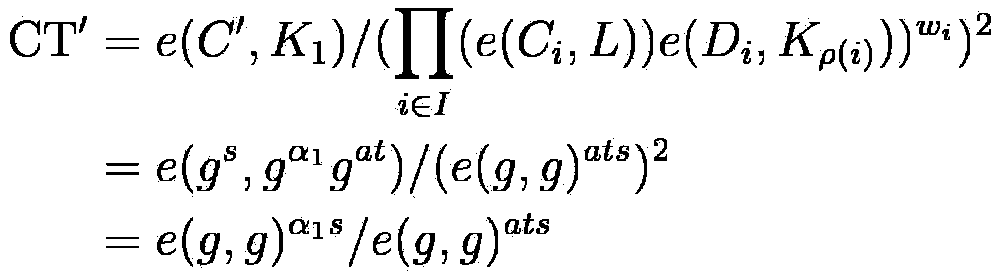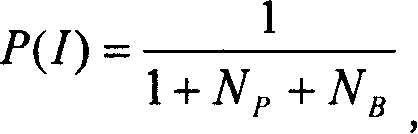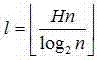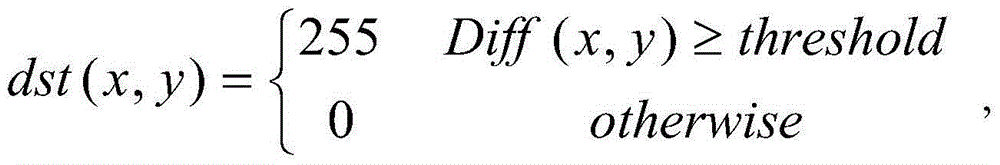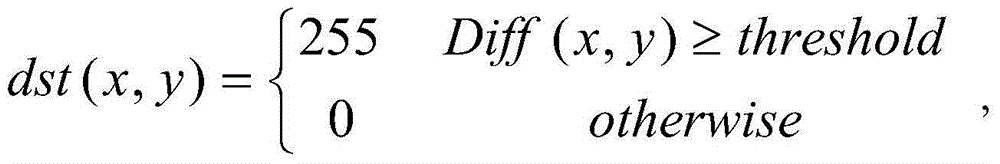Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
795results about How to "Reduce resource overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method, user equipment and base station for transmitting uplink control information
ActiveCN103209483AReduce resource overheadImprove resource utilizationError prevention/detection by using return channelNetwork traffic/resource managementChannel state informationTelecommunications
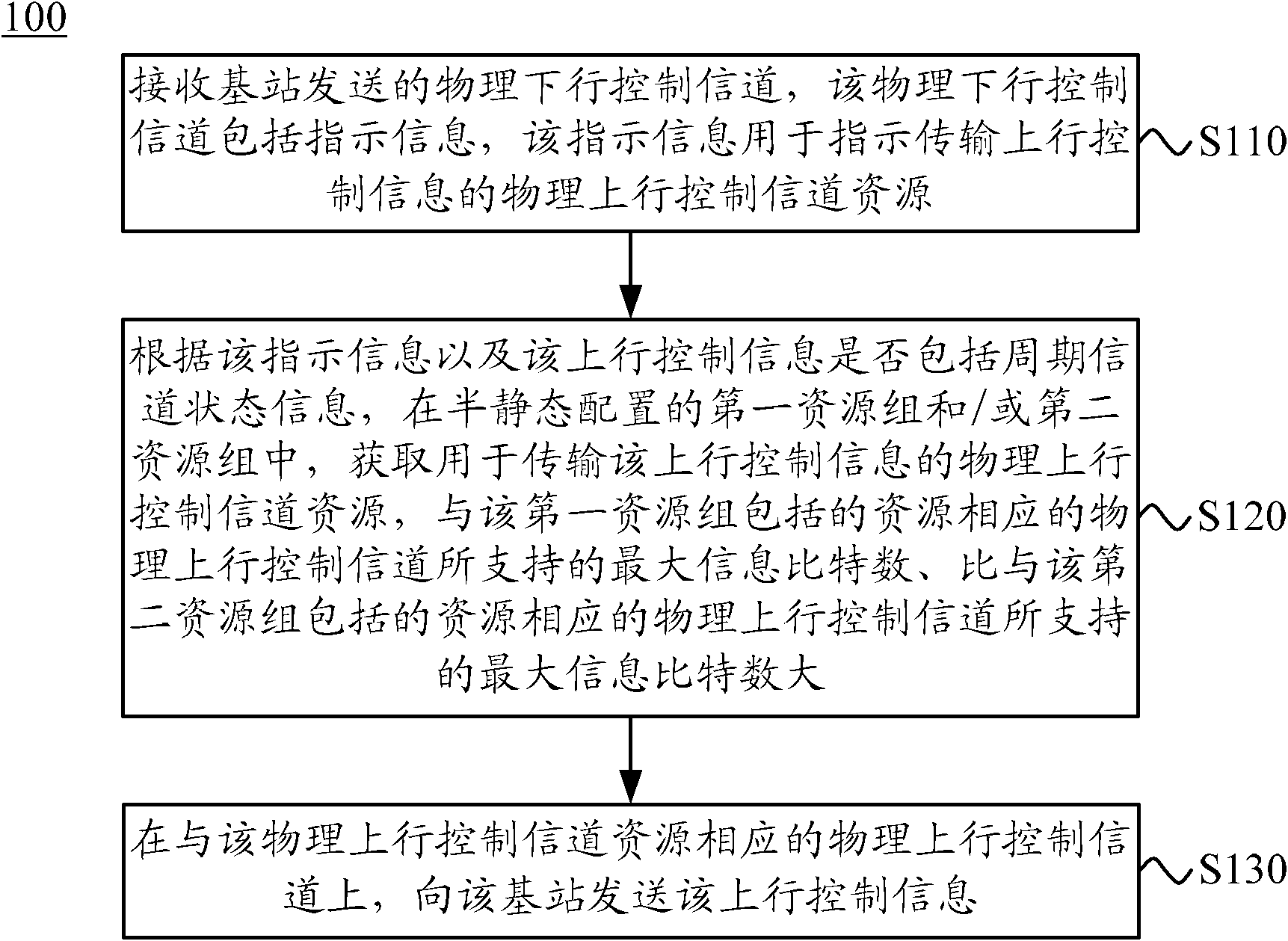
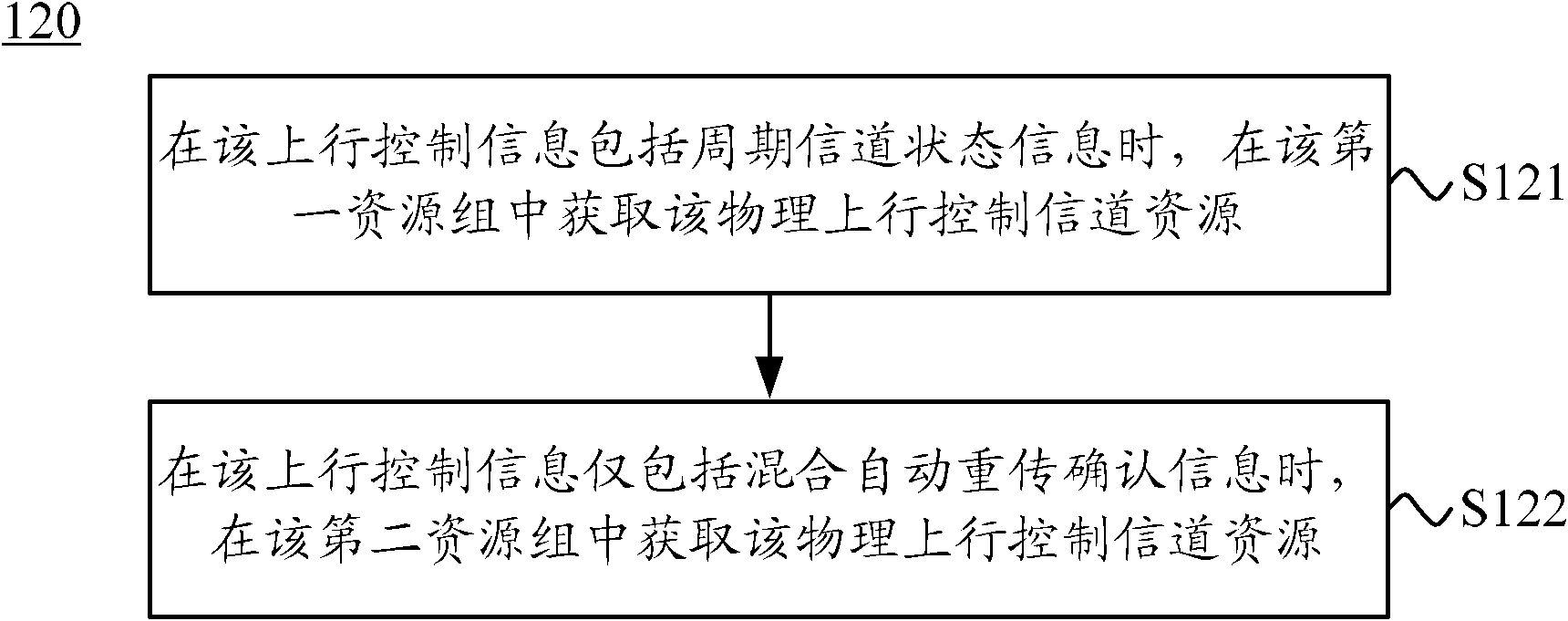
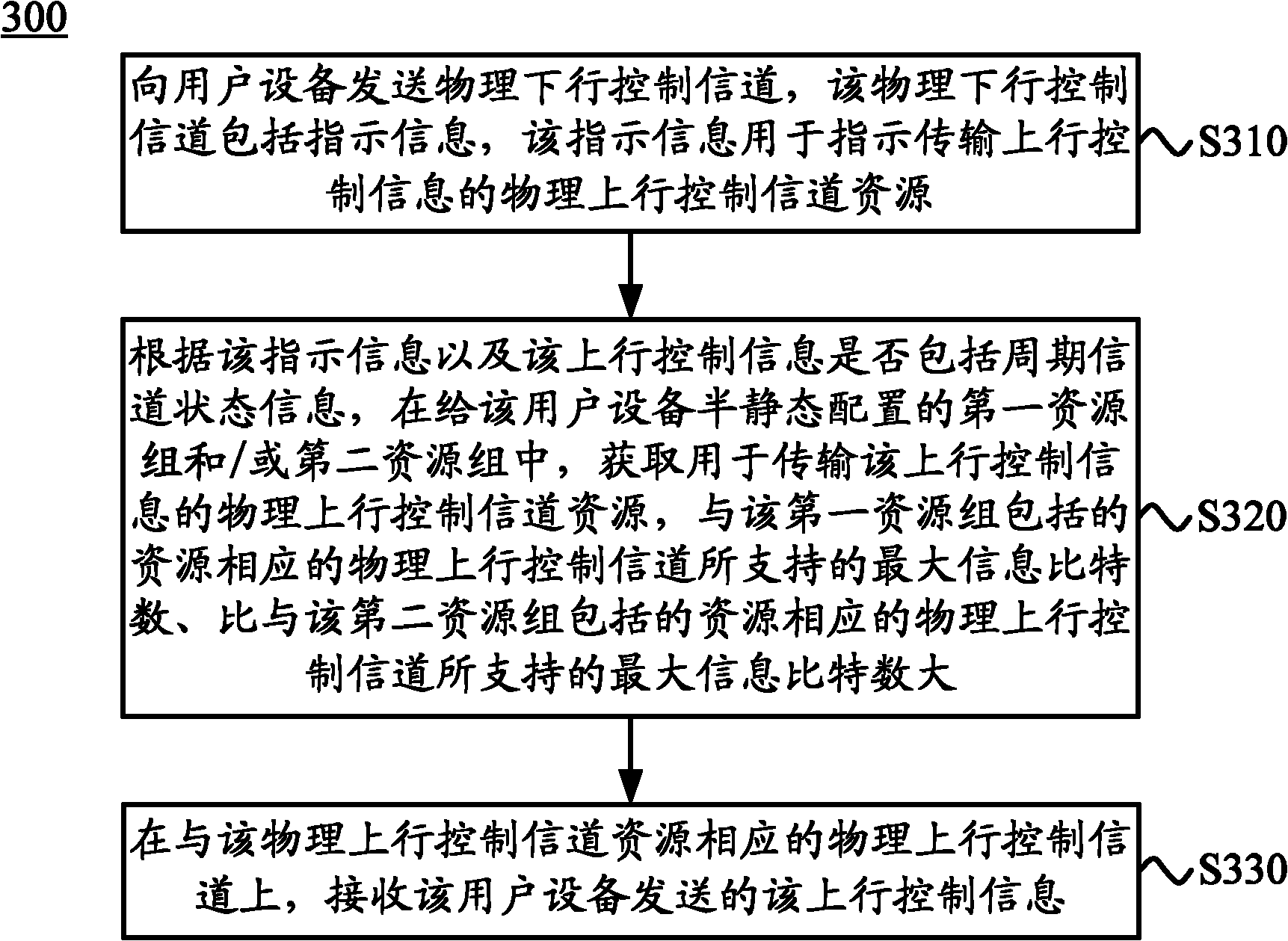
The invention discloses a method, user equipment and a base station for transmitting uplink control information. The method comprises receiving a physical downlink control channel sent from the base station, wherein the physical downlink control channel comprises indication information used for indicating physical uplink control channel resources used for transmitting the uplink control information; acquiring the physical uplink control channel resources used for transmitting the uplink control information in a first resource group and or a second resource group which are configured in a semi-static state according to whether period channel state information included in the indication information and the uplink control information or not; and sending the uplink control information to the base station on a physical uplink control channel corresponding to the physical uplink control channel resources. The method, the user equipment and the base station for transmitting the uplink control information can transmit the uplink control information, reduce resource expenses of the physical uplink control channel in transmission of the uplink control information and improve the resource utilization rate.
Owner:HUAWEI TECH CO LTD
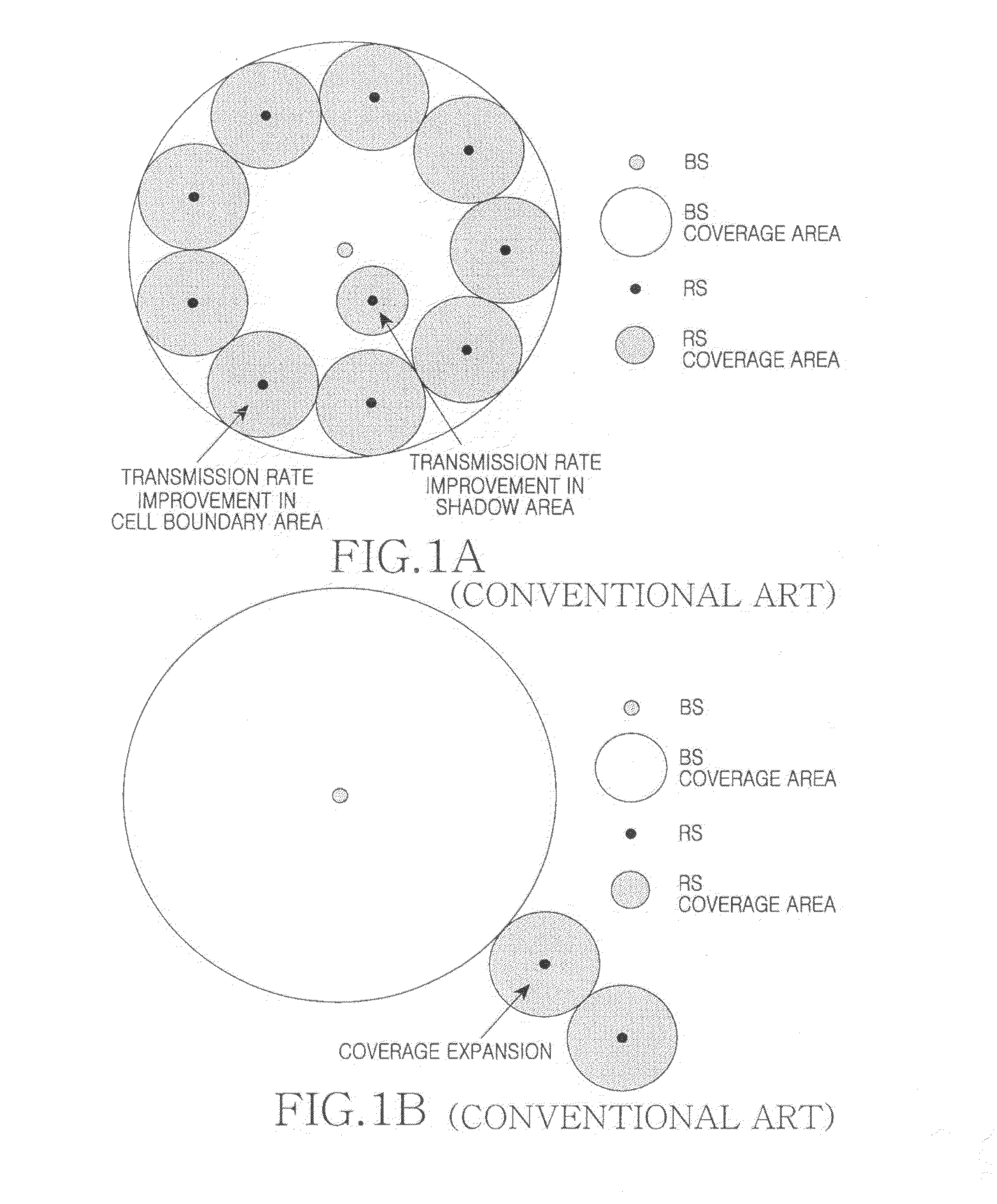
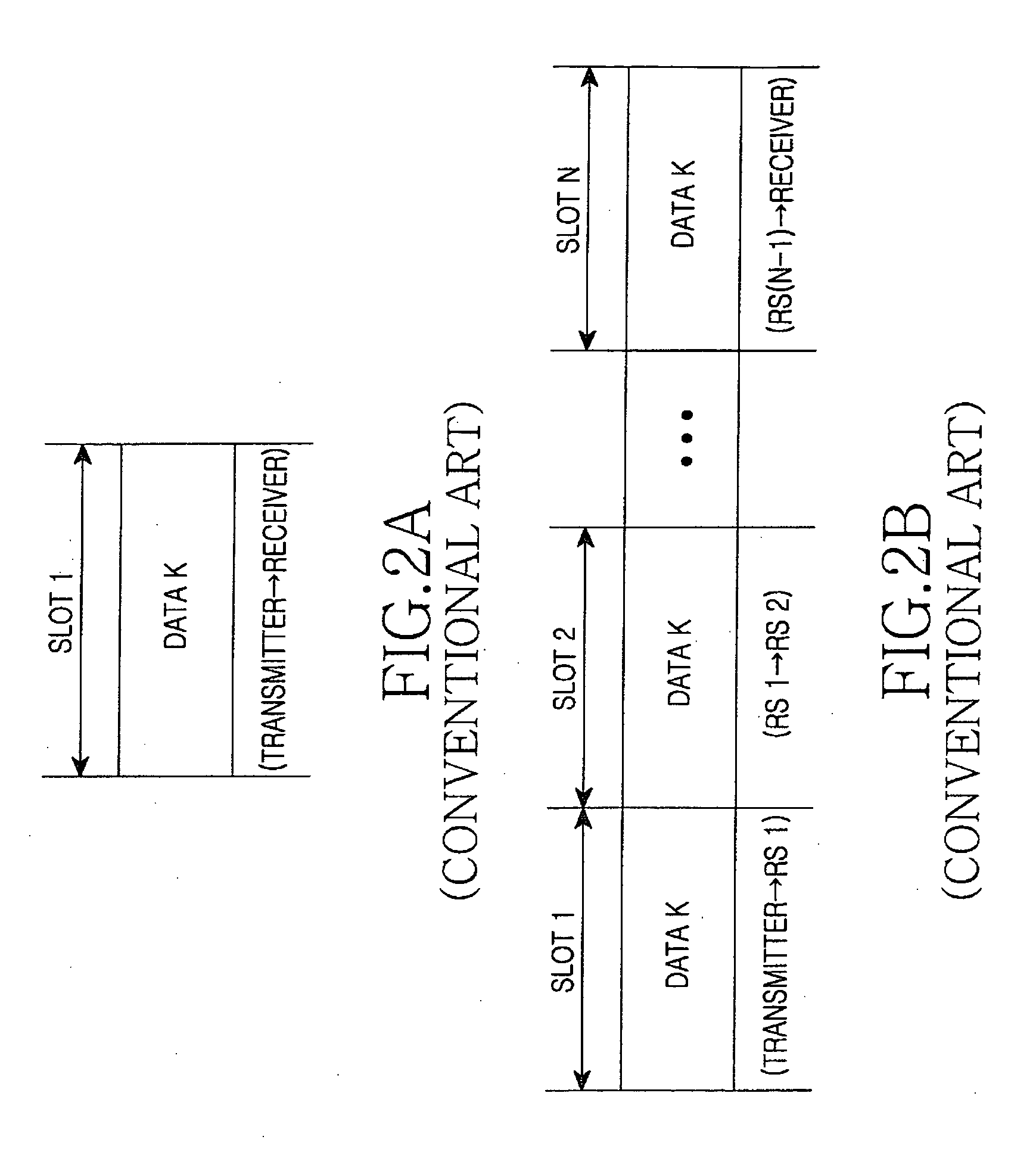
Apparatus and method for operating relay link in relay broadband wireless communication system
InactiveUS20080232296A1Reduce resource overheadReduce in quantityFrequency-division multiplex detailsTime-division multiplexCommunications systemBroadband
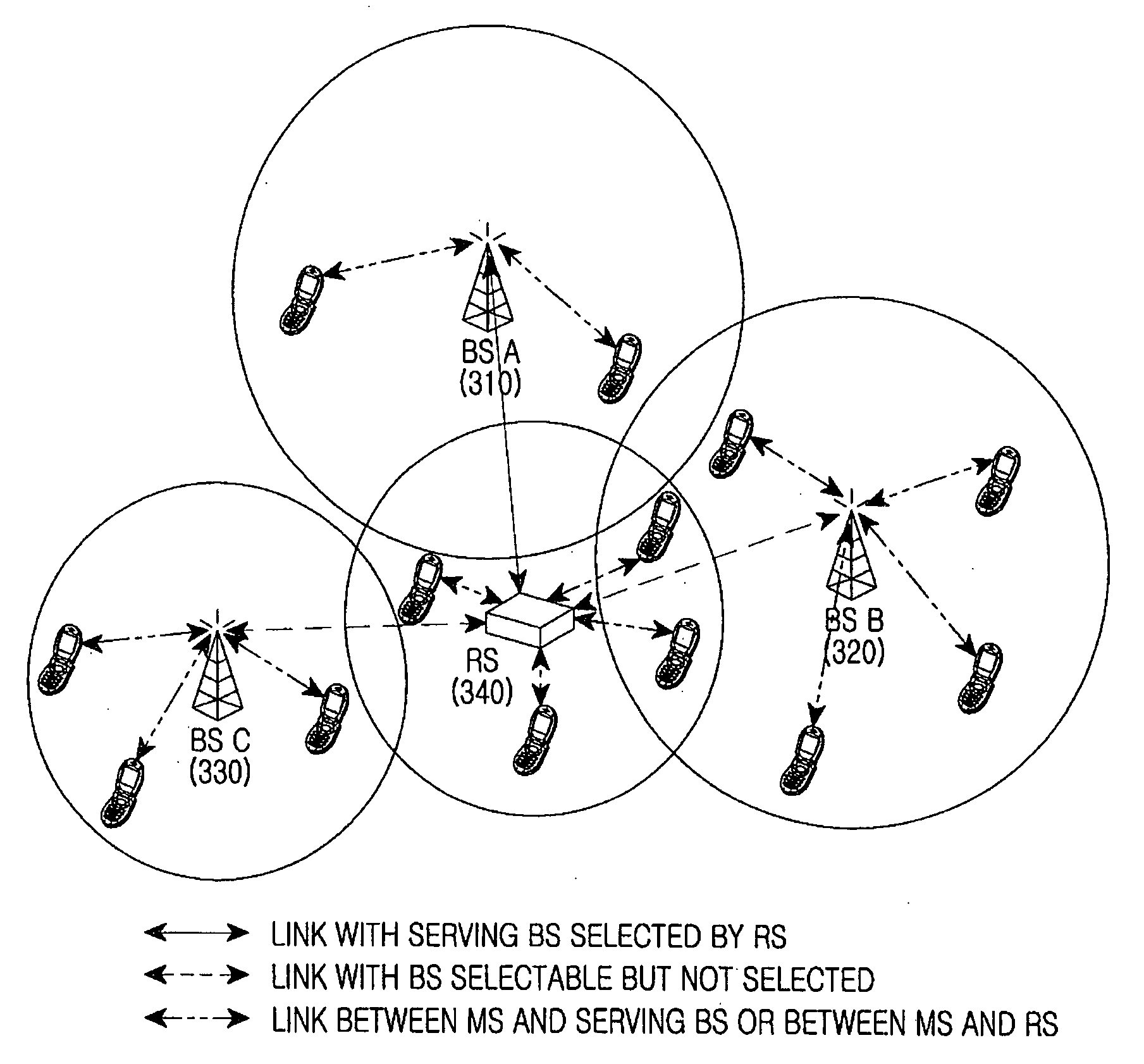
Provided is a relay broadband wireless communication system. The relay broadband wireless communication system includes a plurality of base stations, and one or more relay stations. The base stations perform communication with a relay station placed within a coverage area and generate state information to be provided to the relay station. The one or more relay stations are disposed at a location allowing communication with the plurality of base stations and select one or more serving base stations based on state information received from each of the base stations.
