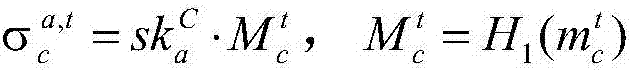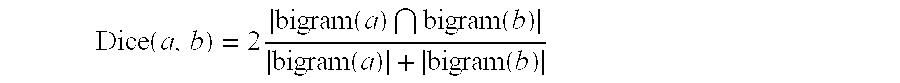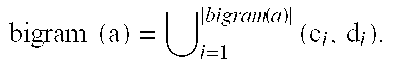Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
376 results about "Three party" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Tripartisme (French: [tʁi.paʁ.tism]) was the mode of government in France from 1944 to 1947, when the country was ruled by a three-party alliance of communists, socialists and Christian democrats, represented by the French Communist Party (PCF), the French Section of the Workers' International (SFIO) and the Popular Republican Movement (MRP), ...
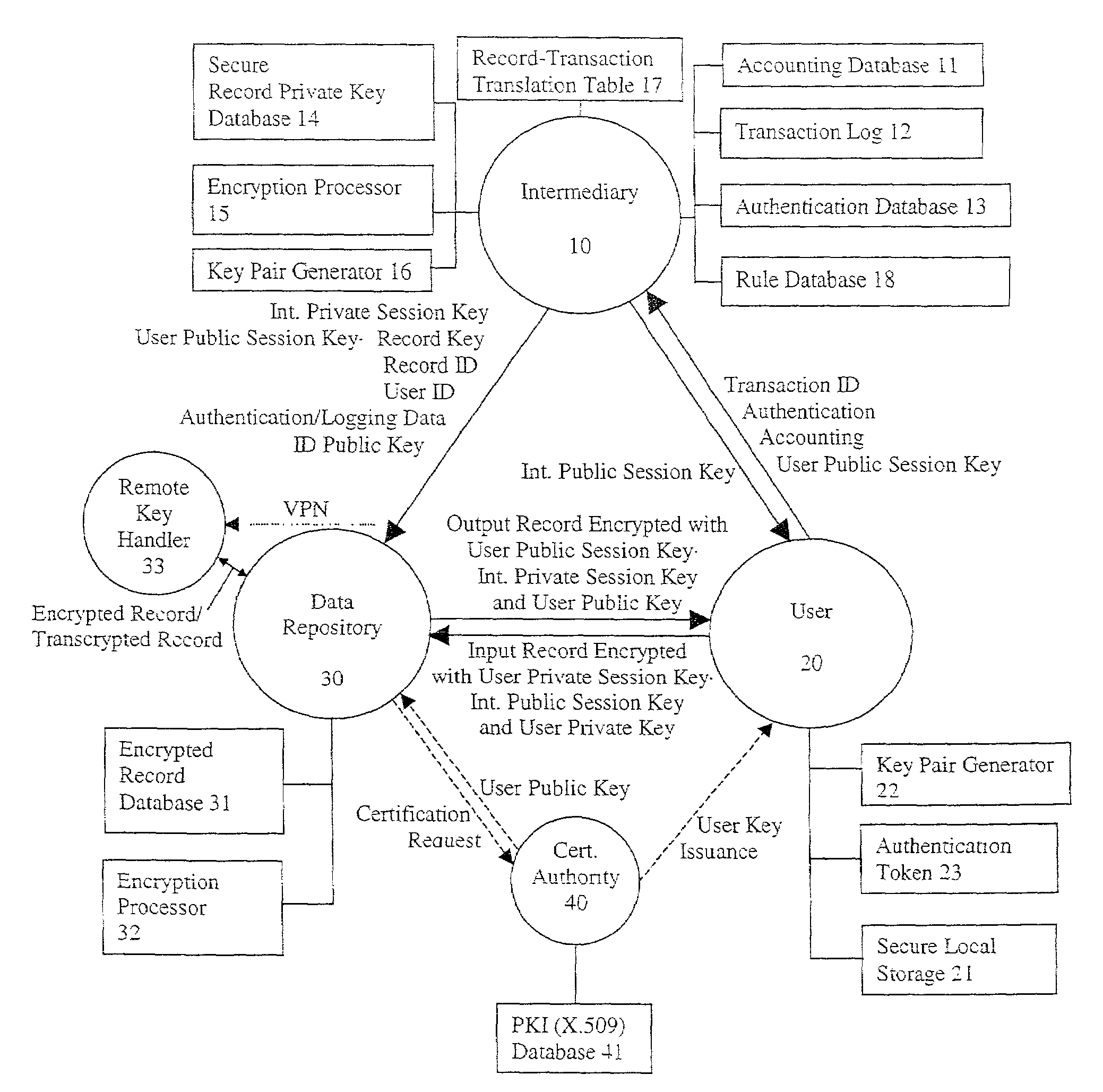
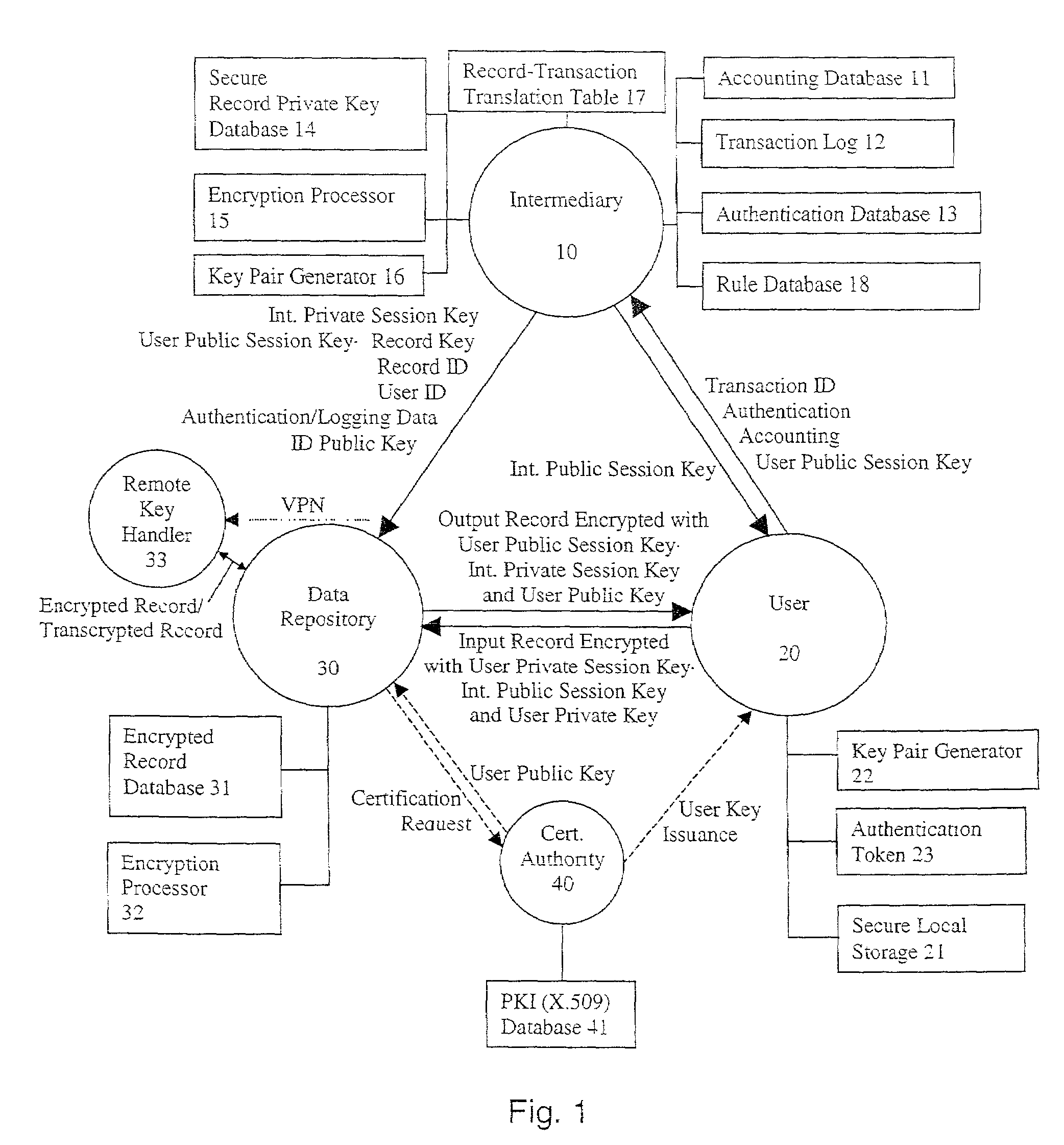
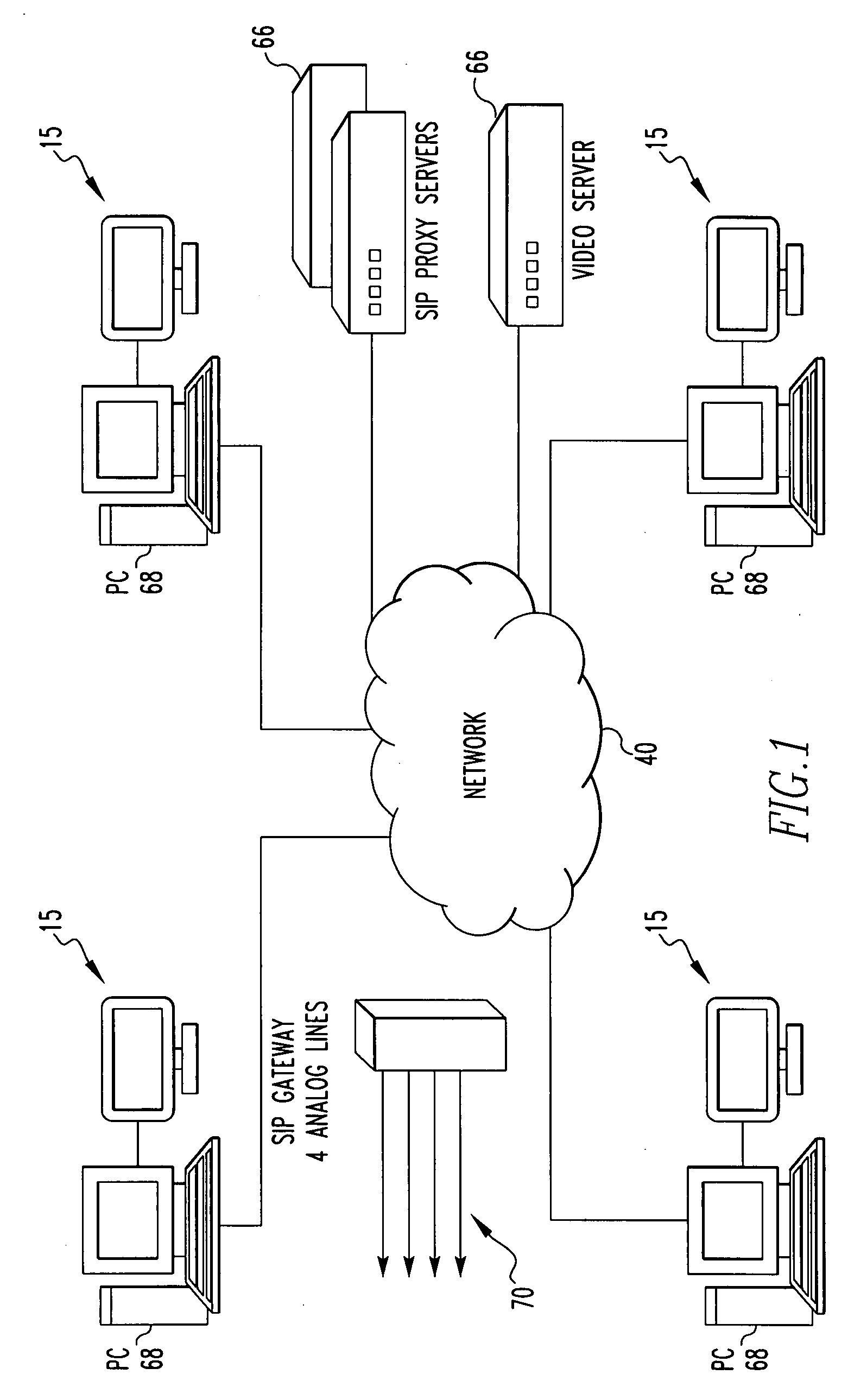
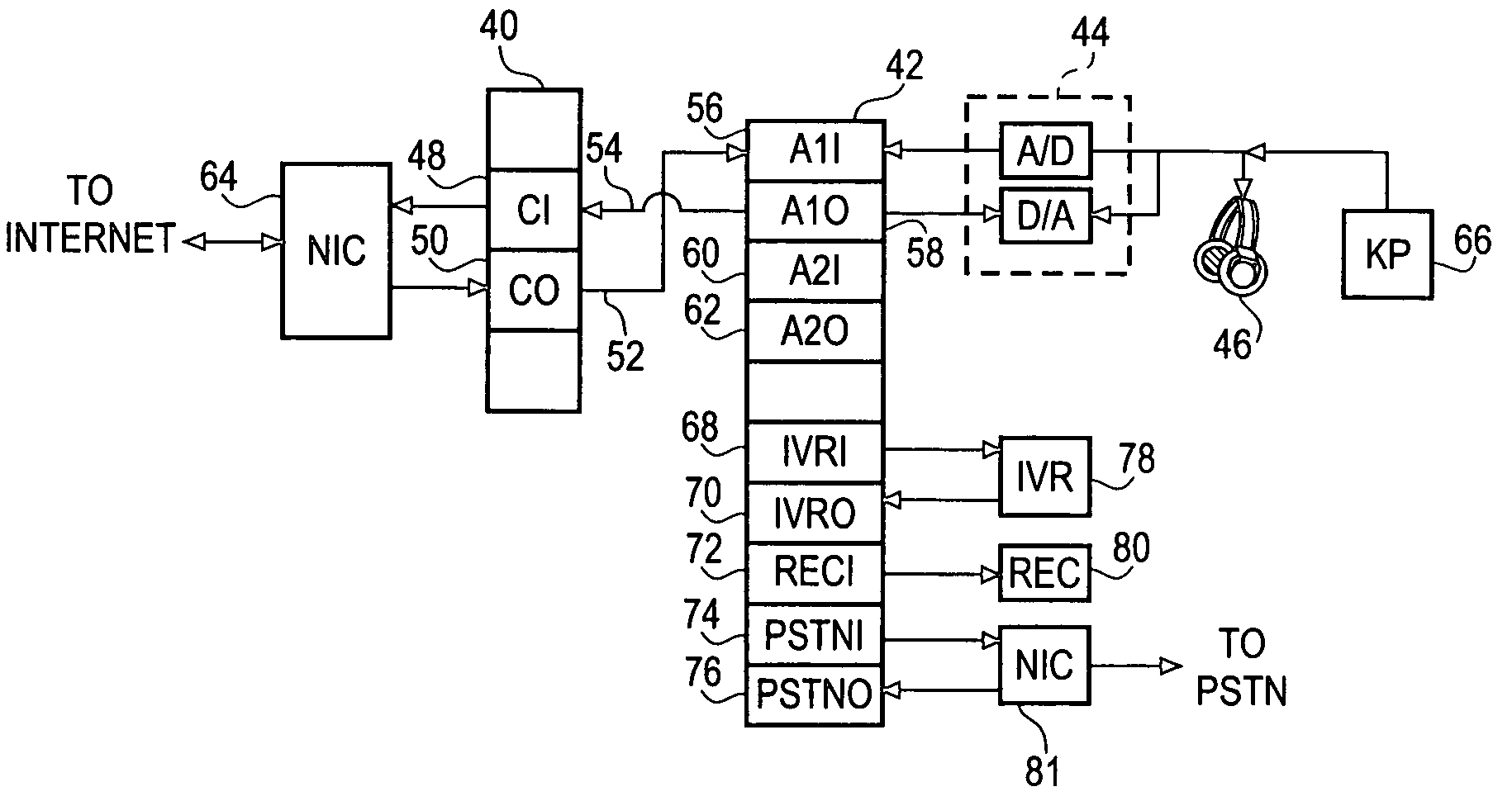
System and method for secure three-party communications
ActiveUS7181017B1Reduce liabilityReduce riskKey distribution for secure communicationTime limitThree party
A system and method for communicating information between a first party and a second party, comprising identifying desired information, negotiating, through an intermediary, a comprehension function for obscuring at least a portion of the information communicated between the first party and the second party, communicating the encrypted information to the second party, and decrypting the encrypted information using the negotiated comprehension function. Preferably, the intermediary does not itself possess sufficient information to decrypt the encrypted information, thus allowing use of an “untrusted” intermediary. The comprehension function may be dynamic with respect to its response to the negotiated comprehension function, and thus permit limitations on the use of the information by the second party. For example, the decryption of the encrypted information may be time limited.
