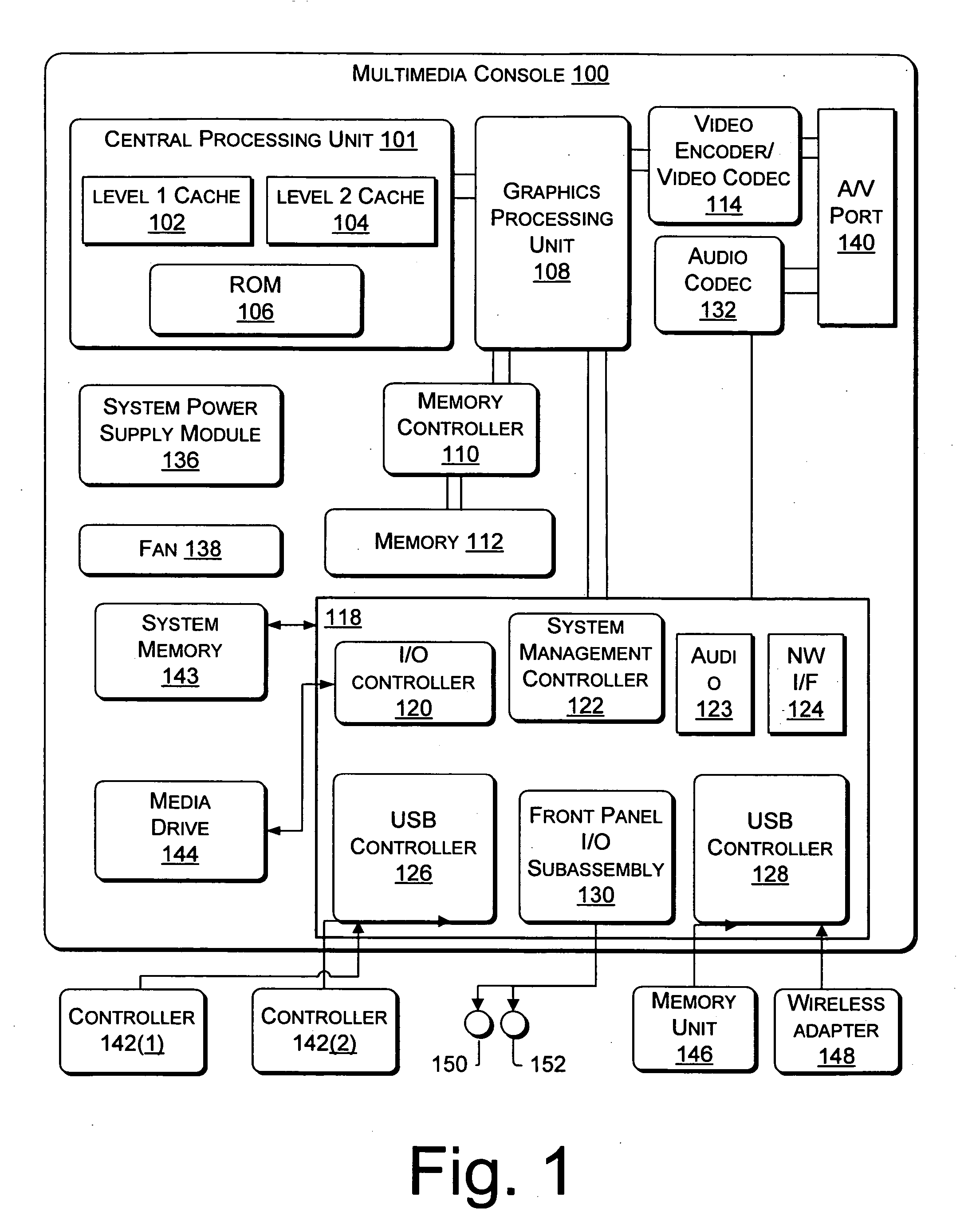
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2048 results about "Time limit" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A time limit or deadline is a narrow field of time, or a particular point in time, by which an objective or task must be accomplished. Once that time has passed, the item may be considered overdue (e.g., for work projects or school assignments). In the case of work assignments or projects that are not completed by the deadline, this may adversely affect the employee's performance rating. In the case of school assignments, essays or reports submitted after the deadline, marks or grades may be deducted from the student's assessment.
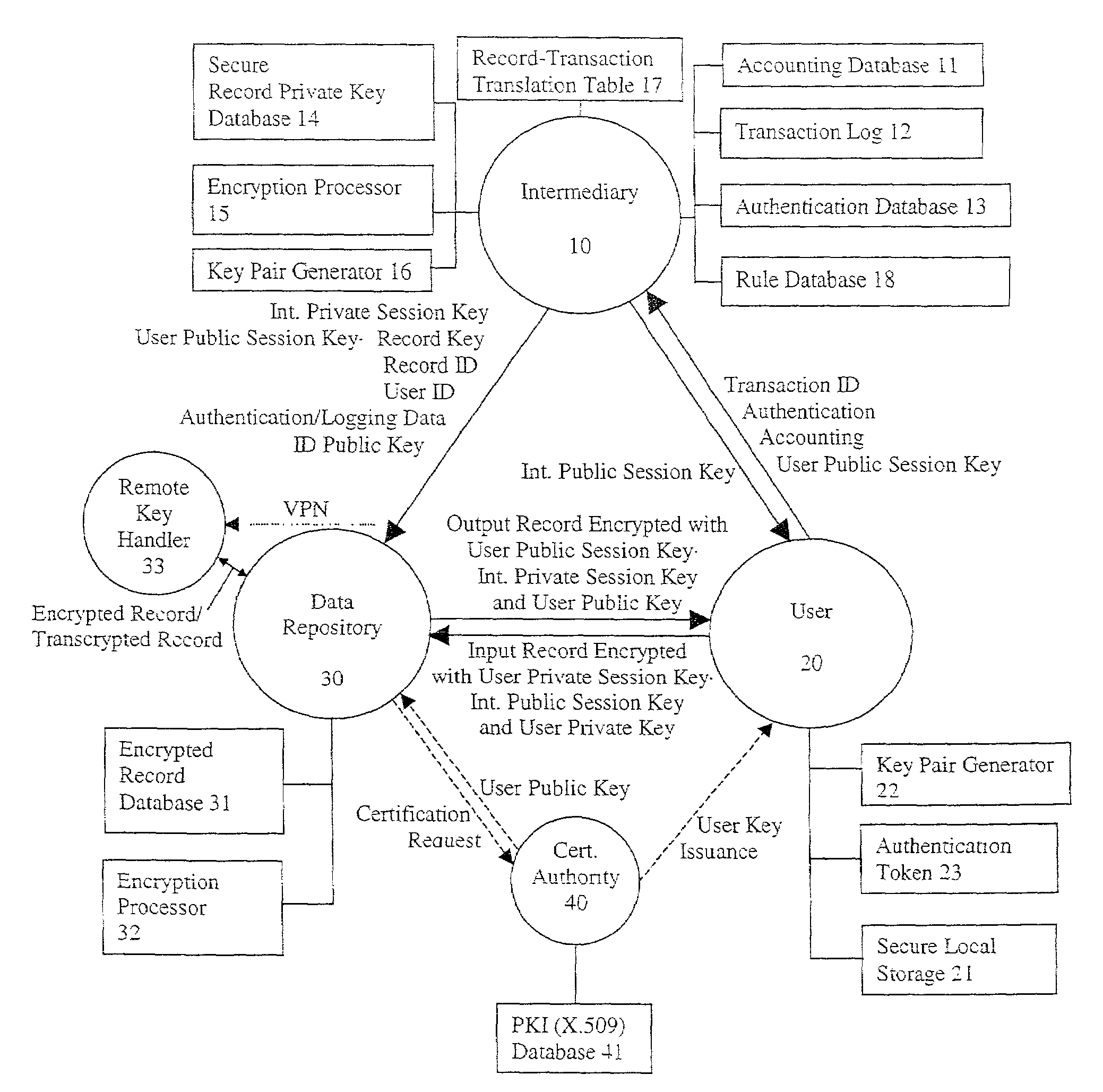
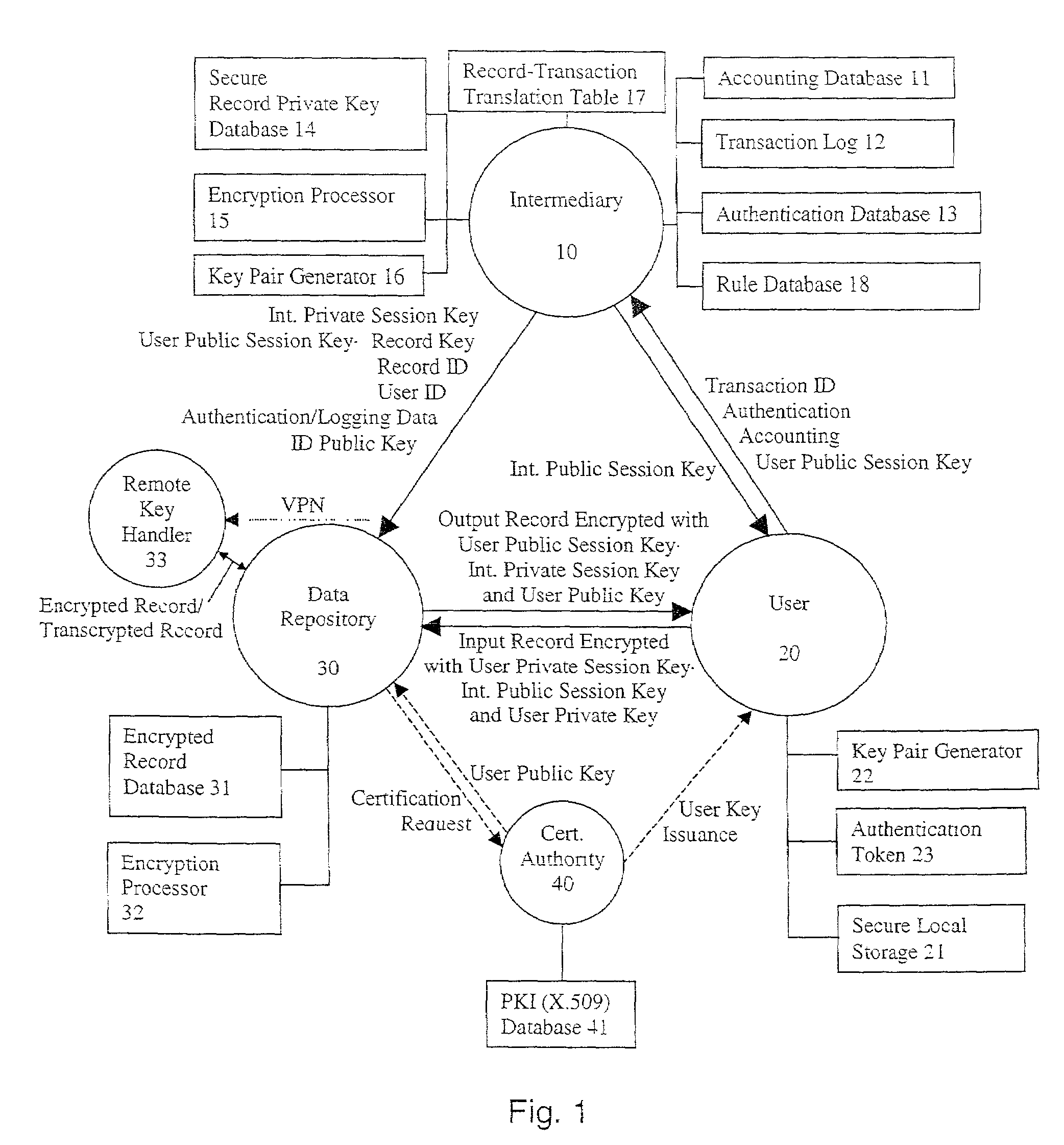
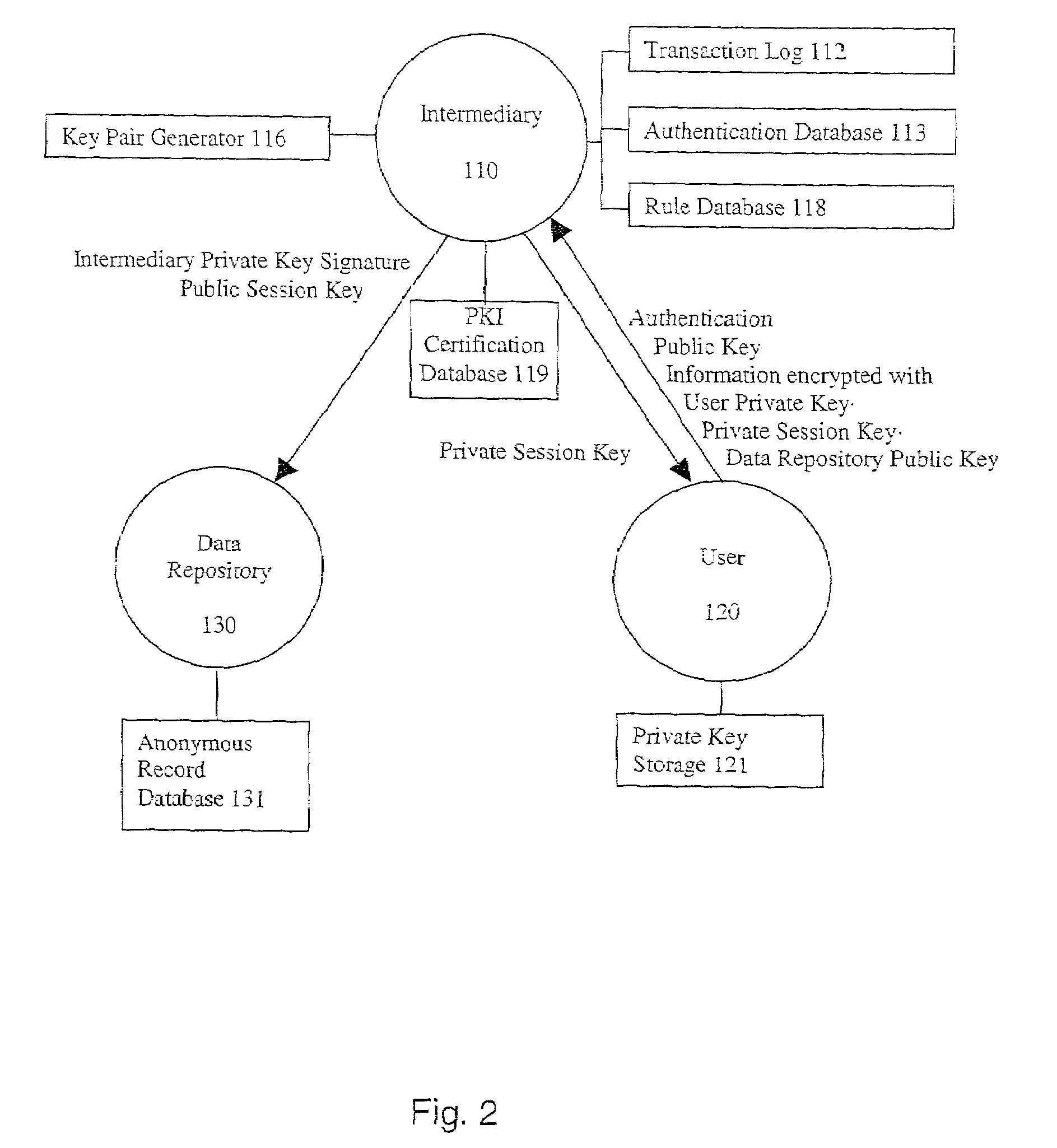
System and method for secure three-party communications
ActiveUS7181017B1Reduce liabilityReduce riskKey distribution for secure communicationTime limitThree party
A system and method for communicating information between a first party and a second party, comprising identifying desired information, negotiating, through an intermediary, a comprehension function for obscuring at least a portion of the information communicated between the first party and the second party, communicating the encrypted information to the second party, and decrypting the encrypted information using the negotiated comprehension function. Preferably, the intermediary does not itself possess sufficient information to decrypt the encrypted information, thus allowing use of an “untrusted” intermediary. The comprehension function may be dynamic with respect to its response to the negotiated comprehension function, and thus permit limitations on the use of the information by the second party. For example, the decryption of the encrypted information may be time limited.
Owner:RPX CORP
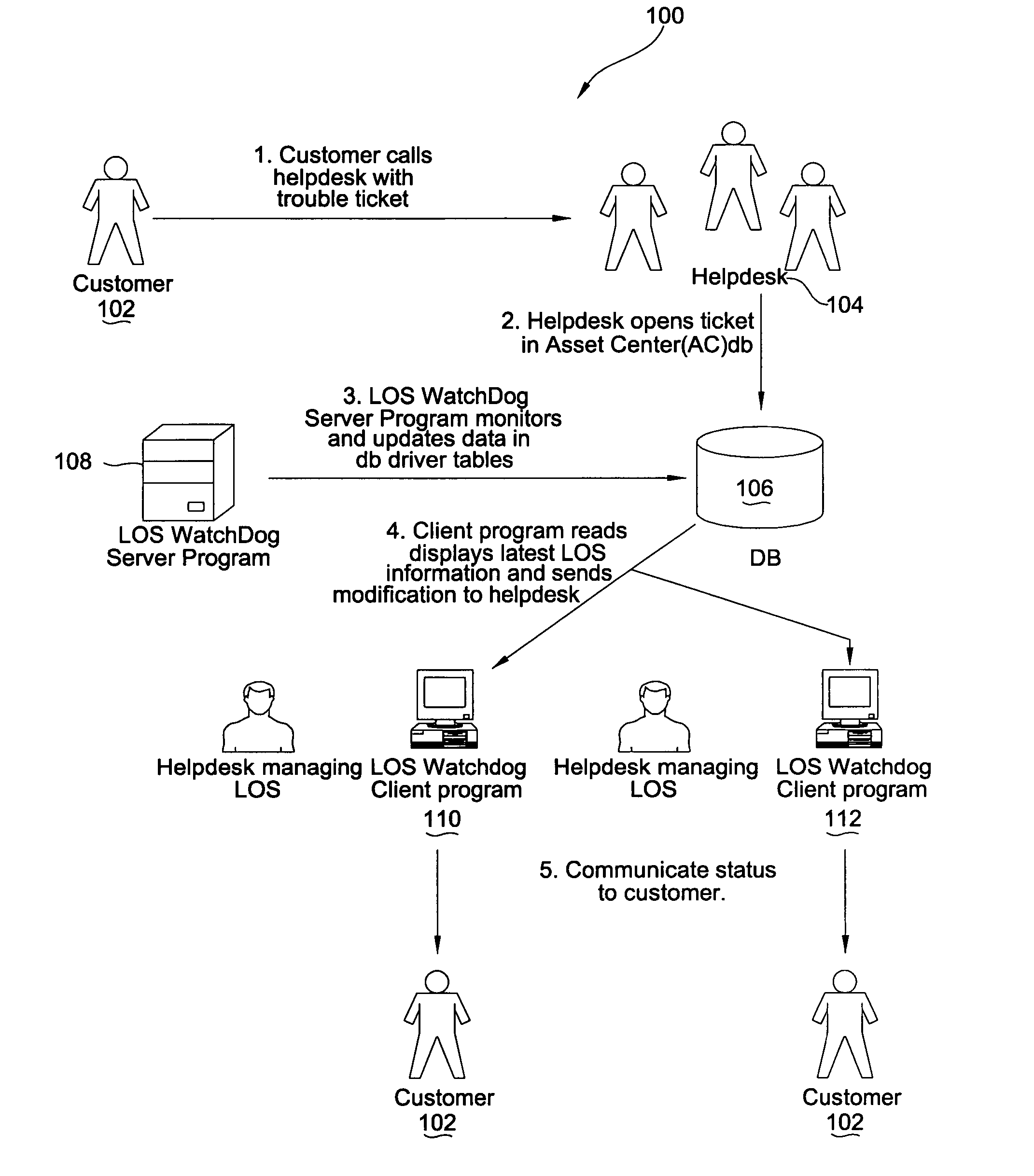
Information technology service request level of service monitor
A method, system, and computer program product for monitoring service tickets for information technology (IT) service providers to ensure that levels of service regarding resolving problems identified by a customer are met is provided. In one embodiment, a monitoring server inspects a service ticket in a database to determine a deadline for when a problem associated with the service ticket must be resolved. The server then determines a deadline approaching alert time. This deadline approaching alert time is a time at which a help desk user must be notified that the deadline for resolving the problem must be met is approaching. The server then alerts the help desk user that the deadline for resolving the problem is approaching when the deadline approaching alert time is reached. If the problem is not resolved by the deadline, the server periodically alerts the help desk user when times for status updates, which have been specified by a level of service agreement for updating the customer of the status of resolution of problems that have past deadline, are approaching, thereby ensuring that the IT provider meets its obligations to the customer.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
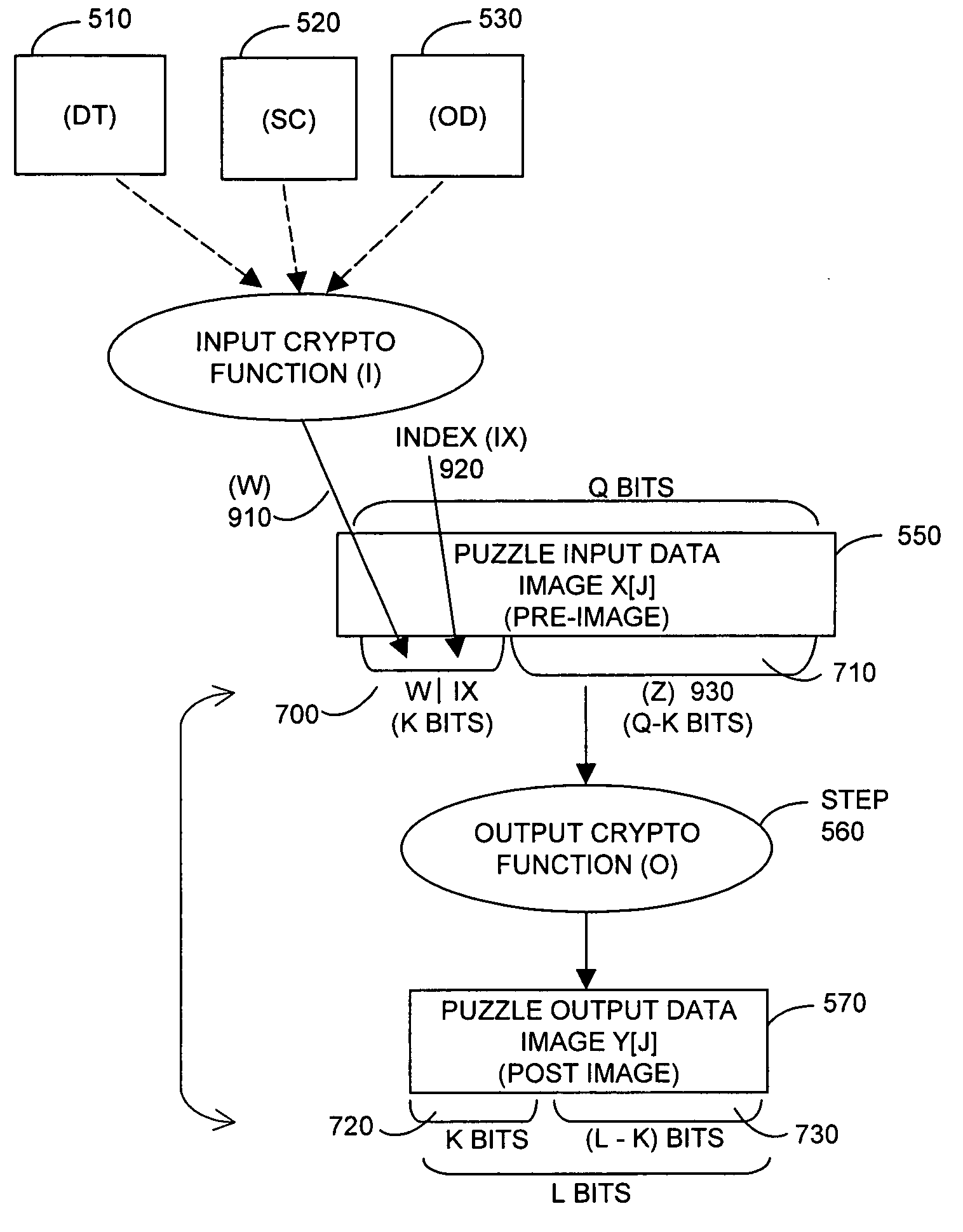
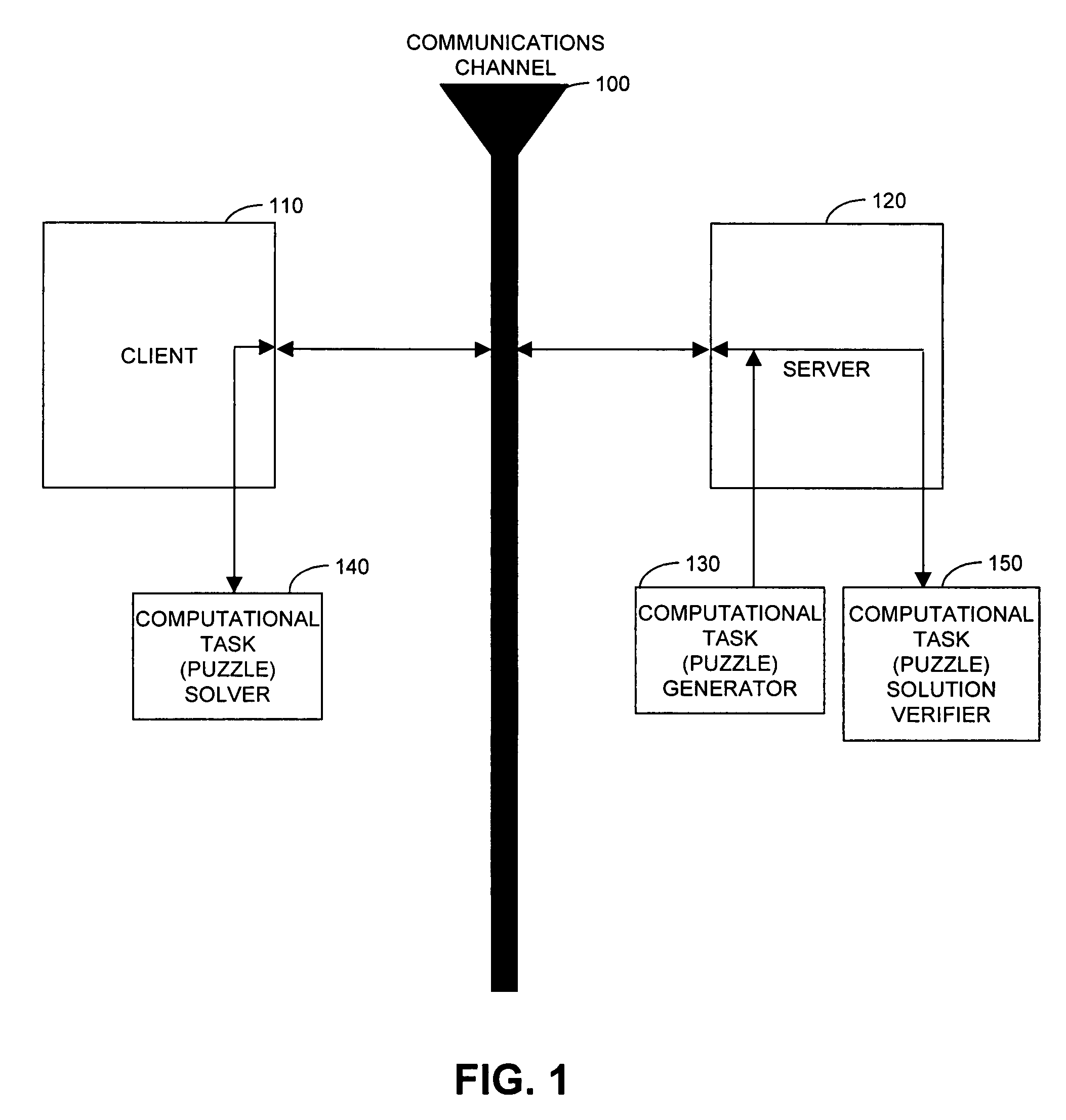
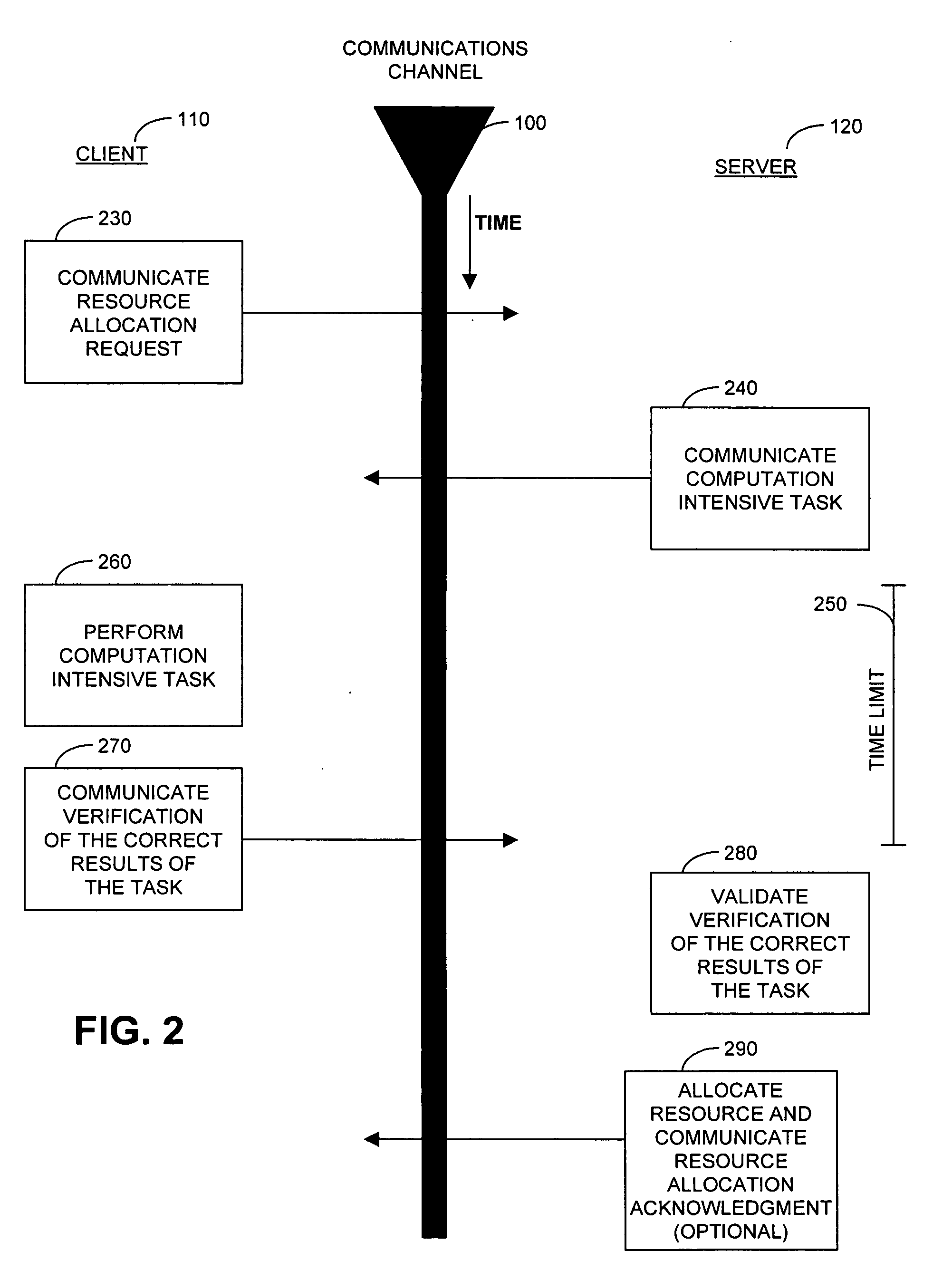
Cryptographic countermeasures against connection depletion attacks
InactiveUS7197639B1Ensure correct executionDigital data processing detailsUser identity/authority verificationCountermeasureTime limit
This invention relates to cryptographic communications methods and systems that protect a server from a connection depletion attack. Specifically, the invention presents a method for allocating a resource comprising the steps of receiving a resource allocation request from a client, imposing a computational task and a time limit for correct completion of the task upon the client, verifying that the task was performed correctly within the time limit, and allocating the resource if the task was correctly performed within the time limit.
