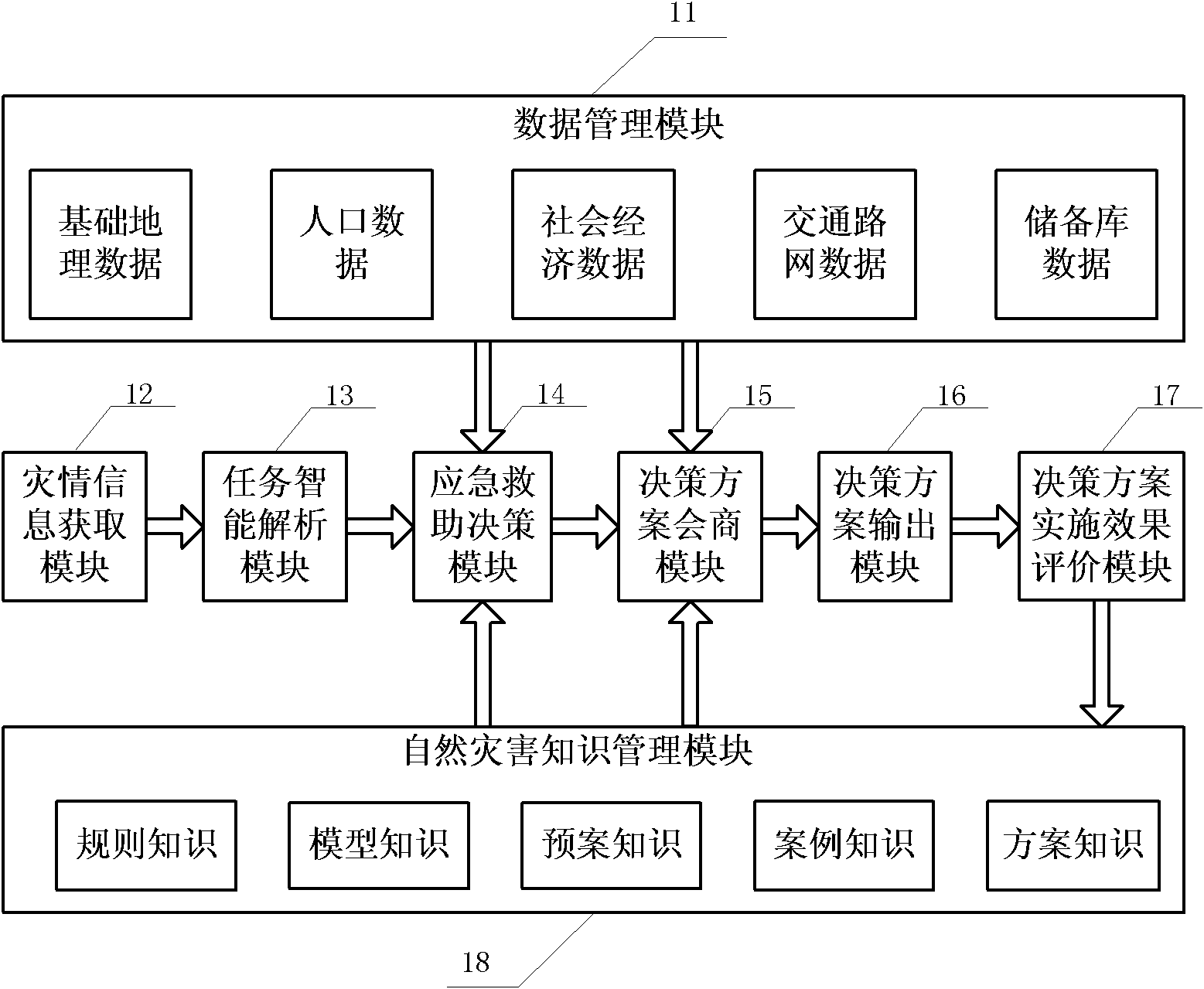
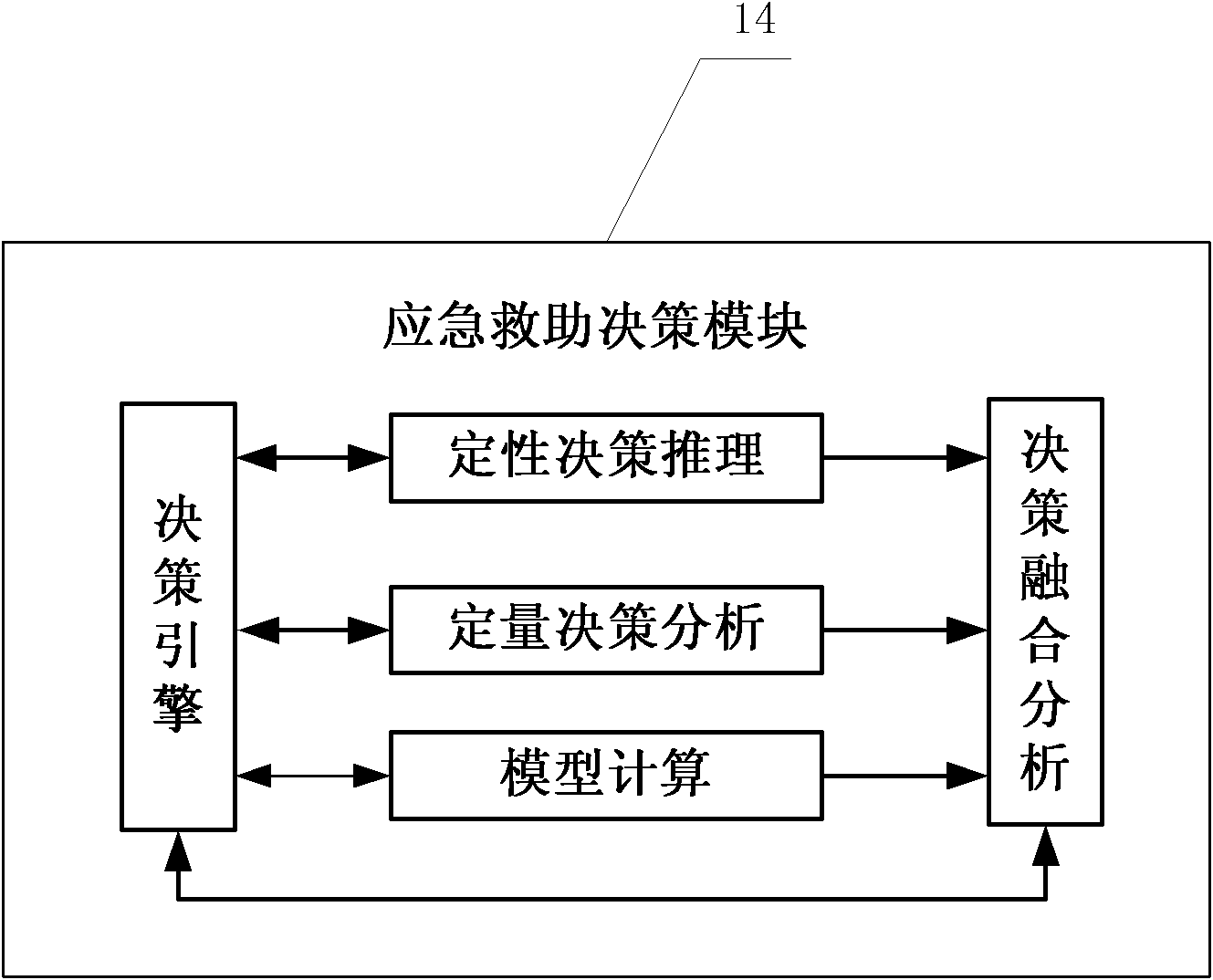
Emergency rescue decision making system aiming at natural disasters and method thereof
The invention discloses an emergency rescue decision making system aiming at natural disasters and a method thereof. A hardware platform comprises a disaster information data input terminal, a database, an application server, a client decision making terminal, a comprehensive natural-disaster knowledge management terminal, a consultation terminal and a printing terminal; a software platform comprises a disaster information acquisition module, an task intelligent analysis module, an emergency rescue decision making module, a decision making scheme consultation module, a decision making scheme output module, a data management module and a natural disaster knowledge management module. By utilizing the emergency rescue decision making system, after the disaster information is obtained, the intelligent analysis of the decision making task is carried out, decision making is carried out under the support of basic data and knowledge, synergetic consultation of experts can be carried out on the obtained feasible scheme, the decision making scheme is output and implemented, the effect of implementing the decision making scheme is evaluated, and the implemented scheme is successfully stored. In the emergency rescue decision making system, according to the whole process of natural disaster development, corresponding emergency rescue measures are given, decision making support is provided for emergency rescue of the government, and the loss caused by natural disasters is reduced.
