Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
527 results about "Mutual exclusion" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
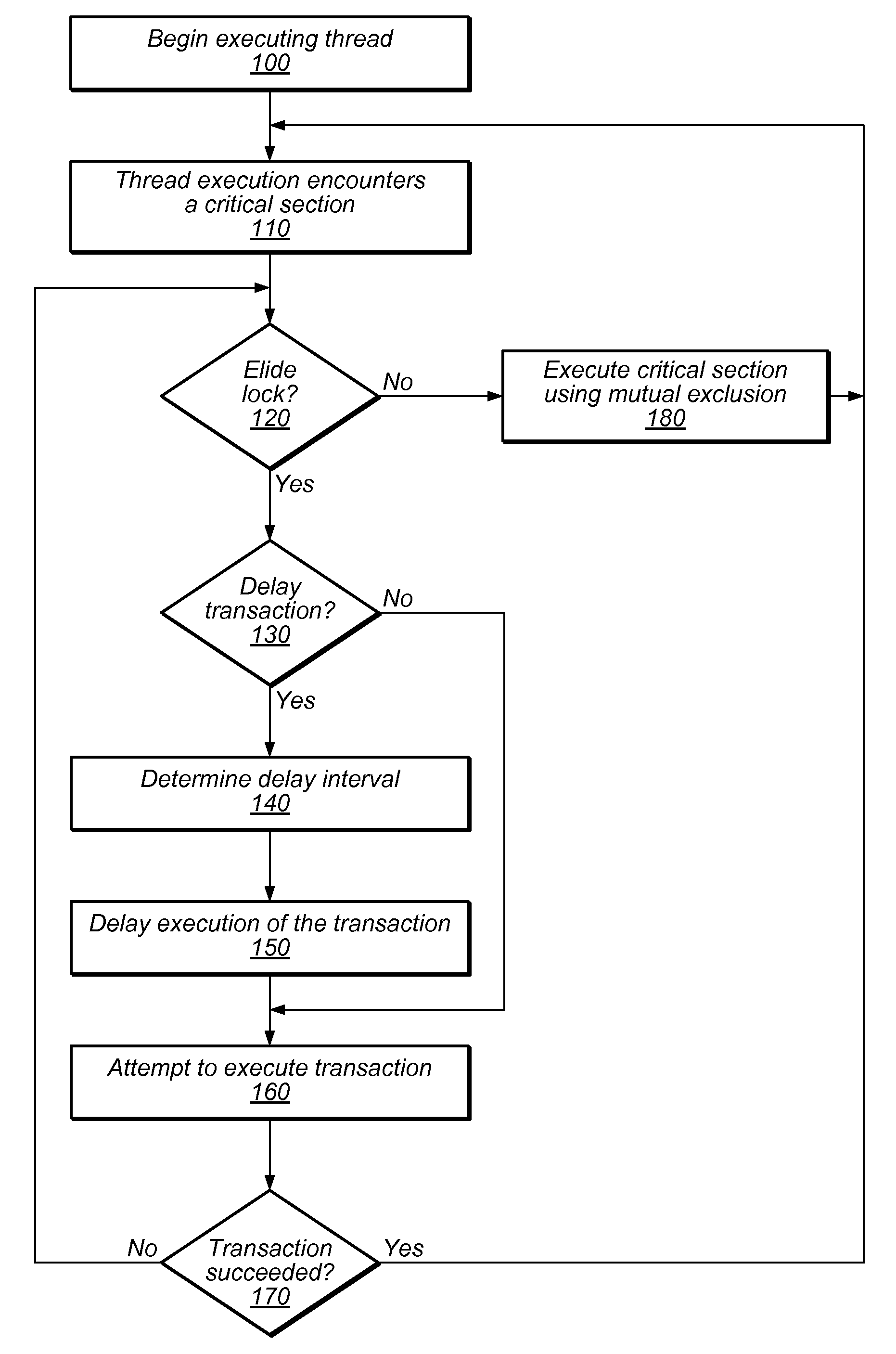
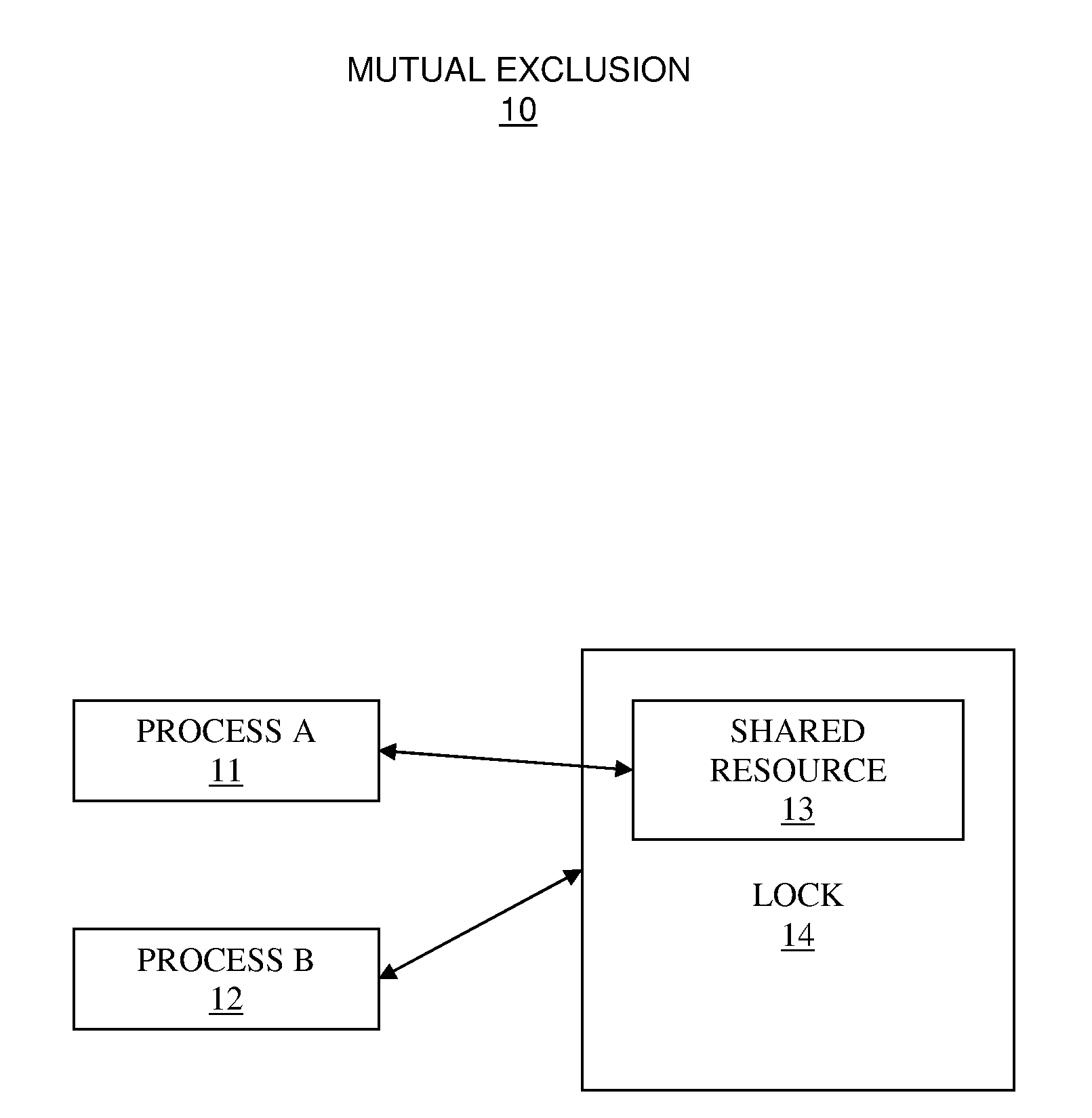
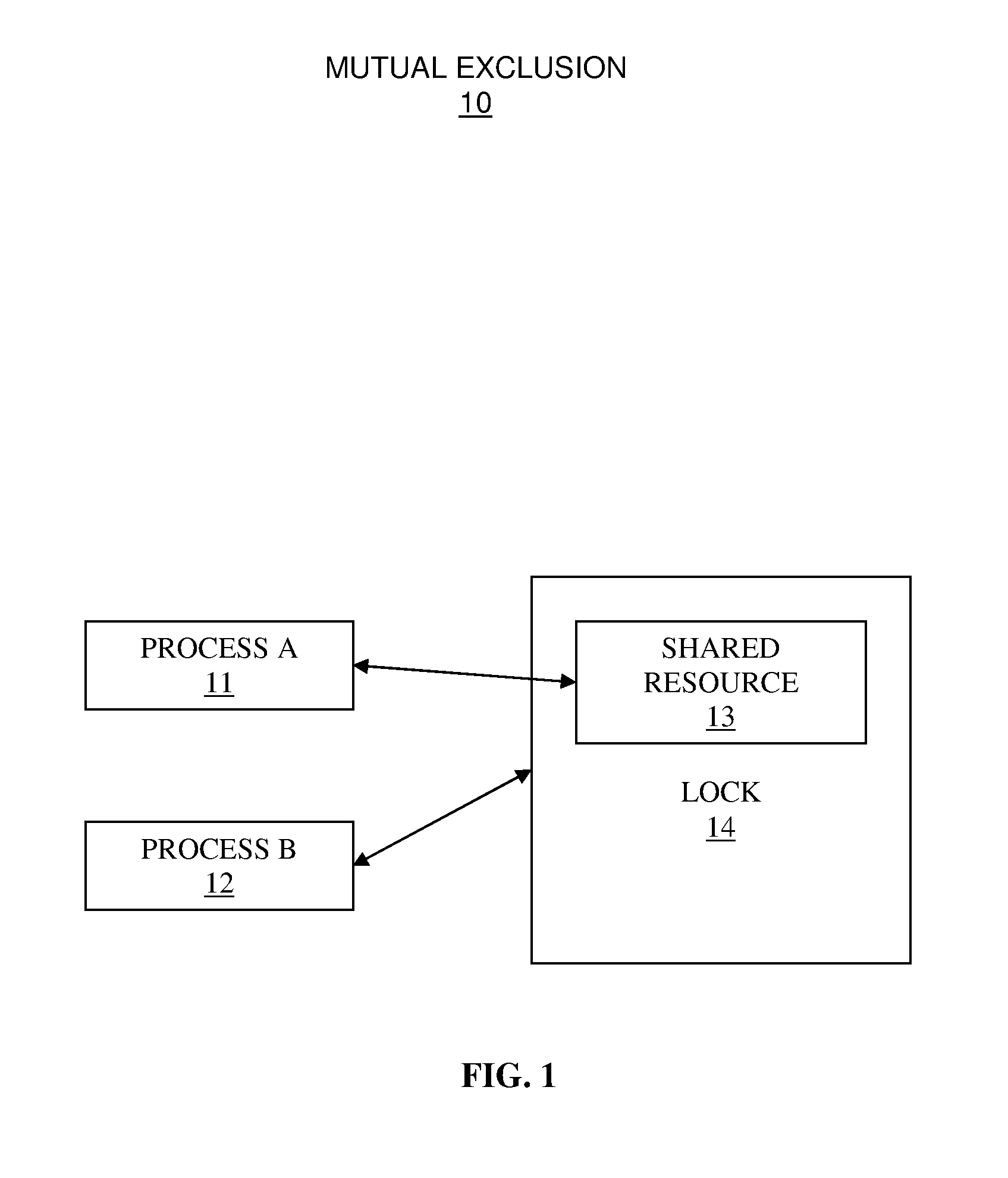
In computer science, mutual exclusion is a property of concurrency control, which is instituted for the purpose of preventing race conditions; it is the requirement that one thread of execution never enters its critical section at the same time that another concurrent thread of execution enters its own critical section.
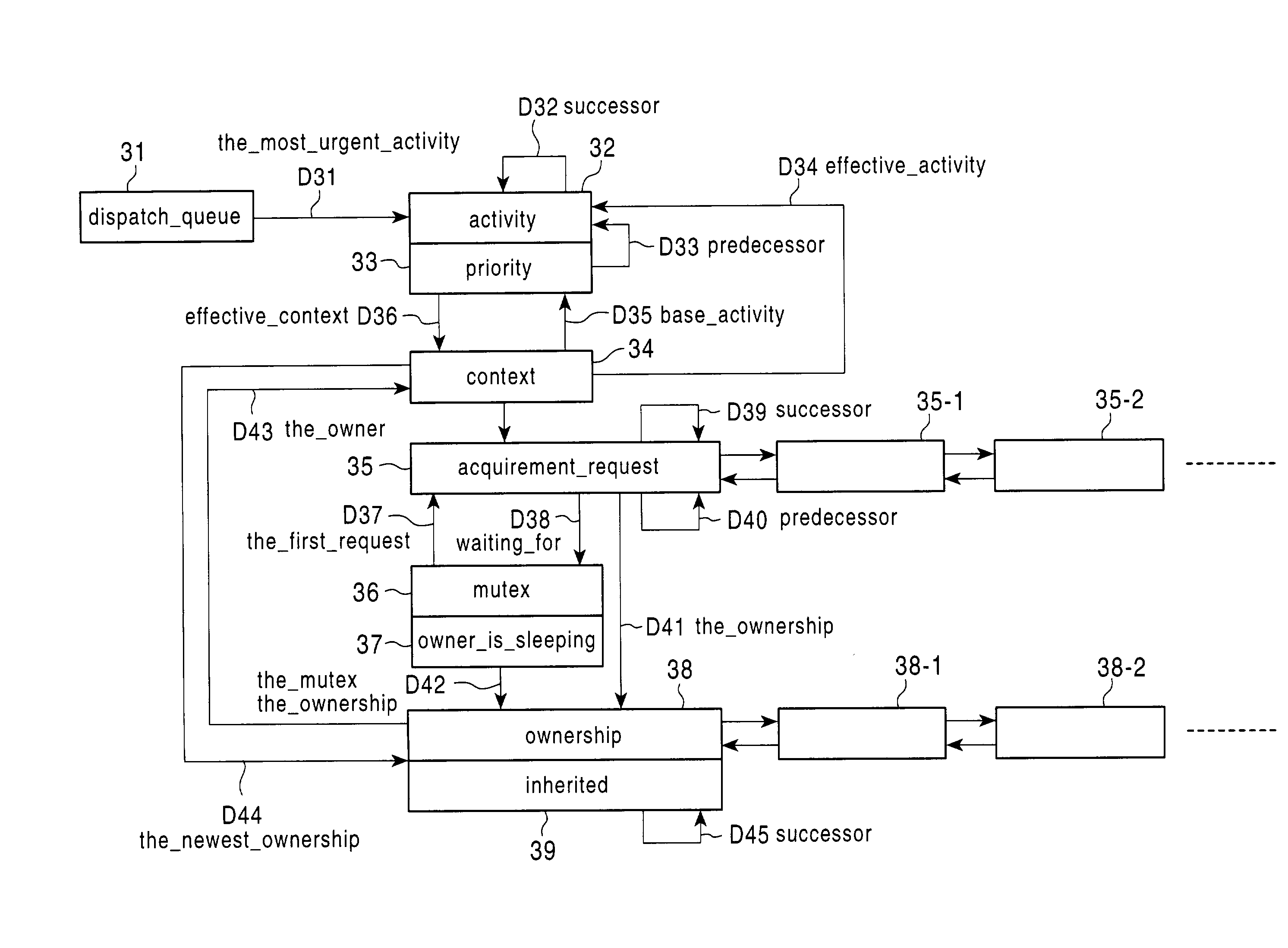
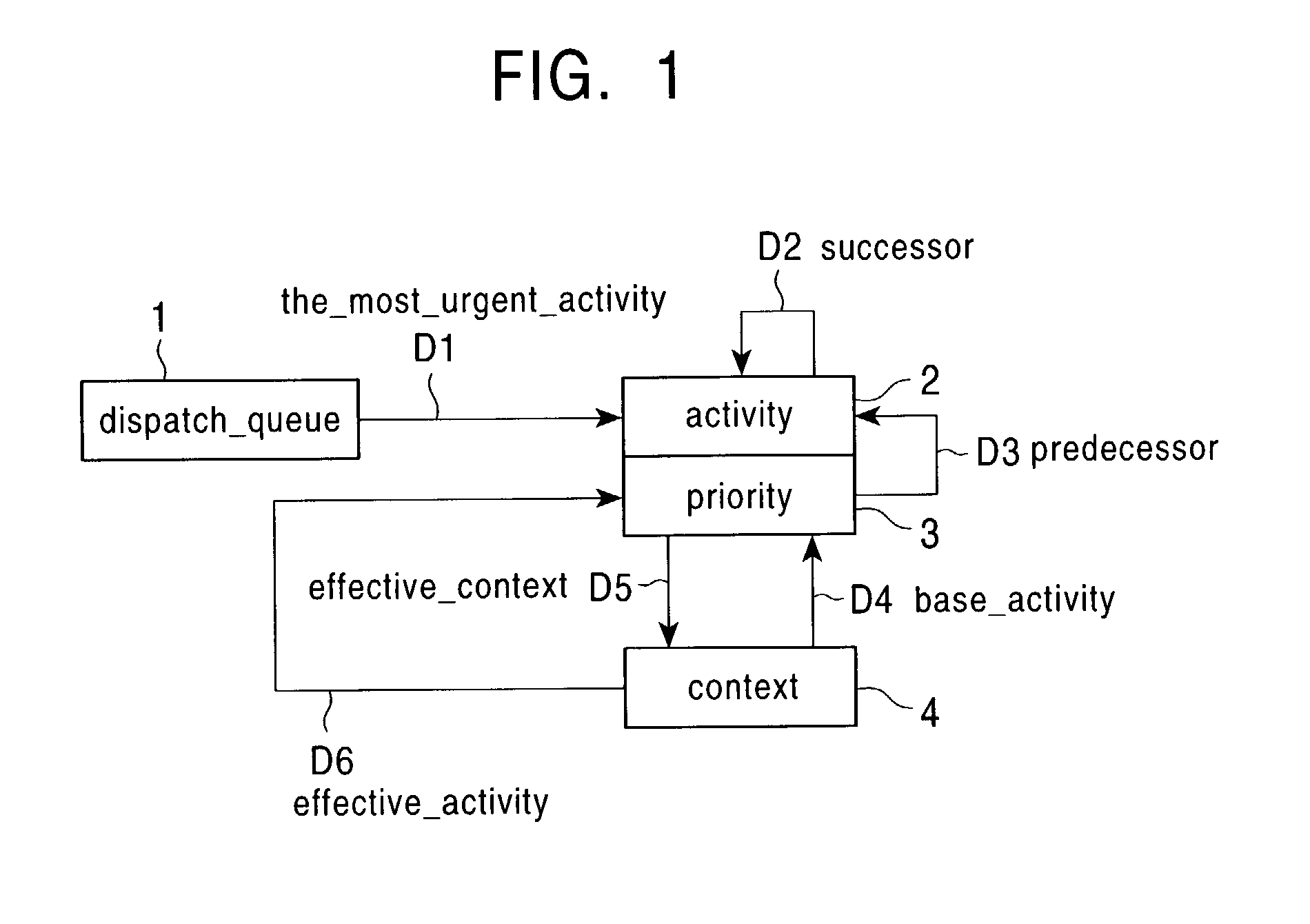
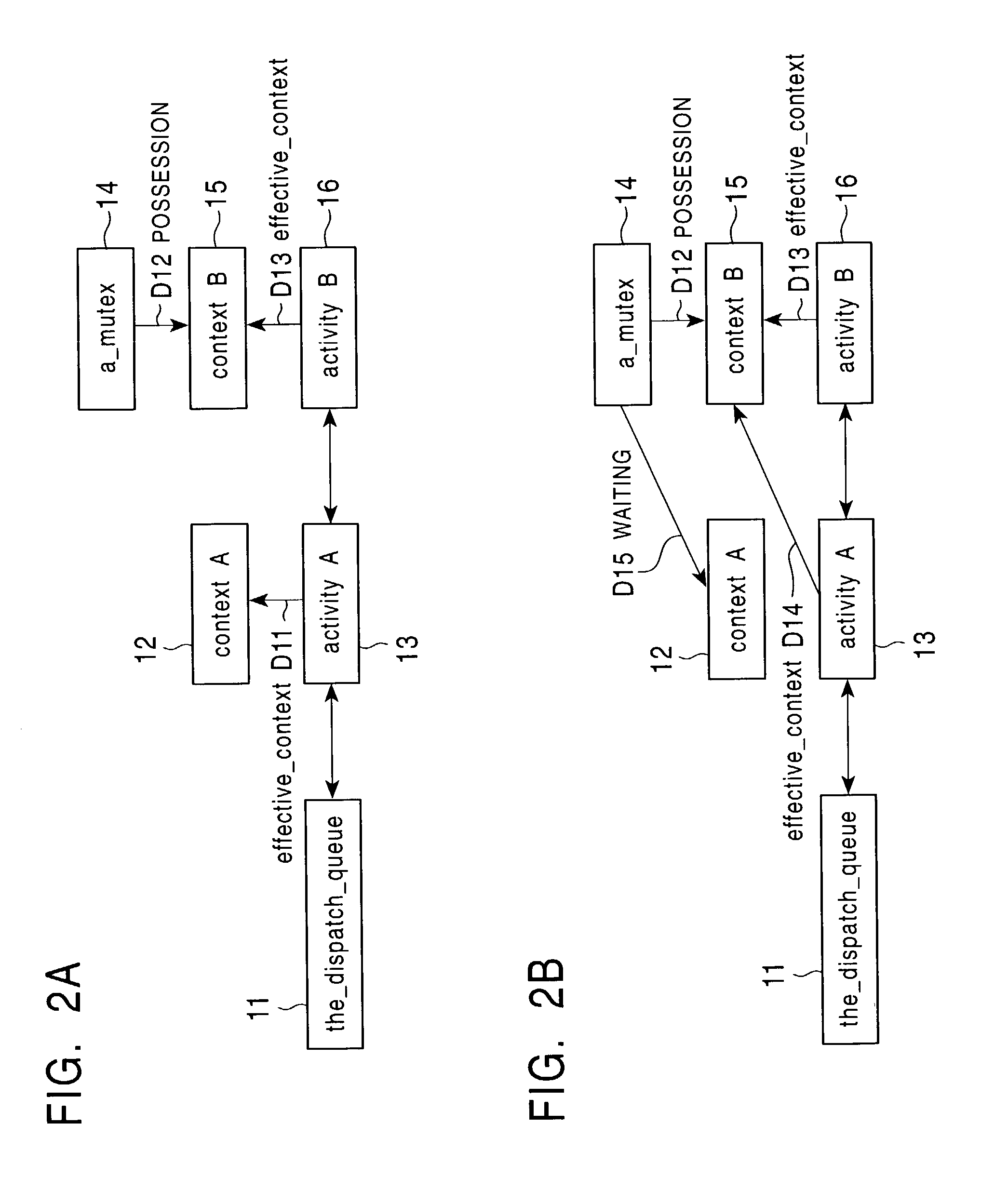
Task management system
InactiveUS7302686B2Shorten the timeReduce overheadProgram initiation/switchingMultiple digital computer combinationsTask managementMutual exclusion
A task management system that inherit priority and that can reduce the queue operation required for transition to / return from a mutual exclusion awaiting state The task management system can execute a task without considering its priority, start or stop a server task and inherit priority without operating the dispatch queue. The task management system includes activity retaining information, context retaining information, and a dispatch queue used to select the highest priority task. Information on a task is divided and managed by the activity and the context, where each activity is inserted into / deleted from the dispatch queue. When the priority of a task is inherited by another task, only the correspondence between activity and context is changed.
