Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
33results about How to "Meet privacy requirements" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
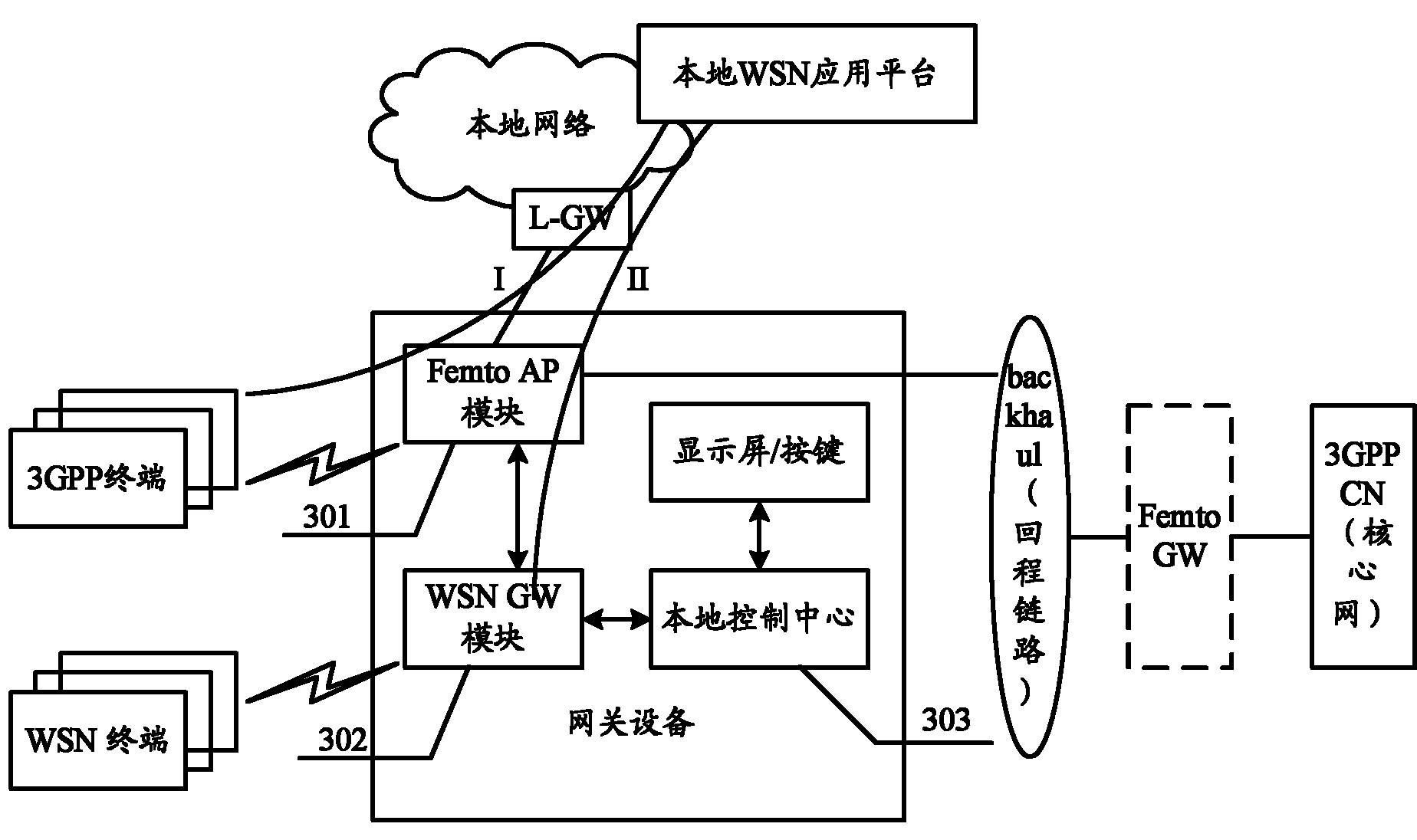
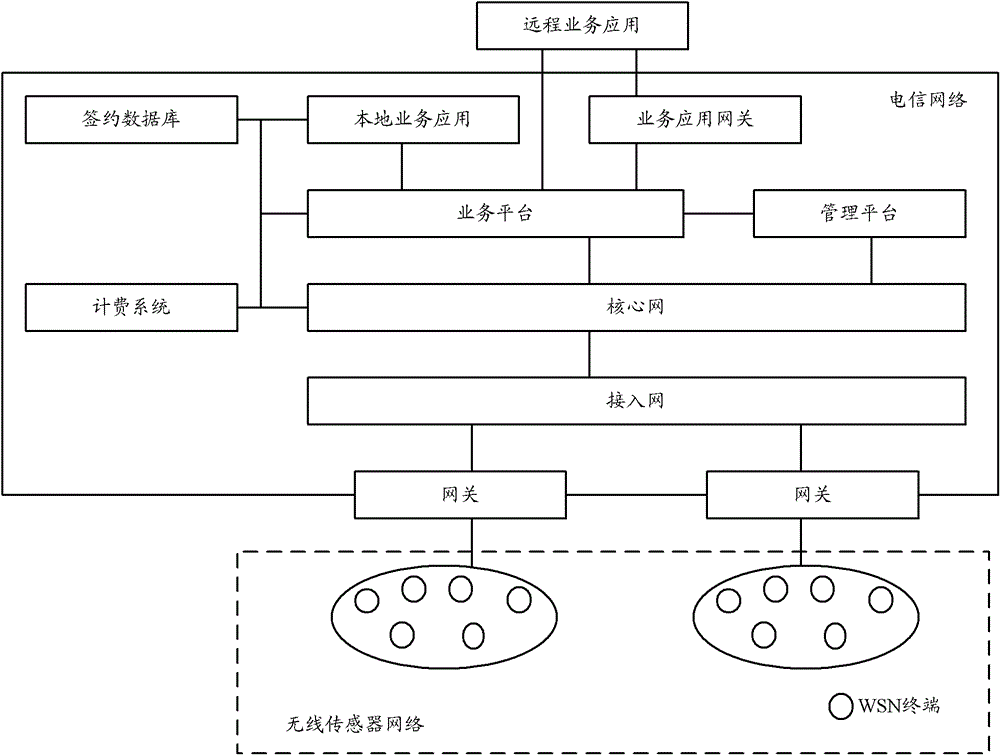
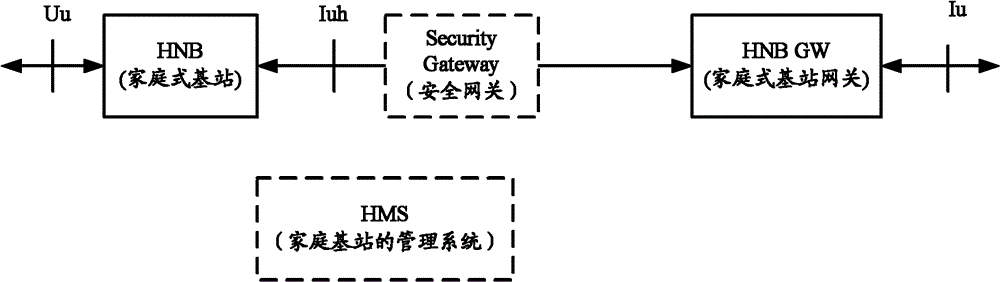
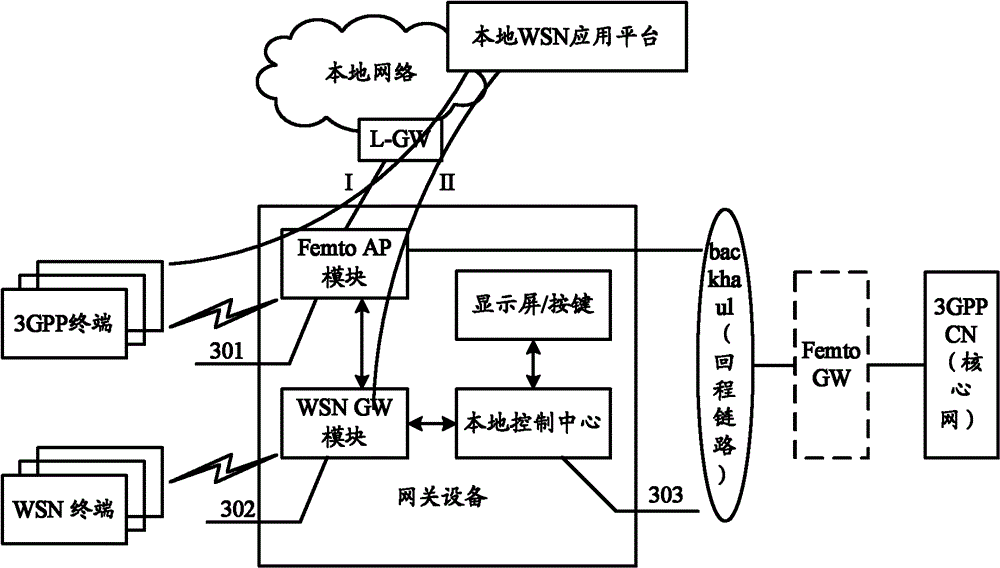
Gateway equipment, method for using gateway equipment and information transmission method and equipment
ActiveCN102098237AMeet privacy requirementsAchieve integrationConnection managementNetwork connectionsLine sensorHome Node B
The invention discloses gateway equipment, a method for using the gateway equipment, an information transmission method and information transmission equipment. The information transmission method comprises the following steps of: accessing a local network through a direct tunnel established between local gateways on the basis of a local Internet protocol (IP) access technology and establishing an end-to-end logic link between a 3rd generation partnership project (3GPP) terminal and a local wireless sensor network application platform to transmit control information and service data information between the 3GPP terminal and the local wireless sensor network application platform; and accessing the local network through a direct tunnel established between a Femto access point (AP) module and the local gateway and establishing an end-to-end link between a wireless sensor network and the local wireless sensor network application platform to transmit control information and service data information between the wireless sensor network and the local wireless sensor network application platform. By the methods and the equipment, fusion of a telecommunication network and the Internet of things can be realized by effectively utilizing the position advantage of a 3rd generation / long term evolution (LTE) network home node B.
Owner:DATANG MOBILE COMM EQUIP CO LTD
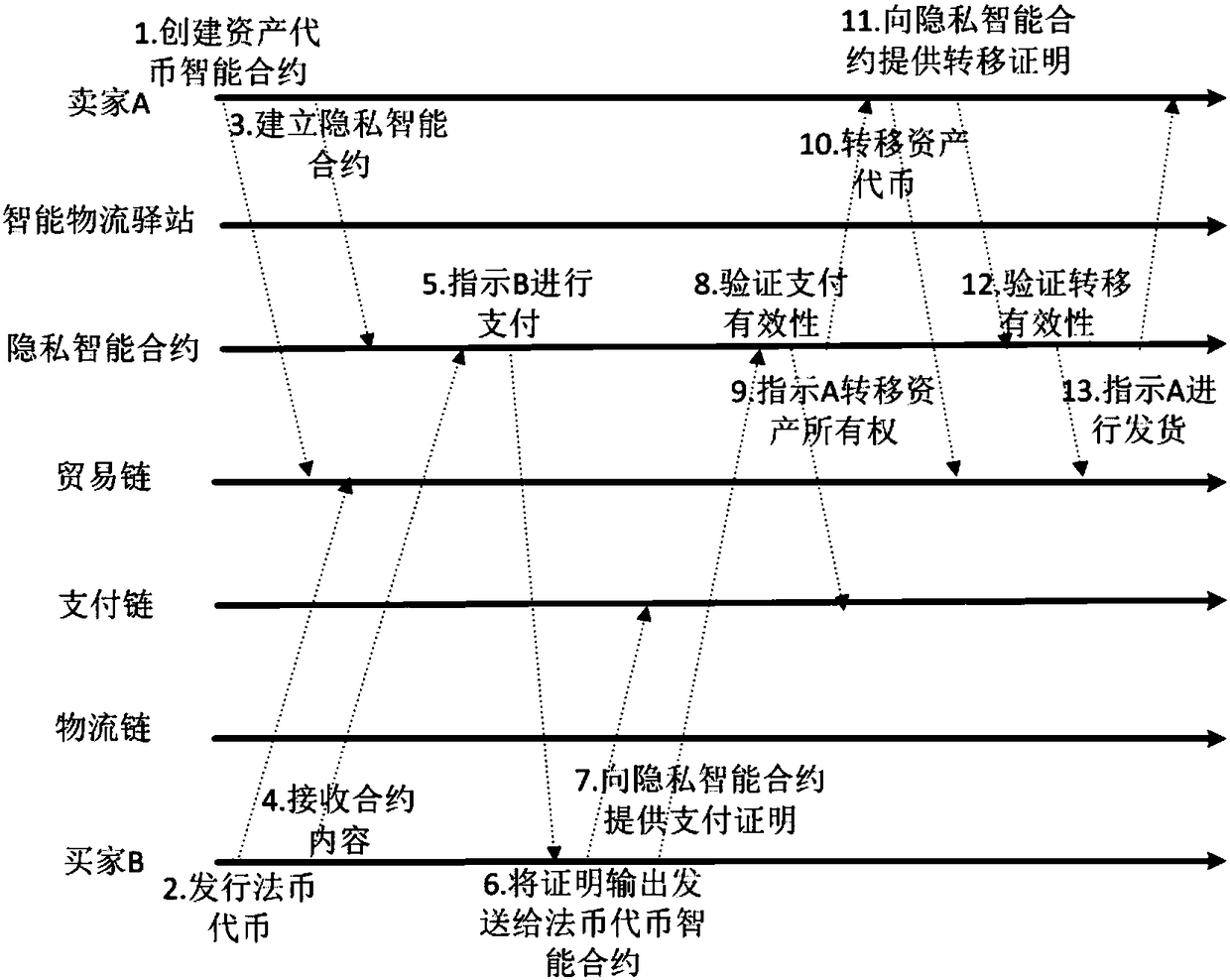
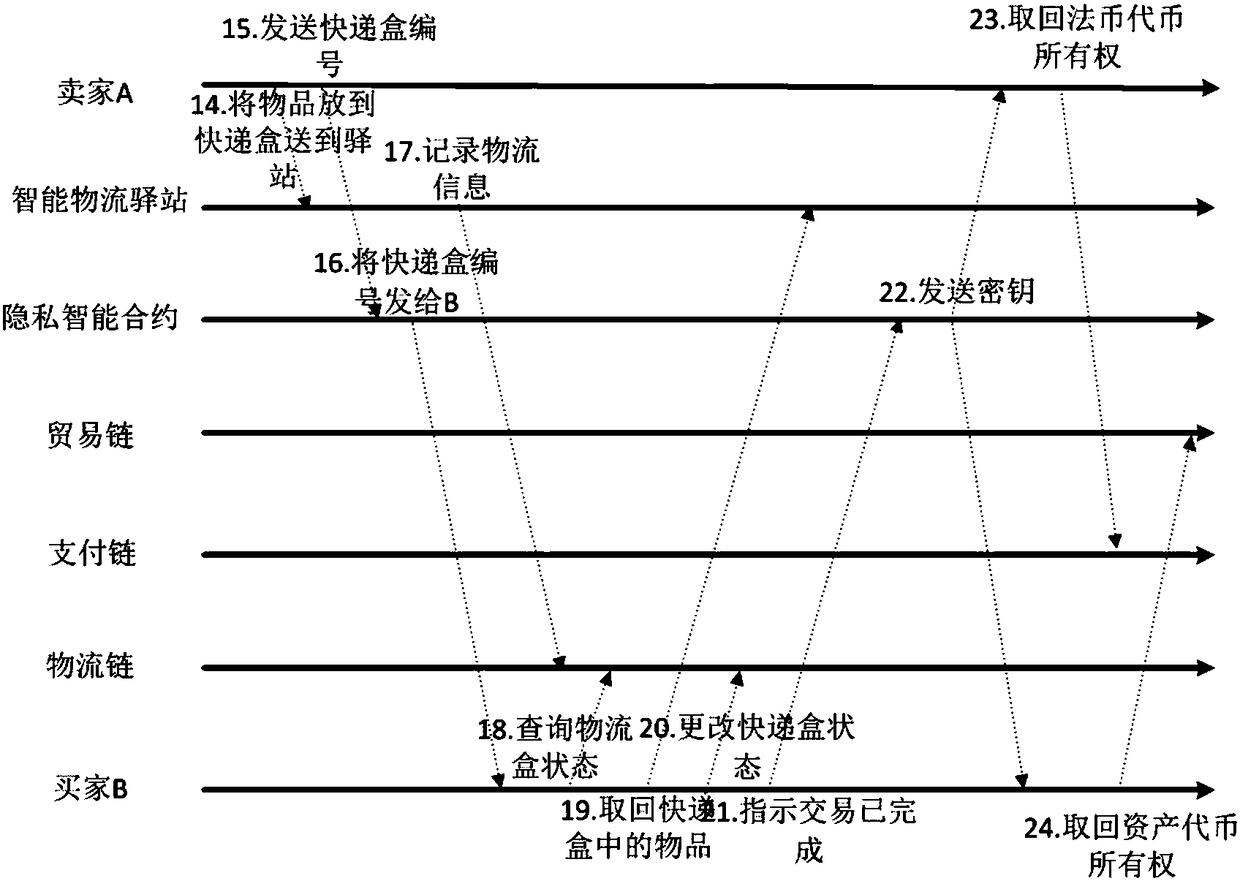
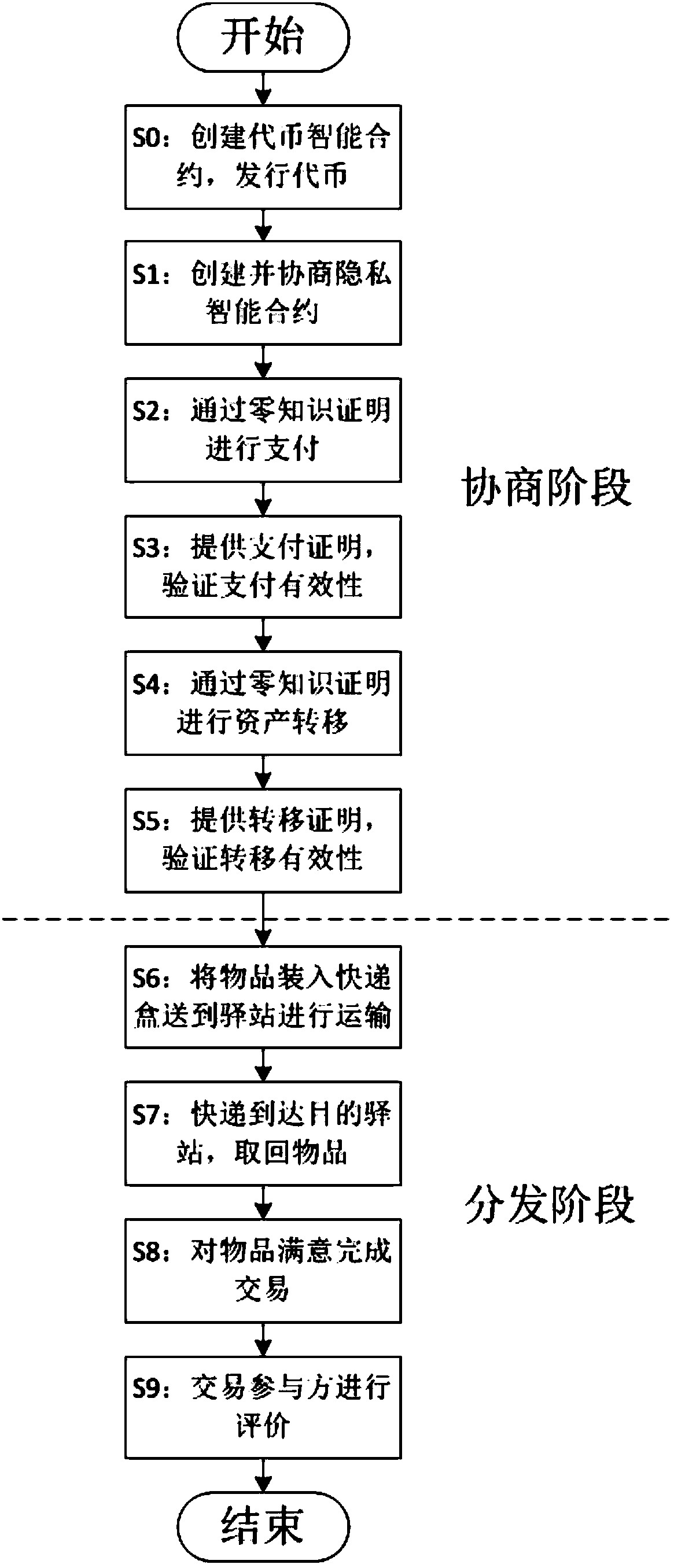
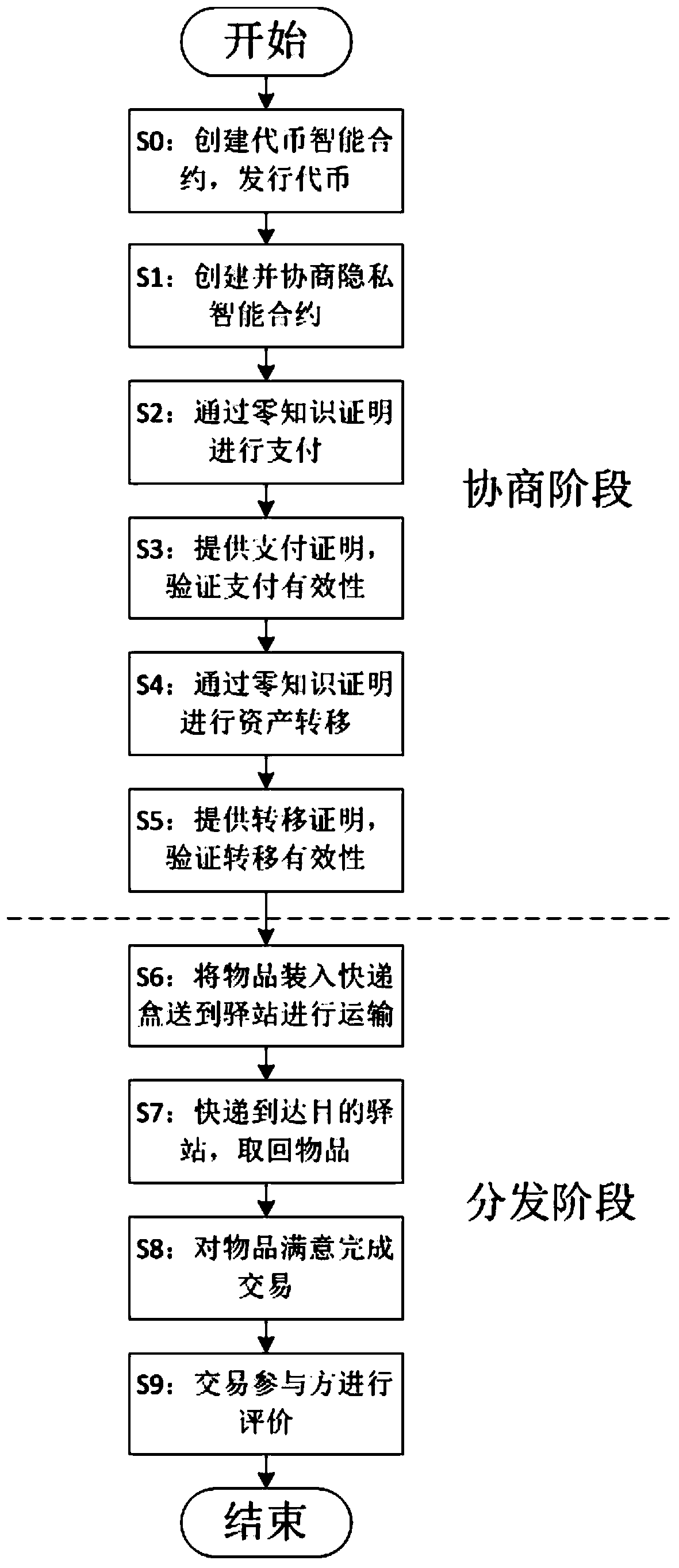
Privacy protection transaction method based on blockchain technology in electronic commerce
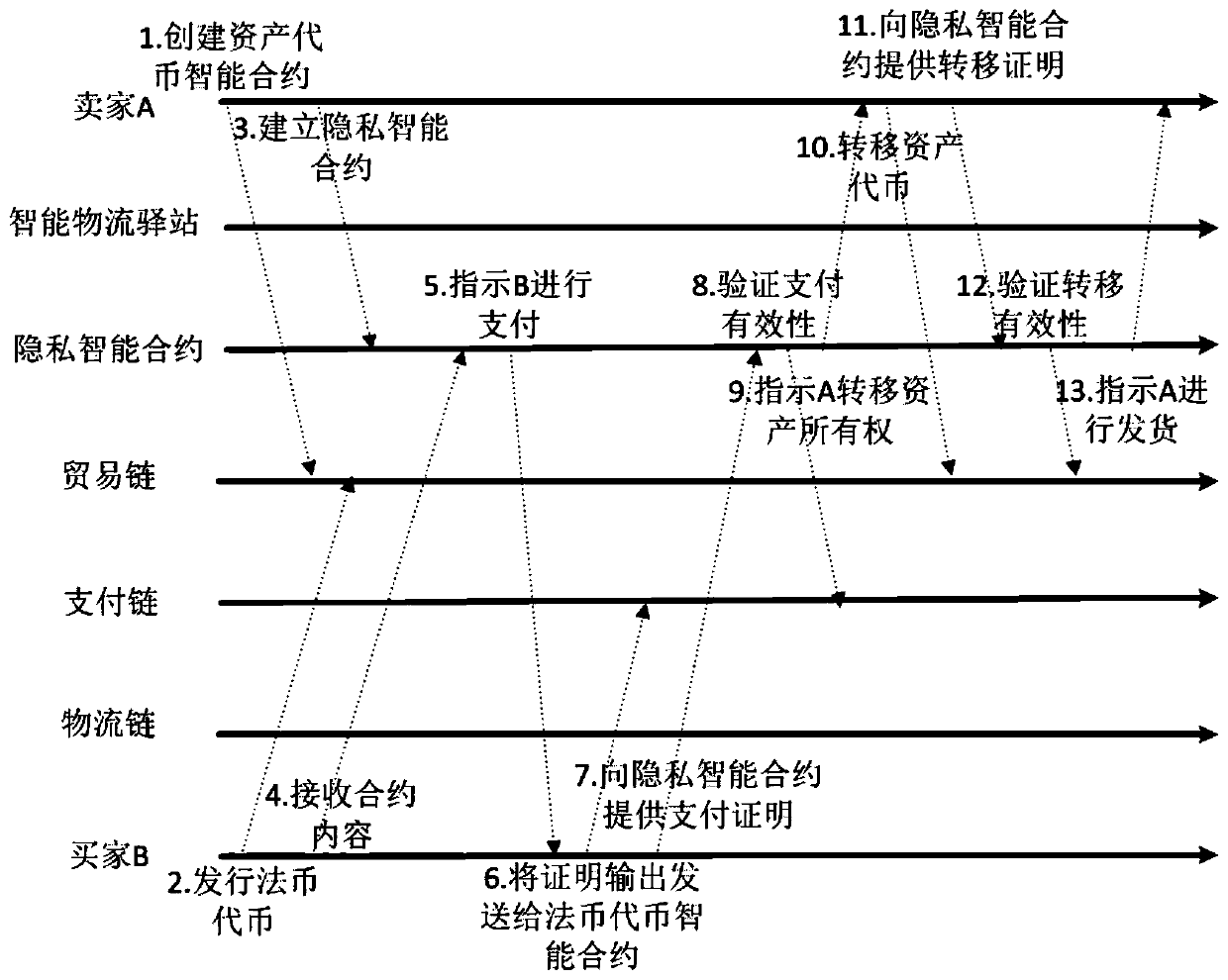
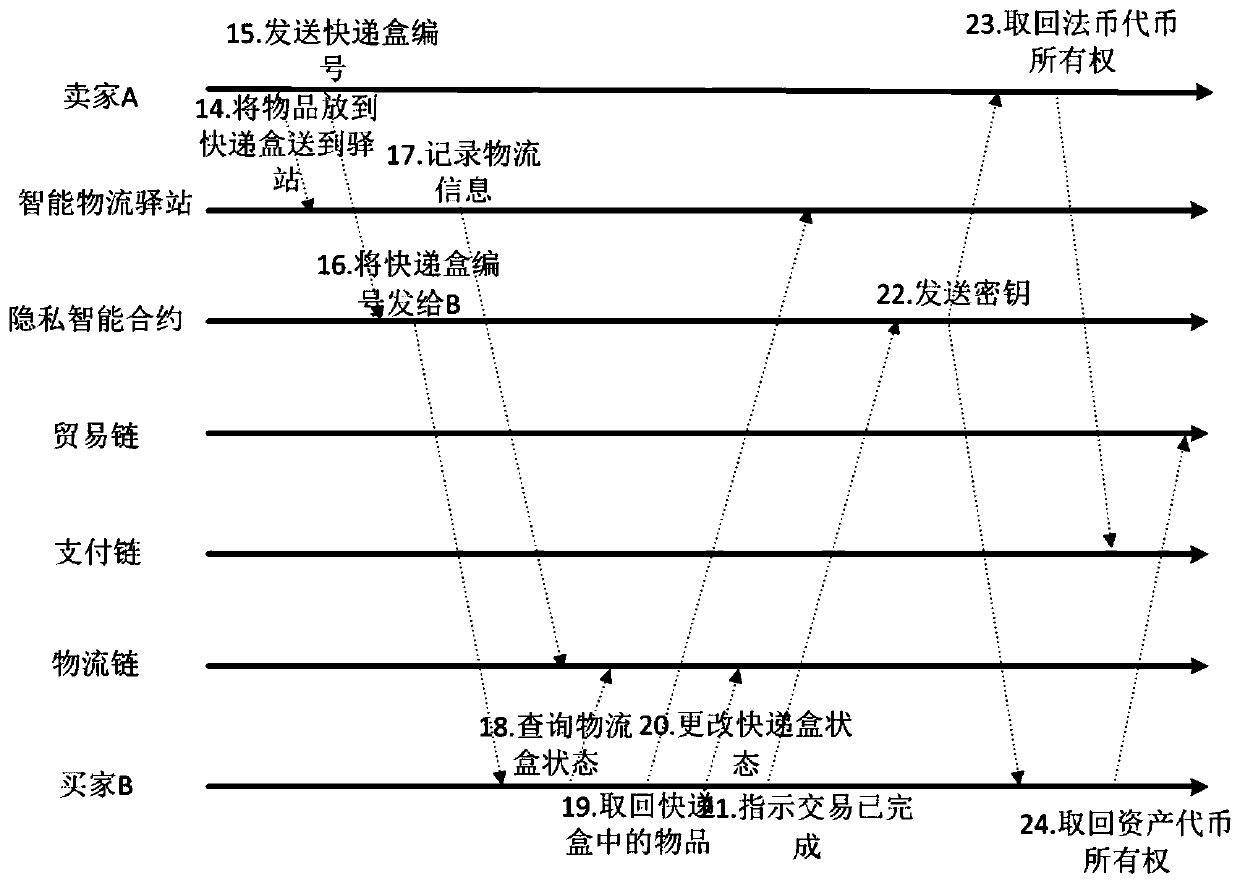
ActiveCN108389046AEase of evaluationMeet privacy requirementsFinanceDigital data protectionData privacy protectionLogistics management
