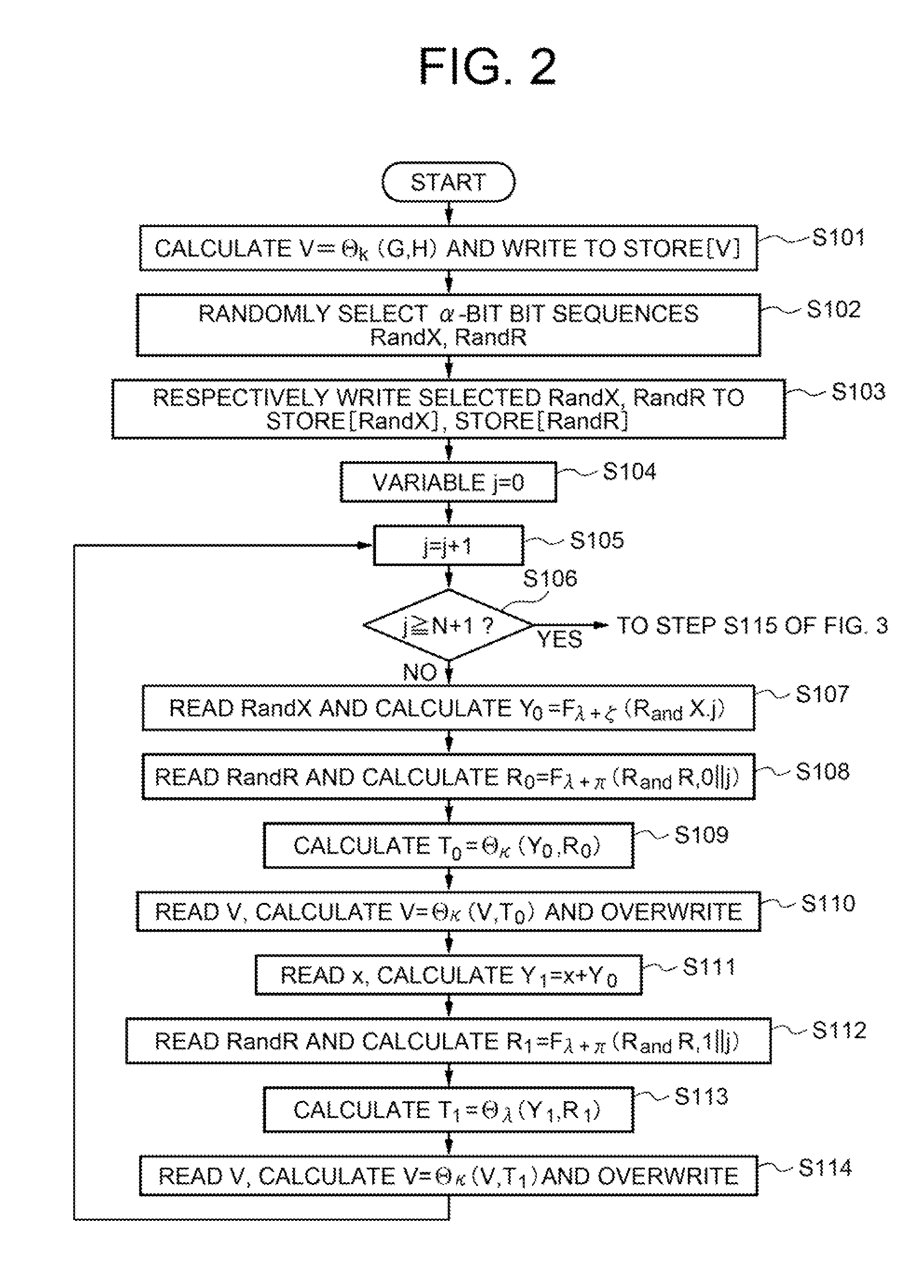
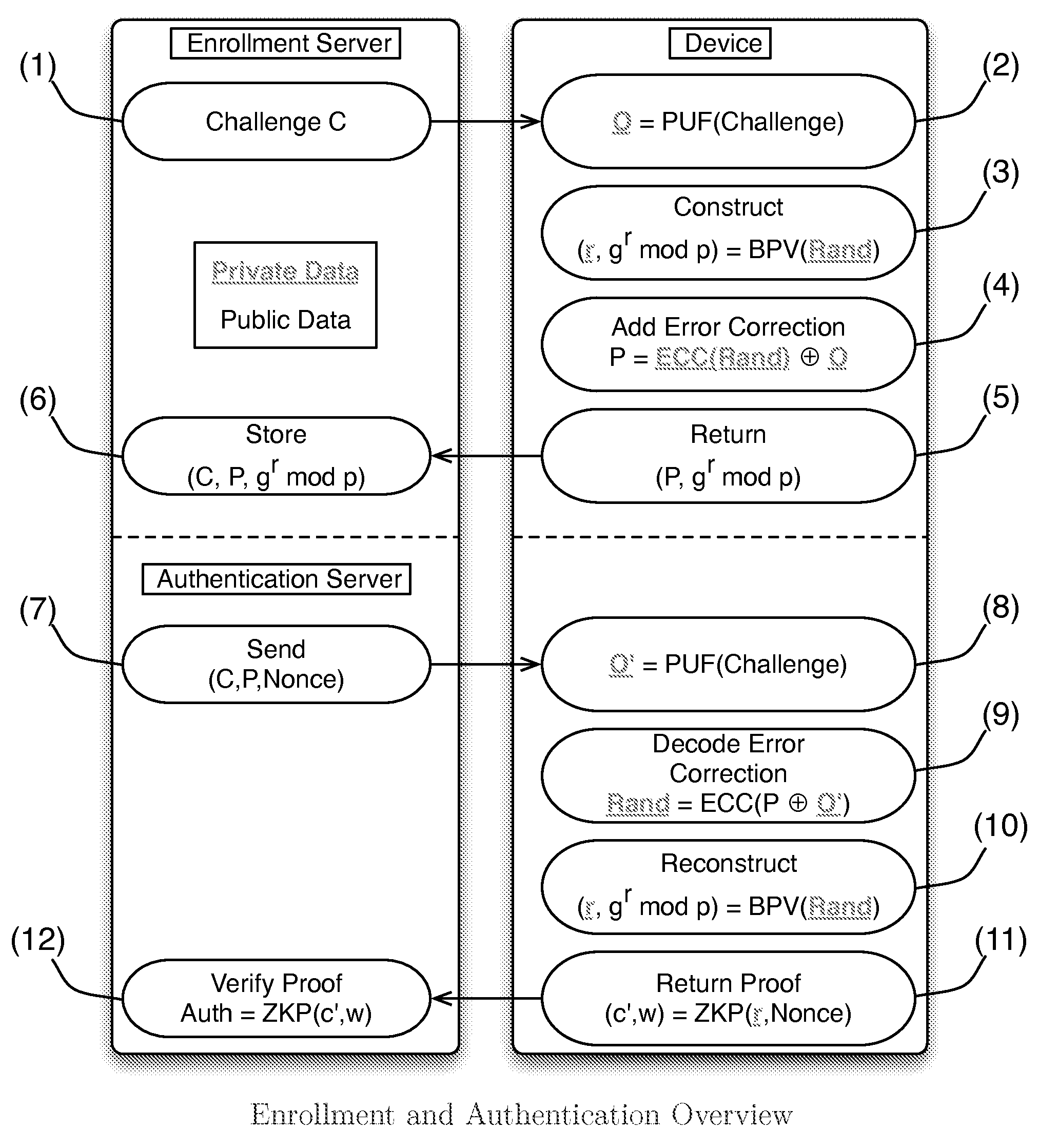
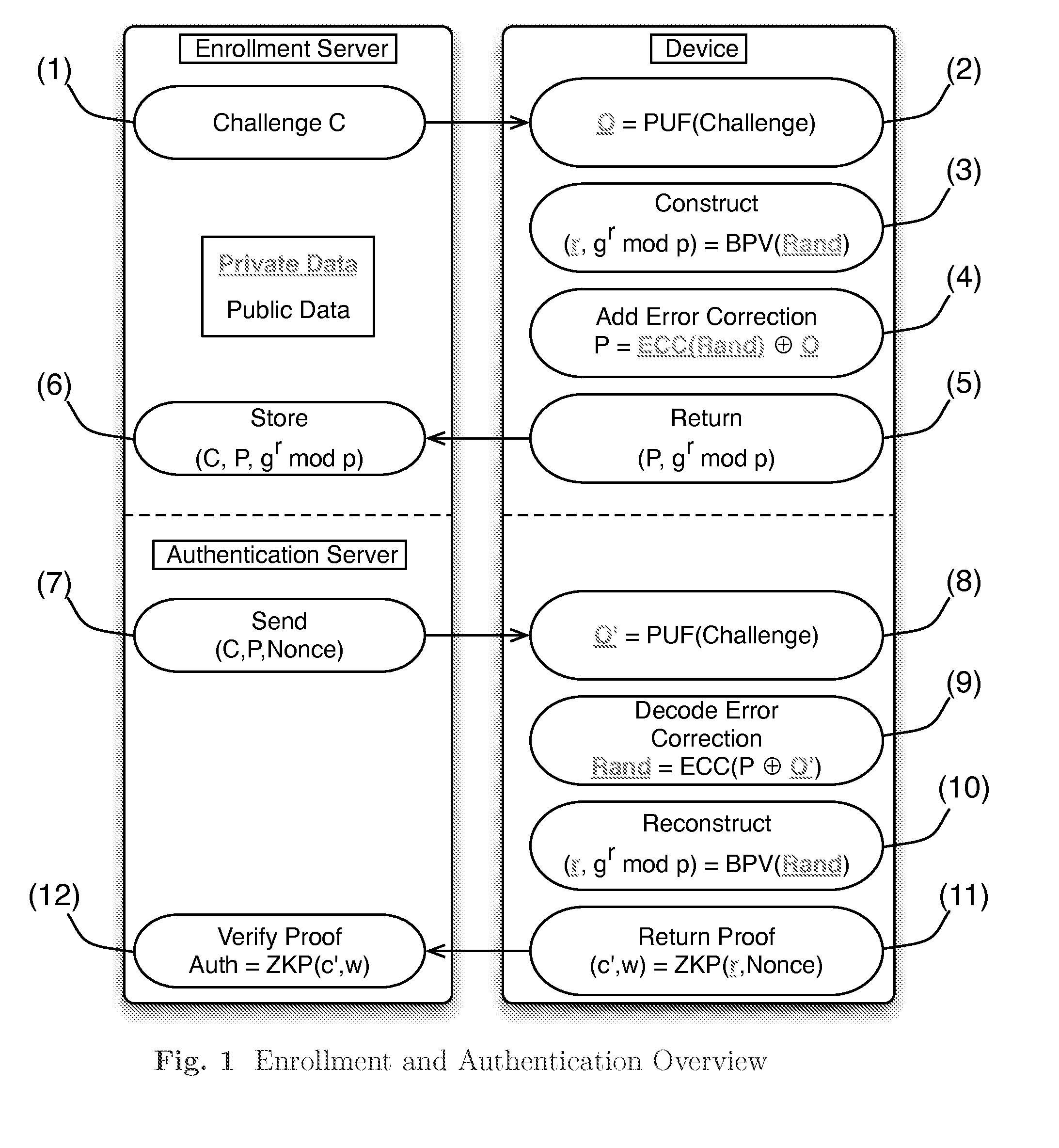
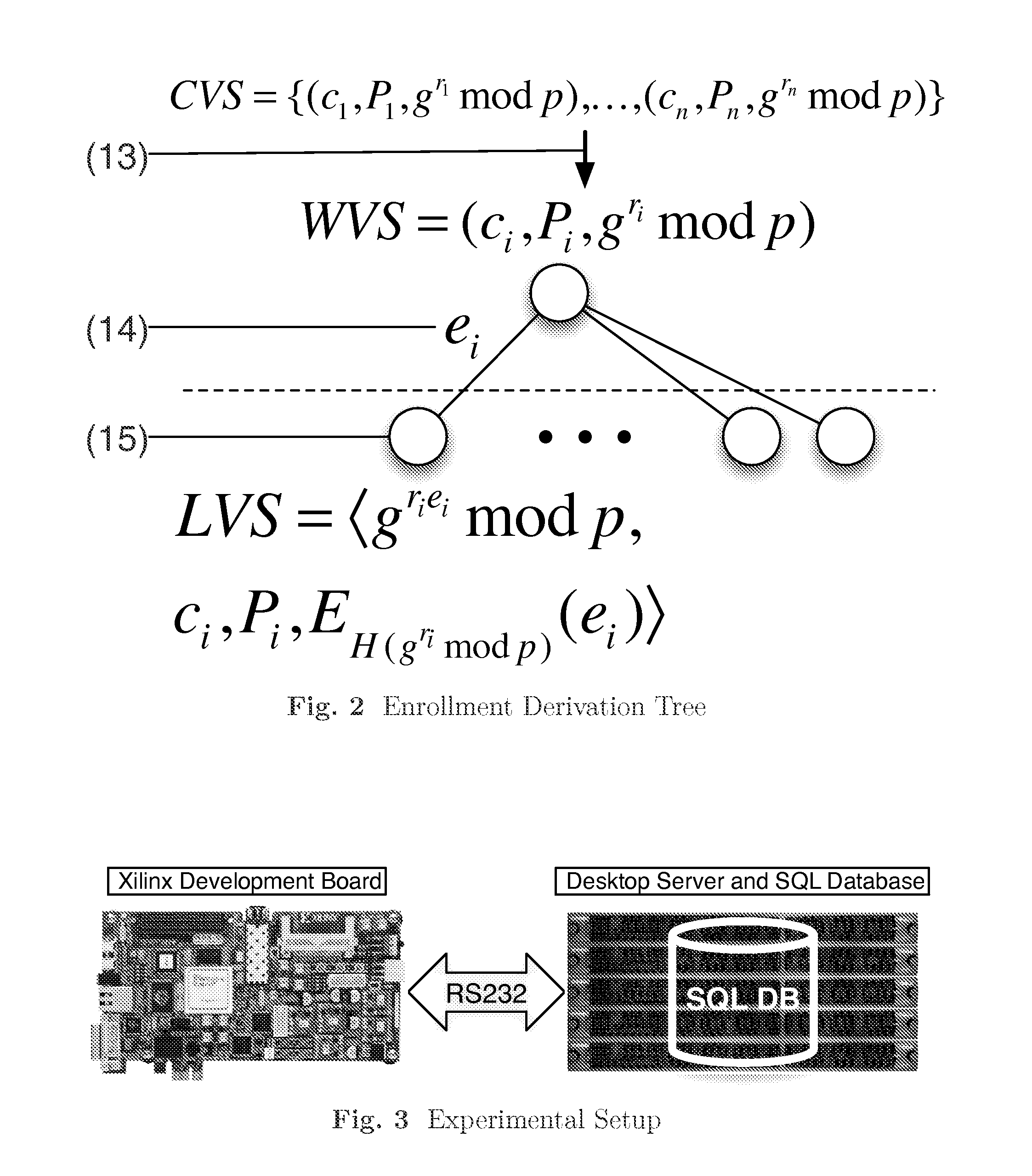
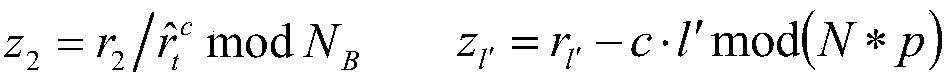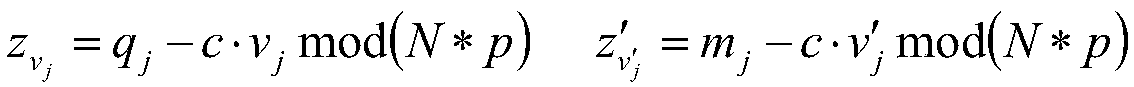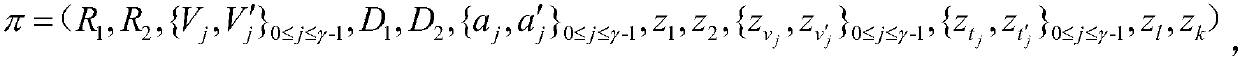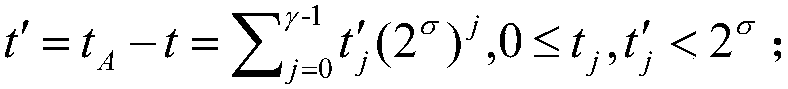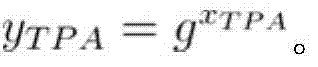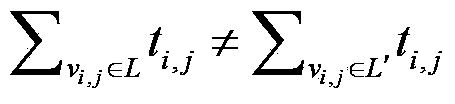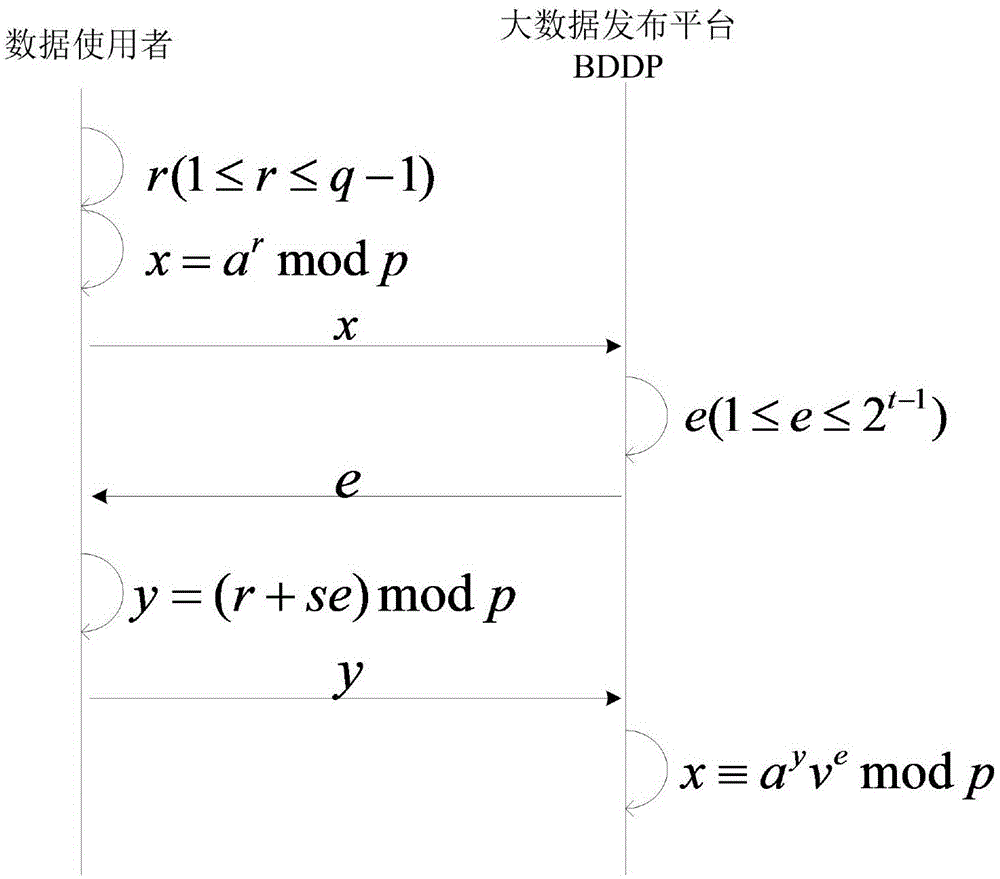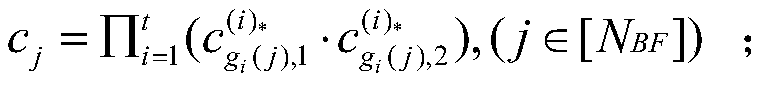Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
406 results about "Zero-knowledge proof" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptography, a zero-knowledge proof or zero-knowledge protocol is a method by which one party (the prover) can prove to another party (the verifier) that they know a value x, without conveying any information apart from the fact that they know the value x. The essence of zero-knowledge proofs is that it is trivial to prove that one possesses knowledge of certain information by simply revealing it; the challenge is to prove such possession without revealing the information itself or any additional information.
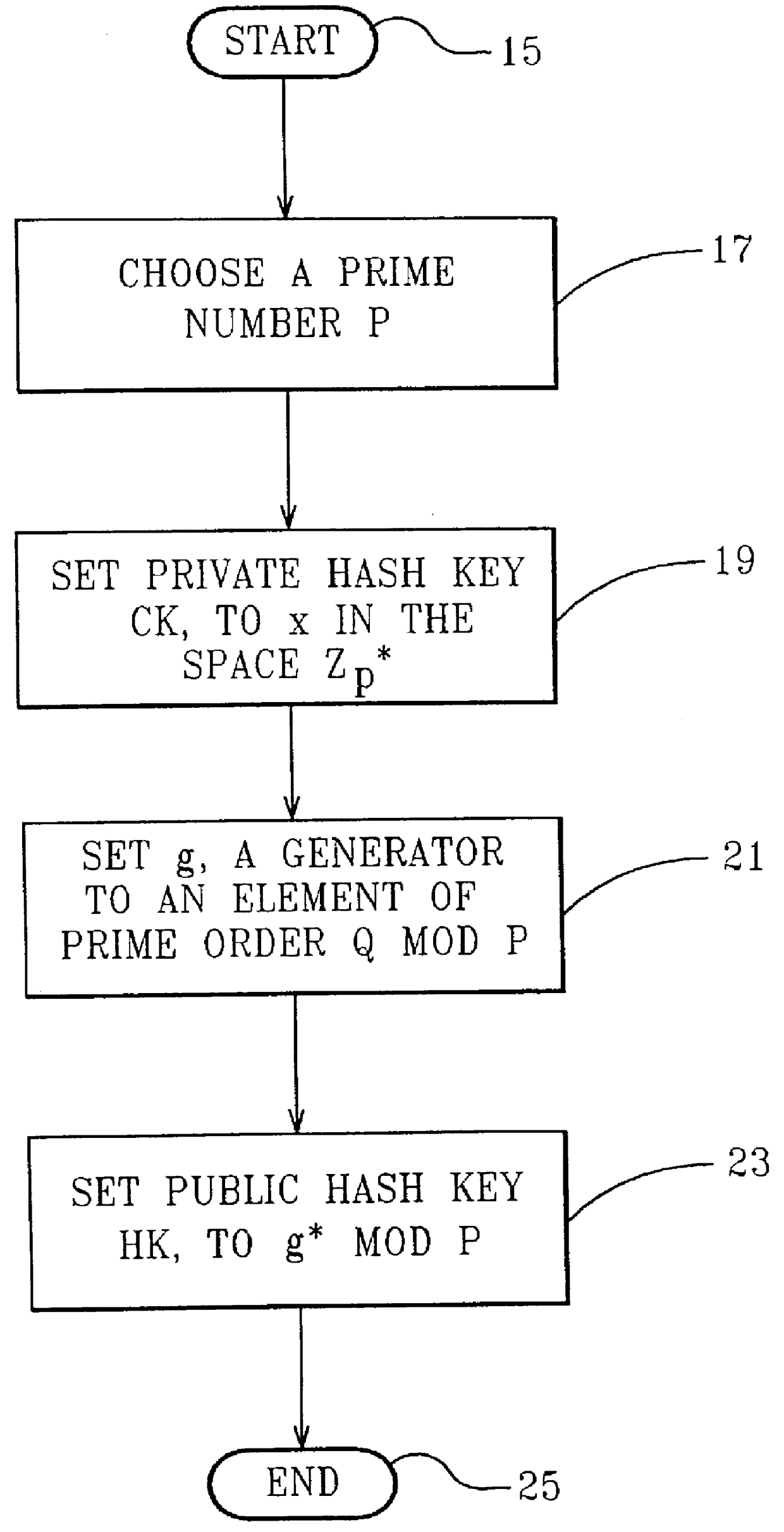
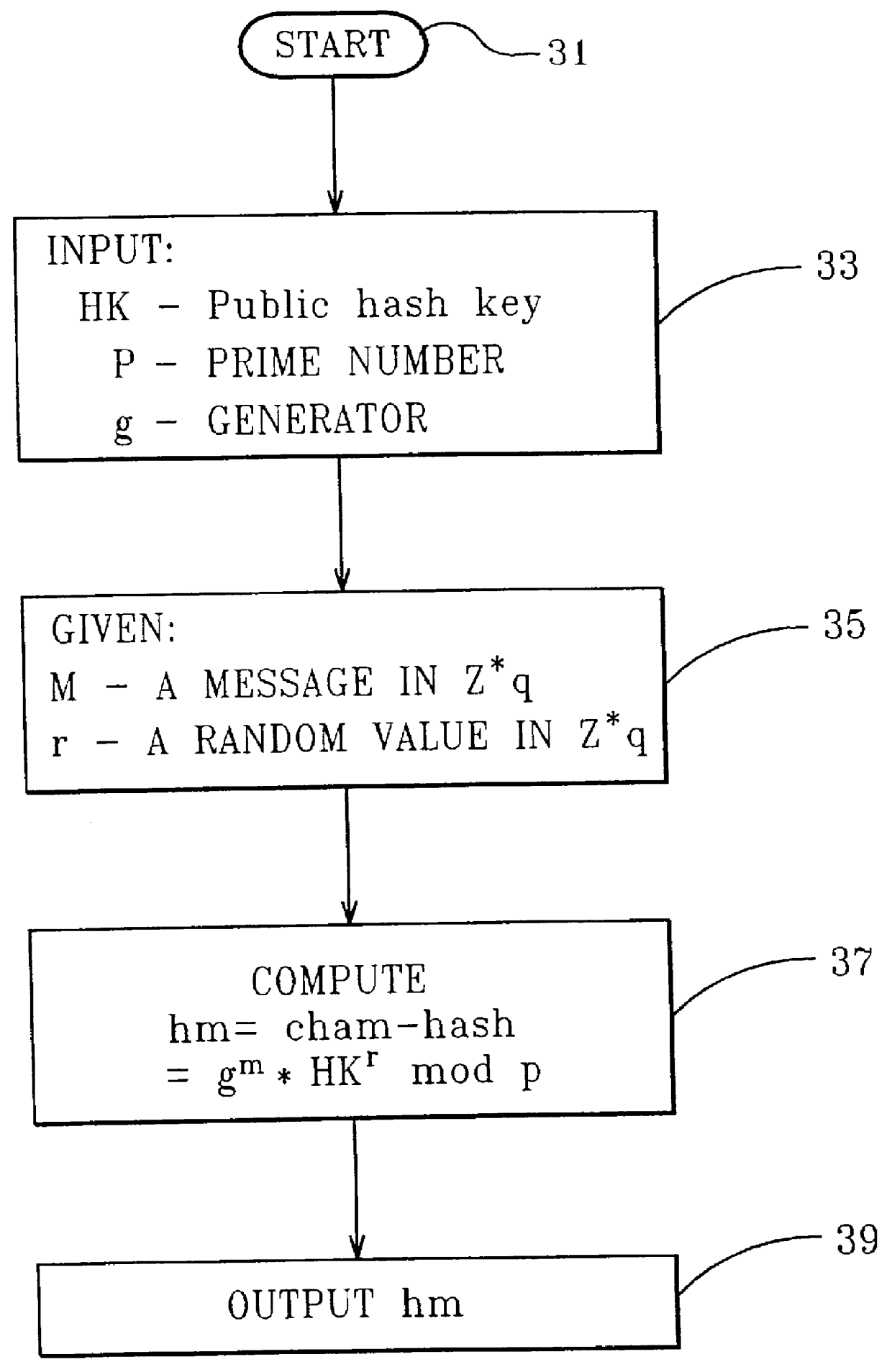
Chameleon hashing and signatures
InactiveUS6108783AImprove performanceSimple and cost-effective constructionPublic key for secure communicationUser identity/authority verificationThird partyHash function
A method for providing a digital signature, "chameleon signatures", which provide the signer of a digital signature exclusive control to disclose the contents of the signed information to third parties. The signatures are closely related to "undeniable signatures", but allow for simpler and more efficient realizations. The method is essentially non-interactive requiring no communication between sender and receiver and do not involve the design and complexity of zero knowledge proofs on which traditional undeniable signatures are based. The method employs a combination of standard digital signing methods with a unique hash functions. These hash functions are characterized by the non-standard property of being collision resistant for the signer but collision tractable for the recipient.