Owner:RPX CORP
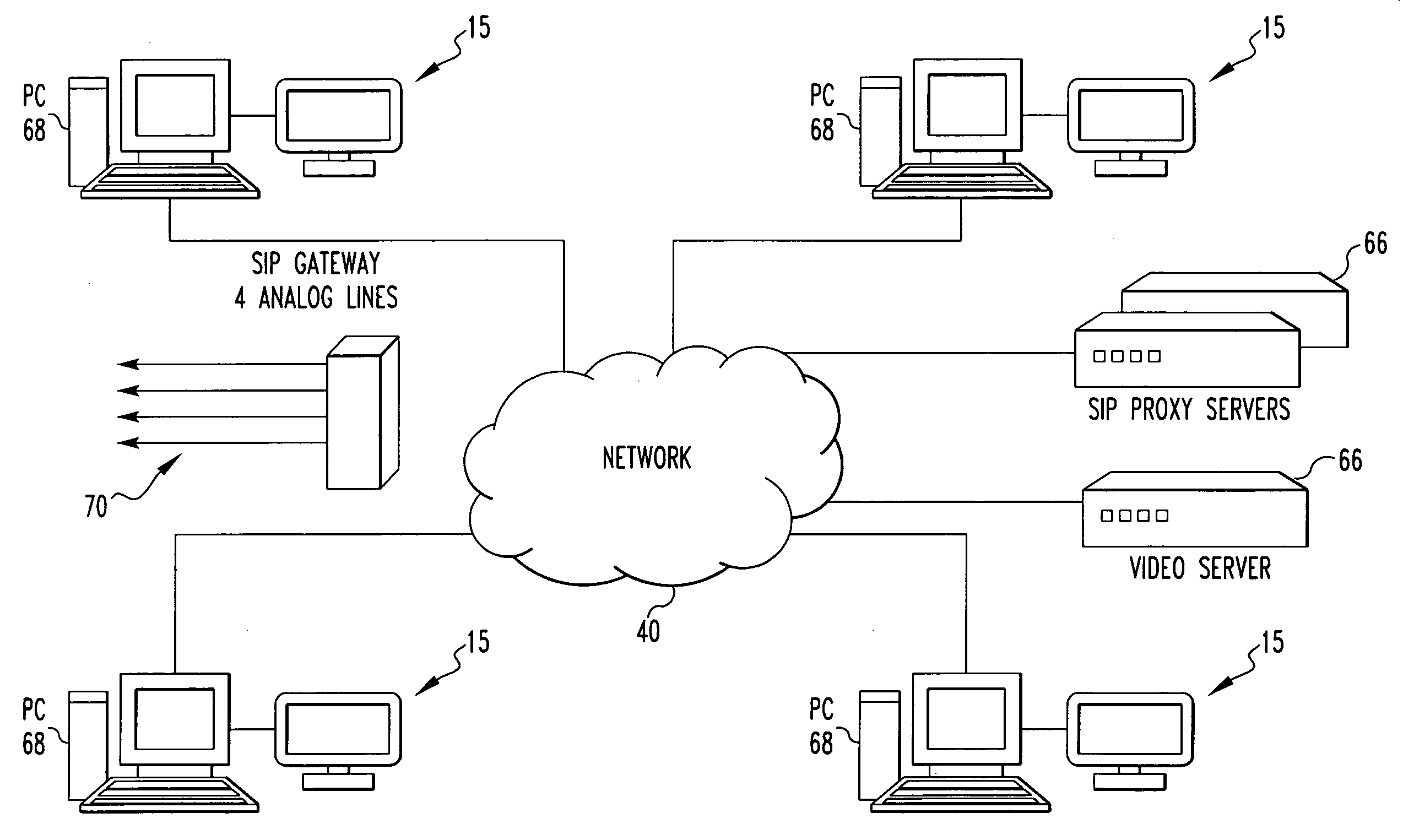
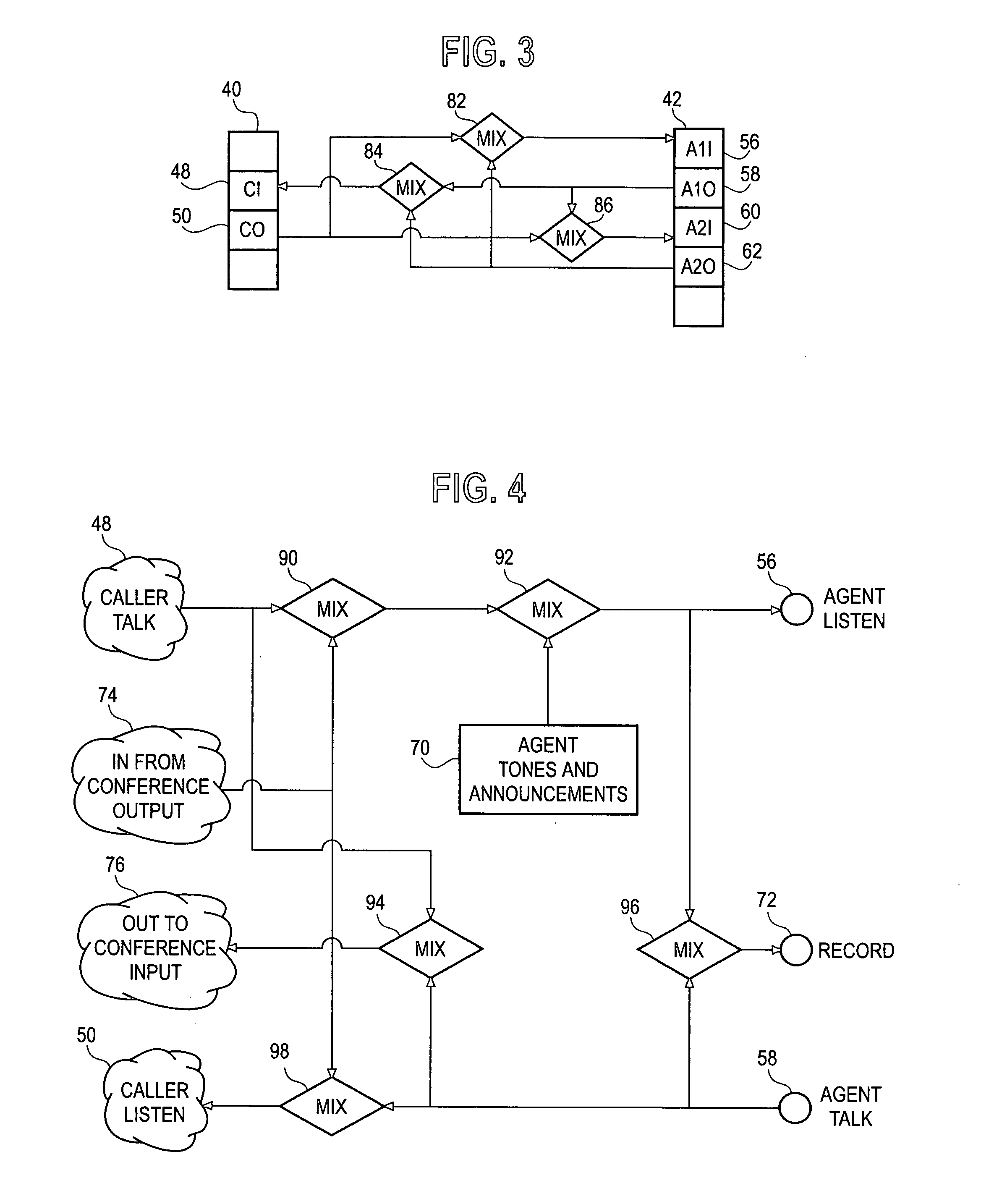
Conference layout control and control protocol
InactiveUS20070291108A1Effective controlReduction of intermediate node processingMultiplex system selection arrangementsSpecial service provision for substationDisplay deviceRTP Control Protocol
A teleconferencing system includes a network. The system includes a plurality of nodes in communication with each other to form a conference. Each node having a video display with a display layout, at least one of the nodes individually controlling at least partially the display layout of each node in the conference with a specific format able to be unique for each node. A method for providing a teleconference including the steps of forming a conference with a plurality of nodes in communication with each other through a network. Each node having a video display with a display layout. There is the step of controlling individually with at least one of the nodes at least partially the display layout of each node in the conference with a specific format able to be unique for each node. A teleconferencing node. A teleconferencing system includes a network. The system includes a plurality of nodes in communication with each other through the network to form a conference. Each node communicating only a change to the other nodes when the change occurs. A method for conducting a telecommunications conference between at least three parties includes the steps of establishing a conference between the party. There is the step of making a change to the conference. There is the step of communicating only the change to the parties.
Owner:TELEFON AB LM ERICSSON (PUBL)
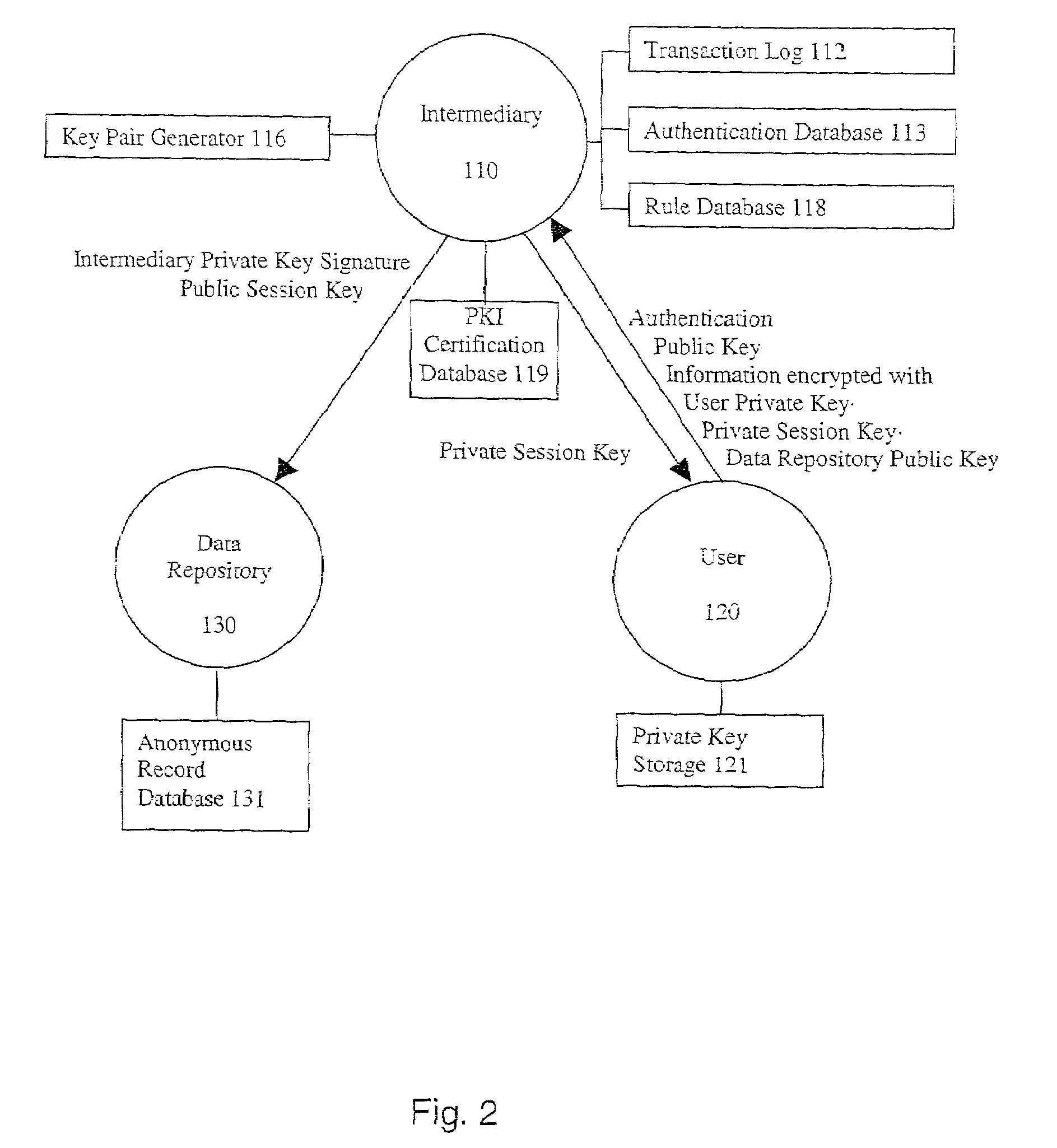
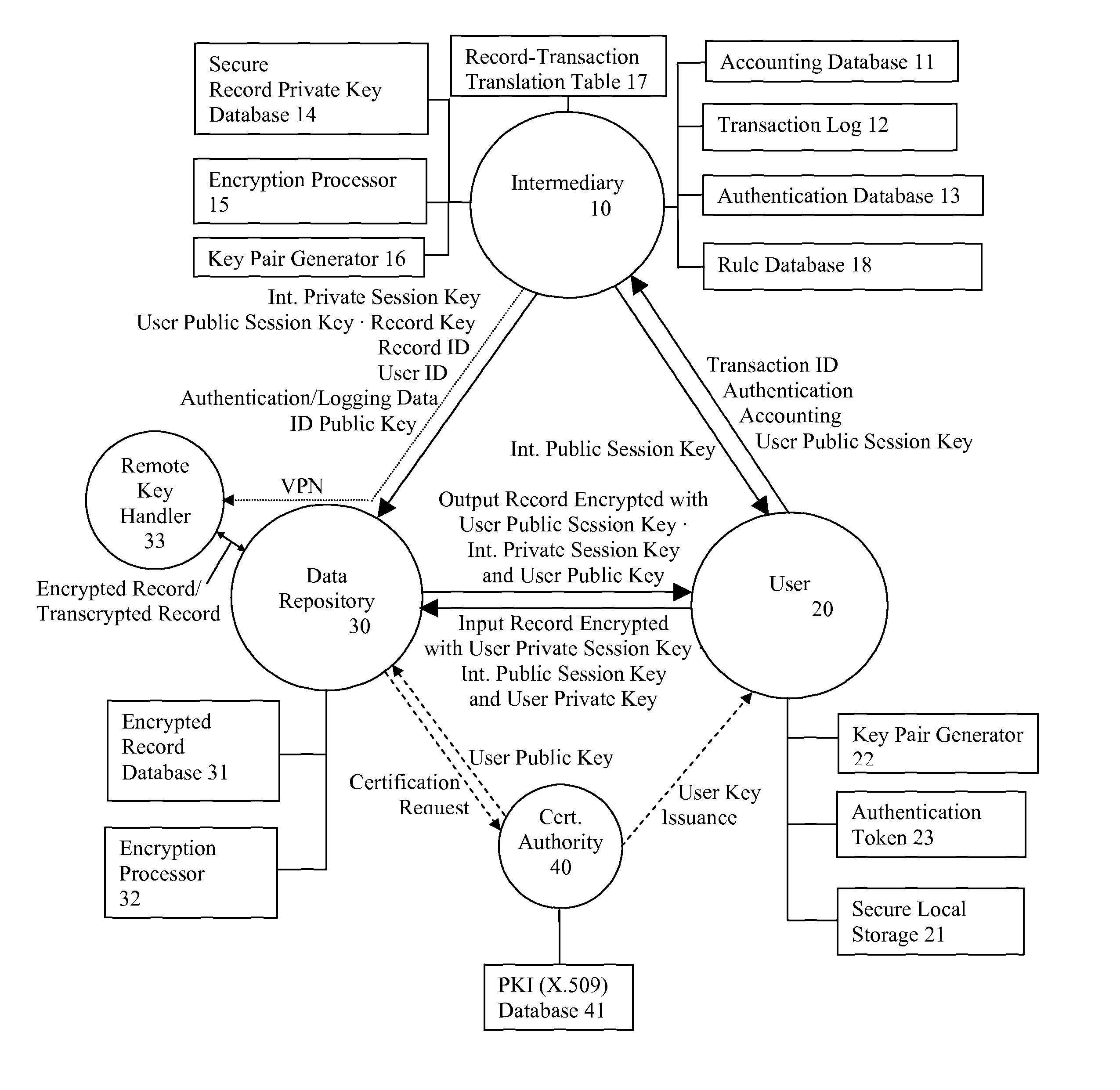
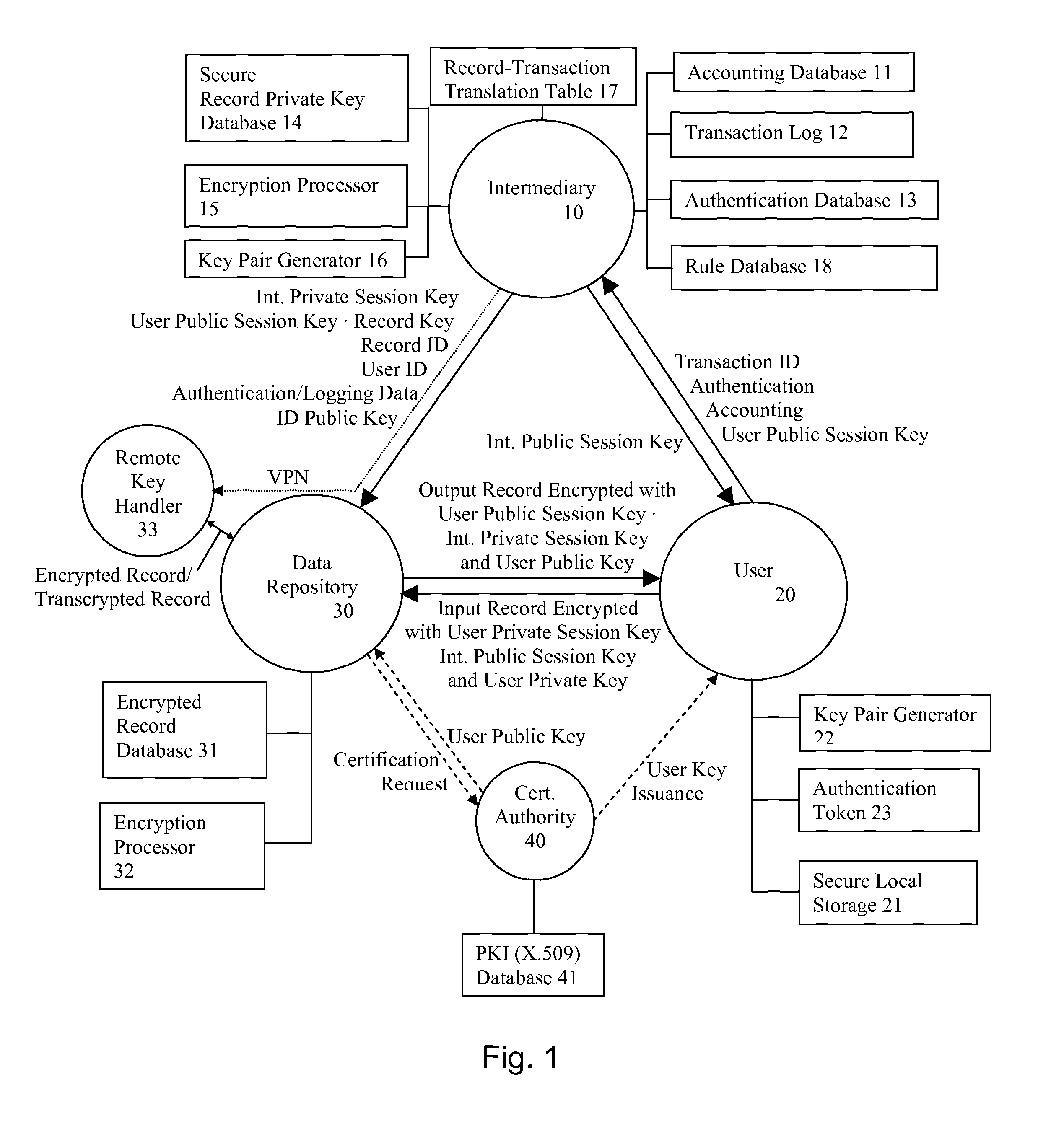
System and method for secure three-party communications
InactiveUS7869591B1Reduce liabilityReduce riskKey distribution for secure communicationSecret communicationKey exchangeTranscoding
A system and method for communicating information between a first party and a second party, comprising the steps of receiving, by an intermediary, an identifier of desired information and accounting information for a transaction involving the information from the first party, transmitting an identifier of the first party to the second party, and negotiating, by the intermediary, a comprehension function for obscuring at least a portion of the information communicated between the first party and the second party. The data transmission may be made secure with respect to the intermediary by providing an asymmetric key or direct key exchange for encryption of the communication between the first and second party. The data transmission may be made secure with respect to the second party by maintaining the information in encrypted format at the second party, with the decryption key held only by the intermediary, and transmitting a secure composite of the decryption key and a new encryption key to the second party for transcoding of the data record, and providing the new decryption key to the first party, so that the information transmitted to the first party can be comprehended by it.