The invention discloses a privacy protection transaction method based on a blockchain technology in electronic commerce. The method comprises the following steps that: adopting the blockchain technology which comprises a privacy smart contract and a zero-knowledge proof to protect the private information of a user; taking the privacy smart contract as a bridge between a buyer and a seller in a transaction period; adopting the zero-knowledge proof to issue a confidentiality token and create a confidentiality transaction; and combining the blockchain, an industrial data space and the Internet ofThings technology to establish infrastructure, and establishing an integrated platform for logistics business management in a distribution way. By use of the method, private information can be hiddenfor dispatchers, private information, including, identity, address, telephone number and the like, can be hidden for sellers, in addition, the method also can be used for other blockchain applicationscenes with a data privacy protection requirement, in addition, blockchain characteristics can be fully utilized, and therefore, the evaluation problem of an electronic commerce platform can be improved.
Owner:XI AN JIAOTONG UNIV
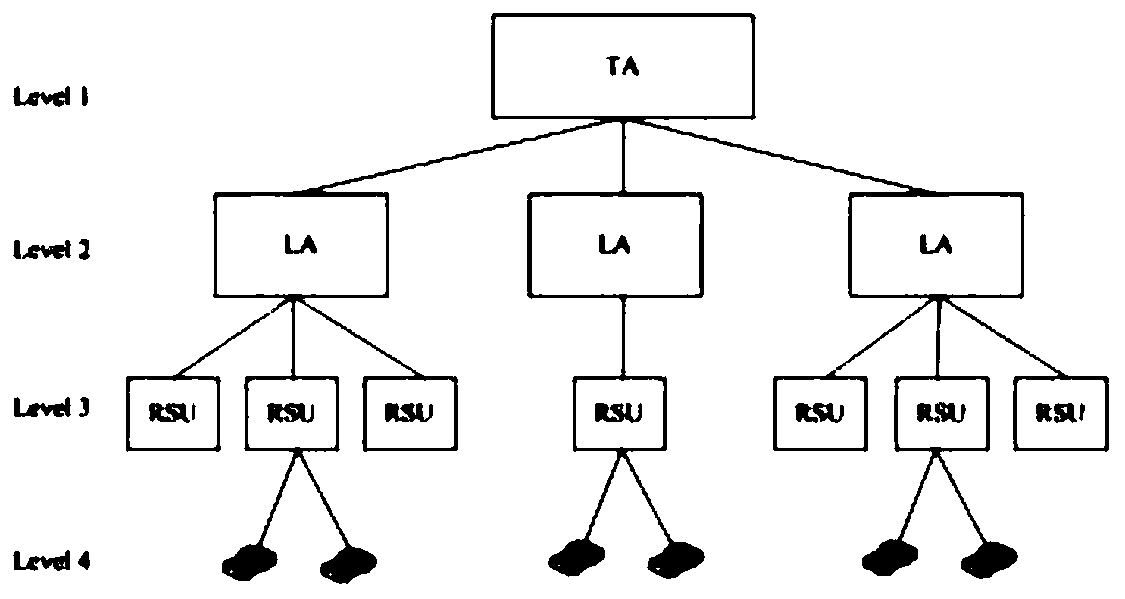
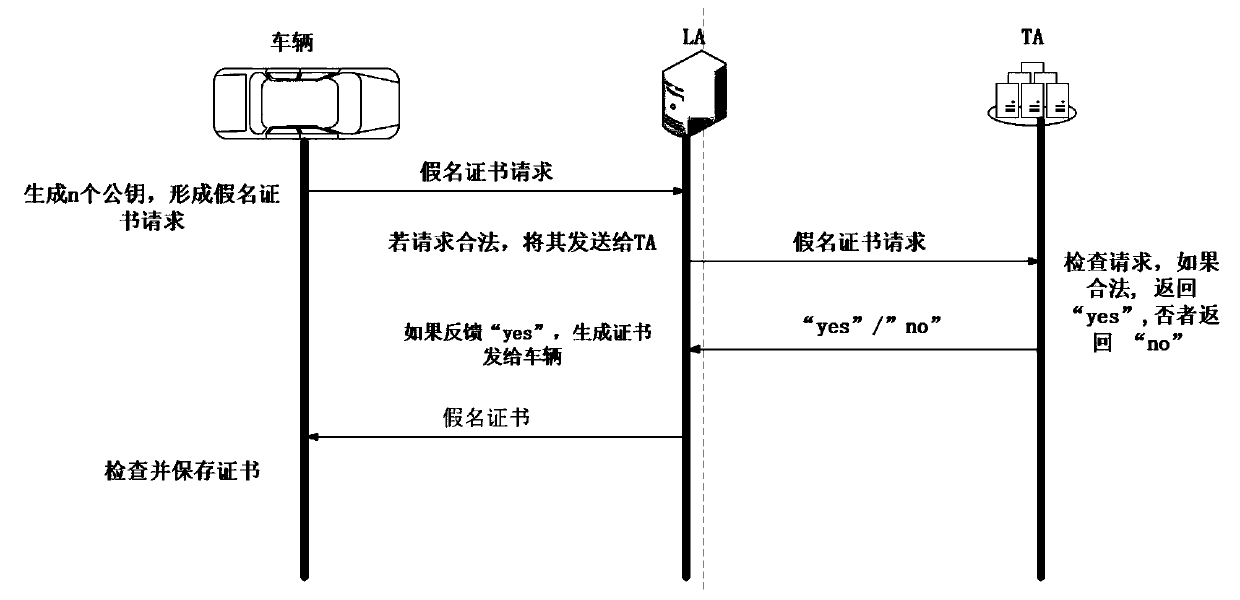
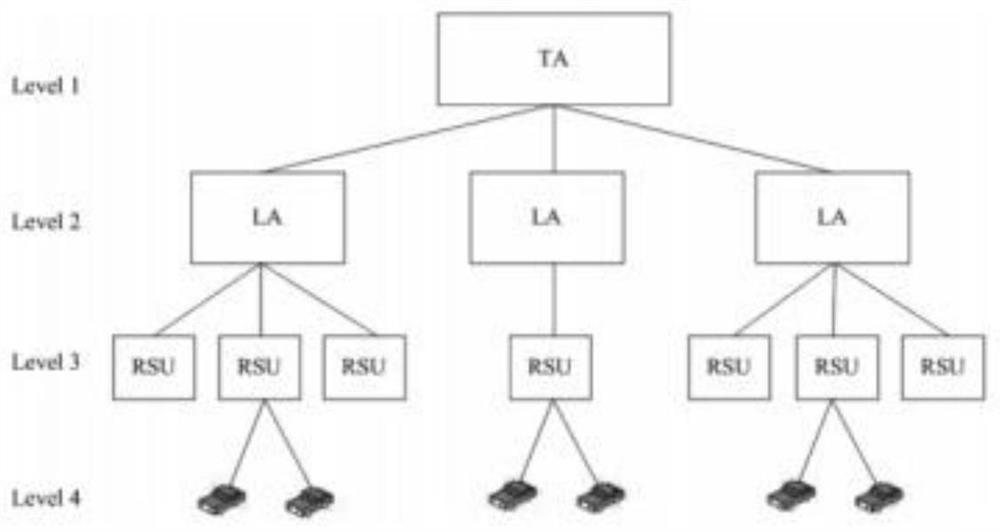
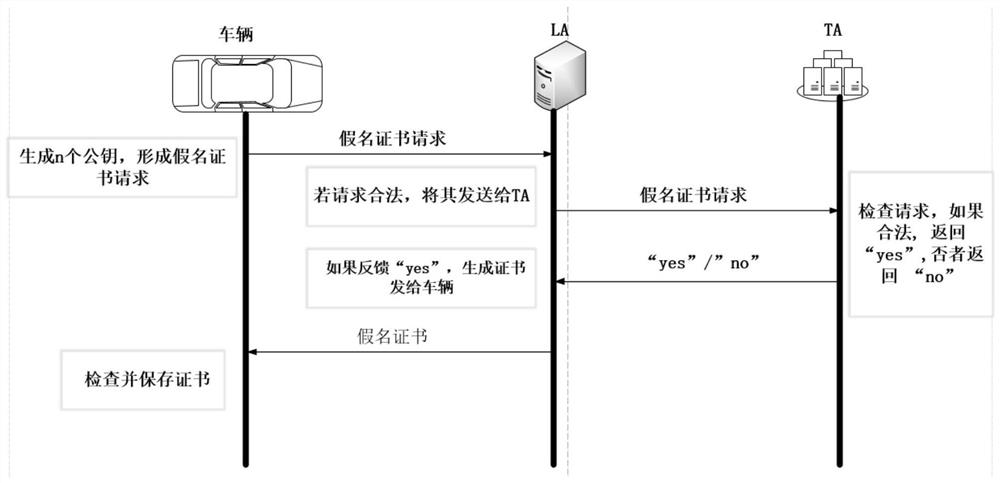
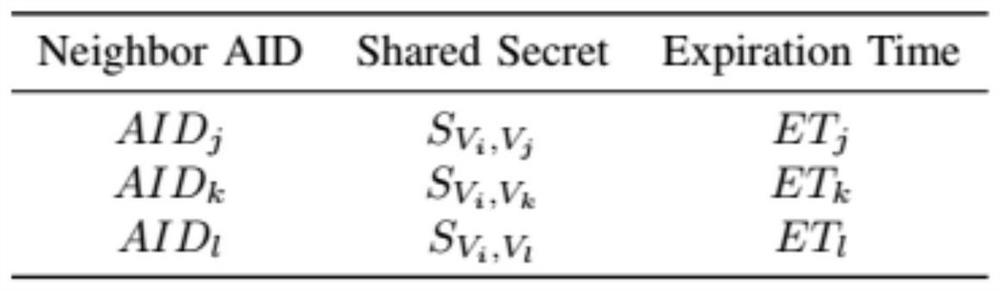
An inter-vehicle message anonymous authentication method and system in an Internet of Vehicles environment
ActiveCN109788482AShort timeMeet privacy requirementsKey distribution for secure communicationUser identity/authority verificationHash-based message authentication codeThe Internet
The invention relates to an inter-vehicle message anonymous authentication method and system in an Internet of Vehicles environment, in the method, each vehicle has a unique identity, and in communication, a short-term pseudonymous certificate needs to be obtained through TA authentication in advance and is used for proving the legal identity of the vehicle. The vehicle negotiates with each neighbor vehicle a communication authentication secret key through the pseudonym certificate, and then based on the communication secret key, signature and signature verification can be realized through simple and rapid HMAC. Compared with a previous message authentication mode, the method has the advantages that the time required for message authentication each time is shortened on the whole, and the environment of vehicle information communication is improved.
