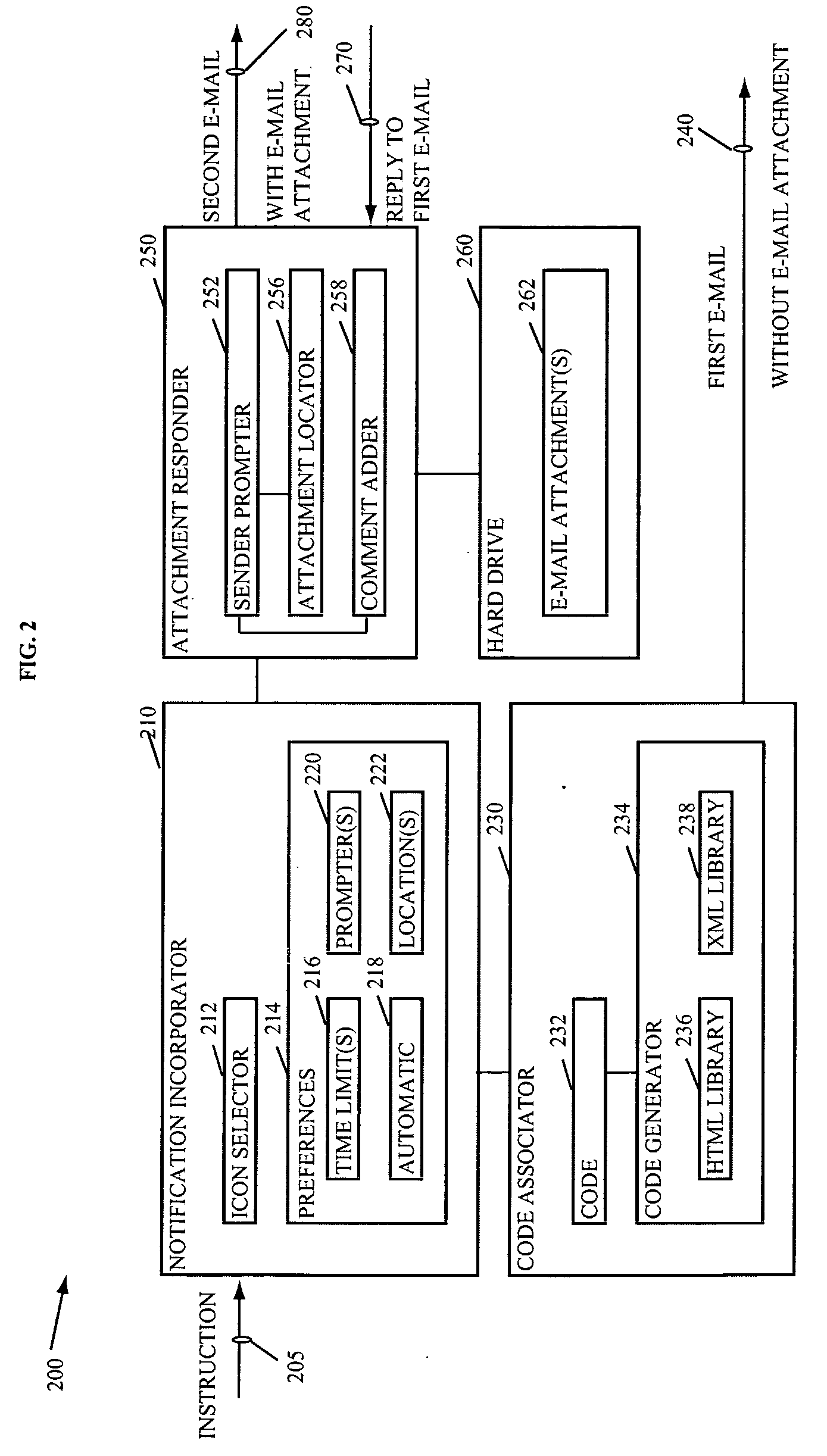
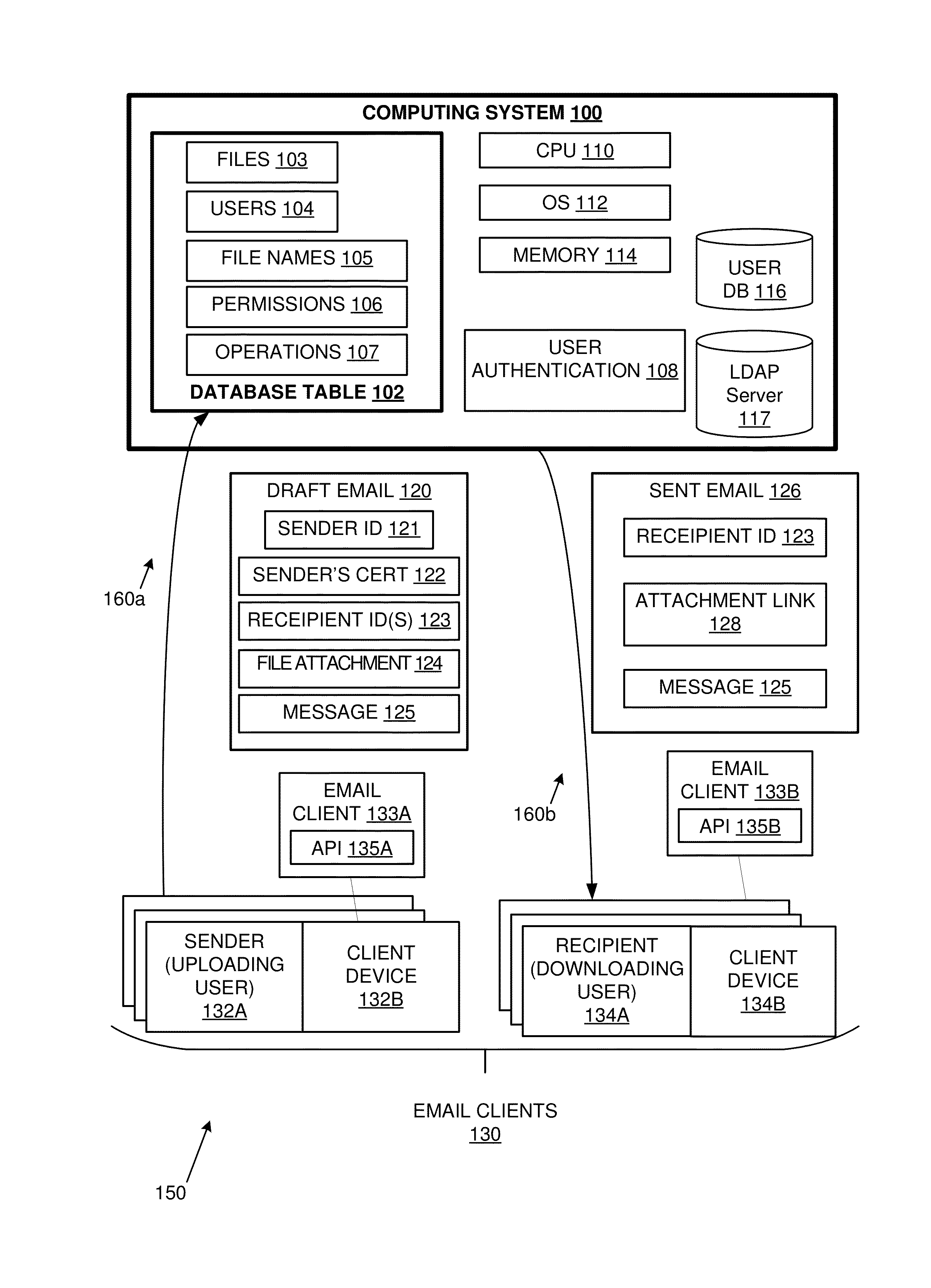
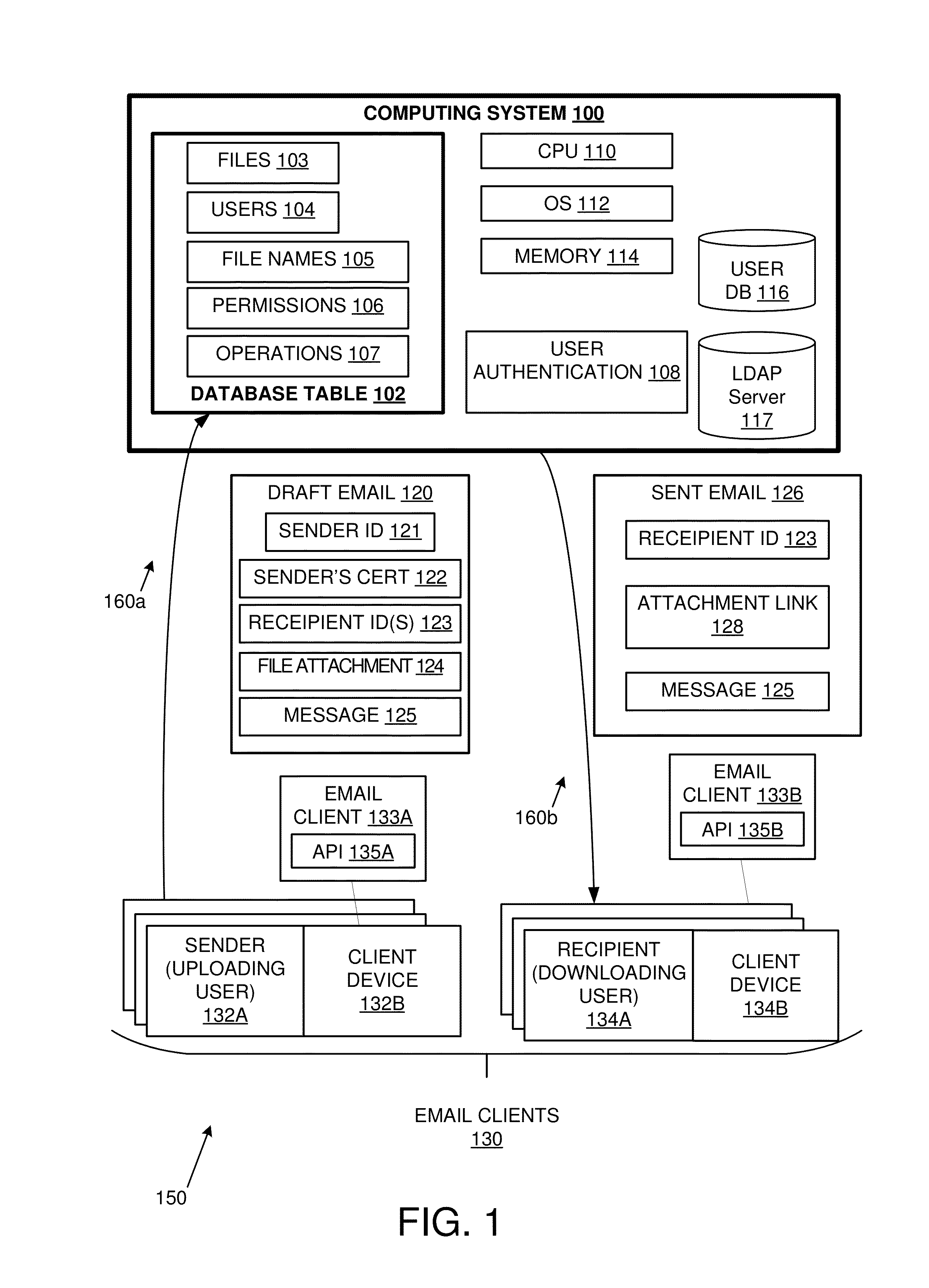
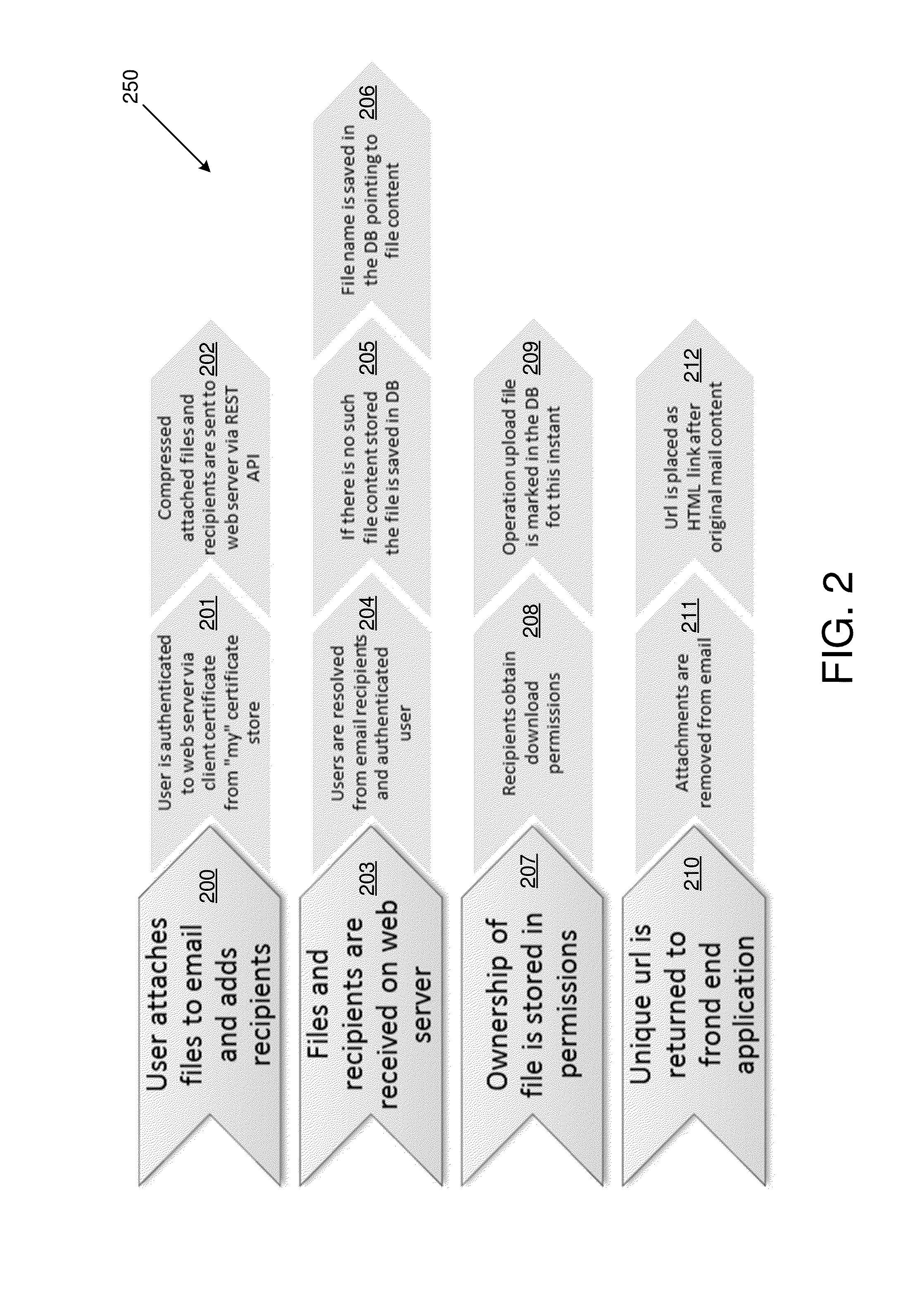
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
237 results about "Email attachment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
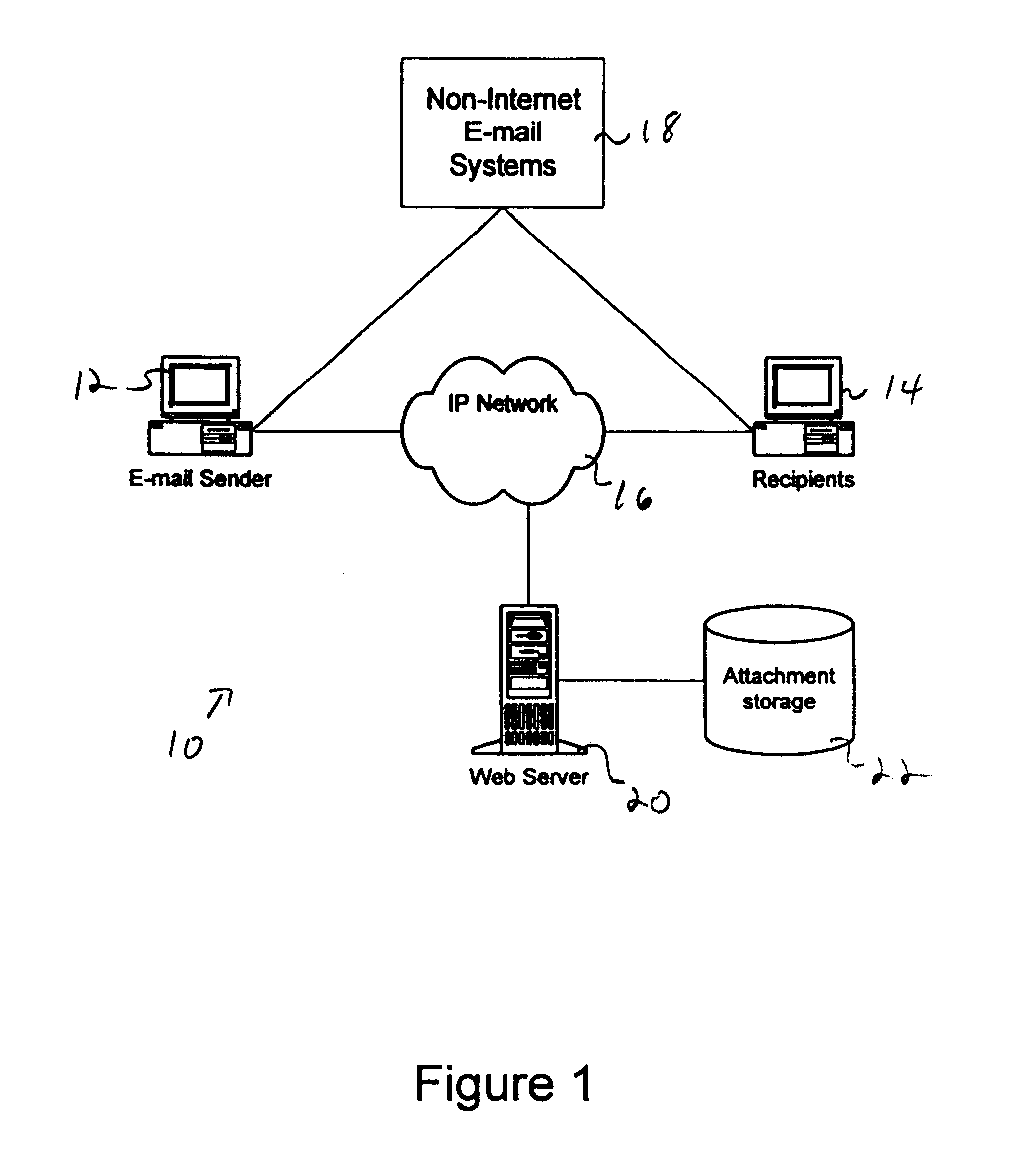
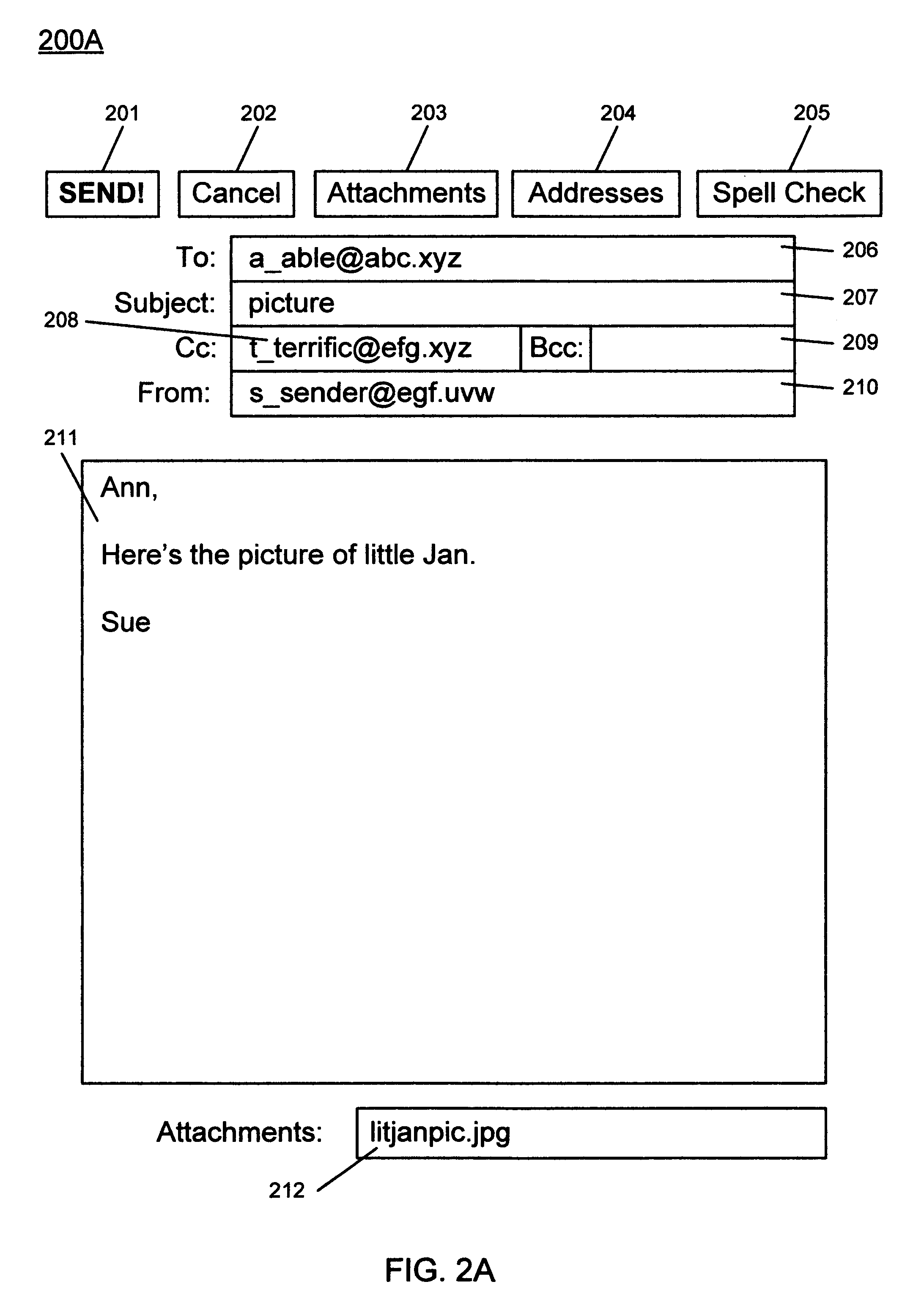
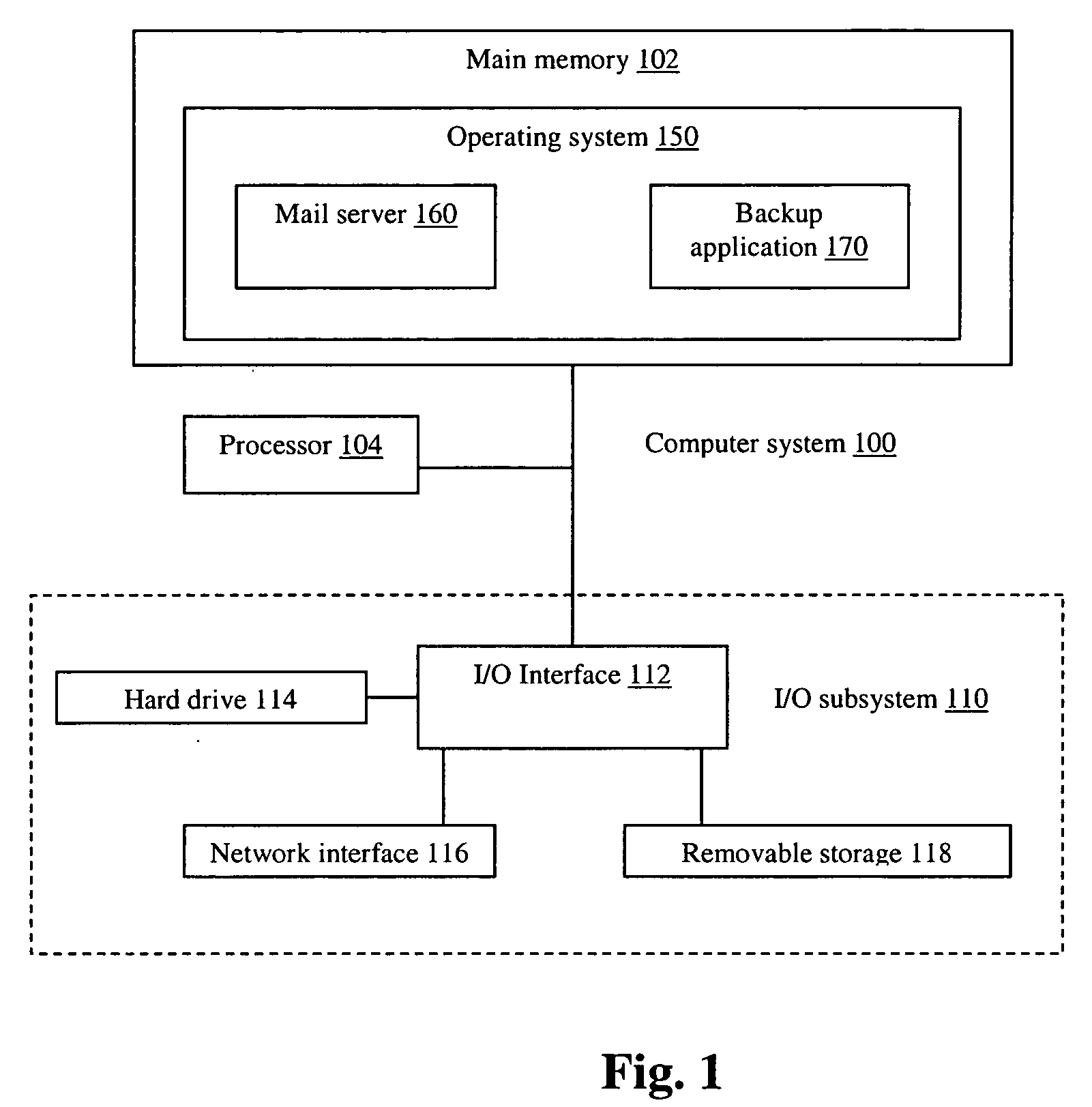
An email attachment is a computer file sent along with an email message. One or more files can be attached to any email message, and be sent along with it to the recipient. This is typically used as a simple method to share documents and images. A paper clip icon is the standard indicator for an attachment in an email client.
