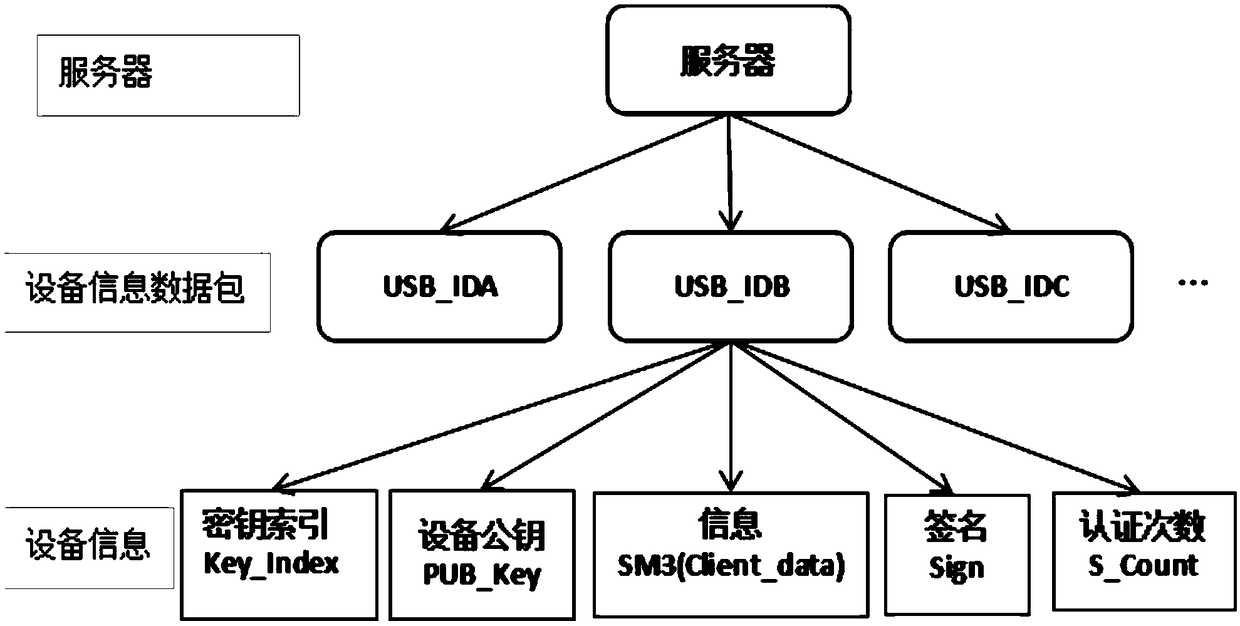
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
340results about How to "Ensure communication security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
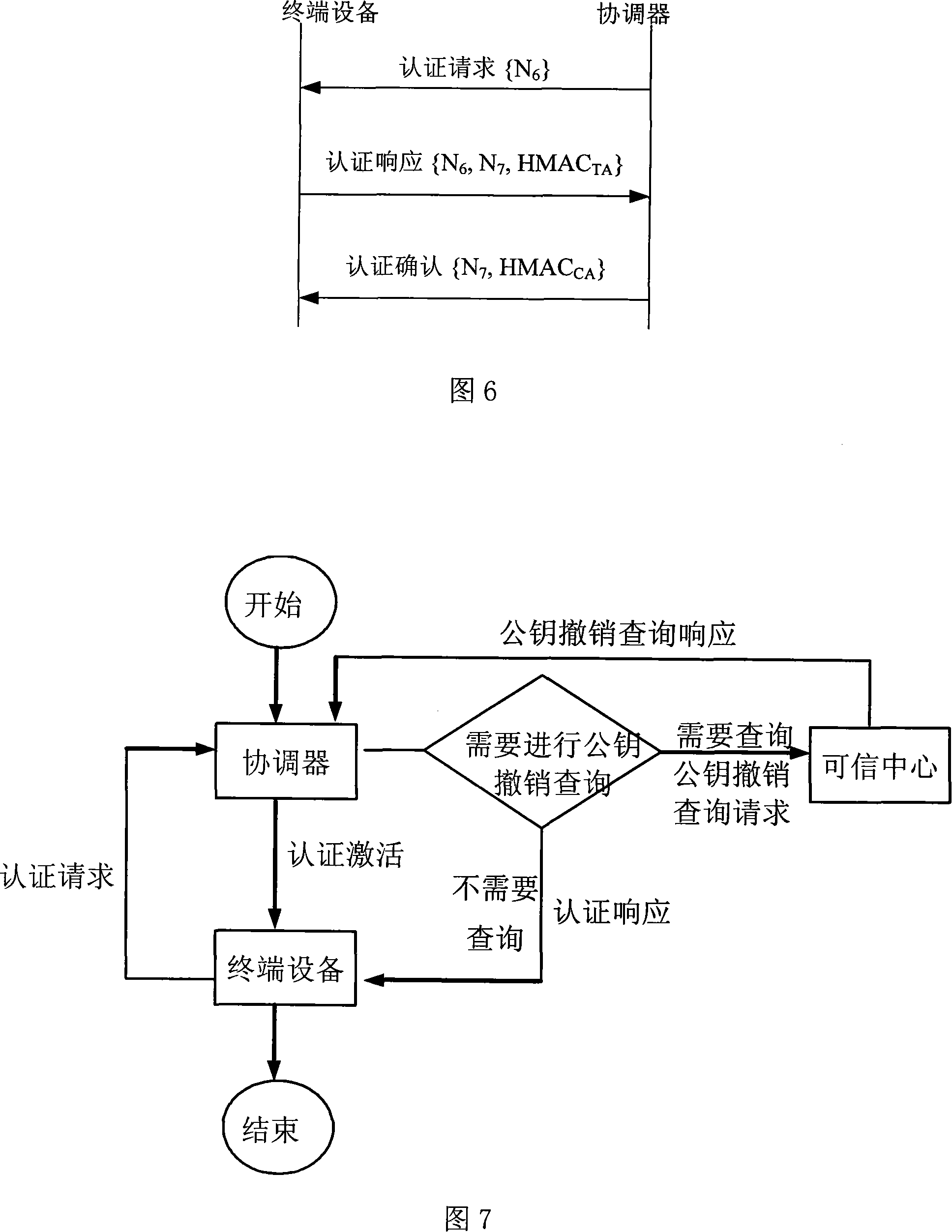
Safety communication secret key negotiation interaction scheme
ActiveCN104506534AGuarantee authenticityEnsure communication securityKey distribution for secure communicationUser identity/authority verificationThe InternetNetwork service
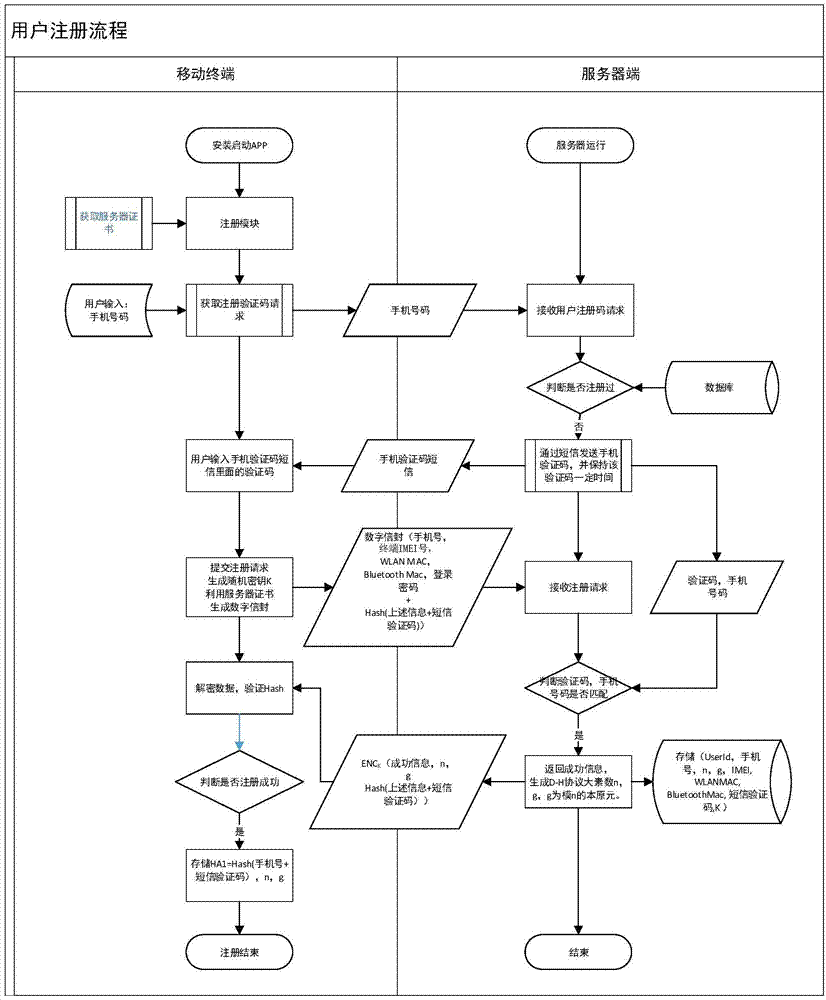
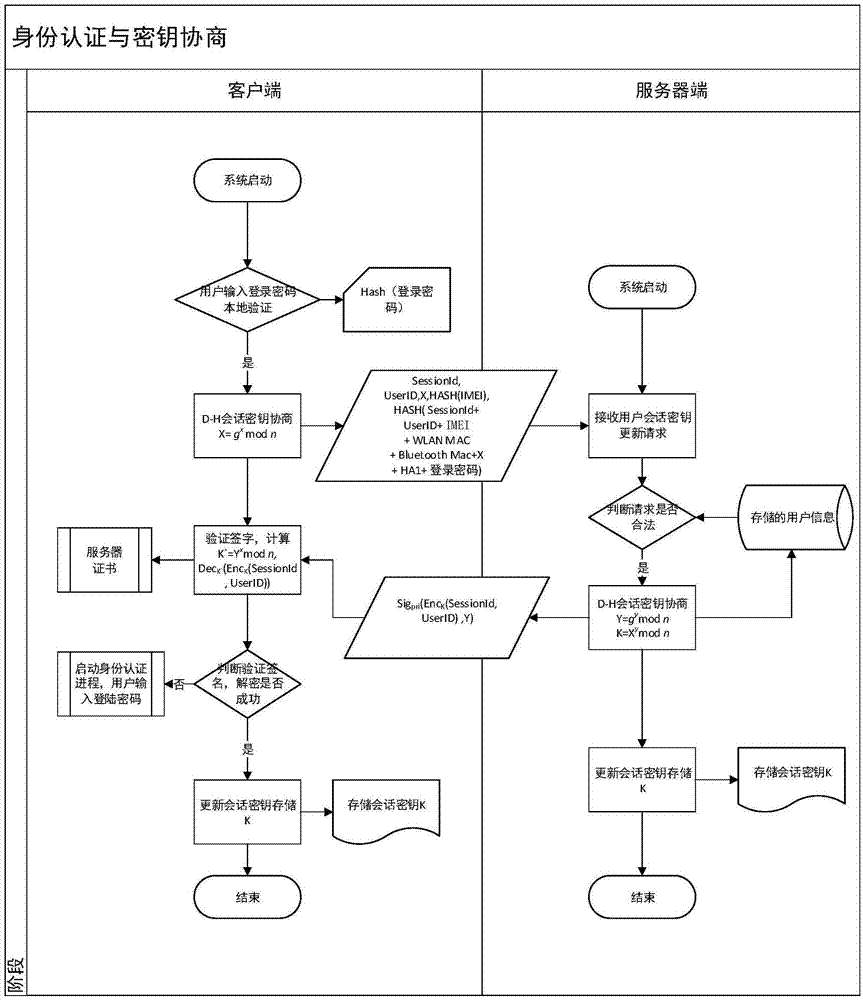
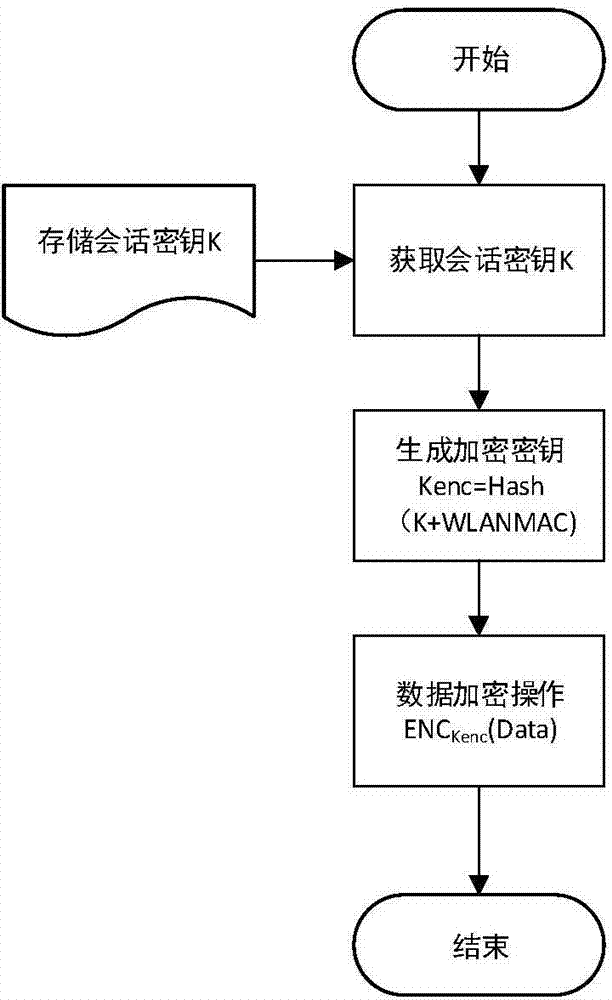
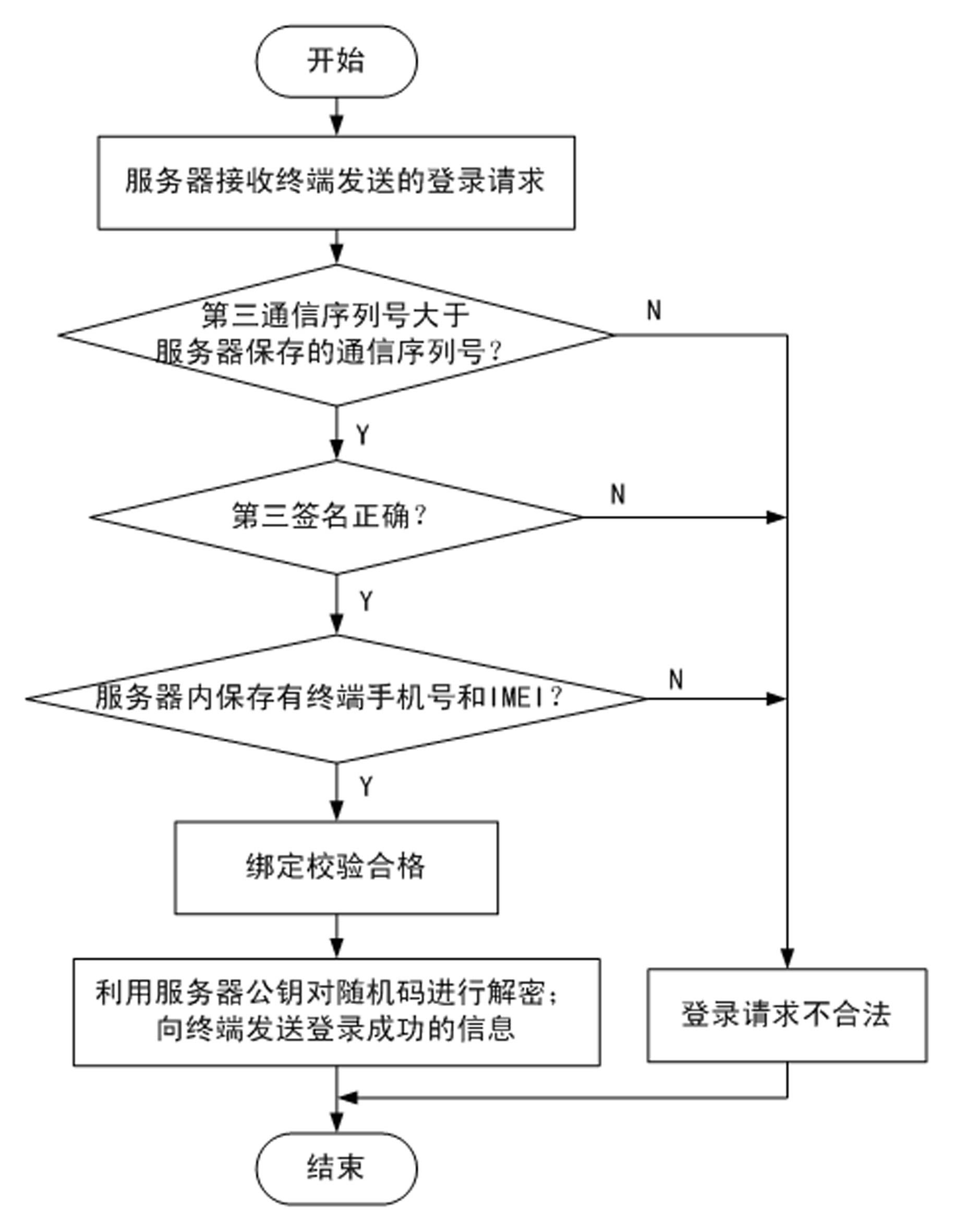
The invention provides a method for safety communication between an application on a mobile terminal and a network server. Shared secrets of a user and a server are overlapped and bound with an identification code of mobile intelligent terminal equipment and a mobile phone number of the user by utilizing a cryptology; then the obtained product is applied to an identity authentication system to implement authentication on a client side; a digital certificate and a digital signature mechanism are utilized to implement authentication on the server; a session key is established with a network server by utilizing a Differ-Hellman secret key negotiation protocol so as to carry out safety data communication. The method is characterized in that the shared secrets are overlapped and bound with identification code of the machine and the mobile phone number of the user and the shared secrets are updated regularly; even though information is stolen by an attacker, a system still cannot be influenced. The user not only needs to provide a login password, but also needs to use the system on designated equipment. The method can ensure that the user carries out safety communication with the server on internet by the mobile equipment.