Owner:WUHAN UNIV
Platform and method for personal information protection based on personal information universal coding
ActiveCN102970302ADoes not affect the sorting workDoes not affect internal processesTransmissionInformation dataAuthentication
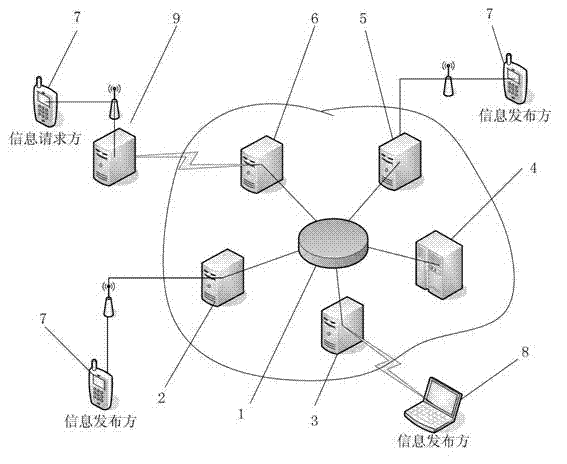
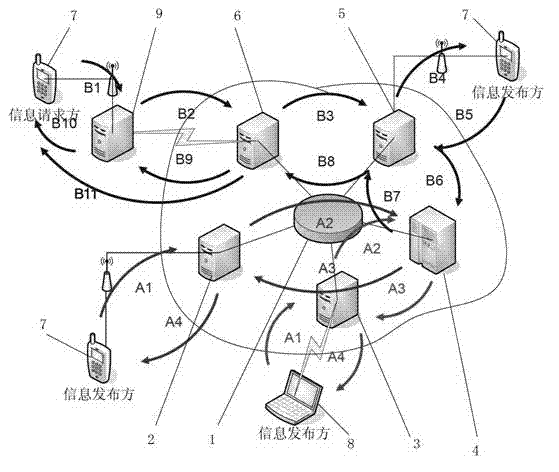
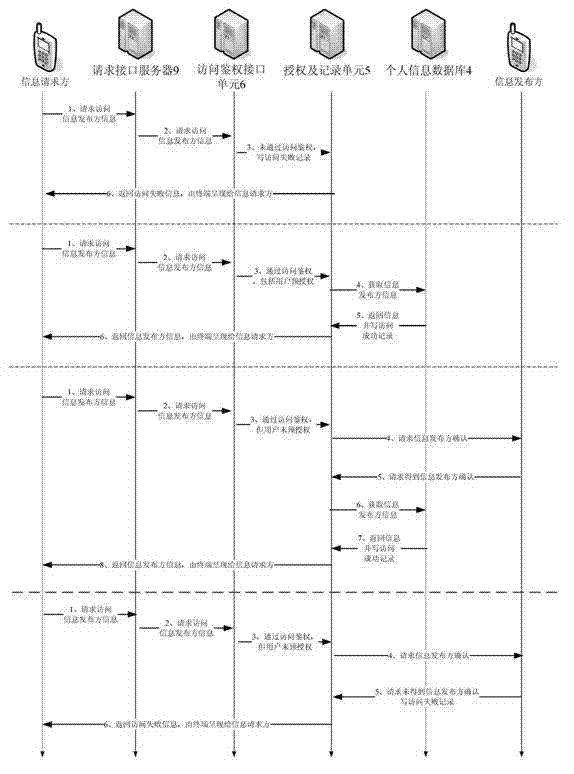
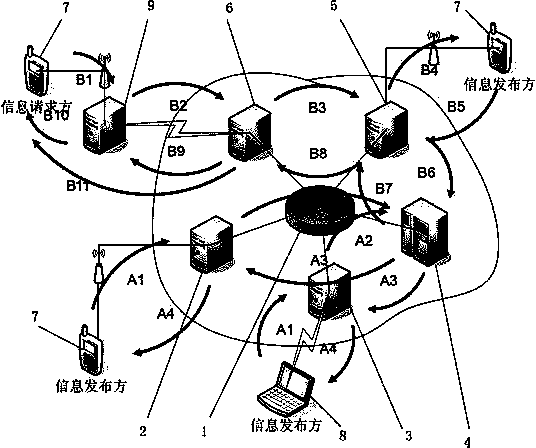
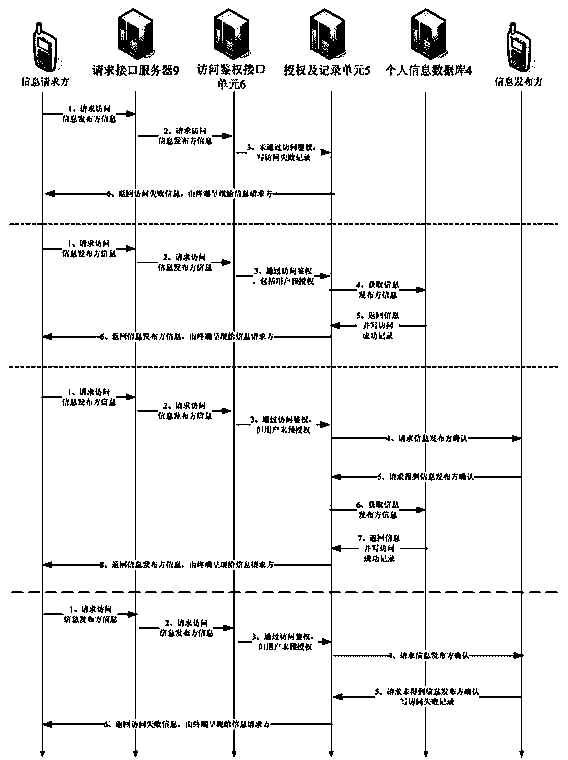
The invention relates to a platform and a method for personal information protection based on personal information universal coding, wherein an access management unit, a personal information database and an access authentication interface unit are connected with an information control unit; the access management unit as well as an authorization and record unit are further connected with the terminal equipment of an information publish party respectively, and the access authentication interface unit is connected with the terminal equipment of an information request party; the information control unit is used for providing registration service for the information publish party which accesses via the access management unit, and generating a unique personal information universal code for the information publish party; the access management unit is used for providing interface service for the access of the information publish party to the information control unit; and the access authentication interface unit is used for performing authentication and audit on the access authentication request according to the personal information universal code, of the information request party, and performing personal information data transmission. Because the platform for personal information protection disclosed by the invention is a platform independent from mail delivery networks, E-business networks and other government departments or units and especially used for storing personal information data, the platform is not a link in a personal information interest chain, and the position of the platform ensures the profession of providing service for the information publish party.
Owner:韩明岐
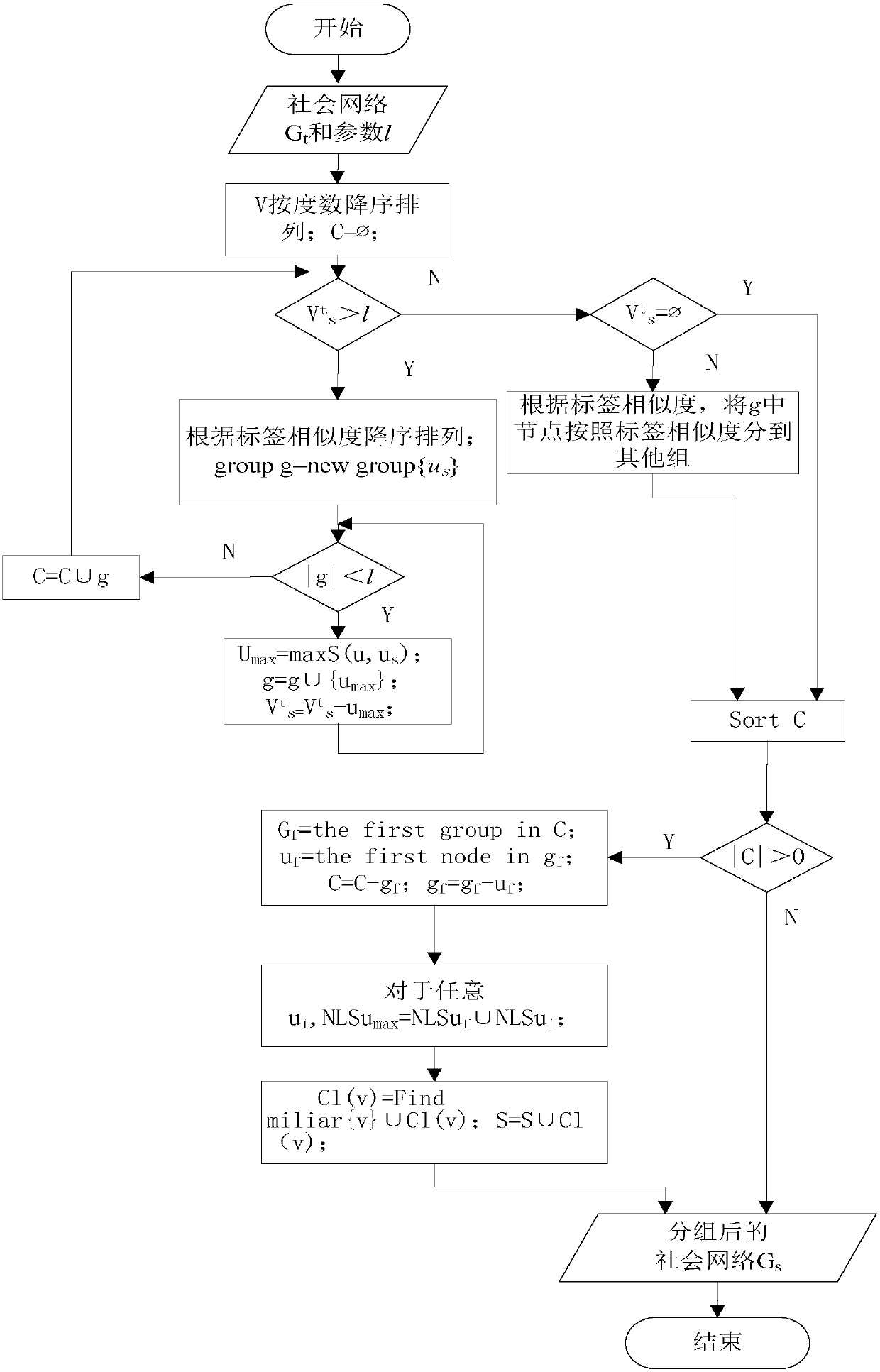
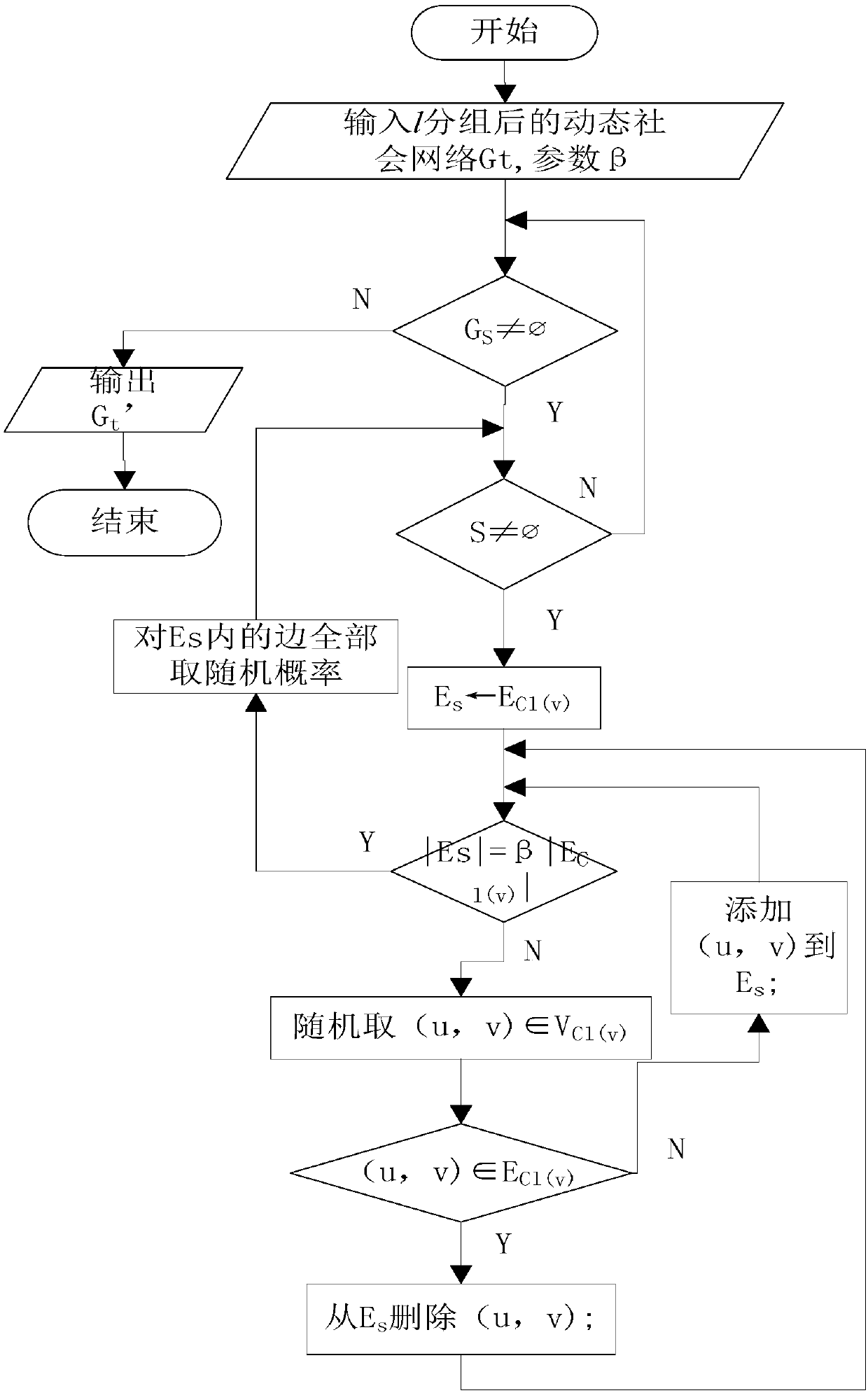
Anonymous method for preventing attack of labeled neighbor in social network dynamic release
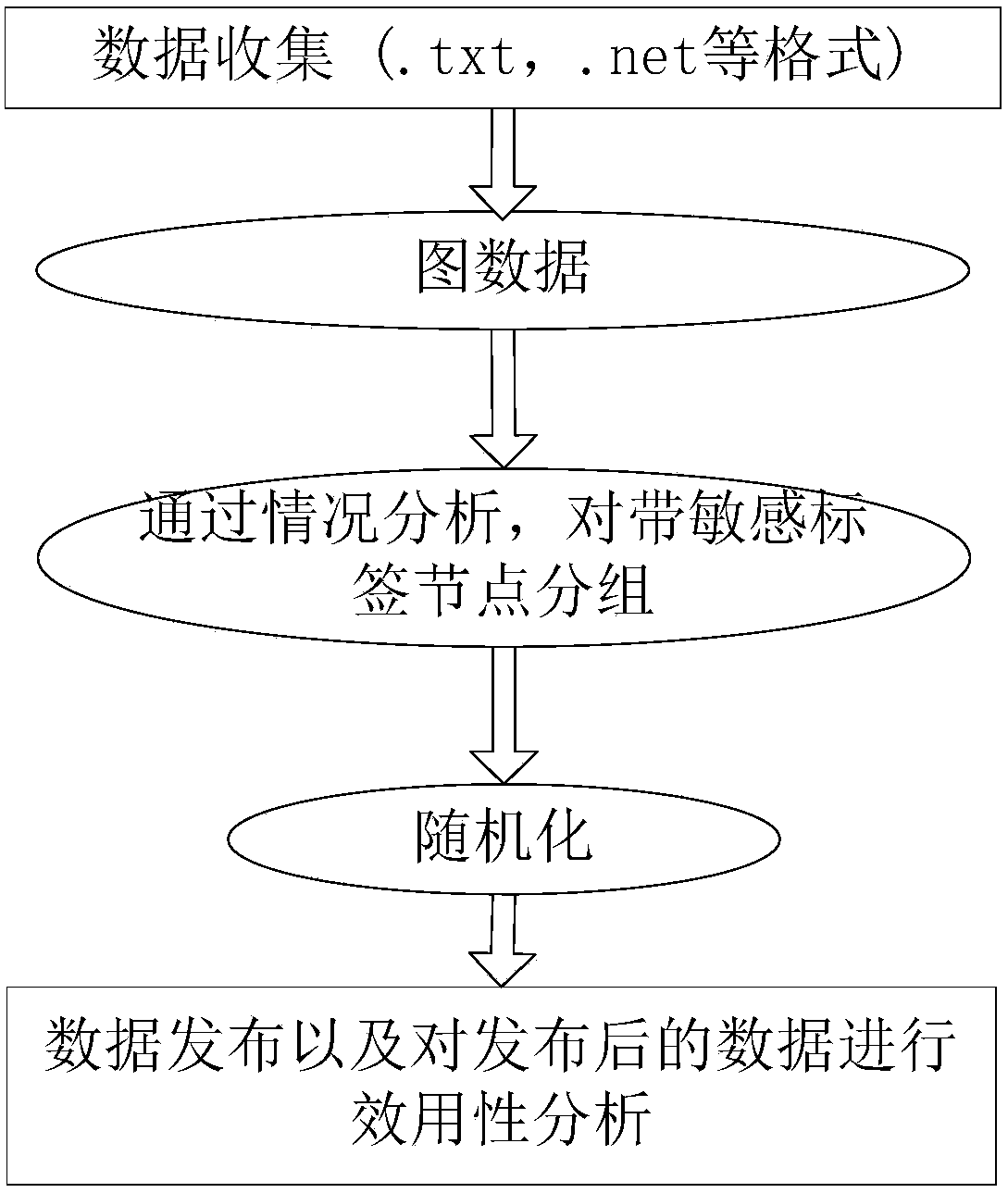
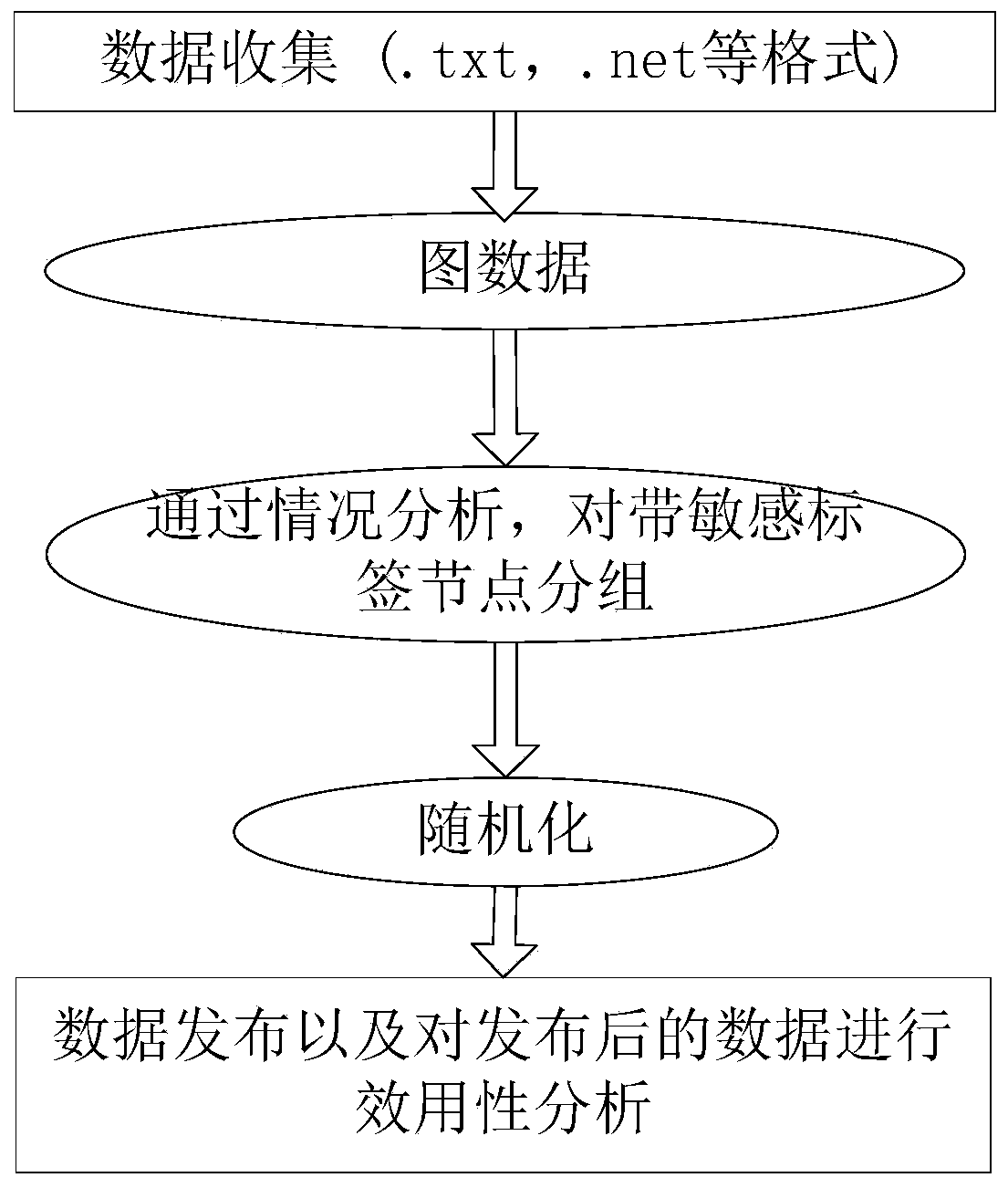
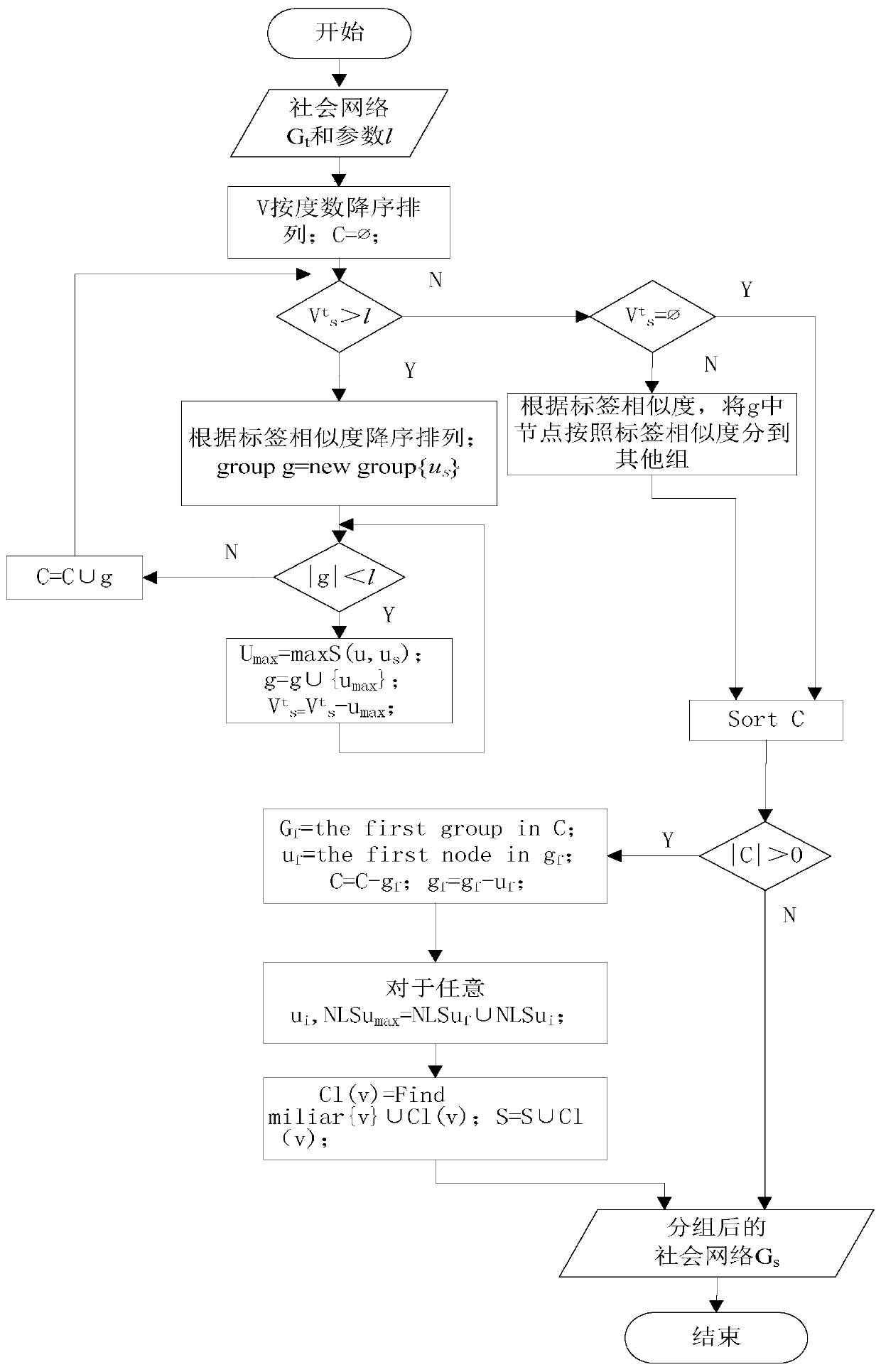
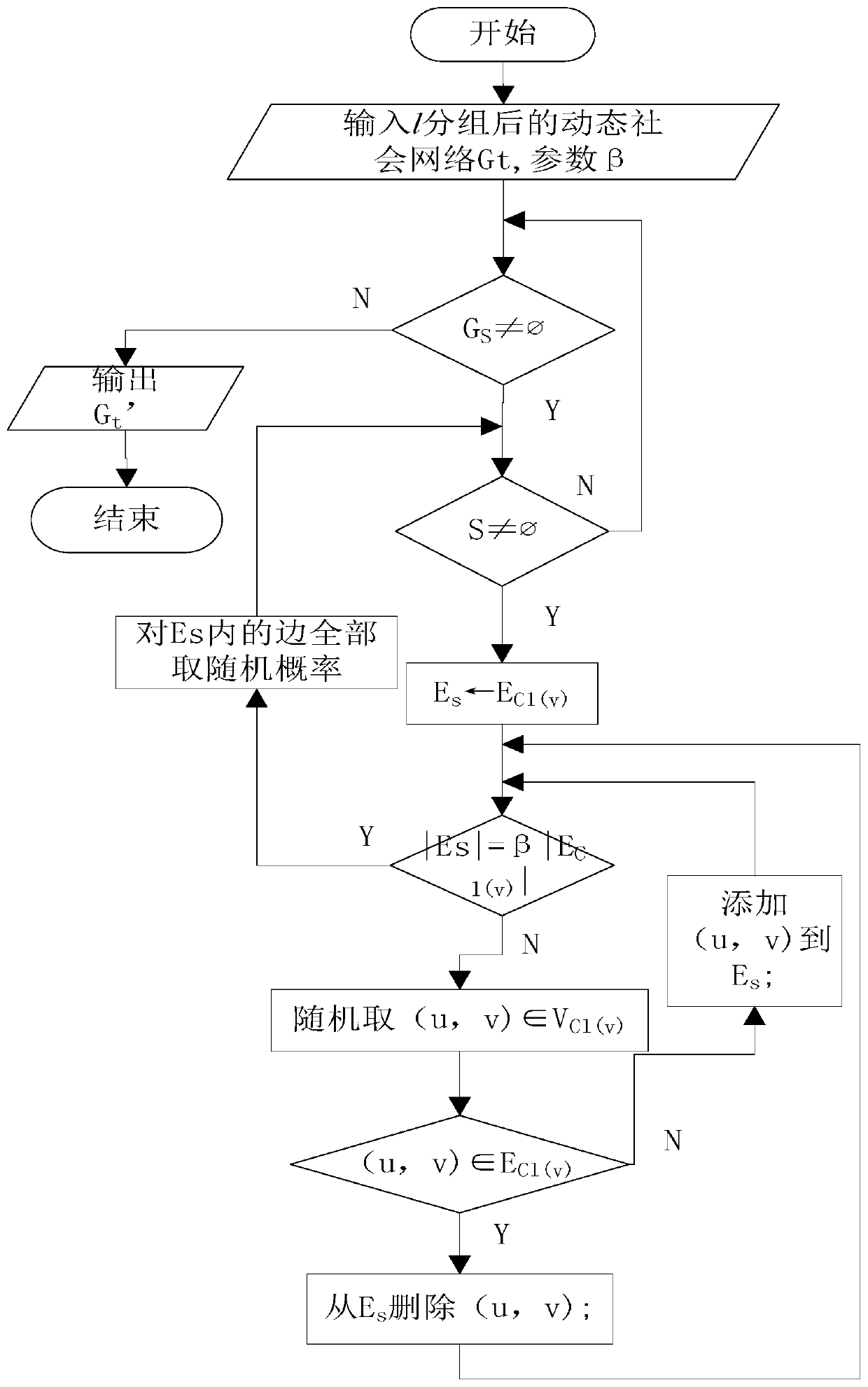
The invention discloses an anonymous method for preventing an attack of a labeled neighbor in social network dynamic release. A design algorithm based on neighbor label similarity is used for distributing nodes into proper groups, meanwhile neighbor structure and degree information of the nodes in the same group in an original social network is also considered, an used StruSim method is improved based on the algorithm, and thus the privacy requirement is met; structural similarity of the nodes in the group is improved to be ready for an next operation, and thus a social network chart after t moment grouping is acquired by using the method. The chart structure is changed by a random disturbing method, edges are randomly added or deleted, then a fuzzy method is used, each edge has the corresponding probability of existing in the social network, so that the probability of an attacker for uniquely determining an individual with a sensitive label is not more than 1 / l. According to the method, only the labeled neighbor information with the sensitive label is disturbed, so that the quantity of undetermined charts is reduced, and data availability is improved.