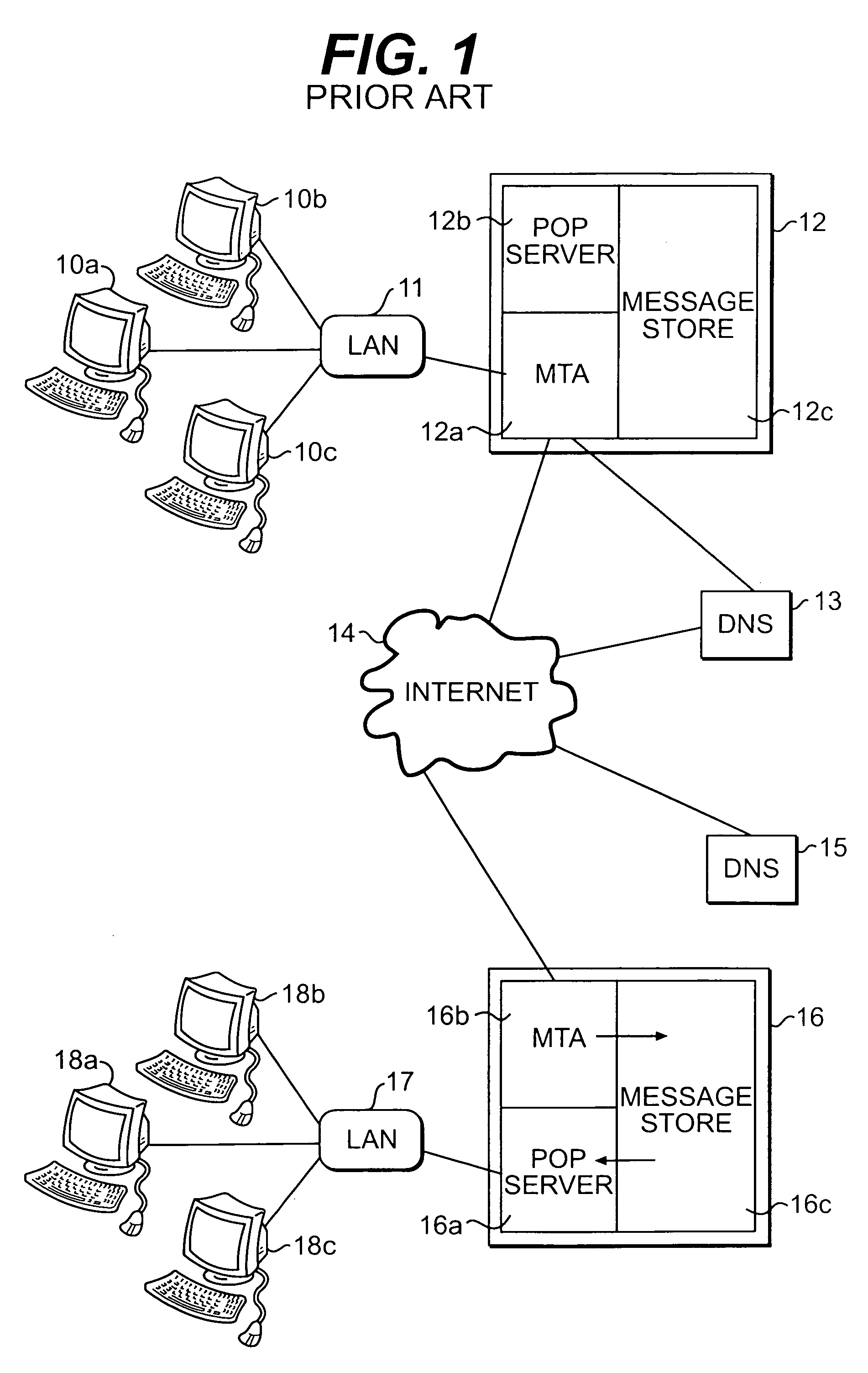
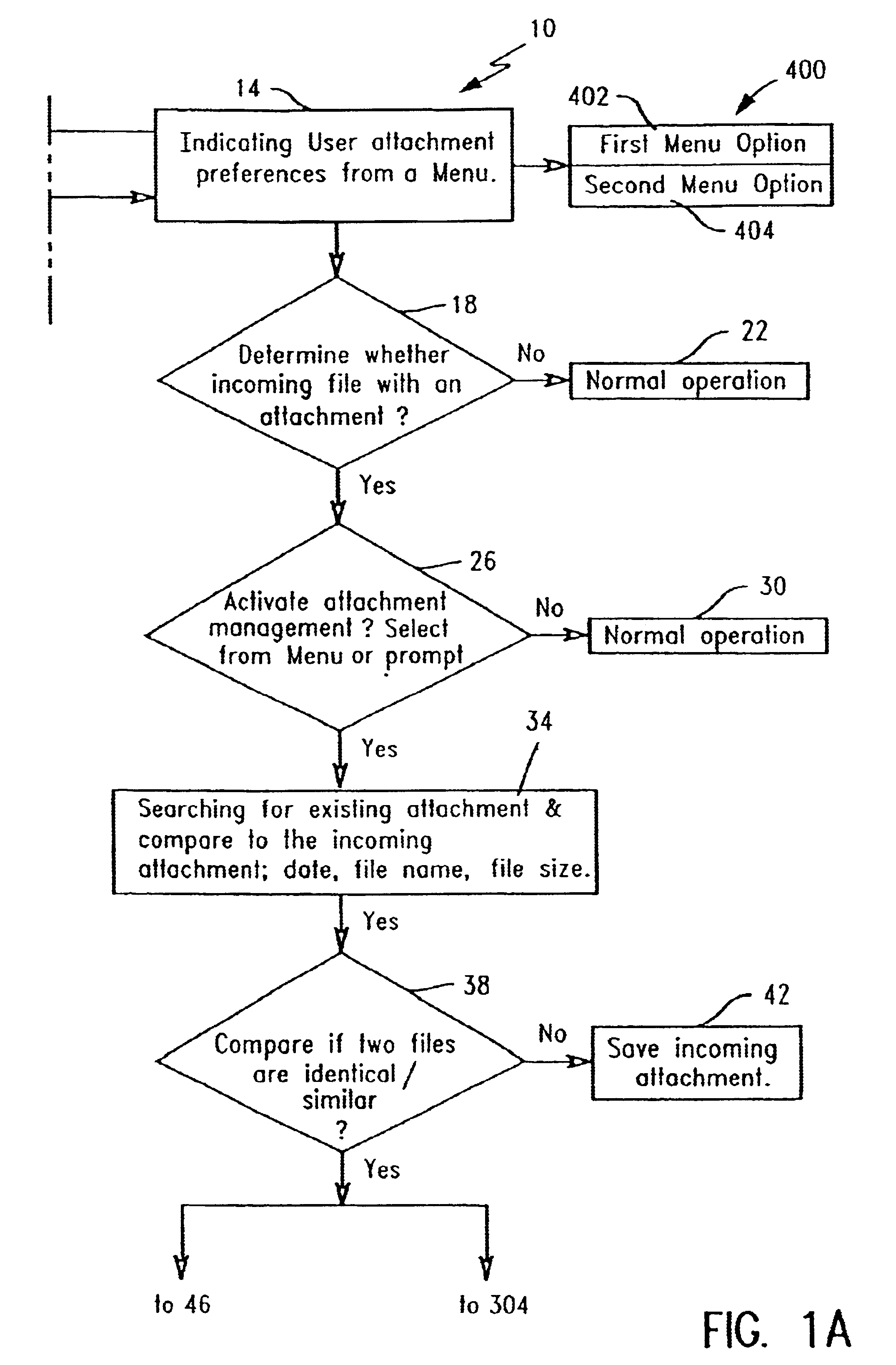
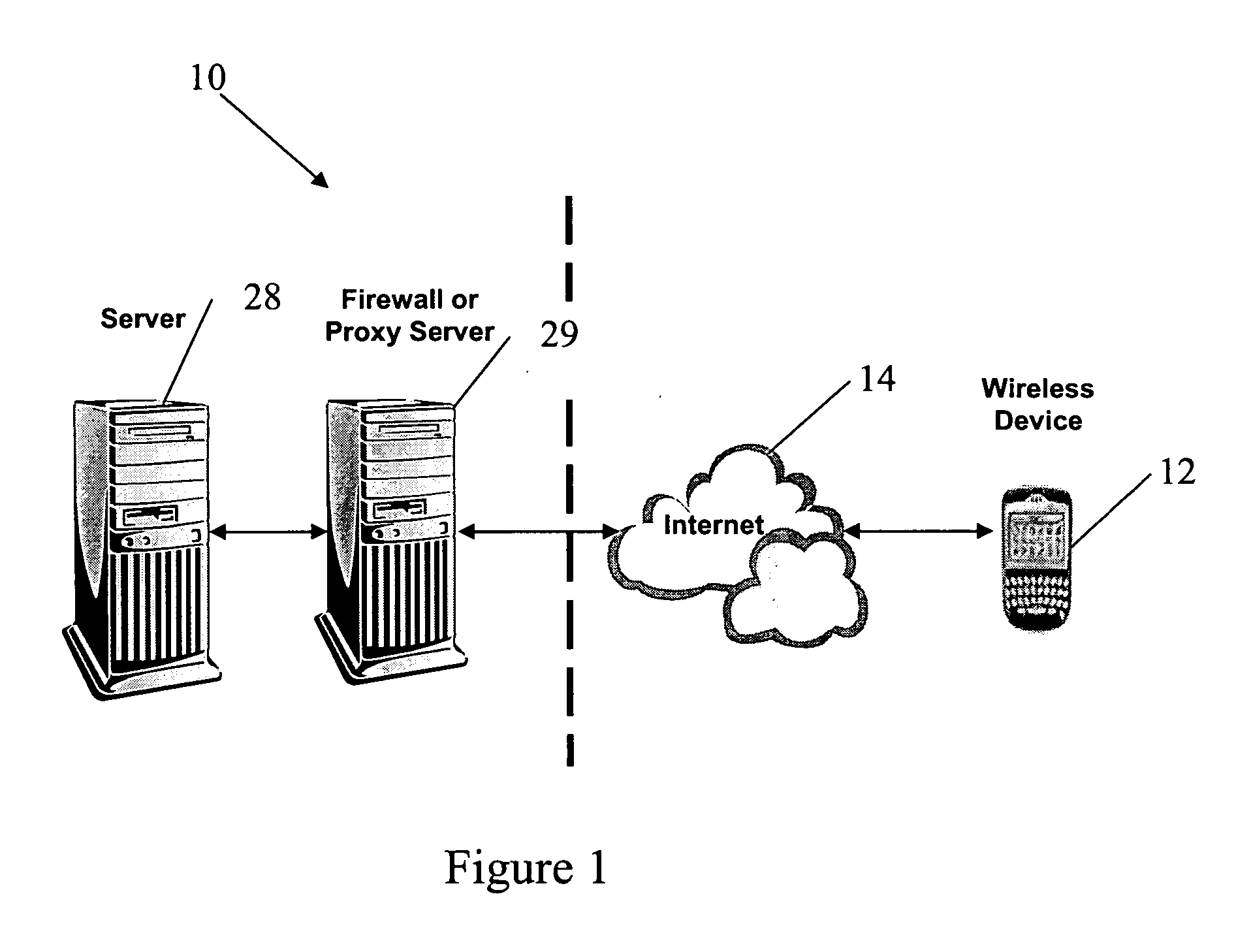
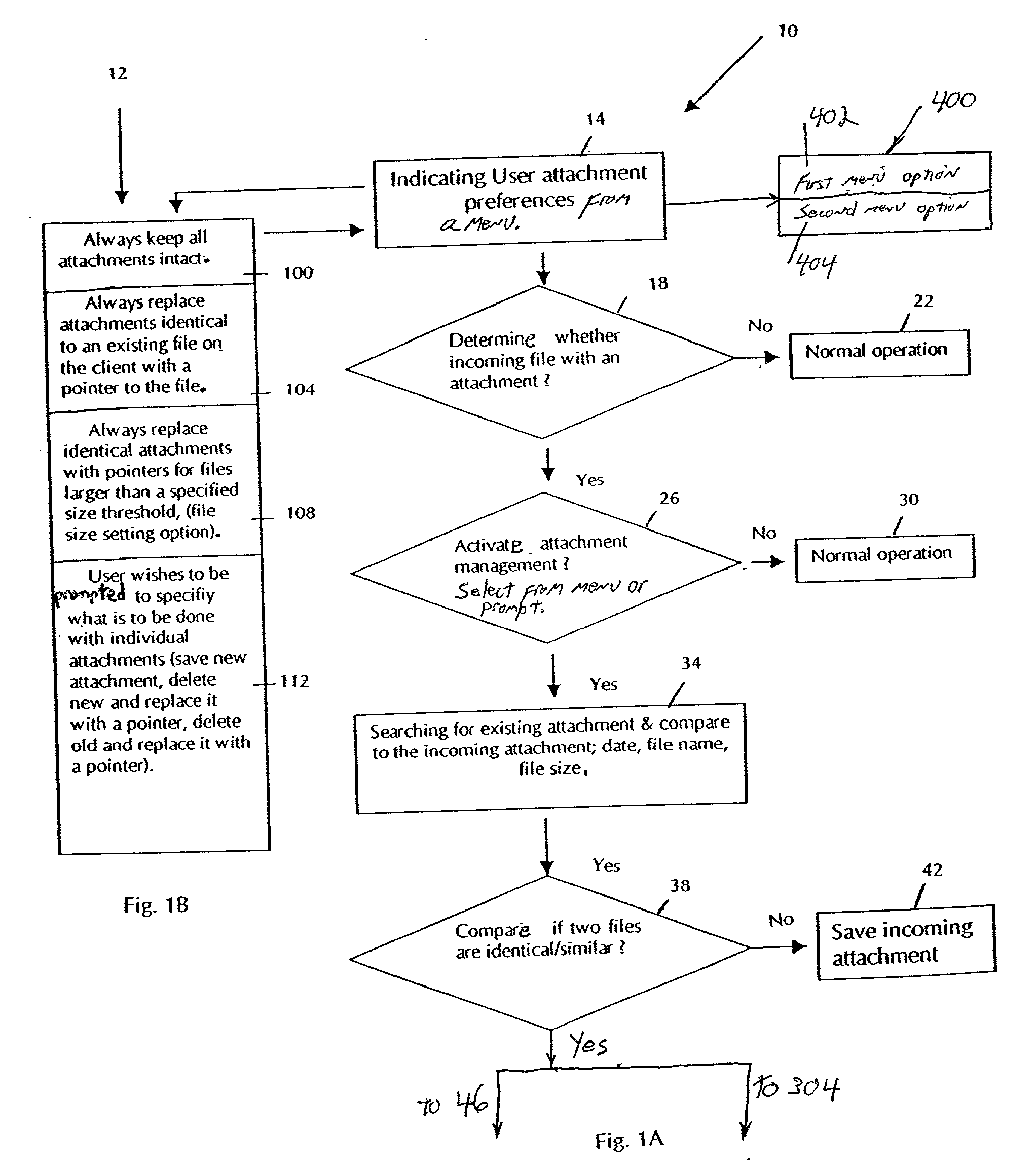
System and methodology for optimizing delivery of email attachments for disparate devices
InactiveUS20020016818A1Digital data information retrievalMultiple digital computer combinationsDevice typeWireless handheld devices
An e-mail system that re-packages message attachments optimized for delivery to wireless handheld devices is described. The preferred embodiment provides an optimization of the e-mail deliveries to allow for the recipients to receive e-mail attachments at a time and in a size / format as desired. The preferred embodiment compares the size of attached images to the capabilities of the type of the recipient client device, and preempts delivery of the original format of those attachments if they are determined to be burdensome or overwhelming. In cases wherein these attachments would strain the capabilities of the recipient devices' wireless bandwidth and / or display features, the original attachments are removed from the messages and do not accompany the e-mail delivery. Any detached attachment is saved in a network media-sharing repository, and can be subsequently accessed via a link (e.g., URL) referencing that storage address. Recipients can specify their wireless handheld device types, and opt to receive transformations of this type of attachment as a default substitute in subsequent e-mail deliveries. In cases wherein the recipient has previously used multiple types of client devices when receiving messages from the system, the present invention applies a transformation on the current attachment that corresponds to the least capable in the set of those multiple devices. Recipients may also elect to receive the URL for the network storage address of copies of either the original and / or transformed attachments.
Owner:SYNIVERSE ICX CORP
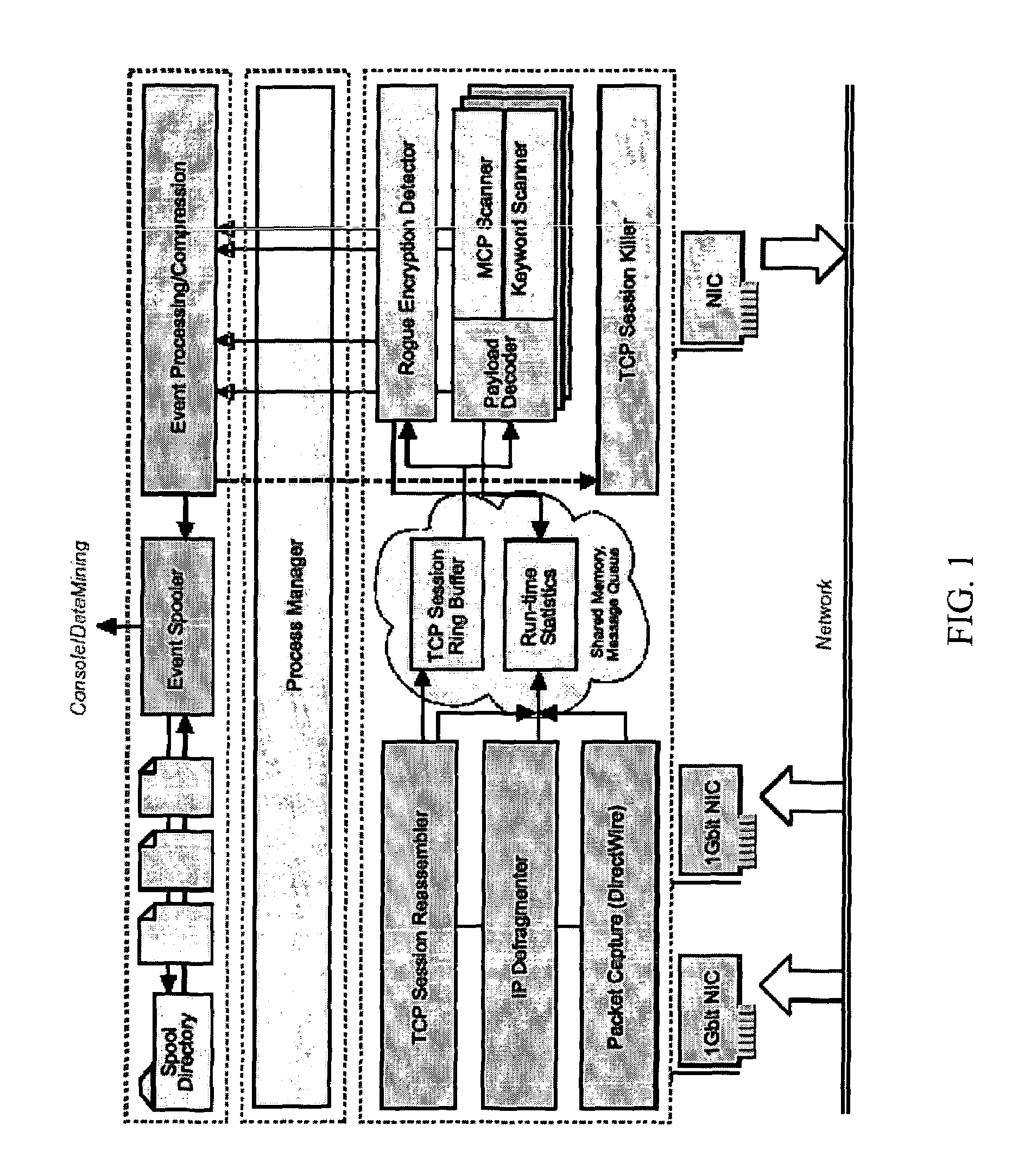
High-performance network content analysis platform
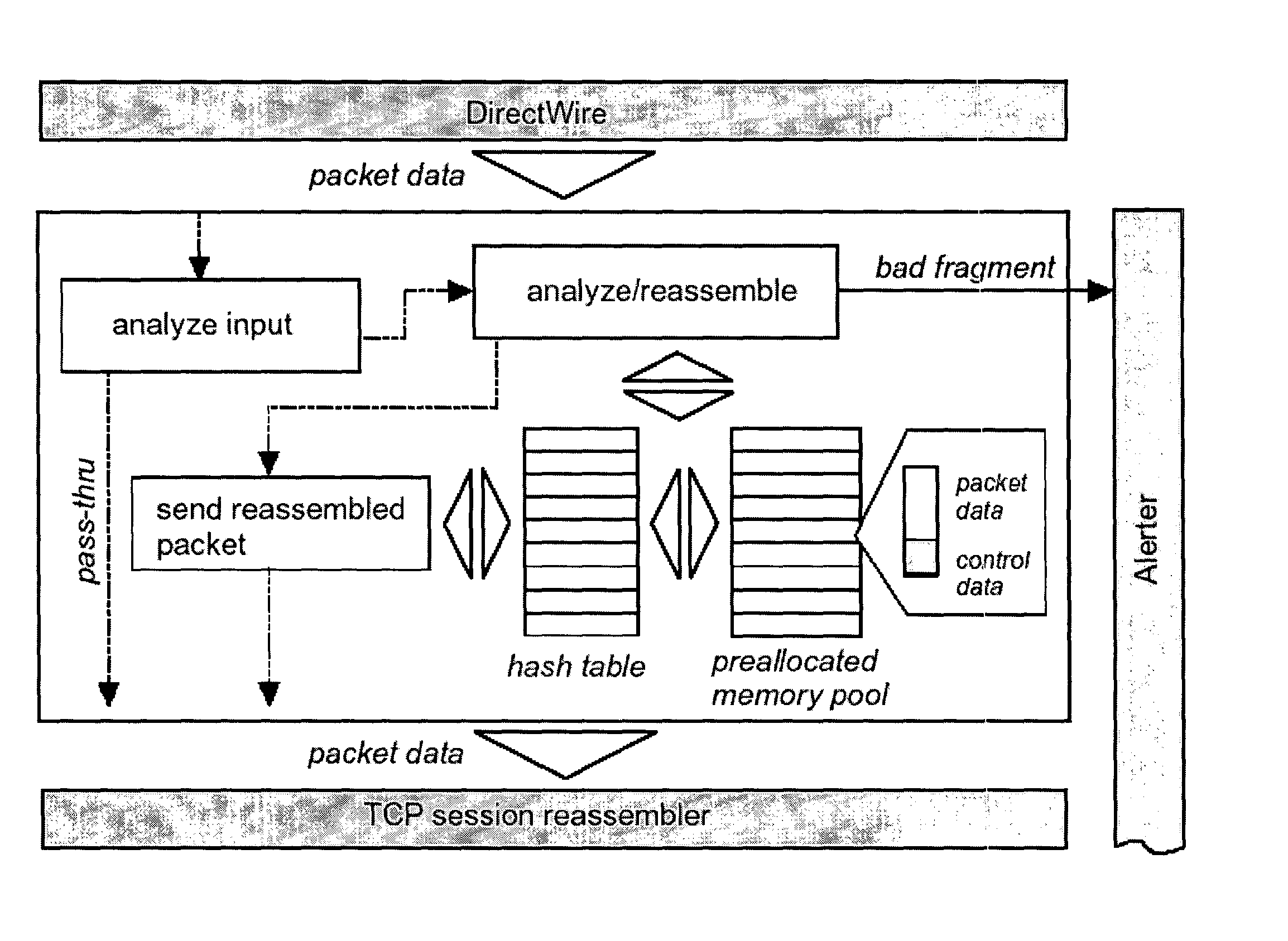
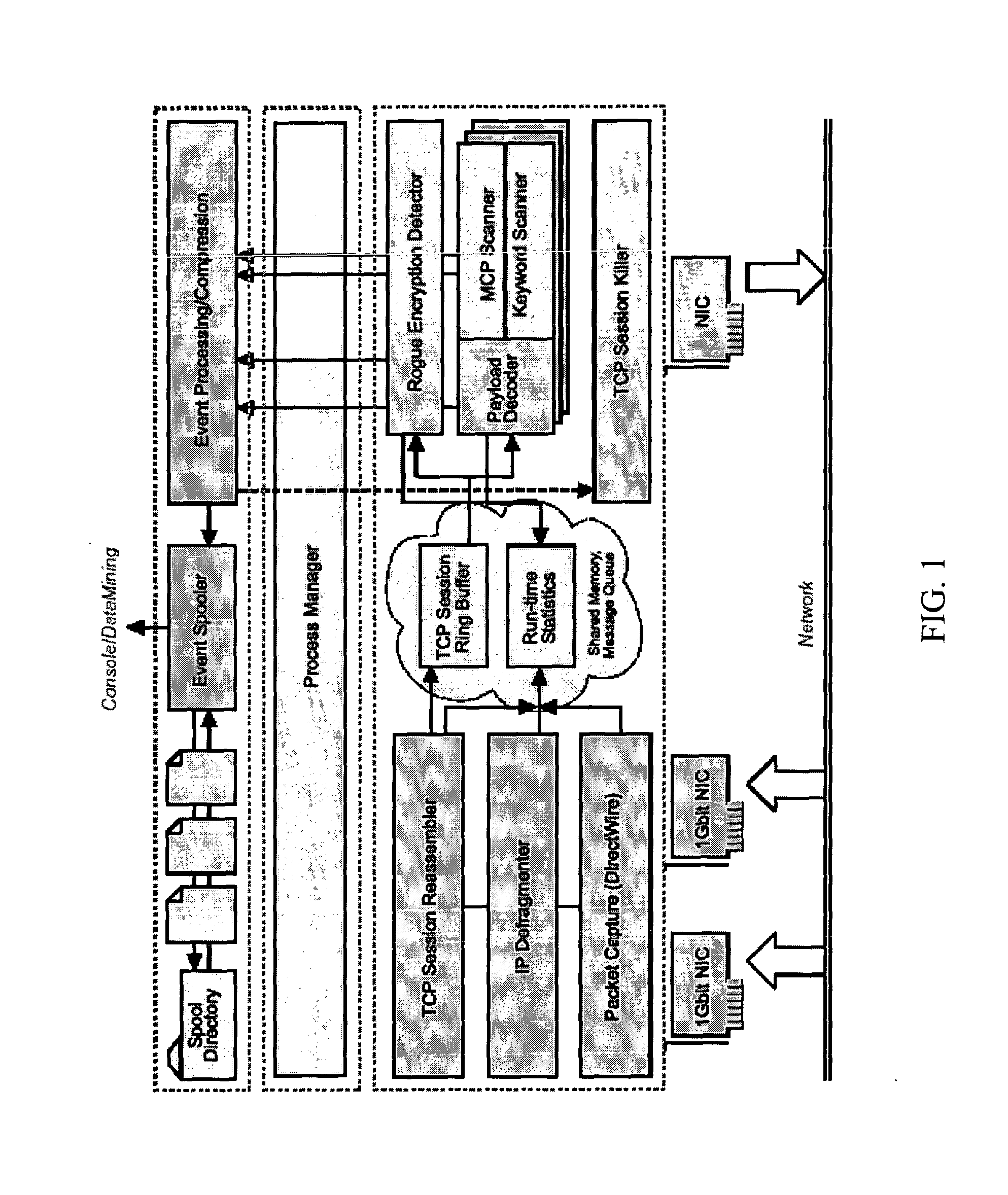
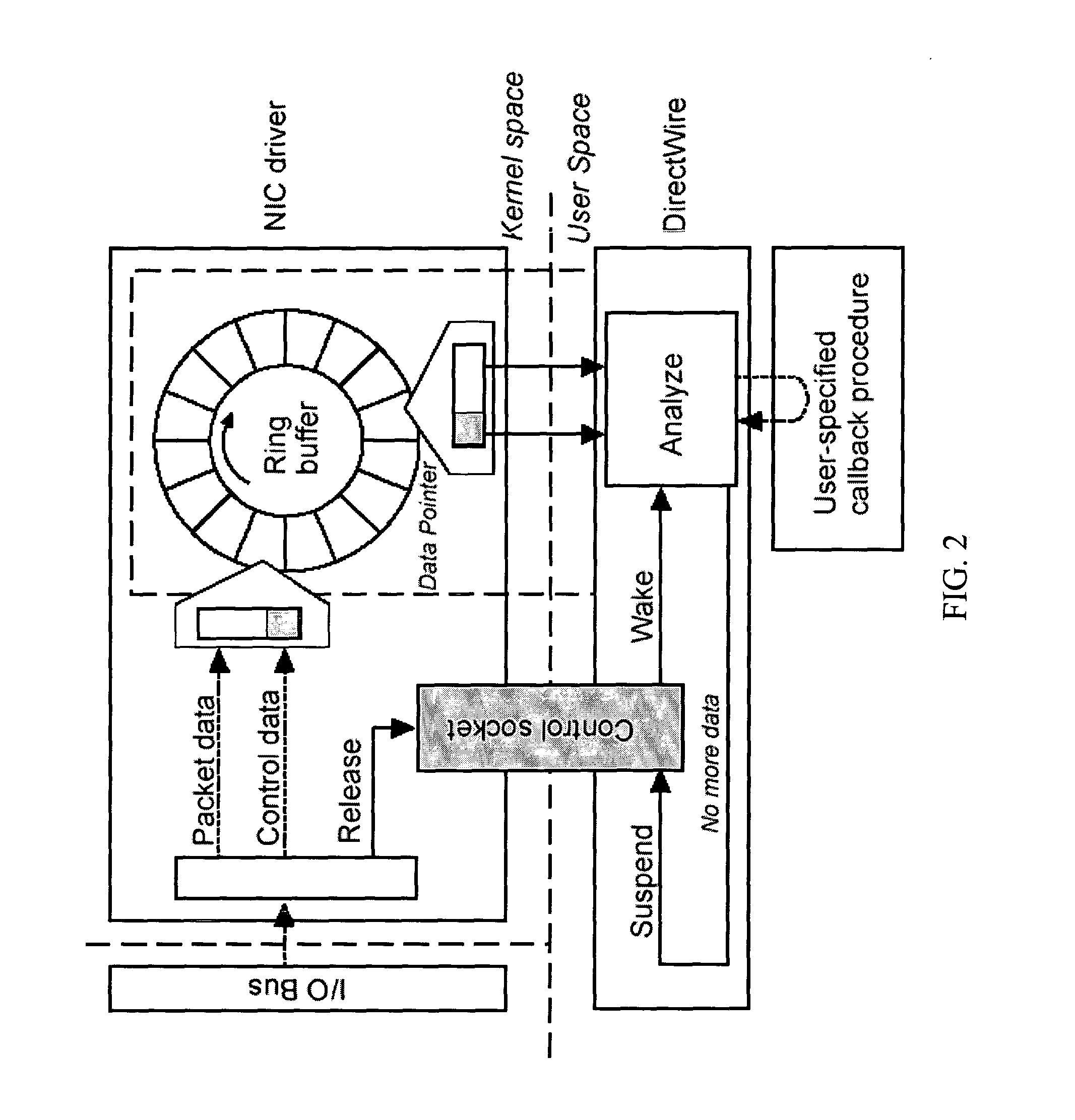
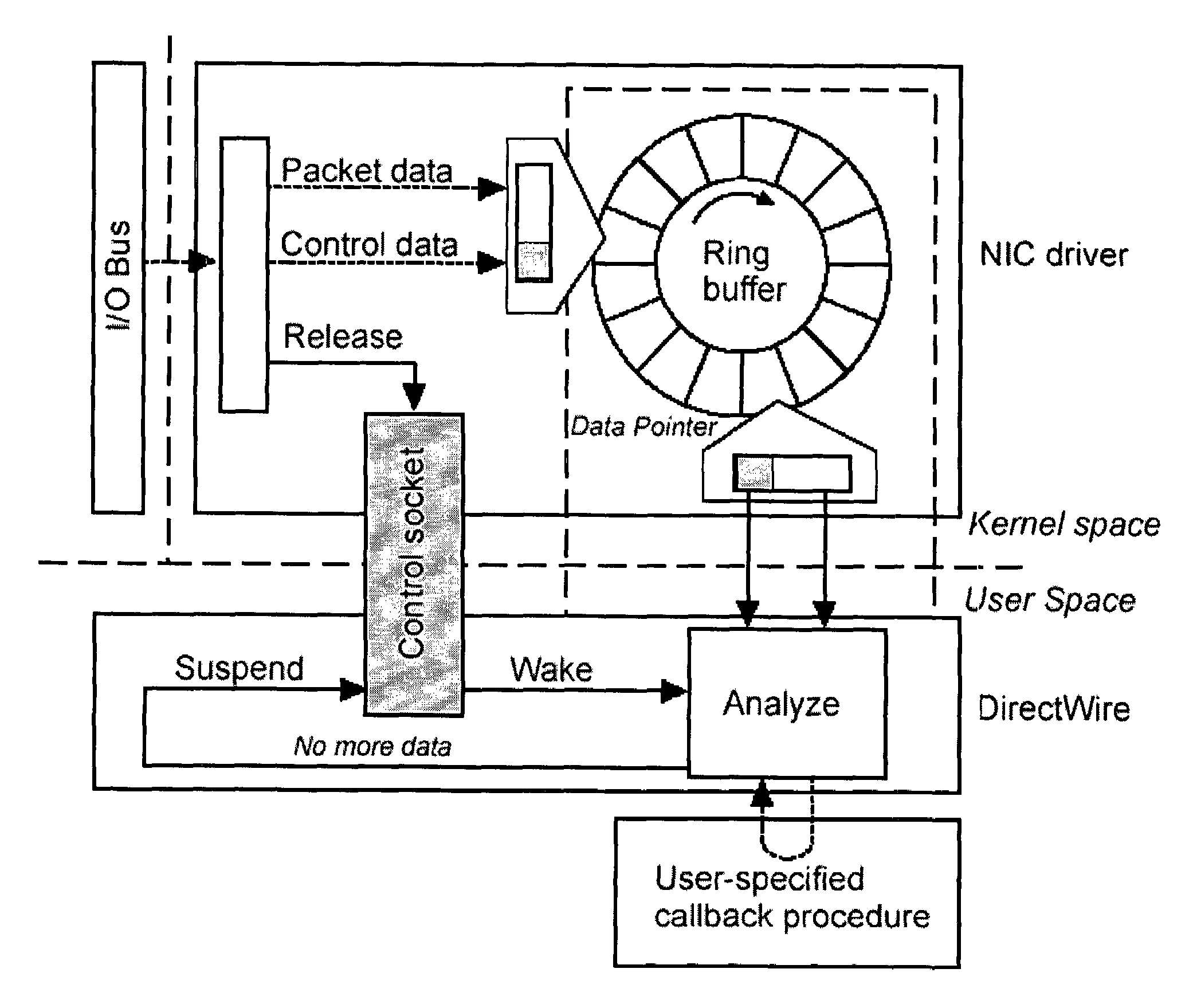
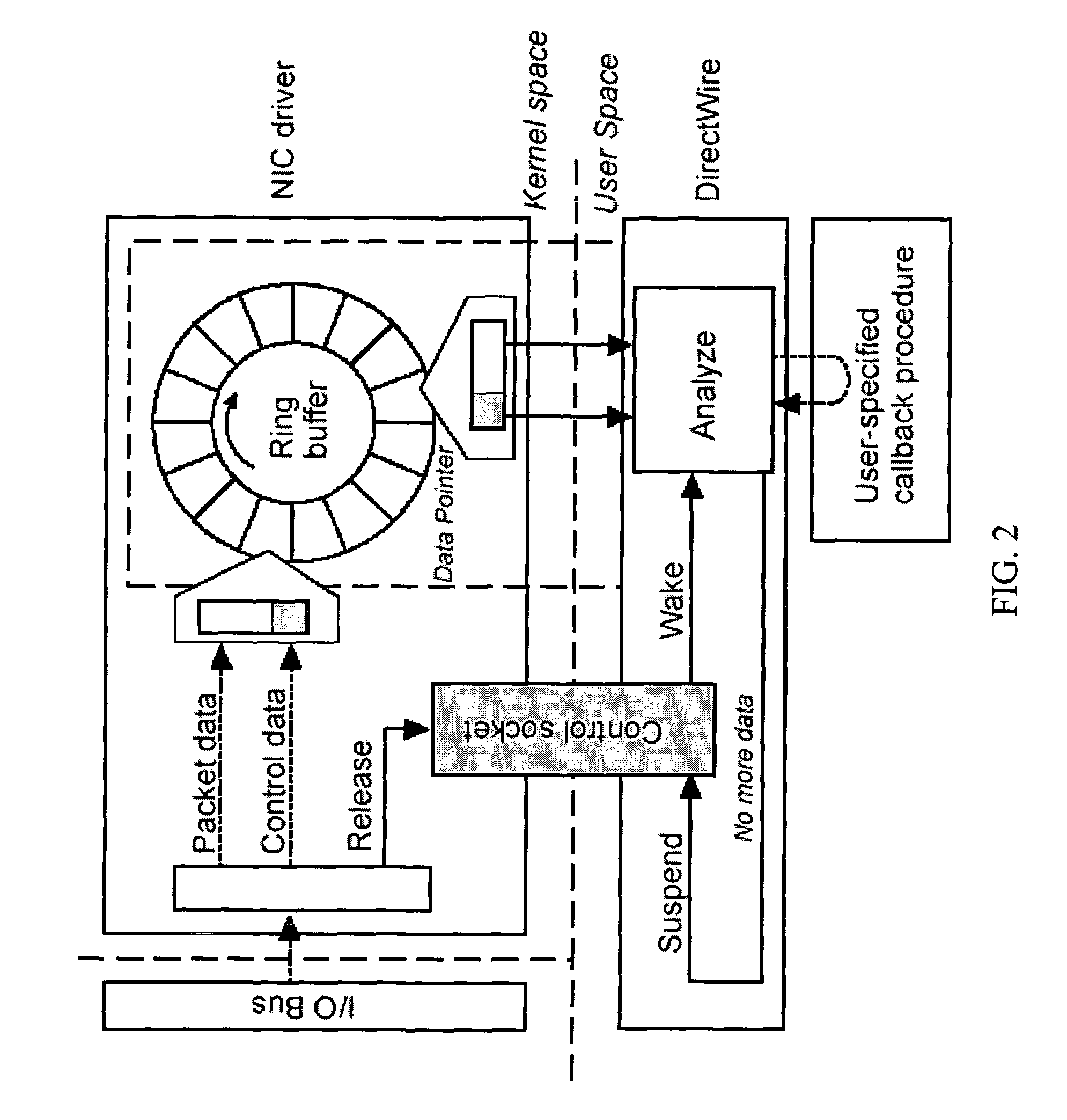
ActiveUS20050055399A1Prevent leakageDigital data processing detailsAnalogue secracy/subscription systemsData streamEmail attachment
One implementation of a method reassembles complete client-server conversation streams, applies decoders and / or decompressors, and analyzes the resulting data stream using multi-dimensional content profiling and / or weighted keyword-in-context. The method may detect the extrusion of the data, for example, even if the data has been modified from its original form and / or document type. The decoders may also uncover hidden transport mechanisms such as, for example, e-mail attachments. The method may further detect unauthorized (e.g., rogue) encrypted sessions and stop data transfers deemed malicious. The method allows, for example, for building 2 Gbps (Full-Duplex)-capable extrusion prevention machines.
