Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2971results about How to "Reduce disadvantages" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
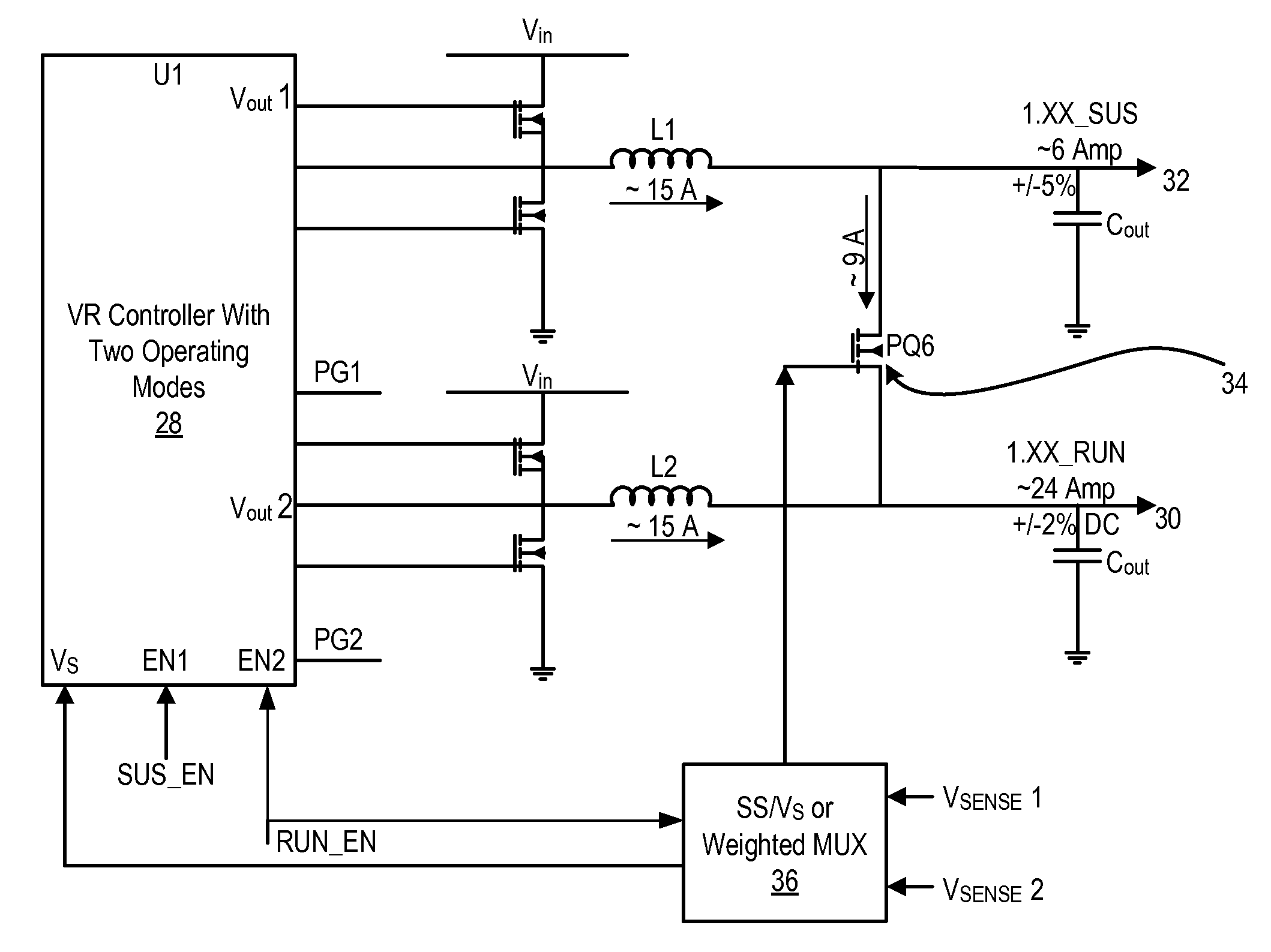
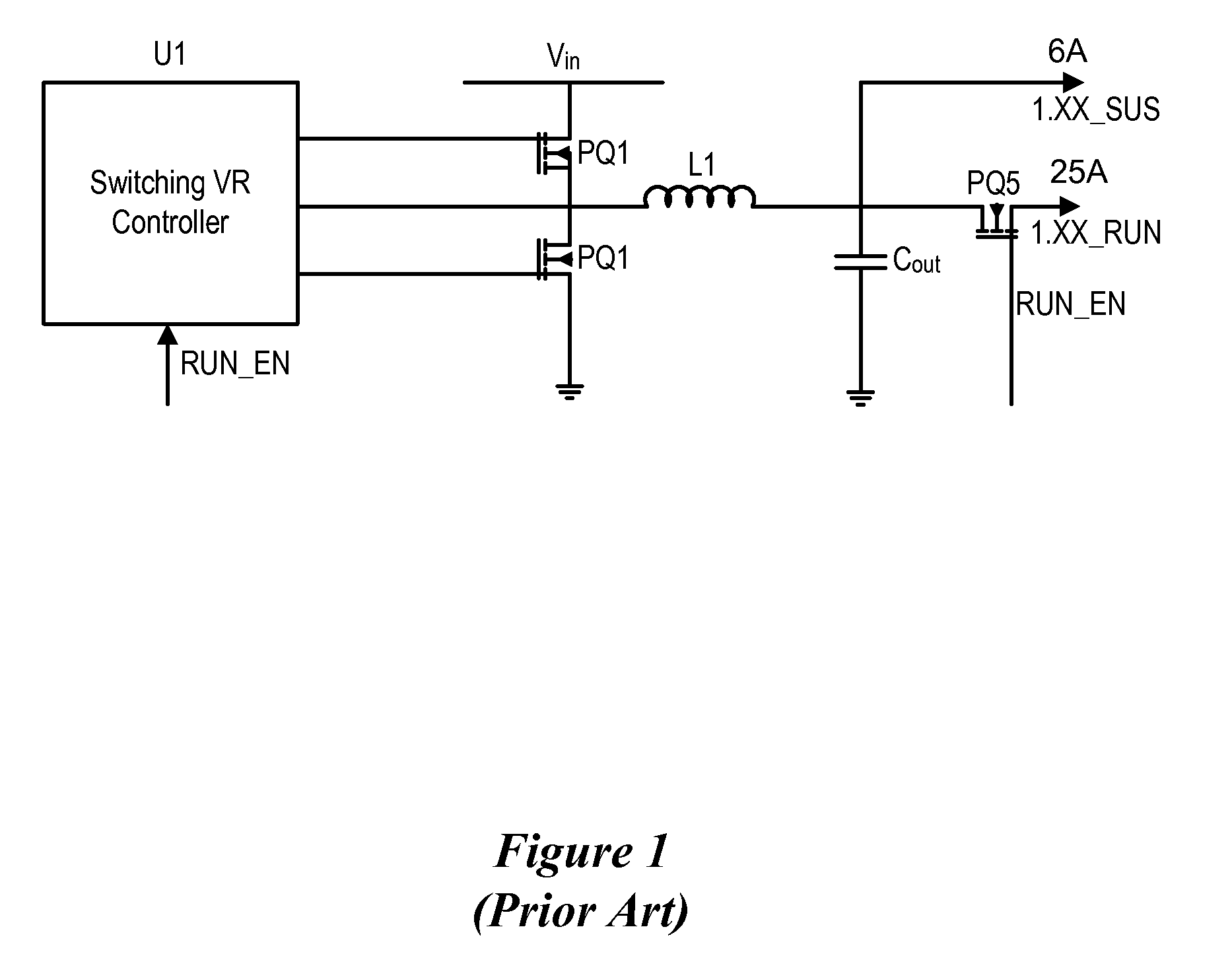
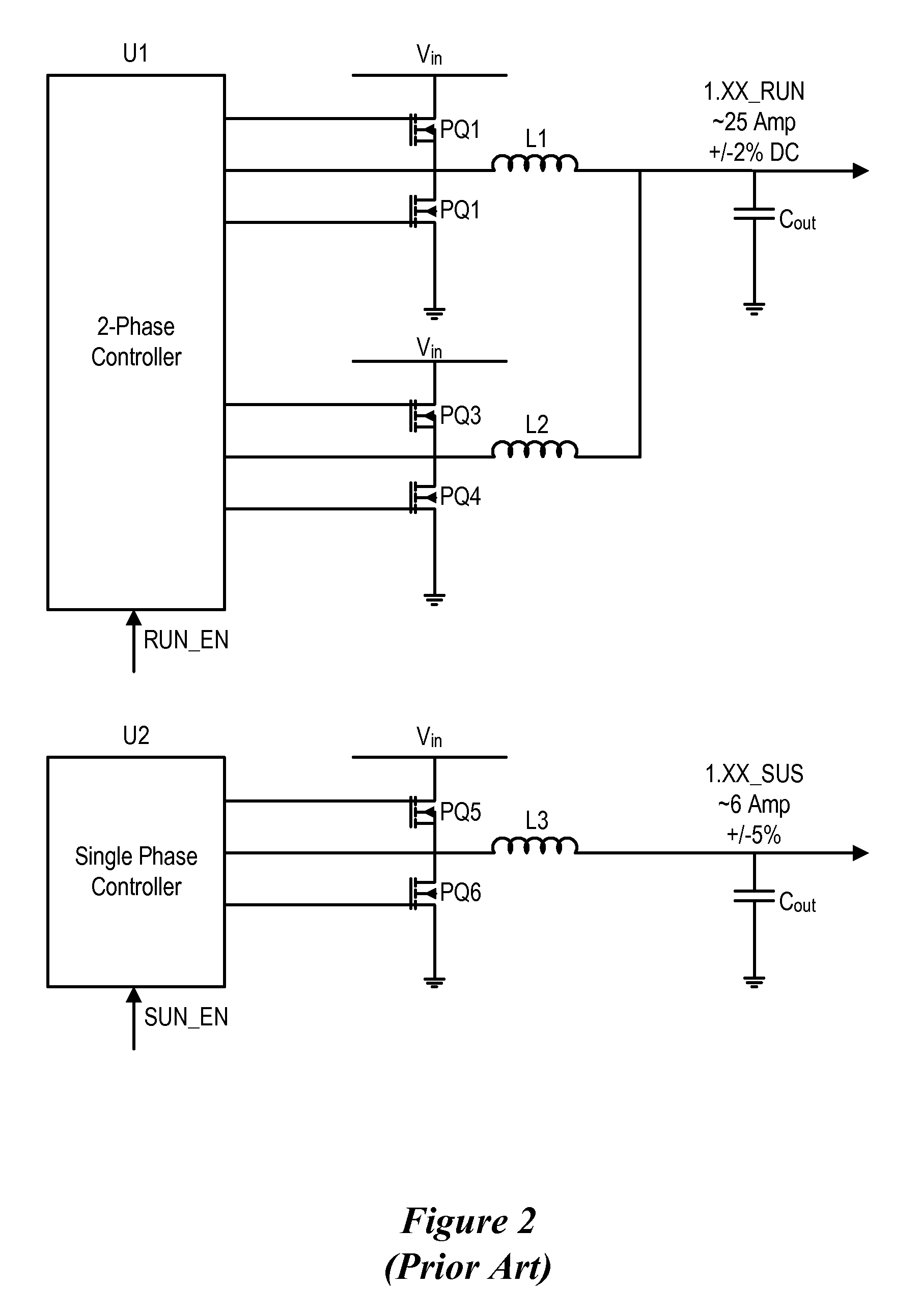
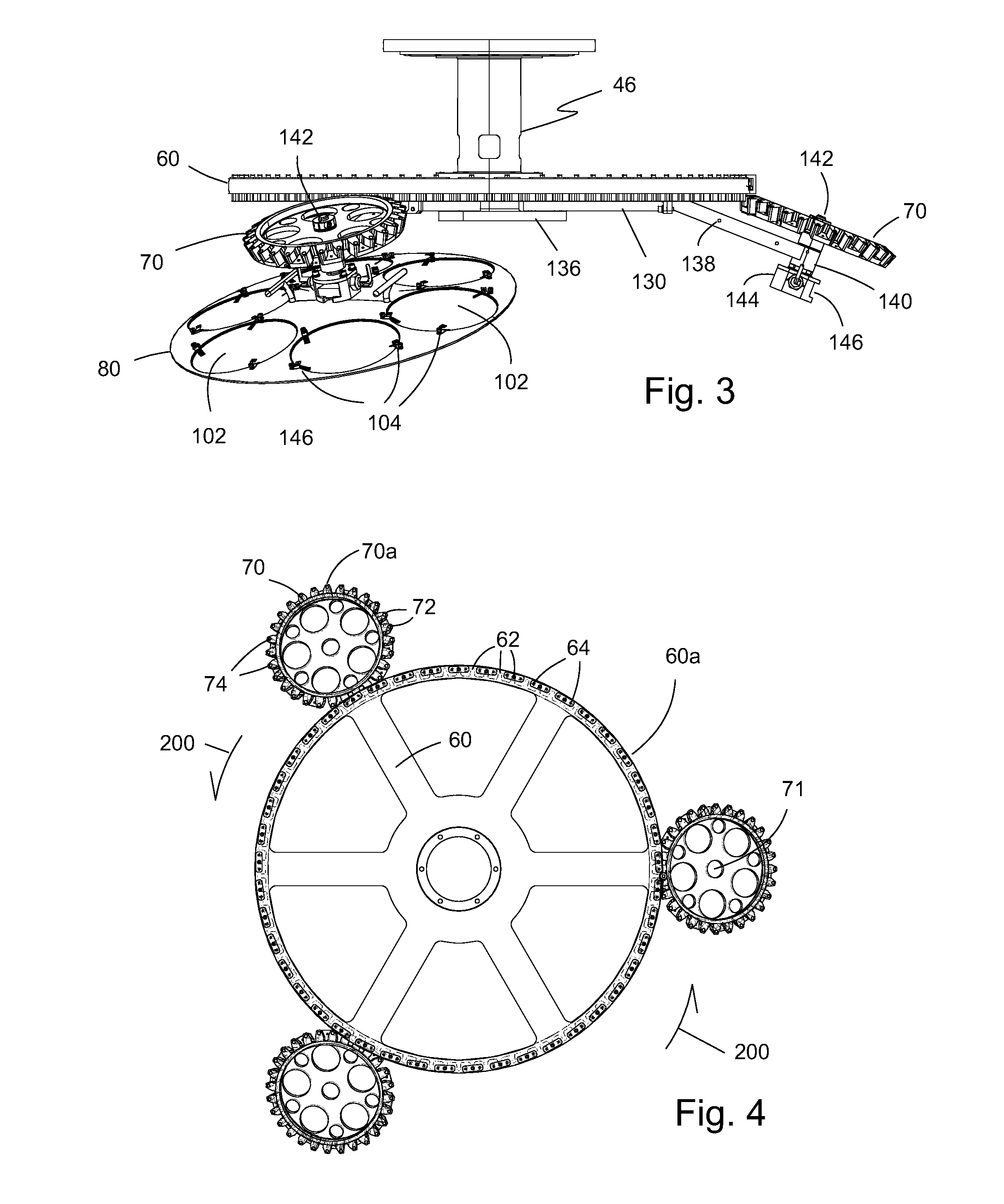
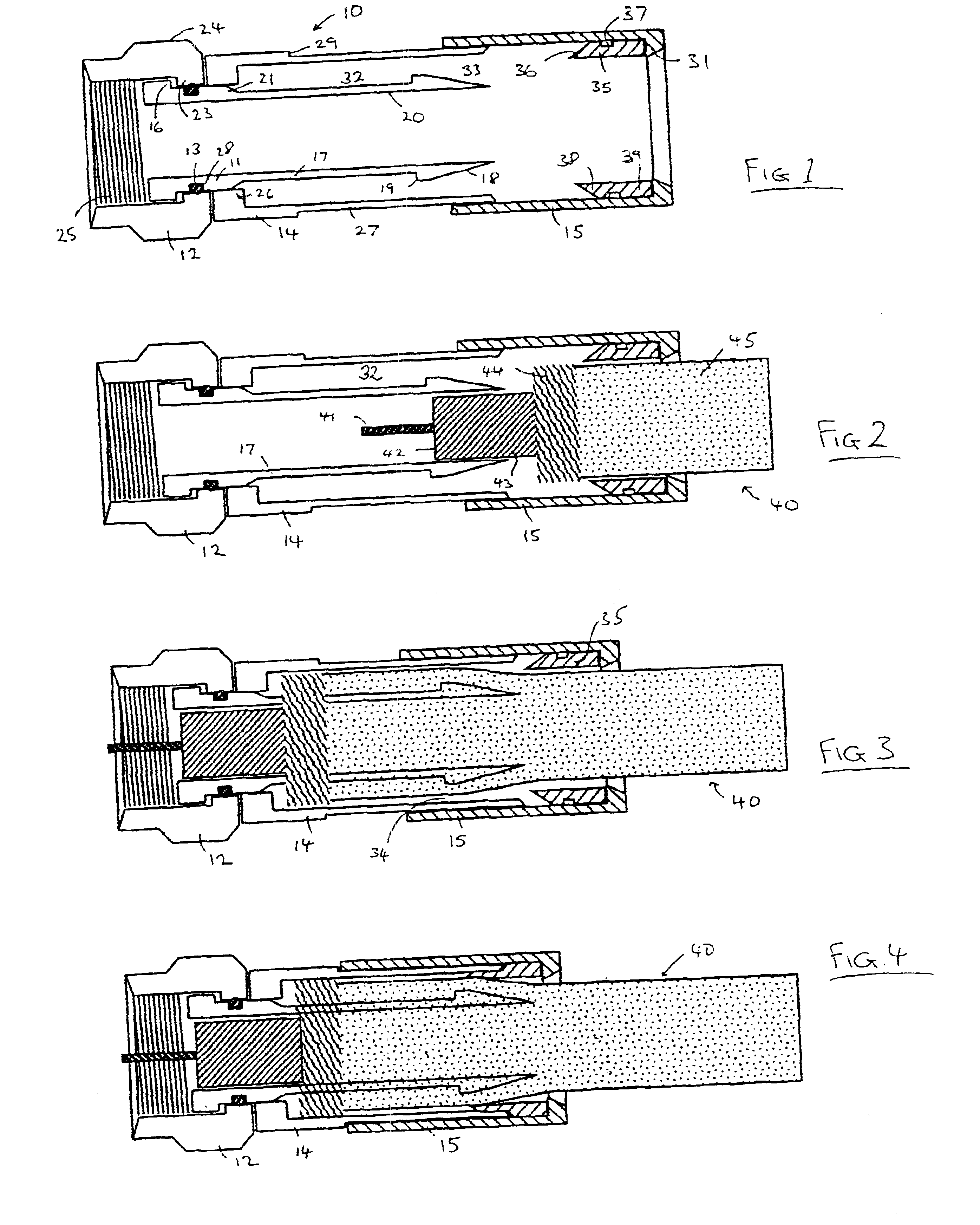
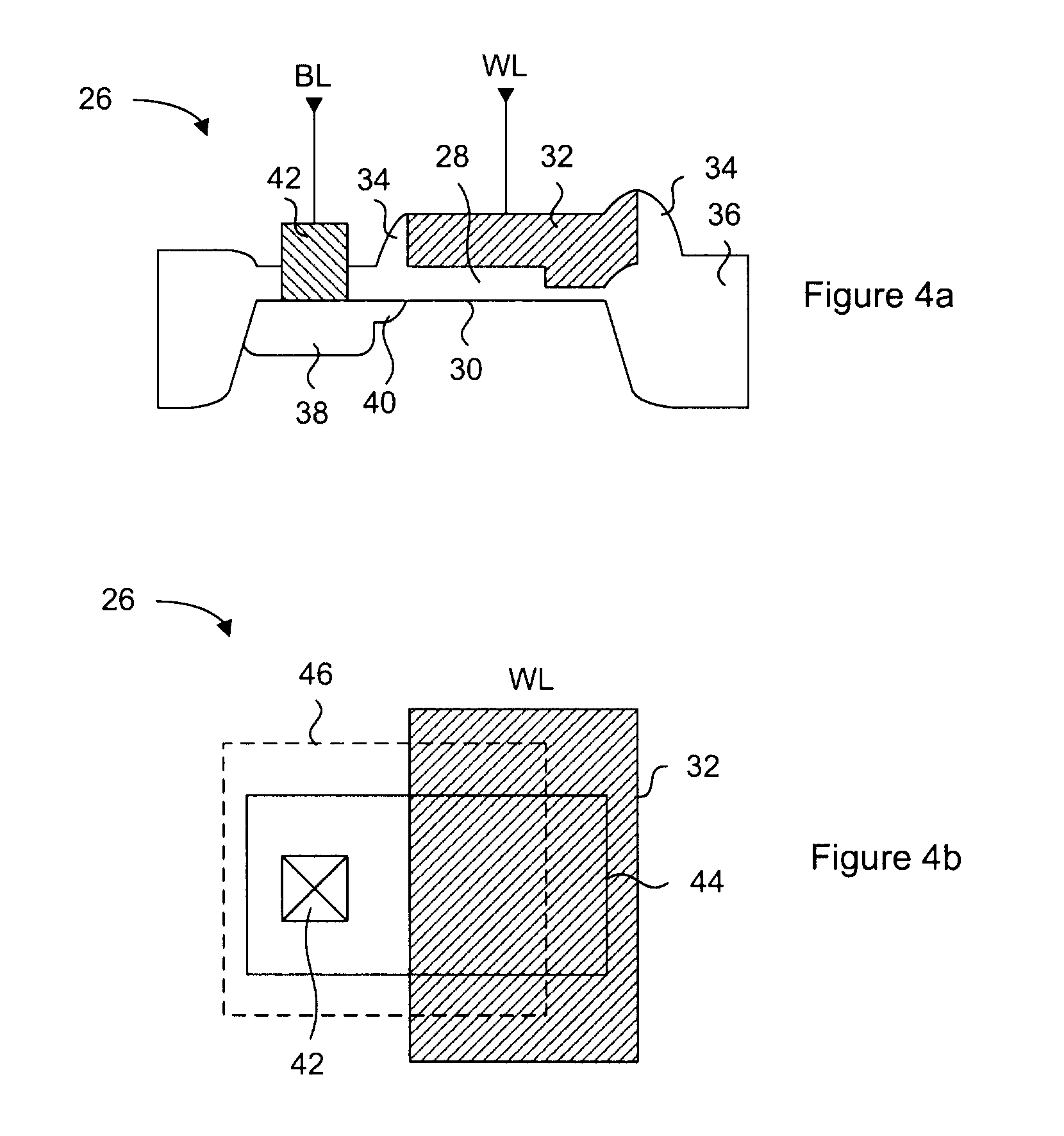
System and method for powering an information handling system in multiple power states
ActiveUS8063619B2Reduce disadvantagesReduce problemsElectric signal transmission systemsDc network circuit arrangementsMOSFETVoltage regulation
Power is supplied to an information handling system chipset with a single voltage regulator having dual phases. A first phase of the voltage regulator provides power to a low power state power rail in an independent mode to support a low power state, such as a suspend or hibernate state. A second phase of the voltage regulator provides power to a run power state power rail in combination with the first phase by activation of a switch, such as a MOSFET load switch, that connects the low power state power rail and the run power state power rail. Voltage sensed from both power rails is applied to control voltage output so that the run power state power rail is maintained within more precise constraints than the low power state power rail.
Owner:DELL PROD LP
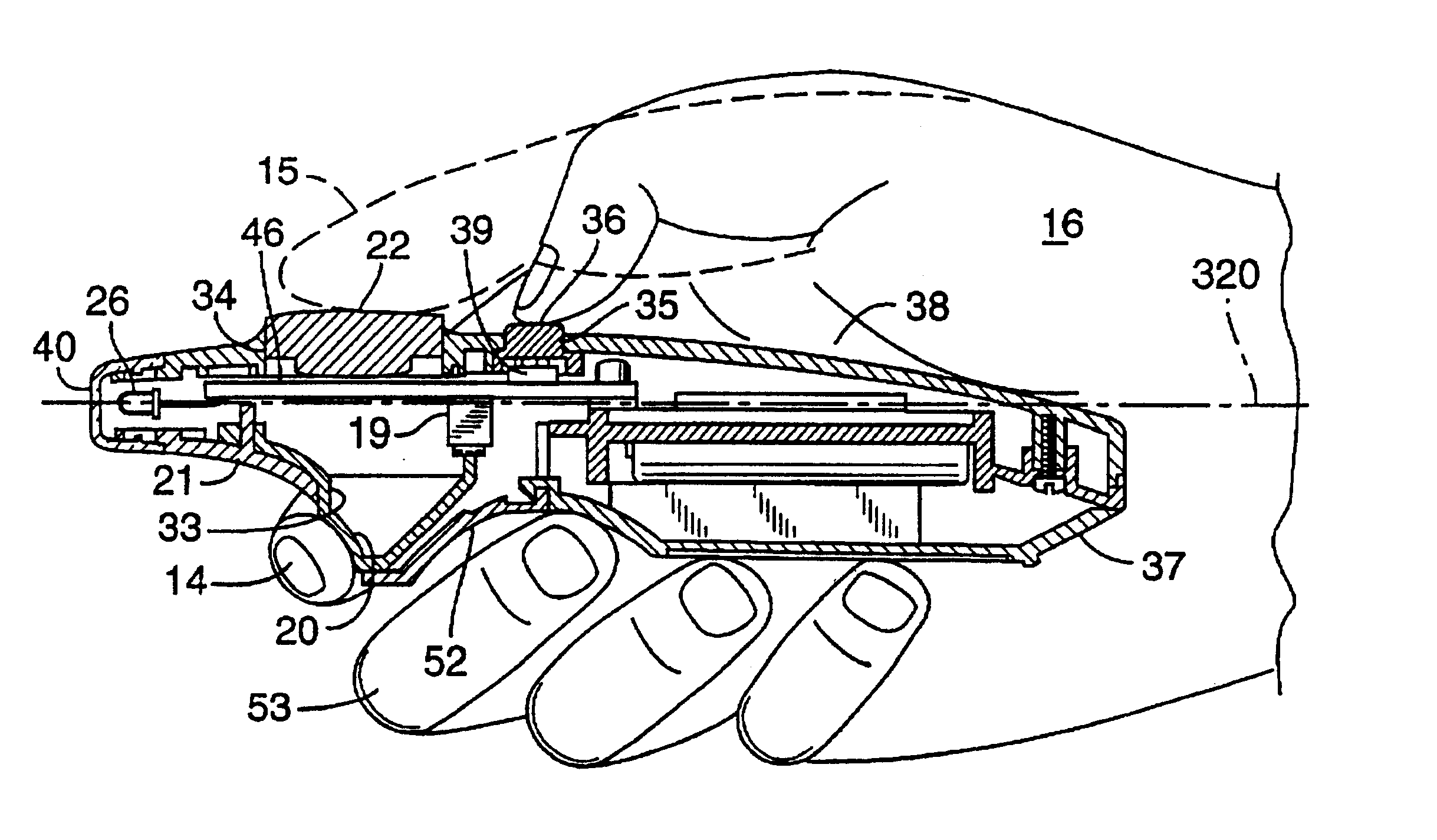
Trigger operated electronic device
InactiveUS6850221B1Reduce disadvantagesCathode-ray tube indicatorsElectric switchesFinger pressureElectronic equipment
A device particularly for use with a computer comprises a housing for location at least partly between two fingers of a user's hand and an electronic circuit mounted on a board within the housing. The circuit includes a switch responsive to pressure selectively to open and close an electronic circuit, and conductive elements arranged on the board mounting the electronic circuit. A first control element is mounted with the housing and responsive to finger pressure such that pressure applied to the first control element causes the element to operate the switch. The first control element is movable with respect to a hinge such that finger action acts to cause the control element to swivel as a trigger about the hinge and thereby interact with the switch. The second control element includes a flexible material mounted such that pressure applied to the flexible material in different directions and positions acts to change the electrical relationship between the conductive elements on the board and thereby vary an output signal from the electronic circuit. The rear portion of the housing includes a receptacle for receiving removable battery means for powering the electronic circuit. There is an infra-red output signal transmitted to a receiver for operating the computer. The first control element is located substantially below the second control element, and the first control element being in a bottom face of the housing.