Owner:IBM CORP
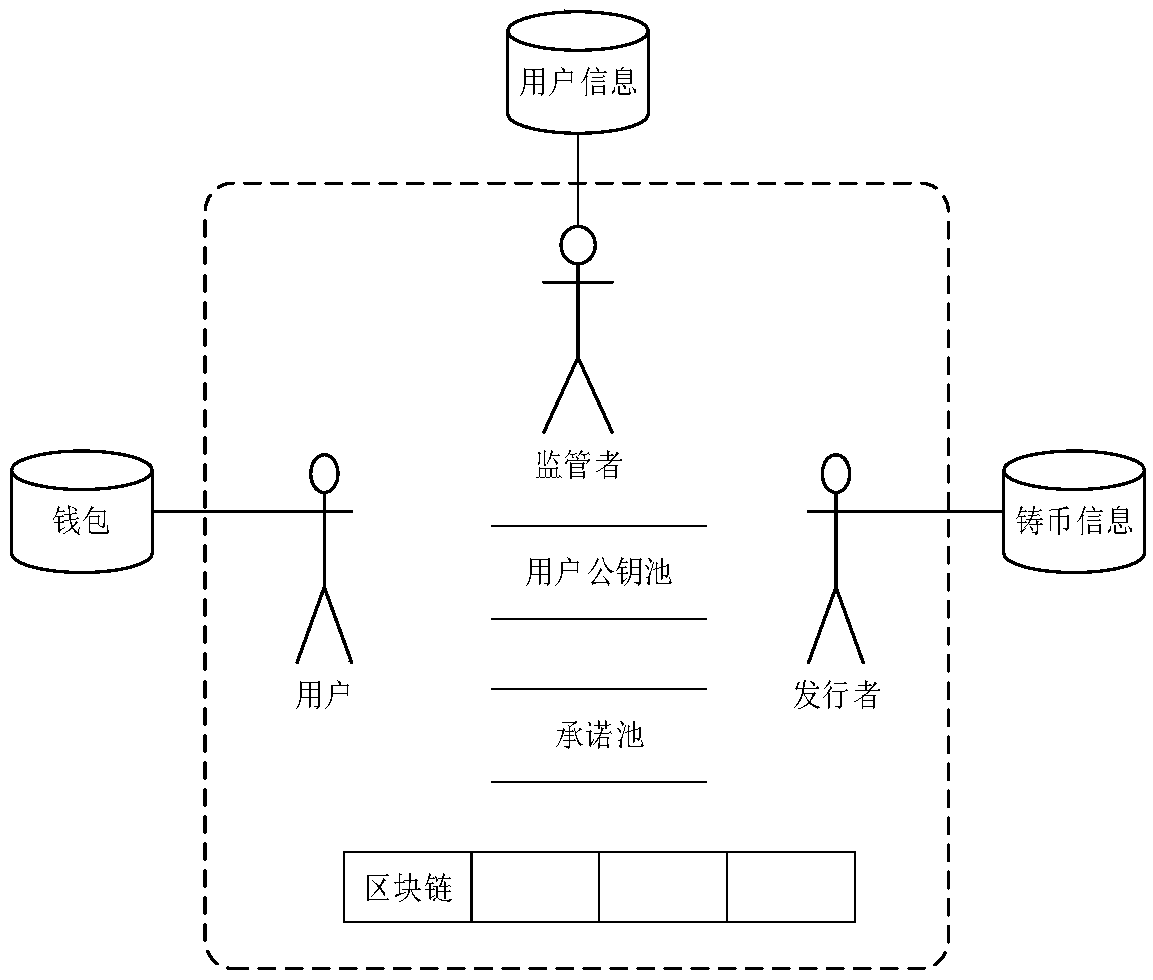
Anonymous transfer method and system based on block chain, and storage medium
ActiveCN108764874AGuaranteed privacyRealize anonymous transferFinancePayment protocolsTransfer systemChain network
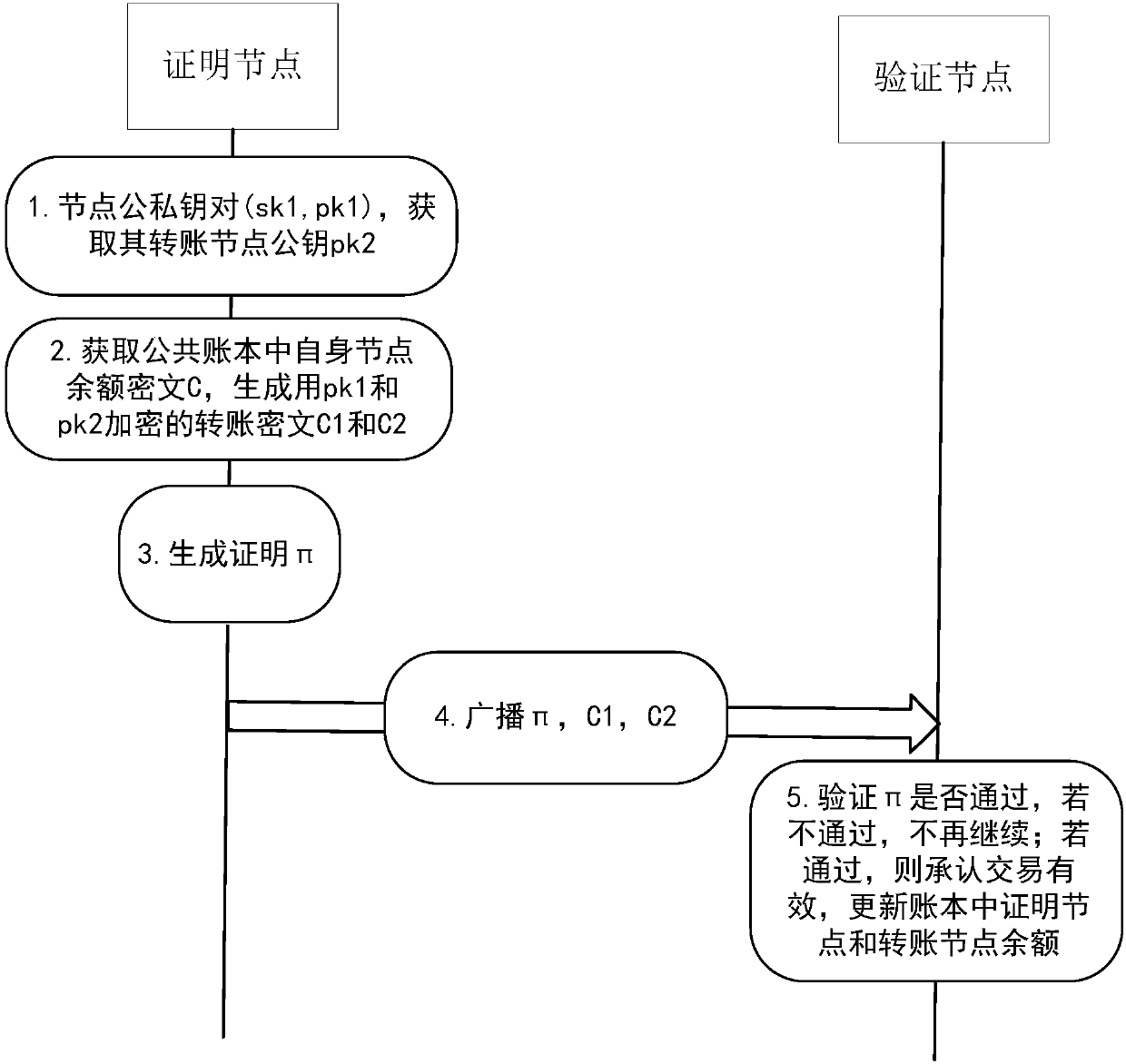
The invention discloses an anonymous transfer method based on a block chain. The method comprises the steps that a first node initiates a transfer transaction request to a second node, and receives public key information returned by the second node; the first node generates transaction information of a current transaction and sends the transaction information to the second node, wherein the transaction information comprises a new currency commitment generated based on the public key information, a transaction amount encrypted based on the public key information, and a zero knowledge proof; thesecond node verifies the transaction amount encrypted based on the public key information, and if the verification is passed, the transaction information is published in a block chain network, so that a miner node can perform verification and bookkeeping on the current transaction; and the miner node verifies proof contents in the zero knowledge proof, and if the verification is passed, the transaction is determined to be valid and the transaction information is recorded in the block chain. The invention furthermore discloses an anonymous transfer system based on the block chain and a computer readable storage medium. According to the method and the system, anonymous transfer is realized, so that the privacy of information of two transaction parties of block chain-based transfer is guaranteed.
Owner:WEBANK (CHINA)
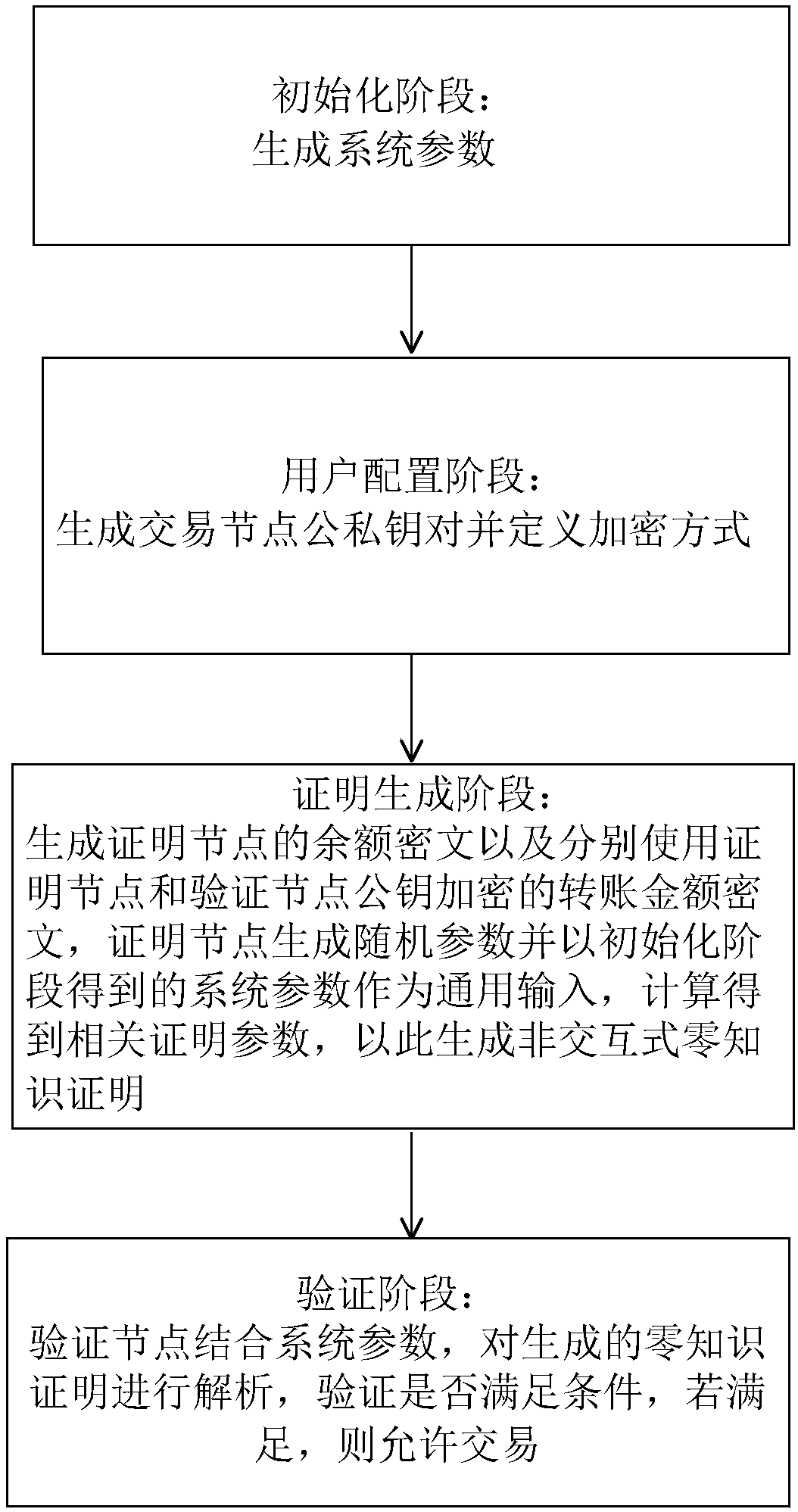
Zero knowledge proving method suitable for protecting privacy of block chain, and medium
ActiveCN108418689AReduce consumptionUser identity/authority verificationProtocol authorisationGeneration processCiphertext
The invention discloses a zero knowledge proving method suitable for protecting the privacy of a block chain, and a medium. UTXO of Bitcoins and a balance model of Ethereum can be supported, and wellcombined with a smart contract, so that the security of the scheme can be further enhanced, the application scene of the scheme can be extended, and aiming at a zero knowledge certificate designed bya specific algebraic structure of a transaction, even a light node can also generate a proving process. The technical scheme is as follows: the method comprises a system parameter in an initializationphase (including a generation process and meaning of the parameter), a specific process of generating the zero knowledge certificate in a certificate generating phase (including ciphertext generatedin the process, and involved formula and parameter), and a verification phase (including verification formula and condition).
Owner:JUZIX TECH SHENZHEN CO LTD +1
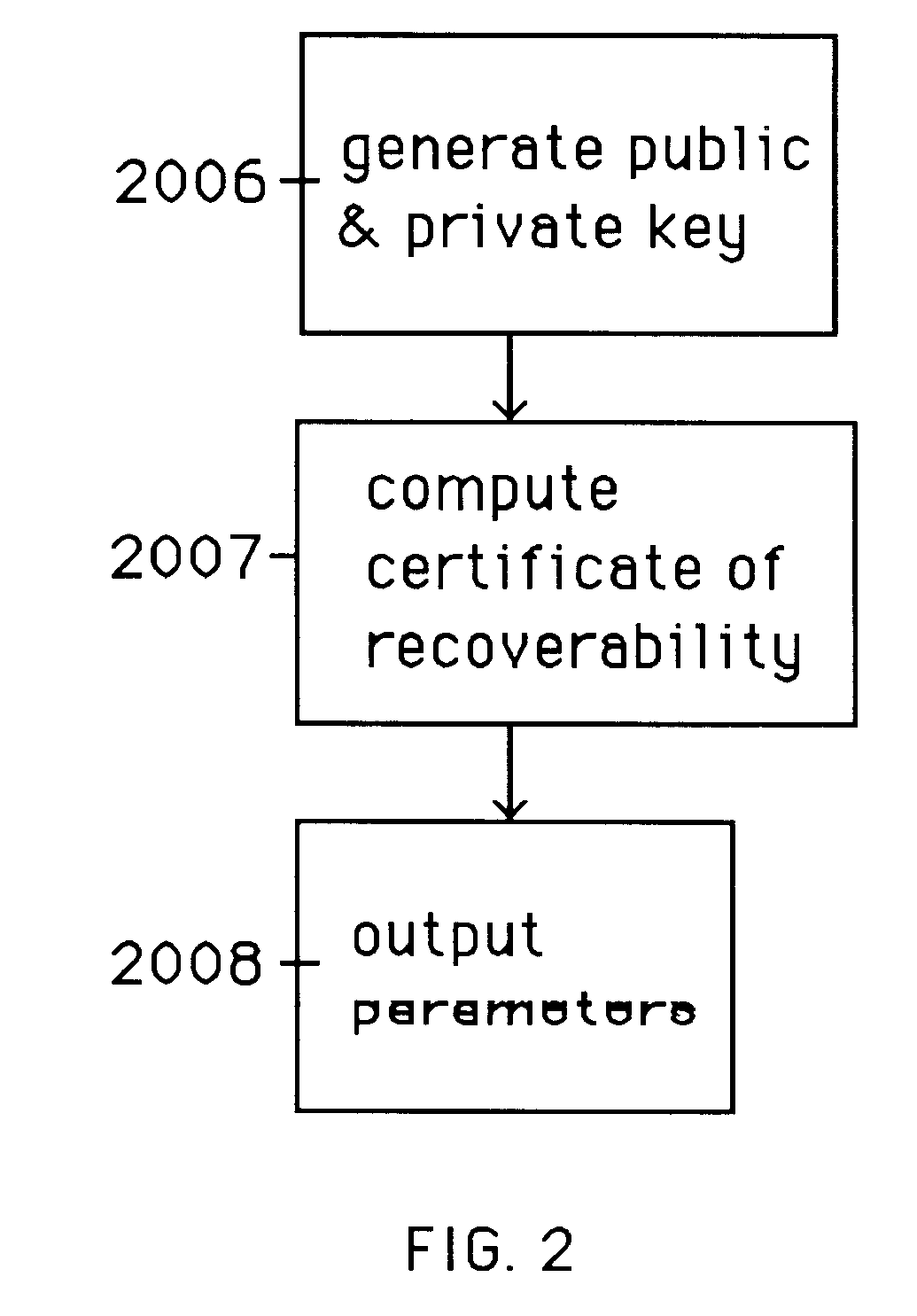
Auto-recoverable and auto-certifiable cryptostem using zero-knowledge proofs for key escrow in general exponential ciphers
InactiveUS6282295B1Fast and easy disseminationEasy to handleKey distribution for secure communicationPublic key for secure communicationTrusted authorityValidation methods
A method is provided for an escrow cryptosystem that is essentially overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The keys generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key is recoverable by the escrow authorities. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". The proof and verification method involves one party proving to a second party that a third party can gain access to an encrypted value. In addition, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware. The system is efficient and can be implemented as a "drop-in" replacement to an RSA or ElGamal cryptosystem. The system is applicable for lawenforcement, file systems, e-mail systems, certified e-mail systems, and any scenario in which public key cryptography can be employed and where private keys or information encrypted under public keys need to be recoverable. The system security relies solely on the security of cipher systems involved whose security has been extensively studied in the past.
Owner:CRYPTOPEAK SECURITY LLC
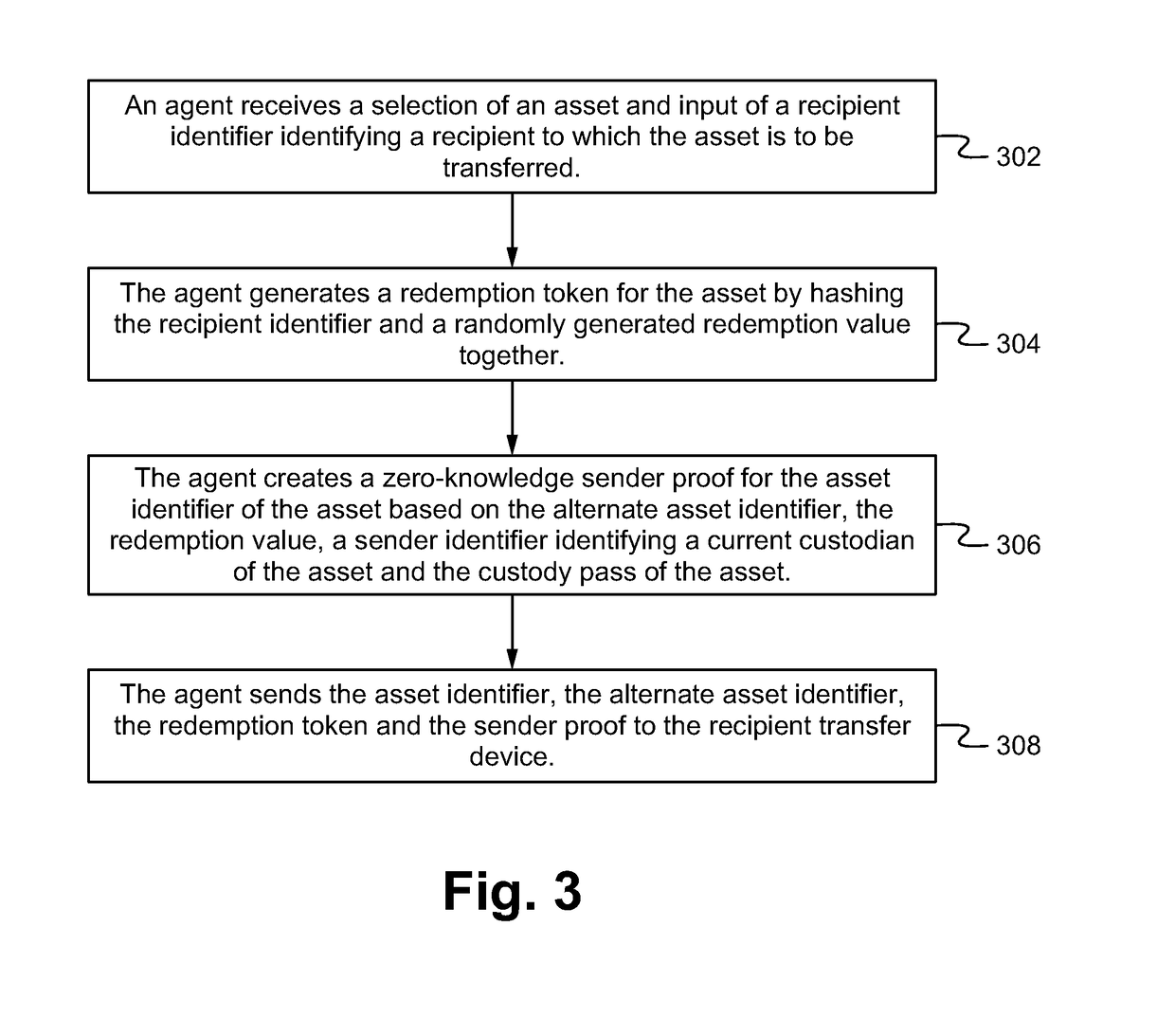
Secure and confidential custodial transaction system, method and device using zero-knowledge protocol
PendingUS20190034923A1Rule out the possibilityPrevent leakageEncryption apparatus with shift registers/memoriesAnonymous user systemsZero-knowledge proofKnowledge level
A system, device and method of confidential secure custodial transfers of asset between entities utilizing transaction agents implemented via a distributed ledger (e.g. a blockchain). In particular, the transaction agents securely record each of the transactions on the ledger utilizing obfuscated or proxy data state such that information about the transactions cannot be gleaned from the ledger. In particular, the transaction agents are able to enforce business rules of the system by requesting zero-knowledge proofs from participants to the transaction (e.g. sender and recipient) in place of actual data for the transaction. The zero-knowledge proofs are able to be designed to prevent an observer of the distributed ledger from determining any information of the transaction that is taking place.
Owner:CHRONICLED INC
Method for protecting privacy of smart contract of block chain, and medium
ActiveCN108418783AIncrease flexibilityImprove privacyFinanceUser identity/authority verificationZero-knowledge proofUser privacy
The invention discloses a method for protecting the privacy of a smart contract of a block chain, which can verify correction of a transaction while covering transaction details, and can verify validity and effectiveness of an operation while protecting the user privacy. The technical scheme of the method is as follows: addition is used for homomorphically encrypting privacy data in the block chain, and non-interactive zero knowledge is generated in the transaction process for proving the effectiveness of the transaction.
