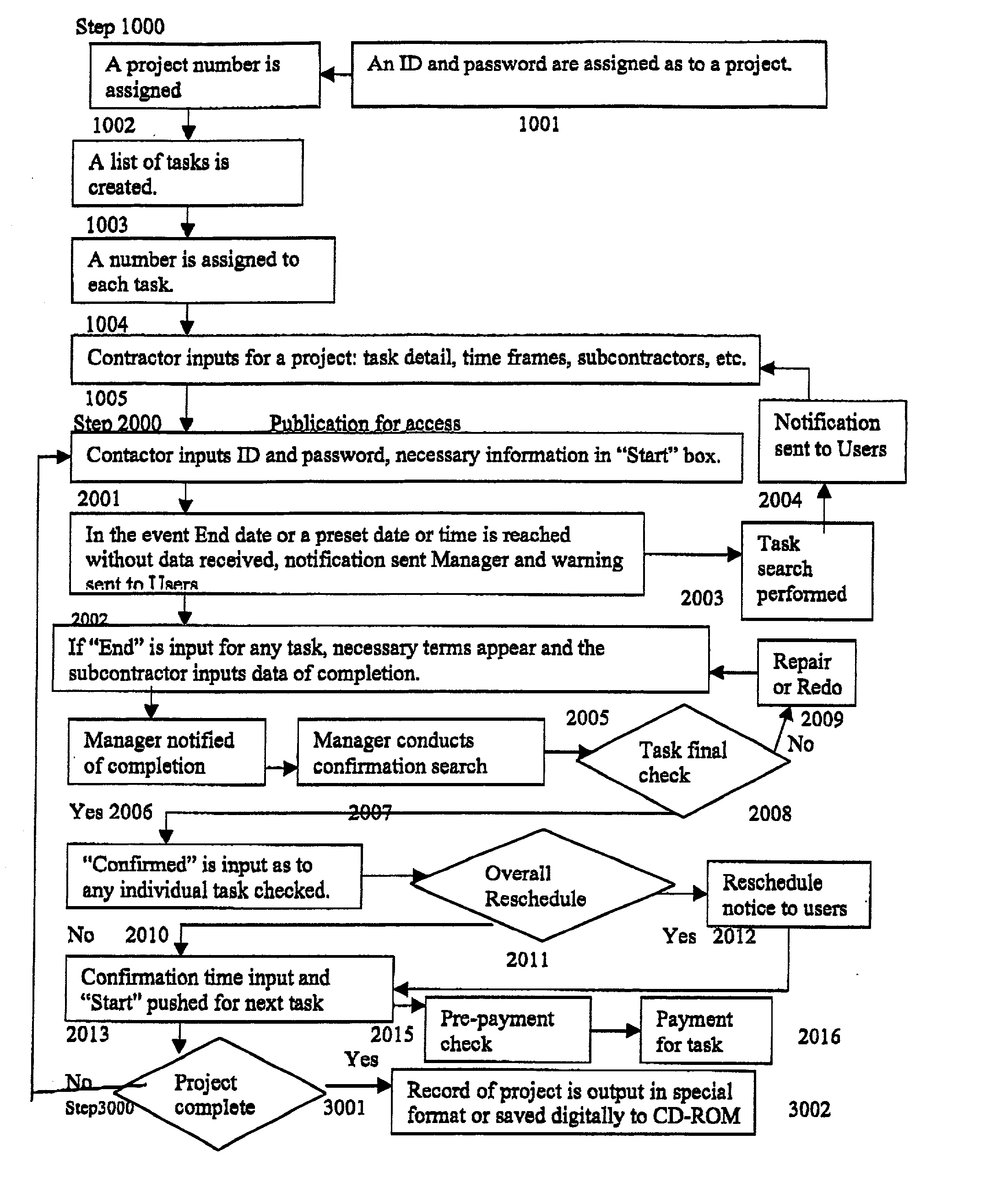
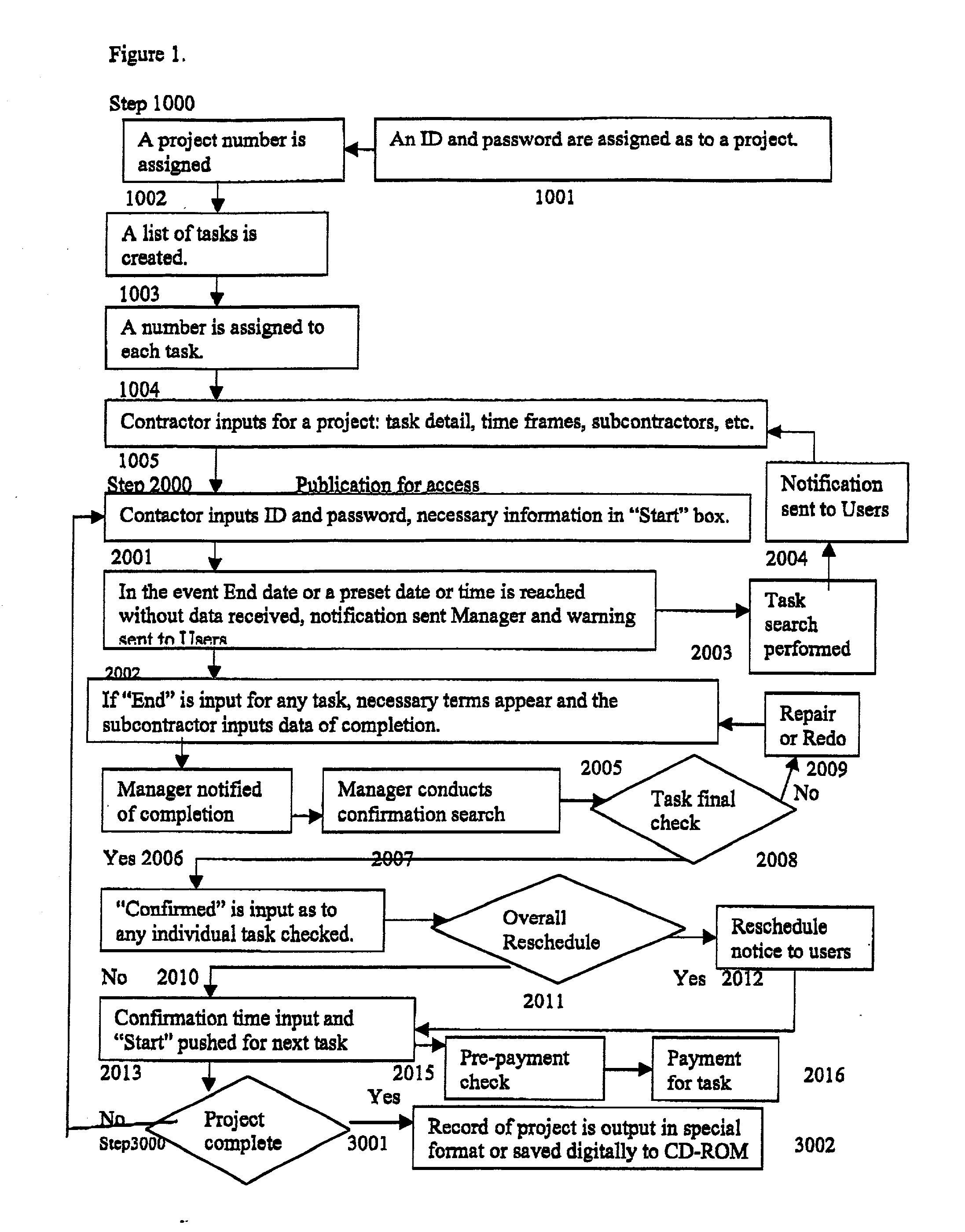
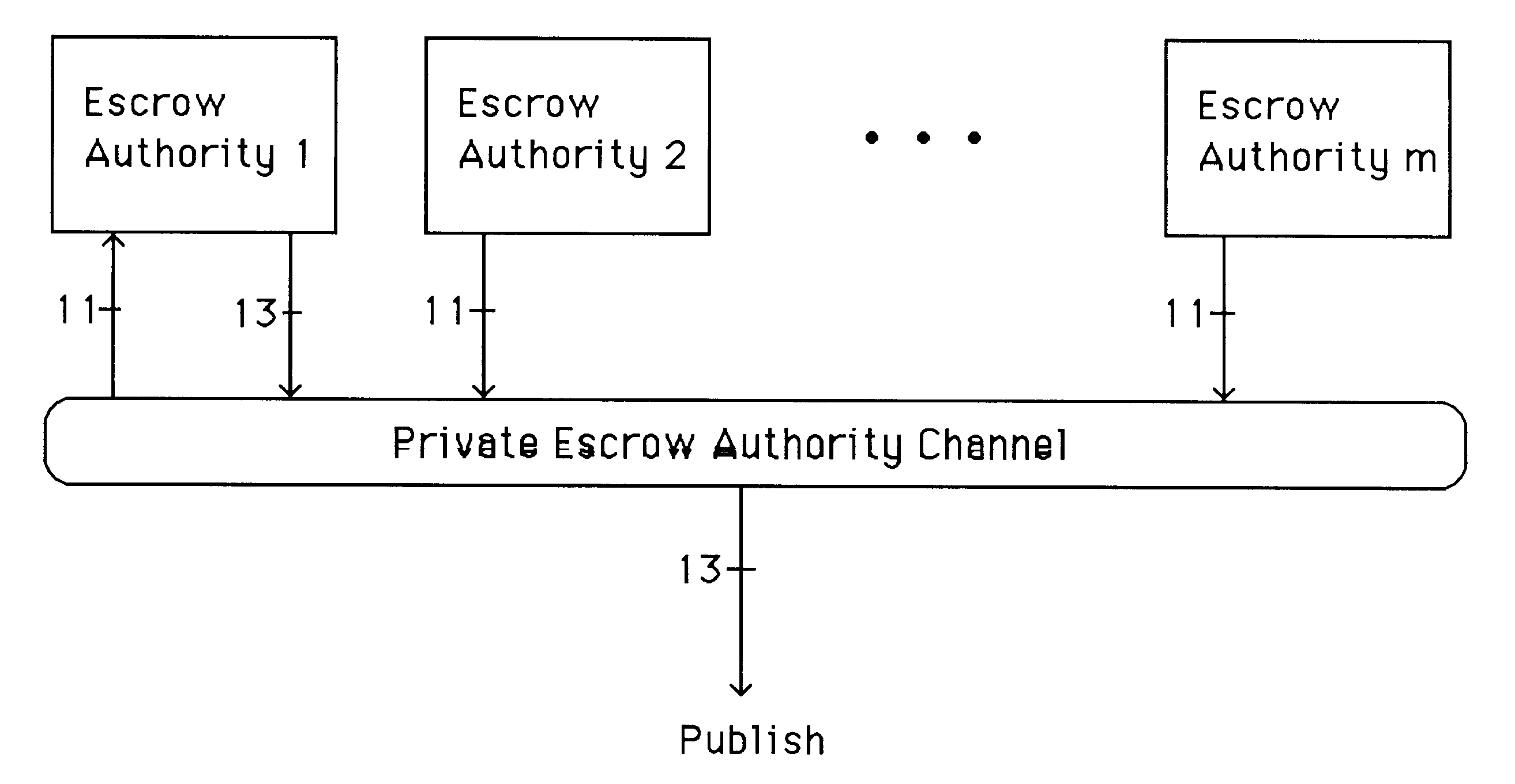
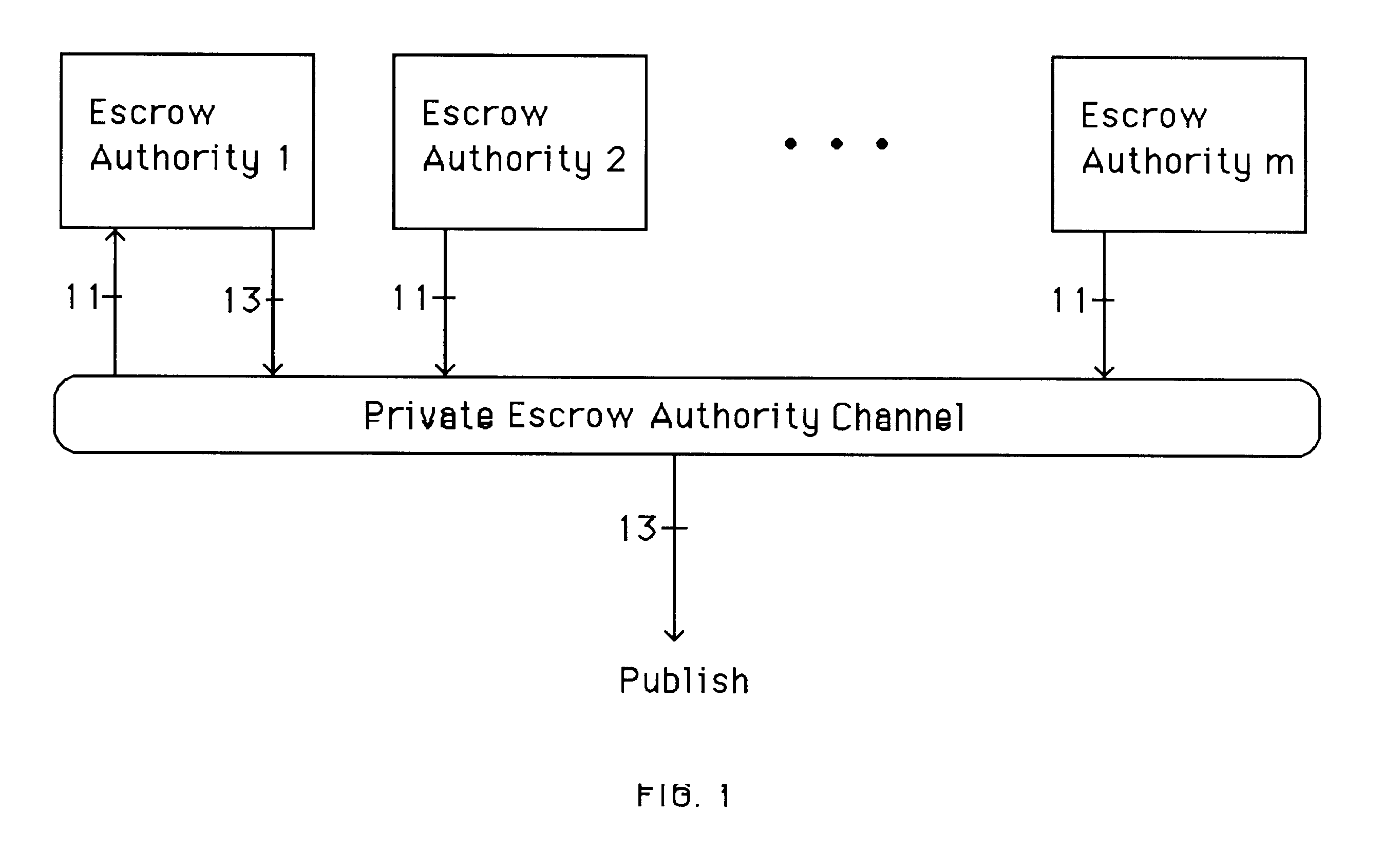
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
248 results about "Escrow" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
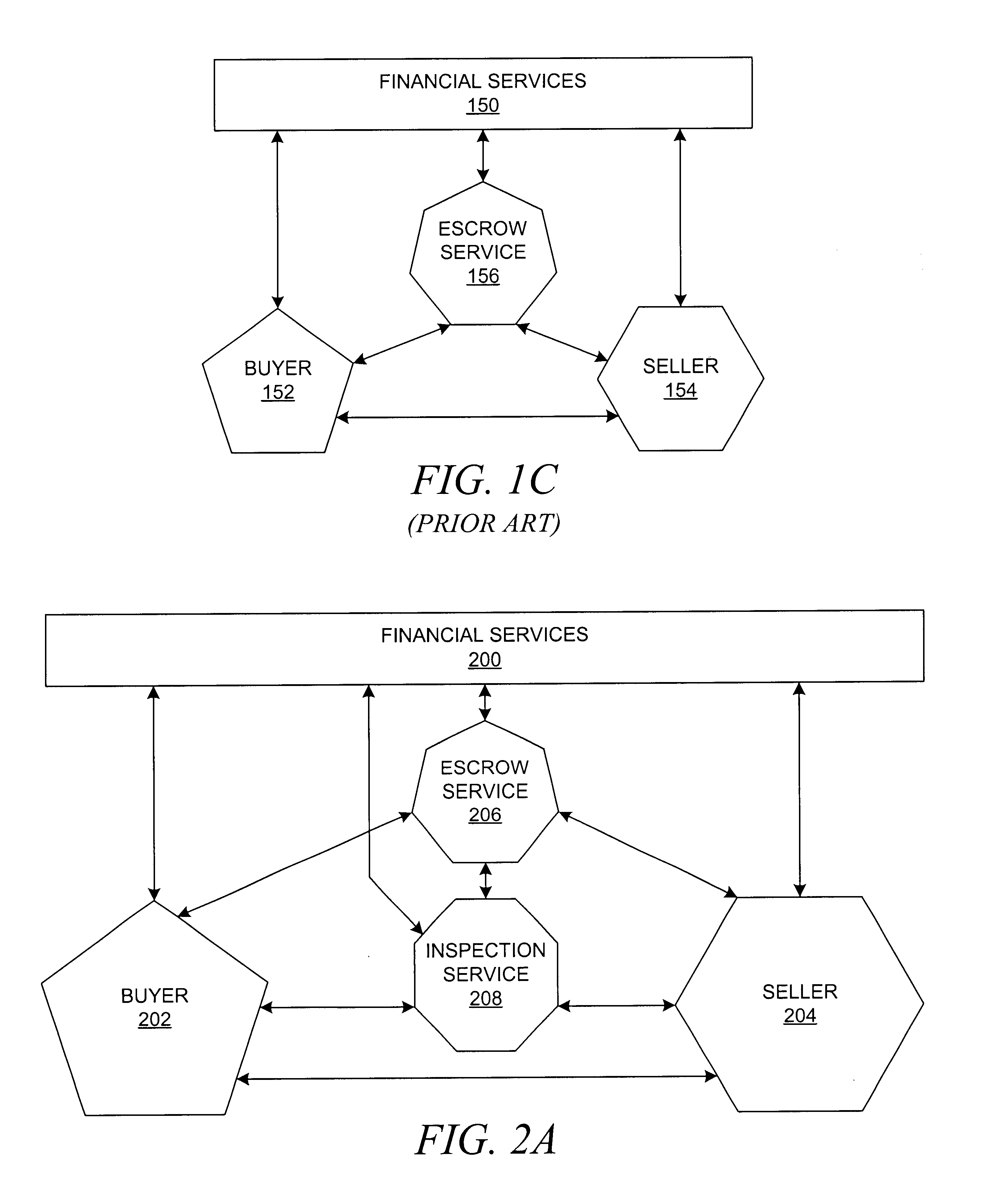
Being in escrow is a contractual arrangement in which a third party (the stakeholder or escrow agent) receives and disburses money or property for the primary transacting parties, most generally, used with plentiful terms that conduct the rightful actions that follow. The disbursement is dependent on conditions agreed to by the transacting parties. Examples include an account established by a broker for holding funds on behalf of the broker's principal or some other person until the consummation or termination of a transaction; or, a trust account held in the borrower's name to pay obligations such as property taxes and insurance premiums. The word derives from the Old French word escroue, meaning a scrap of paper or a scroll of parchment; this indicated the deed that a third party held until a transaction was completed.
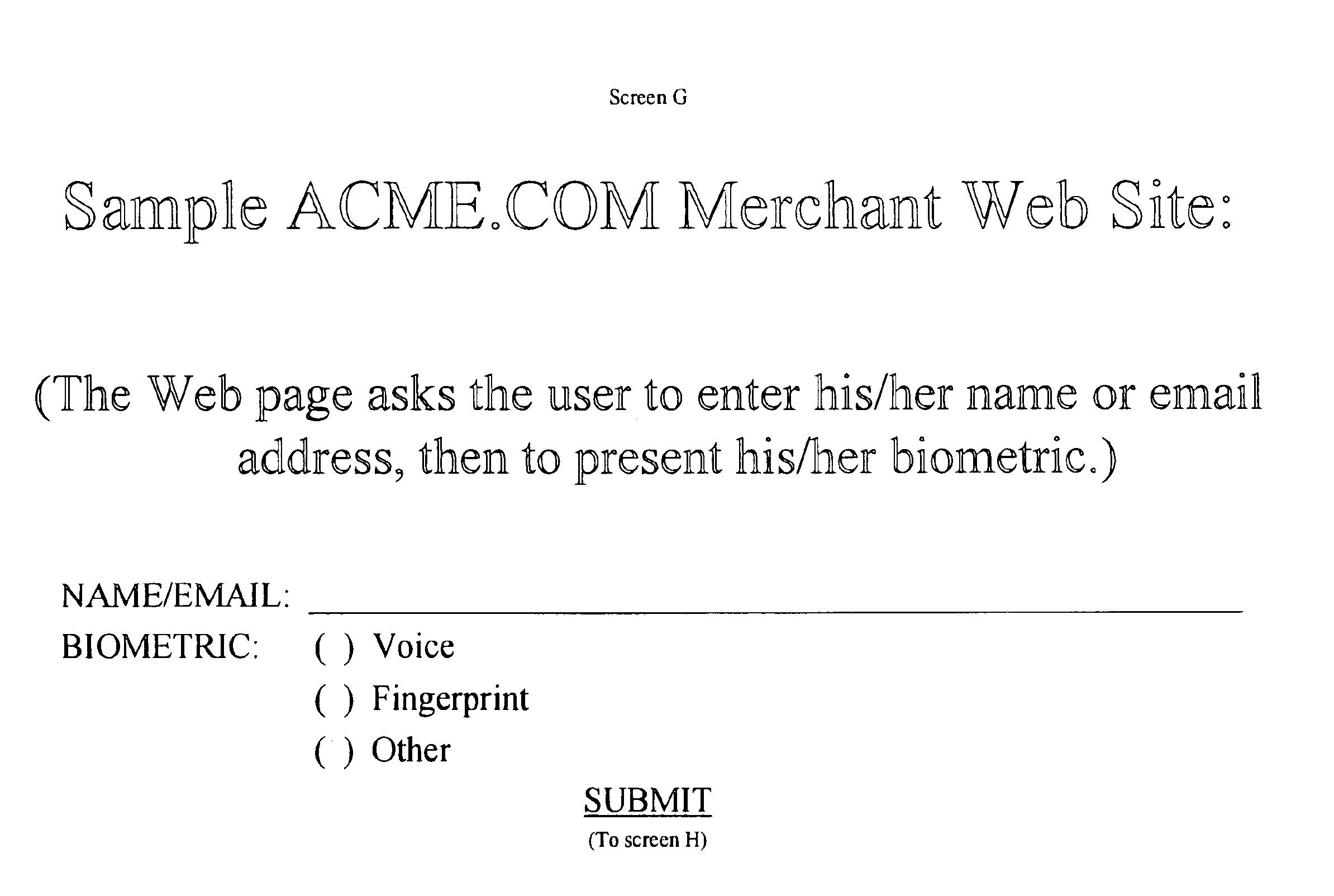
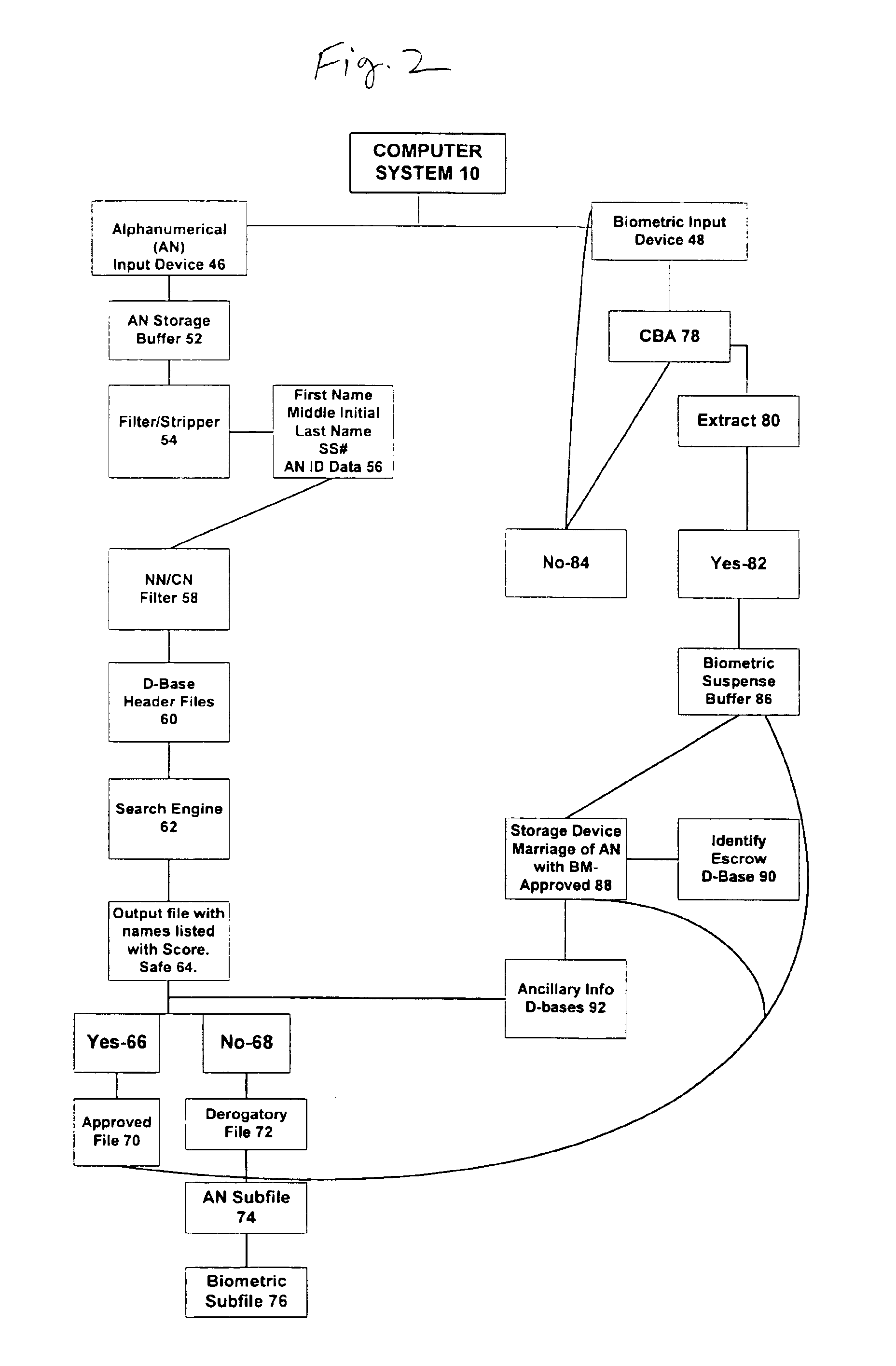
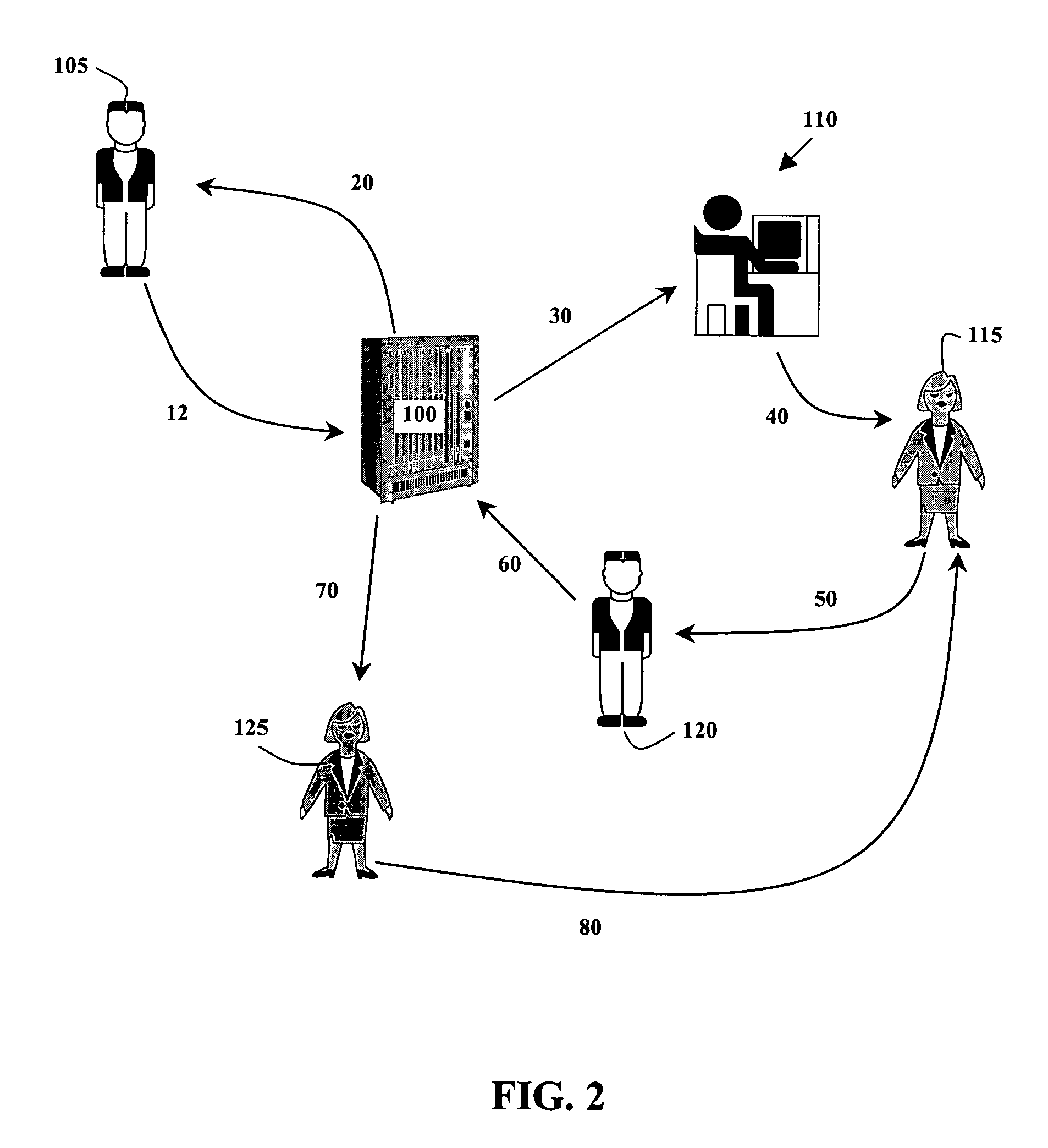
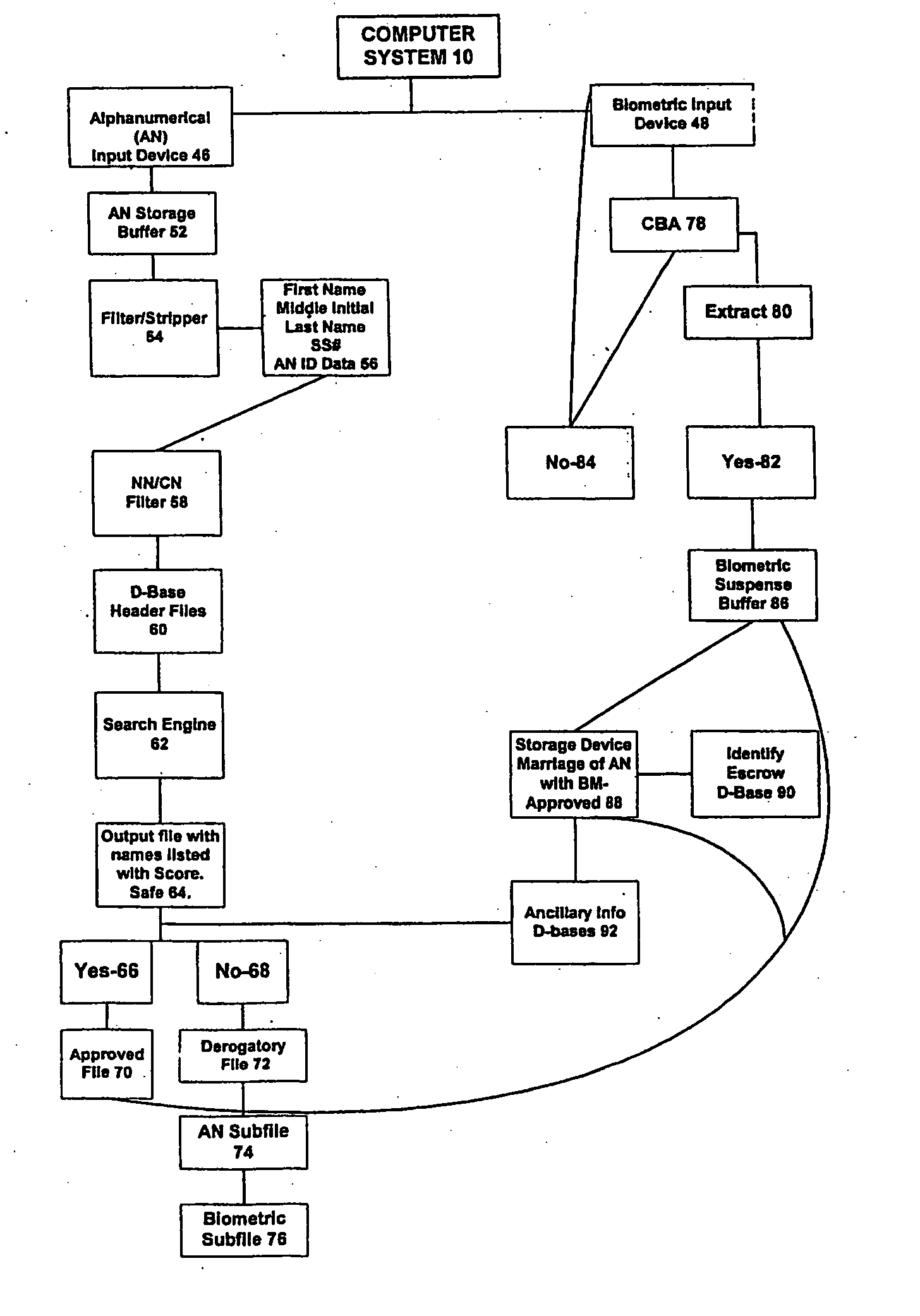
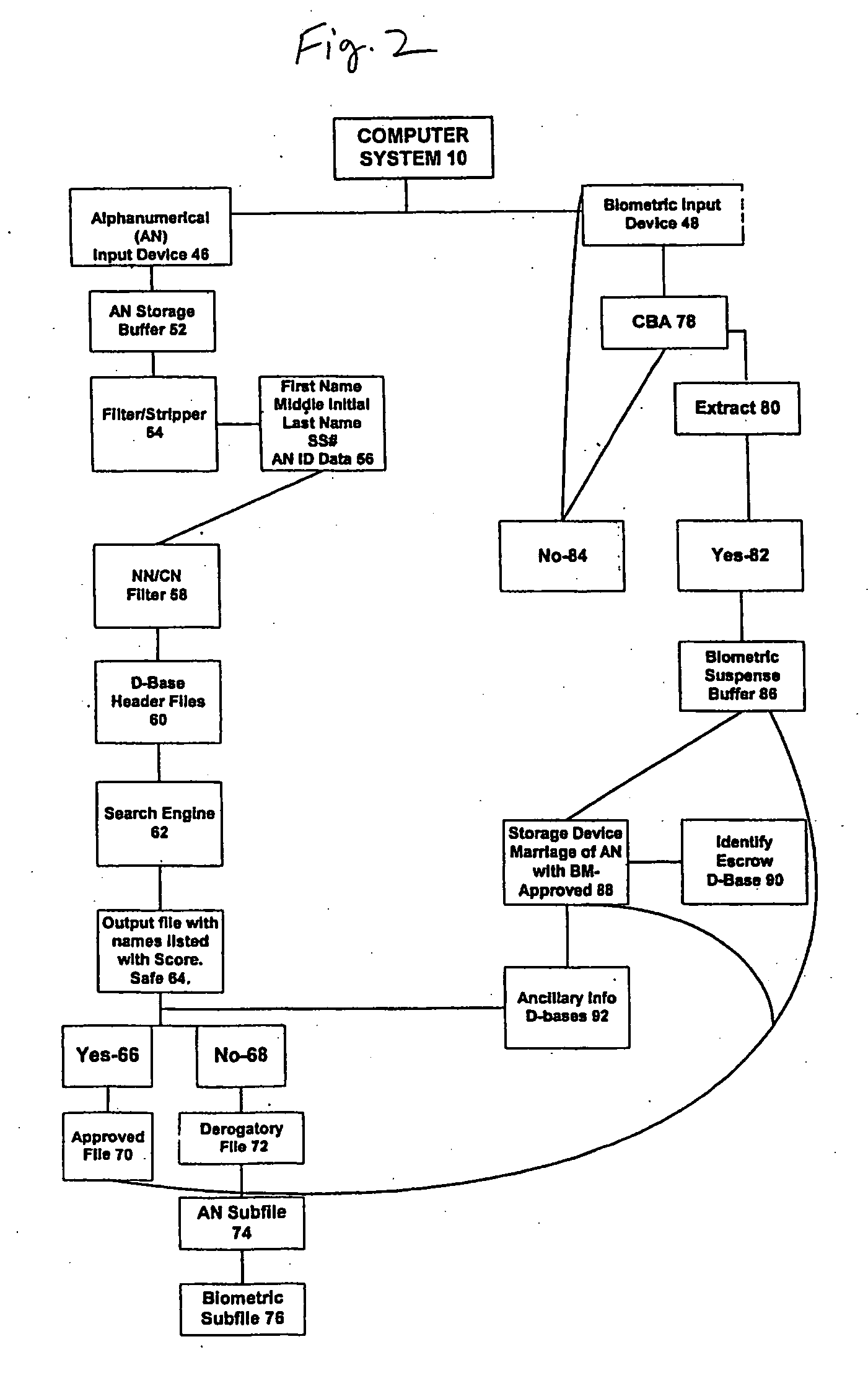
System and method for verification of identity
InactiveUS6871287B1Secure deliverySafe handlingFinanceDigital data processing detailsBiometric dataUser input
A system and method for the identification and verification of a user is provided. The disclosed invention has an enrollment system which includes (i) an alphanumeric input device; (ii) a biometric input device; (iii) a header file database having a plurality of identities; (iv) a search engine in communication with the header file database that searches the database for identifies that match alphanumeric data input by a user according to a predetermined first set of criteria; (v) a processor to score the set of identities matched by the search engine according to a predetermined second set of criteria, and determine that the user's input alphanumeric data based on the score is not suspicious; and (vi) an identity escrow database which receives an approved identity data signal based on the acceptability of the score, and is capable of receiving a biometric identity data signal input by the user to the biometric input device, the escrow database further capable of creating at least one subfile within the escrow database for each user comprising the approved identity data signal and the biometric data signal.
