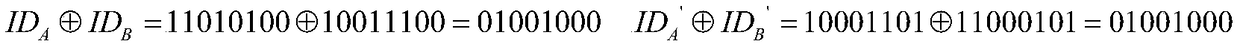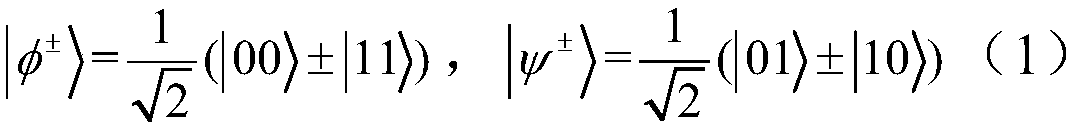Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
219results about How to "Implement identity authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
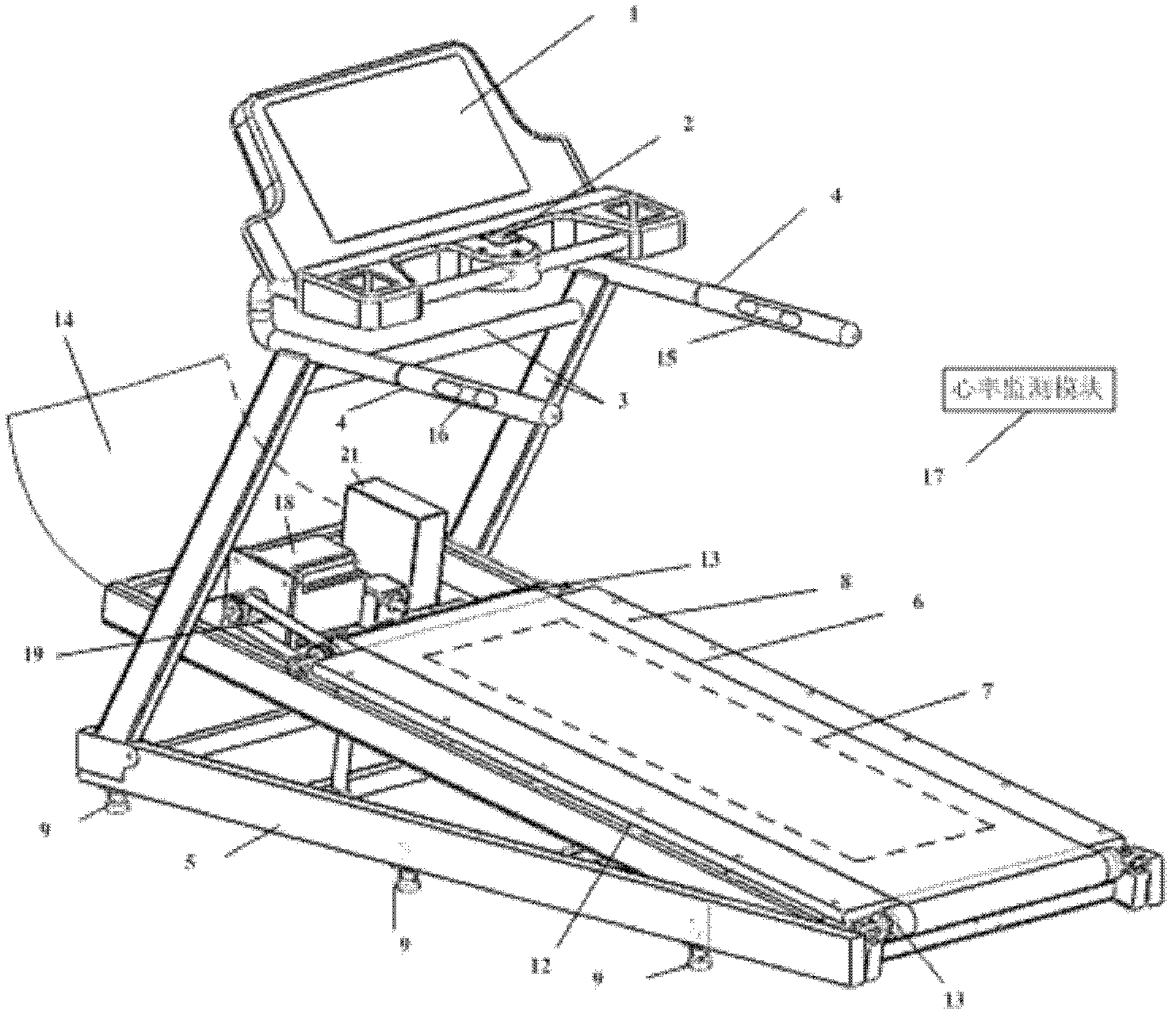
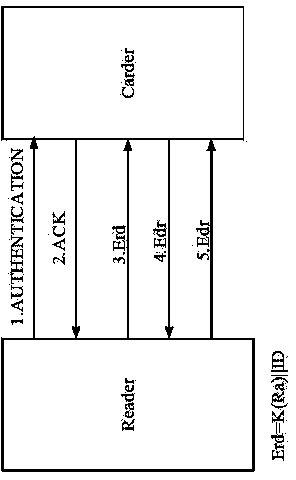
Intelligent running machine
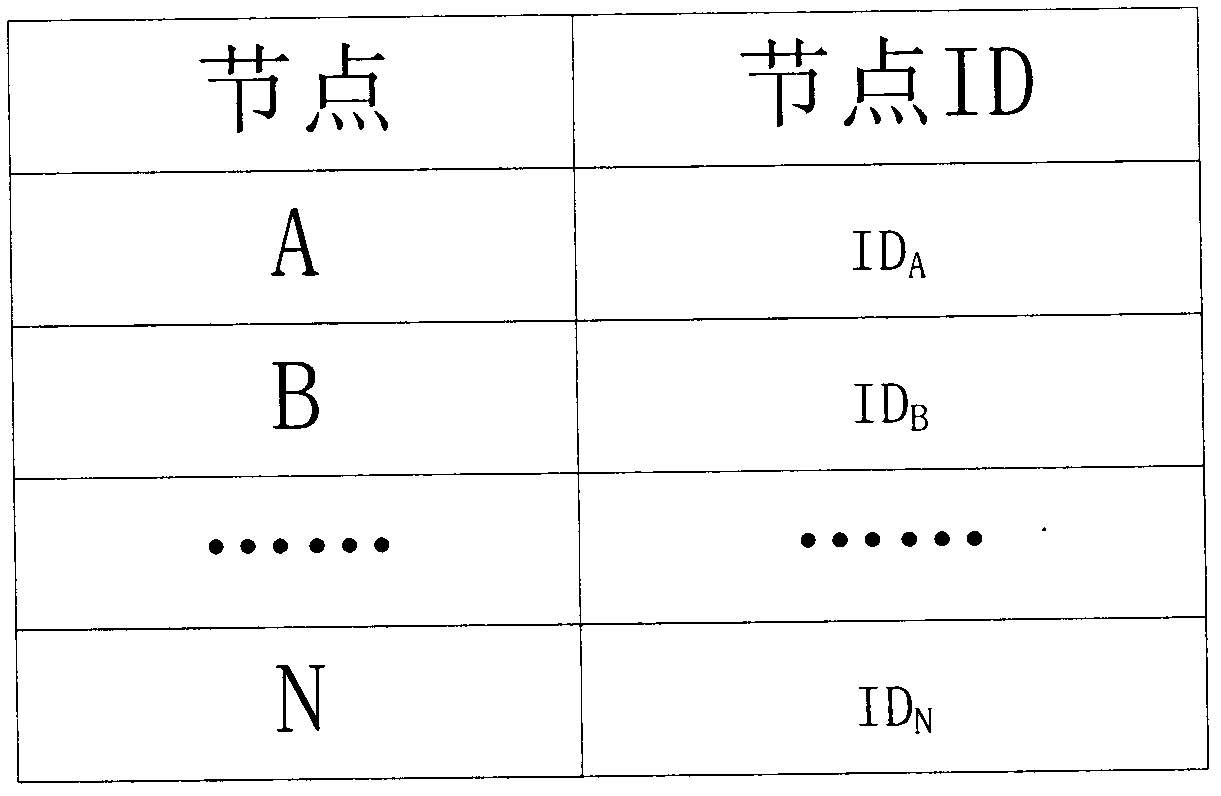
ActiveCN102357284AReduce shockAvoid shockMovement coordination devicesMuscle exercising devicesRelational modelData acquisition
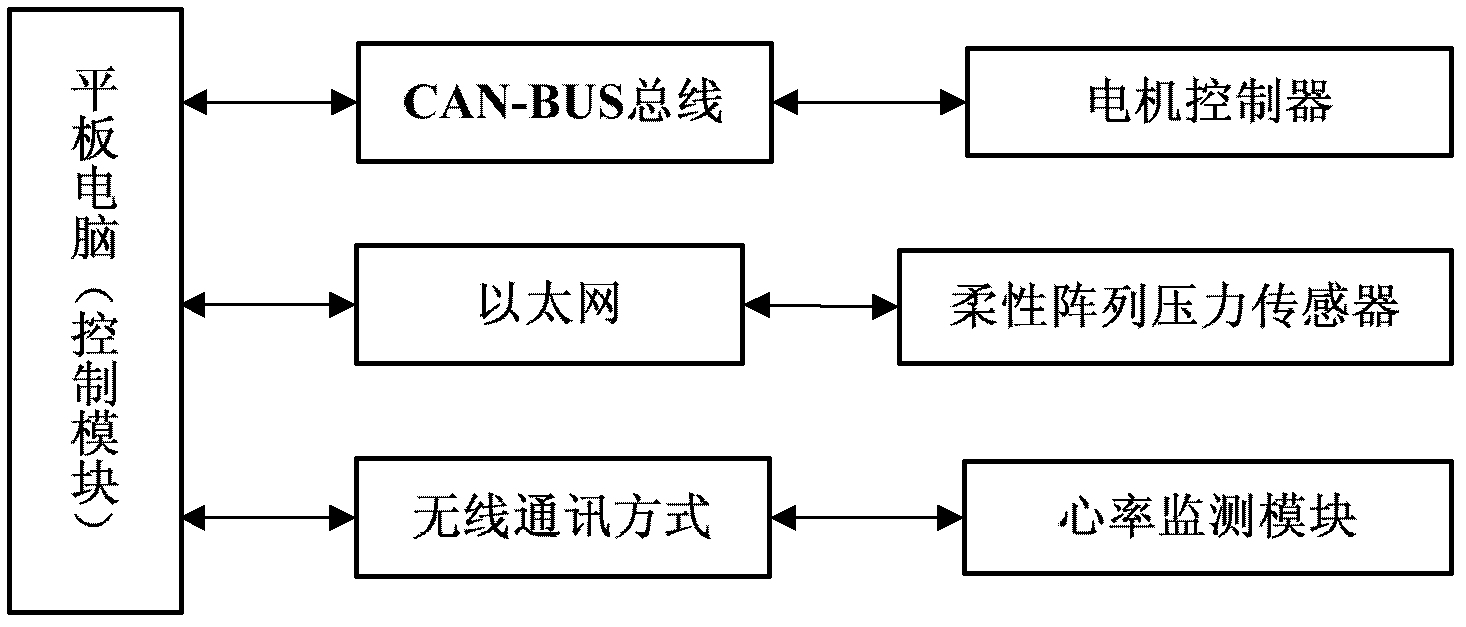
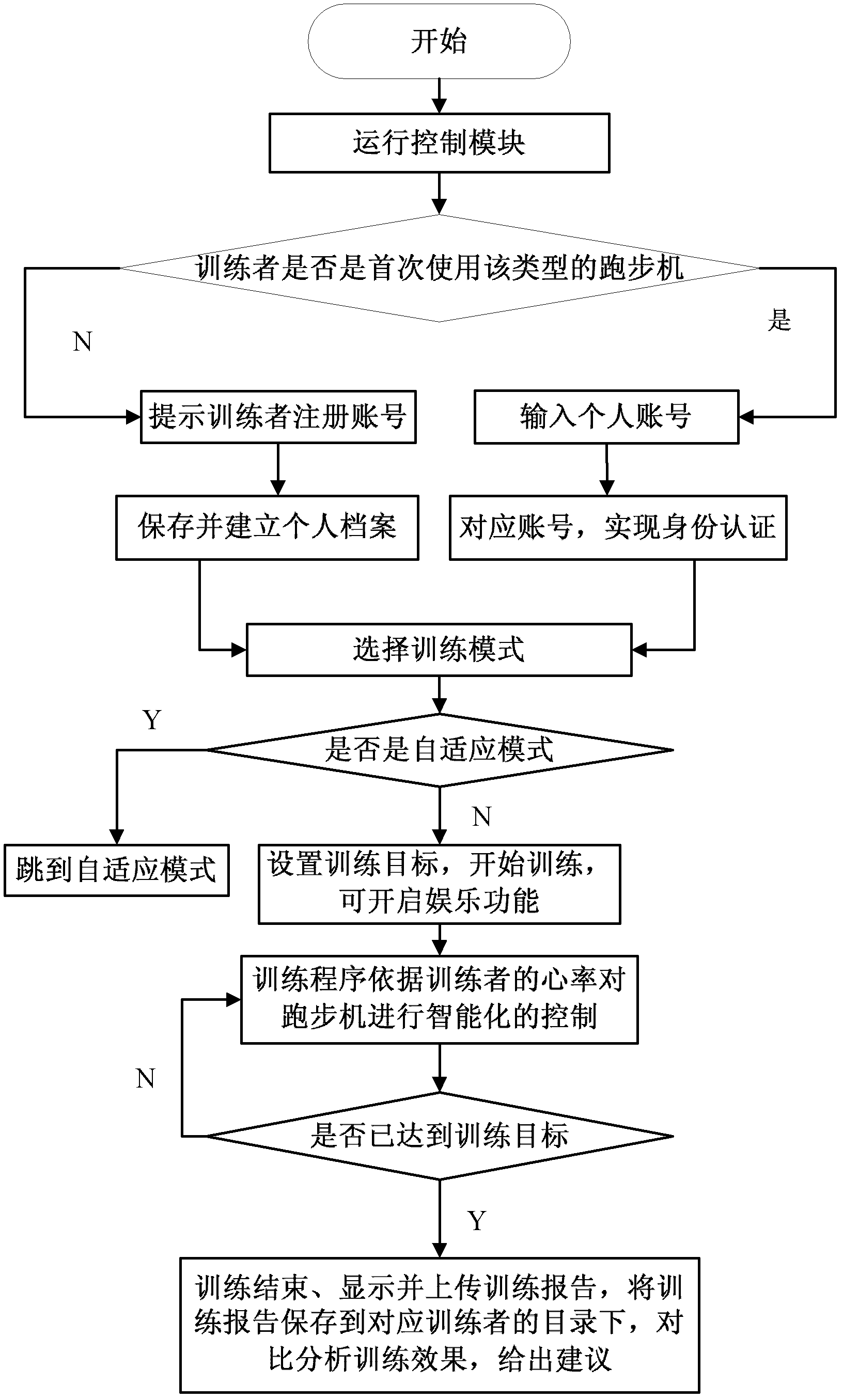
The invention relates to the field of exercise equipment, in particular to an intelligent running machine. The intelligent running machine comprises a running machine body, a tablet personal computer which is arranged on the running machine body, a flexible array pressure sensor which is arranged on the running machine body, a control module which is arranged on the tablet personal computer, a data acquisition module and a motor drive module. An internet function is integrated in the control module of the running machine, and each running machine uploads a relationship model and a training program which are established according to individual characteristics through network to a server for storage so as to realize identity authentication. Multiple kinds of training modes and virtual scenes are integrated in the control module; the training program which meets an exerciser is customized in a personalized way; foot pressure distribution information of the exerciser, which is detected bythe flexible array pressure sensor, and the real-time heart rate which is sent by a heart rate monitoring module are received in real time; running speed, gradient and the like can be adjusted automatically; safety of the exerciser can be guaranteed; and training modes can be enriched and training efficiency can be improved.
Owner:HEFEI INSTITUTES OF PHYSICAL SCIENCE - CHINESE ACAD OF SCI
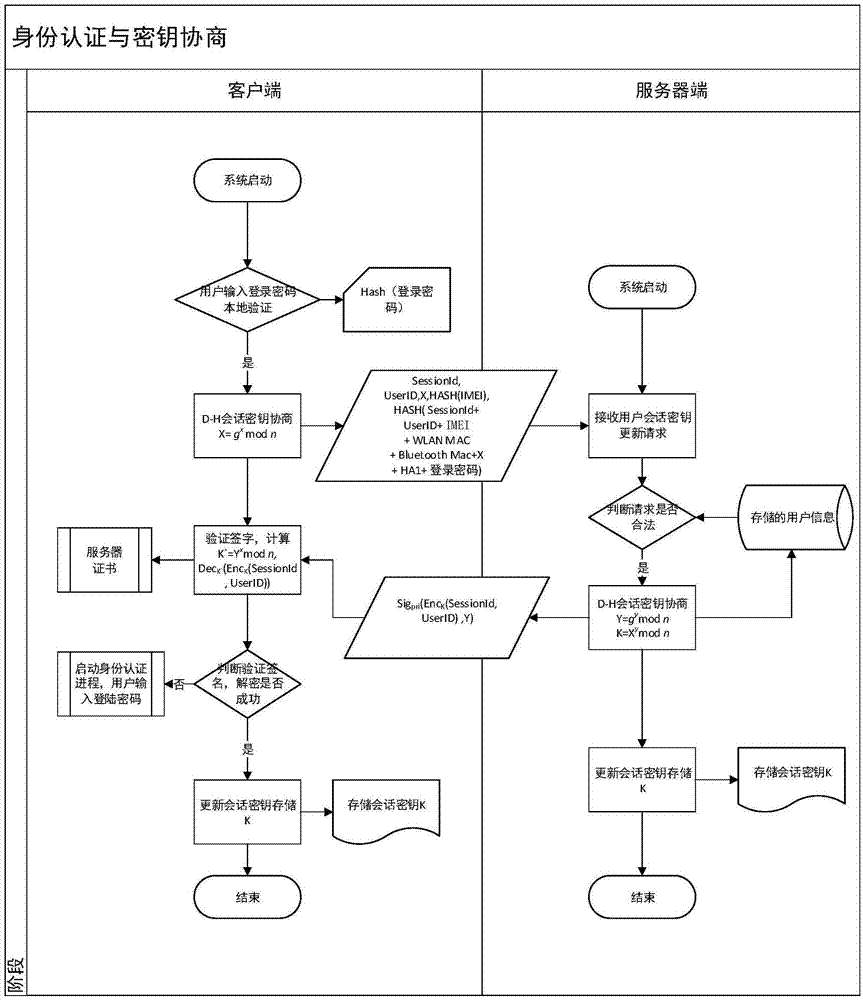
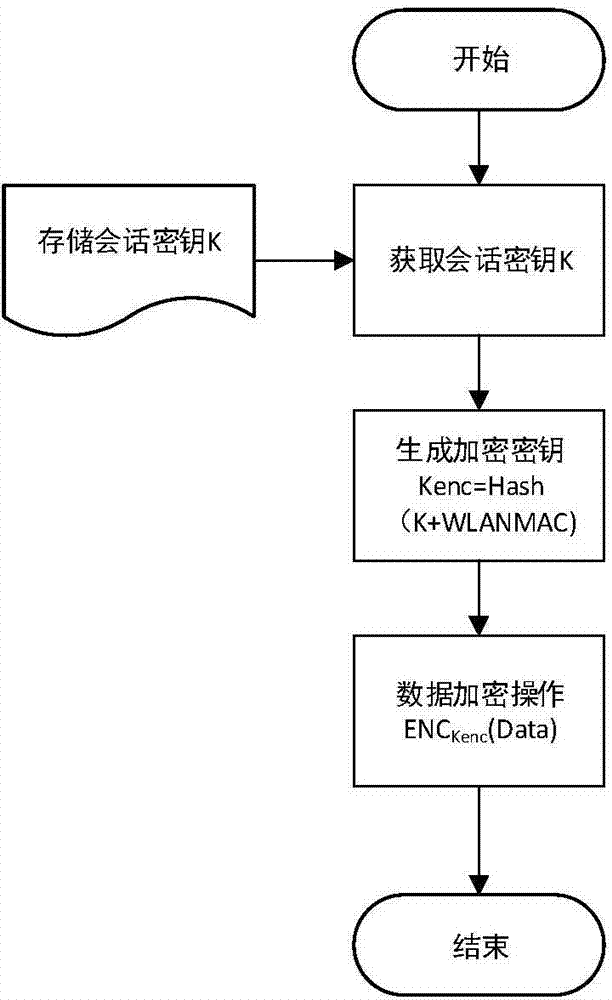
Safety communication secret key negotiation interaction scheme
ActiveCN104506534AGuarantee authenticityEnsure communication securityKey distribution for secure communicationUser identity/authority verificationThe InternetNetwork service
The invention provides a method for safety communication between an application on a mobile terminal and a network server. Shared secrets of a user and a server are overlapped and bound with an identification code of mobile intelligent terminal equipment and a mobile phone number of the user by utilizing a cryptology; then the obtained product is applied to an identity authentication system to implement authentication on a client side; a digital certificate and a digital signature mechanism are utilized to implement authentication on the server; a session key is established with a network server by utilizing a Differ-Hellman secret key negotiation protocol so as to carry out safety data communication. The method is characterized in that the shared secrets are overlapped and bound with identification code of the machine and the mobile phone number of the user and the shared secrets are updated regularly; even though information is stolen by an attacker, a system still cannot be influenced. The user not only needs to provide a login password, but also needs to use the system on designated equipment. The method can ensure that the user carries out safety communication with the server on internet by the mobile equipment.