Owner:EMC IP HLDG CO LLC
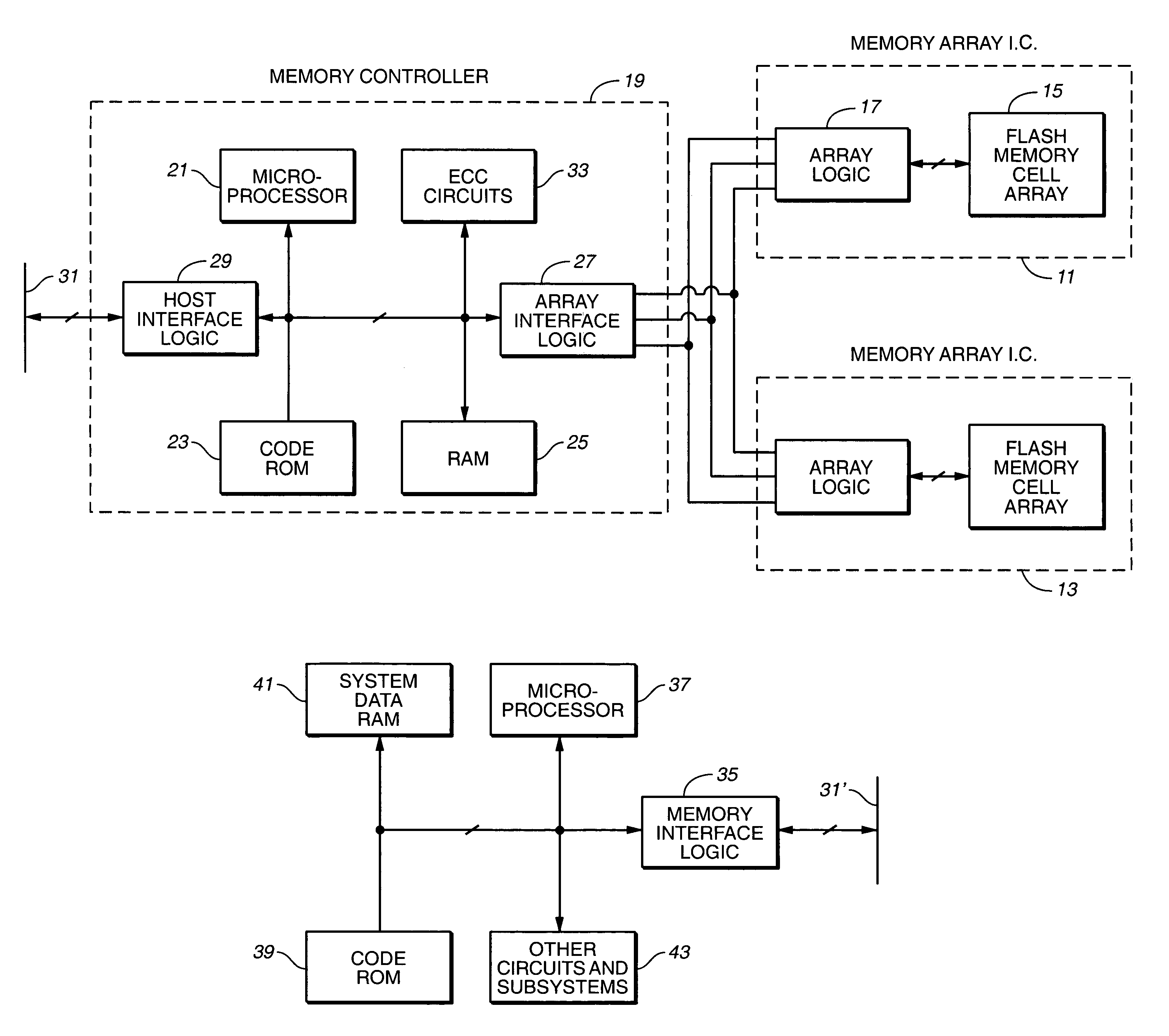
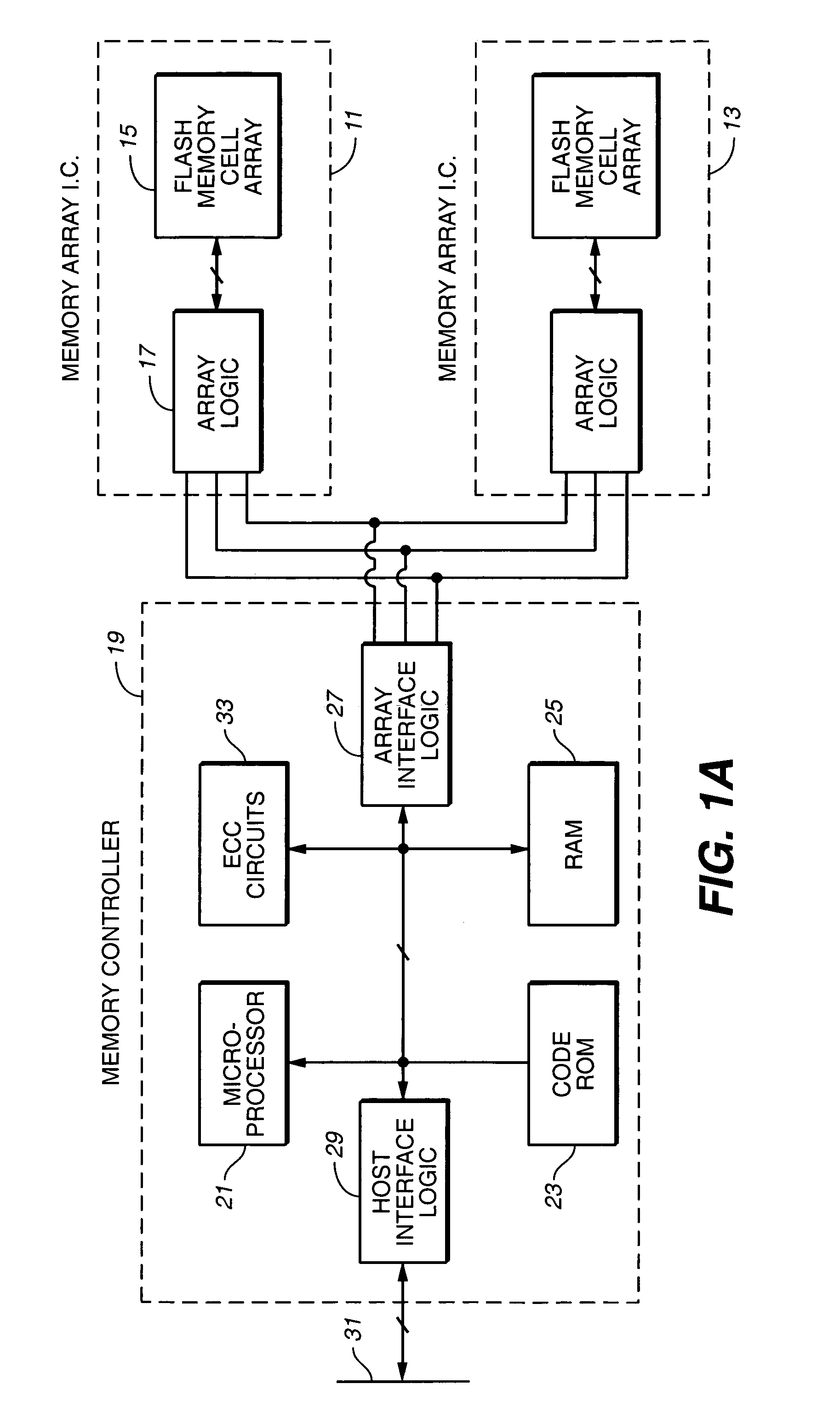
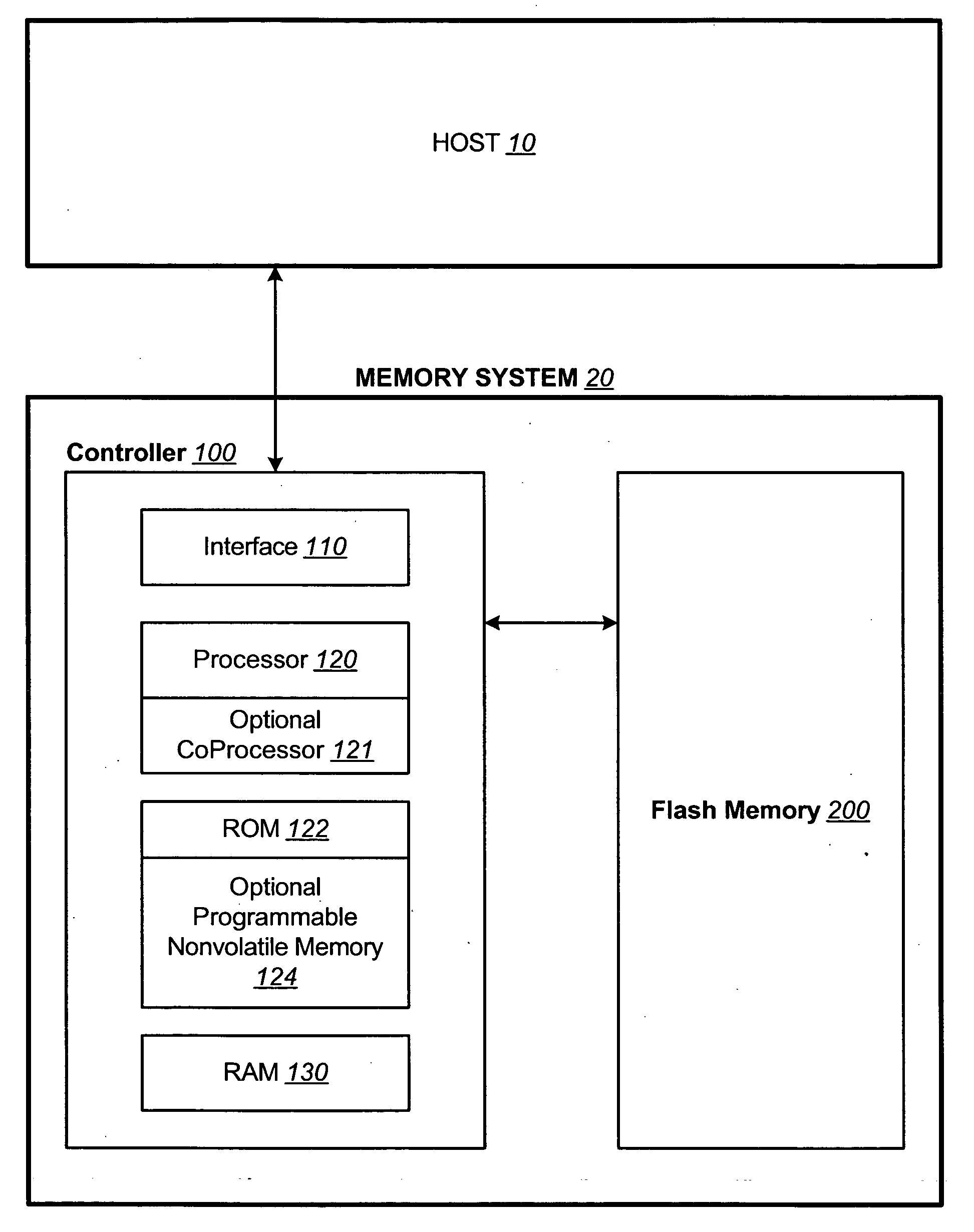
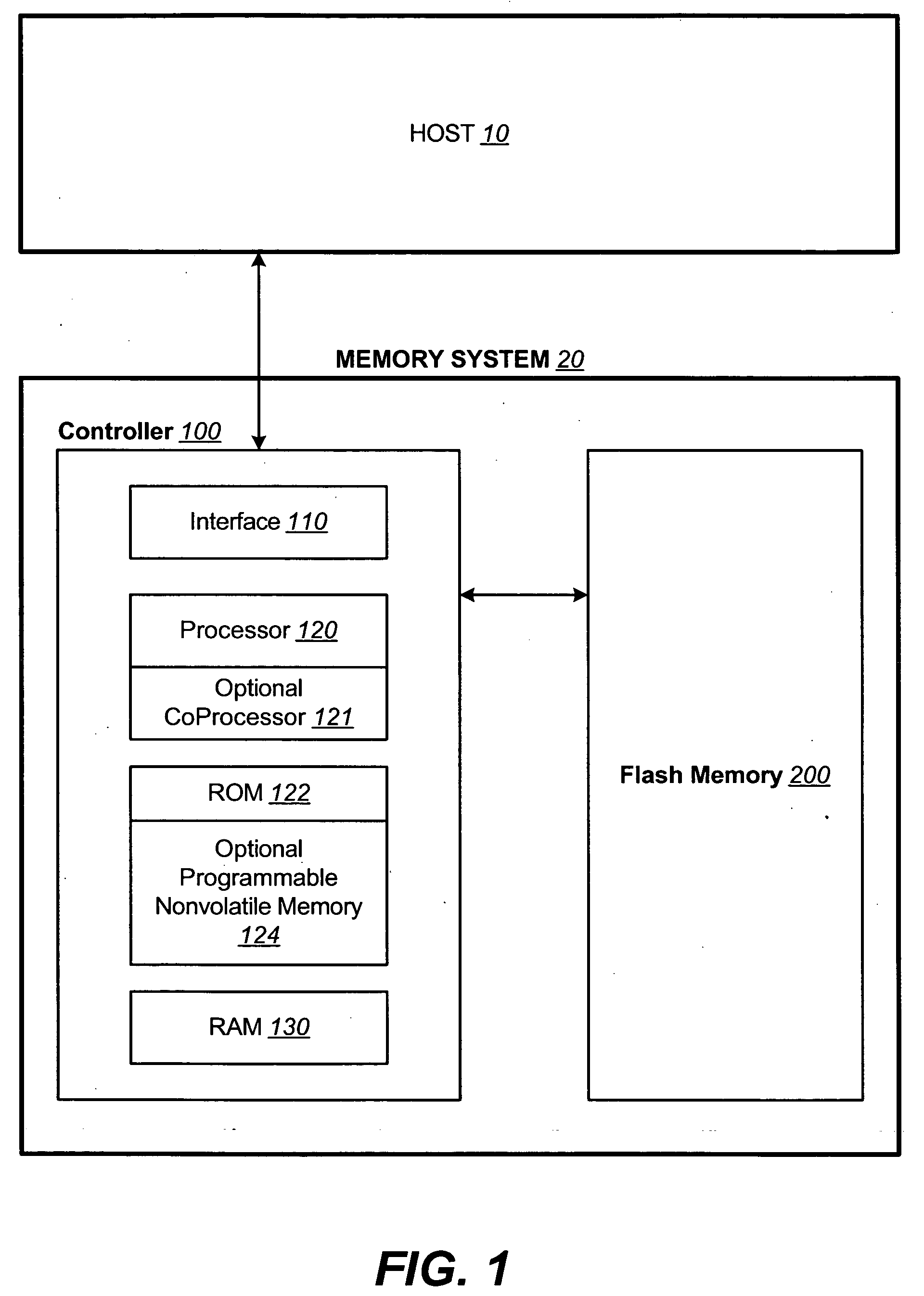
Corrected data storage and handling methods
InactiveUS7173852B2Data disturbanceReduce storage dataRead-only memoriesDigital storageData integrityTime limit
In order to maintain the integrity of data stored in a flash memory that are susceptible to being disturbed by operations in adjacent regions of the memory, disturb events cause the data to be read, corrected and re-written before becoming so corrupted that valid data cannot be recovered. The sometimes conflicting needs to maintain data integrity and system performance are balanced by deferring execution of some of the corrective action when the memory system has other high priority operations to perform. In a memory system utilizing very large units of erase, the corrective process is executed in a manner that is consistent with efficiently rewriting an amount of data much less than the capacity of a unit of erase. Data is rewritten when severe errors are found during read operations. Portions of data are corrected and copied within the time limit for read operation. Corrected portions are written to dedicated blocks.
Owner:SANDISK TECH LLC
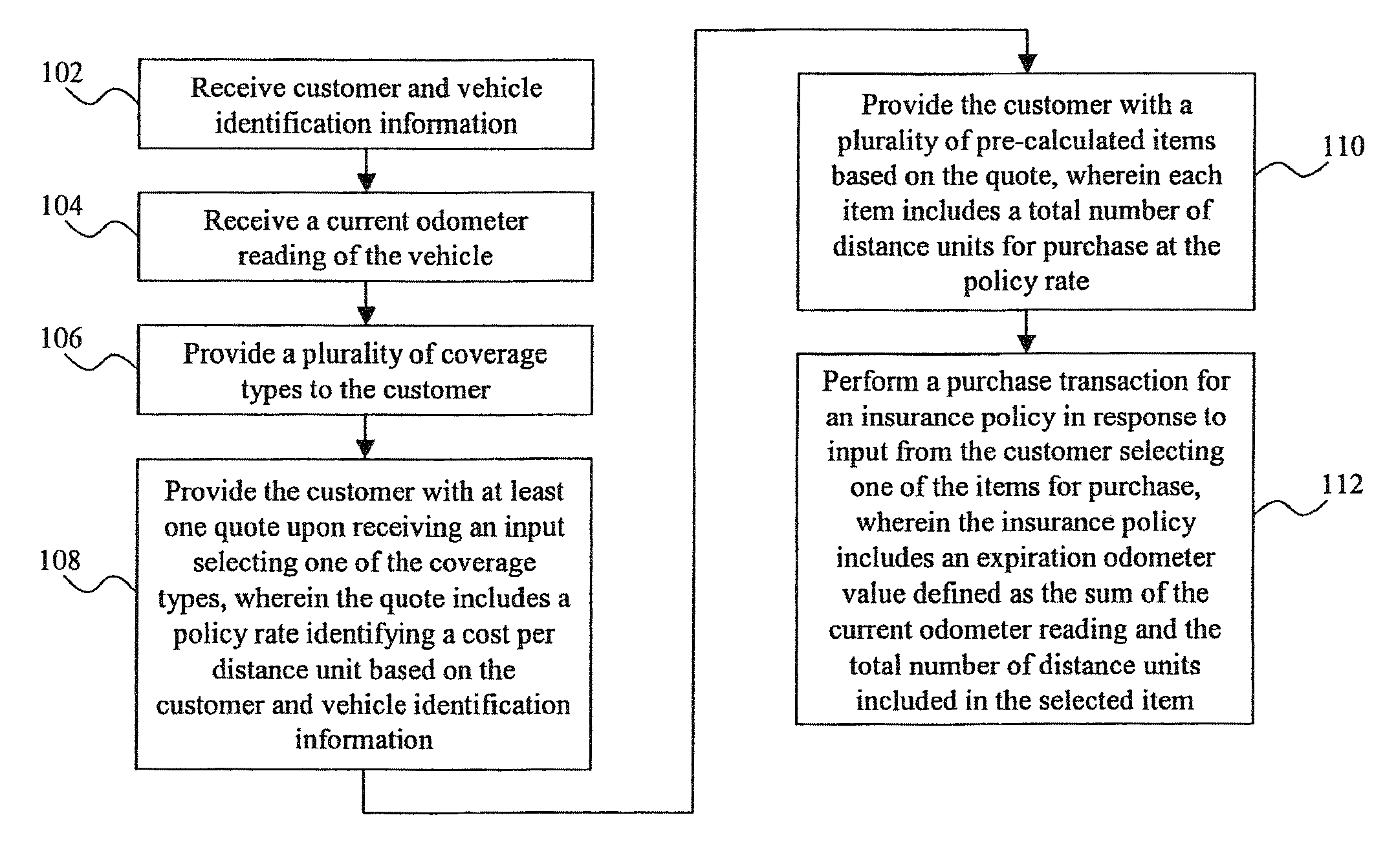
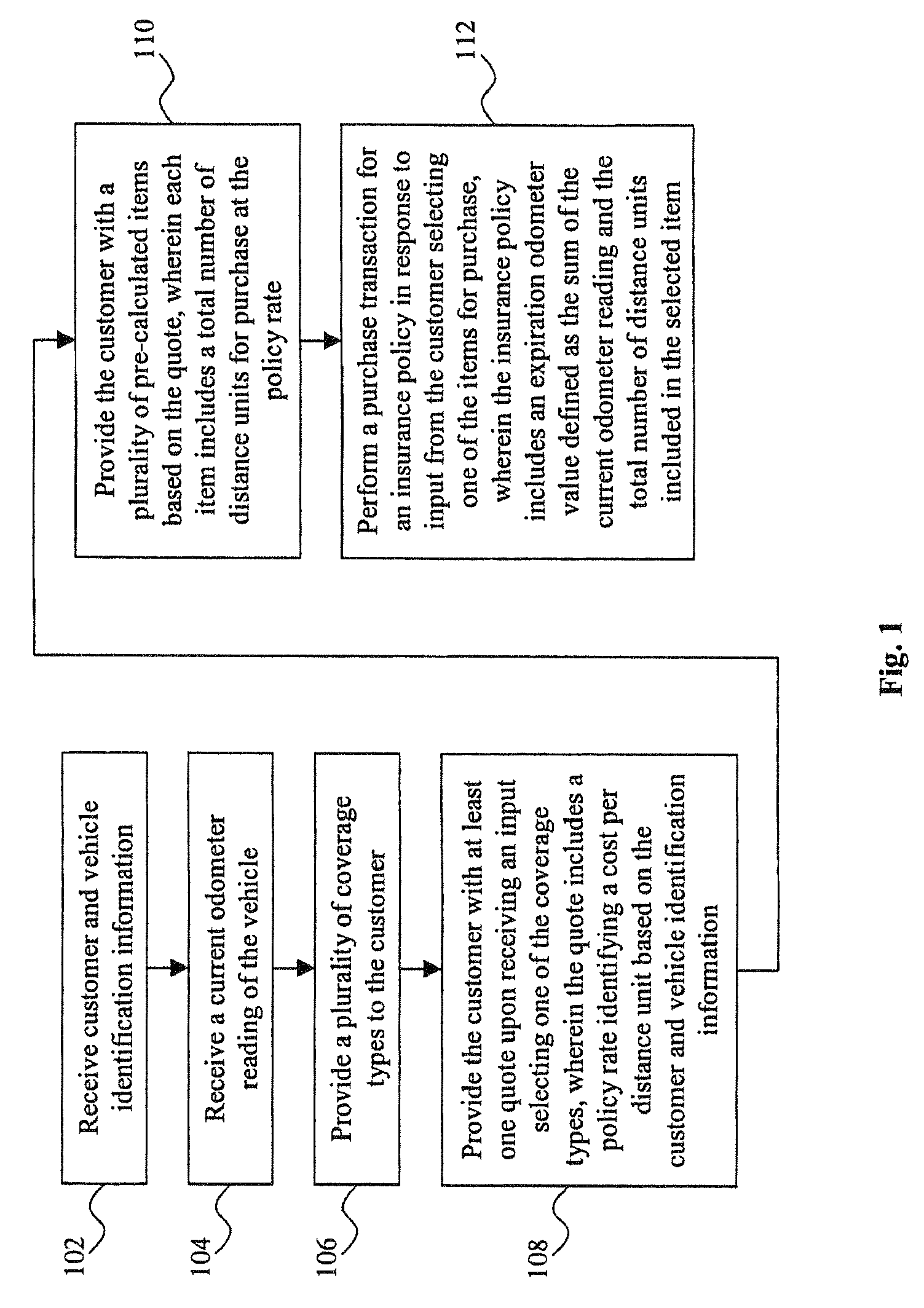
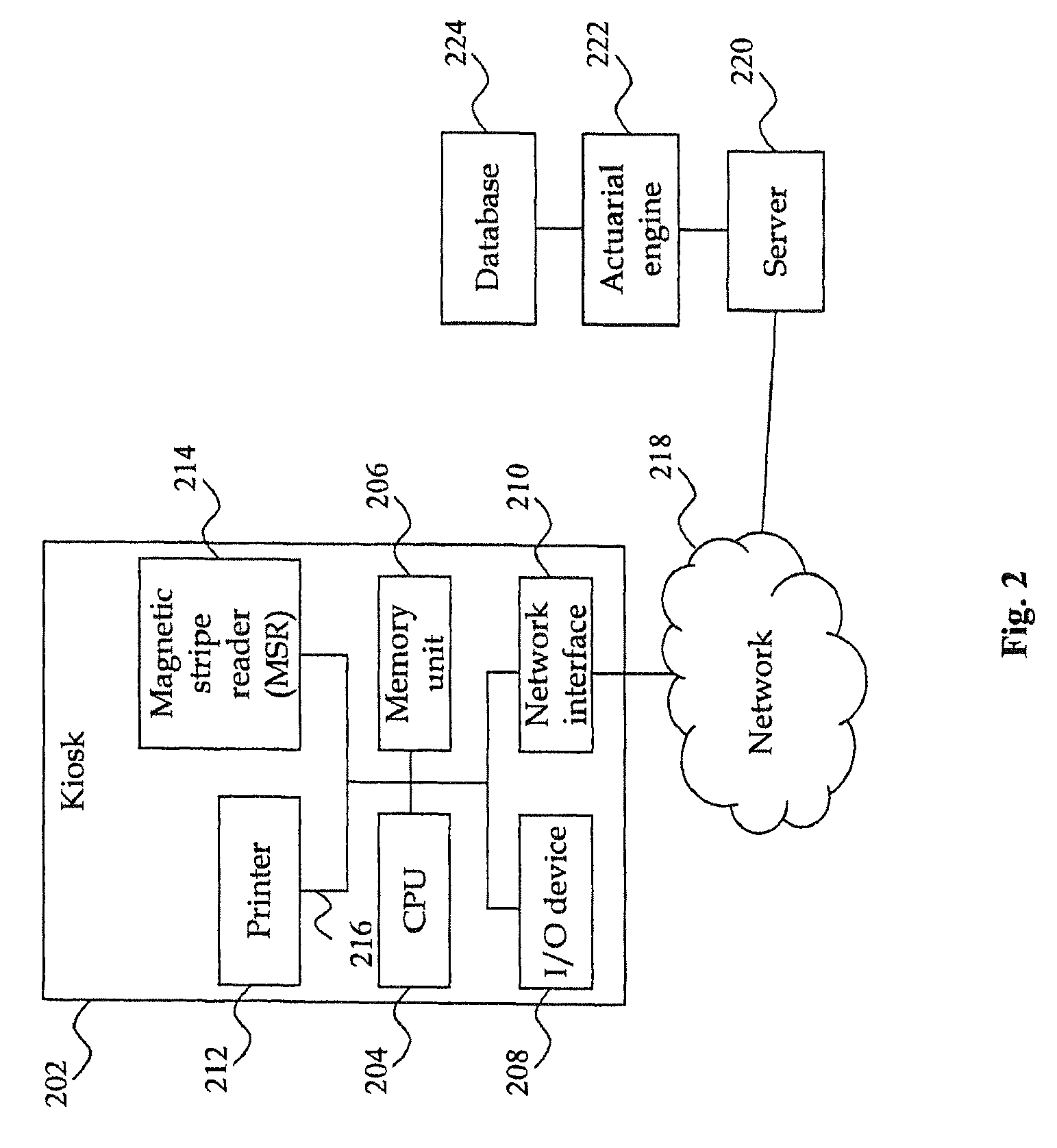
System and method for the assessment, pricing, and provisioning of distance-based vehicle insurance
A method for assessing, pricing, and provisioning distance-based vehicle insurance is disclosed. Receiving identification information of a customer and an associated vehicle, a current odometer reading of the vehicle, and a garaging location of the vehicle is disclosed. The customer is provided with a quote including a policy rate identifying a cost per distance unit based on the customer and vehicle identification information and the garaging location. Performing a purchase transaction for an insurance policy in response to the customer selecting one of the items for purchase, wherein coverage provided by the insurance policy expires based on the earlier of an odometer expiration value occurring and a predetermined time limit is disclosed. The expiration odometer value is the sum of the current odometer reading and the total number of distance units included in the selected item. The current odometer reading is not audited prior to or during the purchase transaction.