Owner:JUZIX TECH SHENZHEN CO LTD +1
Privacy protection transaction method based on blockchain technology in electronic commerce
ActiveCN108389046AEase of evaluationMeet privacy requirementsFinanceDigital data protectionData privacy protectionLogistics management
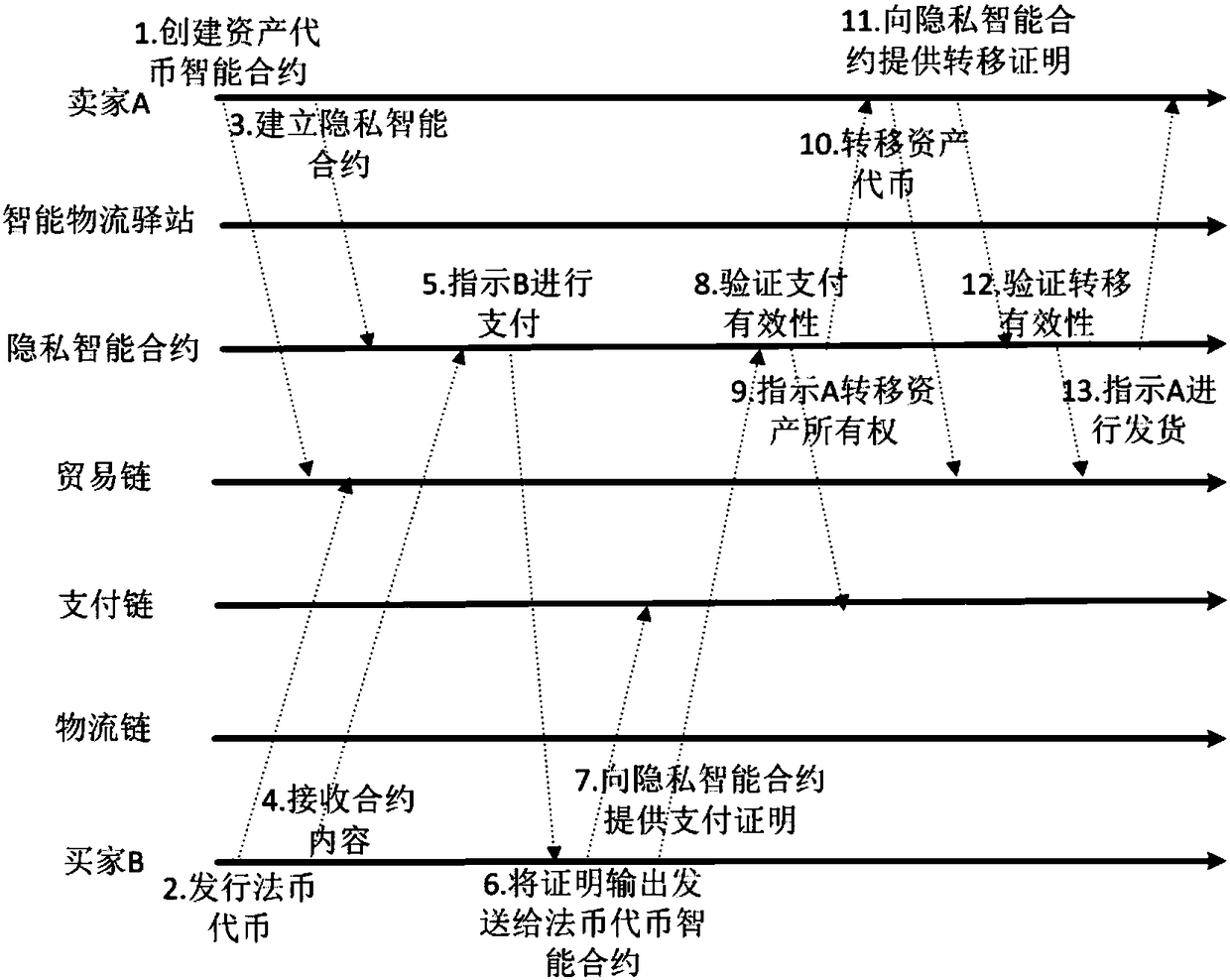
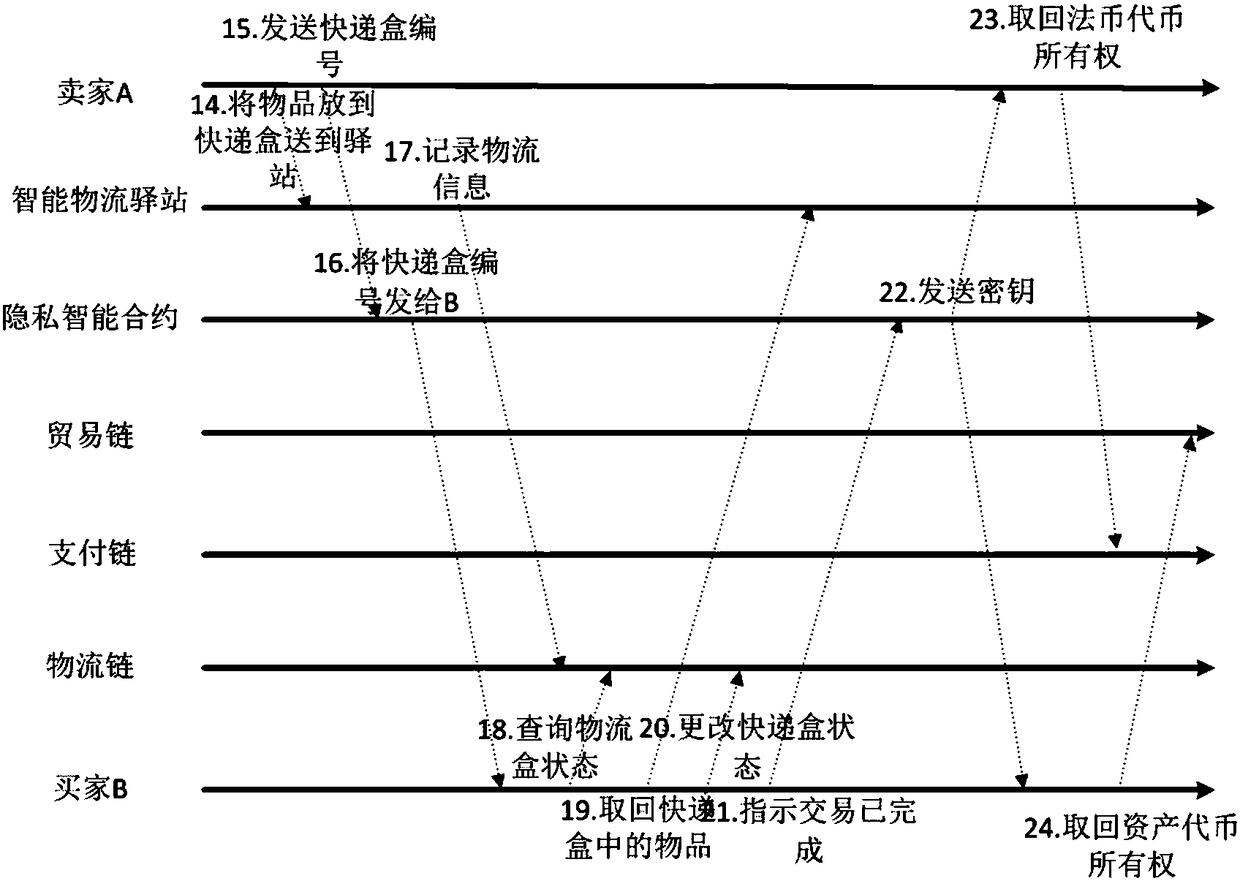
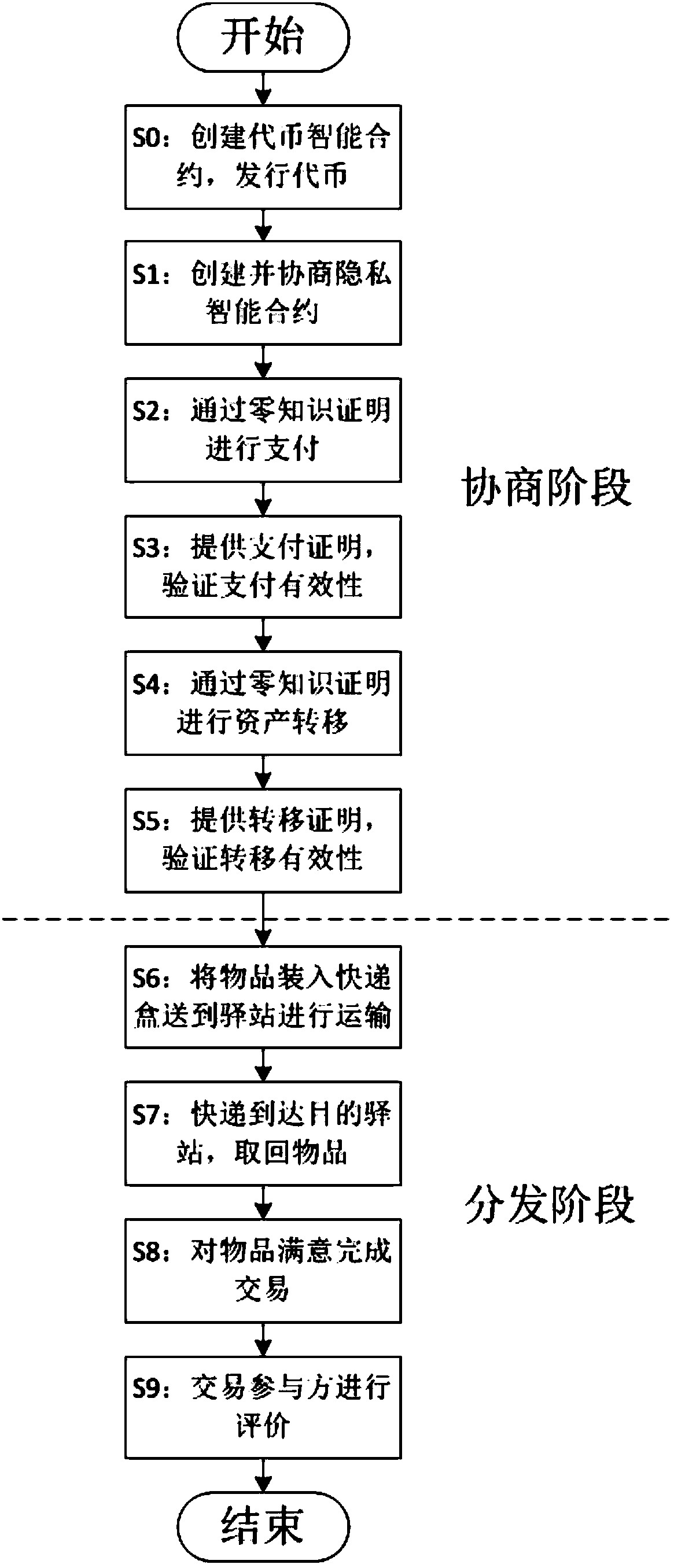
The invention discloses a privacy protection transaction method based on a blockchain technology in electronic commerce. The method comprises the following steps that: adopting the blockchain technology which comprises a privacy smart contract and a zero-knowledge proof to protect the private information of a user; taking the privacy smart contract as a bridge between a buyer and a seller in a transaction period; adopting the zero-knowledge proof to issue a confidentiality token and create a confidentiality transaction; and combining the blockchain, an industrial data space and the Internet ofThings technology to establish infrastructure, and establishing an integrated platform for logistics business management in a distribution way. By use of the method, private information can be hiddenfor dispatchers, private information, including, identity, address, telephone number and the like, can be hidden for sellers, in addition, the method also can be used for other blockchain applicationscenes with a data privacy protection requirement, in addition, blockchain characteristics can be fully utilized, and therefore, the evaluation problem of an electronic commerce platform can be improved.
Owner:XI AN JIAOTONG UNIV
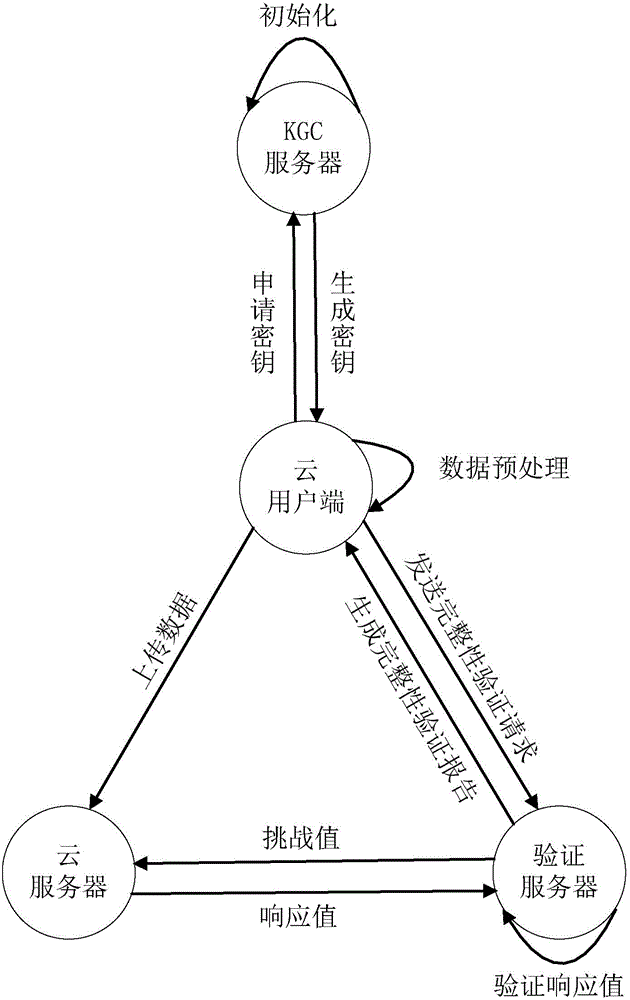
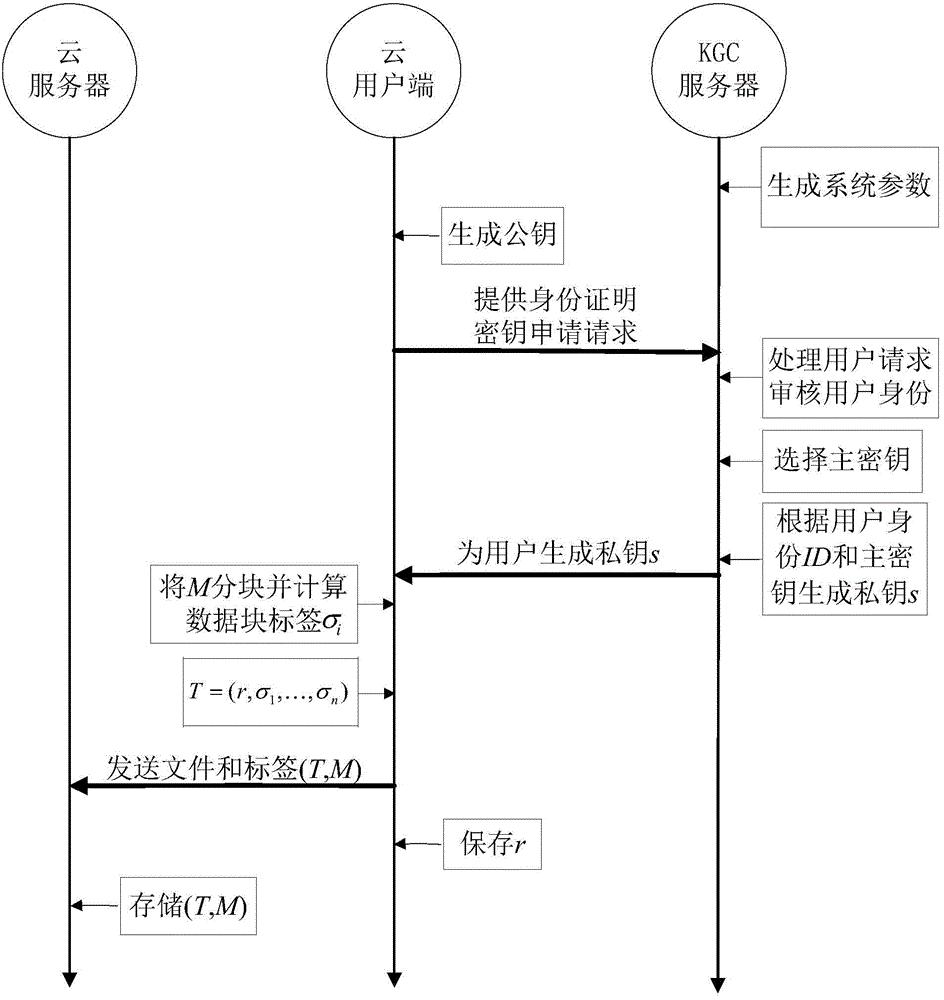
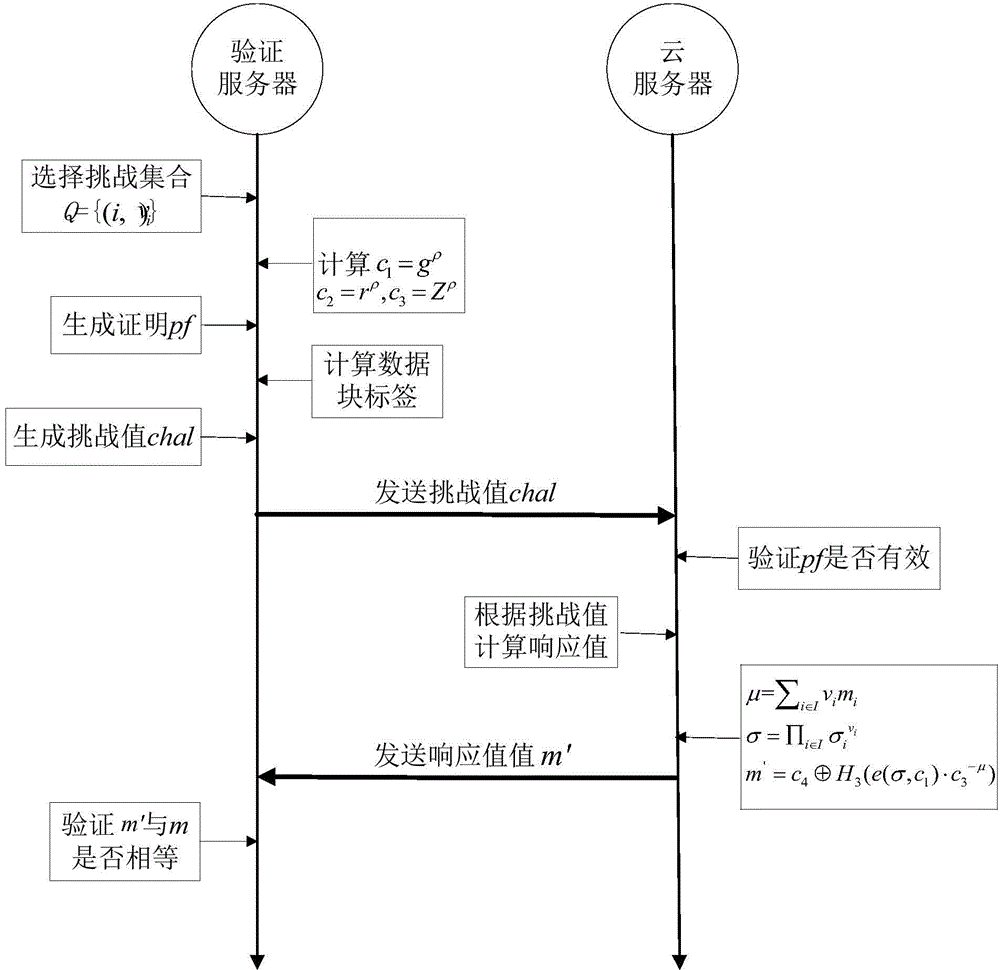
Remote data completeness verification method facing cloud storage
ActiveCN103699851AFlexible control over transparencyRealize protection controlDigital data protectionTransmissionThird partyData integrity
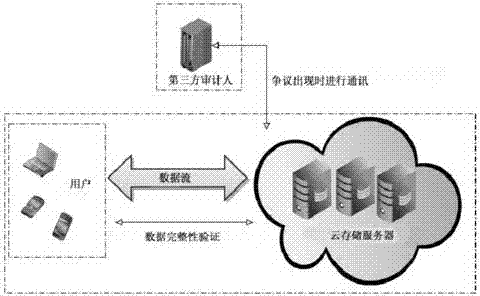
The invention provides a remote data completeness verification method facing cloud storage. According to the method, the aggregate signature and specified certifier signature technology is utilized, the verification function on the user data completeness by users and the third party auditors is realized, and meanwhile, the information of users for data completeness is enabled not to be leaked; the verification information transparency control is realized through the zero knowledge proving technology, and when the dispute exists between the users and a server, the third party auditors can generate the undeniable high-confidence-degree proving through the non-interactive zero knowledge proving technology. According to the method, under the condition that a cloud storage service provider is incredible, the accuracy of the cloud data completeness verification can also be ensured, and the method provided by the invention has the advantages that the realization is easy, the cost is low, the data protection performance is high, the third party audit is supported, the privacy protection mechanism is flexible, and the like.
Owner:HANGZHOU YUANTIAO TECH CO LTD
Data storage method based on identity in cloud computing and integrity verification method based on identity in cloud computing
InactiveCN104811450ALow costReduce complexityUser identity/authority verificationCloud userCloud storage
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Fair electronic voting protocol based on blockchain
InactiveCN107833135ASupport voteFinancePublic key for secure communicationPaymentTrusted third party
The invention belongs to the field of information safety, and provides a fair electronic voting protocol based on blockchain. According to the fair electronic voting protocol, technology such as blockchain, threshold signature scheme, commitment mechanism and zero-knowledge proving and a cryptography method are utilized; based on manners of time commitment and deposit-in-security payment, a no-trusted-third-party electronic voting scheme based on the blockchain and a prime number is presented, and a voting condition of supporting a plurality of candidates can be realized. The fair electronic voting protocol is composed of an initial period, a commitment period, a ballot period and an auditing period. Each voter performs voting on different candidates through selecting different prime numbers which are in one-to-one correspondence with the candidates. The voter pays the deposit-in-security and then performs voting. If a dishonest behavior occurs in the voting process, the deposit-in-security of the voter is used for compensating other voters, thereby ensuring high fairness in the voting process. The fair electronic voting protocol can be used for realizing fair and safe electronic voting.
Owner:SUN YAT SEN UNIV
Secure two-party collaboration SM2 signature method
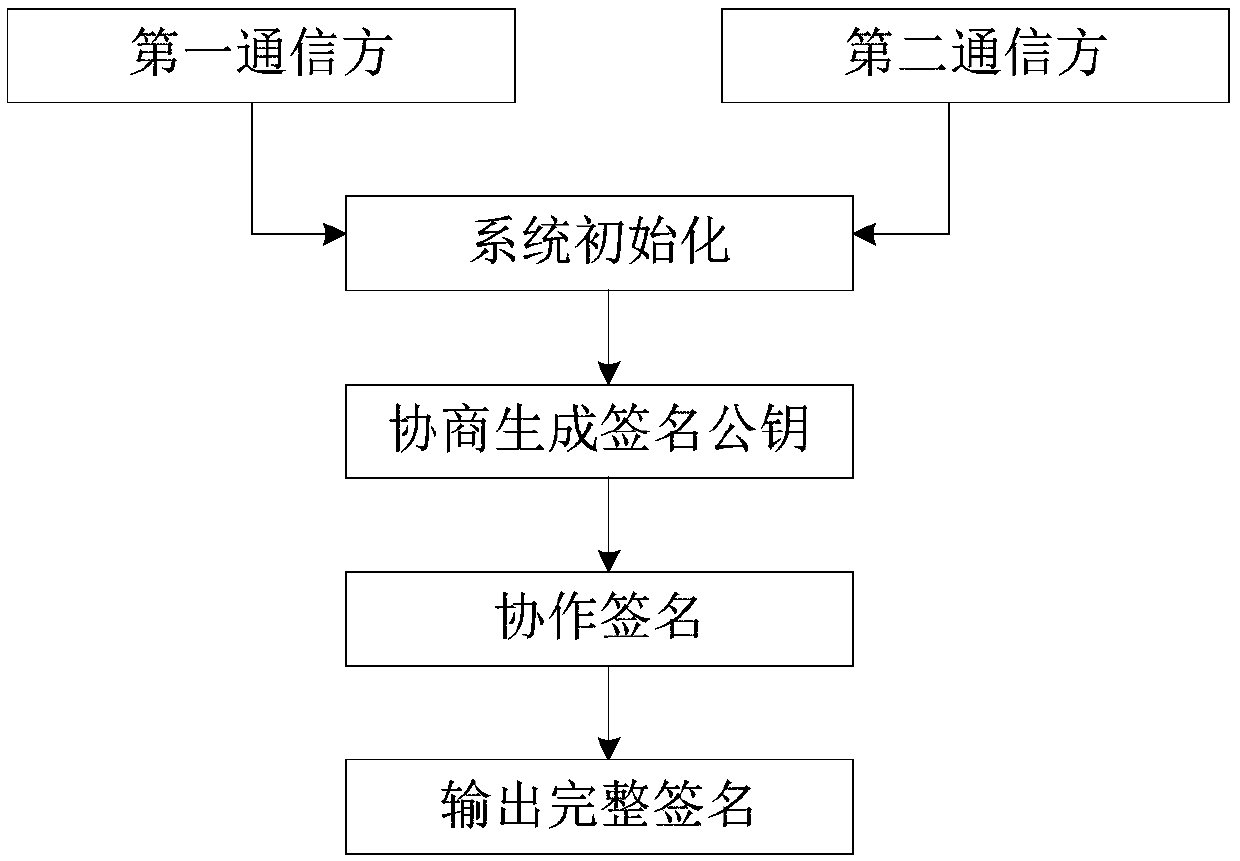
ActiveCN108667626AAvoid attackImprove securityKey distribution for secure communicationPublic key for secure communicationPlaintextMan-in-the-middle attack
The invention provides a secure two-party collaboration SM2 signature method consisting of steps of system initialization, negotiation generation of a signature public key, collaborative signature andoutput of a complete signature. According to the secure two-party collaboration SM2 signature method provided by the invention, prior to the negotiation of the signature public key and the collaborative signature, the both communication parties authenticate the identity of the opposite party by using the zero knowledge proof technology, the correctness of outputting the complete signature is ensured by using the promise technology, it is ensured that the first communication party does not need to decrypt a received ciphertext by using the homomorphic encryption technology, the operation of the corresponding ciphertext can be realized, and a timestamp mechanism is added to ensure that the both communication parties can output the complete signature only when the identity of the first communication party, the current time and the position information of the first communication party are consistent, so that the security of the system is greatly improved, the loss caused by the leakage ofa signature private key is reduced, and the man-in-the-middle attack can be prevented. The secure two-party collaboration SM2 signature method provided by the invention has higher security and can beused in an environment in which a communication channel is not safe.
Owner:SHAANXI NORMAL UNIV +1
Decentralized Customer-Controlled Credit Verification
Systems and methods for decentralized distribution of verifiable information, such as financial information, without requiring resort to centralized information system at the time of a query or other request for information. A decentralized method includes the steps of creating a digital wallet, issuing / receiving an issued verifiable digital credential signed by a credential issuer acting as a trust anchor for a claim contained in the verifiable digital credential, storing the verifiable digital credential within the digital wallet, receiving a request for verified information, and providing the verifiable digital credential, including the claim, from the digital wallet. The verification of information may occur as a zero-knowledge proof such that a required standard is verified as satisfied without disclosing more information about a consumer or other user than is absolutely necessary.
Owner:FINICITY CORP
Block chain model with the privacy protection function
ActiveCN108171511APrivacy protectionAttack resistanceKey distribution for secure communicationUser identity/authority verificationSource Data VerificationCiphertext
The invention discloses a block chain model with the privacy protection function. The block chain model is formed by a minimum trustrank administrator, a private part, and a public part. The minimum trustrank administrator is used for assisting in transaction; the private part is used for defining input information of all sides participating in transaction and sending and receiving of the information and defining relevant calculations during the transaction process and verification of relevant data during the transaction process; and the public part is used for ensuring fairness of the transaction. On the basis of currency encryption, a block chain is constructed by using a distributed anonymous mechanism, zero-knowledge verification, overtime penalties, and packaging methods. Realizationof currency generation and usage, and conversion into basic currency having the privacy protection function relays on zk-SNARK and related data in a ciphertext mode are verified, so that the user is able to realize data verification while the user information is not leaked.