Owner:SAMSUNG ELECTRONICS CO LTD
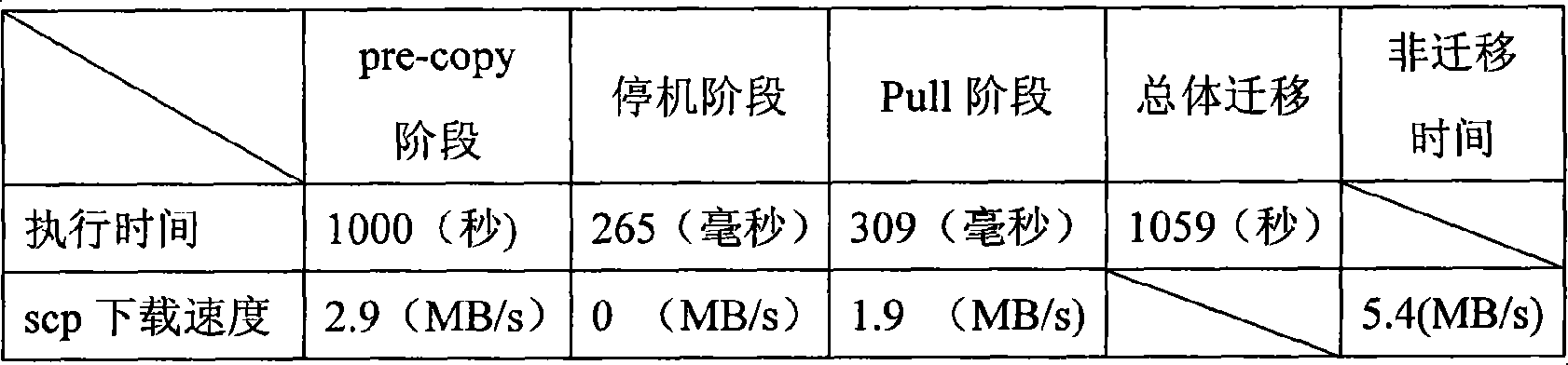
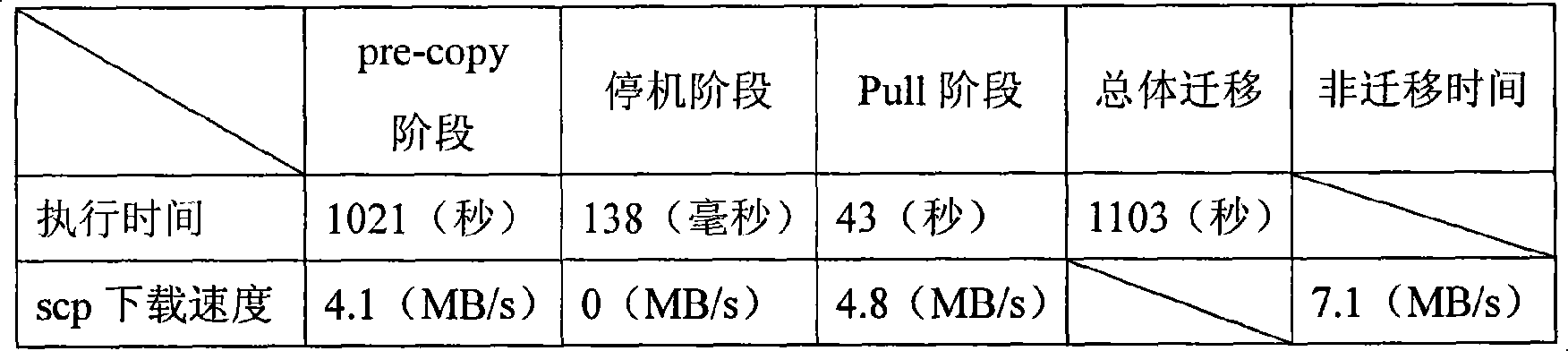
Dummy machine external storage on-line migration method
InactiveCN101101562AAvoid dependencyReduce downtimeMultiprogramming arrangementsSoftware simulation/interpretation/emulationExternal storageComputer science
The invention related to method for online transporting external storage (ES) of virtual machine (VM). In Push stage, the method includes following steps: sending data of all ES of VM to destination host (DH); manager of VM monitors ES access of VM in current procedure for sending ES, records update state of ES block in the sending procedure, and marks dirty blocks of written dirty ES; sending dirty blocks to DH form source host (SH) circularly till presetting condition is reached; the method stops sending data of ES and enters into halt stage; based on information of recording update state of ES to determine remnant dirty blocks of ES and sizes, and to send all remnant dirty blocks to DH form SH. In pull stage, based on information of recording update state of ES to carry out synchronous operation for remnant dirty blocks. The invention guarantees: very short halt time, not dependent on hardware environment of shared ES, and applicable to distributed environment.
Owner:PEKING UNIV
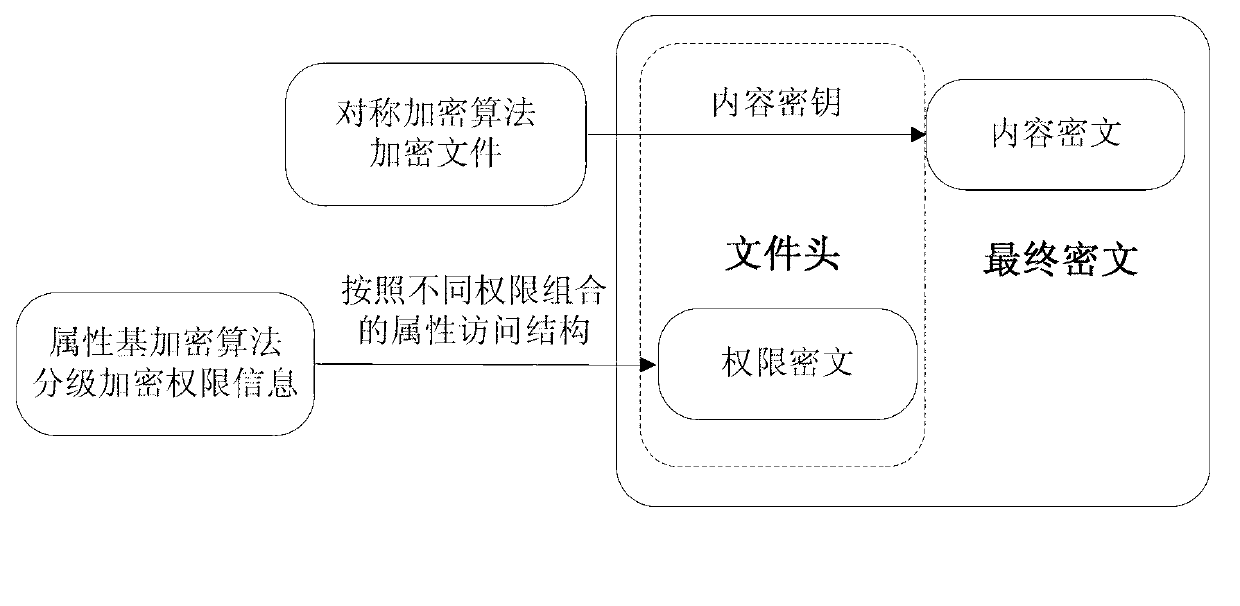
Multistage authority management method for cloud storage enciphered data sharing
ActiveCN103107992AReduce complexityEasy to implementTransmissionAttribute-based encryptionCiphertext
The invention relates to a multistage authority management method for cloud storage enciphered data sharing. The methods such as attribute based encryption, access control and authority management are used for providing a reliable method for access and multistage authority management of a shared cipher text in the cloud storage environment. Through mixing encrypt system, the multistage authority management method for cloud storage enciphered data sharing comprises steps: firstly applying a symmetric encryption algorithm to encrypt data, and generating a content cipher text; then adopting the attribute based encryption to encrypt according to different authority information, and generating an authority cipher text; adopting the attribute based encryption scheme to encrypt a symmetric key and the authority cipher text, regarding the symmetric key and the authority cipher text as a file header of the content cipher text, and generating a final cipher text. The multistage authority management method for cloud storage enciphered data sharing has the advantages of being convenient to achieve, strong in user information protectiveness, fine in authority control grit and the like. Under the premise that a server is not credible, the flexible and extensible authority management to the shared enciphered data is supported, the privacy and the security of the user data and authority information are effectively ensured, and the multistage authority management method for cloud storage enciphered data sharing has good practical value and wide application prospect in the cloud storage field.
Owner:HANGZHOU YUANTIAO TECH CO LTD
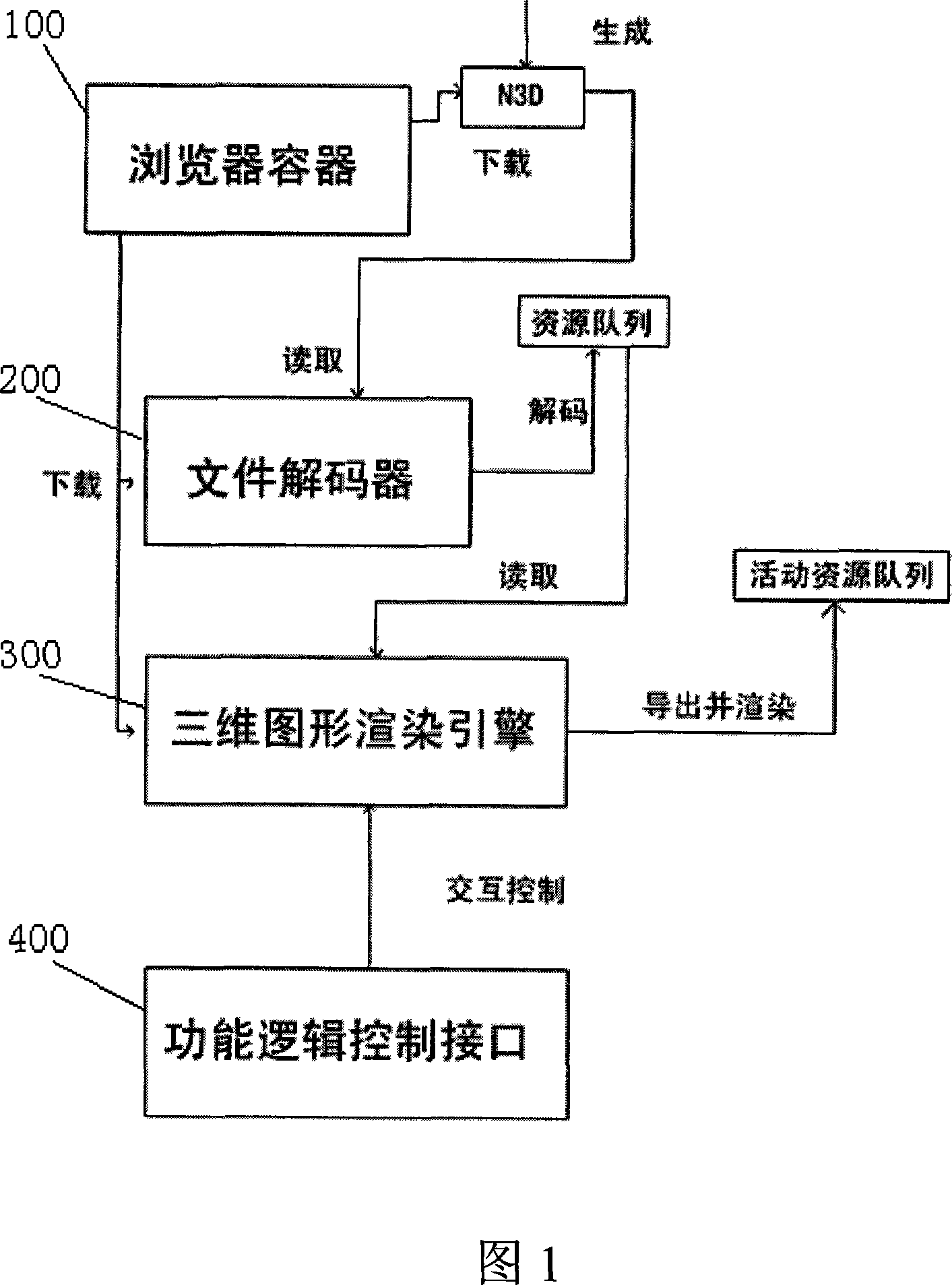
Three-dimensional web page realizing method based on browser
InactiveCN101067827AReduce file sizeImprove interactivitySpecial data processing applications3D-image renderingGraphicsWeb page
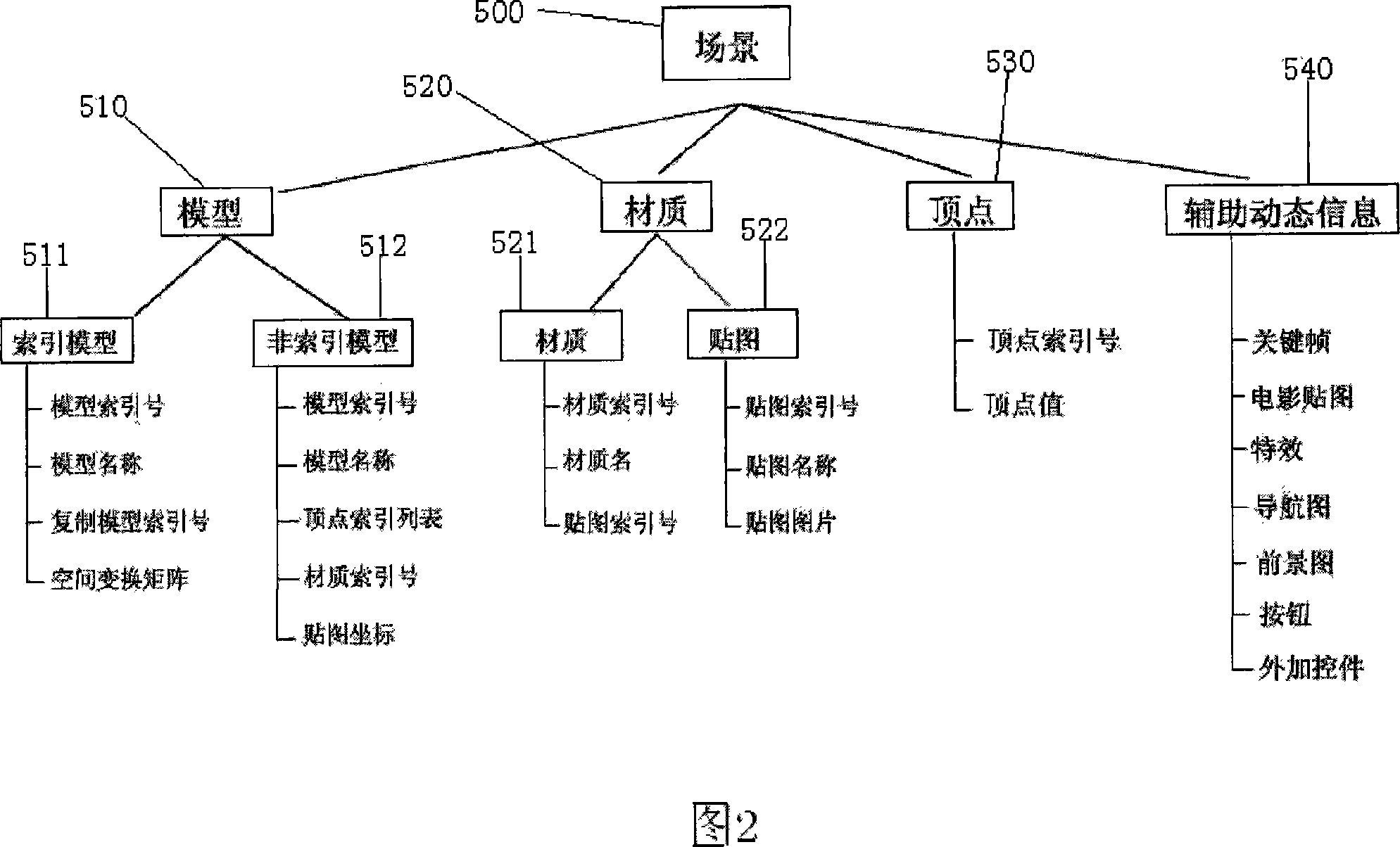
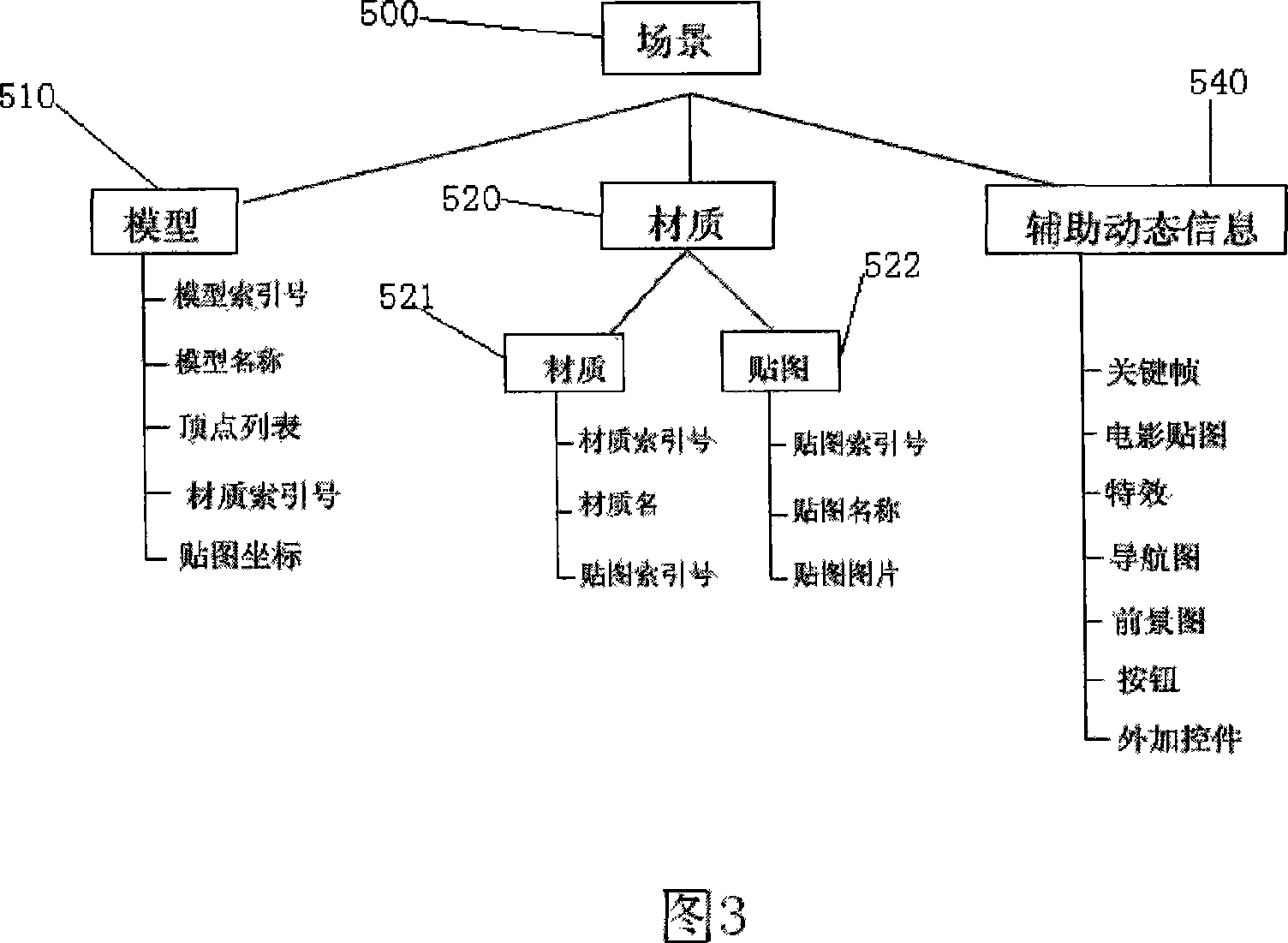
This invention provides a realization method for 3-D webs of a browser including four systems to finish the work: a browser container, a file decoder, a 3-D graph romance engine and a functional logic control interface, and the basic flow includes: a, collecting conversion model data to store them to a specific format, b, utilizing a browser to load the file decoder, the 3-D graph romance engine and 3-D web file dynamically, c, decoding the file timely by the file decoder to put it in a scene resource queue, d, starting up the engine to read the resource queue and generate an active resource queue and carry out real time romance, e, realizing mutual motion with the browser by the functional logic control interface.