Owner:STATE FARM MUTAL AUTOMOBILE INSURANCE COMPANY
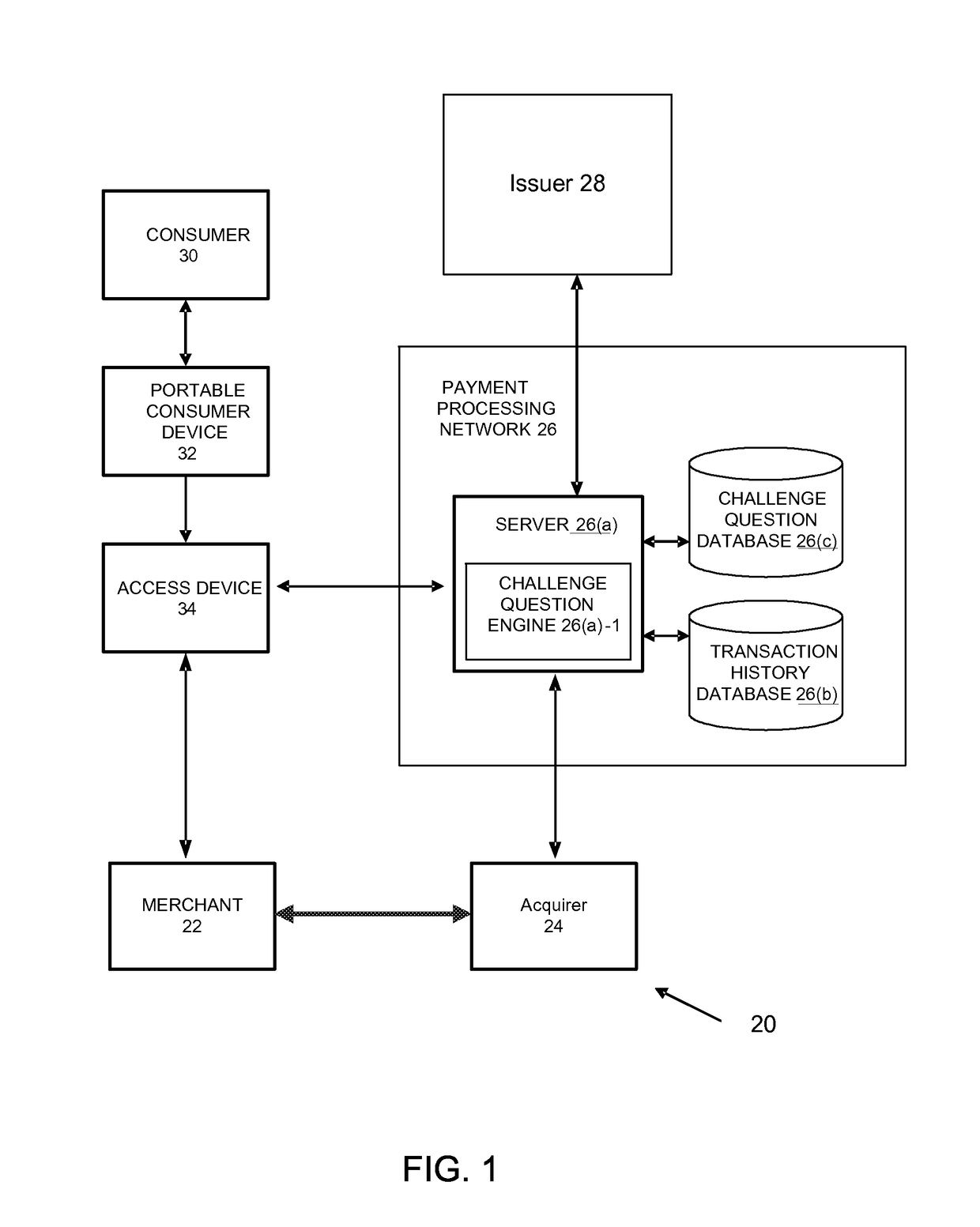
Cardless challenge systems and methods
Owner:VISA USA INC (US)
Method for providing financial and risk management
InactiveUS20020019804A1Reduce riskIncrease revenue generationFinancePayment architectureTime limitComputer science
A method for marketing, assessing, underwriting, insuring and managing loans comprising marketing information and training for financial institutions, criteria for employment, credit history, and loan property type, insurance for loss limited by a predetermined amount, and tracking and servicing of a loan including collection and liquidation in the event of default. The invention further comprises status reporting, and liquidation of loans prior to expiration of the term of a loan.
Owner:WK CAPITAL ADVISORS
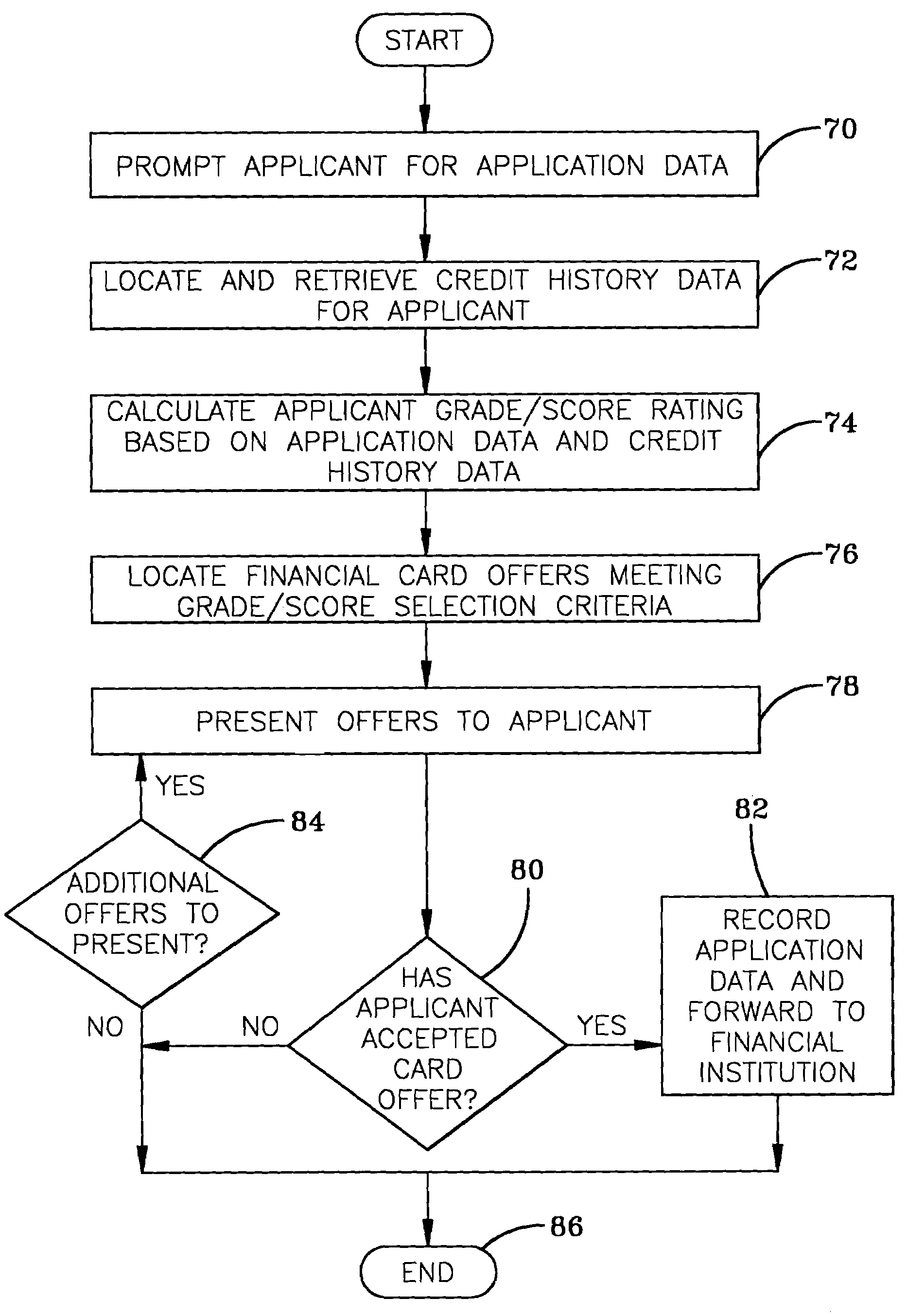
Real-time financial card offer and application system
A system is disclosed for presenting financial card (e.g., credit card, debit card) offers to potential customers. Financial card applicant selection criteria and financial card term data are provided by participating financial institutions. An applicant interested in applying for a new financial card accesses the system via the Internet / World Wide Web. The applicant provides personal and financial data that are then analyzed in conjunction with data from outside sources (such as credit bureaus) to determine a financial risk rating for the applicant. The rating is used to locate financial card offers appropriate for the applicant. The applicant then peruses the offers and chooses one that meets his or her personal selection criteria. The applicant's data is then forwarded for processing to the participating financial institution that made the selected offer.
Owner:BLOCK FINANCIAL
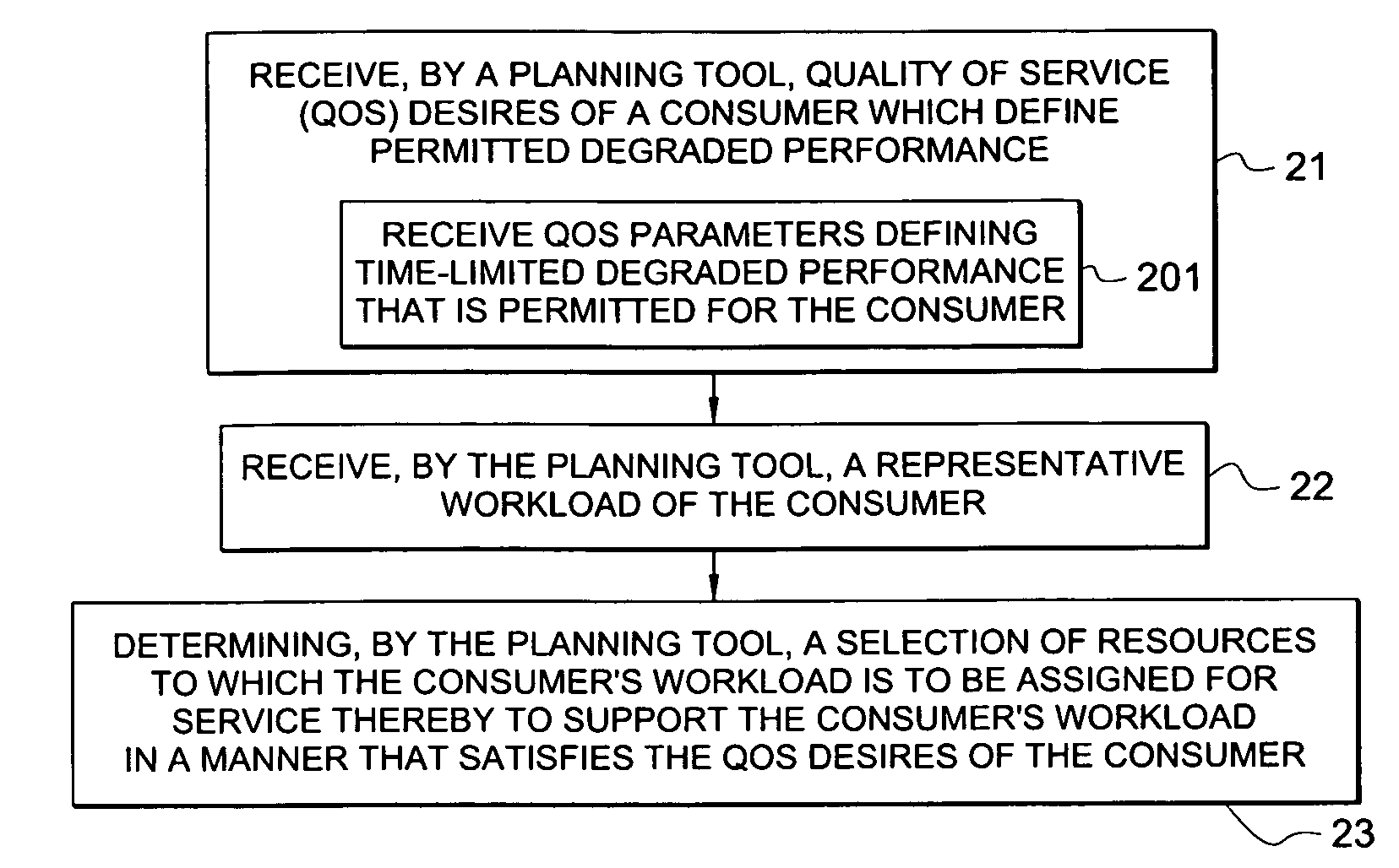
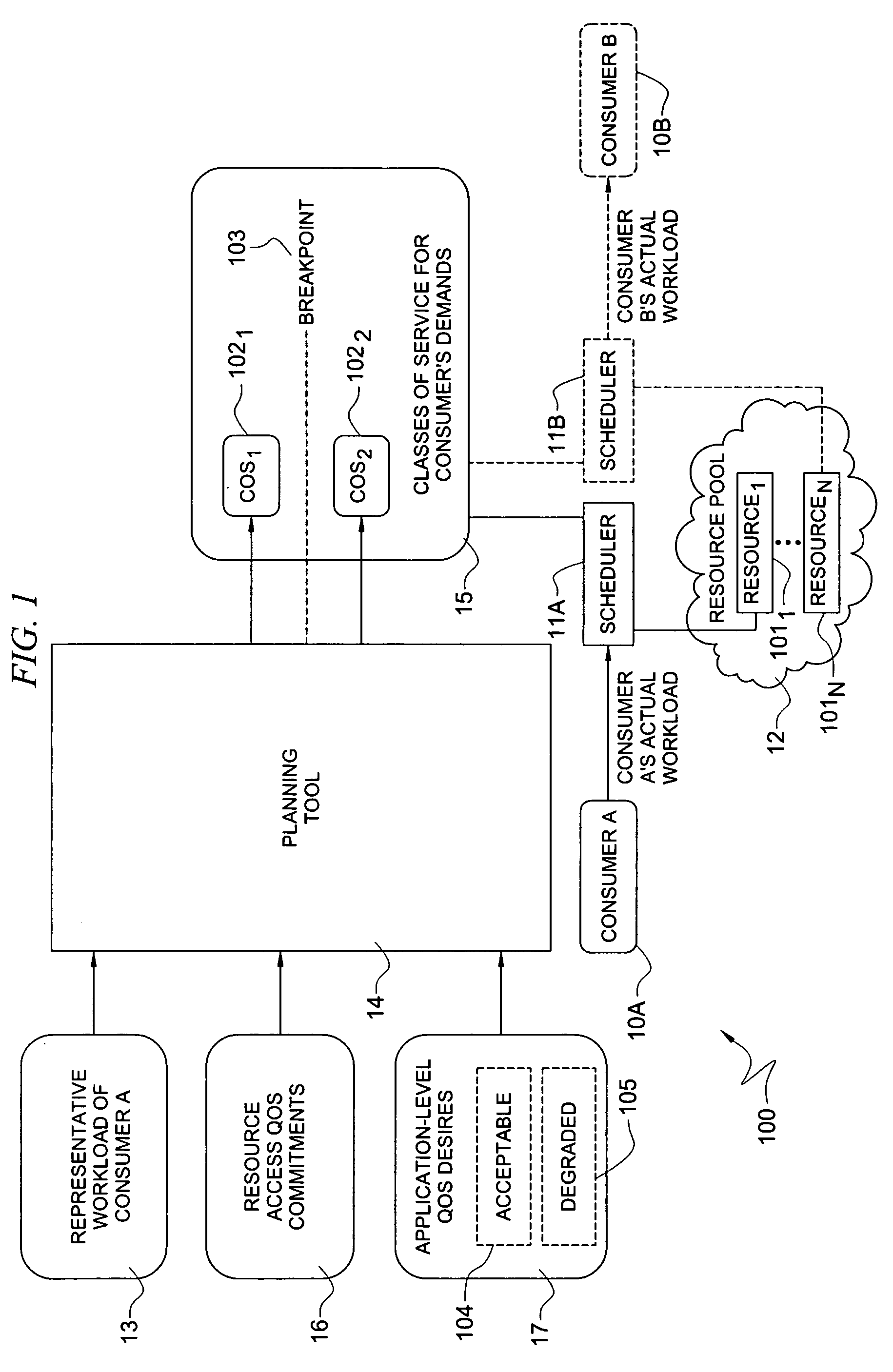
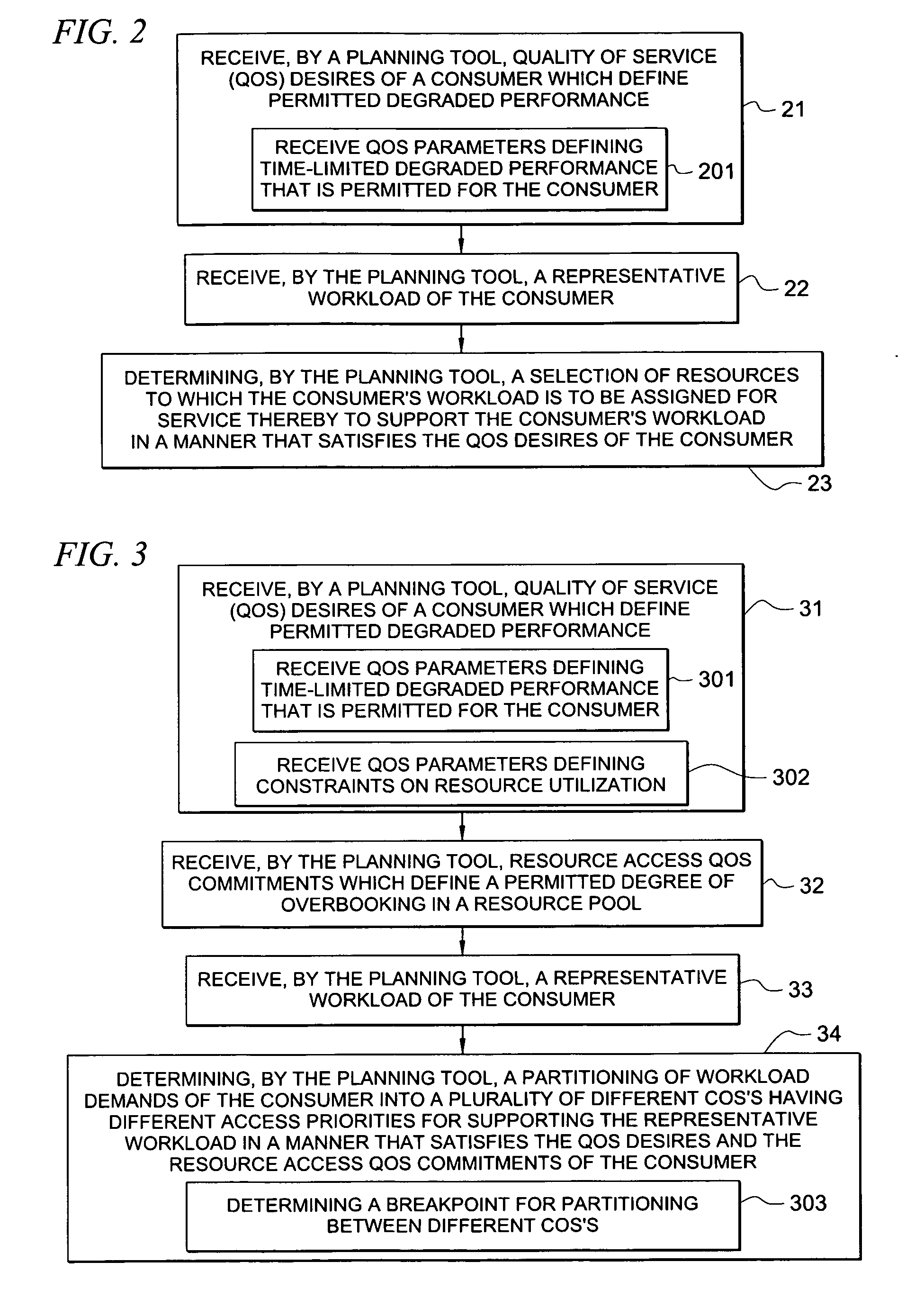
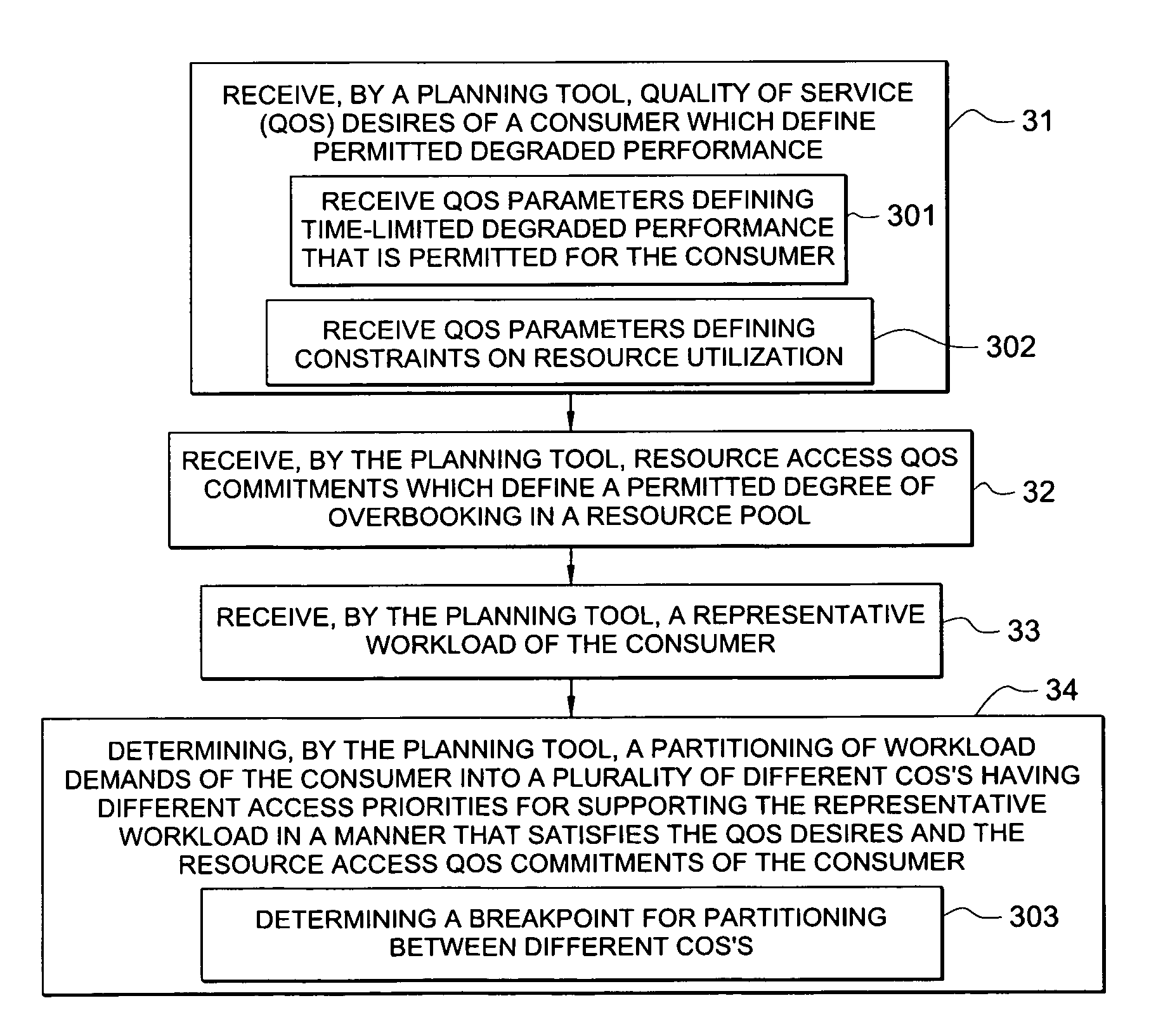
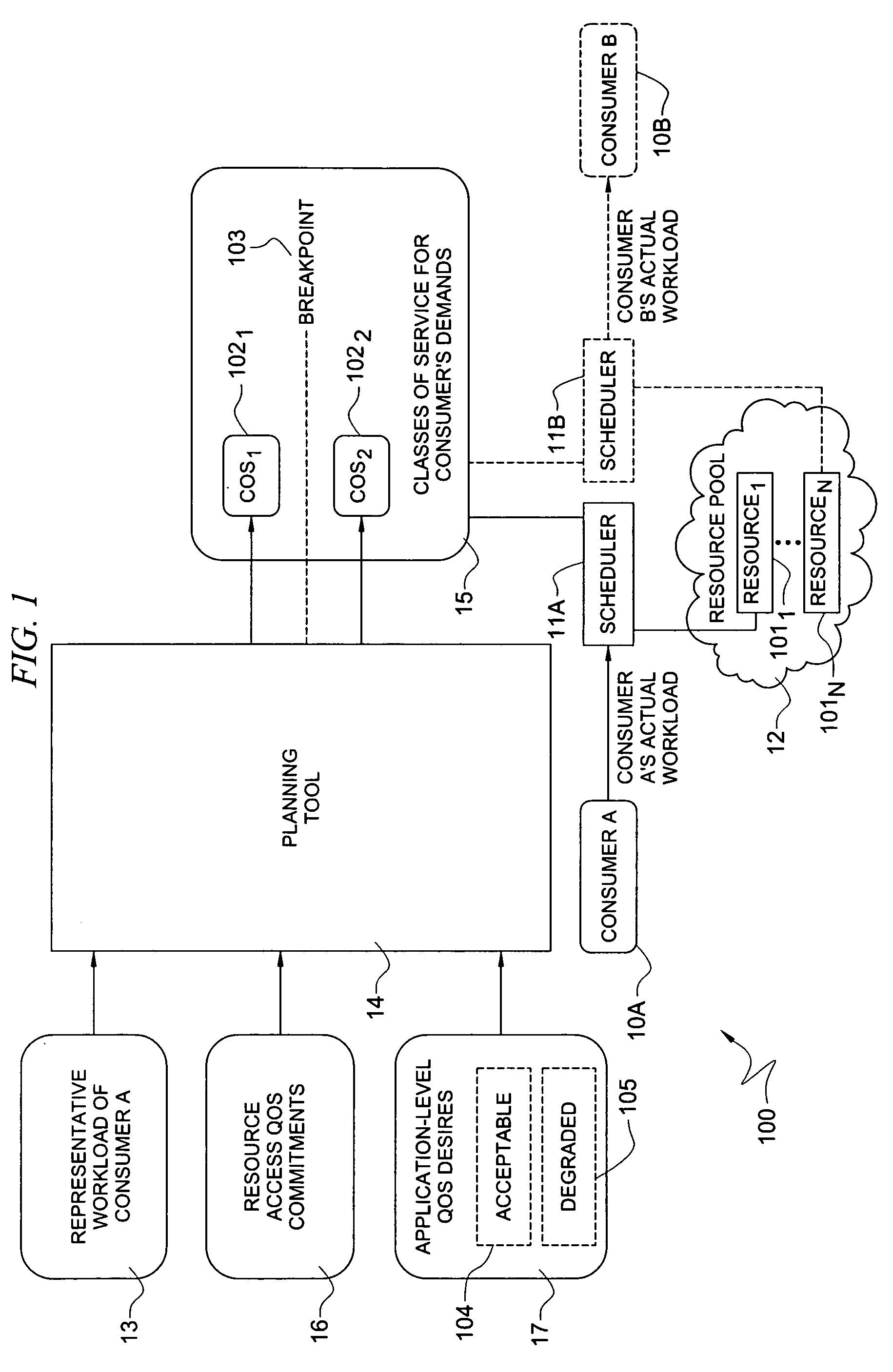
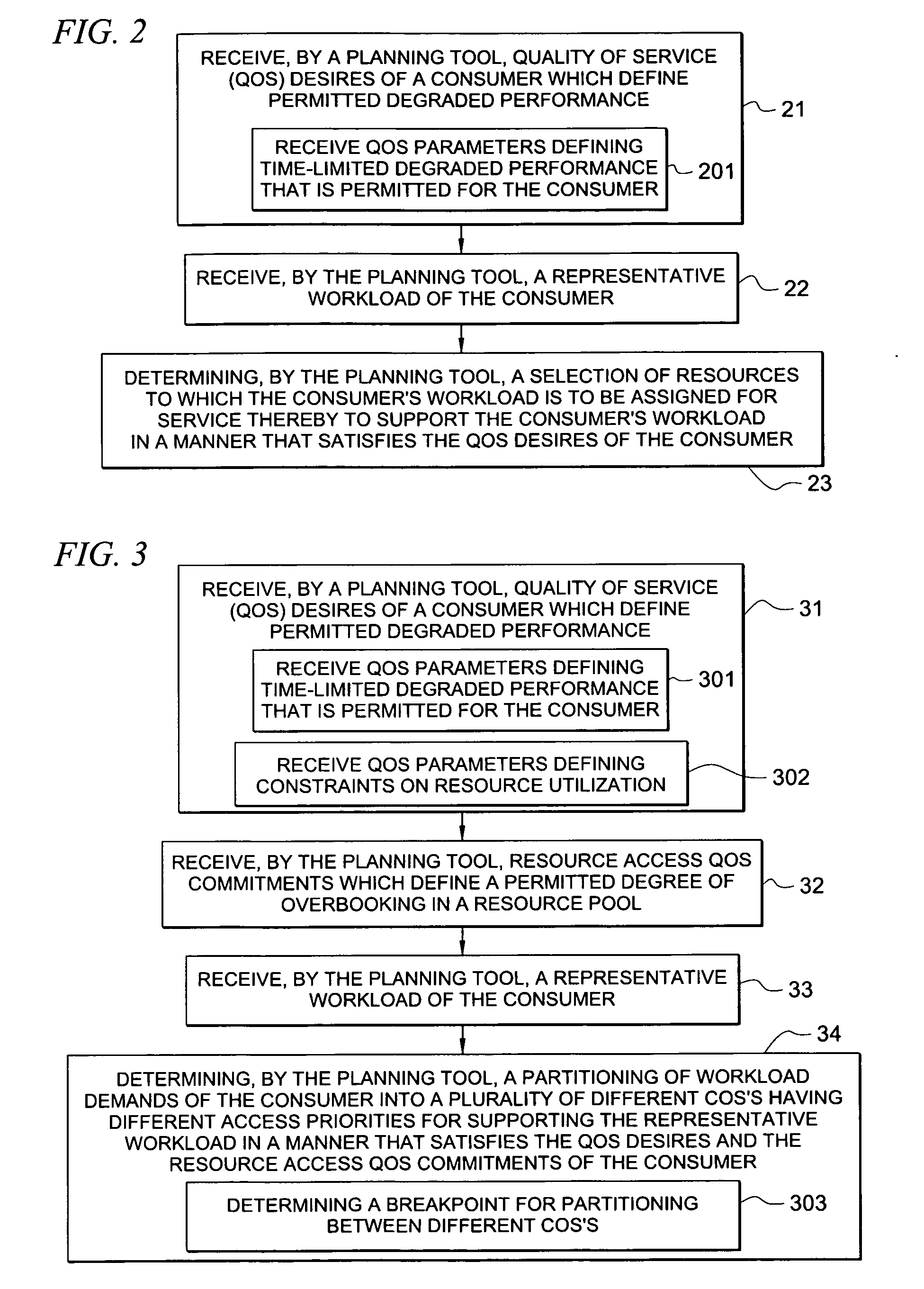
System and method for determining allocation of resource access demands to different classes of service based at least in part on permitted degraded performance
A method comprises receiving into a planning tool a representative workload for a consumer. The method further comprises receiving into the planning tool quality of service desires of the consumer which define permitted degraded performance. In certain embodiments, the permitted degraded performance is time-limited wherein demands of the representative workload may exceed a pre-defined utilization constraint for at least one resource servicing the demands for no more than a pre-defined amount of contiguous time. The planning tool determines an allocation of demand of the consumer for each of a plurality of different classes of service (COSs). In certain embodiments, a first COS provides guaranteed resource access for servicing demand allocated thereto, and a second COS provides non-guaranteed resource access for servicing demand allocated thereto. In certain embodiments, the allocation of demand to the different COSs may be determined for both a normal mode and a failure mode of operation.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
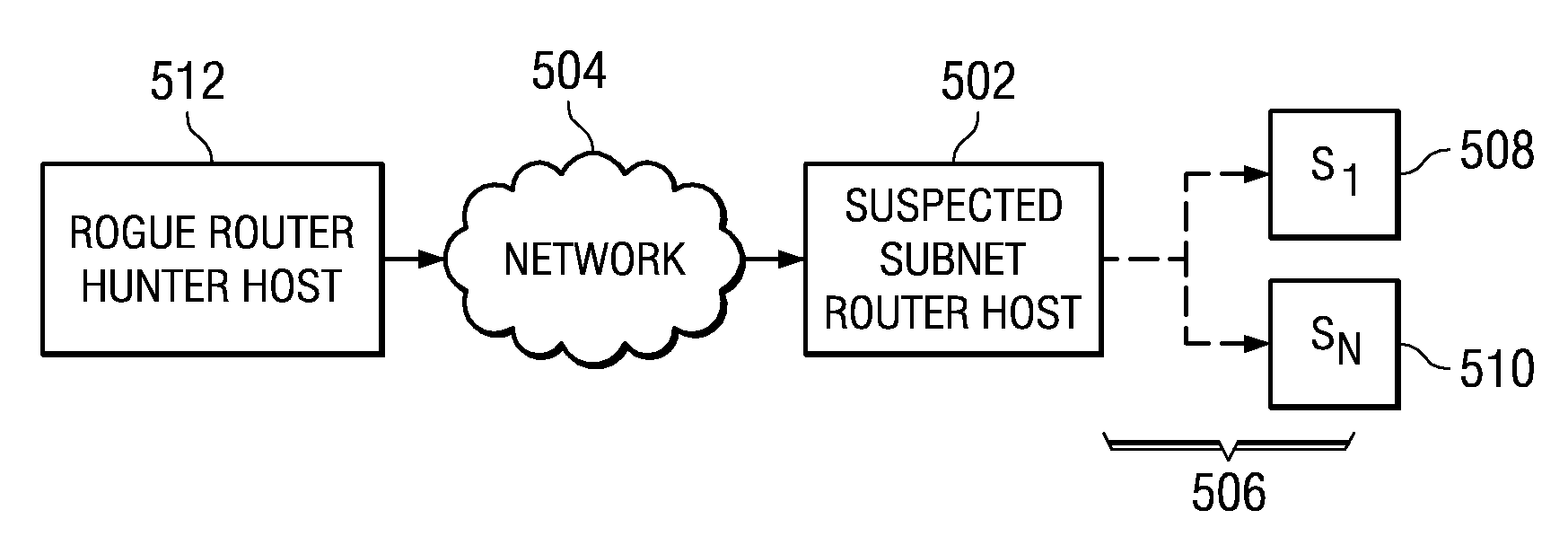
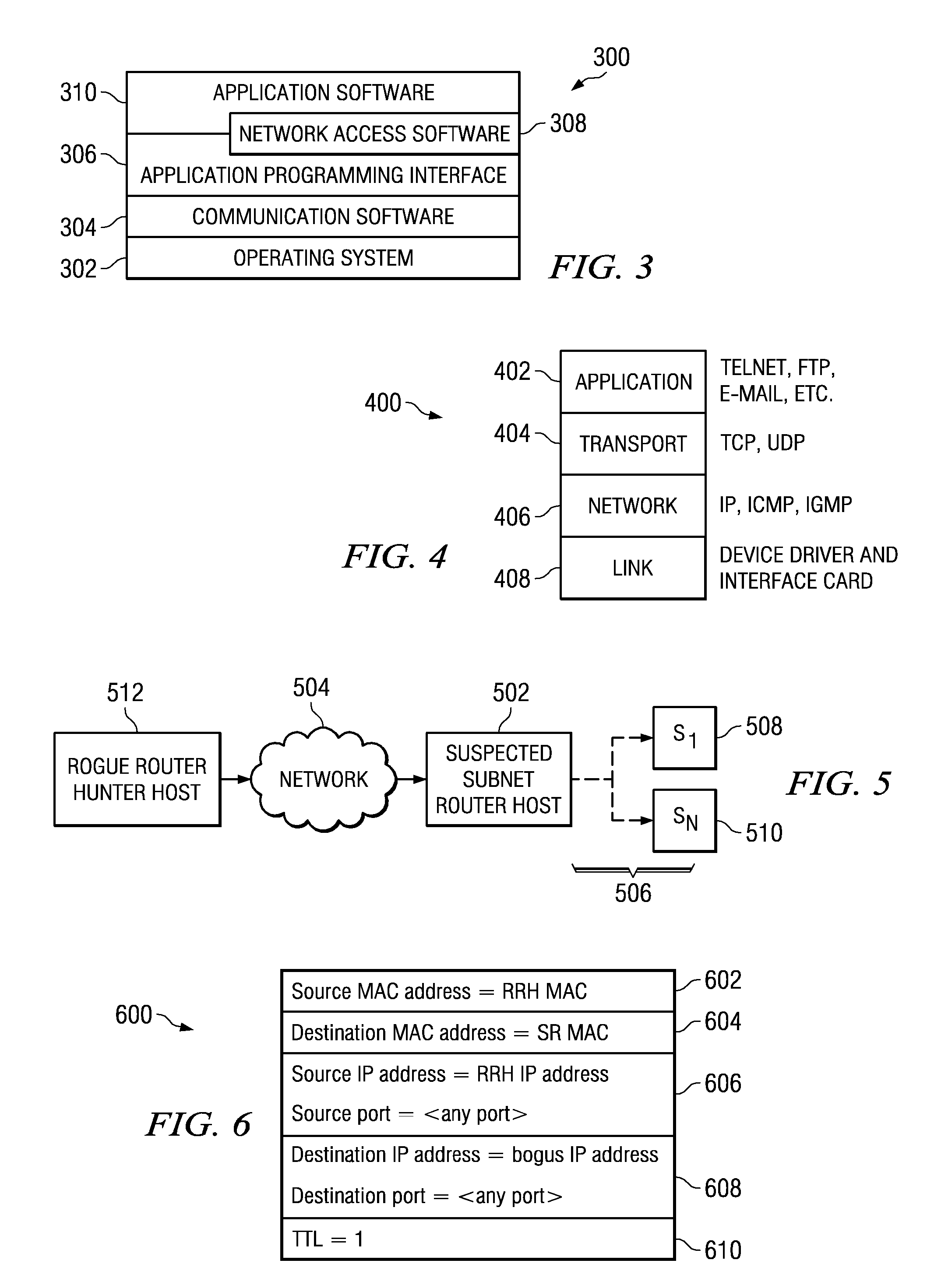
Rogue router hunter
InactiveUS7991877B2Digital computer detailsPlatform integrity maintainanceData processing systemTime limit
A computer implemented method, data processing system, and computer program product for discovering an unauthorized router in a network. The process in the illustrative embodiments first obtains a physical address of a suspected router or destination device. A data packet is created which comprises at least a destination media access control field, a destination internet protocol field, and a time-to-live field, wherein the destination media access control field comprises the physical address of the destination device, wherein the destination internet protocol field comprises a bogus internet protocol address, and wherein the time-to-live field comprises a value indicating the data packet has exceeded a time limit. The data packet is sent to the destination device using the physical address in the destination media access control field. If a time exceeded message is received from the destination device, the destination device is determined to be enabled for routing.
