Identity authentication method and system
A technology of identity authentication and identity information, applied in the electronic field, can solve problems such as bringing great convenience to users, and achieve the effect of ensuring legitimacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
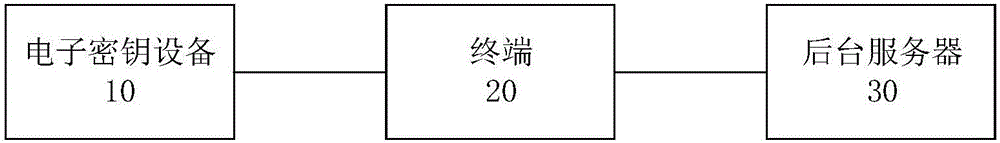
[0025] This embodiment provides an identity authentication system, such as figure 1 As shown, the system includes: an electronic key device 10, a terminal 20, and an authentication server 30.
[0026] In this embodiment, the working principle of each device is described as follows.
[0027] The electronic key device 10 is used to access the terminal 20, power on to initialize, wait to receive instructions issued by the terminal 20, and perform button detection; the electronic key device 10 is used to determine that the button is allowed when a button is detected Whether the flag is set, if the button flag is allowed to be set, scan the button to obtain the key value of the pressed button, and according to the obtained key value, determine the instruction type corresponding to the pressed button; electronic key device 10 is used for When an instruction issued by the terminal 20 is received, it is determined whether the received instruction is an instruction in a preset format. If it...
Embodiment 2
[0066] This embodiment provides a remote account opening system, such as figure 1 As shown, the remote account opening system adopts the identity authentication system in Embodiment 1. The difference between this embodiment and embodiment 1 is that in this embodiment: the terminal 20 is also used to send an account opening request to the authentication server 30, and the account opening request carries at least a user identity, which can be a bank card number, The serial number of the electronic key device 10, the plain text of ID card information, etc. can be used to uniquely identify the user's identity. The user identity has the same meaning as the user identity in Embodiment 1, and contains the same content; the authentication server 30, It is used to open an account matching the user's identity according to the account opening request.
[0067] As an optional implementation of the embodiment of the present invention, the terminal 20 is also used to obtain the identity authen...
Embodiment 3
[0071] This embodiment provides an identity authentication method, which is applied to the identity authentication system in Embodiment 1.
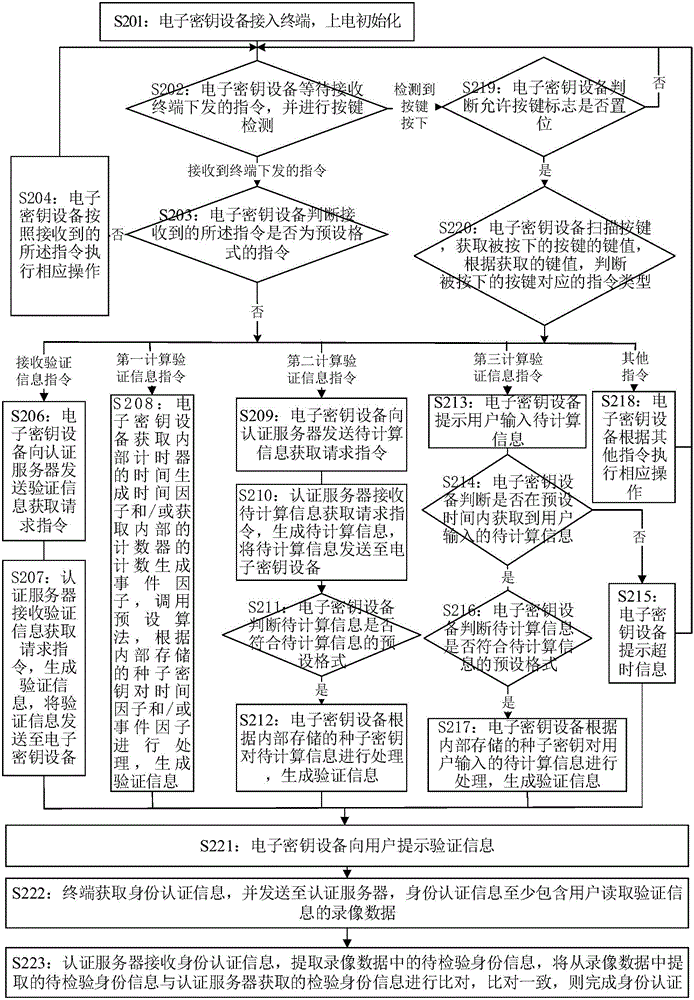
[0072] figure 2 This is a flowchart of the identity authentication method provided in this embodiment. The method mainly includes the following steps (S201 to S223):
[0073] S201: The electronic key device is connected to the terminal and initialized after power-on;
[0074] The electronic key device in this embodiment is a device with a signature function issued by the bank to the user when the user opens an account, including a KEY with a signature function, a smart card, or a device that integrates a KEY card, for example, ICBC U-Shield, Agricultural Bank Kbao , Bank of China e-Ling and other equipment. The terminal can be a PC, a pad (tablet computer), a smart phone and other devices that support electronic key devices. The electronic key device can be connected to the terminal through a wired way (such as a USB interface, a headset int...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com