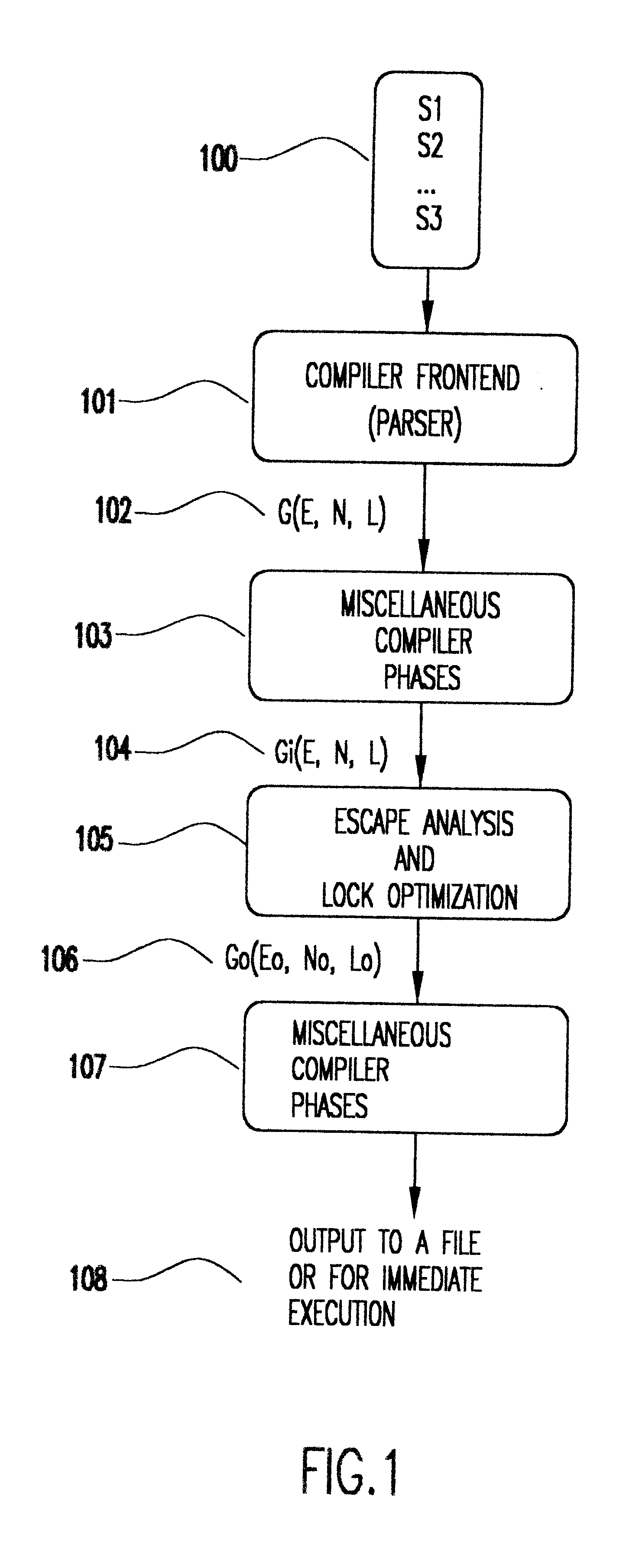
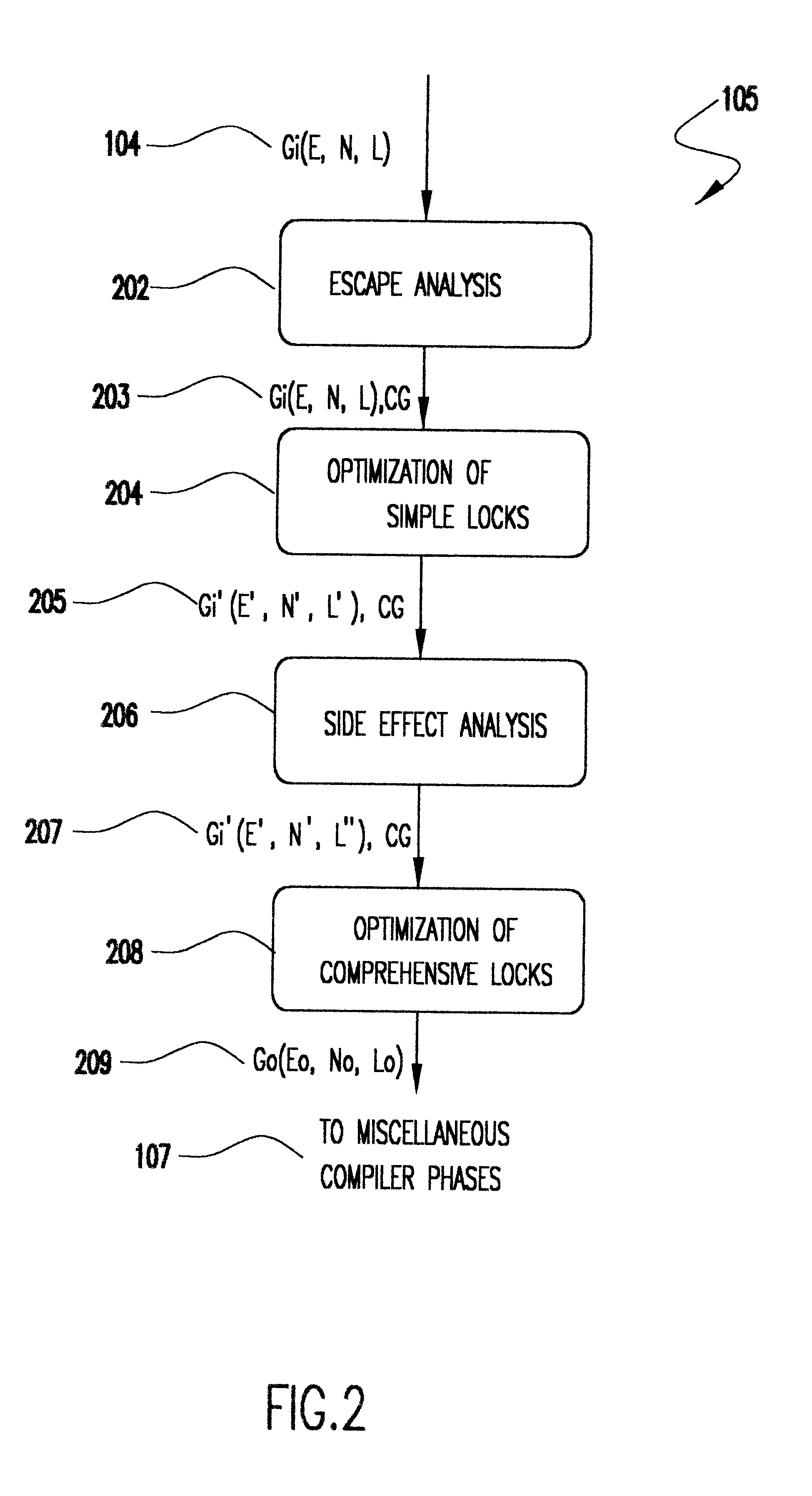
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3482 results about "Computer processing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
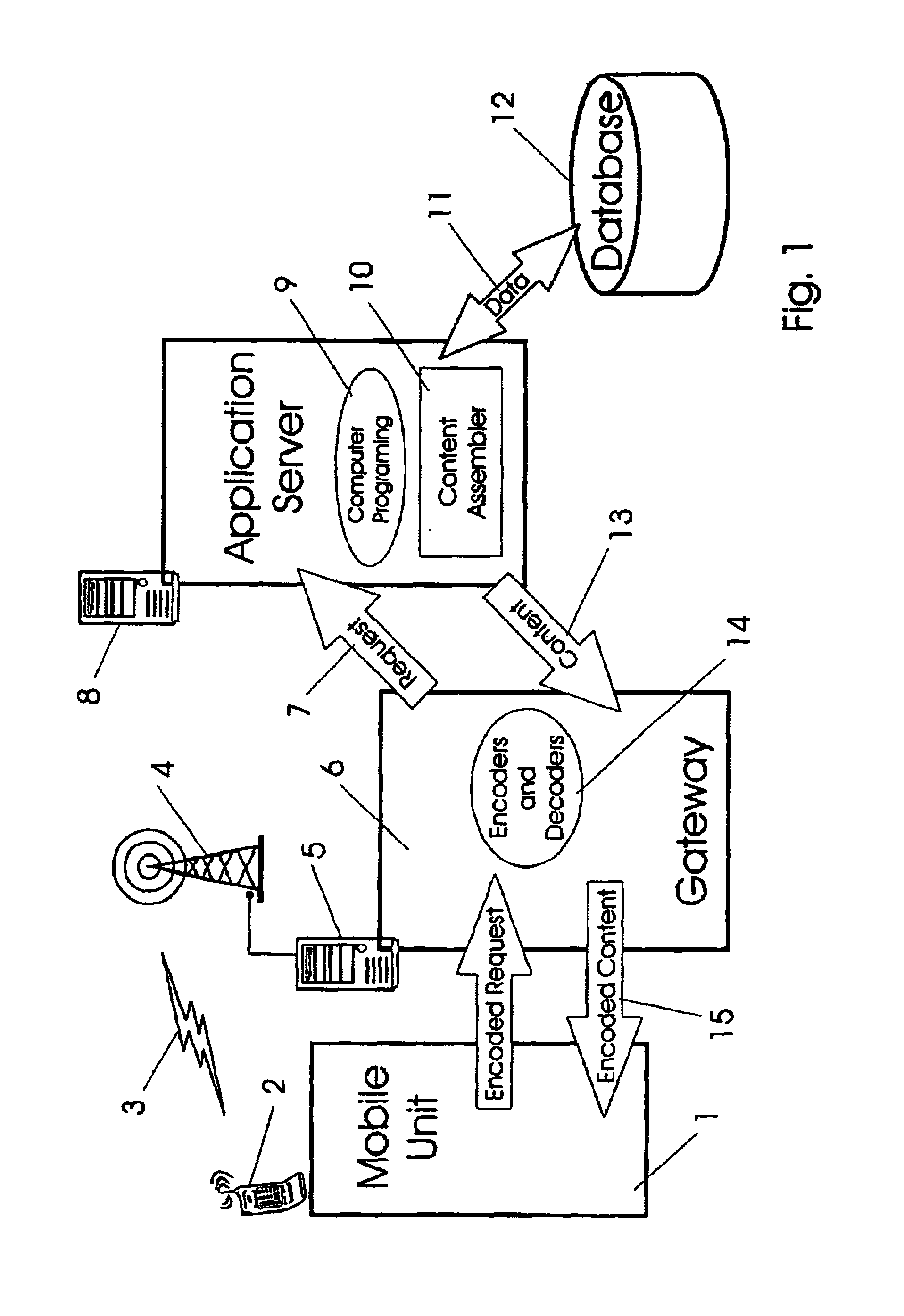
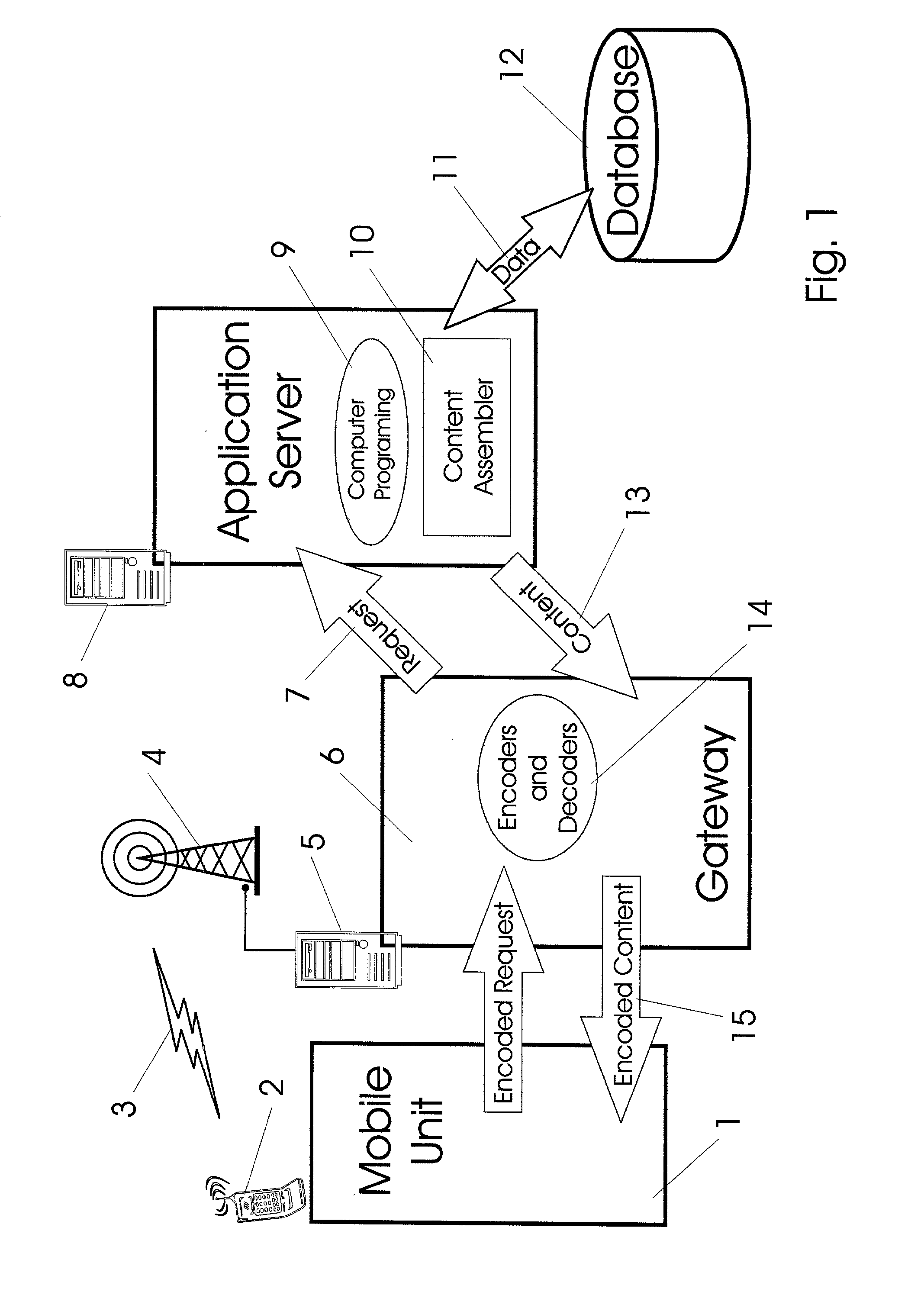
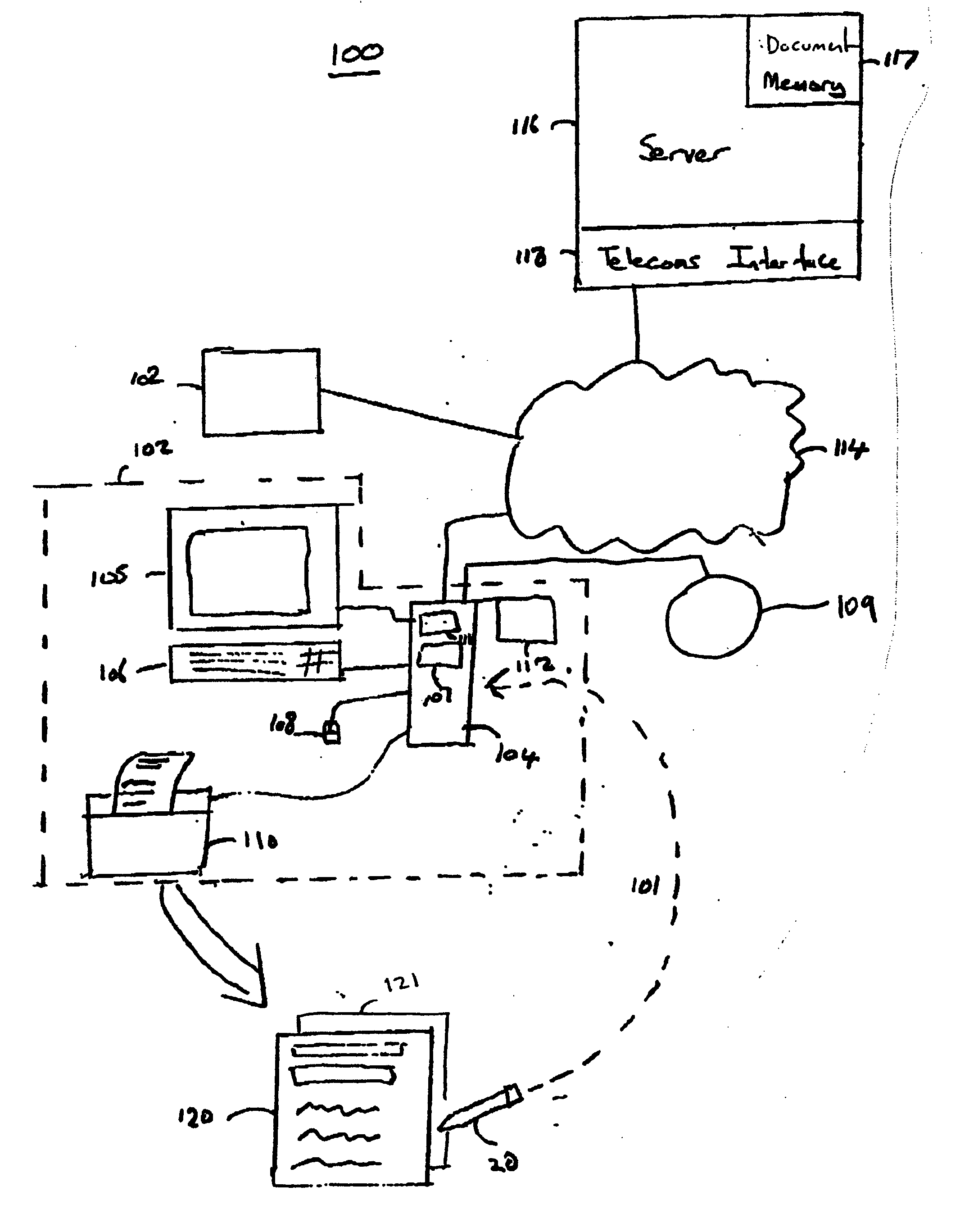
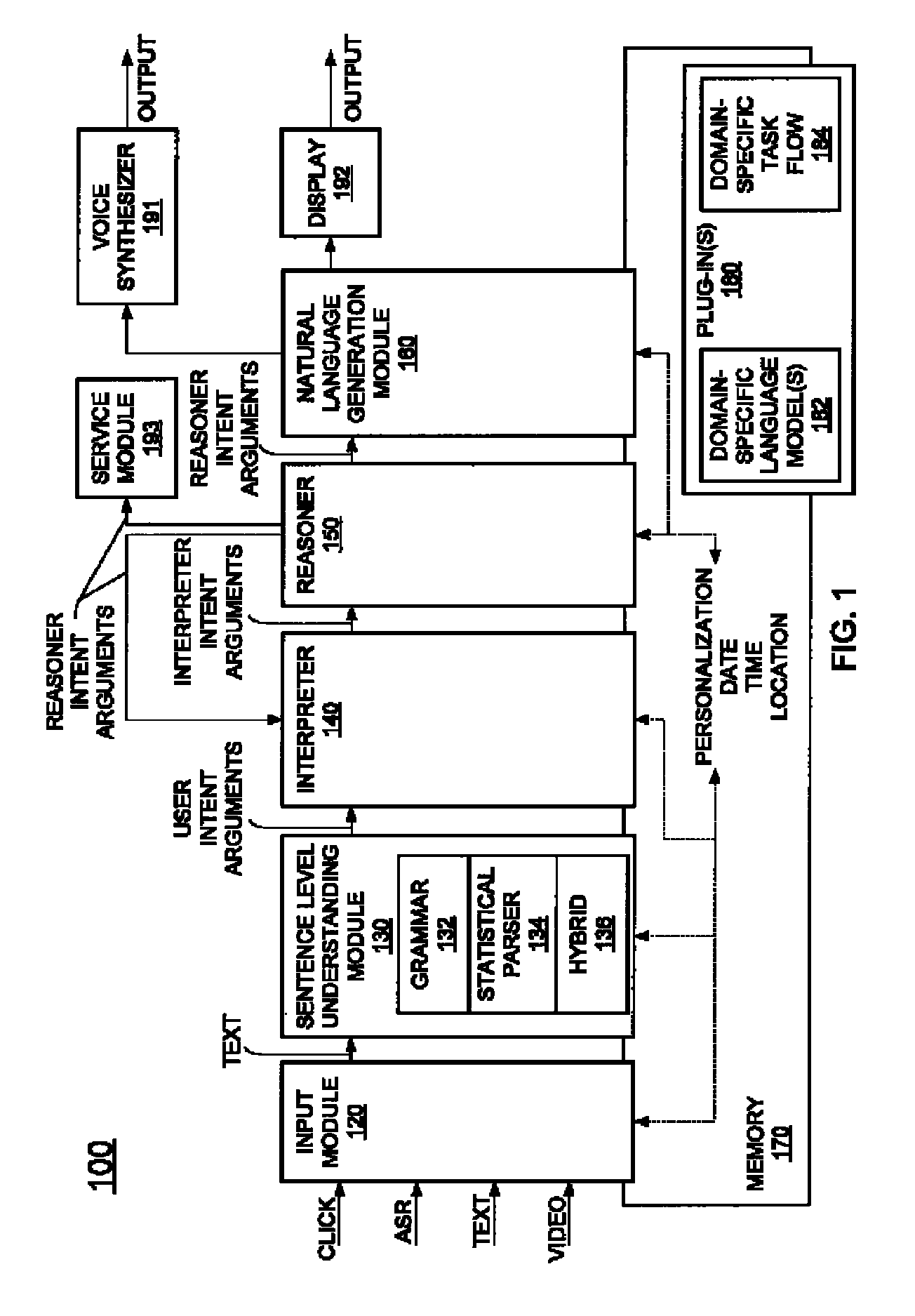
Generic virtual personal assistant platform
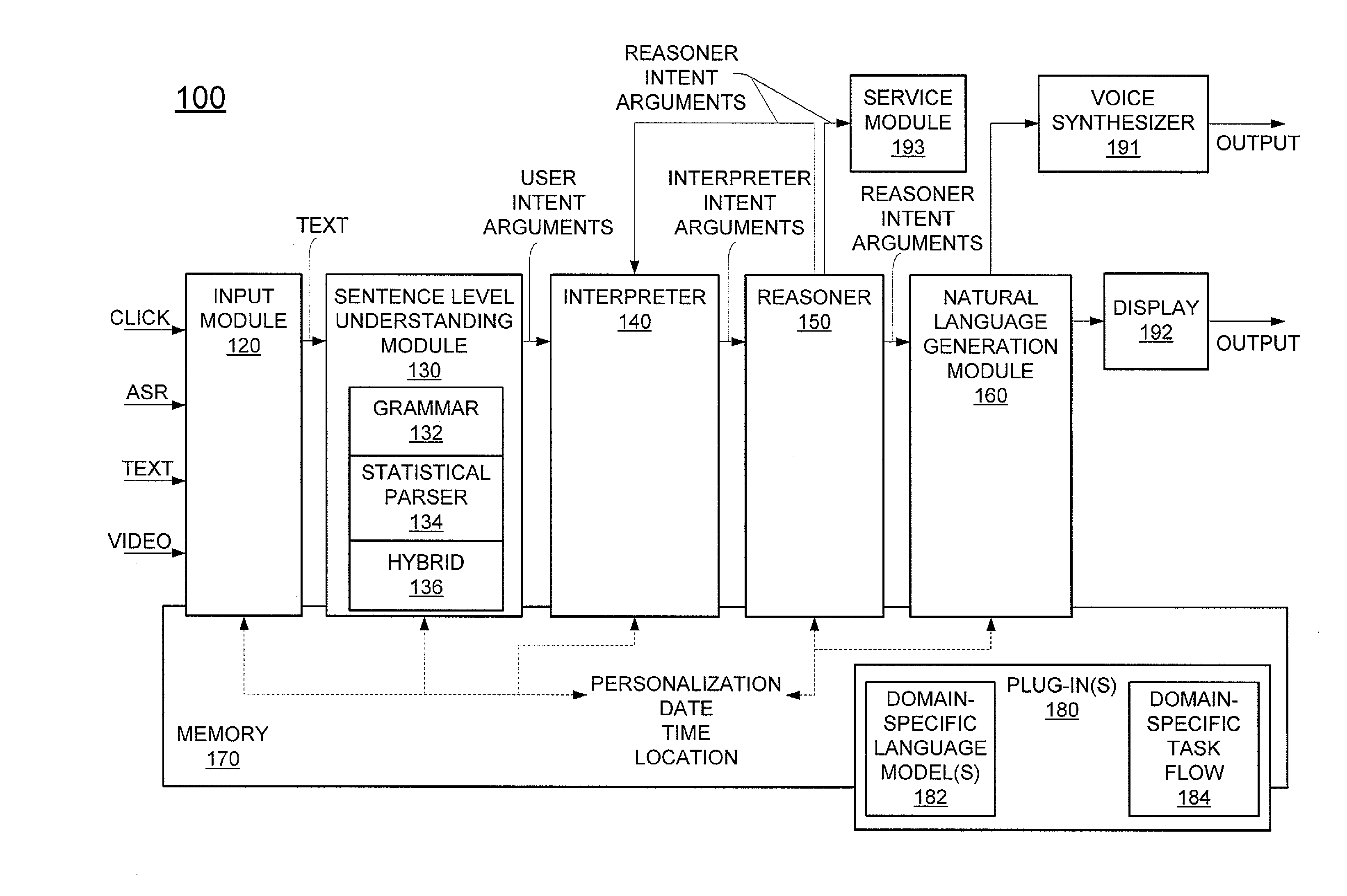
ActiveUS20130152092A1Natural language translationMultiprogramming arrangementsLanguage understandingA domain
A method for assisting a user with one or more desired tasks is disclosed. For example, an executable, generic language understanding module and an executable, generic task reasoning module are provided for execution in the computer processing system. A set of run-time specifications is provided to the generic language understanding module and the generic task reasoning module, comprising one or more models specific to a domain. A language input is then received from a user, an intention of the user is determined with respect to one or more desired tasks, and the user is assisted with the one or more desired tasks, in accordance with the intention of the user.
