Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
171results about How to "Safety of tradement" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
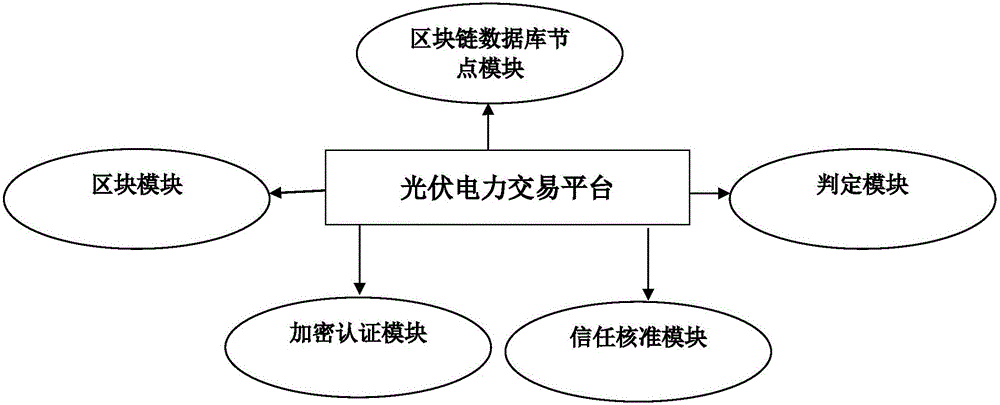
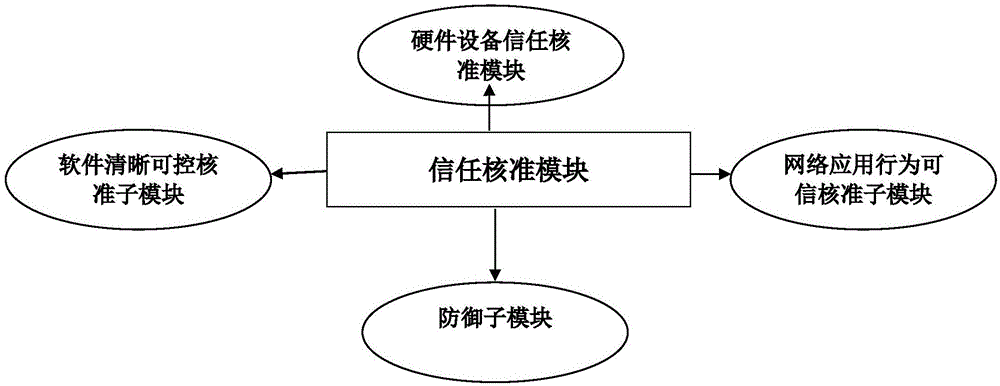
Trusted power grid transaction platform based on block chain technology
InactiveCN106296359AThe transaction is validConduct complianceBuying/selling/leasing transactionsSystems intergating technologiesElectric power transmissionPower grid
The invention provides a trusted power grid transaction platform based on block chain technology. The trusted power grid transaction platform comprises the components of (1), a power chain database node module which stores electric power transaction database copies at a plurality of nodes; (2), a block module, wherein the block chain database is divided into a plurality of blocks which are related with electric power transaction, wherein each block comprises detailed information of transaction; (3) an encryption authentication module which acquires whole-network authentication through combining and encrypting transaction details and signatures of two parties or signature of one party; (4), a trust approval module which is connected with the encryption authentication module and is used for establishing a trusted power grid transaction system of the block chain; and (5), a determining module which determines a fact that the transaction is effect on the condition that encryption records that correspond with all nodes are consistent, and adds the transaction into a historical transaction chain; and if the block is ineffective, the information of a role breaking node is modified through consistent option of the nodes. The trusted power grid transaction platform safely and reliably perform various kinds of power grid transactions and furthermore improves credibility of the block chain technology.
Owner:SHENZHEN FANXI ELECTRONICS CO LTD
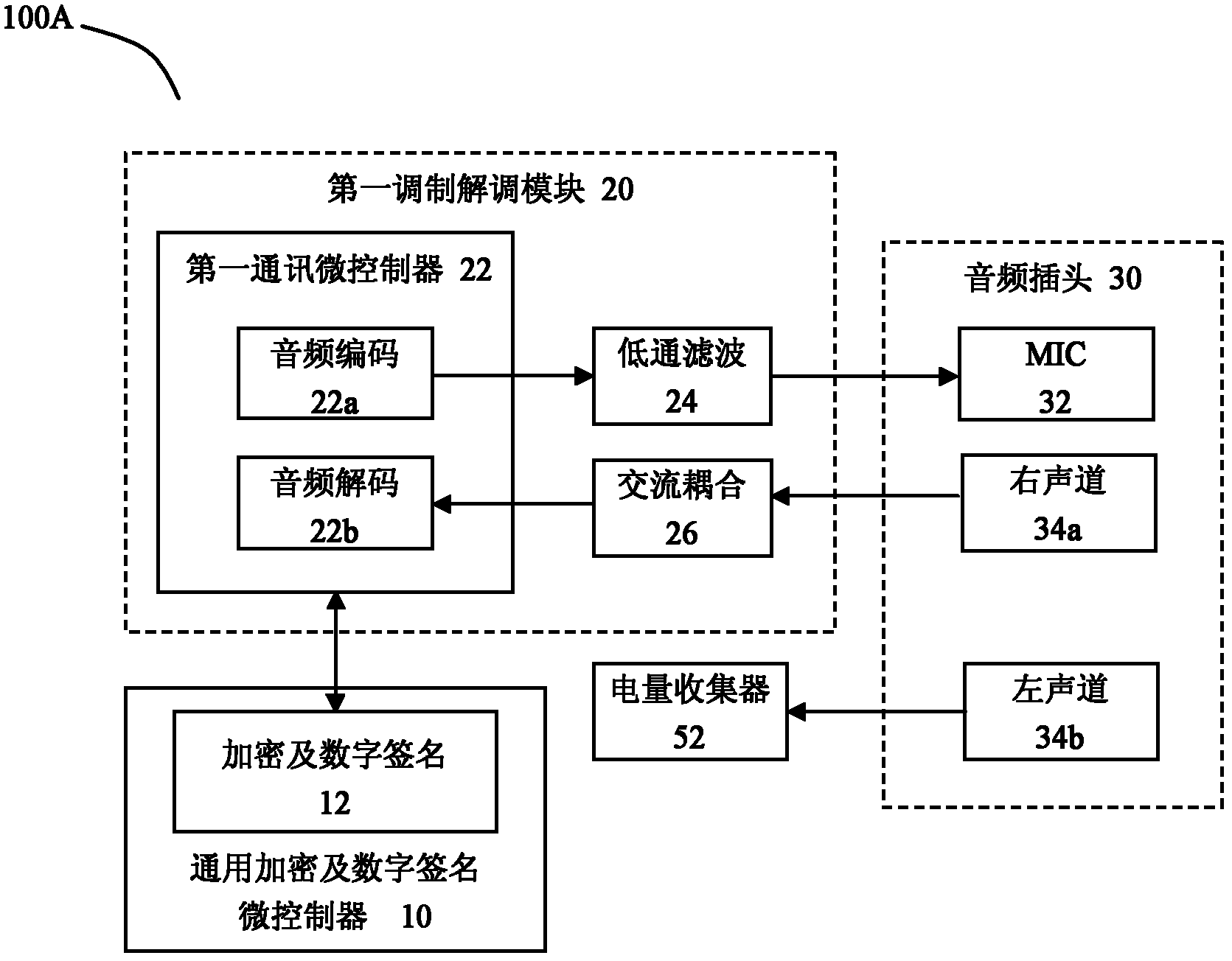
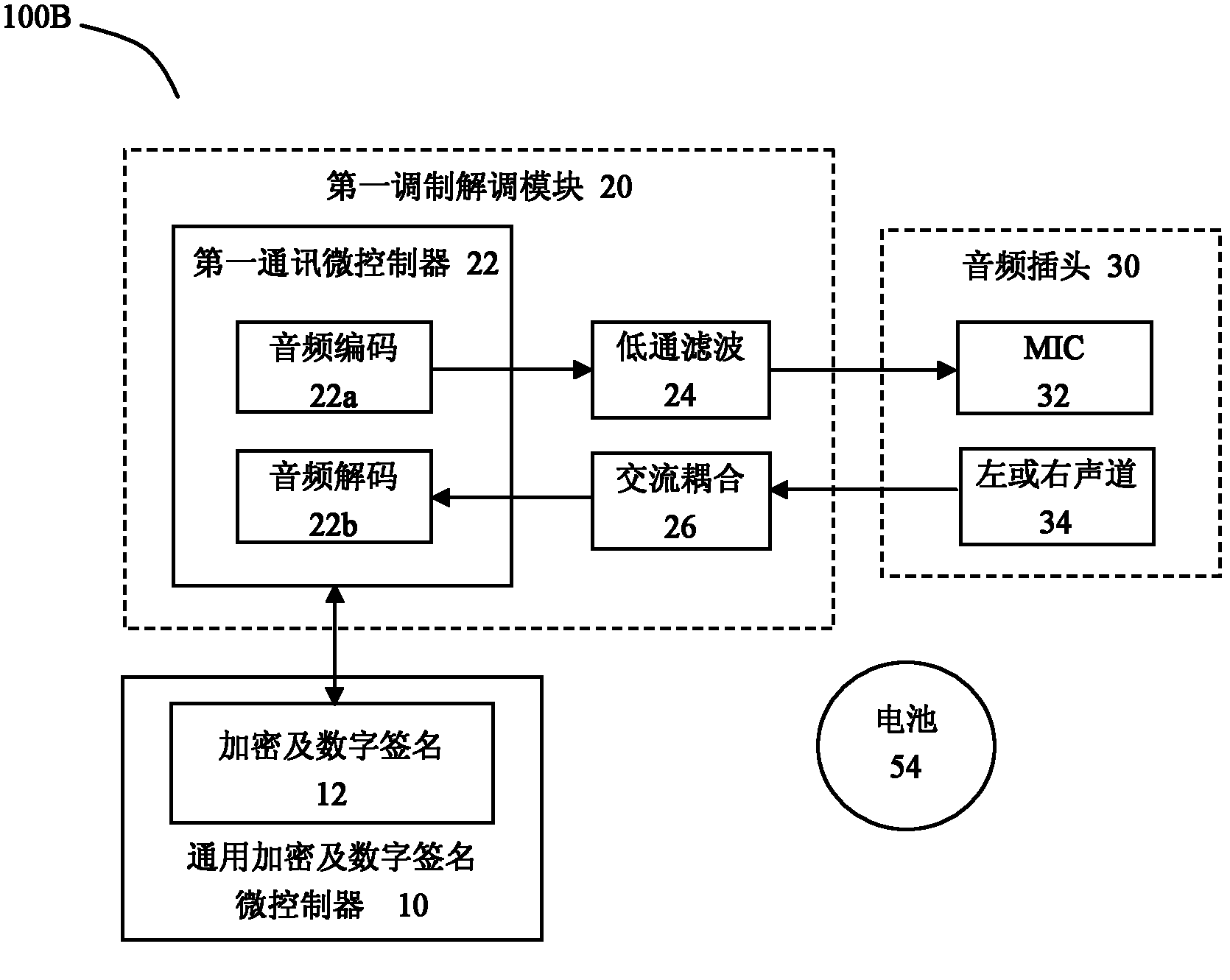
Digital certificate safety lock device and digital certificate authentication system and method
InactiveCN102255730AVersatility and applicabilityEnsure safetyUser identity/authority verificationAuthentication systemInternet bank
The invention relates to a digital certificate safety lock device and a digital certificate authentication system and method. The digital certificate safety lock device comprises a universal encryption and digital signature microcontroller, an audio plug and a first modulation and demodulation module, wherein the universal encryption and digital signature microcontroller is provided with an encryption and digital signature module and a storage for storing a digital certificate, a key of the digital certificate and encryption and decryption algorithms; and the first modulation and demodulation module is used for modulating data information from the encryption and digital signature module for transmitting through an MIC (Microphone) pole of the audio plug, demodulating a signal received from a first sound channel pole of the audio plug and transmitting the demodulated signal to the encryption and digital signature module. The digital certificate safety lock device is provided with a universal audio interface plug which has high university and adaptability and can support communication terminals such as mobile phones, tablet computers, PDAs (Personal Digital Assistants) or PCs (Personal Computers) and the like, with audio interfaces. Due to the functions of independent hardware signature, digital certificate encryption and the like, the security of application logon and transactions of Internet banks or enterprises can be ensured to the maximum extent.
