Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
252 results about "Limited capacity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
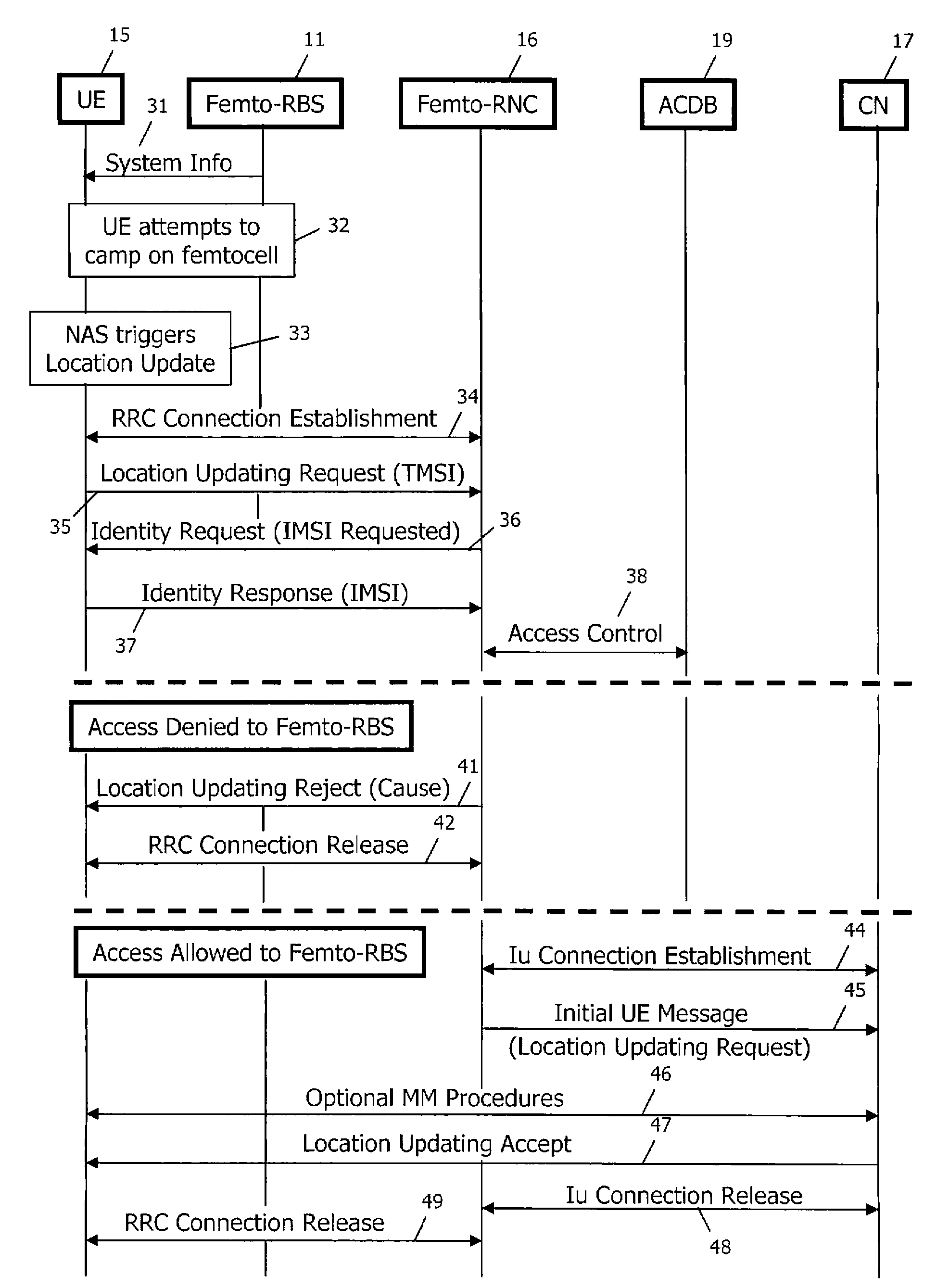
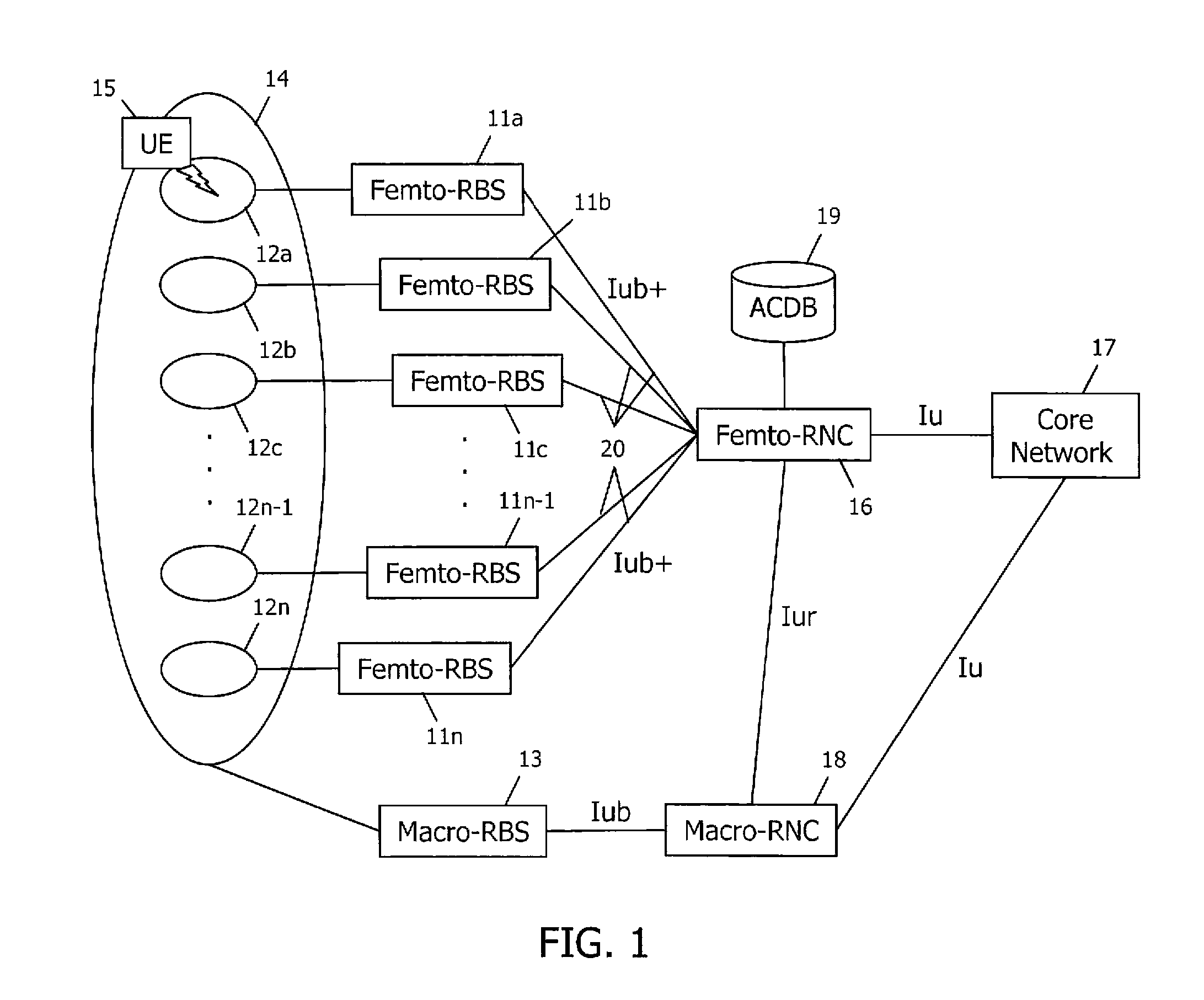
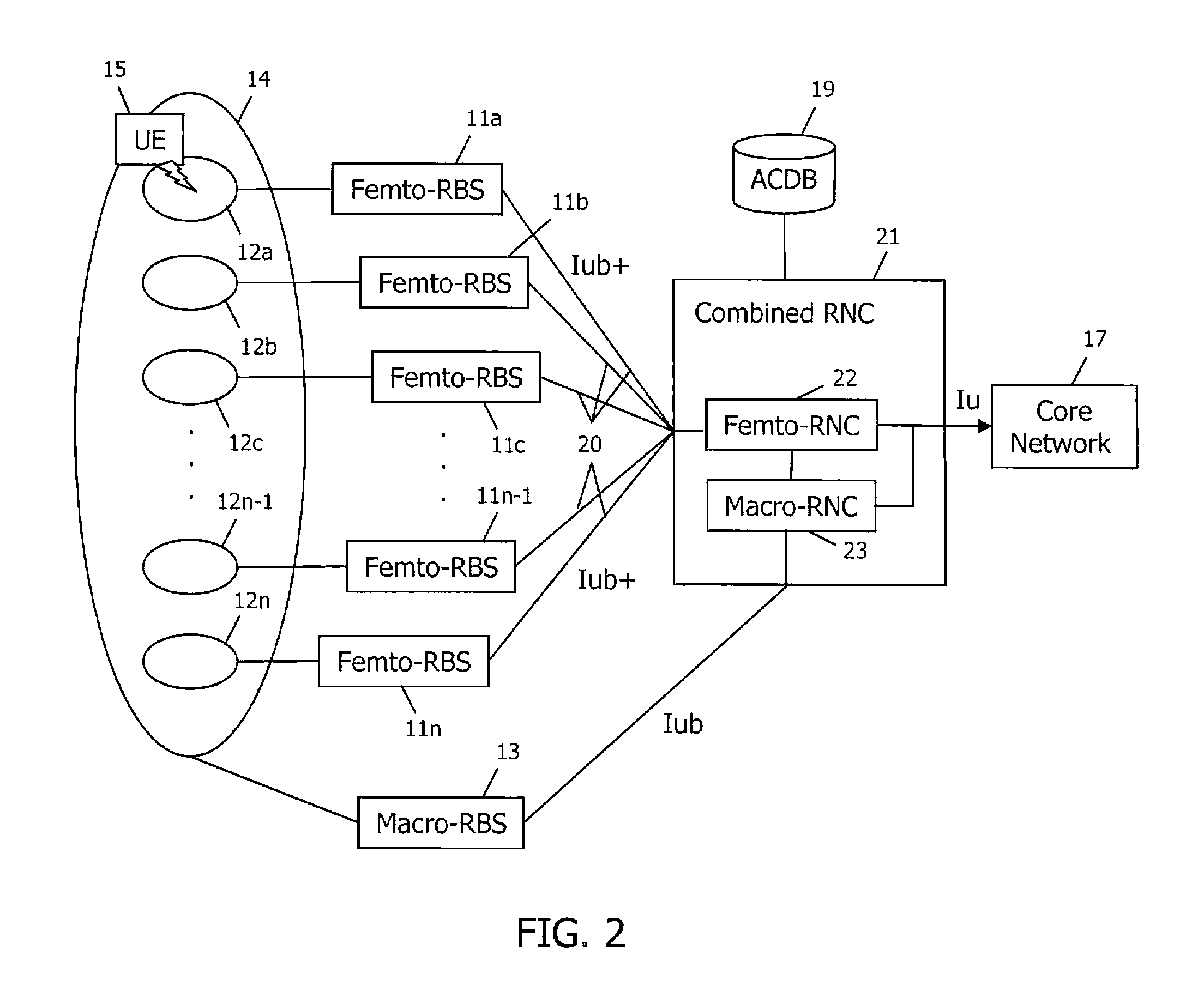
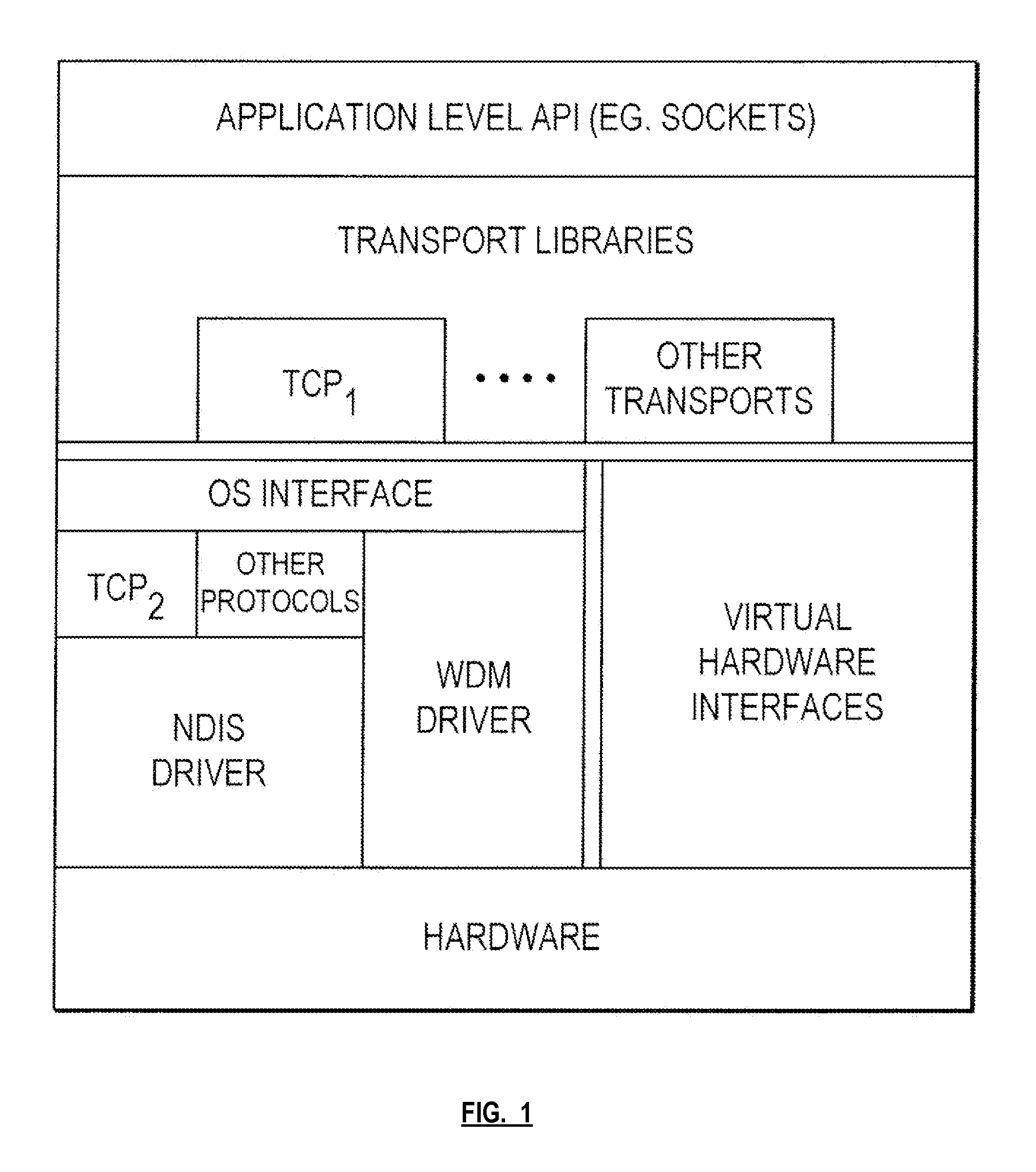
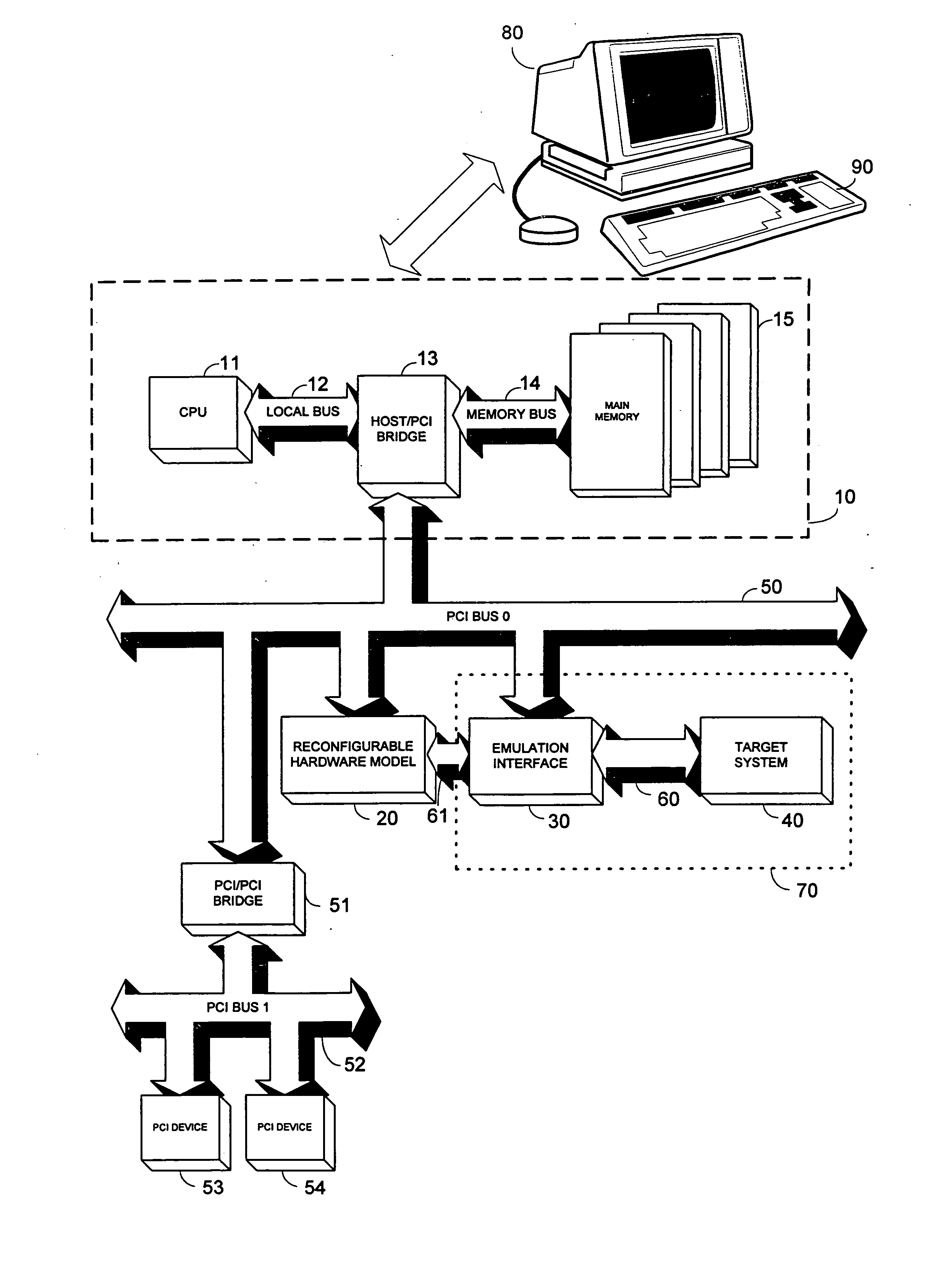
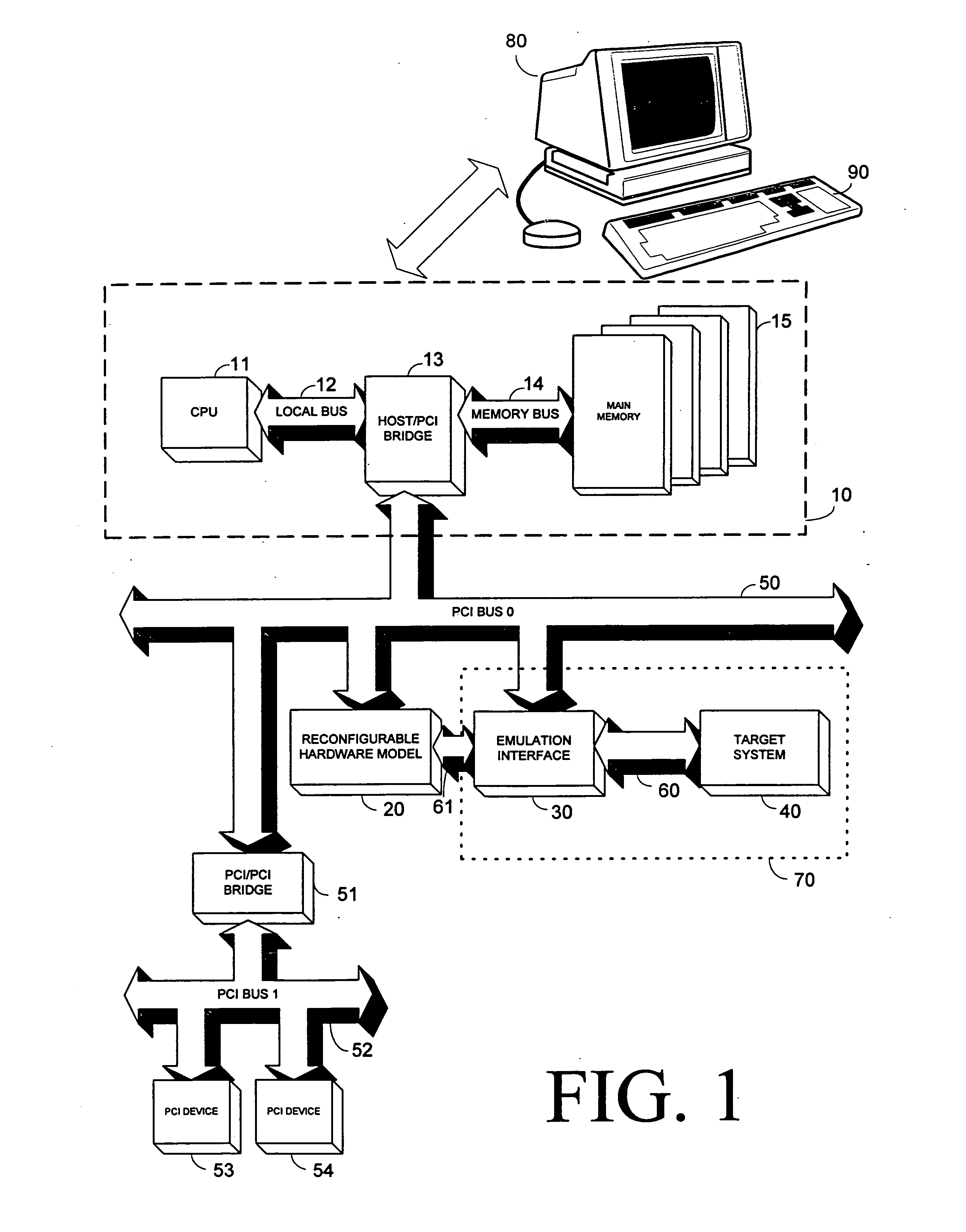
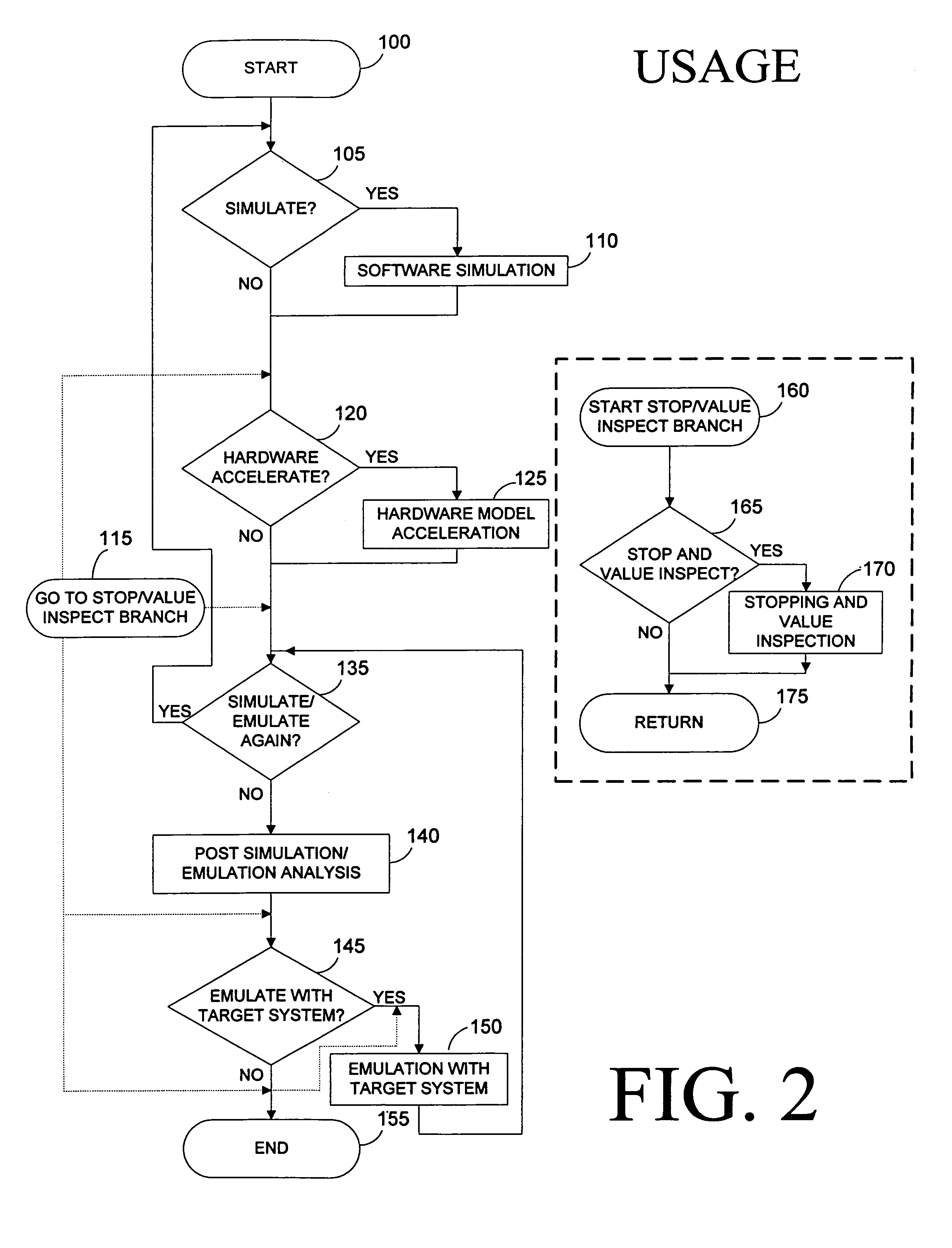
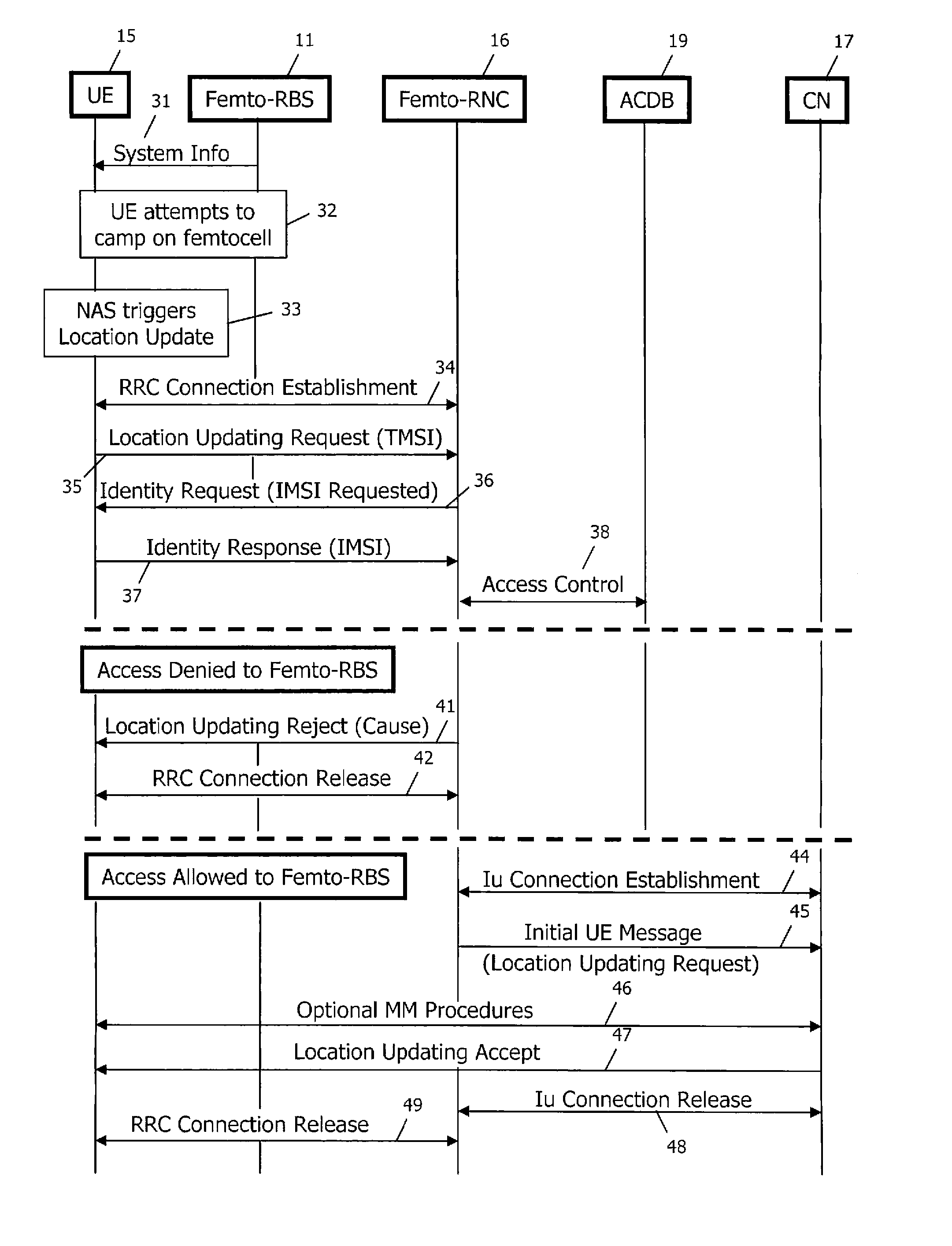
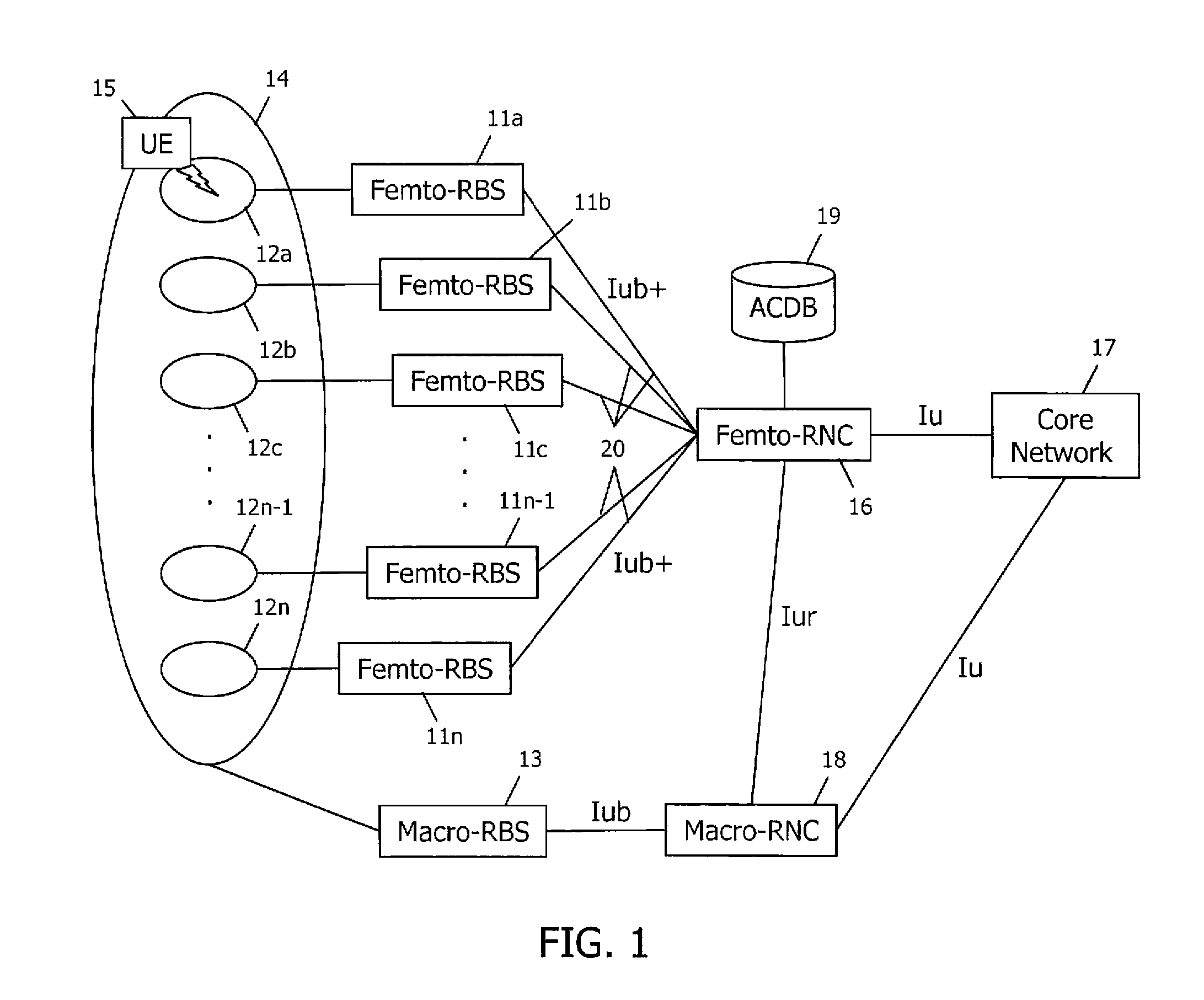
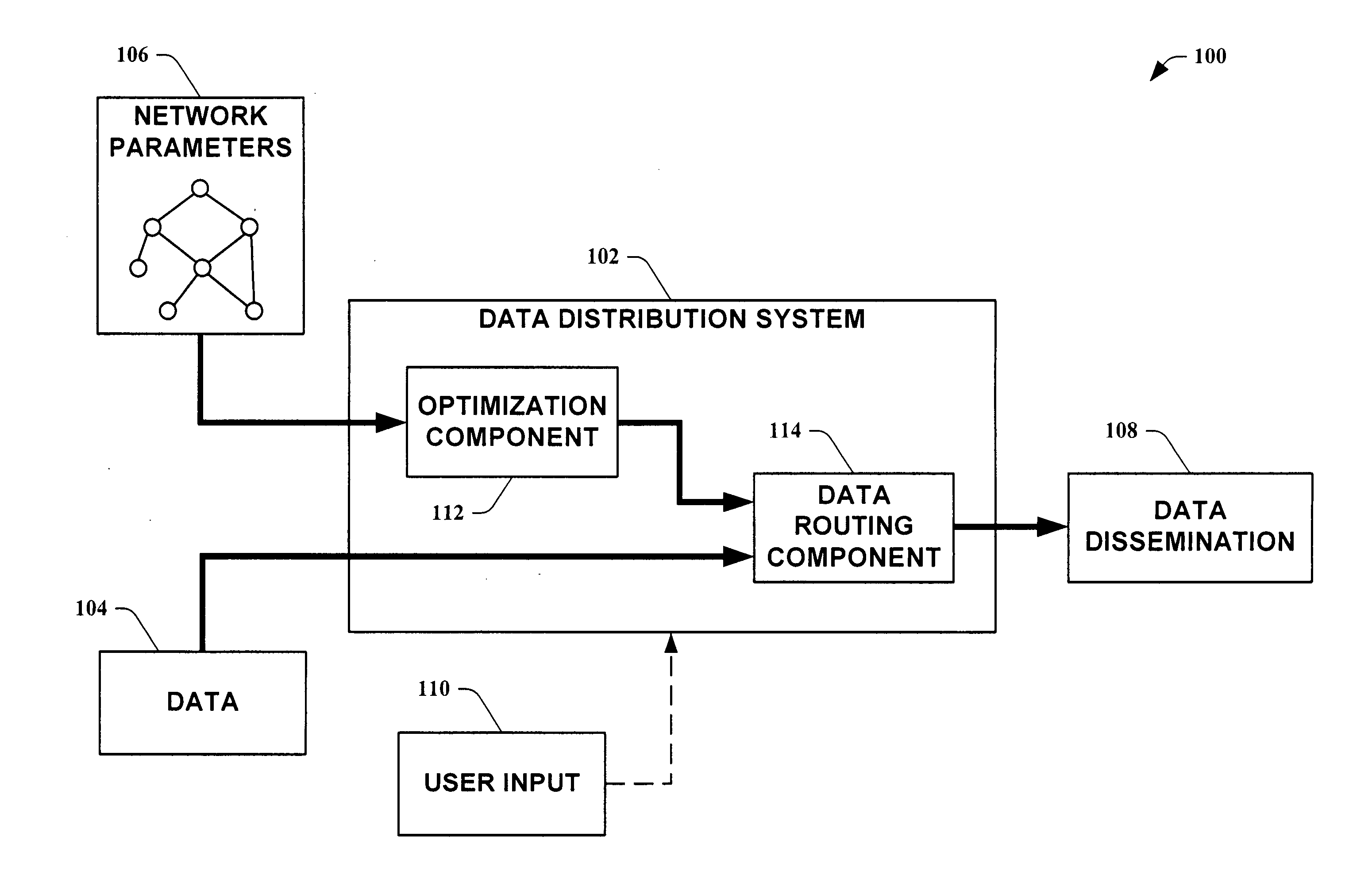
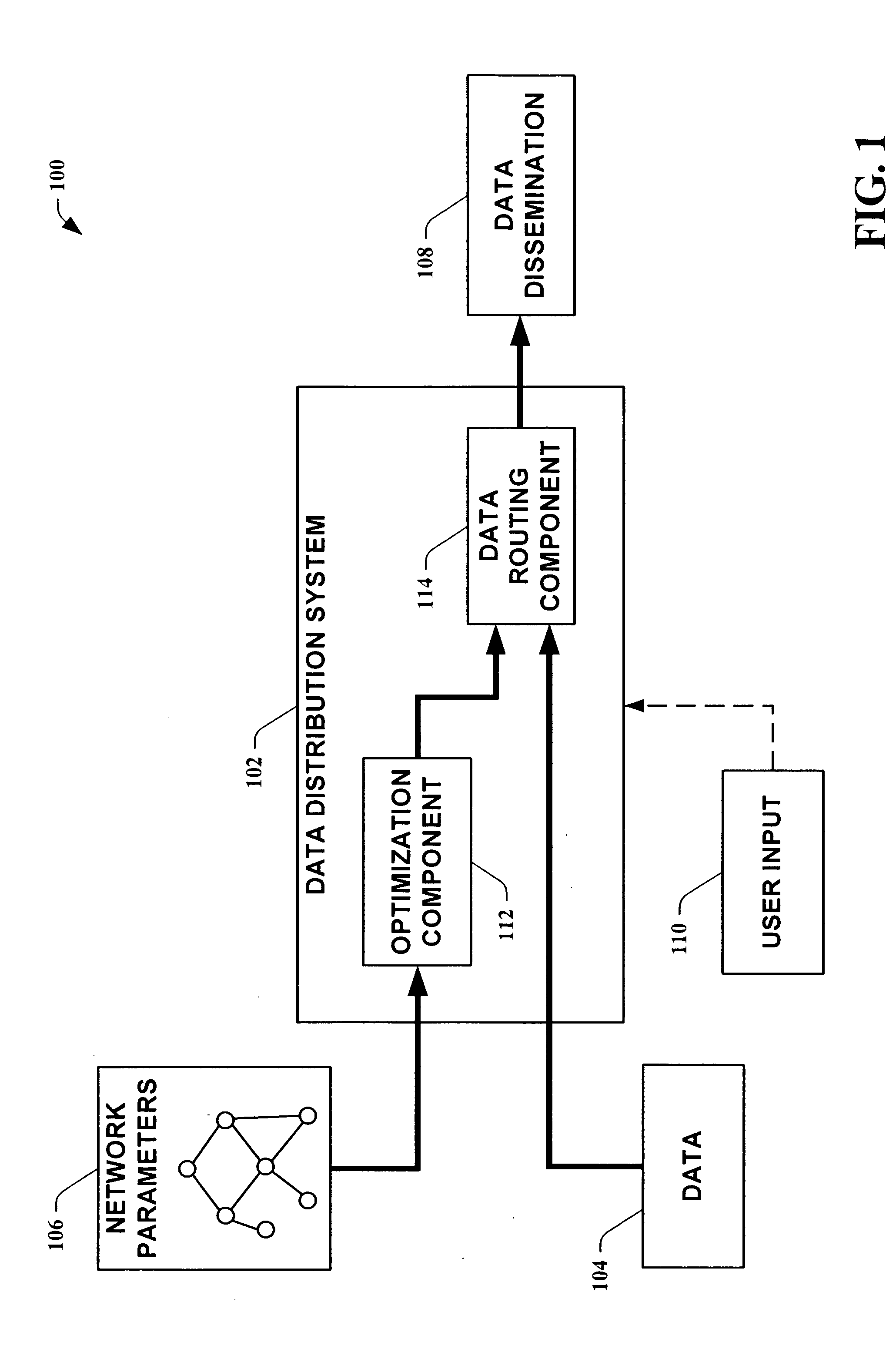
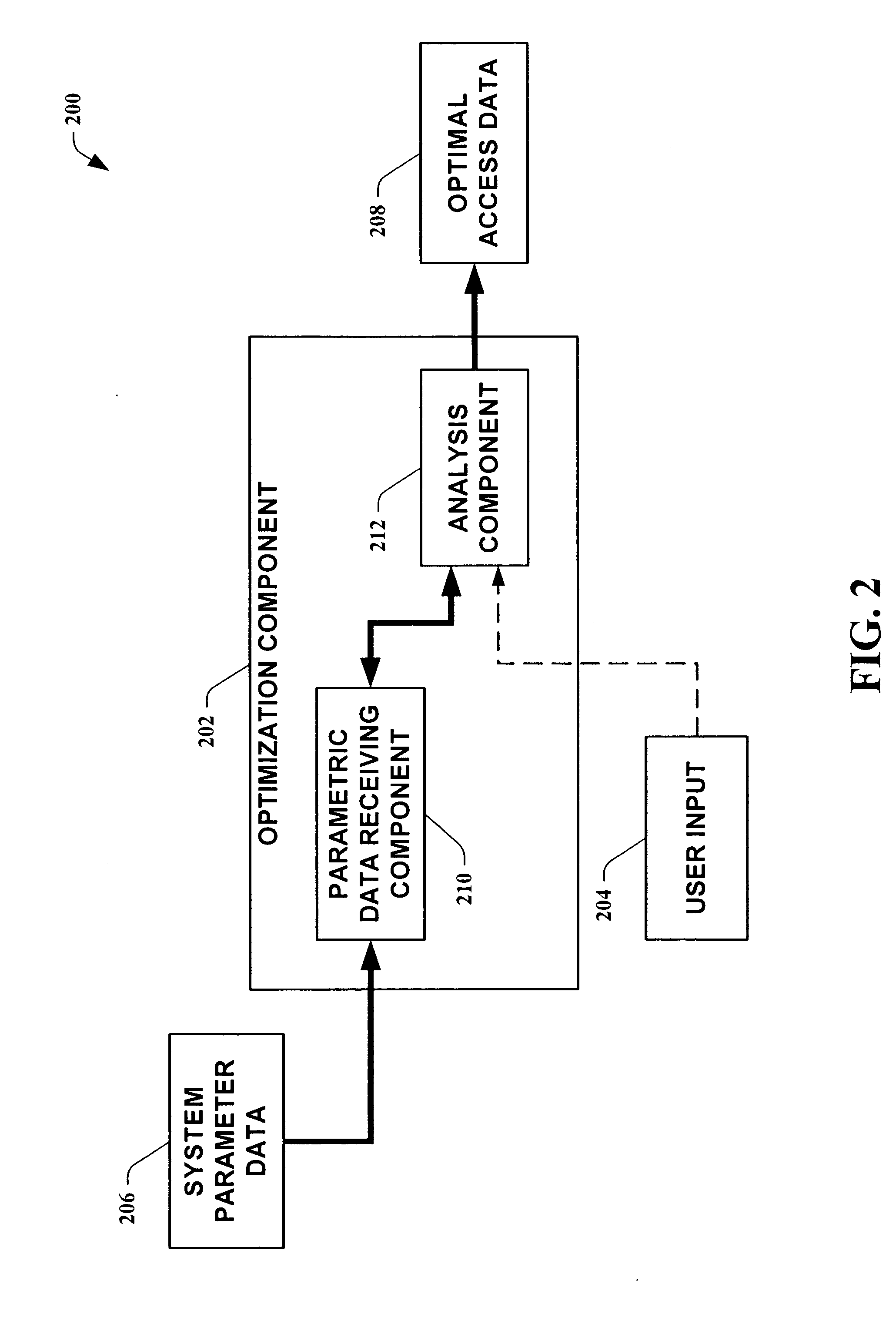
Access control in a mobile communication system
ActiveUS20070270152A1Reduce loadRisk minimizationAssess restrictionNetwork topologiesAccess networkRadio networks
A method and radio network controller (RNC) in a radio access network (RAN) for controlling access to a cellular telecommunication system. Upon receiving an access request from a given user equipment (UE) through a given radio base station (RBS), the RNC retrieves authorization information from an access control database within the RAN. The authorization information indicates whether the given UE is authorized to access the system through the given RBS. The RNC alternatively grants access or denies access to the UE based on the retrieved authorization information. The RBS is particularly useful for controlling access through small cells with limited capacity.
Owner:TELEFON AB LM ERICSSON (PUBL)
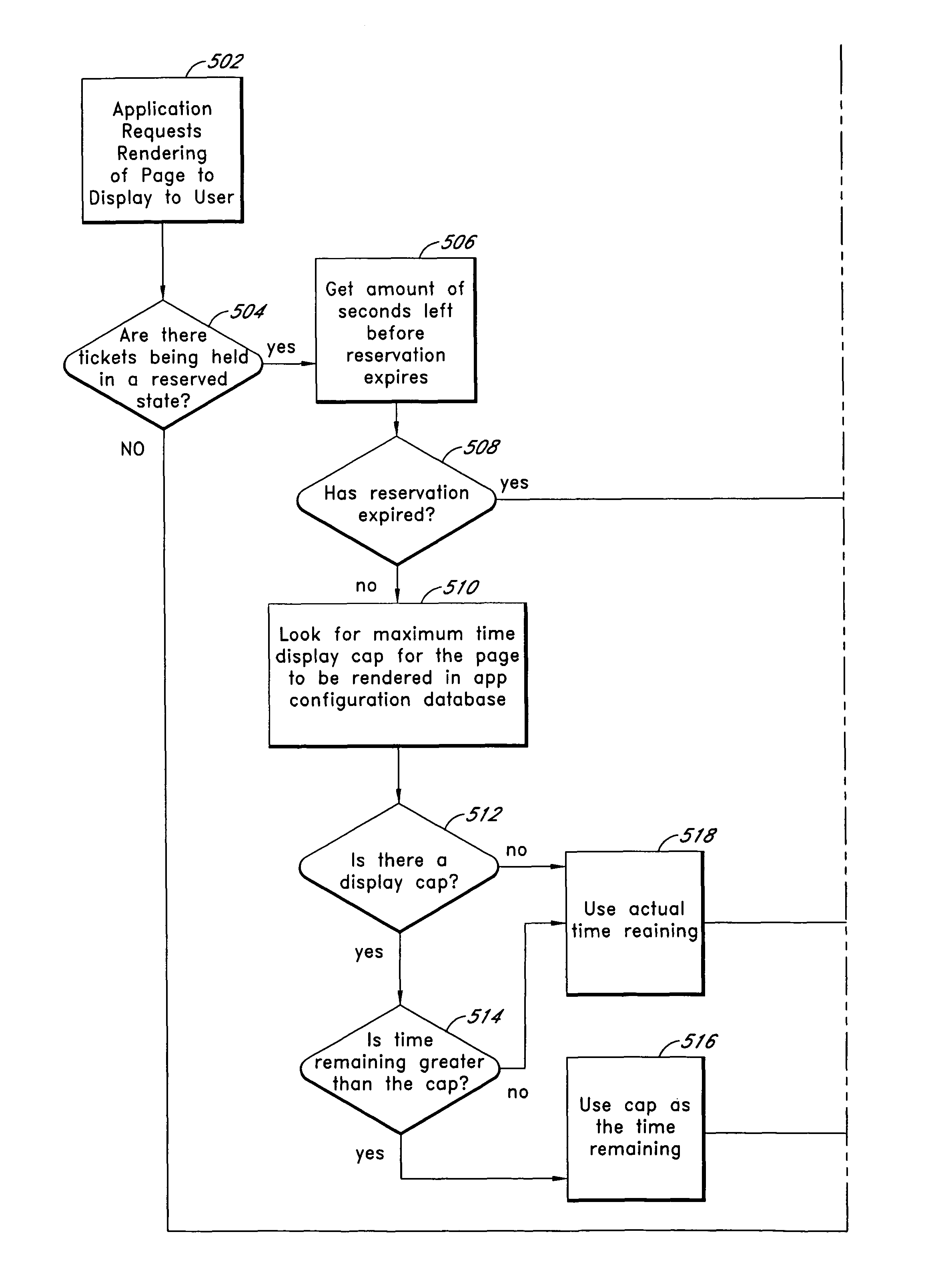
Systems and methods for queuing access to network resources
One embodiment of the present invention provides apparatus and methods for queuing access by large numbers of Internet or other network-based users to networked systems and resources with limited capacity. In one example embodiment, a queuing system provides user access to network resources, such