Owner:GUANGXI NORMAL UNIV
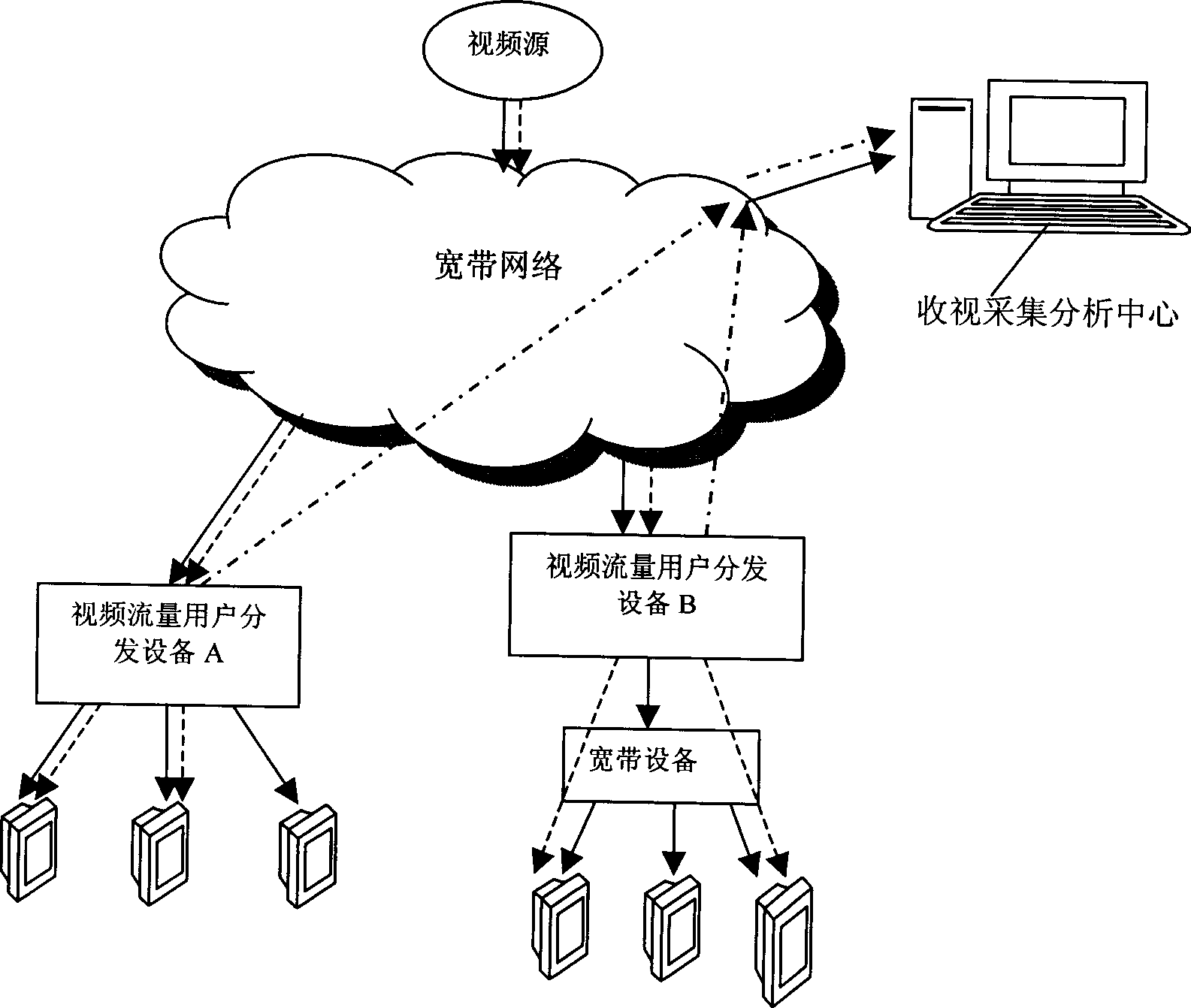
Method and system for obtaining received visual information in wideband video-frequency system
InactiveCN1774066AMeet privacy requirementsAvoid overheadBroadcast services for monitoring/identification/recognitionTwo-way working systemsComputer networkWideband
Owner:HUAWEI TECH CO LTD
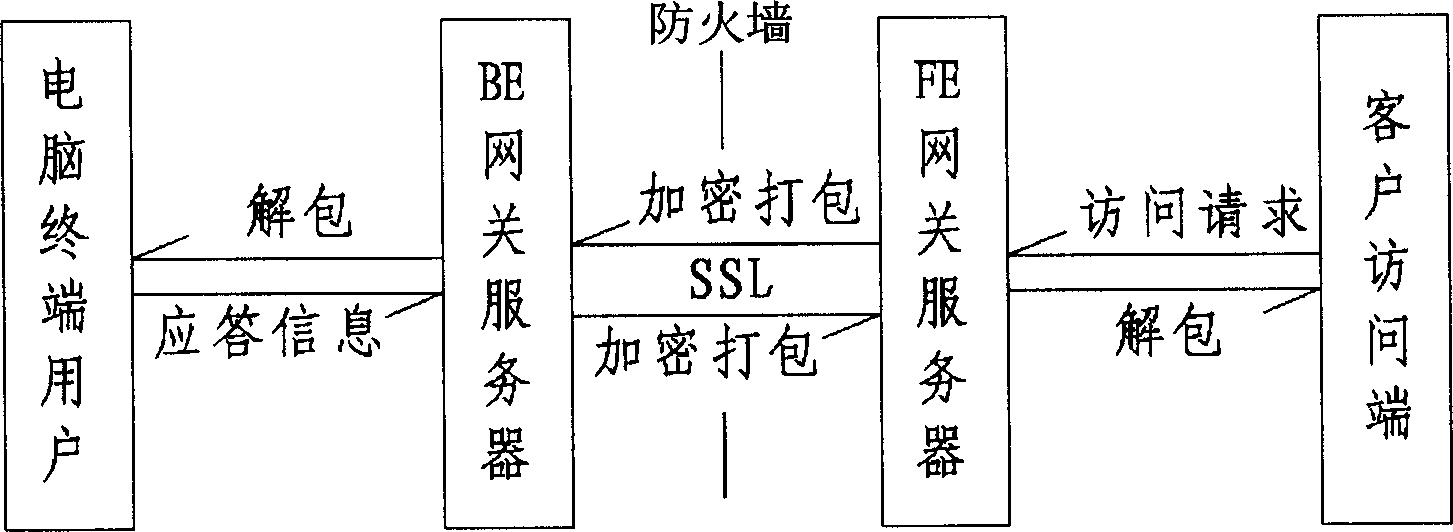
Method for realizing virtual private network by using SSL protocol to build channel of firewall
InactiveCN1697451AReduce the likelihood of being attackedMeet privacy requirementsNetworks interconnectionNetwork connectionsPrivate networkComputer terminal
From inner BE gateway server through SSL, firewall channel builds connection with FE gateway server. When client access end sends an access request to user at computer terminal, the information of request is encrypting packed by a service program at FE gateway server first. Next, through SSL connection, the packed information is transmitted to BE gateway server. Then, Unpacked by service program at BE gateway server, information is sent to user at computer terminal. After receiving the access information from the client access end, user at computer terminal sends out response information to the client access end through following steps: the response information is encrypting packed by a service program at BE gateway server first. Next, through SSL connection, the packed information is transmitted to FE gateway server. Then, unpacked by service program at FE gateway server, the response information is sent to the client access end.
Owner:北京立通无限科技有限公司
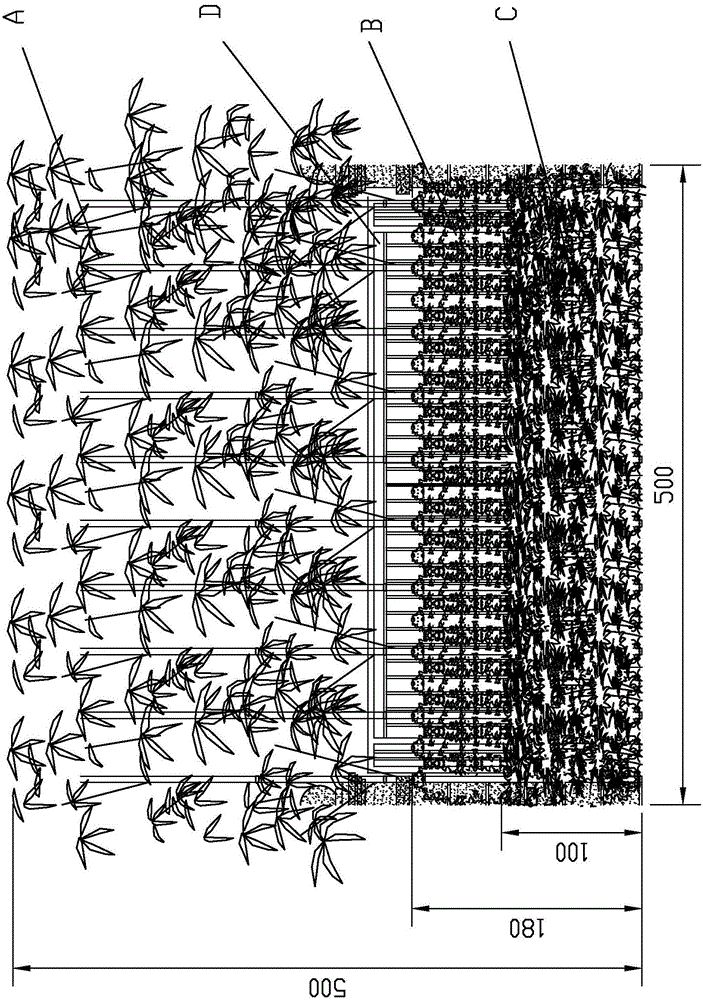
Plant allocation method used for hollowed fence inner side greening
The invention discloses a plant allocation method used for hollowed fence inner side greening. Key points of a technical scheme of the method are that plant combination allocation is divided into A, B, and C layers according to different height levels; B-layer planting stocks are close to a fence D; A-layer planting stocks are planted on the outer side of the B-layer planting stocks; and C-layer planting stocks are fully planted on a lower layer of the A-layer planting stocks. Plant allocated on the same A layer is any one selected from phyllostachys iridescens, phyllostachys bumbusoides, phyllostachys propinqua, phyllostachys violascens, phyllostachys aureosulcata, and phyllostachys heteroclada. Plant allocated on the same B layer is any one selected from euonymus japonicus column, euonymus japonicus column, viburnum odoratissimum column, and photinia fraseri column. Plant allocated on the same C layer is any one selected from fatsia japonica, aucuba japonica, and nandina domestica. With the application of the plant allocation, resident privacy requirements can be satisfied, and an ecological living space with senses of belonging and comfort can be built. The plant allocation also has a noise-reducing function. With the method, a high-efficiency energy-saving city residential area noise-reducing plant mode can be created.