Owner:QINGDAO WEIZHIHUI INFORMATION
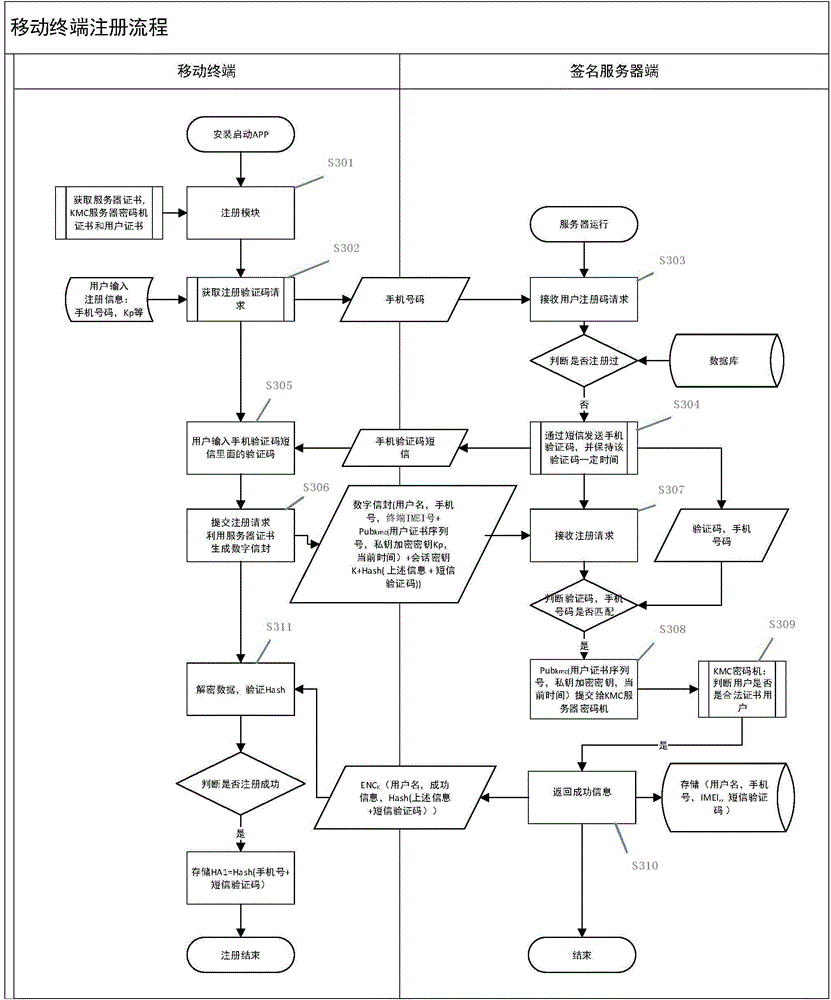
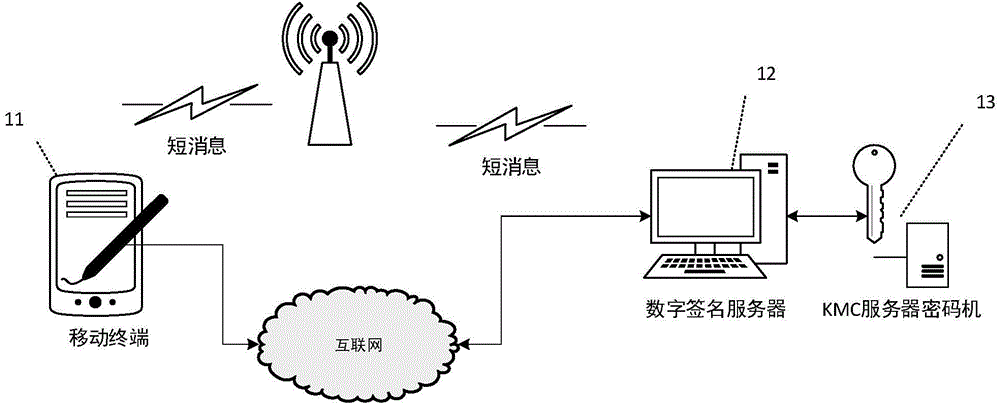
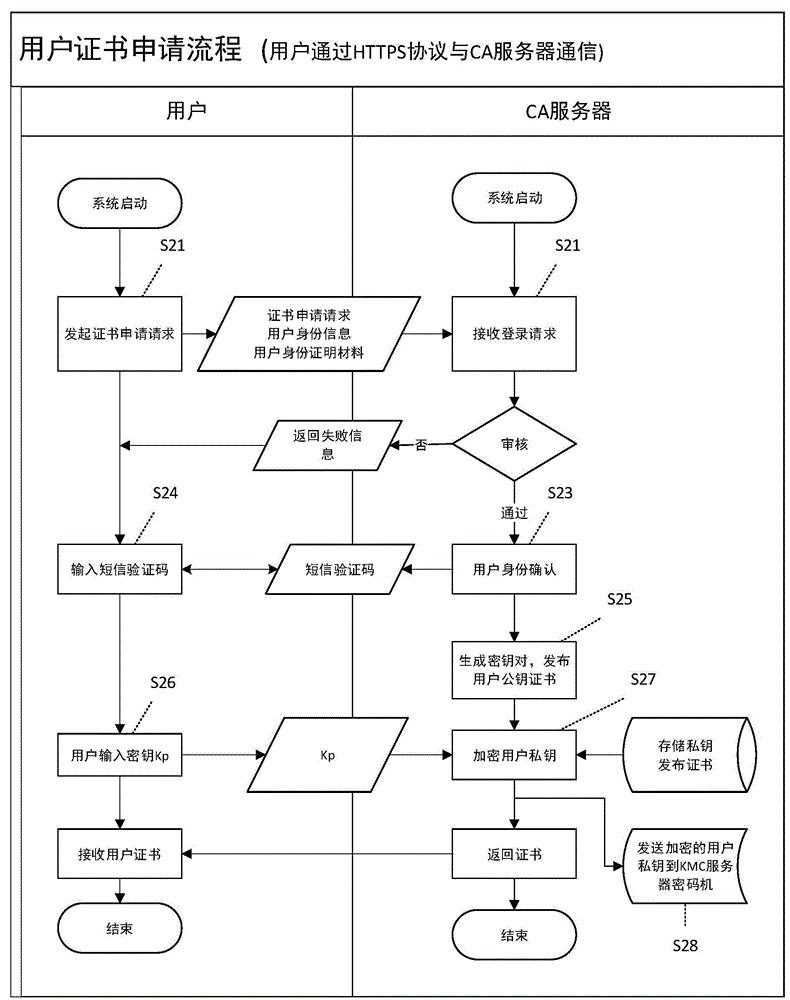
Digital signature method for escrowing private key of mobile terminal
ActiveCN104618120ALower performance requirementsGood adaptabilityUser identity/authority verificationComputer securityText messaging
The invention discloses a digital signature method for escrowing the private key of a mobile terminal. The mobile terminal needs to provide digital signature service in the development of e-government application, however, at present, the mobile terminal is lack of a safety condition providing a private key saving digital signature, the private key is likely to be stolen by a hacker at the mobile terminal, so that the digital signature cannot be realized directly by the mobile terminal. The invention provides a digital signature technology for the mobile terminal. The digital signature technology comprises the mobile terminal, a signature server and a KMC server cipher machine. The signature server is responsible for managing the signature private key of the user, all private keys of the system are encrypted and then saved in the cipher machine, the encrypted user' private key is mastered by the user, and the cipher machine is only communicated with the signature server. When a certificate is downloaded by a user, the terminal application packs a Hash value in digital signature and user identity information together to form digital signature request message, the digital signature request message is sent to the signature server through a short message, after the user request validation is passed, the cipher machine is called, and after the user' private key is digitally signed, the result is returned to the user to complete the digital signature process.
Owner:QINGDAO WEIZHIHUI INFORMATION
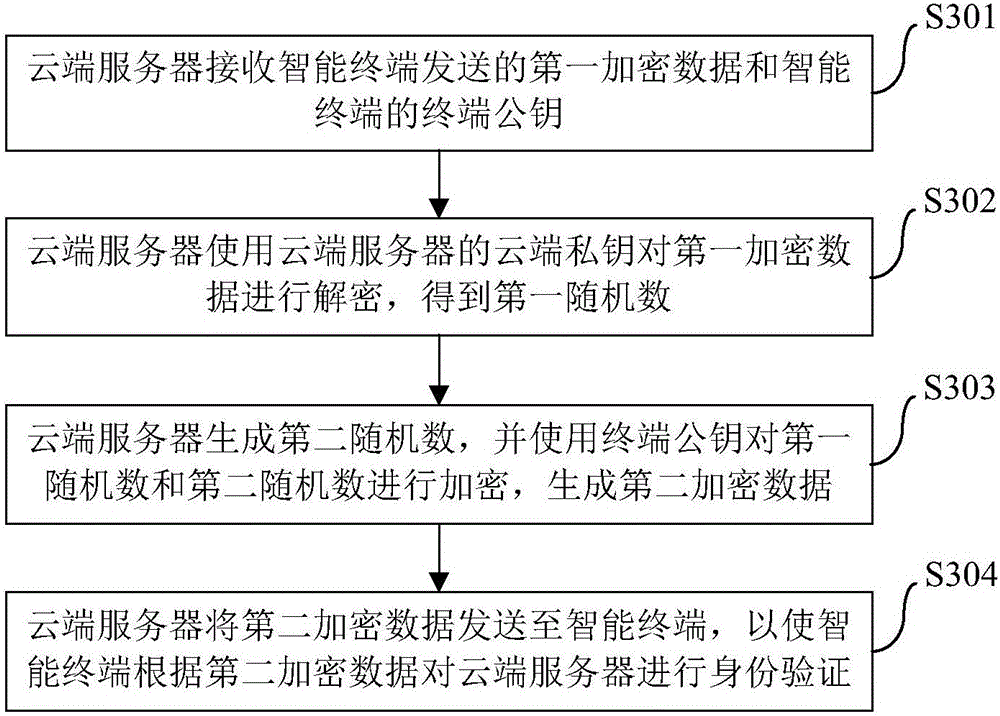
Identity authentication method, apparatus and system
ActiveCN106656481AImplement identity authenticationMaintain securityKey distribution for secure communicationComputer terminalEncryption
The invention brings forward an identity authentication method, apparatus and system. The identity authentication method comprises the following steps: an intelligent terminal generating a first randomized number and generating a terminal public key and terminal private key which form a pair; the intelligent terminal encrypting the first randomized number by use of a prestored cloud public key so as to obtain first encryption data; the intelligent terminal sending the first encryption data and the terminal public key to a cloud server; the intelligent terminal receiving second encryption data sent by the cloud server and decrypting the second encryption data by use of the terminal private key; and if a decryption result comprises the first randomized number, the intelligent terminal confirming that the cloud server succeeds in identity authentication. The identity authentication method simplifies operation steps, reduces operation resources, at the same time, maintains more secure data channels, promotes development of Internet of things and improves user experience.
Owner:MIDEA SMART TECH CO LTD +1
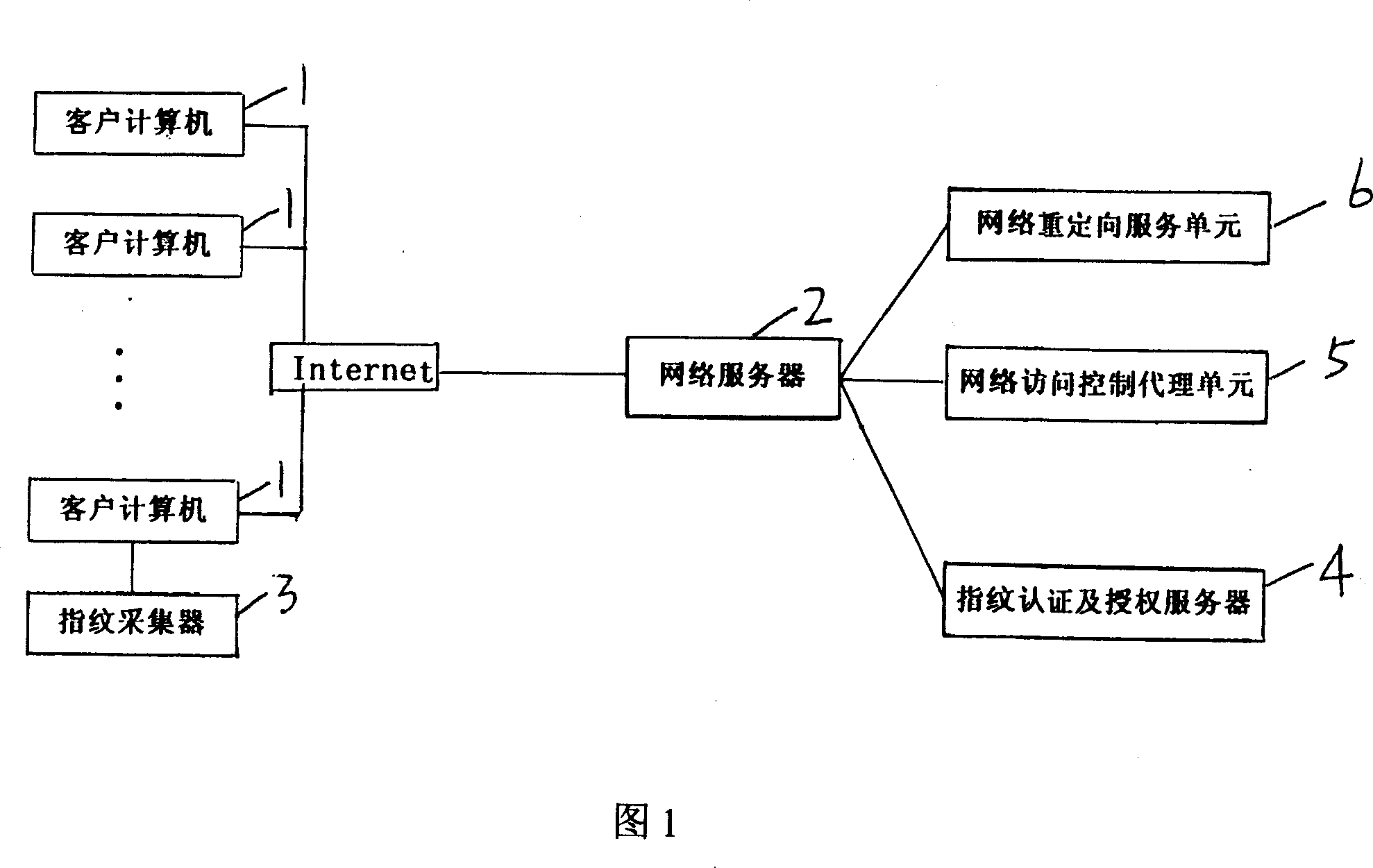
Network access control system and its control method
InactiveCN101034981AImplement access controlImprove confidentialityUser identity/authority verificationCharacter and pattern recognitionNetwork access serverInformation transmission
The invention discloses a network access control system, comprising network reorienting service unit and network access control agent unit installed on network server, fingerprint authentication and authorization server connected with the network access control agent unit, and client end computer equipped with fingerprint collector. And the system implements control of the network server access, and has an obvious advantage of being able to complete interactive information encryption between network browser and network server and access control of the network server only in need of simple configuration without changing client's network environment and second development, where the system implements secrecy and integrity of information transmission and interaction by PKI technique, and implements user ID authentication by fingerprint recognition technique, and implements access control of the network server by united access authorization mechanism.
Owner:上海品伟数码科技有限公司
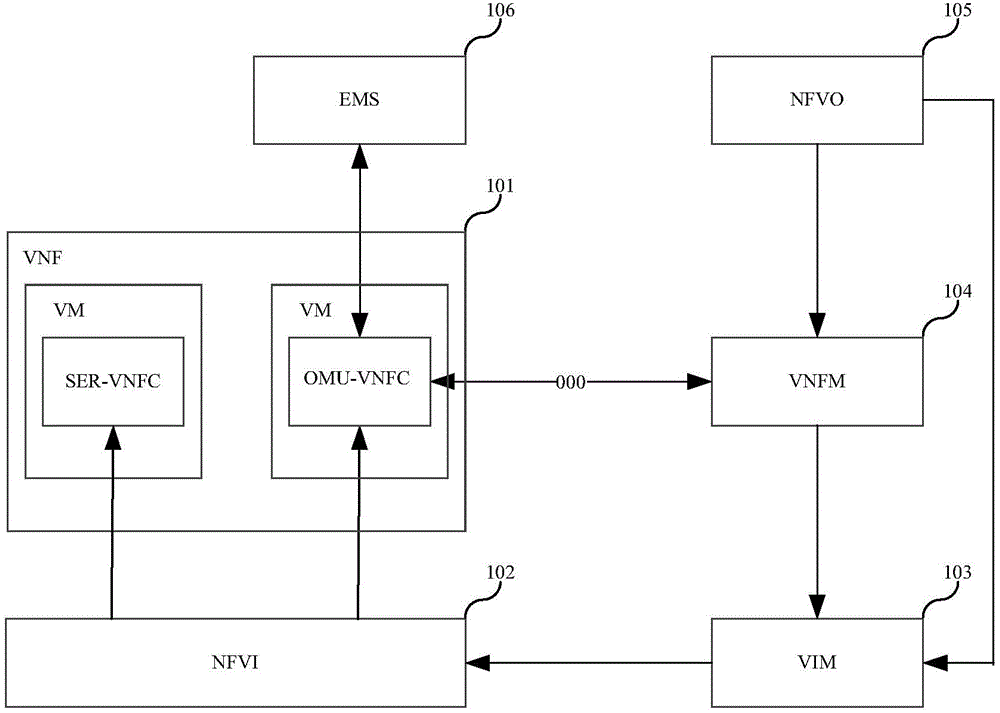
Identity authentication method and device
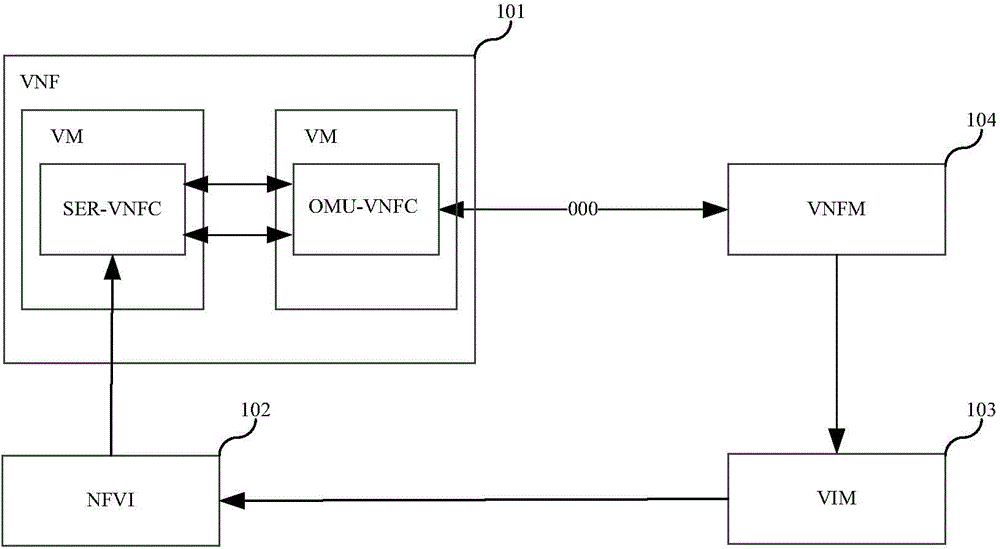
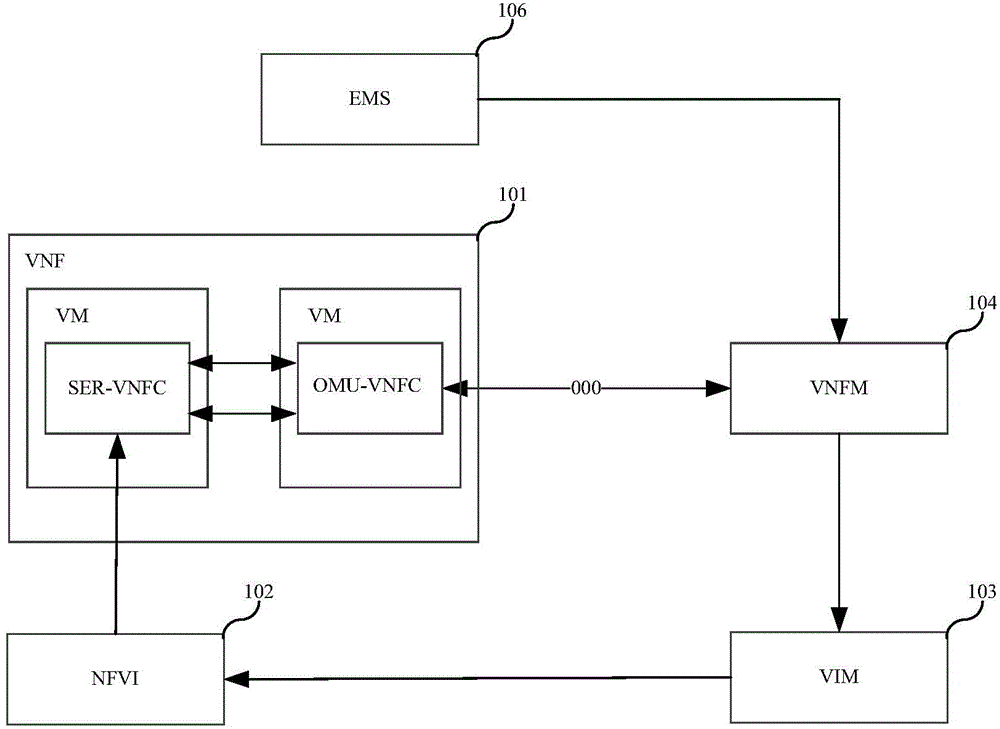
ActiveCN104580208AImplement identity authenticationImprove efficiencyUser identity/authority verificationProgram controlAuthentication
The invention discloses an identity authentication method and device which are applied to an NFV system and can adapt to the dynamic change of the system. The NFV system comprises a VNF which comprises a first VNFC and a second VNFC. The identity authentication method comprises the steps that a public key and a private key of the first VNFC and a public key and a private key of the second VNFC are generated; the private key of the first VNFC and the public key of the second VNFC are written into or sent to the first VNFC; the public key of the first VNFC and the private key of the second VNFC are written into or sent to the second VNFC; the public key and the private key of the first VNFC and the public key and the private key of the second VNFC are used for identity authentication of the first VNFC and the second VNFC.
Owner:HUAWEI TECH CO LTD
Identity-based unmanned aerial vehicle key management and networking authentication system and method
ActiveCN109218018AImprovements to computing inequalityImprove reliabilityKey distribution for secure communicationPublic key for secure communicationAuthentication serverAuthentication system
The invention belongs to the technical field of a device for verifying the identity or credentials of a system user, and discloses an identity-based unmanned aerial vehicle key management and networking authentication system and a method thereof. The ground authentication server is responsible for generating and distributing system parameters, identity information and keys required by the unmannedaerial vehicle for key management and network authentication. UAV authentication client is the main body of the system; Through mutual cooperation, the key pairs of UAV for network authentication canbe generated in a distributed manner, and the identity authentication and key agreement between UAV can be realized by using the key pairs. The invention improves the problem of unequal calculation of nodes in the key management of the UAV network existing in the prior art, enhances the reliability of the system, and realizes the key management of the UAV self-organization. The two-way authentication between UAV nodes ensures the credibility and authenticity of both sides of the communication. Using identity public key and bilinear pairing implementation, the computational overhead is less and the implementation efficiency is improved.