Owner:EDENTIFY INC
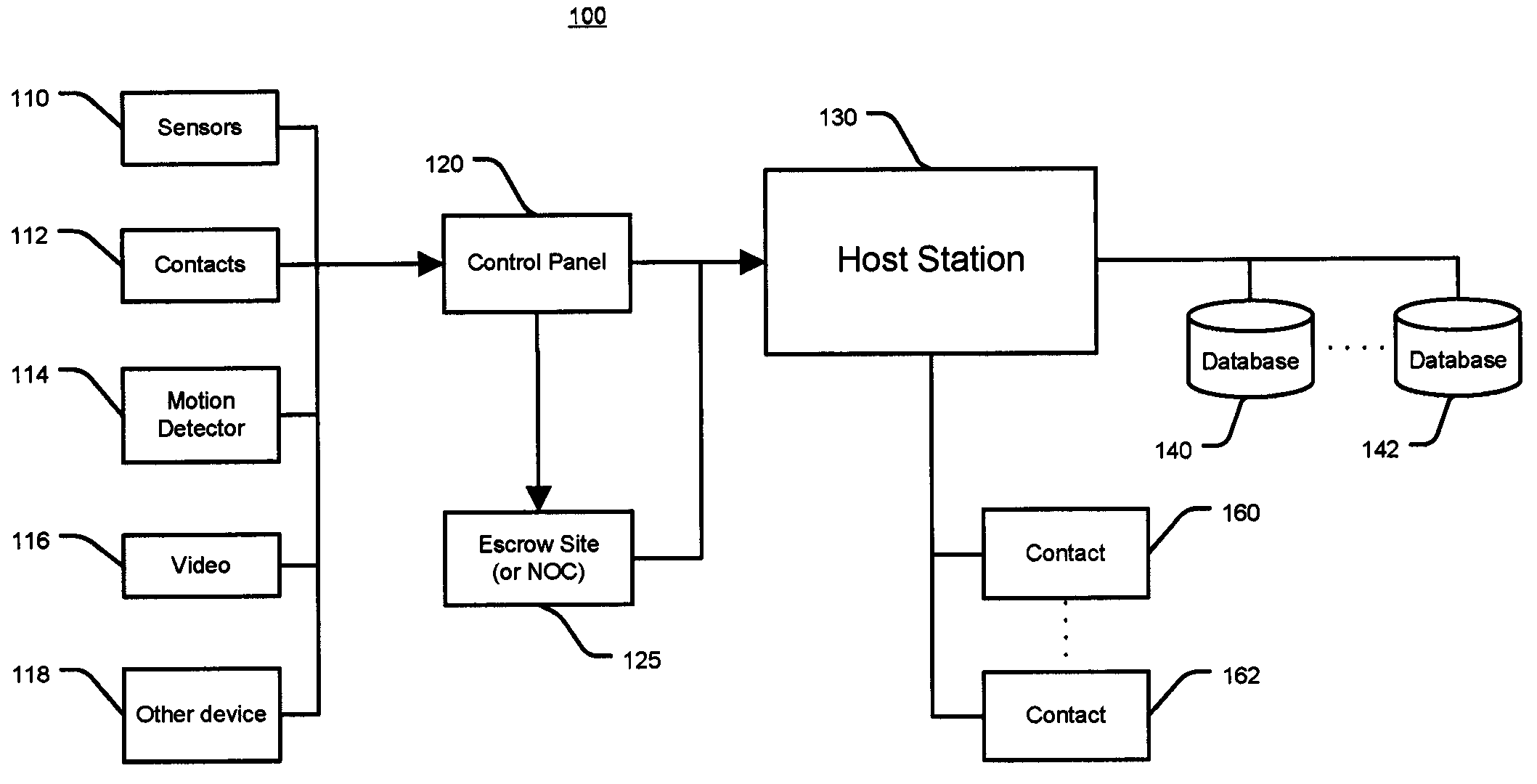
System and method for alarm signaling during alarm system destruction
ActiveUS7619512B2Frequency-division multiplex detailsTime-division multiplexEngineeringPredictive analytics
Owner:ALARM COM INC
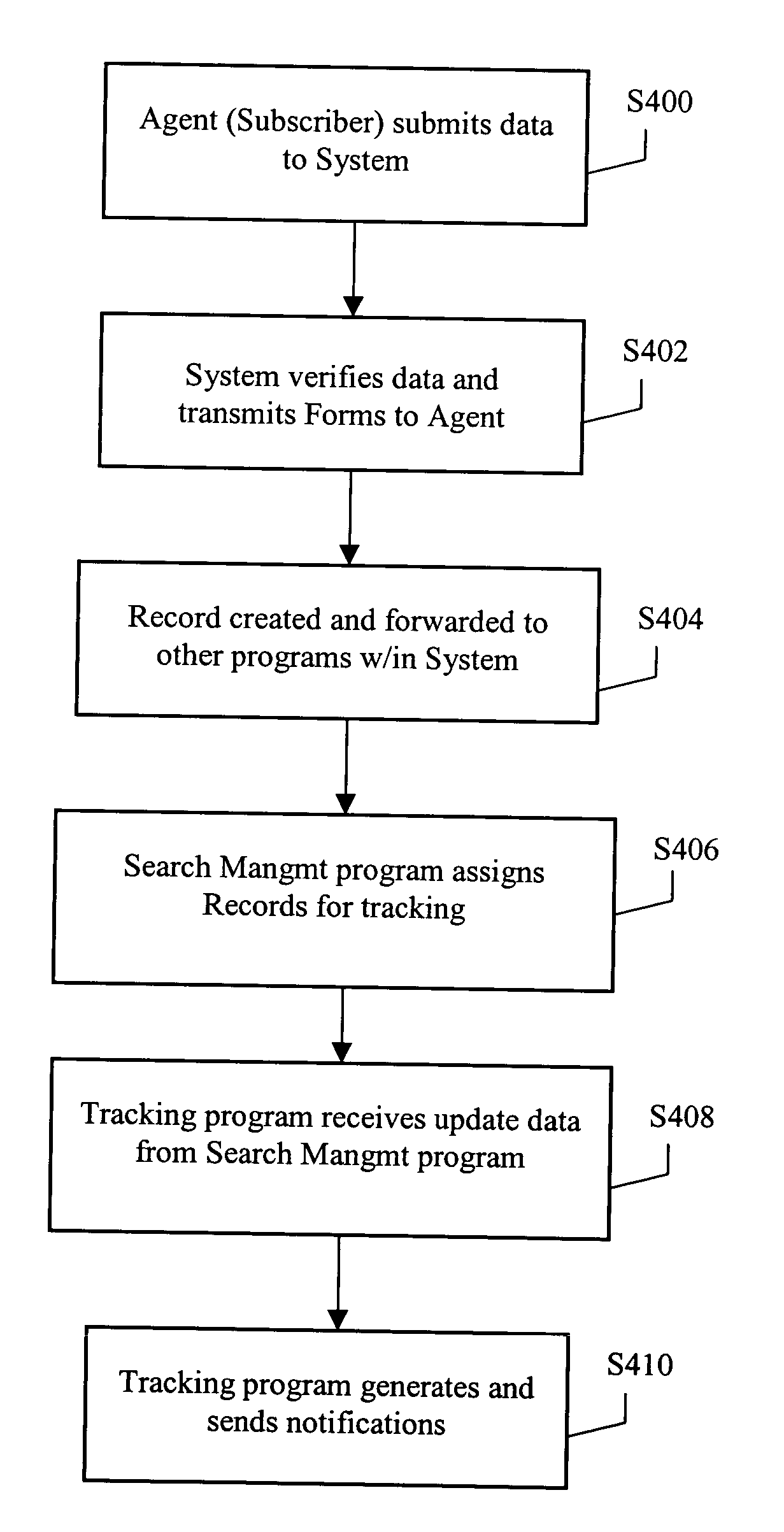
System and method for automated release tracking
A real estate transaction and release tracking system ensures deeds of trust, liens and other encumbrances are released in a timely manner after a specified (or statutory) period of time following settlement of a real estate transaction. Based on information provided by an agent, such as an escrow agent or a settlement agent, the system creates a unique electronic record for each real estate transaction entered by the agent. The system tracks lien status information, either automatically from other computers or via manual input from searchers, and uses this status information to track each real estate transaction. The system monitors the records and indicates when a lien holder has failed to release their lien after a statutory time period that begins after the passing of the settlement date. When the statutory time period has passed, the system can generate a number of forms, including a demand letter as controlled optionally by the system or the user. The demand letter can be sent to the lien holder demanding them to release the lien. If the lien is not thereafter released, further legal documents can be generated and sent to a law firm or enforcement agent for legal action to be taken against the delinquent lien holder.
Owner:REQUIRE HLDG LLC
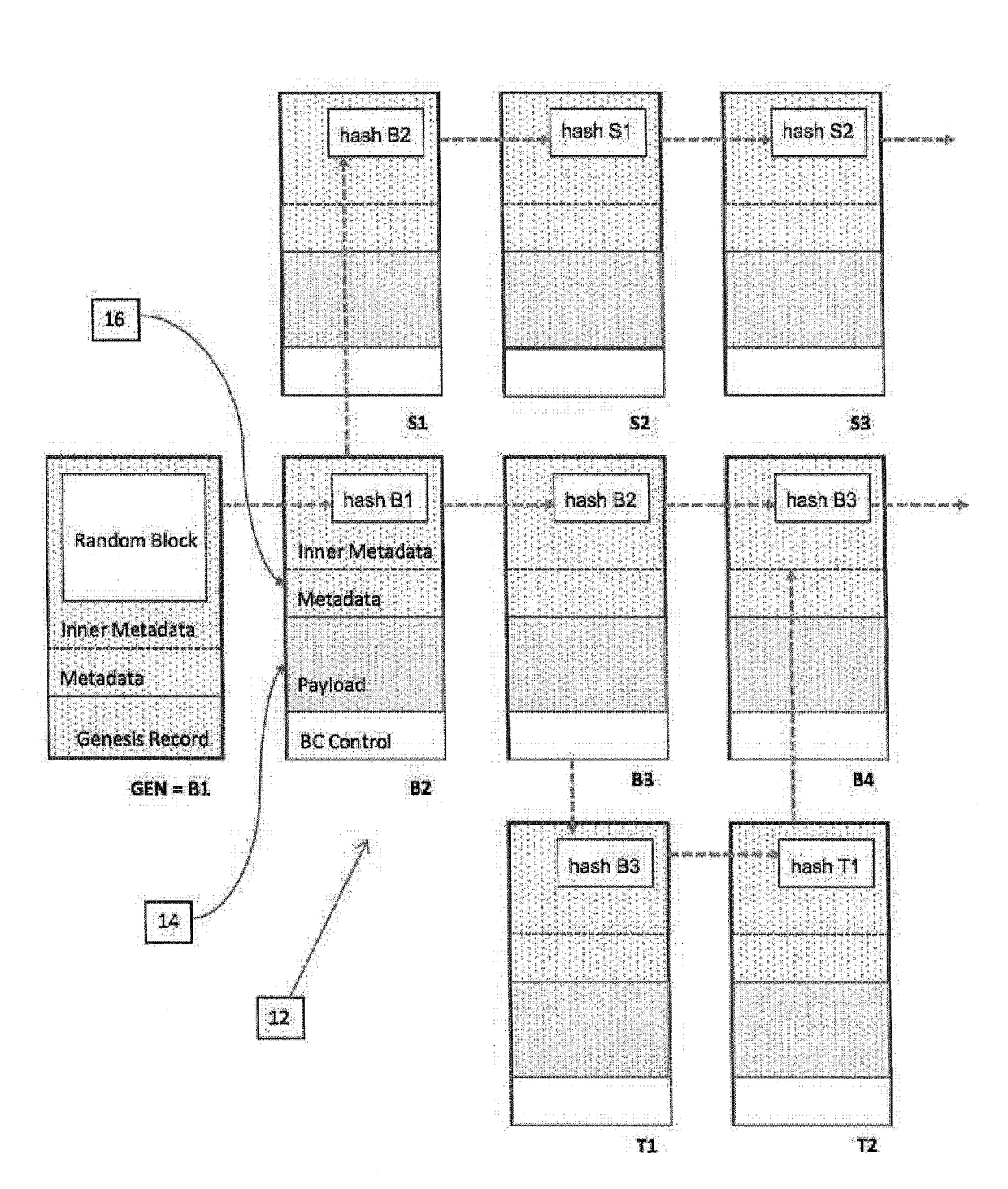
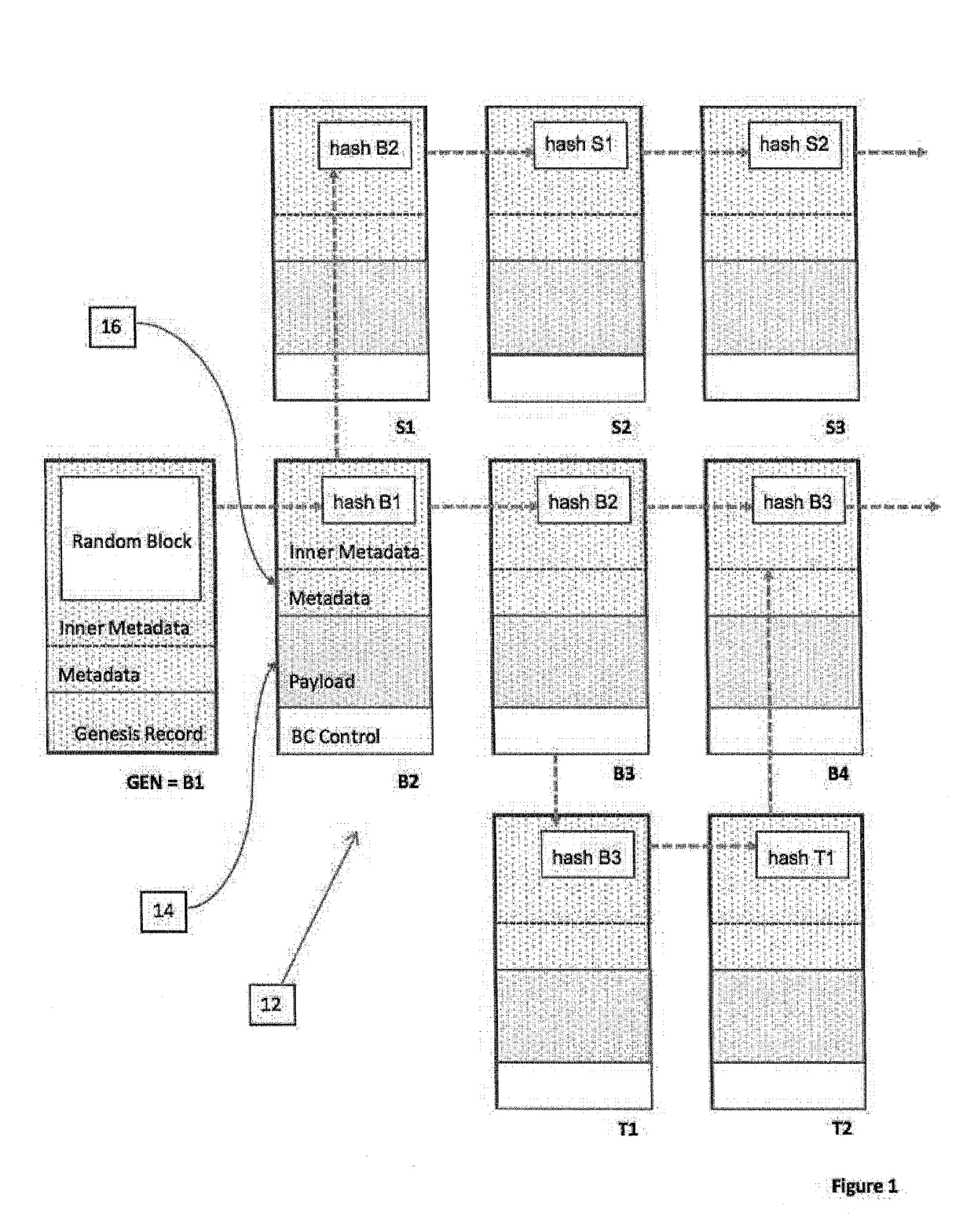
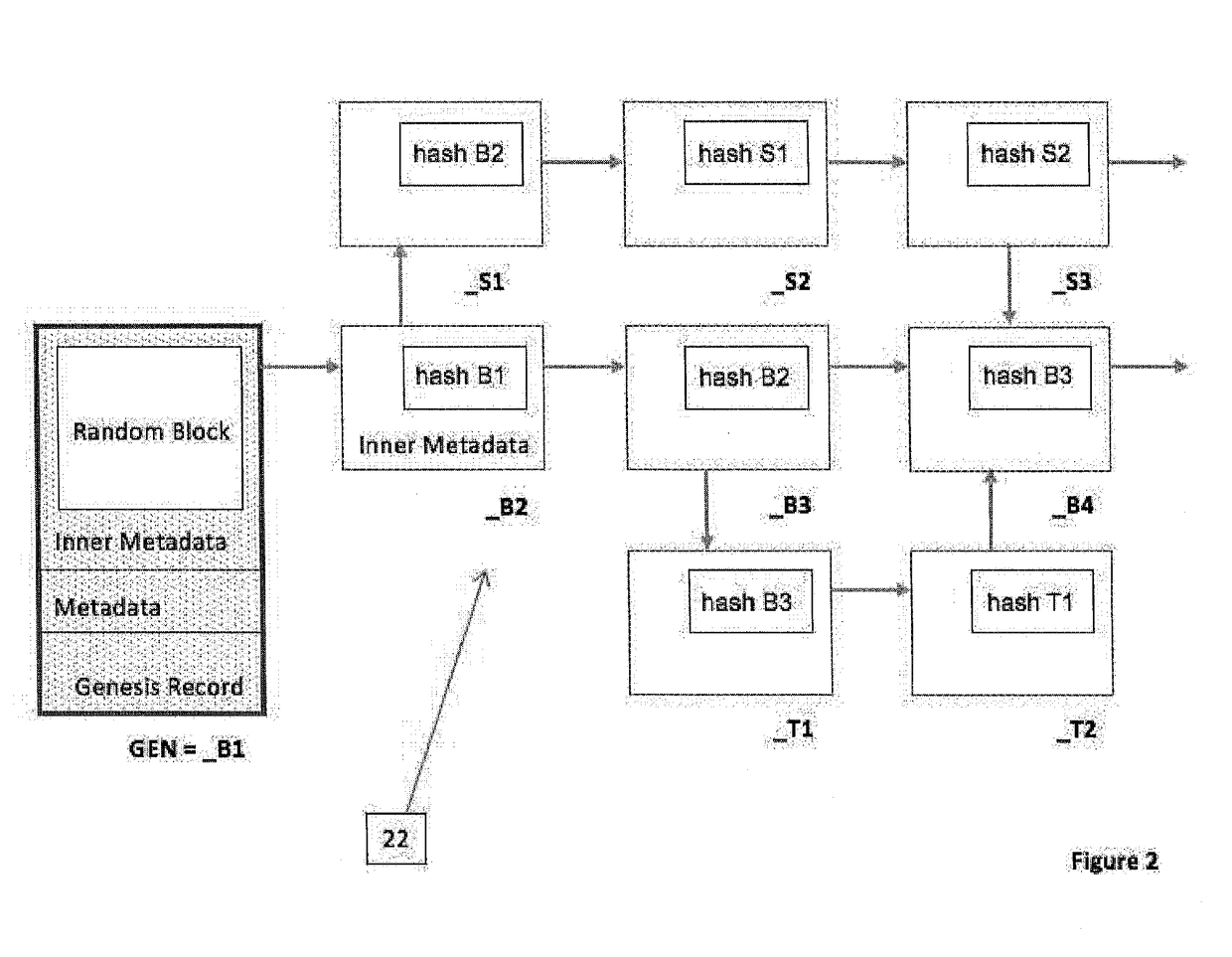
System and method for data management structure using auditable delta records in a distributed environment
A system and method of recording data from a number of devices in a distributed network system in a manner adaptable for auditing the device output. The devices may include one or more control, sensor, edge, or peripheral computing devices physically separate in the distributed network system and in communication with a control server. Such distributed networks systems are common in SCADA or IoT applications. The content stream of data records output from the devices are recorded; a payload stripped stream of data records which are stripped of the payload are recorded and preferably retained by an escrow service. The metadata of the data records includes the hash value of one or more predecessor data records. The hash values are calculated based on the payload and a linkage function, preferably a cryptographic function. A comparison of hash values of the payload stripped stream and the content stream provides the audit ability.
Owner:OLEA NETWORKS
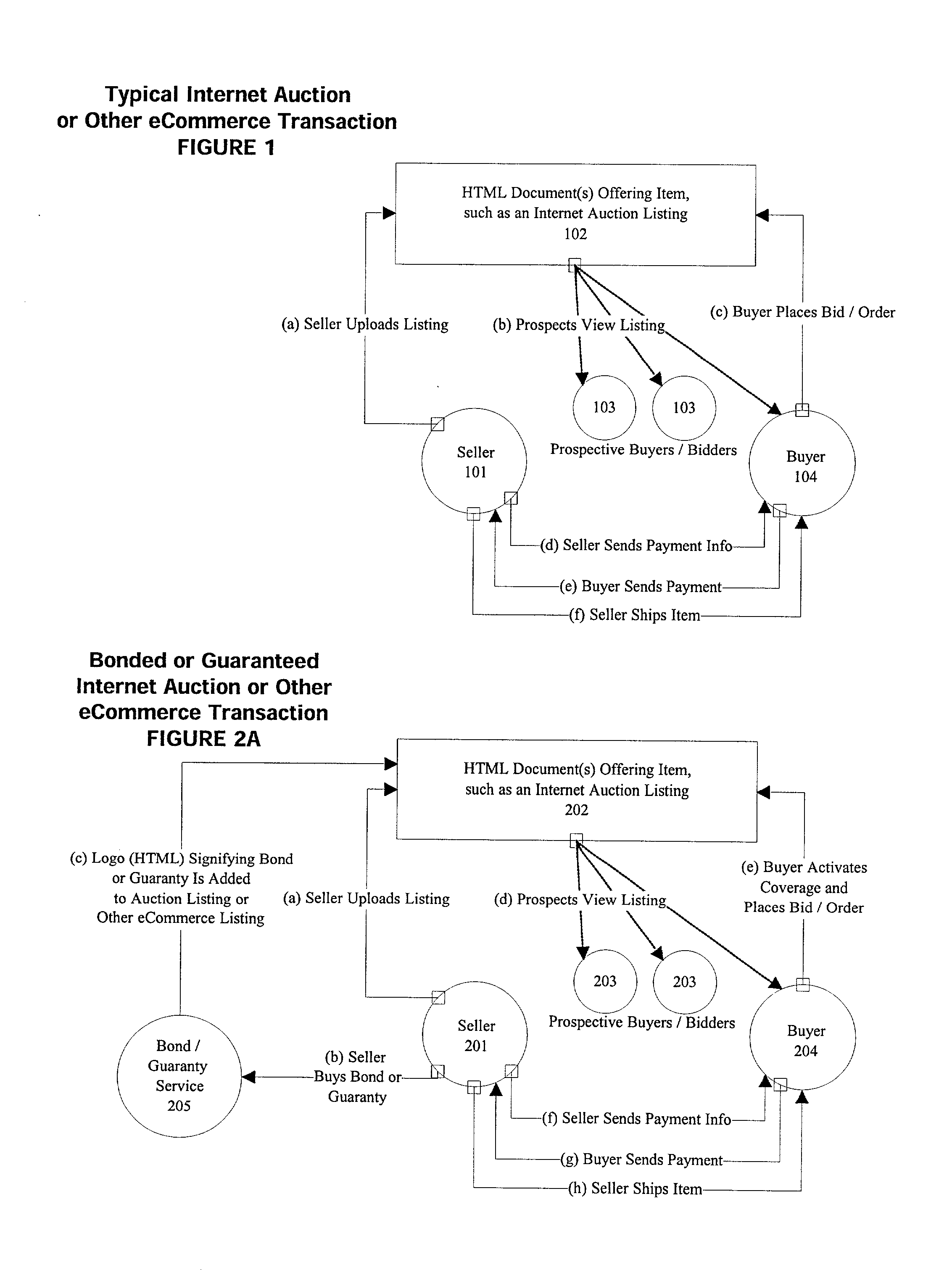
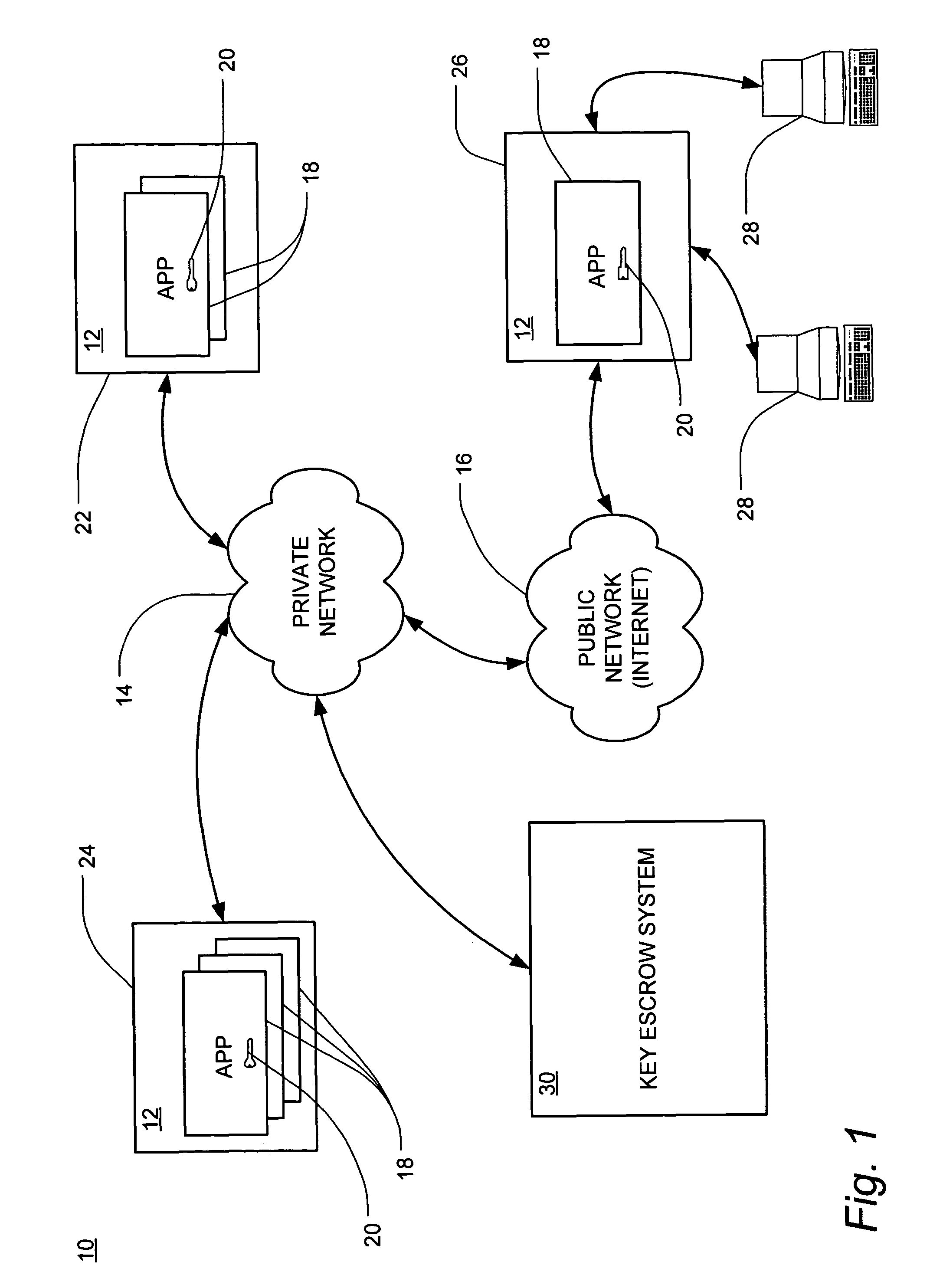
System for conducting business over the internet
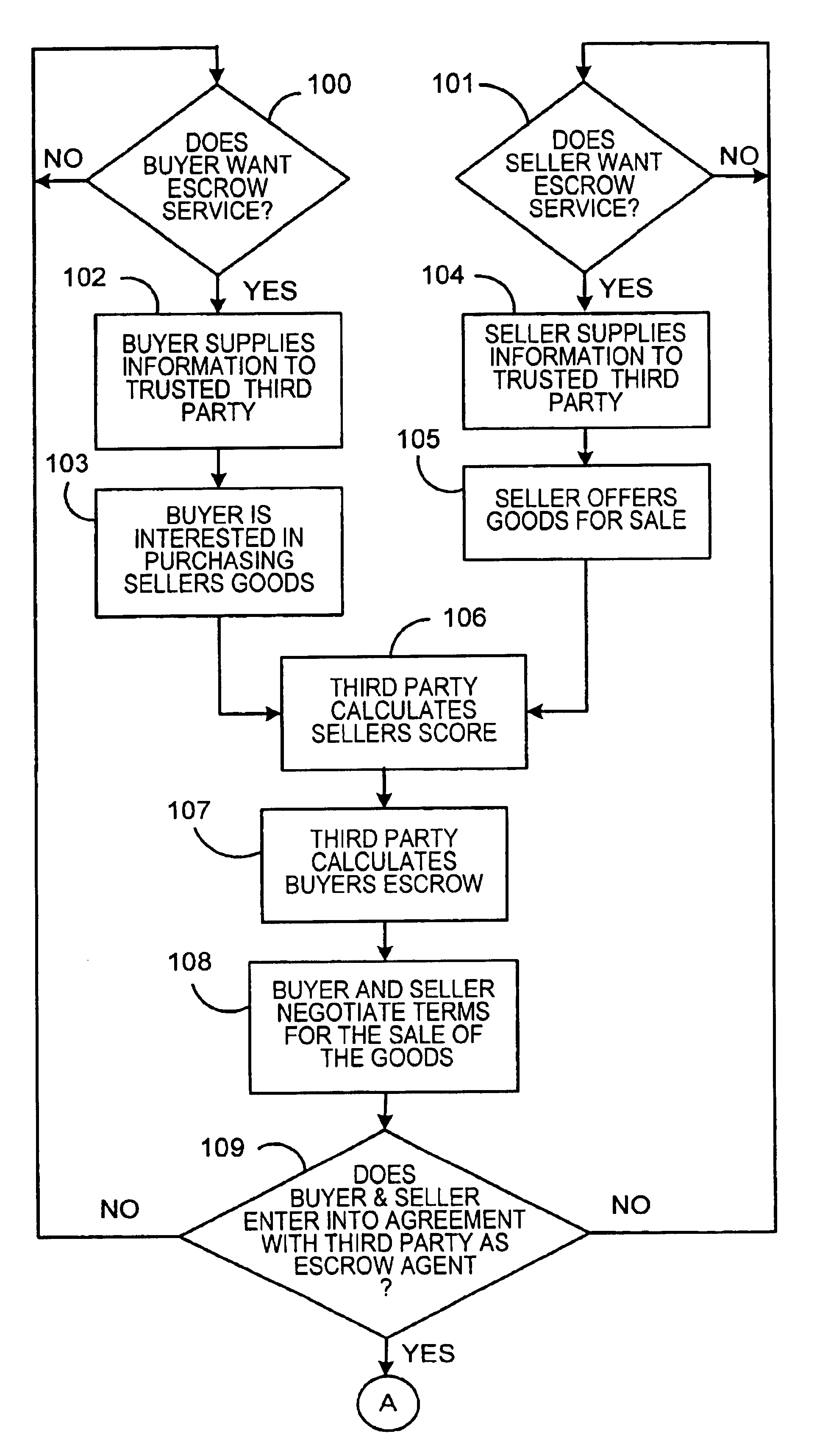
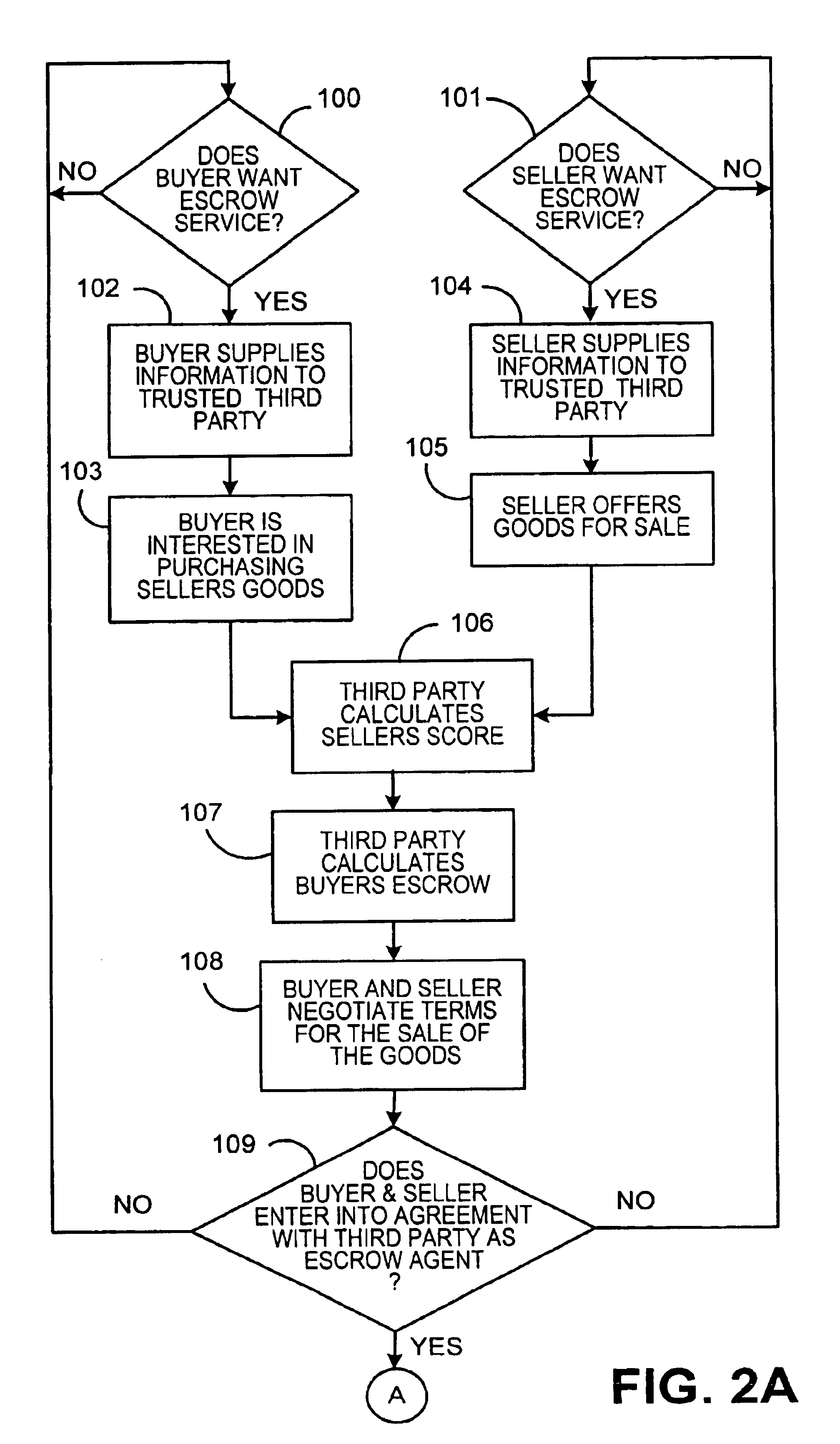
An Internet-based system that allows a buyer and a seller to obtain information about each other while remaining somewhat anonymous. The system provides historic information to buyer and seller by having a trusted third party give the buyer and seller the other party's trading history information without revealing the actual identity of the parties. A buyer registers with the trusted third party by submitting an online application. The trusted third party establishes a credit score for the buyer. A seller registers with the trusted third party by submitting an online application. The trusted third party establishes a score for the seller based upon the seller's trading history, reputation and financial standing. When the buyer chooses to purchase a product from a seller over the Internet, certain parameters i.e., dollar value of transaction, type of purchase, level of current outstanding credit available, credit score, etc. are substituted into an algorithm to determine the maximum purchase amount that may be financed at what terms and how much money the buyer will have to place in escrow. The buyers escrow may be furnished to the trusted third party by credit cards, ACH, wire transfer, etc. If the trusted third party is not satisfied with the seller's score, the trusted third party may require the seller to post a bond for some or all of the seller's transactions.