Owner:SRI INTERNATIONAL
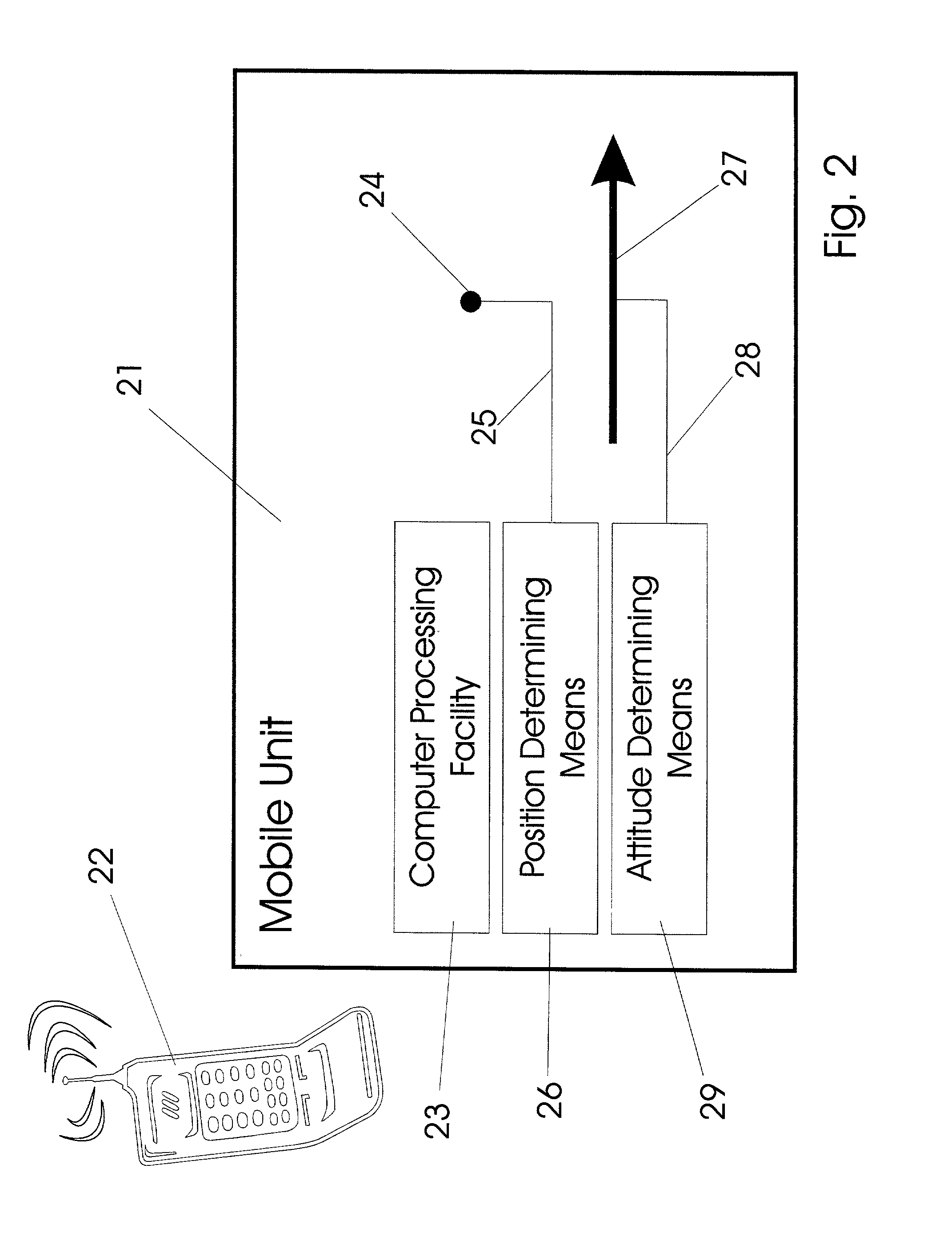
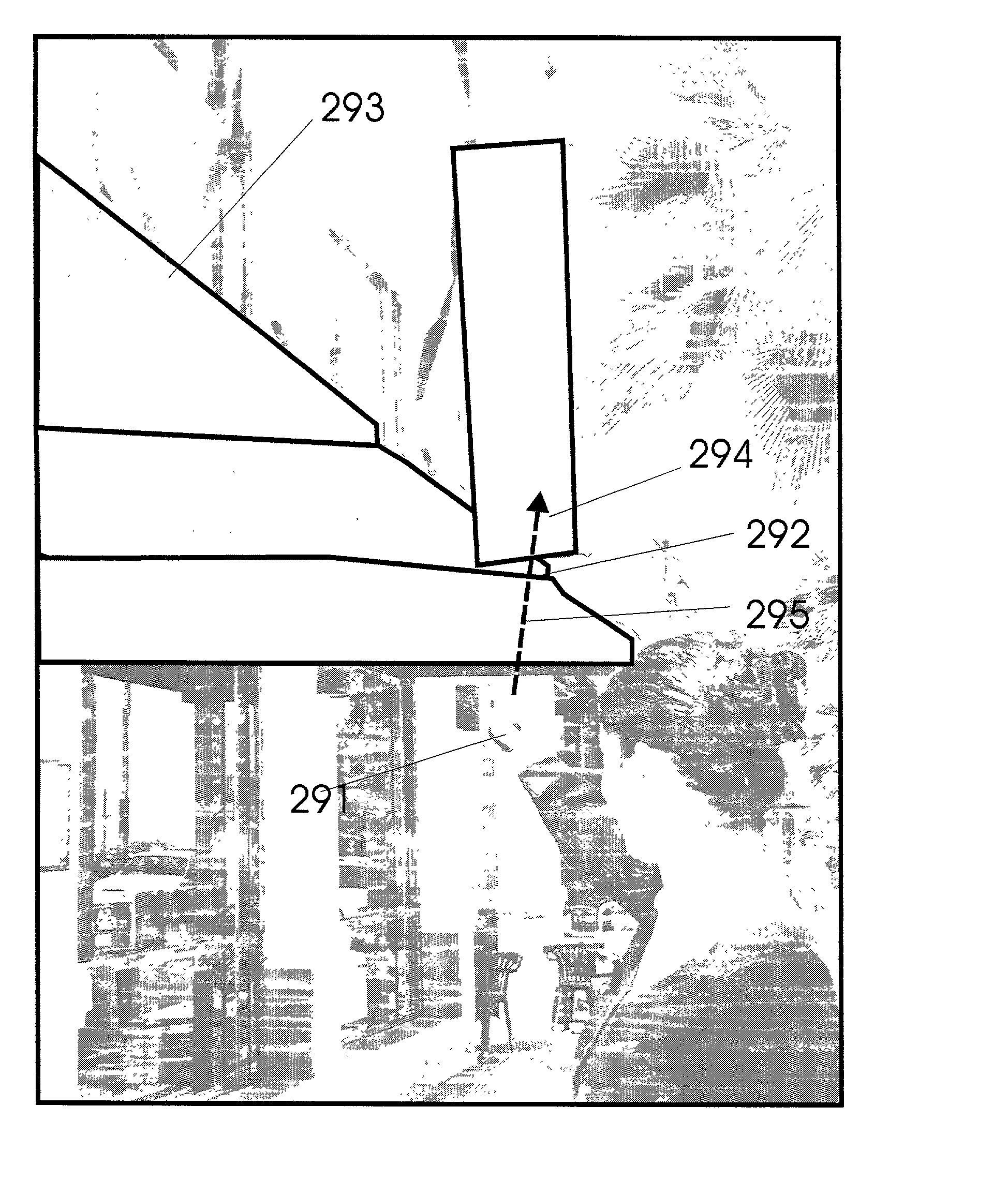
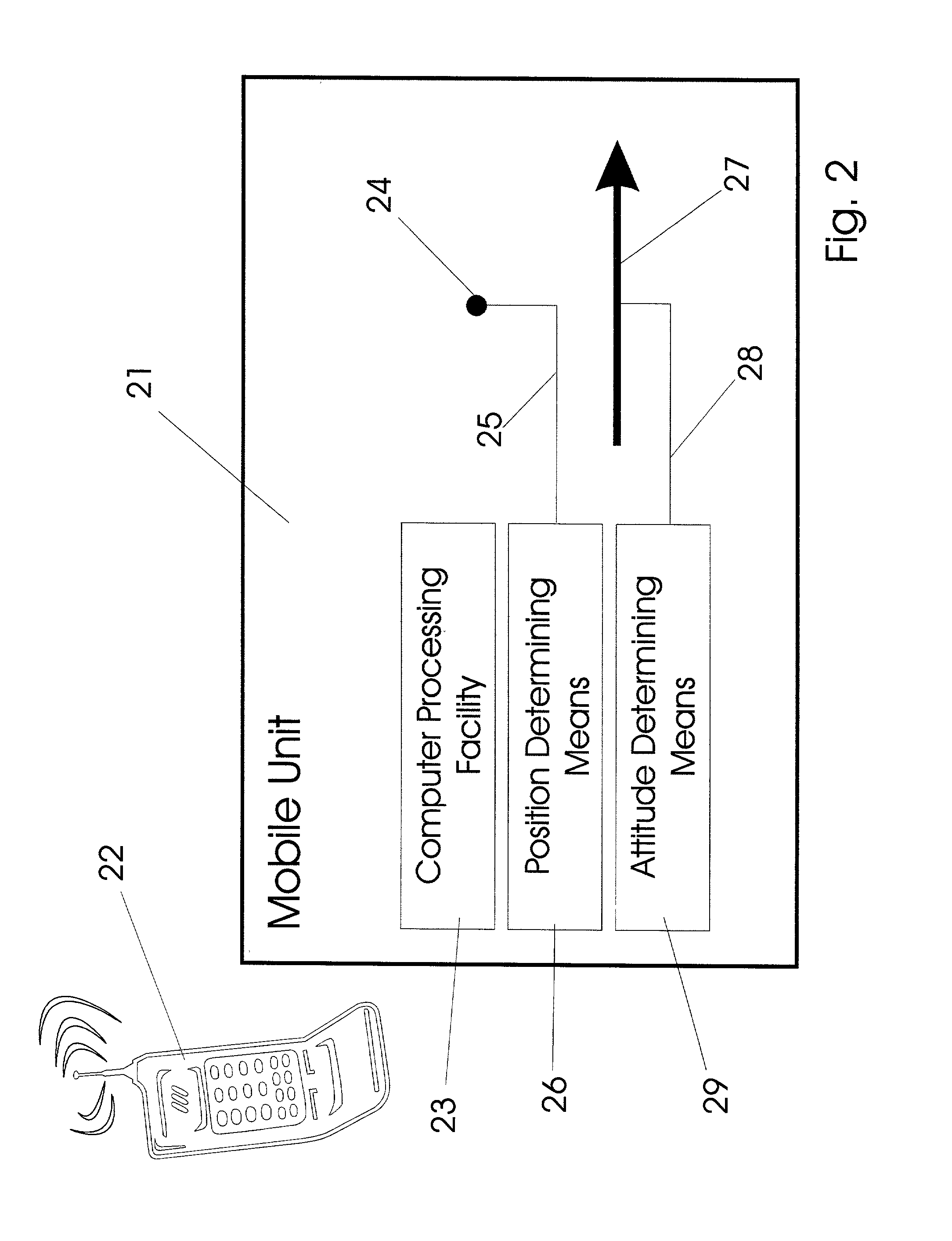
Pointing systems for addressing objects
InactiveUS7031875B2Navigational calculation instrumentsDigital data processing detailsHand heldHand held devices
Systems are arranged to provide a user information which relates to objects of interest. A user may point a hand held device toward an object to address it. The device determines which objects are being addressed by making position and attitude measurements and further a reference and search of a database containing preprogrammed information relating to objects. Information relating to objects determined as objects presently being addressed is thereafter presented at a user interface. Devices of these systems include a point reference, a direction reference, a position determining support, attitude determining support, a computer processor and database, and a user interface. Methods of systems include the steps of addressing an object, determining position and attitude, searching a database, and presenting information to a user.
Owner:GEOVECTOR
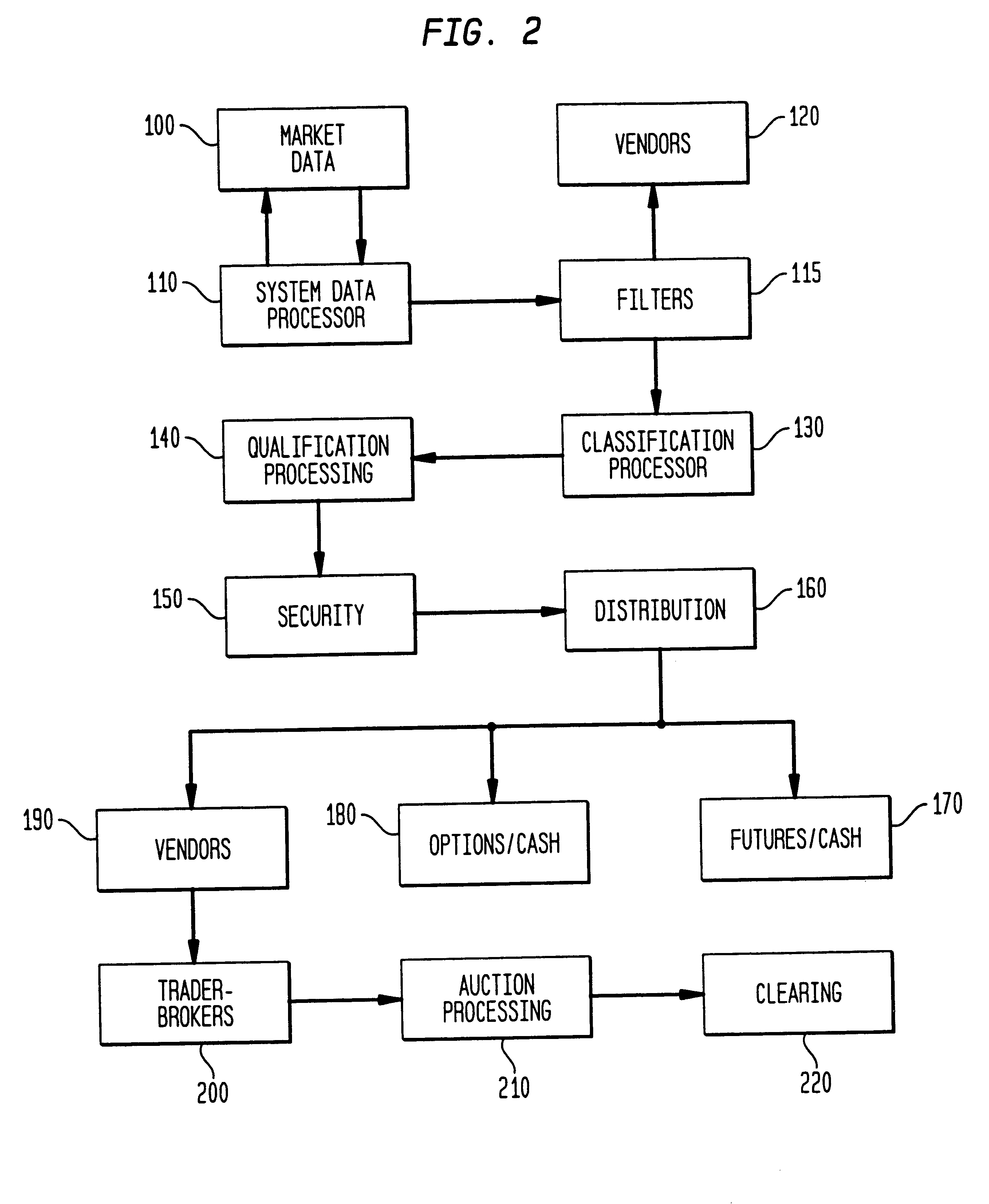
Automated price improvement protocol processor
InactiveUS6850907B2Distribute quicklyFast exchangeFinanceBuying/selling/leasing transactionsData processing systemProtocol processing
A data processing system for implementing transaction management of auction-based trading for specialized items such as fixed income instruments. The data processing system provides a highly structured trading protocol implemented through a sequence of trading paradigms. The system employs a distributed computer processing network linking together a plurality of commonly configured program controlled workstations. The protocol and its program controlling logic enhances trading efficiency, rewards market Makers, and fairly distributes market opportunity to system users.
Owner:CANTOR FITZGERALD LP +1
Pointing systems for addressing objects
InactiveUS20020140745A1Quickly availableNavigational calculation instrumentsDigital data processing detailsHand heldHand held devices
Systems are arranged to provide a user information which relates to objects of interest. A user may point a hand held device toward an object to address it. The device determines which objects are being addressed by making position and attitude measurements and further a reference and search of a database containing preprogrammed information relating to objects. Information relating to objects determined as objects presently being addressed is thereafter presented at a user interface. Devices of these systems include a point reference, a direction reference, a position determining support, attitude determining support, a computer processor and database, and a user interface. Methods of systems include the steps of addressing an object, determining position and attitude, searching a database, and presenting information to a user.
Owner:GEOVECTOR
Robotic extraction cleaner with dusting pad
An vacuum cleaning robot has a drive system adapted to autonomously move a base housing along a horizontal surface and is controlled by a computer processing unit. A dusting assembly is mounted to the base housing and is adapted to selectively rest on a surface to be cleaned. A suction source draws dirt and debris through a suction nozzle and deposits the same in the recovery tank. A power source is connected to the drive system and to the computer processing unit. The computer processing unit is adapted to direct horizontal movement of the base housing within boundaries of the surface to be cleaned based upon input data defining said boundaries.
Owner:BISSELL INC
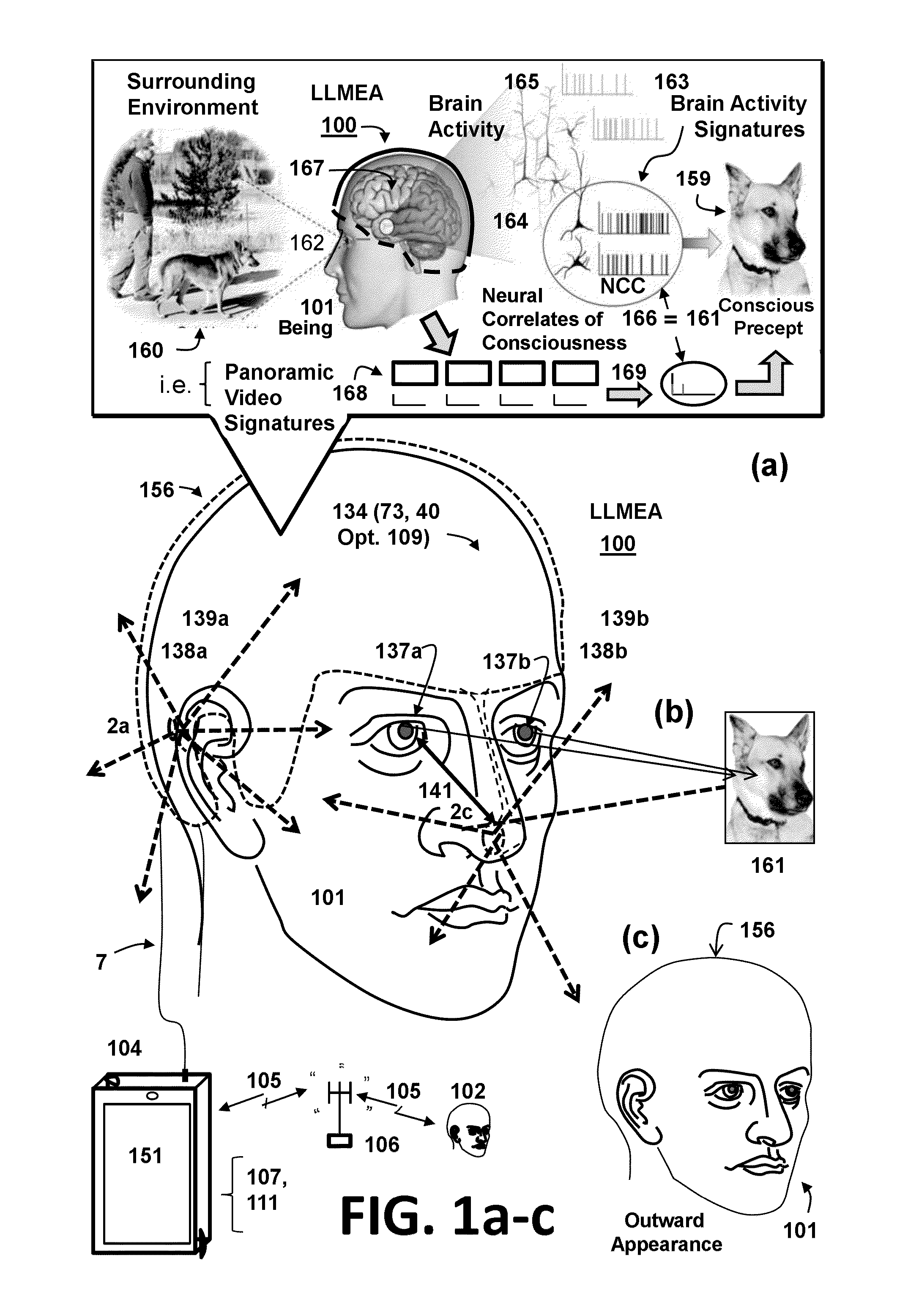
Mobile user borne brain activity data and surrounding environment data correlation system
ActiveUS9101279B2High resolutionEasy to navigateTelevision system detailsBioelectric signal measurementActivity sensingHuman–computer interaction
A mobile user borne brain activity data and surrounding environment data correlation system comprising a brain activity sensing subsystem, a recording subsystem, a measurement computer subsystem, a user sensing subsystem, a surrounding environment sensing subsystem, a correlation subsystem, a user portable electronic device, a non-transitory computer readable medium, and a computer processing device. The mobile user borne system collects and records brain activity data and surrounding environment data and statistically correlates and processes the data for communicating the data into a recipient biological, mechanical, or bio-mechanical system.
Owner:VIRTUAL VIDEO BY RITCHEY LLC
Mapping defects or dirt dynamically affecting an image acquisition device
Defects such as dirt, dust, scratches, blemishes, pits, or defective elements or pixels in a CCD, scanner, photocopier, or image acquiring device are dynamically detected by processing a plurality of images via a computer. A pristine object of calibration is not required. Stationary components of the video images are found and detected so as to produce a low false alarm probability. Text segmentation and measurement of total deviation based on variability related to high-frequency components of the video image are employed to prevent applying the process or method to printed text or graphics. Additional techniques optionally employed are median filtering, sample area detection, and dynamic adjustment of scores. In special cases, only moderately blank documents are used. The dynamic defect detection allows defect compensation, defect correction, and alerting the operator of defects.
Owner:FOTONATION LTD
Locking and unlocking mechanism for controlling concurrent access to objects
InactiveUS6247025B1Data processing applicationsDigital data information retrievalNormal caseSpin locks
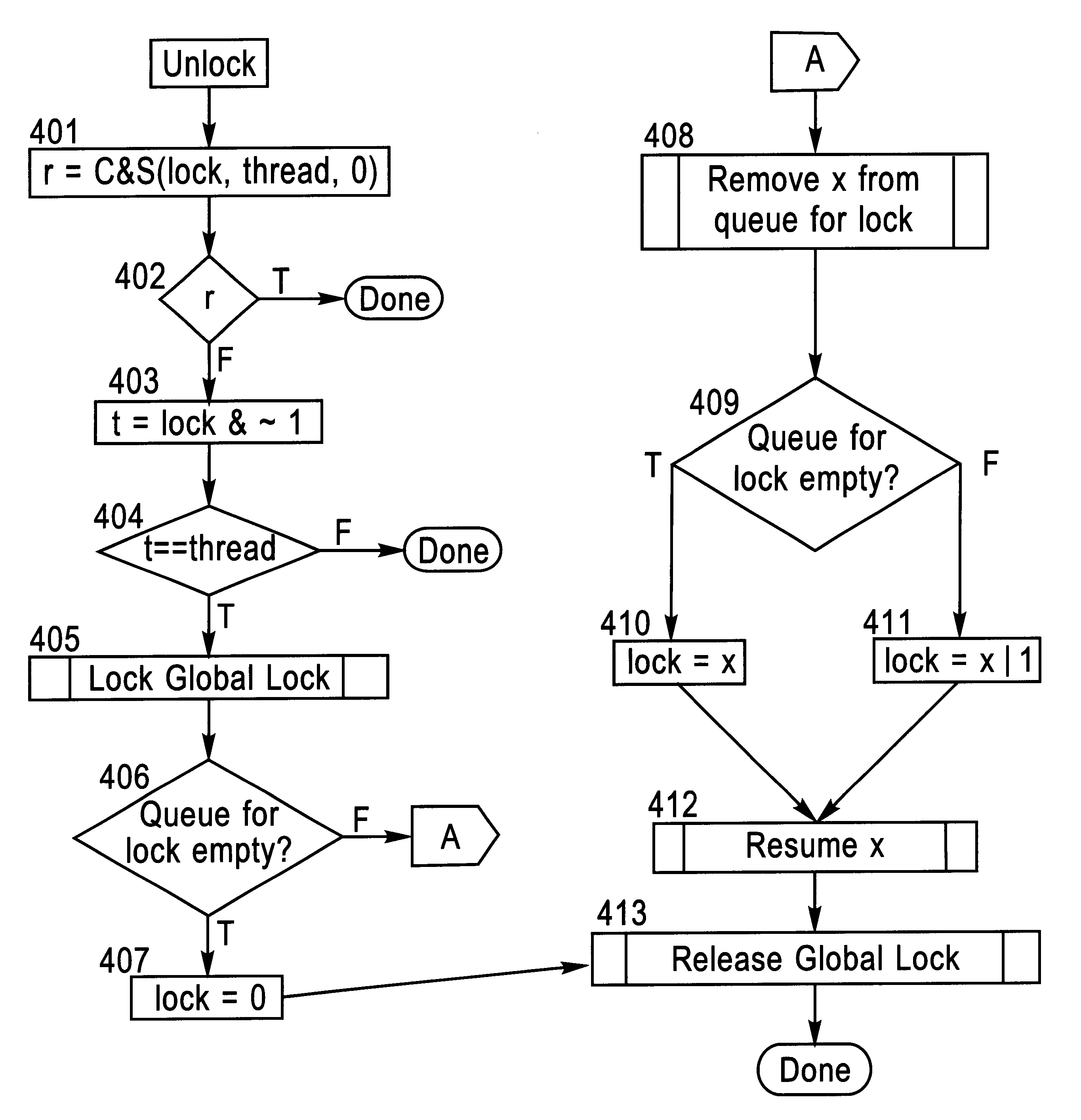
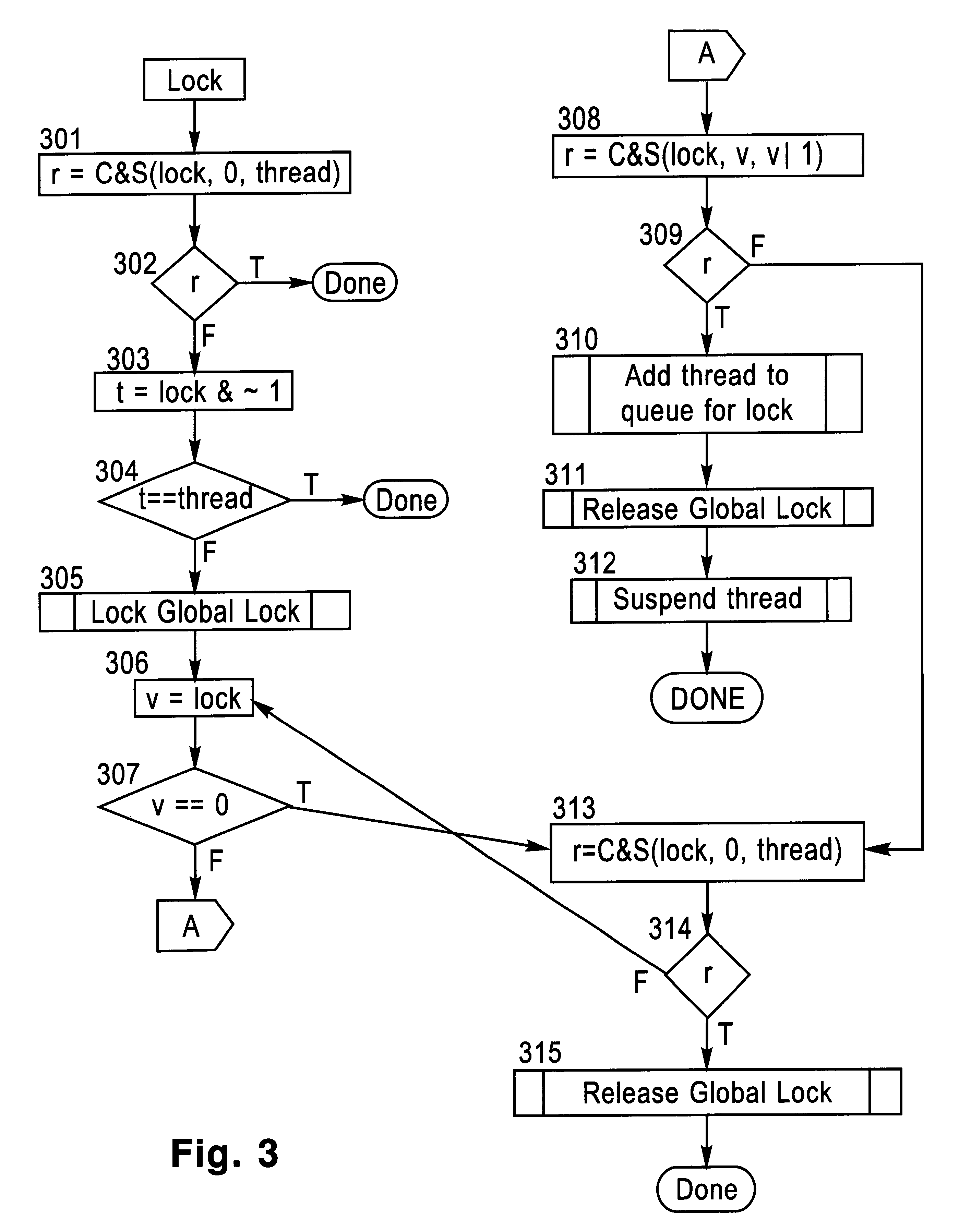
A lock / unlock mechanism to control concurrent access to objects in a multi-threaded computer processing system comprises two parts: a thread pointer (or thread identifier), and a one-bit flag called a "Bacon bit". Preferably, when an object is not locked (i.e., no thread has been granted access to the object), the thread identifier and Bacon bit are set to 0. When an object is locked by a particular thread (i.e., the thread has been granted access to the object), the thread identifier is set to a value that identifies the particular thread; if no other threads are waiting to lock the object, the Bacon bit is set to 0; however, if other threads are waiting to lock the object, the Bacon bit is set to "1', which indicates the there is a queue of waiting threads associated with the object. To lock an object, a single CompareAndSwap operation is preferably used, much like with spin-locks; if the lock is already held by another thread, enqueueing is handled in out-of-line code. To unlock an object, in the normal case, a single CompareAndSwap operation may be used. This single operation atomically tests that the current thread owns the lock, and that no other threads are waiting for the object (i.e., the Bacon bit is "0'). A global lock is preferably used to change the Bacon bit of the lock. This provides an lock / unlock mechanism which combines many of the desirable features of both spin locking and queued locking, and can be used as the basis for a very fast implementation of the synchronization facilities of the Java language.
