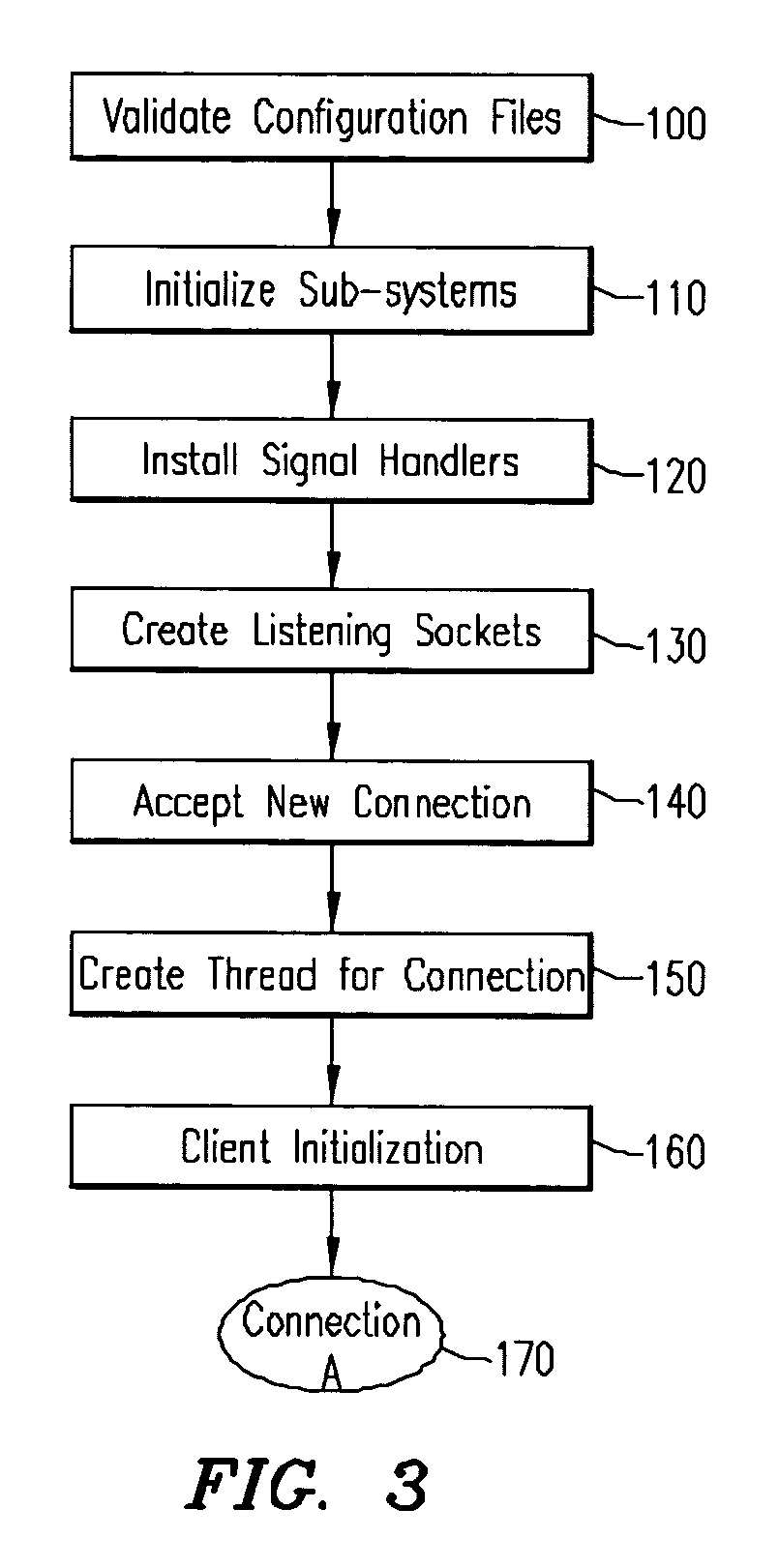
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
174results about How to "Save network bandwidth" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
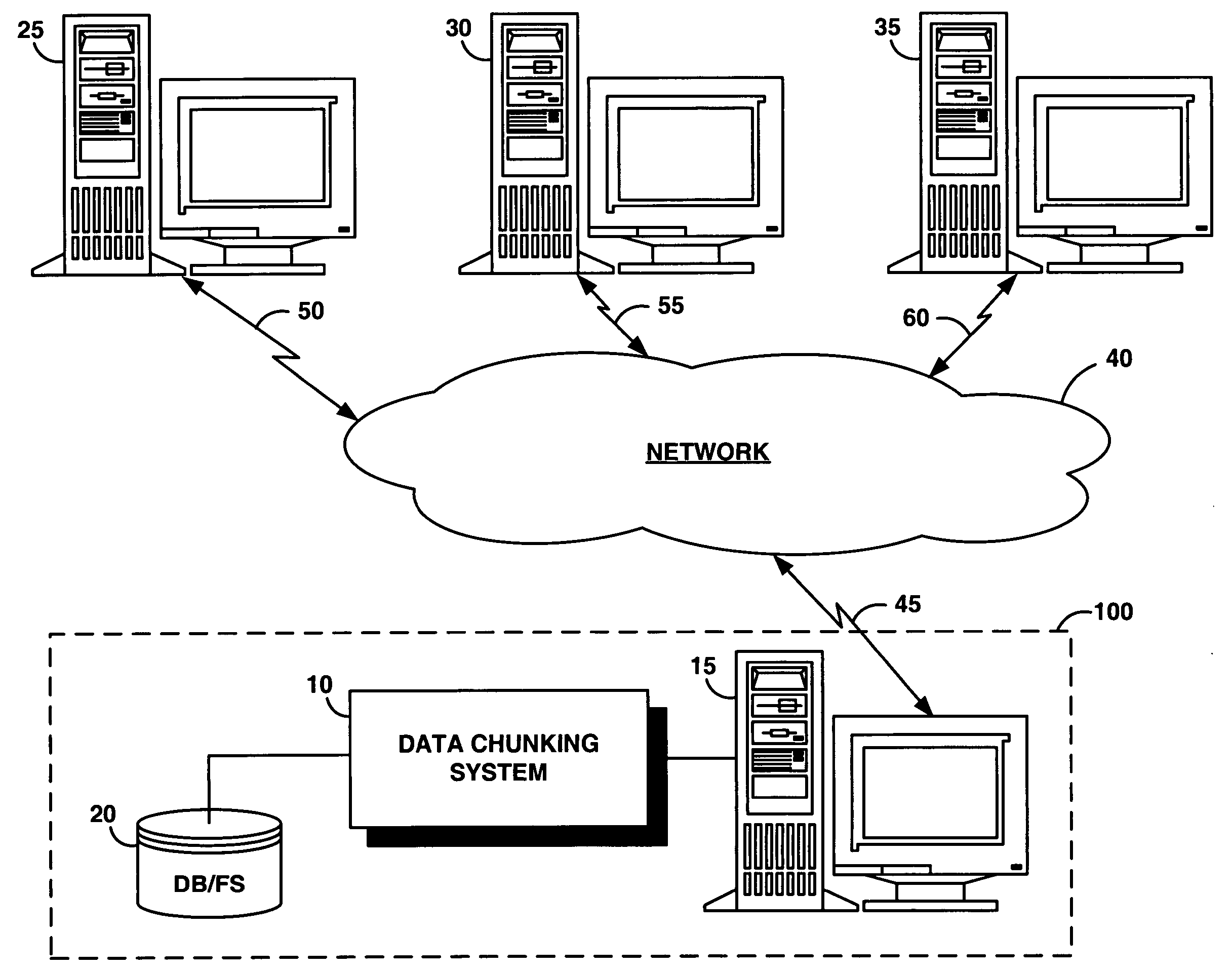
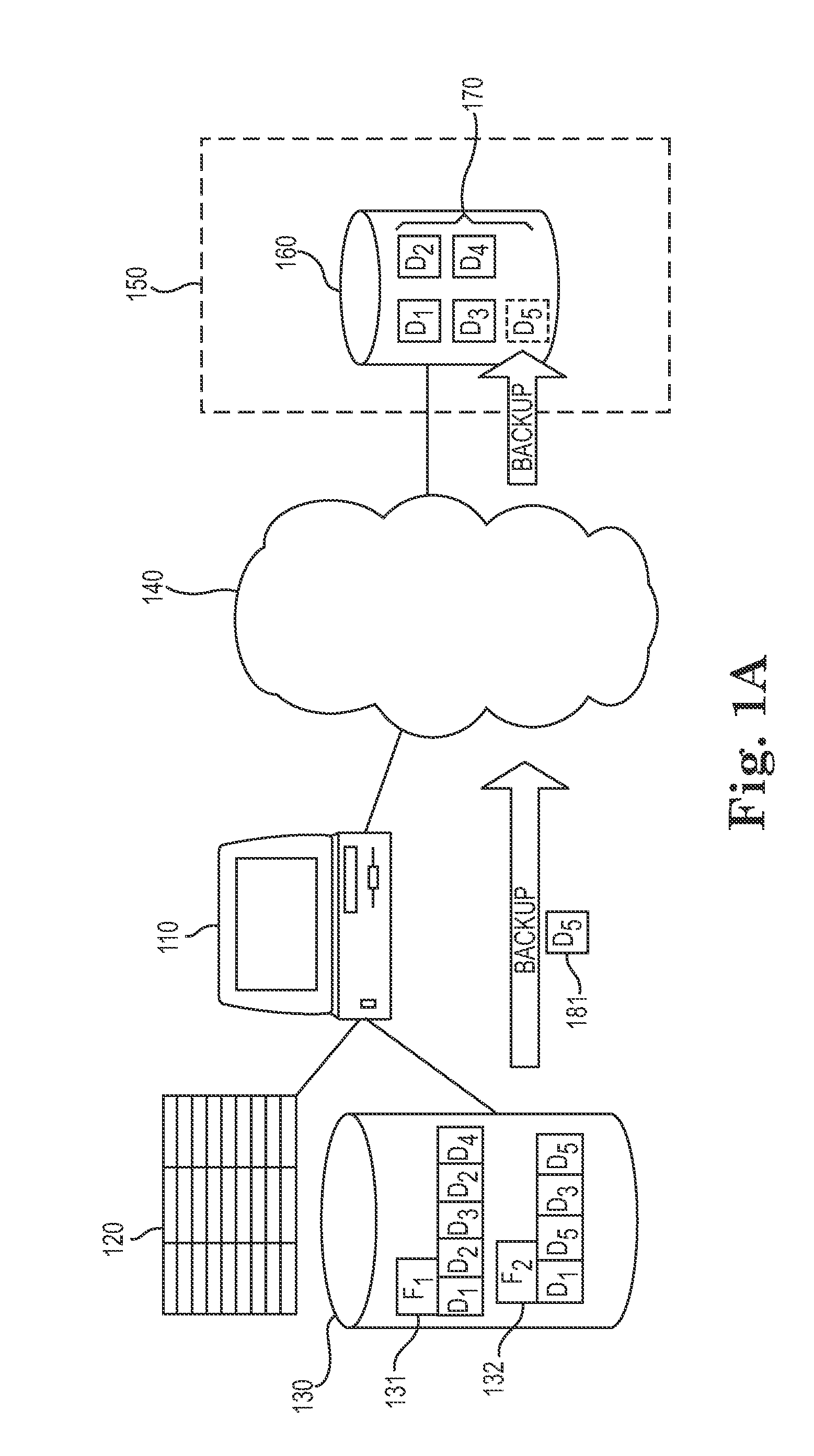
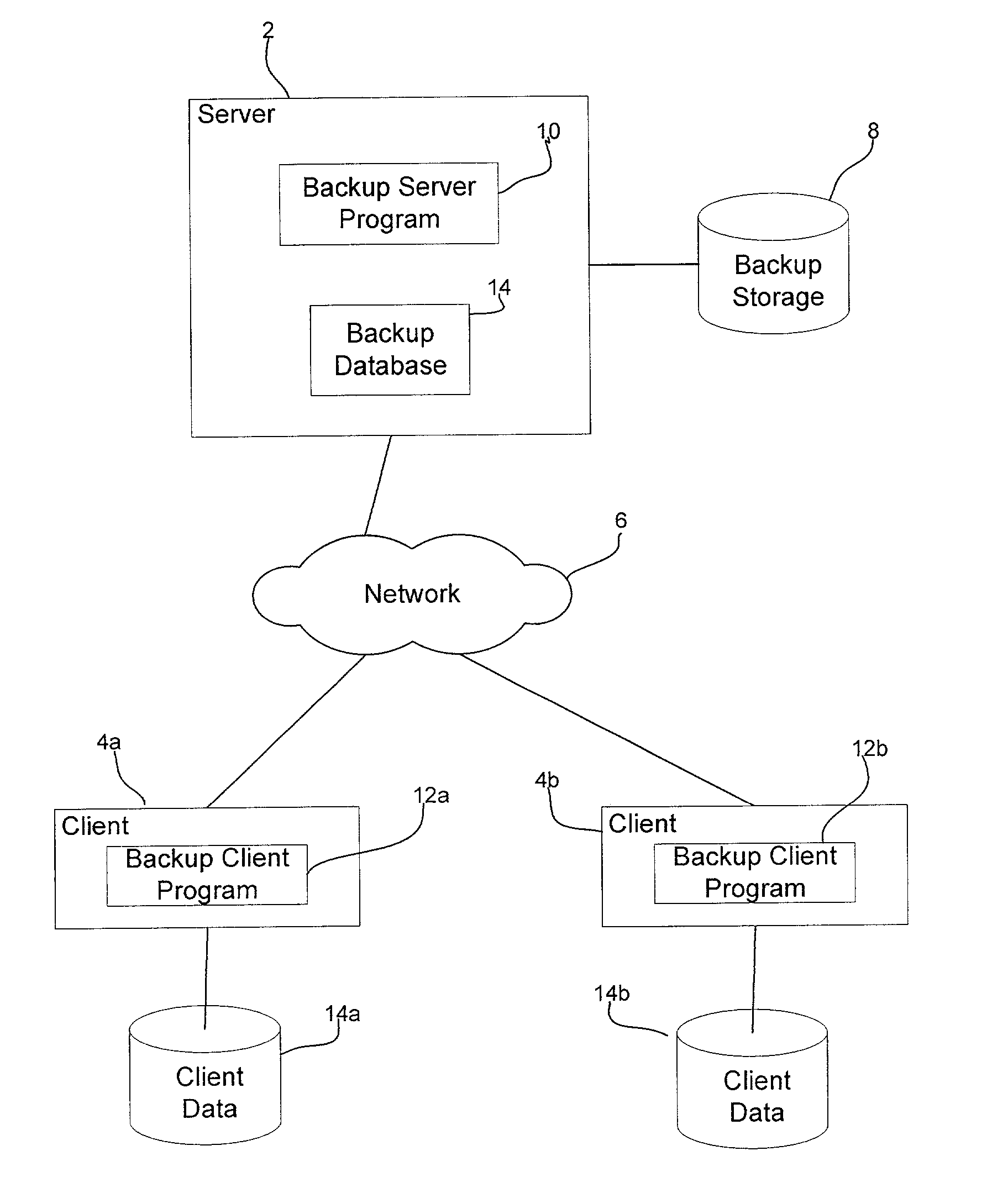
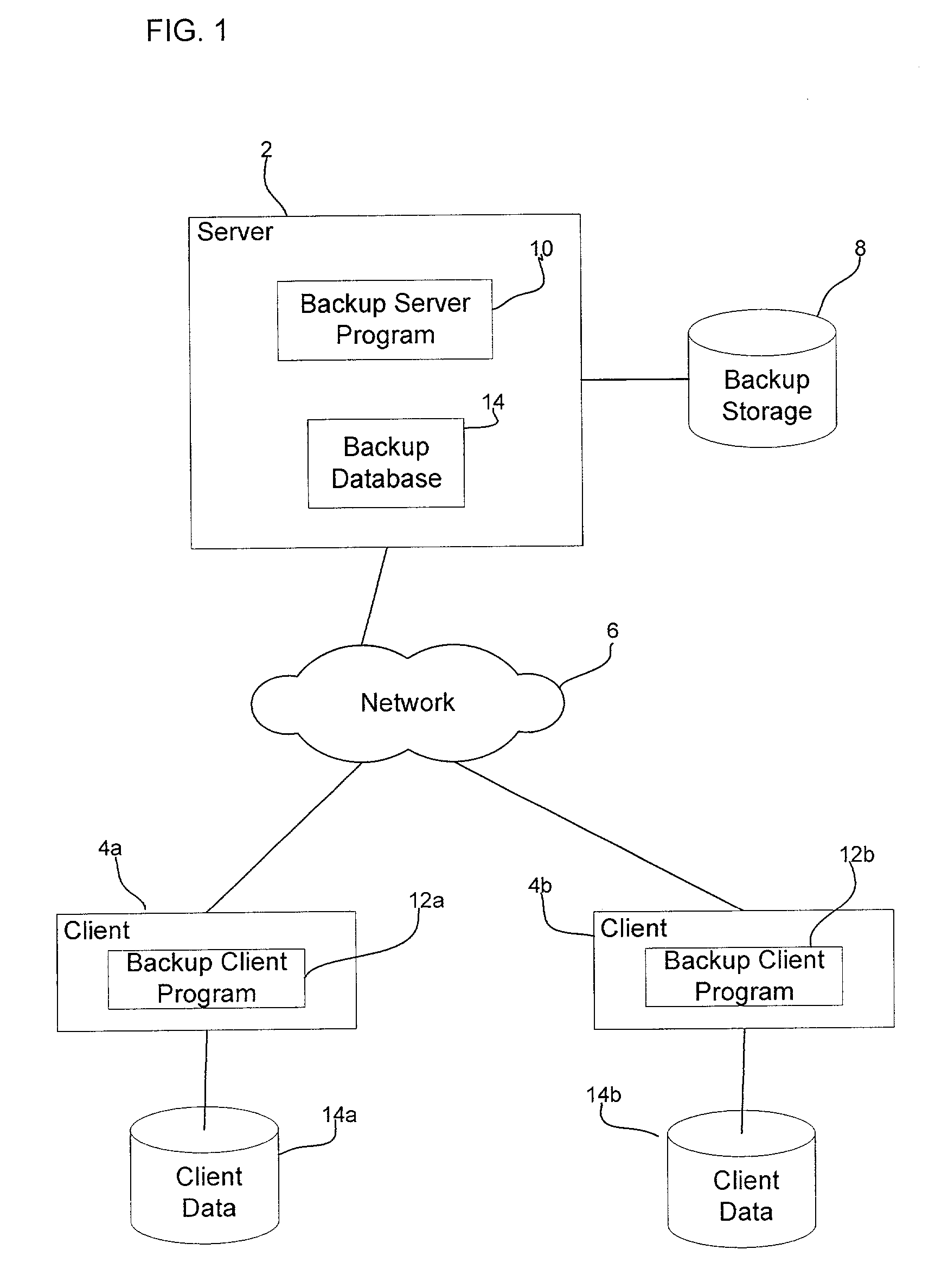
System and method for dividing data into predominantly fixed-sized chunks so that duplicate data chunks may be identified
InactiveUS20050091234A1Maximizes data storage efficiencyLow costData processing applicationsDigital data information retrievalData matchingTheoretical computer science
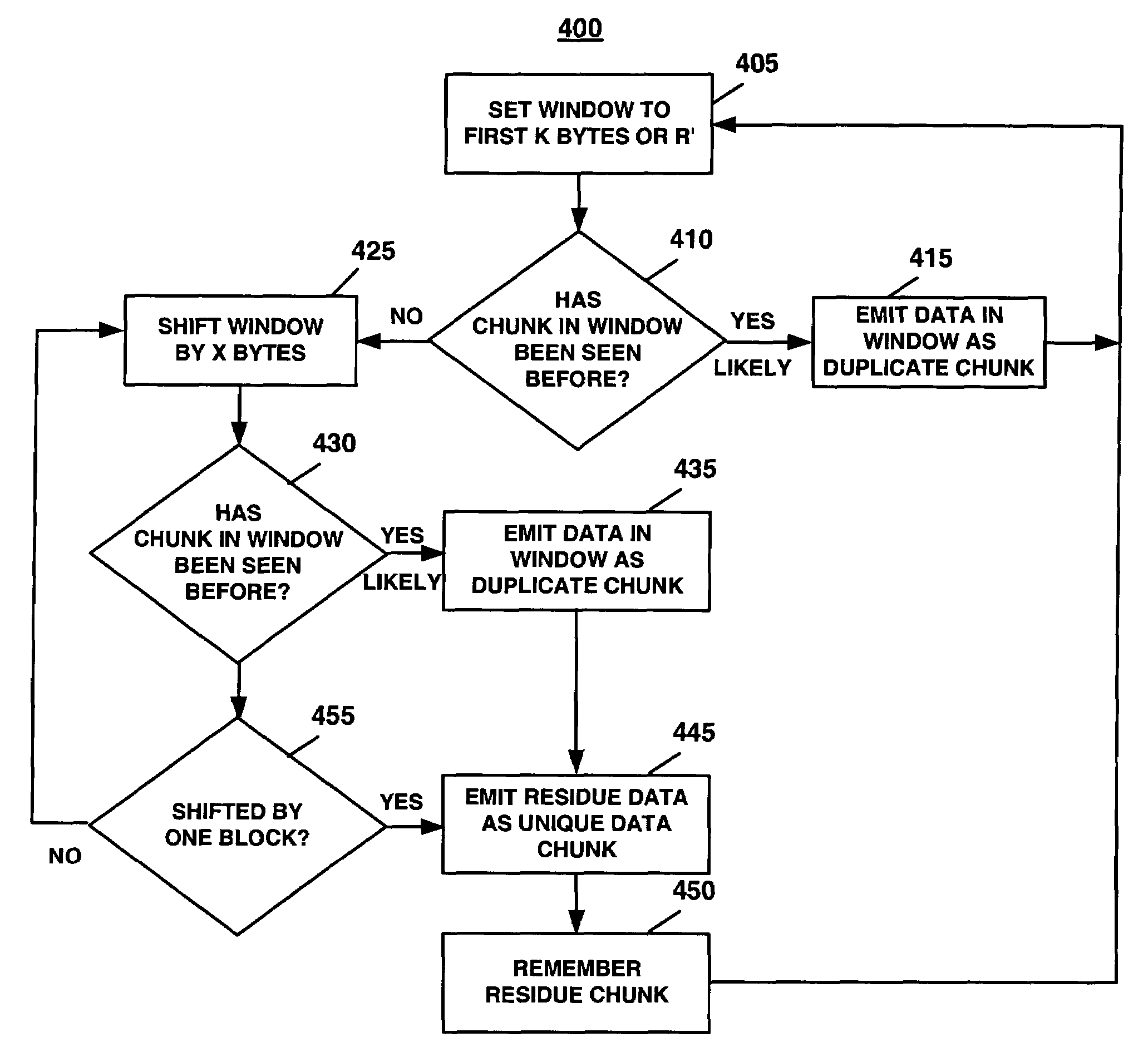
A data chunking system divides data into predominantly fixed-sized chunks such that duplicate data may be identified. The data chunking system may be used to reduce the data storage and save network bandwidth by allowing storage or transmission of primarily unique data chunks. The system may also be used to increase reliability in data storage and network transmission, by allowing an error affecting a data chunk to be repaired with an identified duplicate chunk. The data chunking system chunks data by selecting a chunk of fixed size, then moving a window along the data until a match to existing data is found. As the window moves across the data, unique chunks predominantly of fixed size are formed in the data passed over. Several embodiments provide alternate methods of determining whether a selected chunk matches existing data and methods by which the window is moved through the data. To locate duplicate data, the data chunking system remembers data by computing a mathematical function of a data chunk and inserting the computed value into a hash table.