Owner:FIDELIS SECURITY SYSTEMS
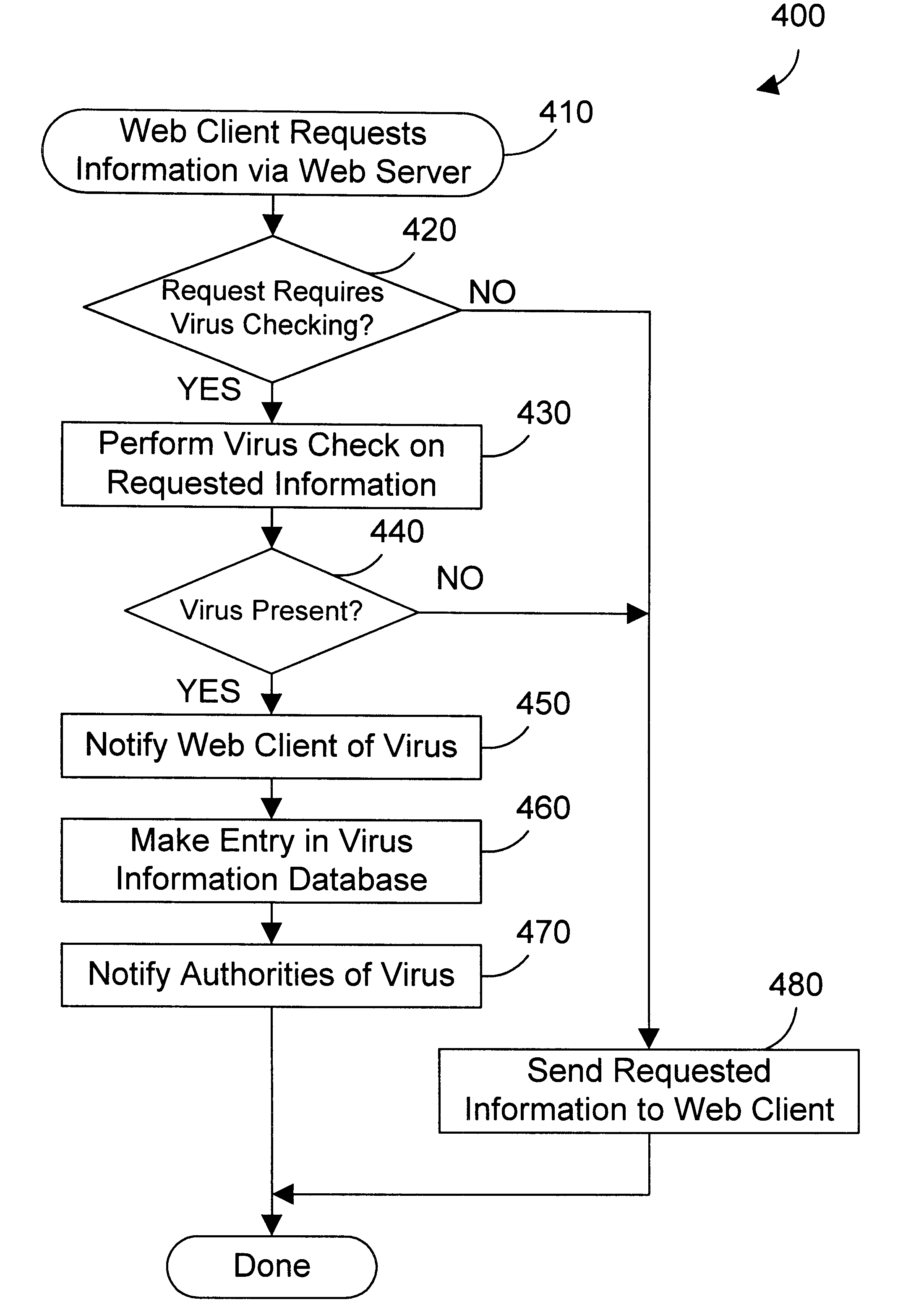
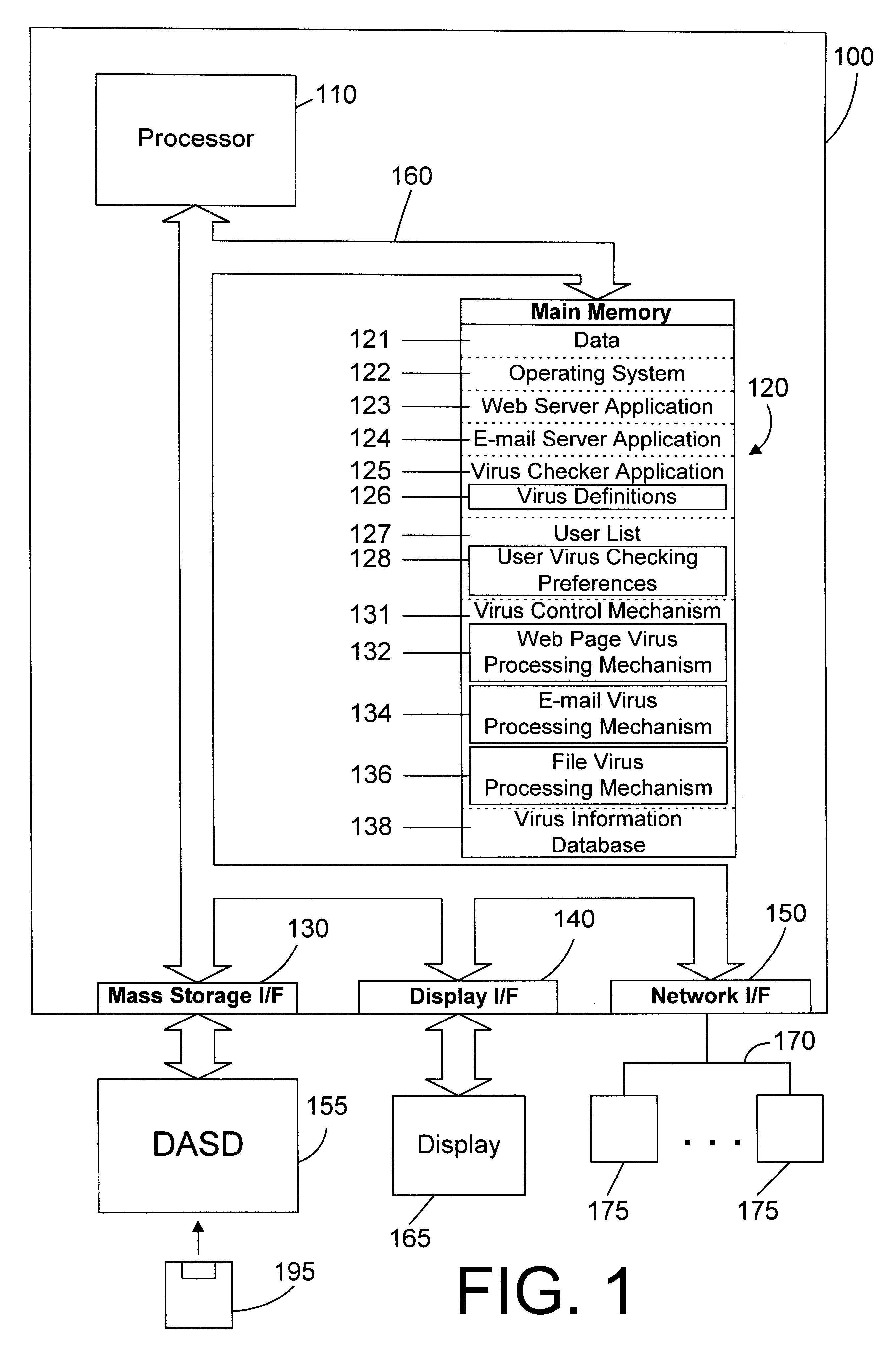
Web server apparatus and method for virus checking
InactiveUS6785732B1Eliminate needPrevent proliferationMemory loss protectionDigital data processing detailsWeb serviceUniform resource locator
A web server computer system includes a virus checker and mechanisms for checking e-mails and their attachments, downloaded files, and web sites for possible viruses. When an e-mail message contains a detected virus, the message is discarded, and both the sender and recipient are informed via e-mail that the message contained a virus. When an e-mail attachment contains a detected virus, the attachment is deleted, and the e-mail message without the attachment is sent to the web client, along with a message explaining that the e-mail message had an attachment that was automatically deleted because it had a virus. When a downloaded file contains a virus, the downloaded file is deleted, and an error message is sent to the web client to inform the web client that the requested file had a virus. When a requested web site (i.e., Uniform Resource Locator (or URL)) has been labeled as a source for a known virus, a message is sent to the web client stating that a virus may have been downloaded from that URL. In addition, if the requested URL has not been labeled as a source for a known virus, but it contains links that have been so labeled, the web page is processed before being sent to the user to identify those potentially dangerous links. In this manner a web server can perform virus checking of different types of information real-time as the information is requested by a web client. In addition, a web client may also request that the server perform virus checking on a particular drive on the web client. If this case, the web server may receive information from the web client drive, scan the information for viruses, and inform the web client whether any viruses were found. In the alternative, the web server may download a client virus checker to the web client and cause the client virus checker to be run on the web client. The preferred embodiments thus allow a virus checker on a web server to dynamically scan incoming data, and to scan web clients coupled to the web server, thereby eliminating the need for virus checking software to be installed on each web client.
Owner:FINJAN BLUE INC
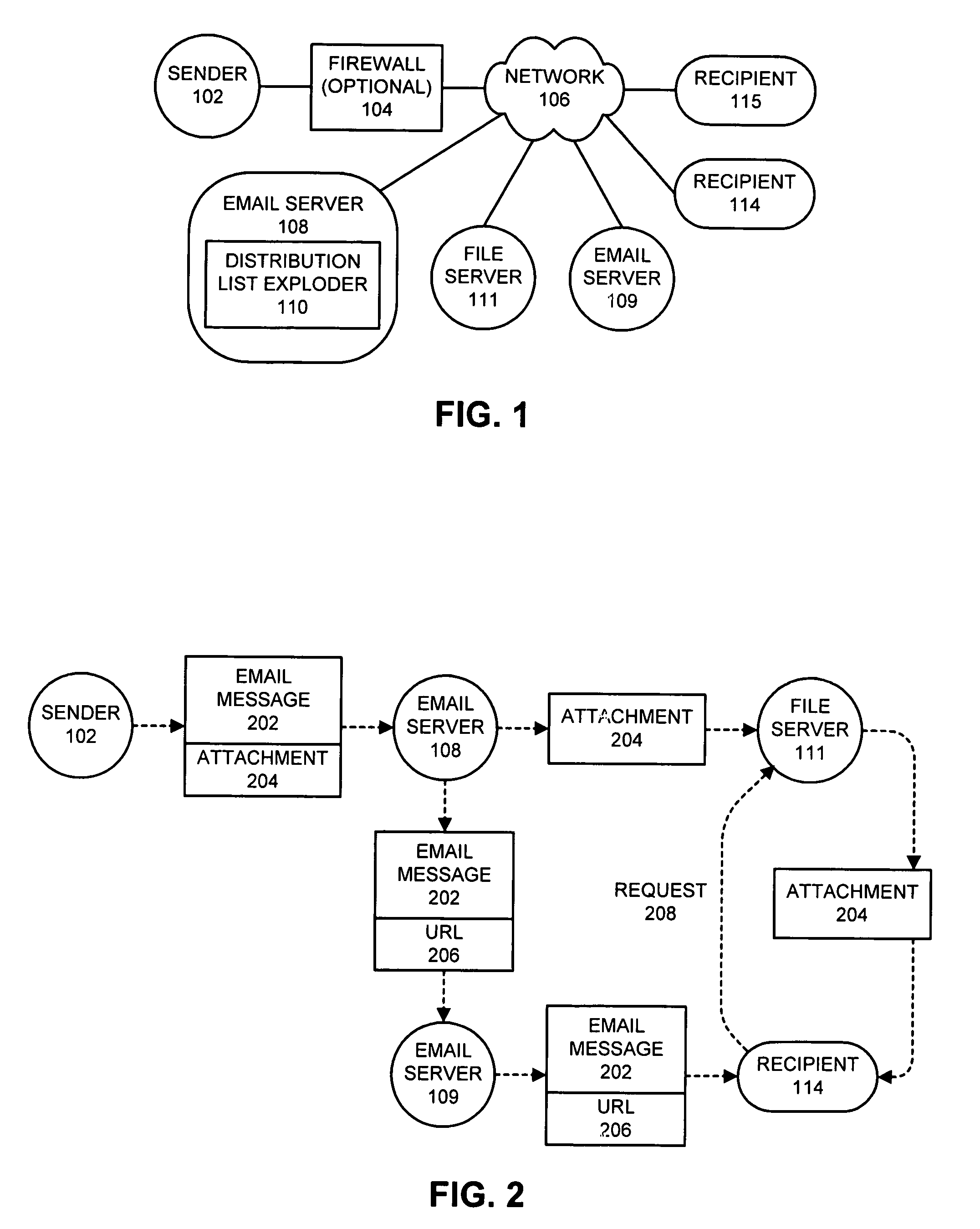
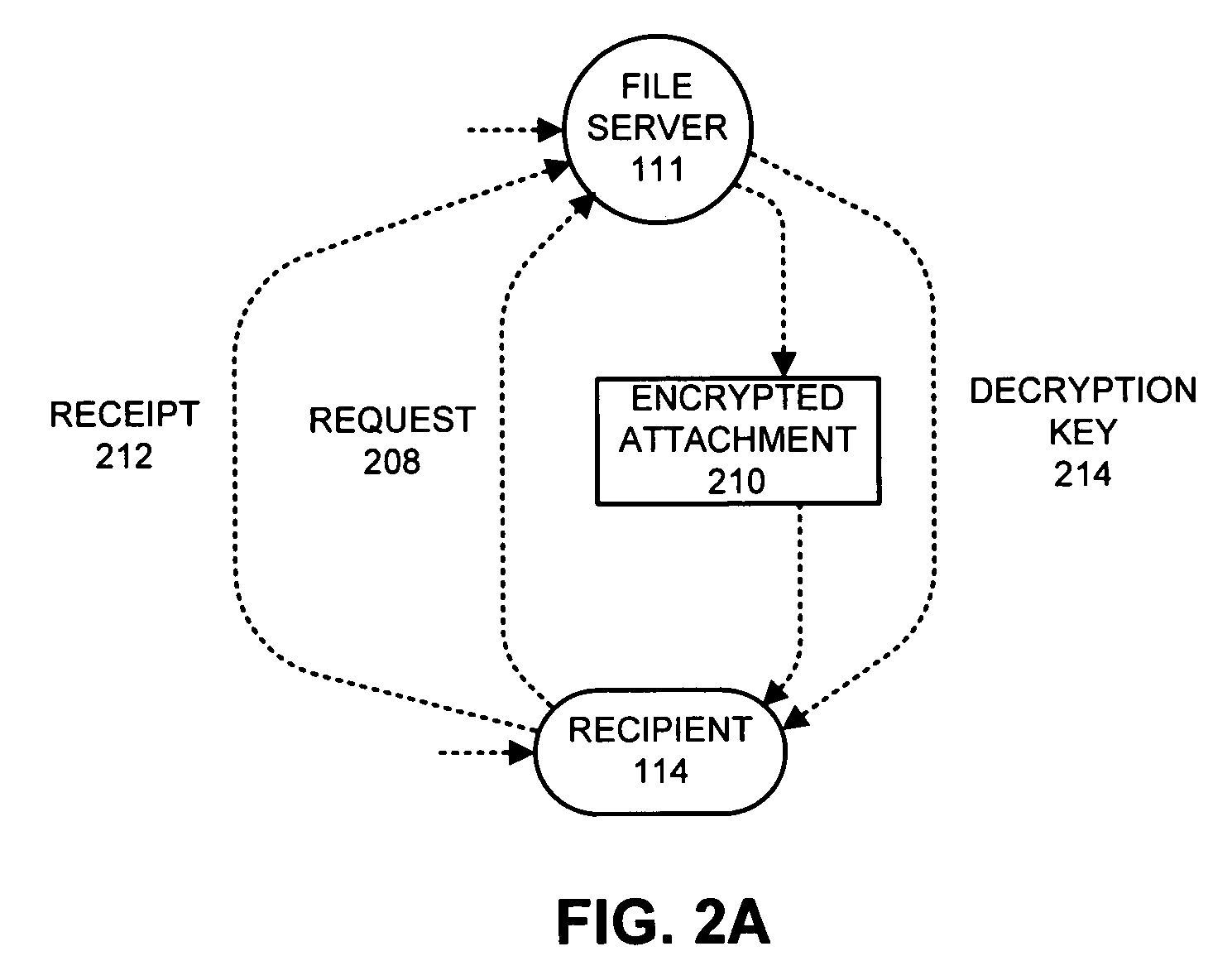
Facility for distributing and providing access to electronic mail message attachments
InactiveUS6839741B1Unauthorized memory use protectionMultiple digital computer combinationsEmail attachmentElectronic mail
A facility stores attachments for electronic mail messages so that the messages may be transmitted to the intended recipients without the attachments. The recipients may then review and / or download the attachments by contacting the facility. This facility is especially useful in instances wherein the attachments are large. The facility eliminates the need to store multiple copies of the attachment throughout a system; thus consuming a great deal of memory space. In addition, the facility prevents the recipient from extensive delays that are often associated with downloading email messages that contain large attachments via a dial-up connection with a low transmission rate. The facility may be realized as a server and may be a web server so as to provide access to the attachments via an IP network.
Owner:VERIZON PATENT & LICENSING INC
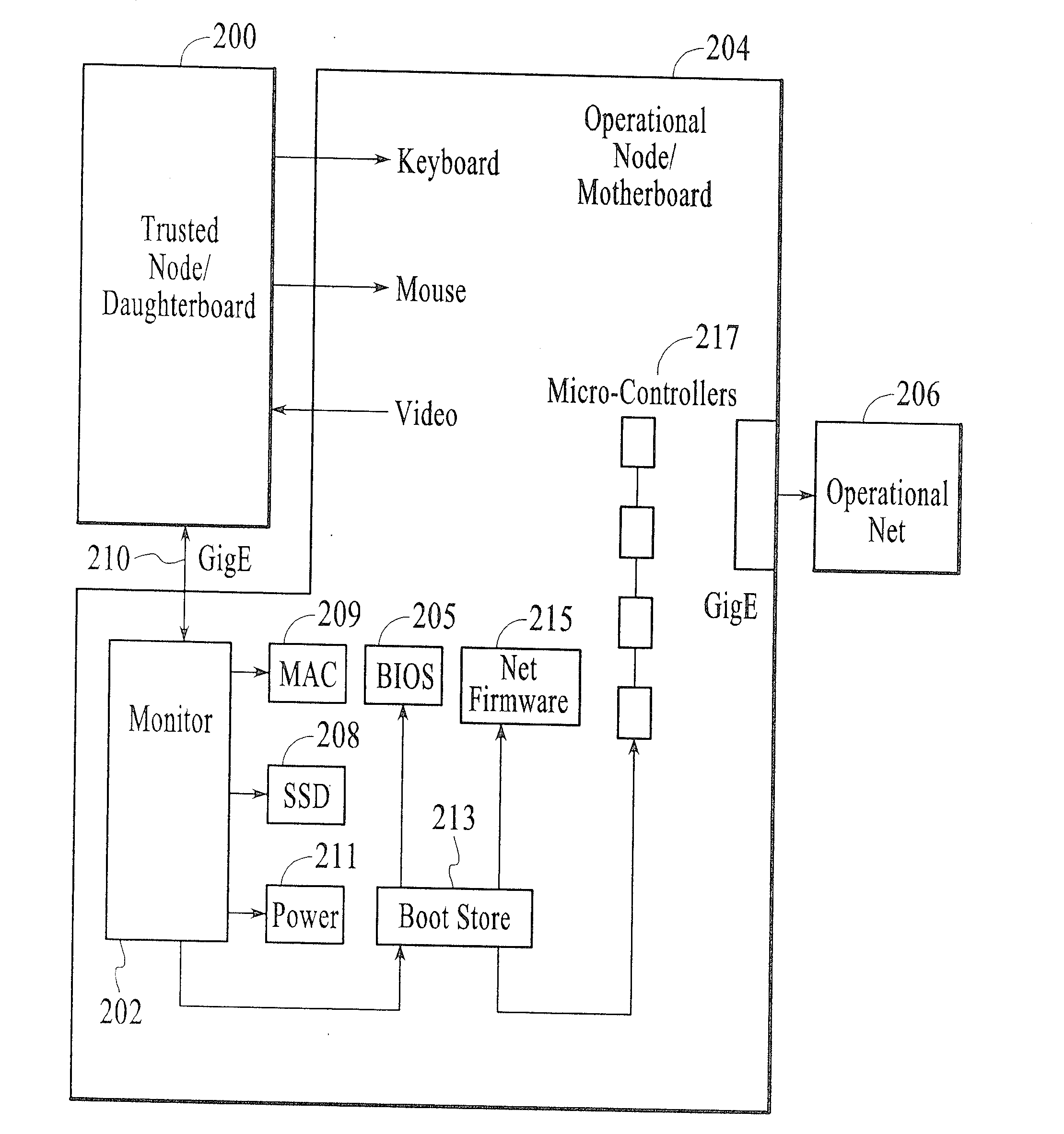
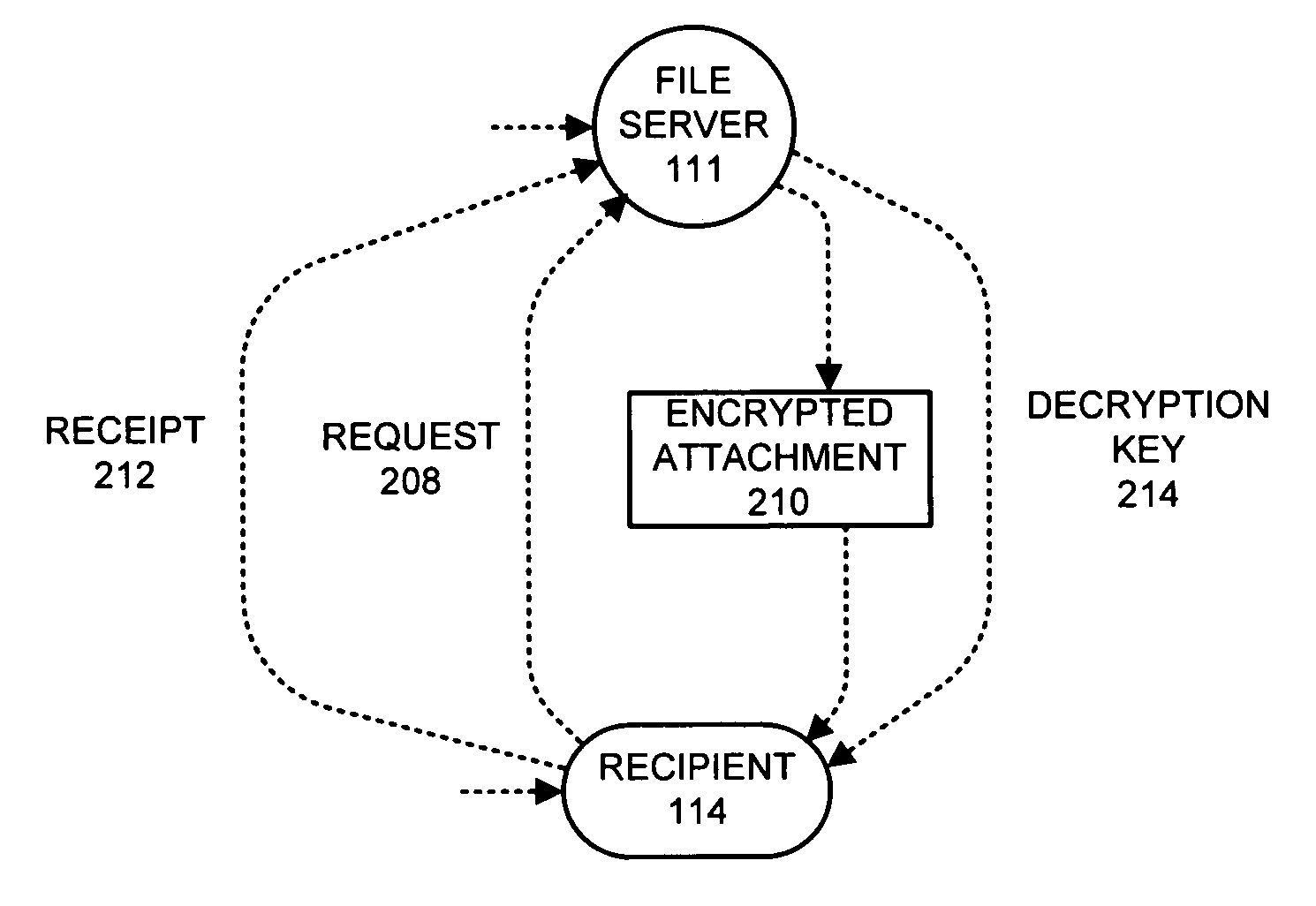
System and method for providing secure reception and viewing of transmitted data over a network
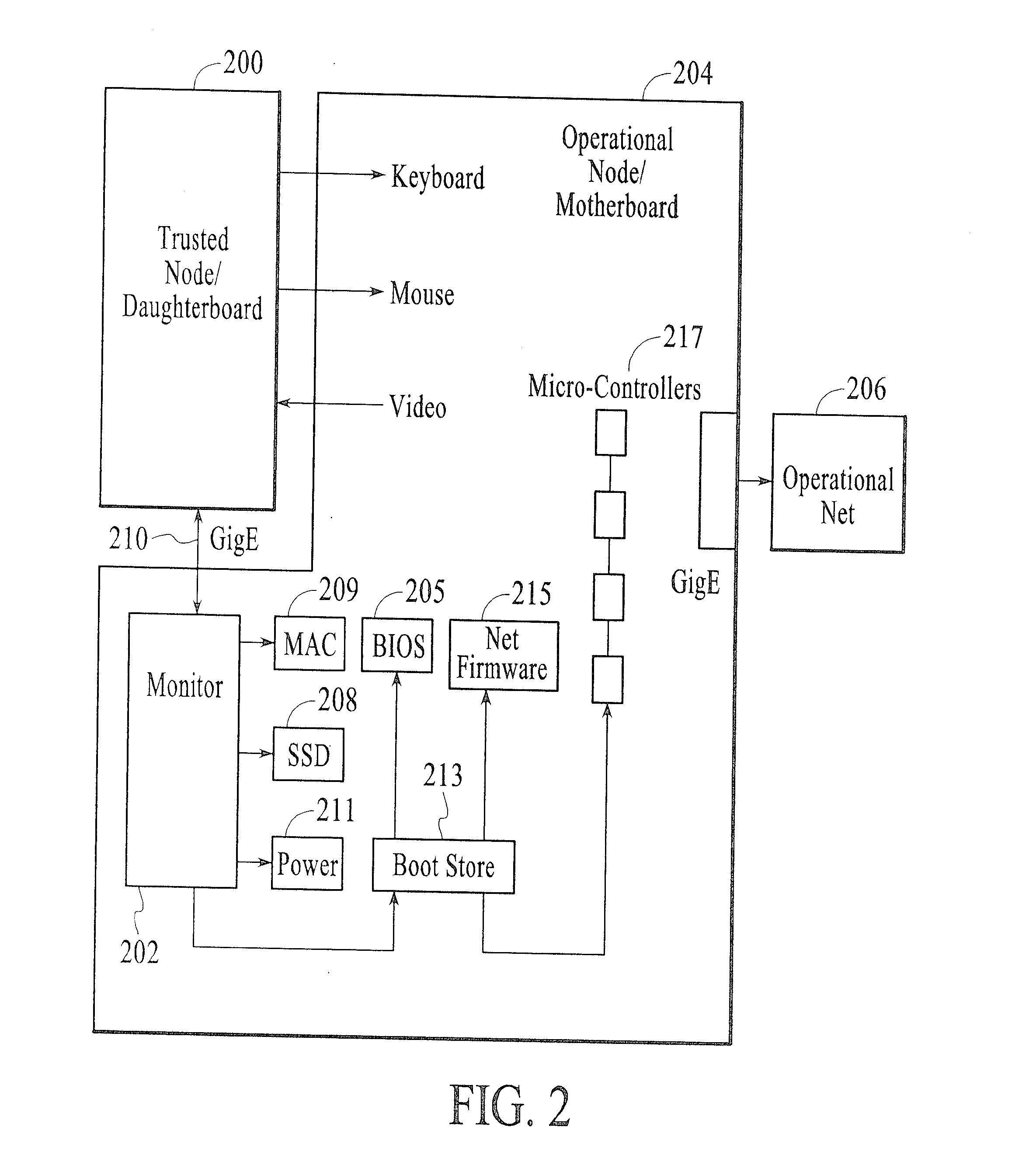
InactiveUS20110113231A1Memory loss protectionError detection/correctionComputer networkEmail attachment
A method and system for securely opening an e-mail attachment in a computer processing environment having a trusted node daughterboard connected to at least one operational node motherboard with an e-mail processing system operatively coupled to the trusted node daughterboard. The method includes the steps of when an e-mail attachment is to be opened, sending a power on signal from the trusted node daughterboard to the operational node motherboard when it is desired to utilize the operational node motherboard for opening an e-mail attachment. Pre-boot data is then requested from the operational node motherboard and is sent from the trusted node daughterboard to the operational node motherboard to enable operation of the operational node motherboard for securely opening an e-mail attachment.