Owner:IBM CORP
System and method for providing secure reception and viewing of transmitted data over a network
InactiveUS20110113231A1Memory loss protectionError detection/correctionComputer networkEmail attachment
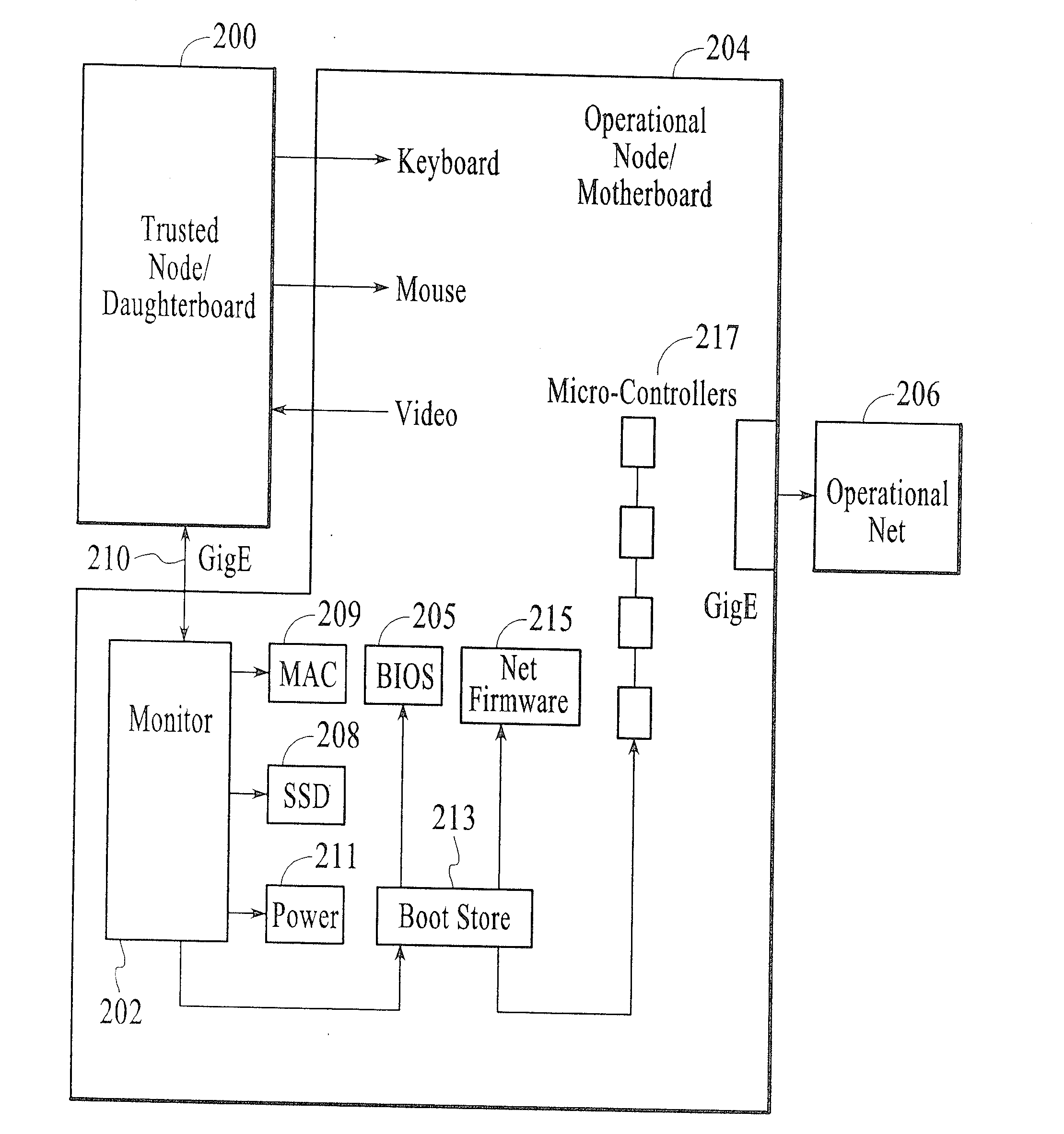
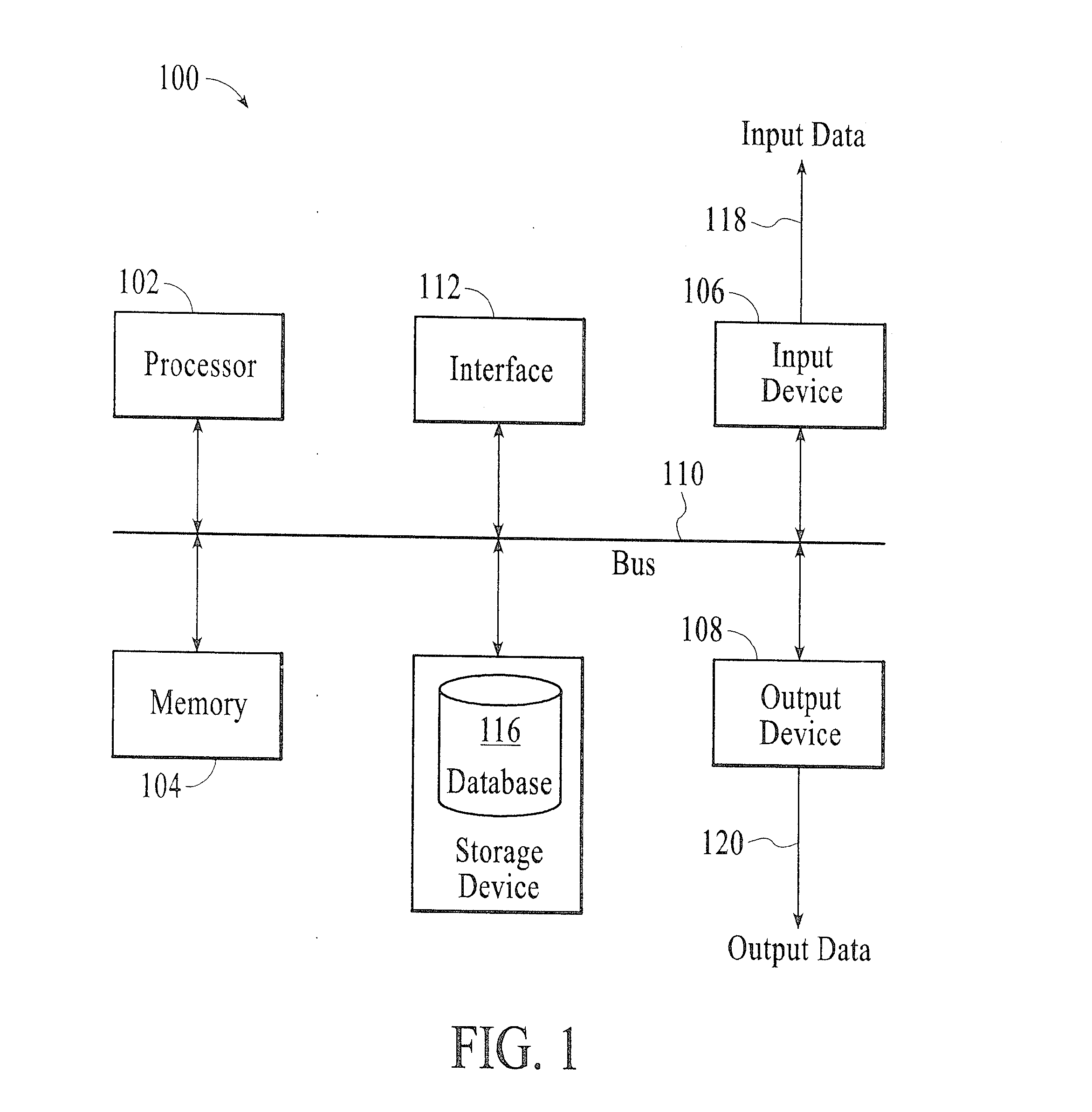
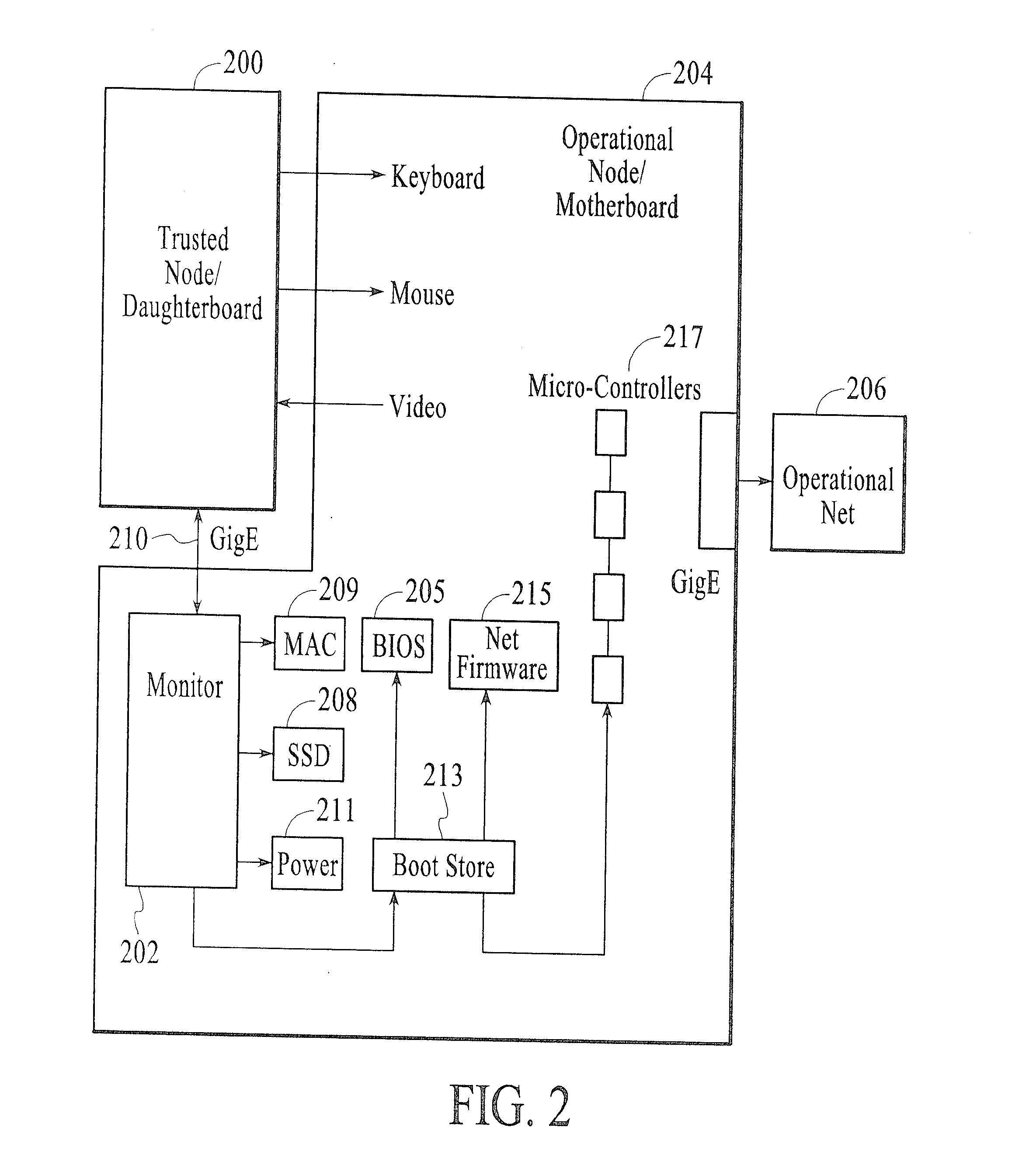
A method and system for securely opening an e-mail attachment in a computer processing environment having a trusted node daughterboard connected to at least one operational node motherboard with an e-mail processing system operatively coupled to the trusted node daughterboard. The method includes the steps of when an e-mail attachment is to be opened, sending a power on signal from the trusted node daughterboard to the operational node motherboard when it is desired to utilize the operational node motherboard for opening an e-mail attachment. Pre-boot data is then requested from the operational node motherboard and is sent from the trusted node daughterboard to the operational node motherboard to enable operation of the operational node motherboard for securely opening an e-mail attachment.
Owner:KAMINSKY DANIEL
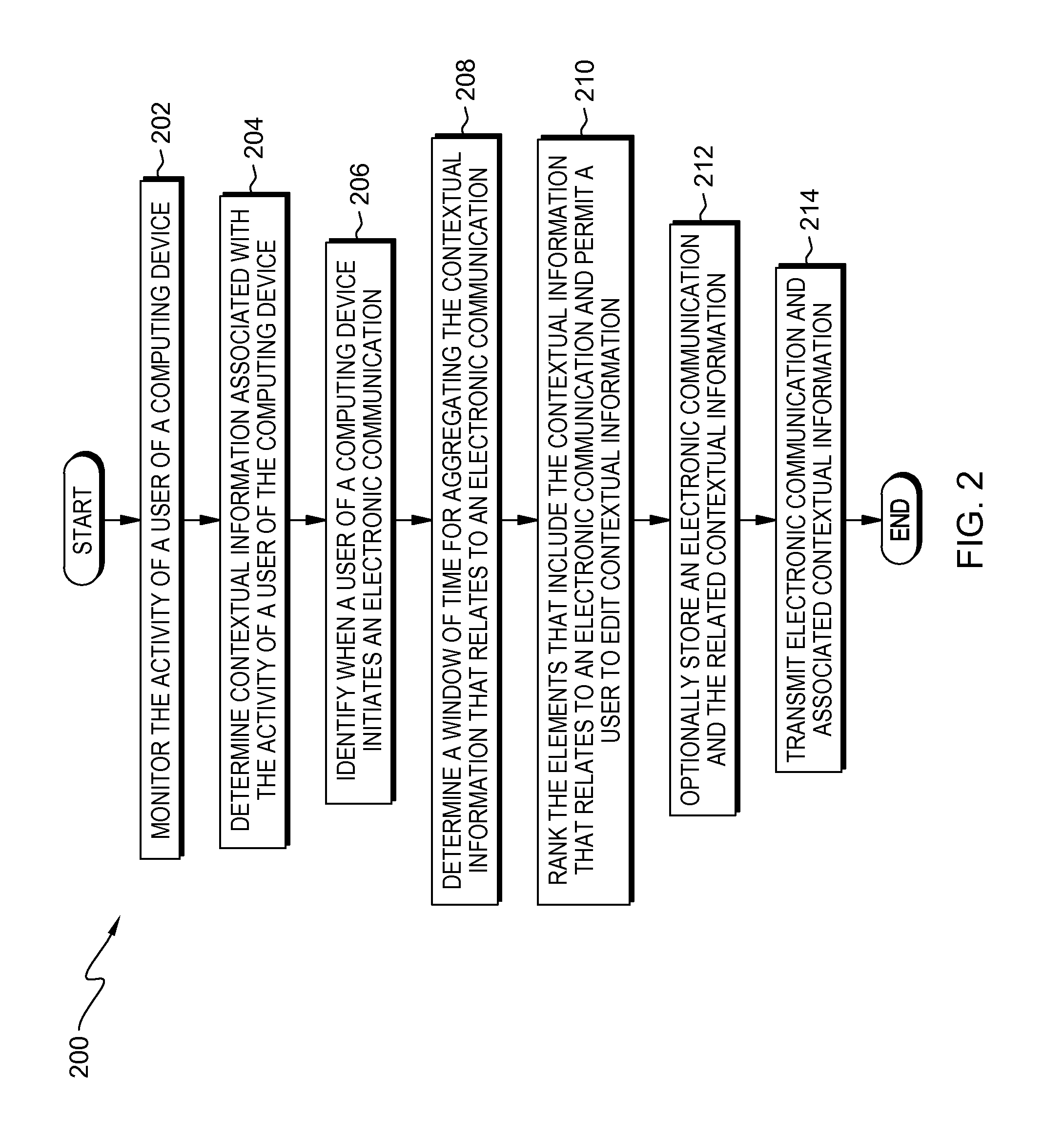
Associating contextual information with electronic communications
InactiveUS20170006094A1Memory architecture accessing/allocationUnauthorized memory use protectionElectronic communicationComputer science
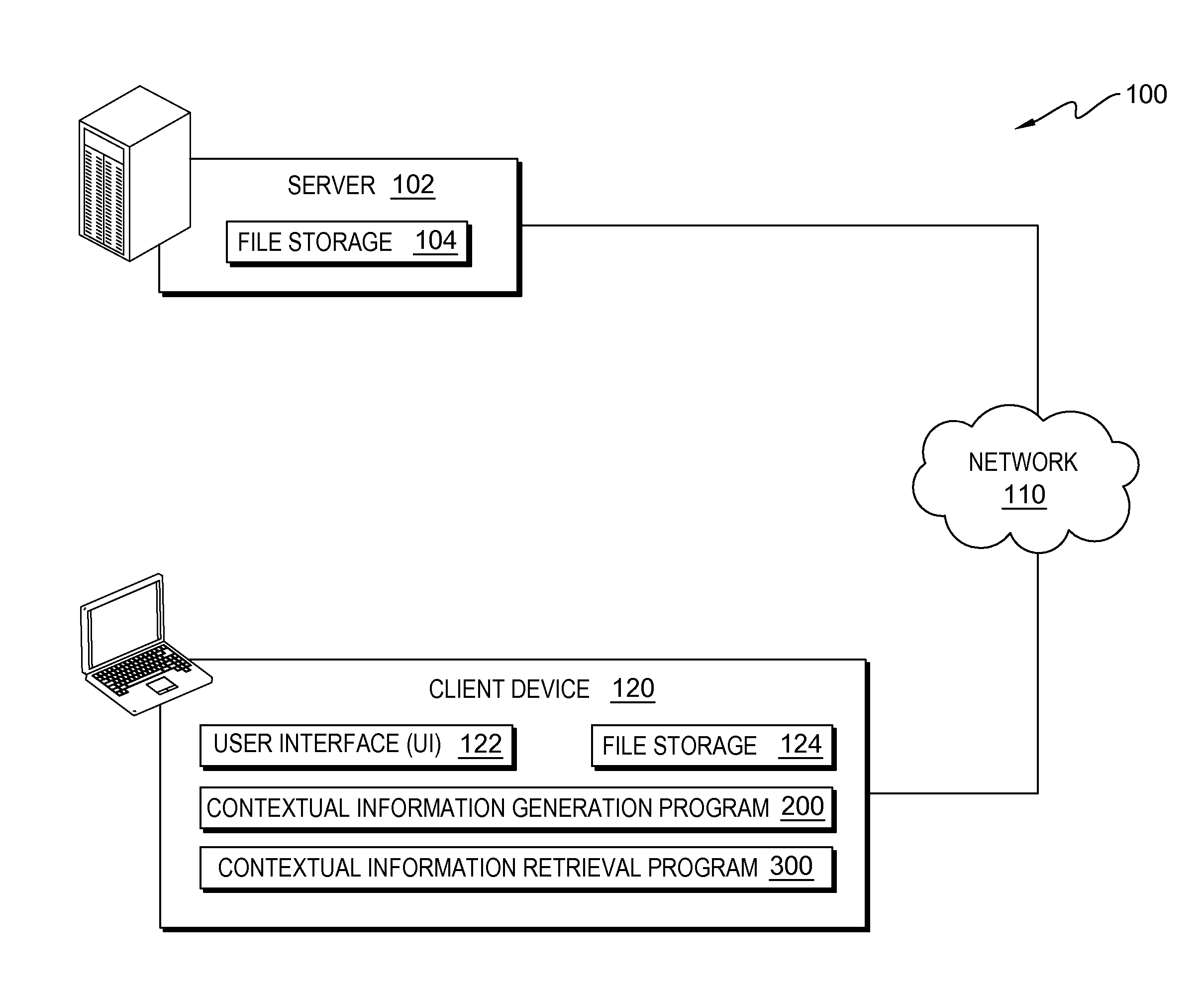
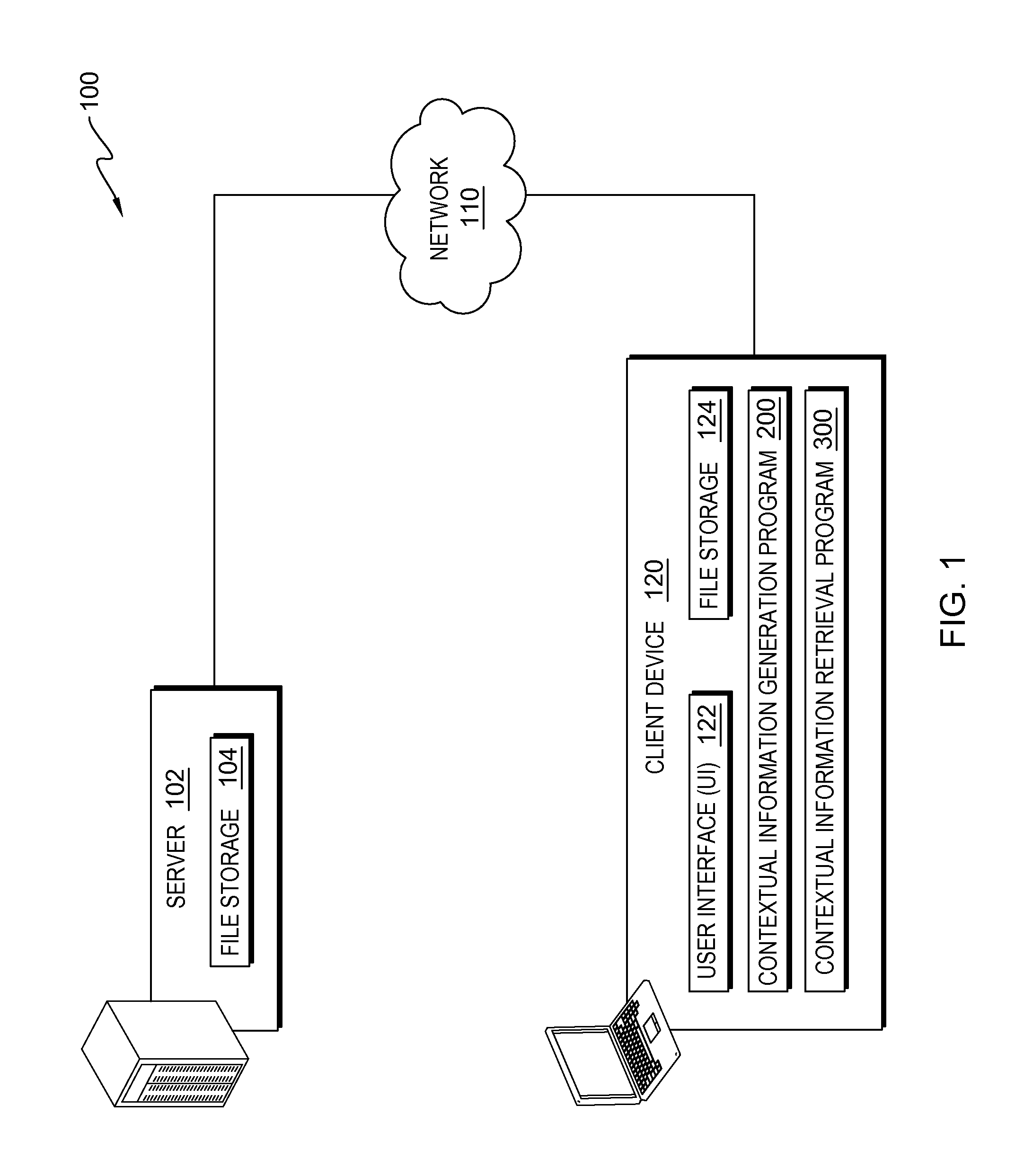
A method for associating contextual information with an electronic communication. The method includes a computer processor monitoring one or more activities of a user of a computing device, and determining contextual information respectively associated with the one or more monitored activities of the user, wherein contextual information includes information describing the one or more monitored activities. The method further includes identifying the user initiating an electronic communication and a time that the user of the computing device initiates the electronic communication. The method further includes determining at least one of the one or more monitored activities that occur within a window of time, relative to the time that the user of the computing device initiates the electronic communication, and storing the contextual information respectively associated with the at least one of the one or more monitored activities that occurred within the window of time in association with the electronic communication.
