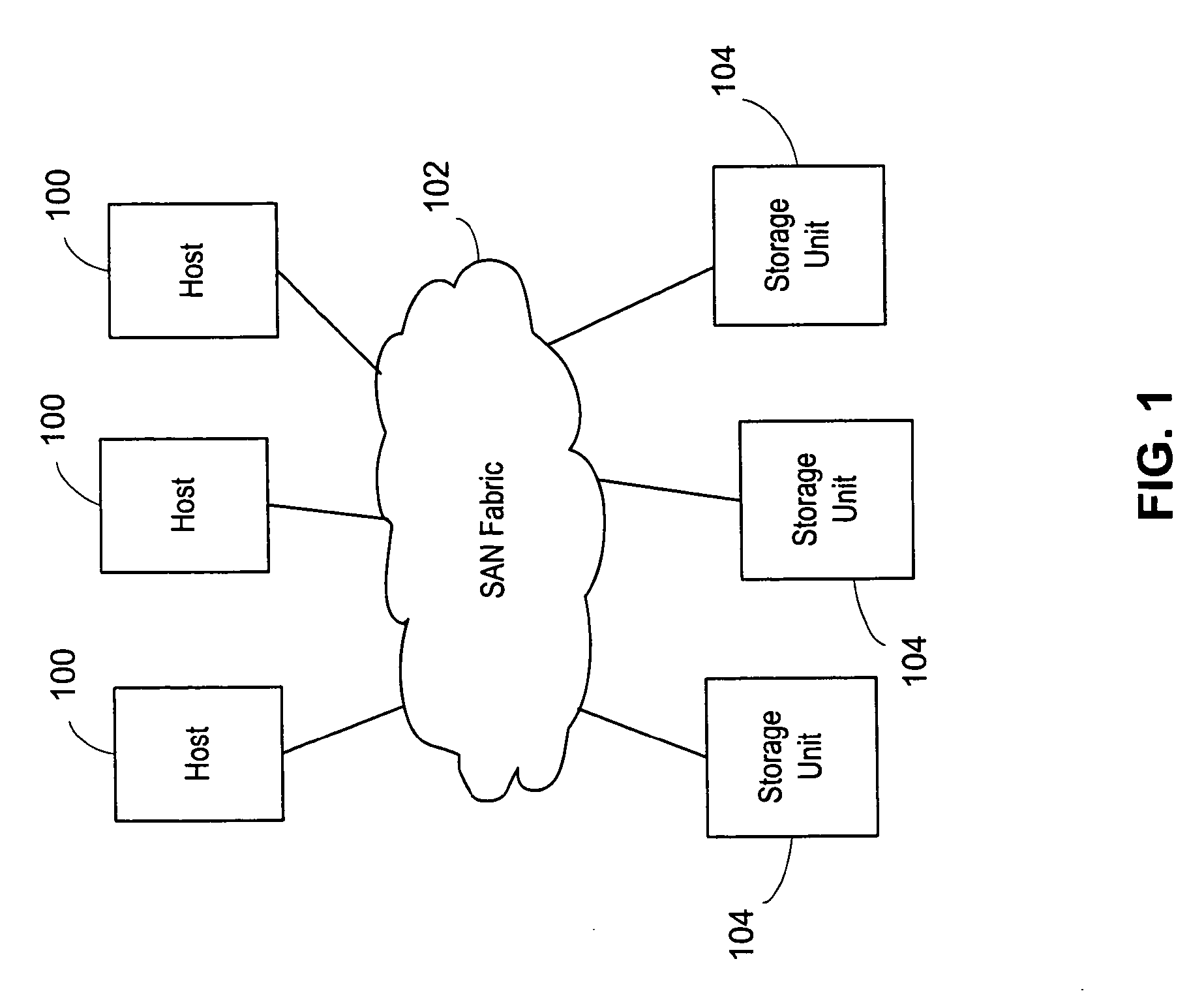
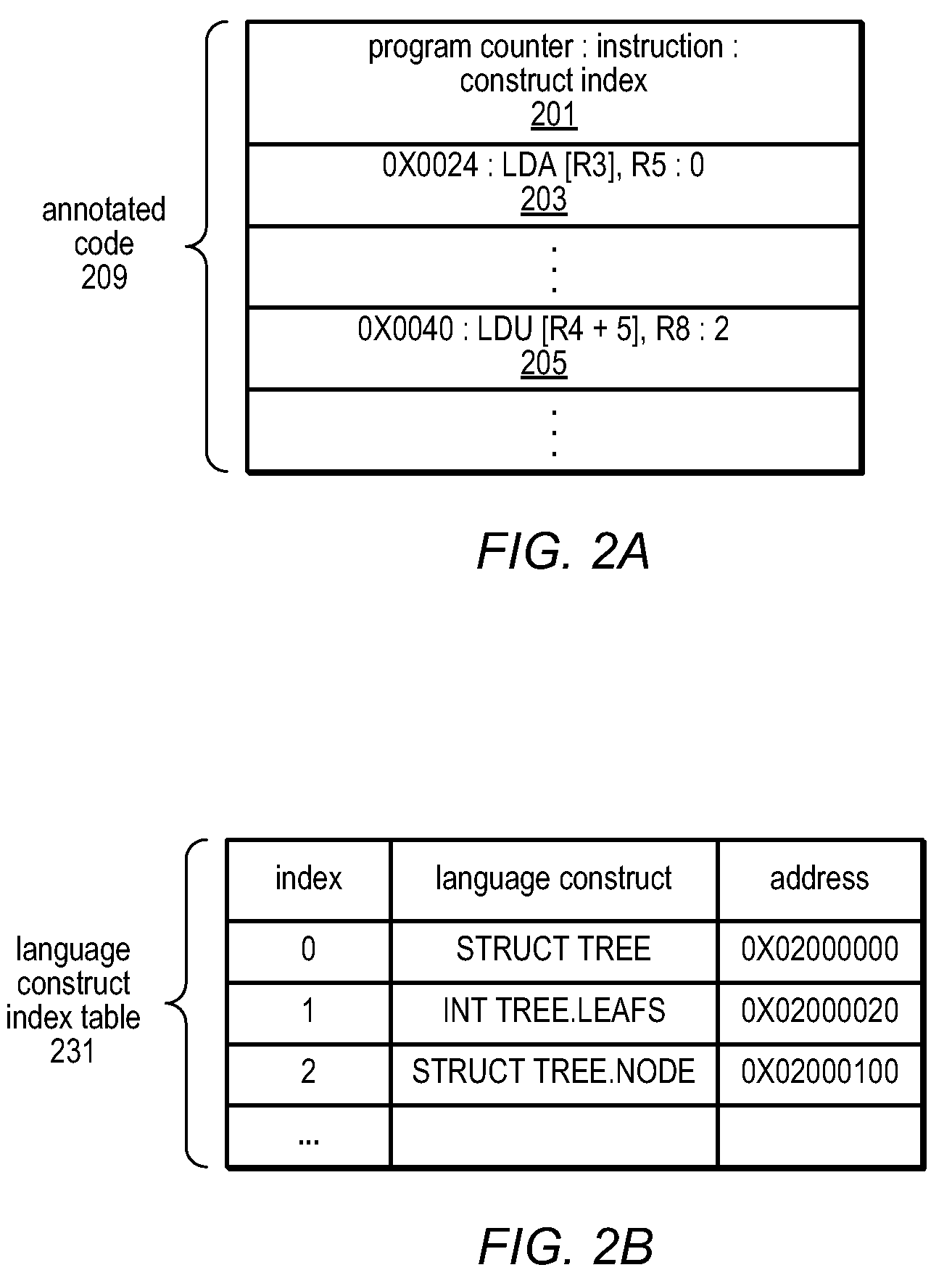
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
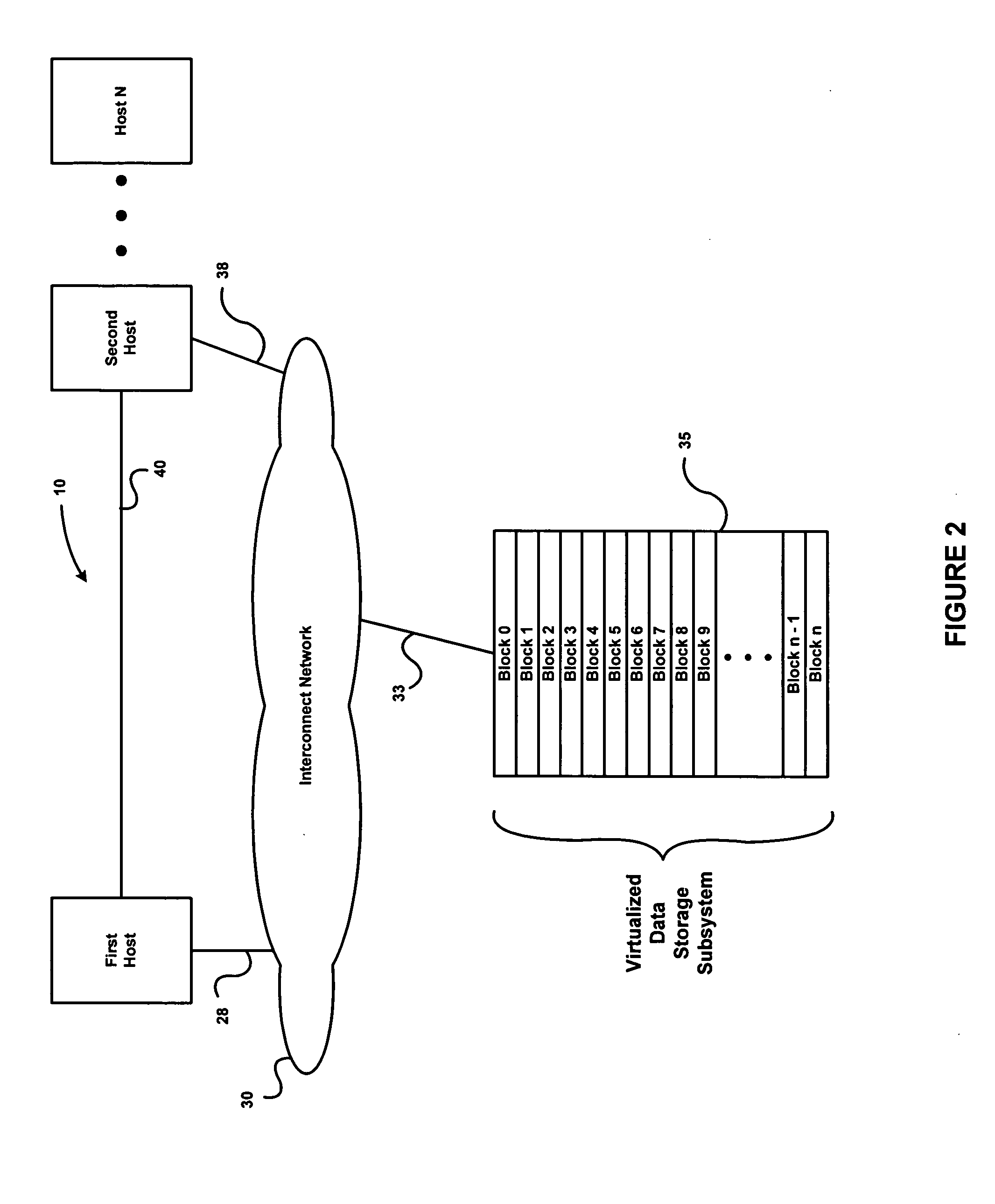
732 results about "Data space" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
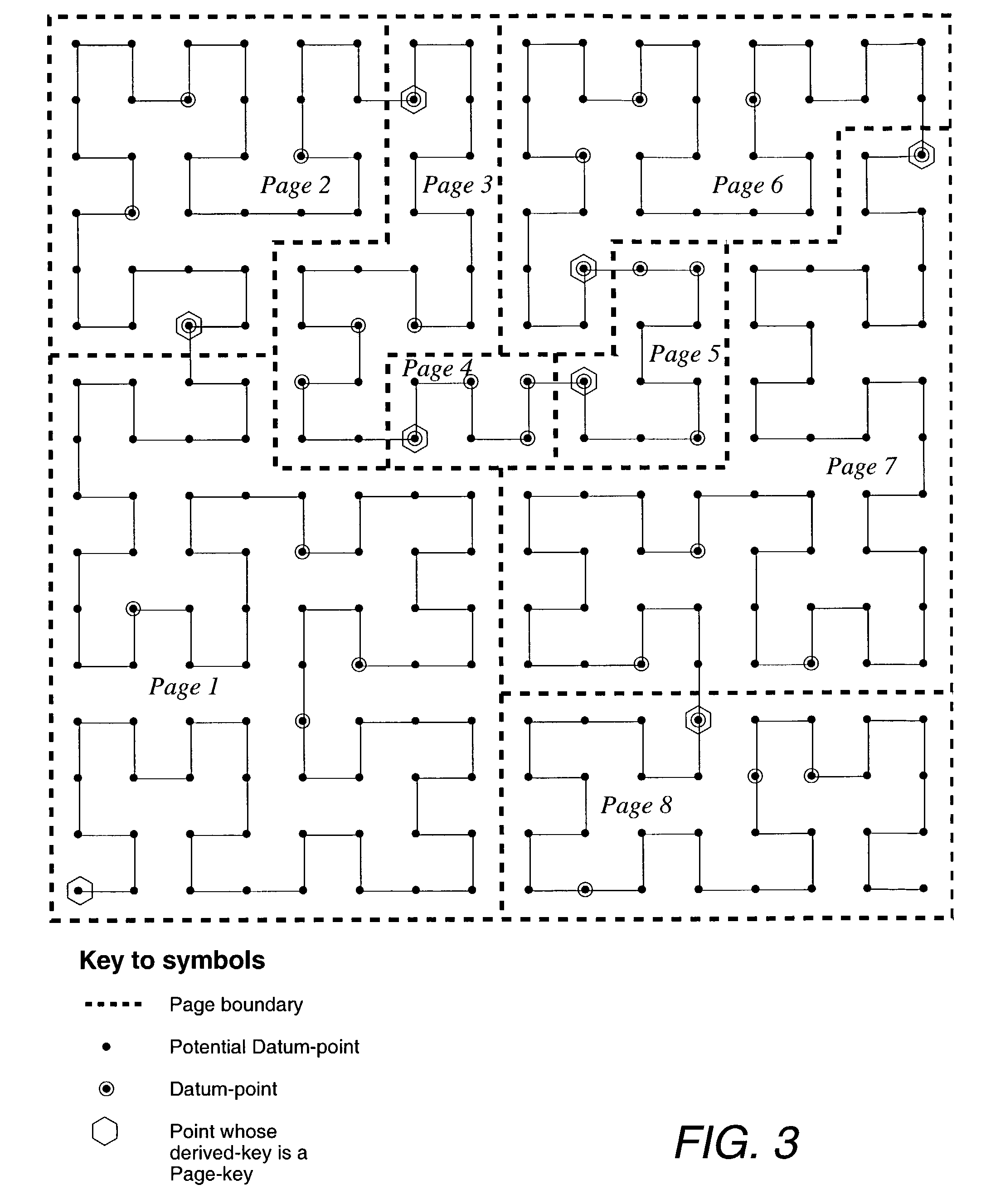
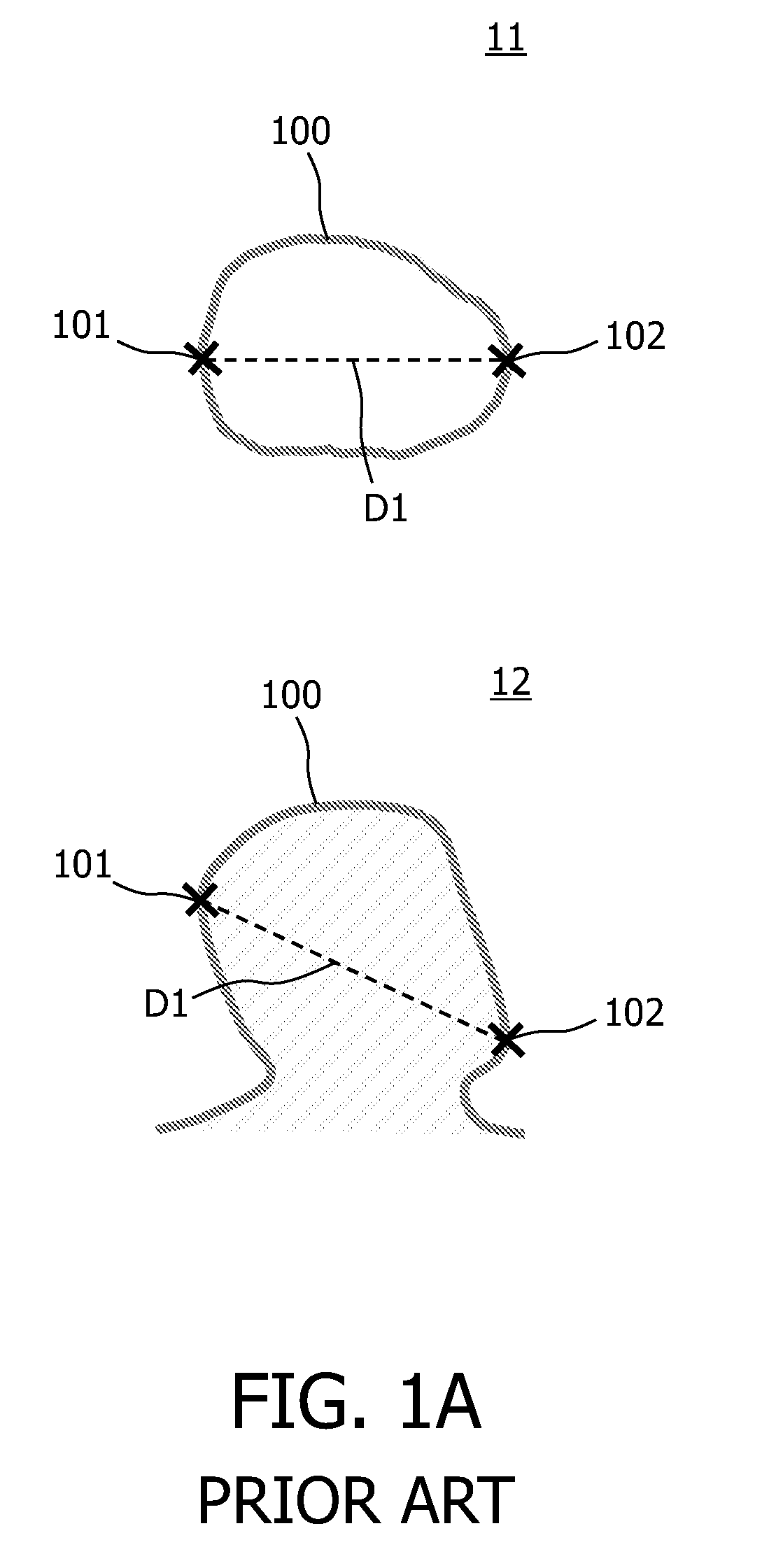
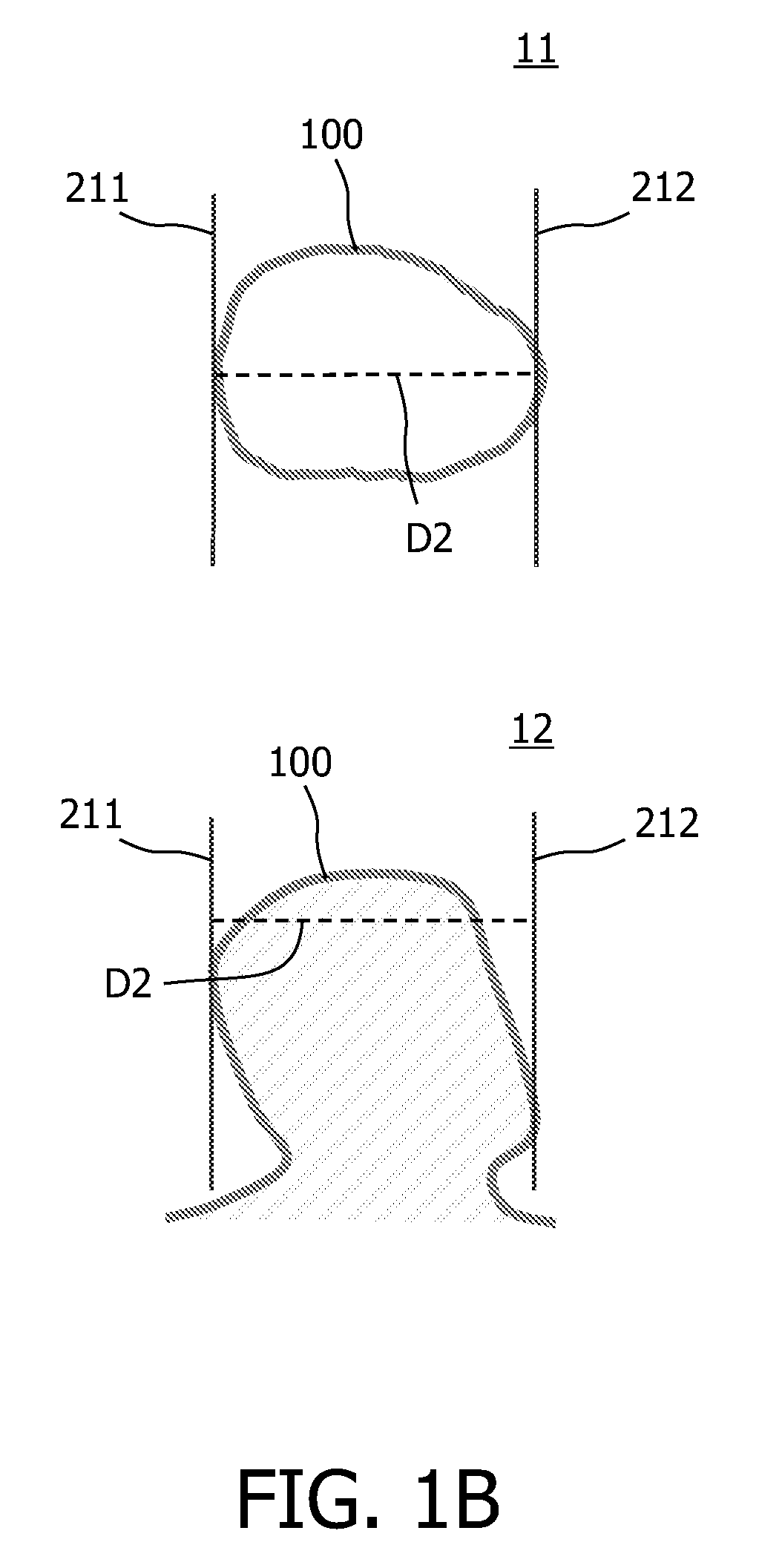
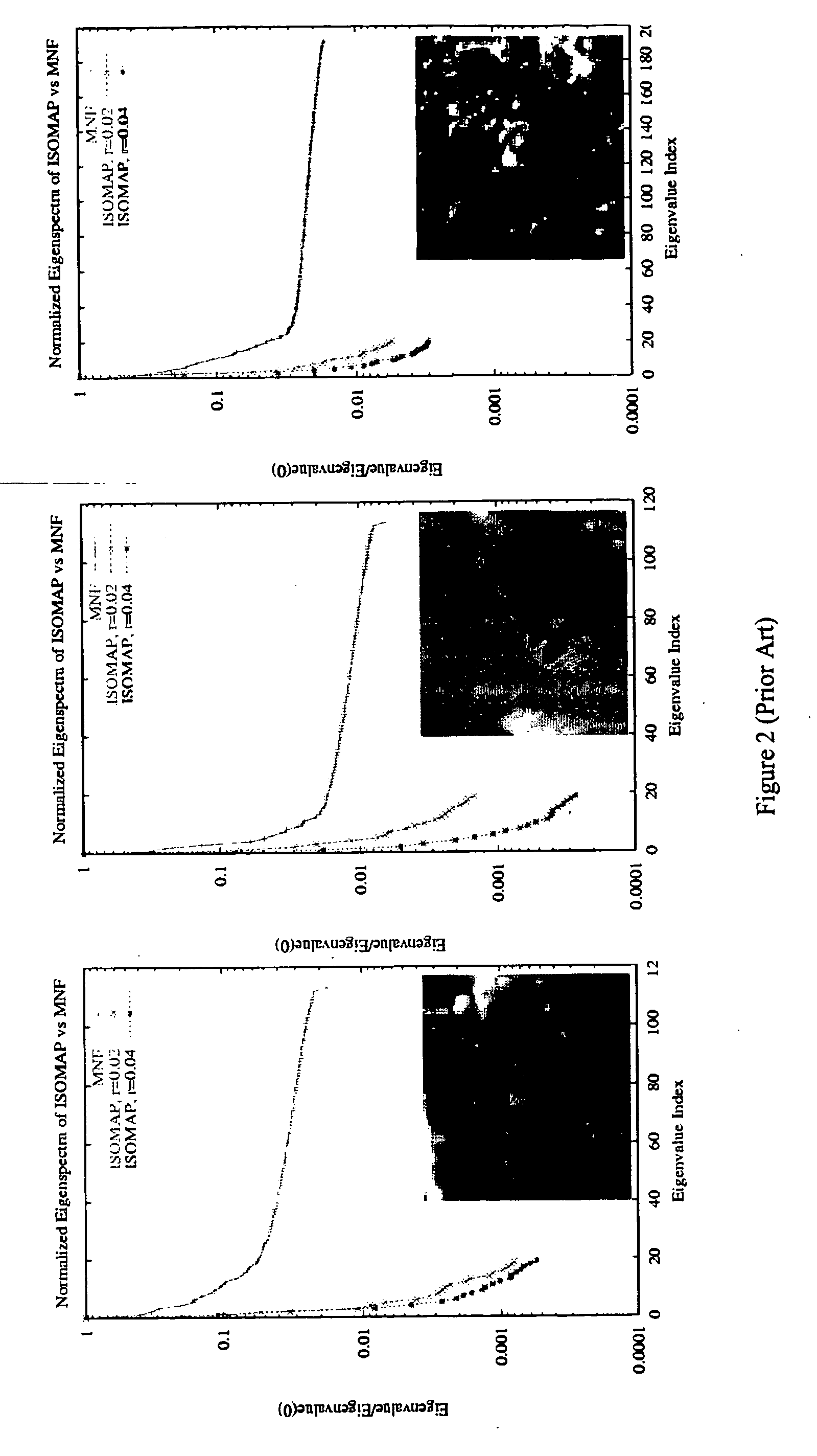
The data spacing is taken as the square spacing perpendicular to the plane of continuity that would give the same number of samples, n(u), as actually found. Practice has shown that using a volume 2 to 3 times the data spacing leads to reasonably stable results.
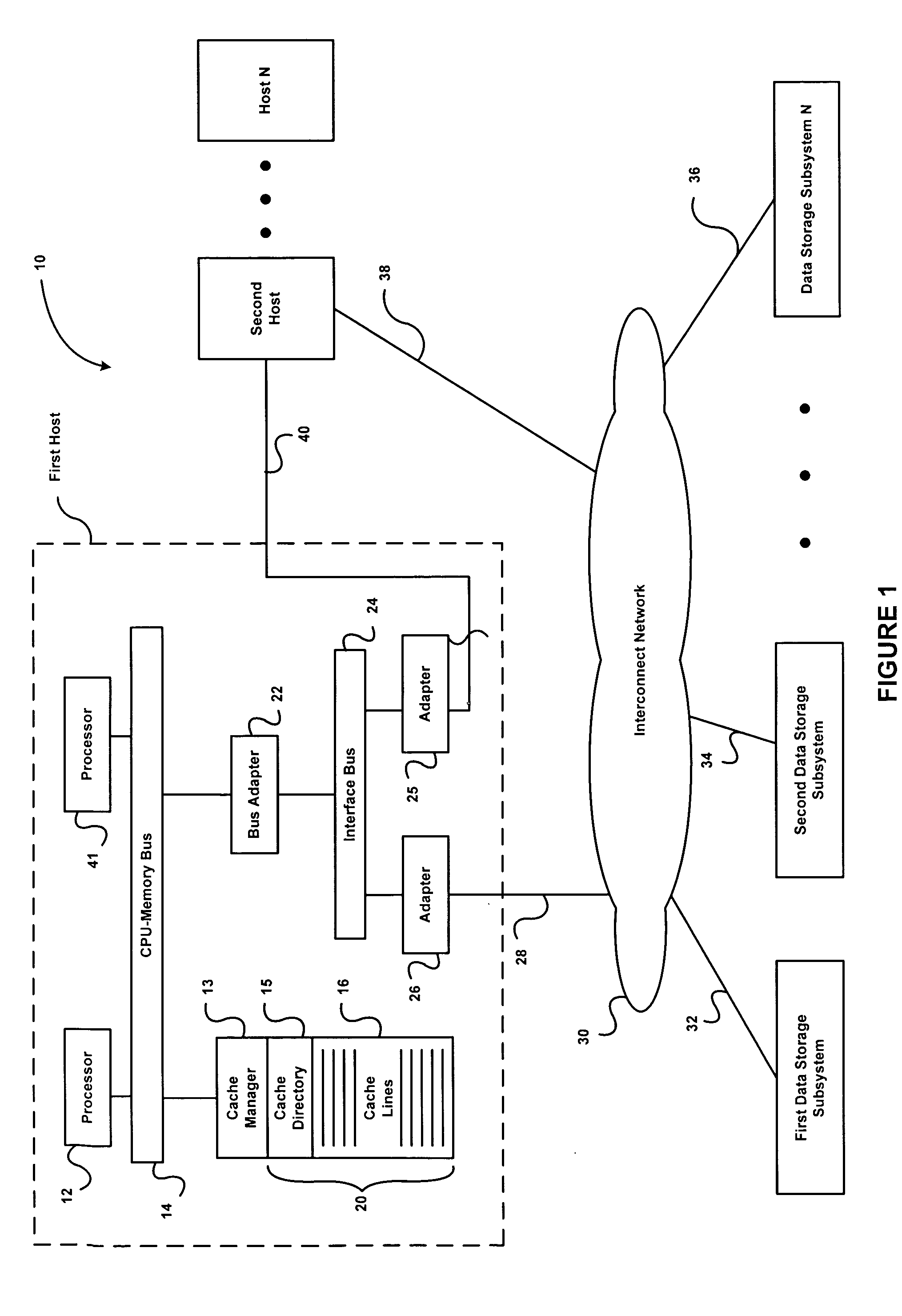
Coil array autocalibration MR imaging
InactiveUS6289232B1Shorten the timeEasy accessDiagnostic recording/measuringSensorsData spaceIn vivo
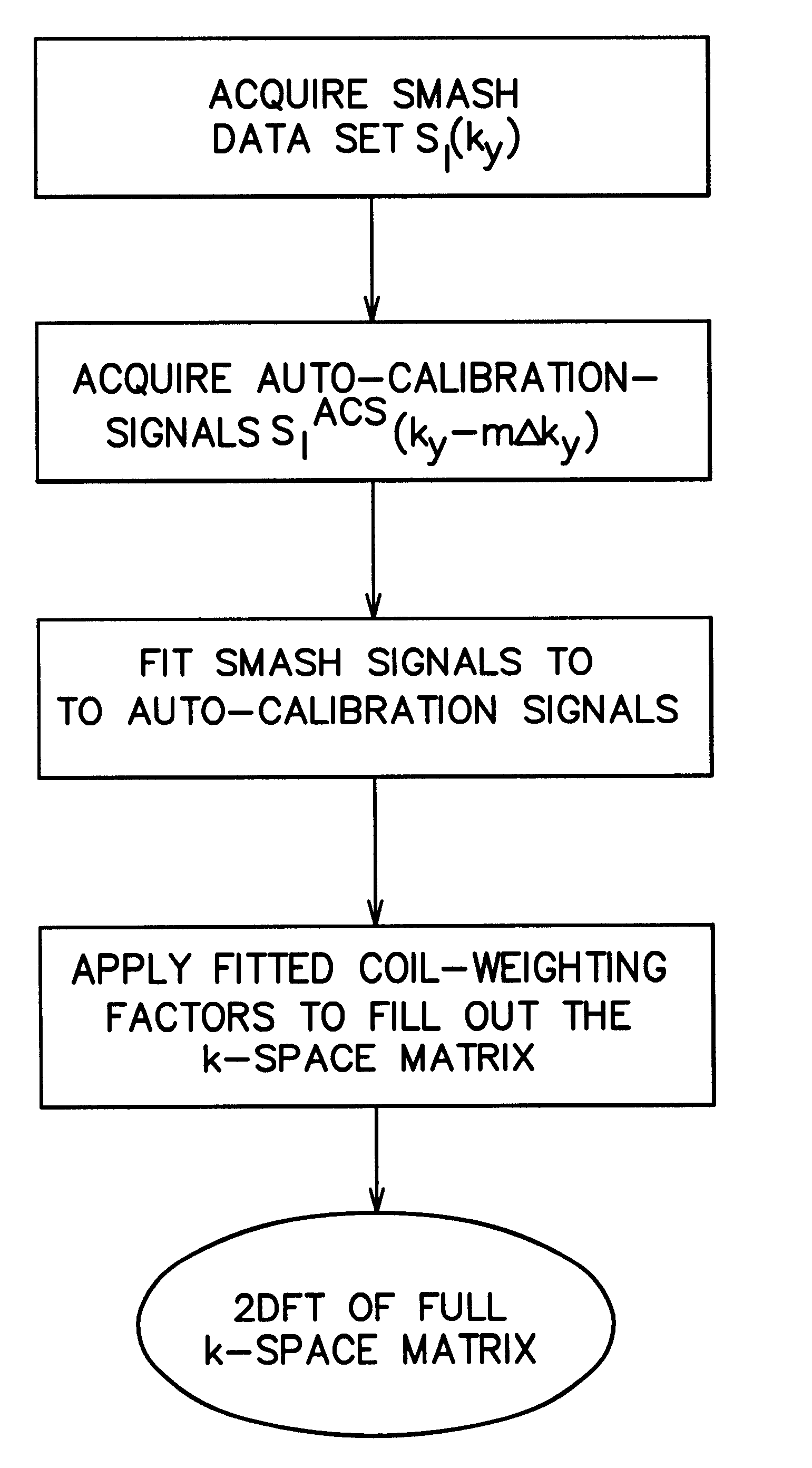
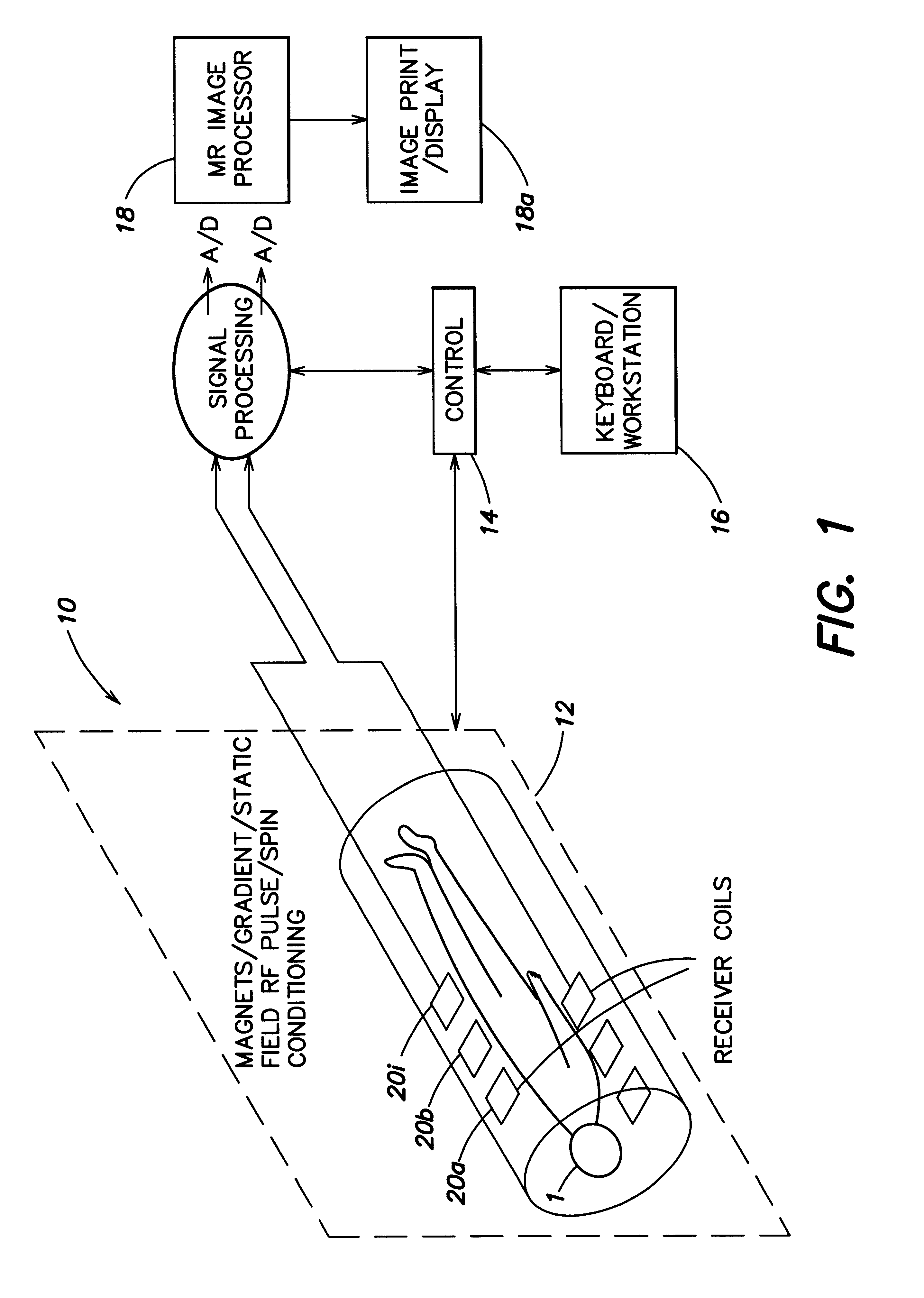
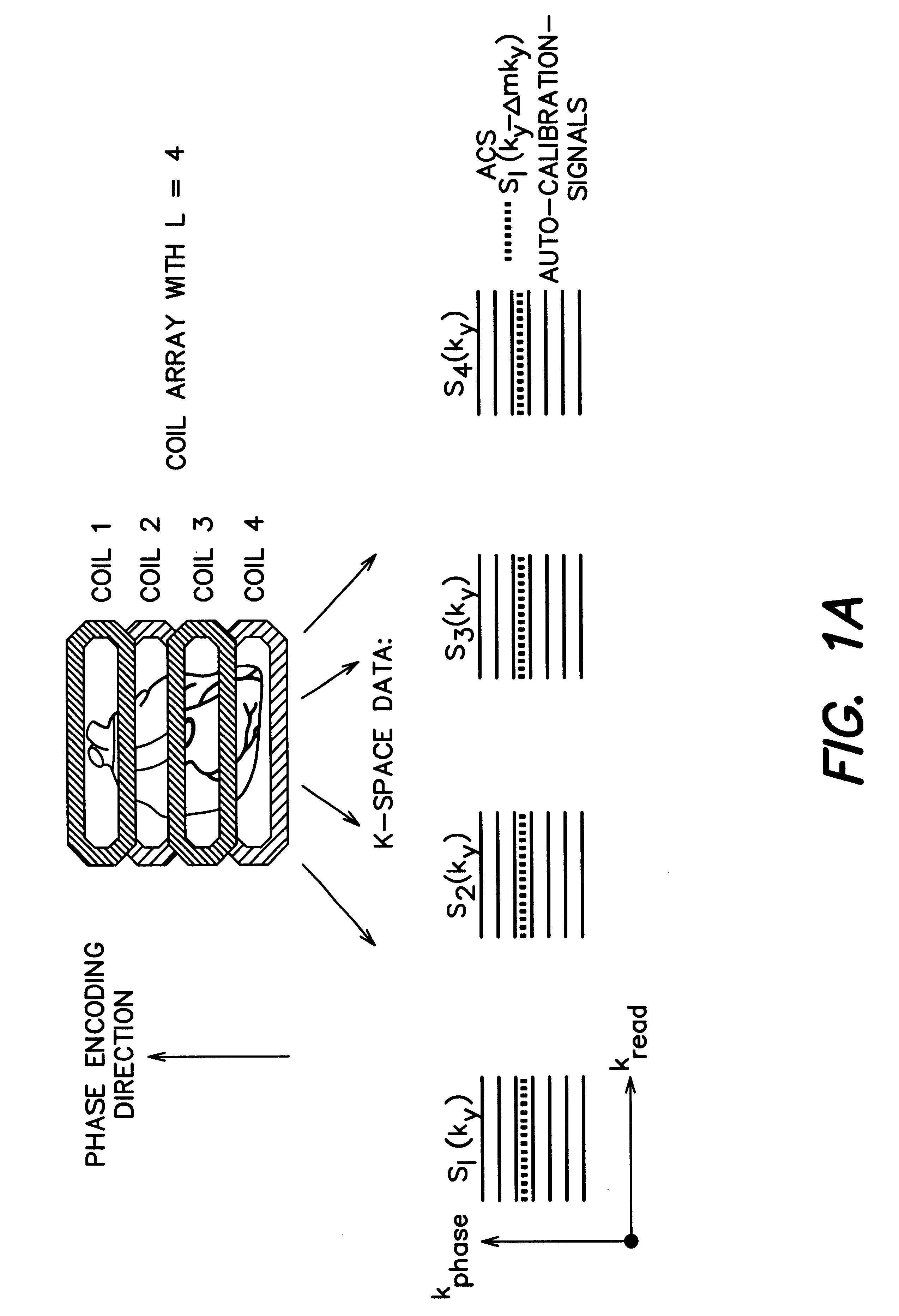
A magnetic resonance (MR) imaging apparatus and technique exploits spatial information inherent in a surface coil array to increase MR image acquisition speed, resolution and / or field of view. Magnetic resonance response signals are acquired simultaneously in the component coils of the array and, using an autocalibration procedure, are formed into two or more signals to fill a corresponding number of lines in the signal measurement data matrix. In a Fourier embodiment, lines of the k-space matrix required for image production are formed using a set of separate, preferably linear combinations of the component coil signals to substitute for spatial modulations normally produced by phase encoding gradients. One or a few additional gradients are applied to acquire autocalibration (ACS) signals extending elsewhere in the data space, and the measured signals are fitted to the ACS signals to develop weights or coefficients for filling additional lines of the matrix from each measurement set. The ACS lines may be taken offset from or in a different orientation than the measured signals, for example, between or across the measured lines. Furthermore, they may be acquired at different positions in k-space, may be performed at times before, during or after the principal imaging sequence, and may be selectively acquired to optimized the fitting for a particular tissue region or feature size. The in vivo fitting procedure is readily automated or implemented in hardware, and produces an enhancement of image speed and / or quality even in highly heterogeneous tissue. A dedicated coil assembly automatically performs the calibration procedure and applies it to measured lines to produce multiple correctly spaced output signals. One application of the internal calibration technique to a subencoding imaging process applies the ACS in the central region of a sparse set of measured signals to quickly form a full FOV low resolution image. The full FOV image is then used to determine coil sensitivity related information and dealias folded images produced from the sparse set.