Owner:QINGDAO WEIZHIHUI INFORMATION
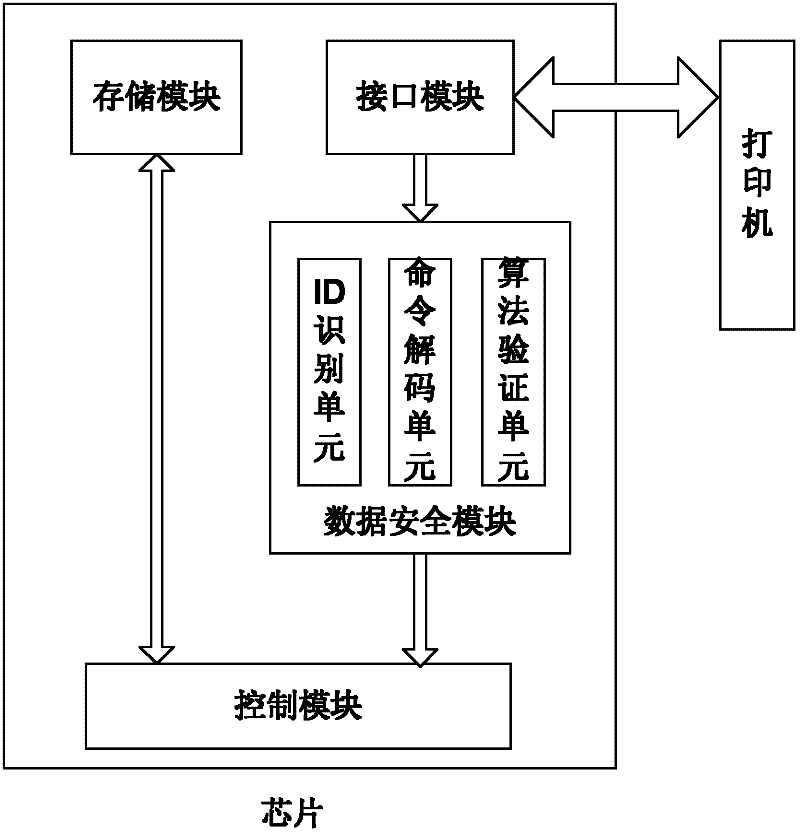
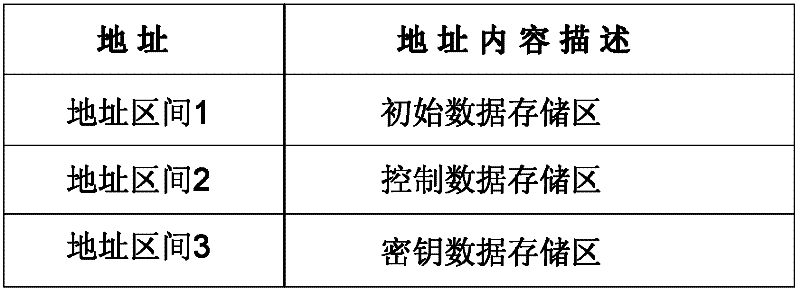
Chip, data communication method for chip, consumable container and imaging equipment
InactiveCN102231054AImprove reliabilityAvoid crackingElectrographic process apparatusPrintingExternal dataStructure of Management Information
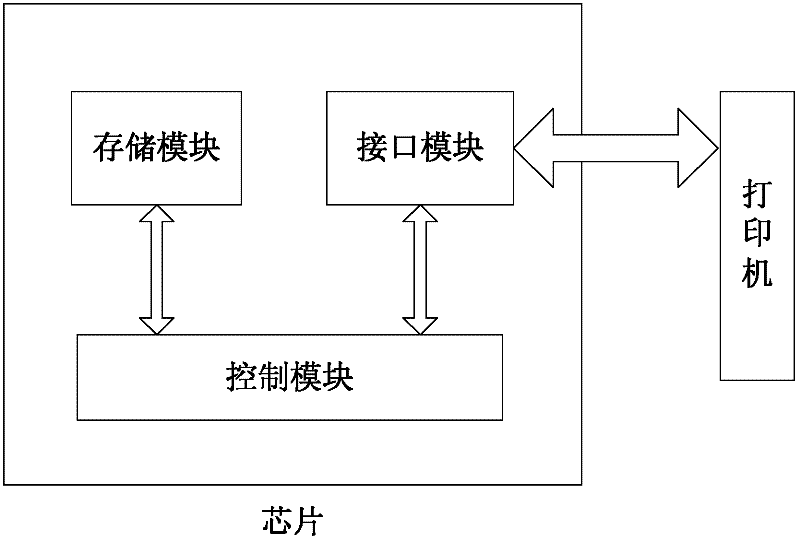
The invention provides a chip of a consumable container, which comprises a storage module, a control module, an interface module and a data safety module. The storage module is used for storing initial data, printing data, control data and key data; the interface module is used for realizing data communication between the storage module and the control module; the data safety module is respectively connected with the interface module and the control module, and is used for identifying a type and a content of data communicated between a printer and the chip, encrypting matched data in a selected safe mode and decrypting the data; the control module is connected with the storage module and is used for controlling data communication between the chip and the printer and the access operation of the data of the storage module and external data and sending a corresponding control command to the chip according to a safety module processing result so as to realize data communication; and the same keys are stored in the printer and the chip. The invention also provides a data communication method for the chip, the consumable container with the chip structure, and imaging equipment with the consumable container. The safety of the communication data of the chip can be protected.
Owner:ZHUHAI TIANWEI TECH DEV CO LTD
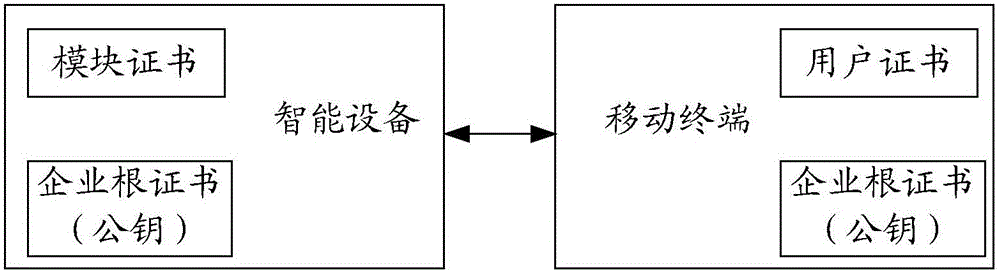
Method and device for secure communication in Internet of Things
InactiveCN105791272AEnsure communication securityPrevent eavesdropping risksKey distribution for secure communicationUser identity/authority verificationSecure communicationCommunications security
The invention provides a method and a device for secure communication in Internet of Things. For communication between devices of any two parties, namely a first device and a second device, in the Internet of Things with interconnected devices of three parties, namely a cloud platform, an intelligent device and a mobile terminal, the first device executes the following steps of carrying out identity validity judgement with the second device through a method for verifying a digital signature of a digital certificate; and communicating with the second device when the first device and the second device both successfully pass through the identity validity judgement. Through adopting the method for verifying the digital certificate to carry out identity authentication on various interconnected intelligent devices in the Internet of Things, and the security control of bidirectional authentication is realized in a process for communication between the intelligent devices, so that the security risks that the devices are counterfeit and the opposite terminal is forged are effectively prevented and the communication security of the intelligent device is guaranteed. After identity authentication, the encrypted communication is carried out, so that the hacking risk is effectively prevented and the communication security is more completely guaranteed.
Owner:QINGDAO HAIER INTELLIGENT HOME TECH CO LTD
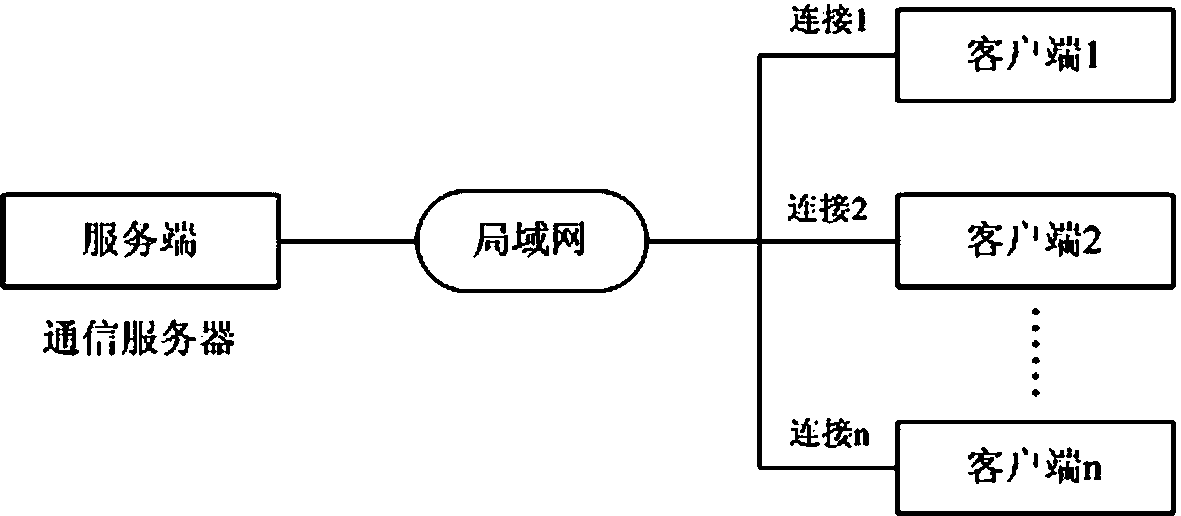
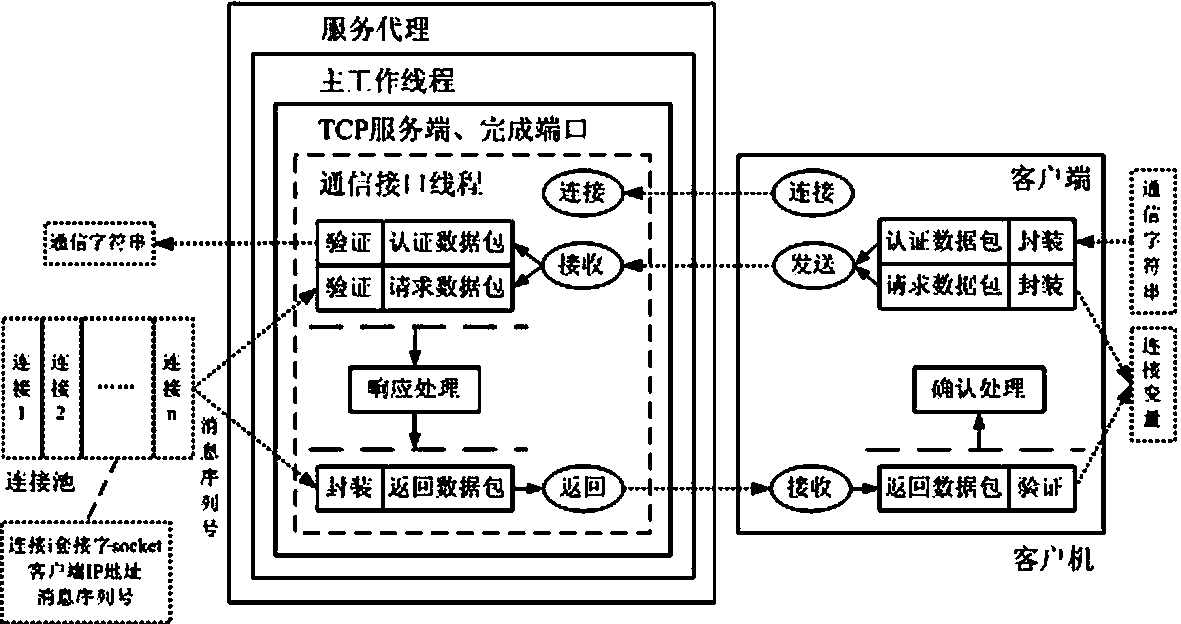
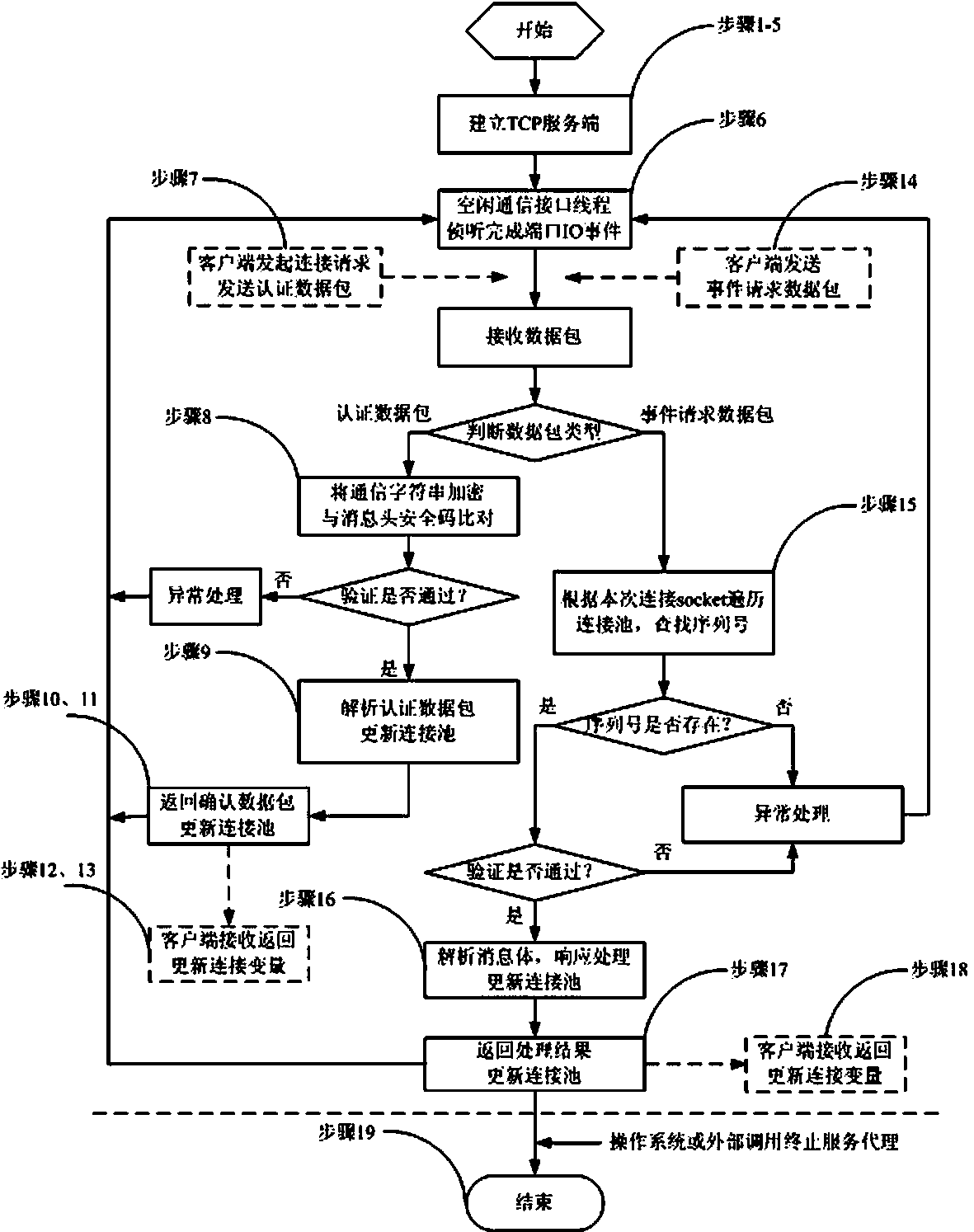
Multilink safety communication method based on completion port model
InactiveCN103391289AImprove scalabilityEasy to implementError preventionSecure communicationCommunication interface
The invention provides a method for supporting multilink concurrence safety communication between a server and multiple clients and relates to a multilink safety communication method based on a completion port model. The method includes that a main worker thread at a communication server is embedded into an application service of a Windows system to run, a transmission control protocol (TCP) communication server is built according to the completion port model, meanwhile a fixed number of communication interface threads are built to conduct communication with the clients in an asynchronous mode, and the parallel processing capability of the server is improved. In an interaction process, after any client builds the TCP connection, two communication parties must adopt a handshake mechanism to ensure connection legality and adopt connection pool queues or local variables to dynamically maintain message serial numbers in the following data receiving and transmitting process, data transmitted by any party on the legal connection are packaged again according to the data package structure definition, and the receiving party adopts a safety verification algorithm to verify the data packages and regroup the plurality of data packages according to the precedence order of the message serial numbers.