Owner:IBM CORP
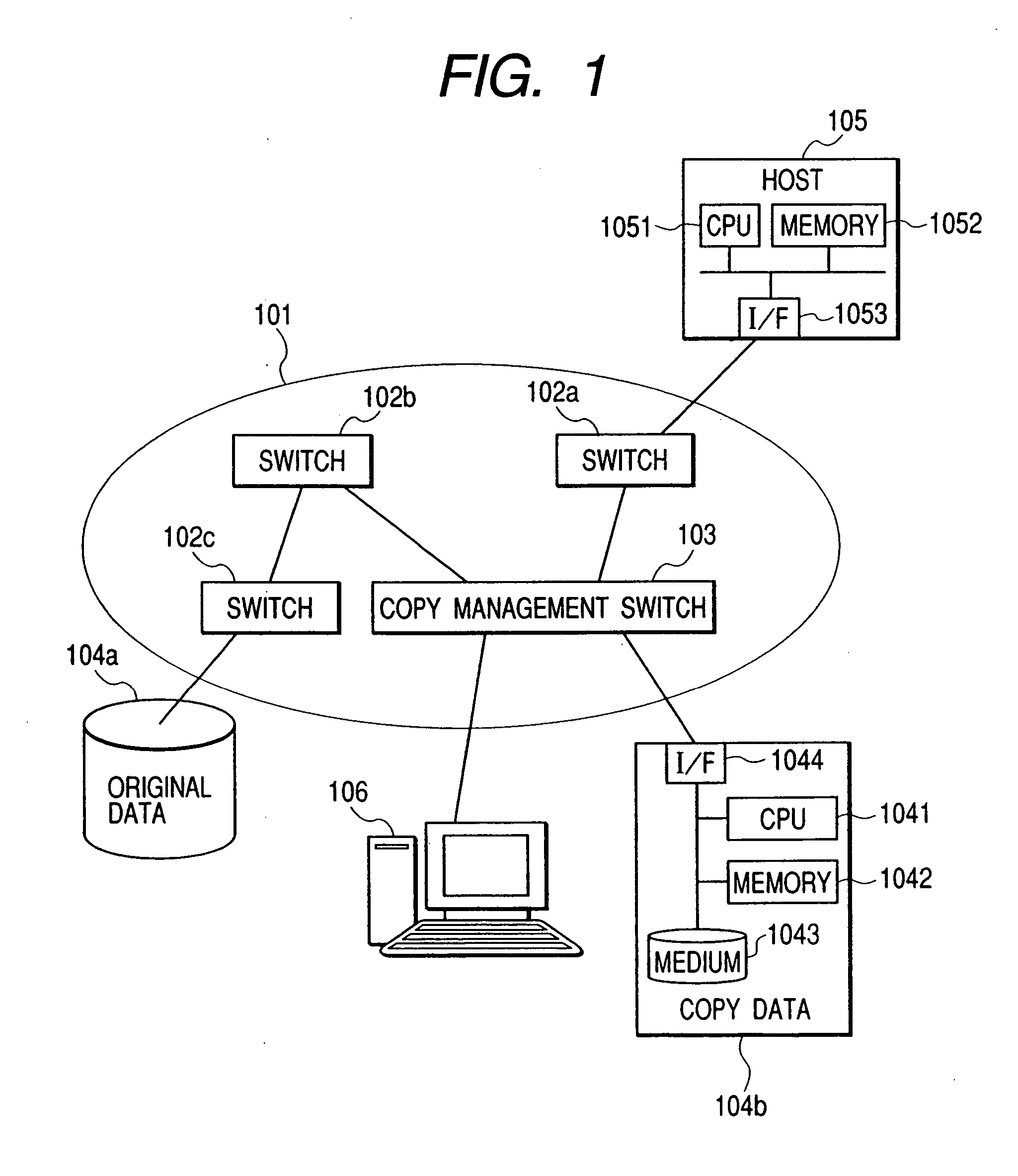
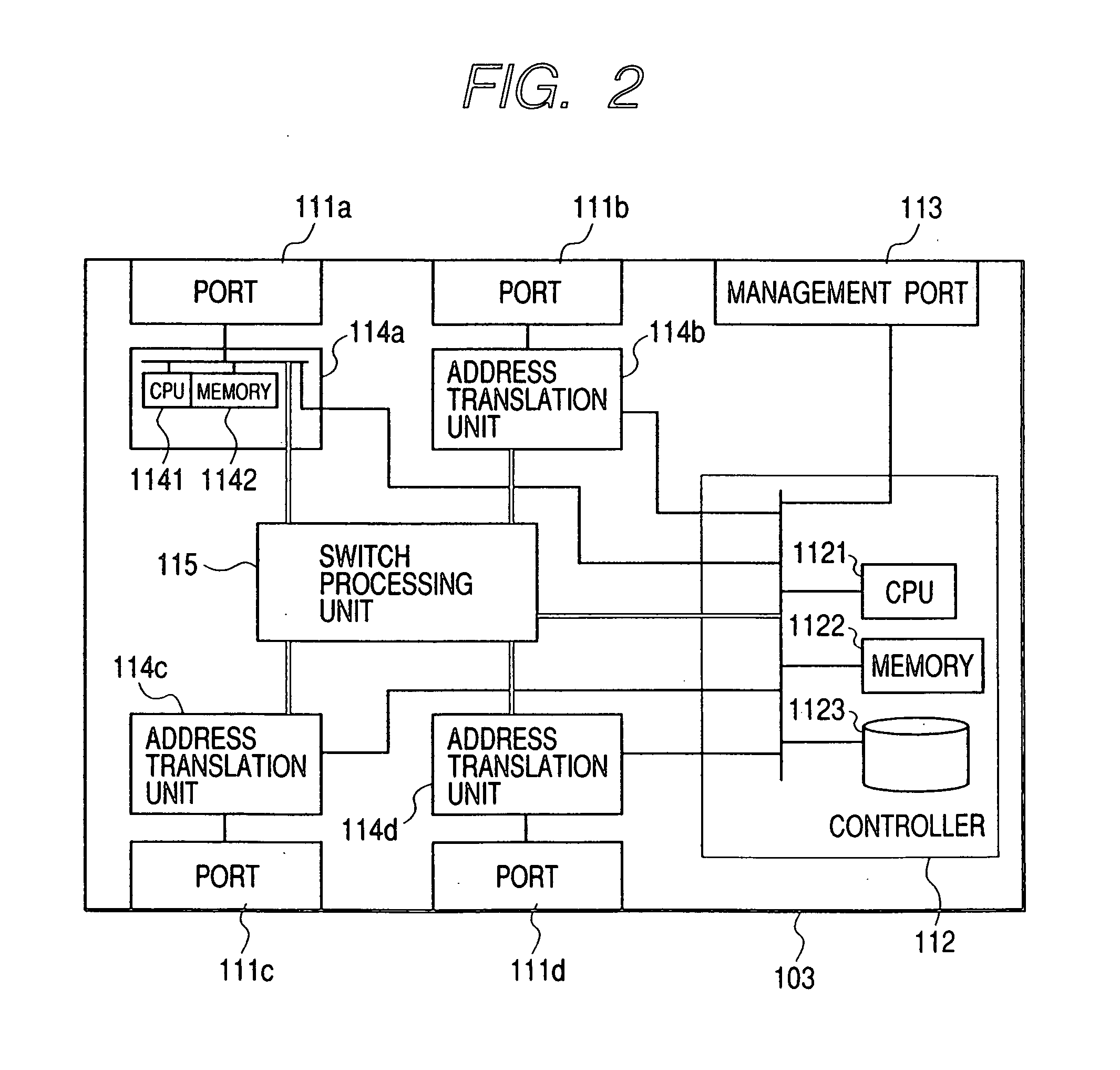
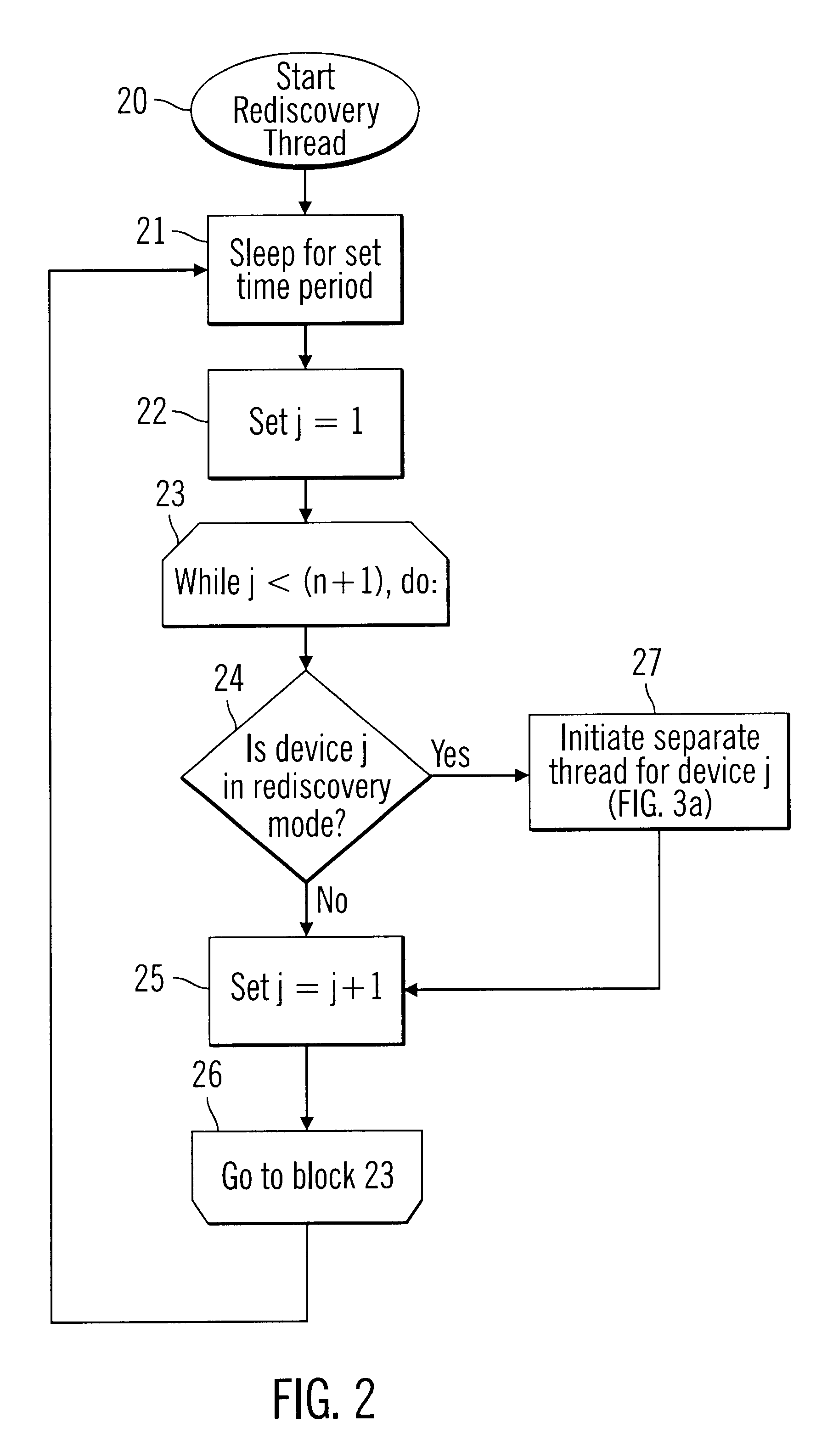
Network system and its switches
InactiveUS20060187908A1SpeedSave network bandwidthMultiplex system selection arrangementsDigital data information retrievalNetwork connectionData transmission
Owner:HITACHI LTD
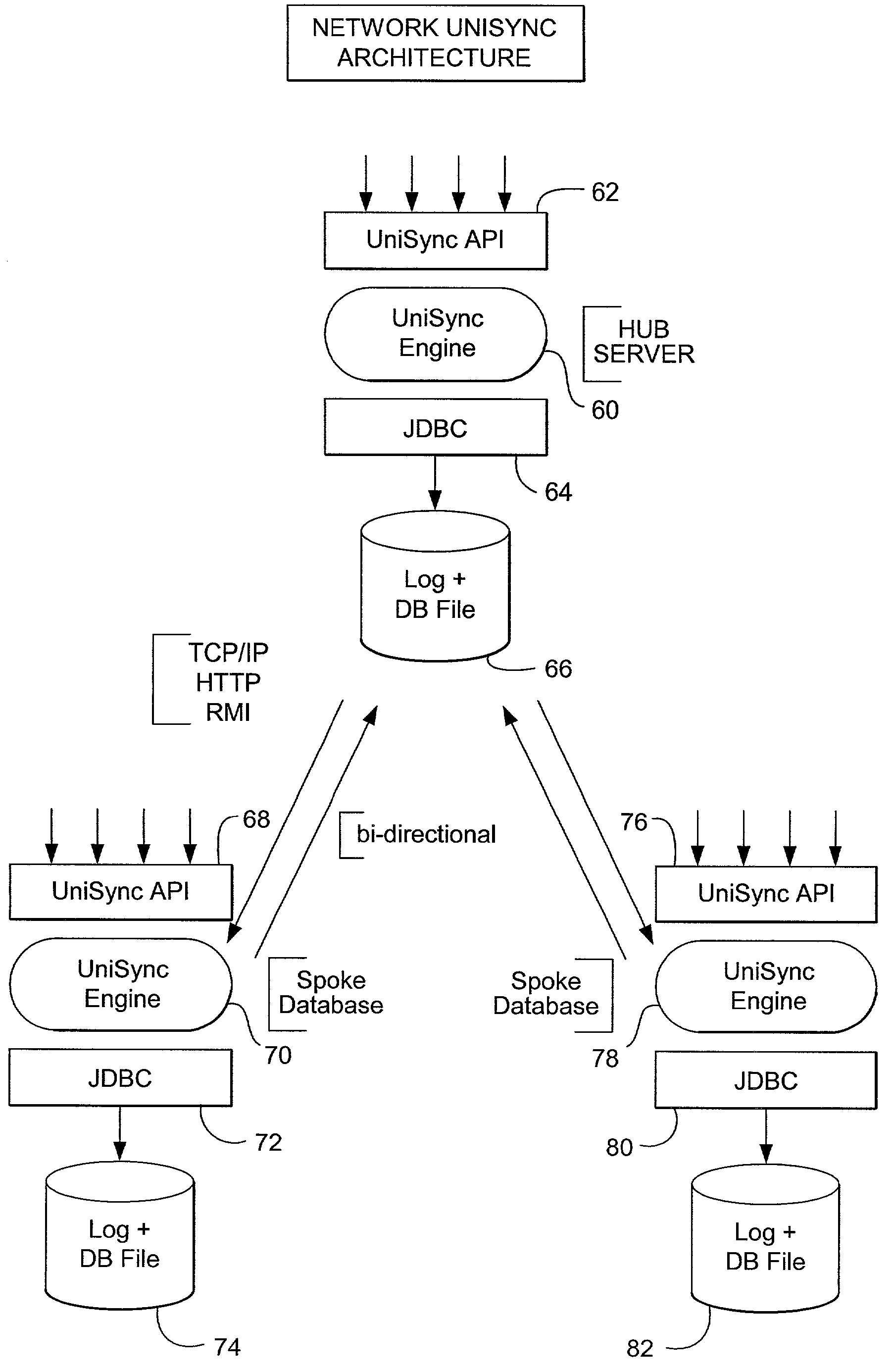
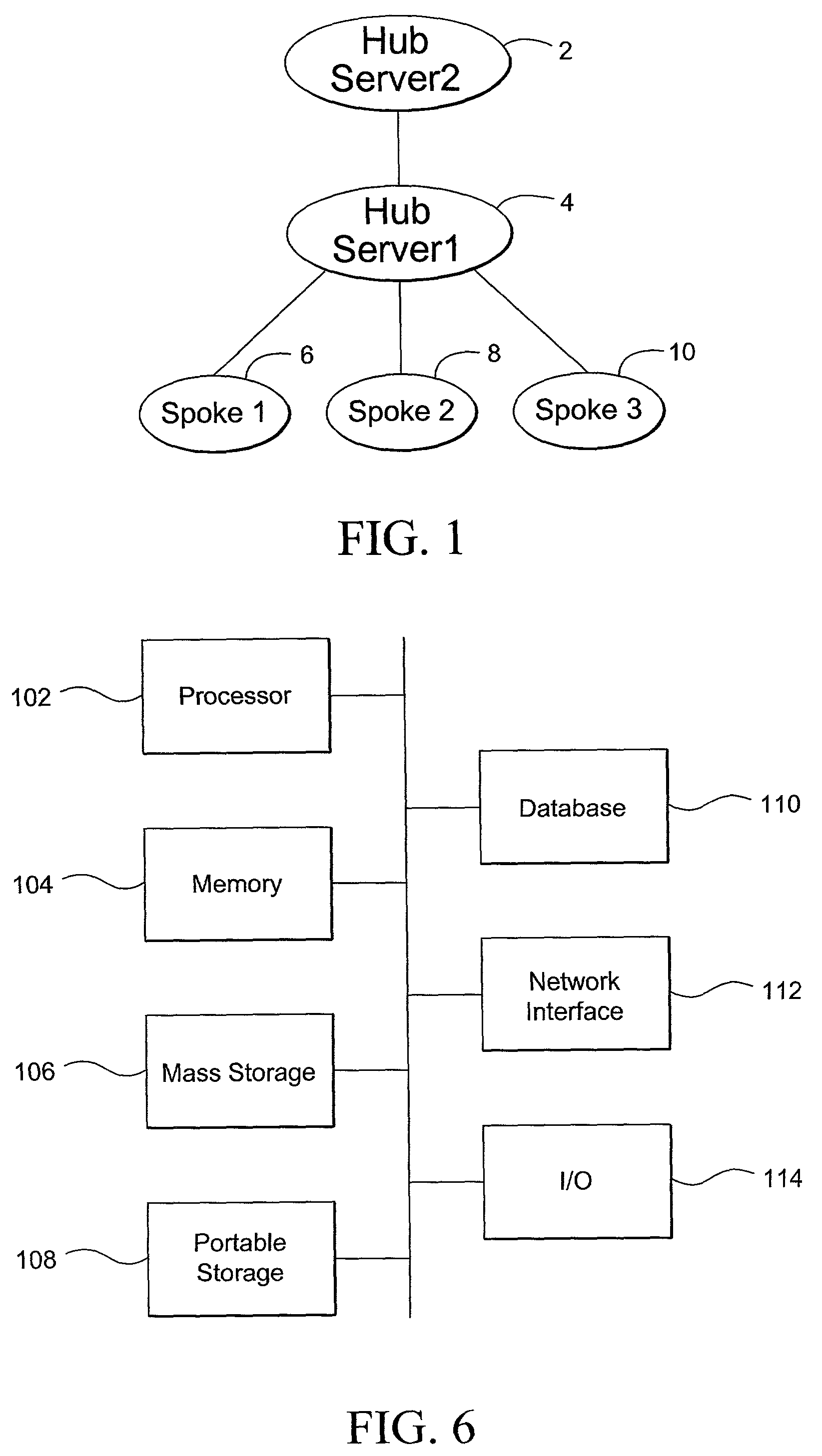
Universal synchronization
InactiveUS20050055382A1Easy to operateGood serviceDatabase distribution/replicationSpecial data processing applicationsOperational systemApplication programming interface
A technology for bi-directional synchronization between at least two entities. Examples of entities include databases, operating system files, applications, email, etc. The two entities can communicate using any appropriate protocol and the two entities can be provided by different vendors using different designs. The synchronization technology includes an Application Programming Interface that enables developers to provide synchronization functionality as an integral part of their distributed applications. Additionally, conflict resolution during synchronization can be customized to suit the particular application. The synchronization technology allows for the management of data anywhere and enables developers to distribute application data and code across multiple tiered environments to applications and users located anywhere.
Owner:POINTBASE
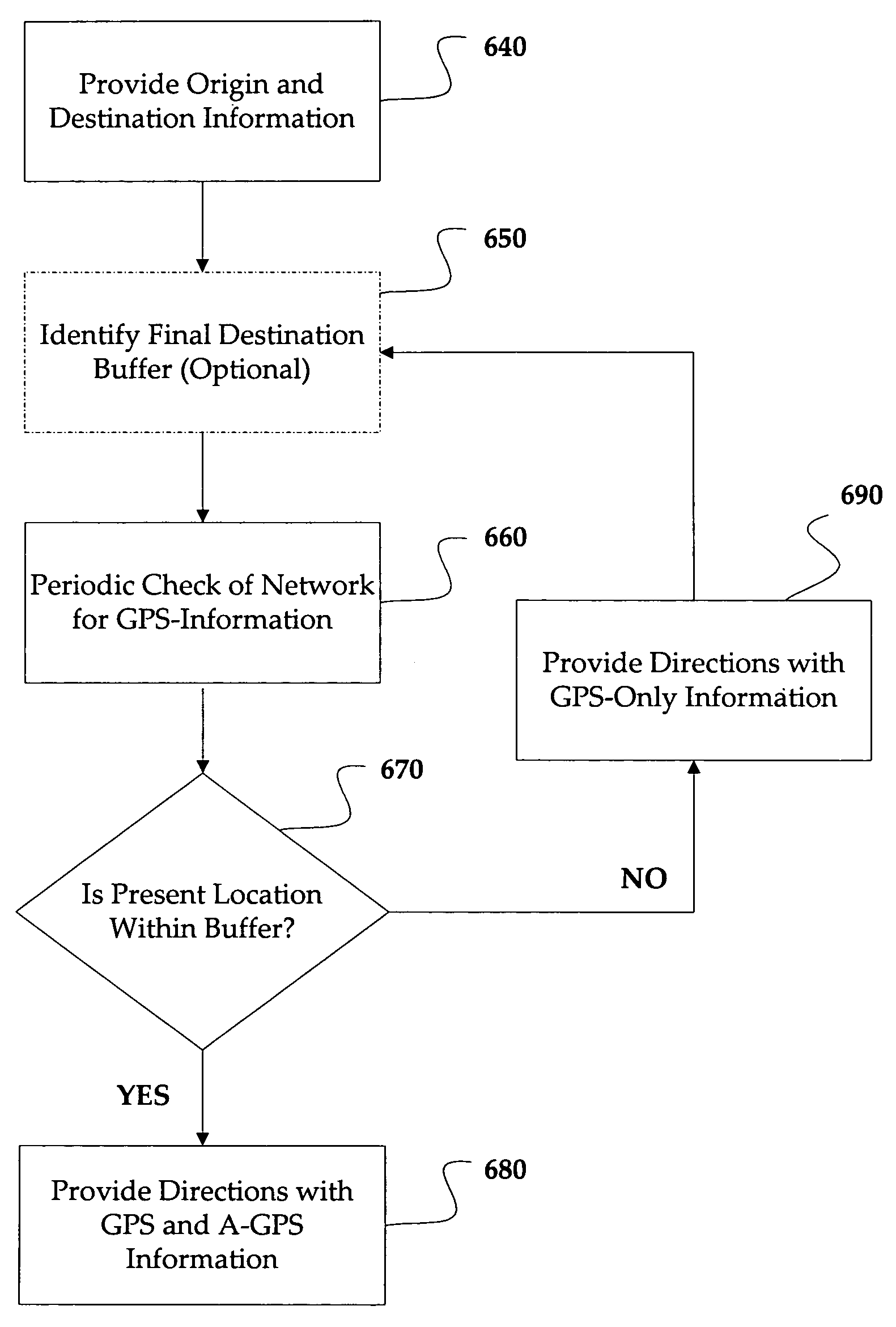
Intelligent utilization of resources in mobile devices
InactiveUS7026984B1Save battery powerSave network bandwidthPower managementPosition fixationComputer moduleBiological activation
A programmable intelligent activation module to intelligently allow access to GPS resources is provided. In accordance with pre-programmed settings, an intelligent activation module will control the frequency by which a GPS module is allowed to access a GPS or GSM network in order to acquire location information of a mobile device equipped with GPS equipment. By controlling access to a GPS or GSM network, network resources such as bandwidth are conserved unless actually needed as is determined by the intelligent activation module. Similarly, battery resources for the mobile device are also conserved in that unnecessary activation of the GPS module is prevented until such activation is actually needed. The intelligent activation module can be programmed with a variety of settings including speed, map deltas, final destination information, or settings as pre-determined by a user of the mobile device.
Owner:CINGULAR WIRELESS II LLC
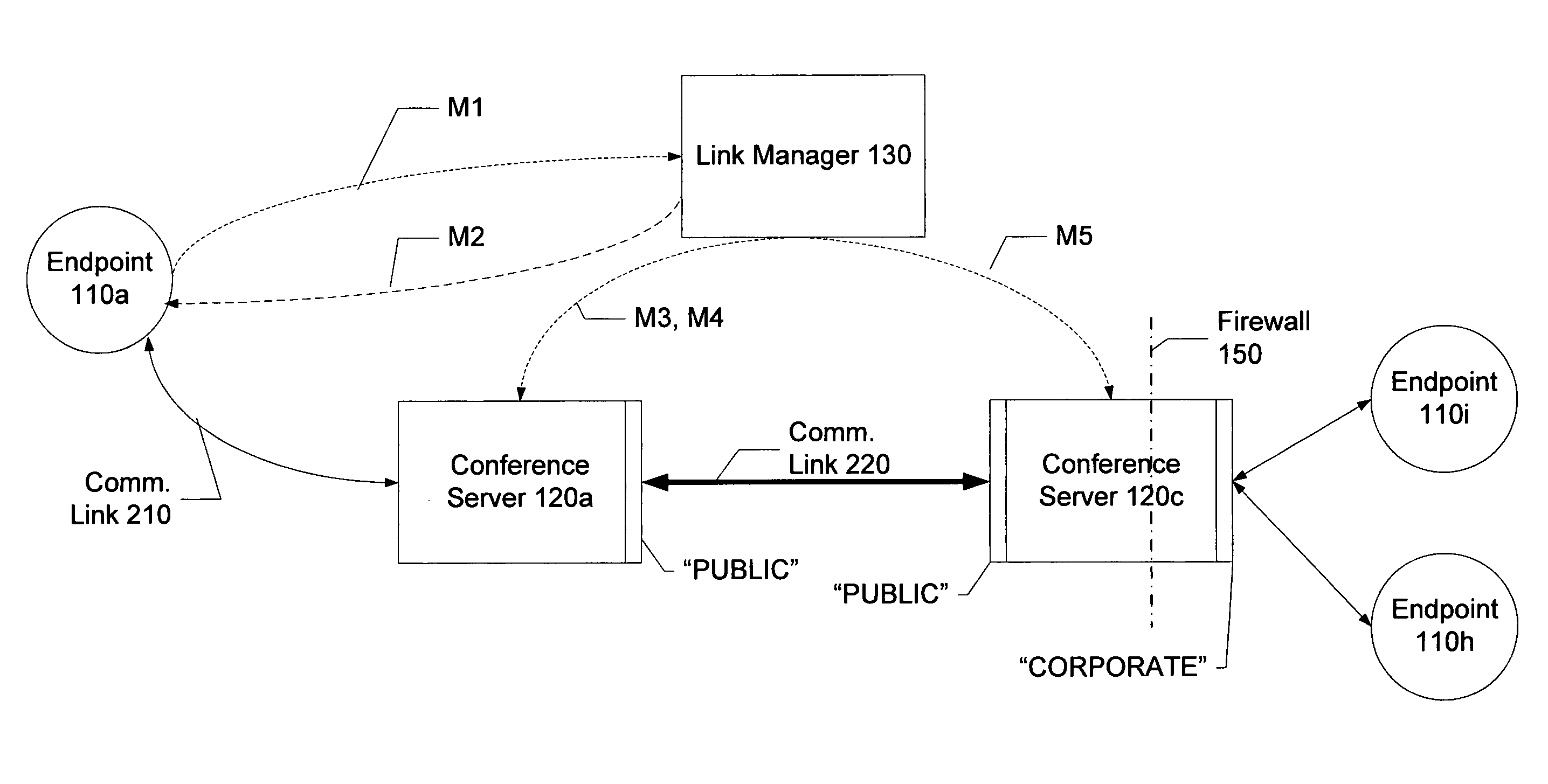
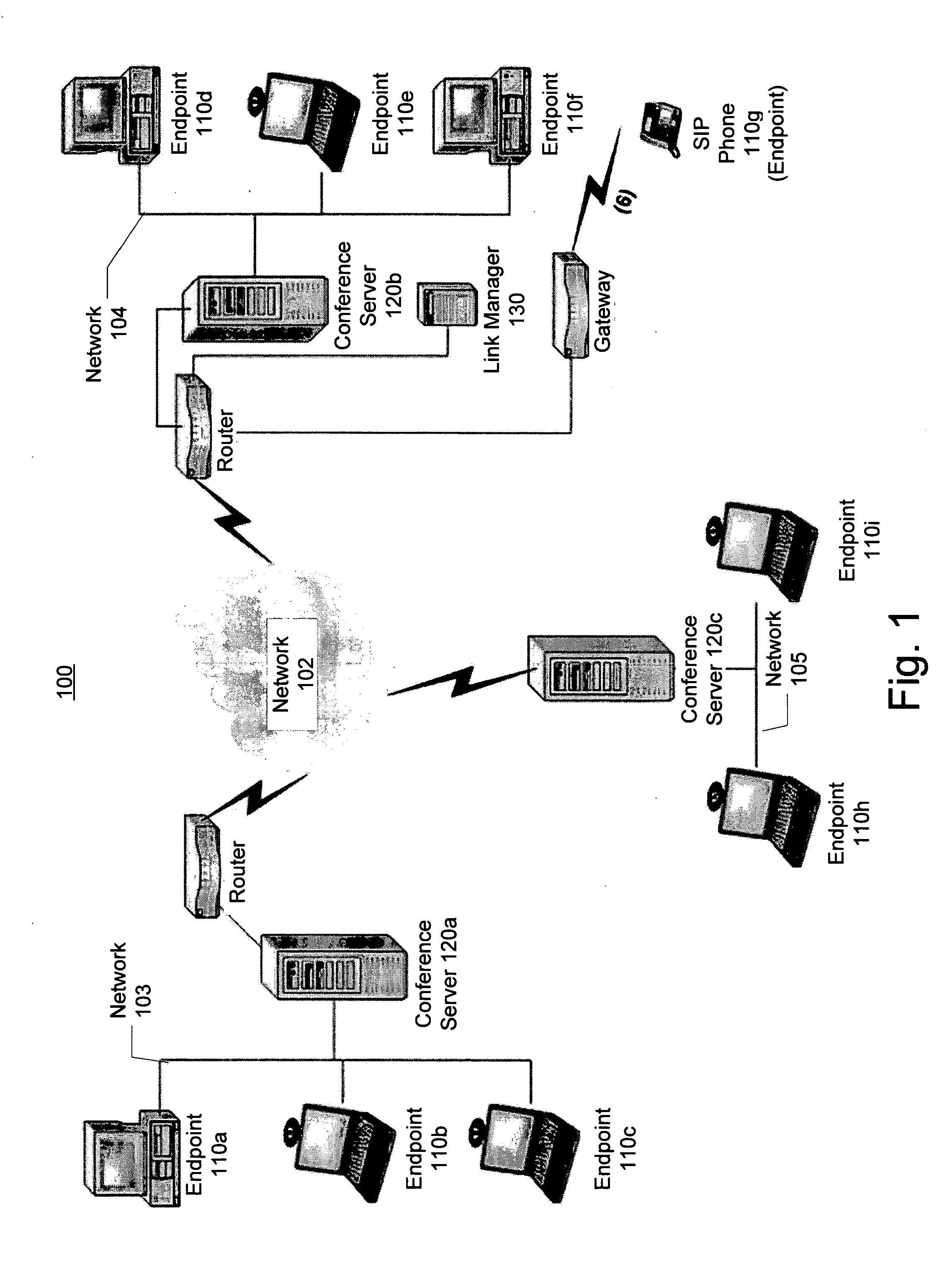
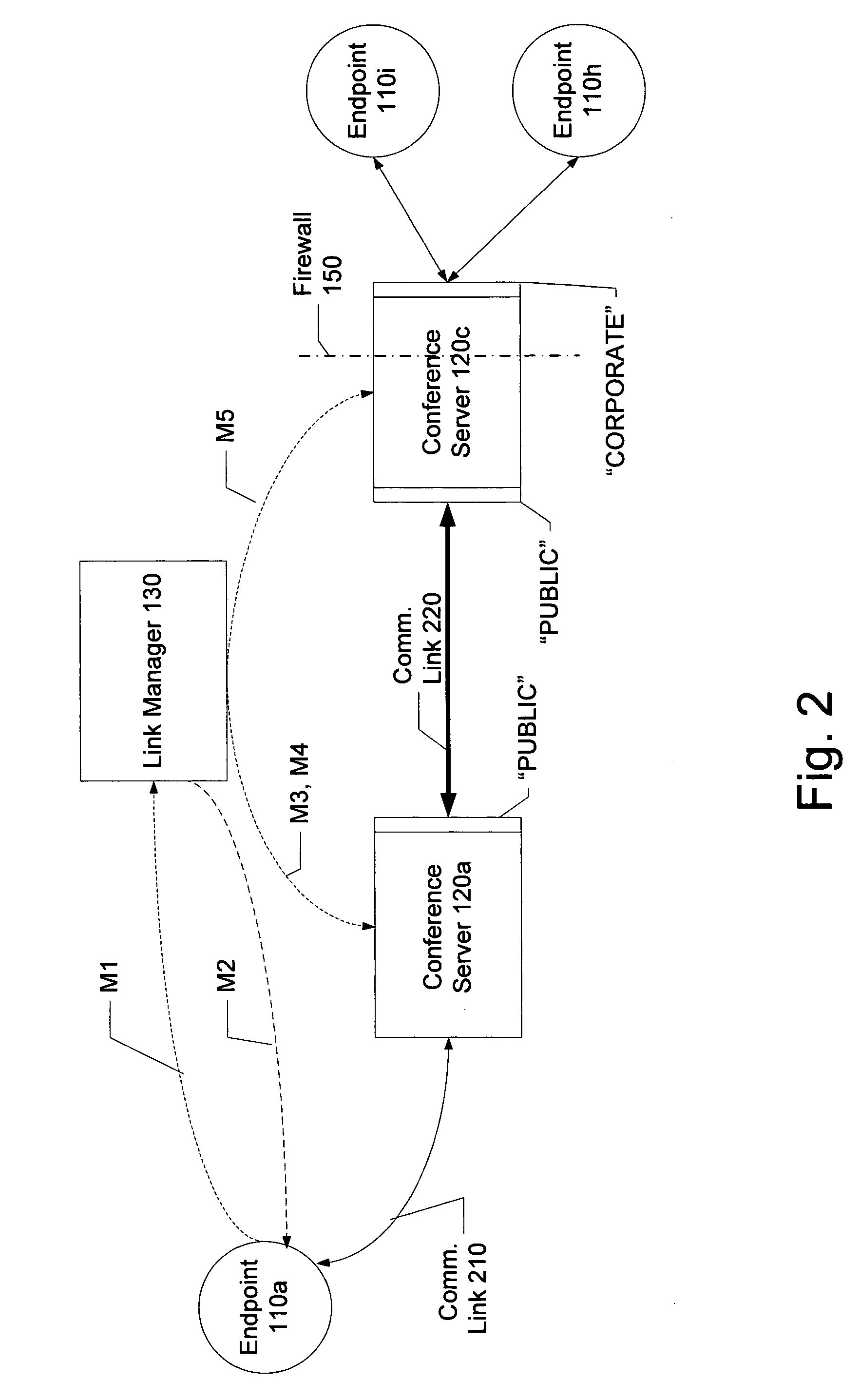
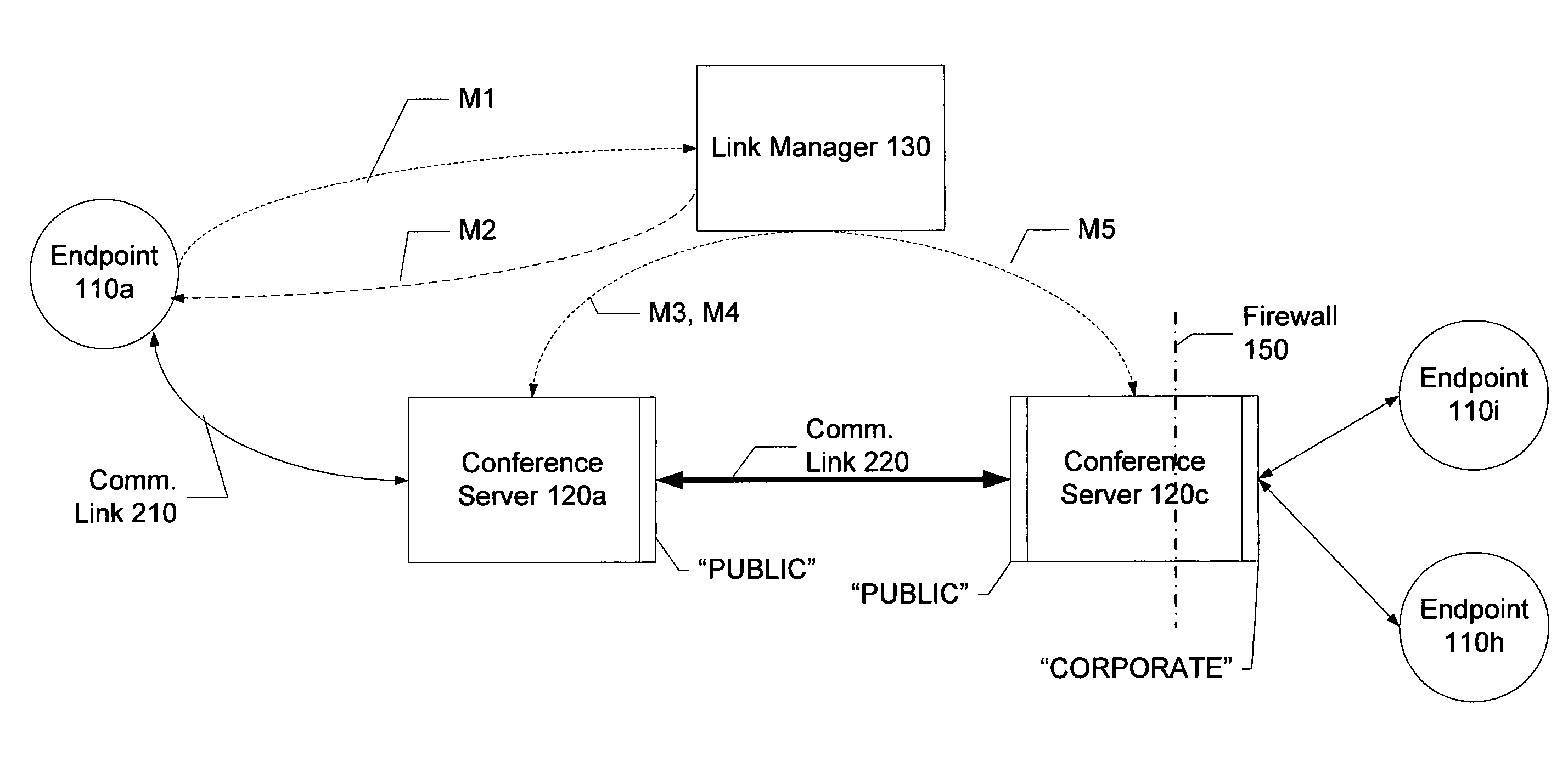
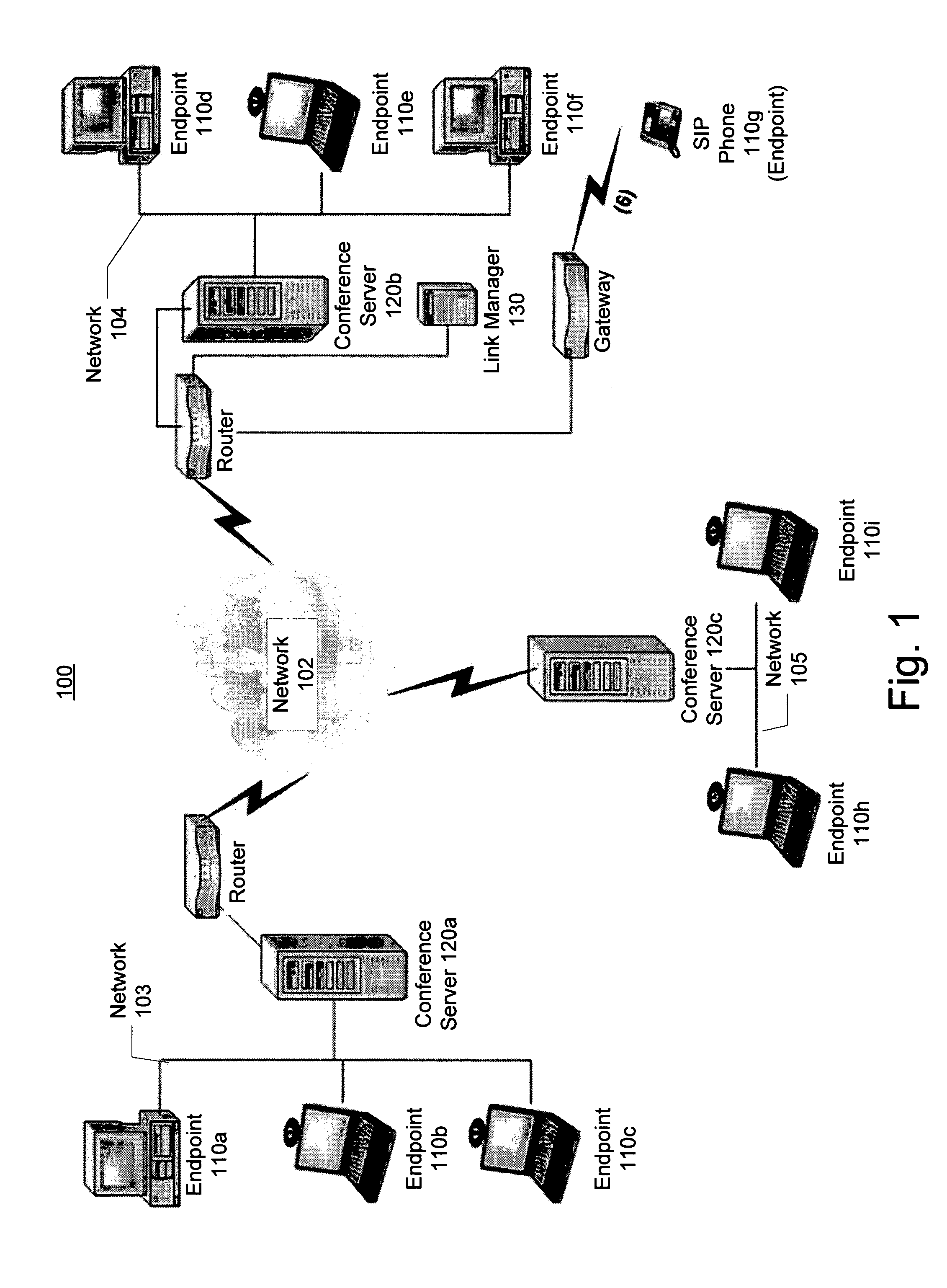
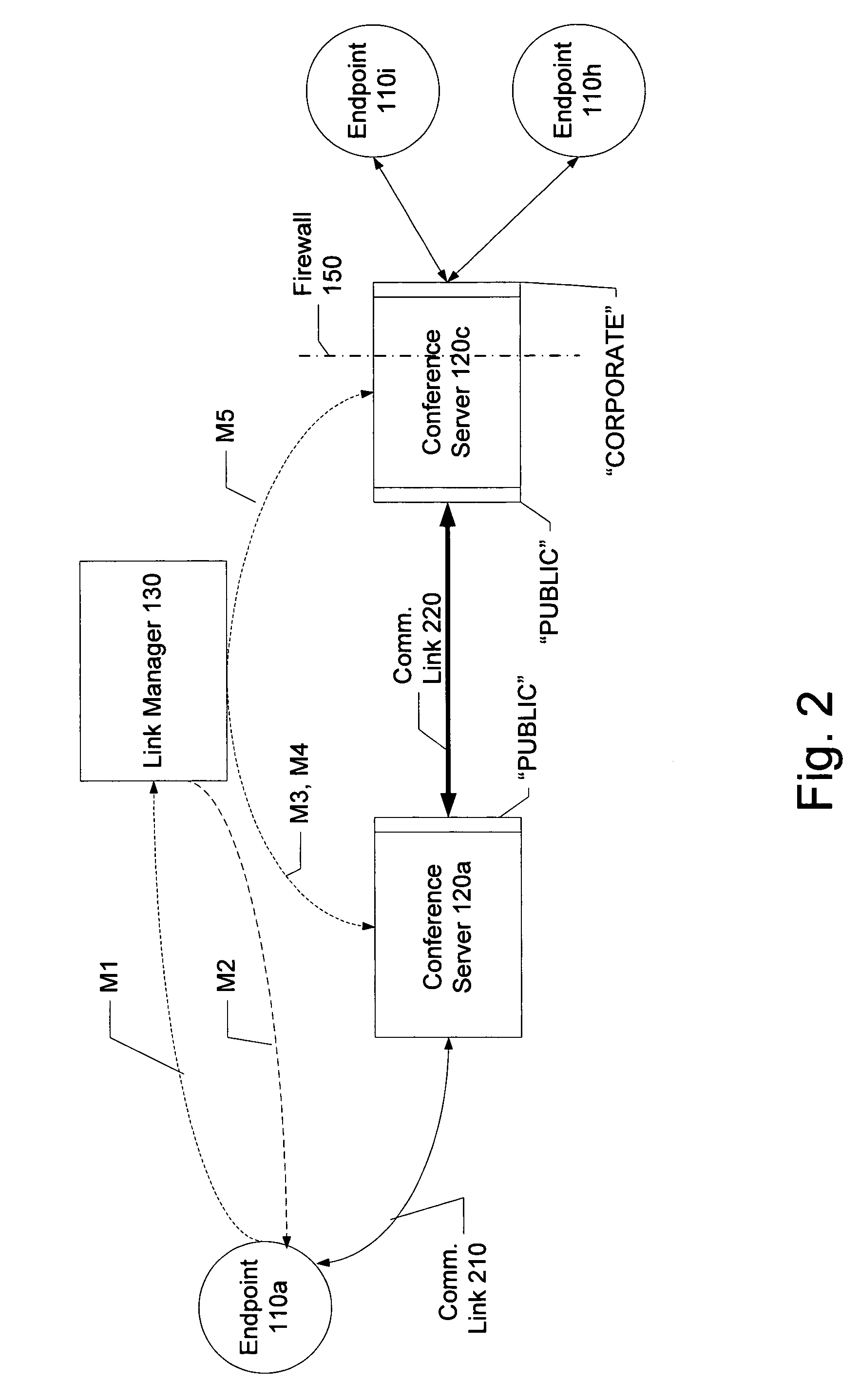
Distributed multipoint conferencing with automatic endpoint address detection and dynamic endpoint-server allocation
ActiveUS20050108328A1Save network bandwidthMultiplex system selection arrangementsSpecial service provision for substationIp addressServer allocation
An embodiment of the invention is a multipoint conferencing system having the ability to dynamically assign an endpoint to a “closest” one of multiple conference servers is disclosed. In one embodiment, when an endpoint first connects to the conferencing system, its Endpoint ID (e.g., IP address, E164 address) is determined. Based on the Endpoint ID, the conferencing system selects the most appropriate ones of the conference servers to act as the endpoint's “local” conference server. That is, the endpoint will transmit and receive conference data from other endpoints via the selected conference server. If no other endpoints across the network happen to be viewing a particular endpoint's video stream, the stream is not provided to the network, thus conserving network bandwidth. An embodiment further creates appropriate linking between conference servers automatically, manages conference server topology and determines link type (e.g., Unicast vs. Multicast linking) automatically.