Owner:KAMINSKY DANIEL
Replacing an email attachment with an address specifying where the attachment is stored
InactiveUS7054905B1User identity/authority verificationMultiple digital computer combinationsInternet privacyEmail attachment
One embodiment of the present invention provides a system that replaces an attachment to an email message with a reference to a location where the attachment is stored. Upon receiving the email message, the system examines the email message to determine if the email message includes an attachment. If the email message includes the attachment, the system stores the attachment at a location on a communication network from which the attachment can be retrieved. The system also modifies the email message by replacing the attachment with a reference specifying the location of the attachment, and sends the modified email message to a recipient of the email message. In one embodiment of the present invention, the recipient receives the modified email message and uses the reference specifying the location of the attachment to retrieve the attachment across the communication network.
Owner:ORACLE INT CORP
High-performance network content analysis platform
ActiveUS7467202B2Prevent leakageDigital data processing detailsAnalogue secracy/subscription systemsData streamKeyword analysis
One implementation of a method reassembles complete client-server conversation streams, applies decoders and / or decompressors, and analyzes the resulting data stream using multi-dimensional content profiling and / or weighted keyword-in-context. The method may detect the extrusion of the data, for example, even if the data has been modified from its original form and / or document type. The decoders may also uncover hidden transport mechanisms such as, for example, e-mail attachments. The method may further detect unauthorized (e.g., rogue) encrypted sessions and stop data transfers deemed malicious. The method allows, for example, for building 2 Gbps (Full-Duplex)-capable extrusion prevention machines.
Owner:FIDELIS SECURITY LLC
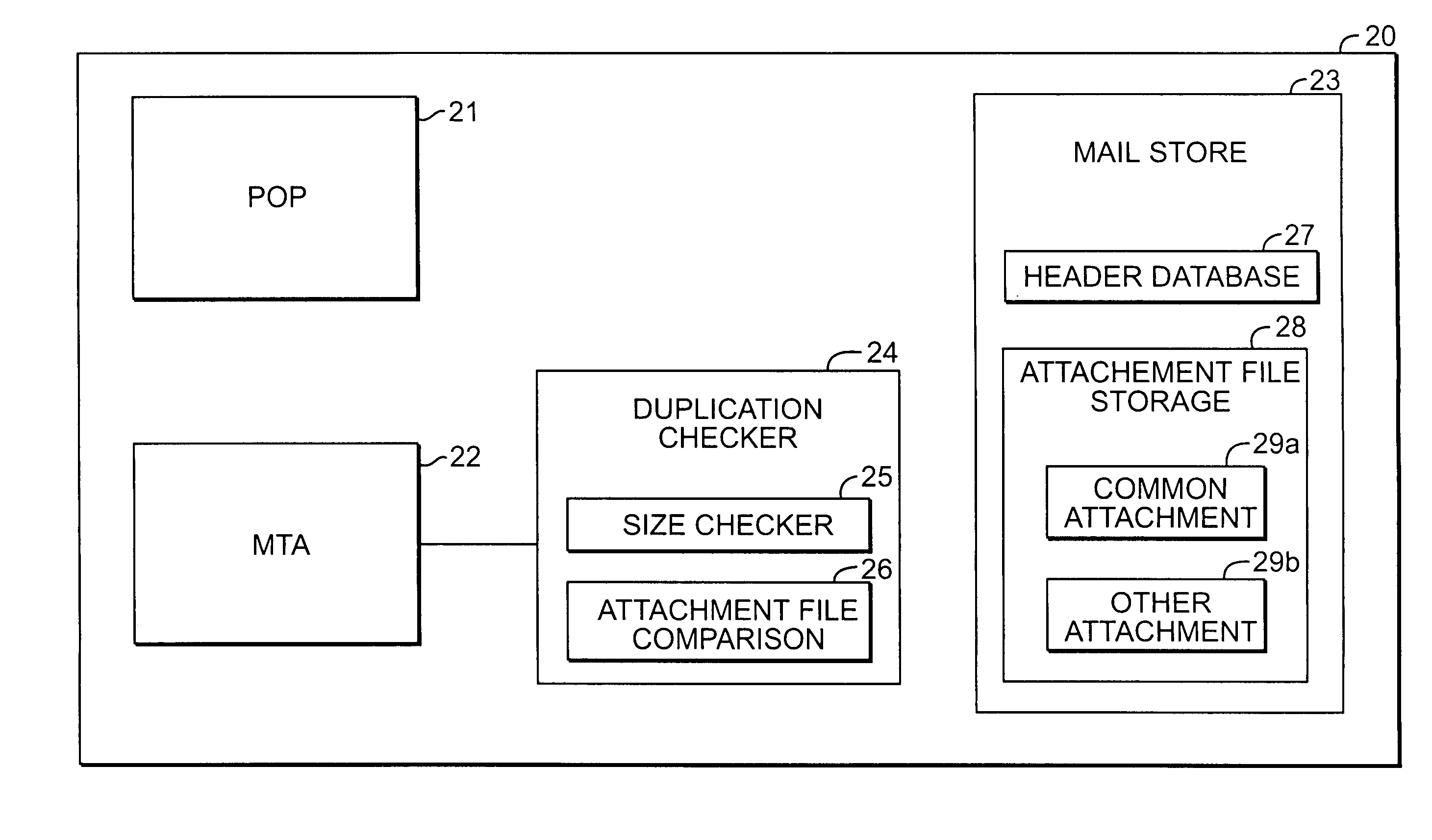
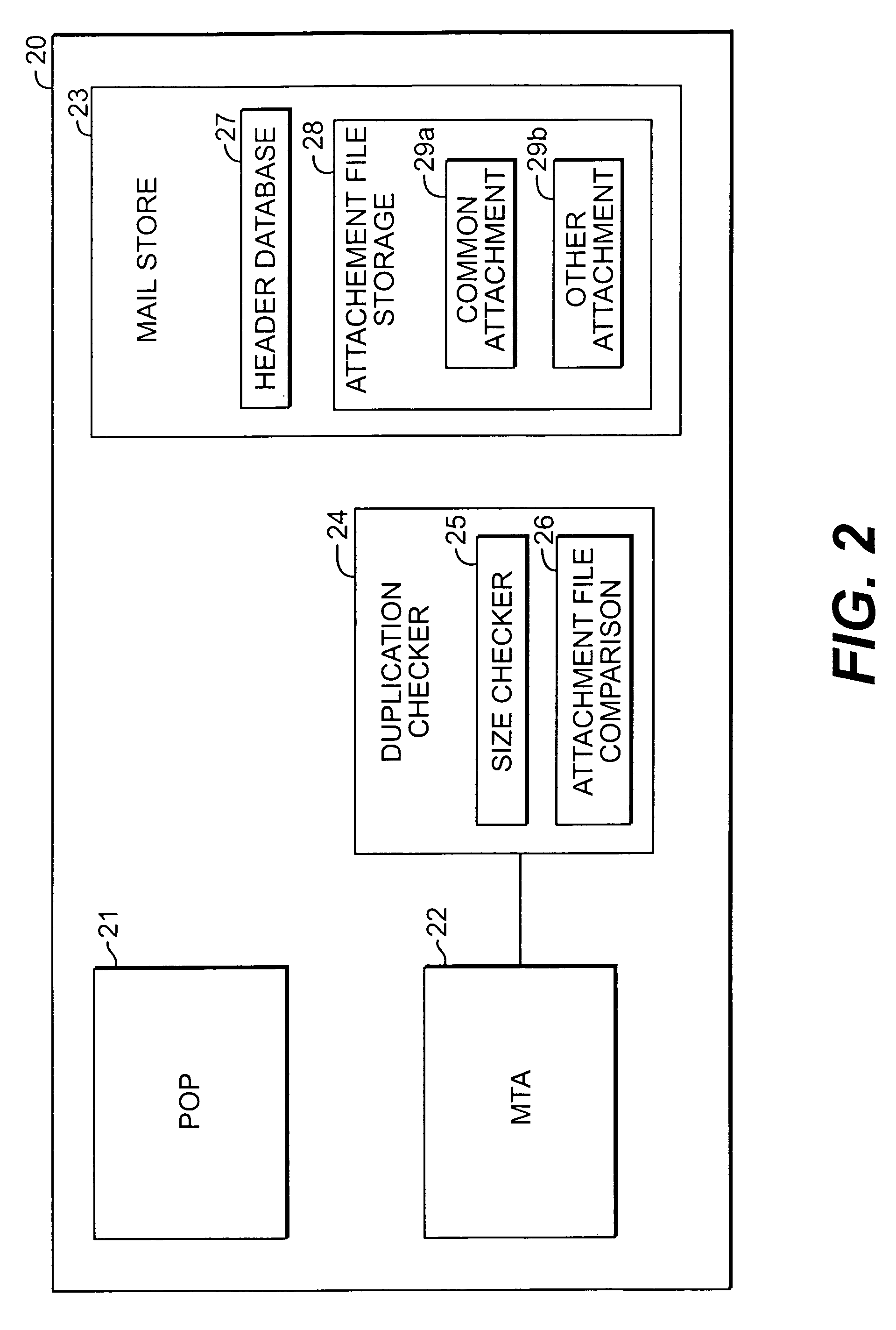
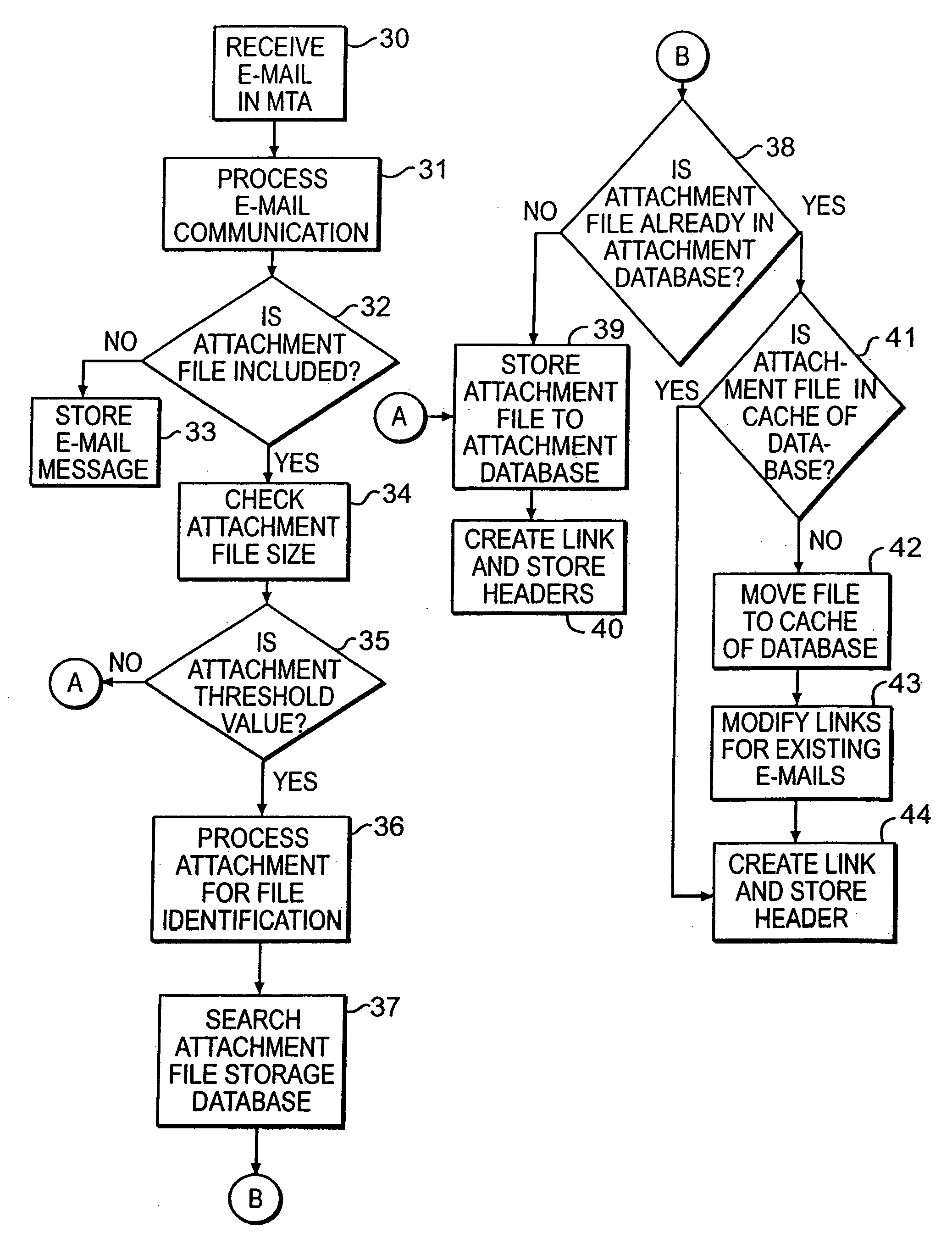
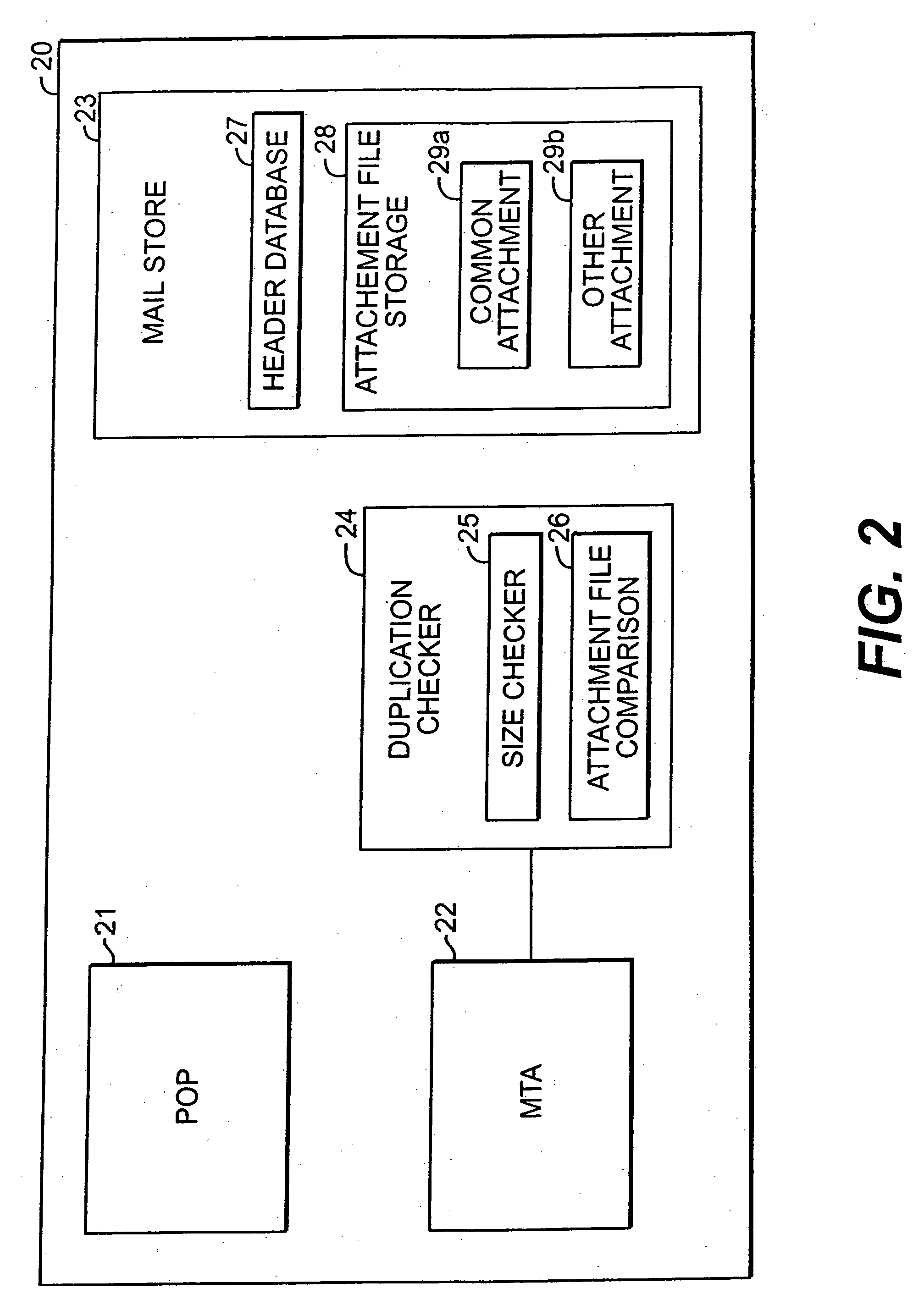
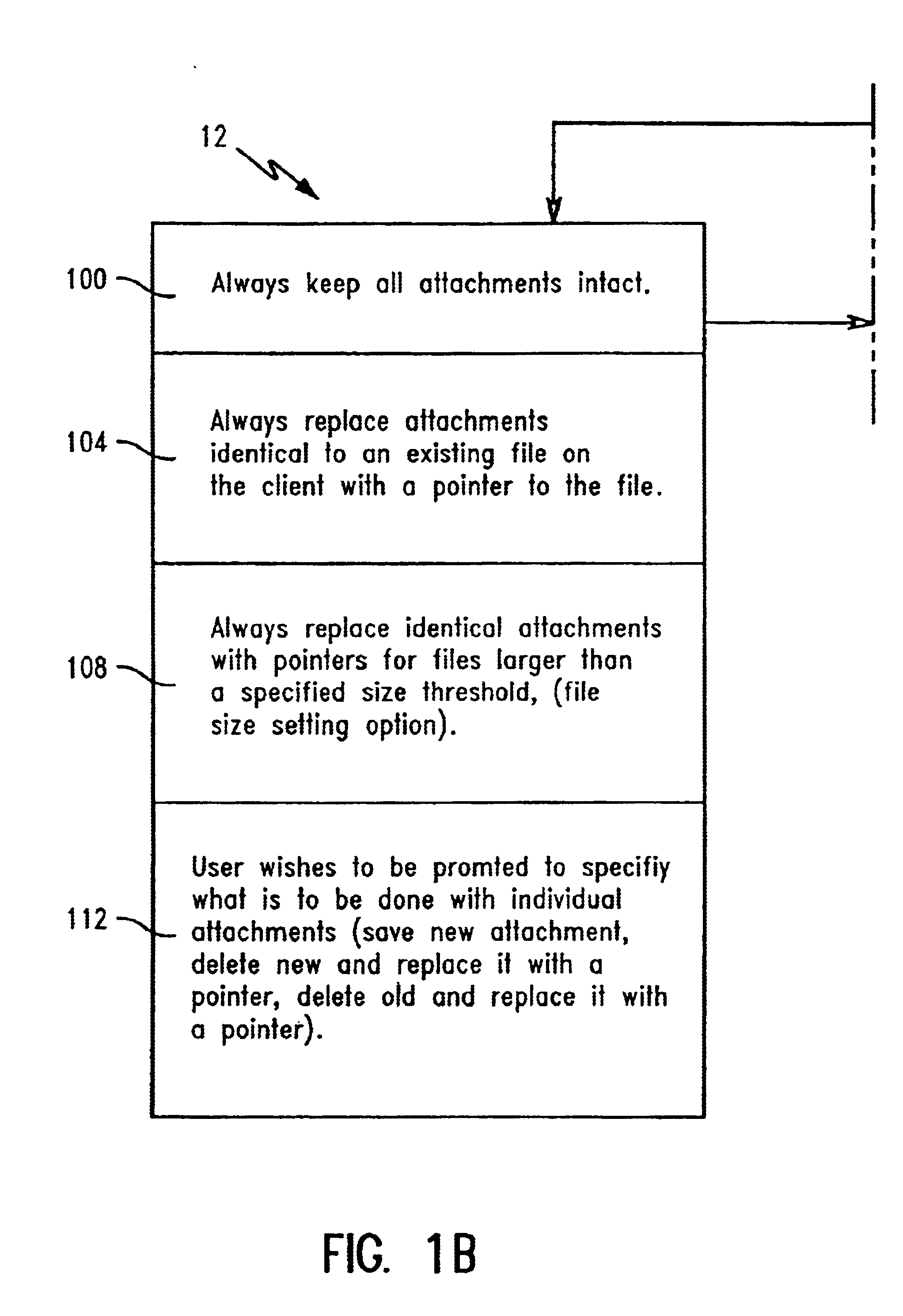
Method and apparatus for minimizing storage of common attachment files in an e-mail communications server
InactiveUS7003551B2Multiple digital computer combinationsOffice automationCommunications systemEmail attachment
The present invention provides an e-mail communications system that minimizes the number of duplicate copies of common attachment files to e-mail communications that are stored in the mail store of an e-mail server. When the e-mail server receives an e-mail attachment file that is larger than a threshold size, the server performs a database search for another copy of the attachment file in the mail store. If another copy is located, the system creates a pointer in the mail store that associates the located attachment file with the e-mail for the additional recipient(s). Attachment files are deleted only after the recipients of the associated e-mail communications delete each of the respective e-mails.
Owner:LINKEDIN
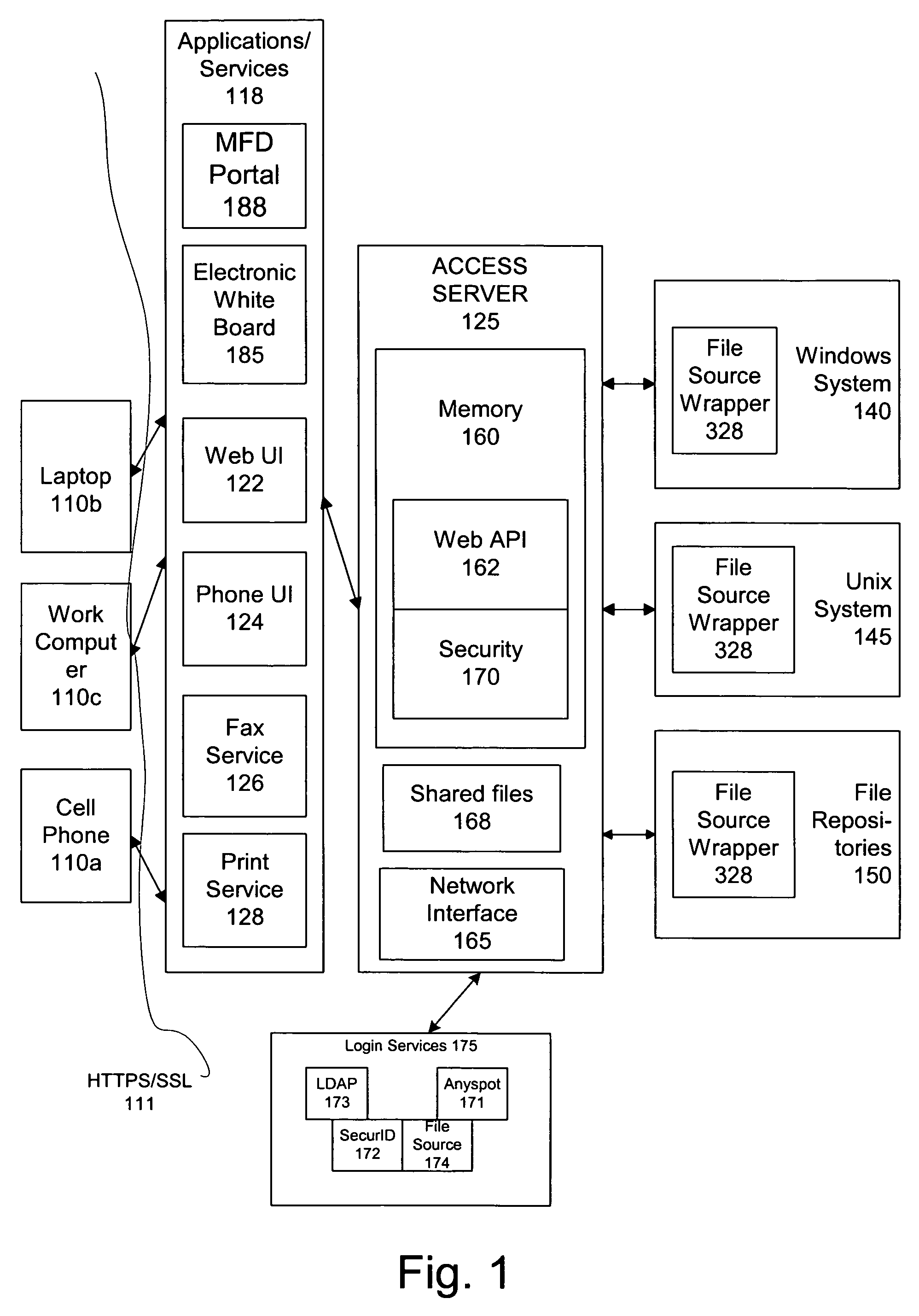
Remote file management using shared credentials for remote clients outside firewall
InactiveUS7412447B2Data processing applicationsMetadata multimedia retrievalEmail attachmentClient-side
An access server allows secure access to commonly used files stored on multiple file sources from a variety of client devices. The access server extracts a list of file sources associated with the user, and accesses each of those sources. The server is then configured to extract a list of most recently used files by the current user as well as information associated with those files. The access server also processes electronic mail attachments. The access server intercepts electronic mail messages containing attachments, and transmits the attachments to a file server.
