A security vulnerability automatic verification system based on a crowd test platform
An automatic verification and vulnerability technology, applied in the field of network security, can solve the problems of failure to deal with vulnerabilities, difficult vulnerability discovery and verification, false positives, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
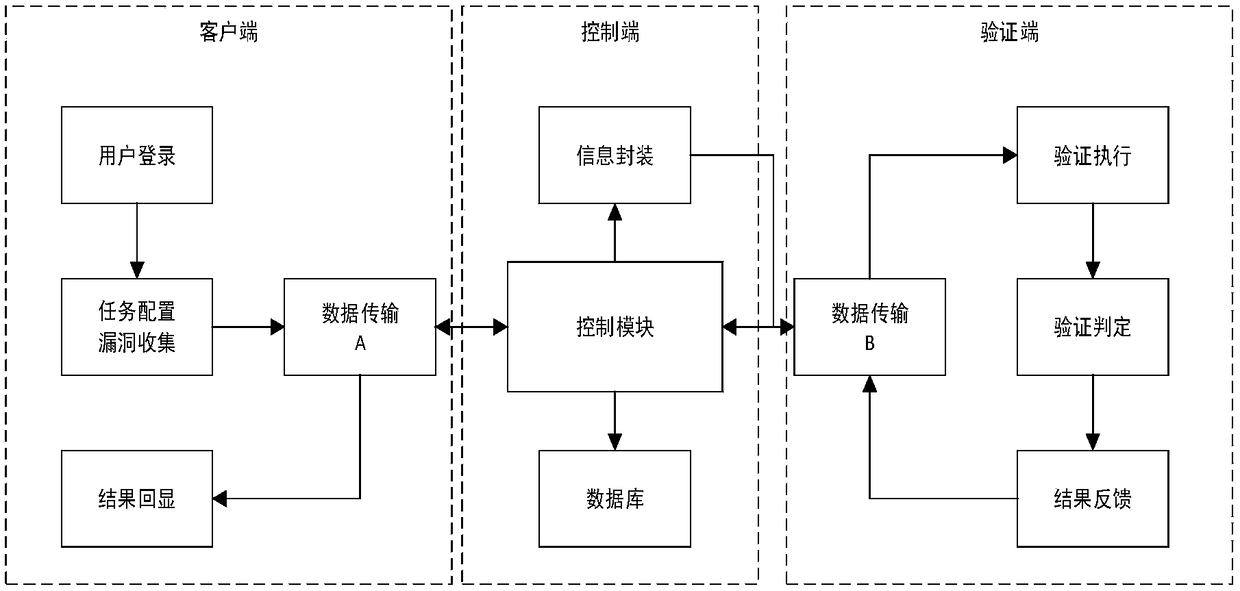
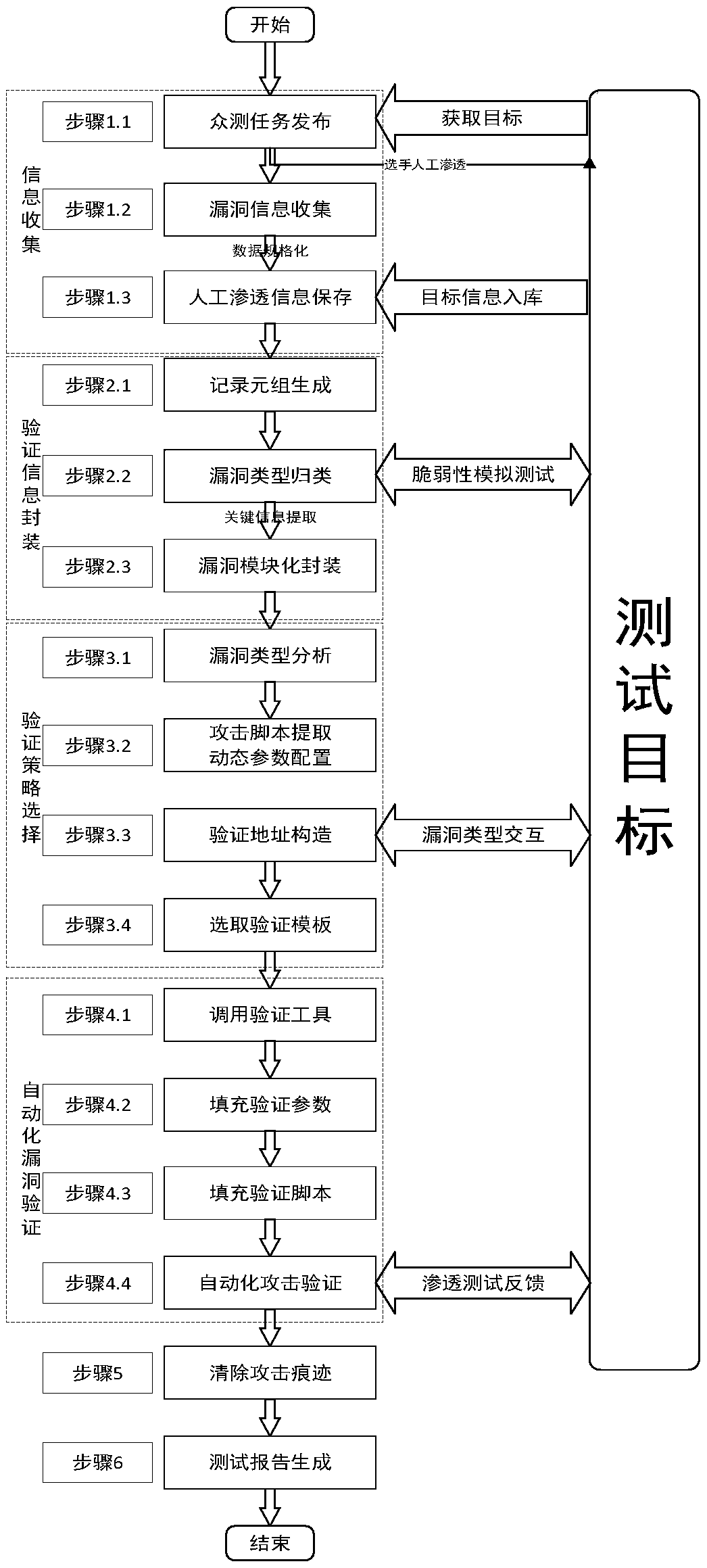
[0064] Such as figure 1 , figure 2As shown, the method of the present invention is developed by combining Java with python scripting language, and the public testing platform adopts a standard interface, which can be docked with other security systems. The overall system module topology of the vulnerability automation verification platform is shown in Figure 1, which is divided into three parts: client, control end and verification end.
[0065] The client includes front-end and back-end user login, task configuration, task submission, result display, and data transmission module A. The task configuration module is responsible for configuring the vulnerability samples submitted by the public testers and the information corresponding to the vulnerabilities; the result display module is responsible for echoing the progress and results of the vulnerabil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com