Owner:BETH ISRAEL DEACONESS MEDICAL CENT INC
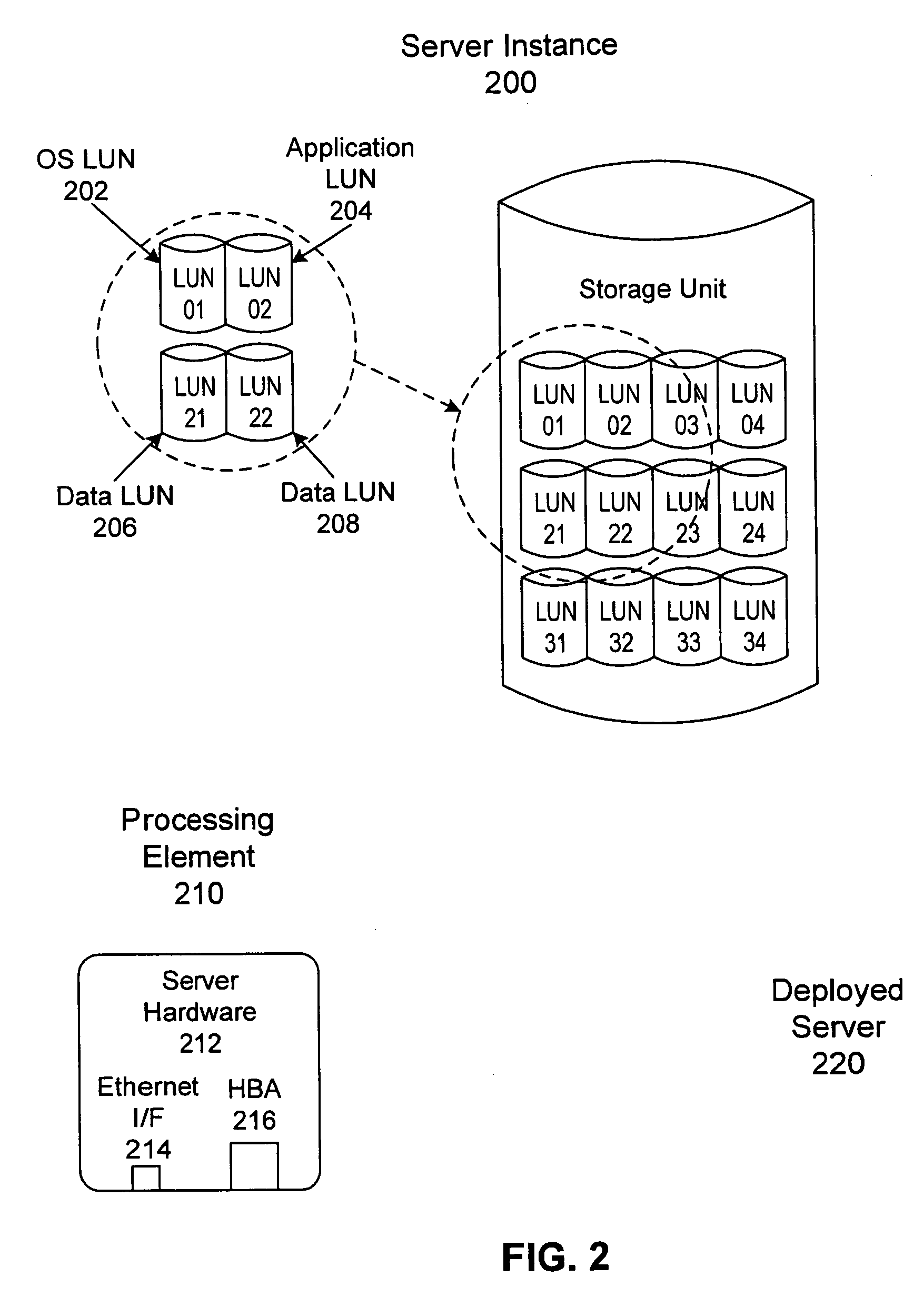
Automated deployment of operating system and data space to a server
InactiveUS20060173912A1Simple processEasy to deploySpecial data processing applicationsSoftware deploymentGraphicsOperational system
A server instance, which is a collection of LUNs, containing an operating system, any applications and data storage. A processing element is the physical hardware. The combination is a server as normally understood. Templates are used to define server instances and server types to simplify deploying a server instance to a processing element. A graphical user interface provides the templates where the particular storage groups are identified and then server instances are created from lists of operating systems, applications, and available storage. The management service processor is a PXE server and provides the necessary software to identify the components of the processing element and correlate between the processing element and a server instance. The management service processor then automatically provides software to the processing element to allow it correctly boot. The management service processor manages the interconnection of the processing element and the relevant LUNs.
Owner:BROCADE COMMUNICATIONS SYSTEMS
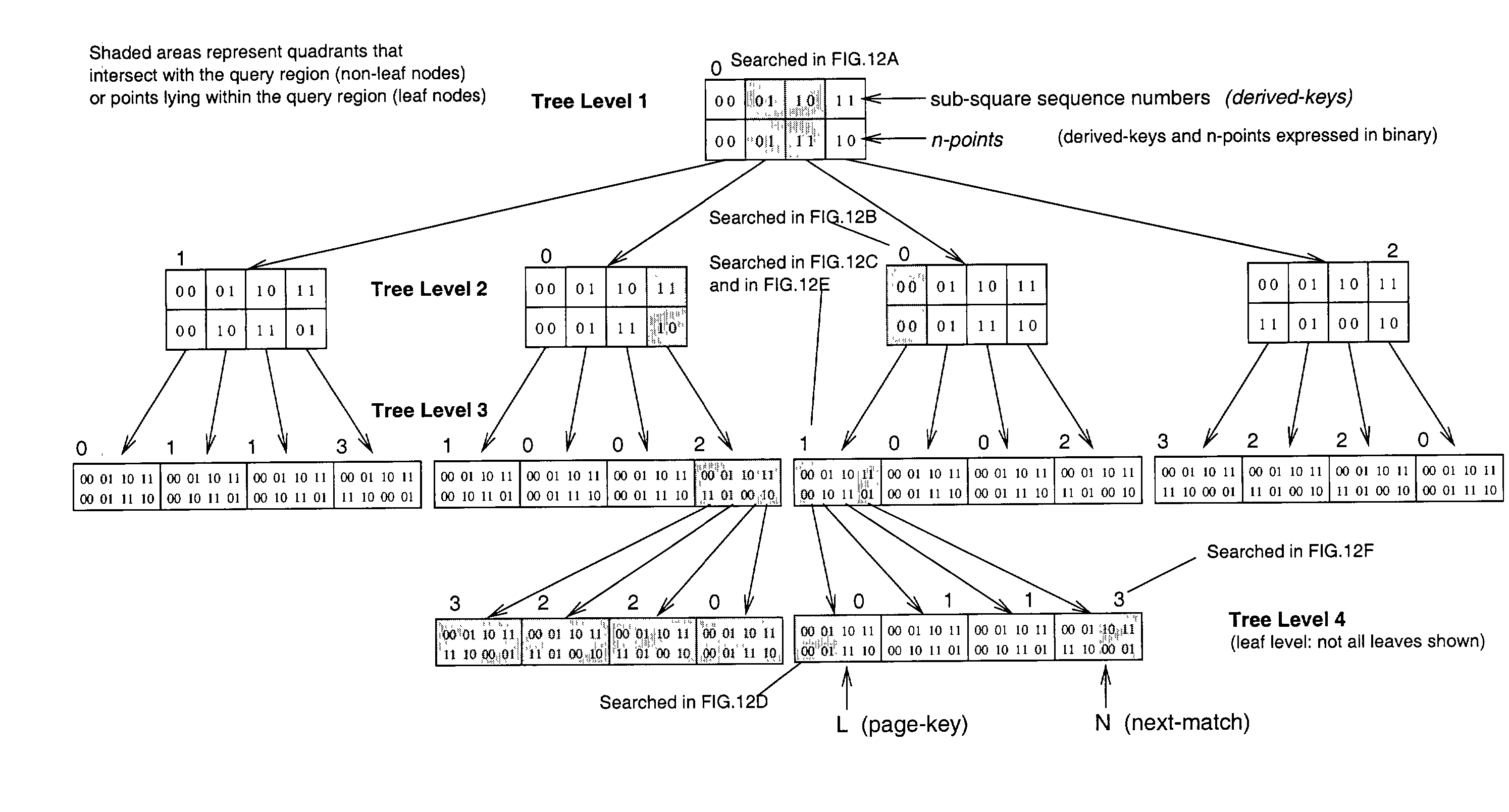
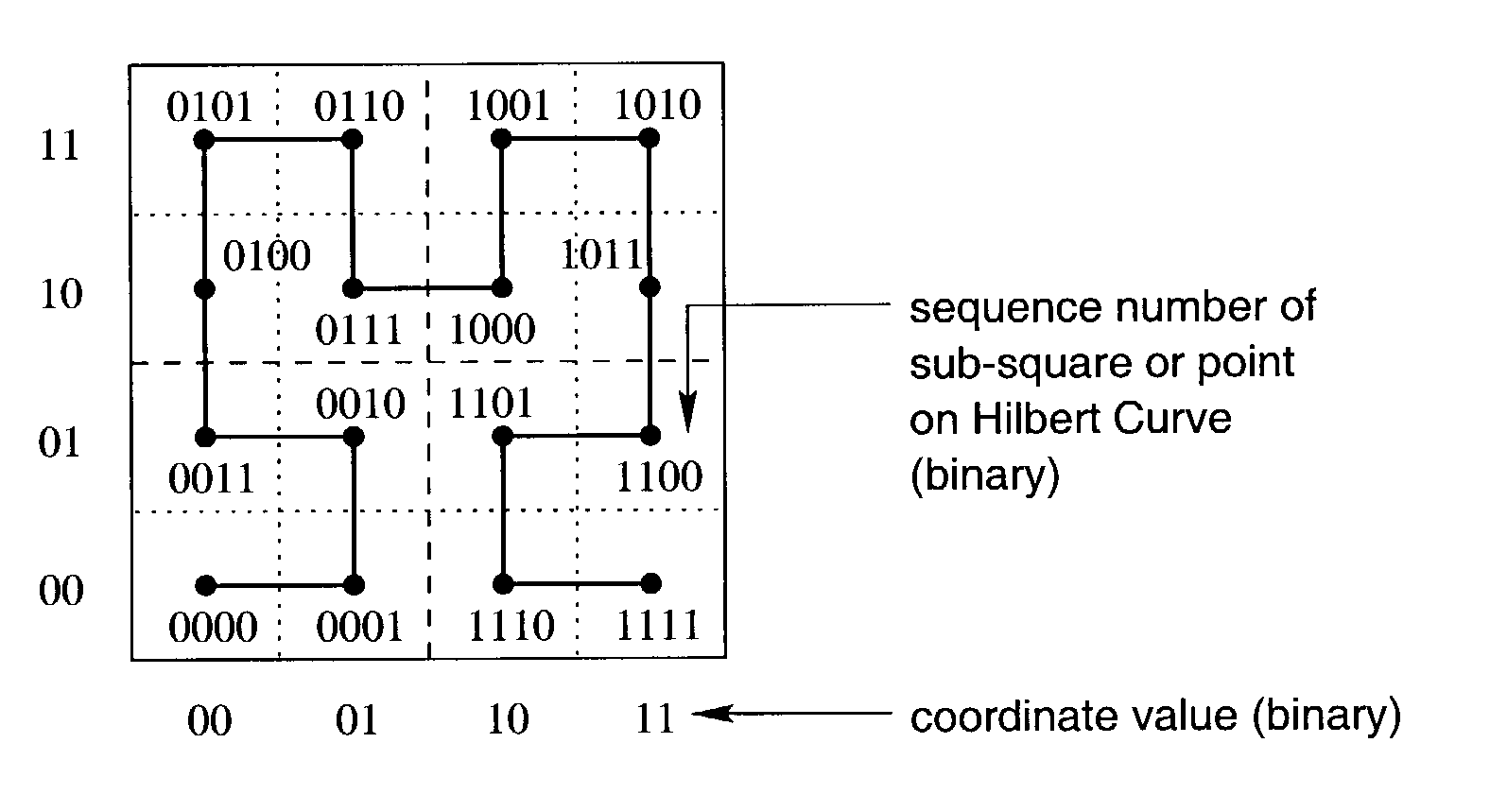
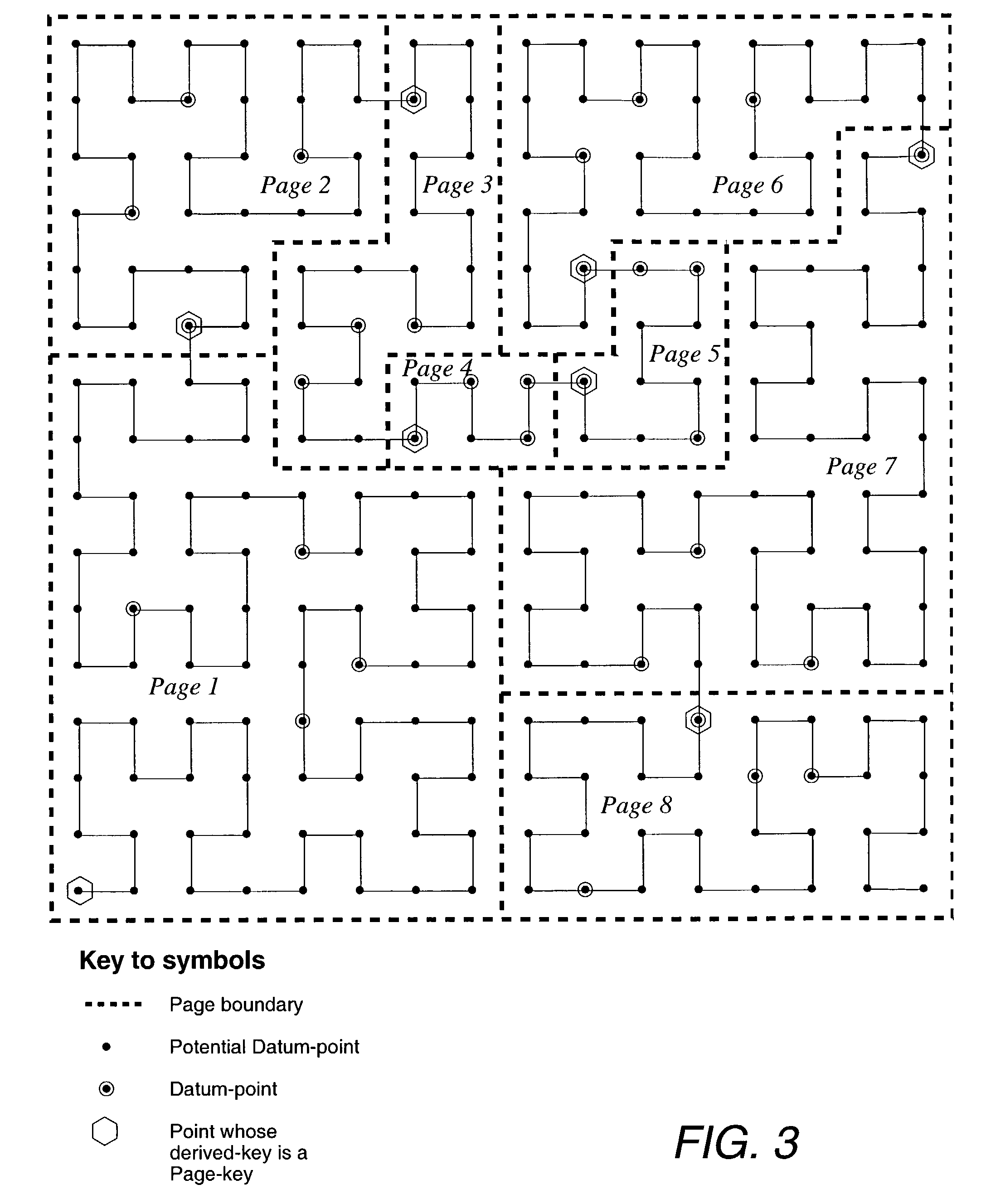
Method of storing and retrieving multi-dimensional data using the hilbert curve
InactiveUS20030004938A1Data processing applicationsDigital data information retrievalData spaceHilbert space
An improved method of partitioning and indexing multi-dimensional data that maps the data to one-dimensional values according to the sequence in which an approximation of a Hilbert space-filling curve passes through all of the points corresponding to potential multi-dimensional data in a data space. Data is partitioned into pages, each corresponding to a length of Hilbert curve. A page identifier is the sequence of the first point on its corresponding Hilbert curve section. The mapping orders data and also orders the data pages that contain data within a database. Mapping multi-dimensional data to one-dimensional values enables the data to be indexed using any one-dimensional index structure. The practical application of the indexing method is made viable and useful by the provision of a querying algorithm enabling data to be selectively retrieved in response to queries wherein all or some of the data that lies within a rectangular space within multi-dimensional space is required to be retrieved. The querying algorithm identifies pages whose corresponding curve sections intersect with a query region. The first intersecting page is found by calculating the lowest one-dimensional value corresponding to a possible multi-dimensional data value or point within the query region, and looking up in the index to find which page may contain this point. The next intersecting page, if it exists, is found by calculating the lowest one-dimensional value equal to or greater than the identifier of the next page to the one just identified. This new lowest one-dimensional, if found, is used to look up in the index and find the next page intersecting with the query region. Subsequent pages to be found, if any, are determined in a similar manner until no more are found. Pages found to intersect the query region can be searched for data lying within the query region.