Owner:IBM CORP
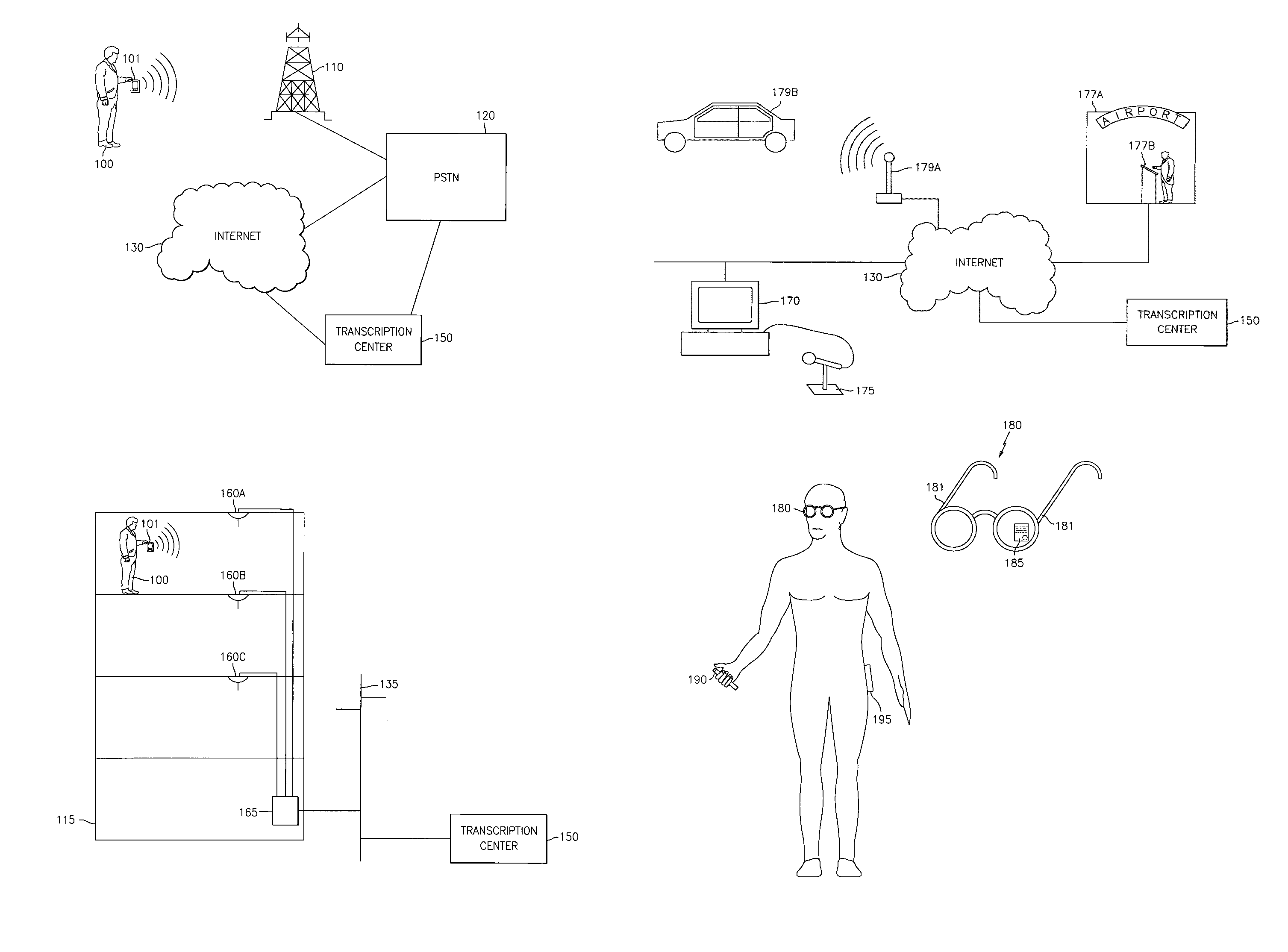
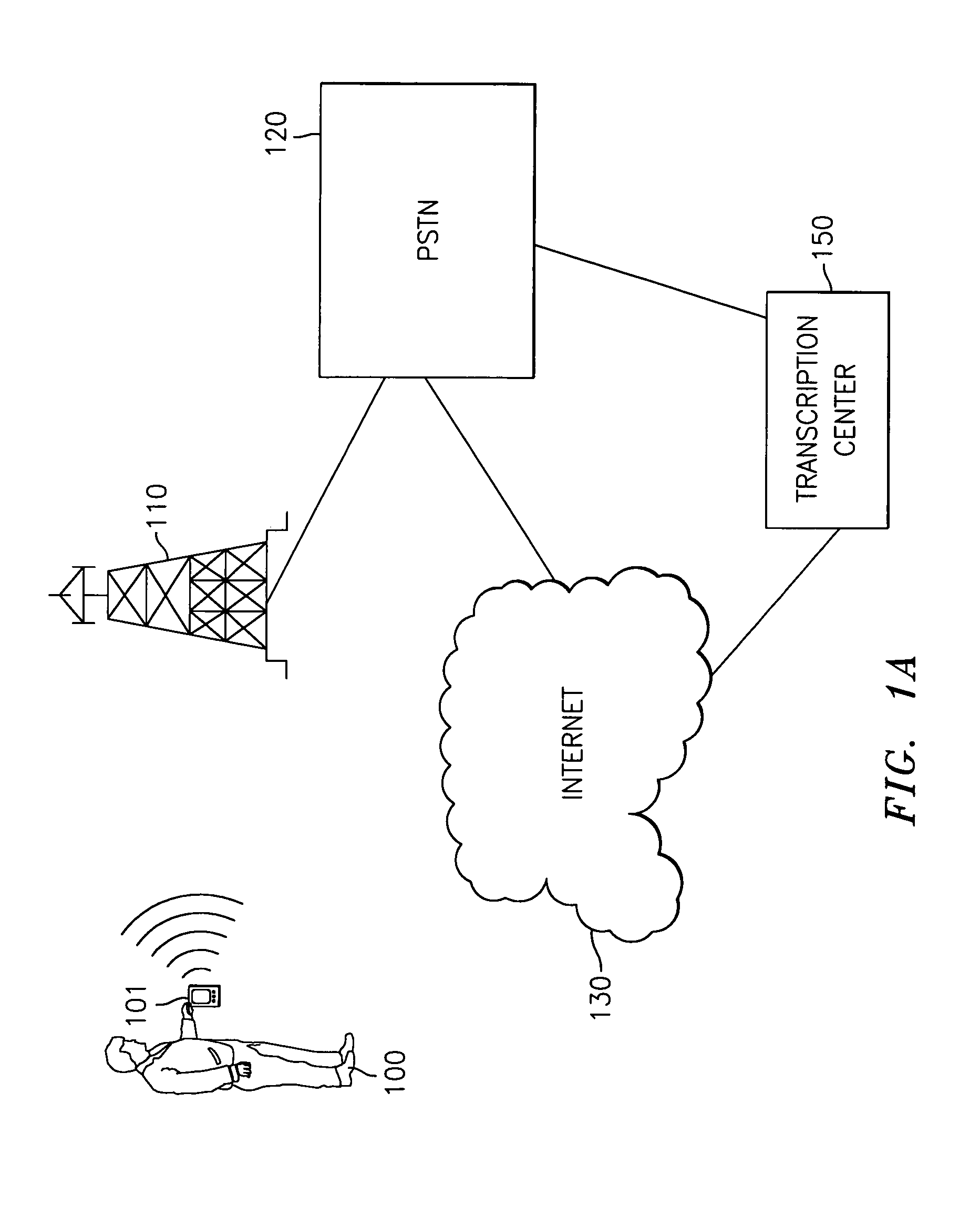
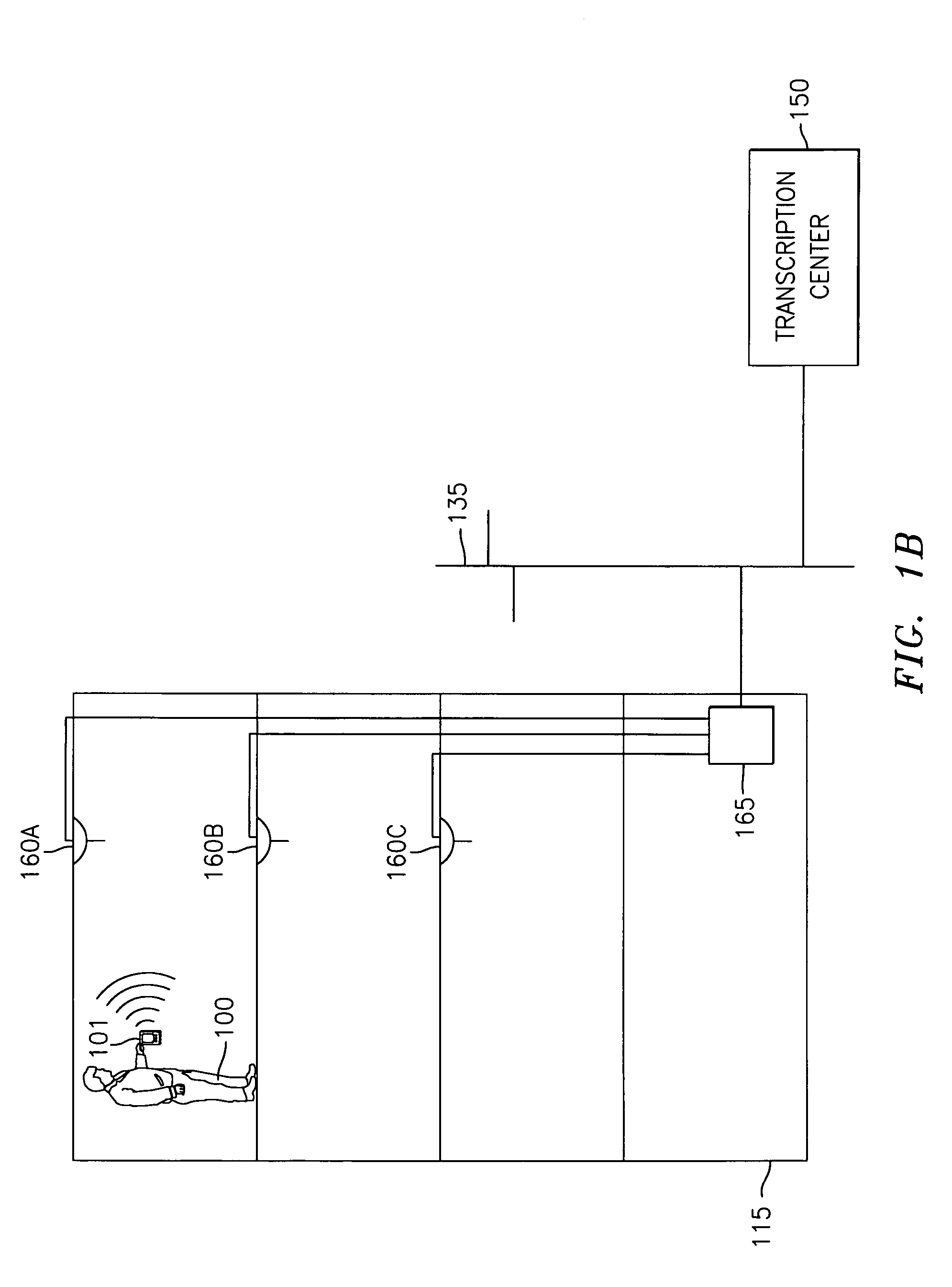
Real-time remote transcription or translation service
InactiveUS6980953B1Cost-effectiveCost-effective to serviceNatural language translationSpeech recognitionComputer networkTranslation service
A system and method is provided for real time transcription or translation services. In one aspect of the system and method, a user requests transcription / translation service with certain service parameters. It is determined what resources can be used for such service, and, if all the service parameters can be met, the service is performed. Resources include live stenographers or translators, and computer processing power. If all the service parameters can not be met, it is determined whether to perform the service by meeting only some of the service parameters. These determinations may be programmed into the system beforehand. In another aspect of the system and method, a user makes a request for transcription / translation service, and the request is displayed so that stenographers or translators may make bids to perform the transcription / translation service. In some embodiments, the request is only displayed to those stenographers or translators who are determined to be able to perform the service. Bids are received and stored. The user chooses whether or not to accept a bid.
Owner:NUANCE COMM INC
Systems and methods for providing data privacy in a private distributed ledger
ActiveUS20170289111A1Multiple keys/algorithms usageUser identity/authority verificationData bankDistributed ledger
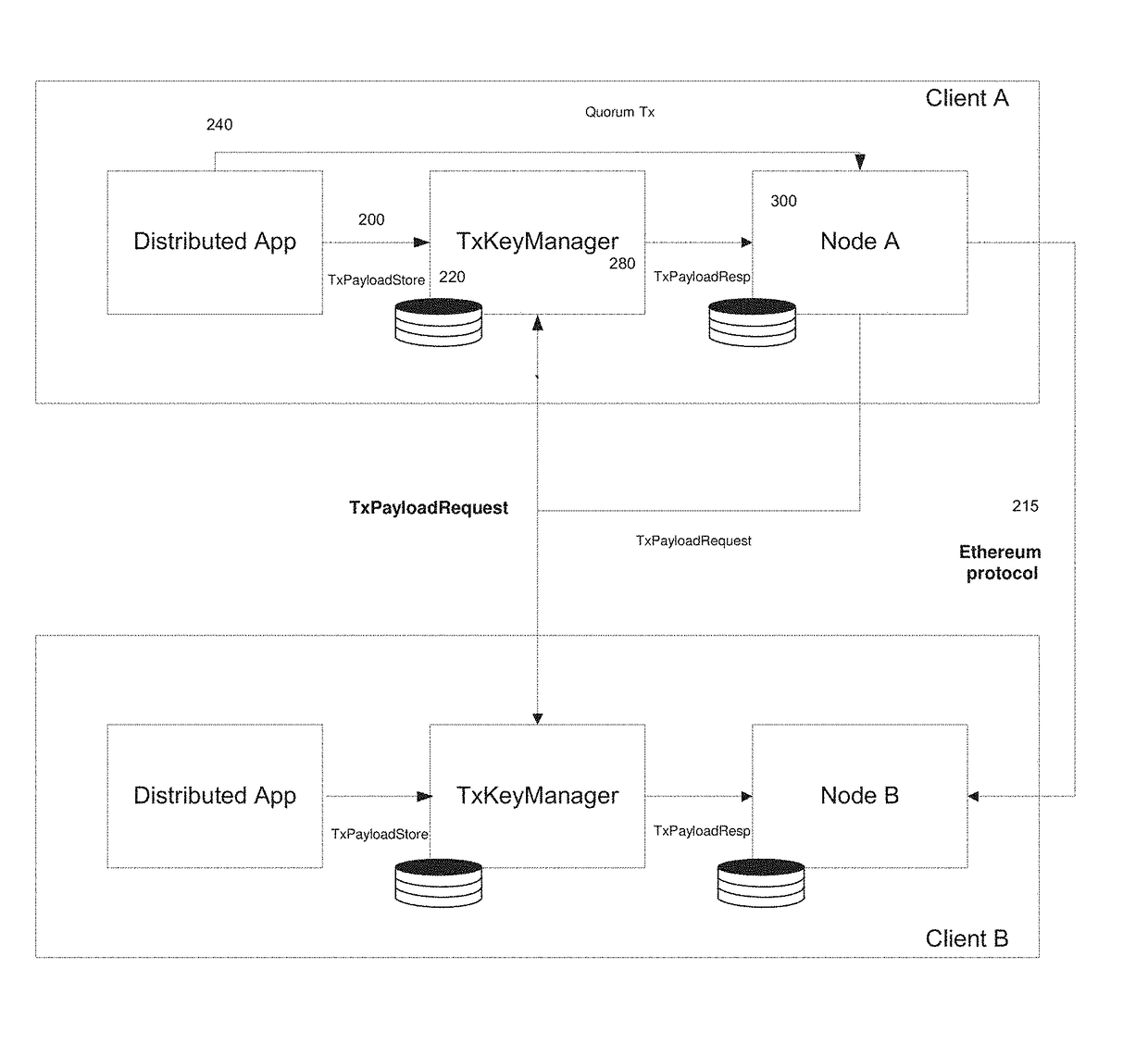
Systems and methods for providing data privacy in a private distributed ledger are disclosed. According to another embodiment a distributed ledger network may include a first node comprising a first node computer processor and hosting a central ledger comprising a plurality of entries for public transactions and private transactions, wherein the entries for public transactions comprise transaction payloads for the respective public transaction, and the entries for private transactions comprise a cryptographic hash digest of a transaction payload for the respective private transaction; and a plurality of second nodes each comprising a second node computer processor and hosting a public database comprising the public transactions, and a private database comprising transaction payloads for the private transactions to which the node is a party.
Owner:CONSENSYS SOFTWARE INC
System and method of interfacing co-processors and input/output devices via a main memory system
ActiveUS20120204079A1Memory architecture accessing/allocationError detection/correctionComputer moduleMemory bus
A system for interfacing with a co-processor or input / output device is disclosed. According to one embodiment, the system includes a computer processing unit, a memory module, a memory bus that connects the computer processing unit and the memory module, and a co-processing unit or input / output device, wherein the memory bus also connects the co-processing unit or input / output device to the computer processing unit.
Owner:RAMBUS INC
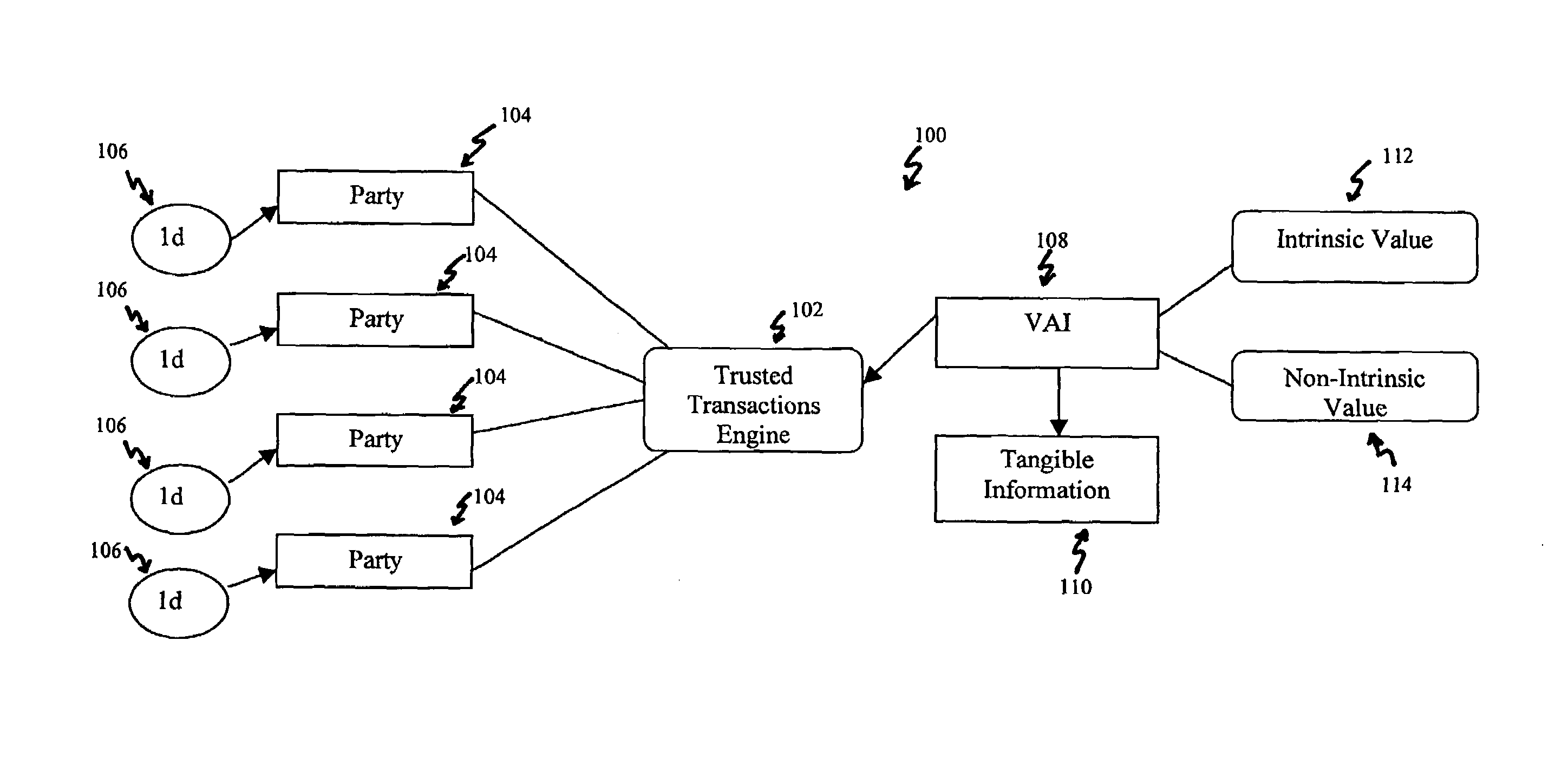
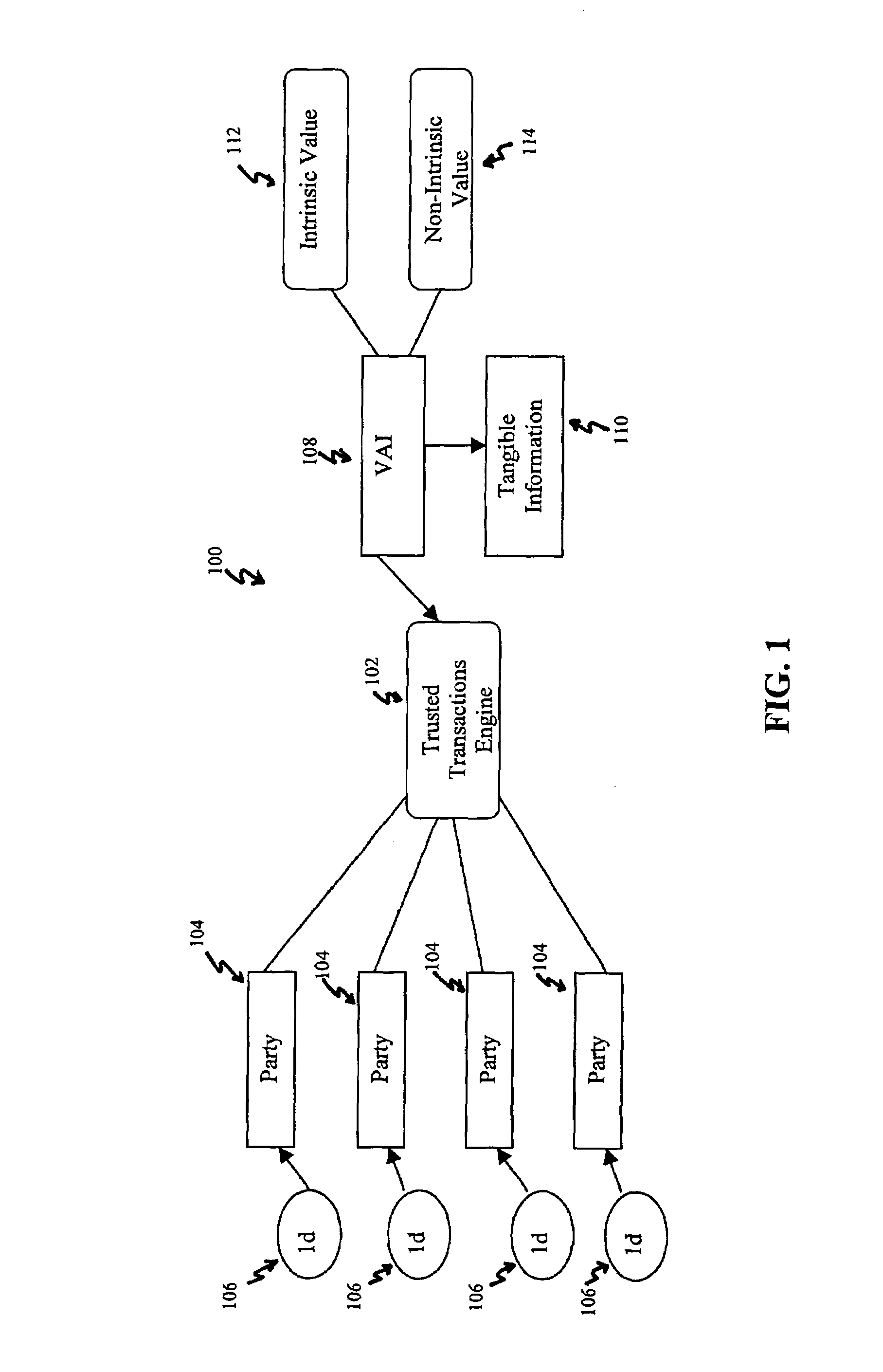
Systems, methods and devices for trusted transactions
InactiveUS7159116B2Convenient transactionLittle processing resourceMultiple keys/algorithms usagePublic key for secure communicationThe InternetSubject matter
The invention discloses a system for enhancing trust in transactions, most particularly in remote transactions between a plurality of transactional parties, for instance a seller and buyer(s) of goods and / or services over a public computer network such as the internet. Trust is disclosed to be a multivalent commodity, in that the trust that is to be enhanced relates to information about the subject matter of the transactions (e.g., the suitability of the goods and services sold), the bona fides of the supplier of the goods and services, the appropriateness of a pricing structure for a particular transaction or series of transactions, a quantum of additional transactional value that may be imparted to the transactional relationship, security of information exchange, etc. An important contributor to trust for such aspects of the transaction is disclosed to be the use of highly-secure steganographic computer processing means for data identification, authentication, and transmission, such that confidence in the transaction components is enhanced. By providing an integrated multivalent system for enhancing trust across a variety of categories (for a variety of transaction species, including those in which the need for trust is greater on the part of one party than of another, as well as those in which both require substantial trust enhancement), the invention reduces barriers to forming and optimizing transactional relationships.
Owner:WISTARIA TRADING INC
Associating electronic documents, and apparatus, methods and software relating to such activities
InactiveUS20050188306A1Other printing matterDigital data processing detailsElectronic documentEngineering
A method of associating a first electronic document with a second electronic document comprising having a first physical paper identifier (130) having pen-readable coding (12) which codes for an identifier for the first electronic document, and reading the coding of the first electronic document with a pen (20) to acquire information enabling the identity of the first electronic document to be established, and communicating that identity to a computer processor (107), and using the processor (107) to associate the identified first electronic document with the second electronic document.
Owner:HEWLETT PACKARD DEV CO LP
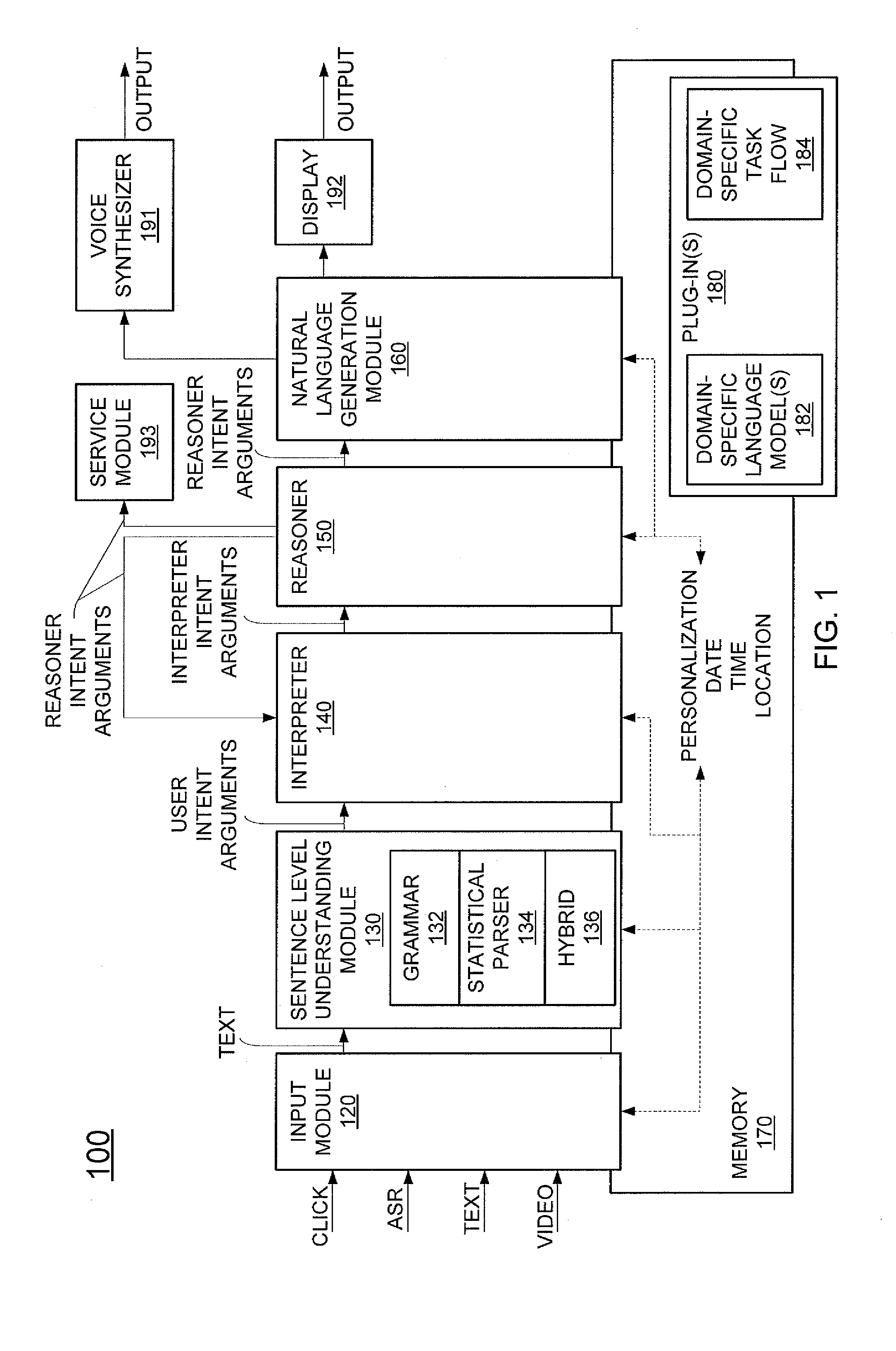
Generic virtual personal assistant platform
ActiveUS9082402B2Natural language translationMultiprogramming arrangementsLanguage understandingA domain
A method for assisting a user with one or more desired tasks is disclosed. For example, an executable, generic language understanding module and an executable, generic task reasoning module are provided for execution in the computer processing system. A set of run-time specifications is provided to the generic language understanding module and the generic task reasoning module, comprising one or more models specific to a domain. A language input is then received from a user, an intention of the user is determined with respect to one or more desired tasks, and the user is assisted with the one or more desired tasks, in accordance with the intention of the user.