Owner:PITNEY BOWES INC
Cryptographic key backup and escrow system
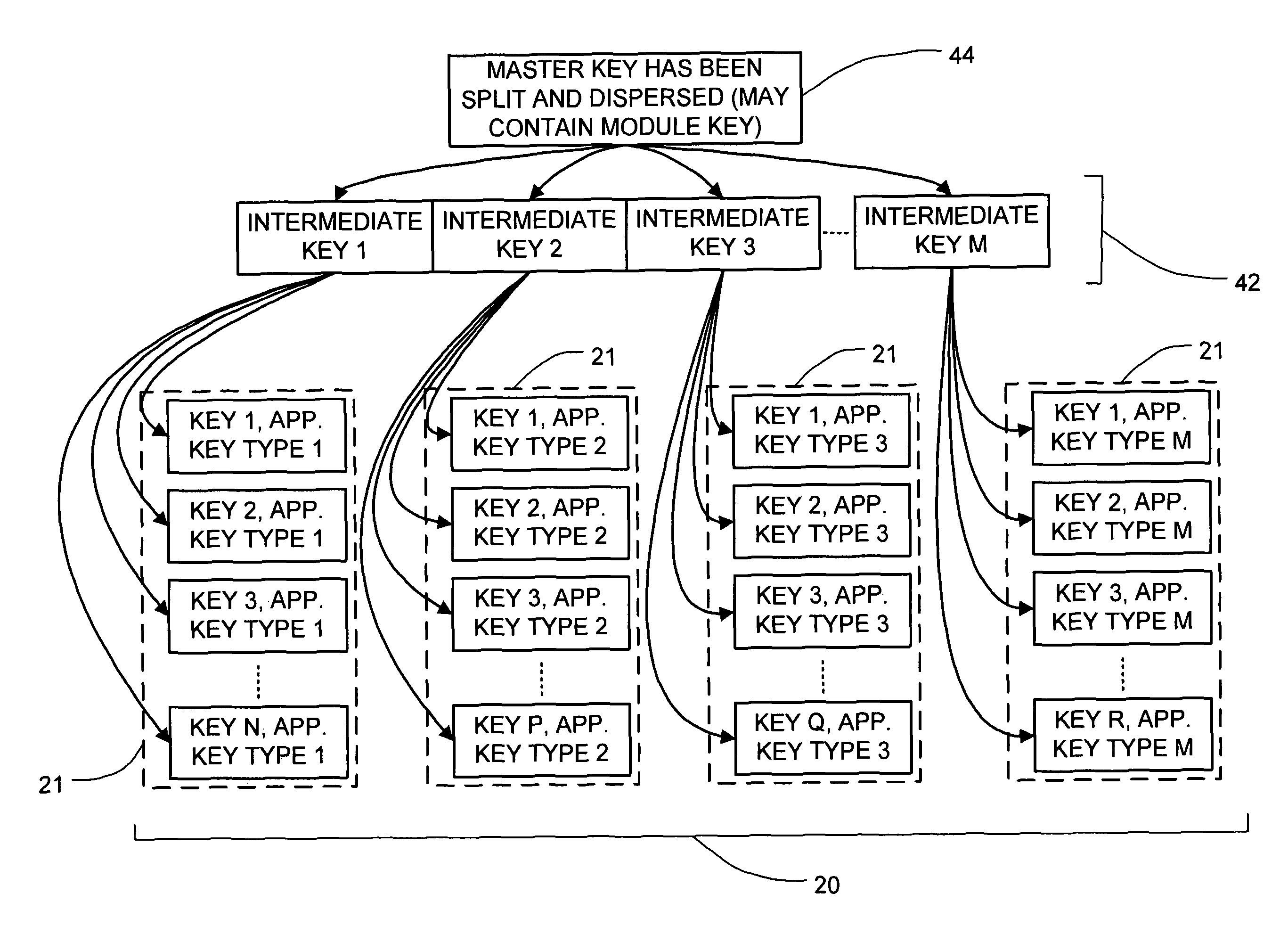
ActiveUS20050138374A1Verify integrityKey distribution for secure communicationHardware security moduleMaster key
A system for securely storing application keys is comprised of a database system, a peripheral hardware security module and cryptographic keys, wherein cryptographic keys comprise application keys, intermediate keys and a master key. Application keys are grouped according to characteristic and are associated with a particular intermediate key, which is utilized to scramble and descramble application keys within the associated group. Intermediate keys are associated with the master key, which is utilized to scramble and descramble the intermediate keys. Scrambling and descrambling of keys is performed within the peripheral hardware security module.
Owner:WELLS FARGO BANK NA
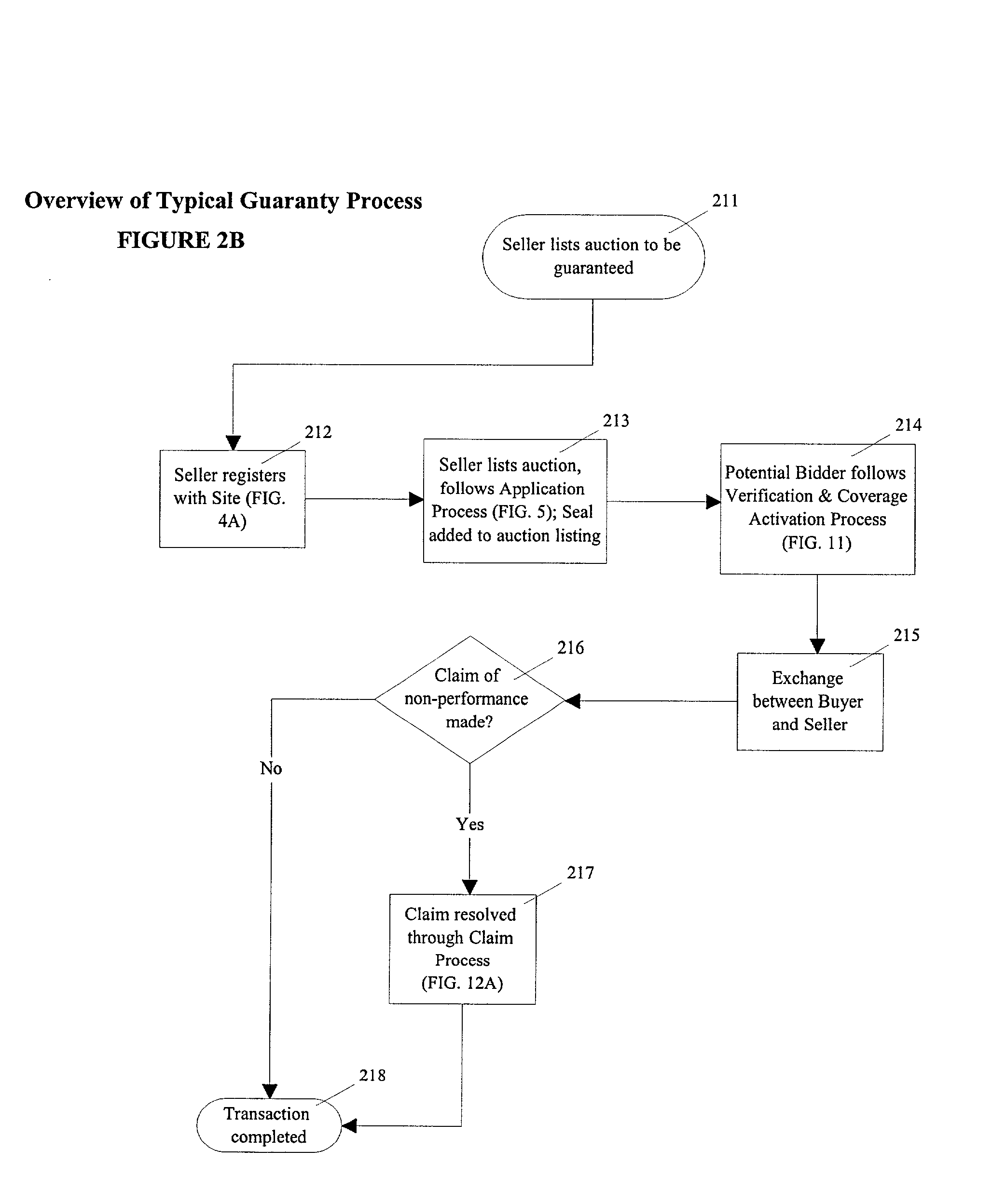
Electronic bond & guaranty process and business method
Disclosed is a method by which suretyship bonds and guaranties can be purchased and deployed over the Internet in real time, providing automatic application evaluation and policy binding. The principal's credit card information is used in a repeating cycle of pre-authorized charges so that the card account serves as effective collateral. A bond seal image, safeguarded against piracy, appears in Web pages indicating the existence of bond coverage. A dynamically updated gauge displays the margin of coverage available under the bond at any given moment. Means of integrating the information technology of auction site and surety company are also disclosed. The invention makes possible an unprecedented level of security in user-to-user auction environments and eliminates the need for online escrow services. Means of accepting bidder deposit accounts is also disclosed, enabling automatic, electronic payment the moment an Internet auction closes and eliminating the need for online payment services.
Owner:HARRISON JR SHELTON E
System and method for verification of identity
InactiveUS20050216953A1Secure deliverySafe handlingDigital data processing detailsCharacter and pattern recognitionThird partyBiometric data
A system for verifying identities comprising an enrollment system having: (i) at least one alphanumeric input device; (ii) at least one biometric input device; (iii) at least one header file database having a plurality of identities; (iv) at least one search engine, said search engine in communication with said header file database such that said search engine first receives an alphanumeric data signal which has been input into said alphanumeric input device by the user, and then searches said database for identities that match the alphanumeric data according to a predetermined first set of criteria; (v) a processor to score the set of identities matched by said search engine according to a predetermined second set of criteria, said processor capable of determining the acceptability or unacceptability of said user's input alphanumeric data based on said score; and (vi) an identity escrow database which is in communication with said processor and receives from said unit an approved identity data signal based on the acceptability of the score, said escrow database additionally in communication with said biometric input device capable of receiving at least one biometric identity data signal input by the user to said biometric input device, said escrow database further comprising means for coupling the approved identity data signal and the biometric identity data signal to create at least one subfile within the escrow database for each user comprising the approved identity data signal and the biometric data signal. The present invention further comprises a verification system for verifying the identity of said user after the user has enrolled in the enrollment system. The verification system has means for processing a second input biometric data signal input by the user to the biometric input device to match the user's preexisting biometric data in said escrow database according to a predetermined third set of criteria. The verification system has an output device for transmitting to a third party whether or not a match was located within said escrow database for said user. The present invention further relates to a method and system for providing a warranty against the theft of a user's identity.
Owner:ELLINGSON JOHN F
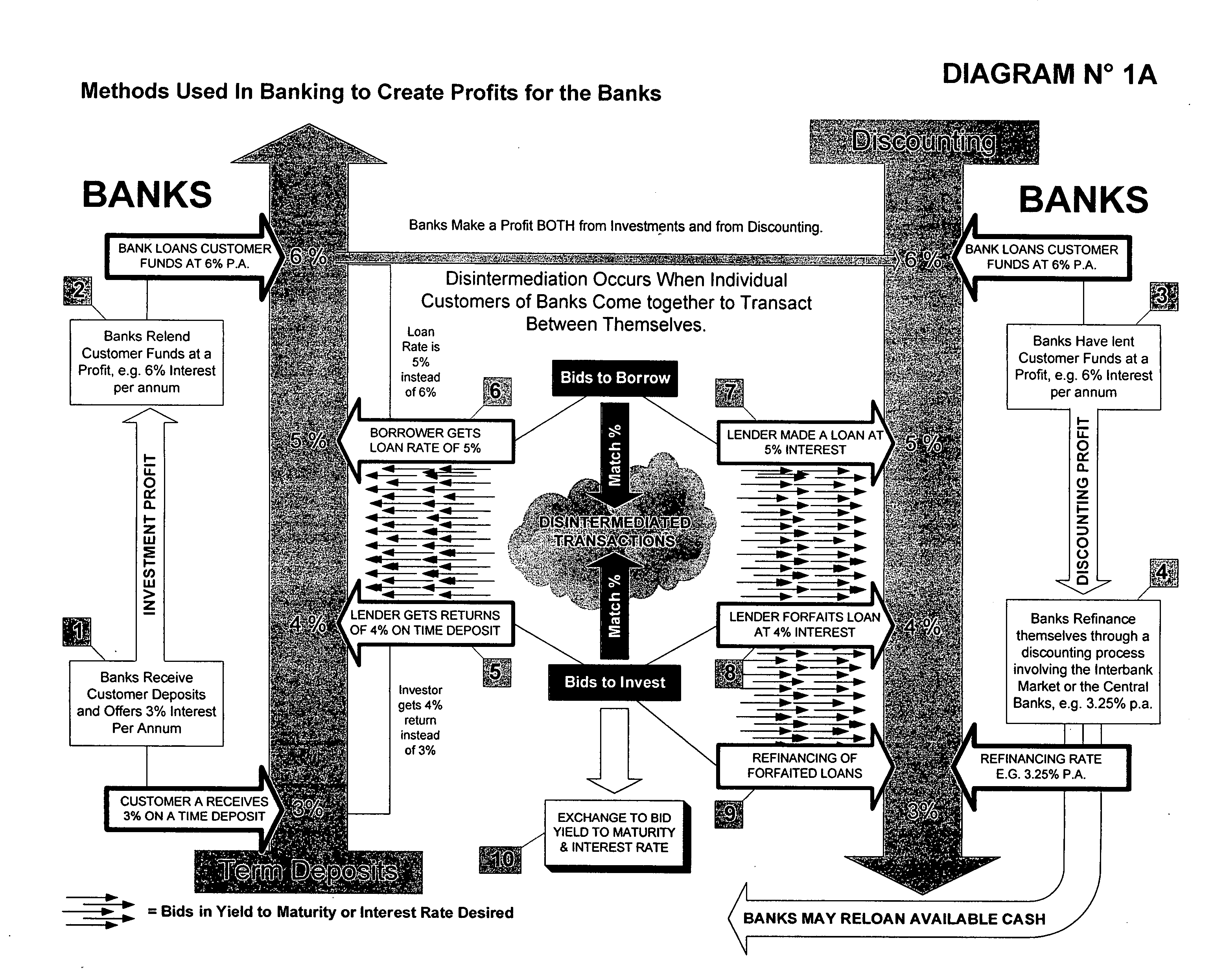
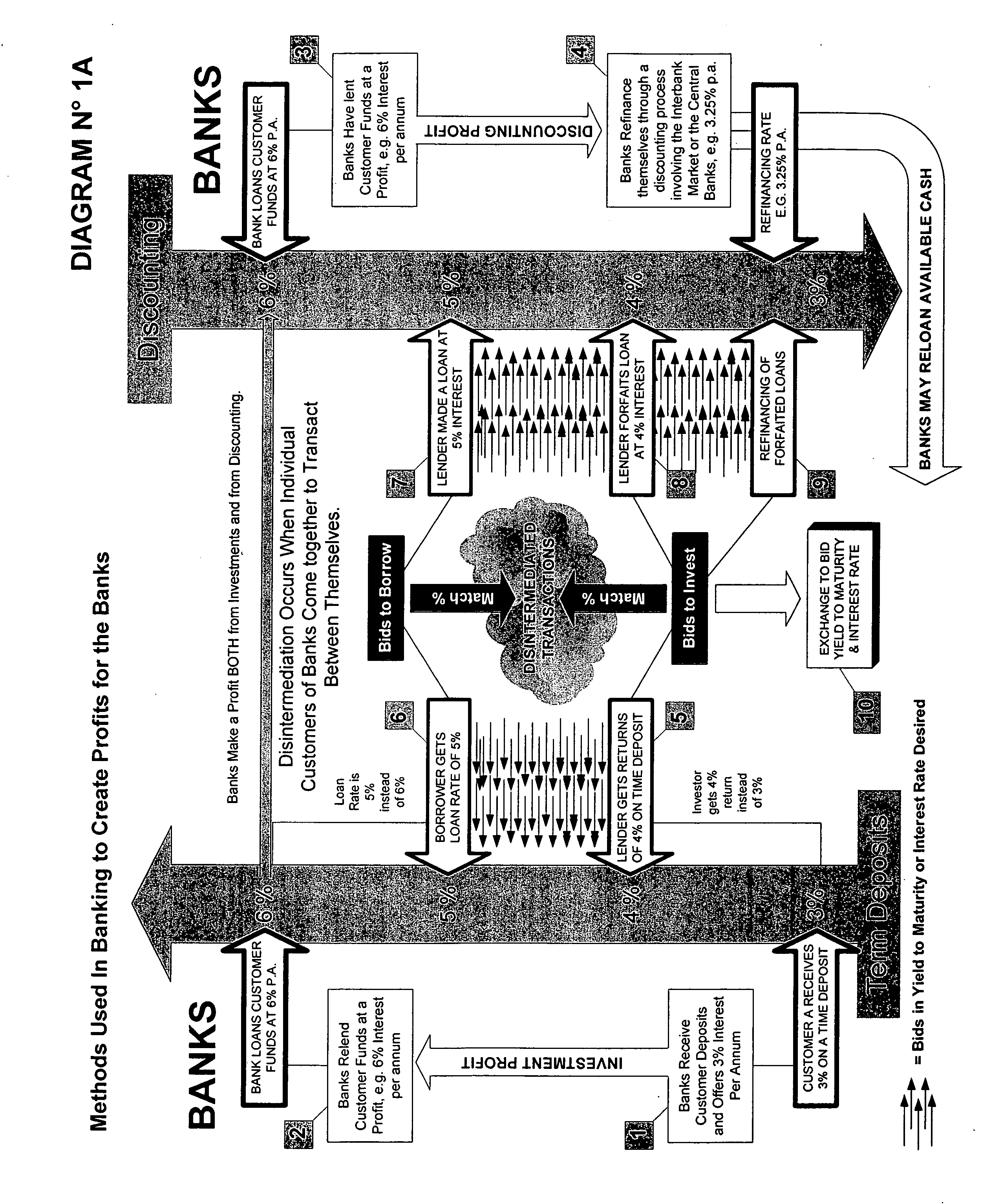
System & method for the creation of a global secure computerized electronic market-making exchange for currency yields arbitrage
InactiveUS20060155638A1Facilitates online interactionInstantly closeFinanceFinancial transactionFinancial trading
A multi-participant financial transaction with no downside risks that results in a net profit for all participants when the transaction is accomplished according to certain required steps, including the step of having simultaneously closings in escrow. A multi-step approach to issuing and selling custom-designed, specially engineered and underwritten securities or bank instruments is also described.
Owner:DE LA MOTTE ALAIN L
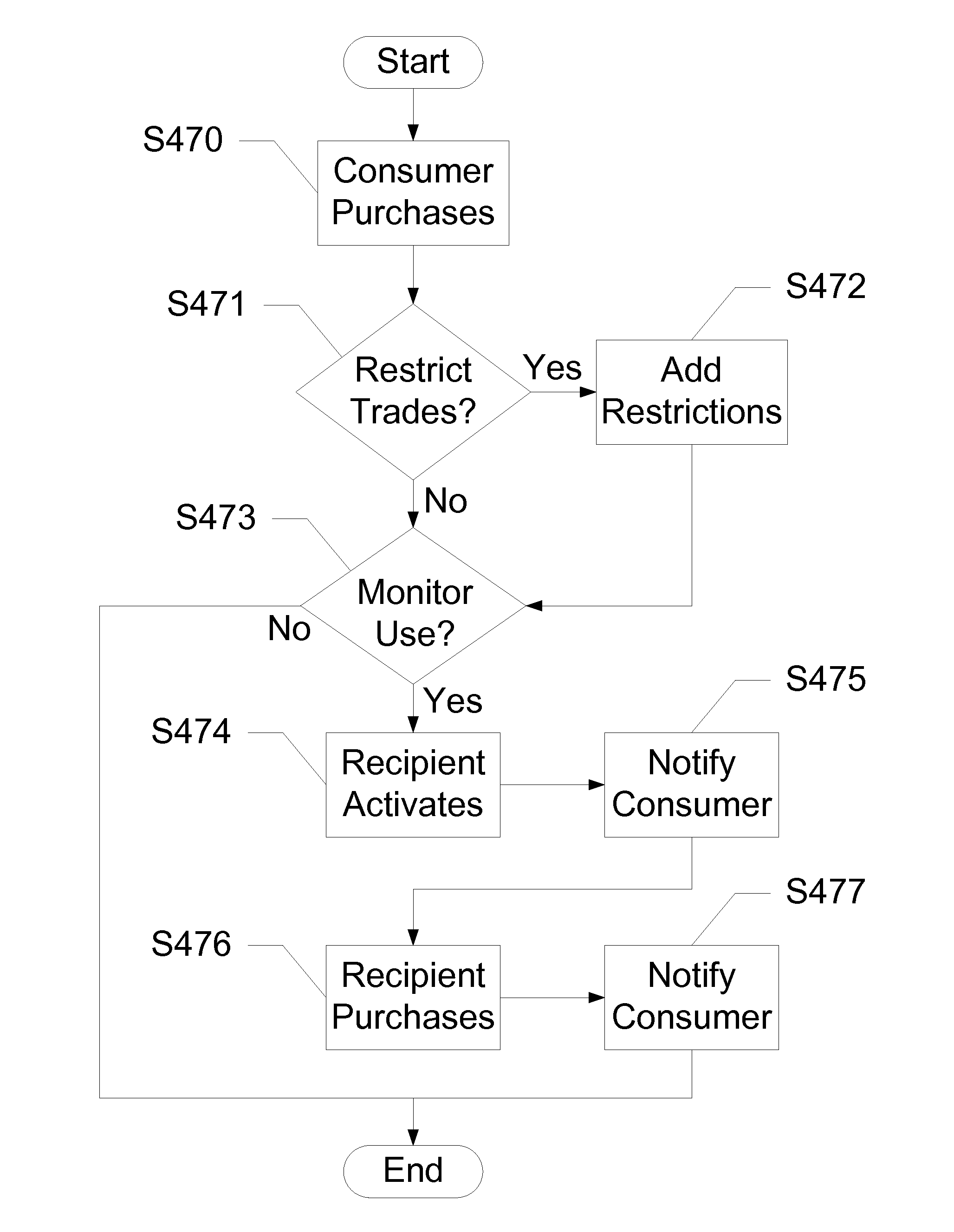
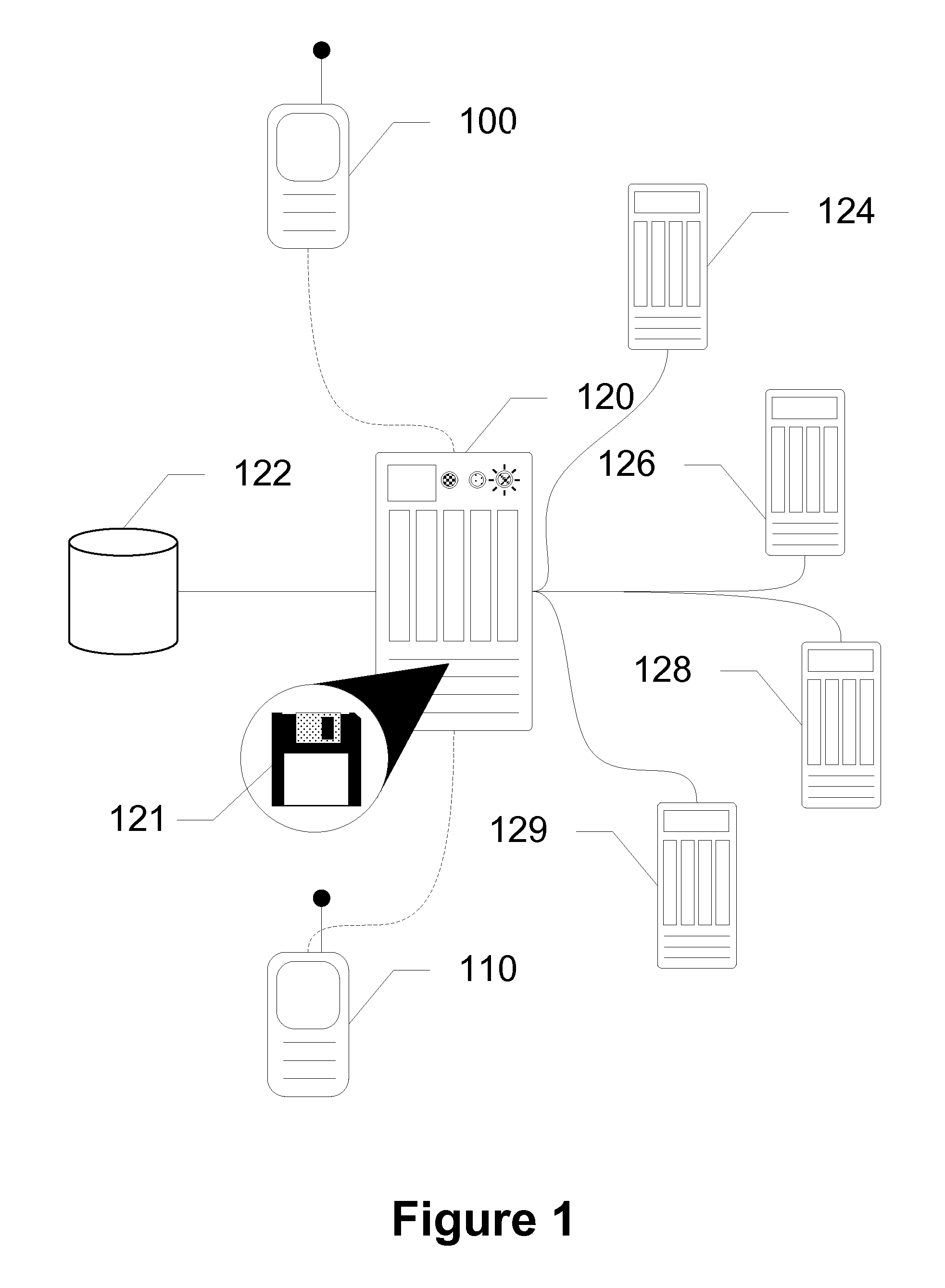
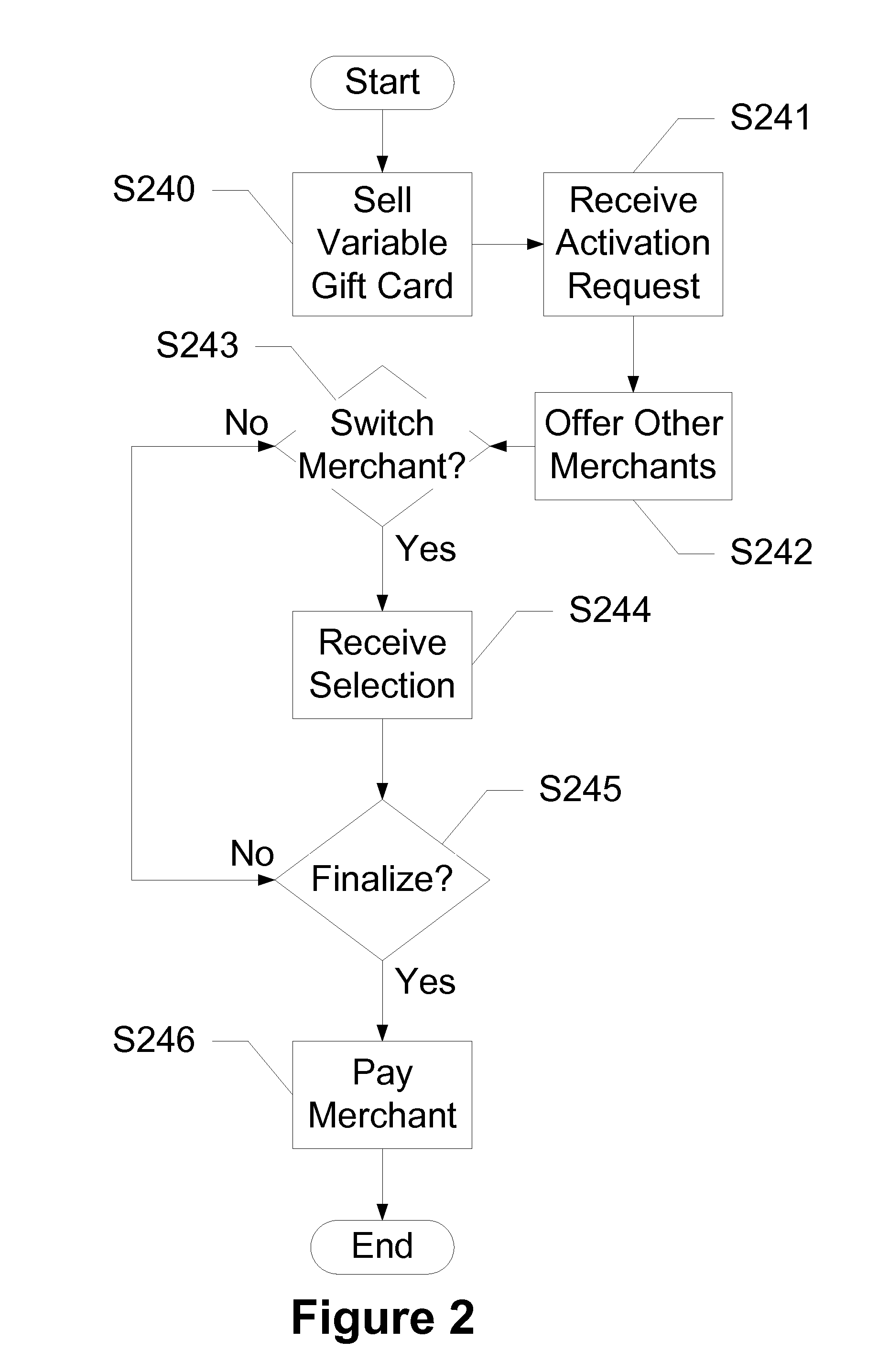
Flexible Mobile Gift Cards
Devices, systems and methods are disclosed which relate to allowing a recipient of a closed-loop gift card to select one of a plurality of merchants toward which to apply the value. A consumer buys a variable gift card from a service provider for a set amount. The consumer pays the service provider that amount, but the service provider holds that amount in escrow. The consumer sends the gift card to a recipient with a predetermined merchant. The recipient receives the gift card and decides not to use the gift card for the predetermined merchant, but for a desired merchant. The recipient requests the service provider to change the merchant. The service provider requests a final confirmation before delivering the amount from escrow to the desired merchant, and the gift card is ready for use. If the recipient does desire to use the predetermined merchant, the recipient simply contacts the service provider for activation, where the service provider transfers the amount to the predetermined merchant.