Owner:SMK LINK ELECTRONICS
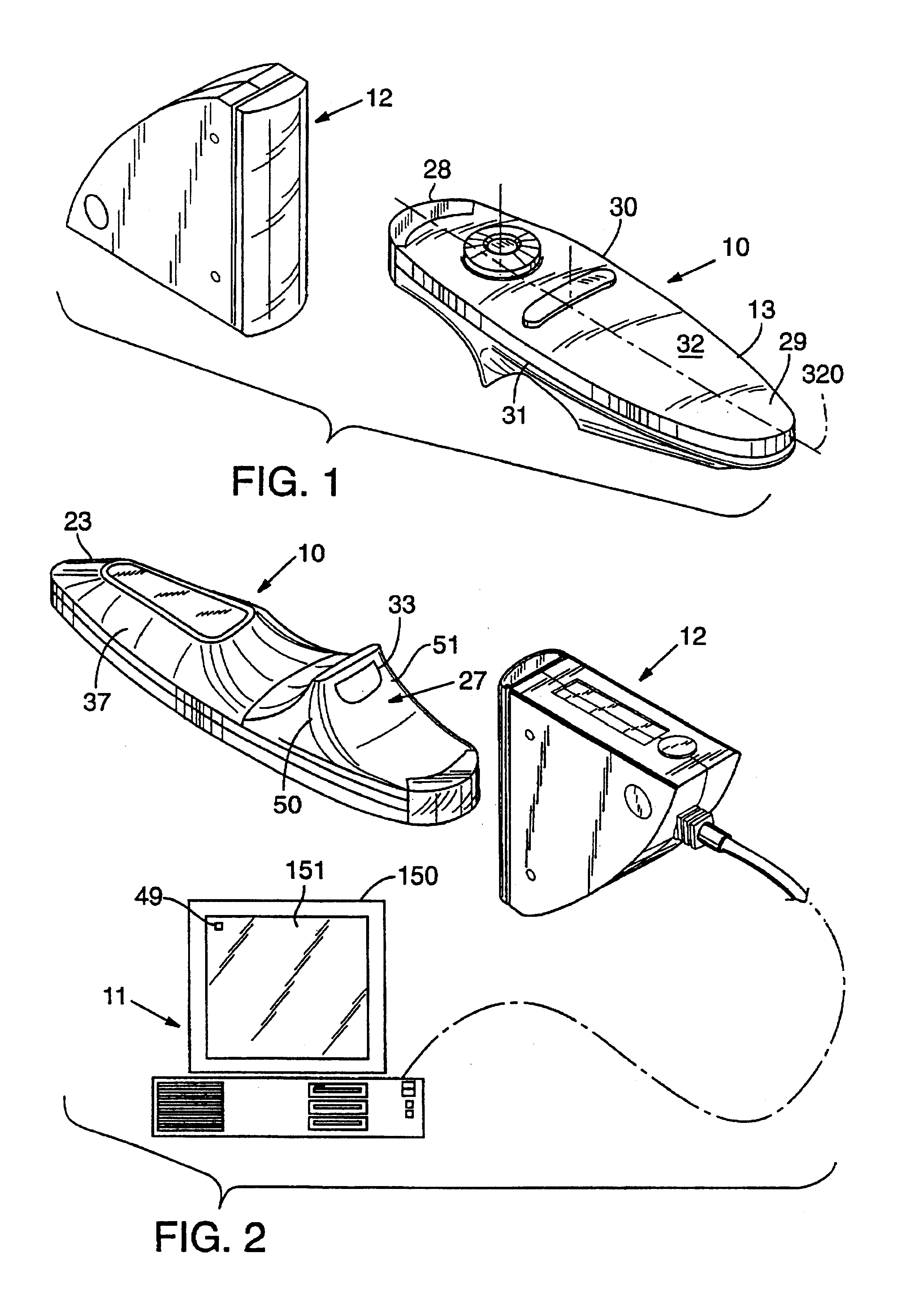
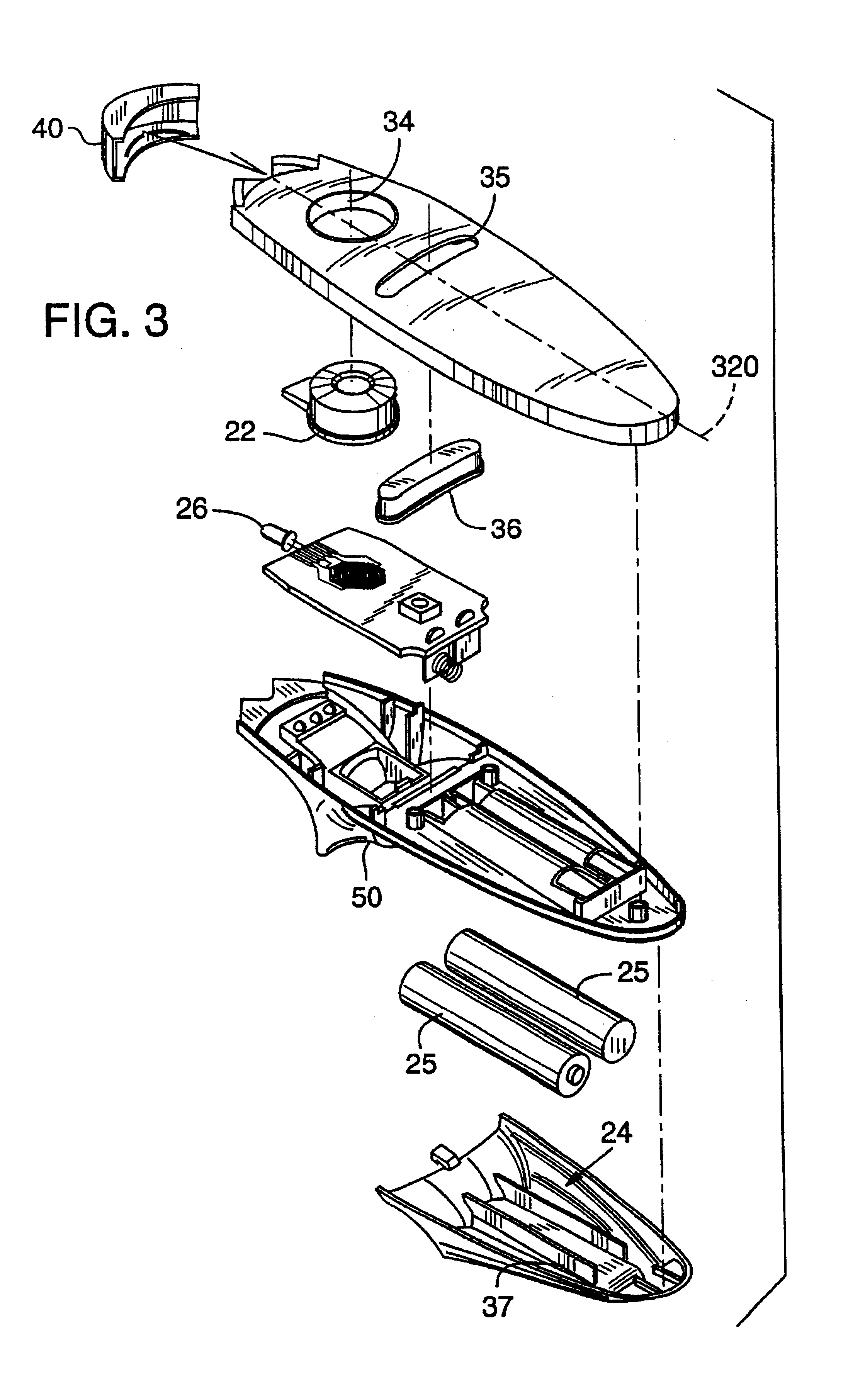
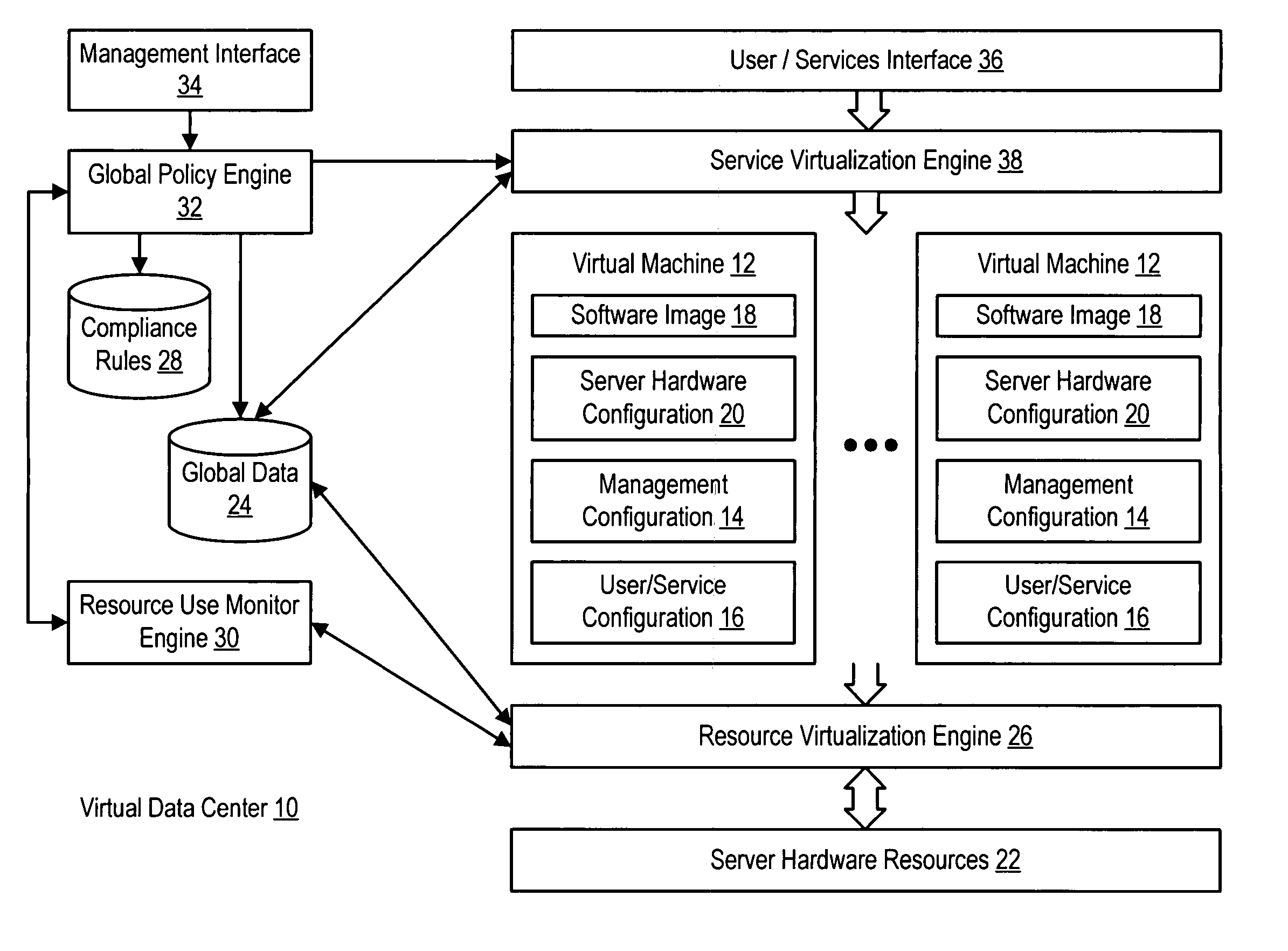
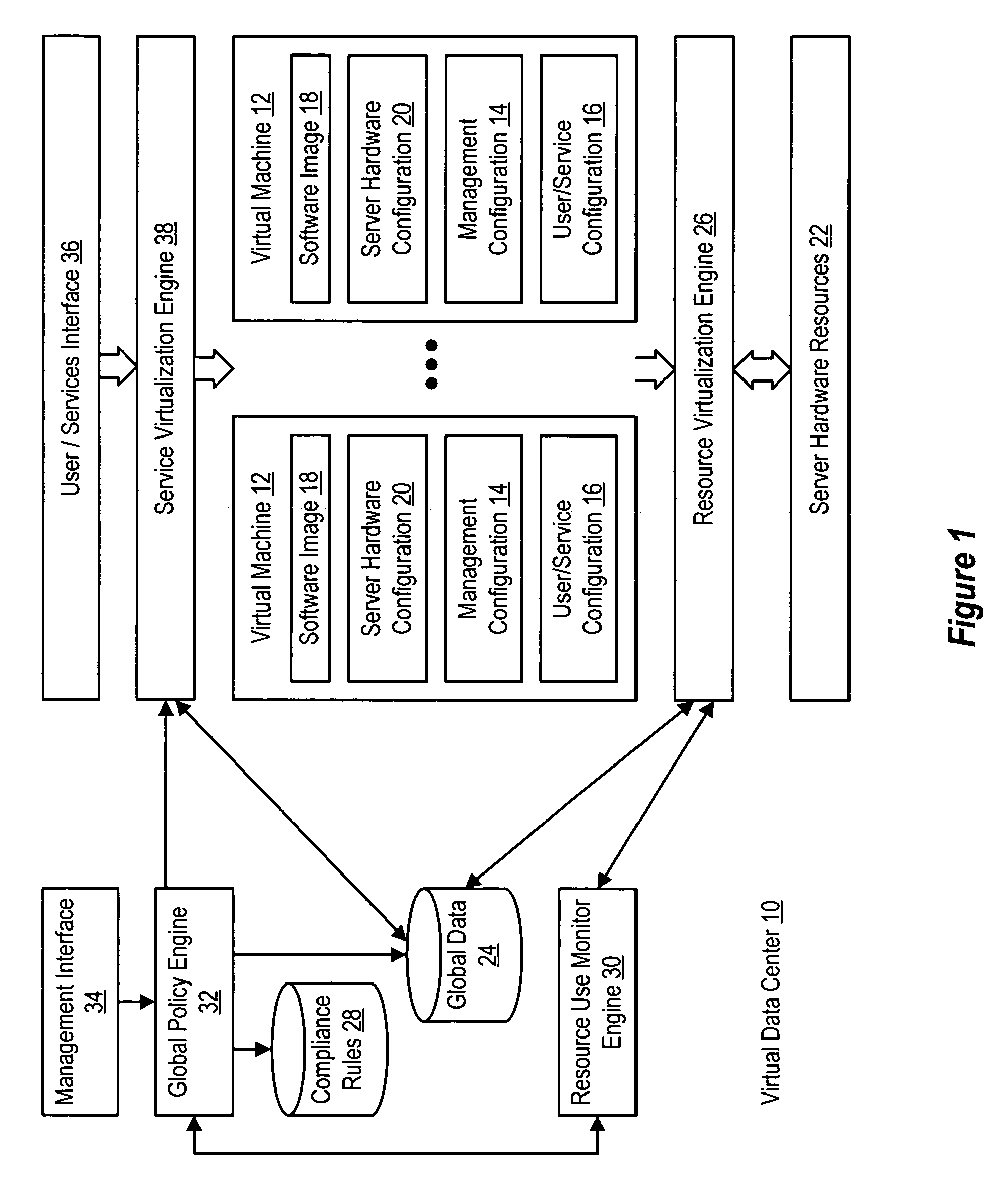
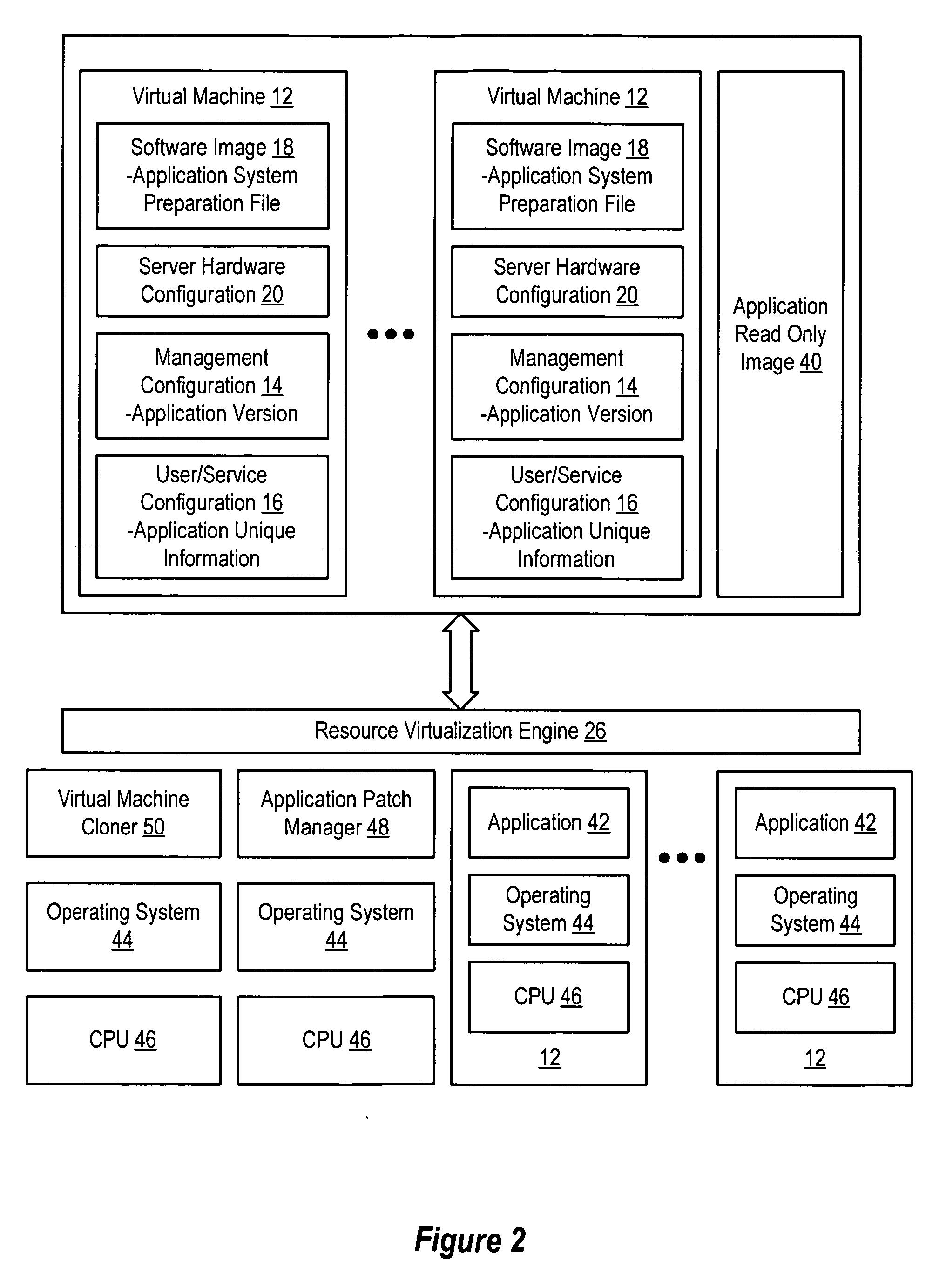
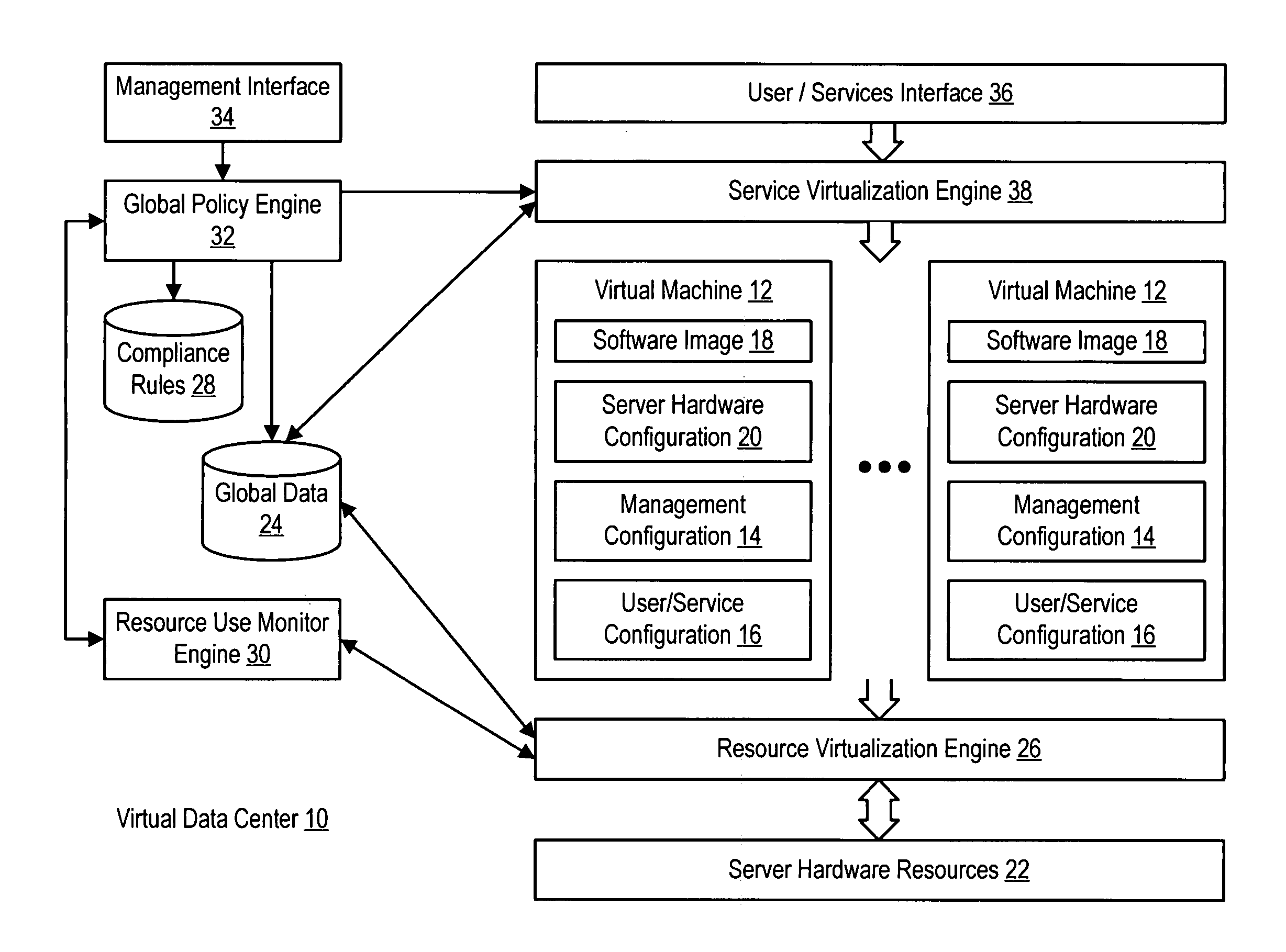
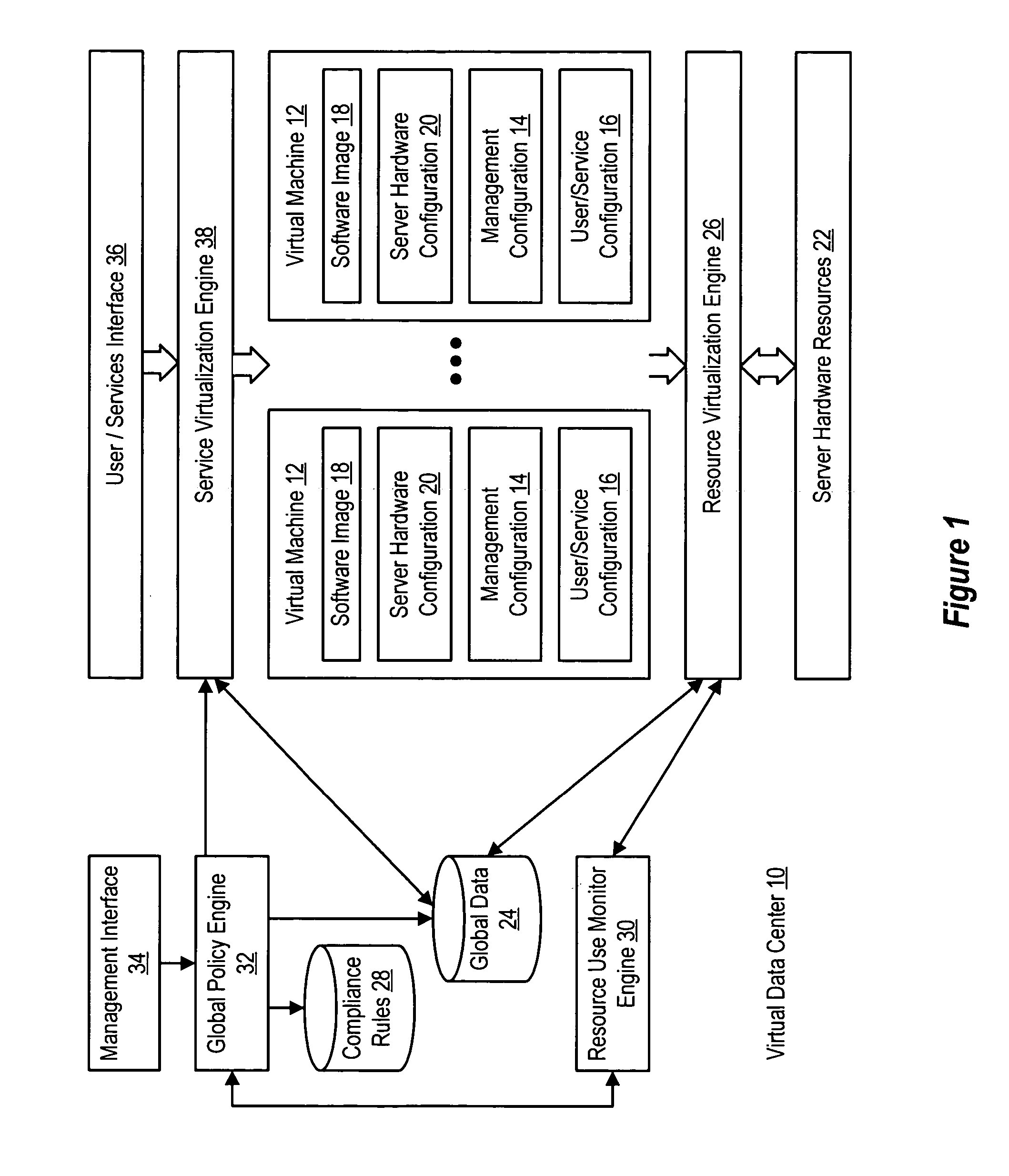
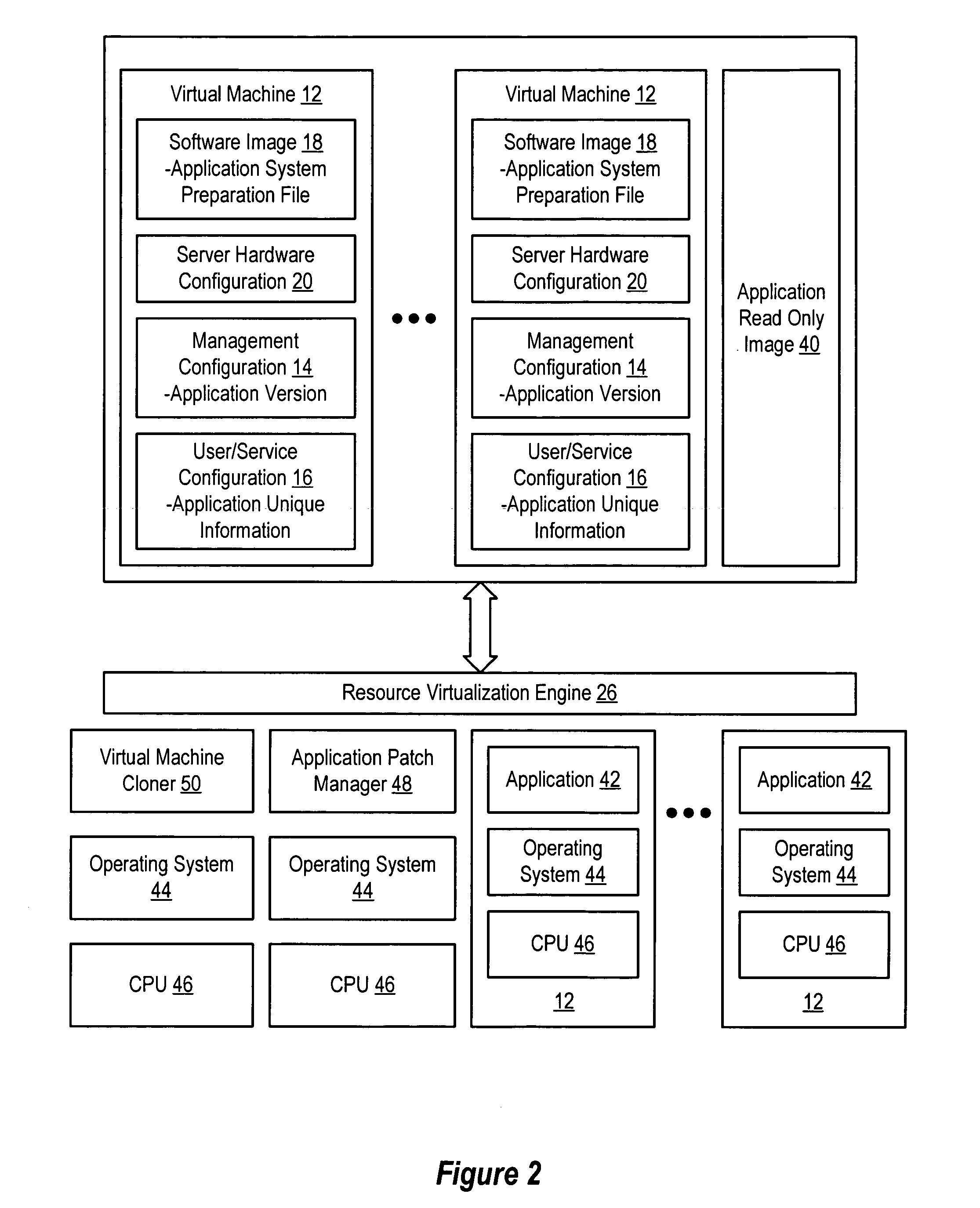
System and method for centralized software management in virtual machines
InactiveUS20060184937A1Simplifies management system updateSimple dataSoftware simulation/interpretation/emulationMemory systemsMaintenance releaseData center
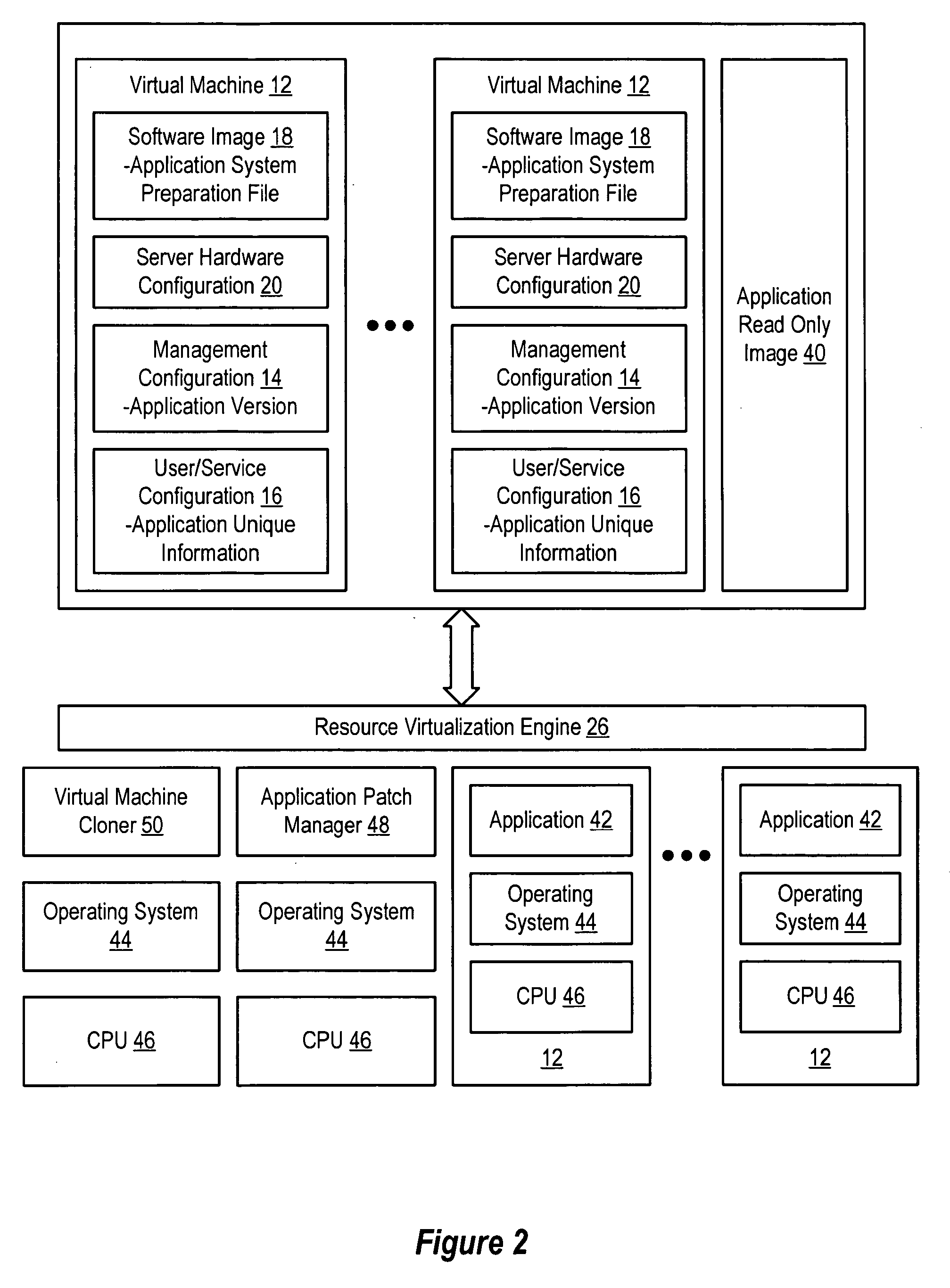
Virtual machines of a virtual data center generate runtime instances with a software image, hardware configuration, management configuration and user / service configuration. Virtual data center resource use is monitored by reference to the management configuration of runtime instances, such as for environmental controls like power, cooling and balancing, or for policy limitations on users, software or hardware. Users or services generate runtime instances of stored virtual machines by reference to the user / service configuration, such as pricing or priority. In one example embodiment, the virtual machine software image comprises an application system preparation file that populates a read only application image common to plural virtual machines. Information unique to each virtual machine with respect to the application is maintained in the user / service configuration of the virtual machine and version information is maintained in the management configuration of the virtual machine. Updates to the application across each virtual machine are performed by updating the read only image or any of its configuration information for hardware configuration, management configuration or user / service configuration.
Owner:DELL PROD LP
Power tool
A power tool includes a body housing a motor with a first output shaft and an attachment for engagement with the output shaft. The attachment includes an output shaft which transmits rotational motion derived from the rotational motion of the motor and further includes a gear mechanism enabling a gear change in rotational speed between its input and output. A combination of the body and the attachment thereby provides a plurality of serially-coupled gear mechanisms.
Owner:BLACK & DECKER INC
Device for improving the visibility conditions in a motor vehicle
ActiveUS7065432B2Improve the situationReduce disadvantagesDigital data processing detailsInstrument arrangements/adaptationsVisibilityMobile vehicle
The invention relates to a device for improving the visibility conditions in a motor vehicle, having a radiation source for infrared radiation for irradiating the surroundings of the vehicle, having an infrared-sensitive camera for taking images of at least part of the irradiated surroundings, having a display unit for displaying collected image data, and having a control unit for controlling the device. Furthermore, a sensing unit for a recommended maximum velocity vmax is provided and is connected to the control unit. A velocity sensor which is connected to the control unit is provided in such a way that the control unit causes the display to be switched off when the vehicle velocity v exceeds the maximum velocity vmax. The display is preferably switched on when the vehicle velocity v drops below the maximum velocity vmax.
Owner:AI CORE TECH LLC
Non-contact magnetic drive assembly with mechanical stop elements
ActiveUS20130095973A1Improve throughputMinimizing particulate contaminationVacuum evaporation coatingSemiconductor/solid-state device manufacturingMechanical driveVacuum deposition
A non-contact magnetic drive assembly with mechanical stop elements for a vacuum deposition system employing a lift-off process having a HULA configuration featuring a plurality of magnets coupled in an annular orientation to a central ring and an orbital ring, each magnet of the orbital ring becomes superposed with a magnet of the central ring as the orbital ring rotates, and a central drive component driving either the central ring, the orbital ring around the central ring or both simultaneously, the central drive component provides a rotational speed allowing non-contact, magnetic drive rotation of the orbital ring around the central ring until a difference between a magnetic drive torque of the superposed magnets and the rotational speed of the central drive component causes the superposed magnets to decouple enabling mechanical drive rotation by interactive contact between a plurality of central ring teeth and a plurality of orbital ring.
Owner:FERROTEC USA CORP
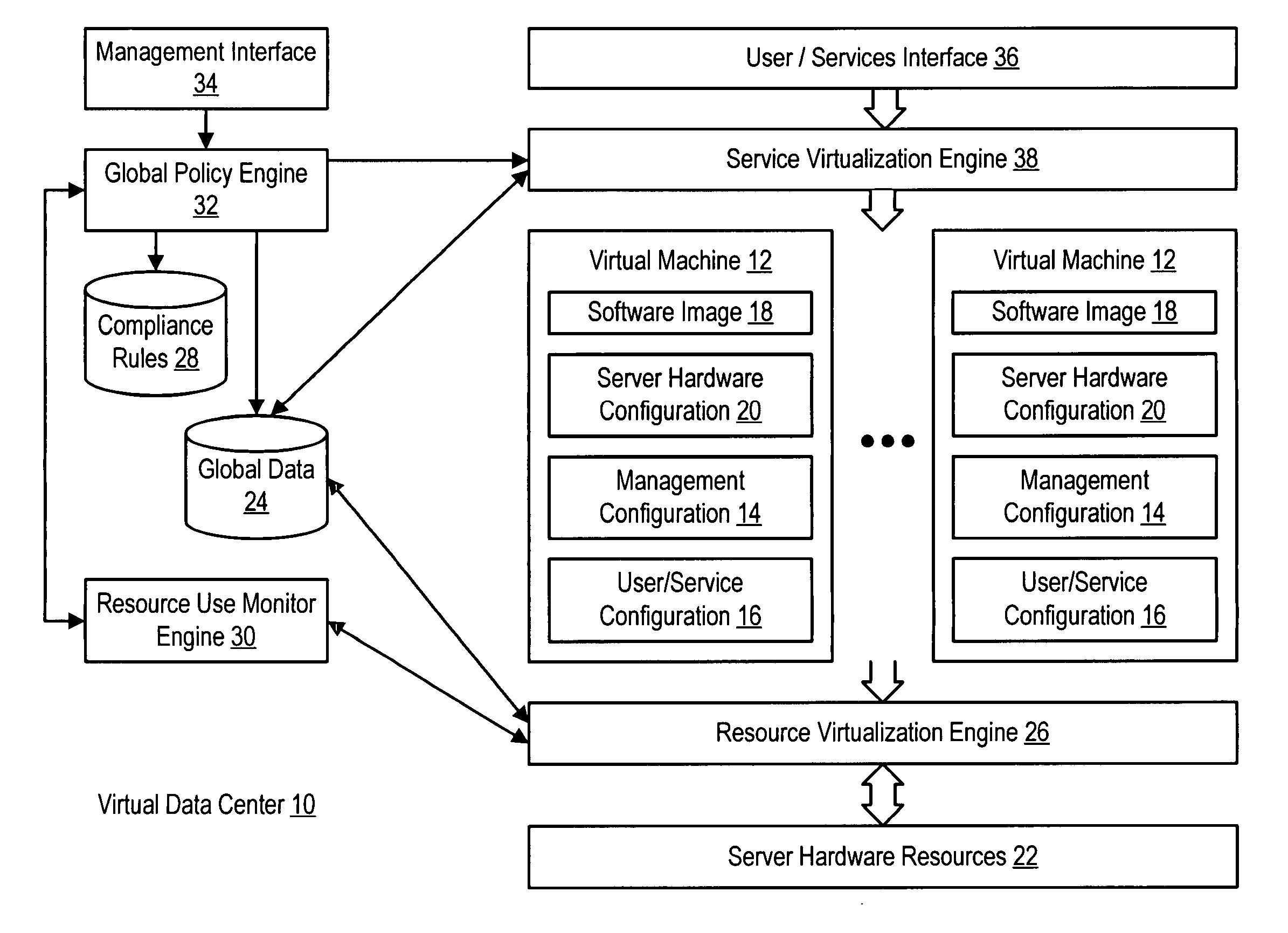
System and method using virtual machines for decoupling software from management and control systems
InactiveUS20060184936A1Simplifies management system updateSimple dataSoftware simulation/interpretation/emulationMemory systemsMaintenance releaseData center
Virtual machines of a virtual data center generate runtime instances with a software image, hardware configuration, management configuration and user / service configuration. Virtual data center resource use is monitored by reference to the management configuration of runtime instances, such as for environmental controls like power, cooling and balancing, or for policy limitations on users, software or hardware. Users or services generate runtime instances of stored virtual machines by reference to the user / service configuration, such as pricing or priority. In one example embodiment, the virtual machine software image comprises an application system preparation file that populates a read only application image common to plural virtual machines. Information unique to each virtual machine with respect to the application is maintained in the user / service configuration of the virtual machine and version information is maintained in the management configuration of the virtual machine. Updates to the application across each virtual machine are performed by updating the read only image or any of its configuration information for hardware configuration, management configuration or user / service configuration.