as that of a ticketing system. A ticket queue queues a request received from a client system. A request processing module causes the client system to repeatedly transmit messages to the system during a first period, and in response to determining that the client system has ceased transmitting messages during the first period, the request is remove from the queue and / or cause the request goes unfulfilled.
Owner:LIVE NATION ENTERTAINEMENT INC
Method for equitable bandwidth allocation for content distribution networks
ActiveUS7801177B2Optimize allocationReduce capacityError preventionFrequency-division multiplex detailsPerformance functionContent distribution
Owner:TELCORDIA TECHNOLOGIES INC
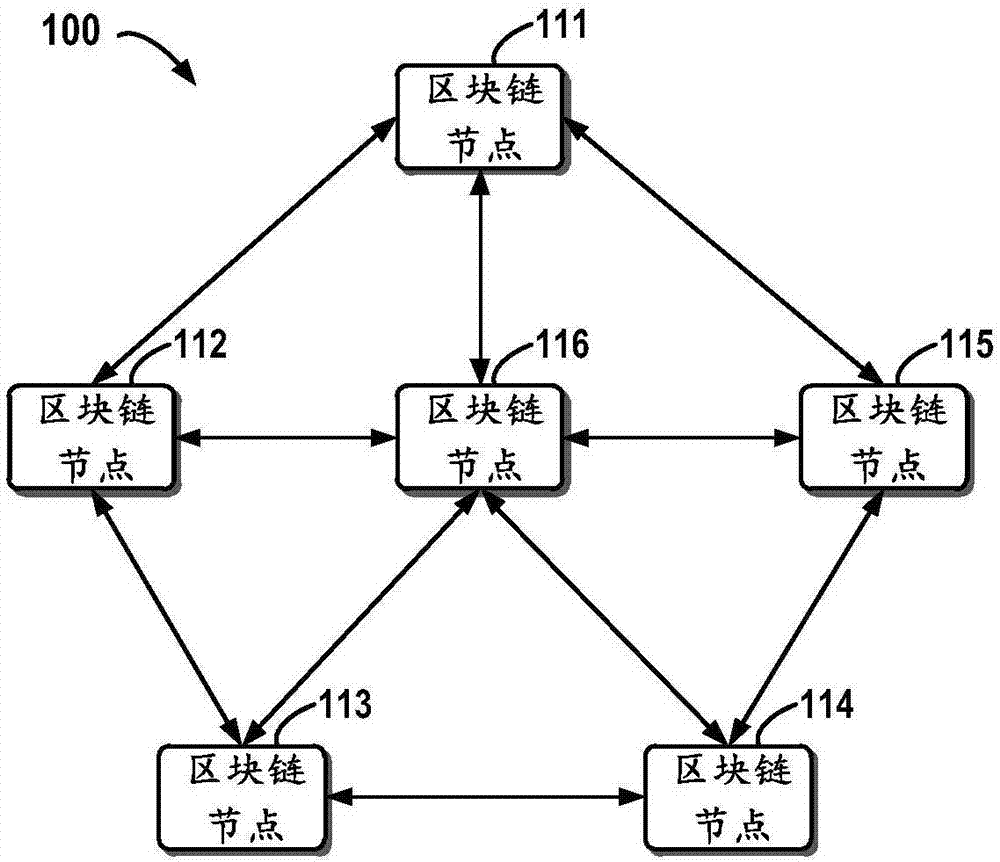
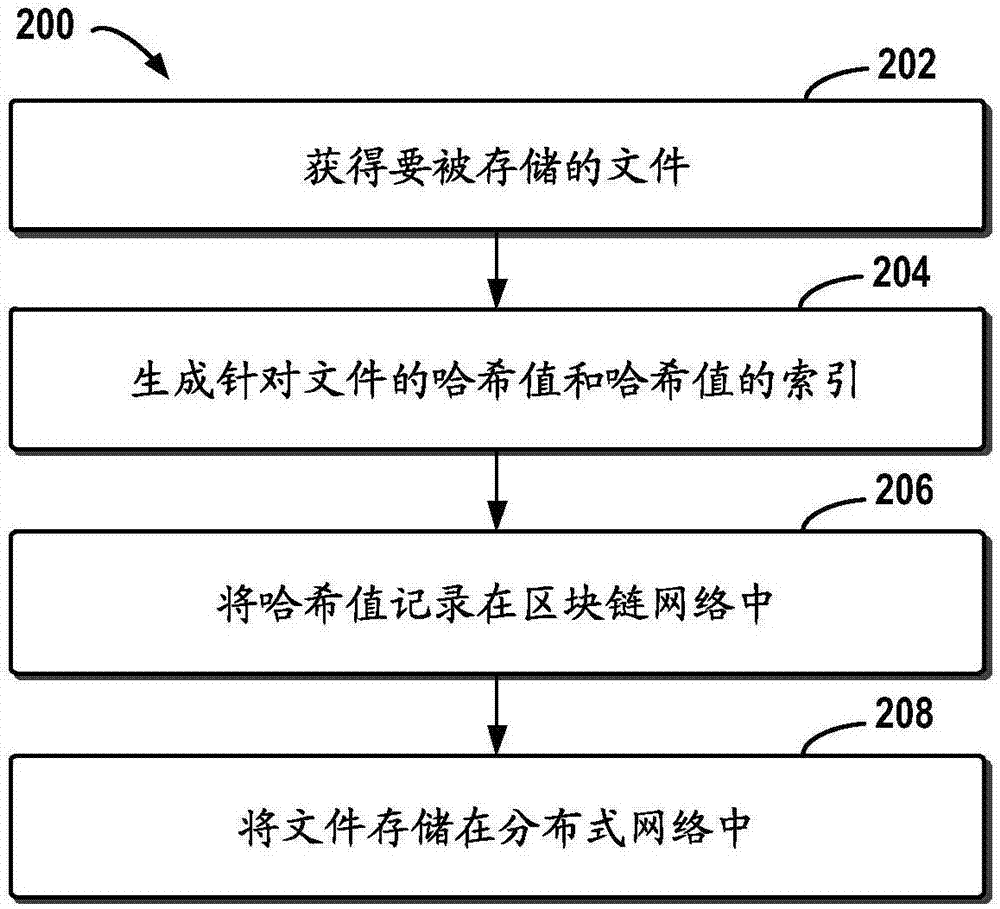
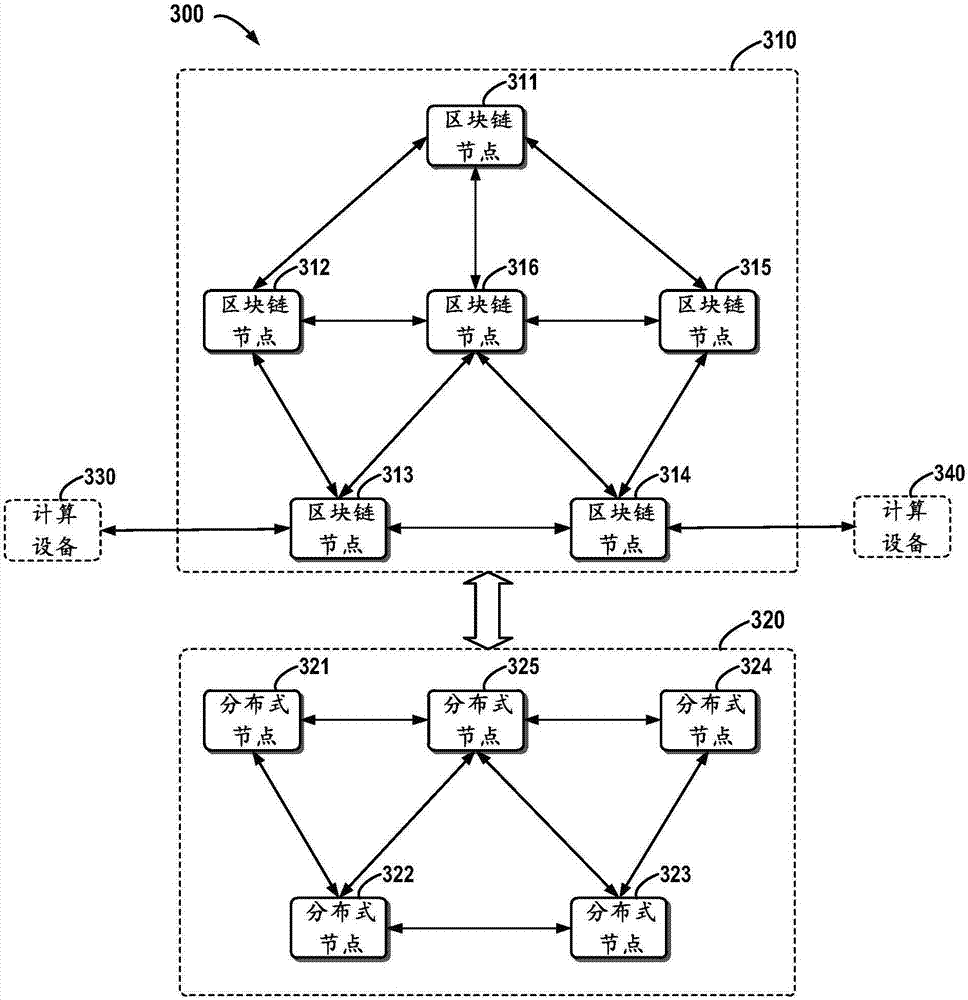
Block chain-based distributed storage
InactiveCN107273410ASolve the problem of limited node capacityAchieve tamper resistanceFile access structuresSpecial data processing applicationsTamper resistanceDistributed File System
The embodiment of the disclosure relates to block chain-based distributed storage, and discloses a block chain-based distributed storage method. The method includes: obtaining a file which needs to be stored, and generating a hash value and an index of the hash value for the file. The method also includes: recording the hash value in a block chain network, and storing the file in a distributed network, wherein the file is located on the basis of the hash value in the distributed network. Therefore, according to the embodiment of the disclosure, tampering proofing and the distributed storage of the file can be realized through combining a block chain and a distributed file system, thus the problem of the limited capacity of block chain nodes is solved, and the authenticity and the availability of the stored file are effectively guaranteed.