Owner:LAWDER JONATHAN KEIR
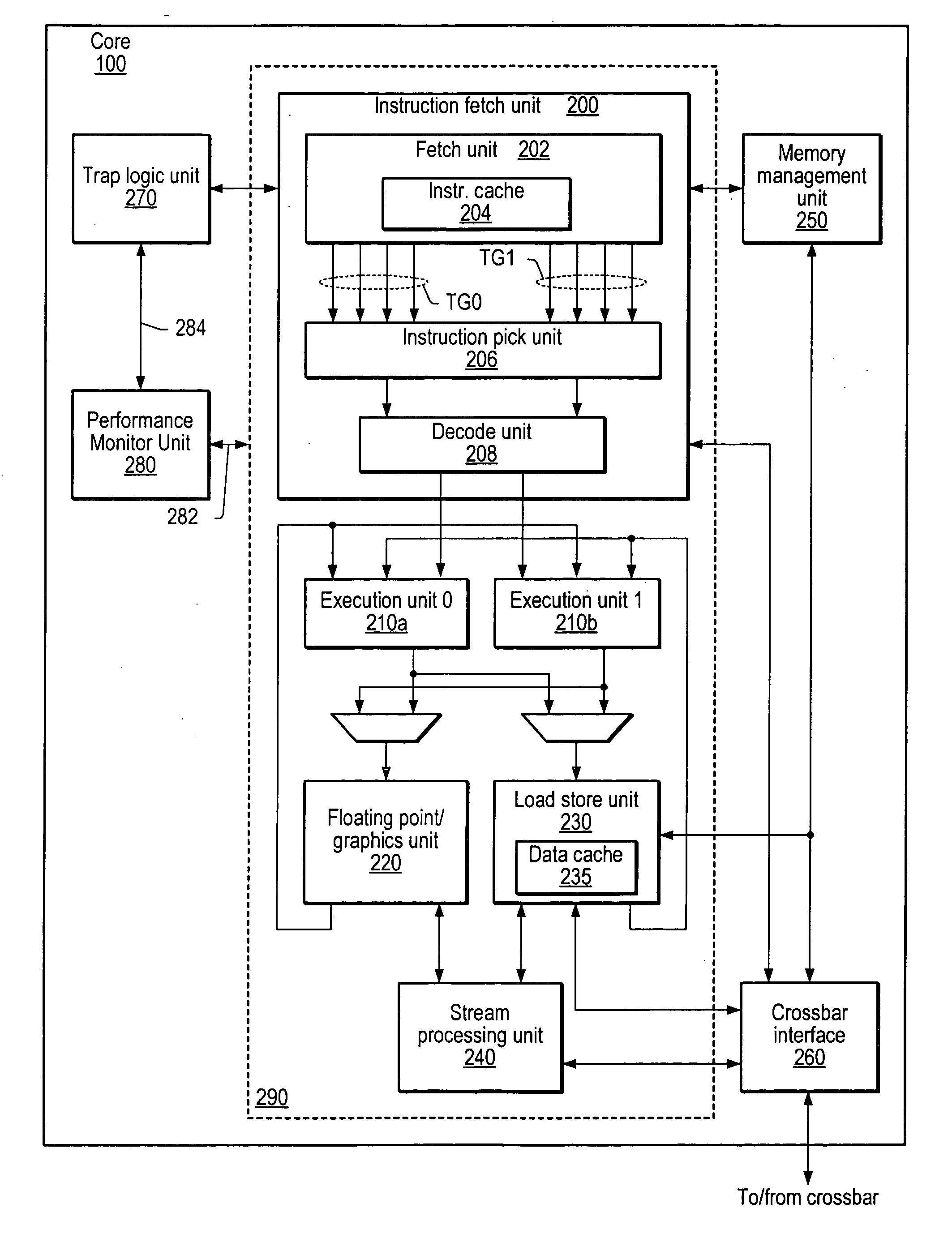
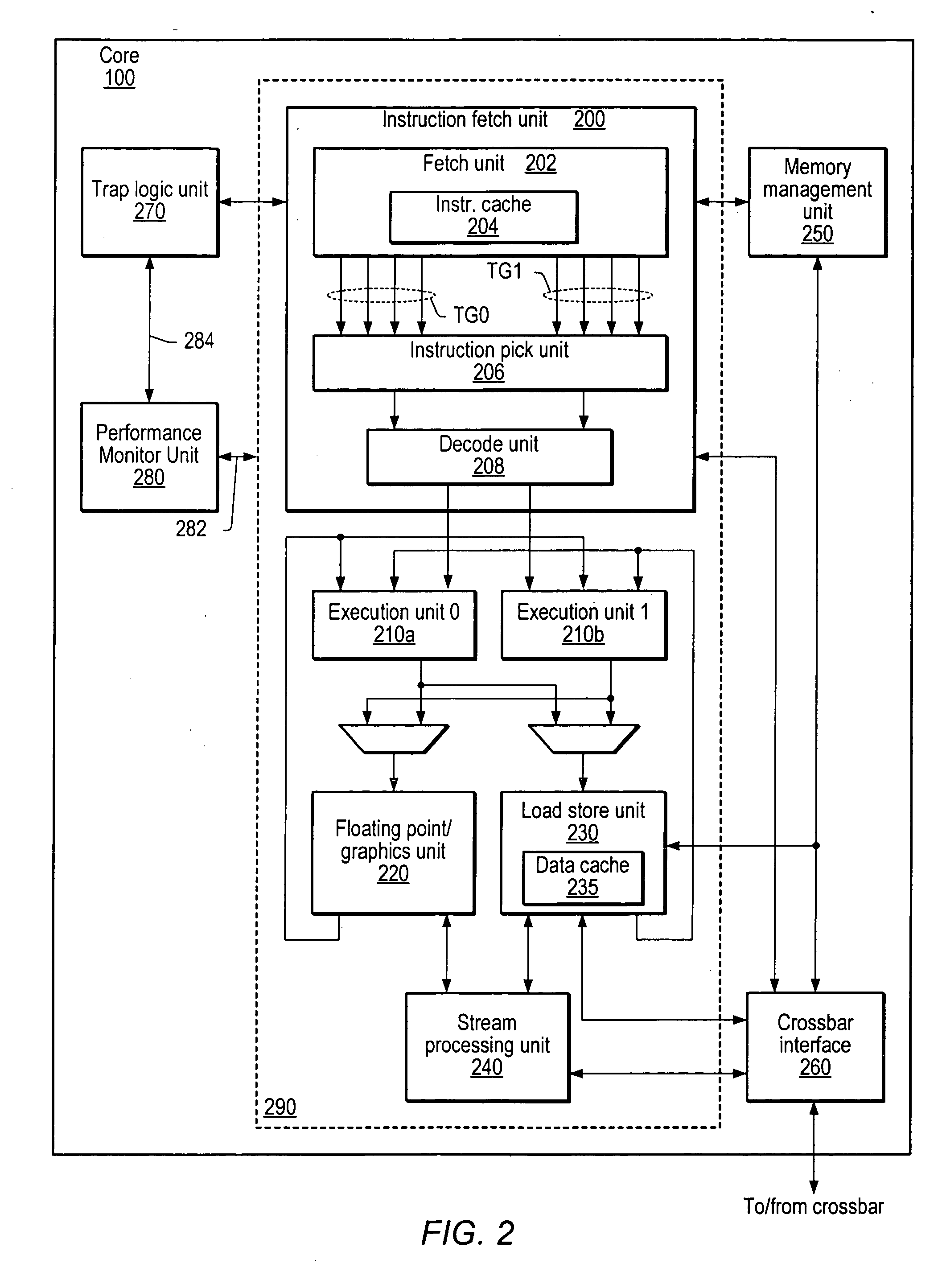
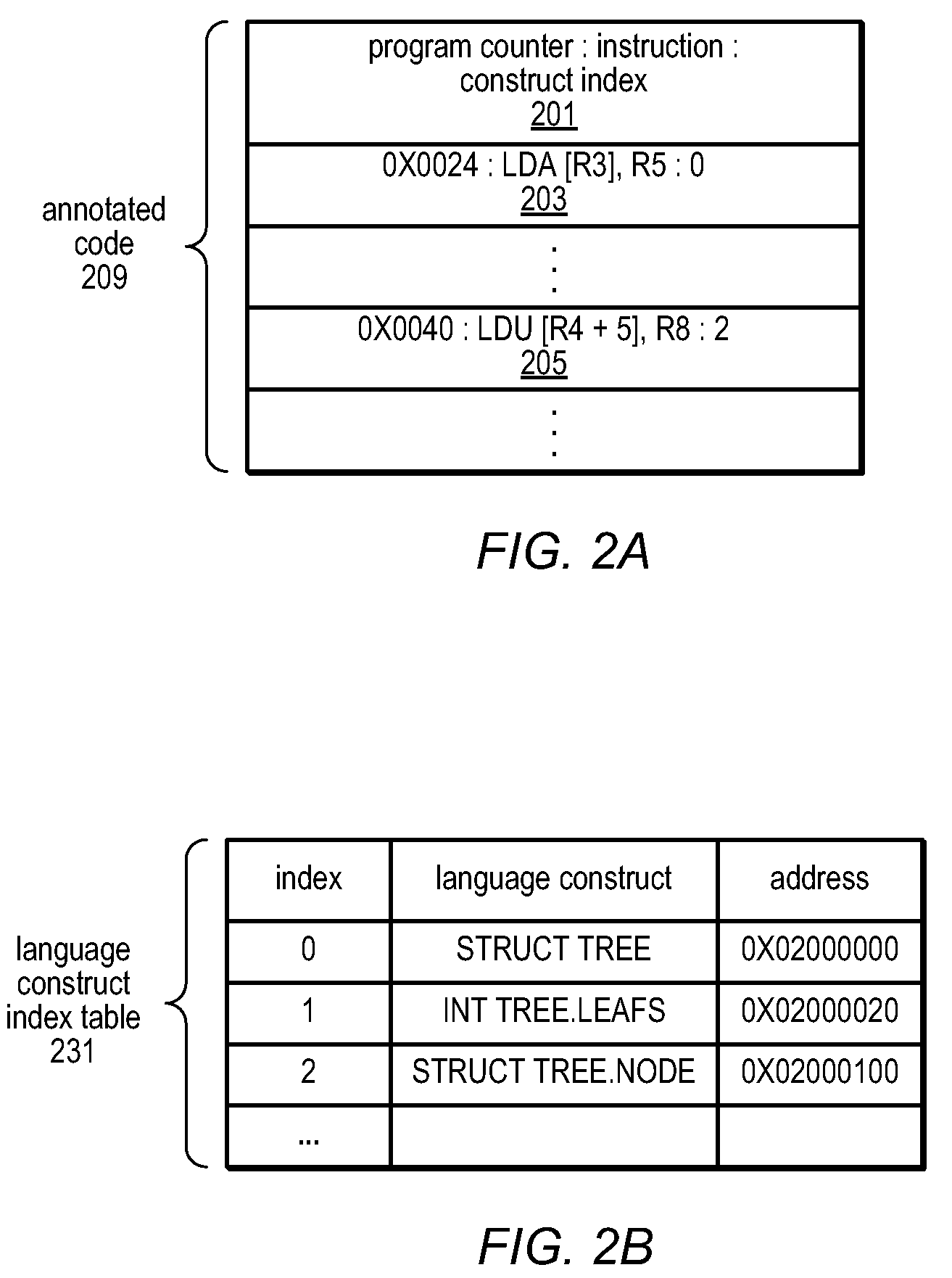
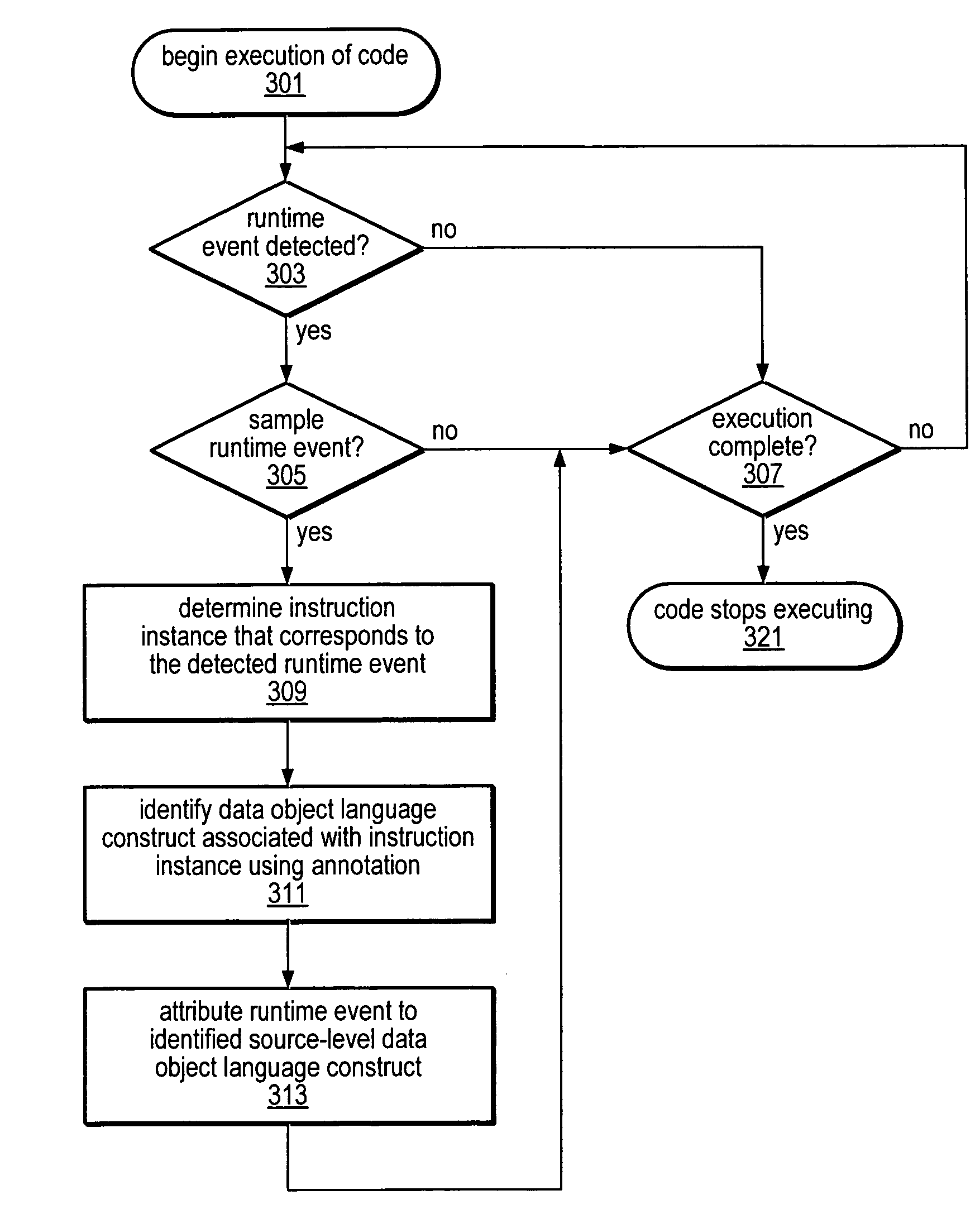
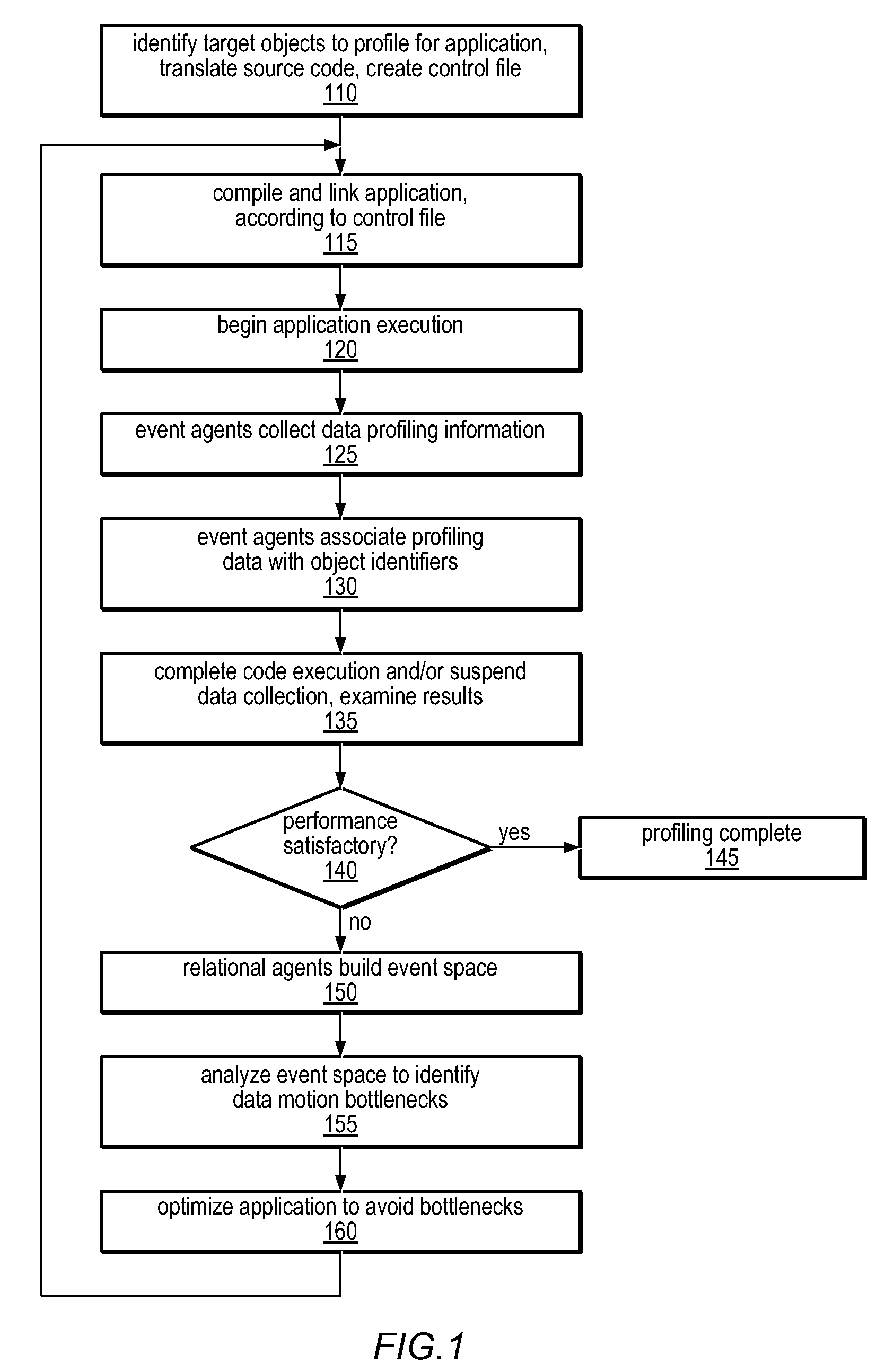
Method and apparatus for precisely identifying effective addresses associated with hardware events
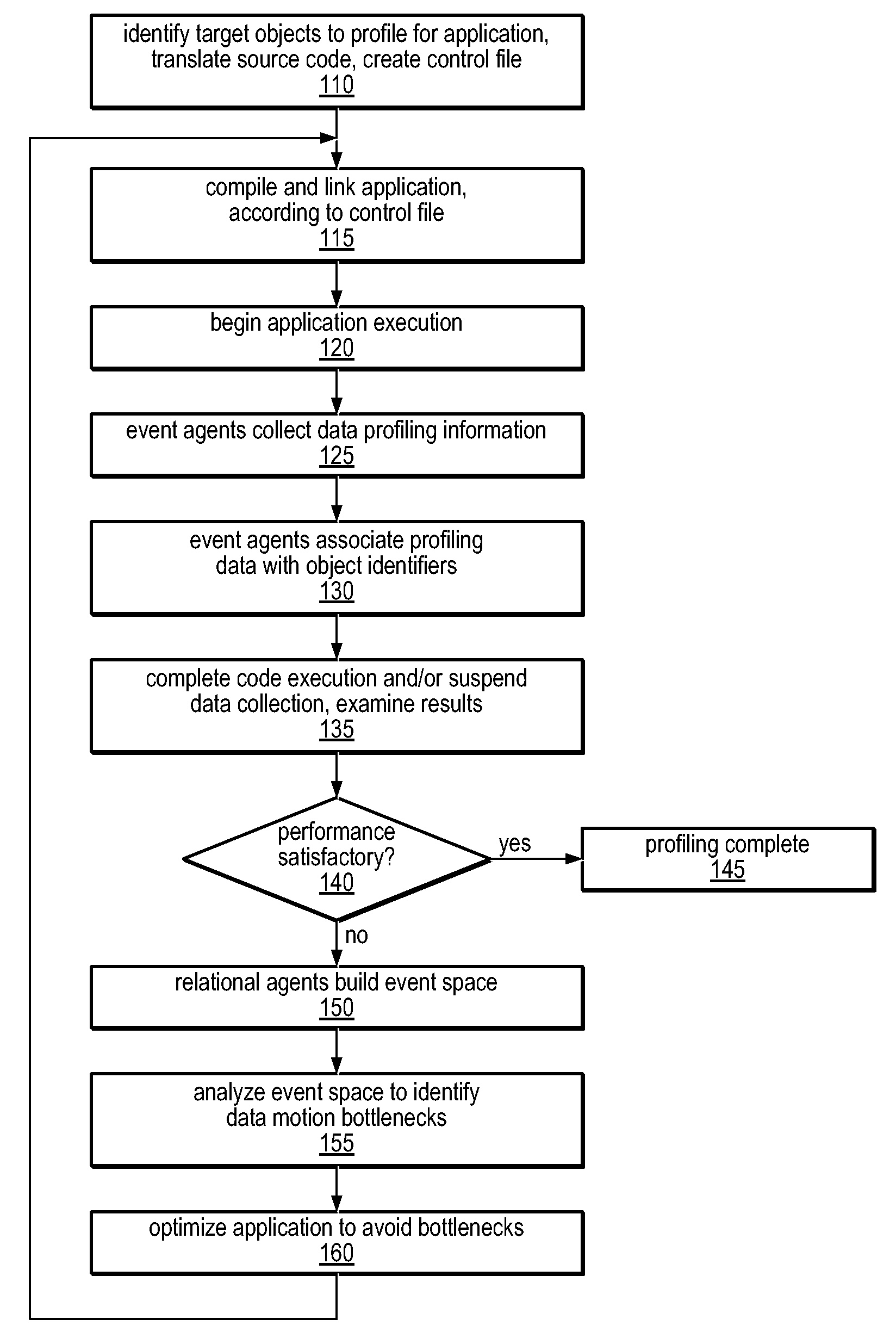
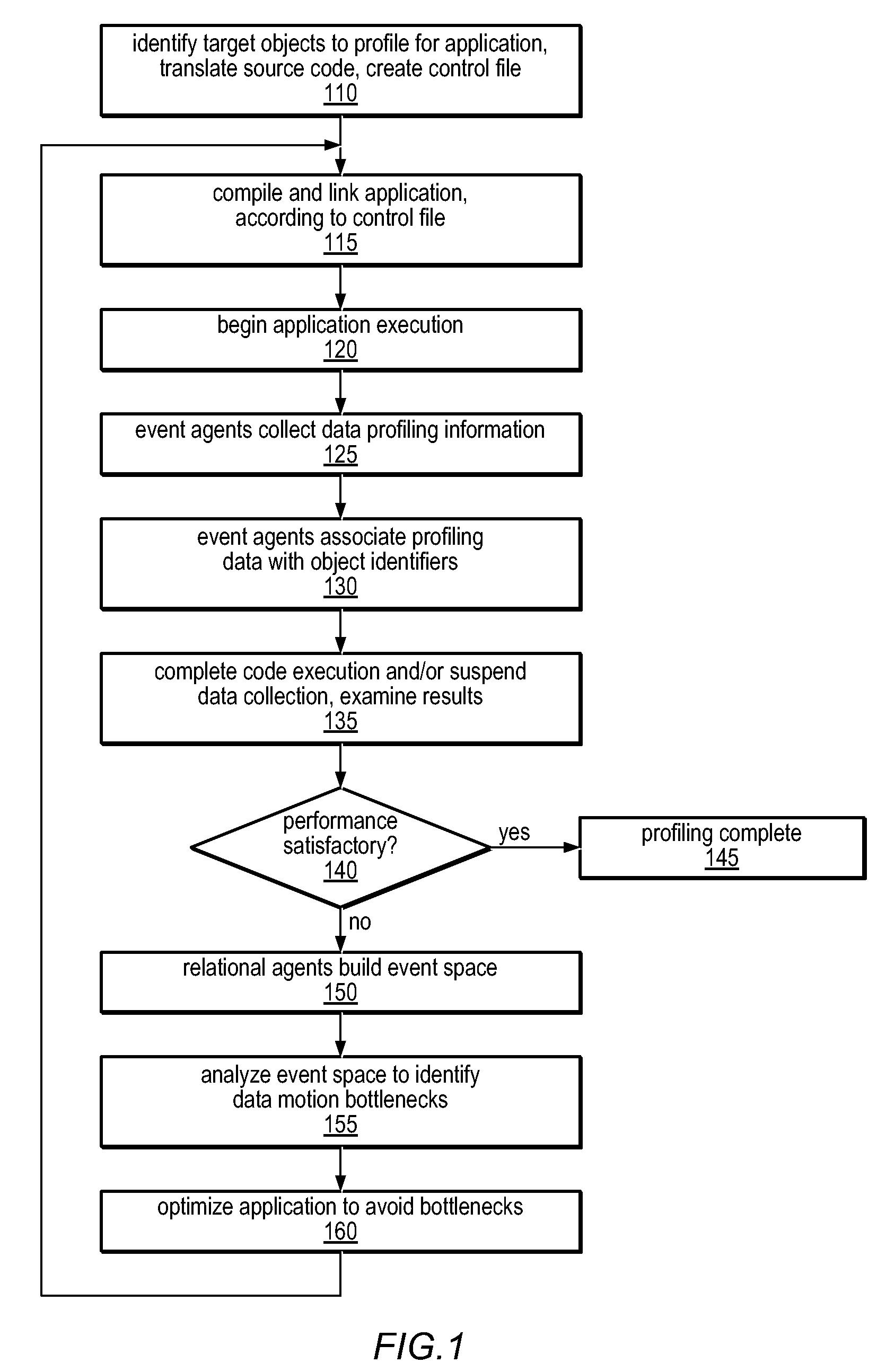
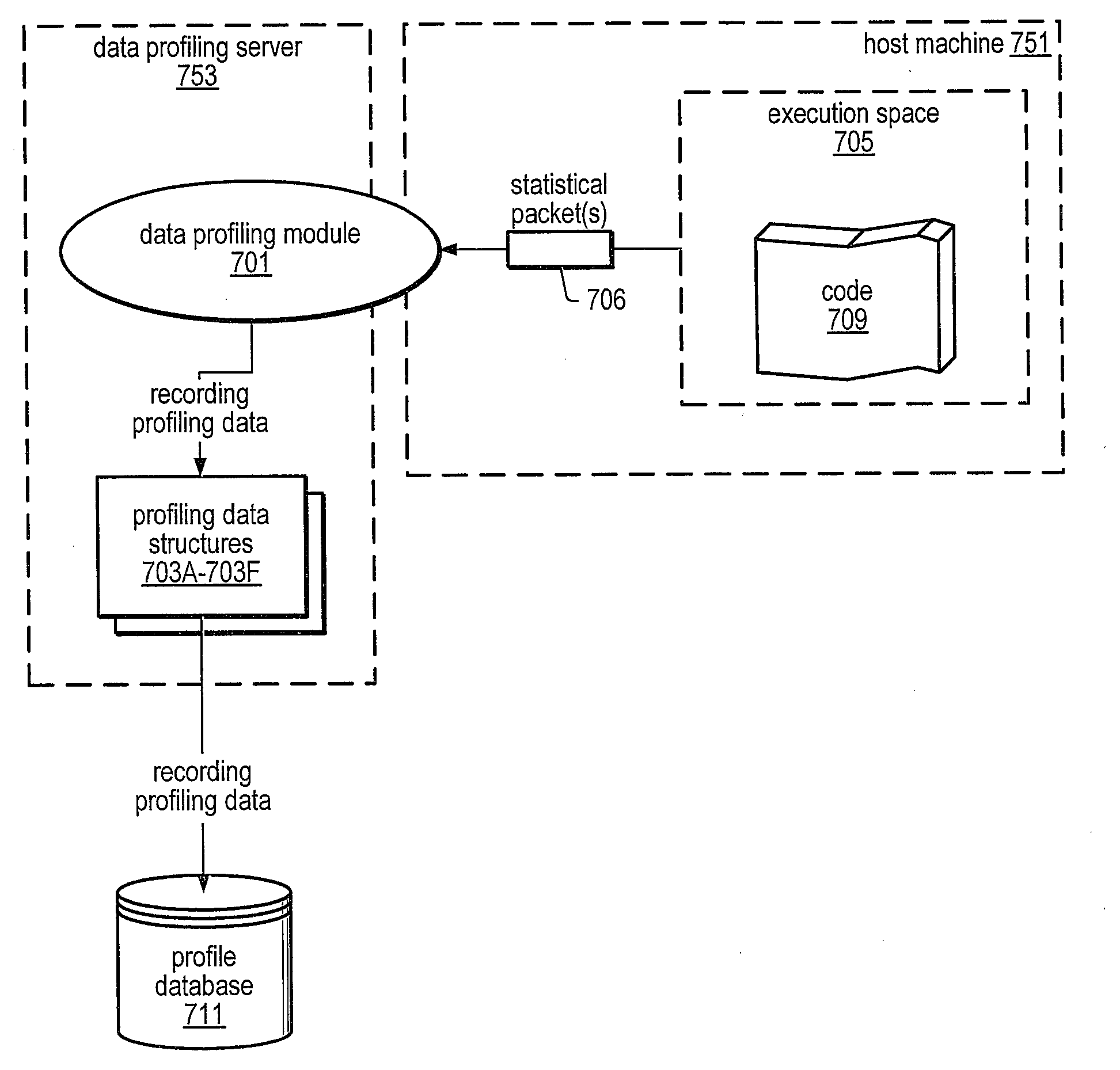
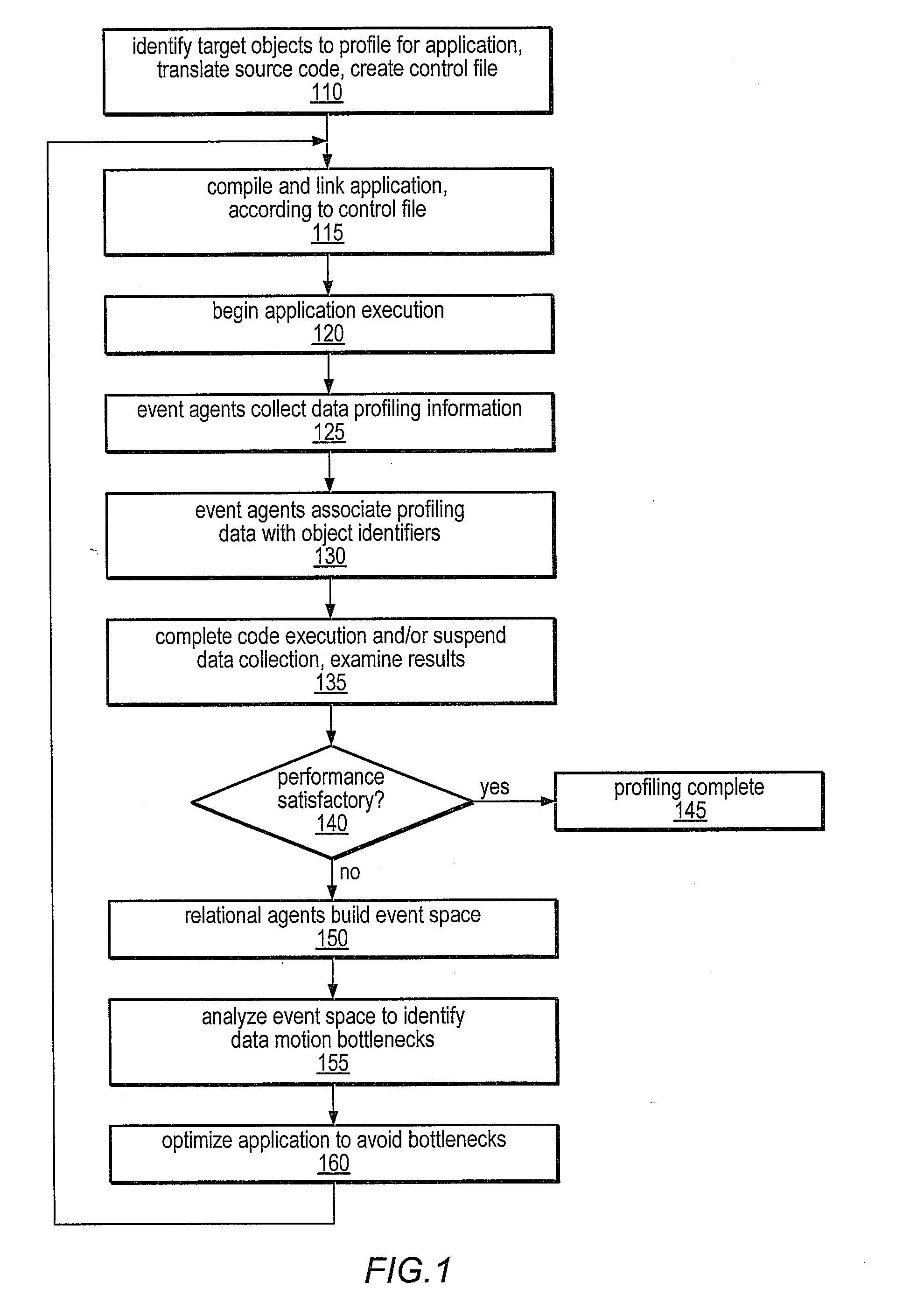
A system and method for precisely identifying an instruction causing a performance-related event is disclosed. The instruction may be detected while in a pipeline stage of a microprocessor preceding a writeback stage and the microprocessor's architectural state may not be updated until after information identifying the instruction is captured. The instruction may be flushed from the pipeline, along with other instructions from the same thread. A hardware trap may be taken when the instruction is detected and / or when an event counter overflows or is within a given range of overflowing. A software trap handler may capture and / or log information identifying the instruction, such as one or more extended address elements, before returning control and initiating a retry of the instruction. The captured and / or logged information may be stored in an event space database usable by a data space profiler to identify performance bottlenecks in the application containing the instruction.
Owner:ORACLE INT CORP
Capturing data changes utilizing data-space tracking
InactiveUS7085787B2Maximum efficiencyData processing applicationsDigital data information retrievalOriginal dataData space
Owner:INT BUSINESS MASCH CORP
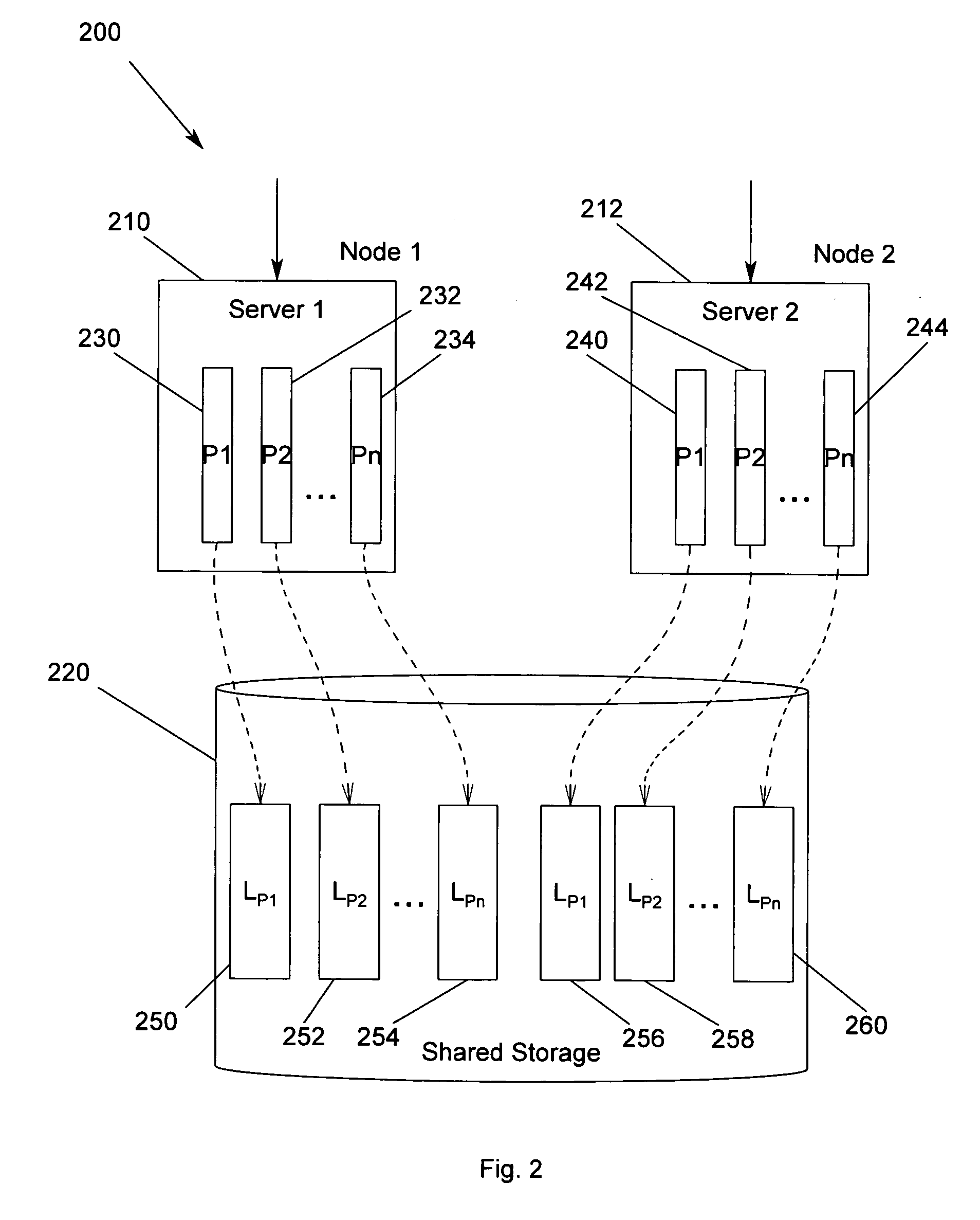
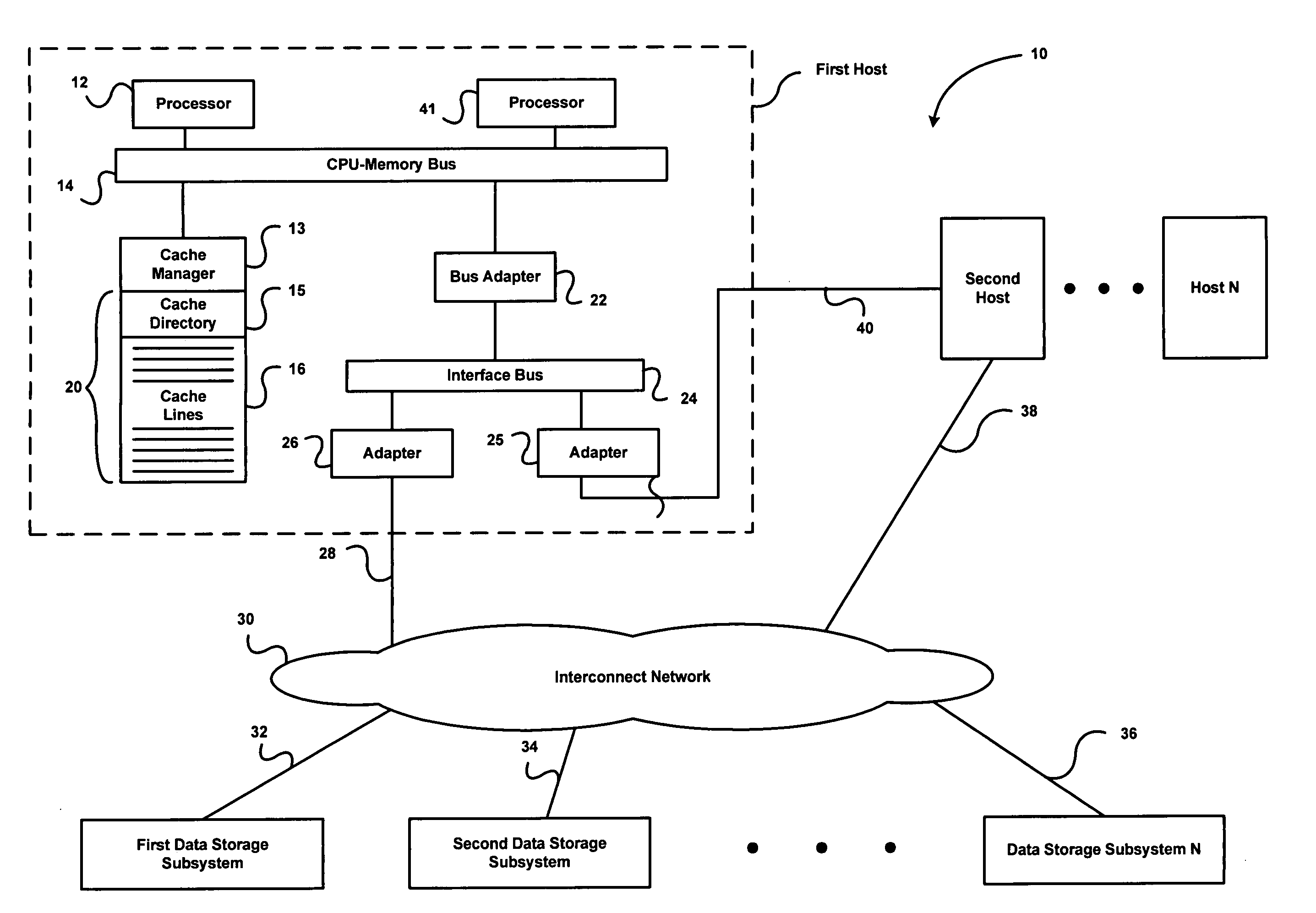
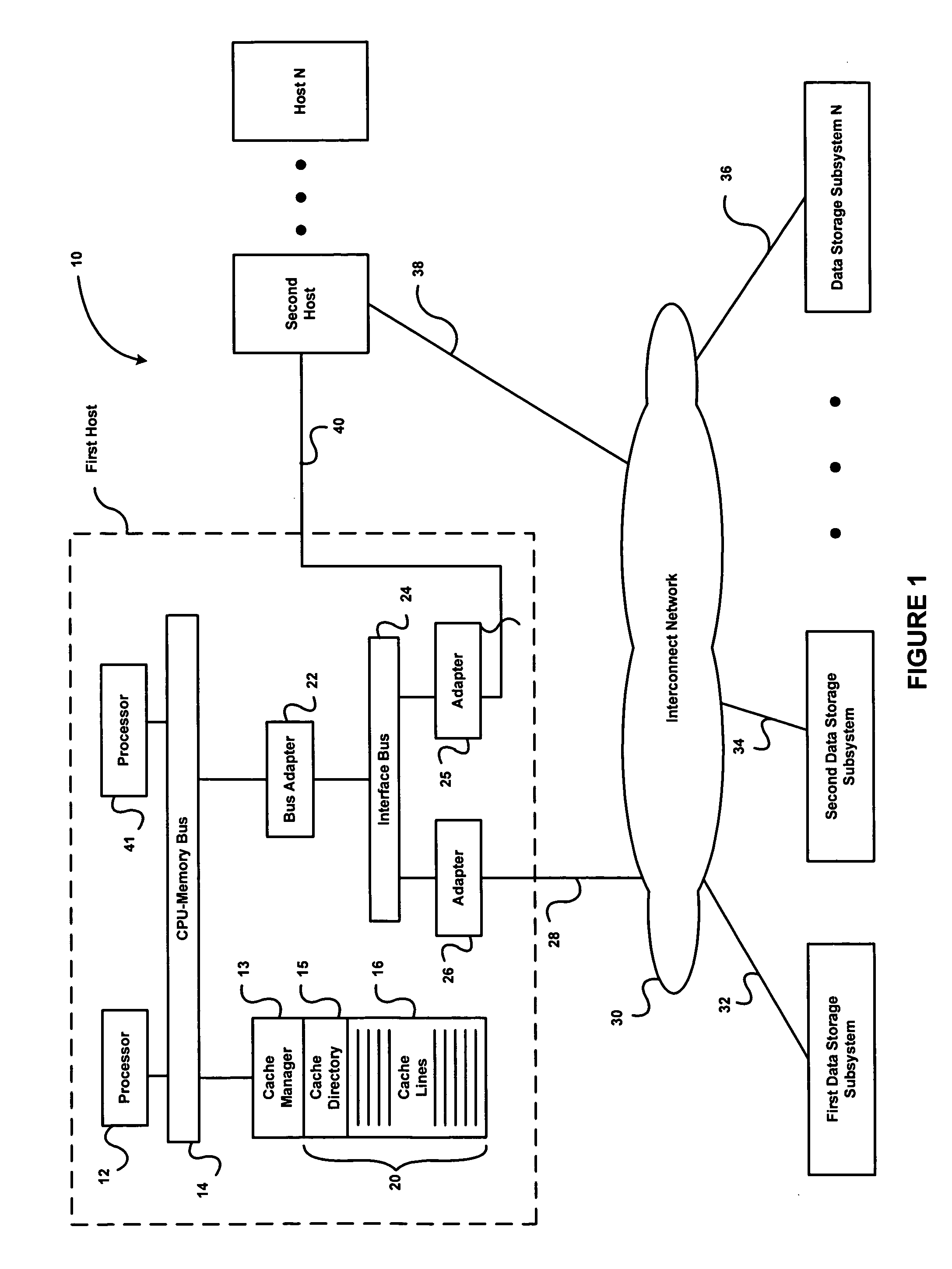
Method, apparatus and program storage device for providing failover for high availability in an N-way shared-nothing cluster system
A method, apparatus and program storage device for providing failover for continuous or near-continuous availability in an N-way logical shared-nothing cluster system is disclosed. Cluster application data space partitions are assigned to each node in the cluster and each node's or server software's internal architecture is partitioned in accordance with the application data partitions assigned to the node. Cluster-integrity protection is performed. A failover and recovery protocol is performed based upon the assigned partitions and the partitioned and bound internal architecture. Containment of the impact of failure is provided such that most of the application data space partitions are not impacted. Affected partition sets are failed over fast and in constant time and so actual load on the surviving nodes does not affect failover duration. When shared storage is not provided, synchronous log replication may be used to facilitate failover and log-based recovery.