Owner:上海创图网络科技股份有限公司
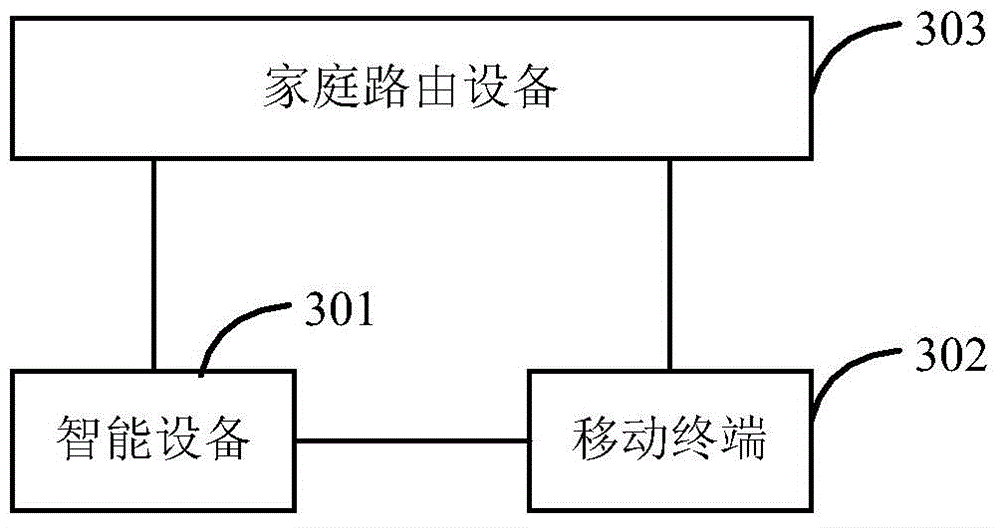
Smart device network access method and device
ActiveCN104618988AReduce transmission loadReduce resource overheadAssess restrictionAccess methodWifi network
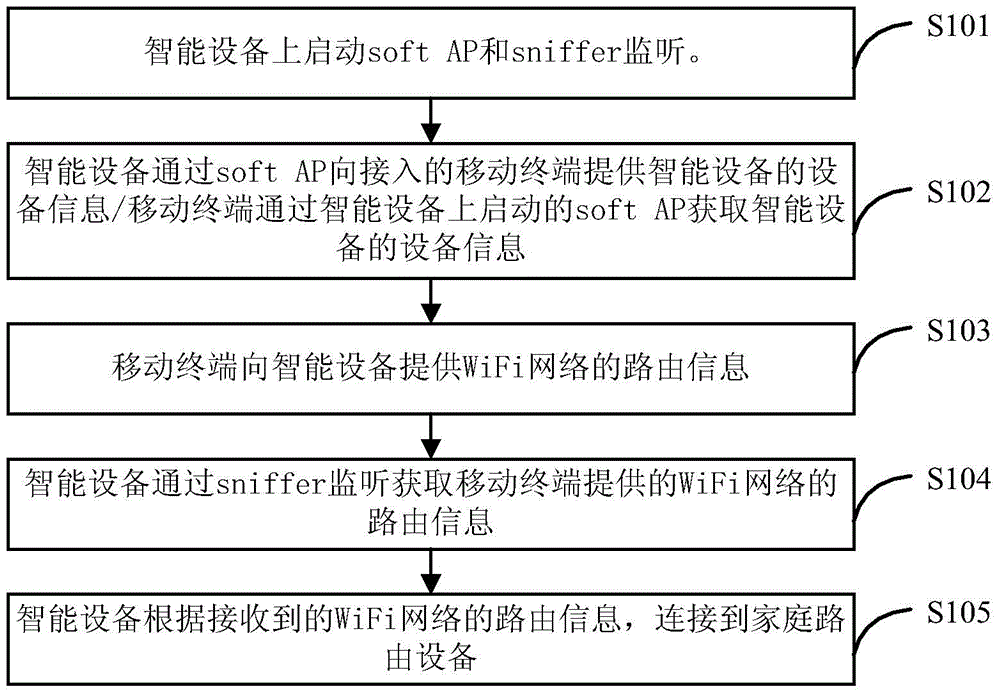
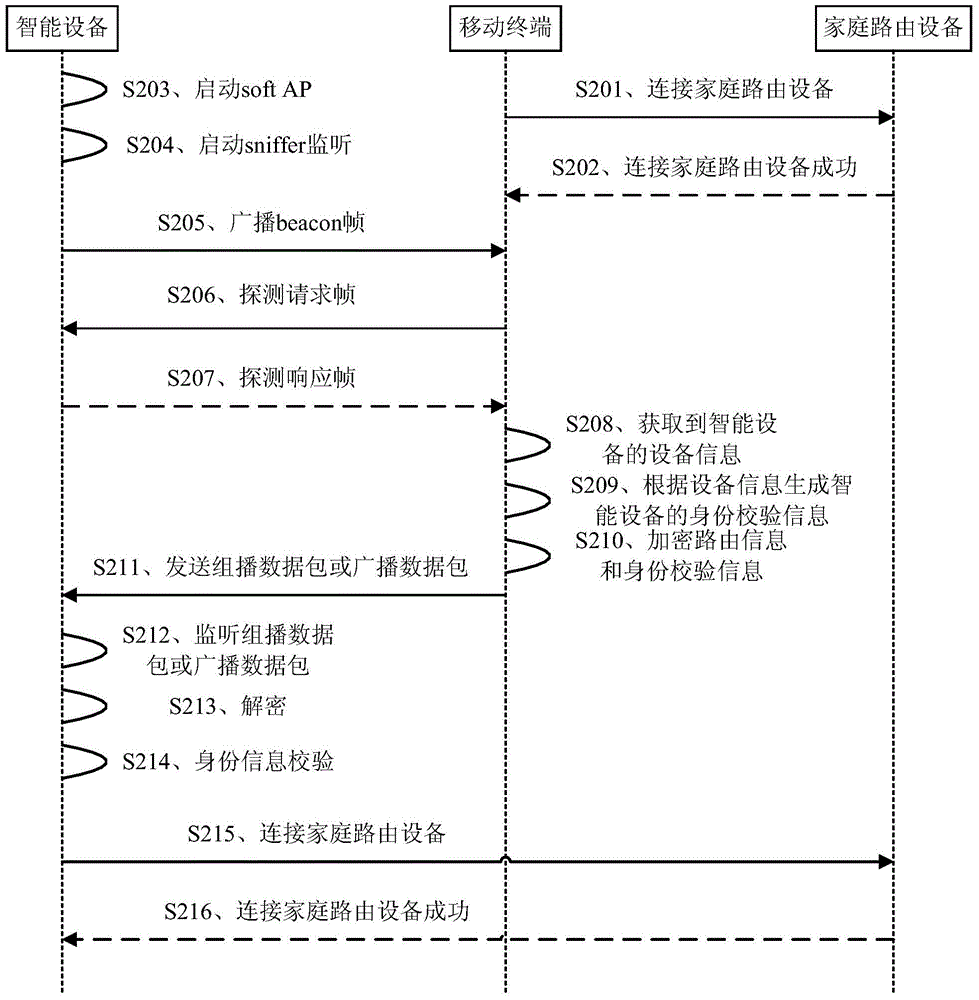
The invention provides a smart device network access method and device. The smart device network access method includes that: a soft access point soft AP and a sniffer on a smart device are started for monitoring; the smart device provides its device information to a mobile terminal where the soft AP is accessed, and acquires route information of a WiFi network provided by the mobile terminal through sniffer monitoring; the smart device is connected with a household route device according to the received route information. According to the smart device network access method, when the smart device is accessed into the wireless network, the mobile terminal does not need wireless network connection switching, so the smart device can be accessed into the wireless network quickly and conveniently, the network transmission load is low, and wireless network resource expenditure is small.
Owner:QINGDAO HAIER INTELLIGENT HOME TECH CO LTD
Apparatus and method for performing group-based m2m communication
InactiveUS20130029716A1Communication throughput be improveEfficient managementBroadcast service distributionRadio transmissionMachine to machineBase station
Disclosed are an apparatus and method for performing group-based machine to machine (M2M) communication. According to one embodiment of the present invention, a method in which a plurality of M2M communication devices from a group, and a specific M2M communication device which is a member of the group performs communication with a base station, comprises the following steps: transmitting, to the base station, a first message for requesting network registration; receiving, as a response to the first message, a second message containing information on the representative M2M communication device which is a representative of the group; and transmitting, to the representative M2M communication device, data to be transmitted to the base station on the basis of the second message.
Owner:LG ELECTRONICS INC
Outsourcing decryption method of attribute-based encryption based on ciphertext policy
InactiveCN104022868AReduce the burden onEfficient and safe decryptionKey distribution for secure communicationUser identity/authority verificationThird partyCiphertext
The invention provides a highly-efficient safe outsourcing decryption method based on the attribute encryption in mobile cloud computing environment. The method comprises the following steps: system initialization; a data owner encrypting a file and uploading the file to a cloud service provider; an authorization organization generating secret keys; a third party transforming ciphertexts; and a mobile terminal user decrypting the file. According to the method, targeted for the mobile cloud computing environment, by utilizing a ciphertext policy attribute-based encryption shared data method, according to the requirement of limited operation and storage capacity of a mobile terminal, and under the premise of guaranteeing data security, a portion of complex decryption tasks are outsourced to the third party; and by utilizing outsourcing decryption, secret key decomposition technique and matching algorithm, unnecessary bilinearity pairing operation is reduced, and a reliable method is provided for the mobile terminal to carry out rapid decryption.
Owner:HANGZHOU NORMAL UNIVERSITY
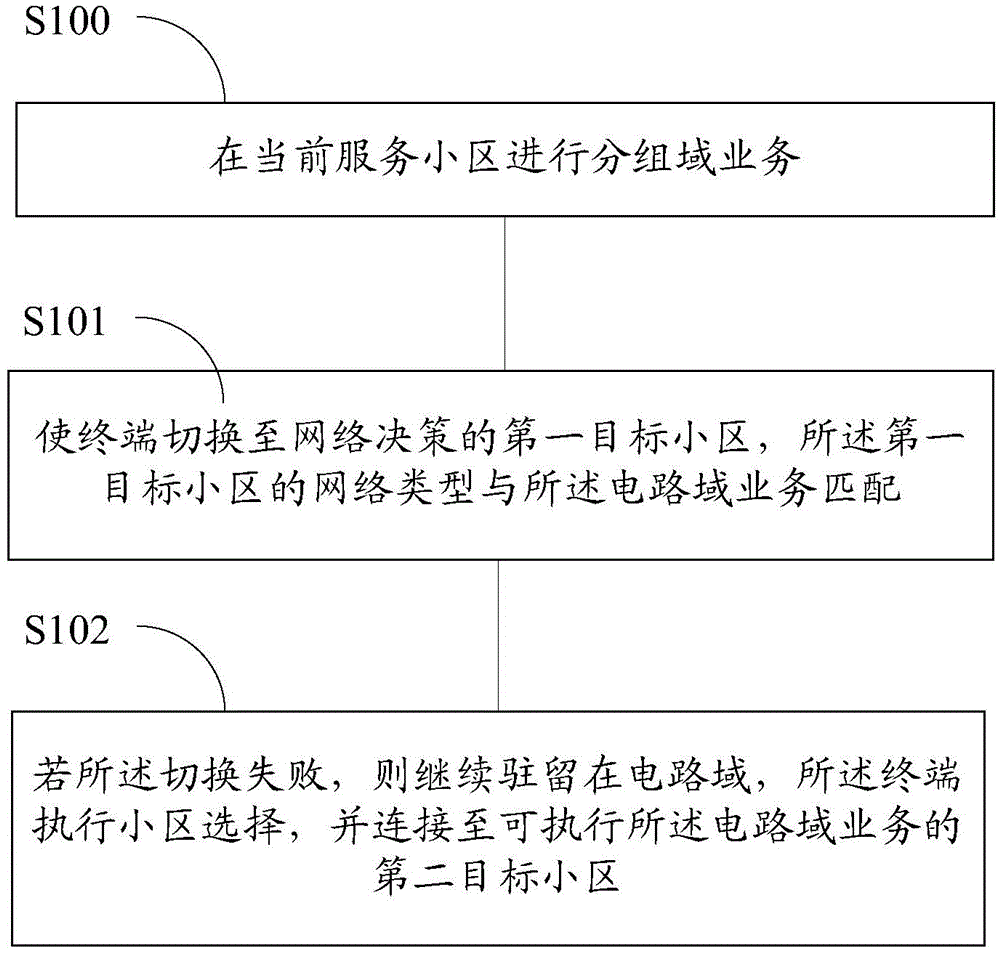
Network switching method based on circuit switched domain fall back CSFB
ActiveCN105338583AImprove experienceReduce resource overheadAssess restrictionCommunication qualityCell selection
The present invention relates to a network switching method based on circuit switched domain fall back CSFB, comprising: performing a packet switched domain service in a current service cell that does not support a circuit switched domain service; switching a terminal to a first target cell for network decision, the network type of the first target cell matches the circuit switched domain service; if the switching is failed, continuing retaining in the circuit switched domain; performing cell selection by the terminal; and connecting to a second target cell that can perform the circuit switched domain service. The network switching method of the present invention can improve the success rate for establishing a call when the network switching based on a CSFB process is failed, thereby improving communication quality.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
Pronunciation quality evaluating method for language learning machine
InactiveCN1763843AWith interactive functionImprove performanceSpeech recognitionLearning machineComputer-aided
The invention discloses a pronunciation quality evaluation method of language study machine in the computer subsidiary language study and phonetic technique domain, which is characterized by the following: extracting exercise phonetic feature; exercising standard pronunciation model; forming standard pronunciation network; detecting phonetic end; extracting evaluation phonetic feature; searching optimum path; calculating the mark of pronunciation quality. The method displays objective and stable evaluation, which constitutes imbedded English study system and mutual human-machine education and oral English self-detection.
Owner:TSINGHUA UNIV
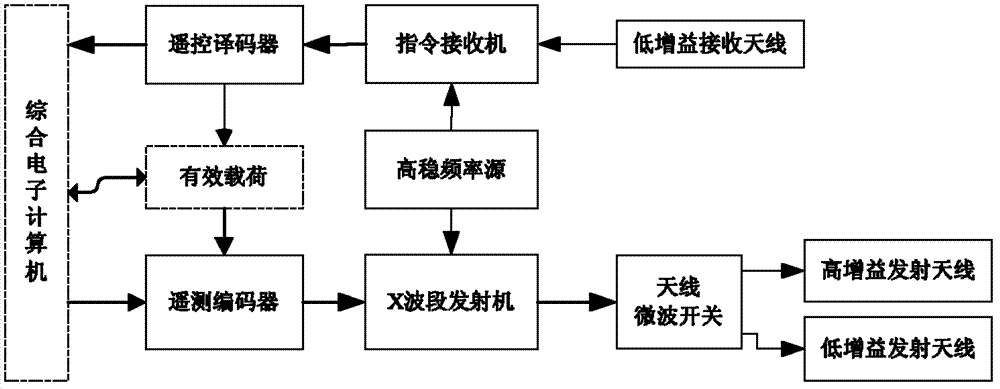
A measurement and control communication method for a deep space probe and a measurement and control communication system for a deep space probe
InactiveCN103368638AReduce weightReduce development difficultyRadio transmissionFrequency standardTransmitter
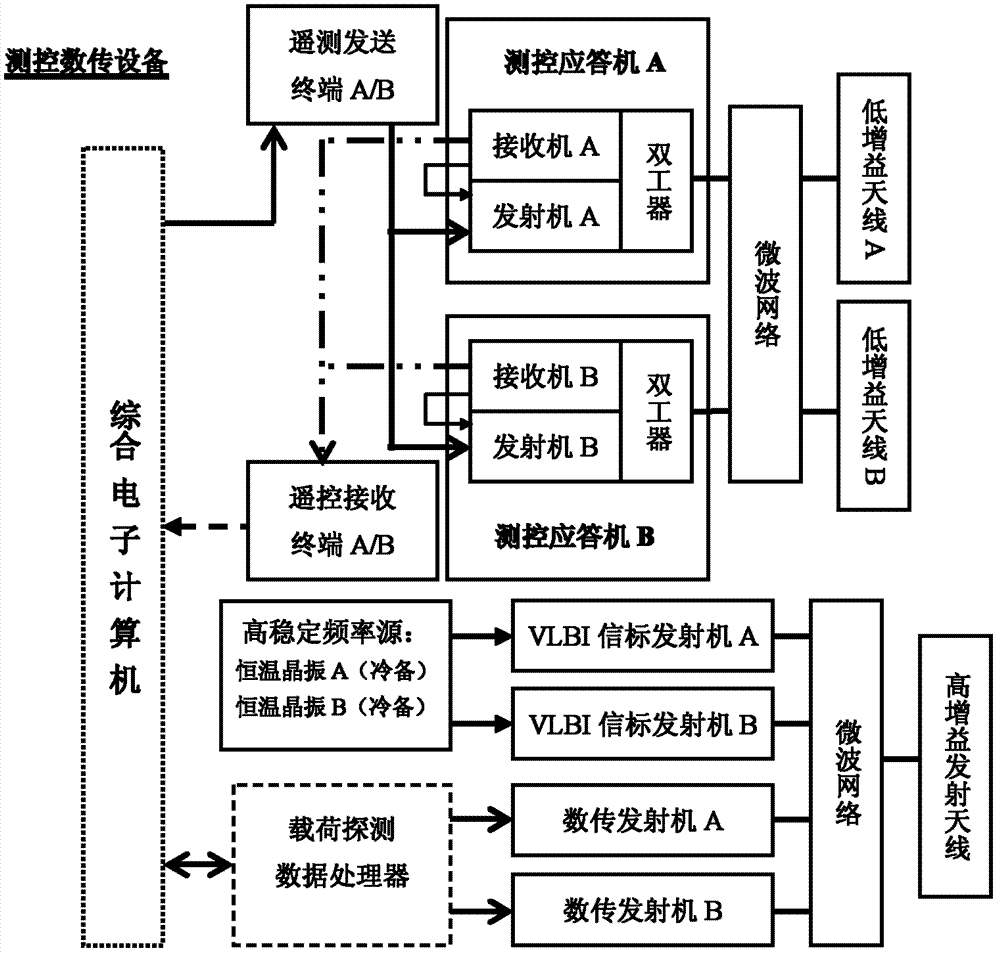
The invention provides a measurement and control communication method for a deep space probe and a measurement and control communication system for a deep space probe. The method is used for achieving information interaction between an earth station and a deep space probe and measurement of a probe track. The method comprises following steps. Four microwave radio signal channels are disposed between the deep space probe and the earth station by using an uplink carrier frequency and a downlink carrier frequency and comprise a telecontrol instruction channel, a telemetry data channel, a scientific data channel, and a VLBI track measurement beacon channel. Three channel signals including engineering telemetry data, scientific probing data, and VLBI track measurement beacon are combined into a downlink transmission signal. Finally, a transmitter is used to complete a transmitting function of all downlink transmission signals. A track measurement beacon is generated by using a frequency standard signal of a high-stability frequency source and is transmitted to an earth VLBI measuring network. Using a Doppler frequency speed measurement and signal interference angle measurement manner, the earth VLBI measuring network completes the track measurement tack of the deep space probe.