Owner:AT&T MOBILITY II LLC
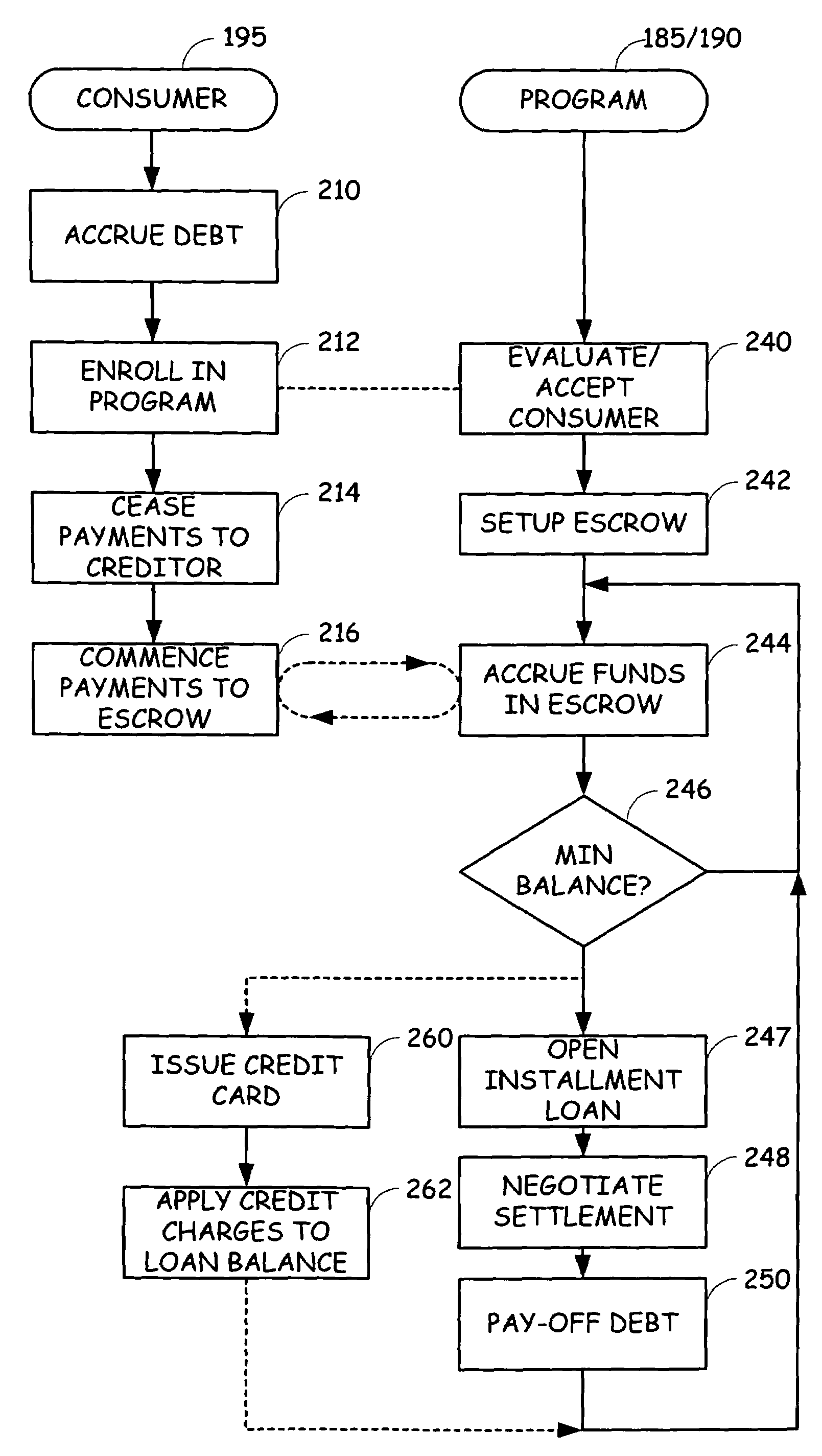
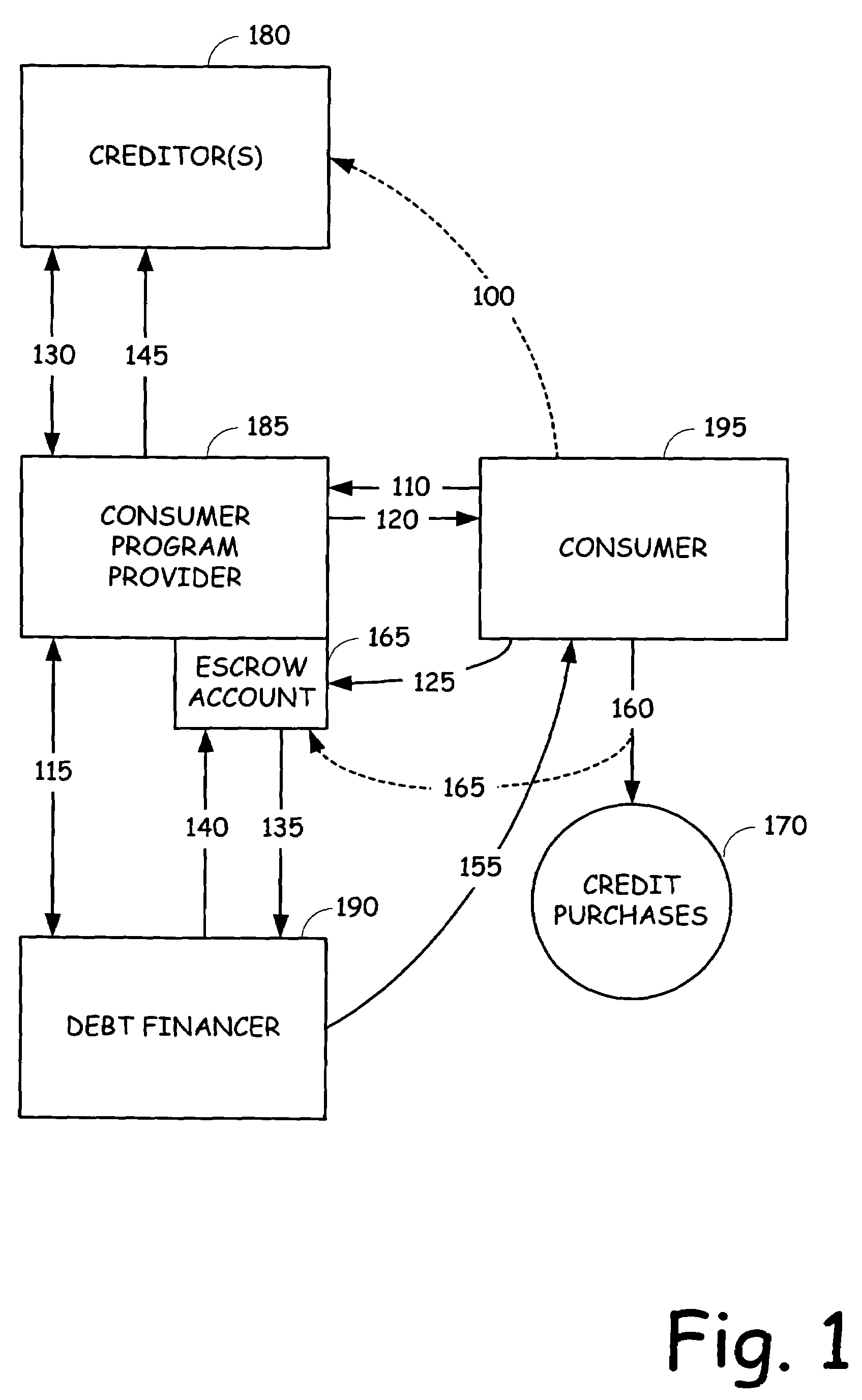
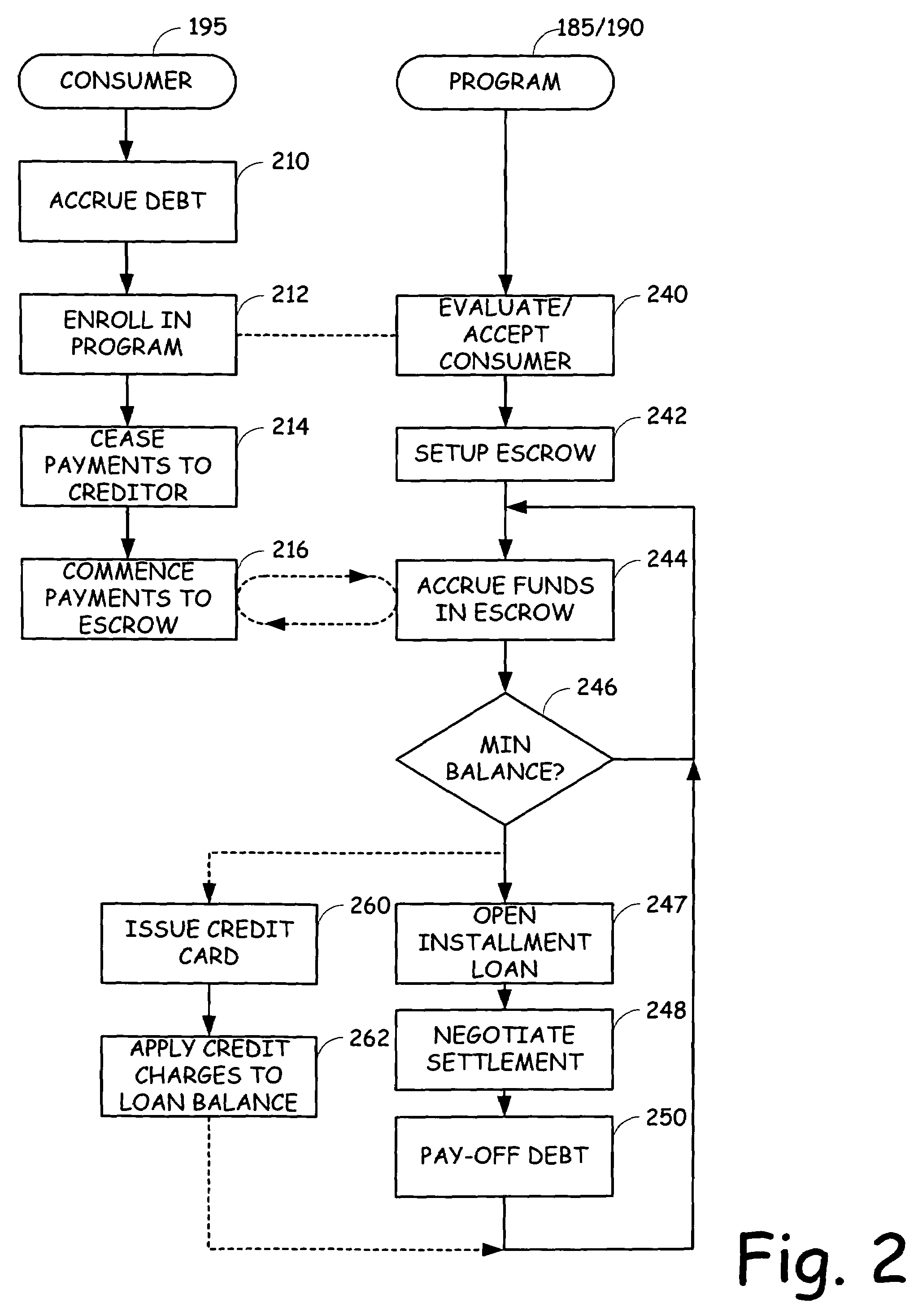
Combined debt consolidation and settlement program
A customer is assisted in recovering from indebtedness by combining a debt consolidation / settlement program with an installment loan. The customer is qualified for an installment loan with a value based on the amount of outstanding indebtedness or possibly based on the anticipated discounted balance. The customer is required to make payments into an escrow account for a period of time to ensure that the customer is credit worthy. One or more of the creditors are then approached in an effort to negotiate a discounted settlement amount in exchange for the reception of immediate reconciliation of the debt owed. A portion of the negotiated discount is retained for compensation, which can be provided to the debt settlement provider and / or the bank finding the installment loan. The balance is passed through to the customer.
Owner:CC SERVE
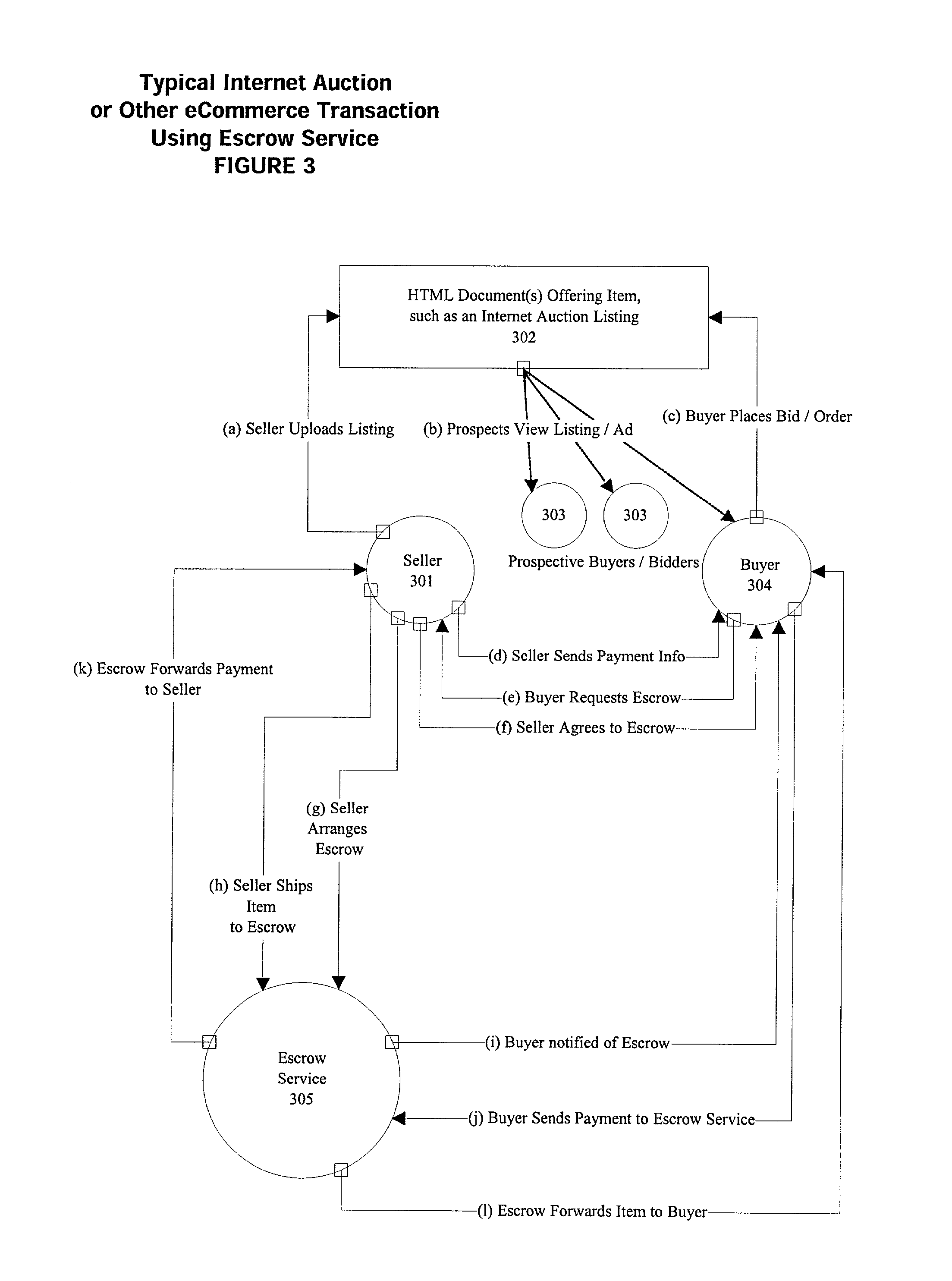
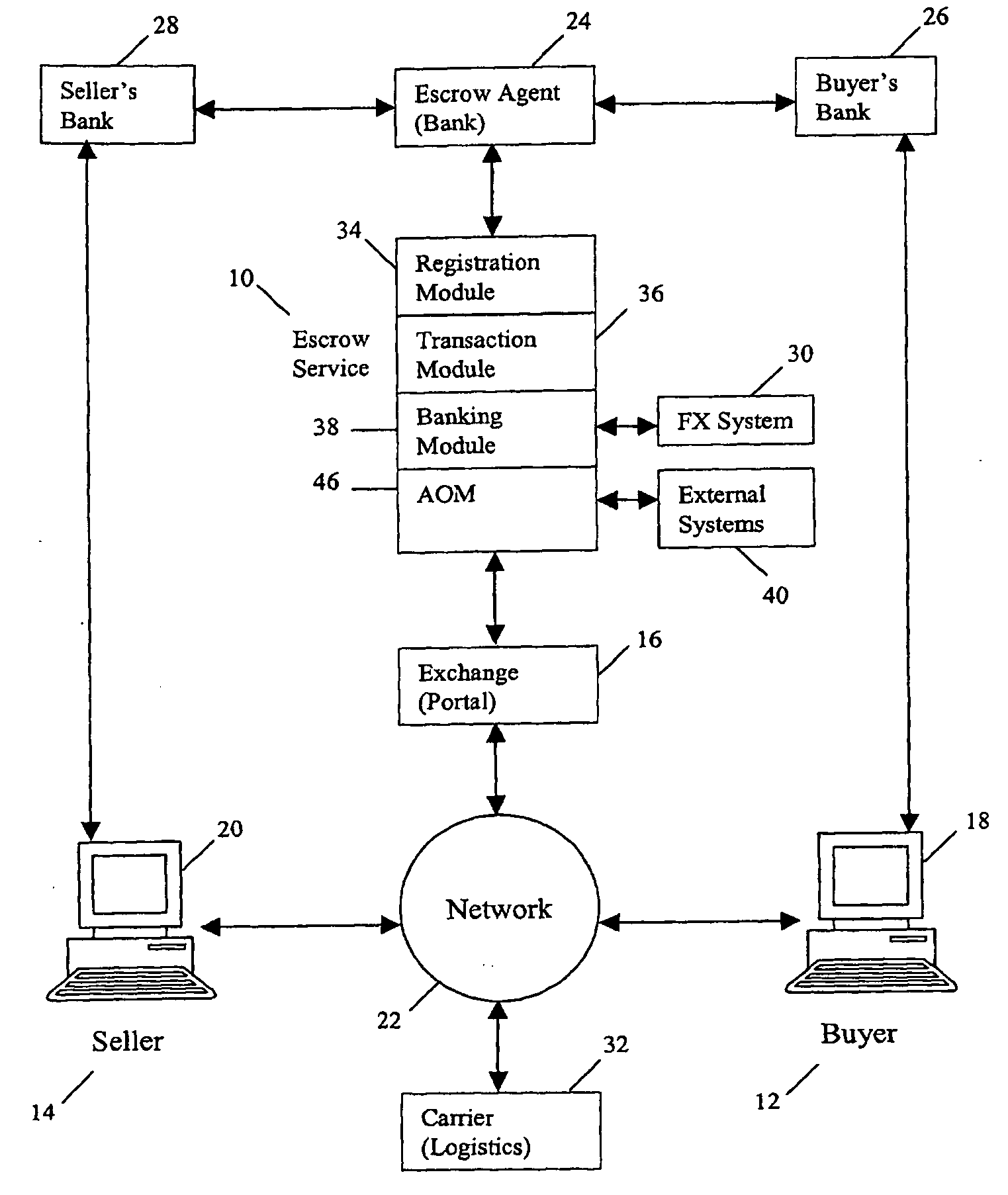
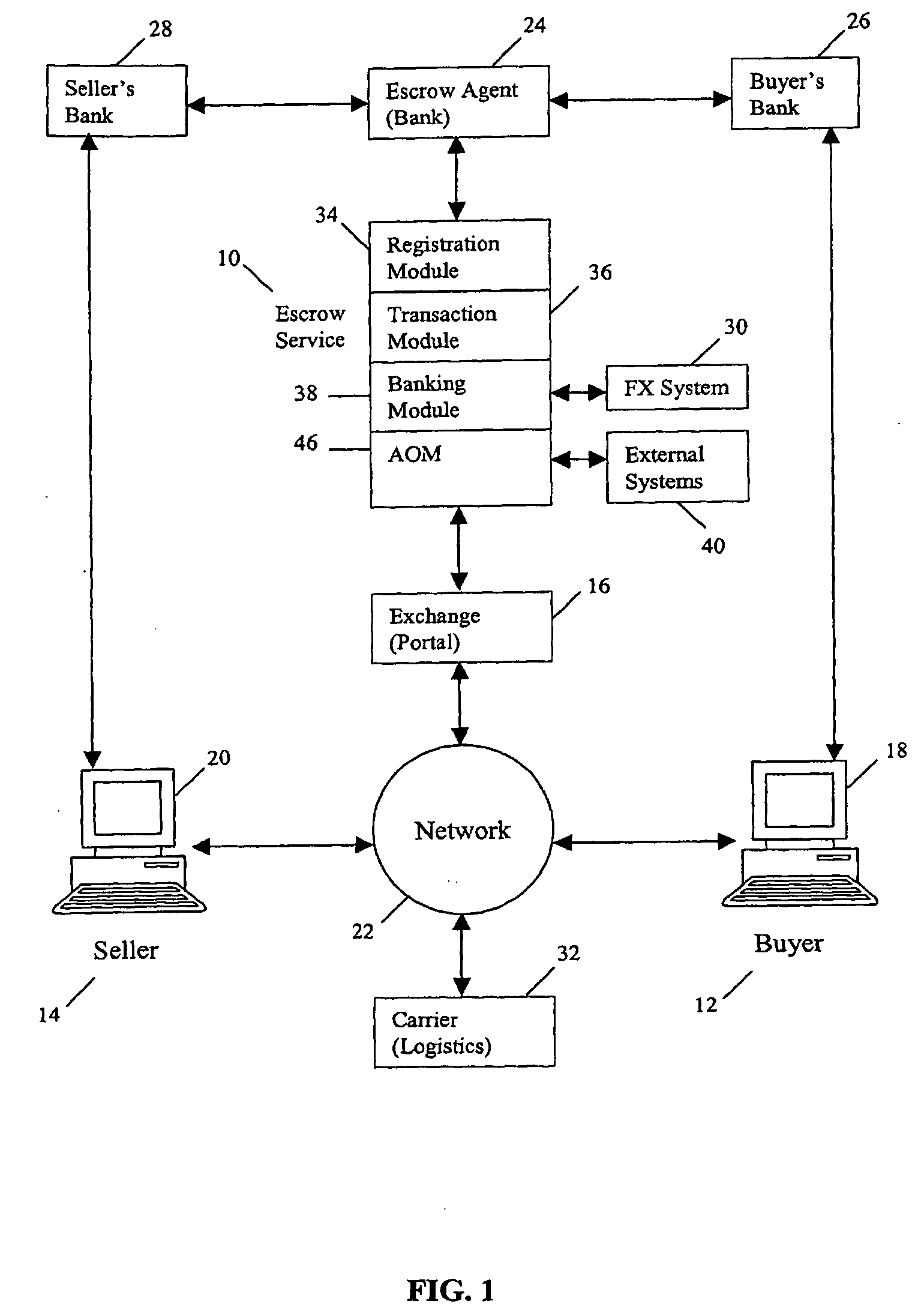
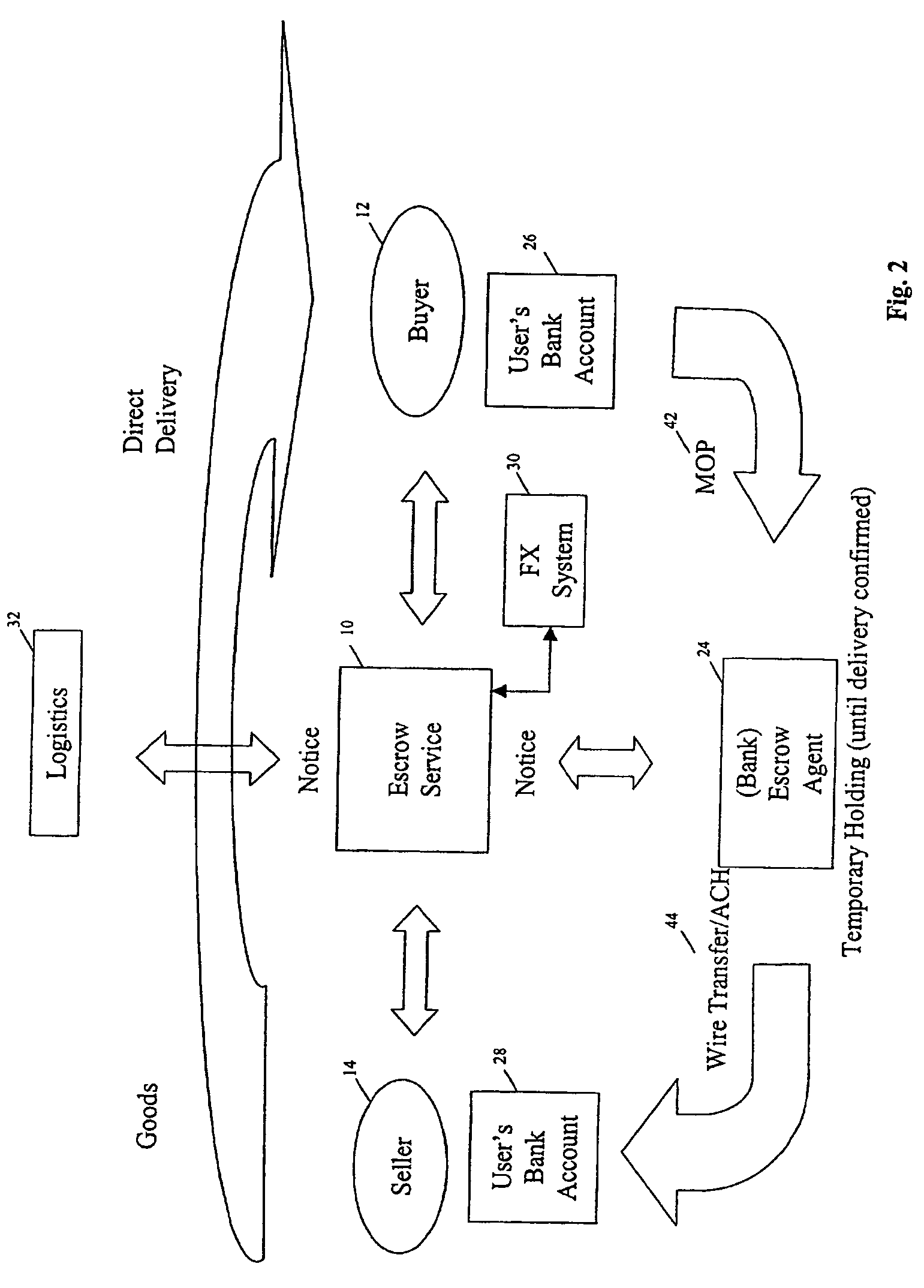
Method and system for multi-currency escrow service for web-based transactions
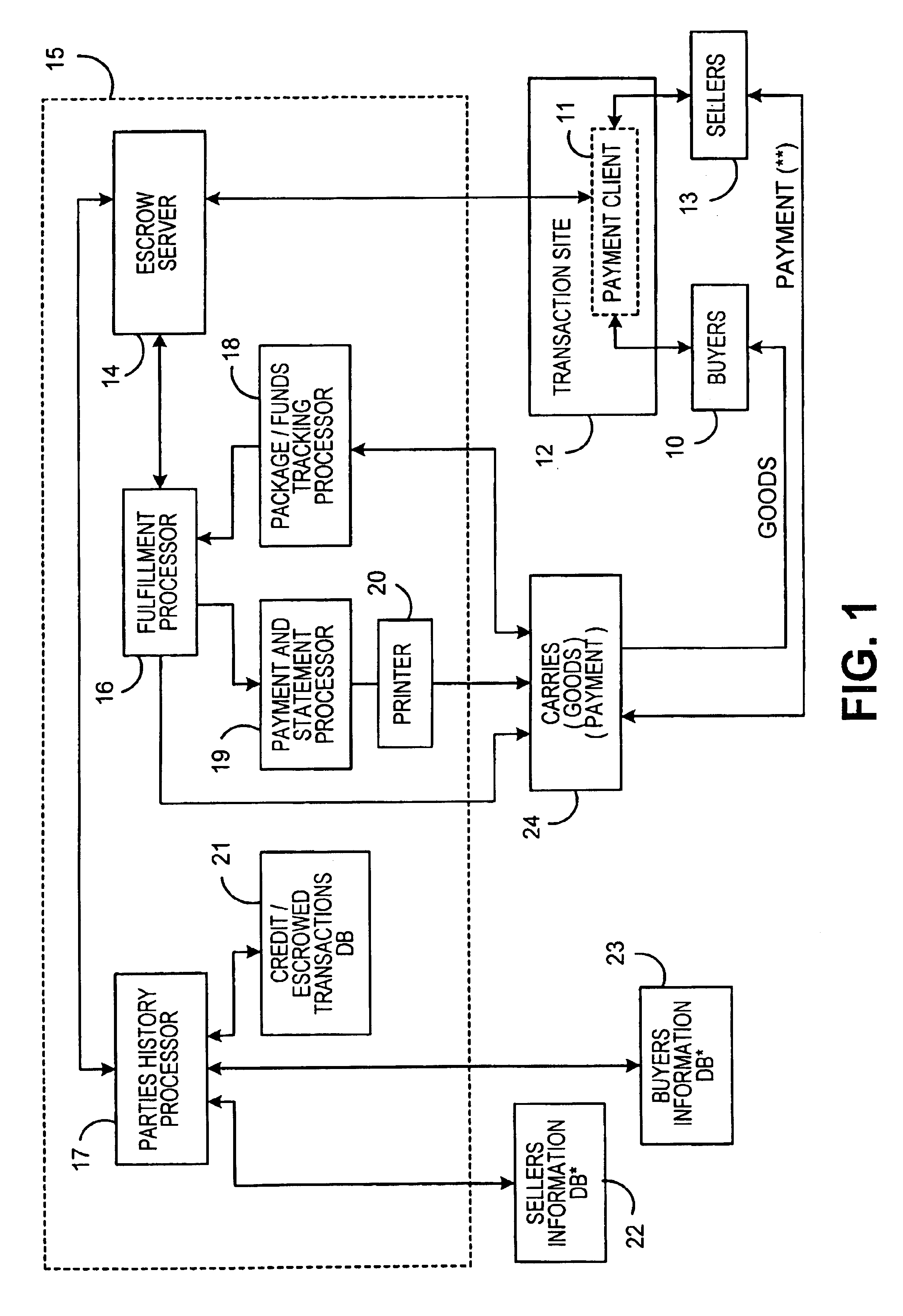
A method and system for escrow service for web-based transactions, such as multi-currency web-based transactions, is web-accessible and accepts registrations from exchanges and / or portal partners. The completion of registration and transactions is allowed to entitled users who access the system via the web. The system maintains an internal banking engine to act as a deal manager, messaging service and accounts sub-ledger and escrows funds entrusted to it. The transaction process is composed of a number of transaction statuses, and reporting of those statuses to users is accomplished online and via web query. The system provides local currency / multi-currency capability and supports several methods of payment, such as credit cards, authorized Automated Clearing House (ACH) or equivalent direct debit / credit and wire transfer payments, and all funds movements are electronic. The system supports transaction level detail through its banking engine accounts; funds movements from its currency accounts, and escrows funds to currency based escrow accounts. Buyers completing goods / services inspections after delivery initiate settlements.
Owner:CITIBANK
Method and system for handling escrow arrangements
A method and system are provided for supplying information to users about each stage of a multi-stage project before dispensing funds. The method includes inputting a set of terms for dispensing funds for each stage of a multi-stage project. Data is recorded related to the terms for dispensing funds. Funds are dispensed after the completion of each stage of the multi-stage project, wherein completion of each stage is dependent upon viewing and approving each stage of the multi-stage project.