Owner:RPX CORP
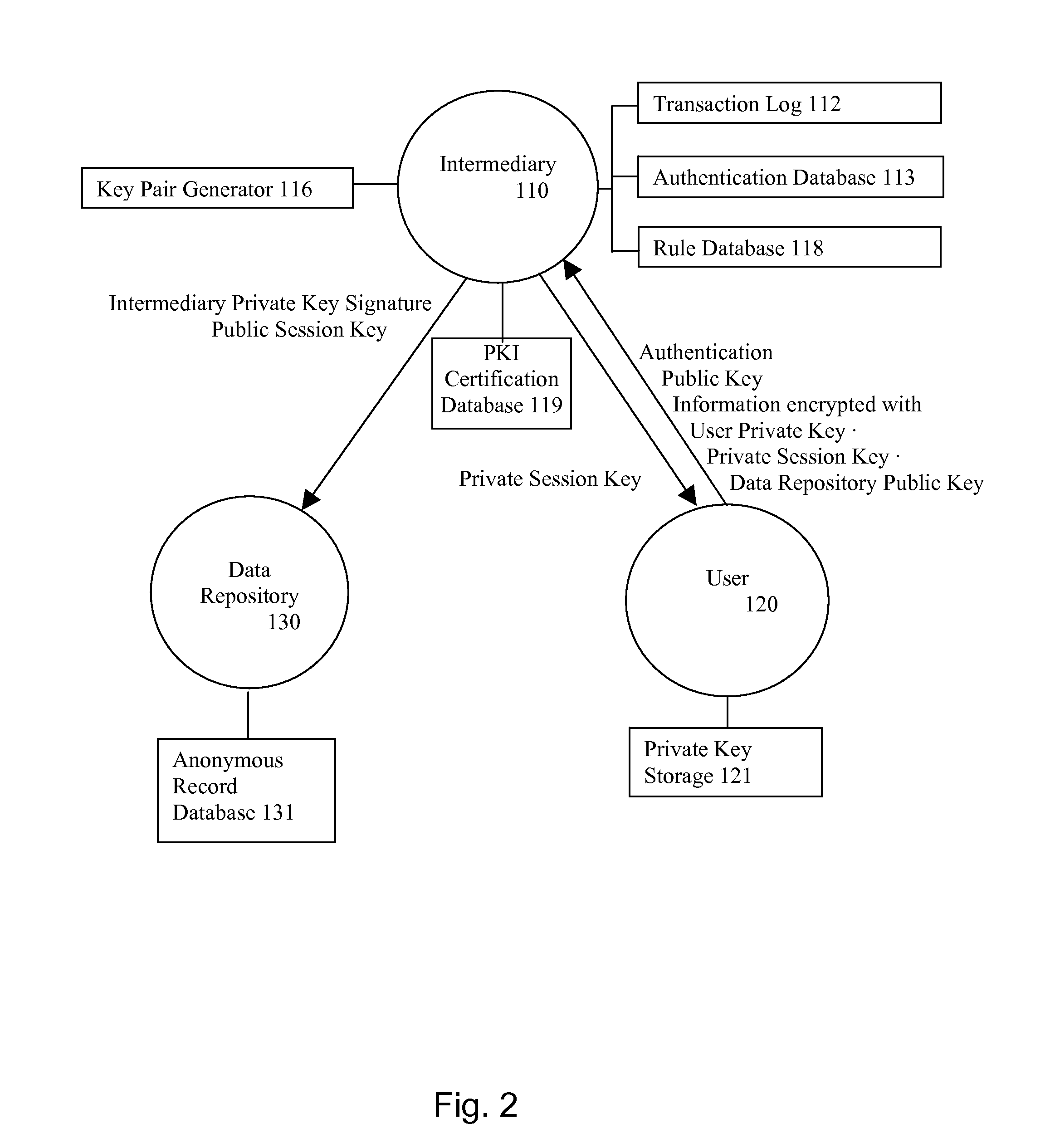
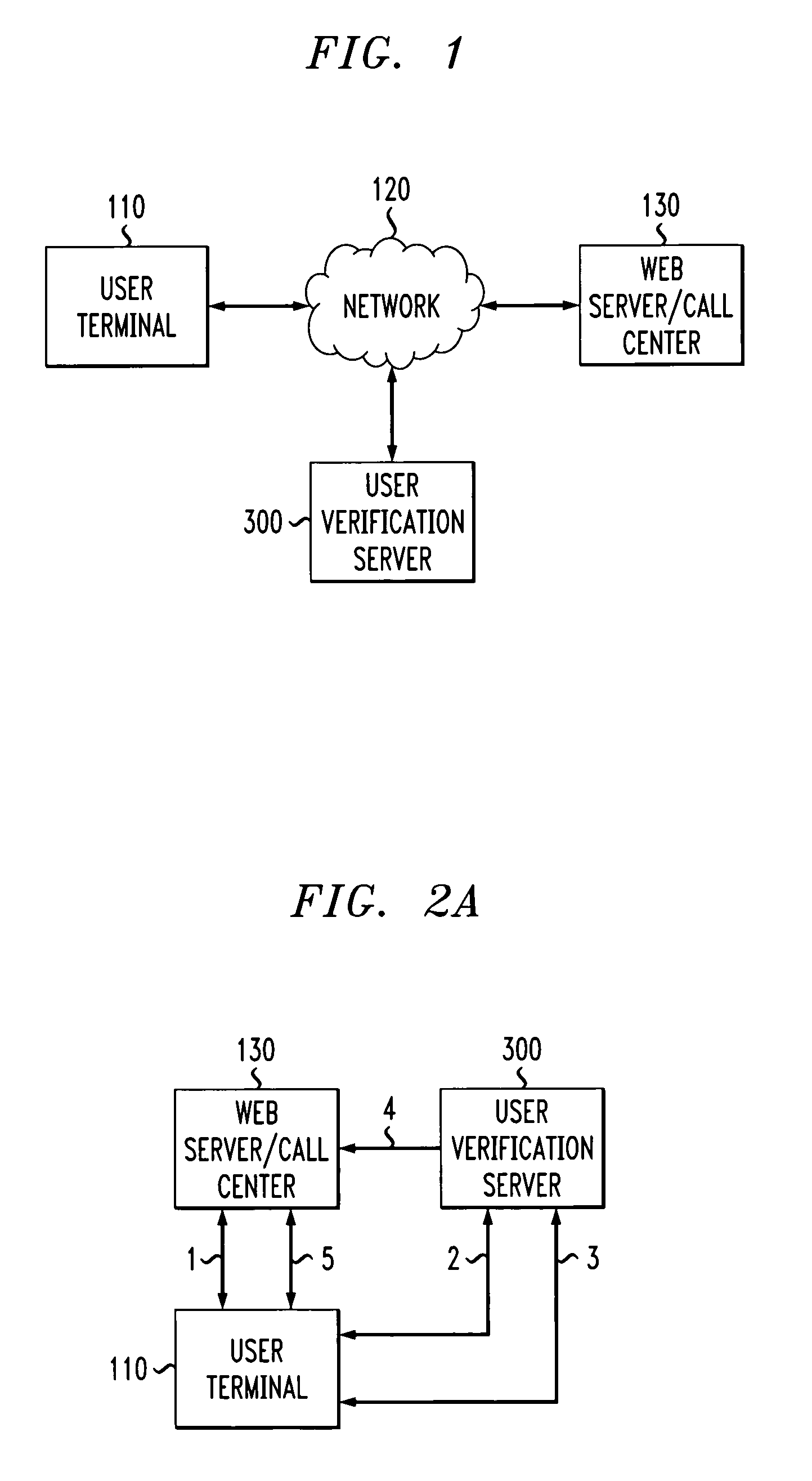
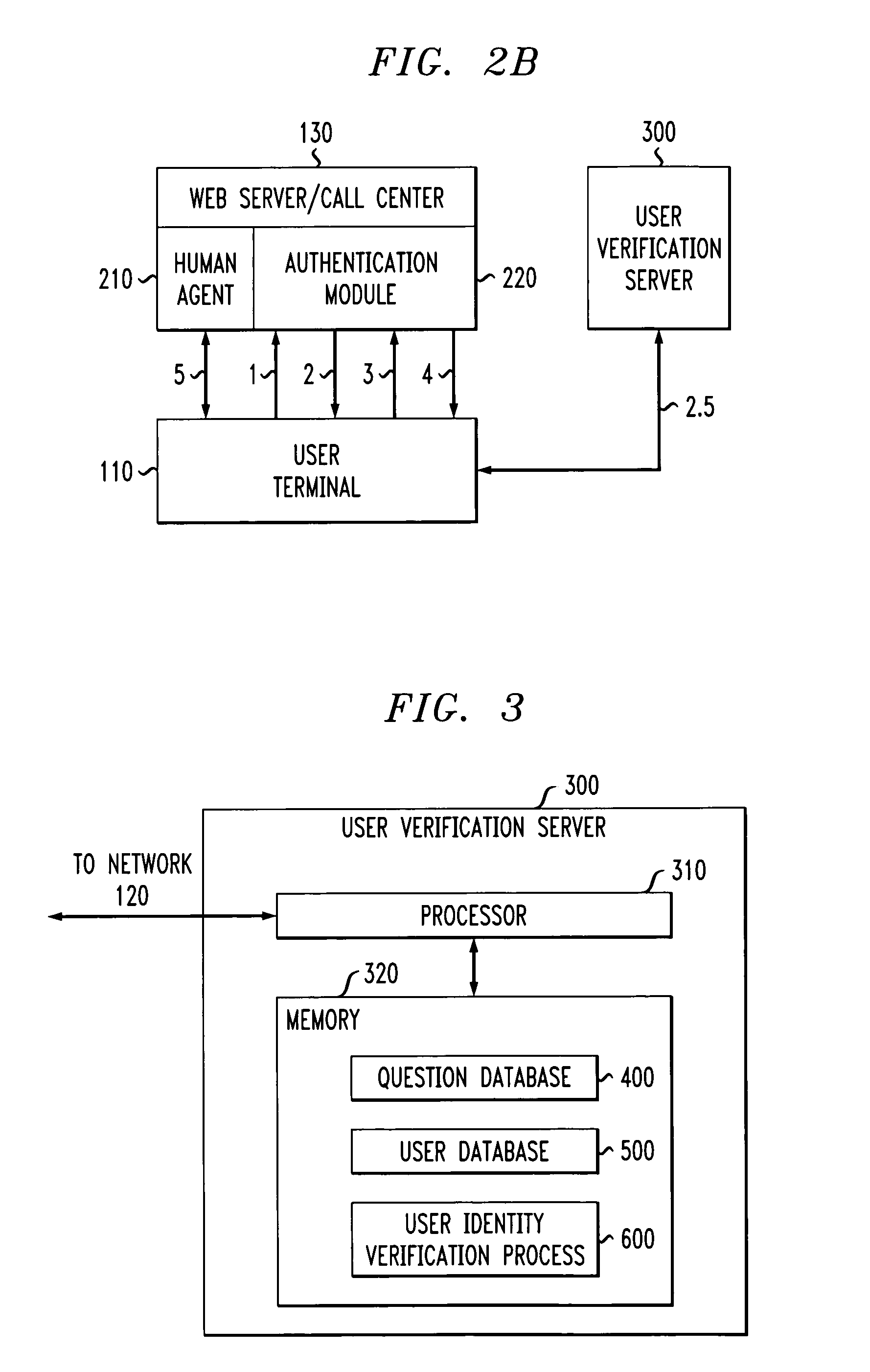
Method and apparatus for authenticating a user using three party question protocol
InactiveUS20050039056A1Digital data processing detailsSpecial service for subscribersUser verificationHuman agent
A three party authenticating protocol is disclosed. During an enrollment phase, a user contacts a call center and is directed to a user verification server. The user verification server instructs the user to select and answer a number of questions that will be used for verification. The selected questions along with identifying indices for each question are stored at the user's location and at the user verification server. The user verification server sends the question indices to the call center, which in turn sends these indices to the user to obtain answer indices for each question. During a verification phase, the user contacts the call center and an authentication module asks the user to provide an asserted identity. The authentication module provides a random selection of question indices from those selected by the user. The user provides answer indices for each question to the authentication module. If the number of correctly matching answers exceeds a threshold, then the user is verified. Otherwise, the user fails verification. After verification, the user is transferred from the authentication module of the call center to a human agent for further processing.
Owner:AVAYA INC
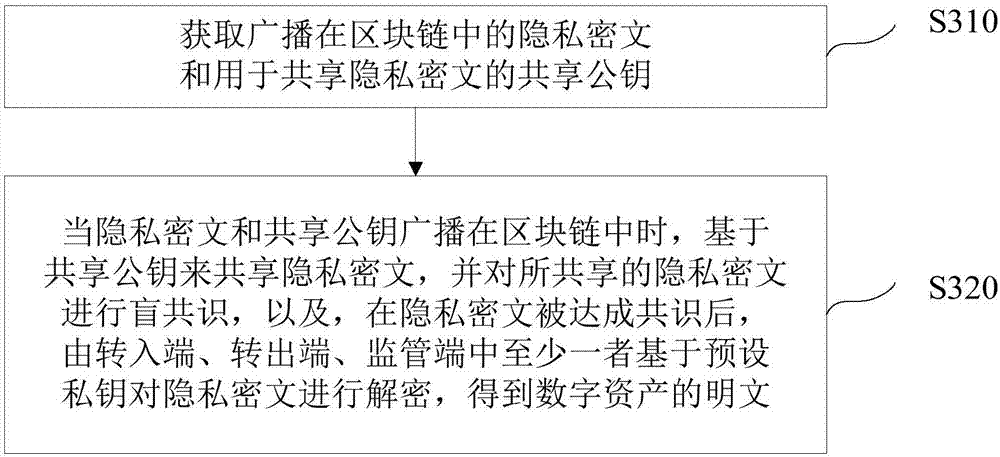
Blockchain-based digital asset processing method and device
ActiveCN106982205AProtection of privacySmooth circulationKey distribution for secure communicationDigital data protectionPlaintextCiphertext
The invention discloses a blockchain-based digital asset processing method and device. The method comprises the following steps: receiving private ciphertext for a digital asset circulated from a sending end to a receiving end through a blockchain, and a preset public key; and obtaining a sharing public key for sharing the private ciphertext based on the preset public key, so that when the private ciphertext and the sharing public key are broadcast in the blockchain, blockchain nodes on the blockchain can share the private ciphertext based on the sharing public key and reach a blind consensus on the shared private ciphertext, and after the consensus on the private ciphertext is reached, the private ciphertext can be decrypted by at least one of three parties, i.e., the sending end, the receiving end and a monitoring end, based on a preset private key to obtain plaintext of the digital asset. The method and device provided by the embodiment of the invention has the advantages that the privacy right of a user is protected; under the premise of privacy protection, the single general digital asset can be smoothly circulated within one blockchain or among multiple blockchains, and a total currency amount remains unchanged; and a monitoring party other than the transaction parties can monitor transaction information at any time.
Owner:中钞信用卡产业发展有限公司杭州区块链技术研究院 +1
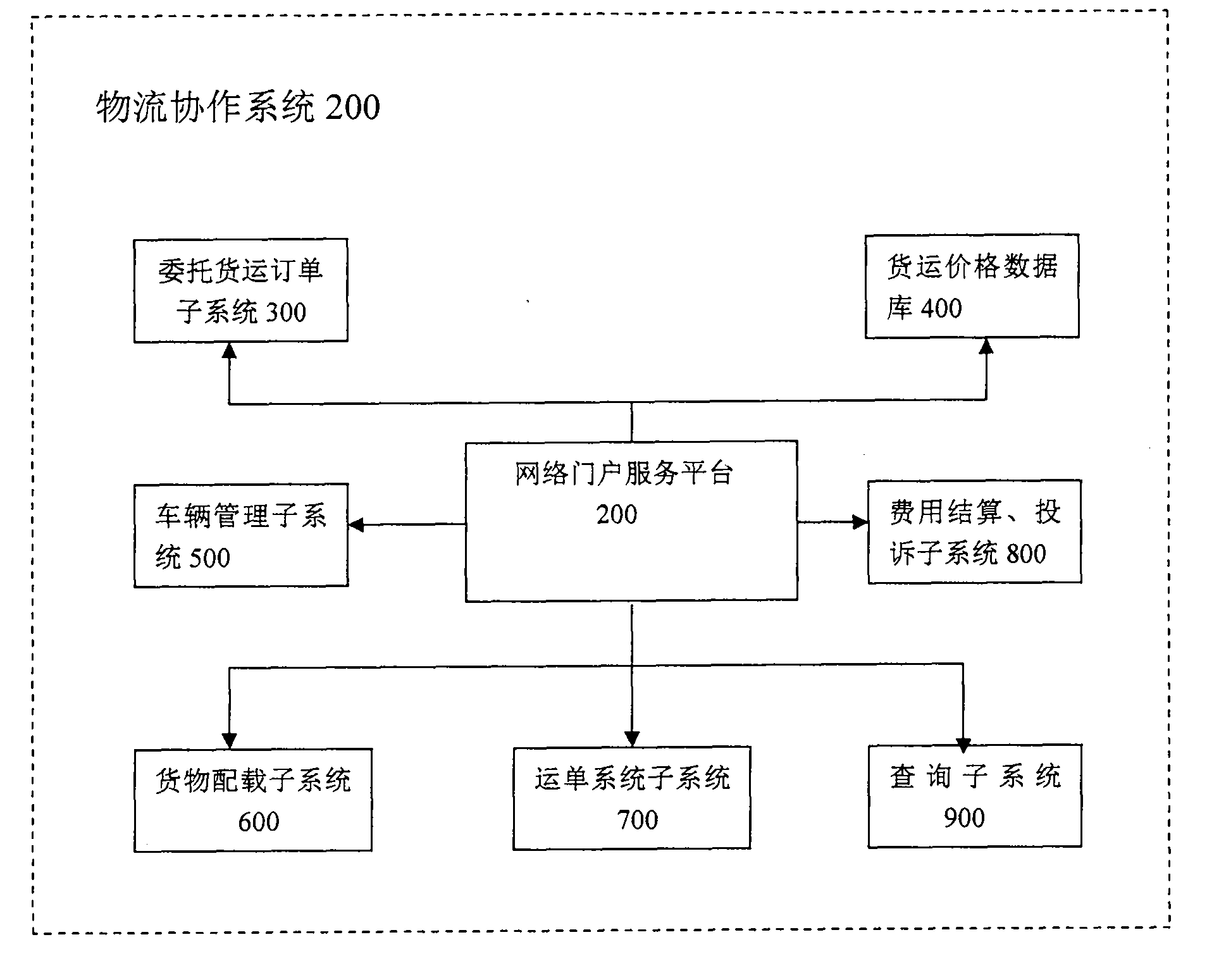
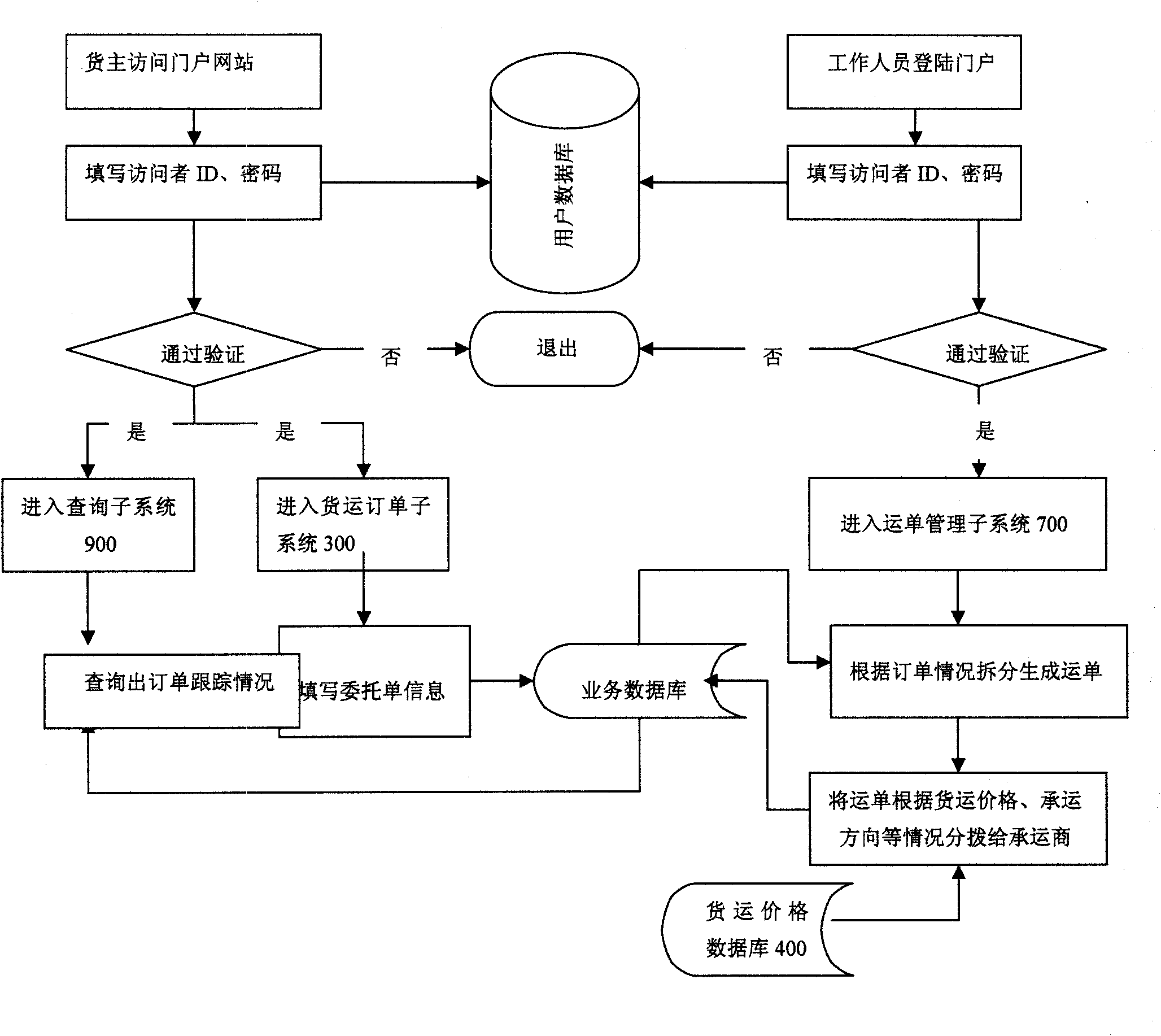
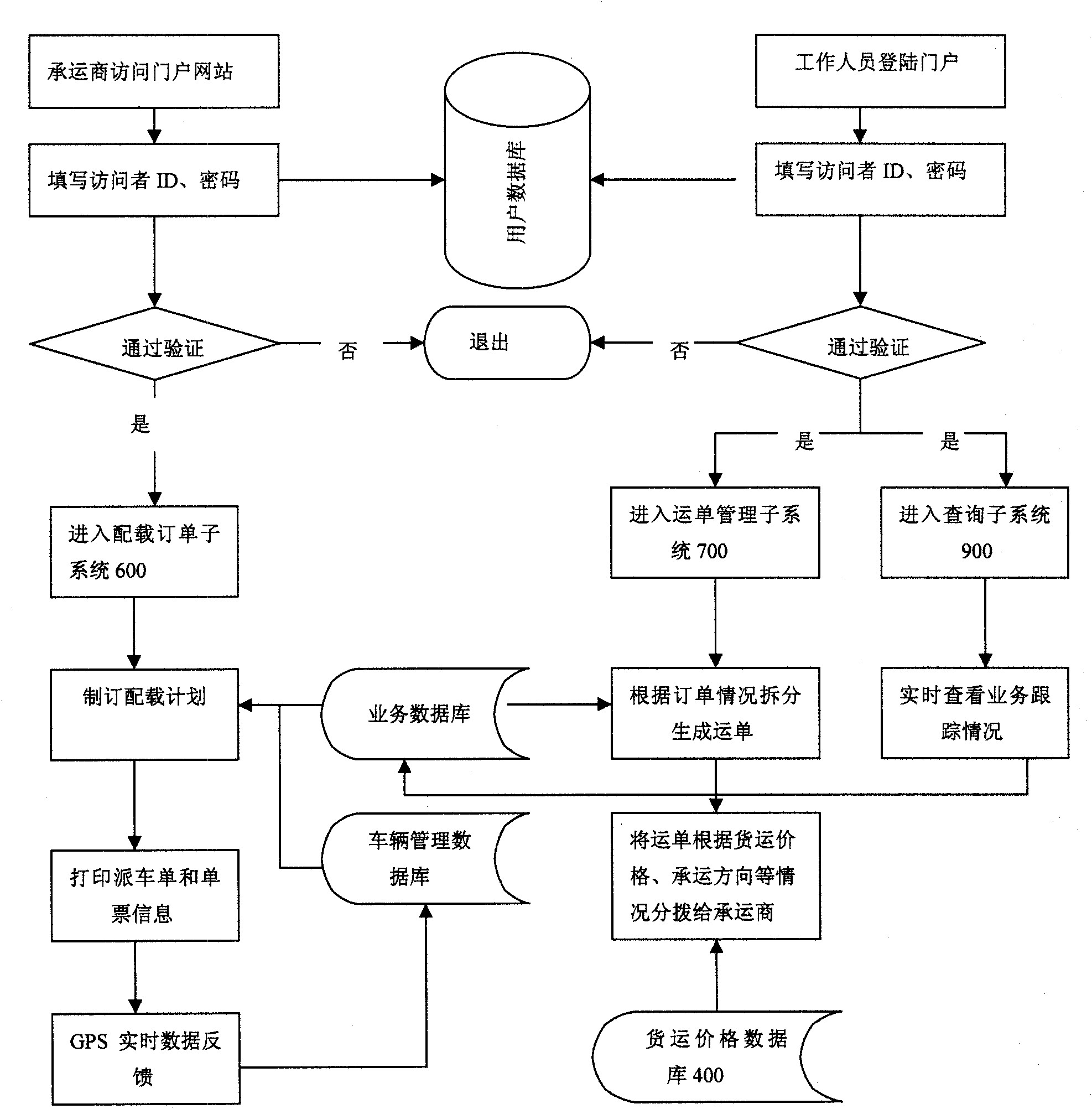
Transportation management method based on joint collaboration of logistics company, shipper and carrier
InactiveCN101923666AHigh transparencyImprove tightnessLogisticsLogistics managementNetworking protocol
The invention relates to a transportation management method based on the joint collaboration of a logistics company, a shipper and a carrier. The transportation management method comprises the following steps: the logistics company creates a transportation management system network platform; the shipper and the carrier visit the system network platform through the network protocol, and the logistics company signs a contract with the shipper and the carrier and delivers order information with forwarding order number according to the contract to the carrier and the shipper; the carrier adjusts according to the vehicle scheduling plan and single vote information and feedbacks the information to the system network platform; the logistics company performs expense settlement based on the information, accepts complaints and settles claims; and the network platform provides a real-time query system, so that the relevant information of accepted goods and the account statement can be checked in real time. The invention has the advantages that the shipper, the logistics company and the carrier share the total process of forwarding transportation, so that the competitiveness of a supply chain is increased; the information asymmetry caused by regional difference is solved, a supply of goods can be organized at different places, so that return vehicles of the carrier can be avoided from being empty, and benefits are brought for three parties of supplier, customer and service provider.