Owner:广州京盛数码科技有限公司
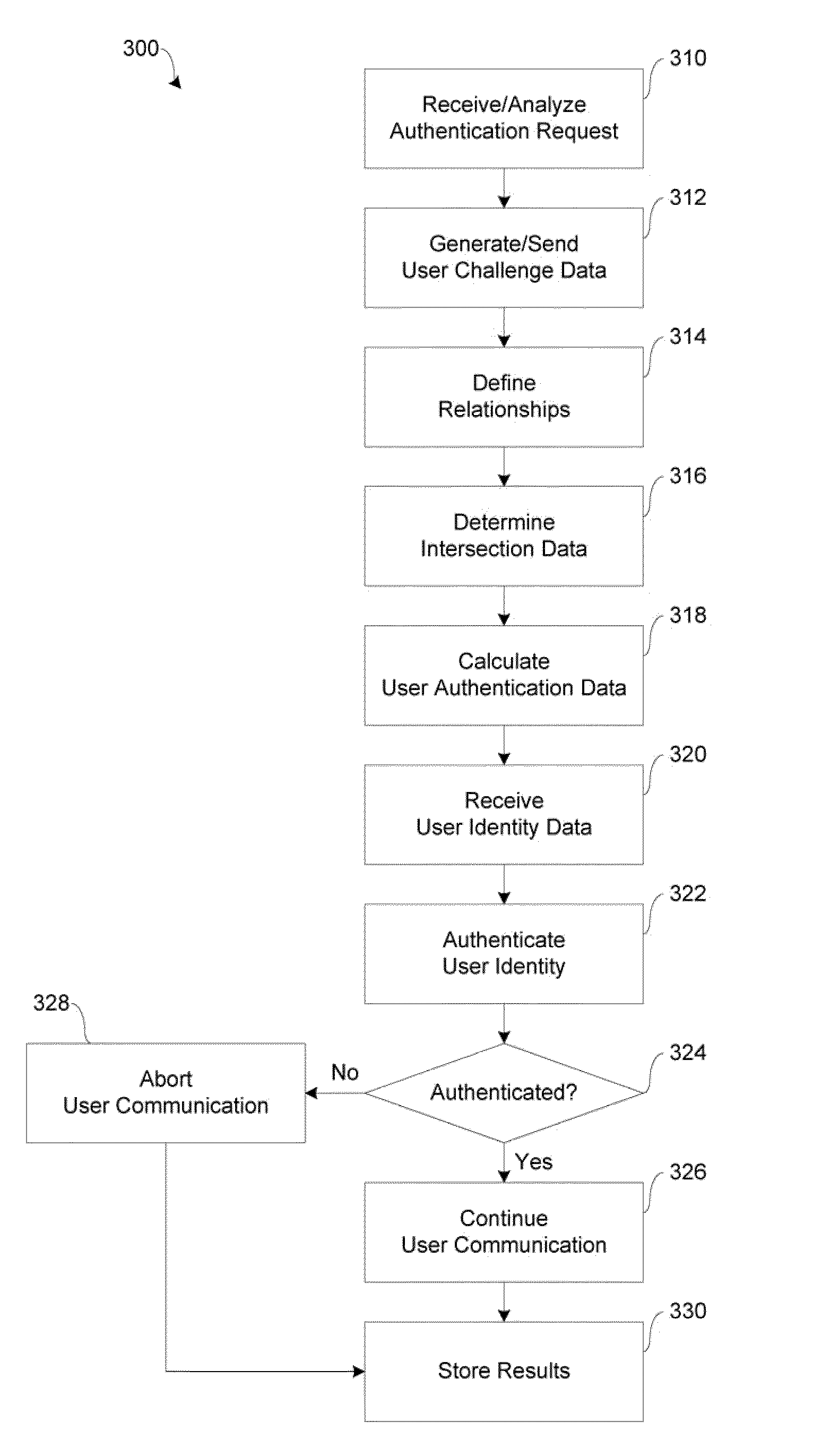
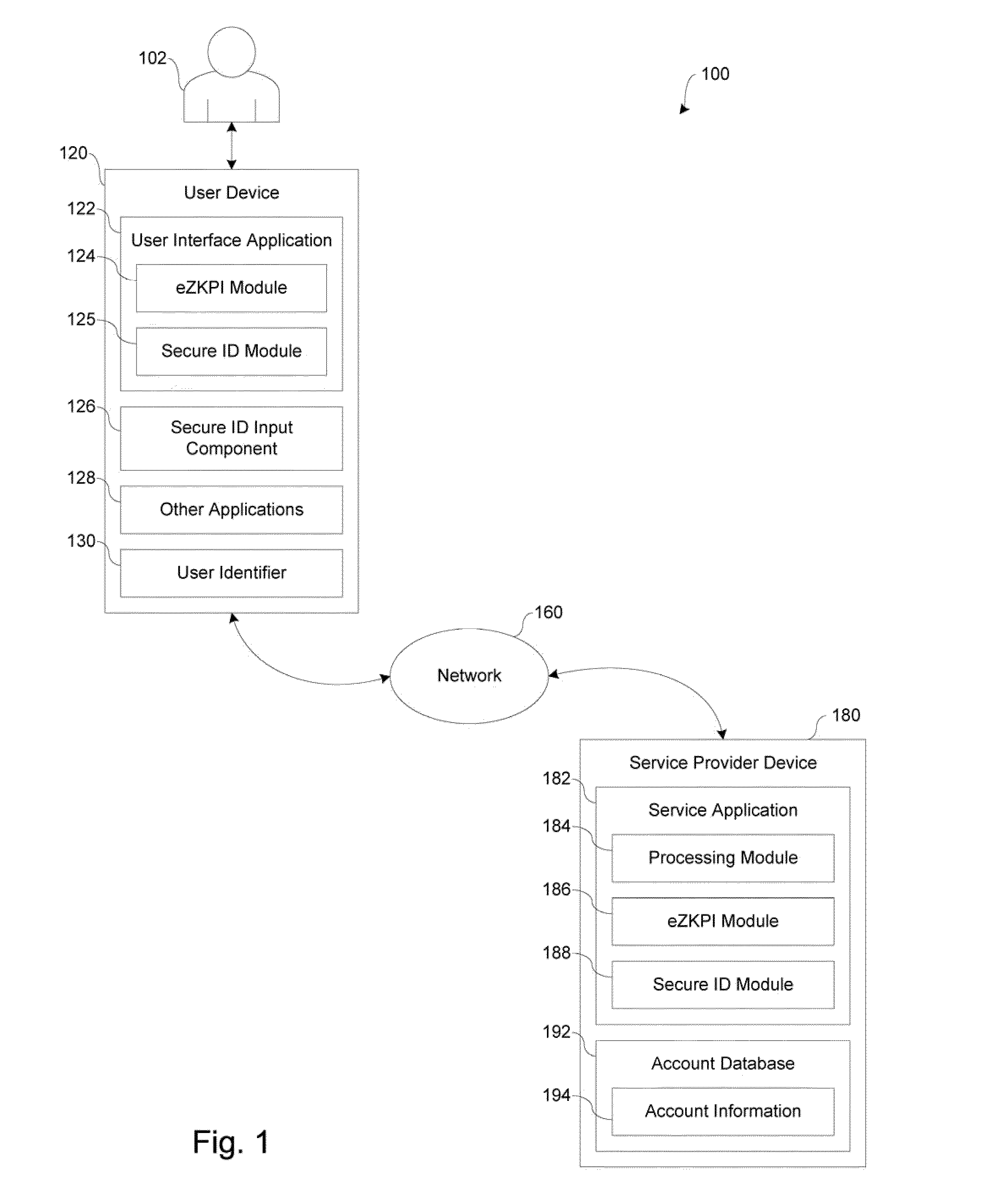
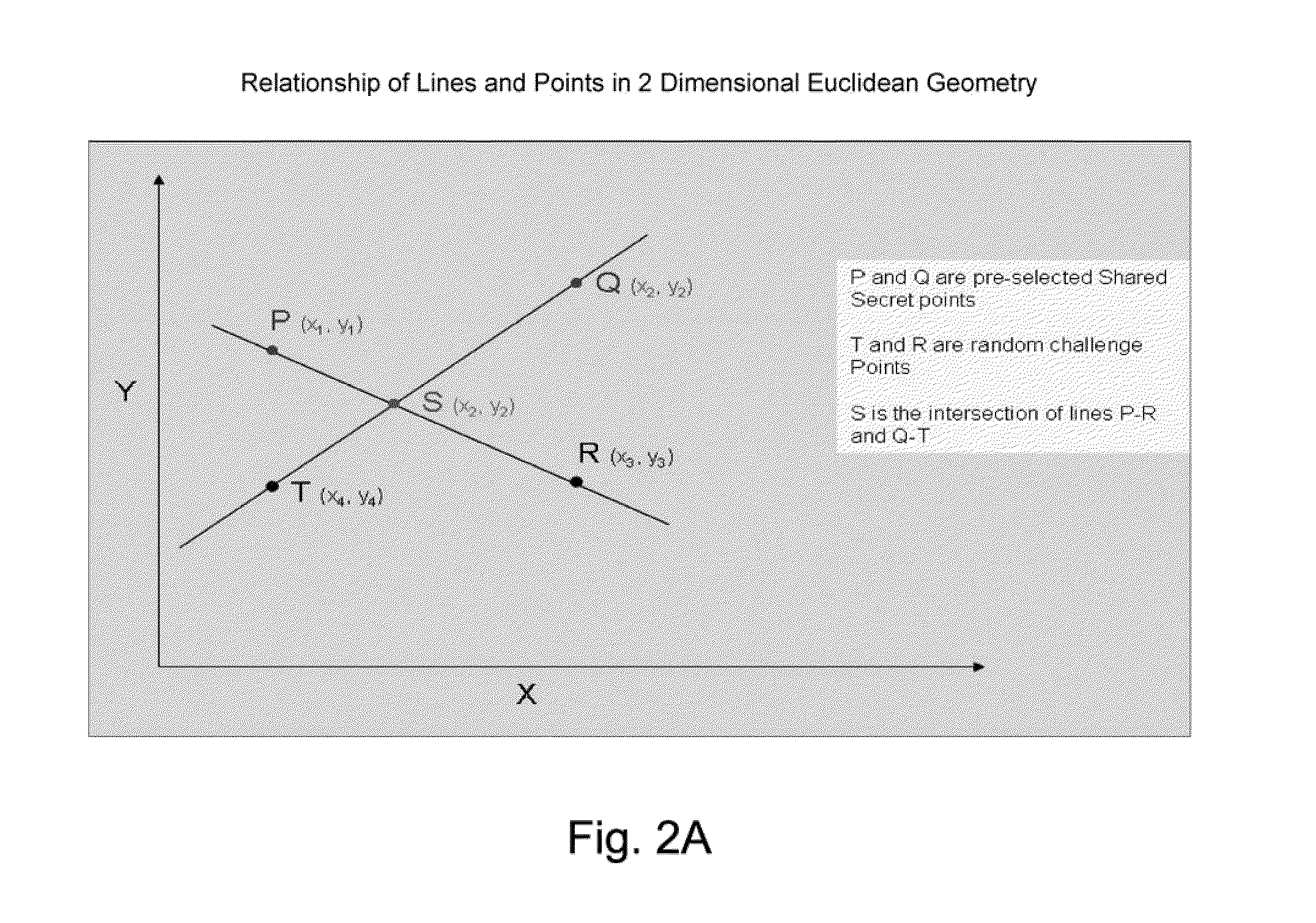
Systems and methods for facilitating user authentication over a network
ActiveUS20110138454A1Strong mutual authenticationFacilitate user authenticationDigital data processing detailsUser identity/authority verificationWeb applicationApplication server
In accordance with embodiments of the present disclosure, systems and methods for facilitating network transactions include user authentication over a network by providing strong mutual authentication of client web application to server side application server, providing session encryption key negotiation after authentication to continue encryption during communication, and providing a high-level encryption technique referred to as an effective zero knowledge proof of identity (eZKPI) algorithm. In various implementations, the eZKPI algorithm is adapted to couple something the user Knows (e.g., a password or personal identification number) with something the user Has (e.g., a secure identification card) to create a stronger identity authentication proof for access to a mobile device and applications running on the mobile device.
Owner:PAYPAL INC
Secure communication authentication method and system in distributed environment
InactiveUS20160119141A1Reduce disadvantagesImprove aspectUser identity/authority verificationDigital data authenticationSecure communicationThird party
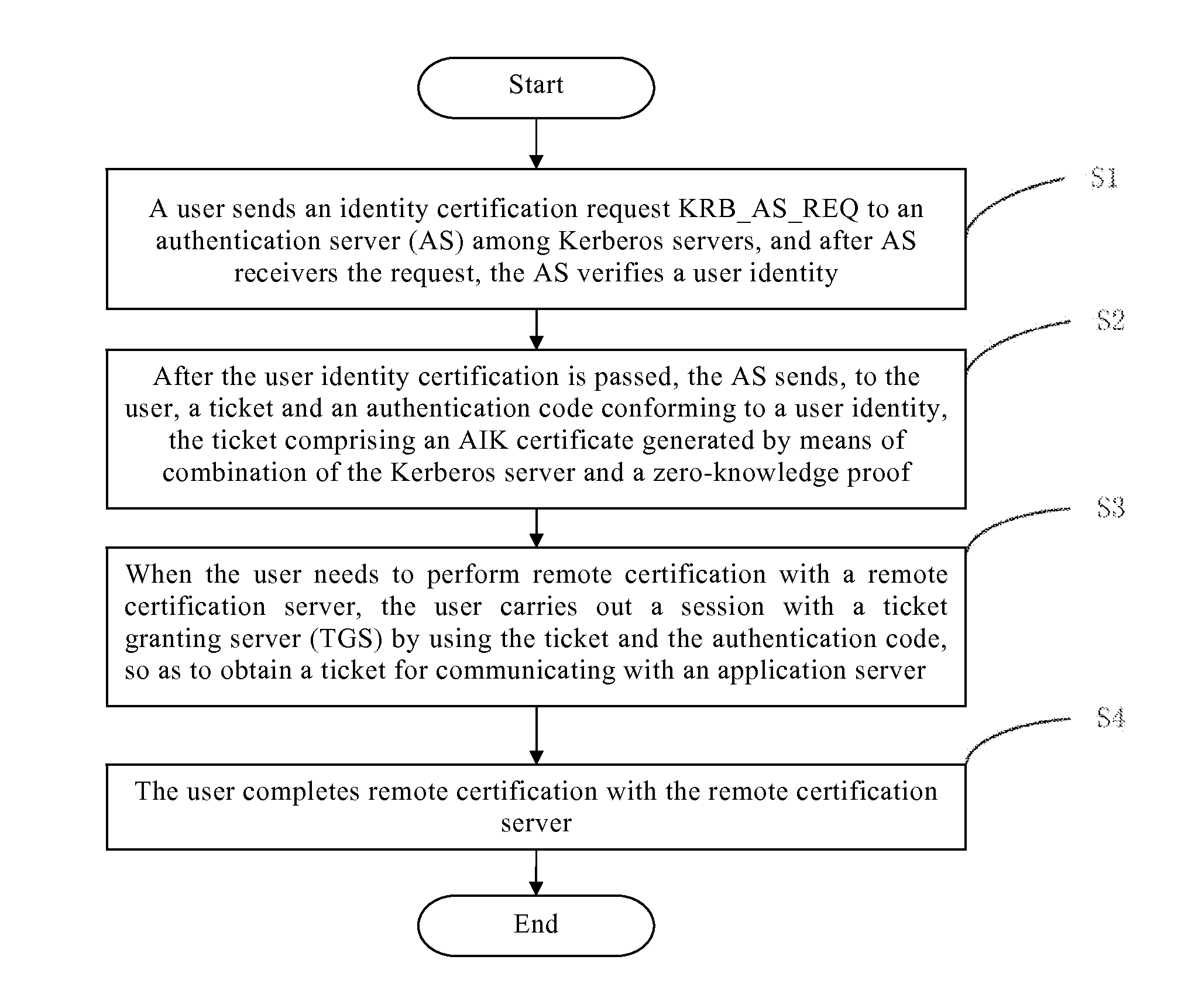
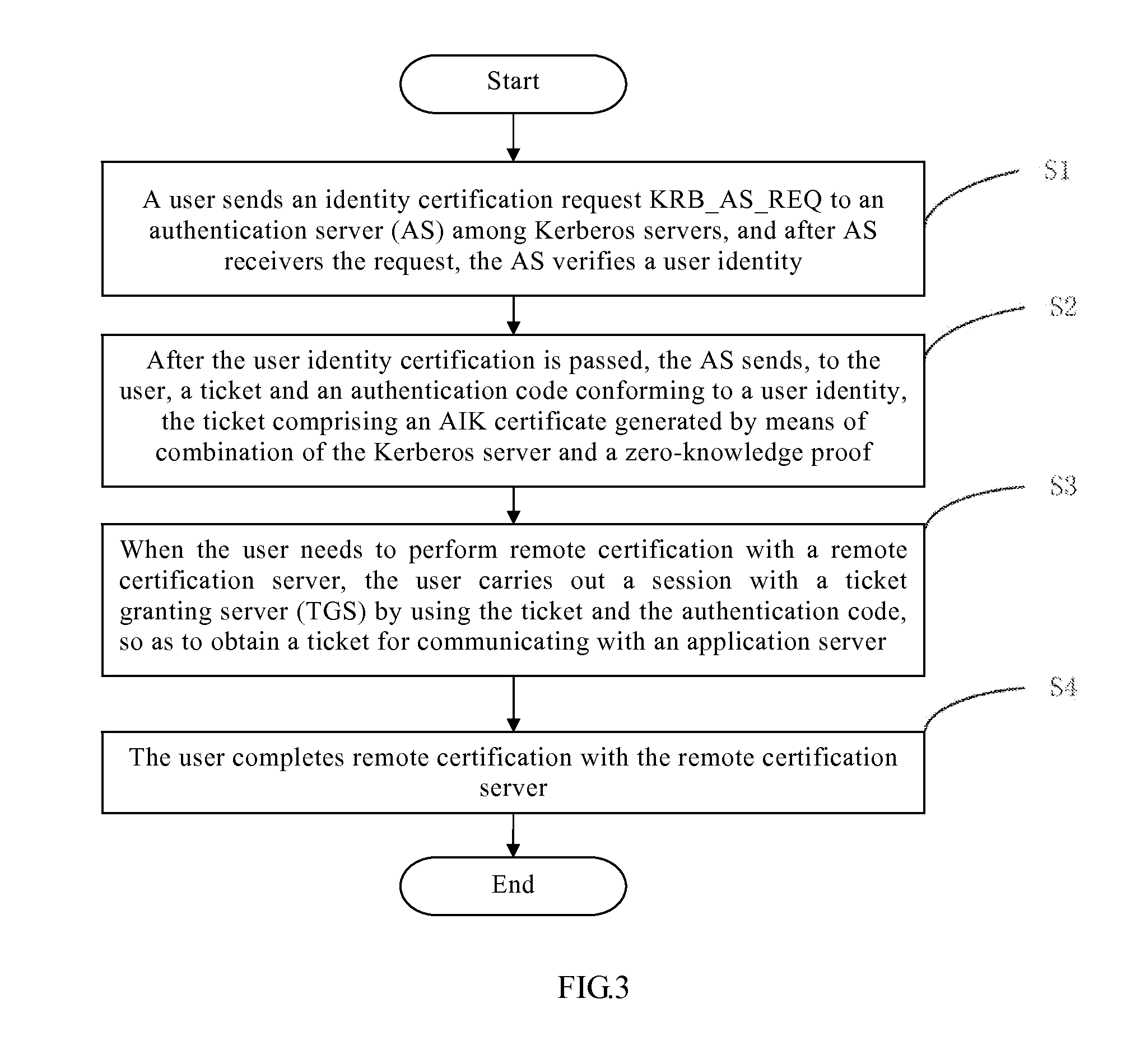
The present invention relates to a secure communication authentication method and system in a distributed environment. By using the method and the system of the present invention, disadvantages in a platform identity certification process in TCG remote certification are alleviated, a method for platform identity certification is expanded, and by combining three technologies, that are, zero-knowledge proof, a Kerberos framework and a virtual TPM, a new verification method is designed, which is mainly intended to make improvement in the aspects in the existing method such as platform information exposure, a trusted third-party bottleneck and complexity avoidance. By using the method and the system of the present invention, the problems of privacy exposure and efficiency in mutual verification between remote servers in the existing distributed system.
Owner:PEKING UNIV FOUNDER GRP CO LTD +2
Attribute protection based multiple authorization center encryption method
InactiveCN103401839APrivacy protectionAddress access controlPublic key for secure communicationUser identity/authority verificationUser privacyEngineering
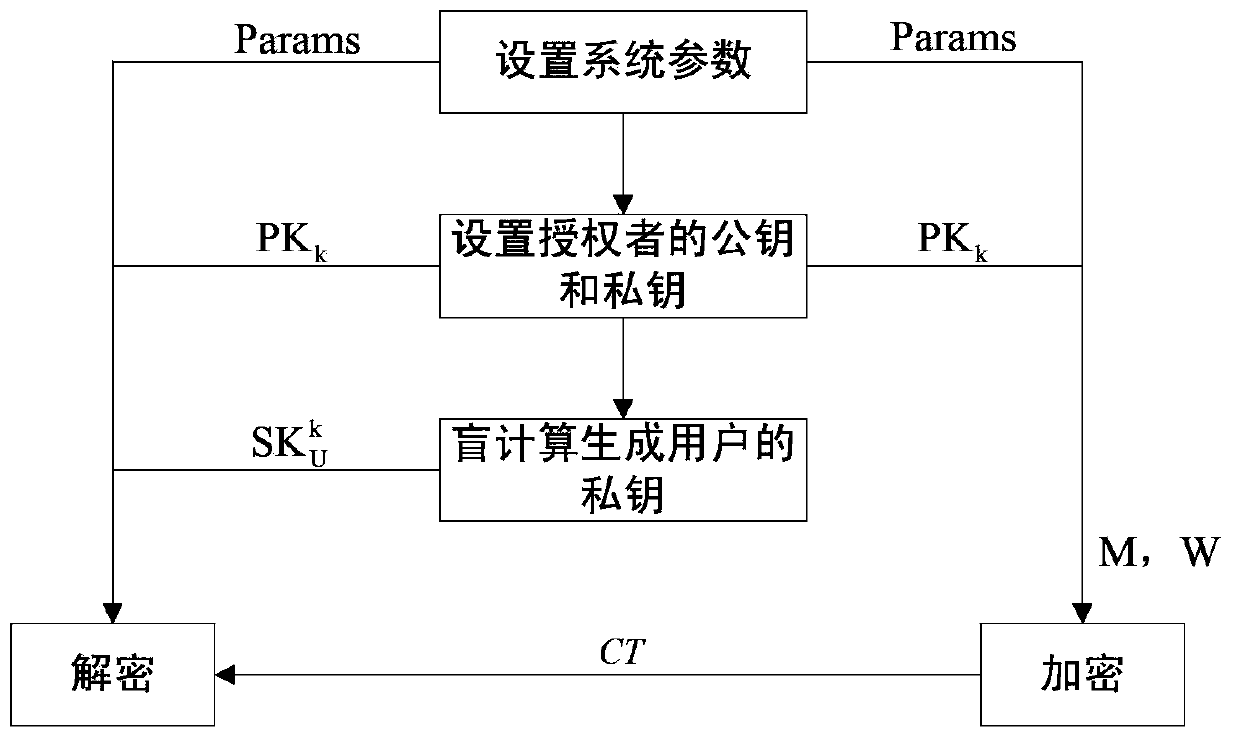
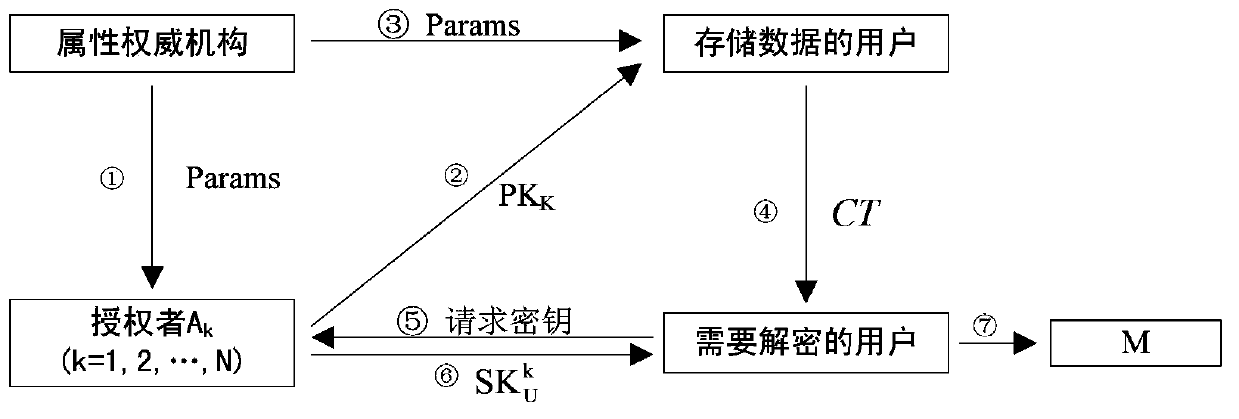
The invention provides an attribute protection based multiple authorization center encryption method. The method comprises the steps of setting system parameters first, and then setting a public key and a private key of an authorized person, wherein the public key is used for encrypting data, and the private key is used for generating a private key of a user. The private key of the user is generated by adopting a method of blind calculation, and the private key of the user is used for decrypting messages. According to the method provided by the invention, two-party safety blind calculation is executed between the user and the authorized person; commitment is carried out on a user global identification code (GID) by using a method of completely concealing the commitment, thereby preventing a malicious authorized person from collecting attributes of the user through tracking the user global identification code (GID); a zero-knowledge proof method enables a certifier to let a verifier believe certain attribute information is correct under the condition of not providing any useful information to the verifier, thereby protecting the user privacy; and the method is used for solving problems of access control and safety in cloud calculation, and the system operation efficiency is high.