Owner:吴沙林 +1
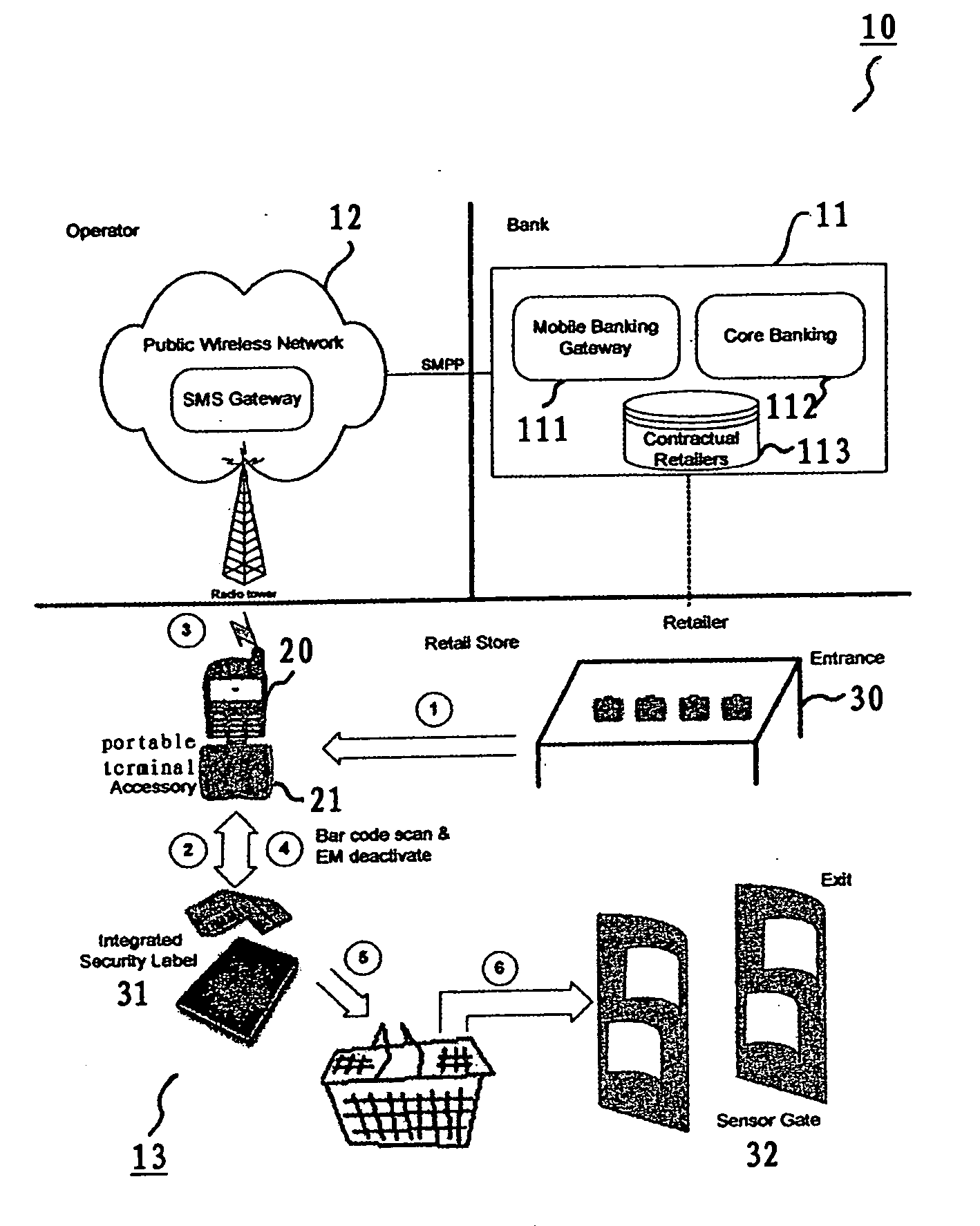
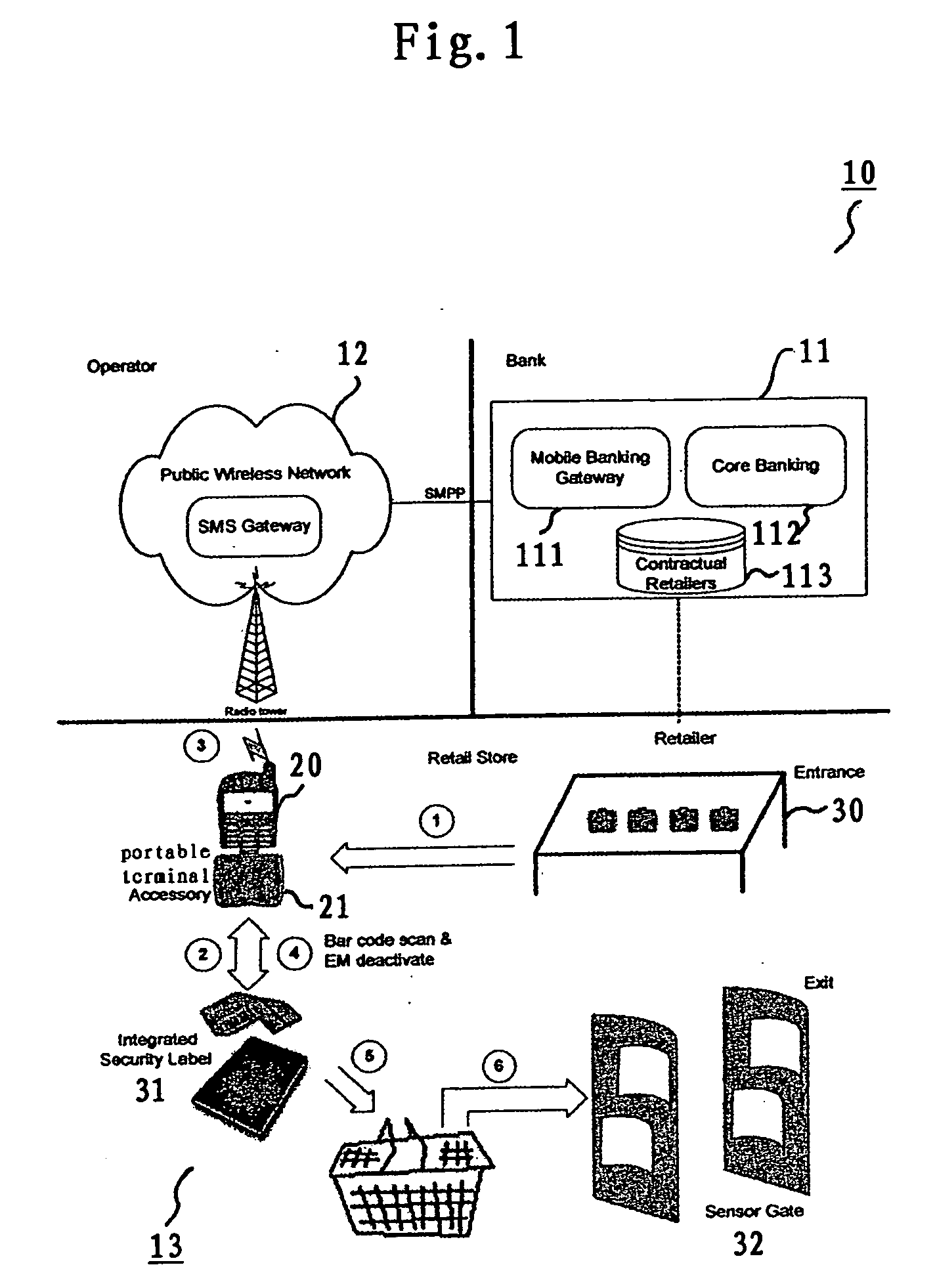
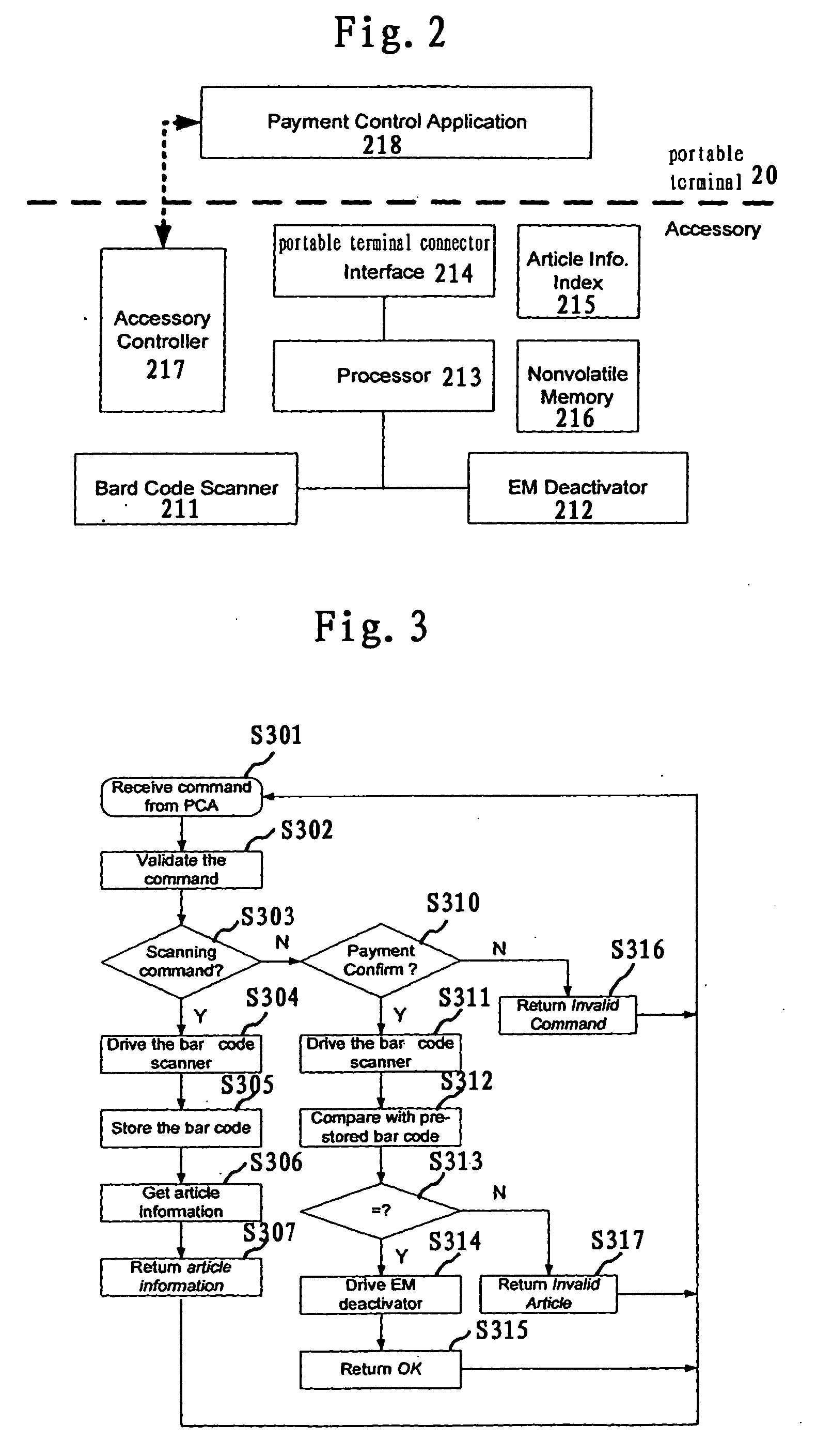
Mobile banking and anti-theft tag based smart portable checkout terminal, system, and method thereof
InactiveUS20060043175A1Reduce waiting timeReduce investmentCredit registering devices actuationCash registersComputer terminalEngineering
A mobile banking and anti-theft tag based portable checkout terminal, checkout system and checkout method for a retail environment are disclosed. A portable terminal accessory is designed for a portable terminal to acquire the article information related to the selected article that a customer in a retail environment wishes to purchase. The portable terminal is connected to the portable terminal accessory to receive the article information via scanning a tag attached to the article and to conduct the checkout processing with a customers bank through wireless communication.
Owner:IBM CORP
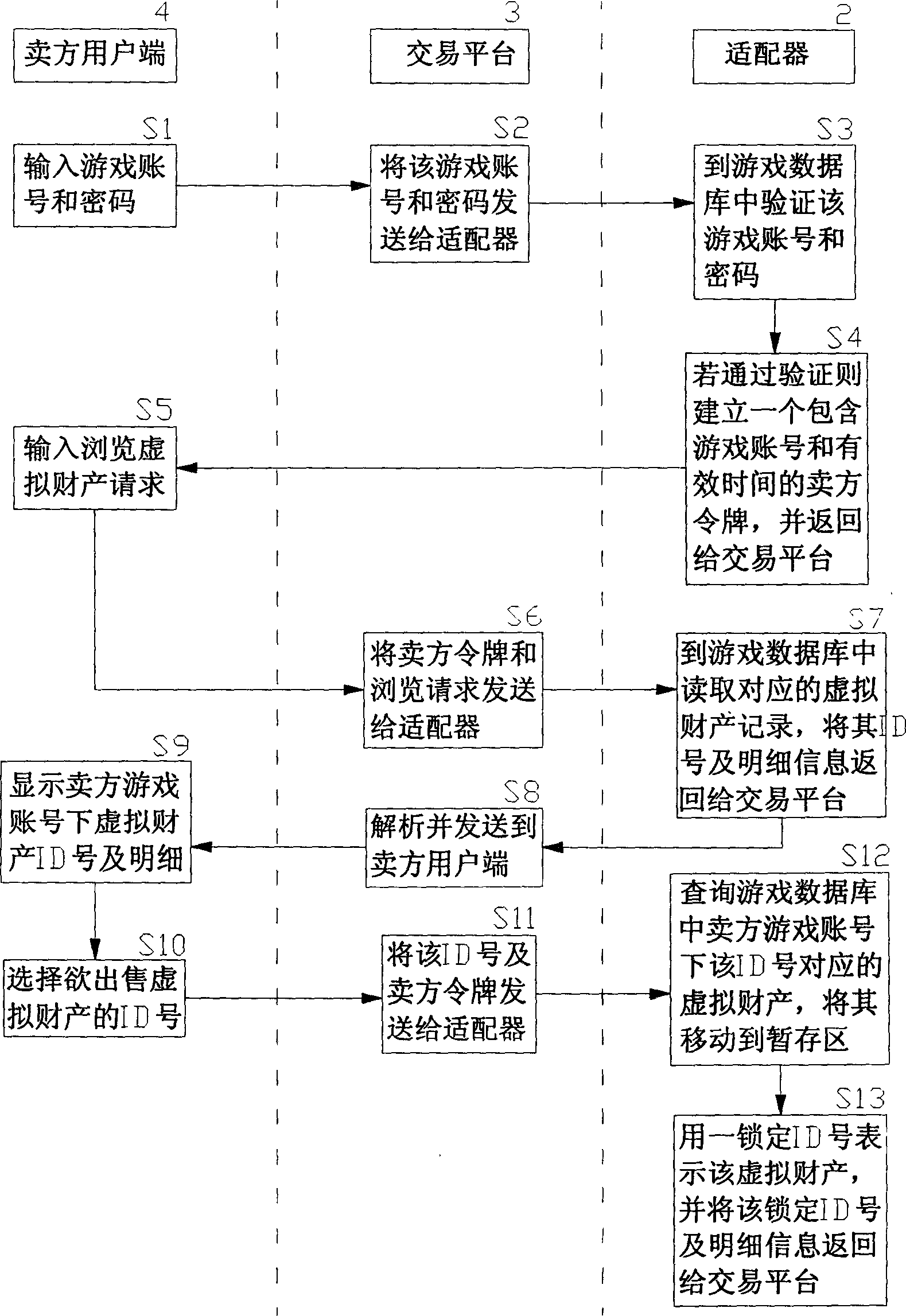
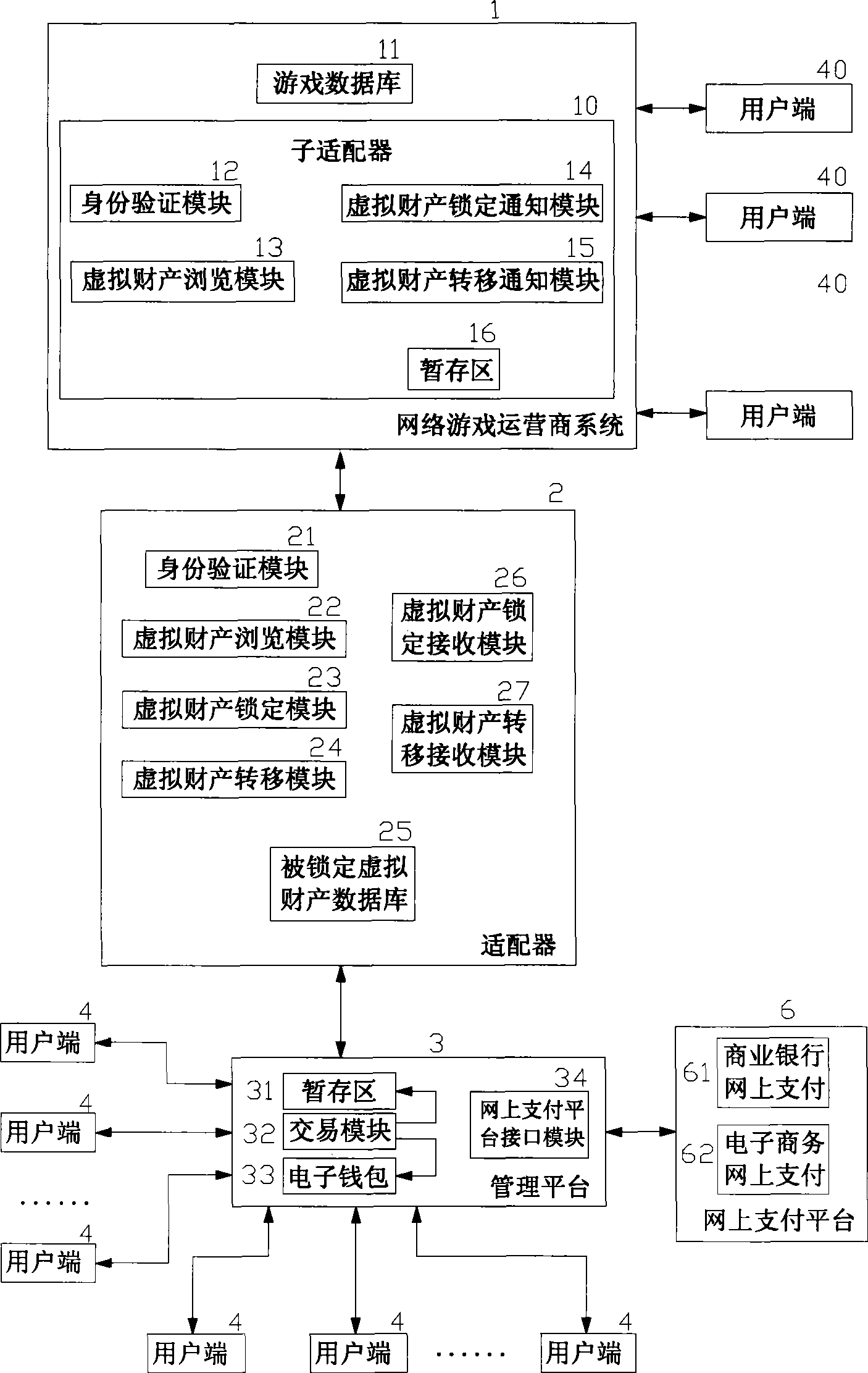