Owner:SHANGHAI DIANRONG INFORMATION TECH CO LTD
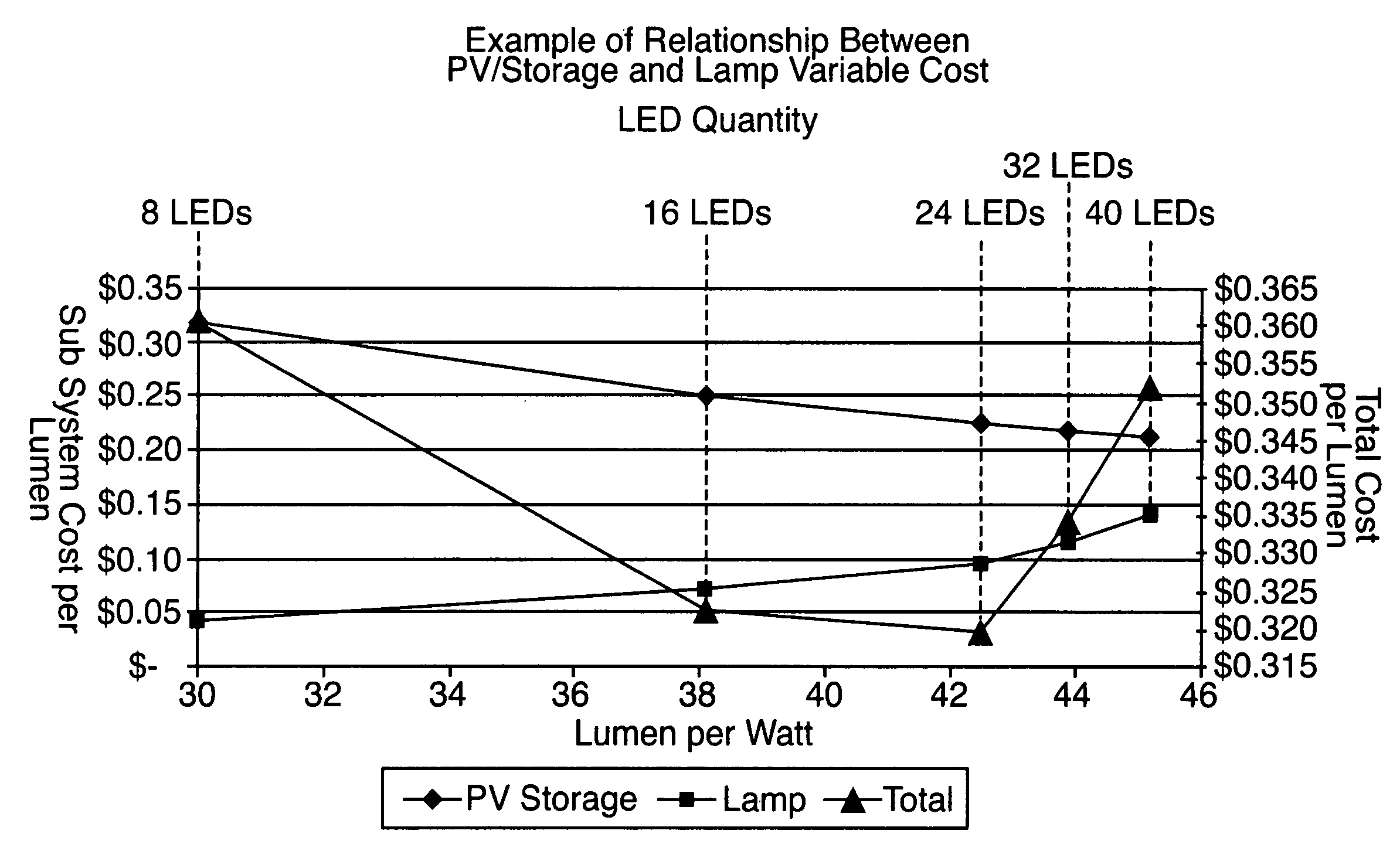
LED lighting system
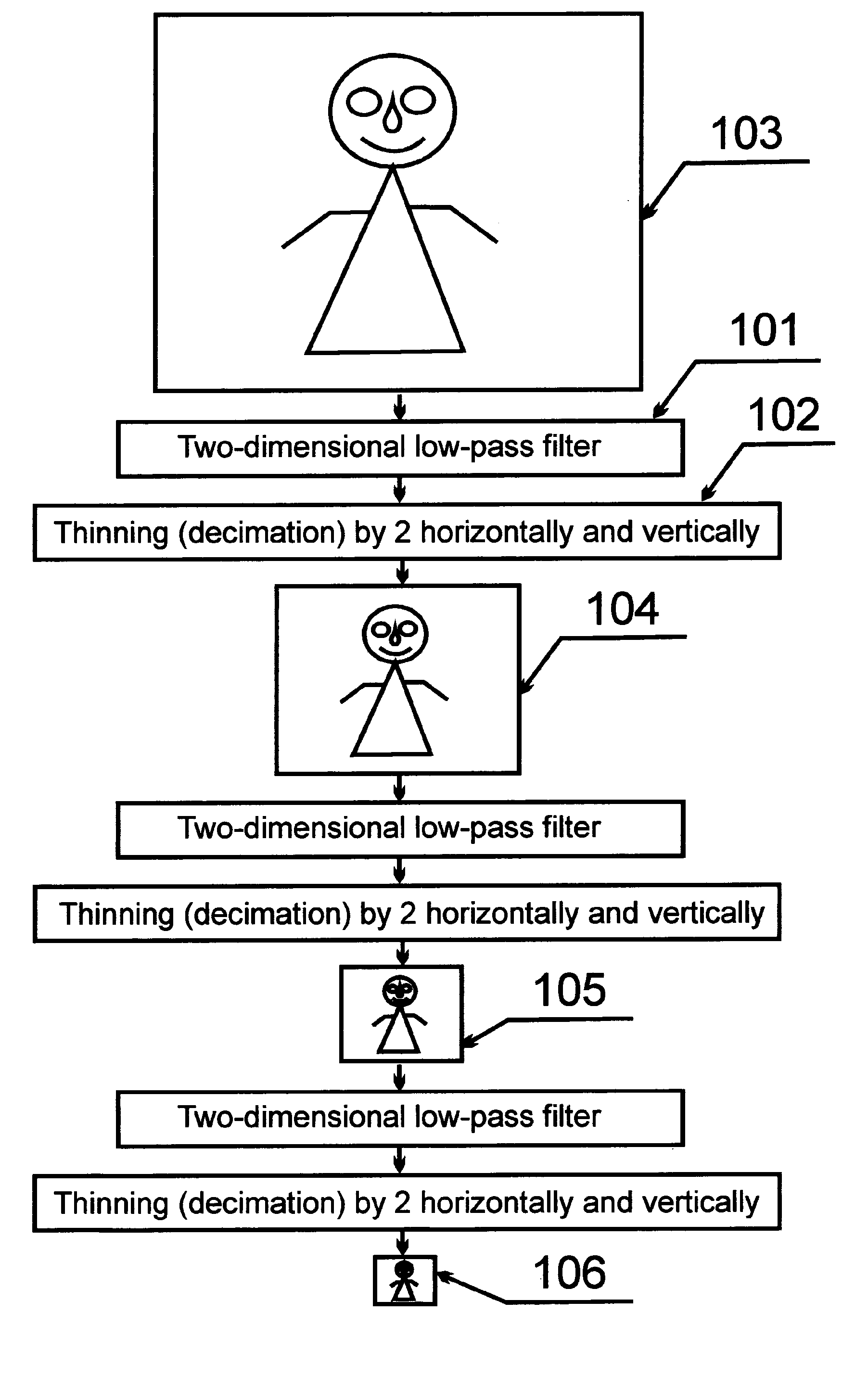
InactiveUS20060149607A1Improve luminous efficiencyImprove efficiencyData processing applicationsElectrical apparatusEffect lightEngineering
A method for optimizing an LED lighting system cost includes steps of determining LED costs, power source costs, and total costs associated with a plurality of LED quantities, and identifying a lowest total cost as an optimal cost. A LED lighting system includes an LED operated by a constant-current driver at less than its maximum current capacity. A programmable controller including a feedback routine is used to compensate for intensity drift as an LED ages. Other embodiments of LED lighting systems include multiple LEDs producing light having various spectrums to optimize the lighting system efficiency and the effectiveness. A charge controller including an MPPT routine is advantageously employed with a LED lighting system powered by a limited-capacity power source.
Owner:SOLARONE SOLUTIONS
Method of encoding digital signals (variants), method of decoding digital signals (variants), device for implementation thereof (variants), and system for image transmission via limited throughput communication channels (variants)
InactiveUS20100226569A1Quality improvementImprove compression efficiencyCode conversionCharacter and pattern recognitionSystematic variationSelf adaptive
The invention relates to systems for a transmission of images via channels of communication with a limited capacity by means of application of compression of the images. The technical result consists in an increase of the compression degree upon encoding, and it allows to fulfill the transmission of such encoded images via the channel of communication with the limited capacity, therewith a high degree of the compression is provided without of increase of computational power of encoding device and without of distortions upon decoding. The result is obtained by the usage of more effective method of interpolation of restored subsamples, in this method there is used an adaptive and applicative set of samples, which restore a quantized signal, and this set of the samples allows to improve an accuracy of the interpolation with a number of the subsamples, which is necessary for the right interpolation that is simultaneously decreased one.
Owner:SIF CODEC
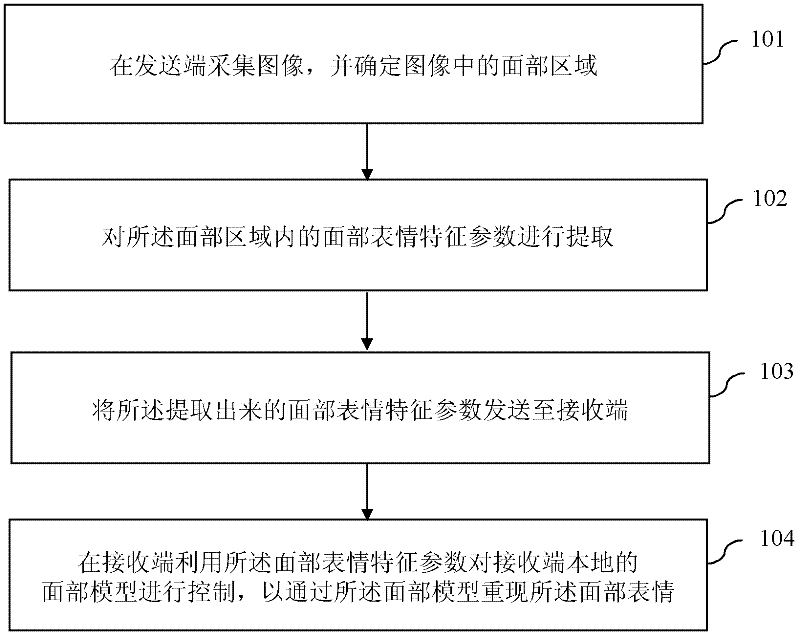
Image communication method and system based on facial expression/action recognition
InactiveCN102271241AReduced transfer rate requirementsTelevision conference systemsCharacter and pattern recognitionFace modelFeature parameter
The invention discloses an image communication method and system based on facial expression / action recognition. In the image communication method based on facial expression recognition, firstly, an image is collected at the sending end, and the facial area in the image is determined; The facial expression feature parameters in the region are extracted; then the extracted facial expression feature parameters are sent to the receiving end; finally, the receiving end uses the facial expression feature parameters to control the local facial model of the receiving end to pass the The facial model reproduces the facial expression. The application of the present invention can not only enhance user experience, but also greatly reduce the requirement on the information transmission rate of the video bearer network, realize more effective video communication, and is especially suitable for wireless communication networks with limited network bandwidth and capacity.
Owner:BEIJING UNIV OF POSTS & TELECOMM
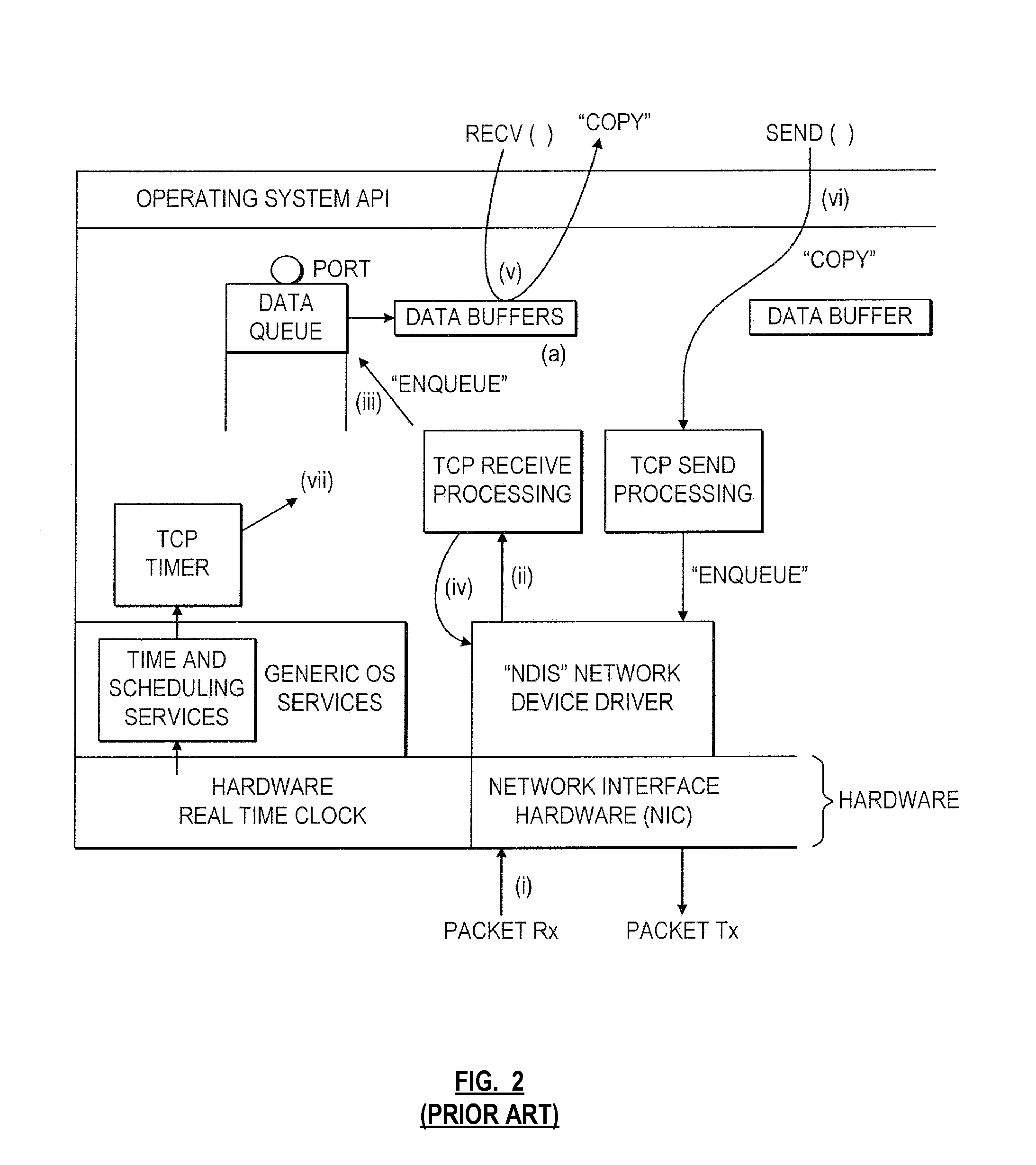
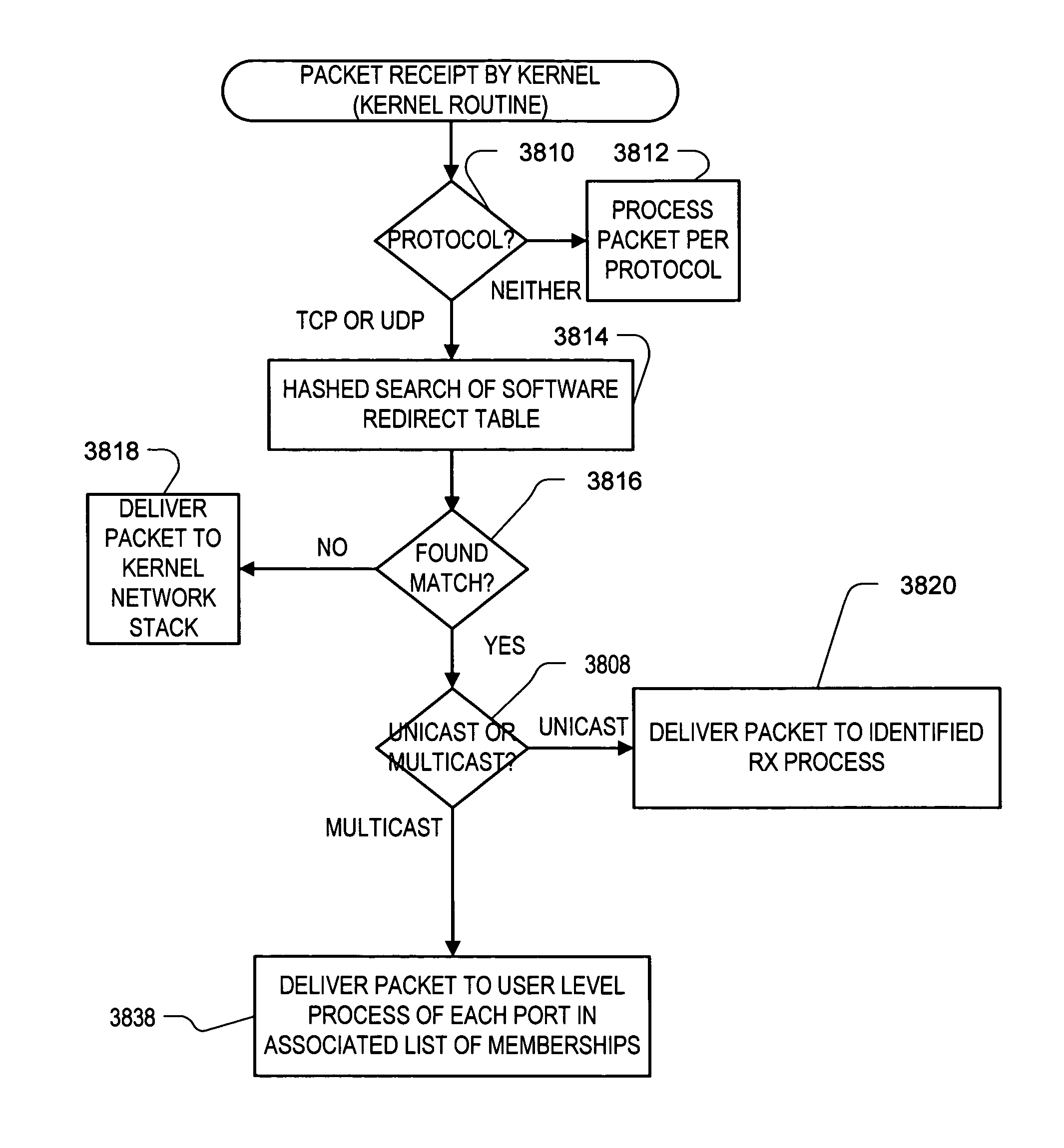
Method and apparatus for multicast packet reception
ActiveUS20120113987A1Special service provision for substationData switching by path configurationNetwork packetMulticast packets
Roughly described, incoming data packets are delivered by the NIC directly to at least two user level endpoints. In an aspect, only filters that cannot be ambiguous are created in the NIC. In another aspect, the NIC maintains a filter table supporting direct delivery of incoming unicast and multicast data packets to one user level endpoint. Additional requests to join the same multicast group cause replacement of the NIC filter with one in the kernel. In another aspect, a NIC has limited capacity to maintain multicast group memberships. In response to a new multicast filter request, the kernel establishes it in the NIC only if the NIC still has sufficient capacity; otherwise it is established in the kernel.
Owner:XILINX INC
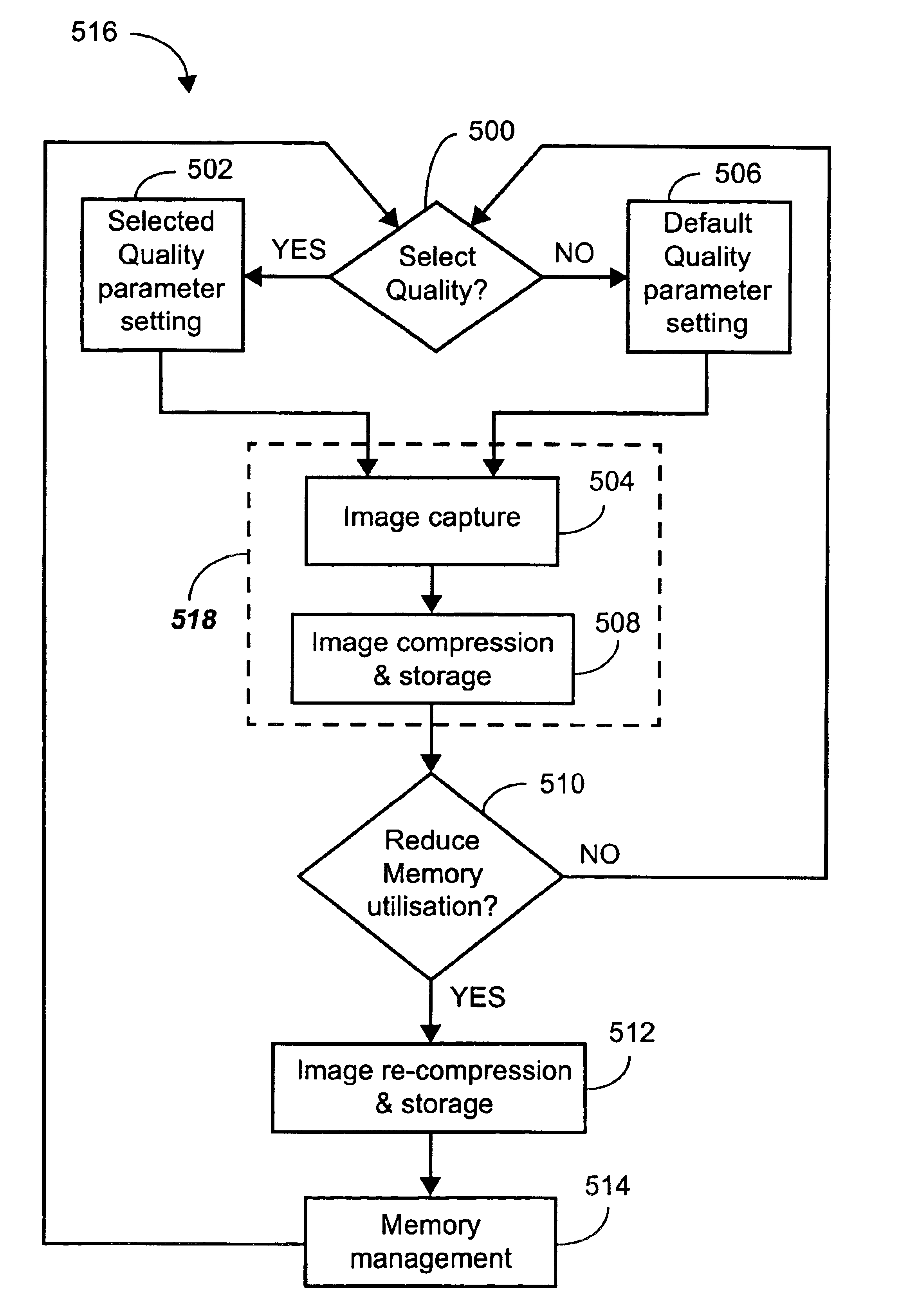
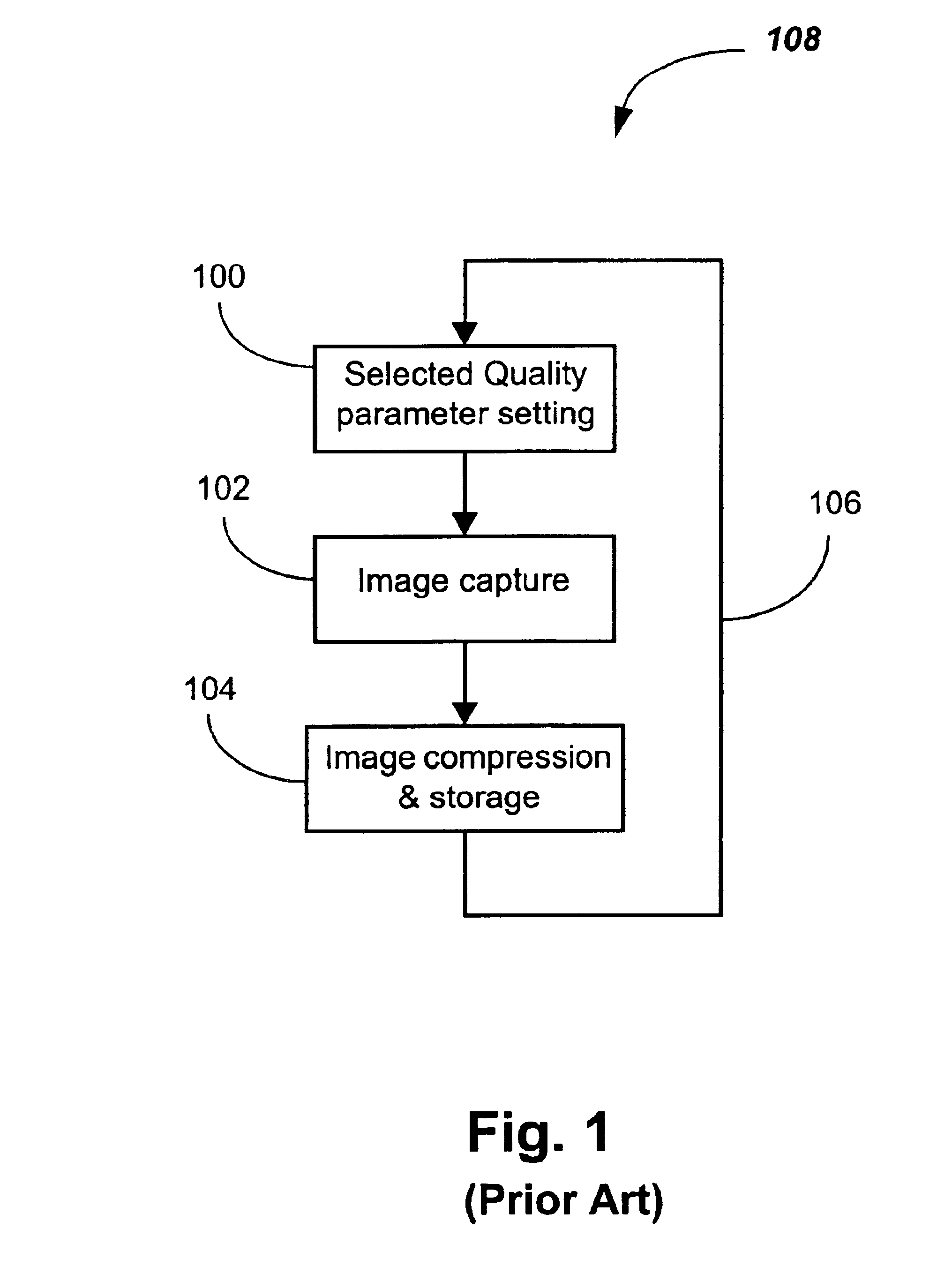
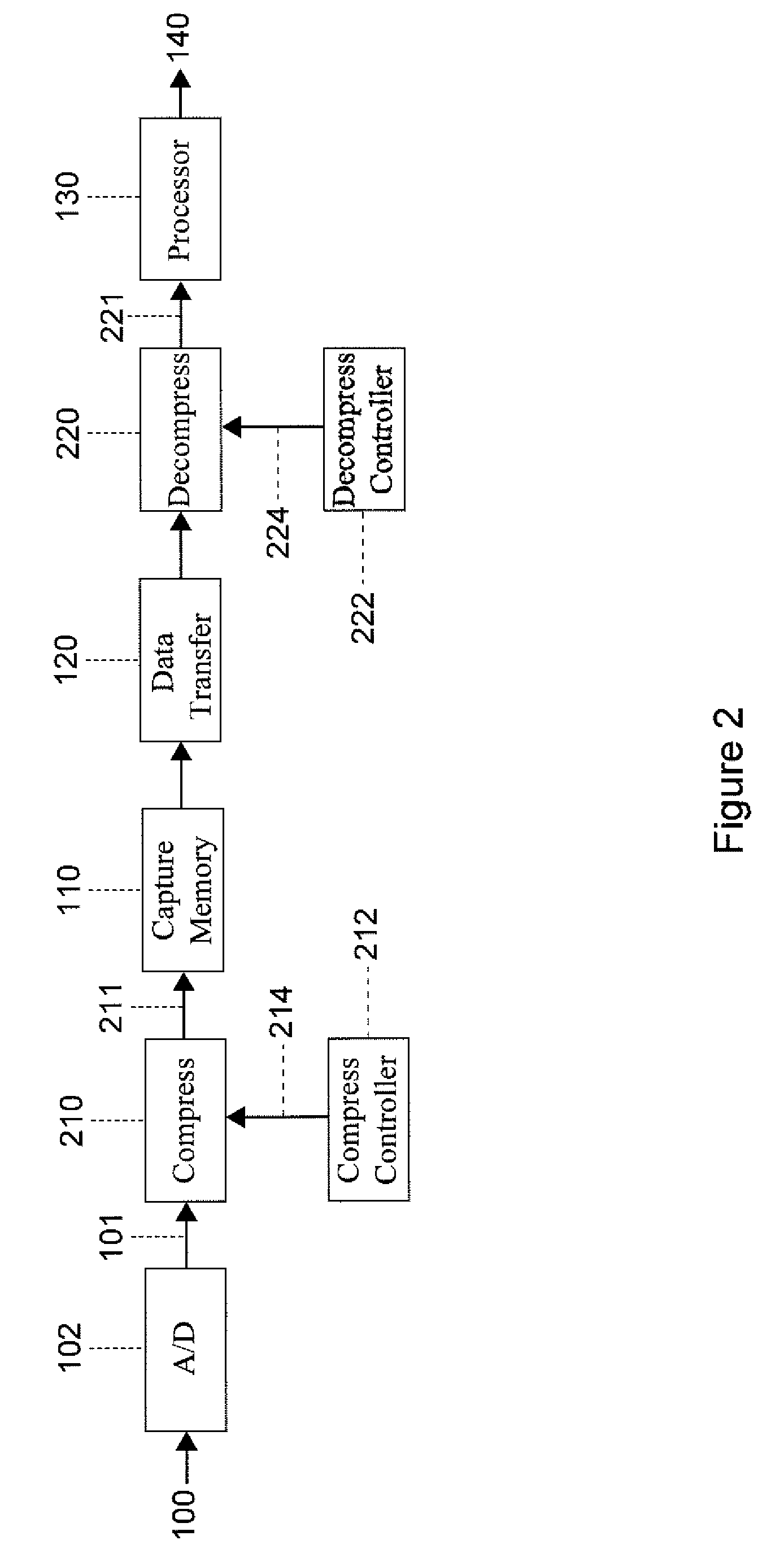
Memory management of compressed image data
InactiveUS6999626B2Recovering memory capacityDigital data processing detailsPicture reproducers using cathode ray tubesReduction factorComputer science
A method is disclosed for recovering image memory capacity, in relation to an image which has been encoded using a linear transform according to a layer progressive mode into L layers, L being an integer value greater than unity, the L layers being stored in an image memory having a limited capacity. The method comprises defining a Quality Reduction Factor (700), being a positive integer value, identifying at least one of the L layers corresponding to the Quality Reduction Factor, and discarding (702) said at least one of the L layers in progressive order in accordance with the Quality Reduction Factor, thereby recovering said memory capacity.