Owner:上海美华系统有限公司
Multi-signature transaction information processing method for data transaction platform based on block chain
ActiveCN107038578AEnsure information securityEnsure safetyPayment protocolsInformation processingPayment
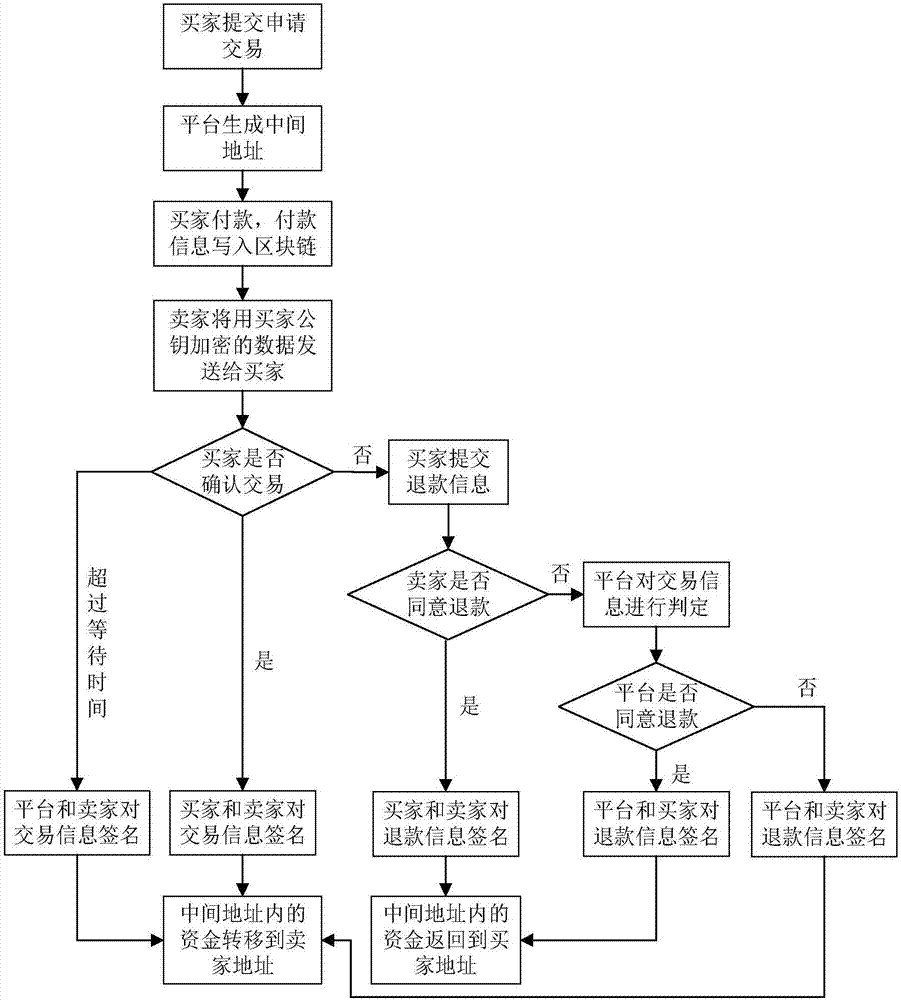
The invention discloses a multi-signature transaction information processing method for a data transaction platform based on a block chain. Each of a buyer and a seller generates a transaction key pair at self client, and the data transaction platform generates and distributes a single transaction key pair for each transaction process; the seller releases data to be transacted on the block chain via the data transaction platform; after the buyer submits a transaction application, an intermediate address is generated according to a three-party public key, money is transferred to the intermediate address after payment, and the seller receives the money, writes the money into the block chain, then encrypts data and sends the encrypted data to the buyer; after the buyer receives the data, if transaction is acknowledged, the double parties sign, and the money is transferred to the address of the seller; and if objection exists, the data transaction platform makes a judgment, and determines to transfer the money to the buyer or the seller according to the judgment result. Data and transaction information during transaction of the double parties are processed in a special regional chain manner, and meanwhile, the data transaction platform cannot embezzle the transaction money, so that the security of digital assets during transaction is further guaranteed.
Owner:浙江数秦科技有限公司
Network identity verification method based on internet third party biological characteristic validation
InactiveCN101316169AGuaranteed reliabilityEnsure safetyUser identity/authority verificationCharacter and pattern recognitionMultiple encryptionApplication software
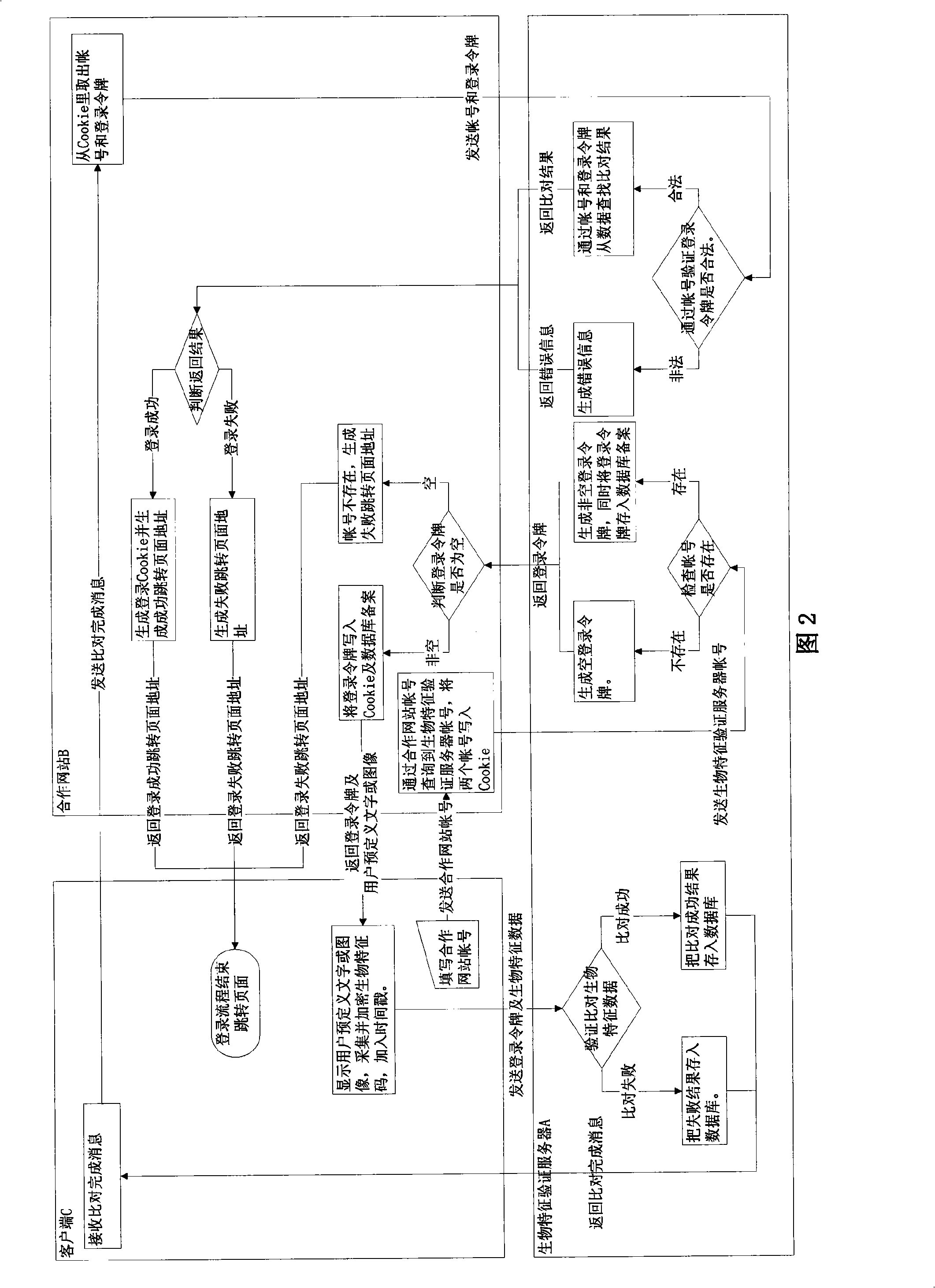
The invention provides a network identity authentication method based on the biological characteristic authentication of a third party on the Internet. The biological characteristics (fingerprint, human face, iris, lip membrane and so on) are used as the identity identification of the user, the user can obtain an authentication request from the third party by submitting the biological characteristic codes through a client terminal widget provided by the third party, the identity authentication is carried out through the request password process and the matching algorithm, the Internet identity authentication can be carried out through a fully cooperative website or an application program provided by a cooperative network in a self-help mode, the third party provides request interfaces containing the registration, verification, reset of the biological characteristics, binding information,etc., the third party needs not to know the name of the user in the cooperative website or the application program provided by the cooperative network, thus avoiding to obtain the other information of the user in the cooperative website or the application program provided by the cooperative network, the reliability at the service terminal and the communication safety among the three parties can be guaranteed through the complete active service request of the cooperative website or the application program provided by the cooperative network, the Cookie, SSL, multi-encryption, digital signature of the widget, user-defined words or pictures,etc.
Owner:张曌 +2
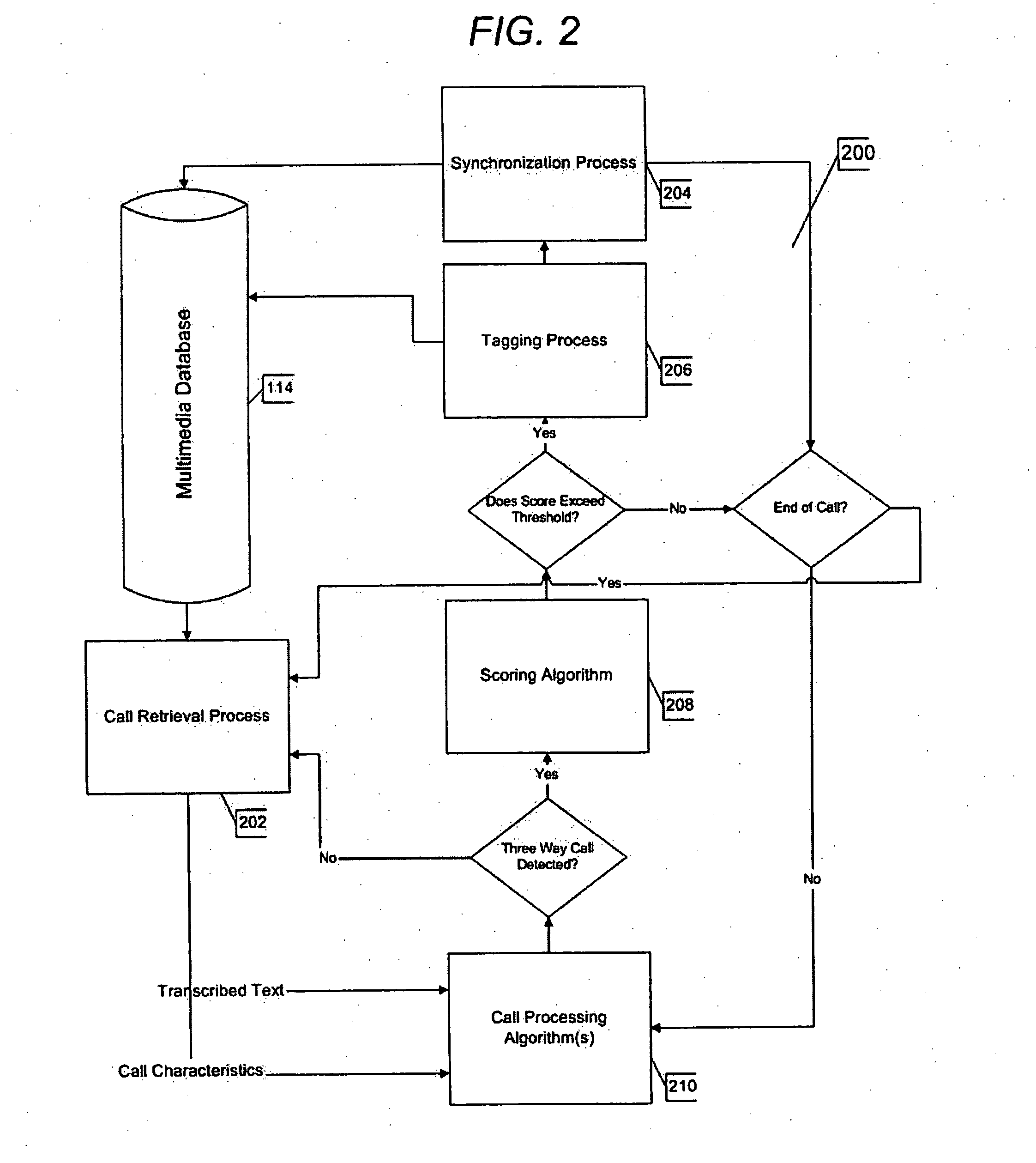
System and method for three-way call detection
ActiveUS20080198978A1Way accurateAccurate detectionDevices with voice recognitionAutomatic call-answering/message-recording/conversation-recordingSubvocal recognitionHuman language
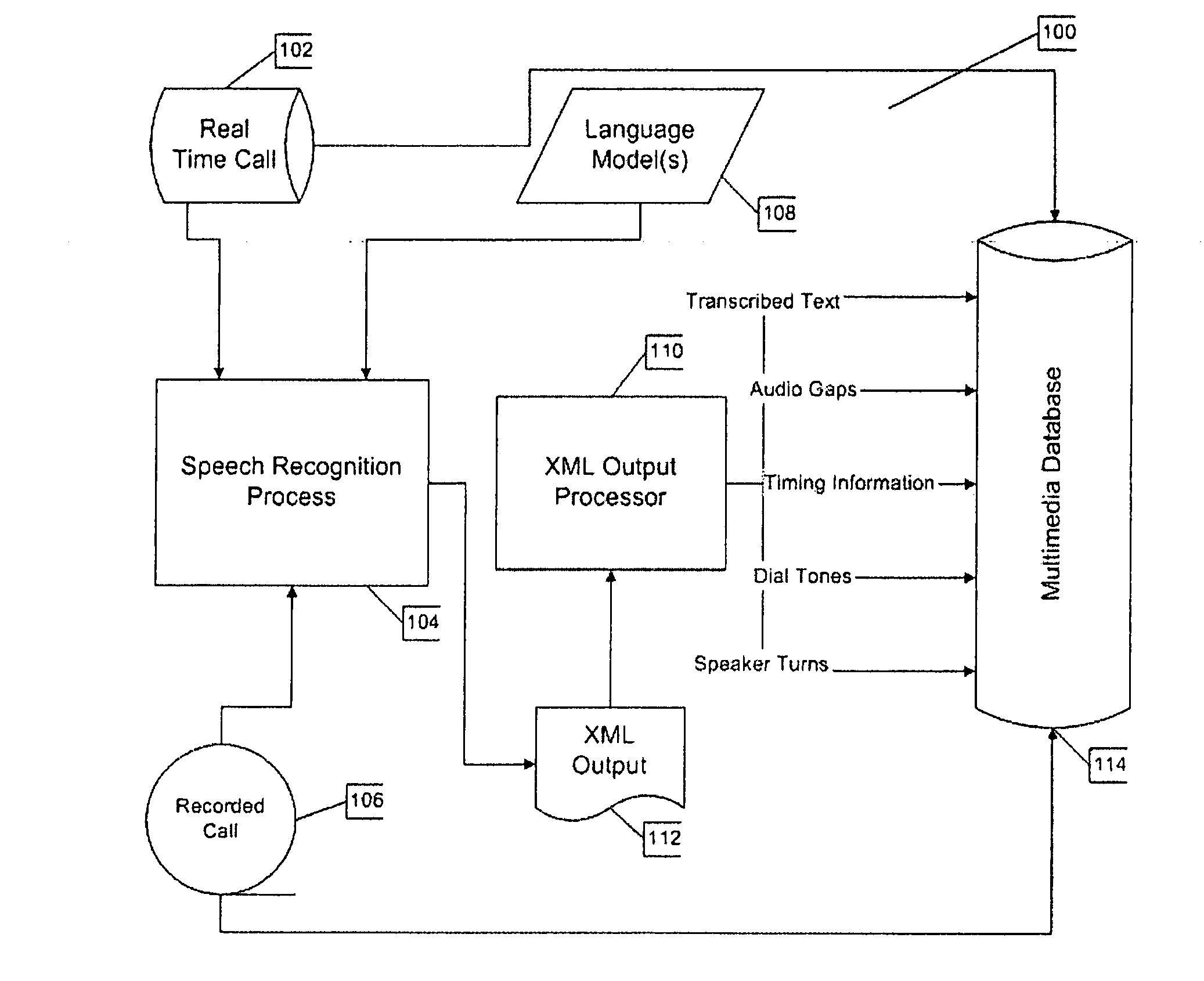
A system for detecting three-way calls in a monitored telephone conversation includes a speech recognition processor that transcribes the monitored telephone conversation and associates characteristics of the monitored telephone conversation with a transcript thereof, a database to store the transcript and the characteristics associated therewith, and a three-way call detection processor to analyze the characteristics of the conversation and to detect therefrom the addition of one or more parties to the conversation. The system preferably includes at least one domain-specific language model that the speech recognition processor utilizes to transcribe the conversation. The system may operate in real-time or on previously recorded conversations. A query and retrieval system may be used to retrieve and review call records from the database.