Owner:FUJIFILM BUSINESS INNOVATION CORP
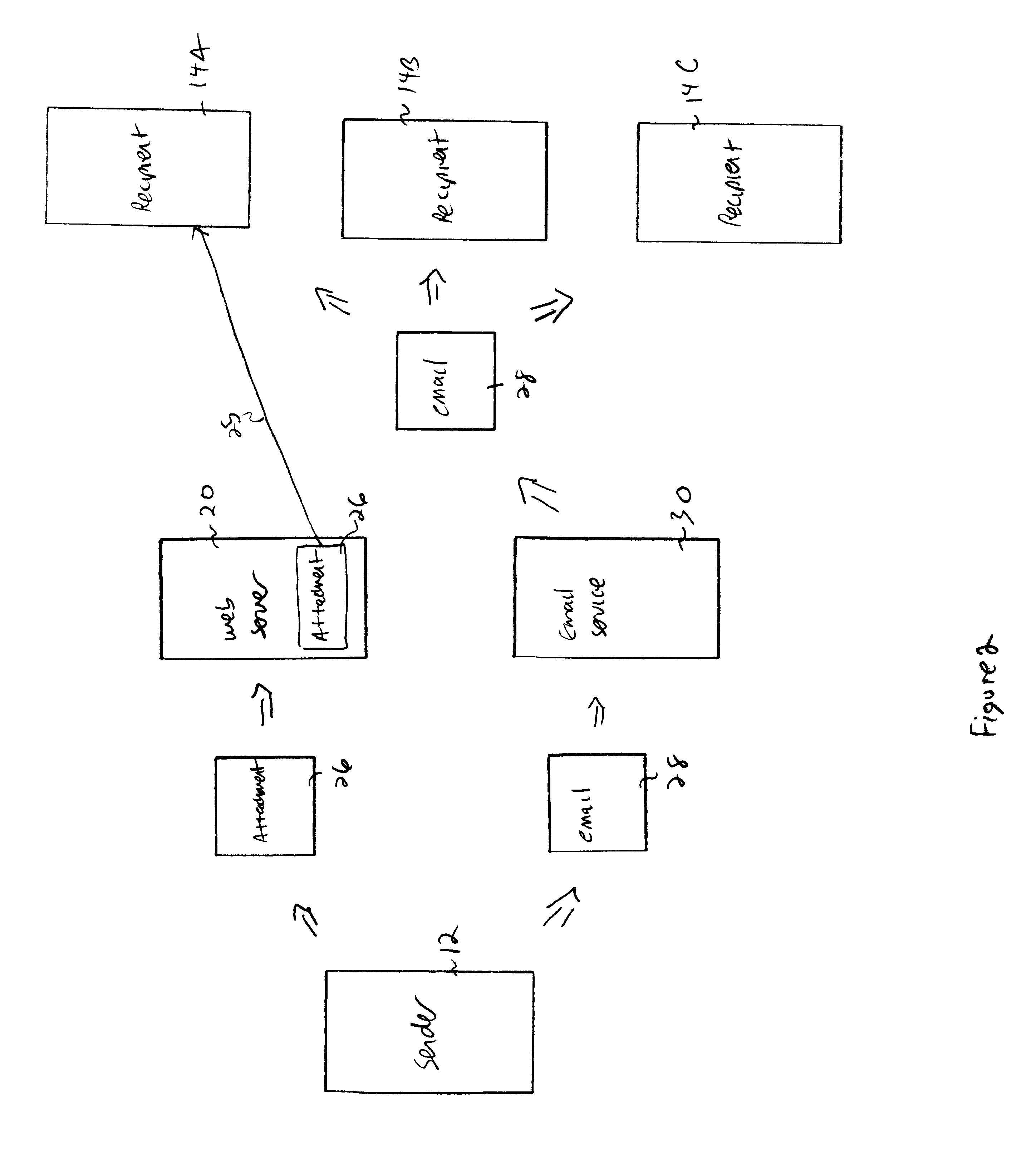
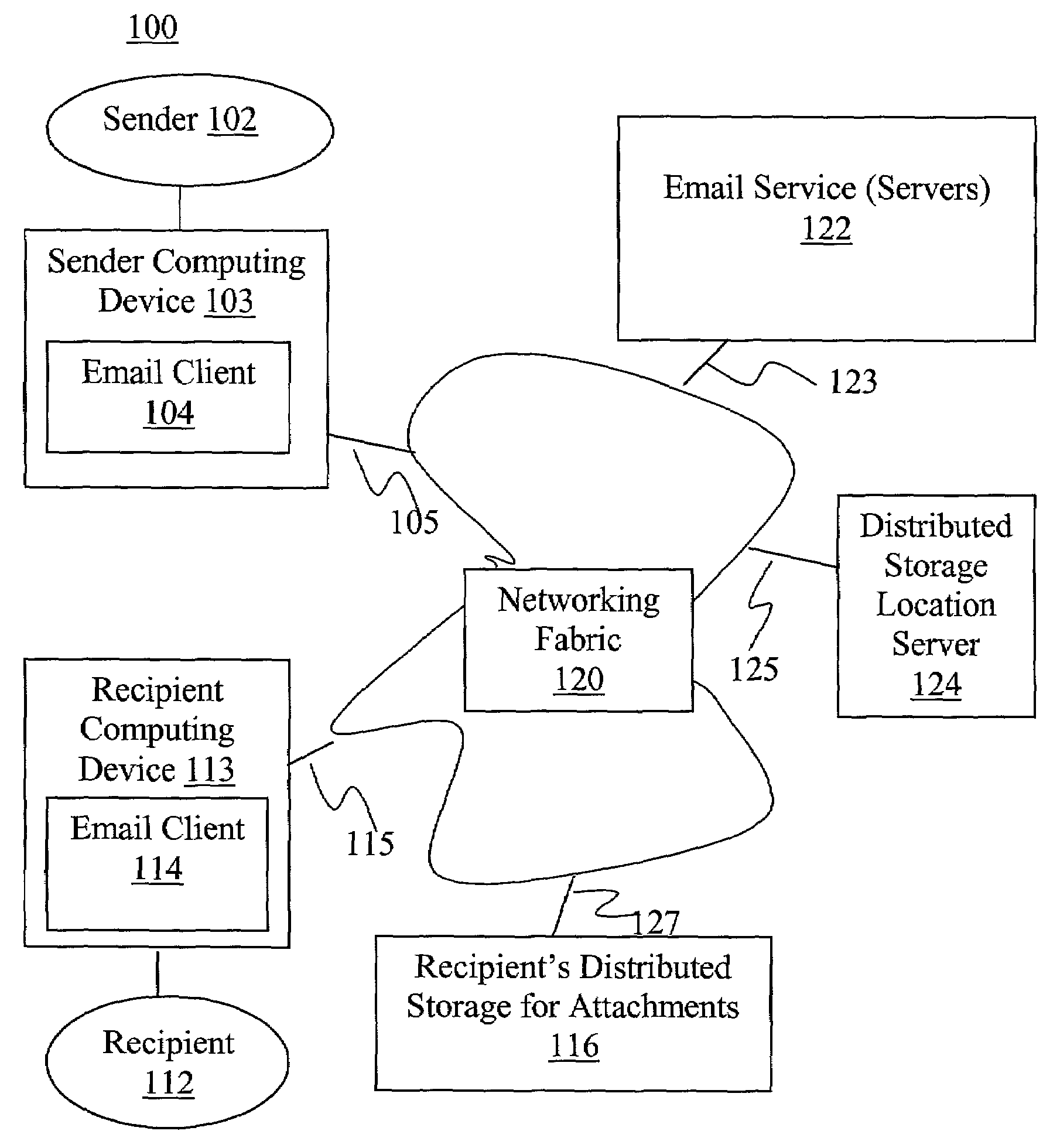
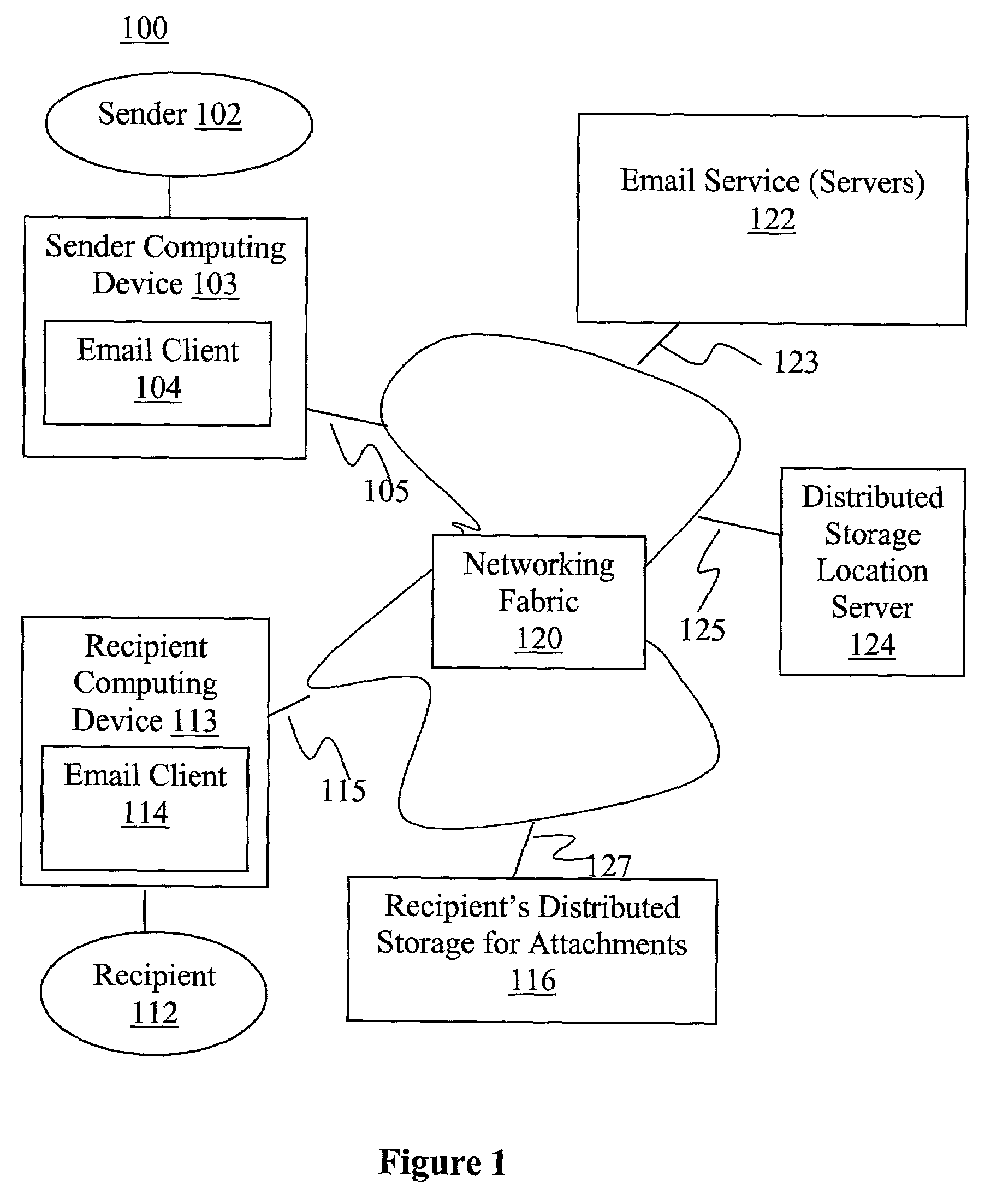
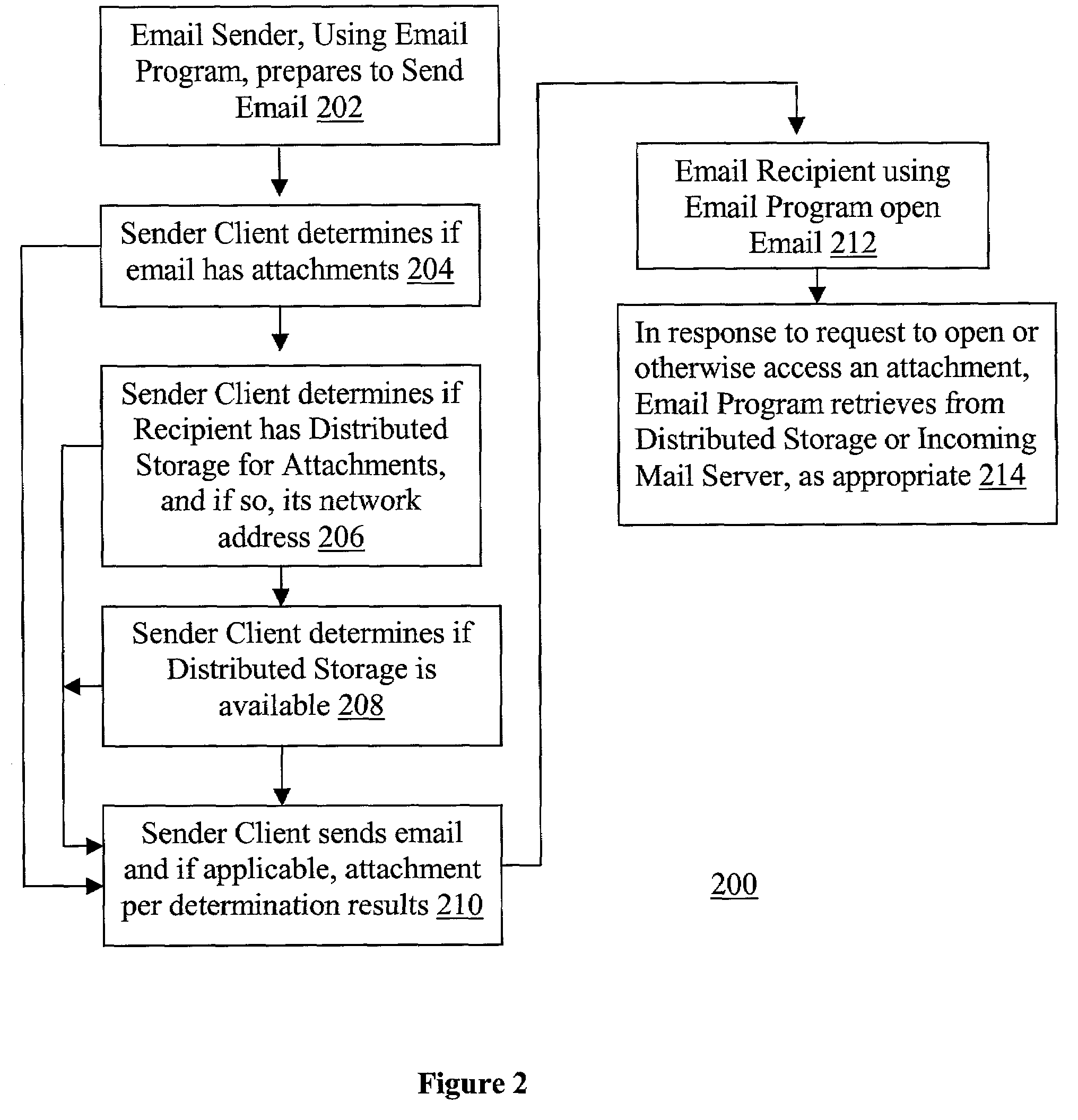
Enhanced email-distributed attachment storage
InactiveUS7257639B1Multiple digital computer combinationsData switching networksEmail attachmentNetwork addressing
A sender email client, in response to a request to send an email with attachment, determines whether a recipient of the email has distributed storage separate from an incoming email server of the recipient for storing email attachments. If so, a location server is consulted for the distributed storage's network address and its availability is determined. The send request is then serviced accordingly. An email service, in response to receiving an email with attachment, determines whether a recipient of the email has distributed storage for storing email attachments. If so, its network address and availability are likewise determined. The attachments are forwarded to the recipient's distributed storage for storage, when it becomes available. An email recipient client, in response to a request to access an email attachment, retrieves the attachment from the recipient's distributed storage or the incoming email server, as appropriate.
Owner:MICROSOFT TECH LICENSING LLC
Visual content browsing with zoom and pan features
InactiveUS20070263007A1Improve securityImprove reliabilityEnergy efficient ICTDigital data information retrievalElectronic documentEmail attachment
Owner:DIGIMEDIA TECH LLC
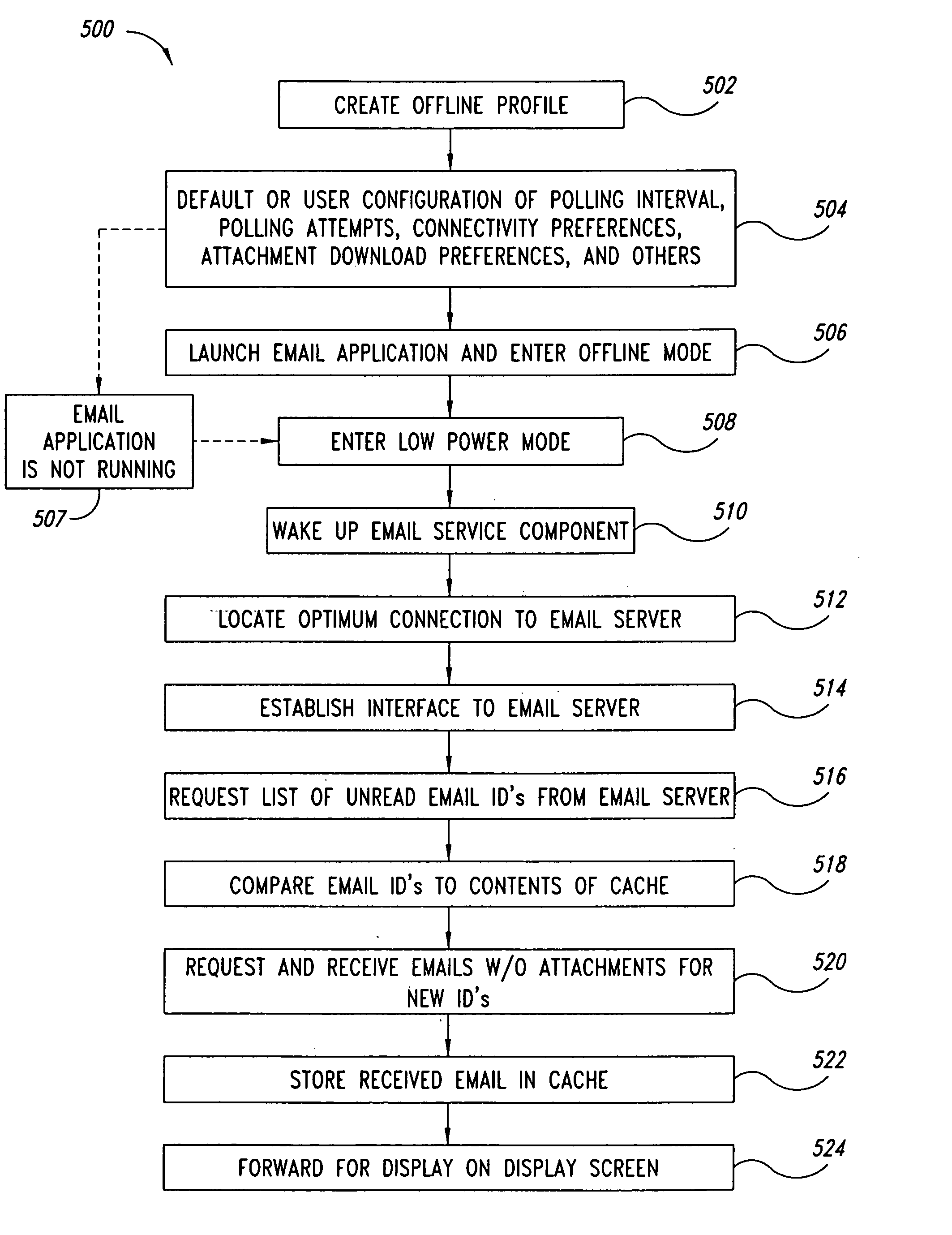
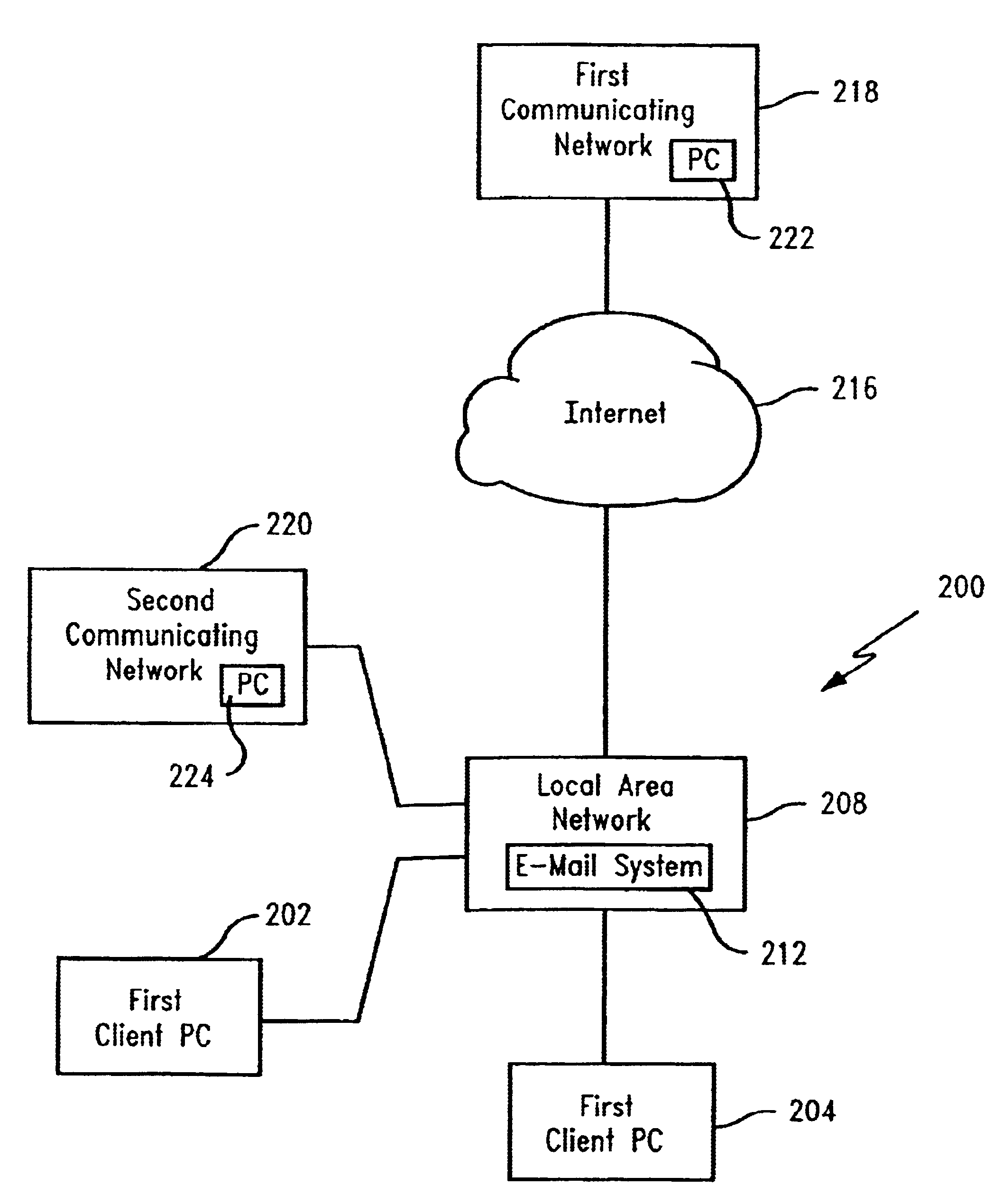
Method and system for email synchronization for an electronic device
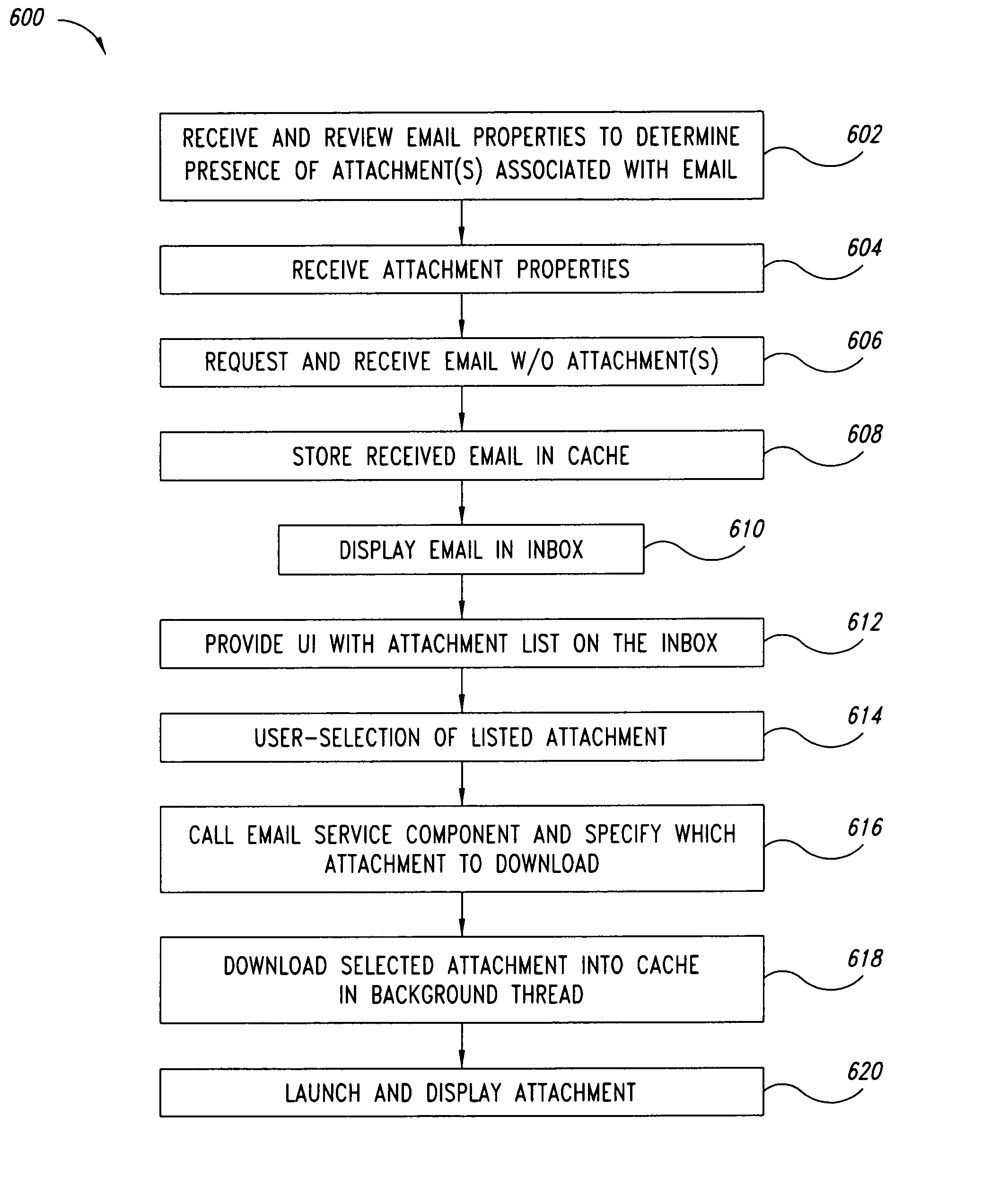
An electronic device, such as a hand-held portable computer, is provided with client-side email capability that allows emails to be independently downloaded from a server, regardless of an operating mode of an email application and without using the standard email retrieval mechanism of the email application. The emails are periodically downloaded without attachments in response to a poll of the server and if a sufficient high-speed connection to the server is available, and then the downloaded email is locally stored in a local cache of the portable computer. Attachments associated with downloaded emails stored in the local cache can be selectively downloaded, via a background process, from the server independently of the operating mode of the email application and during any suitable power state of the electronic device. Synchronization of attachments to emails in the local cache is also independently performed, thereby bypassing synchronization that is normally performed by the email application while in the online mode.
Owner:VULCAN PORTALS
Method and apparatus for minimzing storage of common attachment files in an e-mail communications server
InactiveUS20060095527A1Multiple digital computer combinationsOffice automationCommunications systemEmail attachment
The present invention provides an e-mail communications system that minimizes the number of duplicate copies of common attachment files to e-mail communications that are stored in the mail store of an e-mail server. When the e-mail server receives an e-mail attachment file that is larger than a threshold size, the server performs a database search for another copy of the attachment file in the mail store. If another copy is located, the system creates a pointer in the mail store that associates the located attachment file with the e-mail for the additional recipient(s). Attachment files are deleted only after the recipients of the associated e-mail communications delete each of the respective e-mails.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for managing email attachments for an electronic device
InactiveUS20050076085A1Multiple digital computer combinationsElectric digital data processingHand heldEmail attachment
An electronic device, such as a hand-held portable computer is provided with client-side email capability that allows emails to be independently downloaded from a server, regardless of an operating mode of an email application and without using the standard email retrieval mechanism of the email application. The emails are periodically downloaded without attachments in response to a poll of the server and if a sufficient high-speed connection to the server is available, and then the downloaded email is locally stored in a local cache of the portable computer. Attachments associated with downloaded emails stored in the local cache can be selectively downloaded, via a background process, from the server independently of the operating mode of the email application and during any suitable power state of the electronic device. Synchronization of attachments to emails in the local cache is also independently performed, thereby bypassing synchronization that is normally performed by the email application while in the online mode.