Owner:HOHAI UNIV
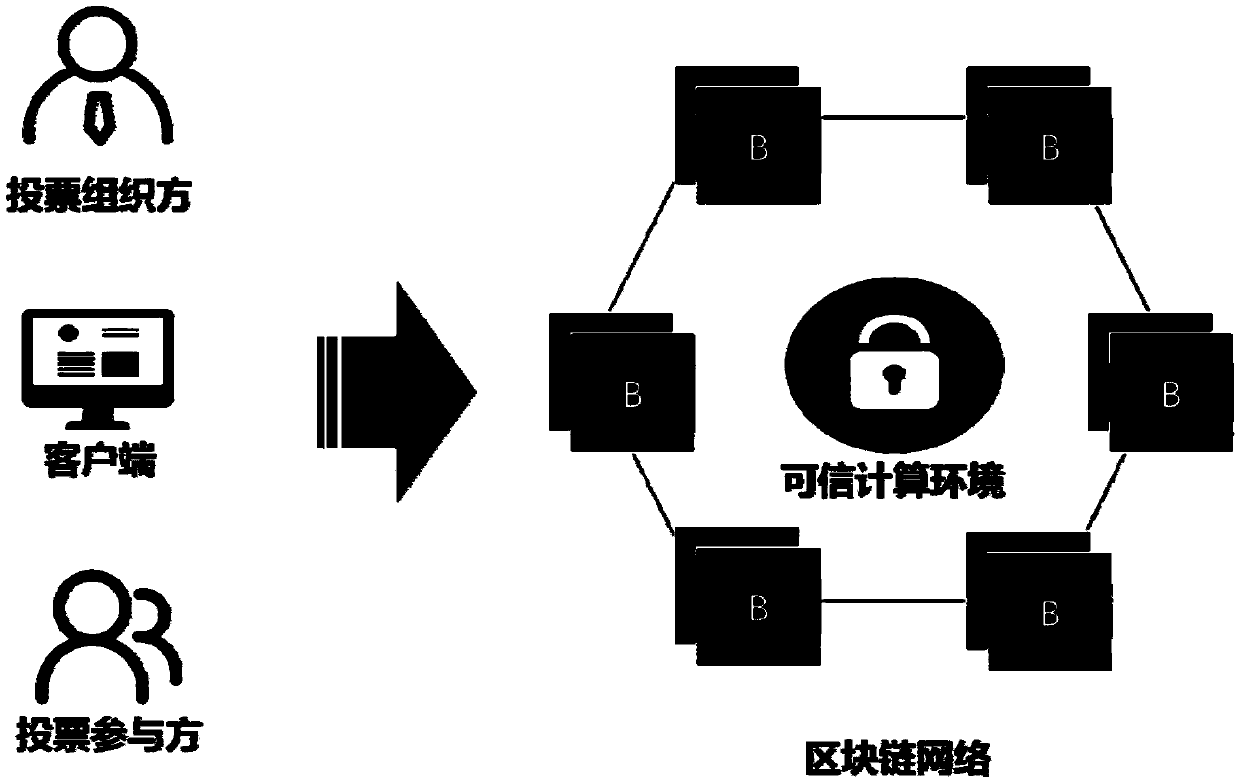
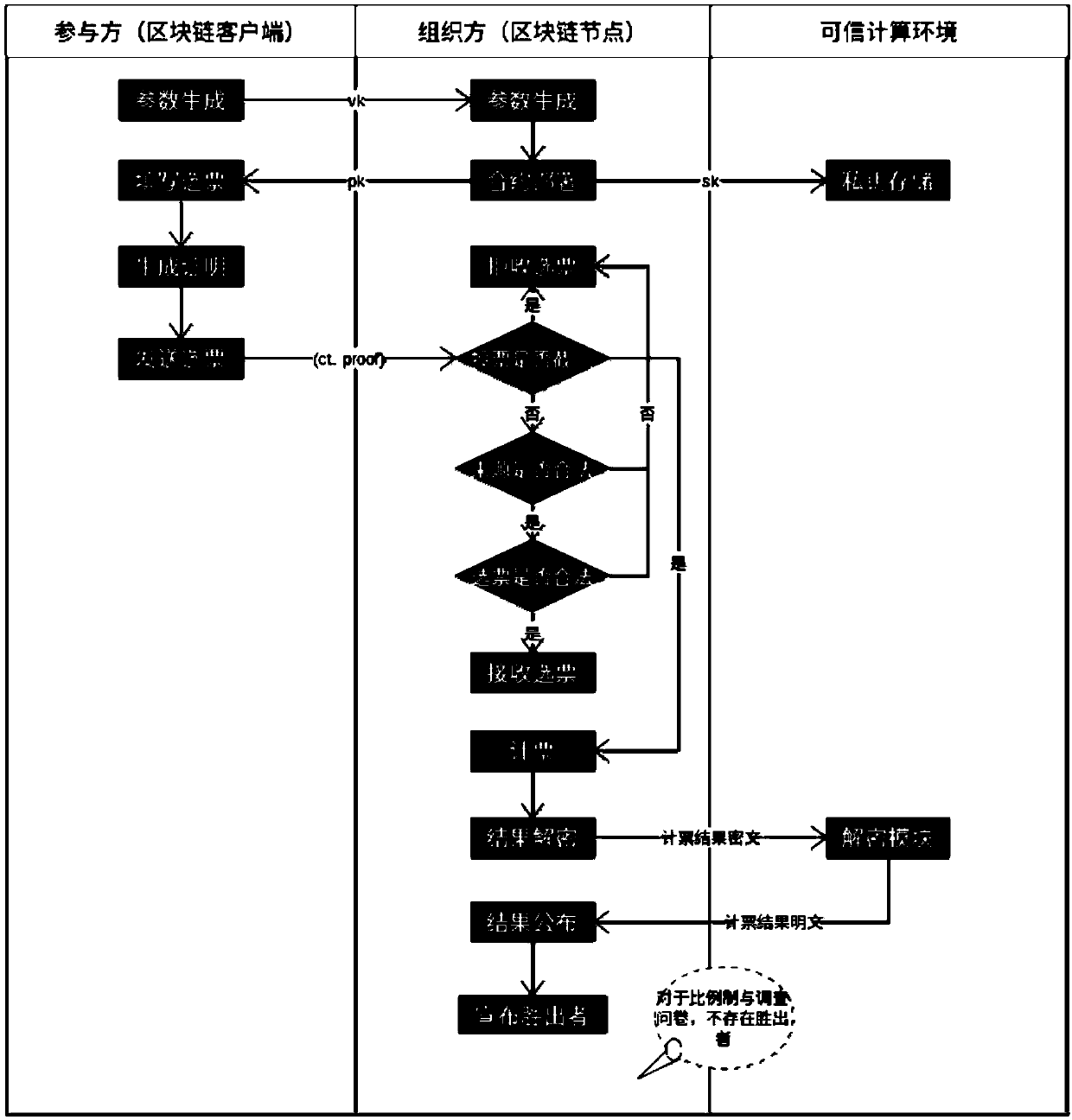
Anonymous electronic voting method based on blockchain technology
ActiveCN109523683ALow costImprove efficiencyVoting apparatusCommunication with homomorphic encryptionTrusted ComputingZero-knowledge proof
The invention discloses an anonymous electronic voting method based on a blockchain technology. According to the anonymous electronic voting method, voting contents are hidden through a homomorphic encryption algorithm, meanwhile, vote validity is ensured through a zero-knowledge proof technology, vote collecting, and the vote counting process and result disclosure are all conducted on a blockchain system, wherein voting results are decrypted through a dependable computing environment, the problem that a private key makes contact with a network in the voting result decrypting process under a traditional way is solved, and the anonymous attribute of voting is protected in the true sense.
Owner:HANGZHOU QULIAN TECH CO LTD
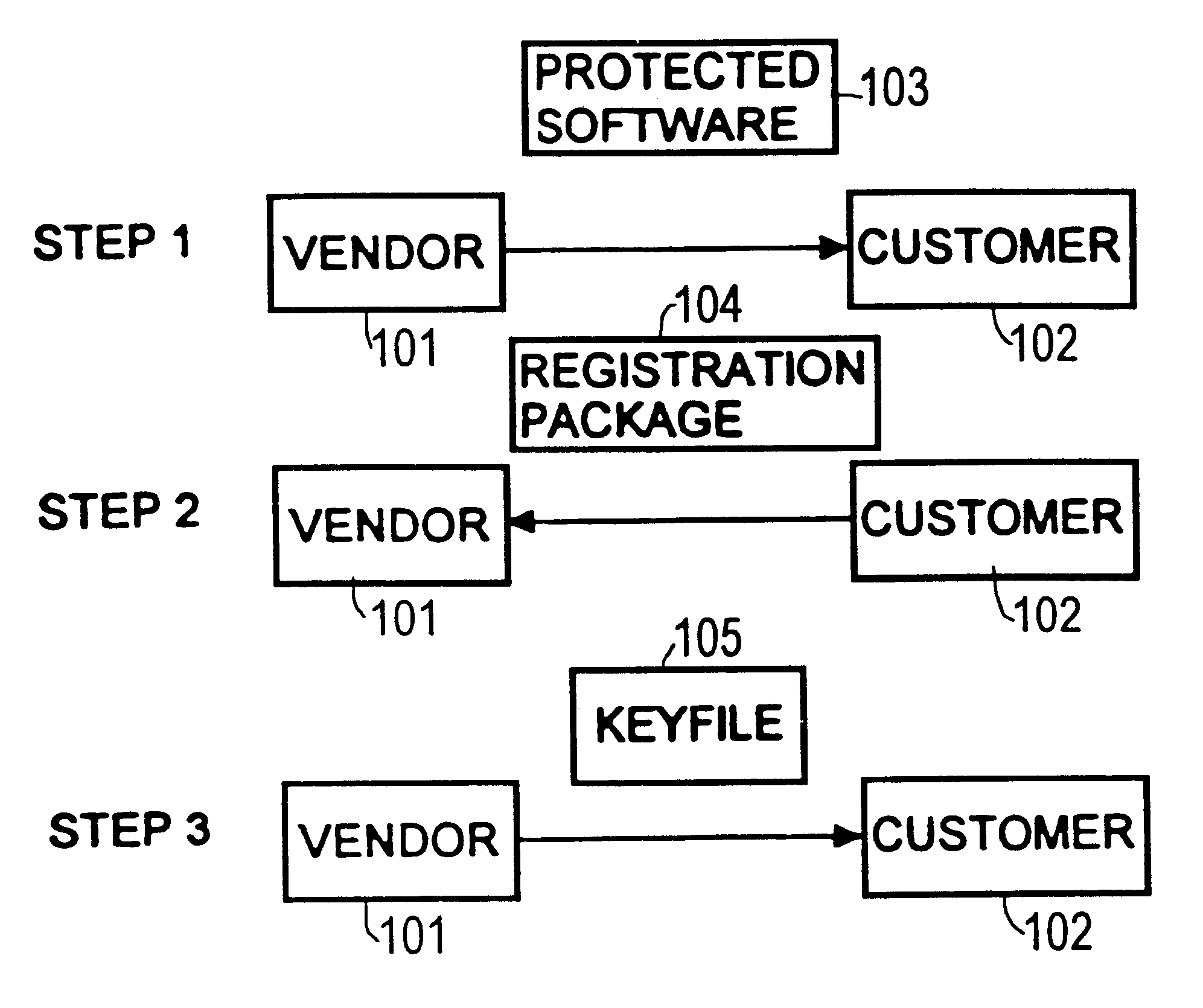
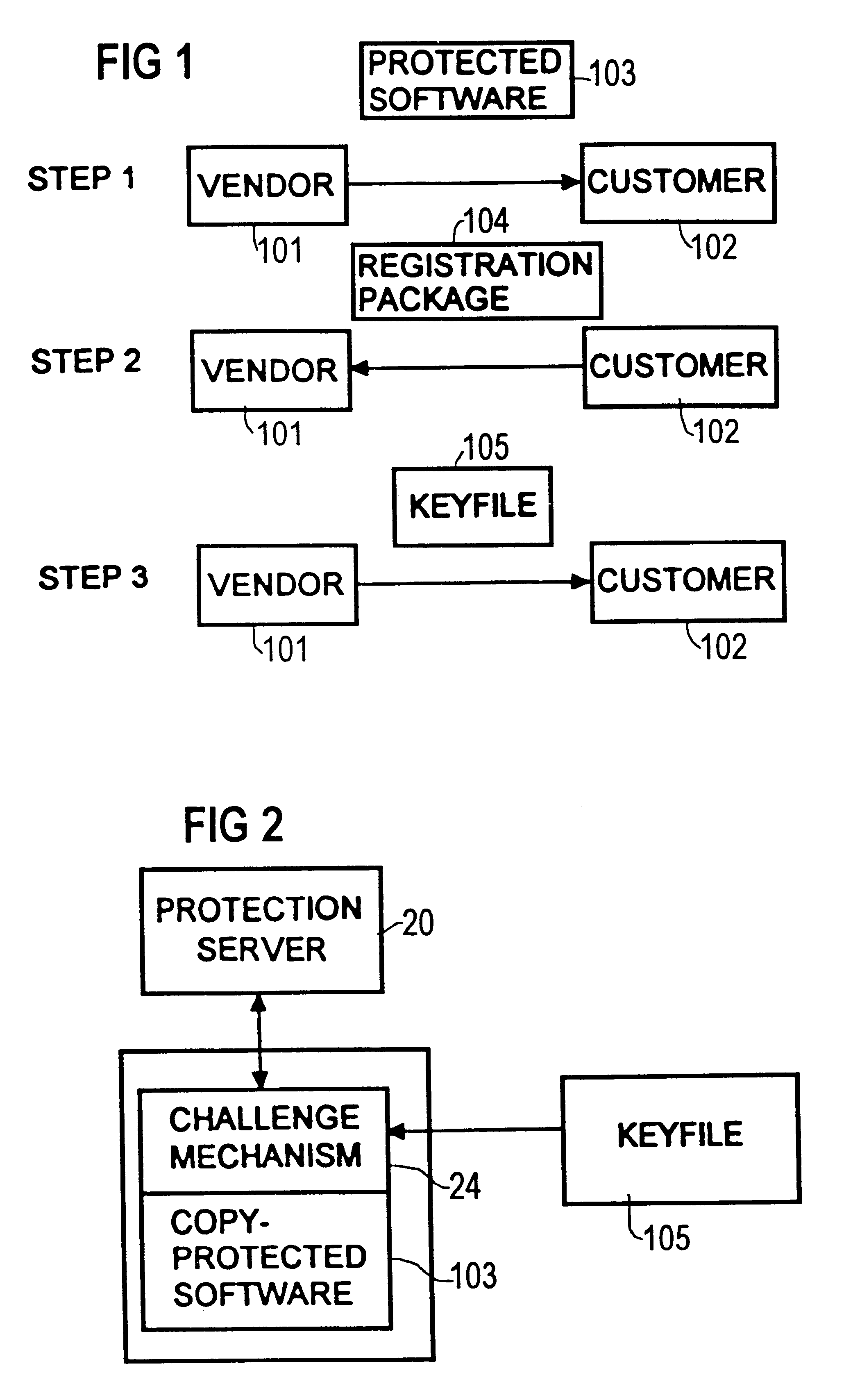
Computer system for protecting software and a method for protecting software
InactiveUS6678665B1Optimization mechanismSatisfies requirementDigital data processing detailsUser identity/authority verificationComputerized systemZero-knowledge proof
A method for protecting an item of software, wherein at least one challenge means is associated with said protected item of software, and at least one response means accesses one private keying material. The challenge means has no access to said private keying material. The response means proves to the challenge means that the response means has access to the private keying material using an asymmetric probabilistic proof, e.g., zero knowledge proof. The challenge means validates this proof using the public keying material that corresponds to the response means' private keying material.
Owner:FUJITSU SIEMENS COMP GMBH
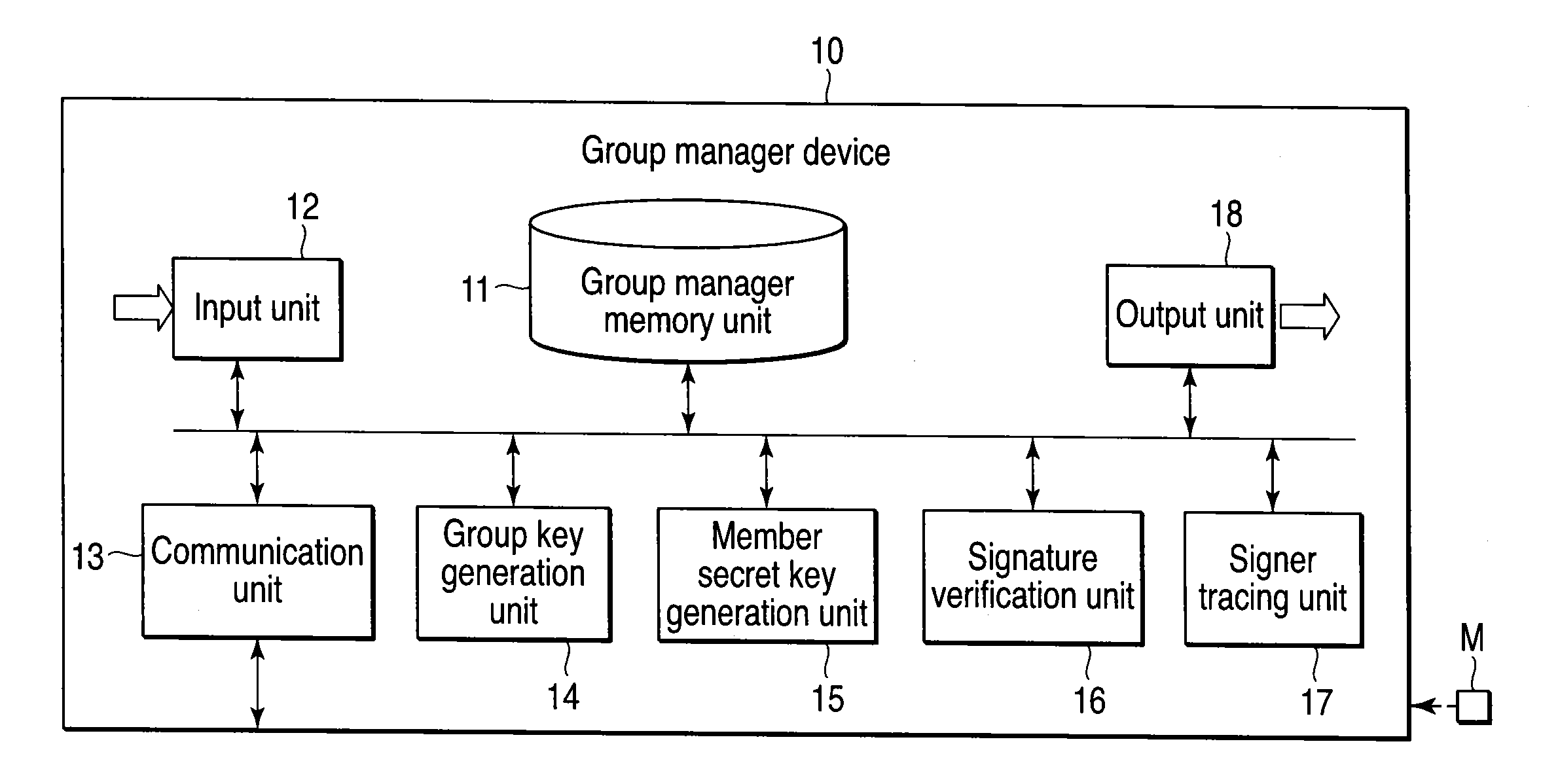
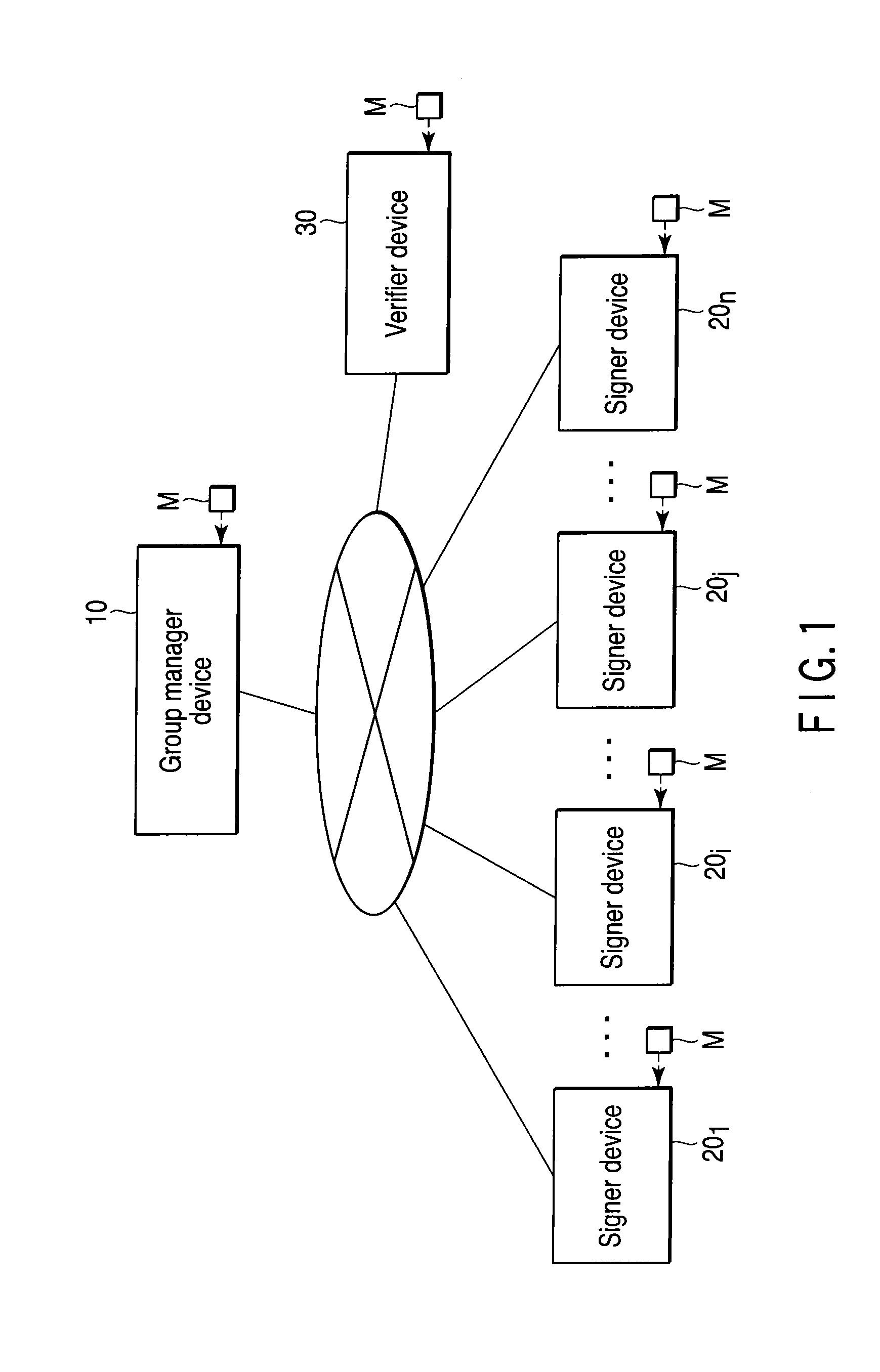
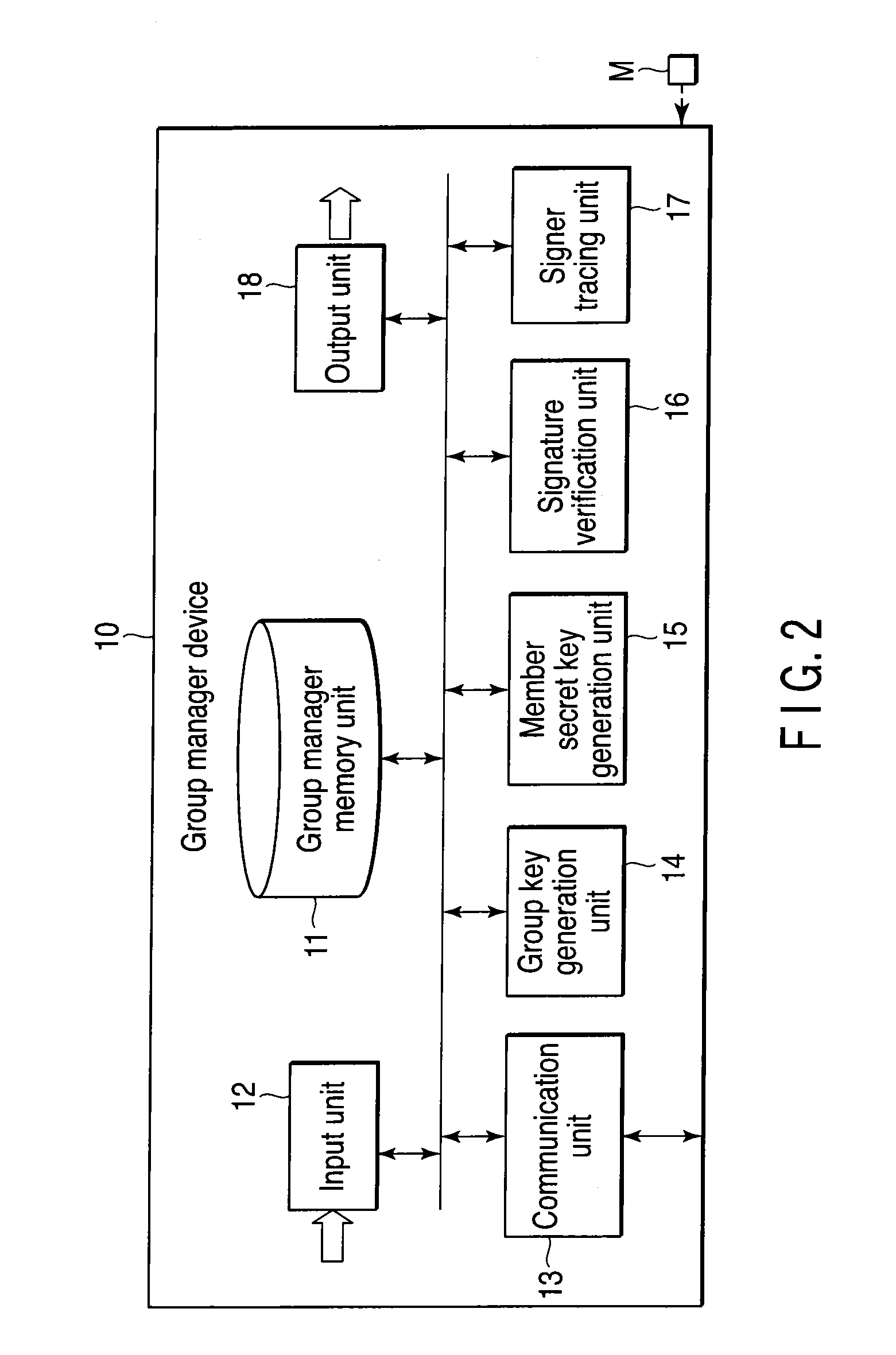
Group signature system, device, and program
ActiveUS20100169656A1Reduce the amount of calculationIncrease computing speedMultiple keys/algorithms usageUser identity/authority verificationZero-knowledge proofComputer security
A group signature system includes a group manager device, a signer device and a verifier device capable of communicating with each other, each device using a group signature scheme. The group manager device generates a group secret key, a group public key, a member secret key and a signer tracing information. The signer device generates an encrypted text data of the signer tracing information, and a zero-knowledge proof showing that the signer device knows the member secret key and the encrypted text data is correctly generated based on the signer tracing information. The signer device transmits, to the verifier device, a group signature composed of the encrypted text data and the zero knowledge proof, and the message. The verifier device verifies correctness of the group signature and transmits the verified result to the signer device.