Owner:J HOME
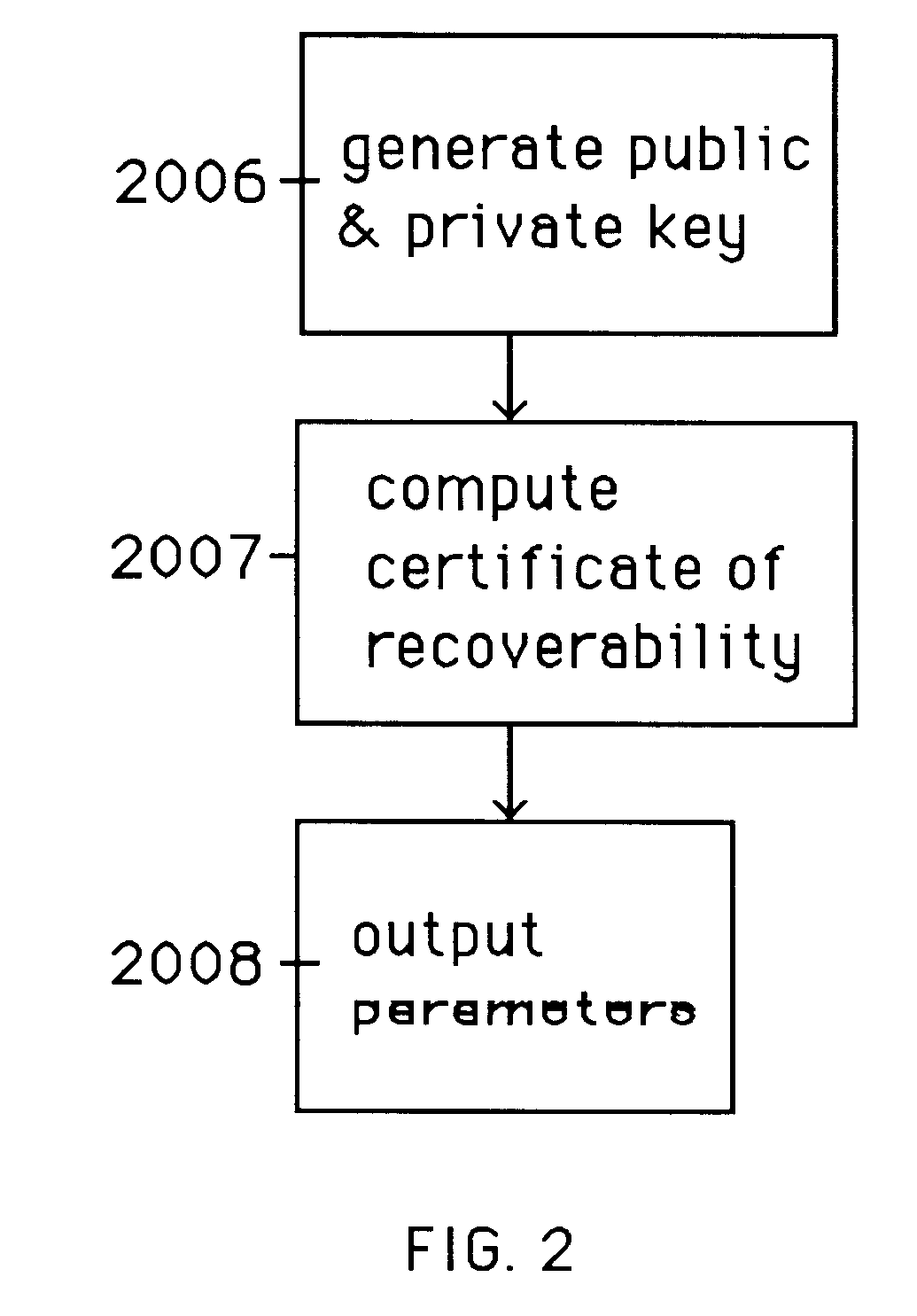
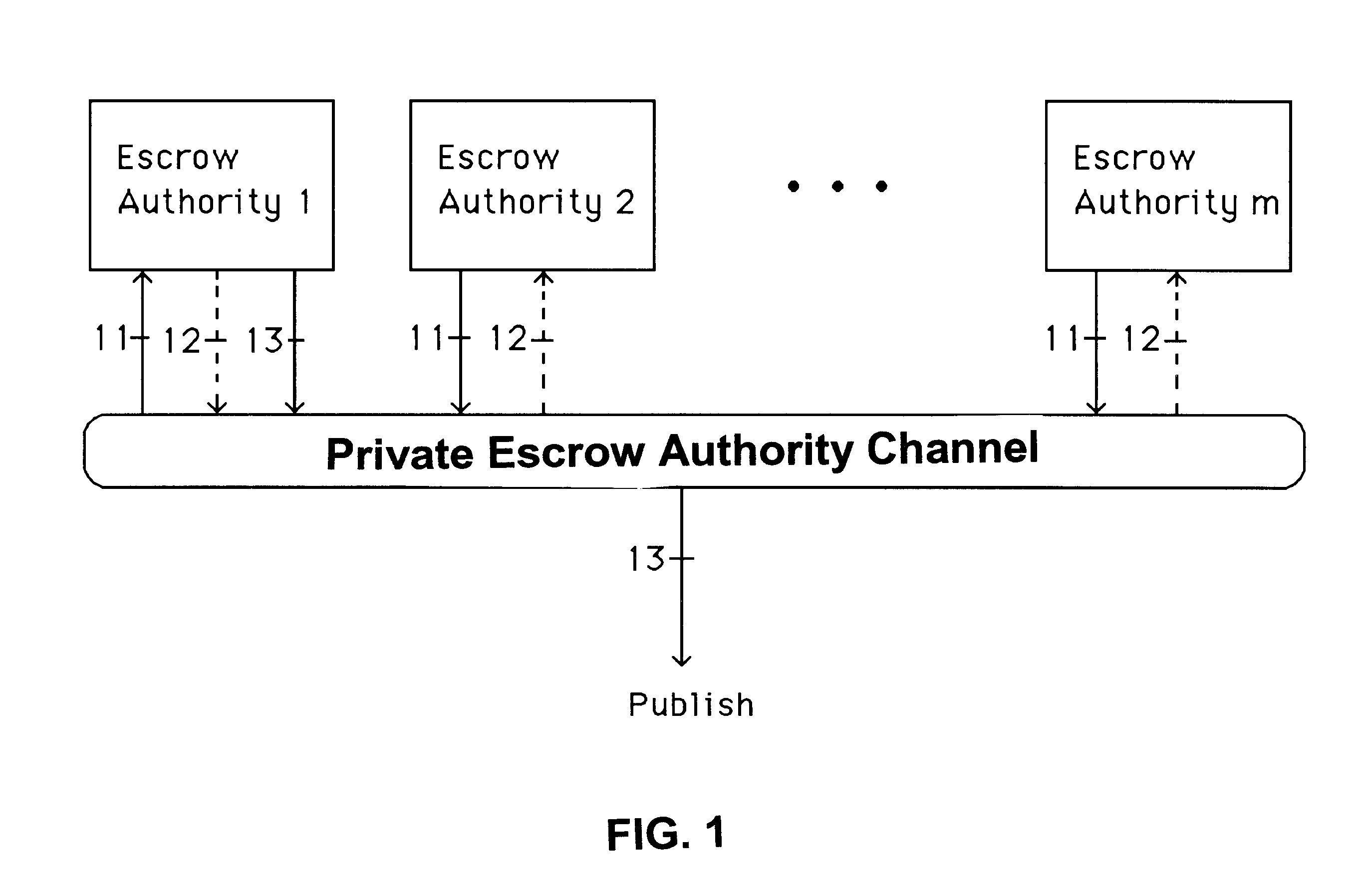
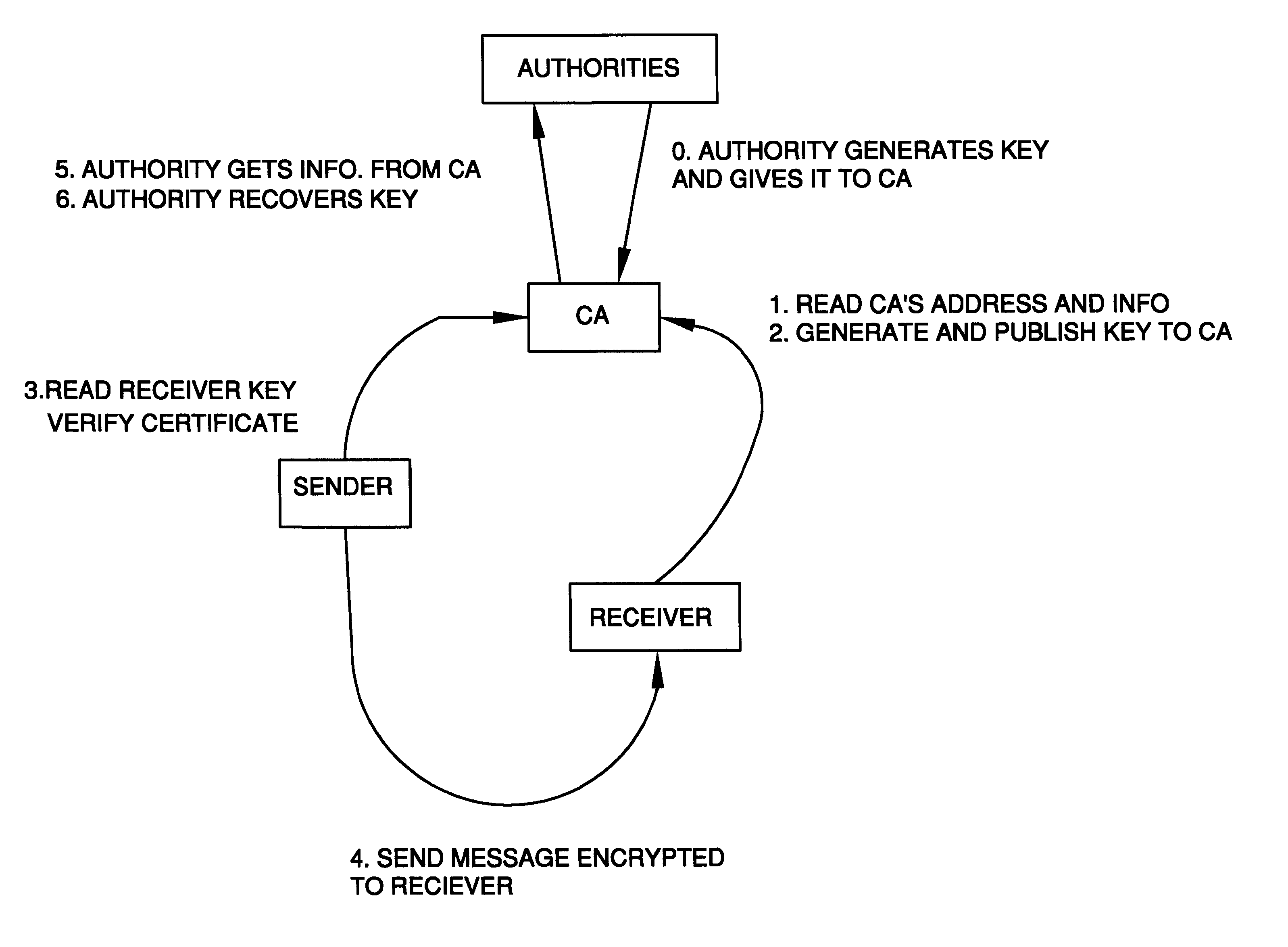
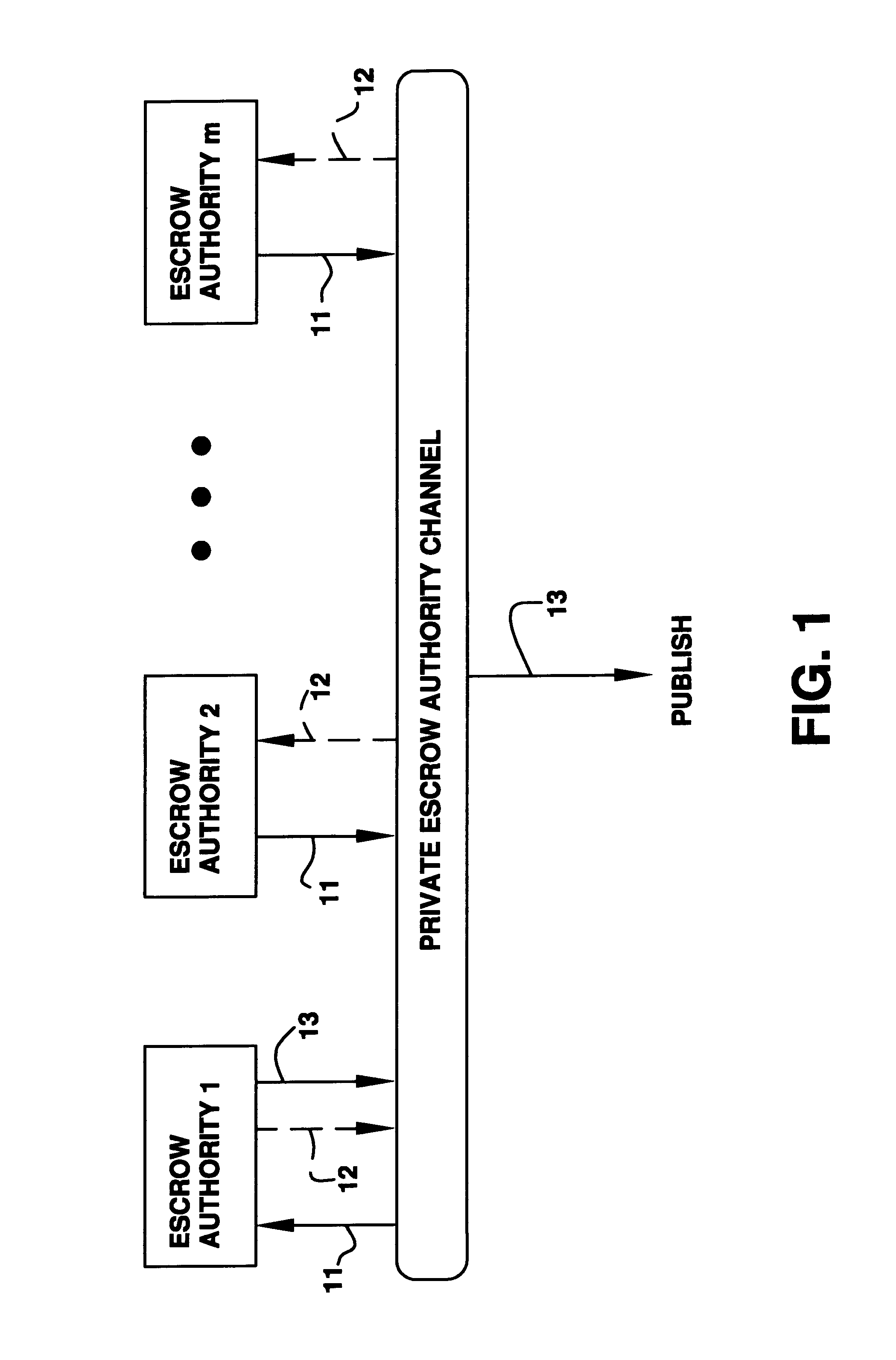
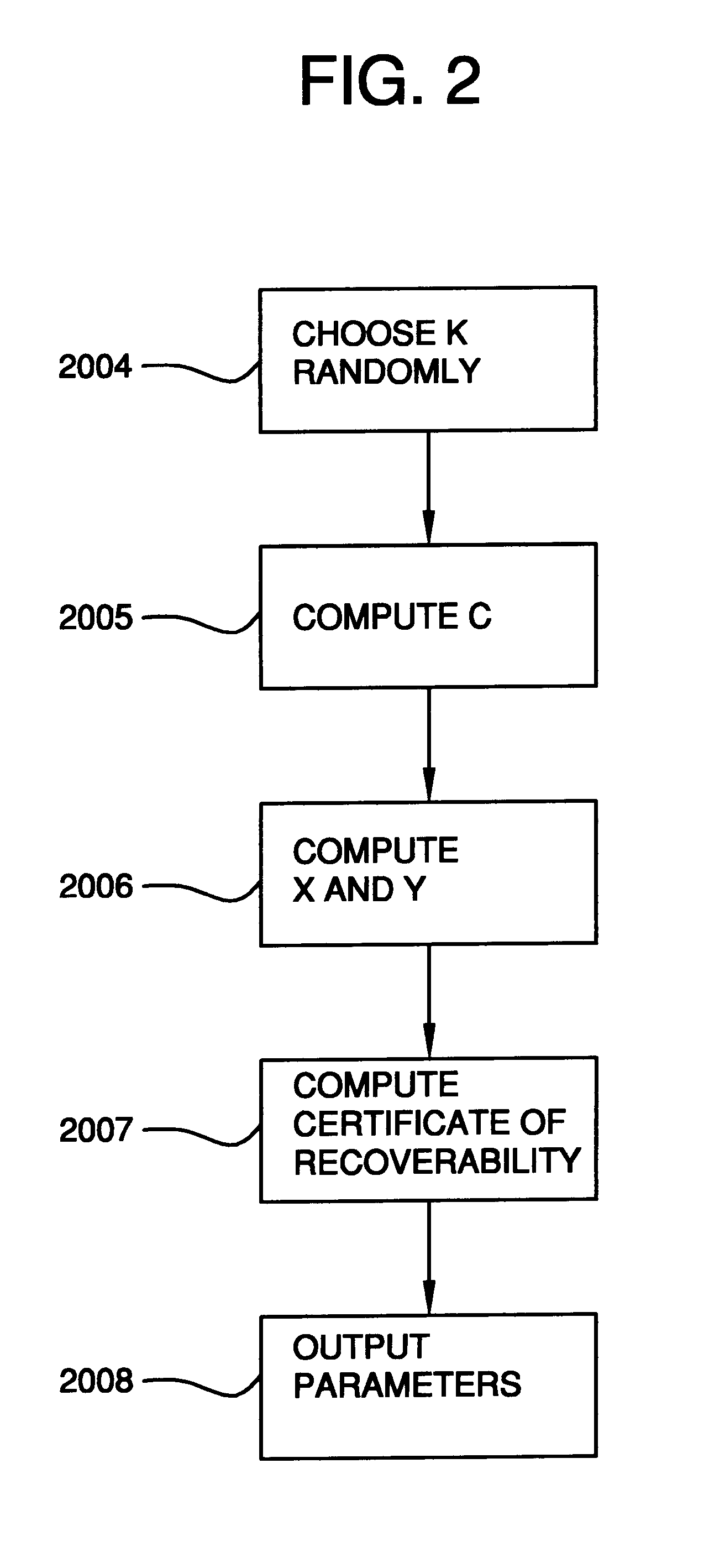
Auto-recoverable and auto-certifiable cryptostem using zero-knowledge proofs for key escrow in general exponential ciphers
InactiveUS6282295B1Fast and easy disseminationEasy to handleKey distribution for secure communicationPublic key for secure communicationTrusted authorityValidation methods
A method is provided for an escrow cryptosystem that is essentially overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The keys generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key is recoverable by the escrow authorities. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". The proof and verification method involves one party proving to a second party that a third party can gain access to an encrypted value. In addition, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware. The system is efficient and can be implemented as a "drop-in" replacement to an RSA or ElGamal cryptosystem. The system is applicable for lawenforcement, file systems, e-mail systems, certified e-mail systems, and any scenario in which public key cryptography can be employed and where private keys or information encrypted under public keys need to be recoverable. The system security relies solely on the security of cipher systems involved whose security has been extensively studied in the past.
Owner:CRYPTOPEAK SECURITY LLC
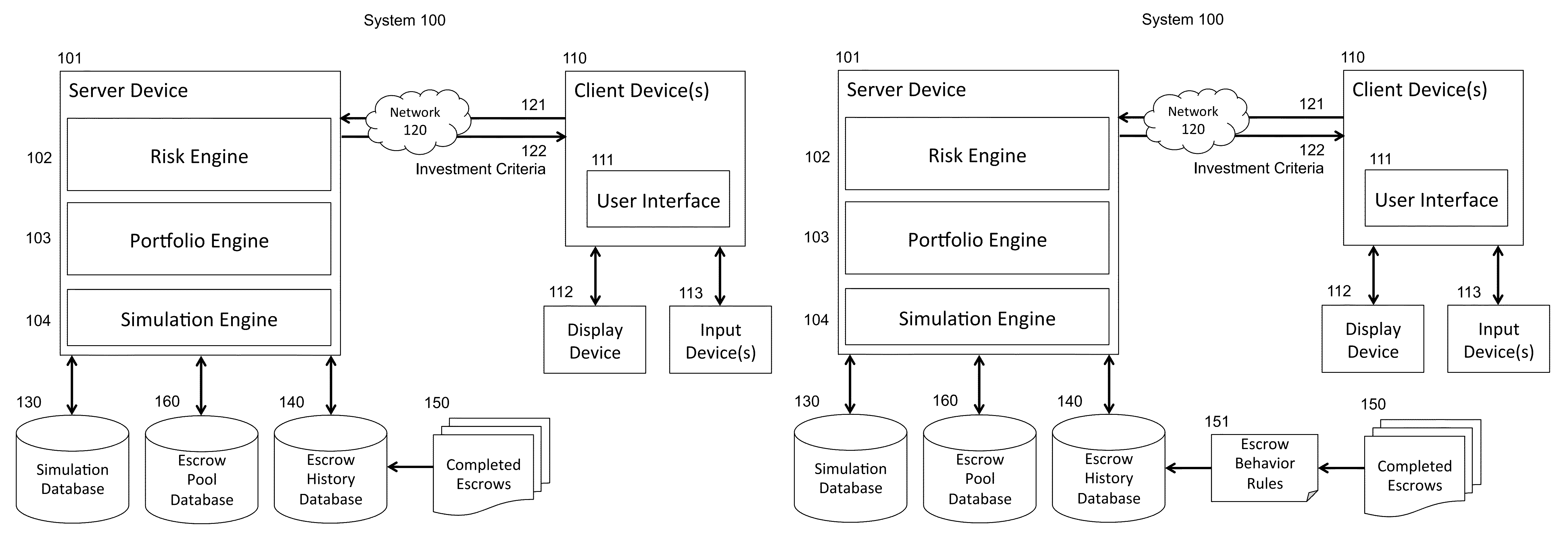
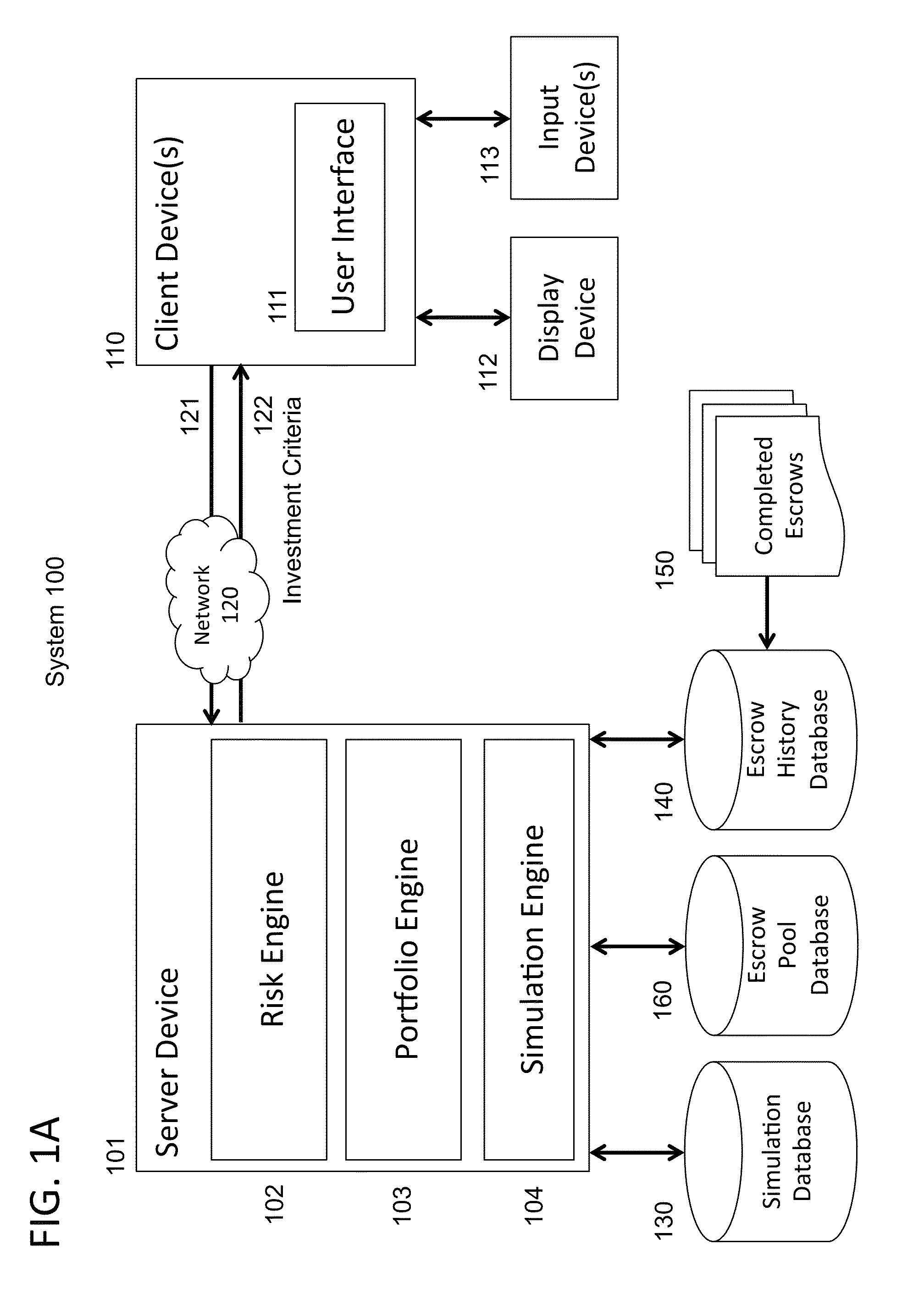
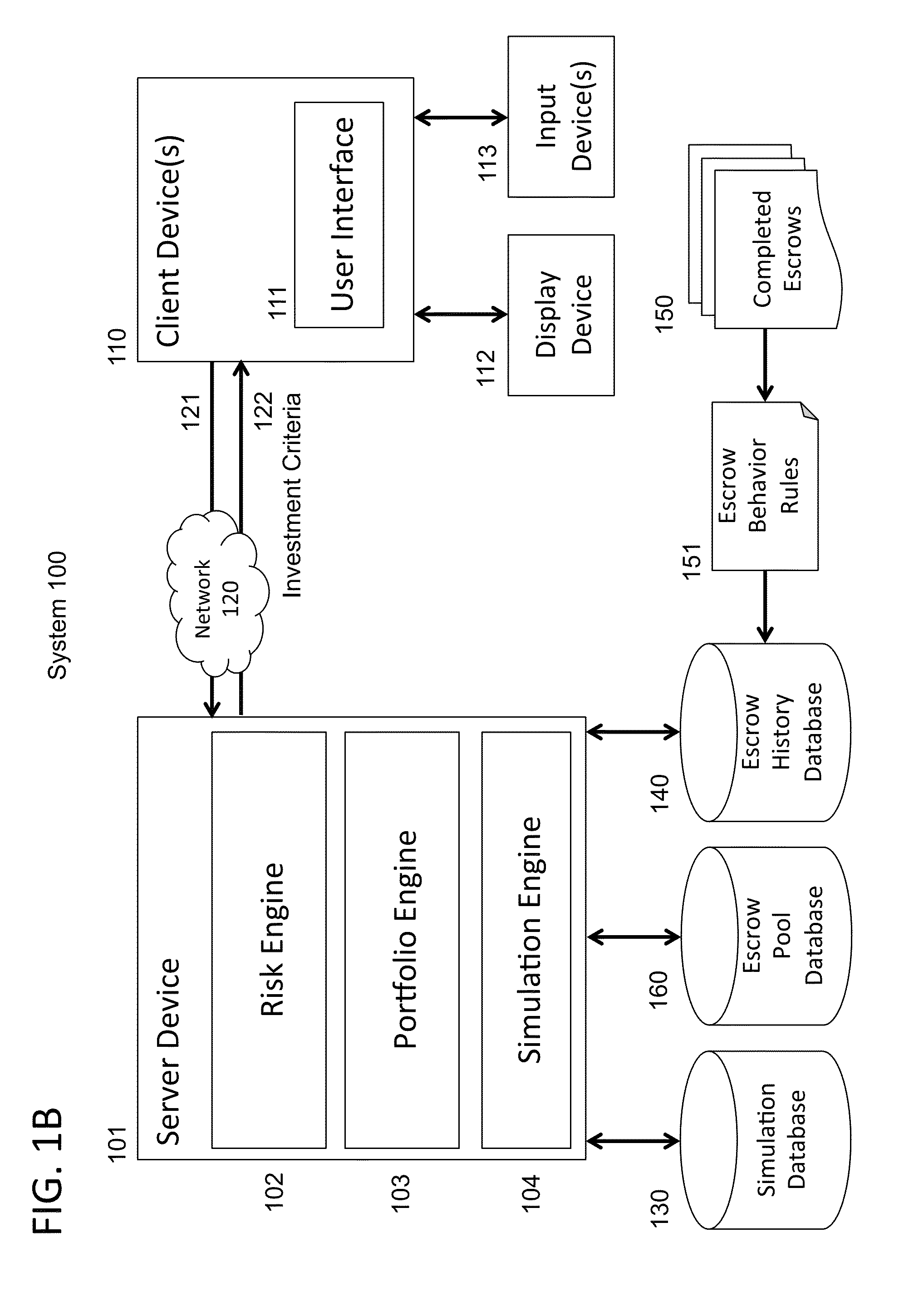
System and method of generating investment criteria for an investment vehicle that includes a pool of escrow deposits from a plurality of merger and acquisition transactions
An automated method is provided for generating investment criteria for an investment vehicle that includes a pool of escrow deposits from a plurality of merger and acquisition transactions. An escrow history database is maintained of data derived from historical behavior of escrows from a plurality of previous merger and acquisition transactions. An escrow pool database is maintained of current escrow deposit data from a plurality of current merger and acquisition transactions. The escrow pool database includes the current deposit amounts in the pool of escrow deposits, and stated terms governing the release of each deposit amount in the pool of the escrow deposits. A set of investment criteria for selecting an asset pool is generated using a processor operating on the escrow history database and the escrow pool database. The set of investment criteria includes maturity metrics selected from the group consisting of weighted average maturity, convexity, and maturity distribution profile.
Owner:ACQUIOM HLDG LLC
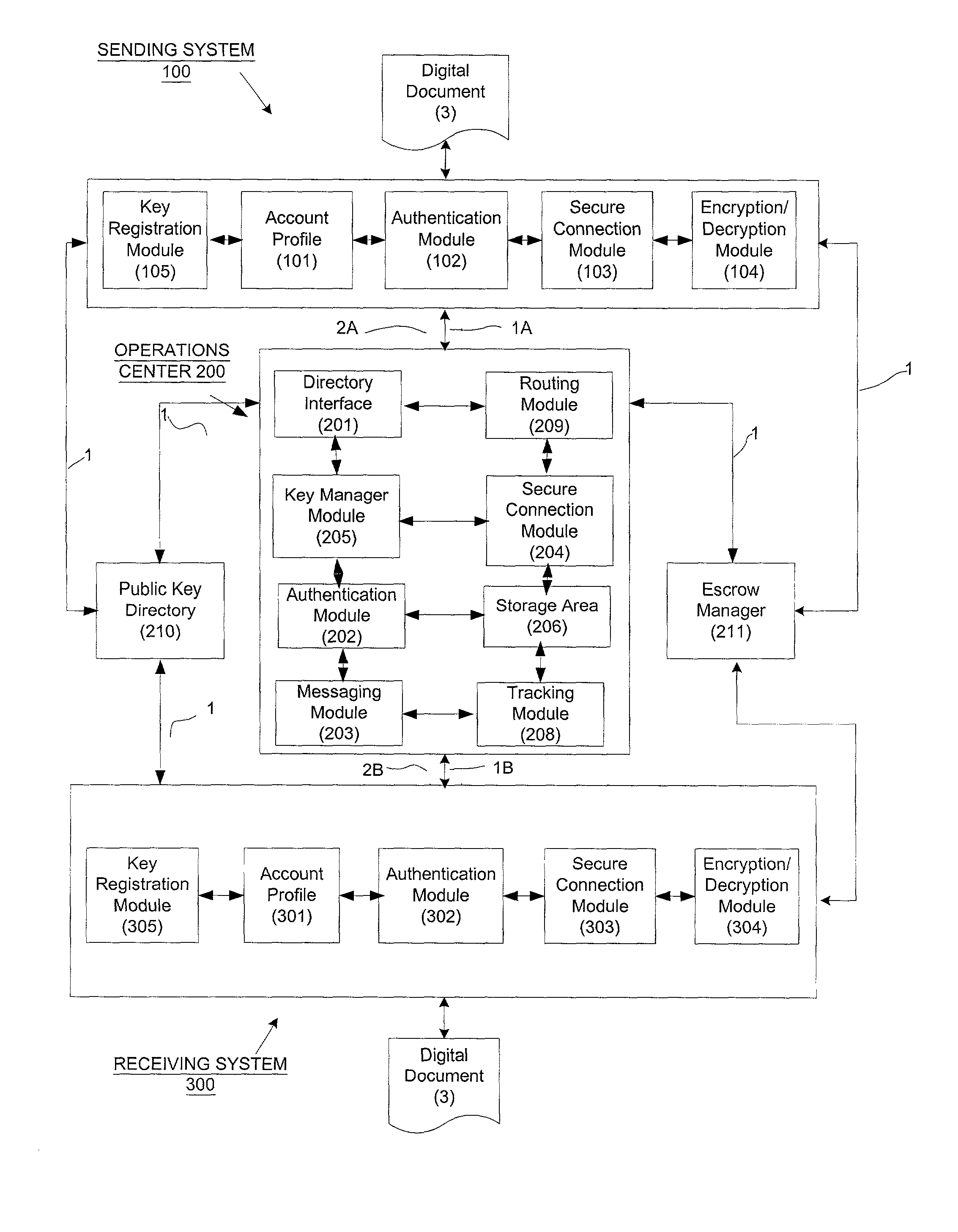
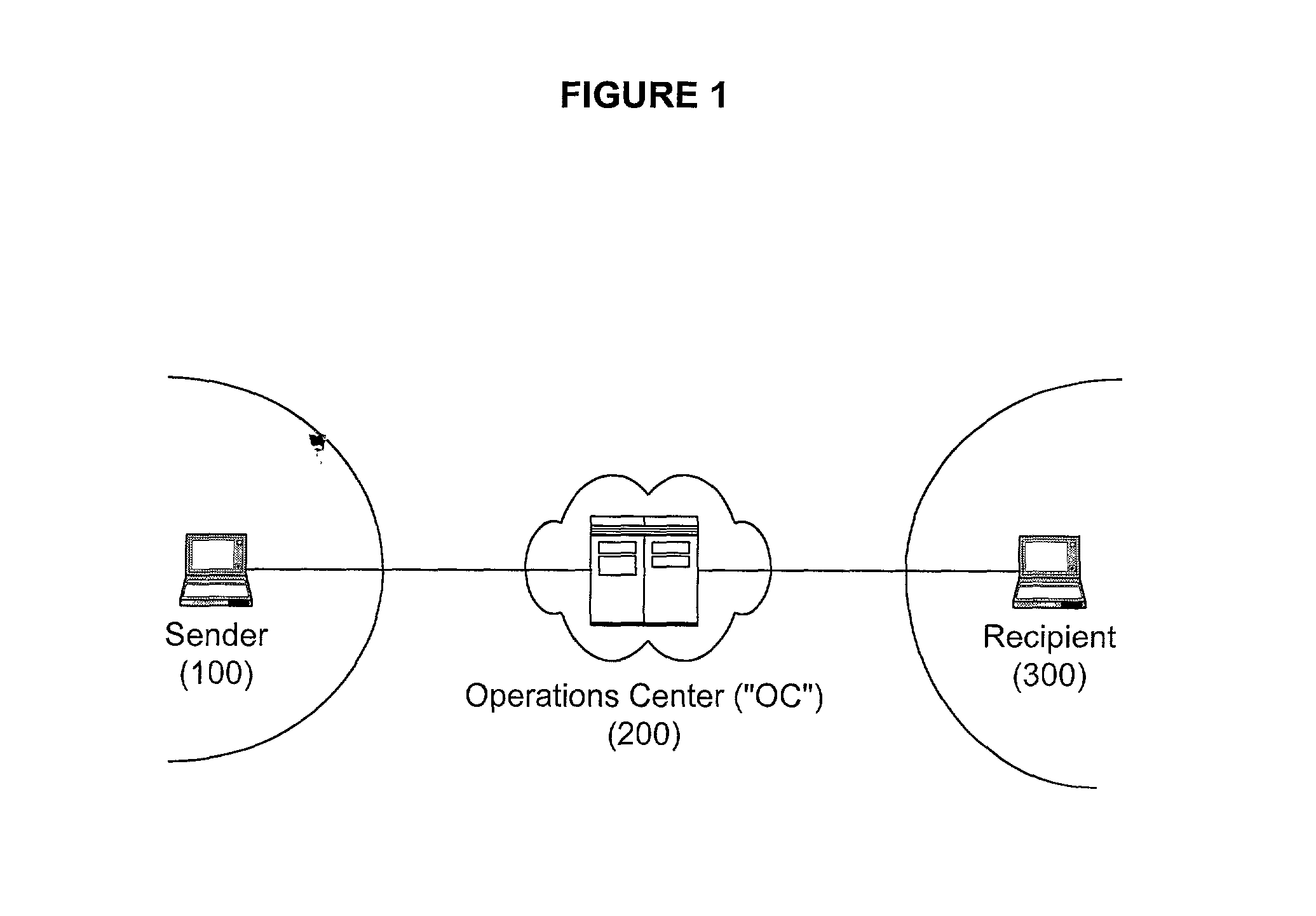
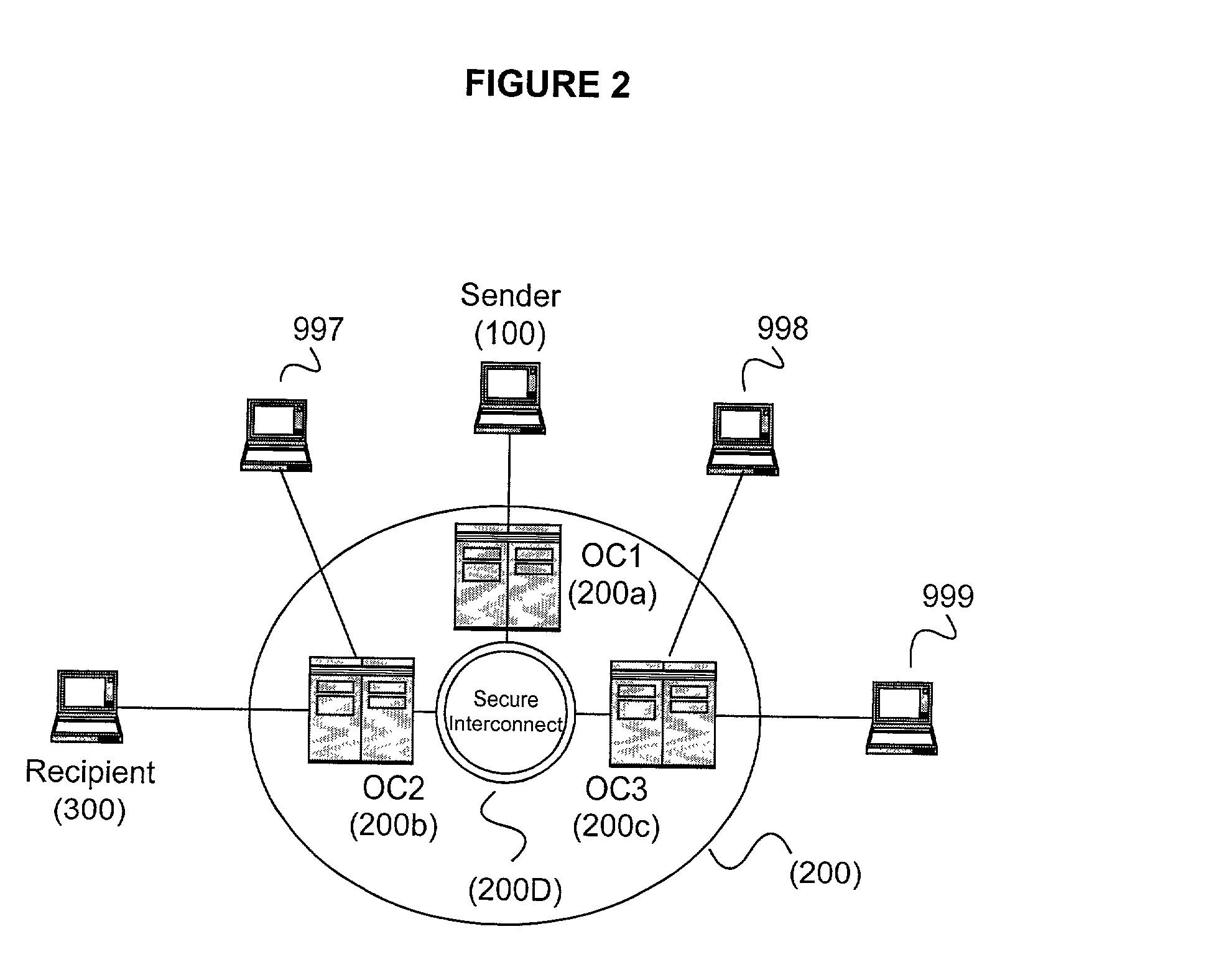
Secure and reliable document delivery using routing lists
InactiveUS20020129238A1Safe and reliable deliveryEffective trackingDigital data processing detailsUser identity/authority verificationEscrowEncryption
An operations center (OC) (200) acts as an intermediary for securely and reliably transmitting a document (3) from a sender (100) to a next recipient (300) on a routing list. The OC (200) identifies (464) a recipient (300) from the next stage of the routing list and provides either the recipient's public key (404) or an escrow encryption key (406). The OC (200) optionally can authenticate the sender (100) and / or the recipient (300), thus increasing security.