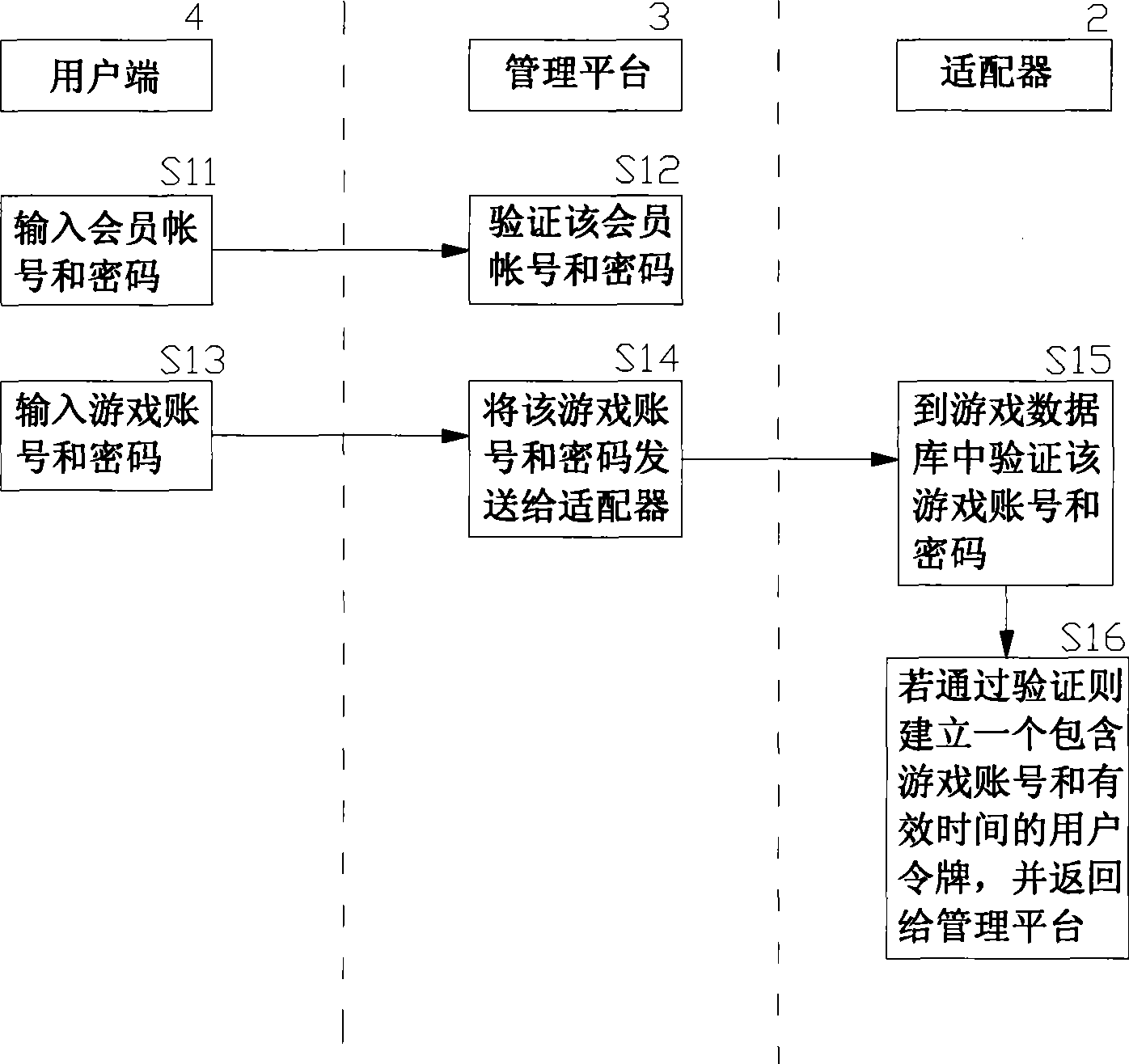
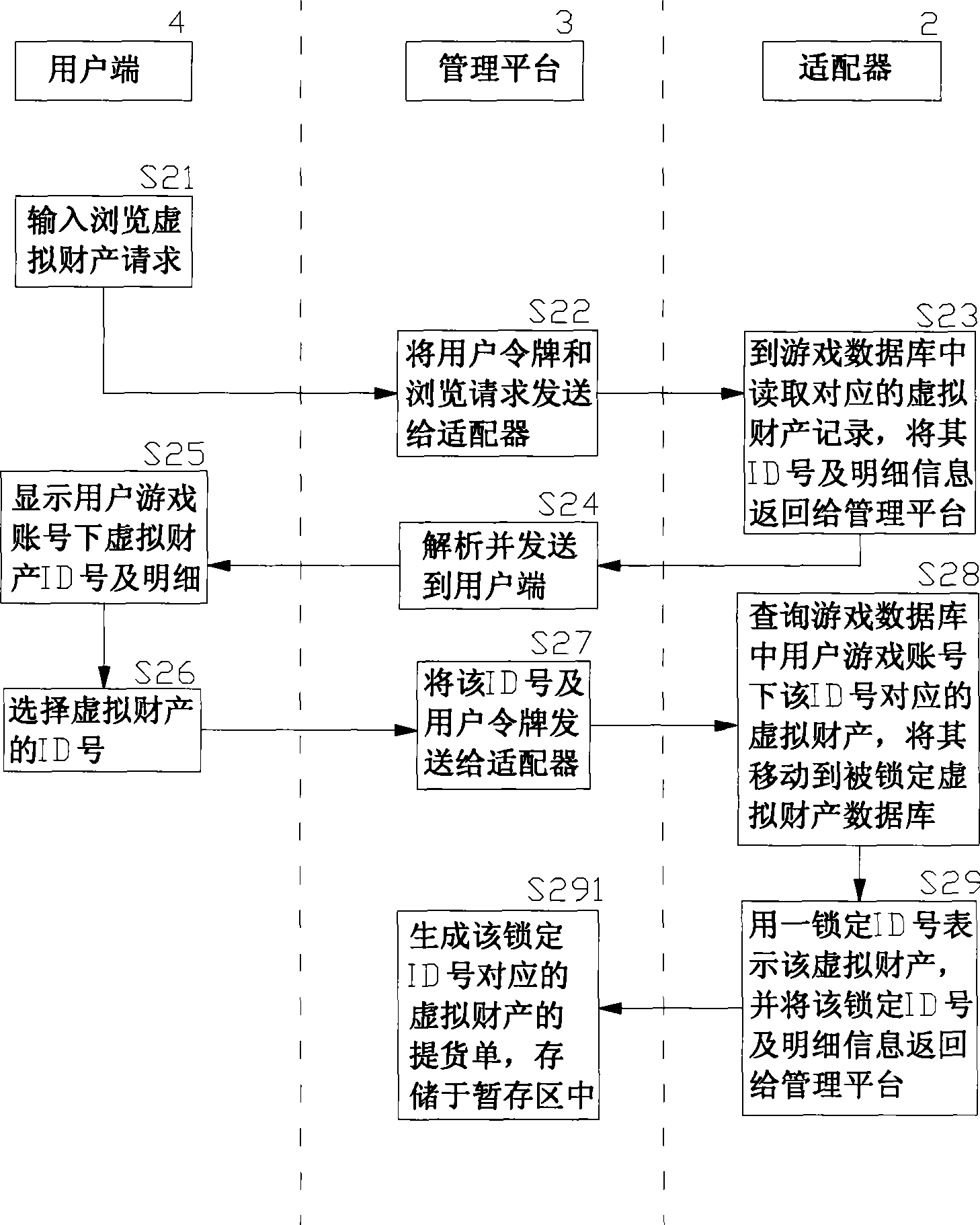
On-line payment method and system for network game virtual property trade
InactiveCN1818958AReduce crimeRealize complete online transactionPayment architectureCommerceVirtual propertyPayment
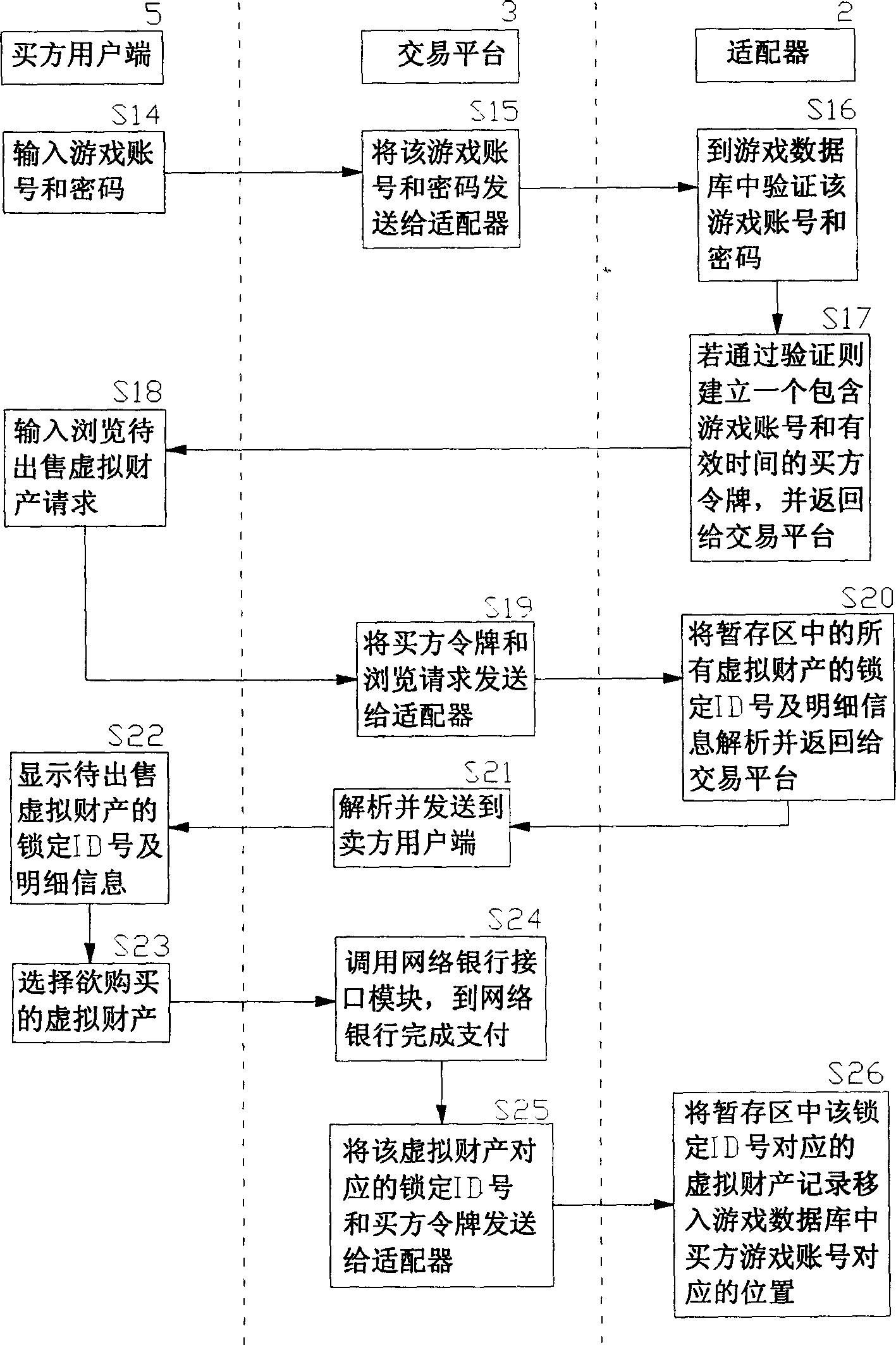
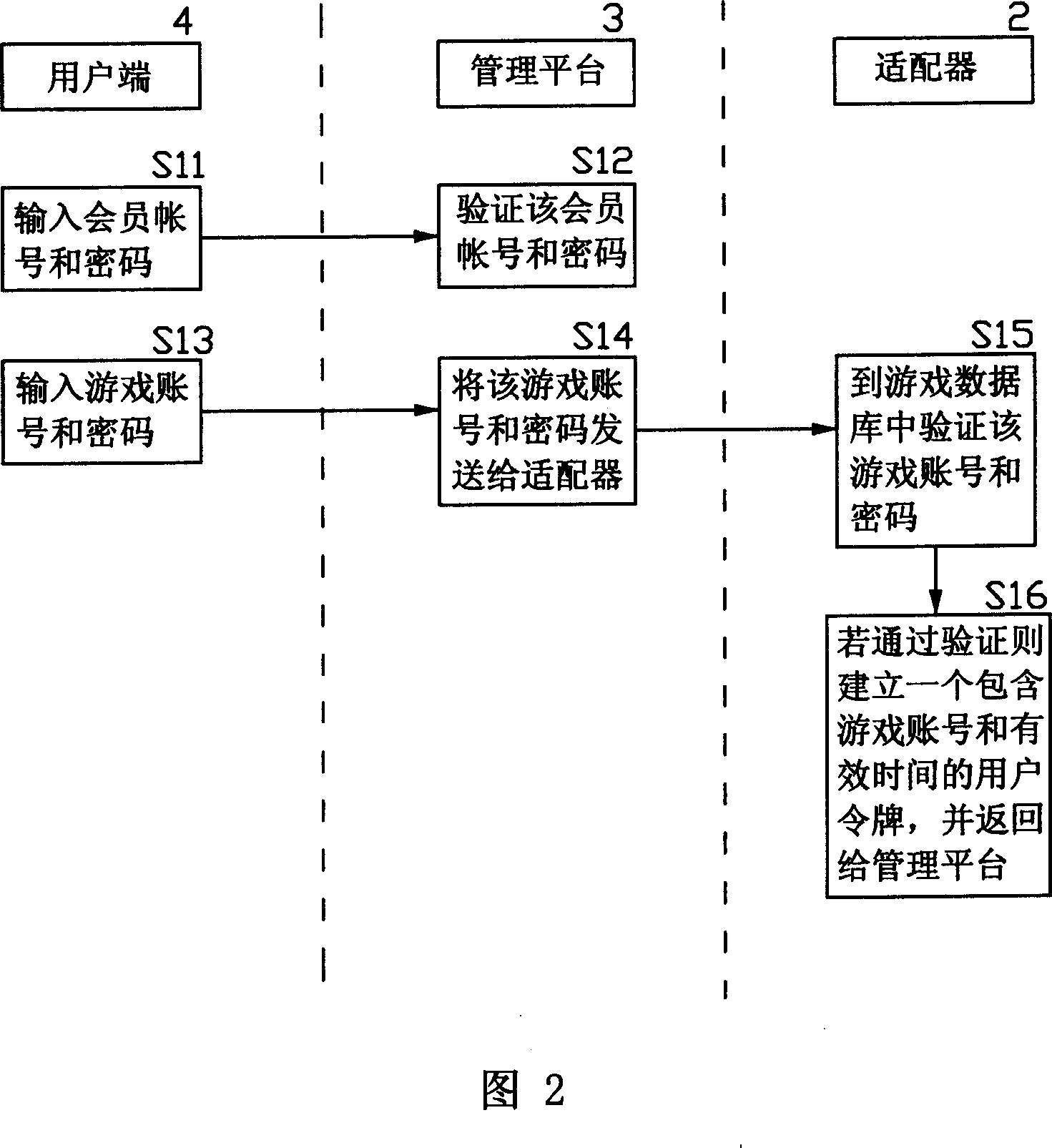
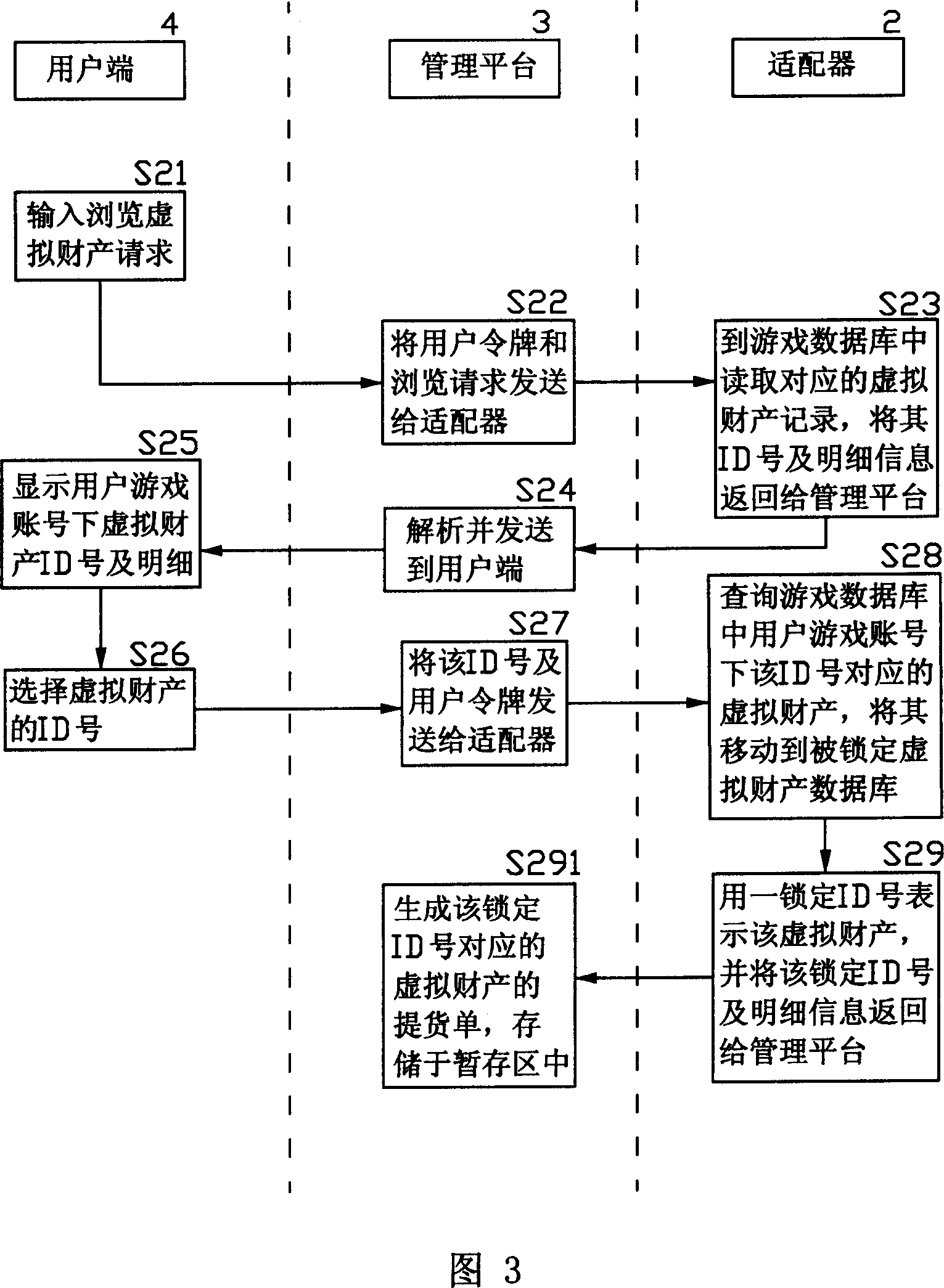
An online deliver method and system of the online-game dummy property exchange, the main principium is: establishing the exchange platform that has the function of online delivery and the user end that support multi-business end, setting a adapter between the exchange platform and the online-game organizer, exchange the data in the game database between the exchange platform and the online-game organizing system, to achieve the corresponding relation of the dummy property and the game account that form in the online-game and change by the operation of the business end, that can realize deliver really and safely of the online-game dummy property.