Owner:CANON KK
Inter-chip communication system
InactiveUS20050102125A1Decrease in performanceMultiple digital computer combinationsCAD circuit designData packCommunications system
Owner:CADENCE DESIGN SYST INC
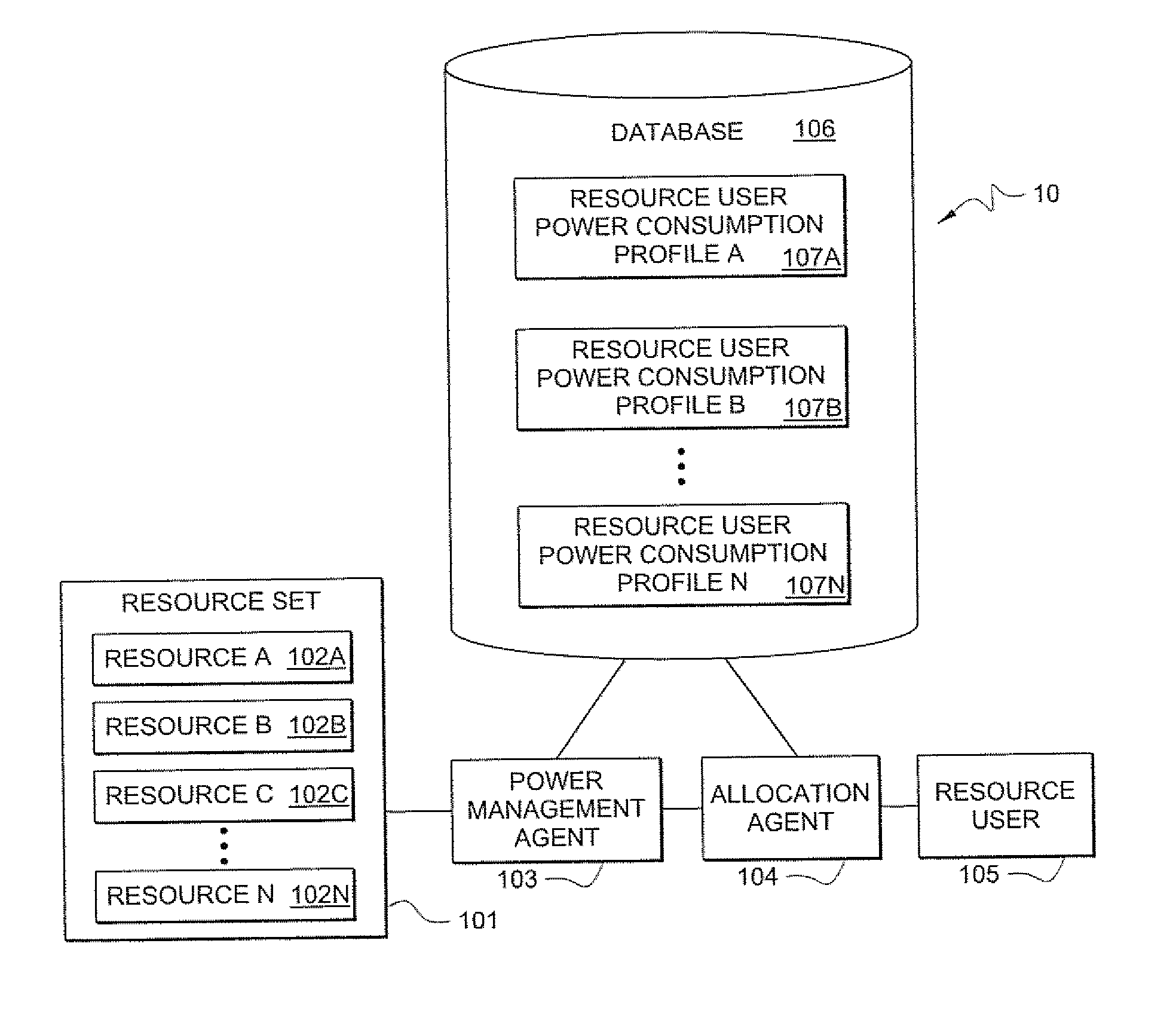
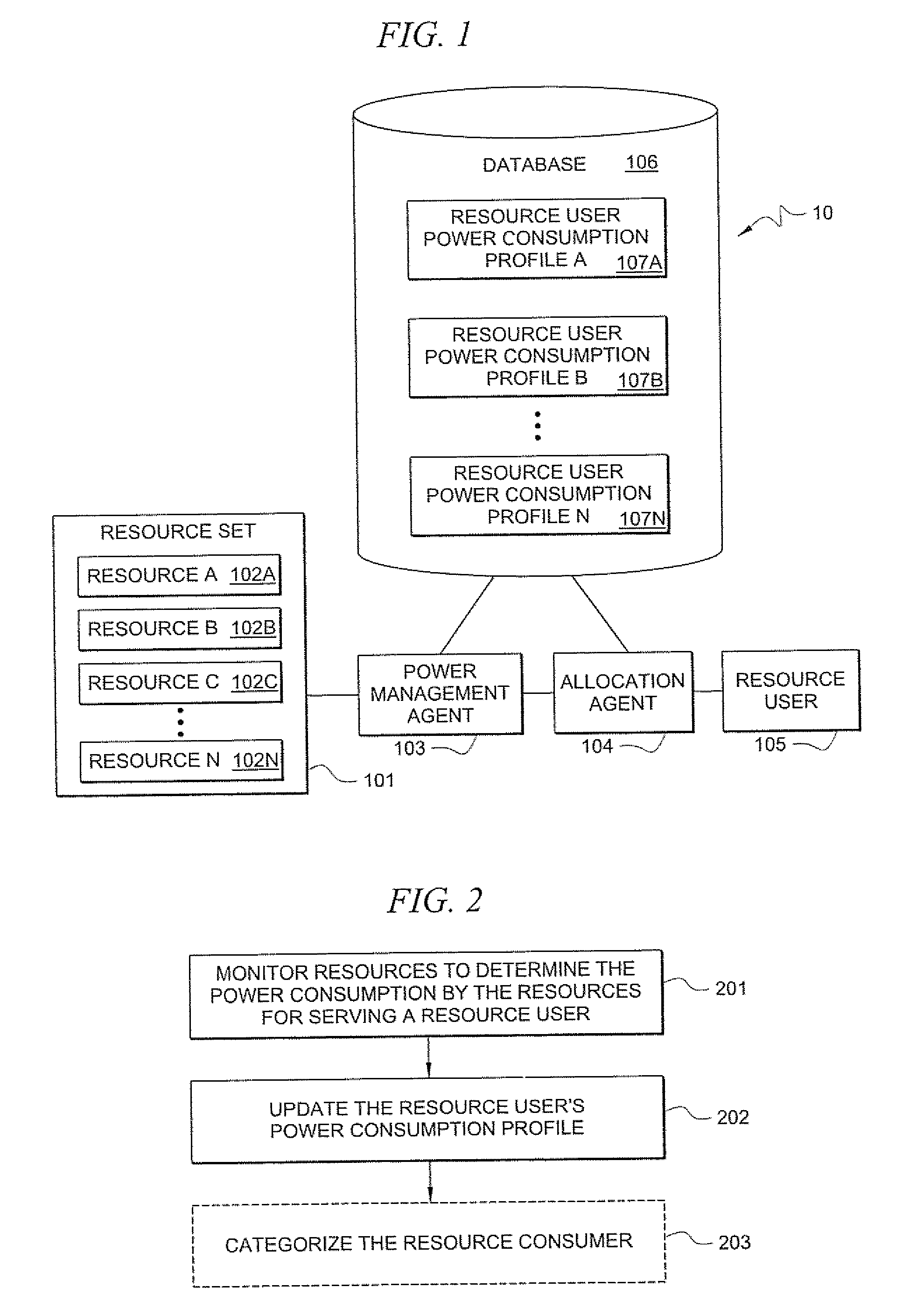
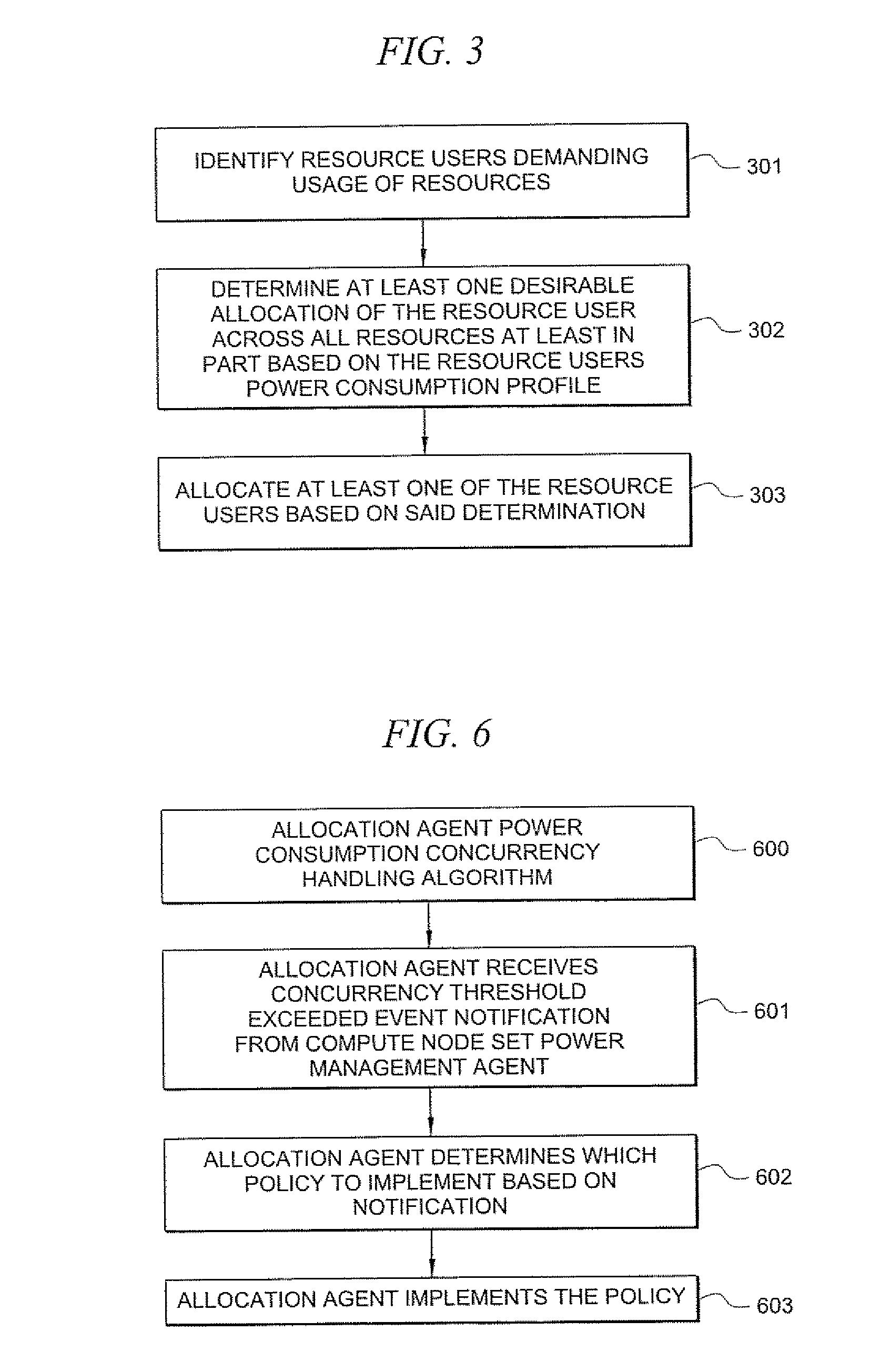
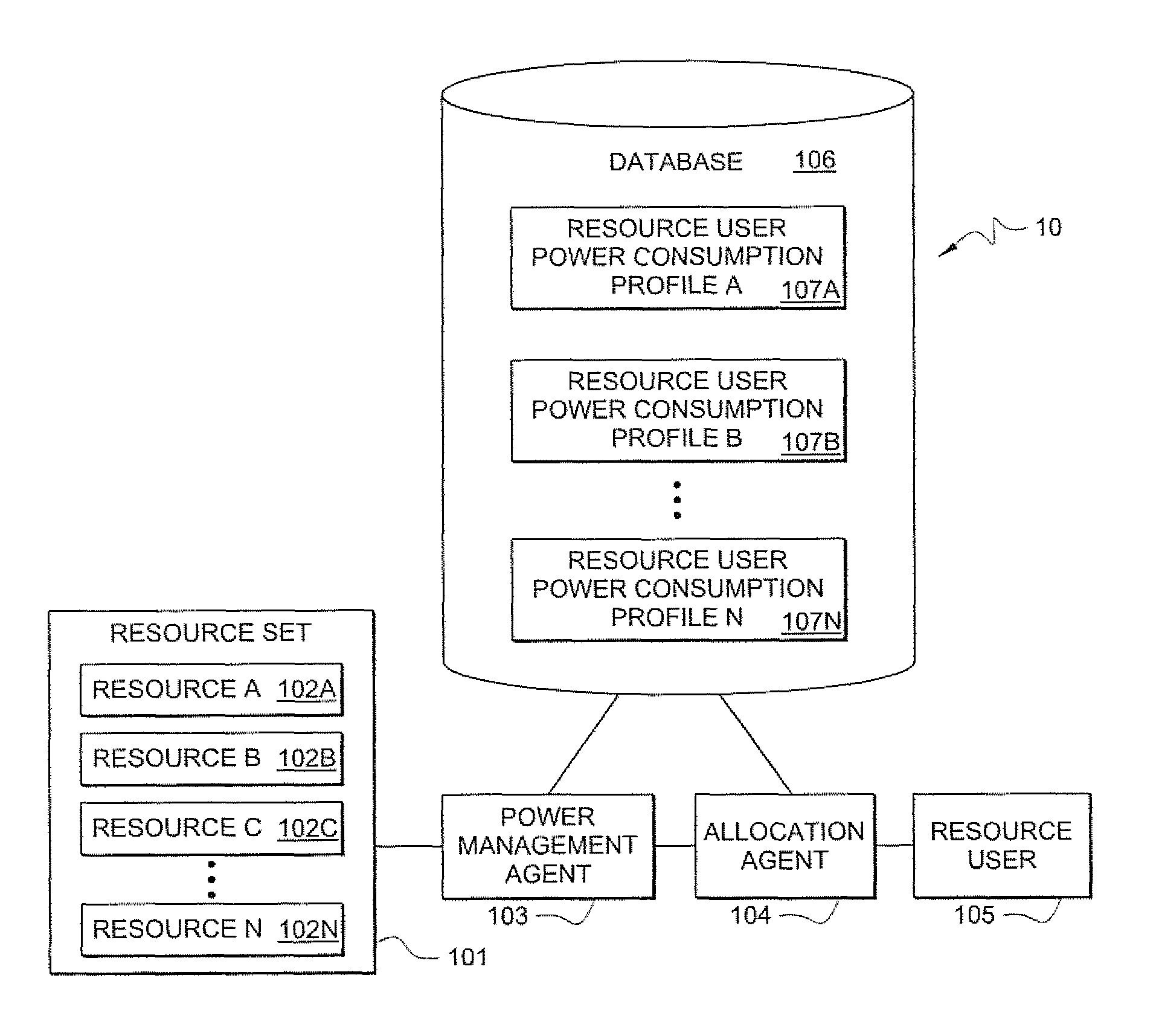
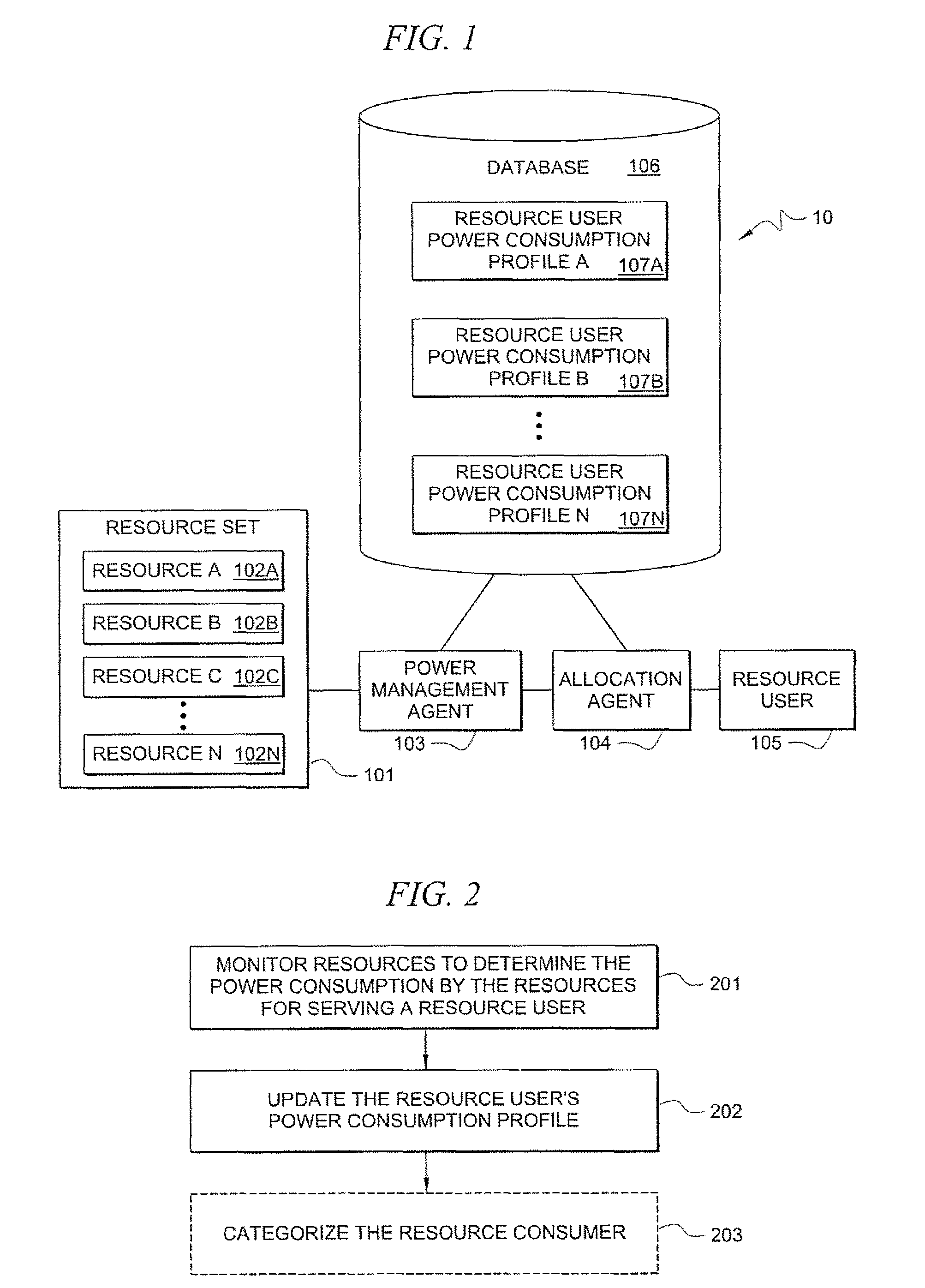
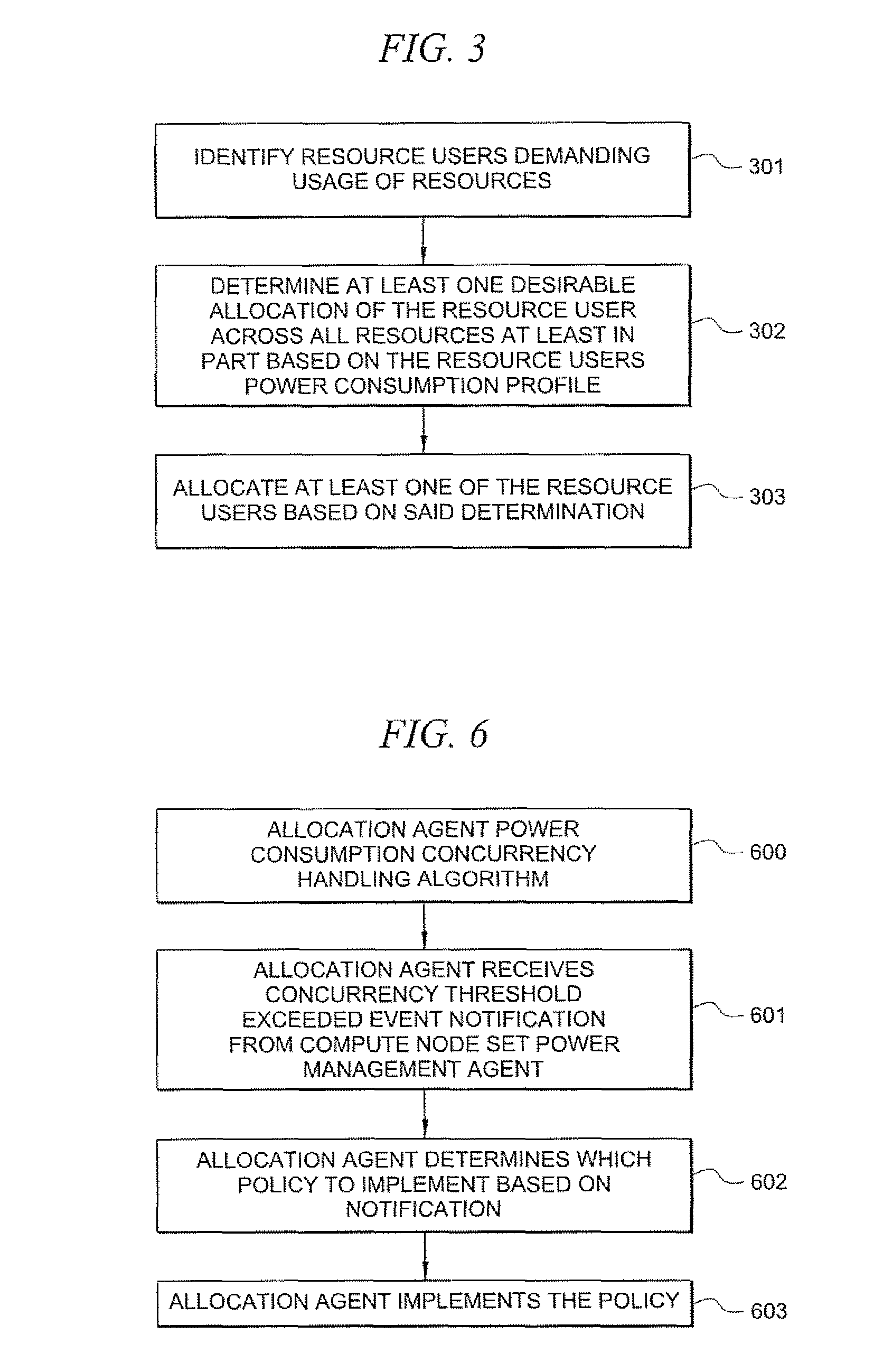
Systems and methods for determining power consumption profiles for resource users and using the profiles for resource allocation
According to one embodiment, a system comprises a plurality of resources. The resources may be any limited-capacity computing resource that is capable of serving a computing demand of a resource user. A resource user refers to any entity which consumes computing capacity of a resource. The system comprises at least one power consumption profile associated with a respective resource user. The system also comprises at least one power management agent for measuring power consumption by ones of the plurality of resources in serving computing demands of the resource user, wherein said power consumption profile contains information based at least in part on the measured power consumption. The system also comprises at least one allocation agent for dynamically allocating the resource user to at least one of the resources based at least in part on the resource user's power consumption profile.
Owner:HEWLETT PACKARD DEV CO LP
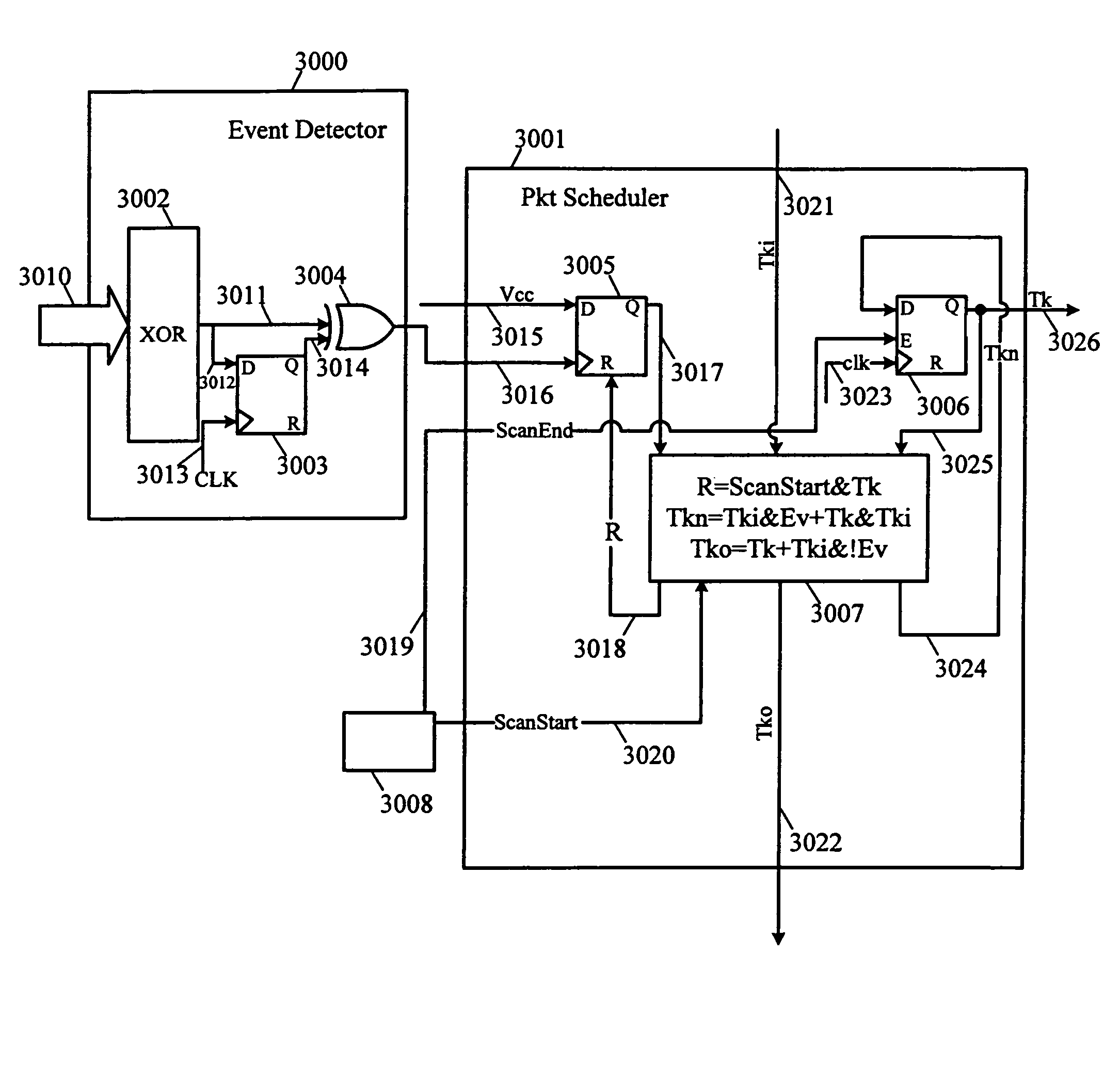
Inter-chip communication system
InactiveUS7512728B2Decrease in performanceMultiple digital computer combinationsCAD circuit designCommunications systemPacket scheduling
The complexity of user designs, the limited capacity of FPGA chips, and the limited number of chip pinouts have resulted in the development of inter-chip communication technology that necessitates the transfer of a large amount of data across a limited number of pins in the shortest amount of time. The inter-chip communication system transfers signals across FPGA chip boundaries only when these signals change values. Thus, no cycles are wasted and every event signal has a fair chance of achieving communication across chip boundaries. The inter-chip communication system includes a series of event detectors that detect changes in signal values and packet schedulers which can then schedule the transfer of these changed signal values to another designated chip. Working with a plurality of signal groups that represents signals at the separated connections, the event detector detects events (or changes in signal values). When an event has been detected, the event detector alerts the packet scheduler. The packet scheduler employs a token ring scheme as follows. When the packet scheduler receives a token and detects an event, the packet scheduler “grabs” the token and schedules the transmission of this packet in the next packet cycle. If, however, the packet scheduler receives the token but does not detect an event, it will pass the token to the next packet scheduler. At the end of each packet cycle, the packet scheduler that grabbed the token will pass the token to the next logic associated with another packet.