Owner:PERIMETER INTERNETWORKING CORP
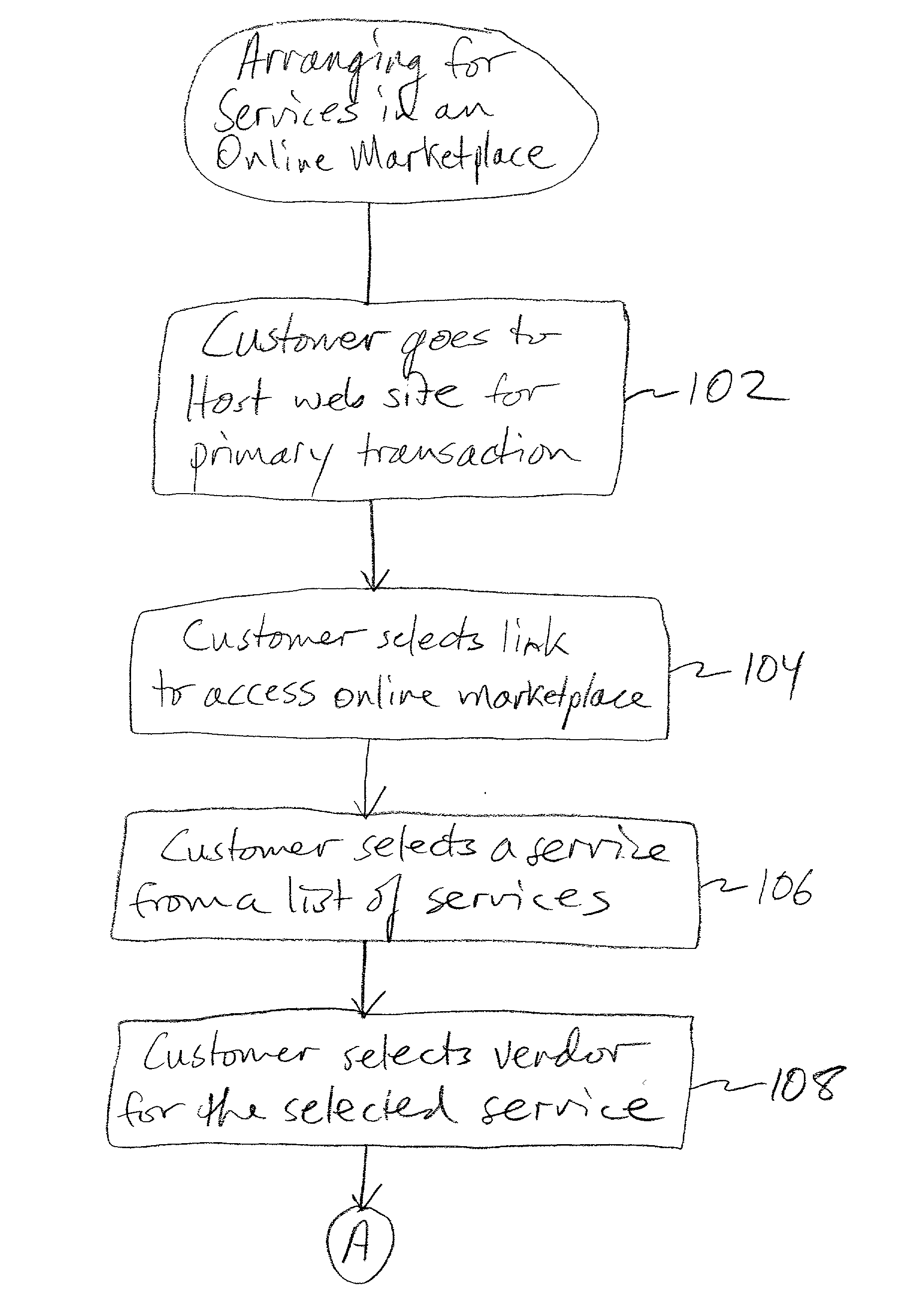
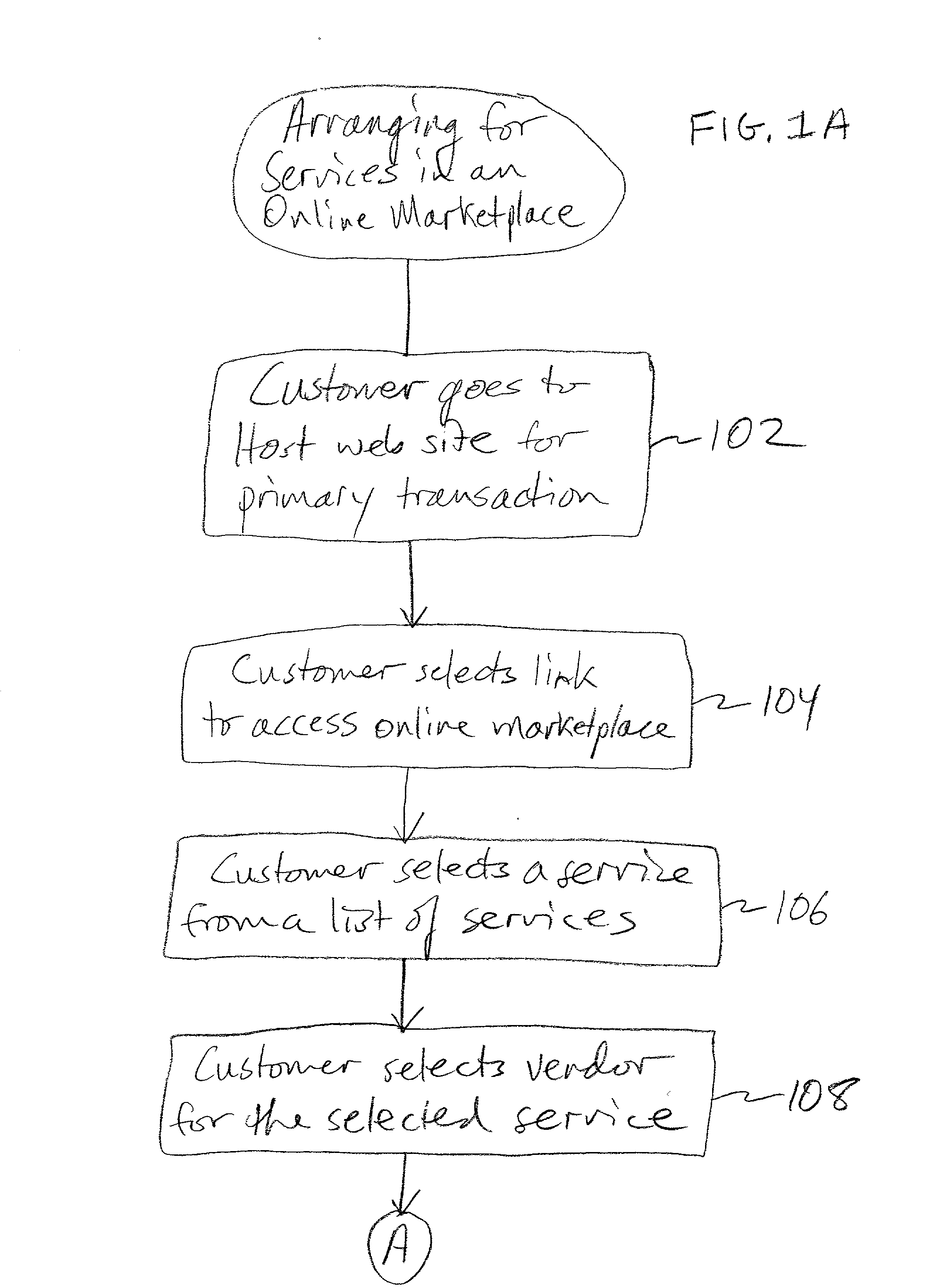
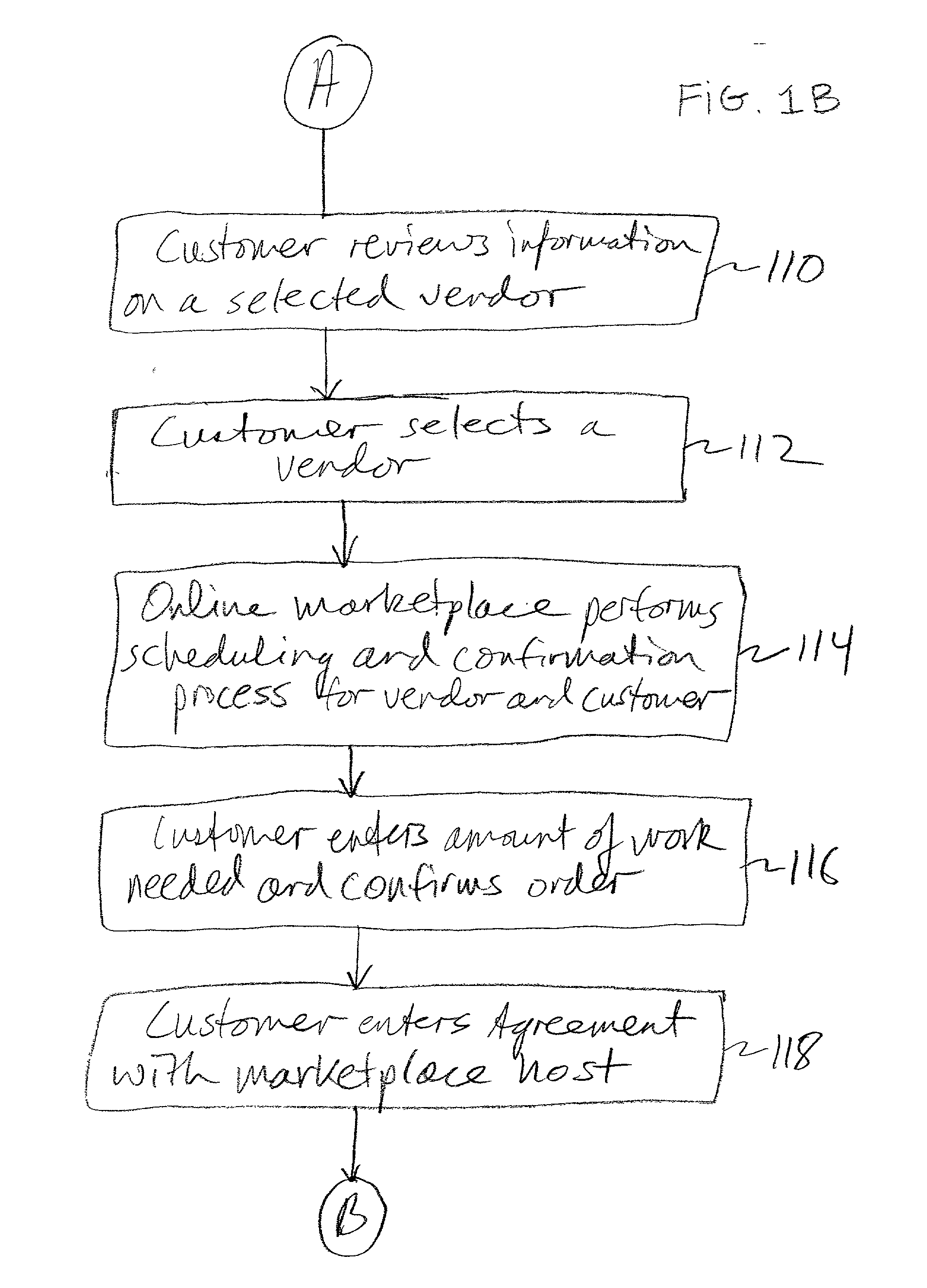
Online marketplace for moving and relocation services
Methods and systems for operating an online marketplace for the sale of services associated with self-help moving and relocating are described. A customer enters an online marketplace where service providers offer services relating to moving and relocating, specifically in the "do-it-yourself" moving field. The venue for the online marketplace is an Internet web site or a site on a computer network and is operated by a host that determines which service providers will be listed on the site. A typical self-help moving customer may enter the marketplace after completing an initial transaction with the host, such as reserving a moving truck or trailer and other moving equipment. In many instances this transaction is what initially draws the customer to the site. Once in the marketplace, the customer can view informational content on numerous vendors providing services relating to moving and relocating. Based on the estimates provided by the marketplace, the customer selects the vendor and "purchases / prepays for" his services on the marketplace. The funds are held in escrow until the transaction is fulfilled to the customer's satisfaction. The customer is provided a confirmation code. The code is given to the service provider upon completion of the job. This is the key that unlocks the funds. The marketplace also does not release the funds unless and until all parties are satisfied with the transaction. The customer selects the vendor that best suits the needs and budget of the customer by viewing rates, reviews, ratings, customer feedback, and background information on the vendor. In this manner control over the transaction lies more with the customer than with the vendor
Owner:U HAUL INT
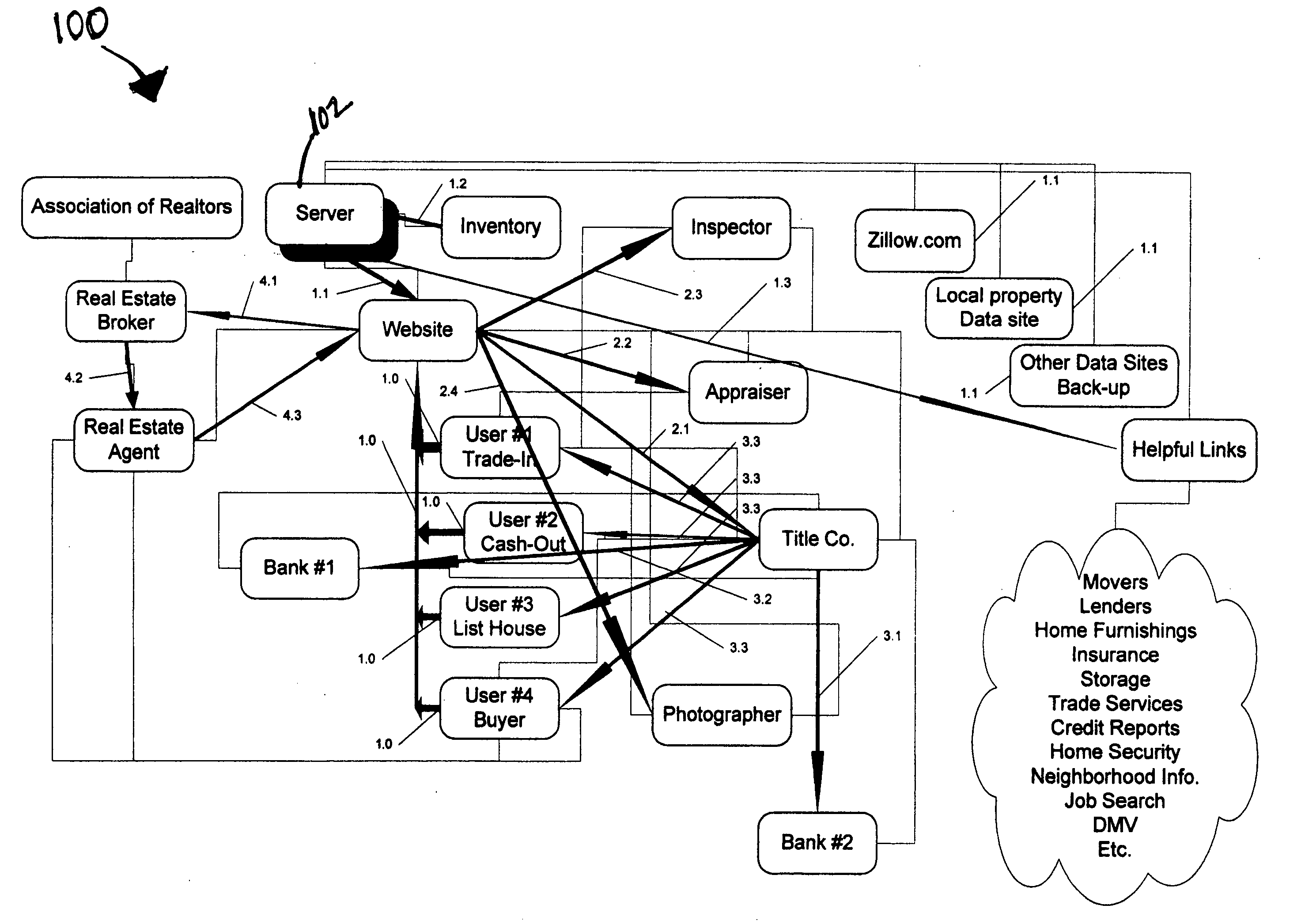
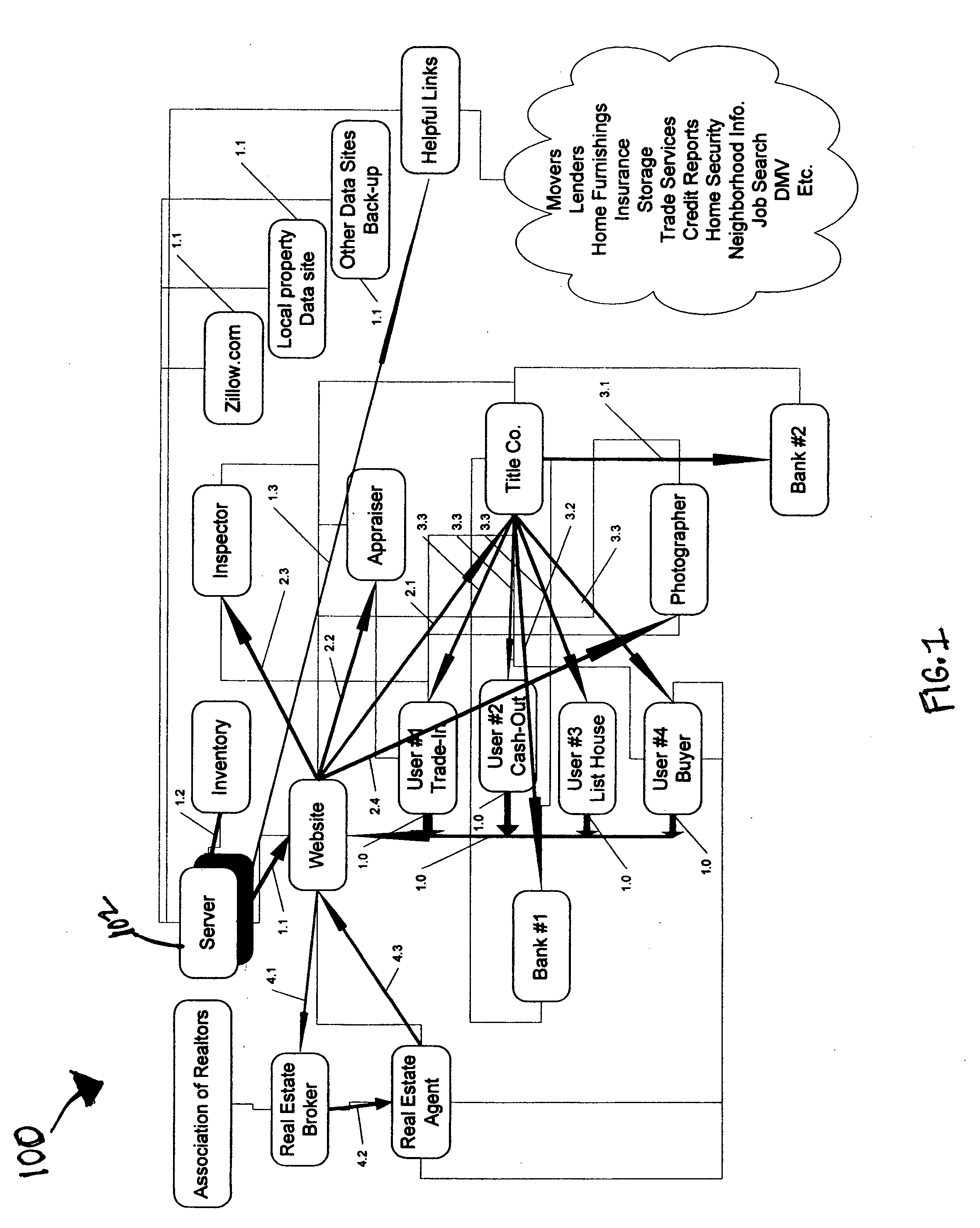
Methods and systems for real estate transactions
A communication hub to facilitate one or more real estate transactions is provided. The communication hub includes a memory to inventory available properties and a pool of appraisers, contracts, inspectors, and the like that may be scheduled via the communication hub to perform necessary or desired services. The communication hub further operates to initiate an escrow and title search for each inventoried or listed property to facilitate cash-out, trade-in, sale, or purchase of the inventoried or listed property.
Owner:SUXESS
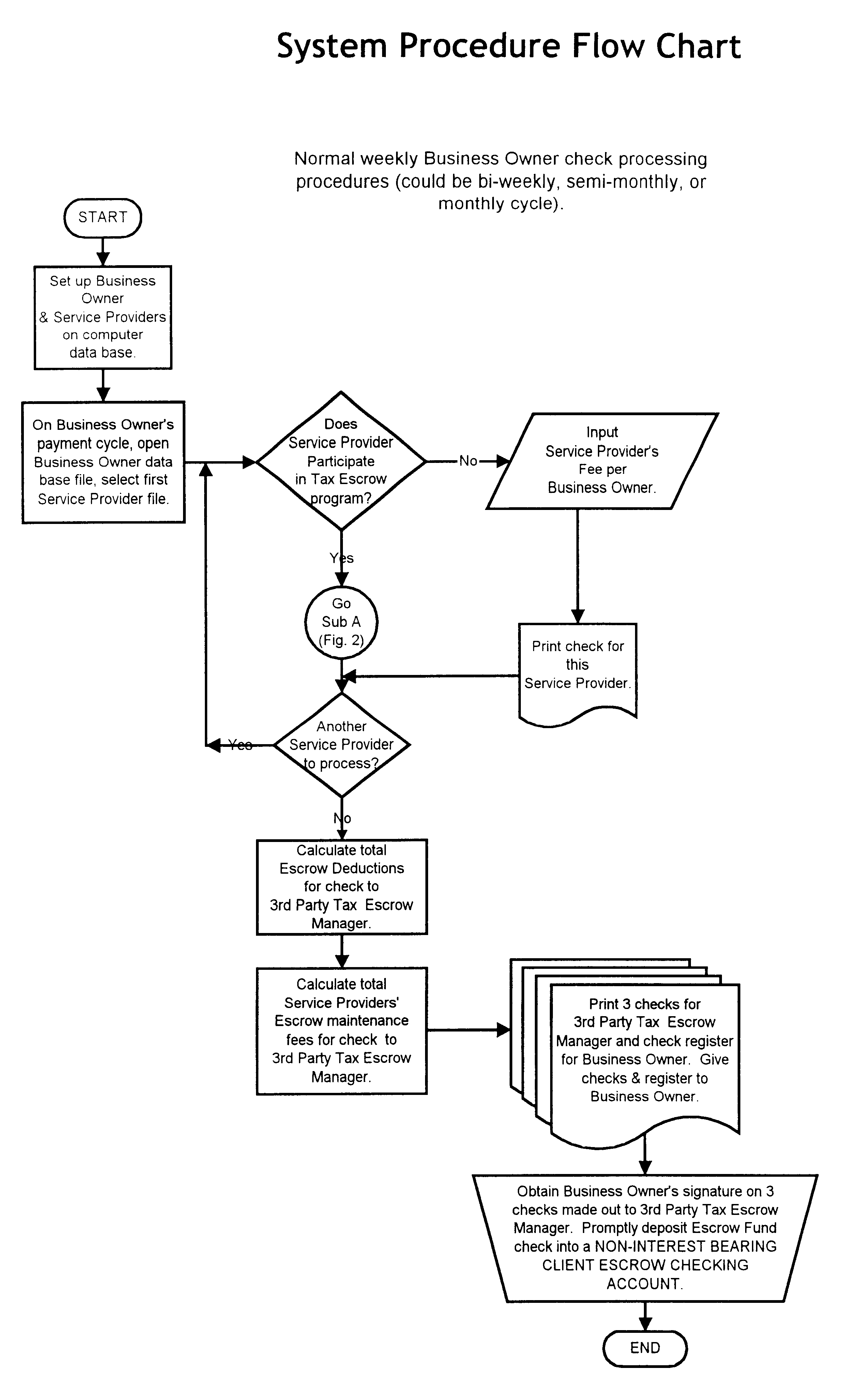
Tax escrow system for independent contractors
InactiveUS6898573B1Reducing noncompliance and nonpayment of taxesReduce paperworkComplete banking machinesFinanceThird partyInternet privacy
The system ensures the timely payment of taxes due a taxing authority while protecting the solvency of an independent service provider. The contracting entity retains a third-party escrow manager who oversees payments made by the contracting entity to an independent service provider. The third-party escrow manager estimates tax liability owed by the independent service provider to a tax authority based upon data provided to the third-party escrow manager by the independent service provider. The third-party escrow manager deposits a portion of monies owed to the independent service provider by the contracting entity for services provided in an escrow account. The escrow account is used by the independent contractor to pay monies owed to the taxing authority in a timely manner when due.
Owner:E PAYCON
System and process for escrow of payments
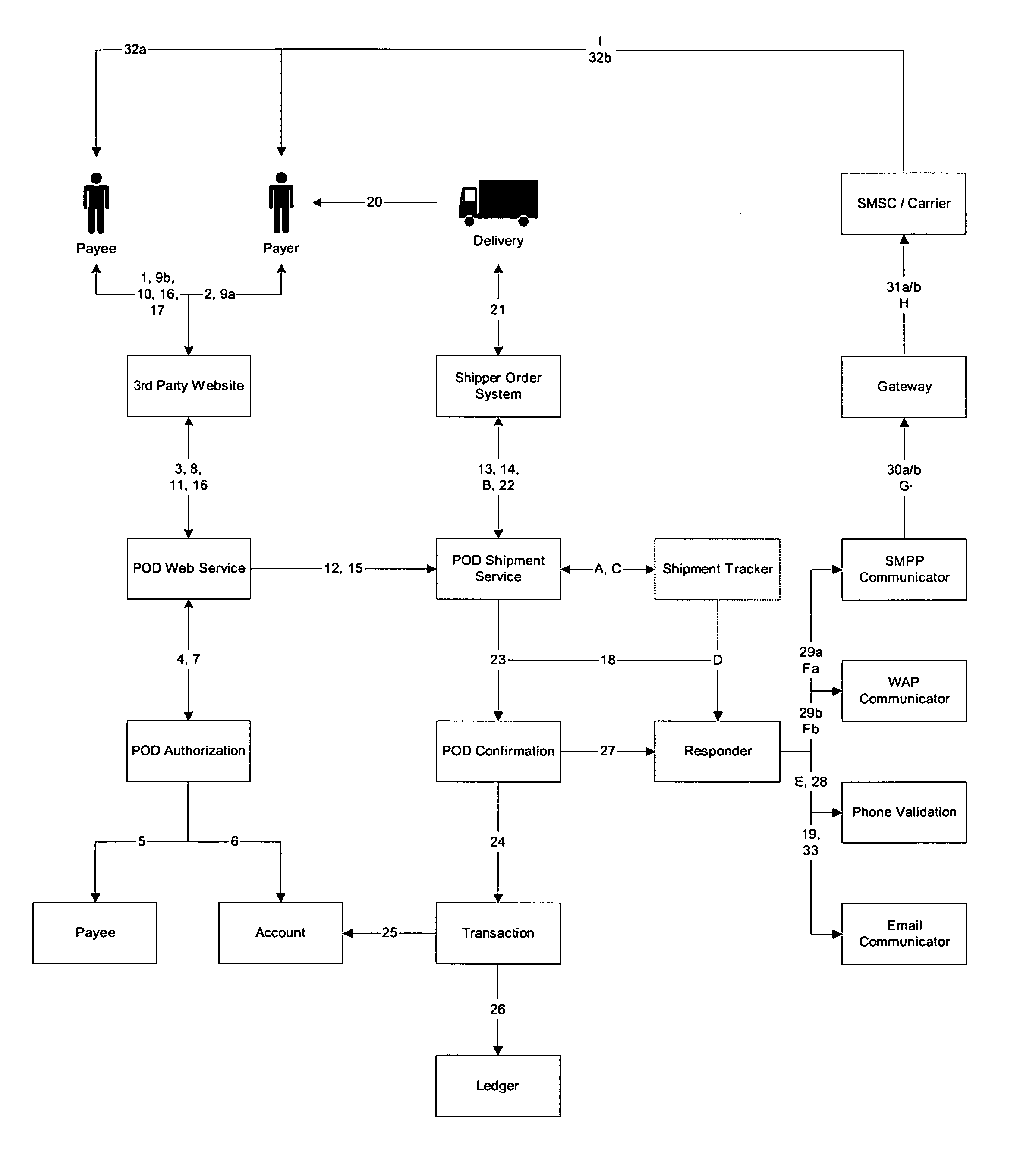
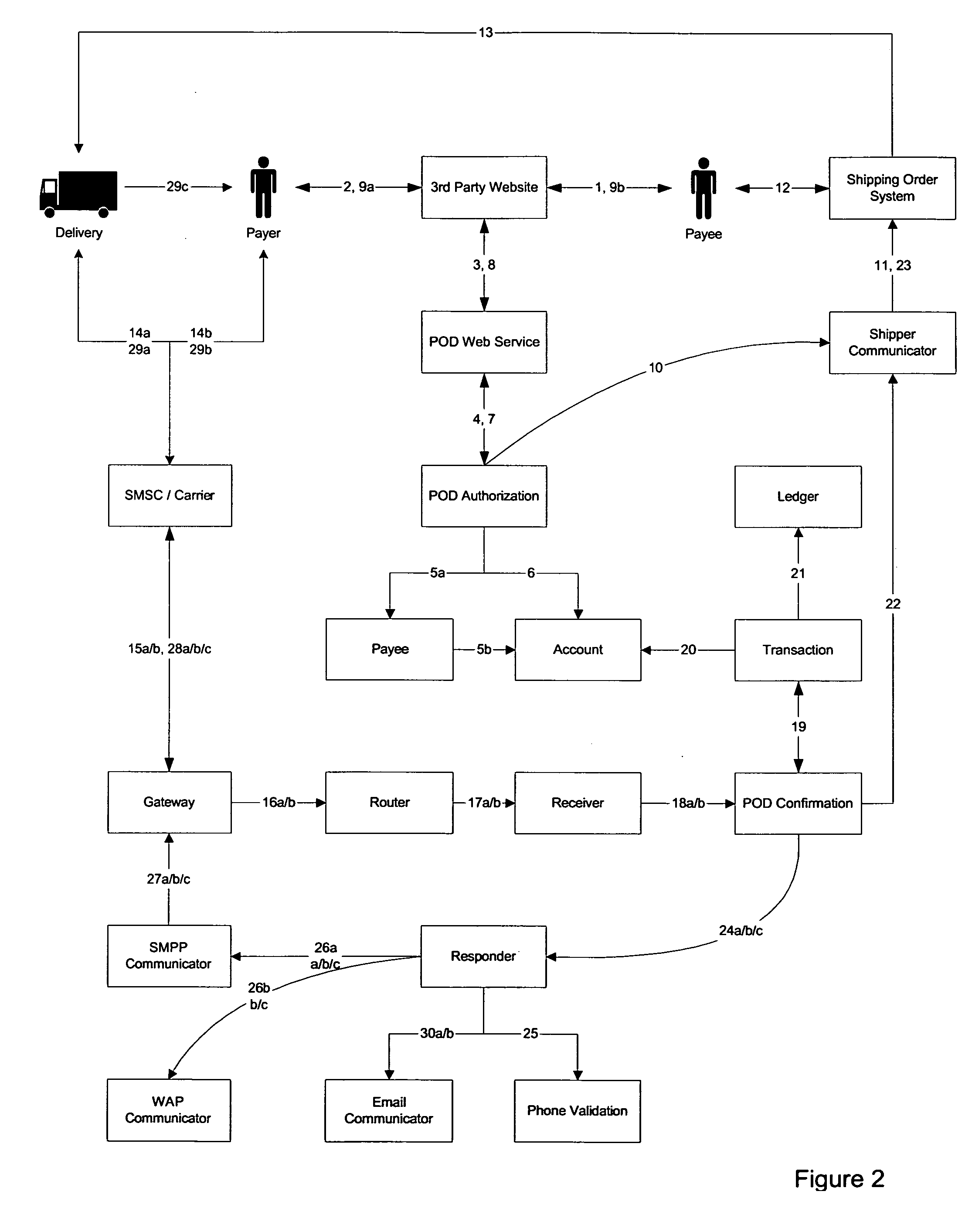
InactiveUS20060253339A1Facilitate electronic communicationCommercePayments involving neutral partyPaymentElectronic communication
Escrow services involve an escrow agent who facilitates an exchange between two parties, typically a payer and a payee. The “cash on delivery” (“C.O.D.”) service is akin to an escrow service, although carriers do not favor C.O.D. services due to their costs. The claimed invention is a method and system which provides an escrow service akin to a C.O.D. service, allowing a carrier to provide the equivalent of a C.O.D. service while shifting payment management to the escrow agent. The system embodying the claimed invention includes electronic devices facilitating electronic communications between the payer and the payee to the transaction. In one embodiment, such electronic communications are provided via the short message service (SMS) feature available on mobile phones and include a notification to the payee that the purchased item was successfully delivered and that the escrowed funds shall be released and delivered to payee.