Owner:GOODHOPE CORP
Method and system for processing network service by utilizing multifactor authentication method
InactiveCN102780674ASafety of tradementMessaging/mailboxes/announcementsTransmissionUser inputComputer terminal
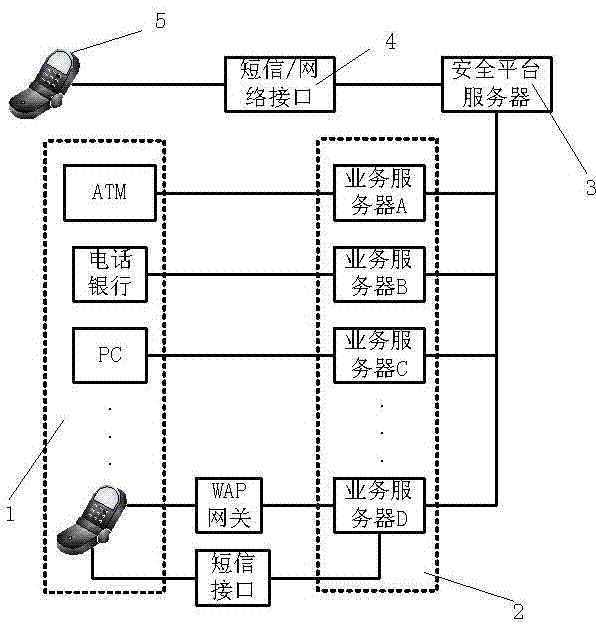
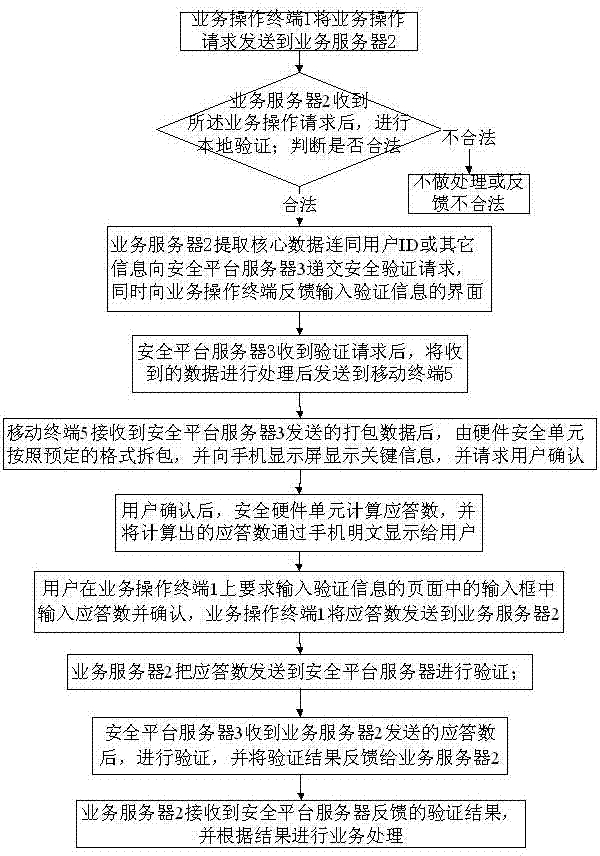
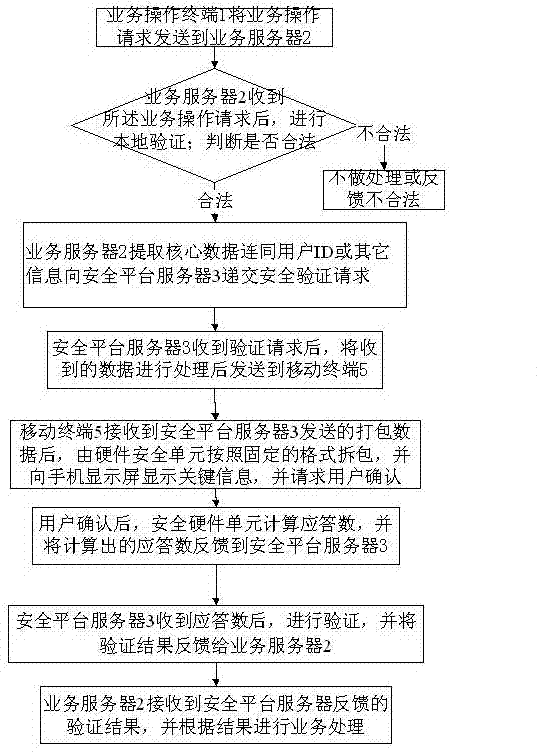
The invention discloses a method and a system for processing network service by utilizing a multifactor authentication method. The method comprises the following steps that a service operation terminal sends a service operation request to a service server; after receiving the service operation request, the service server carries out local authentication; after authentication is successful, a safety authentication request is submitted to a safety platform server; after receiving the authentication request, the safety platform processes the authentication request and then sends data to a mobile terminal corresponding to a user; after receiving data, the mobile terminal calculates the data and displays the data in a clear text for the user; the user inputs and confirms a response number on the service operation terminal; the service operation terminal sends the response number to the service server; the service server sends the response number to the safety platform server; after receiving the response number, the safety platform server authenticates the response number and feeds back the authentication result to the service server; and the service server receives the feedback authentication result and carries out service processing according to the result. According to the scheme disclosed by the invention, the network service processing is safer.
Owner:TSINGHUA TONGFANG CO LTD
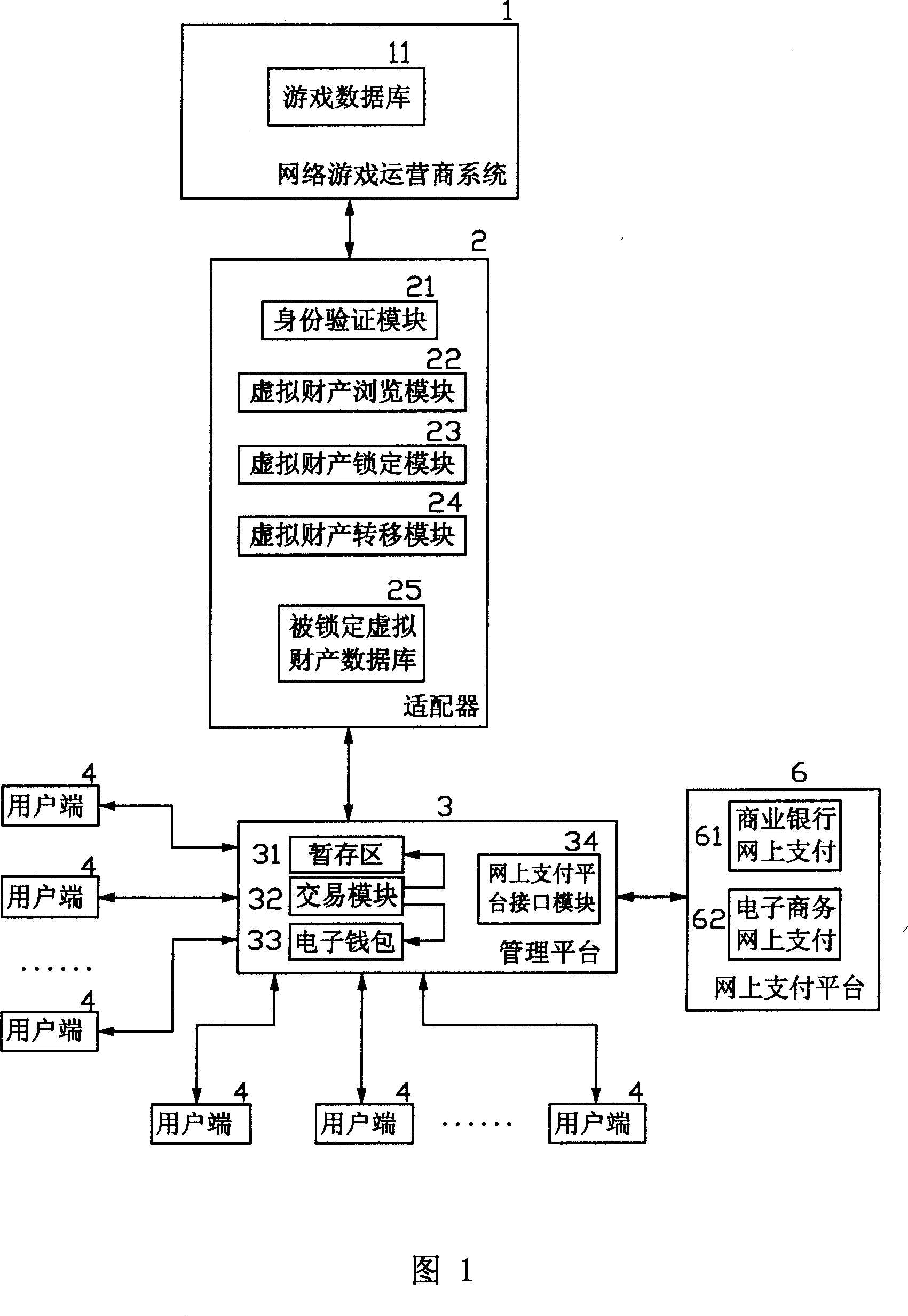
Network game virtual property on-line trading management method and system
InactiveCN101425164ARealize depositAchieve transferCommerceSpecial data processing applicationsVirtual propertyPayment
The invention relates to a method and a system for managing online transaction of virtual property of a network game, which has the main principle that a management platform which has the functions of online consignation, transfer, transaction, payment, and the like and can support a plurality of user ends is built; an adapter is arranged between the management platform and a network game operator system; and the data transaction can be carried out between the management platform and a data base of the network game operator system through a series of standardized definition made to the adapter, so that the online consignation, transfer, transaction and payment of the virtual property of the network game can be operated at the user ends.
Owner:好旺角(厦门)电子科技有限公司
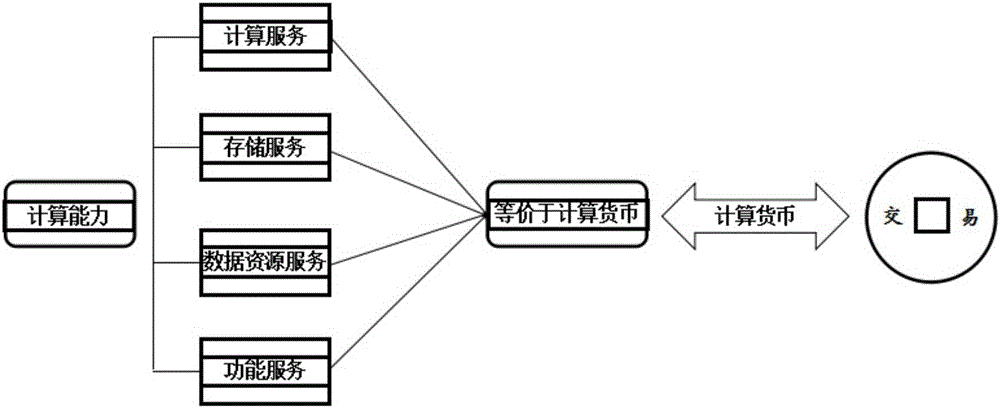
Computing power transaction system and method based on blockchain
InactiveCN106682884ATransaction traceableActive tradingPayment circuitsPayment schemes/modelsDigital currencyOperating system
The invention belongs to the technical field of blockchain and provides a computing power transaction method based on blockchain, comprising the steps of registering and loading information of a computing power provider to blockchain, equalizing computing powers to a computing currency, and registering and loading to the blockchain, wherein the computing powers include computing service, storage service, function services, and data resource services, and the computing currency refers to a digital currency acting as payment and buying media for various computing powers under the support of various computing services for data in an ecological system, such as collection, processing and storage. A computing power transaction system based on blockchain comprises a registering module and a computing currency generating module. By using the computing power transaction method and system based on blockchain and equalizing computing powers to a computing currency for transaction, transactions are traceable and active, have diversified forms and are secured.
Owner:TIANJIN MIYOU TECH
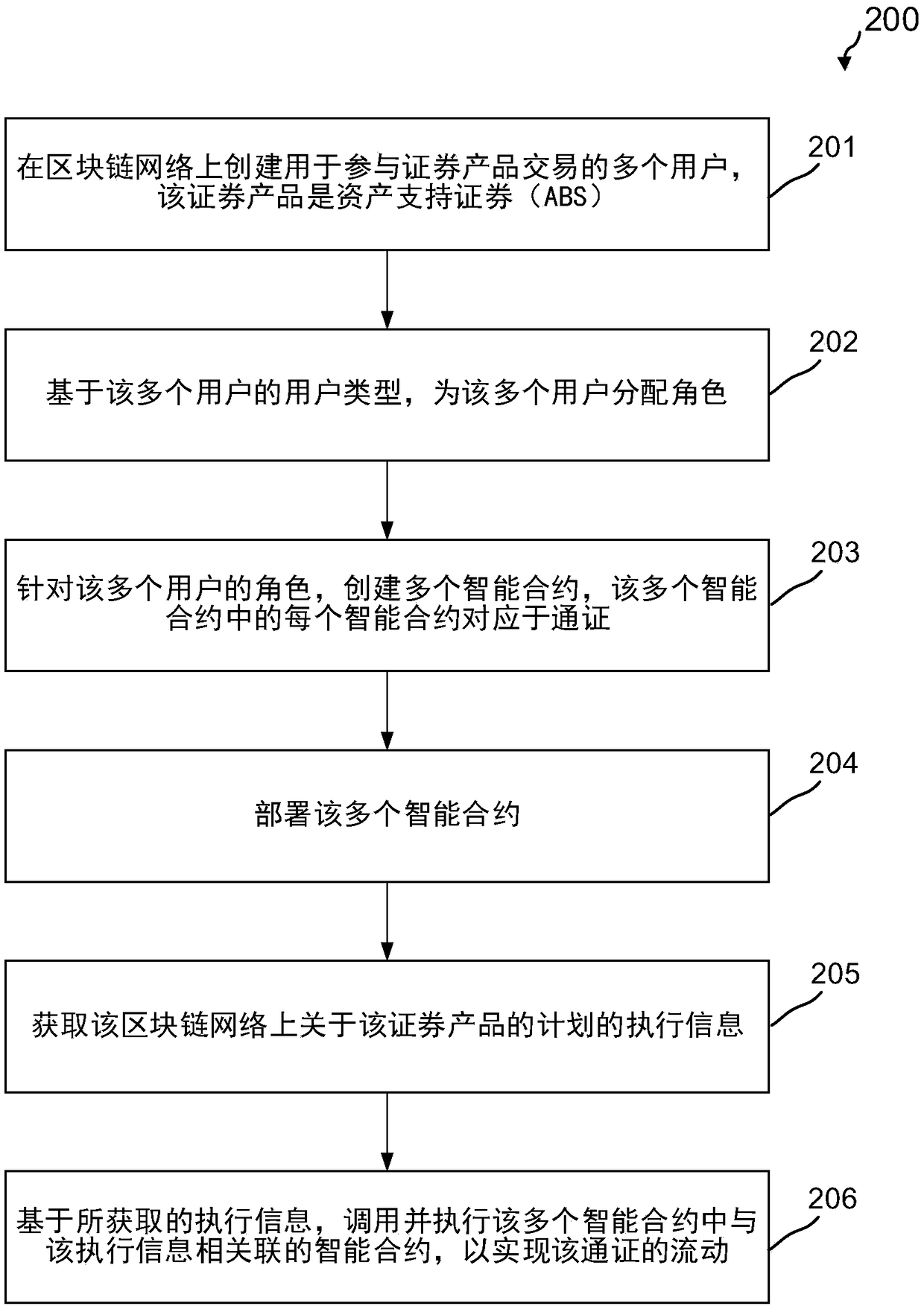
Securities product processing method and device for asset generalization based on block chain
InactiveCN109360103ASafety of tradementReduce or save on service chargesFinanceSmart contractChain network
Embodiments of the present disclosure disclose a block chain-based securities product processing method, the method comprising: creating a plurality of users for participating in securities product trading on a block chain network, the securities product being asset-backed securities (ABS); assigning roles to the plurality of users based on user types of the plurality of users; creating a plurality of smart contracts for the roles of the plurality of users, each smart contract of the plurality of smart contracts corresponding to a pass; deploying the plurality of smart contracts; obtaining execution information on a plan for the securities product on the block chain network; and invoking and executing an intelligent contract associated with the execution information among the plurality ofintelligent contracts based on the obtained execution information to realize the flow of the pass. The method according to embodiments of the present disclosure can improve flexibility and dynamic scalability by dynamically deploying smart contracts, reduce various user costs, and intelligently handle risks.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD
Password dynamic enciphering inputmethod of public emipering mode
InactiveCN1599313ARealize dynamic generationNot afraid of leaksMultiple keys/algorithms usageUser identity/authority verificationPasswordComputerized system
An electronic random numeral generator generates three ciphered safe levels and a random unpredictable dynamic key to be input to the real password, a user selects primary, middle and high three different levels selected by user, an input unit transmits the request information to CPU which generates dynamic key according to the levels and ciphers all numerals and symbols used in the password to be displayed to the user together with the ciphered numerals and symbols in light of this key and their relationship, the user transmits the ciphered real password to the CPU by the input unit to be deciphered and sent out by an output unit. If the password is right, it is allowed to access, if not, it is refused, the memory unit is used for storing real password and corrected real password.
Owner:常志文
Network game virtual assets on-line management method and system
InactiveCN101082941AGuarantee safe and reliableTransactions are more flexibleApparatus for meter-controlled dispensingCommerceVirtual propertyData exchange
The invention discloses an on-line managing method and system for virtual asset of network game, which is characterized by the following: building on-line managing platform with register, transfer, transaction and payment to support user end; establishing an accommodator between management platform and operational businessman of network game; giving a series of standardizing definition for accommodator; exchanging data between managing platform and game database of operational businessman of network game; realizing on-line register, transfer, transaction and payment of virtual asset of network game for user end.