Owner:AVAYA INC +2
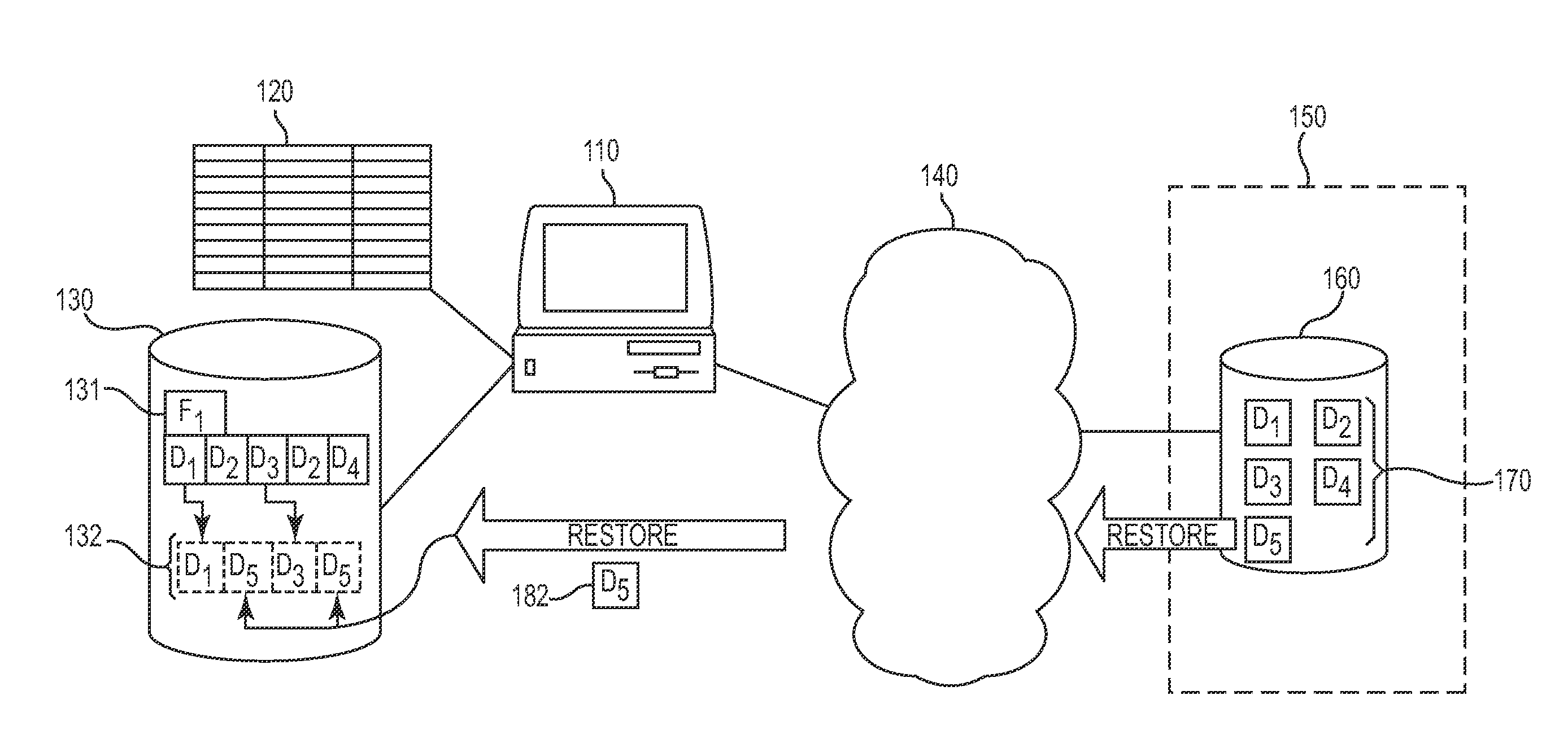
Approach for optimizing restores of deduplicated data
InactiveUS20110218969A1Reduce the amount of processingImprove efficiencyError detection/correctionDigital data processing detailsData fileClient data
Various techniques for improving the performance of restoring deduplicated data files from a server to a client within a storage management system are disclosed. In one embodiment, a chunk index is maintained on the client that tracks the chunks remaining on the client for each data file that is stored to and restored from the storage server. When a specific file is selected for restore from the storage server to the client, the client determines if any local copies of this specific file's chunks are stored in files already existing on the client data store. The file is then reconstructed from a combination of these local copies of the file chunks and chunks retrieved from the storage server. Therefore, only chunks that are not stored or are inaccessible to the client are retrieved from the server, reducing server-side processing requirements and the bandwidth required for data restore operations.
Owner:IBM CORP
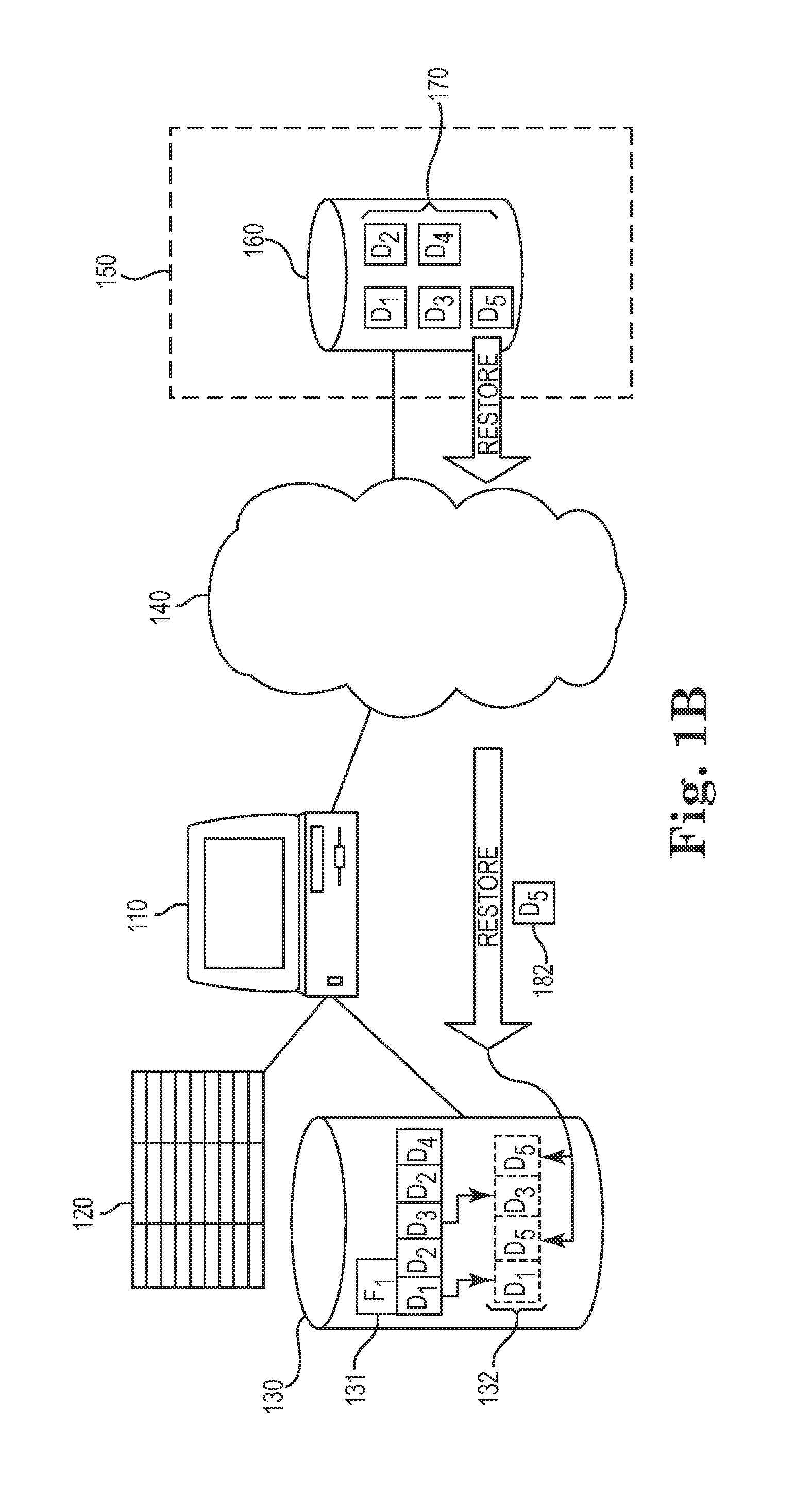
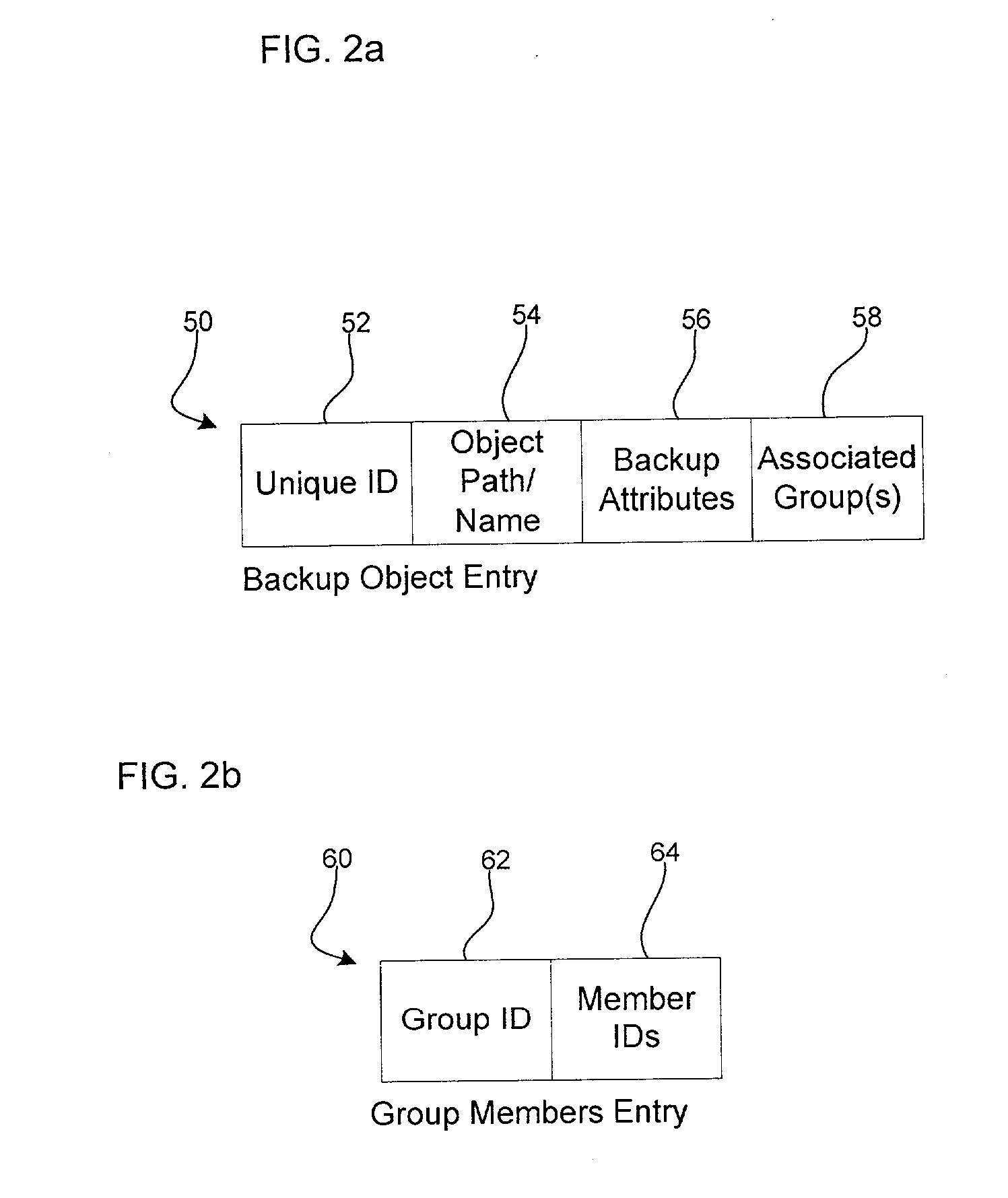
Method, system, and program for grouping objects
InactiveUS20030196052A1Avoids needSave network bandwidthData processing applicationsMemory loss protectionObject storeComputer science
Provided are a system, method, and program for grouping backup objects stored in backup storage. A backup group is created and a plurality of backup objects are added as members of the backup group in separate backup transactions. The backup objects added to the backup group are stored to backup storage.
Owner:IBM CORP
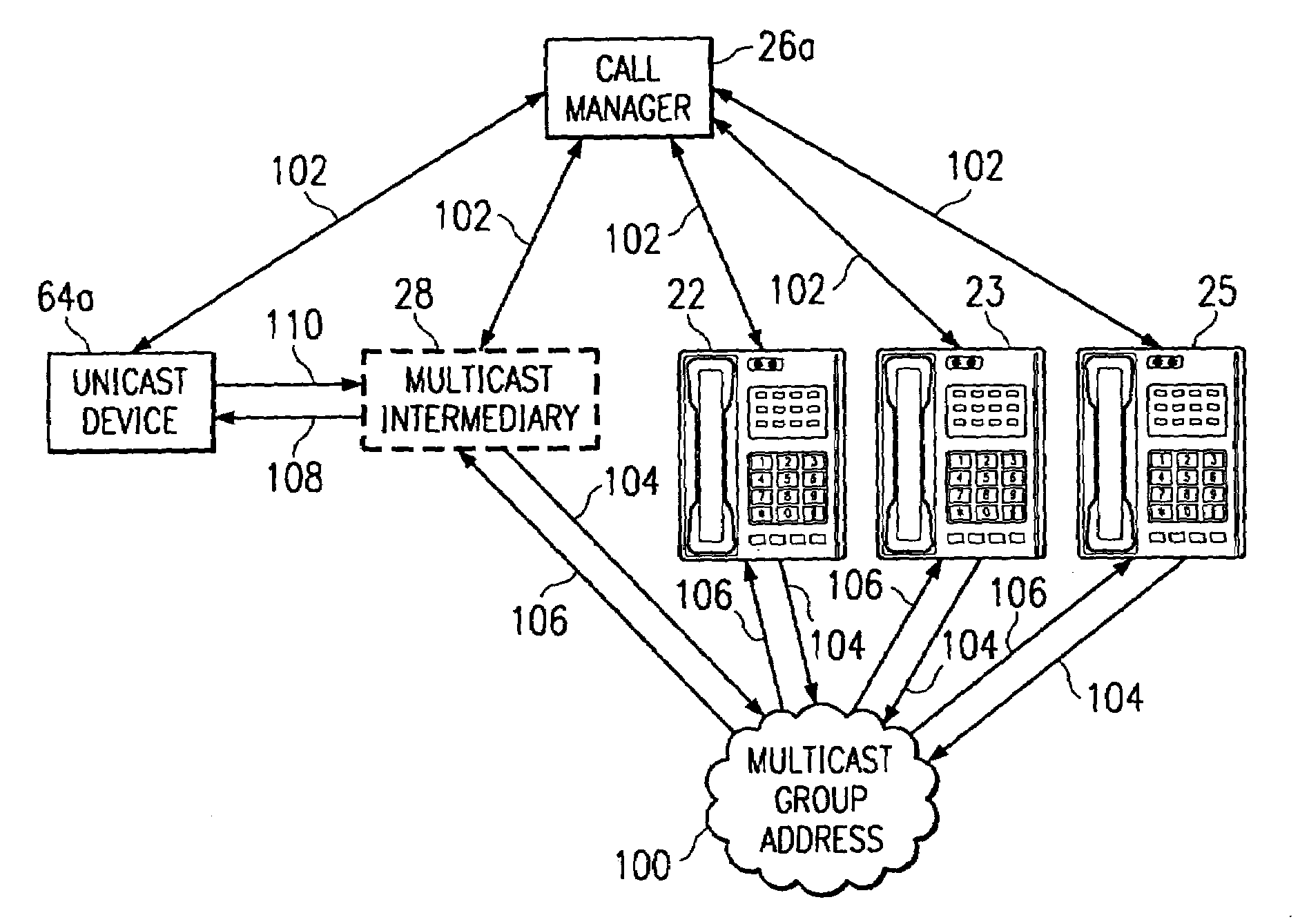
System and method for enabling multicast telecommunications
InactiveUS7079495B1Eliminates and reduces disadvantage and problemEffectively participate in a telecommunication sessionSpecial service provision for substationInterconnection arrangementsMulticast addressComputer science
A communication network is provided that includes a unicast telephony device, and a plurality of multicast telephony devices operable to receive multicast media streaming transmitted to a multicast group address. The communication network further includes a multicast intermediary operable to receive multicast media streaming sent to the multicast group address. The multicast intermediary is further operable to communicate the media streaming to the unicast telephony device to enable the unicast telephony device to participate in the multicast communication with the multicast telephony devices.