Owner:XIDIAN UNIV +1
Intelligent charging access system for electric automobile
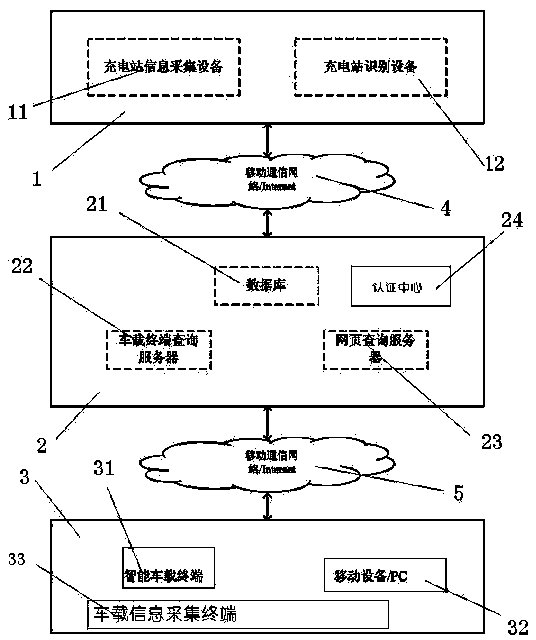
ActiveCN104022549AImplement identity authenticationEliminate limited occupancyBatteries circuit arrangementsElectric powerAutomotive engineeringElectricity
The invention discloses an intelligent charging access system for an electric automobile. The intelligent charging access system for the electric automobile comprises an intelligent charging leading system and a vehicle certification system based on a wireless communication network. The intelligent charging leading system comprises a central server, a mobile communication network, the Internet, a charging station end data collecting system and a vehicle-mounted information collecting terminal. The intelligent charging access system can provide accurate charging station distribution information for a user, and the user is led to be access to a specific charging pile in a charging station to be charged according to the vehicle information of the user. The central server can accept inquiry of various modes from a user end and combine with the battery parameter of the automobile and the preferences or requirement of the user to make a reasonable charging planning and decision scheme. The vehicle certification system is used for achieving identity certification and the payment condition of legal users, so that the fact that illegal automobiles occupy limited charging resources (such as charging files and electricity) is avoided, and the privacy of the user and the safety of data are protected.
Owner:SHANDONG TIANHAI TECH
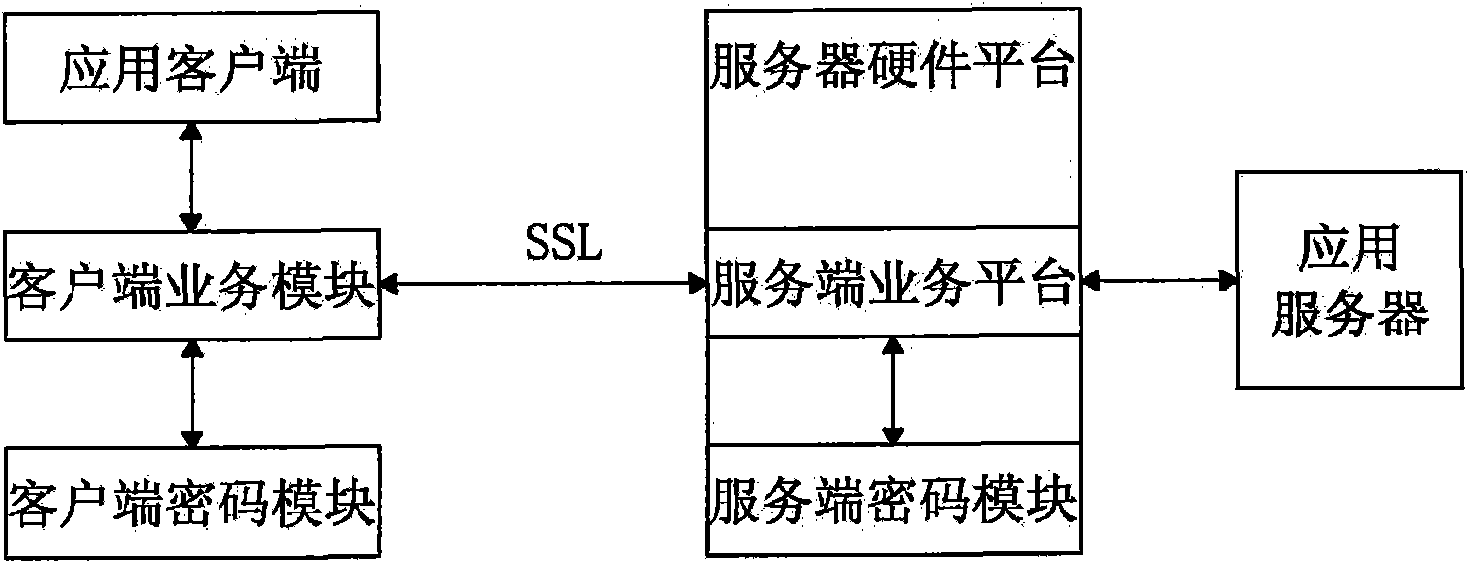
Security certificate gateway
InactiveCN102111349ARealize data transmission securityAchieving Valid AuthenticationNetwork connectionsInternet Authentication ServiceRemote desktop
The invention discloses a security certificate gateway, comprising a client crypto module, a client business module, a service business module and a service crypto module, wherein the client business module is used as an agent of an application client and used for calling the client crypto module and the service business module interactively to build an encrypted connection; and the service business module is used for calling the service crypto module and the service business module to build a secure encrypted channel. Based on the high-strength identity authentication service, the high-strength data link encryption service and the digital signature and authentication service of a digital certificate, the gateway provided by the invention effectively protects secure access of network resources, and supports B / S applications of a hypertext transport protocol (HTTP) and hypertext transfer protocol secure (HTTPS) as well as common C / S applications of a file transfer protocol (FTP), a remote desktop and the like.
Owner:KOAL SOFTWARE CO LTD
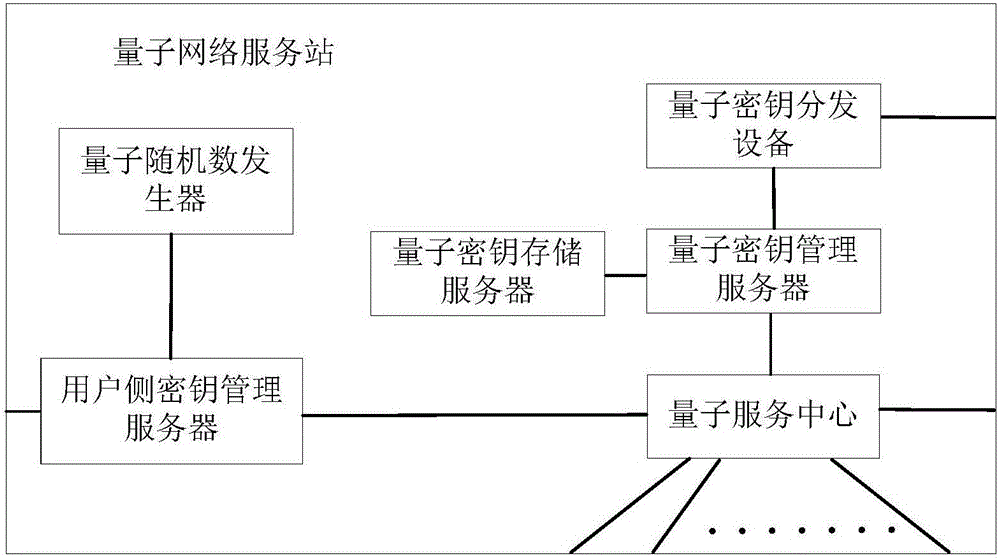
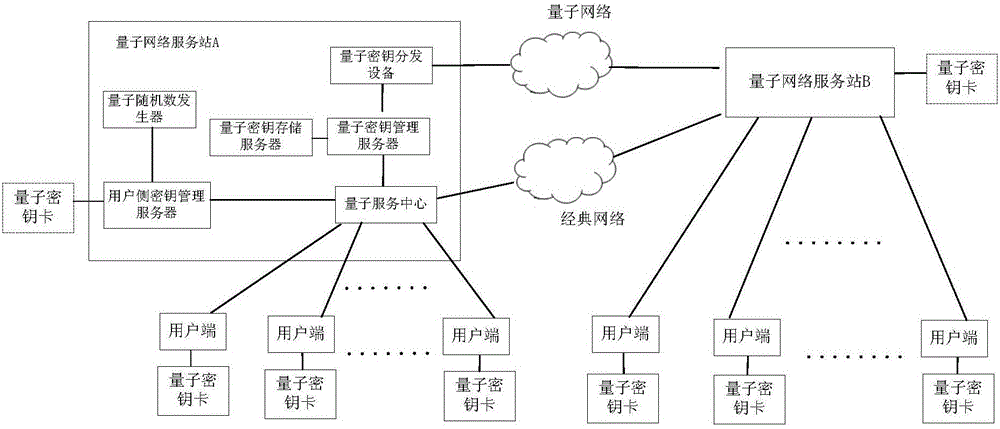
Quantum network service station and quantum communication network
PendingCN106452739APrevent illegal tampering and secret theftFix security issuesKey distribution for secure communicationQuantumQuantum network
The invention discloses a quantum network service station and a quantum communication network. The quantum network service station comprises a quantum service center used for forming a communication connection with each user side, and the quantum network service station is further provided with a true random number generator used for generating true random numbers; a user side key management server used for storing the true random numbers in the station and writing the true random numbers in a user specific device to form corresponding user side keys between the user side key management server and the user specific device, wherein the user side keys are separately applied to the encryption communication between the user sides and the quantum service center. According to the quantum network service station and the quantum communication network disclosed by the invention, the problem of access use and security of a quantum network terminal is solved by using a quantum key card.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
Novel authentication mechanism for encrypting vector
InactiveCN101355422AObvious superiorityImmune to cryptographic attack methodsPublic key for secure communicationUser identity/authority verificationCryptosystemKey generation
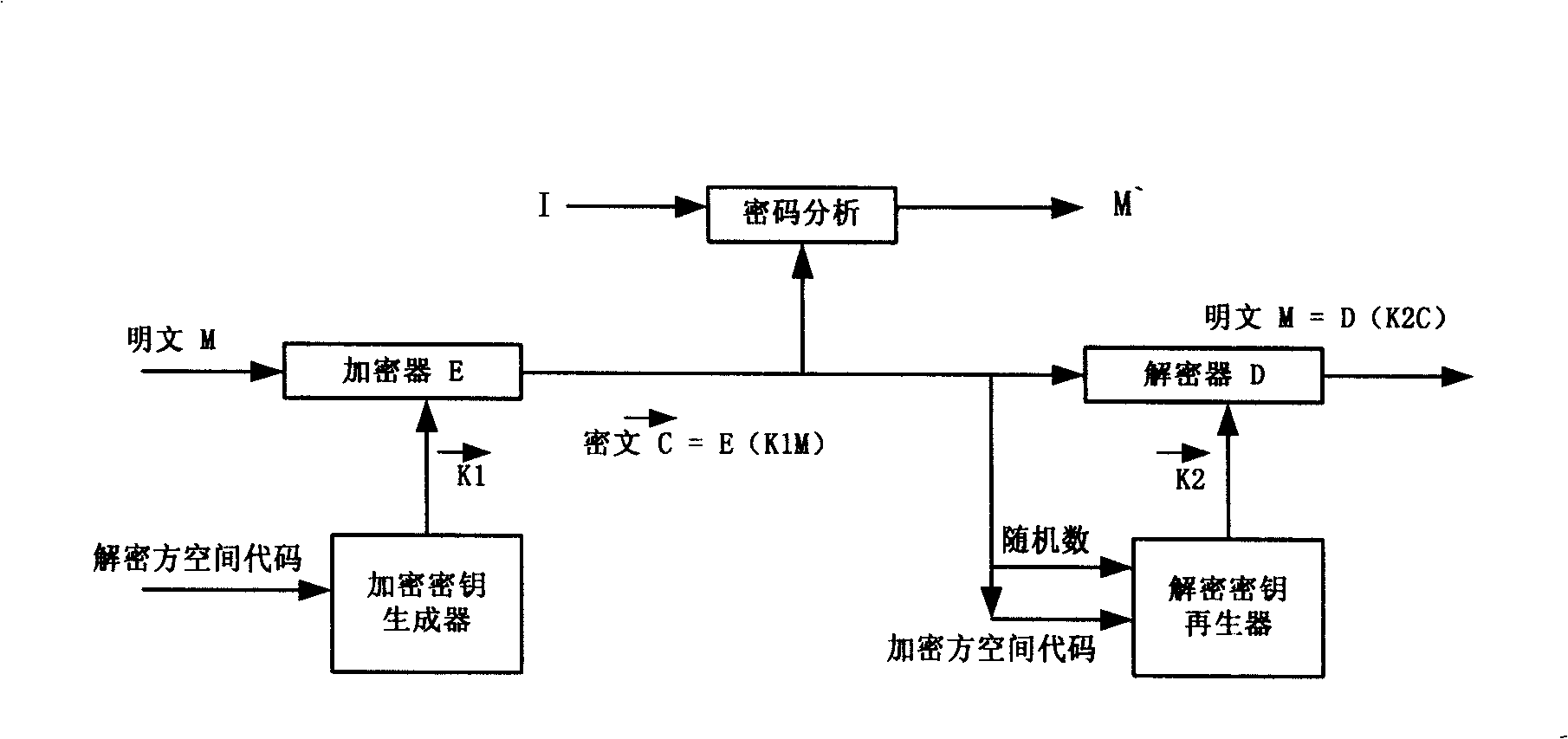
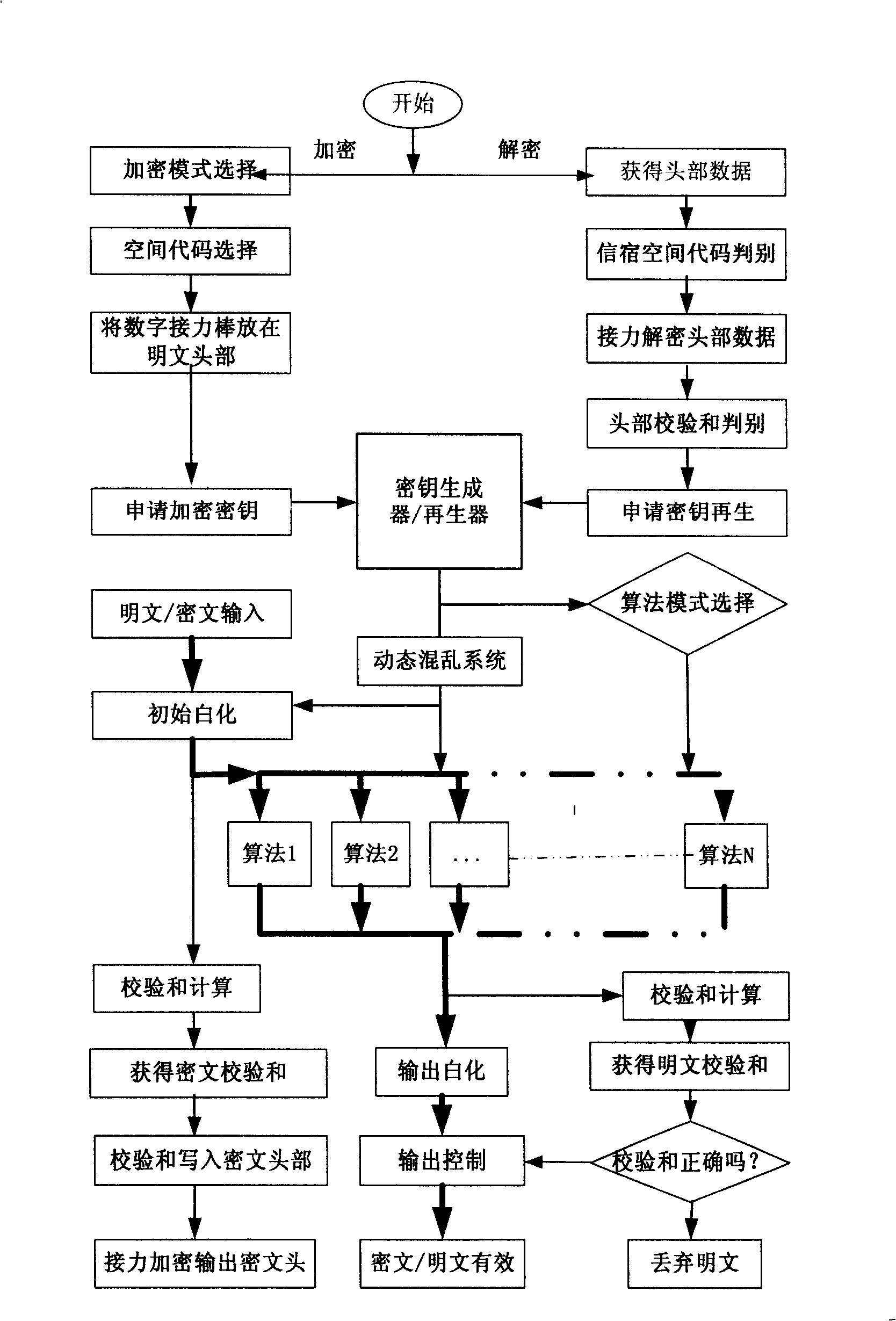
The invention discloses a novel vector encryption authentication mechanism and relates to a vector cryptography method, belonging to the technical field of information security. The method comprises the following steps: a cipher system selects a large number encryption key space M which is twice divided into 2*2 encryption key subspaces which are provided with 2 vectors with different orientations in order that each cipher system of the system possesses a unique encryption key subspace and a unique decryption key subspace; according to the method, the novel vector encryption authentication mechanism can be constructed; the mechanism adopts a hardware tamperproof encryption key generation / regeneration technology to realize the secondary division of the large number encryption key space and endow the encryption key with vector property; and the mechanism adopts a dissymmetrical symmetric algorithm array for encryption / decryption, thereby realizing high strength security, anti-replay, integral control, identity authentication and digital signature and having no problem of the management of the encryption key.
Owner:冯振周
Method for encryption authentication on Ad hoc network transmission layer protocol
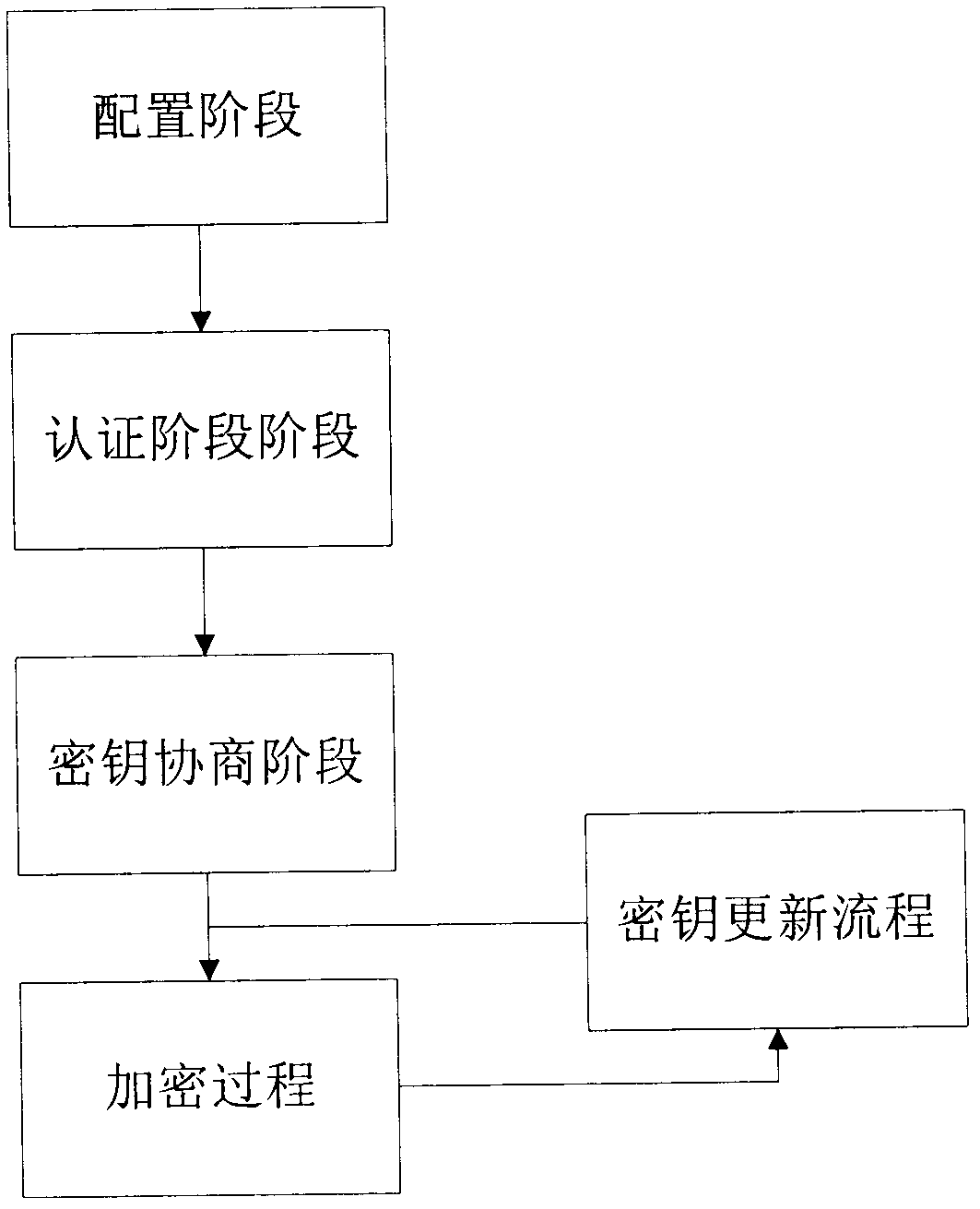
ActiveCN101980558AImplement identity authenticationLittle overheadNetwork traffic/resource managementWireless network protocolsHand shakesExclusive or
The invention discloses a method for encryption authentication on an Ad hoc network transmission layer protocol, which comprises five parts and 18 steps, wherein the five parts are a configuration stage, an authentication stage, a key negotiation stage, an encryption process and a key update flow. The encryption authentication method of the invention is applied to a hand shaking process in the end-to-end communication between two nodes in a multihop Ad hoc network, wherein the two nodes pass through message authentication code verification (MAC) for mutual verification; after the authentication successes, key negotiation is performed by using an elliptic curve diffie-hellman (ECDH) algorithm; and a subsequent message is encrypted by using a shared key acquired in the key negotiation process as a key material and by using an advanced encryption standard (AES) algorithm, and a key update flow is initiated in a communication process. In the authentication and key negotiation process, an exclusive or gate (XOR) algorithm is used for encrypting authentication information and key negotiation information, the safety is high, the efficiency is high, the system expense is small, and the encryption strength is high; and thus, the method has a promising application prospect in the technical field of wireless networks.