Owner:中船凌久高科(武汉)有限公司
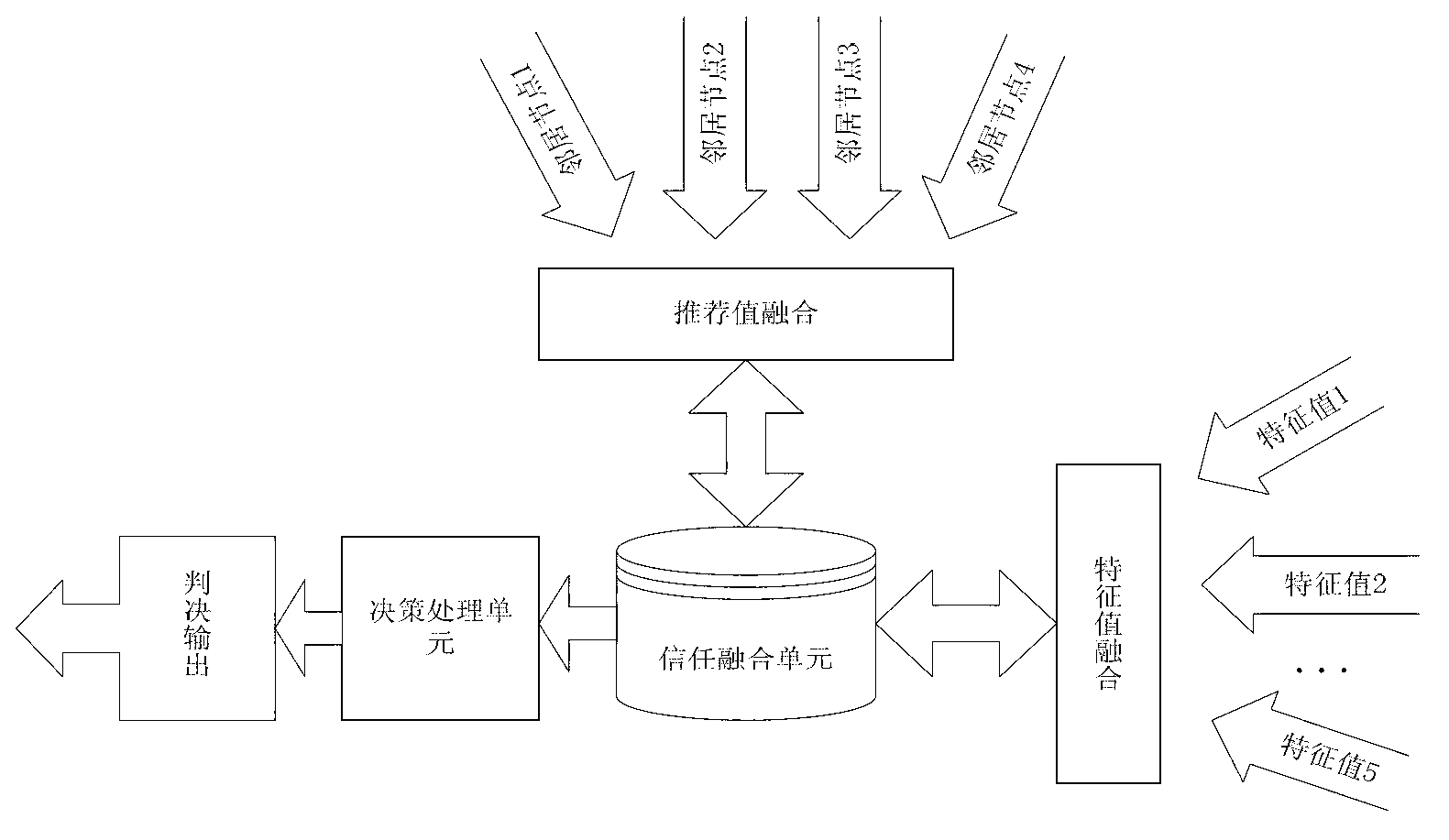
Method for detecting network anomaly of wireless sensor based on trust evaluation
InactiveCN102802158AEnsure communication securityGuaranteed accuracySecurity arrangementComputer hardwareWireless sensor networking
The invention discloses a method for detecting network anomaly of a wireless sensor based on trust evaluation. The method comprises a monitoring step, a fuzzification step, a DS fusion step, a recommended information processing step, and a determining step. A main process is collecting node behavior characteristics, calculating a trust value thereof through a fuzzy theory and a DS evidence theory, determining node operating states by a judging mechanism, and finding malicious nodes, so that effectiveness of data collected by network is ensured. Through monitoring behavior of evaluated nodes, abnormal nodes existed in the network are detected, and the abnormal nodes are broadcasted to neighbor nodes so as to prevent the abnormal nodes destroy normal operation of the whole network.
Owner:HUNAN UNIV
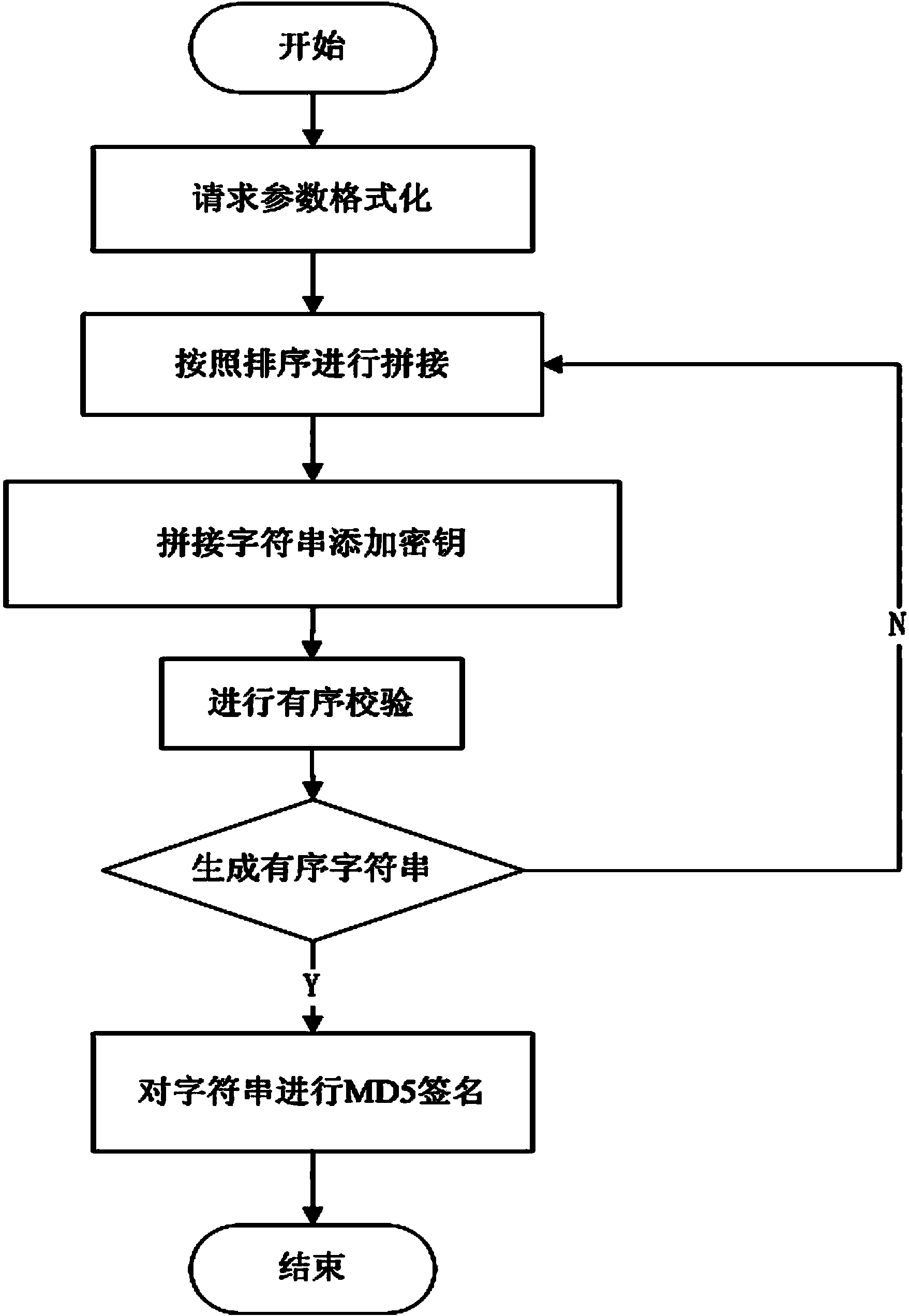
Signature algorithm for server validation
InactiveCN103973695AEnsure communication securityPrevent key theftUser identity/authority verificationServer-sideEncryption
The invention provides a signature algorithm for server validation. The signature algorithm includes the following achievement steps: when a WEB front-end server communicates with a background server, a signature is added to a request parameter, character strings are formed through a specific combination of the parameters and are spliced, the finally obtained character strings are subjected to MD5 signature to serve as a communication passing parameter; the signature is recomputed when a server end receives a request, whether the request parameter is consistent with the passing parameter is judged, and if not, it is indicated that the call request is forged or tampered with. Compared with the prior art, the signature algorithm for server validation guarantees safety in the passing process through multi-hierarchy encryption, and guarantees accuracy in the receiving process by using a matched algorithm of the signature algorithm on the server.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
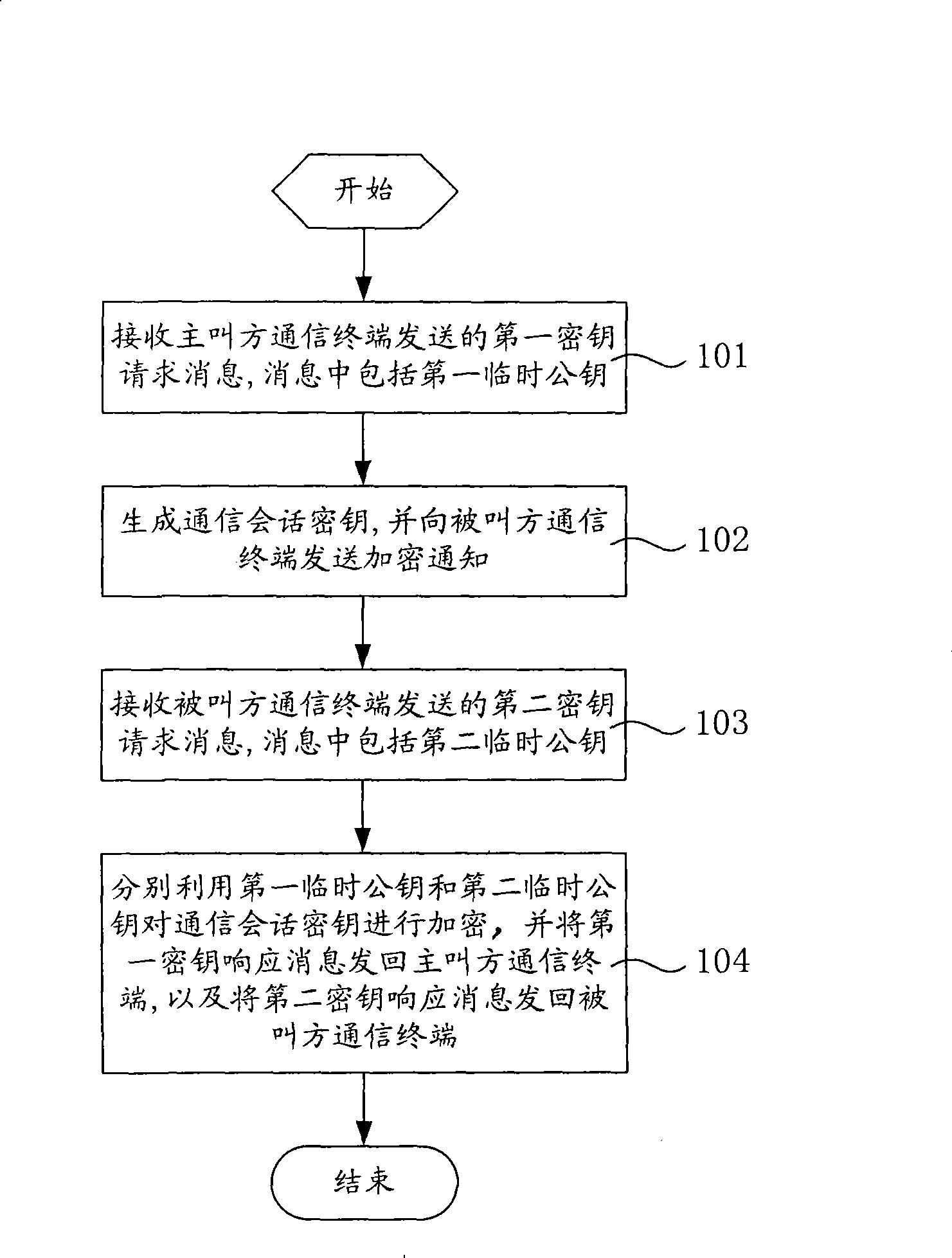
Session cipher key distributing method and system
InactiveCN101383698AEnsure communication securityKey distribution for secure communicationPublic key for secure communicationDistribution methodDistribution system
The invention relates to a session key distribution method which comprises the steps as follows: a first key request message sent by a calling party communication terminal is received, and the first key request message includes a first temporary public key; a communication session key is generated according to the first key request message, and a cryptographic notification message is sent to a called party communication terminal; a second key request message sent by the called party communication terminal is received, and the second key request message includes a second temporary public key; the communication session key is encrypted by respectively using the first temporary public key and the second temporary public key, and a first key response message is sent back to the calling party communication terminal, and a second key response message is sent back to the called party communication terminal. The invention relates to a session key distribution system. The invention realizes the distribution of the keys of the two communication parties having encryption requirements at the network side, utilizes the asymmetric key way to protect the session key, and ensures the safety of the session key transmission; and the session key is distributed by the network side to cause the communication terminals to be free of complex key management.