Owner:CISCO TECH INC
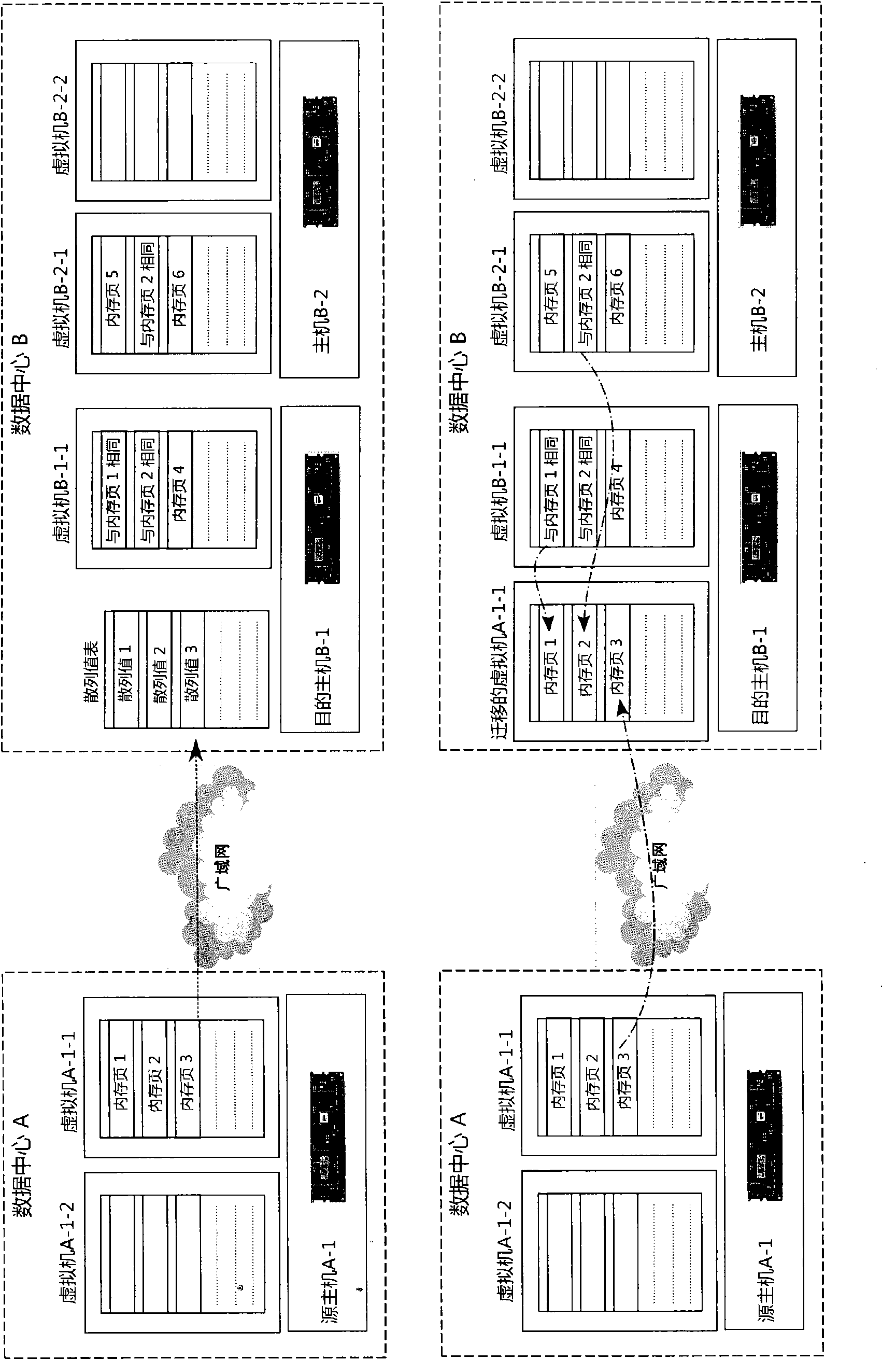
Method and system for dynamic migration of WAN virtual machines
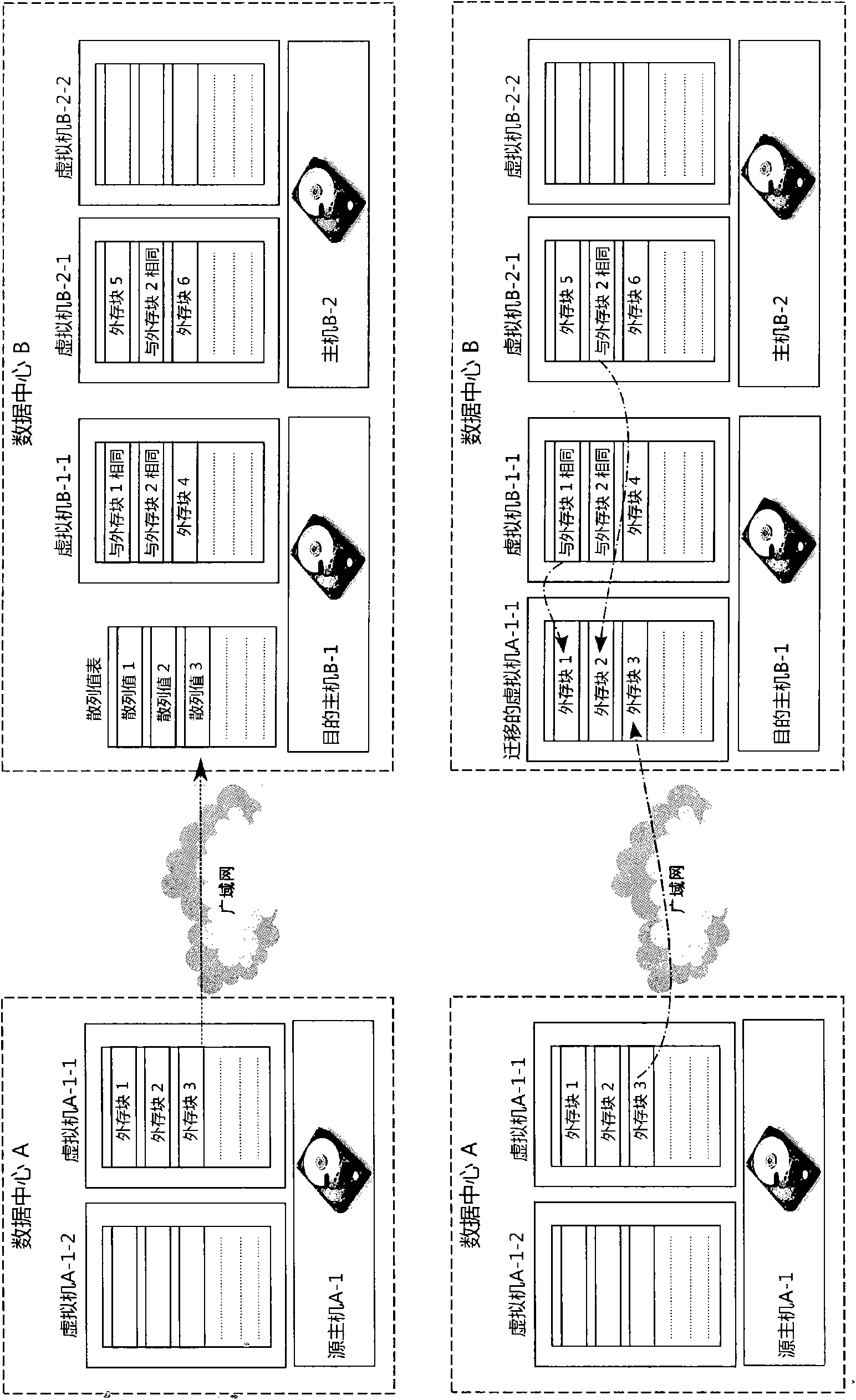
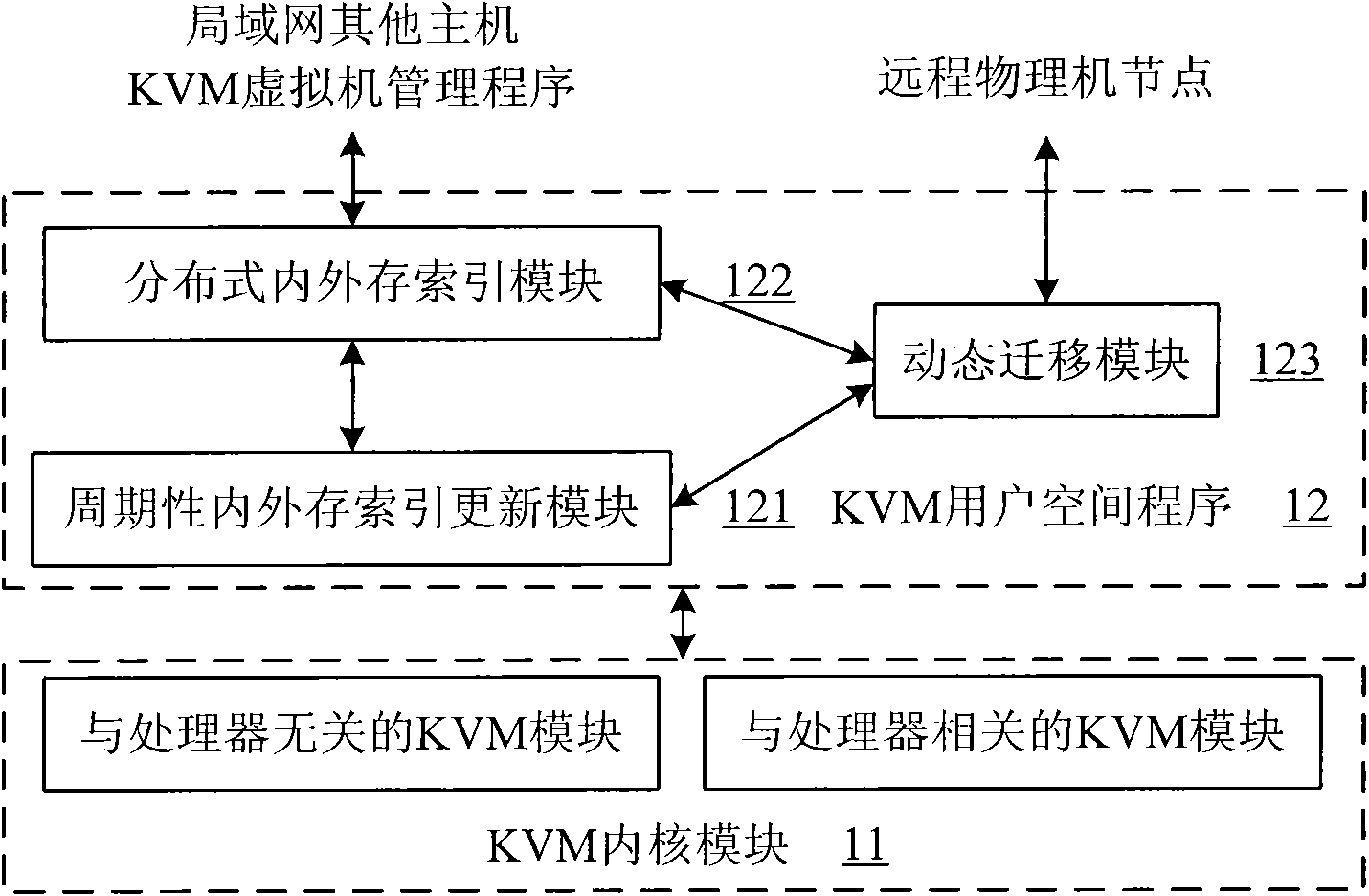
ActiveCN102455942AImprove migration efficiencySave network bandwidthProgram initiation/switchingTransmissionHosting environmentVirtual machine
The invention provides a method for dynamic migration of WAN (Wide Area Network) virtual machines. The method aims to perform dynamic migration of one or more virtual machines from a source host to a destination host in a wide area network. The method comprises the following steps of: establishing a distributed index of the internal memory and external memory data of all virtual machines in operation in a data center to which the destination host belongs, thus forming a destination host environment; in the migration process of the virtual machines, retrieving the internal memory and external memory data of the virtual machines in the source host in the destination host environment, and transmitting the internal memory and external memory data not present in the destination host environment only through the wide area network; and simultaneously, in the transmission process, marking internal memory and external memory dirty blocks by the virtual machine manager of the source host, iteratively sending the internal memory and external memory dirty blocks until reaching a stop condition, and then stopping the transmission of the internal memory and external memory, causing the virtual machines in the source host to enter a stop stage, and starting the virtual machines by the destination host. The method is capable of reducing the network bandwidth occupied by the migration of the virtual machines in the wide area network and shortening the time of the dynamic migration of the virtual machines.
Owner:CHINA STANDARD SOFTWARE
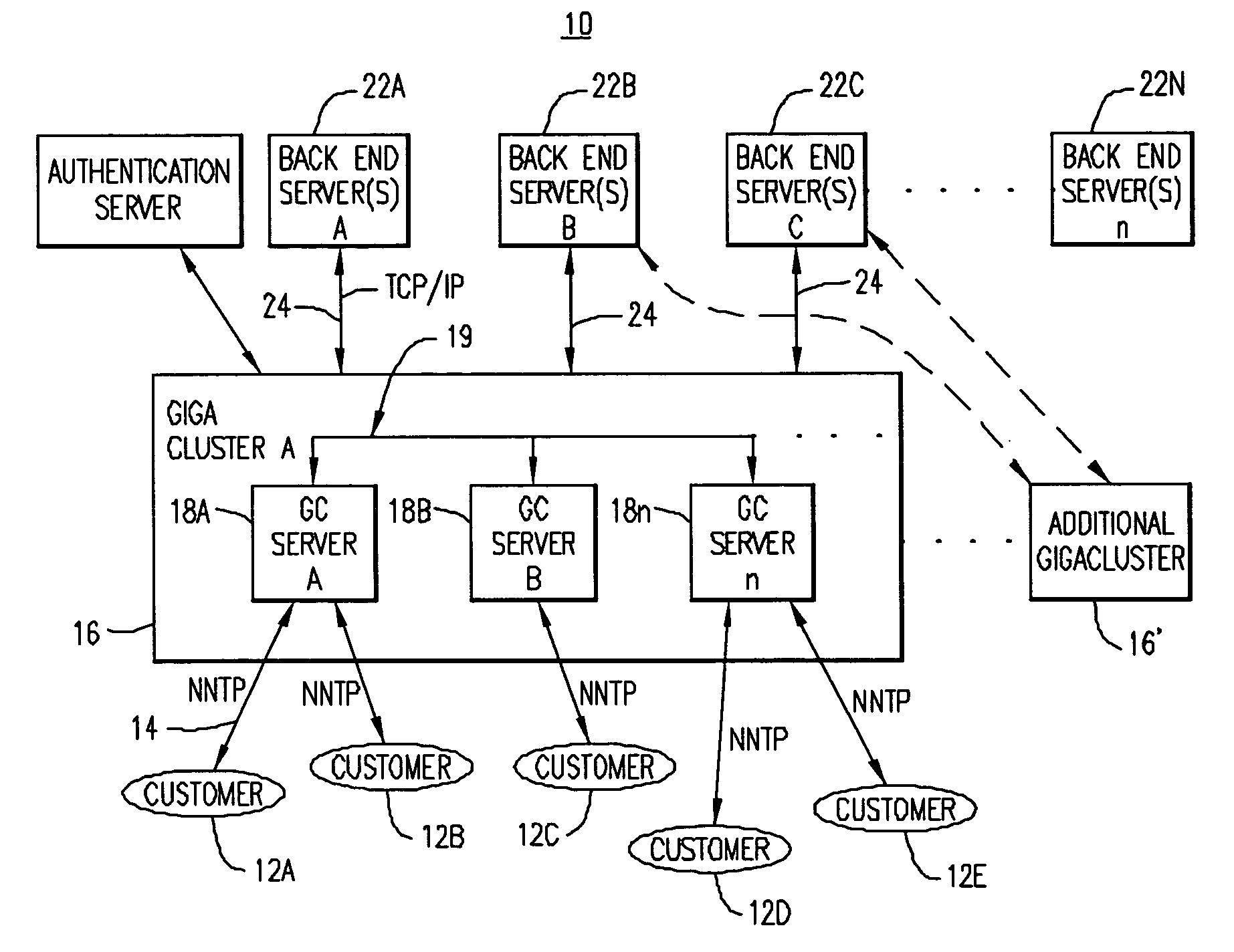
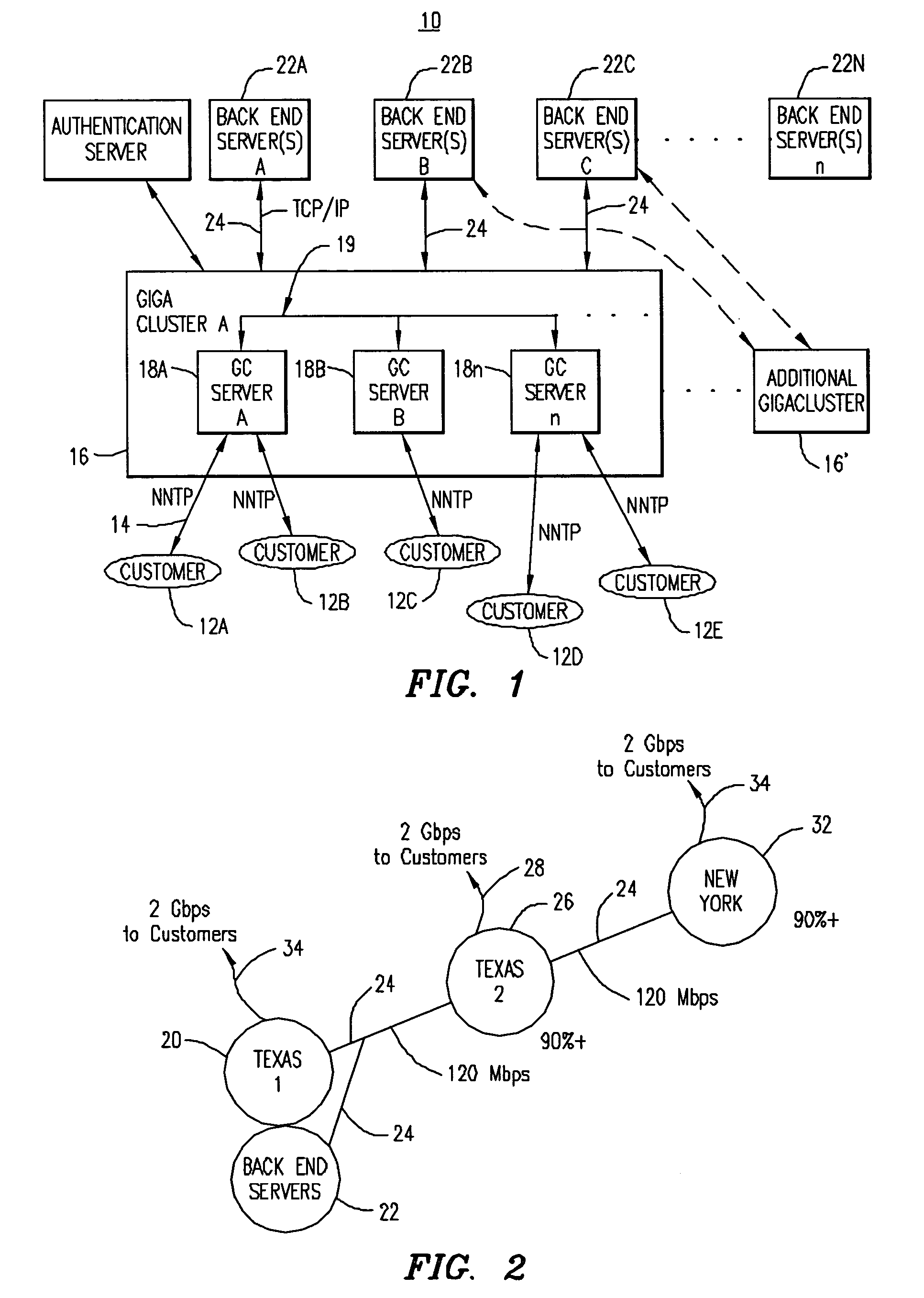
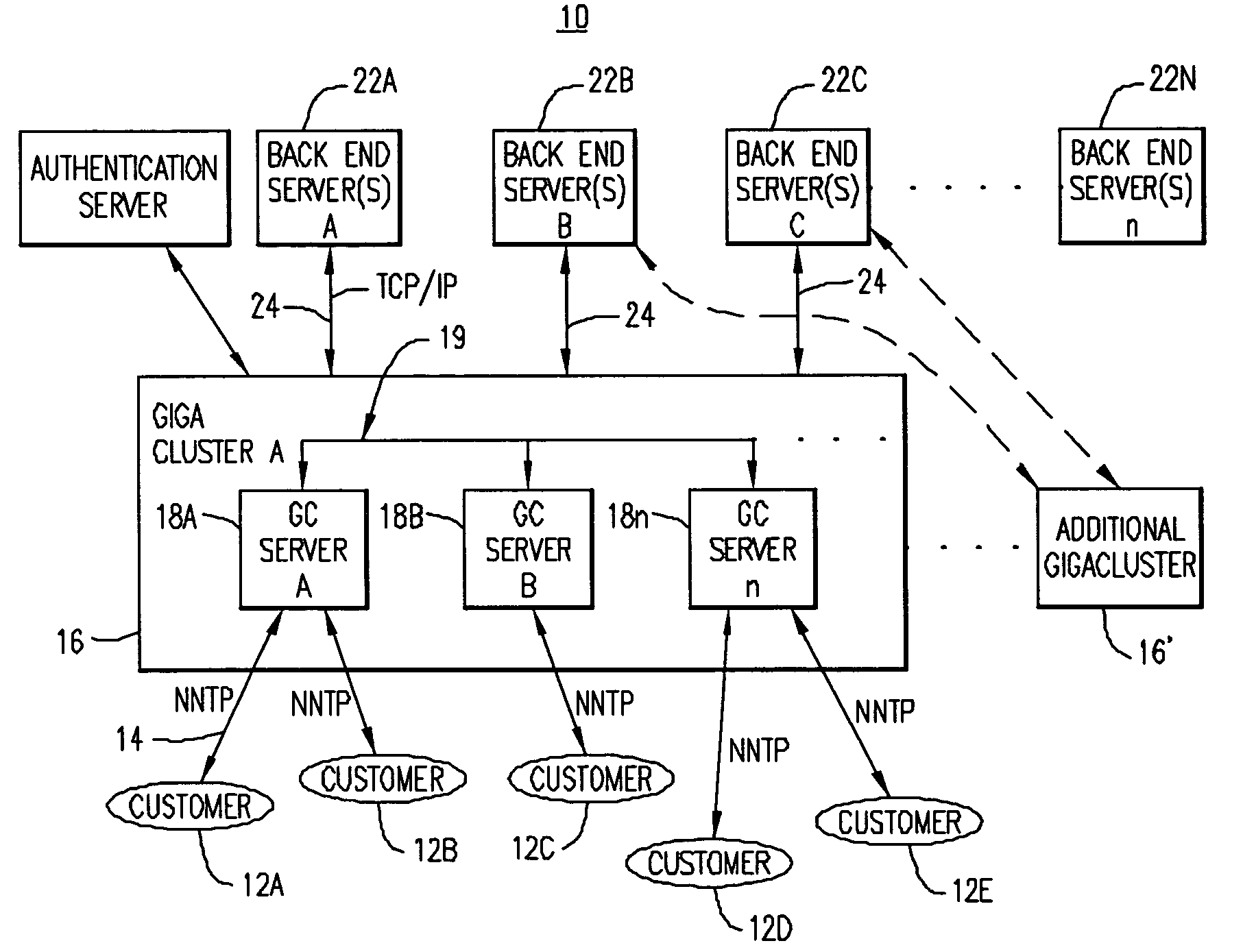
Caching, clustering and aggregating UseNet server
ActiveUS20040122910A1Reduce usageHandling failureDigital data information retrievalMultiple digital computer combinationsCache serverClient-side
A cluster of data caching servers that provide UseNet service to customers. The cluster of data caching servers cache articles and data requested by customers after retrieving the articles and data from a backend server / server farm. The cluster of data caching servers are adapted to share their cache memories with the other clustered servers in the cluster such that, if an article is requested by a client and the article has already been stored in one of the clustered server's cache memories, there is no requirement to retrieve all the requested article from the backend server.