Owner:IBM CORP
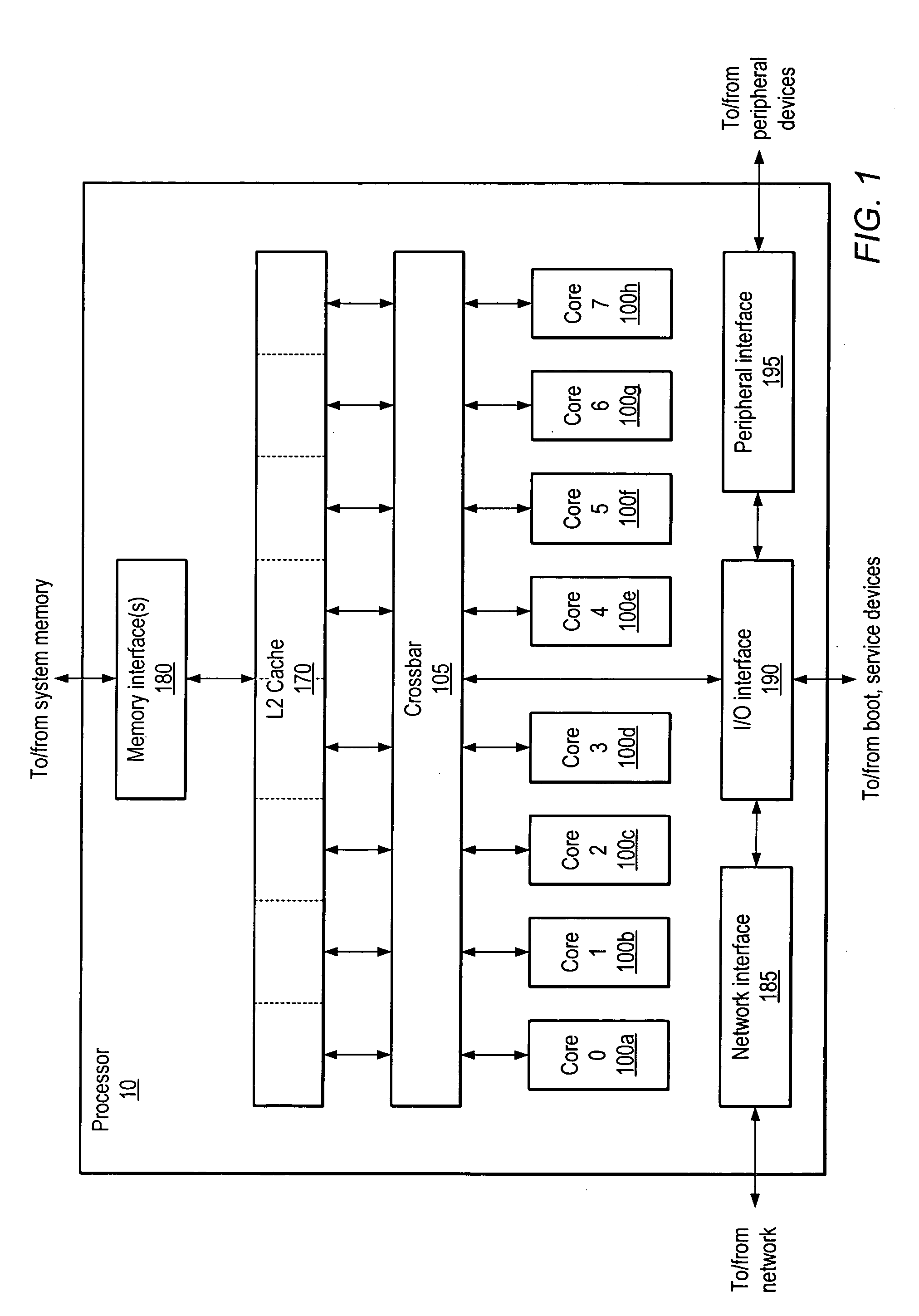
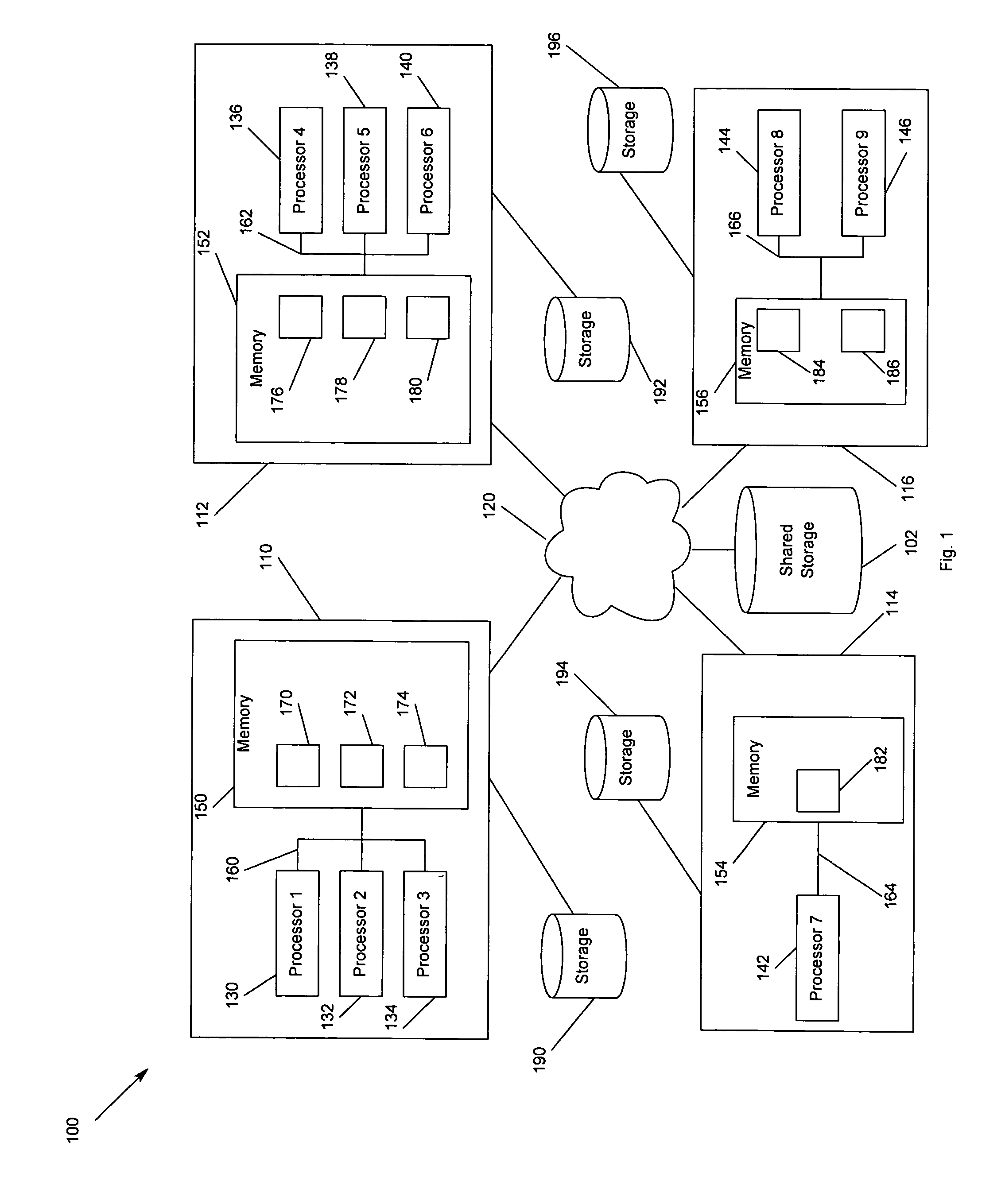
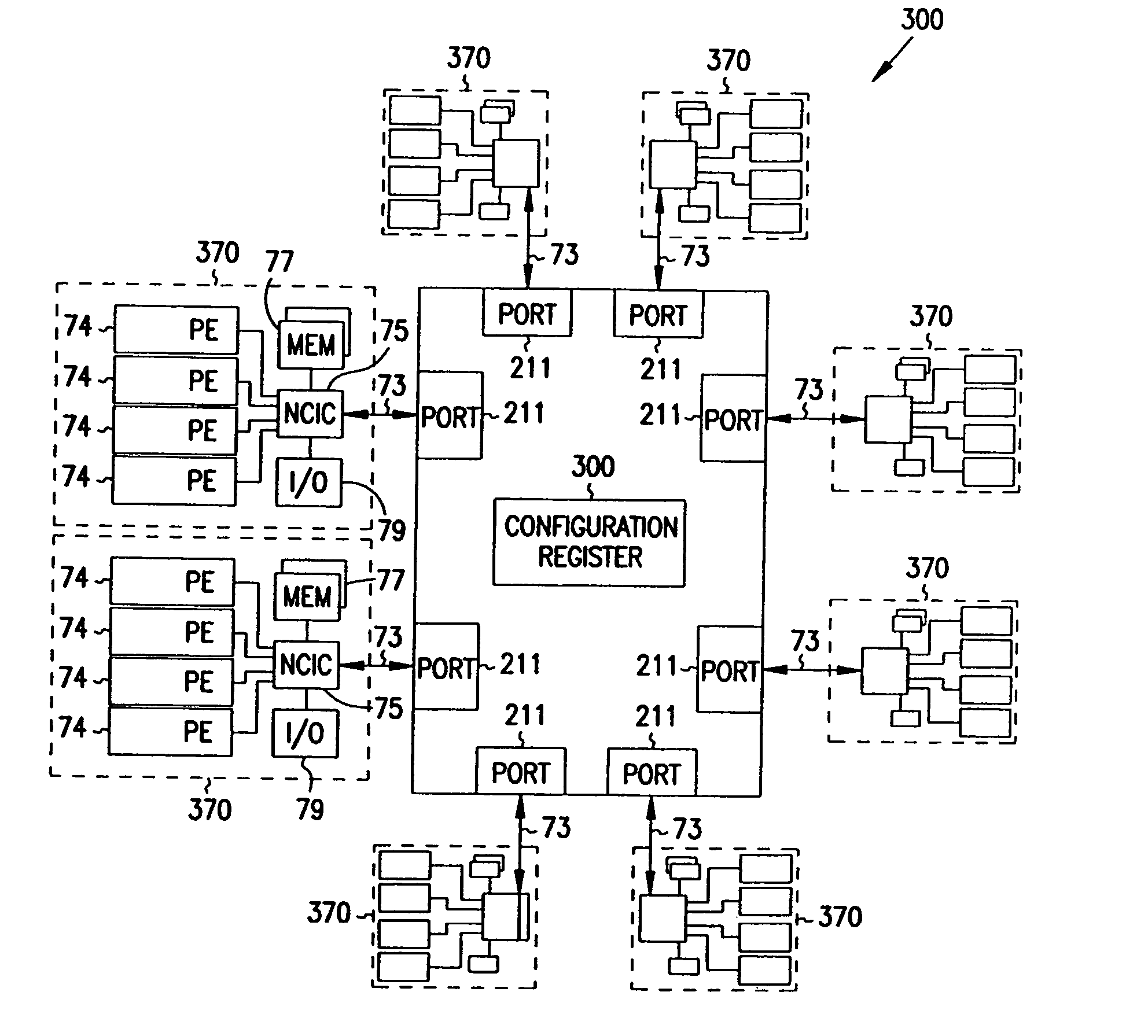
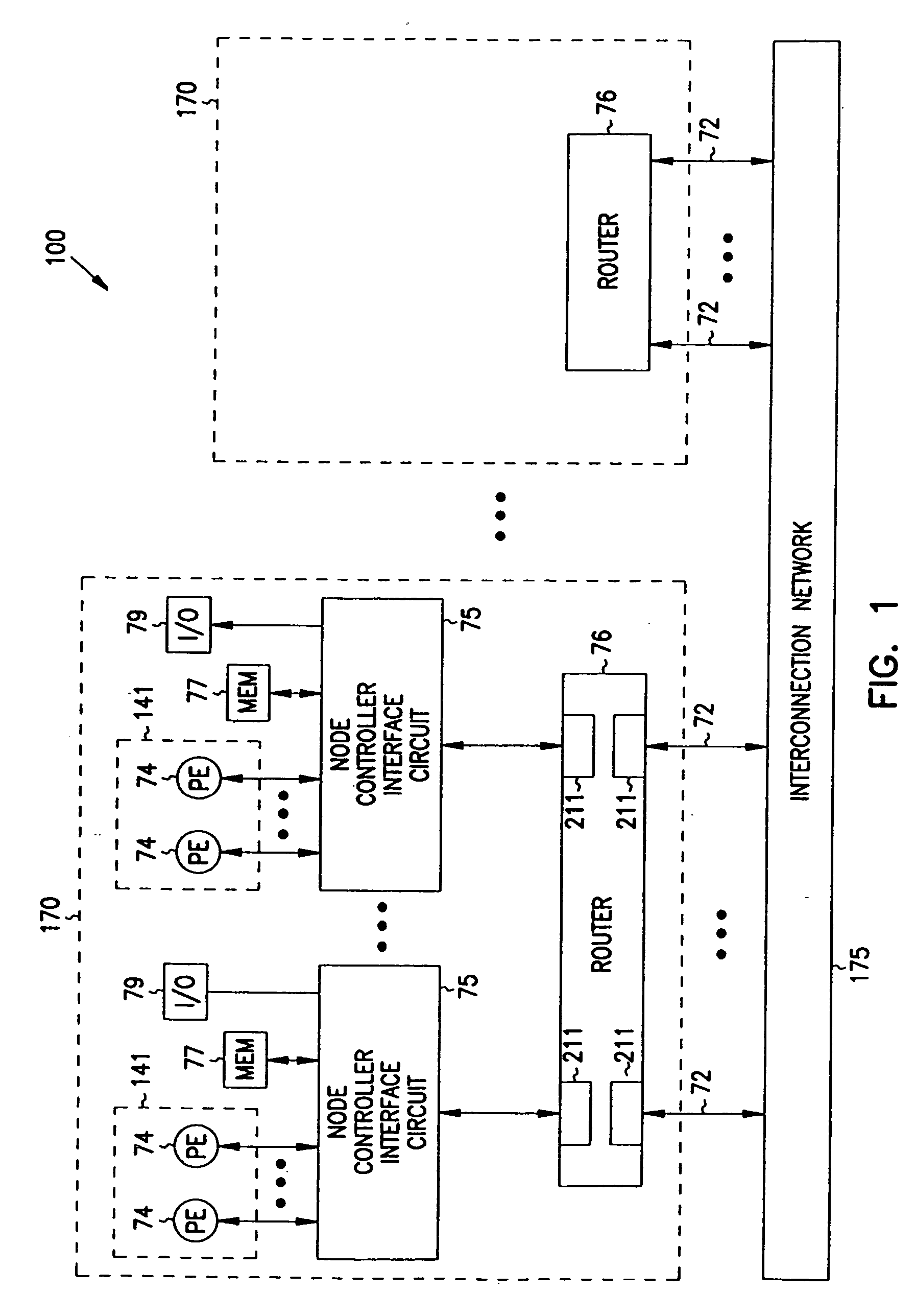
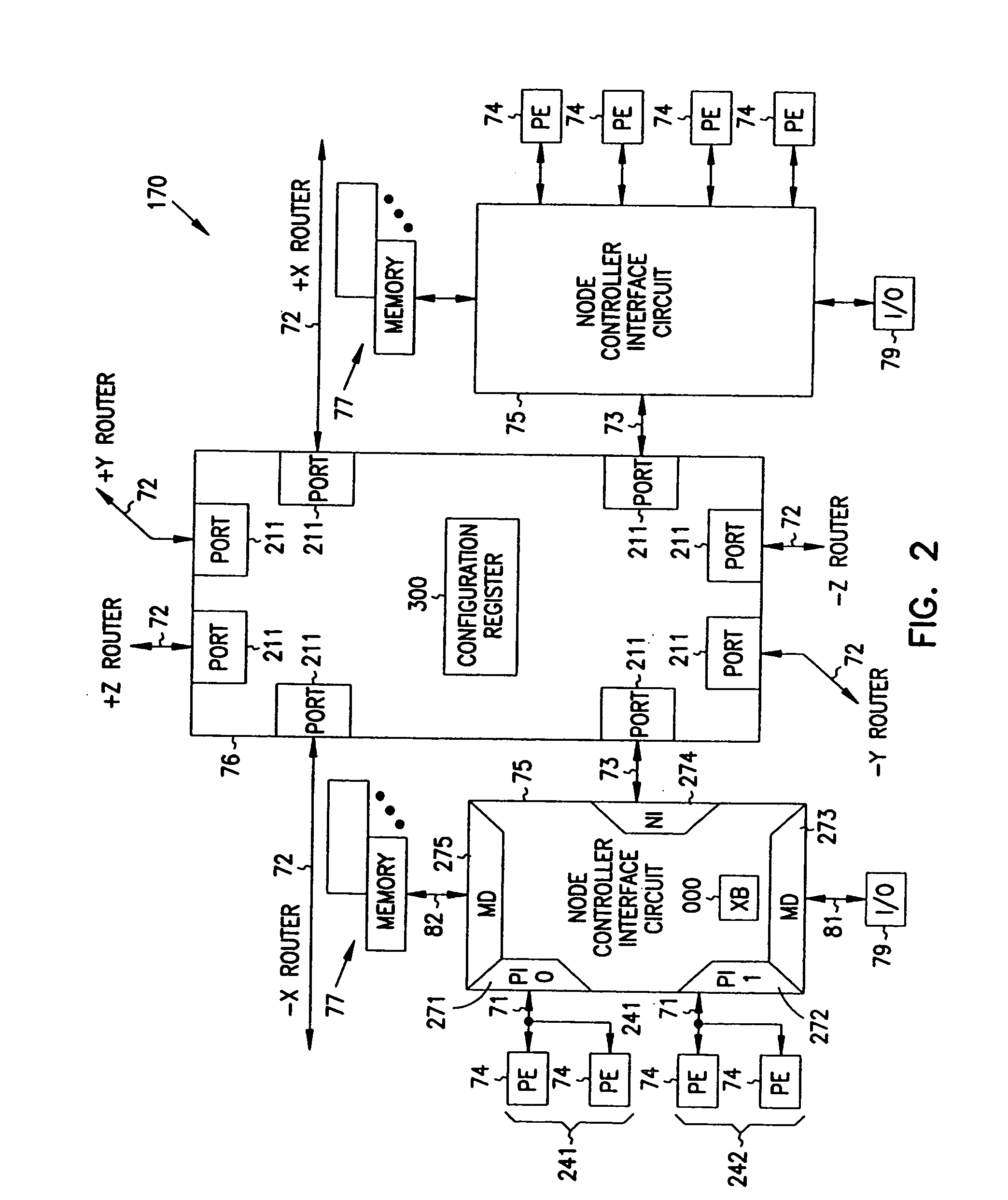
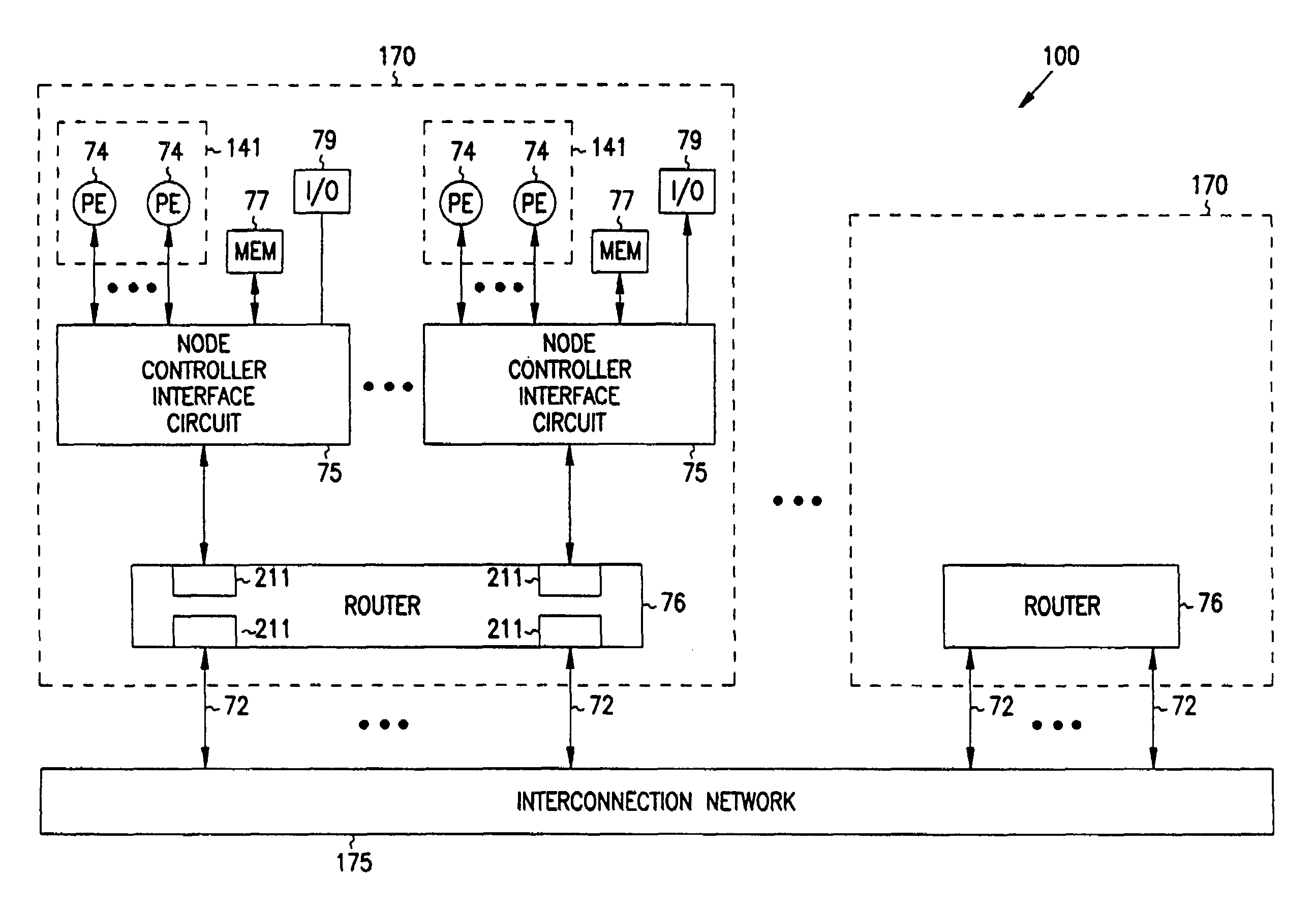
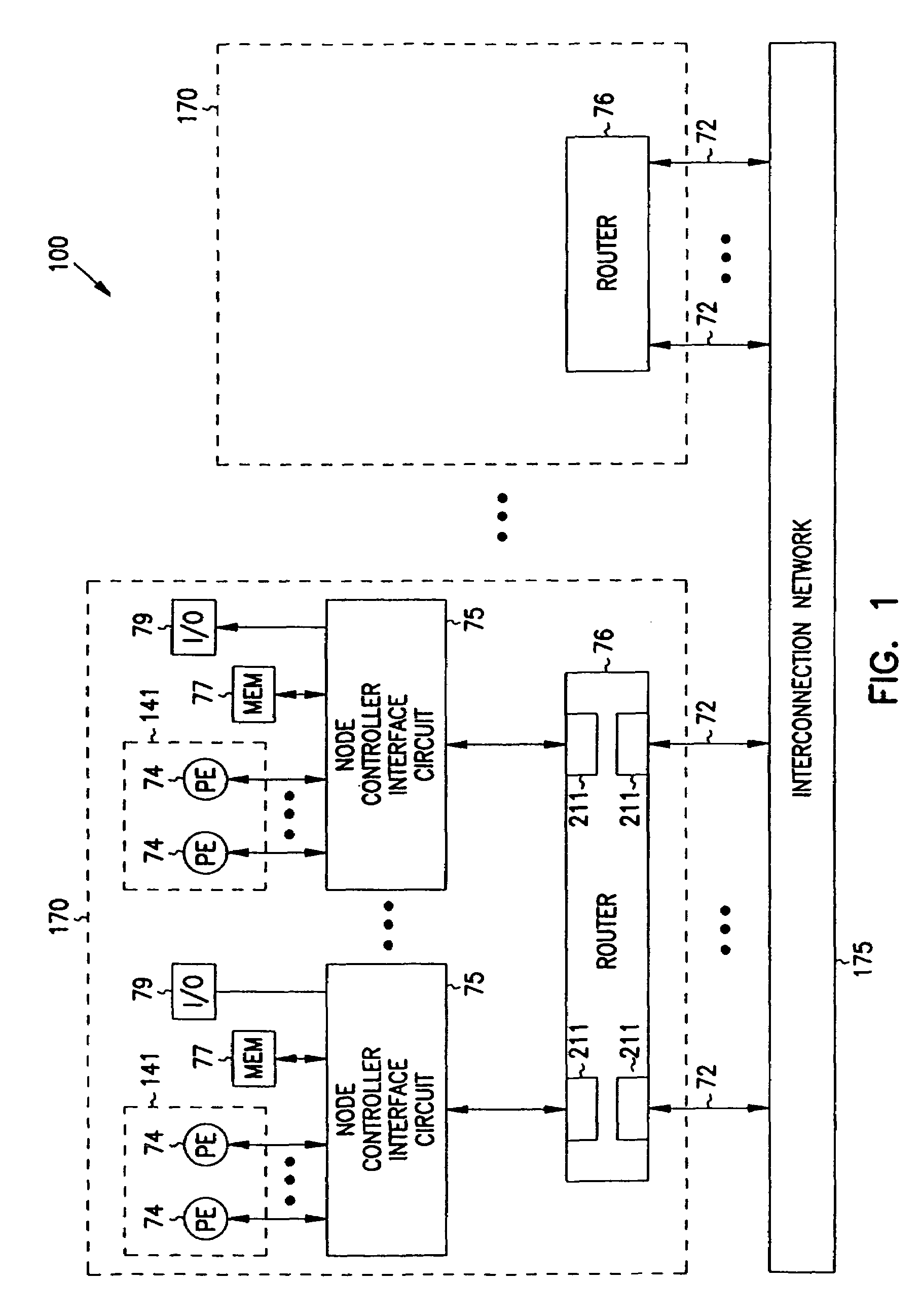
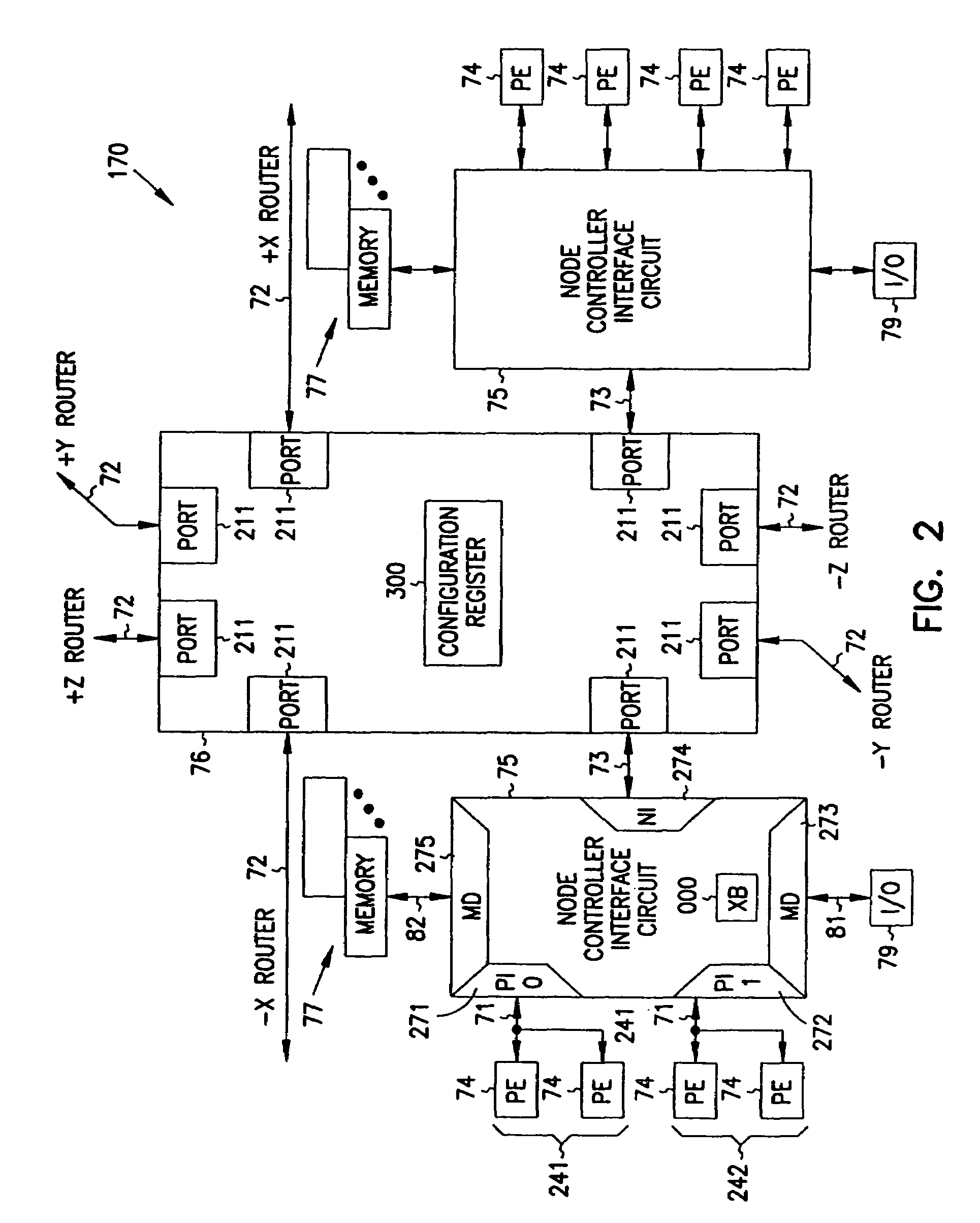
Multiprocessor node controller circuit and method
InactiveUS20050053057A1Ease of parallel processingImprove welfareMultiplex system selection arrangementsMemory adressing/allocation/relocationMemory addressCrossbar switch
Improved method and apparatus for parallel processing. One embodiment provides a multiprocessor computer system that includes a first and second node controller, a number of processors being connected to each node controller, a memory connected to each controller, a first input / output system connected to the first node controller, and a communications network connected between the node controllers. The first node controller includes: a crossbar unit to which are connected a memory port, an input / output port, a network port, and a plurality of independent processor ports. A first and a second processor port connected between the crossbar unit and a first subset and a second subset, respectively, of the processors. In some embodiments of the system, the first node controller is fabricated onto a single integrated-circuit chip. Optionally, the memory is packaged on plugable memory / directory cards wherein each card includes a plurality of memory chips including a first subset dedicated to holding memory data and a second subset dedicated to holding directory data. Further, the memory port includes a memory data port including a memory data bus and a memory address bus coupled to the first subset of memory chips, and a directory data port including a directory data bus and a directory address bus coupled to the second subset of memory chips. In some such embodiments, the ratio of (memory data space) to (directory data space) on each card is set to a value that is based on a size of the multiprocessor computer system.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
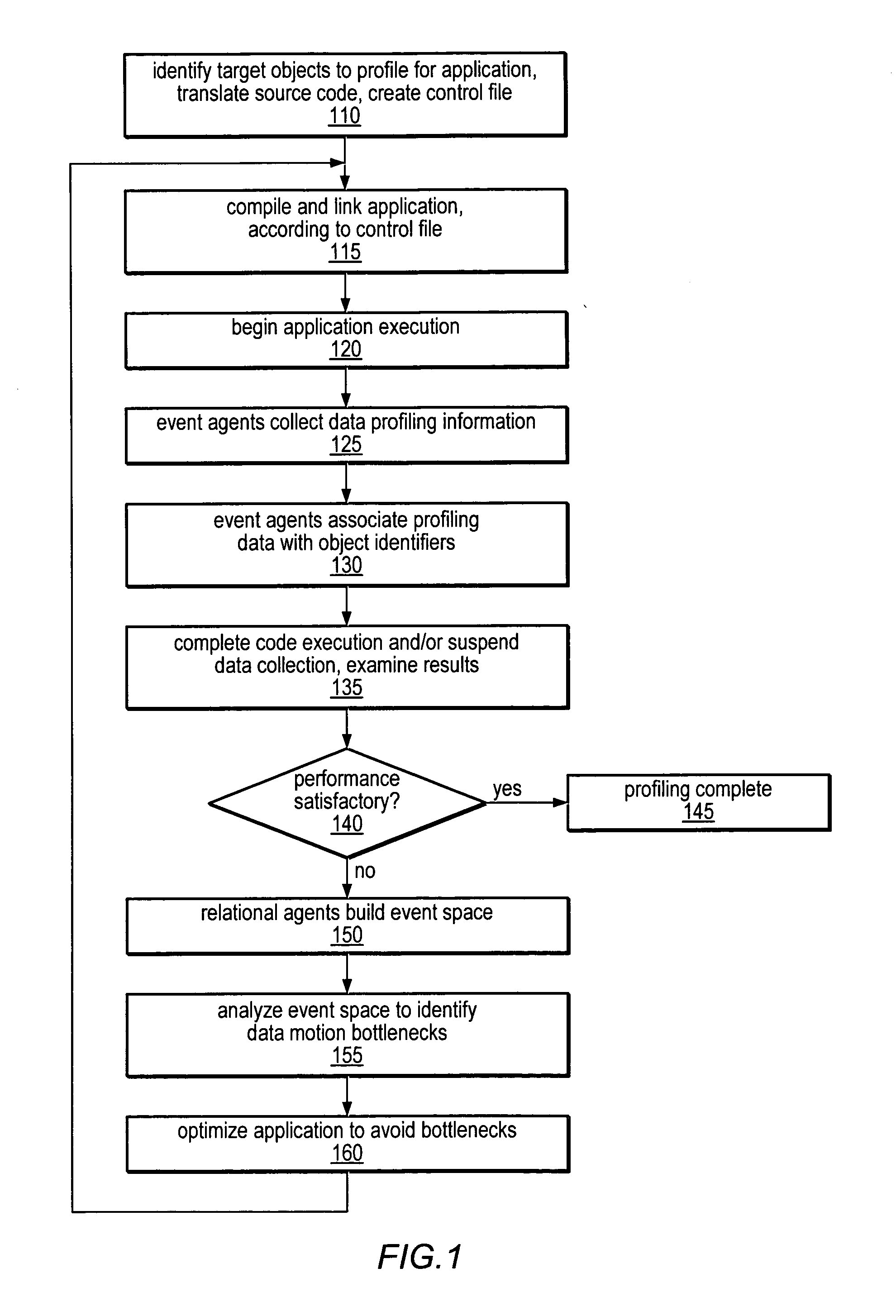
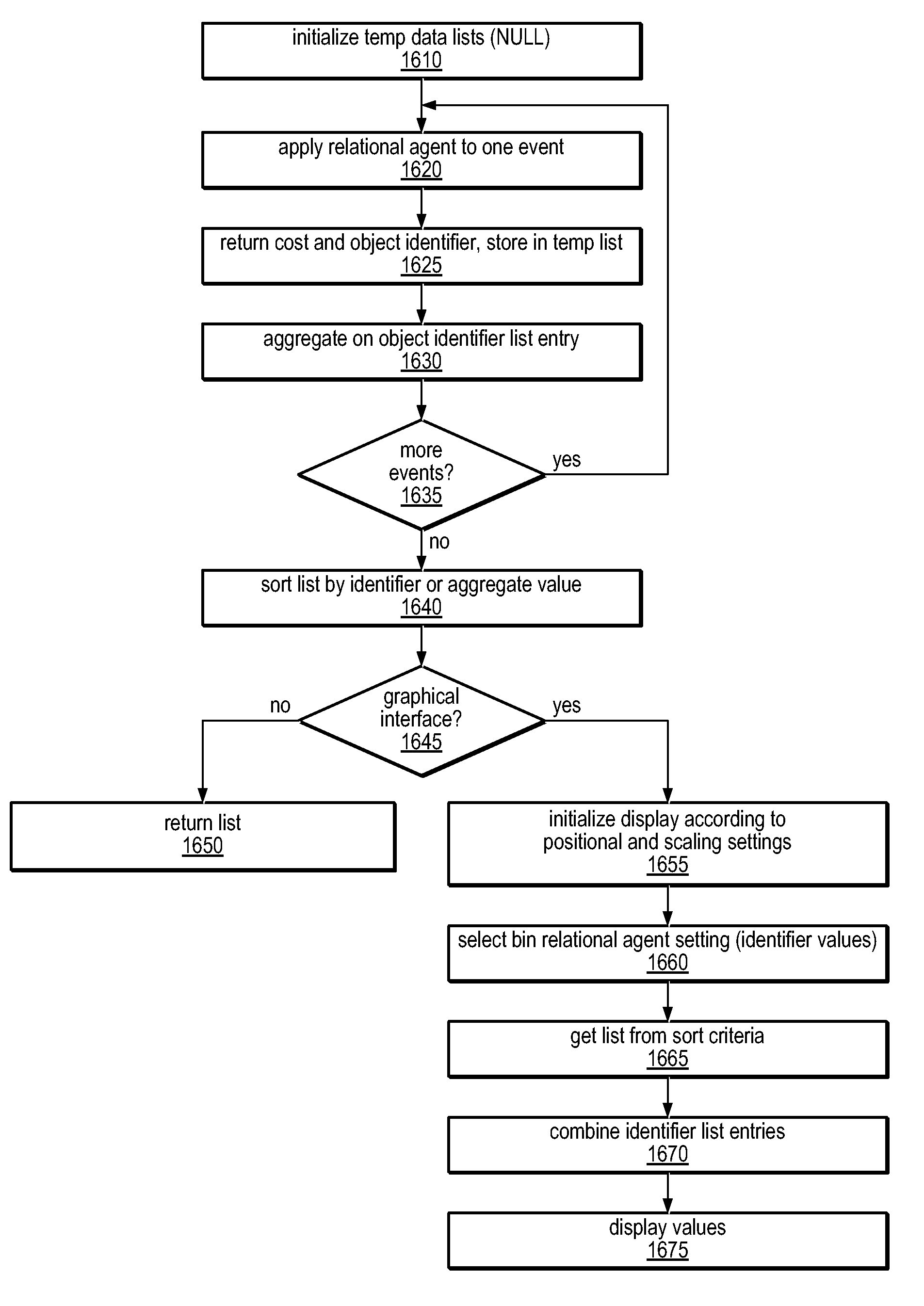
Method and Apparatus for Computing User-Specified Cost Metrics in a Data Space Profiler
ActiveUS20080127149A1Software engineeringSpecific program execution arrangementsCost metricData space
A system and method for profiling a software application may include means for defining a custom cost metric that includes a cost metric identifier and a cost function. The cost function may apply a mathematical formula to data extracted from an event set to calculate a respective cost metric value for each of one or more events in the event set. The data extracted from the event set may include one or more respective profiling object identifiers and one or more other respective costs associated with each of the one or more events. A cost associated with an event in the event space may be associated with a function or basic block of instructions. The cost function may include a distribution formula for attributing at least a portion of the cost associated with a function or basic block to each of the instructions comprising the function or basic block.
Owner:ORACLE INT CORP
Profile refinement for integrated circuit metrology
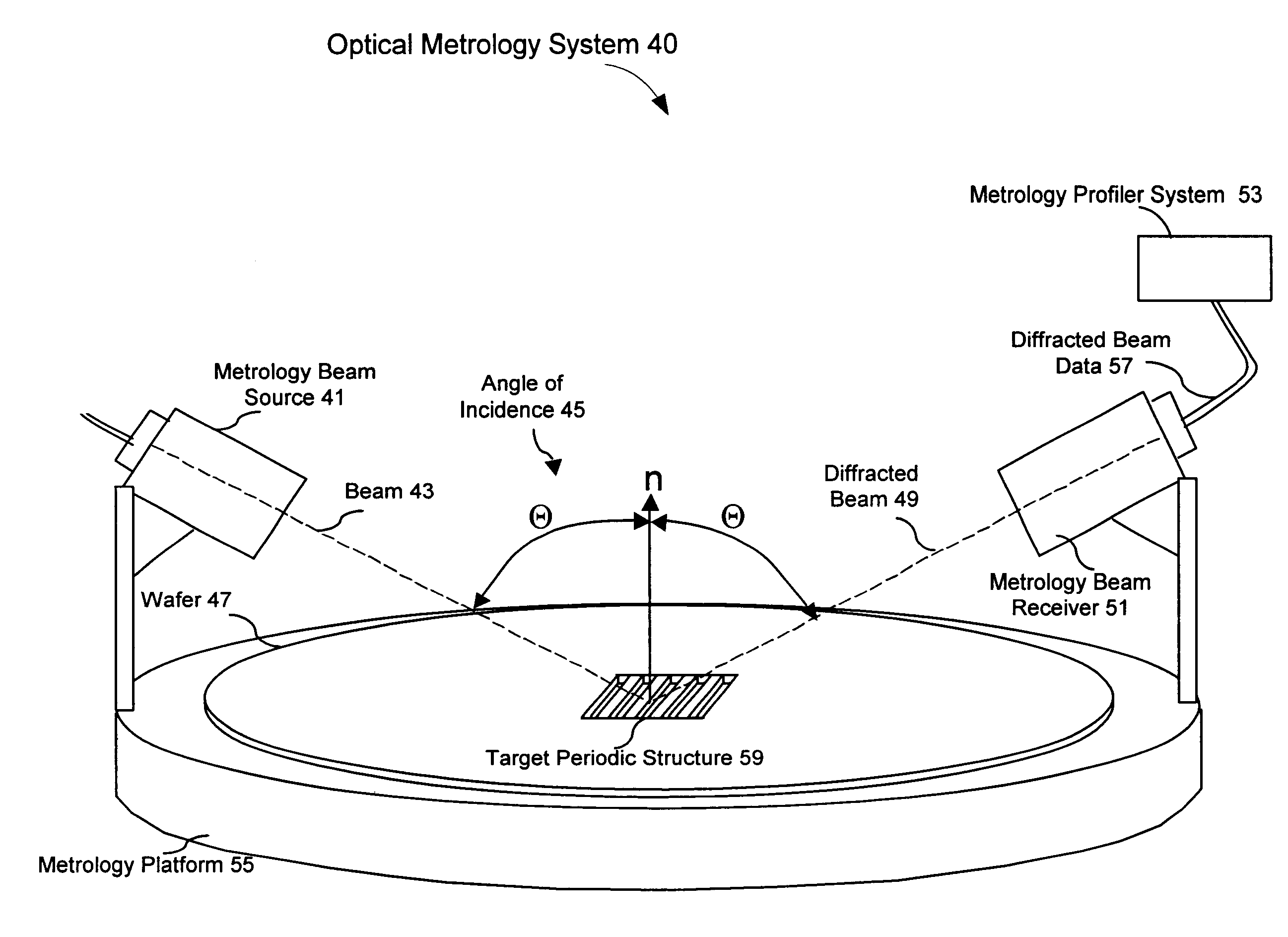
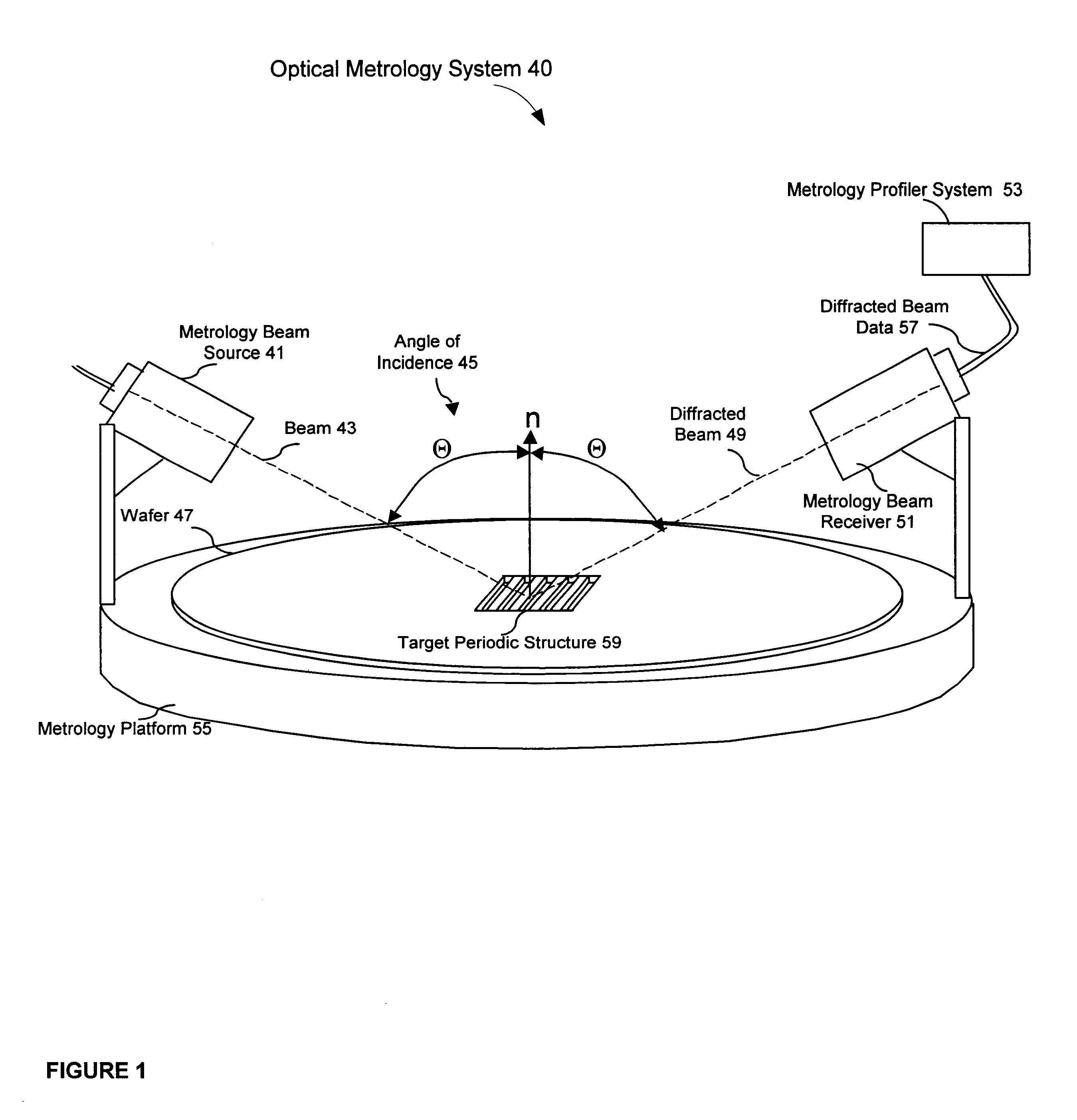
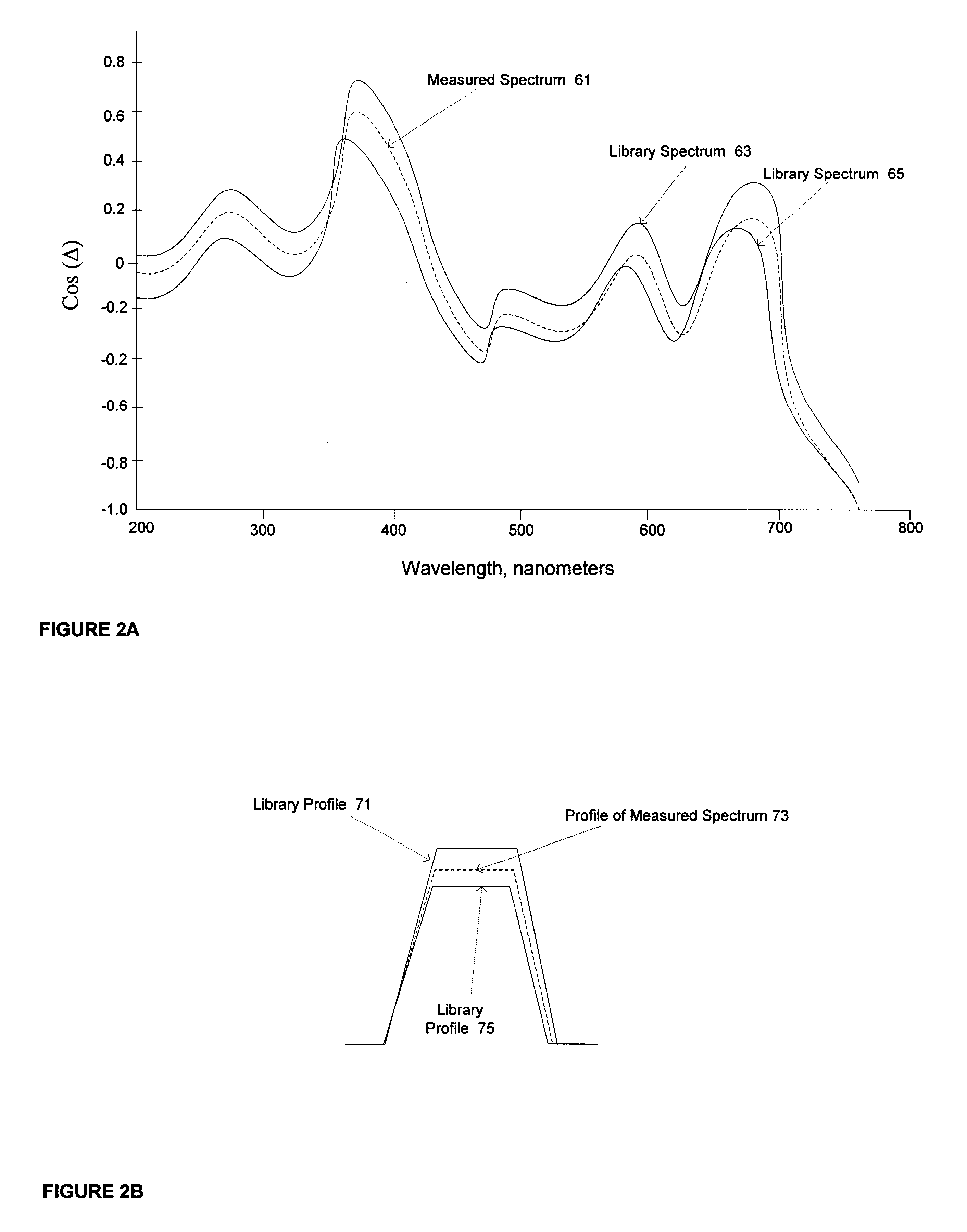
InactiveUS6609086B1Minimize cost functionAmplifier modifications to reduce noise influenceScattering properties measurementsMetrologyData space
The present invention includes a method and system for determining the profile of a structure in an integrated circuit from a measured signal, the signal measured off the structure with a metrology device, selecting a best match of the measured signal in a profile data space, the profile data space having data points with a specified extent of non-linearity, and performing a refinement procedure to determine refined profile parameters. One embodiment includes a refinement procedure comprising finding a polyhedron in a function domain of cost functions of the profile library signals and profile parameters and minimizing the total cost function using the weighted average method. Other embodiments include profile parameter refinement procedures using sensitivity analysis, a clustering approach, regression-based methods, localized fine-resolution refinement library method, iterative library refinement method, and other cost optimization or refinement algorithms, procedures, and methods. Refinement of profile parameters may be invoked automatically or invoked based on predetermined criteria such as exceeding an error metric between the measured signal versus the best match profile library.