Owner:HEFEI INSTITUTES OF PHYSICAL SCIENCE - CHINESE ACAD OF SCI
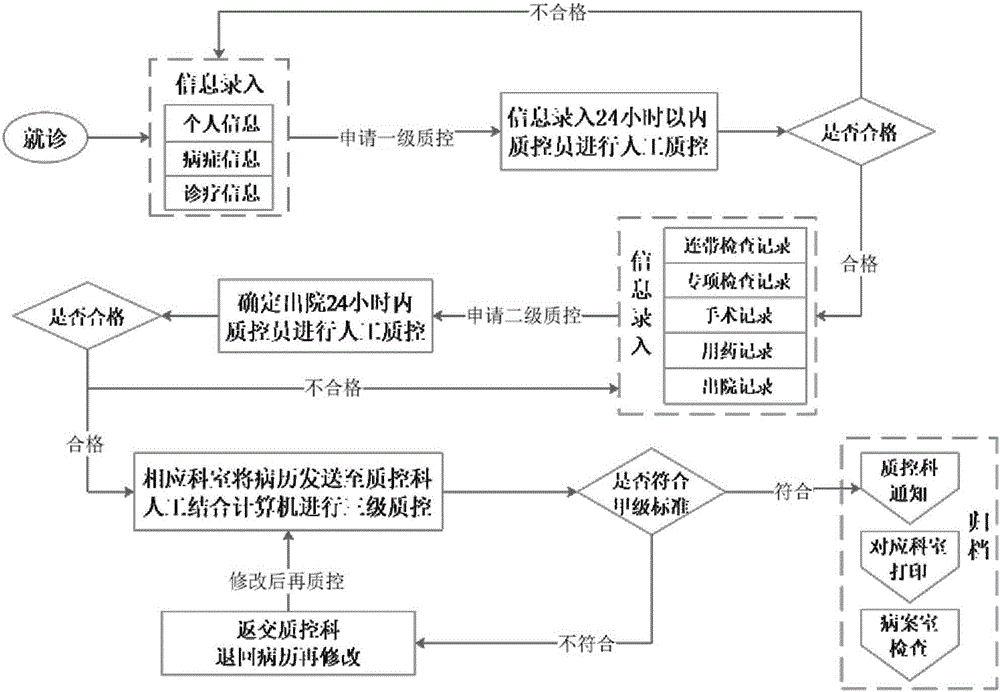
Knowledge-based electronic medical record quality control method
ActiveCN106682397AHighly structuredFine granularitySpecial data processing applicationsPatient-specific dataMedical recordData center
The invention discloses a knowledge-based electronic medical record quality control method. The method includes: by a closed loop type design structure, designing and making quality control semantic judgment rules and inputting time limit rules in an initial stage; allowing middle-stage data to enter a mobile terminal taking Raspberry Pi as a key design, wherein an analysis module combined with the NLP (natural language processing) natural language learning technology is embedded in the terminal; after quality control is finished, uploading synchronous data to a data center for storage and management; by the data center, acquiring common templates in medical record data by means of big data analysis, establishing an error correction knowledge base, and designing and constructing a database and an integrated environment to realize data sharing with internal modules of an error detection quality control terminal. By adoption of the knowledge-based electronic medical record quality control method, data of the data center are sampled and inspected regularly to further guarantee data correctness. Therefore, error detection, integration and analysis of structural medical record data can be realized, mass data and artificial intelligence processing technologies under an intelligent medical environment are utilized completely, medical record quality control cost is reduced, construction of the error correction knowledge base is realized, and quality control algorithm and rule quality is improved.
Owner:江西中科九峰智慧医疗科技有限公司
Energy monitoring system and software based on Internet of Things and cloud computing
InactiveCN105893629AGuaranteed availabilityEnsure safetyHardware monitoringEnergy efficient computingMonitoring systemStructure of Management Information
The invention discloses an energy monitoring system based on Internet of Things and cloud computing. The system comprises a data collecting layer, a data transmission layer and an application management layer, wherein the data collecting layer comprises various metering instruments with a remote data transmission function, the data transmission layer comprises a concentrator and a plurality of collectors, the collectors are connected with the various metering instruments of the data collecting layer, the collectors are connected with the concentrator to perform data concentration, the application management layer comprises a cloud computing platform, a client and a management platform, the client and the management platform are connected with the cloud computing platform, and the concentrator is connected with the cloud computing platform. The energy monitoring system is simple in structure, convenient to build, low in cost, easy to expand, easy to maintain and capable of greatly comprehensively promoting the energy conservation and emission reduction strategy of China.
Owner:江苏斯因信息科技有限公司
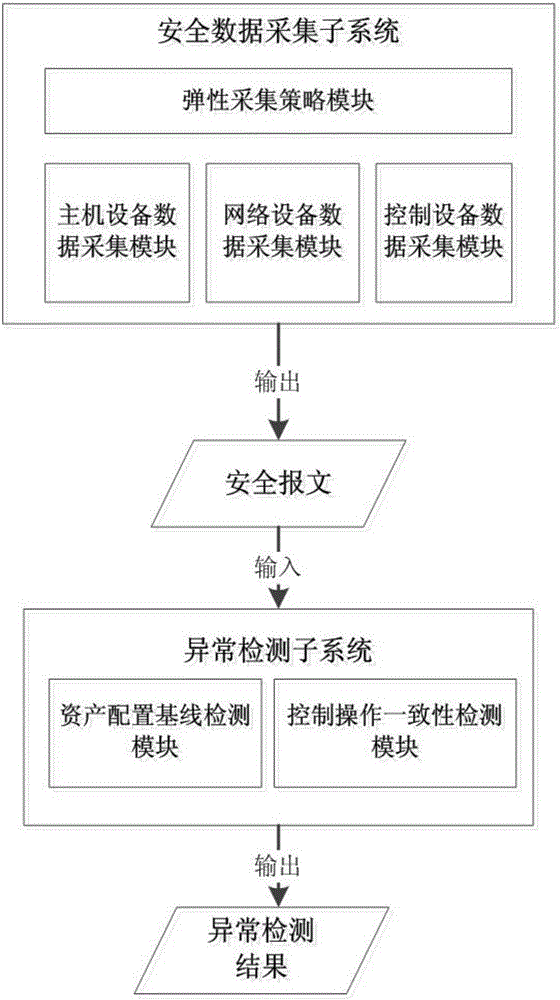
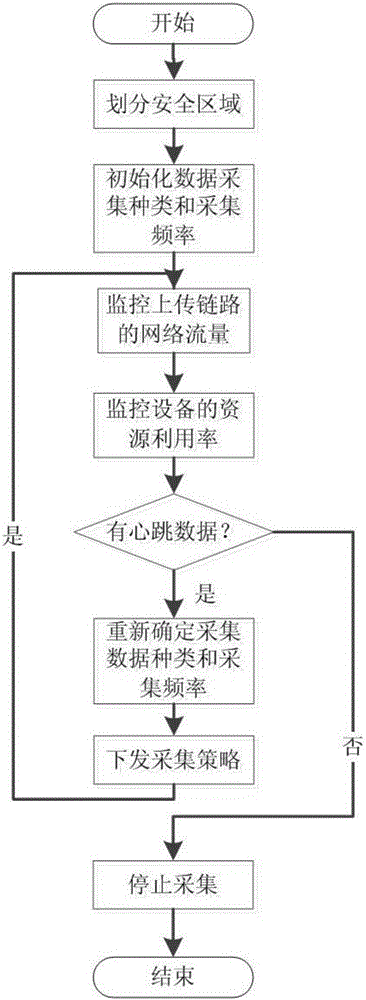
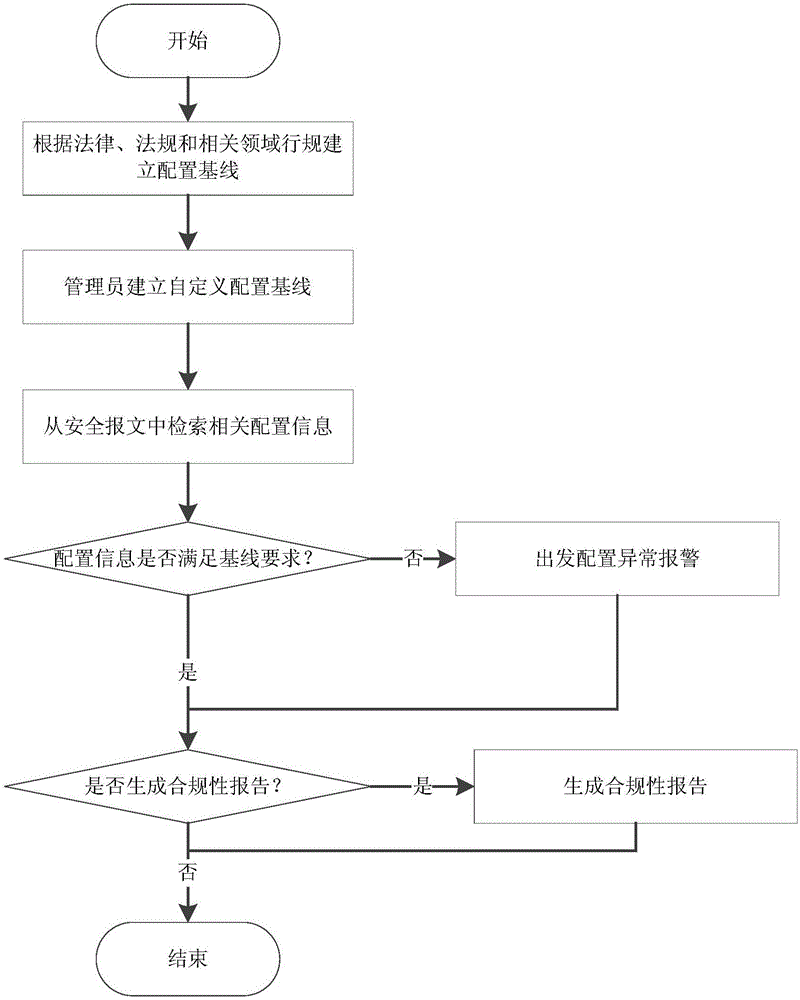
Safety data acquisition and anomaly detection method and system facing industrial control network
ActiveCN105959144AGuaranteed availabilityGuaranteed reliabilityData switching networksAnomaly detectionData acquisition