Owner:TOSHIBA DIGITAL SOLUTIONS CORP +1
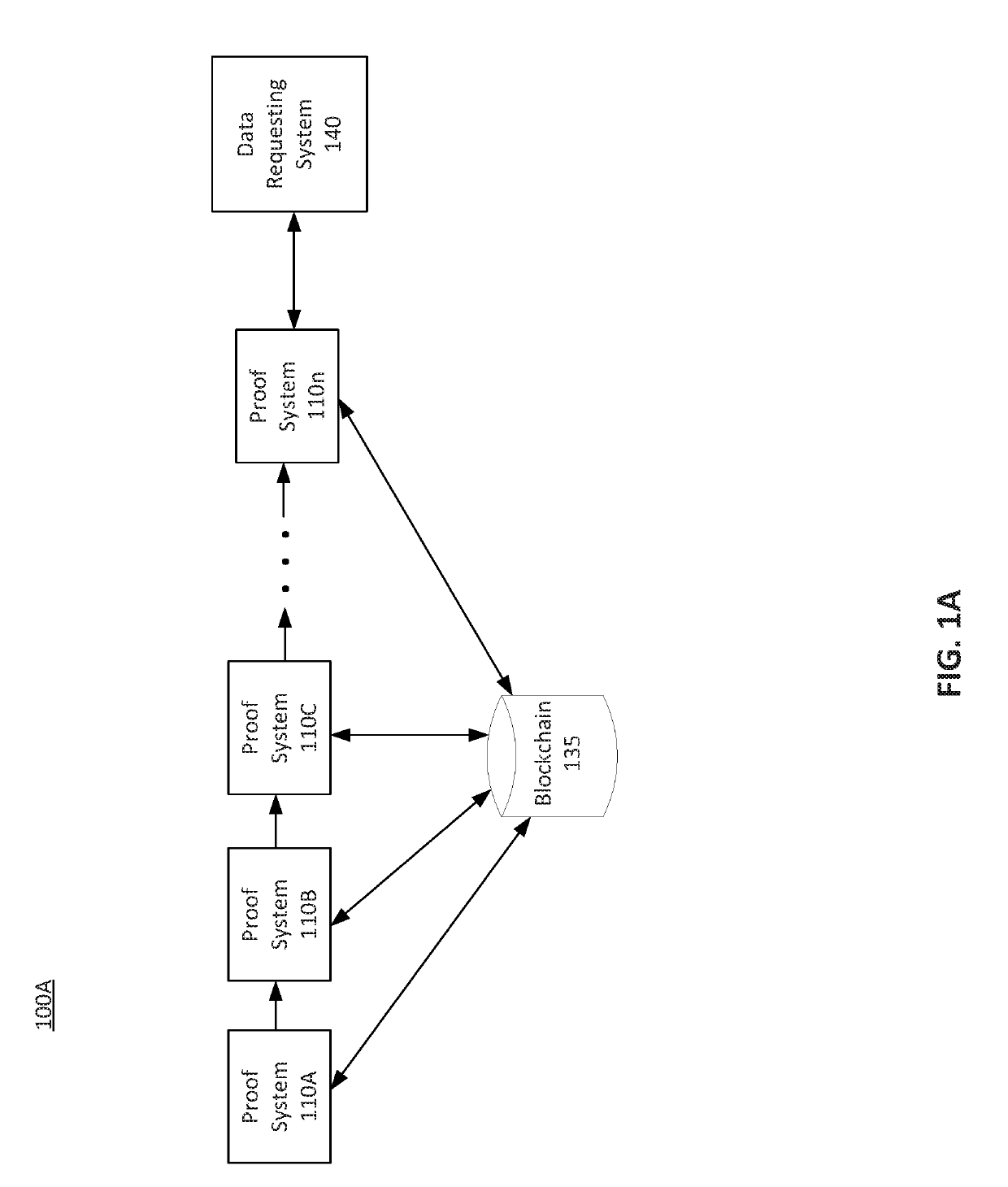
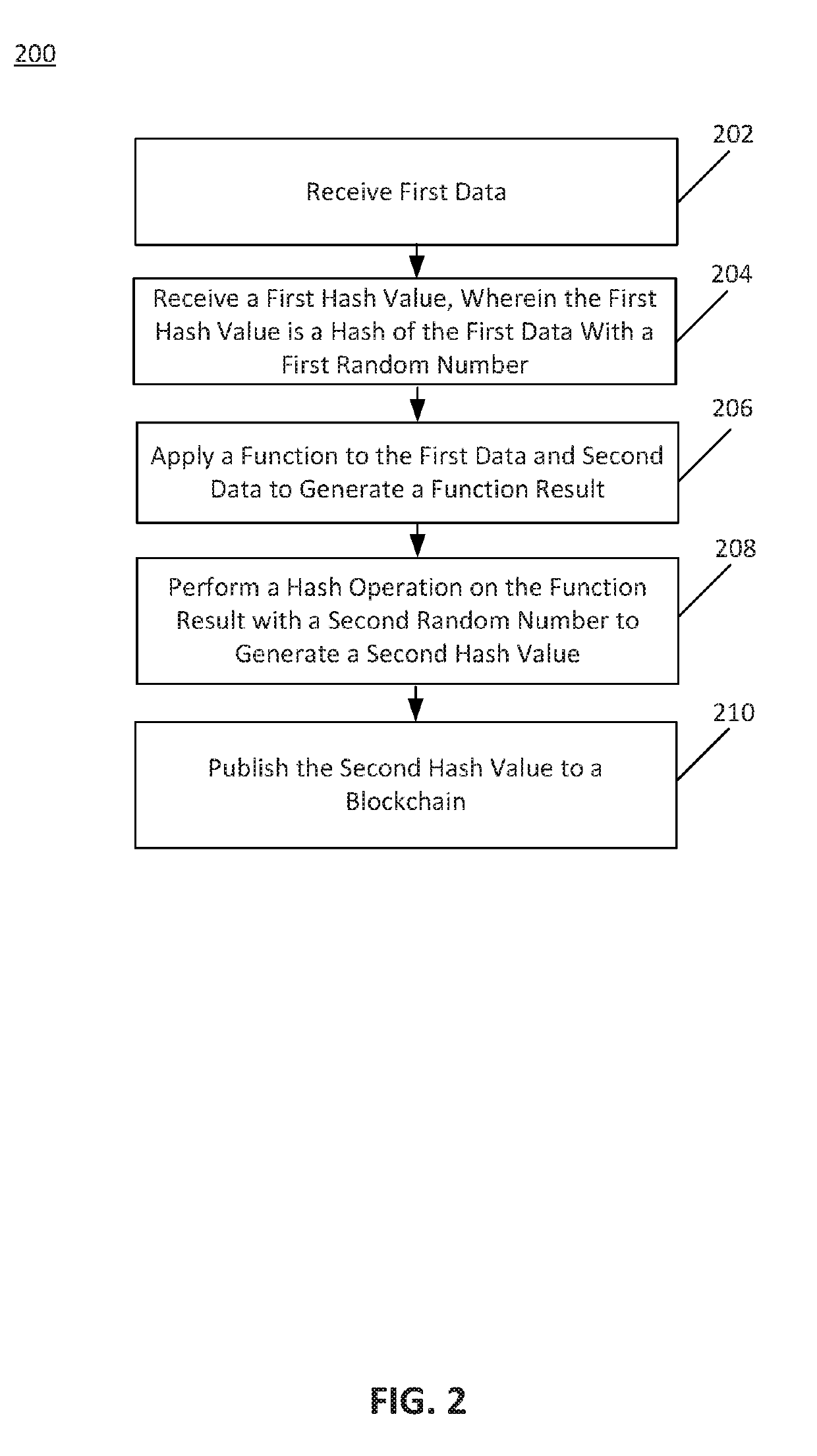
Proof chaining and decomposition
ActiveUS20190229919A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesAnalysis dataDecomposition
Disclosed herein are system, method, and computer program product embodiments for generating and chaining zero-knowledge proofs (“ZKPs”) using proof chaining. A proof may be divided into different components to analyze data in a series and / or parallel manner using chained proof systems. The proof systems may generate hash values indicating that particular functions were applied to the instances of the underlying data. The hash values may prove that a particular function was applied to instances of the underlying data. Using the proof chaining configuration, a data supply system may generate a ZKP allowing a data requesting system to trust a function result without needing to receive the underlying data.
Owner:QED IT SYST LTD
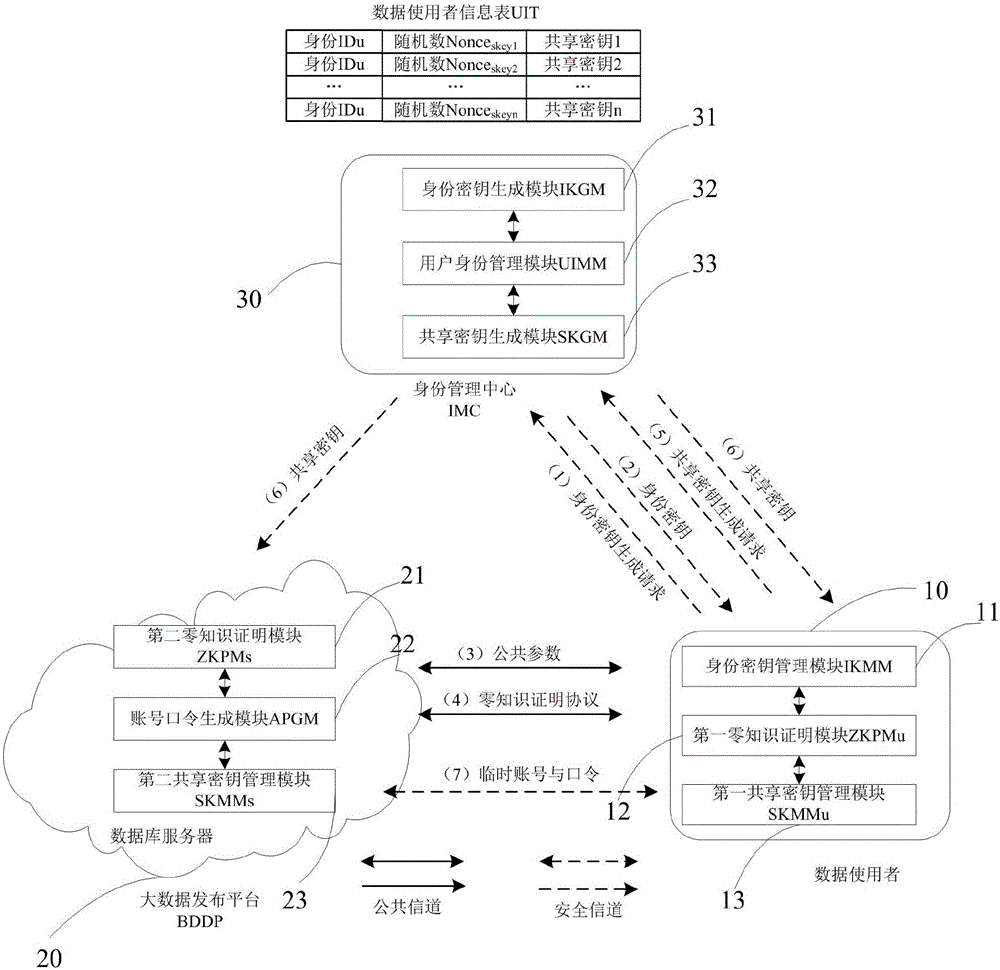
Zero-knowledge proof-based method and system for protecting user identity privacy
ActiveCN105024823ANormal analysisDo not reveal identity informationUser identity/authority verificationTemporary Account NumberPassword
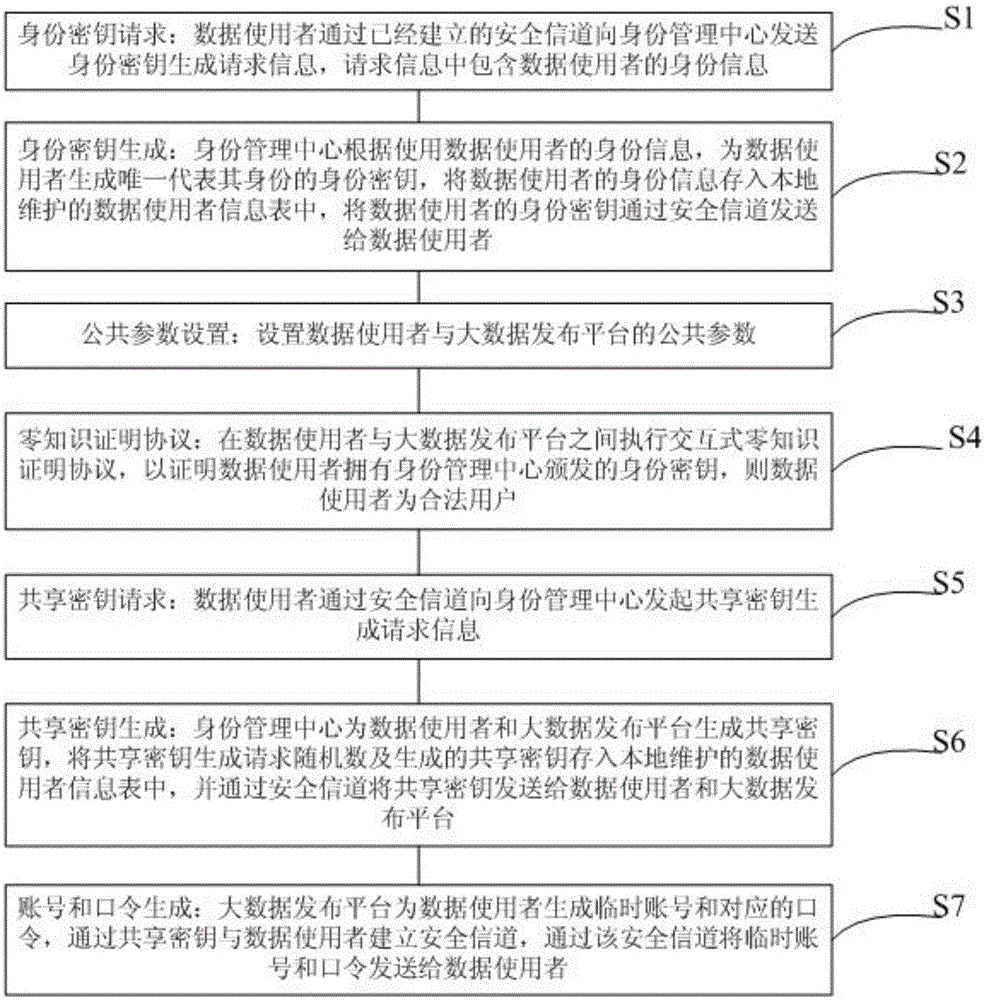
A zero-knowledge proof-based method for protecting user identity privacy comprises the steps as follows: S1, identity secret key requesting: a data user transmits identity secret key generation request information to an identity management centre via an established secure channel; S2, identity secret key generation: the identity management centre uses the identity information of the data user; S3, public parameter setting: public parameters of the data user and a big-data releasing platform are set; S4, zero-knowledge proof protocol execution: an interactive zero-knowledge proof protocol is executed between the data user and the big-data releasing platform; S5, shared secret key requesting: the data user transmits shared secret key generation request information to the identity management centre via the secure channel; S6, shared secret key generation: the identity management centre generates a shared secret key for the data user and the big-data releasing platform; S7, account number and password generation: the big-data releasing platform generates a temporary account number and a corresponding password for the data user and establishes the secure channel.
Owner:NO 709 RES INST OF CHINA SHIPBUILDING IND CORP
Zero-knowledge proof system, zero-knowledge proof device, zero-knowledge verification device, zero-knowledge proof method and program therefor
InactiveUS20110246779A1User identity/authority verificationSecurity arrangementTheoretical computer scienceDiscrete logarithm
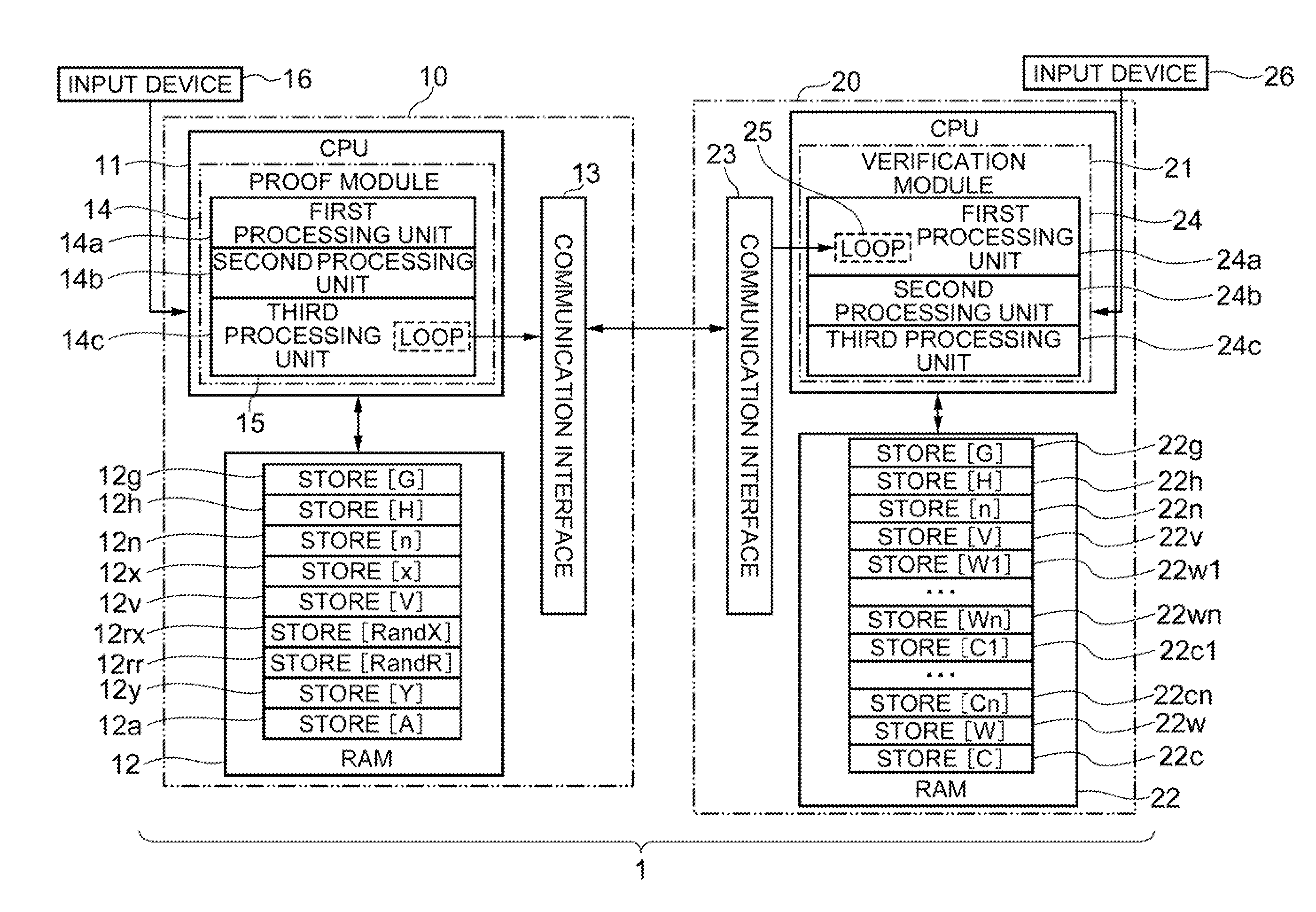
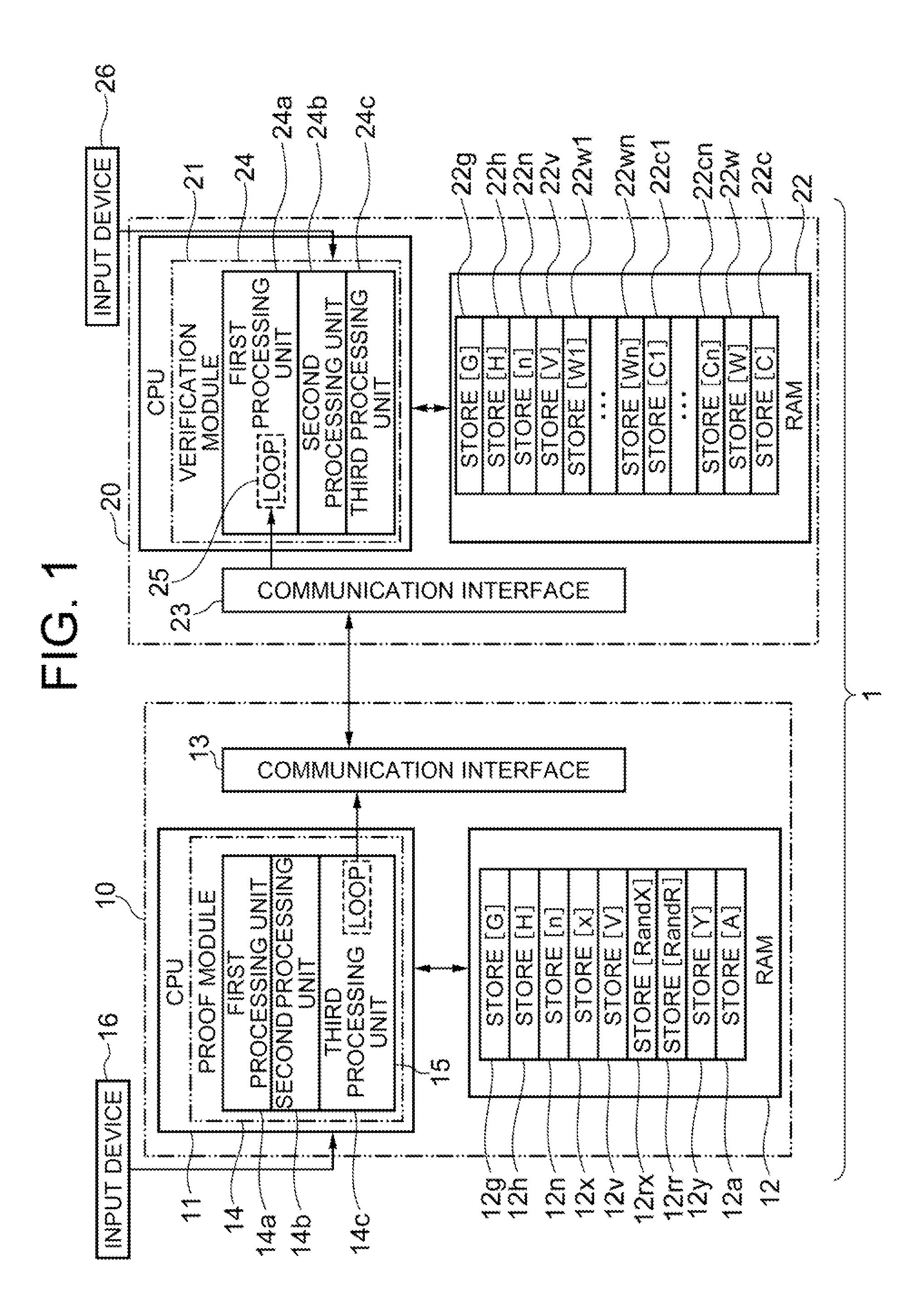
Provided is a zero-knowledge proof system that allows a discrete-logarithm zero-knowledge proof. The zero-knowledge proof device includes a temporary memory unit that stores pseudorandom numbers and previously determined hash values, a first processing unit that calculates multiple pseudorandom numbers and performs multiple iterations of processing to calculate hash values based on the calculated pseudorandom numbers and the information stored in the temporary memory unit, a second processing unit that determines some of the multiple pseudorandom numbers based on the hash values, and a third processing unit that re-calculates some of the pseudorandom numbers and sends the hash values obtained to a zero-knowledge verification device. The zero-knowledge verification device includes a temporary memory region, a data receiving module that sequentially receives new input data, and a processing module that overwrites hash values including variables and input data, as variables into the temporary memory region each time the input data are received.