Owner:BEIHANG UNIV
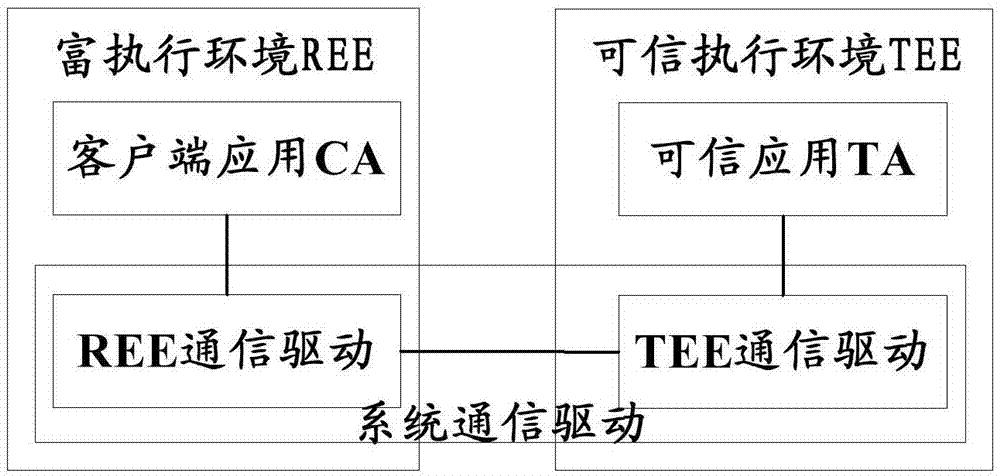
Authentication method and system in trust execution environment
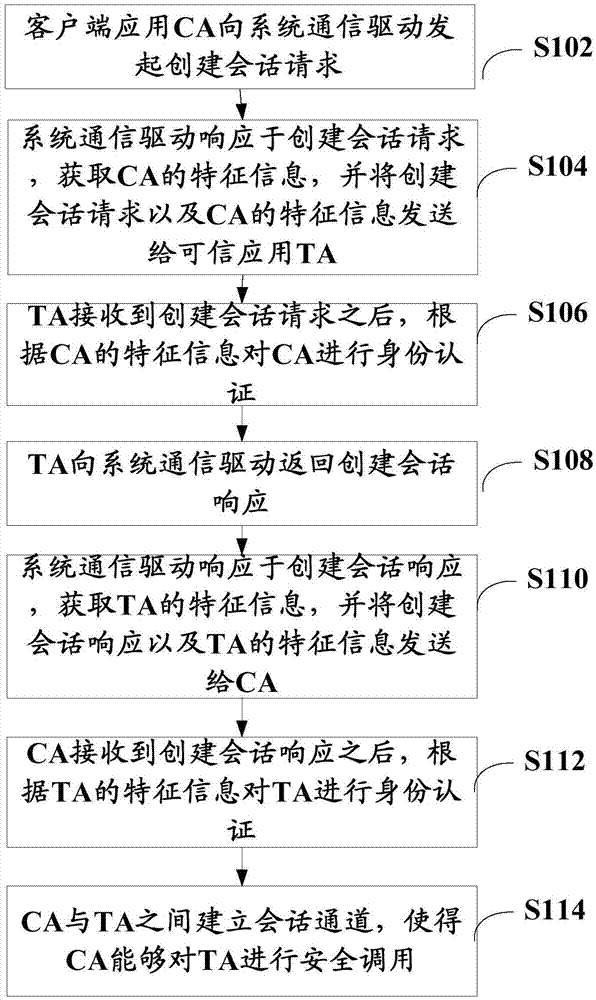
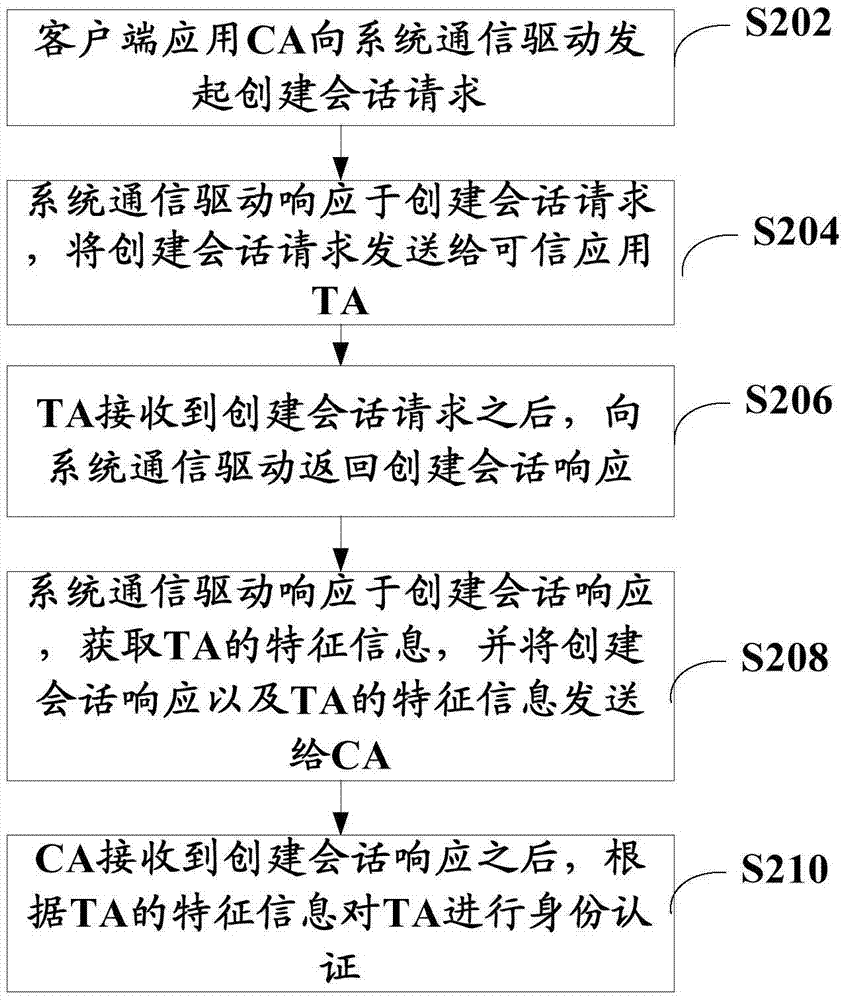
ActiveCN106936774AImplement identity authenticationImprove securityUser identity/authority verificationClient-sideAuthentication
The invention discloses an authentication method and system in a trust execution environment, and relates to the technical field of mobile terminals. The authentication method comprises the following steps: a system communication drive acquires feature information of a client application CA, and sends a trust application TA to the CA to perform the identity authentication; and / or the system communication drive acquires the feature information of the TA, and sends the CA to the TA to perform the identity authentication. The identity authentication between the client application and the trust application is accomplished through the cooperation of the system communication drive, and the security is improved.
Owner:CHINA TELECOM CORP LTD
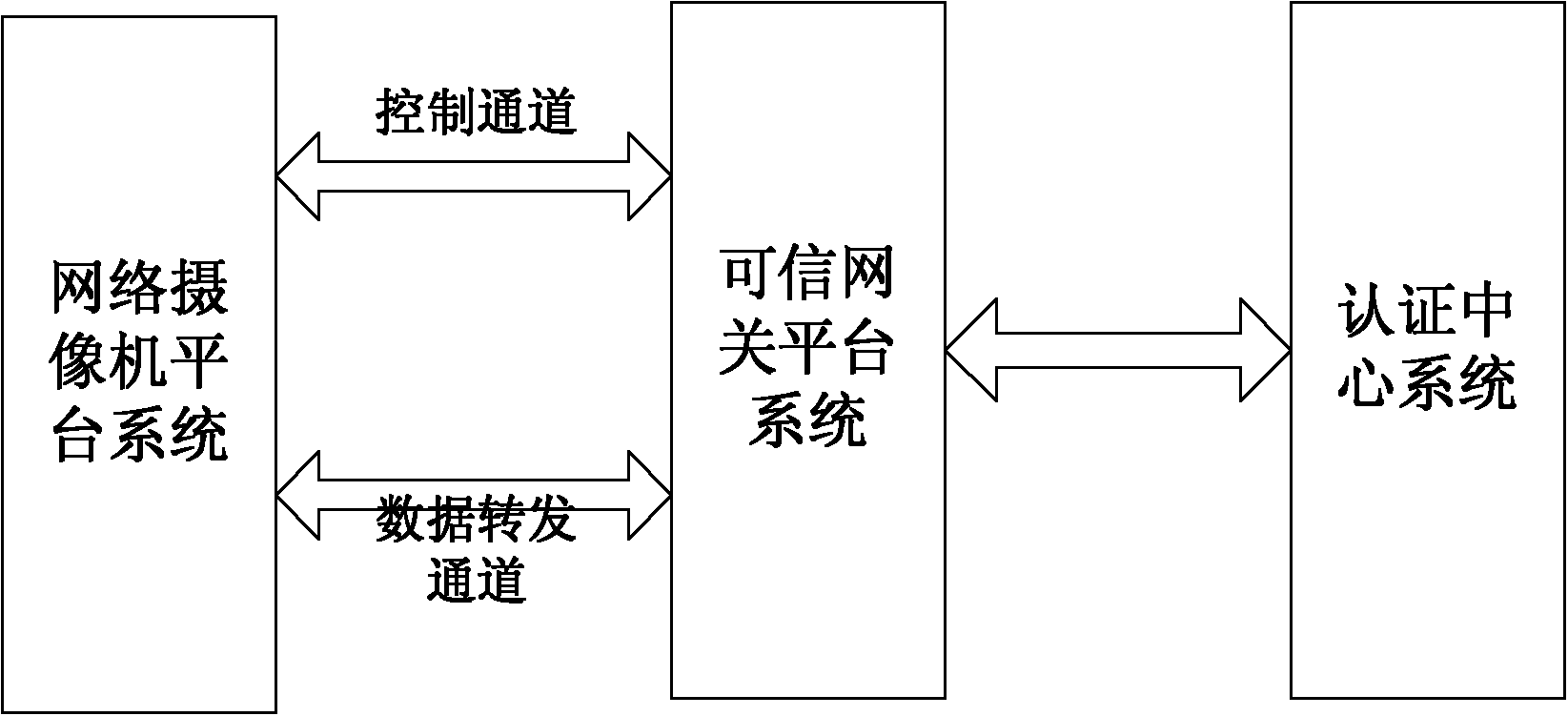
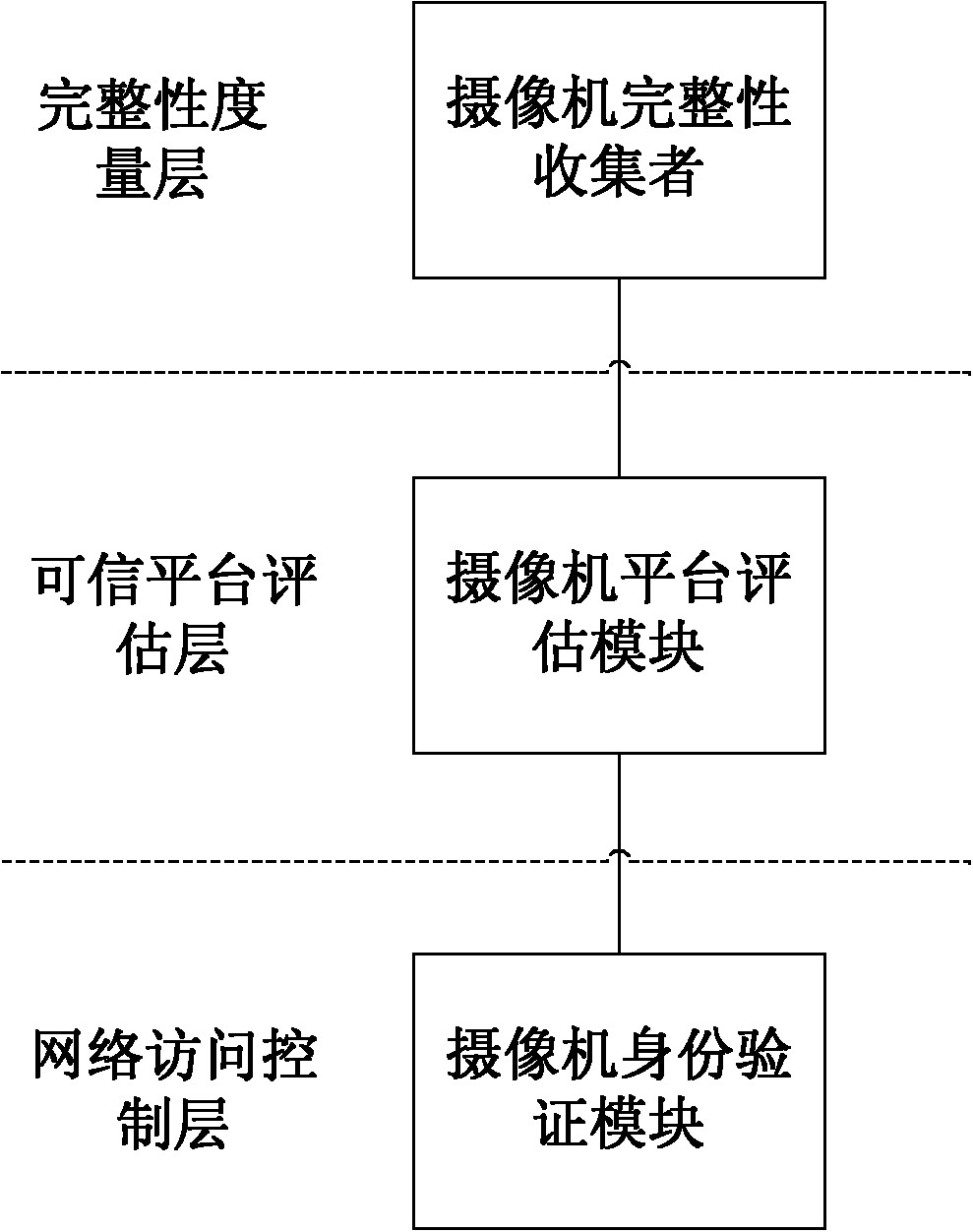
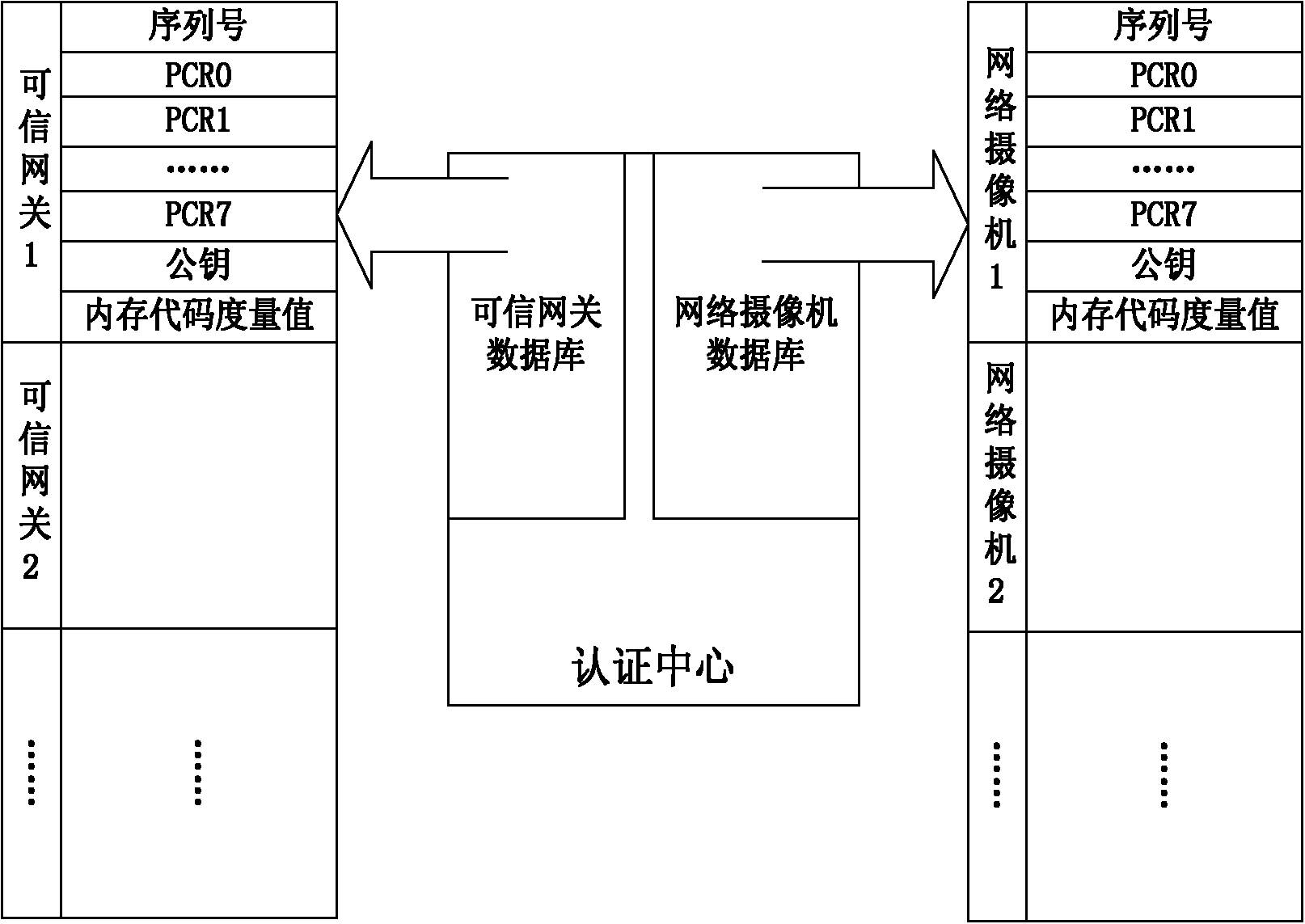
Network camera identity authentication method based on TPCM
ActiveCN103888257AImplement identity authenticationReduced authenticationUser identity/authority verificationClosed circuit television systemsProcessor registerMemory code
The invention provides a network camera identity authentication method based on a TPCM. The method is characterized in that a network camera and a reliable gateway adopt a self-signing mode to generate a digital certificate which comprises a value of a platform configuration register and a measurement result of a memory code segment in operation. An authentication center verifies validity of the digital certificate and confirms identity of the verified party. Advantages are that a measurement value in the starting process of equipment is stored in the platform configuration register so that hardware of the network camera and the reliable gateway is ensured to be unchanged. Reliability of equipment identity is ensured from the aspect of software via measurement of the memory code segment. Besides, a signature secret key is generated by a TPCM chip and bound with the hardware platform state of the equipment so that the digital certificate is difficult to forge.
Owner:BEIJING UNIV OF TECH
Identity authentication system of network user and method
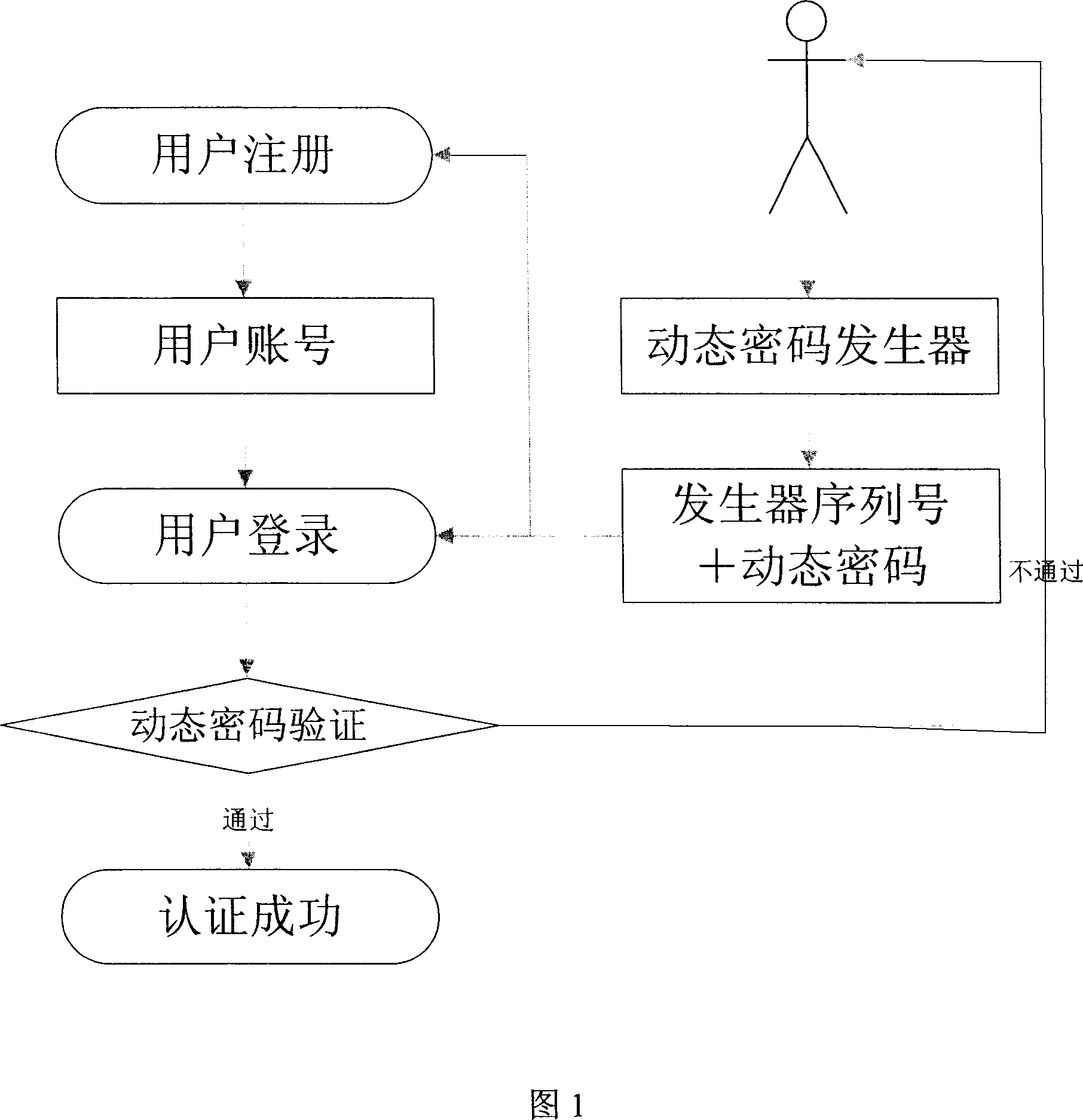
InactiveCN1992590AImplement identity authenticationSimple structureMultiple keys/algorithms usageUser identity/authority verificationPasswordNetizen
The invention discloses a network user identification authentication system, including the client computer, the dynamic password generator and the server, in which the said computer connects to the server through communication network, and the said dynamic password generator connects to the computer, and the said server has the dynamic password checking module. The invention also discloses a network user identification authentication method, including: firstly, the user registers, and then, the client processes login application, and the dynamic password generator generates dynamic password, and then the computer transmits the user identification and dynamic password to the server though communication network, and then, the dynamic password checking module of the server checks the dynamic password, thereby determining the legality of the login application. The authentication architecture of the system in the invention is simple and easy to operate, and it can make users easily login whether or not knowing the network operation, and greatly improve the system's security performance.