Owner:SRI INTERNATIONAL
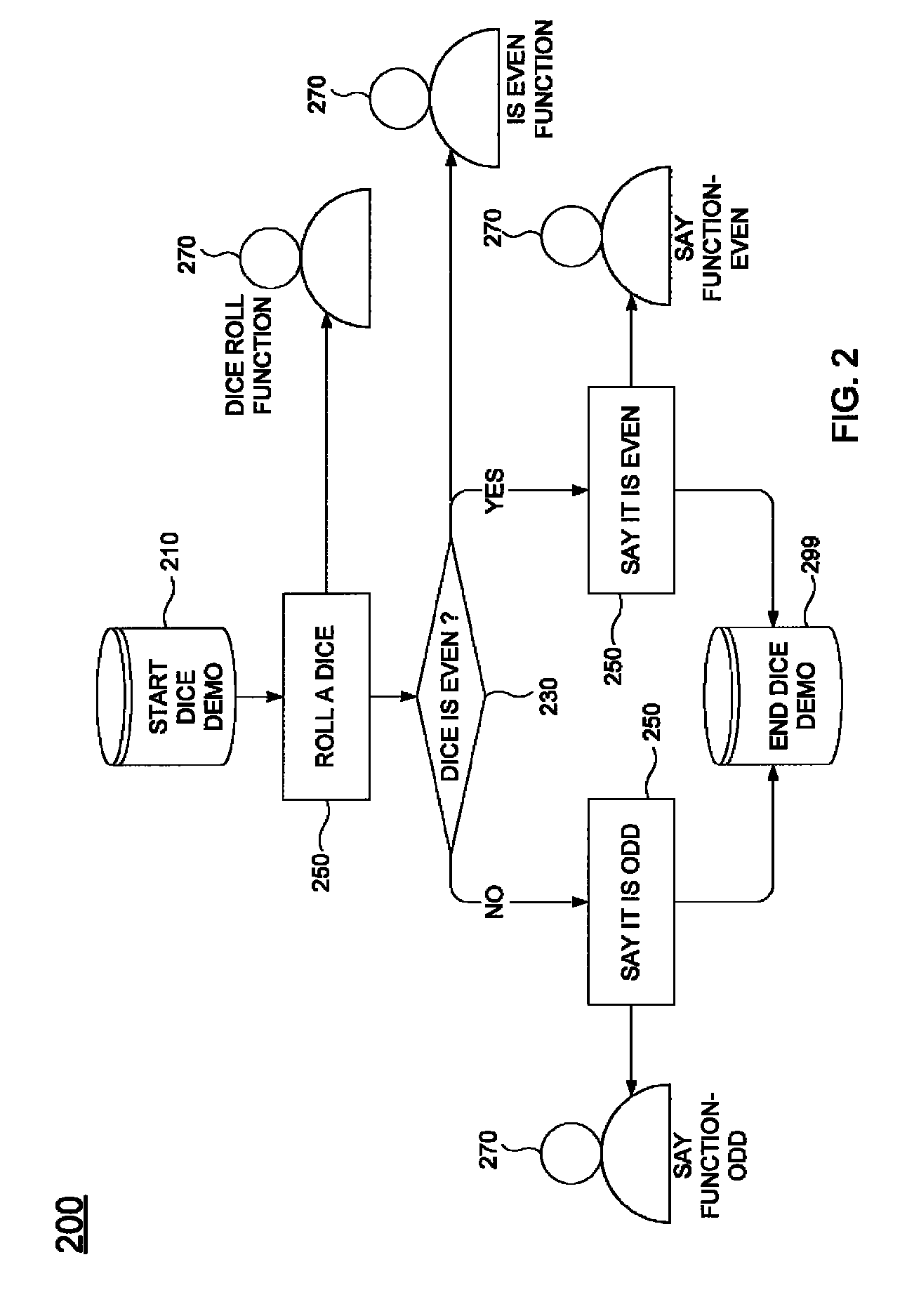
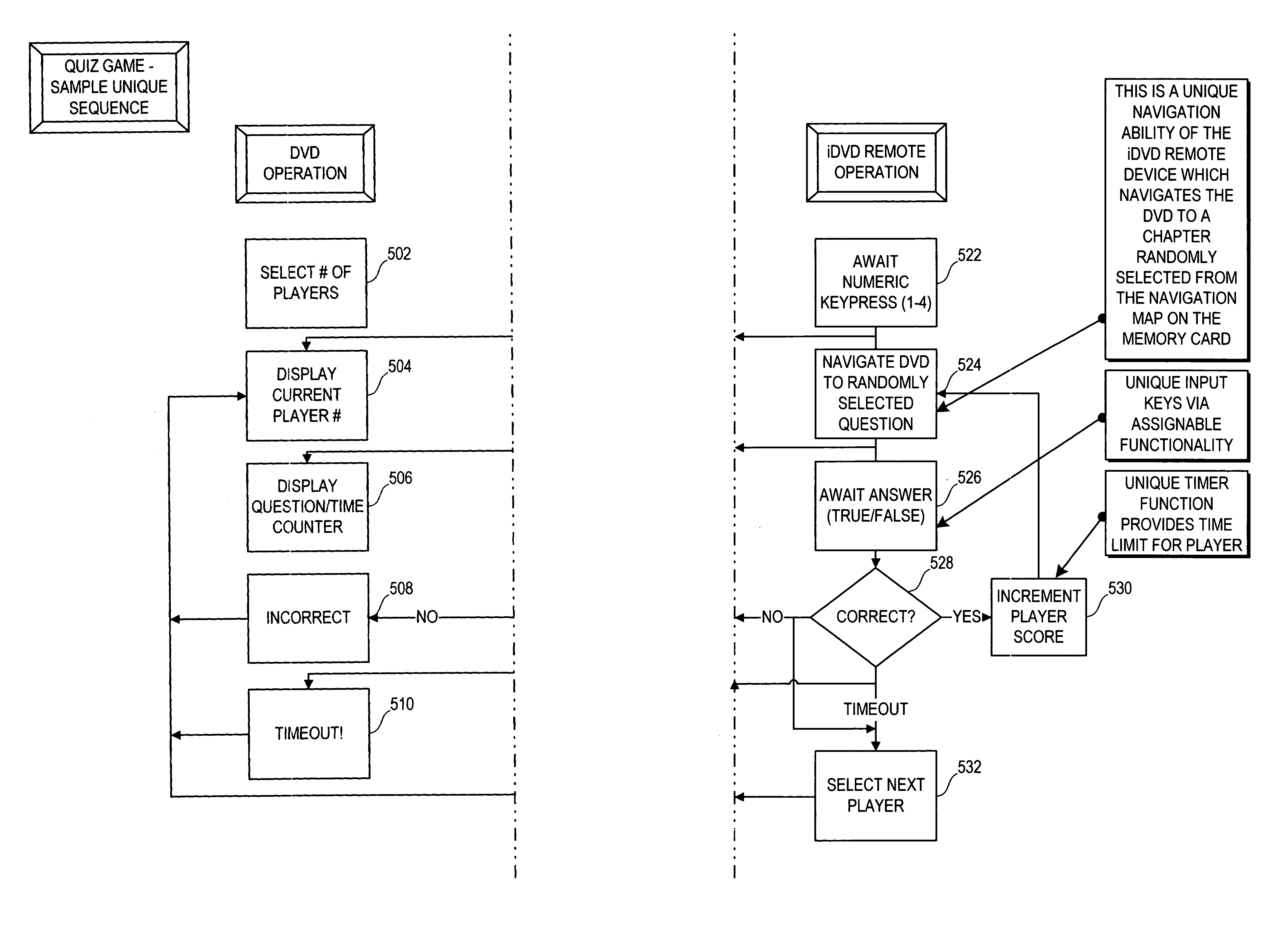
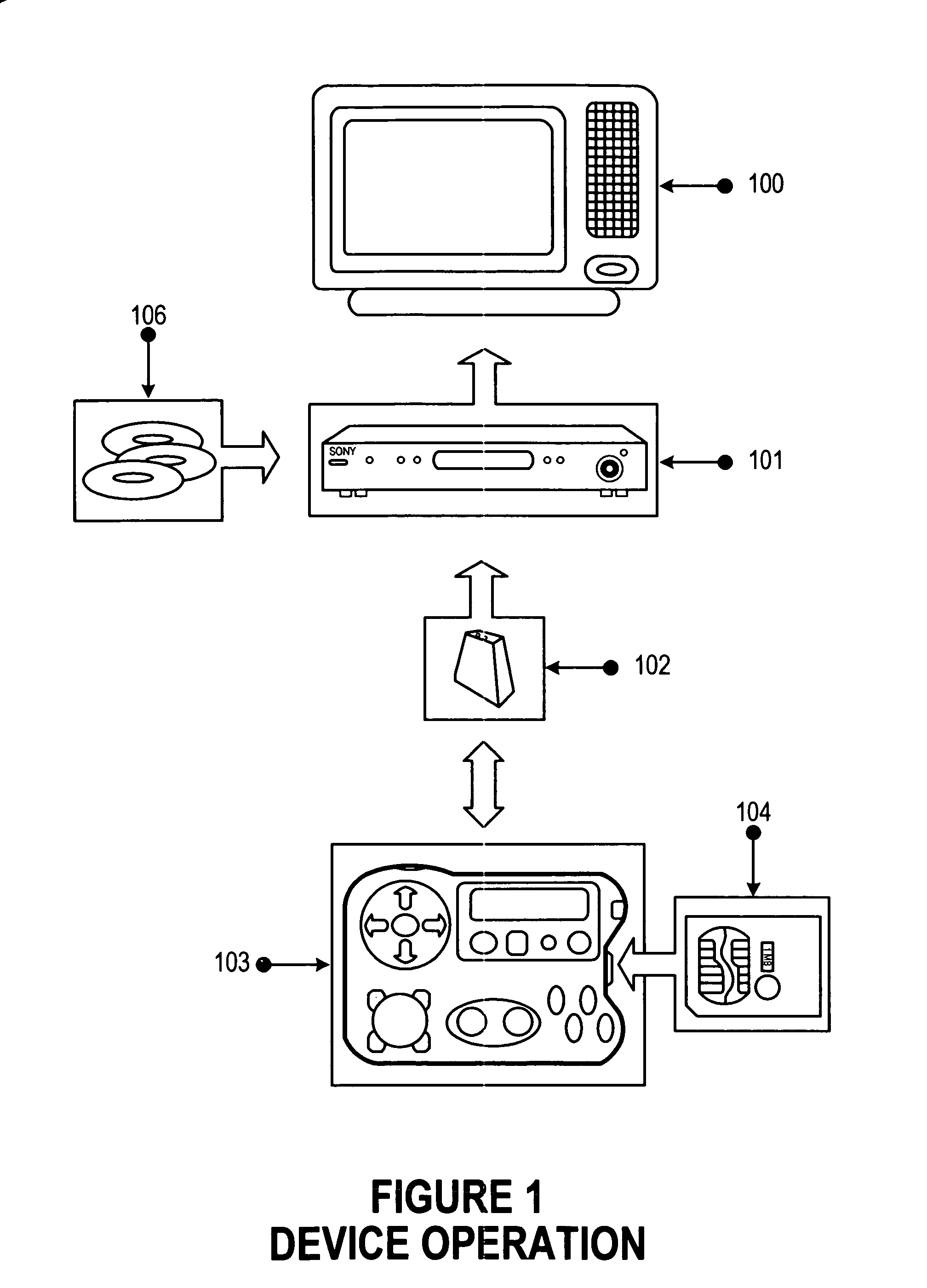
Remote control for providing interactive DVD navigation based on user response
InactiveUS7003598B2Improve the level ofTelevision system detailsDigital data processing detailsDigital videoComputer graphics (images)
A game control unit includes a computer processor for executing game logic stored on a removable memory device. Rich, audiovisual content for the interactive gaming experience is provided on a digital video disk (DVD) in small clips which are selectively played back in a standard DVD player under control of the game control unit. Specifically, the game control unit mimics standard remote control signals to control playback of the audiovisual content by the DVD player.
Owner:BRIGHT ENTERTAINMENT
Systems and methods for a disaster recovery system utilizing virtual machines running on at least two host computers in physically different locations
ActiveUS20060085792A1Minimal disruptionError detection/correctionMultiprogramming arrangementsTelecommunications linkCommunication link
The present invention is directed to systems and methods for providing disaster recovery services using virtual machines. The invention provides an inexpensive and minimally intrusive way to provide disaster recovery services including recovery of the state of computer processors and devices. The system includes a production host and a backup host that communicate via a communications link. The state of the processor and devices on the production host are periodically stored onto backup host and can be restored in the event of an emergency. Additionally, the invention includes two business methods for utilizing the system and methods for providing disaster recovery services.
Owner:MICROSOFT TECH LICENSING LLC
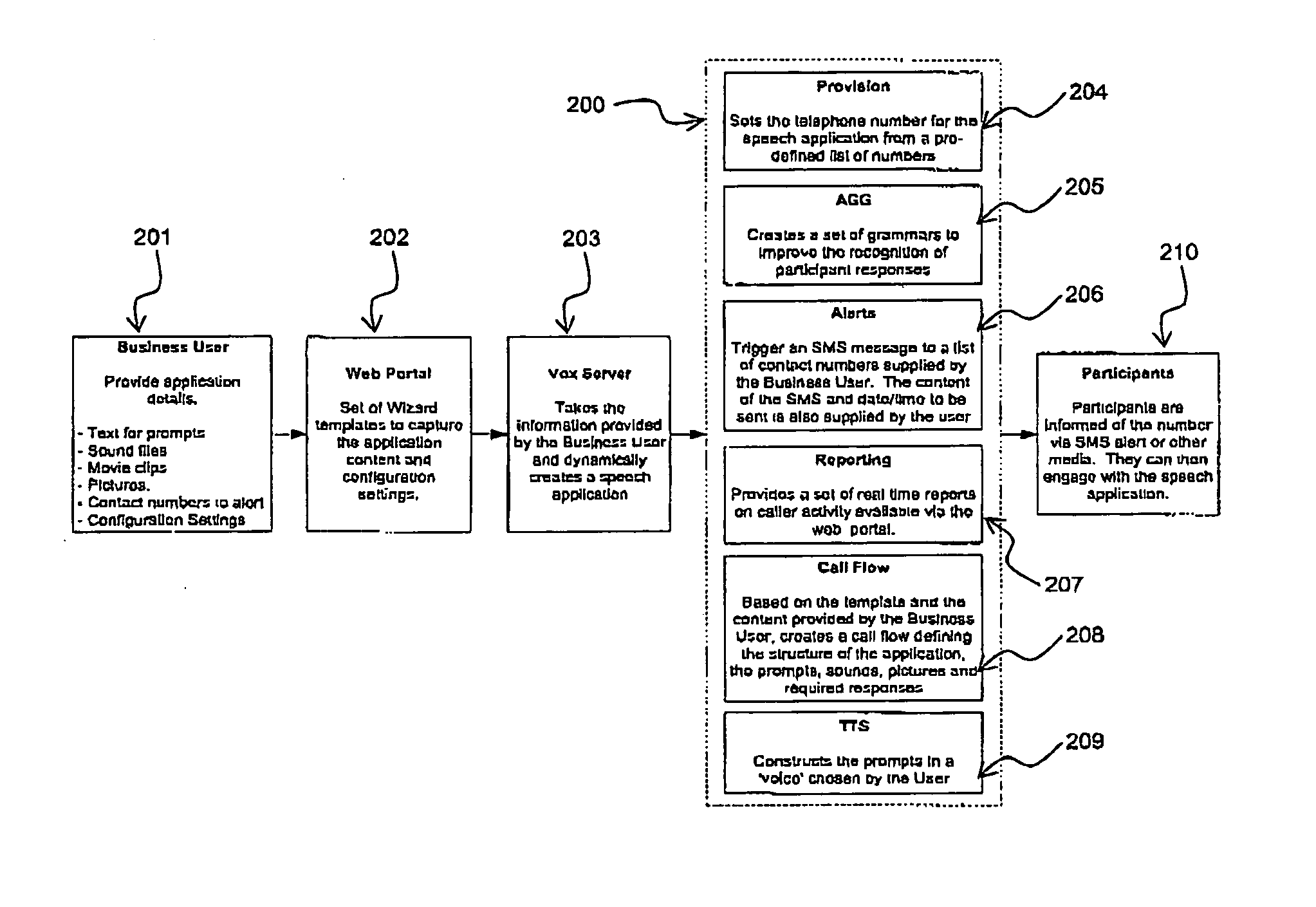
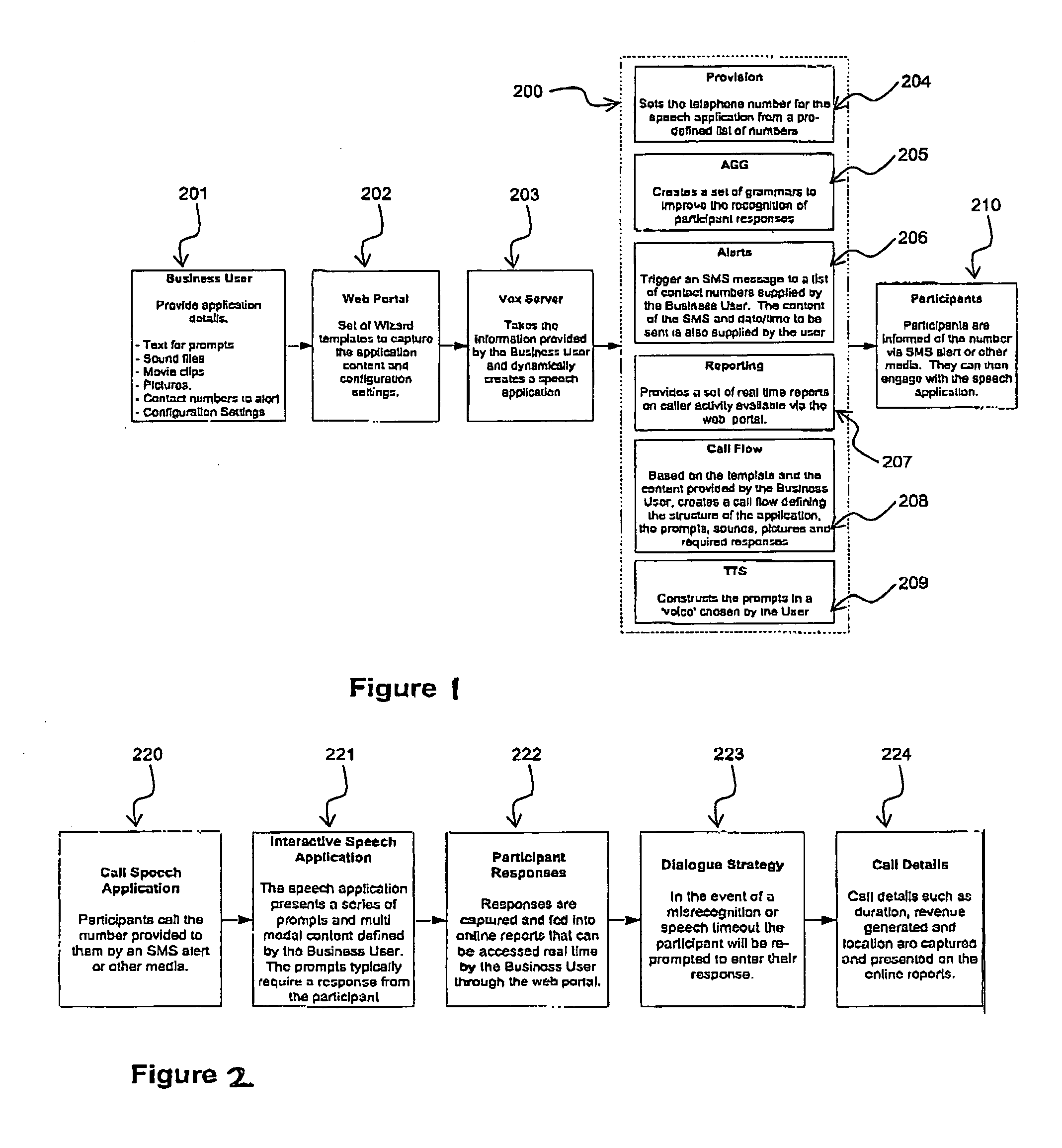
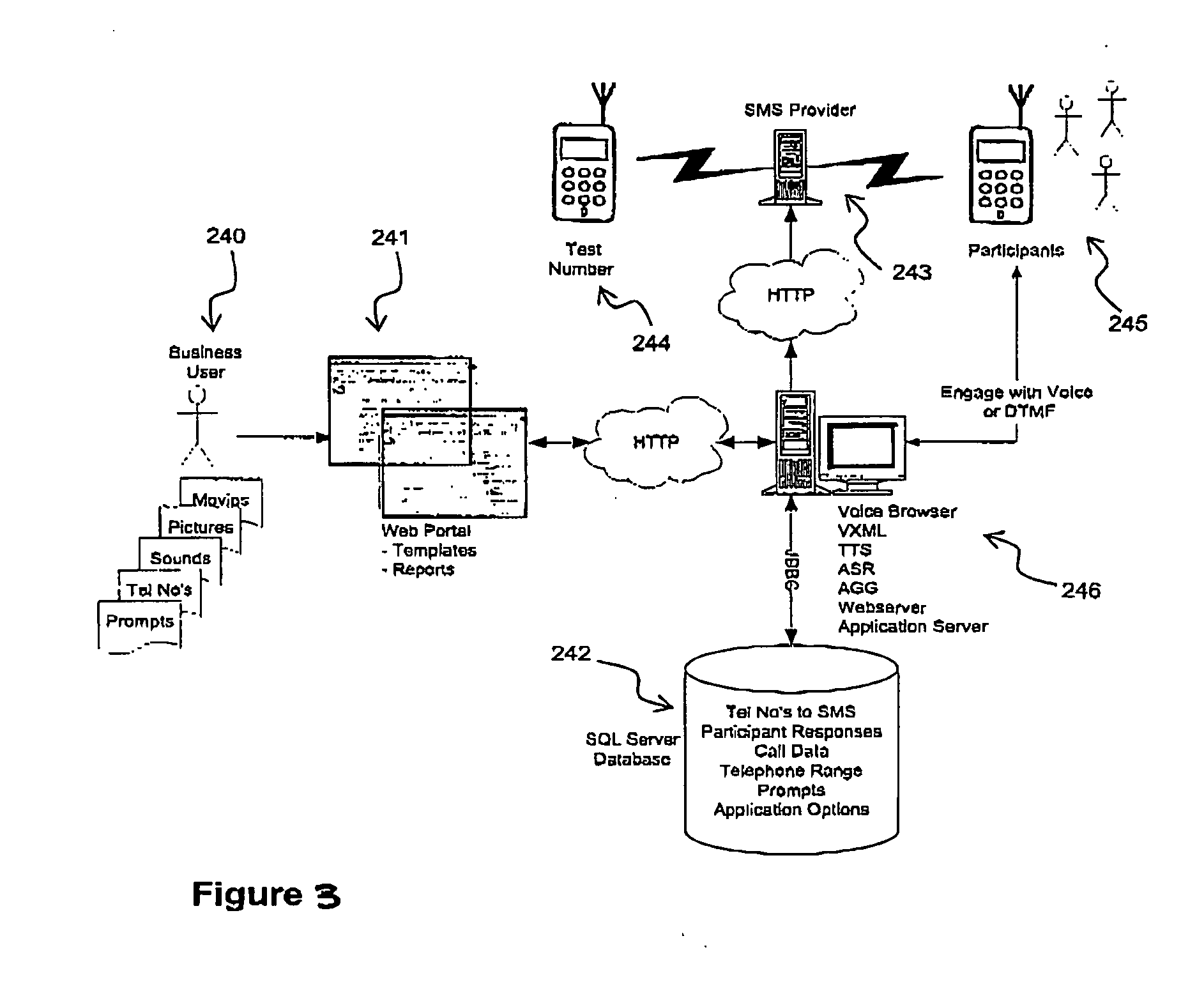
Automated speech-enabled application creation method and apparatus
InactiveUS20050125232A1Easy to useConstrain complexitySpeech recognitionMarketingSpeech soundEmbedded system
A system for creating and hosting speech-enabled applications having a speech interface that can be customised by a user is disclosed. The system comprises a customisation module that manages the components, e.g. templates, needed to enable the user to create a speech-enabled application. The customisation module allows a non-expert user rapidly to design and deploy complex speech interfaces. Additionally, the system can automatically manage the deployment of the speech-enabled applications once they have been created by the user, without the need for any further intervention by the user or use of the user's own computer processing resources.
Owner:VOX GENERATION LTD
3-D imaging multiple target laser radar
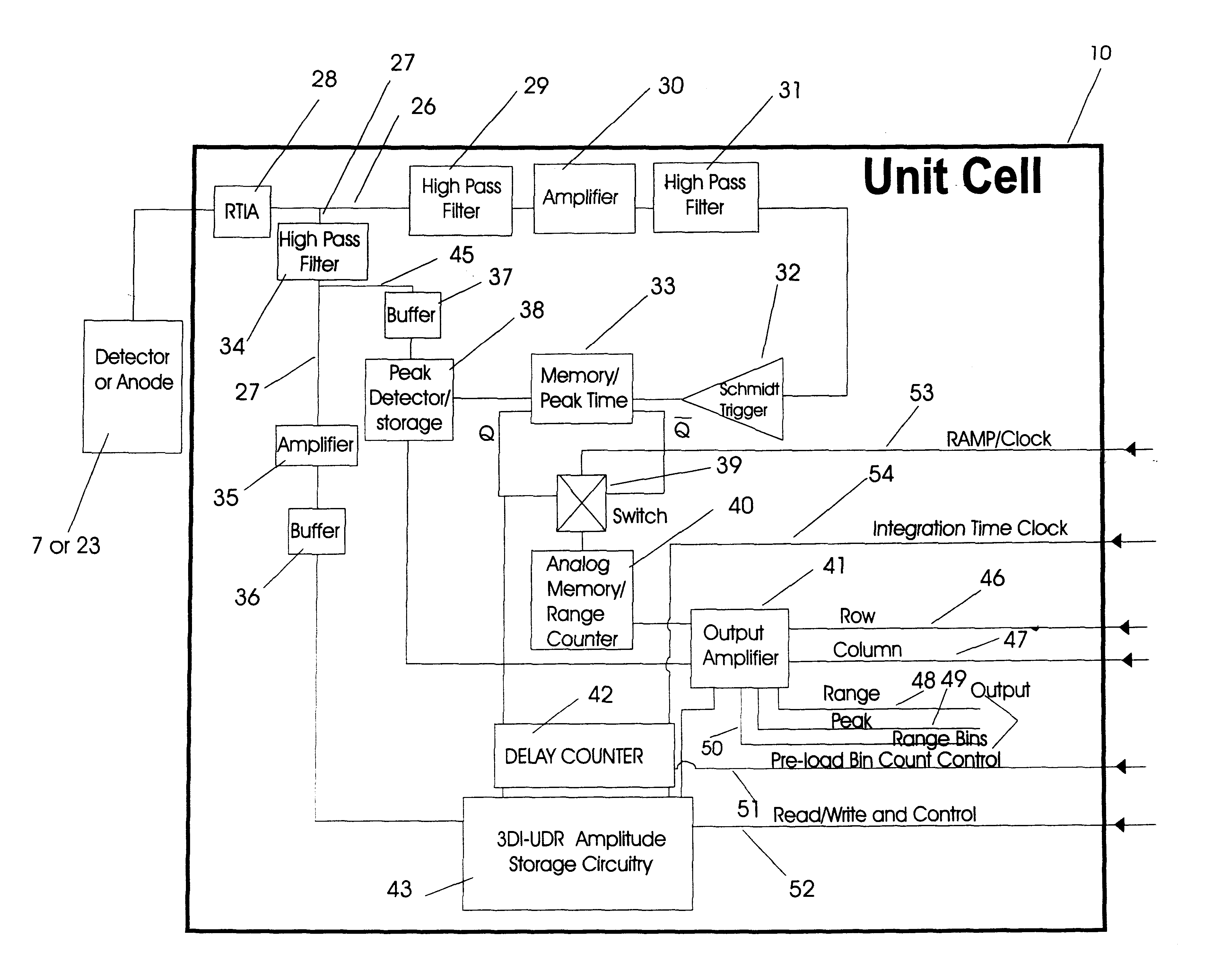
InactiveUS6414746B1Accurately determineOptical rangefindersSolid-state devicesElectronIntegrated circuit
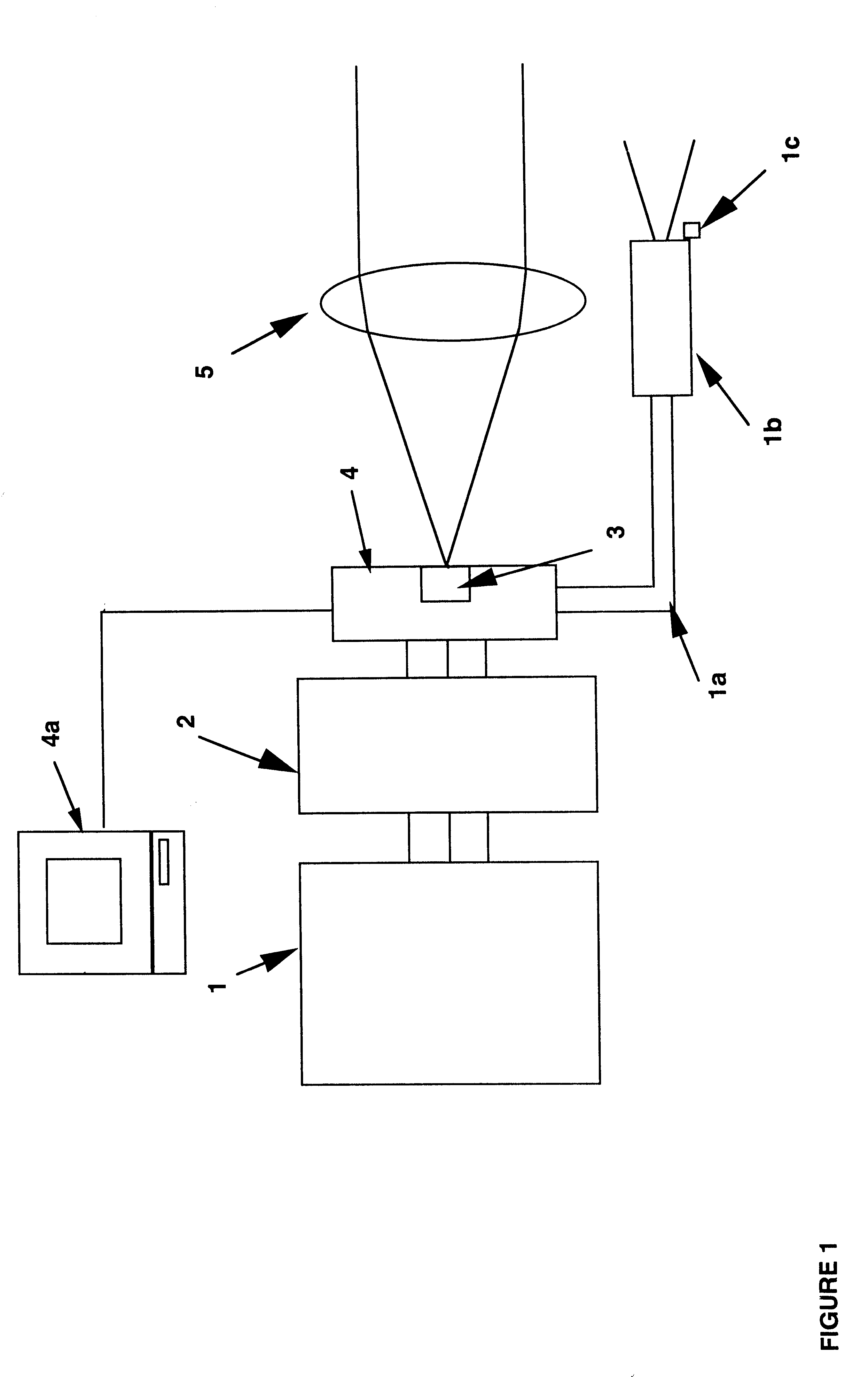
A three dimensional imaging device is presented which uses a single pulse from a pulsed light source to detect objects which are obscured by camouflage, fog or smoke but otherwise enveloped by a light-transmitting medium. The device simultaneously operates in two modes, light reflected from the nearest object is processed to form a three-dimensional image by an array of pixels. This first image is based upon the light-pulse transit time recorded in each pixel. Each pixel also contains a high-speed analog memory that sequentially stores reflected signals at a repeated time interval. The first reflection acts as a time base that controls when the analog memory begins or ends the storage sequence. The first return could be from a camouflage net and the amplitudes of the return signals, after the first return, would then be from objects behind the net. Computer processing these amplitudes reveals the three-dimensional nature of the obscured objects.The device consists of the pulsed light source, optics for collecting the reflected light, a sensor for detecting the light and converting it to electrical data, drive and output electronics for timing and signal conditioning of data generated by the sensors and a computer for processing the sensor data and converting it to a three dimensional image. The sensor collects and processes the light data in a unique manner, first converting it to electricity by a number of alternate detector technologies and then using integrated circuit chips which consist of a two dimensional array of electronic pixels also called unit cells. The two dimensional array defines two dimensions of the image. Stored within each unit cells is data associated with the third dimension, ranges of targets, and amplitudes of target reflections. This data is read out of the integrated circuit chip in the time interval between laser pulses to a processing computer. The processing computer corrects the data and, by means of computer algorithms specific to the device, converts the data to a three-dimensional image of one or more targets. This image may be viewed or processed electronically to isolate targets.