Owner:TOKYO ELECTRON US HOLDINGS INC
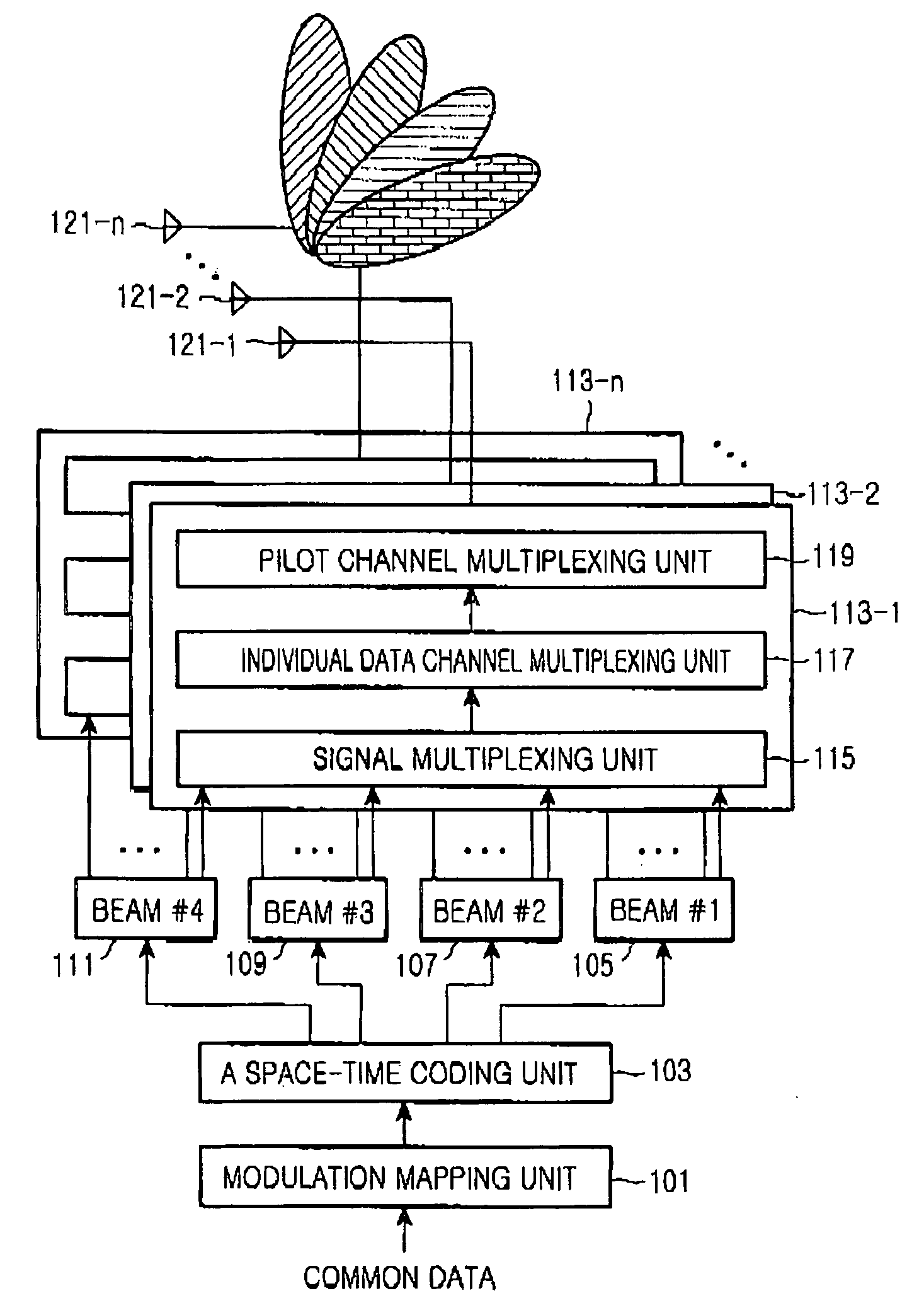
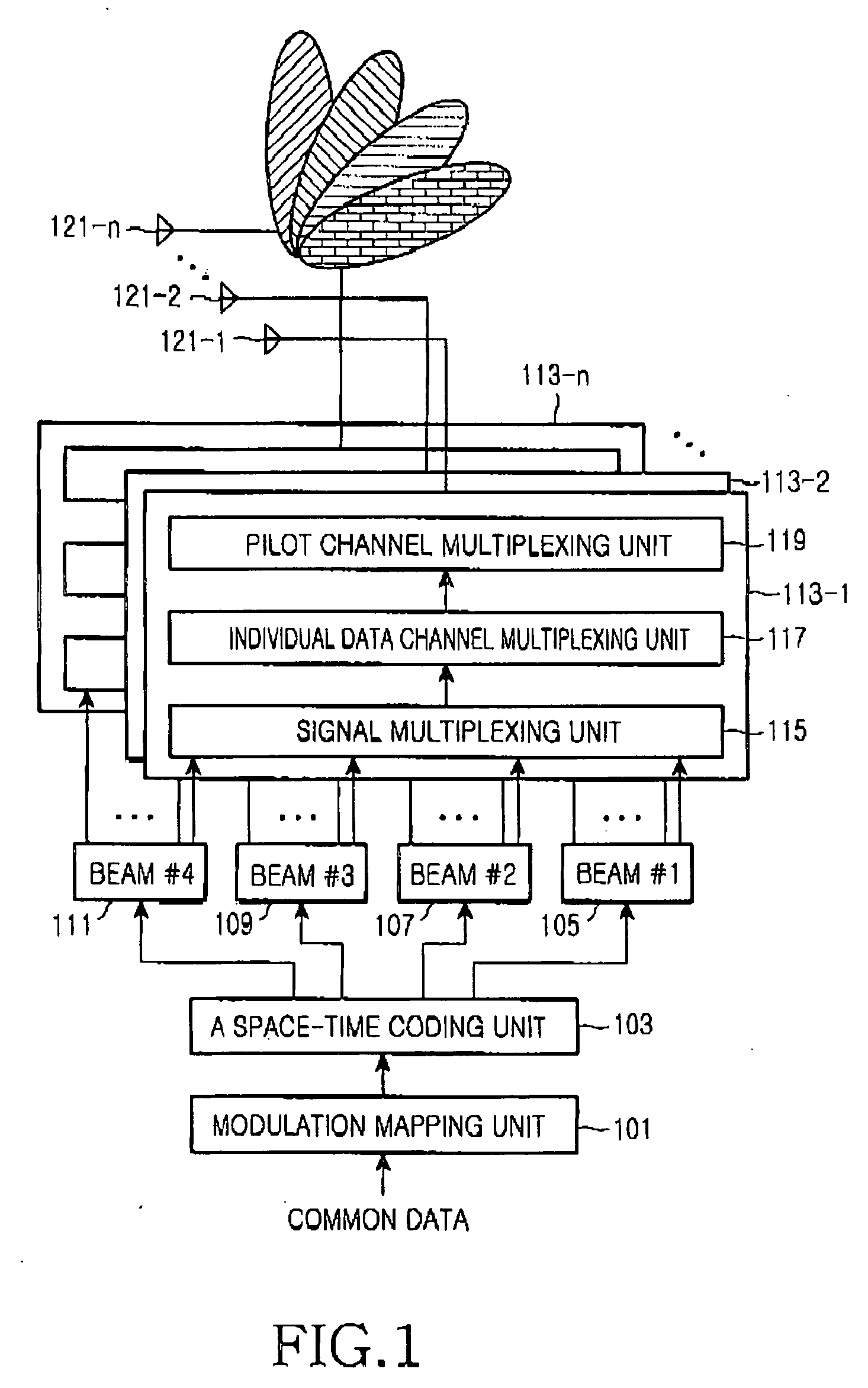
System and method for transmitting common data in a mobile communication system
InactiveUS20050073976A1Spatial transmit diversityBroadcast service distributionTelecommunicationsTransfer system
A common channel transmission system and method for transmitting common data to multiple users by means of a multibeam. A common data coding means space-time codes the common data throughout all beams included in the multibeam. A data transmission means assigns the common data space-time coded by the common data coding means to all beams included in the multibeam and transmits the common data to the multiple users.
Owner:SAMSUNG ELECTRONICS CO LTD
Management of file system snapshots
ActiveUS20060271604A1Data processing applicationsDigital data information retrievalFile systemData space
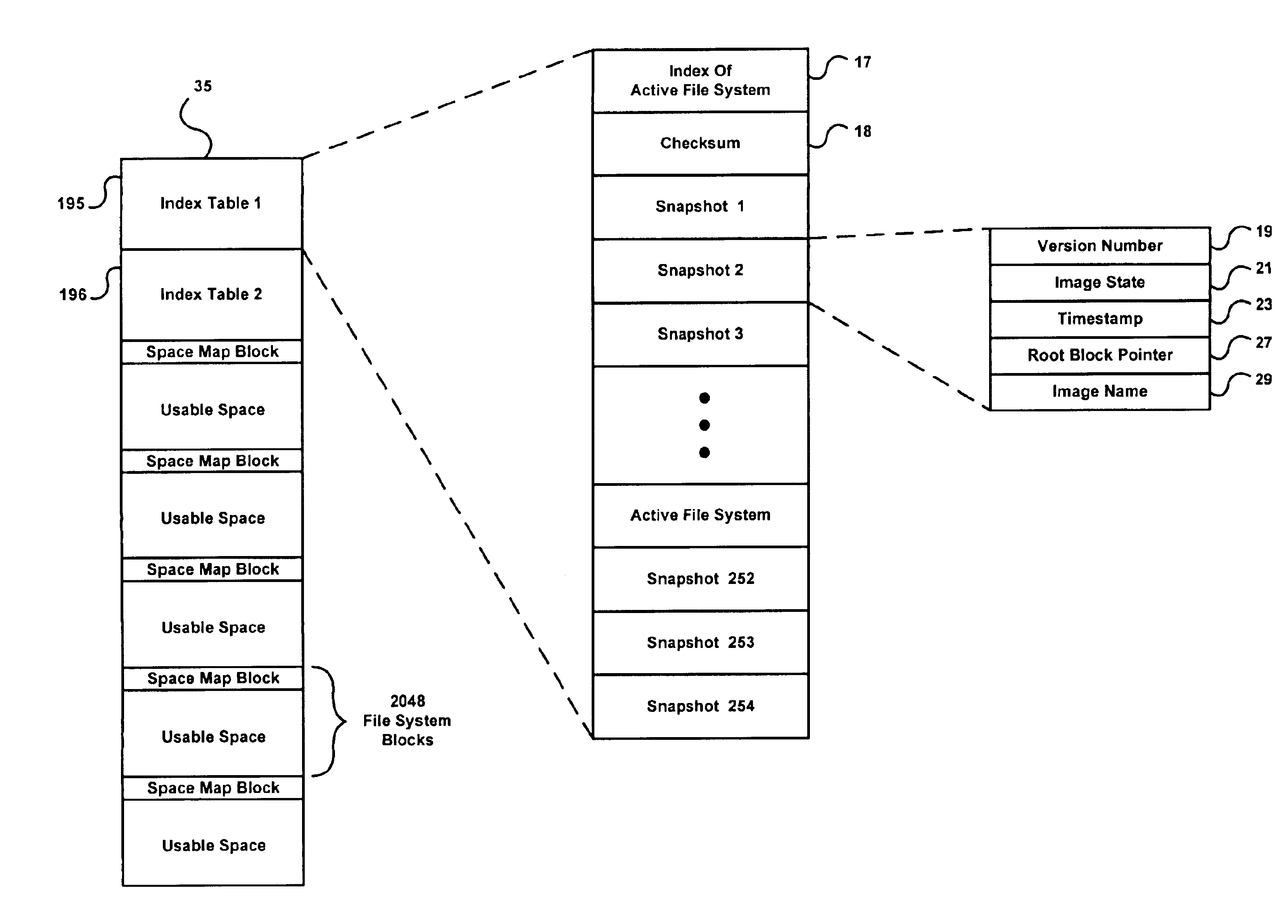
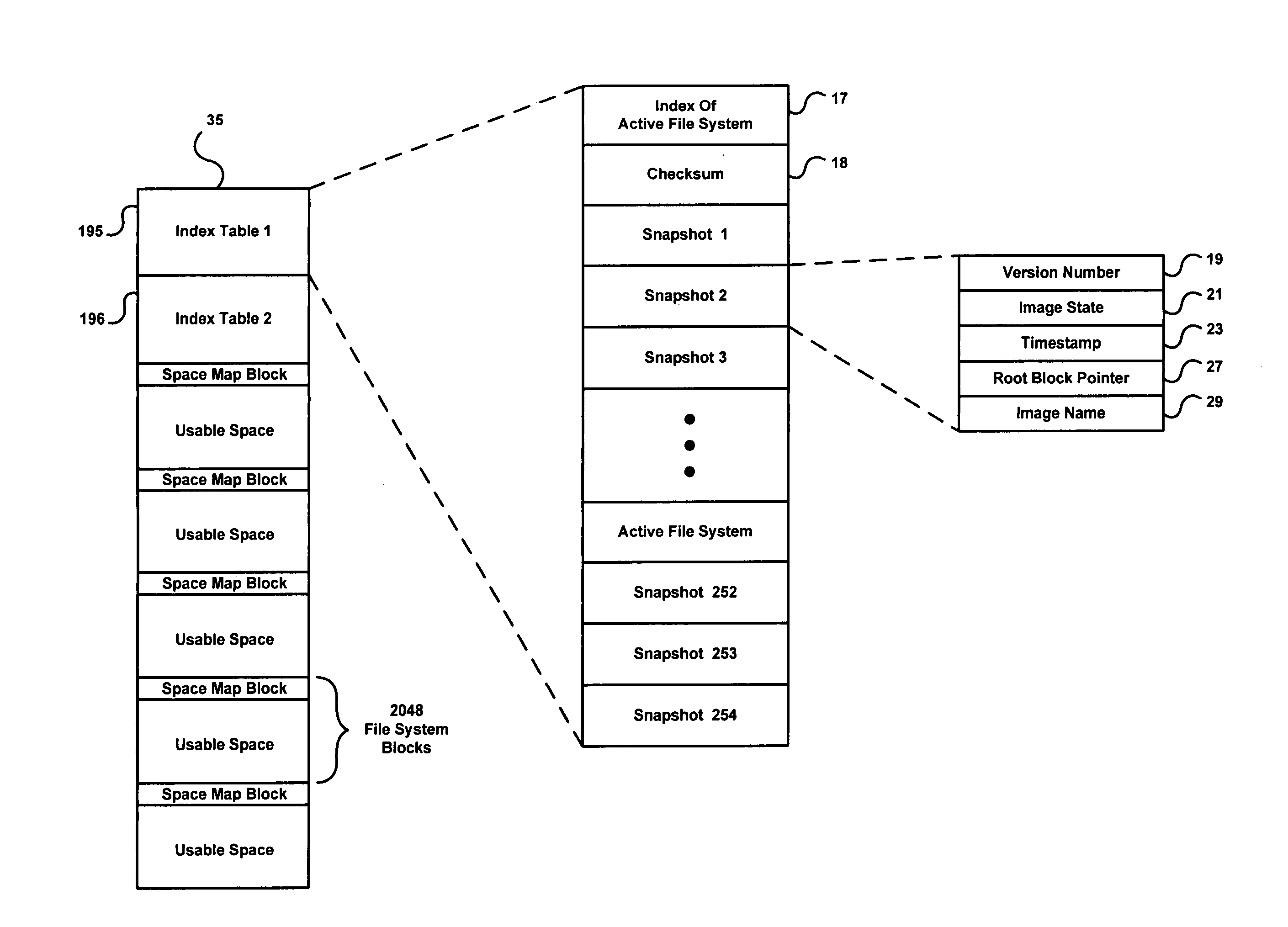
The present invention relates to methods and systems of snapshot management of a file system in a data storage system. To represent the snapshots, the invention maintains pointers to the root block pointer of each snapshot. When the active file system is modified, this invention avoids overwriting any blocks used by previous snapshots by allocating new blocks for the modified blocks. When the invention needs to put an established block in a new location, it must update a parent block to point to the new location. The update to the parent block may then require allocating a new block for the new parent block and so forth. Parts of the file system not modified since a snapshot remain in place. The amount of space required to represent snapshots scales with the fraction of the file system that users modify. To maintain snapshot integrity, this invention keeps track of the first and last snapshots that use each block in space map blocks spread throughout the file system data space. When users delete snapshots, this invention may use a background process to find blocks no longer used by any snapshot and makes them available for future use.
Owner:ORACLE INT CORP
Capturing data changes utilizing data-space tracking
InactiveUS20060074951A1Significant storage space efficiencySignificant processing efficiencyData processing applicationsDigital data information retrievalData spaceOriginal data
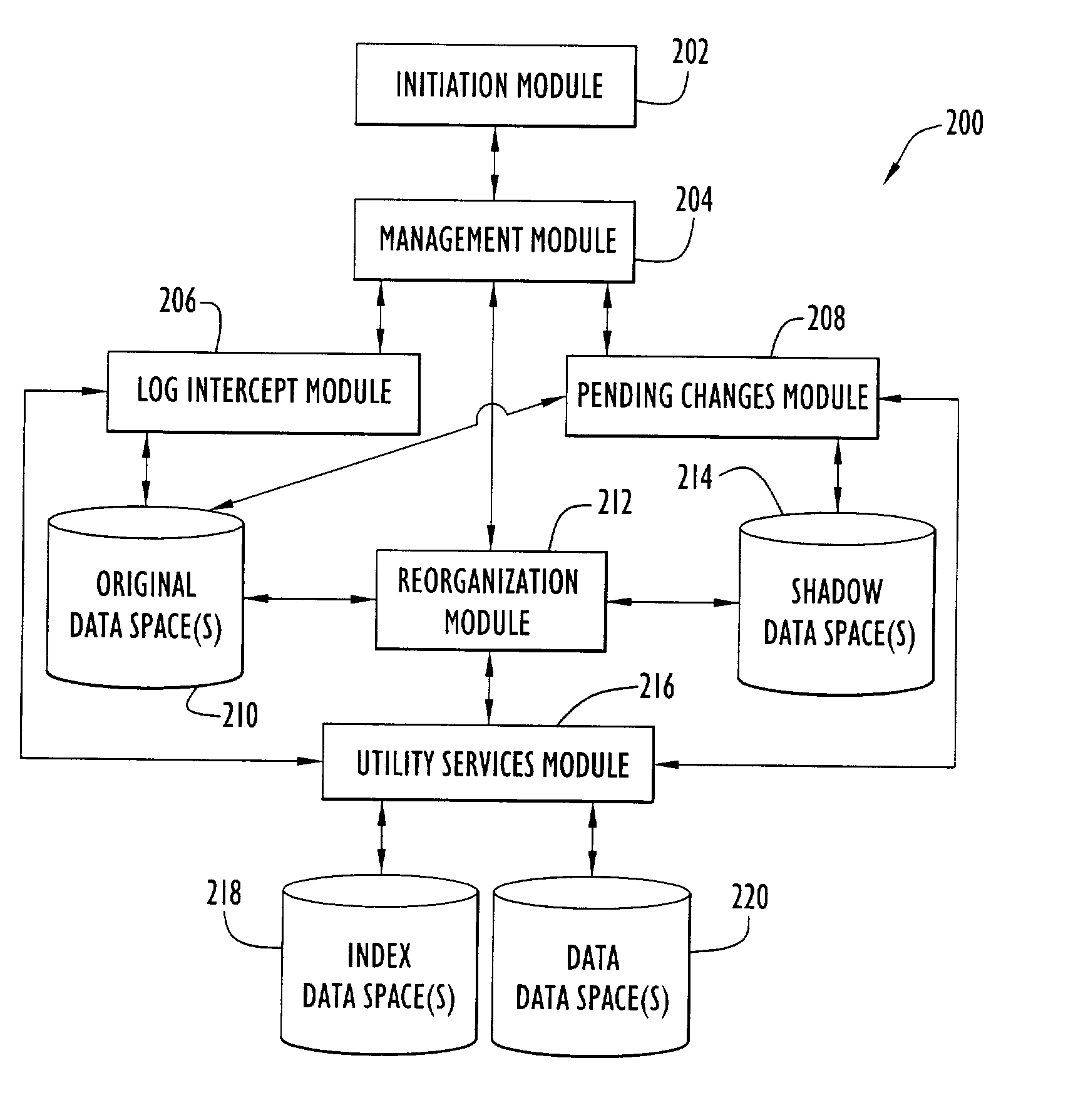
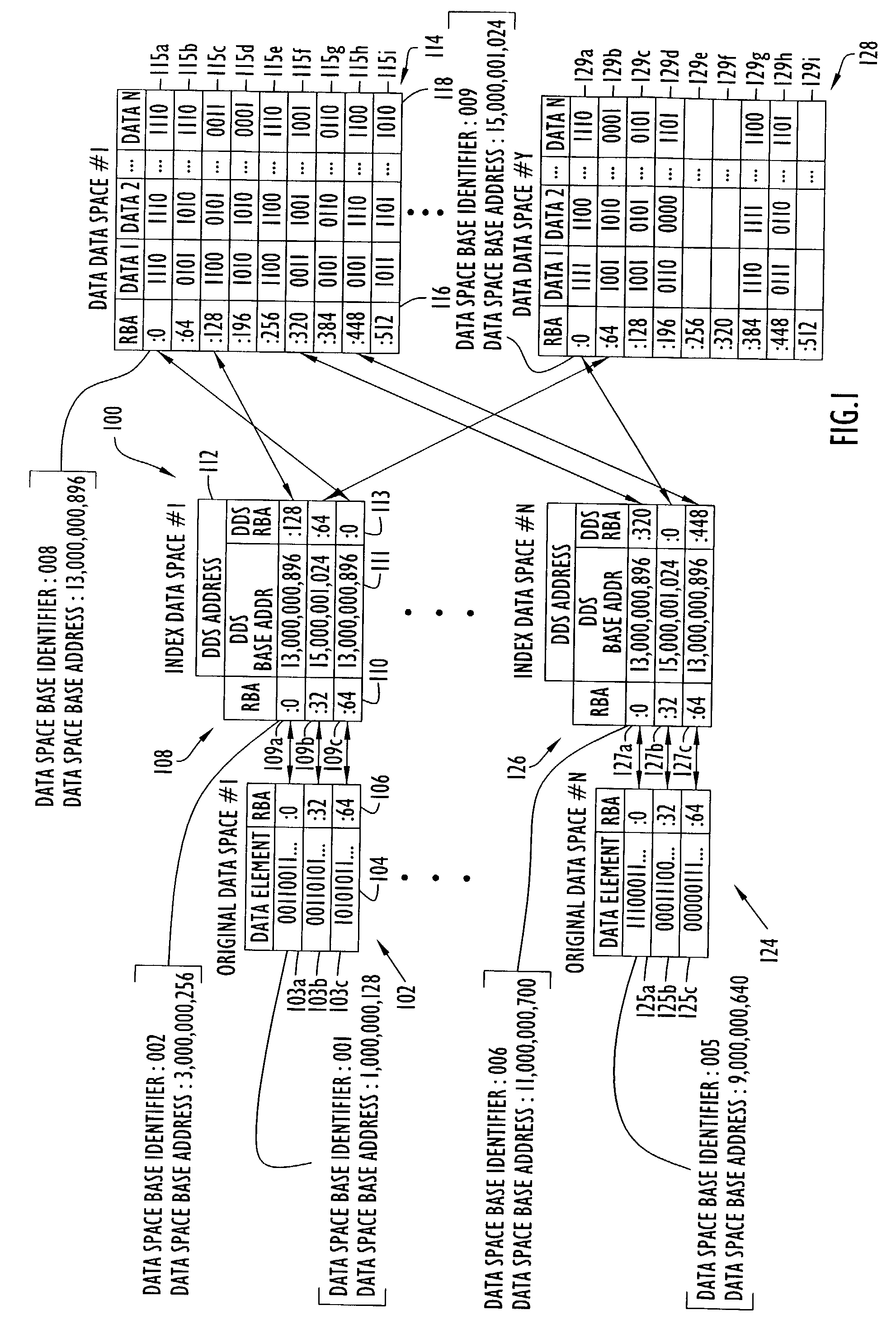
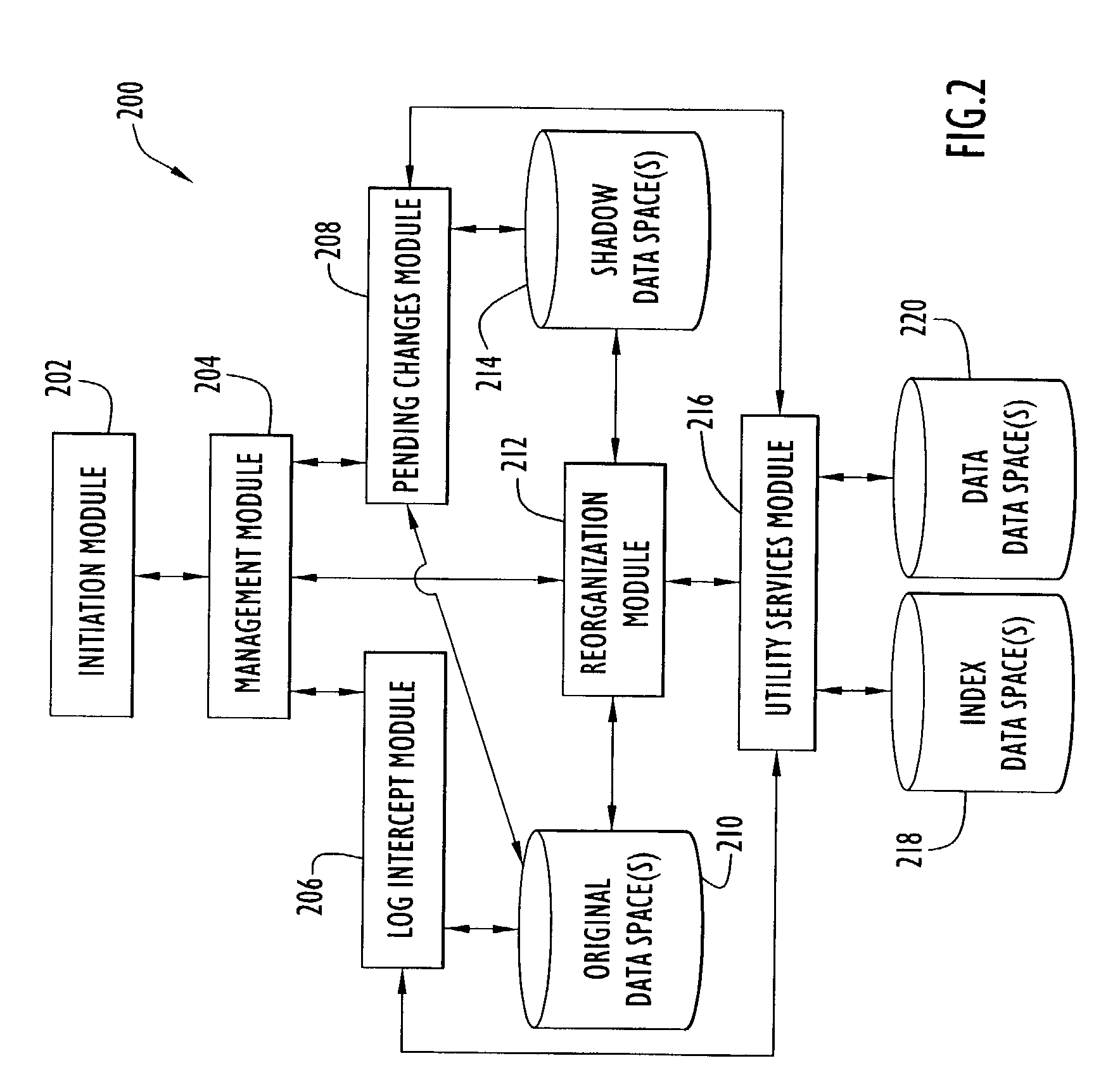
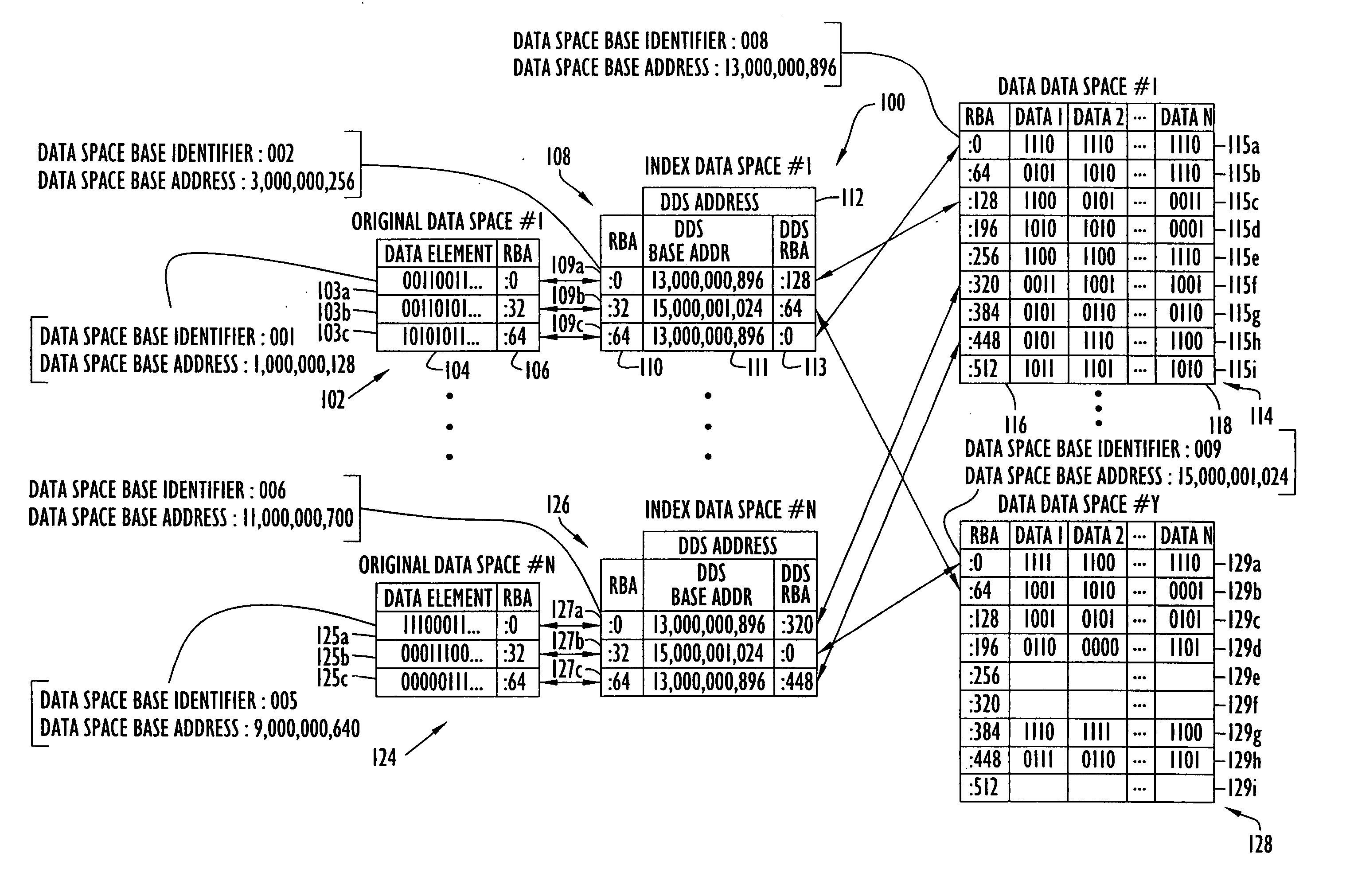
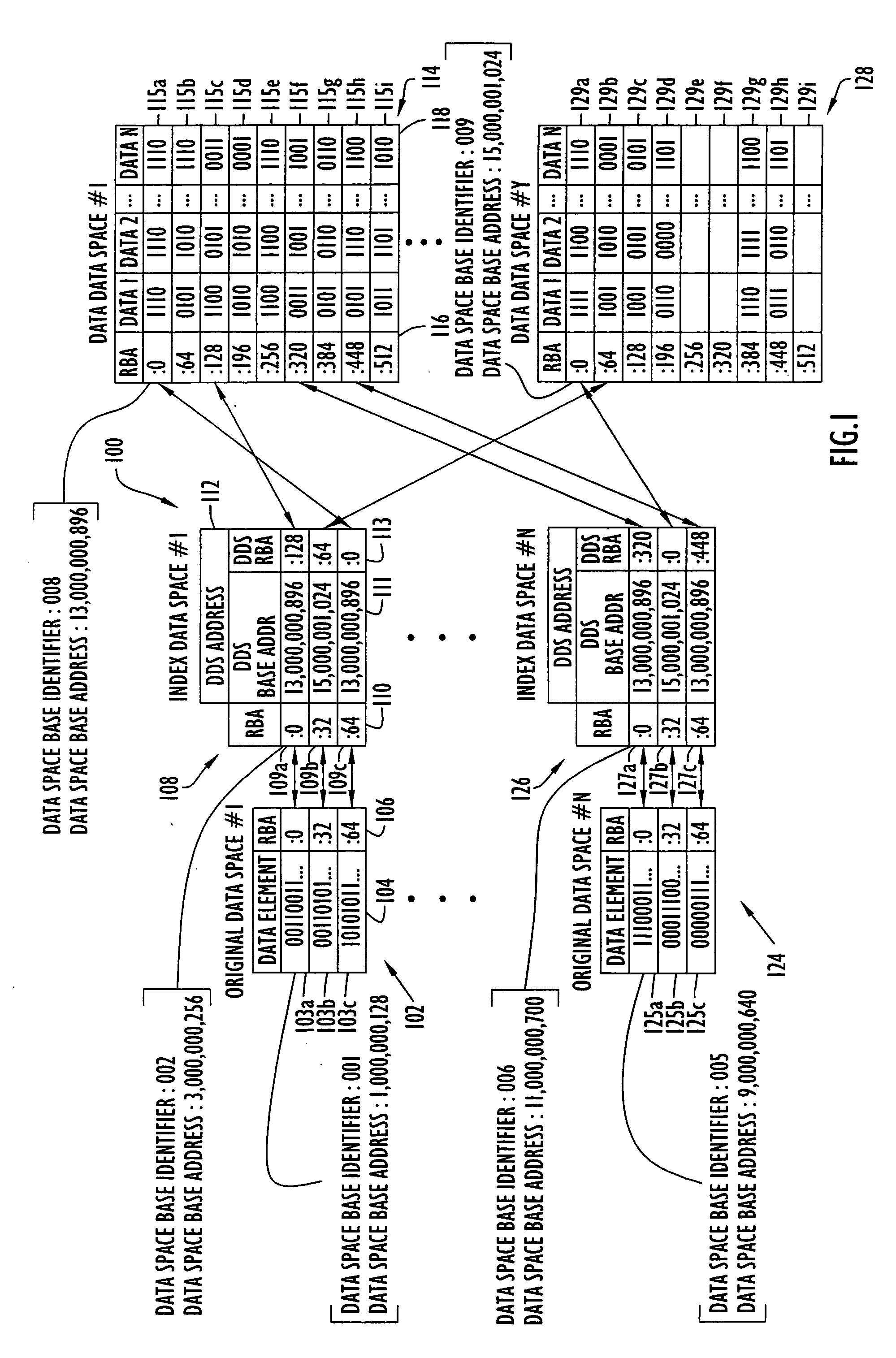
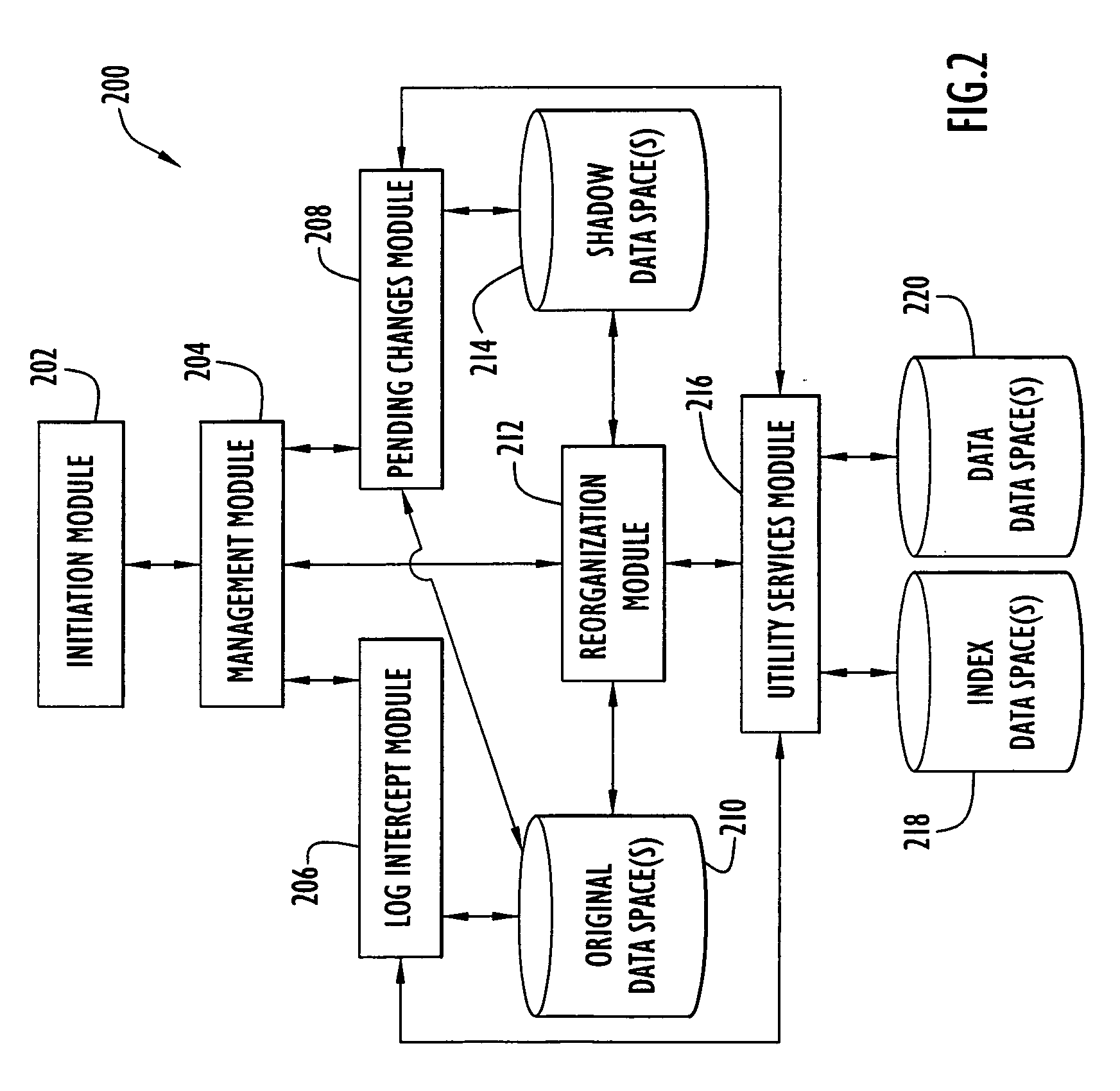
An on-line reorganization facility (ORF) uses index data-spaces that point to other data-spaces, referred to as data data-spaces, to efficiently track and coordinate information about the data-elements in an original data-space operated upon by a reorganization process. A relative base address of a data-element in an index data-space can be derived from a relative base address of a data-element in an original data-space, and vice versa. An index data-space data-element contains a location of a data-element in a data data-space that tracks change information related to a corresponding data-element in the original data-space. Tracked changes are later applied to the newly reorganized data-space to assure consistency and integrity of the data. Tracked changes include the location in the original data-space where the change occurred and a flag indicting the type of change.