The invention discloses a safety data acquisition and anomaly detection method and system facing an industrial control network. The safety data acquisition and anomaly detection method comprises two parts: safety data acquisition and anomaly detection, wherein for the safety data acquisition part, the multi-layer and multi-type of safety data in the industrial control network is acquired based on an elastic acquisition strategy, and a safety message with a unified format is formed; and for the anomaly detection part, the safety message is analyzed and anomaly of asset allocation in the industrial control network is discovered through detection by means of configuration of a baseline, and anomaly of the operation behavior in the industrial control network is discovered through control and operation of consistency detection. The safety data acquisition and anomaly detection method and system face the industrial control network, and can improve the capability of the industrial control network of opposing APT attack, on the basis of guaranteeing the availability and reliability of the industrial control network.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Method for uniformly distributing data in cloud storage
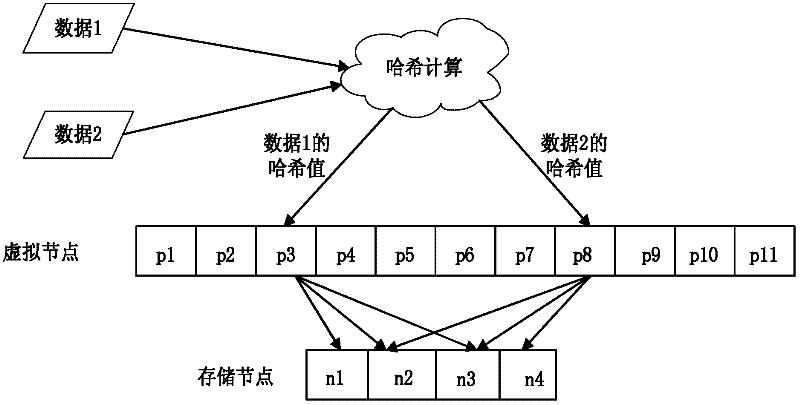
ActiveCN102457571AImprove equalization performanceGuaranteed availabilityTransmissionHash functionData needs
The invention relates to a method for uniformly distributing user data in a cloud storage system, which comprises the following steps of: setting a total number of virtual nodes and a number of copies in the cloud storage system; setting a distribution weight of each storage node in the cloud storage system; determining the number of virtual nodes to be distributed according to the total number of the virtual nodes, the total number of the copies and the distribution weight of each node in the cloud storage system; uniformly distributing three copies of all the virtual nodes onto different storage nodes according to the number of the virtual nodes to be distributed of each node in the cloud storage system; when the data need to be stored, mapping the data to a certain virtual node by a hash function and then respectively storing three copies of the data into the three copies of the acquired virtual nodes; and when the storage nodes are added in or removed from the cloud storage system, acquiring information of the virtual nodes to be redistributed, recalculating the number of virtual nodes to be distributed of each available storage node and then redistributing the virtual nodes.
Owner:CHINA STANDARD SOFTWARE
Evaluation method and system for network burst affair
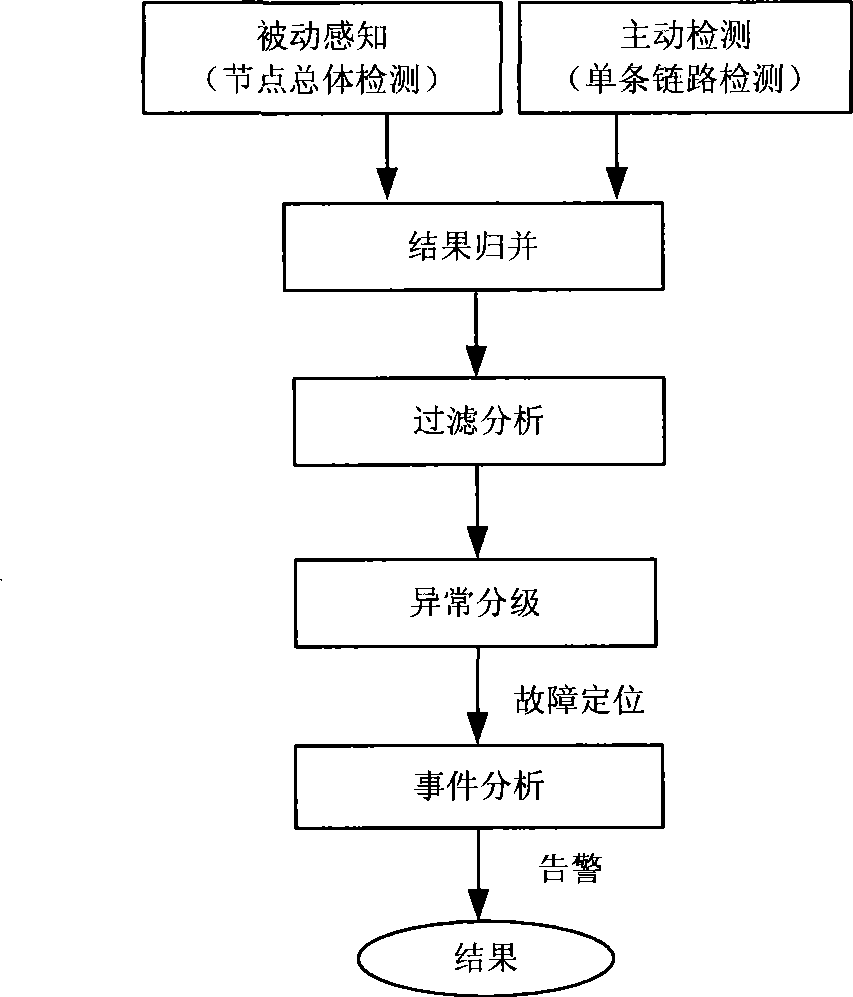
InactiveCN101483547AReduce loadReduce resource overheadData switching networksQuality of serviceNetwork link
The present invention discloses a method for measuring and evaluating network burst damage event, wherein the method comprises the following steps: passive perceiving and active detecting burst event; filtering and analyzing after merging the result; dividing the event grade according to the merging result, realizing the positioning to the fault reason; determining whether an adjustment of protocol mechanism should be executed according to the grade; and checking the whole condition of adjusted network for ensuring the correctness. The invention also provides a system for measuring the network burst damage event. The system comprises a router control module, an array management algorithm module, a network management module and an off-line calculating module. The problem to be settled by the invention is cause that the router has a flow perceiving capability, realize whether the full-network link and node operate normally and whether the burst damage event is generated. The result is notified in time for adjusting the protocol mechanism. The invention provides criterion for the protocol adjustment thereby increasing the usability and reliability of network node and link and finally guaranteeing the service quality of network.