Owner:CHINA TELECOM CORP LTD
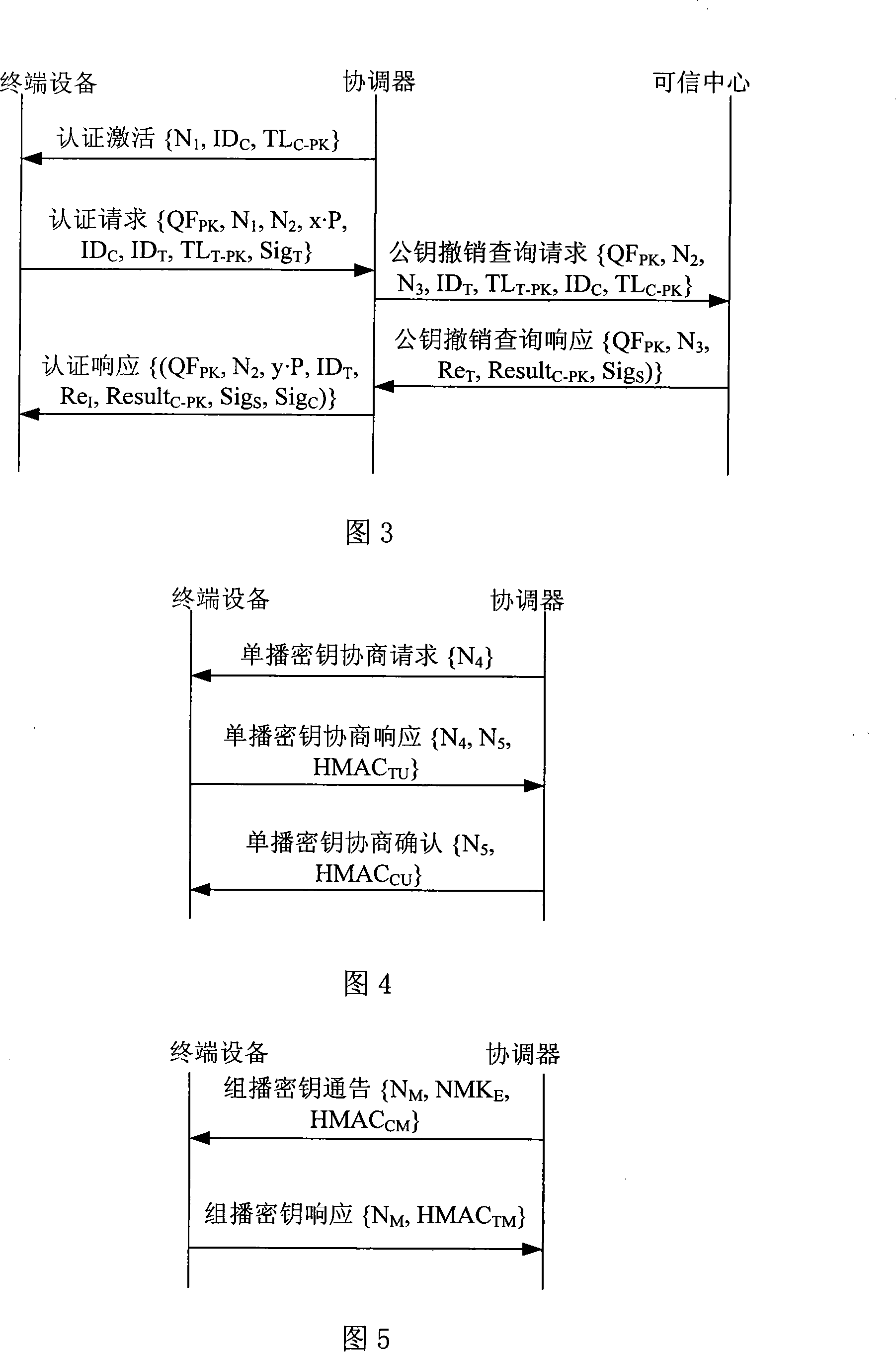
Authentication accessing method of wireless multi-hop network
InactiveCN101232378AImprove securityImprove performanceKey distribution for secure communicationPublic key for secure communicationAccess methodBeacon frame
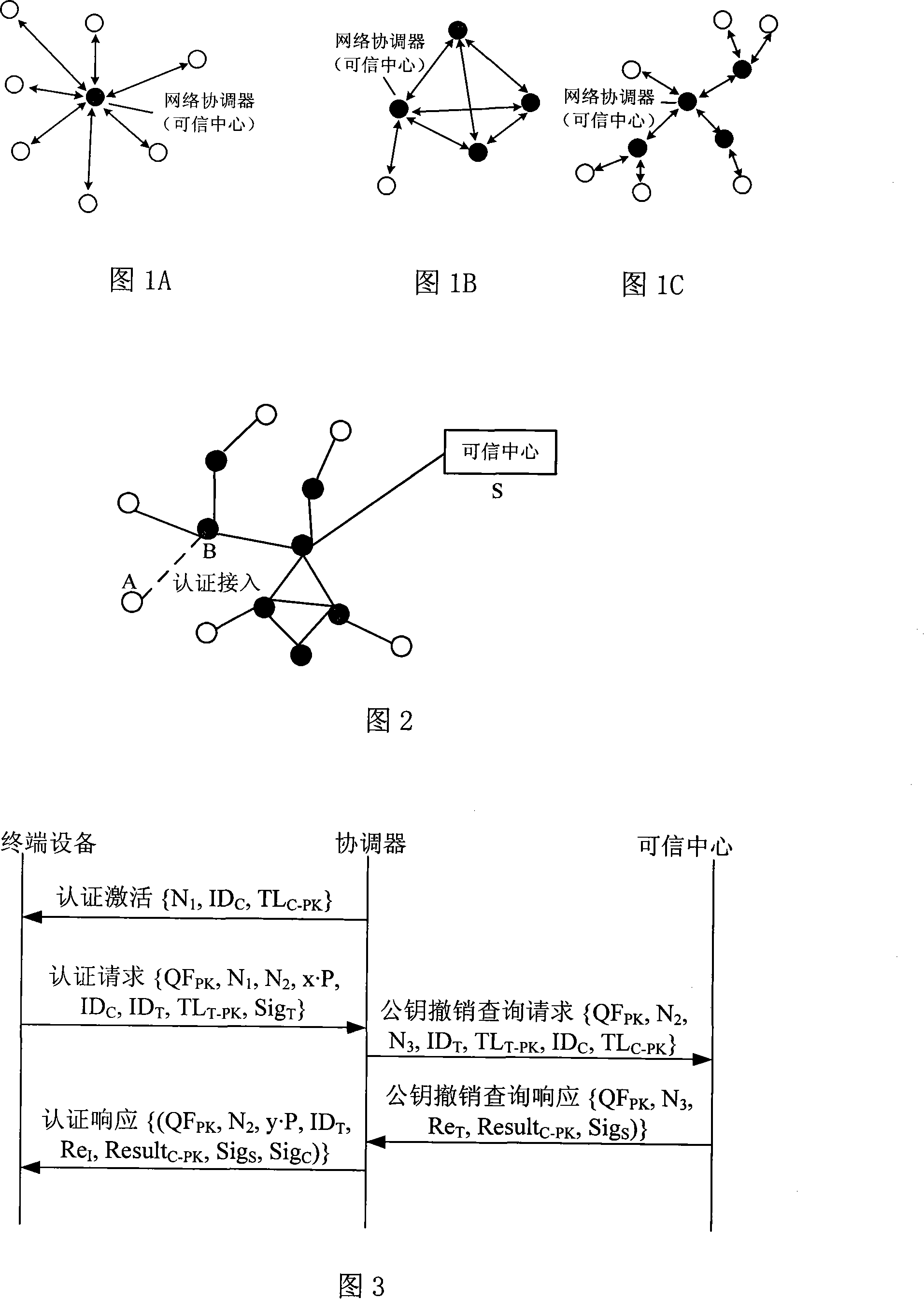
The invention relates to an authentication access method of a wireless multi-hop network. The invention is applicable to the safety application protocol of the WAPI framework method (TePA, the access control method which is based on the triple peer-to-peer identification) during the application on the specific network which includes a wireless LAN, a wireless MAN and a wireless PAN. A terminal equipment and a coordinator have the port control ability, the terminal equipment selects the authentication and key management suit and sends the connection request to command the coordinator after the broadcast beacon frame of the coordinator, the coordinator carries out the authentication together with the terminal equipment according to the selected authentication and key management suit by the terminal equipment, the connection response command is sent to the terminal equipment after the finish of the authentication; the terminal equipment and the coordinator carries out the control to the ports according to the authentication result, so as to realize the authentication access of the wireless multi-hop network. The invention solves the technical problem of the safety hidden trouble of the prior authentication method of the wireless multi-hop network.
Owner:CHINA IWNCOMM
Key processing method in dual connectivity mode and device
ActiveUS20160249210A1Ensure communication securityAvoid failureConnection managementSecurity arrangementCommunications securityKey generation
Embodiments of the present disclosure disclose a key processing method in dual connectivity mode and a device, which ensure communication security of UE in dual connectivity mode. The method according to the embodiments of the present disclosure includes: of a first base station and a second base station that have a communication connection to a terminal each, receiving, by the second base station, first request information sent by the first base station, where the first request information is used to request the second base station to generate a key used for communication with the terminal, and generating, by the second base station based on a security key carried in the first request information, the key used for communication with the terminal.
Owner:HUAWEI TECH CO LTD
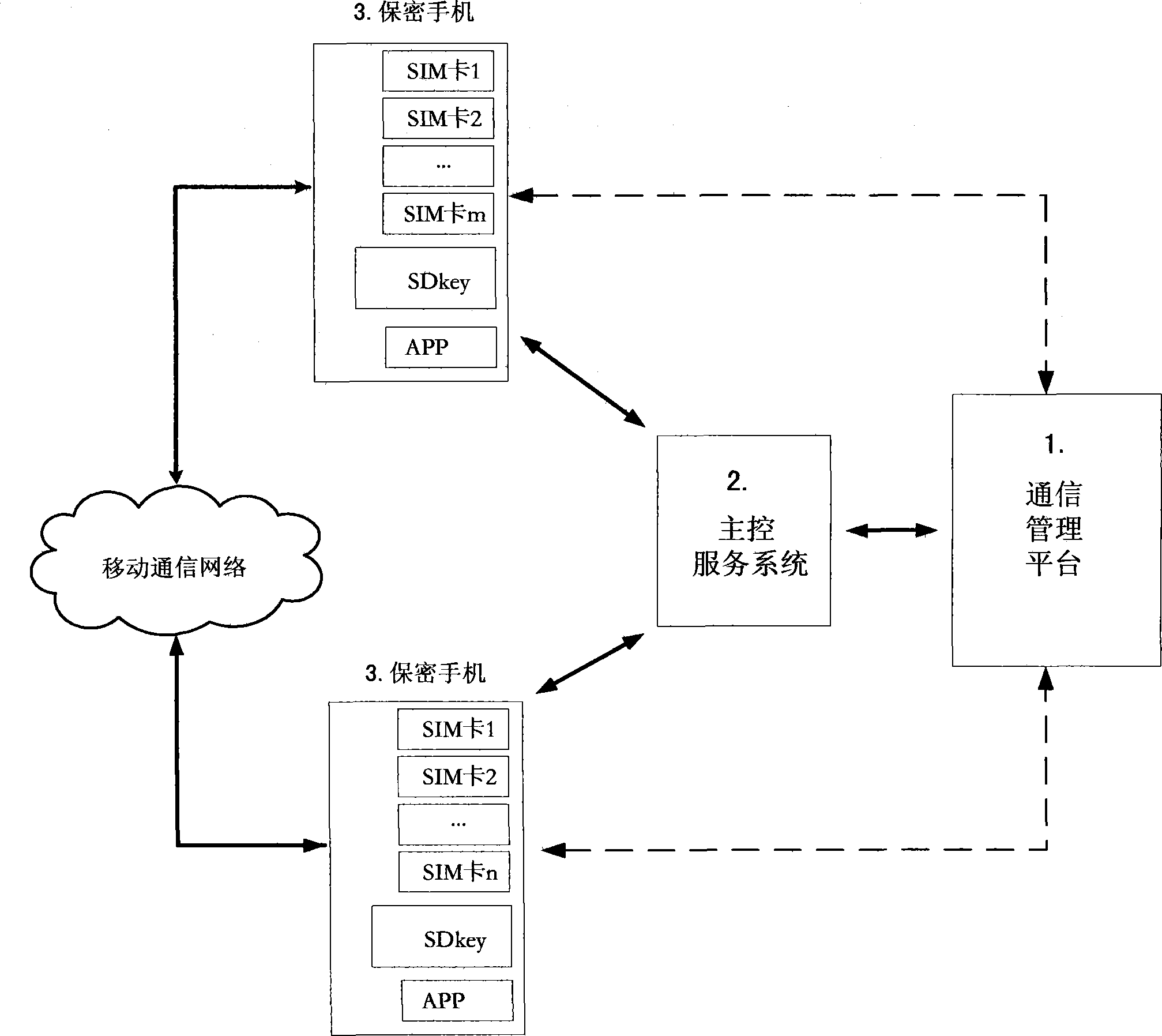
Secrete communication system and method for smart phone
ActiveCN104333455APrevent illegal eavesdroppingPrevent eavesdroppingUser identity/authority verificationSecurity arrangementCiphertextEavesdropping
The invention belongs to the technical field of information safety, in particular to secrete communication of a smart phone. According to the technical scheme, a secrete communication system for the smart phone comprises a communication management platform (1), a main control service system (3) and a plurality of secrete mobile phones (3). Compared with the technology and method for the other secrete mobile phones, the secrete communication system and method use an encryption crushing technology and a recombination decryption technology to transmit complete communication information through x mobile communication signal channels, and each mobile communication signal path transmits one part of cipher-text fragments of a voice data unit or a short message; people cannot restore the complete cipher-text not to mention the plain text of the voice or the plain text of the short message through eavesdropping any one of the mobile communication signal channels, and therefore, the illegal eavesdropping on the mobile communication network is effectively avoided; the voice data or short message encryption, decryption and crushing recombination are performed in a customized SD key in the secrete mobile phone, and the rogue program eavesdropping to the secrete mobile phone terminal can be effectively avoided.
Owner:BEIJING CHERILEAD TECH
A Method of Ensuring the Security of Client Software
InactiveCN102299930AEnsure communication securityNormal use will not be harmfulUser identity/authority verificationCommunications securityClient-side
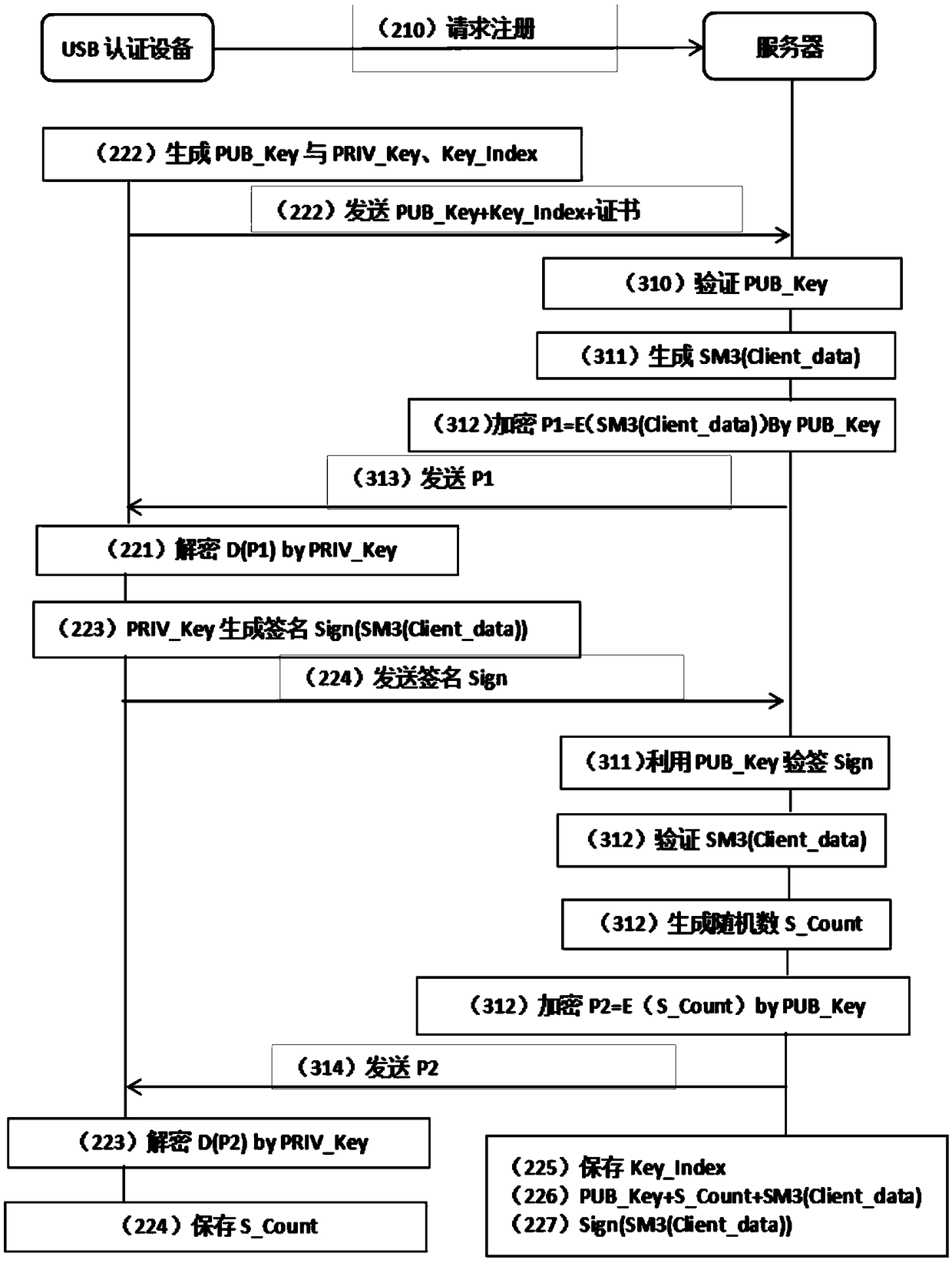
The invention discloses a method for ensuring the security of client software. The method comprises the following steps of: 1, downloading the software by using a terminal, and adding terminal identity authentication information into a software packet by using a server; 2, transmitting a binding request to the server by using the terminal; 3, verifying the legality of the binding request, and if the binding request is legal, transmitting a binding success information to the terminal; 4, verifying the legality of the binding success information; 5, transmitting a login request to the server by using the terminal; 6, verifying the legality of the login request, and if the login request is legal, transmitting a login success information to the terminal; and 7, verifying the legality of the login success information, and if the login success information is legal, keeping a session. By the method, the software can be better prevented from being falsified; the security of communication between the terminal and the server can be ensured; replay attacks can be effectively prevented; the software can be detected whether to be falsified or not; and even though a hacker downloads the software and attacks the server by falsifying the software, only the terminal cannot be used normally and the normal use of other users may not be influenced.
Owner:北京无限新锐网络科技有限公司
Wireless multi-hop network authentication access method based on ID
InactiveCN101222772AImprove securityImprove performanceUser identity/authority verificationNetwork topologiesCommunications securityAccess method
The invention provides an access authentication method in ID based wireless multi-hop network, which is applicable to the security application protocol when WAPI frame method (TePA, an access control method based on triplet peer authentication) is applied on specific network including wireless local area network, wireless metropolitan area network and wireless personal area networks. The methods comprises the following steps that: a non-controlled port and a controlled port are defined; a coordinator transmits a beacon frame; a terminal equipment sends a command for connection request; the coordination conducts authentication with the terminal equipment; after the authentication is successful, the coordinator opens the controlled port and sends a connection response command; the terminal equipments receive the connection response commands and opens the controlled ports so as to get access to the network. The method of the invention solves the technical problem that the prior wireless multi-hop network has safety hidden danger in access authentication method and ensures the communication security between the terminal equipment and the coordinator.