Owner:SONY CORP
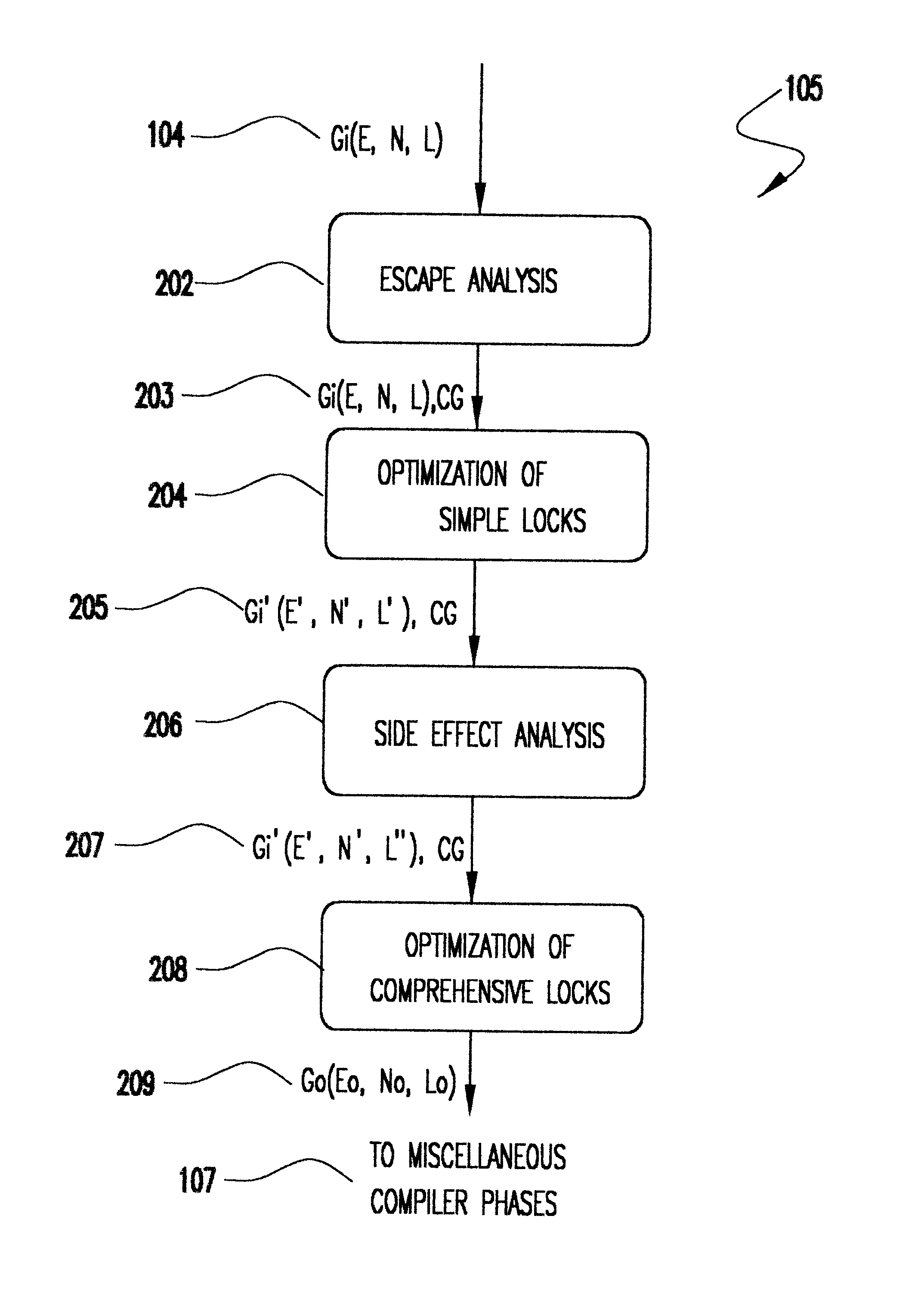
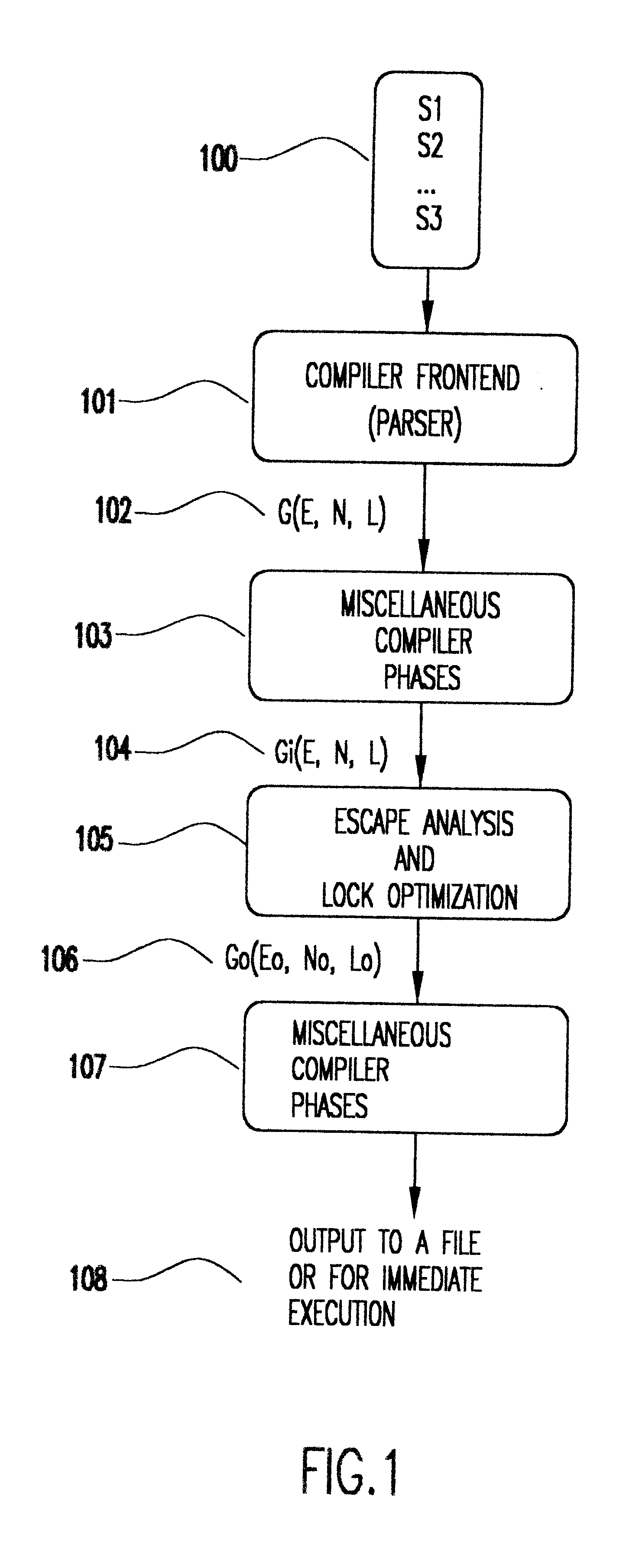
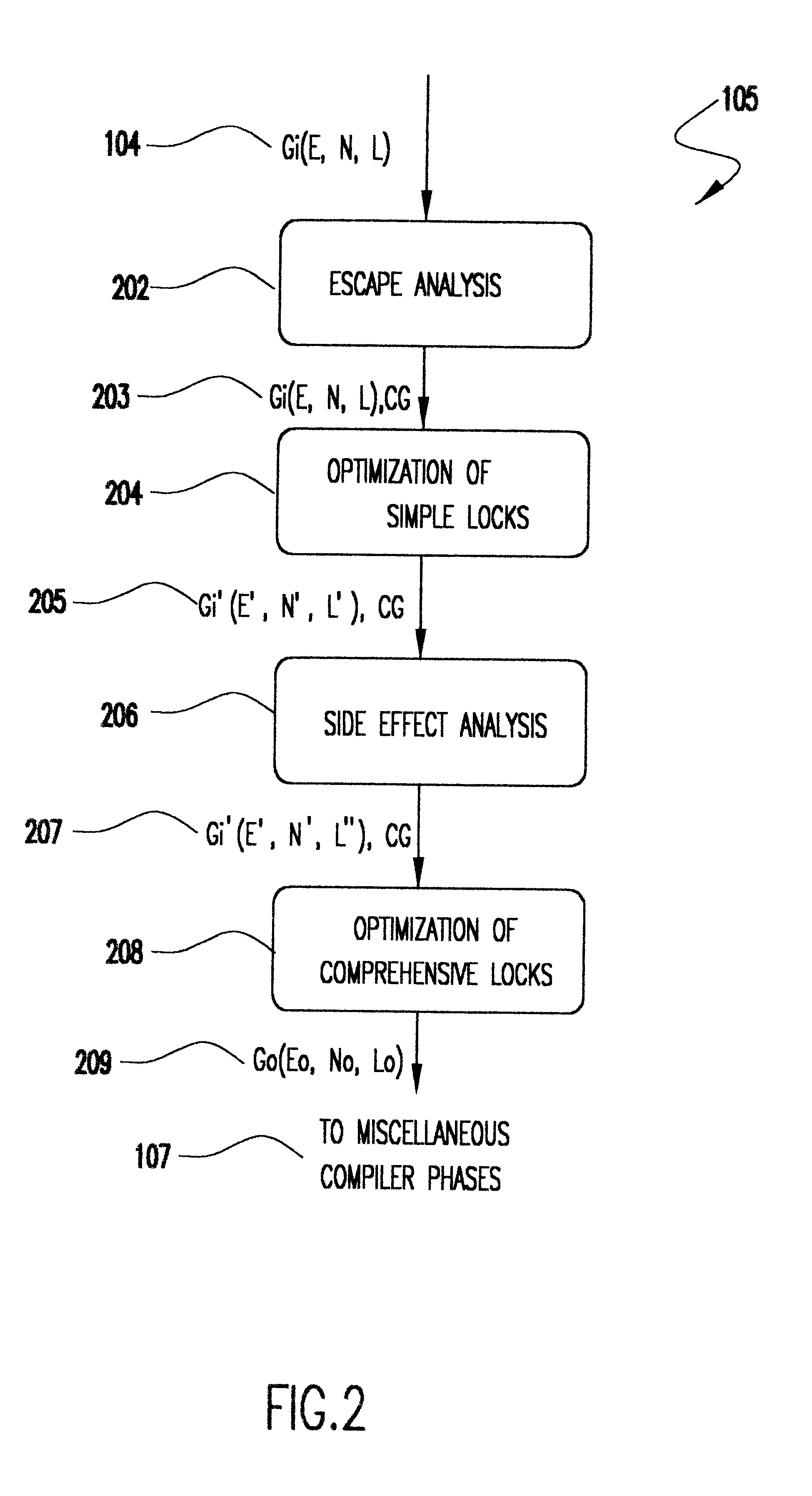
Method for optimizing locks in computer programs
InactiveUS6530079B1Easy to operateProgram synchronisationSoftware engineeringProgram planningSemantics
A method and several variants for using information about the scope of access of objects acted upon by mutual exclusion, or mutex, locks to transform a computer program by eliminating locking operations from the program or simplifying the locking operations, while strictly performing the semantics of the original program. In particular, if it can be determined by a compiler that the object locked can only be accessed by a single thread it is not necessary to perform the "acquire" or "release" part of the locking operation, and only its side effects must be performed. Likewise, if it can be determined that the side effects of a locking operation acting on a variable which is locked in multiple threads are not needed, then only the locking operation, and not the side effects, needs to be performed. This simplifies the locking operation, and leads to faster programs which use fewer computer processor resources to execute; and programs which perform fewer shared memory accesses, which in turn not only causes the optimized program, but also other programs executing on the same computing machine to execute faster. The method also describes how information about the semantics of the locking operation side effects and the information about the scope of access can also be used to eliminate performing the side effect parts of the locking operation, thereby completely eliminating the locking operation. The method also describes how to analyze the program to compute the necessary information about the scope of access. Variants of the method show how one or several of the features of the method may be performed.
Owner:IBM CORP
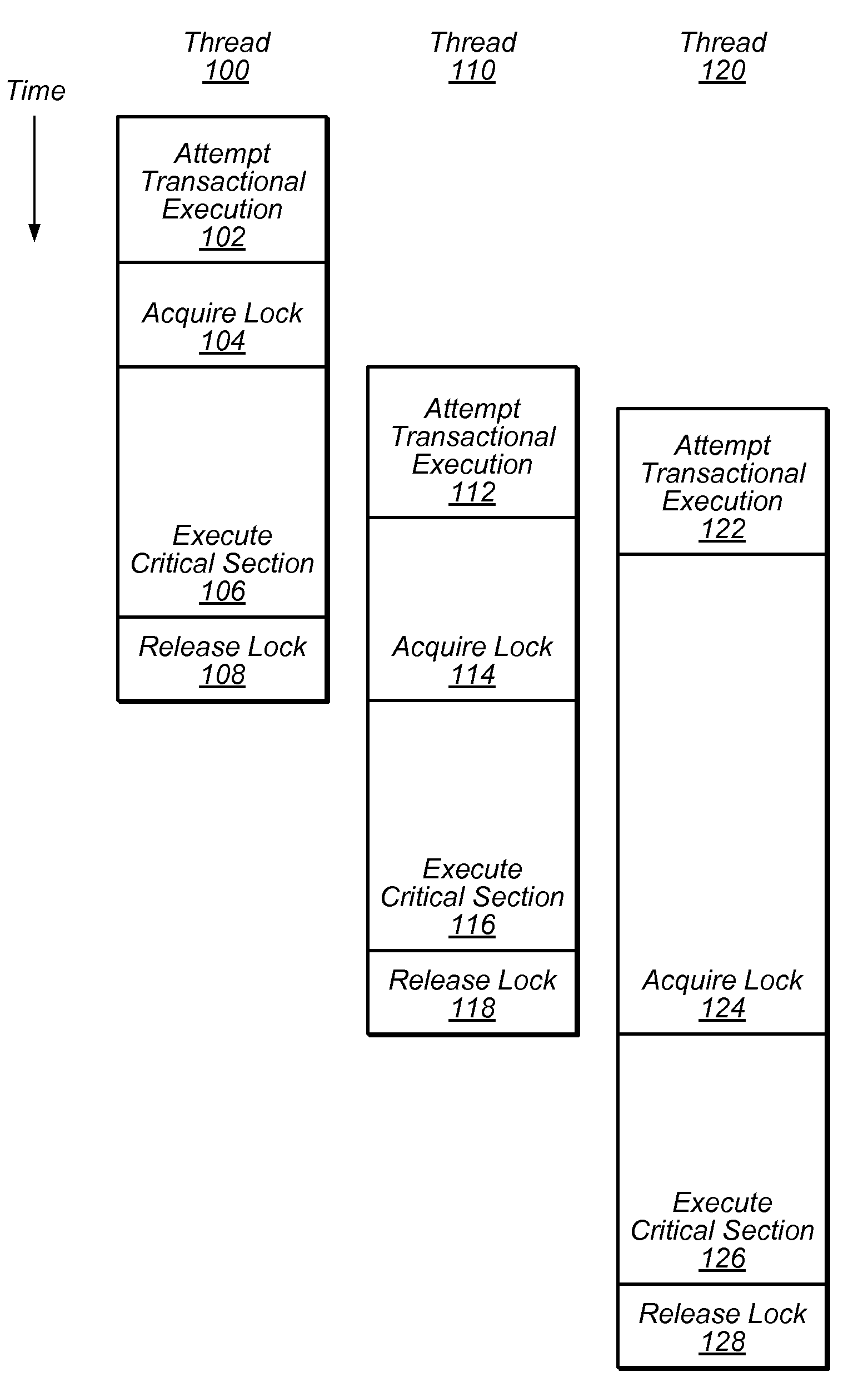
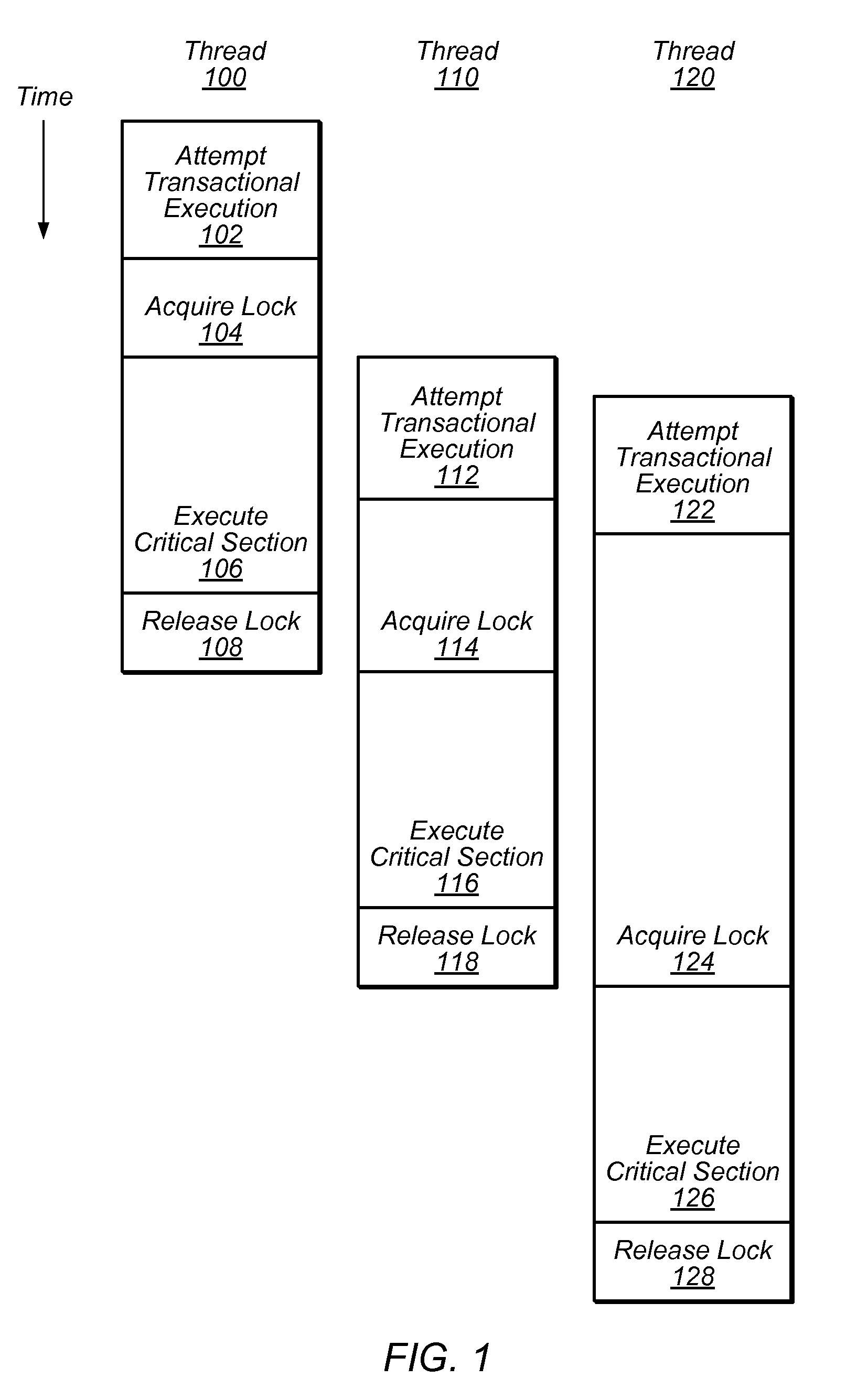
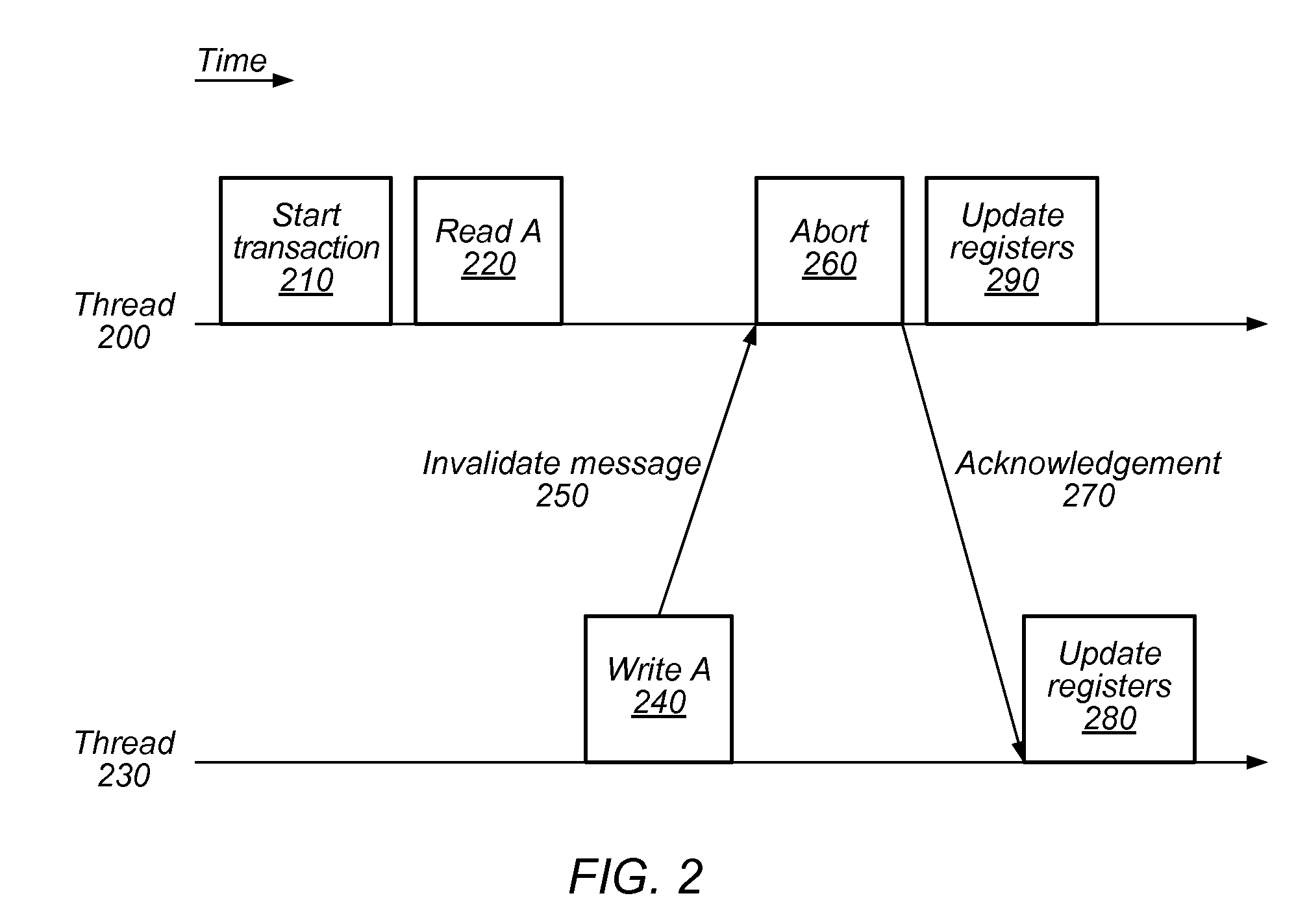
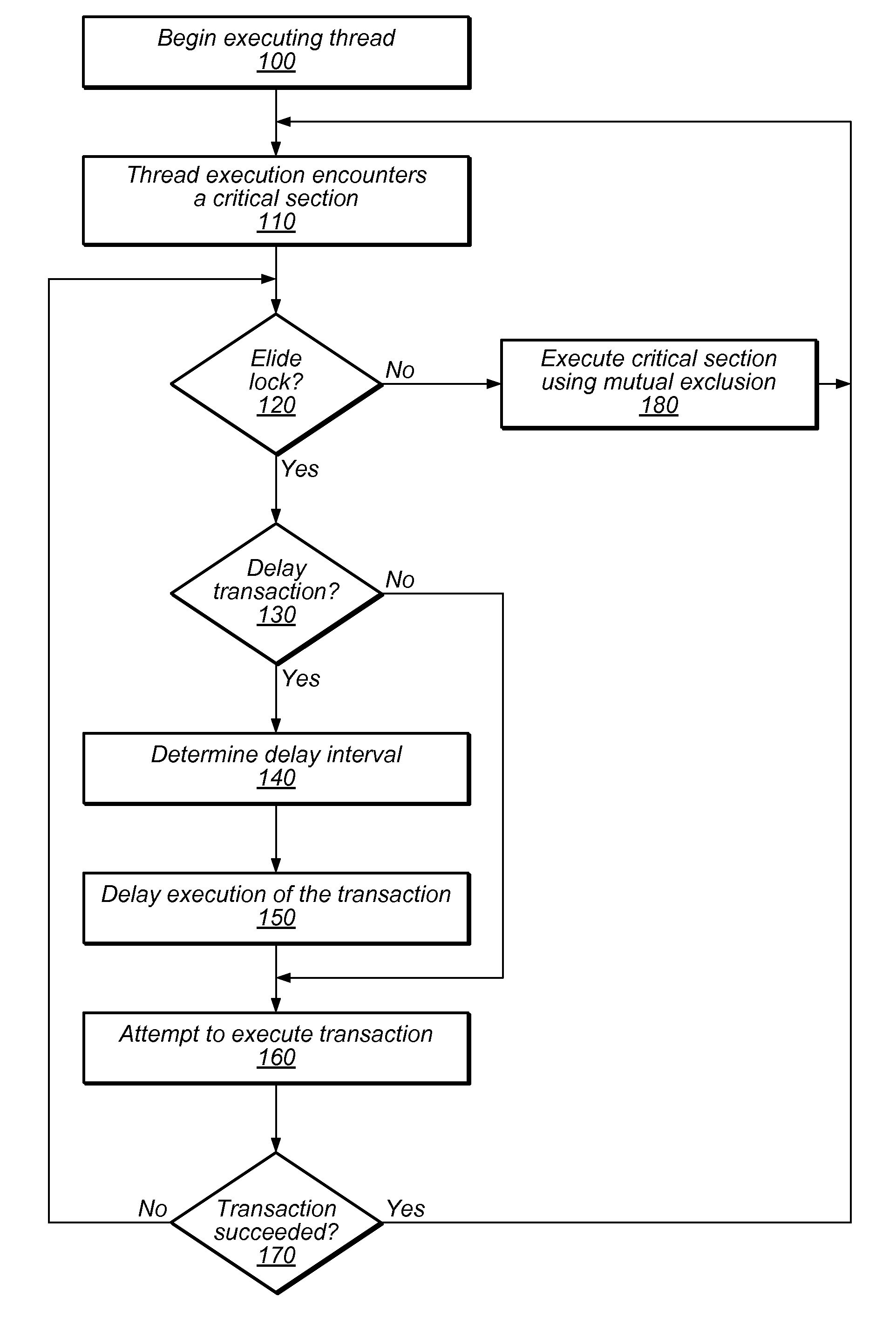
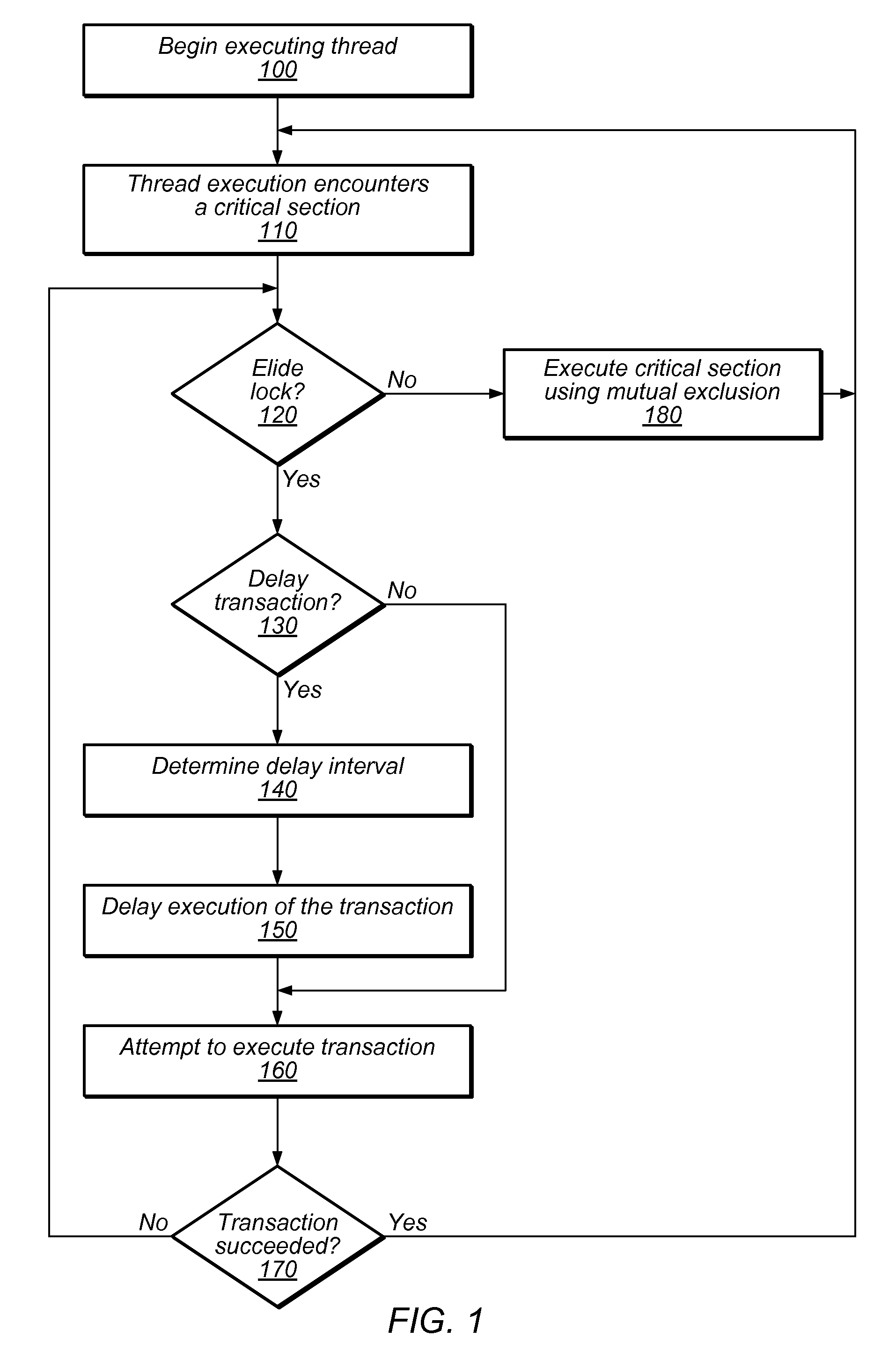
System and Method for Reducing Serialization in Transactional Memory Using Gang Release of Blocked Threads
ActiveUS20100138836A1Reduce the impactProgram synchronisationMemory systemsCritical sectionParallel computing
Transactional Lock Elision (TLE) may allow multiple threads to concurrently execute critical sections as speculative transactions. Transactions may abort due to various reasons. To avoid starvation, transactions may revert to execution using mutual exclusion when transactional execution fails. Because threads may revert to mutual exclusion in response to the mutual exclusion of other threads, a positive feedback loop may form in times of high congestion, causing a “lemming effect”. To regain the benefits of concurrent transactional execution, the system may allow one or more threads awaiting a given lock to be released from the wait queue and instead attempt transactional execution. A gang release may allow a subset of waiting threads to be released simultaneously. The subset may be chosen dependent on the number of waiting threads, historical abort relationships between threads, analysis of transactions of each thread, sensitivity of each thread to abort, and / or other thread-local or global criteria.