Owner:THE PLA INFORMATION ENG UNIV
Cloud file storage system and method
InactiveCN103577503AEasy to storeEnsure safetyFile access structuresTransmissionUser needsTerminal equipment
The invention provides a cloud file storage system and a cloud file storage method, which are applied to cloud computing servers. The cloud computing servers are connected with terminal equipment and a plurality of cloud servers. The cloud file storage system and the cloud file storage method can be used for dividing files uploaded by the terminal equipment into a plurality of data blocks, and storing each data block into the corresponding cloud server through the network in a scattering manner. When a user needs to use the files, the cloud file storage system can download all the data blocks of the data file from the corresponding cloud server through the network, combining the downloaded data blocks into the data file needed by the user, and transmitting the data file to the terminal equipment of the user. After the system and the method are implemented, a mass of files can be stored in the distributed cloud servers after being split in the scattering mode, so that the storage of the files is facilitated, and the safety and the usability of the files are ensured.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Virtualization-based credible server trust chain construction method
ActiveCN105095768AIntegrity guaranteedGuaranteed confidentialityPlatform integrity maintainanceVirtualizationOperational system
The invention discloses a virtualization-based credible server trust chain construction method, and belongs to the field of server information credibility. The method comprises the steps that characteristics of a could data center are combined, a credible server is used as a foundation, link firmware, a virtual host, a virtual operation system and a hardware and software integrated trust chain of an upper layer application are constructed, and integrity, confidentiality and availability of a cloud host system in data processing and service operation are ensured.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Permission data validation method, device and system
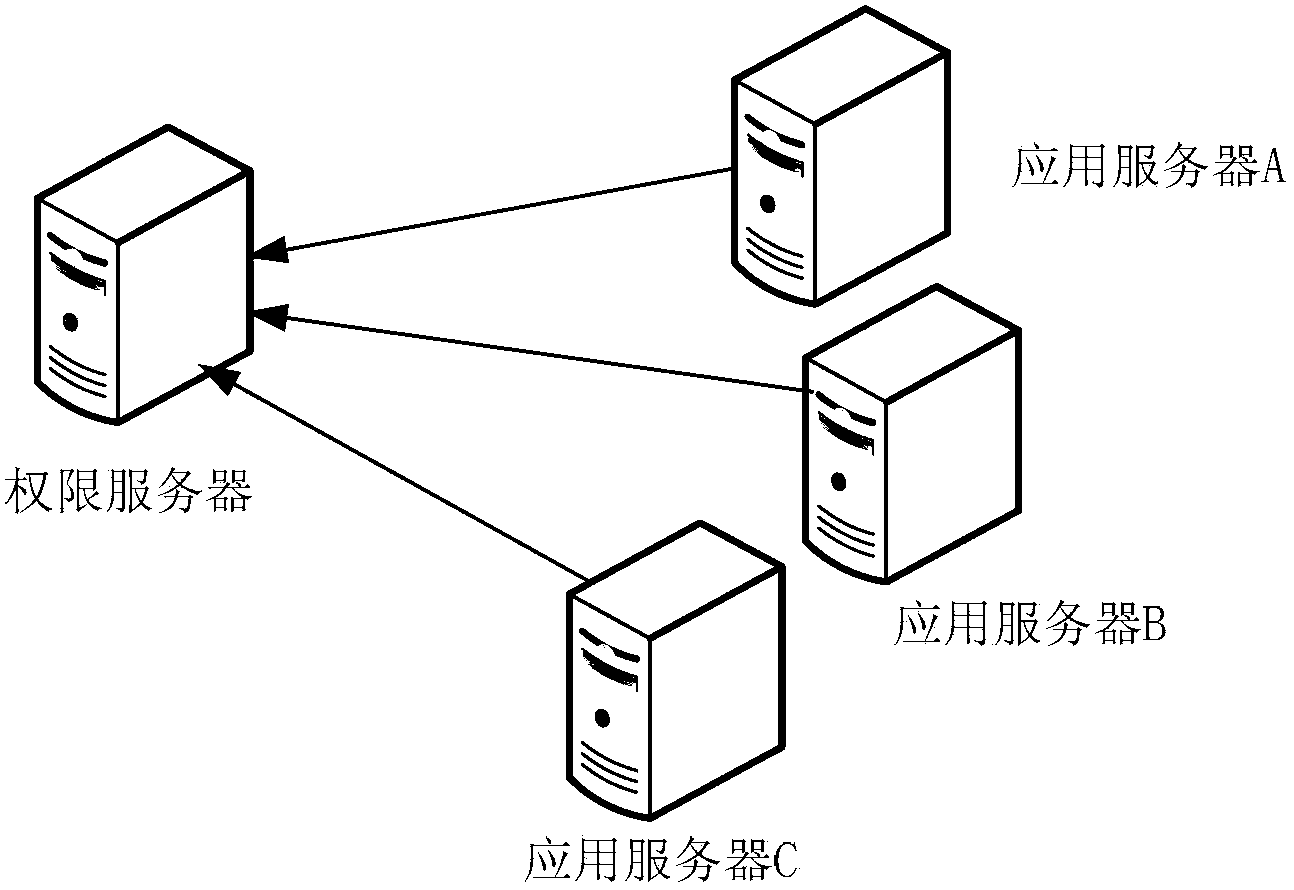
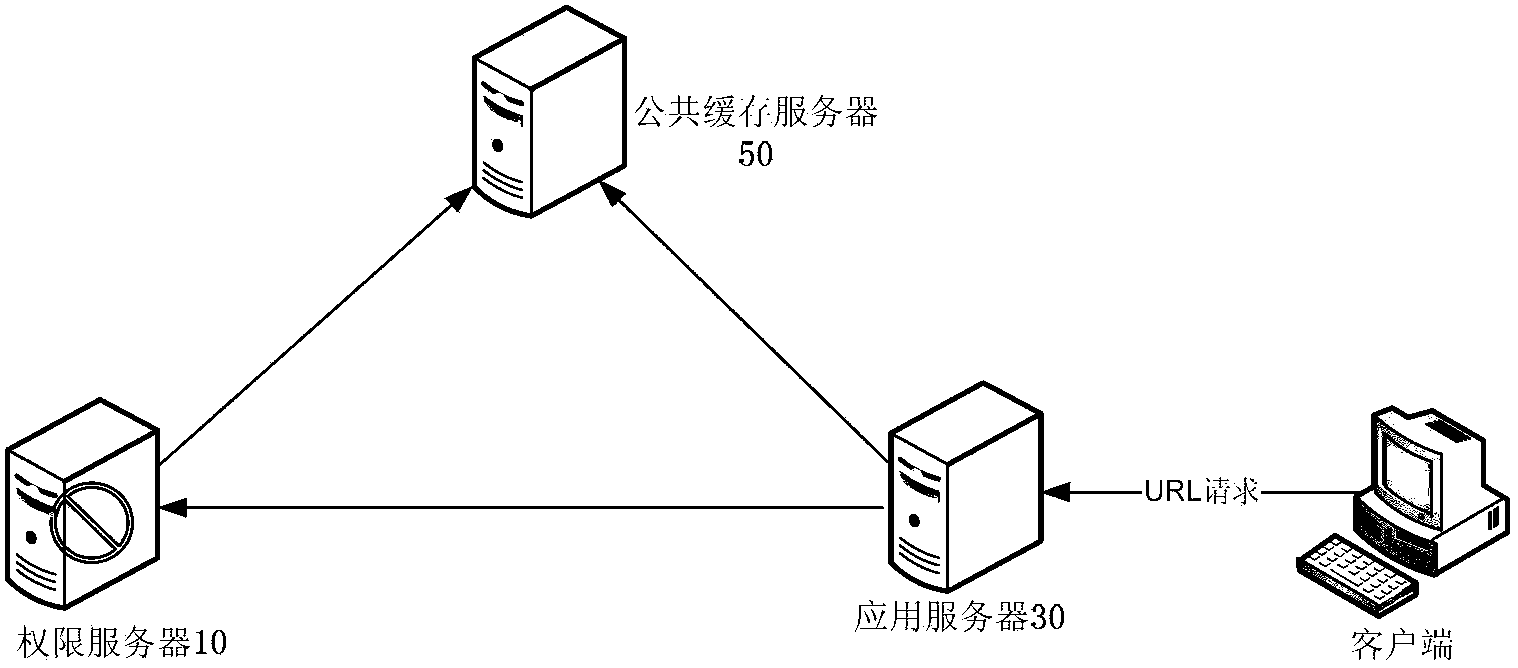
ActiveCN103490886AGuaranteed availabilityFix inaccessible issuesUser identity/authority verificationData validationApplication server
The invention discloses a permission data validation method, device and system. The method comprises the steps of using a server to receive permission data access information of a client terminal, processing the permission data access information according to a keyword generative rule to generate a permission validation keyword, sending the permission validation keyword to a public cache server to conduct validation to obtain a validation result corresponding to the permission validation keyword, returning the validation result to the client terminal under the condition that the validation result is successfully got back through the public cache server, and under the condition that the validation result is not successfully returned through the public cache server, using a permission server to inquire to obtain the corresponding validation result according to the received permission validation keyword by using a remote calling interface to have access to the permission server. By means of the permission data validation method, device and system, a permission service on an application server is still available and the availability of supply chain system colonies is not influenced when the permission server breaks down.