Owner:NAT SPACE SCI CENT CAS
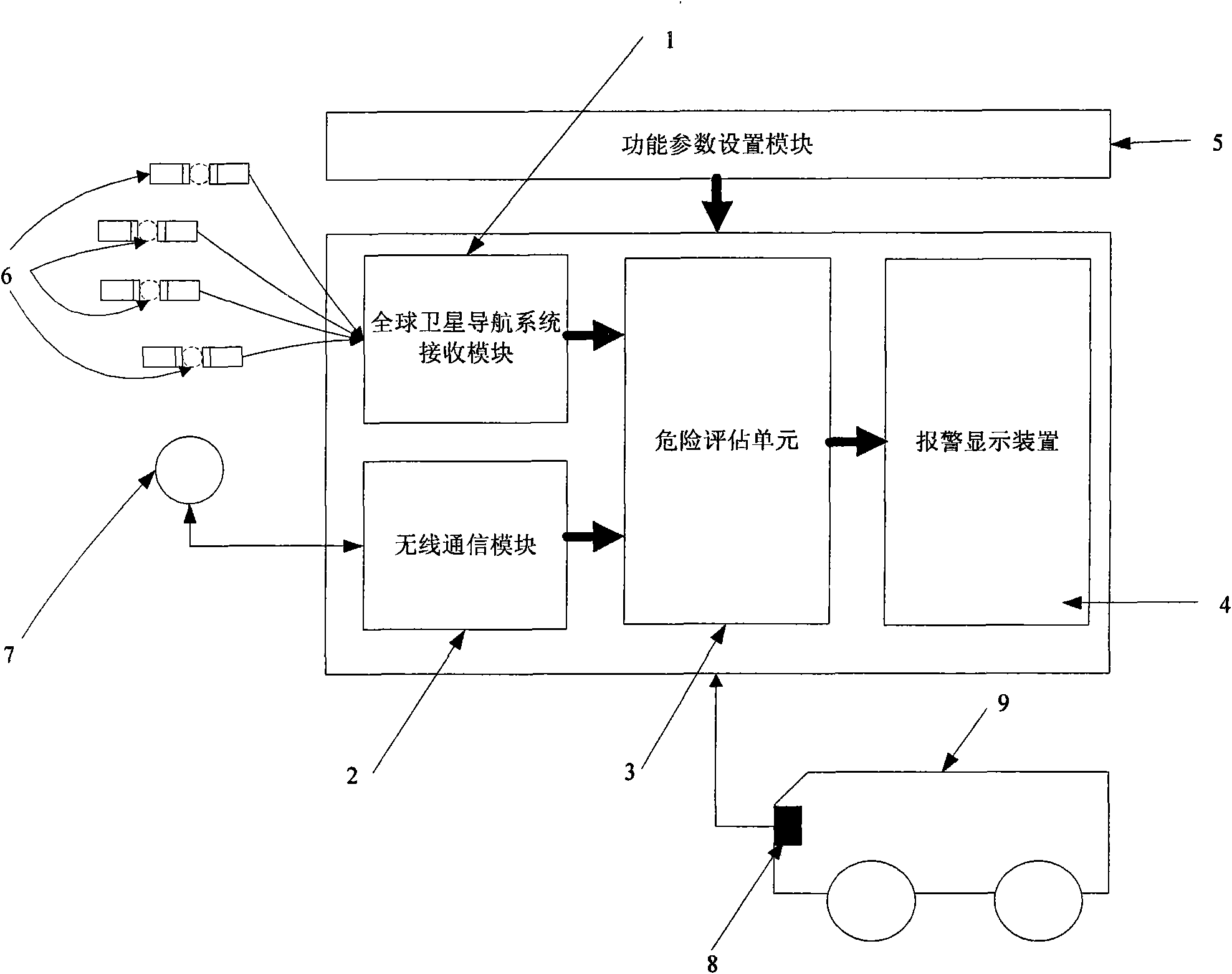
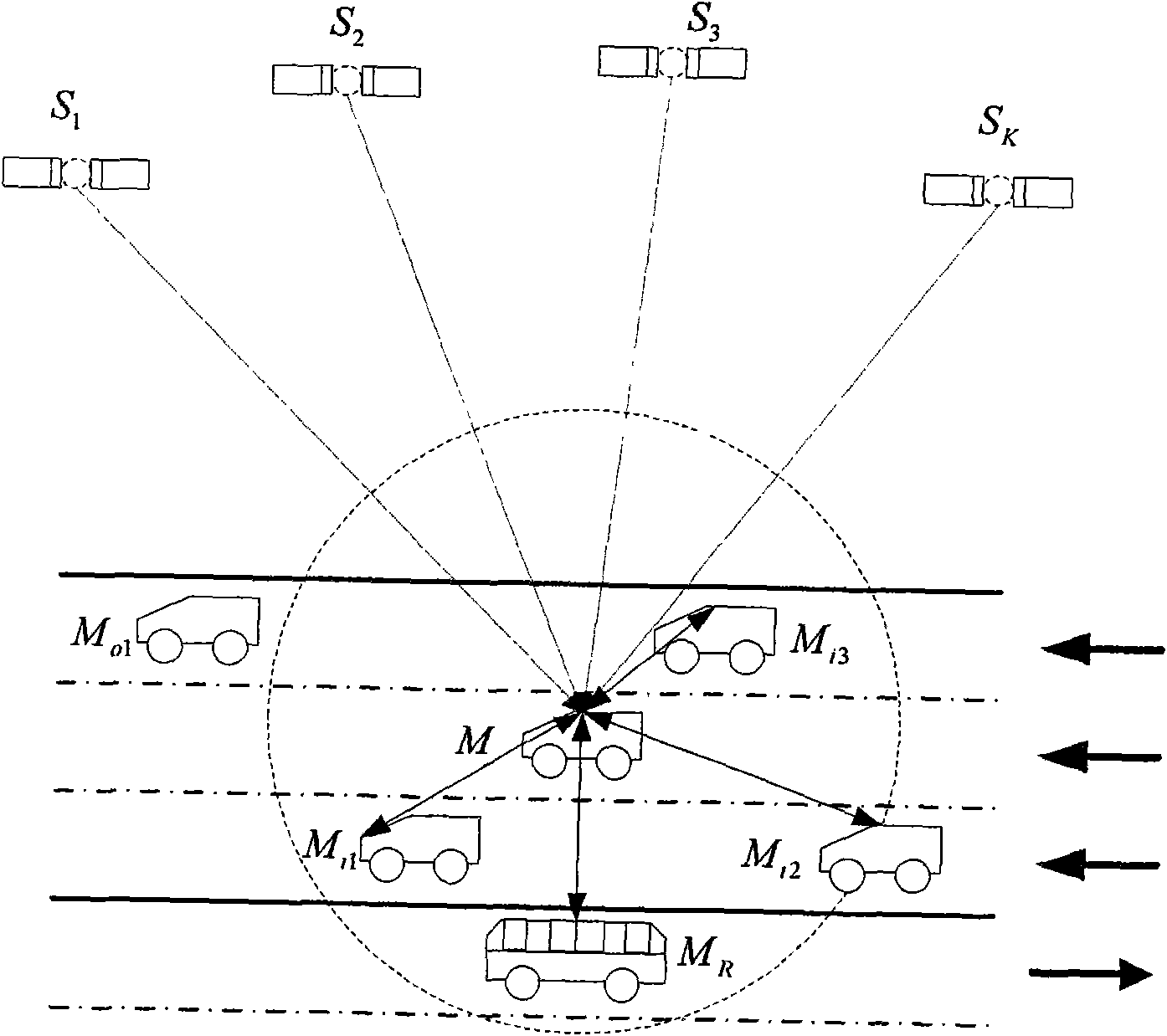
Early warning method when automobile closes at high speed and early warning device
InactiveCN101625797AEfficient use ofLower performance requirementsAnti-collision systemsPosition fixationDisplay deviceEngineering
The invention discloses an early warning method when an automobile closes at high speed and an early warning device. The method comprises the following steps: when the automobile drives at high speed, a navigation signal of a global navigation satellite system defines drive parameter information of the automobile, wireless net receives the drive parameter information of circumambient automobiles, the two drive parameter information are sent into a danger assessment unit, and the danger assessment unit judges whether the danger is existed to send an early warning signal. The device comprises a receiving module of the global navigation satellite system, a warless communication module, the danger assessment unit and a warning display device. The invention is the early warning method when the automobile closes at high speed and the early warning device, having simple and compact structure, low cost, convenient installation, wide application range and high safety.
Owner:NAT UNIV OF DEFENSE TECH
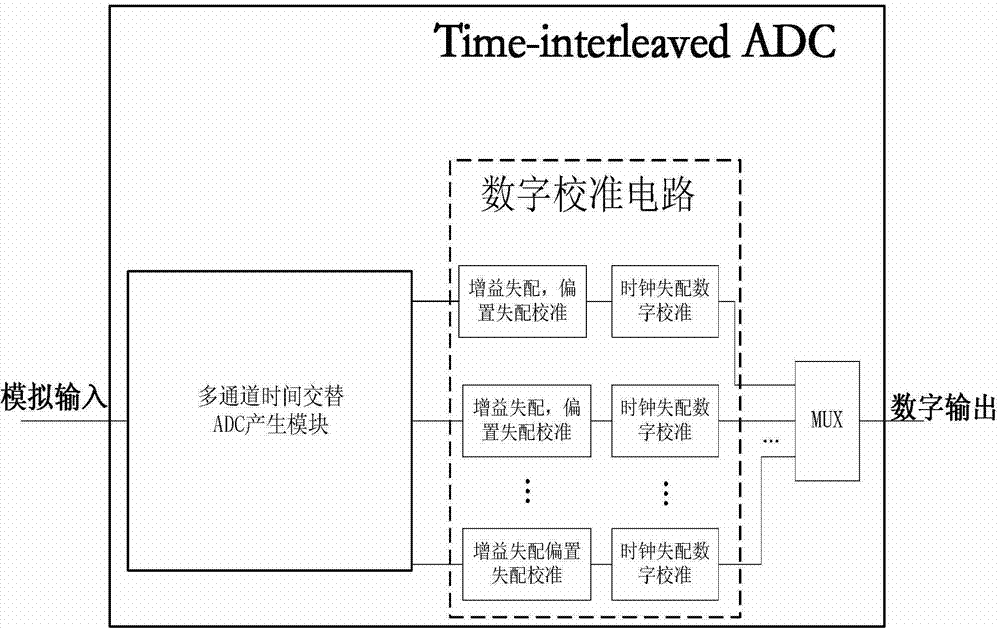
Mismatch error calibration method for multi-channel high-speed parallel alternate sampling system
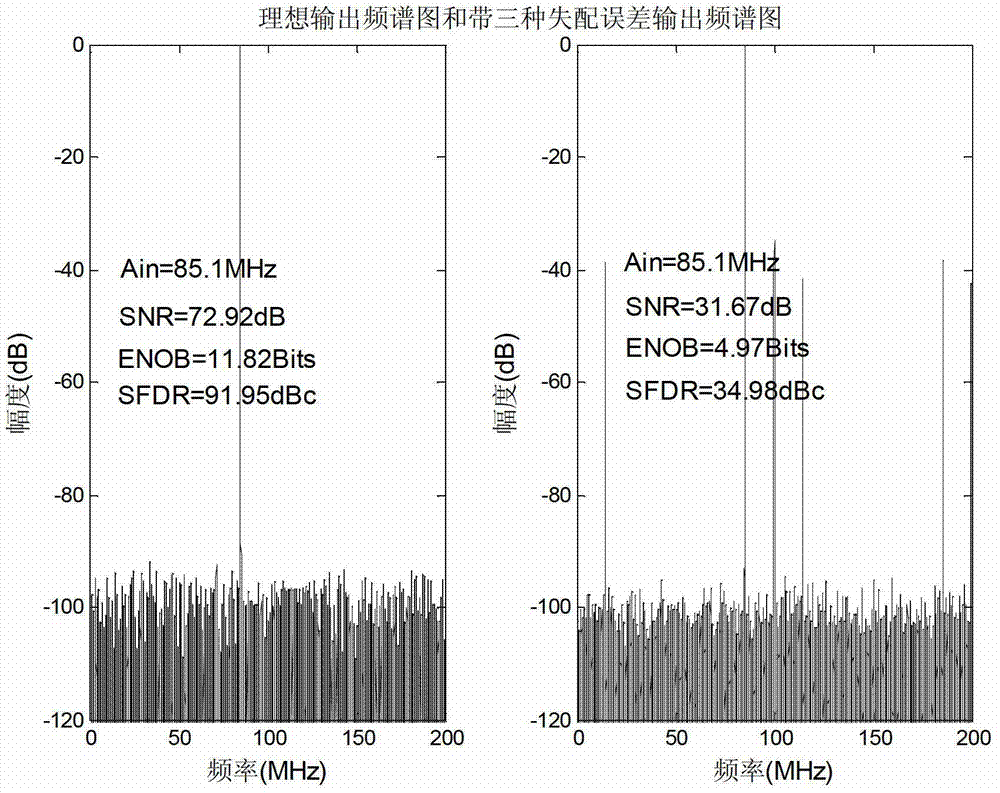
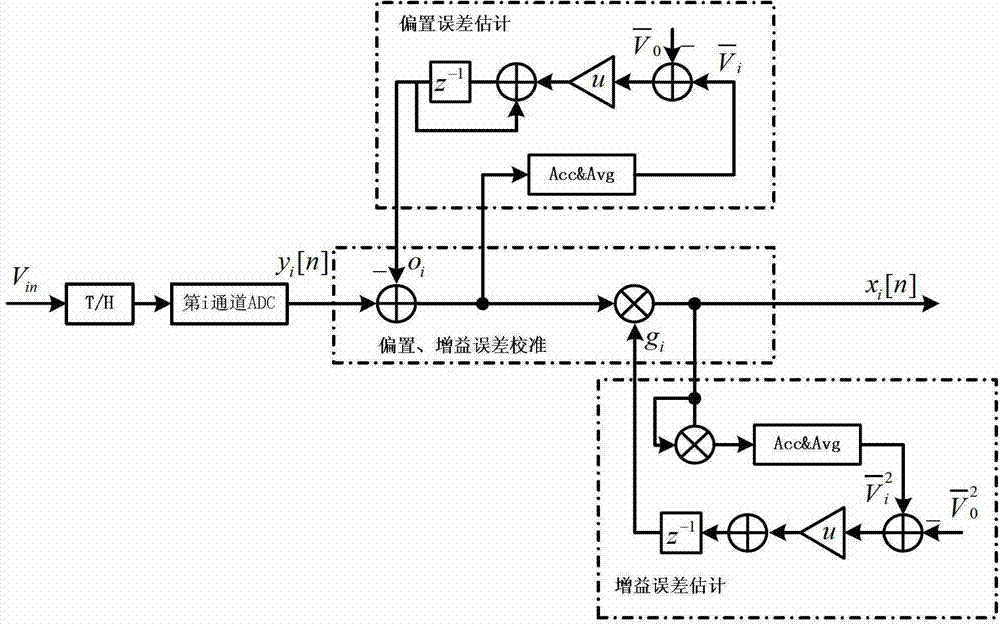
InactiveCN102857225AReduce complexityFast approachAnalogue/digital conversion calibration/testingSelf adaptiveComputer science
The invention provides a mismatch error calibration method for a multi-channel high-speed parallel alternate sampling system, which is characterized by comprising an offset and gain mismatch error calibration step and a time mismatch error calibration step, wherein the time mismatch error calibration step comprises the estimation of time mismatch error and the calibration based on the estimation of time mismatch error. The mismatch error calibration method for a multi-channel high-speed parallel alternate sampling system can estimate and calibrate three kinds of mismatch errors online and in real time, and is a self-adaption calibration method for blind signals. When the external environment is changed, a filter coefficient is not required to be regulated, a calibration module is further not required to be designed again, and the three kinds of mismatch errors can be estimated and calibrated online and in real time. Compared with the prior art, the mismatch error calibration method for a multi-channel high-speed parallel alternate sampling system has lower complexity and can calibrate and output effective data in real time.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Demodulating method for multi-stream data and system thereof
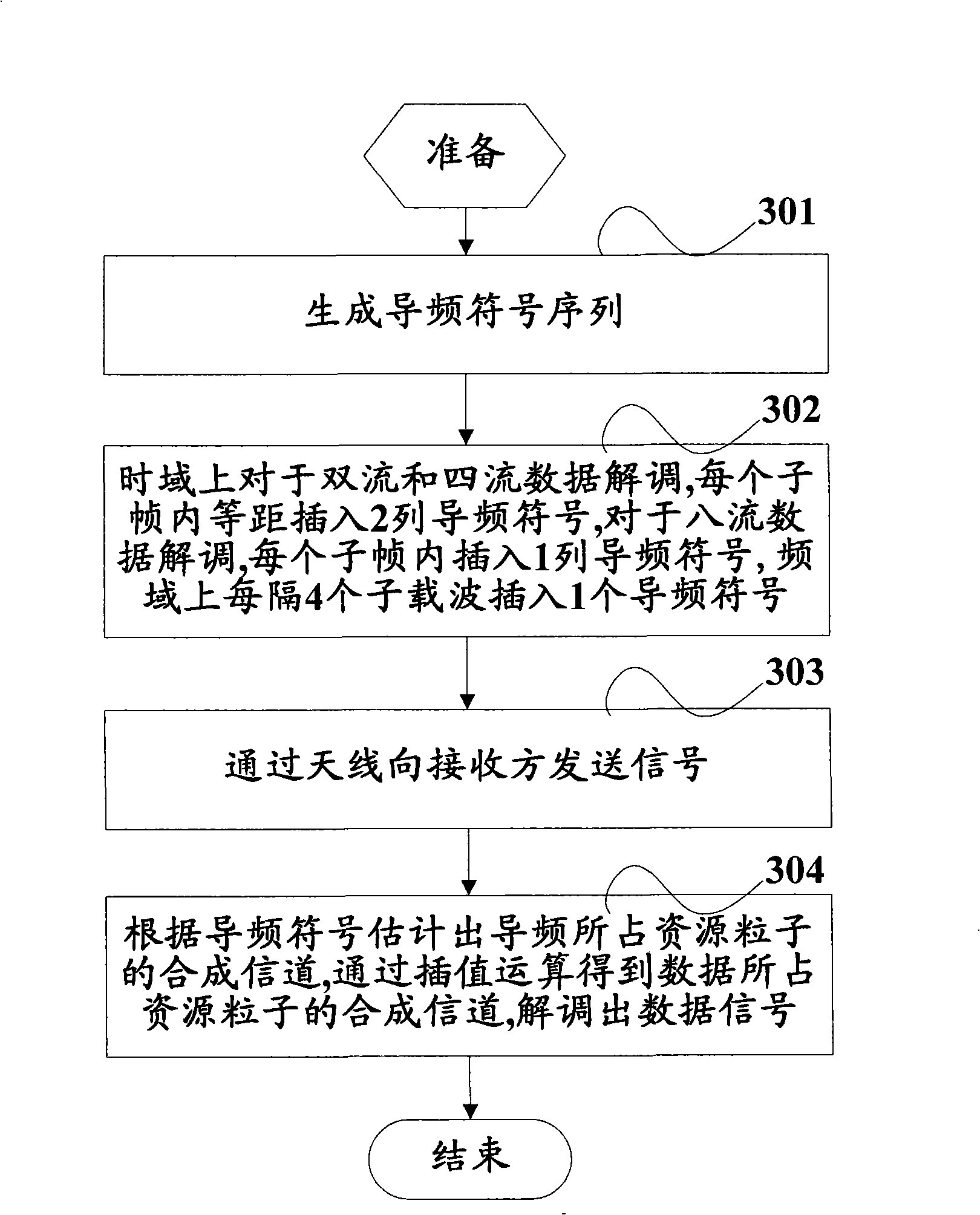
InactiveCN101540751AReduce resource overheadGuaranteed CompatibilityMulti-frequency code systemsTransmitter/receiver shaping networksTime domainData stream
The invention provides a demodulating method for multi-stream data and a system thereof. The demodulating method comprises the steps as follows: a pilot frequency symbol sequence is generated; for double-stream and four-stream data demodulation, two rows of pilot frequency symbols are equidistantly inserted in time domain correspondingly to each data stream in a pair of resource blocks; for eight-stream demodulation, one row of pilot frequency symbols are inserted in time domain while one pilot frequency symbol is inserted in every four sub-carrier-waves correspondingly to each data stream ina resource block, wherein, the pilot frequency and the data employ the same pre-coding mode; signals are sent to a receiver by an antenna; composite channel of resource particles, which is occupied by the pilot frequency, is estimated according to the inserted pilot frequency symbols when the signals are received by the receiver; the composite channel of resource particles, which is occupied by the data signals, is acquired by interpolation algorithm, thereby obtaining the data signals by demodulating. The special pilot frequency designed by the invention considers influence of factors, such as performance, spending and the like, thus having excellent compatibility with LTE Release 8.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method and system for configuring discontinuous reception (DRX) parameters in long term evolution system
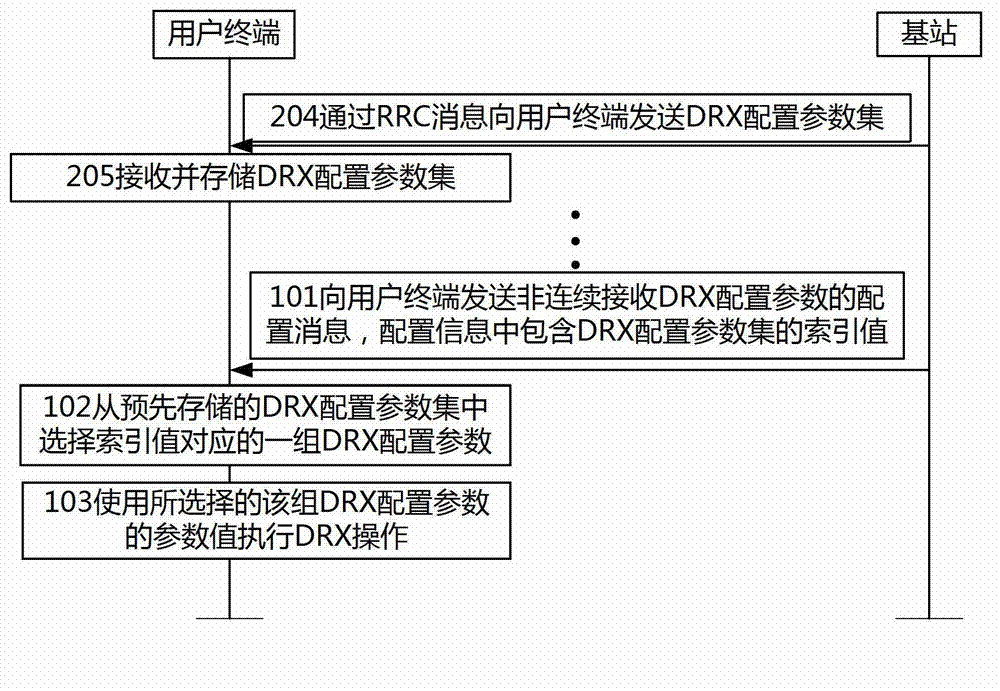
ActiveCN103945505AReduce overheadReduce resource overheadPower managementHigh level techniquesResource utilizationBase station
The invention discloses a method and system for configuring discontinuous reception (DRX) parameters in a long term evolution system. The method comprises: a base station sending a configuration message of a DRX configuration parameter, wherein the configuration message comprises indexes of a group of DRX configuration parameters in a DRX configuration parameter set, the DRX configuration parameter set comprises at least one group of DRX configuration parameters, the indexes are corresponding to one group of DRX configuration parameters in the DRX configuration parameter seat, and the group of DRX configuration parameters comprise parameter values of multiple DRX configuration parameters; and a user terminal, in response to the configuration message, selecting the group of DRX configuration parameters corresponding to the indexes from a prestored DRX configuration parameter set, and executing DRX operation by use of the parameter values of the selected group of DRX configuration parameters. By using the technical scheme provided by the invention, the cost of occupied signalings after the base station carries out DRX parameter configuration on the user terminal is reduced, and the resource utilization rate is improved.
Owner:CHINA TELECOM CORP LTD
Method and device for detecting whether target object is blocked, electronic equipment and storage medium
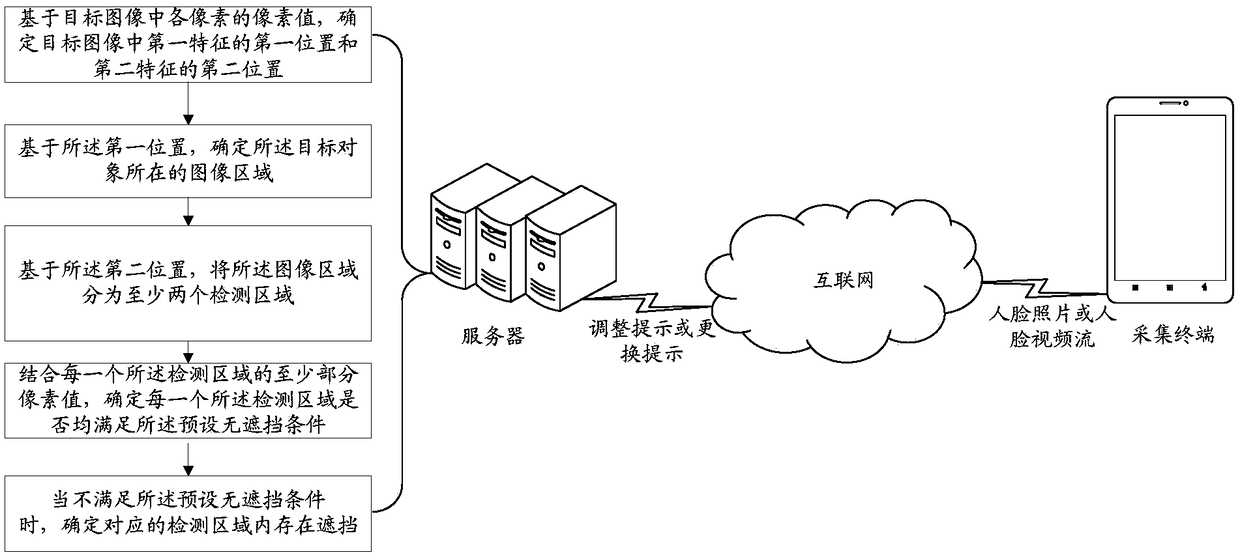
ActiveCN108319953AReduce the amount of calculationReduce computational complexityCharacter and pattern recognitionOcclusion detectionElectric equipment
The embodiments of the invention disclose a method and a device for detecting whether a target object is blocked, a piece of electronic equipment and a storage medium. The method includes the following steps: determining a first position of a first feature and a second position of a second feature in a target image based on the pixel values of the pixels in the target image, wherein the first feature is the outer contour feature of a target object in the target image, the second feature is the feature of an interfering sub-object in the target object, and the interfering sub-object is a sub-object which interferes with occlusion detection in the target object; determining an image region where the target object is located based on the first position; dividing the image region into at leasttwo detection regions based on the second position; determining whether each detection region satisfies a preset no-occlusion condition based on at least part of the pixel values of each detection region; and if any detection region does not satisfy the preset no-occlusion condition, determining that there is occlusion in the detection region.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Internet protocol security (IPSEC) tunnel data transmission method and device thereof
ActiveCN103139222AImprove processing efficiencyReduce resource overheadNetworks interconnectionIPsecField data
The invention relates to the communication field data transmission, in particular to an Internet protocol security (IPSEC) tunnel data transmission method and an IPSEC tunnel data transmission device. The invention provides the IPSEC tunnel data transmission method and the IPSEC tunnel data transmission device. Due to the fact that IP messages of the same kind are combined and compressed through a coprocessor and the like, an IPSEC tunnel model data are packaged to send by an outer network card. Due to the fact that after fragmentation IP message data are rebuilt, the coprocessor is uncompressed and the like, the rebuilt IP message data are divided into each different original IP message and sent through an inner network card, and a data transmission performance of an IPSEC tunnel can be largely improved. Data processing is carried out through the networks, a network data receiver and a network data sending device. The IPSEC tunnel data transmission method and the IPSEC tunnel data transmission device are mainly used in the field of the IPSEC tunnel data transmission.