Owner:CADENCE DESIGN SYST INC
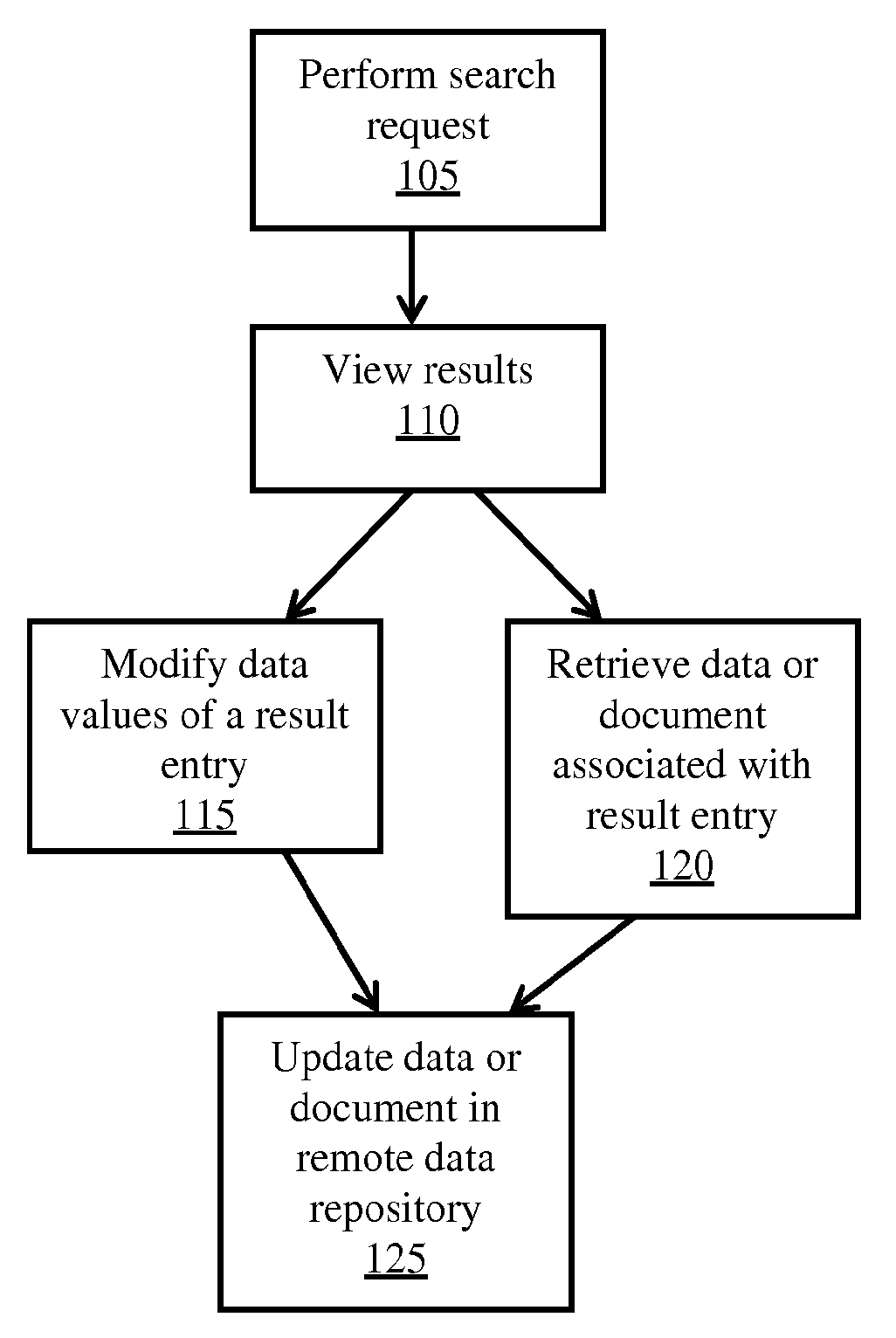
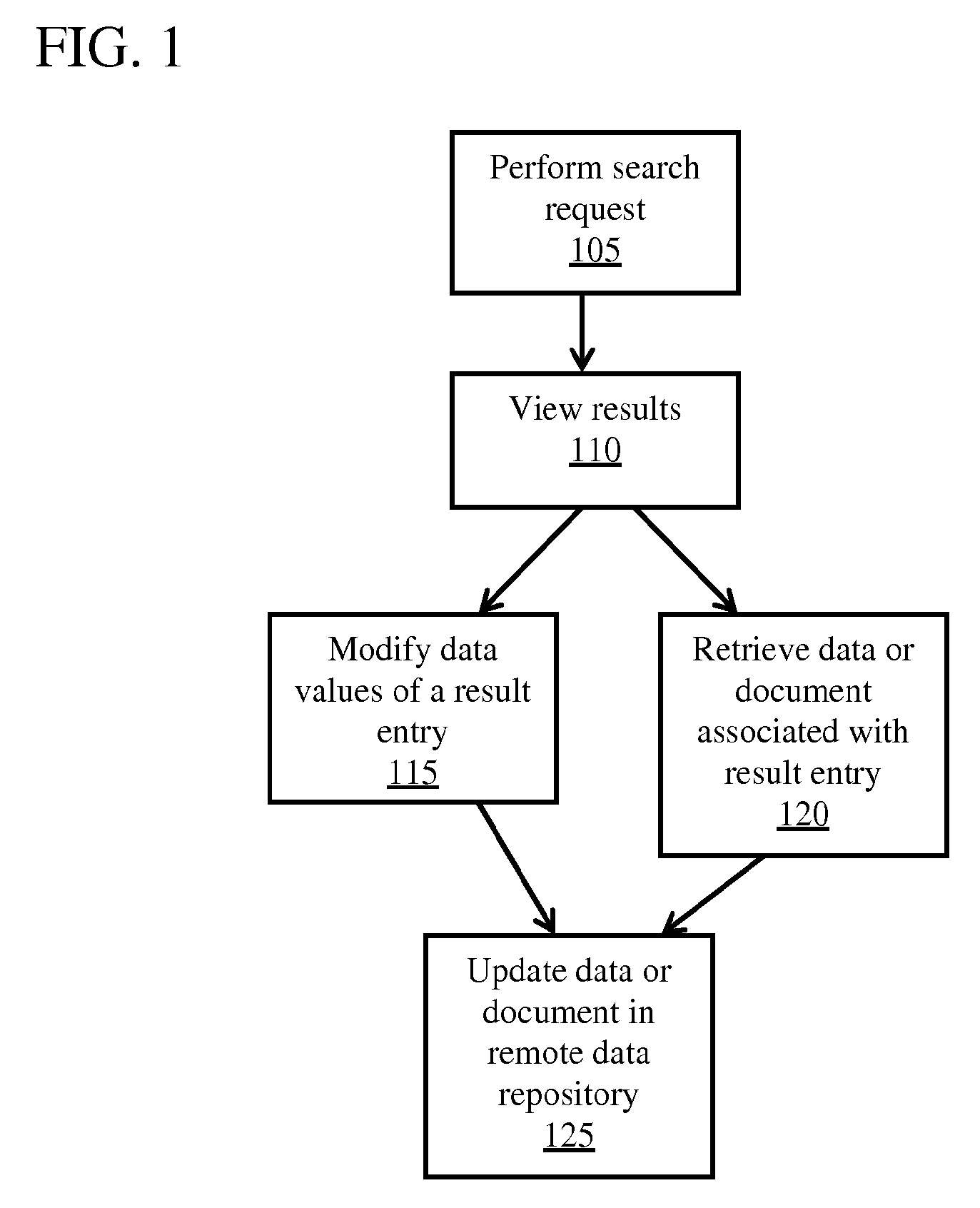
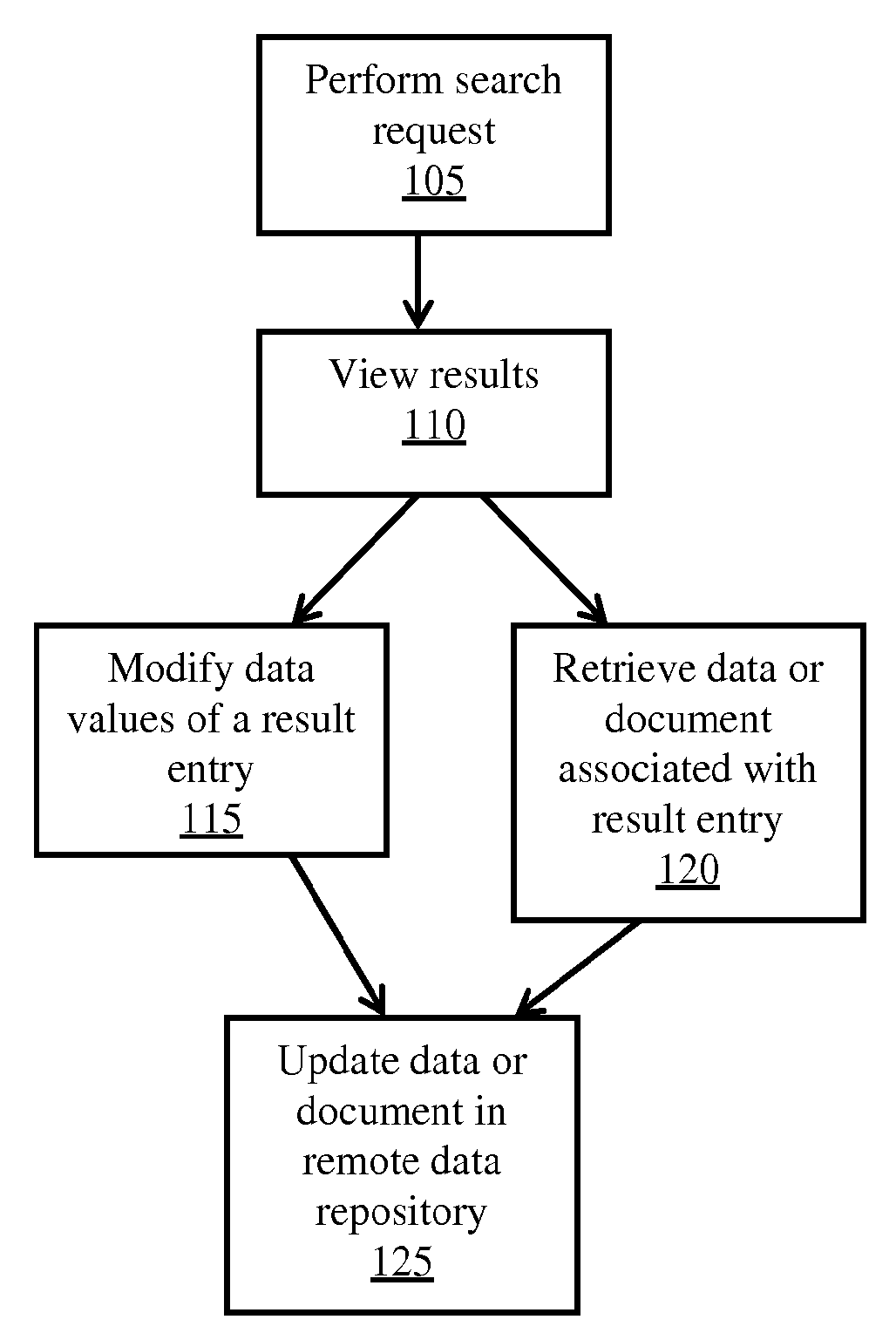
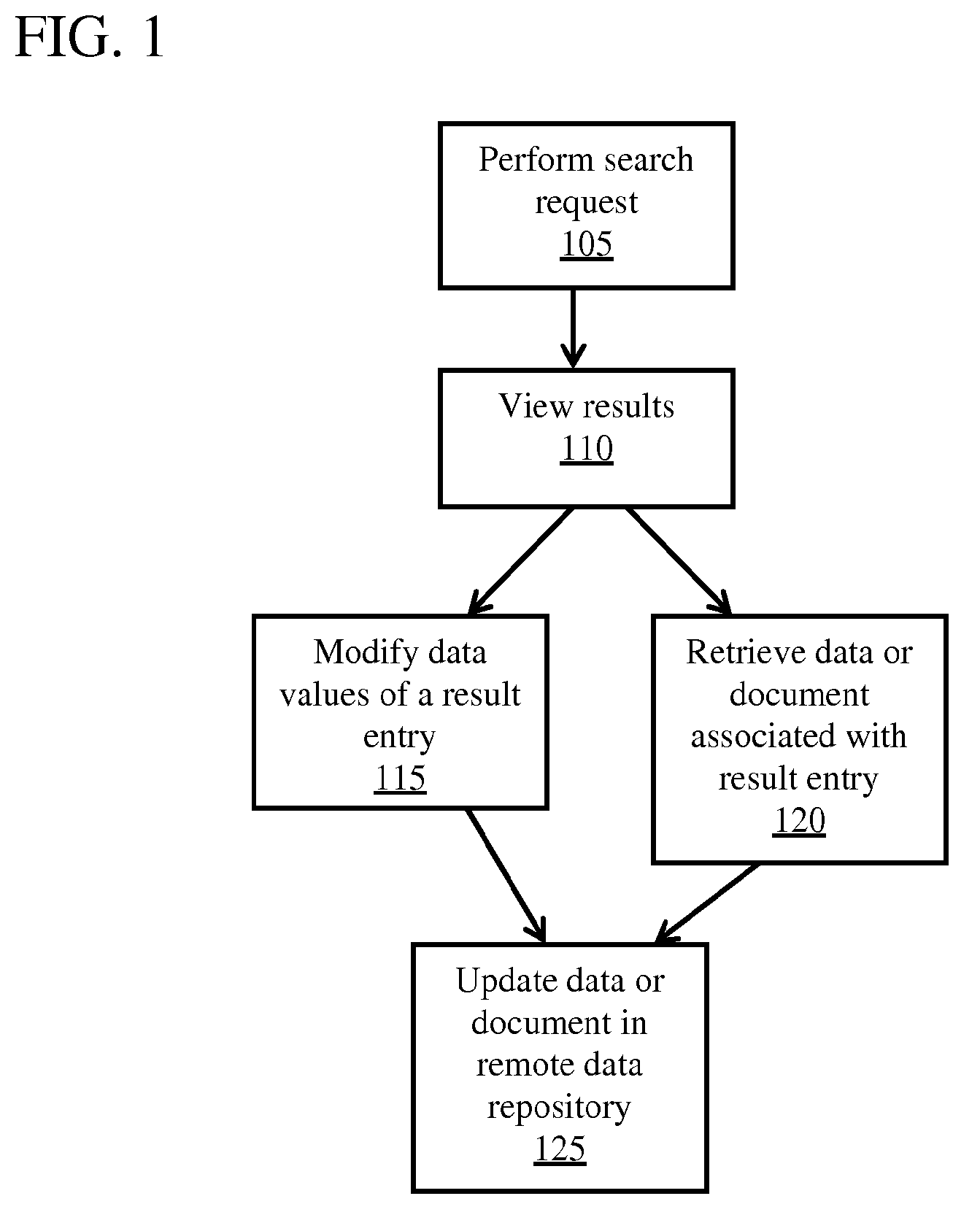
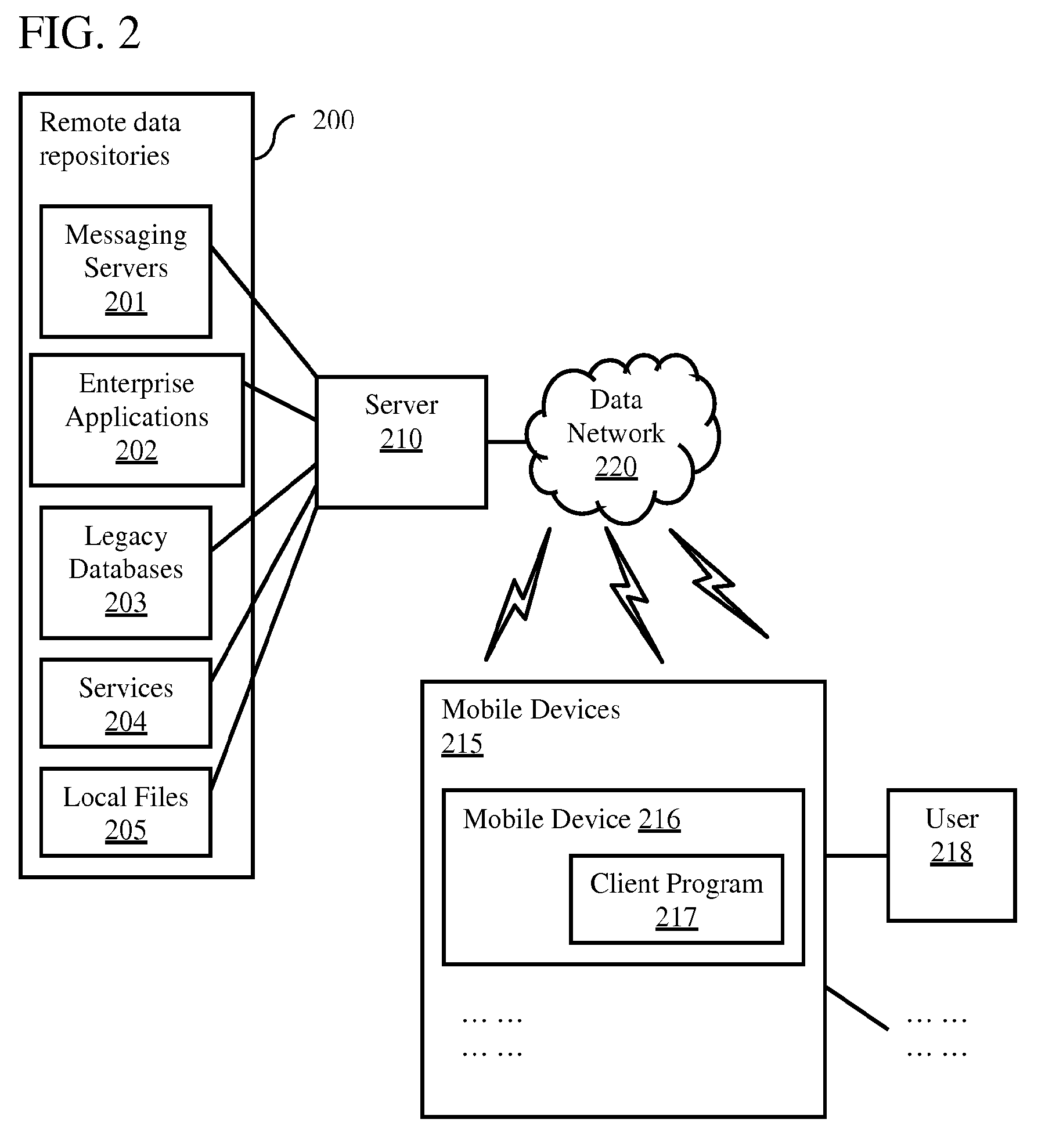
Remote Access of Heterogeneous Data
InactiveUS20090234823A1The process is convenient and fastConvenient and efficient accessDigital data information retrievalDigital data processing detailsDocument preparationCellular telephone
A method and system for providing remote access to heterogeneous information sources from computing devices including but not limited to personal computers, laptop computers, PDAs, cellular telephones is presented. A middle-tier server is provided in a multi-tier environment for allowing a data-centric approach to accessing, modifying and updating content located at remote data sources. The middle-tier server provides functionality for a mobile (or similar) user to perform a search query, request for document and / or data, update remote data, and perform commands on remote data sources. In addition, the middle-tier server manages the authentication of the user in sessioned or sessionless mode. In particular, search query results are processed such that the results answer a search query. That is, rather than simply providing a list of document matches, the middle-tier server extracts information from the document that answers the search query most appropriately. Finally, the middle-tier server, using user preferences, device capabilities and settings, transforms the result, document or data into an appropriate format that is suitable for the device, user and communication network. This allows the user to easily process and view the document on a (possibly limited capacity / functionality) device.
Owner:STATE CAPITAL RESOURCES
Access control in a mobile communication system
ActiveUS7941144B2Reduce loadRisk minimizationAssess restrictionNetwork topologiesRadio networksSmall cell
A method and radio network controller (RNC) in a radio access network (RAN) for controlling access to a cellular telecommunication system. Upon receiving an access request from a given user equipment (UE) through a given radio base station (RBS), the RNC retrieves authorization information from an access control database within the RAN. The authorization information indicates whether the given UE is authorized to access the system through the given RBS. The RNC alternatively grants access or denies access to the UE based on the retrieved authorization information. The RBS is particularly useful for controlling access through small cells with limited capacity.
Owner:TELEFON AB LM ERICSSON (PUBL)
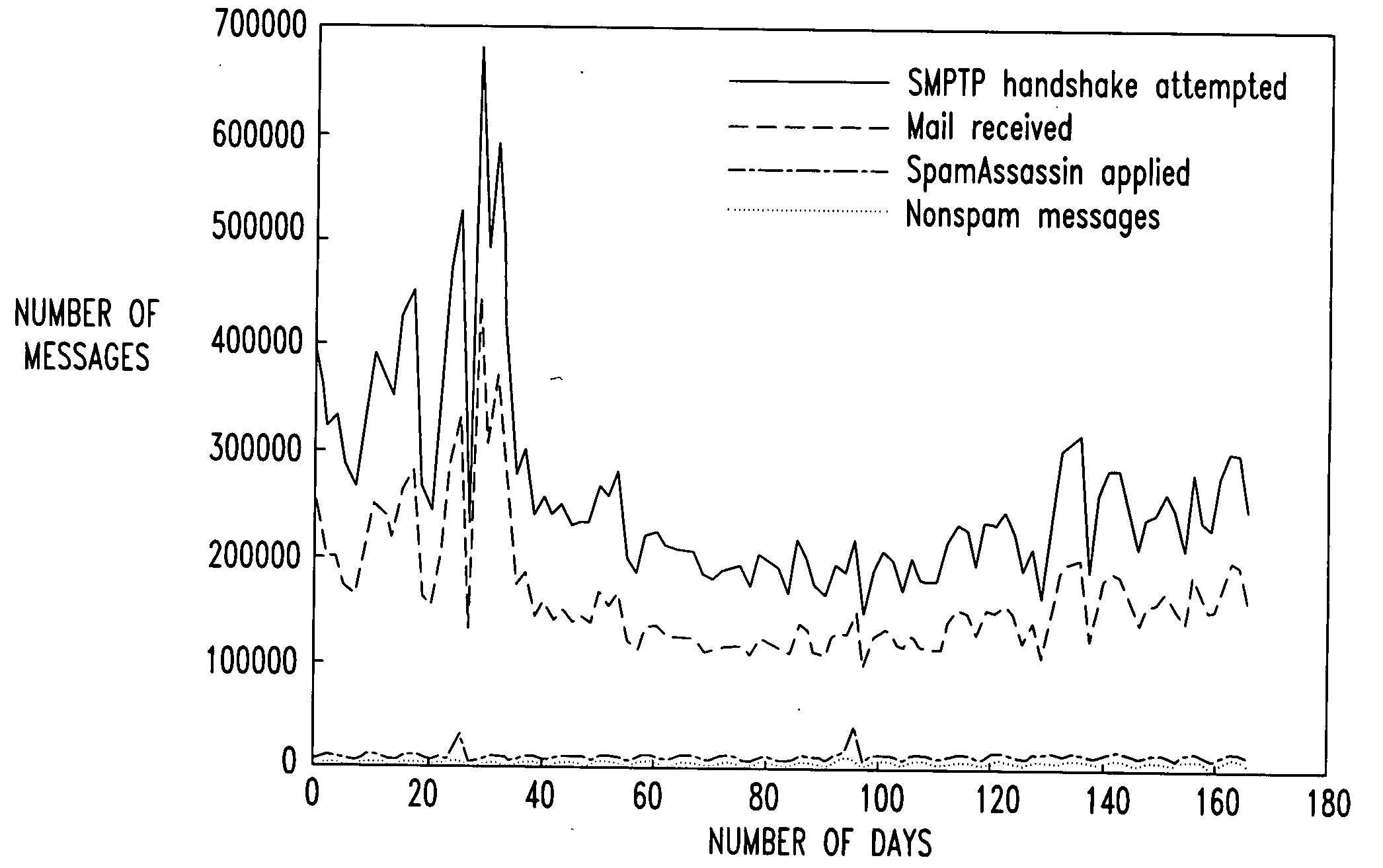
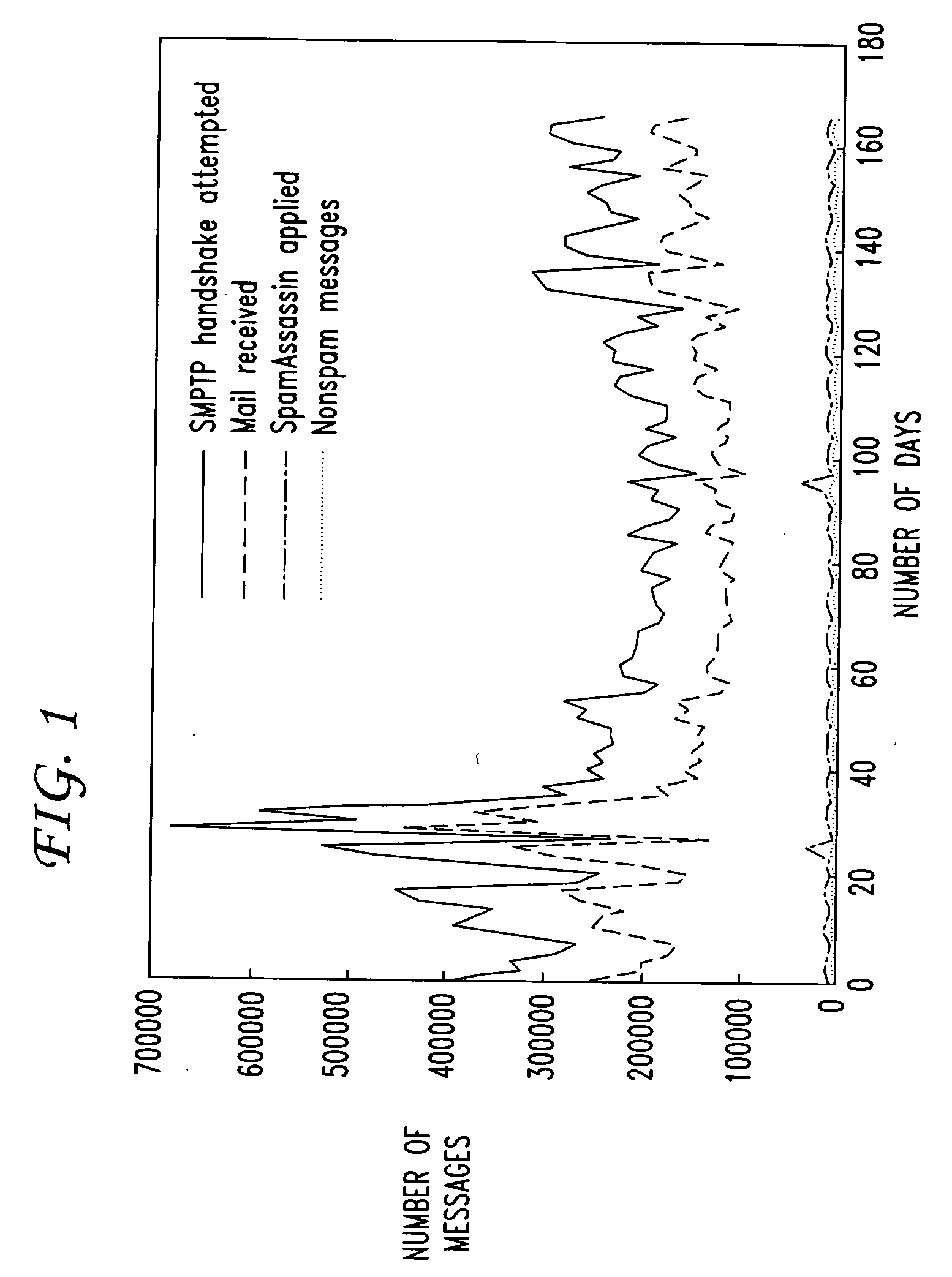
Managing email servers by prioritizing emails
InactiveUS20090113016A1Improve abilitiesReduce capacityMultiple digital computer combinationsData switching networksDistributed computingElectronic mail
Disclosed are email server management methods and systems that protect the ability of the infrastructure of the email server to process legitimate emails in the presence of large spam volumes. During a period of server overload, priority classes of emails are identified, and emails are processed according to priority. In a typical embodiment, the server sends emails sequentially in a queue, and the queue has a limited capacity. When the server nears or reaches that capacity, the emails in the queue are analyzed to identify priority emails, and the priority emails are moved to the head of the queue.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Frequency resolution using compression
InactiveUS20080123731A1Frequency domain resolutionImprove detection accuracySpectral/fourier analysisCode conversionSpectrum analyzerImage resolution
In a frequency analysis system, such as a signal detection system or a spectrum analyzer, the frequency domain resolution is enhanced by compression and decompression of the signal samples. The limited capacity of the data storage and / or data transfer resources limit the number of samples that can be stored or transferred. A compressor forms a compressed signal prior to data transfer or storage. A decompressor decompresses the compressed signal prior to transformation to the frequency domain, by a fast Fourier transform or other frequency domain transform. The frequency domain resolution is enhanced because more decompressed samples are available for the frequency domain transform. The compressor and decompressor apply computationally efficient algorithms that can be implemented to operate in real time.
Owner:ALTERA CORP
Remote access of heterogeneous data
InactiveUS7882122B2The process is convenient and fastConvenient and efficient accessDigital data information retrievalDigital data processing detailsDocument preparationCellular telephone
A method and system for providing remote access to heterogeneous information sources from computing devices including but not limited to personal computers, laptop computers, PDAs, cellular telephones is presented. A middle-tier server is provided in a multi-tier environment for allowing a data-centric approach to accessing, modifying and updating content located at remote data sources. The middle-tier server provides functionality for a mobile (or similar) user to perform a search query, request for document and / or data, update remote data, and perform commands on remote data sources. In addition, the middle-tier server manages the authentication of the user in sessioned or sessionless mode. In particular, search query results are processed such that the results answer a search query. That is, rather than simply providing a list of document matches, the middle-tier server extracts information from the document that answers the search query most appropriately. Finally, the middle-tier server, using user preferences, device capabilities and settings, transforms the result, document or data into an appropriate format that is suitable for the device, user and communication network. This allows the user to easily process and view the document on a (possibly limited capacity / functionality) device.
Owner:STATE CAPITAL RESOURCES
Method and apparatus for multicast packet reception
ActiveUS8116312B2Special service provision for substationData switching by path configurationNetwork packetMulticast packets
Roughly described, incoming data packets are delivered by the NIC directly to at least two user level endpoints. In an aspect, only filters that cannot be ambiguous are created in the NIC. In another aspect, the NIC maintains a filter table supporting direct delivery of incoming unicast and multicast data packets to one user level endpoint. Additional requests to join the same multicast group cause replacement of the NIC filter with one in the kernel. In another aspect, a NIC has limited capacity to maintain multicast group memberships. In response to a new multicast filter request, the kernel establishes it in the NIC only if the NIC still has sufficient capacity; otherwise it is established in the kernel.