Owner:ALIBABA GRP HLDG LTD
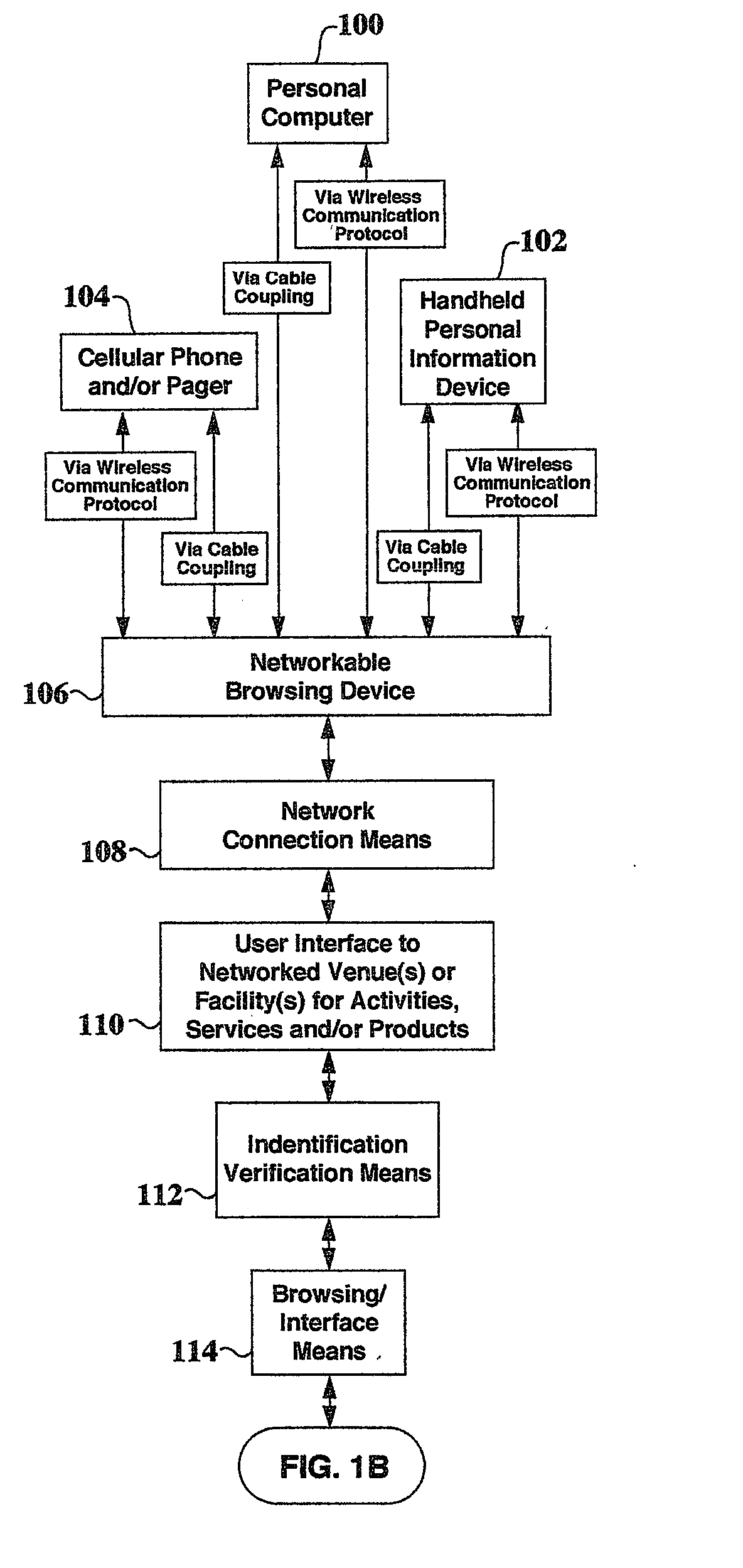
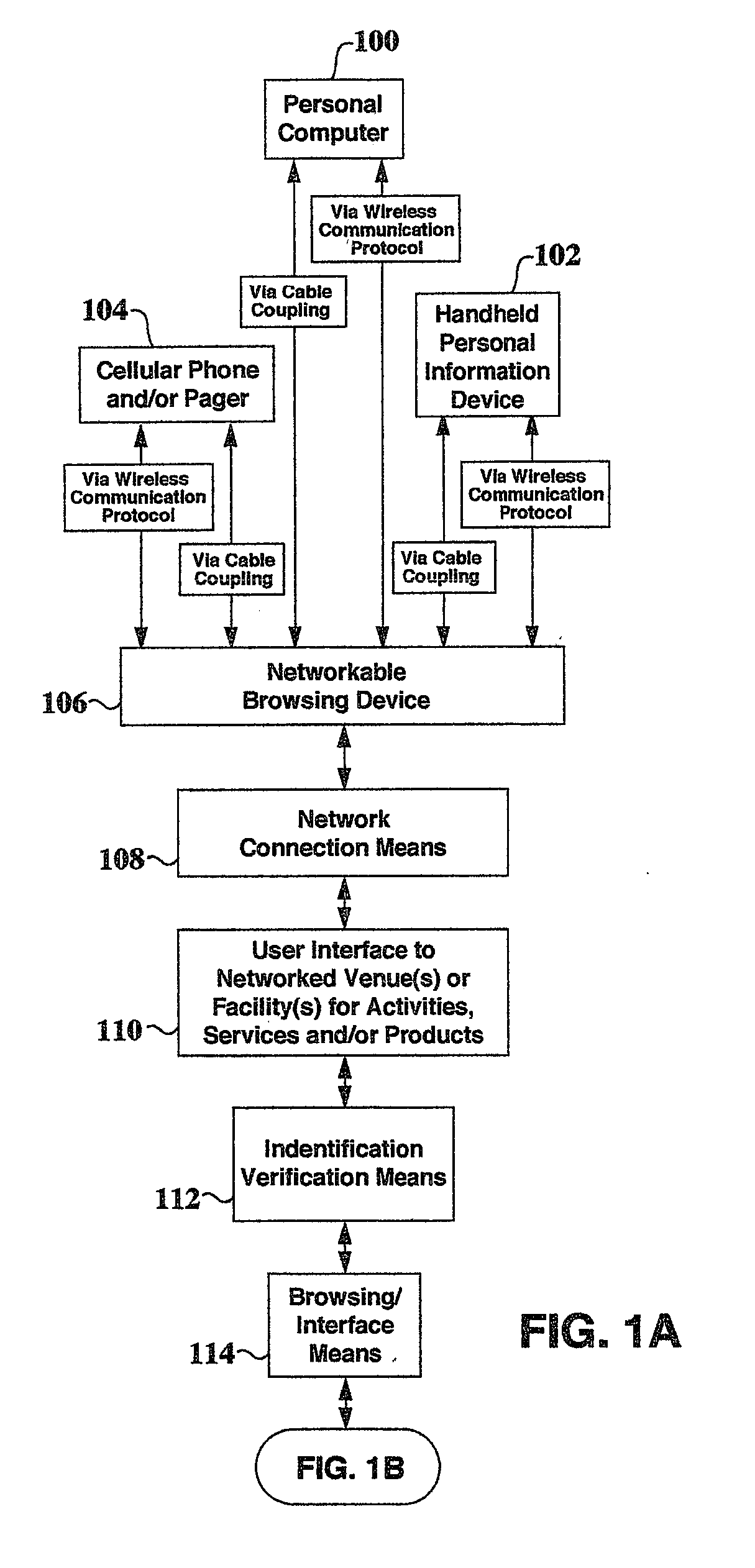
Portable electronic device, external basic device, method for coupling the portable electronic device to an external basic device and using the external basic device for coupling the portable electronic device
InactiveUS20130236192A1Improve compatibilityImprove data transfer rateElectromagnetic wave systemClose-range type systemsElectrical conductorEnergy absorption
A portable electronic device includes a functional processor for providing an electronic functionality, an optical data transmitter for conductor-less, optical data communication with an external basic device and an energy supplier for an energy absorption by means of an inductive coupling from a magnetic field emitted by the external basic device and for supplying the functional processor and the data transmitter with energy based on the energy absorbed from the external magnetic field.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
Method for estimating remaining time and capacity of battery
ActiveCN102655549AImprove experienceHigh precisionElectrical testingSubstation equipmentCurrent electricElectrical battery
The invention discloses a method for estimating the remaining time of a battery, which comprises the following steps: S1, reading a reference curve of the battery, wherein the reference curve is initially generated according to the nominal capacity of the battery; S2, acquiring current battery parameters, wherein the parameters include the current voltage, the current electric current, and the discharge time; S3, judging whether the battery is in a floating, discharge or equalized charging state; S4, calculating the remaining time T of the battery in the state of floating; S5, calculating the remaining time of the battery in the state of discharge; and S6, calculating the discharge time of the battery in the state of equalized charging. The invention also discloses a method for estimating the remaining capacity of a battery. According to invention, a remaining time estimation result and a remaining capacity estimation result are coherent, and the accuracy is higher, so that while the availability is ensured, the user experience is greatly increased.