Owner:PALM ECO TOWN DEV CO LTD
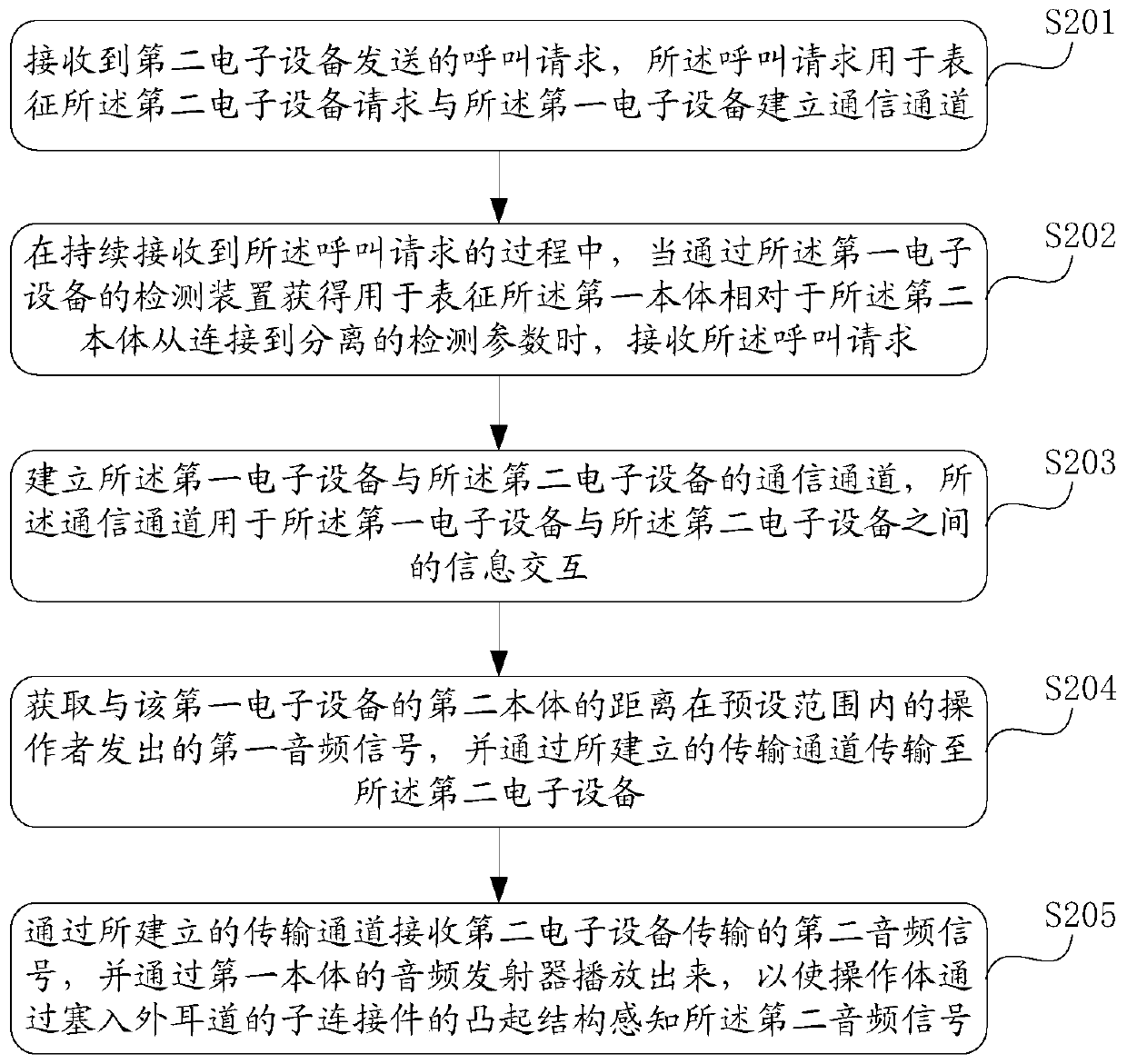
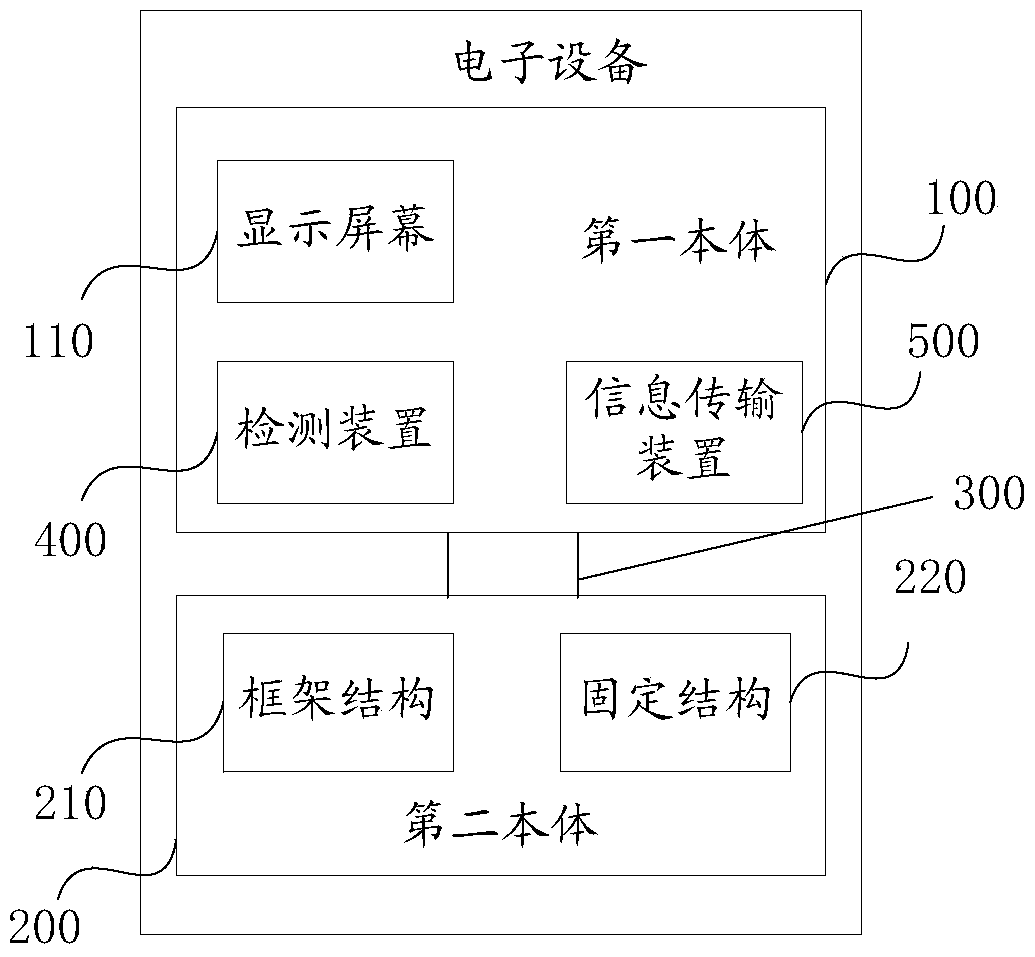
Communication control method and electronic equipment
ActiveCN105991832AReal-time portabilityFeel goodSubstation equipmentTransmission channelCommunication control
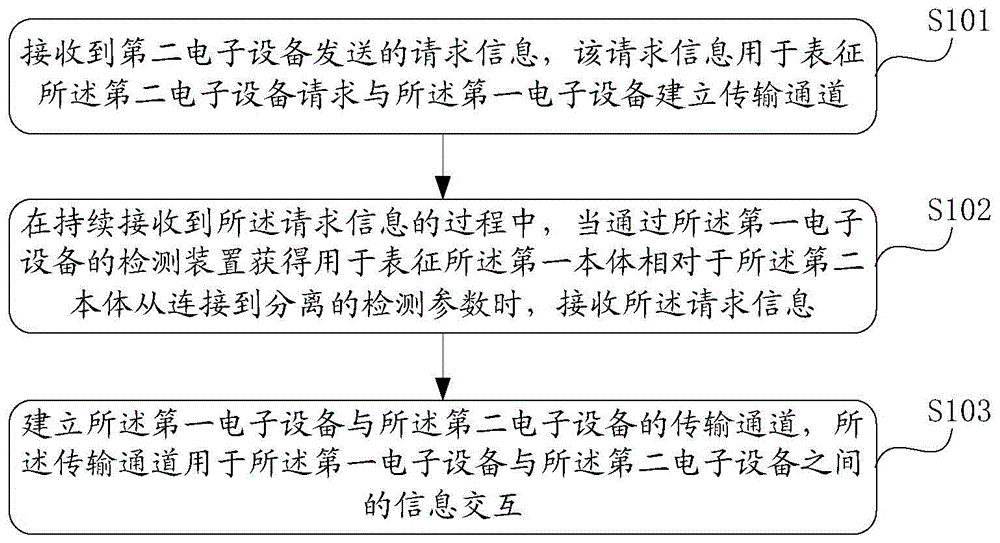
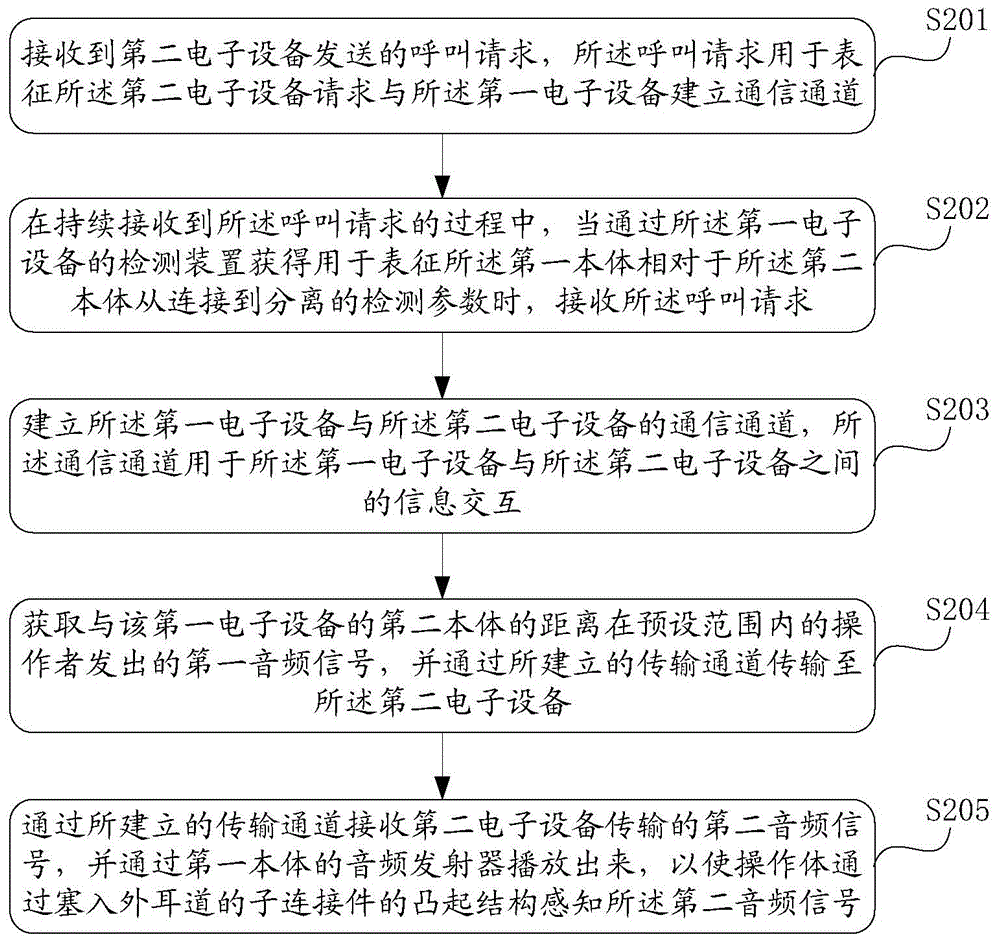
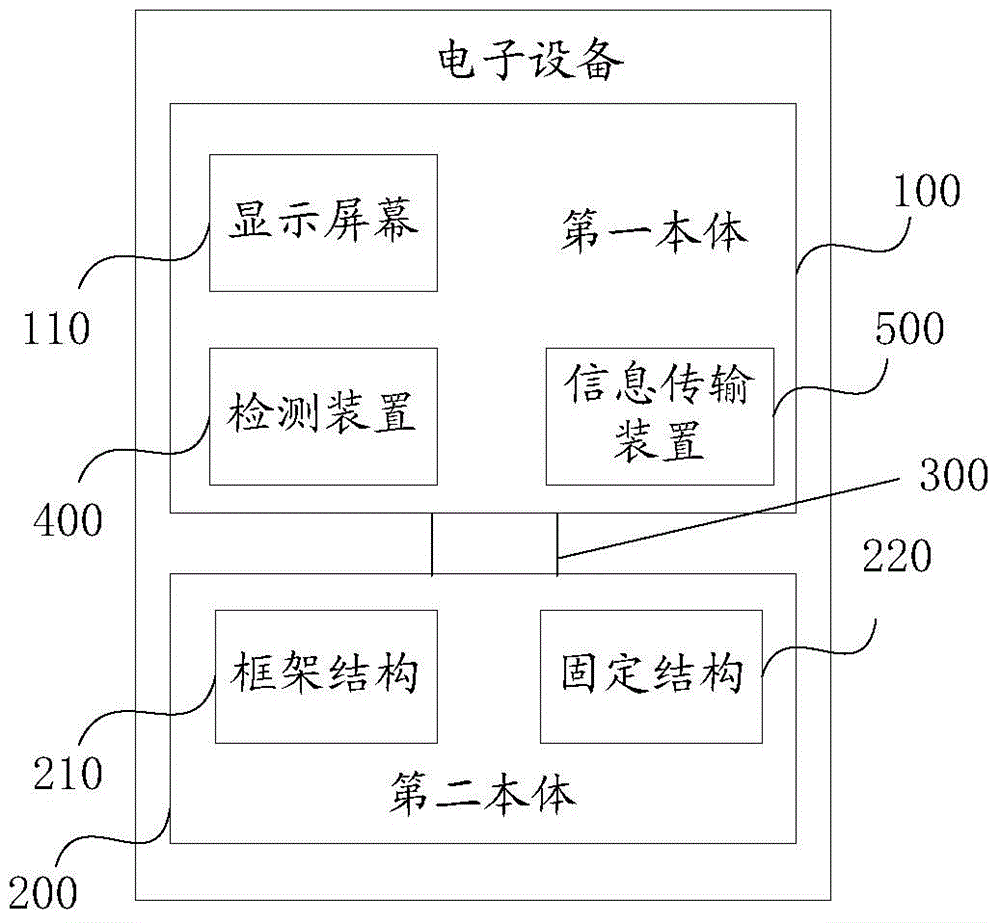
The invention provides a communication control method and electronic equipment. The communication control method is applied to first electronic equipment, a second body of the first electronic equipment comprises a frame structure and a fixing structure used for fixing the first electronic equipment onto an operation body, and the electronic equipment forms a ring shape when the first electronic equipment is fixed on the operation body; a first body comprises a display screen, is connected with or separated from the frame structure of the second body through a first connector; during the process of continuously receiving request information sent from second electronic equipment by the first electronic equipment, the first electronic equipment receives the request information when acquiring detection parameters used for representing states from connection to separation of the first body relative to the second body by means of a detection device of the first electronic equipment, and establishes a transmission channel between the first electronic equipment and the second electronic equipment, so as to achieve information exchange between the first electronic equipment and the second electronic equipment, avoiding leakage of the transmitted information, and satisfying the privacy requirements for answering and making phone calls of the user.
Owner:LENOVO (BEIJING) CO LTD
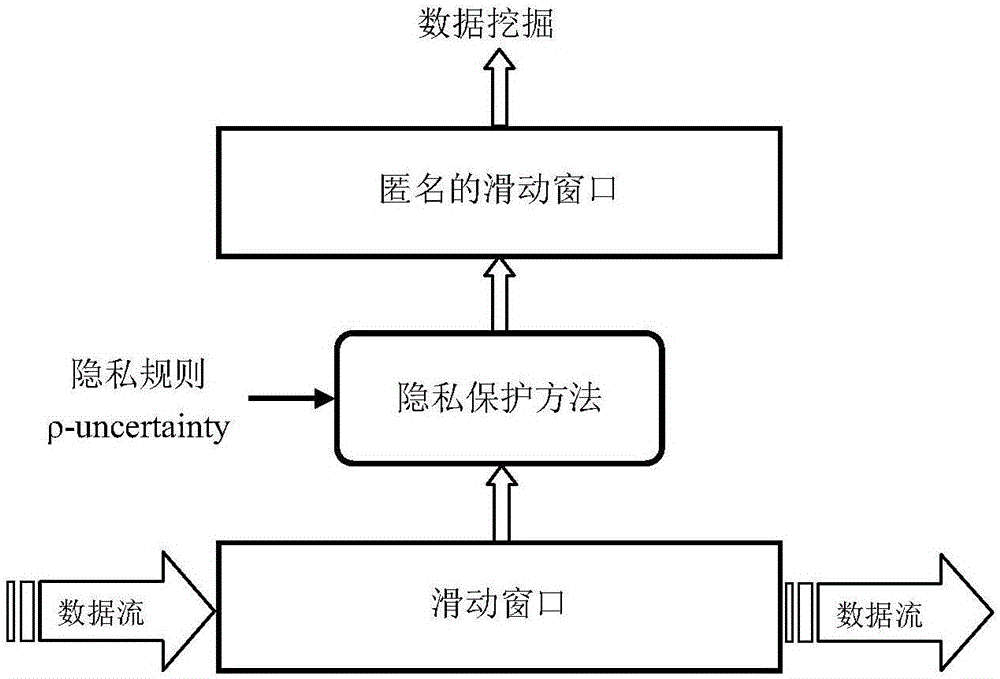
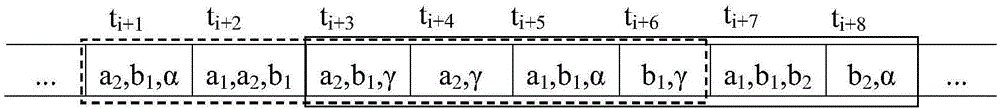
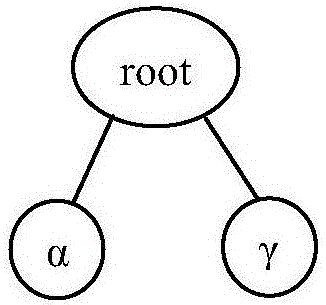
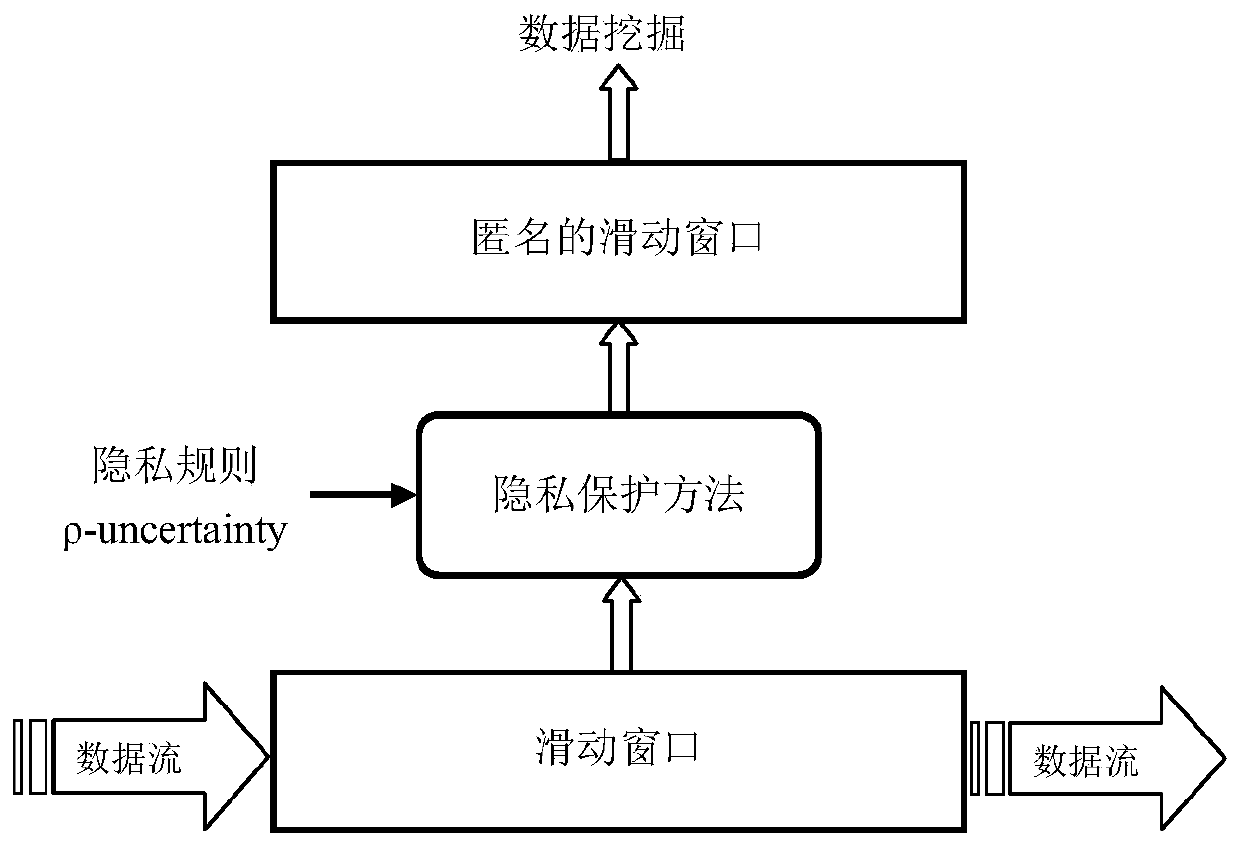
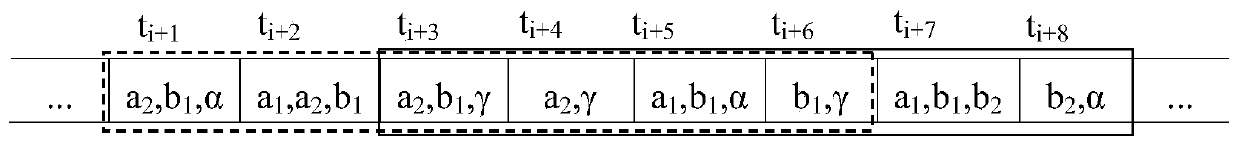
Privacy protection method for transactional data flow publishing
ActiveCN106778346AMassiveEasy to handleDigital data protectionSpecial data processing applicationsData streamData information
The invention discloses a privacy protection method for transactional data flow publishing, data are anonymous by adoption of sliding windows, the recent data information can be well processed by the sliding windows, and therefore privacy requirements can be ensured to be satisfied by any sliding window and data validity is maintained as much as possible, thereby facilitating analysis by data miners.