Owner:SUN MICROSYSTEMS INC
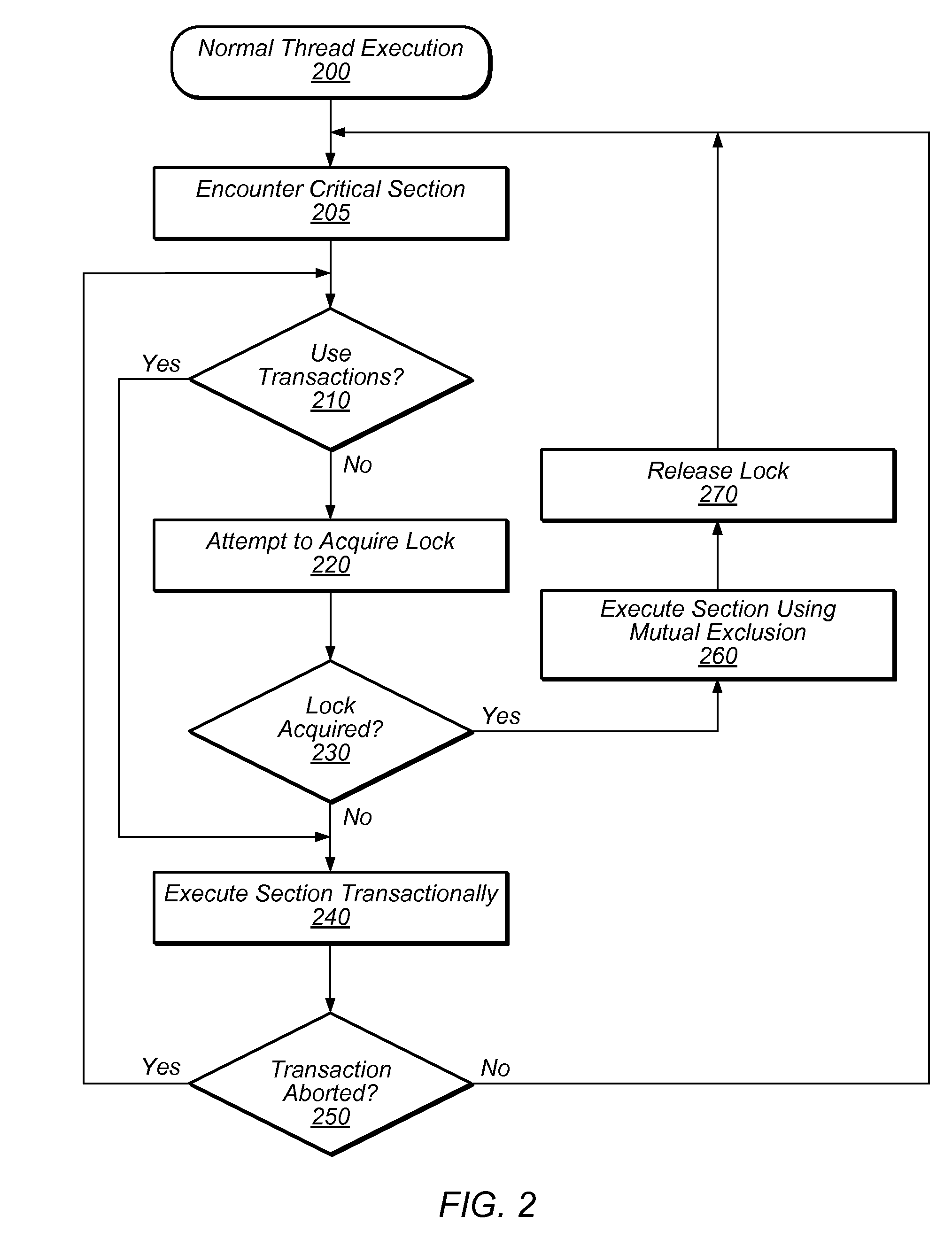
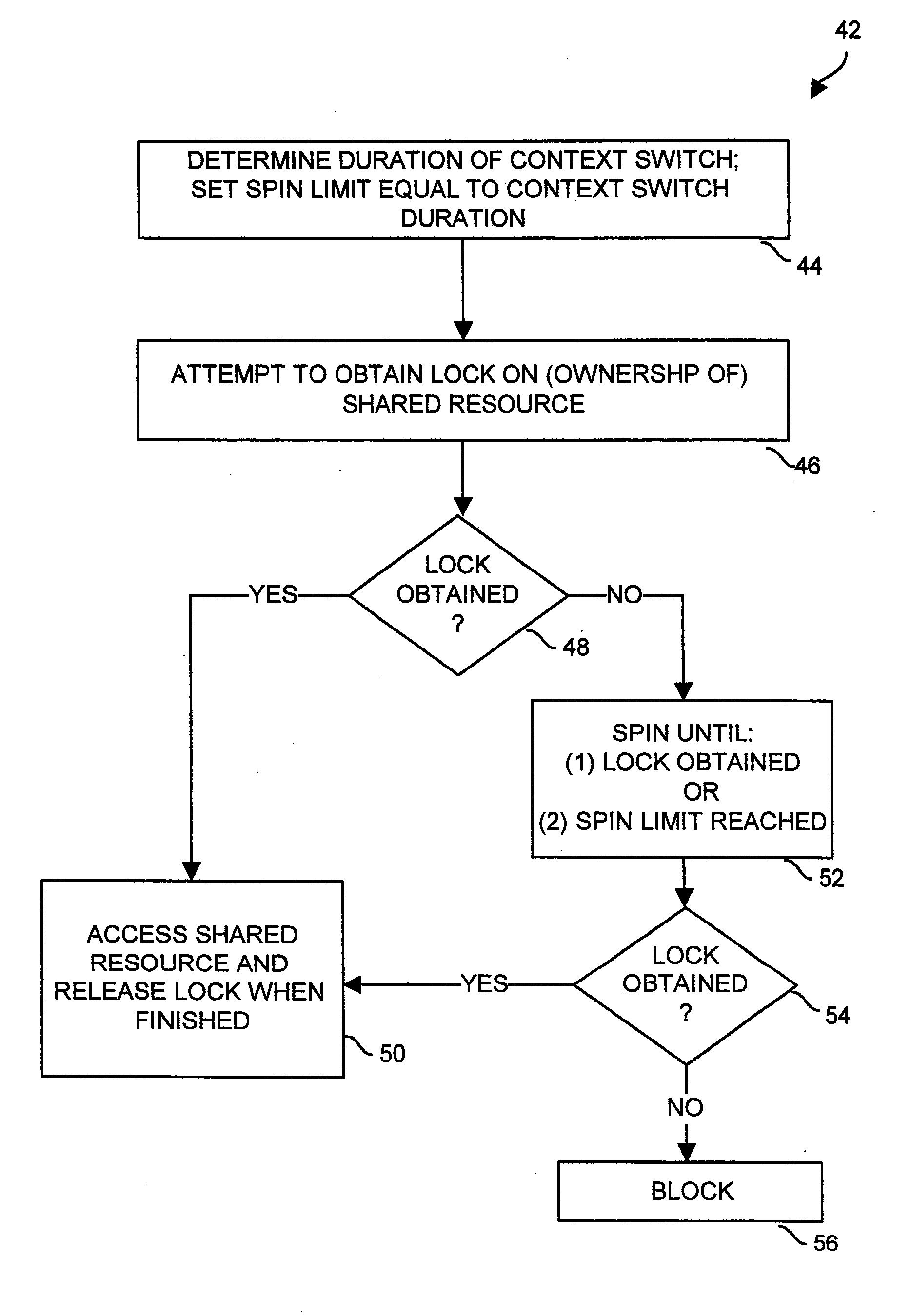
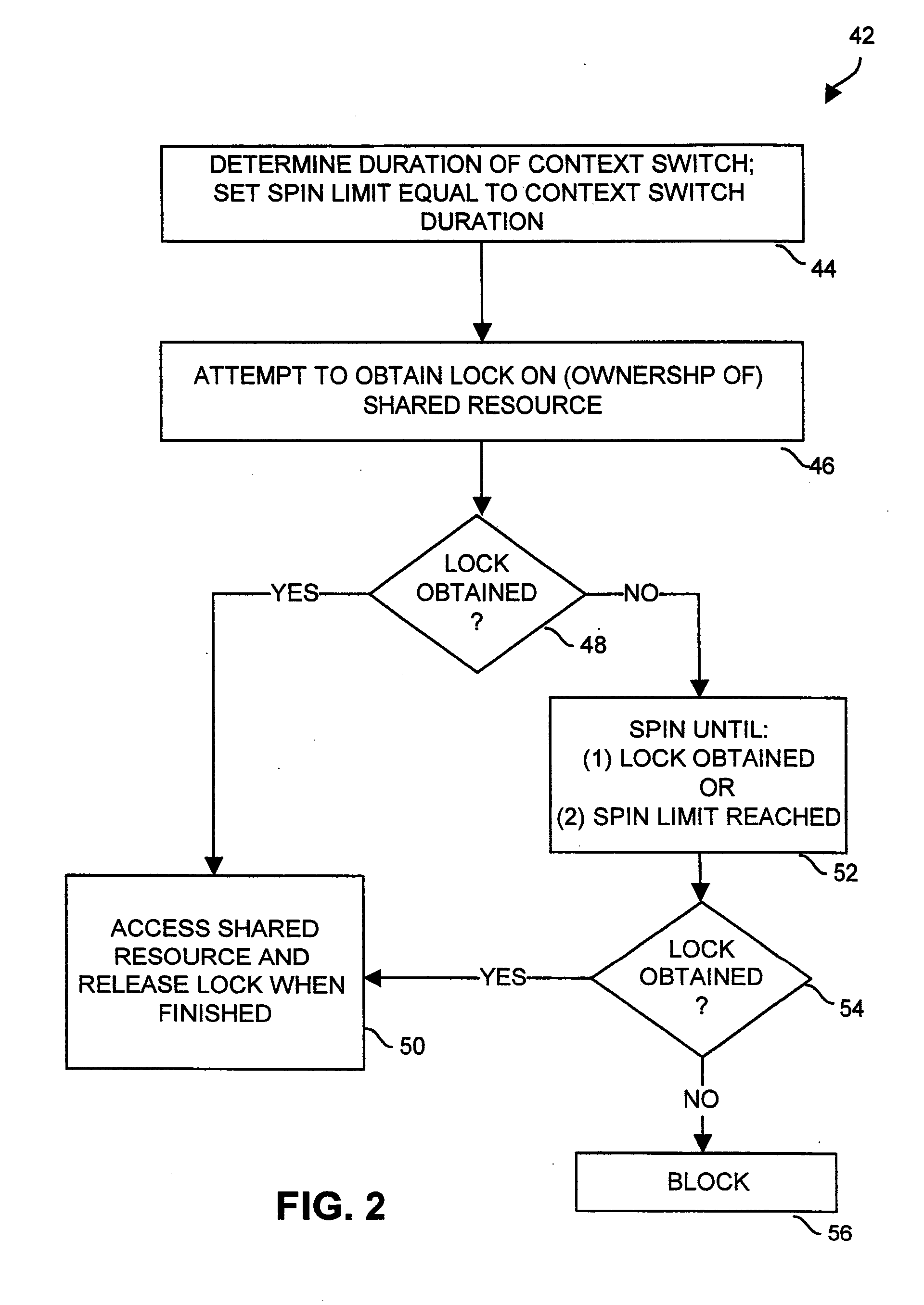
Adaptive spin-then-block mutual exclusion in multi-threaded processing
ActiveUS20090328053A1Avoid excessive delayMiss migrationMemory systemsProgram saving/restoringSpinsEngineering
Adaptive modifications of spinning and blocking behavior in spin-then-block mutual exclusion include limiting spinning time to no more than the duration of a context switch. Also, the frequency of spinning versus blocking is limited to a desired amount based on the success rate of recent spin attempts. As an alternative, spinning is bypassed if spinning is unlikely to be successful because the owner is not progressing toward releasing the shared resource, as might occur if the owner is blocked or spinning itself. In another aspect, the duration of spinning is generally limited, but longer spinning is permitted if no other threads are ready to utilize the processor. In another aspect, if the owner of a shared resource is ready to be executed, a thread attempting to acquire ownership performs a “directed yield” of the remainder of its processing quantum to the other thread, and execution of the acquiring thread is suspended.
Owner:ORACLE INT CORP
System and Method for Managing Contention in Transactional Memory Using Global Execution Data
ActiveUS20100138841A1Improve system performanceMemory systemsTransaction processingResource consumptionCritical section
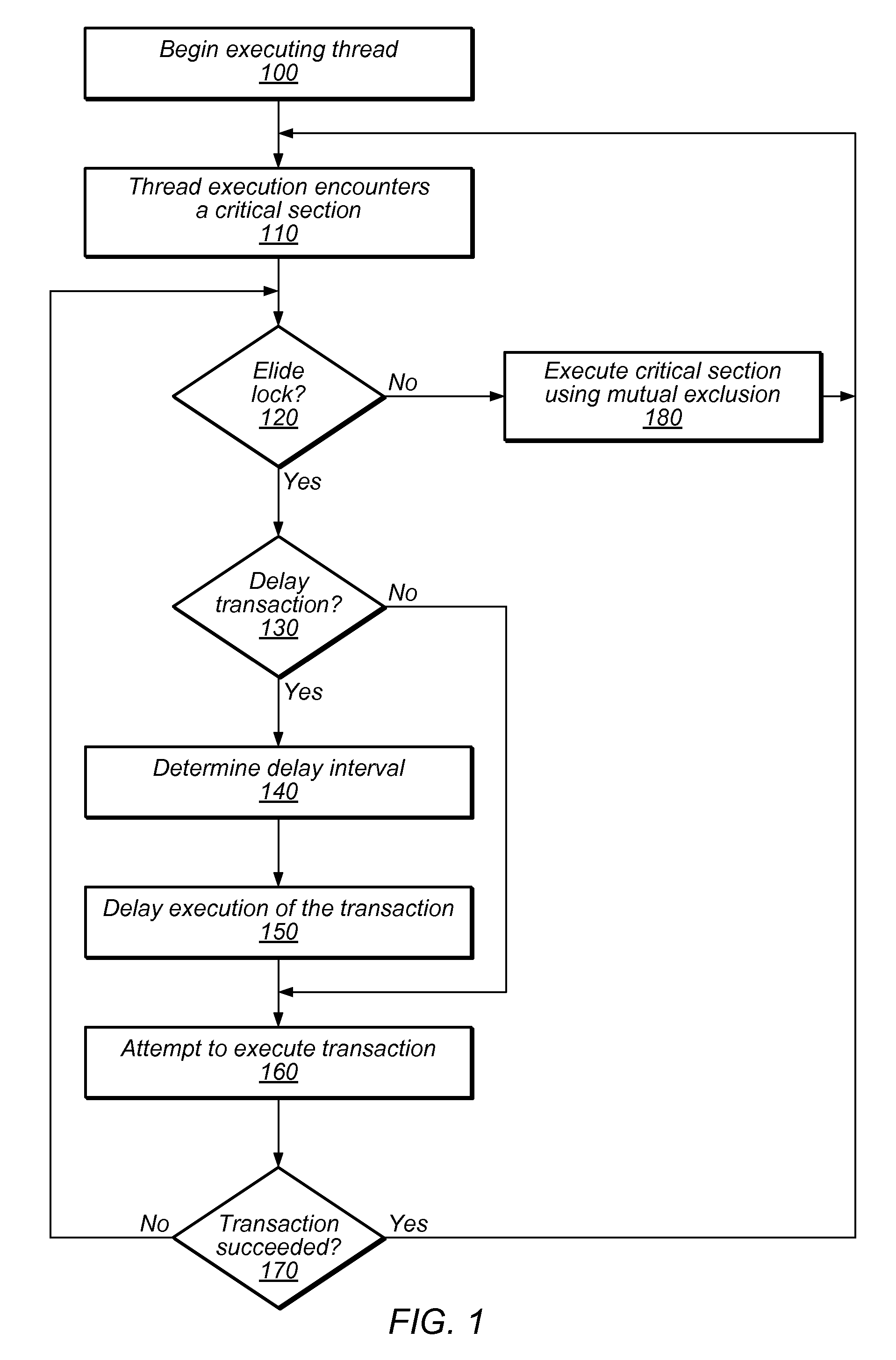
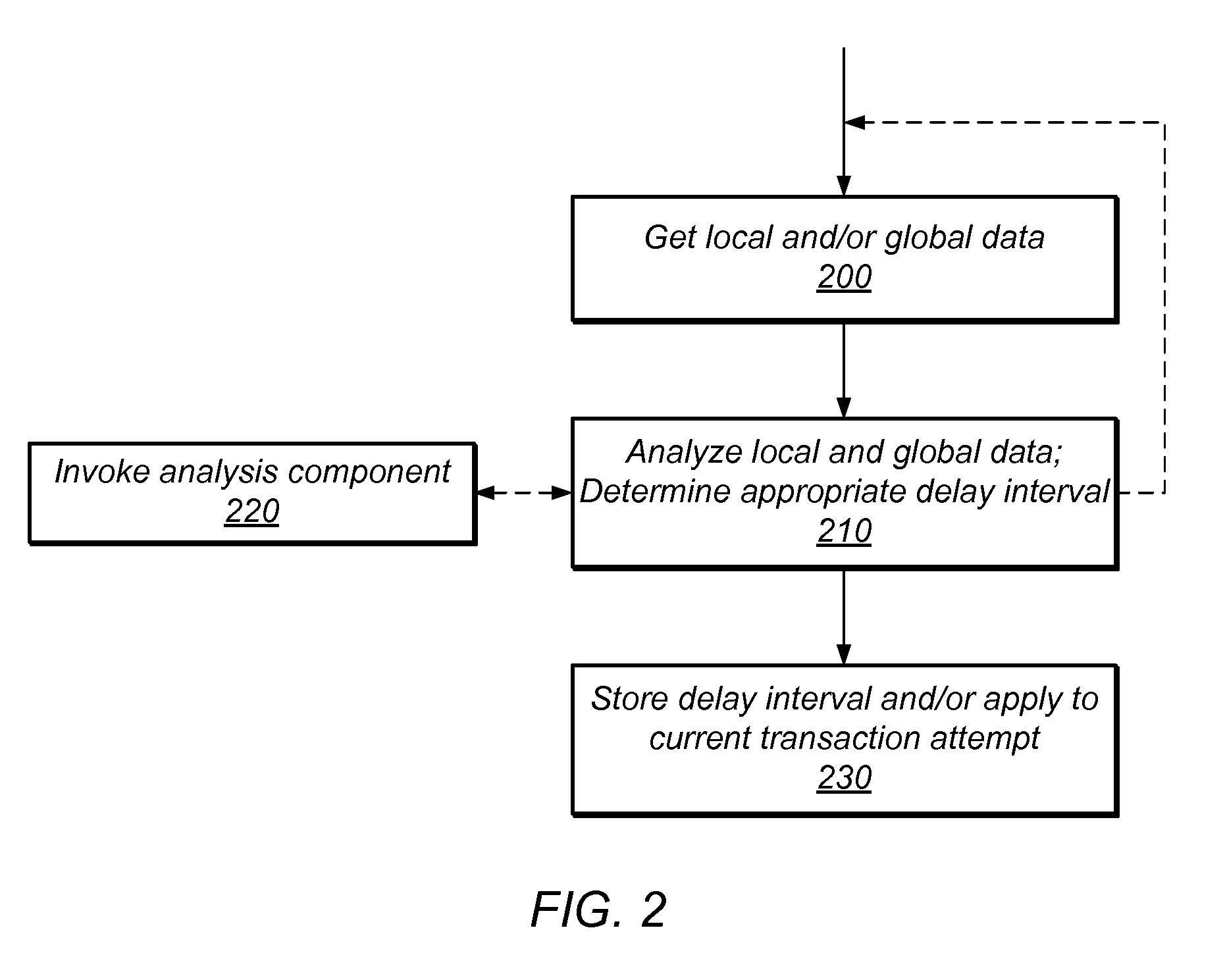
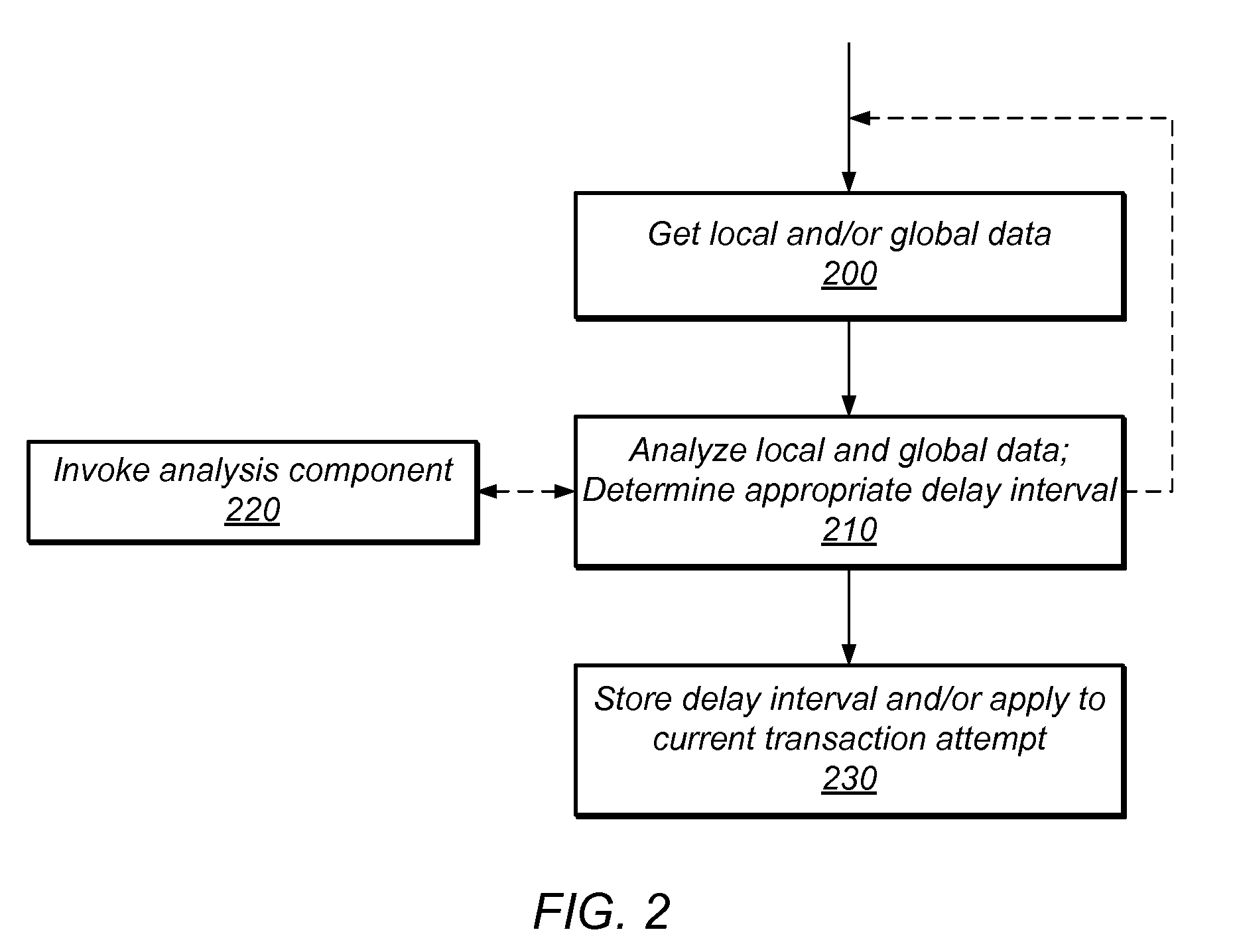
Transactional Lock Elision (TLE) may allow threads in a multi-threaded system to concurrently execute critical sections as speculative transactions. Such speculative transactions may abort due to contention among threads. Systems and methods for managing contention among threads may increase overall performance by considering both local and global execution data in reducing, resolving, and / or mitigating such contention. Global data may include aggregated and / or derived data representing thread-local data of remote thread(s), including transactional abort history, abort causal history, resource consumption history, performance history, synchronization history, and / or transactional delay history. Local and / or global data may be used in determining the mode by which critical sections are executed, including TLE and mutual exclusion, and / or to inform concurrency throttling mechanisms. Local and / or global data may also be used in determining concurrency throttling parameters (e.g., delay intervals) used in delaying a thread when attempting to execute a transaction and / or when retrying a previously aborted transaction.
Owner:ORACLE INT CORP
Queue-based spin lock with timeout
InactiveUS6965961B1Easy to scaleProgram synchronisationUnauthorized memory use protectionSpin locksReal-time computing
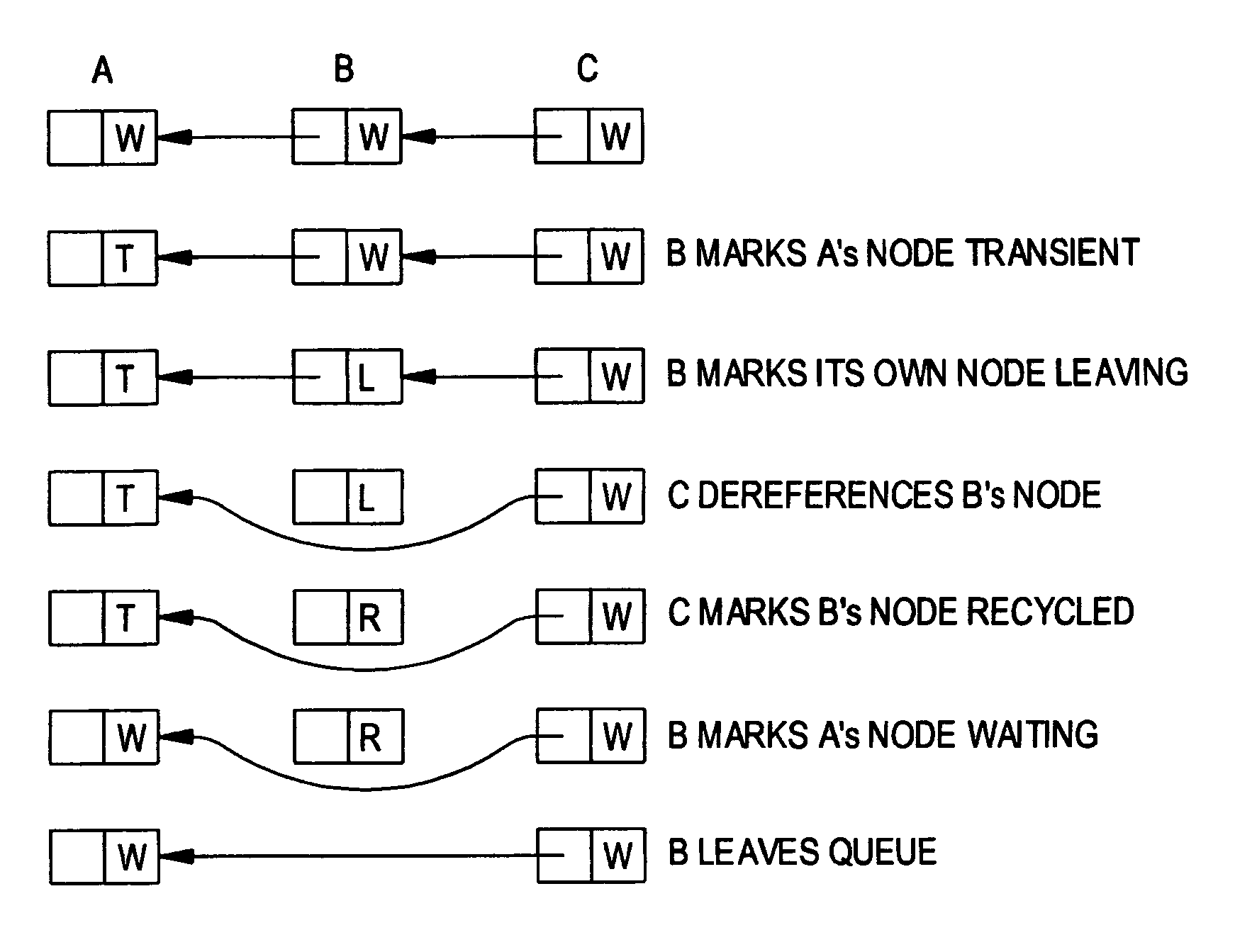
A queue-based spin lock with timeout allows a thread to obtain contention-free mutual exclusion in fair, FIFO order, or to abandon its attempt and time out. A thread may handshake with other threads to reclaim its queue node immediately (in the absence of preemption), or mark its queue node to allow reclamation by a successor thread.