Owner:VULCAN PORTALS
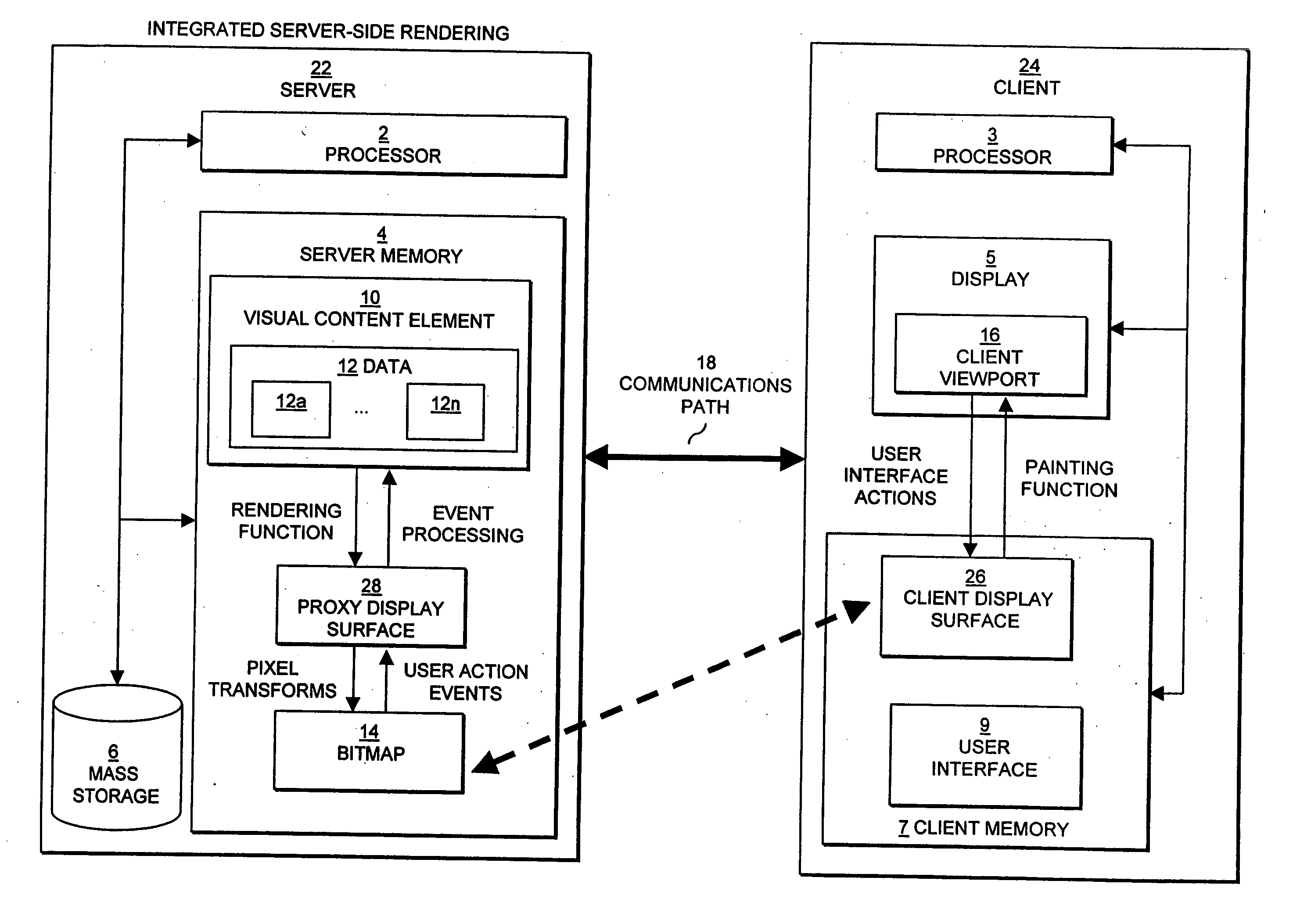
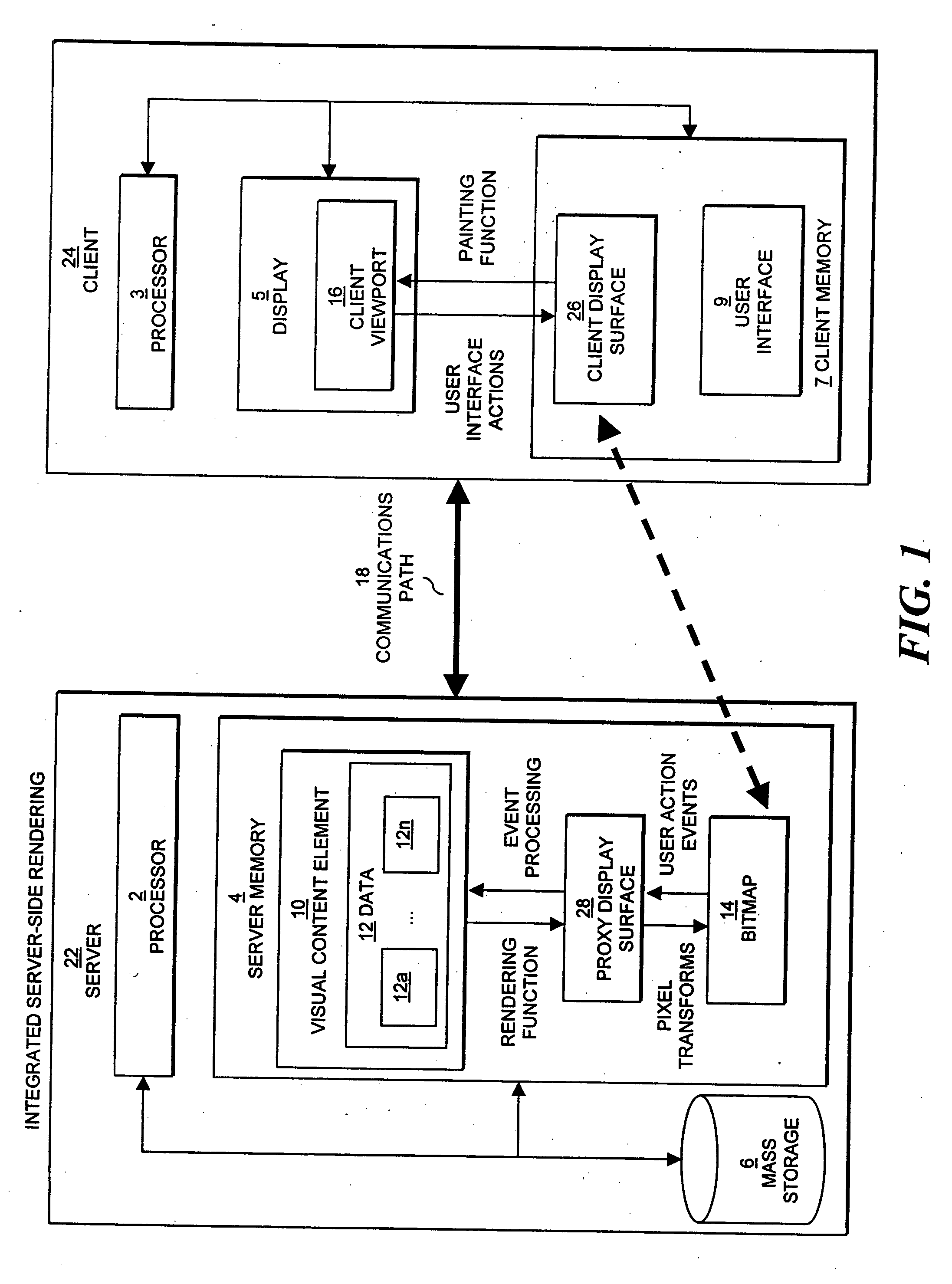
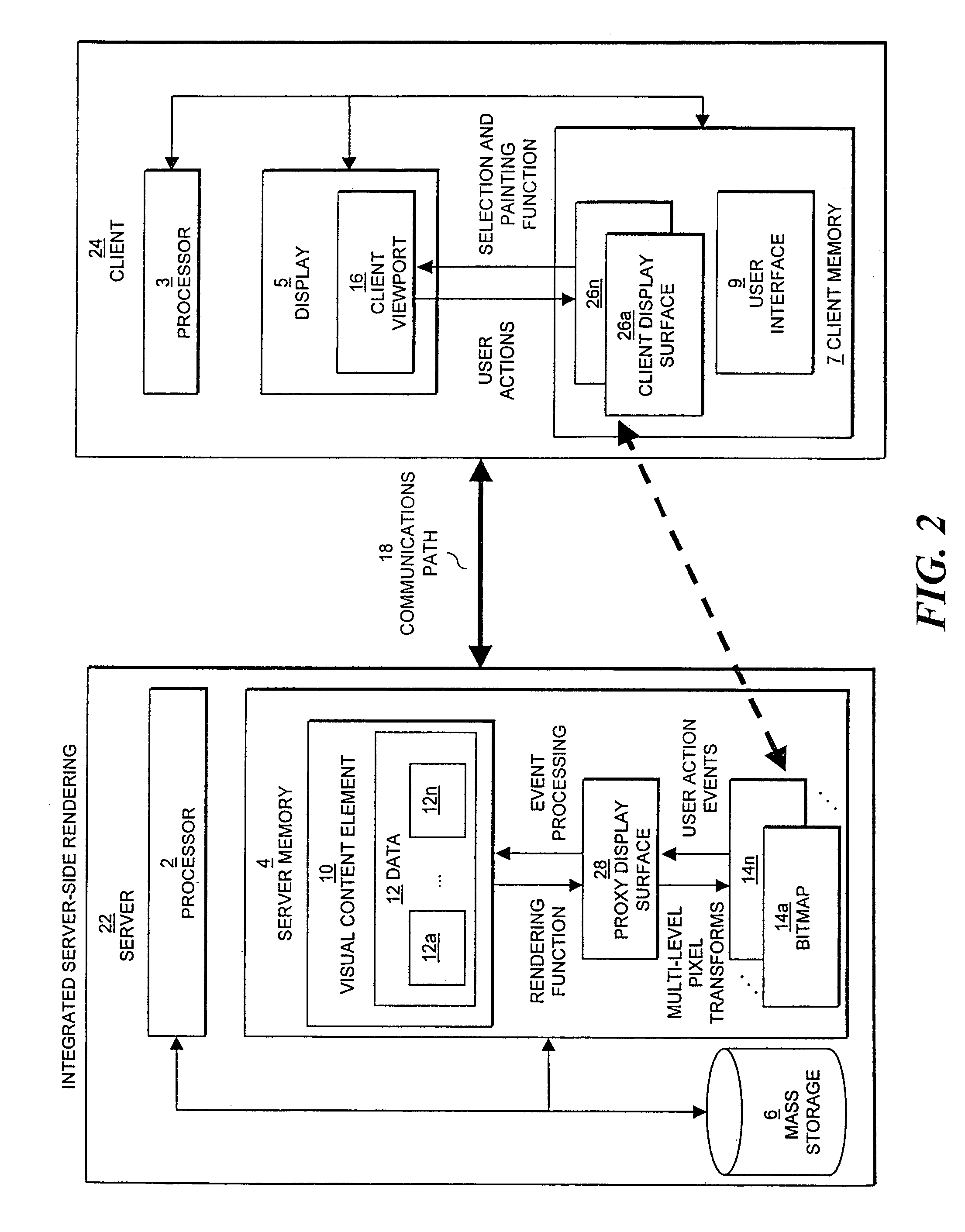
Visual content browsing using rasterized representations
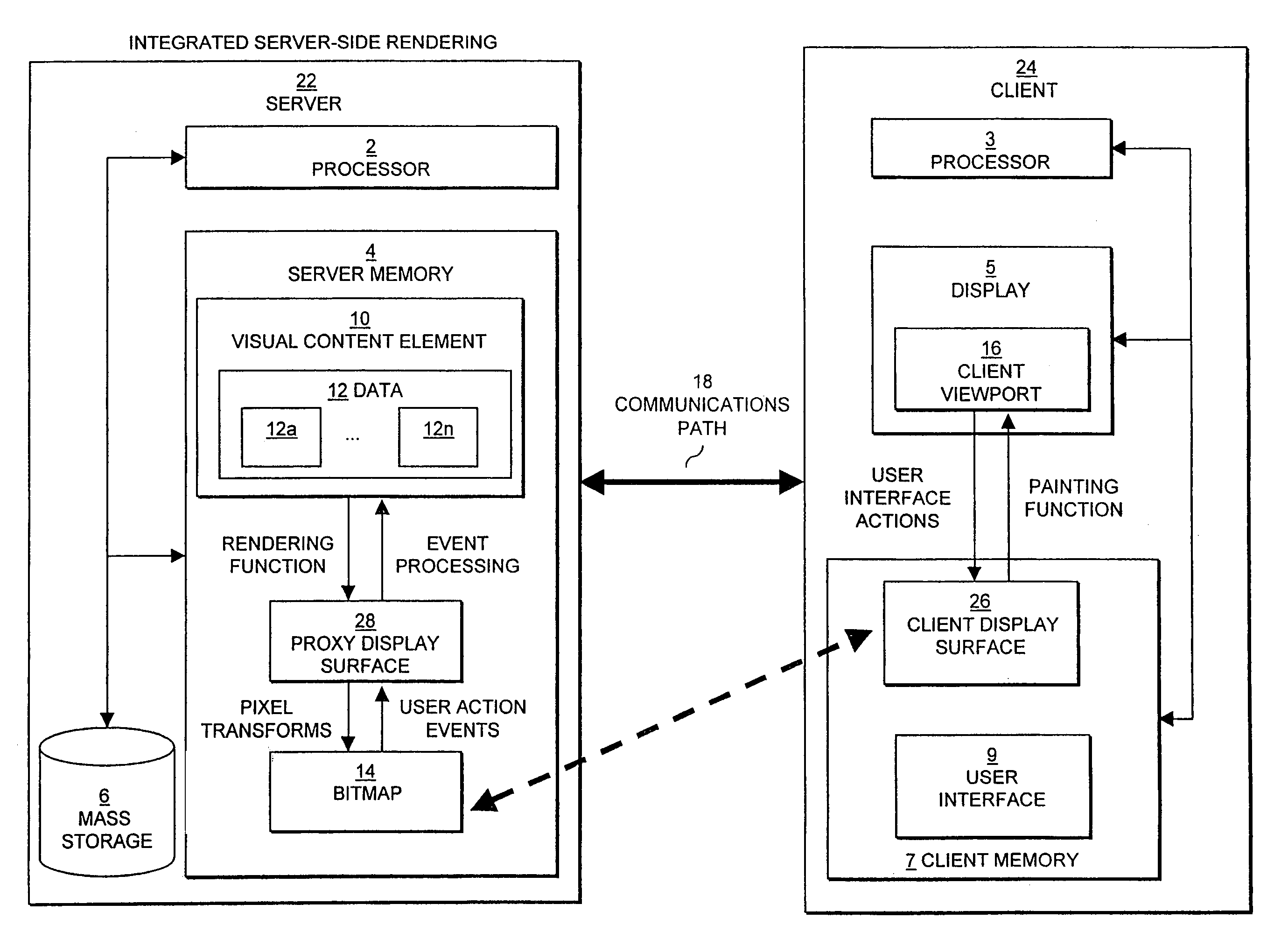
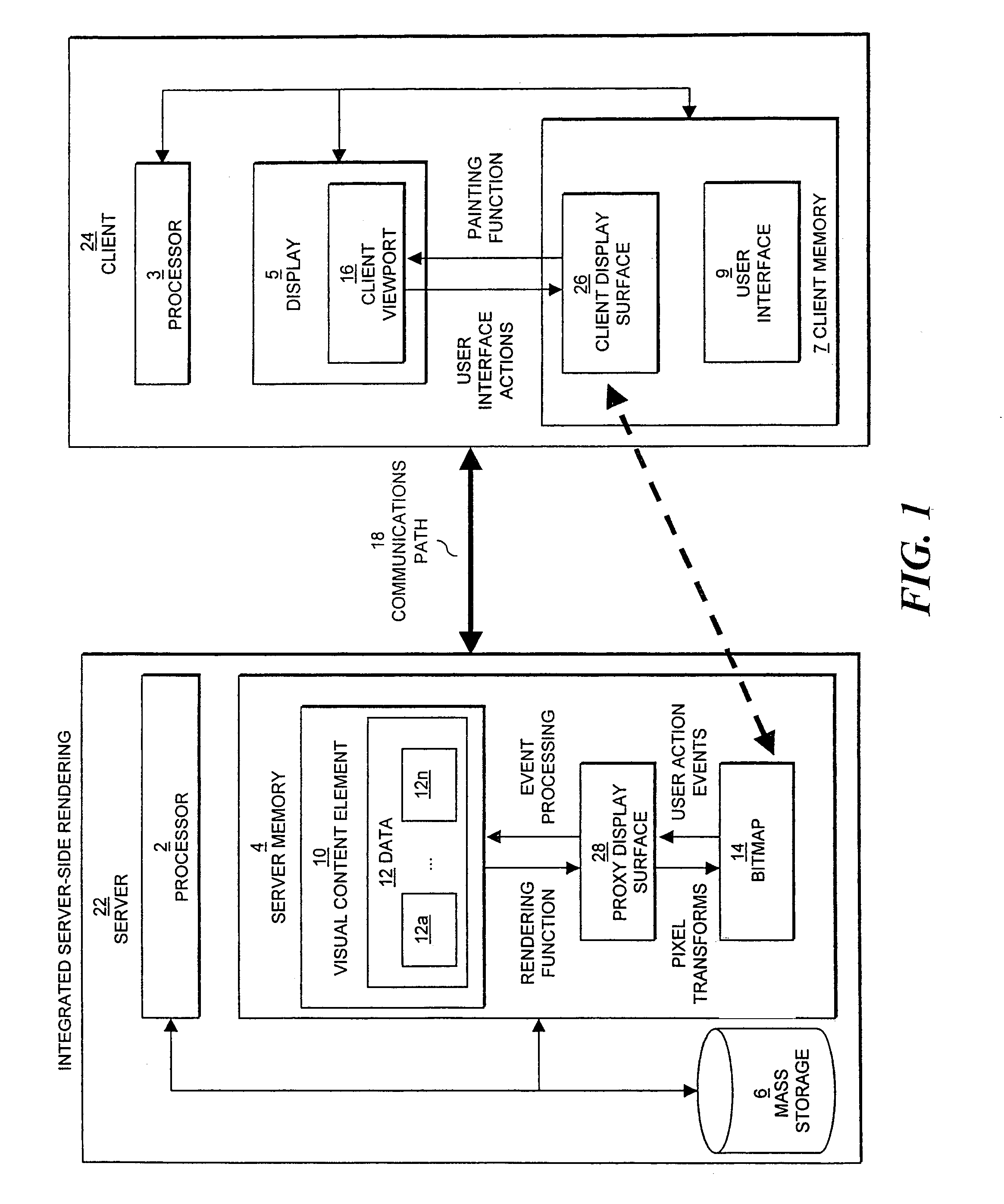
InactiveUS7242406B2Improve performanceEasy to optimizeEnergy efficient ICTDigital data information retrievalDatabase queryElectronic document
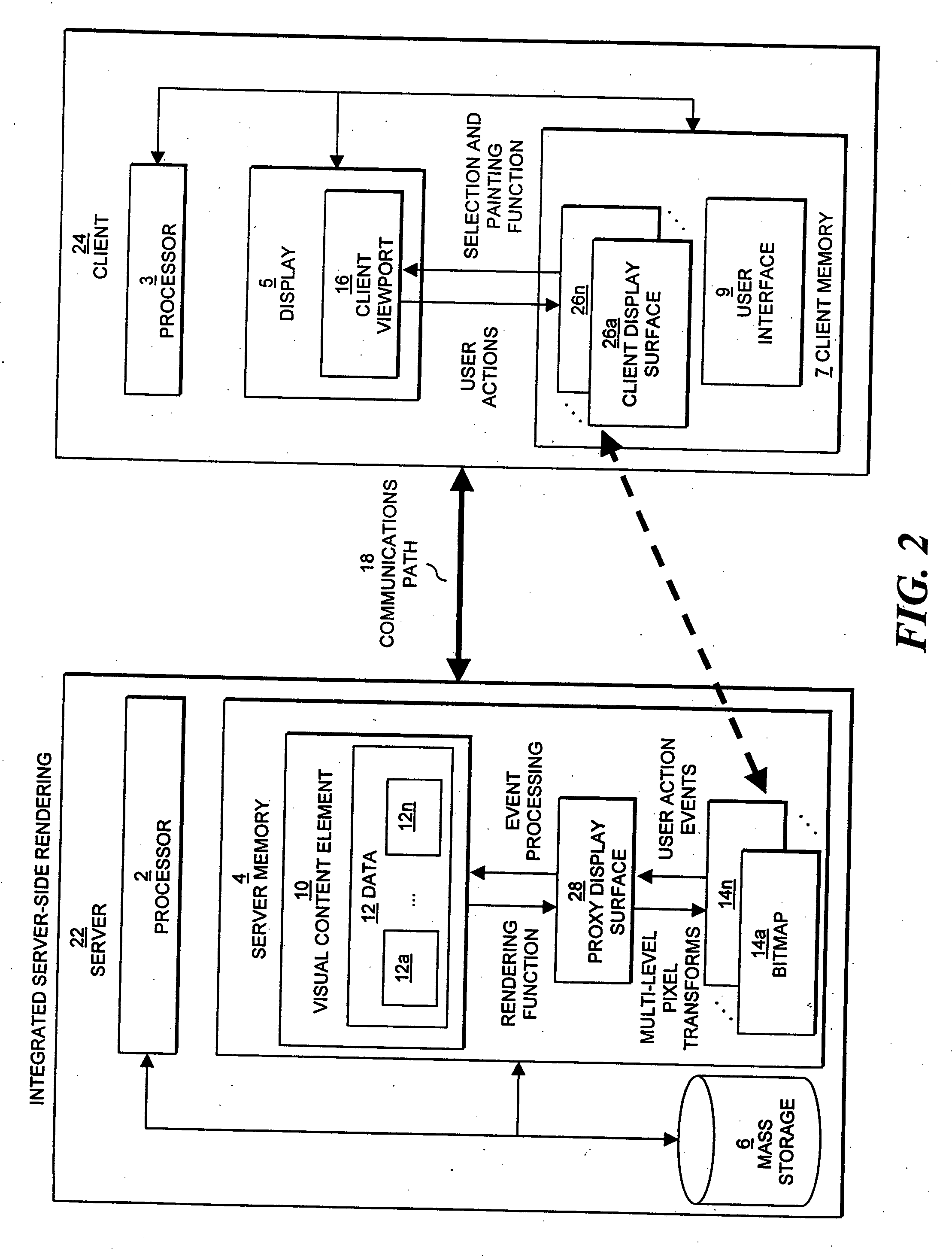
The present invention relates to display of visual content on a client device using server-side rasterization of visual content. Visual content is rendered on a server system, transformed into bitmaps compatible with the display attributes of a client device, and transmitted for display on the client device. The invention allows the server to perform, in effect, as a remote browser for displaying Web pages, e-mail, e-mail attachments, electronic document and forms, database queries and results, drawings, presentations, and images at the client device. The approach is “remote” because the server does the rendering and the client provides the interface; “multi-level” because rendered visual content is represented as a multi-level set of raster representations; and constitutes a “browsing system” because the client and server share data about the source visual content element being browsed, and the client performs a specific browsing function assisted by the server.
Owner:DIGIMEDIA TECH LLC
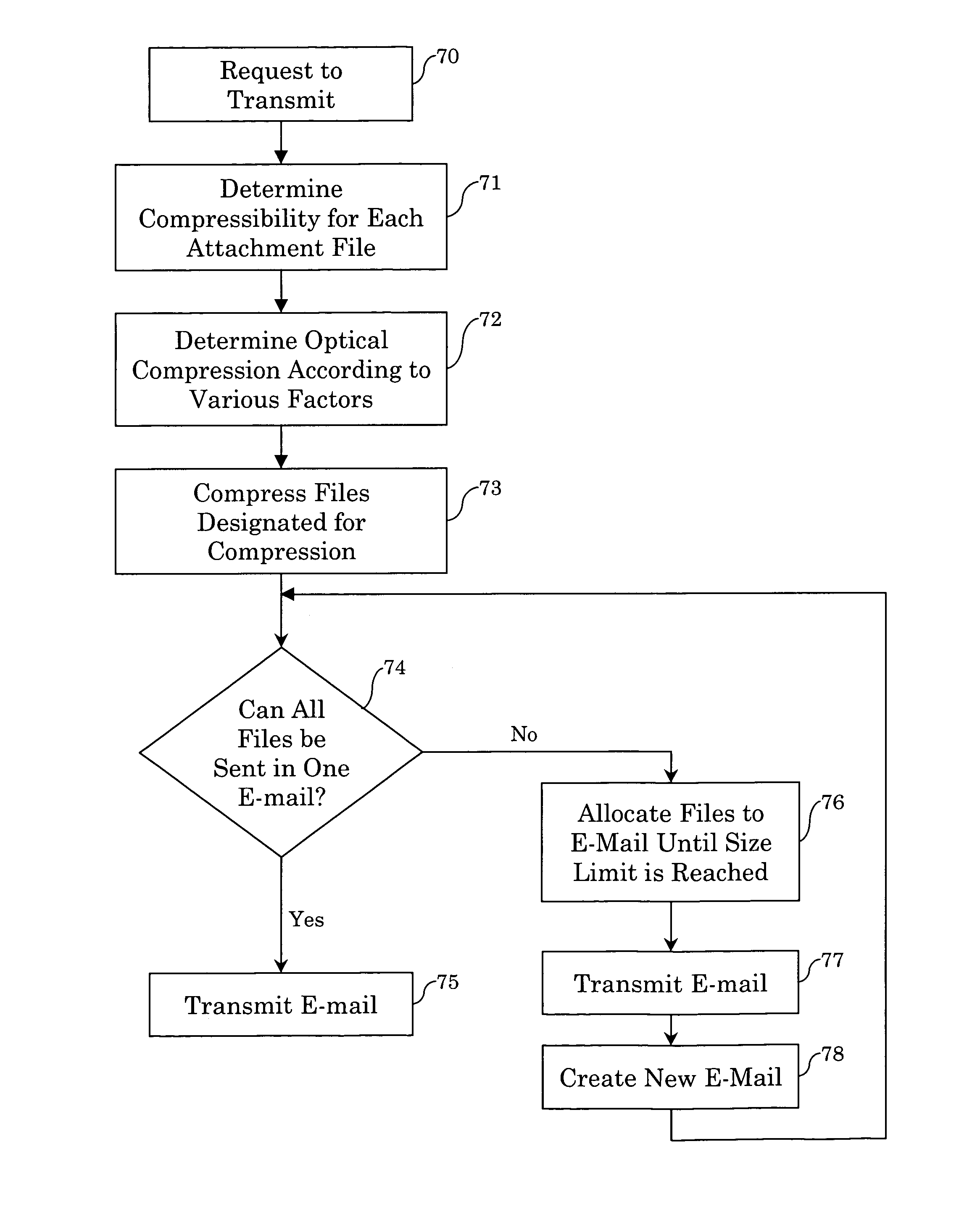
Method and apparatus for compressing attachments to electronic mail communications for transmission
InactiveUS7089286B1Compression is selectiveMaximize sizeMultiple digital computer combinationsData switching networksCommunications systemEmail attachment
The present invention is directed to a method and system for compressing attachments to electronic mail communications for transmission. In an e-mail communications system, a table stores, for each of a plurality of different types of files, a compressibility value corresponding to a percentage by which the file can be compressed in size. An e-mail attachment configuration module is configured to compress each attachment file of a type having a compressibility value greater than a threshold value in an e-mail communication. In another embodiment, the e-mail attachment configuration module compresses a number of the plurality of attachment files according to file size and the corresponding compressibility value, such that the total size of the e-mail communication after compression is maximized and is less than a threshold size. The attachment configuration module can be incorporated into a system for configuring packages of application files, designated from within user applications, to be sent as e-mail attachments in e-mail communications.
Owner:BELLSOUTH INTPROP COR
Online publishing of multimedia content
The method and system disclosed herein publishes user created multimedia content including voice, video, text, pictures, and a combination thereof on one or more publication virtual spaces, simultaneously. A client application, provided on a mobile device, creates and transfers the multimedia content to a publishing service. A protocol is provided for synchronizing user preferences of the publication virtual spaces between the client application and the publishing service. The multimedia content may be transferred as a single multimedia file, data segments, or electronic mail attachments to a back end service of the publishing service via a front end service. The back end service creates a multimedia object from the transferred multimedia content. The back end service splices targeted advertisements with the multimedia object. The multimedia object is transferred from the back end service to the front end service and then published on the publication virtual spaces chosen by the user.