Owner:CONTINENTAL AUTONOMOUS MOBILITY US LLC
Retail store method and system
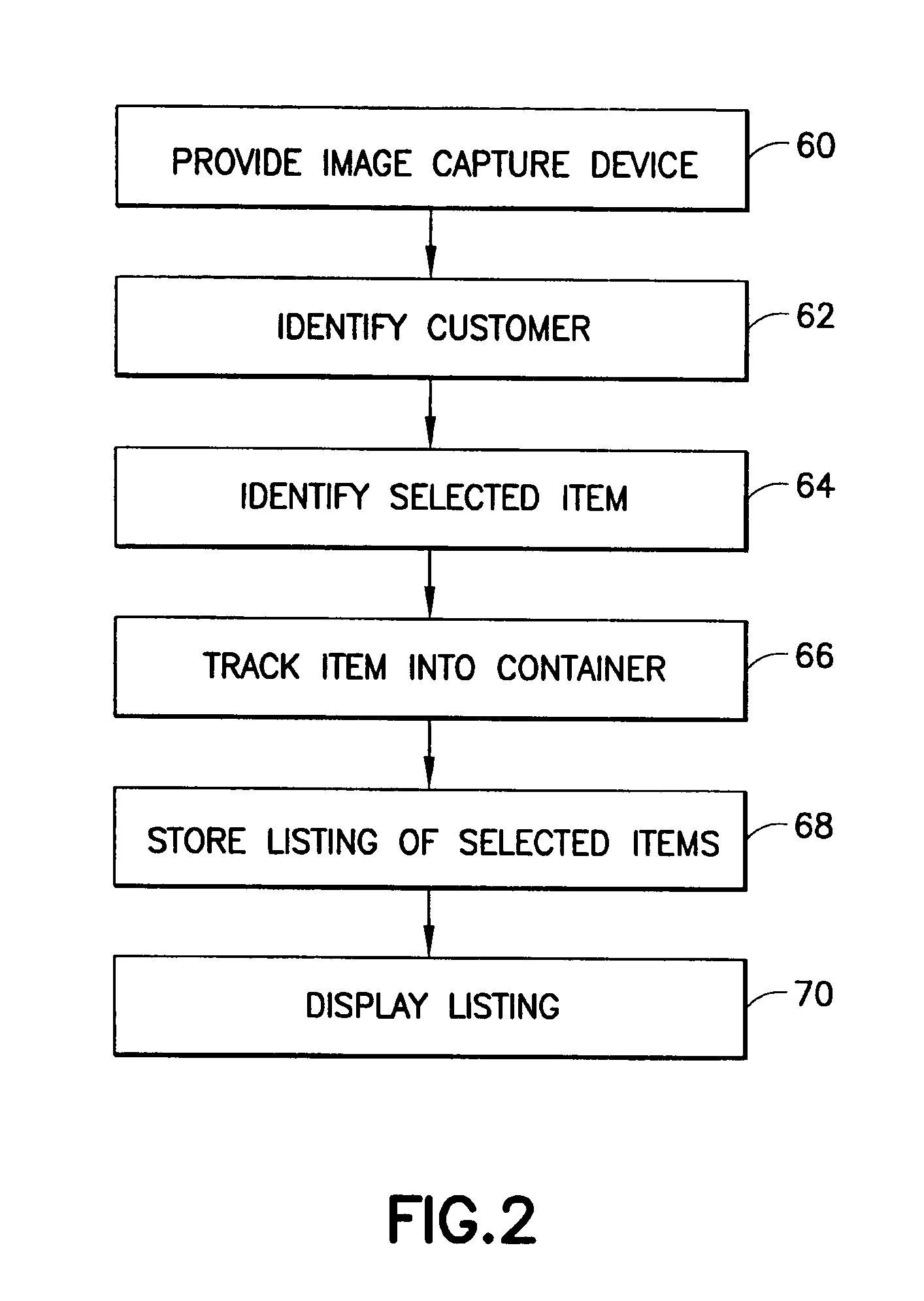
InactiveUS20060032915A1Increase capacityImprove operational capabilitiesCredit registering devices actuationColor television detailsLocation trackingOptical tracking
Image capture devices attached to a computer processor are located in a retail store. Items of merchandise for sale are tracked from their display position to a shopping container using optical tracking software. The software is capable of identifying the items and containers optically. A list of items in each container is maintained in a database. A customer may request a listing of items in a cart at any time via a query. At checkout time, there is no need to scan the items.
Owner:IBM CORP
Mmw contraband screening system
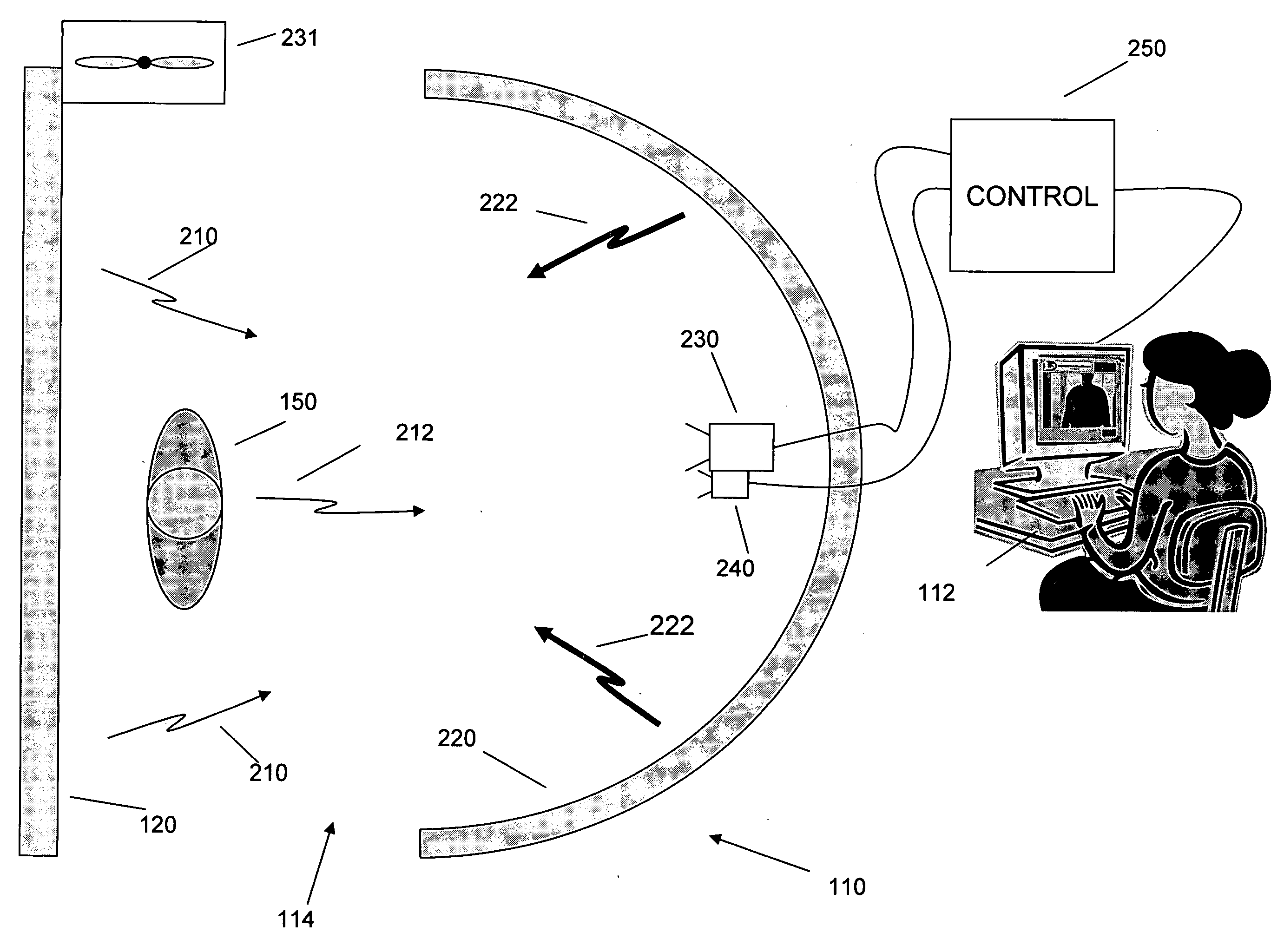
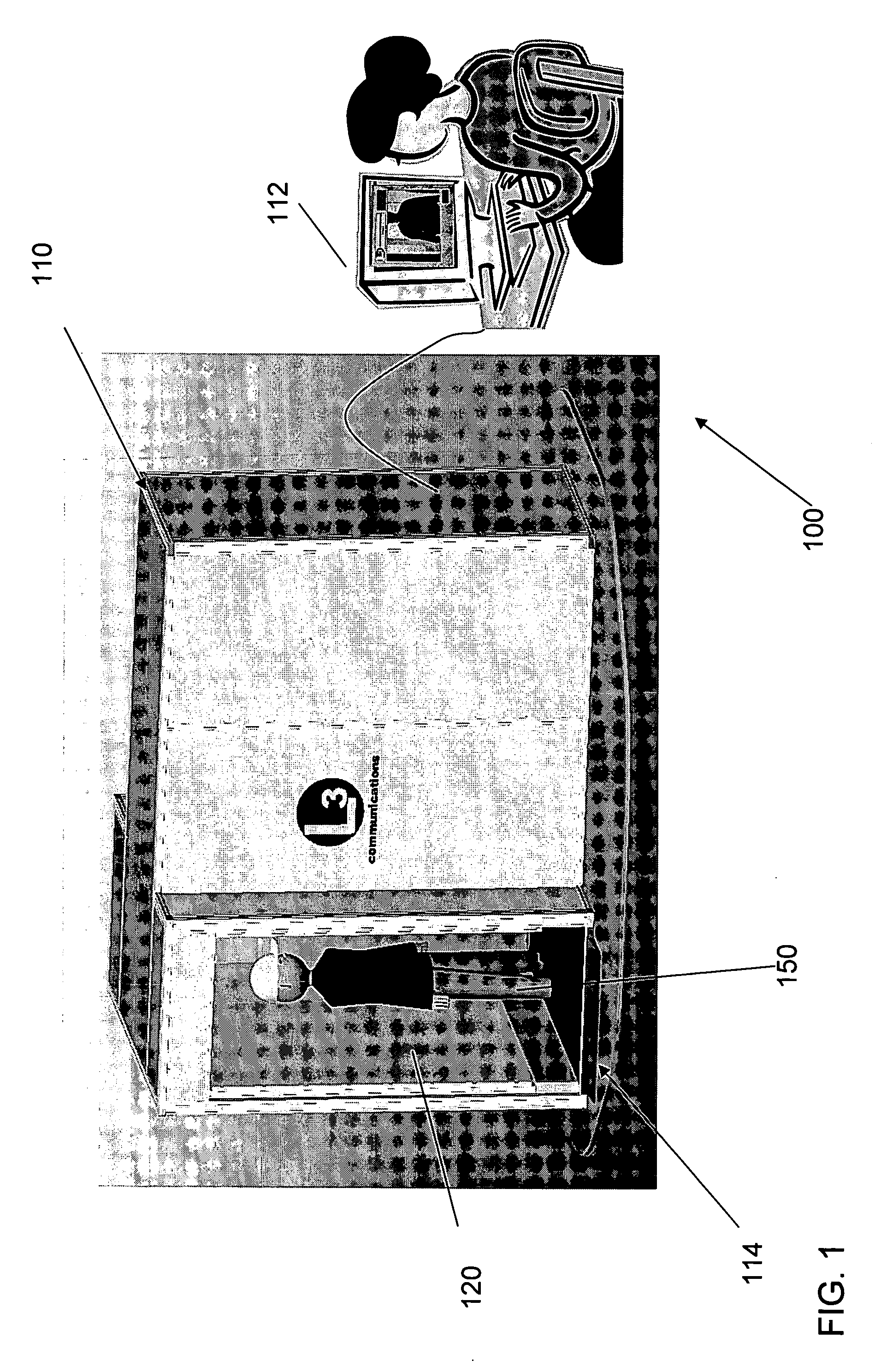
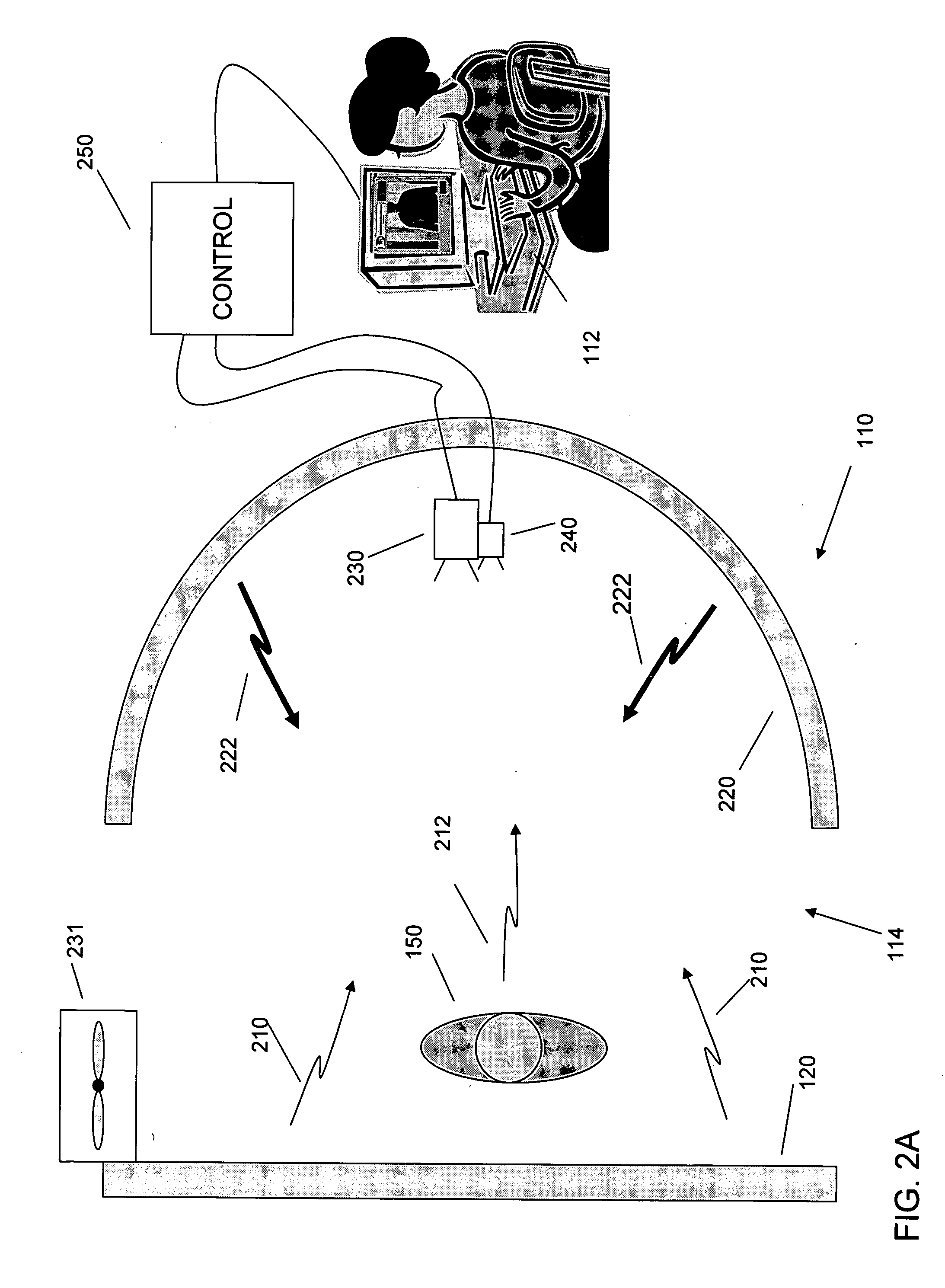
InactiveUS20050110672A1Geological detection using milimetre wavesMaterial analysis using microwave meansTemperature controlCheck point
An inspection system that can detect contraband items concealed on, in or beneath an individual's clothing. The system employs mm wave radiation to detect contraband items. The system is described in connection with a check point security system that includes temperature controlled walls to enhance imaging of contraband items. Also, a mm wave camera is used in conjunction with a camera that forms visible images. To address privacy concerns of displaying images of people made with mm wave cameras that effectively “see through” clothes, the mm wave images are not displayed directly. Rather, computer processing produces indications of suspicious items from the underlying raw mm wave images. The indications of suspicious items are overlaid on the visible image.
Owner:L3 COMMUNICATIONS SECURITY & DETECTION SYSTEMS CORPORATION
File management program
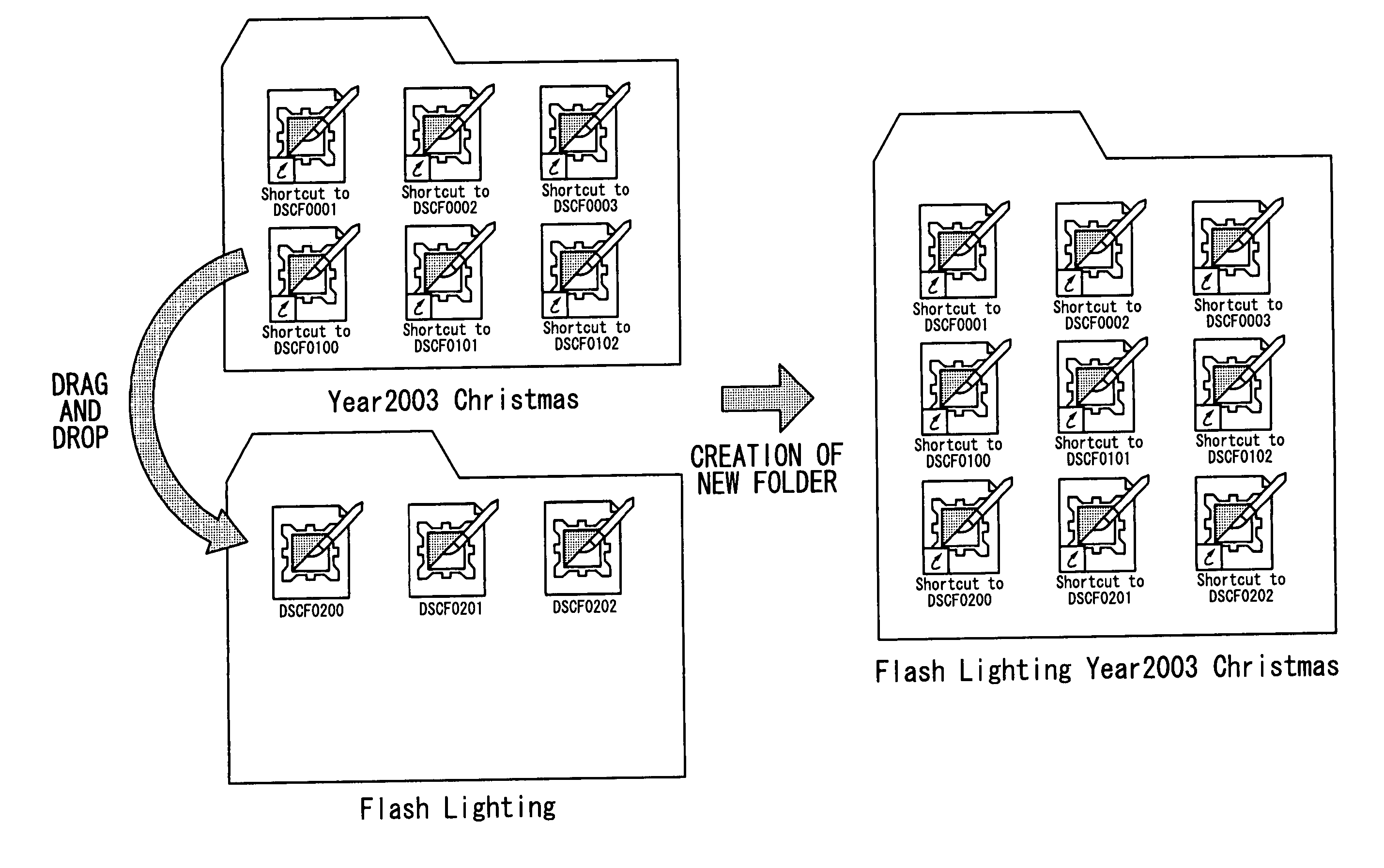
InactiveUS20050177796A1Simplified managementEasy to manageTelevision system detailsColor television detailsDrag and dropComputer science
The computer readable medium has embodied thereon a file management program for processing by a computer, the file management program comprising: a first code segment for, when an icon of a first folder displayed on a display apparatus is dragged and dropped onto another icon of a second folder displayed on the display apparatus, creating a third folder at the same level as the second folder; and a second code segment for copying a file stored in the first folder and a file stored in the second folder into the third folder.
Owner:FUJIFILM CORP
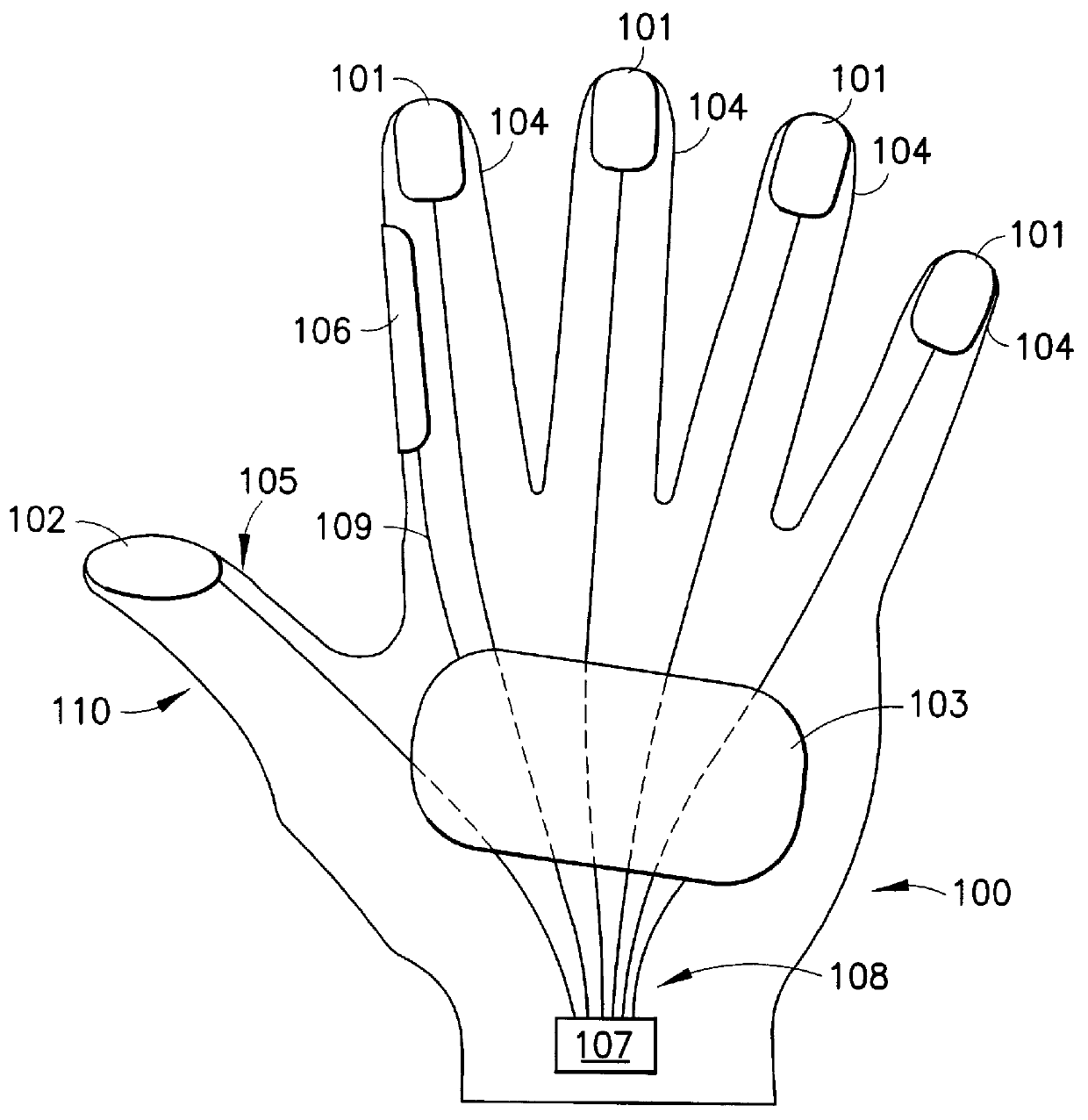
Data input glove having conductive finger pads and thumb pad, and uses therefor
A data input glove including a gloved body at least some of whose fingertip portions have conductive fingertip pad elements thereon, operatively connected to an output connector, and at least one conductive palm pad positioned on a palm portion of the gloved body and operatively connected to an output connector, wherein contact between a finger pad and a palm pad generates a signal. The signal may be processed by computer processor to provide a desired output, e.g., synthesized speech or other analogue or digital output in a suitable medium. The data glove is useful for inputting data in a covert manner, as well as communicationally enabling disabled persons with the aid of a computer, such as a handheld, wearable, or desktop computer.