Owner:GUANGXI NORMAL UNIV
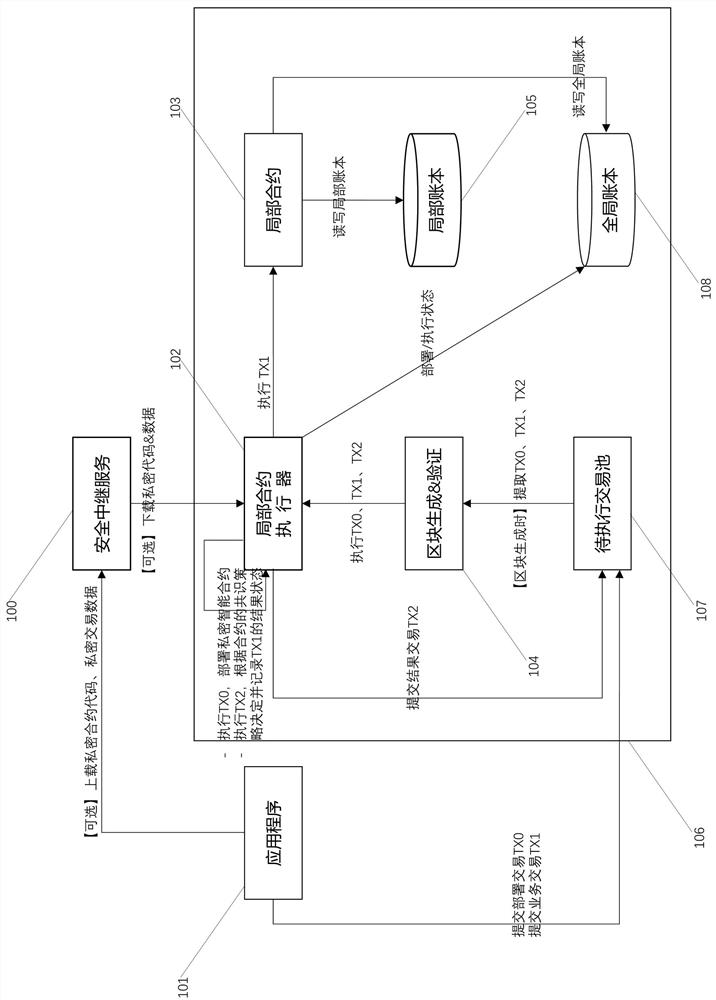
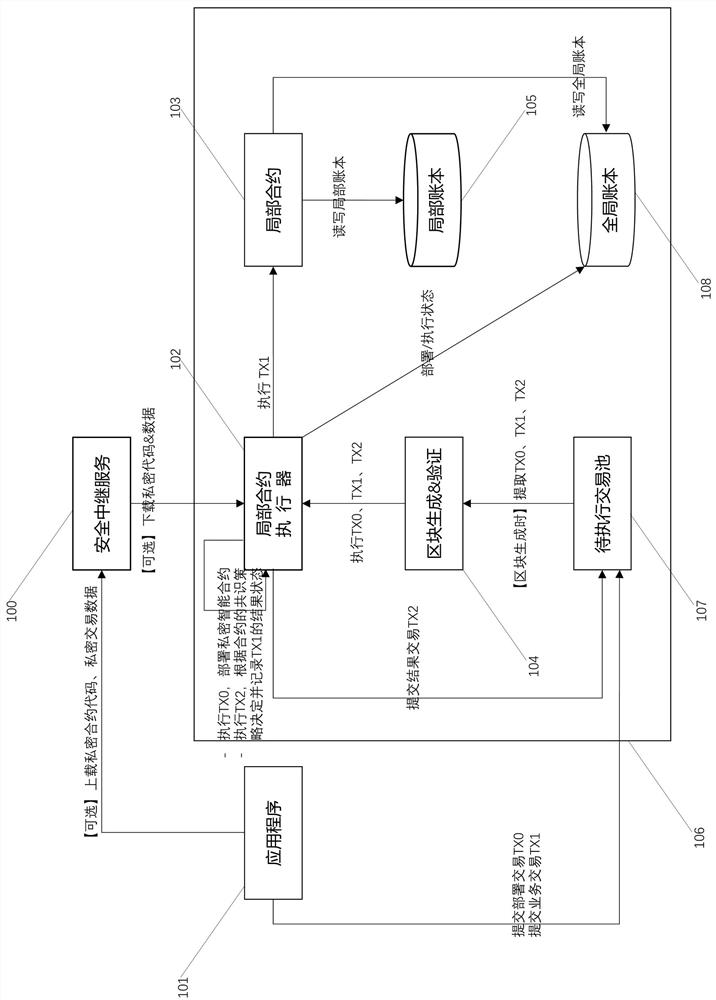
Intelligent contract implementation method and device based on full-chain consensus and local deployment
ActiveCN112580112AIncrease the number of smart contractsMeet privacy requirementsFinanceDigital data protectionTrunkingFinancial transaction
The invention provides an intelligent contract implementation method and device based on full-chain consensus and local deployment, and the method comprises the steps: separating full-chain triggeringfrom local execution of a deployment transaction and a business transaction, and introducing a mode of a local state; and supporting an intelligent contract which combines full-chain-level consensusand contract-level consensus and is locally deployed, locally triggered and locally stored on a blockchain network, namely, supporting a local contract in which data and codes selectively exist at blockchain nodes but participate in full-chain consensus. As most of real scenes are only significant to related parties, the local contract architecture method only needs to be deployed at the related parties, and the local contract architecture method can greatly improve the number of intelligent contracts which can be simultaneously supported by one block chain network on the premise of full-chainconsensus. Moreover, with the assistance of an out-of-chain security relay service, the local contract architecture method can realize a real secure and private smart contract on the premise of full-chain consensus so as to meet the privacy requirement of a real scene.
Owner:北京全息智信科技有限公司
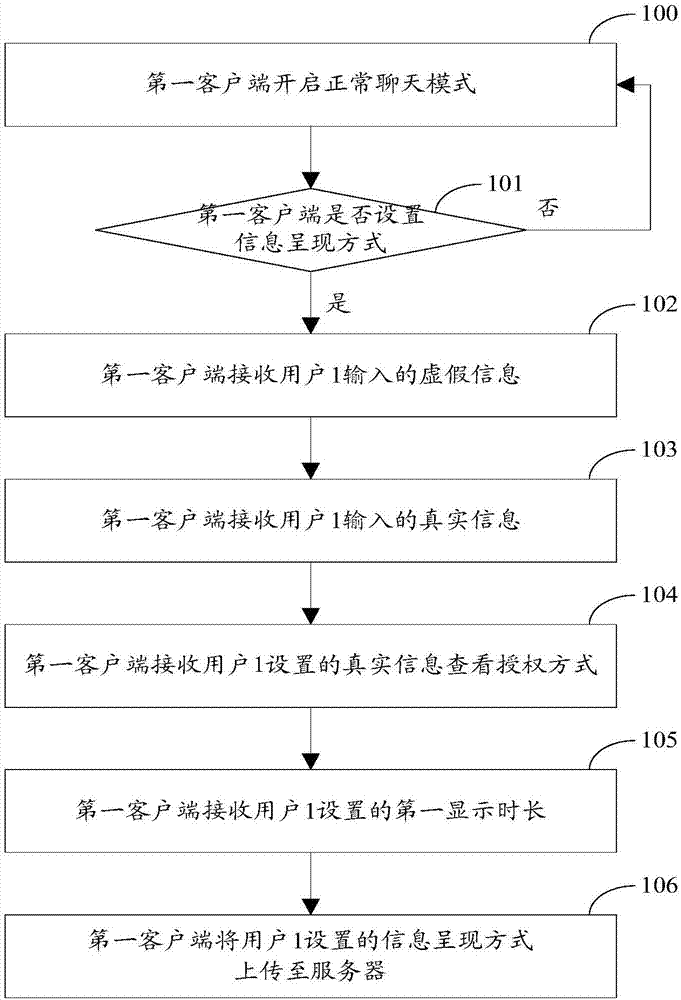
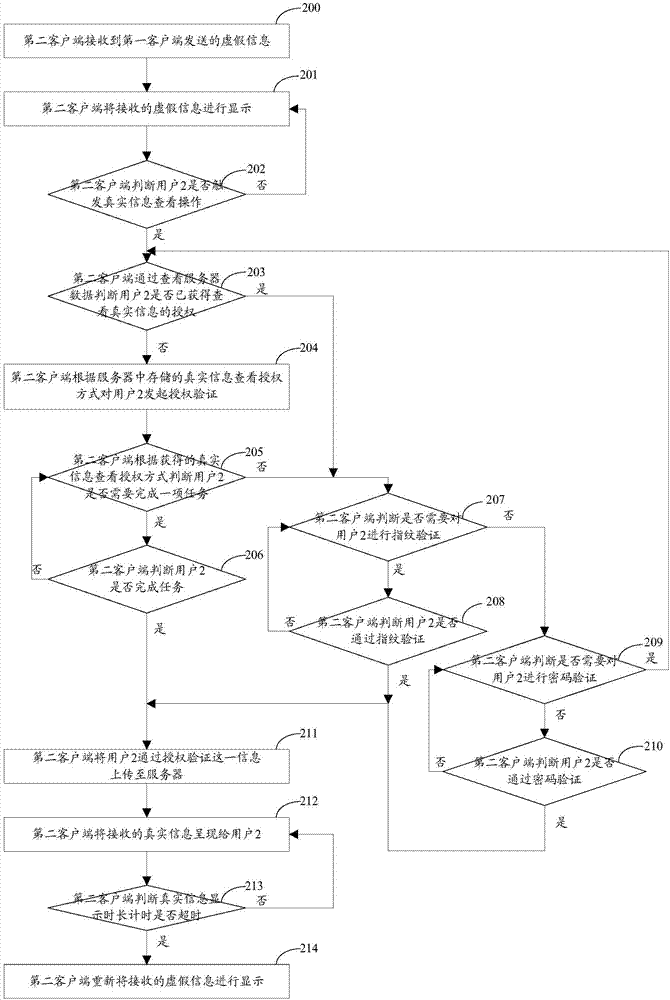
Information presentation method and device based on instant messaging
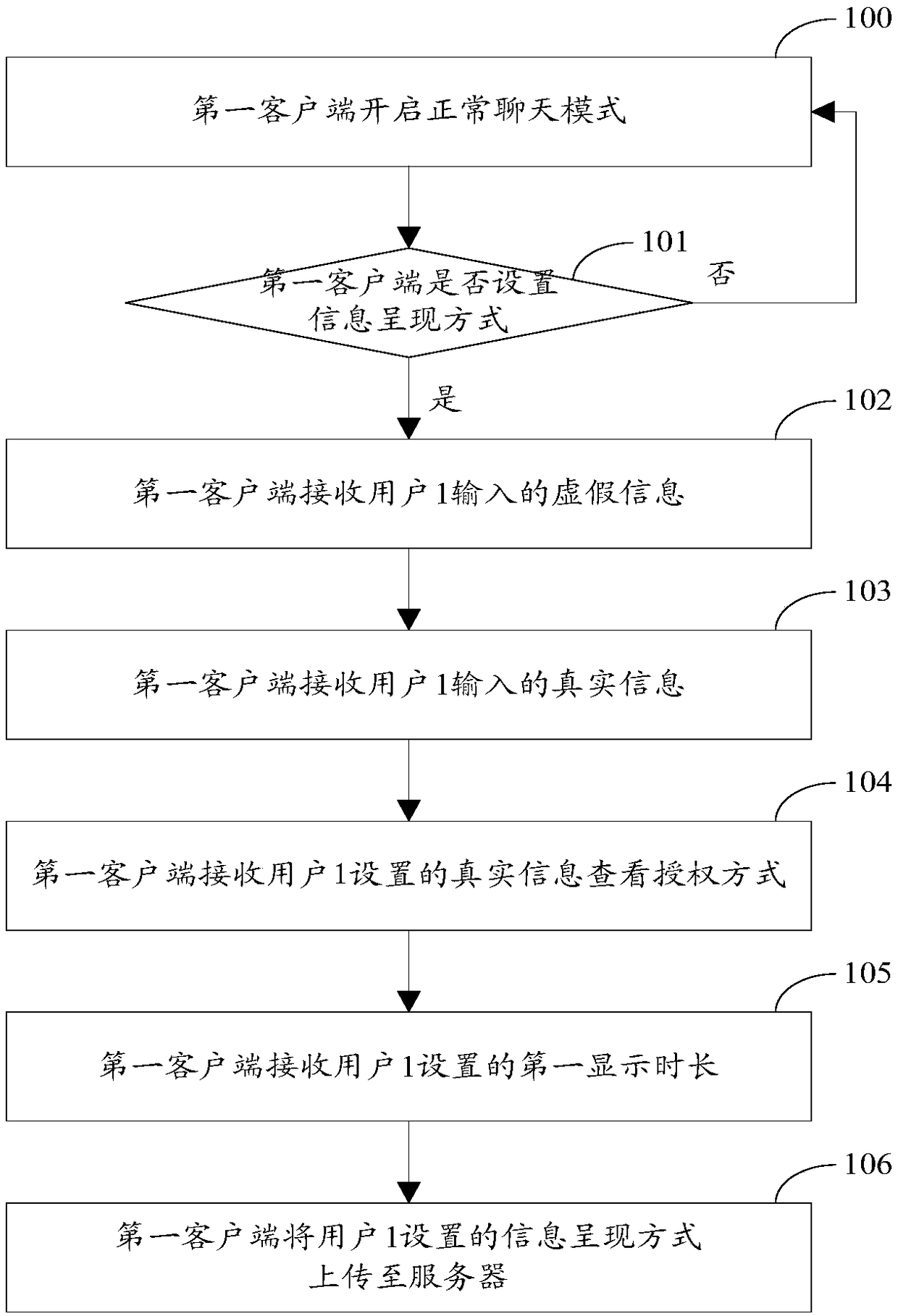
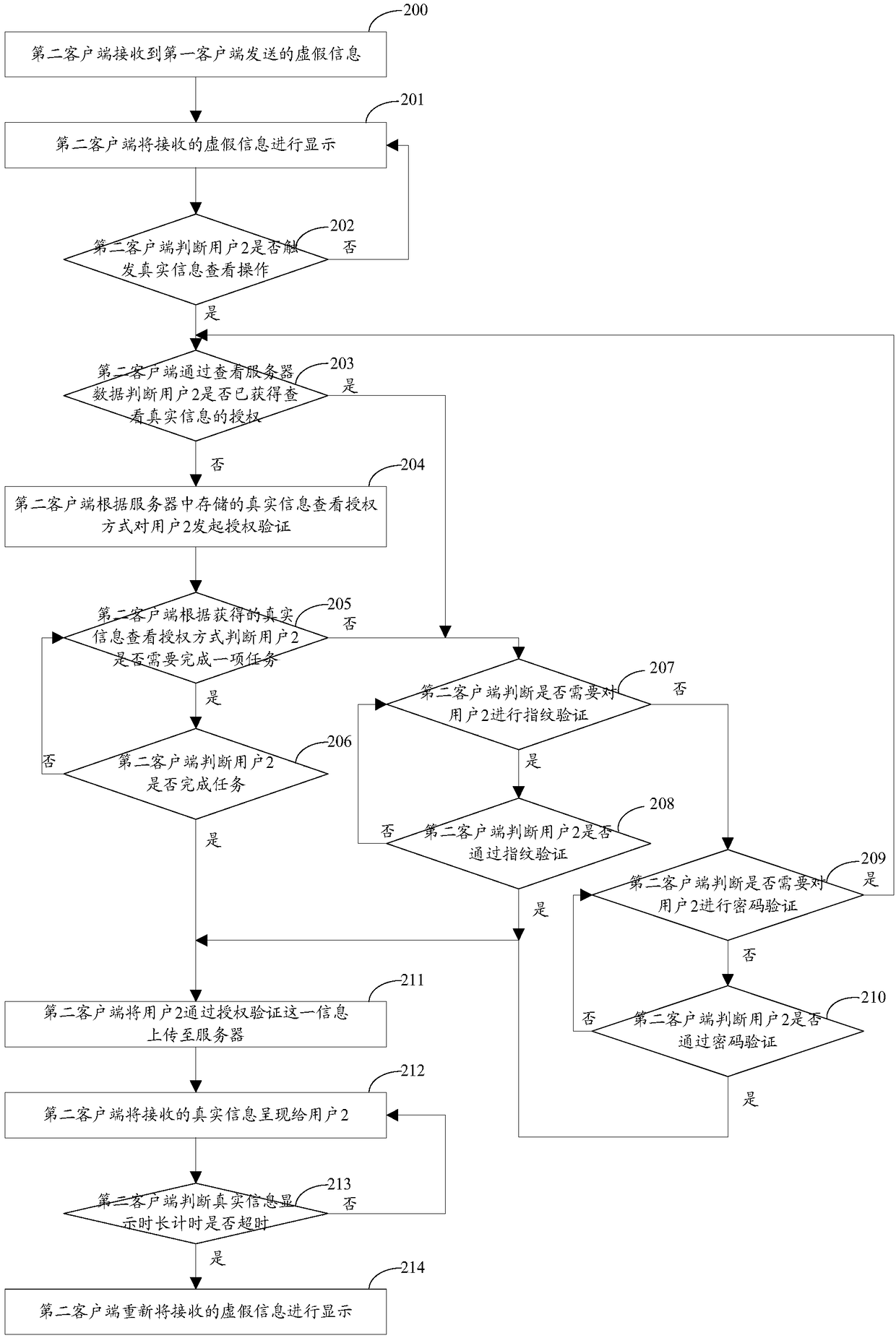
ActiveCN107508799AMeet privacy requirementsPrevent leakageData switching networksAuthorization ModeInformation presentation
The invention relates to the field of the communication, and especially relates to an information presentation method and device based on instant messaging. A privacy requirement on interaction information in the instant messaging process of a user is satisfied. The method comprises the following steps: a server sends false information set by a first client to a second client; the second client triggers a real information check operation after receiving the false information; the server performs the authorization verification on the second client according to a way preset by the first client, and sends real information, set by the first client, corresponding to the false information to the second client after determining that the second client passes the authorization verification; therefore, the privacy requirement on interaction information in the instant messaging process of the user is satisfied, the leakage of the interaction information is avoided, and the messaging process of both messaging parties is more interested through the setting of the real information checking authorization way.
Owner:GREE ELECTRIC APPLIANCES INC
Bed having baby room and being convenient for sexual life
The invention relates to a bed having a baby room and being convenient for sexual life. A bed plate comprises a lifting lying board and a lifting stopping board, wherein the lifting stopping board is arranged at the middle position of the tail part of the lifting lying board; the lifting lying board rises upwards when in use; the lifting stopping board descends downwards; the lifting stopping board and the lifting lying board are arranged on a lifting bottom board; the baby room is arranged on the lifting bottom board below the bed plate; the lifting bottom board rises upwards when in use; an opening is formed in the side of a space between the bed plate and the lifting bottom board; a baby basket is put into the baby room from the opening; and an air window is formed in the position, opposite to the baby room, of the side bed plate. The bed is provided with the baby room and is safe and comfortable, the bed plate is formed by liftable components, the modeling change from a conventional flat bed deformed into a sex bed which is convenient to perform sexual life meets the sex requirements, sexual life of husband and wife is labor-saving, the quality of sexual life can be well improved, and meanwhile, the privacy requirements are also met.