Owner:SHENZHEN REALTIMES TECH
Information security control system
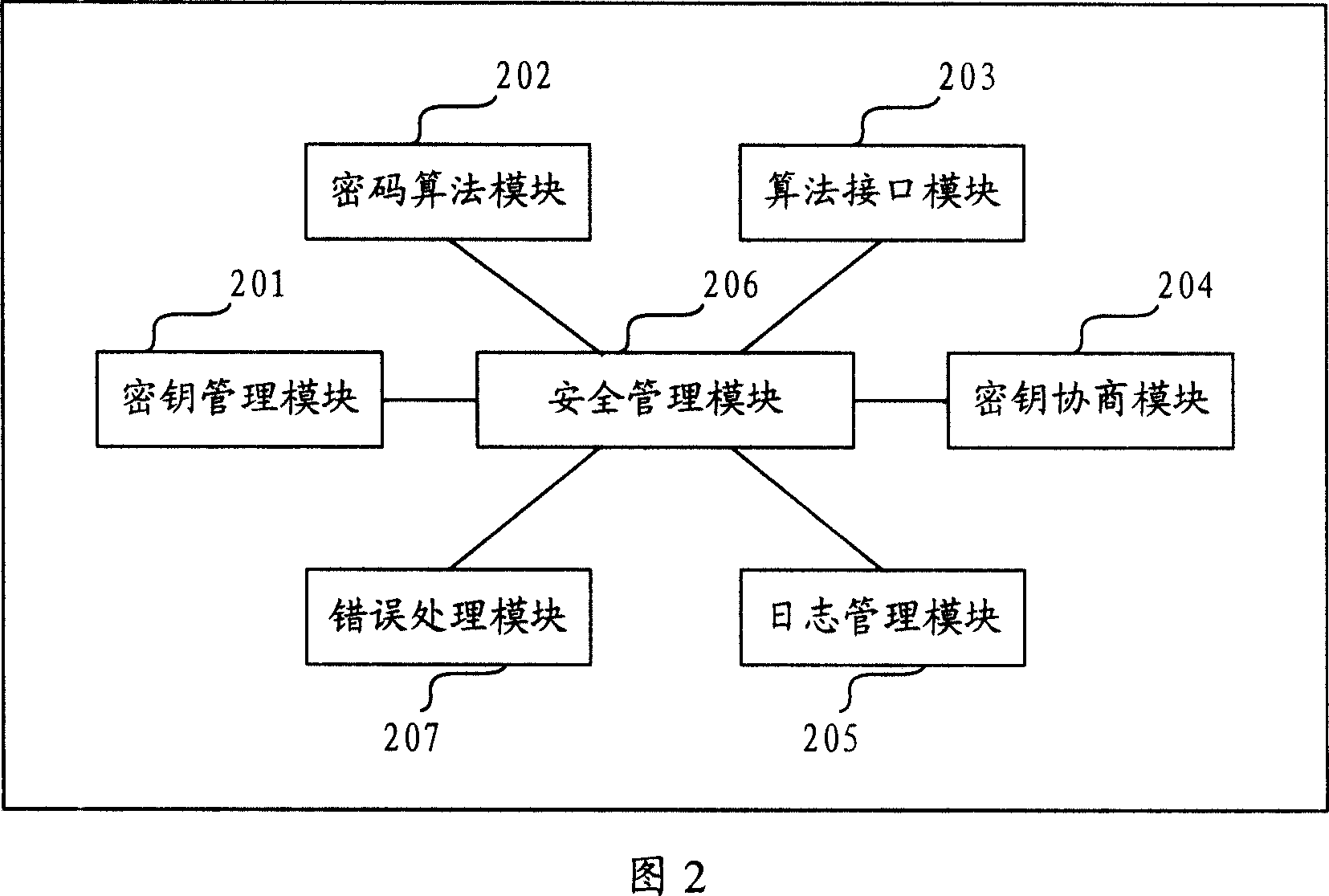
InactiveCN101043335AImplement encrypted transmissionAvoid illegal acquisitionUser identity/authority verificationError processingConfidentiality
The invention provides a control system for the information safety to solve the safe problems existed in the business system, and prevent the important data from leakage and illegal interpolation. The system includes: key management module, key negotiation module, code interface module, log management module, security management module and mistake processing module. The control system for the information safety provided by the invention can combine with the business system closely, and it is classified following the business system on the structure design, the business logic of every hierarchy has the corresponding security control to protect the every aspects of business, and the business safety technical measures cover the every aspect of business system that includes data transmission, data storage, database, files, logs and operation certification and so on, and it can assure the confidentiality, integrality, anti-aggression, usability, anti-repudiation, ID identify and authority control of business system.
Owner:CHINA CONSTRUCTION BANK
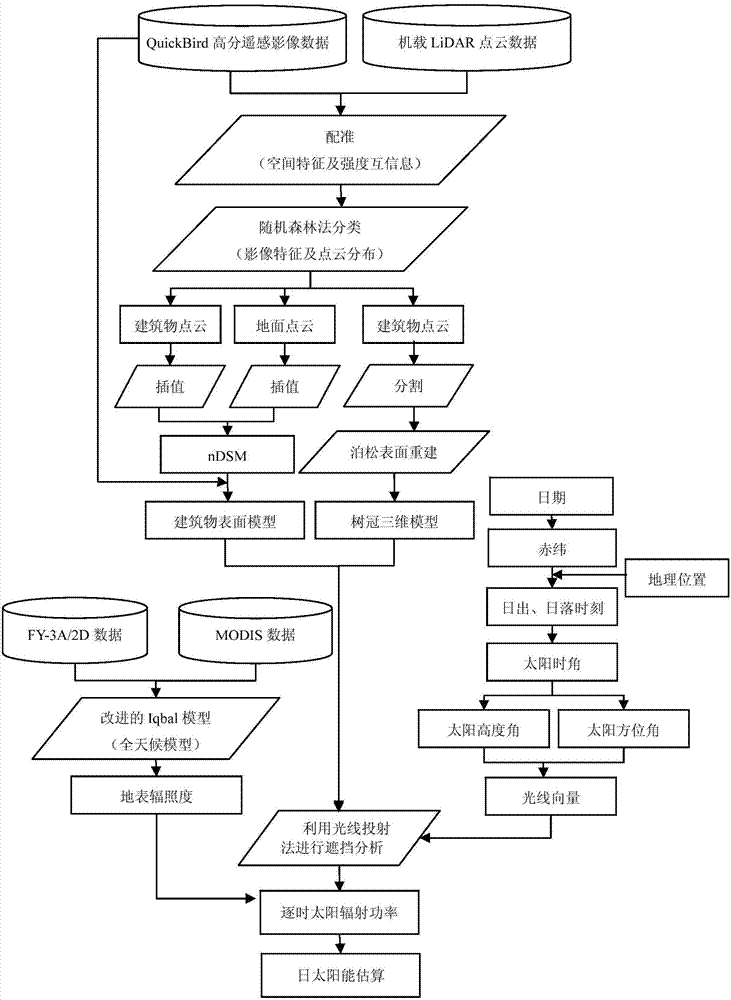
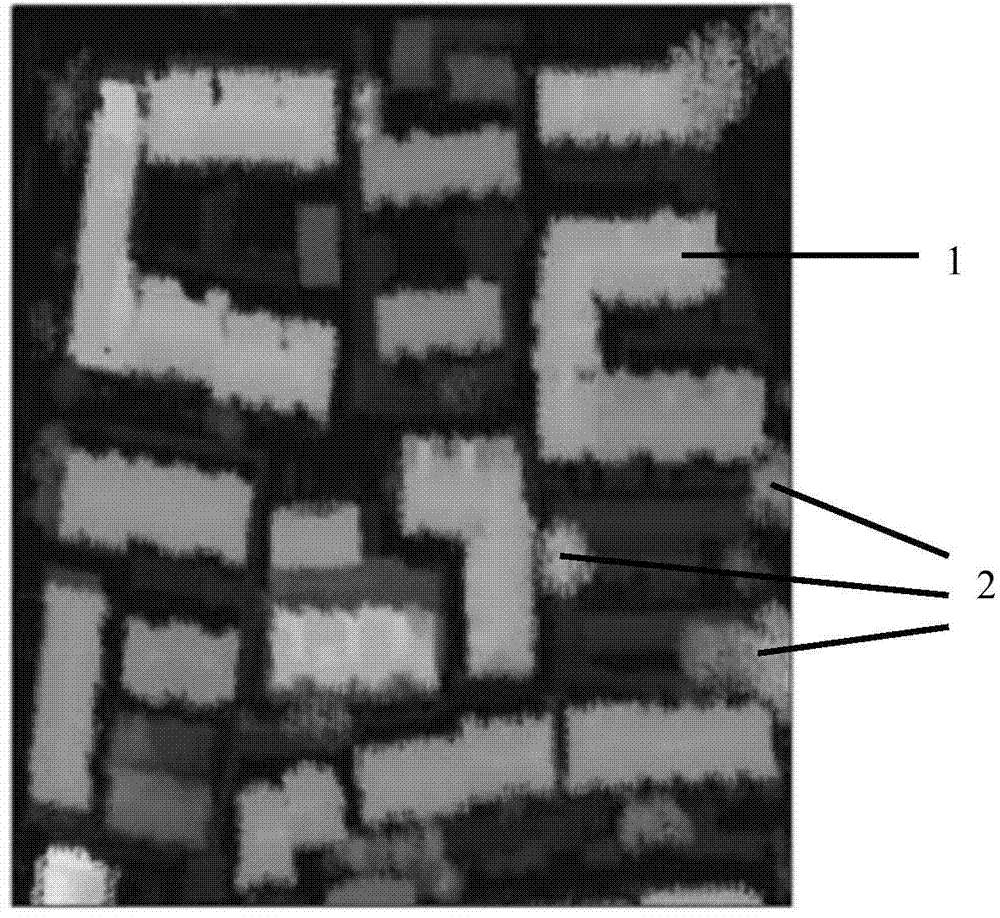
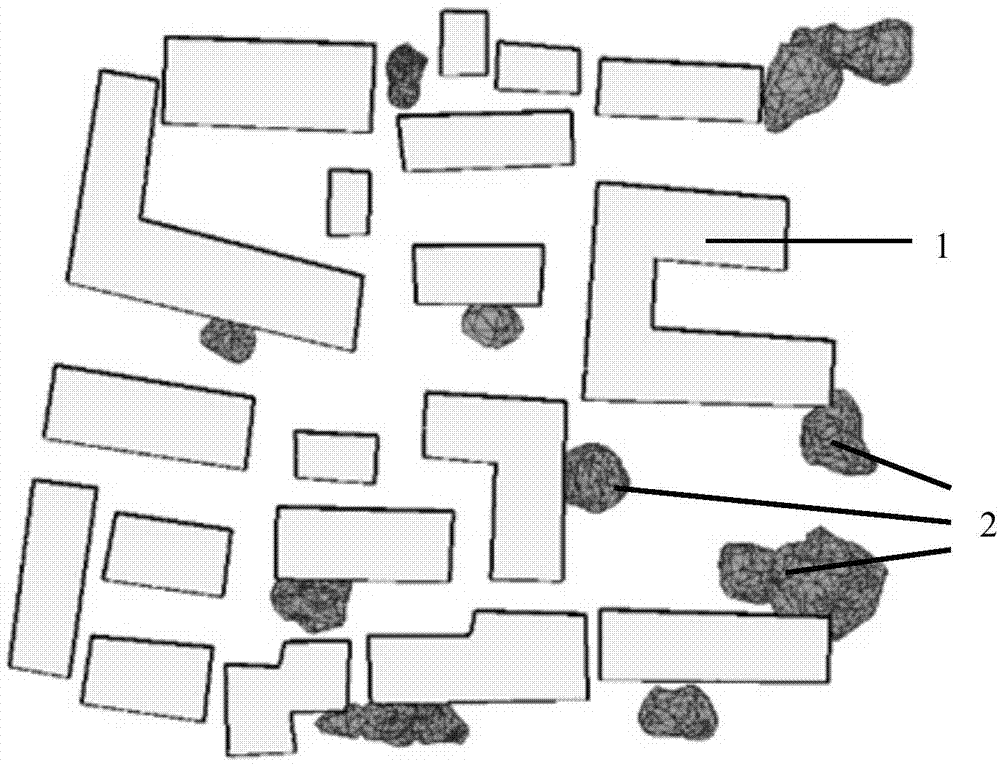
Rapid estimation method for solar energy in construction size
ActiveCN103942420APreserve morphological informationDetails change description idealCharacter and pattern recognitionSpecial data processing applicationsUrban regionBuilding design
The invention discloses a rapid estimation method for solar energy in a construction size. The method includes the steps that by the comprehensive utilization of LiDAR data and high-resolution remote sensing image data, and three-dimension digital surface modeling is performed on objects such as urban constructions and trees; through simulation analysis of the attenuation effect, on direct solar radiation to the ground, of the atmosphere and the sheltering influence, on