Owner:INT BUSINESS MASCH CORP
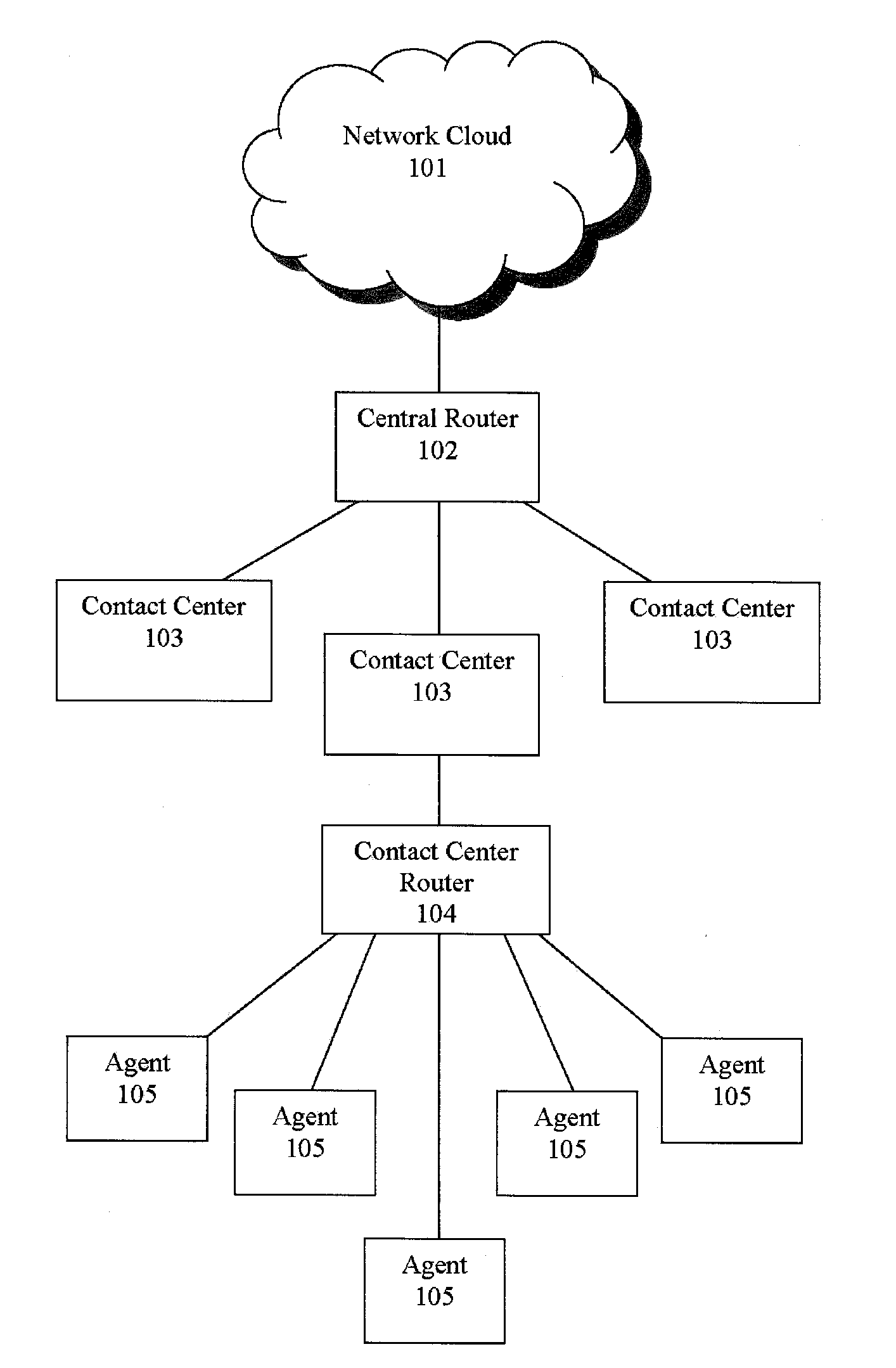
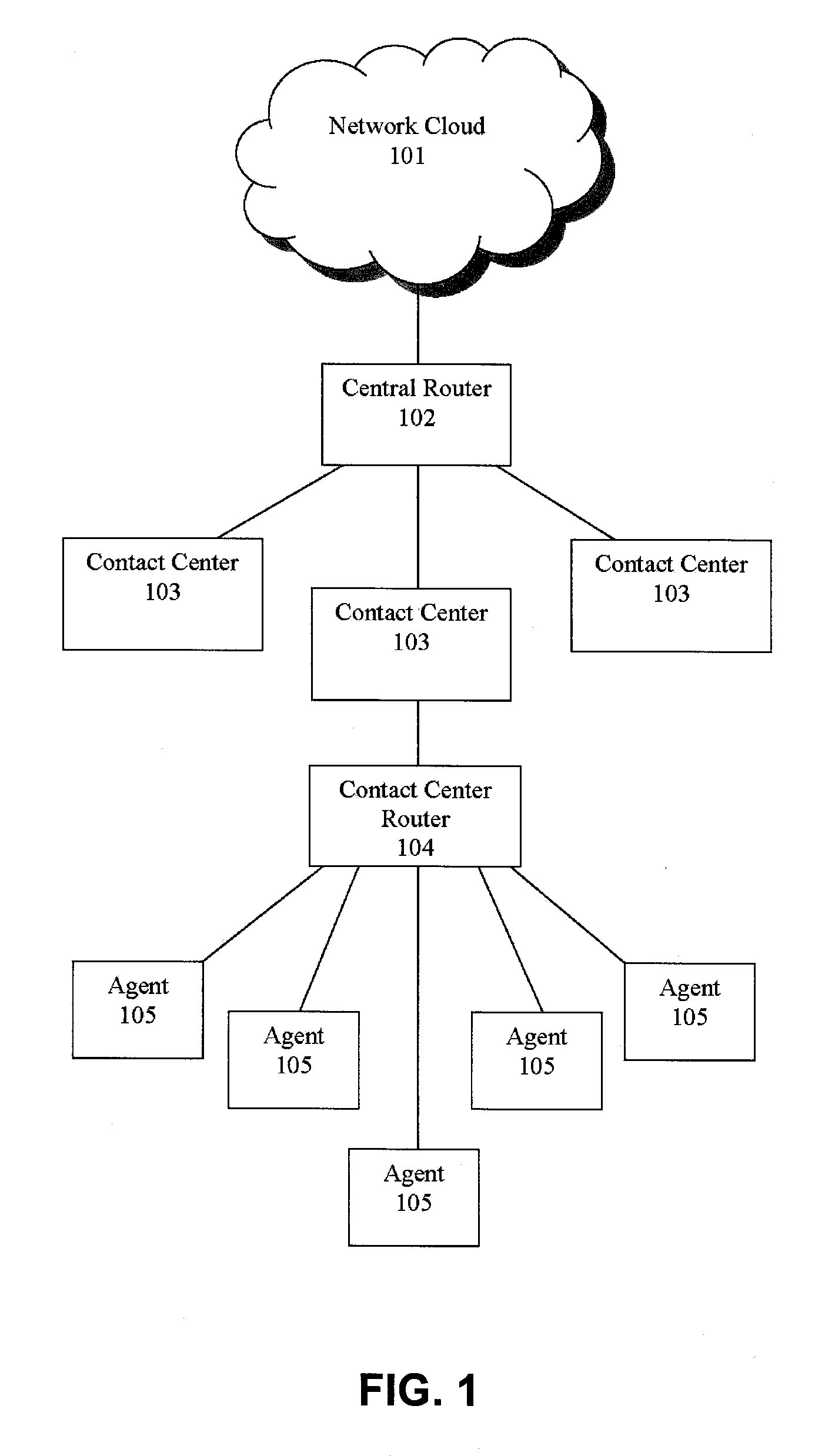
Time to answer selector and advisor for call routing center
Systems and methods are disclosed for routing callers to agents in a contact center, along with an intelligent routing system. An exemplary interface for use with a contact center includes a graphical user element for adjusting a time limit for a caller to be held before routed to an agent according to a pattern matching algorithm where the caller is compared to a set of agents via the pattern matching algorithm and routed to the best matching agent of the set of agents if available prior to the time limit and routed to the best matching agent of available agents if the time limit is exceeded. The interface may further display an estimated effect of the time limit on at least one outcome variable, which may include revenue generation, cost, customer satisfaction, first call resolution, cancellation, or other variable outputs from the pattern matching algorithm(s) of the system.
Owner:AFINITI LTD
Non-volatile memory and method with phased program failure handling
InactiveUS20050166087A1Improve efficiencyReduce overheadMemory architecture accessing/allocationMemory adressing/allocation/relocationError processingTime critical
In a memory with block management system, program failure in a block during a time-critical memory operation is handled by continuing the programming operation in a breakout block. Later, at a less critical time, the data recorded in the failed block prior to the interruption is transferred to another block, which could also be the breakout block. The failed block can then be discarded. In this way, when a defective block is encountered during programming, it can be handled without loss of data and without exceeding a specified time limit by having to transfer the stored data in the defective block on the spot. This error handling is especially critical for a garbage collection operation so that the entire operation need not be repeated on a fresh block during a critical time. Subsequently, at an opportune time, the data from the defective block can be salvaged by relocation to another block.
Owner:SANDISK TECH LLC
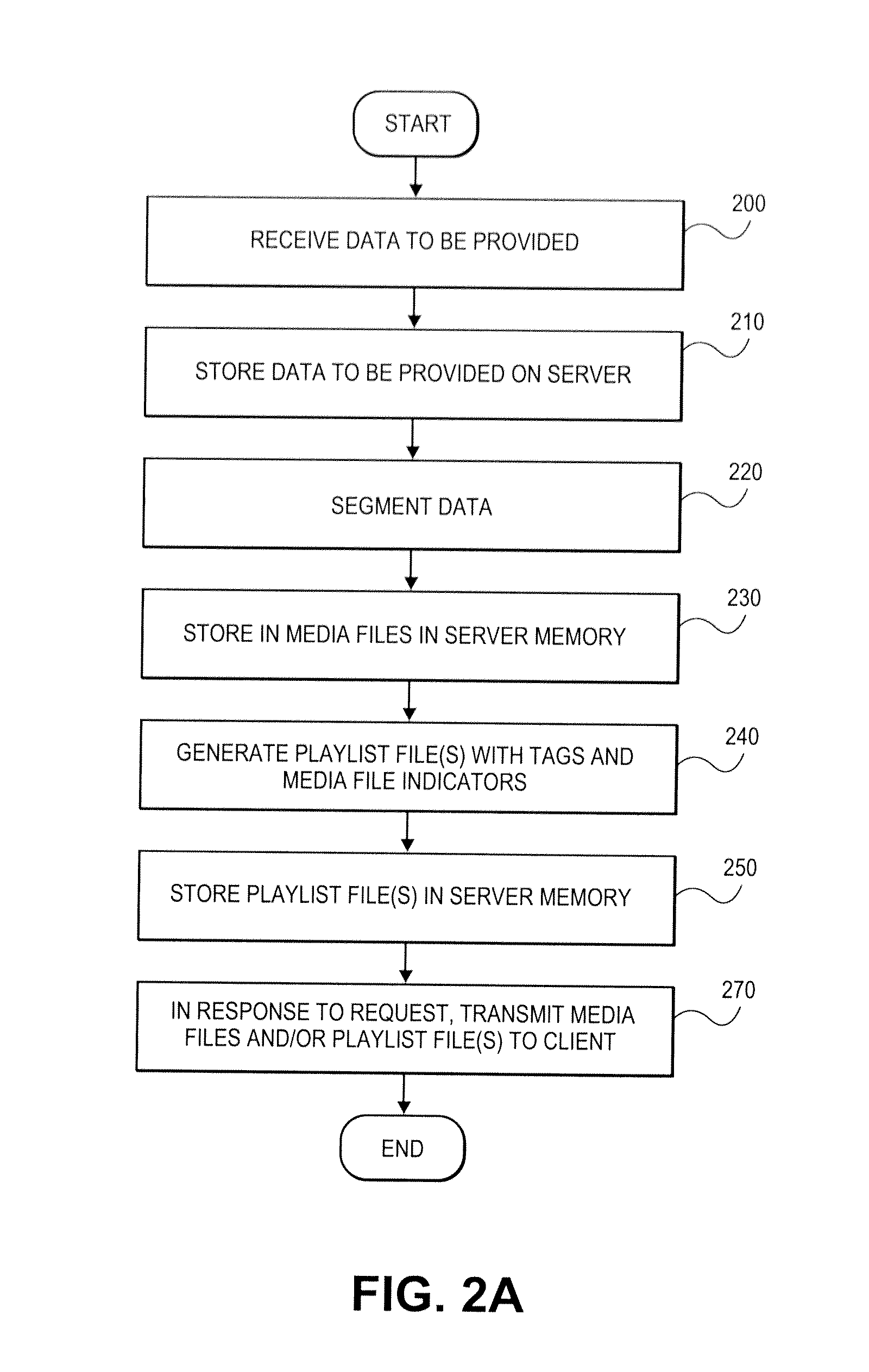
Playlists for real-time or near real-time streaming
ActiveUS20120311094A1Television system detailsMultiple digital computer combinationsTime limitClient-side
Methods, systems and machine readable storage medium for allowing playback of streaming media at playback rates of other than 1× are described. In one embodiment, a method can determine different sets of I-frames that are available before a display deadline, where each set can have a different cadence, and one of the sets can be selected for download and display to achieve playback at other than 1×. Byte range requests from a client device can be used to retrieve each of the I-frames. Other methods, system and media are also described.
Owner:APPLE INC
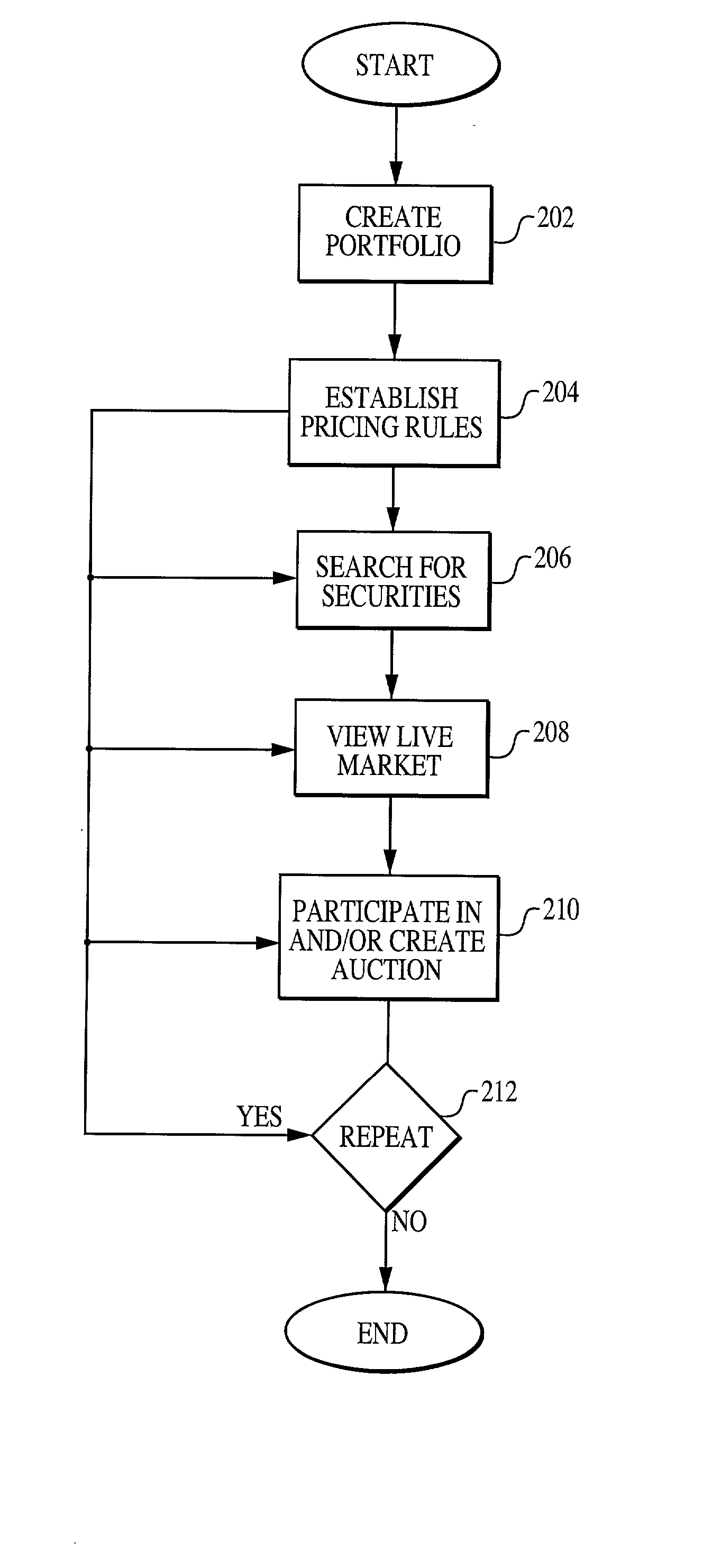
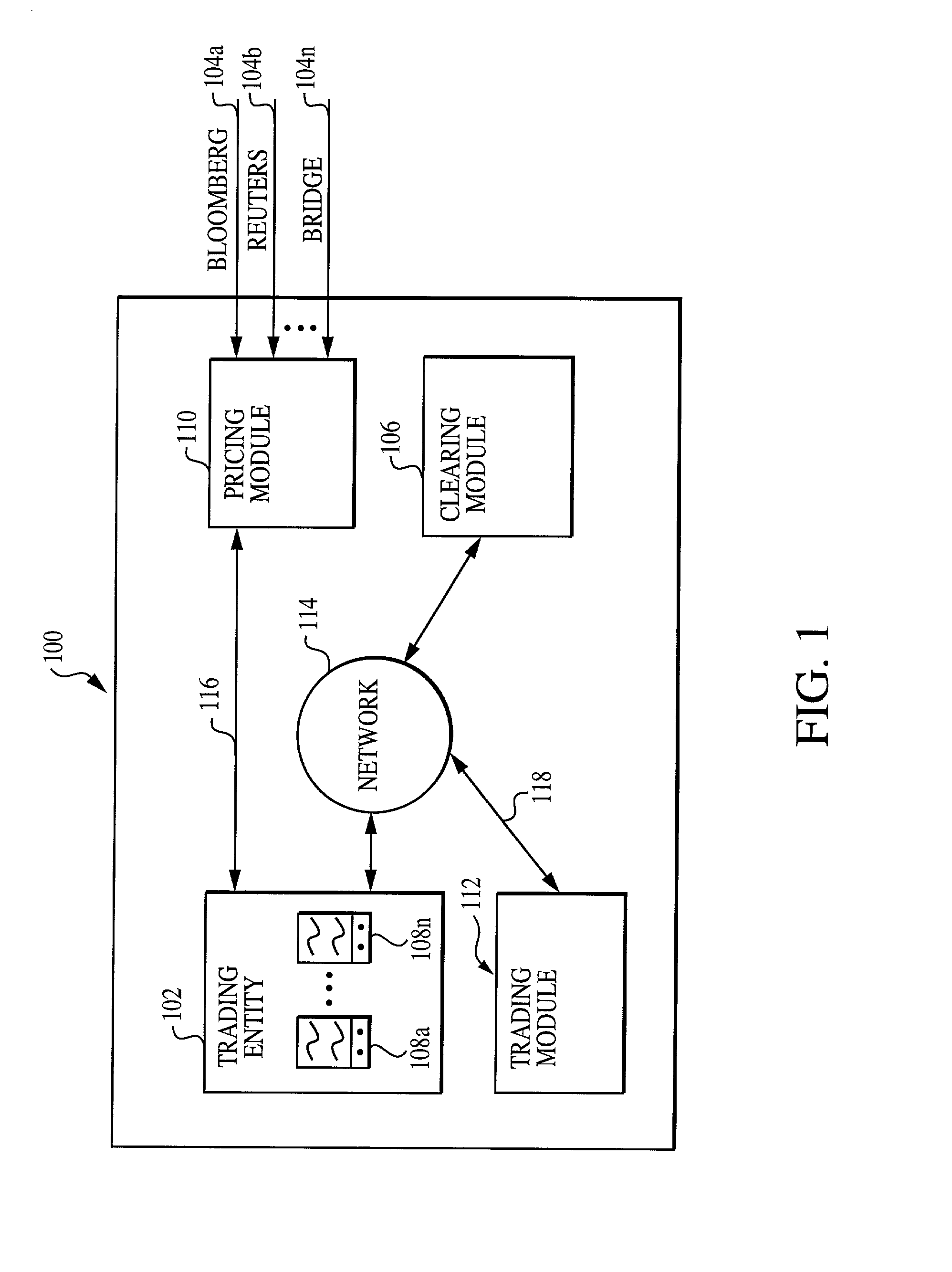
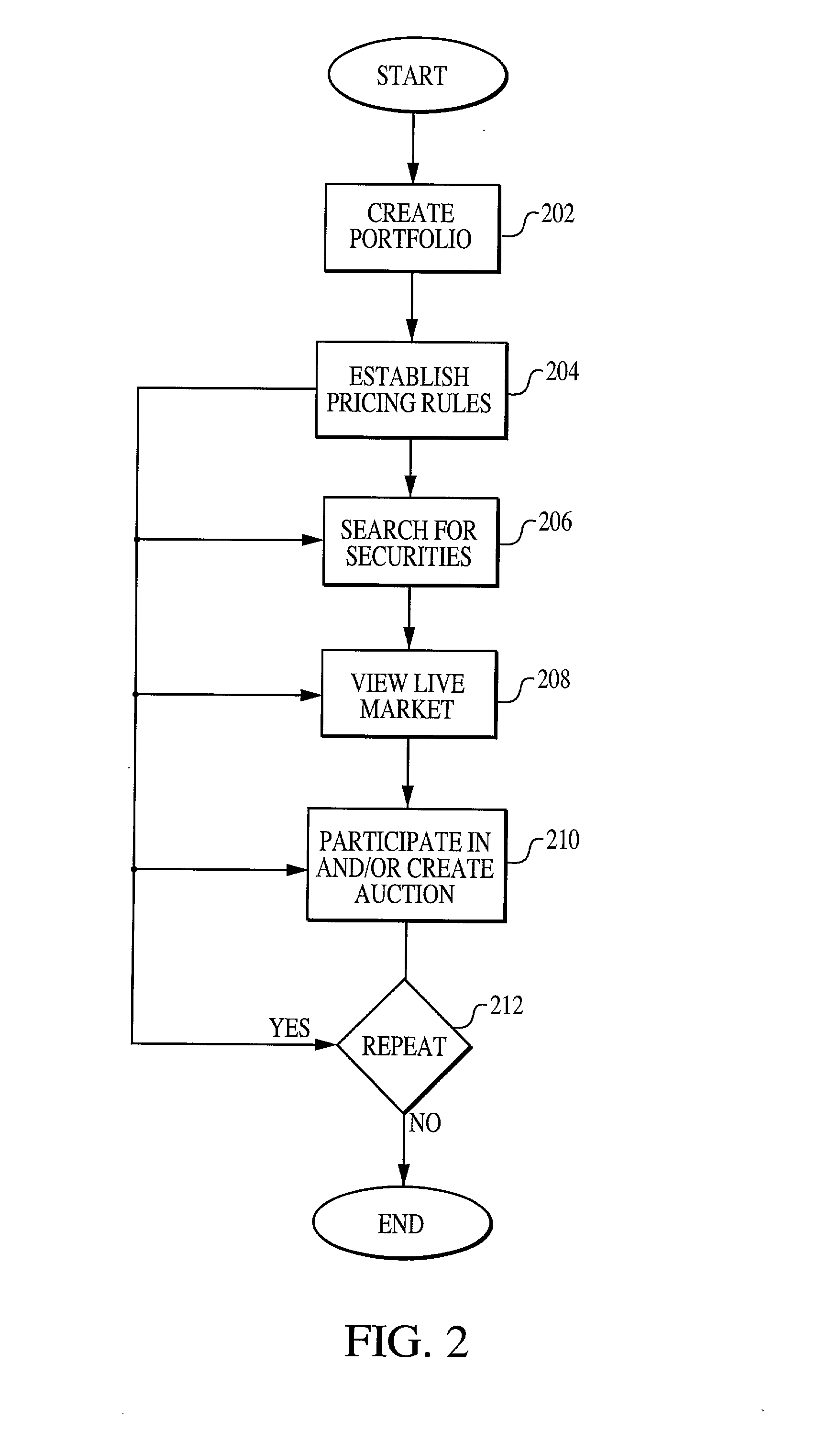
System, medium and method for trading fixed income securities
A system, method and medium for performing electronic fixed income trading that allows users to specify and / or control price and / or time limits associated with potential trades while preserving buyer and seller anonymity. According to at least some of the embodiments of the present invention, a pricing module receives financial information from at least one financial data provider, and transmits the data to one or more trading entities. Purchase and / or sell offers are transmitted to a trading module, and can be defined according to any of a plurality of pricing methods. Depending on the user specified parameters that comprise the offer, the system can automatically place the user into the market, or automatically take the user out of the market. Once a trade is executed, a clearing module monitors and records the transactions executed in clearing the trade.