Owner:IBM CORP
Method and Apparatus for Data Space Profiling of Applications Across a Network
ActiveUS20080114806A1Error detection/correctionMultiple digital computer combinationsData spaceContext specific
A system and method for profiling a network application may include means for operating on context-specific data and costs. The system may include an apparatus for associating local extended address elements with a message sent from a first computing system to a second computing system across a network. The second computing system may store the received information as remote extended address information and may store its own local extended address information. An event agent may capture values of local and / or remote extended address elements in response to detecting the message or another system event and may associate the extended address elements with the message or system event in an event set accessible by a data space profiler. The extended address information may include time stamps. An event agent may determine network latency dependent on time stamps of messages and may generate an event if the latency exceeds a predetermined threshold.
Owner:ORACLE INT CORP
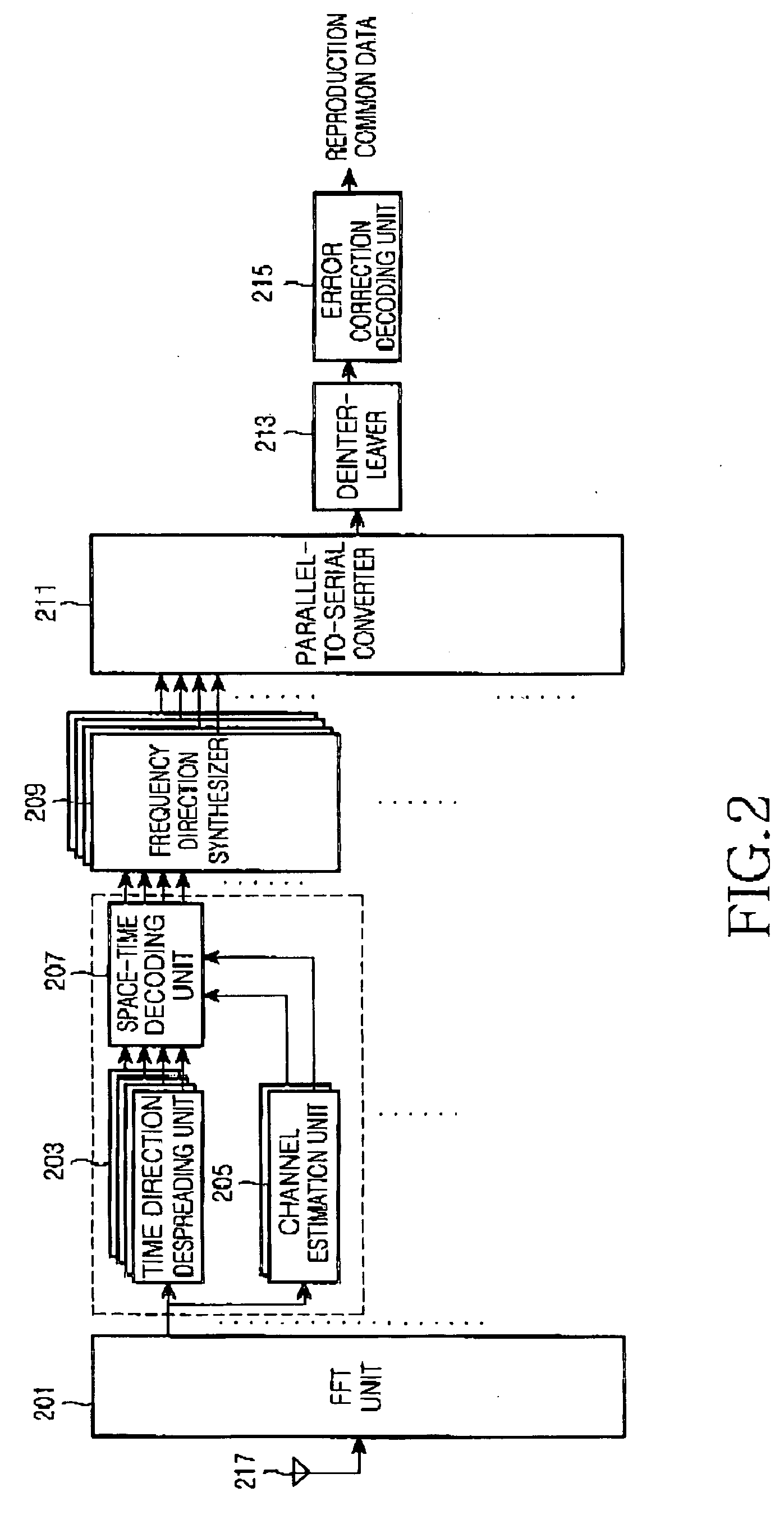
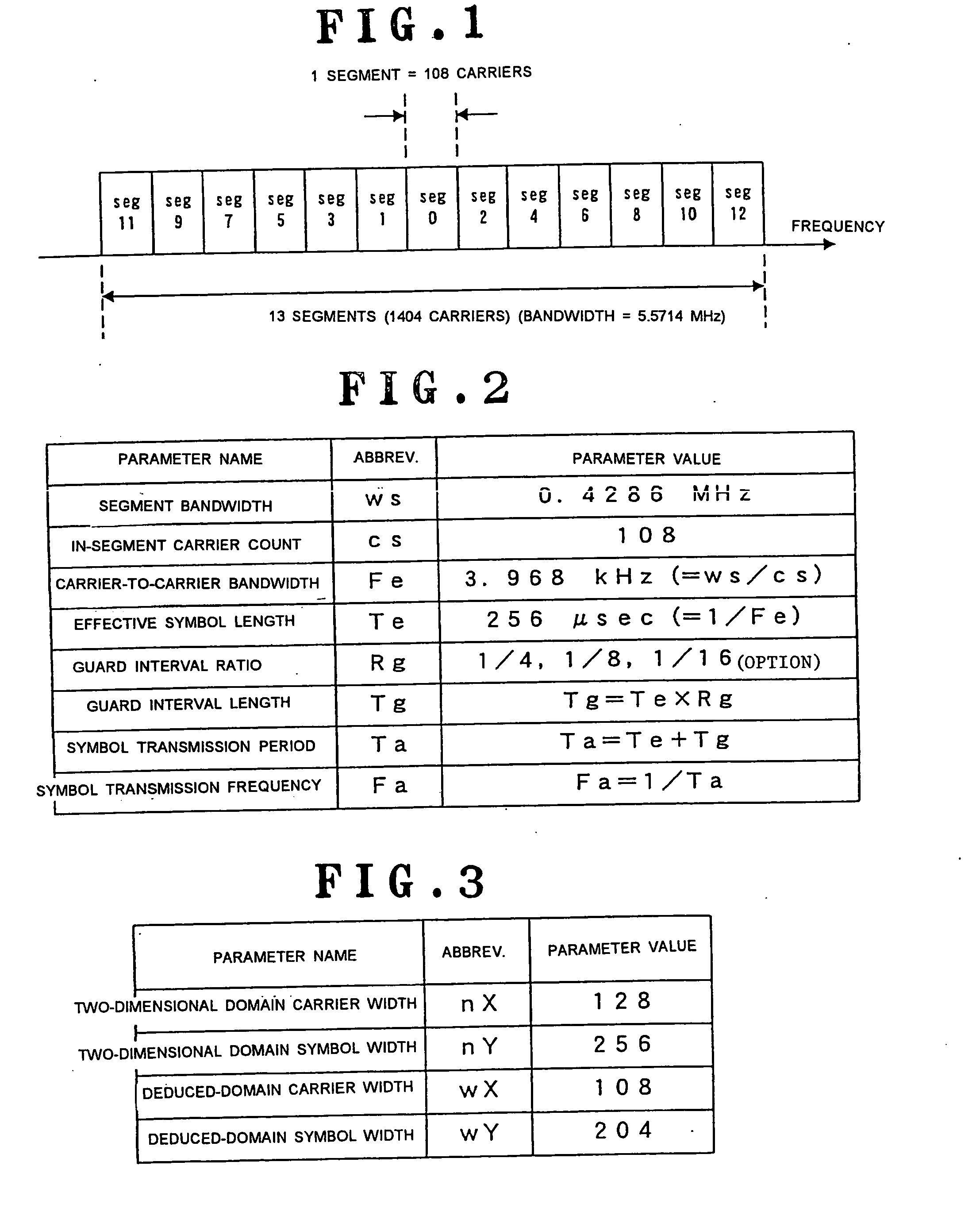
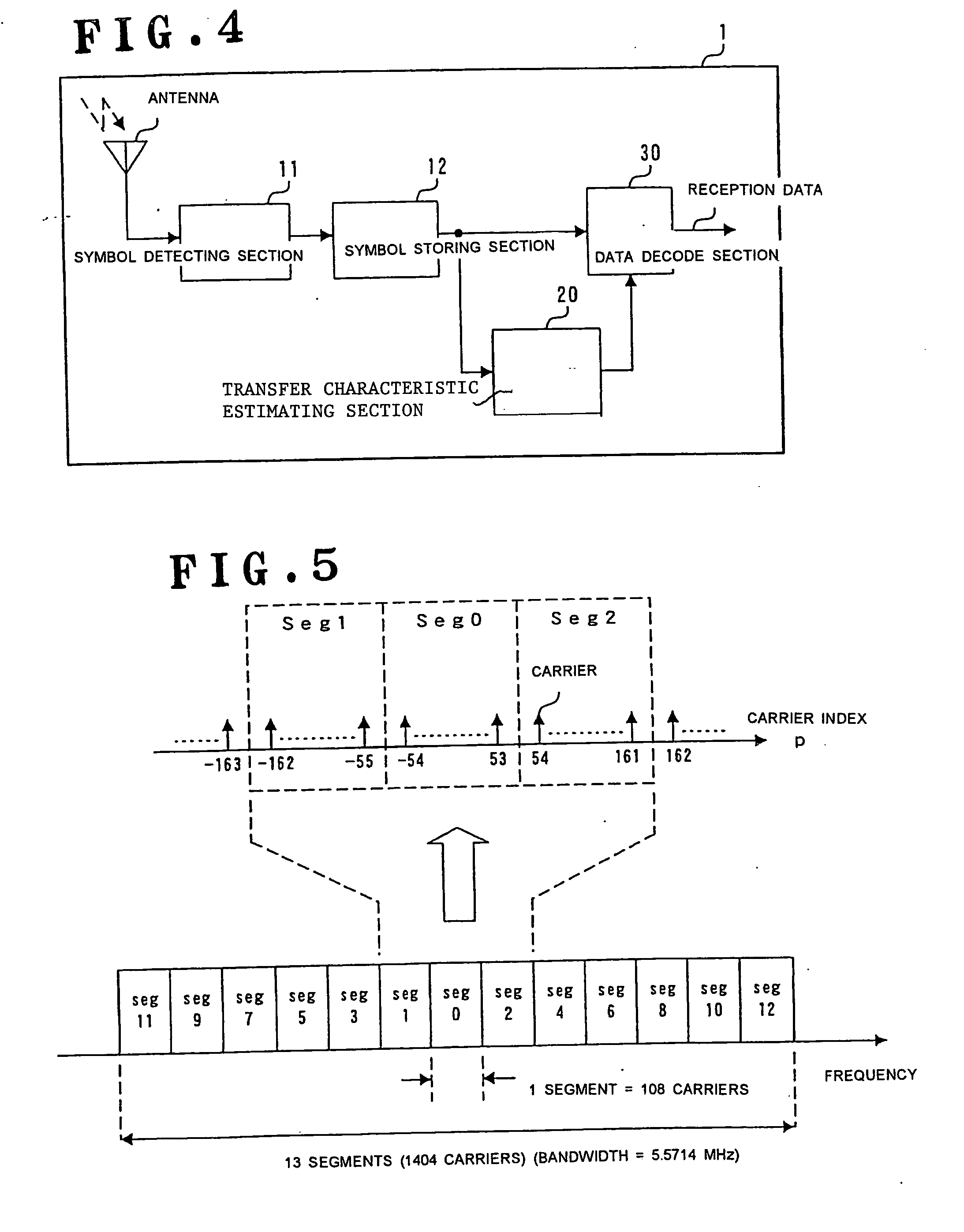
Digital broadcast signal receiving apparatus and method
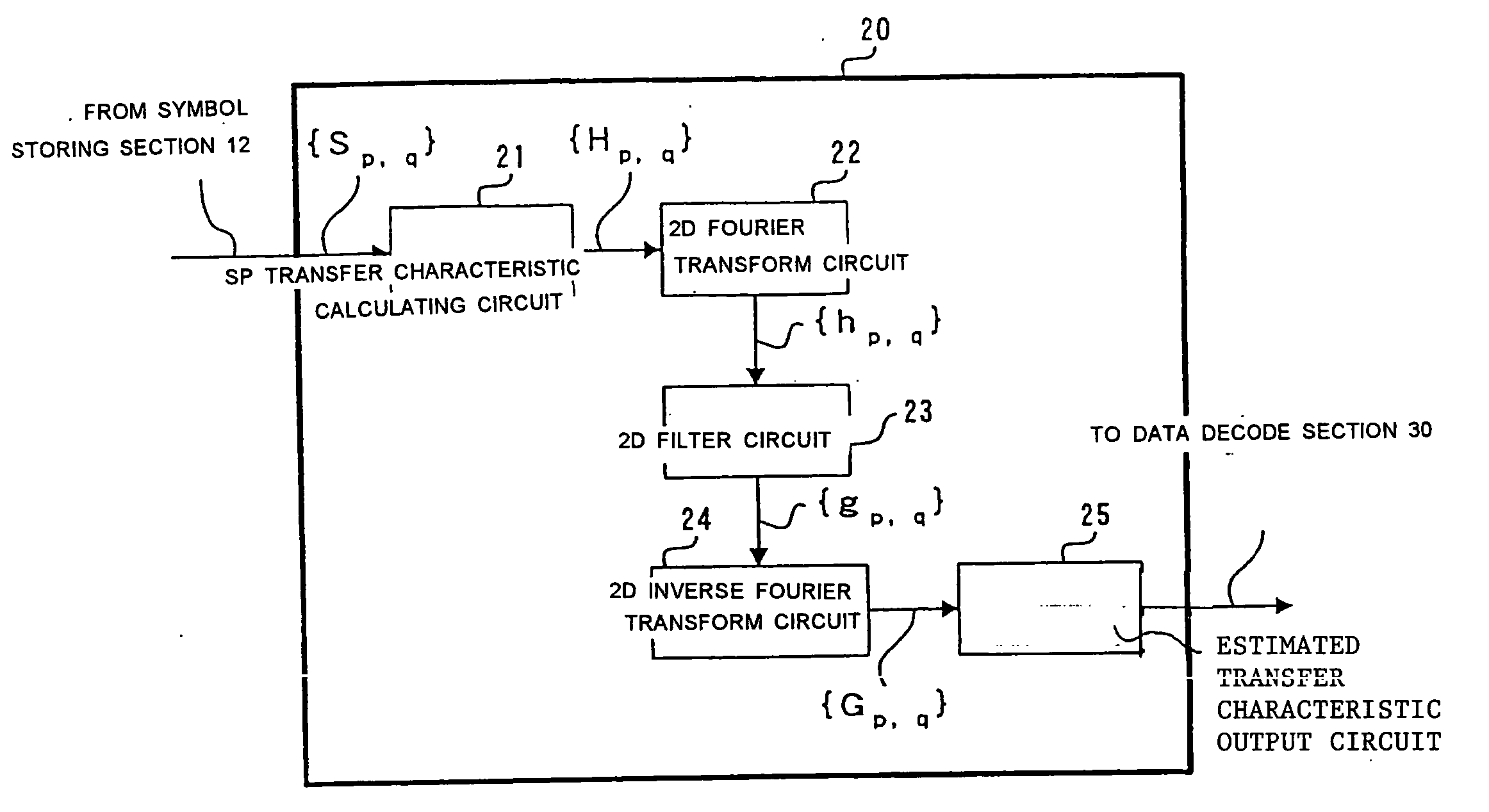
A signal receiving apparatus and method which is high in deduction accuracy of transfer characteristic and less in error rate during signal decoding. For each detection signal of a pilot carrier allotted in an OFDM symbol space, a transfer function thereof is calculated. The transfer function is subjected to two-dimensional Fourier transform as to impulse delay time and symbol frequency thereby generating a two-dimensional data space. A predetermined domain of the two-dimensional data space is extracted by a filter extracting domain. The data included in the extracted domain is subjected to two-dimensional inverse Fourier transform as to carrier frequency and symbol time, thereby generating a deduced transfer function.
Owner:ONKYO KK D B A ONKYO CORP
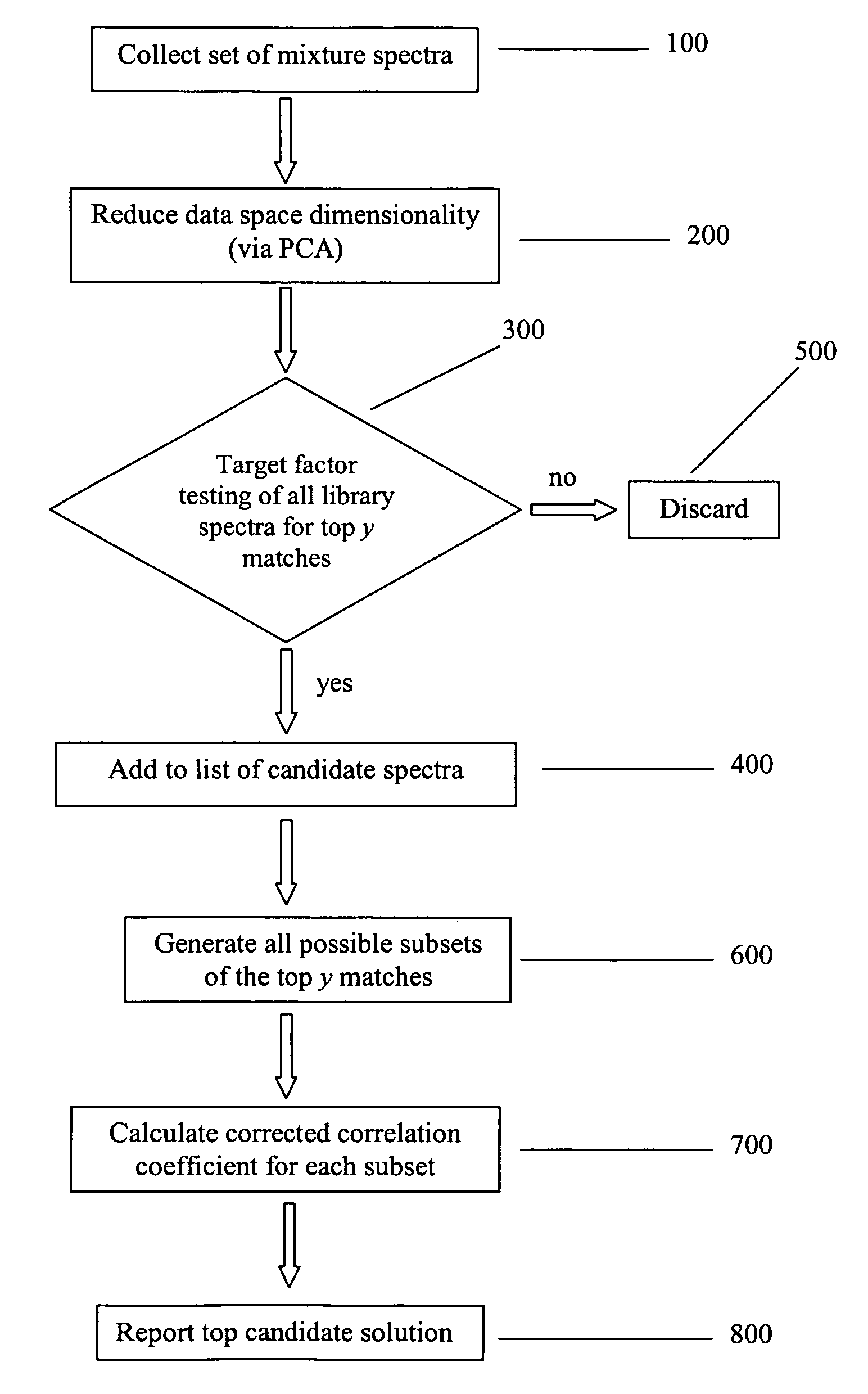
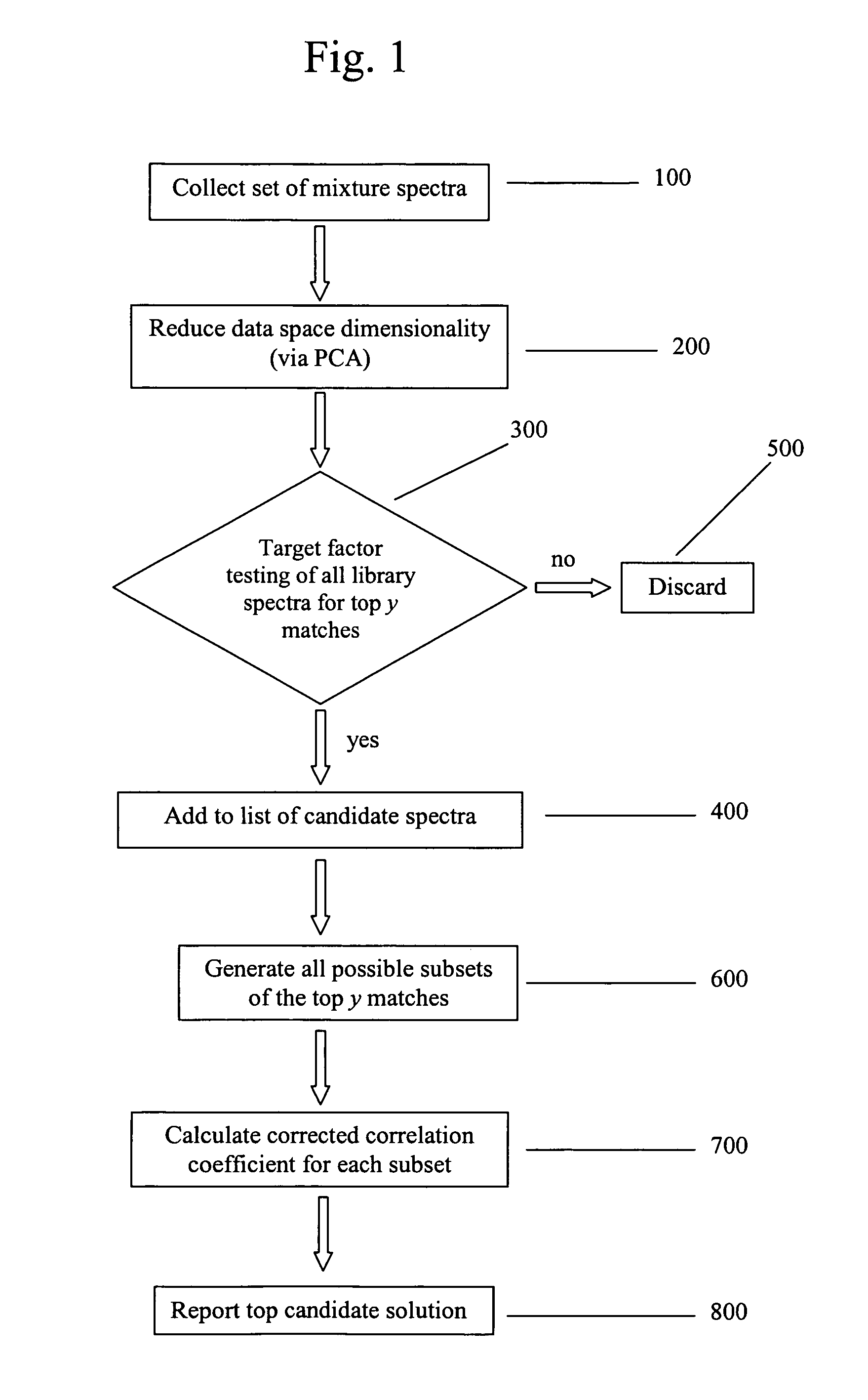
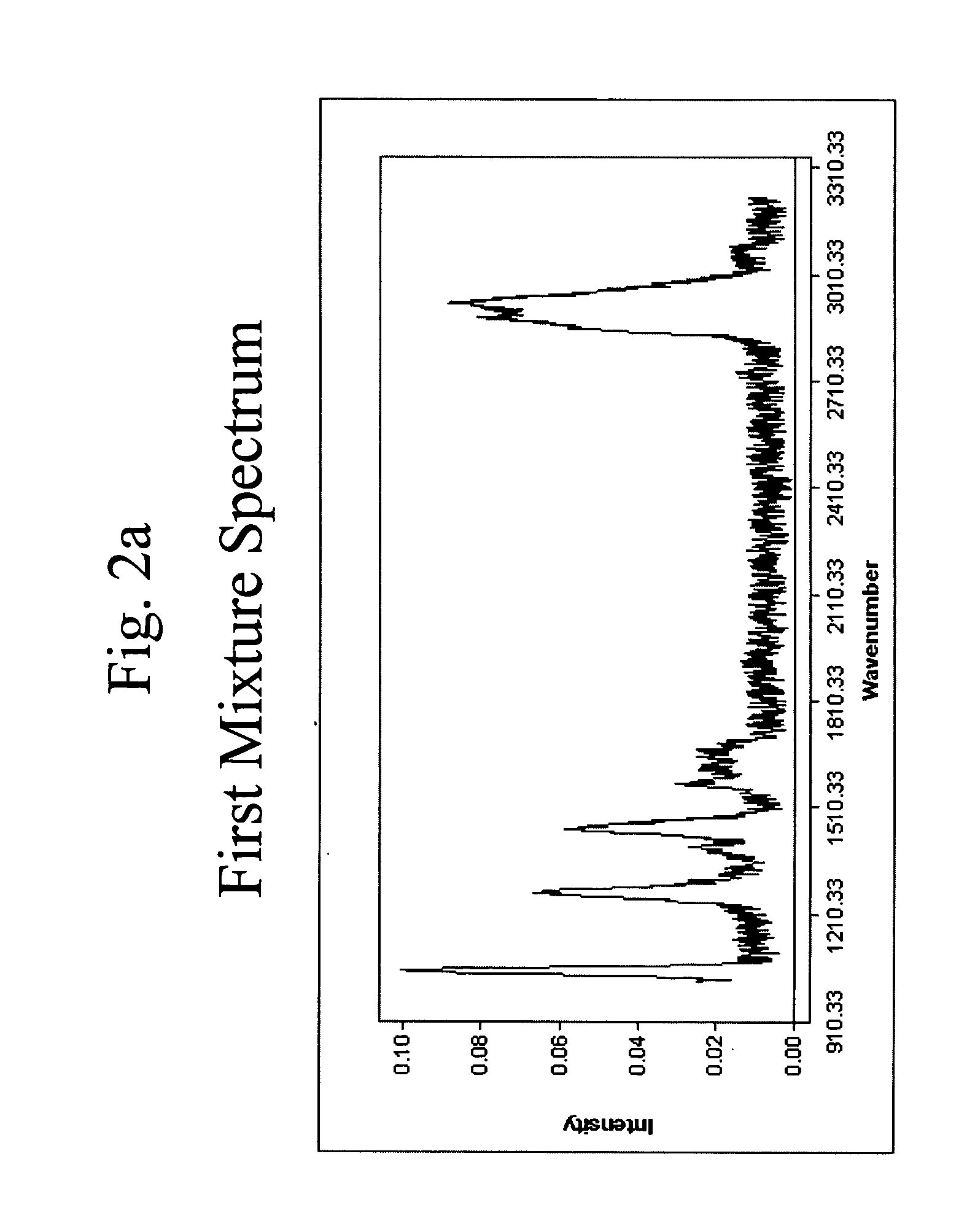
Method for identifying components of a mixture via spectral analysis
ActiveUS7072770B1Easy to detectEasy to identifyMolecular entity identificationSpectrum investigationCorrelation coefficientPresent method
The present invention is directed generally toward the field of spectral analysis and, more particularly, toward an improved method of identifying unknown components of a mixture from a set of spectra collected from the mixture using a spectral library including potential candidates. For example, the present method is directed to identifying components of a mixture by the steps which comprise obtaining a set of spectral data for the mixture that defines a mixture data space; ranking a plurality of library spectra of known elements according to their angle of projection into the mixture data space; calculating a corrected correlation coefficient for each combination of the top y ranked library spectra; and selecting the combination having the highest corrected correlation coefficient, wherein the known elements of the selected combination are identified as the components of the mixture.
Owner:CHEMIMAGE
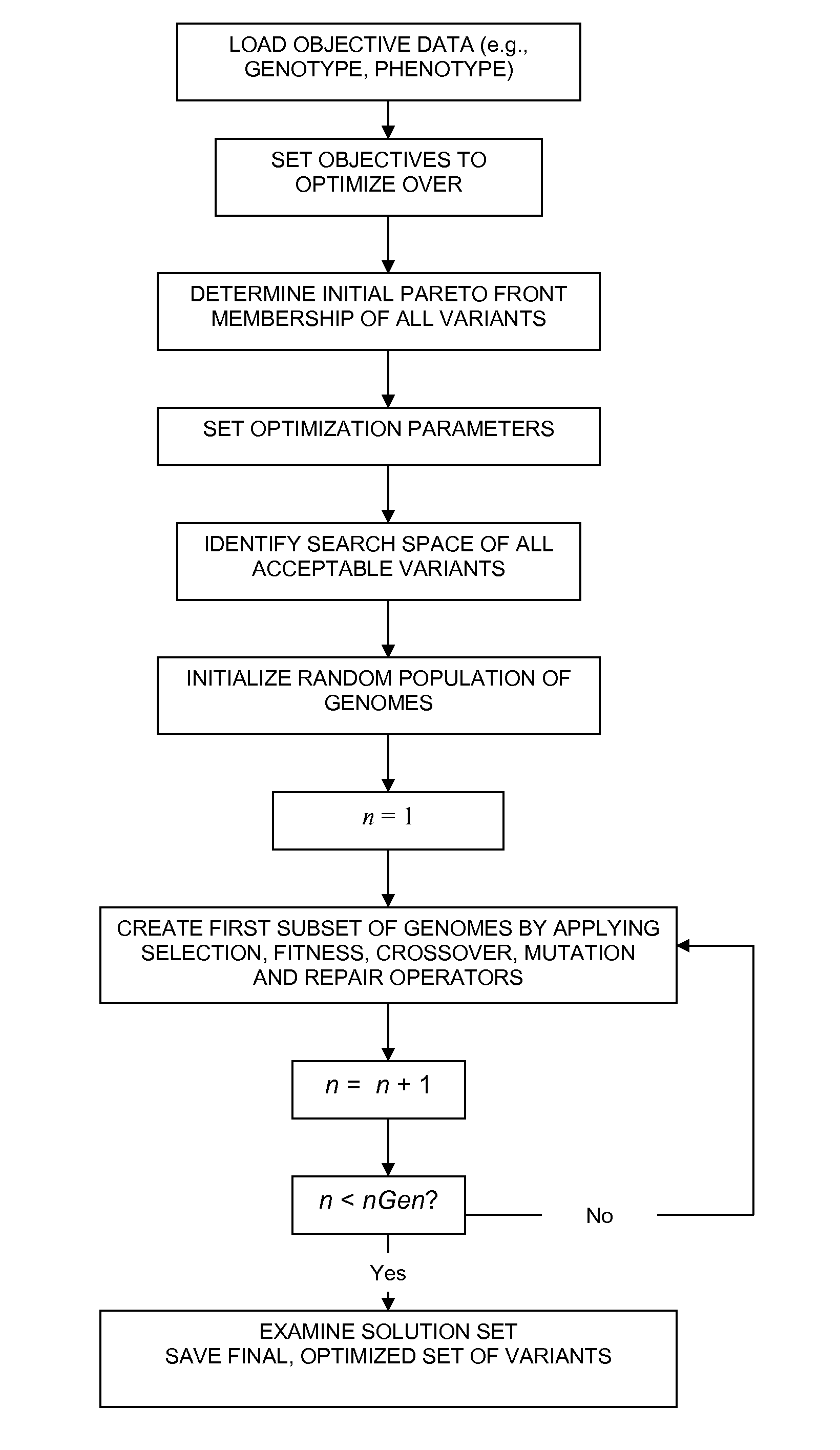
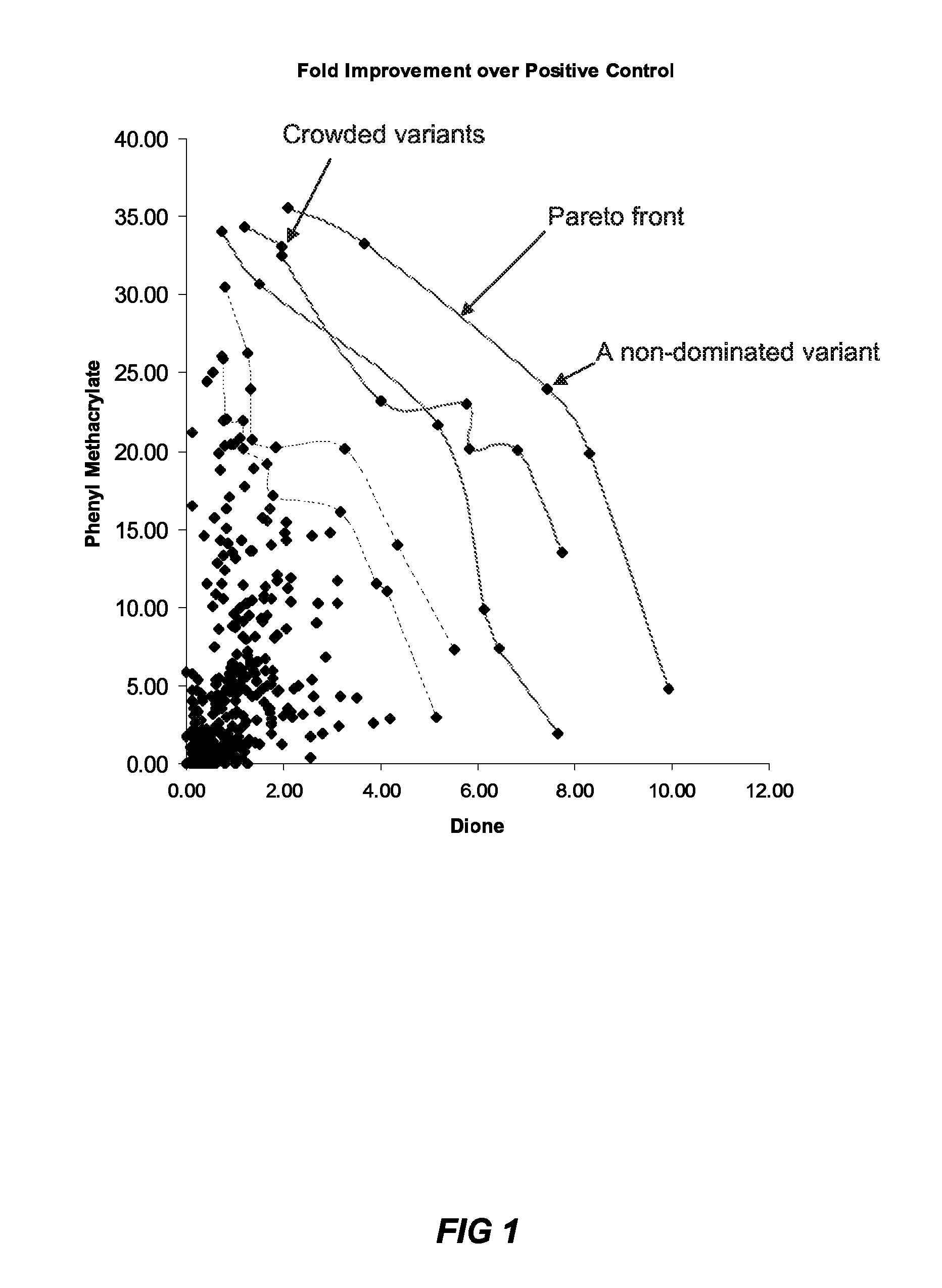
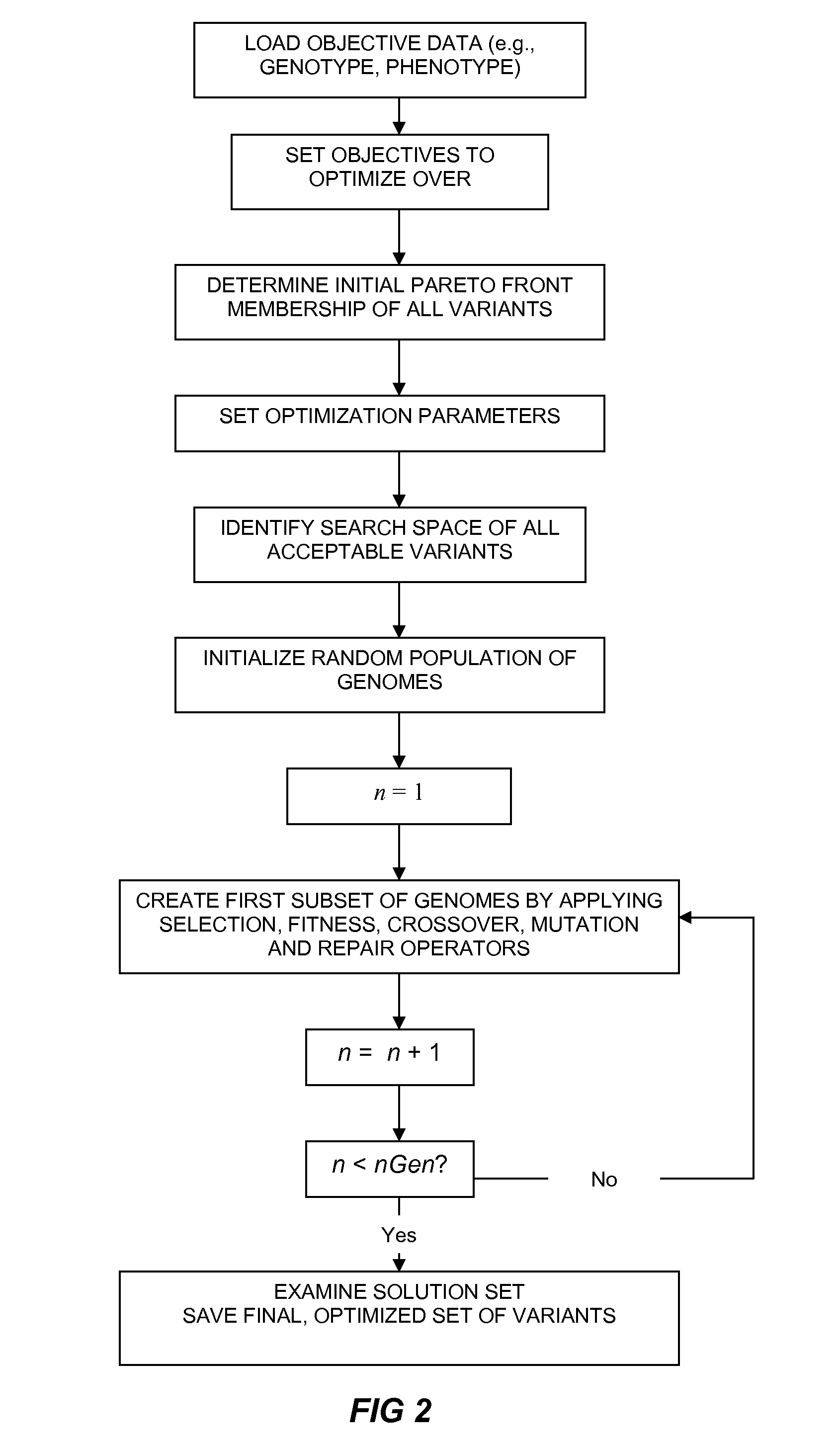
Method of generating an optimized, diverse population of variants
The present disclosure relates to methods of rapidly and efficiently searching biologically-related data space to identify a population set maximally diverse and optimized for sets of desired properties. More specifically, the disclosure provides methods of identifying a diverse, evolutionary separated bio-molecules with desired properties from complex bio-molecule libraries. The disclosure additionally provides digital systems and software for performing these methods.