Owner:YHC CORP
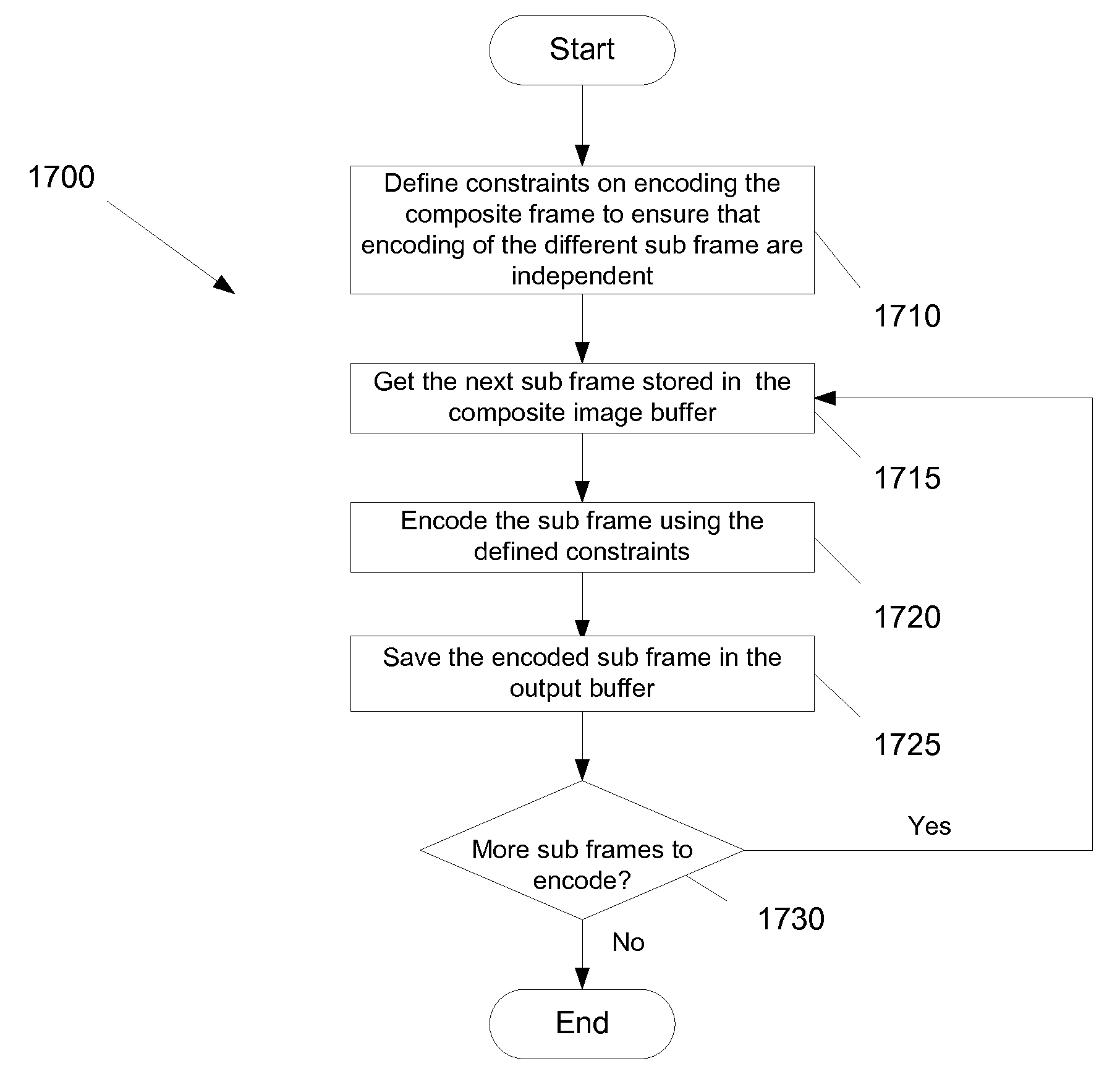
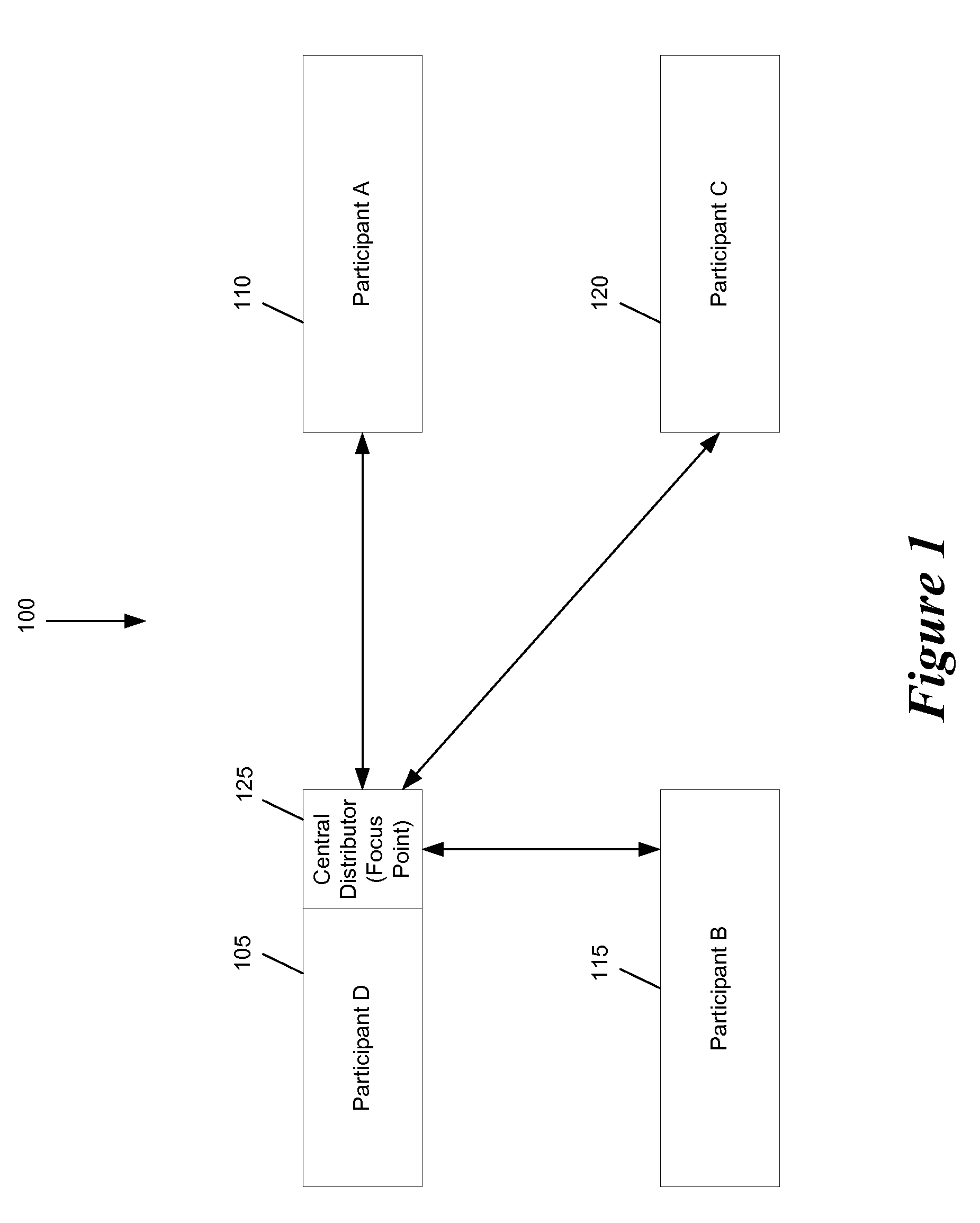
Video encoding in a video conference
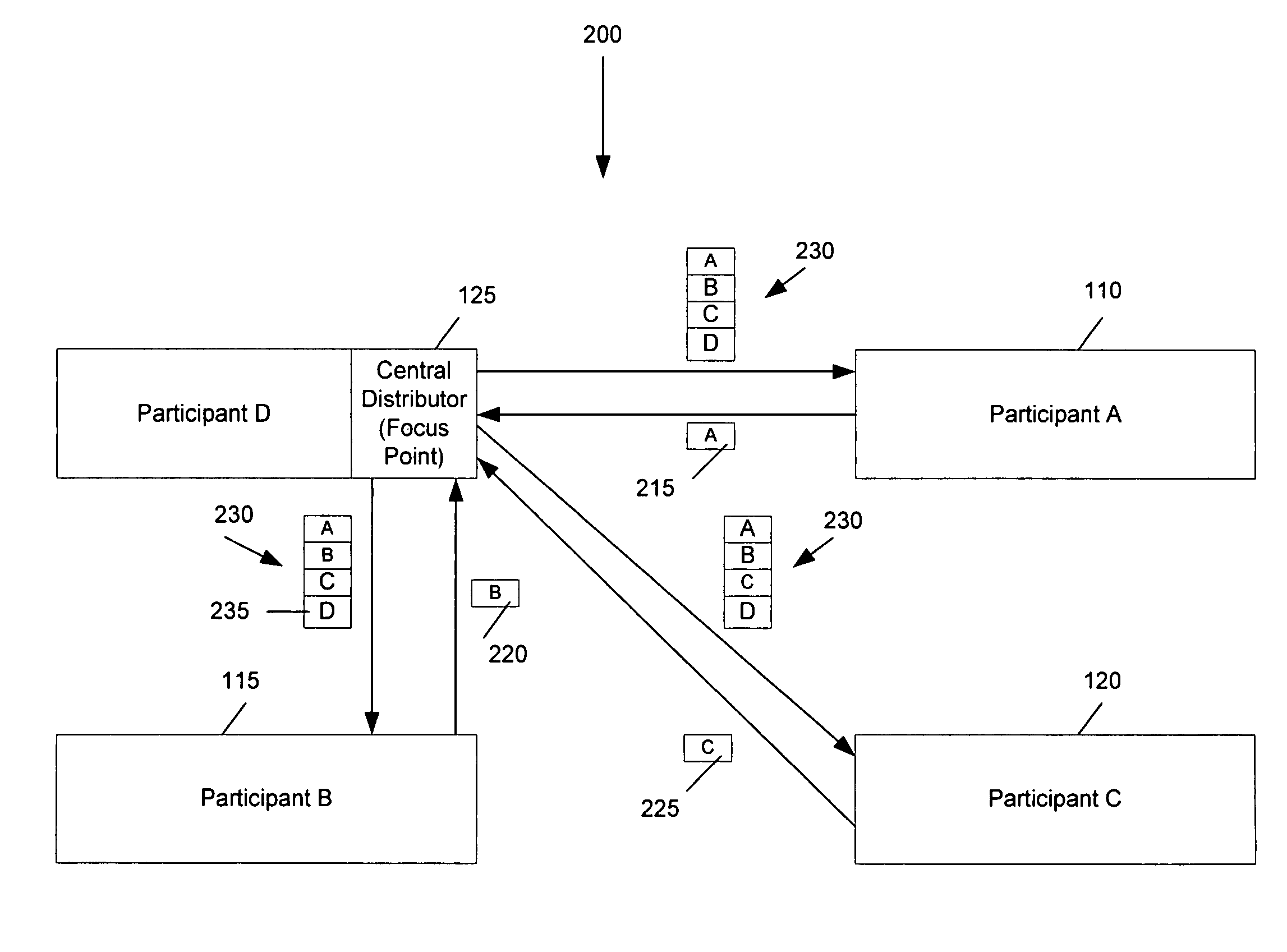
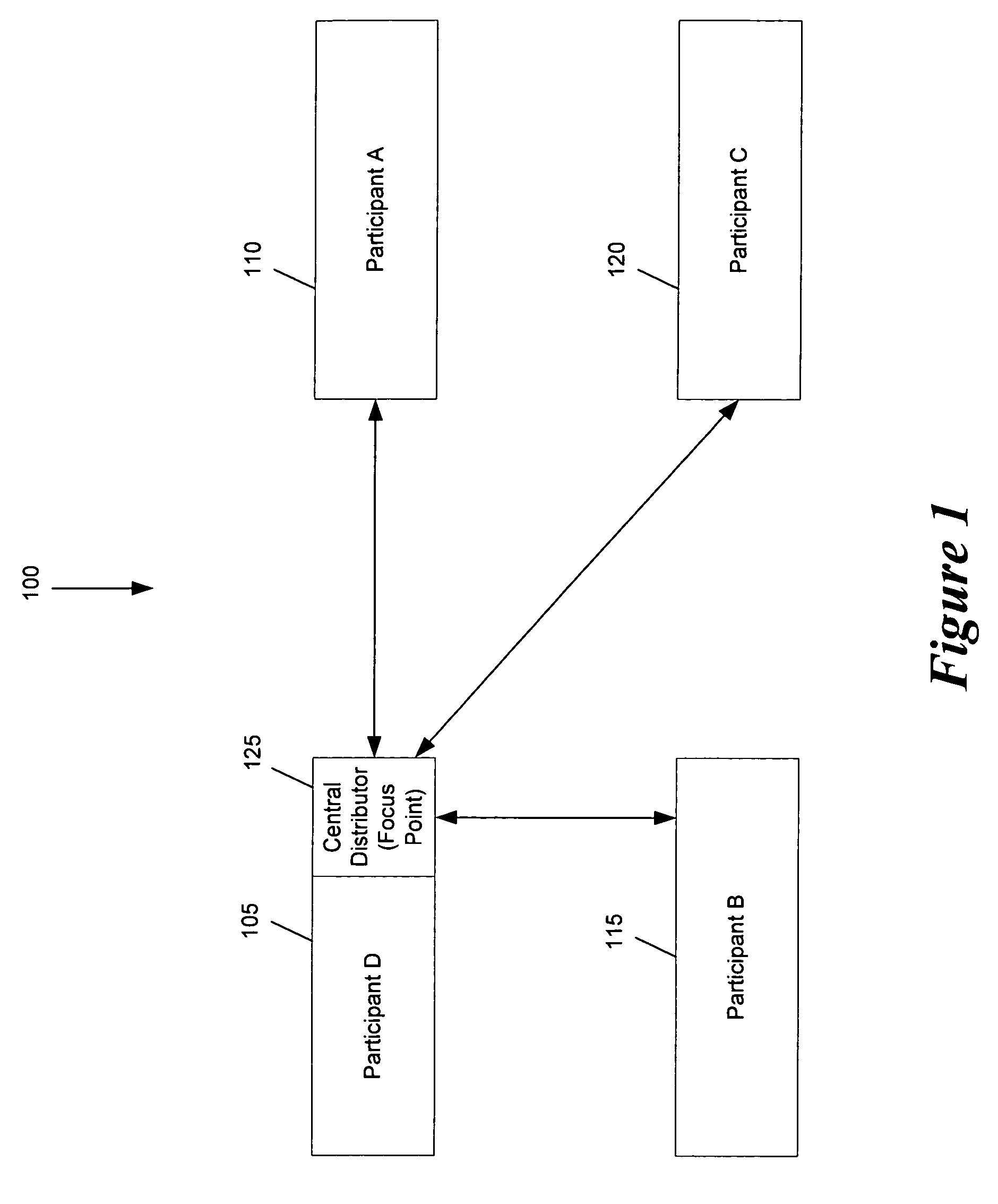
ActiveUS20060244819A1Save network bandwidthTelevision conference systemsTwo-way working systemsComputer graphics (images)Video encoding
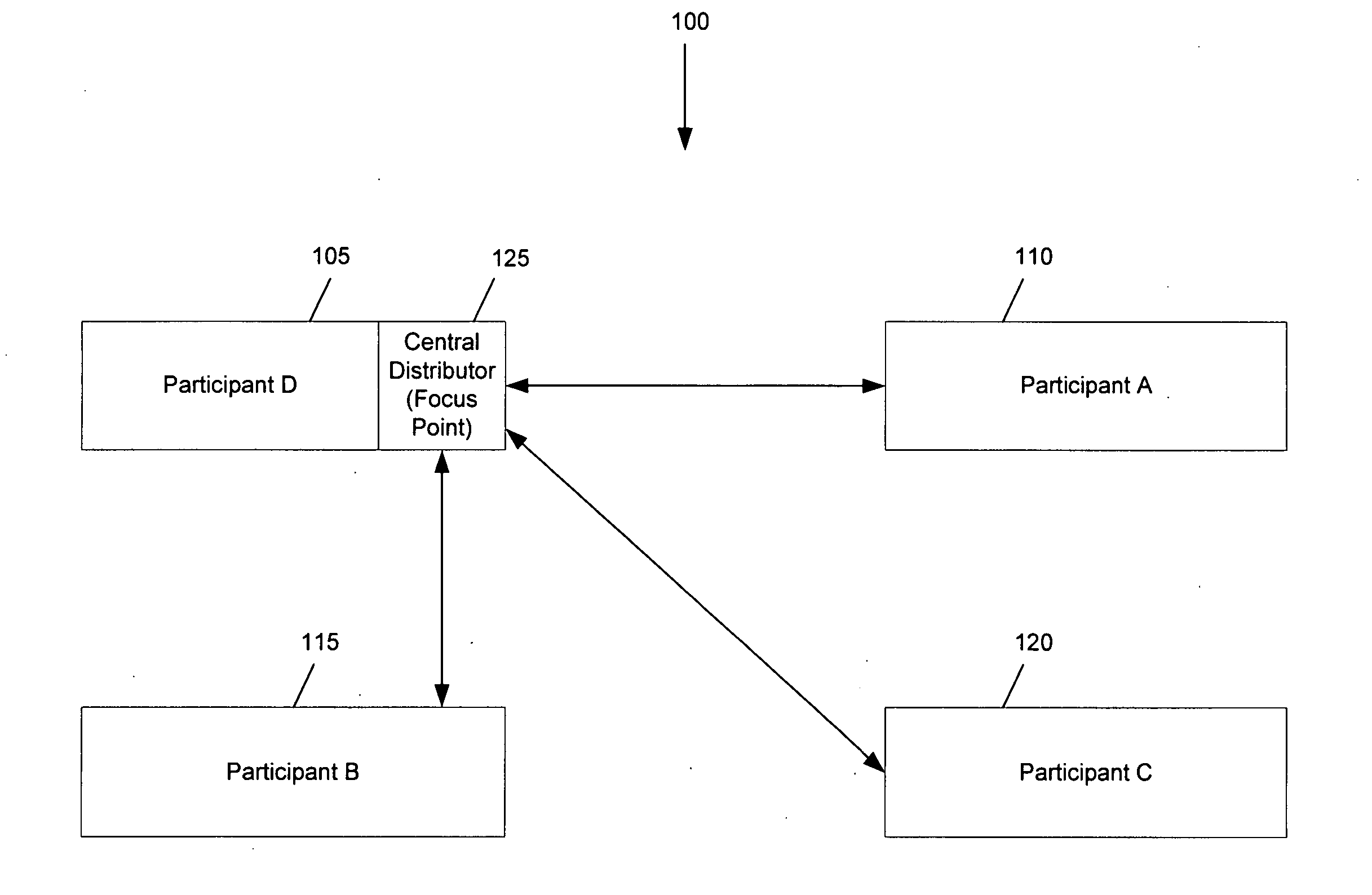
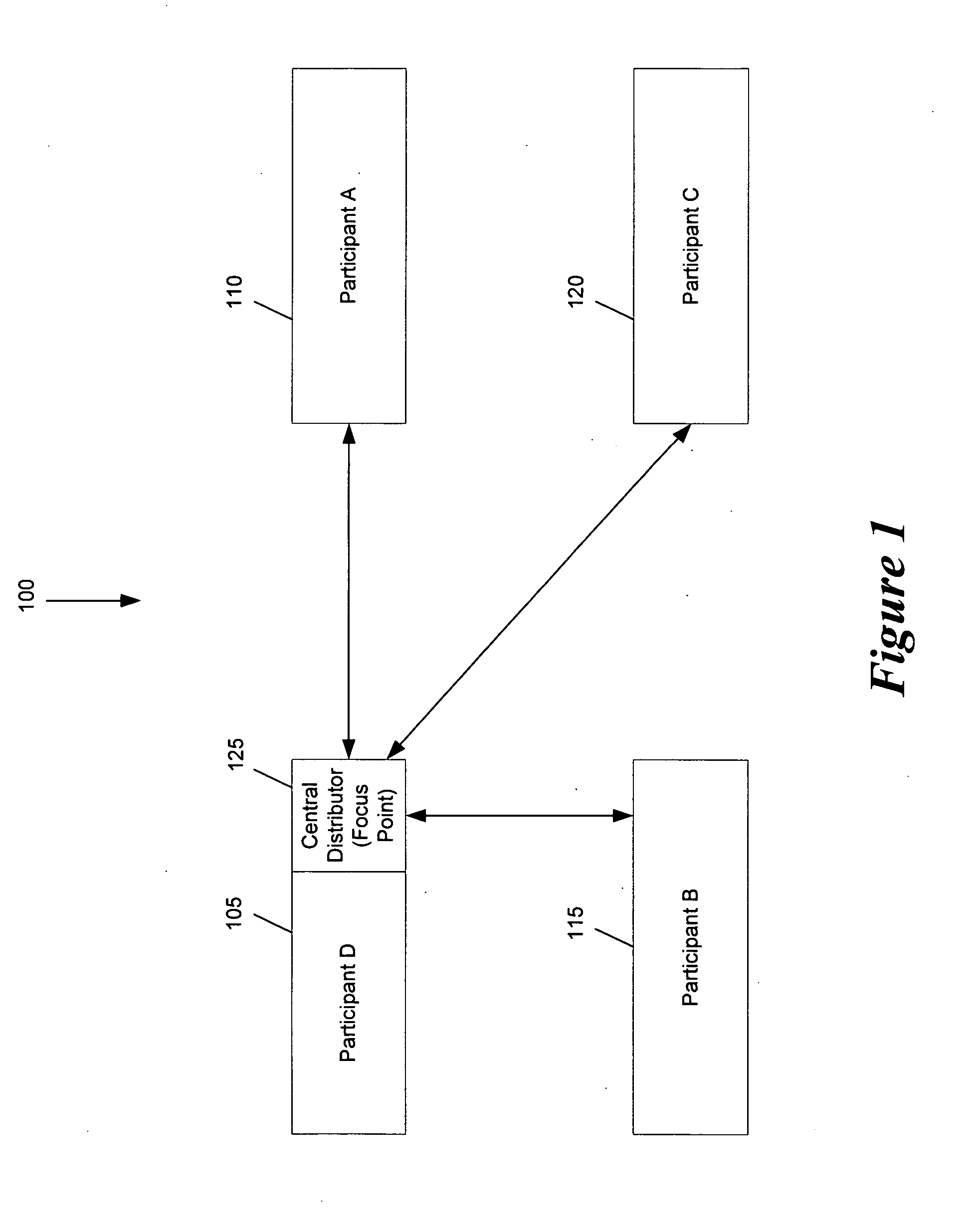
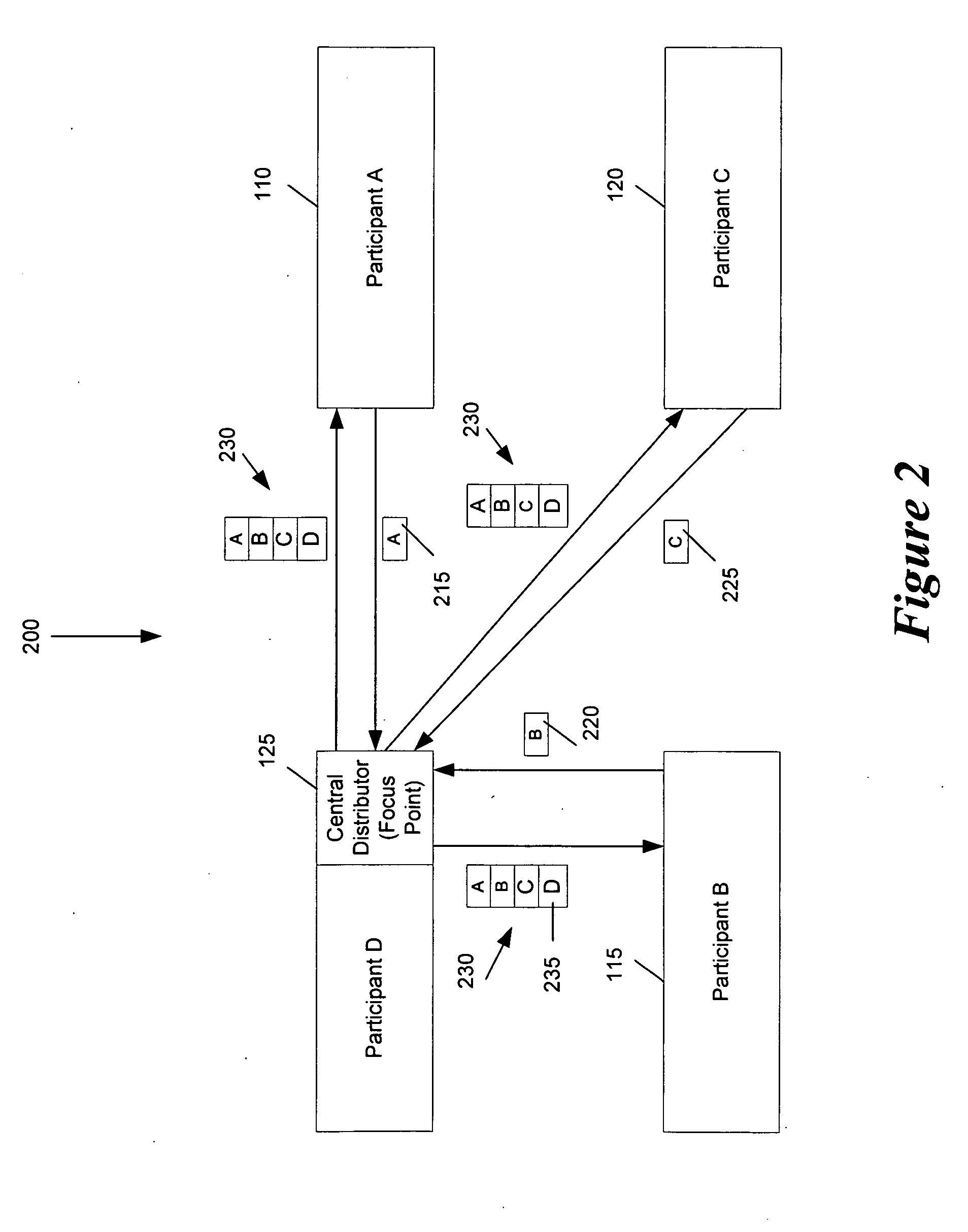
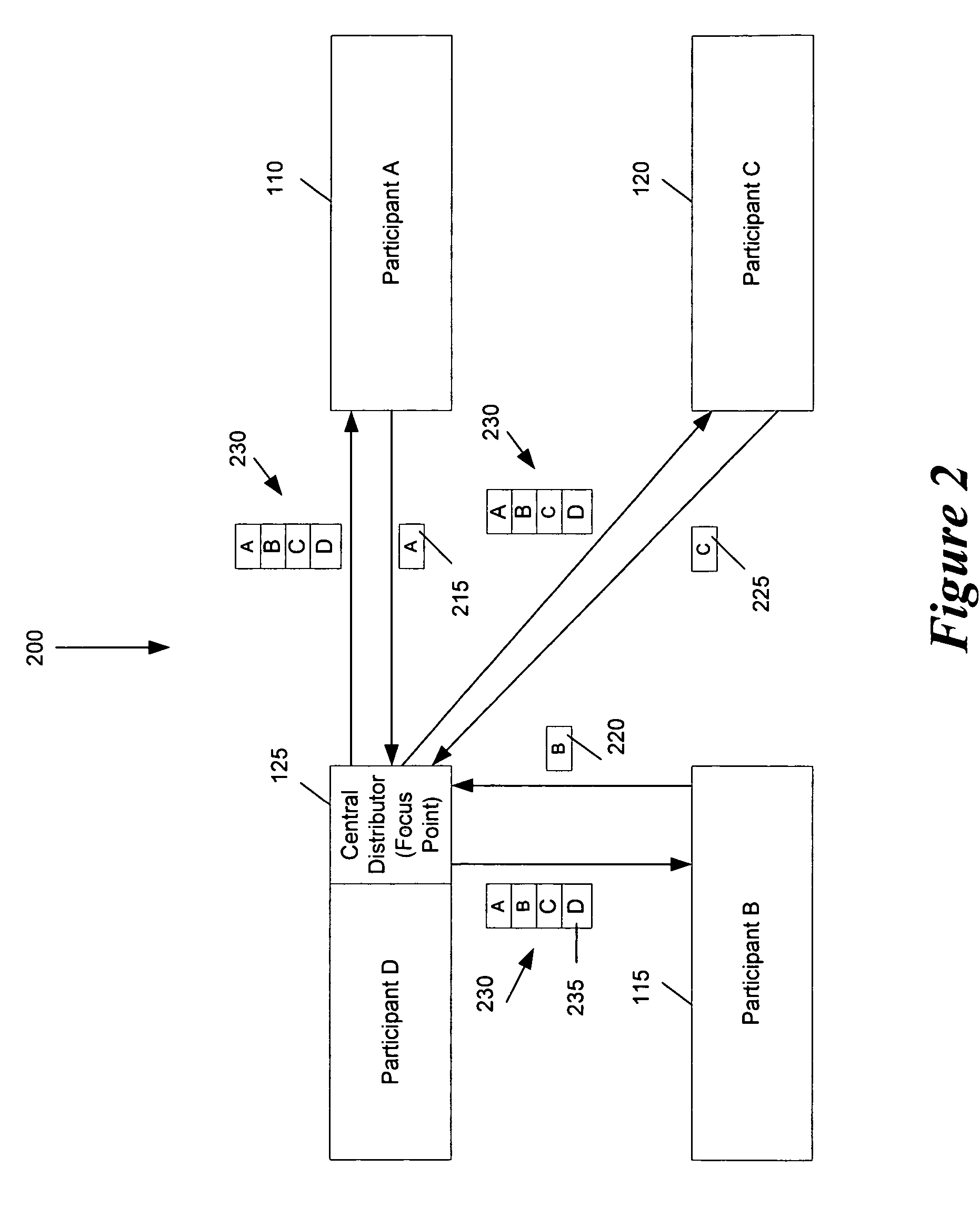
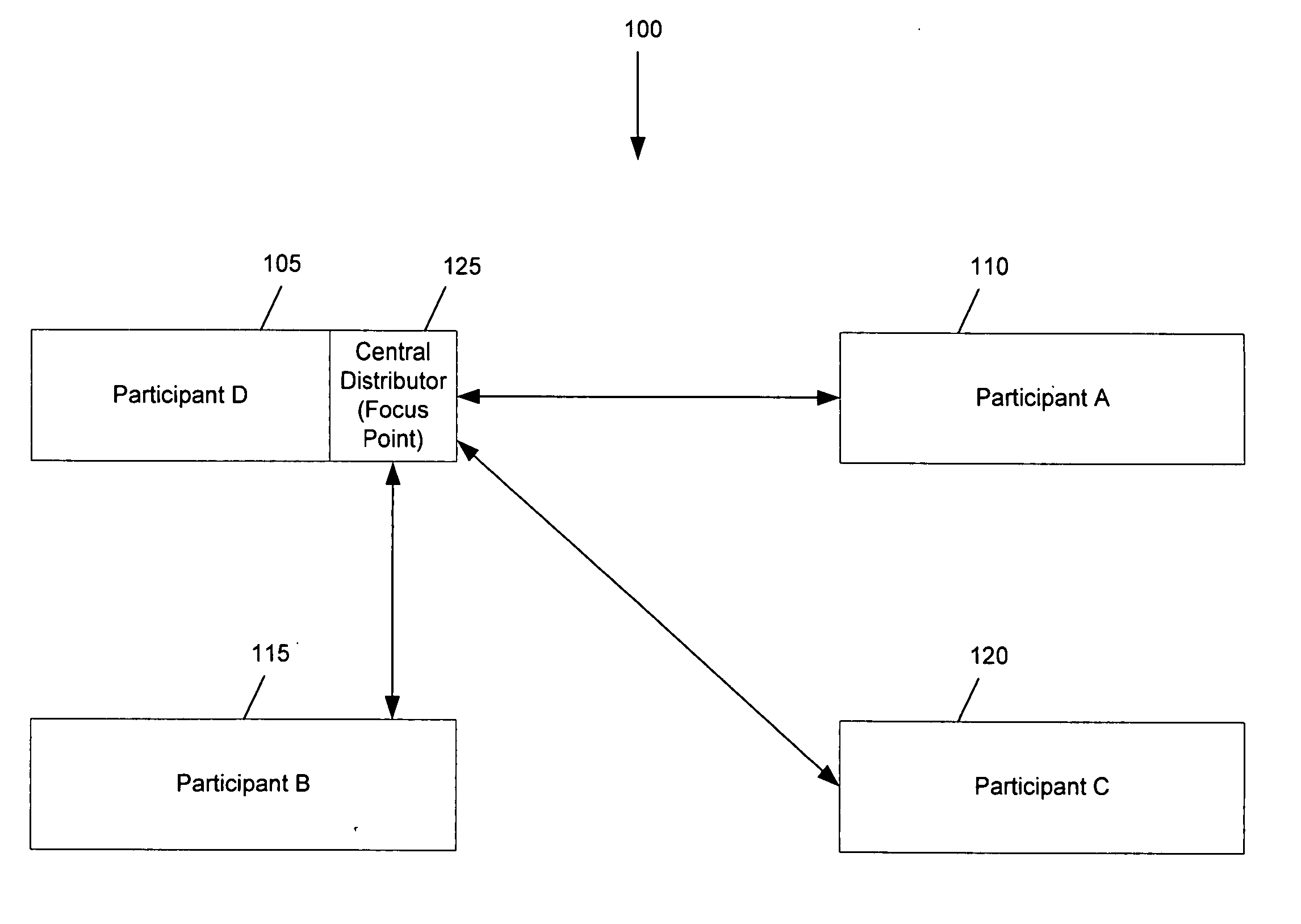
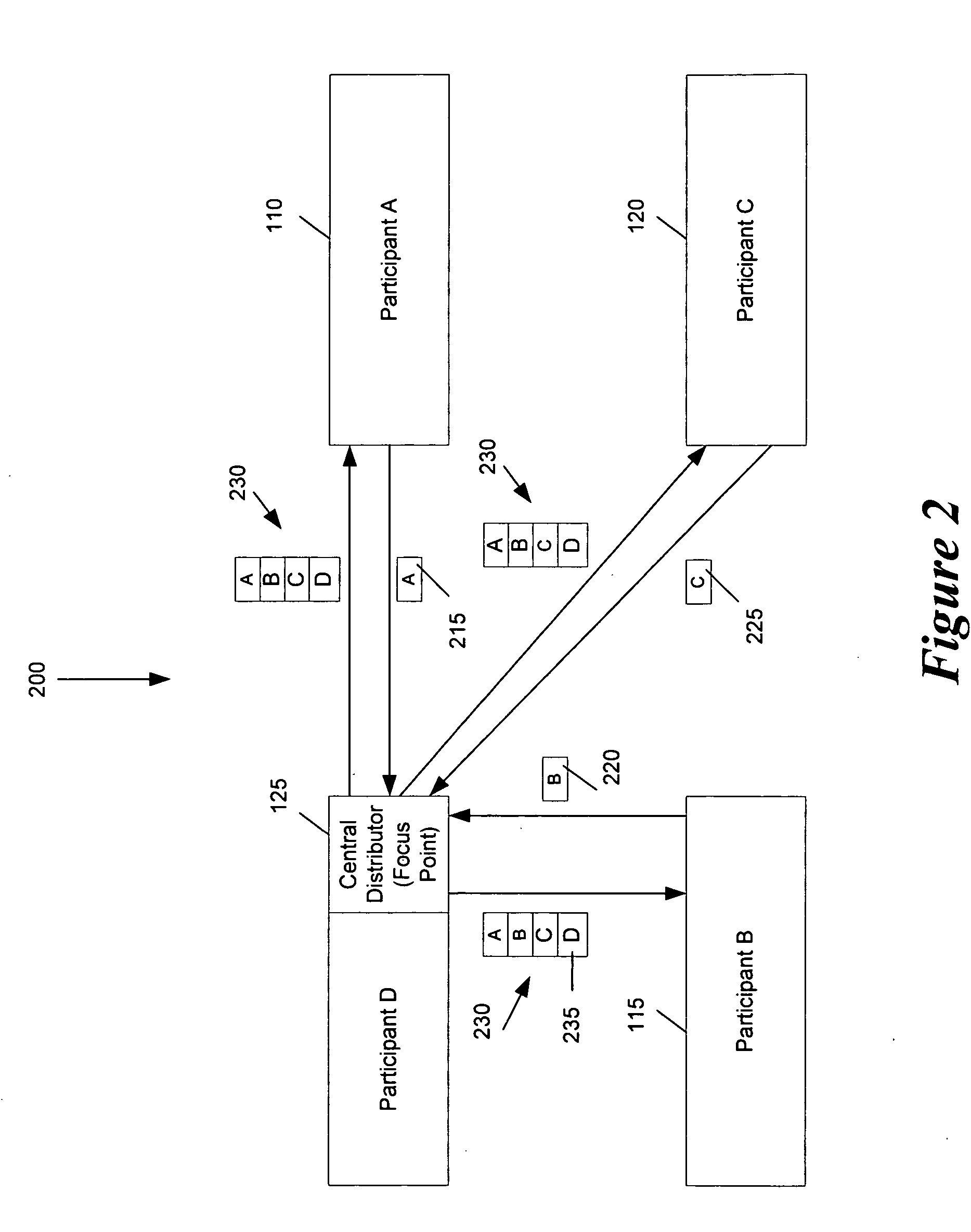
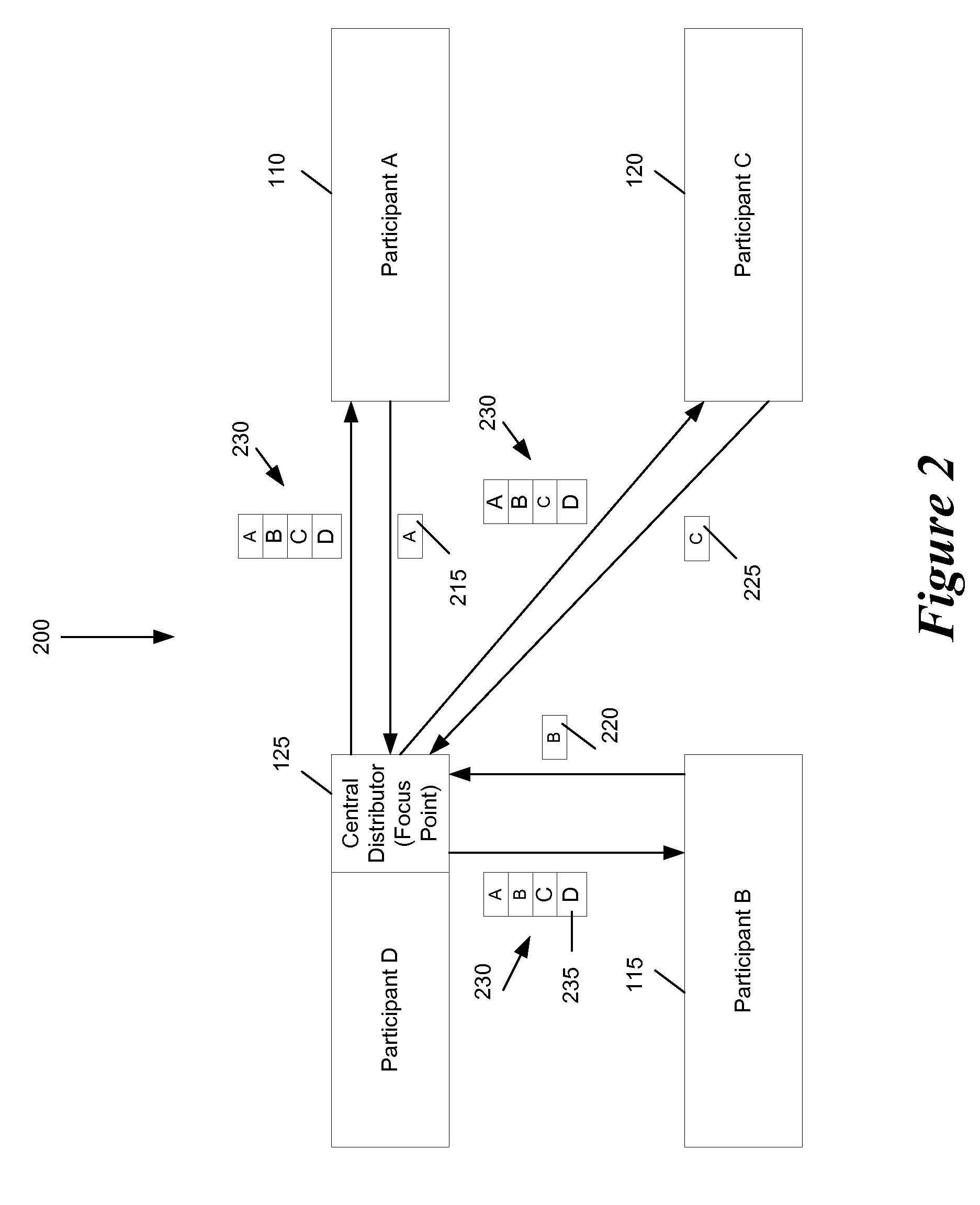
Some embodiments provide an architecture for establishing multi-participant video conferences. This architecture has a central distributor that receives video images from two or more participants. From the received images, the central distributor generates composite images that the central distributor transmits back to the participants. Each composite image includes a set of sub images, where each sub image belongs to one participant. In some embodiments, the central distributor saves network bandwidth by removing each particular participant's image from the composite image that the central distributor sends to the particular participant. In some embodiments, images received from each participant are arranged in the composite in a non-interleaved manner. For instance, in some embodiments, the composite image includes at most one sub-image for each participant, and no two sub-images are interleaved.
Owner:APPLE INC
Caching, clustering and aggregating server
ActiveUS7337214B2Reduce usageHandling failureDigital data information retrievalMultiple digital computer combinationsCache serverBack end server
A cluster of data caching servers that provide UseNet service to customers. The cluster of data caching servers cache articles and data requested by customers after retrieving the articles and data from a backend server / server farm. The cluster of data caching servers are adapted to share their cache memories with the other clustered servers in the cluster such that, if an article is requested by a client and the article has already been stored in one of the clustered server's cache memories, there is no requirement to retrieve all the requested article from the backend server.