Owner:DELL PROD LP
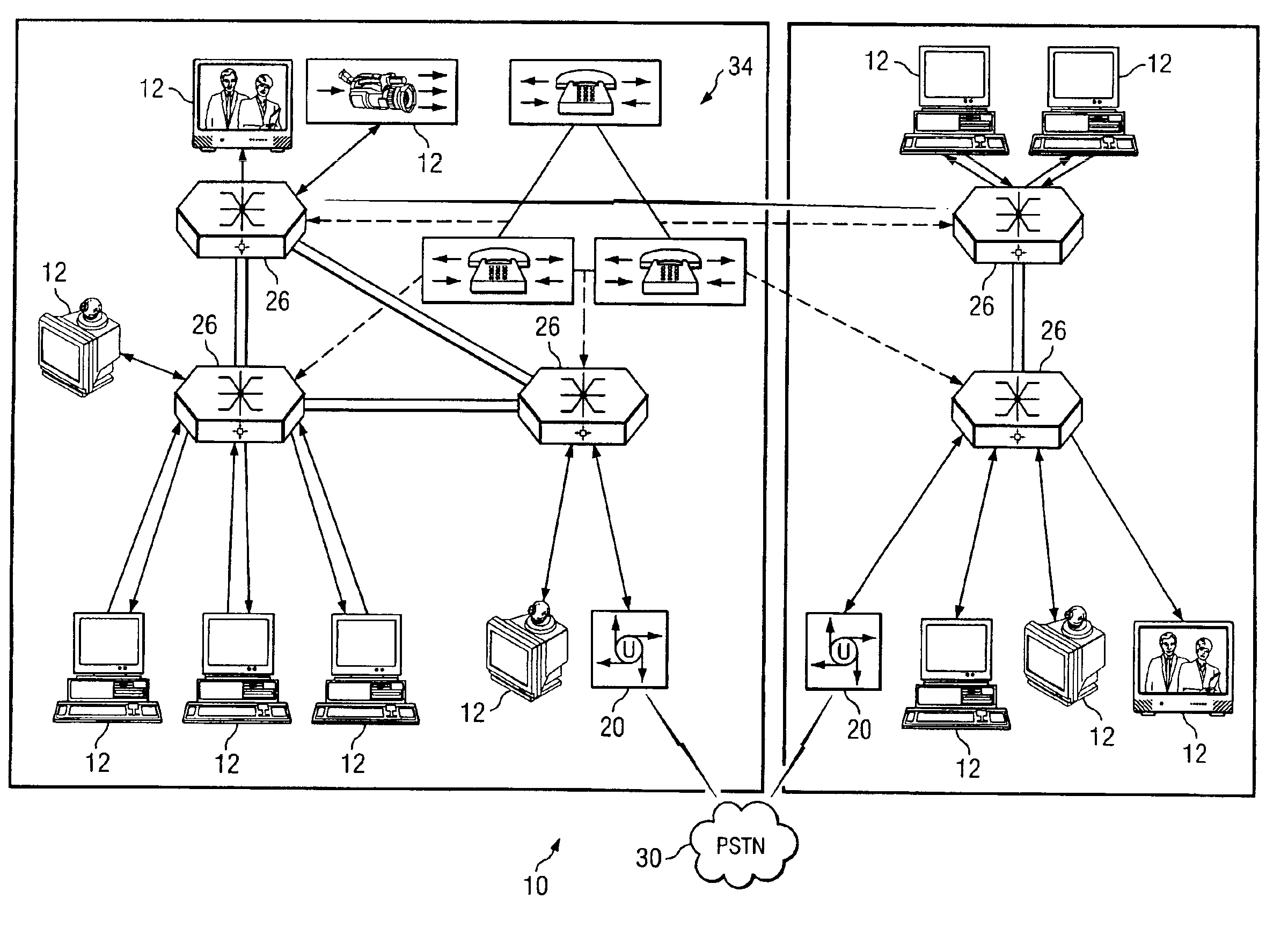
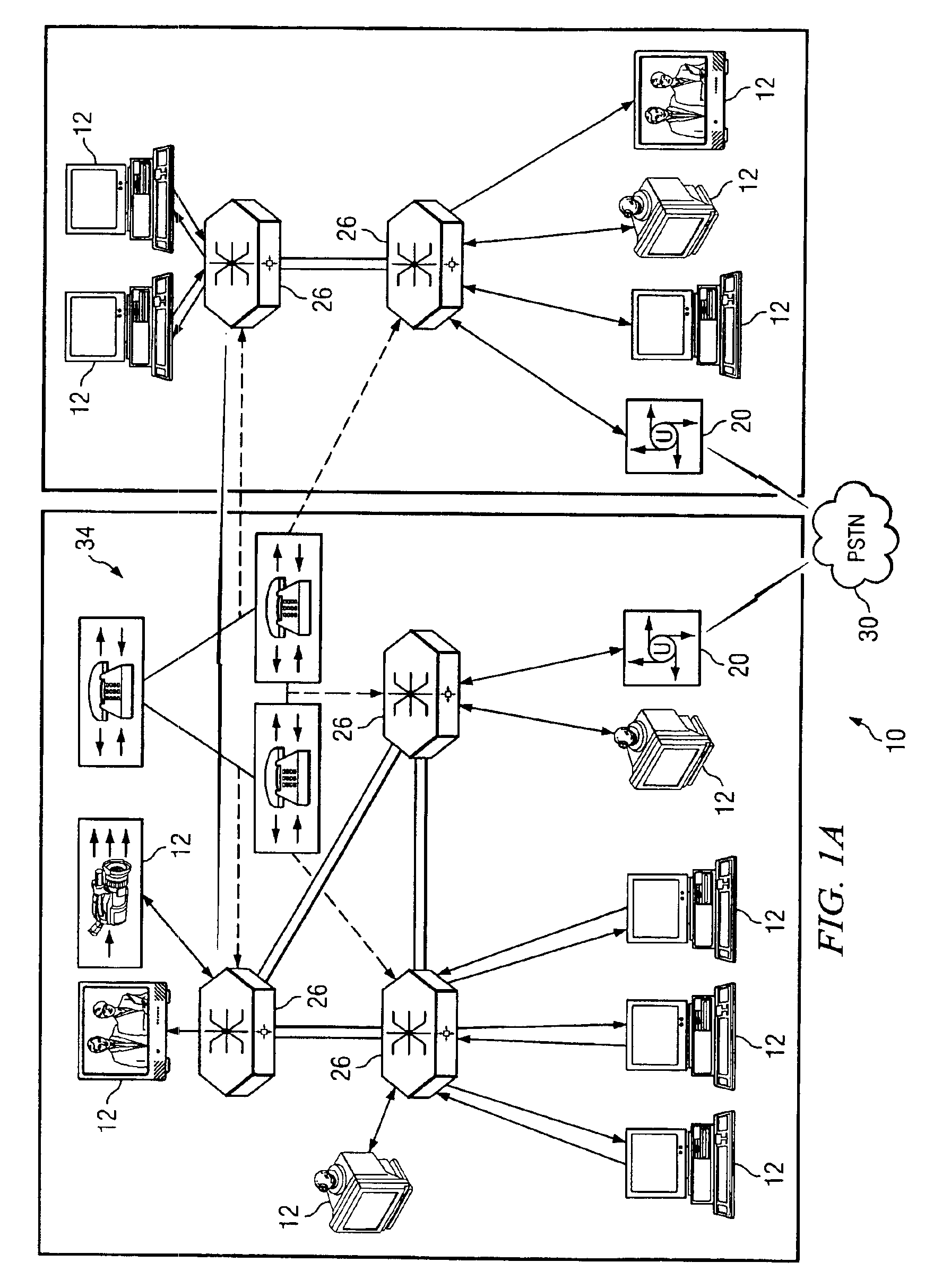
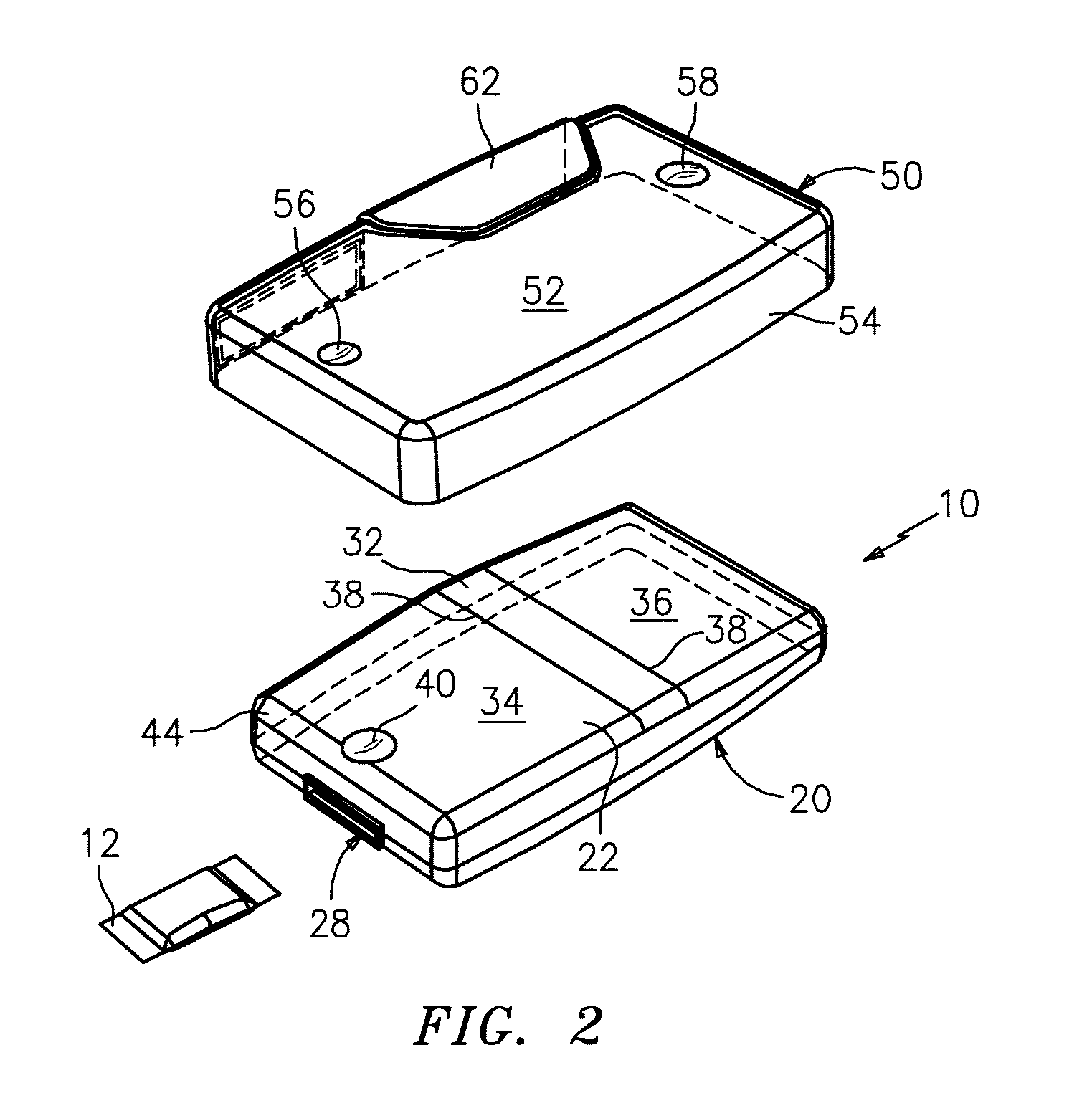
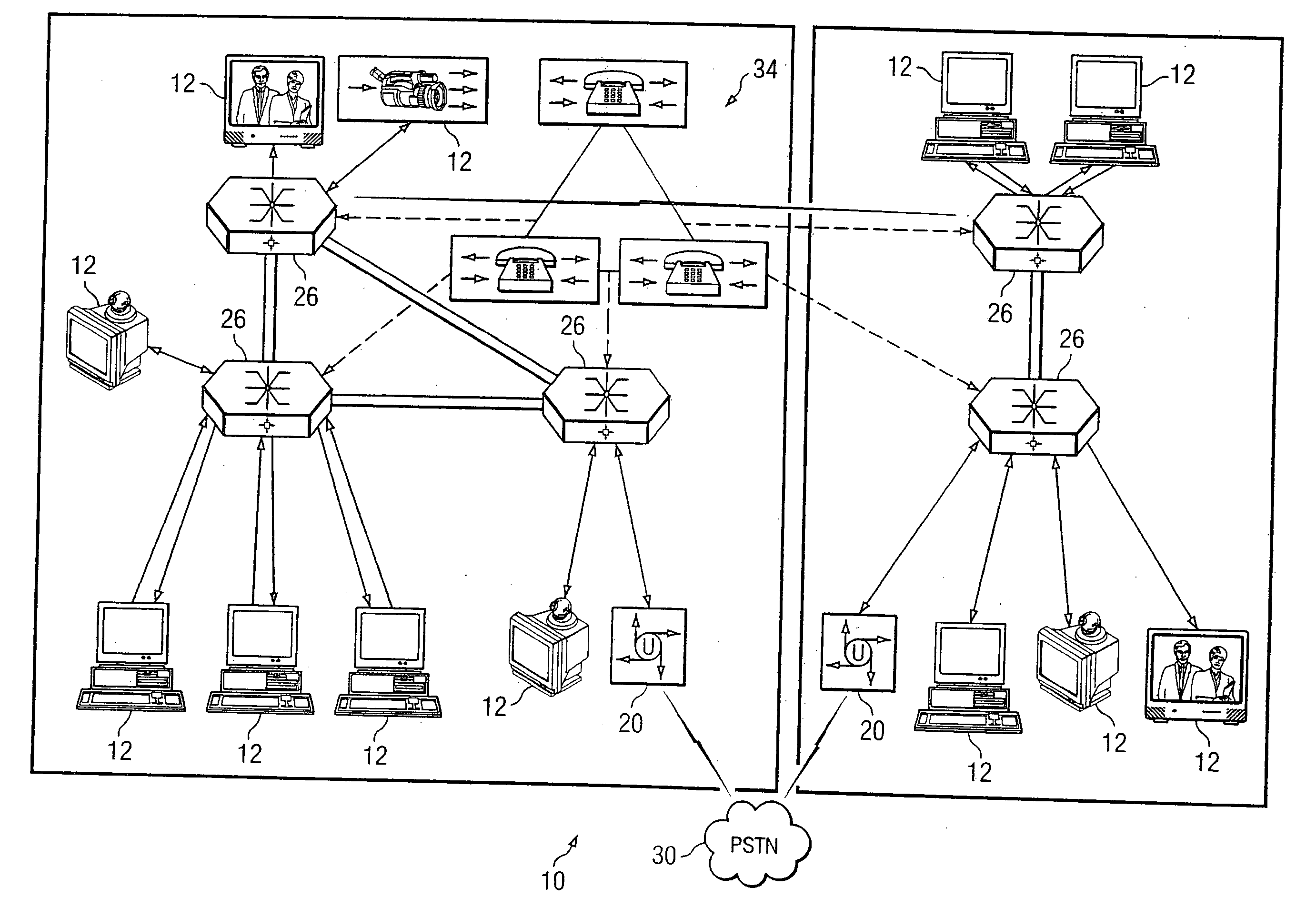
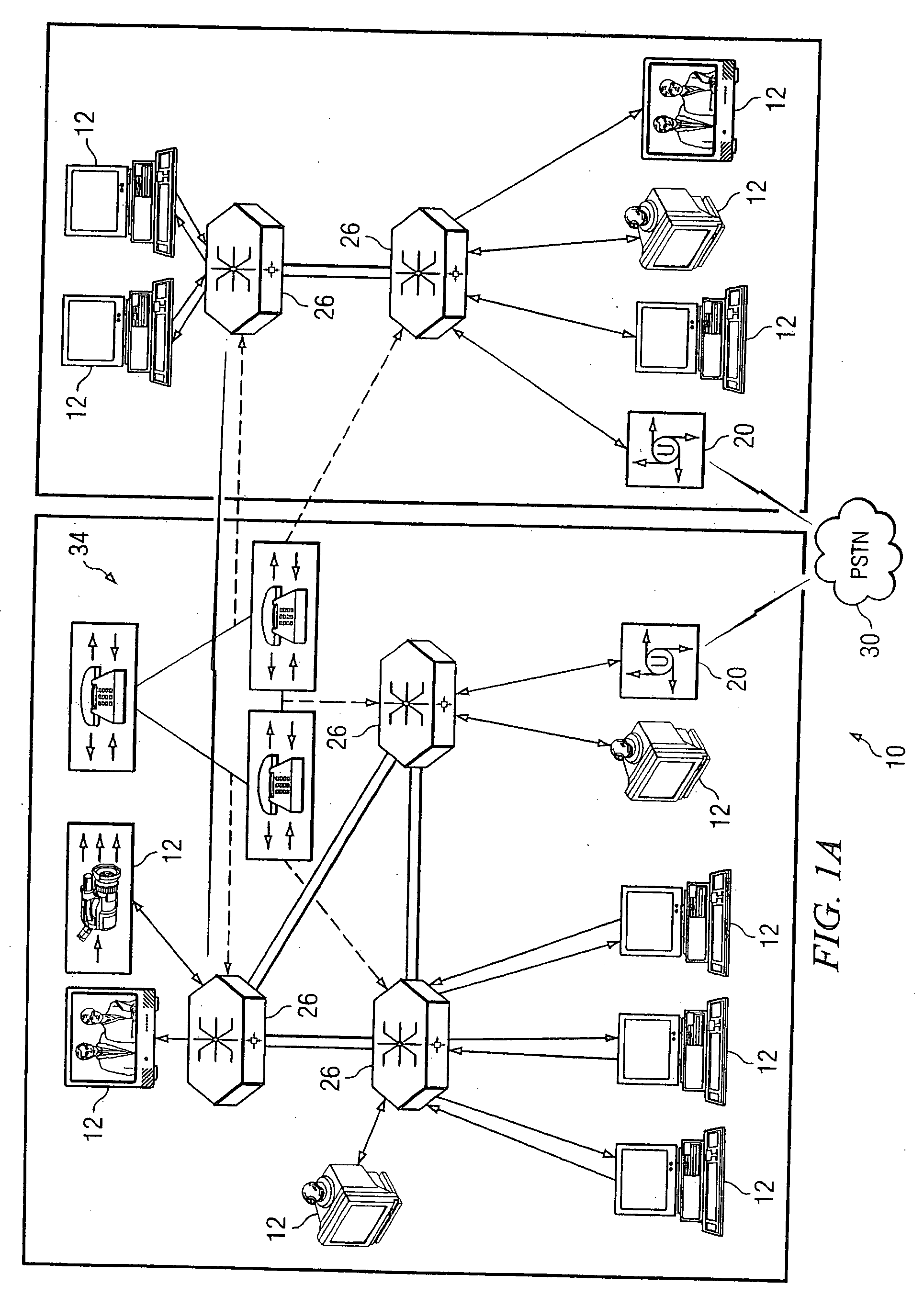
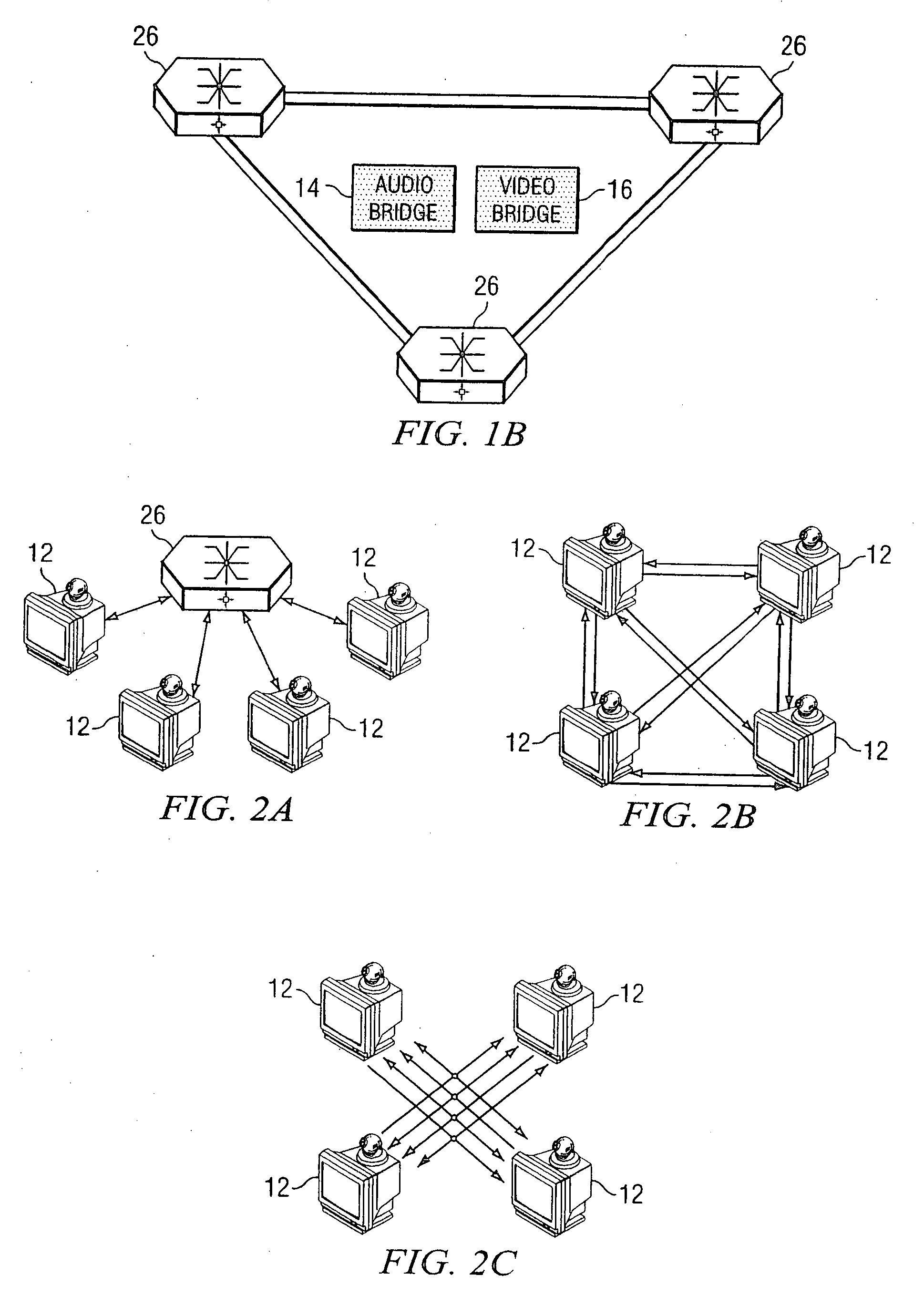
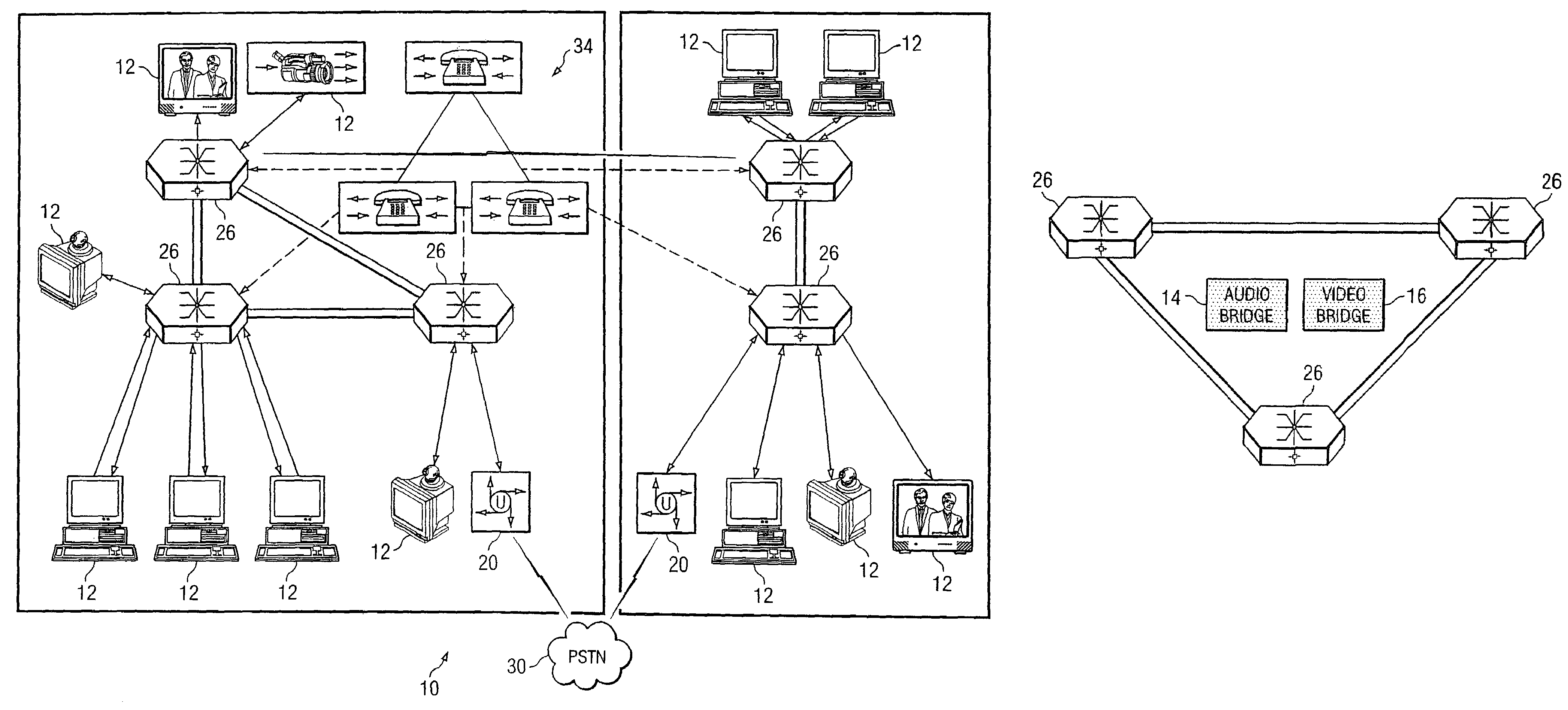
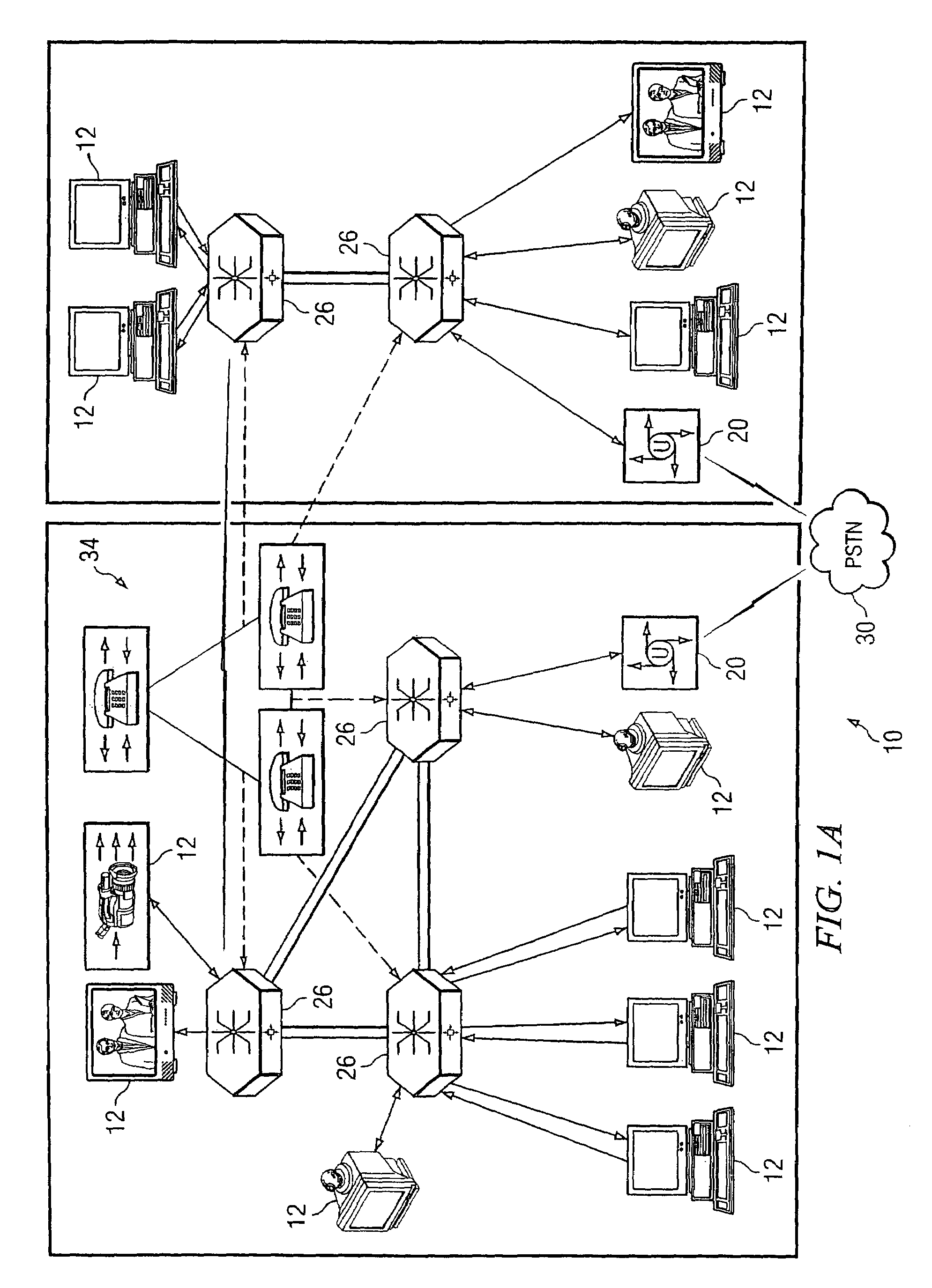
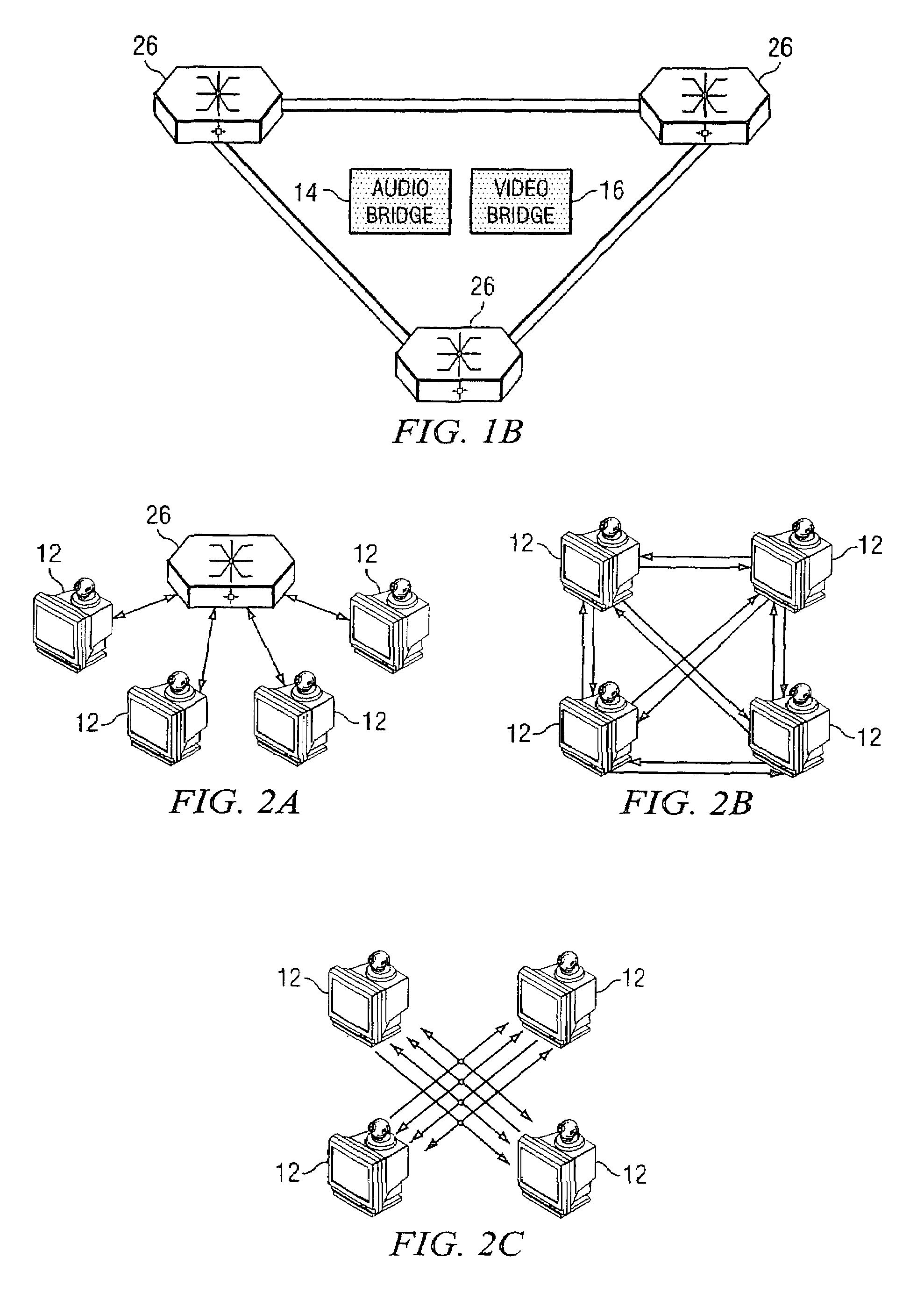
System and method for performing distributed video conferencing
ActiveUS6989856B2Reduce disadvantagesReduce problemsTelevision conference systemsAutomatic exchangesLoudspeakerAudio frequency
A method for executing a video conference is provided that includes receiving one or more audio streams associated with a video conference from one or more end points and determining an active speaker associated with one of the end points. Audio information associated with the active speaker may be received at one or more media switches. One or more video streams may be suppressed except for a selected video stream associated with the active speaker, the selected video stream propagating to one or more of the media switches during the video conference. The selected video stream may be replicated such that it may be communicated to one or more of the end points associated with a selected one of the media switches.