Owner:SINGH GURVINDER
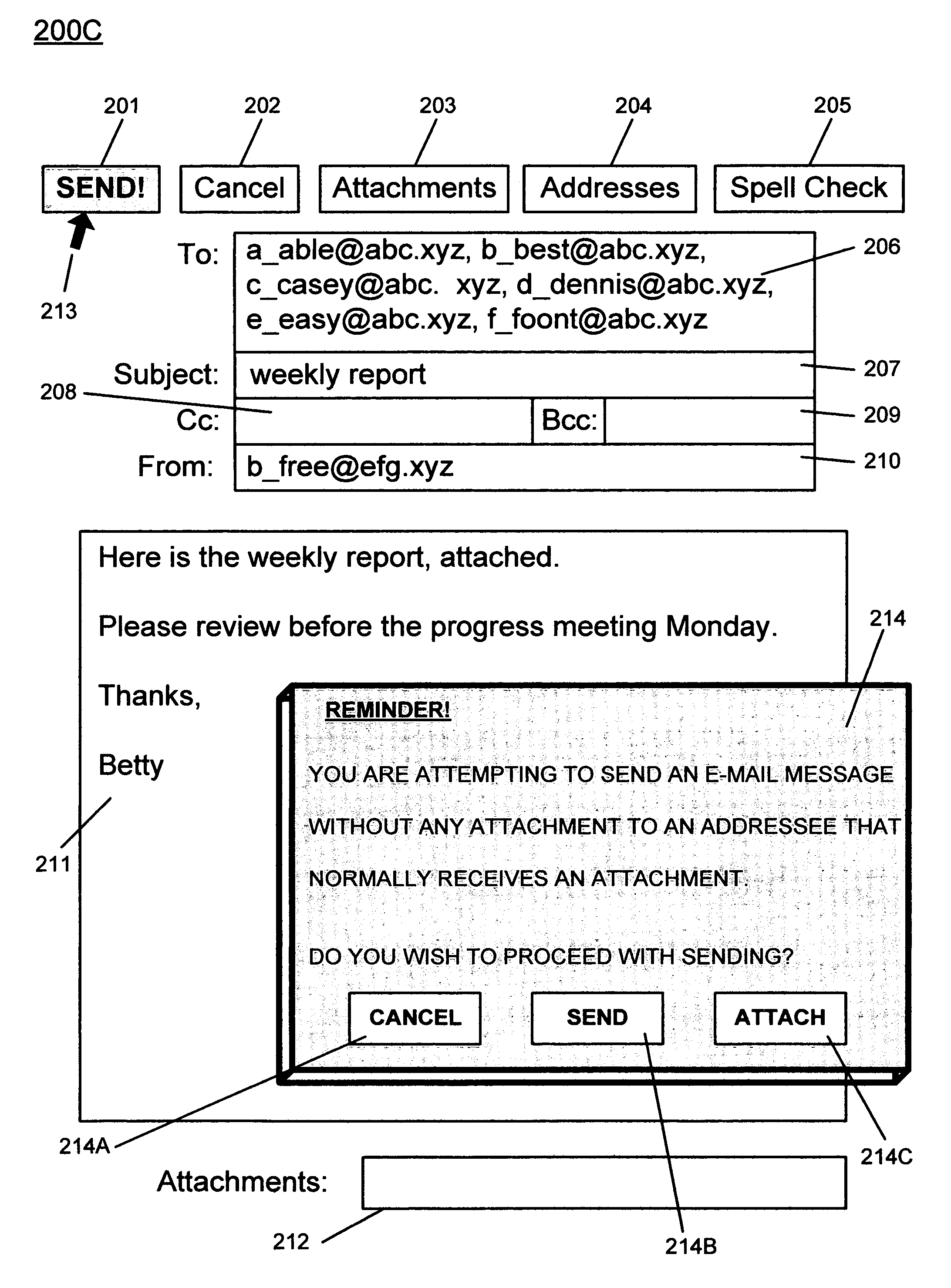
Method of email attachment confirmation
InactiveUS6970908B1Easy and inexpensive implementationWithout annoying a userData processing applicationsMultiple digital computer combinationsEmail addressEmail attachment
The present invention provides a method for automatically determining, and accordingly prompting an email user as to whether an attachment is to accompany an email message prior to transmission of the message. In one embodiment, the present invention provides a method, which can prompt an email user as to whether an attachment is to accompany an email addressed to certain individuals, groups, or organizations, prior to transmission of the message. In one embodiment, a database of certain addressees to whom attachments are frequently transmitted is consulted. In one embodiment, the present invention provides a method, which automatically prompts users based on the content of an email message as to whether an attachment is desired prior to transmission. In one embodiment, a database of certain keywords appearing in message text frequently correlated with attachment inclusion is consulted. In one embodiment, the databases are automatically updated by a self-learning modality.
Owner:MONTEREY RES LLC
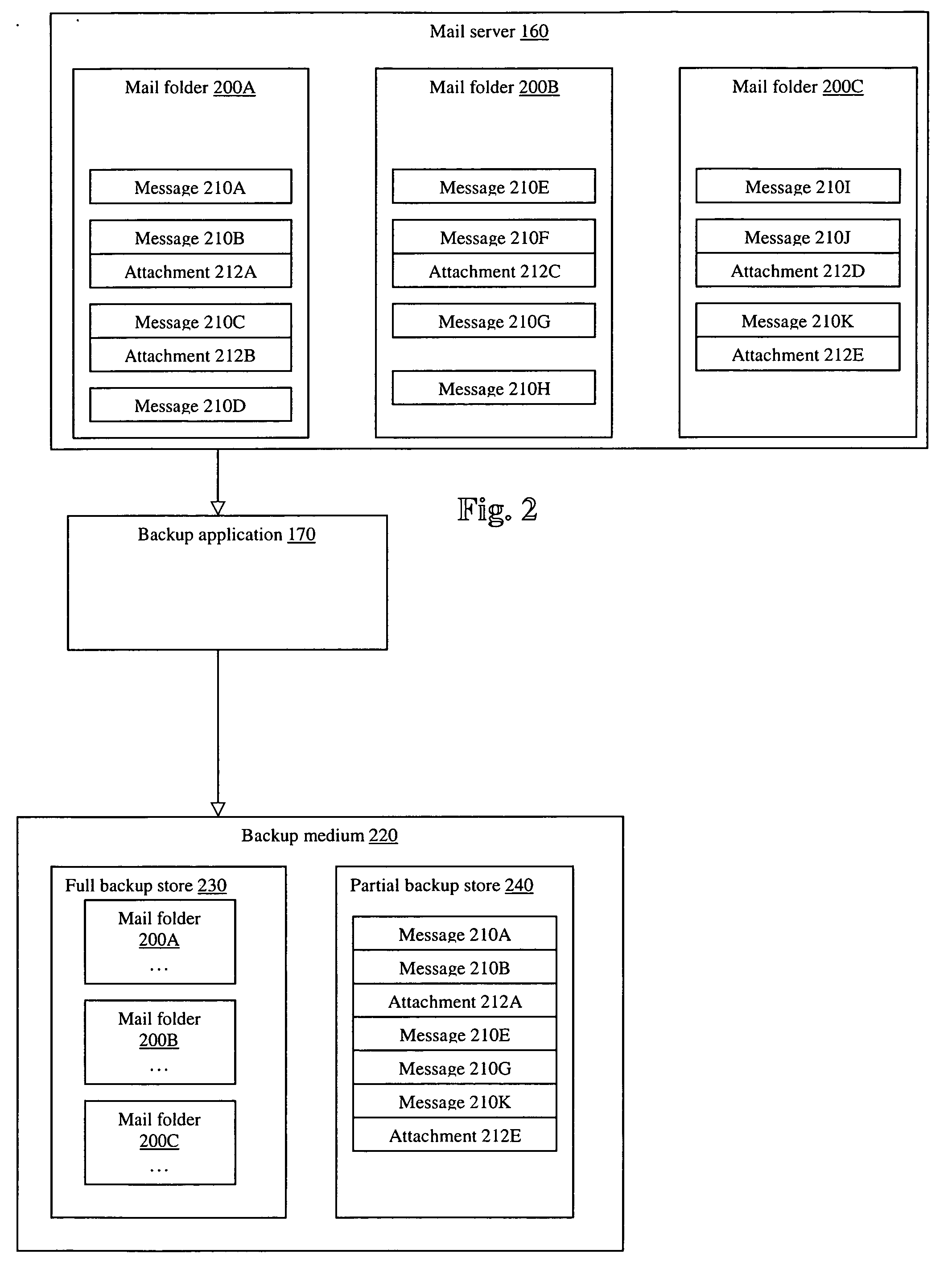
Single instance backup of email message attachments
ActiveUS20050114450A1Error detection/correctionMultiple digital computer combinationsEmail attachmentElectronic mail
A system and method for single instance backup. In one embodiment, a method may comprise storing a plurality of duplicate messages on a mail server, where each of the messages includes a copy of an attachment, and storing a copy of each of the plurality of duplicate messages and one or more copies of the attachment to a backup medium, where the number of copies of the attachment stored on the backup medium is less than the number of duplicate messages stored on the backup medium. For example, only a single copy of the attachment may be stored on the backup medium. In one embodiment storing a copy of each of the plurality of duplicate messages and one or more copies of the attachment may comprise extracting metadata from each of the messages, storing the metadata in an attachment index, storing the metadata with each message on the backup medium, and storing the metadata with the copies of the attachment on the backup medium.
Owner:SYMANTEC OPERATING CORP
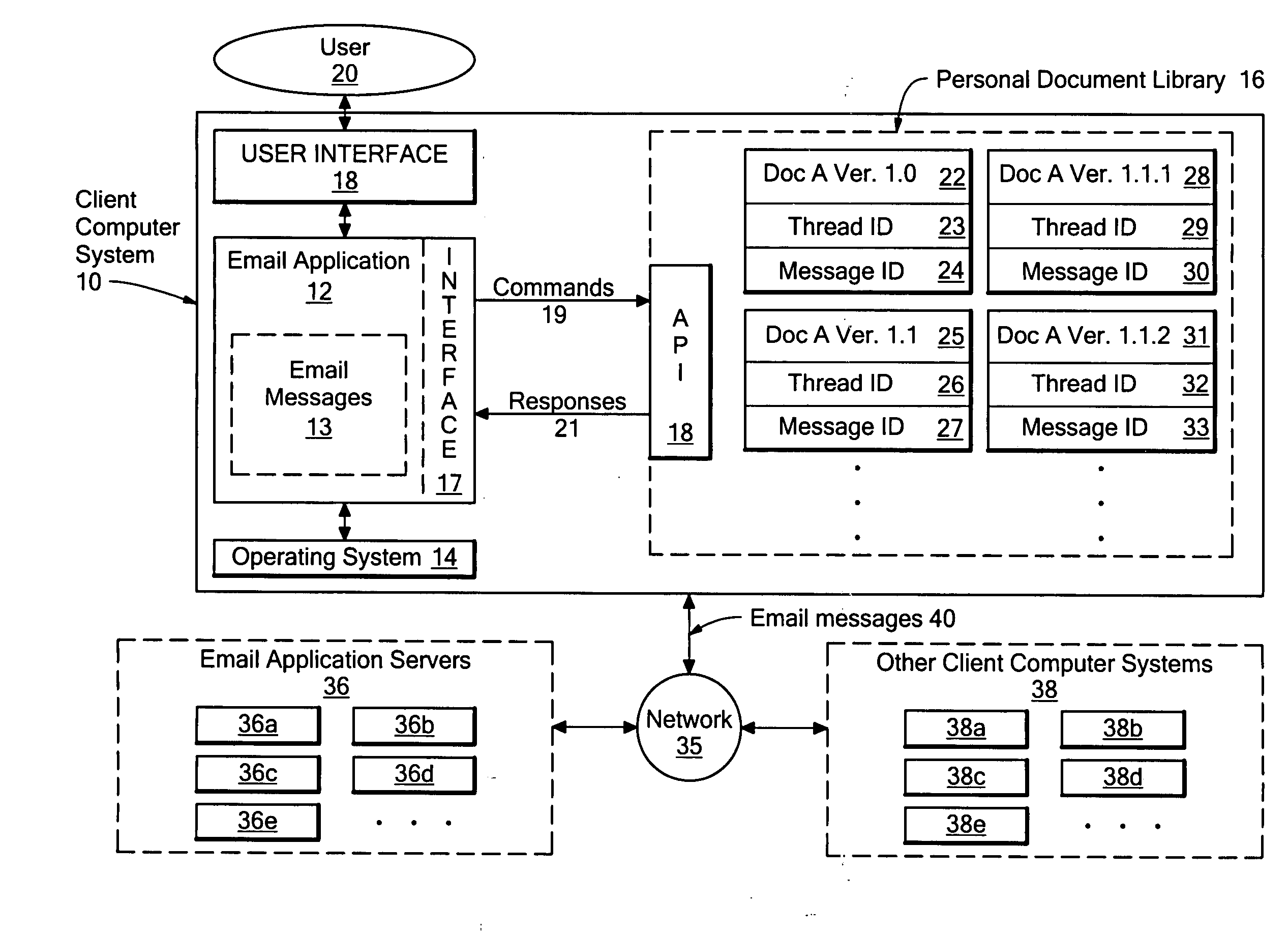
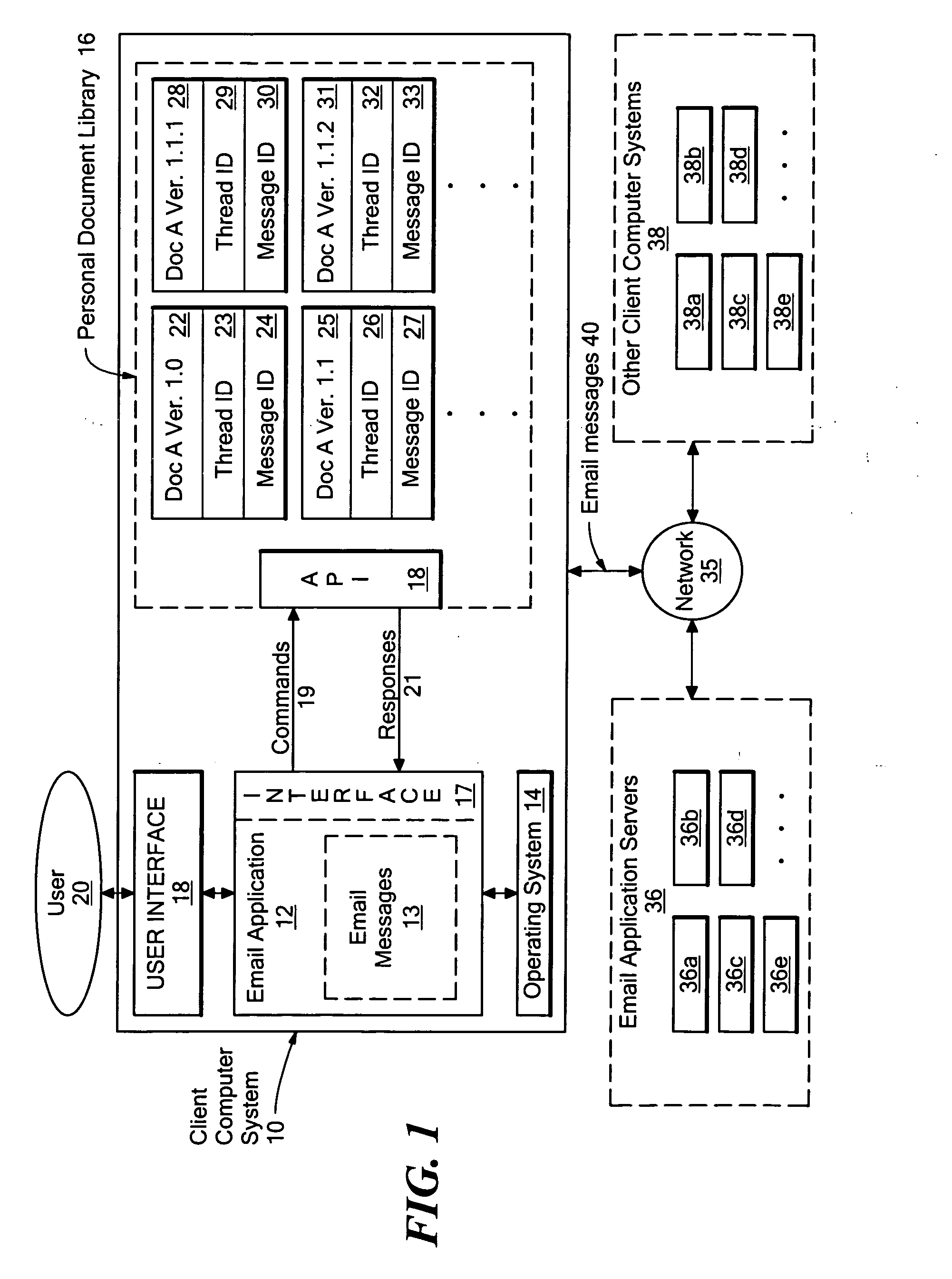
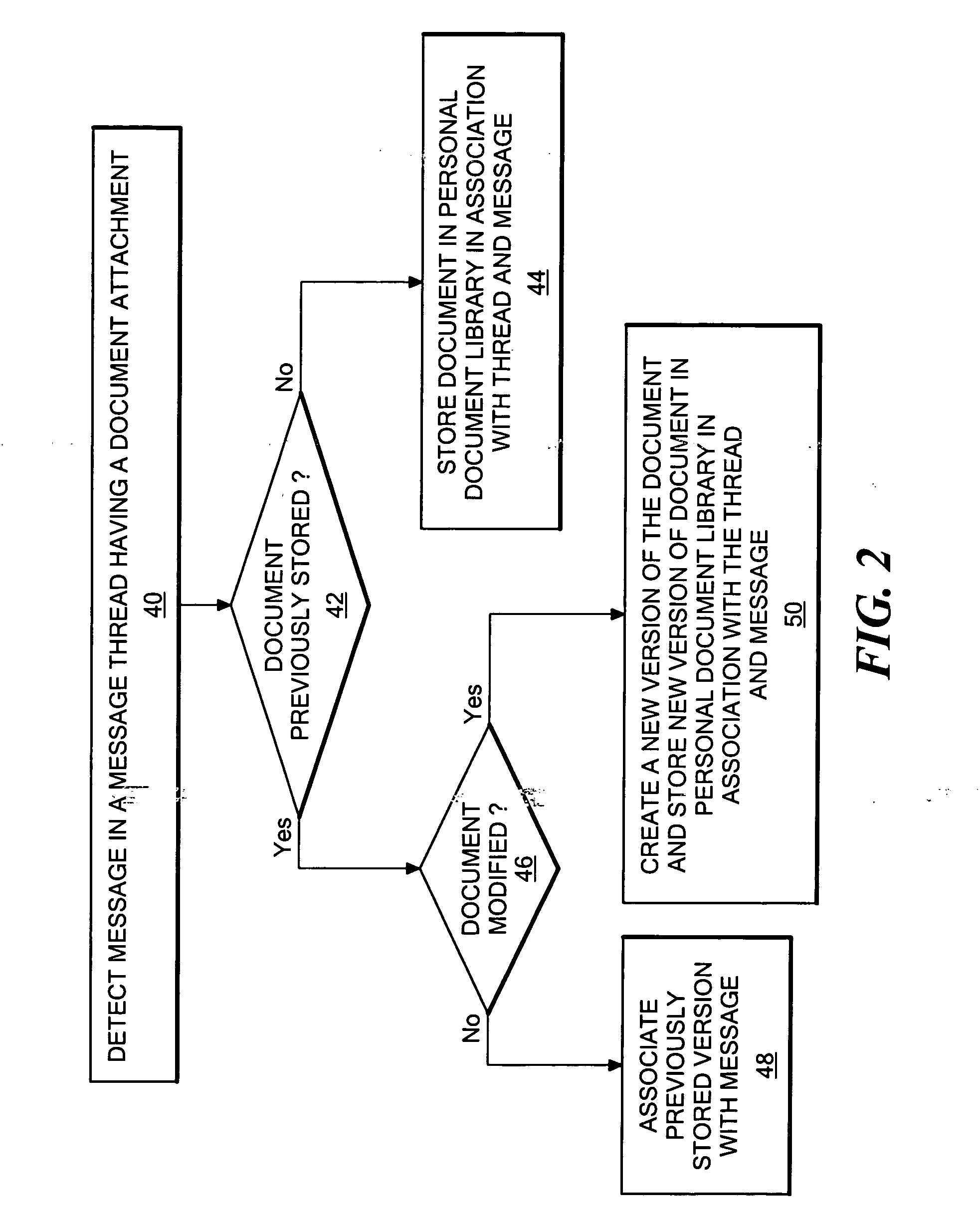
Method and system for providing version control for electronic mail attachments
InactiveUS20070143425A1Conveniently obtainNatural language data processingMultiple digital computer combinationsApplication programming interfaceEmail attachment
A system for providing version control for documents attached to electronic mail messages in which a user's personal document library is used to store documents attached to the email messages the user sends and / or receives. Each time an attached document is transmitted or received within a message thread, a different version of the document is created and stored in the personal document library. The multiple document versions created allow the disclosed system to provide the user with the options of opening the most recent version of an attached document and / or opening the version of the attached document that is associated with the specific opened message. An attached document is represented within an email message using a URL (Uniform Resource Locator), where the stored URL points to the version of the attached document for that message that is stored in the user's personal document library. Through an API (Application Programming Interface) provided by the personal document library, the most recent version of a document can be requested, or another specific version of the document can be indicated for opening.
Owner:IBM CORP
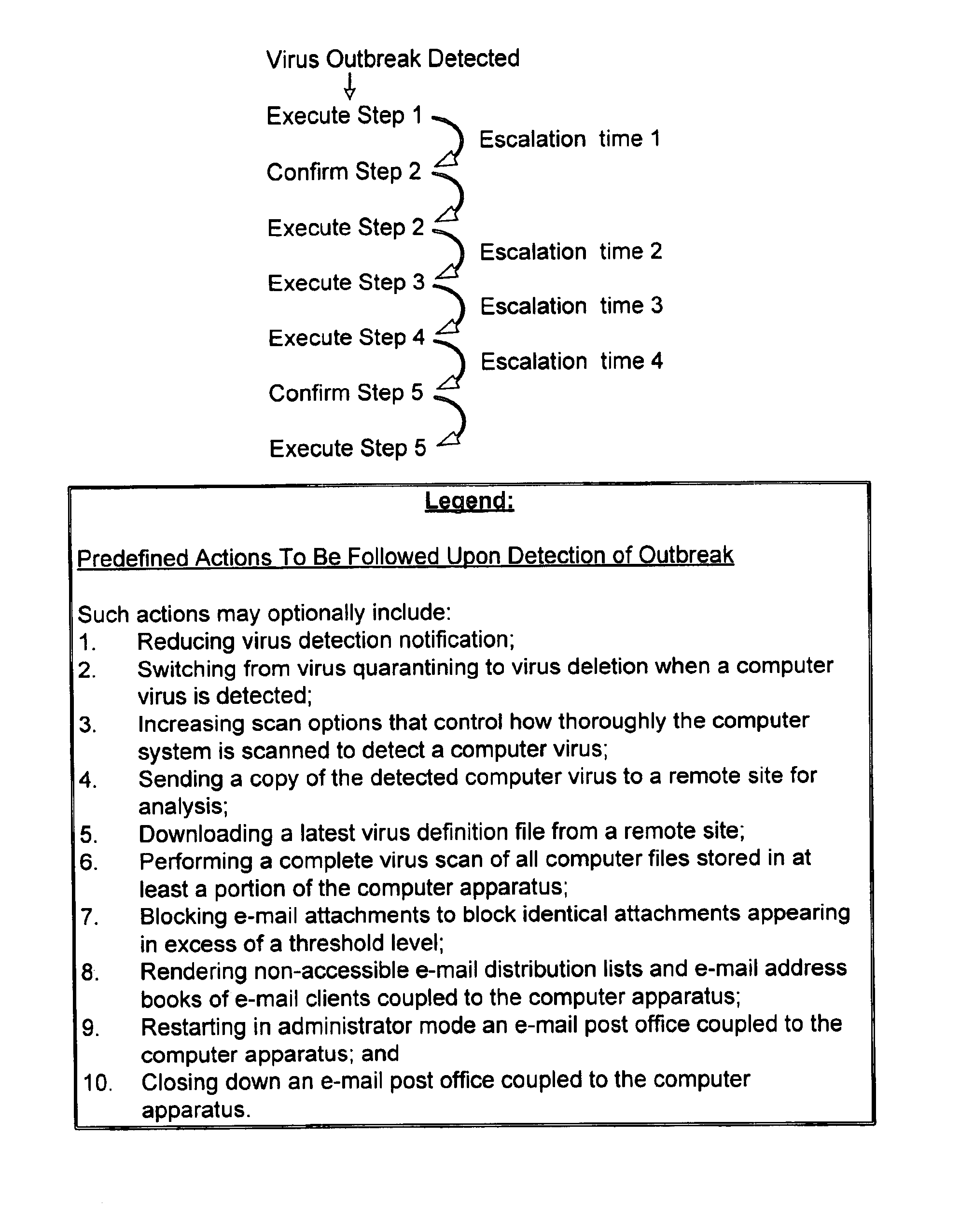
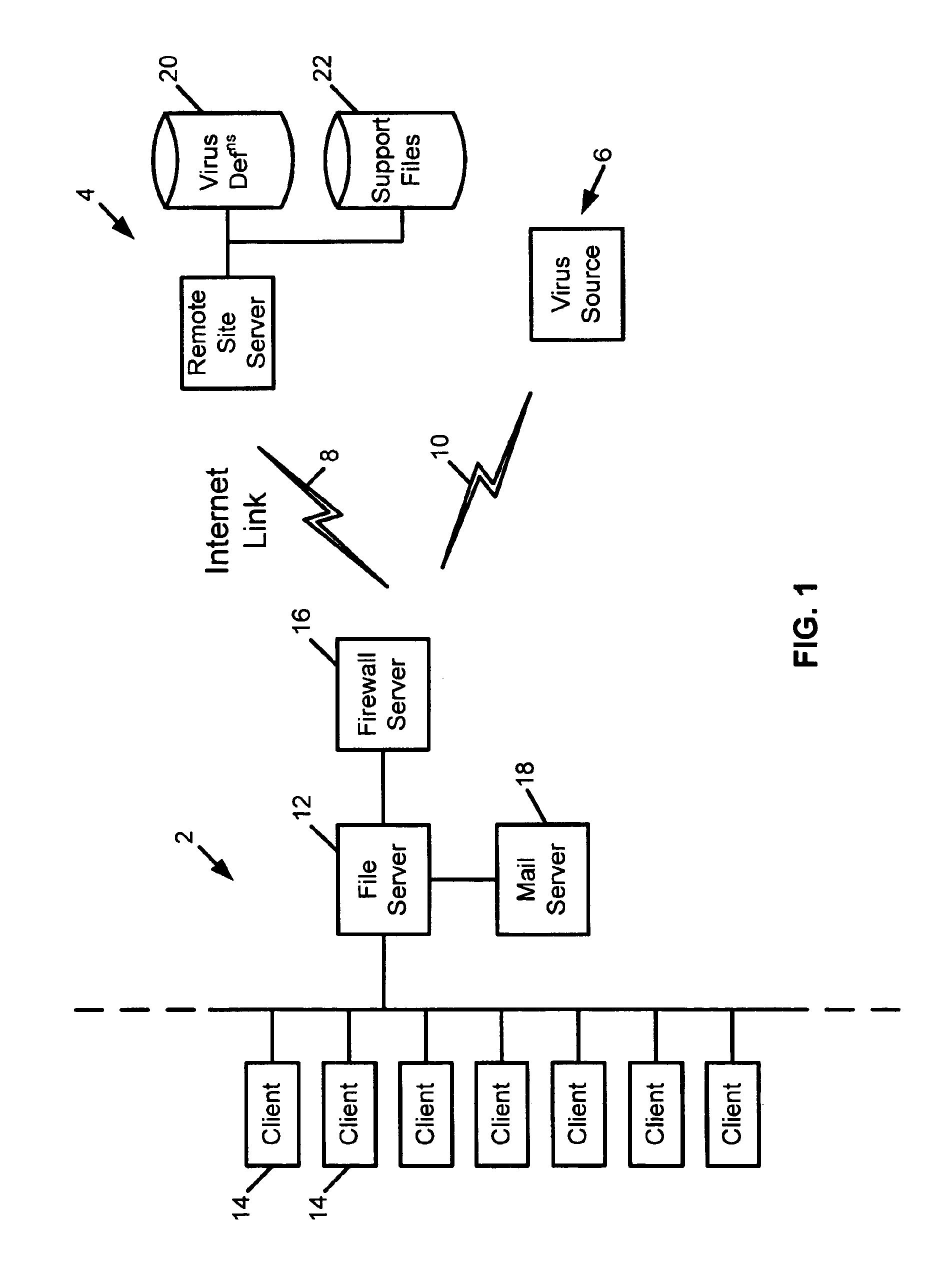
Response to a computer virus outbreak
InactiveUS6898715B1Light loadInhibit computer virus propagationMemory loss protectionUnauthorized memory use protectionAnti virusAddress book
When a computer virus outbreak is detected, a predefined sequence of steps are automatically or manually followed using rule definitions, that may include office hours, to invoke anti-virus counter-measures. The counter-measures can include reducing virus notification, increasing scanning options, blocking E-mail attachments, hiding E-mail address books and the like. The predetermined sequence of actions may be varied with the time of day and day of week.