Owner:YHC CORP
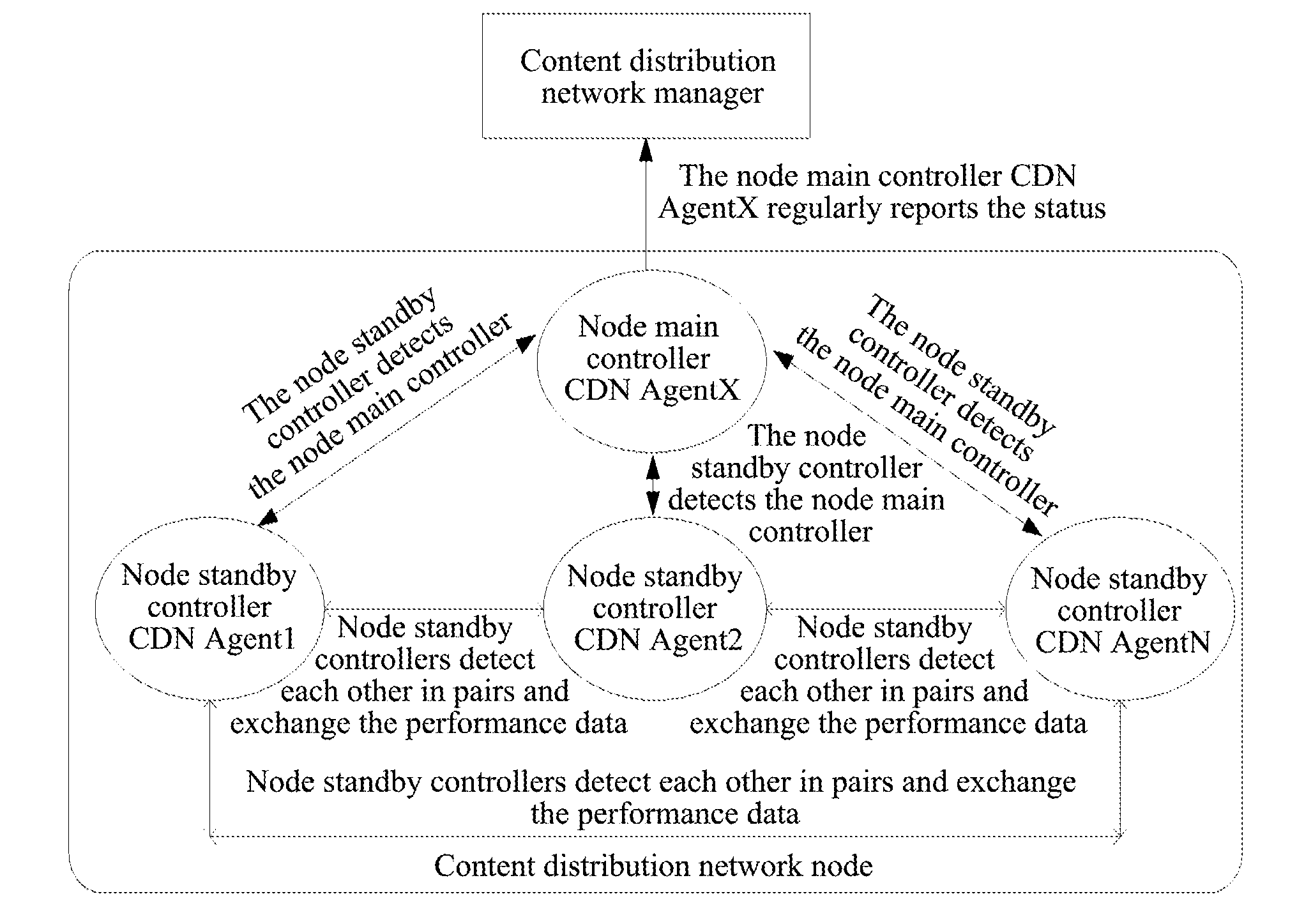
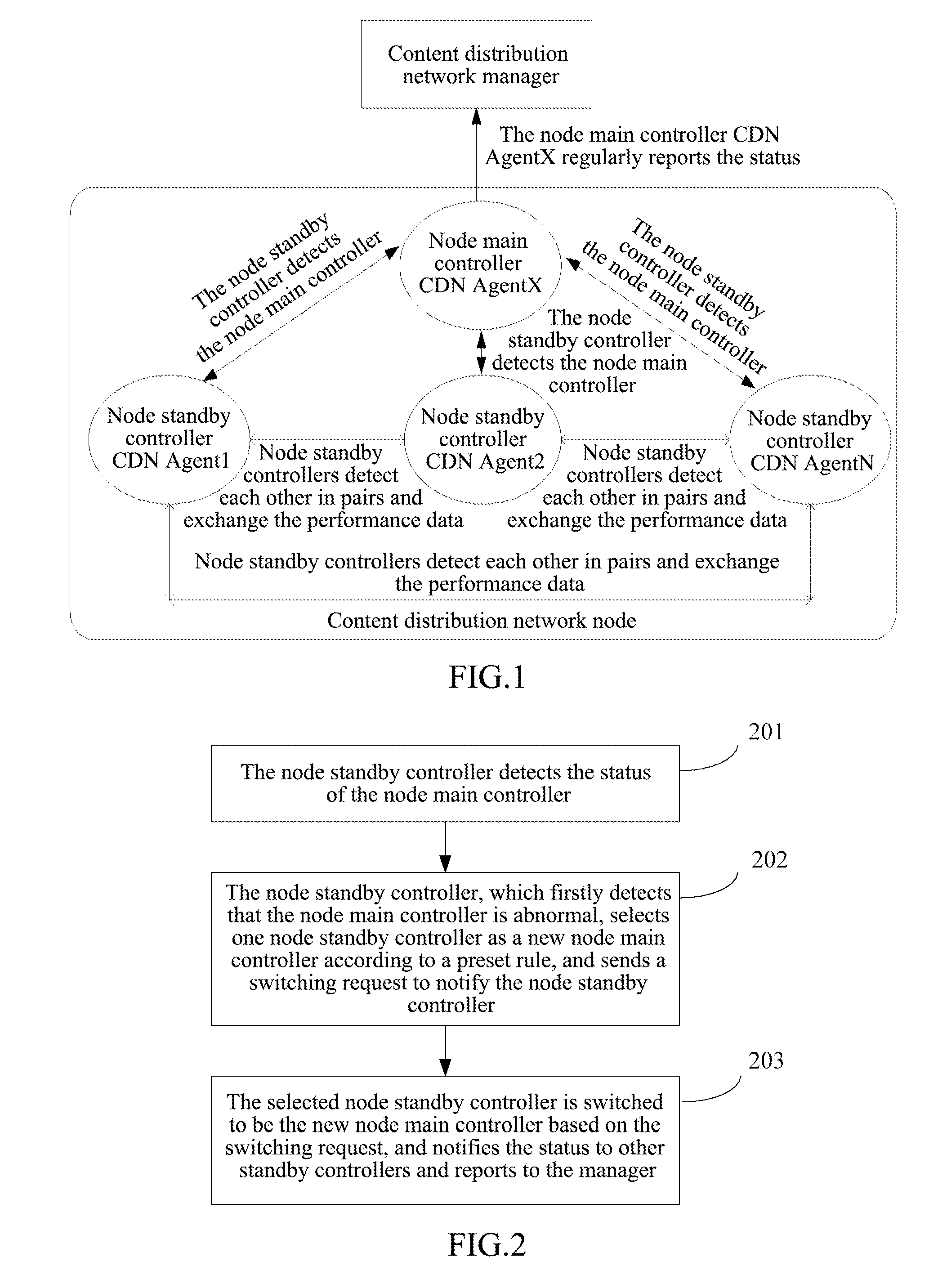
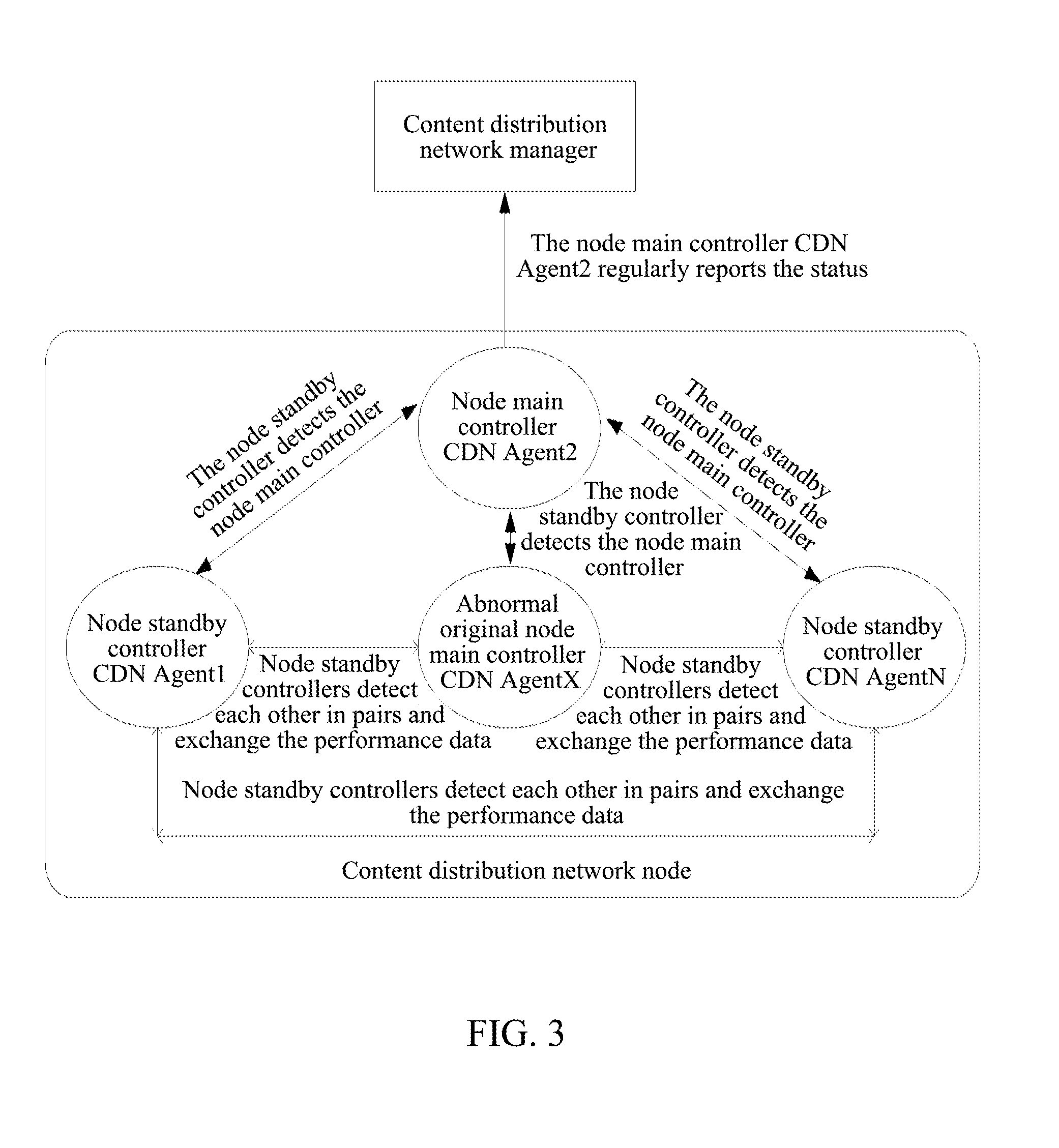
Method for switching node main-standby controllers based on content delivery network (CDN) and cdn thereof
ActiveUS20120151550A1Improve performanceSave bandwidthError preventionError detection/correctionContent distributionEngineering
A method for switching node main-standby controllers based on content distribution network is disclosed by the present invention, including the process that a node standby controller detects the status of the current node main controller, and when the node main controller is abnormal, the node standby controller selects one node standby controller to be the new node main controller by replacement according to a preset rule. A content distribution network is also disclosed by the present invention. The present invention can avoid the problem that a manager changes the node main controller blindly, which is caused by a network anomaly while not the failure of the node main controller, thus the performance of the manager is effectively improved and the bandwidth of the network is saved.
Owner:ZTE CORP
Video processing in a multi-participant video conference
ActiveUS7817180B2Save network bandwidthTelevision conference systemsTwo-way working systemsComputer graphics (images)Video processing
Some embodiments provide an architecture for establishing multi-participant video conferences. This architecture has a central distributor that receives video images from two or more participants. From the received images, the central distributor generates composite images that the central distributor transmits back to the participants. Each composite image includes a set of sub images, where each sub image belongs to one participant. In some embodiments, the central distributor saves network bandwidth by removing each particular participant's image from the composite image that the central distributor sends to the particular participant. In some embodiments, images received from each participant are arranged in the composite in a non-interleaved manner. For instance, in some embodiments, the composite image includes at most one sub-image for each participant, and no two sub-images are interleaved.
Owner:APPLE INC
Method for adding special effect in video communication and video customer terminal
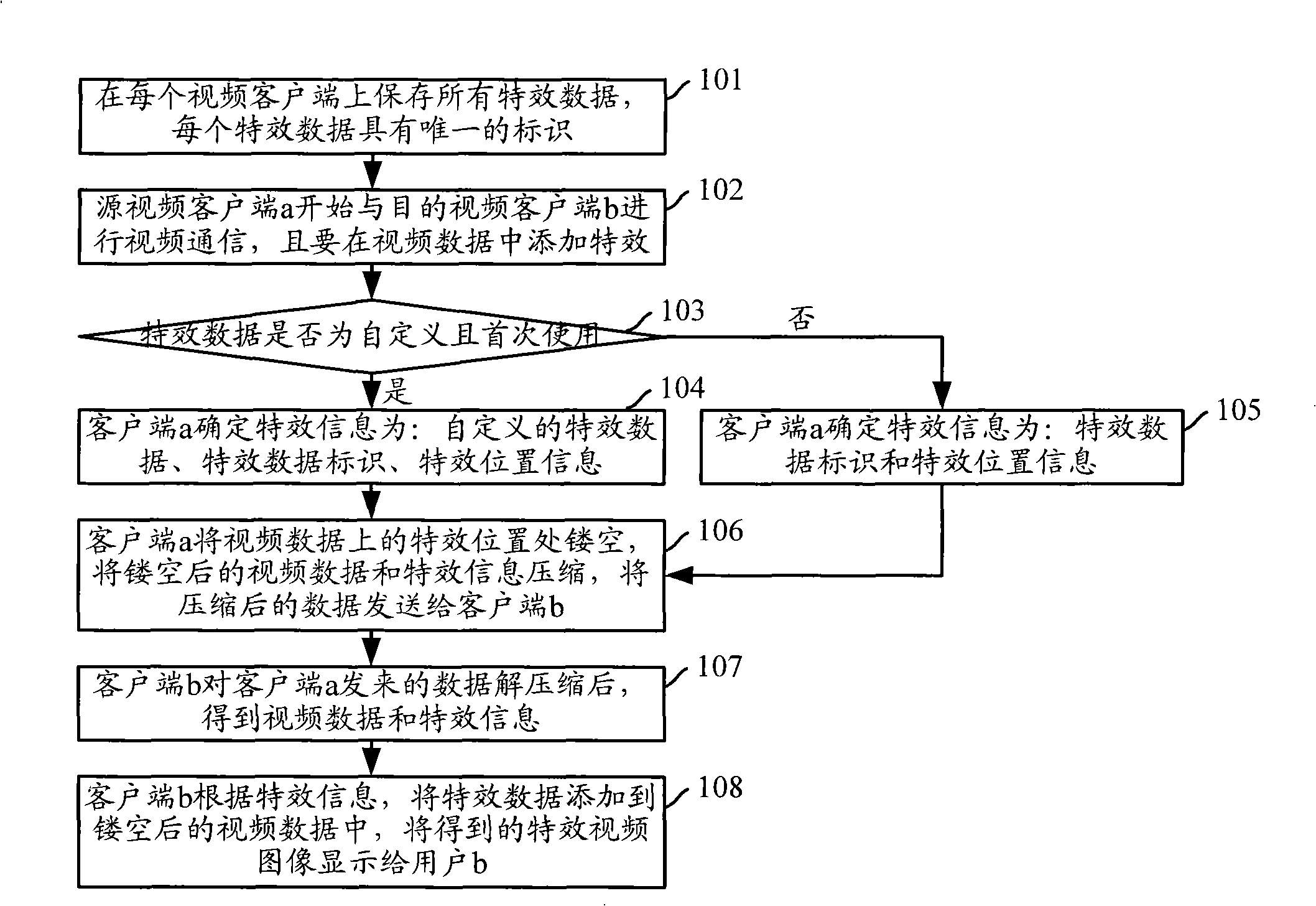
ActiveCN101287093AReduce data volumeSave network bandwidthTwo-way working systemsTransmissionClient-sideSpecial effects
The invention discloses a method for adding special effect in video communication and a video client side thereof. The method disclosed by the invention comprises the steps that: special effect data are preserved at the video client side, and each special effect datum has unique identification; when an original video client side adds the special effect for the video data to be sent, the special effect identification, specific effect position information and the video data are sent to a target video client side which then searches for the special effect datum according to the special effect data identification and adds the special effect datum into the video data according to the special effect position information. The method disclosed by the invention needs not to transmit the special effect data together with the video data every time, thus reducing transmitted data quantity and saving network bandwidth; in addition, the further reduction of the transmitted data quantity and the saving of the network bandwidth can be realized by hollowing-out the special effect position of the video data or setting the special effect position into the same pixel value.
Owner:VIMICRO ELECTRONICS CORP
Computer implemented method and system for transmitting graphical images from server to client at user selectable resolution
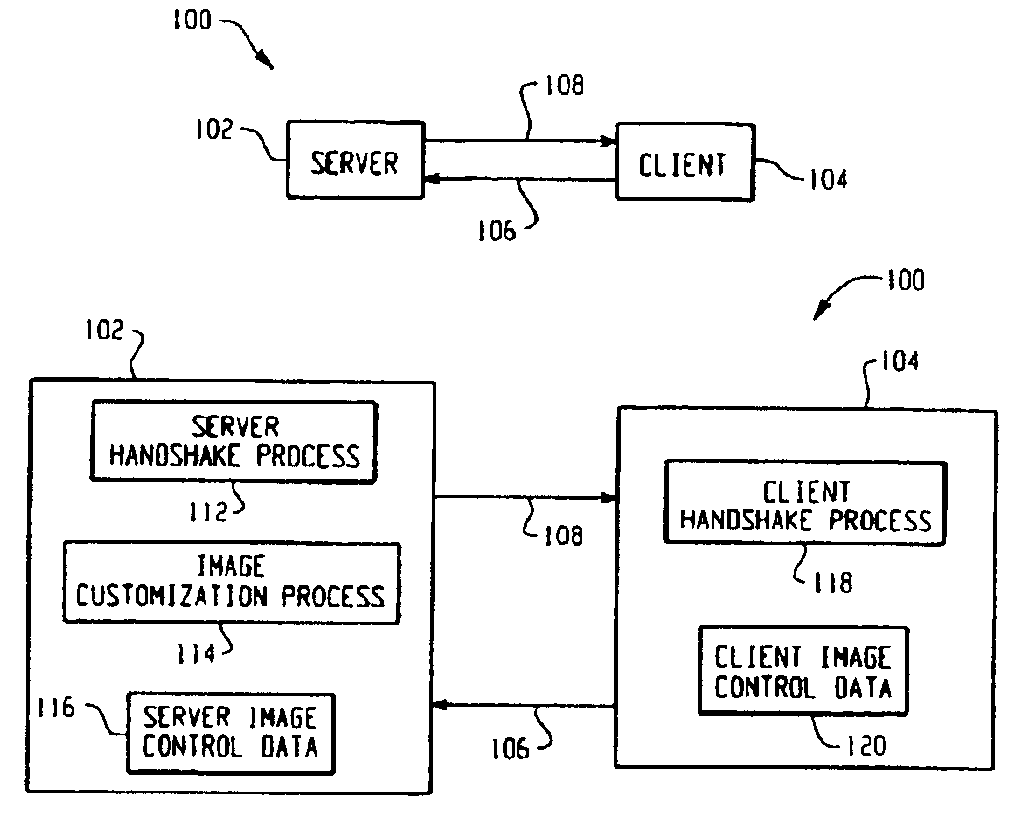
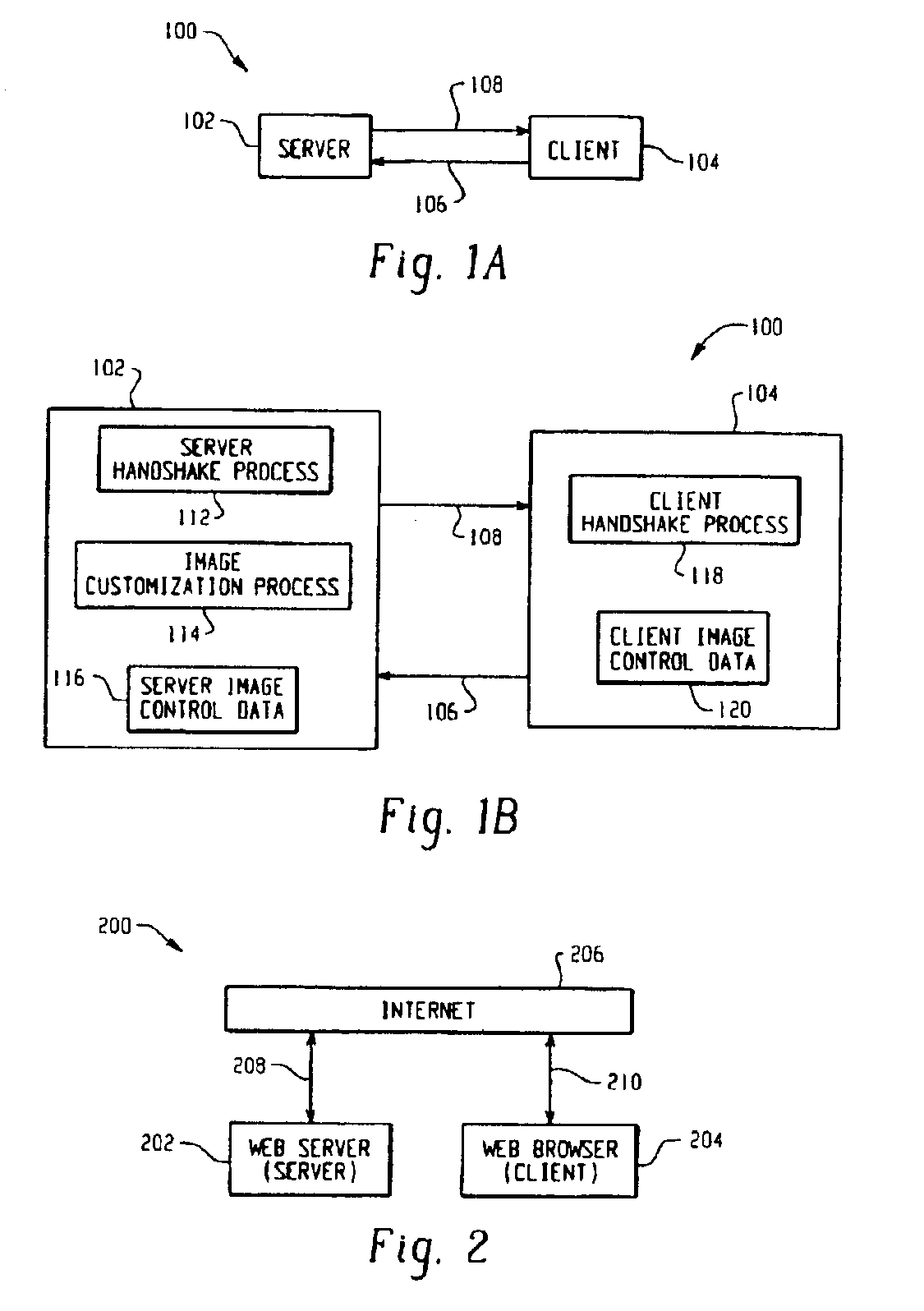
InactiveUS6950101B2Reduce the amount requiredSave network bandwidthDigital data information retrievalNatural language data processingGraphicsImage resolution
Techniques for transmitting graphical images in a network environment are described. According to the techniques, the amount of data of the graphical images that is transmited is customized in accordance with client and / or server supplied information. The techniques enable graphical images to be transmitted more efficiently than previously possible, thus saving precious network bandwidth and reducing transmision time. The invention is particularly suitable for network (Internet or Internet) implementations wherein graphical images often need transferred.
Owner:RAKUTEN INC
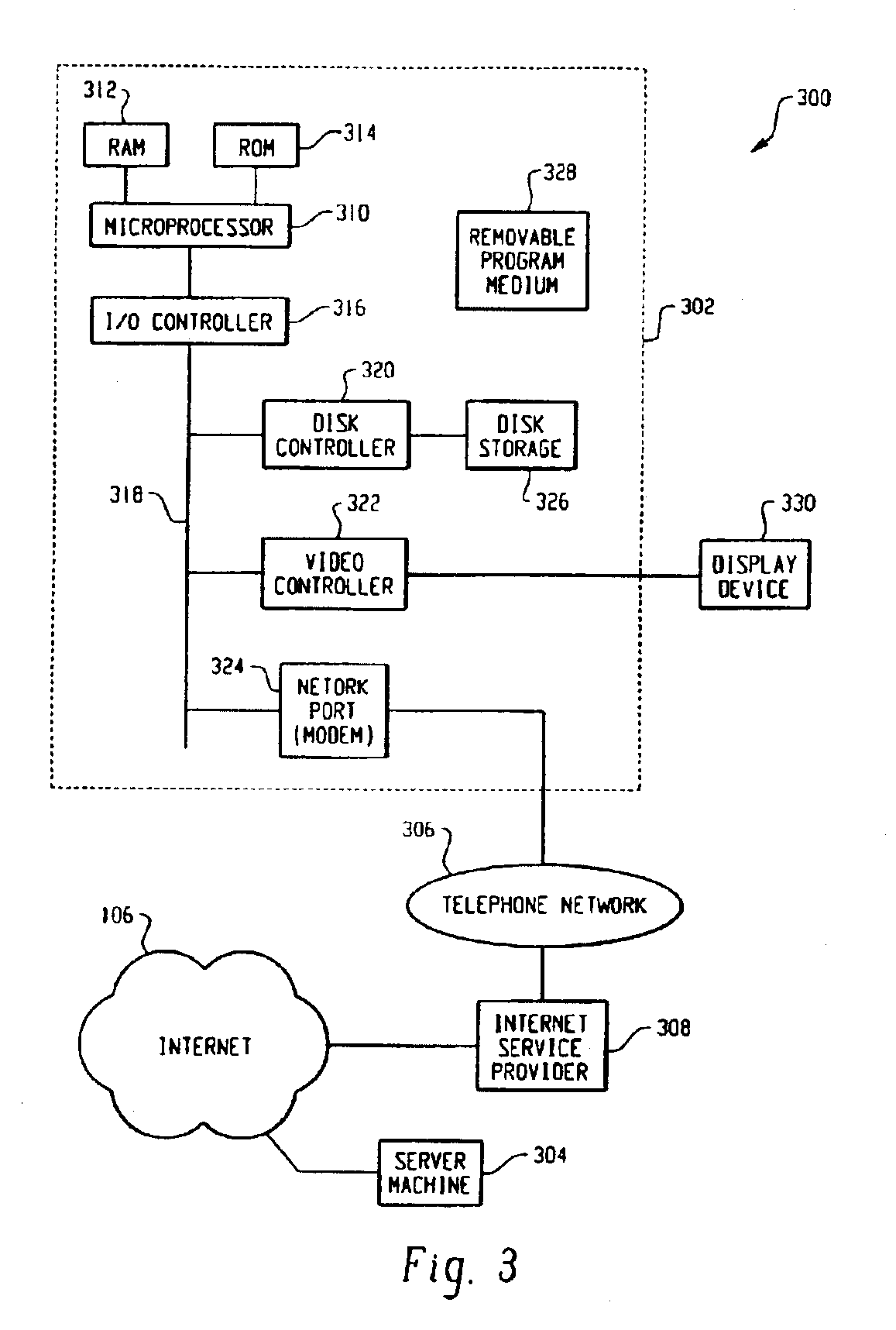
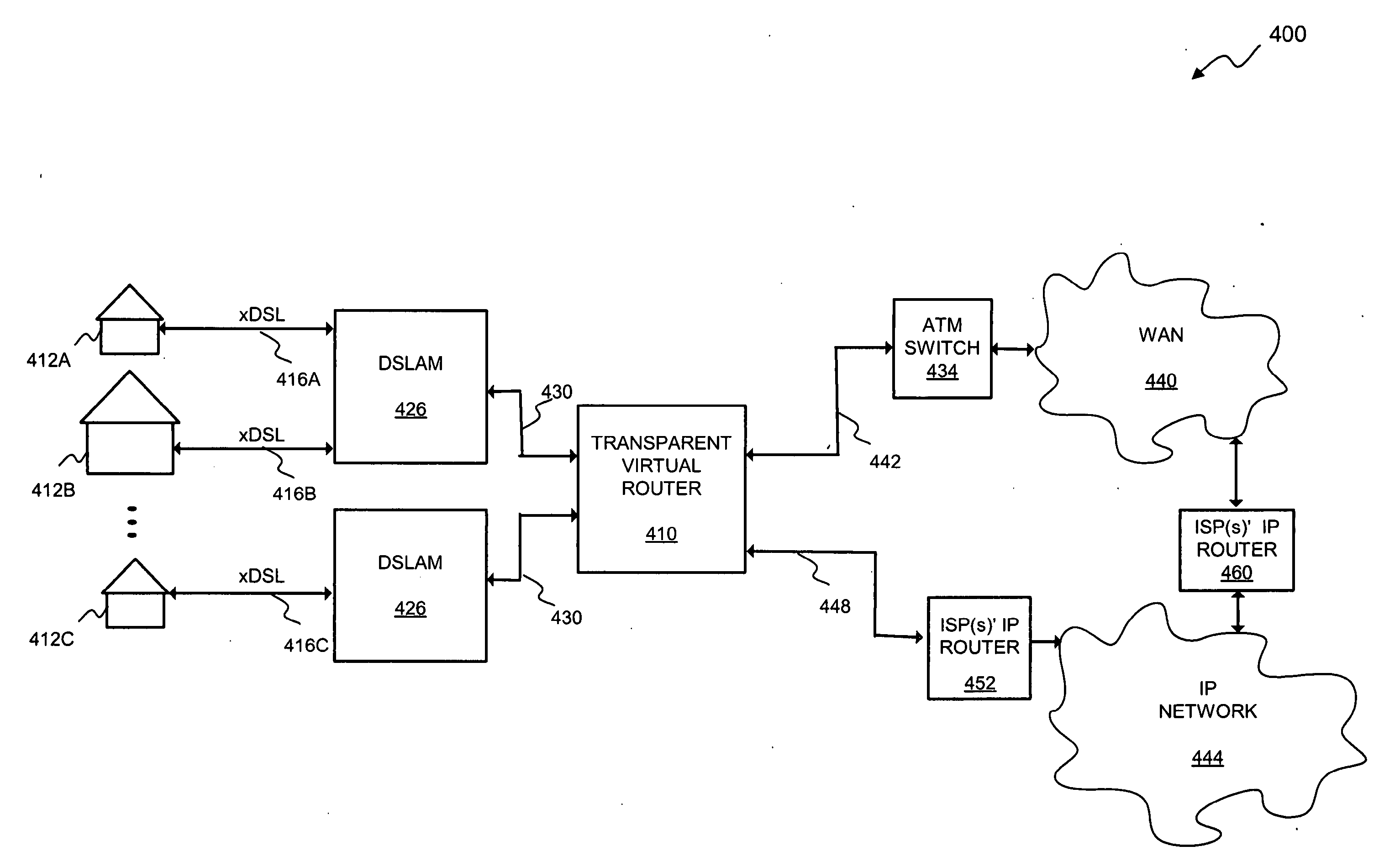
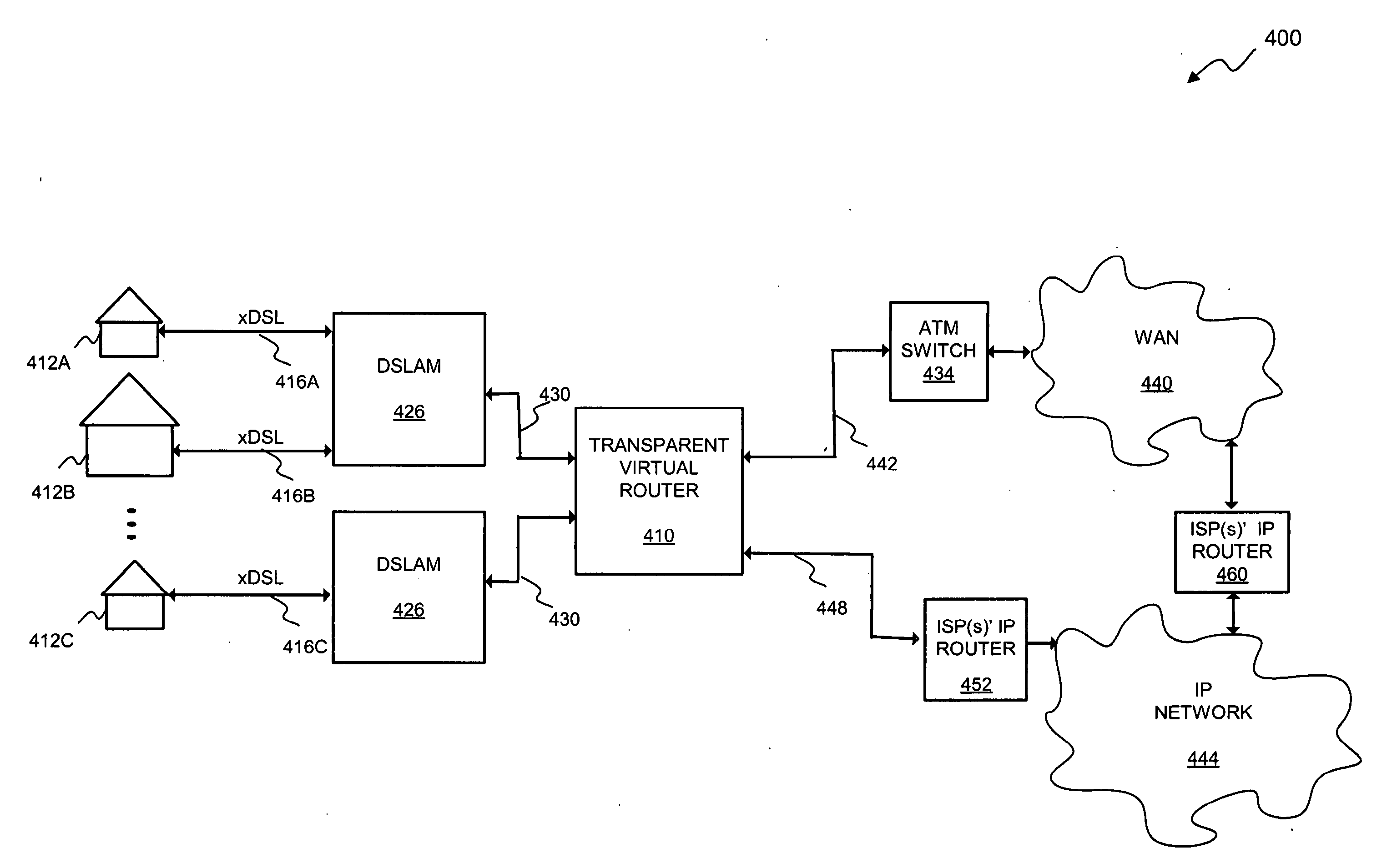
System and Method for Transparent Virtual Routing
InactiveUS20080151906A1Minimal administrativeMinimal operationalDigital computer detailsElectric digital data processingAccess networkRouting table
A transparent routing device disposed within an access network configured in accordance with one or more lower-layer protocols is disclosed herein. The device includes a set of subscriber-side ports. Each of the subscriber-side ports is associated with a plurality of virtual subscriber-side interfaces disposed to effectively terminate a corresponding plurality of subscriber-side connections with subscriber host devices served by the access network. The device further includes at least one network-side port through which communication occurs with an external network in accordance with a higher-layer protocol. A routing table is configured to establish a correspondence between network addresses of the subscriber host devices and the plurality of virtual subscriber-side interfaces. During operation of the device, packets received through the at least one network-side port are forwarded to corresponding ones of the virtual subscriber-side interfaces based upon network addresses of the packets.