Owner:TRUMARKETS
Parking regulation enforcement system
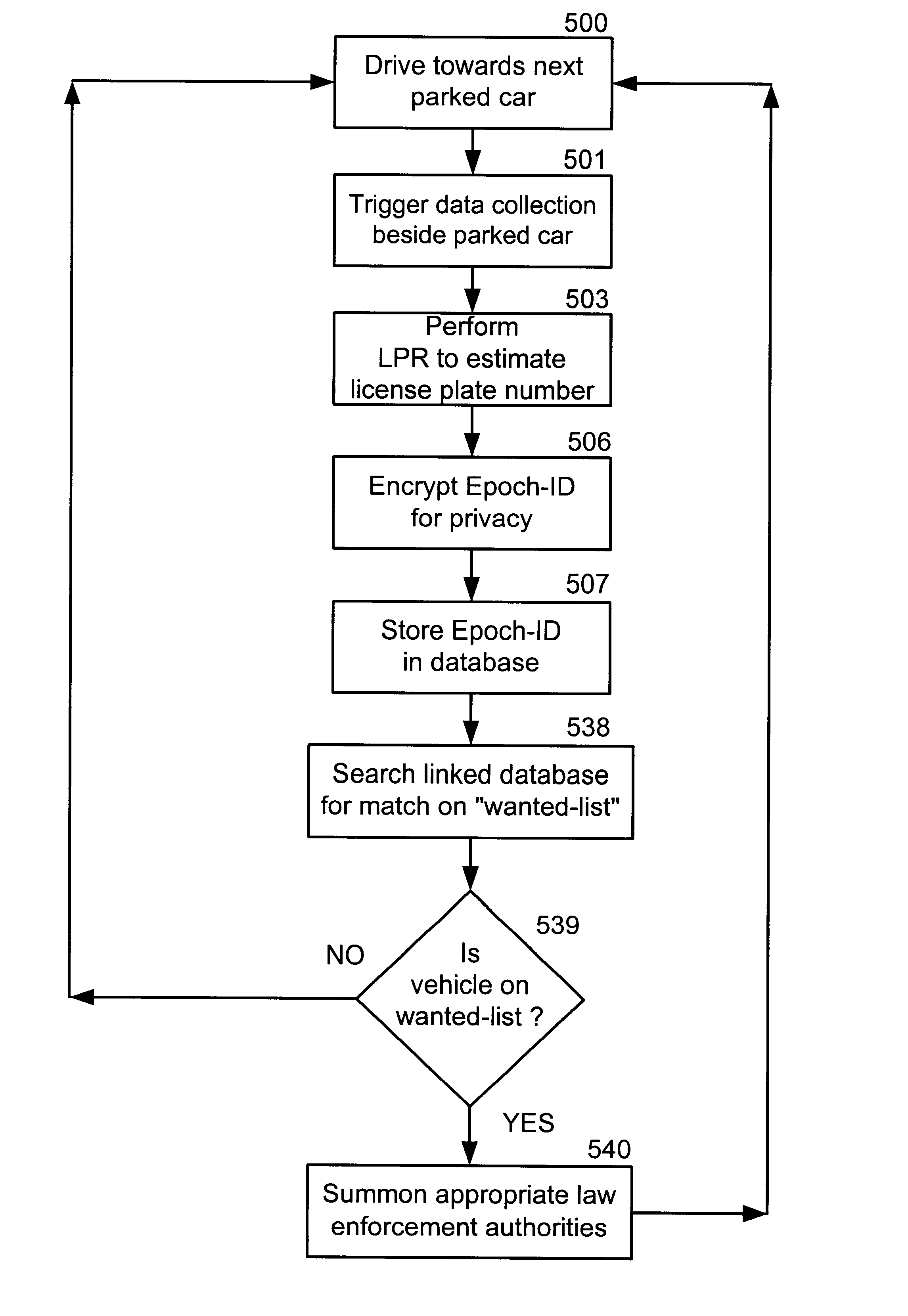
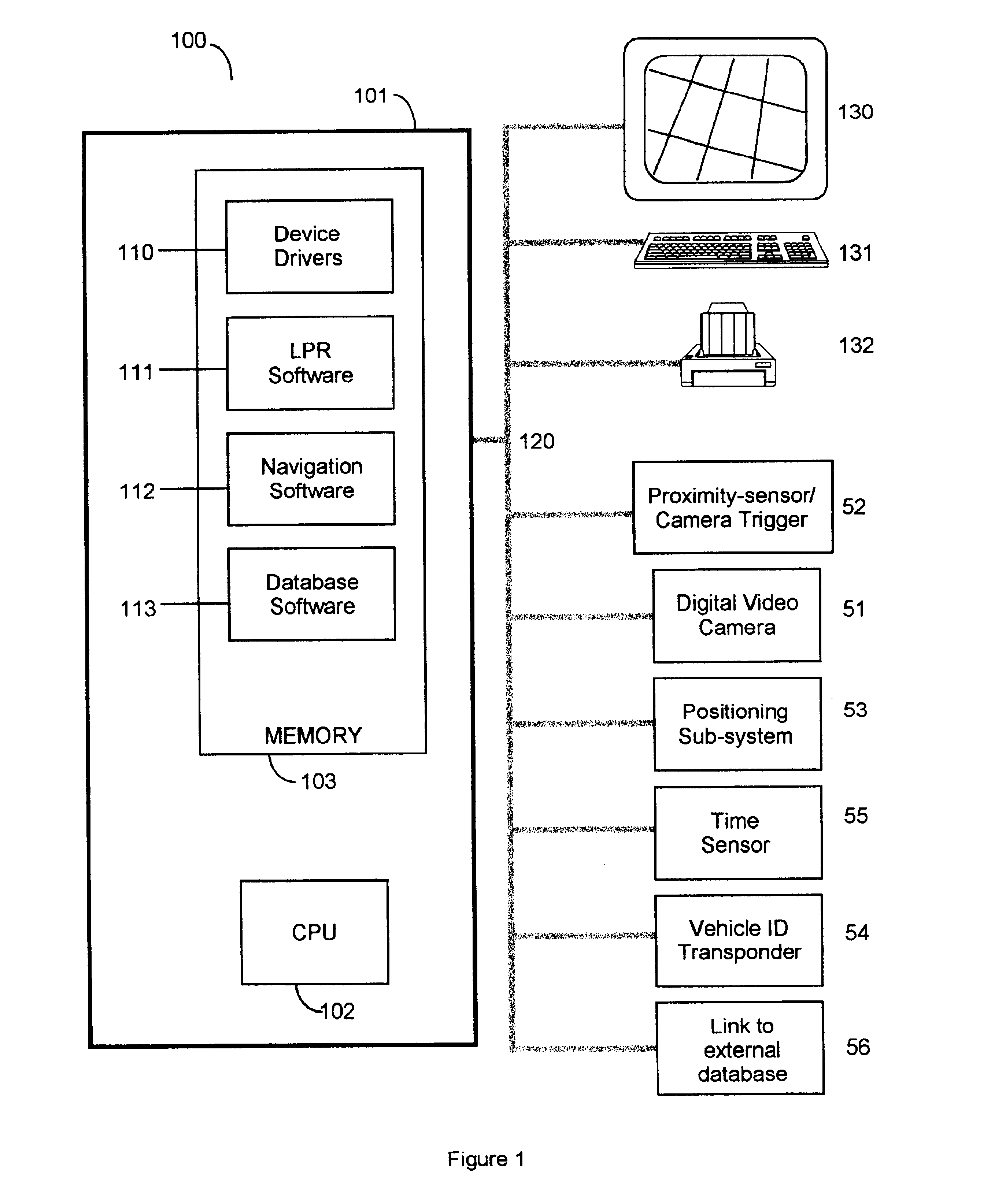
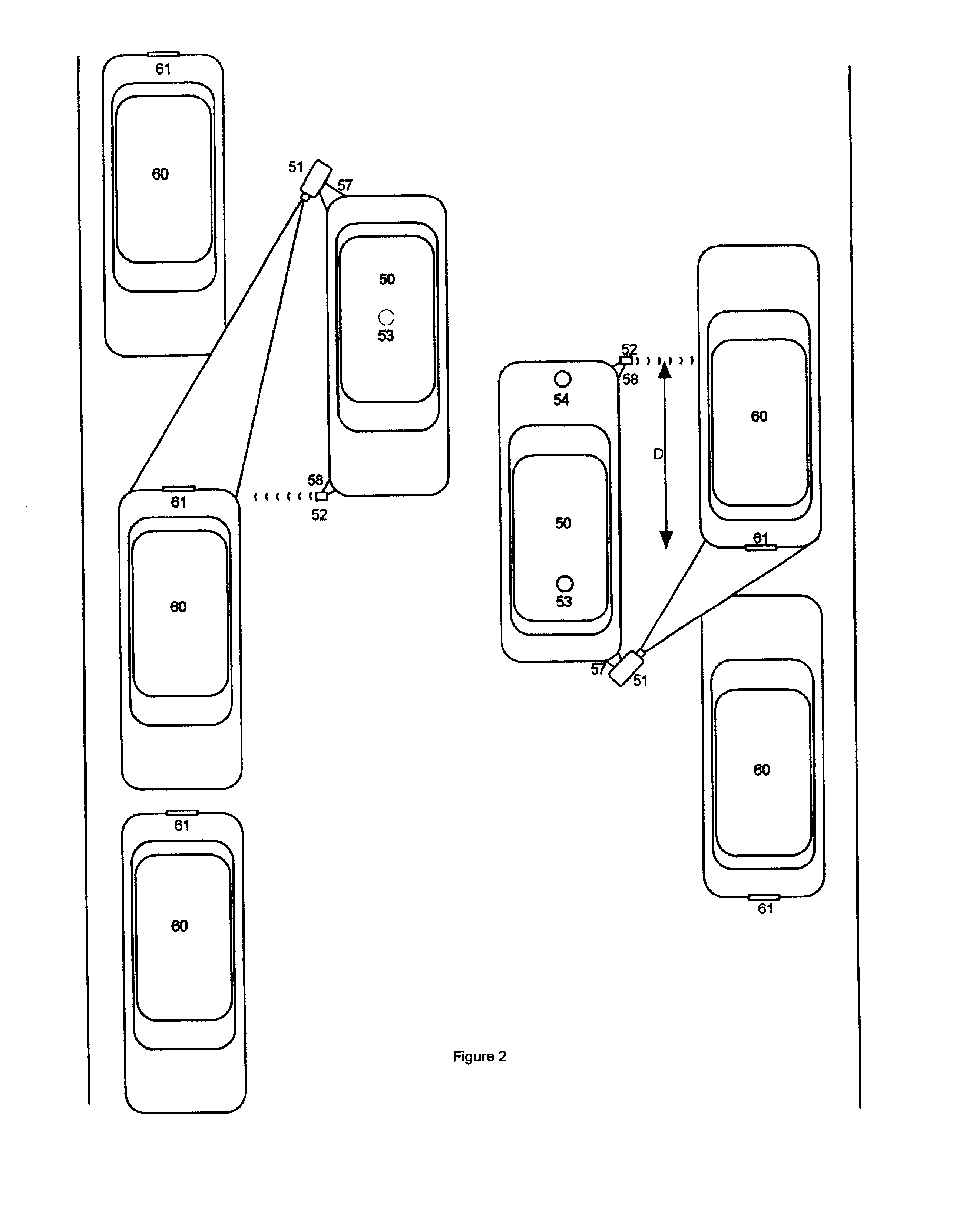
A video camera mounted on a parking enforcement patrol vehicle and connected to a computer near the operator. The system is driven along a patrol route where parked vehicles are governed by a posted time limit. The system enforces the local parking regulation by automatically determining whether or not each parked car has been parked longer than the posted time limit. Violations are detected by applying a License Plate Recognition algorithm to the images. Each license plate number is time-tagged, geo-referenced and entered into a local database. When the patrol vehicle re-traces the patrol route after the posted parking time limit has expired, the database is searched to flag vehicles that were observed at the same location during the previous circuit and therefore in violation of the parking regulations. When the system detects a parking violation, it prints a parking citation that the operator affixes to the offending parked vehicle.
Owner:AUTO VU TECH INC
System and method for determining allocation of resource access demands to different classes of service based at least in part on permitted degraded performance
A method comprises receiving into a planning tool a representative workload for a consumer. The method further comprises receiving into the planning tool quality of service desires of the consumer which define permitted degraded performance. In certain embodiments, the permitted degraded performance is time-limited wherein demands of the representative workload may exceed a pre-defined utilization constraint for at least one resource servicing the demands for no more than a pre-defined amount of contiguous time. The planning tool determines an allocation of demand of the consumer for each of a plurality of different classes of service (COSs). In certain embodiments, a first COS provides guaranteed resource access for servicing demand allocated thereto, and a second COS provides non-guaranteed resource access for servicing demand allocated thereto. In certain embodiments, the allocation of demand to the different COSs may be determined for both a normal mode and a failure mode of operation.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
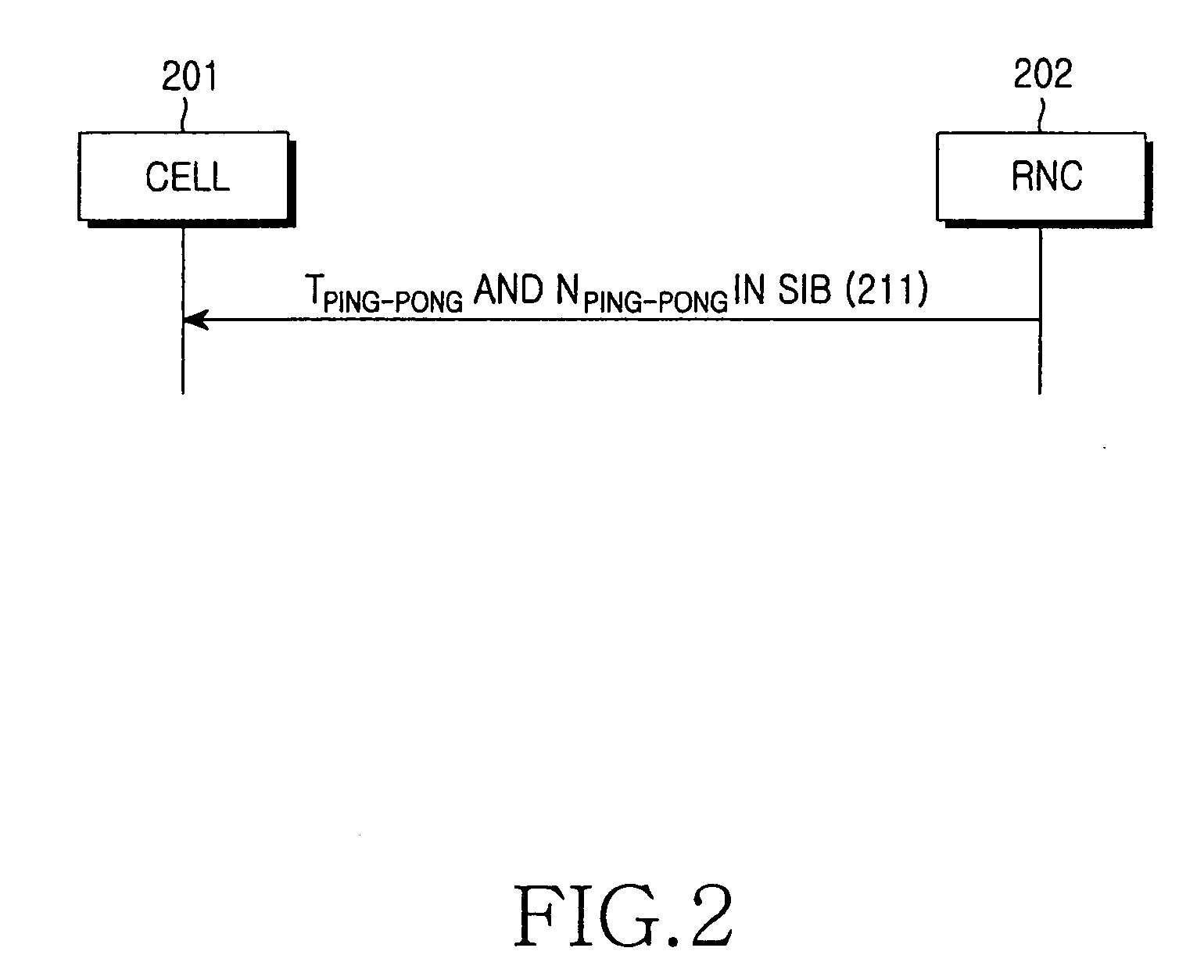
Cell reselection method and apparatus for preventing ping-pong in a mobile communications system
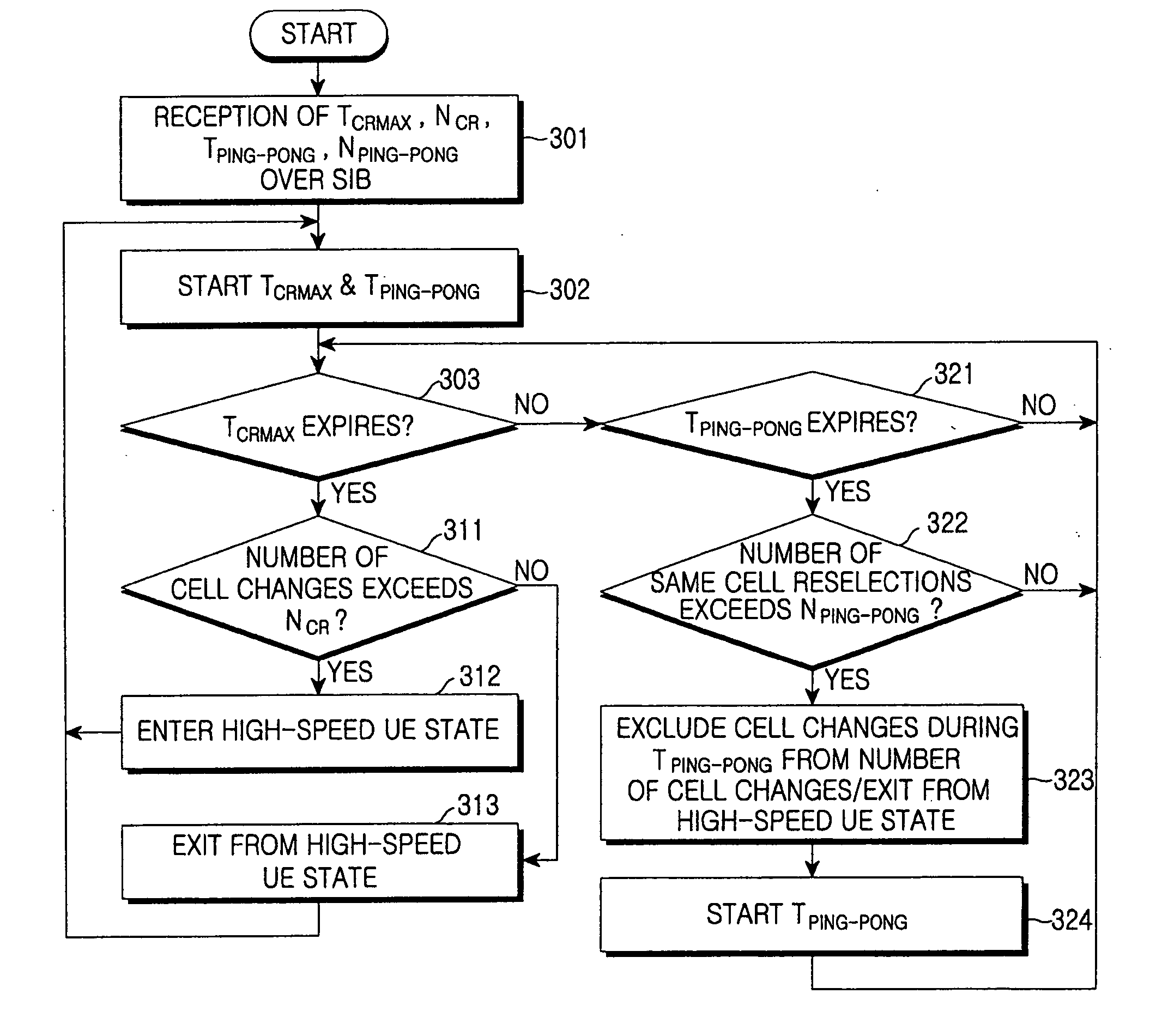
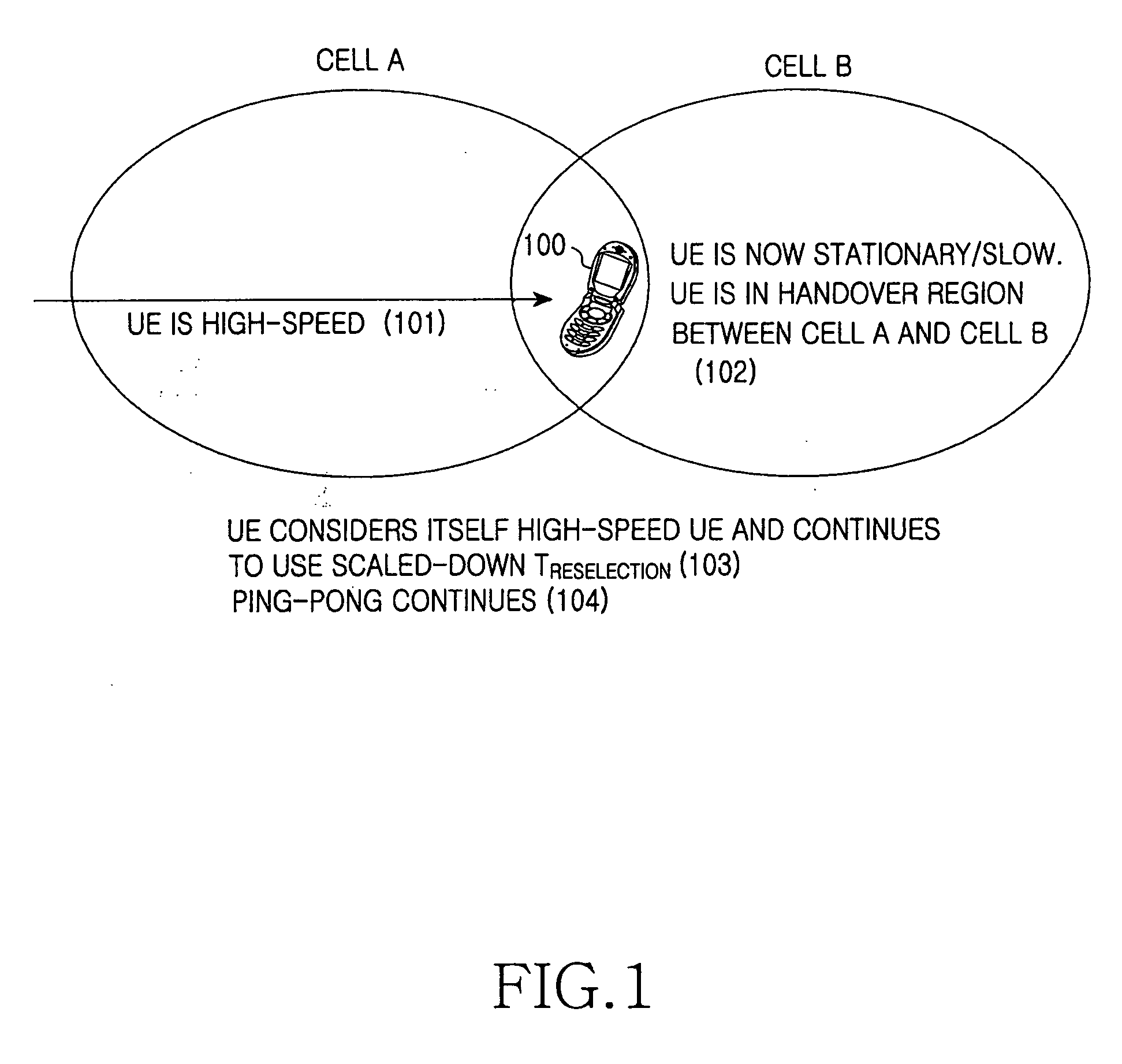
ActiveUS20060258386A1Accurately determineAccurately and efficiently reselectNetwork topologiesRadio transmissionCommunications systemTime limit
A method and apparatus are provided for enabling a UE to perform accurate and efficient cell reselection in a cellular mobile communications system. If reselection to the same cell is repeated, the UE releases itself from a high-speed UE state or excludes the number of reselections to the same cell from the number of cell changes counted for a duration set for deciding as to the high-speed UE state, according to a ping-pong duration threshold and a ping-pong occurrence number threshold. The UE uses a non-scaled down cell reselection time limit in a non-high-speed UE state, and a scaled-down cell reselection time limit in the high-speed UE state. Thus, the UE reselects to a non-serving cell having the highest ranking continuously for the cell reselection time limit.
Owner:SAMSUNG ELECTRONICS CO LTD
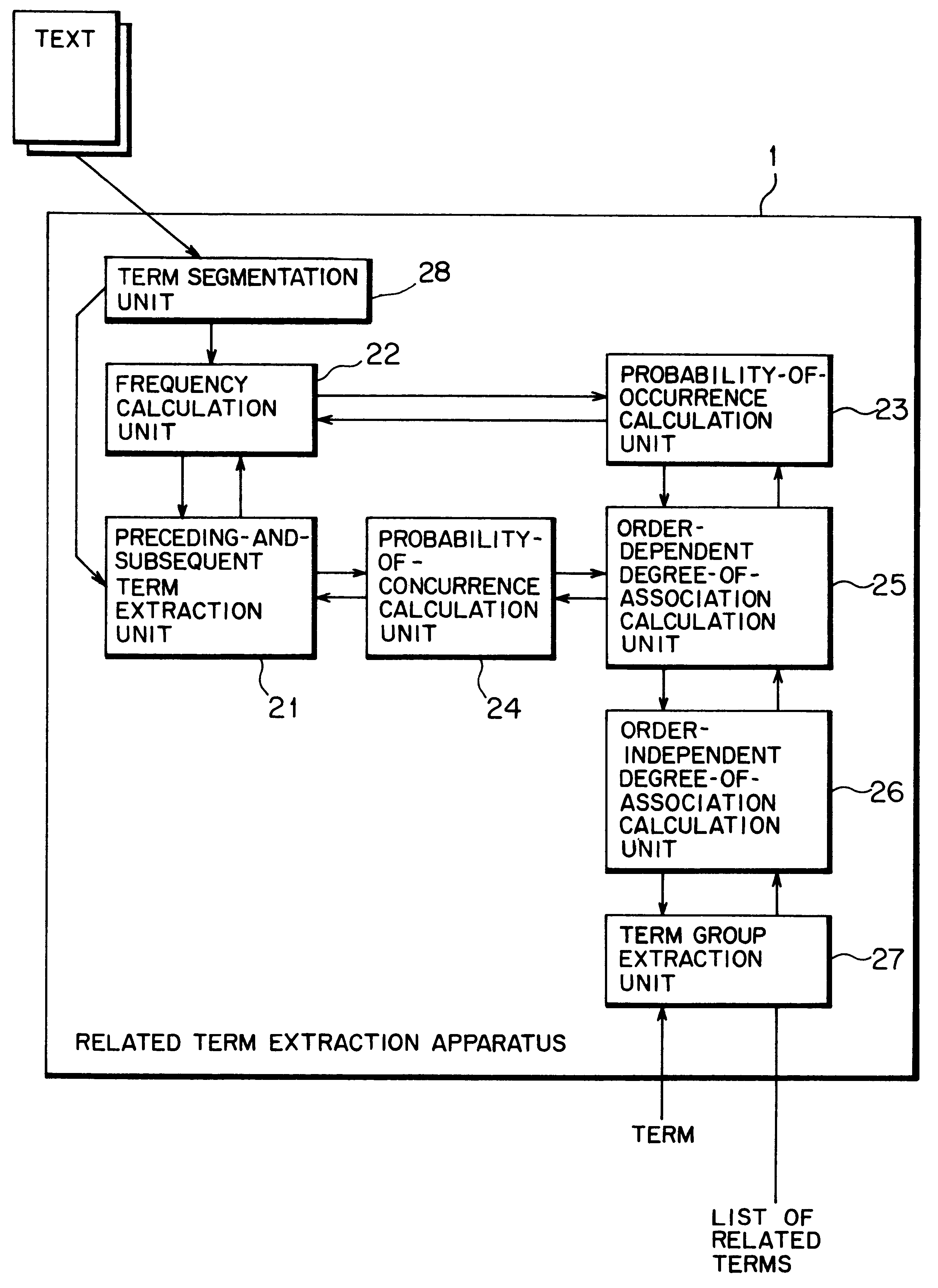
Related term extraction apparatus, related term extraction method, and a computer-readable recording medium having a related term extraction program recorded thereon
InactiveUS6178420B1Easy to understandData processing applicationsDigital data information retrievalAlgorithmTime limit
The present invention is intended to allow a user to easily and precisely extract related terms through use of mutual information without requiring morphological analysis or syntax analysis, by constituting a related term extraction apparatus from preceding-and-subsequent term extraction means for extracting a preceding term occurring prior to a specified term or a subsequent term occurring subsequent to the same in text data; a frequency calculation means for calculating the occurrence frequencies of the specified term, the preceding terms, and the subsequent terms; probability-of-occurrence calculation means for calculating the occurrence probabilities of the preceding and subsequent terms together with the occurrence probability of the specified term; probability-of-concurrence calculation means for calculating the probabilities of the preceding and subsequent terms cooccurring with the specified term; order-dependent degree-of-association calculation means for calculating an order-dependent degrees of the preceding and subsequent terms cooccurring with the specified term; order-independent degree-of-association calculation means for calculating an order-independent degrees of occurrence of the preceding and subsequent terms with the specified term; and term group extraction means for extracting from the text data a group of terms related to the specified term, on the basis of the degree-of-association information calculated by the order-independent degree-of-association calculation means.
Owner:FUJITSU LTD
Programmable key for a security system for protecting merchandise
ActiveUS7737845B2Unauthorized useSufficient powerElectric signal transmission systemsMultiple keys/algorithms usageTime limitEngineering
Owner:INVUE SECURITY PROD INC
Authorisation system
InactiveUS20050262026A1More securityEasy constructionDigital data processing detailsSpecial data processing applicationsHash functionTime limit
Systems and methods for securely authorising an on-line transaction, e.g. involving a micro-payment, between a customer browser and merchant server without the need for special software installed on the customer computer or a SSL connection to the merchant server. The authorisation method involves a double redirection instruction: the initial transaction request is redirected via the customer web browser to a service provider arranged to authenticate the customer, from where the authenticated instruction is further redirected via the customer web browser to a merchant site to complete the transaction. Information identifying the merchant, merchandise, etc. is included in the redirection instruction, and may be encrypted or encoded e.g. using a hash function to prevent tampering. To authorise an authenticated instruction, a cookie containing transaction identification data may be returned to the merchant web server along with the authenticated instruction. Alternatively, the service provider may set a time limit after which the authenticated instruction will no longer be valid.