Owner:胡建平
A method and system for anonymous authentication of messages between vehicles in the Internet of Vehicles environment
ActiveCN109788482BShort timeMeet privacy requirementsKey distribution for secure communicationUser identity/authority verificationInternet privacyIn vehicle
Owner:WUHAN UNIV
Supervisory method and supervisory entity of authorization service of identify providing entity
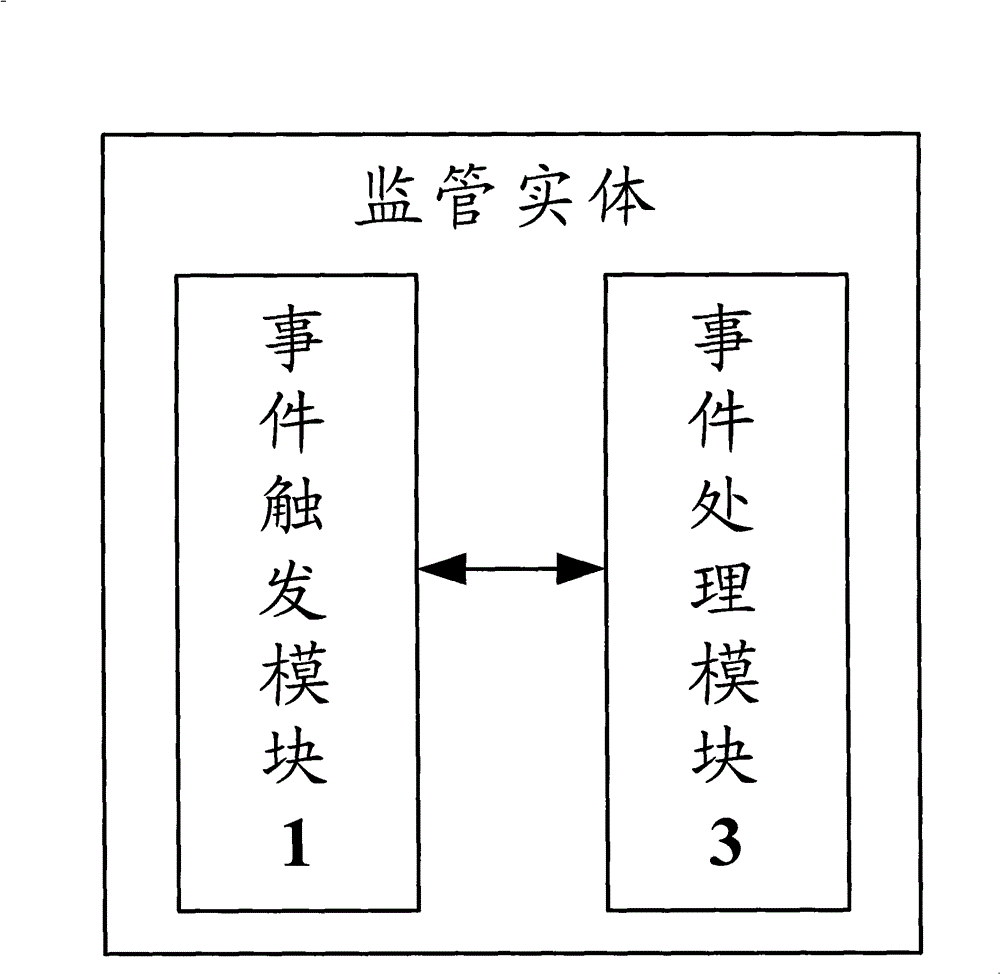
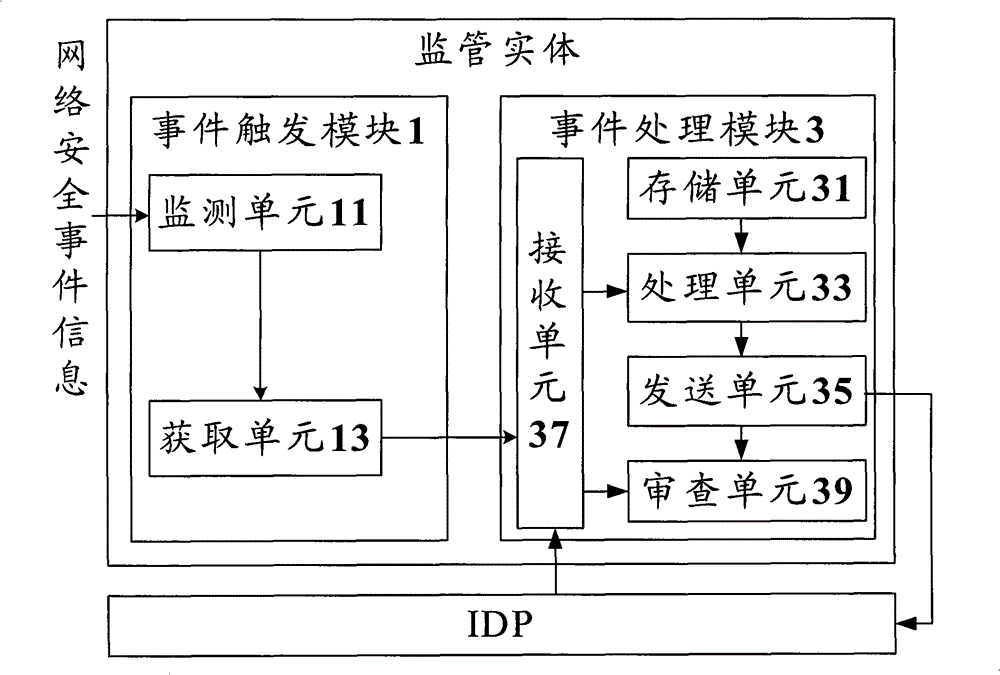
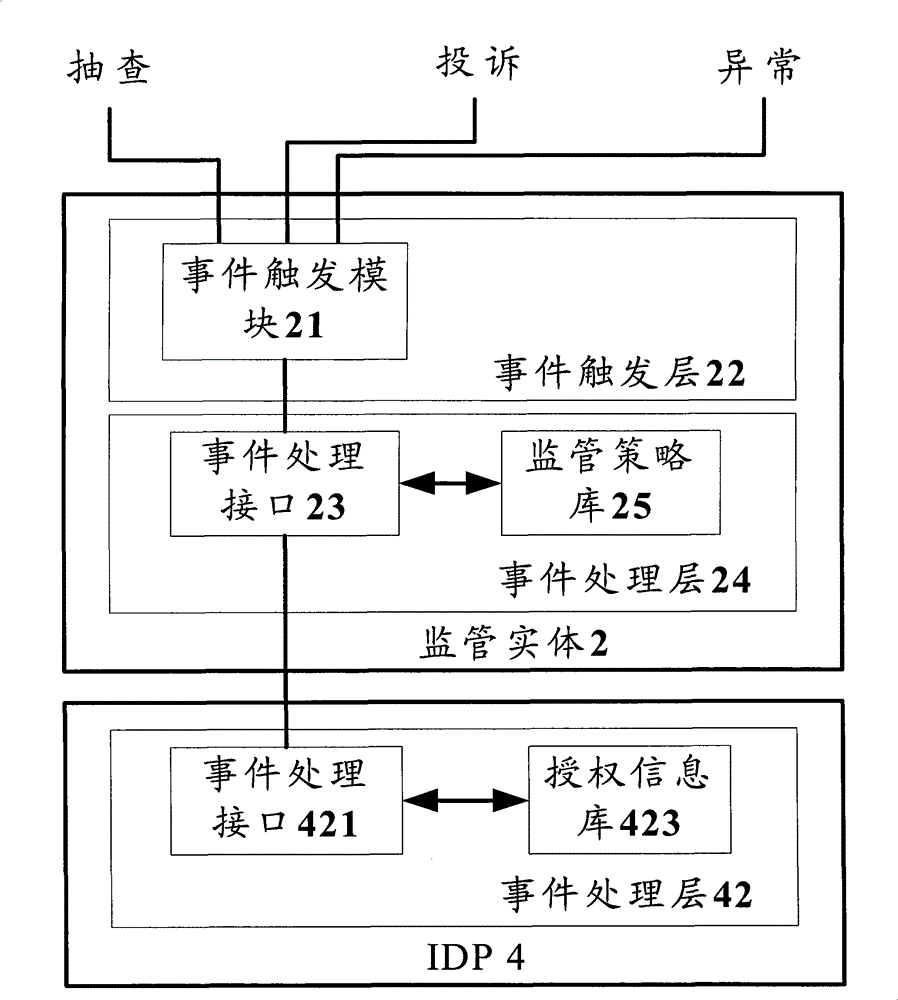
ActiveCN101730100BMeet privacy requirementsEnsure safetySecurity arrangementEvent triggerAuthorization
The invention discloses a supervisory method and a supervisory entity of authorization service of an identify providing entity. The supervisory entity comprises an event trigger module and an event processing module, wherein the event trigger module is used for monitoring and receiving network security event information of different types of network security events; and the event processing module is used for sending a supervisory command to an identify providing entity according to the security event information, and corresponds to authorization information returned by the supervisory command according to the identify providing entity to perform authorization examination to the identify providing entity. According to the technical scheme, the current requirement of a user to privacy can be satisfied, therefore, the network security can be guaranteed, and the disclosure of the identify information of the user can be prevented.
Owner:ZTE CORP
Platform and method for personal information protection based on personal information universal coding
ActiveCN102970302BGuaranteed professionalismPrevent floodingTransmissionInformation controlInternet privacy
The invention relates to a platform and a method for personal information protection based on personal information universal coding, wherein an access management unit, a personal information database and an access authentication interface unit are connected with an information control unit; the access management unit as well as an authorization and record unit are further connected with the terminal equipment of an information publish party respectively, and the access authentication interface unit is connected with the terminal equipment of an information request party; the information control unit is used for providing registration service for the information publish party which accesses via the access management unit, and generating a unique personal information universal code for the information publish party; the access management unit is used for providing interface service for the access of the information publish party to the information control unit; and the access authentication interface unit is used for performing authentication and audit on the access authentication request according to the personal information universal code, of the information request party, and performing personal information data transmission. Because the platform for personal information protection disclosed by the invention is a platform independent from mail delivery networks, E-business networks and other government departments or units and especially used for storing personal information data, the platform is not a link in a personal information interest chain, and the position of the platform ensures the profession of providing service for the information publish party.
Owner:韩明岐
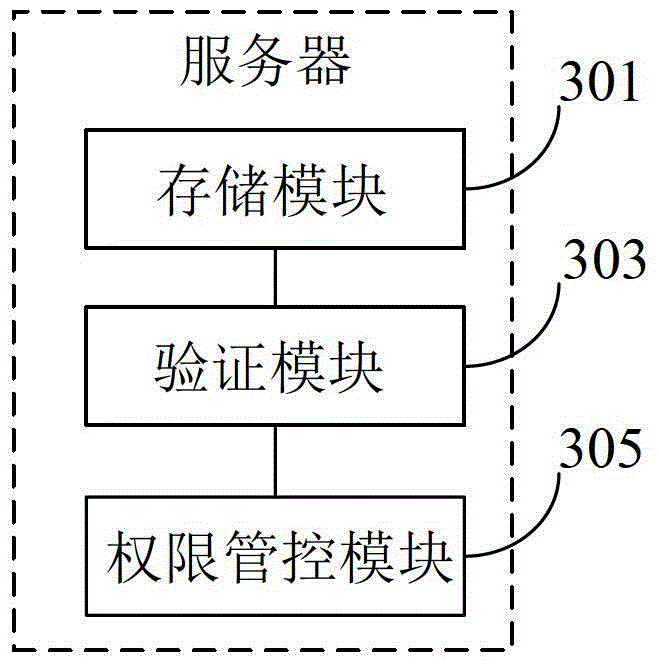
Rights management method, system and server
InactiveCN103400067BEnsure safetyEasy to useMultiple keys/algorithms usageUser identity/authority verificationInternet privacyRights management
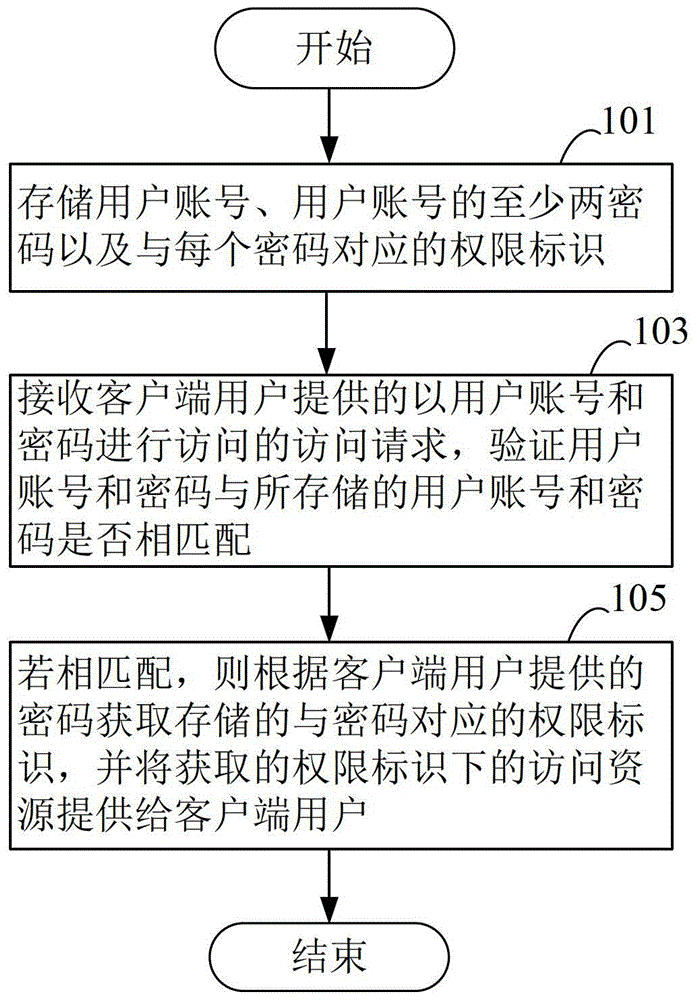
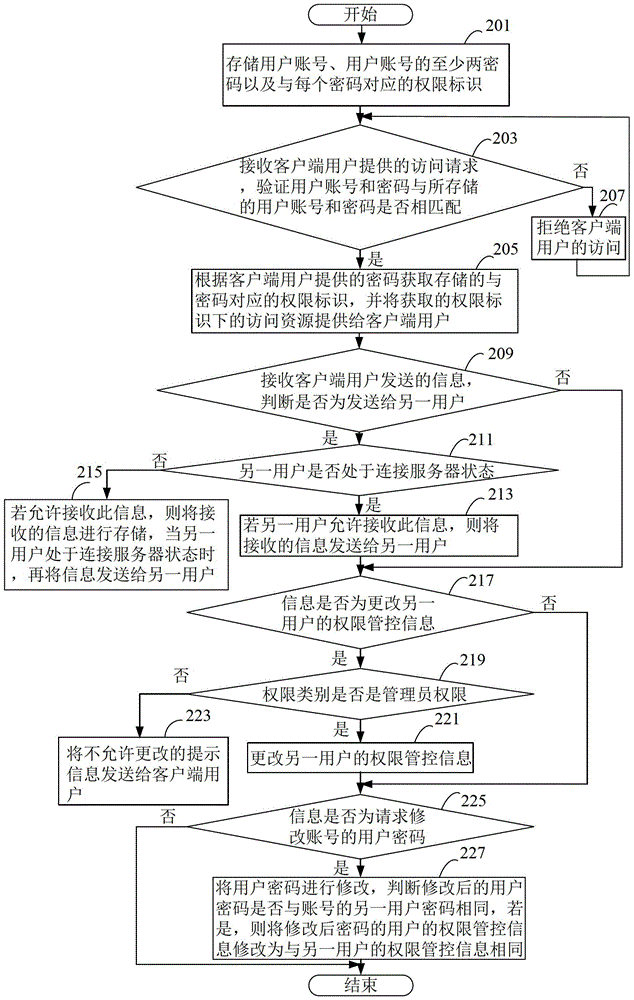
The invention discloses an access control method, system and server, and belongs to the field of information management. The method includes the steps of storing a user account, at least two ciphers of the user account and access identifications corresponding to the ciphers, receiving a visit request which is provided by a client user and used for visiting with a user account and a cipher and verifying whether the user account and the cipher are matched with the stored user account and one stored cipher, obtaining the stored access identification corresponding to the cipher according to the cipher provided by the client user if the user account and the cipher are matched with the stored user account and the stored cipher, and providing visiting resources of the obtained access identification for the client user. According to the access control method, system and server, the visiting resources corresponding to each cipher of the same account can be provided for different users of a client for visiting through control, requirements for privacy of each user can be met, use safety of the account is guaranteed, and convenience is brought to the users during use.
Owner:HISENSE VISUAL TECH CO LTD
A communication control method and electronic device
ActiveCN105991832BReal-time portabilityFeel goodSubstation equipmentTransmission channelCommunication control
The invention provides a communication control method and electronic equipment. The communication control method is applied to first electronic equipment, a second body of the first electronic equipment comprises a frame structure and a fixing structure used for fixing the first electronic equipment onto an operation body, and the electronic equipment forms a ring shape when the first electronic equipment is fixed on the operation body; a first body comprises a display screen, is connected with or separated from the frame structure of the second body through a first connector; during the process of continuously receiving request information sent from second electronic equipment by the first electronic equipment, the first electronic equipment receives the request information when acquiring detection parameters used for representing states from connection to separation of the first body relative to the second body by means of a detection device of the first electronic equipment, and establishes a transmission channel between the first electronic equipment and the second electronic equipment, so as to achieve information exchange between the first electronic equipment and the second electronic equipment, avoiding leakage of the transmitted information, and satisfying the privacy requirements for answering and making phone calls of the user.
Owner:LENOVO (BEIJING) LTD
A smart contract implementation method and device based on full-chain consensus and local deployment
ActiveCN112580112BIncrease the number of smart contractsMeet privacy requirementsFinanceDigital data protectionTrunkingFinancial transaction
The present invention provides a smart contract implementation method and device based on full-chain consensus and local deployment. By separating the full-chain triggering and local execution of deployment transactions and business transactions, and introducing local states, it supports A smart contract that combines full-chain consensus and contract-level consensus, local deployment, local triggering, and local storage, that is, a local contract where data and code selectively exist on blockchain nodes but participate in full-chain consensus. Because most real-world scenarios are only meaningful to the relevant parties and thus only need to be deployed on the relevant parties, this local contract architecture method can greatly increase the number of smart contracts that a blockchain network can support at the same time under the premise of a full-chain consensus. Moreover, supplemented by off-chain security relay services, this local contract architecture method can realize truly secure and private smart contracts under the premise of full-chain consensus, so as to meet the privacy requirements of real-world scenarios.
Owner:北京全息智信科技有限公司
A Privacy Preserving Method for Publishing Transactional Data Streams
ActiveCN106778346BMassiveEasy to handleDigital data information retrievalDigital data protectionData streamSlide window
The invention discloses a privacy protection method for transactional data flow publishing, data are anonymous by adoption of sliding windows, the recent data information can be well processed by the sliding windows, and therefore privacy requirements can be ensured to be satisfied by any sliding window and data validity is maintained as much as possible, thereby facilitating analysis by data miners.
Owner:GUANGXI NORMAL UNIV
Gateway equipment, method for using gateway equipment and information transmission method and equipment
ActiveCN102098237BMeet privacy requirementsEasy to controlConnection managementNetwork connectionsHome Node BTelecommunications network
The invention discloses gateway equipment, a method for using the gateway equipment, an information transmission method and information transmission equipment. The information transmission method comprises the following steps of: accessing a local network through a direct tunnel established between local gateways on the basis of a local Internet protocol (IP) access technology and establishing anend-to-end logic link between a 3rd generation partnership project (3GPP) terminal and a local wireless sensor network application platform to transmit control information and service data information between the 3GPP terminal and the local wireless sensor network application platform; and accessing the local network through a direct tunnel established between a Femto access point (AP) module andthe local gateway and establishing an end-to-end link between a wireless sensor network and the local wireless sensor network application platform to transmit control information and service data information between the wireless sensor network and the local wireless sensor network application platform. By the methods and the equipment, fusion of a telecommunication network and the Internet of things can be realized by effectively utilizing the position advantage of a 3rd generation / long term evolution (LTE) network home node B.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Communication method and server based on social identity
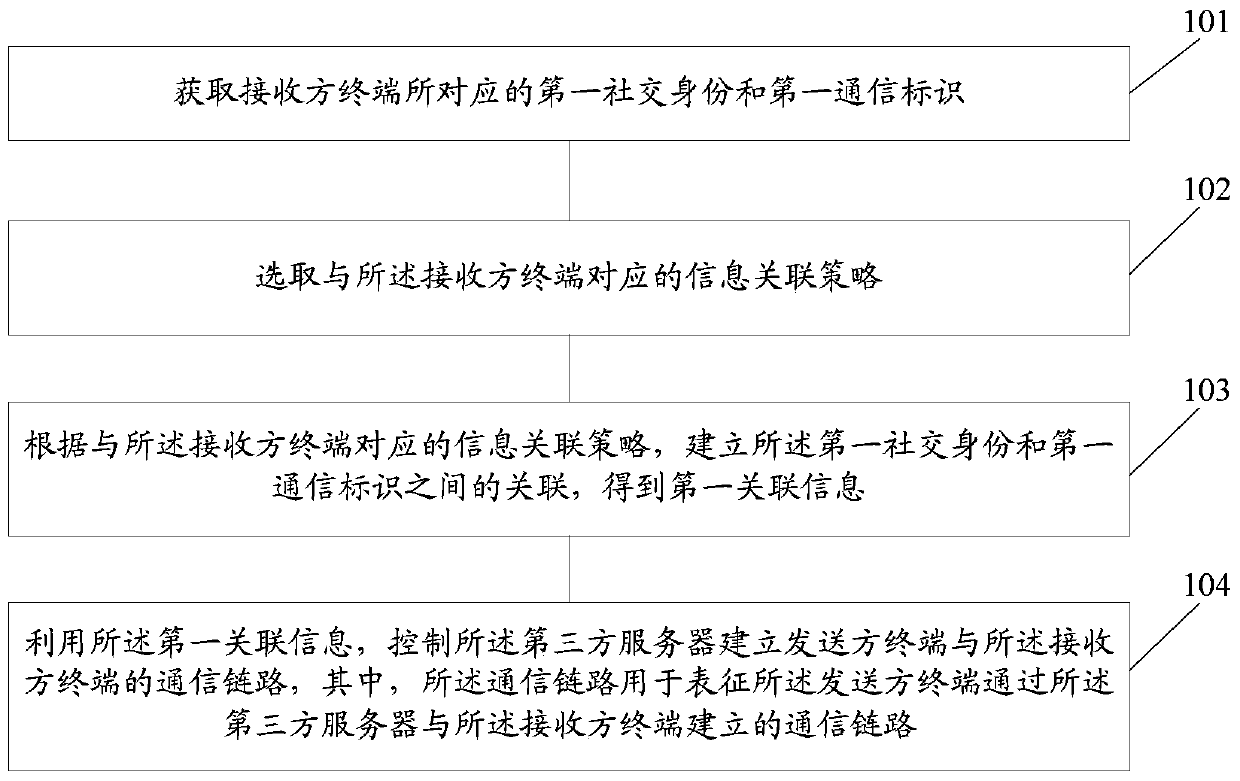
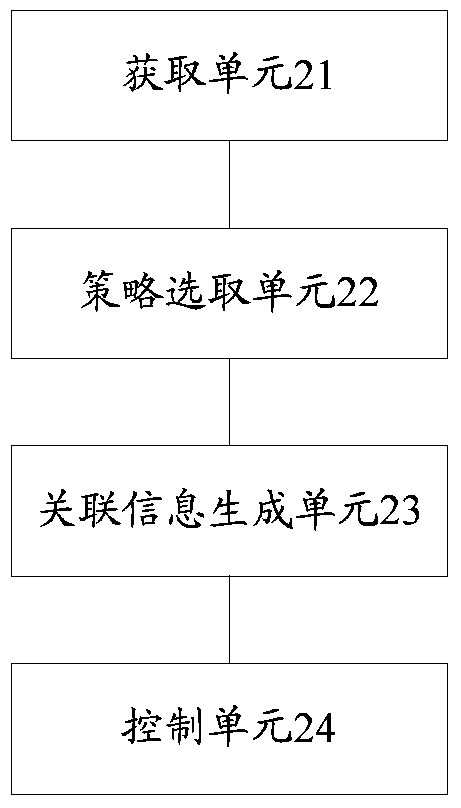
ActiveCN106850703BMeet privacy requirementsImprove experienceData processing applicationsTransmissionThird partyInformation control
The embodiment of the present invention discloses a communication method based on social identity, which is applied to a third-party server; including: obtaining the first social identity and the first communication identification corresponding to the receiving terminal; selecting information corresponding to the receiving terminal An association strategy; according to an information association strategy corresponding to the recipient terminal, establish an association between the first social identity and the first communication identifier to obtain first association information; use the first association information to control the A third-party server establishes a communication link between the sender terminal and the receiver terminal, where the communication link is used to represent the communication link established between the sender terminal and the receiver terminal through the third-party server . The embodiment of the invention also provides a server.