Owner:XILINX INC
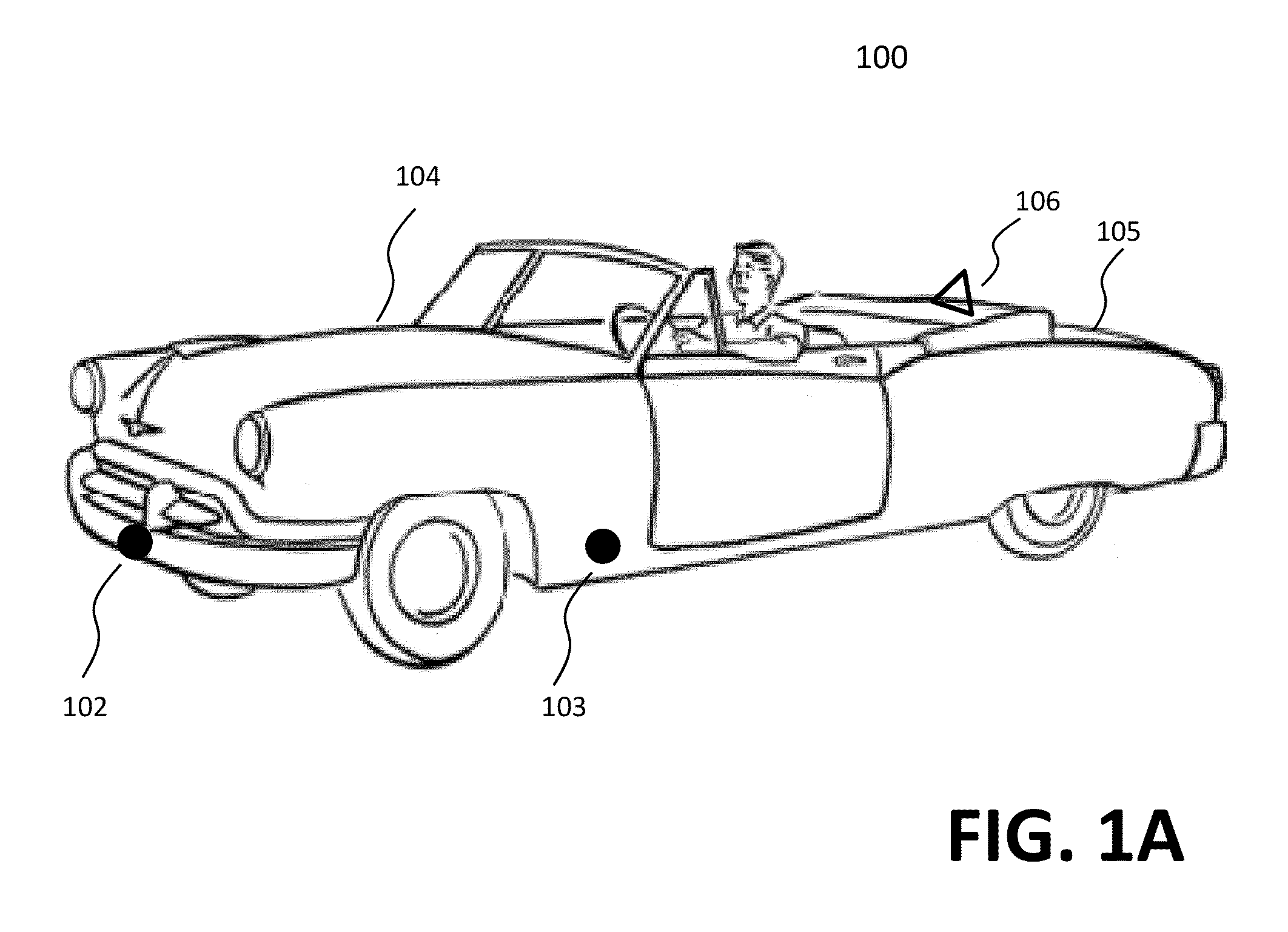
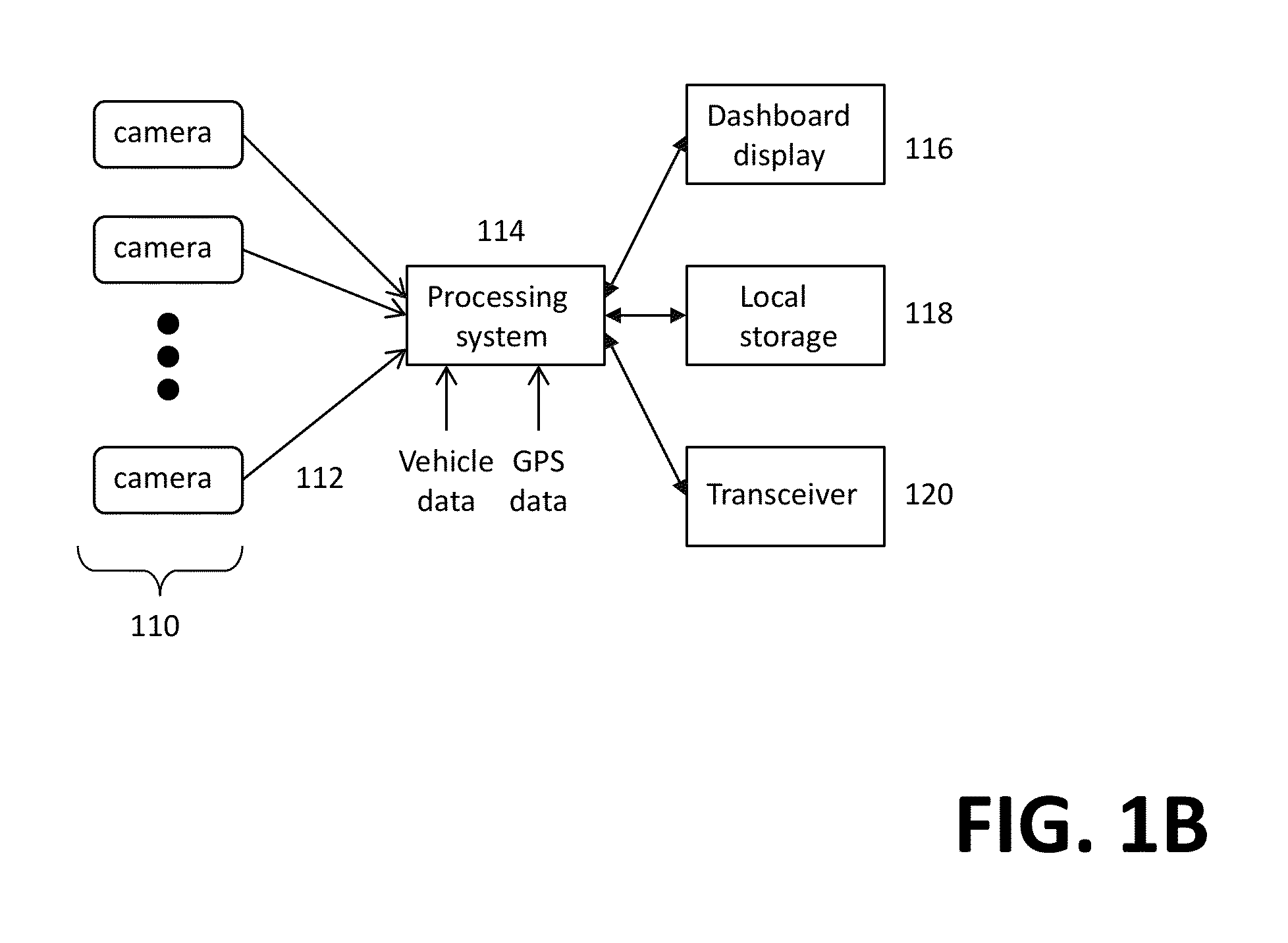
Vehicle monitoring systems
InactiveUS20130083196A1Registering/indicating working of vehiclesColor television detailsMonitoring systemVideo processing
A monitoring system for vehicles is disclosed. At least two cameras are disposed around a vehicle to generate videos or images representing surrounding scenes in which the vehicle is present. Video streams from the cameras are transported via wired means or wireless means to a video processing system. Depending on applications, the video streams are processed to be collectively displayed on a screen (e.g., on the dashboard of the vehicle), analyzed to assist the driver of the vehicle to perform a task, stored in a storage device of limited capacity, or transported to a remote server for remote assistance or analysis.
Owner:SUN MANAGEMENT LLC
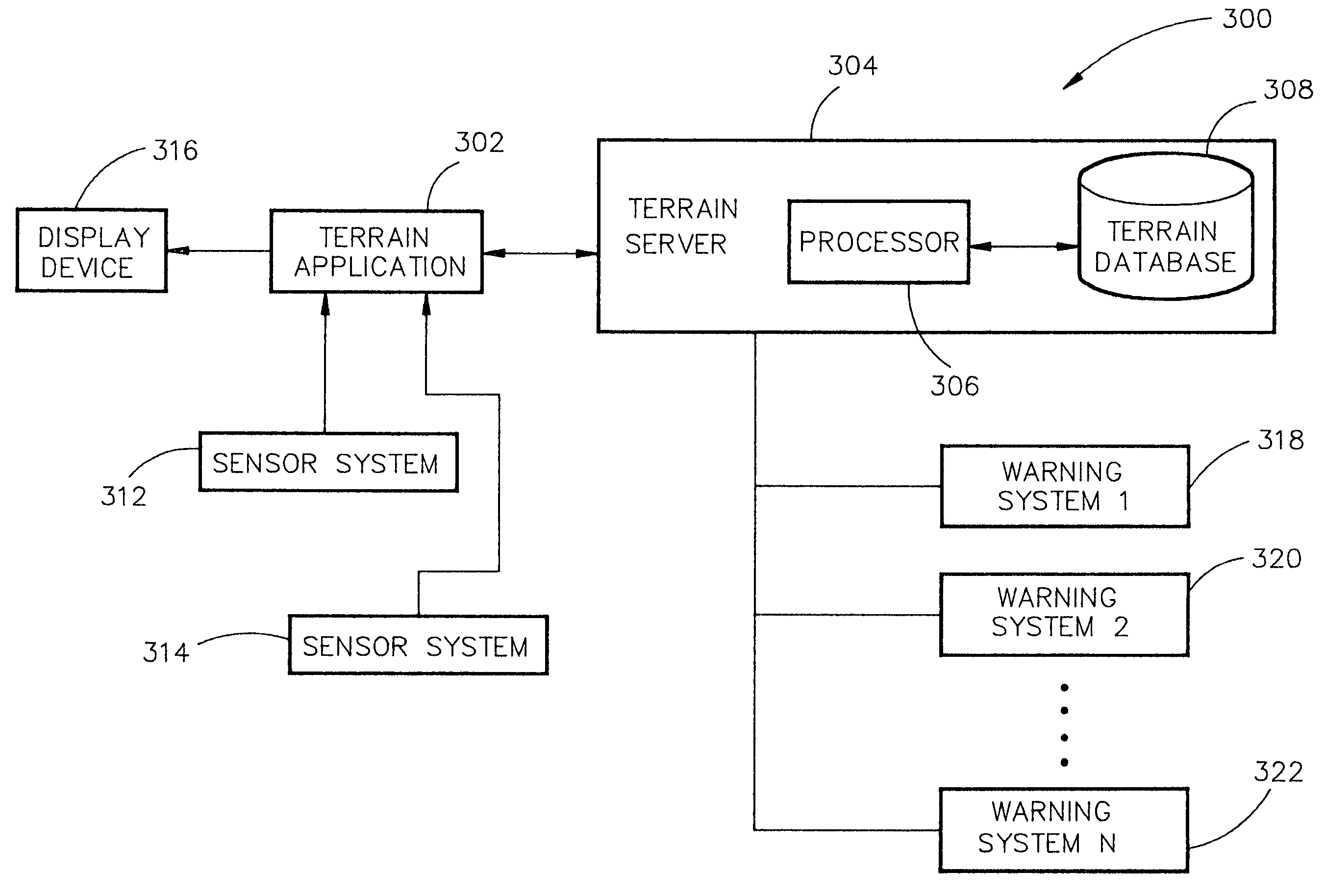
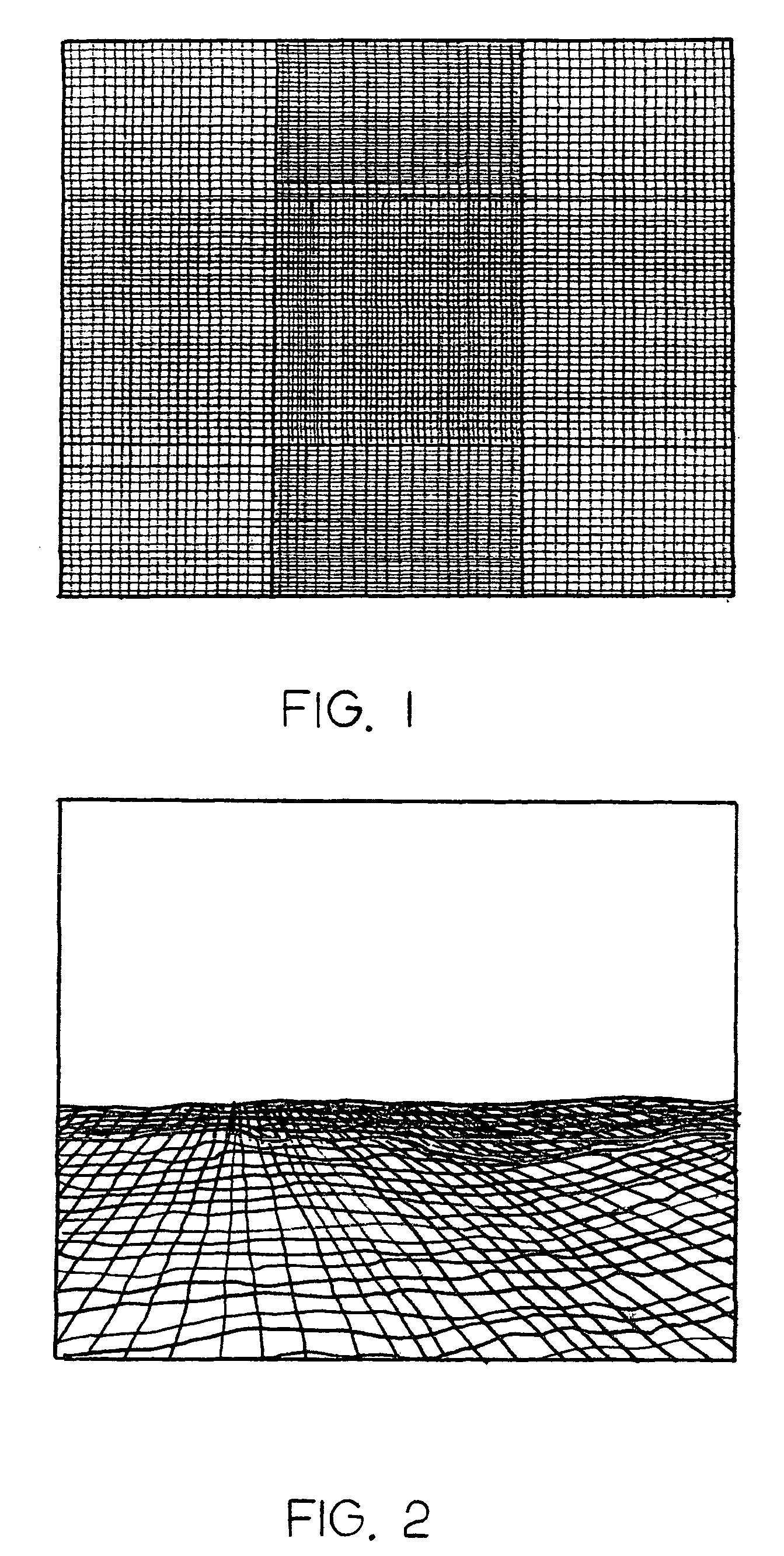
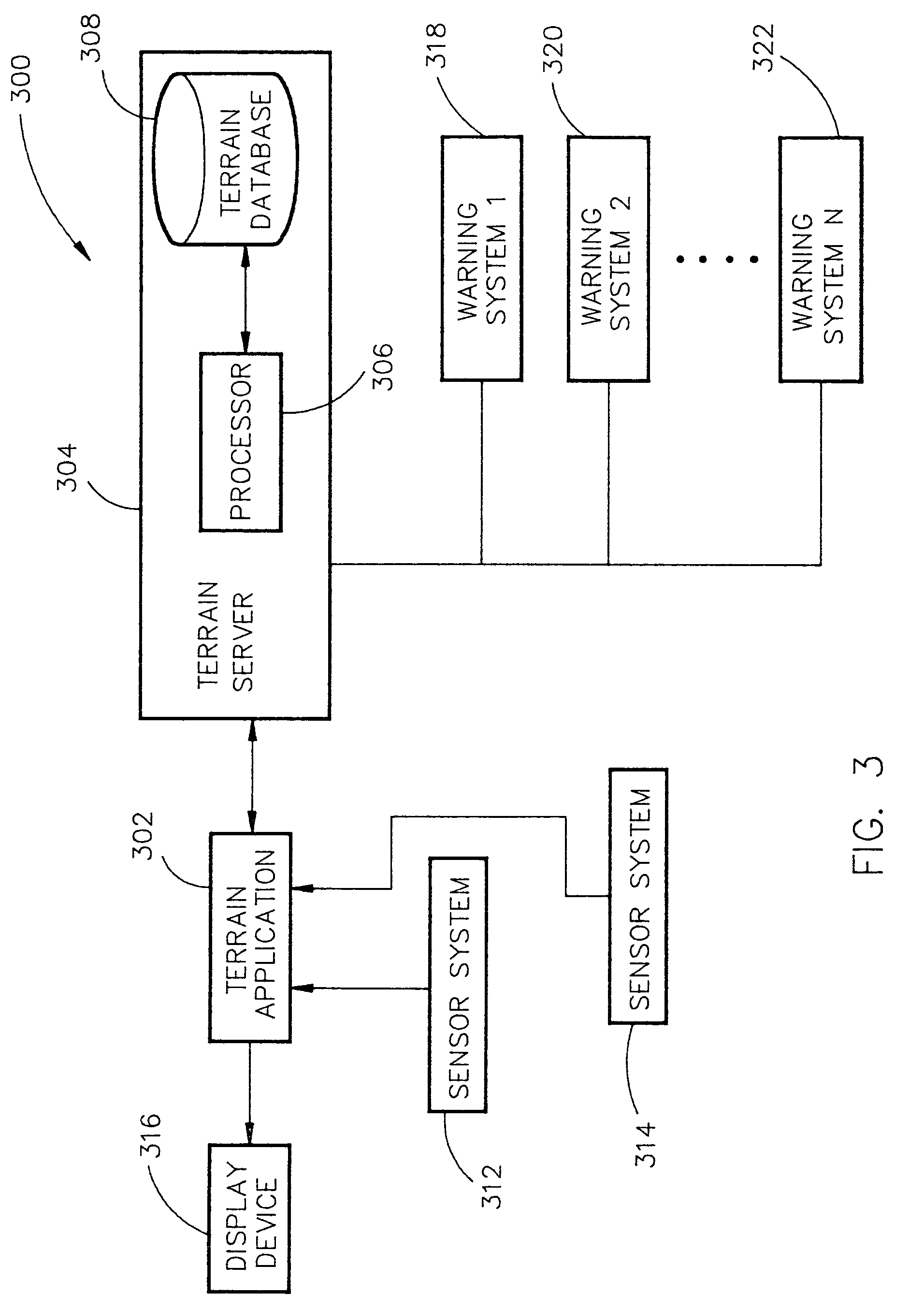
System and method for a safe depiction of terrain, airport and other dimensional data on a perspective flight display with limited bandwidth of data presentation
ActiveUS7262713B1Limited bandwidthReduce usageAnalogue computers for trafficNavigation instrumentsTerrainSystem capacity
The present invention is directed to a system and method for a safe flight display through increasing situation awareness by an optimal presentation, given limited capacity of the system. The system may determine which terrain area needs a detail representation and which area needs a coarse representation. A view-dependent visual error metric may be utilized to define and maintain an error bound and accurately minimize the amount of terrain data being depicted. By performing a breadth-first search on the terrain database, a user can determine amount of geometry to be displayed with limited bandwidth of data presentation. The user may be allowed to scale the application to his / her desired level of detail, given a capacity of the system. Therefore, the system may provide a safe flight display with an anticipated and graceful (all portions of the screen would be given an equal quality representation) degradation in performance upon the choice of the user.
Owner:ROCKWELL COLLINS INC
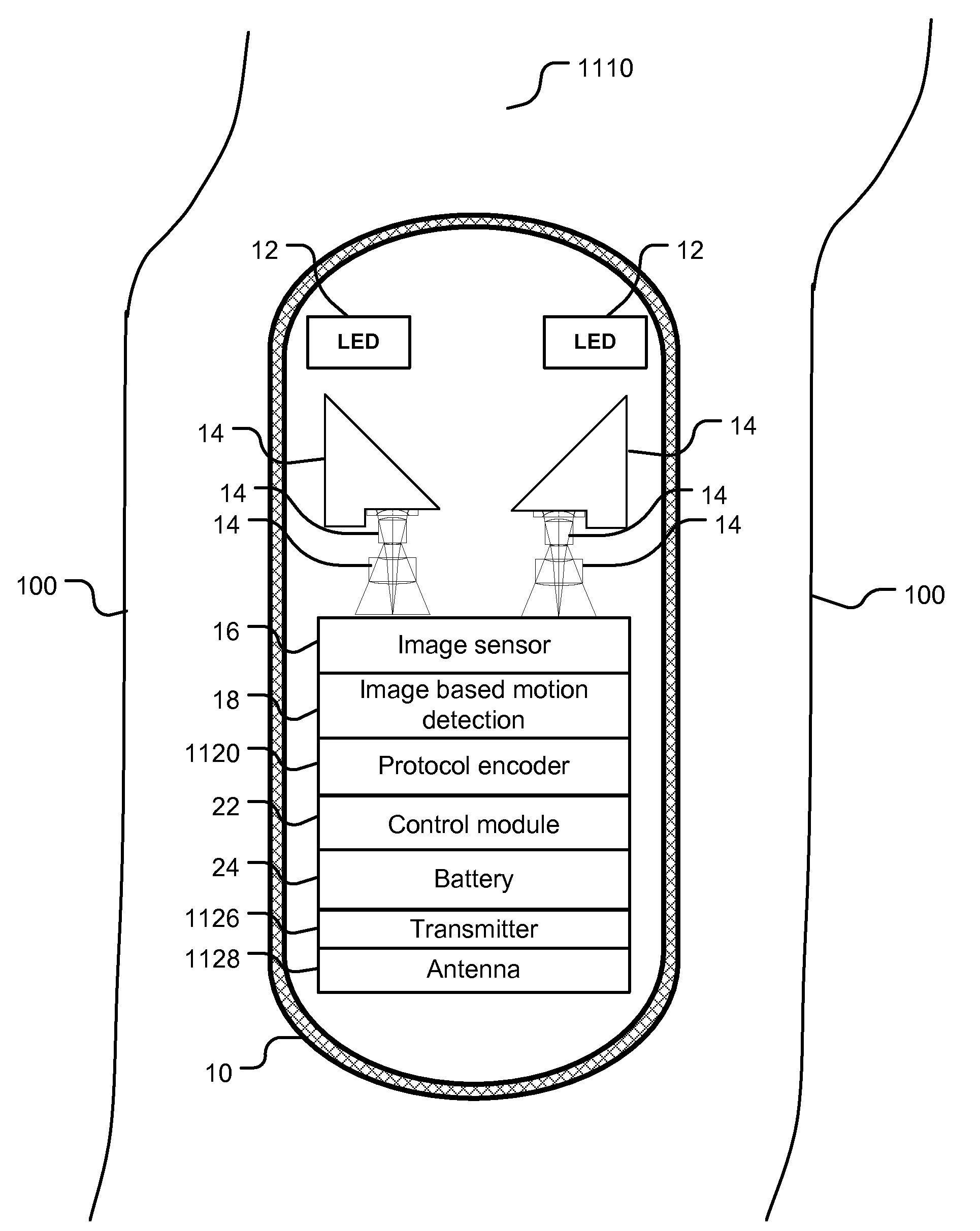
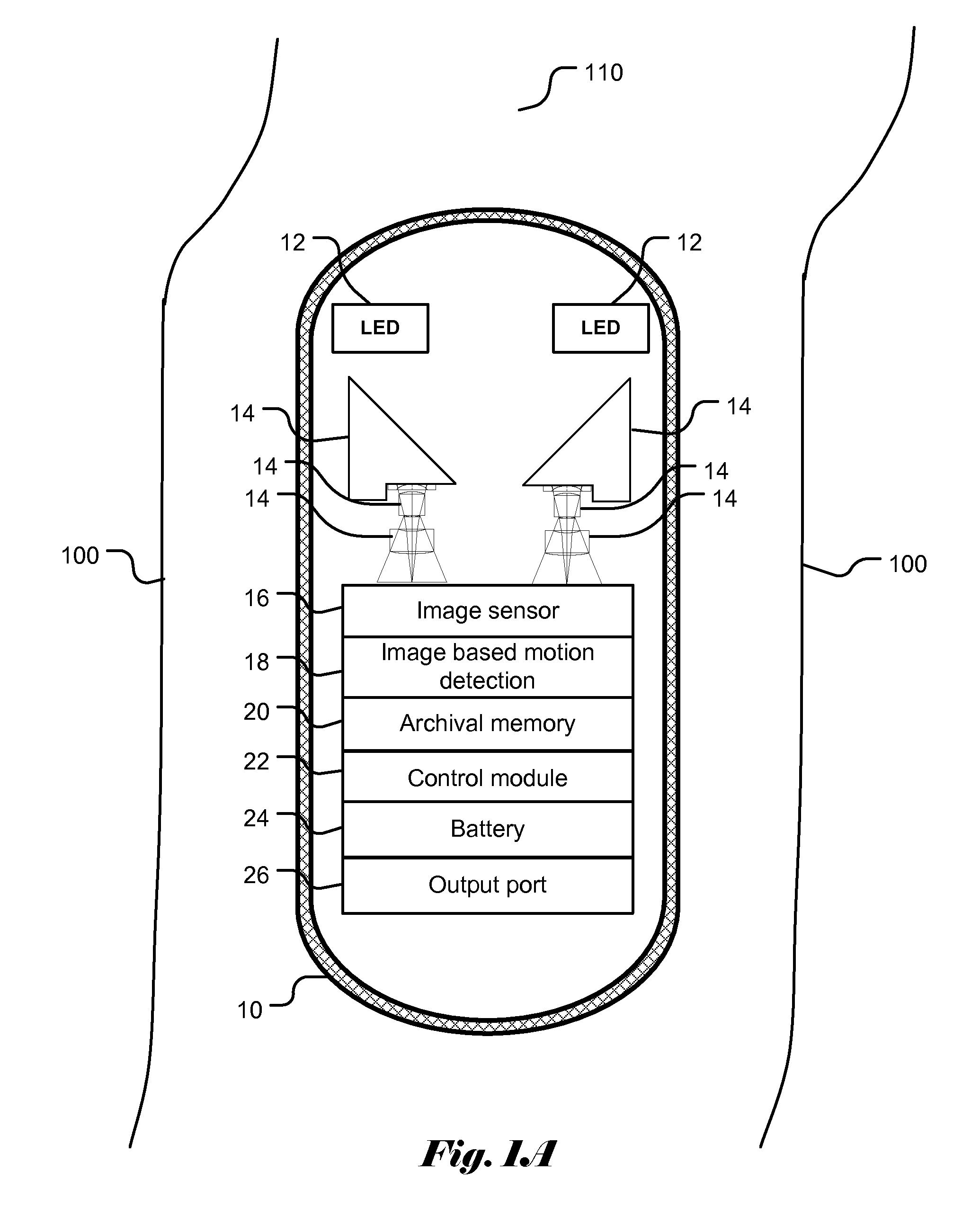
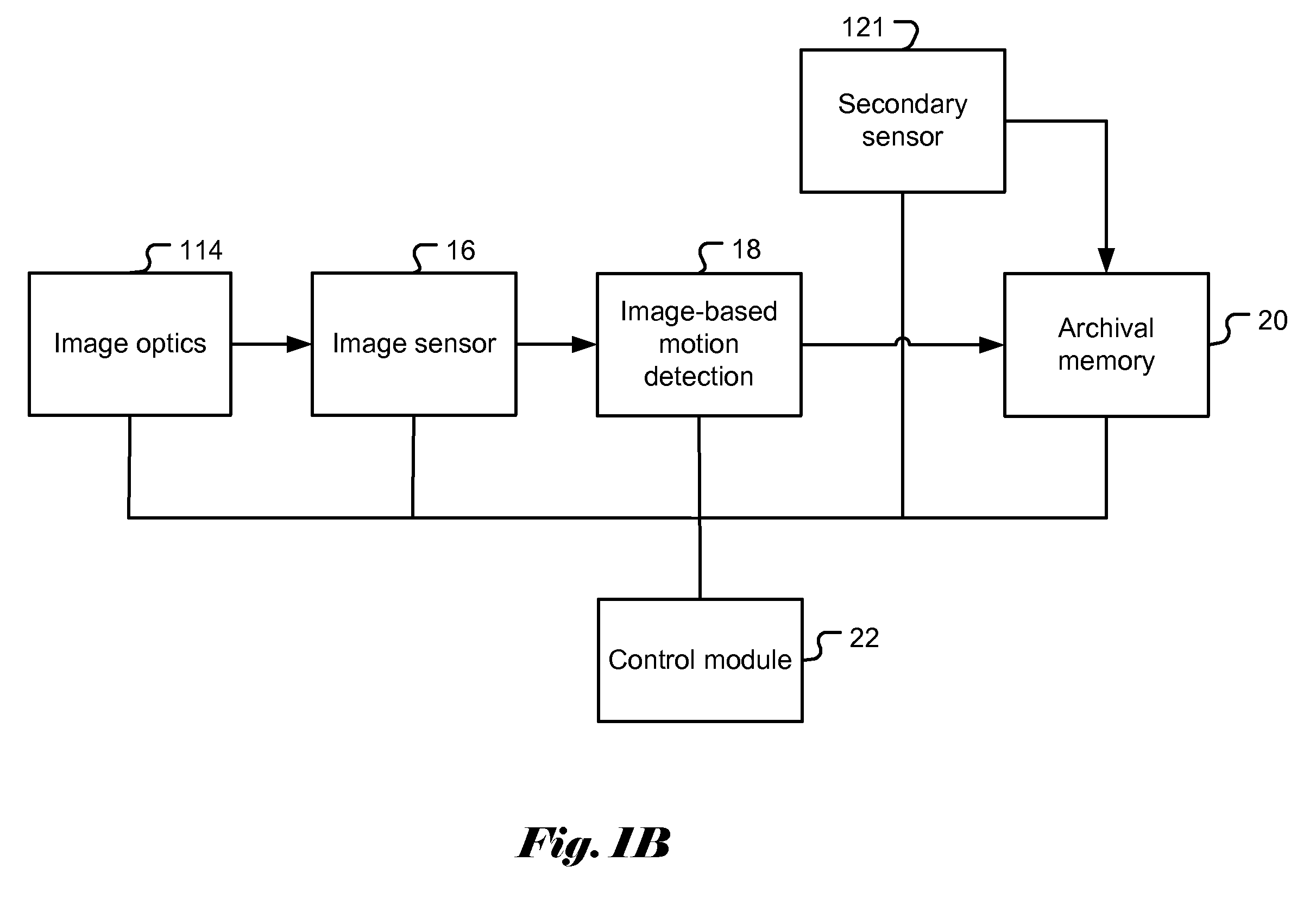
Image capture control for in vivo autonomous camera
ActiveUS20090322865A1Adjustable parametersTelevision system detailsColor signal processing circuitsIntestinal wallsOn board
Systems and methods are provided for motion detection and capture control of video data from a capsule camera system having an on-board storage. The capsule camera system moves through the GI tract under the action of peristalsis and records images of the intestinal walls. The capsule's movement is episodic and jerky. The capacity of the on-board storage is limited. In order to avoid unnecessary capture of images when the capsule camera moves very slowly or stalls, motion detection technique is utilized to help control image capture. Furthermore, an adaptive capture control is disclosed that automatically adjusts the threshold level of capture control to maintain proper image capture. The invented capture control also conserves precious battery power by eliminating capture of unnecessary images when the capsule camera moves too slowly or stalls. The present invention of image capture control and threshold update is also applicable to a capsule camera system having a wireless transmitter instead of an on-board storage.
Owner:CAPSO VISION INC
Systems and methods for determining power consumption profiles for resource users and using the profiles for resource allocation
InactiveUS8037329B2Energy efficient ICTVolume/mass flow measurementResource basedResource allocation
According to one embodiment, a system comprises a plurality of resources. The resources may be any limited-capacity computing resource that is capable of serving a computing demand of a resource user. A resource user refers to any entity which consumes computing capacity of a resource. The system comprises at least one power consumption profile associated with a respective resource user. The system also comprises at least one power management agent for measuring power consumption by ones of the plurality of resources in serving computing demands of the resource user, wherein said power consumption profile contains information based at least in part on the measured power consumption. The system also comprises at least one allocation agent for dynamically allocating the resource user to at least one of the resources based at least in part on the resource user's power consumption profile.