Owner:WATKINS DANIEL ROBERT
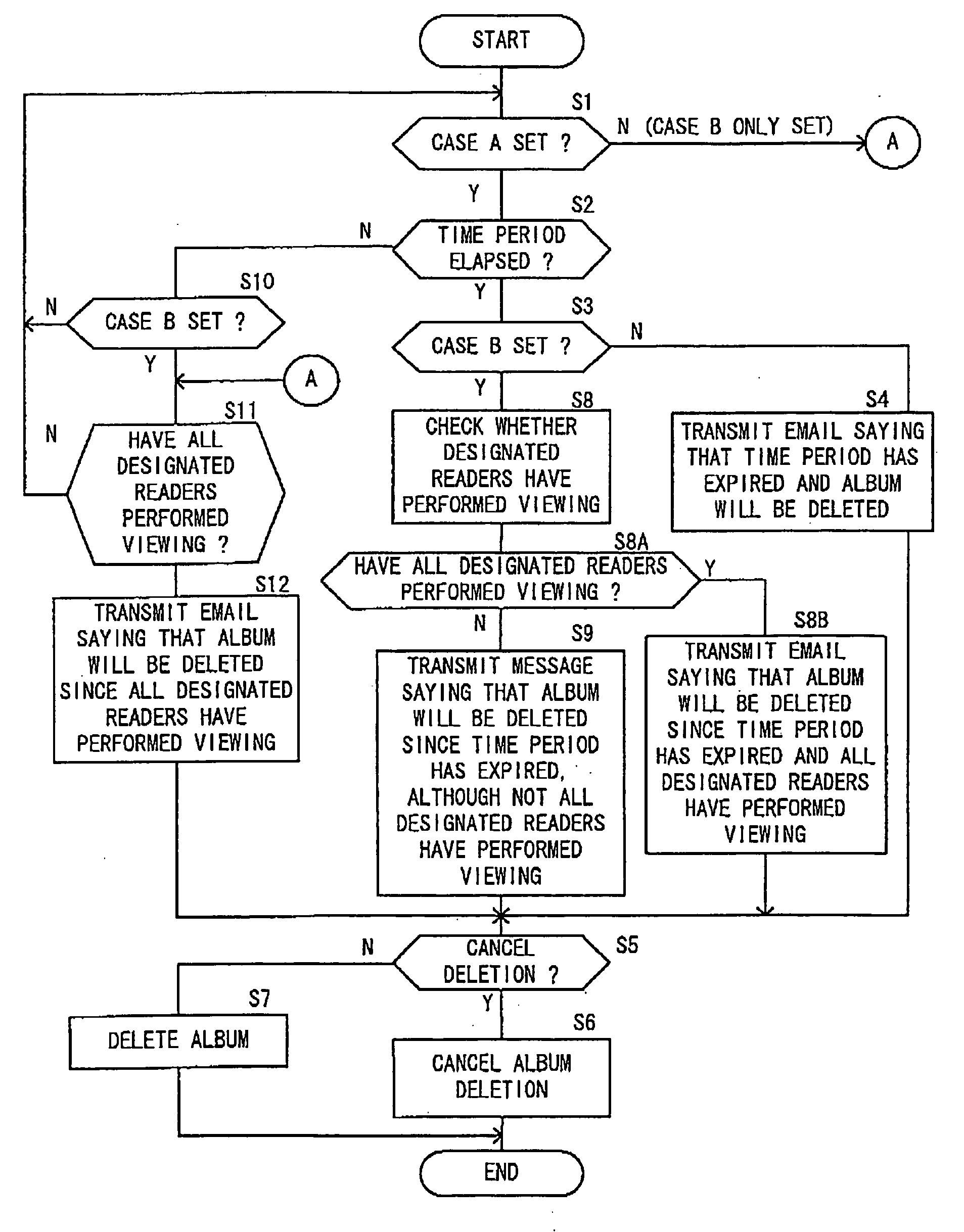
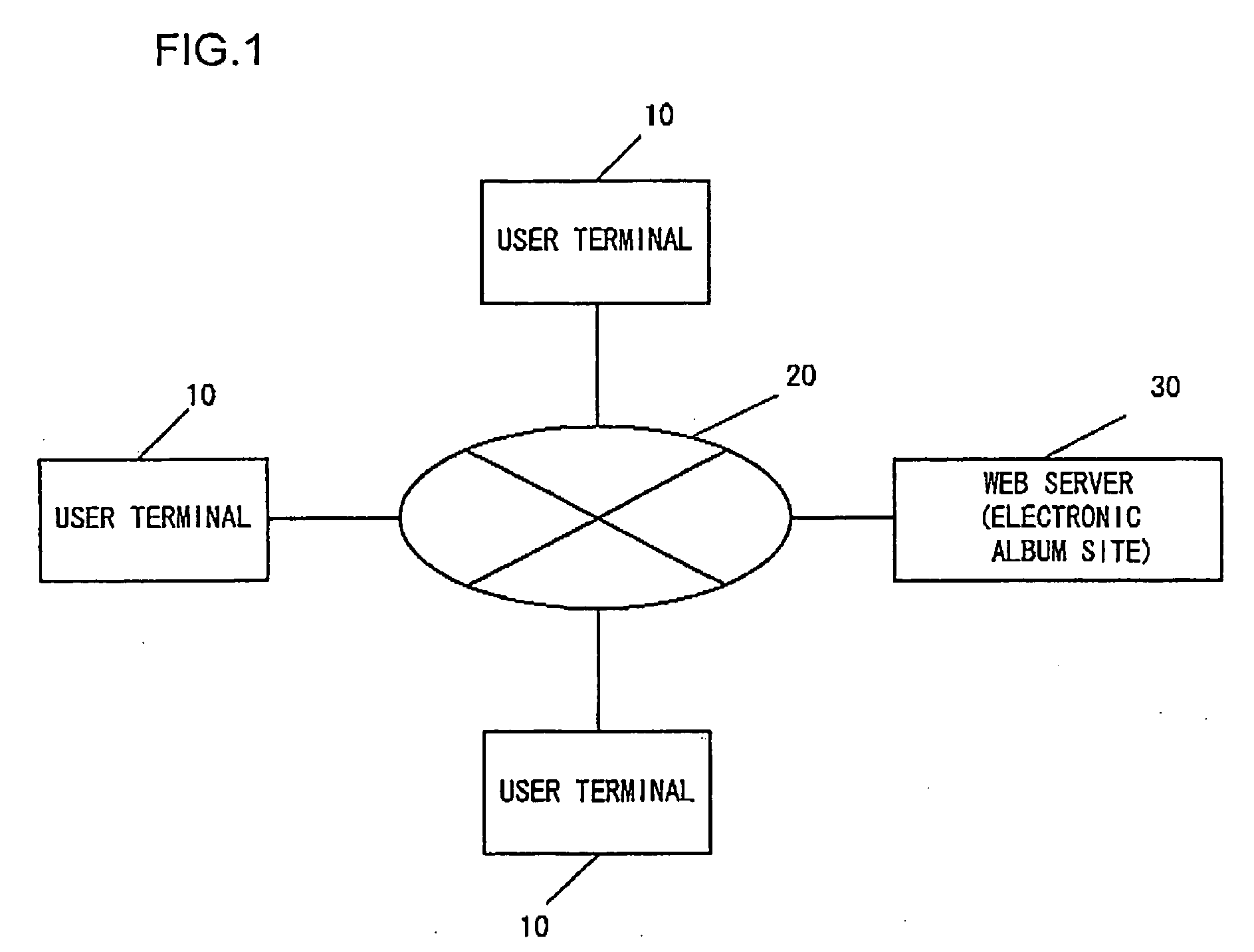
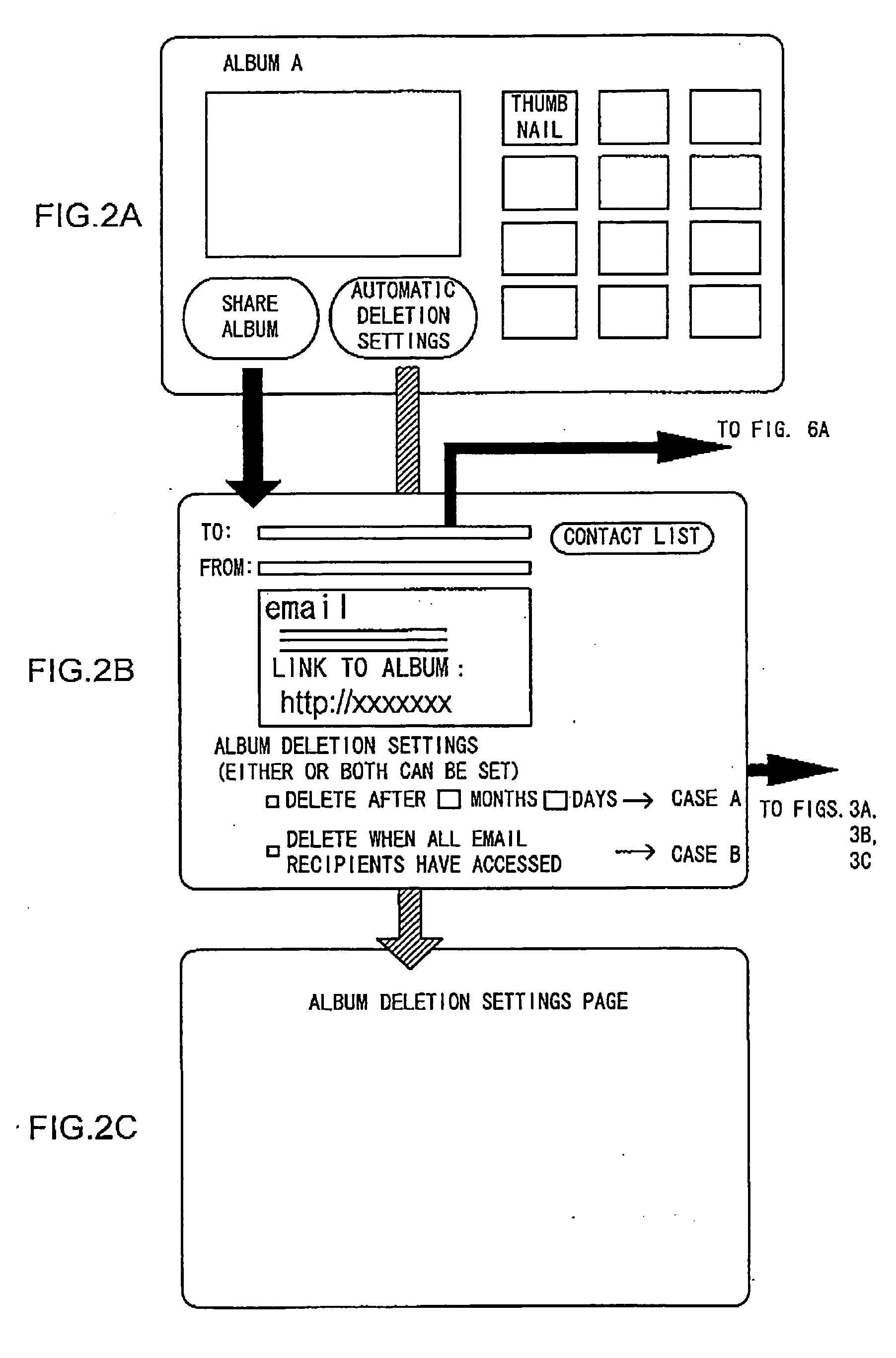
Electronic album providing system and file providing system
The electronic album providing system, with which publishing and viewing of an electronic album by a system user is possible, includes: a first decision unit that detects whether or not a designated reader who has been designated by a publisher has viewed the album, and that decides that a first condition has become valid when a number of persons who have completed viewing to a total number of the designated readers reaches a predetermined value; a second decision unit that decides that a second condition has become valid when a time limit for publishing the album that has been set in advance arrives; and a deletion unit that performs deletion control of the album when at least one of the first condition and the second condition becomes valid.
Owner:NIKON CORP
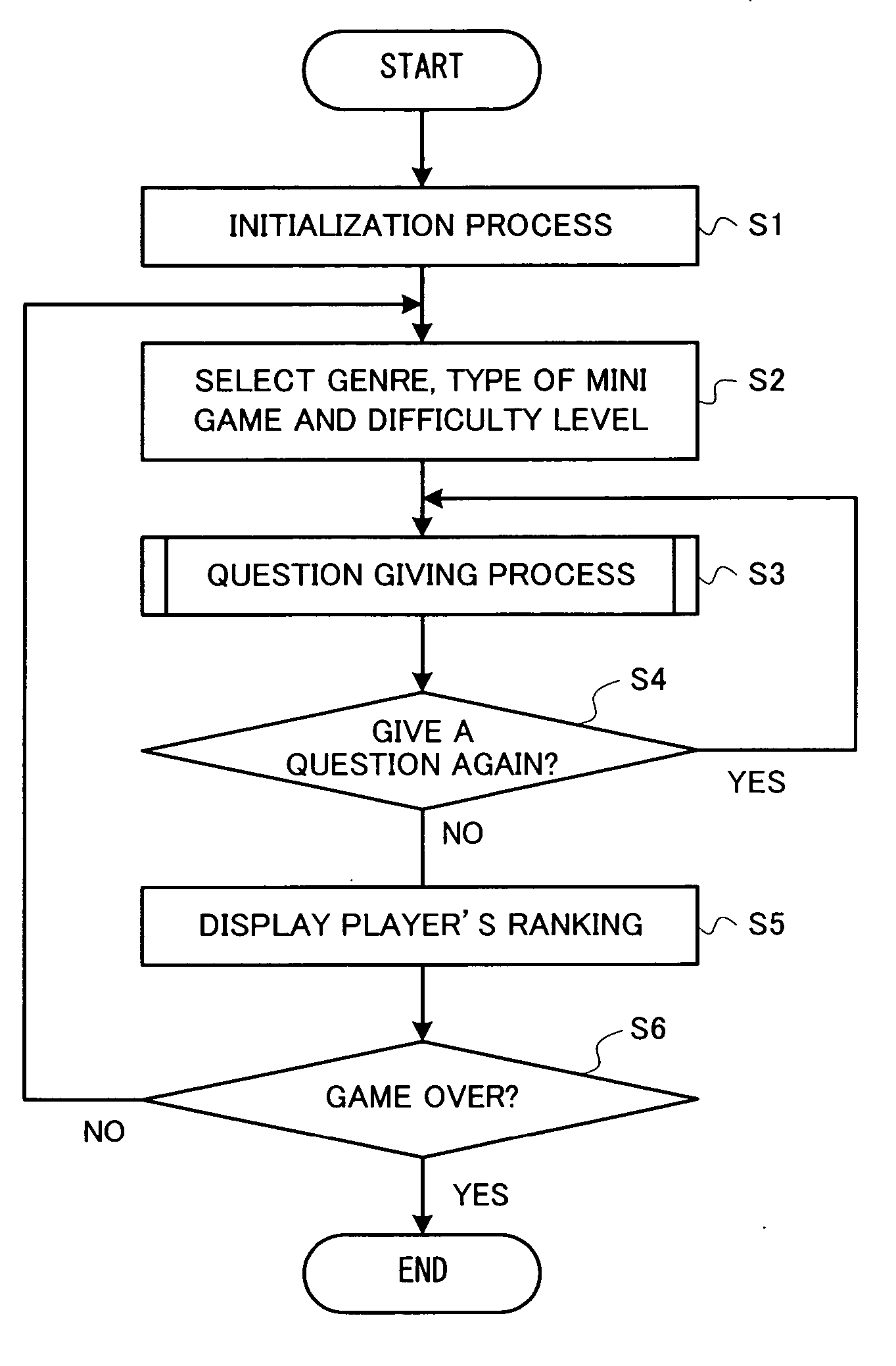
Game program and game device
A game device provides a question to a plurality of players. The game device counts the number of players each having provided an answer to the question or each having provided a correct answer to the question. When the counted number of players reaches a predetermined number of players, a predetermined time limit is set. The game device measures an elapsed time from when the time limit has been set (i.e., a correct answer elapsed time), and stops accepting an answer to the question when the correct answer elapsed time reaches the time limit.
Owner:NINTENDO CO LTD
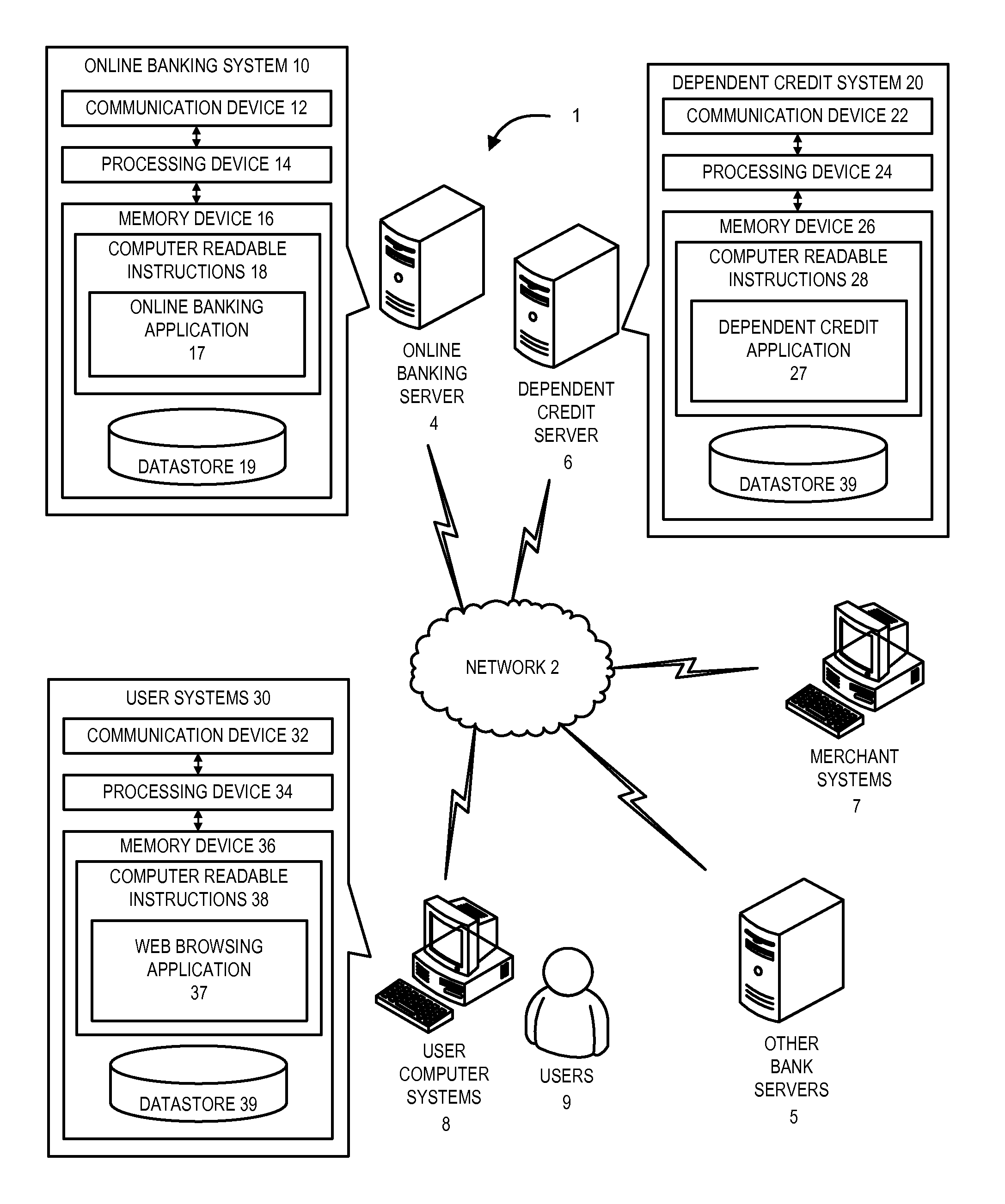
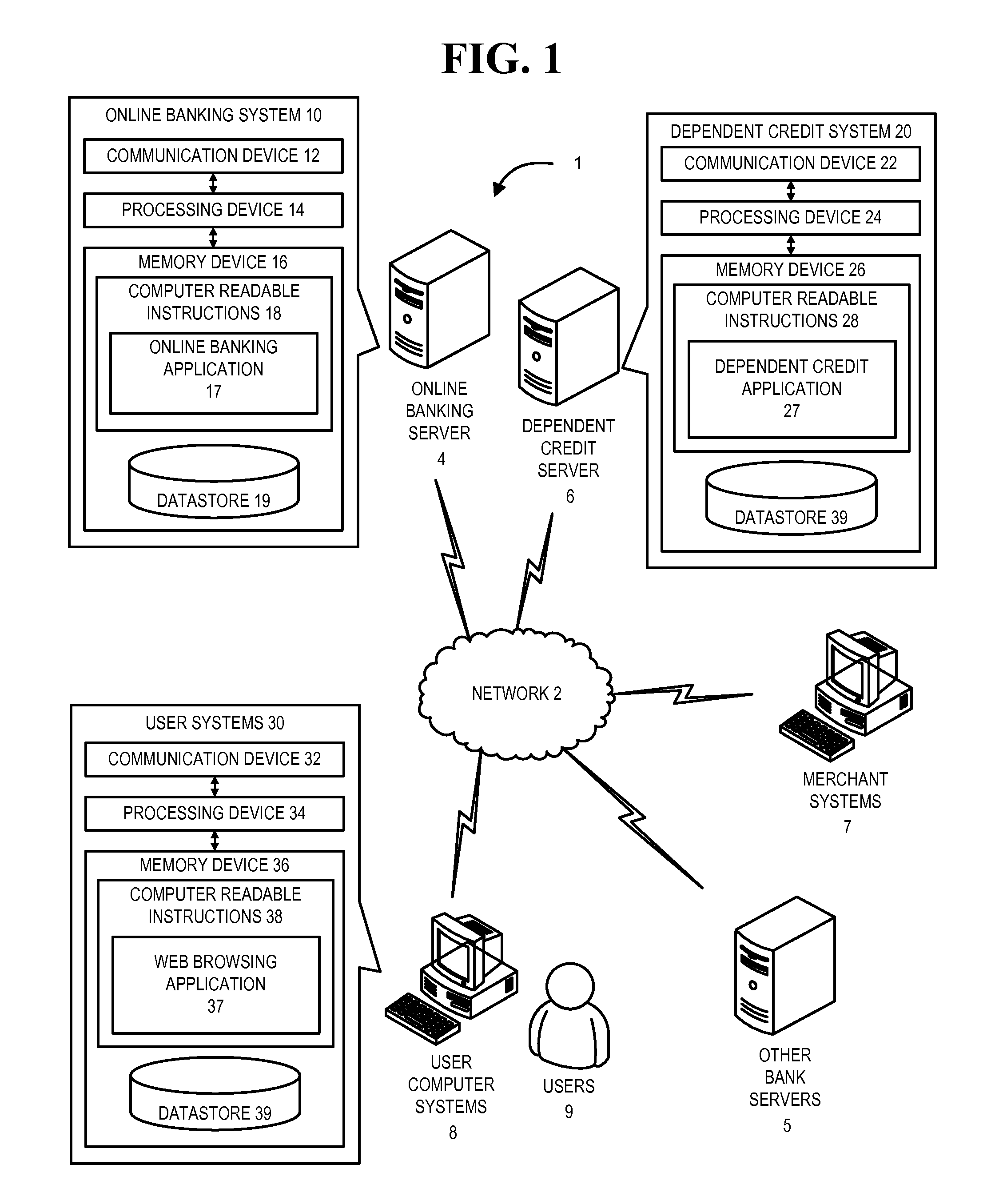
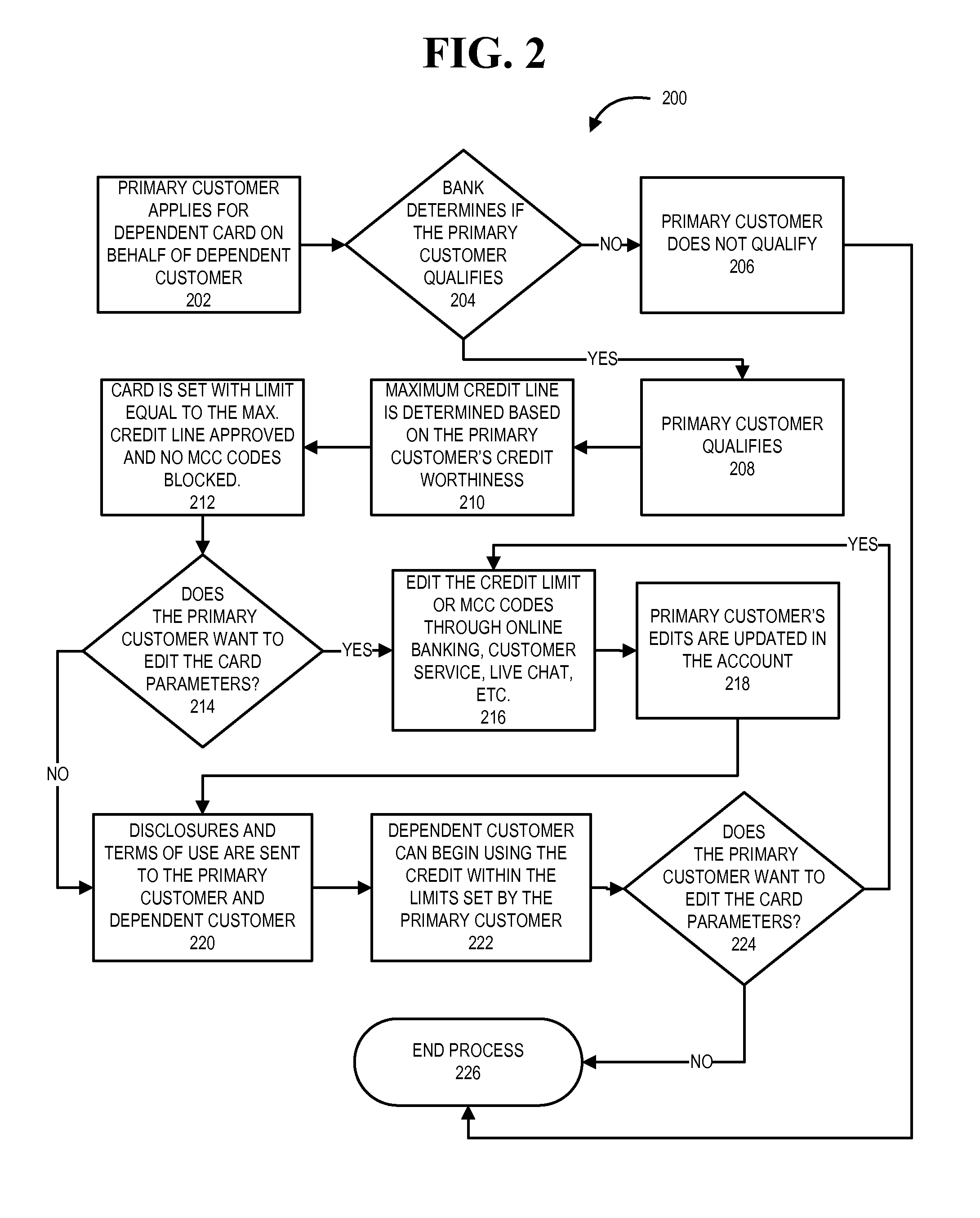
Dependent payment device
The present invention provides embodiments of a dependent payment device, such as a credit card, for allowing a primary customer to control and monitor the transactions made by a dependent customer who is authorized to use the account of the primary customer. The primary customer can control the maximum limit that the dependent customer can spend on the dependent card up to the maximum amount that the financial institution has approved for the primary customer. The primary customer can also block / approve purchases that the dependent customer can make at store or on products by adding MCCs, store names, store types, UPCs, or other product or store identifiers to a list of blocked / approved transactions. The primary customer can set monetary and time limits on the amount and frequency of the transactions the dependent customer can make at stores or on products that have been blocked / approved.