Owner:DSI ITI
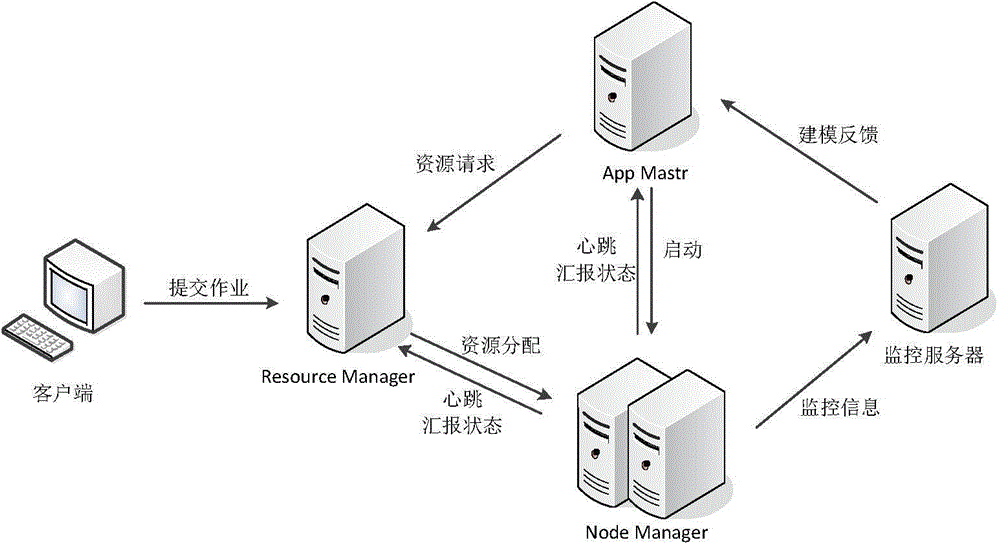
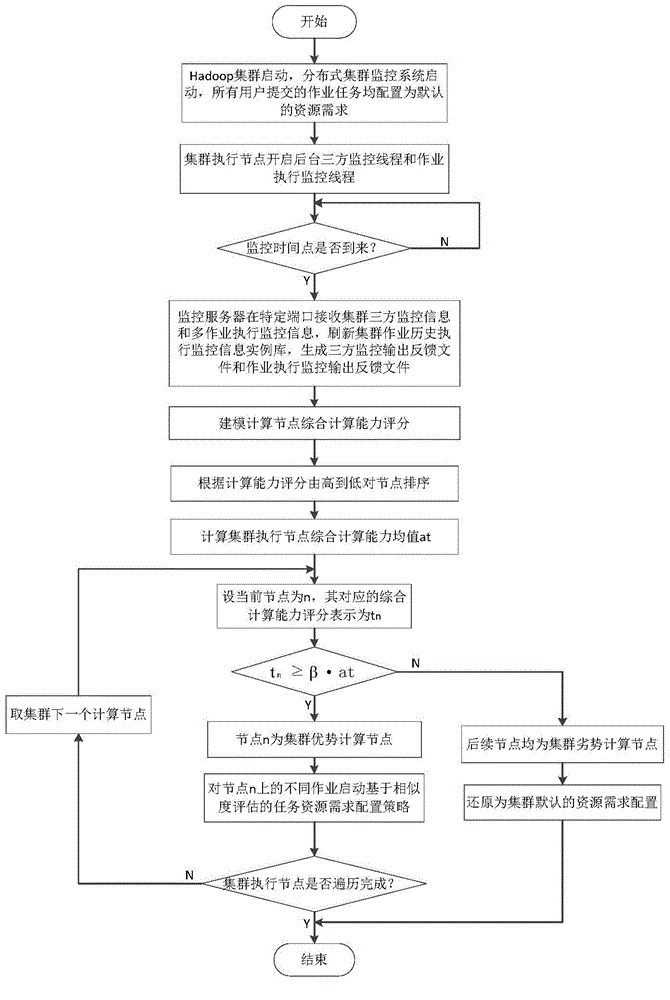
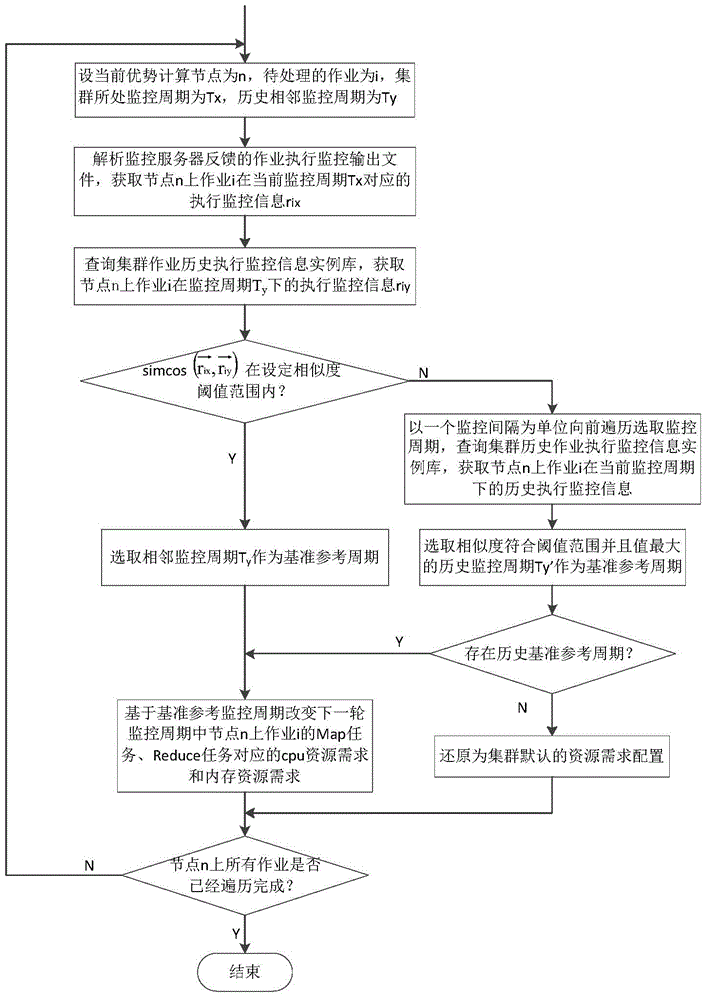
Resource scheduling method under Hadoop-based multi-job environment
ActiveCN104915407AEfficient use ofPromote efficient concurrencyProgram initiation/switchingDatabase distribution/replicationYarnGranularity
The invention discloses a resource scheduling method under a Hadoop-based multi-job environment, which includes: (1) collecting the three-party monitoring information of cluster loads, a Hadoop platform and hardware in real time; (2) collecting the job execution monitoring information of a user on each computing node of a cluster in real time; (3) gathering the three-party monitoring data of the cluster, modeling to evaluate the computing capabilities of the nodes, and dividing the nodes of the cluster into superior computing nodes and inferior computing nodes; (4) if the nodes are the superior computing nodes, then starting a job task resource demand allocation policy based on similarity evaluation; (5) if the nodes are the inferior computing nodes, then returning to a default resource demand allocation policy of the Yarn. The resource scheduling method under the Hadoop-based multi-job environment solves the problem of resource fragments caused by oversize job resource demand division granularity in conventional resource schedulers of the Yarn, can comprehensively take the heterogeneity of cluster nodes and jobs into consideration, and increases the execution concurrency of the cluster by reasonably and effectively allocating the node resources, thus increasing the execution efficiency of the multiple jobs of the Hadoop cluster.
Owner:HUAZHONG UNIV OF SCI & TECH
Method and device for secure communication in Internet of Things
InactiveCN105791272AEnsure communication securityPrevent eavesdropping risksKey distribution for secure communicationUser identity/authority verificationSecure communicationCommunications security
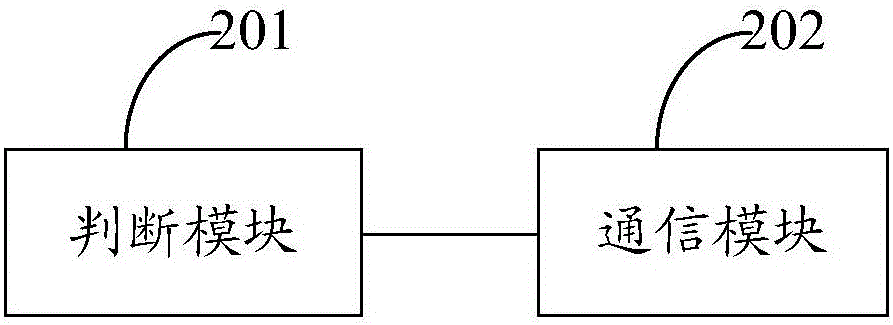
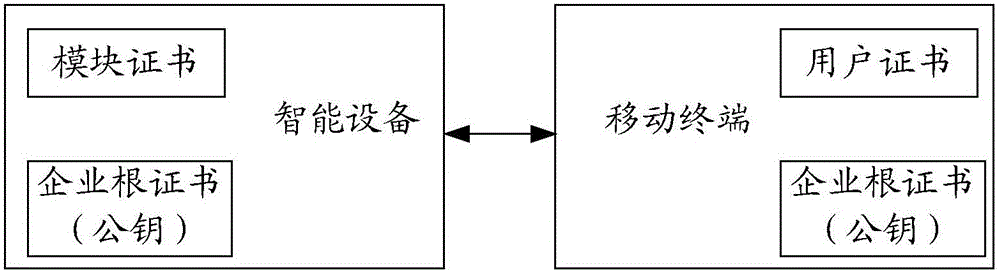
The invention provides a method and a device for secure communication in Internet of Things. For communication between devices of any two parties, namely a first device and a second device, in the Internet of Things with interconnected devices of three parties, namely a cloud platform, an intelligent device and a mobile terminal, the first device executes the following steps of carrying out identity validity judgement with the second device through a method for verifying a digital signature of a digital certificate; and communicating with the second device when the first device and the second device both successfully pass through the identity validity judgement. Through adopting the method for verifying the digital certificate to carry out identity authentication on various interconnected intelligent devices in the Internet of Things, and the security control of bidirectional authentication is realized in a process for communication between the intelligent devices, so that the security risks that the devices are counterfeit and the opposite terminal is forged are effectively prevented and the communication security of the intelligent device is guaranteed. After identity authentication, the encrypted communication is carried out, so that the hacking risk is effectively prevented and the communication security is more completely guaranteed.
Owner:QINGDAO HAIER INTELLIGENT HOME TECH CO LTD
Apparatus for secure computation of string comparators
InactiveUS20090282039A1Rule out the possibilityDigital data information retrievalDigital data processing detailsConfidentialityTheoretical computer science
We present an apparatus which can be used so that one party learns the value of a string distance metric applied to a pair of strings, each of which is held by a different party, in such a way that none of the parties can learn anything else significant about the strings. This apparatus can be applied to the problem of linking records from different databases, where privacy and confidentiality concerns prohibit the sharing of records. The apparatus can compute two different string similarity metrics, including the bigram based Dice coefficient and the Jaro-Winkler string comparator. The apparatus can implement a three party protocol for the secure computation of the bigram based Dice coefficient and a two party protocols for the Jaro-Winkler string comparator which are secure against collusion and cheating. The apparatus implements a three party Jaro-Winkler string comparator computation which is secure in the case of semi-honest participants
Owner:TELECOMM RES LAB
Software based single agent multipoint conference capability
ActiveUS7075900B2Special service provision for substationMultiplex system selection arrangementsVoIP phoneSpeech sound
A method and apparatus are provided for providing a three-party connection among a first, second and third call participant during a voice-over-Internet-Protocol (VoIP) telephone call. The method includes the steps of providing a respective first and second port within a transceiving terminal for receiving VoIP voice information of the VoIP telephone call from the first and second call participants, mixing the VoIP information from the ports of the first and second call participants and transferring the mixed VoIP information to the third call participant.
Owner:WILMINGTON TRUST NAT ASSOC AS ADMINISTATIVE AGENT +1
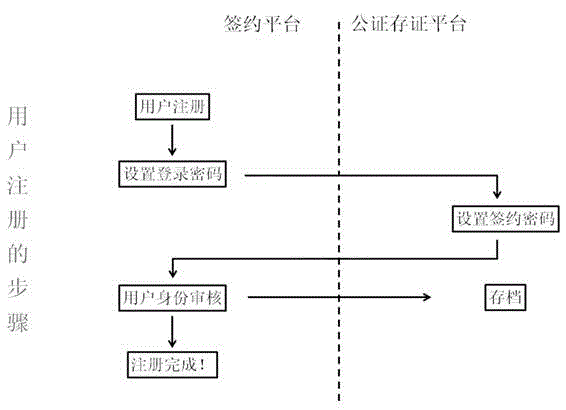
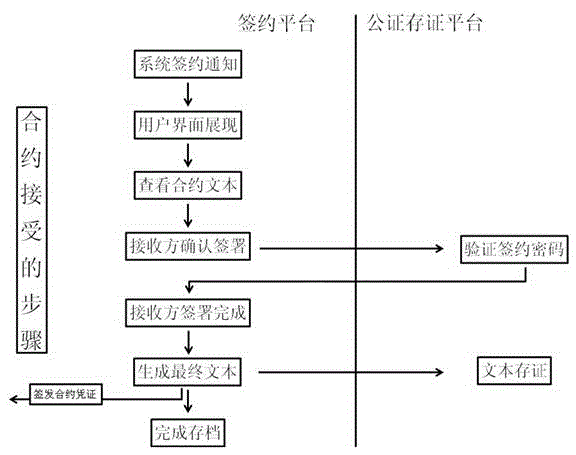
Electronic contract signing method based on the internet
ActiveCN105635169ASolve the problem of confirming the authenticity of meaning expressionCannot be tampered withOffice automationBuying/selling/leasing transactionsThird partyElectronic contracts
The invention discloses an electronic contract signing method based on the internet. After a user registers information, a signing request is initiated; a contract text is directly uploaded to a server for text deposition; the server targets to a notarization and deposition platform; the notarization and deposition platform sends the deposited text contract to a signing platform for signing; a contrast receiver is informed of the singing by the signing platform; after confirming the signing, the receiver skips to the notarization and deposition platform for verification; after the verification is successful, the receiver returns to the signing platform for signing; and filing is carried out. According to the method provided by the invention, the signing platform and the notarization and deposition platform are separated; because of the intervention of a notarization mechanism, the original two-party relationship is changed into a three-party relationship; the data exchange generated by the signing behavior of the user is no longer generated between the user and the signing platform and is deposited by the third party notarization and deposition platform in real time; the three parties cooperate mutually and restrict mutually; and the user rights and interests are ensured.
Owner:江苏慧世联网络科技有限公司
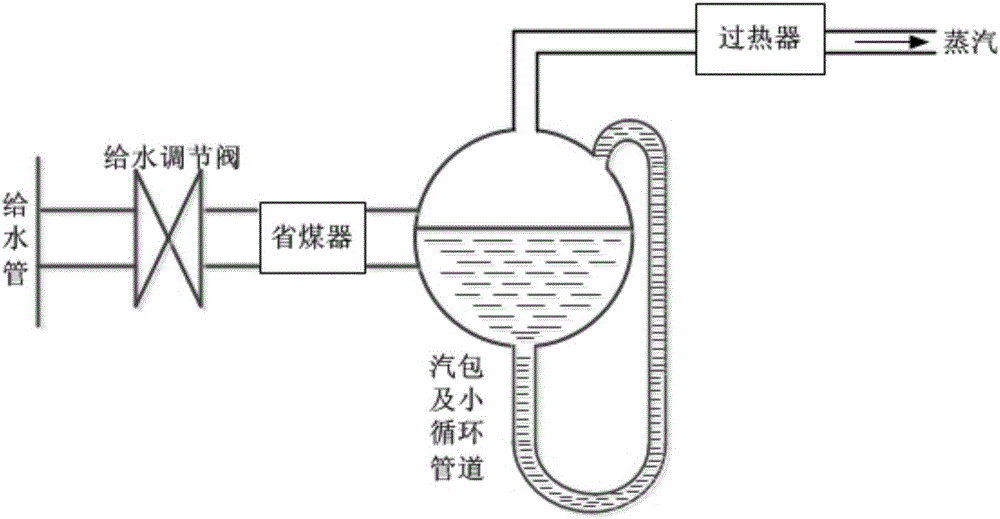
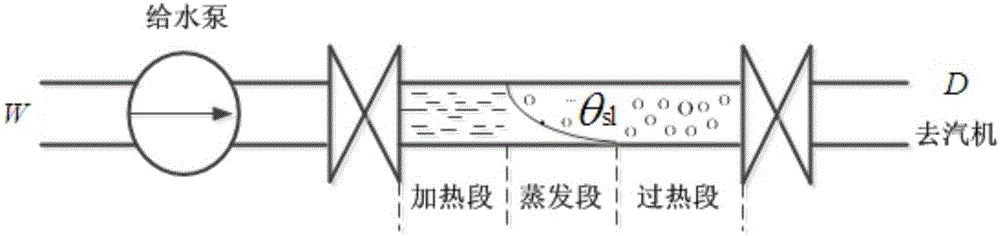
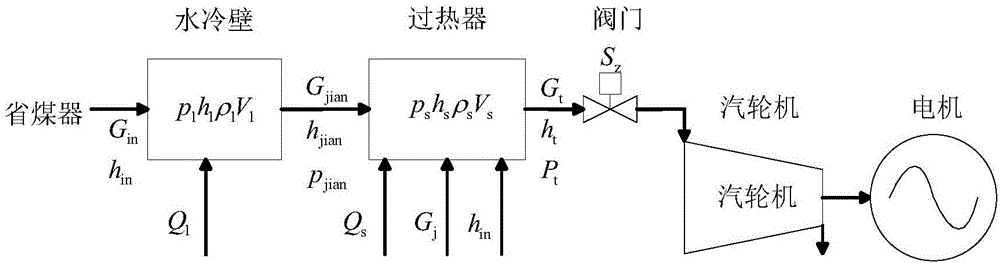
Model used for carrying out primary frequency modulation analysis coordination control on boiler, steam turbine and power grid
ActiveCN106527131AImprove energy utilizationAchieve win-winAdaptive controlNegative feedbackElectric power system
The invention relates to a model used for carrying out primary frequency modulation analysis coordination control on a boiler, a steam turbine and a power grid and particularly relates to a boiler, steam turbine and power grid three-party coordination control supercritical and super-supercritical set coordination control model used for carrying out primary frequency modulation analysis. Control focus of machine-network coordination and machine-furnace coordination in the prior art is a turbo generator set and a power grid, only negative feedback control strategies of grid frequency difference are reflected in a primary frequency modulation control loop, influence on the boiler is not considered, so a hidden safety trouble exists. The method for problem solution is characterized by comprising steps that 1, a DC boiler mechanism model in a supercritical and super supercritical set is established; 2, a supercritical and super supercritical DC boiler controller model is established; 3, a steam turbine primary frequency modulation model is established; 4, an electric power system frequency modulation model including different types of sets is established; and 5, a steam turbine power given signal is corrected. The model is advantaged in that the model is applicable to the boiler, steam turbine and power grid coordination control field.
Owner:黑龙江工研龙创智通云管科技有限公司
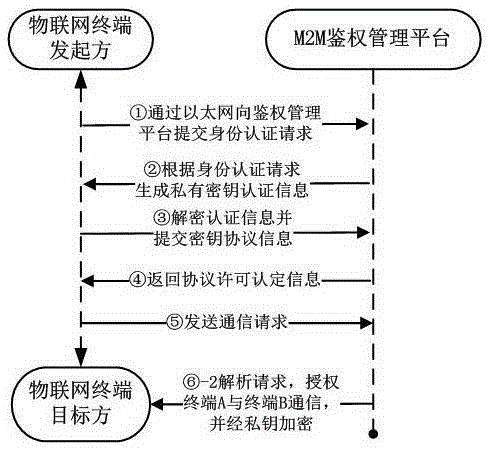
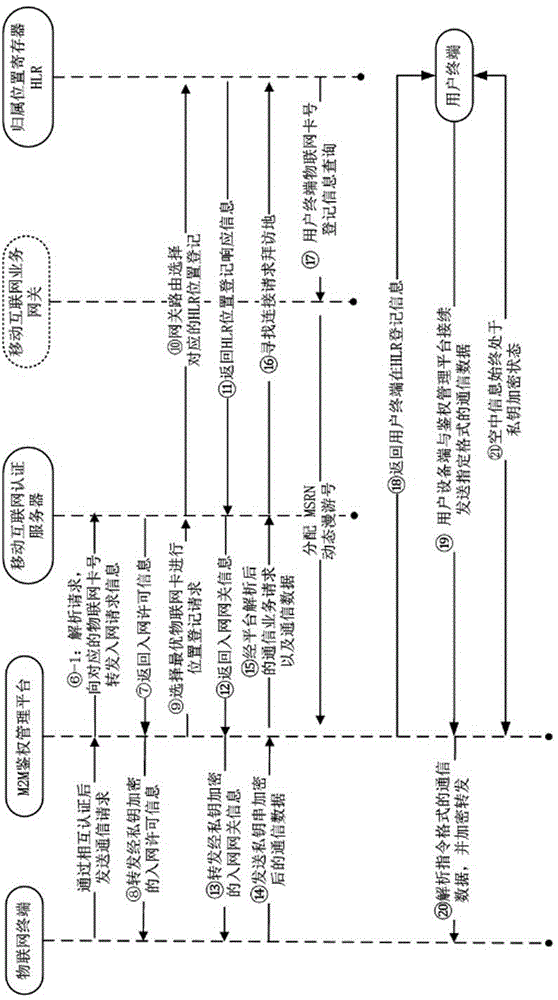
Internet of things information interactive communication method and system
ActiveCN105307108AImprove securityImprove application securityWireless commuication servicesTransmissionThe InternetMedia access control
The invention discloses an Internet of things information interactive communication method and system. The method comprises the following steps that: a cloud authentication management platform correspondingly matches MAC (Media Access Control) of an Internet of things terminal with an Internet of things card number of the Internet of things terminal; when an initiator makes a request of performing interactive communication with a target party to the authentication management platform, the initiator, the authentication management platform and the target party need to perform three-party authentication certification; during authentication of the Internet of things terminal, the authentication management platform selects network parameter information of an optimal Internet of things card of the Internet of things terminal according to a communication object on the basis of weights in order to realize registration and access in a mobile communication network; and when the initiator, the authentication management platform and the target party perform a communication, all communication data is encrypted through a private key, wherein the private key is a dynamic random key string code and is relevant to the Internet of things card number in order that the transmitted communication data can only be resolved and read by the initiator, the authentication management platform and the target party.