Owner:中电科网络安全科技股份有限公司
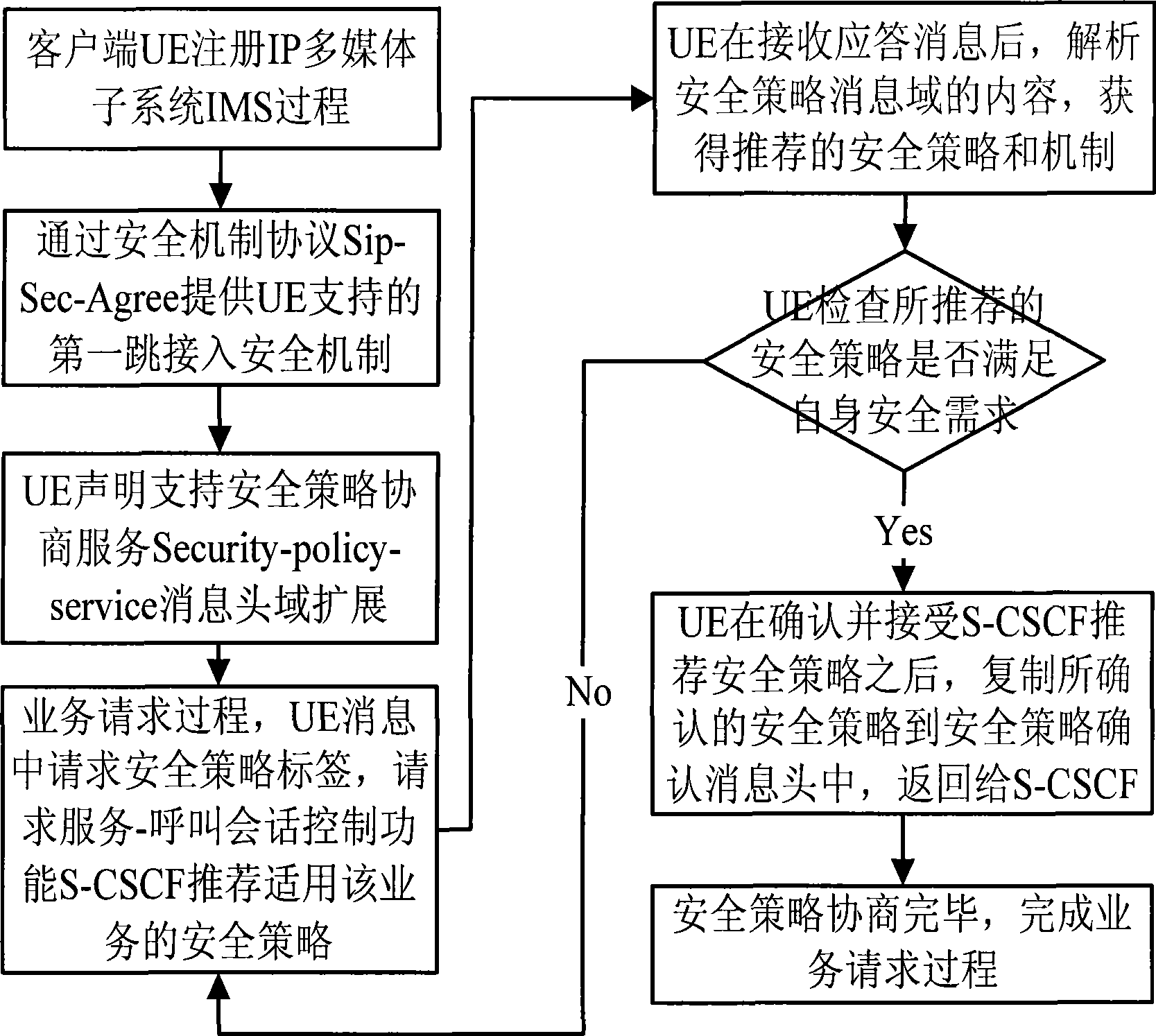
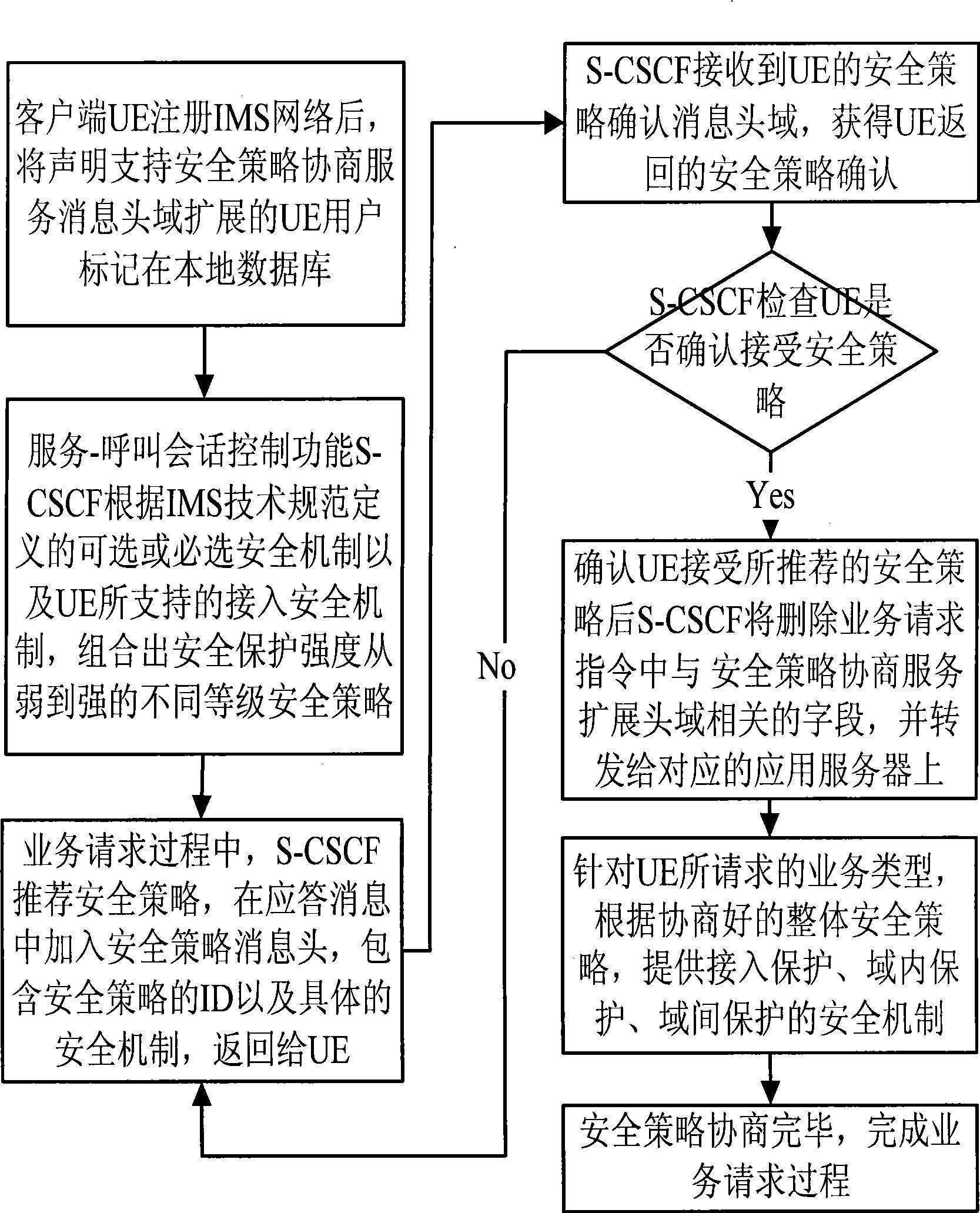
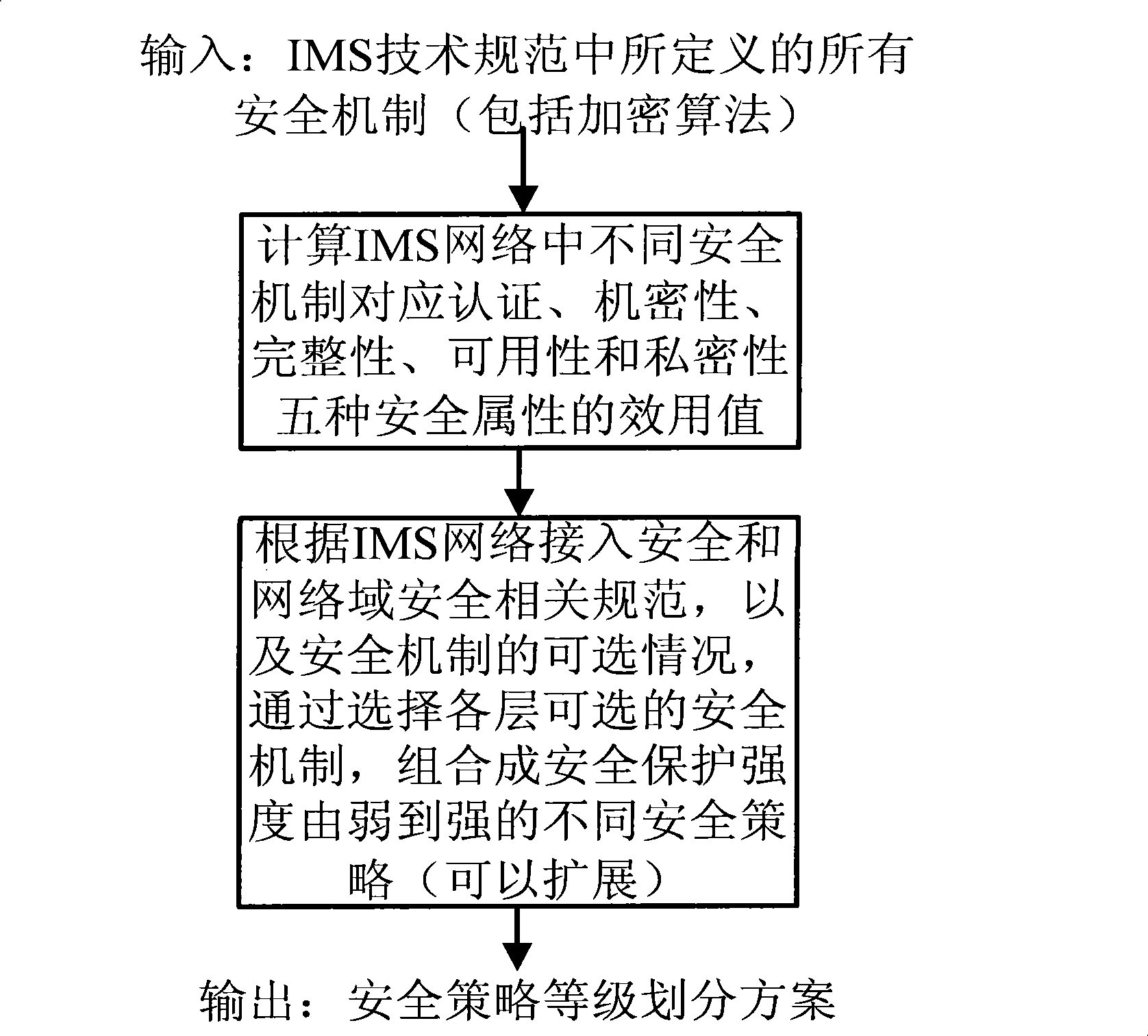
Negotiation control method based on SIP security policy grade in IMS network
InactiveCN101483860ASatisfy service quality assuranceReduce resource overheadSecurity arrangementSession Initiation ProtocolQuality of service
A negotiation control method based on SIP security strategy level in an IMS network provides a negotiation control mechanism based on session initiation protocol (SIP) security strategy level in the IMS network of an IP multimedia subsystem. The method belongs to the field of network safety protection and access control technology, which is characterized in that two aspects are included: 1) According to IMS technical specification, different safety mechanisms are combined to select safety protection strategies from weak to strong, so as to provide a set of integral and unified IMS safety strategy combination for IMS and user equipment (UE) to carry out safety negotiation and strategy selection. 2) Through the newly defined SIP message domain and negotiation process, the method provides negotiation process and SIP message field format for terminals users and IMS operators, so as to allow the IMS operators and the terminal users to negotiate and determine the method of business safety strategy. Eventually, the operators can provide the safety strategies with different safety levels according to different business types and different user types, thus realizing personalized user service quality assurance, reducing resource costs brought by network safety, and realizing the optimal selection strategy for network safety protection and service quality assurance.
Owner:TSINGHUA UNIV
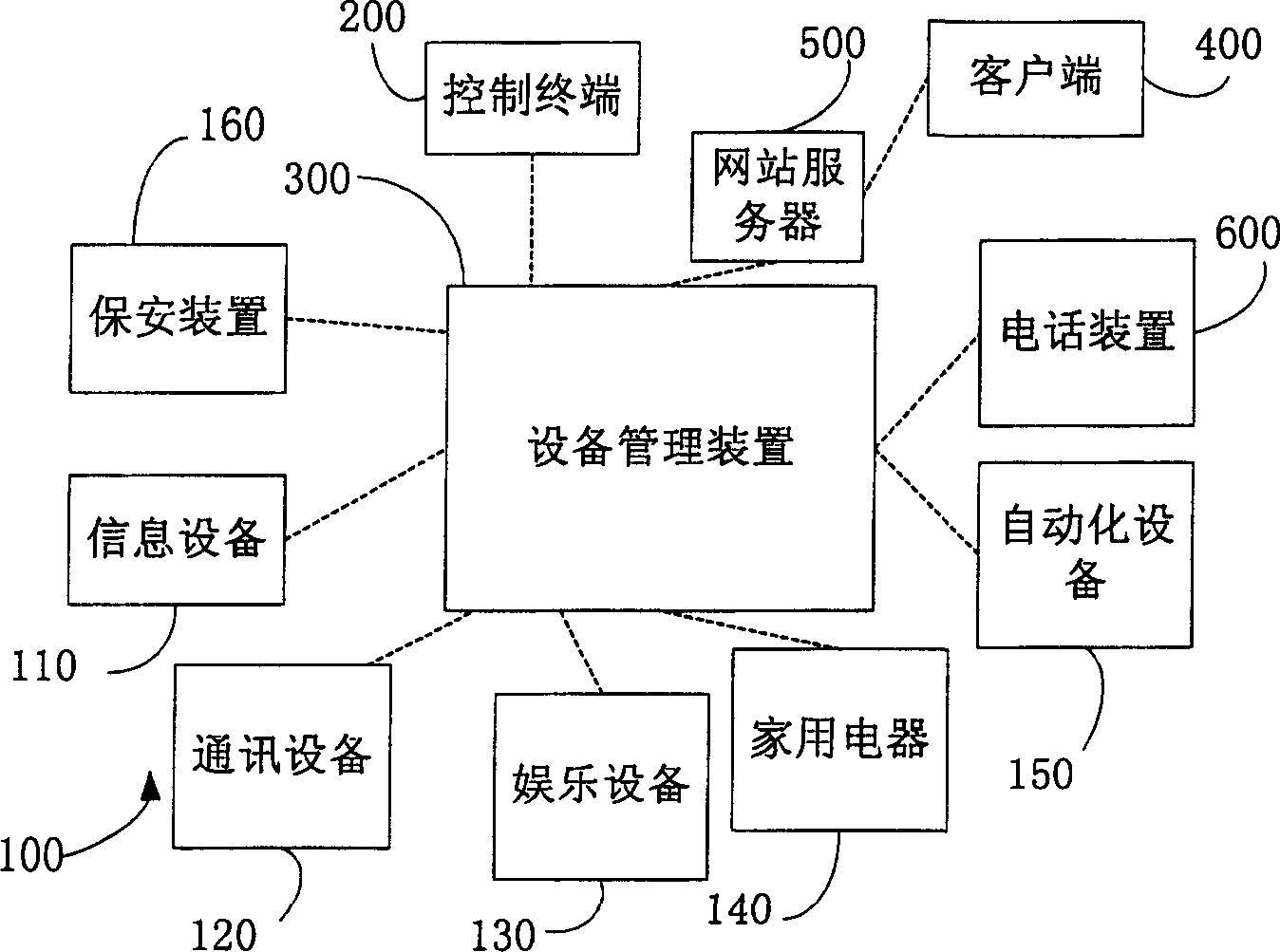
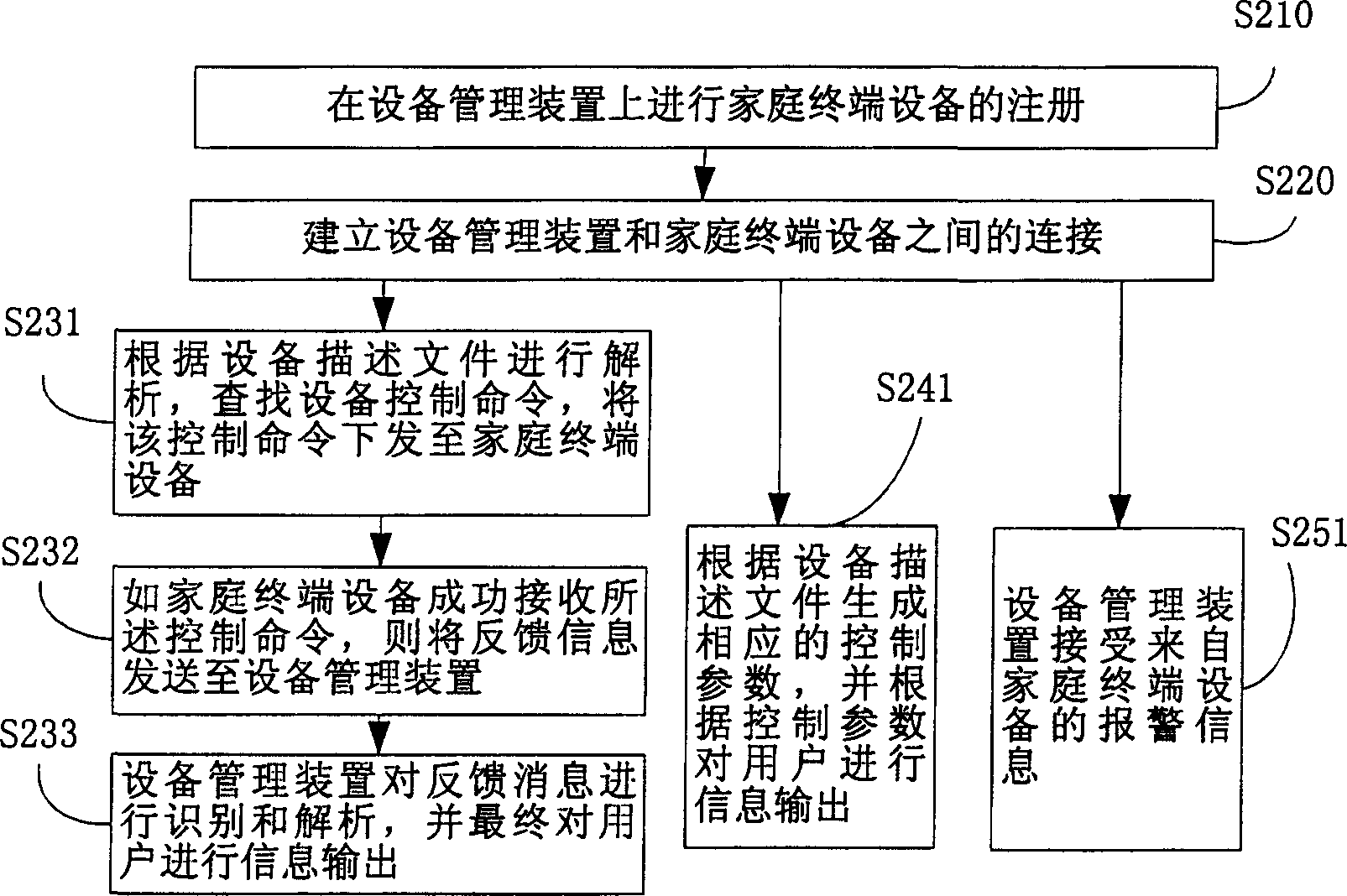
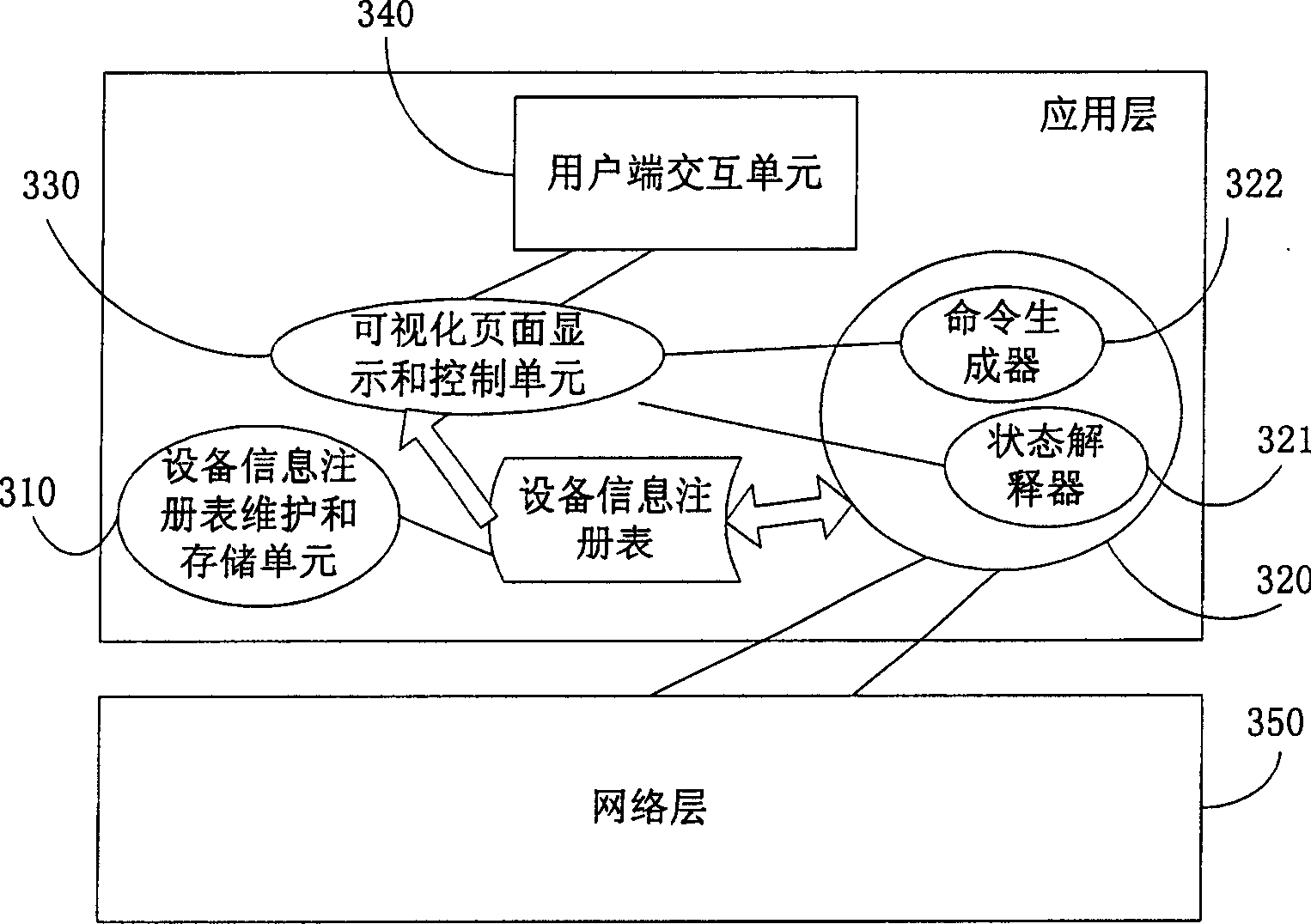
Household network device controlling method and equipment management apparatus
ActiveCN1845505AReduce resource overheadLow costData switching by path configurationUser inputTerminal equipment
The disclosed control method for household network device comprises: the manage device stores data and description file contained index of the terminal device data; it registers the terminal device on manage device and generates device list file according to terminal ID with corresponding relation to description file; the manage device receives directly user control or state query request, resolves the description file, and generates command to the terminal. Besides, it also discloses the corresponding device management device.