Owner:CISCO TECH INC
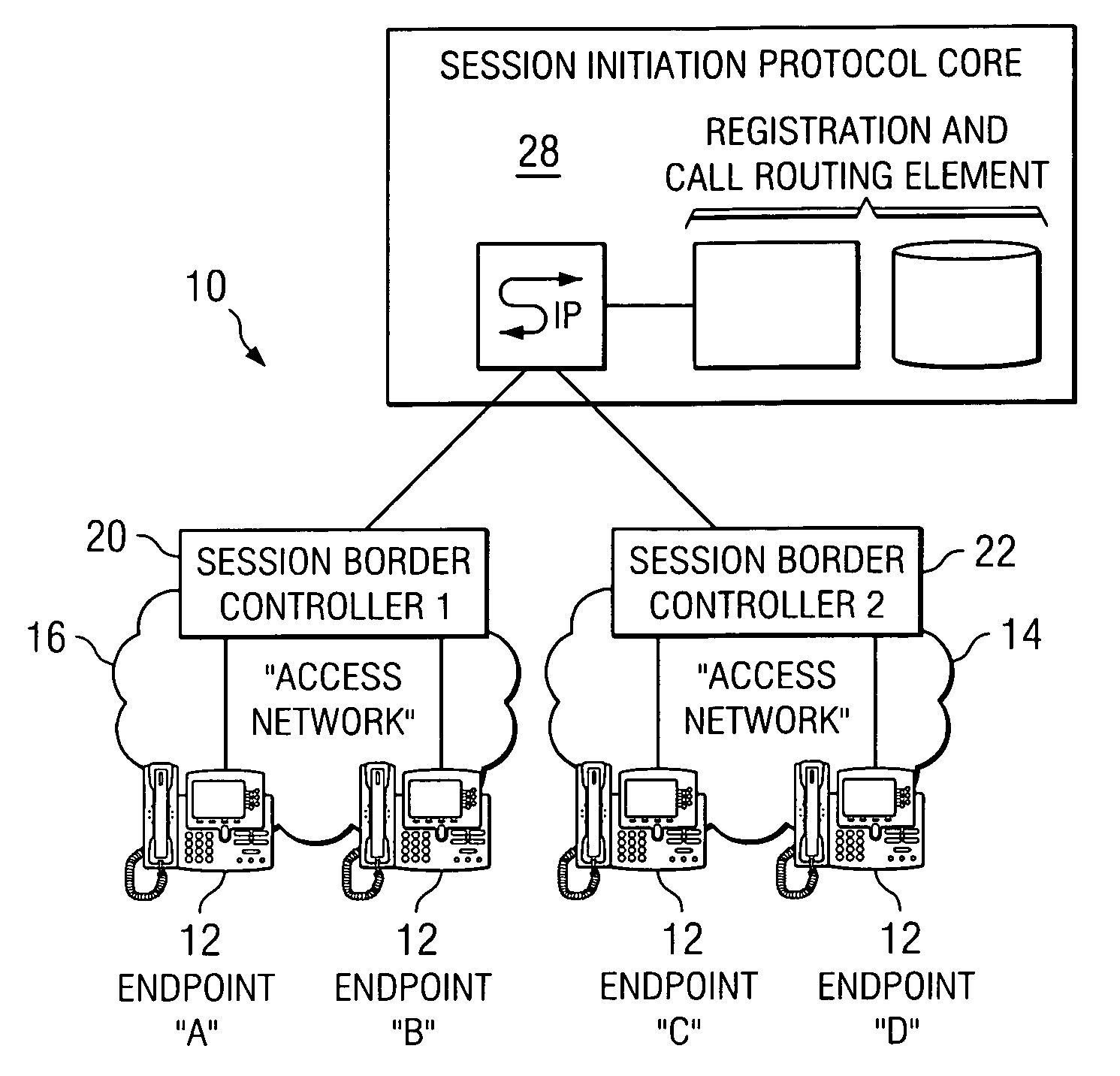
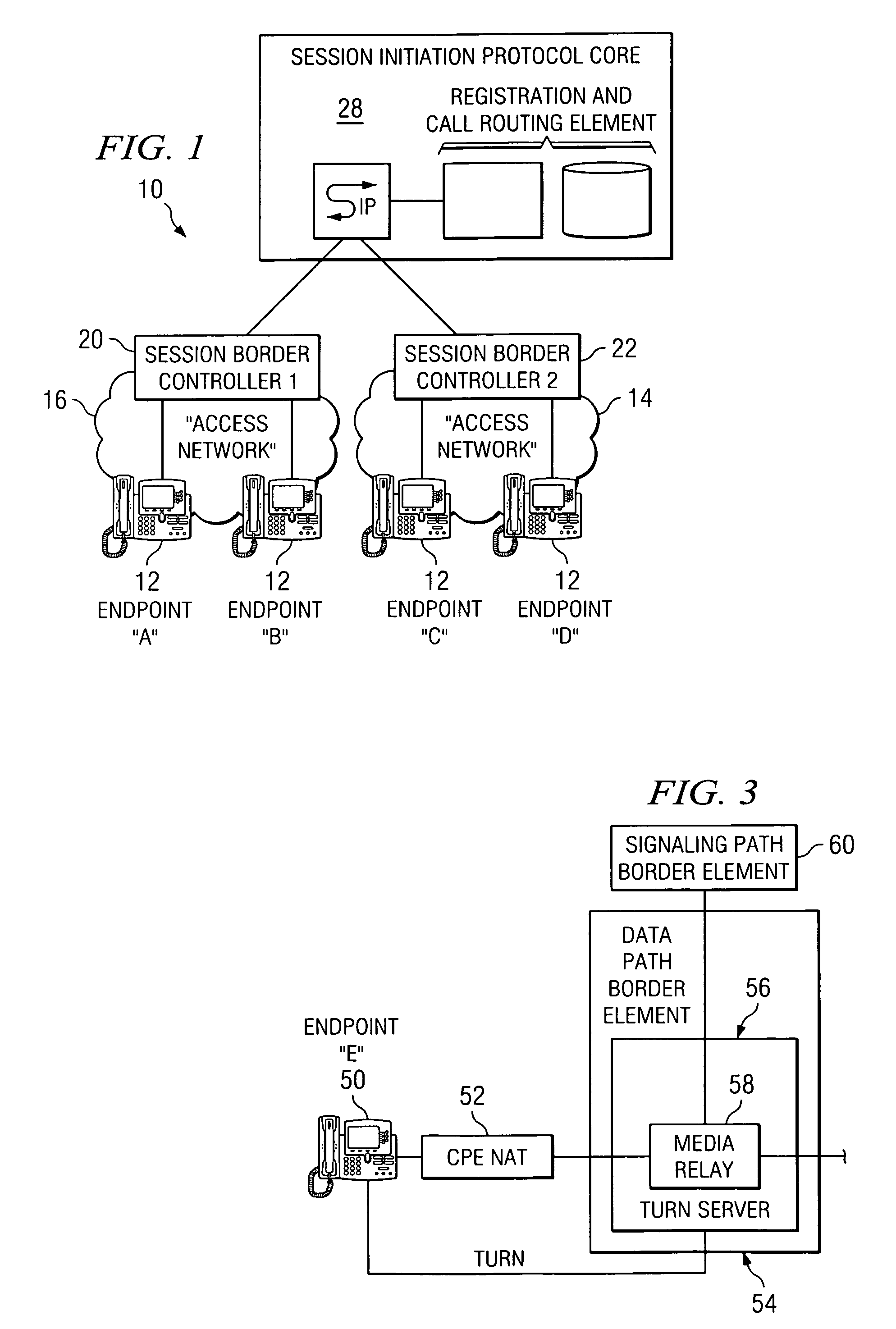
System and method for optimizing communications between session border controllers and enpoints in a network environment
ActiveUS20070019619A1Reduce disadvantagesReduce problemsMultiplex system selection arrangementsSpecial service provision for substationDatapathSession border controller
An apparatus for optimizing communications between session border controllers in a network environment is provided that includes a session border controller (SBC) operable to communicate with a first endpoint and a second endpoint. The SBC is also operable to communicate with a data path border element (DBE) and a signaling path border element (SBE). The DBE is operable to provide a media relay for a communication session involving the endpoints, the media relay being invoked by either of the endpoints using a traversal using relay network address translation (TURN) protocol, which allows the SBC to operate in either of two modes depending on protocol support present in the endpoints.
Owner:CISCO TECH INC
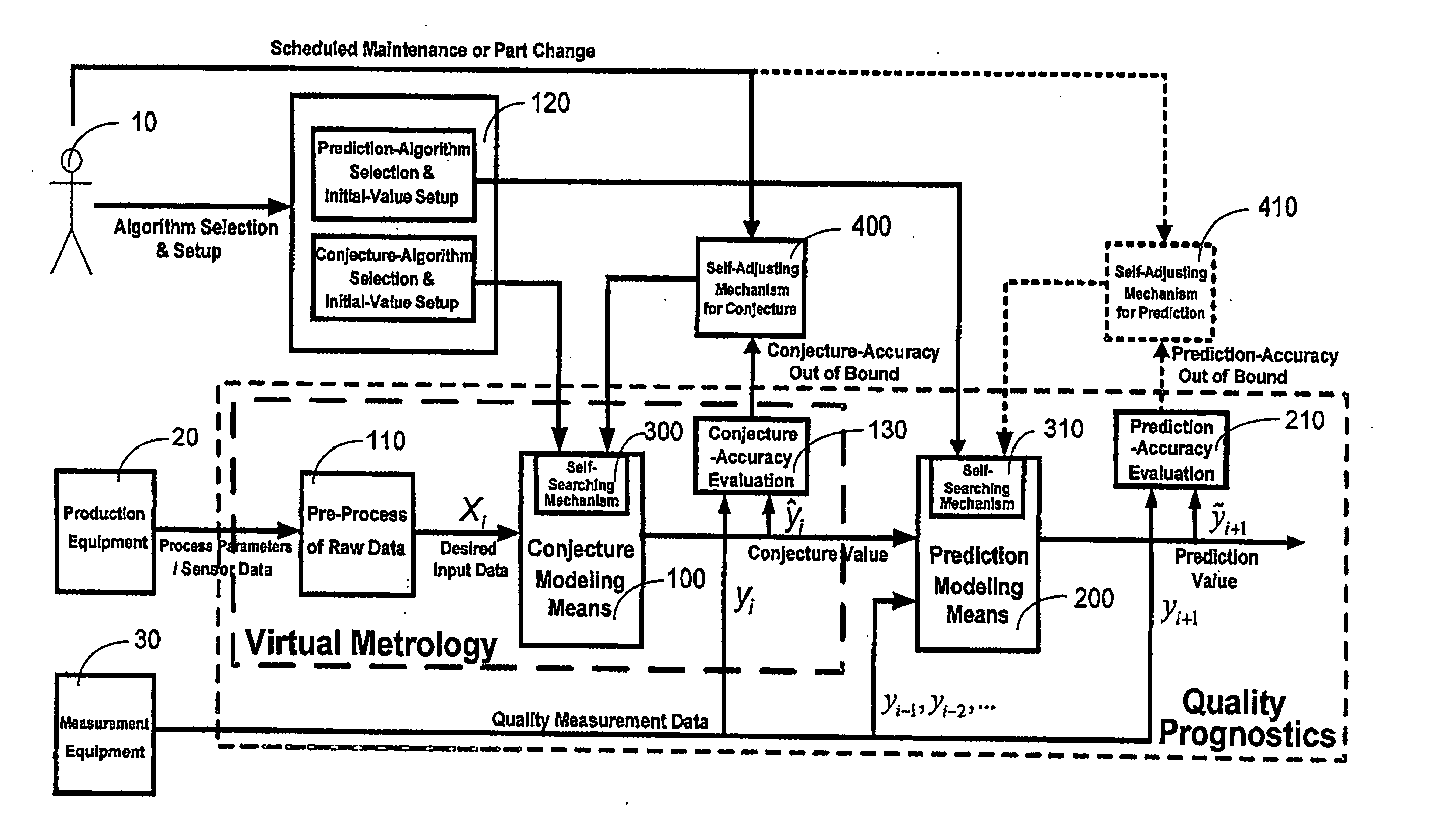
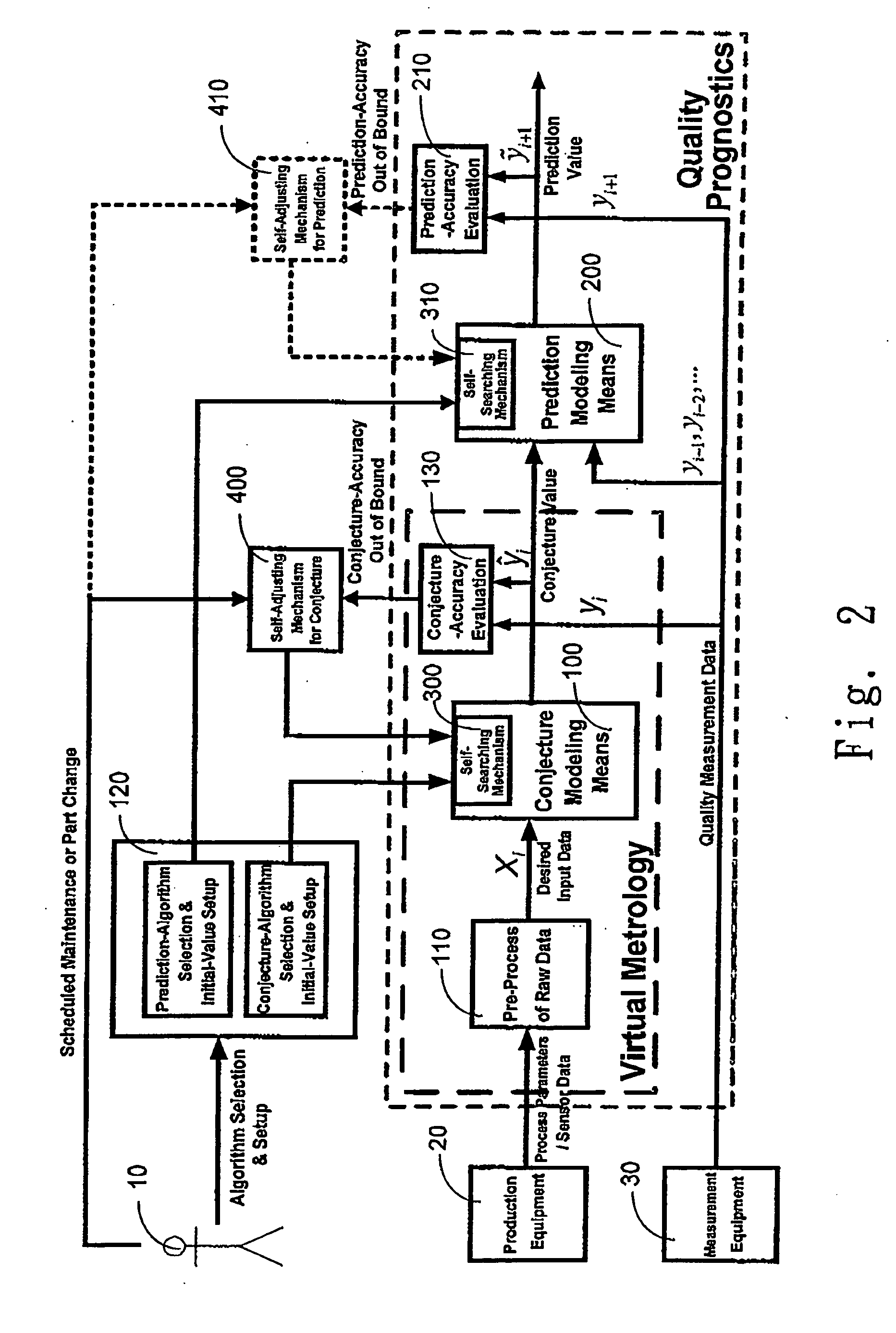
Quality prognostics system and method for manufacturing processes
ActiveUS20050288812A1Reduce disadvantagesImprove availabilityDigital computer detailsSemiconductor/solid-state device manufacturingPredictive systemsPrediction algorithms
A quality prognostics system and a quality prognostics method for predicting the product quality during manufacturing processes are disclosed. The present invention utilizes the current production tool parameters sensed during the manufacturing process and several previous quality data collected from the measurement tool to predict the future product quality. The quality prognostics system is composed of conjecture modeling means and prediction modeling means. The conjecture modeling means itself also can be applied for the purpose of virtual metrology. Further, the quality prognostics method possesses a self-searching means and a self-adjusting means for searching the best combination of various parameters / functions used by the conjecture algorithm or prediction algorithm; and meeting the requirements of new equipment parameters and conjecture / prediction accuracy.
Owner:NAT CHENG KUNG UNIV
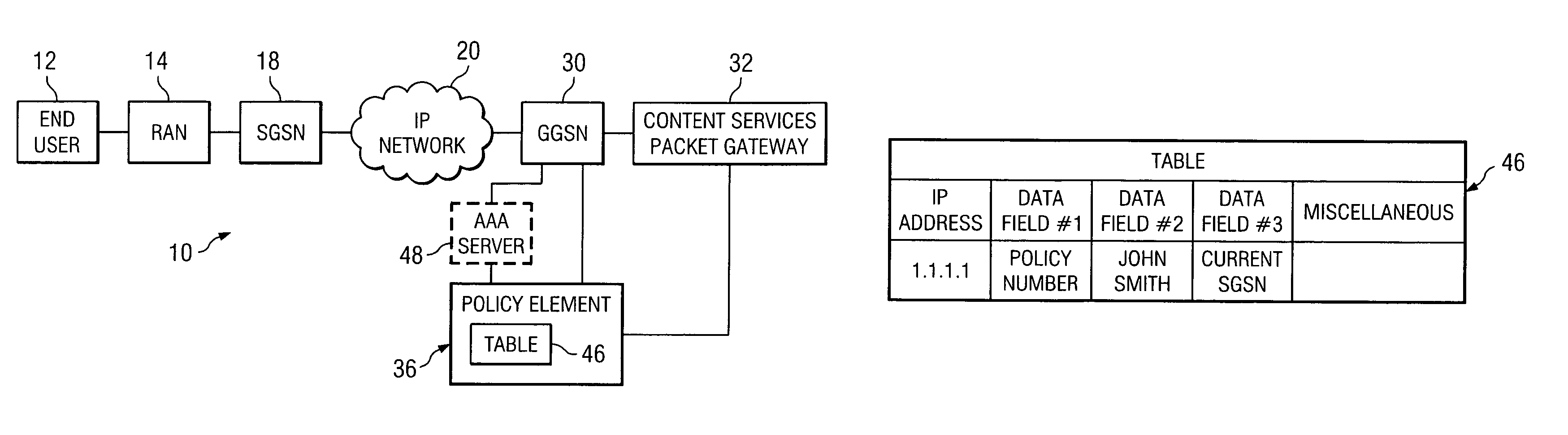
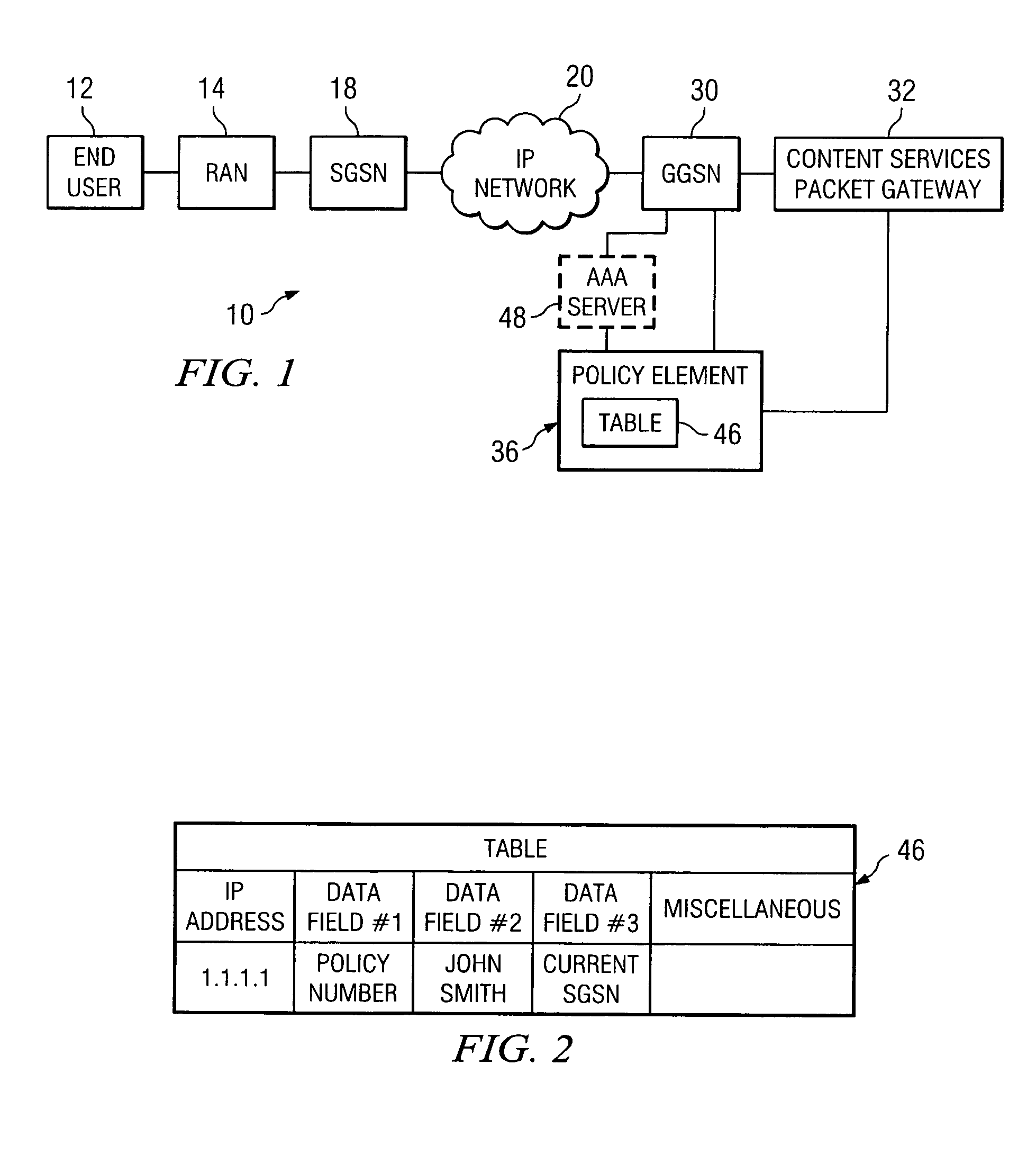
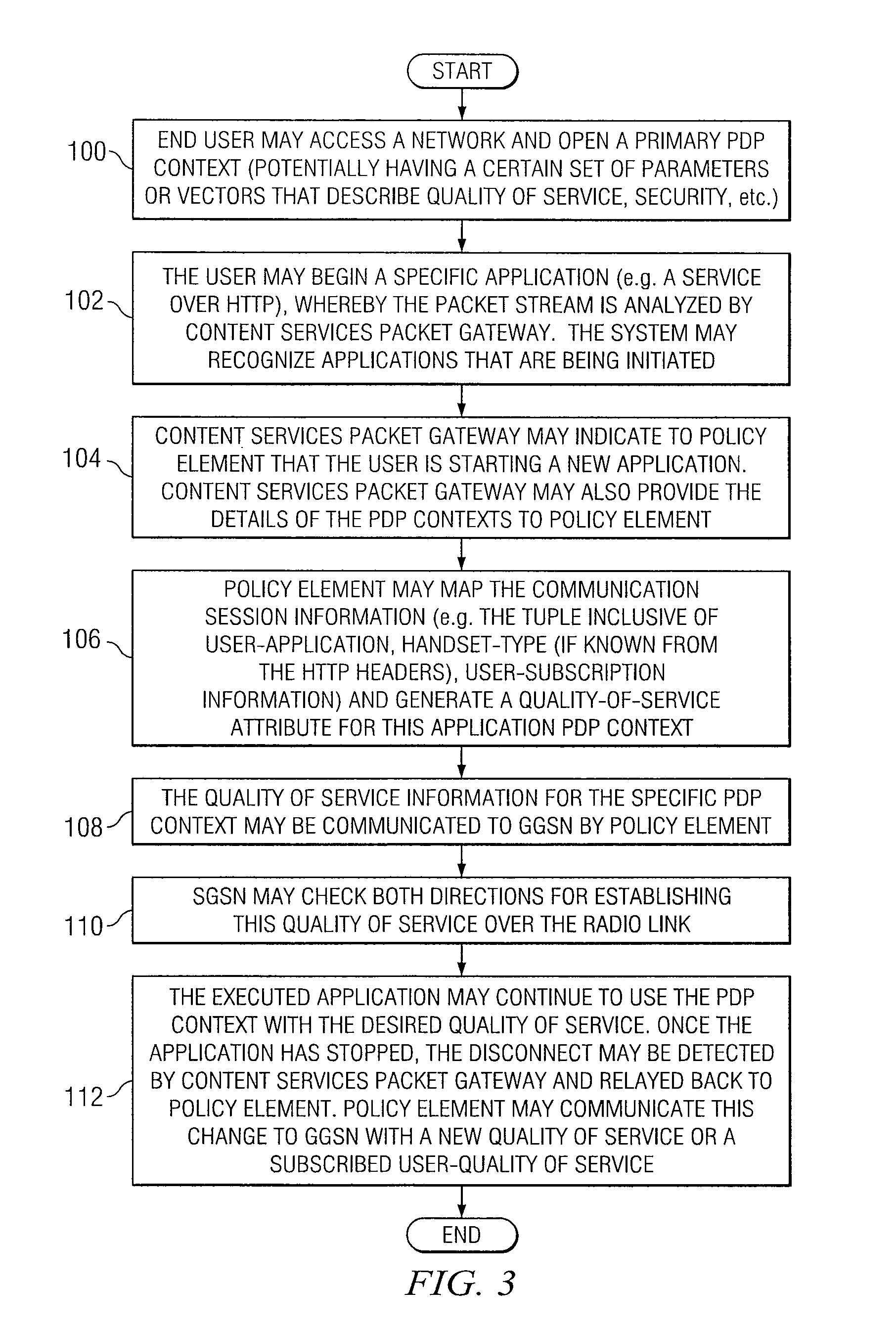
System and method for offering quality of service in a network environment
ActiveUS8050275B1Improve compatibilityFine granularityNetwork traffic/resource managementData switching by path configurationQuality of serviceDistributed computing
A method for providing a quality of service in a network environment is provided that includes receiving communication session information associated with a packet data protocol (PDP) link for an end user. The communication session information may be mapped to the end user in order to generate a quality of service attribute to be communicated to a next destination.
Owner:CISCO TECH INC
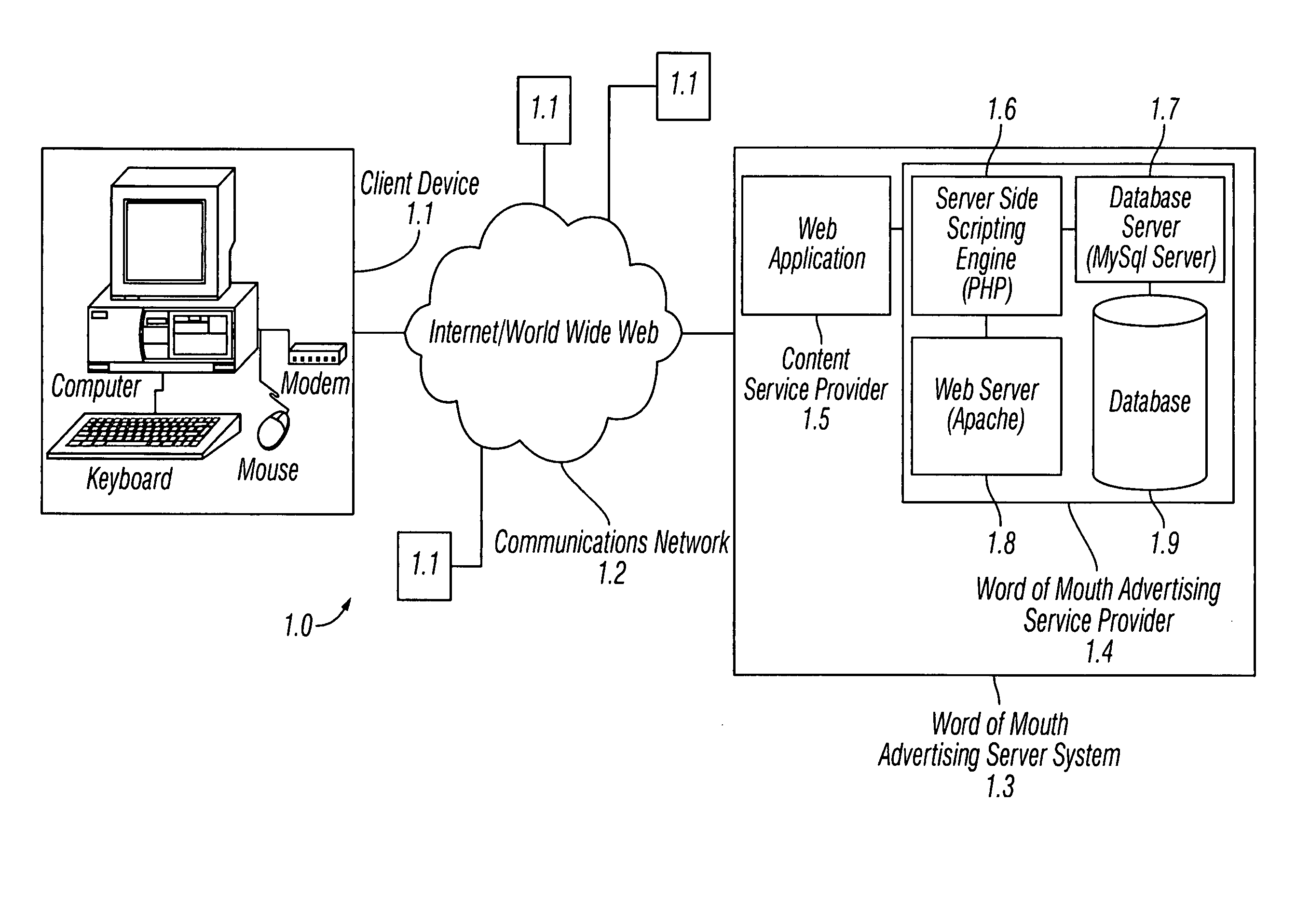
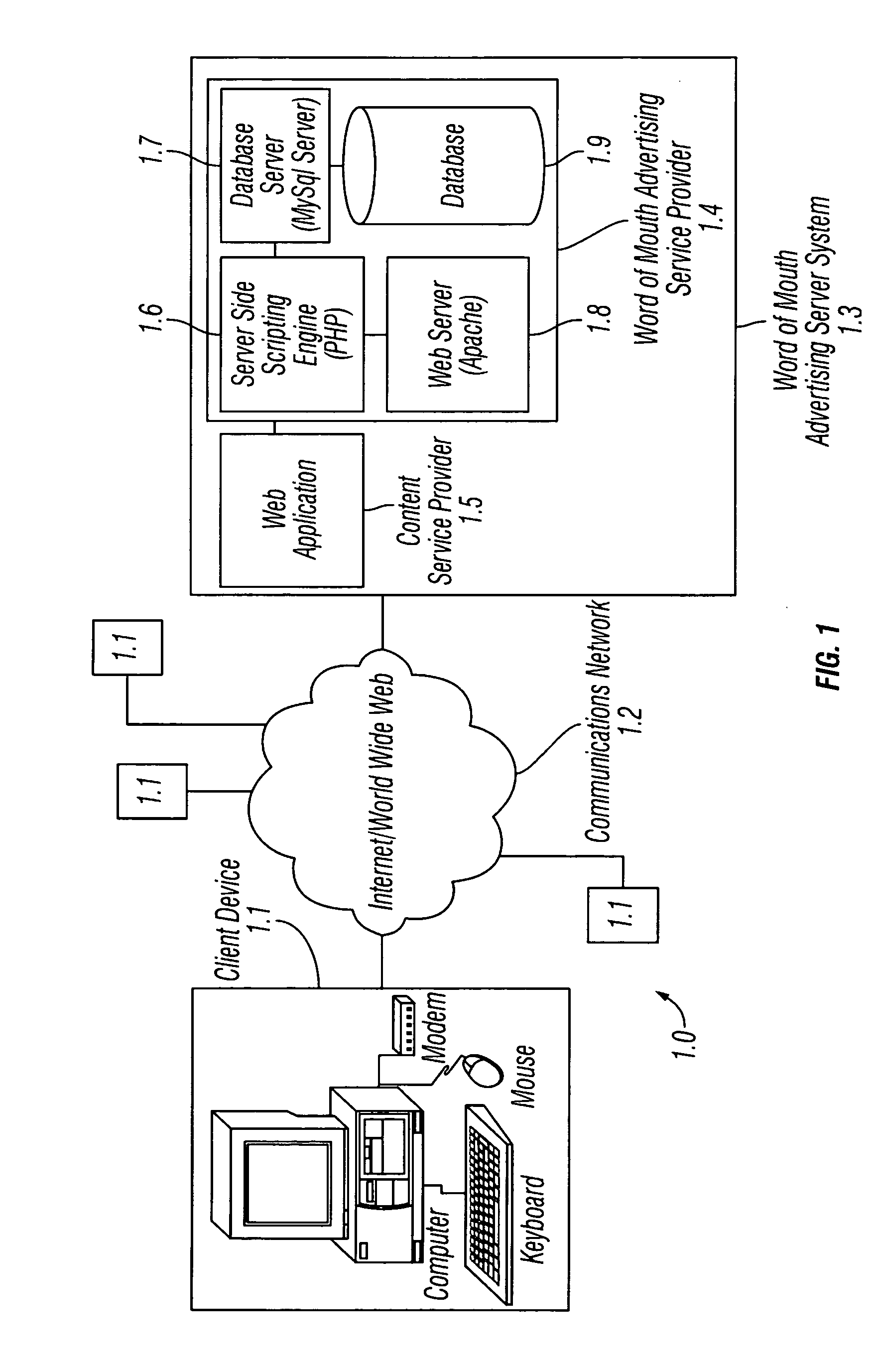
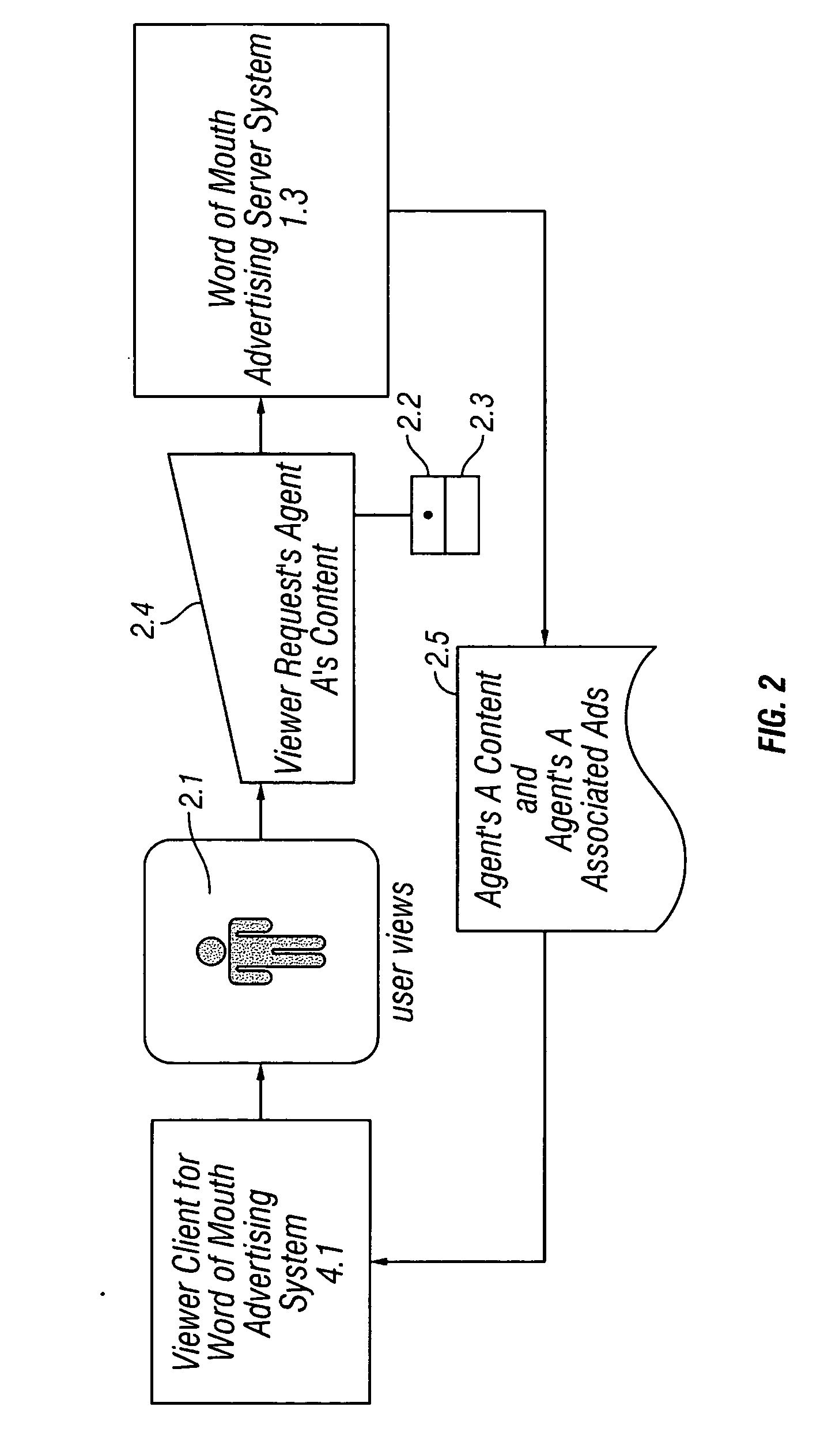
Method and system for word of mouth advertising via a communications network
ActiveUS20050149397A1Reduce disadvantagesEnhanced interactionAdvertisementsSpecial data processing applicationsService providerService provisioning
An advertising method and system allows individuals or groups to interactively select brands from a service provider to associate with their online presence in exchange for the online service, as part of an online service, or for some reward, monetary or otherwise. Individuals or groups select brands from a pool of advertisers based on personal preference and may use them as a means of expression for their online audience as part of an online service. This provides advertisers with self-selected targeted marketing to affinity groups, the online version of word of mouth advertising. Information regarding the online activity of these individuals or groups, including their audience, reach, and influence is used by the service provider in order to calculate the cost to the participating brand advertisers for supplying their advertisements to the service provider's pool as well as to solicit new brand advertisers for the pool.
Owner:RAKUTEN COMMERCE
Coaxial cable connector with integral grip bushing for cables of varying thickness
ActiveUS6848939B2Eliminate needReduce disadvantagesElectrically conductive connectionsSecuring/insulating coupling contact membersShielded cableCoaxial cable
A connector is provided for interconnecting a coaxial cable to an electrical device. The connector has an internal body and an external body which are assembled together, and which can be activated to clamp upon and seal to an inserted coaxial cable without disassembling the external body from the internal body. The external body includes a deformable inner collar that permits the connector to be attached and sealed to cables of varying thickness as are found on common single foil and braid cable, Tri Shield cable and Quad Shield cable.