Owner:HEWLETT PACKARD DEV CO LP
Grouping method in frequency domain distributed video coding
InactiveCN101835044ADecoding quality dropsTelevision systemsDigital video signal modificationNetwork terminationSide information
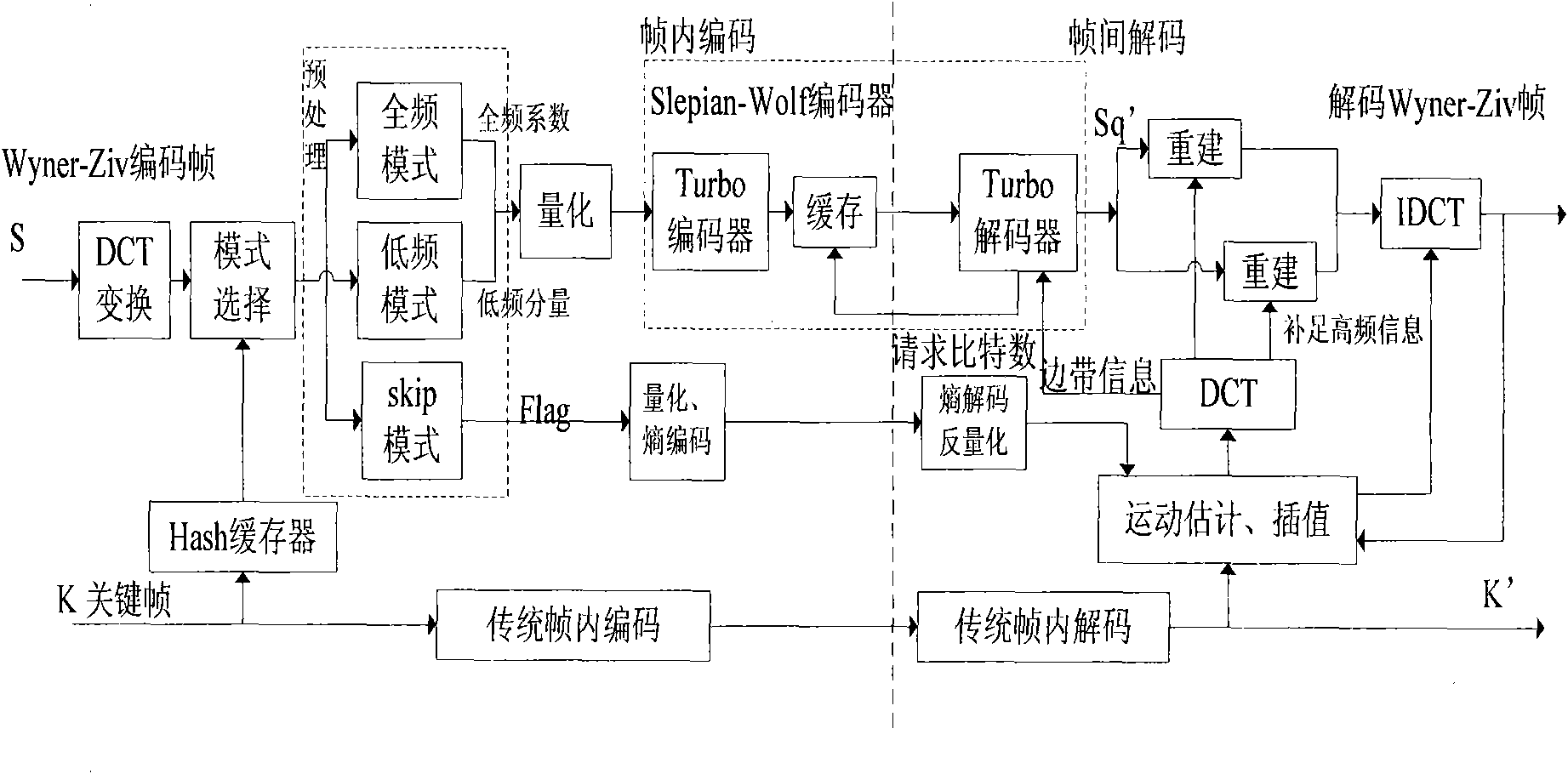
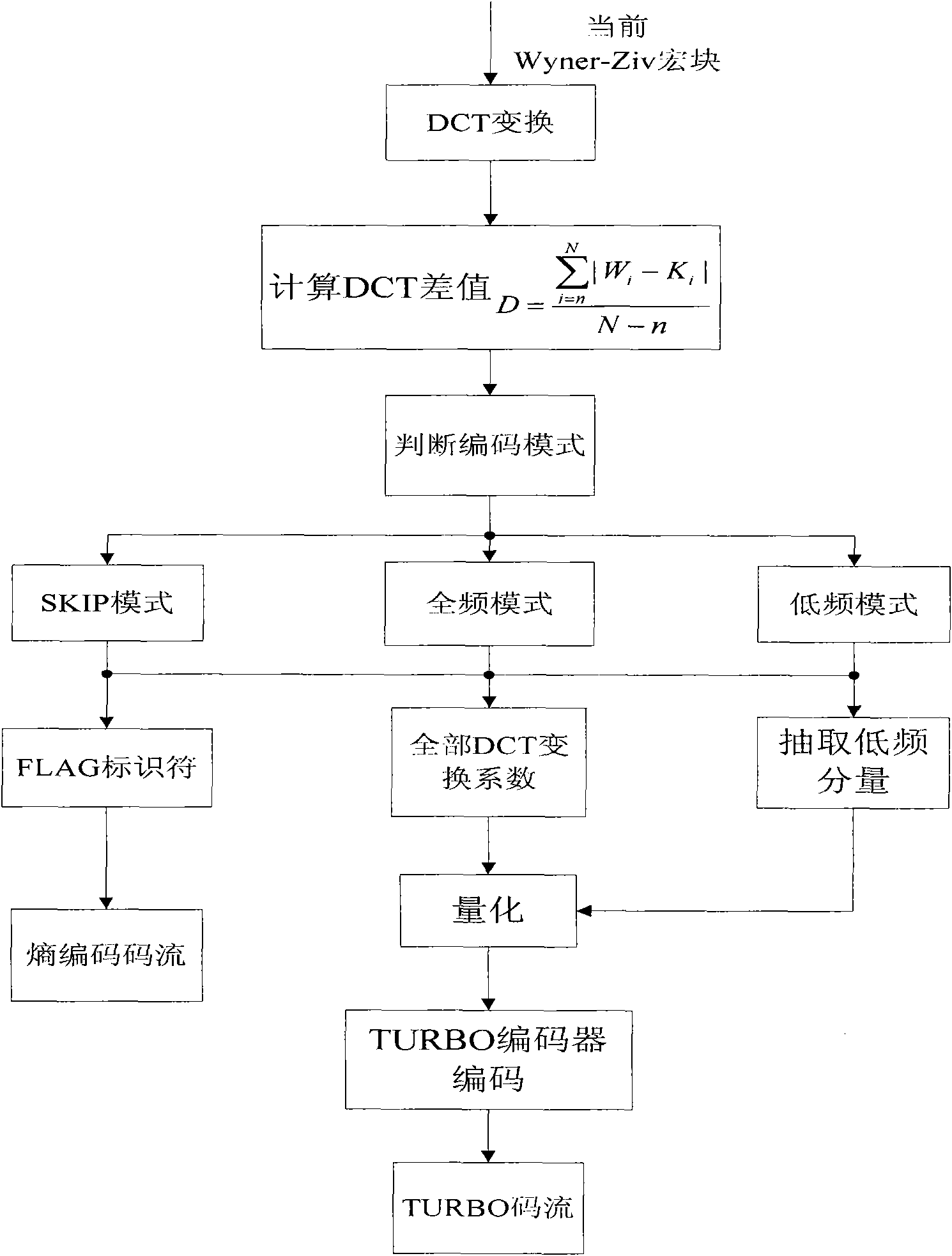
The invention relates to a grouping method in frequency domain distributed video coding, which is improved aiming at a frequency domain Wyner-Ziv video coding scheme provided by a foreign research scholar, Stanford University Professor Bernd Girod, according to the characteristics of a wireless sensor network terminal device, such as low coding complexity, limited storage capacity and capability of transmitting in a network with poor channel quality and the like, and the Wyner-Ziv video coding characteristic. In the method, image frames are divided into three coding modes at a coding end, namely a skip mode, a low frequency mode and a full frequency mode; and combined decoding is performed by respectively selecting a side information estimation method for average interpolation, adaptive search motion estimation interpolation and adaptive search fine motion estimation interpolation according to a corresponding coding mode at a decoding end. The method can realize low bitrate transmission by eliminating a large number of interframe predictions and entropy coding, and also can acquire more accurate side information with low decoding price so as to effectively avoid the reduction of image decoding quality.
Owner:GUANGDONG XUNTONG TECH
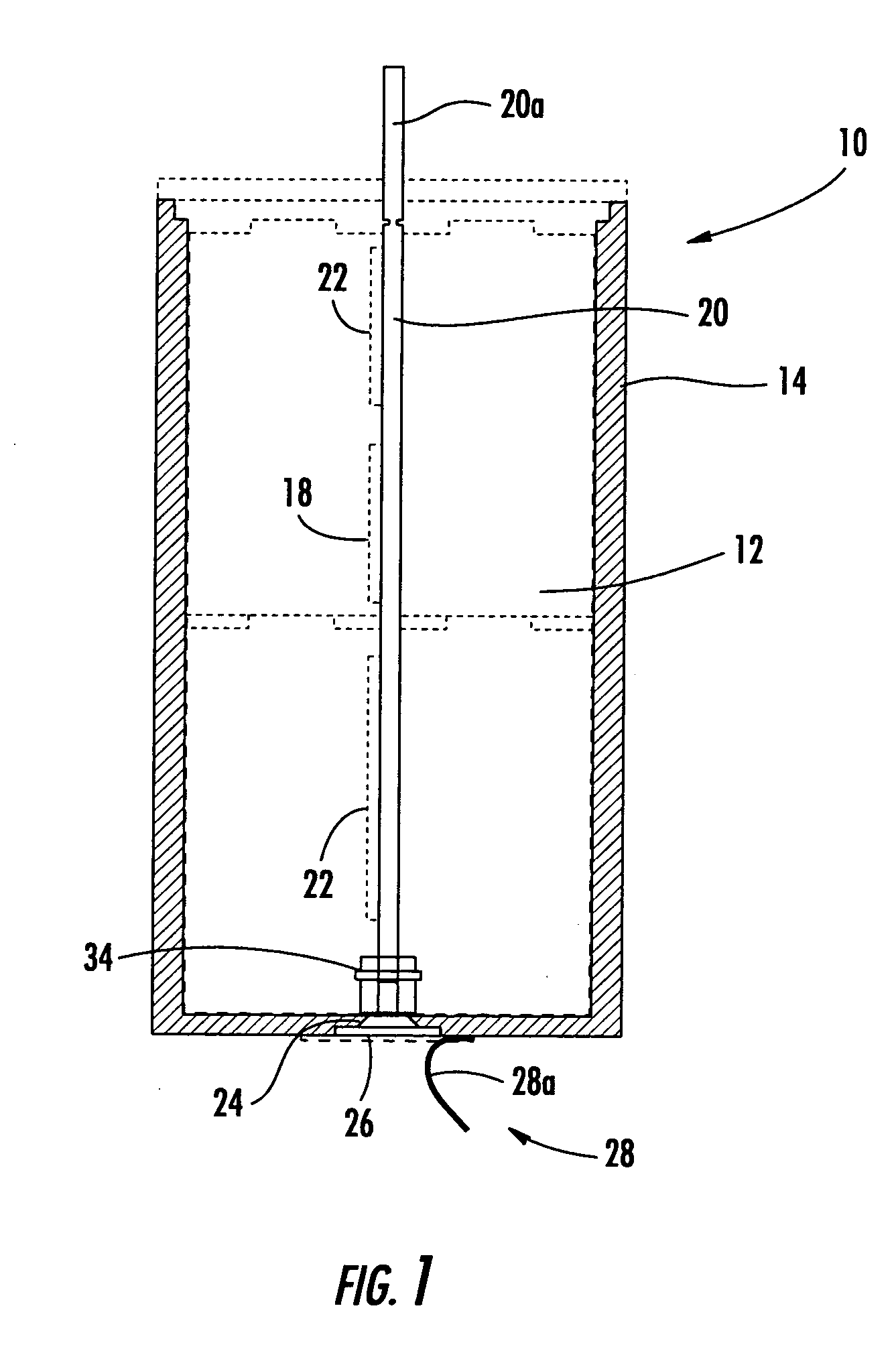
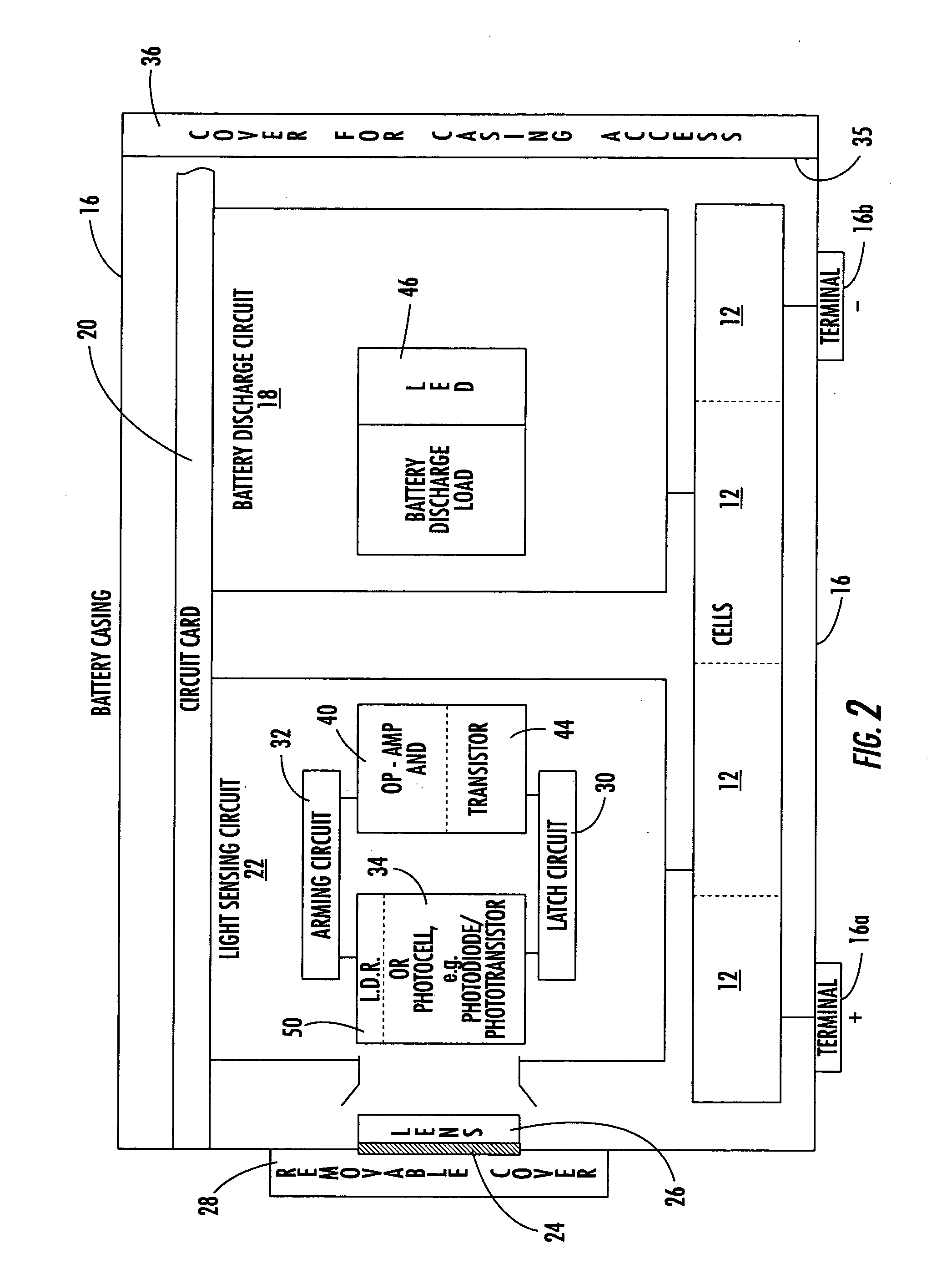
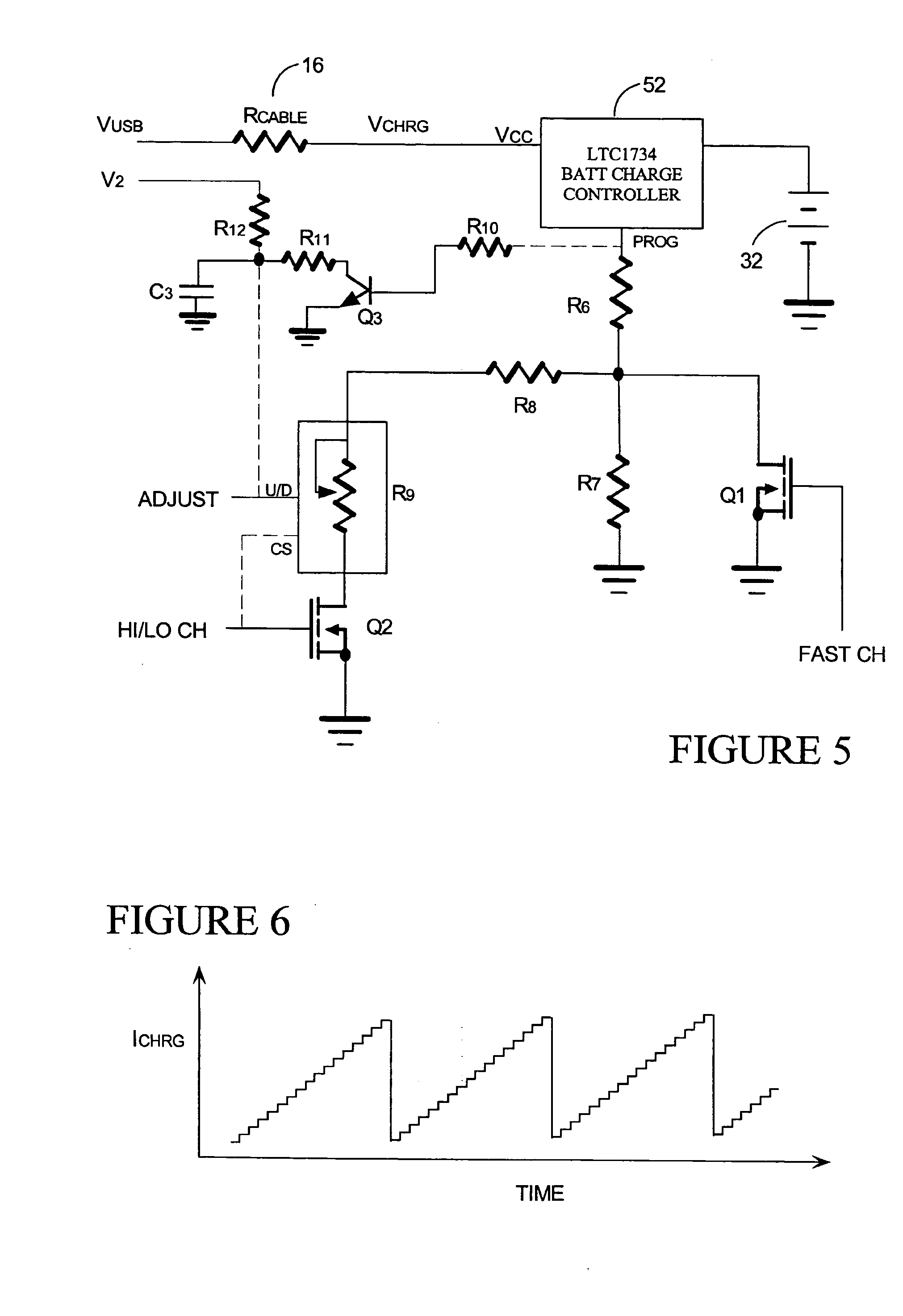
Battery heating circuit
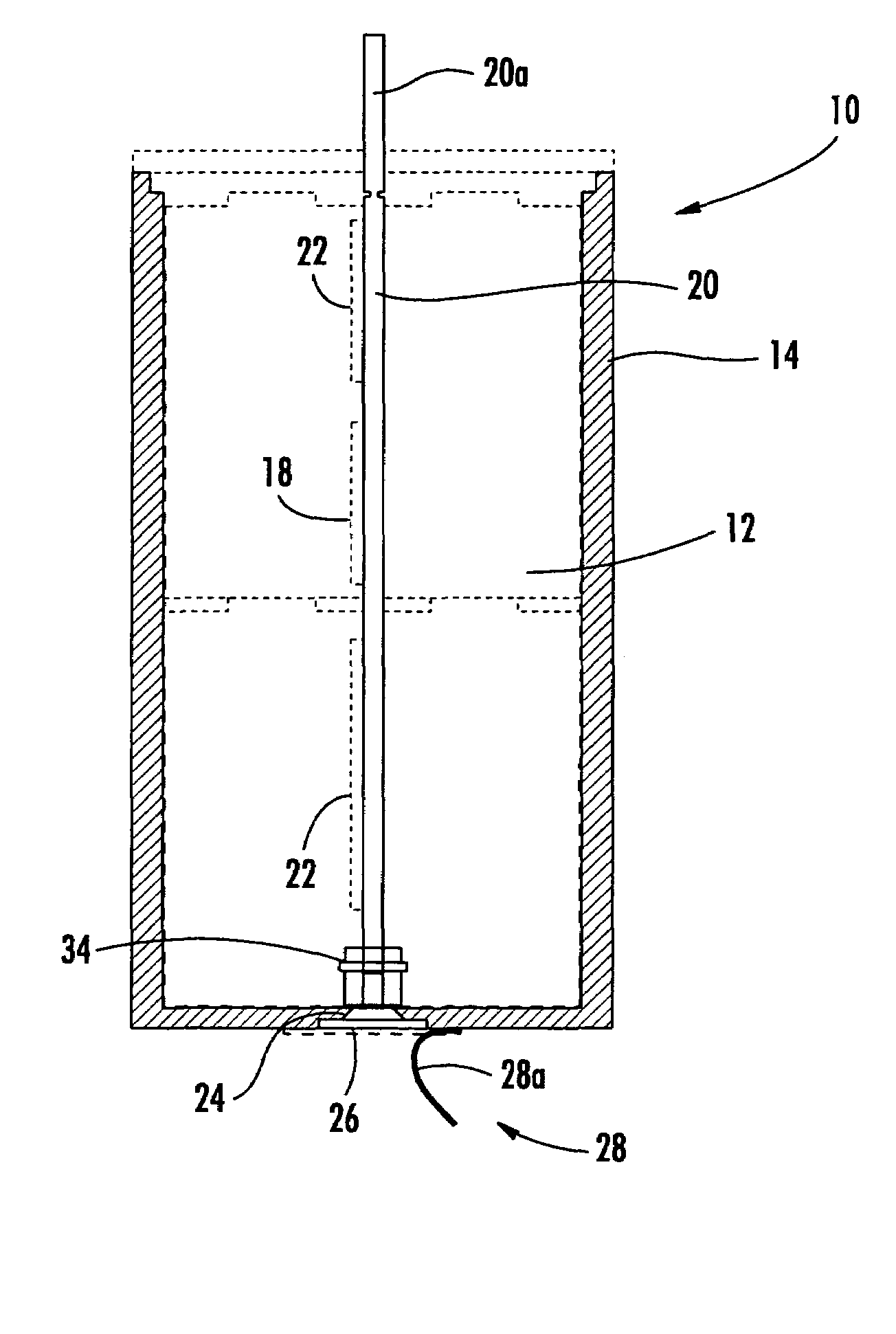
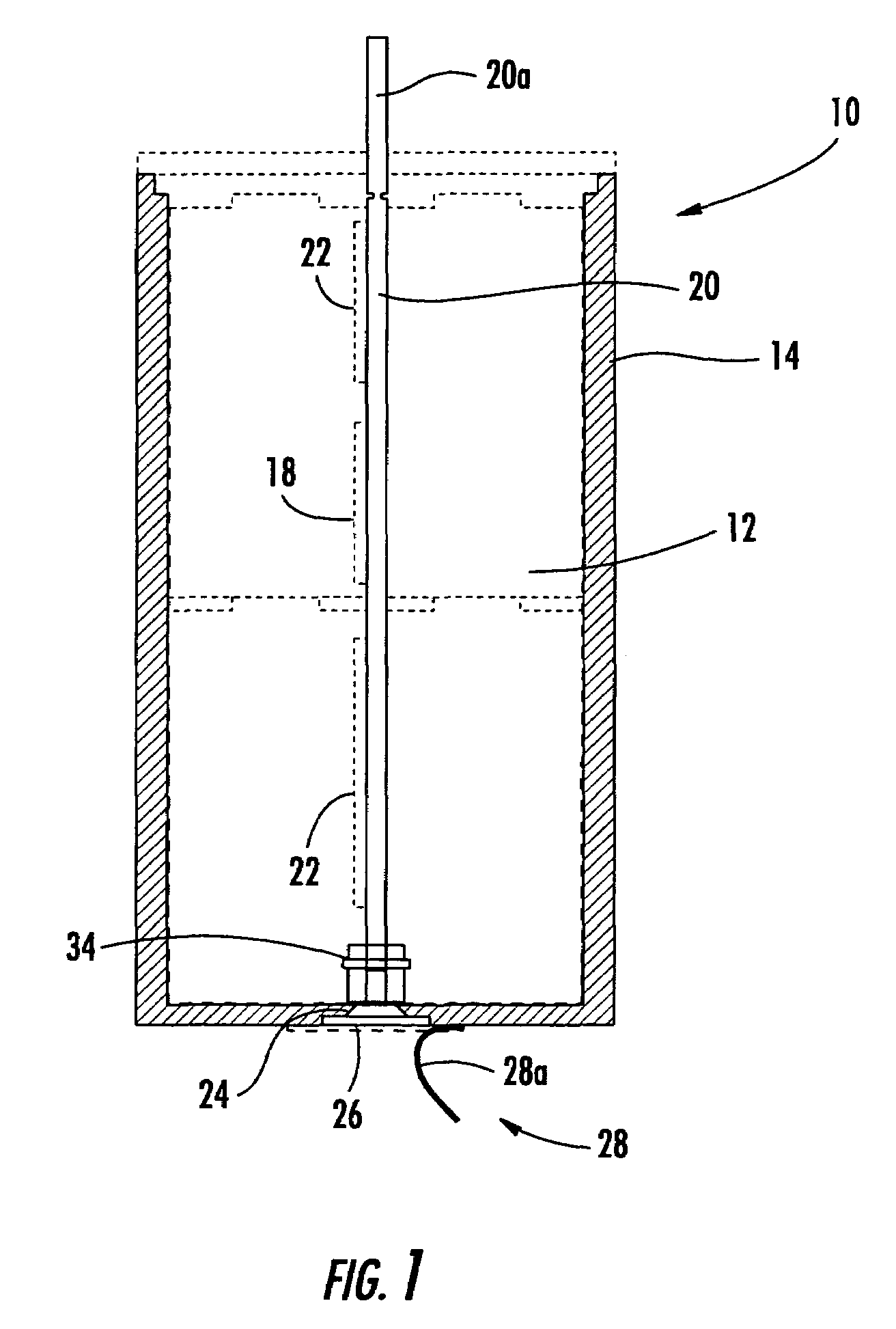
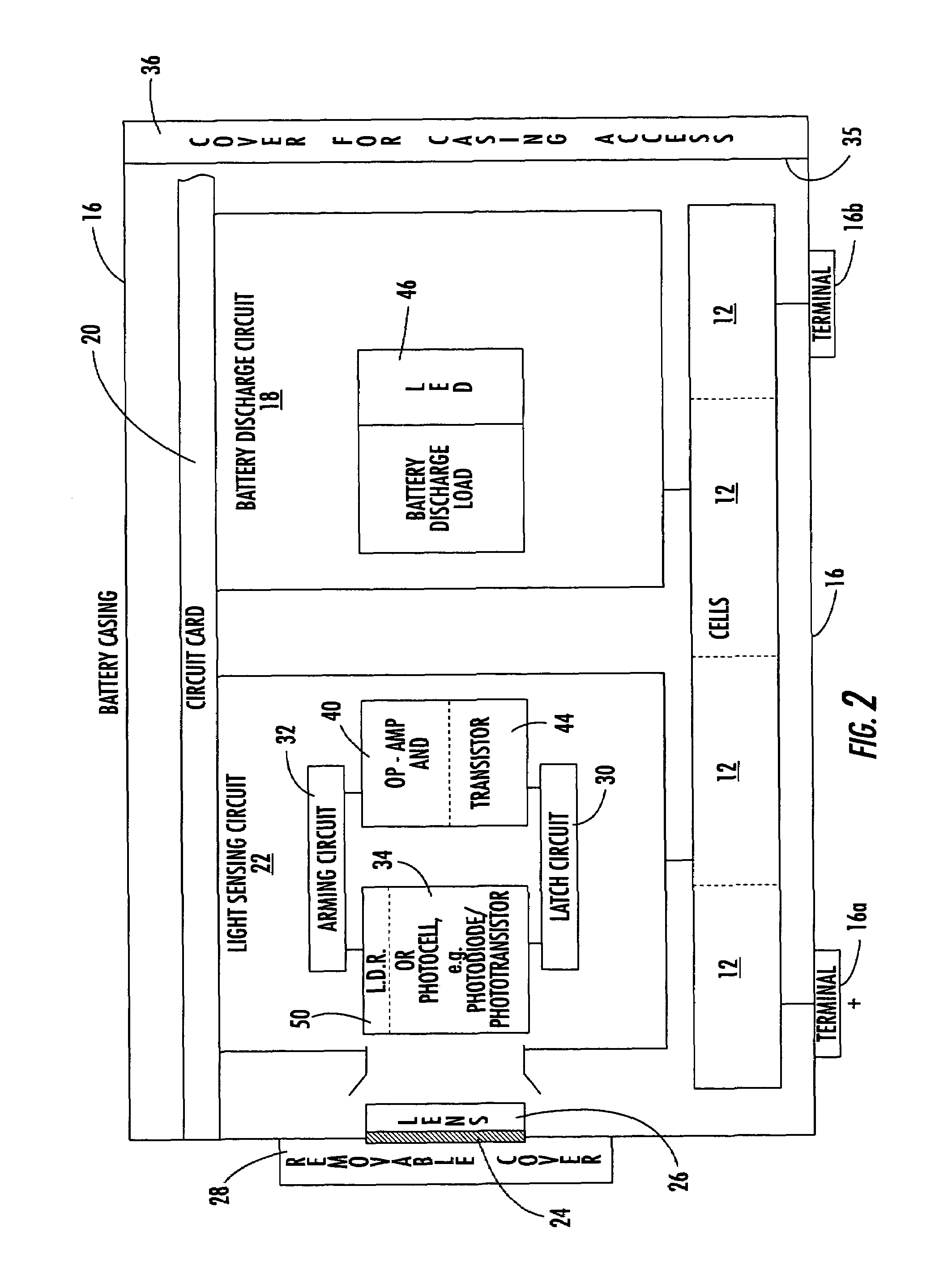
ActiveUS7327122B2Simple circuit designSecondary cellsElectric powerNameplate capacityBattery capacity
A battery delivers its rated capacity when the battery is below a temperature when the available battery capacity is limited. The battery includes a heating element, a temperature sensor, and a switch operatively connected to the heating element and temperature sensor and responsive to the temperature sensor for switching on the heating element and raising the temperature of the battery to allow the battery to deliver its rated capacity when a sensed temperature of the battery is below a temperature where available battery capacity is limited.