Owner:NEC CORP
Authentication System
InactiveUS20150134966A1User identity/authority verificationCoding/ciphering apparatusAuthentication systemZero-knowledge proof
Owner:ANALOG DEVICES INC
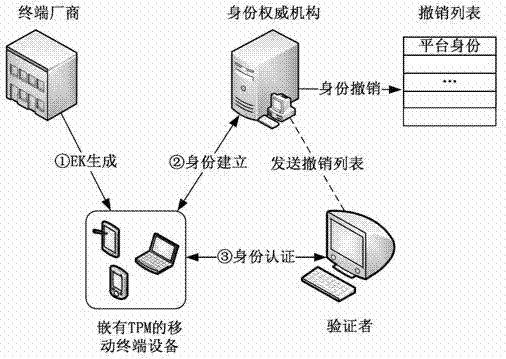
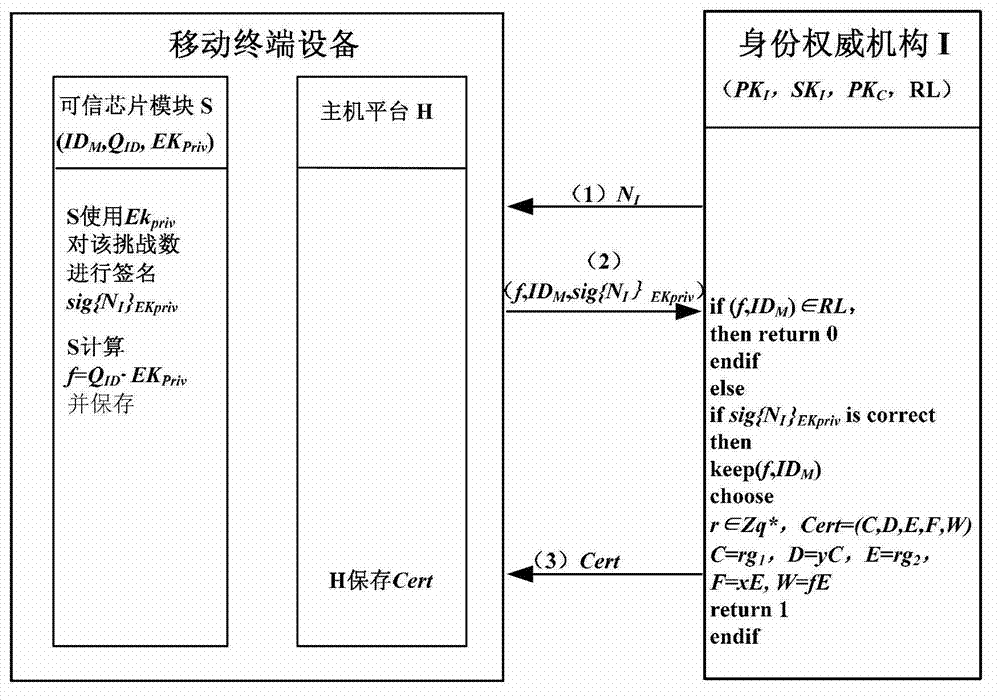
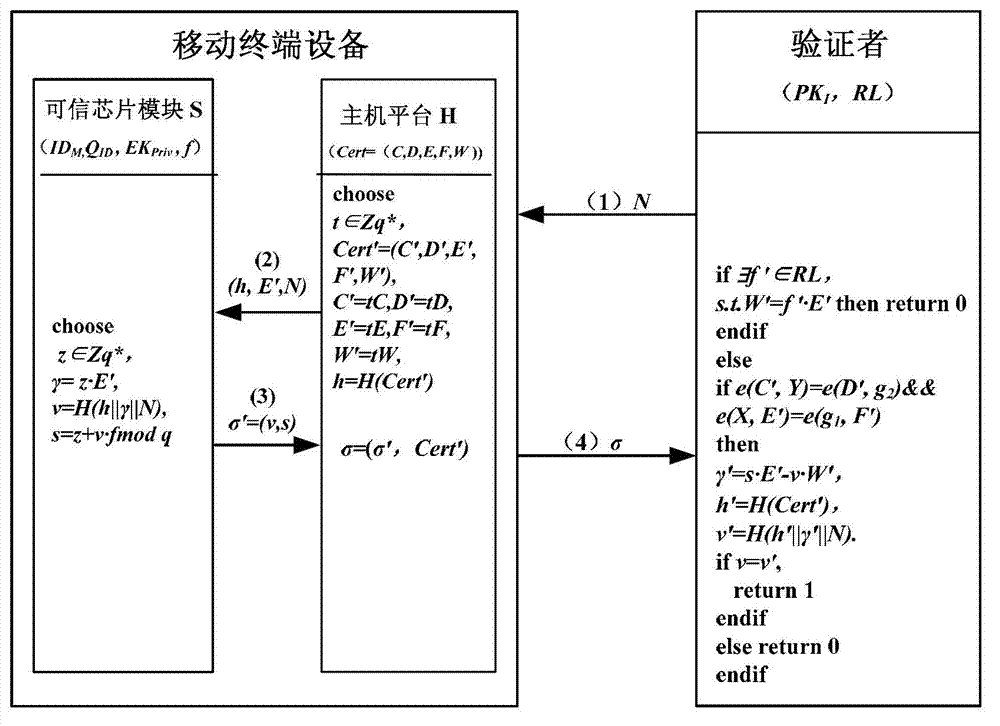
Direct anonymous attestation method applied to credible mobile terminal platform
ActiveCN102970682AReduce computational overheadImprove safety and reliabilitySecurity arrangementThree stageTrusted Platform Module
The invention provides a direct anonymous attestation method applied to a credible mobile terminal platform, which can realize the generation of a platform endorsement key (EK) pair, the establishment and revocation of a platform identity and the authentication of a mobile terminal identity by adopting a method based on identity signature and zero-knowledge proof signature. The method is divided into three stages, namely a system initialization stage, an identity establishment stage and an identity verification stage and comprises 9 steps in total, and the method is specifically as follows: stage 1: system initialization: step 1: performing the system initialization on a manufacturer; step 2: performing the system initialization on an identity authoritative institution; step 3: initializing an equipment EK pair; stage 2: identity establishment: step 4: sending a challenge number; step 5: making a response by terminal equipment; step 6: verifying and issuing an identity certificate; and the stage 3: identity verification: step 7: sending a challenge number; step 8: responding by the terminal equipment; and step 9: verifying the legitimacy of the identity certificate. The method provided by the invention meets the requirements of anonymous authentication for correctness, unforgeability and untraceability, and is suitable for a mobile terminal platform which has limited computational resources and is embedded with a TPM (trusted platform module).
Owner:BEIHANG UNIV
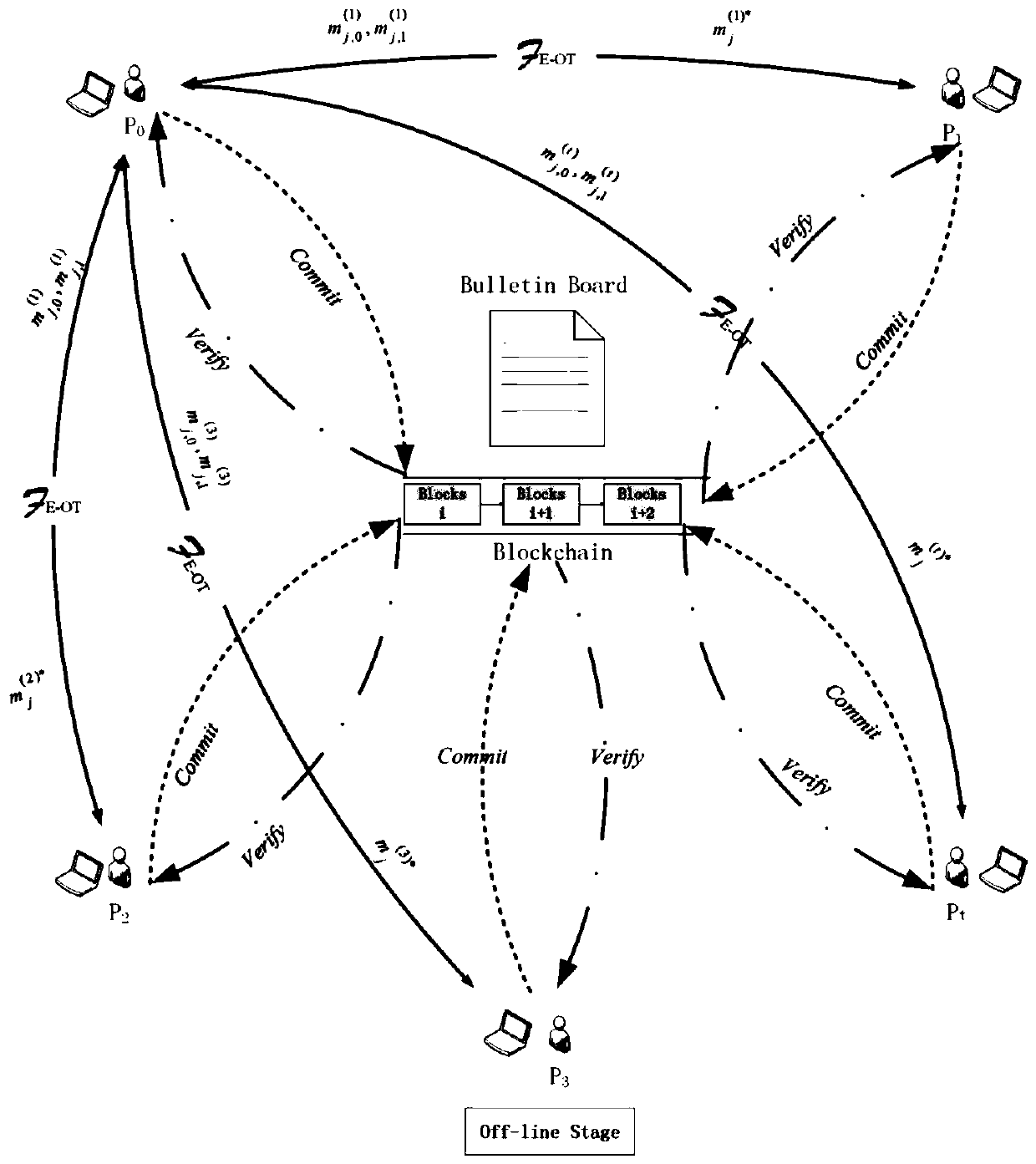
Multi-party privacy set intersection method for resisting malicious enemies
ActiveCN110719159AProtection of rights and interestsConvenient verificationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesInternet privacyEngineering
The invention relates to a multi-party privacy set intersection method for resisting malicious enemies. The method comprises an offline stage and an online stage. In the offline stage, appointment commitment, careless transmission and the like are carried out, and operation is carried out in the online stage; a threshold homomorphic encryption scheme, a non-interactive zero knowledge proof, an improved Bloom filter and the like are mainly used for constructing a protocol. Even if malicious enemies can obtain the Bloom filters and the operation results of all honest parties, the malicious enemies and the operation results cannot leak extra information of all honest participants except the intersection under the condition of aiming at multiple parties. The bulletin board function is achieved, the commitment values of all participants are disclosed together while all the participants send corresponding information to the bulletin board so that the published information can be convenientlyverified in the later period, and malicious behaviors of part of the participants are prevented.
Owner:HENAN NORMAL UNIV
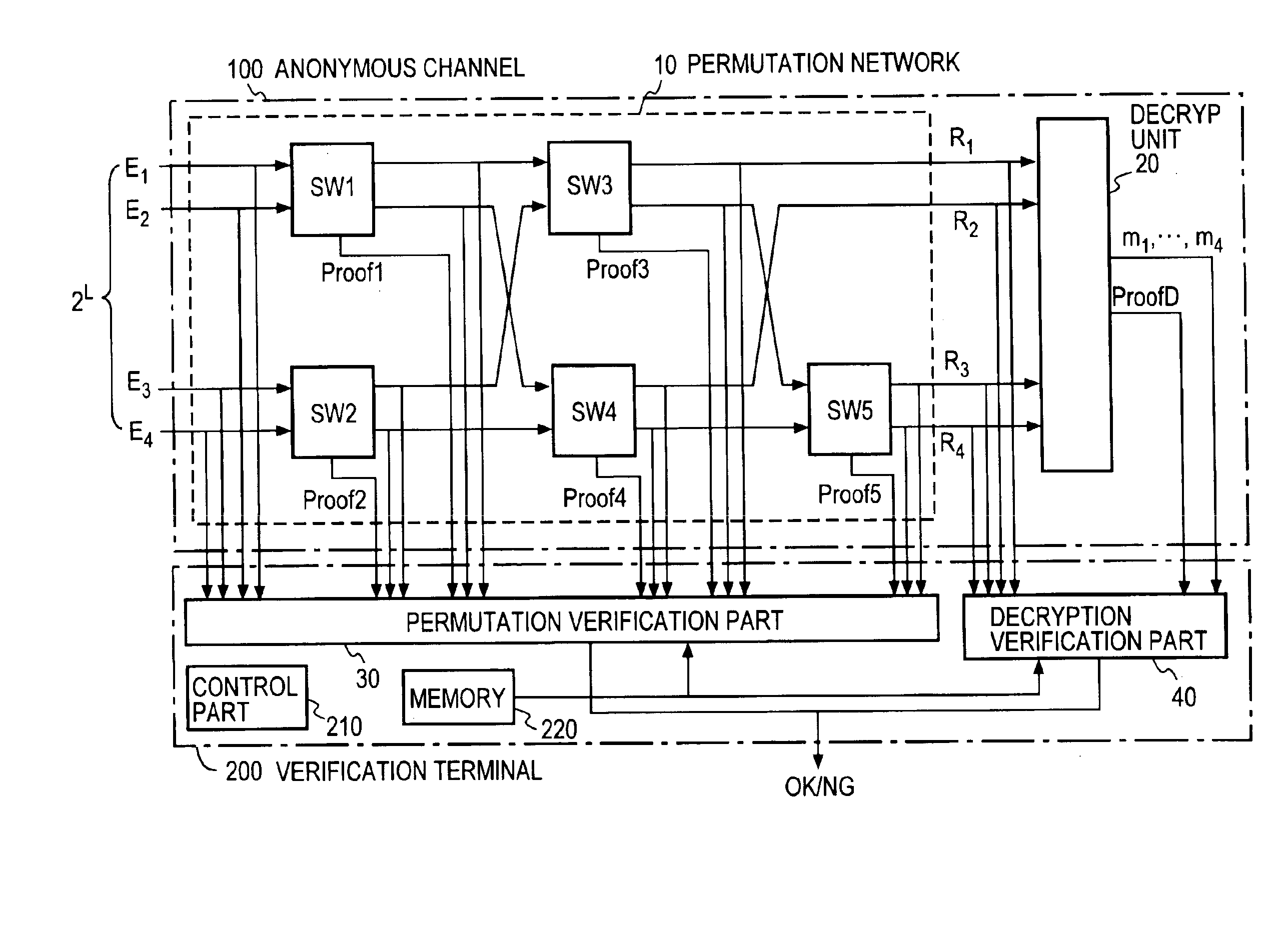
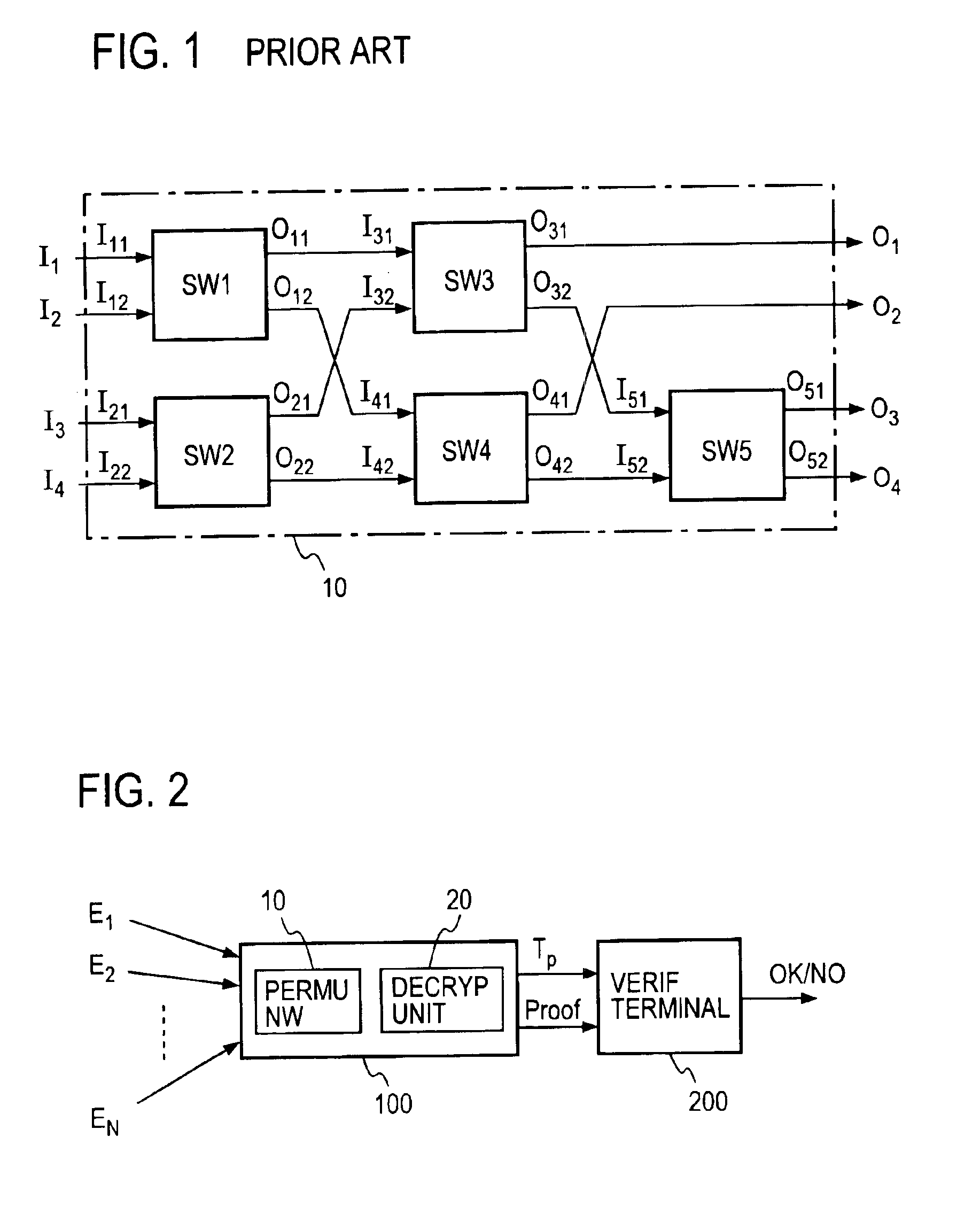
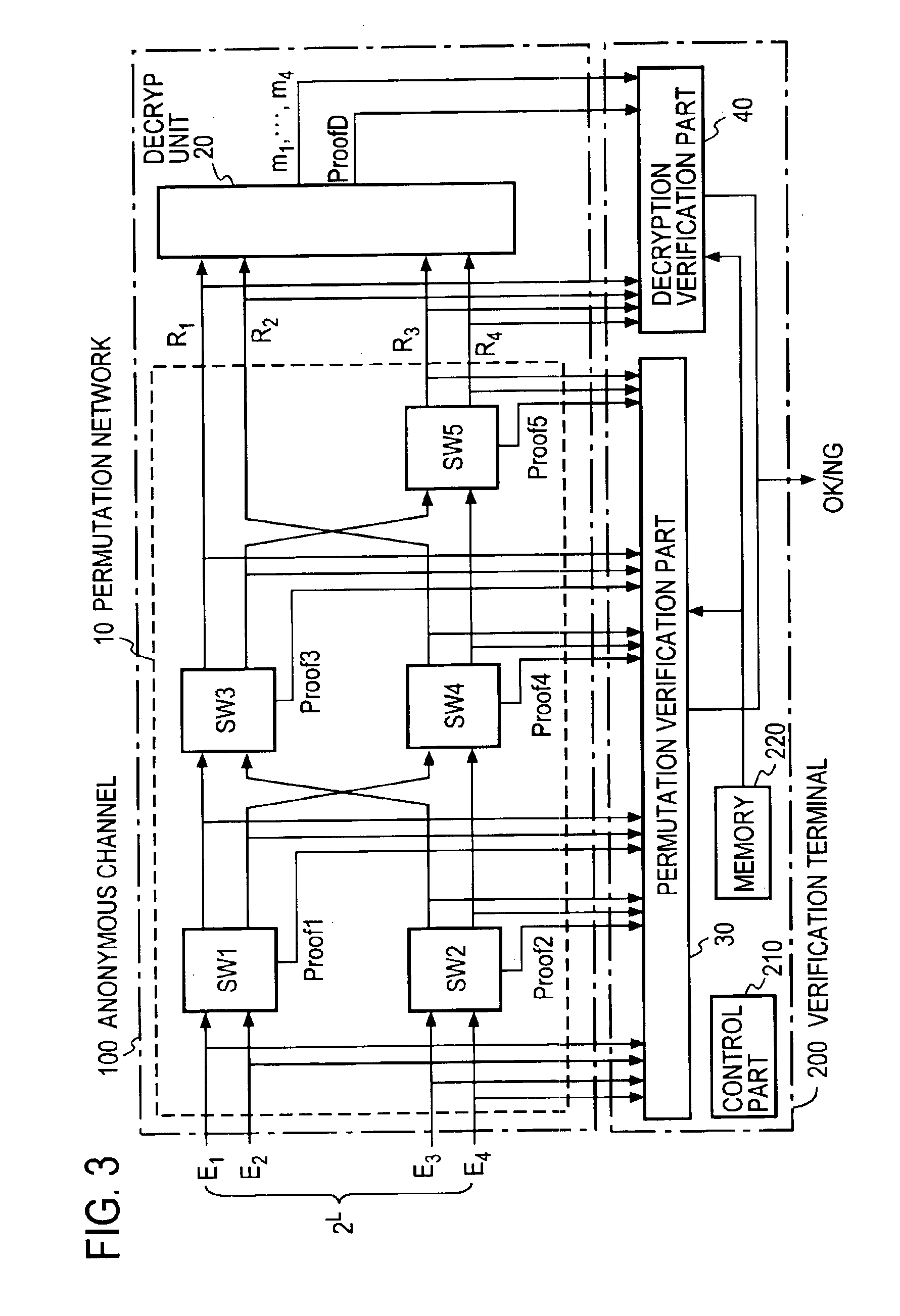
Verifiable anonymous channel
InactiveUS6937728B1Efficiently proveEfficient verificationPublic key for secure communicationUser identity/authority verificationPseudorandom permutationValidator
Two El Gamal ciphertexts, which are input to a two-input two-output unit switching gates SW forming a permutation network, are randomized with a random number and randomly permuted, and a zero-knowledge proof, which proves the correspondence between the inputs and outputs of the switching gates SW, is output to a verifier without revealing the random number and the random permutation. A decryption unit decrypts ciphertexts from a unit switching gate SW in he last column through the use of a secret key, and proves in zero-knowledge the validity of the decryption without revealing the secret key. A verification unit verifies the proof of each unit switching gate and the proof of the decryption unit.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
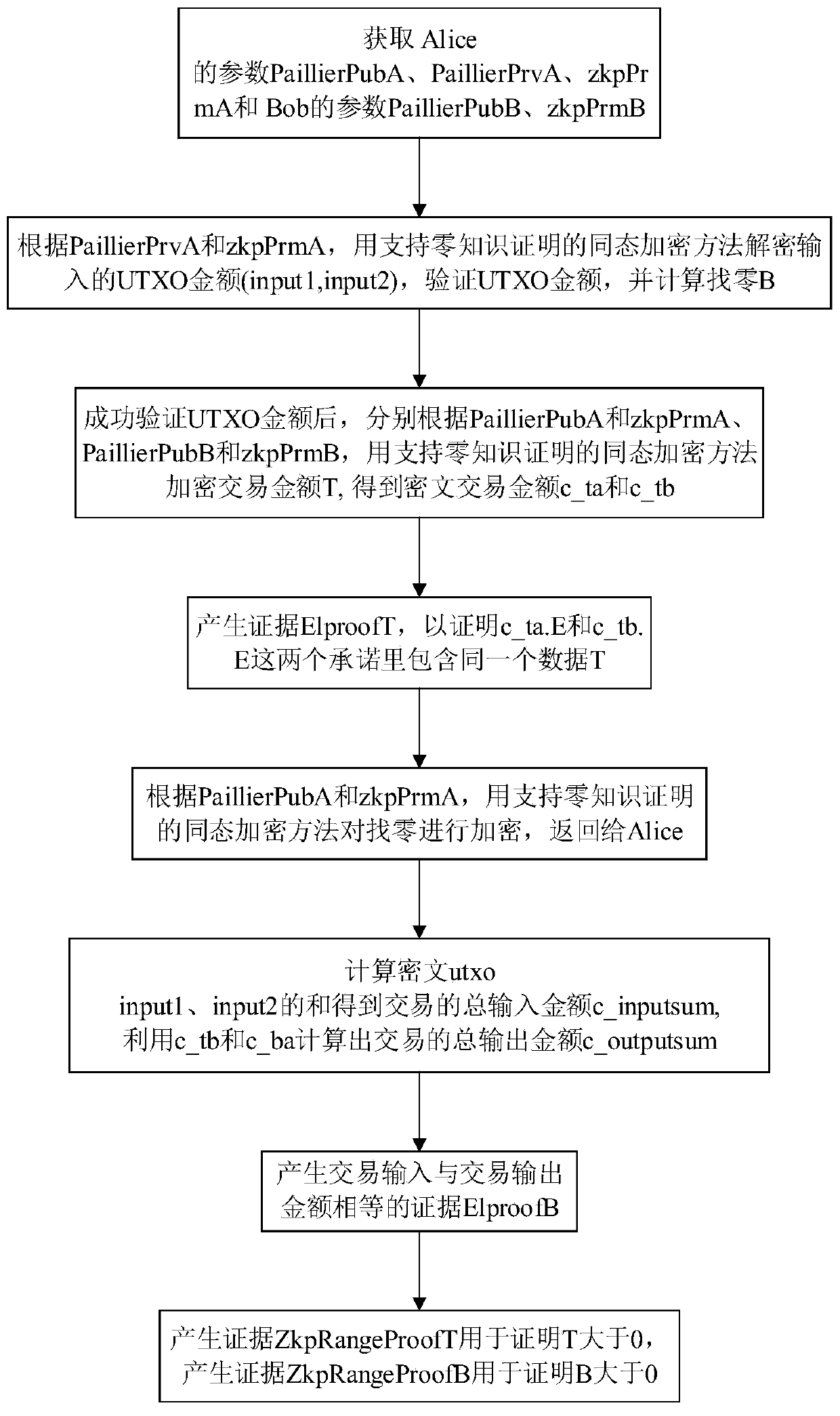
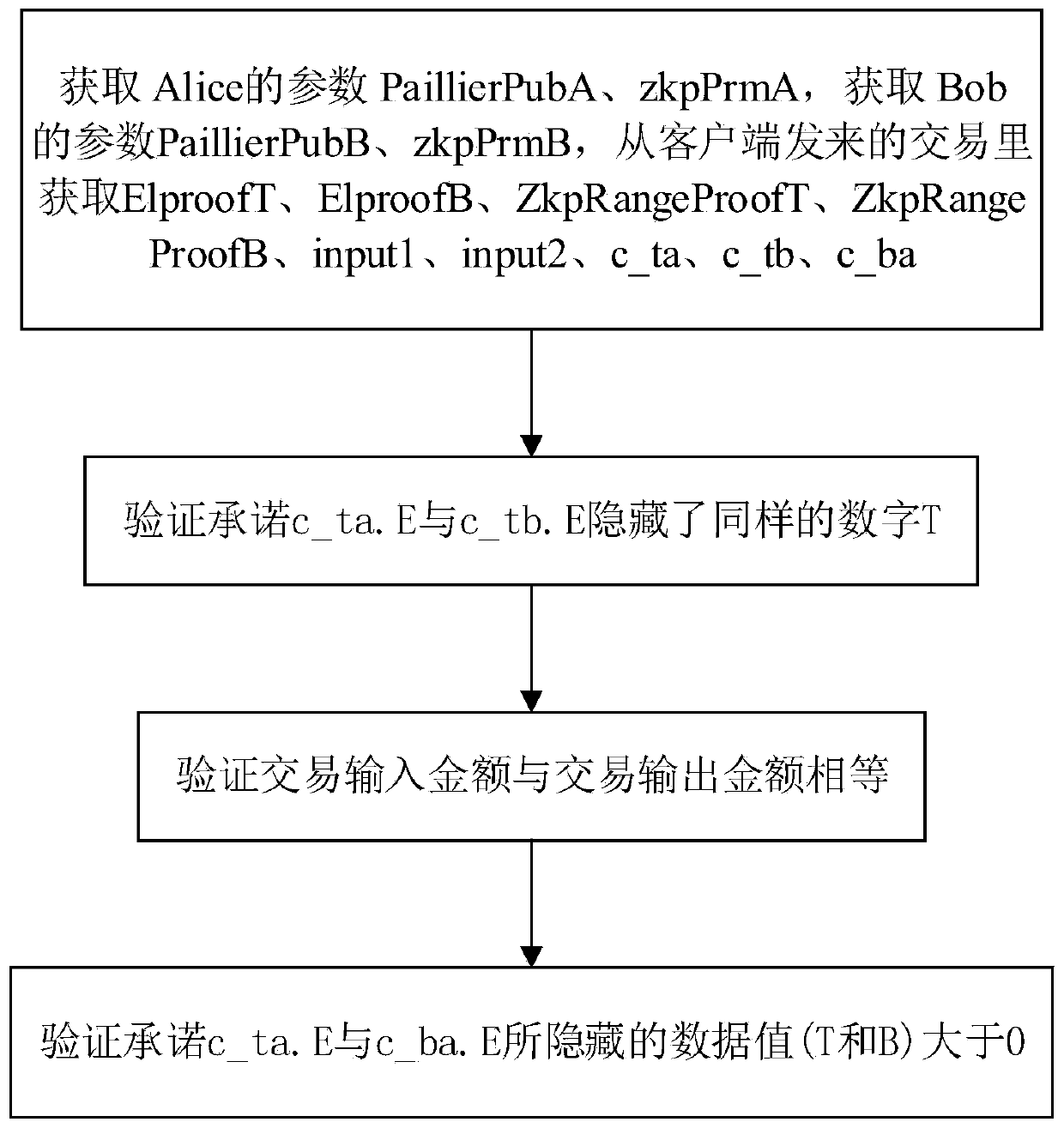
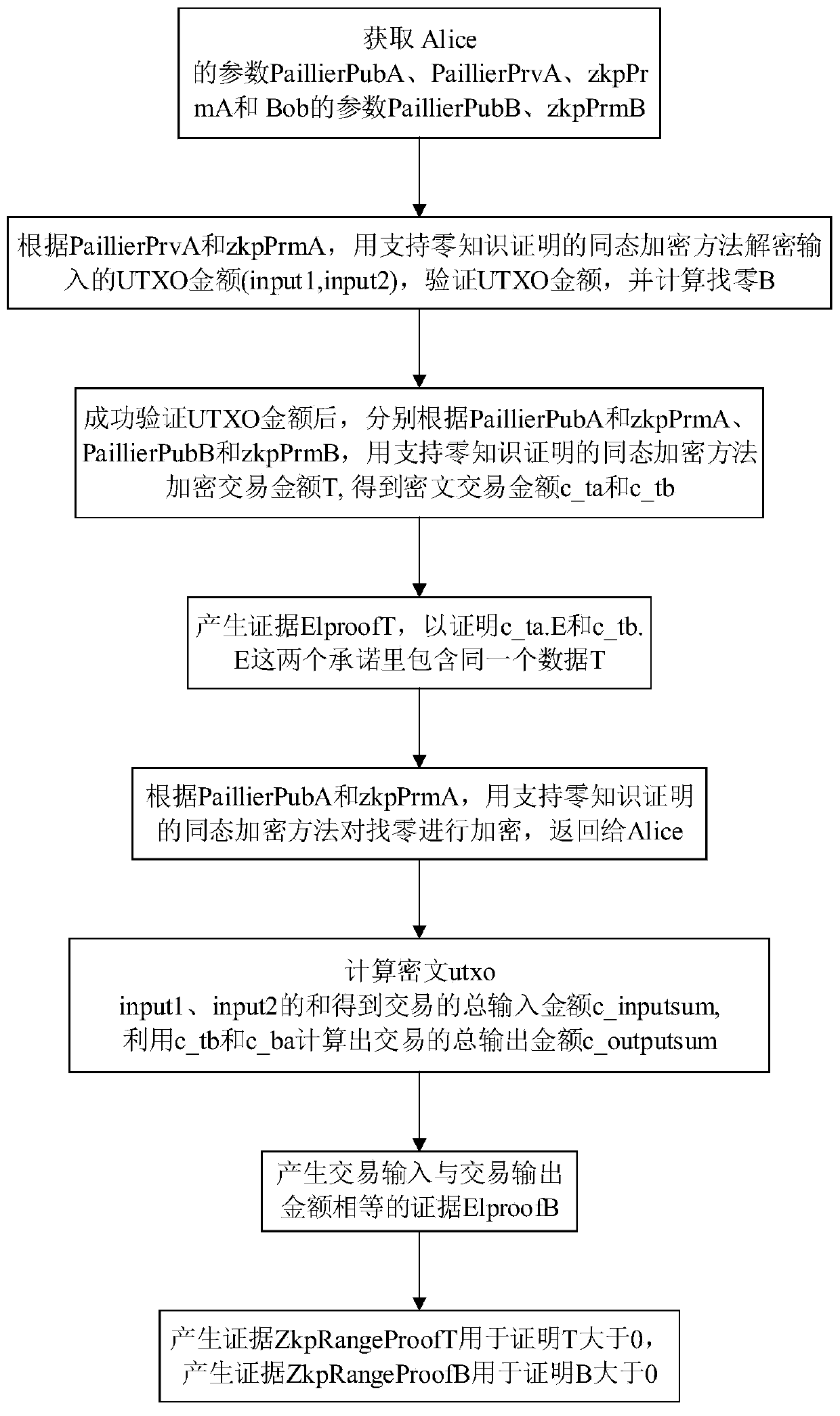
Homomorphic encryption method for encrypting transaction amount and supporting zero knowledge proof
ActiveCN110011781ARange Proof SupportUser identity/authority verificationPayment protocolsPlaintextCiphertext
The invention discloses a homomorphic encryption method for encrypting transaction amount and supporting zero knowledge proof, and belongs to the technical field of information security. The method comprises the following steps: generating a public key, a private key and a zero knowledge parameter according to a zero knowledge proof requirement and a Paillier algorithm; according to a given plaintext, using an encryption algorithm, the public key and the zero knowledge parameter for encryption, and outputting a ciphertext (E, c1 and c2); and according to the given ciphertext, using a decryption algorithm and the private key for decryption, and outputting a plaintext. According to the method, the Paillier homomorphic algorithm is improved; the ciphertext is divided into three parts (E, c1 and c2), the three parts can be used for secreting transaction amount on the whole, and the commitment part E can also be used for proving the zero knowledge range of the transaction amount, so that the Pillier algorithm is combined with the zero knowledge range proof based on FO commitment, and the range proof of the ciphertext is supported. The method can be used for transaction amount encryptionand range proof of an account model, and can also be used for transaction amount encryption and range proof of a UTXO model.