Owner:CHINA MOBILE COMM GRP CO LTD
Garden assembly type rest sentry box
InactiveCN114458057AConvenient for sitting and lyingRest comfortablySunshadesStoolsEngineeringStructural engineering
The garden assembly type rest sentry box comprises a bottom side plate and a top side plate, a top cover is arranged at the top of the bottom side plate in a clamped mode, a plurality of stand columns are fixedly arranged between the top side plate and the bottom side plate, a plurality of matching sleeves are slidably arranged on the outer surfaces of the stand columns, and fence plates are fixedly arranged between the matching sleeves; side hinge rods are hinged between the upper and lower adjacent fence plates, matched connecting bases are arranged at the tops of the bottom side plates and the bottoms of the top side plates, middle columns are rotatably arranged in the matched connecting bases, connecting wheels are rotatably arranged on the two sides of each middle column, connecting grooves are formed in the connecting wheels, and the connecting grooves are connected with the bottom side plates. According to the equipment, the positions of the seats can be adjusted, when the seats are arranged in a staggered mode, stress is uniform, meanwhile, people can sit and lie more conveniently, the equipment can form a wrapping structure on the outer surface of the sentry box to keep out wind and rain, and people can have a rest more comfortably.
Owner:ZHEJIANG COLLEGE OF CONSTR
A method and device for presenting information based on instant messaging
ActiveCN107508799BMeet privacy requirementsPrevent leakageData switching networksAuthorization ModeInformation presentation
The present invention relates to the communication field, in particular to an instant messaging-based information presentation method and device. It is used to meet the user's privacy requirements for the interactive information in the instant messaging process. The method is as follows: the server first sends the false information set by the first client to the second client, and the second client will trigger the real information viewing operation after receiving the false information, then the server will follow the pre-set method of the first client Carry out authorization verification to the second client, after confirming that the second client passes the authorization verification, then send the real information corresponding to the false information setting of the first client to the second client, thus satisfying the user's requirement for instant messaging. The privacy requirement of the interactive information avoids the leakage of the interactive information, and at the same time, the setting of the authorization method for viewing the real information also makes the communication process of the two parties more interesting.
Owner:GREE ELECTRIC APPLIANCES INC
A privacy protection transaction method based on blockchain technology in e-commerce
ActiveCN108389046BEase of evaluationMeet privacy requirementsFinanceDigital data protectionData privacy protectionConfidentiality
The invention discloses a privacy protection transaction method based on a blockchain technology in electronic commerce. The method comprises the following steps that: adopting the blockchain technology which comprises a privacy smart contract and a zero-knowledge proof to protect the private information of a user; taking the privacy smart contract as a bridge between a buyer and a seller in a transaction period; adopting the zero-knowledge proof to issue a confidentiality token and create a confidentiality transaction; and combining the blockchain, an industrial data space and the Internet ofThings technology to establish infrastructure, and establishing an integrated platform for logistics business management in a distribution way. By use of the method, private information can be hiddenfor dispatchers, private information, including, identity, address, telephone number and the like, can be hidden for sellers, in addition, the method also can be used for other blockchain applicationscenes with a data privacy protection requirement, in addition, blockchain characteristics can be fully utilized, and therefore, the evaluation problem of an electronic commerce platform can be improved.
Owner:XI AN JIAOTONG UNIV
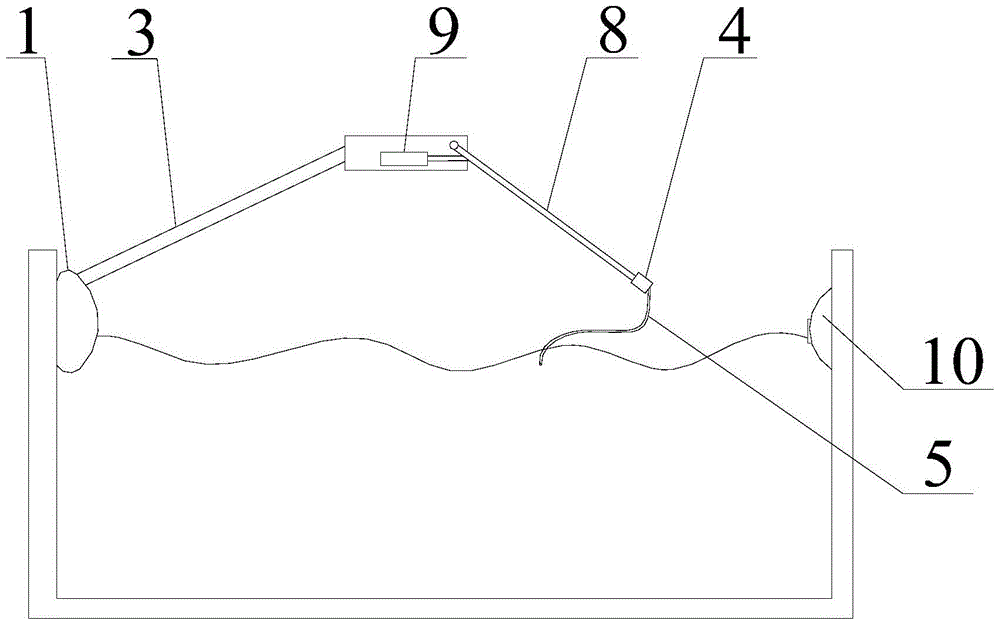
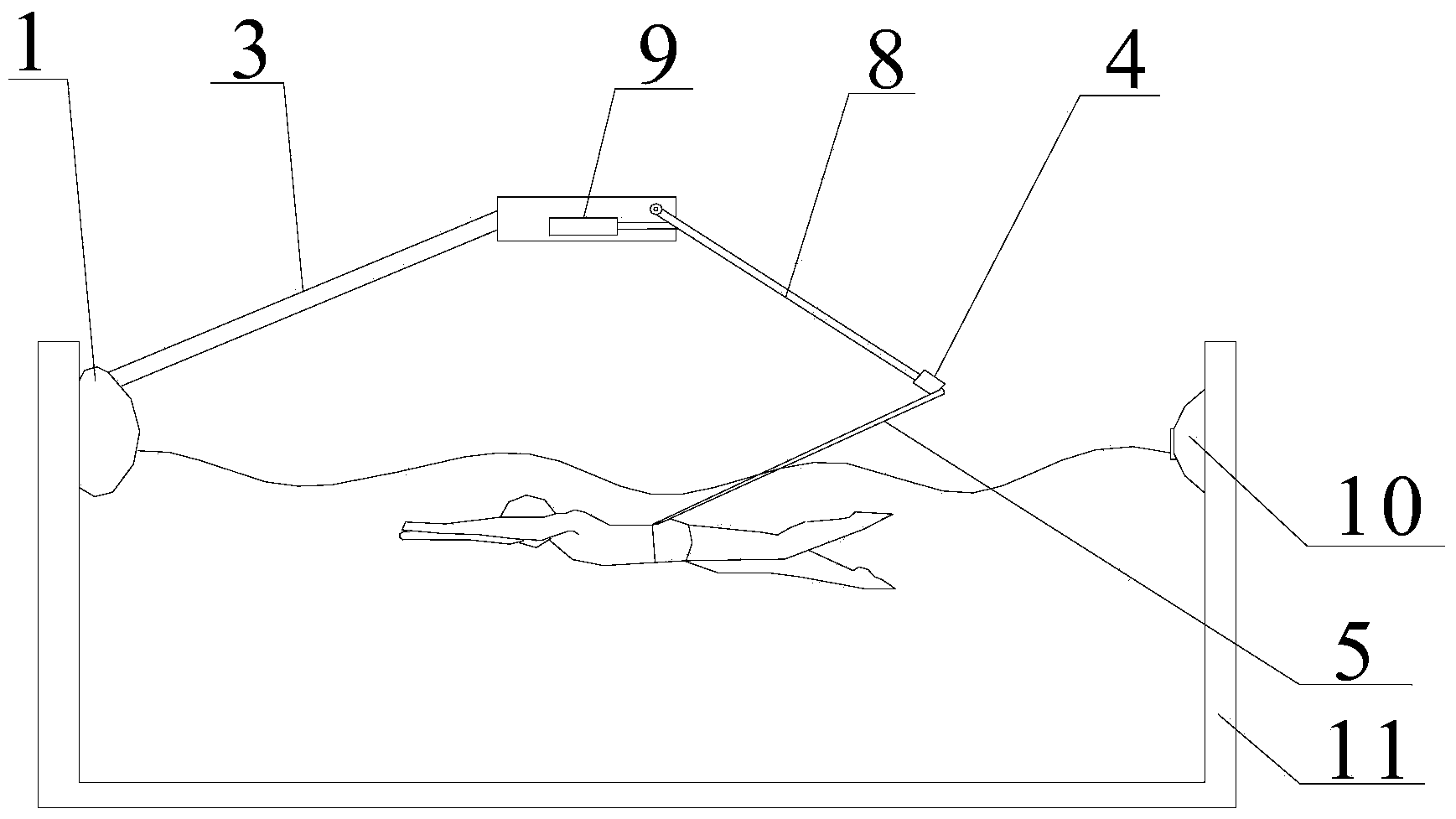
A swimming aid device and a domestic swimming pool
The invention relates to the field of sports auxiliary equipment, in particular to a swimming auxiliary device and a household swimming pool. It includes a host, the shell is connected with a support arm, and the end of the support arm is provided with a tension sensor; the host is provided with a control circuit board, and the control circuit board is provided with a data processing module, a timing module and a power supply module. The swimming auxiliary device and the household swimming pool provided by the present invention, when swimming, select multiple points in each cycle to record the value of the tension through the tension sensor, process it through the data processing module, and convert it into a digital signal and transmit it to the display screen. Displays the distance traveled. Through this auxiliary device, the same exercise effect as the standard swimming pool can be achieved, but compared with the standard swimming pool, it occupies 1 / 400th of the space, saves space, can realize swimming in the bathroom at home, and saves money, satisfying the needs of people. For privacy requirements, the temperature can be adjusted according to personal preference, the environment is hygienic, and the time distance is not limited.
Owner:旌德君创科技发展有限公司
Method and system for obtaining received visual information in wideband video-frequency system
InactiveCN100499800CMeet privacy requirementsAvoid overheadBroadcast services for monitoring/identification/recognitionTwo-way working systemsComputer networkGroup program
A method for obtaining view-in information in wideband video system includes utilizing the corresponding relation of user terminal to multicast group to obtain user terminal information and utilizing user terminal information to determine view-in information on each multicast group program, furthermore providing view-in information of each multicast group program aiming to each kind of user terminal so as to provide overall information service for preparing program reasonably and for arranging program properly.
Owner:HUAWEI TECH CO LTD
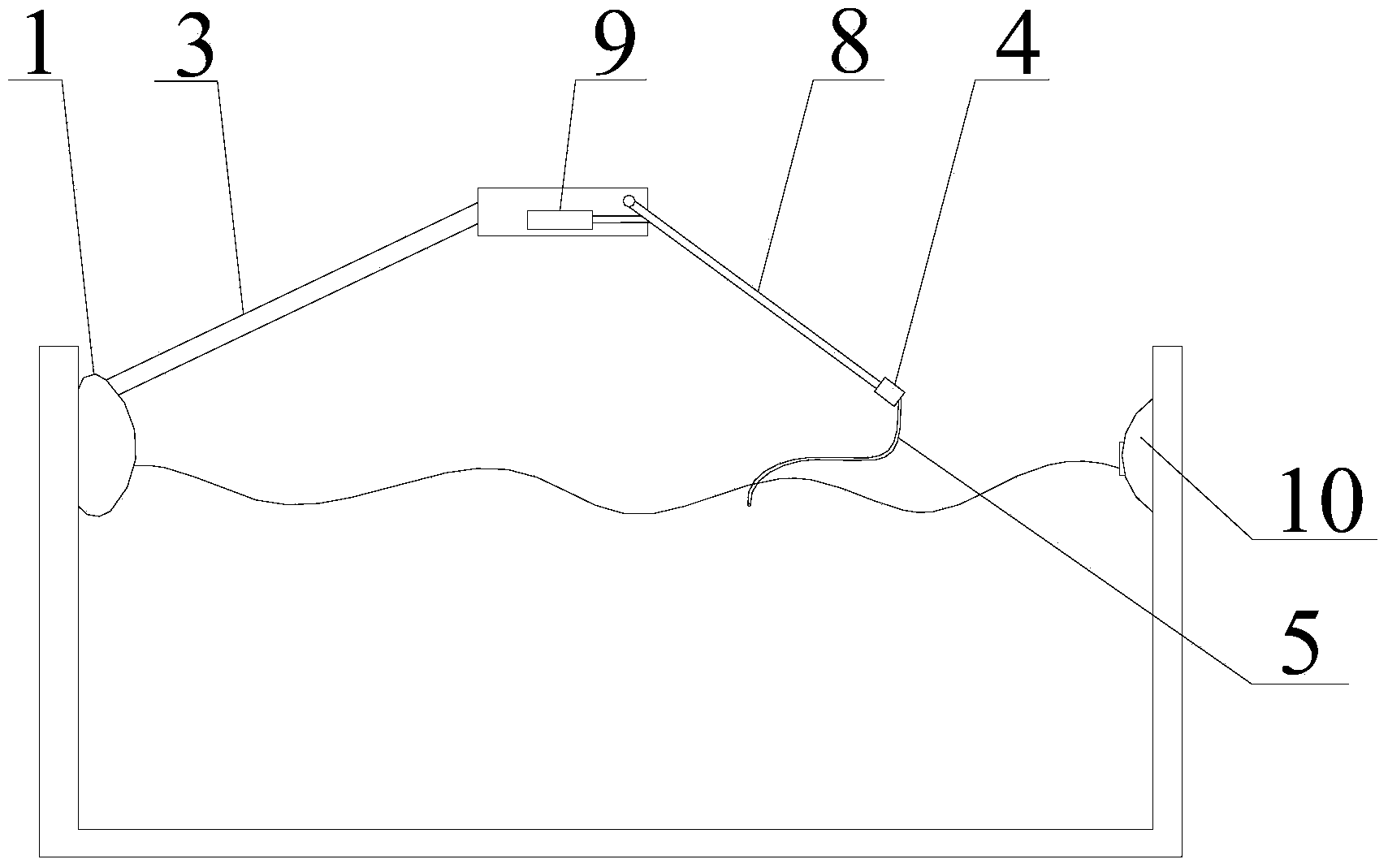
Auxiliary device for swimming and domestic swimming pool
The invention relates to the field of sport auxiliary equipment, in particular to an auxiliary device for swimming and a domestic swimming pool. The auxiliary device for swimming comprises a host, a shell is connected with a supporting arm, a pull force sensor is arranged at the end of the supporting arm, and a data processing module, a timing module and a power supply module are arranged on a control circuit board which is arranged in the host. The auxiliary device for swimming and the domestic swimming pool have the advantages that when swimming, a user selects multiple points in each period and utilizes the pull force sensor for recording pull force numerical values, and the pull force numerical values are processed by the data processing module and converted into digital signals to be transmitted to a display screen, so that swimming distance is displayed; by the aid of the auxiliary device, the user can achieve the same exercising effect in the domestic swimming pool as in a standard swimming pool, but the occupied space of the domestic swimming pool is 1 / 400 of that of the standard swimming pool, and thereby space is saved, swimming in a domestic toilet can be achieved, cost is reduced, requirements of people on privacy are met, the temperature can be regulated according to personal preference, the swimming environment is sanitary, and time and distance are not limited.
Owner:旌德君创科技发展有限公司
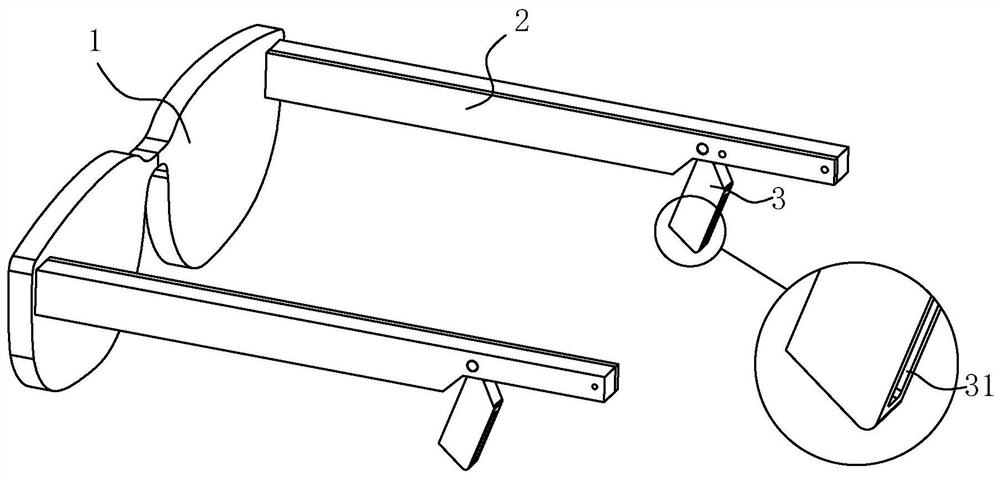
Glasses
The invention provides a pair of glasses. The pair of glasses comprises a glasses frame and two glasses legs symmetrically arranged on the glasses frame; at least one glasses leg is rotatably provided with a loudspeaker module, and each loudspeaker module is provided with a loudspeaker sound outlet hole for transmitting sound to the ear of a user; the glasses legs provided with the loudspeaker modules are provided with accommodating cavities, and the loudspeaker modules have a first state that the loudspeaker modules rotate out of the accommodating cavities and face the ears of a user and a second state that the loudspeaker modules are accommodated in the accommodating cavities; when the loudspeaker modules are in the first state, the loudspeaker sound outlet holes directly face the ears of the user, and the distance between the loudspeaker sound outlet holes and the ears of the user is smaller than a set value; and driving mechanisms for driving the loudspeaker modules to switch between the two states are also arranged in the glasses legs. The position state of the loudspeaker modules can be switched, and especially when the loudspeaker modules are in the first state, the sound effect can be ensured, and the privacy requirement can be met.
Owner:GOERTEK INC
An Anonymous Method to Prevent Tag Neighbor Attacks in Dynamic Publishing in Social Networks
The invention discloses an anonymous method for preventing an attack of a labeled neighbor in social network dynamic release. A design algorithm based on neighbor label similarity is used for distributing nodes into proper groups, meanwhile neighbor structure and degree information of the nodes in the same group in an original social network is also considered, an used StruSim method is improved based on the algorithm, and thus the privacy requirement is met; structural similarity of the nodes in the group is improved to be ready for an next operation, and thus a social network chart after t moment grouping is acquired by using the method. The chart structure is changed by a random disturbing method, edges are randomly added or deleted, then a fuzzy method is used, each edge has the corresponding probability of existing in the social network, so that the probability of an attacker for uniquely determining an individual with a sensitive label is not more than 1 / l. According to the method, only the labeled neighbor information with the sensitive label is disturbed, so that the quantity of undetermined charts is reduced, and data availability is improved.
Owner:GUANGXI NORMAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com