Owner:HAIER GRP CORP +1
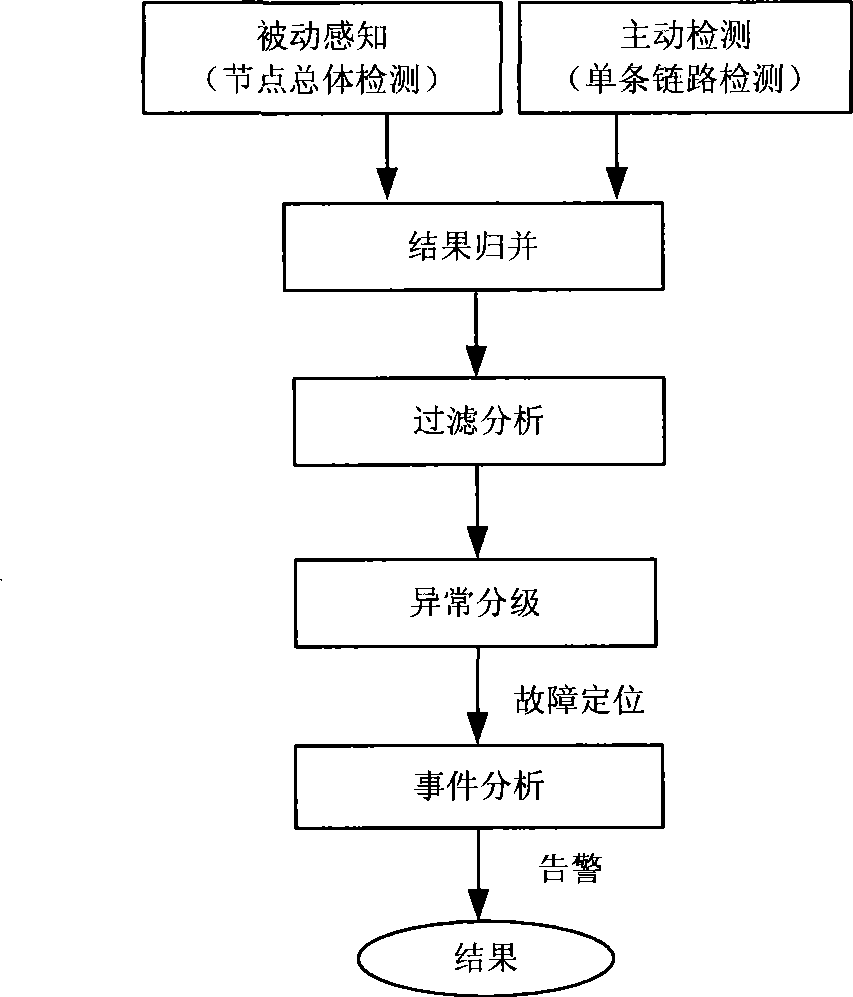
Evaluation method and system for network burst affair
InactiveCN101483547AReduce loadReduce resource overheadData switching networksQuality of serviceNetwork link
The present invention discloses a method for measuring and evaluating network burst damage event, wherein the method comprises the following steps: passive perceiving and active detecting burst event; filtering and analyzing after merging the result; dividing the event grade according to the merging result, realizing the positioning to the fault reason; determining whether an adjustment of protocol mechanism should be executed according to the grade; and checking the whole condition of adjusted network for ensuring the correctness. The invention also provides a system for measuring the network burst damage event. The system comprises a router control module, an array management algorithm module, a network management module and an off-line calculating module. The problem to be settled by the invention is cause that the router has a flow perceiving capability, realize whether the full-network link and node operate normally and whether the burst damage event is generated. The result is notified in time for adjusting the protocol mechanism. The invention provides criterion for the protocol adjustment thereby increasing the usability and reliability of network node and link and finally guaranteeing the service quality of network.
Owner:THE PLA INFORMATION ENG UNIV
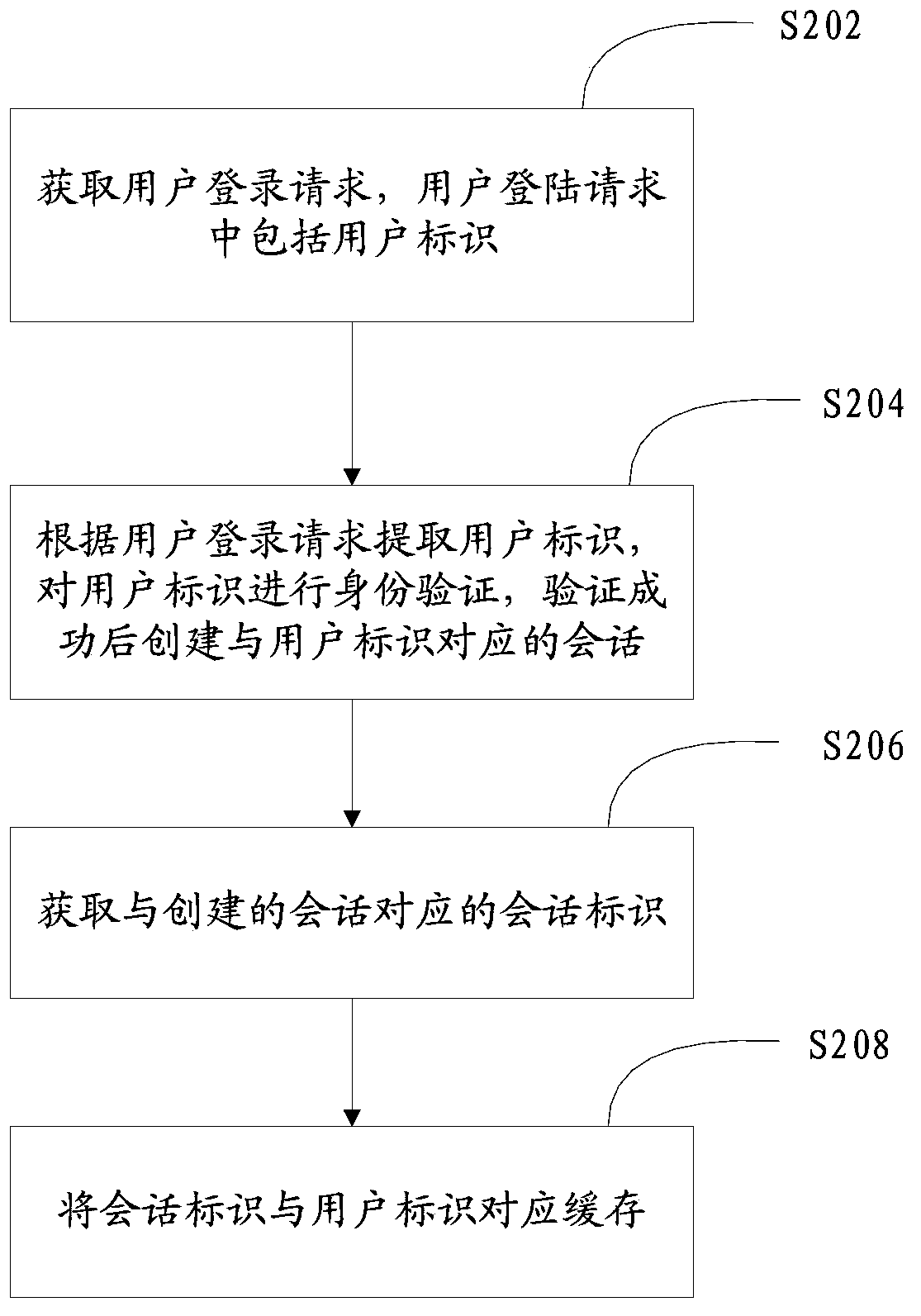
Method and system for maintaining login state of user account
ActiveCN103532919AReduce verification timesRelieve pressureUser identity/authority verificationDigital data authenticationData accessWorld Wide Web
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method for detecting network video quality by network injury tolerance
InactiveCN101227604AReduce resource overheadImprove real-time performancePulse modulation television signal transmissionData switching networksDamage effectsInternet service provider
The invention relates to a method of detecting the quality of a network video through network damage degree, wherein the method reflects the influence degree of network damage effecting the quality of the video according to specific frame sequence type, frame rate, packing condition, frame packet loss rate, namely a rate of a single-frame losing a qualified pockets which obtained according to the network video and corresponding impairment grade of the frame pocket loss rate, and obtains the quality of network video according to an original video quality Q0 and the relation of the influence degree of damaging network and the network video quality (Q); the original video quality and the network video quality are both adopt the same quantification evaluation criteria measurement. Compared with the prior art, the invention has the advantages of considering the different type of frame packet loss has different effect to the video quality and the condition of different impairment grade of the video quality which effects by the different number pocket of a frame losing, thereby the invention has the advantages of low cost of resource develop, good real-time performance, higher estimation accuracy and which can be especially applied for internet service providers or operation businesses to estimate the quality of real-time transmission video.
Owner:SHANGHAI BROADBAND TECH
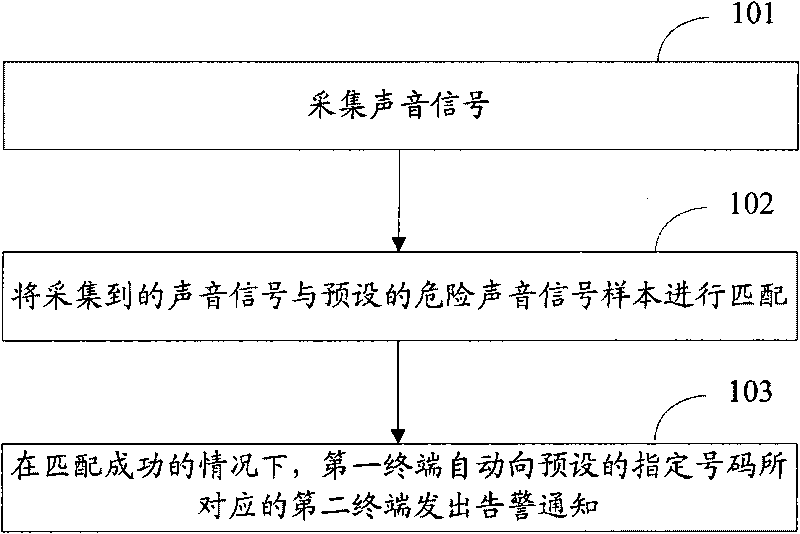
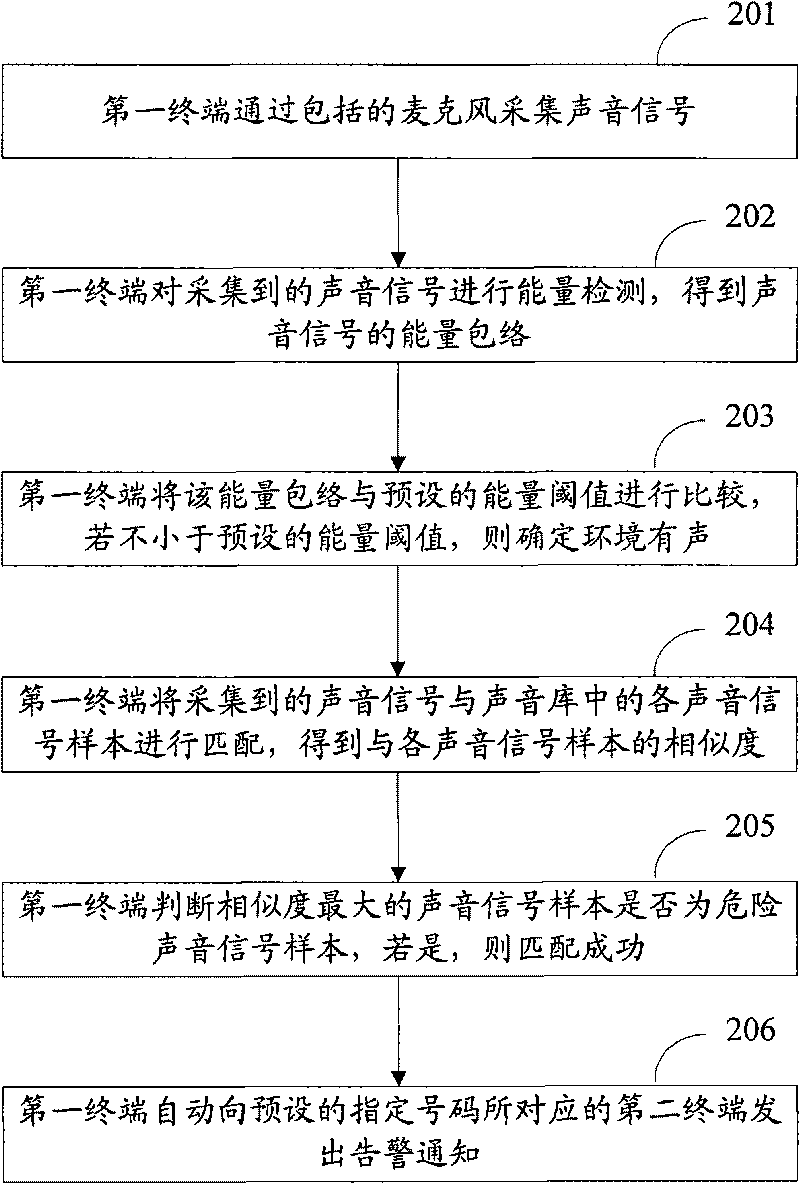
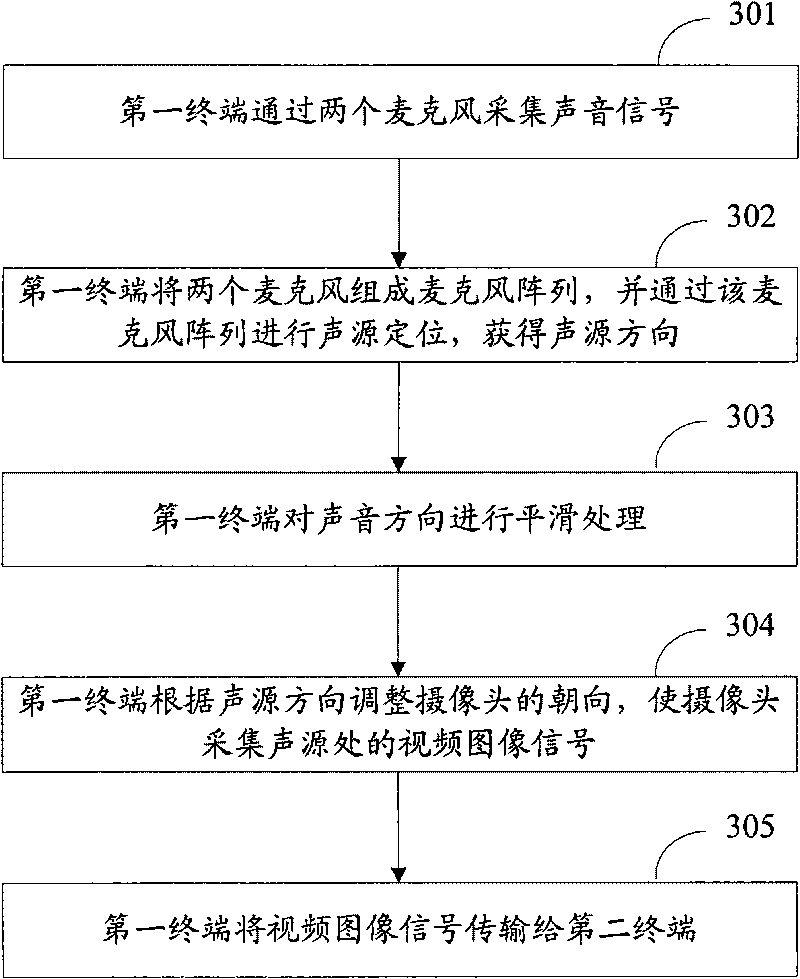
Sound control alarm method and device
InactiveCN101739789ARealize voice-activated alarmReduce resource overheadTelephonic communicationAlarmsComputer terminalComputer science
The invention discloses a sound control alarm method used for realizing alarm when the danger sounds are found. The method comprises the following steps: acquiring the sound signal; matching the acquired sound signal with the preset danger sound signal sample; and under the condition of successful matching, sending the alarm notice to a second terminal corresponding to the preset designated number by a first terminal automatically. The invention also discloses a device for realizing the method.