Owner:CODEXIS INC
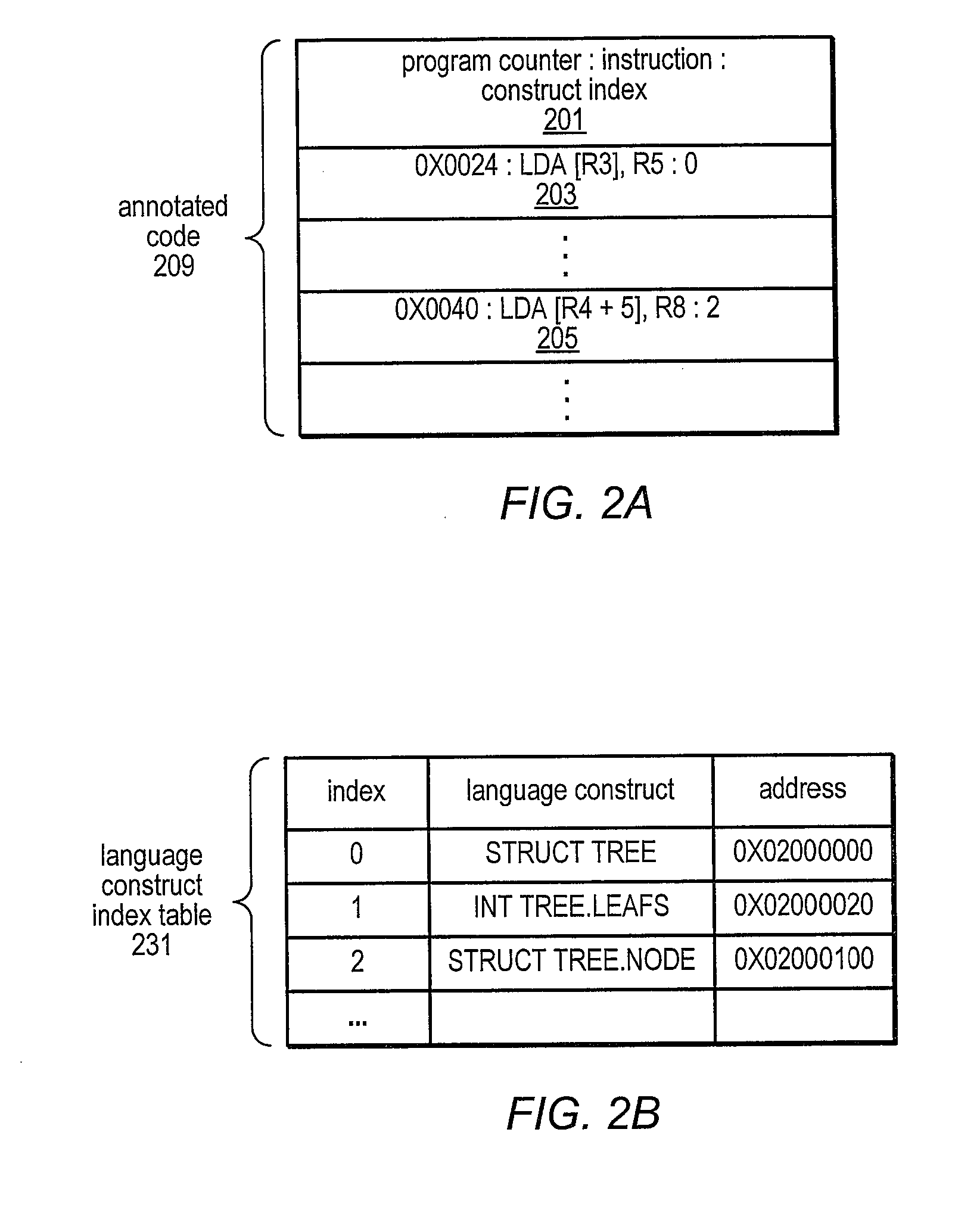
Method and apparatus for identifying instructions associated with execution events in a data space profiler
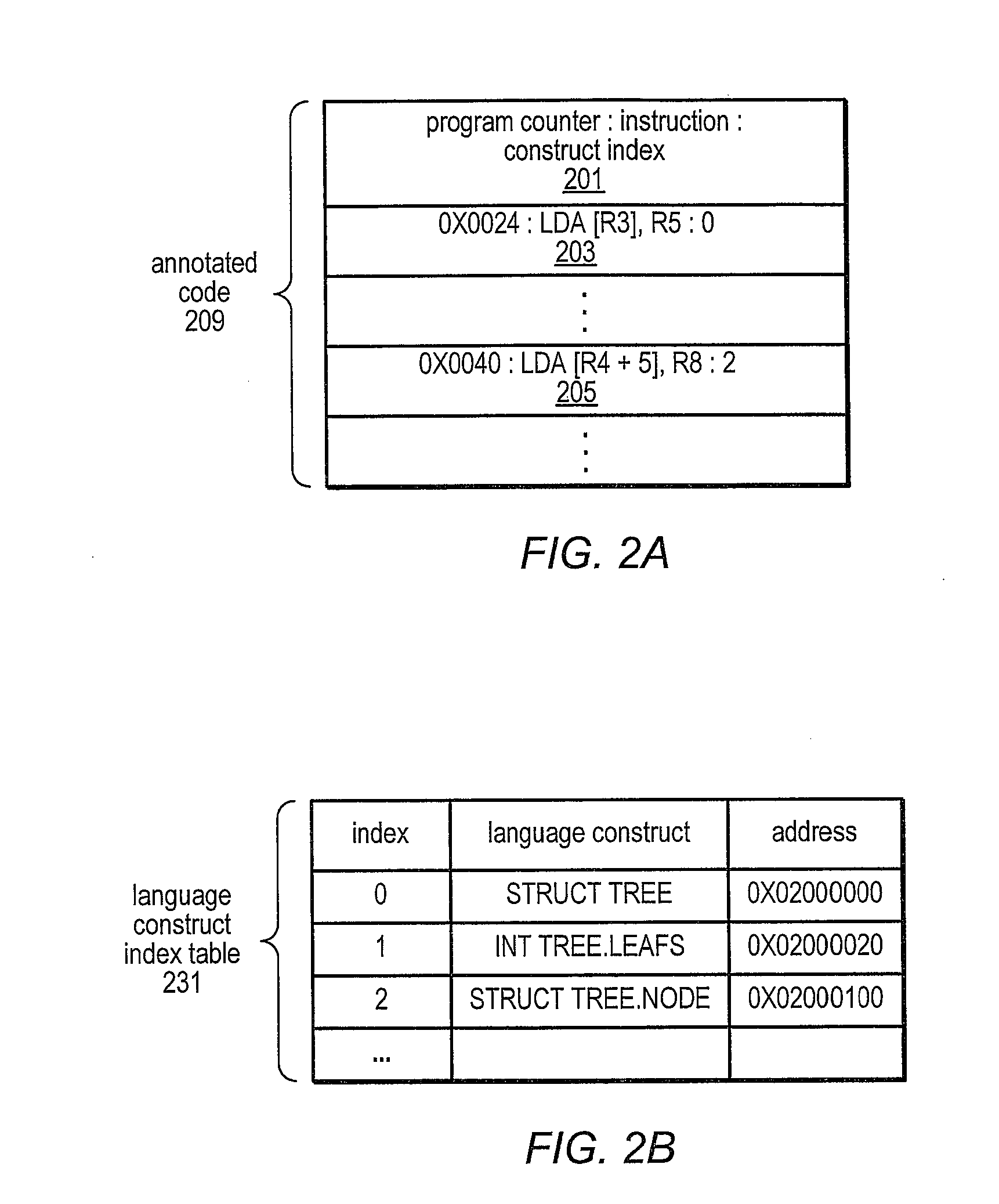
ActiveUS20080127120A1Error detection/correctionSpecific program execution arrangementsEvent typeData space
A system and method for profiling a software application may include means for capturing profiling information corresponding to an instruction identified as having executed coincident with the occurrence of a runtime event, and for associating the profiling information with the event in an event set. In some embodiments, the identified instruction, which may have triggered the event, may be located in the program code sequence at a predetermined position relative to the current program counter value at the time the event was detected. The predetermined relative position may be fixed dependent on the processor architecture and may also be dependent on the event type. The predetermined relative position may be zero, indicating that when the event was detected, the program counter value corresponded to an instruction associated with the event. If the identified instruction is an ambiguity-creating instruction, an indication of ambiguity may be associated with the event.
Owner:ORACLE INT CORP
Caliper for measuring objects in an image
ActiveUS9014441B2Improve visualizationEasy to measureImage analysisCharacter and pattern recognitionData spaceDisplay device
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Method for image data processing
InactiveUS20060251324A1Easy to set upReduce memory costScene recognitionComputer graphics (images)Data space
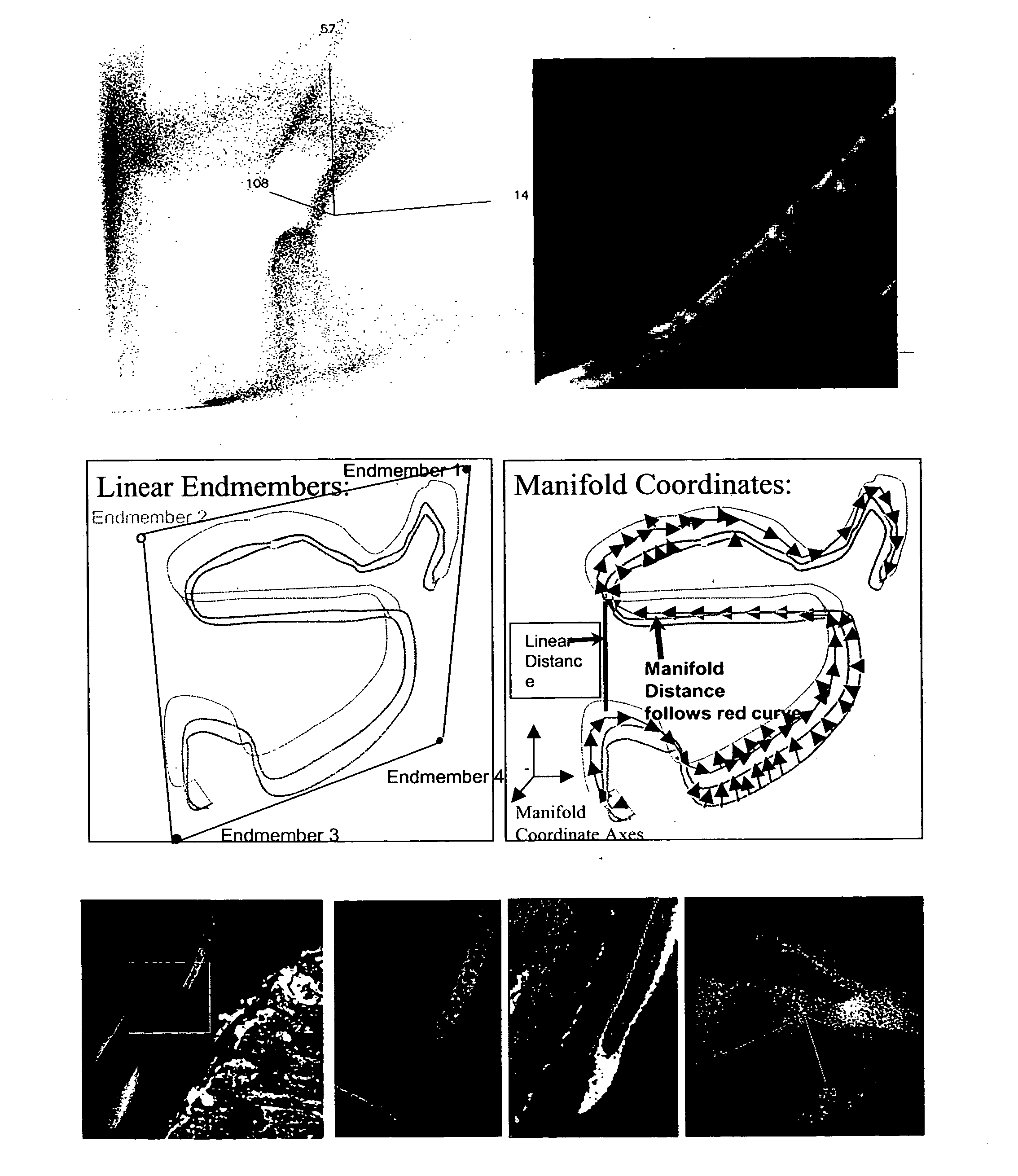
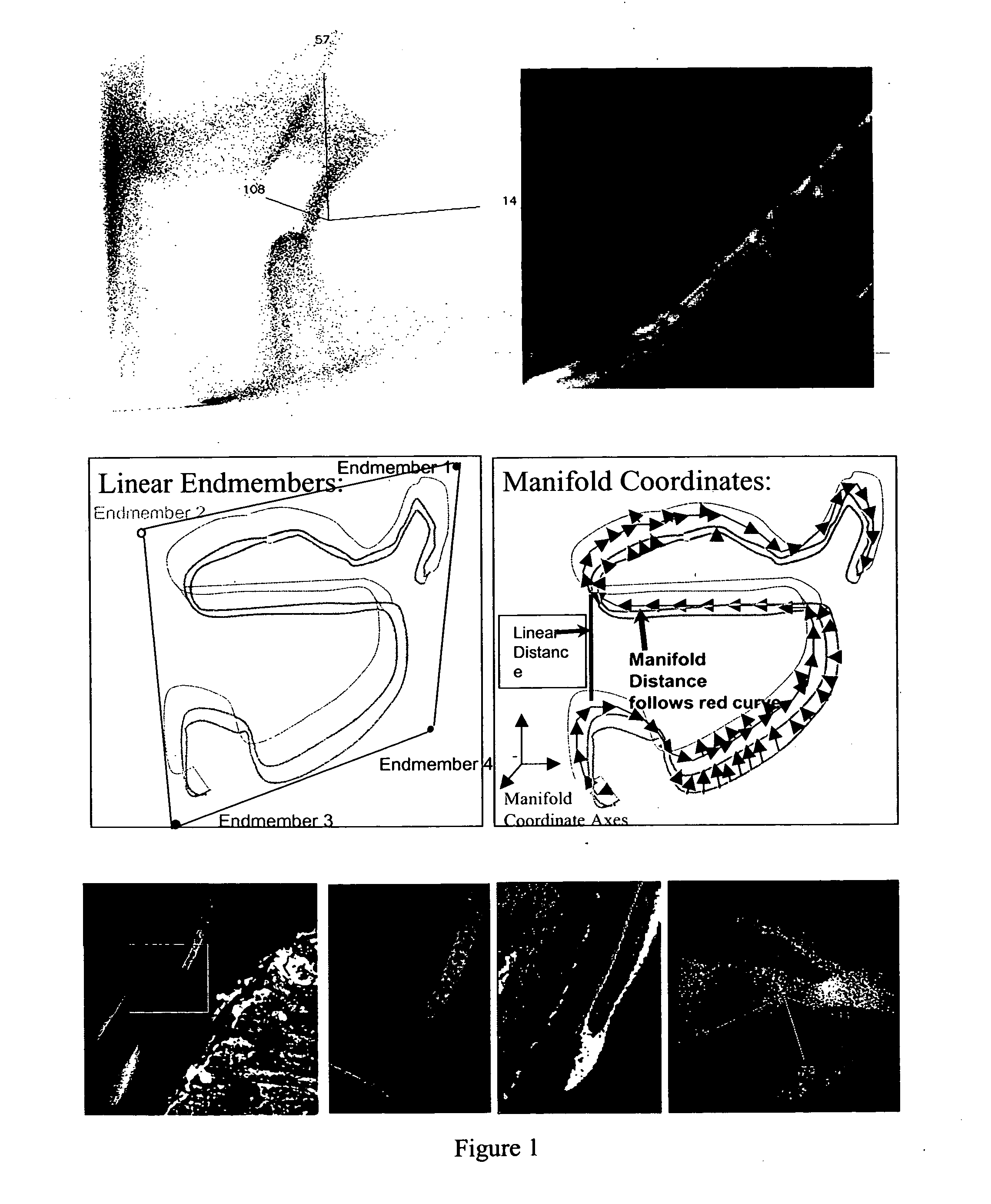
A method for exploiting the nonlinear structure of hyperspectral imagery employs a manifold coordinate system that preserves geodesic distances in the high-dimensional hyperspectral data space. Data representing physical parameters such as a scene is divided into a set of smaller tiles. The manifolds derived from the individual tiles are then aligned and stitched together to complete the scene. Coordinates are derived for a very large although not complete representative subset of the data termed the “backbone”. Manifold coordinates are derived for this representative backbone and then the remaining samples inserted into the backbone using a reconstruction principle using the property of local linearity everywhere on the manifold to reconstruct the manifold coordinates for the samples not originally belonging to the backbone. The output is a global manifold coordinate system, which for topographical image data depicts clearer detail of land and water portions of a scene.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
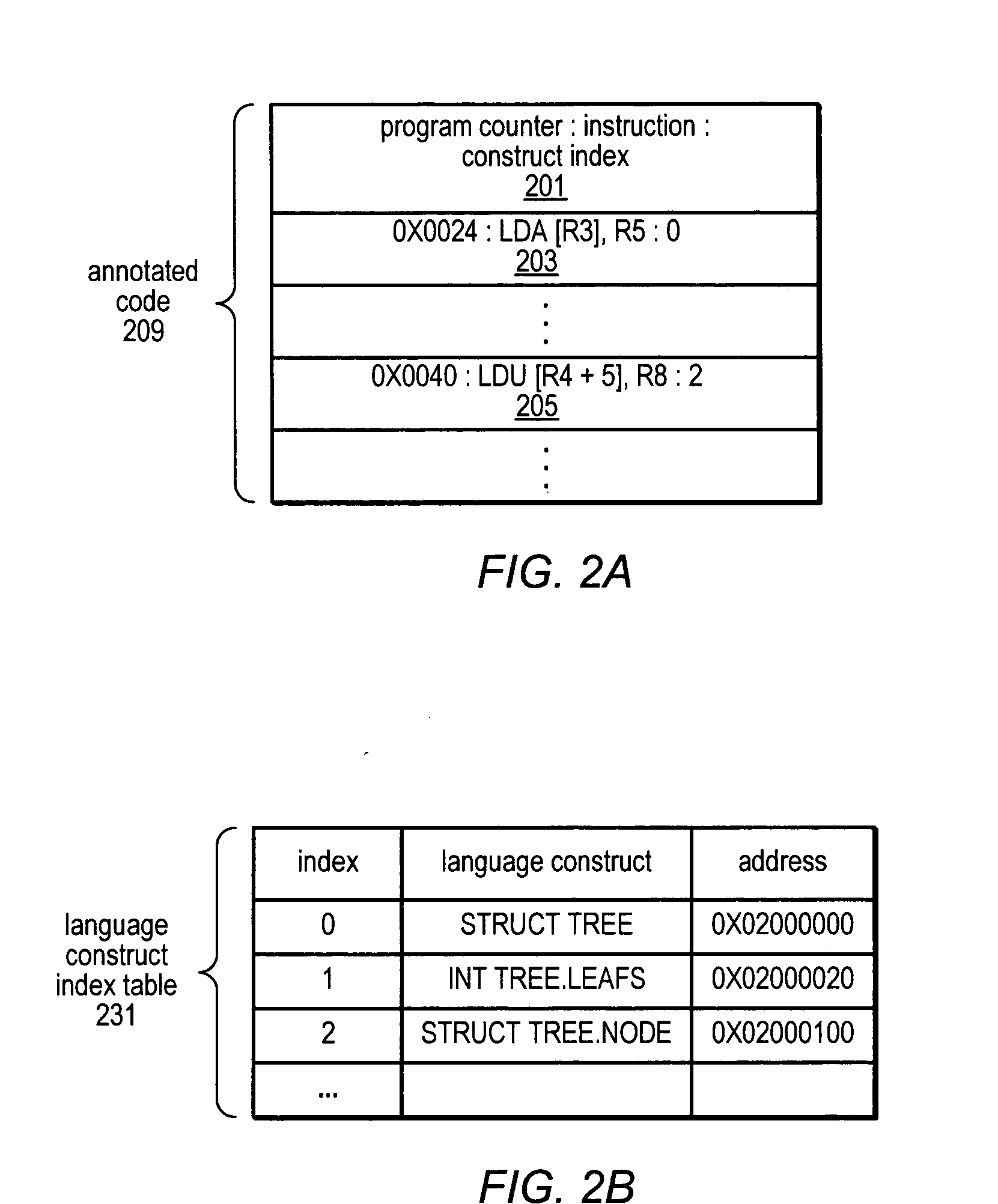
Method and Apparatus for Associating User-Specified Data with Events in a Data Space Profiler
A system and method for profiling a software application may include means for operating on context-specific data and costs. The system may include a descriptor apparatus for specifying identifiers of extended address elements to be profiled and locations for storing corresponding data values. In some embodiments, a list of variables to be included in profiling may be registered with an event agent and values of the variables may be captured in response to detection of a system event. Registering variables to be profiled may involve conveying a list of the variables or a pointer to such a list to the event agent. The event agent may associate the values of the registered variables with the detected system event and may store them in an event space database. The database may be accessed by a data space profiler to identify performance bottlenecks dependent on one or more registered variable values.
Owner:SUN MICROSYSTEMS INC
Method And System For Virtual Fast Access Non-Volatile RAM
ActiveUS20100023672A1Fast read accessFast write accessMemory architecture accessing/allocationMemory adressing/allocation/relocationData spaceDatabase
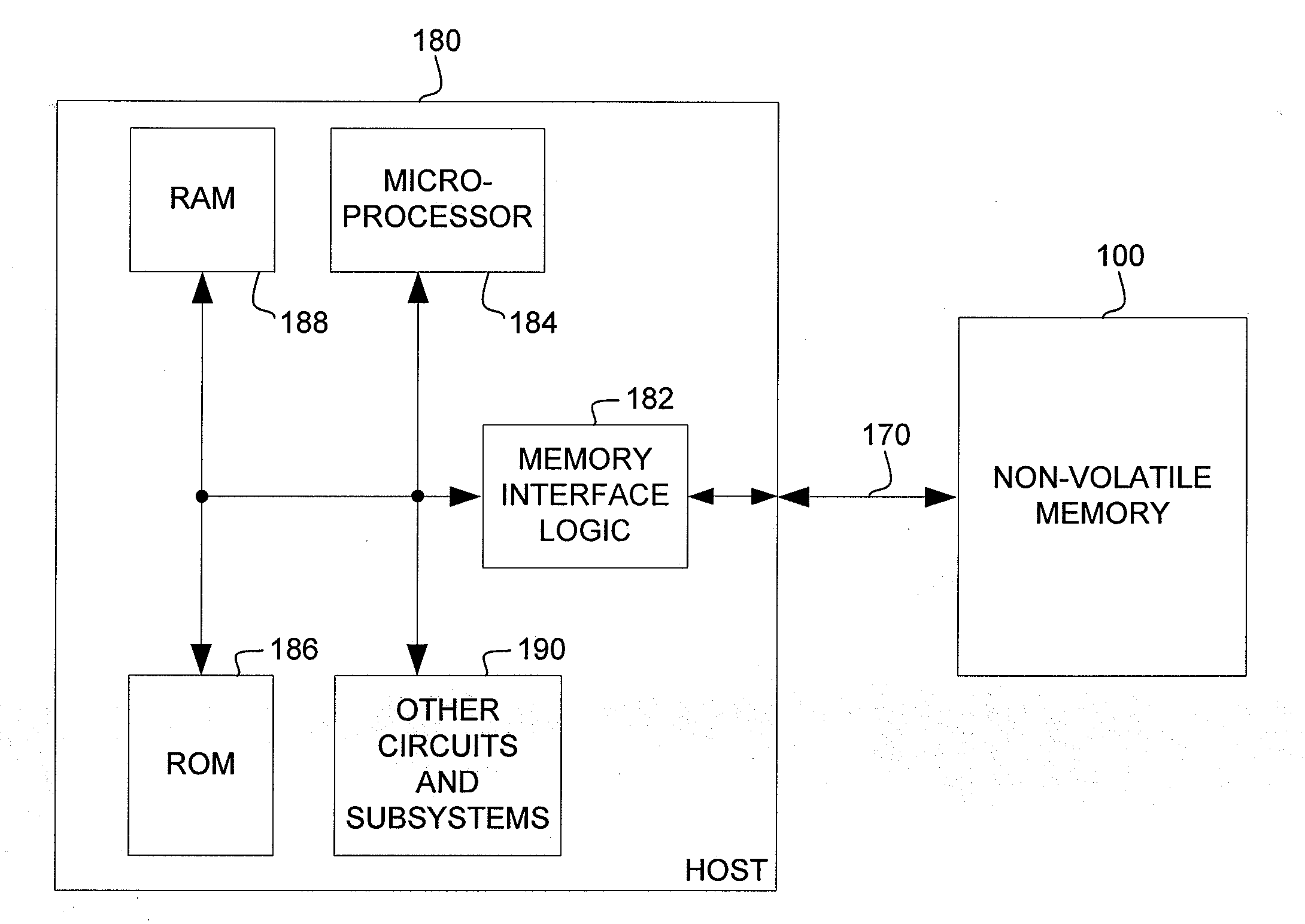
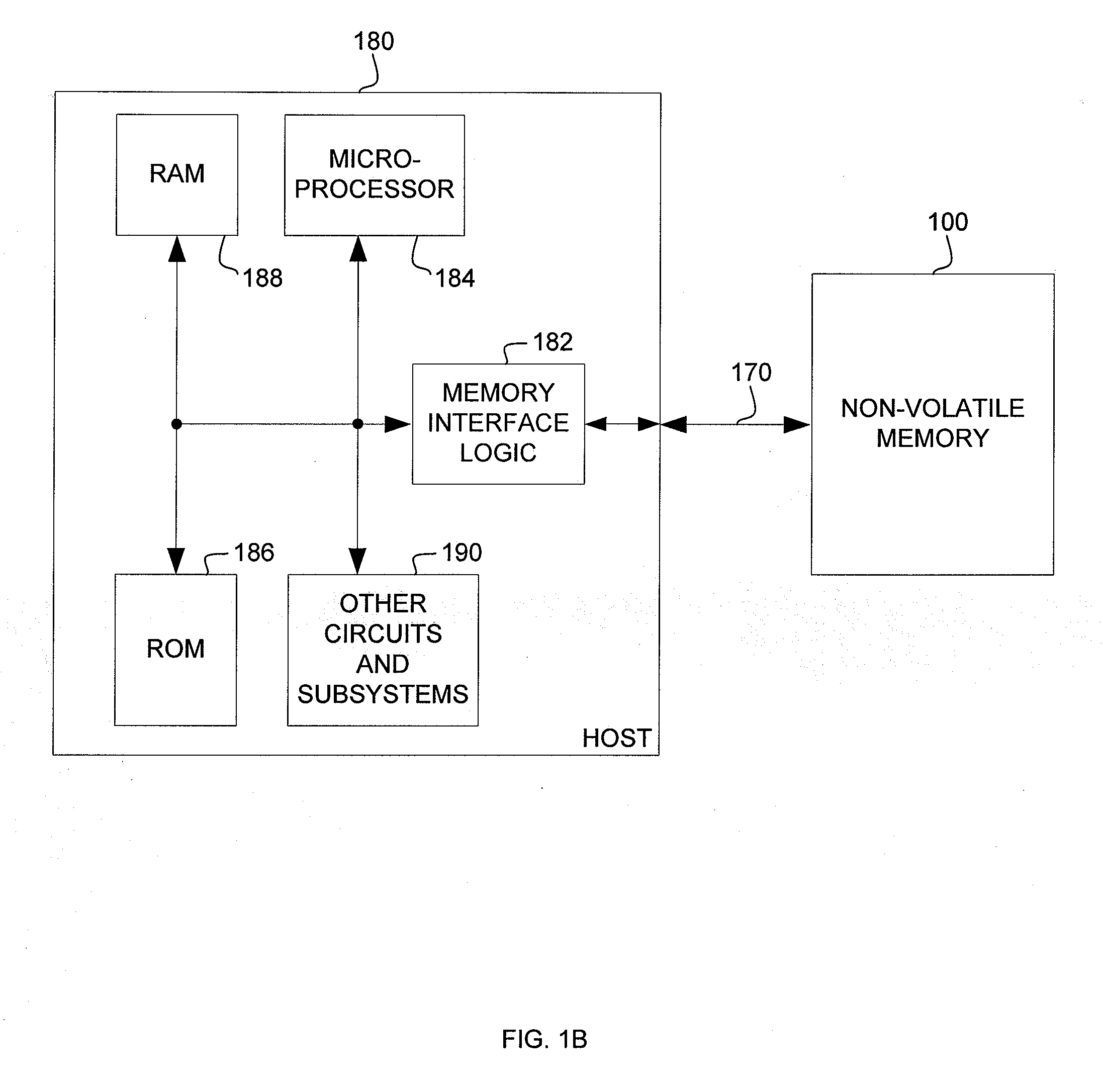
A method of writing data to a non-volatile memory with minimum units of erase of a block, a page being a unit of programming of a block, may read a page of stored data addressable in a first increment of address from the memory into a page buffer, the page of stored data comprising an allocated data space addressable in a second increment of address, pointed to by an address pointer, and comprising obsolete data. The first increment of address is greater than the second increment of address. A portion of stored data in the page buffer may be updated with the data to form an updated page of data. Storage space for the updated page of data may be allocated. The updated page of data may be written to the allocated storage space. The address pointer may be updated with a location of the allocated storage space.
Owner:SANDISK TECH LLC
Snapshots of file systems in data storage systems
ActiveUS20050021565A1Data processing applicationsDigital data processing detailsFile systemData space
The present invention relates to methods and systems of snapshot management of a file system in a data storage system. To represent the snapshots, the invention maintains pointers to the root block pointer of each snapshot. When the active file system is modified, this invention avoids overwriting any blocks used by previous snapshots by allocating new blocks for the modified blocks. When the invention needs to put an established block in a new location, it must update a parent block to point to the new location. The update to the parent block may then require allocating a new block for the new parent block and so forth. Parts of the file system not modified since a snapshot remain in place. The amount of space required to represent snapshots scales with the fraction of the file system that users modify. To maintain snapshot integrity, this invention keeps track of the first and last snapshots that use each block in space map blocks spread throughout the file system data space. When users delete snapshots, this invention may use a background process to find blocks no longer used by any snapshot and makes them available for future use.