Owner:SHENGDA COMP SHANGHAI
Cloud technology-based commodity traceability and consumption flow statistical analysis method and system
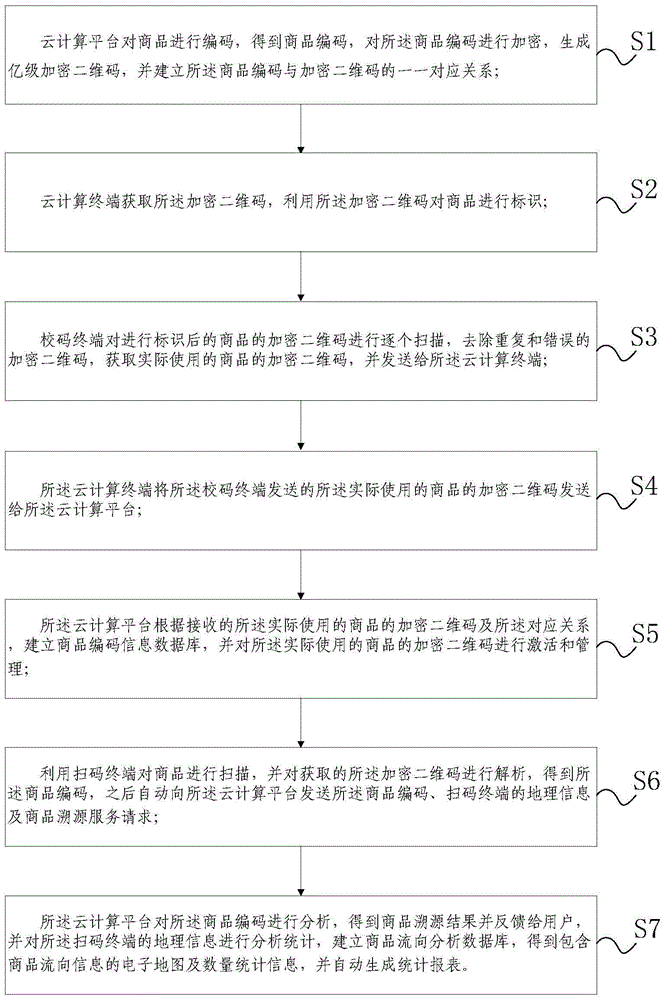
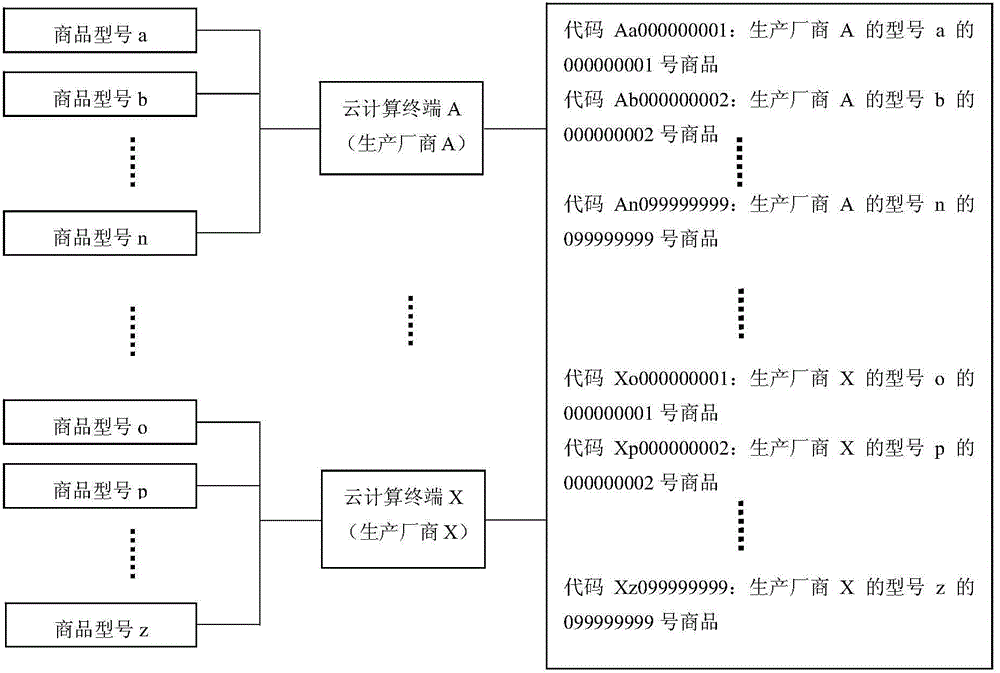
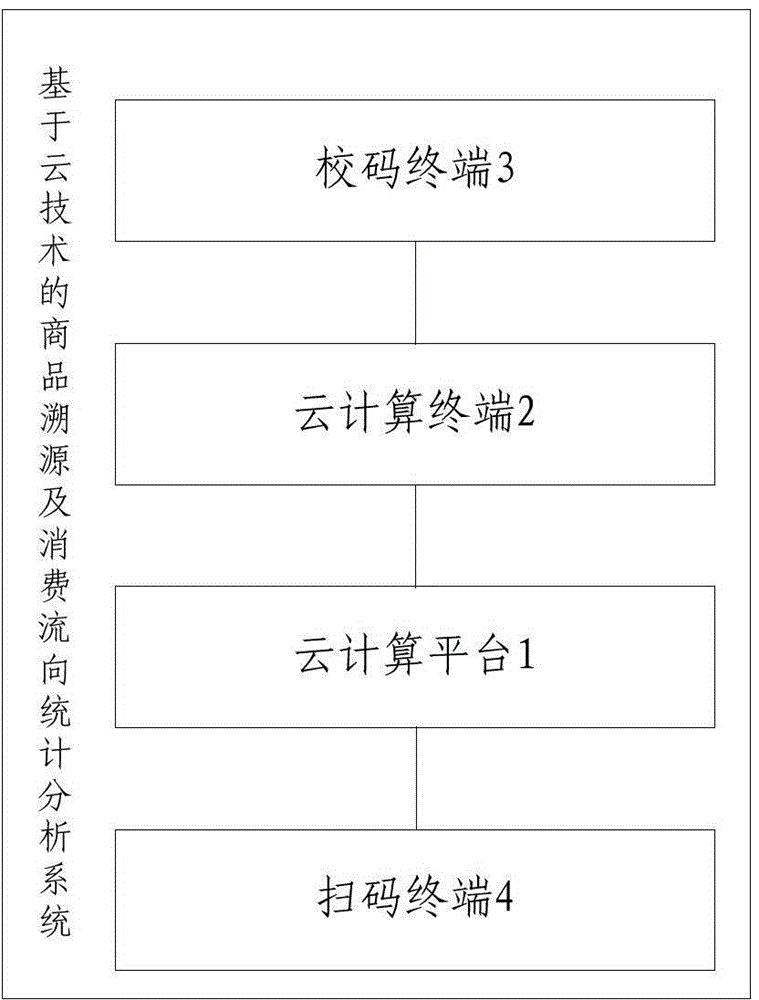
ActiveCN104834999AStrong computing powerImprove performanceResourcesCommerceStatistical analysisBiological activation
The invention discloses a cloud technology-based commodity traceability and consumption flow statistical analysis method and system. According to the cloud technology-based commodity traceability and consumption flow statistical analysis method and system, a cloud technology architecture in which a cloud computing platform and a cloud computing terminal coordinate with each other is adopted, wherein the cloud computing platform is responsible for coding, compression, encryption, generation and activation, assignment and management of hundred-million-level encrypted two-dimension codes and providing traceability services for consumers and providing consumption flow statistical analysis services for enterprises, and the cloud computing terminal is responsible for assigning identifiers for the encrypted two-dimension codes of commodities; since the powerful computing ability and performance of cloud technologies are utilized, and a convenient automated centralized management mode is adopted, the operational efficiency, reliability, flexibility and robustness of the system can be ensured.
Owner:NANJING DASHU INTELLIGENT SCI & TECH CO LTD
Identification authentication method and system
InactiveCN101488111APrevent theftImprove securityUnauthorized memory use protectionAuthentication systemSession key
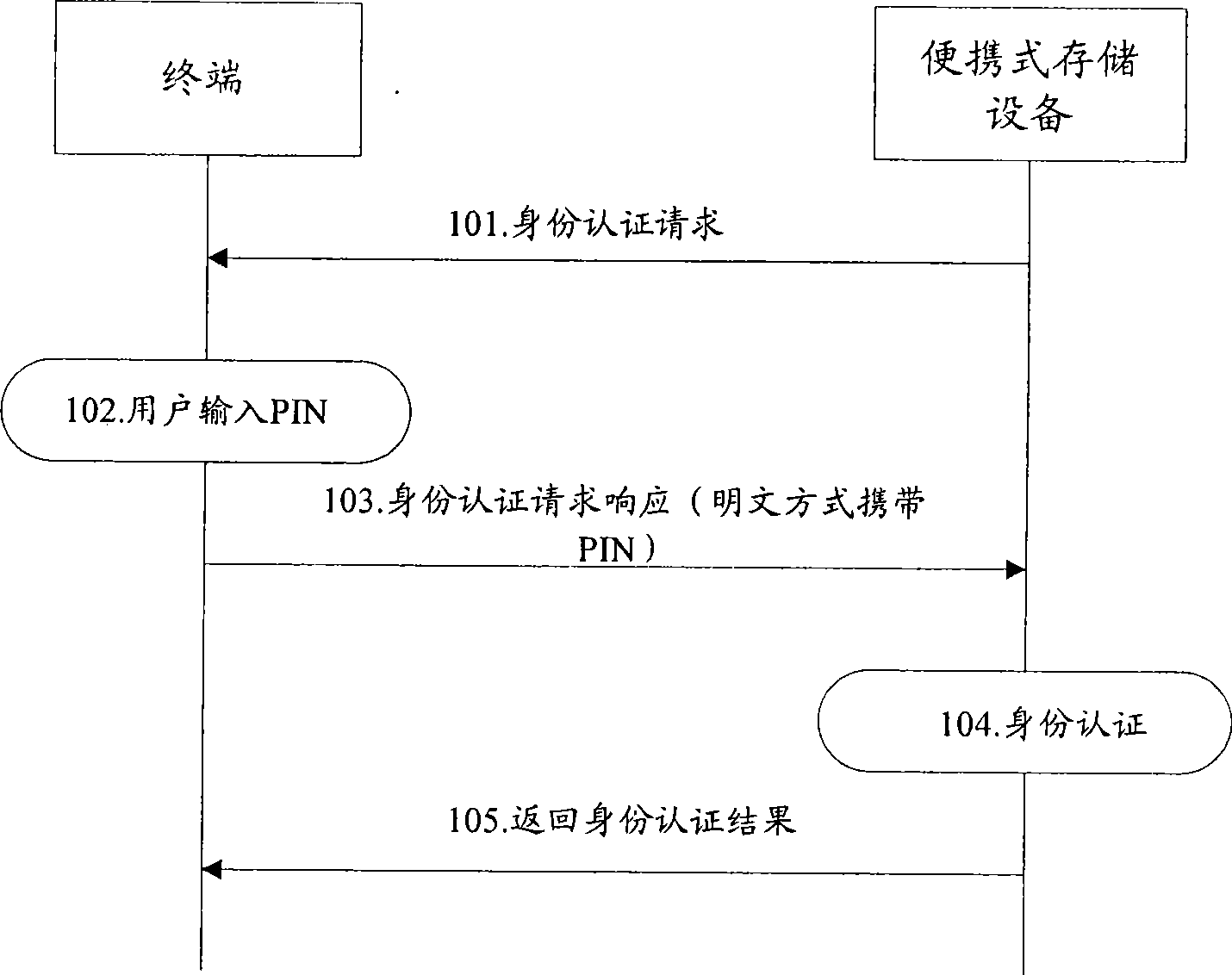
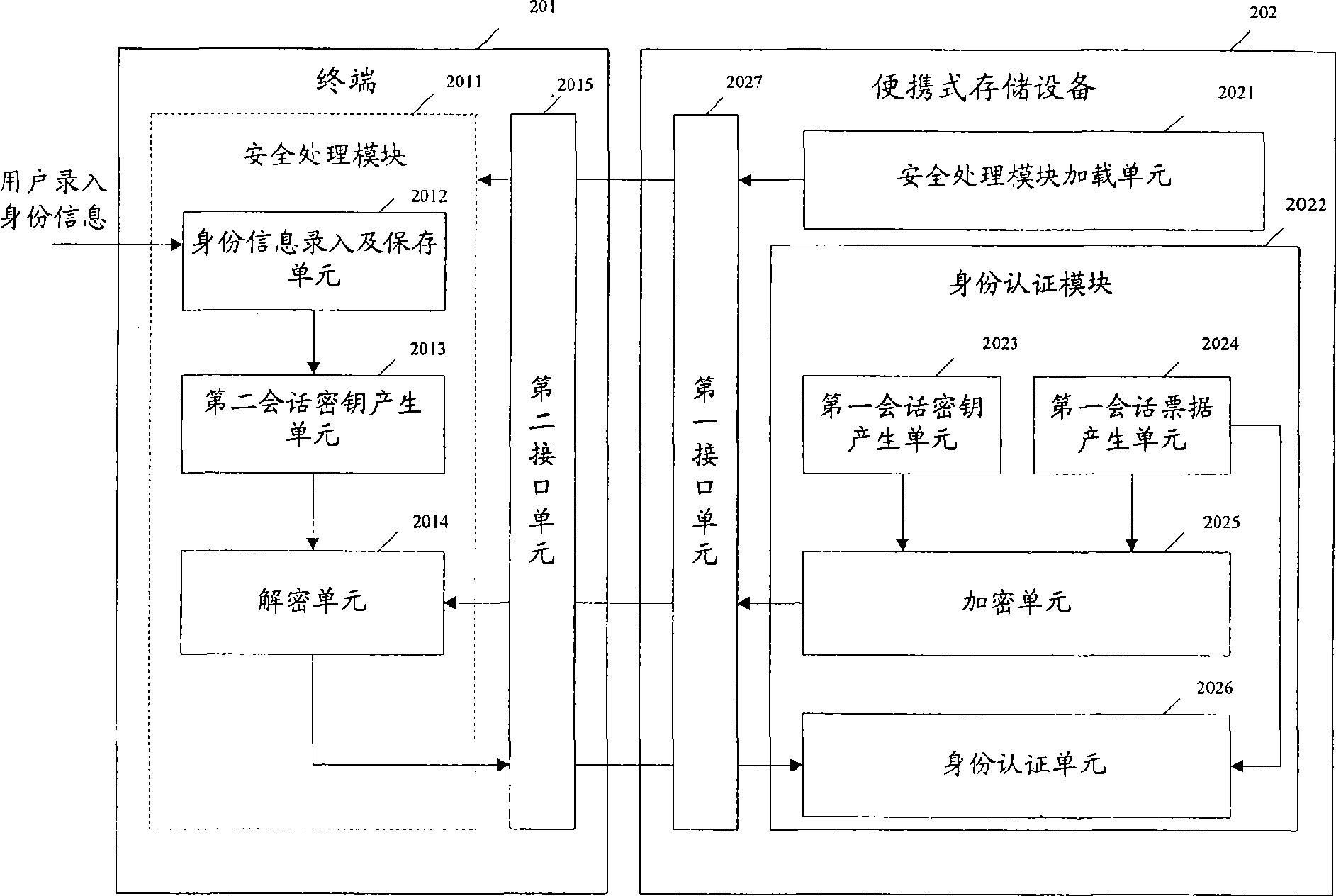
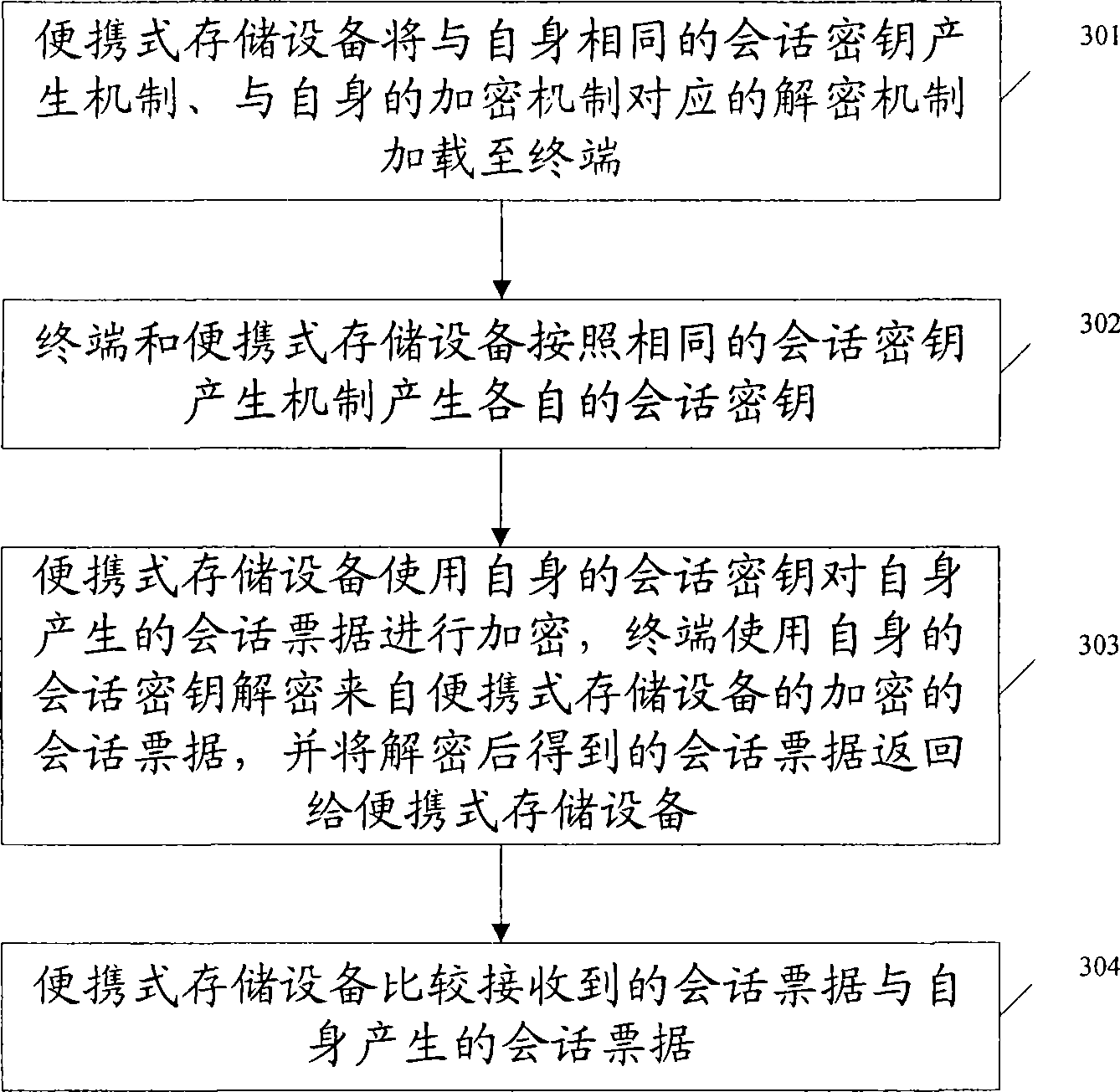
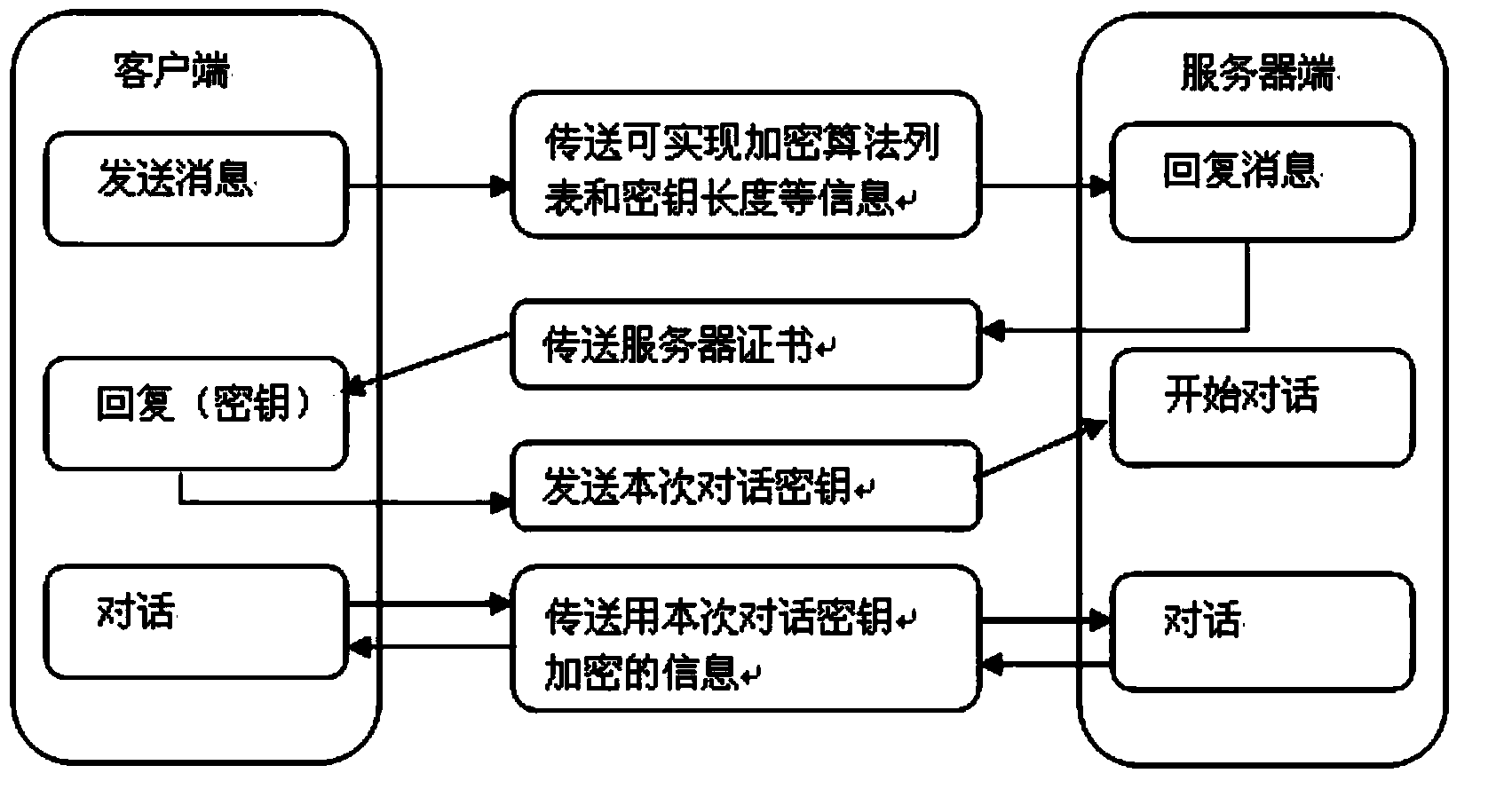
The invention discloses an identity authentication method. Firstly, a portable storage device loads a session key generation mechanism identical to itself and a decrypting mechanism corresponding to an own encrypting mechanism onto a terminal; then, the portable storage device uses an own session key to encrypt a self-produced session ticket; the terminal generates the session key according to the session key generation mechanism identical to the portable storage device, ensures that the own session key decrypts the encrypted session ticket from the portable storage device and returns the session ticket obtained after the decryption to the portable storage device; subsequently, the portable storage device can compare the received session ticket with the session ticket produced by itself, so as to realize the identity authentication. At the same time, the invention also discloses an identity authentication system. The method and the system can improve the safety of the identity authentication between the terminal and the portable storage device.