Owner:MPOWER MOBILE
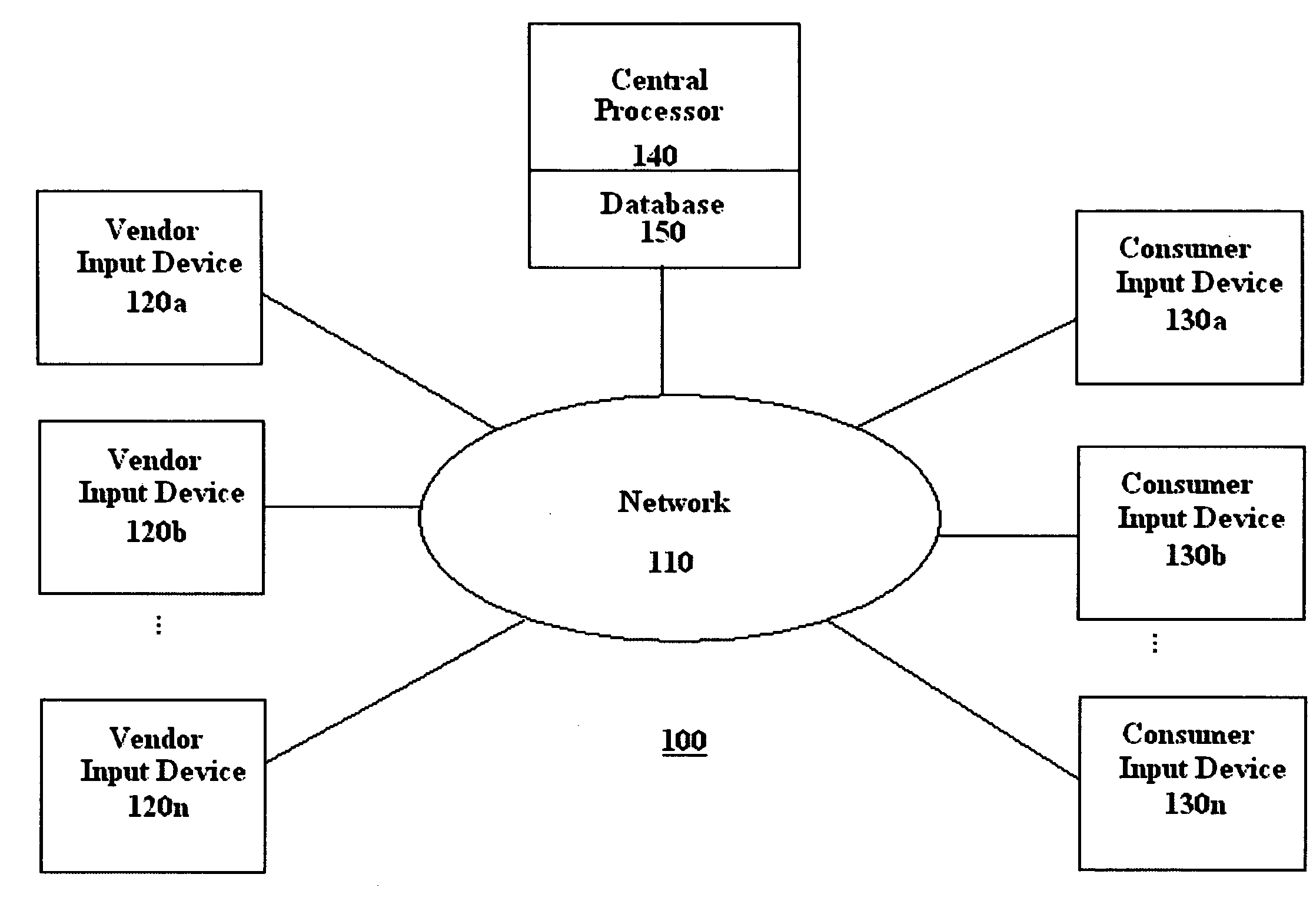
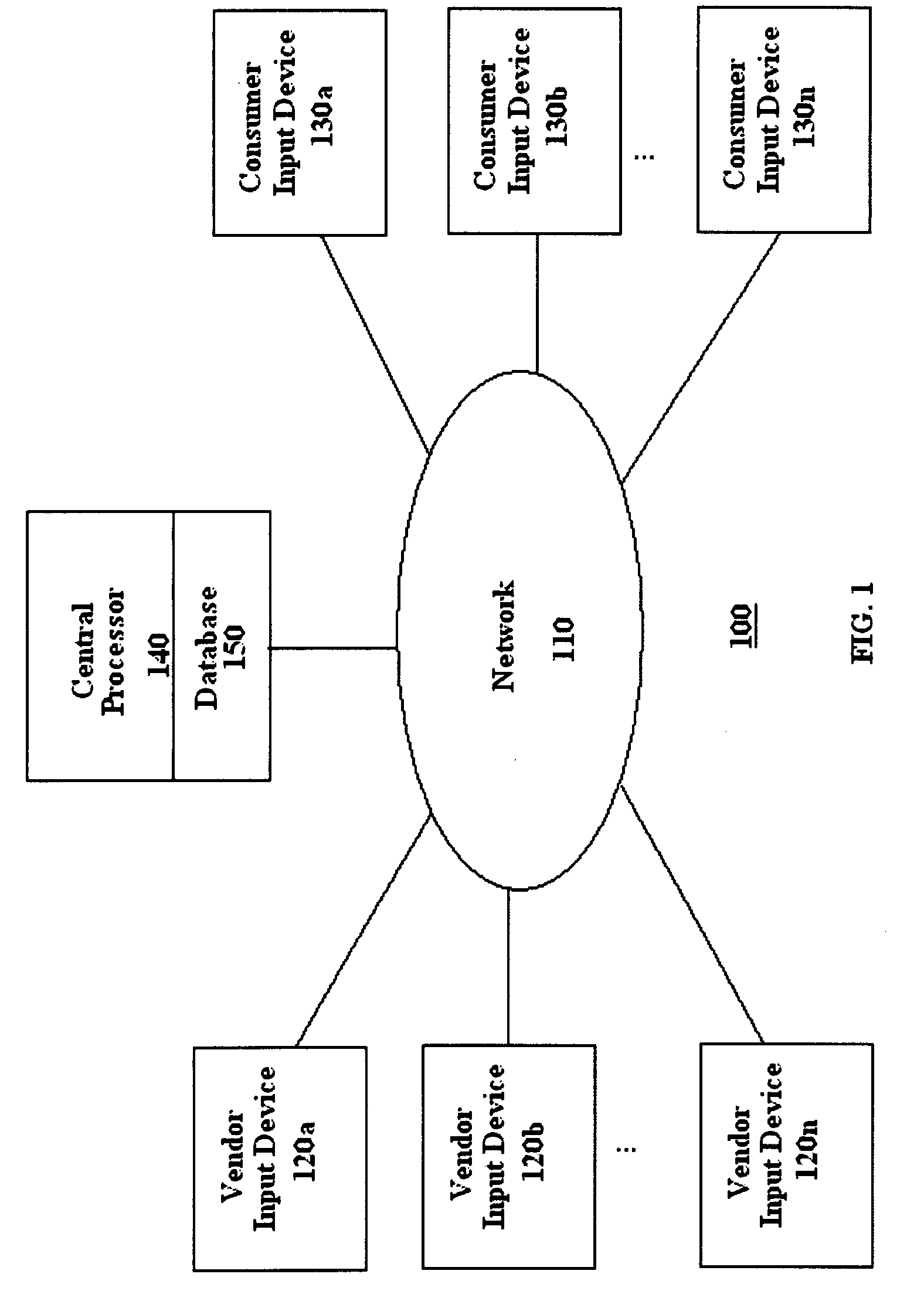
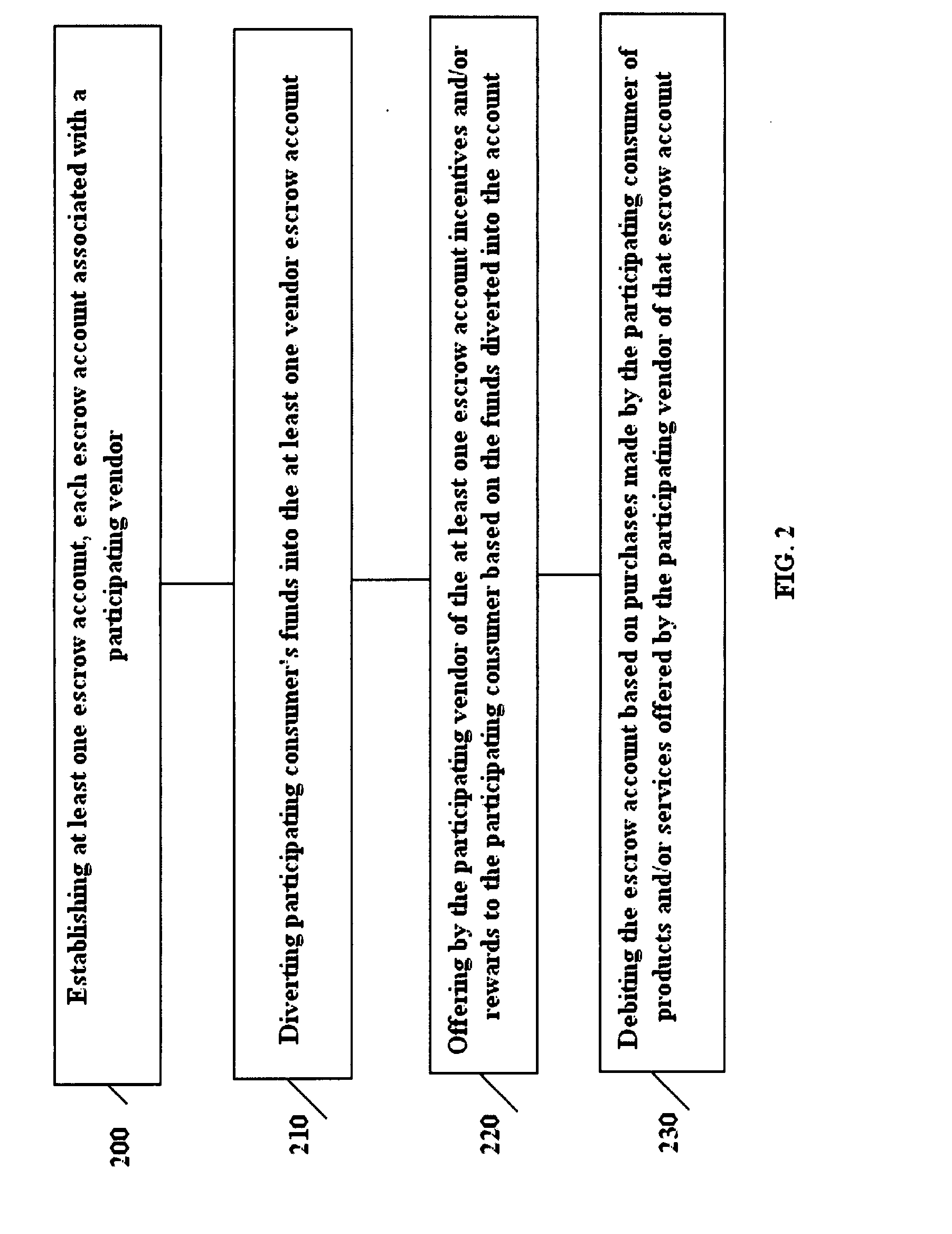
System and method for payment of consumer purchases via vendor escrow accounts
A system and method for payment by a consumer of a purchase from one of a plurality of participating vendors. Each product or service for purchase is classified by a central office into a unique class. A single vendor is permitted for each class of product or service thereby guaranteeing a maximum return of investment. The consumer establishes a vendor escrow account, wherein each vendor escrow accounts is associated with a specific participating vendor. In advance of the purchase, a predetermined amount of funds, as specified by the consumer, is diverted from their paycheck into the vendor escrow account and prohibited thereafter from withdrawal by the consumer. Appropriate funds are debited from the vendor escrow account in payment for the purchase made by the consumer from the associated participating vendor.
Owner:HALL ARTHUR W
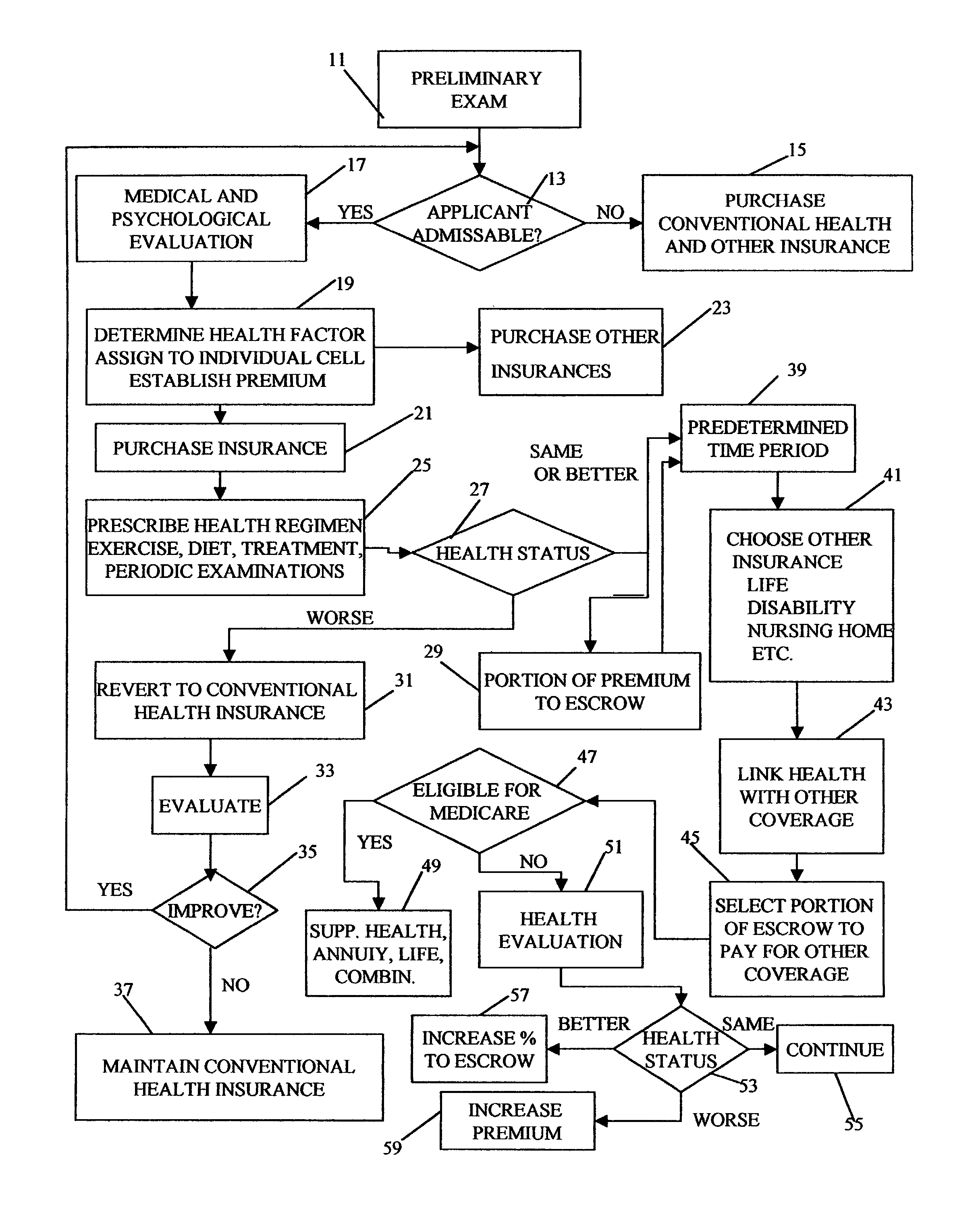
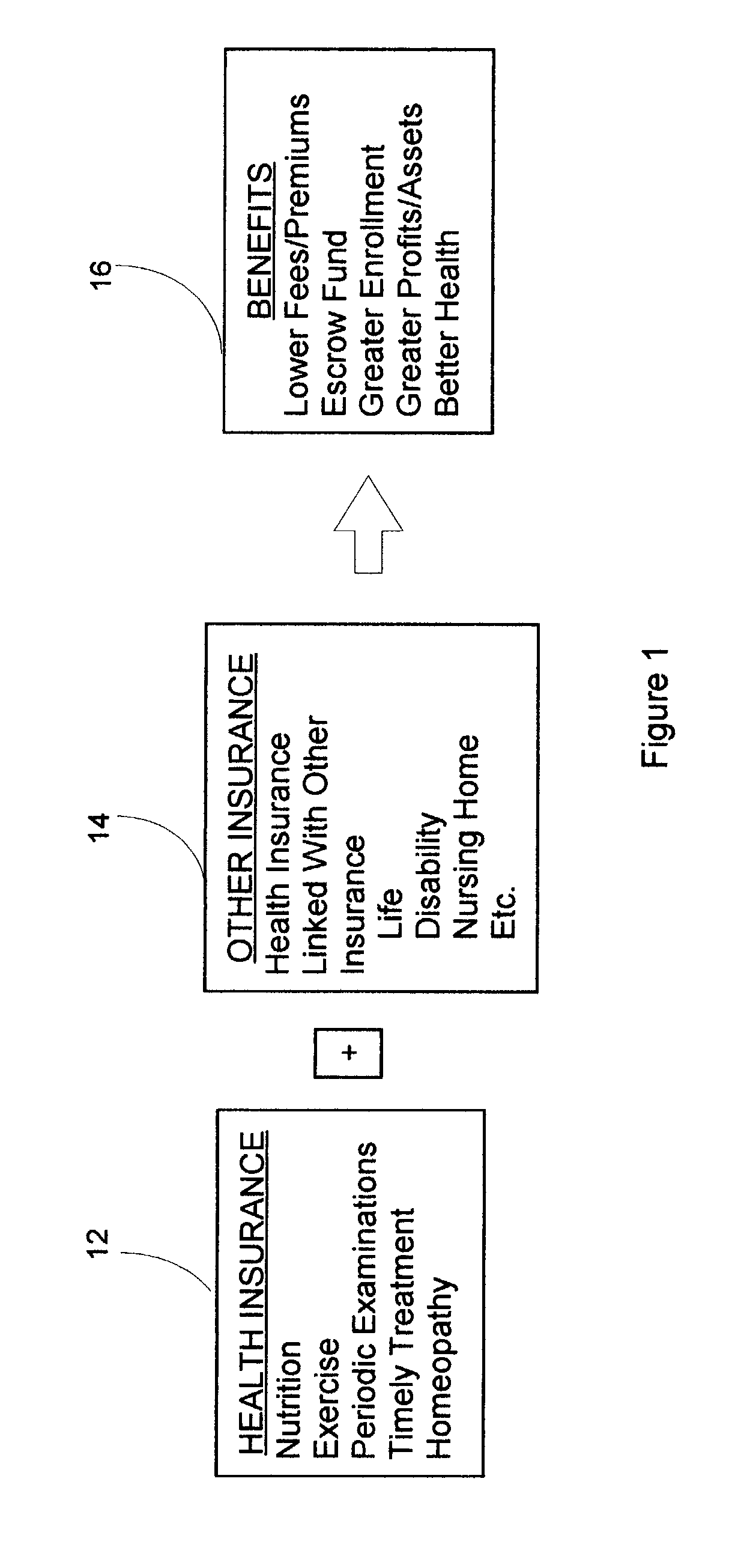
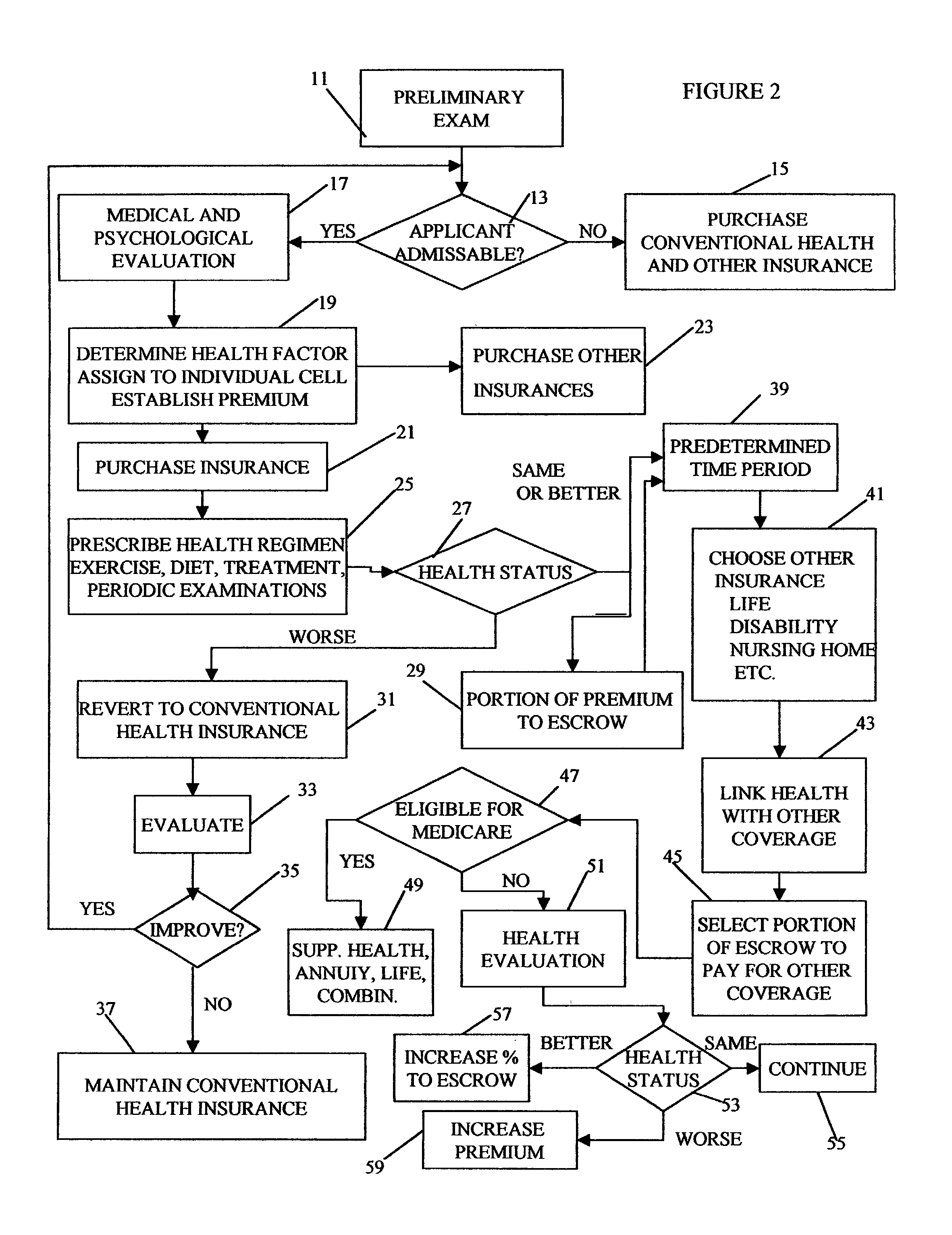
Method for linking insurance policies
ActiveUS7685007B1Reduce morbidityExtend your lifeFinanceHealth insurance managementWaiting periodEscrow
An insurance program that provides improved health care and longevity by emphasizing health improvement and maintenance. After a predetermined waiting period from the time health insurance is purchased, during which the health status of the insured is maintained or improved, the insured may link the health insurance policy with one or more other types of insurance policies, such as; life, disability, nursing home, etc. Throughout the life of the policy, portions of the premiums may be deposited in an escrow account, provided that the health of the insured is maintained or improved, which may be utilized to pay or help pay for the linked insurance and may also be utilized for retirement benefits.
Owner:CHAI INSURANCE CONSULTING GRP
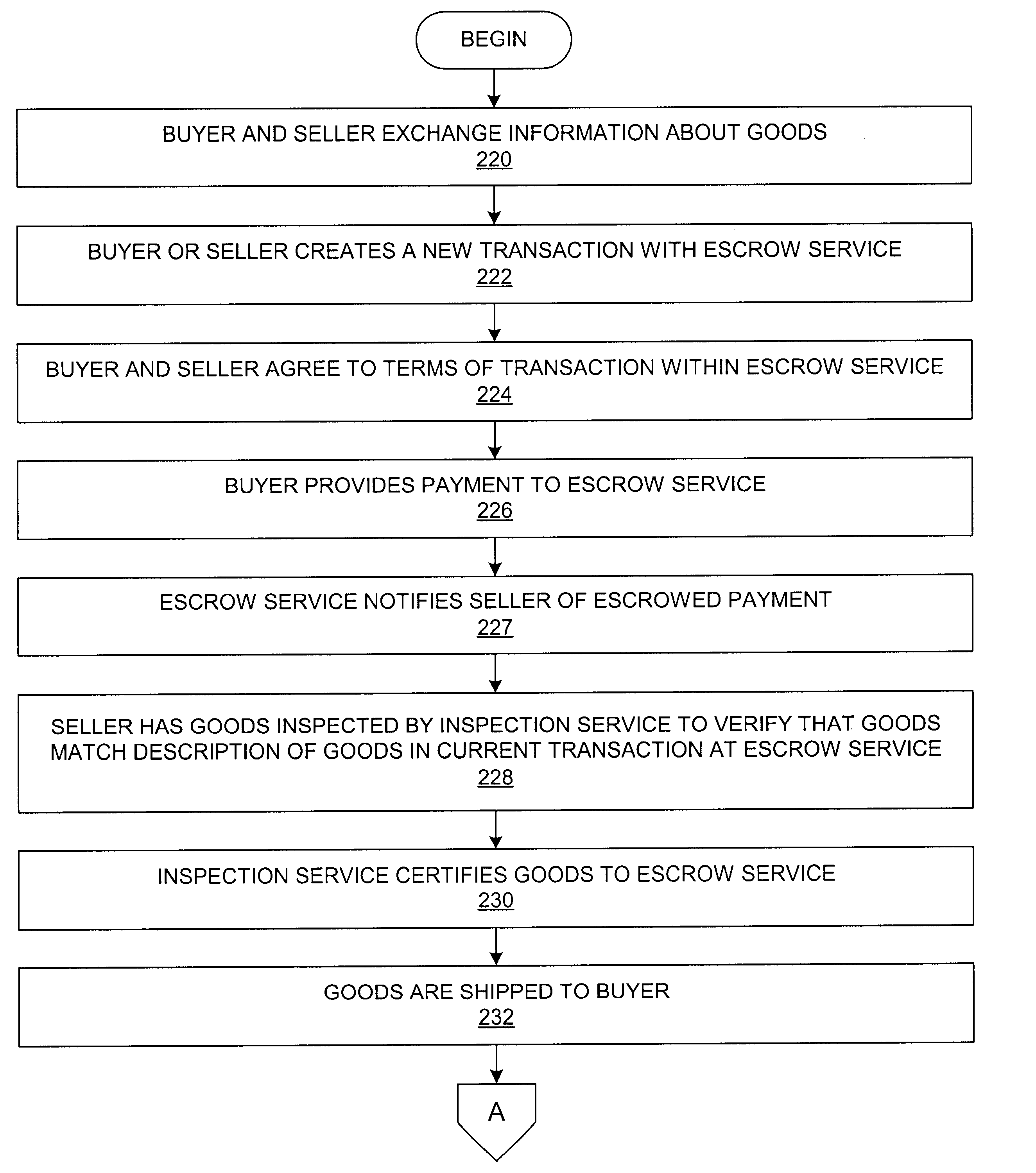
Method and system in electronic commerce for inspection-service-based release of escrowed payments
InactiveUS6865559B2Easy to optimizeFacilitates trustworthy electronic commerceFinanceComputer security arrangementsPaymentThird party
A method, apparatus, system, or computer program product facilitates trustworthy electronic commerce by providing an inspection-service-based release of an escrowed payment for a transaction involving physical goods. An inspection service stands as an independent party at the onset of the transfer of goods between the buyer and the seller. In an attempt to reduce fraudulent behavior by the buyer or the seller, an inspection service inspects the goods, preferably at the point of shipment. A description of the goods has been previously stored in a transaction record that has been previously created within an escrow service. The inspection service may electronically retrieve the description of the goods from the escrow service. The inspection service then determines whether the description of the goods is acceptably similar to the actual condition or type of the goods and generates a certification if they are acceptable similar. The inspection service may then electronically notify the escrow service of the certification, and the escrow service may release the escrowed payment if the goods are accepted by the other party.
Owner:IBM CORP
Auto-Recoverable and Auto-certifiable cryptosystems with RSA or factoring based keys
InactiveUS6389136B1Fast and easy disseminationEasy to handleKey distribution for secure communicationPublic key for secure communicationTrusted authorityComposite number
A method is provided for an escrow cryptosystem that is essentially overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. The keys generated are based on composite numbers (like RSA keys). A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The keys generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key is recoverable by the escrow authorities. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". Furthermore, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware. The system is efficient and can be implemented as a "drop-in" replacement to an RSA or Rabin cryptosystem. The system is applicable for law-enforcement, file systems, e-mail systems, certified e-mail systems, and any scenario in which public key cryptography can be employed and where private keys or information encrypted under public keys need to be recoverable. Another aspect of the system is the possibility to organize it in a hierarchical tree structure, where each element in the tree is an escrow authority (or authorities) capable to recover keys and / or information encrypted under these keys within the subtree rooted at the authority (or authorities) and only within this subtree.
Owner:CRYPTOPEAK SECURITY LLC
Auto-escrowable and auto-certifiable cryptosystems
InactiveUS6202150B1Fast and easy disseminationEasy to handleKey distribution for secure communicationUser identity/authority verificationTrusted authorityTamper proof hardware
A method is provided for an escrow cryptosystem that is overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The key generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key was generated according to the algorithm. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". The cryptosystem is overhead free since there is no additional protocol interaction between the user who generates his or her own key, and the certification authority or the escrow authorities, in comparison to what is required to submit the public key itself in regular certified public key systems. Furthermore, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware.
Owner:CRYPTOPEAK SECURITY LLC
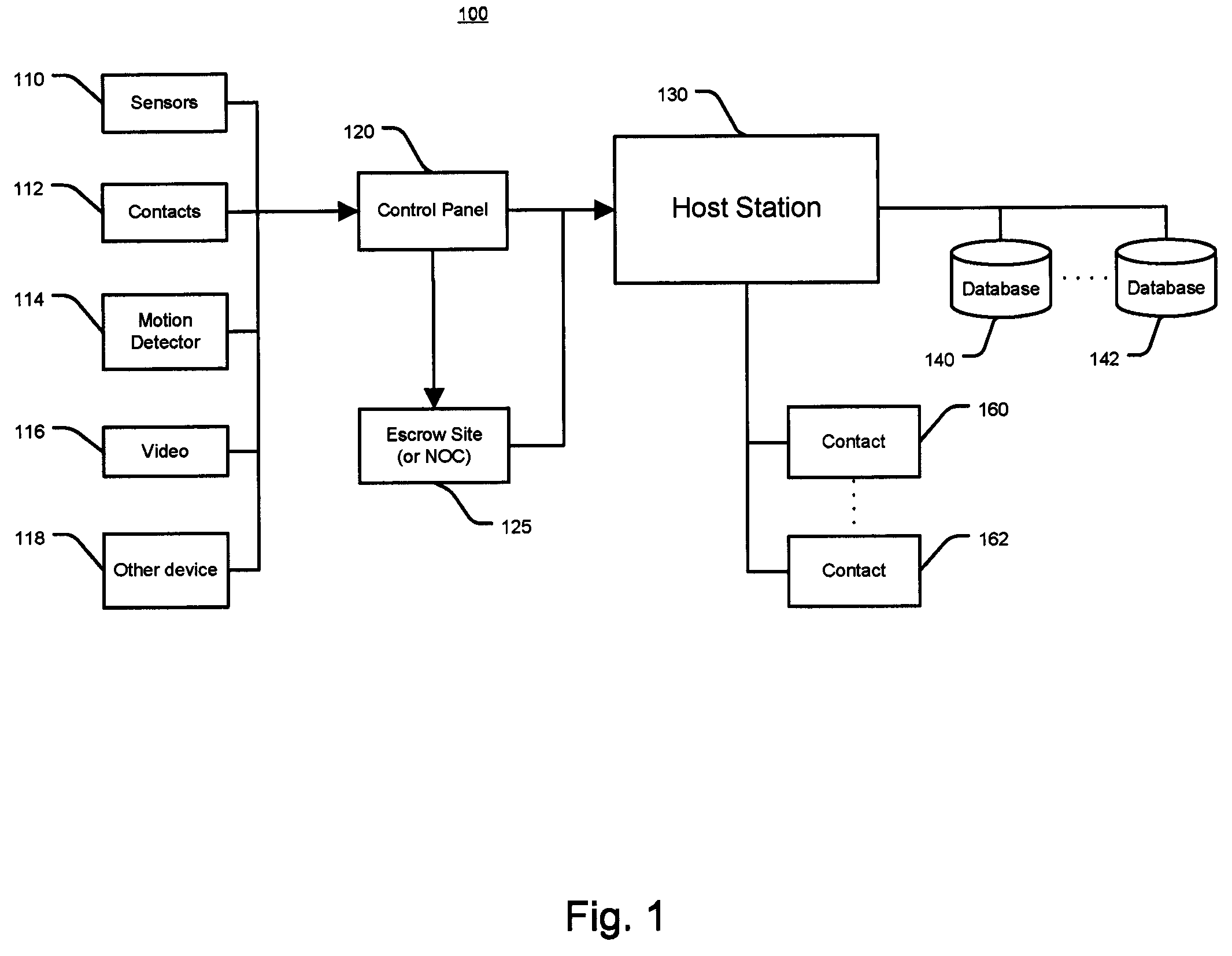
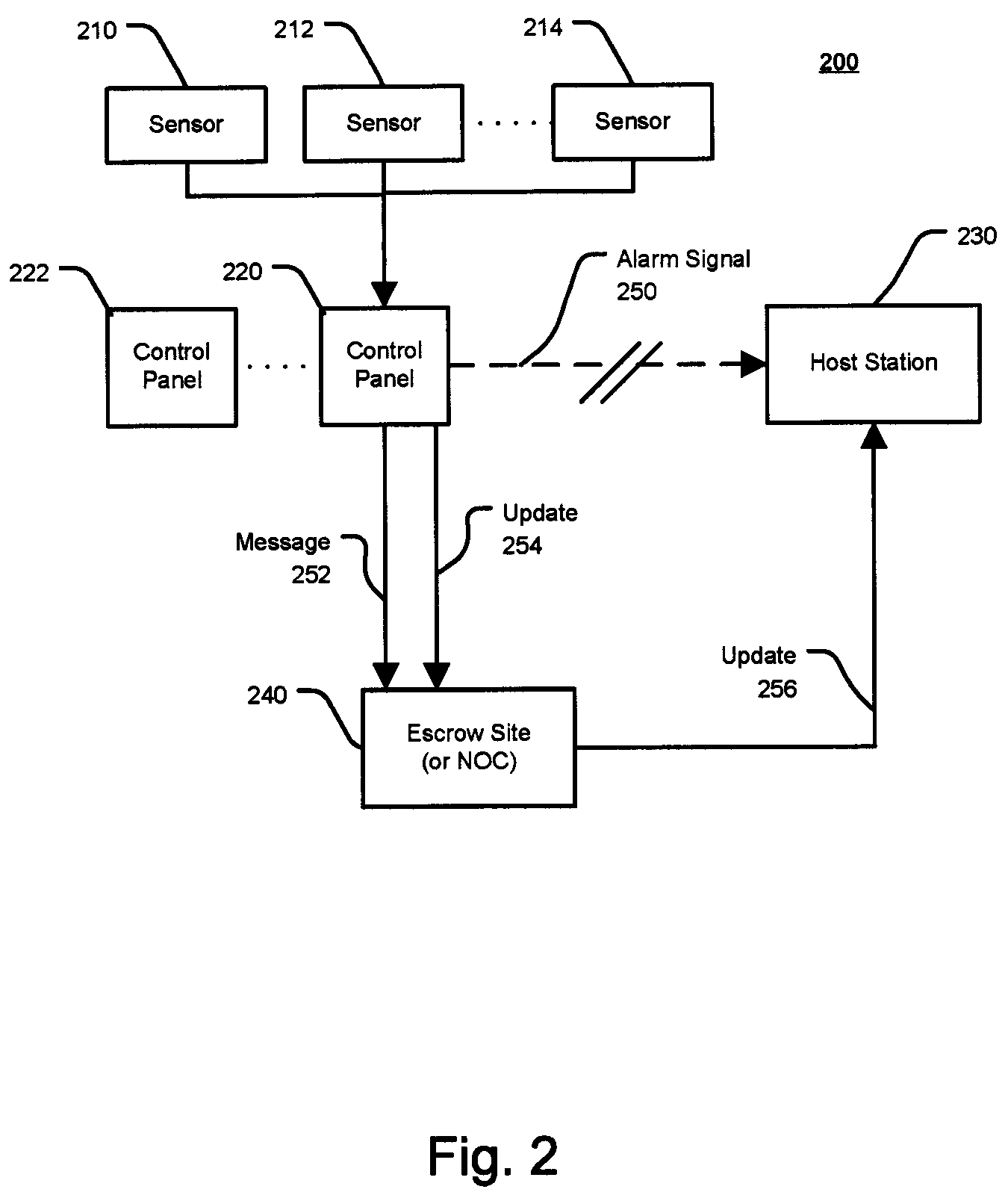
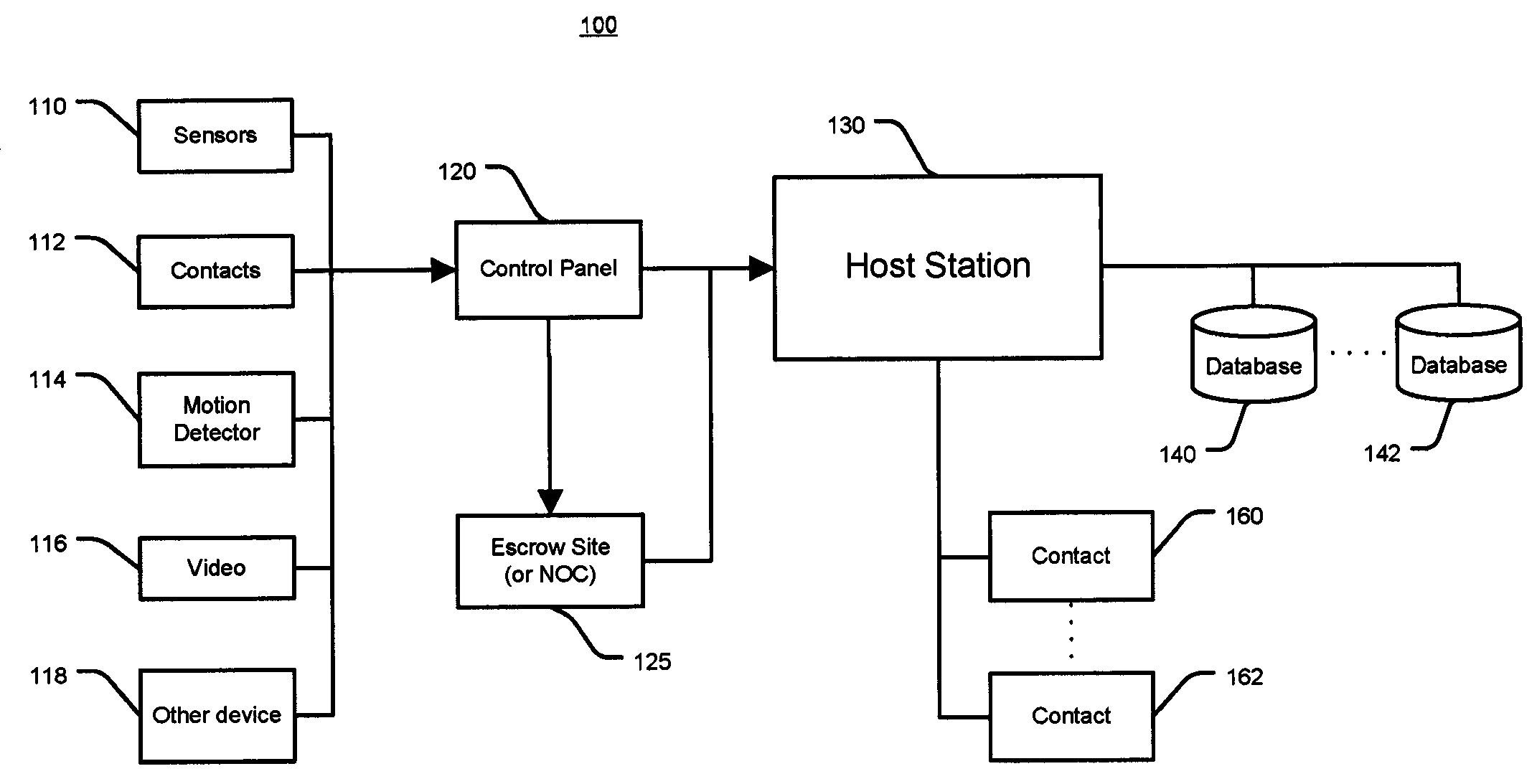
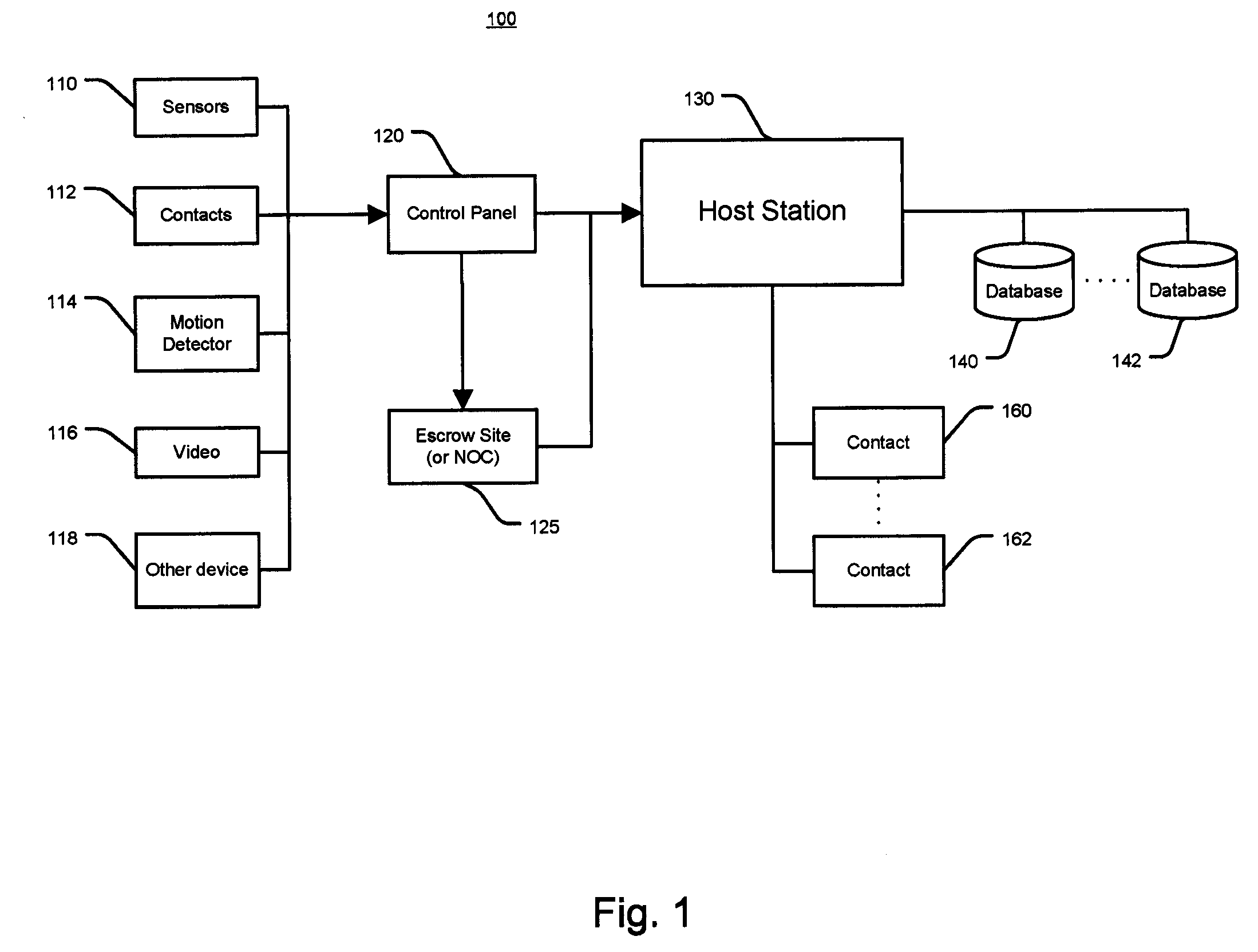
System and Method for Alarm Signaling During Alarm System Destruction
ActiveUS20080079561A1Frequency-division multiplex detailsTime-division multiplexEngineeringPredictive analytics
Embodiments of the present invention provides a system and method for the immediate transmission of a potential alarm to a remote alarm signal escrow site and from the escrow site to a host station in the event where a control panel or an alarm signaling device is tampered with or destroyed by a disablement tactic, e.g., a “crash and smash intrusion.” A system and method may also send an alarm signal during such an attack by using predictive analysis of real-time events.