Owner:GOODHOPE CORP
Visible self-service terminal
InactiveCN101650853AImprove service imageSafety of tradementComplete banking machinesFinanceService level requirementCommand system
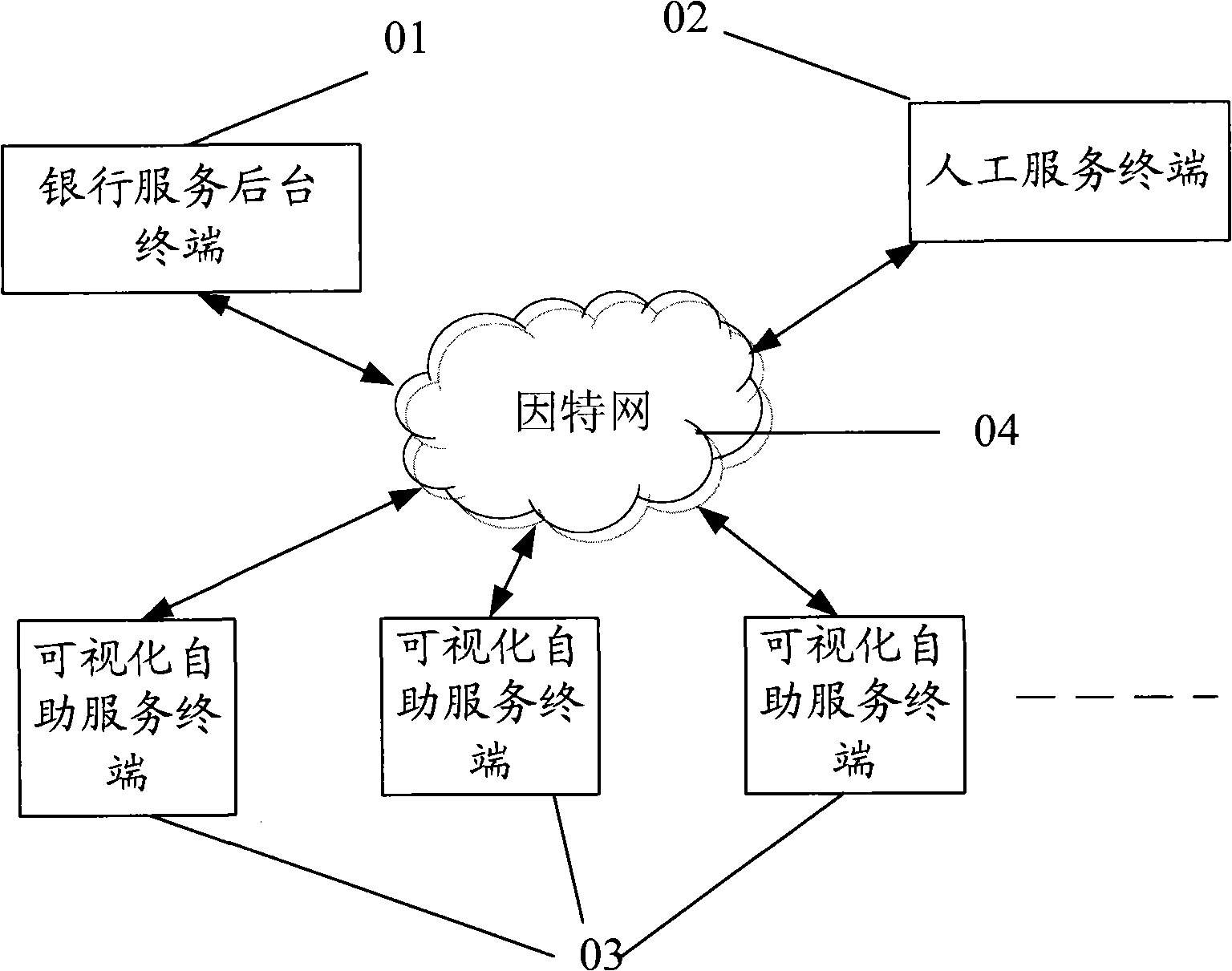
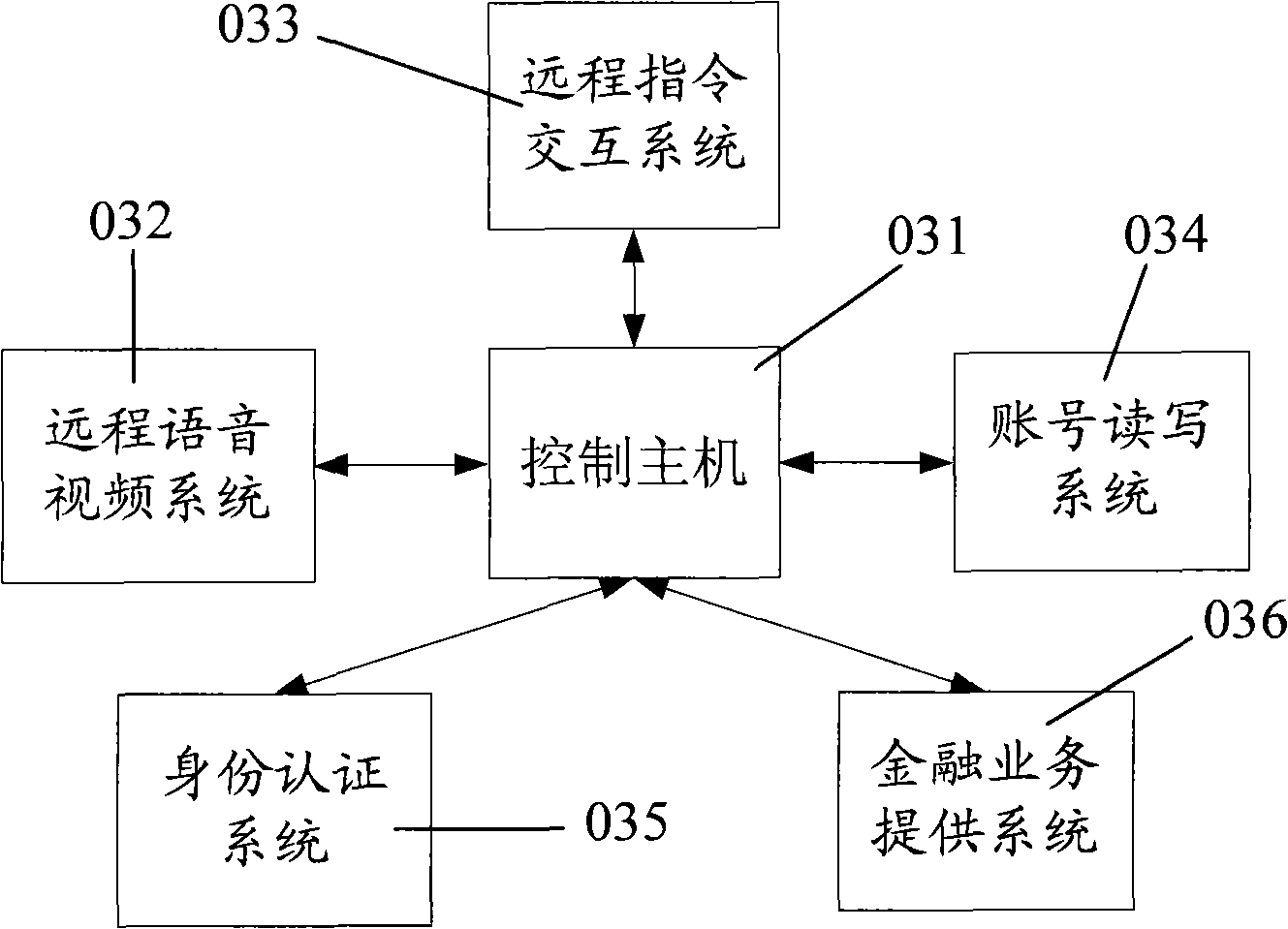
The invention relates to a visible remote interactive self-service terminal capable of processing full-service and meeting requirements of manual intervention services as well as simple self services.The visible self-help service terminal comprises a control host machine, a remote voice and video system, a remote command interactive system, an account number reading and writing system, an identity authentication system and a financial business providing system, wherein the remote voice and video system is used for performing remote voice and video interaction with a manual service terminal; the remote command interactive system is used for performing interaction with the manual service terminal and a bank service background terminal; and the account number reading and writing system, theidentity authentication system and the financial business providing system can meet service requirements. A command system of the manual service terminal is used for performing command control on theremote self-service terminal; and the account number reading and writing system and the identity authentication system perform certificate authority through the bank service background terminal. The introduction of the remote voice and video system ensures that the self-help service terminal is safer and meets more service requirements.
Owner:GRG BAKING EQUIP CO LTD
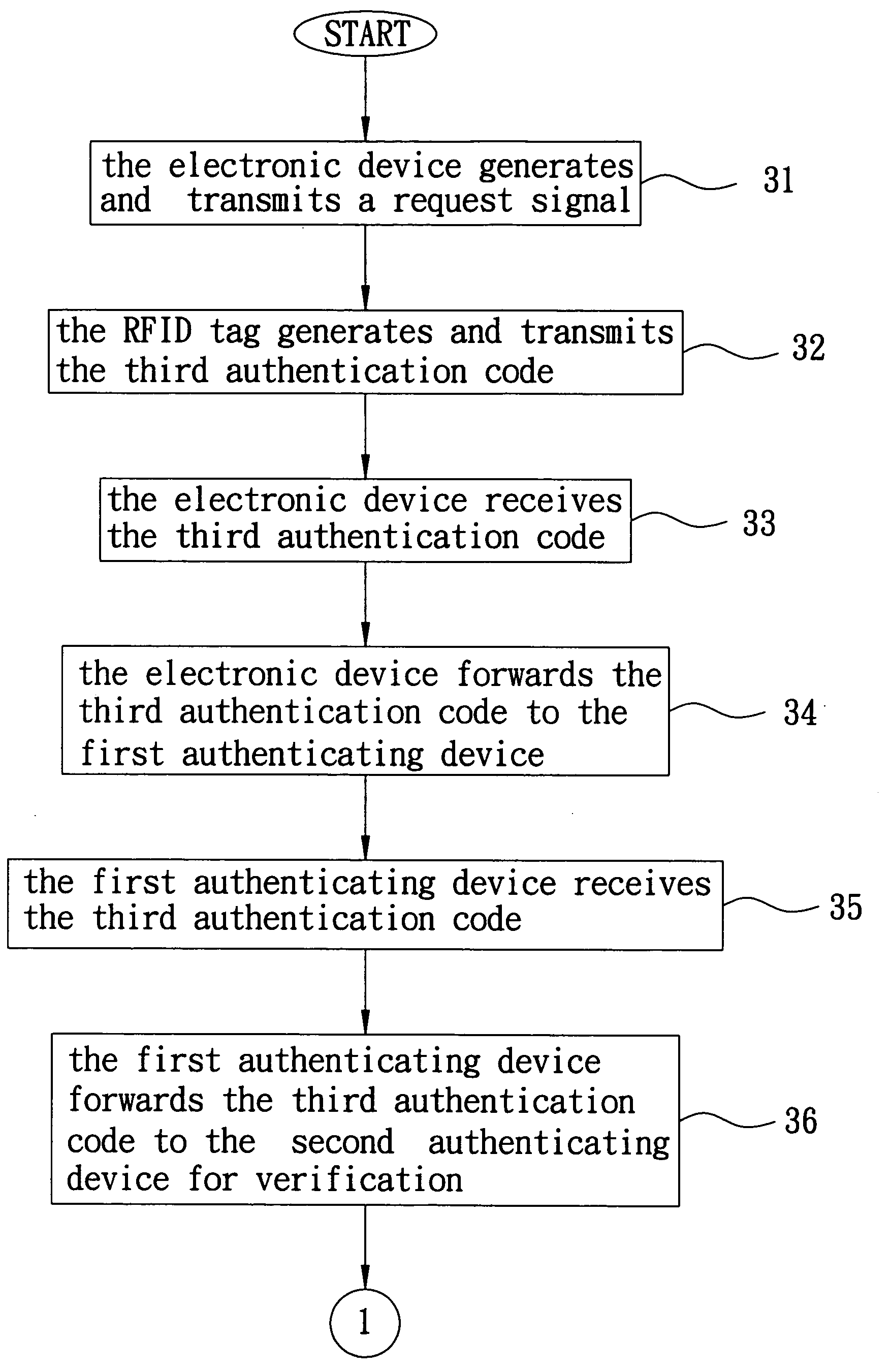
Method and system for verifying authenticity of an object
InactiveUS20080079535A1Verify authenticityEnsure safetyElectric signal transmission systemsMultiple keys/algorithms usageAuthenticationElectronic equipment
A method for verifying authenticity of an object includes the steps of: enabling an electronic device to generate and transmit a request signal; in response to the request signal, enabling an RFID tag to generate a first authentication code based on a varying secret key, a second authentication code based on a unique identification code of the RFID tag and the varying secret key, and a third authentication code that is based on the unique identification code of the RFID tag and the first and second authentication codes, and to wirelessly transmit the third authentication code for reception by the electronic device; and enabling the electronic device to forward the third authentication code received from the RFID tag to an authenticating center for verification. A system, which includes the RFID tag, the electronic device, and the authenticating center, and which performs the method is also disclosed.
Owner:USERSTAR INFORMATION SYST
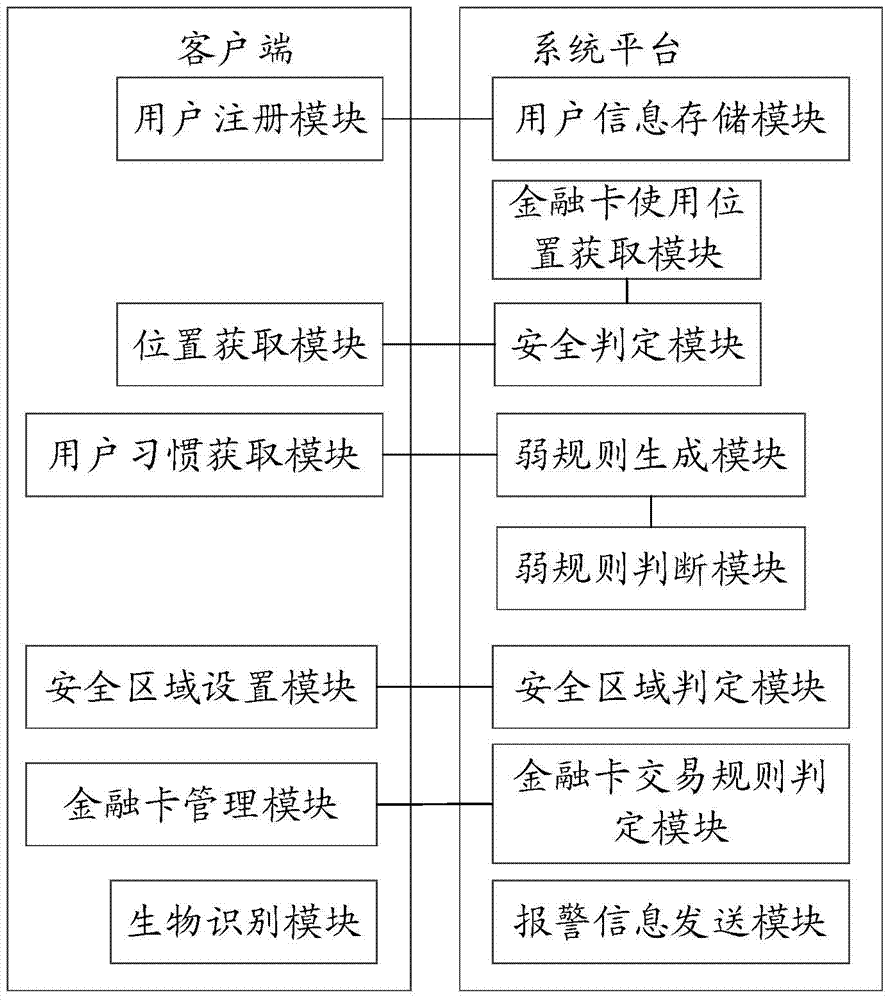
System and method for achieving transaction safety protection of financial card based on location binding
InactiveCN104504566AReduce fraudFraud controlProtocol authorisationStructure of Management InformationService module
The invention relates to a system and a method for achieving transaction safety protection of financial card based on location binding, wherein the system comprises a user registration module which is used for obtaining registration information of a user and financial card information added by the user, and sending the information to a system platform for user registration and financial card addition; a location service module which is used for obtaining location information of a client terminal; the system platform comprises a user information storage module which is used for storing personal information and the financial card information of the user; a financial card using location obtaining module; a safety judgment module which is used for judging whether the transaction is safe based on that whether the using location of the financial card corresponding to the user is in accordance with the location of the client terminal at the same moment. The method and the system for achieving transaction safety protection of financial card based on location binding employing such a structure implement the safety judgment based on the location identification via binding the location of the financial card with the location of the client terminal, thus the transaction of the financial card is more safe and reliable; the method and system have a wider application range.