Owner:POTEVIO INFORMATION TECH
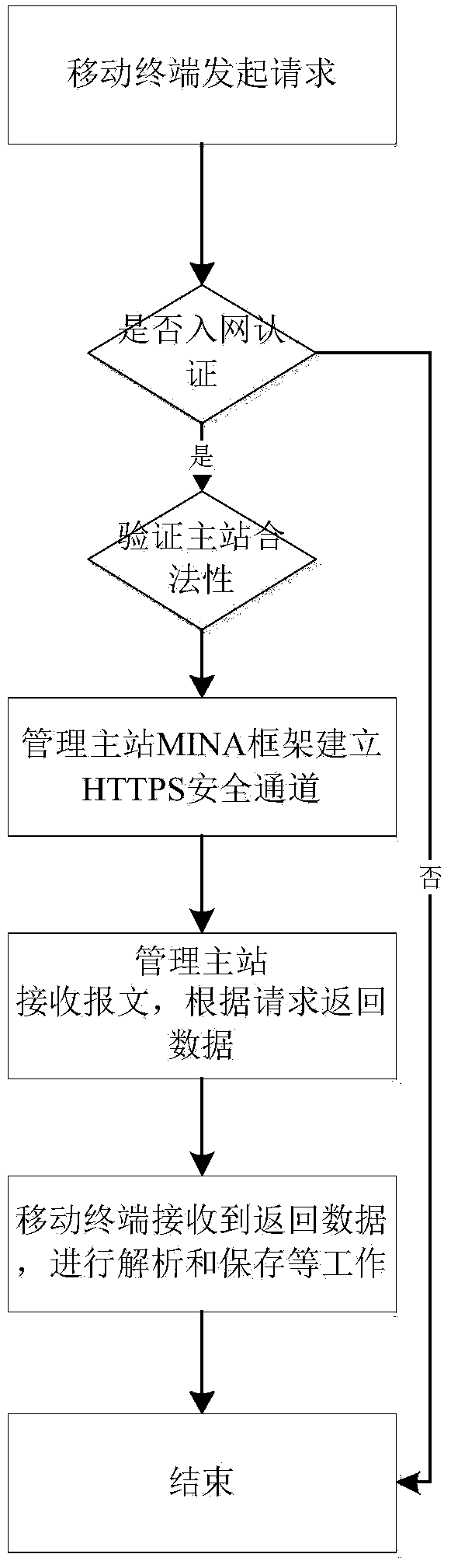
Communication method of power asset management master station system and RFID (radio frequency identification device) terminal
The invention relates to a communication method of a power asset management master station system and an RFID terminal. The method guarantees the identity legitimacy of a client by providing bidirectional authentication for the RFID terminal and the management master station system and encrypting private data and through digital signatures; a terminal layer is mainly composed of the RFID mobile terminal and an RFID reading and writing module and mainly achieves the operations such as field installation, label information inquiry and equipment checking of power grid equipment labels. The communication method of the power asset management master station system and the RFID terminal can guarantee the communication safety between the power asset management master station system and the RFID terminal; two communicating parties can establish safe communication channels therebetween for data transmission only by holding key certificates and being authorized.
Owner:STATE GRID CORP OF CHINA +3
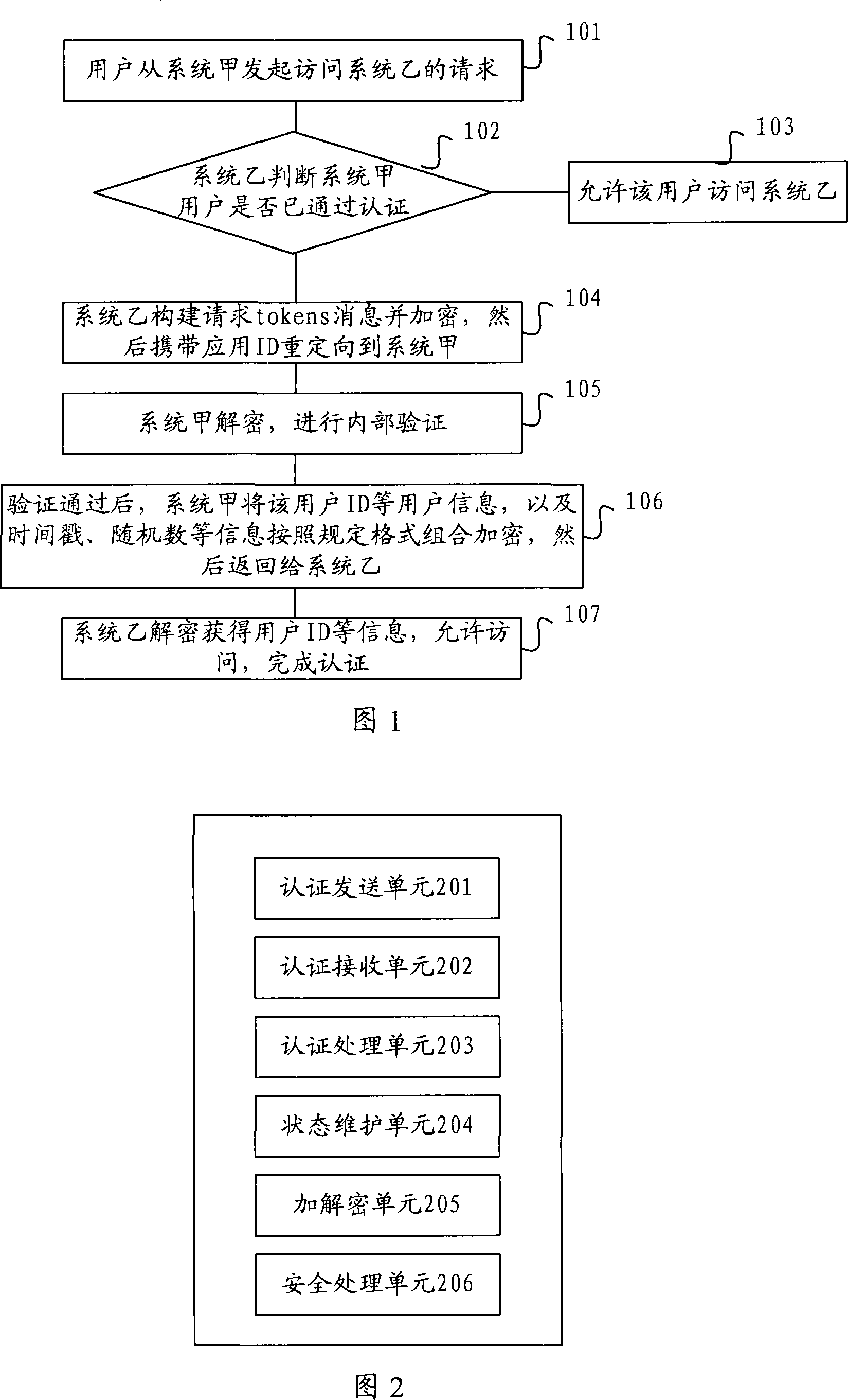
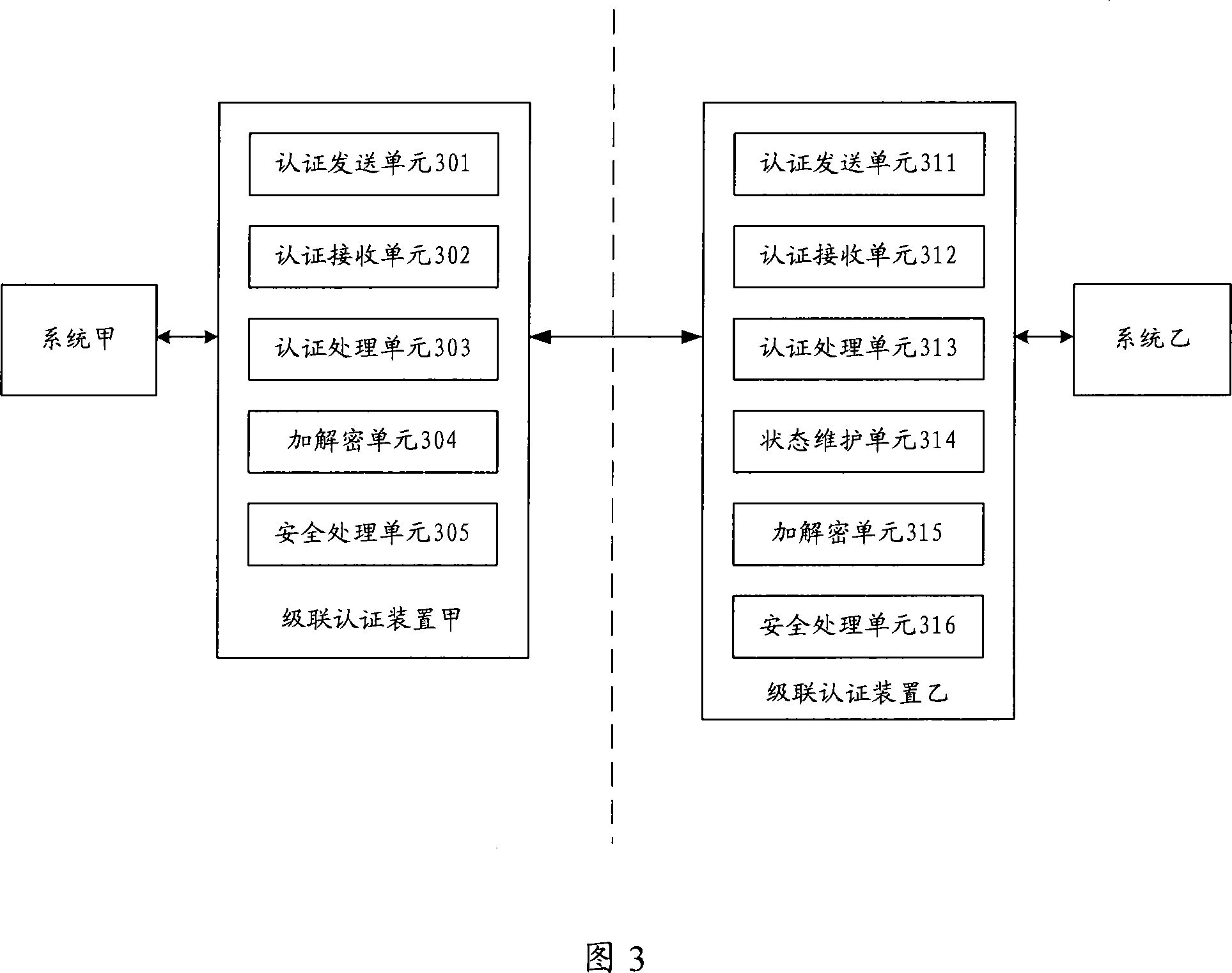
Cascade connection authentication method and device between application systems
InactiveCN101222335AImplement identity authenticationResolve incompatibilitiesKey distribution for secure communicationUser identity/authority verificationExtensibilityEncryption decryption
The invention discloses an application system cascade certification method and a device thereof; the invention can realizes user identity certification of application systems between two or more than two different or identical platforms; the certification method includes that: when a user of the system A initiates a request of visiting a system B from a system A, the system B firstly judges whether the user passes the certification, if the user of the system A does not pass the certification, the system B is directly redirected to the system A which completes the certification; if the user of the system A passes the certification, the information of the successful certification is fed back to the system B, the system B believes that the user is a valid user and allows the user to visit the system B; on the contrary, if a user of the system B visits the system A, the same process is adopted. In the mutual certification process, the data interaction can use a plurality of encryption algorithms, the user can choose the encryption-decryption algorithms by himself, thereby improving the flexibility and the expandability of the system.
Owner:STATE GRID INFORMATION&TELECOMM
Key digital identification method using once variable quantity
InactiveCN1980124AImprove integrityAchieve freshnessUser identity/authority verificationComputer hardwareMessage authentication code
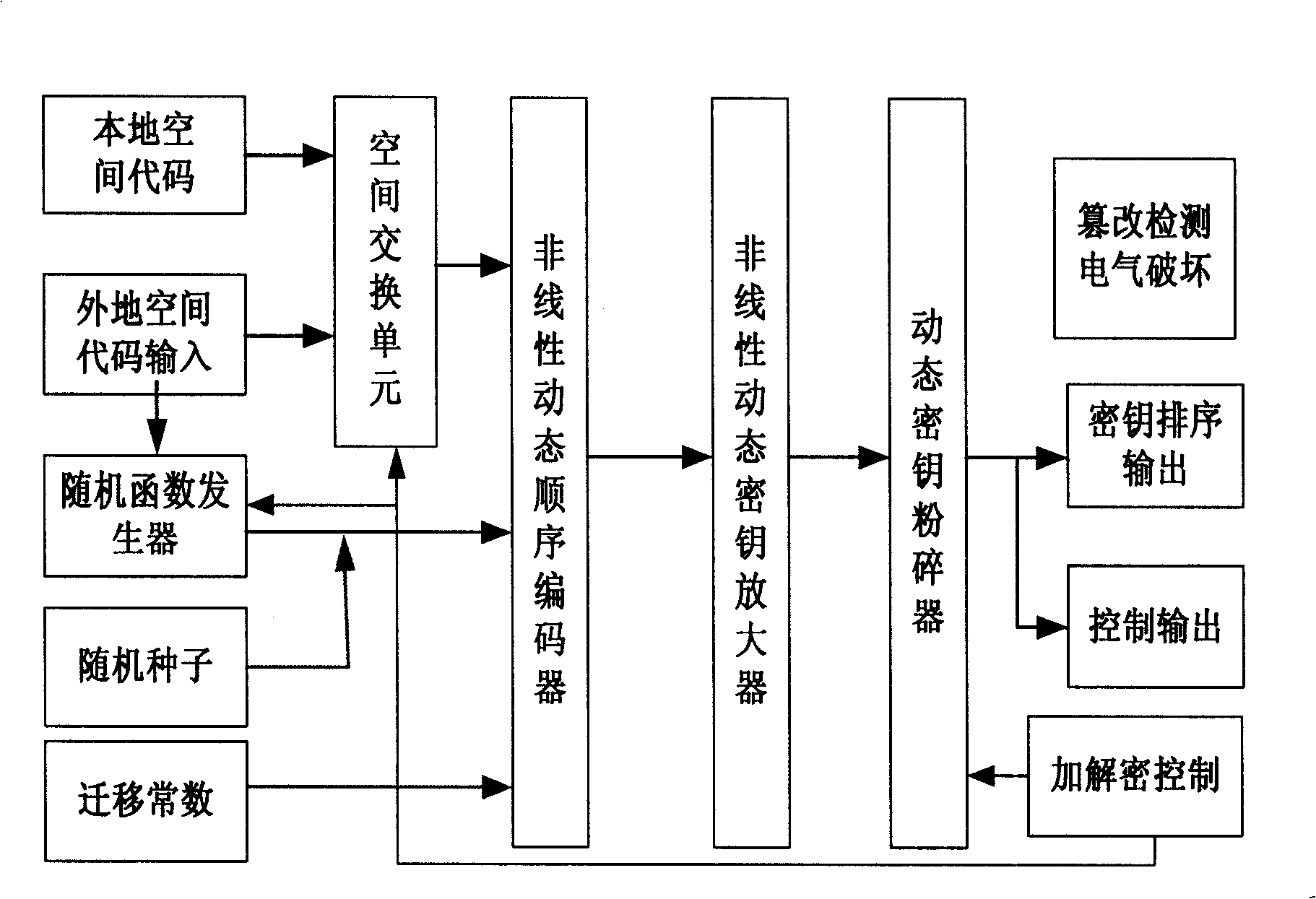
Using message authentication code (MAC) to authenticate message, the invention uses one-off variable. The method includes steps: before using one-off variable, saving range and use state of one-off variable; it must carry out operation for one-off variable and message together to calculate MAC; in authenticating MAC, must authenticate one-off variable, and its state; after using one-off variable, must mark and save use state; for certain cipher key and authentication function, one-off variable is only use for once to authenticate message effectively. Using one-off variable can realize integrality and freshness of authenticating message. Advantages are: synchronous use one-off variable to prevent security attack in many ways, and simple method for realizing complicated authentication application.