Owner:CHINA IWNCOMM
A user authentication device and an authentication method based on a physically non-clonable technology PUF
ActiveCN109040067AImprove privacy and securityUniqueness guaranteedPublic key for secure communicationUser identity/authority verificationUser authenticationNumber generator
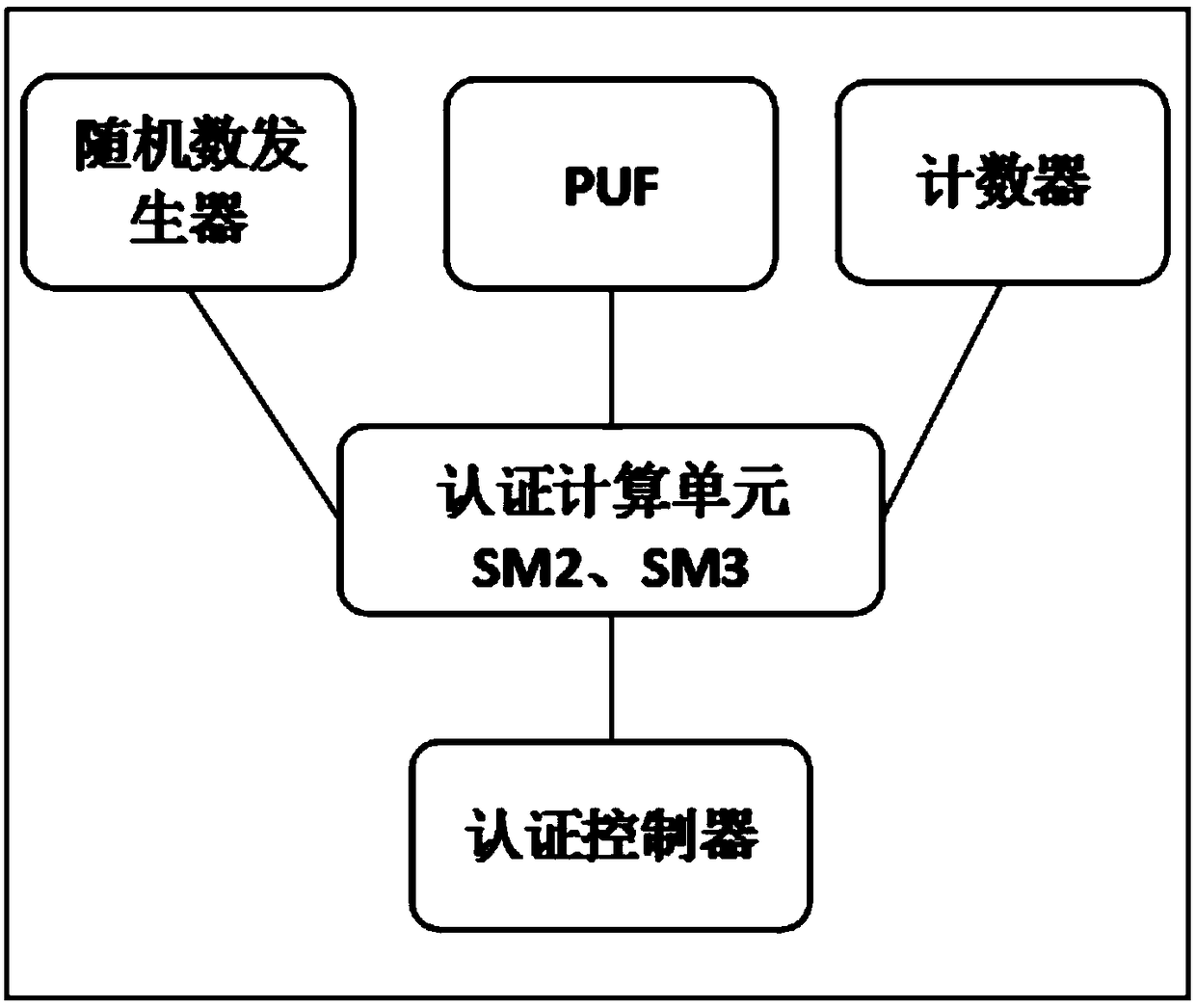
The invention discloses a user authentication device based on a physically non-clonable technology PUF, comprising a physically non-clonable module PUF, an authentication module, an authentication control module, a random number generator and a counter, wherein, the physically non-clonable module PUF is embedded in the authentication device for generating authentication-related key pairs; The authentication module is embedded with an asymmetric algorithm and a digest algorithm to complete the operation to be executed by the authentication; The user can manually control sending authentication request and sending authentication information through the authentication control module; The invention is based on the three principles of simplicity, privacy security and compatibility, and meets therequirements of simplicity, high security and compatibility with a plurality of network servers. The chip inside the device adopts the non-clone technology PUF to ensure the uniqueness of the device,and meets the characteristics of non-clone replication and privacy security of the device.
Owner:GUANGDONG UNIV OF TECH +1
Self-supporting lightning-proof optical cable
ActiveCN101887781AMeet special climate requirementsEasy to layPlastic/resin/waxes insulatorsInsulated cablesShielded cableElectromagnetic field
The invention discloses a self-supporting lightning-proof optical cable. The self-supporting lightning-proof optical cable comprises a cable core, a covered layer and a suspension wire, wherein the cable core is used for transmitting an optical signal and power; the covered layer is covered with the cable core; and the suspension wire is connected with the covered layer. The covered layer comprises a shielding layer, an outer sheath and a ground layer, wherein the shielding layer shields the cable core; the outer sheath coats the shielding layer; and the ground layer is arranged between the cable core and the shielding layer. The self-supporting lightning-proof optical cable of the invention can prevent communication equipment from being damaged by thunder and lightening, effectively prevent an electromagnetic field generated by the shielding cable from disturbing other communication cable signals and prevent external electromagnetic field from disturbing the cable core.
Owner:JIANGSU ZHONGLI GRP CO LTD +3
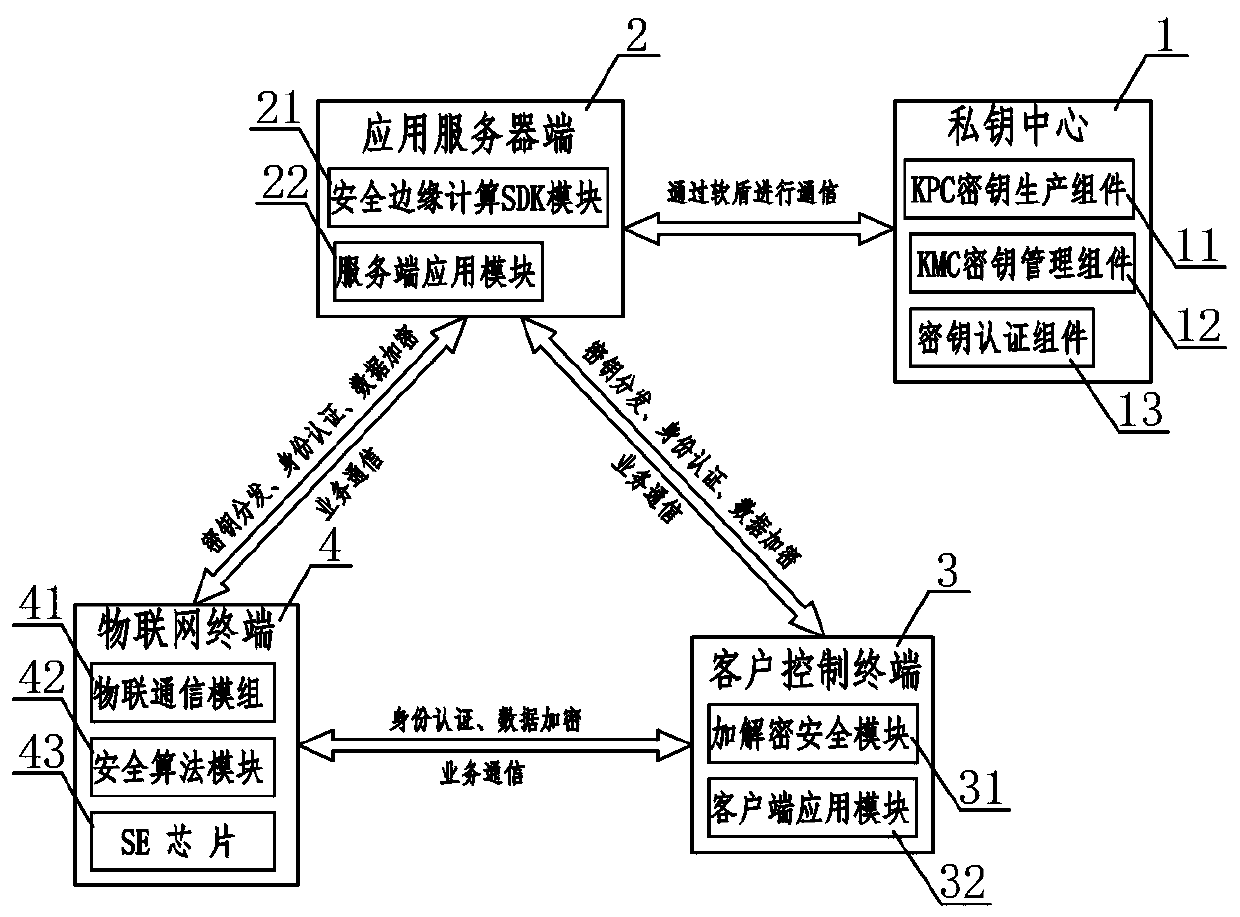
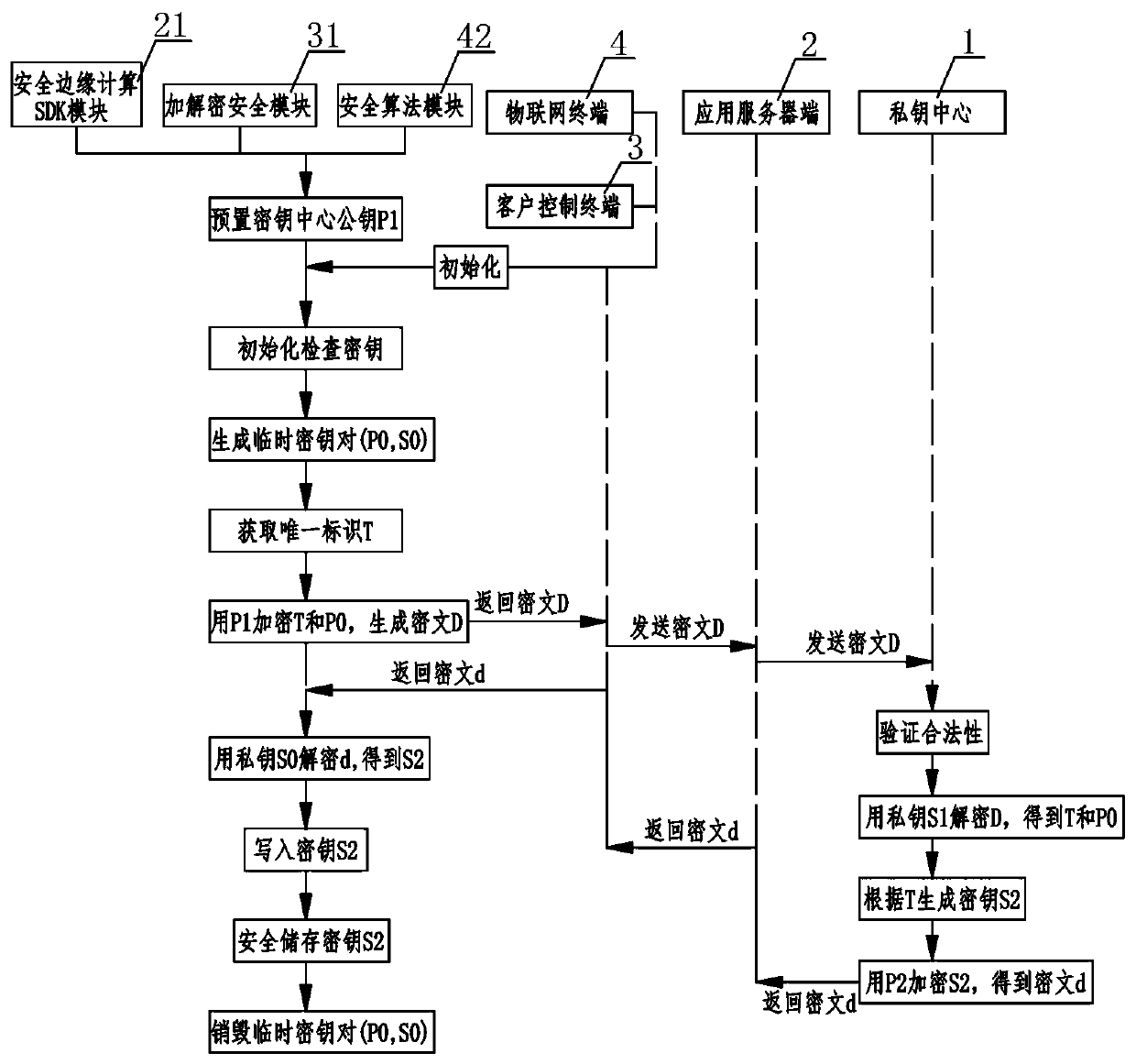
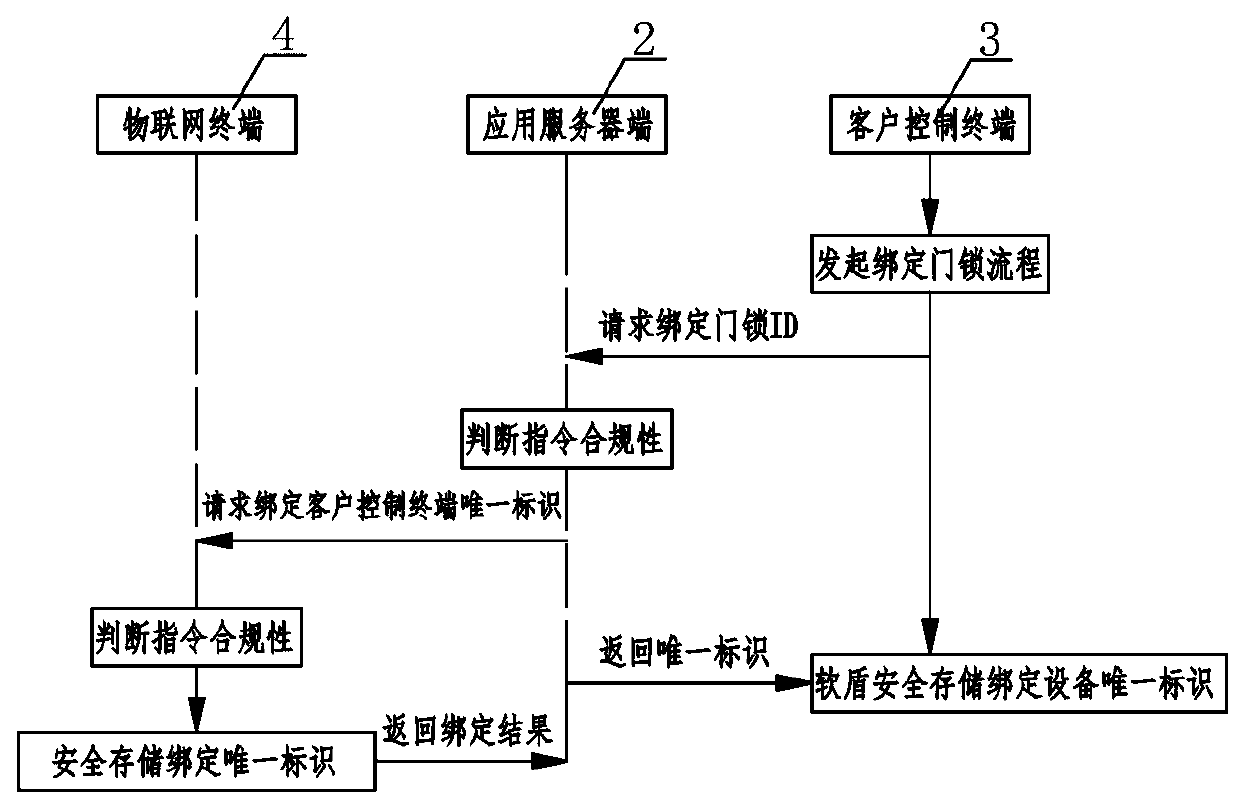
Internet of Things safety management system
ActiveCN110784491AEnsure communication securityAvoid illegal operationTransmissionSafety management systemsThe Internet
The invention relates to an Internet of Things security management system. A private key center and an application server perform communication authentication data transmission through a soft shield;the application server side performs mutual communication of key distribution, identity authentication and data encryption with the client control terminal and the Internet of Things terminal at the same time; mutual communication of identity authentication and data encryption is carried out between the client control terminal and the Internet of Things terminal, wherein the private key center comprises a KPC key production assembly, a KMC key management assembly and a key authentication assembly, the application server comprises a security edge computing SDK module and a server application module, and the client control terminal comprises an encryption and decryption security module and a client application module, and the Internet of Things terminal comprises an Internet of Things communication module, a security algorithm module and an SE chip. According to the Internet of Things security management system, only the user is completely autonomous and controllable in the Internet of Things system, the cloud system does not have the authority of directly operating the user equipment, and the Internet of Things control security level can be effectively improved.