Owner:HUAZHONG UNIV OF SCI & TECH
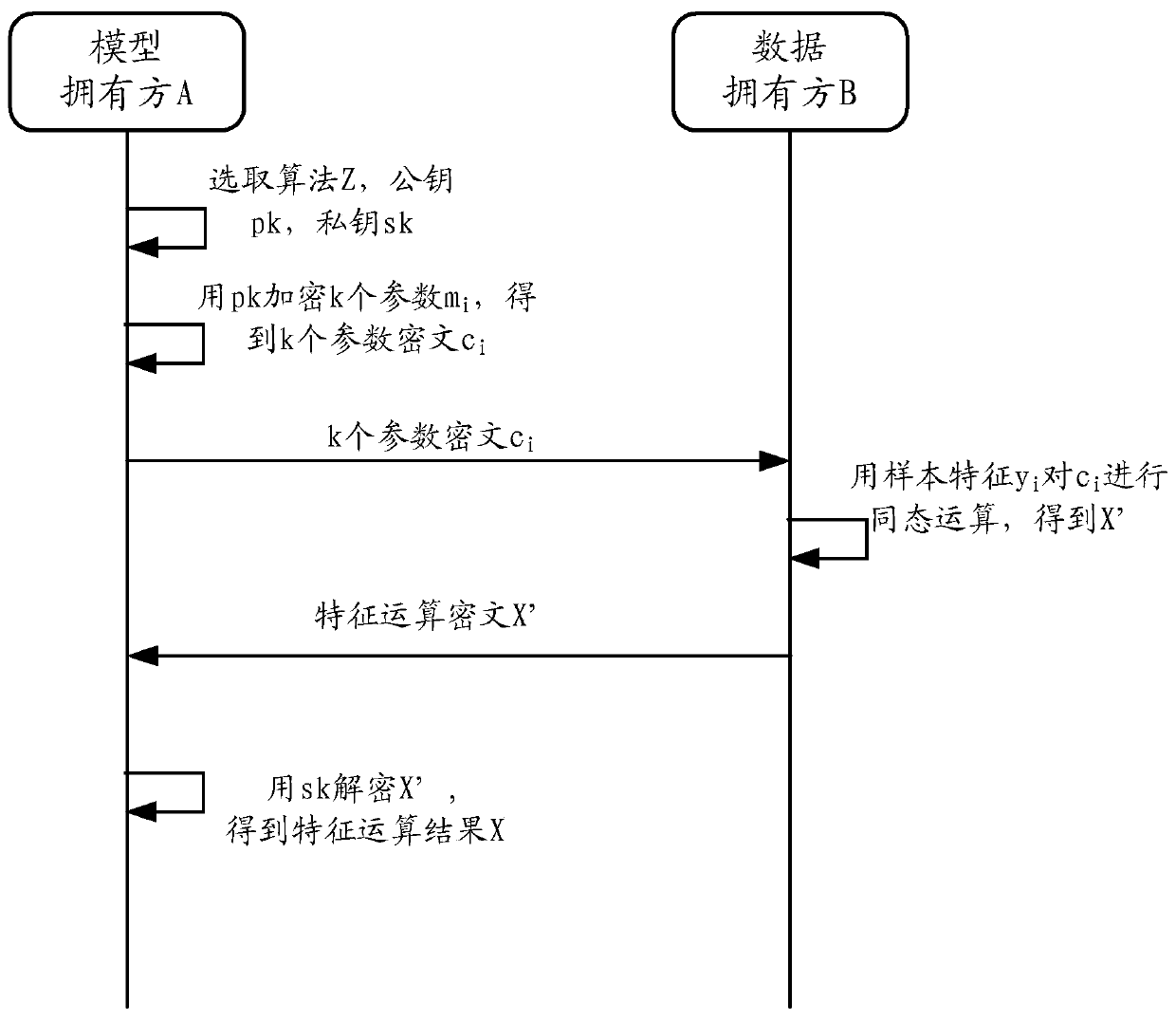
Multi-party joint model data processing method and device
ActiveCN110991655AWon't leakEnsure safetyKey distribution for secure communicationUser identity/authority verificationAlgorithmCiphertext
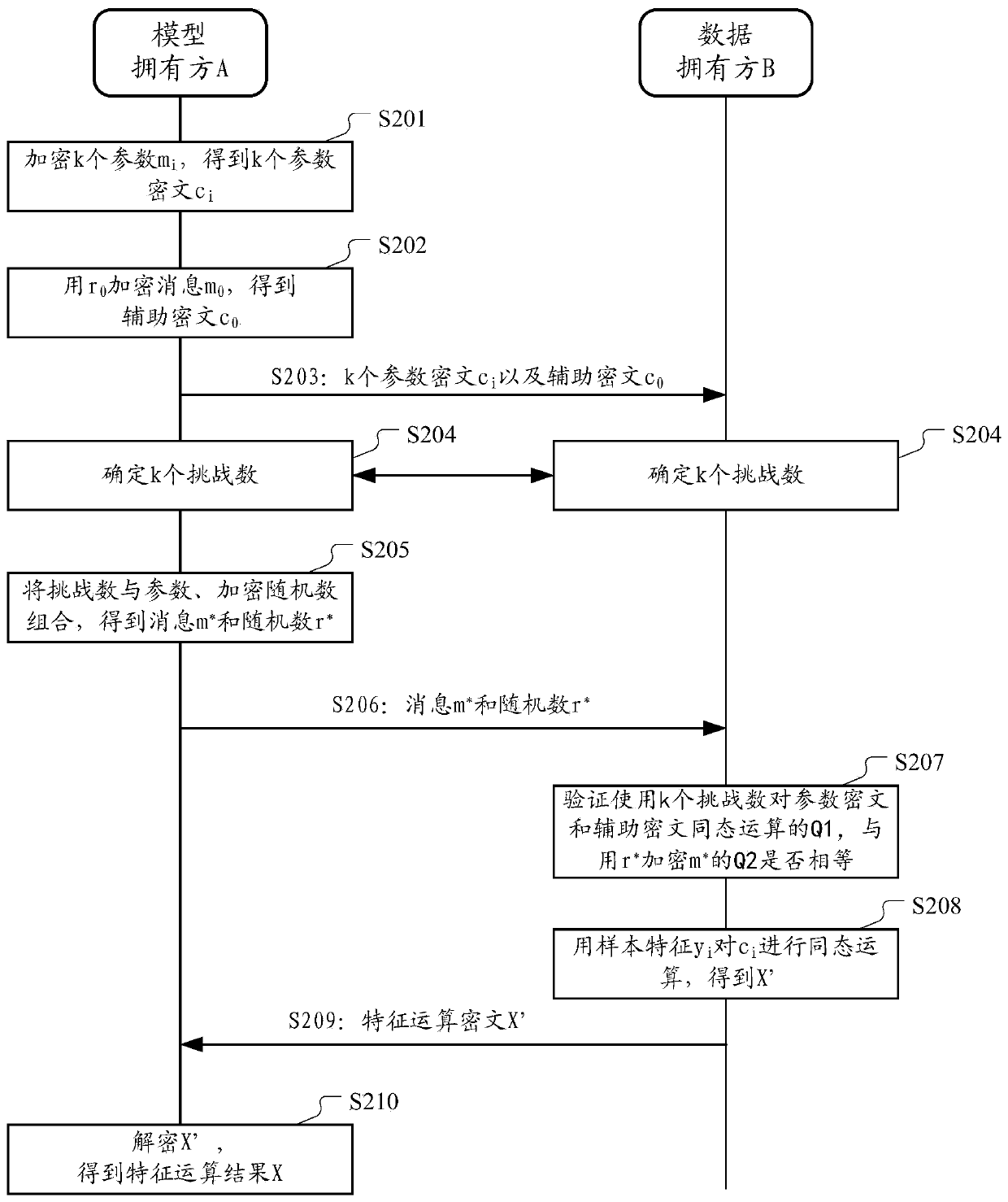
The embodiment of the invention provides a multi-party joint model data processing method and device for protecting data privacy. According to the method, after a model owner performs homomorphic encryption on k model parameters to obtain k parameter ciphertext, a first random number is selected to encrypt a random first message to obtain an auxiliary ciphertext; in addition, the model owner and adata owner jointly determine k challenge numbers. And then, the model owner combines the k challenge numbers with the model parameters and the first message, and the encrypted random number and the first random number to generate a verification random number and a verification message as zero knowledge proof. The data owner may verify whether a result of the homomorphic operation of the parametric ciphertext and the auxiliary ciphertext based on the k challenge number pairs is equal to a result of encrypting the verification message with the verification random number. And under the conditionof the same value, the homomorphic operation is carried out by using the sample characteristics, and the result is returned to the model owners, so that the security of private data of each party inthe model data process is ensured.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Digital certificate management method and system based on block chain, equipment and storage medium
ActiveCN113014392ARaise the barSolve forgeryEncryption apparatus with shift registers/memoriesUser identity/authority verificationSecure communicationGeneration process
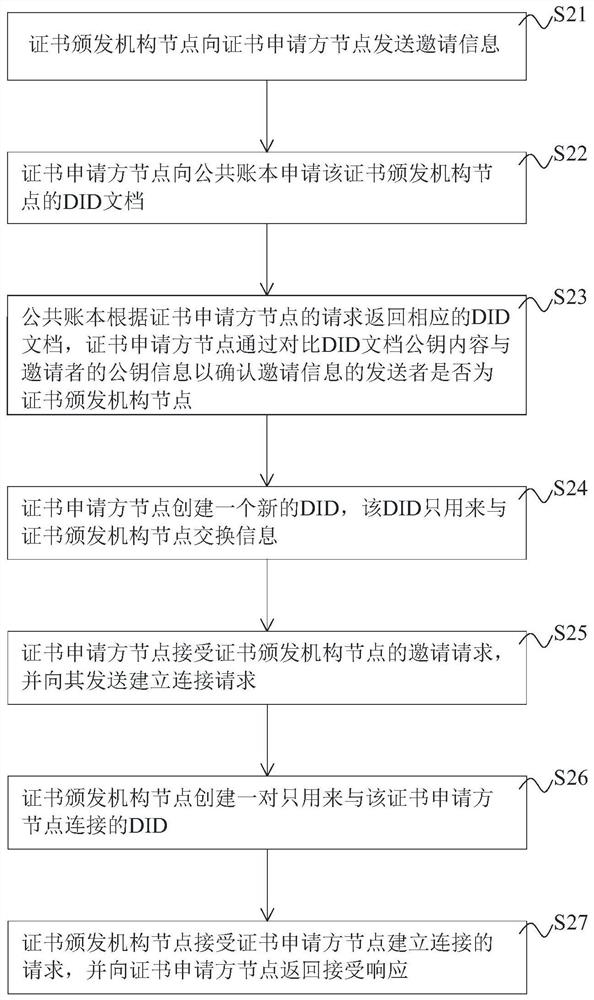
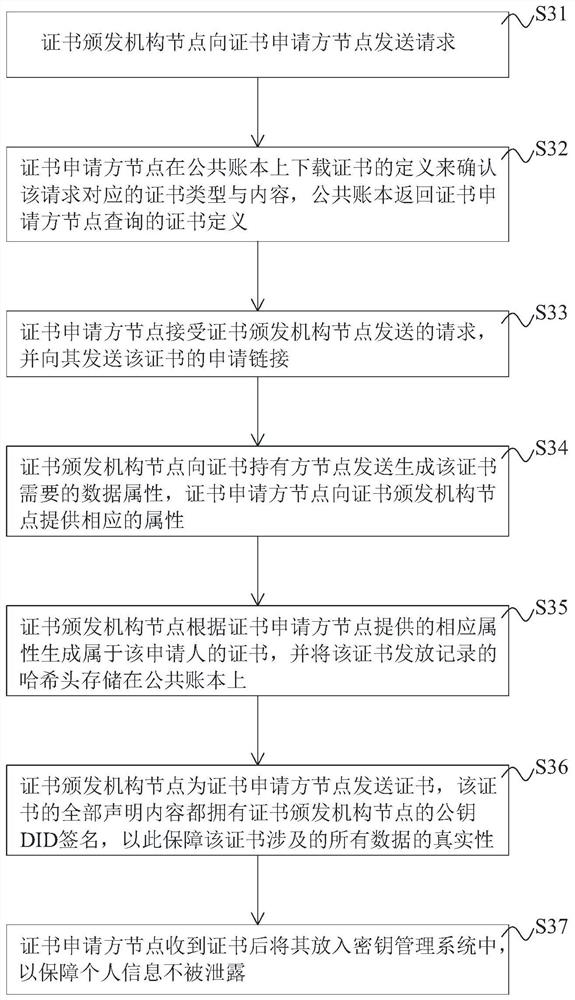
The invention discloses a digital certificate management method and system based on a block chain, equipment and a storage medium, in the method, a certificate template can be issued only after passing through a registration program, strict management and control are carried out from the root of certificate issuing, the certificate template and a sending record of each certificate can be traced, and the problem of certificate counterfeiting is thoroughly solved, the certificate inspection cost can be reduced, and the certificate inspection efficiency is improved. Before a certificate is issued and verified, a secure connection needs to be established between an applicant and an issuer and between a holder and a verifier, and the adopted DID technology provides a basis for secure communication and increases the security of certificate transmission. Besides, the certificate verifier can complete validity verification of the certificate based on the verifiable declaration provided by the holder, and the generation process of the verifiable declaration is combined with cryptographic technologies such as zero-knowledge proof and Merkel tree to selectively disclose certificate attributes, so that the privacy of the certificate holder can be ensured not to be leaked, and the security is improved.
Owner:HUNAN UNIV
Method and device for authenticating zero knowledge proof
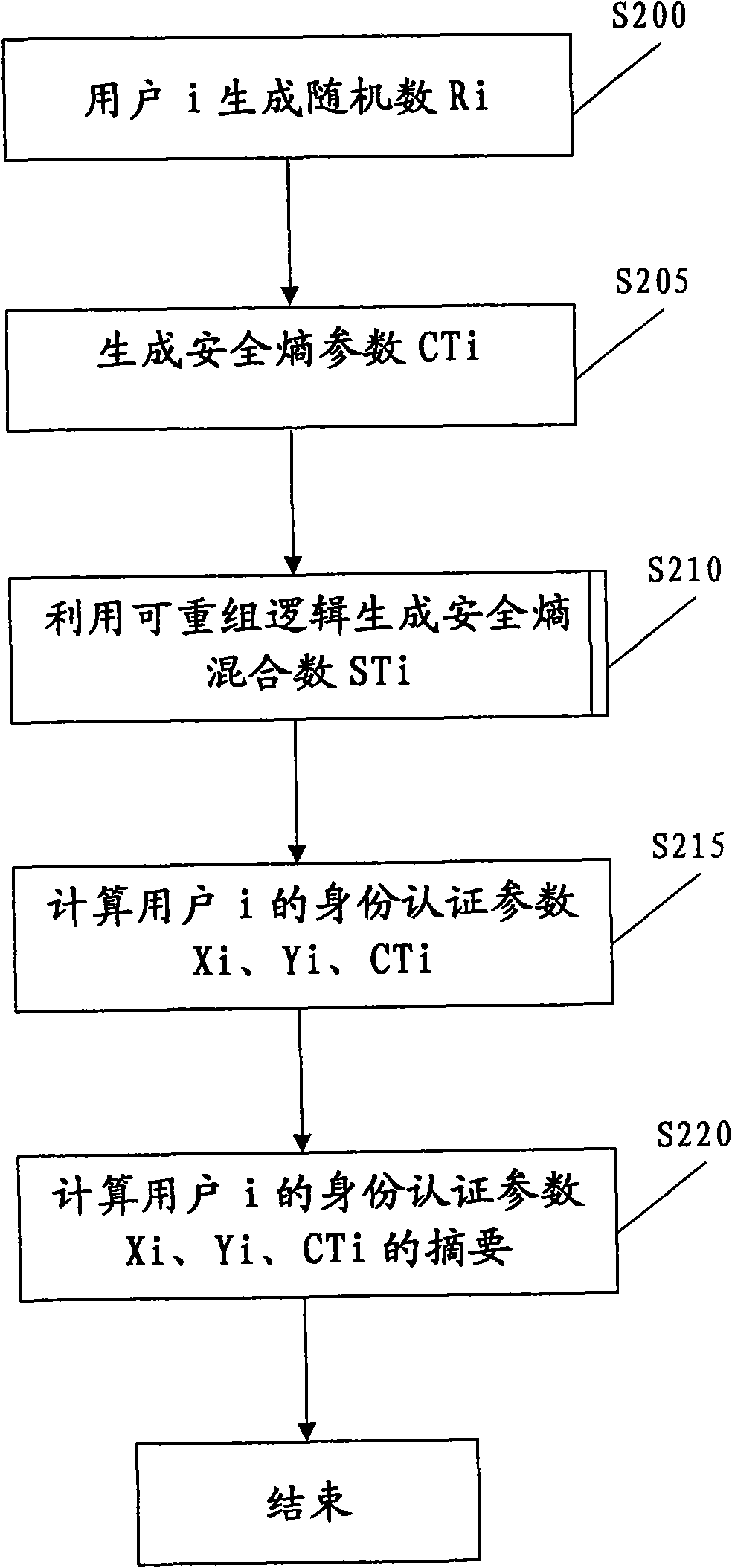
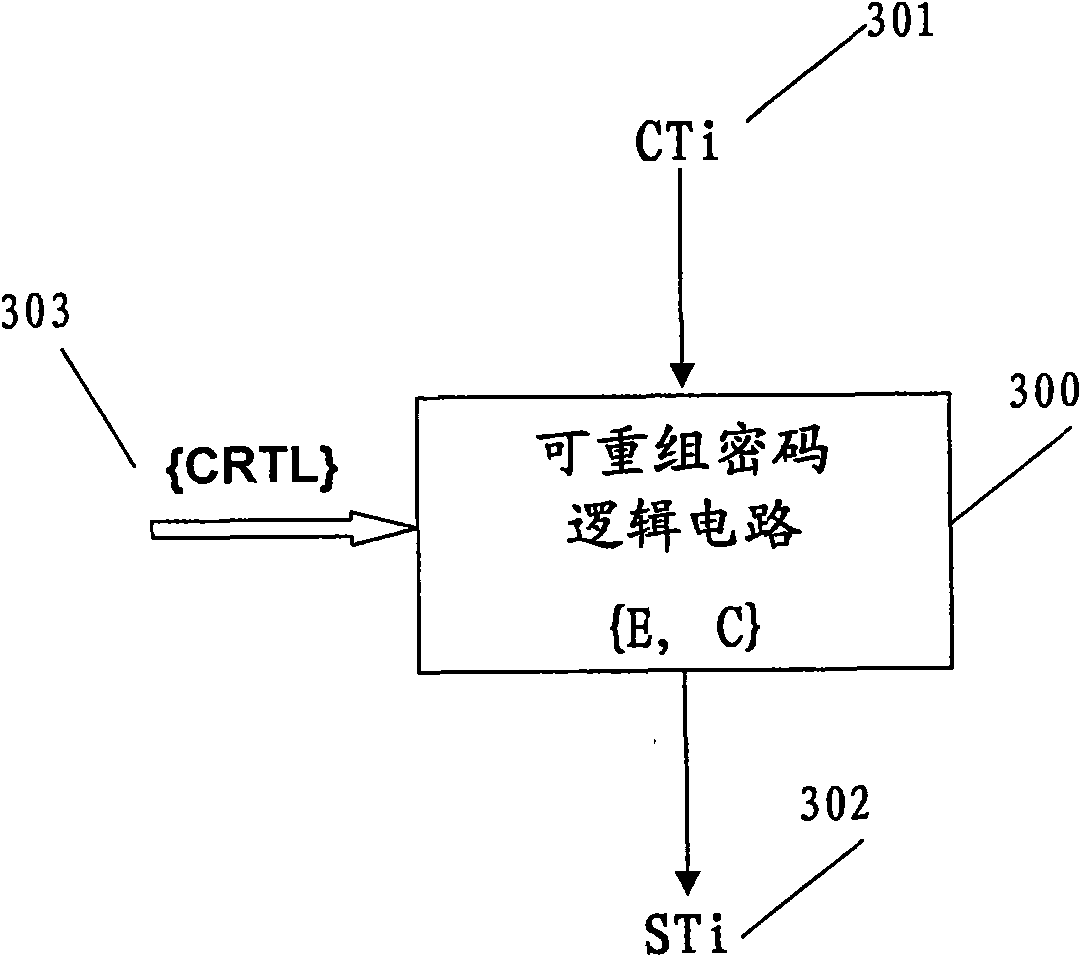
The invention relates to a method and device for authenticating zero knowledge proof. The method is based on a public key system, wherein a public key certificate GCi is allotted to a first user through a first authentication organism, and the public key certificate GCi at least comprises user parameters idi and is published. The method comprises the steps of: generating a first random number Ri and a safety entropy parameter CTi, on the basis of the safety entropy parameter CTi, generating a safety entropy mixing number STi by using a recombination cryptologic circuit; on the basis of the first random number Ri, the safety entropy parameter CTi and the safety entropy mixing number STi, generating a first identity authentication parameter of the first user; sending the first identity authentication parameter to a second user by the first user; and figuring out a public key certificate GCi' of the first user from the received first identity authentication parameter by the second user and comparing the figured-out public key GCi' and the published public key certificate GCi to authenticate the first user.
Owner:深圳市前海多思科技发展有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com