Owner:IDEAL IND INC
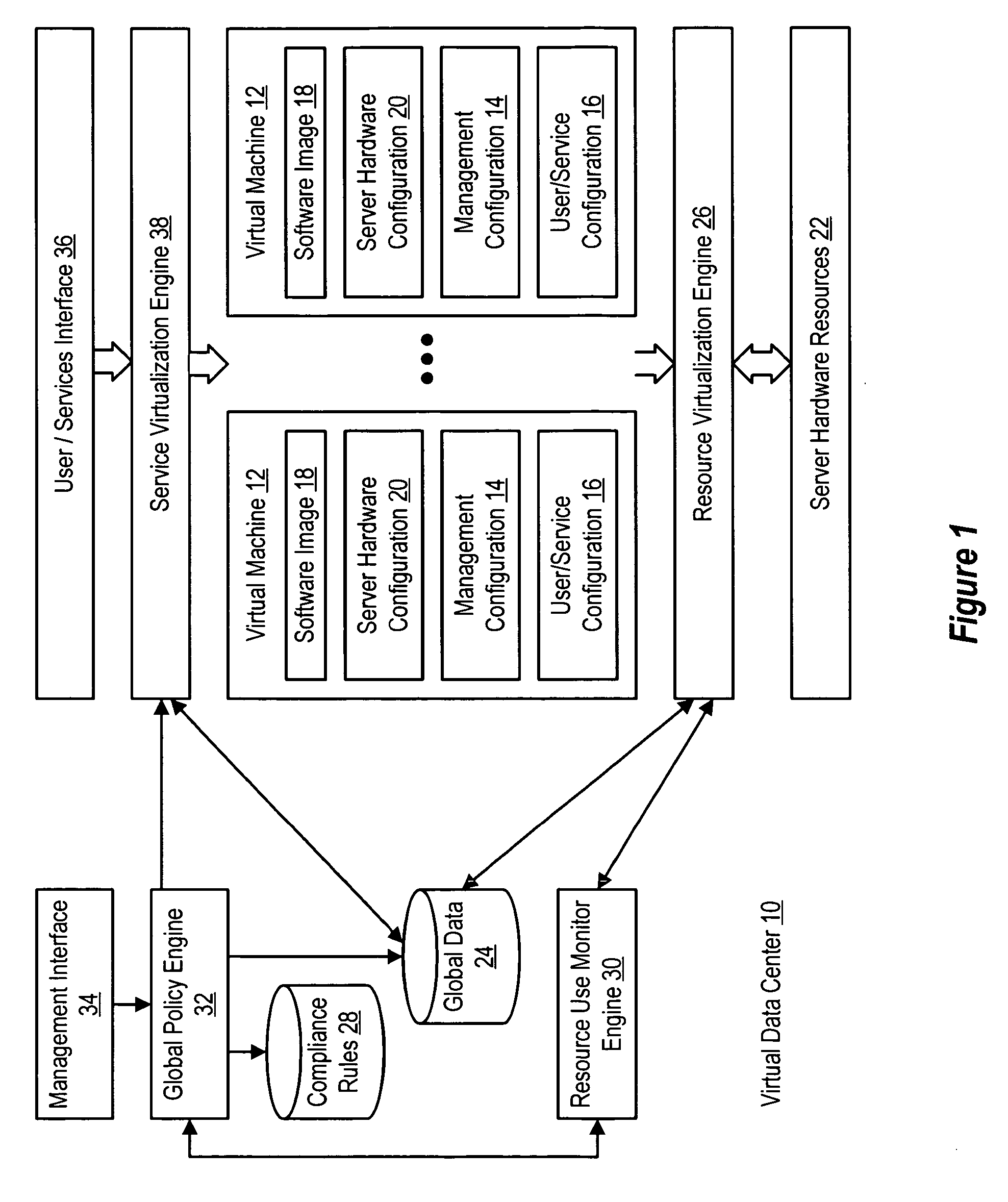
System and method using virtual machines for decoupling software from users and services
InactiveUS20060184935A1Reduce disadvantagesReduce problemsSoftware simulation/interpretation/emulationMemory systemsMaintenance releaseData center
Virtual machines of a virtual data center generate runtime instances with a software image, hardware configuration, management configuration and user / service configuration. Virtual data center resource use is monitored by reference to the management configuration of runtime instances, such as for environmental controls like power, cooling and balancing, or for policy limitations on users, software or hardware. Users or services generate runtime instances of stored virtual machines by reference to the user / service configuration, such as pricing or priority. In one example embodiment, the virtual machine software image comprises an application system preparation file that populates a read only application image common to plural virtual machines. Information unique to each virtual machine with respect to the application is maintained in the user / service configuration of the virtual machine and version information is maintained in the management configuration of the virtual machine. Updates to the application across each virtual machine are performed by updating the read only image or any of its configuration information for hardware configuration, management configuration or user / service configuration.
Owner:DELL PROD LP
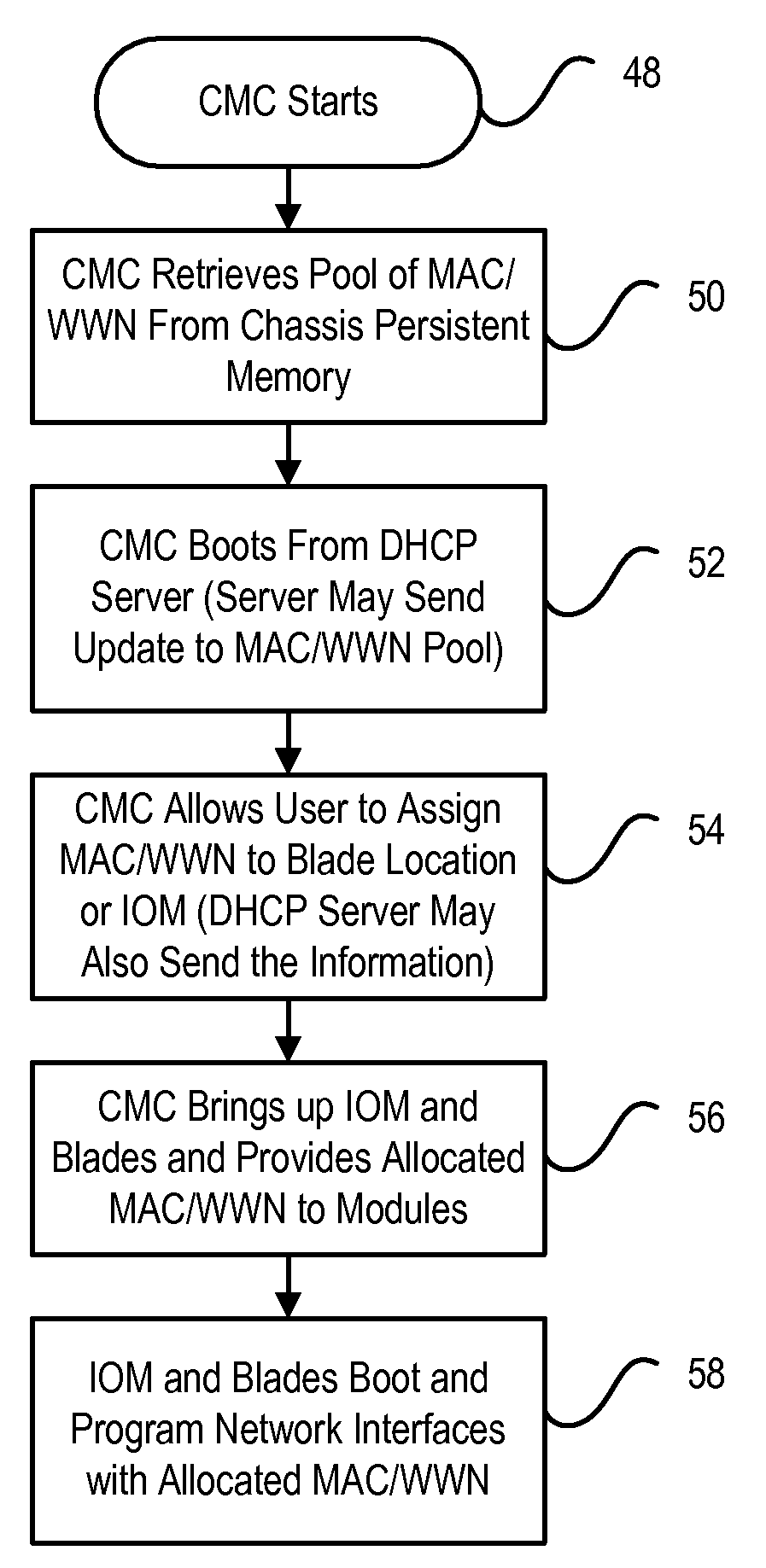
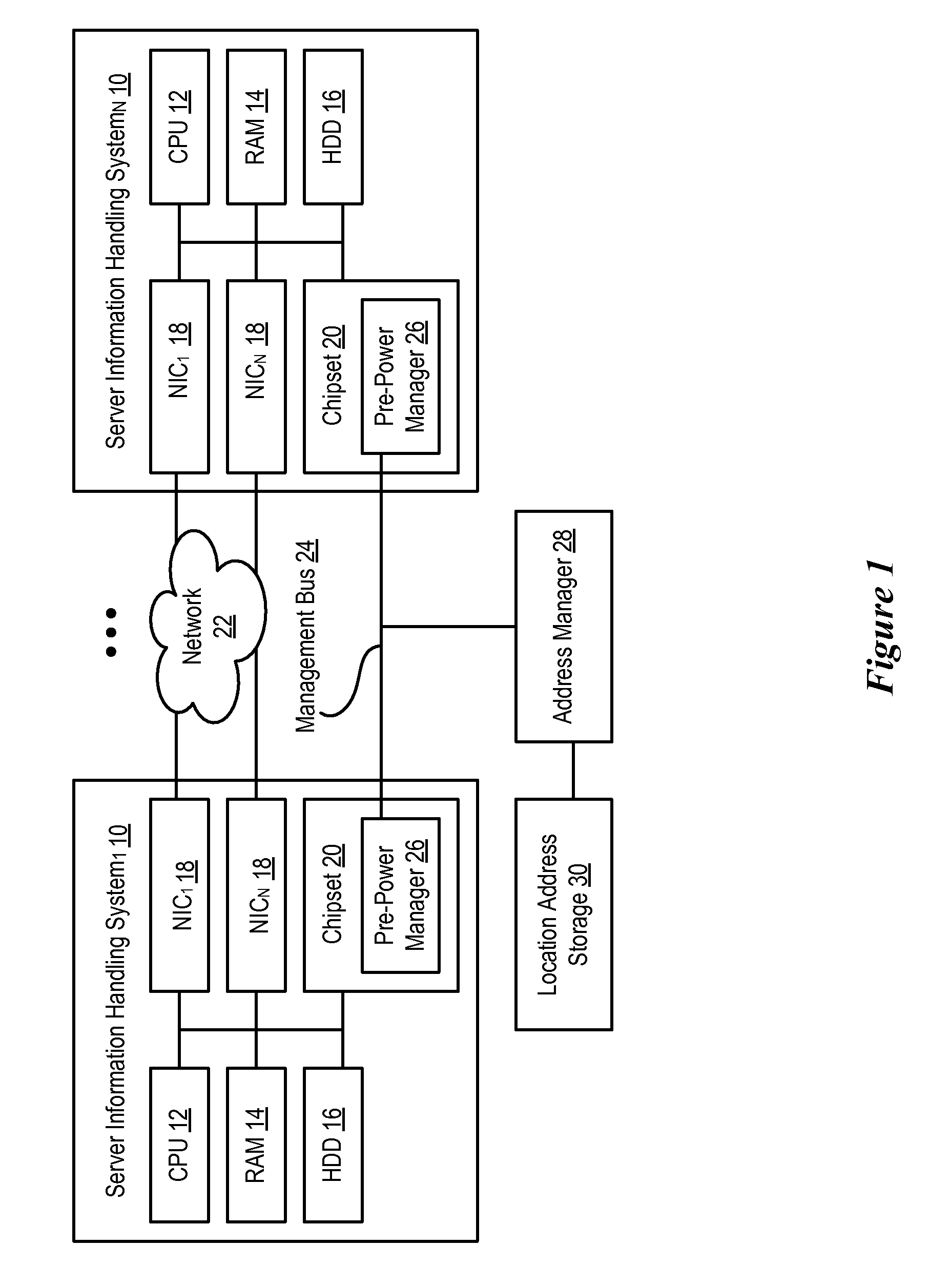
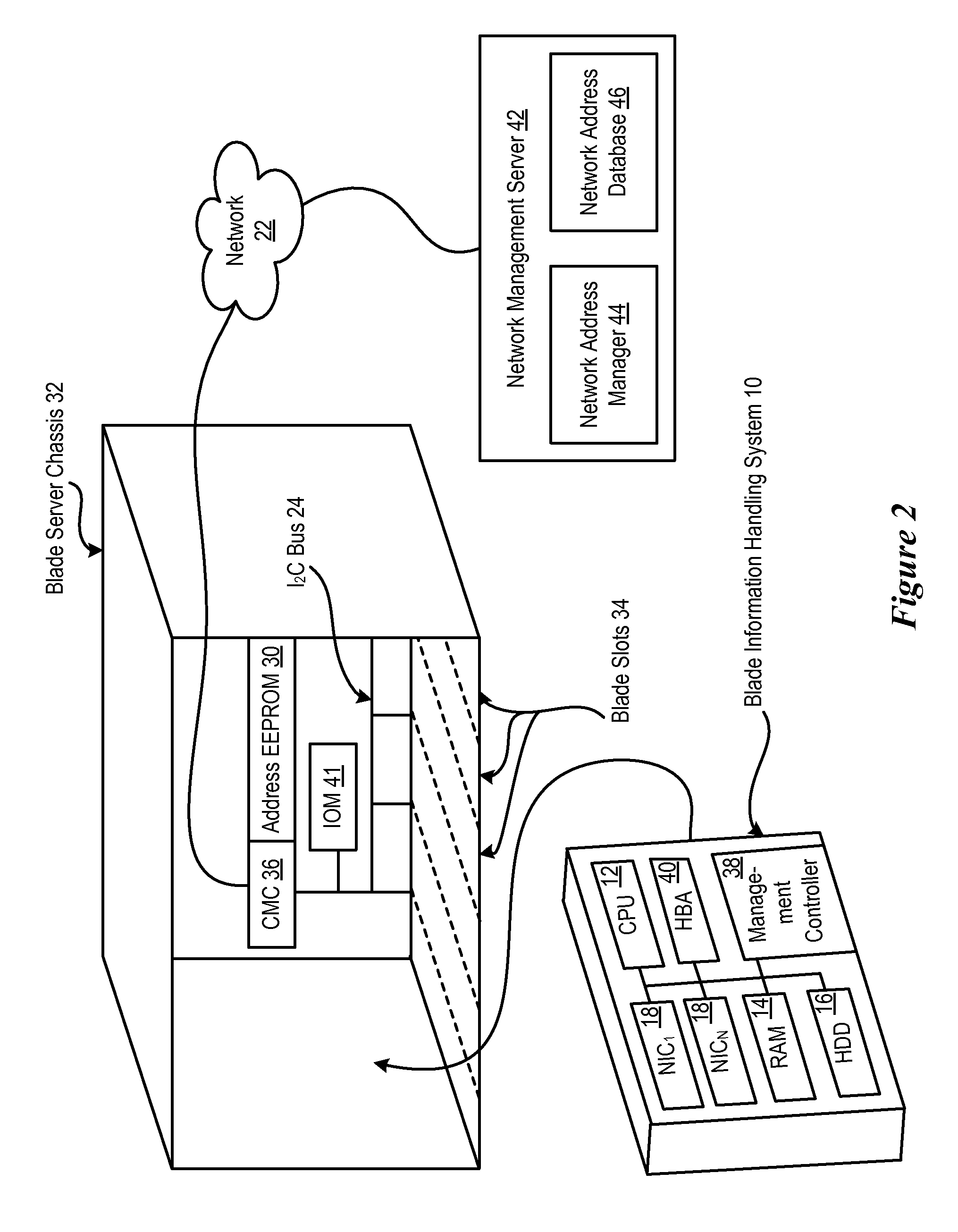
System And Method For Assigning Addresses To Information Handling Systems
ActiveUS20090077208A1Inadvertent duplication is preventedReduce disadvantagesError preventionFrequency-division multiplex detailsNetwork addressingNetwork communication
Information handling system network addresses are managed to support a consistent MAC address for iSCSI and fibre channel host bus adapter. For example, a management controller retrieves a MAC address from persistent memory, such as a network location, and assigns the MAC address to a non-persistent memory of a predetermined information handling system network component so that the MAC address remains consistent even if the network component is replaced. For example, an offload engine that supports network communications with iSCSI receives a MAC address from a network location and applies the MAC address for use by a host bus adapter. Alternatively, an offload engine supports Fibre Channel with World Wide Name or World Wide Identifier address assignments.
Owner:DELL PROD LP
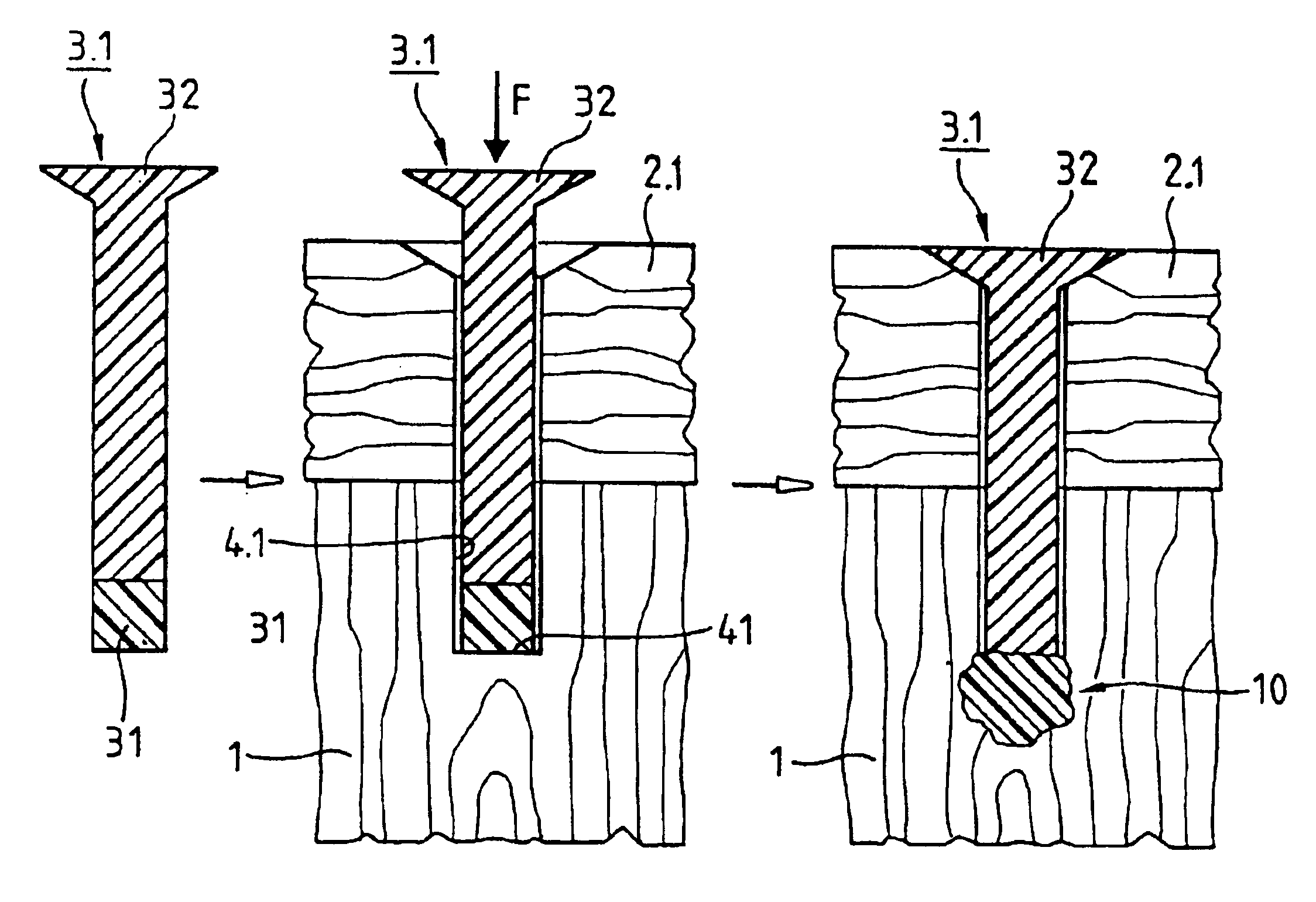
Process for anchoring connecting elements in a material with pores or cavities and connecting elements therefor
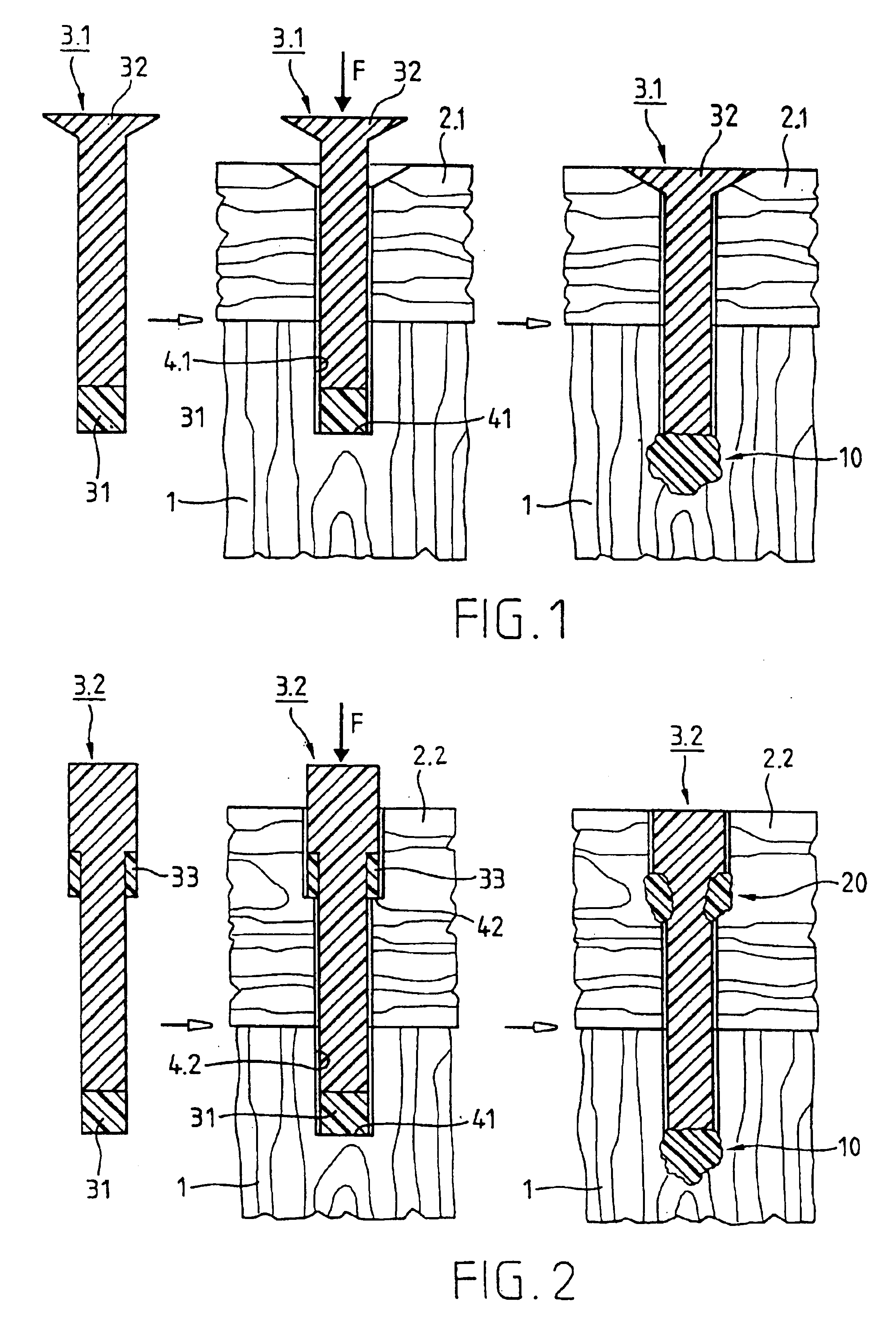
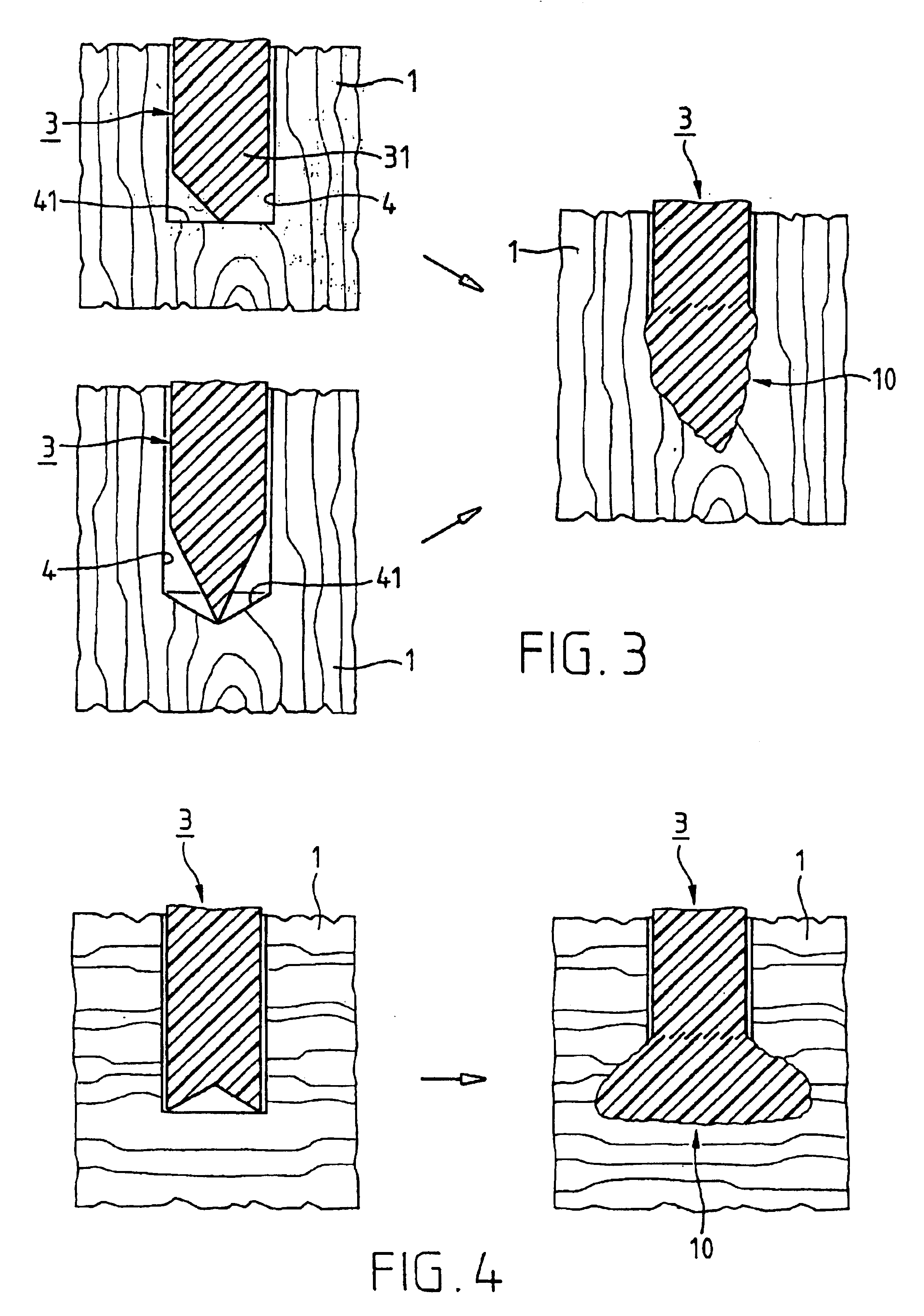
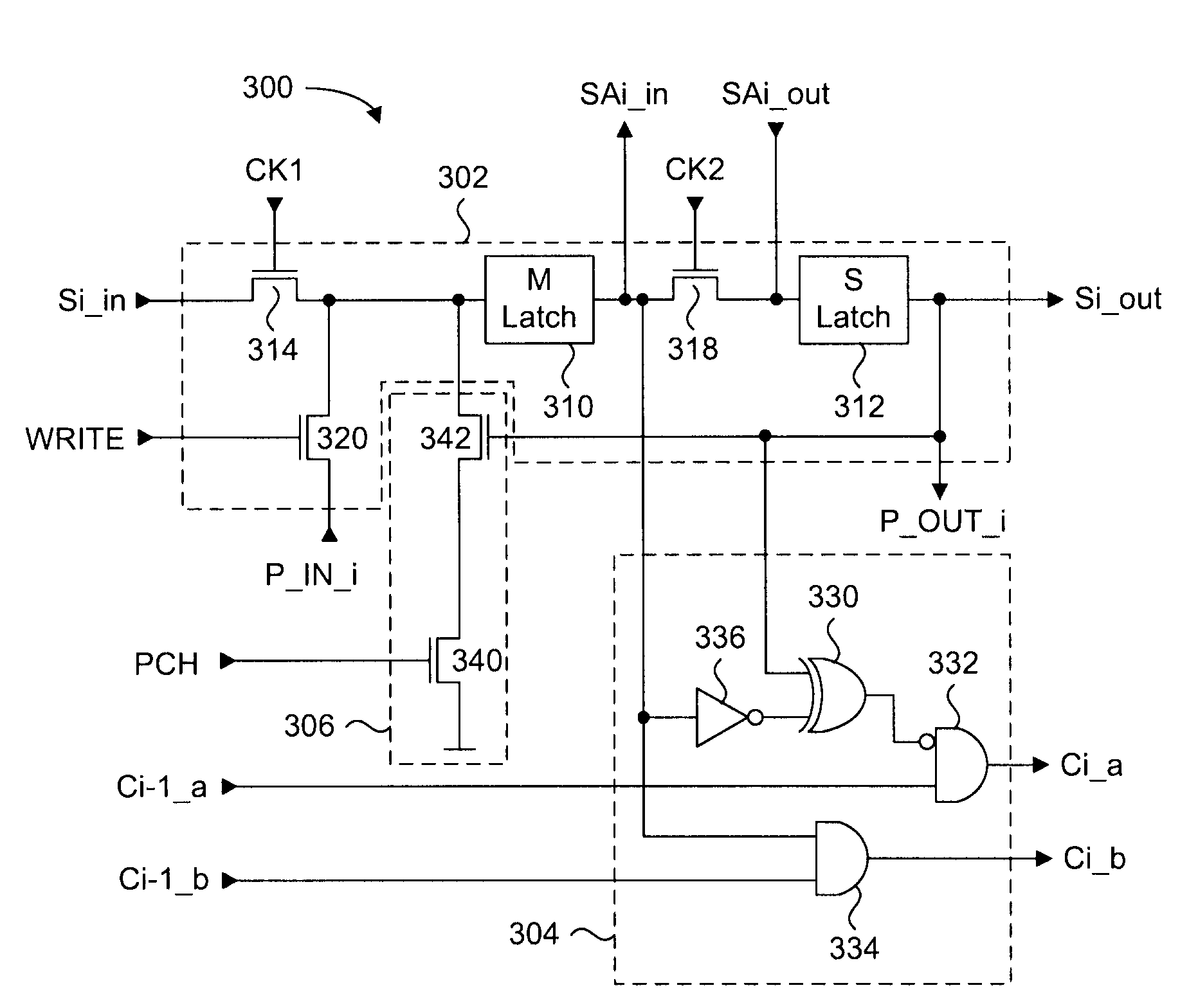
InactiveUS6913666B1Easy to reachReduce disadvantagesRivetsCylinder headsEngineeringUltrasonic vibration
A joining pin (3.2) with which two parts (1 and 2) made from a porous material, particularly wood or a wood-like material, are to be joined together, is anchored in the porous material at predetermined anchoring points (31, 33). For this purpose, a bore (4.2) with a closed inner end (41) is made in the parts (1 and 2). The shape of this bore (4.2) is so matched to the joining pin (3.2) that it can be introduced substantially without force expenditure into the bore and is positionable in a first position. At least one predetermined anchoring point (31, 33) between the joining pin (3.2) and the wall of the bore (4.2) is formed when pressure is built up by pressing the joining pin (3.2) with a pressing force (F) more deeply into the bore to a second position. Energy is supplied in a planned manner to the joining pin (3.2) so that at the predetermined anchoring points (31, 33) the thermoplastic material of the joining pin (3.2) is plasticized. The locally plasticized plastic material is pressed by the local pressure into the porous material of the parts and forms local, macroscopic anchors (10, 20). The joining pin (3.2) is, e.g., made entirely from a thermoplastic material and the energy for plasticizing is supplied thereto by ultrasonic vibration.
Owner:WOODWELDING
Dual function data register
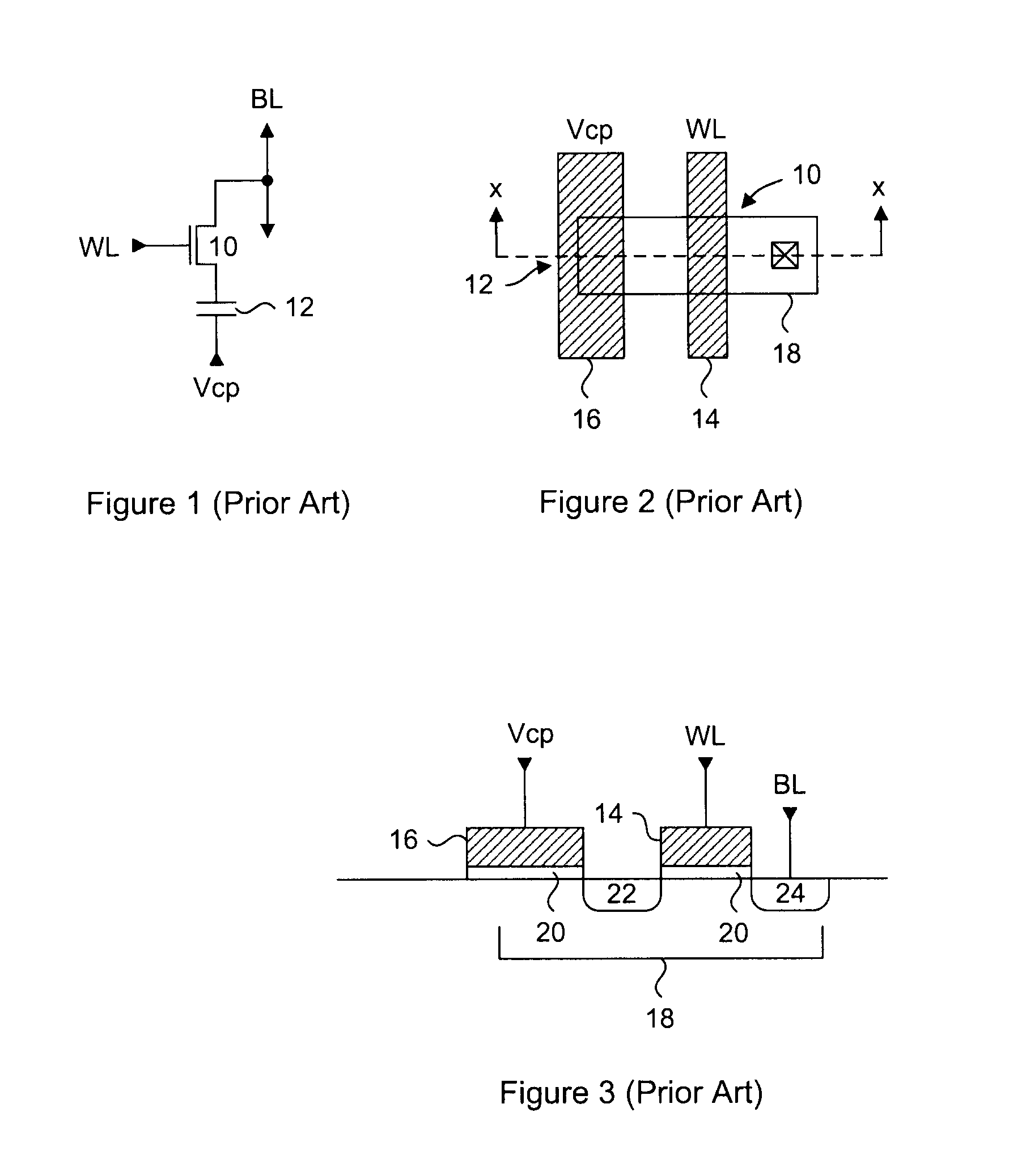
ActiveUS20090290434A1Reduce disadvantagesRead-only memoriesDigital storageProcessor registerTheoretical computer science
A dual function serial and parallel data register with integrated program verify functionality. The master and slave latching circuits of the dual function data register can concurrently store two different words of data. In a program verify operation, the master latch stores program data and the slave latch will receive and store read data. Comparison logic in each register stage will compare the data of both latches, and integrate the comparison result to that of the previous register stage. The final single bit result will indicate the presence of at least one bit that has not been programmed. Automatic program inhibit logic in each stage will prevent successfully programmed bits from being re-programmed in each subsequent reprogram cycle. Either data word can be serially clocked out by selectively starting the shift operations on either the low or high active logic level of a clock signal.