direct solar radiation energy obtained by construction surfaces including roofs and wall faces, by the urban objects, the solar energy obtained by the roofs and the wall faces of the urban constructions and dynamic estimated values are obtained. The rapid estimation method is suitable for specific application of using solar energy resources in the construction size in an urban region, wherein the specific application includes optimal configuration of energy resources, installation of solar photovoltaic equipment, design of green and environment-friendly constructions and the like.
Owner:PEKING UNIV
Digital beam forming and phase fitting method
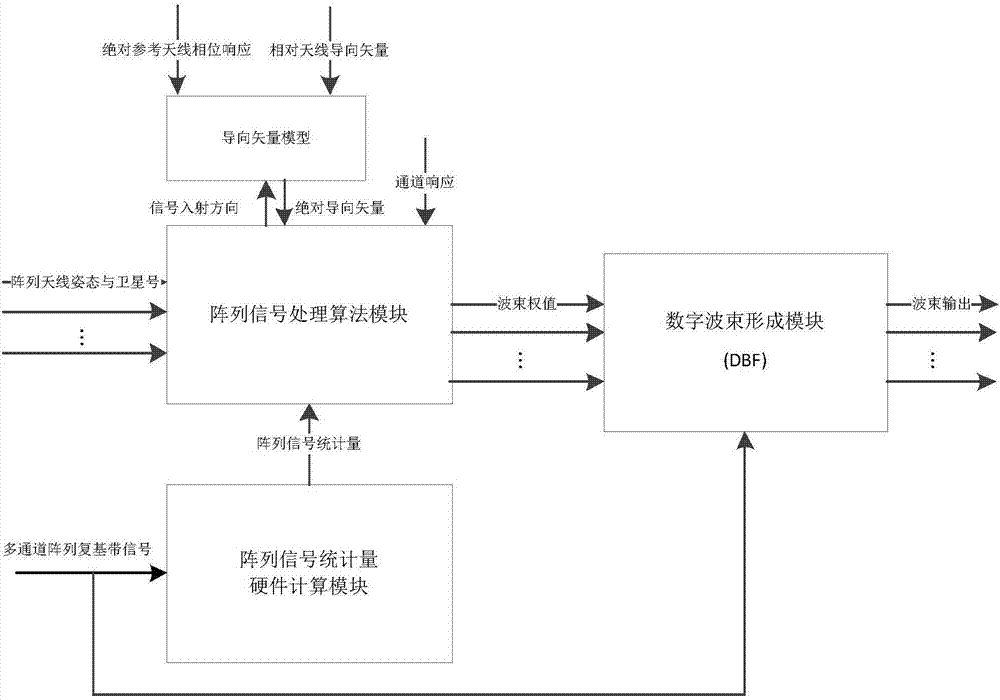
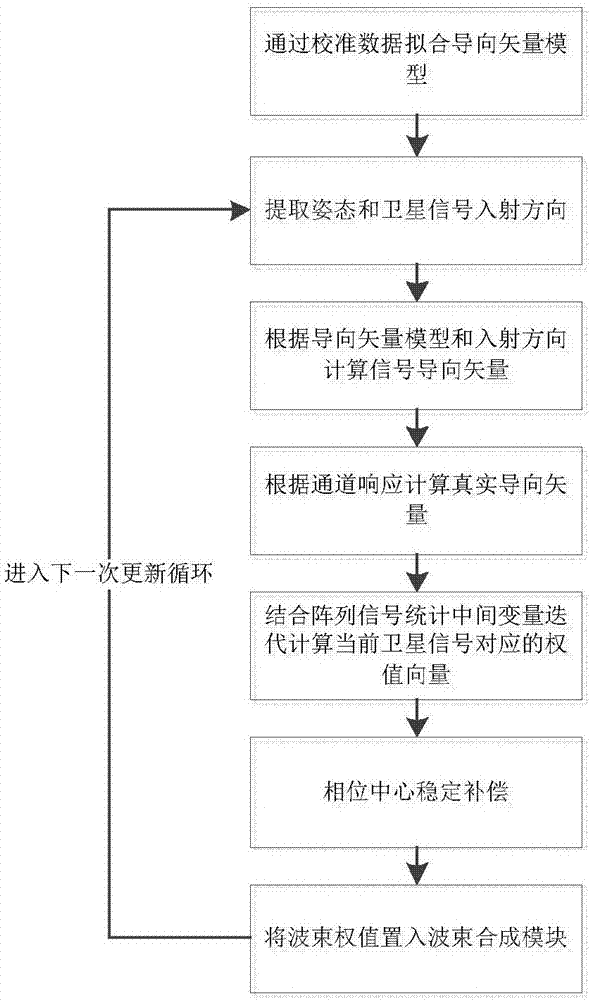
ActiveCN107356943AAchieve stabilizationSuppress interferenceSatellite radio beaconingPhase fittingModel parameters
The invention provides a digital beam forming and phase fitting method, and aims to provide a method capable of suppressing interference, improving the signal to interference and noise ratio and accurately controlling the phase of a beam forming signal. The method is implemented according to the technical scheme that a steering vector model obtains relative steering vectors by using online calibration, accurate absolute steering vectors are acquired by combining absolute phase responses, which are measured in a darkroom, of a reference array element, model parameters of the steering vector are fitted out by combining the existing absolute steering vectors, and an accurate spare steering vector of an antenna array in any direction is acquired; the second-order statistic of the array signal is iteratively calculated through an array signal statistic hardware calculation module, and sent to an array signal processing algorithm module together with an antenna array steering vector and a channel response to calculate an optimal beam weight; and finally, the array signal processing algorithm module imbeds the optimal beam weight into the digital beam forming module to perform real-time digital beam forming and phase fitting and process multi-channel array data and beam output in real time.