Owner:成都工百利自动化设备有限公司
A shielded face recognition method and device
ActiveCN109886167AEasy to handleImage enhancementCharacter and pattern recognitionDiscriminatorFeature extraction
The invention relates to a shielded face recognition method and device. The method comprises the following steps of training a face recognizer by utilizing a face image with an identity mark; traininga face generator, a global face discriminator and a local face discriminator in the generative adversarial network framework by utilizing the non-occluded face image with the identity mark, the corresponding occluded face image, the corresponding face occluded mark graph, the corresponding face semantic segmentation graph and the pre-trained face resolver in combination with the face recognizer;carrying out restoration processing on the input shielded face image by using a face generator to obtain a restored face image; and performing feature extraction or identity classification on the restored face image by using the face recognizer to obtain face features or identity marks, performing face recognition by using the face features, and identifying the identity information of the face byusing the identity marks. The three-party game is realized by adopting the face generator, the face discriminator and the face recognizer, and the shielded face can be repaired and recognized at the same time.
Owner:INST OF INFORMATION ENG CAS
Intelligent media advertisement machine of elevator dynamic monitoring system
The invention relates to an intelligent media advertisement machine of an elevator dynamic monitoring system, and the intelligent media advertisement machine of the elevator dynamic monitoring system adopts a novel playing and managing system of intelligentialized elevator dynamic monitoring media advertisement information. According to an advanced mobile network technology, intelligentialized sensor equipment and data base managing software, a reliable monitoring platform, a monitoring terminal and a monitoring network are designed for the system, the dynamic monitoring management of long-distance intellectualization, informatization and visuality of an elevator is achieved, and a management monitoring platform is provided for remote alarming and monitoring of elevator faults, display and fault records of elevator running conditions, playing and controlling of advertisement media information. Specially, the intelligent media advertisement machine of the elevator dynamic monitoring system effectively solves the problem that mind and body hurts can be caused to trapped people due to the fact that alarms and rescue cannot be sent timely in the conditions of power failures and elevator faults. The information release system of the media advertisement machine can play characters and voices timely to pacify the trapped people, and automatically connects a three-party communication of passengers, a real estate department and a maintenance department. An elevator safety management department carries out a full-time on-line administrative supervision and management of inquiry, review, storage, statistic, monitoring and control.
Owner:TIANJIN AMJOY TECH
On-line client service system and on-line communication method thereof
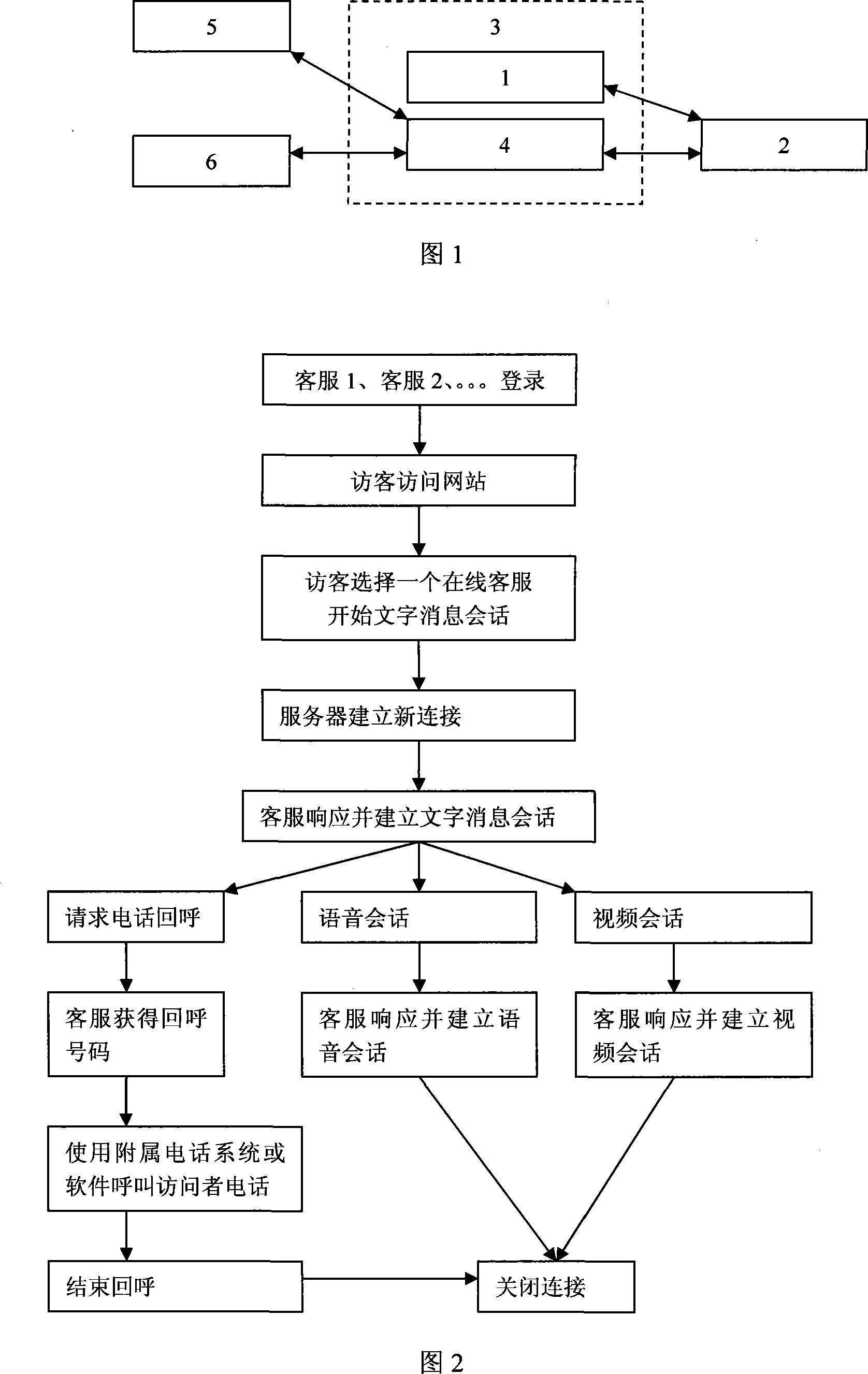
InactiveCN101227487ARealize online communicationMultiple interactivitySpecial service provision for substationSpecial data processing applicationsService personnelWeb service
An on-line client service system and a process of on-line communication are disclosed, especially relating an on-line client service system. Provided are an on-line client service system and the on-line communication process which have much lower cost and stronger function, which comprises client service management program software, a media server, a WEB server and an on-line client service client, wherein the media server is provided with media server program and a database, the WEB server is provided with WEB server program, and the on-line client service client is provided with visitor end program and client service end program which are embedded with WEB server program. Visitors access a web page which has the on-line client service system panel after the client personnel logs in, and choose and double click with a mouse some on-line client service icon, the media server establishes a conversation with the visitor end and the client service end, a conversation window is started and a voice or video conversation is established when conducts the conversation in words, visitors can input a callback number which will be displayed on the client service end, and the client service personnel choose additional three-party calling platform or voip platform, and send a call through using hardware and software.
Owner:厦门纳网科技股份有限公司
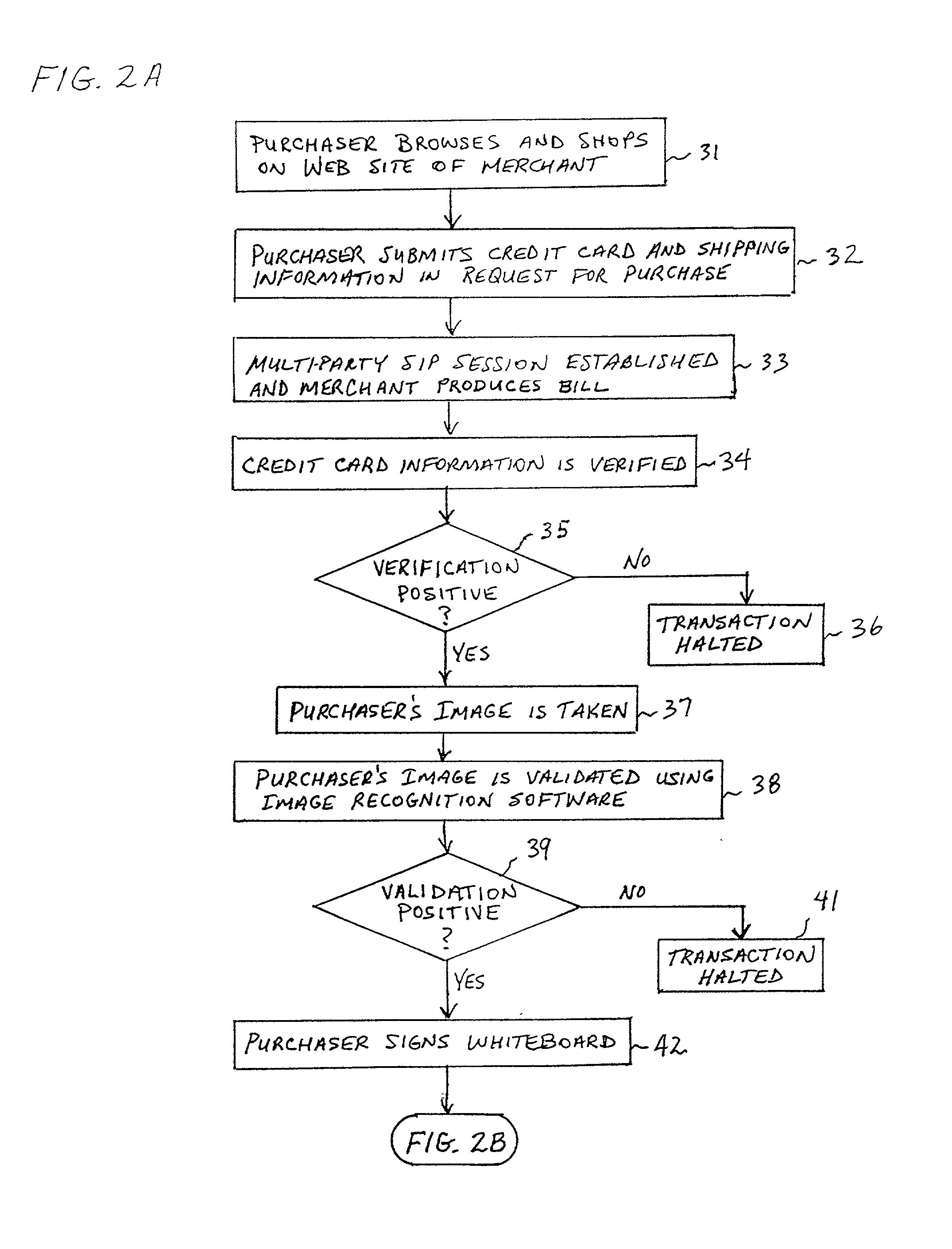
System and method of authorizing an electronic commerce transaction
A system and method of authorizing an electronic commerce transaction between a purchaser using a credit card, an on-line merchant, and a credit card company. A server associated with the merchant receives a purchase request from the purchaser that includes a purchase amount and the purchaser's credit card information. A SIP multi-party conference is established, and information is shared among the three parties through a multicast procedure. A Web camera may take an image of the purchaser when the purchaser sends the purchase request to the merchant. A whiteboard application is used to capture an image of the purchaser's signature. The credit card company verifies the credit card information, authorizes the purchase amount, and validates the purchaser's image and signature utilizing an image recognition program and a database of valid cardholder images and signatures.
Owner:TELEFON AB LM ERICSSON (PUBL)
Expandable storage system and control method based on objects
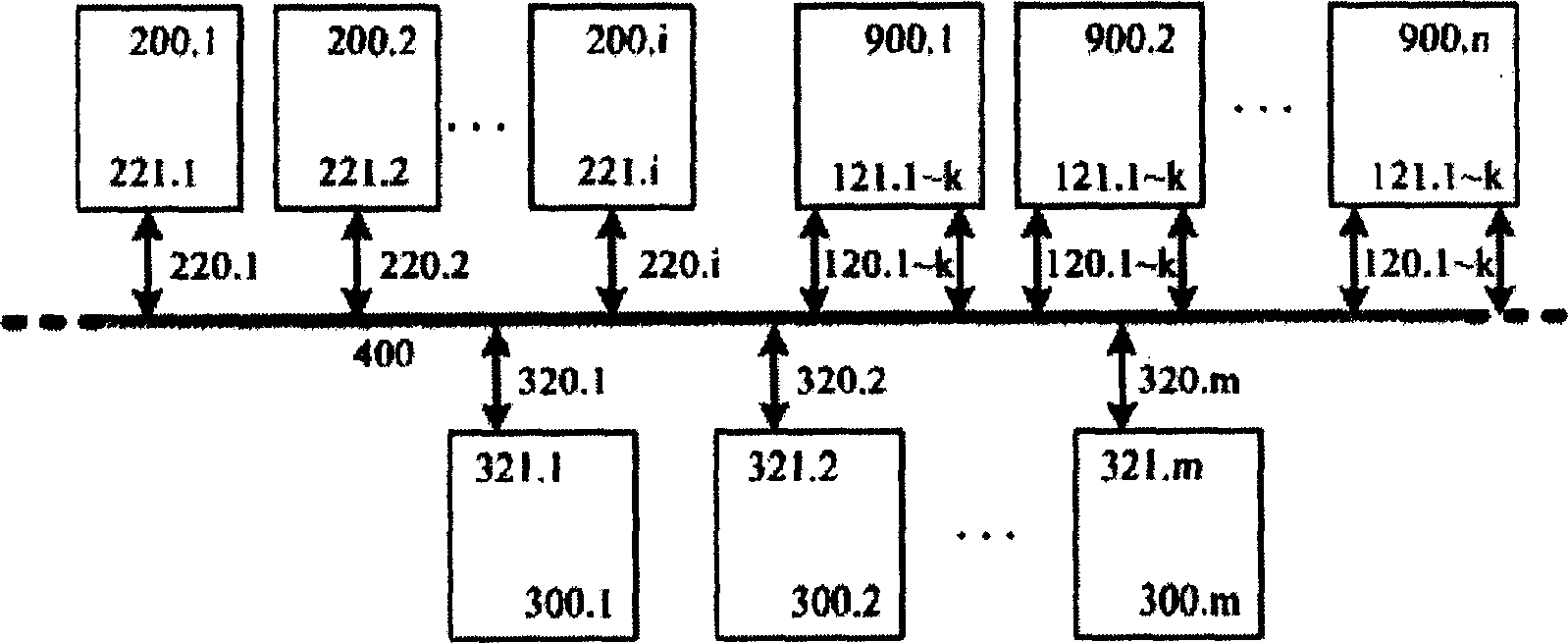
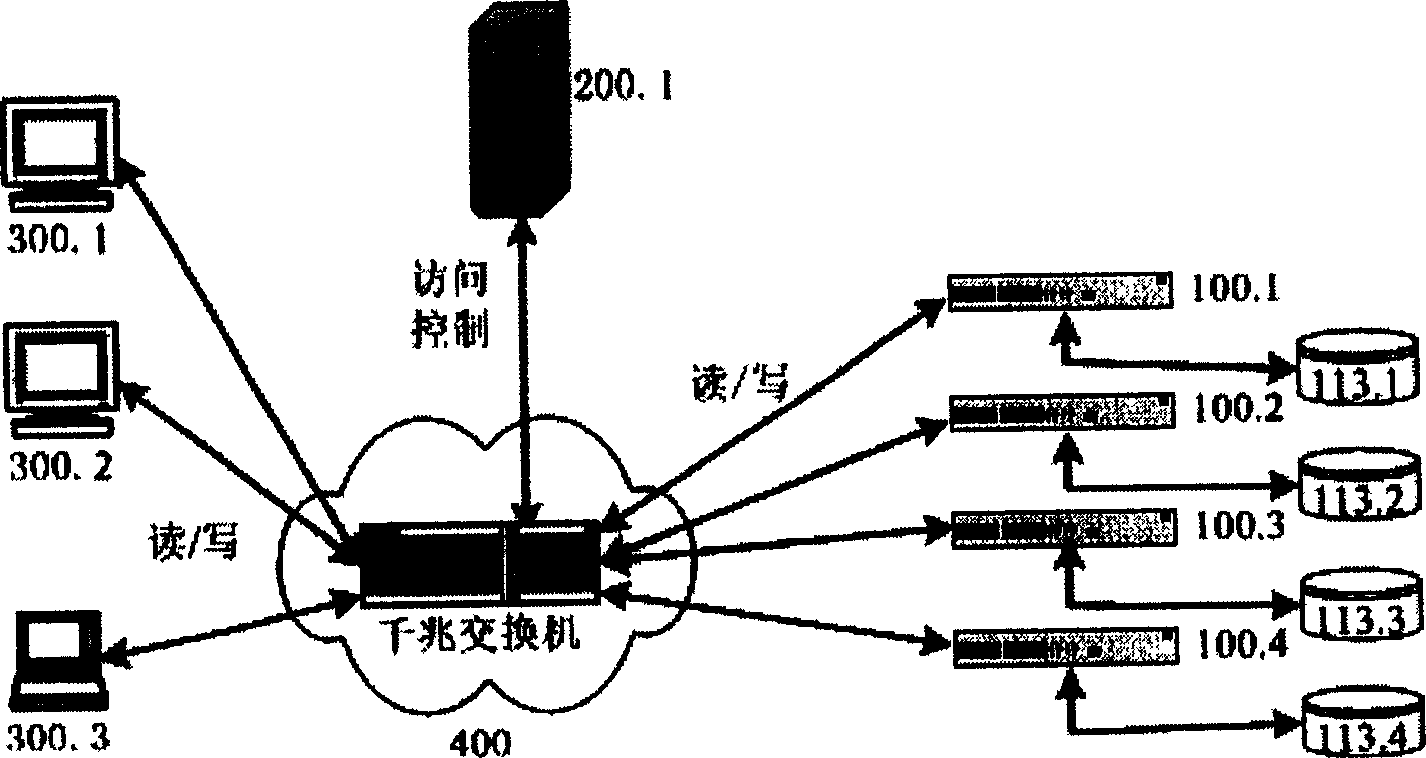
ActiveCN1728665AEasy to expandImprove scalabilityData switching by path configurationSpecial data processing applicationsObject basedAdaptive management
Combining file with block mode, the invention puts forward a brand new object interface in order to overcome disadvantages of system structure and mode of user service in current mass storage system. The system includes I pieces of metadata server, N pieces of object storage node, and M pieces of client end connected to each other. Three parties among client ends, object storage node and severs are realized. The system provides high expandability, and synchronous growth of memory capacity and collective bandwidth of data transmission. Changing traditional data management and control mode, object storage node OSN executes fussy functions for managing data at bottom layer of file system, and MS implements management of metadata. Based on object storage, the system realizes adaptive management function.