Owner:SYNOPSYS INC
Method and system for collecting, sharing and tracking user or group associates content via a communications network
InactiveUS20050203801A1Reduce disadvantagesEfficient methodMultiple digital computer combinationsCommerceInternet auctionsSubsequent revision
A content collection, sharing, and tracking method and system allows individuals or groups to incorporate the content of one another into their own context for creative referenced re-use. Users browse the content of other users and add content to a tool known as a GRAB BAG. Users may be part of affinity groups such as social networks or have common interests such as an interest in a single Internet auction site. The GRAB BAG storage system keeps track subsequent revisions and contexts for the piece of content in all instances where it is grabbed. When users incorporate the content they have grabbed into their own content, it appears with a link to the original author as well as with links to track the dissemination of the original content. The GRAB BAG storage system is created to reference content so that identical items under two different contexts need not be duplicated in full.
Owner:RAKUTEN COMMERCE
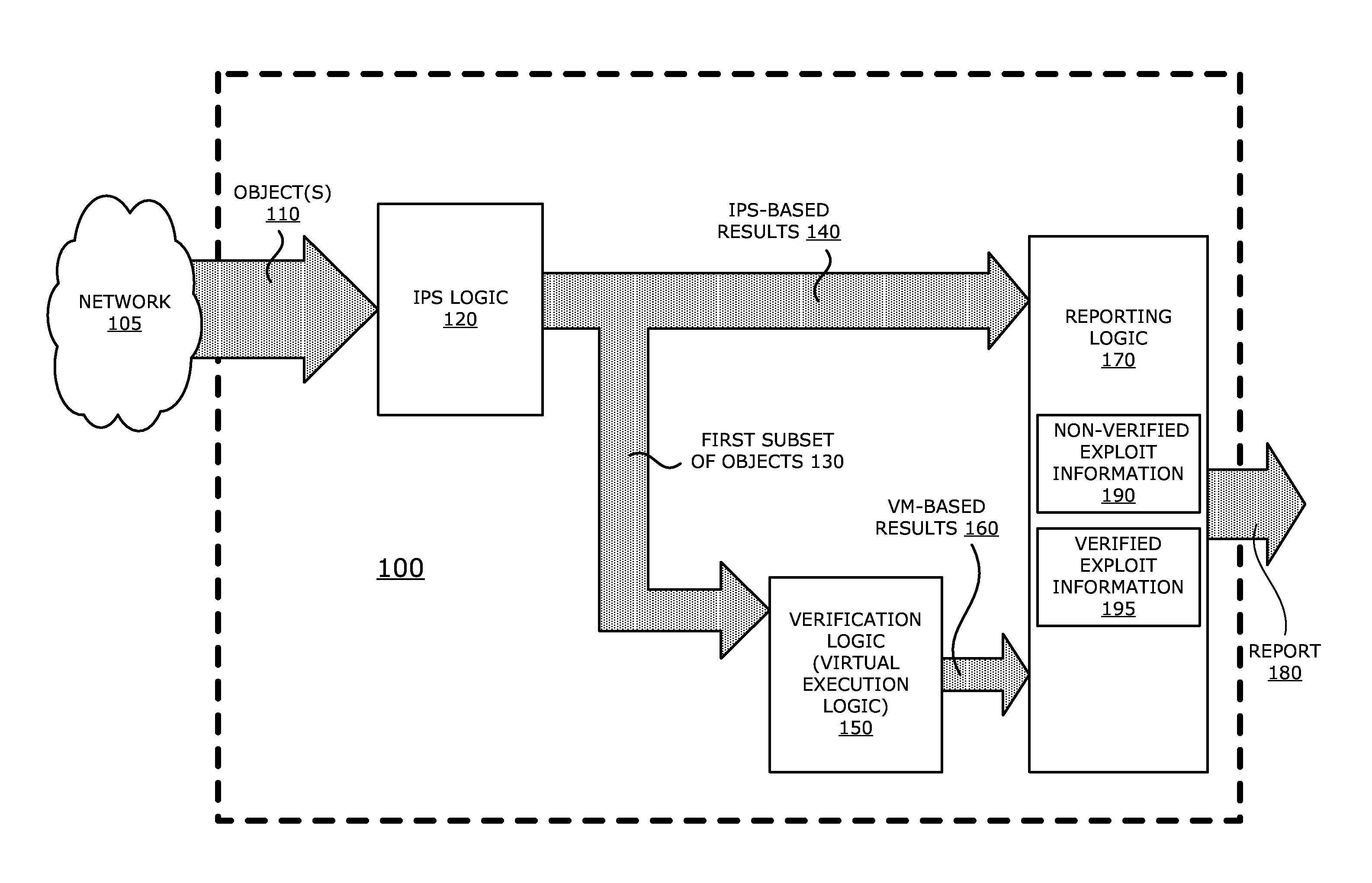
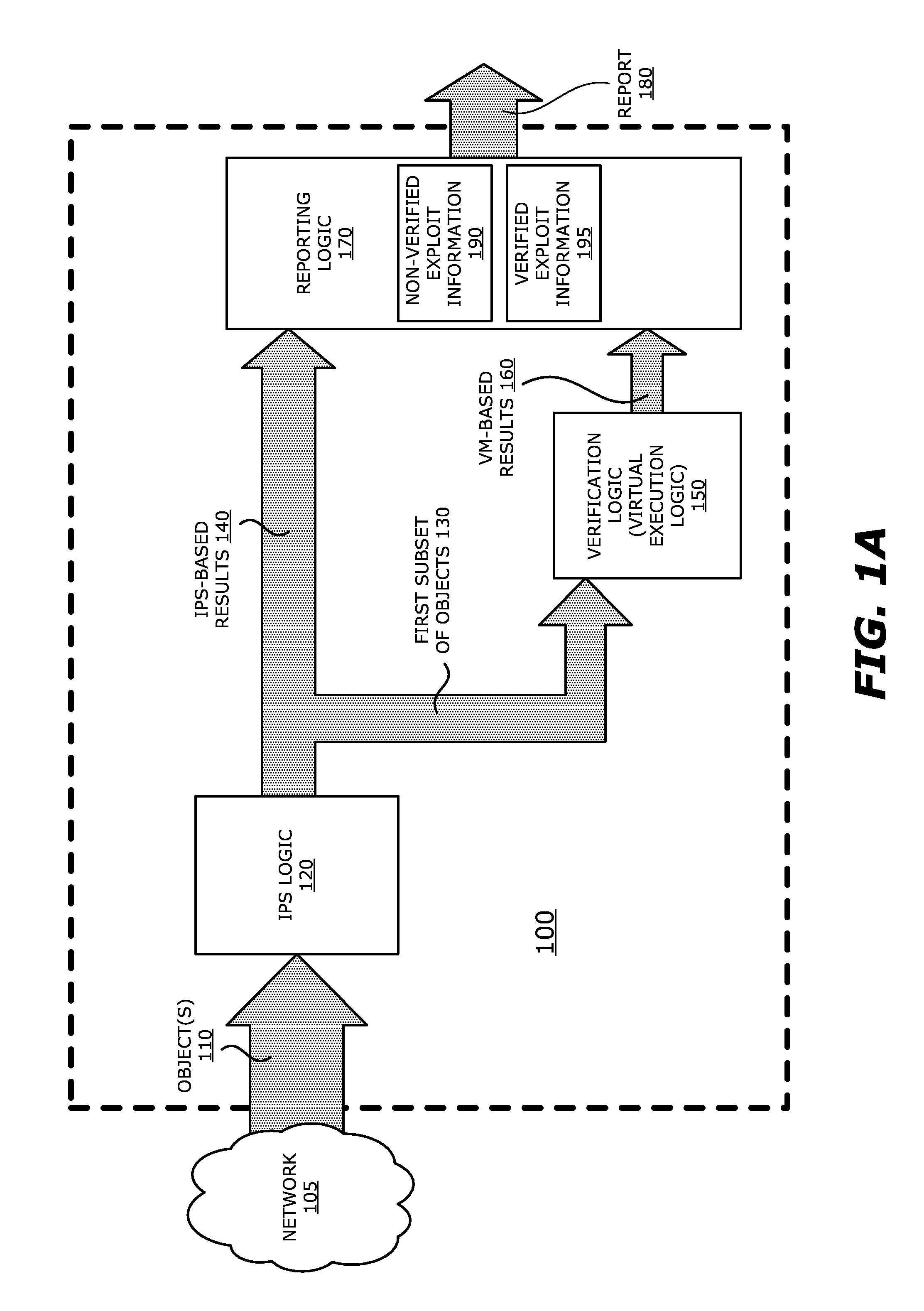
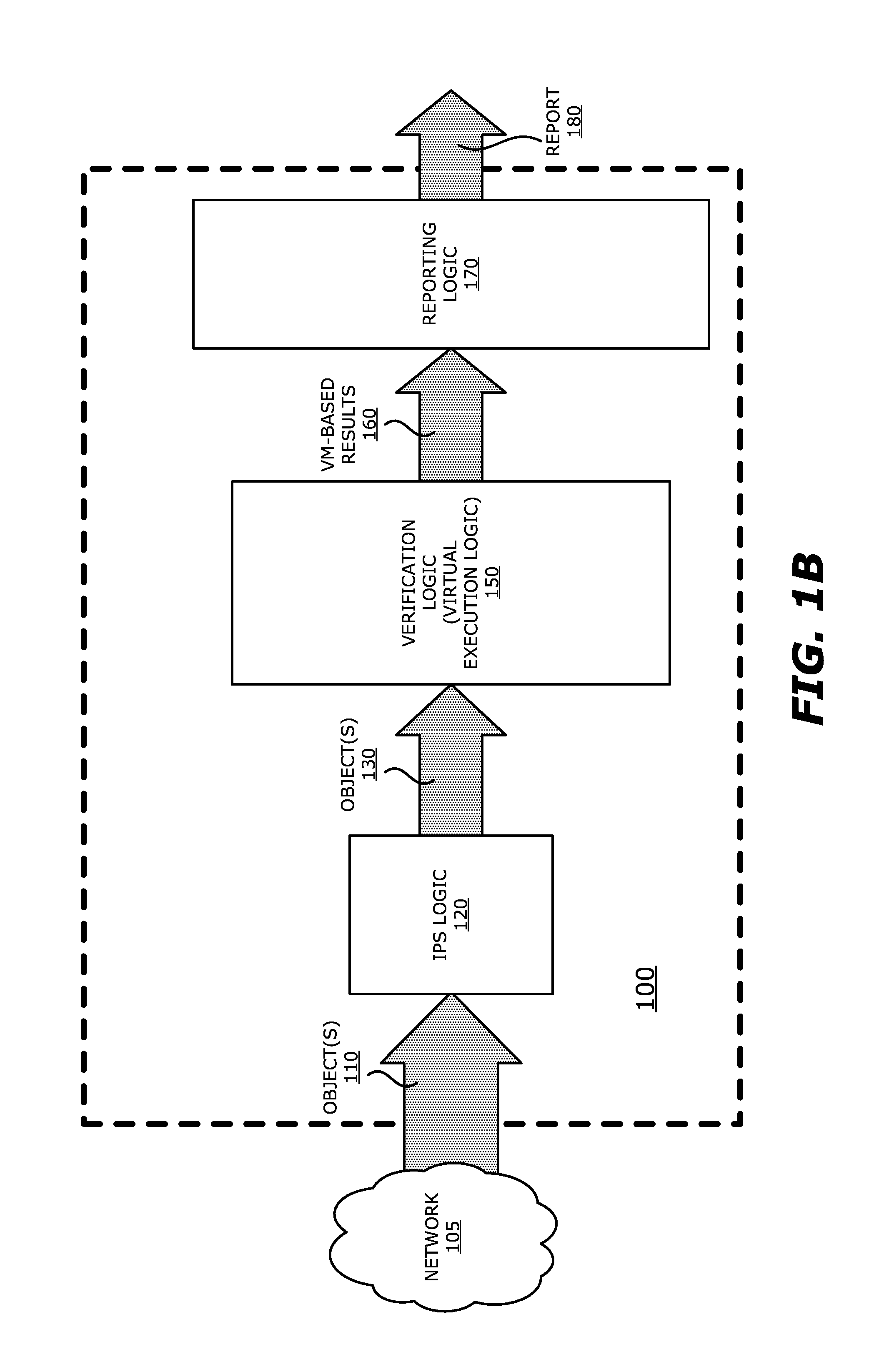
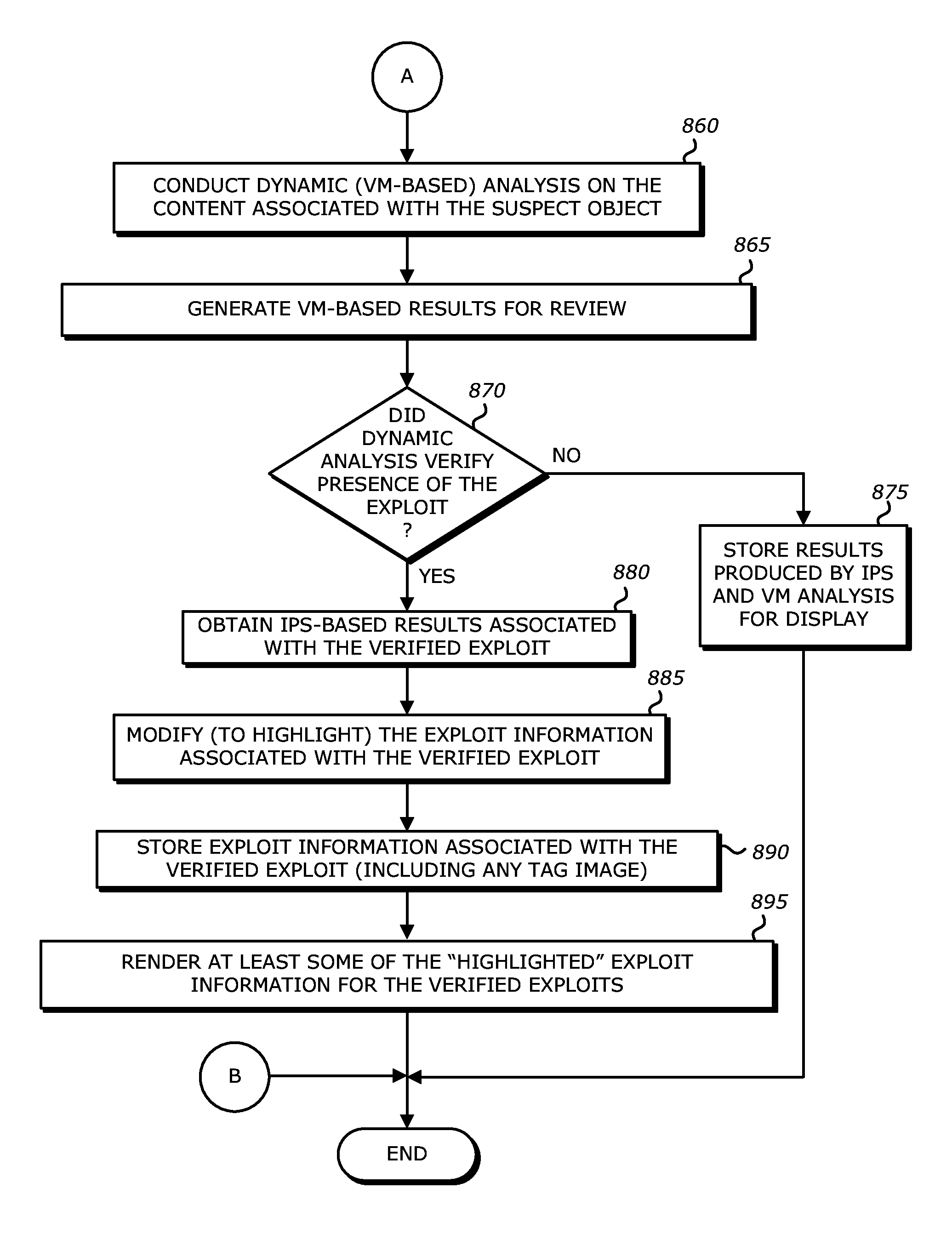
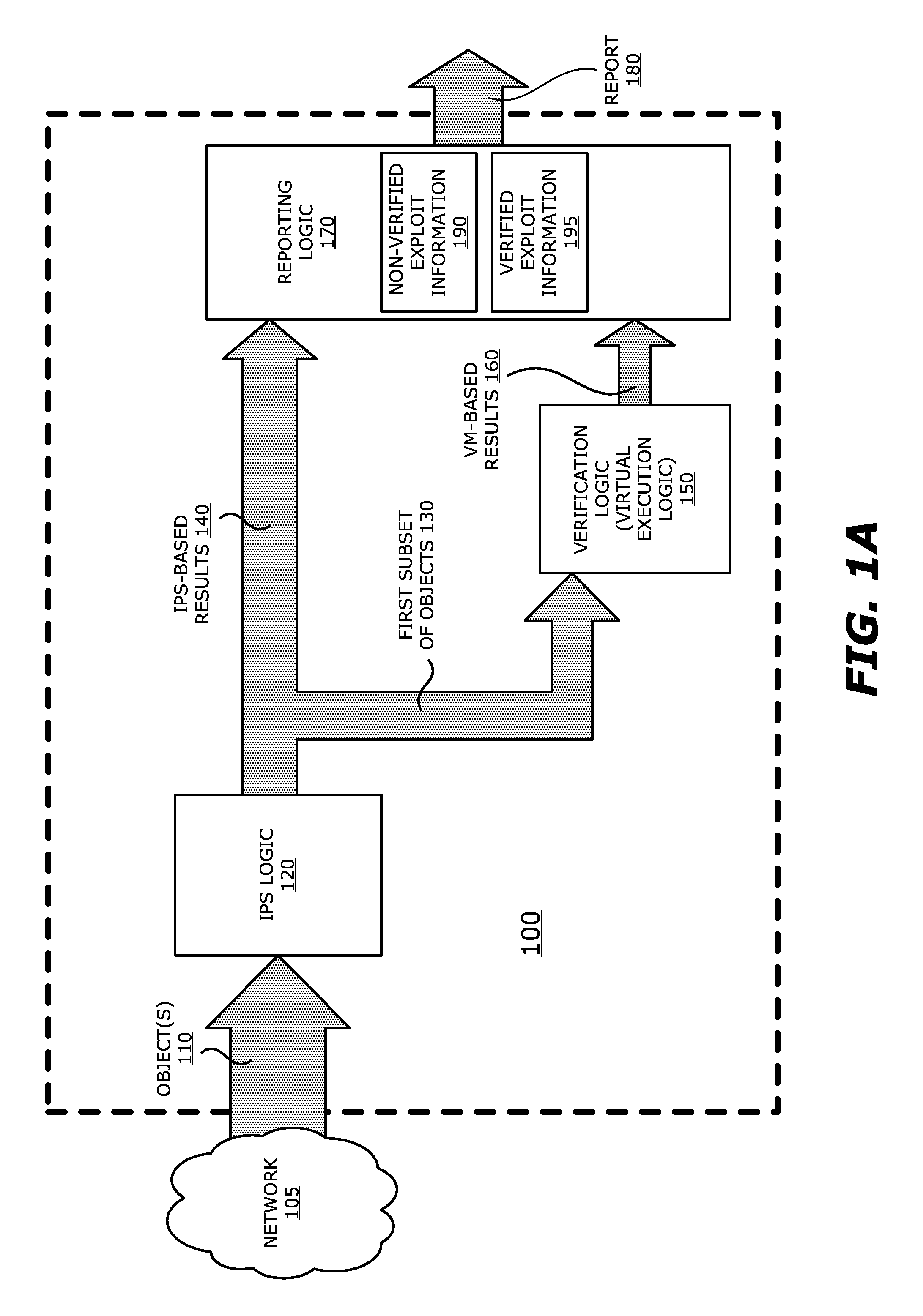
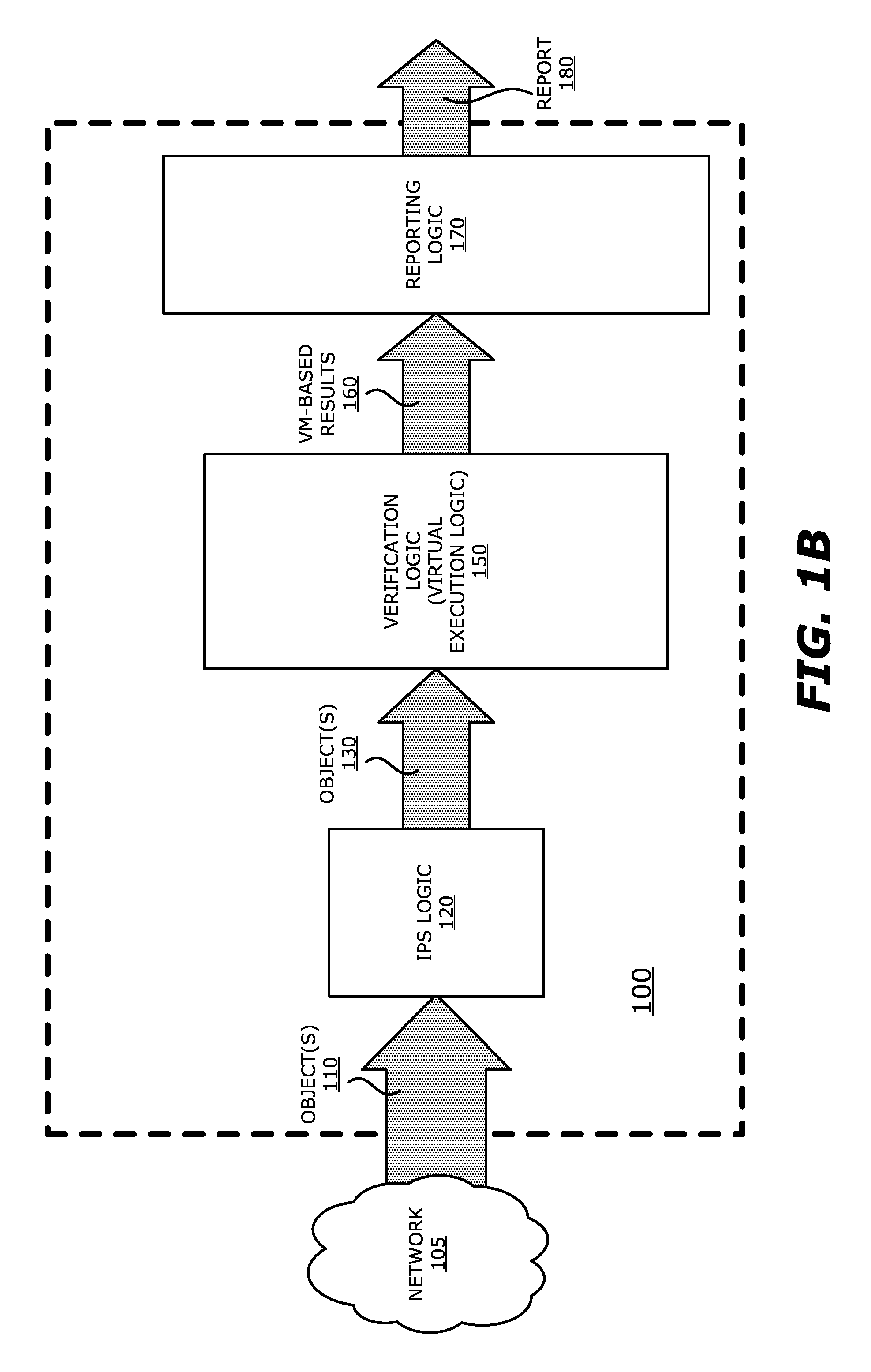
System, apparatus and method for automatically verifying exploits within suspect objects and highlighting the display information associated with the verified exploits
ActiveUS20150186645A1Quickly and easily determineReduce disadvantagesMemory loss protectionError detection/correctionAnomalous behaviorProtection system
According to one embodiment, a threat detection system is integrated with intrusion protection system (IPS) logic and virtual execution logic. The IPS logic is configured to receive a first plurality of objects and filter the first plurality of objects by identifying a second plurality of objects as suspicious objects. The second plurality of objects is a subset of the first plurality of objects and is lesser or equal in number to the first plurality of objects. The virtual execution logic is configured to automatically verify whether any of the suspicious objects is an exploit. The virtual execution logic comprises at least one virtual machine configured to virtually process content within the suspicious objects and monitor for anomalous behaviors during the virtual processing that are indicative of exploits.
Owner:FIREEYE SECURITY HLDG US LLC
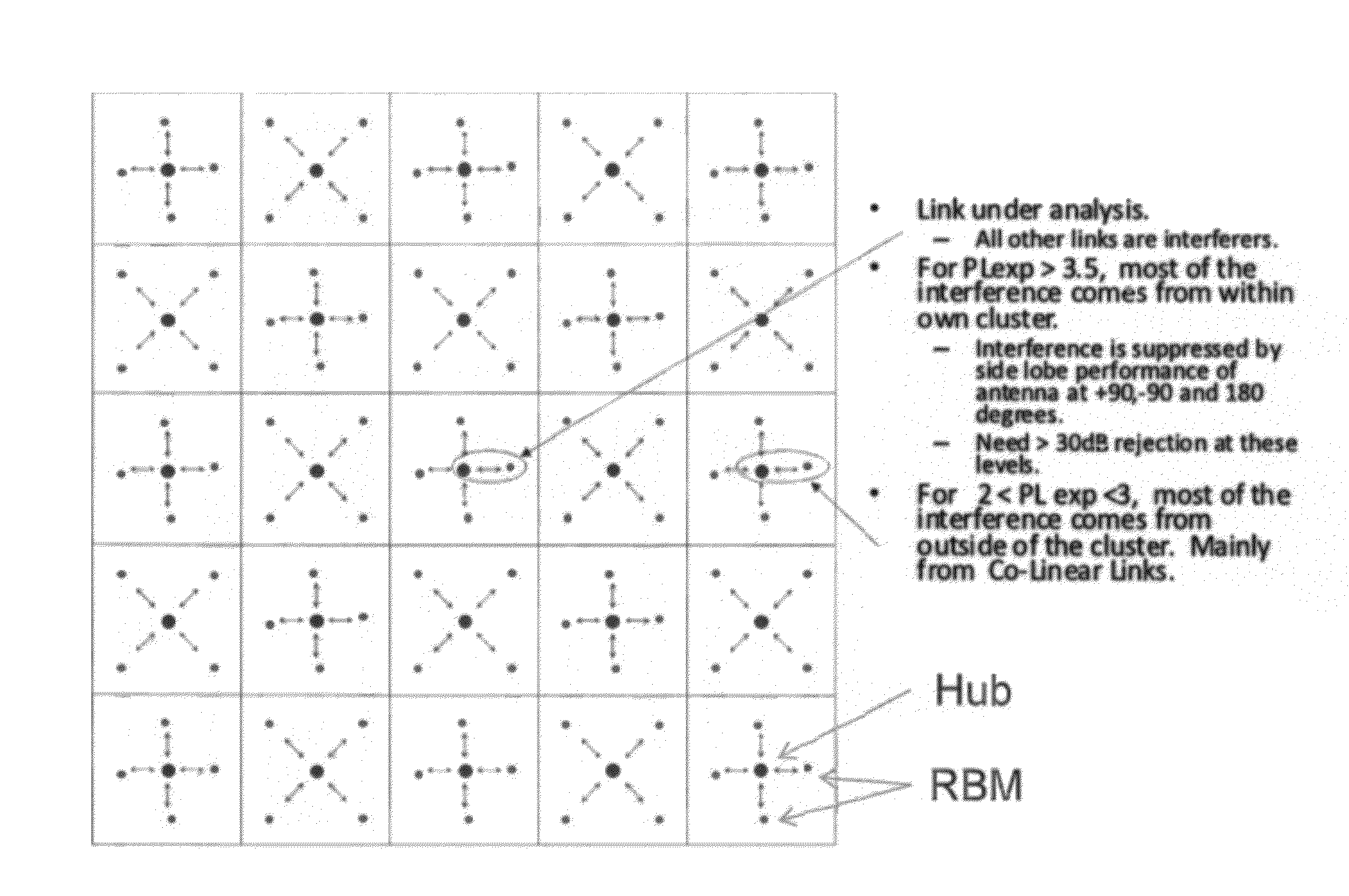
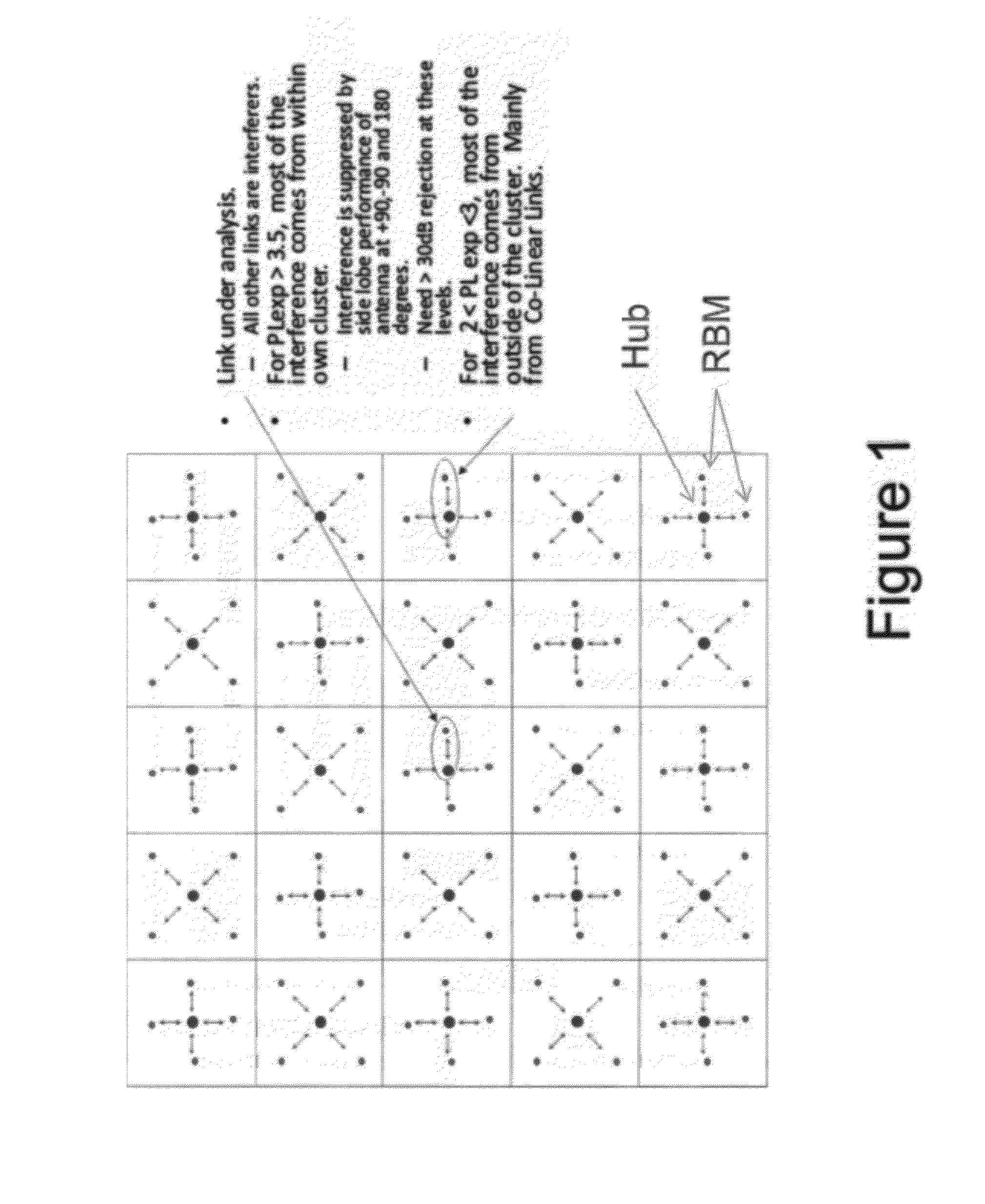
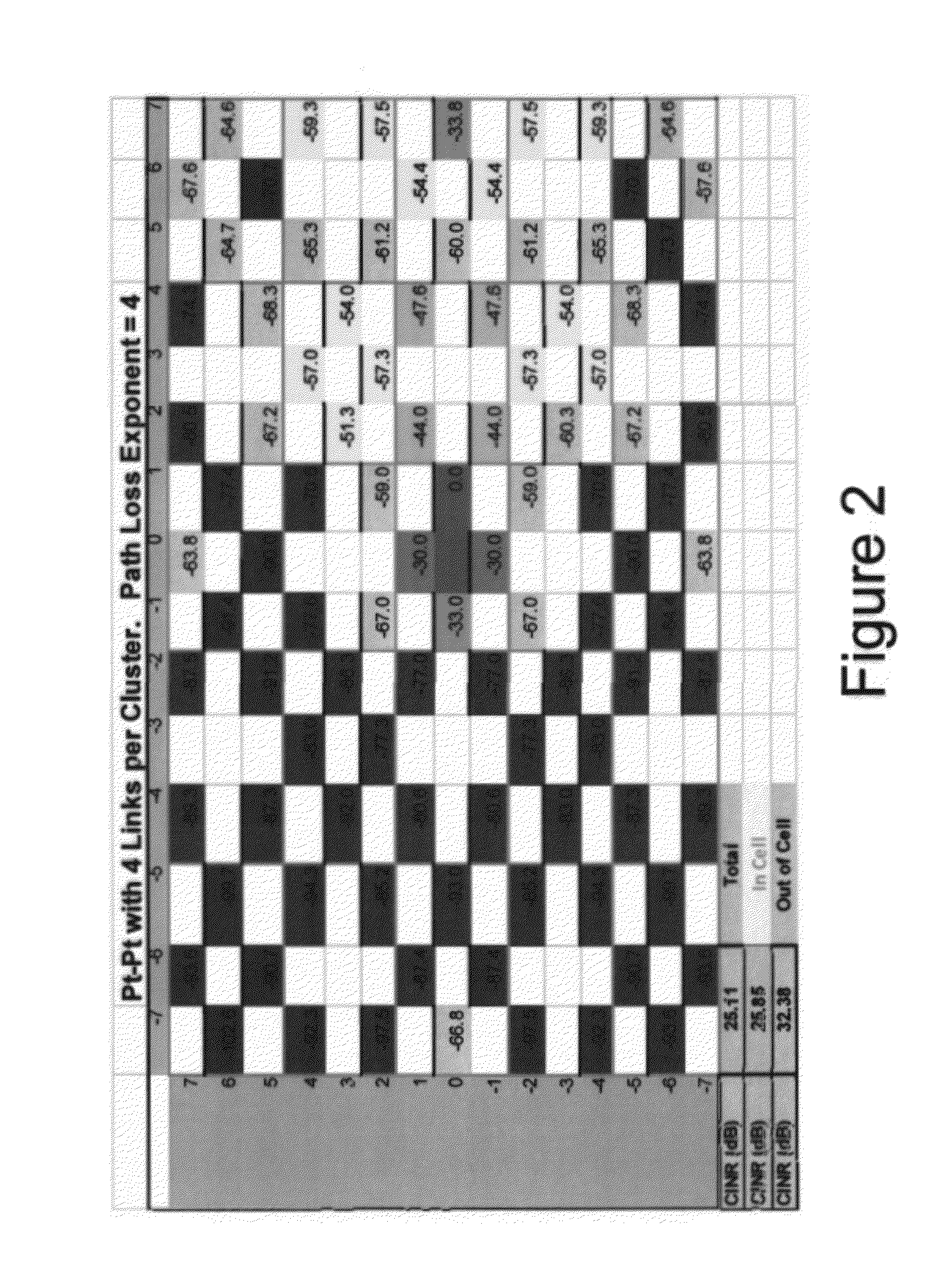
System and Method for Co-Channel Interference Measurement and Managed Adaptive Resource Allocation for Wireless Backhaul
ActiveUS20120236731A1Reduce disadvantagesReduce co-channel interferenceError preventionTransmission systemsResource blockPublic resource
A system, method, and software are provided for measuring co-channel interference in a wireless network with particular application for management of resource allocation for Non Line of Sight (NLOS) wireless backhaul in MicroCell and PicoCell networks. Given the difficulty of predicting the mutual interference between multiple links, DownLink and UpLink co-channel interference are characterized between each Hub and each Remote Backhaul Module Unit periodically during active service. Beneficially, the co-channel interference metrics are used as the basis for intelligently and adaptively managing network resources to substantially reduce interference and increase the aggregate data capacity of the network e.g. by grouping of interfering and / or non-interfering links, and managing resource block allocations accordingly, i.e. assigning common resource blocks preferentially to weakly interfering links or groups of links and allocating different resource blocks or orthogonal channels to strongly interfering links or groups of links.