Owner:ORACLE INT CORP
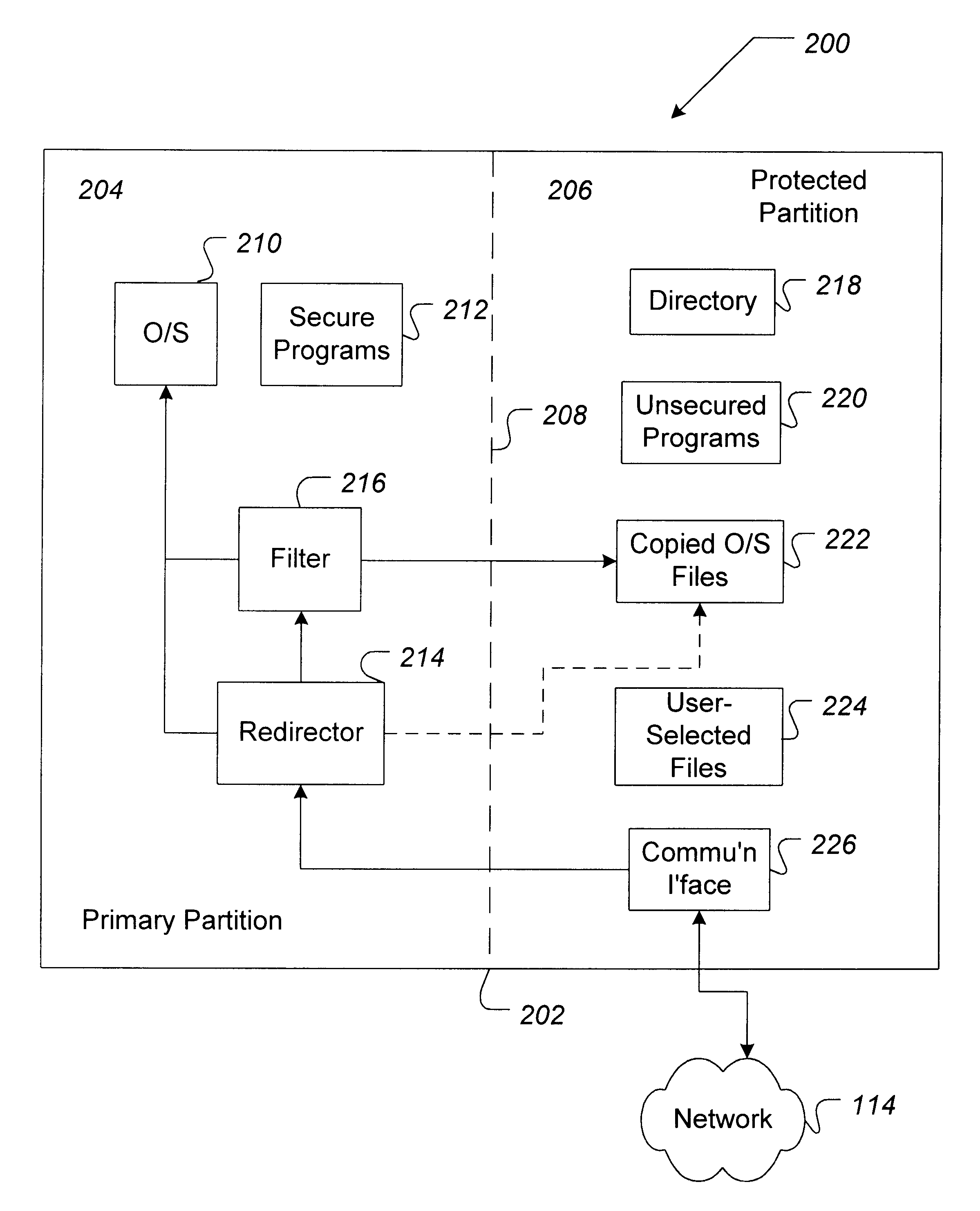
Methods, software, and apparatus for secure communication over a computer network
InactiveUS6192477B1Digital data processing detailsError detection/correctionSecure communicationData space
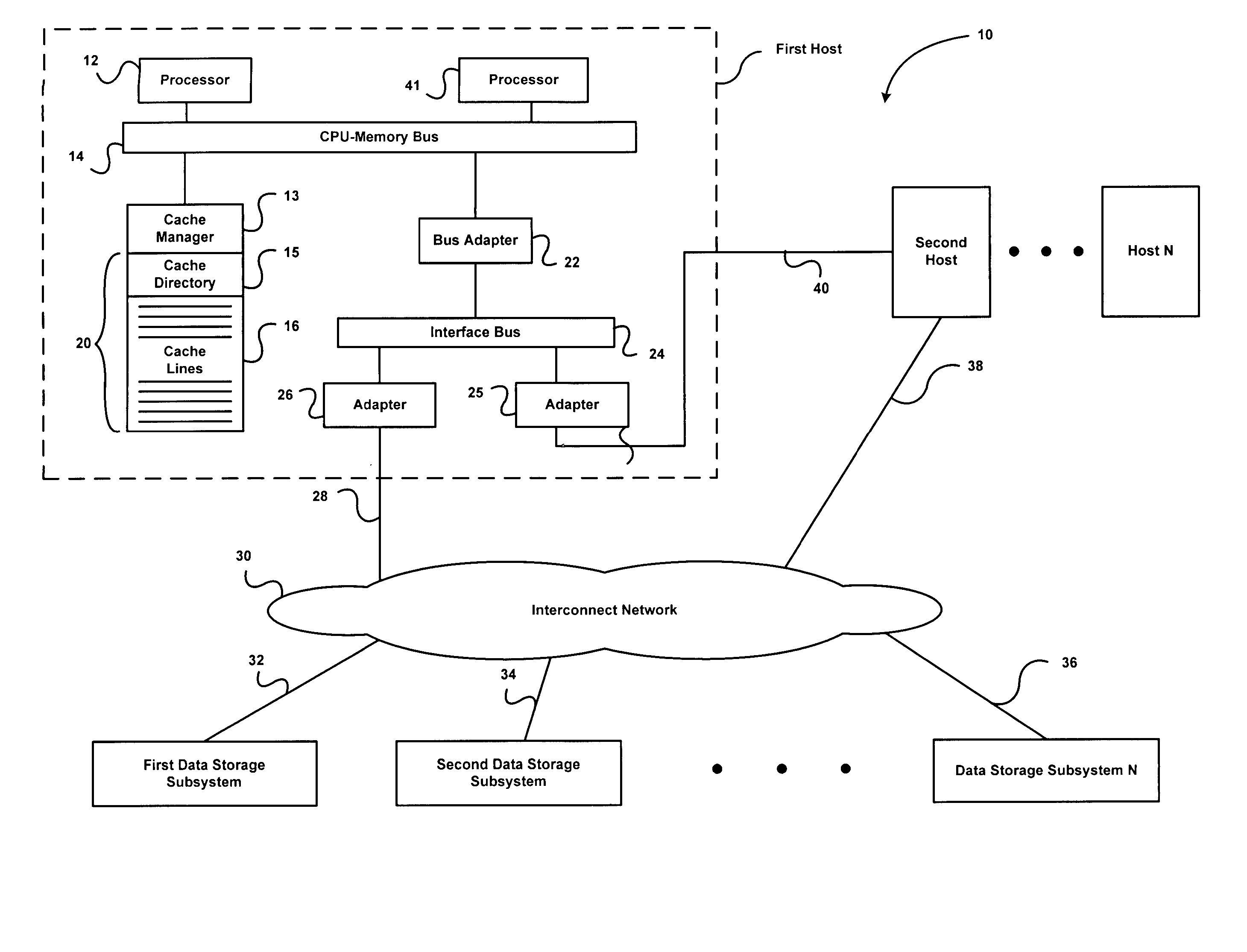
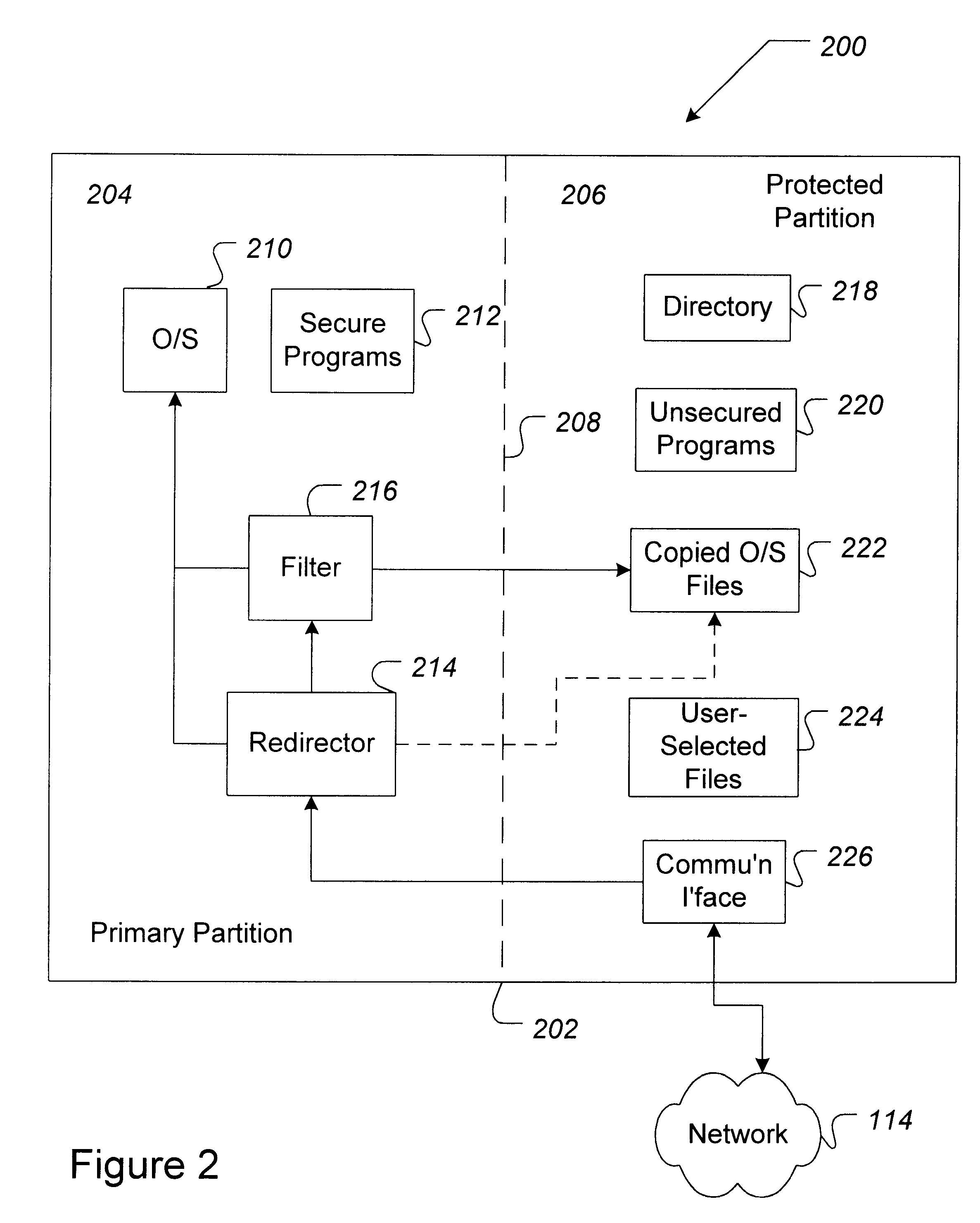
A method for performing secure communication between a first user's computer and second remote computer over a computer network is described. According to one embodiment of this aspect, the data space of the first computer is partition into a first secure portion and a second network interface portion. Communication is established between the first and a second computer, and redirection and filter mechanisms are initialized. An instruction is received by the first computer, analyzed by the redirection mechanism, and passed to the filter if the instruction is a protected instruction. The protected instruction is verified by the filter and processed if the verification is successful.
Owner:DAGG
Snapshots of file systems in data storage systems
Owner:ORACLE INT CORP
Systems and methods of searching for and determining modified blocks in a file system
InactiveUS20100179959A1Digital data information retrievalDigital data processing detailsFile systemData space
The invention relates to a method of determining if a block was modified in a file system by comparing the versions of the base snapshot, the delta snapshot, and the space map block entry (b, e). In another aspect, the invention relates to a method of searching for blocks modified in a tree structured file system. The invention relates to methods and systems of snapshot management of a file system in a data storage system. To represent the snapshots, the invention maintains pointers to the root block pointer of each snapshot. When the active file system is modified, this invention avoids overwriting any blocks used by previous snapshots by allocating new blocks for the modified blocks. When the invention needs to put an established block in a new location, it must update a parent block to point to the new location. The update to the parent block may then require allocating a new block for the new parent block and so forth. Parts of the file system not modified since a snapshot remain in place. The amount of space required to represent snapshots scales with the fraction of the file system that users modify. To maintain snapshot integrity, this invention keeps track of the first and last snapshots that use each block in space map blocks spread throughout the file system data space. When users delete snapshots, this invention may use a background process to find blocks no longer used by any snapshot and makes them available for future use.
Owner:ORACLE INT CORP
Multiprocessor node controller circuit and method
InactiveUS7406086B2Ease of parallel processingImprove welfareMultiplex system selection arrangementsMemory adressing/allocation/relocationMemory addressMemory chip
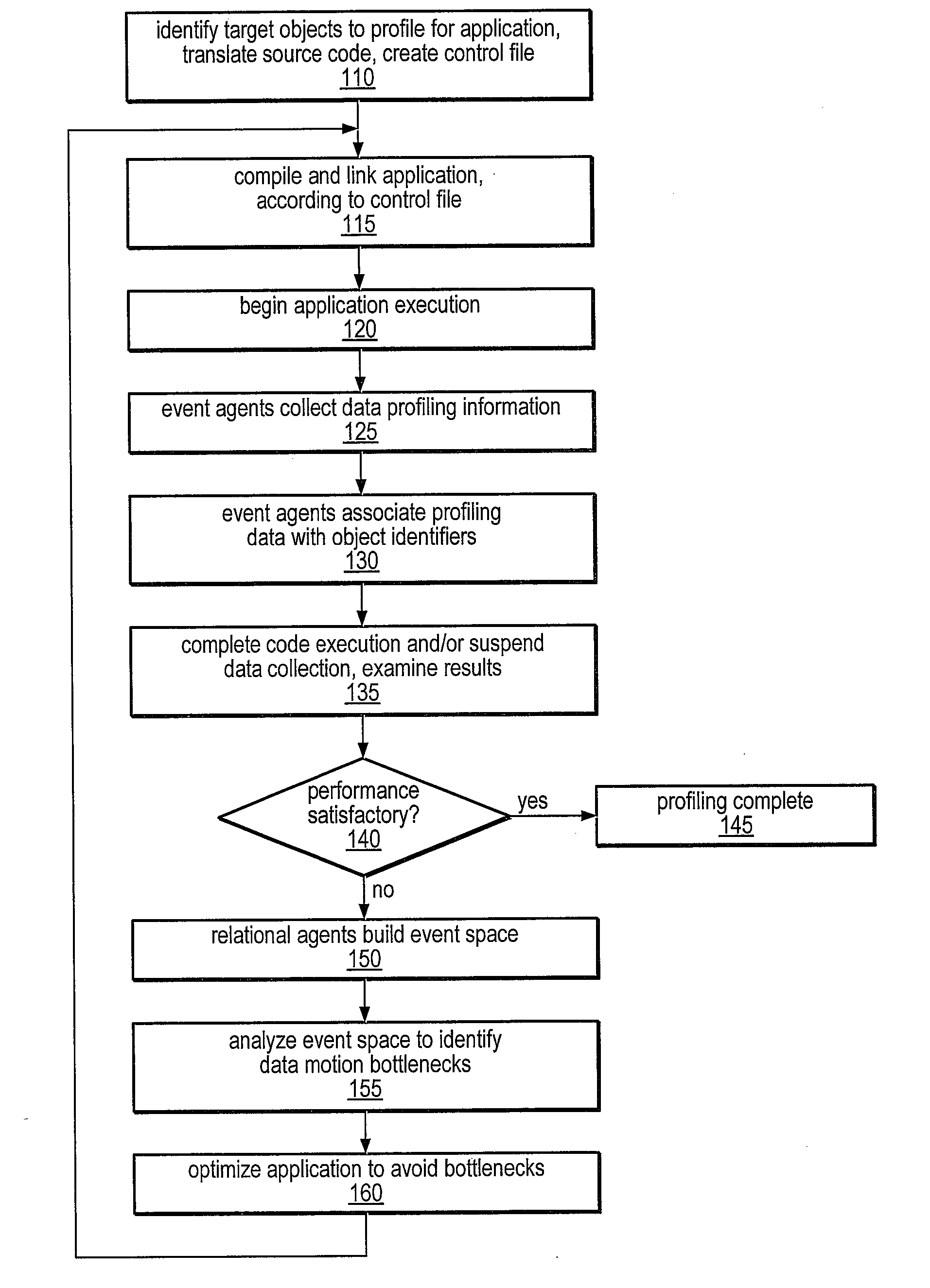
Improved method and apparatus for parallel processing. One embodiment provides a multiprocessor computer system that includes a first and second node controller, a number of processors being connected to each node controller, a memory connected to each controller, a first input / output system connected to the first node controller, and a communications network connected between the node controllers. The first node controller includes: a crossbar unit to which are connected a memory port, an input / output port, a network port, and a plurality of independent processor ports. A first and a second processor port connected between the crossbar unit and a first subset and a second subset, respectively, of the processors. In some embodiments of the system, the first node controller is fabricated onto a single integrated-circuit chip. Optionally, the memory is packaged on plugable memory / directory cards wherein each card includes a plurality of memory chips including a first subset dedicated to holding memory data and a second subset dedicated to holding directory data. Further, the memory port includes a memory data port including a memory data bus and a memory address bus coupled to the first subset of memory chips, and a directory data port including a directory data bus and a directory address bus coupled to the second subset of memory chips. In some such embodiments, the ratio of (memory data space) to (directory data space) on each card is set to a value that is based on a size of the multiprocessor computer system.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Method and apparatus for computing user-specified cost metrics in a data space profiler
A system and method for profiling a software application may include means for defining a custom cost metric that includes a cost metric identifier and a cost function. The cost function may apply a mathematical formula to data extracted from an event set to calculate a respective cost metric value for each of one or more events in the event set. The data extracted from the event set may include one or more respective profiling object identifiers and one or more other respective costs associated with each of the one or more events. A cost associated with an event in the event space may be associated with a function or basic block of instructions. The cost function may include a distribution formula for attributing at least a portion of the cost associated with a function or basic block to each of the instructions comprising the function or basic block.
Owner:ORACLE INT CORP
Method of storing and retrieving multi-dimensional data using the hilbert curve
InactiveUS7167856B2Gain selective accessMinimizes numberData processing applicationsDigital data information retrievalData spaceHilbert space
Owner:LAWDER JONATHAN KEIR
System and method for automated search by distributed elements
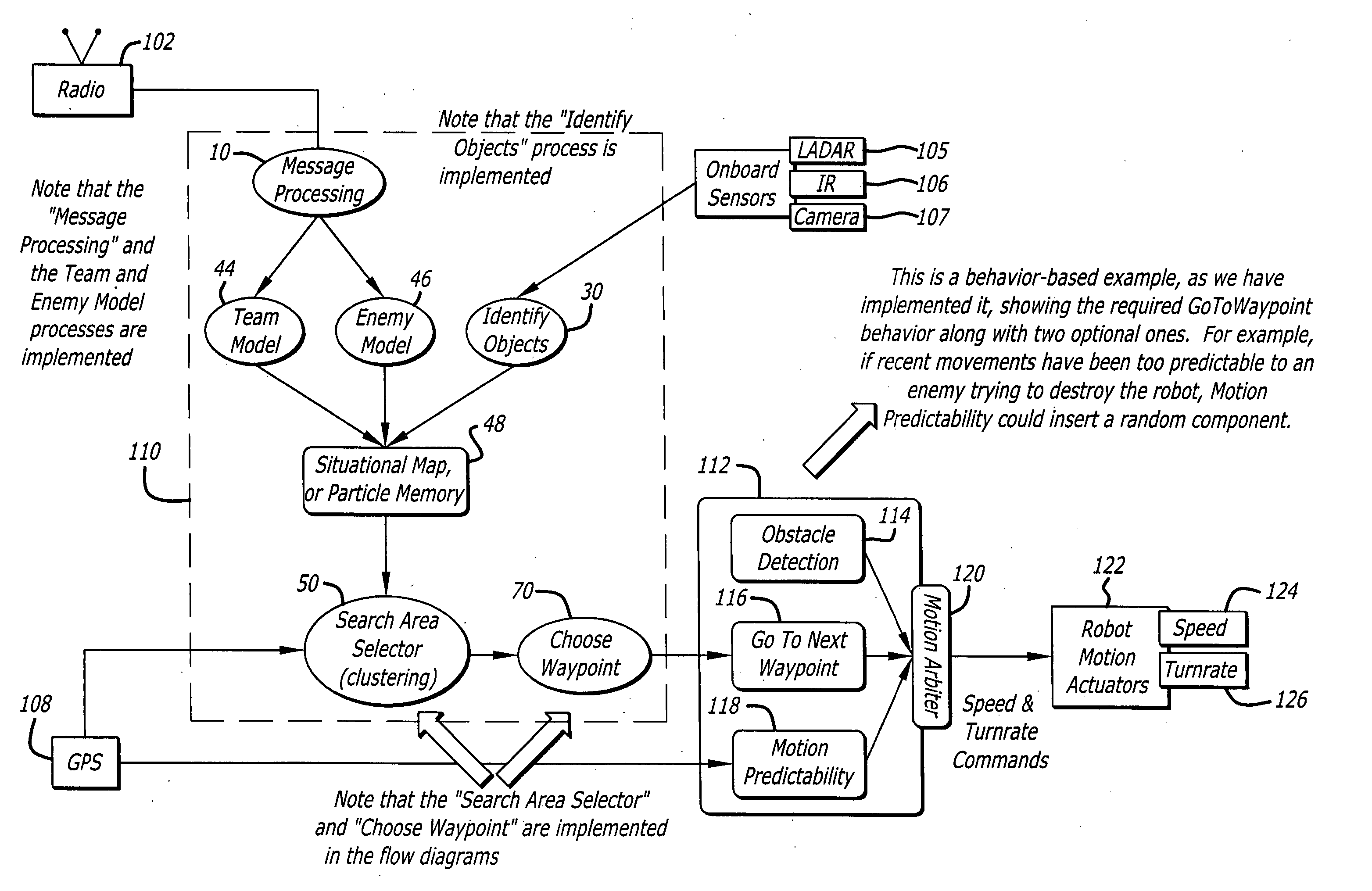
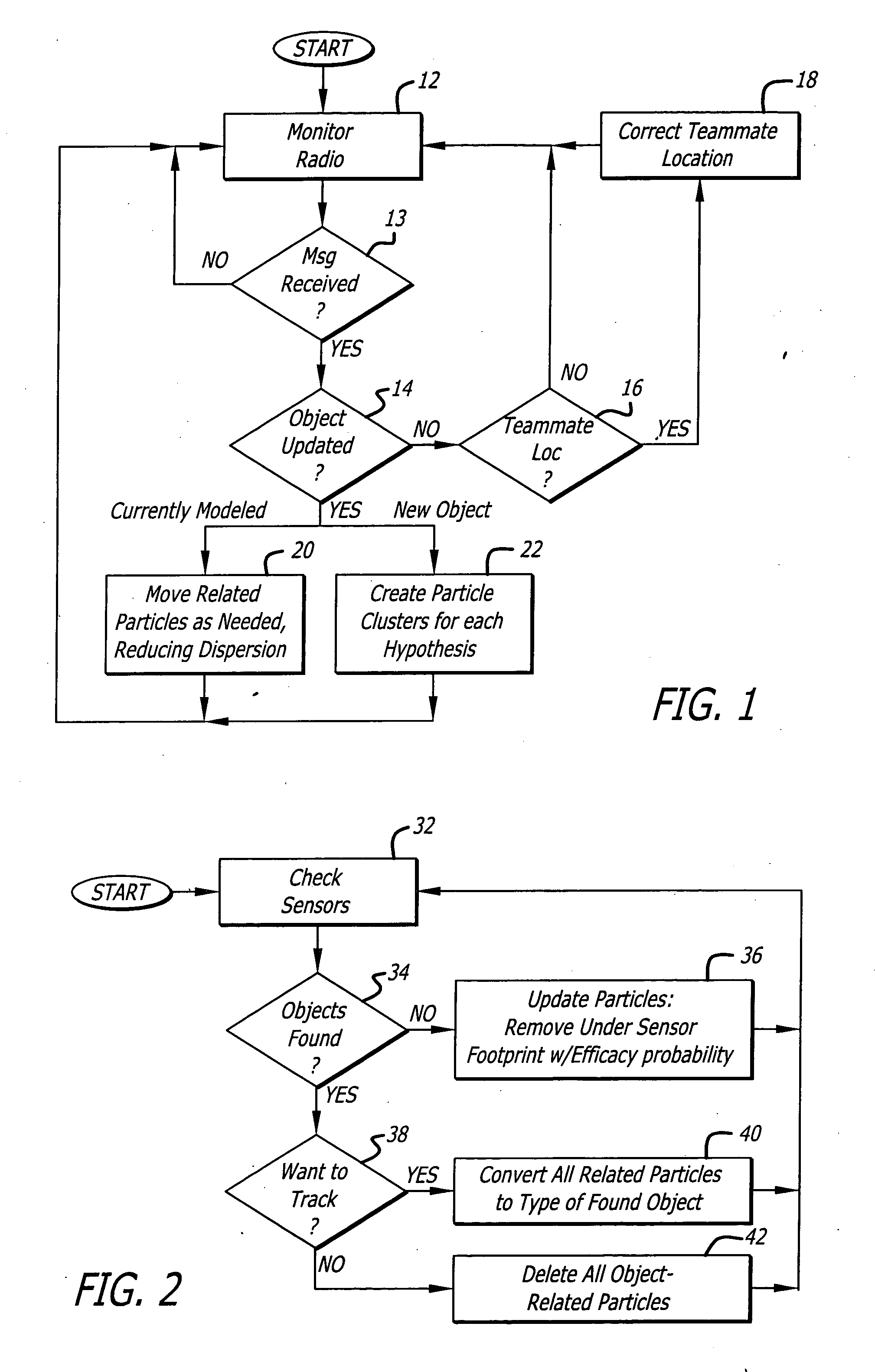
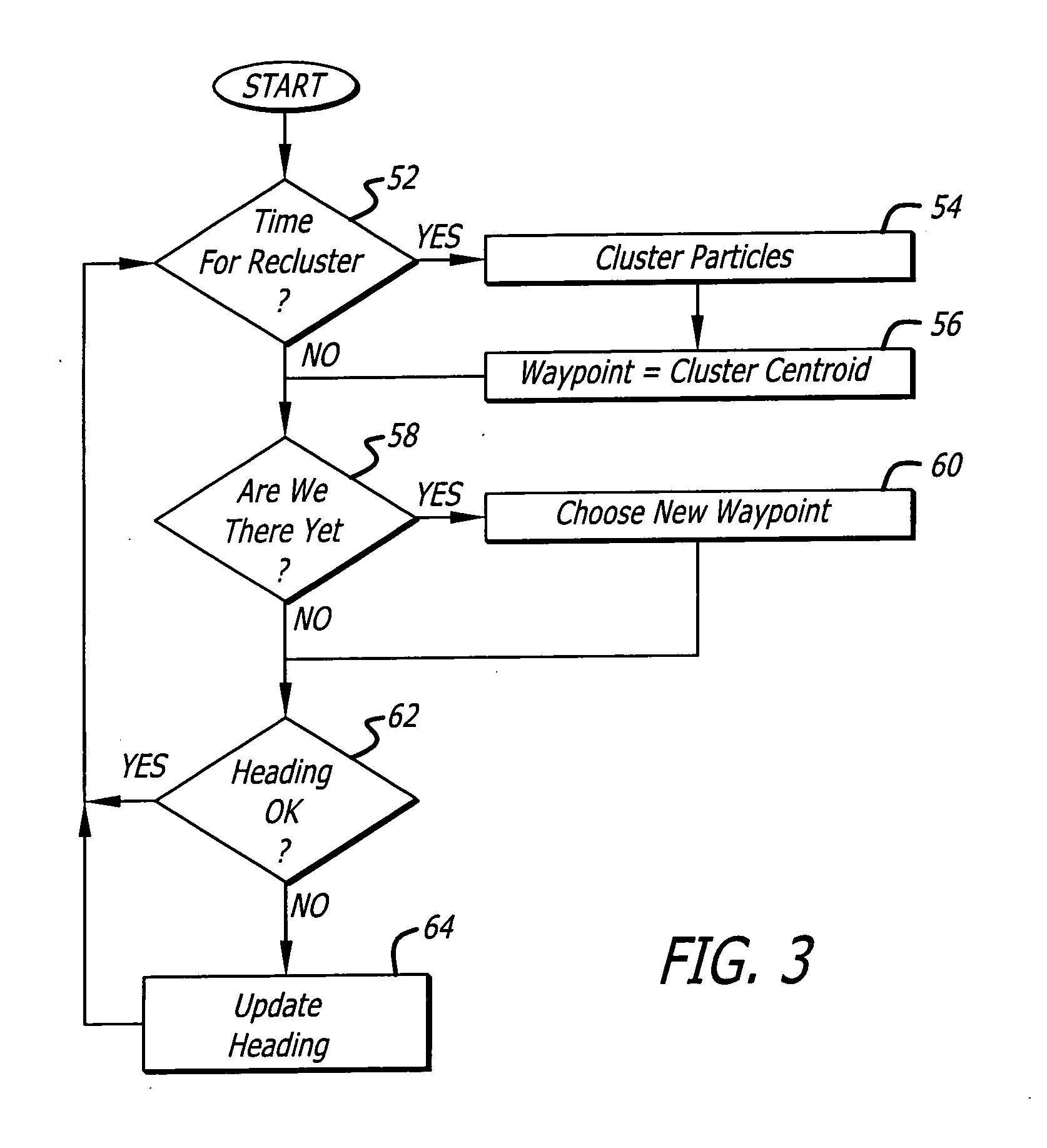
InactiveUS20060015215A1Autonomous decision making processPosition fixationSearch problemProbability representation
A system and method for decentralized cooperative control of a team of agents for geographic and other search tasks. The approach is behavior-based and uses probability particle approach to the search problem. Agents are attracted to probability distributions in the form of virtual particles of probability that represent hypotheses about the existence of objects of interest in a geographic area or a data-space. Reliance on dependable, high-bandwidth communication is reduced by modeling the movements of other team members and the objects of interest between periodic update messages.
Owner:RAYTHEON CO
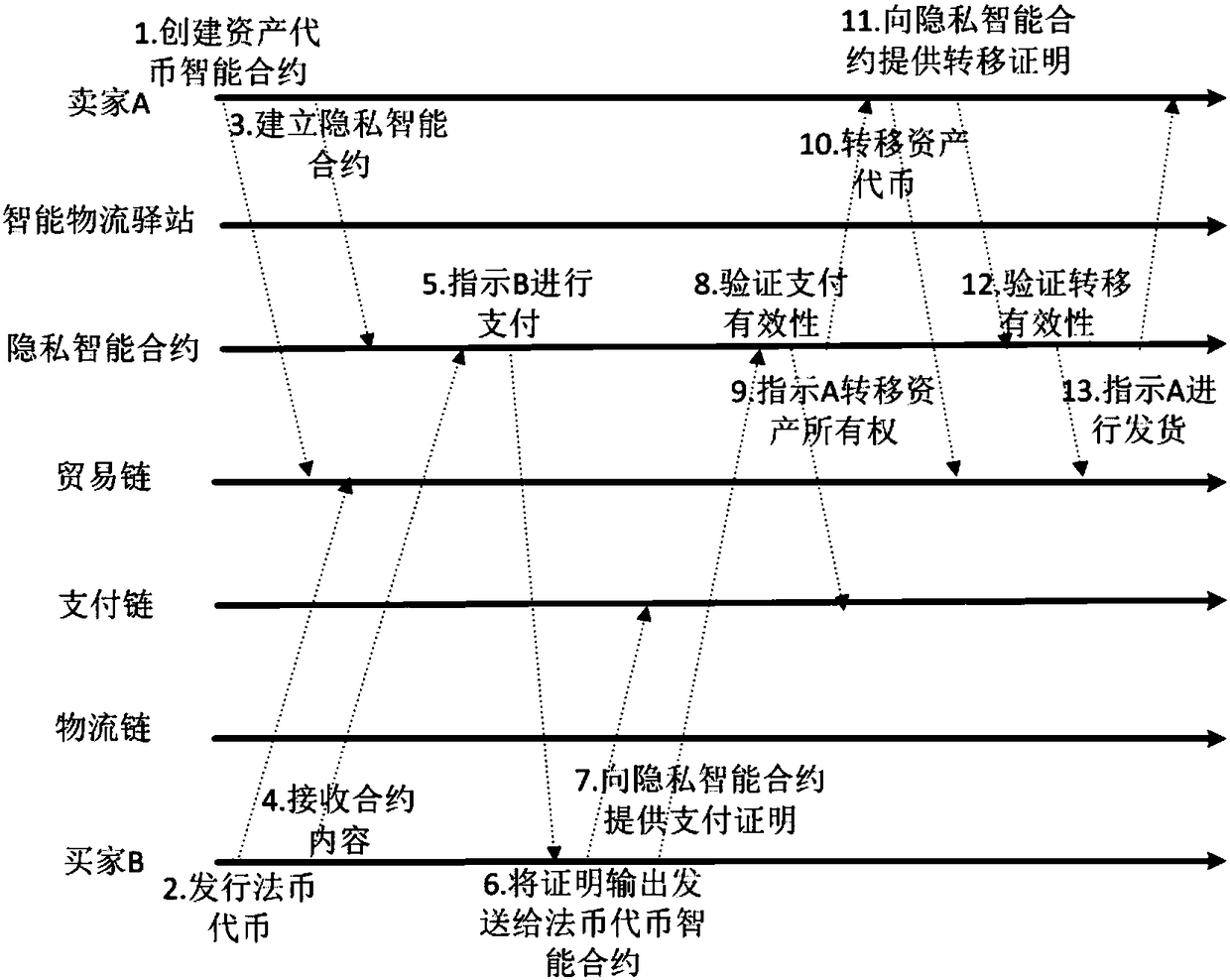
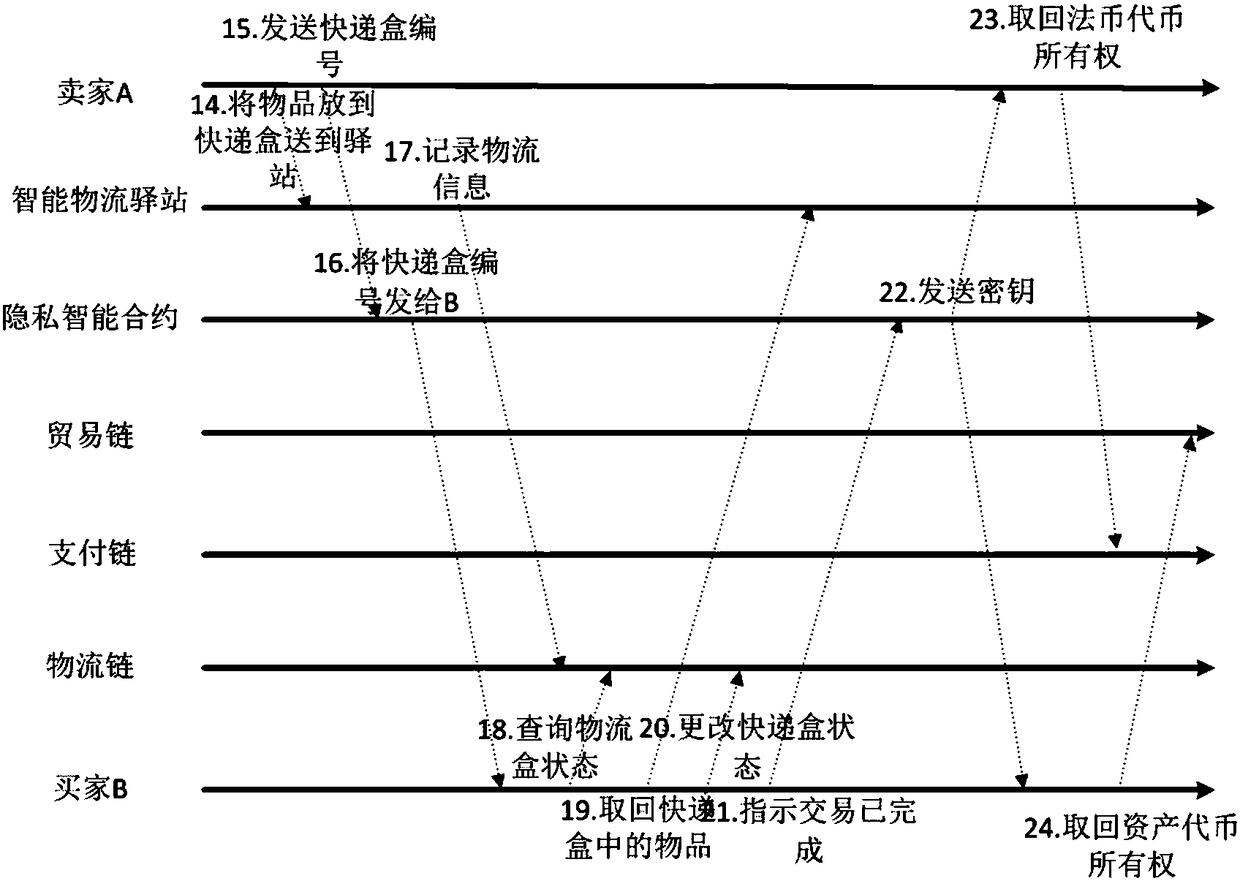
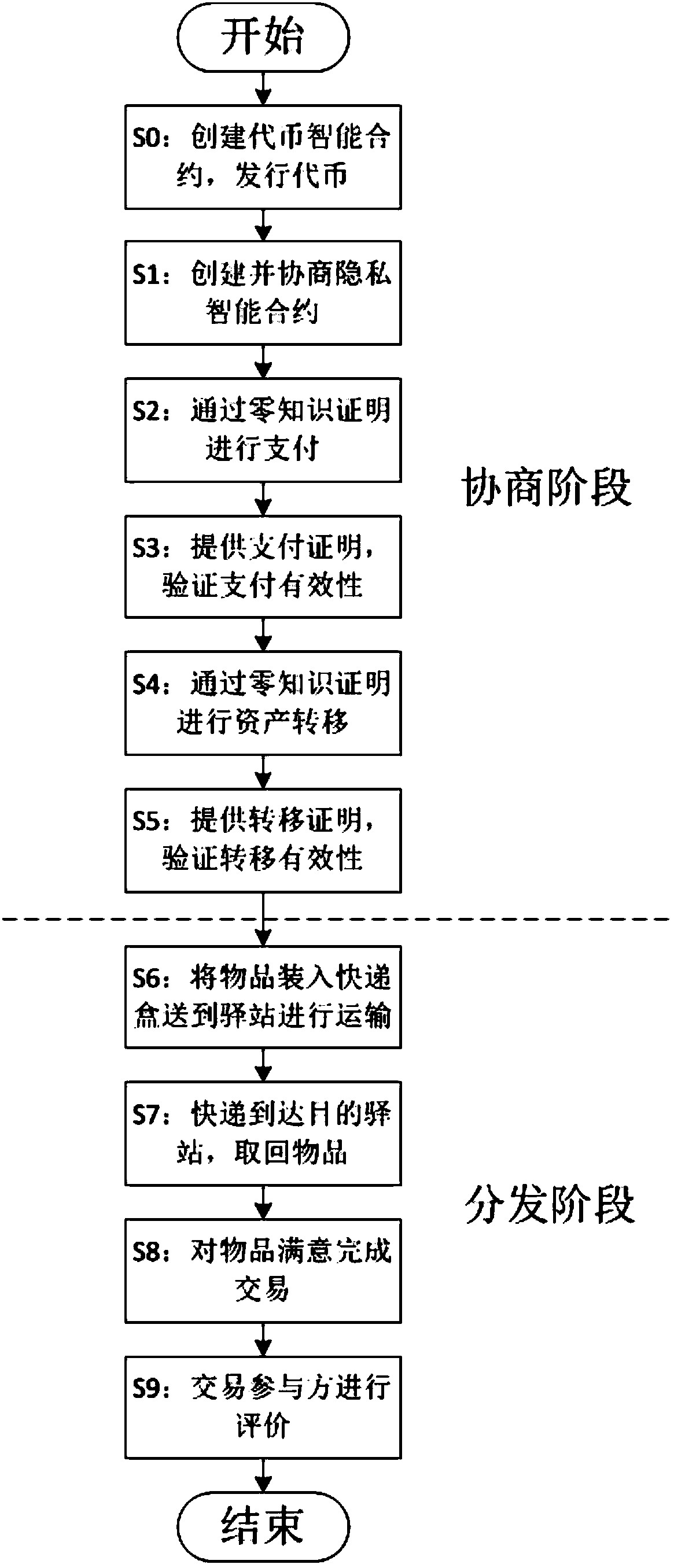
Privacy protection transaction method based on blockchain technology in electronic commerce
ActiveCN108389046AEase of evaluationMeet privacy requirementsFinanceDigital data protectionData privacy protectionLogistics management
The invention discloses a privacy protection transaction method based on a blockchain technology in electronic commerce. The method comprises the following steps that: adopting the blockchain technology which comprises a privacy smart contract and a zero-knowledge proof to protect the private information of a user; taking the privacy smart contract as a bridge between a buyer and a seller in a transaction period; adopting the zero-knowledge proof to issue a confidentiality token and create a confidentiality transaction; and combining the blockchain, an industrial data space and the Internet ofThings technology to establish infrastructure, and establishing an integrated platform for logistics business management in a distribution way. By use of the method, private information can be hiddenfor dispatchers, private information, including, identity, address, telephone number and the like, can be hidden for sellers, in addition, the method also can be used for other blockchain applicationscenes with a data privacy protection requirement, in addition, blockchain characteristics can be fully utilized, and therefore, the evaluation problem of an electronic commerce platform can be improved.
Owner:XI AN JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com