Owner:ALARM COM INC
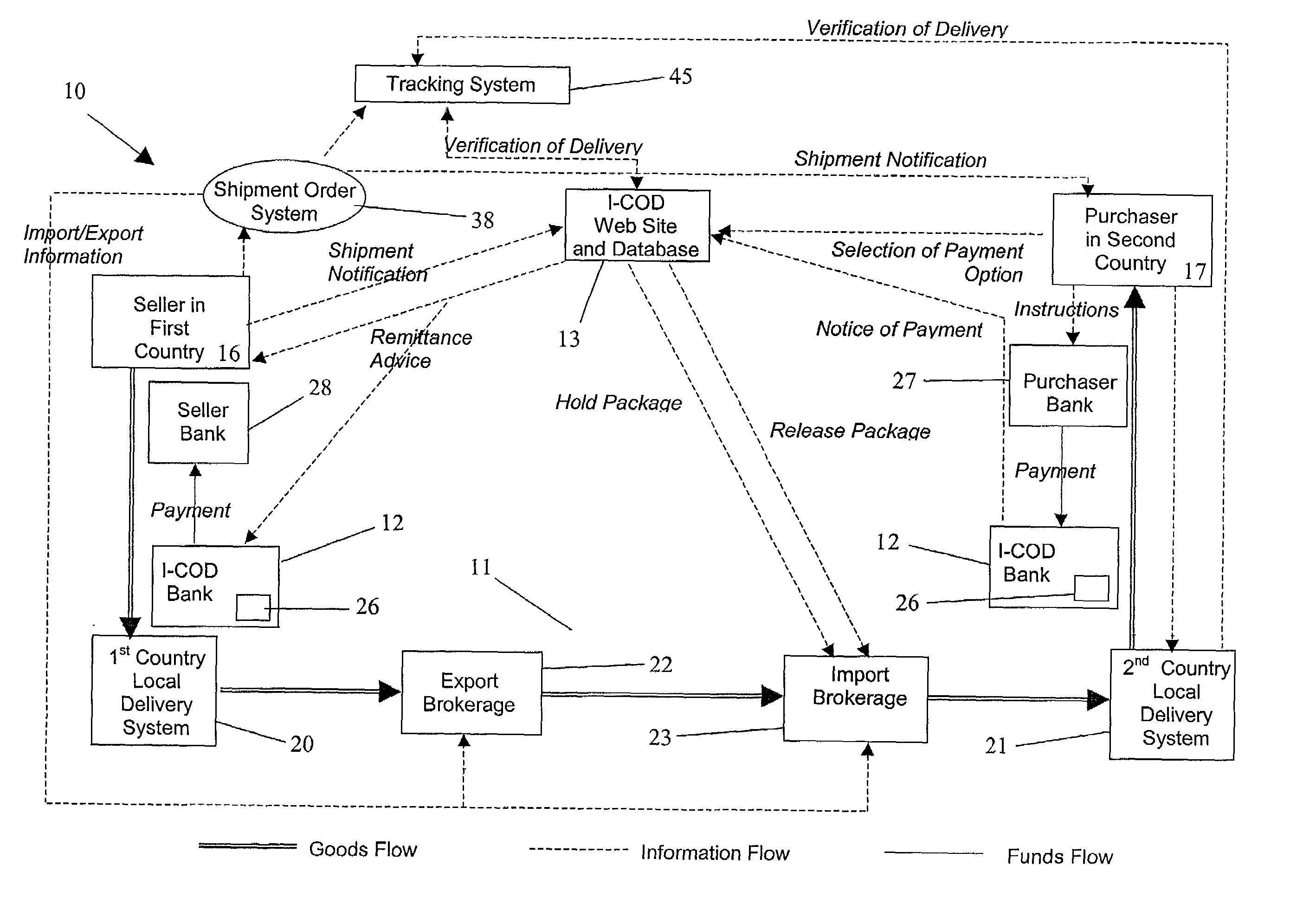
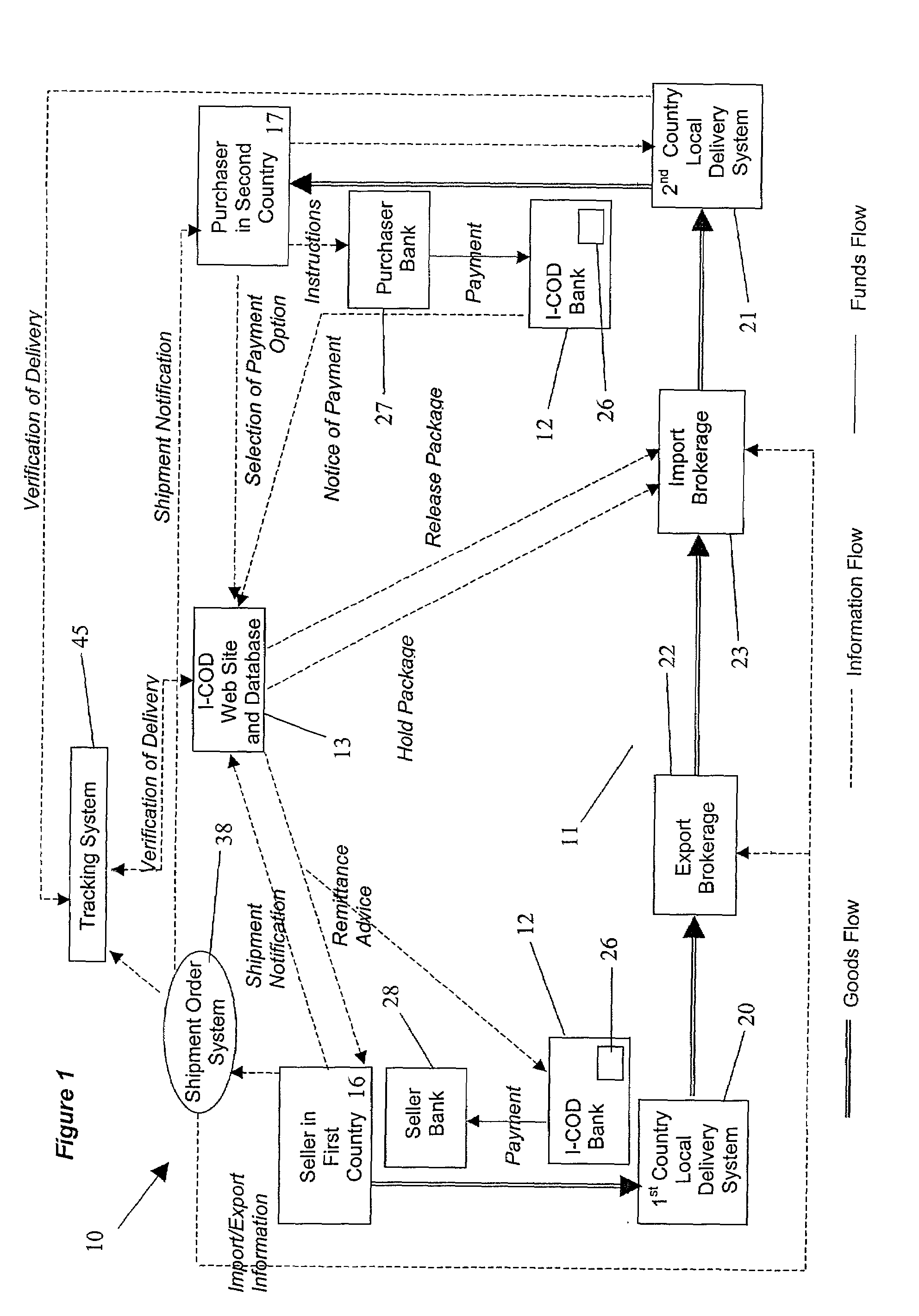
International cash-on-delivery system and method
InactiveUS7249069B2Reduce deliveryExemption stepsBuying/selling/leasing transactionsStacking articlesEngineeringFinancial transaction
An international cash-on-delivery (I-COD) system for completing a transaction between a seller in a first country and purchaser in a second country, wherein the seller has agreed to exchange packaged goods for a payment from the purchaser. The international delivery system includes a delivery service system, a payment system and an information system. The delivery system physically handles delivery of the packaged goods, including import and export clearing, and holding of the packaged goods in escrow at an intermediate location until payment by the purchaser. The payment system handles the flow of funds including receiving payment from the purchaser, holding the payment in escrow and distribution of the payment to the seller upon delivery of the packaged goods. The information system electronically coordinates escrow aspects of both the delivery service system, and the payment system, so as to minimize the risk of the transaction to both the seller and the purchaser.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
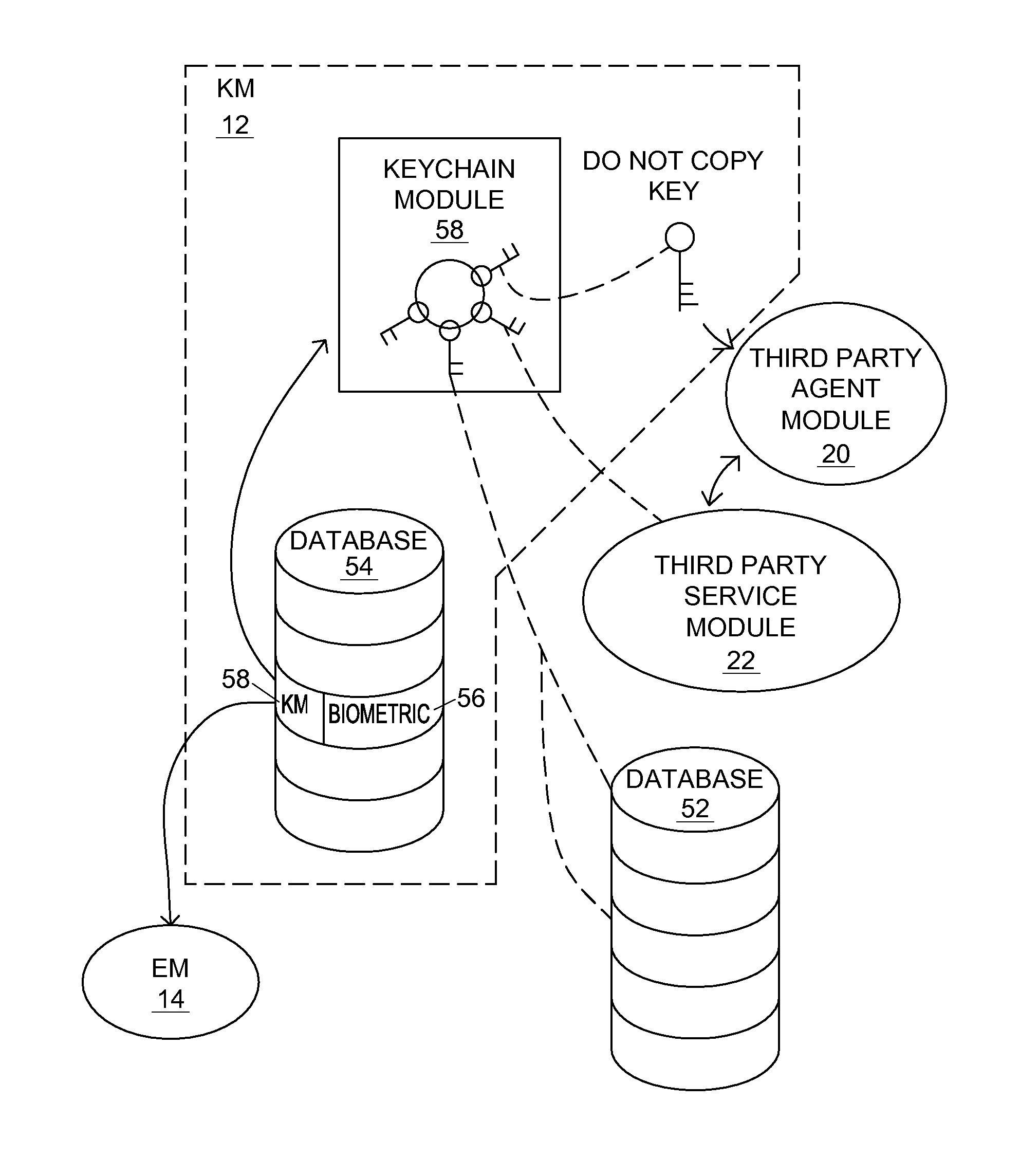
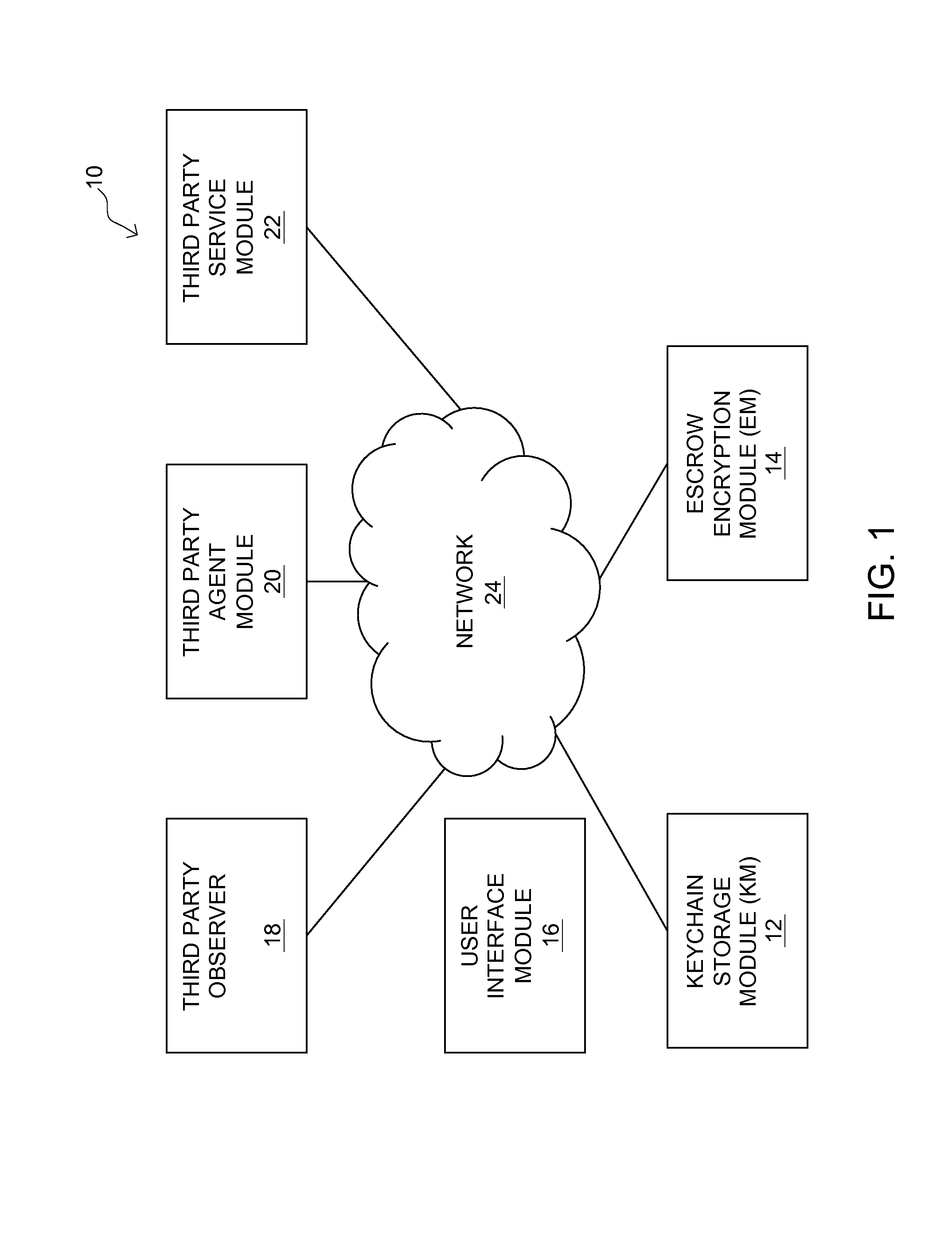
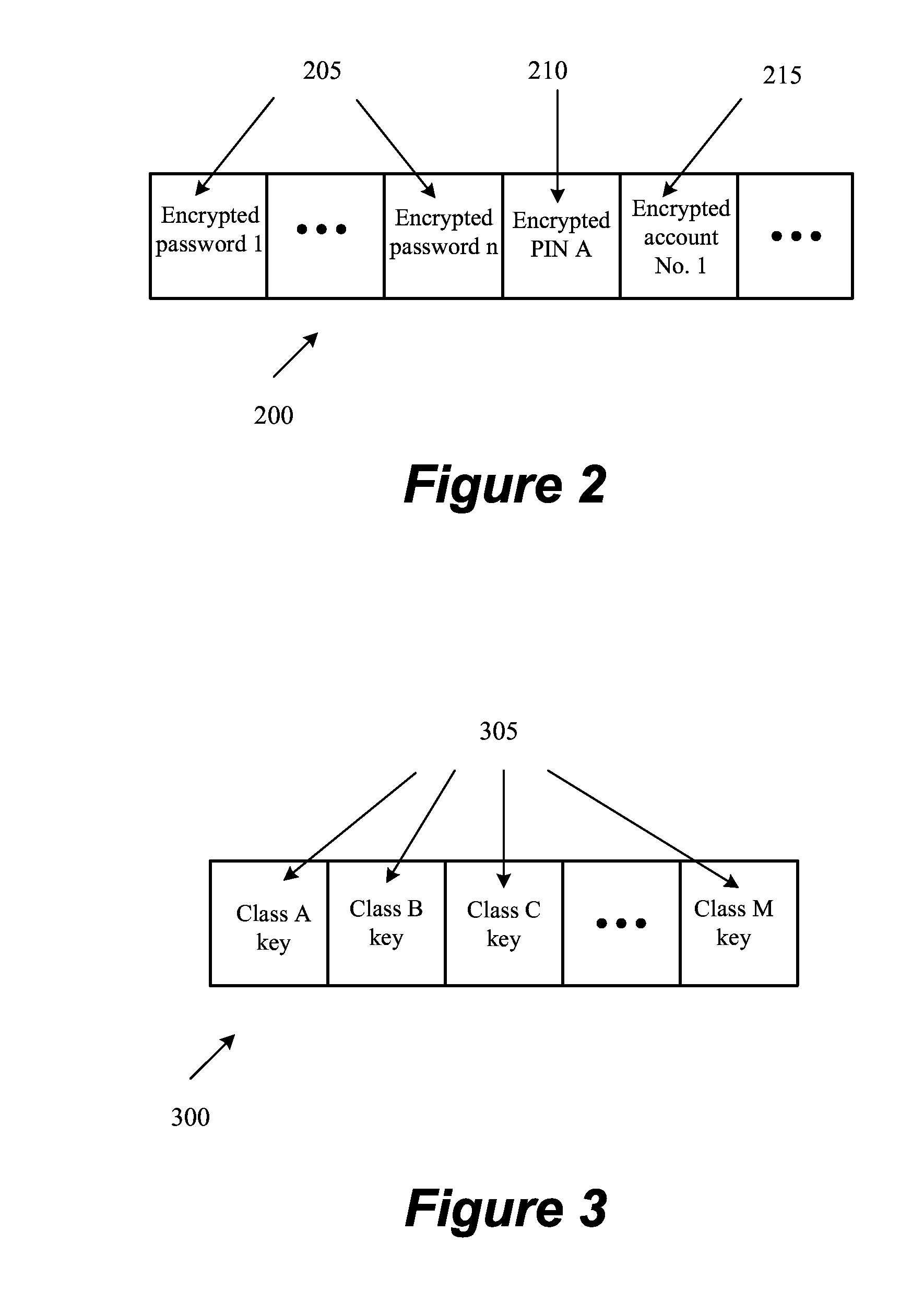
System and method of protecting, storing and decrypting keys over a computerized network
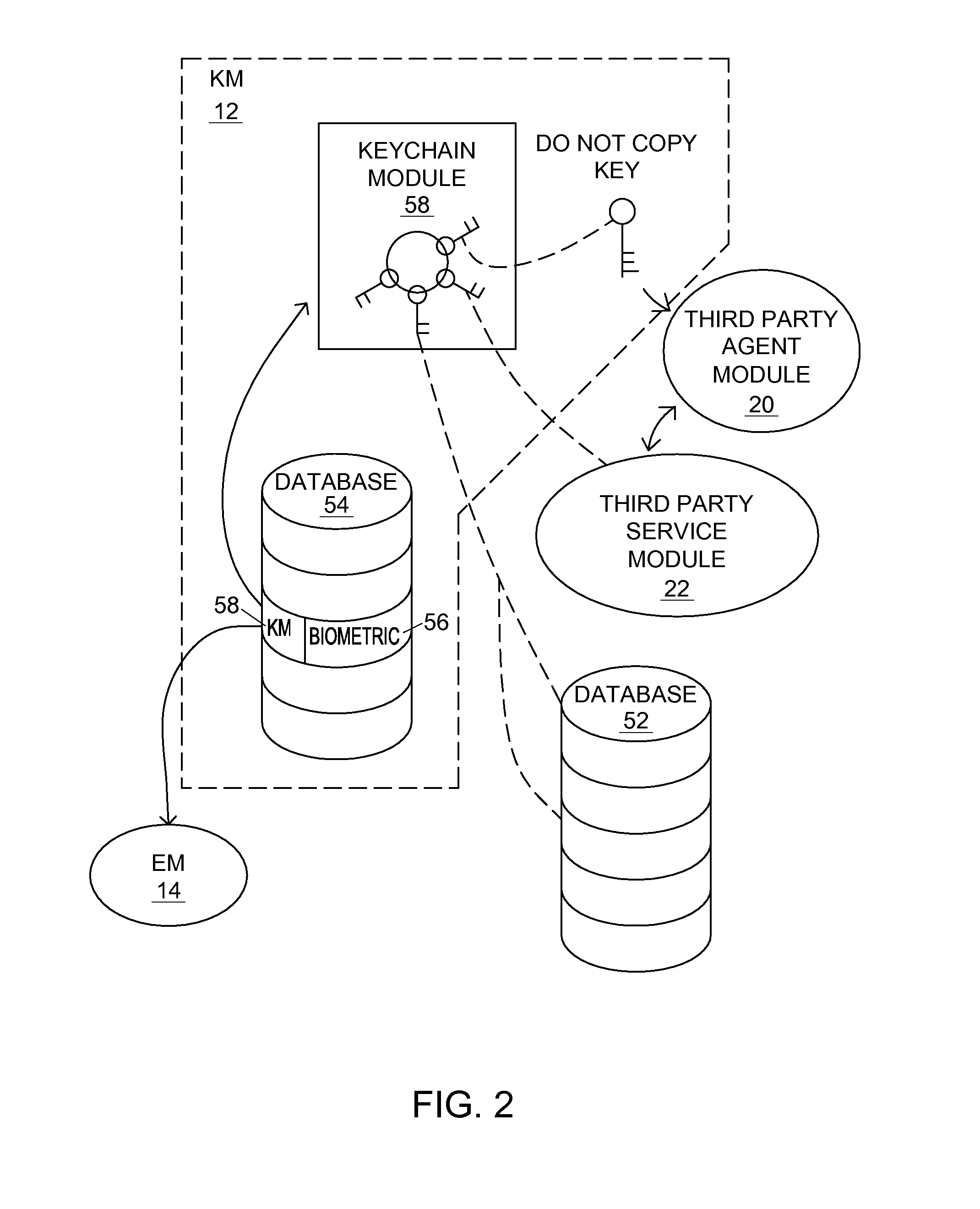
InactiveUS20140211944A1Facilitating key decryptionKey distribution for secure communicationDigital data authenticationBiometricsEscrow
A system and method of protecting, decrypting, and storing encryption keys. An encryption escrow module stores a library of indexed encryption algorithms. A keychain storage module includes a plurality of encrypted keys and / or keychains that are encrypted according to varying encryption algorithms of the encryption escrow module. Biometrics are used to index encrypted keychains to specific algorithms, but the two are kept separate. Since a naked key is never stored and only produced in cooperation with a specific user, the keychain storage module and the encryption escrow module, cracking attempts that compromise only two of the three groups are unable to generate any naked keys.
Owner:LUTZ DANIEL JOSEPH
Cryptographic key backup and escrow system
A system for securely storing application keys is comprised of a database system, a peripheral hardware security module and cryptographic keys, wherein cryptographic keys comprise application keys, intermediate keys and a master key. Application keys are grouped according to characteristic and are associated with a particular intermediate key, which is utilized to scramble and descramble application keys within the associated group. Intermediate keys are associated with the master key, which is utilized to scramble and descramble the intermediate keys. Scrambling and descrambling of keys is performed within the peripheral hardware security module.
Owner:WELLS FARGO BANK NA
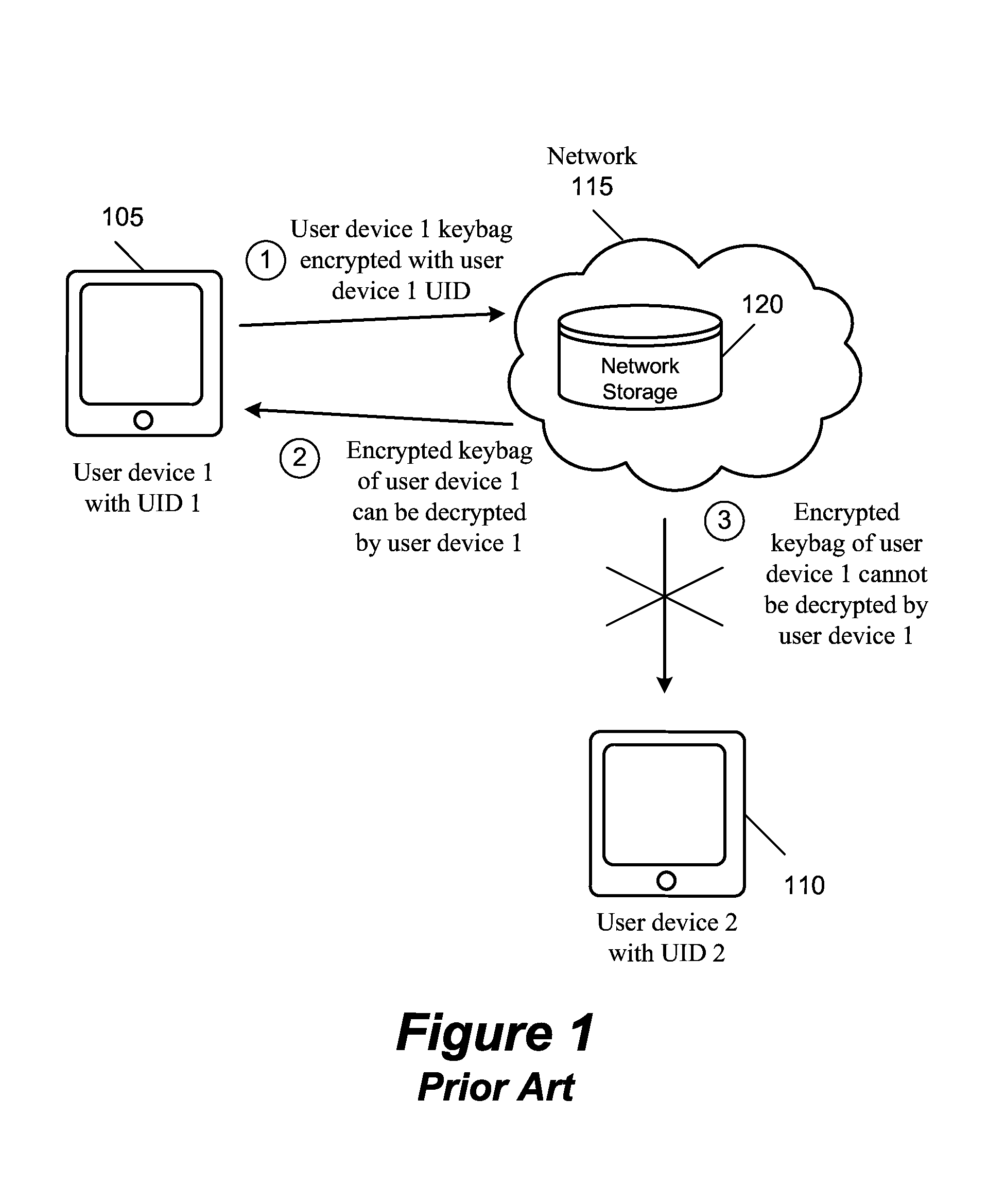
Secure Escrow Service
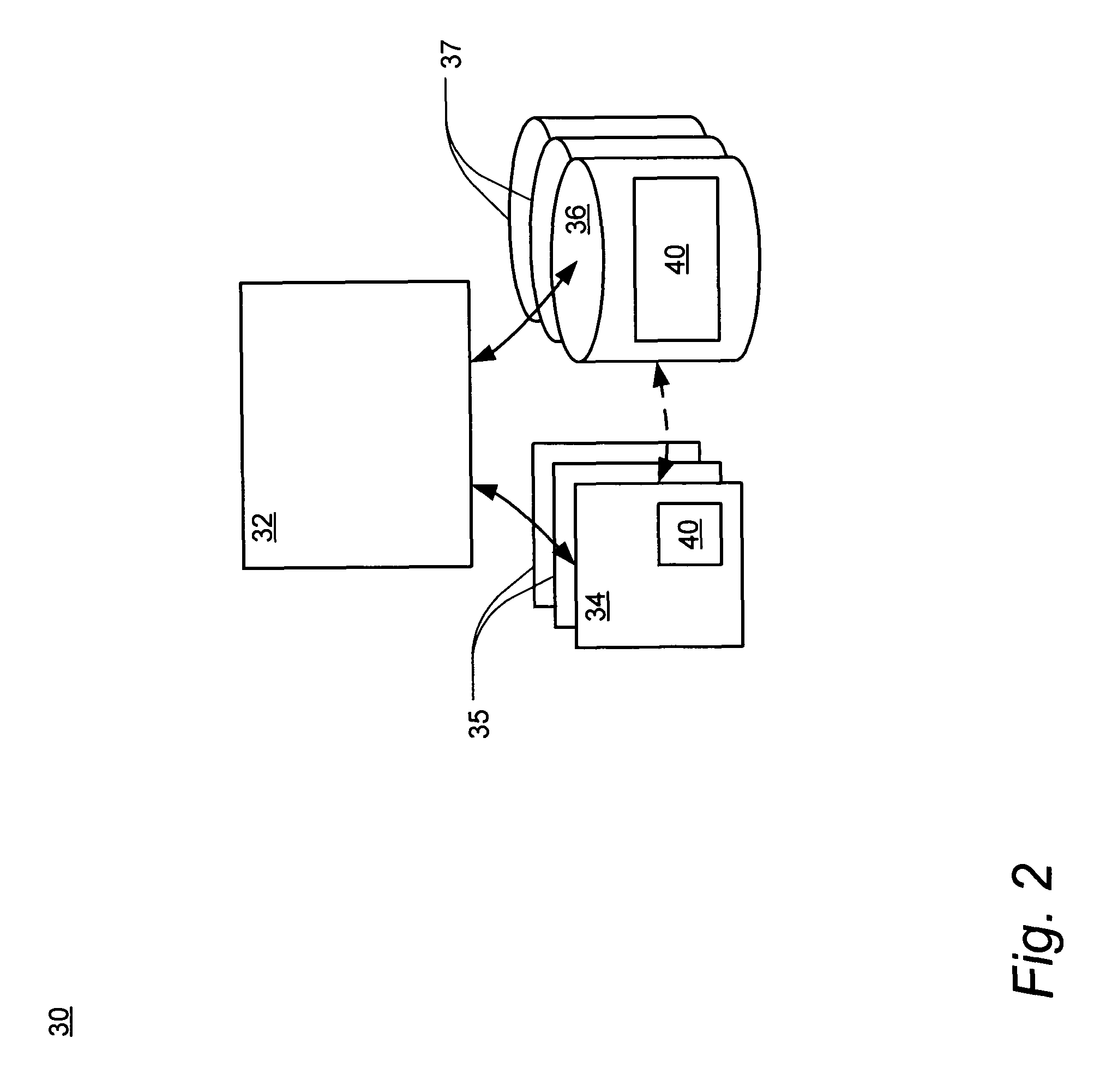
ActiveUS20140093084A1Avoid repetitionKey distribution for secure communicationDigital data protectionEscrowInternet privacy
A method of restoring confidential information items of a first device to a second device by using a set of servers. The method generates a public and private key pair and ties the private key to the hash of executable code of the servers at the time of generating the public and private keys. The method receives the encrypted confidential information items in a secure object which is encrypted with a user-specific key and the public key. The method only provides the confidential information to the second device when the second device provides the same user-specific key as the key that encrypts the secure object and the hash of the executable code of the servers at the time of accessing the private key to decrypt the secure object matches the hash of the executable code running on the servers at the time of generating the private key.
Owner:APPLE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com