Owner:MATHEWS ASSOCS
Battery heating circuit
ActiveUS20050017690A1Simple circuit designIncrease temperatureSecondary cellsElectric powerHeating elementLimited capacity
A battery delivers its rated capacity when the battery is below a temperature when the available battery capacity is limited. The battery includes a heating element, a temperature sensor, and a switch operatively connected to the heating element and temperature sensor and responsive to the temperature sensor for switching on the heating element and raising the temperature of the battery to allow the battery to deliver its rated capacity when a sensed temperature of the battery is below a temperature where available battery capacity is limited.
Owner:MATHEWS ASSOCS
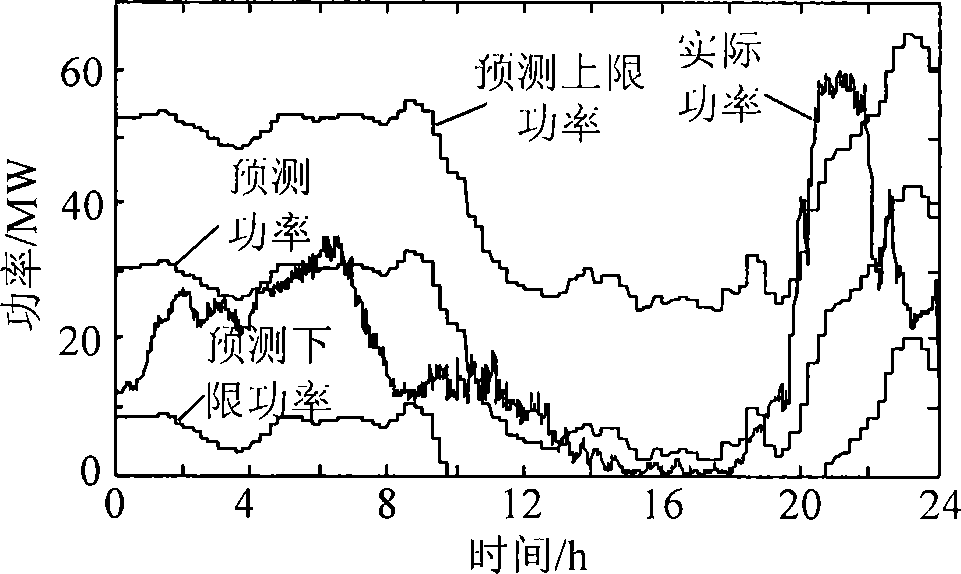
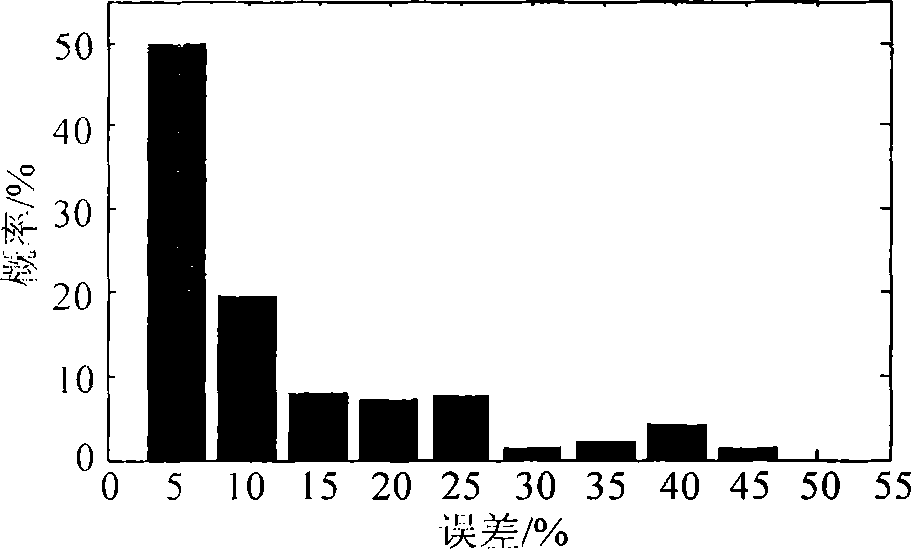
Method and system for tracking wind and electric output plans through energy storage based on predictive power of wind and electricity
ActiveCN104779631AOptimize charge and discharge control coefficientReal-time optimization of charge and discharge control coefficientsEnergy storageAc network load balancingPlanning methodLimited capacity
The invention provides a method and system for tracking wind and electric output plans through energy storage based on predictive power of wind and electricity. The method comprises the following steps: reading the relevant data of a wind power field and an energy storage system; establishing a charging and discharging control strategy of the energy storage system; confirming a target function; confirming charging and discharging control coefficients through a particle-swarm optimization algorithm; confirming the charging and discharging power of the energy storage system according to the charging and discharging control coefficients. The system comprises an acquisition unit, a control unit, a calculating unit, an optimizing unit and a result outputting unit. According to the method and system, each predictive point performs roll poling at a time, and the purpose of optimizing the charging and discharging control coefficients of an energy storage power station in real time is achieved through the particle-swarm optimization algorithm, so that the limited capacity of the energy storage system can be sufficiently utilized; in addition, the target function is set, so that the stage of charge of the energy storage system is kept in an appropriate range as much as possible, the charging and discharging capabilities of the energy storage system are further improved, and finally the capability of tracking planning output, of a wind-storage association system, is improved.
Owner:STATE GRID CORP OF CHINA +1
Systems and methods for approximating optimal distribution via networked systems
InactiveUS20050108071A1Maximize update speedImprove distributionForecastingMultiple digital computer combinationsNetworked systemNetwork data
The present invention leverages an ellipsoid method with an approximate separation oracle to analyze network data routes for data dissemination by a source, yielding an optimization analysis process which compensates for networks with limited capacity links, traditionally an NP-hard problem. In one instance of the present invention, by utilizing a novel generalization of an ellipsoidal means to work with an approximate separation oracle, a primal as well as a dual linear program is solved within the same approximation factor as the approximate separation oracle. Performance of the present invention is within a 1.6 factor.
Owner:MICROSOFT TECH LICENSING LLC
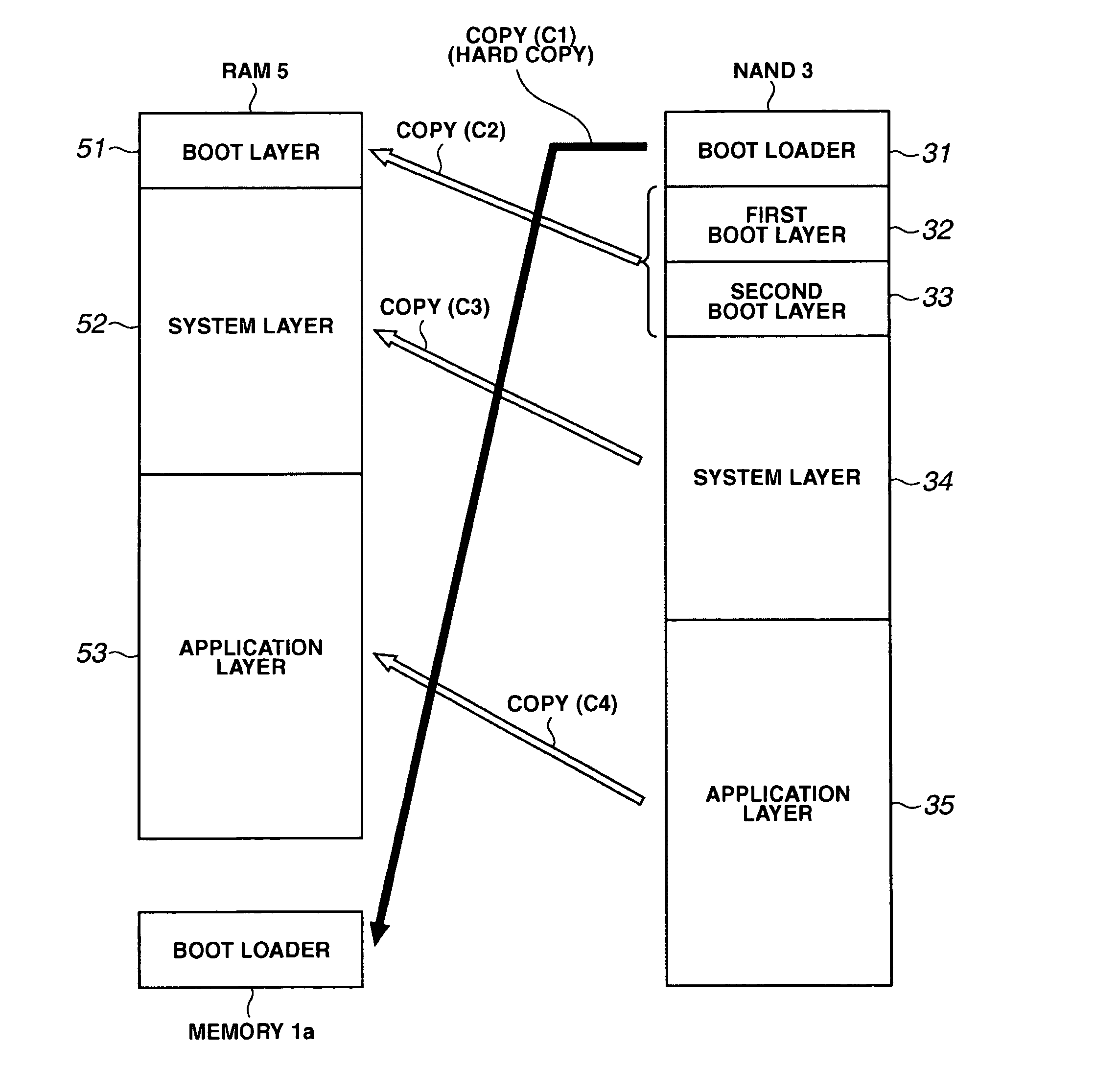
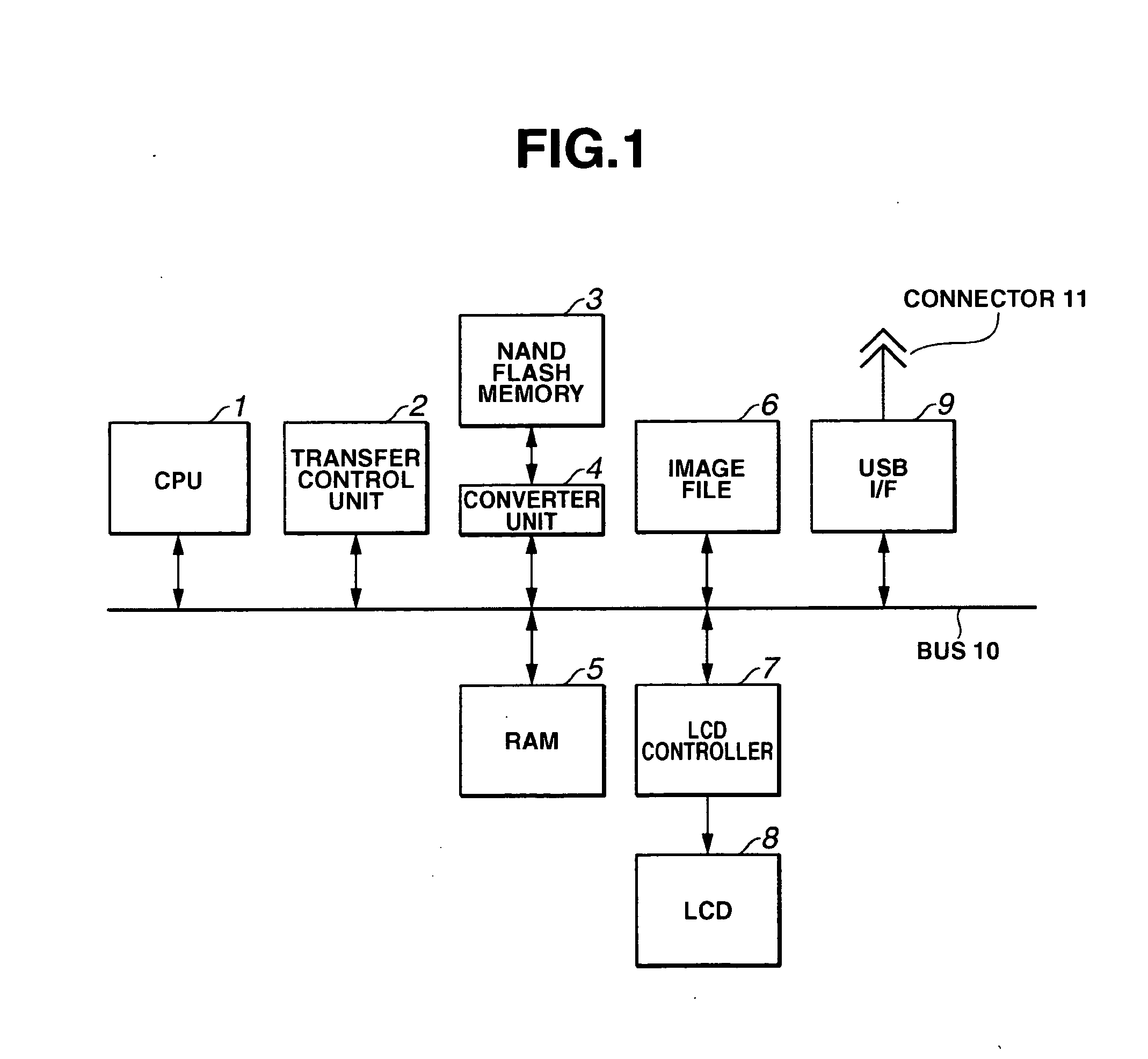
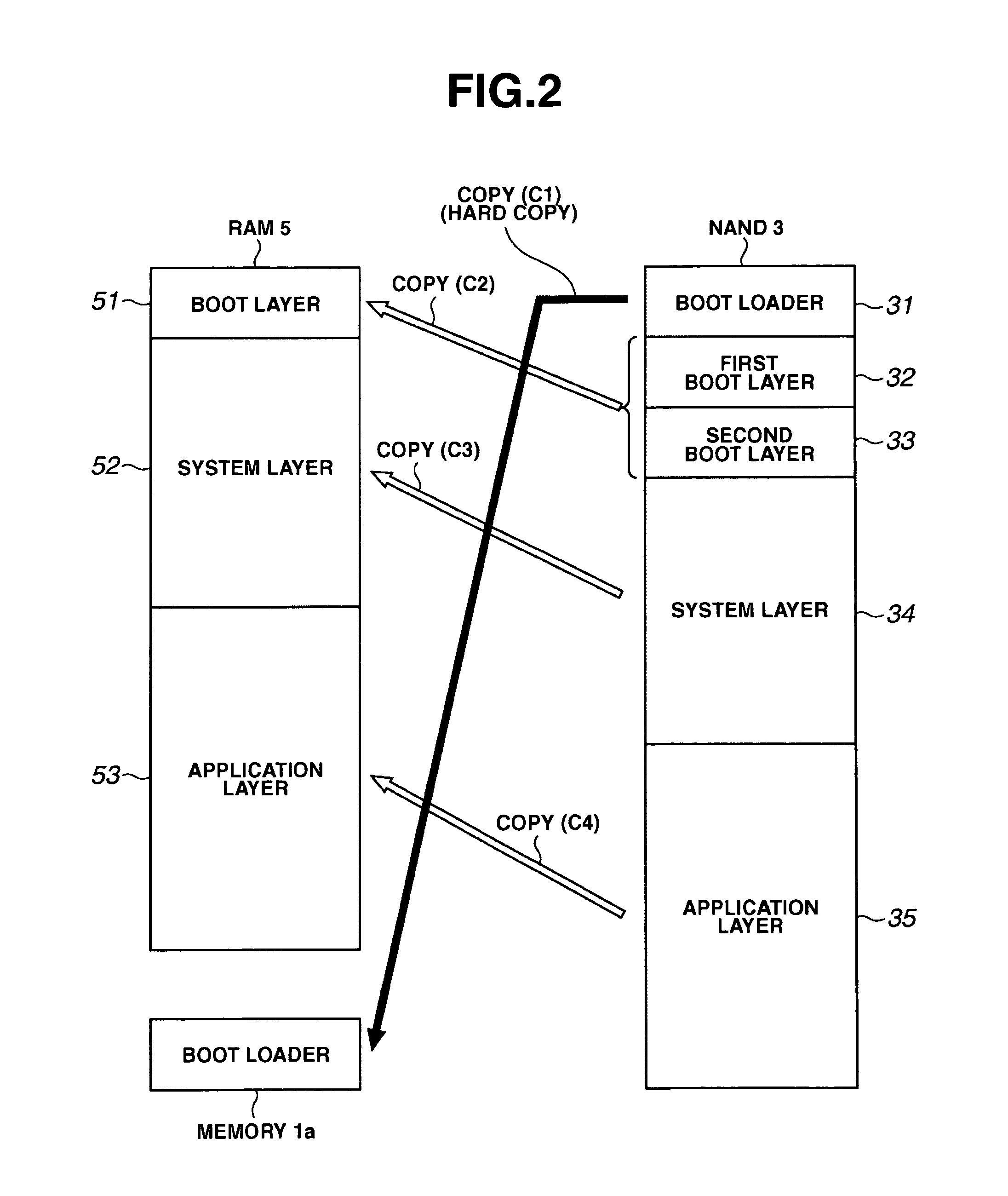
Portable terminal
InactiveUS20060107031A1Not truly reliableImprove reliabilityDigital computer detailsBootstrappingOn-screen displaySecond screen
Screen display matched to the progress of execution of the initialization function in small and inexpensive devices such as a portable terminal is performed. Furthermore, reliability in the event of an error is improved without providing excessive redundancy and with limited capacity in a NAND flash memory storing programs. A first boot layer and a second boot layer of the same content are stored in the NAND flash memory. The boot layer free from errors is copied (C2) to a RAM (step S21), and a boot layer program is executed in the RAM (step S30). A simple logo and the like comprising characters is then displayed (first screen display) (step S32). Next, a system layer program is executed in the RAM (step S40). A screen (second screen display) is then displayed by switching between a plurality of images (step S44).
Owner:KK TOSHIBA
Circuit and method of operation for an adaptive charge rate power supply
InactiveUS20050046391A1Minimize timeMaximize currentVolume/mass flow measurementPower supply for data processingBattery chargeLow voltage
Owner:MALIKIE INNOVATIONS LTD
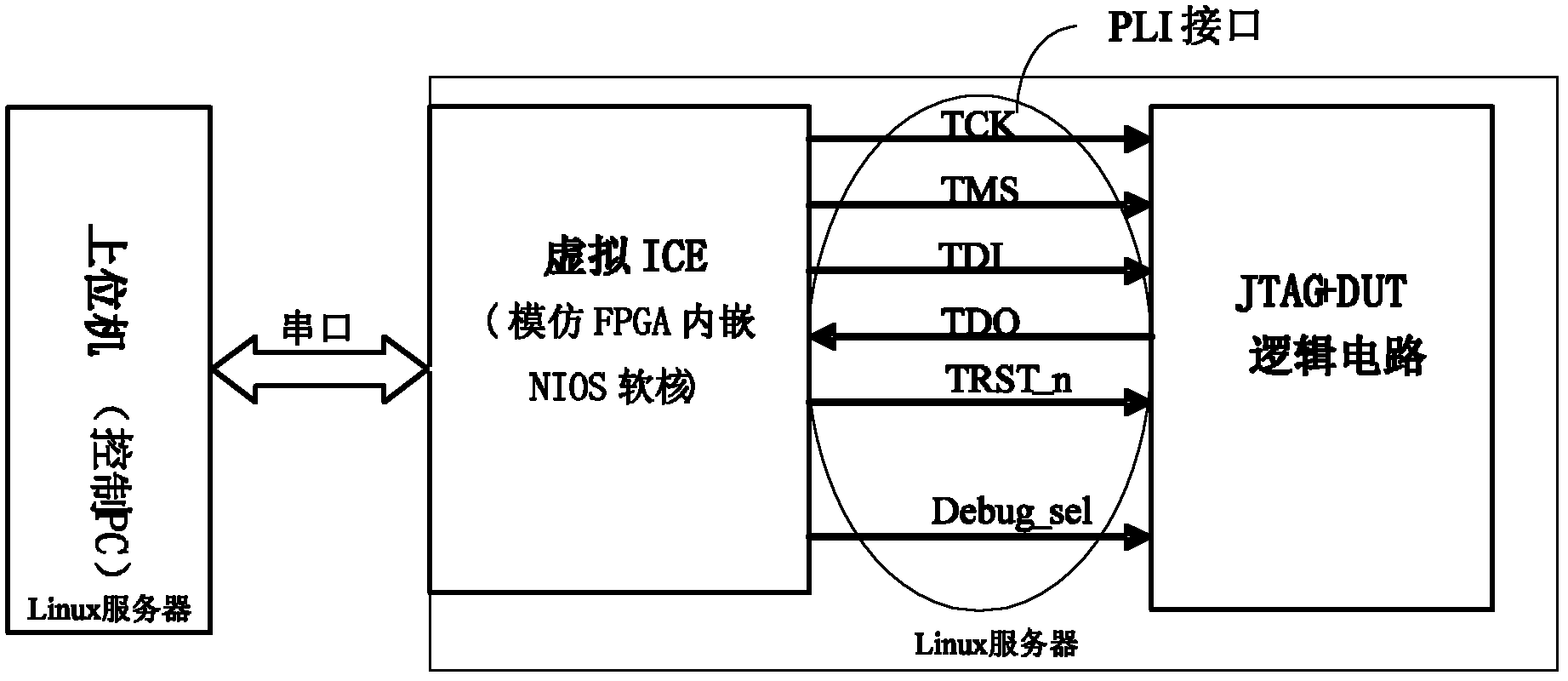
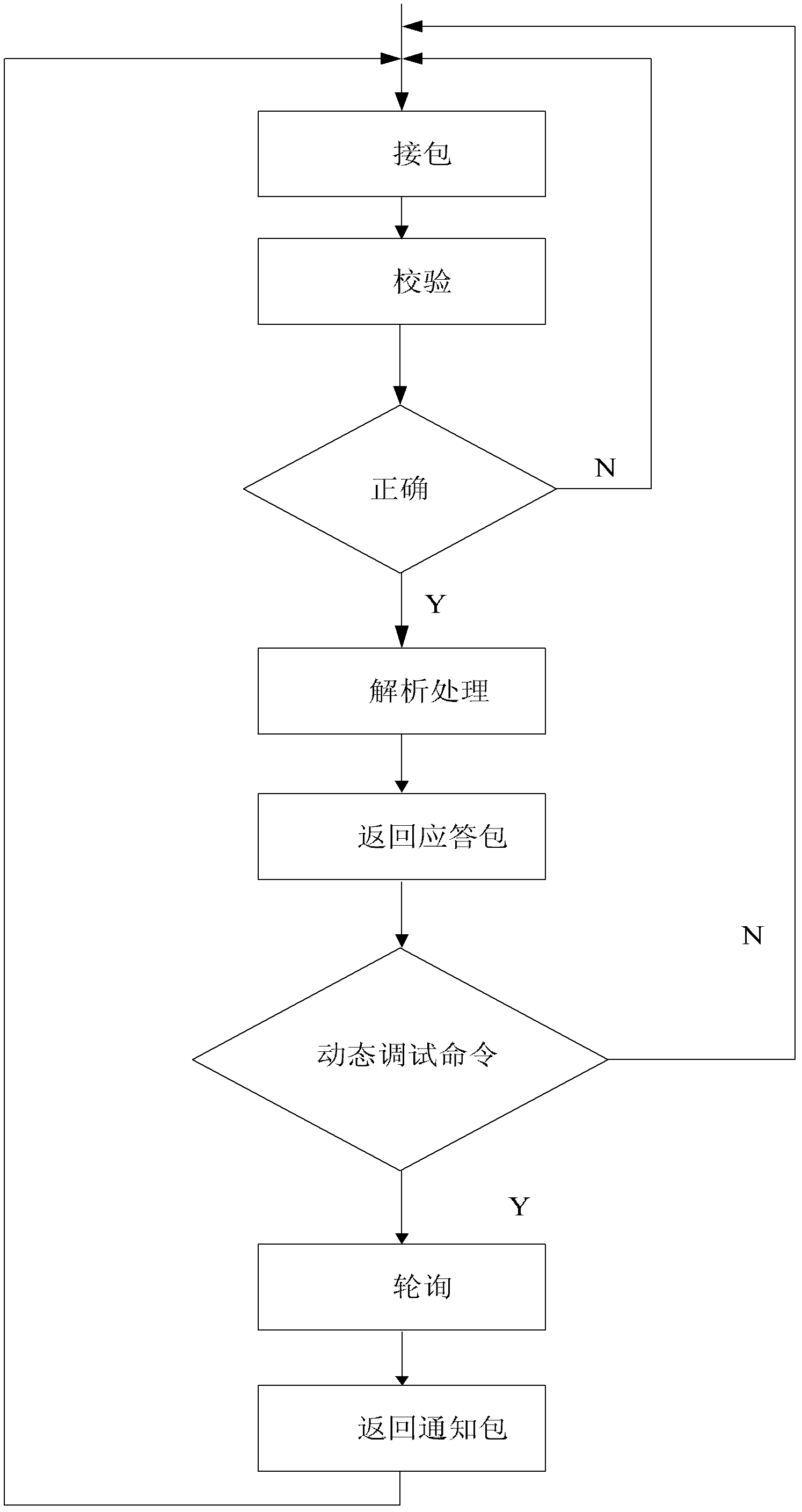
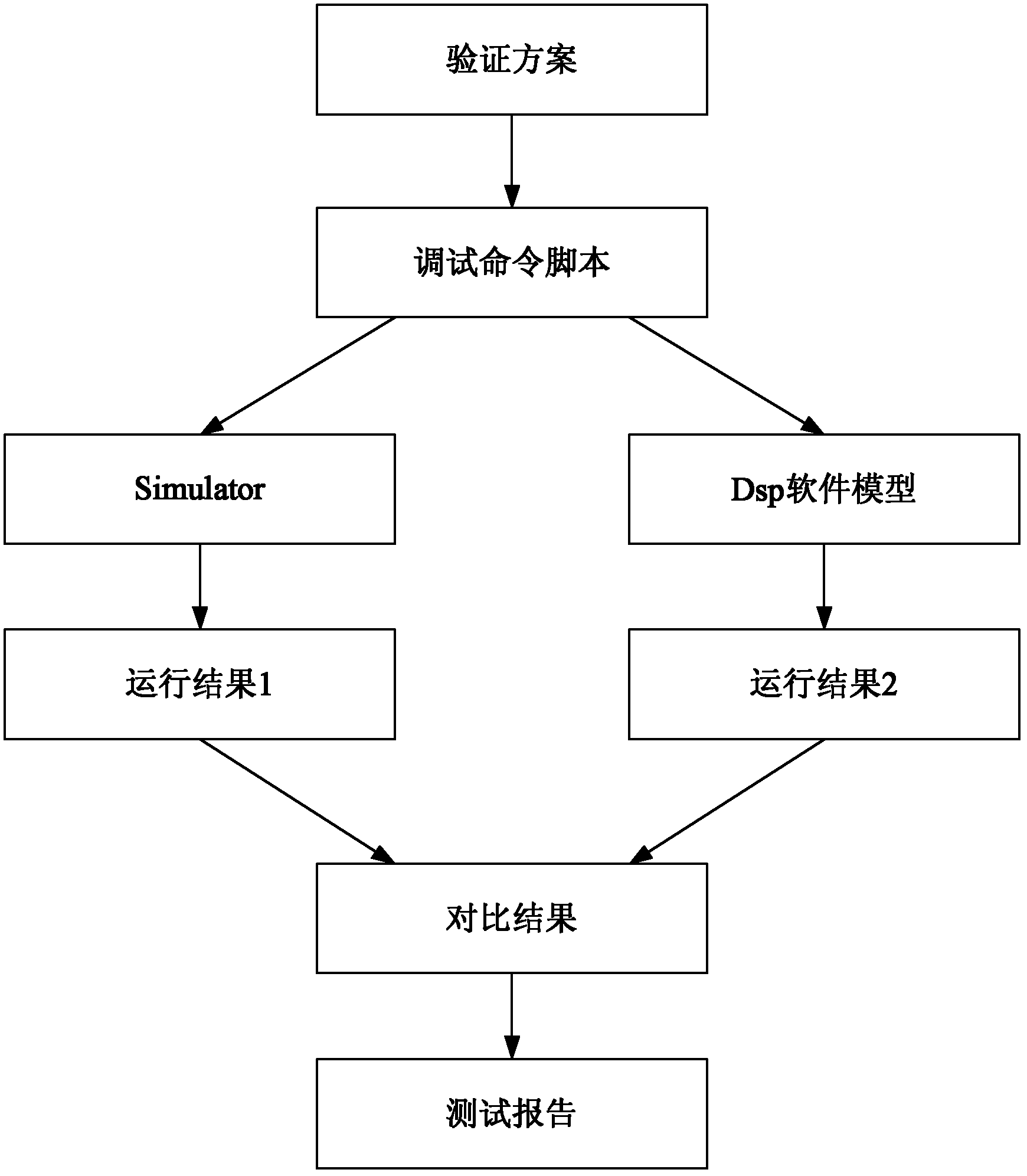
Software-hardware co-verification platform
The invention discloses a software-hardware co-verification platform, which comprises an upper computer, a virtual in-circuit emulator (ICE), a design under verification (DUV) and a communication part, wherein the virtual ICE communicates with the upper computer through a serial port between servers and is connected with the DUV through programming language interfaces (PLIs); the upper computer is realized on a server equipped with a Linux operating system; and the virtual ICE, the PLI and the DUV are realized on another server equipped with a Linux operating system. The verification environment of the verification platform can be realized only by using the servers with relatively large storage space, so that the problem of limited capacity of a software-hardware co-verification product is solved, and system-level verification of a chip at a design front end can be realized; the prices of the servers are low, so that the cost of integrated product development is reduced; and besides, as the software-hardware co-verification platform is completely realized by using software, a lengthy period of hardware debugging is avoided, the development process of the product is accelerated, and precious time is strived for early listing of the product.
Owner:CHINA ELECTRONIC TECH GRP CORP NO 38 RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com