Owner:BLINQ NETWORKS
System, apparatus and method for automatically verifying exploits within suspect objects and highlighting the display information associated with the verified exploits
ActiveUS9306974B1Quickly and easily determineReduce disadvantagesPlatform integrity maintainanceAlarmsAnomalous behaviorProtection system
Owner:FIREEYE SECURITY HLDG US LLC
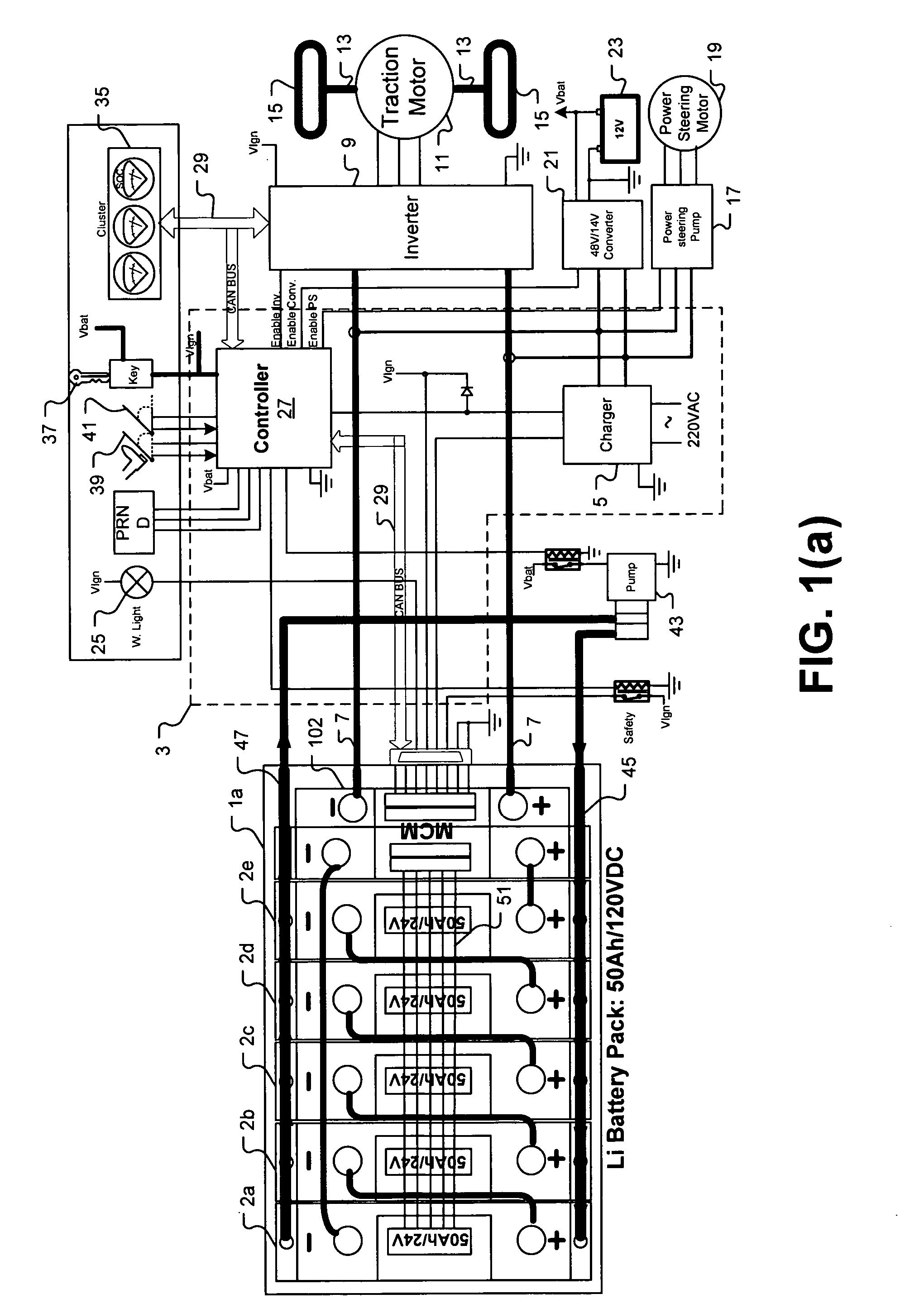
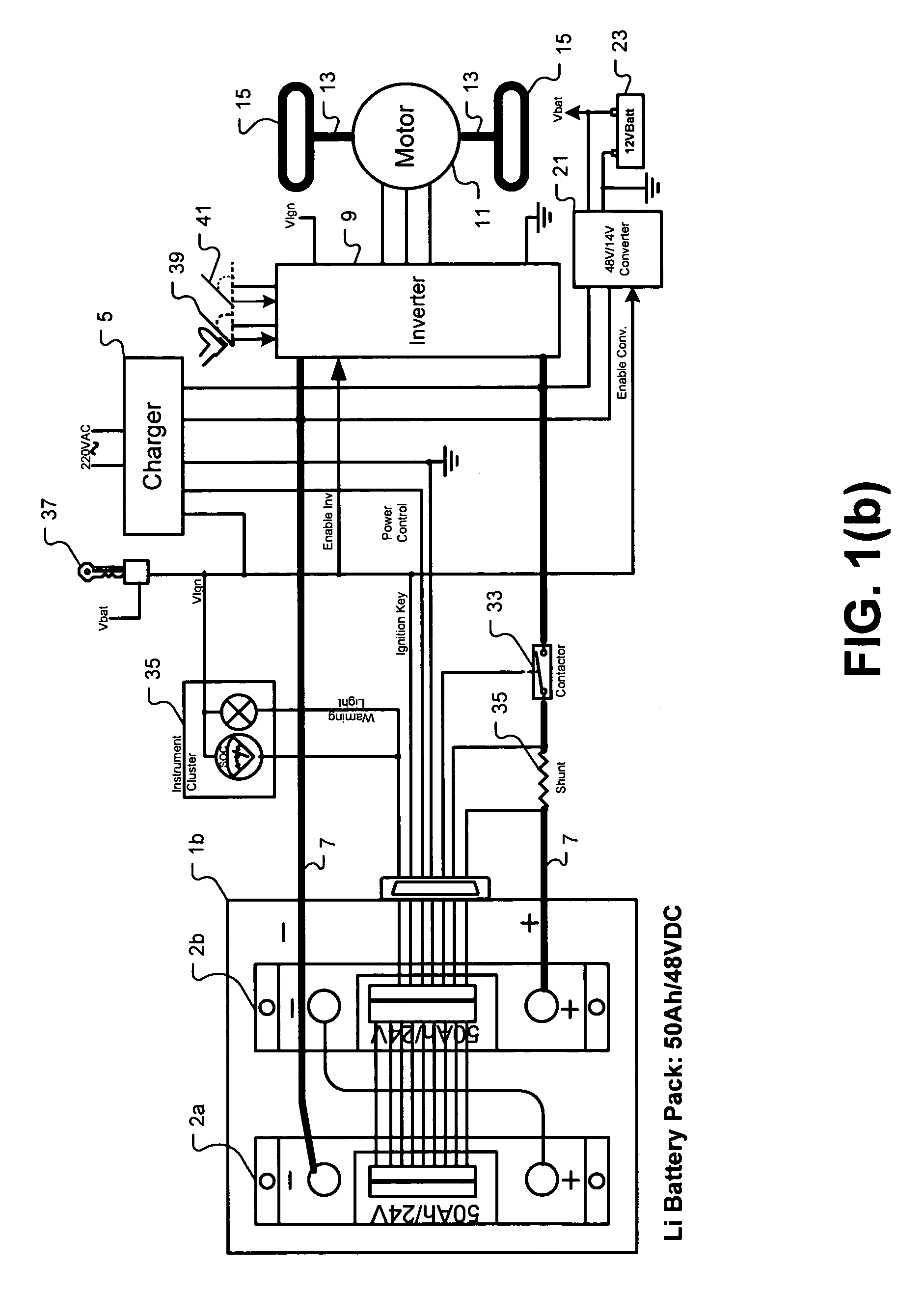
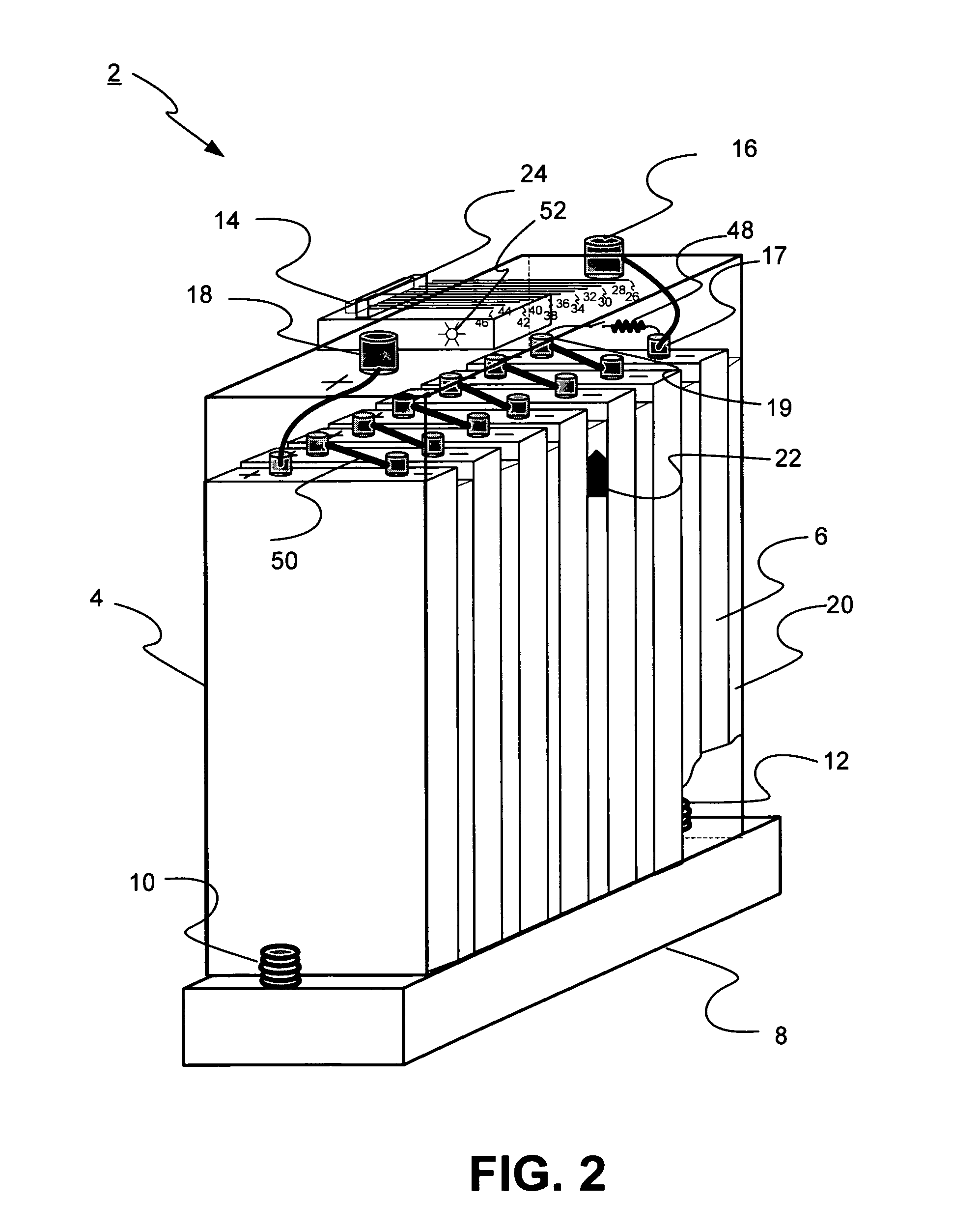
Universal battery module and controller therefor
InactiveUS20070080662A1Easy to integrateMass productionCircuit monitoring/indicationCharge equalisation circuitEmbedded systemBattery pack
A battery pack is provided including universal battery modules and a master control module. By selecting proper rated universal battery modules and connecting them either in series and / or parallel, a high performance and long life battery pack is assembled that is suitable for high power applications such as electrical vehicles whereby the master control module acts as the battery pack control and interface module.
Owner:DELAWARE POWER SYST CORP
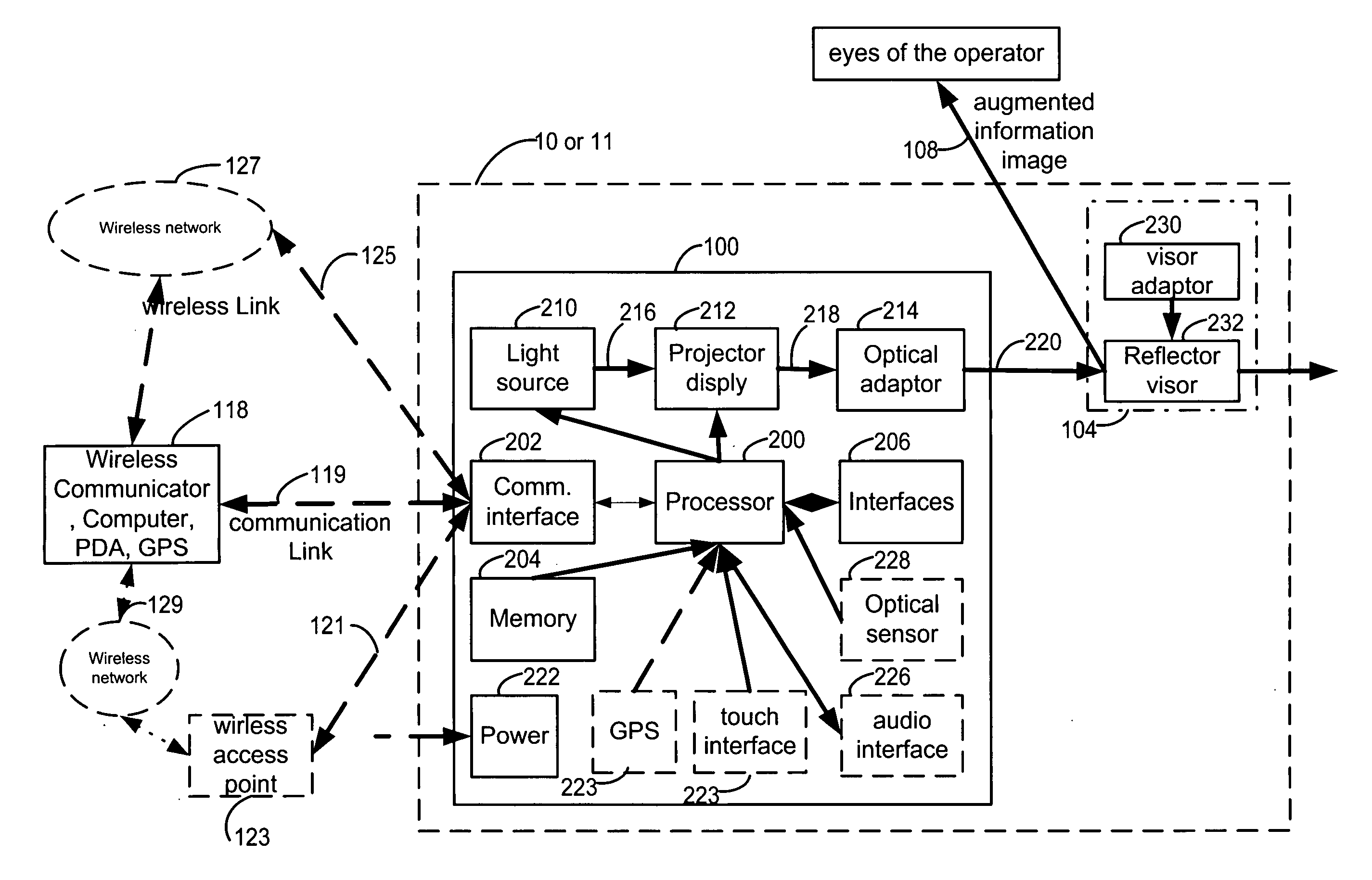
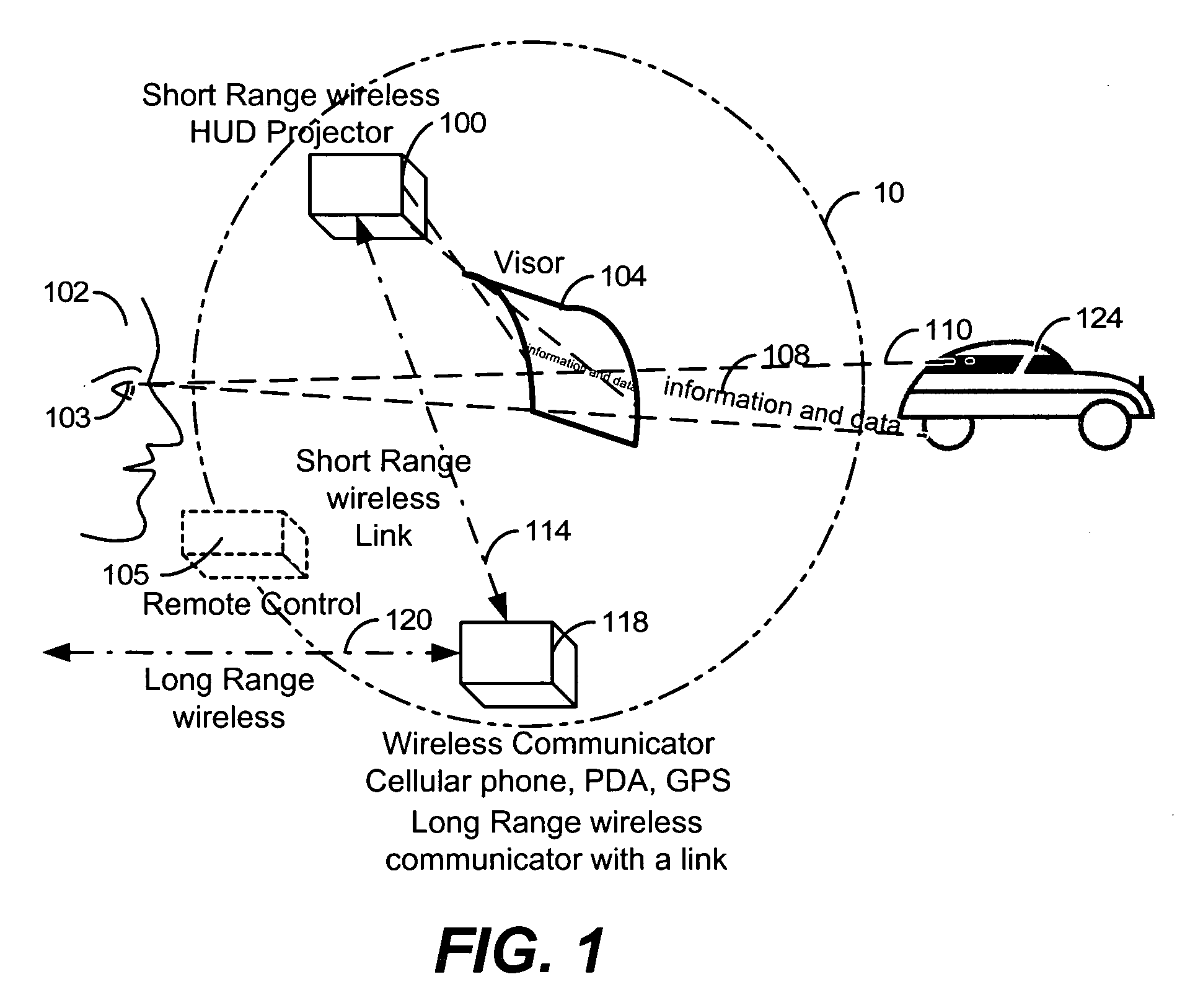
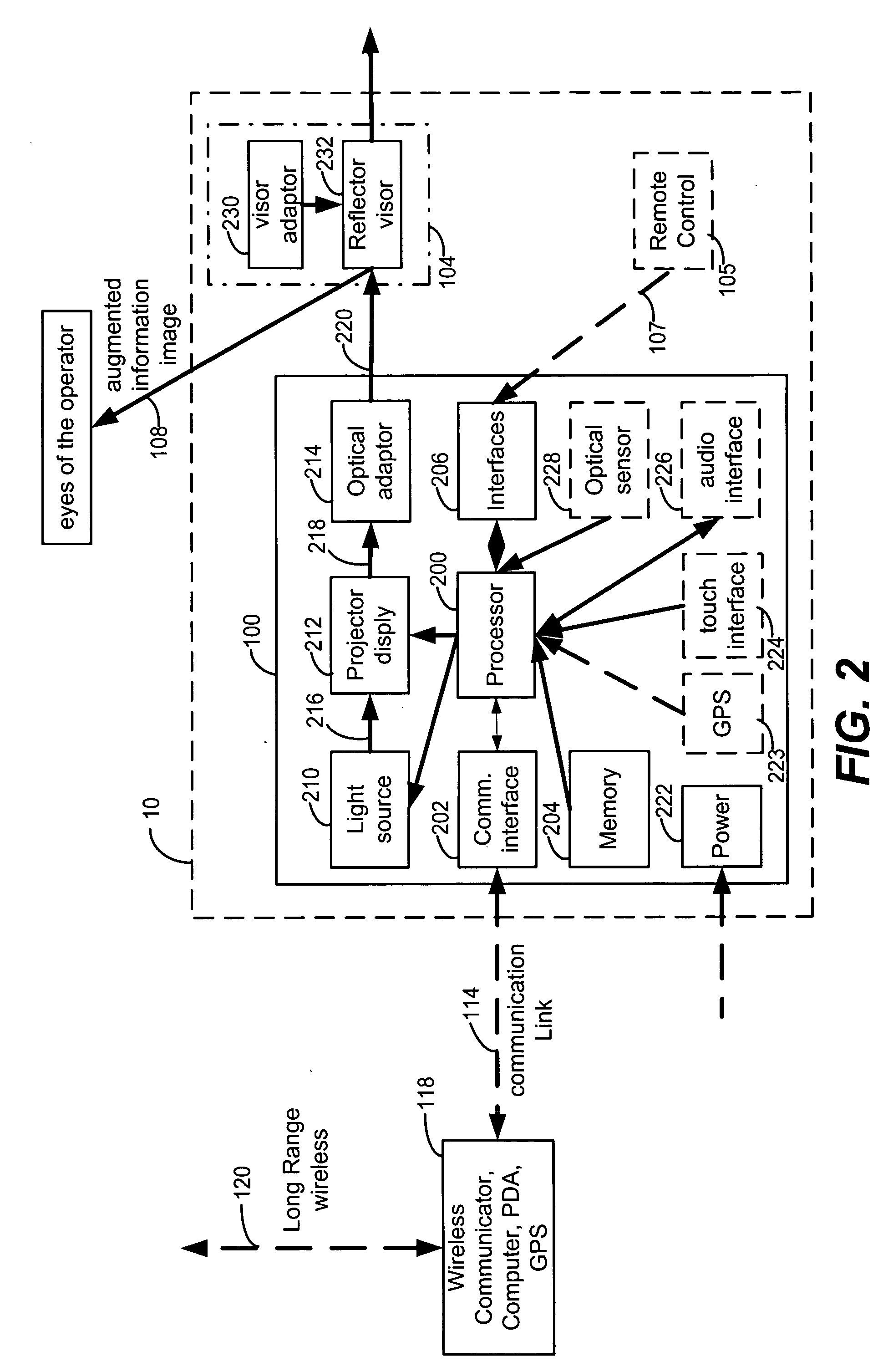
Augmented display system and methods
InactiveUS20060103590A1Safely display augmented dataReduce riskSignalling system detailsCathode-ray tube indicatorsLocation-based serviceGraphics
A mobile augments information system with capabilities of displaying information within field of view of the eyes a vehicle operator. The mobile augments information system includes a Head Up Display (HUD) apparatus consisting of a projector, a selectively reflecting visor and a HUD processing units. The Mobile HUD displays digital information that may be received from external sources such as a cellular phone, navigation system, automotive system, or remote information systems such as Location Based Services (LBS). The data may be received via a wireless link, or a wired link. The mobile HUD may be controlled locally, remotely by a vehicle operator using a wireless remote controller, or using voice commands. The mobile HUD system may also include internal information sources, such as a GPS receiver, or a cellular phone. The mobile augments information system can display textual and graphical information using monochrome or multicolor. Visor may be fixed or dynamically controlled.
Owner:DIVON AVNER
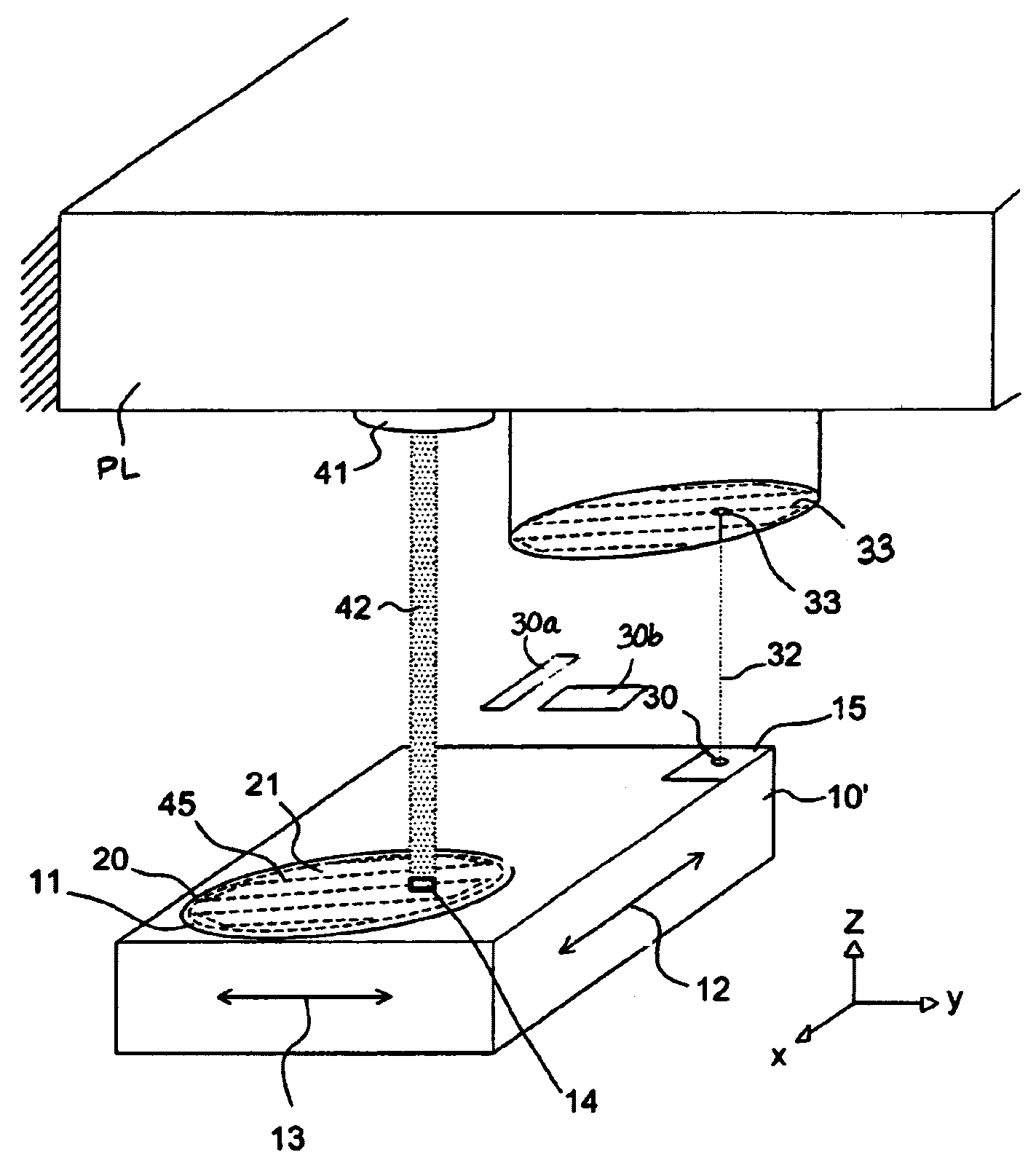
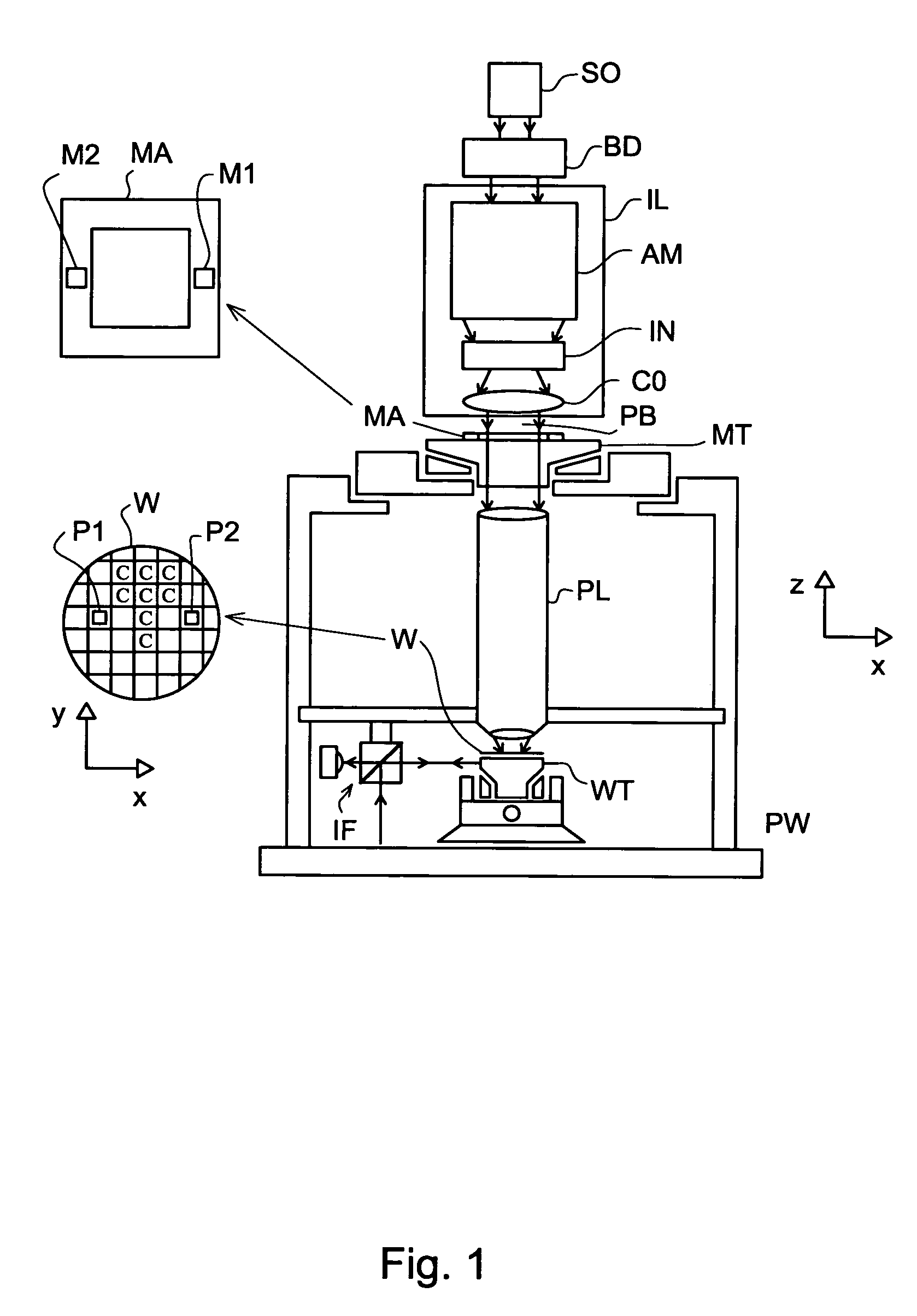
Lithographic apparatus, measurement system, and device manufacturing method
ActiveUS7102729B2Comparable accuracyReduce Algorithmic ComplexityUsing optical meansPhotomechanical exposure apparatusEngineering
The invention pertains to a measurement system for measuring displacement of a moveable object relative to a base in at least a first direction of measurement, the moveable object having at least one reference part that is moveable in a plane of movement relative to the base, the actual movements of the reference part being within an area of said plane of movement that is bounded by a closed contour having a shape. The measurement system comprises a sensor head that operatively communicates with a planar element. The sensor head is mounted onto the base and the planar element being mounted onto the reference part of the moveable object or the other way around, wherein the planar element has a shape that is essentially identical to the shape of the closed contour.