Owner:深圳前海智安信息科技有限公司
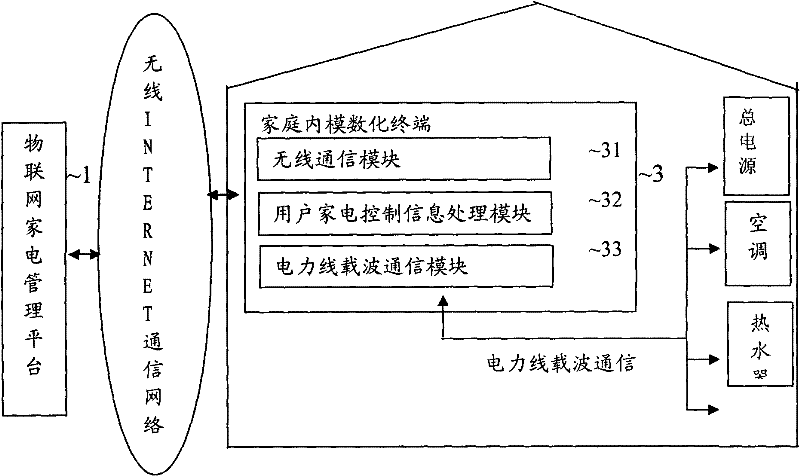
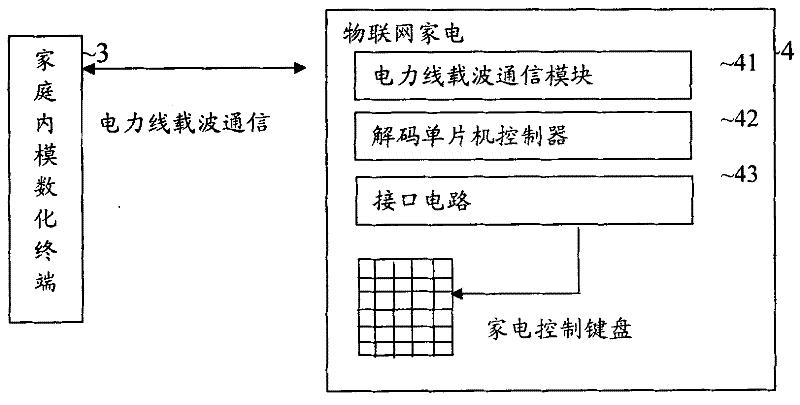
Internet of things home appliance management system and management method
InactiveCN102130802ARealize switch controlRealize parameter settingData switching by path configurationInternet communicationControl function
The invention discloses an Internet of things home appliance management system and an Internet of things home appliance management method. The system comprises an Internet of things home appliance management platform, a plurality of home modular terminals and various home appliances in which decoding singlechip controllers are arranged. The management method comprises the following steps that: the Internet of things home appliance management platform starts the Internet of things home modular terminals by short messages or in an Internet communication mode, so that two-way communication of home appliance control information between the terminals and the management platform is realized; electric wires which pass through the interior of a home are connected with power line carrier communication interfaces included in the various Internet of things home appliances, so that communication with the decoding singlechip controllers arranged in the networked home appliances is realized; and the decoding singlechip controllers in the home appliances carry out instruction identity identification and matching and translate control instructions sent to the controllers into same address codes of each control key in a monitoring program corresponding to a keyboard controlled by the home appliances, so that direct connection with conventional control functions of each home appliance is realized. A simple, easy and low-cost method is provided for managing requirements of the Internet of things home appliances of different manufacturers.
Owner:安徽省皖江质量检测科技有限公司
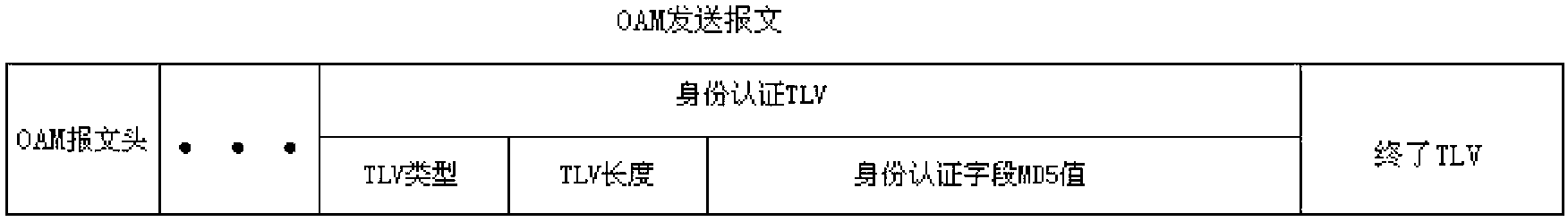
Method and device for setting operation, administration and maintenance (OAM) security authentication
InactiveCN102857521AEnsure communication securityImprove stabilityUser identity/authority verificationCommunications securityThe Internet
The invention provides a method and a device for setting operation, administration and maintenance (OAM) security authentication. The method comprises the following steps of: pre-setting keys on network equipment at two ends of a maintenance entity, and when the network equipment at one end sends an OAM message, adding an identity checking threshold limit value (TLV) field into the sent OAM message, wherein the field comprises a sending end MD5 value, and the sending end MD5 value consists of a sequenceID field and key logic operation; when the network equipment at the other end of the ME, performing corresponding logic operation on the sequenceID field in the message and a locally preset key to obtain a receiving end MD5 value; and comparing the two MD5 values, and if the two MD5 values are the same, determining that the OAM message passes through the authentication, otherwise, abandoning the message. Therefore, the OAM communication security is guaranteed, and equipment for running a continuity fault management (CFM) protocol difficultly suffers from hostile attack of the Internet.
Owner:SUZHOU CENTEC COMM CO LTD
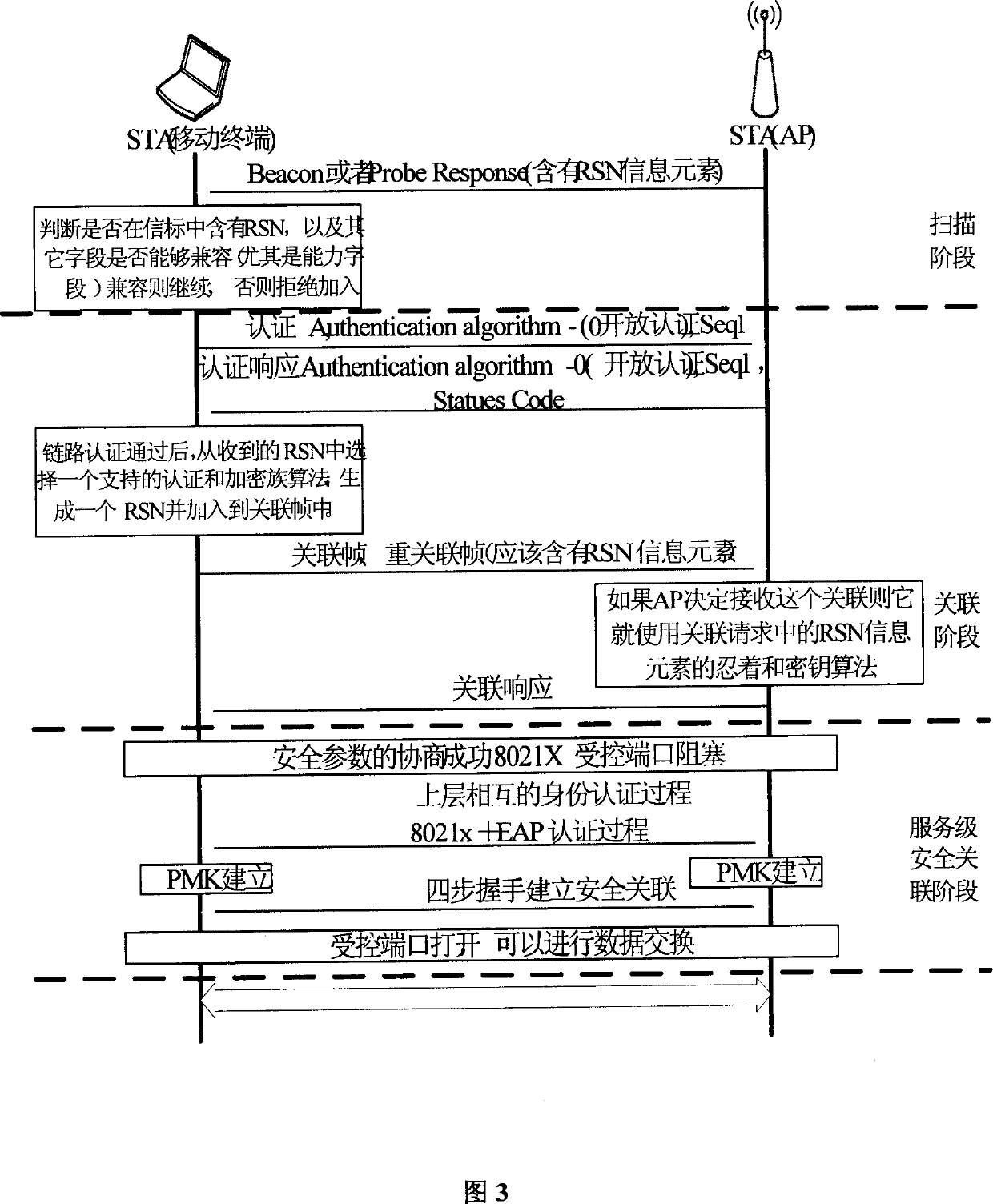
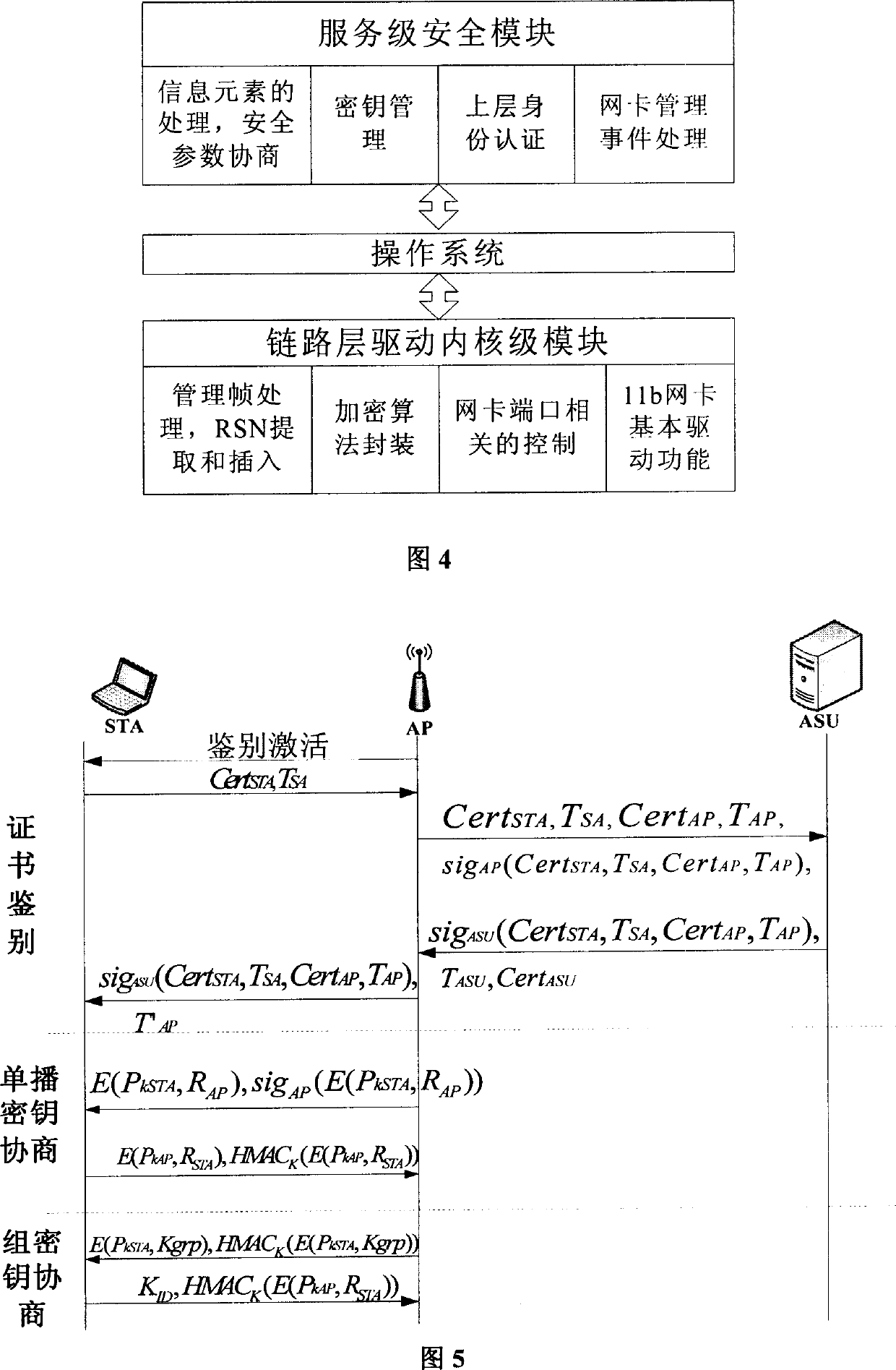
Access method for realizing WLAN multi mode safety identification
InactiveCN1801709AEnsure communication securityAdaptableUser identity/authority verificationData switching by path configurationLocal area networkSecure authentication
The invention discloses an access method to realize multimode security identification in WLAN and solve the problem that the selective access into two protocols of IEEE802.11i and WAPI, which comprises: with the compatibility of two protocols and internet distinguishability, integrating the said two protocols with current wireless network card of IEEE802.11b on link layer in TCP / IP protocol by dividing the protocol identification modules of IEEE 802.11 and WAPI into link level and service level for individual integration; finally, with terminal, recognizing network, selecting opposite identification, and adaptive taking a dialogue with a protocol to access network. This invention has strong adaptability, well compatibility and security in WLAN access.
Owner:KUNSHAN RUIXIANG XUNTONG COMM TECHCO
Communication security processing method, apparatus and system
ActiveCN103718527AEnsure communication securityEffective security isolationTransmissionCommunications securitySecurity domain
The embodiment of the invention discloses a communication security processing method, a relevant apparatus and a system, wherein the method comprises the steps of a security gate receiving a report transferred by a host, and the report is transmitted from a source device to a target device; determining a security domain that a first user belongs to when logging in the source device, and a security domain that a second user belongs to when logging in the target device. If the security domain that a first user belongs to is the same to the security domain that a second user belongs to, conduct security processing to the report according to domain-inside security policy; and if the security domain that a first user belongs to is different from the security domain that a second user belongs to, conduct security processing to the report according to inter-domain security policy. According to the embodiment of the invention, the security domain that a user belongs to can be determined according to the user information, and different security processing policies can be conducted based on whether the security domains are the same or not, therefore, safe isolation is realized, and communication security among users are guaranteed.
Owner:HUAWEI TECH CO LTD
End-to-end speech ciphering method, apparatus and system
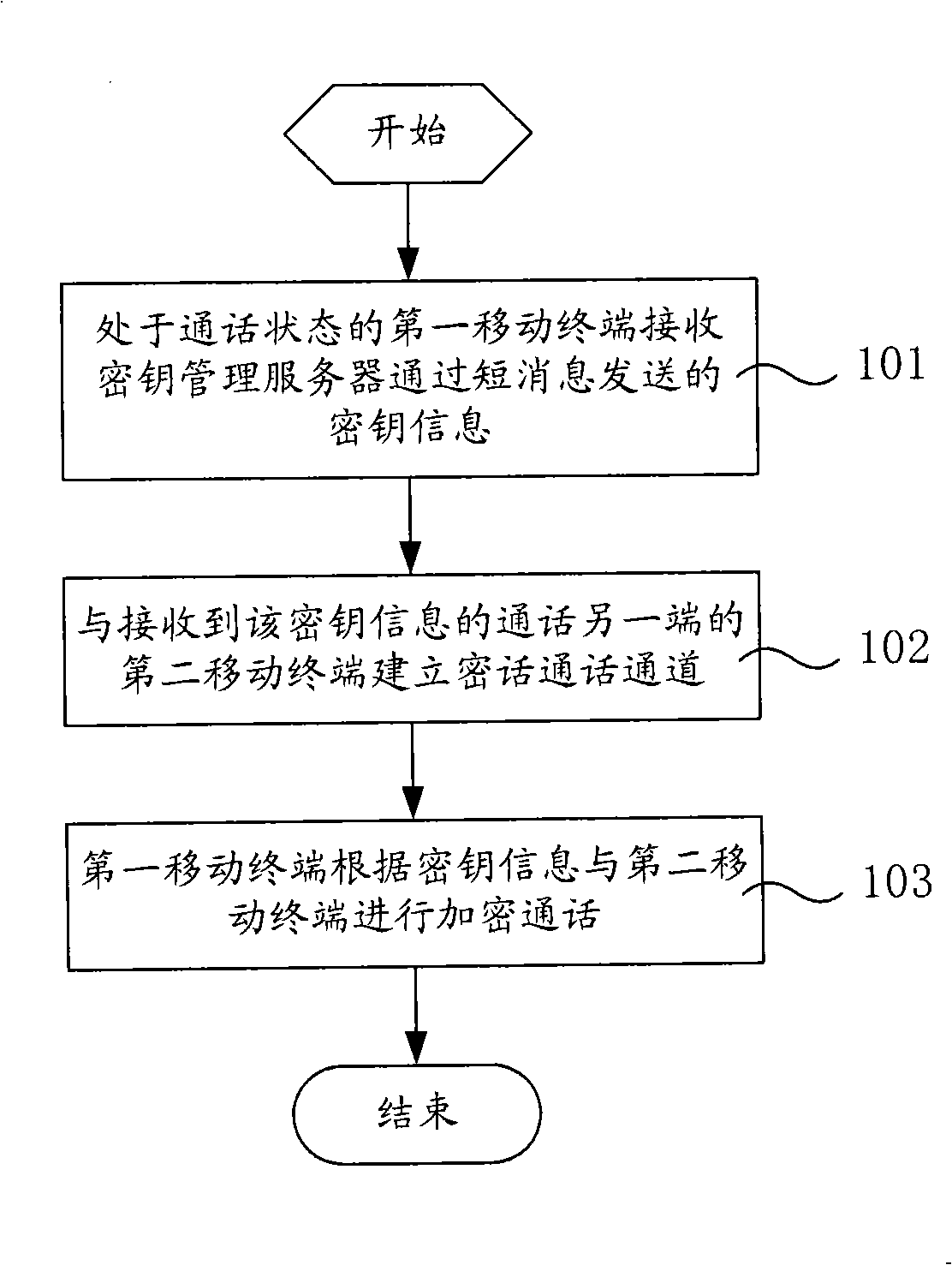
InactiveCN101309281AEnsure communication securityEasy to implementRadio/inductive link selection arrangementsTransmissionComputer hardwareCommunications security
The invention relates to an end-to-end speech encryption method which includes the steps that a first mobile terminal in the conversation mode receives the key information sent by the key management server through a short message and establishes an encryption conversation channel with a second mobile terminal which is the other end of the conversation and receives the key information; when the encryption channel is established, the first mobile terminal has the encrypted conversation with the second mobile terminal according to the key information. The invention also relates to an end-to-end speech encryption device and a system. The called and calling parties in the conversation mode receive the key information sent by the key management server through short messages and realize the encrypted conversation according to the key information so that the end-to-end conversation encryption processing is realized and the communication security is guaranteed; besides, the short message mode has the advantages of simple realization and easy implementation.