Owner:UNIVERSITY OF ROCHESTER
Synchronization mechanism and method for synchronizing multiple threads with a single thread
A host system is provided with a shared resource (such as work queues and completion queues); multiple processors arranged to access the shared resource; and an operating system arranged to allow multiple processors to perform work on the shared resource concurrently while supporting updates of the shared resource. Such an operating system may comprise a synchronization algorithm for synchronizing multiple threads of operation with a single thread so as to achieve mutual exclusion between multiple threads performing work on the shared resource and a single thread updating or changing the state of the shared resource without requiring serialization of all threads.
Owner:INTEL CORP
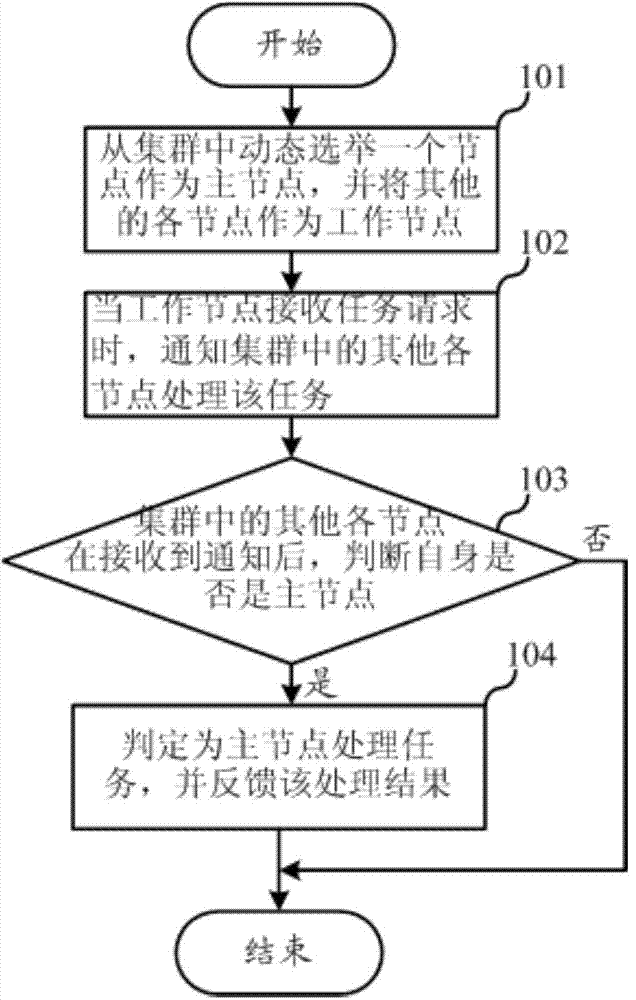
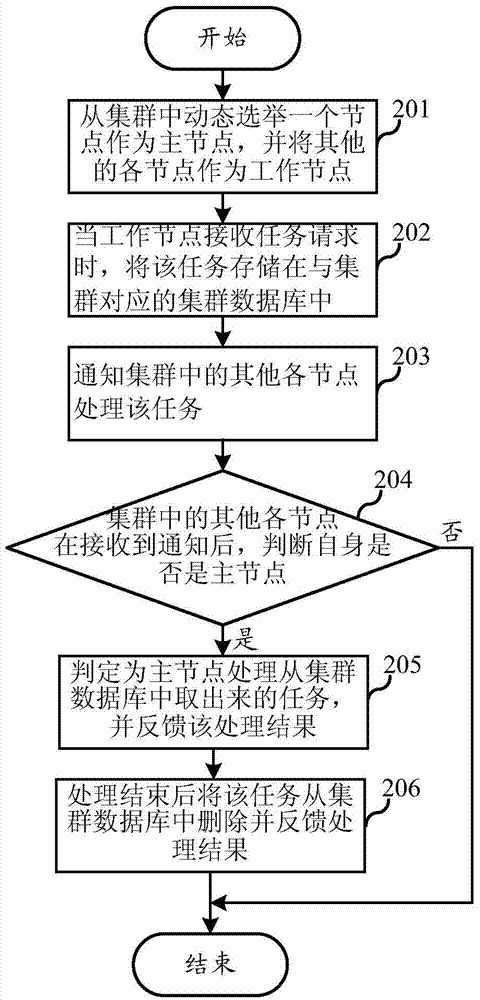
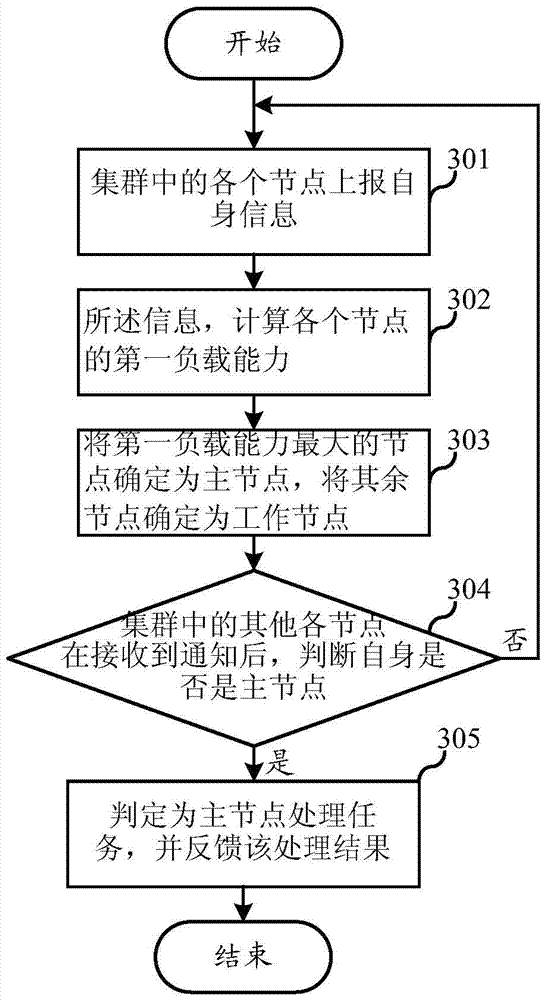
Method and device for data synchronization based on cluster server system
ActiveCN104753994AEnsure consistencyAvoid inconsistenciesTransmissionData synchronizationCloud storage
The invention relates to the field of cloud storage, and discloses a method and a device for data synchronization based on a cluster server system. The method comprises the steps of dynamically electing a master node, and notifying the master node to process in a cluster after worker nodes receive a task, thereby effectively ensuring the data consistency, avoiding mutual exclusion and synchronization between processes of the nodes at the same time, and reducing the system overhead. According to the invention, the cluster server system comprises at least one cluster, the cluster comprises at least three nodes, and the method for data synchronization based on the cluster server system comprises the steps that one node in the cluster is dynamically elected as the master node, and the other nodes act as the worker nodes; if the worker nodes receive a task request, the other nodes in the cluster are notified to process the task; each of the other nodes in the cluster judges whether the node itself is the master node or not after receiving the notice; and if the node is the master node, the master node processes the task and feeds back a processing result.
Owner:HANGZHOU HIKVISION SYST TECH
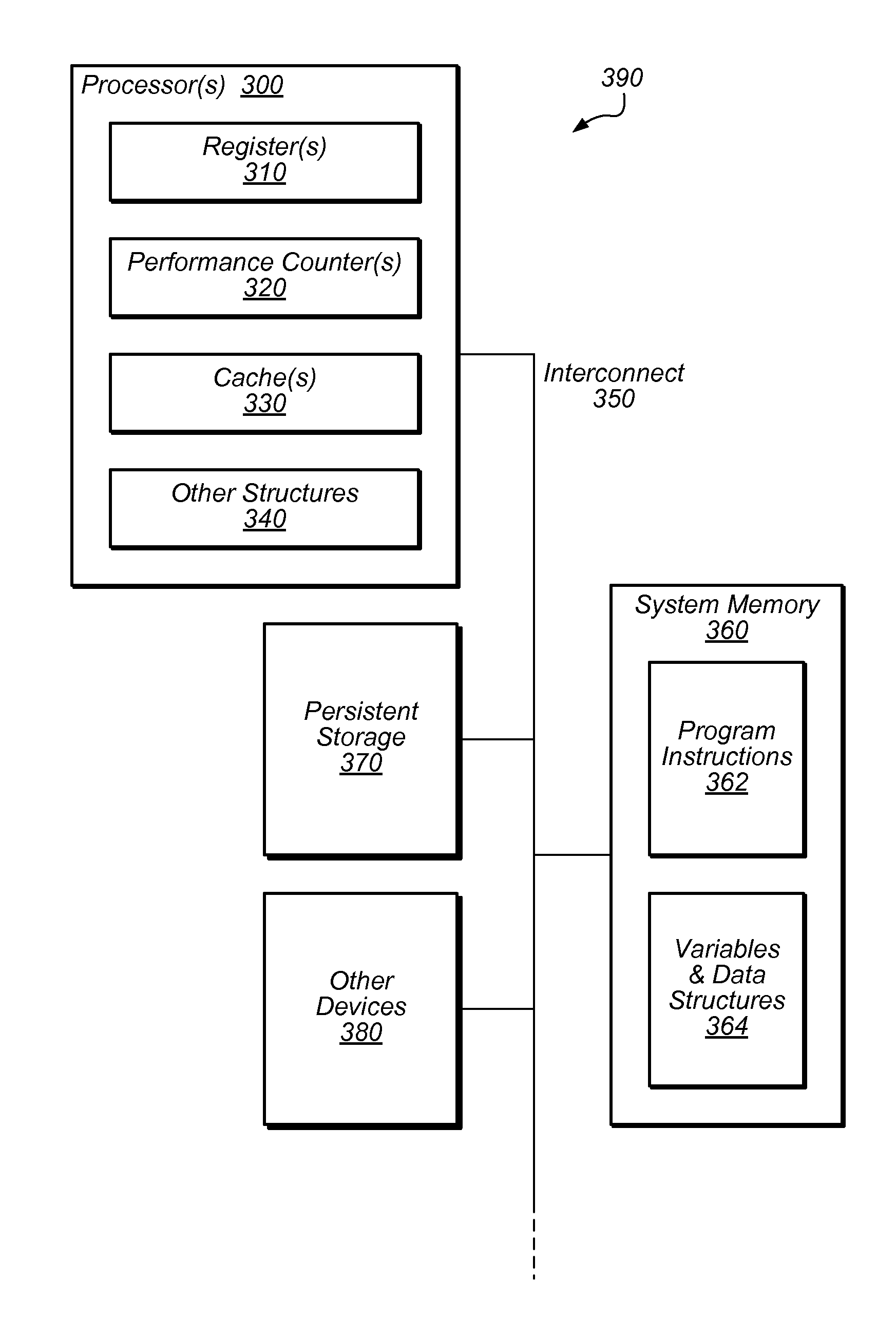
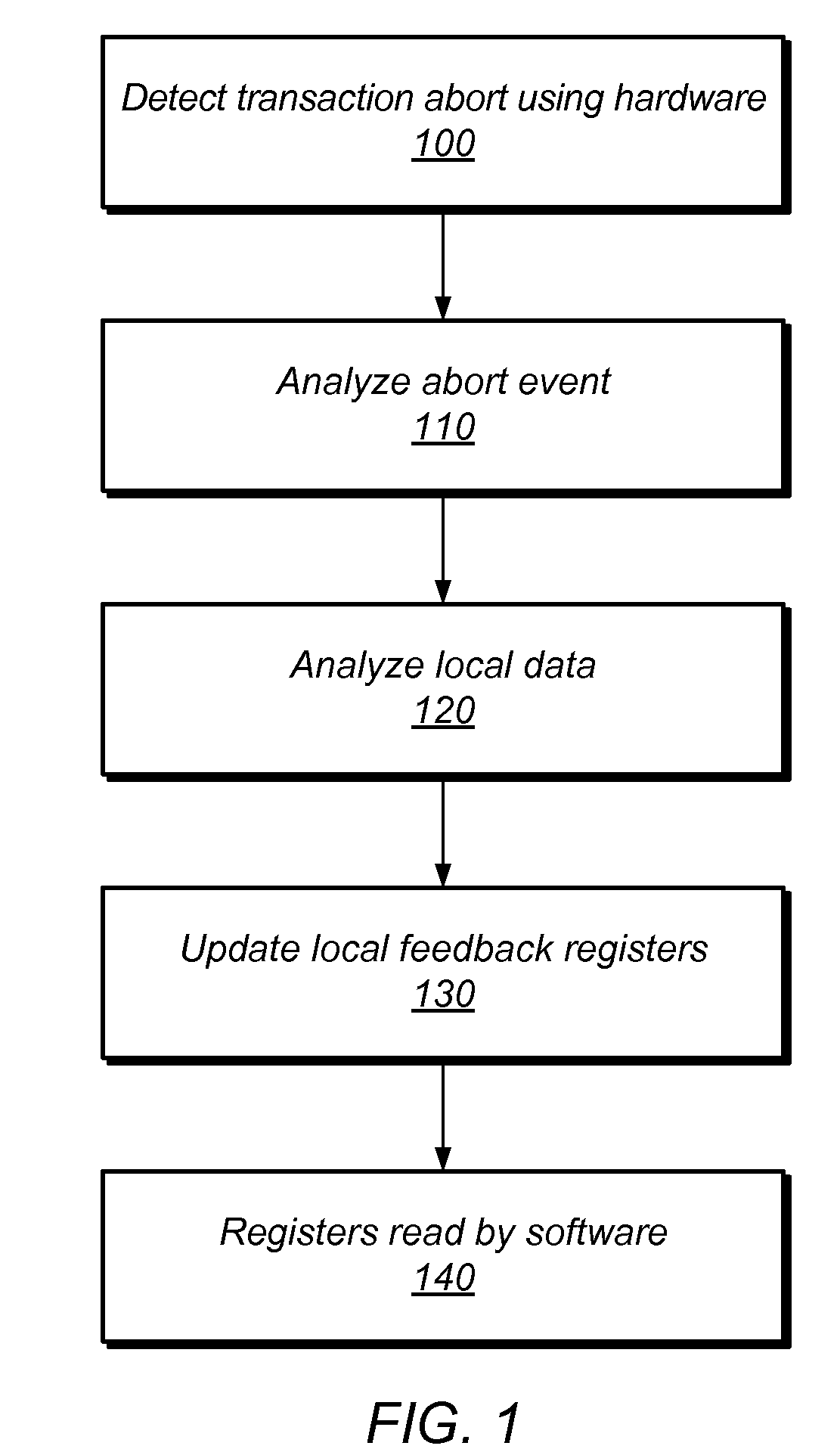
Method and System for Hardware Feedback in Transactional Memory
ActiveUS20100131953A1Memory adressing/allocation/relocationTransaction processingCritical sectionTransactional memory
Multi-threaded, transactional memory systems may allow concurrent execution of critical sections as speculative transactions. These transactions may abort due to contention among threads. Hardware feedback mechanisms may detect information about aborts and provide that information to software, hardware, or hybrid software / hardware contention management mechanisms. For example, they may detect occurrences of transactional aborts or conditions that may result in transactional aborts, and may update local readable registers or other storage entities (e.g., performance counters) with relevant contention information. This information may include identifying data (e.g., information outlining abort relationships between the processor and other specific physical or logical processors) and / or tallied data (e.g., values of event counters reflecting the number of aborted attempts by the current thread or the resources consumed by those attempts). This contention information may be accessible by contention management mechanisms to inform contention management decisions (e.g. whether to revert transactions to mutual exclusion, delay retries, etc.).
Owner:SUN MICROSYSTEMS INC
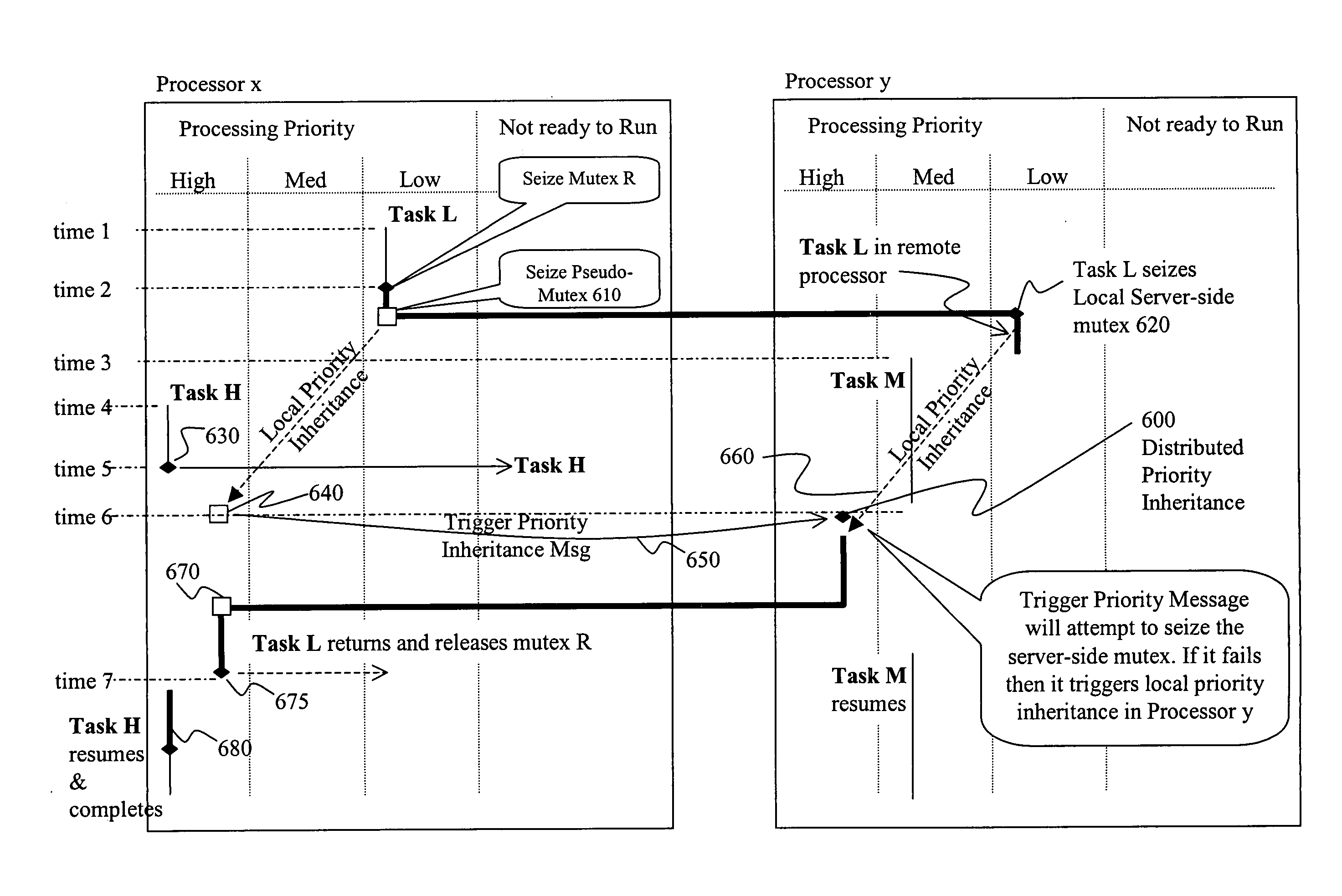
System and method for implementing distributed priority inheritance
ActiveUS20060282836A1Advanced conceptEasy to transportMultiprogramming arrangementsMemory systemsOperational systemReal-time operating system
Priority inheritance is implemented across a distributed system, preferably by use of a mutual exclusion object, referred to as a pseudo-mutex, which provides operations for communicating priority of a task which is held to a different connected processor or node of a network and generating a dummy local command of priority at least equal to that of the held task at the remote processor or node in collaboration with a real-time operating system and middleware. The remote real time operating system then carries out priority inheritance in the normal manner to raise the priority of a blocked task, thus reversing any preemption of that task at the remote processor or node. The increase in priority avoids preemption of lower priority processes and thus increases the execution speed of the executing thread to release the existing lock at an earlier time; allowing a lock to be obtained by the higher priority thread. The middleware serves as an intermediary, communicating messages that include pseudo-mutex arguments or similar communications and requests for enabling priority inheritance across nodes.
Owner:LOCKHEED MARTIN CORP
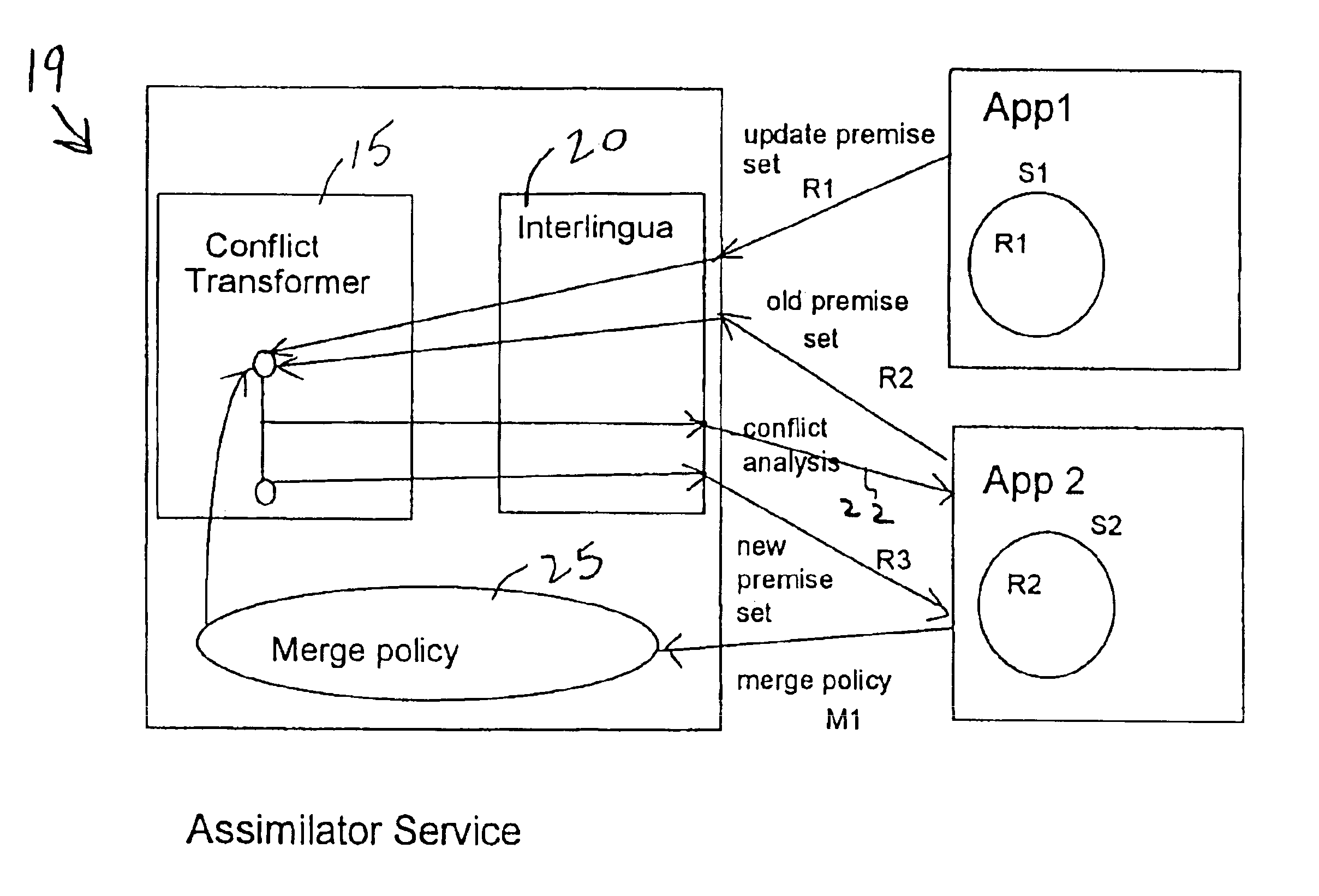
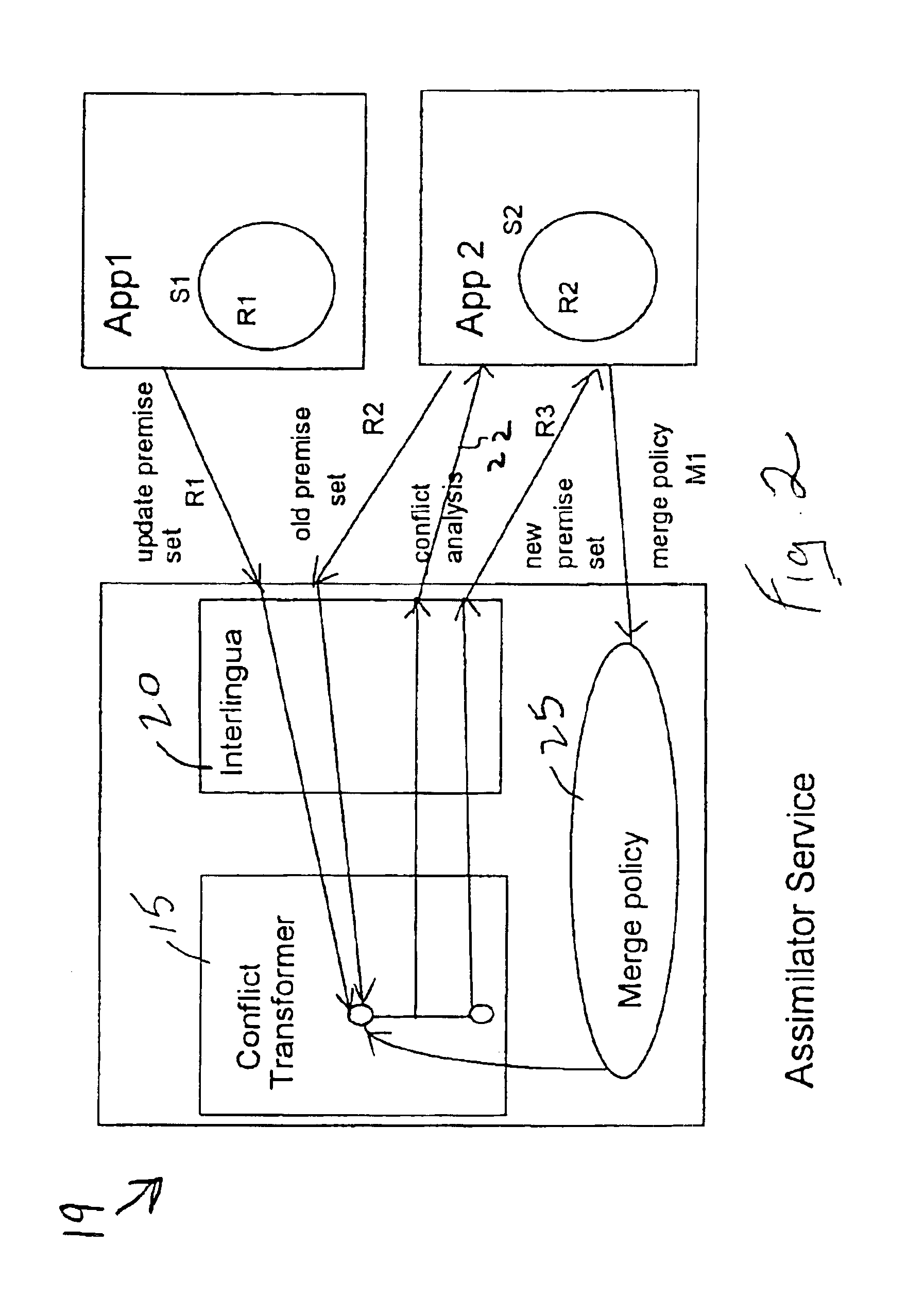
Conflict-handling assimilator service for exchange of rules with merging
InactiveUS6910028B2Easy to useEasy to integrateDigital computer detailsKnowledge representationOriginating applicationRule-based system
A system and method for merging two rulesets provided in rule-based systems associated with originating applications executing at different locations, each ruleset comprising rules in potential conflict with each other, and each ruleset being in a different rule format. The rulesets to be merged are communicated to an assimilator service provided with a merge policy comprising a set of specifications of partially-ordered priorities and / or mutual-exclusion constraints. The rulesets are translated into a common core representation capable of being implemented in any logic program rule engine provided in a rule-based application at any location. The rulesets are assimilated to produce a new merged ruleset comprising logic required for resolving potential conflicts among rules in accordance with the merge policy that is implemented in any logic program rule engine provided at any location. The new merged ruleset is then translated into one of the originating application's rule format.