Owner:GOOGLE TECH HLDG LLC
Method for coping database data in heterogeneous environment
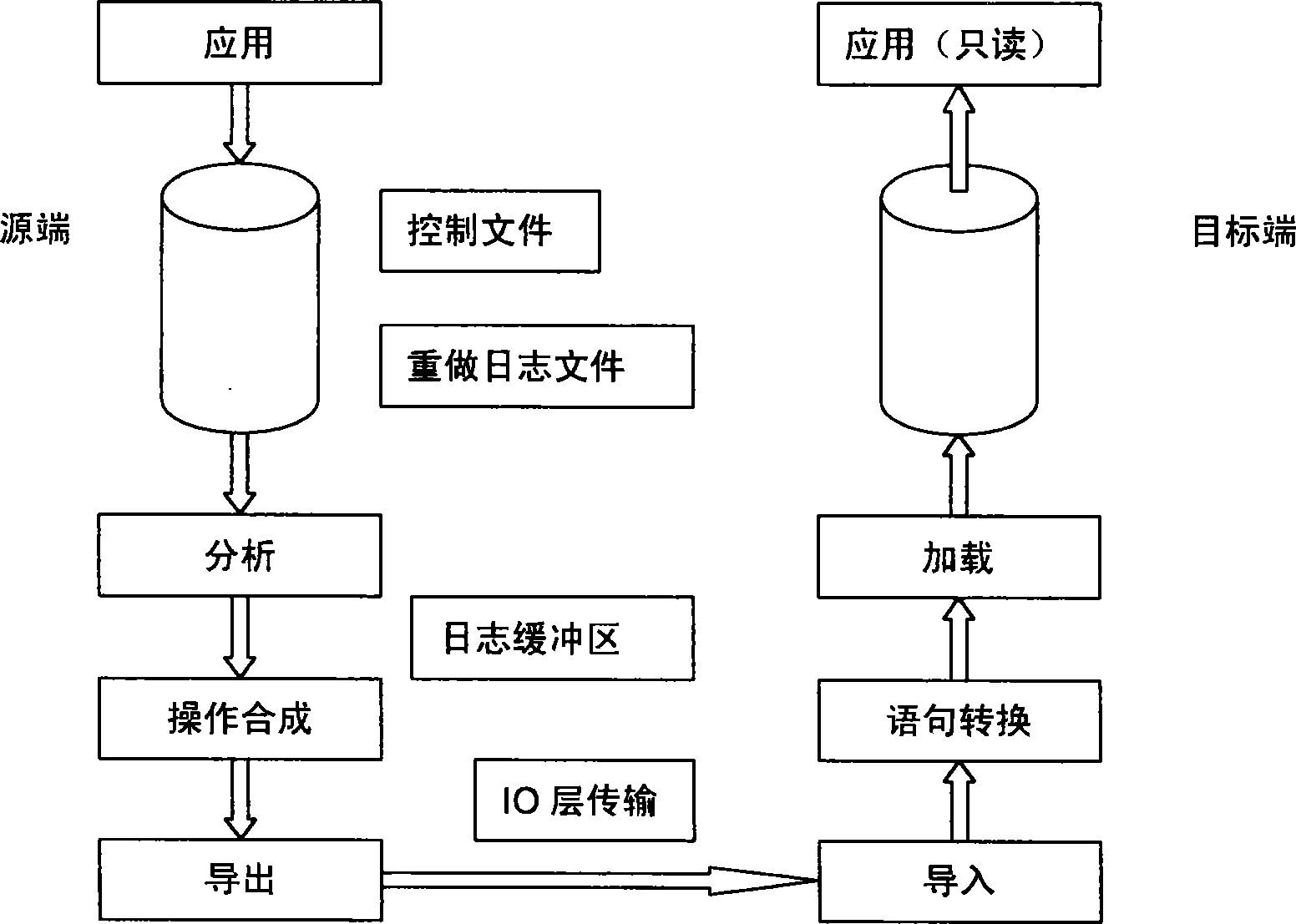
InactiveCN101187888AAvoid lookup timeRapid positioningRedundant operation error correctionSpecial data processing applicationsOperational systemSQL
The invention discloses a method which realizes data reproduction of a database in an isomeric environment, which gains SQL sentences which cause changes of a source end database through analysis of journals of the source end database, and the SQL sentences are organized according to work, then the SQL sentences which are organized are transmitted to a target end database, and the SQL sentences are executed according to the sequence which is executed in the source end database in the target end database to realize reproduction of a database. The method can suit isomeric environments, and has no isomorphic requirements to storing devices, servers, operating systems, and database software of the source end and the target end, and the method has the advantages of excellent adaptability, which occupies little systematic resource and network bandwidth resource.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Video processing in a multi-participant video conference
ActiveUS20060244812A1Save network bandwidthTwo-way working systemsComputer graphics (images)Video processing
Some embodiments provide an architecture for establishing multi-participant video conferences. This architecture has a central distributor that receives video images from two or more participants. From the received images, the central distributor generates composite images that the central distributor transmits back to the participants. Each composite image includes a set of sub images, where each sub image belongs to one participant. In some embodiments, the central distributor saves network bandwidth by removing each particular participant's image from the composite image that the central distributor sends to the particular participant. In some embodiments, images received from each participant are arranged in the composite in a non-interleaved manner. For instance, in some embodiments, the composite image includes at most one sub-image for each participant, and no two sub-images are interleaved.
Owner:APPLE INC
System and method for dividing data into predominantly fixed-sized chunks so that duplicate data chunks may be identified
InactiveUS7281006B2Reduce storageImprove reliabilityData processing applicationsDigital data information retrievalData matchingTheoretical computer science
A data chunking system divides data into predominantly fixed-sized chunks such that duplicate data may be identified. The data chunking system may be used to reduce the data storage and save network bandwidth by allowing storage or transmission of primarily unique data chunks. The system may also be used to increase reliability in data storage and network transmission, by allowing an error affecting a data chunk to be repaired with an identified duplicate chunk. The data chunking system chunks data by selecting a chunk of fixed size, then moving a window along the data until a match to existing data is found. As the window moves across the data, unique chunks predominantly of fixed size are formed in the data passed over. Several embodiments provide alternate methods of determining whether a selected chunk matches existing data and methods by which the window is moved through the data. To locate duplicate data, the data chunking system remembers data by computing a mathematical function of a data chunk and inserting the computed value into a hash table.
Owner:IBM CORP
Method, system and program for establishing network contact
InactiveUS6584503B1Easy to useReestablish communicationDigital computer detailsData switching networksComputer networkComputer printing
Disclosed is a method, system, and program for establishing communication with multiple network devices, such as printers. A detection is made of at least one network device that is not available for communication. A routine is executed at predetermined intervals that sends a message, such as an SNMP message, to each unavailable network device to establish communication with the unavailable network device. A determination is then made as to whether the message sent to each unavailable network device established communication with that network device. Indication is then made that each previously unavailable network device for which the message established communication is available on the network.
Owner:IBM CORP
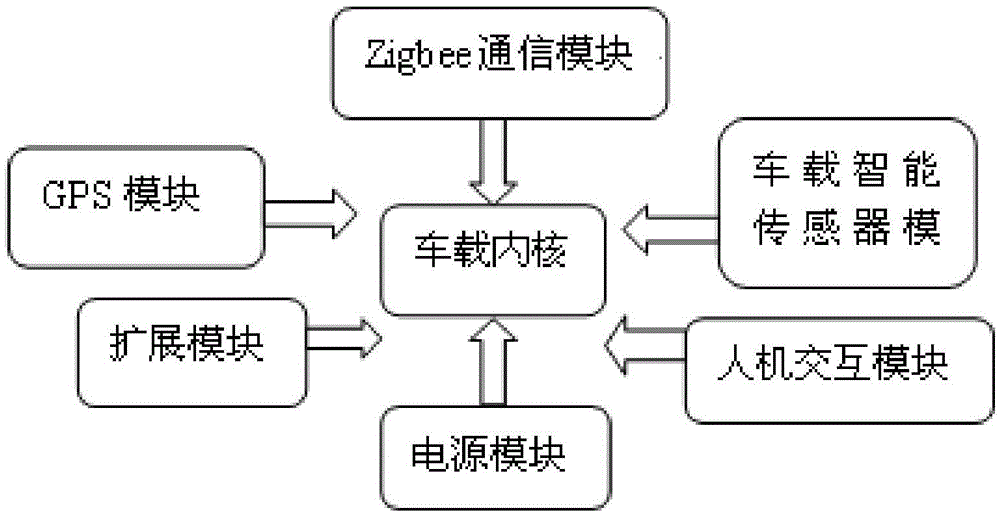
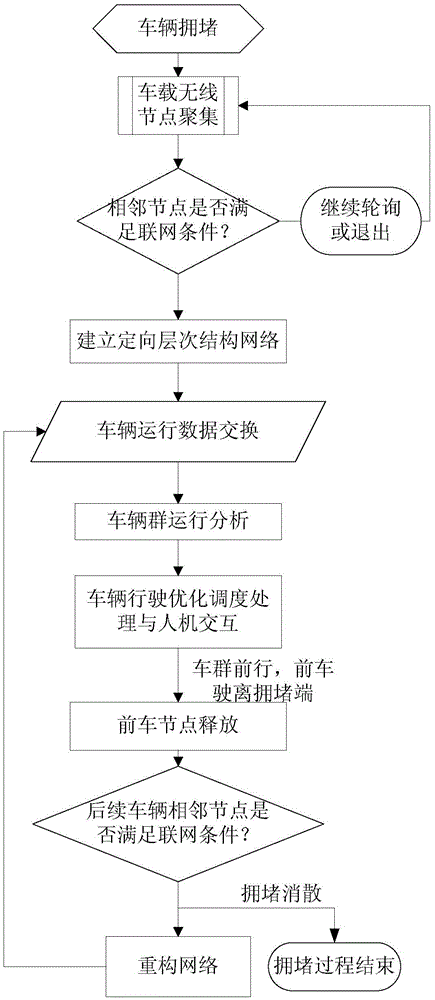
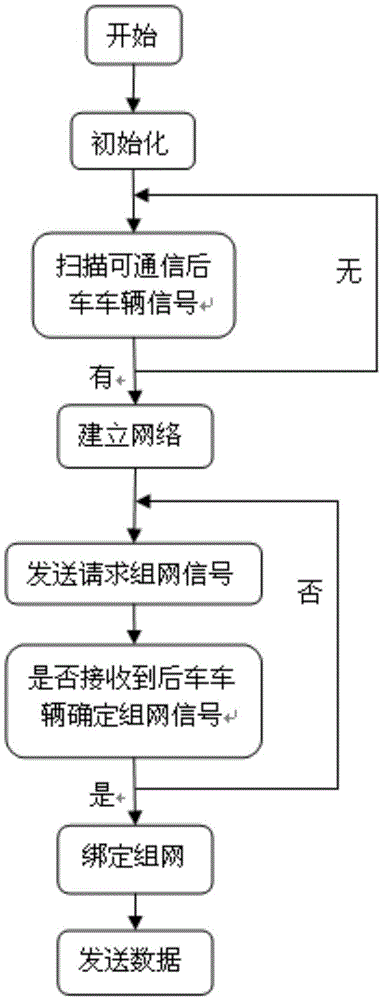
Intelligent traffic flow congestion dispersal method through vehicle group autonomous cooperative scheduling
ActiveCN105631793AGuaranteed purityAvoid serious traffic jamsData processing applicationsRoad vehicles traffic controlMobile vehicleDriver/operator
The invention provides an intelligent traffic flow congestion dispersal method through vehicle group autonomous cooperative scheduling. An intelligent vehicle-mounted terminal and a wireless communication module are integrated, a cooperative scheduling algorithm optimization index and vehicle driving parameter acquisition and processing process is built according to a vehicle following model in the case of traffic flow congestion, the optimization index reflects the vehicle group passing efficiency, the intelligent vehicle-mounted terminal and an adjacent vehicle build a wireless communication network, a guiding instruction is generated according to the cooperative scheduling algorithm and the protocol, a vehicle queuing position and estimated passing time are provided for a driver through a man-computer interface, and the driver is guided to select a proper speed and a proper direction. The method of the invention has the advantages of low cost, high terminal integration, simple mounting, high sensitivity, quick response speed and the like, and is applicable to various motor vehicles, such as freight cars, buses and cars, which run in traffic dense areas such as urban areas and freeways.
Owner:SOUTH CHINA UNIV OF TECH
Acceleration method, equipment and system for network video loading
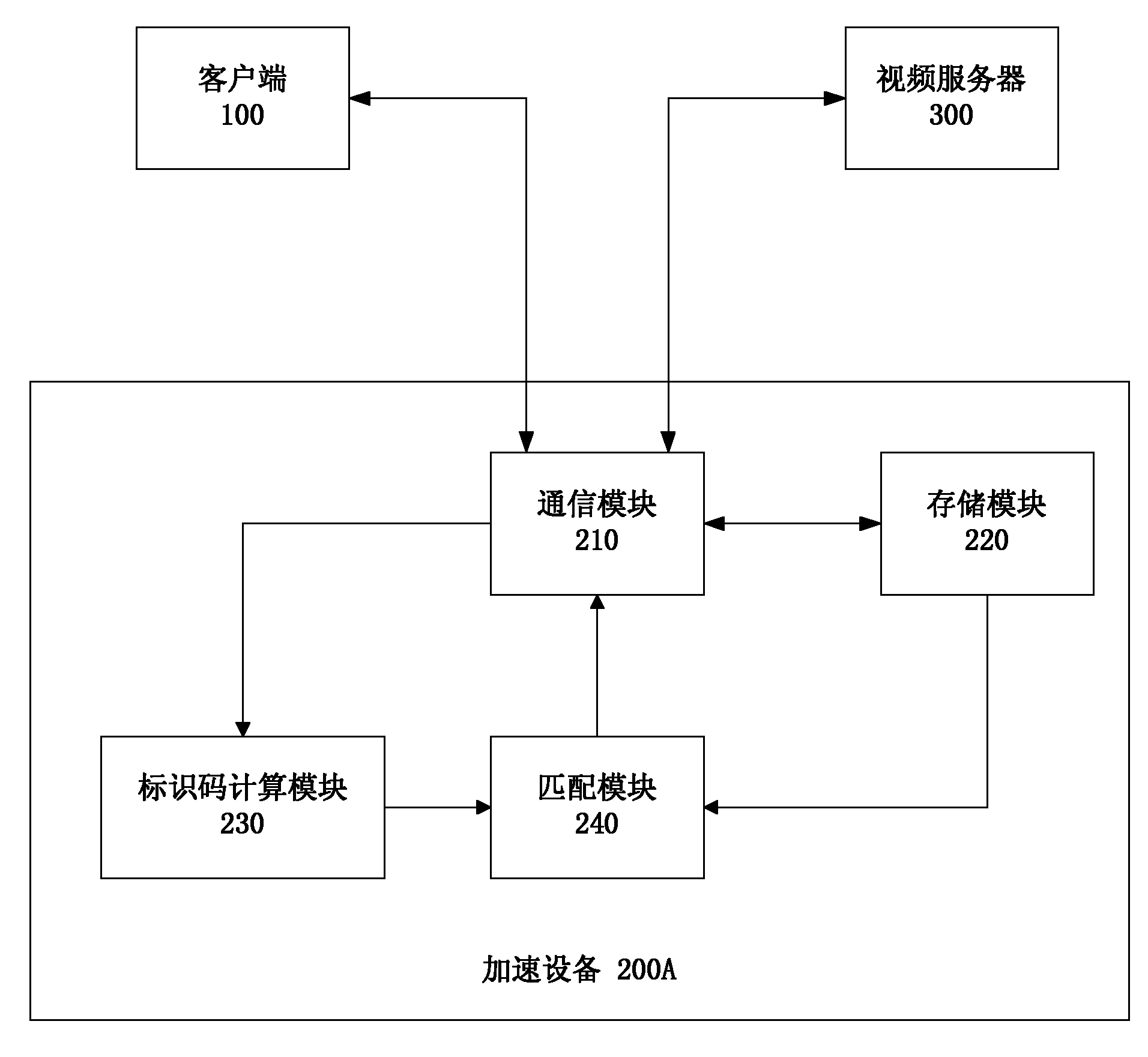
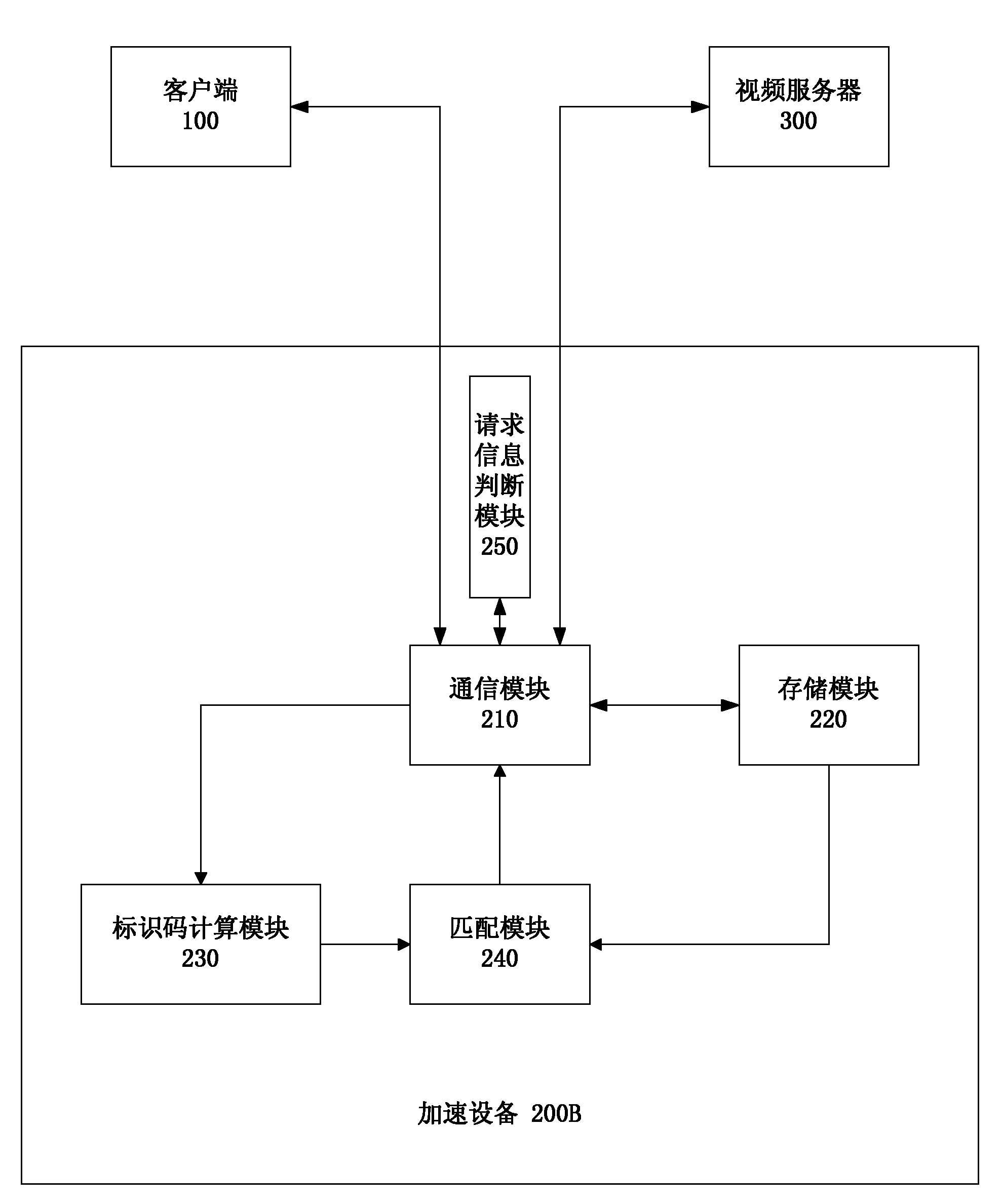
ActiveCN102111685ASave network bandwidthImprove download speedSelective content distributionVideo serverClient-side
The invention discloses an acceleration method, equipment and system for network video loading. The method comprises the following steps: S1, receiving video request information from a client and sending the video request information to a video server; S2, receiving the video data stream of the required video from the video server; S3, after receiving a size-predetermined video fragment, calculating the identification code of the required video according to the video fragment, wherein the identification code can uniquely identify the video; and S4, searching a cached video according to the identification code, stopping receiving the video data stream from the video server if finding the video data matched with the identification code, and sending the found video data to the client, if not finding the video data matched with the identification code, continuing to receive the video data stream from the video server, caching the received video data, and sending the video data to the client. According to the invention, network bandwidth is saved, and video loading speed is accelerated.
Owner:SANGFOR TECH INC
System and method for distributed multipoint conferencing with automatic endpoint address detection and dynamic endpoint-server allocation
ActiveUS7461126B2Save network bandwidthMultiplex system selection arrangementsSpecial service provision for substationIp addressServer allocation
An embodiment of the invention is a multipoint conferencing system having the ability to dynamically assign an endpoint to a “closest” one of multiple conference servers is disclosed. In one embodiment, when an endpoint first connects to the conferencing system, its Endpoint ID (e.g., IP address, E164 address) is determined. Based on the Endpoint ID, the conferencing system selects the most appropriate ones of the conference servers to act as the endpoint's “local” conference server. That is, the endpoint will transmit and receive conference data from other endpoints via the selected conference server. If no other endpoints across the network happen to be viewing a particular endpoint's video stream, the stream is not provided to the network, thus conserving network bandwidth. An embodiment further creates appropriate linking between conference servers automatically, manages conference server topology and determines link type (e.g., Unicast vs. Multicast linking) automatically.
Owner:AVAYA INC +2
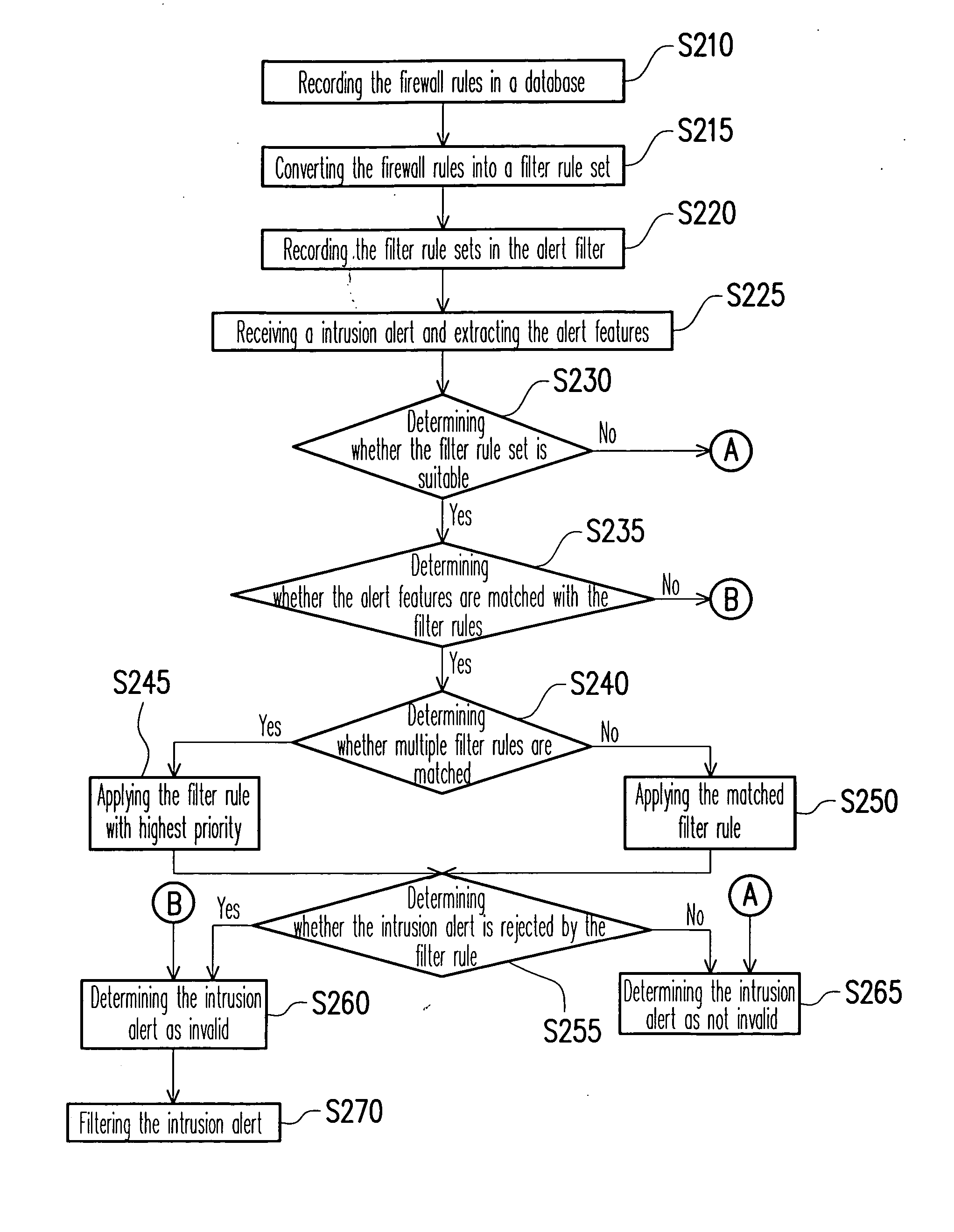
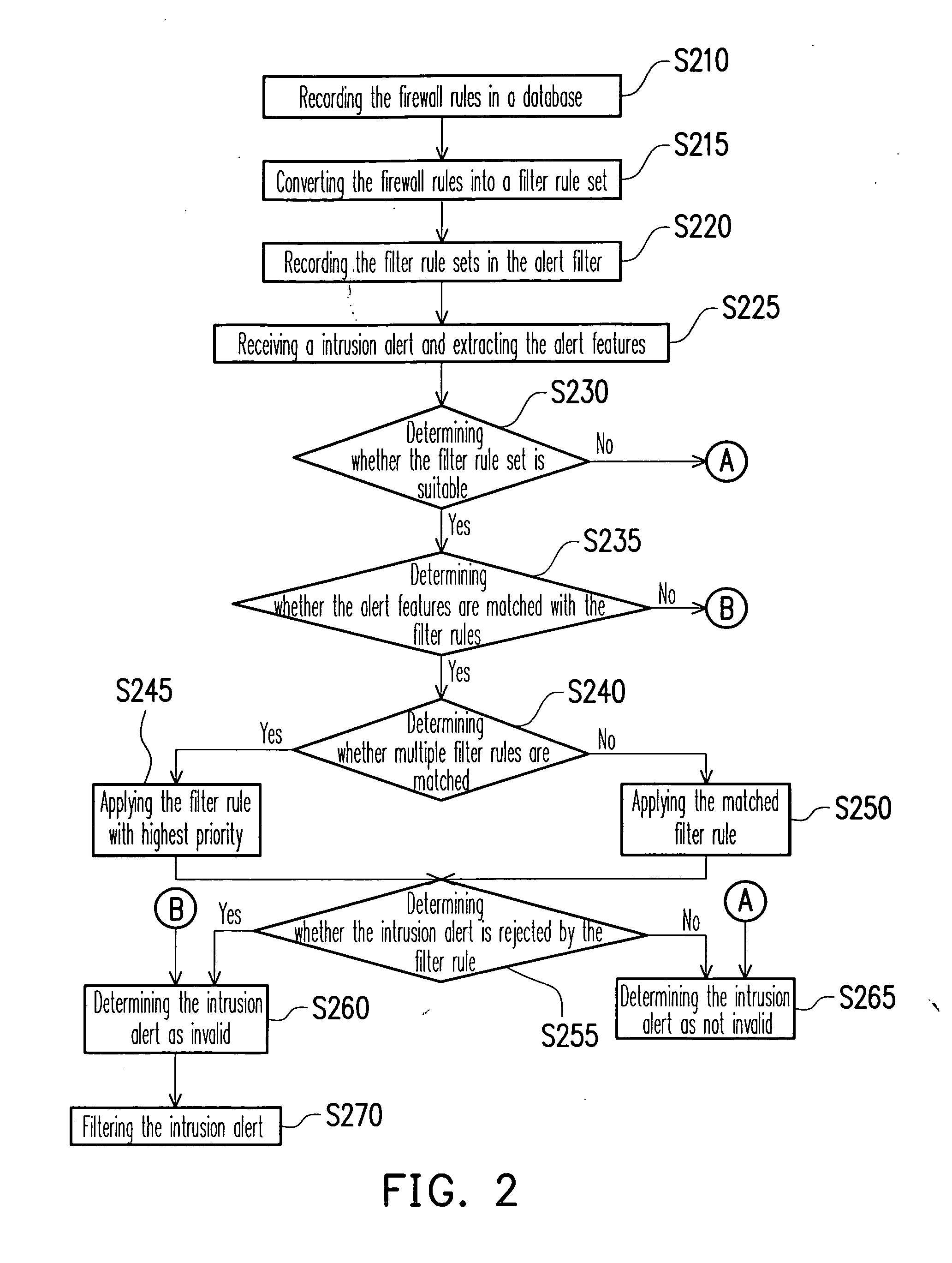
Method for eliminating invalid intrusion alerts
InactiveUS20070136813A1Avoid disadvantagesRapid deploymentMemory loss protectionError detection/correctionFiltering rulesComputer security
The method for eliminating invalid intrusion alerts operates according to a set of filter rules that are generated from given firewall rules. As a filter that implements this method receives an intrusion alert, it directly matches the features of the alert against its own rules, and then decides the validity of the alert. By coupling with the method, various filter-rule sets could be generated for numerous firewalls that may be not on the same specification, and an on-line deployment method could be applied to deploy filter-rule sets for filters. By applying the invention, it is reachable to eliminate invalid intrusion alerts precisely and efficiently, and to deploy quickly and with less manpower.