Owner:MCAFEE LLC
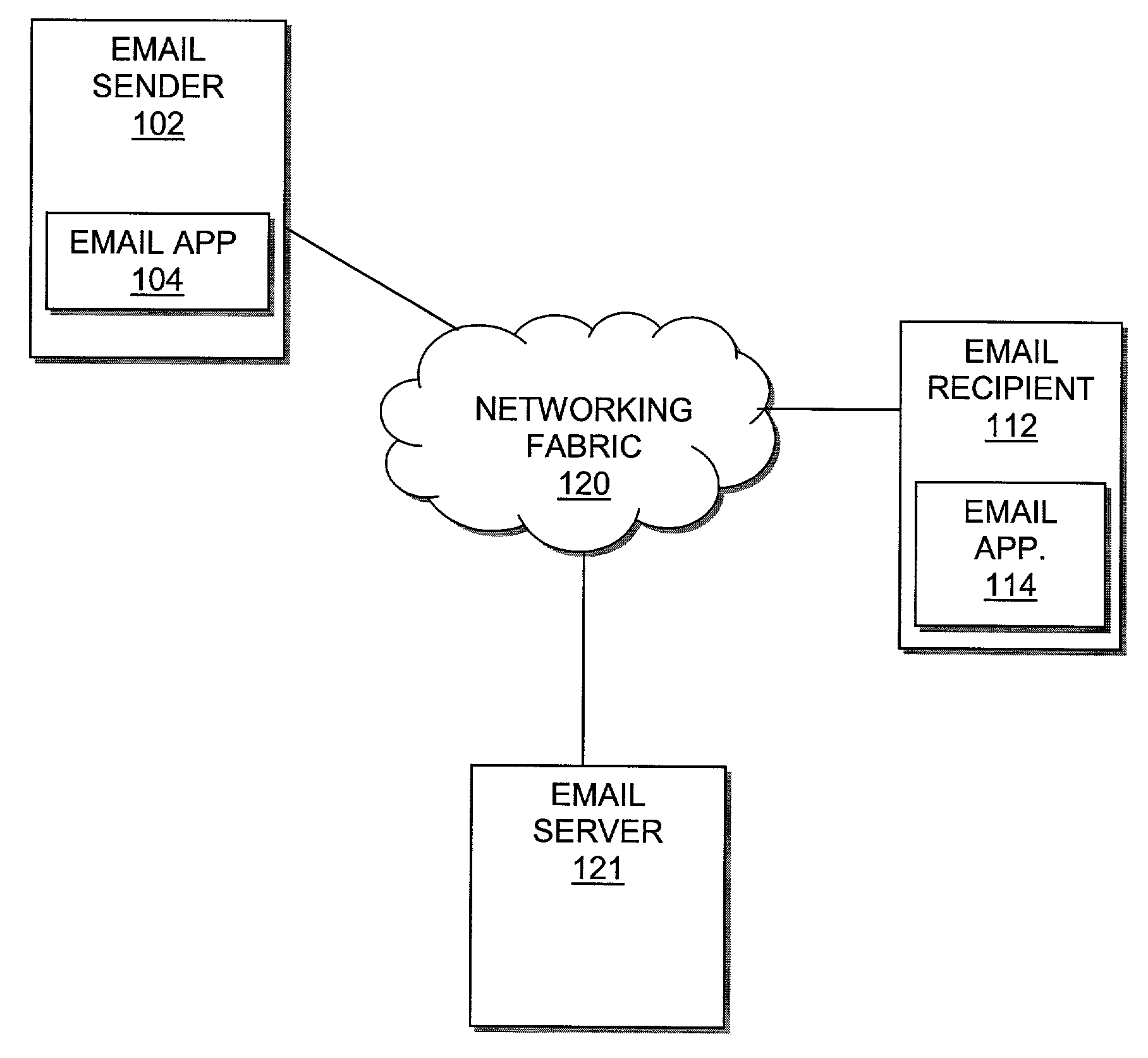
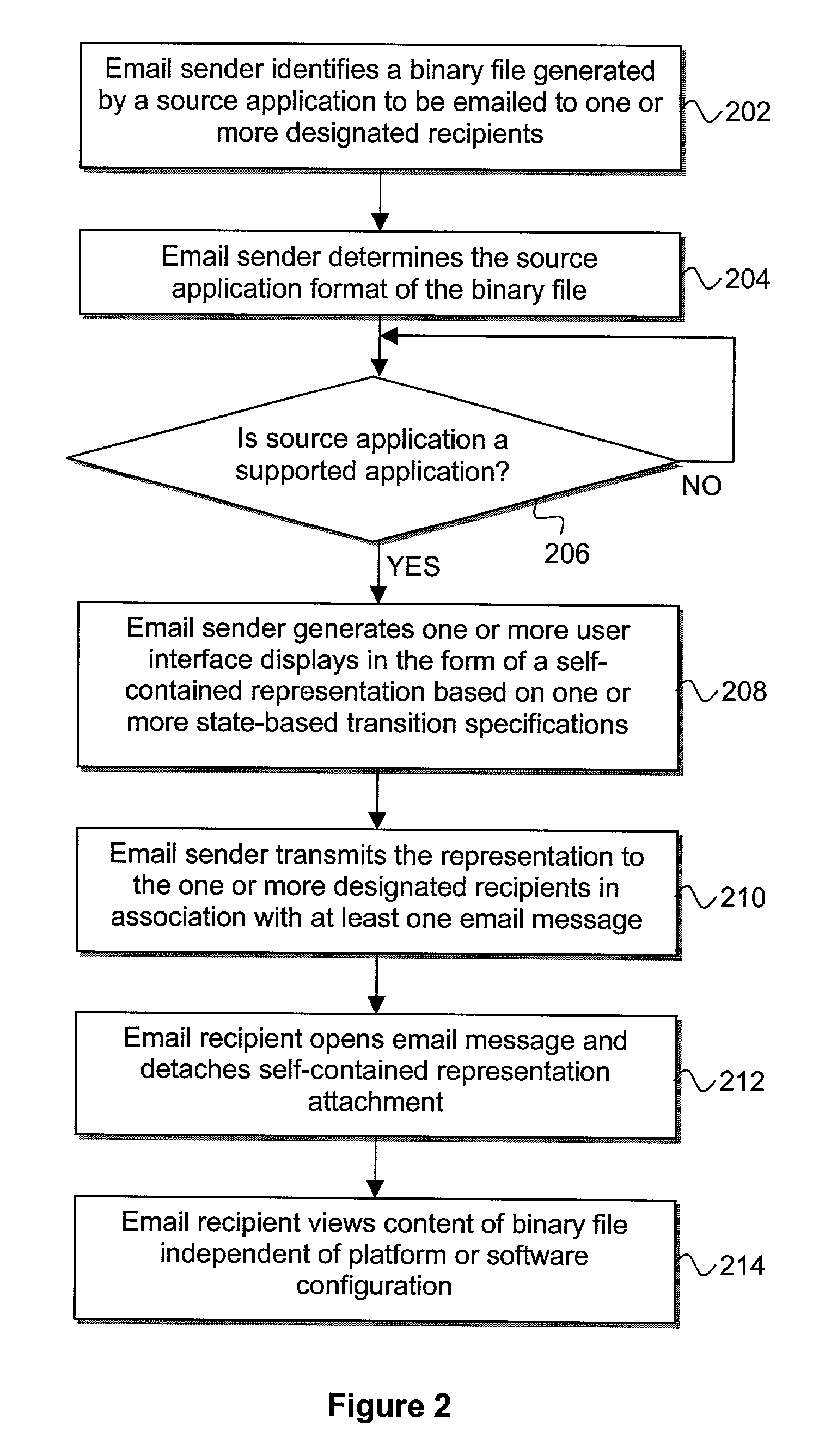
Autonomous rendering of email attachments
InactiveUS7599992B2Multiple digital computer combinationsOffice automationComputer hardwareWeb browser
An enhanced email agent generates a self-contained representation of a binary file attachment for transmission to one or more designated recipients. Each recipient may view the content of the binary file using only a generic web browser and otherwise independent of the software or hardware configuration of the recipient's computing device web browser. In on embodiment, one or more user interface displays are generated based at least in part upon one or more state-based transition specifications so as to enable platform independent viewing of content from the binary file each recipient.
Owner:XEVO INC
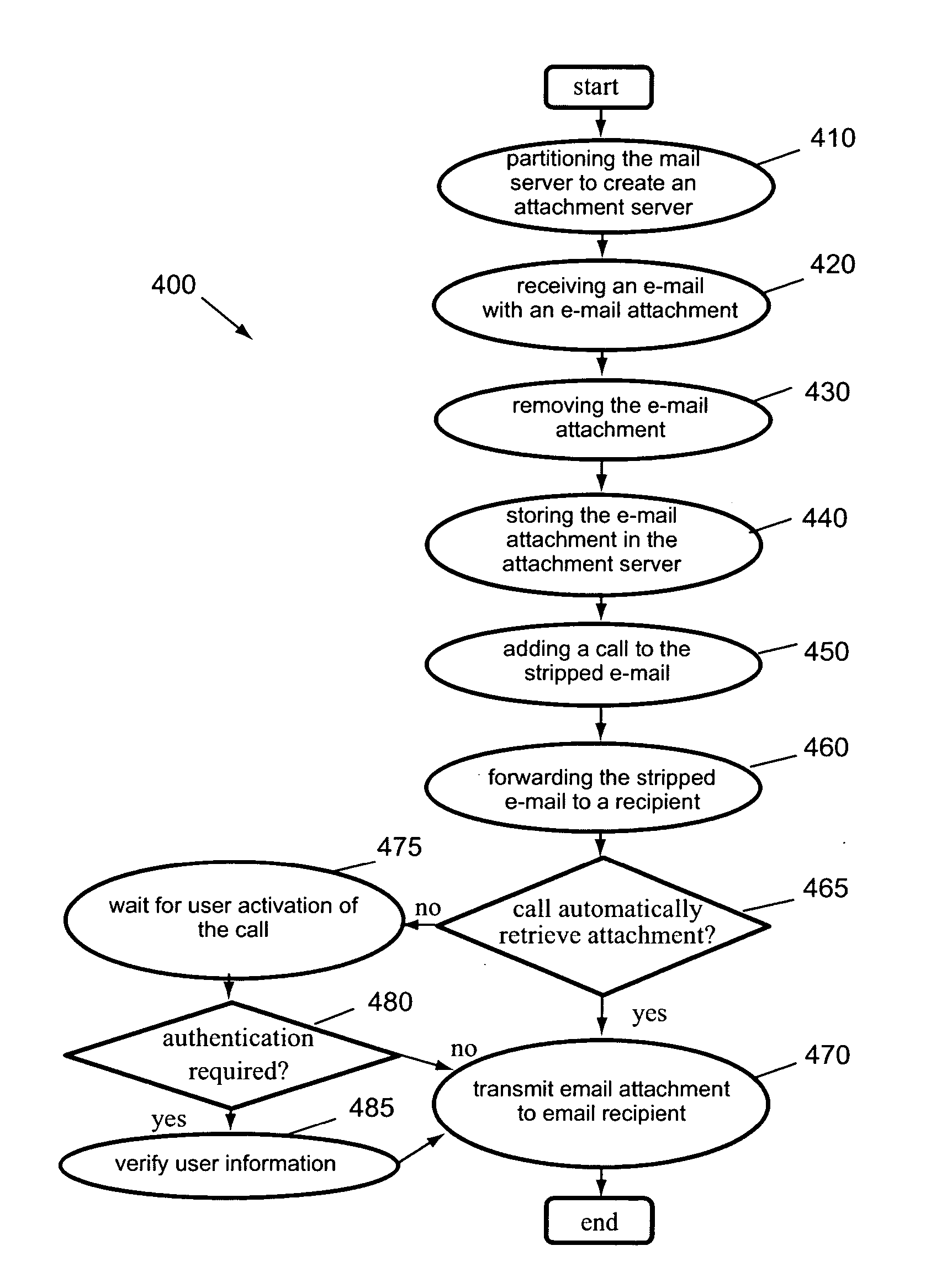
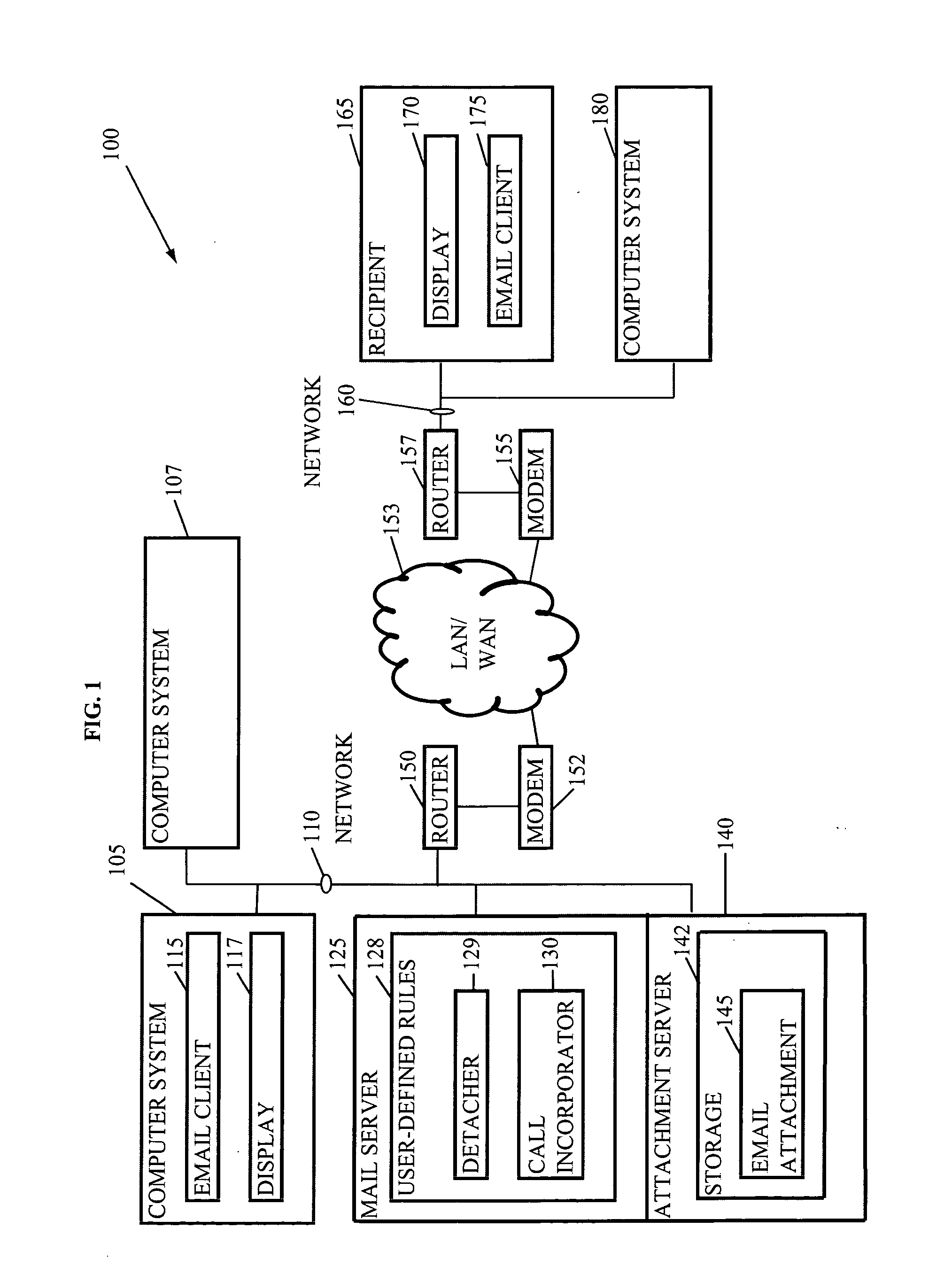
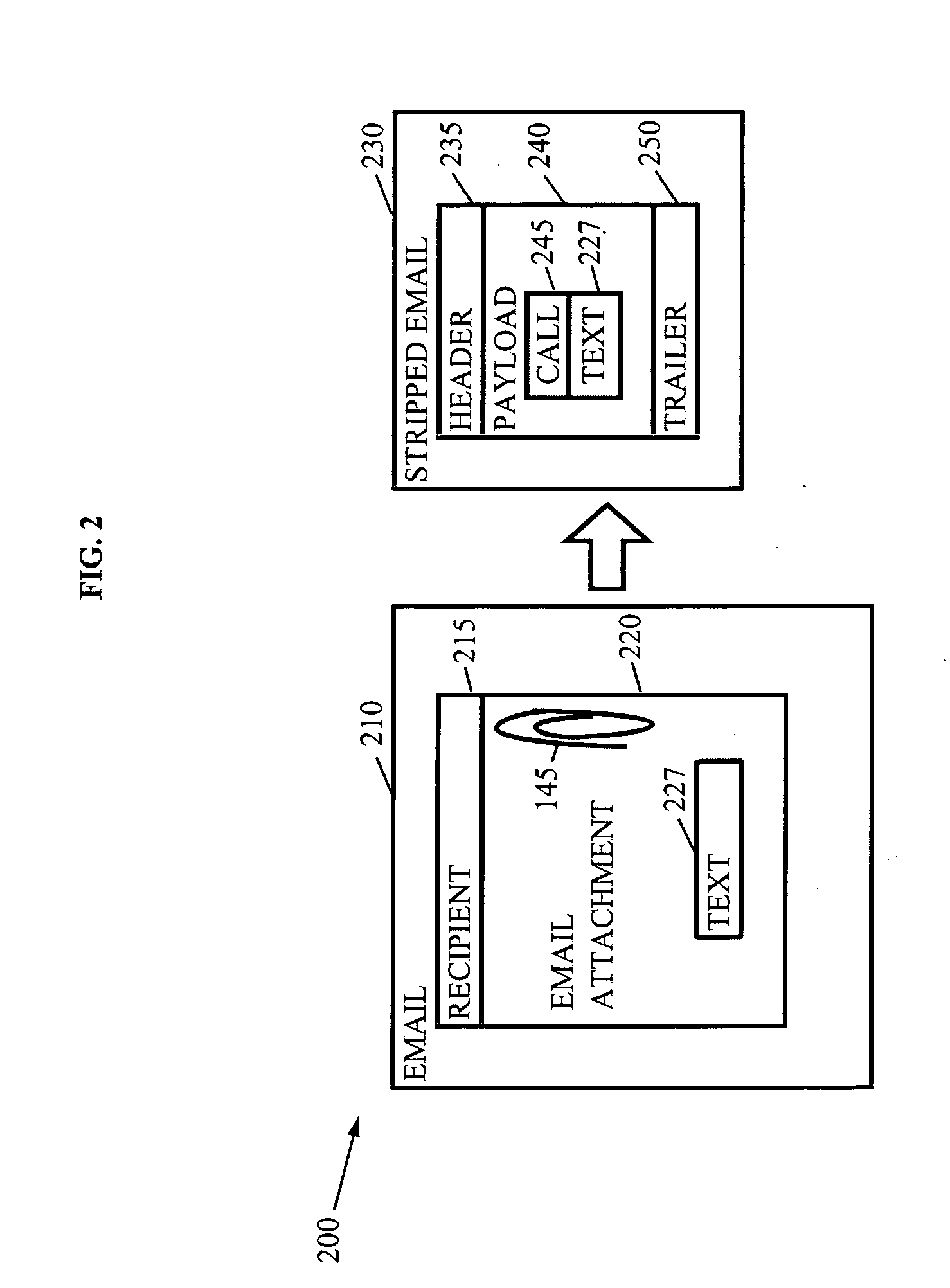
Selective transmission of an email attachment
ActiveUS20050108335A1Multiple digital computer combinationsData switching networksEmail attachmentElectronic mail
Methods, devices, systems, and media are disclosed for replacing an email attachment with a call, and forwarding the email with the call to a user for selective display of the attachment by making a call. One embodiment includes receiving an email on a mail server, wherein the email has the email attachment, and removing the email attachment from the email to produce a stripped email. The embodiment further includes storing the email attachment on a server, adding the call to the stripped email, and forwarding the stripped email with the call for displaying to a recipient.
Owner:SNAP INC
Slide show navigation
InactiveUS20060156240A1Optimization mechanismEasy to viewNatural language data processingTransmissionAnimationThumbnail
Owner:APPLE INC
Method of managing attached document
InactiveUS6915333B2Multiple digital computer combinationsOffice automationEmail attachmentPaper document
Owner:CLOUD SOFTWARE GRP SWITZERLAND GMBH
Method for scaling images for usage on a mobile communication device
InactiveUS20060056604A1Quick ViewReduce the amount requiredCalled number recording/indicationTransmissionEmail attachmentComputer graphics (images)
A process is set forth for scaling images recieved as email attachments, or accesible by a URL link, to fit the device screen of a mobile communication device. A user menu prompt is presented for allowing the user to save the image for subsequent reuse by other device applications such as screensavers, background image useage, or picture viewers, without these device applications having to synchronize with a desktop computer to obtain the image.
Owner:ARIZAN +1
Method of managing attached document
InactiveUS20030115273A1Multiple digital computer combinationsOffice automationEmail attachmentClient-side
A method for managing e-mail attachment files received via a network e-mail system by a user. A first e-mail is received at a client computer which includes a first attachment file from the network e-mail system. The client computer begins searching for a second attachment file included with a second e-mail file, preferably automatically after opening the first e-mail. The files are compared to determine if the first attachment file is another incidence of the second attachment file. If true, the method replaces the first attachment file with an identification which points to the second attachment file. When deleting the second e-mail file, the method searches for a third e-mail file. If the third e-mail file is found and the third e-mail file is the next earliest dated incidence of the second e-mail file, the method provides moving and attaching the second attachment file to the third e-mail file.
Owner:CITRIX SYST INT GMBH
Optional receipt of an email attachment
InactiveUS20050108336A1Multiple digital computer combinationsData switching networksEmail attachmentBiological activation
Methods, devices, systems, and media are disclosed for selective receipt of an e-mail attachment. One embodiment includes receiving an instruction from a sender to add a selectable notification of an email attachment to a first email. Further, the embodiment includes inserting code in the first email to transmit a reply to the sender upon execution of the code by an email client, wherein execution is responsive to activation of the selectable notification by a recipient. Further still, the embodiment includes generating a second email having the email attachment upon receipt of the reply, and transmitting the second email to the recipient in response to the reply.
Owner:IBM CORP
Authorizing access by email and sharing of attachments
ActiveUS20150264111A1Database queryingDigital data processing detailsEmail attachmentElectronic mail
Solutions are provided for authorizing access to and / or sharing of email attachments. An example method may include, by a computing device, detecting an email message with a file attachment. The email message may identify one or more recipients of the file attachment. The file attachment may be stored in a database table. The database table may include at least one permissions entry controlling access by the one or more recipients to the stored file attachment. The file attachment may be replaced in the email message, with a download link to a location in the database table storing the file attachment. The email message may be delivered with the download link to the one or more recipients.
Owner:SAP AG
System, method and program product for authenticating an e-mail and/or attachment
InactiveUS20050015457A1Digital data processing detailsUser identity/authority verificationInternet privacyEmail attachment
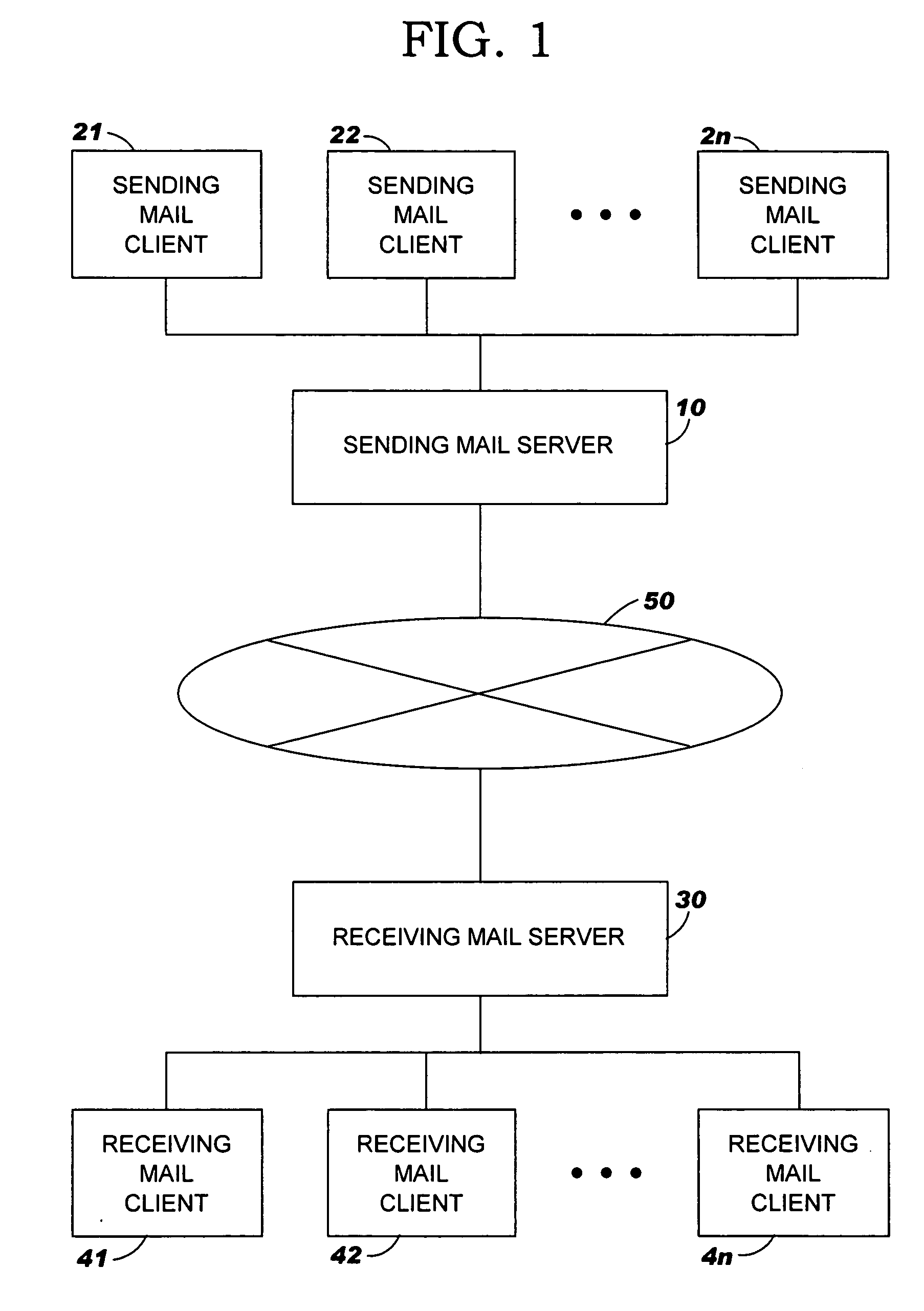
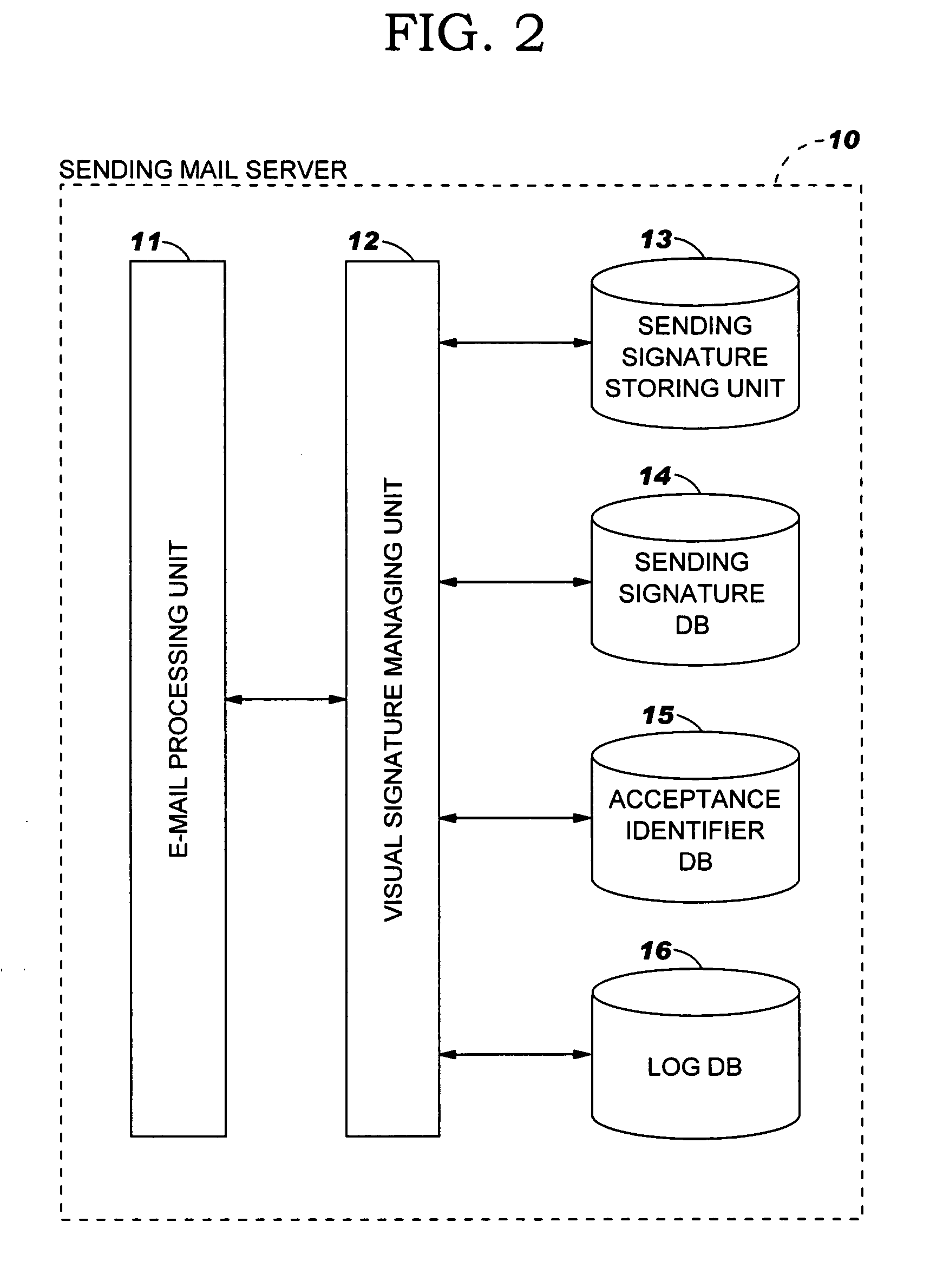
A system, method and program product for authenticating an e-mail. A user requests to register a visual signature image with a sending mail server, and in response, the sending mail server furnishes a first identifier to the user. Subsequently, the user requests the sending mail server to send an e-mail with the visual signature image and supplies the e-mail and first identifier to the sending mail server. In response, the sending mail server validates the first identifier, and sends the e-mail with a second identifier to a receiving mail server. In response, the receiving mail server validates the second identifier. The second identifier identifies an addressee of the e-mail, and the receiving mail server validates the second identifier by comparing the addressee identified by the acceptance identifier to an addressee within the e-mail. The sending mail server embeds the second identifier in the visual signature image and sends the visual signature image with the embedded second identifier to the receiving mail server. The invention also resides in the image representing an originator of an e-mail and / or an attachment to the e-mail; the image is included in the e-mail, an icon for the attachment or the attachment. The image includes an identity of an originator and an identity of a recipient intended by the originator. The e-mail with the added image is sent to the intended recipient. The image and identities of the originator and recipient authenticate the e-mail and / or the attachment
Owner:KYNDRYL INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com