Owner:VIMICRO CORP +1
Information processing method and system, and terminal
ActiveCN108259409AAchieve decouplingReduce resource overheadSelective content distributionSecuring communicationInformation processingMultimedia
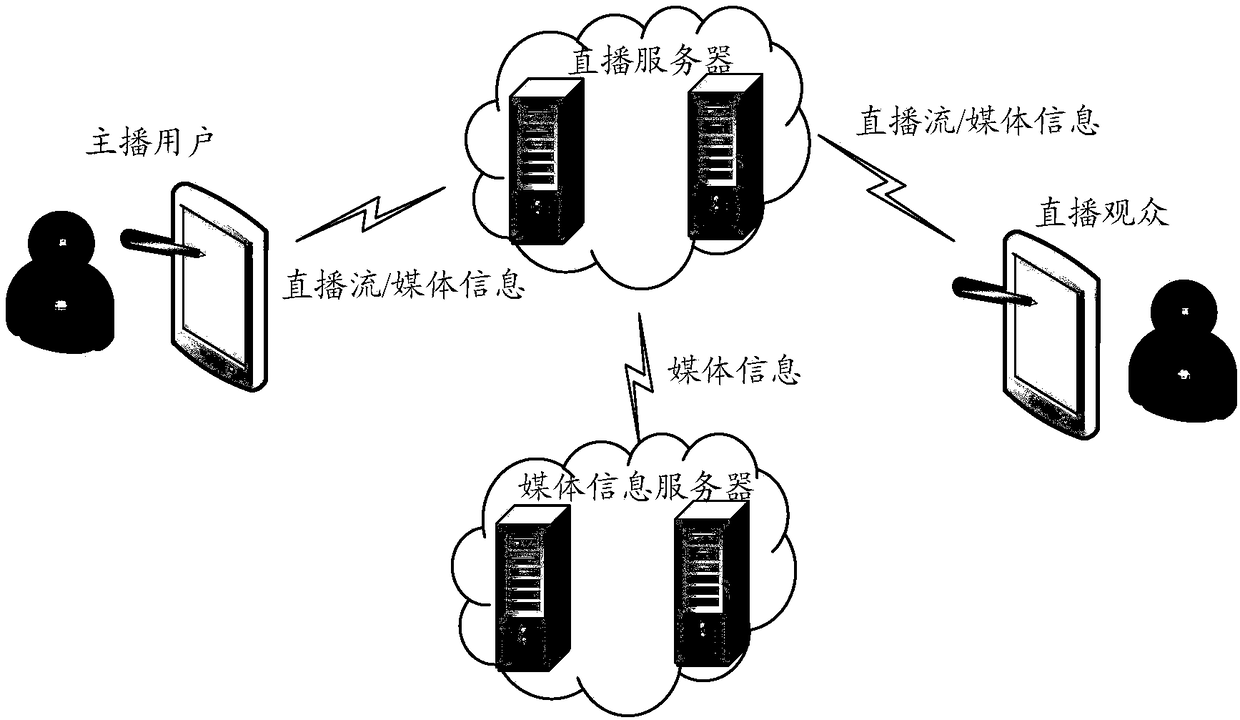
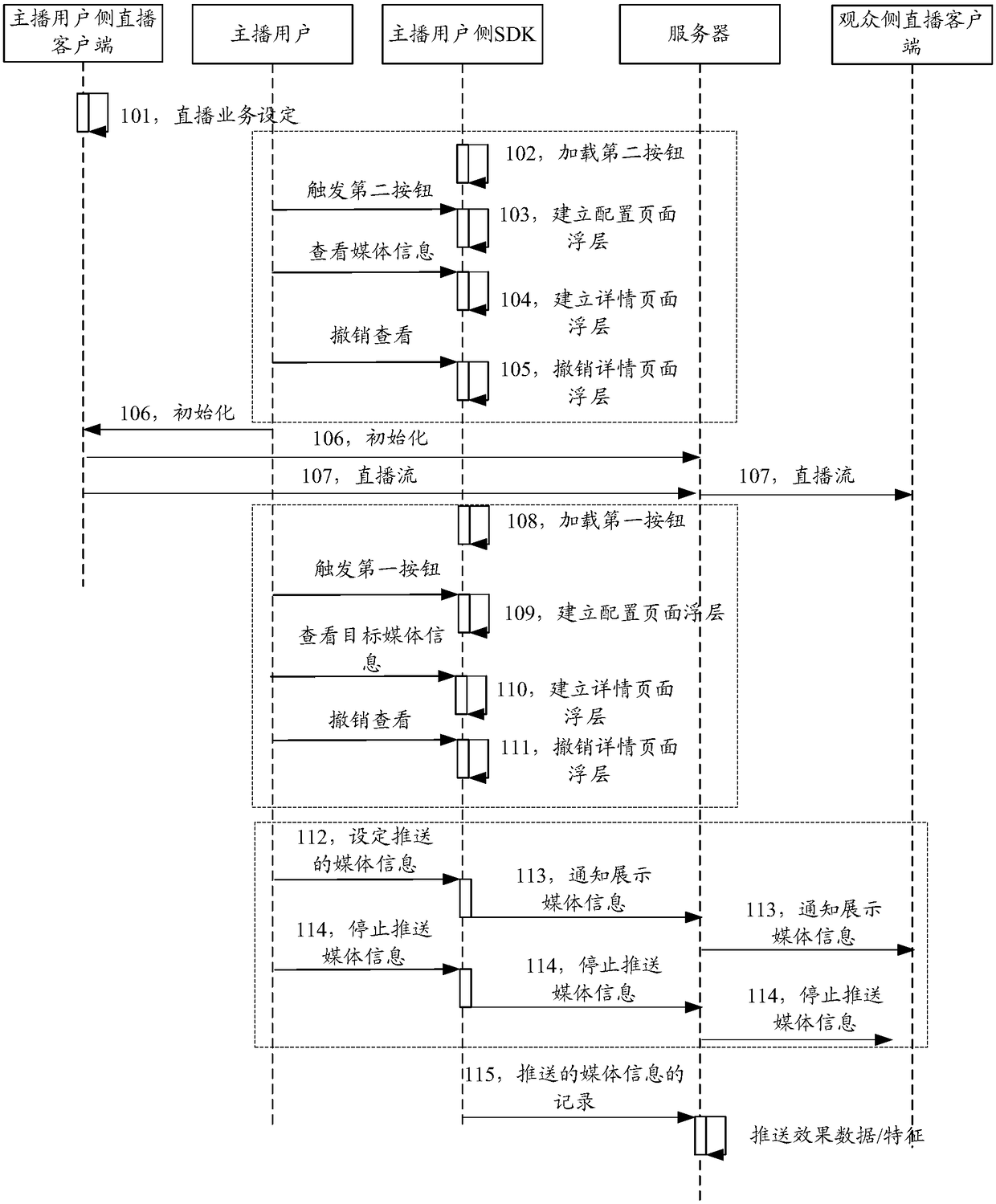
The present invention discloses an information processing method and system, and a terminal. The method comprises the steps of: initializing live business between an anchor user and live audiences; performing media collection of the anchor user side, performing coding of the media information obtained through collection to form a live stream, and sending the live stream to live windows of the liveaudiences for playing; arranging an area configured to push the media information based on a live window of the anchor user; loading candidate media information pushed to the live audiences at the area, and determining media information to be pushed selected by the anchor user; and sending the media information to be pushed into the area configured to push the media information based on the liveaudiences for display.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Location privacy protection method based on l-inquiry
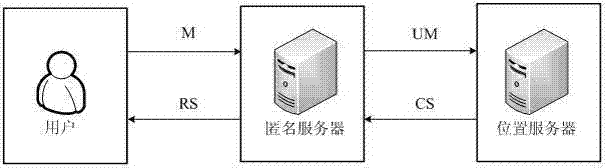
InactiveCN104507048AOvercoming Security FlawsImprove securityLocation information based serviceTransmissionProtection mechanismPrivacy protection
The invention relates to a location privacy protection method based on l-inquiry. The method comprises the following steps that (1) when a user requires location service, an inquiry request is initiated for an anonymous server; (2) the anonymous server constructs an anonymous inquiry request including k users and l inquiry subjects by a method of merging the inquiry requests from the same region at the same moment and inserting the false inquiry on the location k-anonymity basis, and in addition, the anonymous inquiry request is submitted to a location server; (3) the location server respectively carries out inquiry processing on the l inquiry subjects one by one, and then returns a result set obtained through merging the inquiry results to the anonymous server; (4) the anonymous server filters away the false inquiry result from the result set, and then carries out sorting and secondary refinement according to the inquiry subjects of different users, the final location inquiry result is obtained, and is then respectively returned to each user. The method has the advantage that the location privacy protection mechanism security can be improved.
Owner:FUJIAN NORMAL UNIV
Multilingual user interface for an operating system
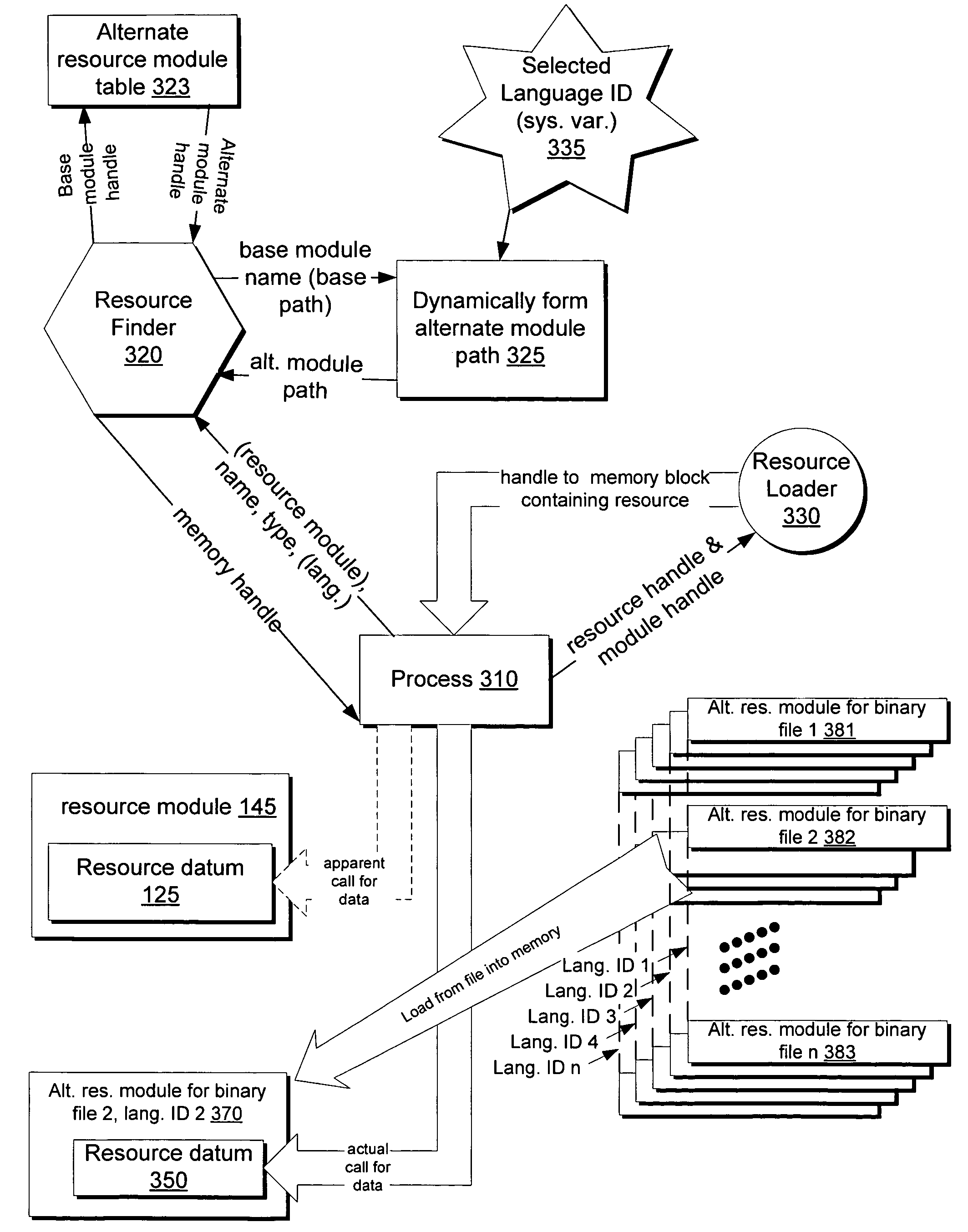
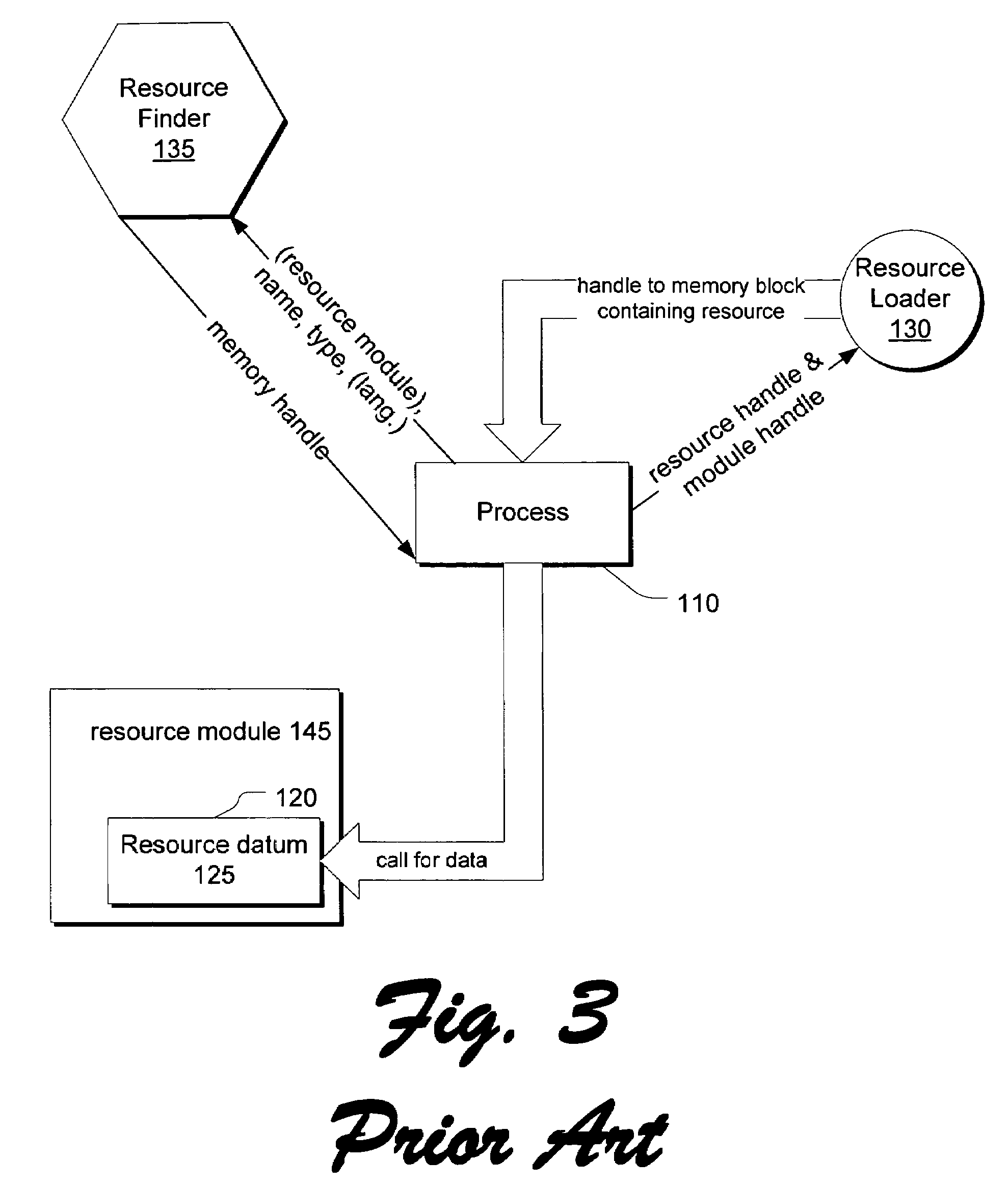
InactiveUS7464334B2Reduce in quantityReduce resource overheadMultiprogramming arrangementsCathode-ray tube indicatorsOperational systemMulti language
In an operating system, a resource handler accepts resource requests from application modules. A resource request identifies a module from which the requested resource is to be obtained. Rather than providing the resource from the identified module, however, the resource handler provides the requested resource from an associated resource module. An association between an executable module and resource modules of different languages is created by a defined file naming convention, optionally using different directories for resource modules of different languages. Some executable modules contain a shared resource reference which can be used to create an association between multiple executable modules and a single set of shared resource modules. A language fallback mechanism allows alternative languages to be used where resource modules of the appropriate language are not available.
Owner:MICROSOFT TECH LICENSING LLC
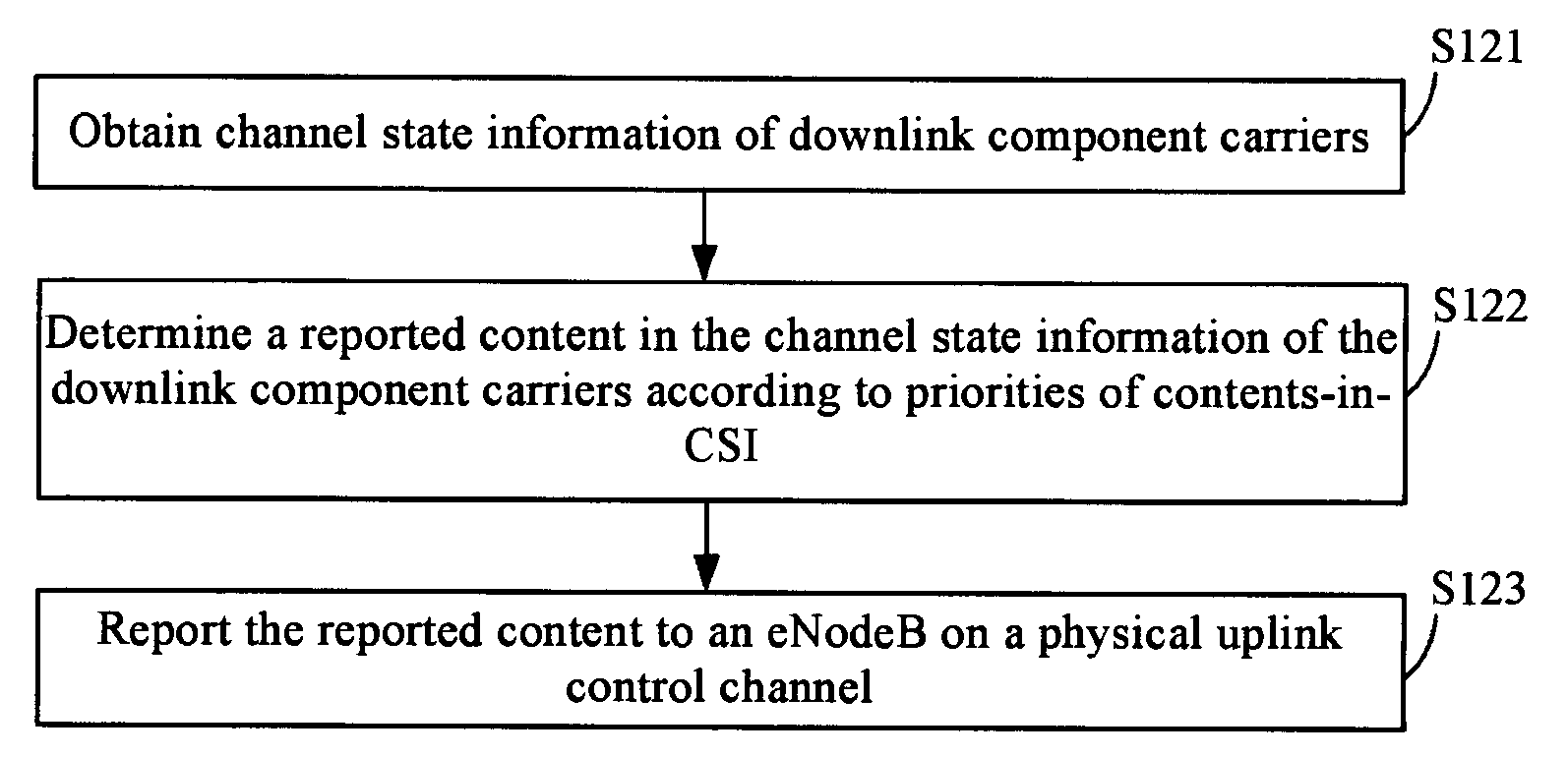
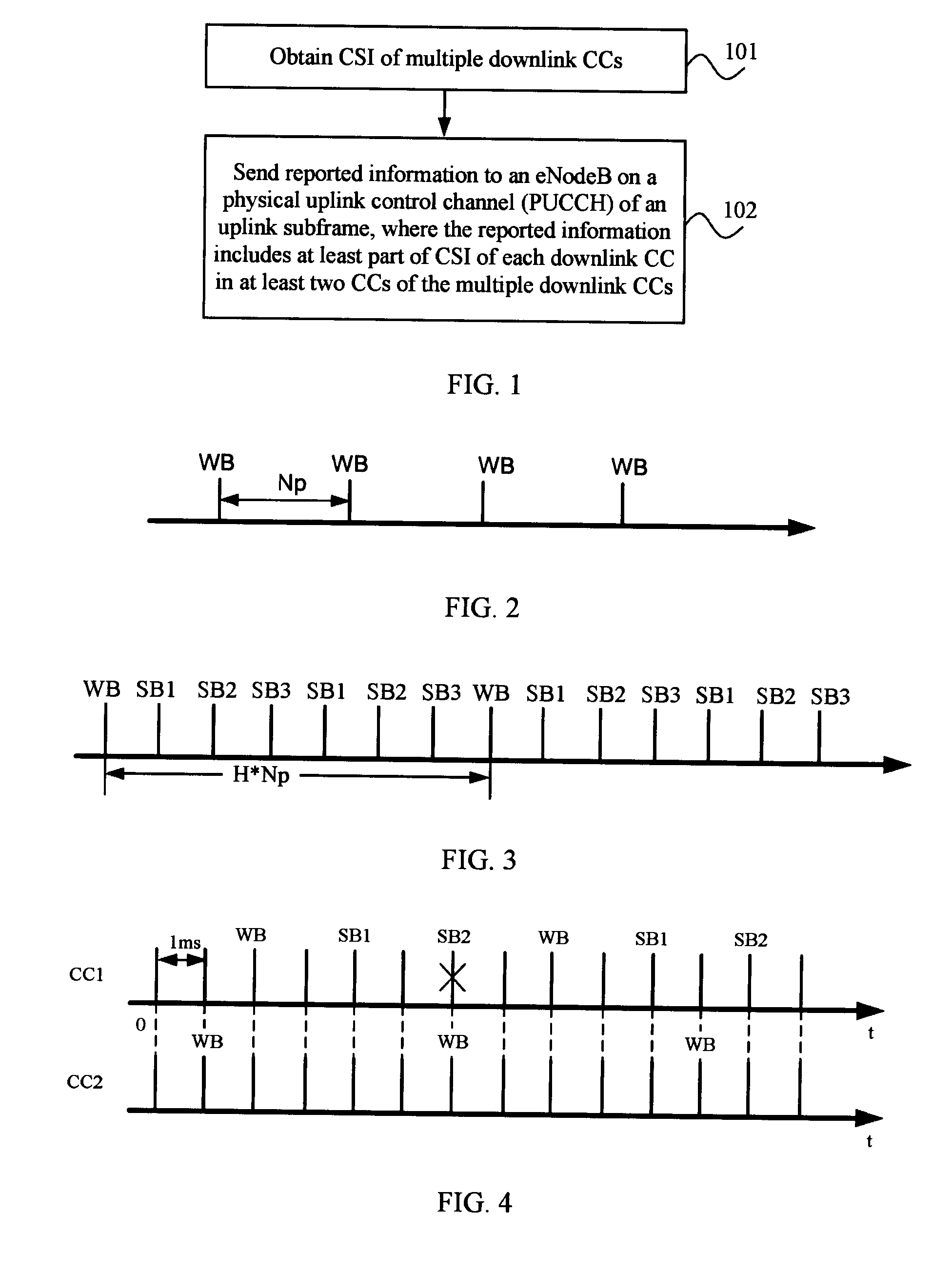
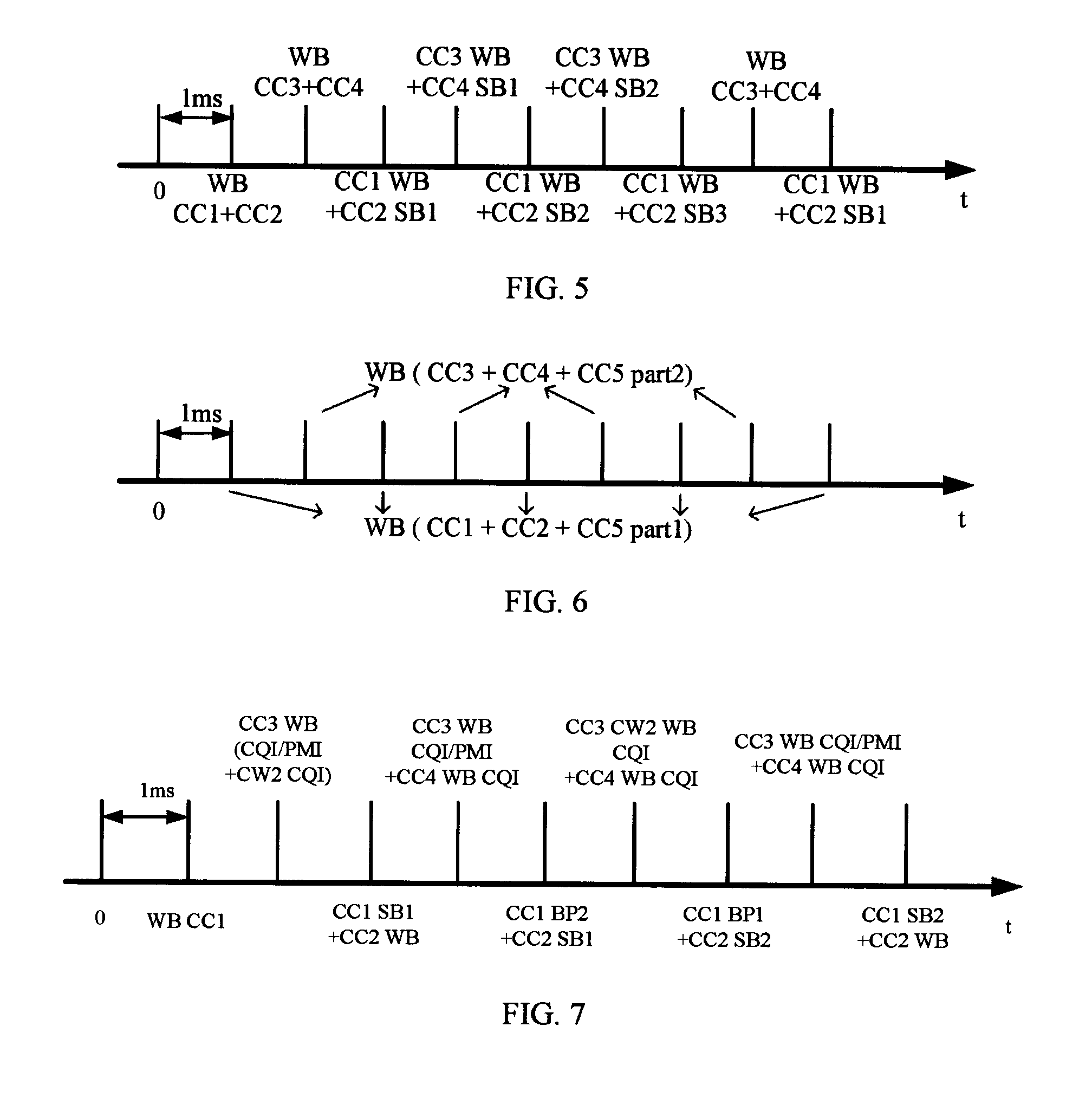
Method for reporting and obtaining channel state information, enodeb, and user equipment
ActiveUS20120327785A1Reduce resource overheadError preventionTransmission systemsChannel state informationTelecommunications
A method for reporting and obtaining channel state information, an eNodeB, and a user equipment are disclosed. The method for reporting channel state information includes: determining a reported content in channel state information (CSI) of downlink component carriers according to priorities of contents-in-CSI, where the CSI of the downlink component carriers includes the reported content and a content that is not to be reported; and reporting the reported content to an eNodeB on a physical uplink control channel (PUCCH). By determining a reported content in CSI according to a priority, the shortage of a CSI reporting resource may be relieved.