Owner:ASML NETHERLANDS BV
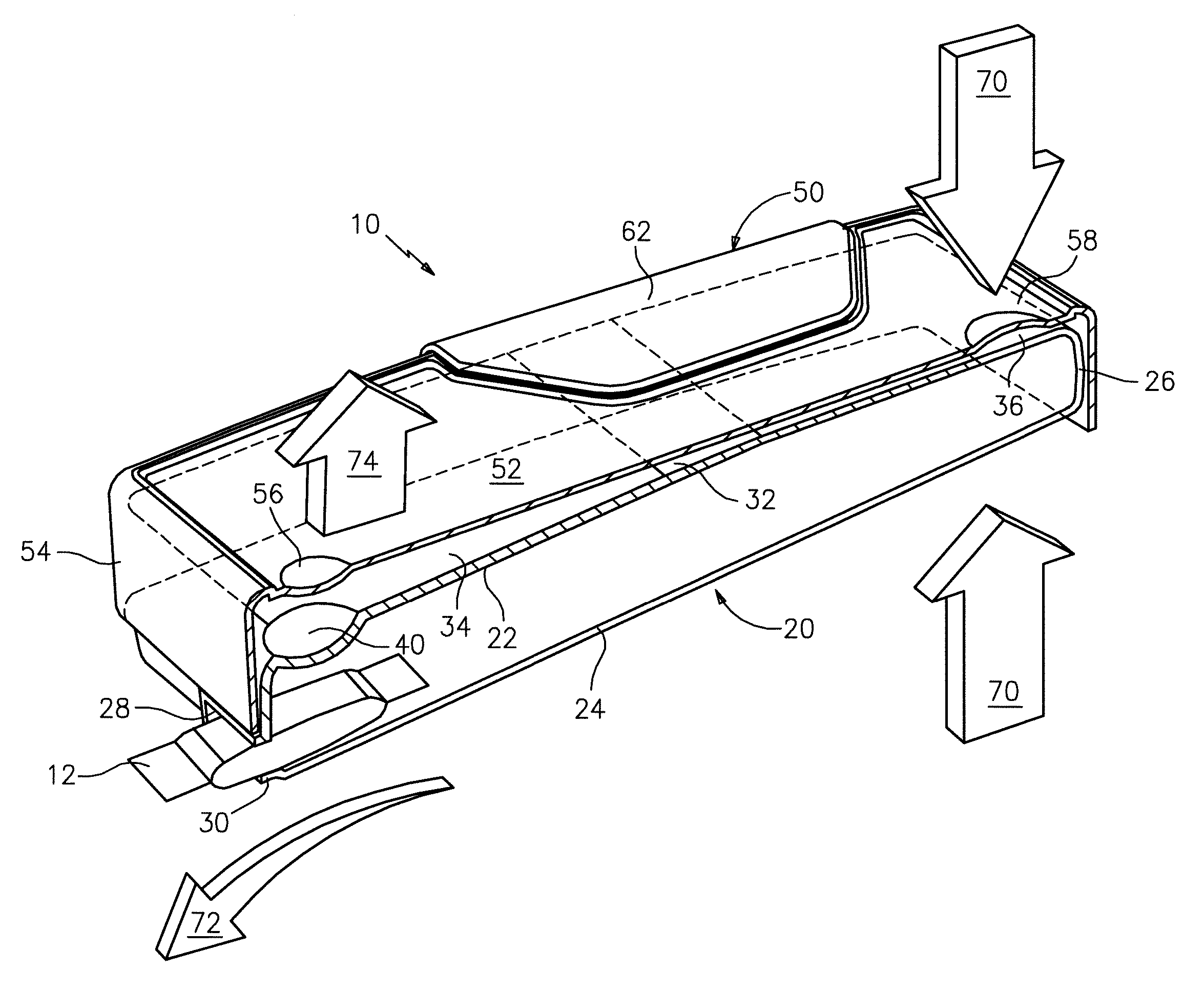
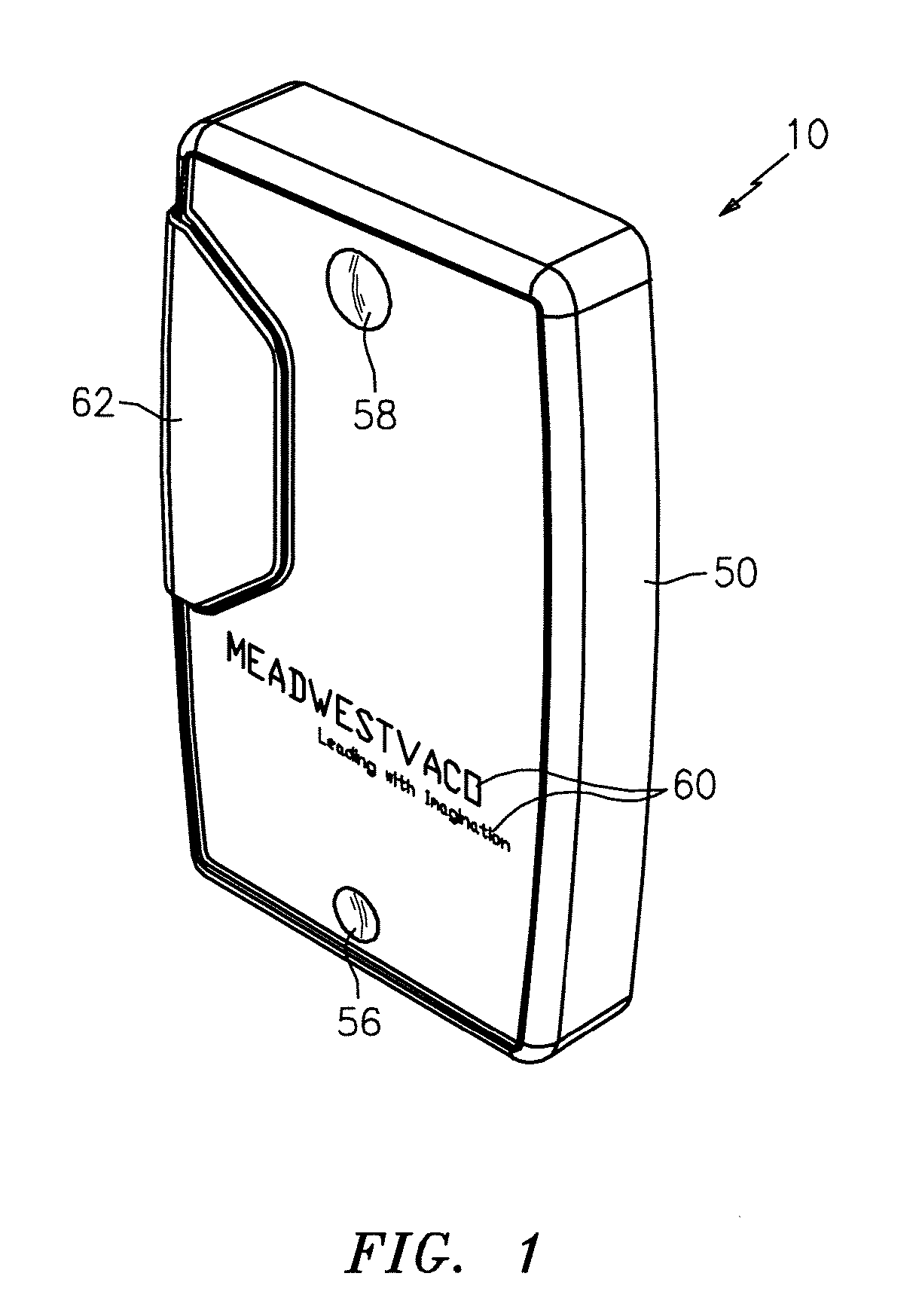
Container with pivoting cover
ActiveUS20100084424A1Reduce disadvantagesEasy to useSmall article dispensingContainer/bottle contructionEngineeringMechanical engineering
Disclosed is a package for storing a product, such as smokeless tobacco, which includes, inter alia, a container that has opposing upper and lower surfaces, and a container sidewall that extends between the upper and lower surfaces to define an interior for storing a plurality of products. The upper surface of the container has an apex intermediate a first region and a second region and the container sidewall defines an opening sized and configured to release at least one of the products. The package also includes an outer cover having an upper section and a cover sidewall depending from the upper section. The outer cover is configured to retain the container and selectively seal the opening. The container pivots about the apex to transition between open and closed positions.
Owner:MEADWESTVACO CORP
System and method for performing distributed video conferencing
ActiveUS20050248652A1Economical conferencingViable solutionTelevision conference systemsAutomatic exchangesLoudspeakerAudio frequency
A method for executing a video conference is provided that includes receiving one or more audio streams associated with a video conference from one or more end points and determining an active speaker associated with one of the end points. Audio information associated with the active speaker may be received at one or more media switches. One or more video streams may be suppressed except for a selected video stream associated with the active speaker, the selected video stream propagating to one or more of the media switches during the video conference. The selected video stream may be replicated such that it may be communicated to one or more of the end points associated with a selected one of the media switches.
Owner:CISCO TECH INC
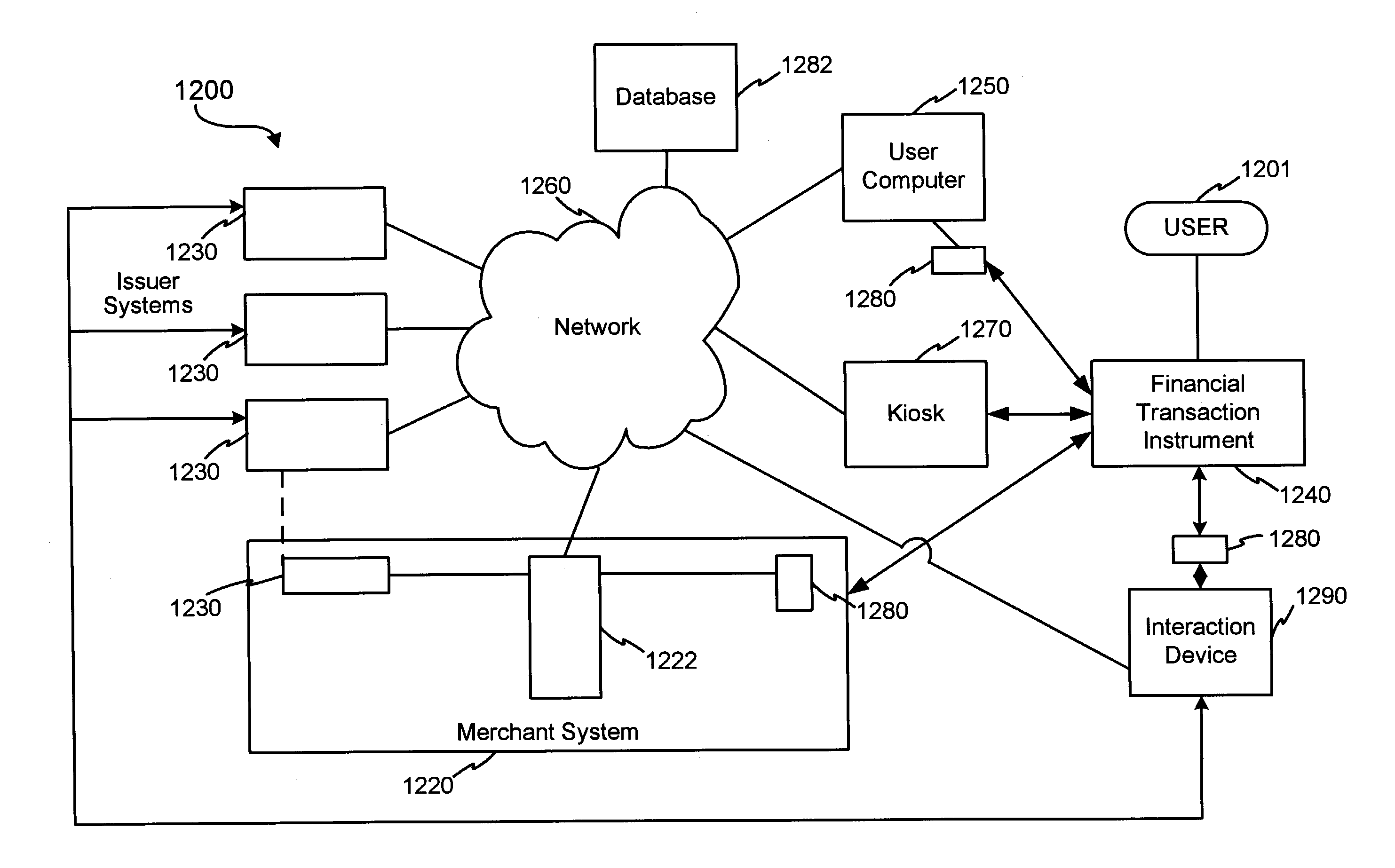
Public/private dual card system and method
InactiveUS20050035192A1Reduce disadvantagesEliminate needComplete banking machinesTicket-issuing apparatusCredit cardOperating system
A system and method for providing a multiple-service card is disclosed. A card member 108 is provided with a single card that serves as both an open transaction instrument and a private retailer transaction instrument. This multiple-service card may have the traditional credit card data on one side of the card, including, for example, the account number, name of the account holder, and the expiration date. The other side of the card may include a magnetic stripe that contains the account information in machine readable form as well as private retailer transaction instrument information. In the system, the primary party and the service partner participants cooperate to complete the processes associated with the provision of the combined card services, including a new account process, card replacement and renewal processes, a service partner cancellation process, and a process for cancellation and / or transfer by a primary party.
Owner:CHARTOLEAUX +1
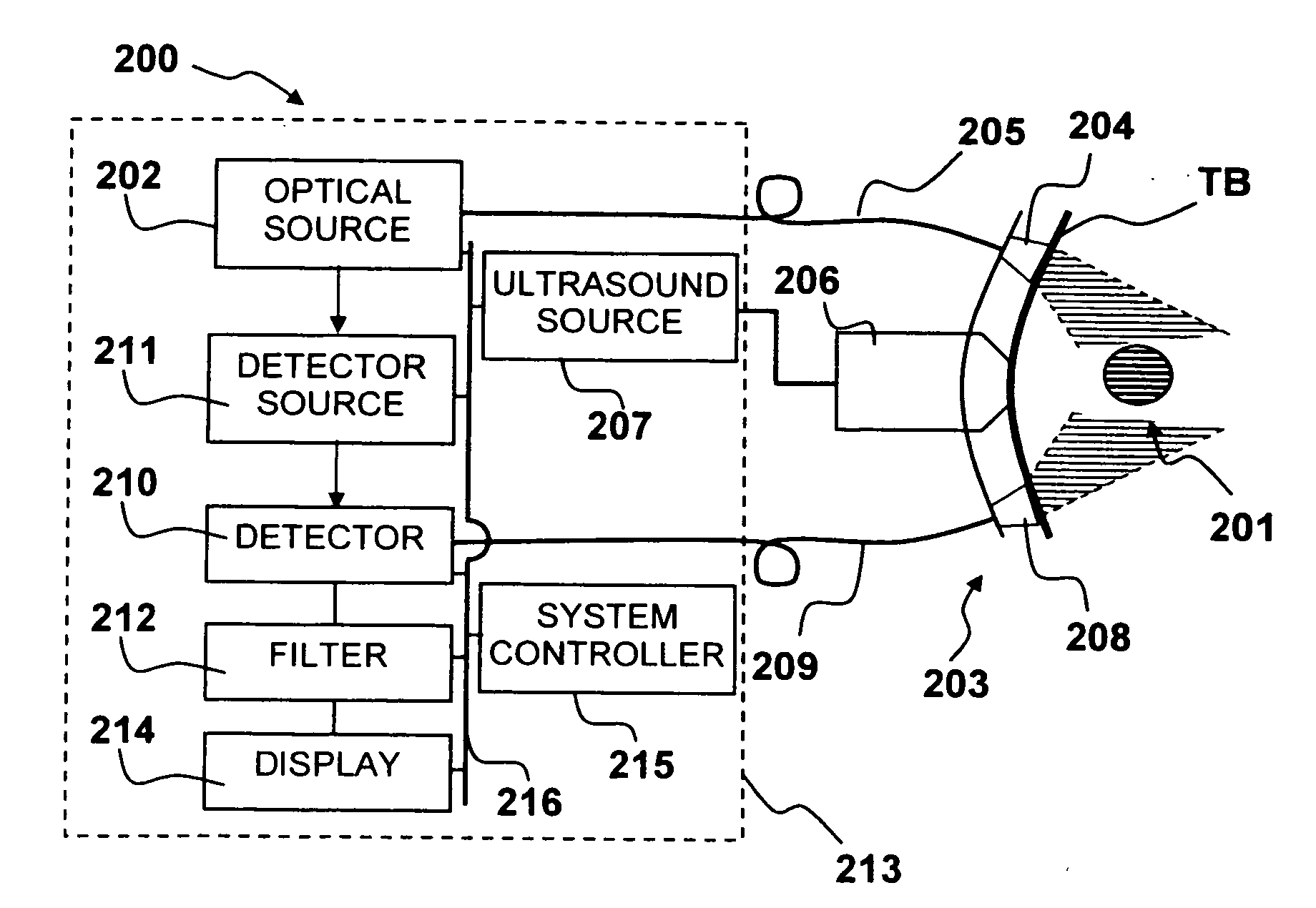
Apparatus and method for non-invasive and minimally-invasive sensing of parameters relating to blood
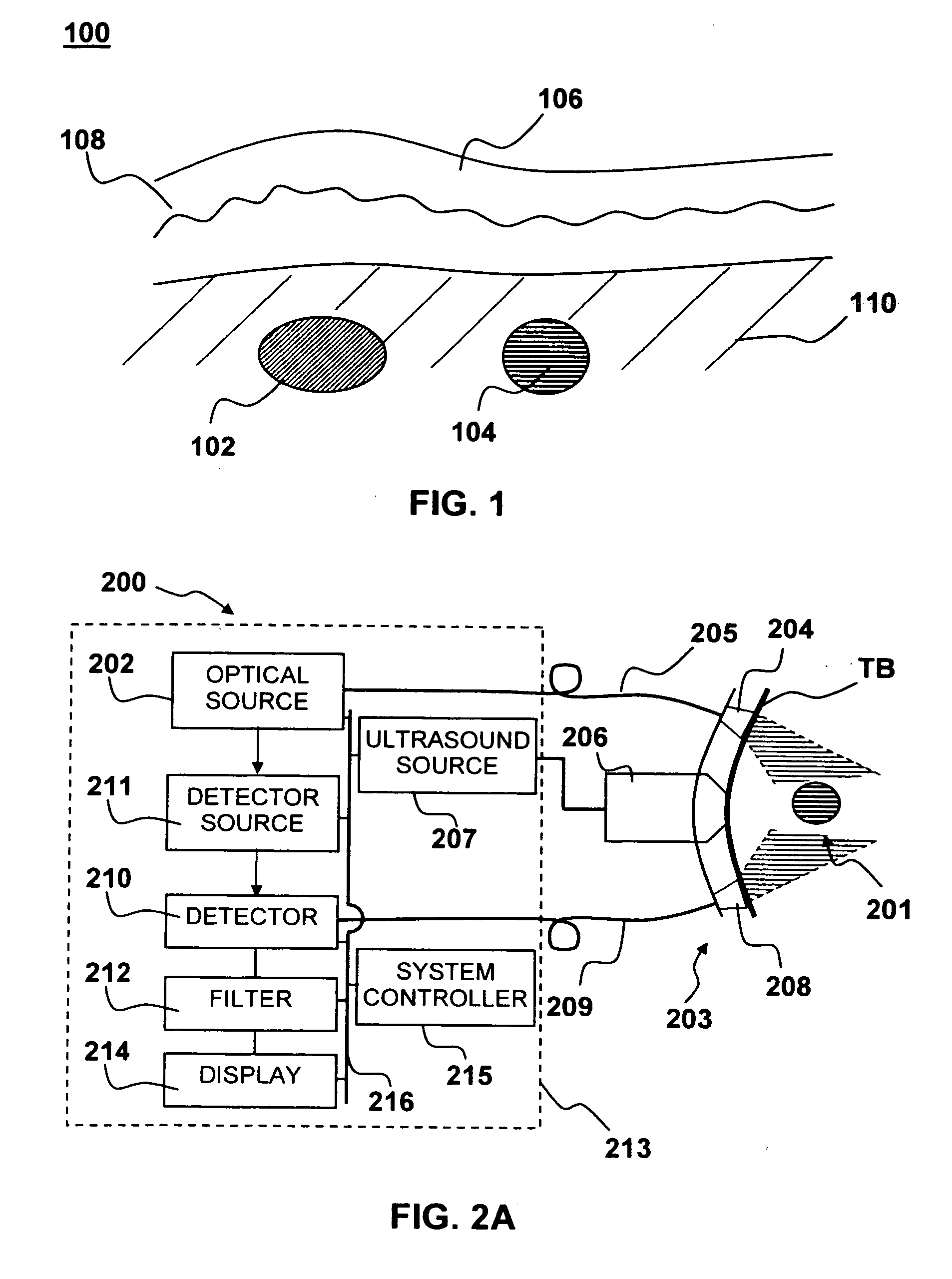
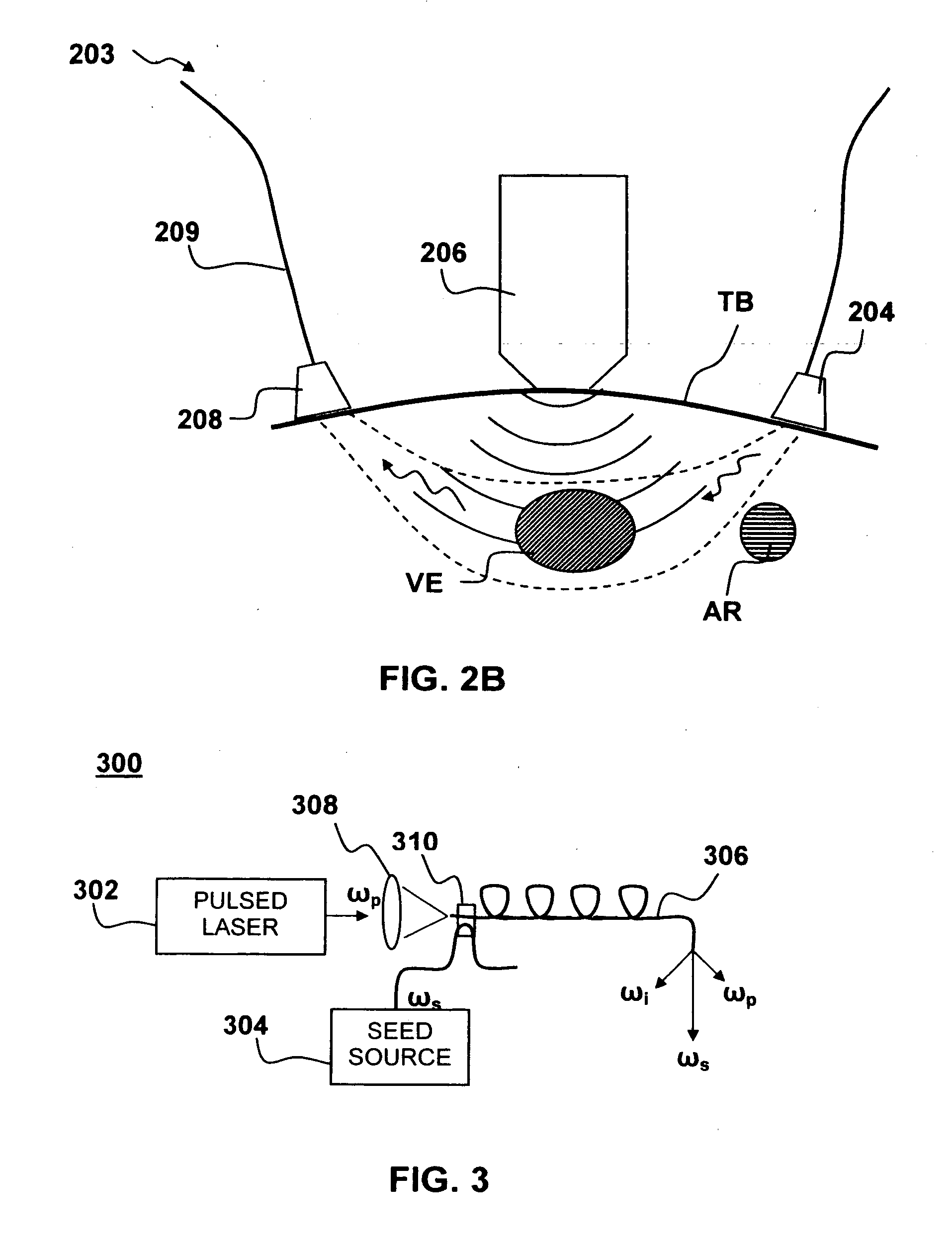
InactiveUS20060253007A1Reduce disadvantagesImprove accuracyDiagnostics using lightOrgan movement/changes detectionNon invasiveThree vessels
Medical diagnostic system, apparatus and methods are disclosed. Optical transmitters generate radiation-containing photons having a specific interaction with at least one target chromophore in a target structure, preferably a blood vessel such as the interior jugular vein. The optical transmitters transmit the radiation into at least a first area including a substantial portion of the target structure and into a second area not including a substantial portion of the target structure. Optical receivers detect a portion radiation scattered from at least the first area and the second area. A processor estimates oxygenation, pH or cardiac output based on the scattered radiation detected from the first area, and the scattered radiation from the second area.
Owner:SKYLINE BIOMEDICAL
System and method for performing distributed video conferencing
InactiveUS7477282B2Reduce disadvantagesReduce problemsTelevision conference systemsSpecial service for subscribersLoudspeakerVideo streaming
A method for executing a video conference is provided that includes receiving one or more audio streams associated with a video conference from one or more end points and determining an active speaker associated with one of the end points. Audio information associated with the active speaker may be received at one or more media switches. One or more video streams may be suppressed except for a selected video stream associated with the active speaker, the selected video stream propagating to one or more of the media switches during the video conference. The selected video stream may be replicated such that it may be communicated to one or more of the end points associated with a selected one of the media switches.
Owner:CISCO TECH INC
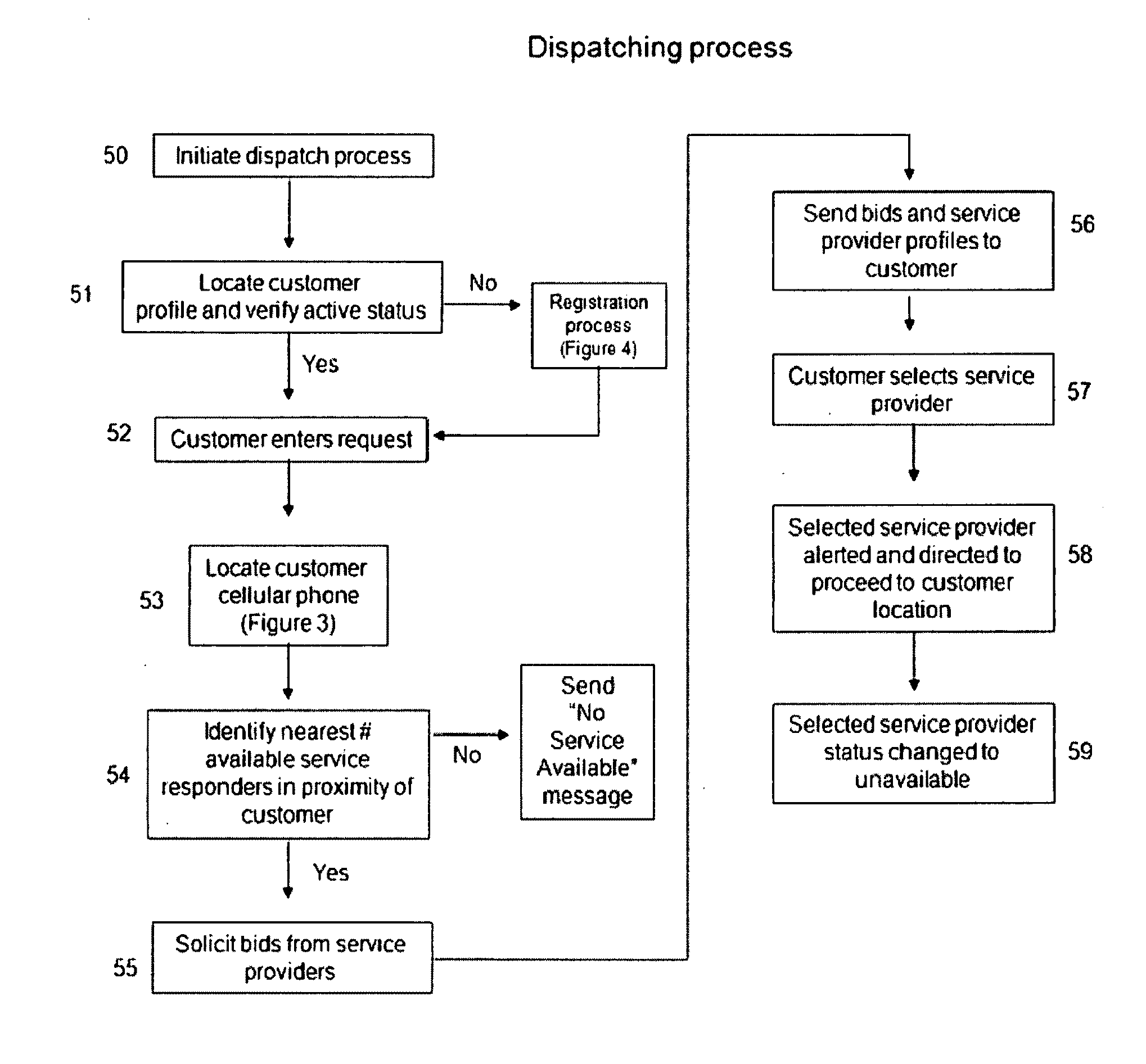
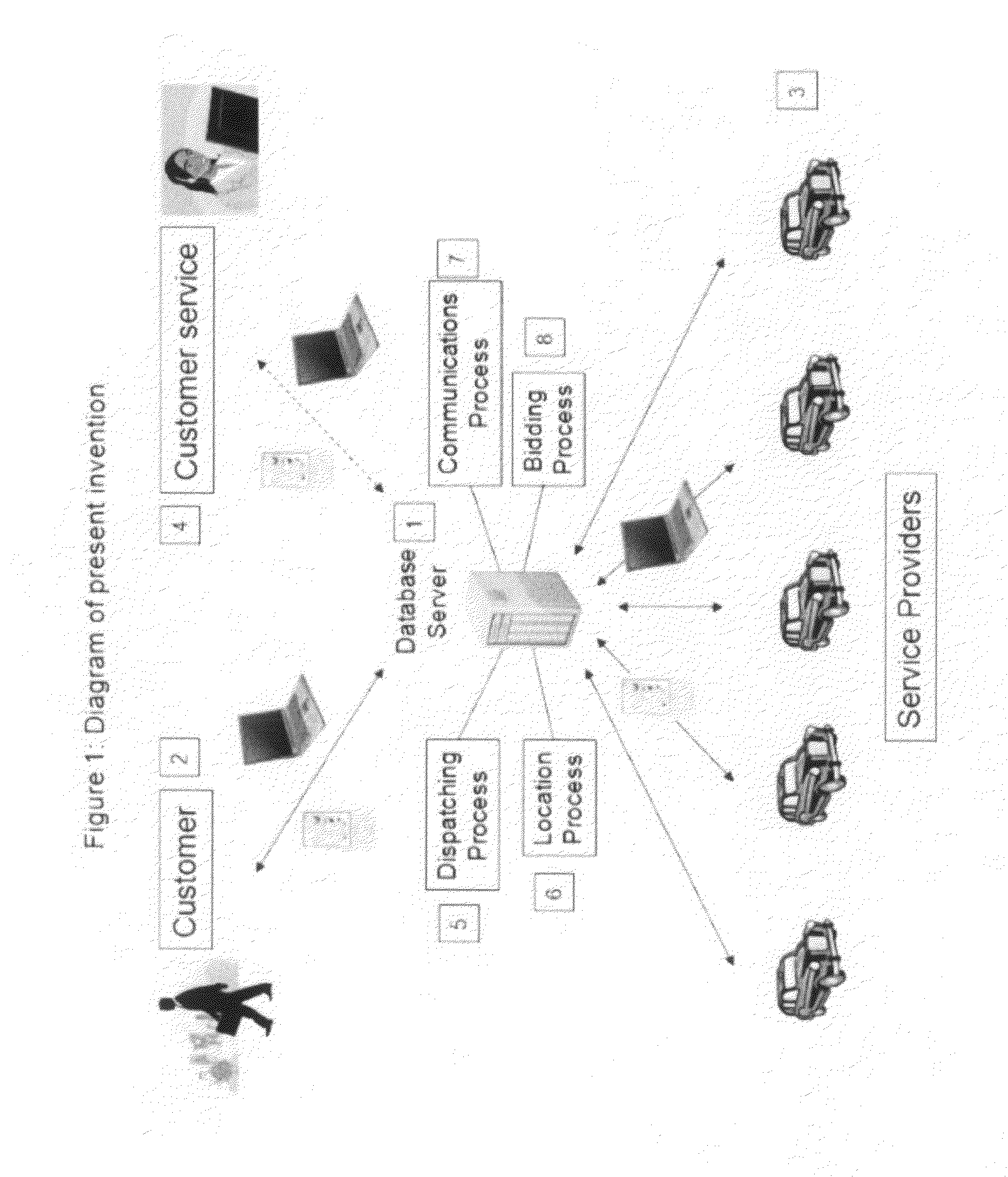
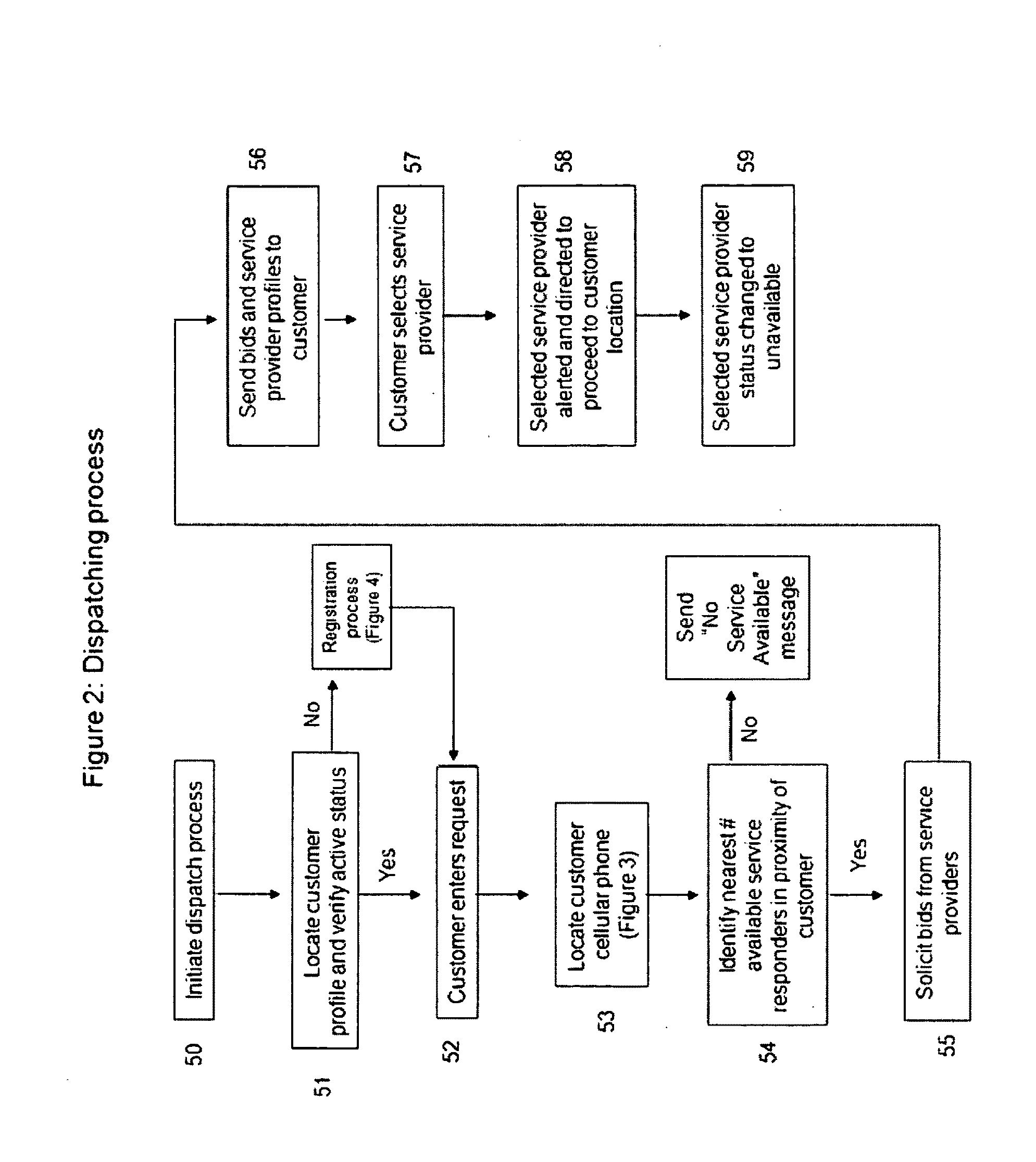
Consumer initiated, service provider direct dispatching system
InactiveUS20090313077A1Convenience to workIncrease in costInstruments for road network navigationTemperatue controlPersonal detailsDirect communication
A customer originated and directed dispatching system to provide direct coordination of requested service to service providers without the need for intermediary dispatching assistance. A database stores records each documenting needed services and customer and service provider profiles. Processing circuitry (which may be one or several networked computers) performs a dispatching process which reviews these records, locates records indicating a need for immediate service, locates the customer, identifies potential service responders, carries out an auction for the requested service and collects a list of potential service provides with their bids and profiles. The processing circuitry also performs a monitoring process which monitors service provider's activities by reviewing the records, and automatically obtained service provider's activity information, and records customer and service provider performance ratings to the database. Communications circuitry enables direct communication between the service provider and the customer as well as updates of the service provider's activity and review customer and service provider performance records.
Owner:WHEELER IV GEORGE Y
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com