Owner:10TH RES INST OF CETC
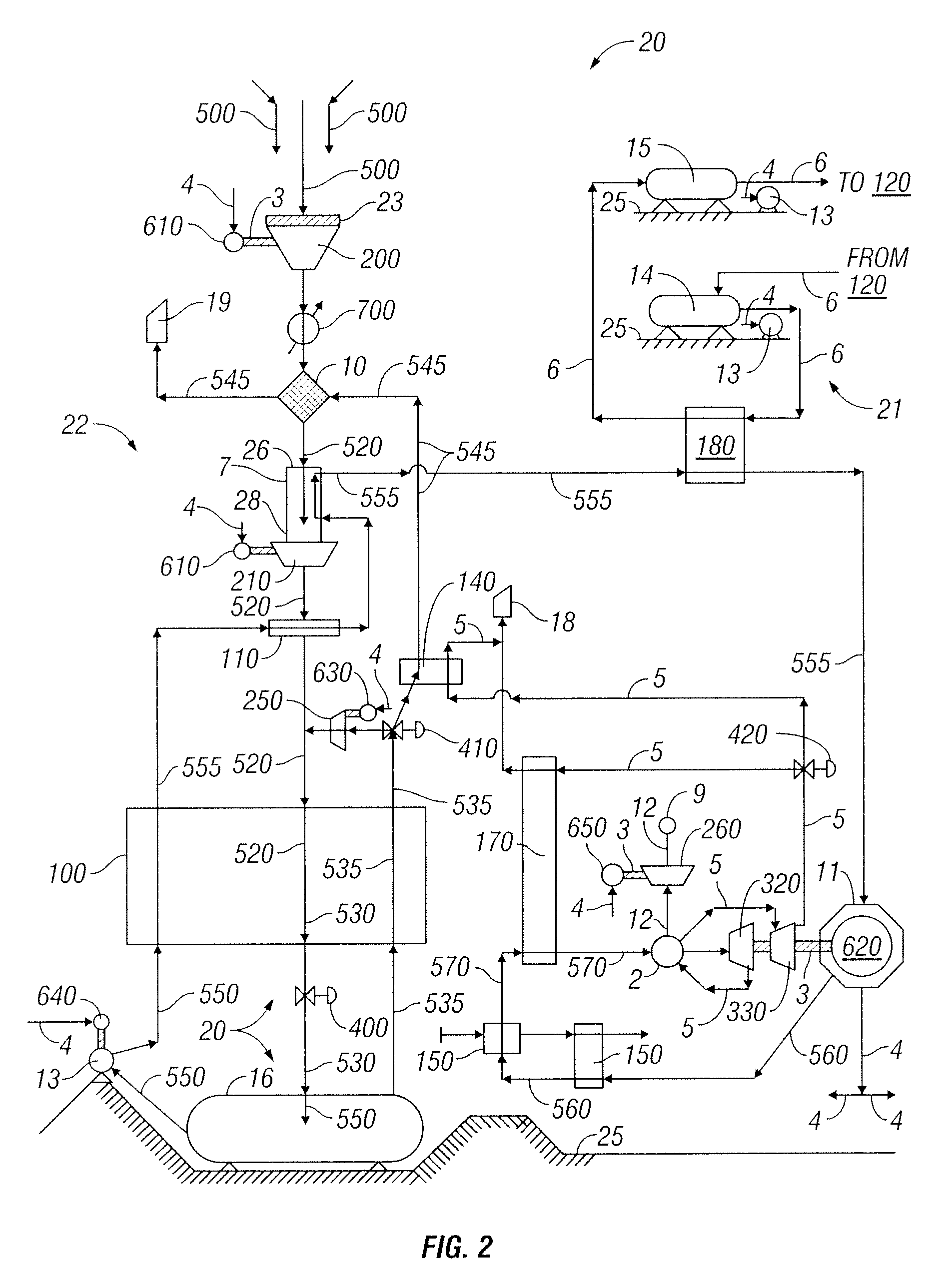
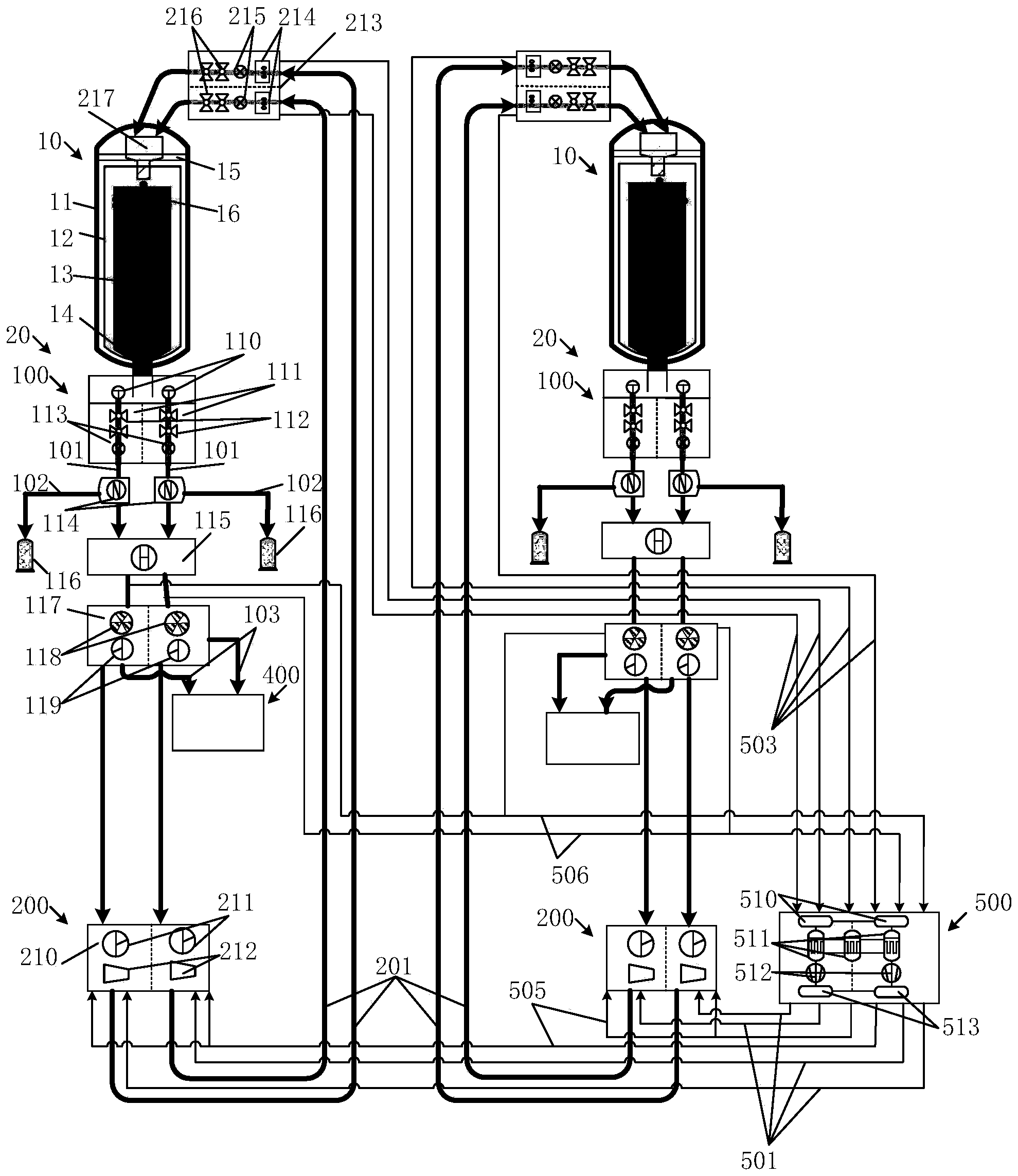
Pebble-bed module type high-temperature gas cooled reactor fuel loading and unloading system
ActiveCN103474113AGuaranteed purityImprove securityNuclear energy generationReactor fuel elementsVacuum pumpingNuclear engineering
The invention relates to a pebble-bed module type high-temperature gas cooled reactor fuel loading and unloading system which comprises a reactor (10), a reactor core fuel circulating system (20), a new fuel loading system (300) and a spent fuel unloading system (400). The reactor (10) comprises a reactor pressure container (11), a graphite coating reactor internal component (12), a central reactor core cylinder (13), a metal reactor internal component (15) and an unloading pipe (14), the reactor core fuel circulating system (20) comprises a reactor core unloading system (100) and a reactor core loading system (200) and further comprises a helium pneumatic conveying system (500), a compressed air pneumatic conveying system (600), a vacuum pumping system (700) and a helium supplying and recycling system (800), and the compressed air pneumatic conveying system (600), the vacuum pumping system (700) and the helium supplying and recycling system (800) are all connected with the helium pneumatic conveying system (500). The helium pneumatic conveying system (500) is further respectively connected with the reactor (10), the reactor core fuel circulating system (20), the new fuel loading system (300) and the spent fuel unloading system (400).
Owner:CHINERGY CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com