Owner:BANK OF AMERICA CORP
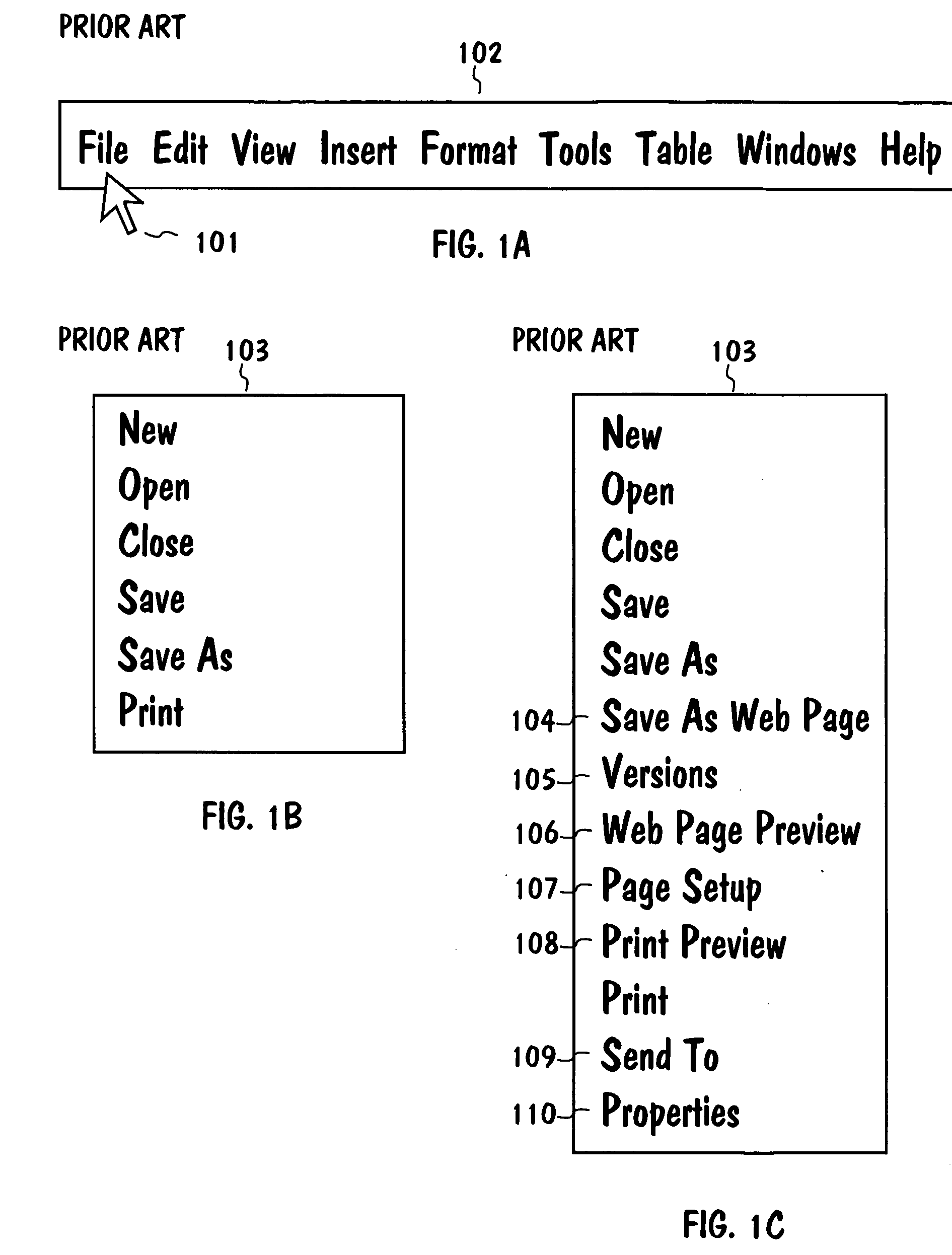
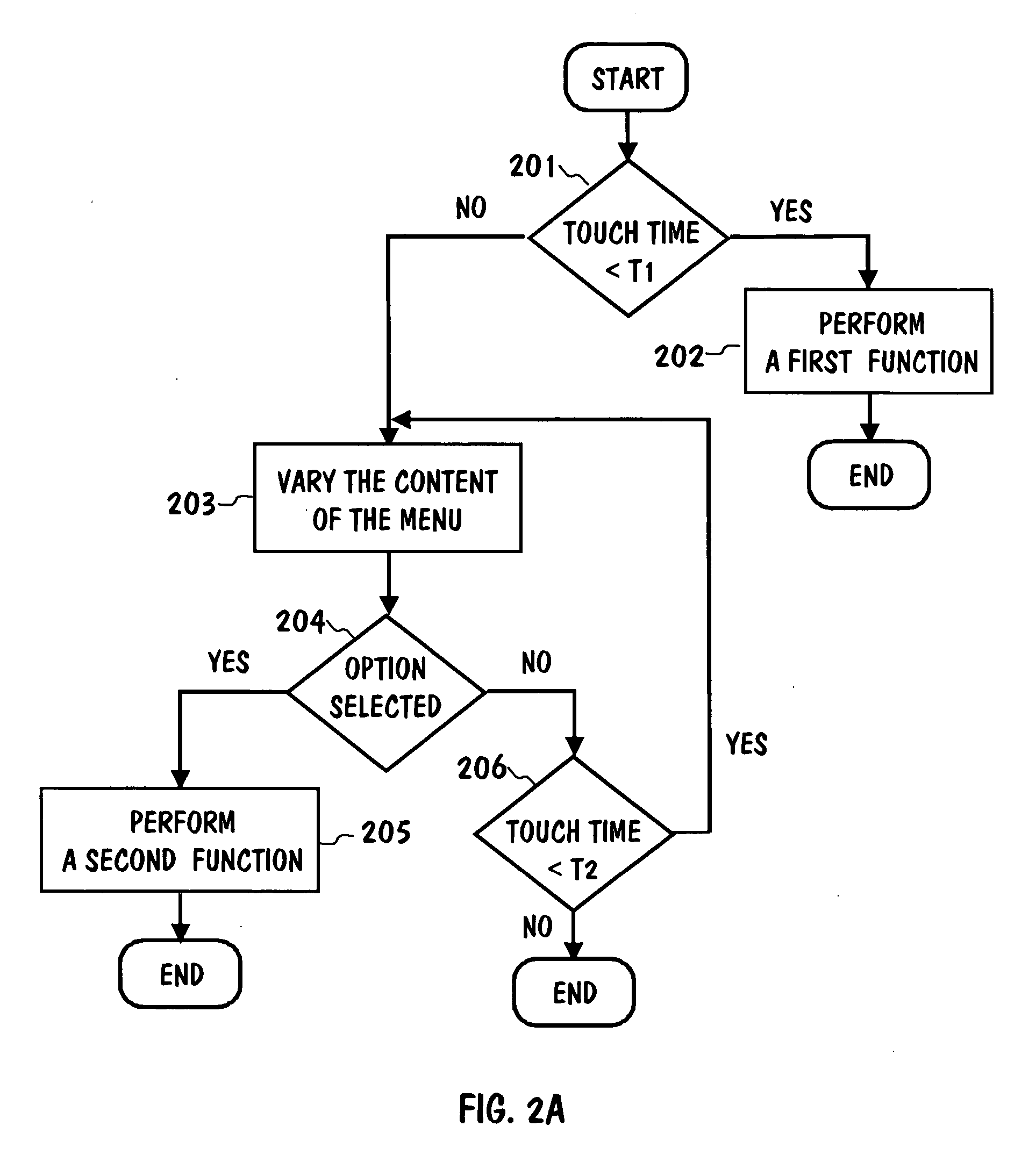
Varying-content menus for touch screens
A method and system implementing menus for touch screens. A touch screen shows at least one menu that can be touched with a probe, which is the user's finger, for example. When the touch time of a menu reaches a predetermined time limit, a user is preferably given feedback indicating that the content of the menu will be varied. Feedback may be visual, audible, or haptic. There are basically two ways to vary the content of a menu. The menu can be enlarged from its default size, so that it contains a greater number of menu options. Alternatively, the content of the menu can be varied so that the size of the menu is constant but at least one of the menu options shown is replaced by another menu option.
Owner:MYORIGO
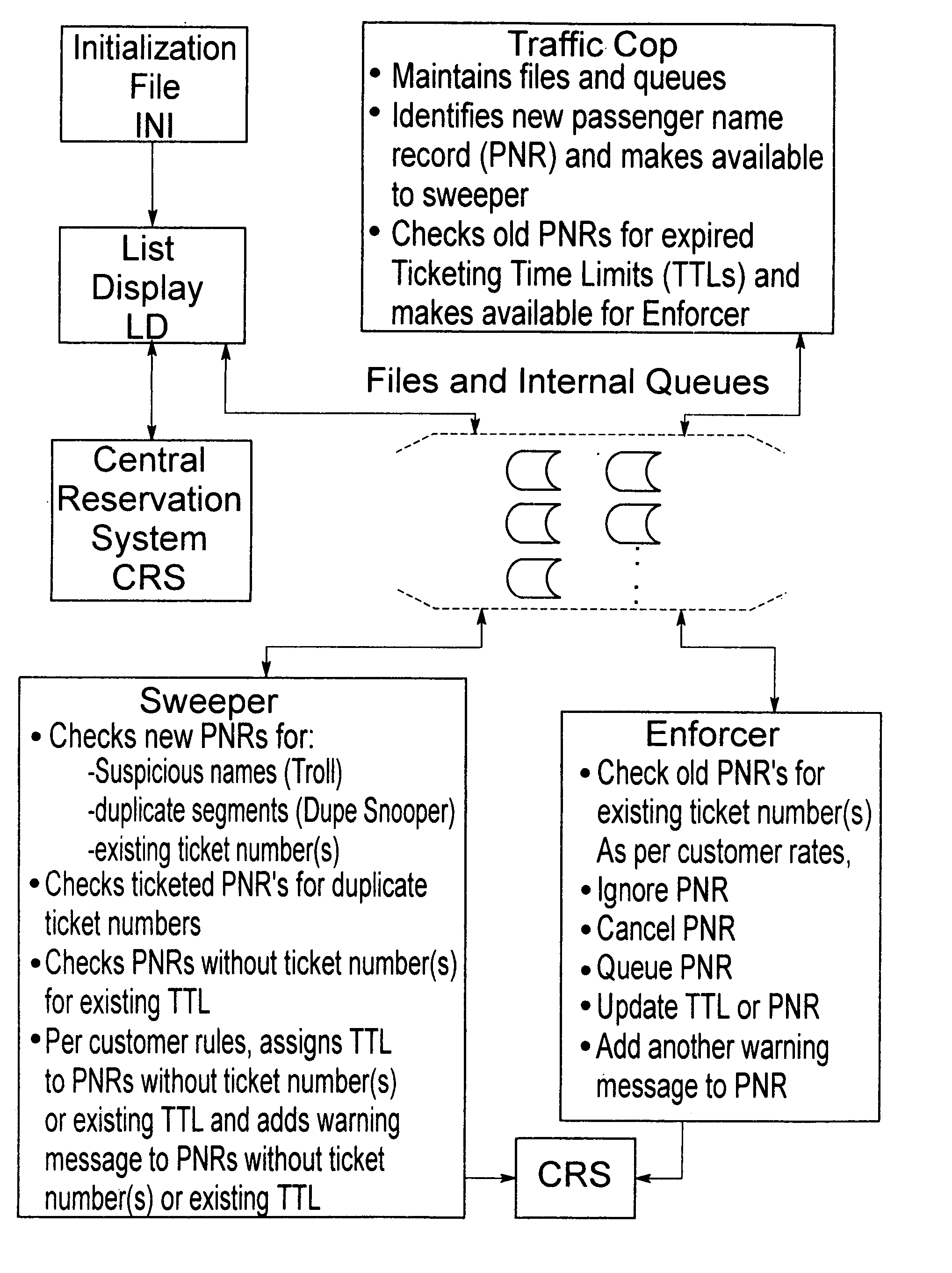
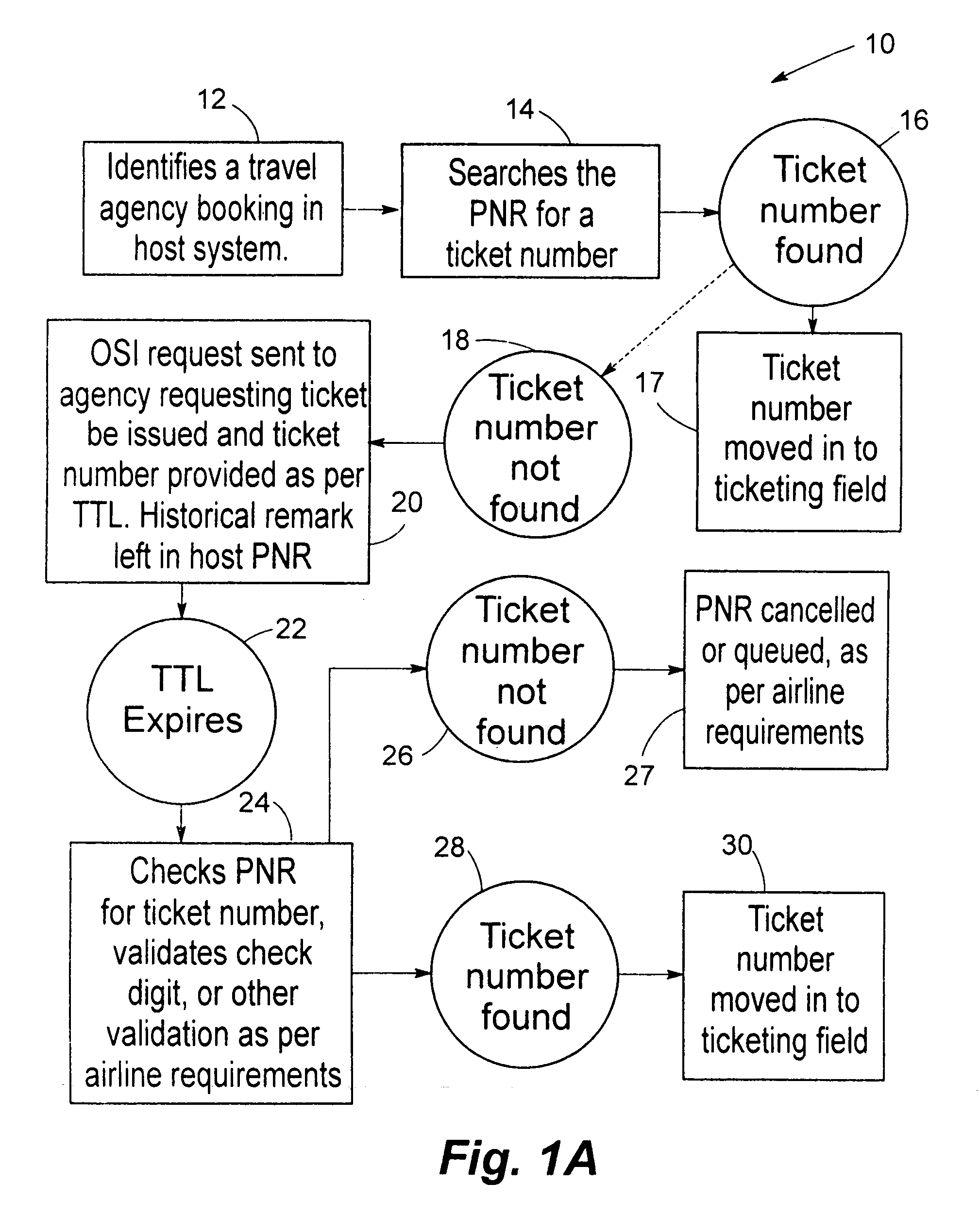
Automated method and system for recognizing unfulfilled obligations and initiating steps to convert said obligations to a fulfilled status or to a null status for resale
InactiveUS7194417B1Increase onboard load factorReduction of lost revenueReservationsSpecial data processing applicationsTime limitComputer science
An automated method and system for identifying date-sensitive entries in a database wherein an obligation must be satisfied relative to the entry according to instructions provided by the beneficiary of the obligation. The method and system of the invention can be practiced from a location remote from the database and are particularly useful in a number of situations and particularly those wherein unticketed reservations are maintained in a storage medium for a time prior to issuance of a ticket to “firm up” the reservation to a ticketed status. The present system and methodology finds particular utility enforcing ticketing time limit rules on travel agency or other reservation and ticket issuers involved in the reserving and ticketing of airline bookings and the like and results in the reduction of no-shows and overbooking while increasing onboard load factors on sold-out flights in particular. The automated system of the invention is capable of operating essentially continually throughout seven days a week and twenty-four hours each day to constantly “firm” all or selected flights of a given carrier. Enforcement of ticket time limit rules can extend at the option of a user to booking class, market, point of sale and the like or any combination thereof.
Owner:AMADEUS REVENUE INTEGRITY
Blood pressure measurement device for measuring at appropriate timing
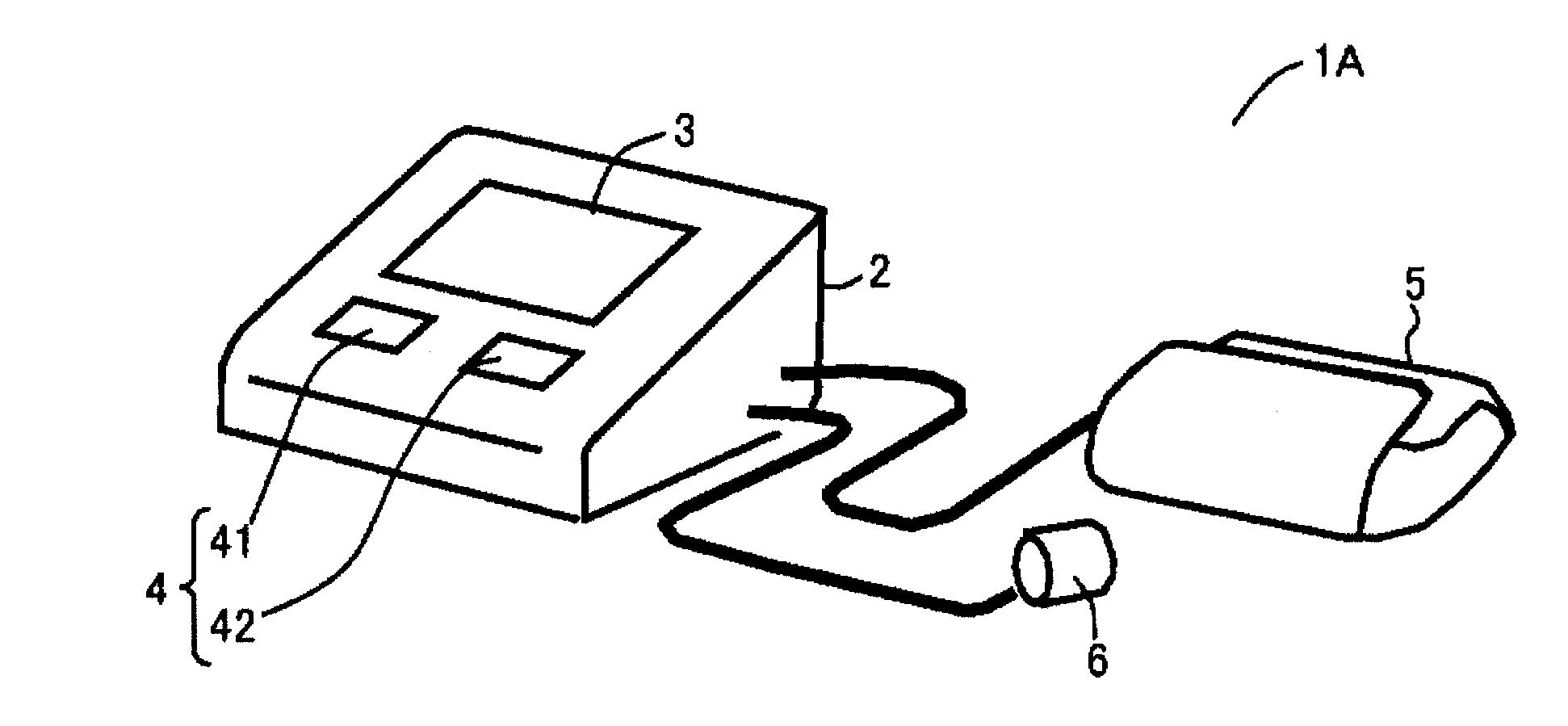
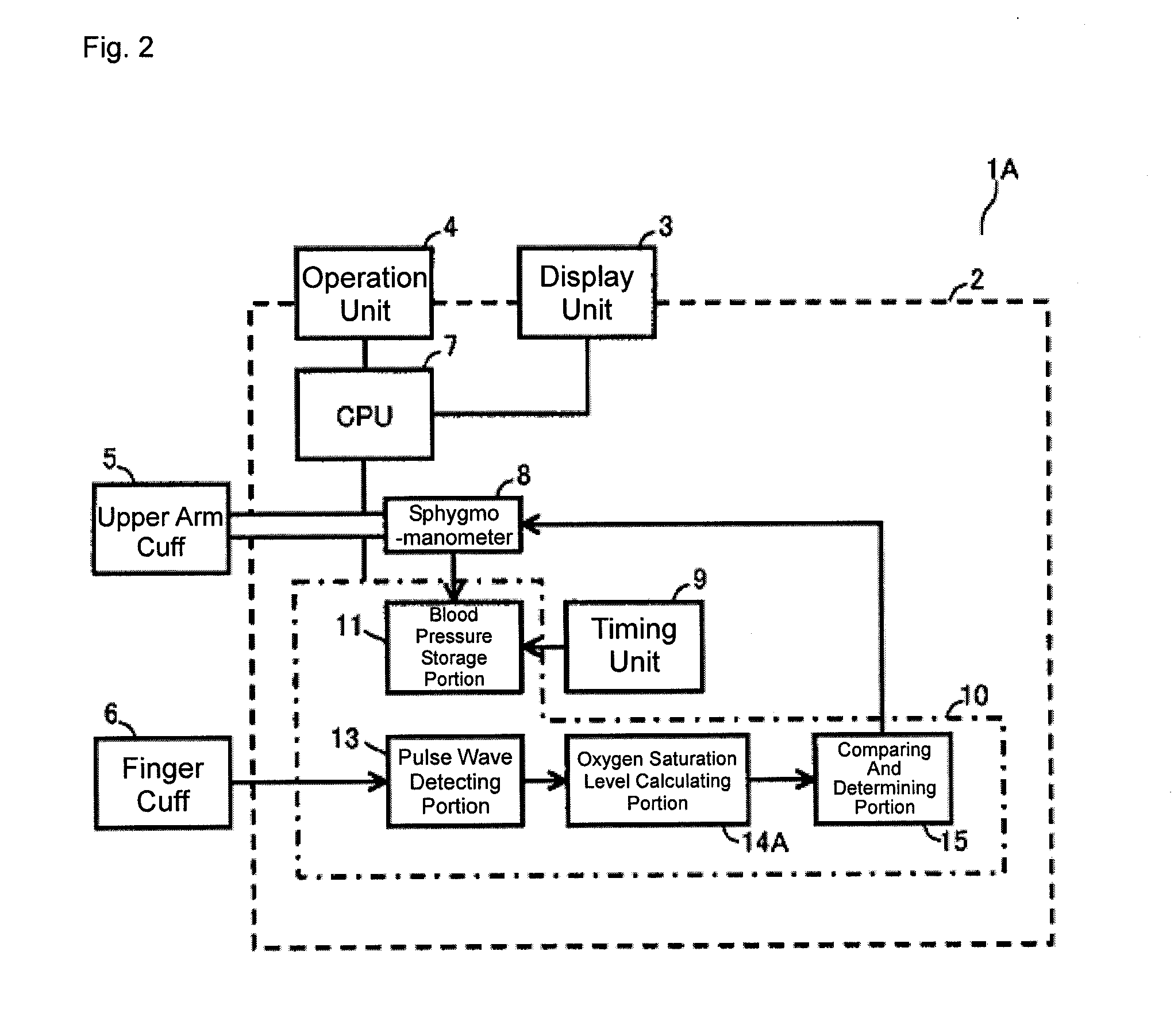
ActiveUS20110230729A1ElectrocardiographyEvaluation of blood vesselsSphygmomanometerMeasurement device
A blood pressure measurement device includes a finger cuff for measuring a blood oxygen saturation level of a subject as physiological information excluding a blood pressure, a pulse wave detecting portion, and an oxygen saturation level calculating portion, where a start of blood pressure measurement in a sphygmomanometer is determined by a comparing and determining portion when a value becomes greater than or equal to a reference value. After the end of the measurement, a time limit for limiting the start of the blood pressure measurement is set. The comparing and determining portion determines not to start the blood pressure measurement within the time limit even if the blood oxygen saturation level becomes greater than or equal to the reference value.
Owner:OMRON HEALTHCARE CO LTD +1
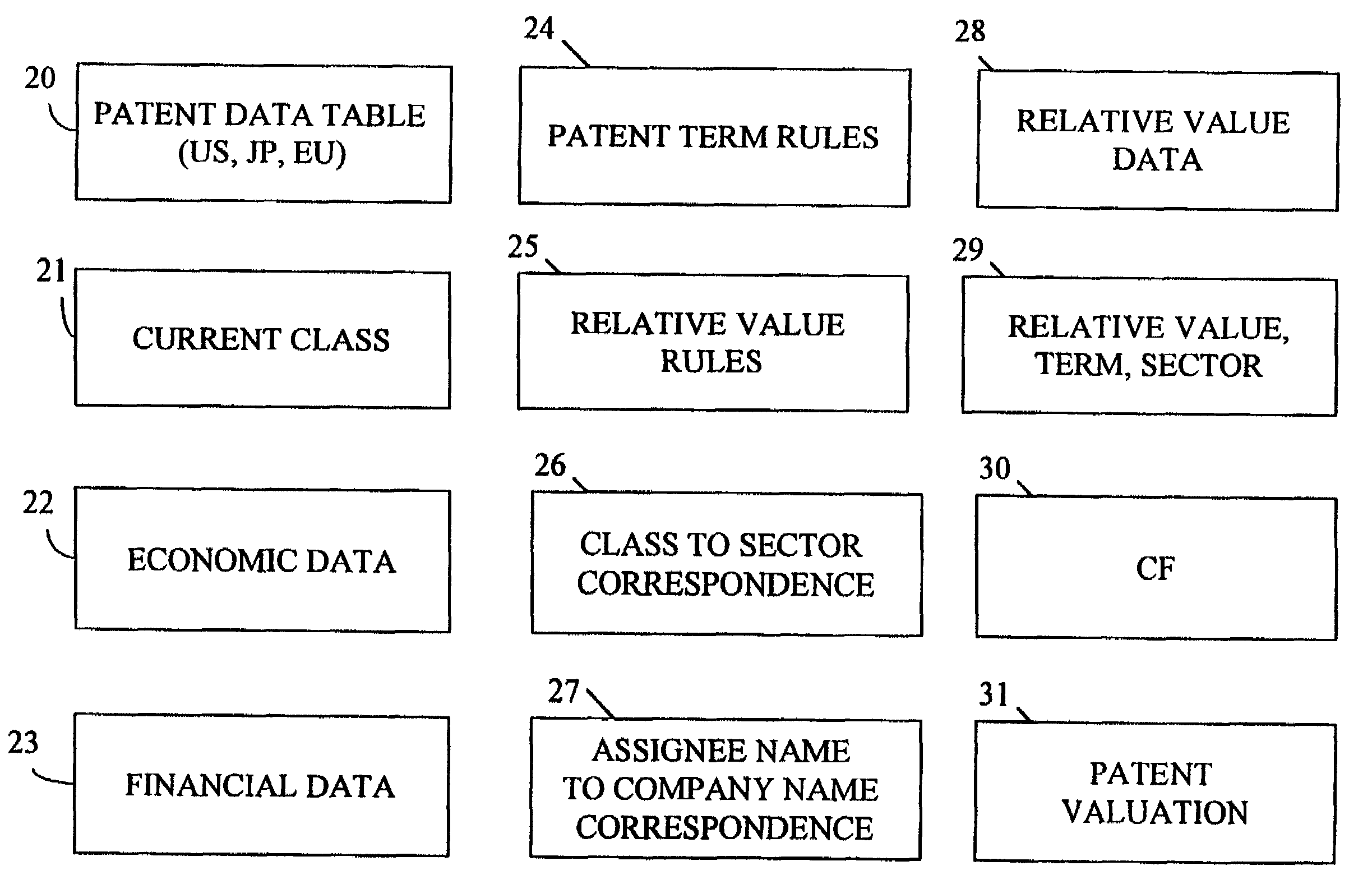
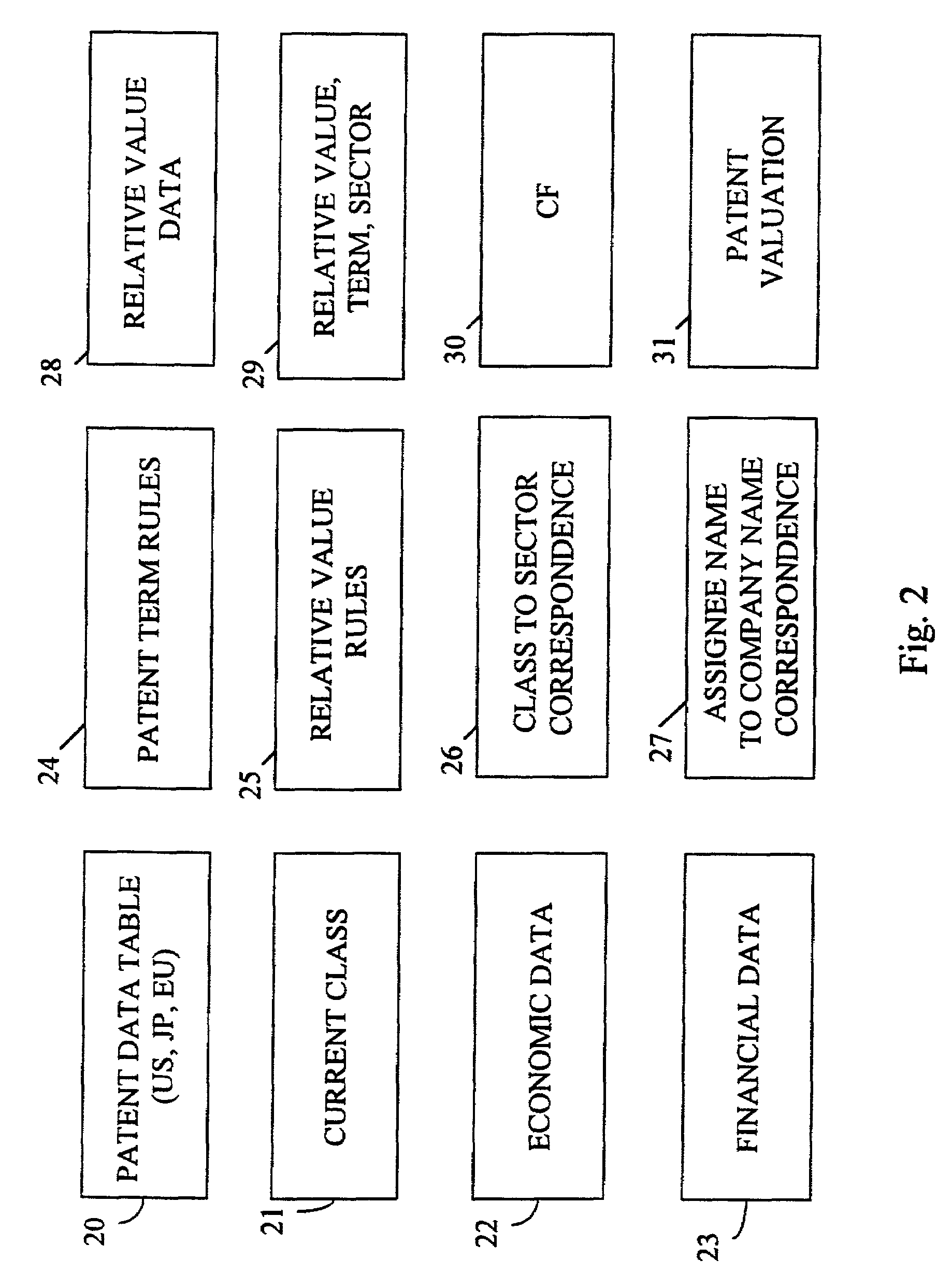
System and method for valuing patents
InactiveUS7676375B1Effective valueImprove accuracyFinanceProduct appraisalPaymentComputerized system
A computer system implementing a macro economic model based upon macroeconomic data and relative value characteristics data of patents that determines nominal values for (1) goods and services and (2) profits generated by sales that are covered by the rights of a patent, implements an income value theory to value the patent based upon the predicted values of profits or goods and services covered by the patent, determines patent terms from patent filing, publication, and issue dates, determines patent assignees from patent data, and uses the value of a company's patents, the patent issuance data and term date data, to determine trends versus time in: the number of a company's enforceable patents; the number of a company's patents obtained; the nominal value of net earnings and of goods and services sold that are covered by the company's patents; the nominal value of the sum of the company's patents, and provides comparisons of those trends between companies, regions, and economic sectors, providing the results of the analysis to users of the computer system. The computer system employs a user database enabling a novel electronic accounting model enabling payment by affiliates, programmed securities trading, and accrediting of investors.