Owner:IBM CORP
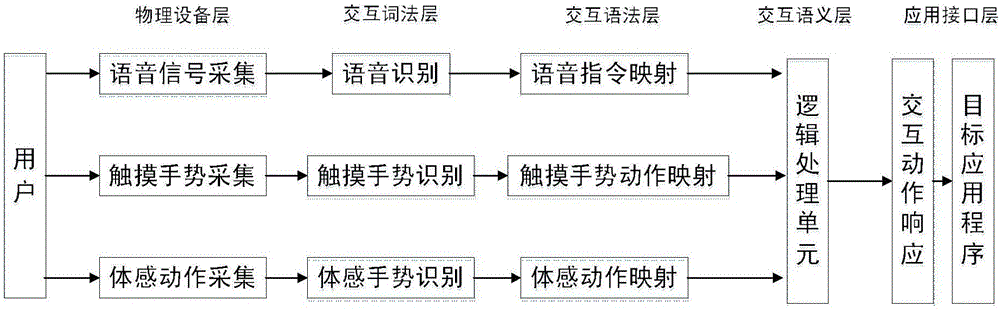
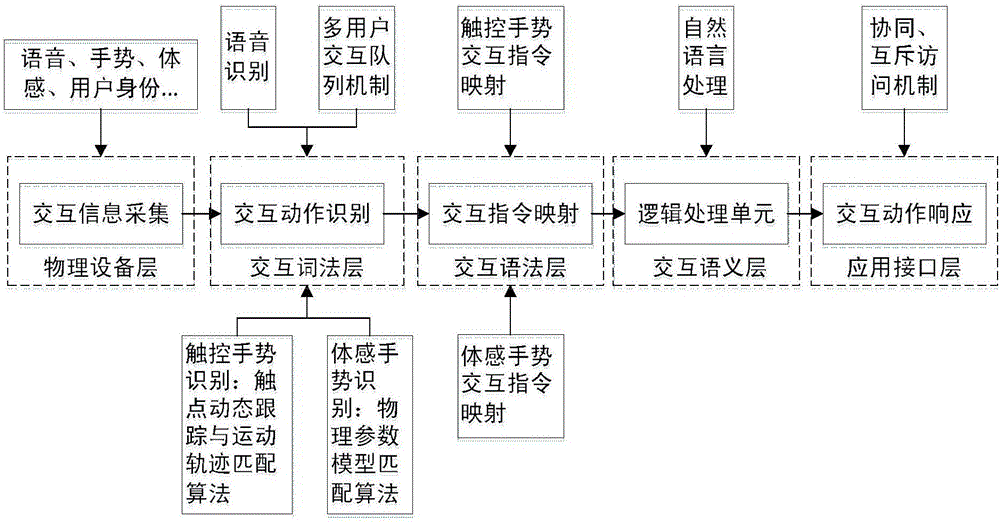
Multi-modal man-machine interaction system and control method thereof
InactiveCN106569613AAchieve consistencyImplement responseInput/output for user-computer interactionSound input/outputCouplingHuman–computer interaction
The invention discloses a multi-modal man-machine interaction system and a control method thereof. The main interaction process comprises: interaction information collection, interaction motion identification, interaction instruction mapping, logic processing unit, and interaction motion response. The interactive identification algorithm of voice, touch gesture and body feeling and gesture is broken through. The method comprises contact dynamic tracking and movement track coupling algorithm, physical parameter model coupling method, multi-user interaction queue mechanism. Touch control / body feeling gesture interaction mapping instruction and logic processing, cooperation / mutual exclusion access mechanism are set; the user control instruction is converted into service instruction of application system scheduling execution; multi-user interaction is supported; the system has strong anti-interference capability and identification efficiency.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
System and method for managing contention in transactional memory using global execution data
ActiveUS8402464B2Improve system performanceResource allocationMemory systemsResource consumptionCritical section
Transactional Lock Elision (TLE) may allow threads in a multi-threaded system to concurrently execute critical sections as speculative transactions. Such speculative transactions may abort due to contention among threads. Systems and methods for managing contention among threads may increase overall performance by considering both local and global execution data in reducing, resolving, and / or mitigating such contention. Global data may include aggregated and / or derived data representing thread-local data of remote thread(s), including transactional abort history, abort causal history, resource consumption history, performance history, synchronization history, and / or transactional delay history. Local and / or global data may be used in determining the mode by which critical sections are executed, including TLE and mutual exclusion, and / or to inform concurrency throttling mechanisms. Local and / or global data may also be used in determining concurrency throttling parameters (e.g., delay intervals) used in delaying a thread when attempting to execute a transaction and / or when retrying a previously aborted transaction.
Owner:ORACLE INT CORP
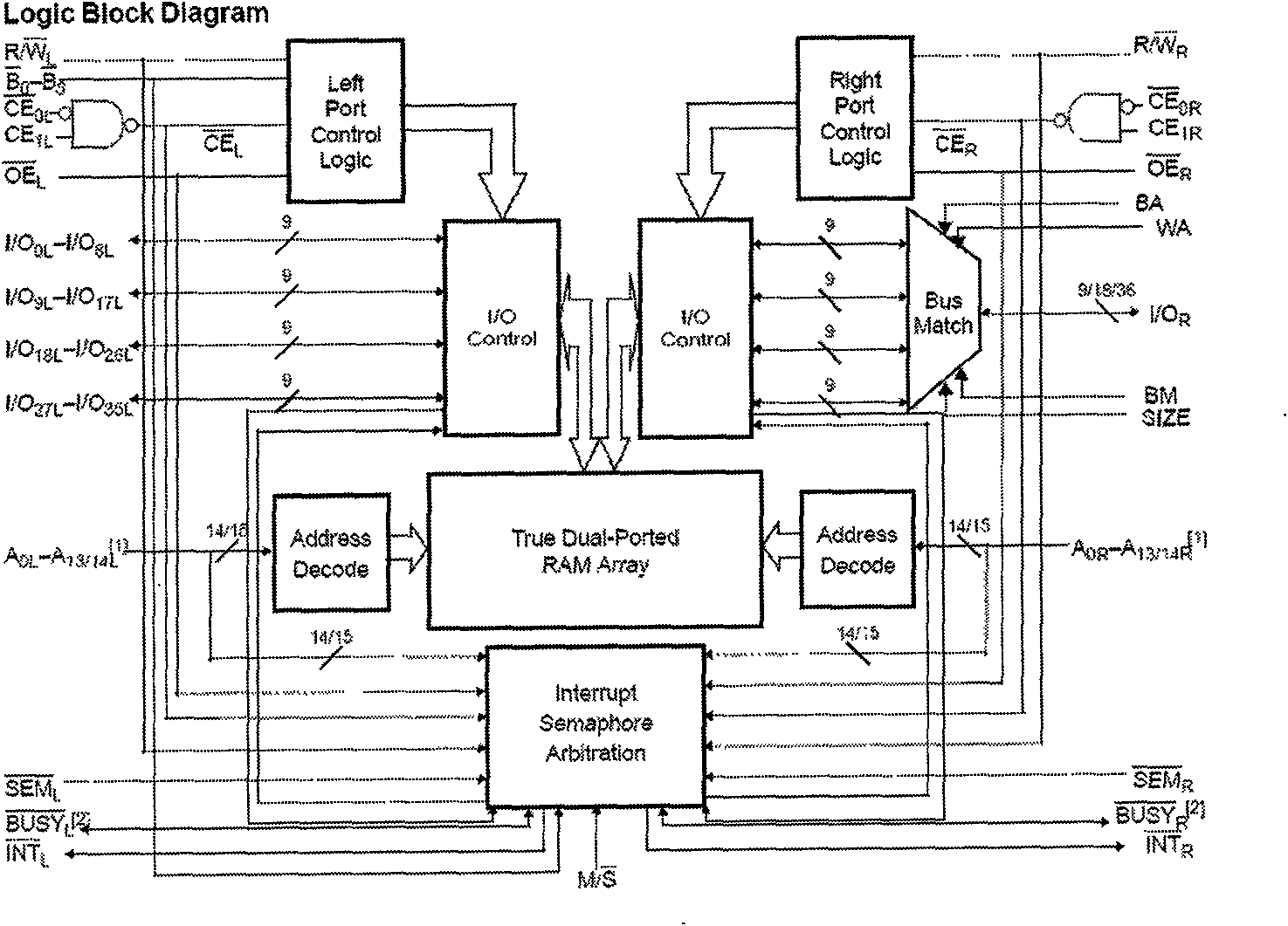
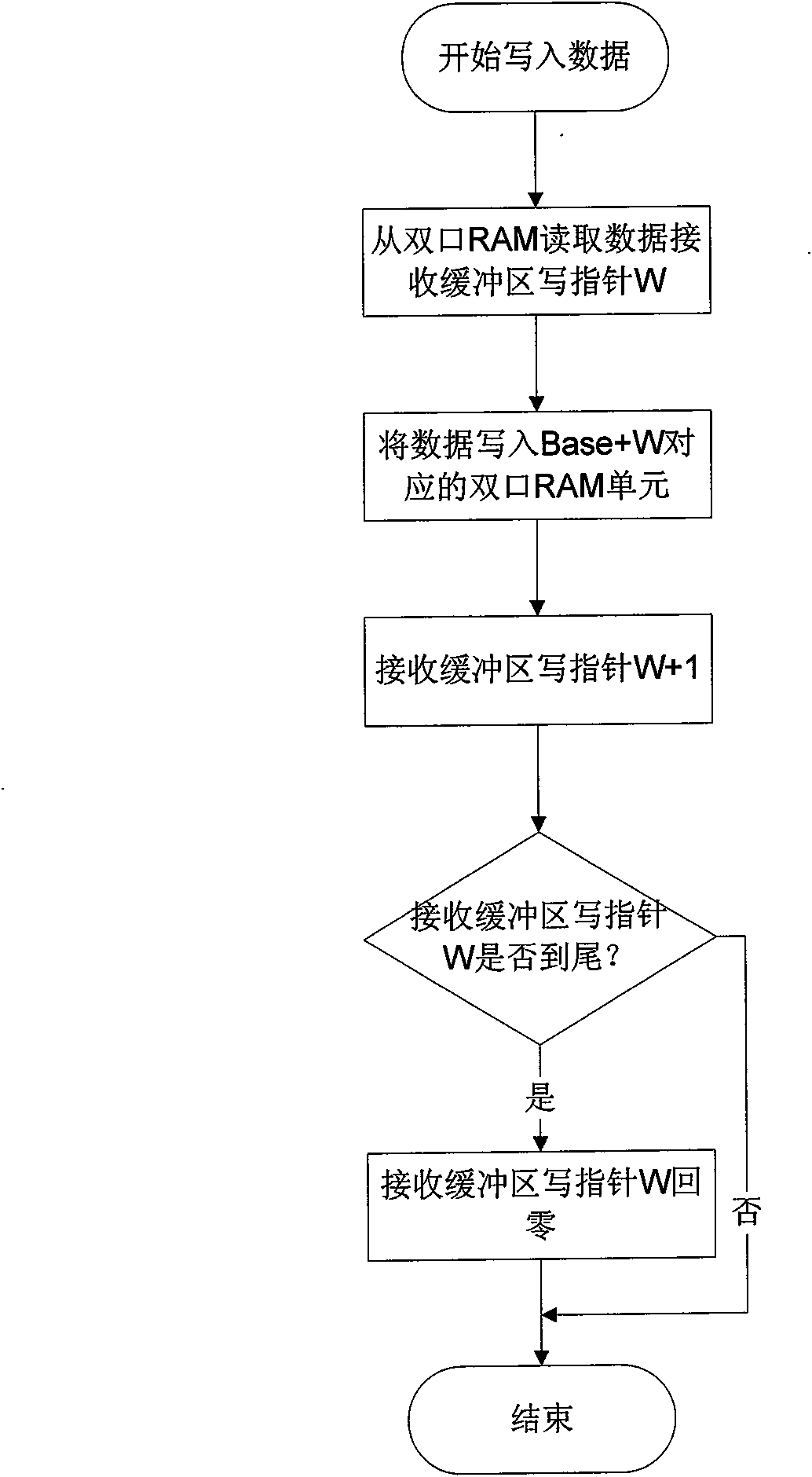
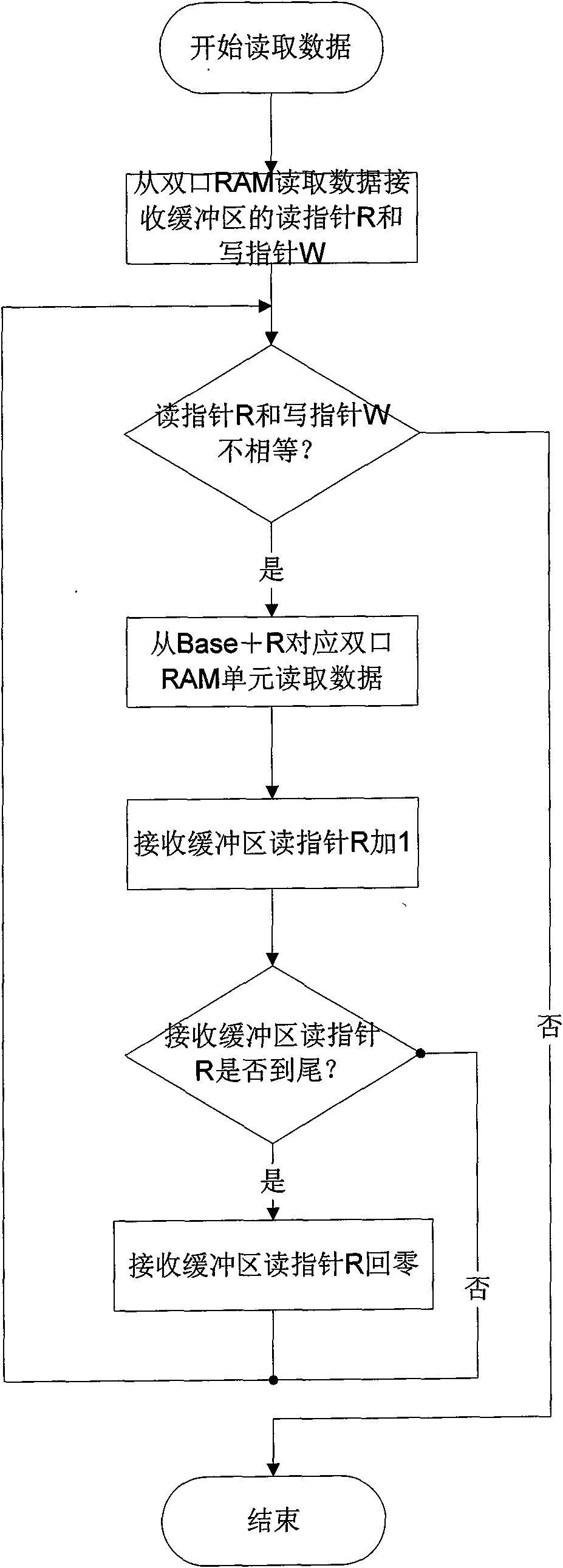
Implementation method of double-port RAM mutual exclusion access
InactiveCN101655824AAvoid competitionImprove real-time performanceElectric digital data processingData accessWrite pointer
The invention relates to an implementation method of double-port RAM mutual exclusion access. The method comprises the following operation steps: 1) dividing a shared data area into a plurality of data areas by an address partitioned mode, and establishing a corresponding software protocol; 2) dividing a shared storage area of a RAM into a plurality of large data areas starting from an initial unit according to the type of exchange data in software partition processing; determining size of the data areas based on practical transmission data; and subdividing the large data areas into a data receive buffer area and a data send buffer area, and defining each buffer area with corresponding data access base addresses and read-write pointers; and 3) in the system, all the communication work of an external system is completed by a slave, while a host is only required to write the date to be sent into the corresponding data buffer area in the double-port RAM or read the required data.
Owner:CHINA TECHENERGY
Method and system for autonomically adaptive mutexes by considering acquisition cost value
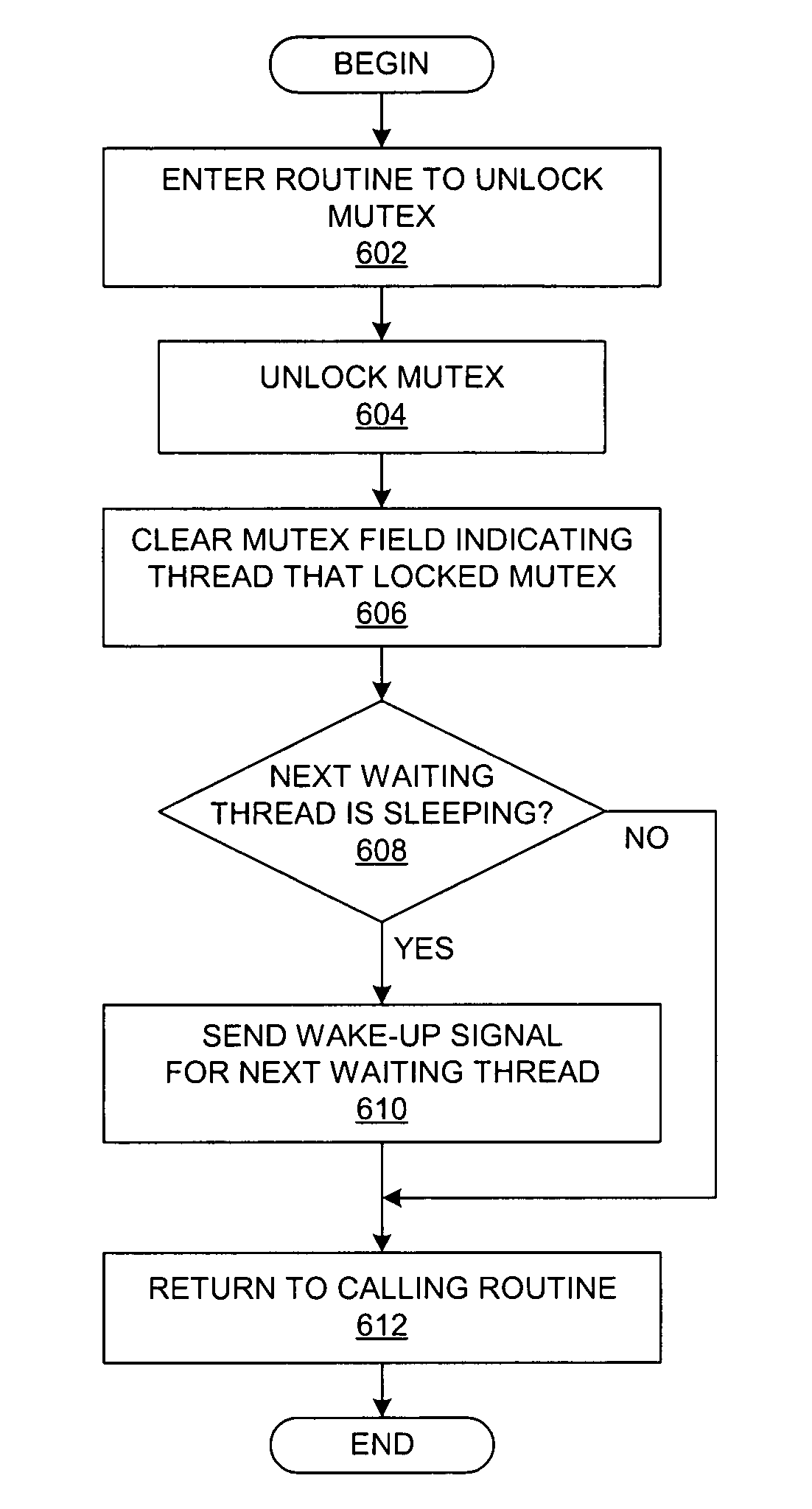
ActiveUS7383368B2Unauthorized memory use protectionMultiprogramming arrangementsData processing systemSleep state
A method for managing a mutex in a data processing system is presented. For each mutex, an average acquisition cost is maintained that indicates an average consumption of computational resources that has been incurred by threads attempting to acquire the mutex. If a thread attempts to acquire a locked mutex, then the thread enters a spin state or a sleep state based on restrictive conditions and the average acquisition cost value for the mutex at that time. A thread-specific current acquisition cost value is maintained that represents the consumption of computational resources by the thread after the initial attempt to acquire the mutex and prior to acquiring the mutex. When the thread acquires the mutex, the thread-specific current acquisition cost value is included into the average acquisition cost value.
Owner:IBM CORP
TICC-paradigm to build formally verified parallel software for multi-core chips
InactiveUS7979844B2Reduce designSimple designSoftware engineeringMultiprogramming arrangementsInitial abstractMulti processor
This invention teaches a way of implementing formally verified massively parallel programs, which run efficiently in distributed and shared-memory multi-core chips. It allows programs to be developed from an initial abstract statement of interactions among parallel software components, called cells, and progressively refine them to their final implementation. At each stage of refinement a formal description of patterns of events in computations is derived automatically from implementations. This formal description is used for two purposes: One is to prove correctness, timings, progress, mutual exclusion, and freedom from deadlocks / livelocks, etc. The second is to automatically incorporate into each application a Self-Monitoring System (SMS) that constantly monitors the application in parallel, with no interference with its timings, to identify and report errors in performance, pending errors, and patterns of critical behavior. This invention also teaches a way of organizing shared-memory for multi-processors that minimizes memory interference, protects data and increases execution efficiency.