Owner:HUAZHONG UNIV OF SCI & TECH
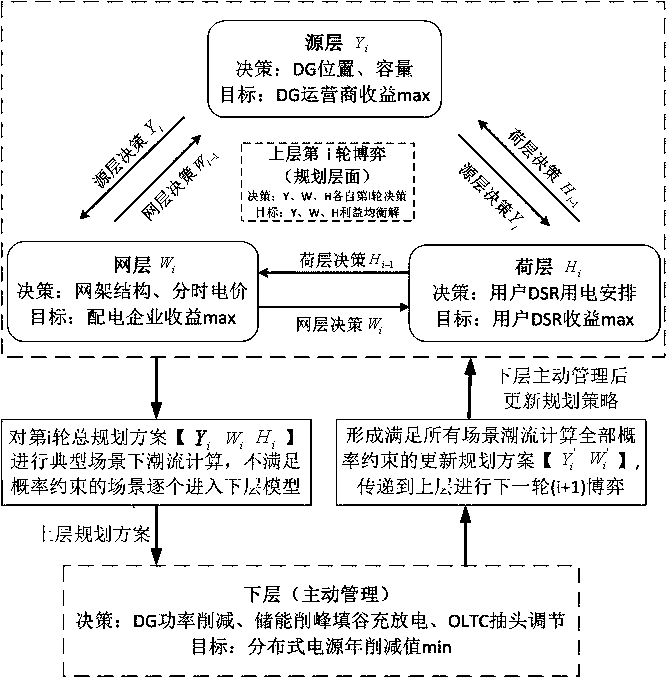
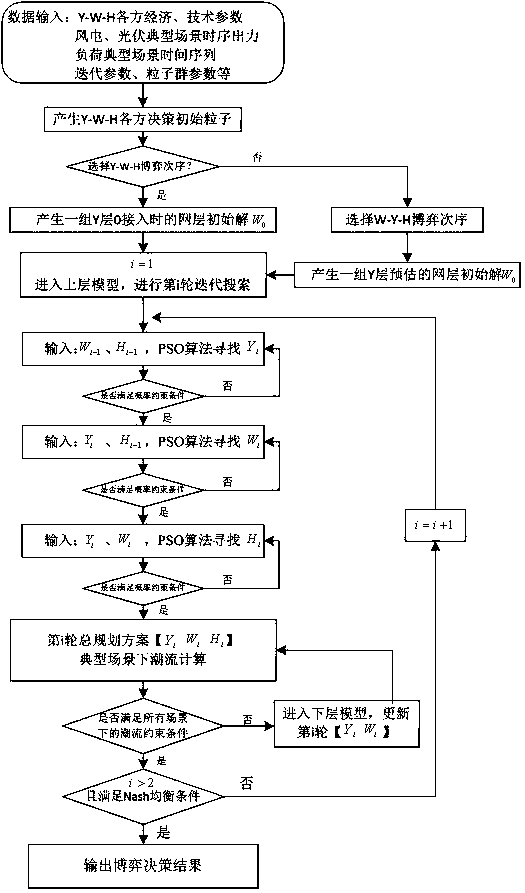
Active power distribution network coordination planning method considering multi-subject benefit game
PendingCN109934487AImprove absorption capacityPromote low carbonBiological modelsResourcesTransformerElectricity market
The invention relates to an active power distribution network coordination planning method considering a multi-subject benefit game. The method comprises the following steps of: firstly, determining respective objective functions and constraint conditions by taking the maximum annual net income as an objective of a network-source-load main body, and respectively establishing independent planning models of a network layer, a source layer and a load layer; then, an upper-layer strategy type game planning model is established with the fact that the three-party subjects achieve respective benefitbalance and stability in the game as an upper-layer target; taking the minimum reduction amount of the distributed power supply corresponding to wind curtailment and light curtailment as a target, andestablishing a lower-layer active management model by considering on-load transformer tap adjustment and energy storage adjustment; information transmission of the upper-layer game planning model andthe lower-layer active management model is considered, and a complete active power distribution network coordination planning model considering the multi-subject benefit game is established. The model established by the invention better adapts to maximization of benefit pursuits of all subjects in the gradually open power market, and the planning scheme solved based on the model can realize 'network-source-load' multi-subject friendly interaction and coordinate the overall planning.
Owner:STATE GRID FUJIAN ELECTRIC POWER CO LTD +3
Method and system for sequencing ciphertexts orienting to homomorphic encryption
ActiveCN103401871AEnsure safetyHomomorphic Encryption ImplementationKey distribution for secure communicationPlaintextCiphertext
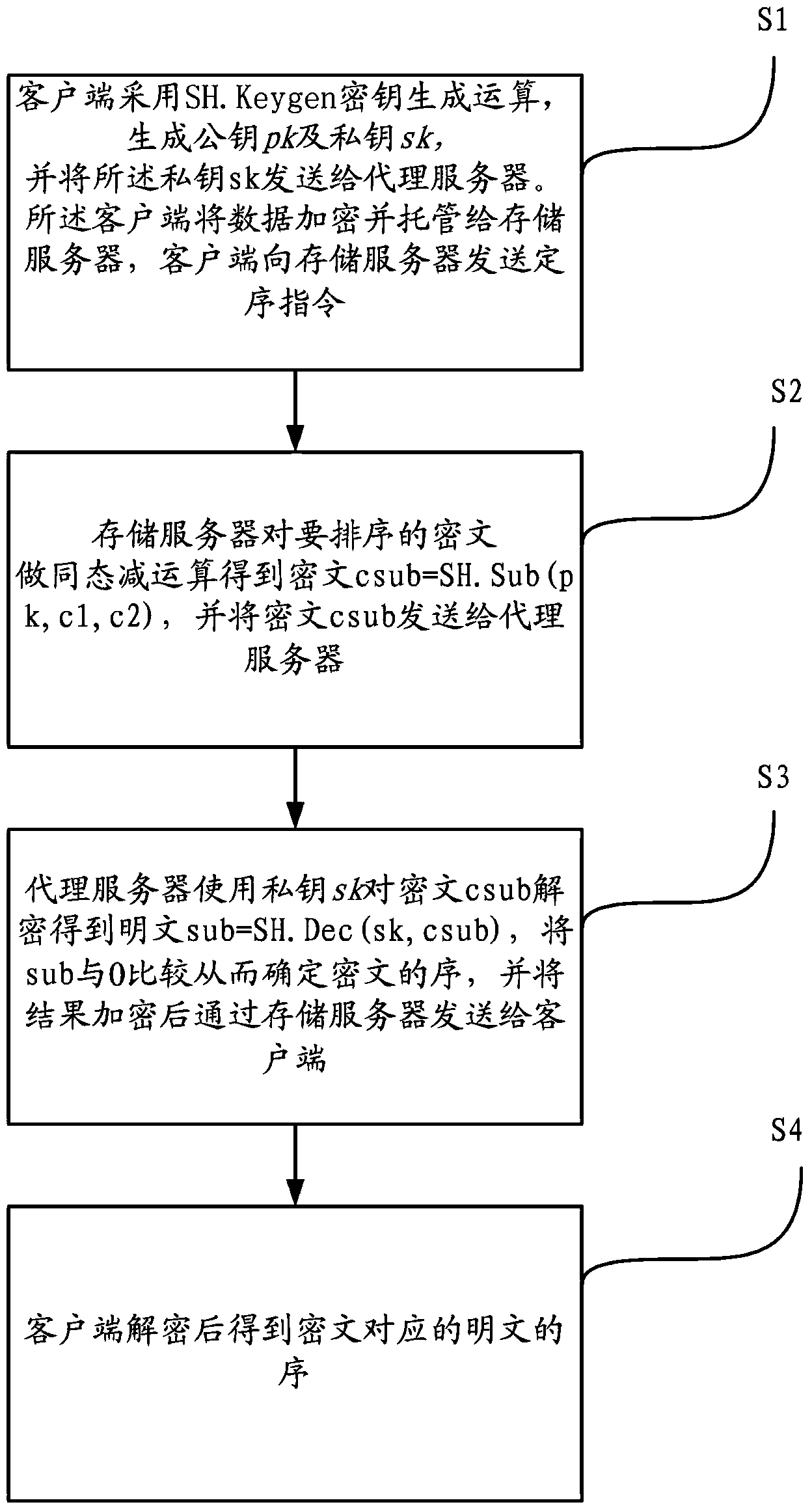
The invention discloses a method and a system for sequencing ciphertexts orienting to homomorphic encryption. The system comprises the following three parties: a client side, a storage server and an agency, wherein the storage server and the agency cannot mutually collude. The method comprises the following steps: an SH. Keygen secret key generation operation is adopted by the client side to generate a pk (public key) and a sk (secret key); the sk is sent to an agency server by the client side; data are encrypted, and are mandated to the storage server by the client side; a sequencing command is sent to the storage server by the client side; homomorphic subtraction operation is carried out on the ciphertexts need to be ranked by the storage server, so as to obtain the ciphertext csub which is equal to SH. Sub (pk, c1, c2); the ciphertext csub is sent to the agency server; the ciphertext csub is decrypted through the agency server by utilizing the sk, so as to obtain a plaintext sub which is equal to SH. Dec (sk, csub); the sub is compared with 0 to determine the sequence of the plaintext; the result is encrypted to be sent to the client side through the storage server; and after the result is decrypted through the client side, so as to obtain the sequence of the plaintext corresponding to the ciphertext, no plaintexts are leaked in the whole process; although the difference of the plaintexts is obtained through the agency server, the plaintexts corresponding to the difference cannot be calculated; and the whole process is safe.
Owner:SUZHOU UNIV
Conference layout control and control protocol
InactiveUS20120086769A1Effective controlReduce processMultiplex system selection arrangementsTelevision conference systemsTeleconferenceTelephony
A teleconferencing system-includes a plurality of nodes in communication with each other to form a conference. At least one of the nodes individually controlling, partially, the display layout of each node in the conference. A method for providing a teleconference including forming a conference with a plurality of nodes through a network. At least one of the nodes controls at least partially the display layout of each node in the conference with a specific format unique for each node. A teleconferencing system includes a plurality of nodes in communication with each other through the network to form a conference. Each node communicating only a change to the other nodes when the change occurs. A method for conducting a telecommunications conference between at least three parties includes establishing a conference between the parties and where there is a change to the conference only the change is communicated to the parties.
Owner:TELEFON AB LM ERICSSON (PUBL)
Blind verifiable cryptographic signature method based on block chain
InactiveCN107040383APrivacy protectionPublic key for secure communicationUser identity/authority verificationAlice and BobDigital signature
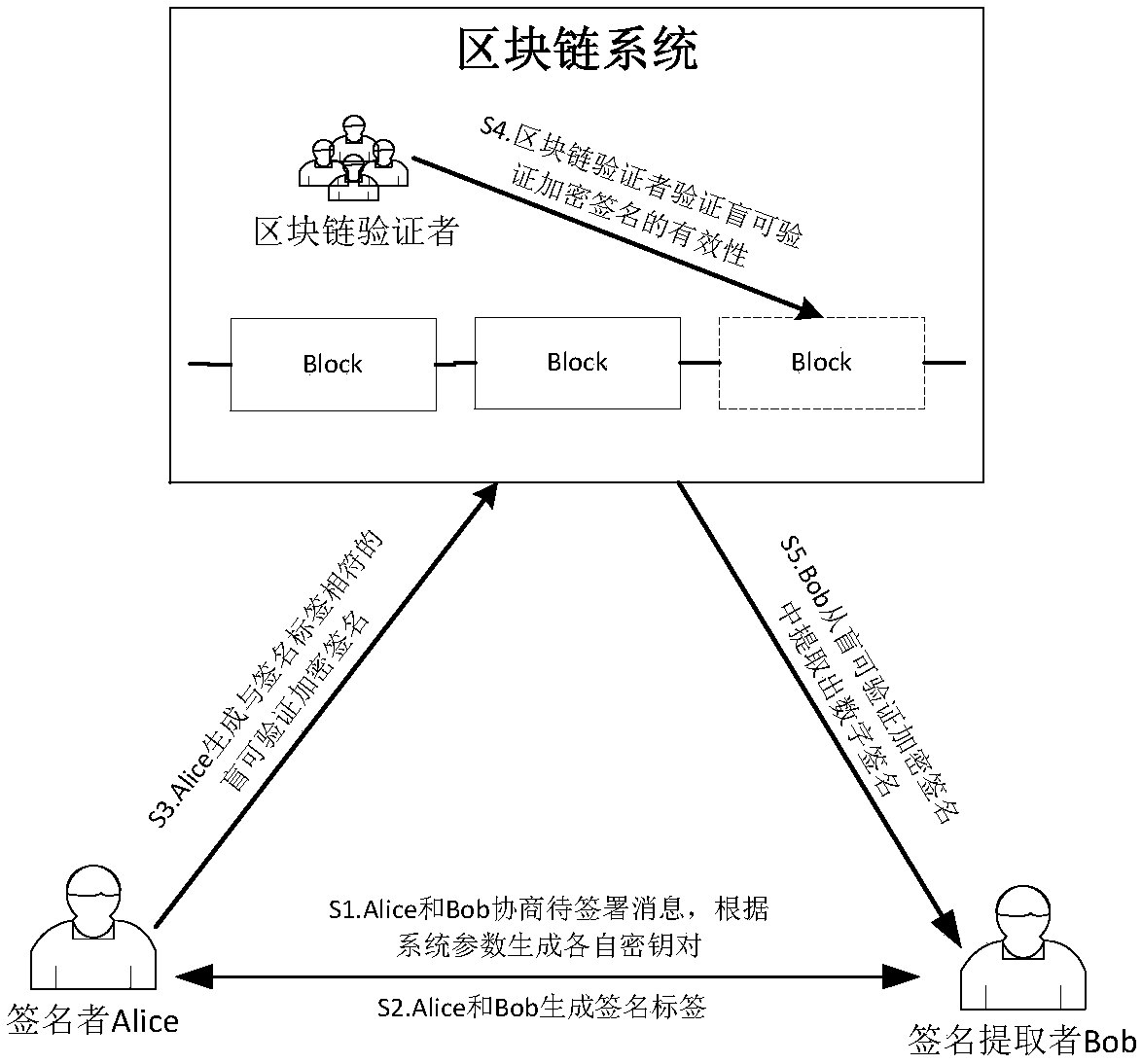
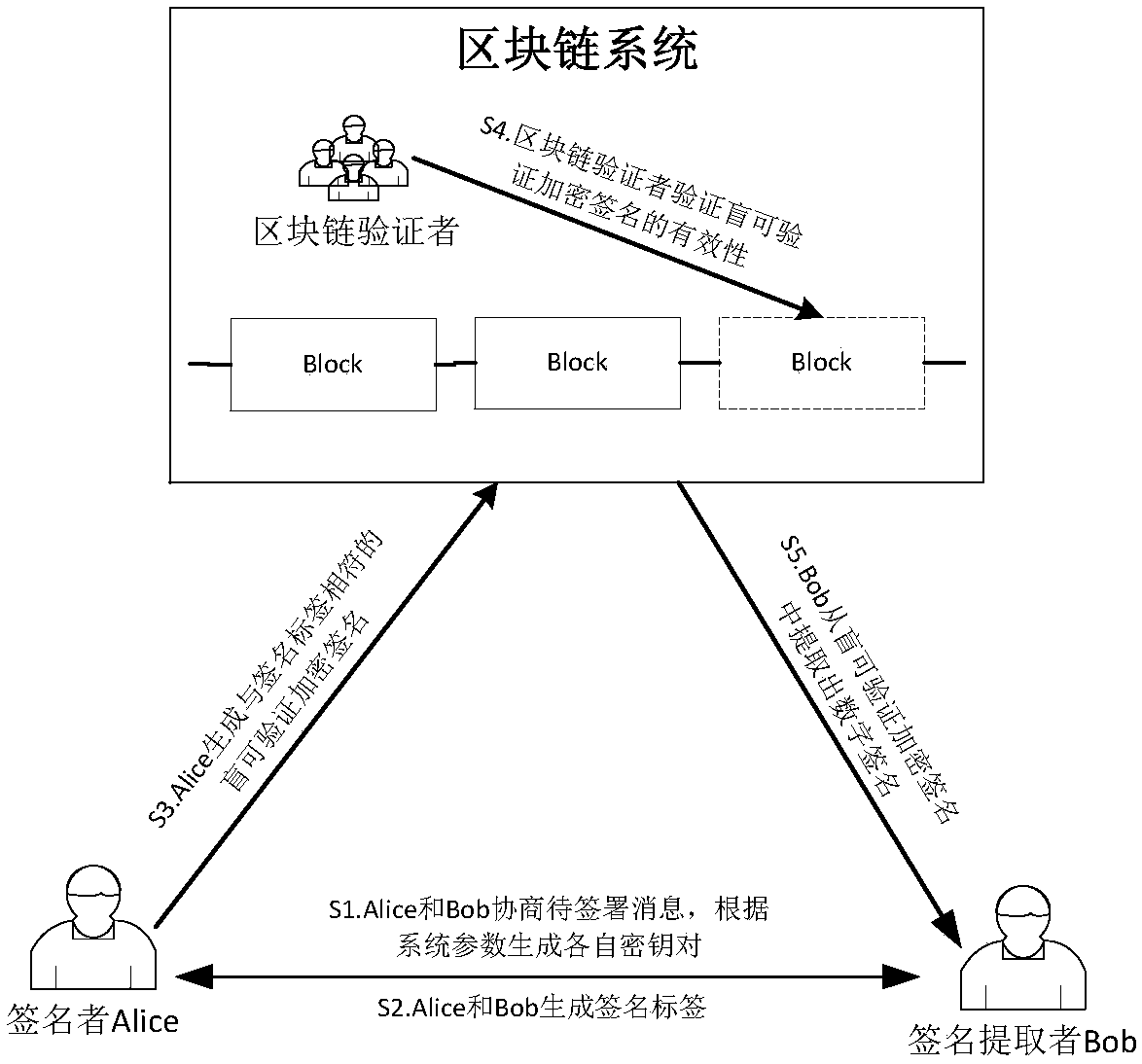
The invention relates to a blind verifiable cryptographic signature method based on a block chain. The method includes three parties: a signer Alice, a signature extractor Bob, and a block chain verifier. The method is implemented in the following steps: Alice and Bob negotiate a message to be signed and generate their own key pairs respectively according to system parameters; Alice and Bob generate signature tags; Alice generates a blind verifiable cryptographic signature that matches the signature tag; the block chain verifier verifies the validity of the cryptographic verifiable cryptographic signature; and Bob extracts a digital signature from the blind verifiable cryptographic signature. The method can be used to construct a fair digital signature exchange protocol that protects privacy in a public block chain environment. The method blindens the public key information of the signer so that a node on a block chain cannot obtain the real digital signature and the public key of the signer aside from verifying the validity of the signature, and the privacy protection for the signer is achieved.
Owner:深圳市数峰科技有限公司
Synchronous monitoring and optimizing system and method used for wireless communication network multi-interface
ActiveCN101431762AImprove optimization efficiencyWireless communicationAccess networkCollection analysis
The invention discloses a simultaneous monitoring and optimizing system for multiple interfaces of wireless communication network, comprising: a terminal test module, a simultaneous and communication control module, an access network and core network signaling monitoring module and a data processing module. The invention further discloses a simultaneous monitoring and optimizing method for multiple interfaces of wireless communication network. The terminal test module as well as the access network and core network signal monitoring module of the invention are respectively in charge of terminal side signaling and parameter collection test as well as signaling collection analysis of access network and core network, synchronizes the collection process of the three parties by the simultaneous and communication control module, and then real-time processing and tabulate statistics are performed for the signaling and parameters by the data processing module, positioning and analyzing the network, thereby greatly improving optimization efficiency of wireless network.
Owner:CHINA MOBILE GRP GUANGDONG CO LTD
Apparatus for dental diagnosis and treatment
An apparatus for dental diagnosis and treatment includes: a dentist's chair disposed near a dental treatment table; an intraoral camera which can capture moving images in the patient's oral cavity and can be fixed near the patient's mouth; a first monitor installed at a position where the three parties comprising a dentist sitting on the dentist chair, the patient lying on his / her back on the dental treatment table, and a dental assistant assisting the diagnosis and treatment can see, the first monitor displaying the image captured by the intraoral camera, and being able to invert the image in the vertical direction and reverse the image in the lateral direction by the dentist; and a recording device which can record the images captured by the intraoral camera.