Owner:INNOVATIONQ
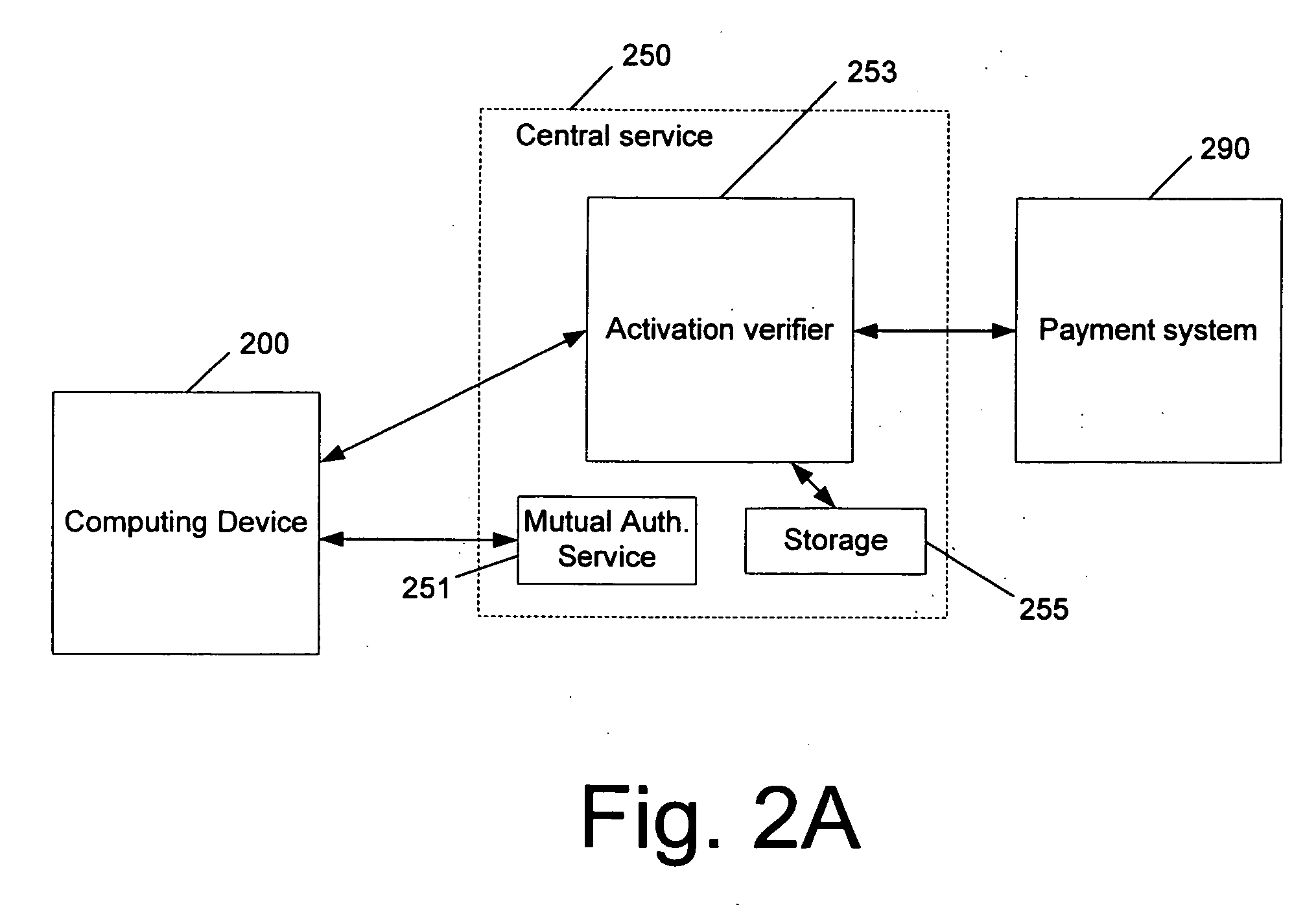
Licensing the use of software to a particular user
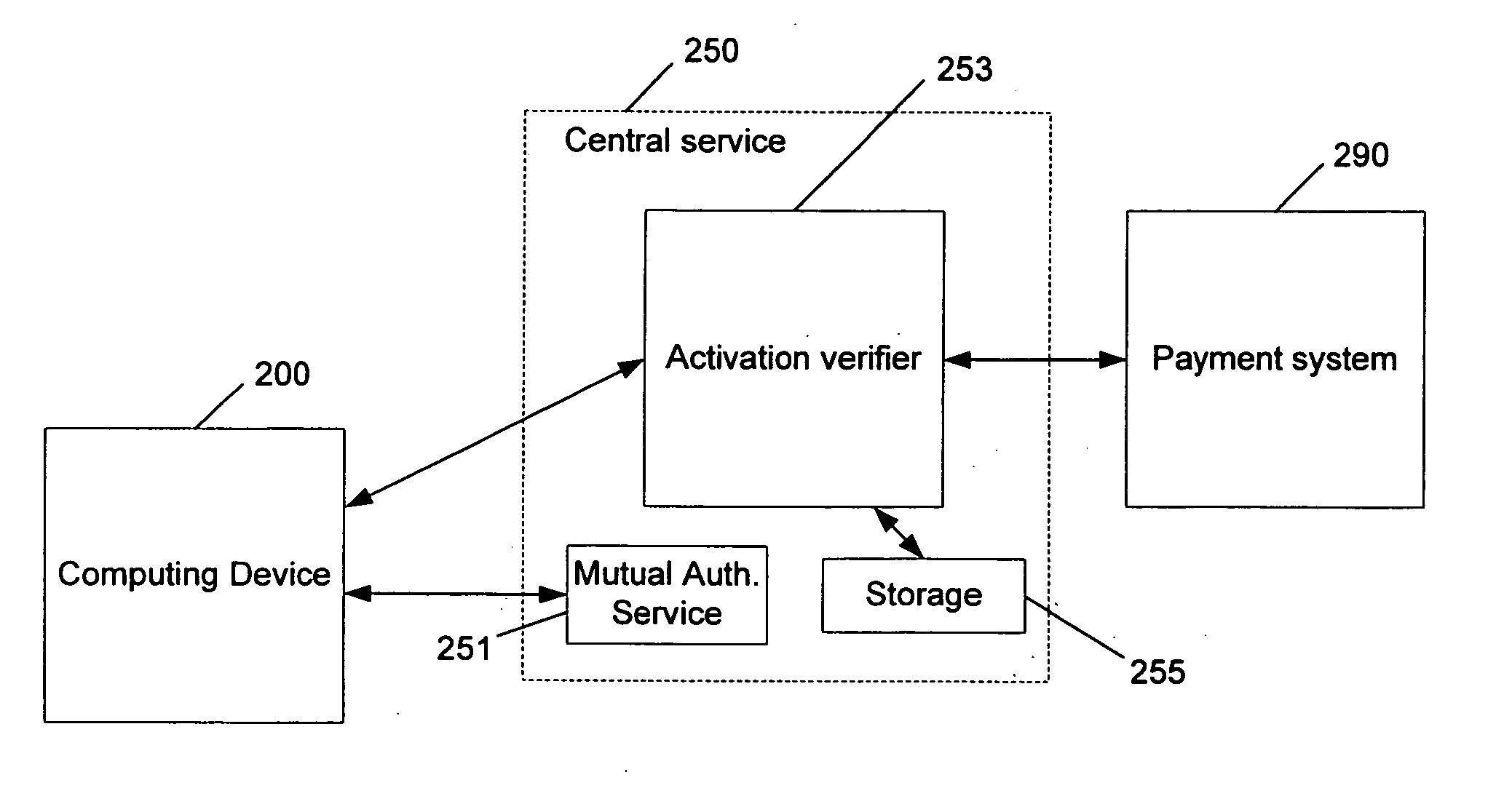
InactiveUS20060048236A1Digital data processing detailsUser identity/authority verificationPaymentTime limit
The use of software is licensed to a particular user, regardless of the computing device on which the software has been launched. A computing device is logged onto a central service. The central service either directly approves the launching of the software or it provides a code to the computing device, which in turn, unlocks the appropriate software (or features of software) residing on, or being used in conjunction with, the computing device. The approval or unlocking code may be provided after payment or another condition is satisfied. The software is usable on any computing device that is logged onto a central server, via a user's valid account. The central service may unlock the software for the entire time a user is logged in to the central service, or there may be a time limit that the user is able to access the software. Authorization to use the software on any computing device may be granted while the user has a valid account or subscription to the service, or may be limited to a predetermined time period (e.g., a rental period of 30 days).
Owner:MICROSOFT TECH LICENSING LLC
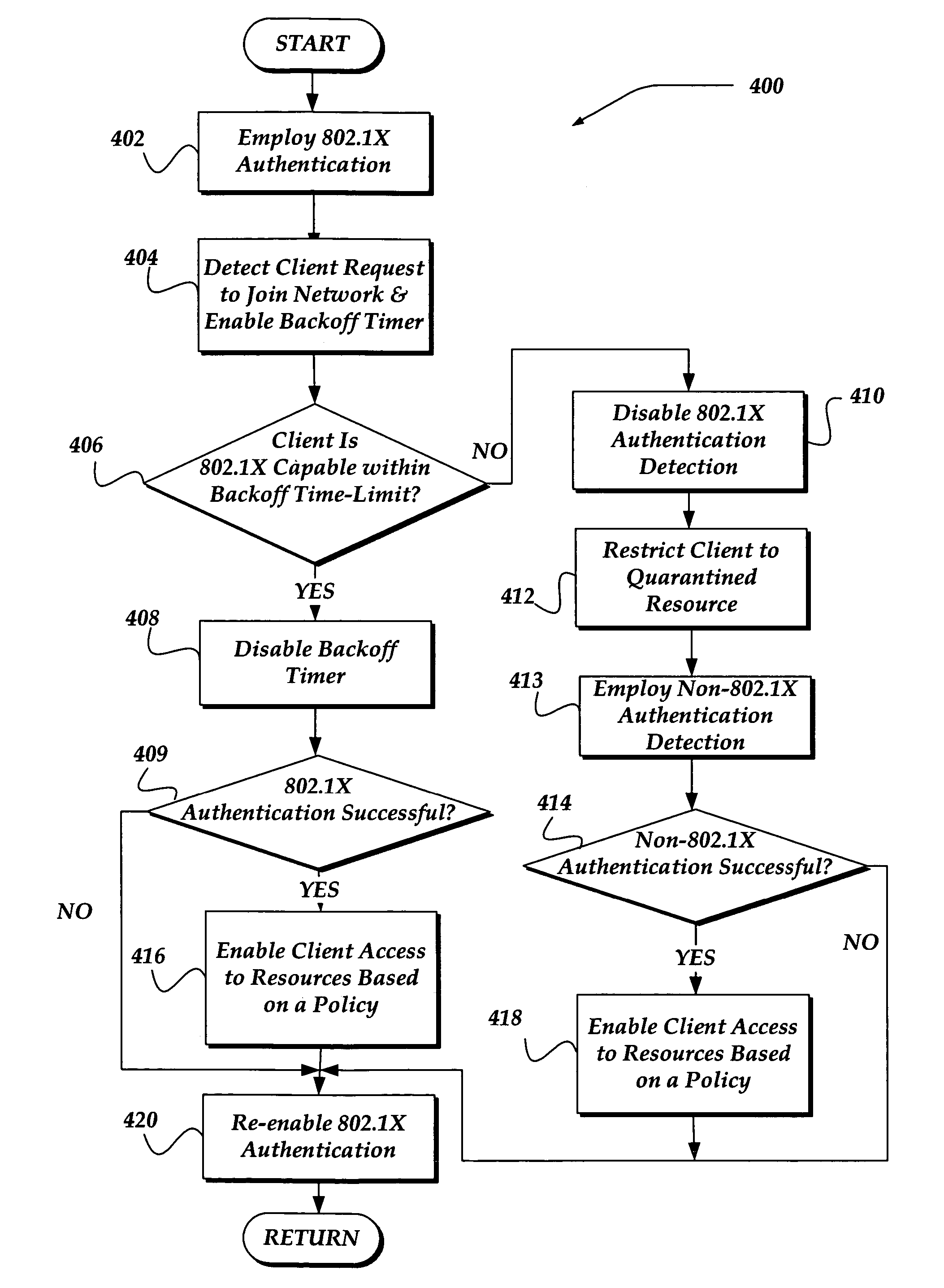
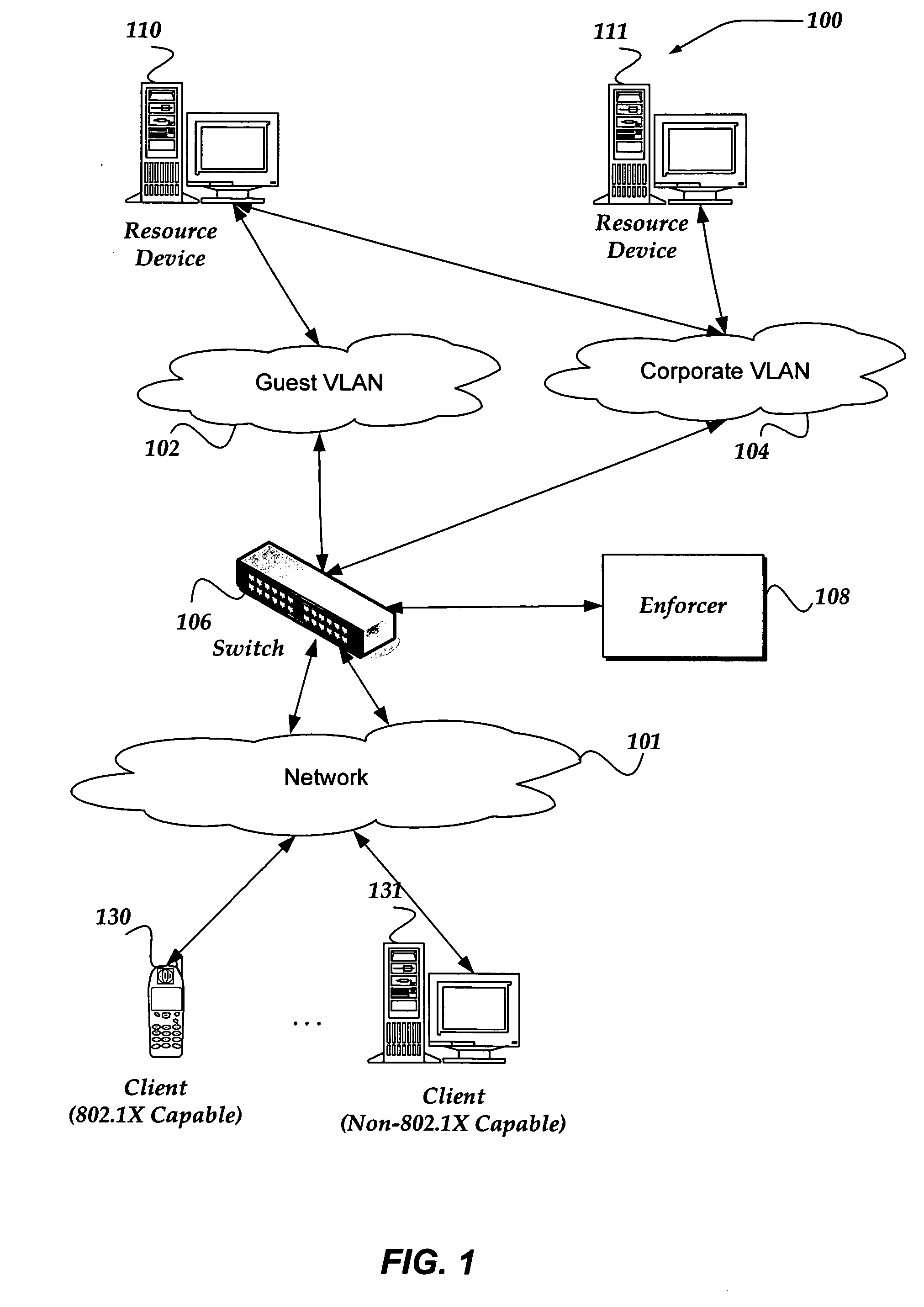
Enabling dynamic authentication with different protocols on the same port for a switch
InactiveUS20060168648A1Digital data processing detailsUser identity/authority verificationPasswordTime limit
The invention enables a client device that does not support IEEE 802.1X authentication to access at least some resources provided through a switch that supports 802.1X authentication by using dynamic authentication with different protocols. When the client device attempts to join a network, the switch monitors for an 802.1X authentication message from the client device. In one embodiment, if the client fails to send an 802.1X authentication message, respond to an 802.1X request from the switch, or a predefined failure condition is detected the client may be deemed incapable of supporting 802.1X authentication. In one embodiment, the client may be initially placed on a quarantine VLAN after determination that the client fails to perform an 802.1X authentication within a backoff time limit. However, the client may still gain access to resources based on various non-802.1X authentication mechanisms, including name / passwords, digital certificates, or the like.
Owner:MCAFEE LLC
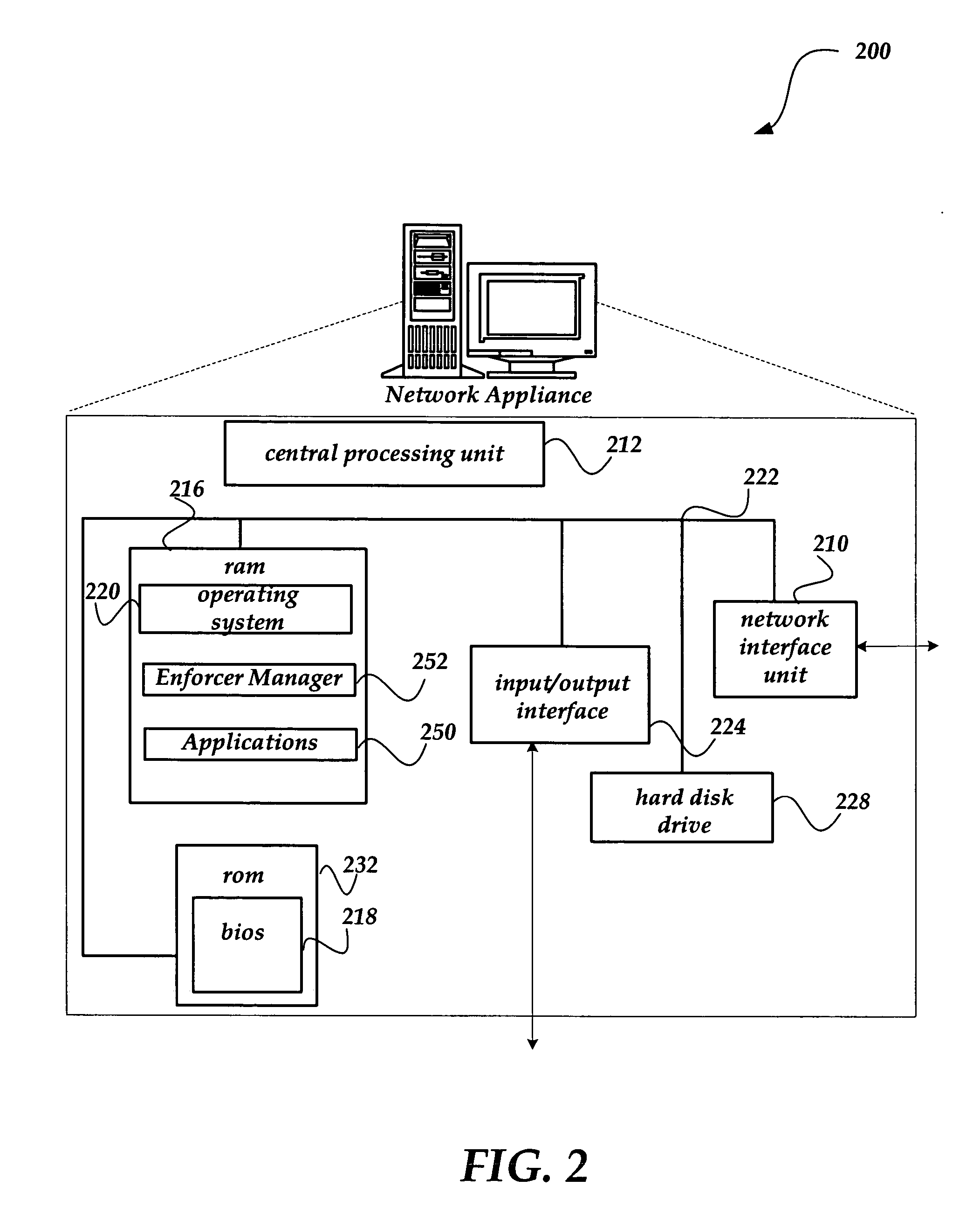
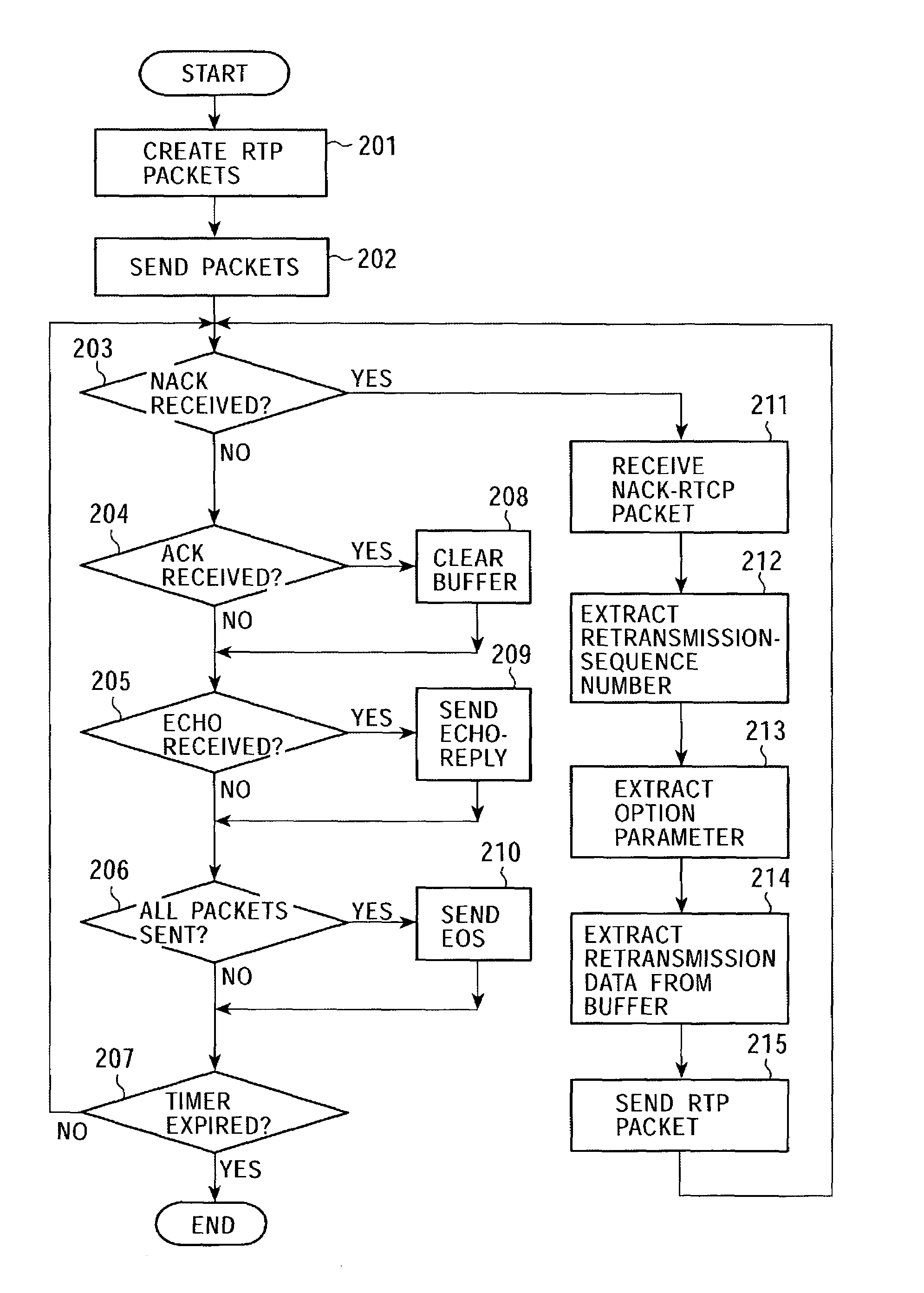
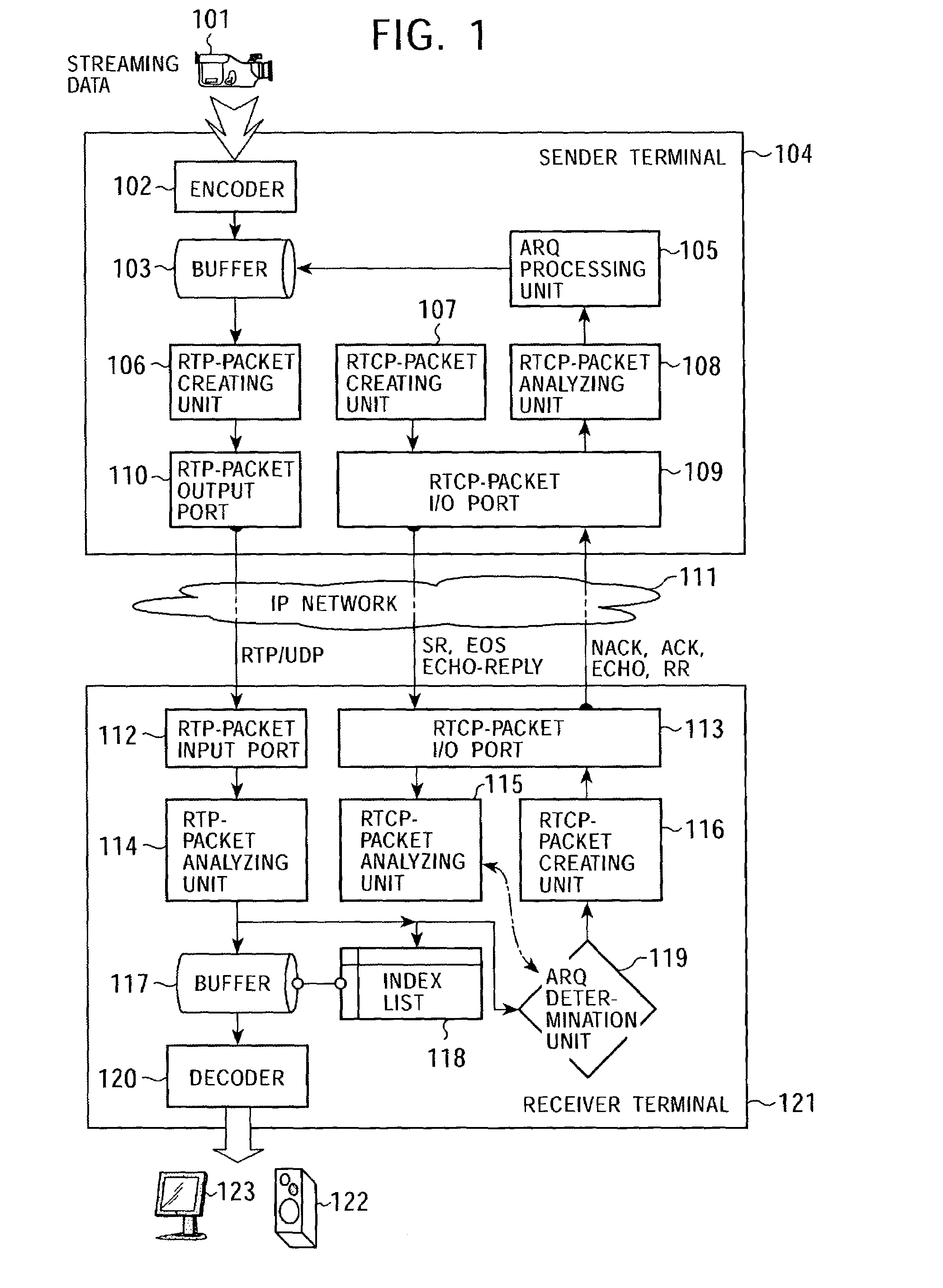
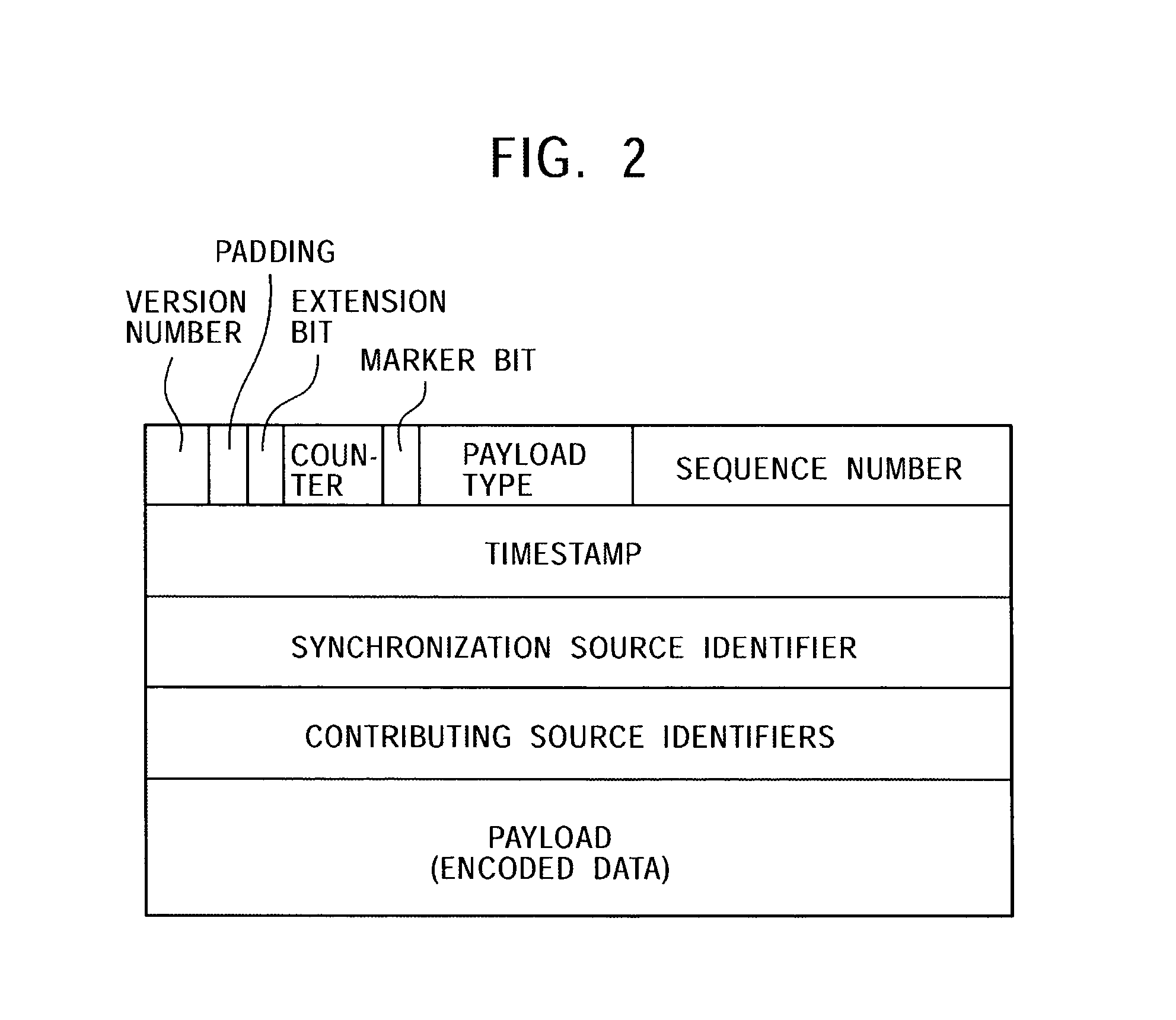
Data communication system, data transmission apparatus, data reception apparatus, data communication method, and computer program
ActiveUS7315898B2Quality improvementEfficient transferError prevention/detection by using return channelFrequency-division multiplex detailsCommunications systemAutomatic repeat request
In a data communication system, the function of automatic repeat request is provided for transmission of packets based on a data communication protocol such as the Real-Time Transport Protocol or the User Datagram Protocol. Lost packets are detected at various timings, for example, when the beginning packet of each frame is received, the final frame of each frame is received, at a time limit of processing, and at a regular interval, and retransmission requests are issued accordingly. A data reception terminal does not issue a retransmission request if associated retransmission data will not be in time for playing with consideration of processing time and roundtrip time, thereby avoiding the transmission of useless retransmission request packets and retransmission packets.
Owner:SONY CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com