Owner:YINLIAN FINANCIAL INFORMATION SERVICE BEIJING CO LTD
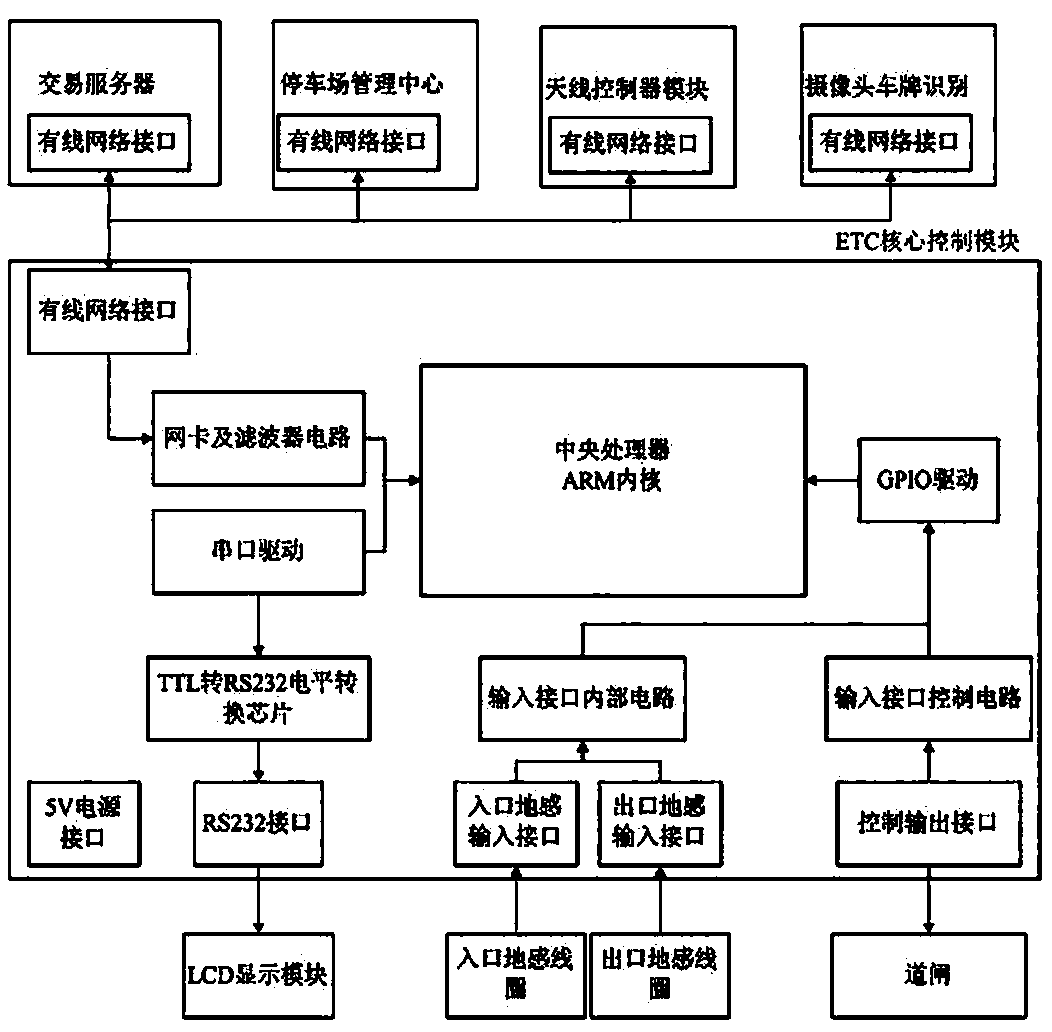
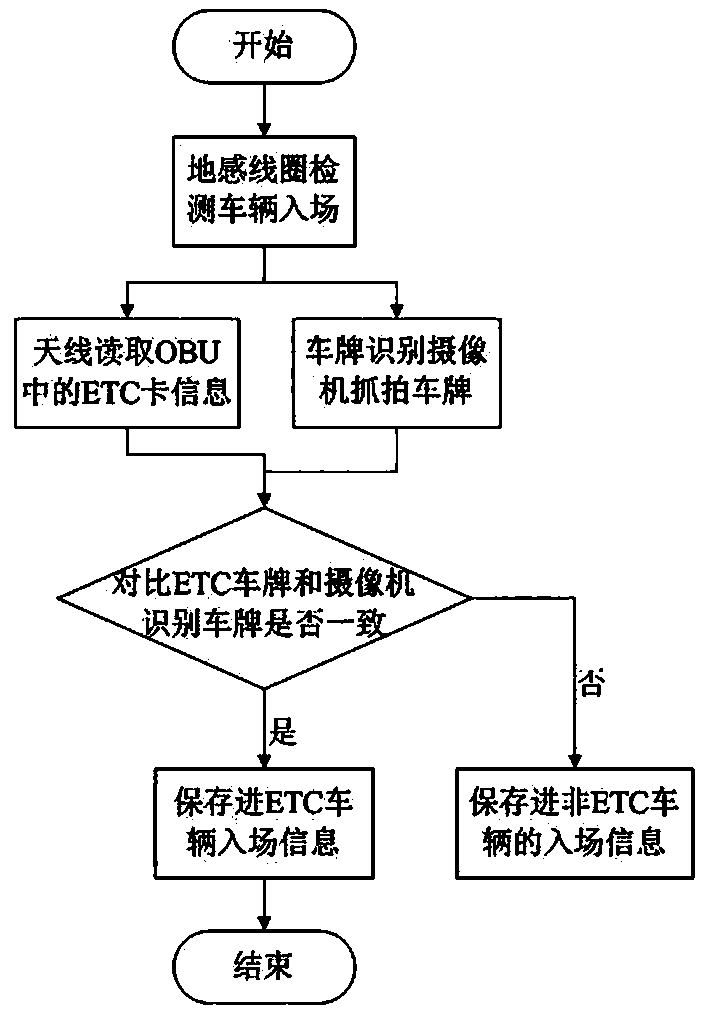
Intelligent parking lot system and method for ETC
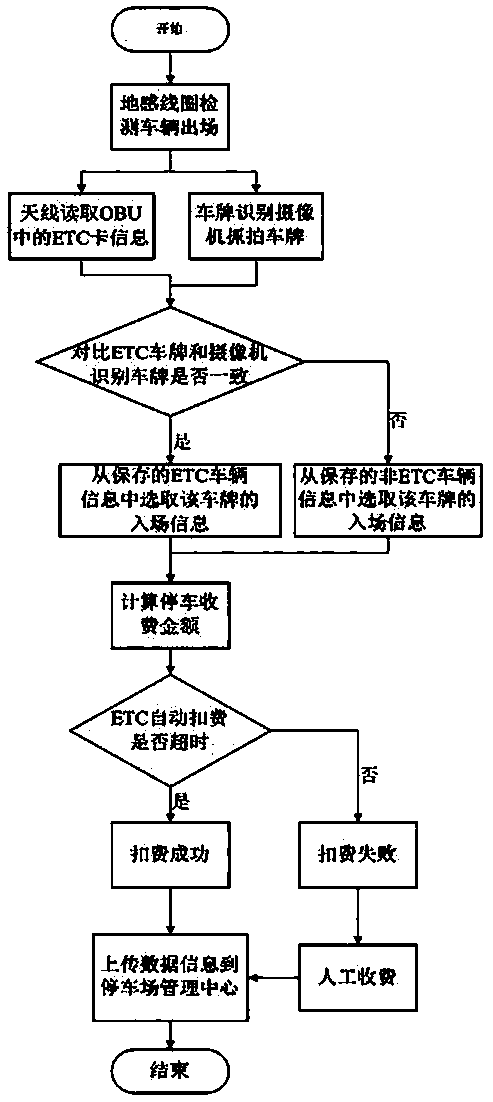
InactiveCN107945293ASave the tedious process of manual billingReduce waiting timeTicket-issuing apparatusPayment architectureControl flowPayment
The invention relates to an intelligent parking lot system and method for ETC, and belongs to the technical field of parking lot charging systems. The intelligent parking lot system comprises an ETC core control module, a transaction server, a background service end of a parking lot management center, an antenna controller module, a camera license plate identification module, an LCD display module, an inlet ground induction coil, an outlet ground induction coil and a barrier gate. The system and method provided by the invention have the advantages that the system structure is reasonable, a control flow is simple, the system stability is high, and payment is efficient and convenient.
Owner:河南省视博电子股份有限公司
A block chain-based distributed data sharing system and method
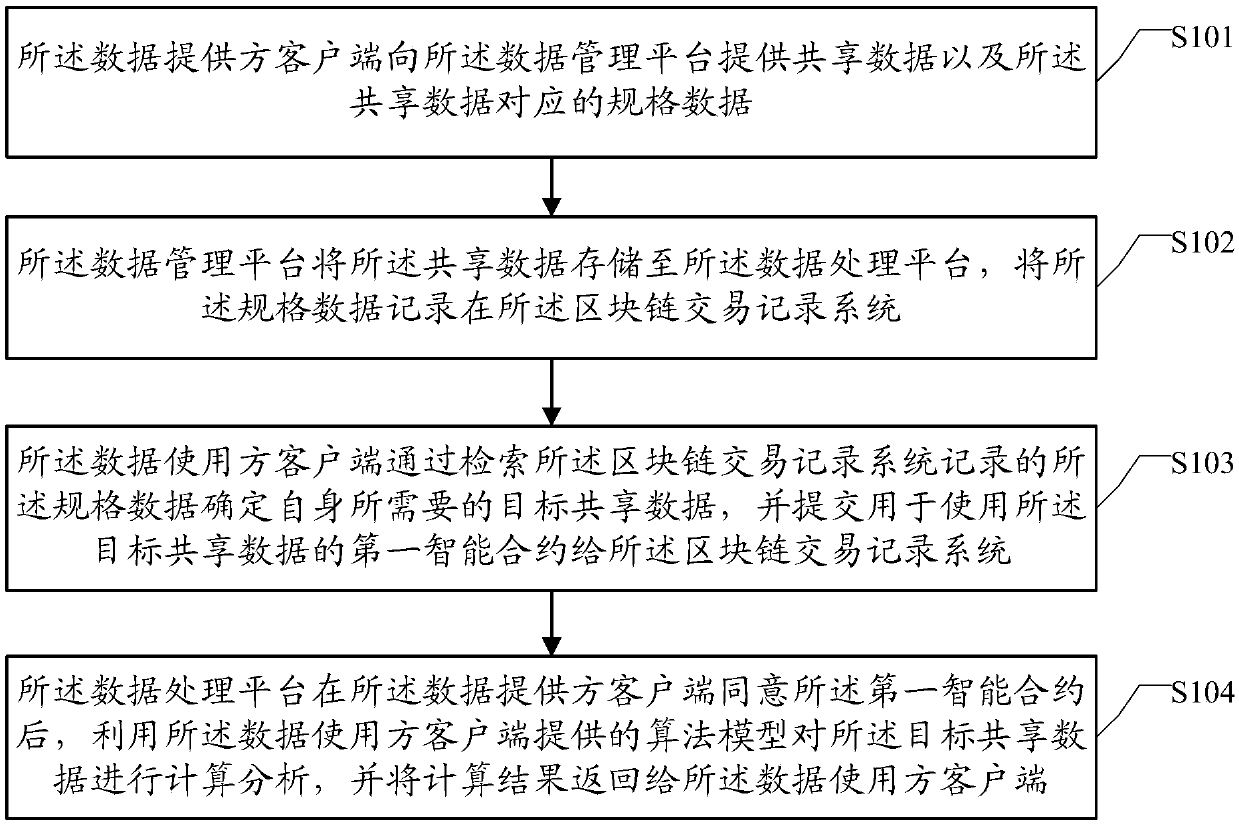
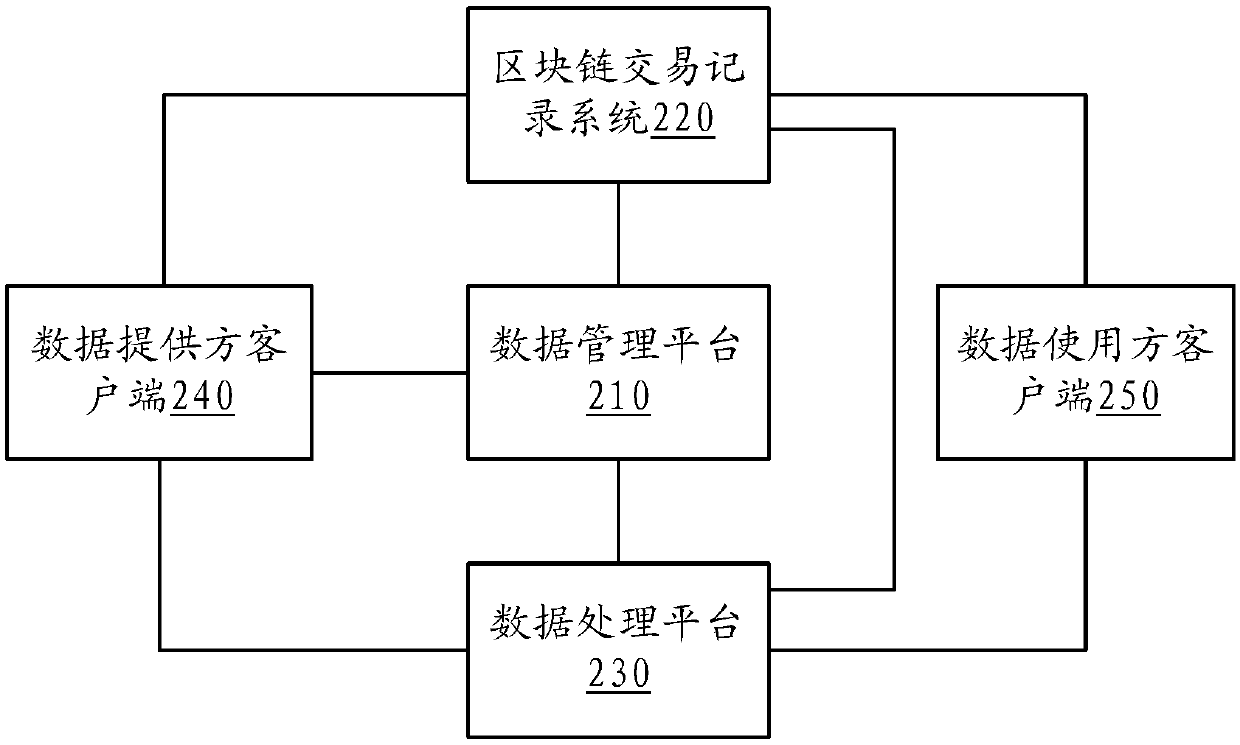
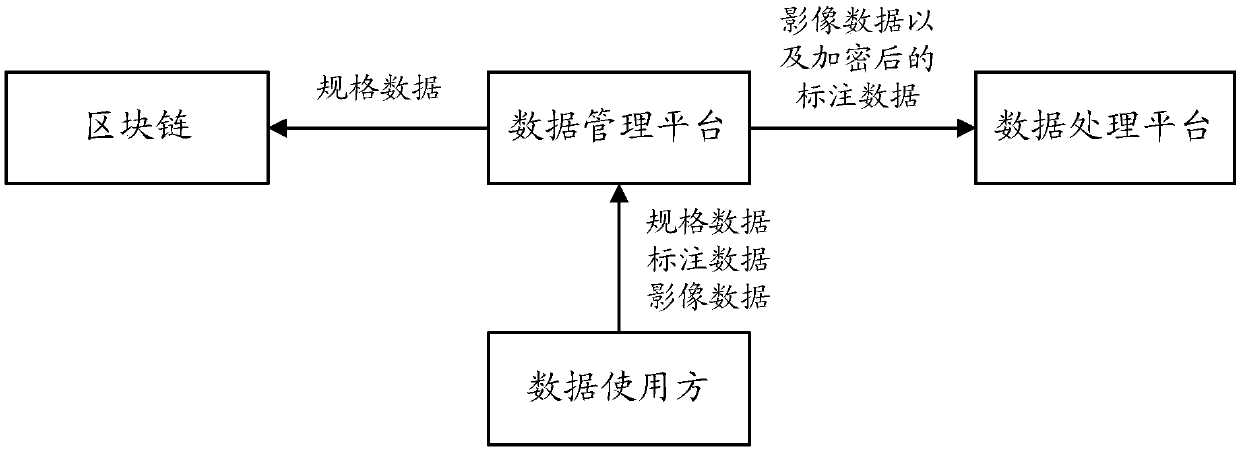
InactiveCN109542856AEnsure safetyGuaranteed privacyDigital data information retrievalFinanceData centerData provider
The invention provides a block chain-based distributed data sharing system and method, which are used for data secure transaction. The system comprises a data management platform, a block chain transaction recording system, a data processing platform, a data provider client and a data user client. The data processing platform puts the data of the data provider and the algorithm model of the data user which meet the requirements of the user into a temporary virtual running environment, Load the algorithm model to calculate and analyze the data, return the calculation results to the data user after the calculation, and upload the data provider and the data user to the temporary virtual environment at the same time, destroy the algorithm model. This decentralized data-sharing mechanism is safer than the current centralized data centers and provides continued value to data providers.