Owner:刘金宏
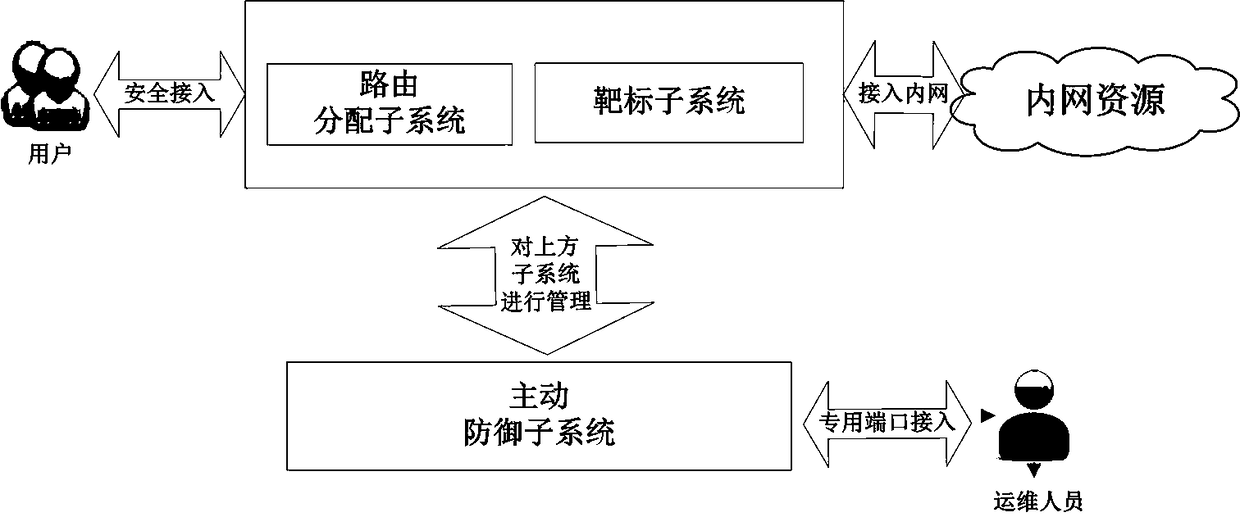
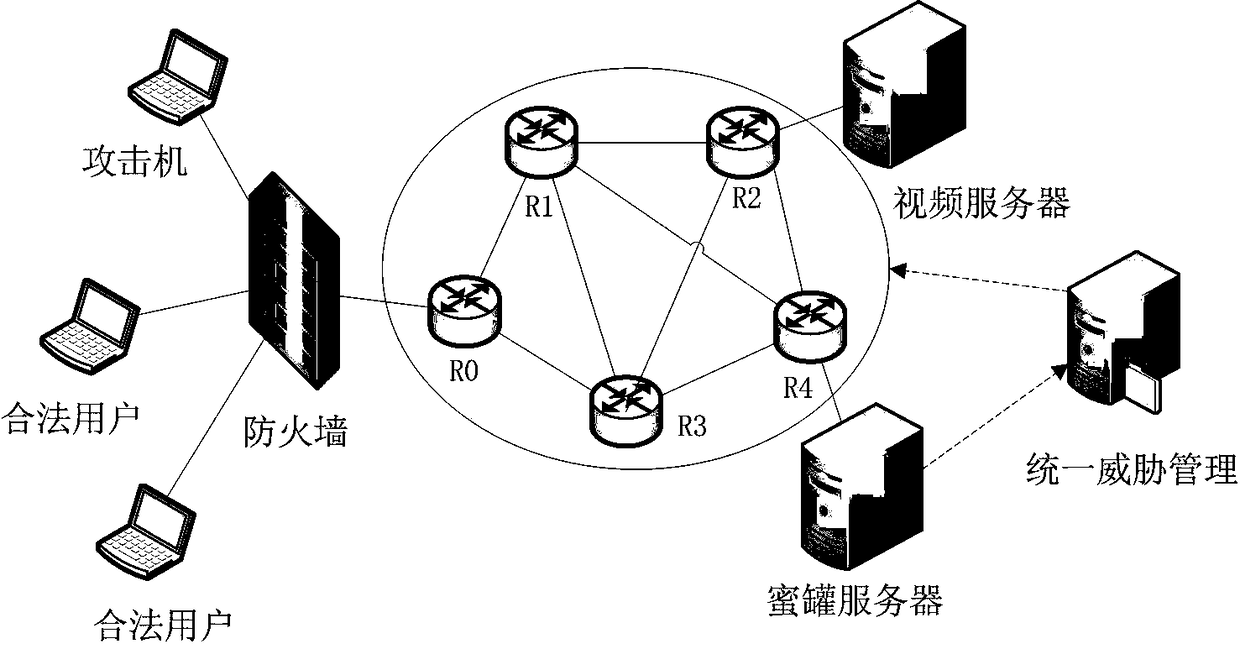
Network dynamic defense system and method
ActiveCN109347830ARealize dynamic changesRealize identificationTransmissionNetwork attackAuthentication
The invention provides a network dynamic defense system and method. The system comprises a route distribution sub-system, a target sub-system and an active defense sub-system. The route distribution sub-system comprises a router, a client and a server; the router is used for detecting legality of users from the client, forwarding legal users which pass the detection to the server and forwarding doubtable users which are failed in the detection to the target sub-system; the target sub-system is used for recording attack behaviors of the doubtable users, performing secondary identity authentication on the doubtable users based on an identity knowledge base, forwarding normal users to the route distribution sub-system again and forwarding the doubtable users to the active defense sub-system;the active defense sub-system is used for extracting and analyzing attack characteristics and backing up and / or restoring important data. By adding dynamicity, randomness and indetermination of the defense system, a system defense capacity is put forth; and the network dynamic defense system increases the attack complexity of attackers and efficiently deals with the network attacks.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
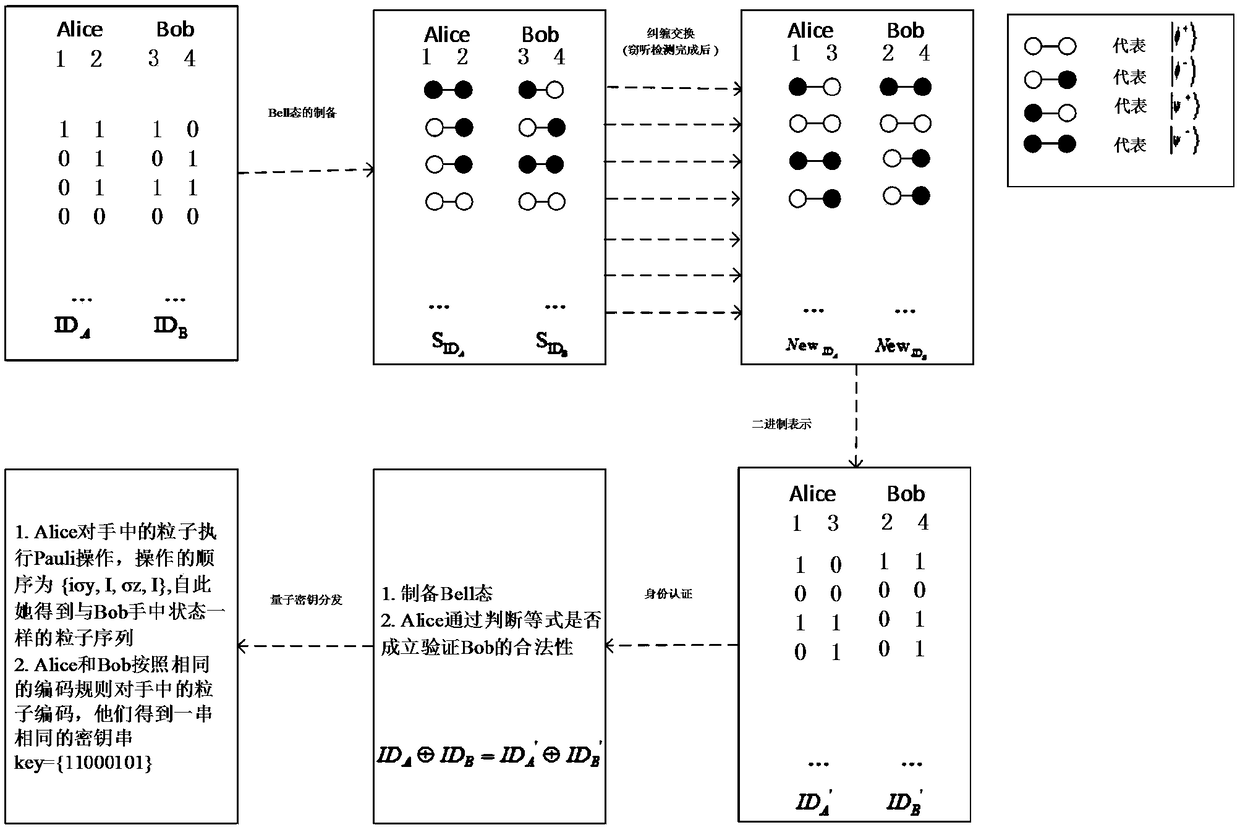
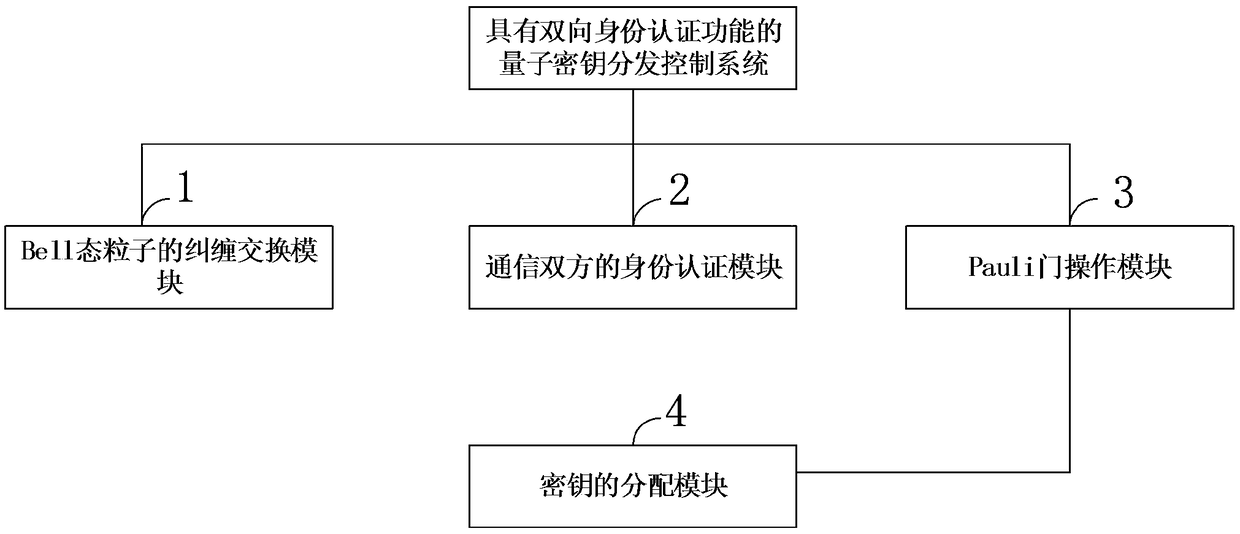
Quantum key distribution method and system with bidirectional identity authentication function
ActiveCN109327308AThe certification process is simple and practicalIncrease profitKey distribution for secure communicationBell stateQuantum gate
The invention belongs to the technical field of network information and discloses a quantum key distribution method and system with a bidirectional identity authentication function. A communication participant uses a binary character string representing the user identity to carry out preparation of a Bell state; encoding and particle exchange are carried out according to a same convention; Bell-based measurement is finished so as to achieve entanglement exchange of the Bell-state particles; after a bitwise XOR operation is carried out, a Pauli gate operation is carried out on any side of bothsides of communication so that the particles in the hand are converted into the Bell-state particles the same as the particles on the opposite side; and both the sides of communication can obtain a same binary character string so as to finish the distribution of secret keys. The quantum key distribution method and system with a bidirectional identity authentication function in the invention improve the use ratio of resources produced during authentication of both the sides of communication; according to the agreement announced by both the sides of communication can identity authentication andkey distribution be realized without the intervention of a third side; the required quantum state is the Bell state of two particles; and the preparation is relatively easy.
Owner:CHENGDU UNIV OF INFORMATION TECH
Method and device for controlling multicast service access by customer device in access network
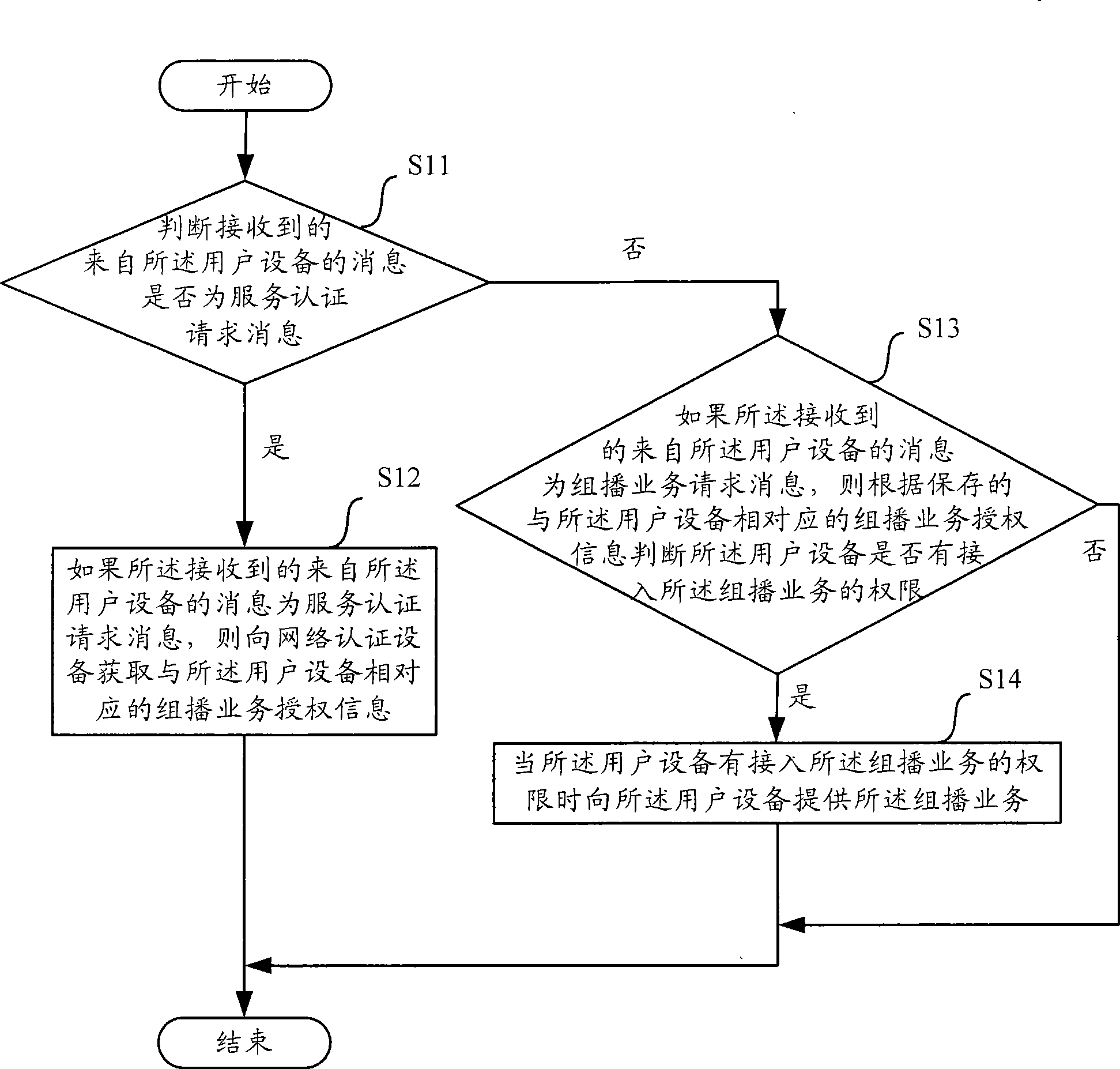
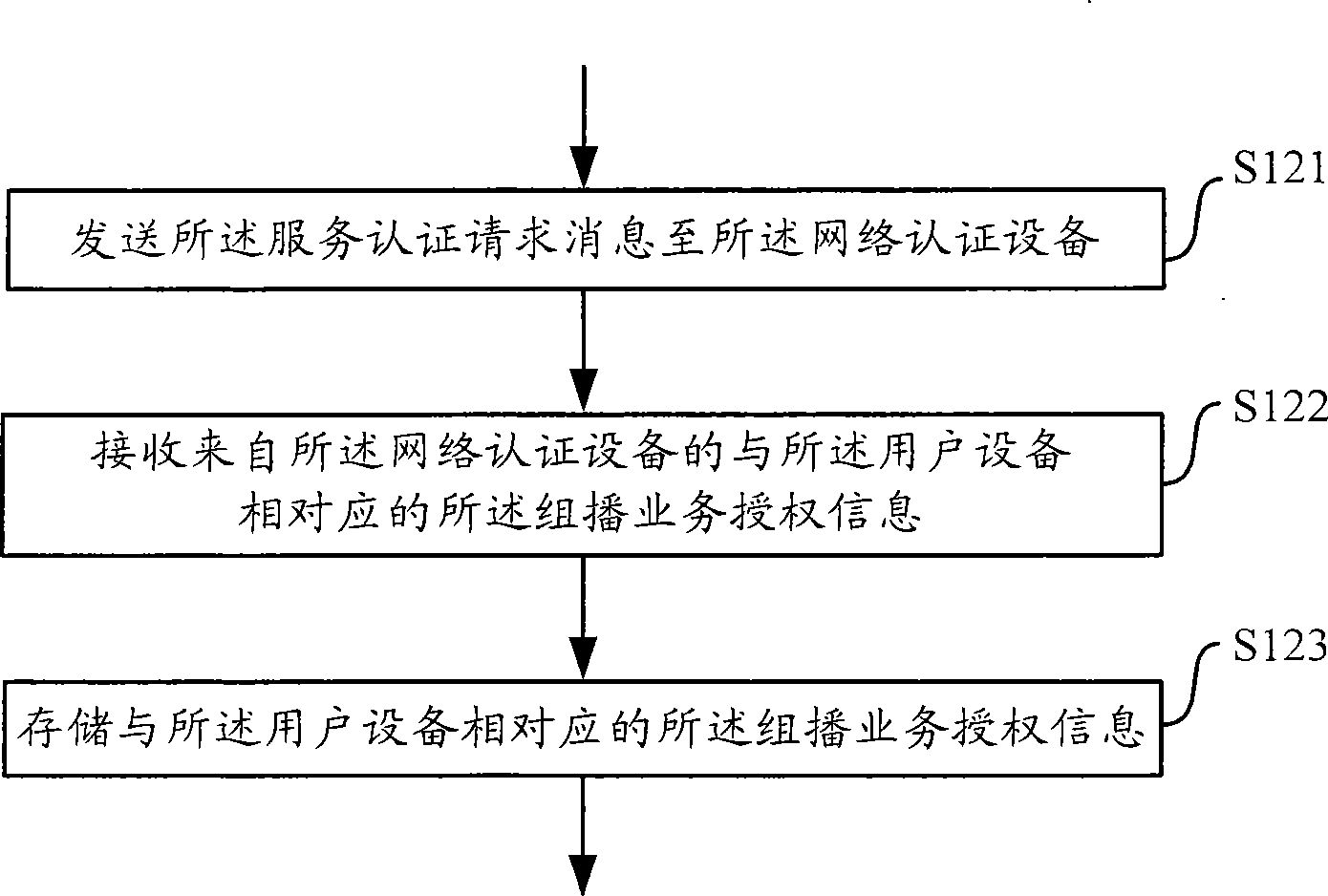
InactiveCN101399718AReduce the number of authenticationsSave network bandwidthSpecial service provision for substationWide area networksWeb authenticationAccess network
The invention provides a method used for controlling the user equipment to access in the multicasting service in the network access equipment and network authentication equipment of the access network and a device thereof; wherein, the invention also provides a method used for controlling the user equipment to withdraw the multicasting service in the network access equipment of the access network and a device thereof; for the user equipment which applies for certain multicasting service, only the status of the user equipment needs to be authenticated; when the user equipment passes the authentication, the network authentication equipment sends the multicasting service access authority corresponding to the user equipment to the network access equipment and memorizes the multicasting service access authority in the network access equipment; detailedly, when the user equipment applies for certain multicasting service in the multicasting service, the network access equipment judges whether the user equipment has the access authority of the multicasting service according to the multicasting service authentication information memorized wherein, and needs not to carry out the status authentication on the user equipment when each multicasting service of the multicasting service is applied by the user equipment.
Owner:ALCATEL LUCENT SHANGHAI BELL CO LTD
Identity authentication method and system
ActiveCN105939197AImplement identity authenticationGuaranteed legalityUser identity/authority verificationAuthentication serverComplete Agreement
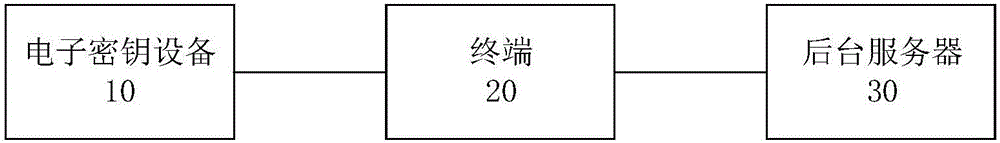
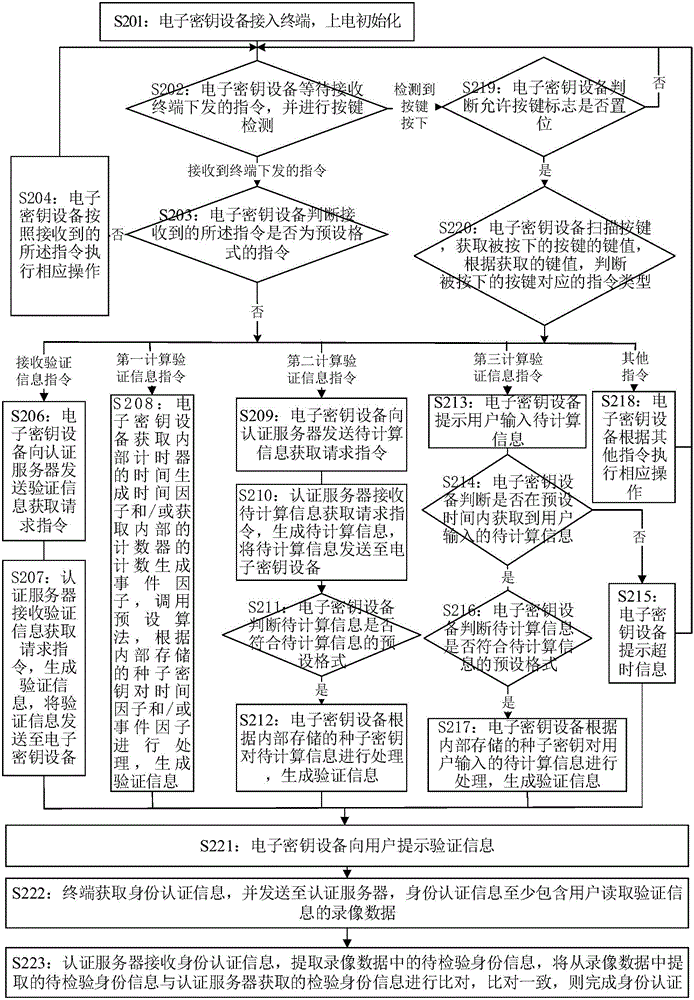
The invention provides an identity authentication method and system. The identity authentication method comprises the steps of connecting an electronic key device to a terminal, electrifying and initializing to obtain verification information, and reminding a user of the verification information; by the terminal, obtaining the identity authentication information and sending the information to an authentication server, wherein the identity authentication information at least comprises record data of reading the authentication information by the user; by the authentication server, receiving the identity authentication information, extracting to-be-verified identity information in the record data, comparing the to-be-verified identity information extracted from the record data with the verified identity information obtained by the authentication server, and finishing the identity authentication is the compared information is in complete agreement.