Owner:FUJIE HIDEHIRO +1
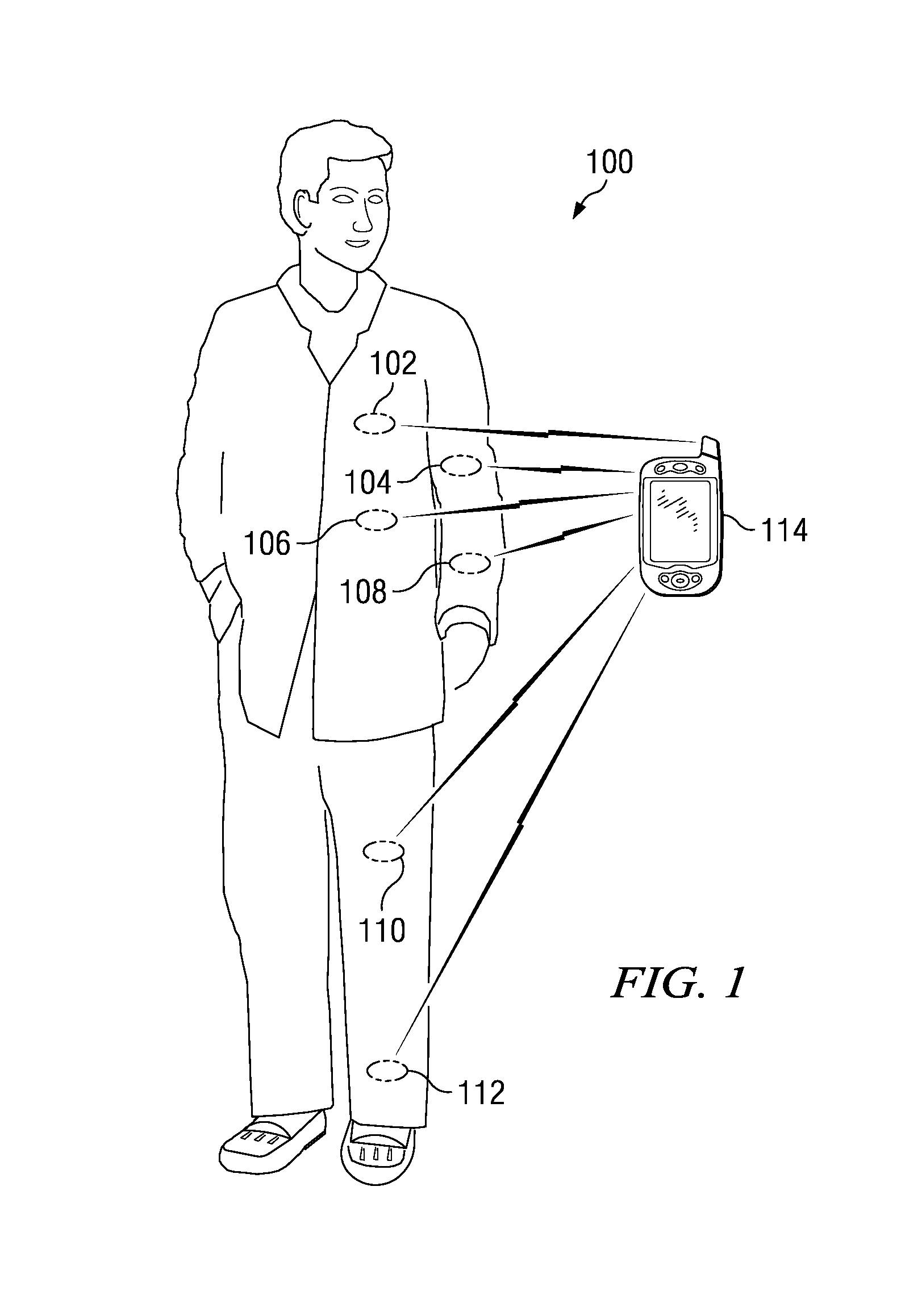
Securing Wireless Body Sensor Networks Using Physiological Data
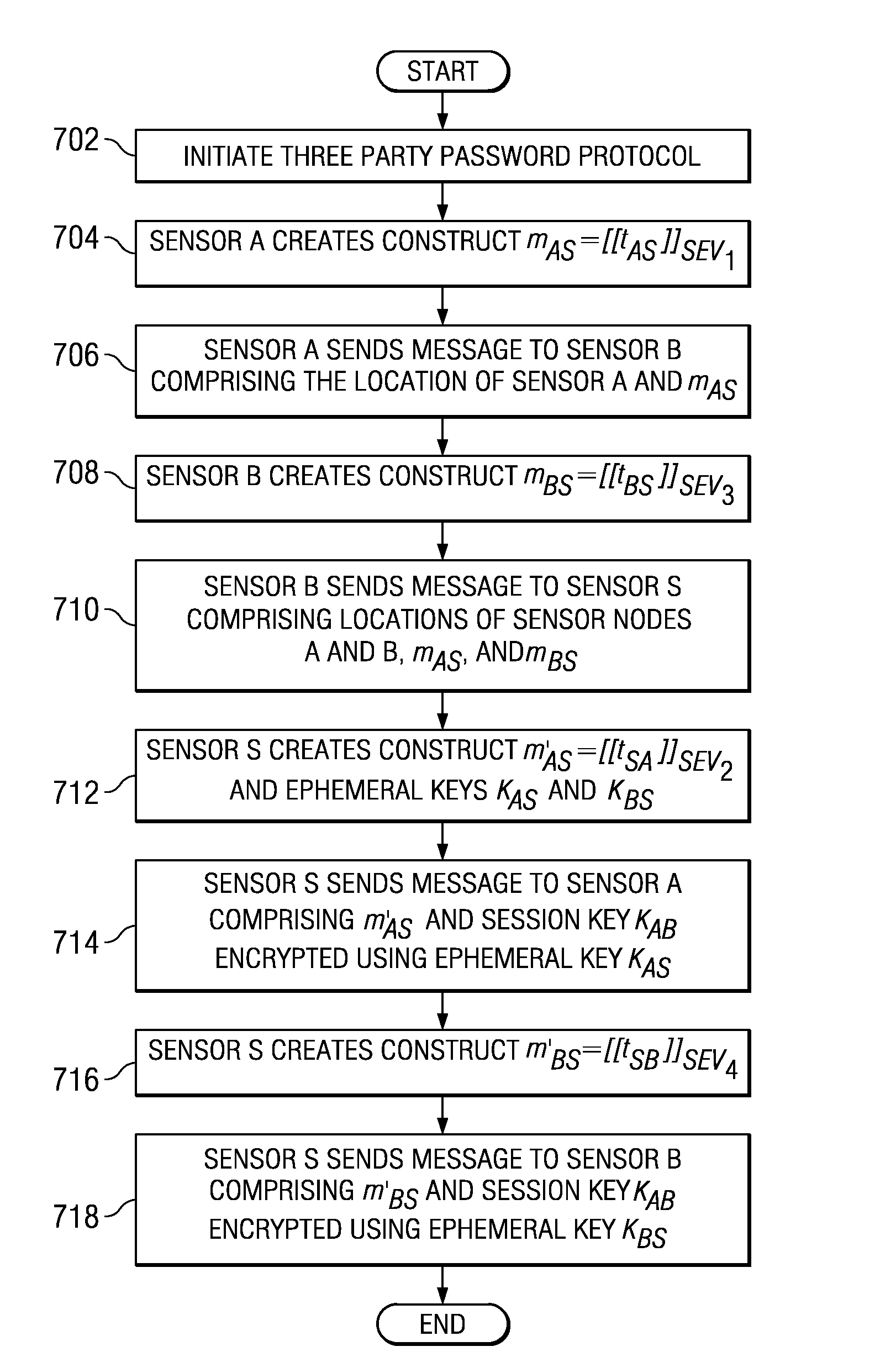
A computer implemented method, apparatus, and computer program product for securing wireless body sensor networks with a three party password protocol. The password protocol combines the Bellare-Rogaway 3PKDP (three-party key distribution protocol) and the Diffie-Hellman password protocol. The three party password protocol also uses physiological values in place of passwords in one of the key exchanges. The other key exchanges in the protocol use symmetric key cryptography. The combination of the Bellare-Rogaway three-party key distribution protocol and the Diffie-Hellman password protocol allows two sensors which do not measure the same environmental data to authenticate and establish keys.
Owner:IBM CORP
GBA (General Bootstrapping Architecture)-based secret key negotiation system and method of telecommunication capability open platform
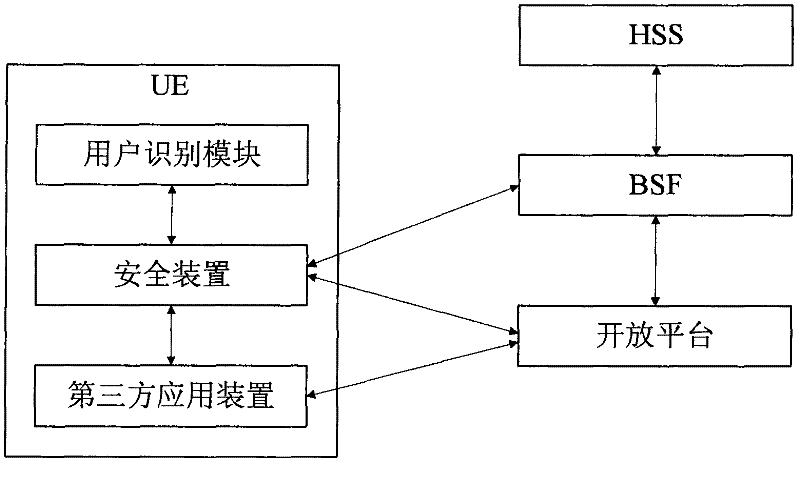
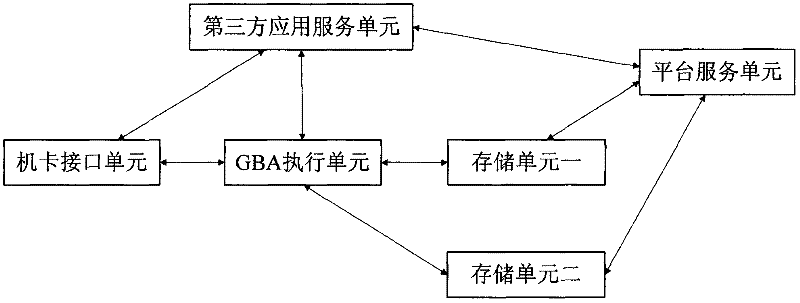
InactiveCN102413464AImprove service efficiencyLower technical barriersSecurity arrangementThird partyOpen platform
The invention relates to a GBA(General Bootstrapping Architecture)-based secret key negotiation system and method of a telecommunication capability open platform. A safety device and a third-party application device are arranged in UE (User Equipment). The GBA-based secret key negotiation method comprises the following steps: the three-party application device sends a registration request message carrying an application identifier to the safety device; the safety device initiates an initialized request message carrying a user identifier, a platform identifier and an application identifier to a BSF (Bootstrapping Service Function); the BSF searches a platform secret key and an application secret key which are stored in local according to the platform identifier and the application identifier, informs the safety device of updating the platform secret key and the application secret key, executes an inter-authentication GBA process with the safety device and finally generates a root secret key according to the application secret key and the application secret key; and the safety device generates a root secret key Ks consistent with the BSF according to the updated platform secret key K_op and the updated application secret key K_app and returns generated local token and validity period to the third-party application device. The GBA-based secret key negotiation system and method of the telecommunication capability open platform, disclosed by the invention, belong to the technical field of mobile communication, and the open platform is capable of effectively authenticating and identifying third-party application.
Owner:EB INFORMATION TECH
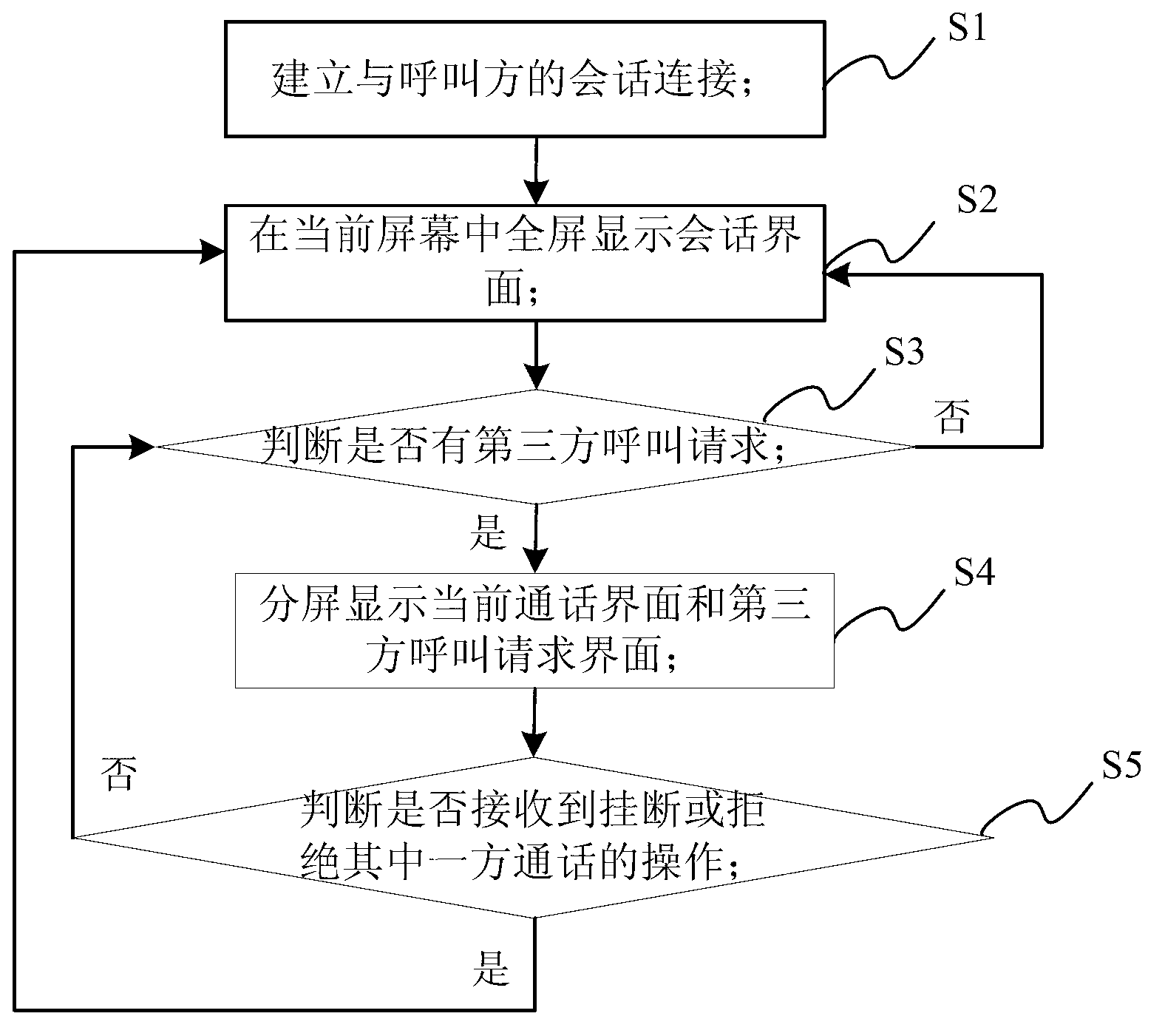
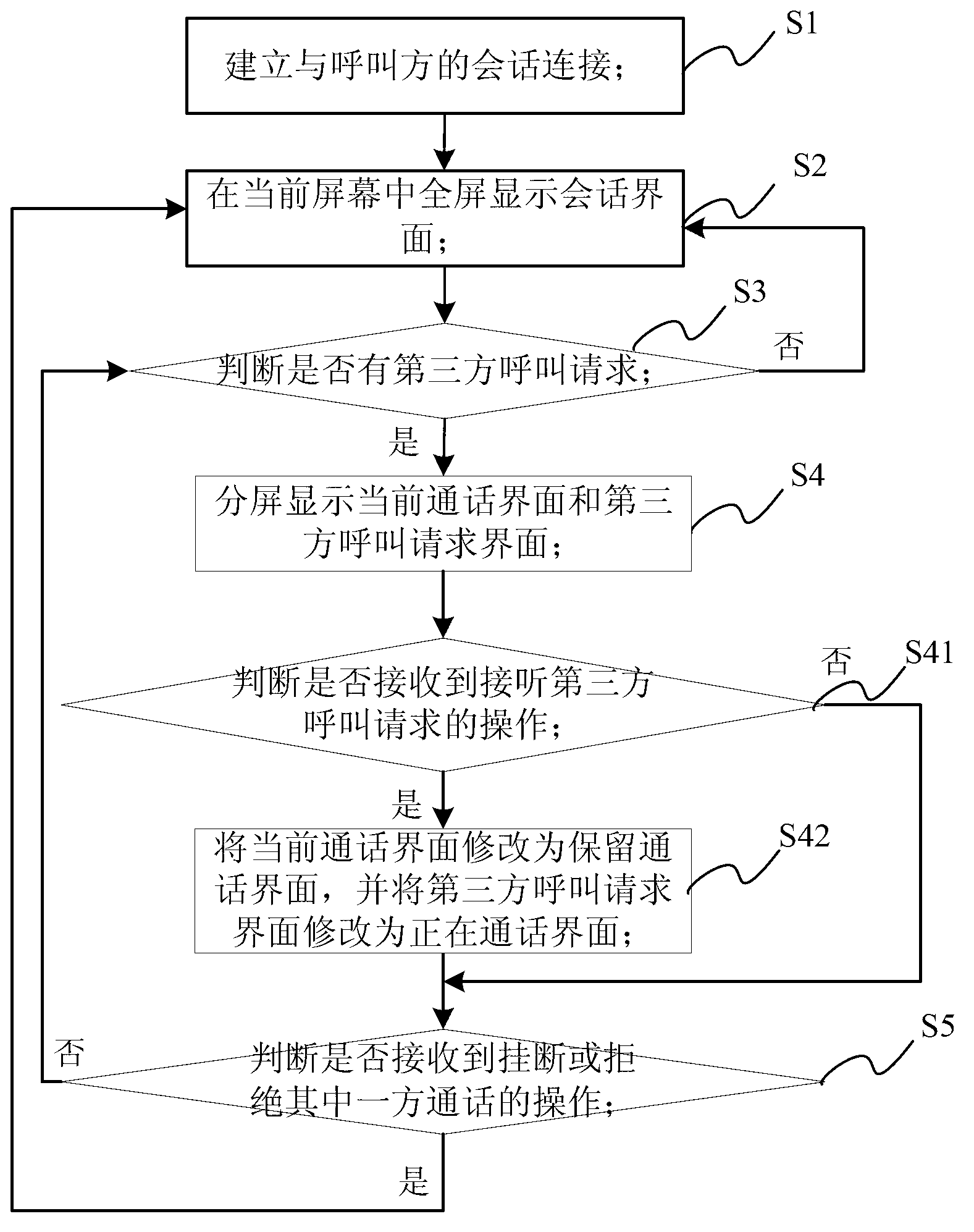
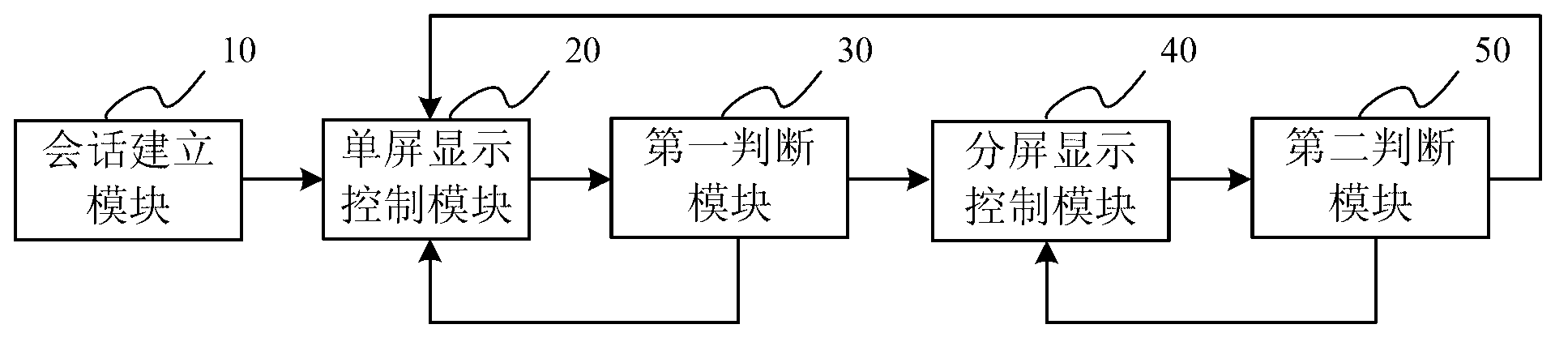
Multiparty call display controlling method, device and mobile terminal
ActiveCN103067585AEasy to operateImprove experienceCalling susbscriber number recording/indicationThird partyCommunication interface
The invention relates to a multiparty call display controlling method, a device and a mobile terminal. The method includes the following steps: (A) establishing conversation connection with calling parties; (B) displaying a conversation interface on a full present screen, then carrying out a step C; (C) judging whether the device has a call request from a third party or not, if yes, carrying out a step D, or, carrying out the step B; (D) diving the present screen into two parts to respectively display an communication interface with conversation established and an interface of the call request of the third party, then carrying out a step E; (E) judging whether operation which requires to hang up or refuse communication with one party is received or not, if yes, returning to the step B, and if no, returning to the step D. Through split-screen display, a three-party communication interface is enabled to be attractive and fast, operation by users is convenient, misoperation is not easy to produce, three-party communication can be easily achieved, even three-party video communication can be achieved, and user experience is improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com