Owner:上海基诺联生物科技有限公司
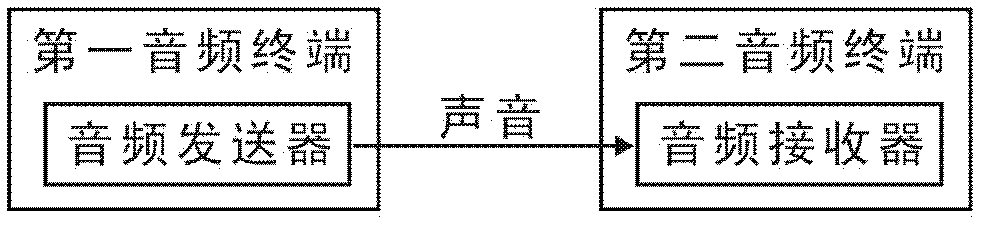
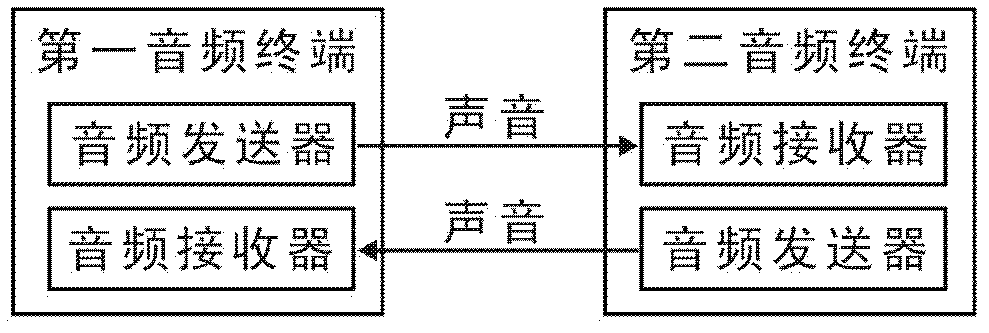
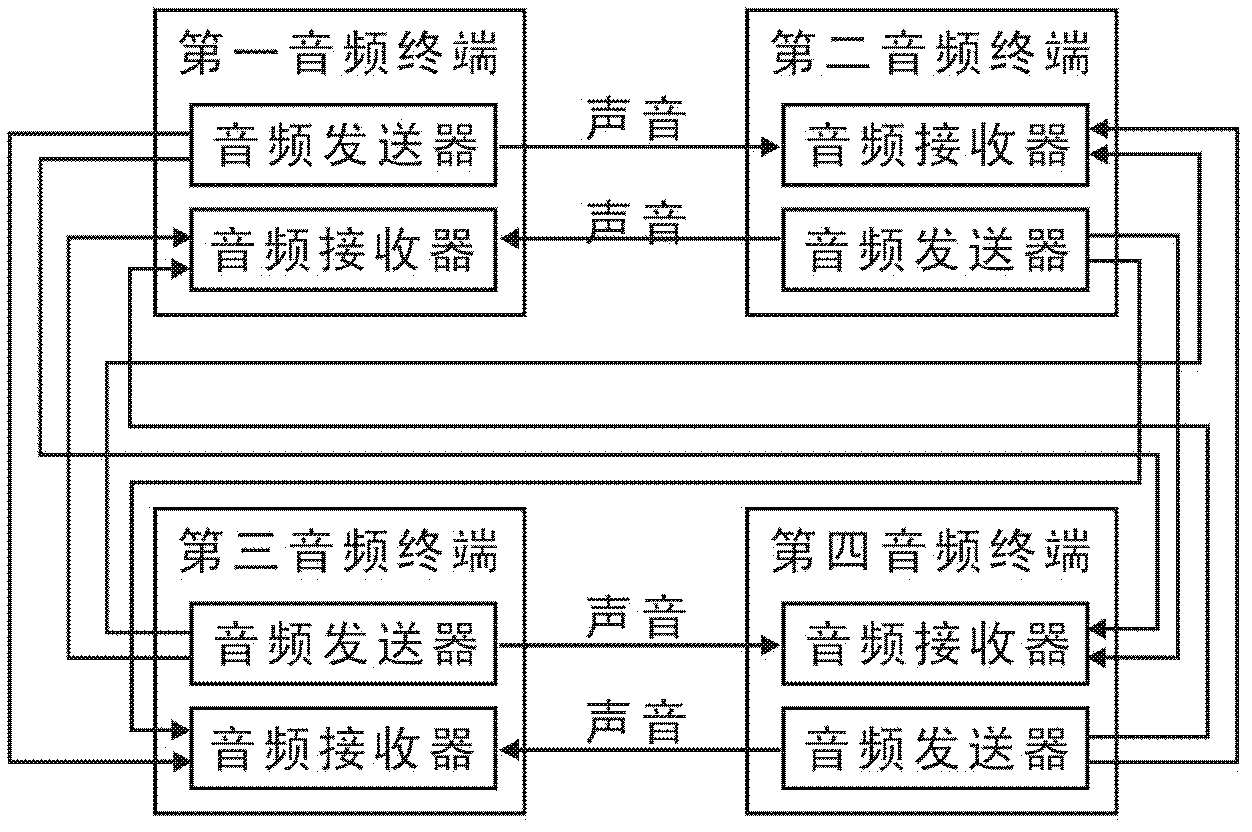
Audio data transmission system, audio data transmission method and application thereof
InactiveCN102325224ASafety of tradementConvenient transactionSpeech analysisSubstation equipmentDigital dataFinancial transaction
The invention discloses an audio data transmission system, which comprises two or more audio terminals, and an audio transmitter for converting digital application data signals into voice signals and an audio receiver for converting voice signals into digital application data signals are arranged in each audio terminal. The invention also discloses an audio data transmission method; a rule of corresponding conversion between digital application data signals and voice signals is first established; at a transmitting end, digital application data signals are first converted into voice signals according to the rule of conversion, and the voice signals are then transmitted; and at a receiving end, the voice signals transmitted by the transmitting end are converted into the digital application data signals according to the rule of conversion. The invention also discloses the application of the audio data transmission system and the audio data transmission method in close range electronic transaction within one meter. By means of the invention, mobile phones and other mobile terminals can be utilized to directly carry out safe, convenient and quick close range electronic transaction.
Owner:CHENGDU MOBO NETWORK TECH
E-shop system
InactiveCN101645157AConvenient transactionSafety of tradementCommerceSpecial data processing applicationsCommunity orPayment
The invention relates to the technical field of an E-shop, in particular to a convenient and fast E-shop system which can combine with communities, shops, etc. Compared with the prior art, the E-shopsystem combines with service items correlative to life, such as shopping streets, community services, movies, games, and the like, provides an online trading platform for merchandise, and provides face-to-face trade for the merchandise and after-sale services. By adopting on-line shopping or reserving, the E-shop system uniformly examines, verifies, bargains and purchases the merchandise. Using amember registration system set on the network, the E-shop system can realize home-delivery service at the communities or family-run shops, can adopt cash transaction and on-line payment mode, can setup community service points at each resident community or residential area, has the advantages of convenient and fast shopping, safe and reliable transaction and the like, has stable after-sale services protection, can be taken as supermarkets at the door of home, and leads each consumer to experience the enjoyment and the convenience of the on-line shopping.
Owner:庄秀宝
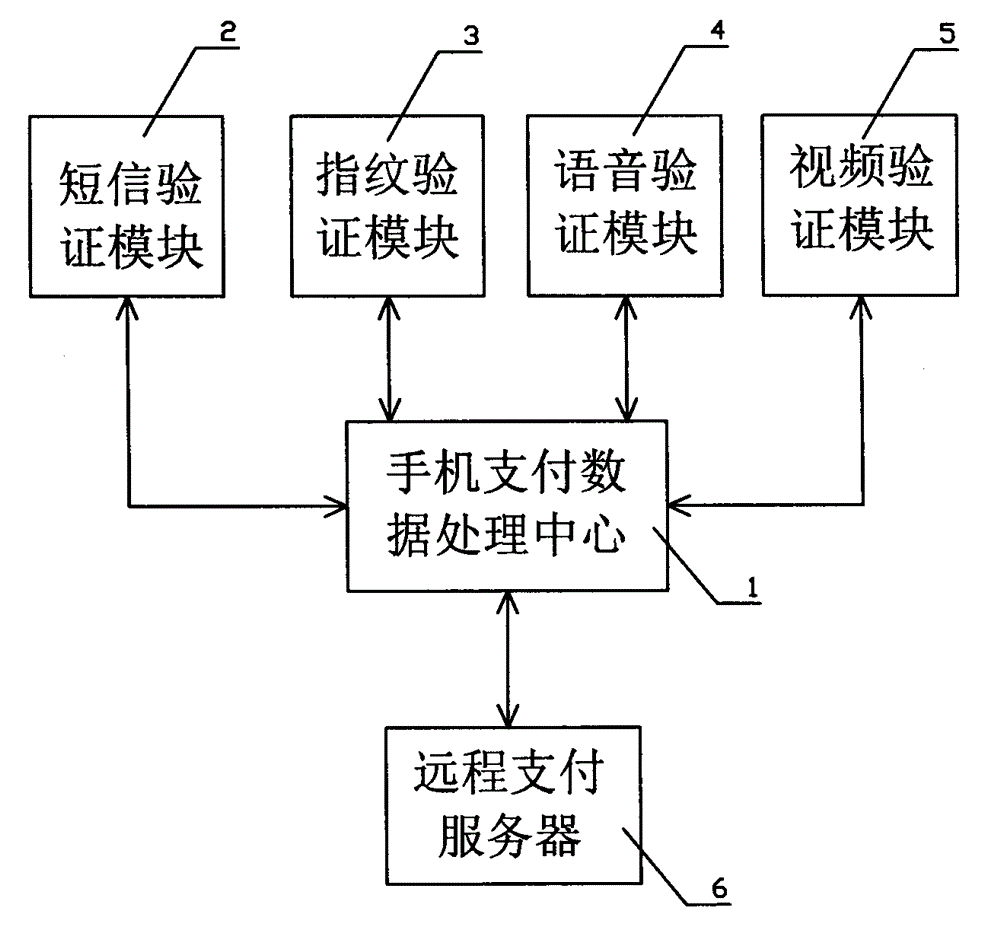
Mobile phone payment system
The invention provides a mobile phone payment system, which has the advantages of being safer in transaction and optional in security levels. The mobile phone payment system comprises a mobile phone payment data processing center (1), a short message verification module (2), a fingerprint verification module (3), a voice verification module (4), a video verification module (5) and a remote payment server (6), wherein the short message verification module (2), the fingerprint verification module (3), the voice verification module (4) and the video verification module (5) are independent functional units built in a mobile phone and each comprise corresponding software and hardware; the fingerprint verification module (3) comprises a fingerprint sensor and a fingerprint analysis and comparison program; the voice verification module (4) comprises a microphone, a loudspeaker and a voice identification program; the video verification module (5) comprises a camera and a video identification program; and the short message verification module (2), the fingerprint verification module (3), the voice verification module (4) and the video verification module (5) are all uniformly controlled by the mobile phone payment data processing center (1).
Owner:南宁市锋威科技有限公司
Method, mobile terminal, server and system for identity authentication
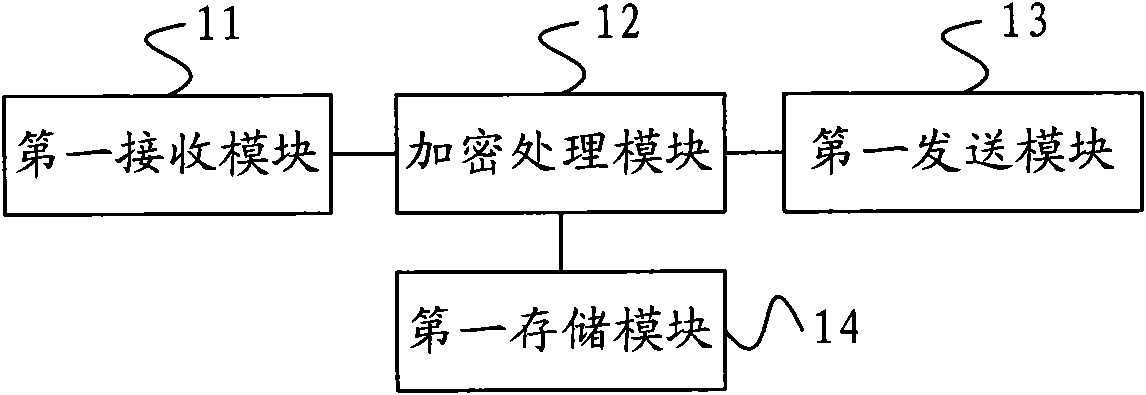
InactiveCN101594611ASafety of tradementEasy to operateSecurity arrangementNetwork data managementQuality of serviceMobile phone
The invention provides a method, a mobile terminal, a server and a system for identity authentication. The method comprises the following steps of: identifying information transmitted by a mobile terminal to a user identity identification module by a mobile terminal network banking encryption card, if the identified information is an authentication character string transmitted by a far-end server and used for identity authentication, encrypting the authentication character string by the stored user digital certificate, and obtaining a first encryption character string; and returning the first encryption character string obtained by the mobile terminal network banking encryption card to the far-end server for identity authentication. Due to the arrangement of the mobile terminal network banking encryption card between the mobile phone and the SIM card, the network banking trade of the user by the mobile phone is safer and more convenient, and the operation is easy; moreover, as for the user, the user can make the network banking trade by the mobile phone at any time and in any place, so that the quality of service is improved.
Owner:北京钱袋宝支付技术有限公司
Method for identity authentication, mobile terminal, server, and identity authentication system
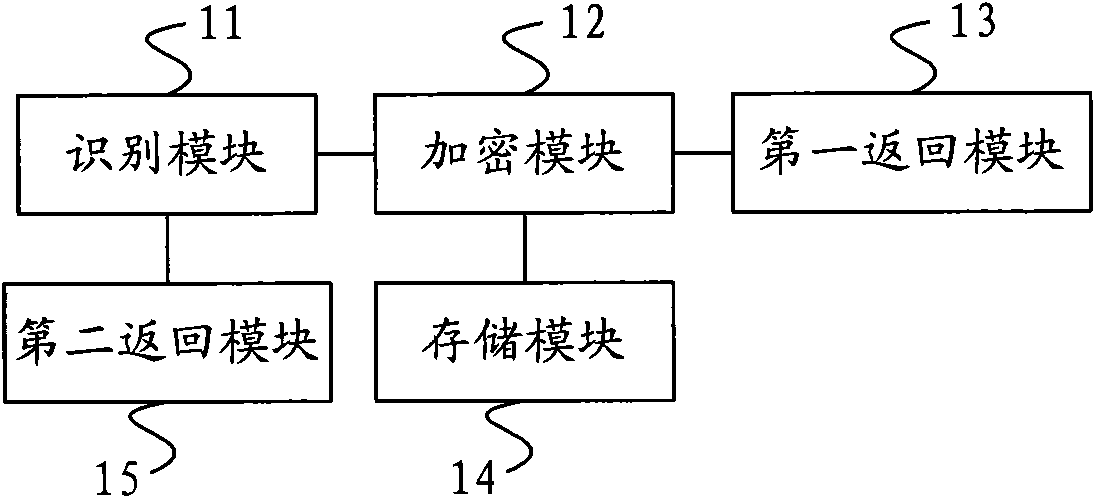
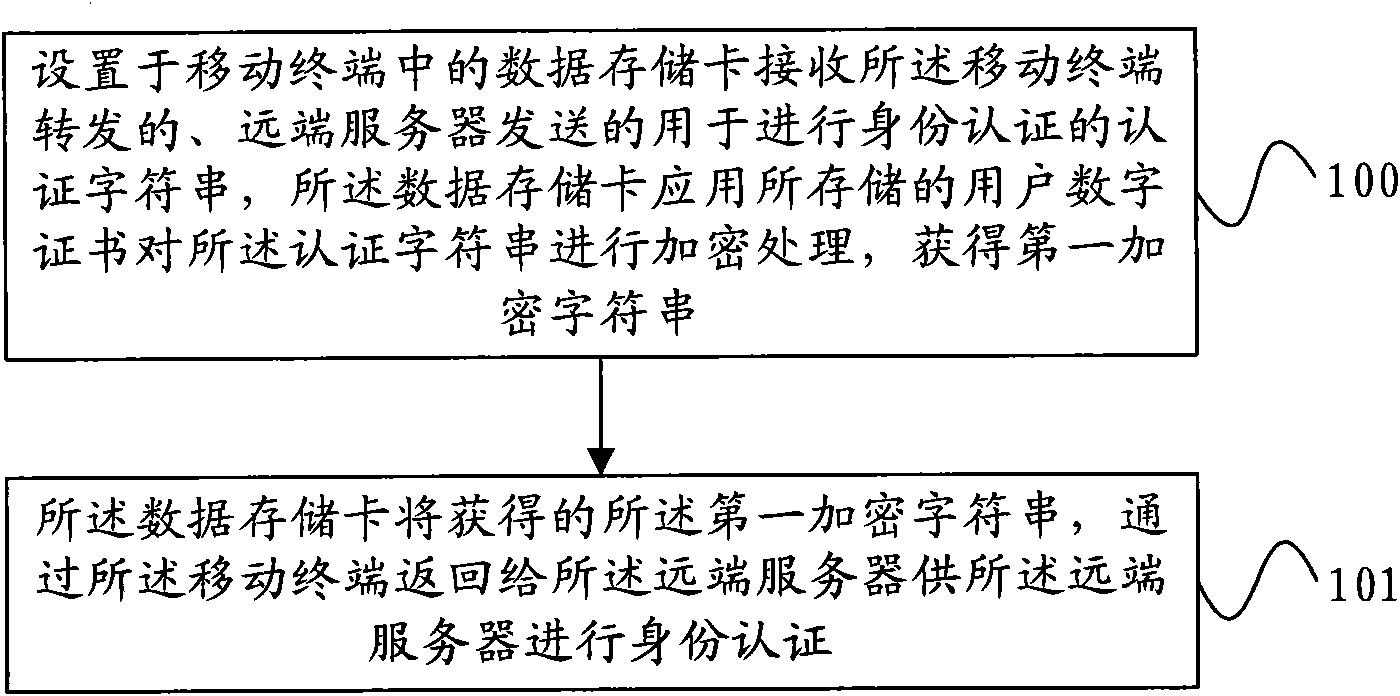
ActiveCN101605325AImplement identity authenticationSafety of tradementUser identity/authority verificationWireless network protocolsQuality of serviceAuthentication system
The invention provides a method for identity authentication, a mobile terminal, a server and an identity authentication system. A data storage card arranged in the mobile terminal receives an authentication character string for identity authentication, which is forwarded by the mobile terminal and sent by a remote server; the data storage card applies a stored user digital certificate to encrypt the authentication character string to obtain a first encrypted character string; and the data storage card returns the obtained first encrypted character string to the remote server through the mobile terminal to facilitate the identity authentication of the remote server. The data storage card of the mobile terminal stores the user digital certificate used for the user identity authentication to realize the identity authentication of a user, so that ebanking service carried out by the user through a mobile phone is more safe and convenient, and has simple operation; and for the user, the user can carry out the ebanking service at all times and places through the mobile phone, and the service quality is improved.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
Polymer compositions and methods for shielding radioactivity
InactiveUS20050203229A1Prevent leakageSafety of tradementPolyurea/polyurethane coatingsShieldingDepleted uraniumScrap
A urethane based polymer composition is provided that exhibits superior shielding properties during and after exposure to high level radiation. The composite is formed by mixing a liquid isocyanate monomer, preferably 4,4′-diisocyanate monomer with a liquid phenolic resin, preferably phenol formaldehyde resin, and a phosphate ester flame retardant. An optional pyridine catalyst may be added to shorten the cure time. The resulting composition cures at room temperature and can be utilized in several manners, including spraying or pouring the composition prior to curing over radioactive material to prevent leakage of radiation. The uncured composite can be sprayed on the walls of a room or container to prevent leakage of radiation and can also be used to contain radiation prior to demolition. The uncured composite can also be molded into bricks or panels for use in construction. In a preferred embodiment, the polymer composition further incorporates radioactive waste, namely depleted uranium oxide, and can be used in conjunction with specially designed containers for storing radioactive material. The resulting polymer / waste composition cures at room temperature and does not deteriorate or suffer structural damage when exposed to higher levels of gamma radiation, nor do the mechanical or chemical properties undergo any detectable change. The composition is resistant to biodegradation and combustion, and does not creep or shrink during thermal cycling.