Owner:HARMON STEVE
Management and distribution of surgical supplies within an RFID enabled network
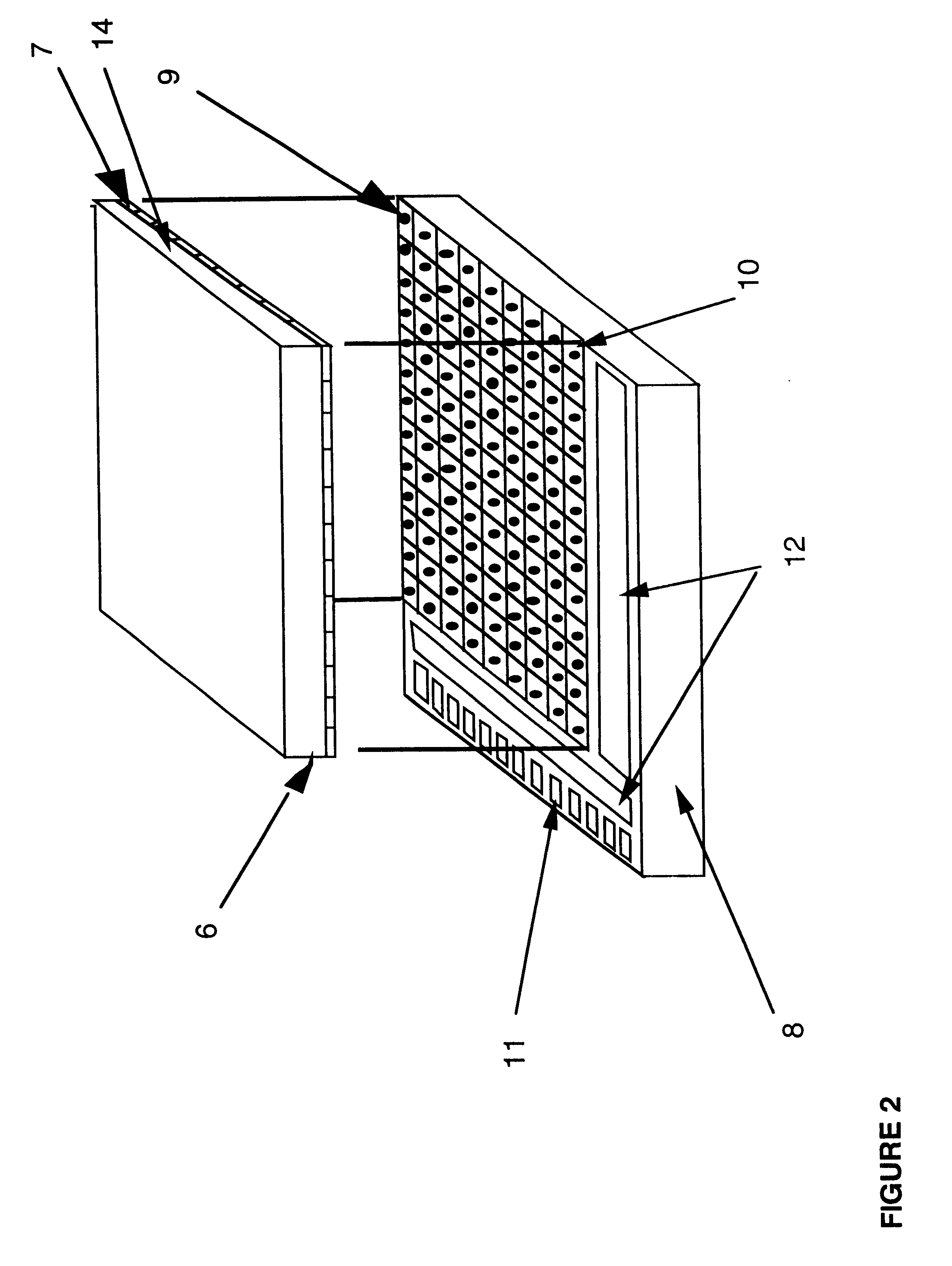
InactiveUS7142118B2Efficiency parameters to be monitoredImprove quality controlData processing applicationsDigital data processing detailsWide areaQuality control
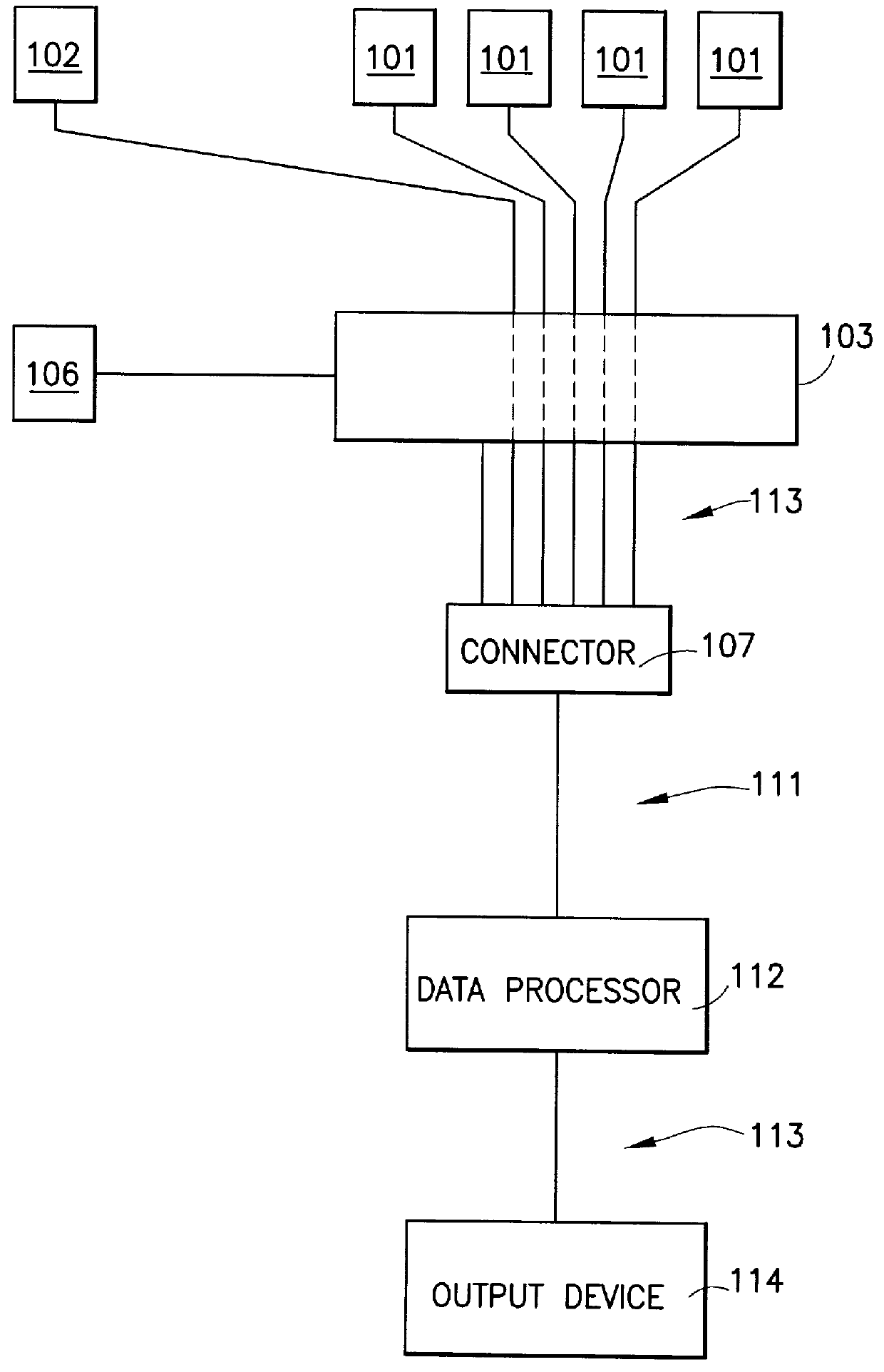
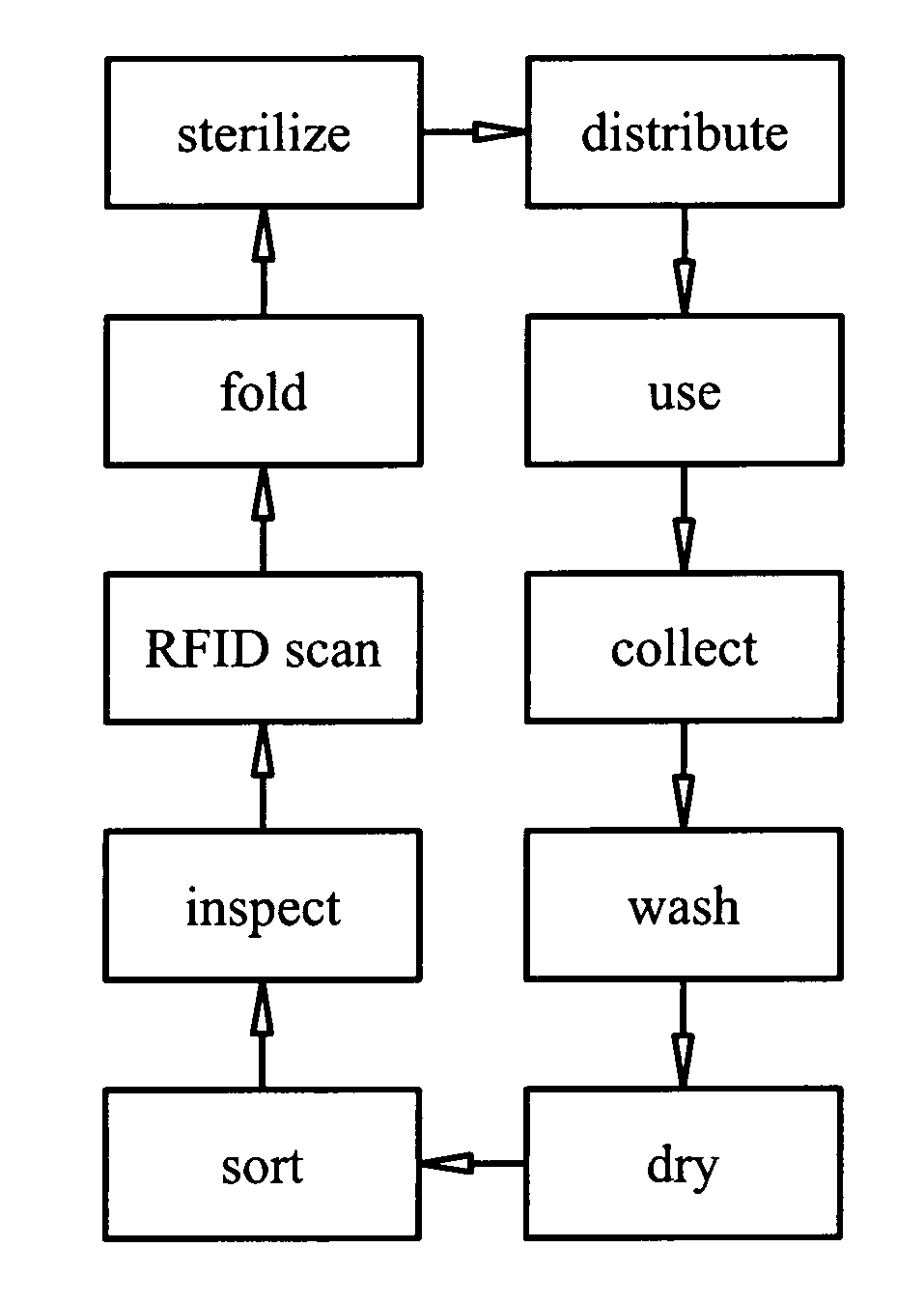
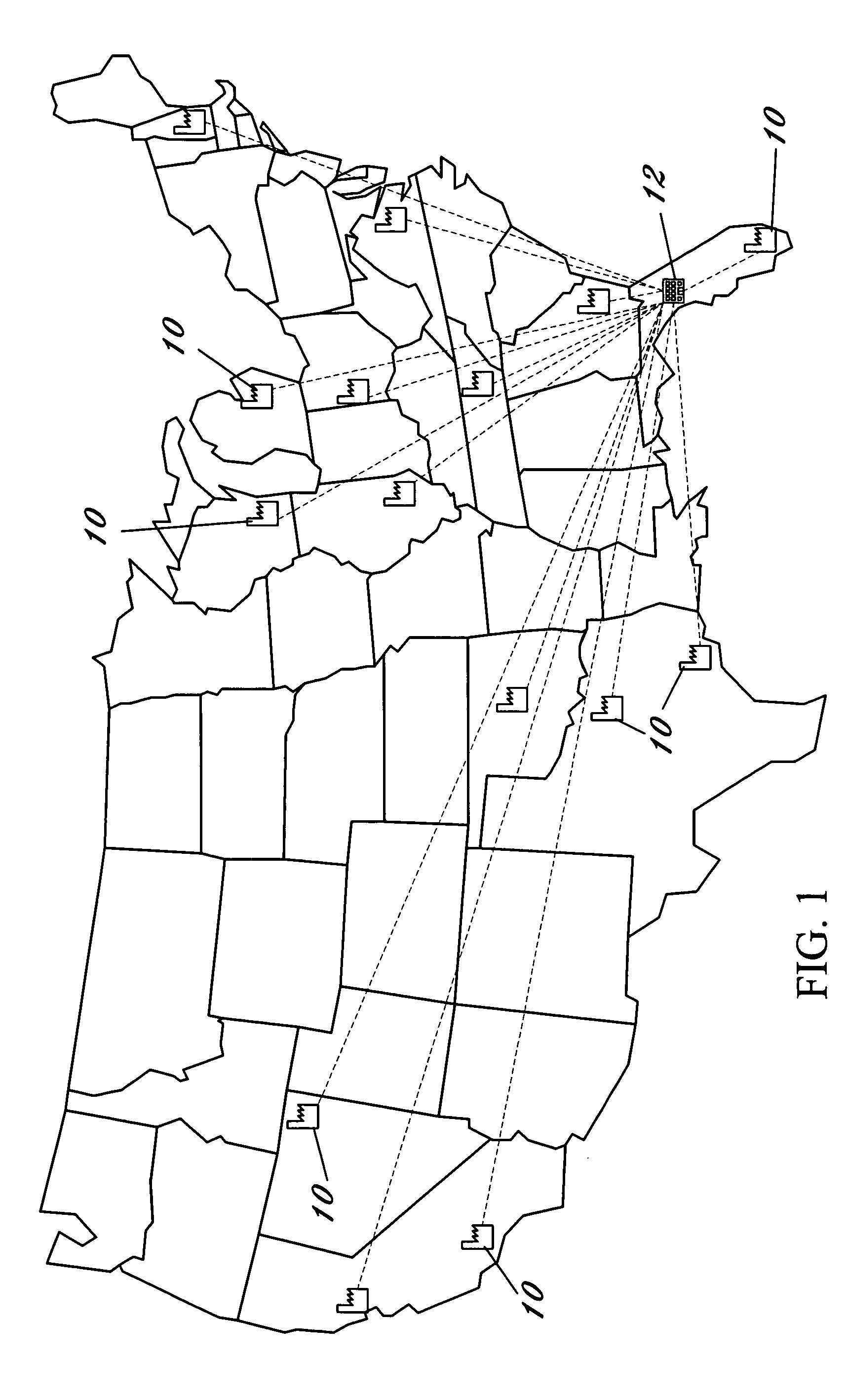
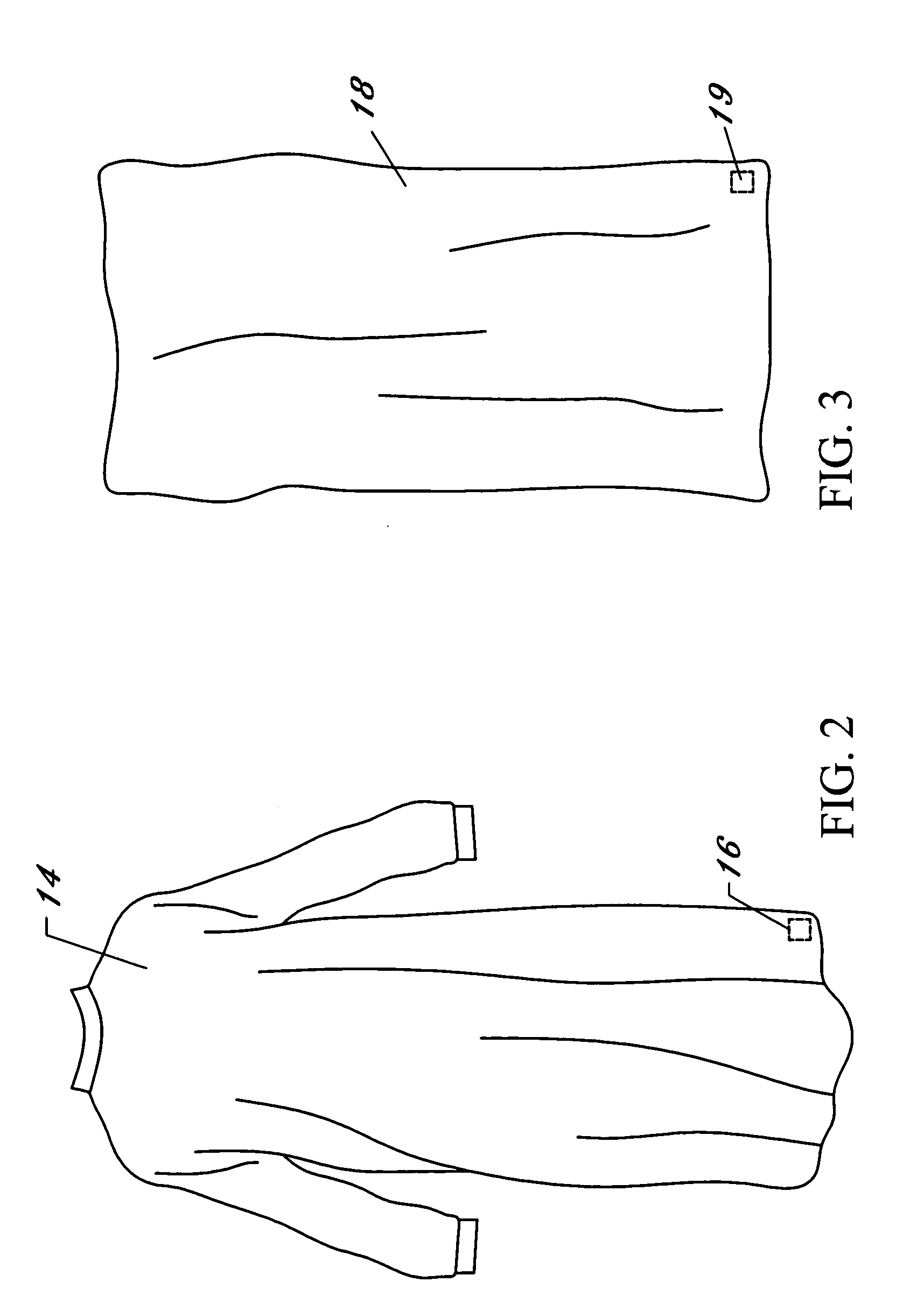
The present invention contributes to advancements in the art of inventory management and distribution by providing a system and method for processing, distributing, and tracking reusable inventory items. Reusable articles, such as surgical garments and accessories, are adapted with radio frequency identification (“RFID”) tags having unique identification numbers. A “reader” is used to retrieve stored information from the tags without requiring direct contact or clear line-of-sight. The reusable articles are processed and distributed using an inventory management system wherein lifecycle data is obtained for each reusable article. The reusable articles are distributed to the end users from central processing facilities, used, returned, cleaned, inspected, folded, sterilized, and returned to inventory for re-distribution. Periodic quality control inspections are conducted in response to predetermined usage parameters. The use of RFID tags and a corresponding computer network allows for the acquisition of data corresponding to each reusable article within a distribution system having multiple remote distribution and processing facilities. The acquired data is transmitted to a central computer processing system via a secured wide area computer network for use and analysis. Data processing computer servers at each remote distribution and processing facility electronically linked to a central data processing server provide a fail-safe network for acquired data.
Owner:SRISURGICAL EXPRESS
Transfer of knowledge from a human skilled worker to an expert machine - the learning process
InactiveUS20090132088A1Improve operational sensitivityComputer controlSimulator controlSoftware engineeringLearning methods
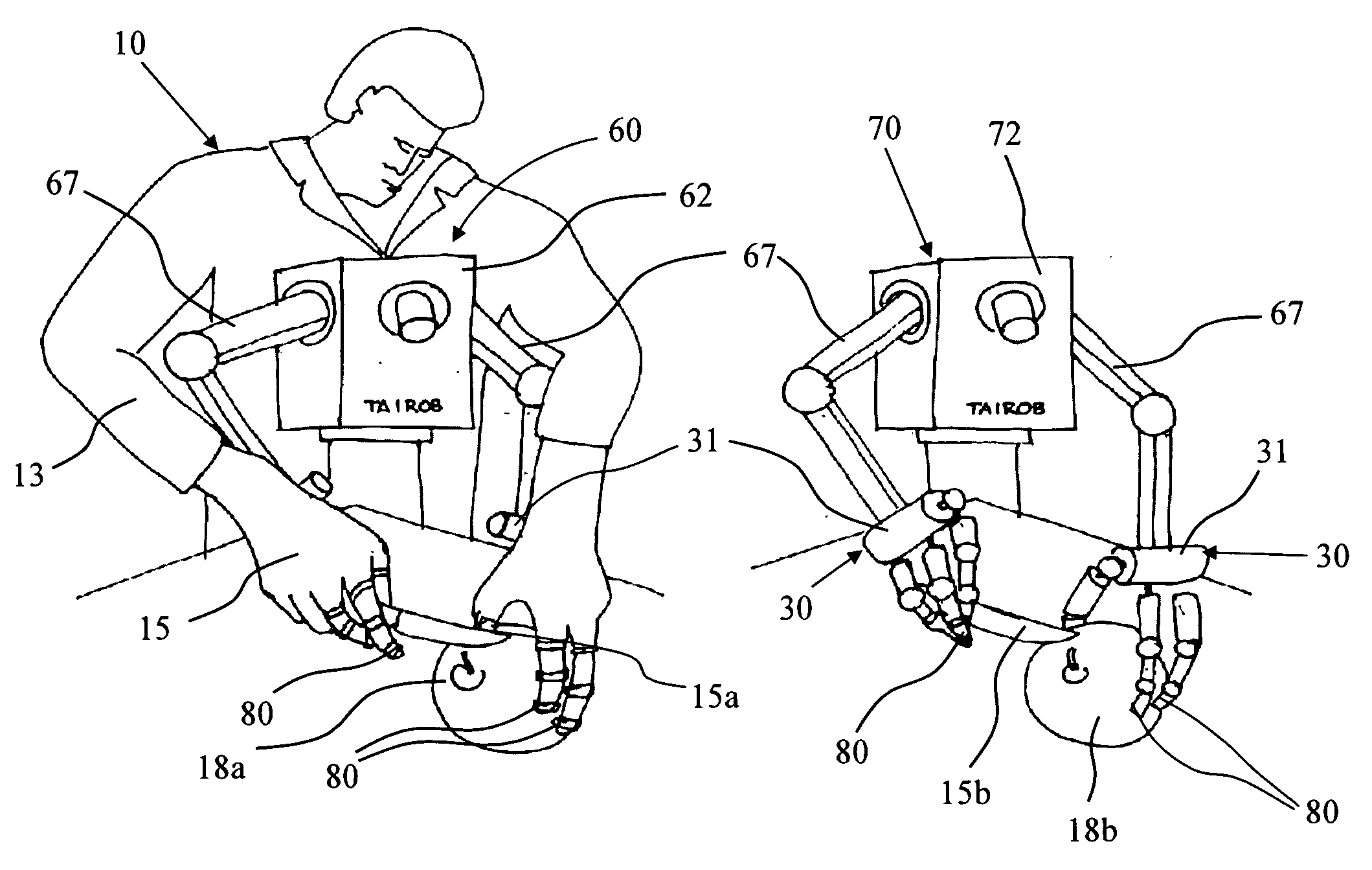
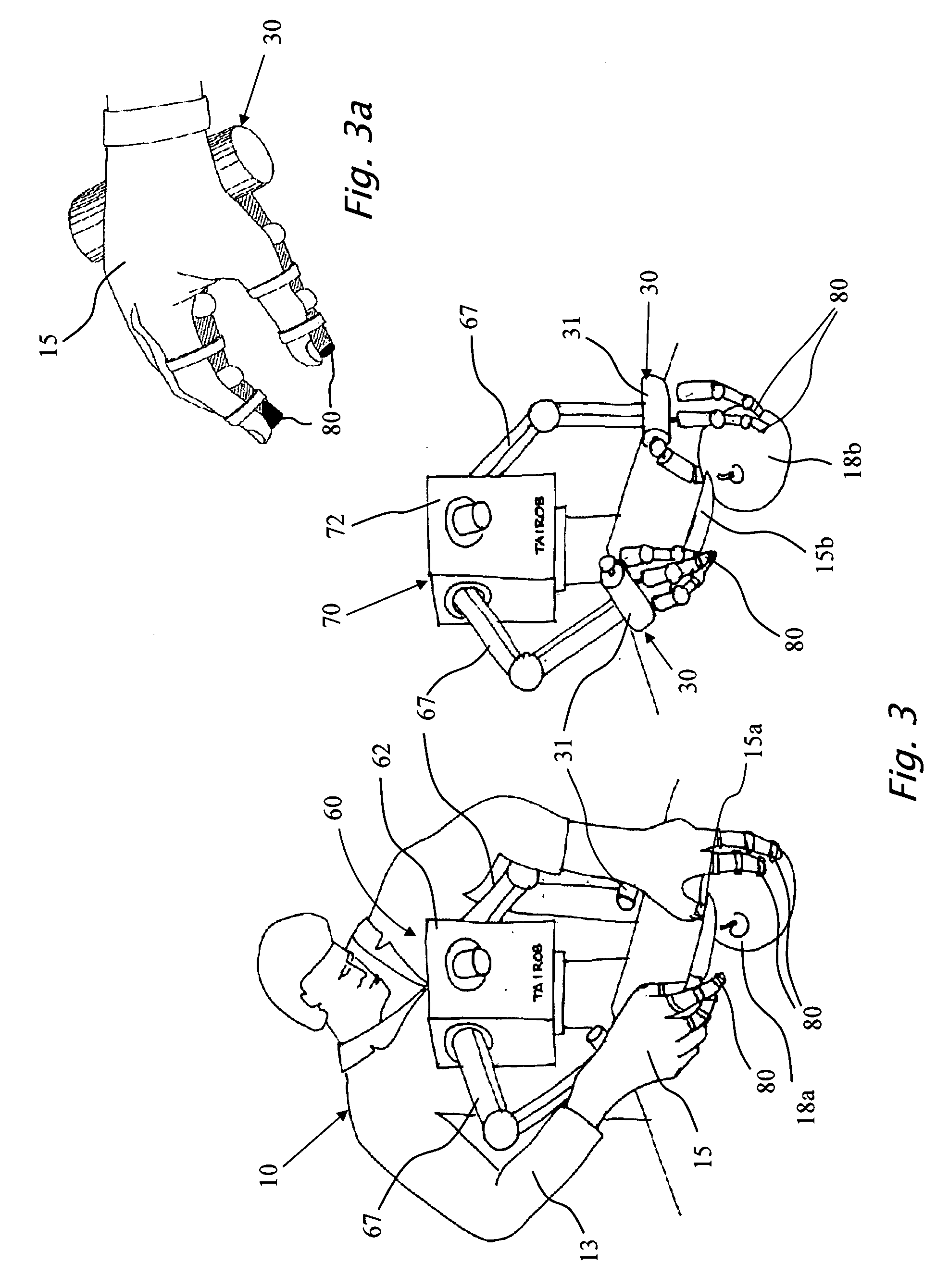
A learning environment and method which is a first milestone to an expert machine that implements the master-slave robotic concept. The present invention is of a learning environment and method for teaching the master expert machine by a skilled worker that transfers his professional knowledge to the master expert machine in the form of elementary motions and subdivided tasks. The present invention further provides a stand alone learning environment, where a human wearing one or two innovative gloves equipped with 3D feeling sensors transfers a task performing knowledge to a robot in a different learning process than the Master-Slave learning concept. The 3D force\torque, displacement, velocity\acceleration and joint forces are recorded during the knowledge transfer in the learning environment by a computerized processing unit that prepares the acquired data for mathematical transformations for transmitting commands to the motors of a robot. The objective of the new robotic learning method is a learning process that will pave the way to a robot with a “human-like” tactile sensitivity, to be applied to material handling, or man / machine interaction.