Owner:EDSS INC
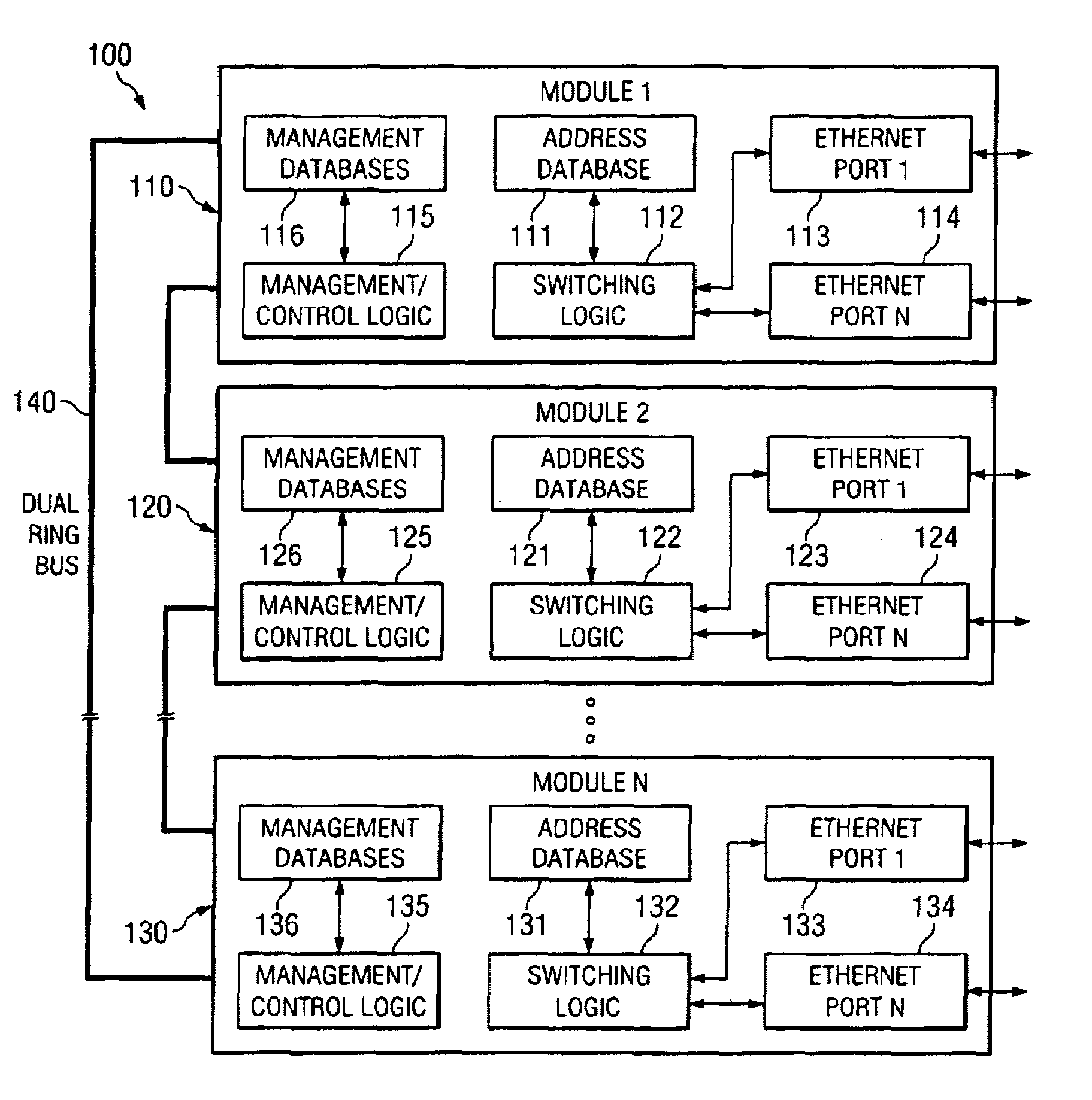
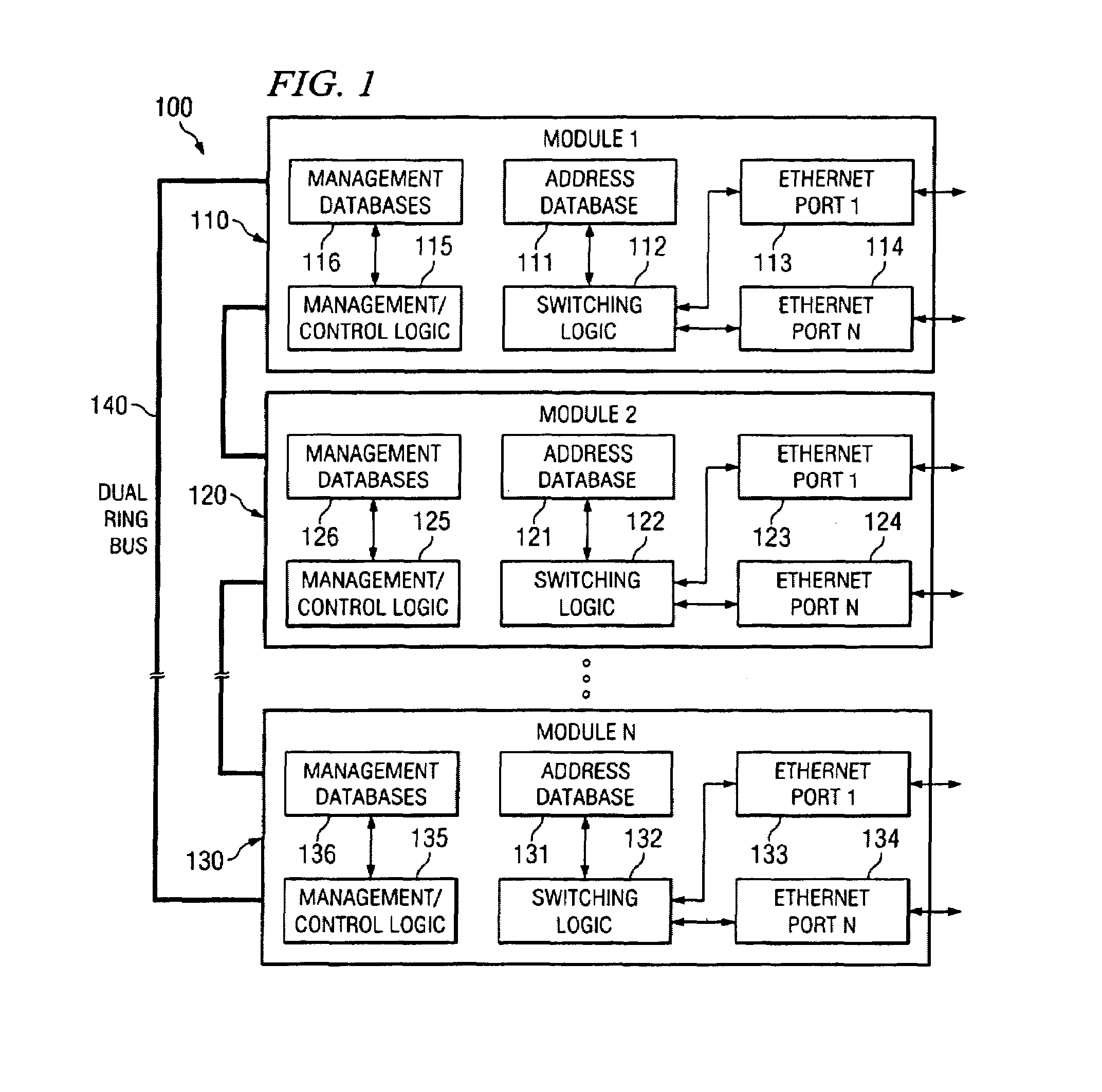
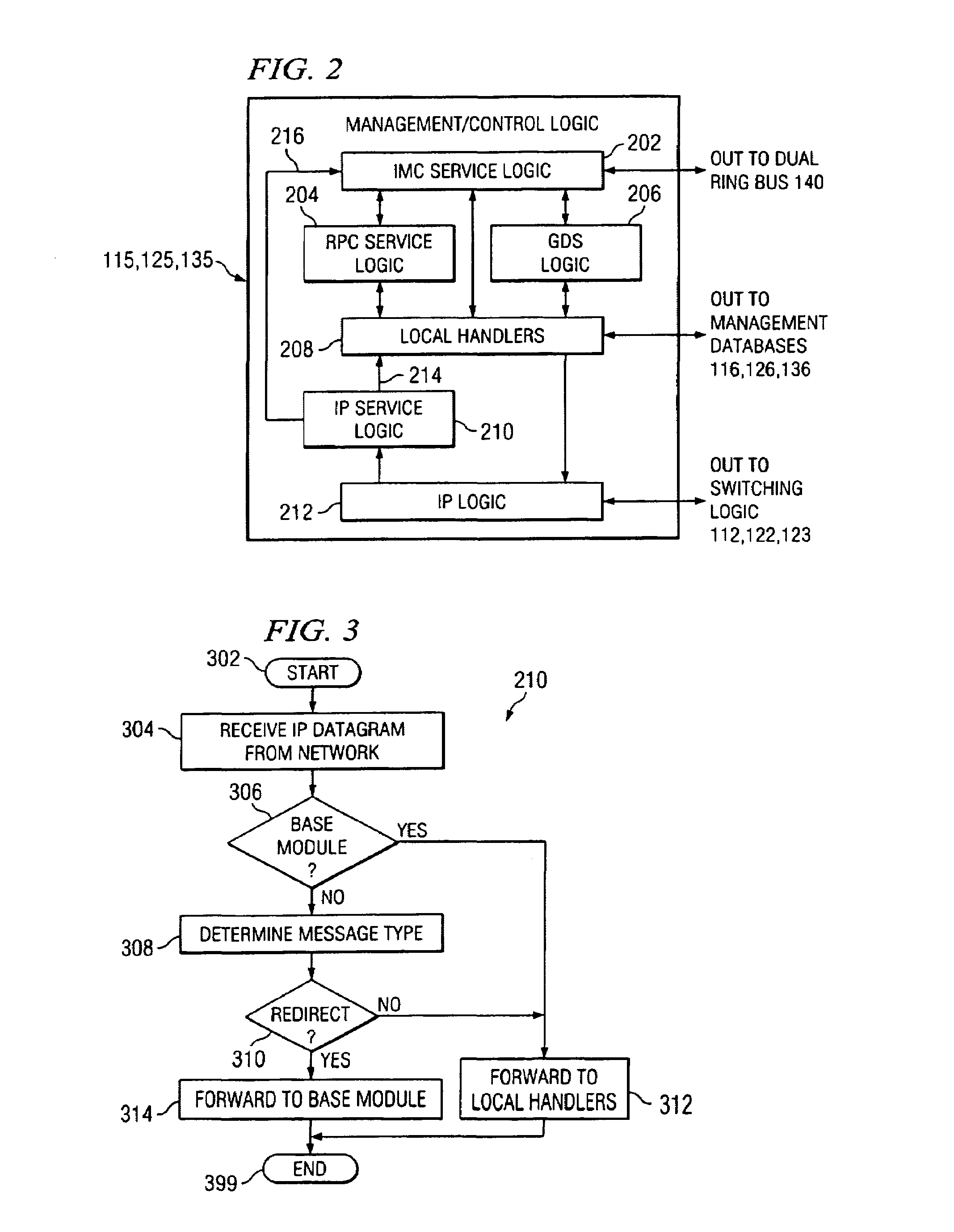
Decentralized management architecture for a modular communication system
InactiveUS6981034B2Reduce the amount requiredMultiplex system selection arrangementsBatteries circuit arrangementsCommunications systemModularity
A decentralized management model enables a plurality of interconnected modules to be managed and controlled as an integrated unit without requiring any one of the interconnected modules to operate as a fully centralized manager. One of the interconnected modules is configured to operate as a base module, which coordinates certain network management operations among the interconnected modules. Each of the interconnected modules is capable of sending and receiving management and control information. Each of the interconnected modules maintains a segmented management database containing network management parameters that are specific to the particular module, and also maintains a shadowed management database containing network management parameters that are common to all of the interconnected modules in the stack. Management and control operations that do not require synchronization or mutual exclusion among the various interconnected modules are typically handled by the module that receives a management / control request. Management and control operations that require synchronization or mutual exclusion among the various interconnected modules are handled by the base module.
Owner:AVAYA INC
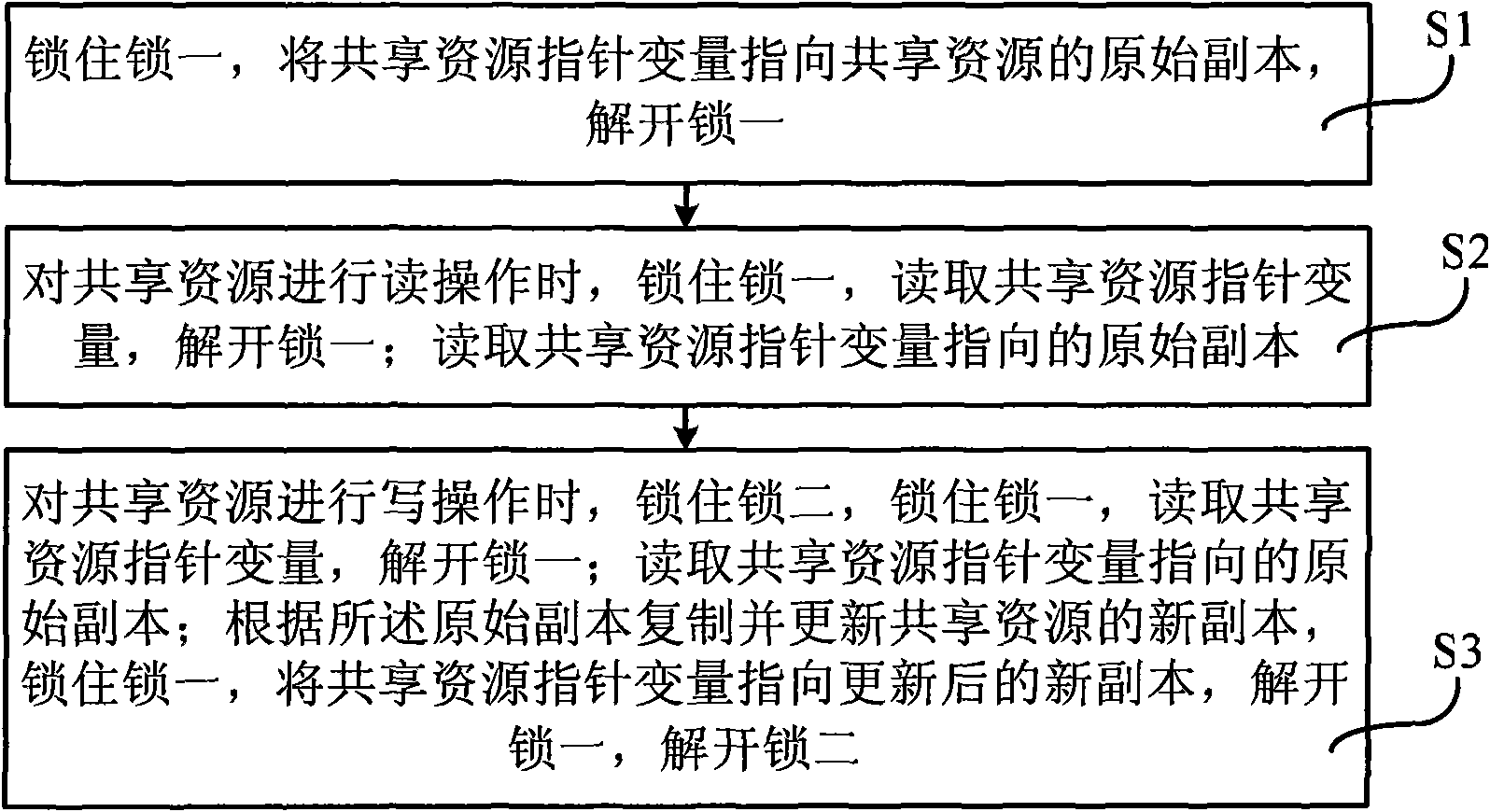
Synchronous method performing mutual exclusion access on shared resource, device and network equipment
InactiveCN101631328AReduce complexityImprove performanceWireless communicationRound complexityShared resource
The invention provides a synchronous method performing mutual exclusion access on shared resource, a device and network equipment. The invention accesses the shared resource by introducing shared resource pointer variable, establishes a copy of the shared resource when performing writing on the shared resource to be specially used for resource update, uses two locks to respectively protect the shared resource pointer variable and the shared resource copy, simplifies the introduction of complex shared resource into introduction of pointer variable, thus reducing the complexity of critical region operation, improving the system performance, ensures plural readers and one writer to access the shared resource simultaneously, achieving the effect of self sole occupation of data, and enhancing the system concurrency rate to a great degree.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
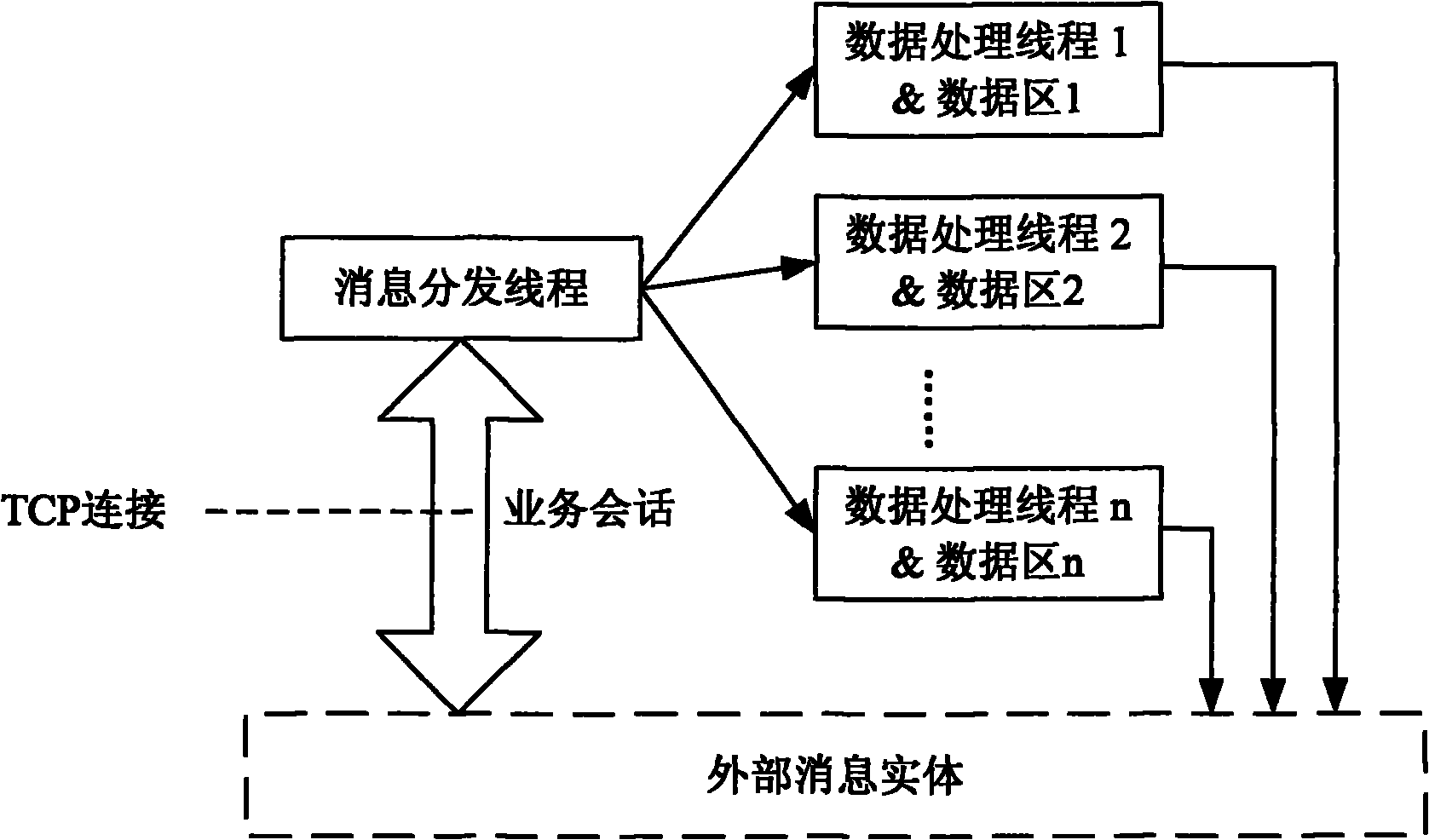
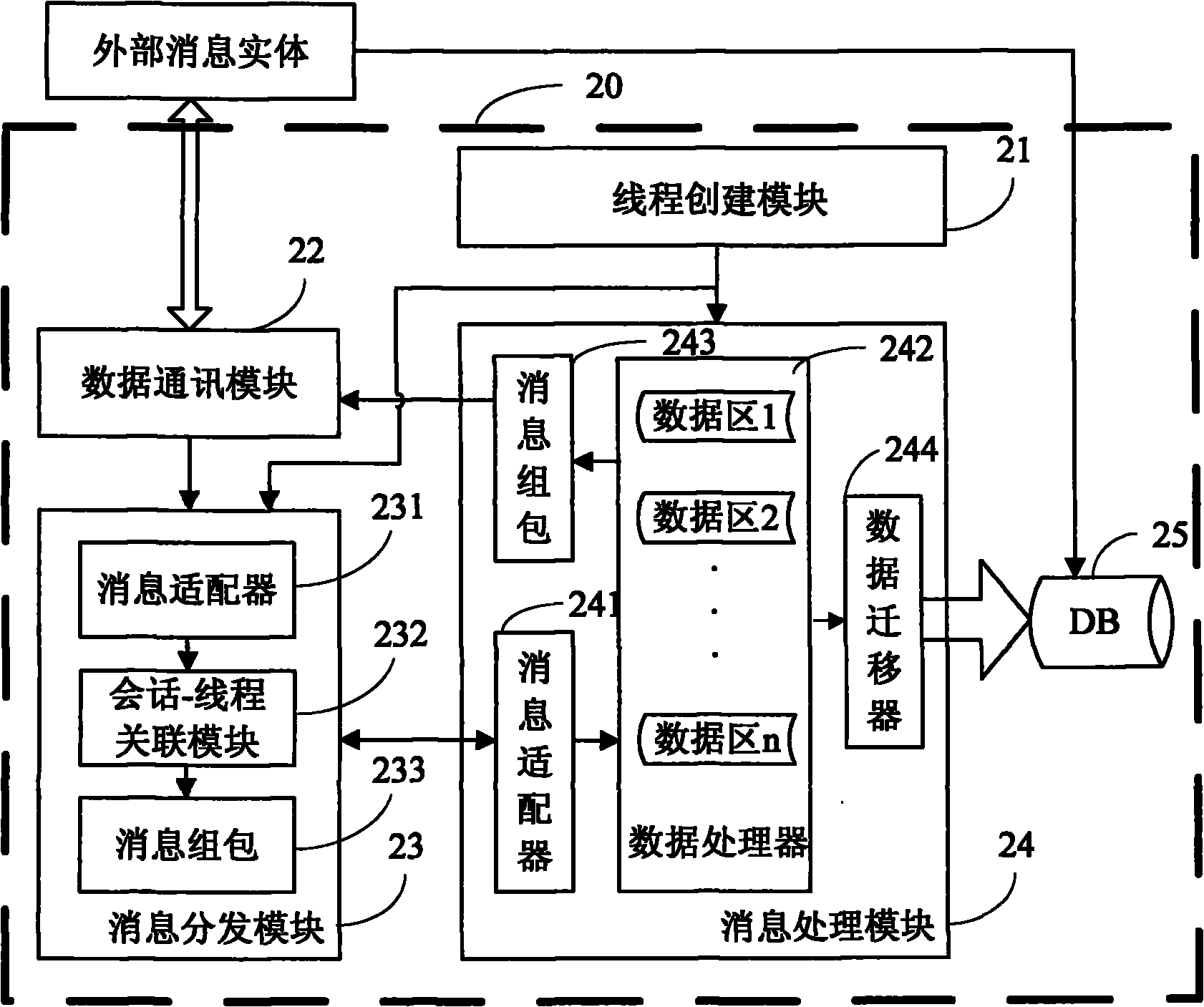
Method for processing business conversational application with multi-thread and device thereof
InactiveCN101882089AAchieve runnabilityAchieve consistencyInterprogram communicationMessage deliveryApplication software
The invention discloses a method for processing business conversational application with a multi-thread and a device thereof. The method comprises that a business conversational application program creates and activates a message delivery thread and a plurality of data processing threads in advance, and allocates a data area only associated with each data processing thread for each data processing thread; when receiving message from an external message entity, the message delivery thread only associates the business conversation of the message with one data processing thread, and deliveries the message to the data processing thread; when receiving the message delivered by the message delivery thread, the data processing thread performs the corresponding process to the corresponding data area according to the status of the message, and feeds back the processed result to the external message entity. The invention avoids the defects of synchronization and mutual exclusion mechanism, and greatly reduces the complexity of the system process while ensuring the safe and effective operation of the system.
Owner:ZTE CORP
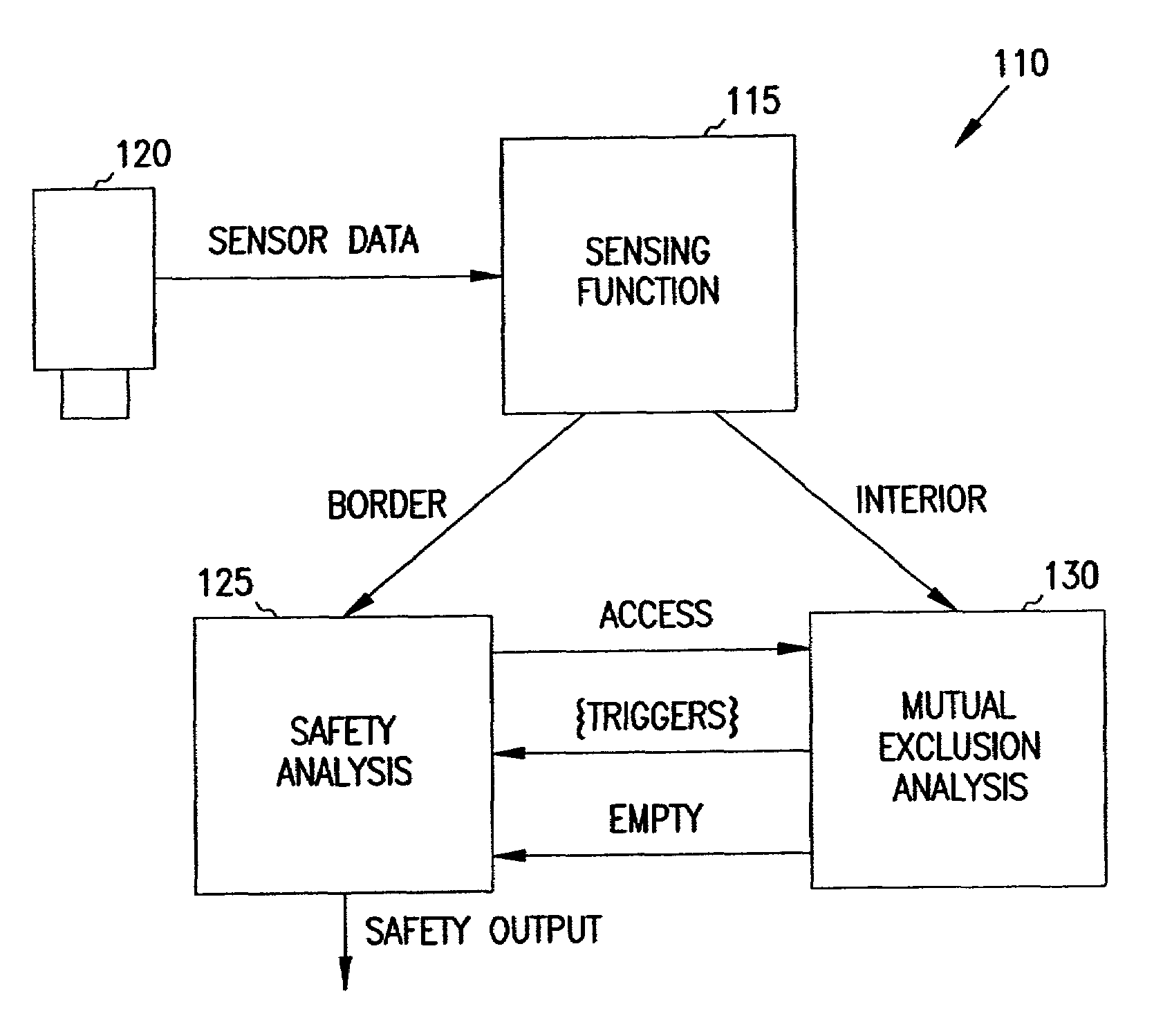
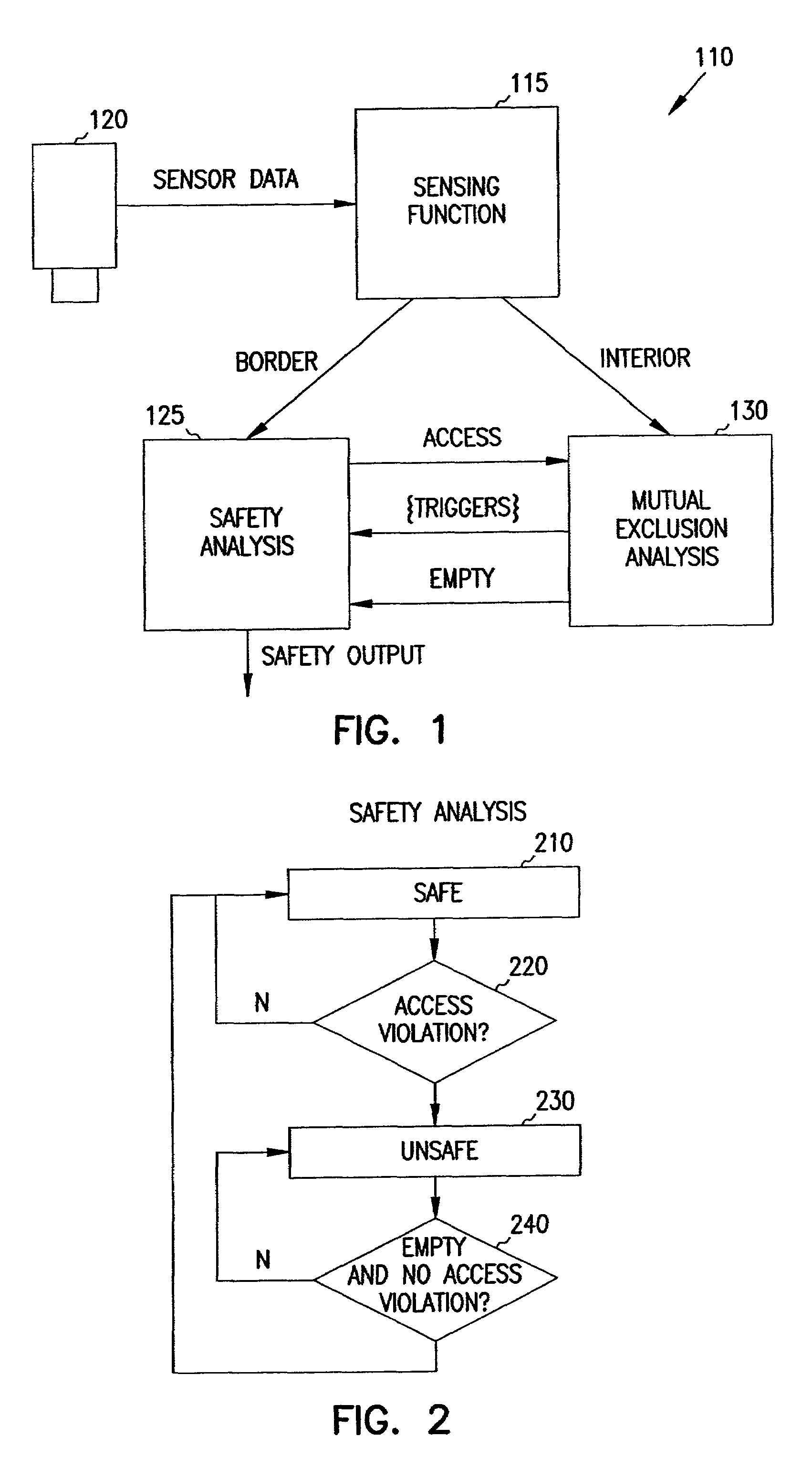
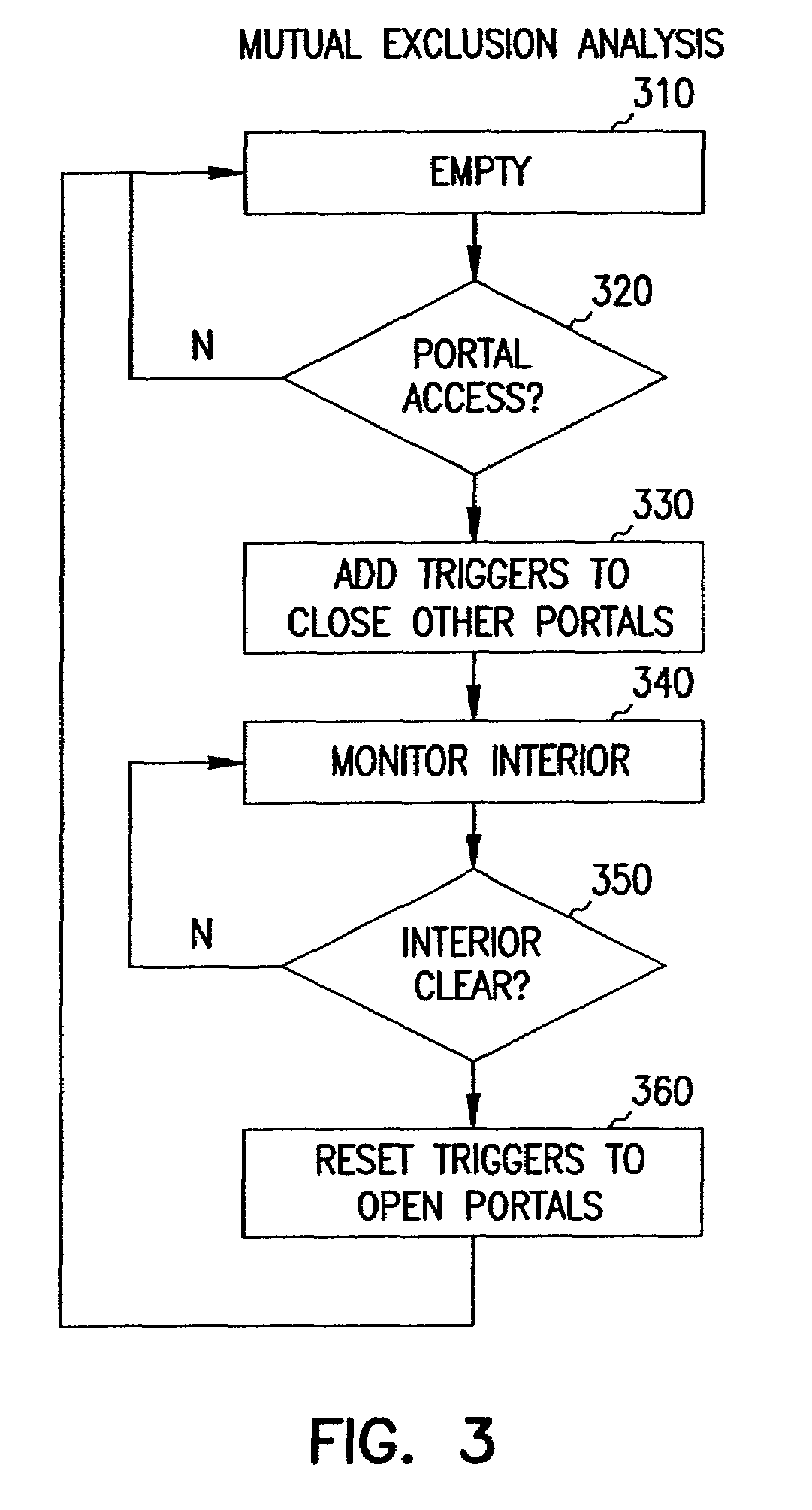
Machine safety system with mutual exclusion zone
A safety system receives access monitoring information from sensors to detect intrusion into a mutual exclusion zone by either an operator or mechanical equipment. The border of the mutual exclusion zone is segmented into portals that allow both the operator and equipment to access a common work area such as for loading material. When intrusion into one of the portals is detected, intrusion into any other selected portals triggers a safety violation. Access to the mutual exclusion zone via the other portals is prohibited until the interior of the zone is determined to be empty again.