Owner:HUAWEI TECH CO LTD
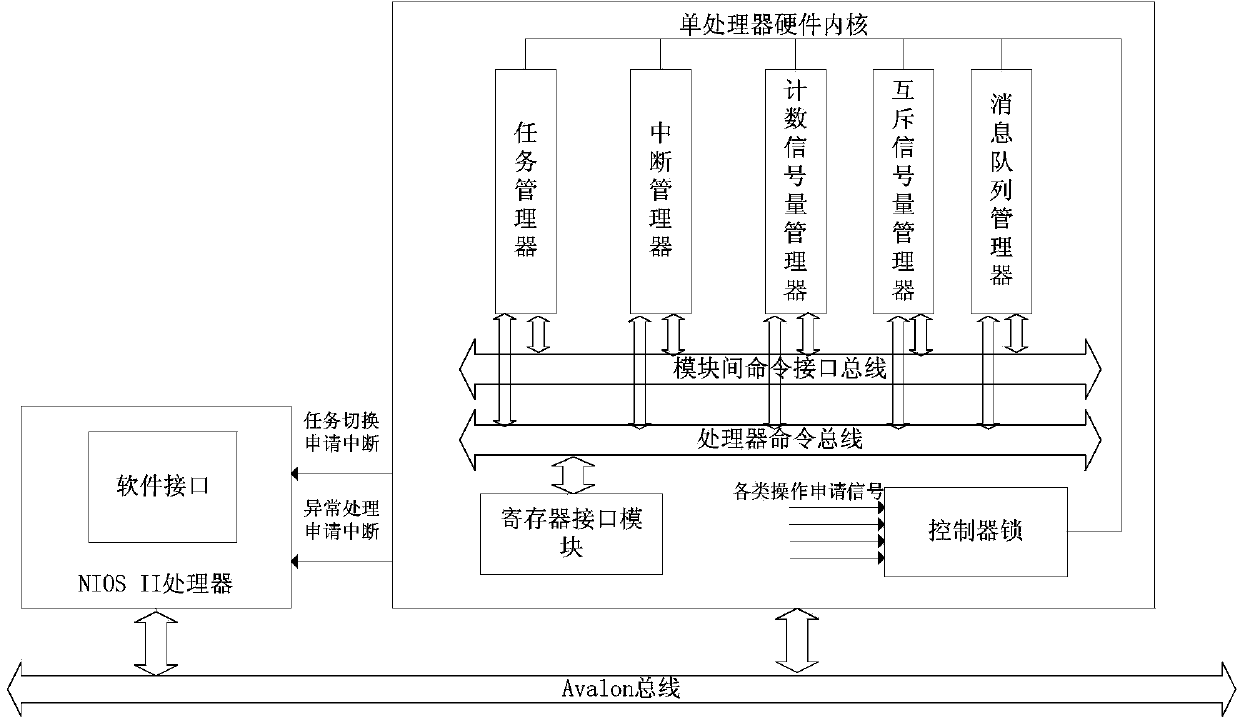
Realization method of real-time operating system of component-based hardware
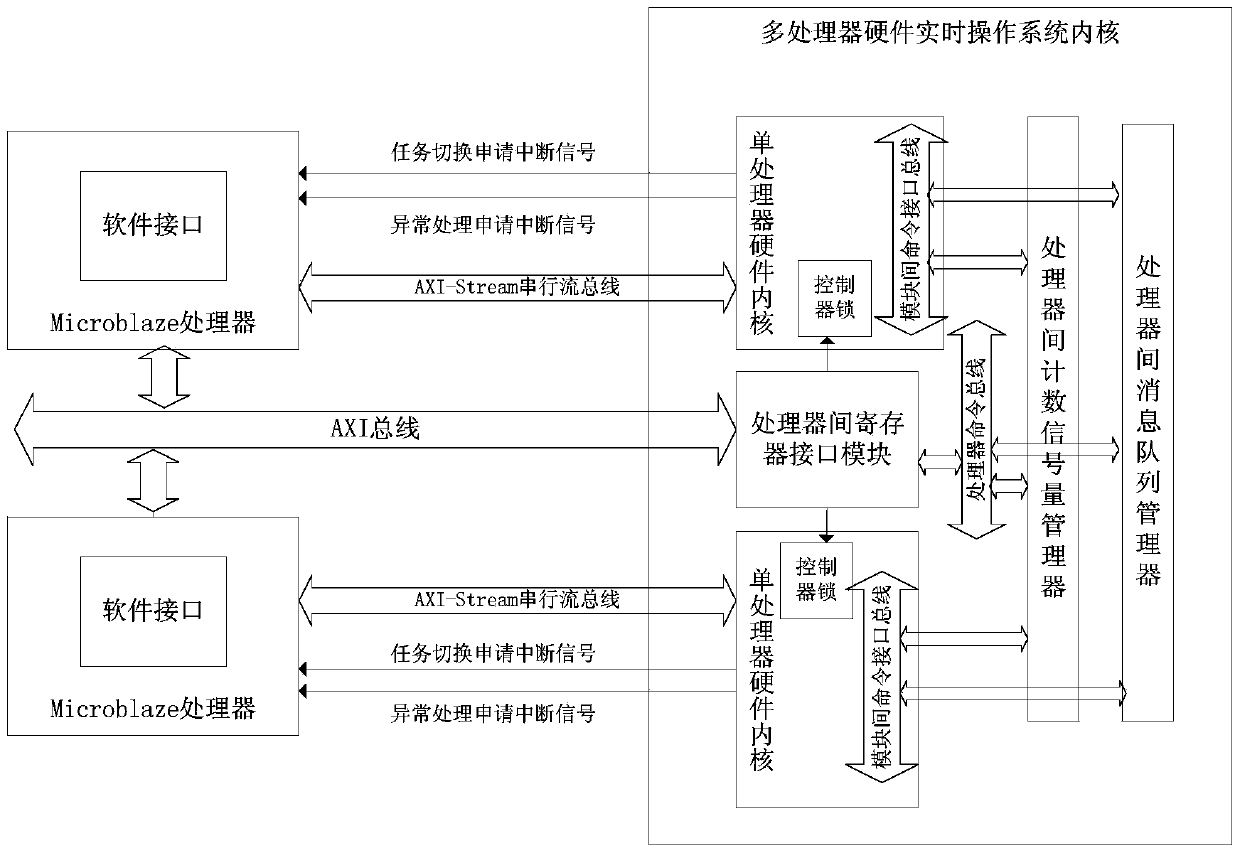
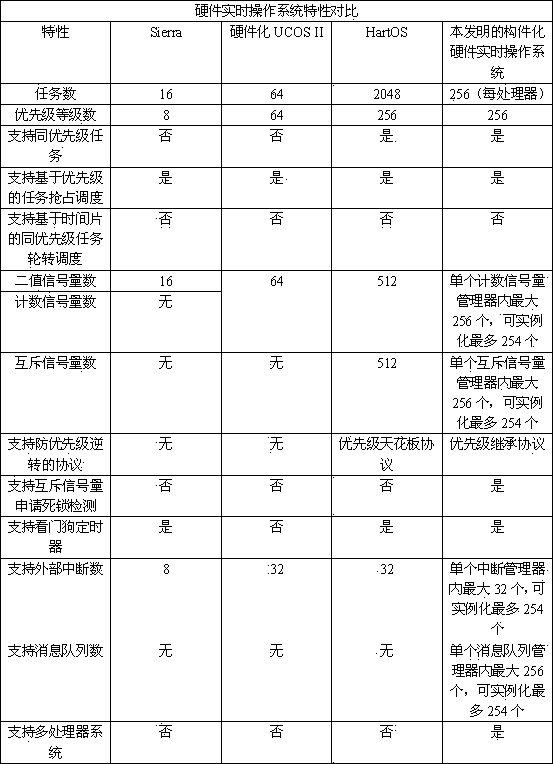
InactiveCN103440171AReduce overheadImprove performanceProgram initiation/switchingMessage queueProcessor register
The invention discloses a realization method of a real-time operating system of component-based hardware. The method comprises the following steps of: firstly, dividing the real-time operating system into two parts including a hardware inner core and a software interface; then, realizing the communication of a task manager, an interruption manager, a counting semaphore manager, a mutual exclusion semaphore manager and a message queue manager of the real-time operating system by component-based manner in the hardware inner core; enabling the hardware inner core to be communicated with software by a register interface module; synchronizing all the managers by a controller lock; enabling the mangers to be communicated by standard inter-mould command interface buses; and finally, realizing an inter-processor counting semaphore manager and an inter-processor message queue manager and realizing the hardware inner core of a multiprocessor real-time operating system. According to the realization method, the inner core of the hardware real-time operating system is realized by a component-based manner so that the cuttability and the expandability of the system are improved greatly and the flexibility of the software is realized by the real-time operation of the hardware.
Owner:ZHEJIANG UNIV
Data acquisition method and equipment
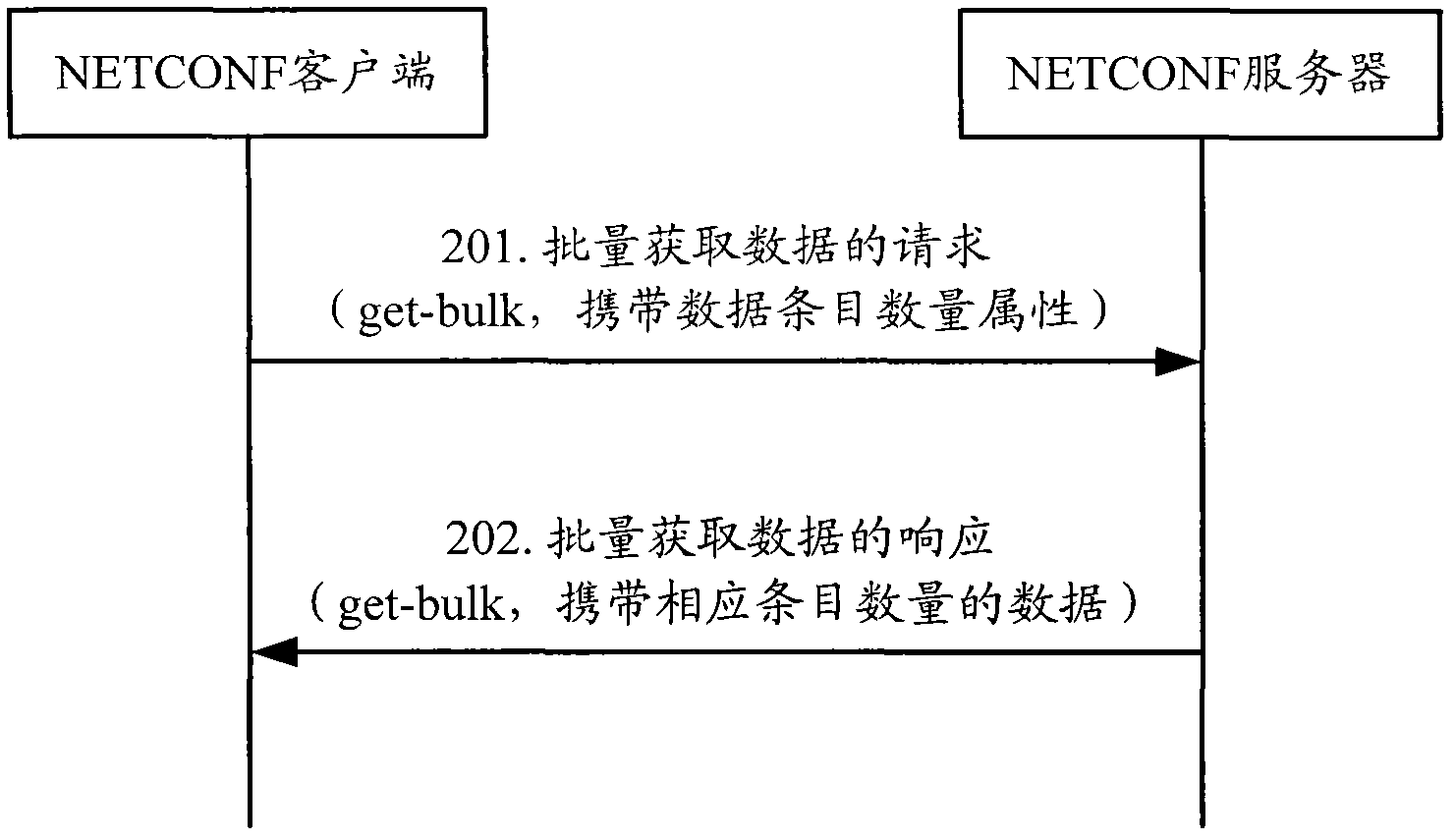
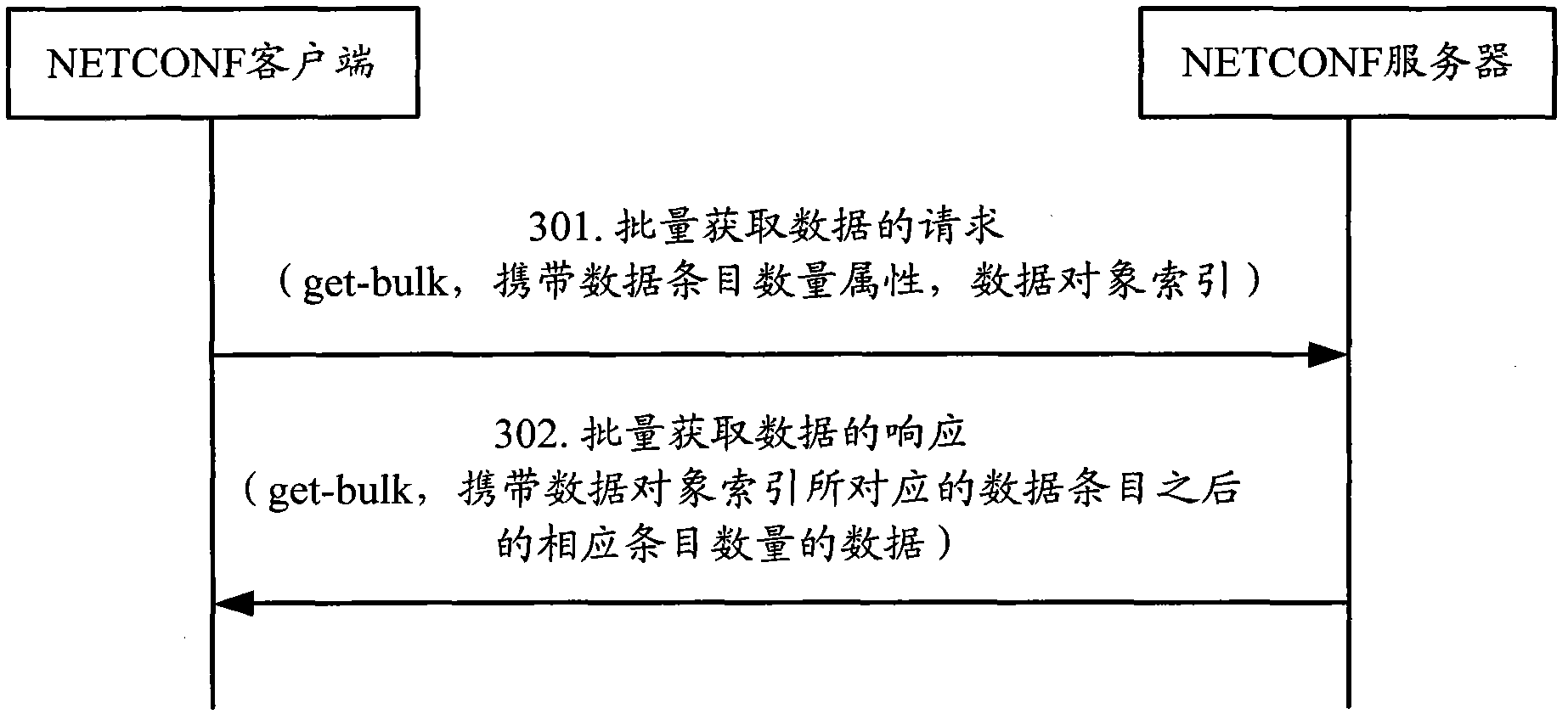
InactiveCN102355374AReduce resource overheadImprove convenienceData switching networksNetworked systemData acquisition
The invention discloses a data acquisition method and equipment which are applied to a network system containing a server and client, wherein the server and the client communicate with each other through an NETCONF (network configuration) protocol. The method provided by the invention comprises: the client sends a request for acquiring data in batches to the server, wherein the request carries data item quantity information; and the client receives a response of acquiring data in batches returned by the server, wherein the response carries corresponding item quantity of data inquired by the server. According to the invention, the problems of large resource expenses and non-flexible implementation caused by acquiring a large quantity of data based on the NETCONF protocol can be solved.
Owner:NEW H3C TECH CO LTD
Door opening and closing detection method based on monitoring videos
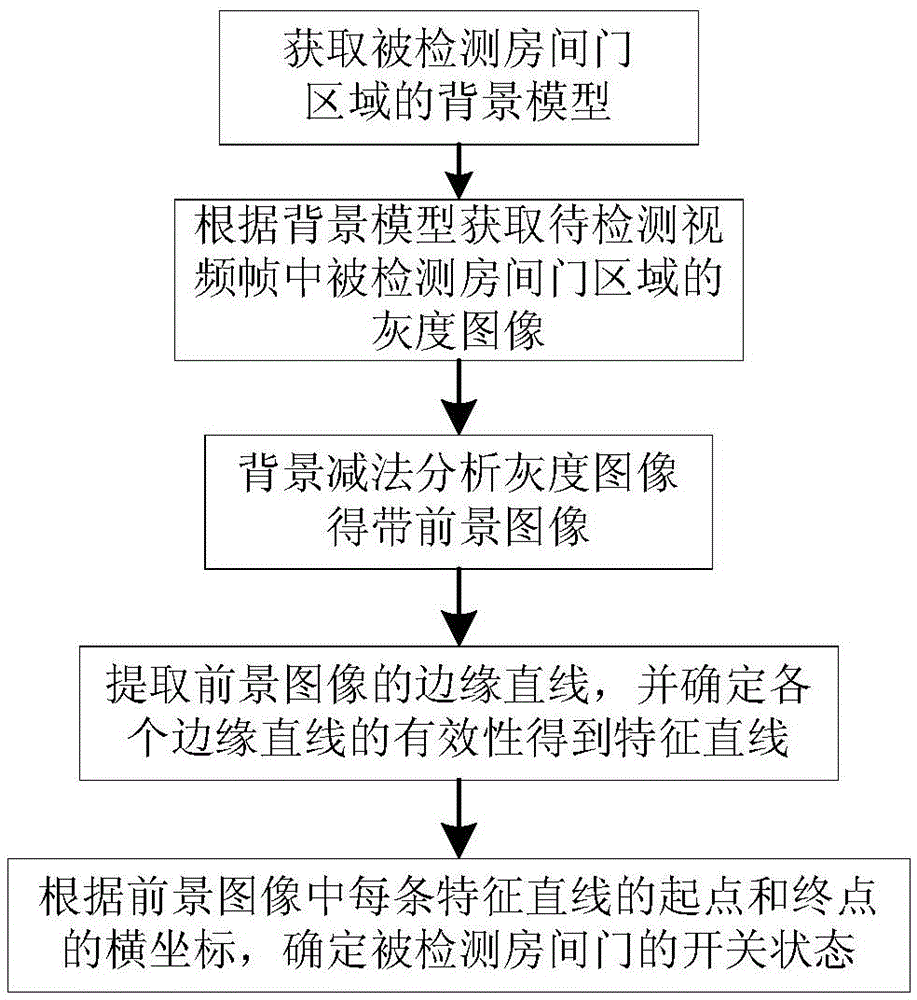
ActiveCN103986906AAvoid interferenceImprove securityTelevision system detailsCharacter and pattern recognitionVideo monitoringForeground detection
The invention discloses a door opening and closing detection method based on monitoring videos. A corresponding image frame when a detected room door is closed serves as a reference frame, a background model of the detected room door is obtained according to the reference frame, background subtraction is carried out on a room door area in a detected video frame through the background model to work out a foreground image, and the opening and closing state of the detected door is determined by extracting a feature straight line of the foreground image and then using the horizontal position of the feature straight line and a door crack in the background model. The door opening and closing detection method based on monitoring videos achieves the function of automatically detecting the opening and closing state of the room door through the simple combined technologies such as motion foreground detection and digital image processing, and is simple, low in resource expense and suitable for the application of an embedded type system like video monitoring. The whole room door area is directly detected, the opening and closing state is determined according to the door crack position, the inference generated when a person or an object shields the room door is effectively avoided, the detection accuracy is high, universality is high, no monitoring blind spot exits, and the safety coefficient of monitoring is improved.
Owner:HANGZHOU TOPZEN INFORMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com