Owner:TAIROB
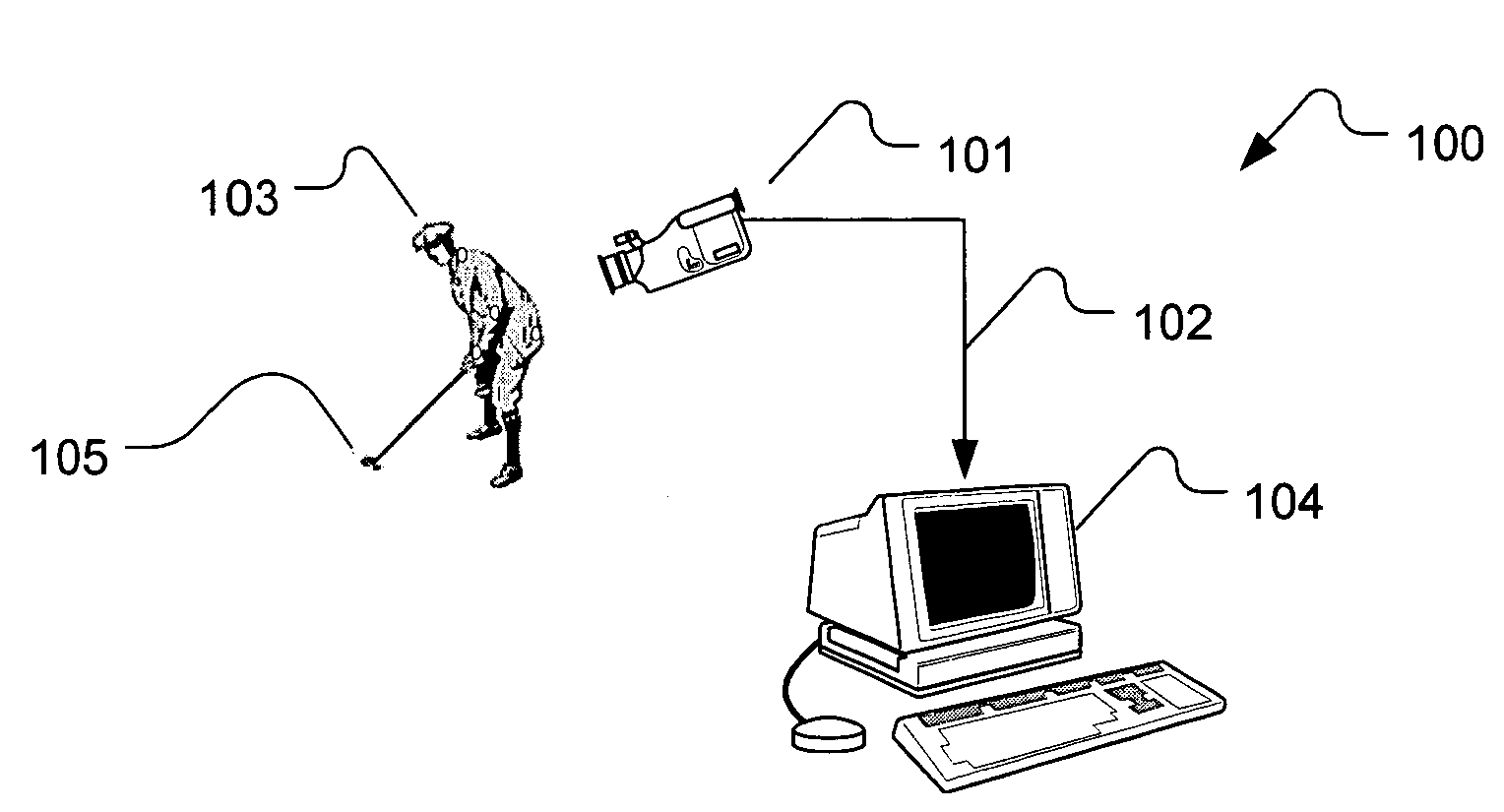
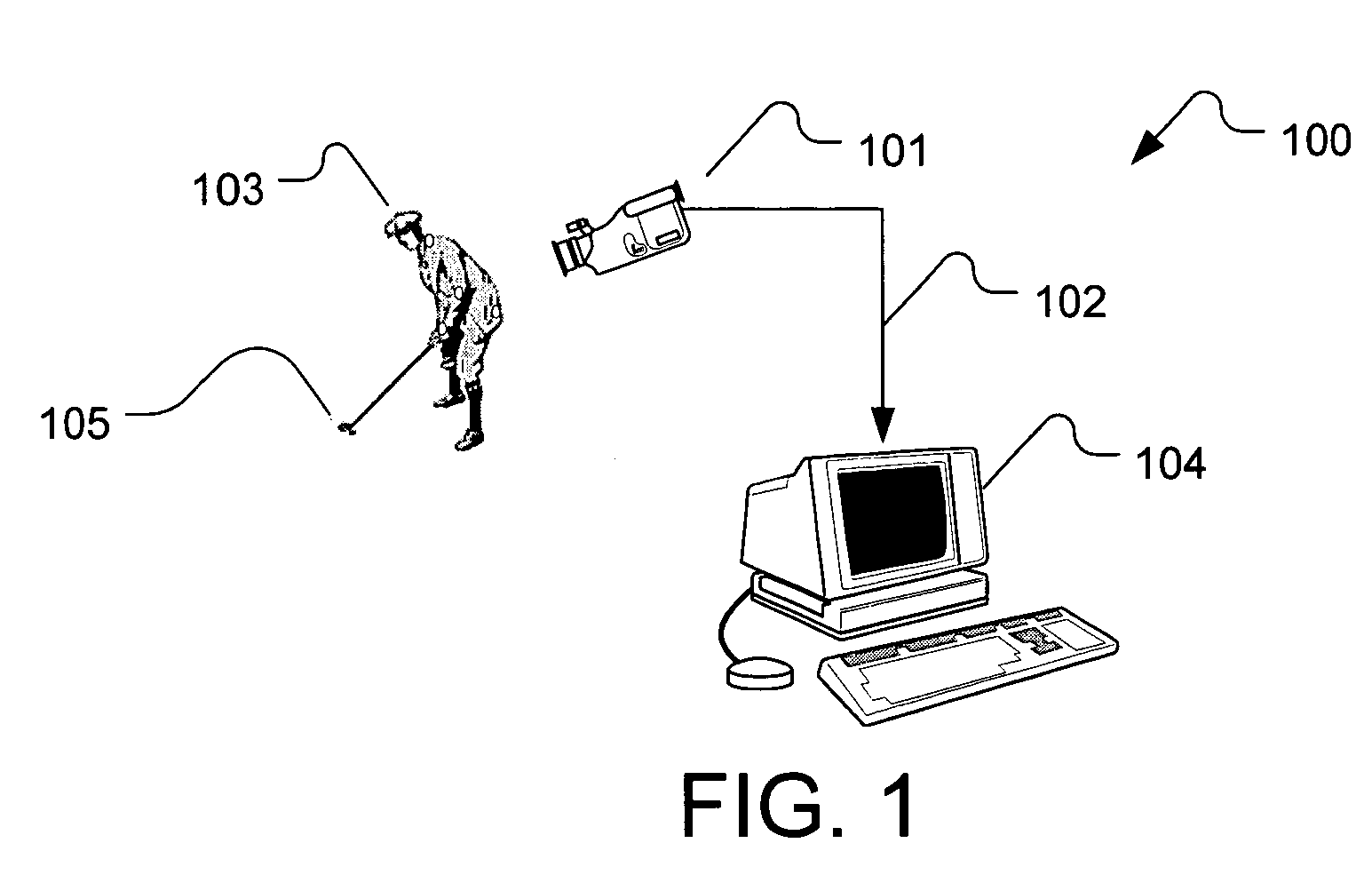
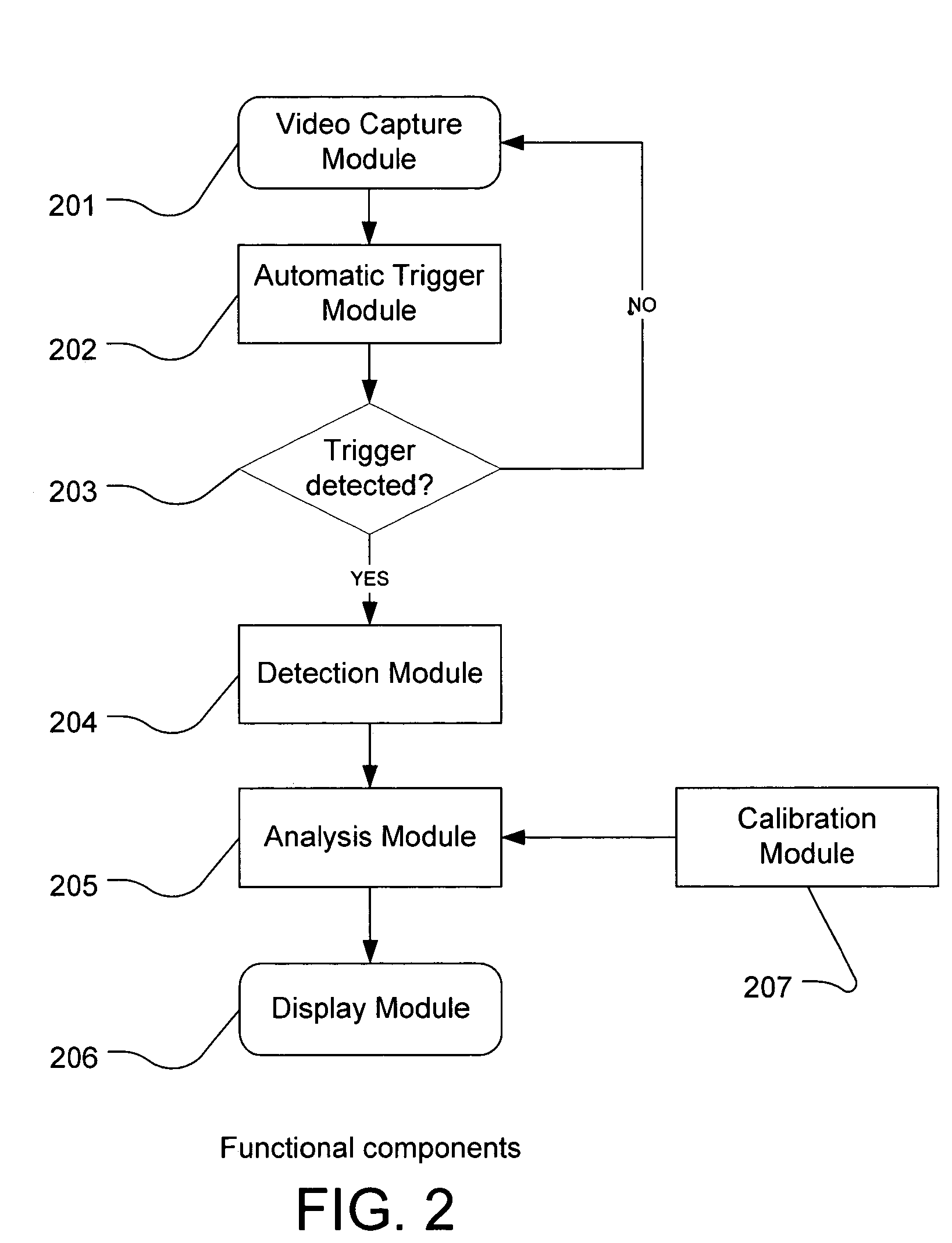
Method and system for physical motion analysis and training of a golf club swing motion using image analysis techniques
The analysis tool is a system and method for providing athletic training and instruction as it pertains to a golf club swing motion, specially a golf putting stroke motion. The analysis tool provides analysis information to a user from the analysis of at least one video image recording device. The motion of the golf club during the swing or stroke is determined by processing the video image frame data collected by the video image recording device(s). The resulting measurements are displayed by the computer processing environment and presented to the user numerically or pictorially for the purposes of instruction and improvement.
Owner:MCNITT MICHAEL J
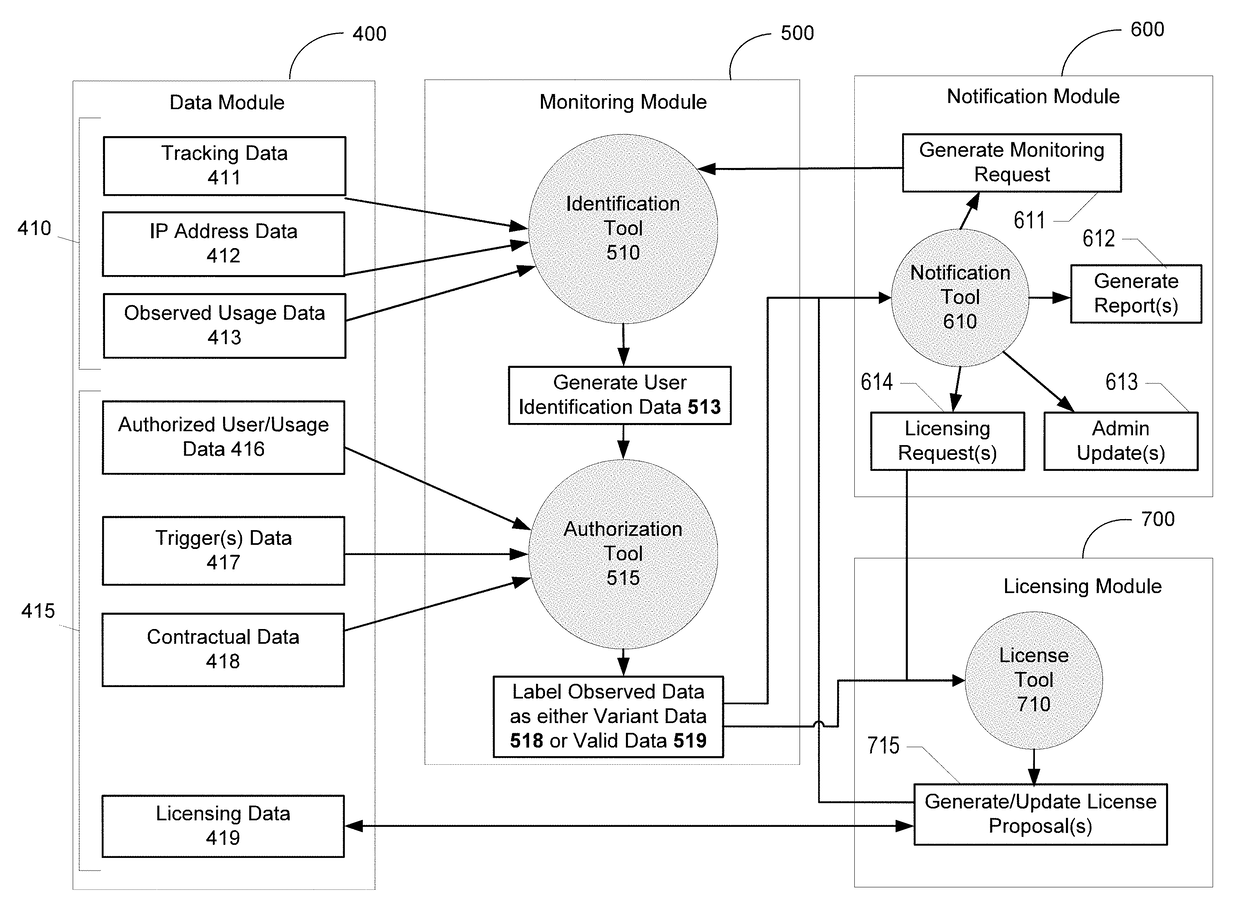
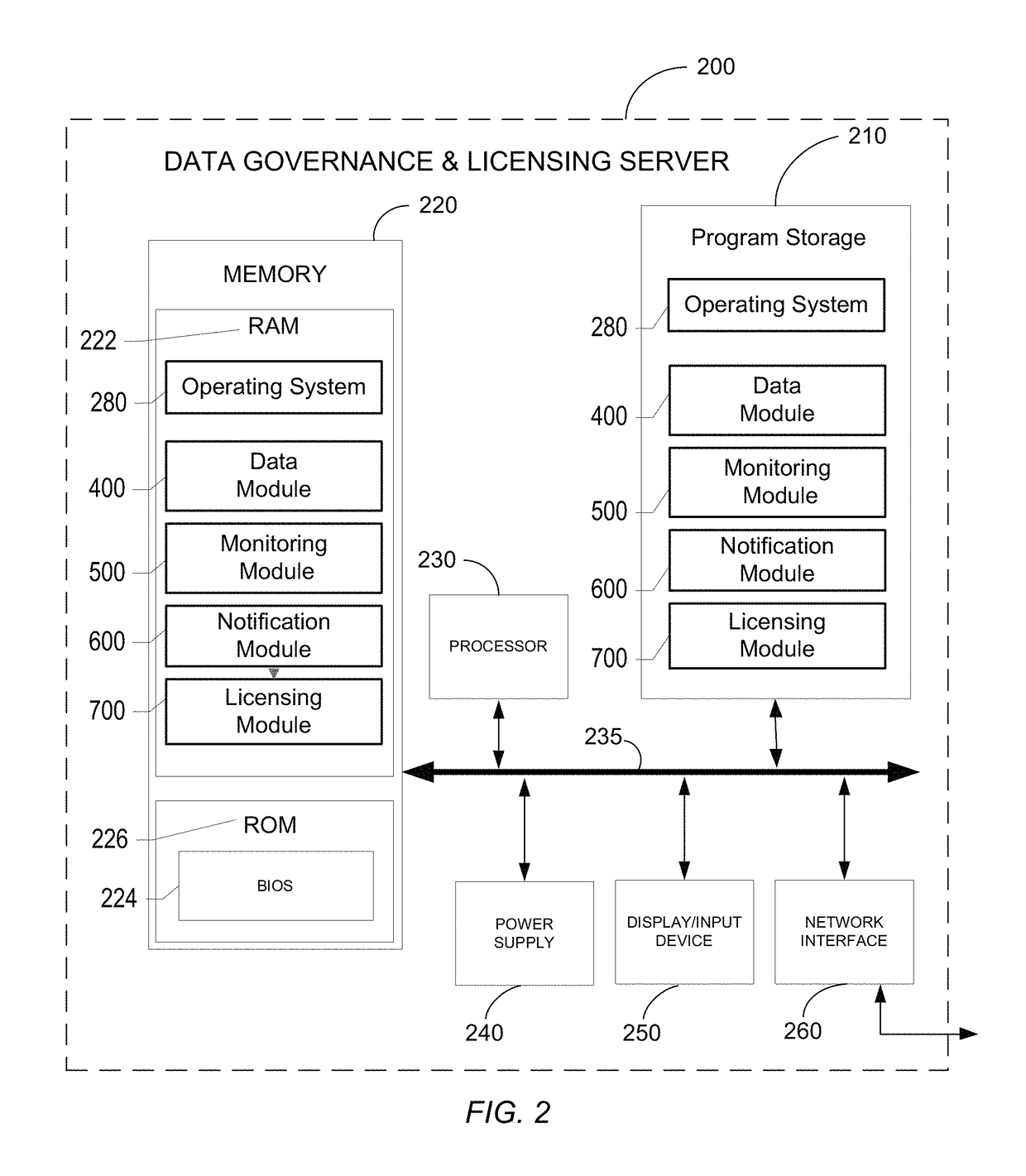
Systems, methods, and computer program products for data governance and licensing
Various embodiments provide a data governance and licensing system for monitoring usage of tracking data associated with transport of a plurality of packages and for facilitating licensing arrangements in connection therewith. In certain embodiments, the system comprises: one or more memory storage areas containing a variety of data and one or more computer processors. The one or more computer processors are configured to: receive observed data associated with access of tracking data by at least one accessing party; analyze at least a portion of the observed data to determine identification data for the accessing party; compare the identification data and the authorized user data to determine whether the accessing party is an authorized party; determine whether one or more discrepancies exist between the observed data and either generic usage data or authorized user data; and if so, generate either a license proposal or a license revision request.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
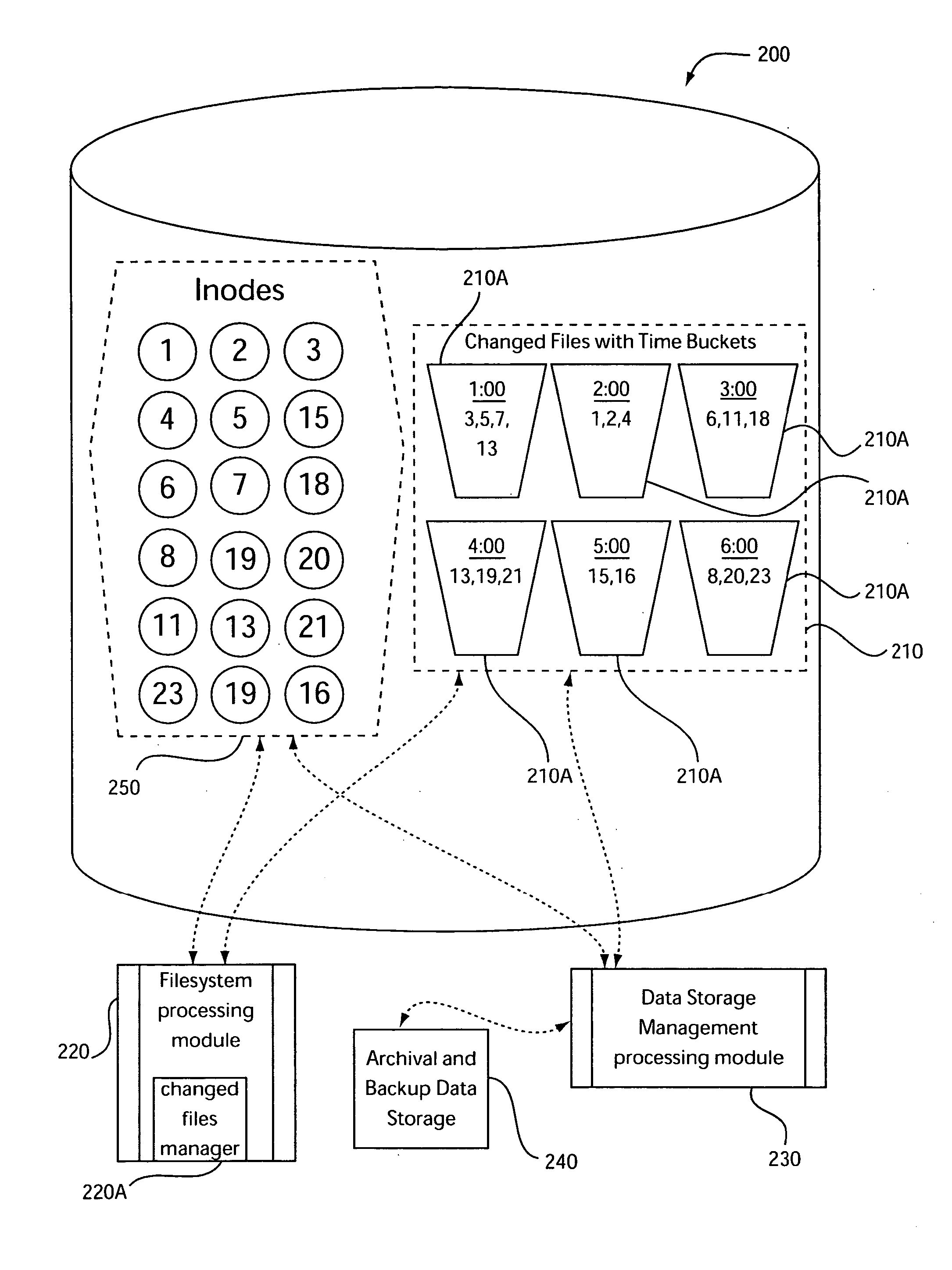
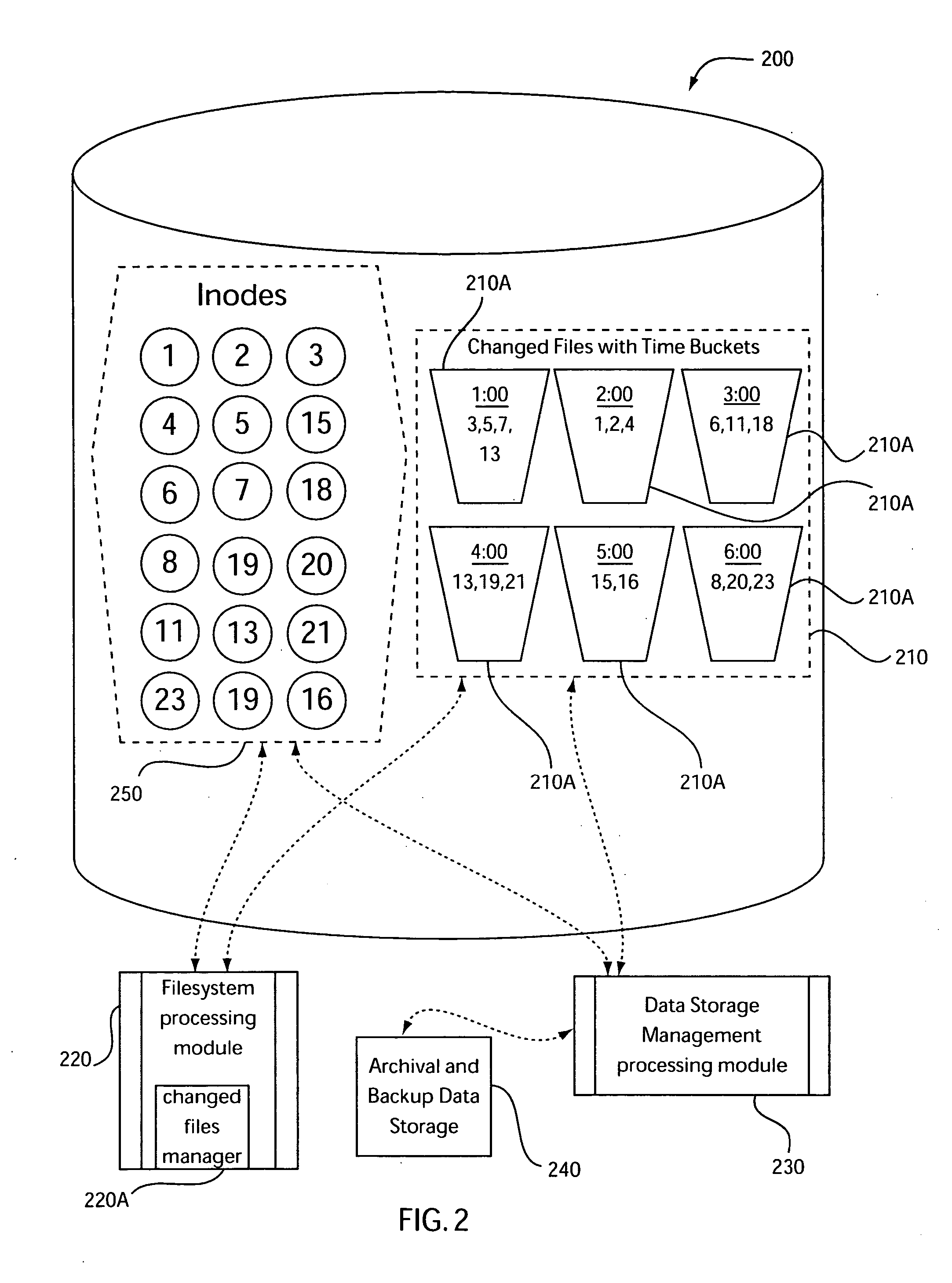
Changed files list with time buckets for efficient storage management
InactiveUS20060259527A1File access structuresSpecial data processing applicationsTimestampManagement object
There is provided, in a computer processing system, an apparatus for managing object data. The apparatus includes a changed objects manager for creating and managing a changed objects list that at least identifies the objects that have changed based on time of change. The changed objects list is associated with a plurality of time buckets. Each of the plurality of time buckets is associated with a respective date and time period and with object change records for objects having a timestamp falling within the respective date and time period. Each of the object change records is associated with a unique object identifier and the timestamp for a corresponding one of the objects. The timestamp specifies a date and a time corresponding to a latest one of a creation time or a most recent update time for the corresponding one of the objects.
Owner:IBM CORP
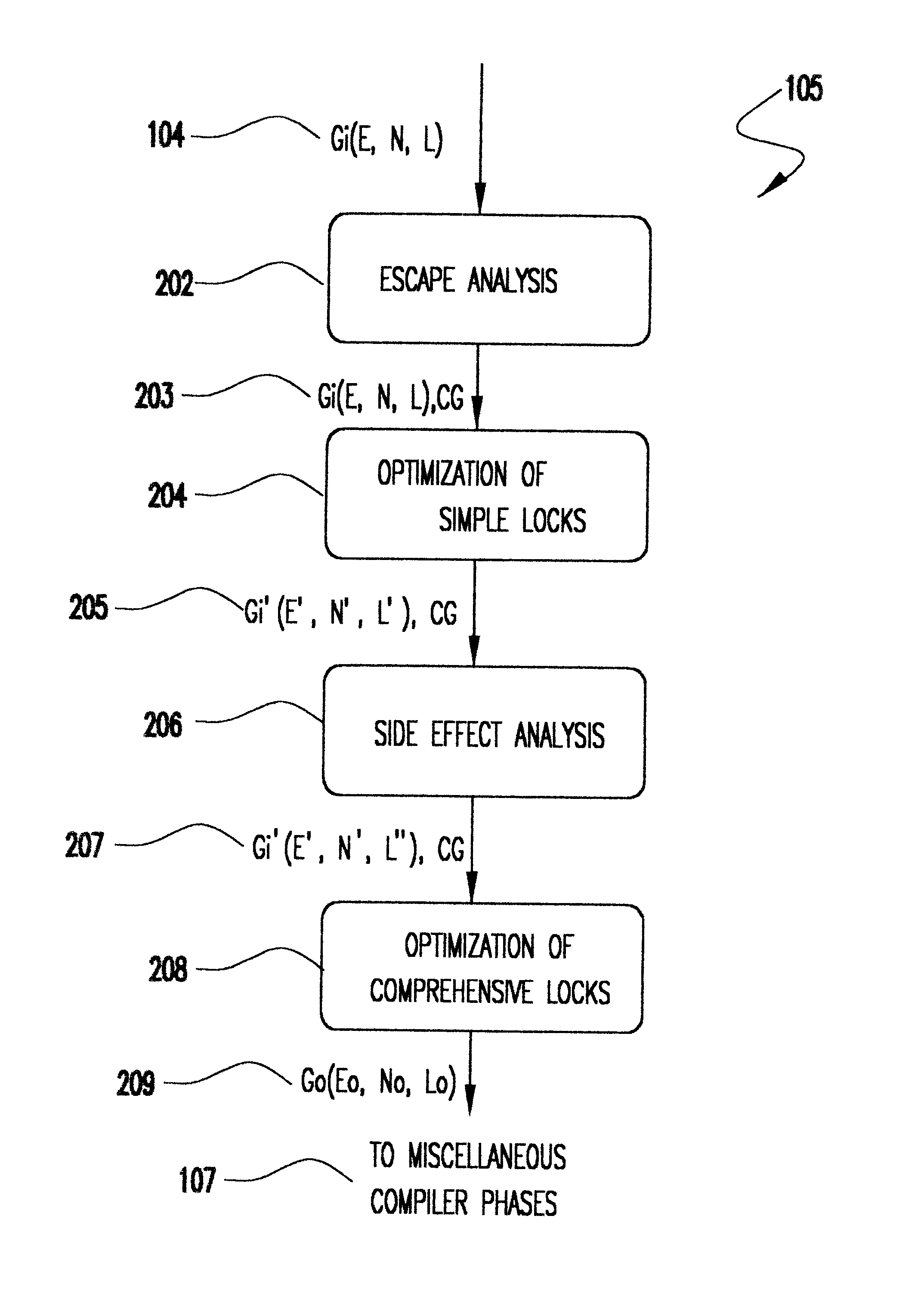
Method for optimizing locks in computer programs
InactiveUS6530079B1Easy to operateProgram synchronisationSoftware engineeringProgram planningSemantics
A method and several variants for using information about the scope of access of objects acted upon by mutual exclusion, or mutex, locks to transform a computer program by eliminating locking operations from the program or simplifying the locking operations, while strictly performing the semantics of the original program. In particular, if it can be determined by a compiler that the object locked can only be accessed by a single thread it is not necessary to perform the "acquire" or "release" part of the locking operation, and only its side effects must be performed. Likewise, if it can be determined that the side effects of a locking operation acting on a variable which is locked in multiple threads are not needed, then only the locking operation, and not the side effects, needs to be performed. This simplifies the locking operation, and leads to faster programs which use fewer computer processor resources to execute; and programs which perform fewer shared memory accesses, which in turn not only causes the optimized program, but also other programs executing on the same computing machine to execute faster. The method also describes how information about the semantics of the locking operation side effects and the information about the scope of access can also be used to eliminate performing the side effect parts of the locking operation, thereby completely eliminating the locking operation. The method also describes how to analyze the program to compute the necessary information about the scope of access. Variants of the method show how one or several of the features of the method may be performed.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com