Owner:NAT CHUNG SHAN INST SCI & TECH
System and Method for Transparent Virtual Routing
InactiveUS20080212598A1Minimal administrativeMinimal operationalNetwork connectionsWide area networksNetwork addressVirtual user
A transparent routing device disposed within an access network configured in accordance with one or more lower-layer protocols is disclosed herein. The device includes a set of subscriber-side ports. Each of the subscriber-side ports is associated with a plurality of virtual subscriber-side interfaces disposed to effectively terminate a corresponding plurality of subscriber-side connections with subscriber host devices served by the access network. The device further includes at least one network-side port through which communication occurs with an external network in accordance with a higher-layer protocol. A routing table is configured to establish a correspondence between network addresses of the subscriber host devices and the plurality of virtual subscriber-side interfaces. During operation of the device, packets received through the at least one network-side port are forwarded to corresponding ones of the virtual subscriber-side interfaces based upon network addresses of the packets.
Owner:GOOGLE TECH HLDG LLC
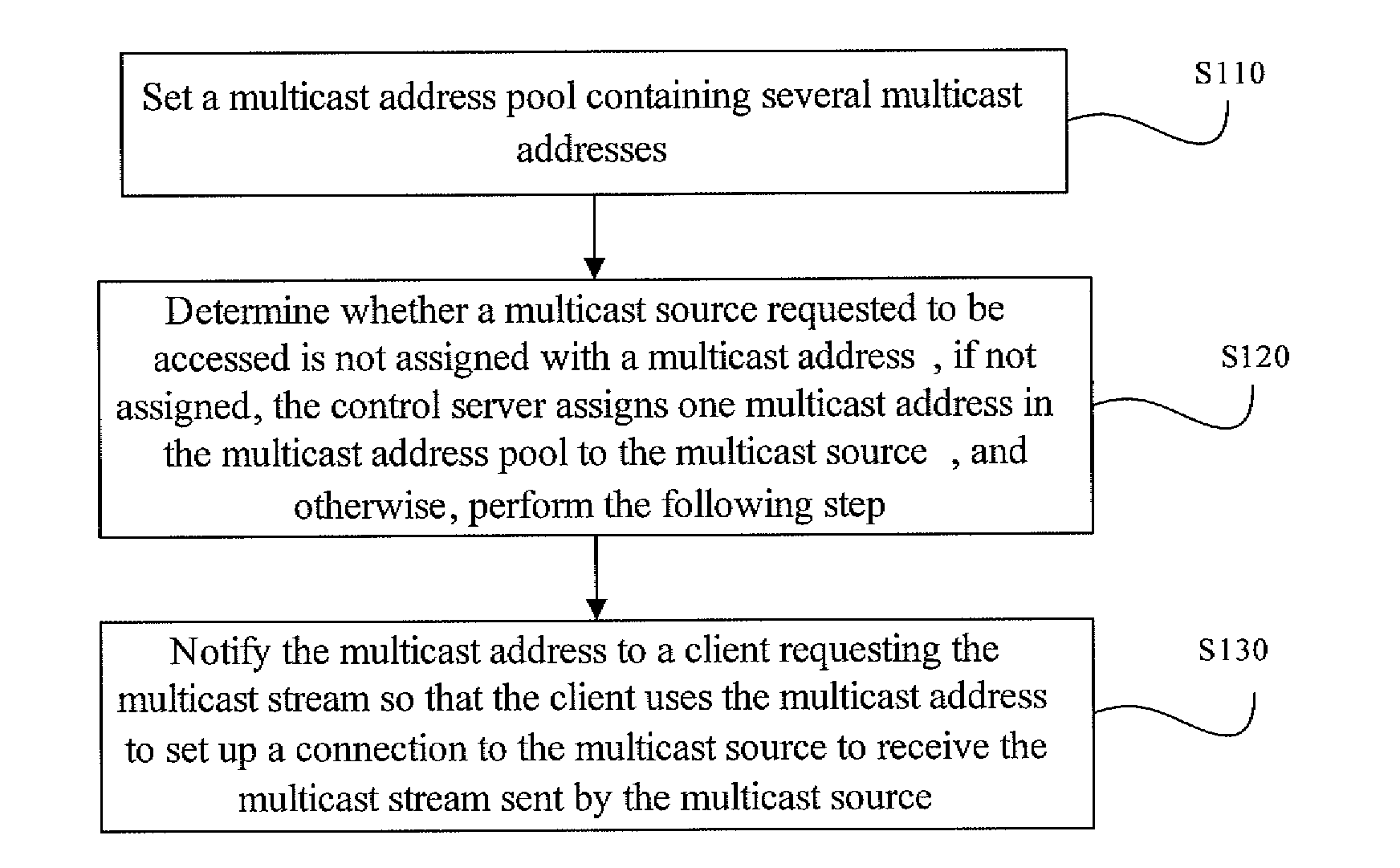
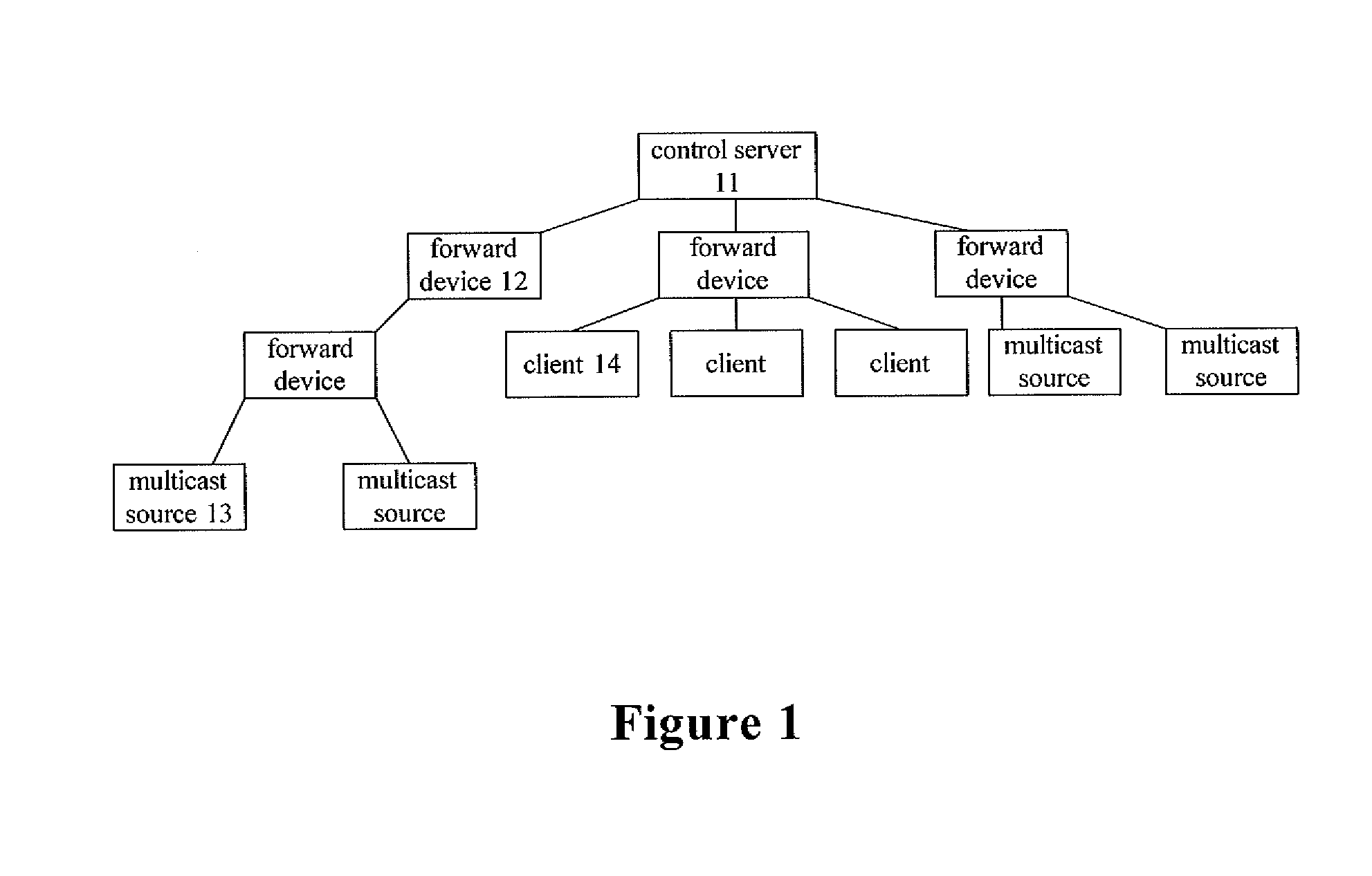
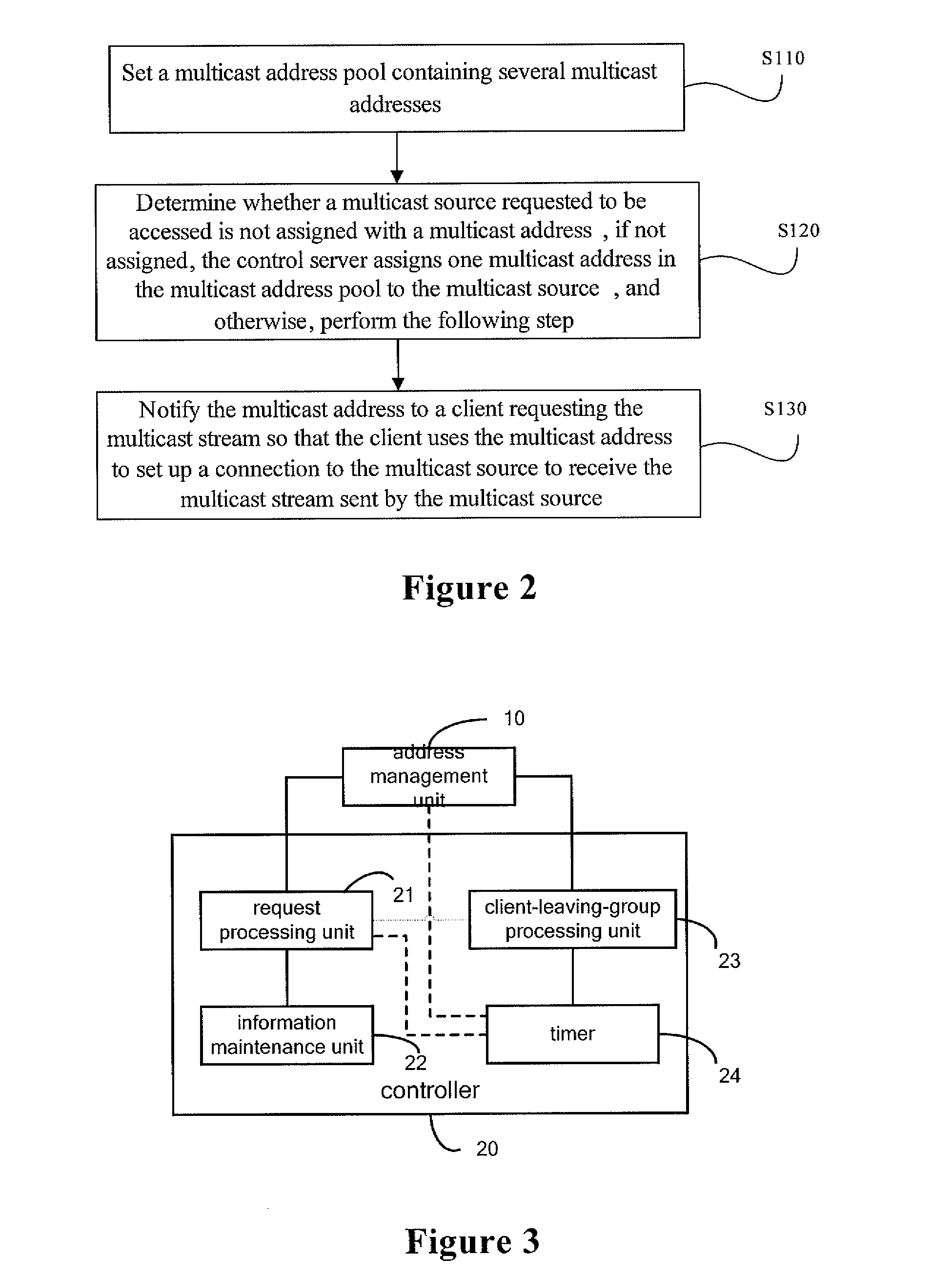
Method for deploying multicast network, multicast network and control server
InactiveUS20090190587A1Save resourcesSave network bandwidthSpecial service provision for substationData switching by path configurationClient-sideMulticast network
The present invention discloses a method for deploying a multicast network, which includes a control server, several multicast sources and clients. The method includes: setting a multicast address pool containing several multicast addresses, determining whether a multicast address is assigned to a multicast source requested to be accessed; if no multicast address is assigned to the multicast source, assigning one multicast address in the multicast address pool to the multicast source, and otherwise, notifying a client requesting a multicast stream of the multicast address so that the client uses the multicast address to set up a connection to the multicast source so as to receive the multicast stream sent by the multicast source. The present invention further discloses a multicast network and control server. According to the present invention, not only multicast address resources but also network bandwidth as well as multicast route table entries of forward devices can be saved.
Owner:NEW H3C TECH CO LTD
Video encoding in a video conference
ActiveUS7692682B2Save network bandwidthTelevision conference systemsTwo-way working systemsVideo encodingComputer graphics (images)
Some embodiments provide an architecture for establishing multi-participant video conferences. This architecture has a central distributor that receives video images from two or more participants. From the received images, the central distributor generates composite images that the central distributor transmits back to the participants. Each composite image includes a set of sub images, where each sub image belongs to one participant. In some embodiments, the central distributor saves network bandwidth by removing each particular participant's image from the composite image that the central distributor sends to the particular participant. In some embodiments, images received from each participant are arranged in the composite in a non-interleaved manner. For instance, in some embodiments, the composite image includes at most one sub-image for each participant, and no two sub-images are interleaved.
Owner:APPLE INC
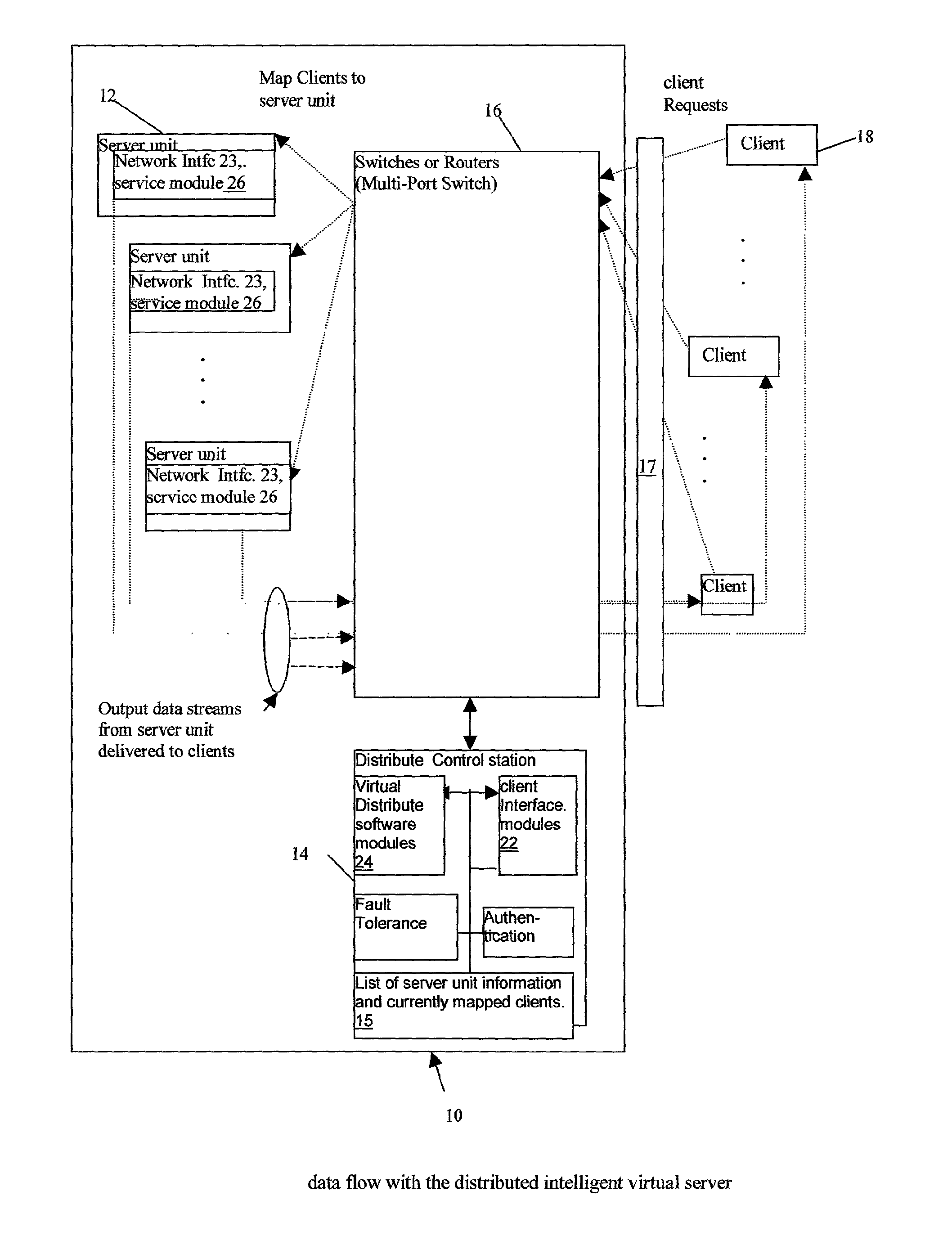
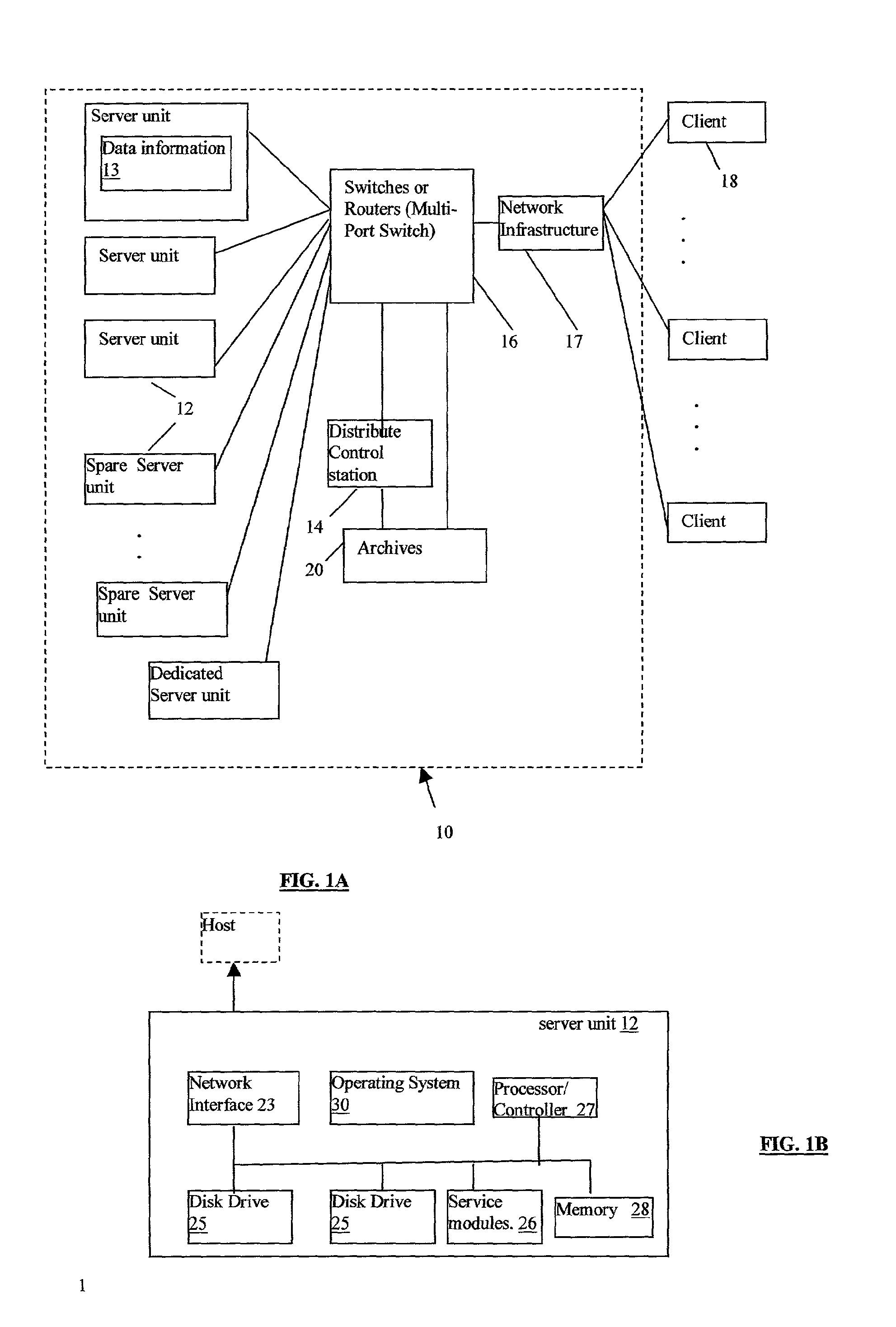
Distributed Intelligent Virtual Server
InactiveUS20110093740A1Capacity of the virtual server can be scale upImprove abilitiesDigital data processing detailsComputer security arrangementsDistribution controlTelecommunications link
A intelligent distributed virtual server for providing distributed services to a plurality of clients, including one or more servers units, each server units storing data and providing service for accessing by one or more clients; one or more switches and routers for connecting the clients to the server units and to provide a communication link; and a distribution control station connected to the clients and the server units via the switches and routers, wherein the distribution control station receives a request for a service from a client, and selectively establishes a data link between that client and an server unit, which stores the requested data and provides service, such that the server unit provides the data stream to the client via the communication link, independent of other server units. Therefore, it provides distributed computing cross intra-net or Internet and it provides scalability and all intelligent services such as fault handling, security and others.
Owner:RPX CORP
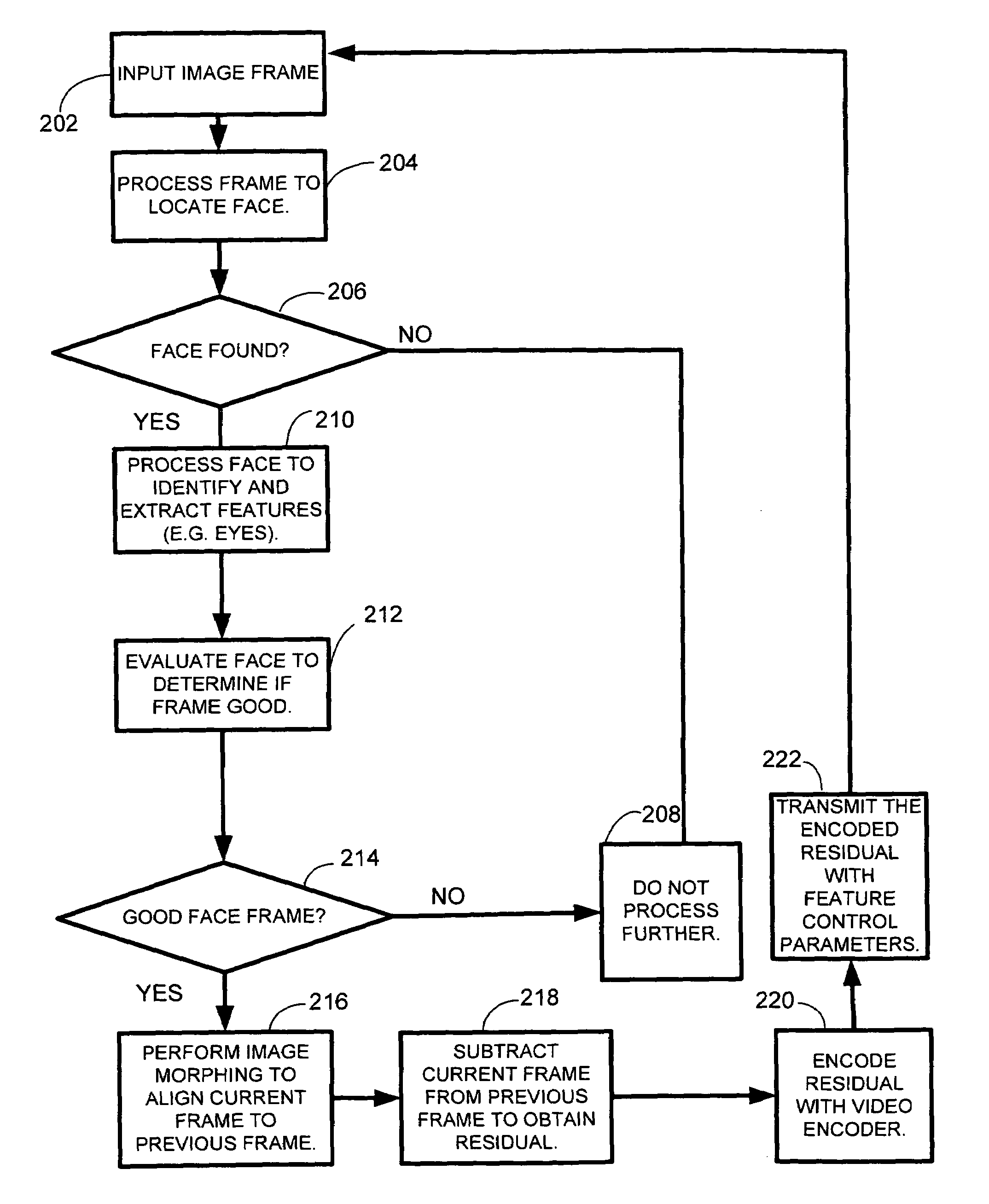
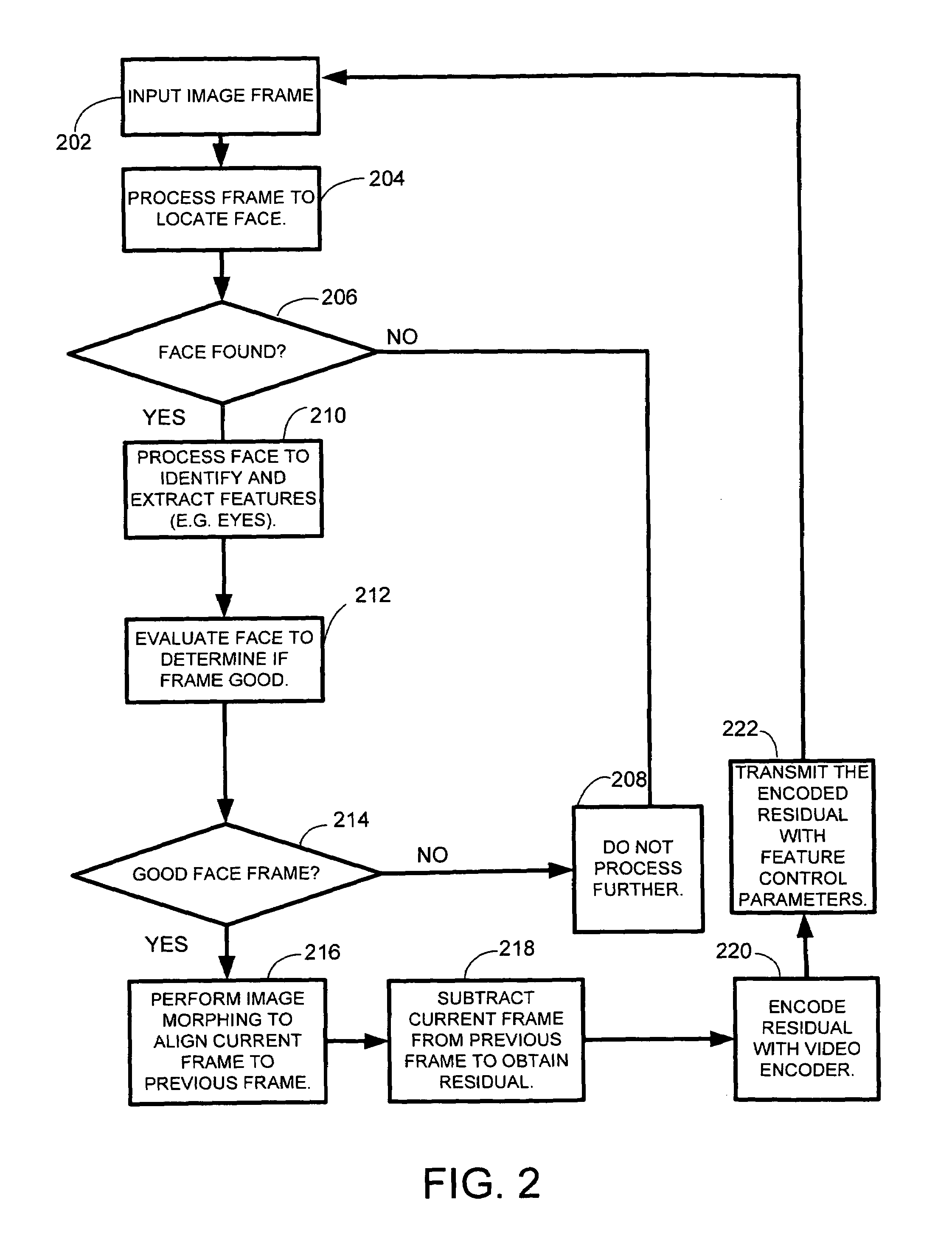
System and method for very low frame rate video streaming for face-to-face video conferencing
ActiveUS7583287B2Reduces the video frame-rateIncrease frame rateTwo-way working systemsMorphingSystem usage
A real-time low frame-rate video compression system and method that allows the user to perform face-to-face communication through an extremely low bandwidth network. At the encoder side, the system is able to automatically select only a few good faces from the original sequence with high visual quality and compress and transmit them. At the decoder side, the system use image-morphing based rendering method to generate a normal frame-rate video. Experimental results show that the system is superior to more traditional video codecs for low bit-rate face-to-face communication.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com