Owner:CHINA TELECOM CORP LTD
Data transmission method, system and apparatus in internet of things
ActiveCN106375390AEfficient data transferEnsure communication securityTransmissionOriginal dataDigital signature
The present invention relates to a data transmission method in an internet of things. Data is transmitted between terminals in an internet of things environment; a transmit end sends original data to network data transmission devices; the network data transmission devices sequentially add a digital signature to each piece of data; and the final network data transmission device verifies all digital signatures of the received data, determines that the data is from the transmit end through a set path, and then sends the original data to a receive end. The present invention further provides a data transmission system in the internet of things and a data transmission apparatus in the internet of things. The data is singed when passing each hardware device in transmission, a later receiving device can verify the signature, so that multiple nodes on one communication chain are managed safely and effectively, the whole communication chain is ensured to communicate safely, and a non-credit person is prevented from intruding and controlling the device.
Owner:北京爱接力科技发展有限公司
Submarine cable for power grid interlink of offshore oil platform
InactiveCN101916616AGood chemistryStrong communication functionPower cables with screens/conductive layersCommunication cablesOcean bottomElectricity
The invention relates to a submarine cable for a power grid interlink of offshore oil platforms, which is characterized in that a plurality of offshore platform power stations on a plurality of offshore oil drilling platforms distributed in a sea area are connected through submarine cables so as to form a small-sized grid-connected power system. The submarine cables are compound type submarine cables, which are provided with submarine optical cable units and optical fibers with the voltage class of 35KV and the cross section of 3*(150-250)mm<2>. The submarine cables have excellent electric, physical and chemical properties, are beneficial to enhancing the communication capability of the grid interlink among all oil fields, and can effectively guarantee the effectiveness of optical fiber communication, greatly enhance the anti-torque capability of the optical fibers and ensure the smooth communication of the power grid interlink.
Owner:CHINA NAT OFFSHORE OIL CORP +2
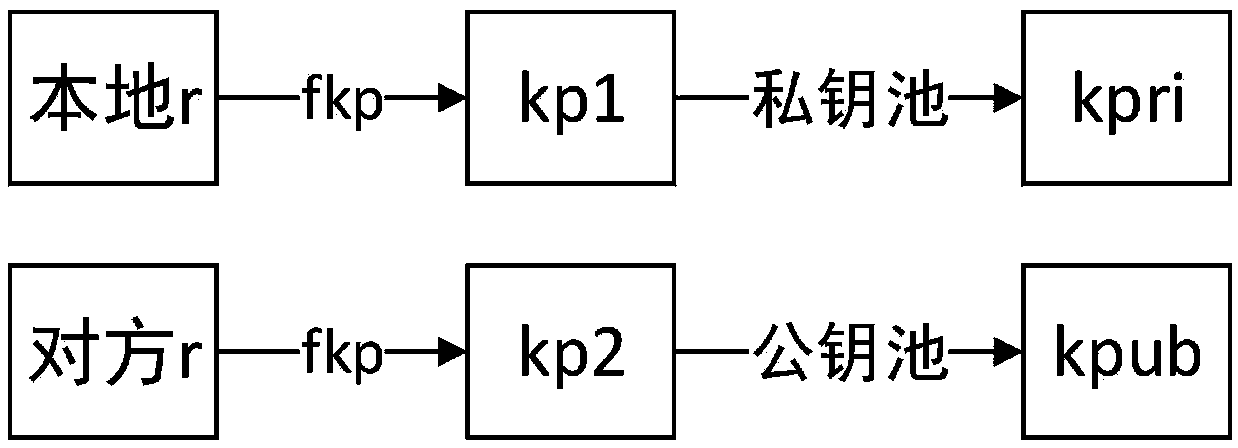
Anti-quantum-computing key negotiation method based on asymmetric key pools
InactiveCN109450623AReduce the possibilityWon't get and crackKey distribution for secure communicationMultiple keys/algorithms usageKey exchangeCommunications security
The invention relates to an anti-quantum-computing key negotiation method based on asymmetric key pools. The method includes a group. The group includes a plurality of use ends. The key pools are stored in quantum key cards configured for all the use ends, and include private key pools of the current parties and public key pools of the other members of the group. Equal negotiation keys are obtained through interaction of parameters of all the parties and the key pools of the current parties, and then key negotiation of every two terminals is realized. The quantum key card are independent hardware isolation equipment, greatly reduces possibility of stealing the keys by malicious software or malicious operations, and also cannot be obtained and cracked by quantum computers; and in the group,an asymmetric key exchange manner is adopted to realize key negotiation between objects, key sharing of two communication parties is realized, other objects cannot get corresponding shared keys, andcommunication security of the two communication parties in the group is guaranteed.
Owner:RUBAN QUANTUM TECH CO LTD
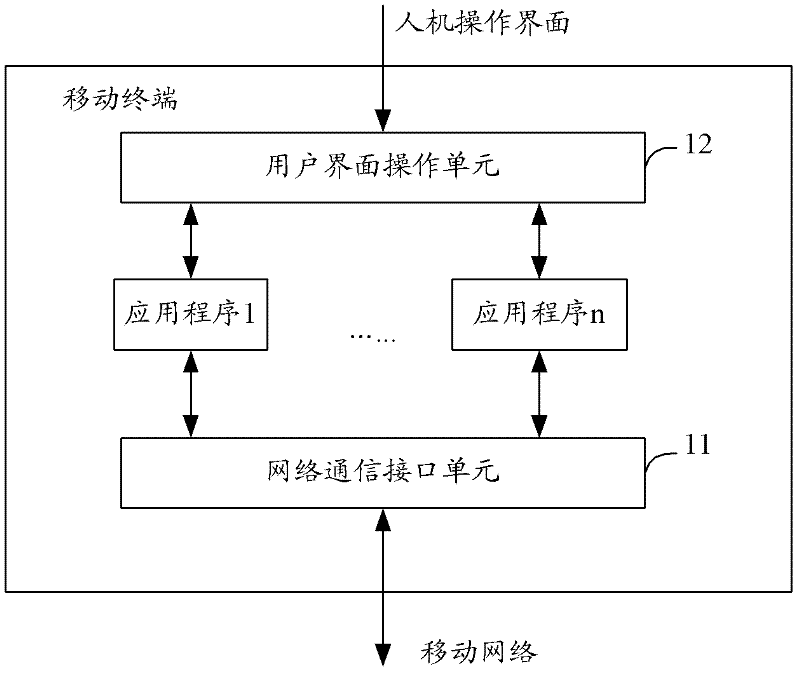
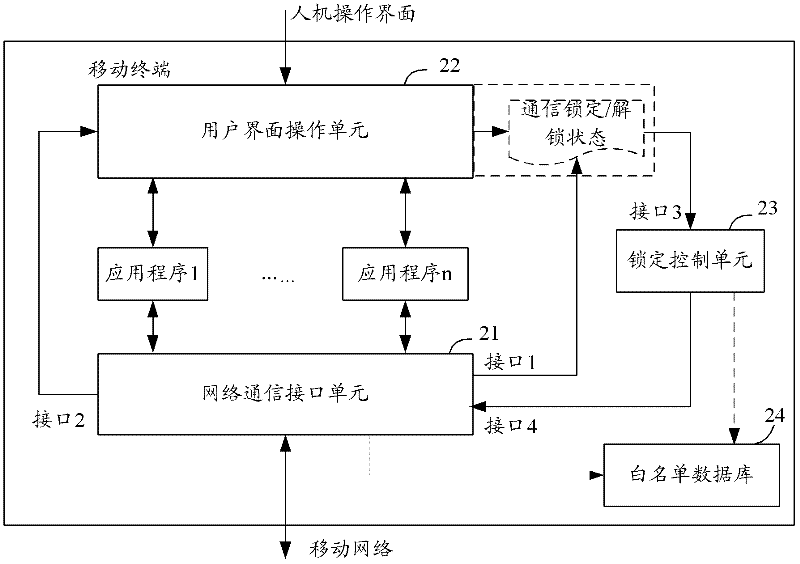
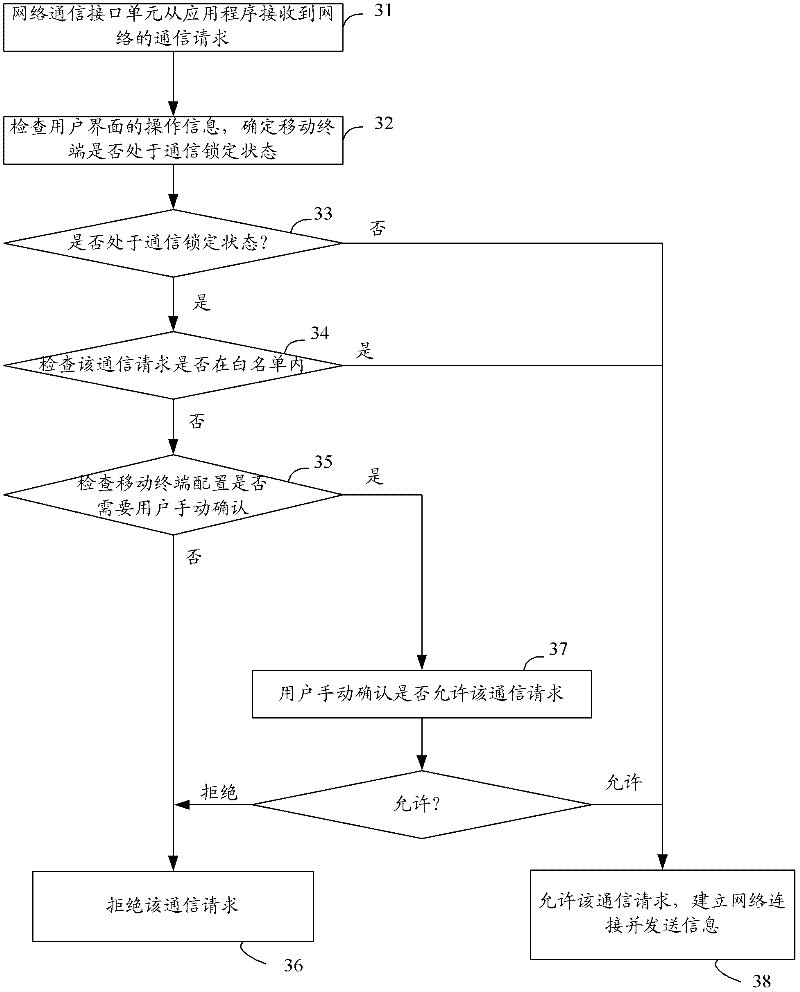
Method for mobile terminal to possess communication function of locking and unlocking, and mobile terminal thereof
InactiveCN102244858AEnsure communication securityPrevent leakageNetwork data managementCommunications securityMobile Web
The invention provides a method for a mobile terminal to possess communication functions of locking and unlocking, and the mobile terminal thereof. The method comprises the following steps: through monitoring operation conditions of a mobile terminal user interface, when a communication unlocking state of the mobile terminal is converted into a locking state, closing a function of communication between the mobile terminal and mobile network, wherein the communication is initiated by the mobile terminal; when the communication locking state of the mobile terminal is converted into the unlocking state, automatically opening the function of communication between the mobile terminal and the mobile network, wherein the communication is initiated by the mobile terminal. The function of active external communication can be locked when the mobile terminal is in the locking state. When the mobile terminal is in the unlocking state, the function of active external communication can be automatically recovered. Communication safety of the mobile terminal can be guaranteed. Information leakage and communication cost losses can be avoided, wherein the information leakage and the communication cost losses are caused by initiating external communication which is controlled by malicious programs or viruses when the mobile terminal is in a standby state which means the locking state.
Owner:王冬梅
Sensor network distributed access control method capable of protecting user privacy
InactiveCN102088462ADefend against compromise attacksGuaranteed anonymityNetwork topologiesTransmissionUser privacyRing signature
The invention discloses a sensor network distributed access control method capable of protecting user privacy. The method comprises the following steps: broadcasting a pre-established group access list pool to all of the network users by a network owner, and loading the group access list pool in all of sensor nodes; generating request information and ring signature information by a network user when the network user proposes an access requirement, transmitting the request information and the ring signature information to a sensor node to be accessed, wherein the request information includes a user random number; after the sensor node to be accessed receives the request information and the ring signature information, checking the request information according to the group access list pool to determine whether the request information is valid; refusing the request information if the request information is invalid; and determining whether the ring signature information is correct by the sensor node if the request information is valid, if correct, transmitting the data requested by the network user to the network user via the sensor node, otherwise, refusing the request information.
Owner:ZHEJIANG UNIV
Information protection method and device based on link layer discovery protocol
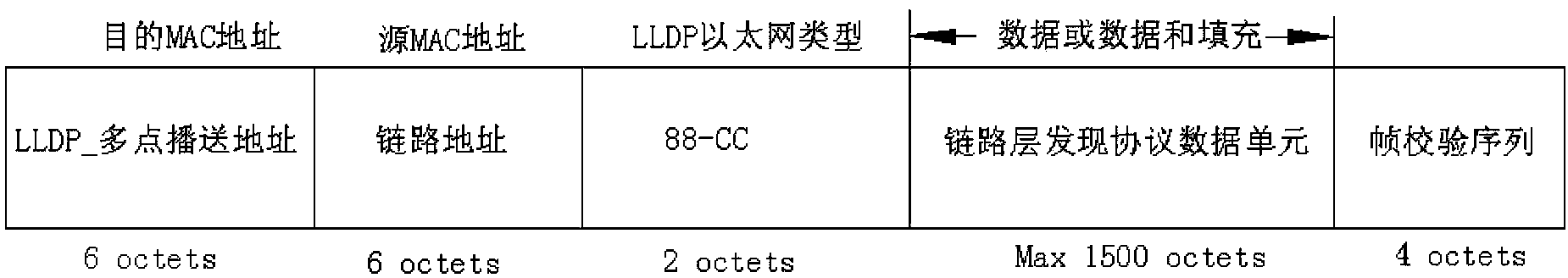
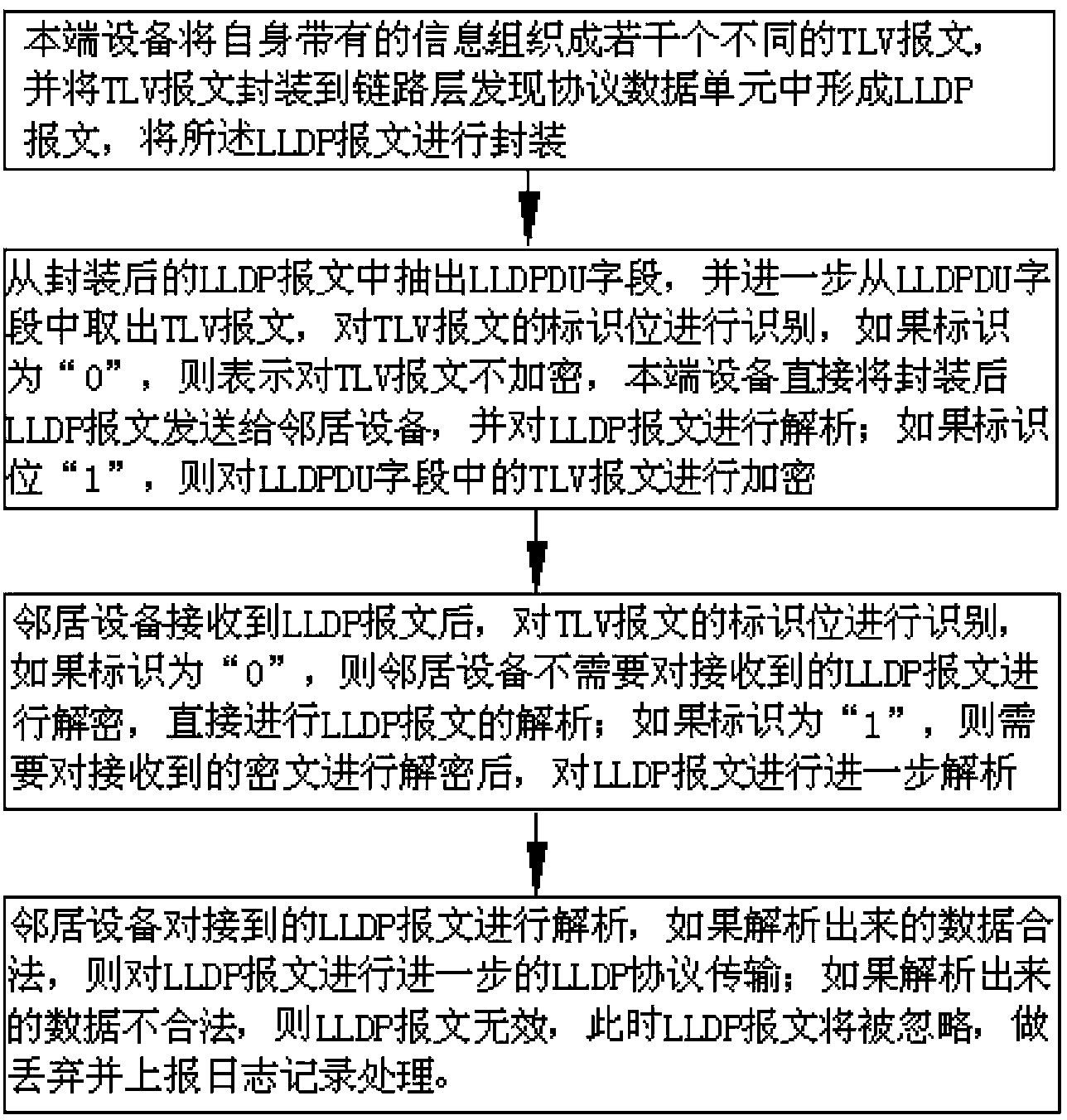
InactiveCN103441983AEnsure communication securityNot vulnerable to malicious attacksTransmissionHigh level techniquesCommunications securityKnowledge organization
The invention discloses an information protection method and device based on a link layer discovery protocol. The information protection method includes the steps that a home terminal device organizes self-carried information to form a plurality of different TLV messages, encapsulates the TLV messages into a data unit of the link layer discovery protocol to form LLDP messages, draws out LLDPDU fields encapsulated in the LLDP messages, carries out encryption on the TLV messages in the LLDPDU fields, and sends the encrypted cryptographs to a neighbor device adjacent to the home terminal device; the neighbor device decrypts the cryptographs, and carries out further analysis on the received LLDP messages to finish information interaction. According to the information protection method and device, an encryption method for both communication parties of a LLDP protocol is introduced, the information protection method and device ensure communication safety of the LLDP protocol, enable the device for operating the LLDP protocol to be not easily influenced by hostile attacks from the Internet and other aspects, and improve the safety of protocol operation.