Owner:TENDYRON CORP
Quantum authorization management method based on EPR pair and entanglement swapping
ActiveCN107070664AImplement identity authenticationDetailed authority divisionKey distribution for secure communicationUser identity/authority verificationThird partyTrusted third party
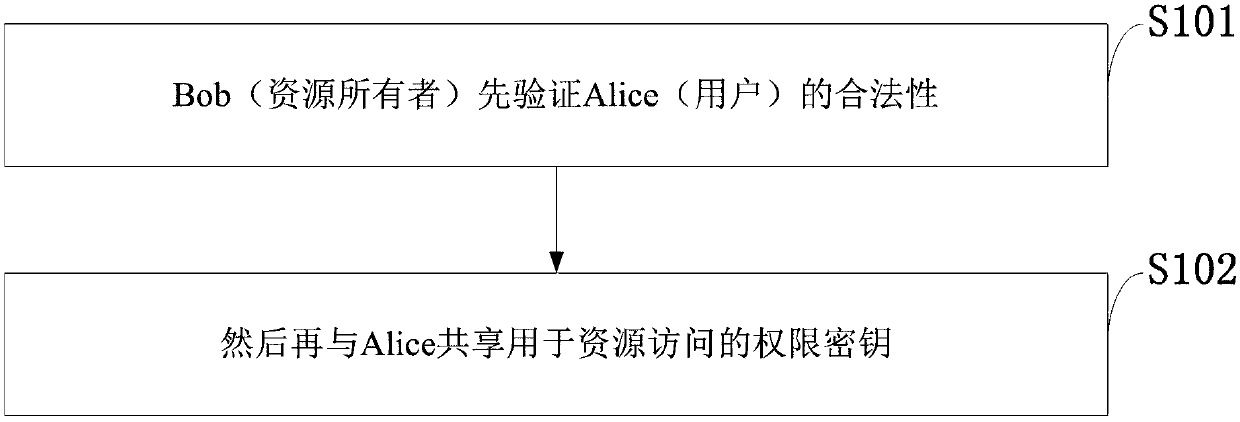
The invention discloses a quantum authorization management method based on EPR pair and entanglement swapping. Bob, a resource owner, firstly verifies validity of a user Alice, and then shares a permission key applied to resource access with Alice; the permission division is the finely grained permission division. According to the protocol in the method provided by the invention, identity authentication and finely grained permission division are achieved without the existence of a semi-trusted third party. In addition, as checking of CHSH inequality violation during a checking period is eavesdropped, even Eve controls or provides a quantum carrier source and measurement equipment, Eve cannot acquire any secret information, and thus side channel attacks from Eve can be defended. According to the method provided by the invention, authorized division is extended to finely grained permission division. According to the method provided by the invention, identity authentication is achieved, and permission of accessing some resources is granted to legal users. The protocol in the method provided by the invention can also defend side channel attacks from Eve.
Owner:CHENGDU UNIV OF INFORMATION TECH
Security chip based on PUF and zero knowledge proof, application method, system and medium
ActiveCN110324151AImplement identity authenticationAchieve tamper resistanceUser identity/authority verificationDigital signatureZero-knowledge proof
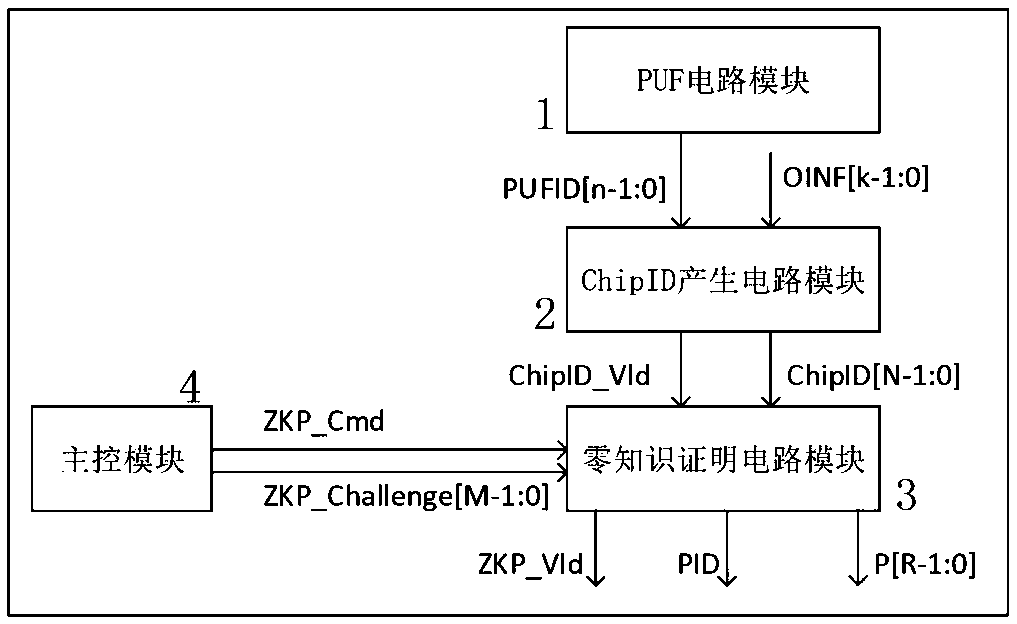
The invention discloses a security chip based on PUF and zero knowledge proof, an application method, a system and a medium. The security chip based on PUF and zero knowledge proof comprises a PUF circuit module, a ChipID generation circuit module, a zero knowledge proof circuit module and a main control module. The zero knowledge proof circuit module comprises a first execution circuit used for generating a publicable zero knowledge identification number PID and a second execution circuit used for generating a proof code P. An identity authentication application method comprises the step of realizing the identity authentication method based on the lightweight security chip based on the security chip. The identity authentication method does not need a complex interactive protocol. The request end and the server end only need to execute zero knowledge proof calculation. Compared with a digital signature and authentication method based on a public key cryptographic algorithm, the identity authentication method is simpler and has the advantages of good universality, high security, low authentication overhead, simple authentication process and the like.
Owner:北京智涵芯宇科技有限公司
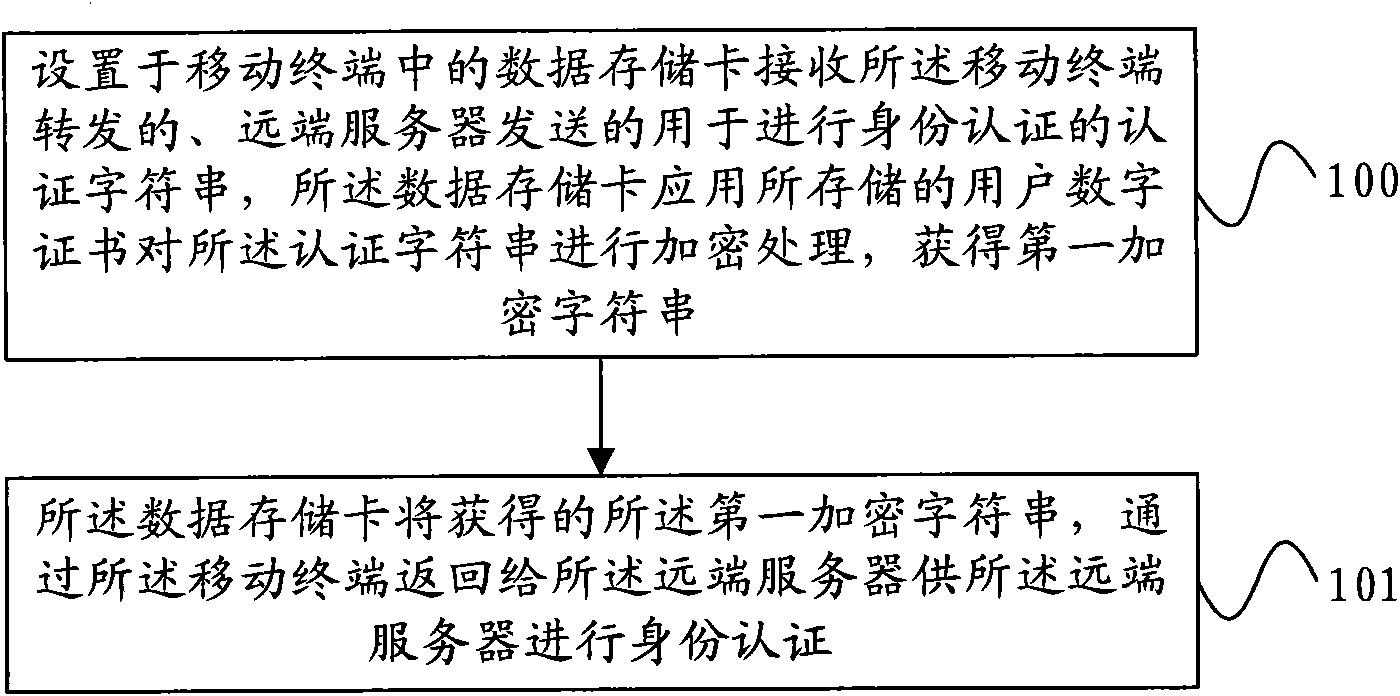
Method for identity authentication, mobile terminal, server, and identity authentication system
ActiveCN101605325AImplement identity authenticationSafety of tradementUser identity/authority verificationWireless network protocolsQuality of serviceAuthentication system
The invention provides a method for identity authentication, a mobile terminal, a server and an identity authentication system. A data storage card arranged in the mobile terminal receives an authentication character string for identity authentication, which is forwarded by the mobile terminal and sent by a remote server; the data storage card applies a stored user digital certificate to encrypt the authentication character string to obtain a first encrypted character string; and the data storage card returns the obtained first encrypted character string to the remote server through the mobile terminal to facilitate the identity authentication of the remote server. The data storage card of the mobile terminal stores the user digital certificate used for the user identity authentication to realize the identity authentication of a user, so that ebanking service carried out by the user through a mobile phone is more safe and convenient, and has simple operation; and for the user, the user can carry out the ebanking service at all times and places through the mobile phone, and the service quality is improved.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
Smart identity authentication method and device for rail transit device
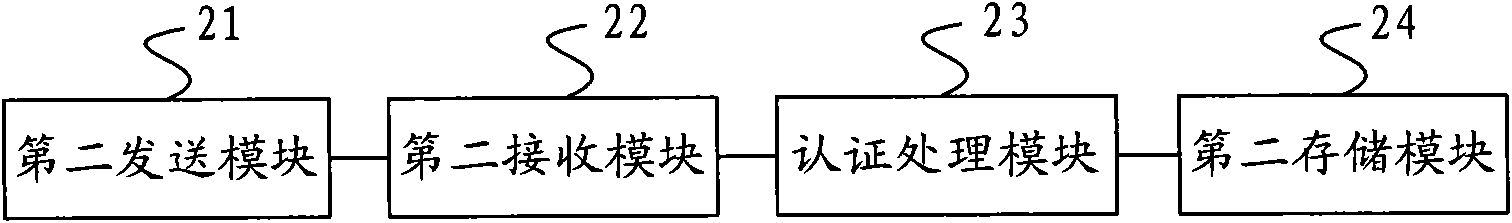
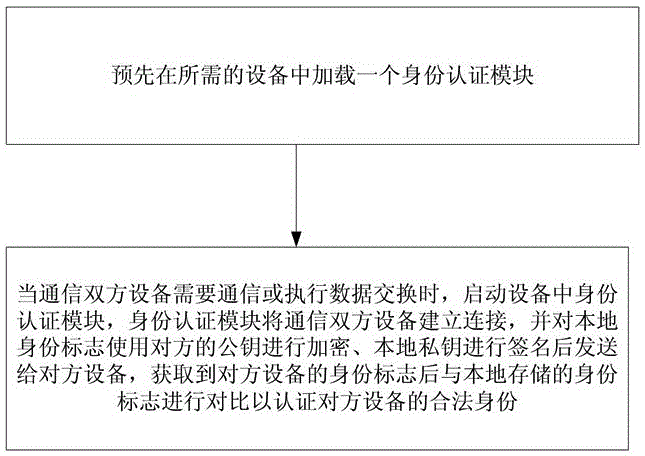
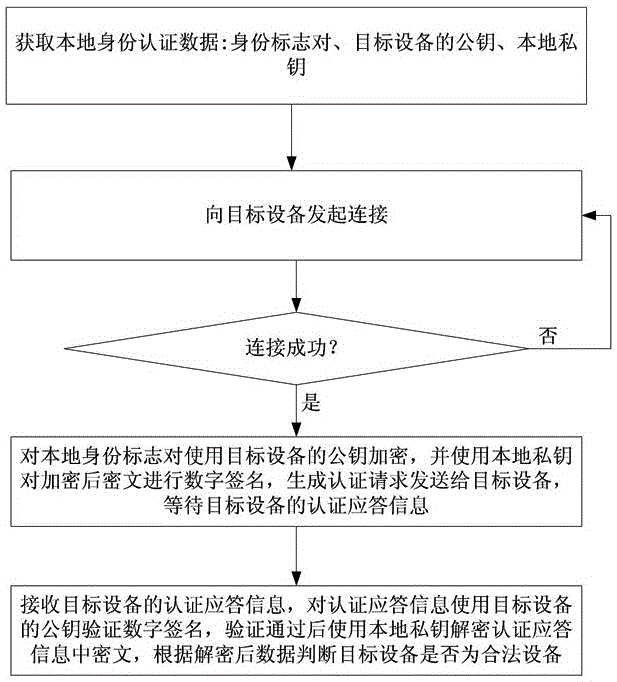
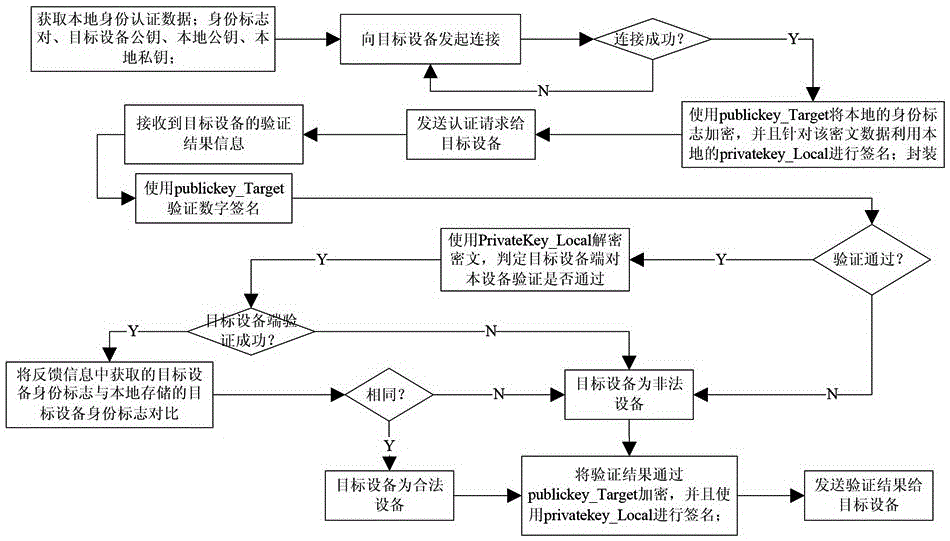
ActiveCN106850680AImplement identity authenticationImprove information securityDigital data authenticationTransmissionComputer moduleData exchange
The invention discloses a smart identity authentication method and device for a rail transit device. The method comprises the steps of 1), preloading an identity authentication module in a required device; and 2), when two communication party devices need to communicate or perform data exchange, the identity authentication module in the device is started, the connection between the two communication party devices is established by the identity authentication module, a local identity mark is encrypted through a public key of an opposite party and is signed by a local private key and then is sent to an opposite device, and after the identity mark of the opposite device is obtained, the identity mark is compared with a locally stored identity mark, thereby authenticating the legal identity of the opposite device. The method and the device are applicable to the rail transit device for realizing smart identity authentication, and the method and the device have the advantages that the realization method is simple, the required cost is low, the identity authentication efficiency is high and the method and the device are safe and reliable.
Owner:ZHUZHOU CSR TIMES ELECTRIC CO LTD
Remote safe meter reading method
ActiveCN103778773AImplement identity authenticationRealize functionElectric signal transmission systemsUser identity/authority verificationSecurity levelRemote meter reading
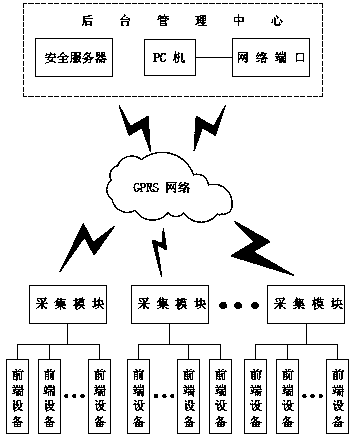
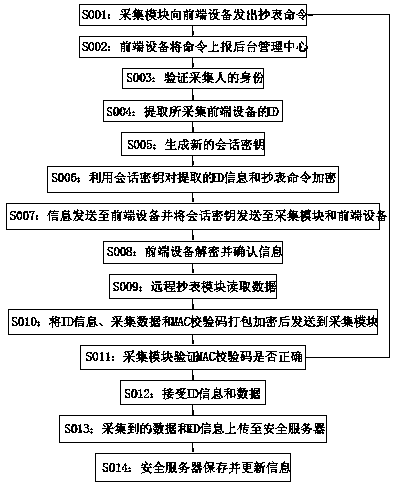
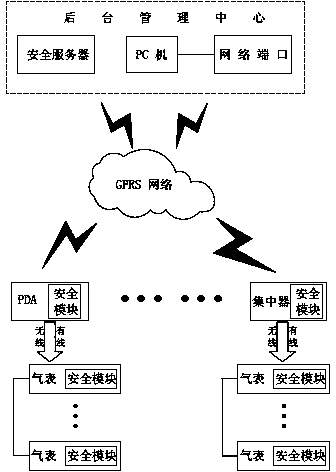
The invention discloses a remote safe meter reading system, comprising a background management center, a collection module and front-end equipment. A remote safe meter reading method comprises the following processes: 1) sending a meter reading command by the collection module; 2) reporting the command to the background management center; 3) validating the identity of a gatherer; 4) extracting an identity (ID) of the collected front-end equipment; 5) generating a new session key; 6) encrypting the extracted ID information and metering reading command; 7) transmitting information to the front-end equipment, and transmitting the session key to the collection module and the front-end equipment; 8) decrypting and confirming information by the front-end equipment; 9) reading data by the remote meter reading module; 10), packaging and encrypting the ID information, collected data and MAC check code and then transmitting to the collection module; 11) receiving the ID information and data; 12) uploading the data to a safety server; and 13) storing and updating information by the safety server. The functions of identity authentication and data encryption are achieved in the remote meter reading process, and the security level is greatly improved.
Owner:山东微分电子科技有限公司
Energy-efficient identity authentication method in multi-level clustering wireless sensor network
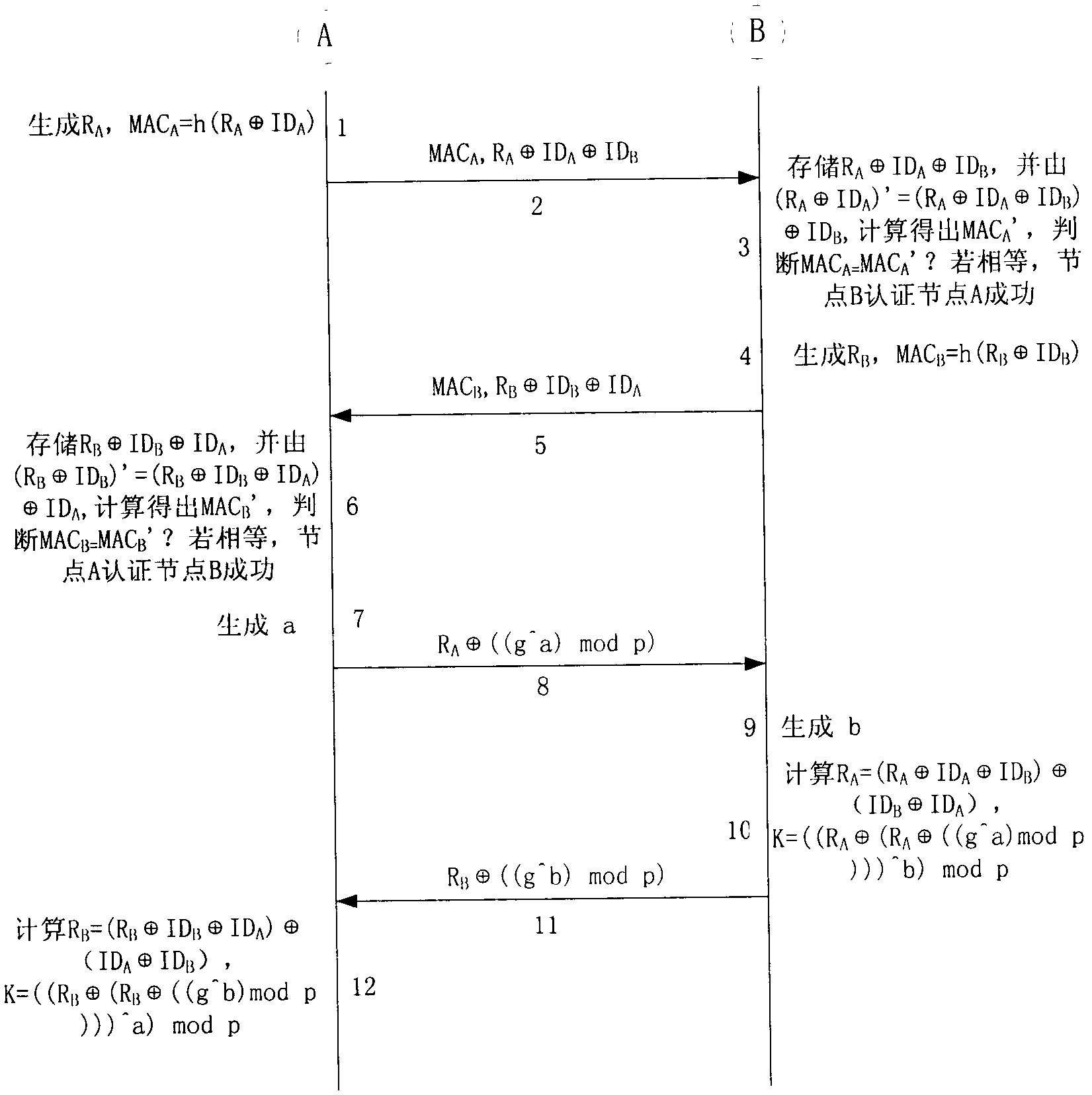
ActiveCN102612035AKeep your identity safeAvoid the authentication processEnergy efficient ICTNetwork topologiesMobile wireless sensor networkWireless mesh network
The invention provides an energy-efficient identity authentication method in a multi-level clustering wireless sensor network, which belongs to the technical field of computer networks. According to the method disclosed by the invention, a symmetric encryption algorithm is taken as the basis, a base station is used for transferring identity information, and all the nodes only need to be subjected to double-way identity authentication with cluster head nodes according to the characteristics of the multi-level clustering wireless sensor network, so that the unnecessary authentication process is avoided. According to the energy-efficient identity authentication method disclosed by the invention, the energy-efficient whole-network necessary identity authentication can be realized in the multi-level clustering wireless sensor network, and identity safety of the nodes of the whole network can be ensured at minimum energy cost.
Owner:福建汇智数字通达科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com