Owner:HONEYWELL INC
Dual network card cooperative handover method based on train position
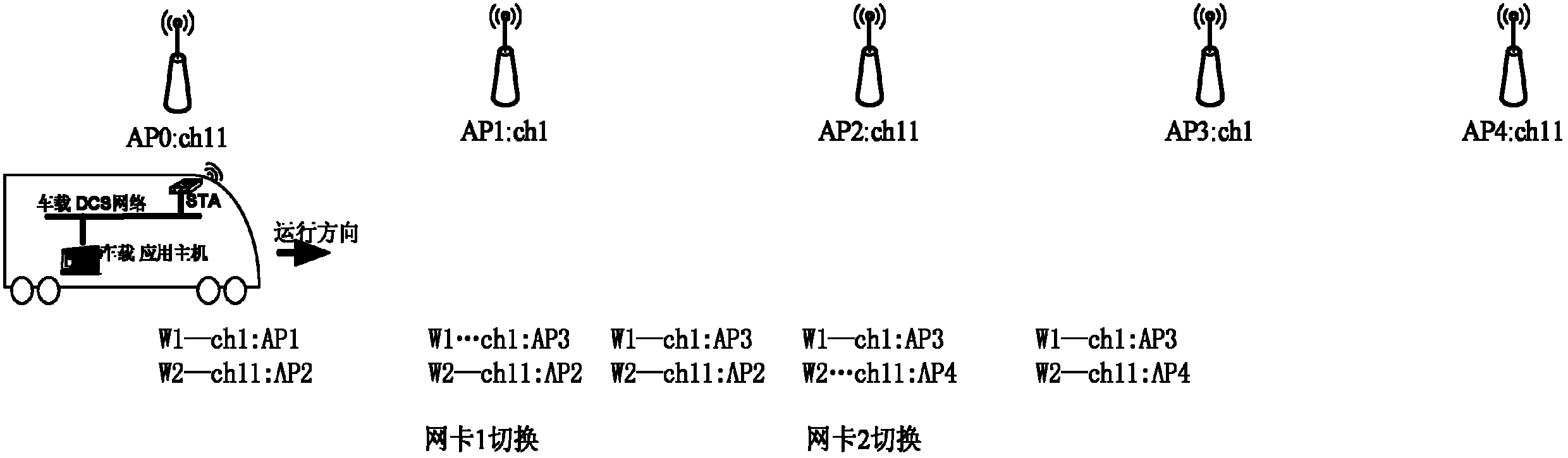
ActiveCN102497655ANo packet loss due to switchingPacket loss occursWireless communicationPacket lossDual network
A dual network card cooperative handover method based on a train position is characterized in that current position information of a train is obtained through two methods, namely information of all access points (AP) beside a track obtained by scanning through a vehicle-mounted single threaded apartment (STA) in an area is obtained through background scanning, and single-network-card fast active roaming handover of the vehicle-mounted STA is conducted by combining an AP information data base beside the track. Simultaneously, dual network cards cooperate to work through a mutual exclusion lock, the fact that at most only one network card performs roaming switching at the same moment is guaranteed, and at least one network card keeps reliable data transmission, thereby enabling the vehicle-mounted STA to provide a fast roaming handover function with zero handover time and zero packet loss for an upper-layer application system of the track, and achieving stable and reliable vehicle-ground data bidirectional transmission. Handover time of a handover algorithm is zero, and a phenomenon of losing packets caused by handover can not occur.
Owner:NANJING NRIET IND CORP
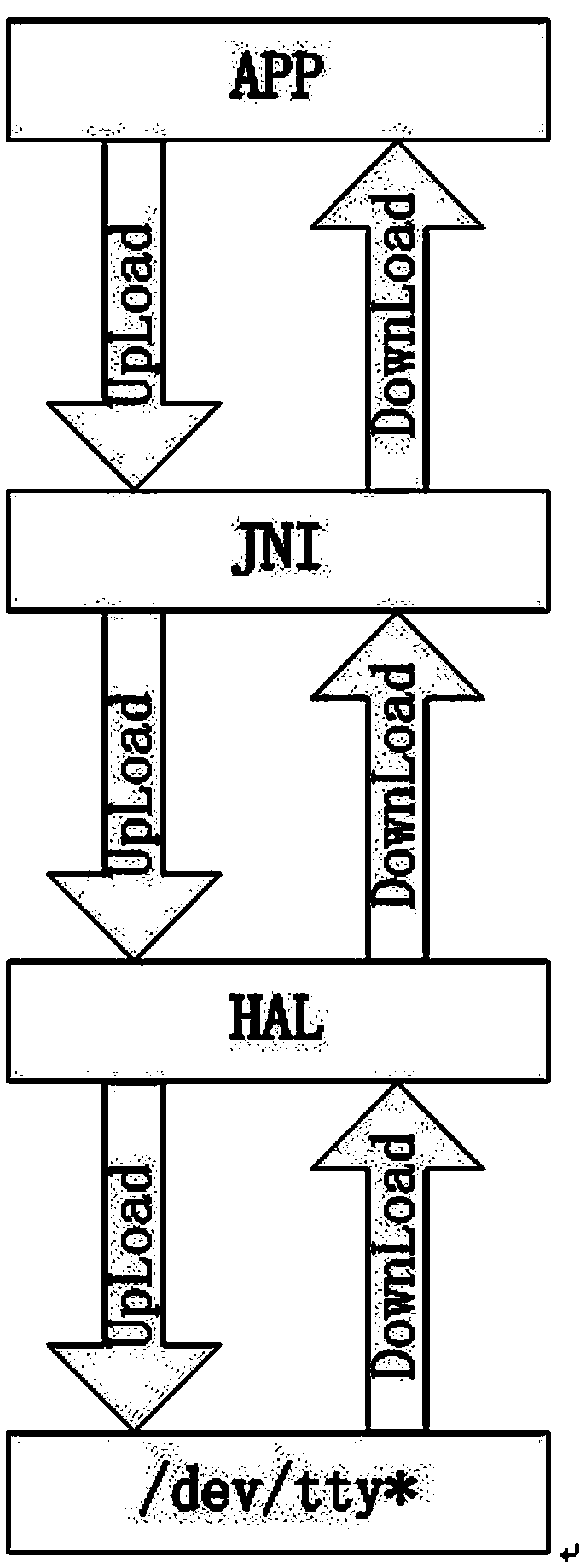
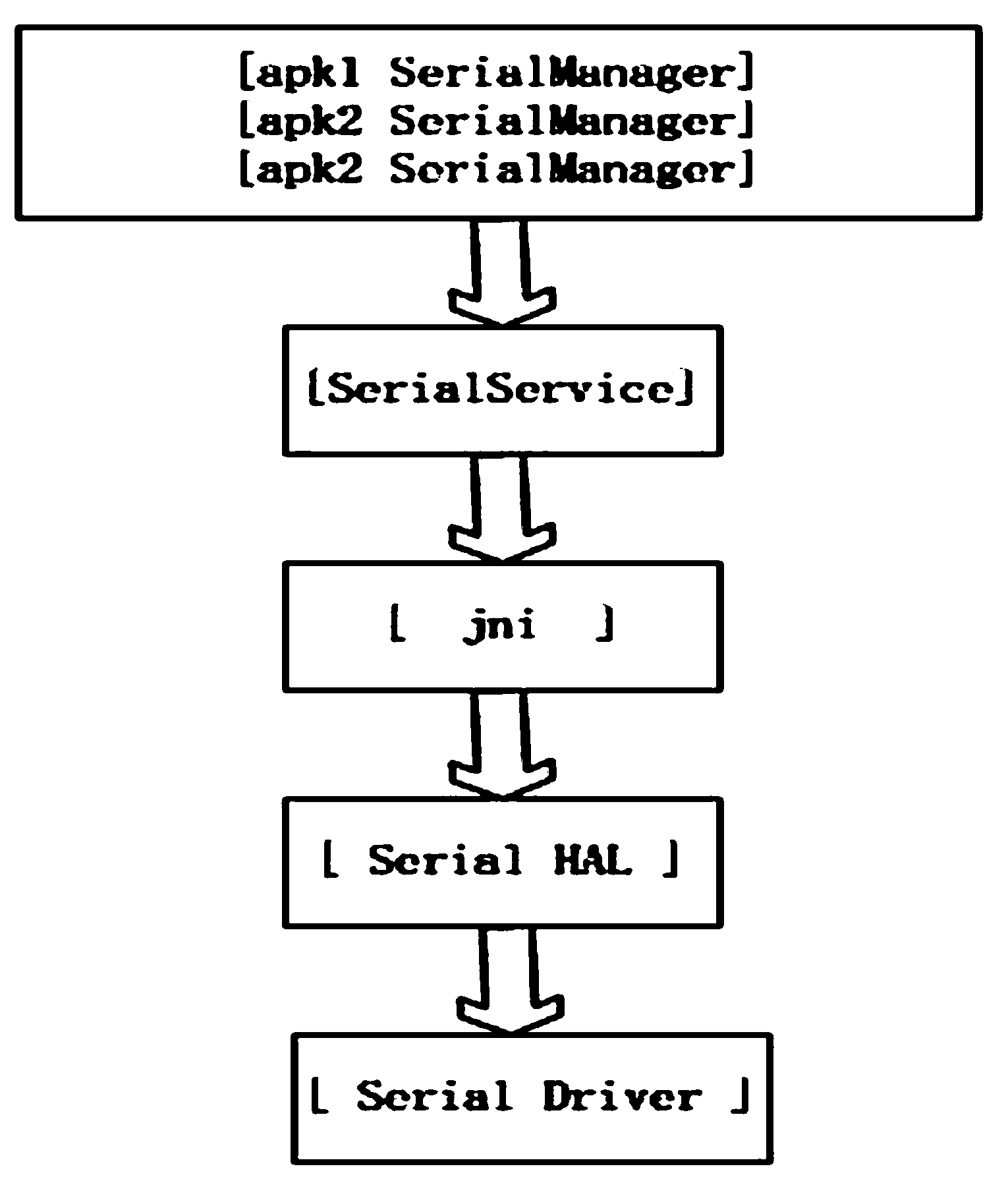
Universal serial device communication module based on Android system
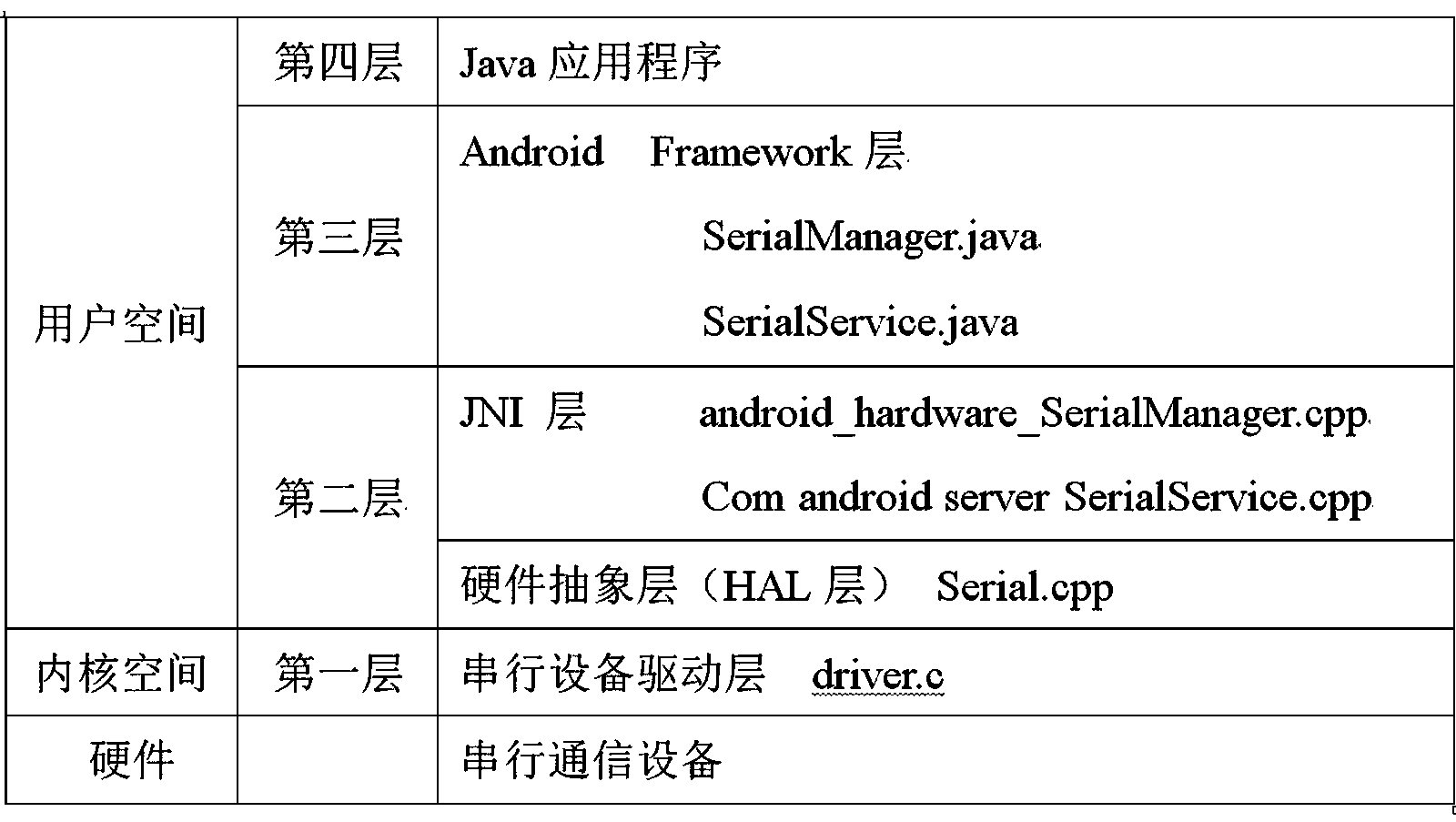
InactiveCN103353839AApplied to the convenience of calling devices with serial portsEasy to callSpecific program execution arrangementsLinux kernelApplication software
The invention provides a universal serial device communication module based on an Android system, which can realize calling to various serial devices under the Android system, and provides a solution for mutual exclusion produced when various (APK) application processes access to the same serial device at the same time. The universal serial device communication module is in operation on a Linux kernel and under an Android frame, and comprises a serial device drive layer, a hardware abstraction layer, a Framework layer and a JNI (Java Native Interface) layer. The universal serial device communication module provides convenience for the Android system to be applied in industries needing to call the serial devices.
Owner:杭州竞航科技股份有限公司
Method for enhancing efficiency in mutual exclusion
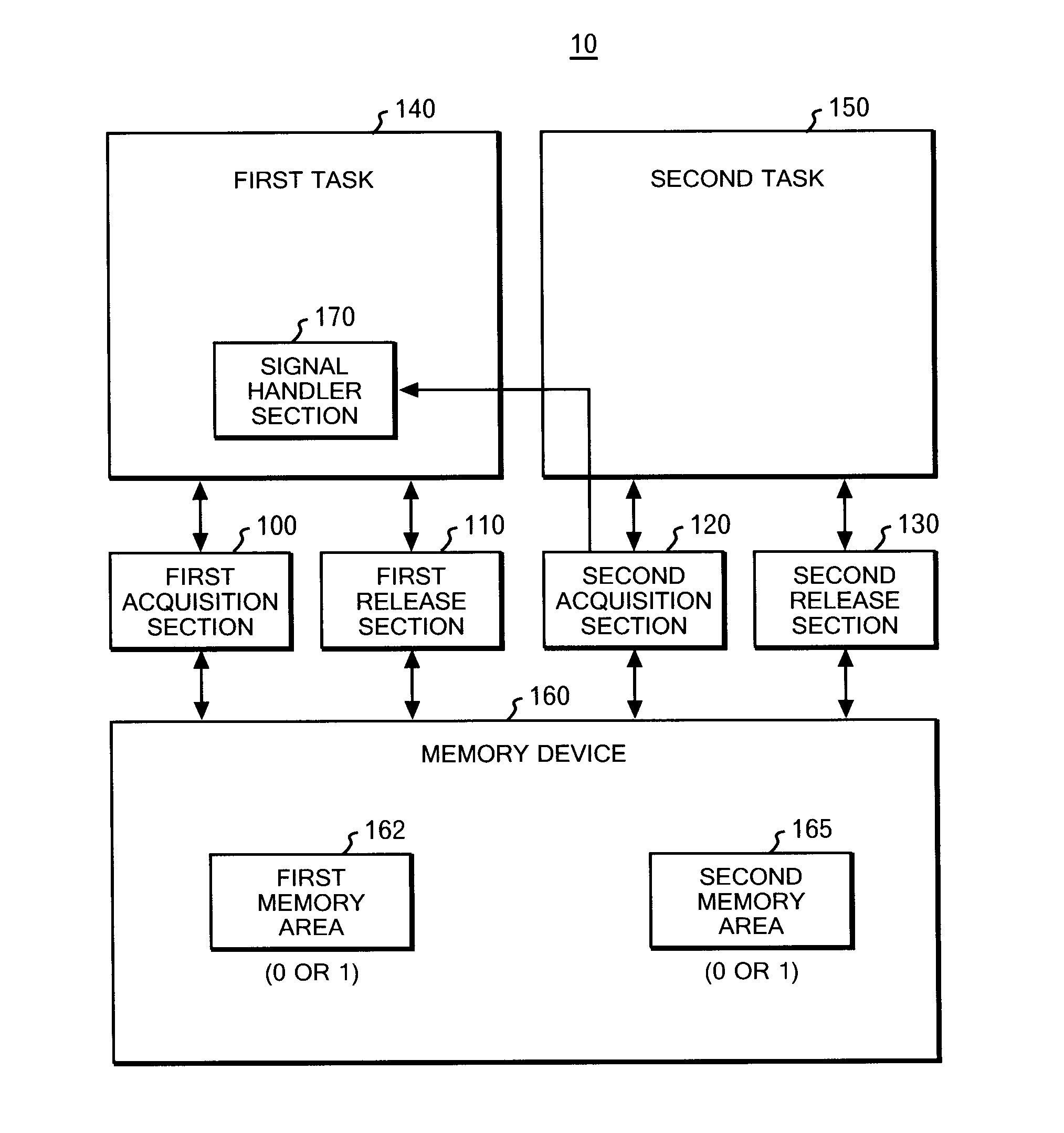
A system of the present invention includes: a memory device which includes a first memory area for storing first information indicating that a first task acquires or attempts to acquire a lock, and a second memory area for storing second information indicating that a second task acquires or attempts to acquire the lock, and in which a time lag may occur between a time when the first task issues a writing instruction and a time when the written content is enabled to be referred to by the second task; a first acquisition section which reads the second memory area after issuing a writing instruction to write the first information to the first memory area in response to a request from the first task, and which makes a reply indicating a success of the lock acquisition on condition that the second information is not read; and a second acquisition section which writes the second information to the second memory area in response to a request from the second task, which enables the written content to be referred to by the first task, which thereafter executes a write-reflection process for enabling the content written in the first memory area by the first task to be referred to by the second task, which reads the first memory area after completion of the write-reflection process, and which makes a reply indicating a success of the lock acquisition on condition that the first information is not read from the first memory area.
Owner:IBM CORP
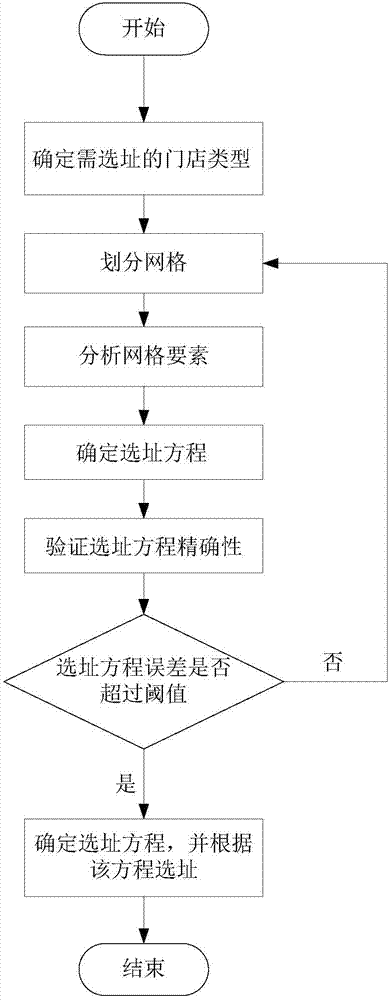
Site selection method
ActiveCN108009677AUniversal applicabilityFast site selectionForecastingComplex mathematical operationsLogistics managementComputer science
The invention relates to the technical field of big data, in particular to a site selection method, and aims at solving the problem that existing site selection methods are long in time consumption, high in cost, inaccurate and difficult to understand, and do not consider mutual exclusion factors. The site selection method specifically comprises the following steps of: 1, determining store type which needs site selection; 2, dividing grids; 3, analyzing grid elements; 4, determining a site selection equation; 5, verifying accurate of the site selection equation; and 6, completing site selection according to the site selection equation. The method is suitable for the store site selection in the fields of commercial retail industry, logistics industry, conference and exhibition industry, financial industry, catering industry, tourist industry, real estate industry, advertising industry, information consulting service industry, public utilities and the like.
Owner:黑龙江鑫联华信息股份有限公司
Backoff protocols and methods for distributed mutual exclusion and ordering
A system for and method of implementing a backoff protocol and a computer network incorporating the system or the method. In one embodiment, the system includes: (1) a client subsystem that generates a request for access to a shared resource and (2) a server subsystem that receives the request, returns a LOCKED indicator upon an expectation that the shared resource is unavailable and otherwise returns a FREE indicator, the client subsystem responding to the LOCKED indicator by waiting before regenerating the request for the access.
Owner:ALCATEL-LUCENT USA INC +1
Method and apparatus for resource access synchronization
InactiveUS7100161B2Efficient and reliableMultiprogramming arrangementsMemory systemsAccess controlMutual exclusion
A resource access control mechanism for a multi-threaded computing environment associates a sequence of one or more mutexes with a resource. When a requesting thread attempts to access the resource, a mutex is locked and allocated to the requesting thread, and if a previous mutex in the sequence is present, an attempt to lock the previous mutex is made. If the previous mutex is already locked, the requesting thread is suspended until the previous mutex is unlocked.
Owner:ORACLE INT CORP
System and method for dynamically adaptive mutual exclusion in multi-threaded computing environment
InactiveUS20090307707A1Overcome disadvantagesProgram synchronisationMemory systemsCritical sectionSelf adaptive
A system and associated method for mutually exclusively executing a critical section by a process in a computer system. The critical section accessing a shared resource is controlled by a lock. The method measures a detection time when a lock contention is detected, a wait time representing a duration of wait for the lock at each failed attempt to acquire the lock, and a delay representing a total lapse of time from the detection time till the lock is acquired. The delay is logged and used to calculate an average delay, which is compared with a suspension overhead time of the computer system on which the method is executed to determine whether to spin or to suspend the process while waiting for the lock to be released.