Owner:SUZHOU CENTEC COMM CO LTD
Inter-application communication method, client side and application process manager of online application platform
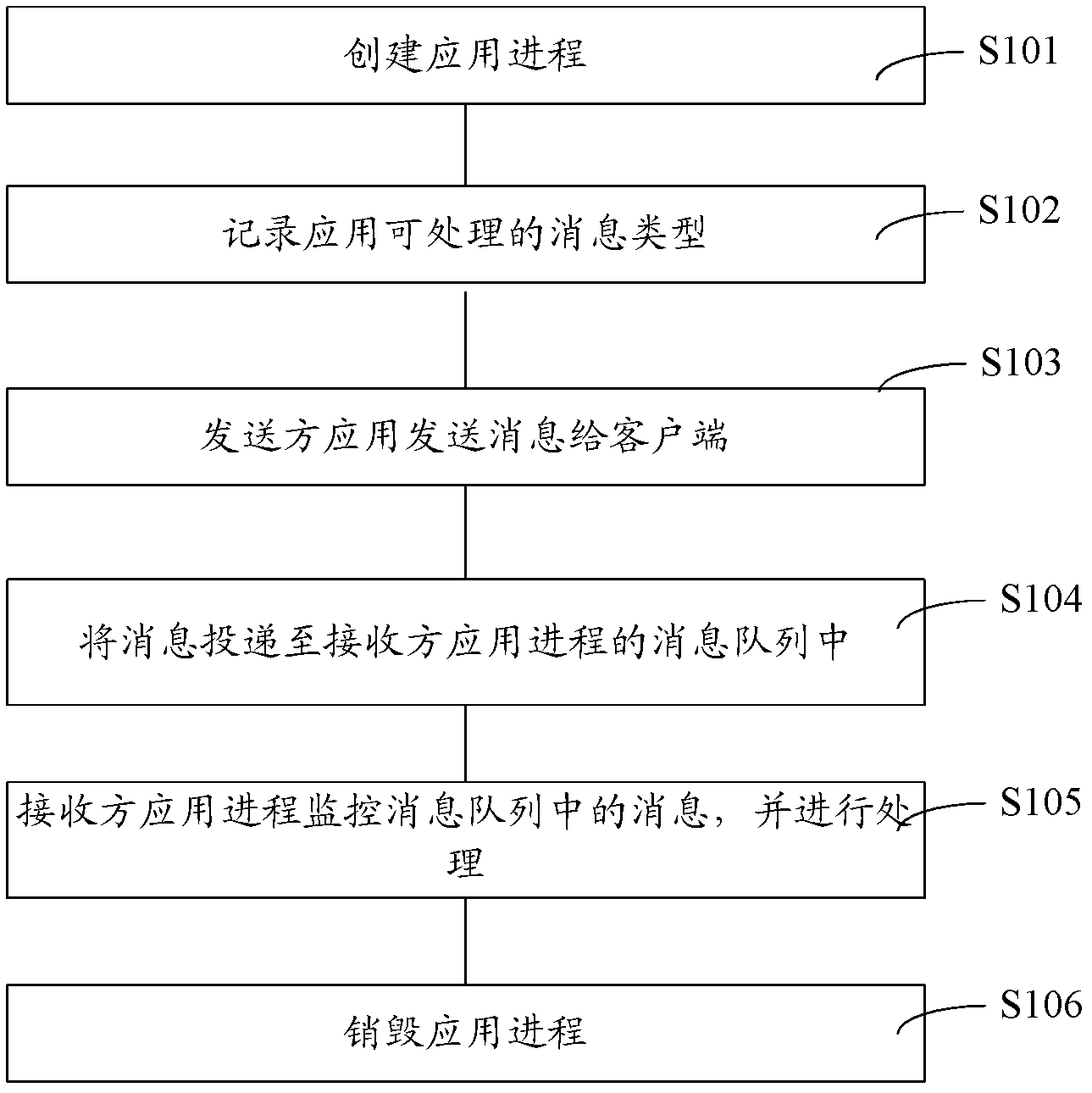
InactiveCN102662776AAvoid participationAvoid authorization processInterprogram communicationTransmissionMessage queueInformation transmission
The invention provides an inter-application communication method of an online application platform. The inter-application communication method comprises the following steps: a client side of the online application platform starts an application and creates an application process according to a predetermined communication protocol; the processable message type of the application is recorded; when inter-application communication is carried out, a message from a sender application is received and delivered into a message queue of one application process corresponding to a receiver application; the application process corresponding to the receiver application monitors and processes the message in the message queue; and when the sender application or the receiver application quits, the application process is destroyed. The invention also provides a client side of the online application platform and an application process manager of the online application platform, wherein the client side comprises multiple applications and an application process manager; and the application process manager of the online application platform comprises a process creating interface, a process message sending interface and a process destroying interface. The introduced user participation and authorization procedures due to a safety factor in information transmission are avoided fundamentally.
Owner:厦门格畅科技有限公司
Method and device for security authentication
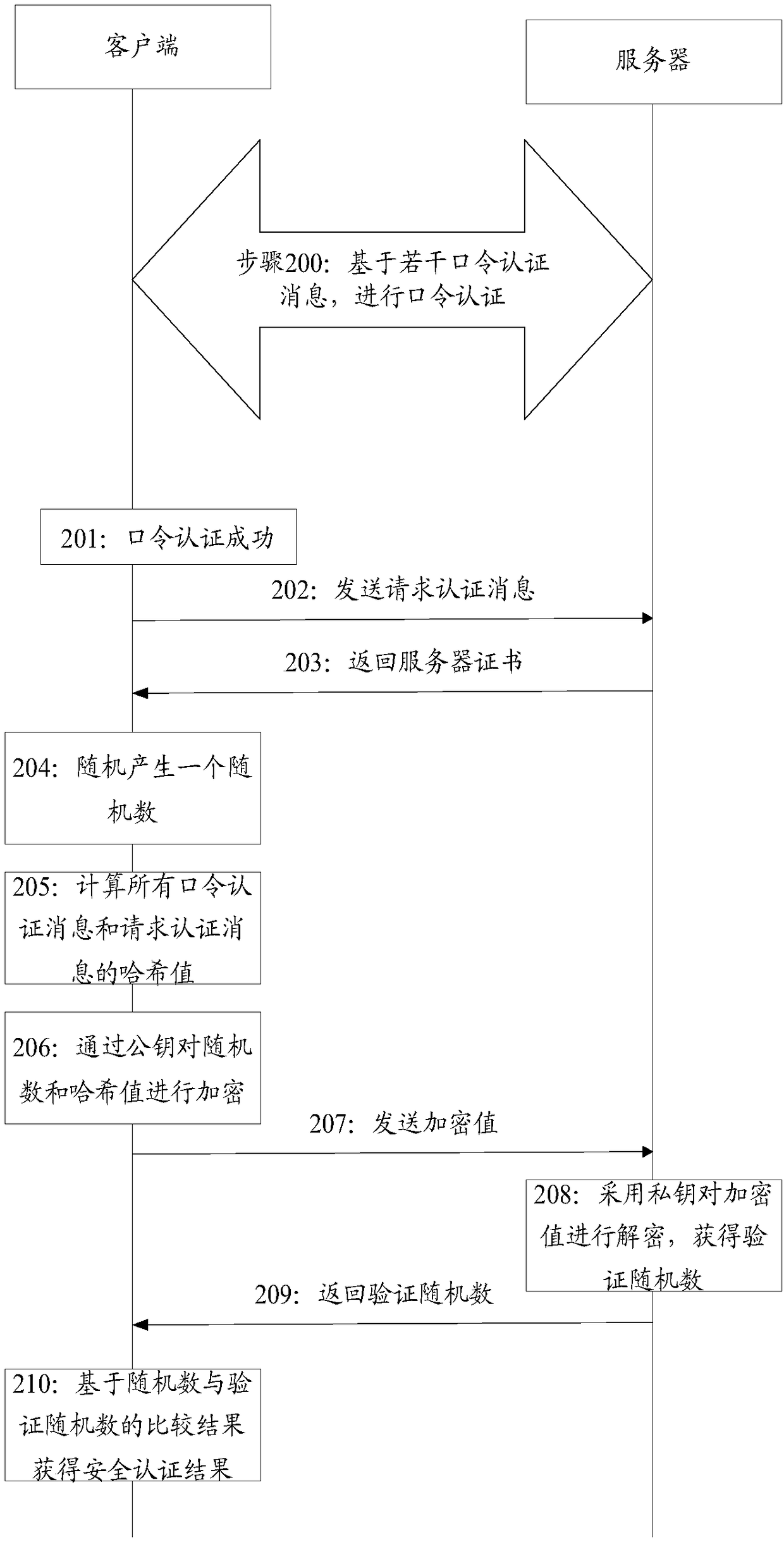
ActiveCN109309565AEnsure communication securityGuaranteed correctnessKey distribution for secure communicationPublic key for secure communicationCommunications securityWeb authentication
Embodiments of the invention disclose a method and device for security authentication. The method comprises the following steps: performing password authentication with a server based on a transmittedpassword authentication message to obtain a password authentication result; sending an authentication request message to the server when determining that the password authentication result characterizes password authentication success; and performing security authentication by the way of digitally signing all interaction messages through the server, and performing digital signature verification through the client, or by way of performing public key encryption by the client on the local random numbers and all the interaction messages, and verifying the random numbers returned by the server. Thus, the identity correctness of both communication parties is ensured by the way of combining the password authentication with digital signature, or combining the password authentication with public key encryption, thereby avoiding network attacks such as message leakage and malicious information tampering during the communication, improving the reliability of network authentication, and guaranteeing the user's communication security.
Owner:CHINA MOBILE COMM LTD RES INST +1
Vehicle node certificate updating method based on Vehicle to X (V2X) network
ActiveCN105812131APrevent crackingEnsure communication security and non-repudiationKey distribution for secure communicationUser identity/authority verificationPublic key infrastructureComputer security
The invention discloses a vehicle node certificate updating method based on a Vehicle to X (V2X) network. A vehicle node applies for an updated certificate from a PKI (Public Key Infrastructure) system via a roadside node; the PKI system sends part of private keys to the vehicle node; the vehicle node generates a new public key and a new private key using the part of private keys and part of private keys generated per se, generates a certificate using the new private key, and sends the certificate to the PKI system; the PKI system verifies the validity and the accuracy of the certificate; and after the certificate passes the verification, the PKI system updates the certificate of the vehicle node using the public key generated by the vehicle node, and issues the updated certificate to the whole network. The updated certificate, the new public key and the new private key are all generated using part of private keys of the PKI system and part of private keys of the vehicle node, and only the vehicle node has node private keys, so the information issued by the vehicle node can be effectively prevented from being decrypted by the PKI system, and the security and the non-repudiation of communication of the vehicle node in the V2X network are guaranteed.
Owner:DATANG GOHIGH INTELLIGENT & CONNECTED TECH (CHONGQING) CO LTD
Application server by-passing method and service type call session control functional equipment
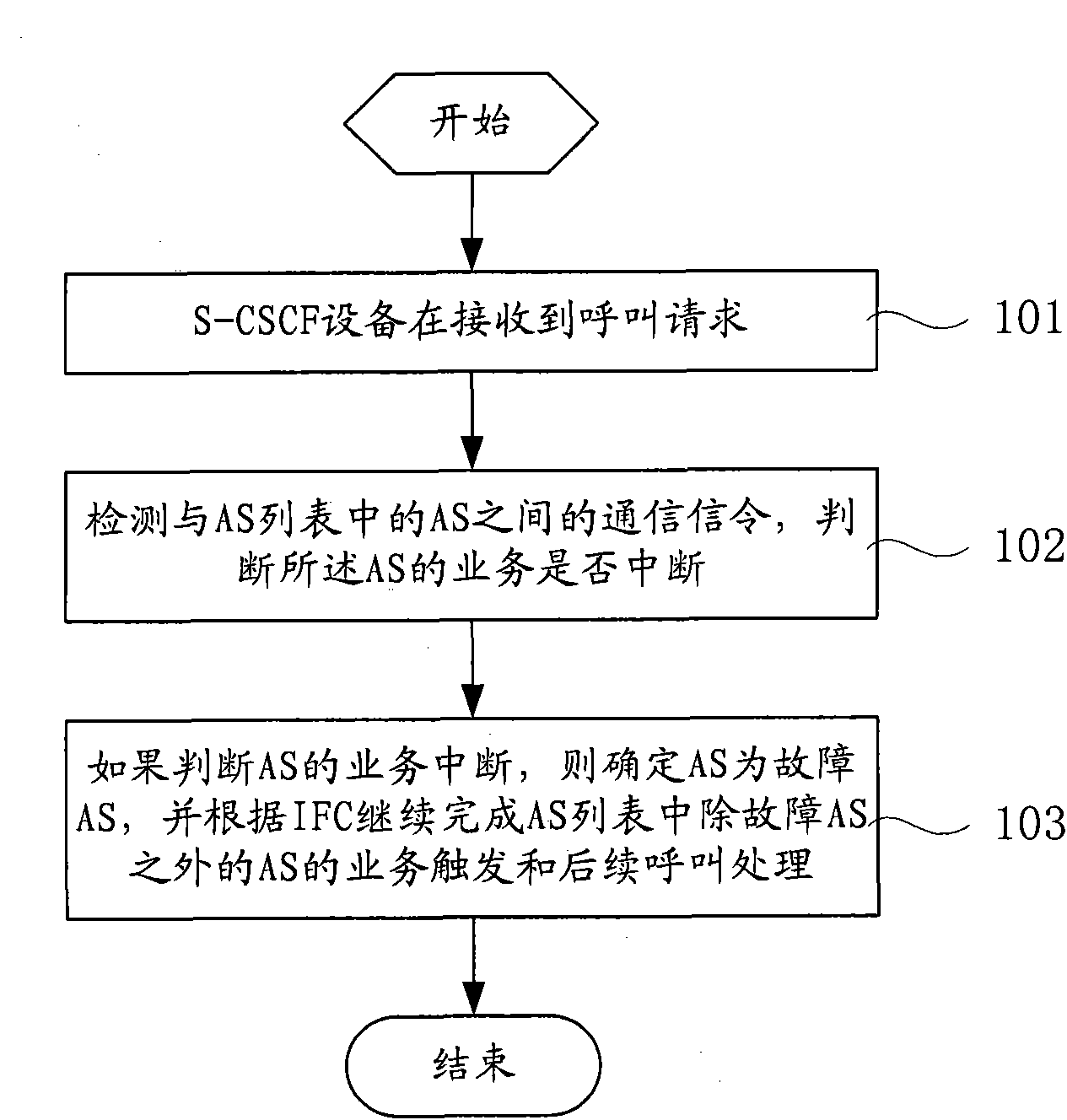
ActiveCN101895915AEnsure communication securityConnection managementWireless network protocolsCommunications securityApplication server
The invention relates to an application server by-passing method, which comprises: when service type call session control functional equipment receives a call request, detecting a signaling used for communication between the service type call session control functional equipment and an application servers in an application server list, and determining if the service of the application server is interrupted; if service of the application service is interrupted, determining the application server as a fault application server; and according an initial filtration rule, continuing to complete the service triggering and subsequent call processing of application servers excluding the fault application server in the application server list. The invention also relates to the service type call session control functional equipment. In the invention, through a by-pass AS mode, that the call of a user cannot be interrupted due to the fault in a certain AS is ensured. In case of interruption between an S-CSCF and a PES / PSS AS, the communication safety of the user can be guaranteed to a maximum degree by by-pass operation, so the possibility for the large-area interruption of an IMS service is lowered greatly.
Owner:CHINA TELECOM CORP LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com