Owner:IBM CORP
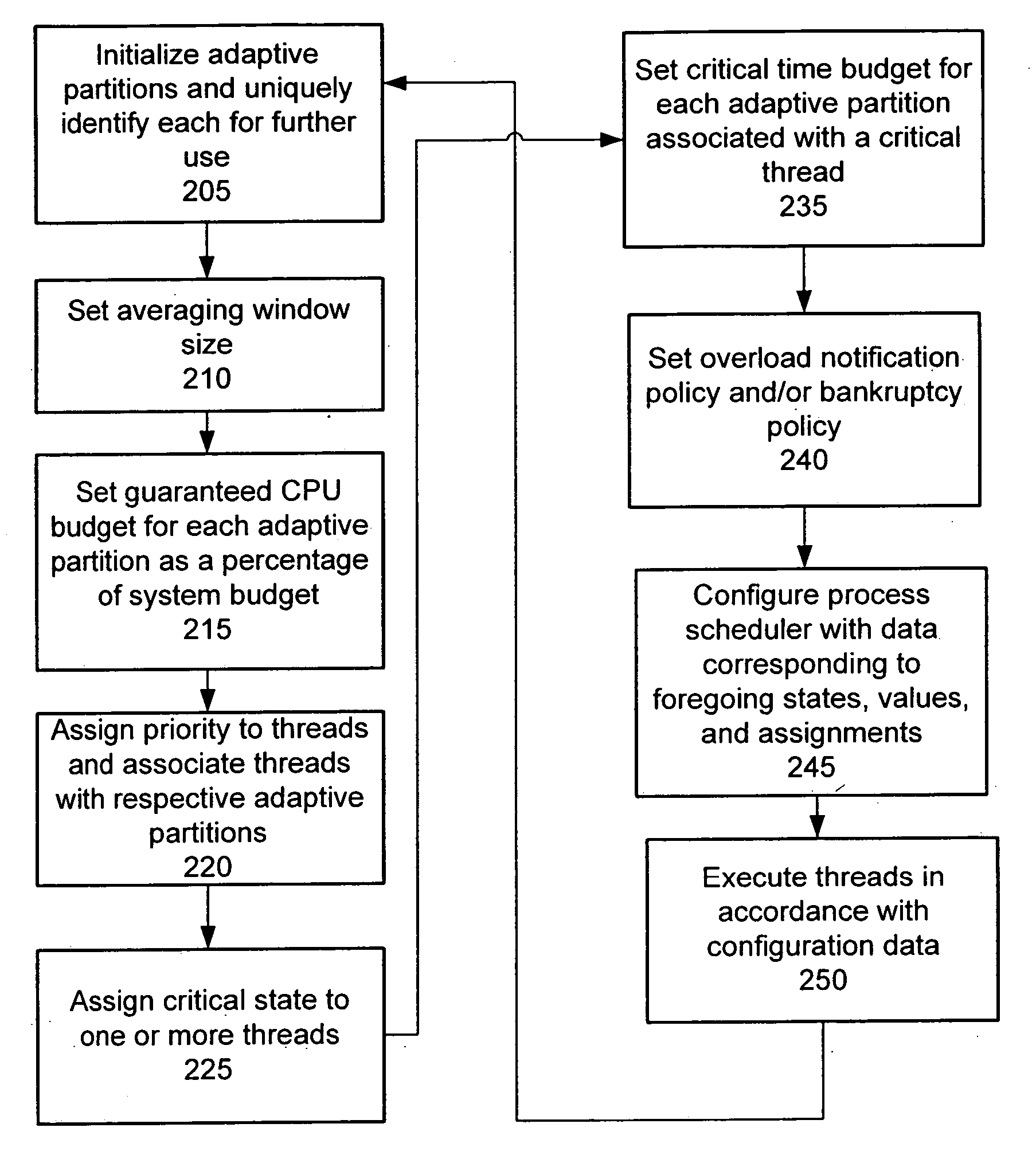
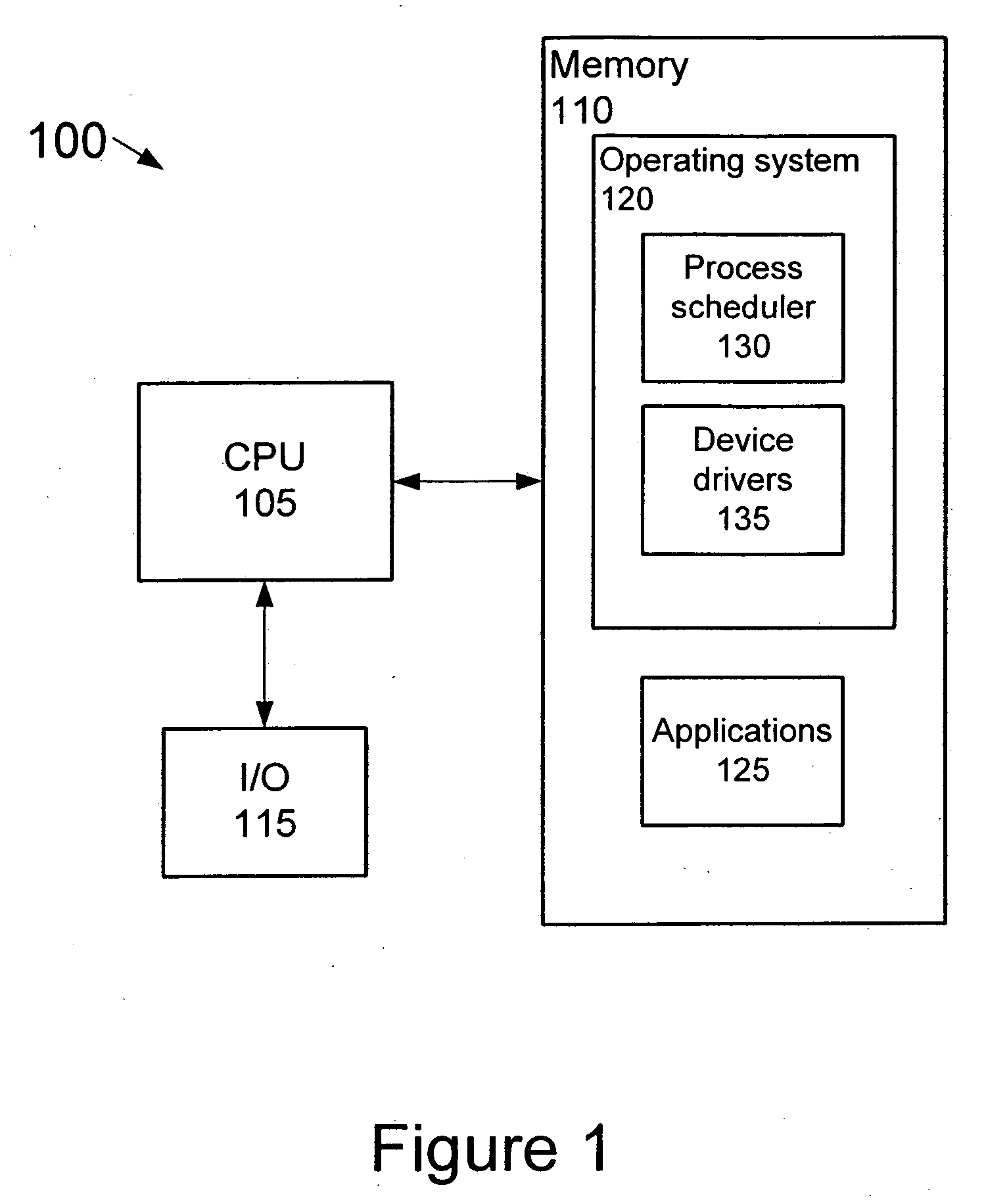
Process scheduler having multiple adaptive partitions associated with process threads accessing mutexes and the like
ActiveUS20070061809A1Multiprogramming arrangementsMultiple digital computer combinationsParallel computingProcessor assignment
Owner:MALIKIE INNOVATIONS LTD
Realization method of real-time operating system of component-based hardware
InactiveCN103440171AReduce overheadImprove performanceProgram initiation/switchingMessage queueProcessor register
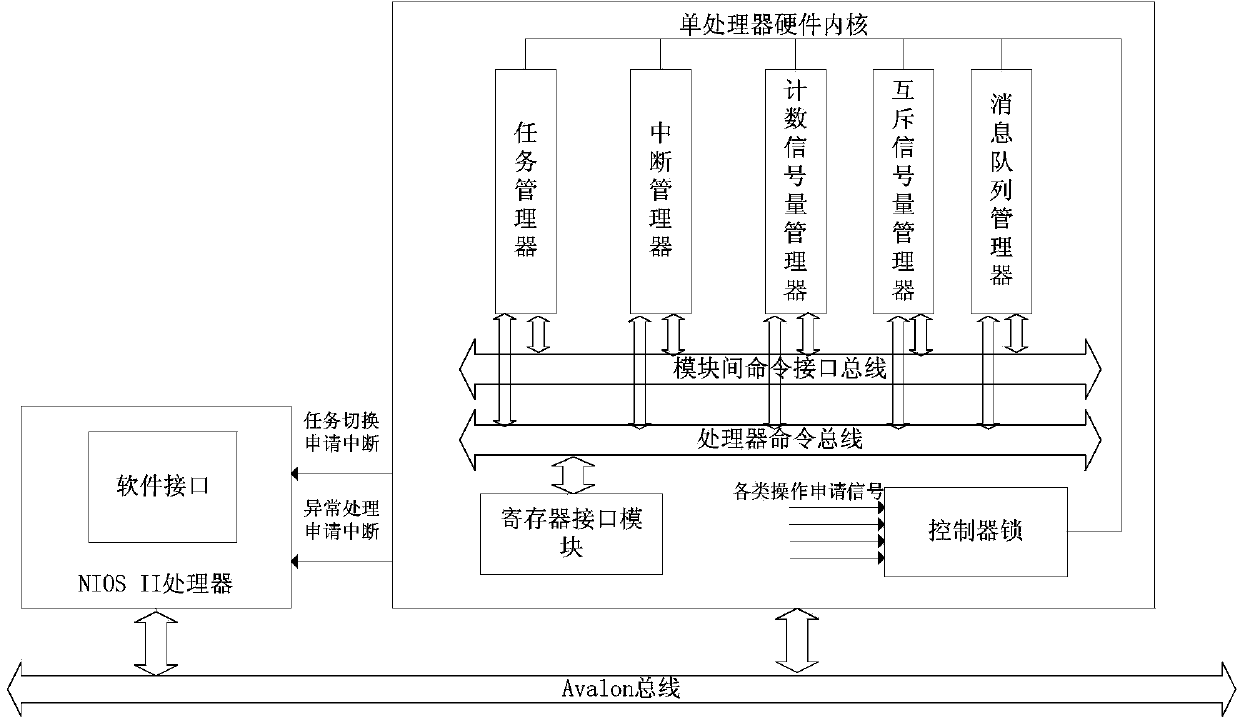
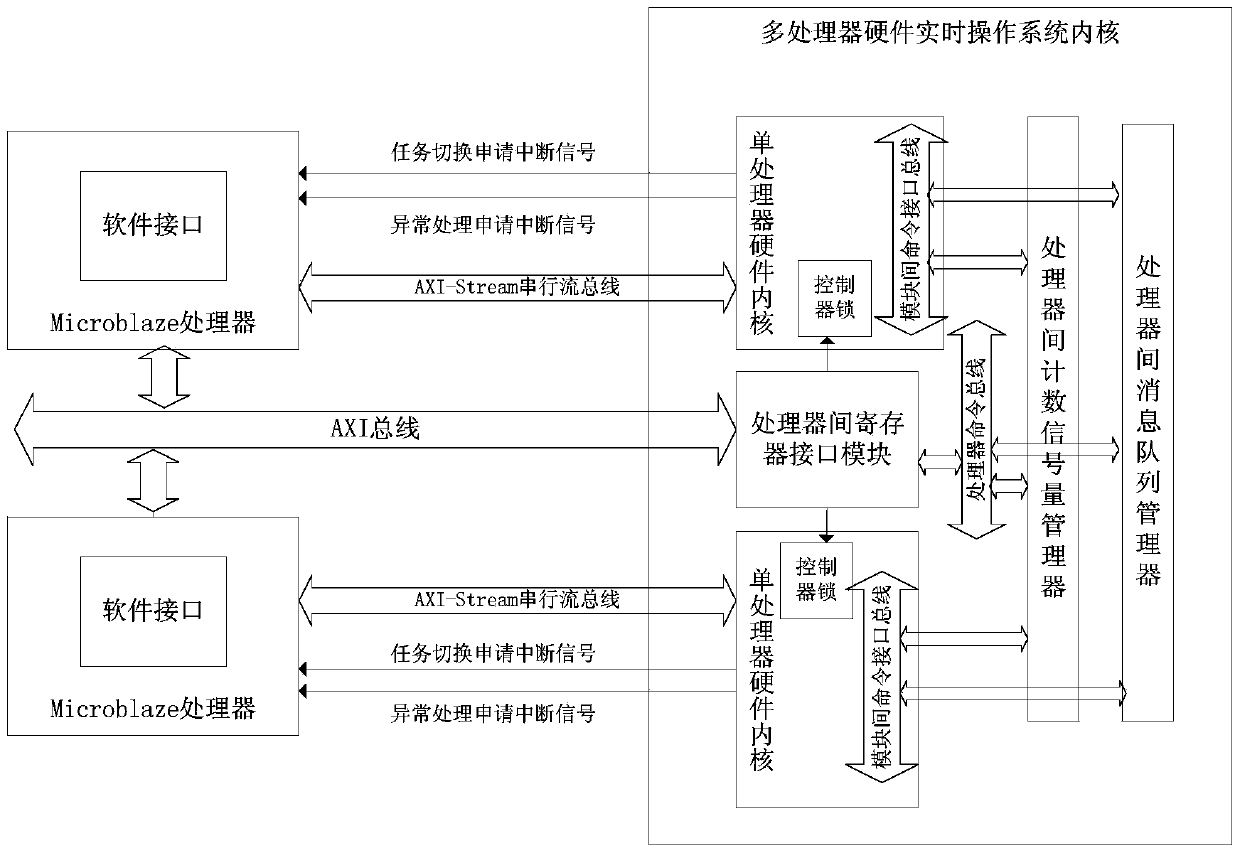
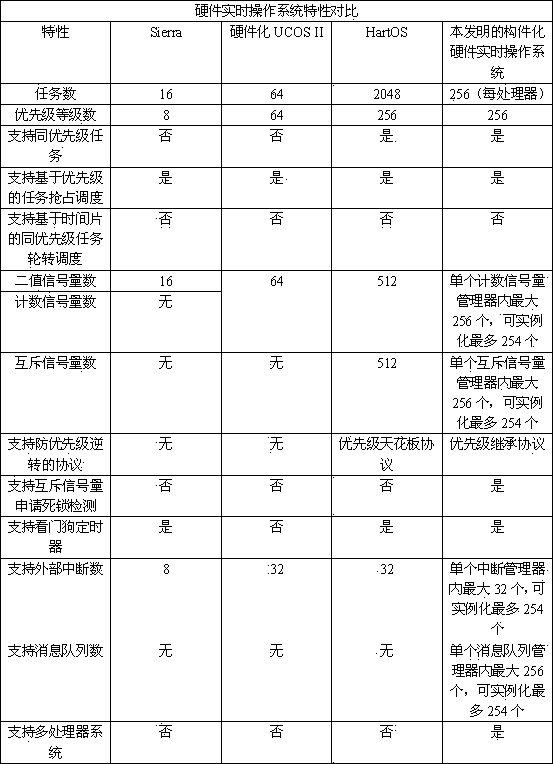
The invention discloses a realization method of a real-time operating system of component-based hardware. The method comprises the following steps of: firstly, dividing the real-time operating system into two parts including a hardware inner core and a software interface; then, realizing the communication of a task manager, an interruption manager, a counting semaphore manager, a mutual exclusion semaphore manager and a message queue manager of the real-time operating system by component-based manner in the hardware inner core; enabling the hardware inner core to be communicated with software by a register interface module; synchronizing all the managers by a controller lock; enabling the mangers to be communicated by standard inter-mould command interface buses; and finally, realizing an inter-processor counting semaphore manager and an inter-processor message queue manager and realizing the hardware inner core of a multiprocessor real-time operating system. According to the realization method, the inner core of the hardware real-time operating system is realized by a component-based manner so that the cuttability and the expandability of the system are improved greatly and the flexibility of the software is realized by the real-time operation of the hardware.
Owner:ZHEJIANG UNIV
Send-Side Matching Of Data Communications Messages
InactiveUS20120066284A1Program synchronisationMultiple digital computer combinationsComputing systemsCollective operation
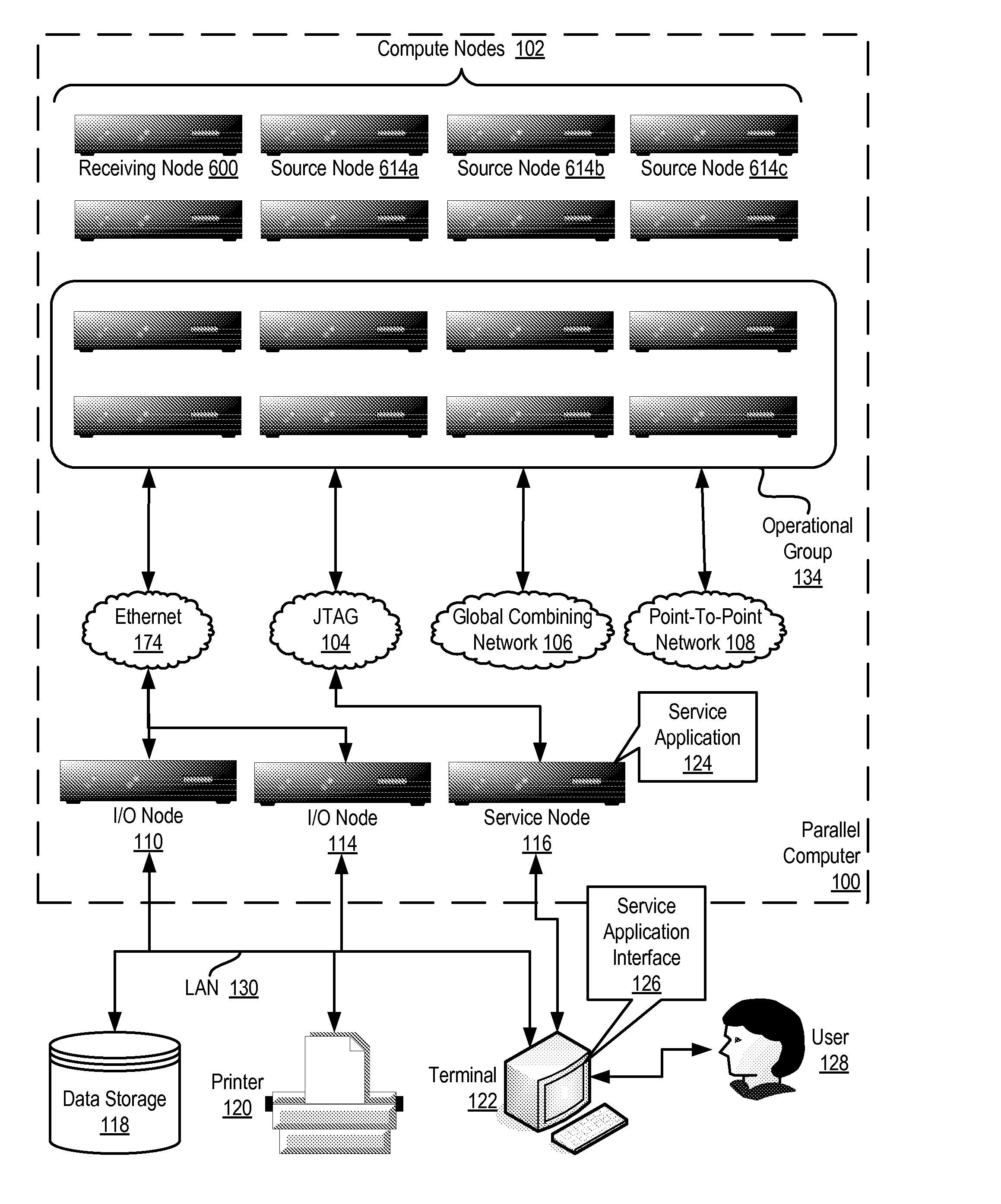
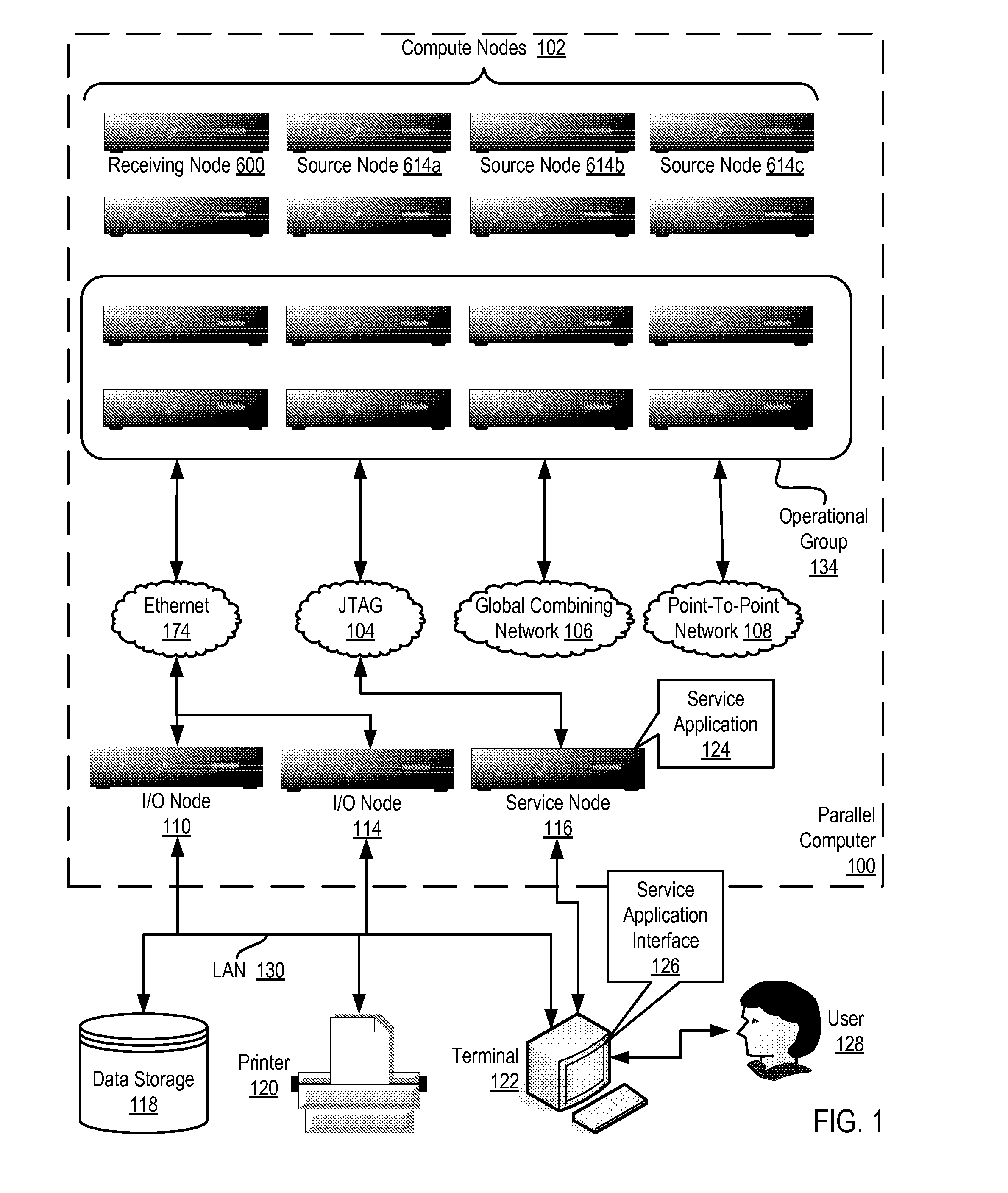
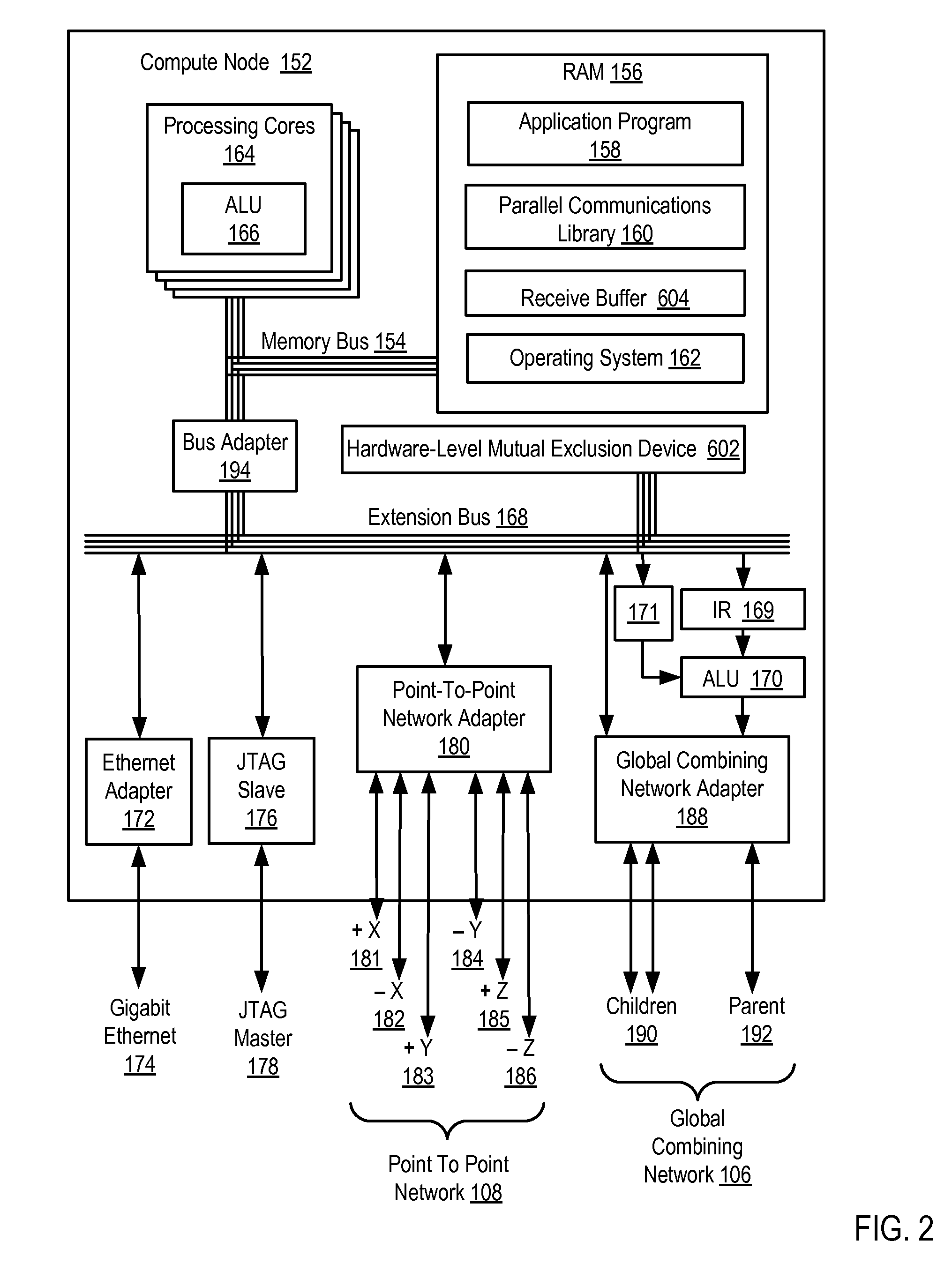
Send-side matching of data communications messages in a distributed computing system comprising a plurality of compute nodes organized for collective operations, including: issuing by a receiving node to source nodes a receive message that specifies receipt of a single message to be sent from any source node, the receive message including message matching information, a specification of a hardware-level mutual exclusion device, and an identification of a receive buffer; matching by two or more of the source nodes the receive message with pending send messages in the two or more source nodes; operating by one of the source nodes having a matching send message the mutual exclusion device, excluding messages from other source nodes with matching send messages and identifying to the receiving node the source node operating the mutual exclusion device; and sending to the receiving node from the source node operating the mutual exclusion device a matched pending message.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com