Owner:SOUNDARARAJAN RENGARAJAN
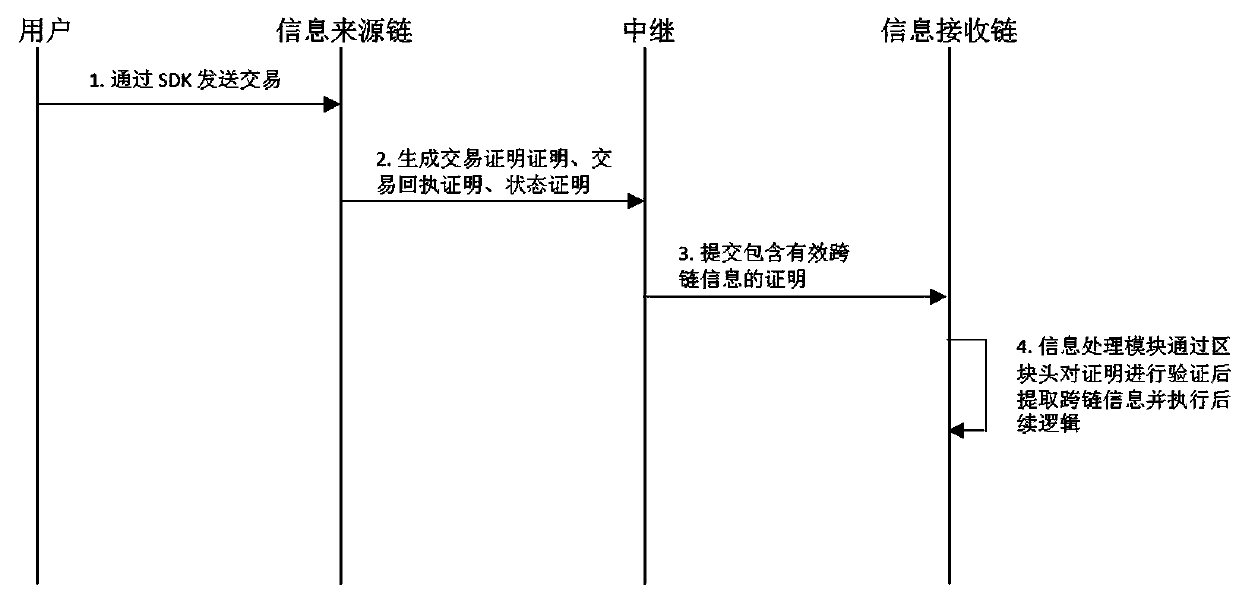
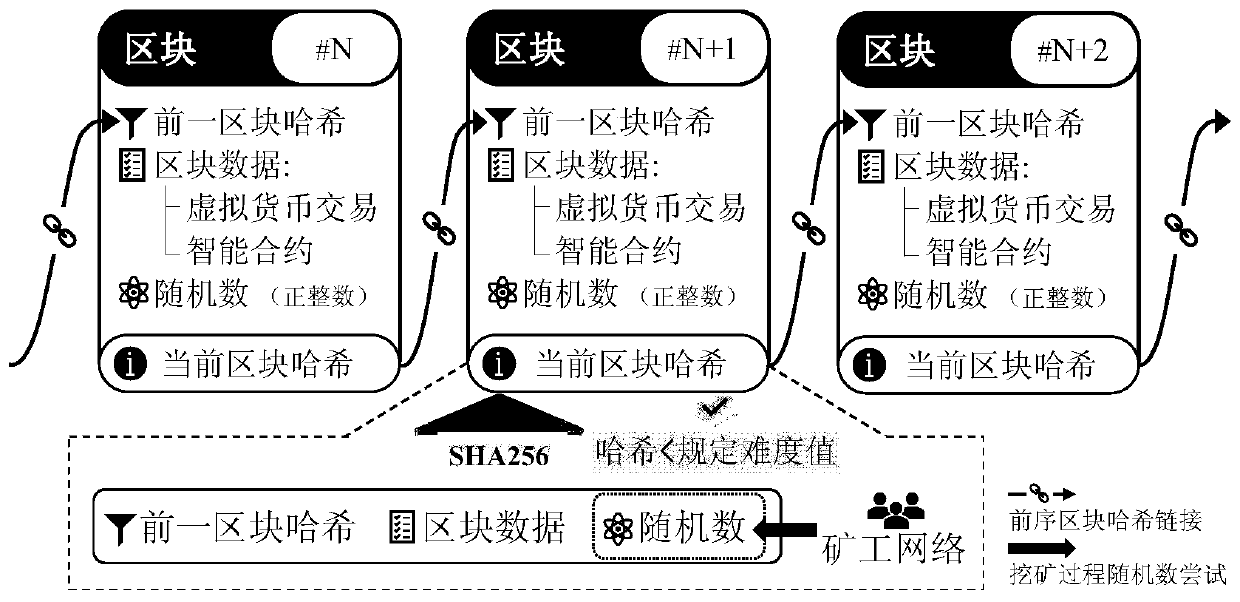
Cross-chain information verification method based on light node technology
ActiveCN111159293ASafe deliverySafety of tradementFinanceDatabase distribution/replicationInformation processingTrunking
The invention discloses a cross-chain information verification method based on a light node technology, and the method comprises the following steps: S1, achieving a light node of an information source chain on an information receiving chain, wherein the light node synchronizes block head information through the connection with all nodes on the information source chain; S2, deploying a cross-chaininformation processing module on the information receiving chain; S3, realizing a decentralized relay; s4, verifying the block head from the information source chain through the light node, wherein the cross-chain information processing module receives the verified block head of the information source chain and then stores the verified block head; s5, verifying the received transaction certificate, transaction receipt certificate or state certificate after transaction execution according to the stored transaction root, transaction receipt root or state root in the block head, and extracting and subsequently processing the cross-chain information contained in the certificate after the verification is passed by the cross-chain information processing module.
Owner:HANGZHOU ABMATRIX TECH CO LTD
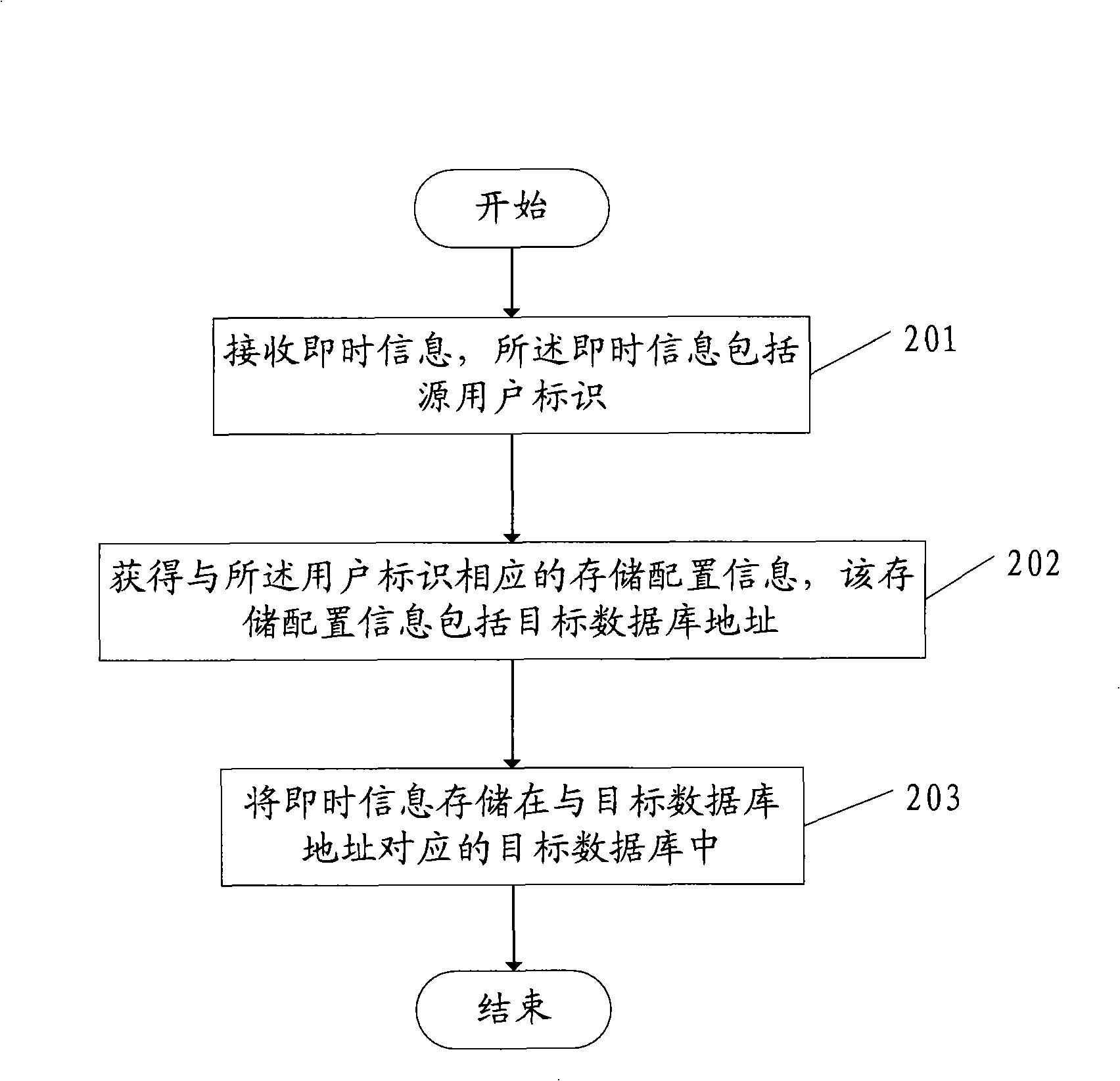
Method and system for storing instant information
InactiveCN101330431ASafety of tradementGood trade creditStore-and-forward switching systemsInformation storageData mining
The invention discloses an instant message storage method and a system thereof. The method comprises the following steps: receiving an instant message comprising user identification; acquiring storage allocation information corresponding to the user identification, which comprises a target database address; storing the instant message in a target database corresponding to the target database address. In this way, instant messaging records related to a user are stored in the target database corresponding to the user identification in a centralized manner, so as to avoid the problems such as low searching efficiency and high cost in the prior art caused by traversing each server in a cluster in order to acquire the instant messaging records of the user, and prevent the server performance from being affected thereby.
Owner:ALIBABA GRP HLDG LTD
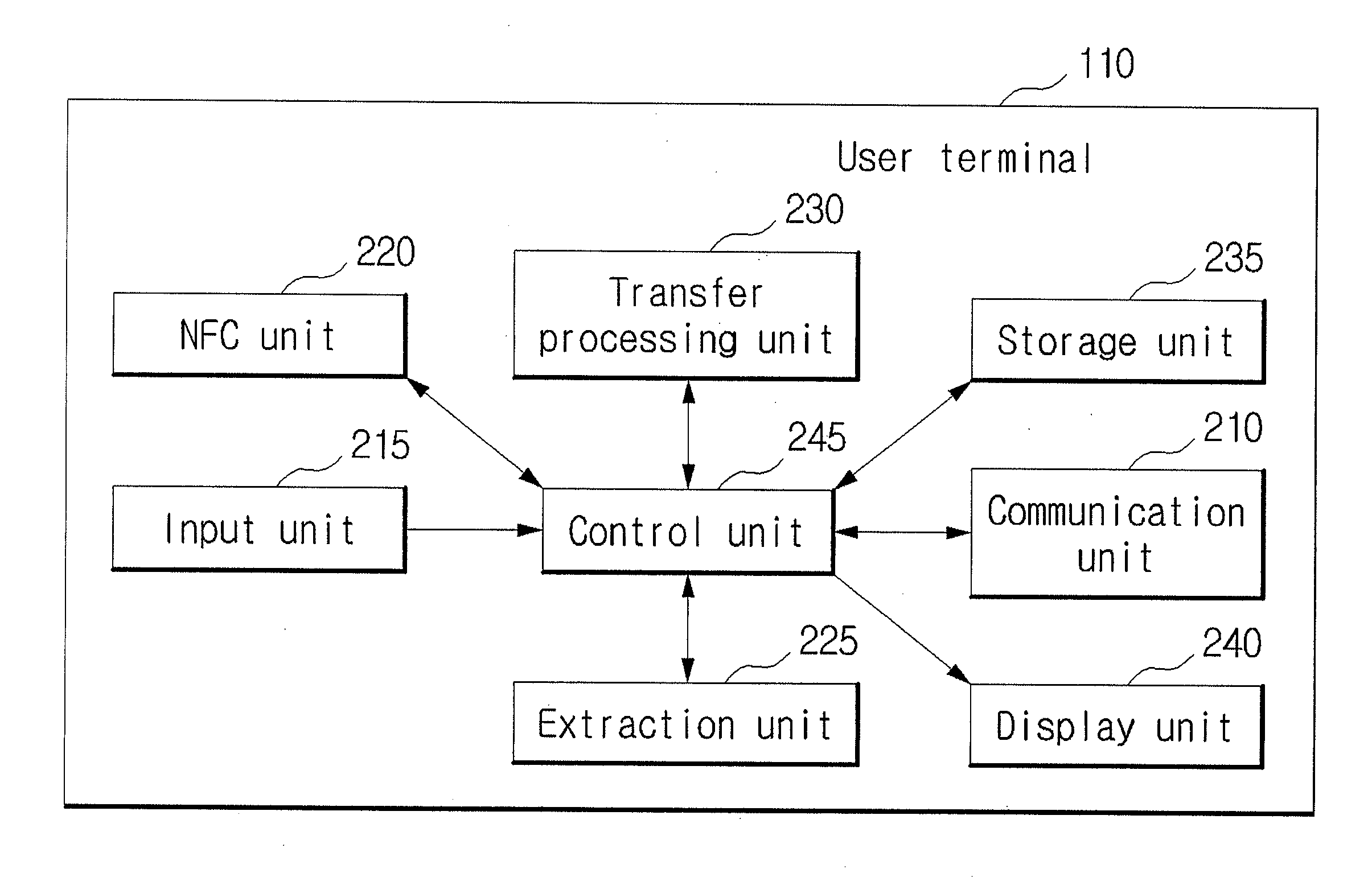
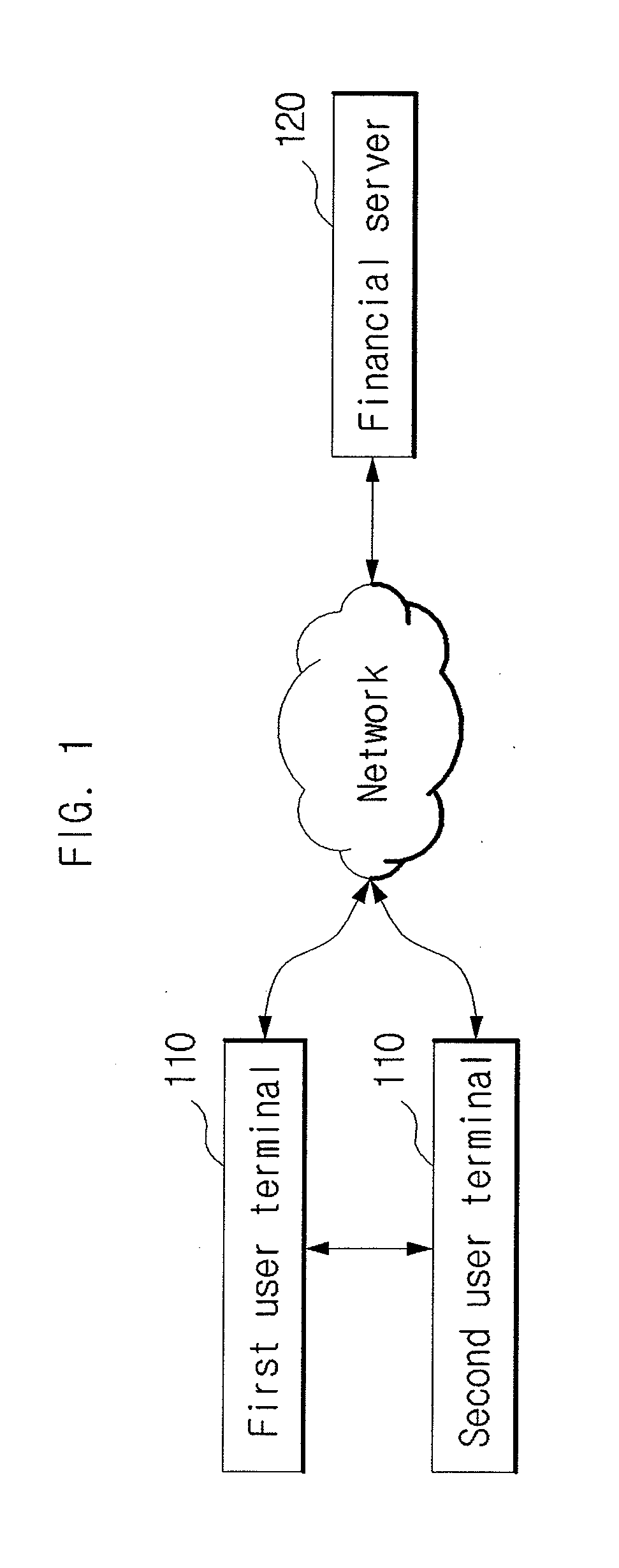
Method and system for providing financial service
InactiveUS20120173433A1Traffic minimizationImprove securityDebit schemesProtocol authorisationDeposit accountComputer terminal
A system and a method for providing a financial service. The system for providing a financial service can include: a first user terminal which signs financial transaction information with a pre-stored first private key, the financial transaction information including withdrawal account information, a PIN of the withdrawal account, deposit account information and amount information; a second user terminal which receives the signed financial transaction information by being connecting with the first user terminal through near field communication and which further signs the signed financial transaction information with a pre-stored second private key; and a financial server configured to transfer an amount corresponding to the amount information from an account of the withdrawal account information to an account of the deposit account information.
Owner:KT CORP
Method, device and system for transaction by mobile phone
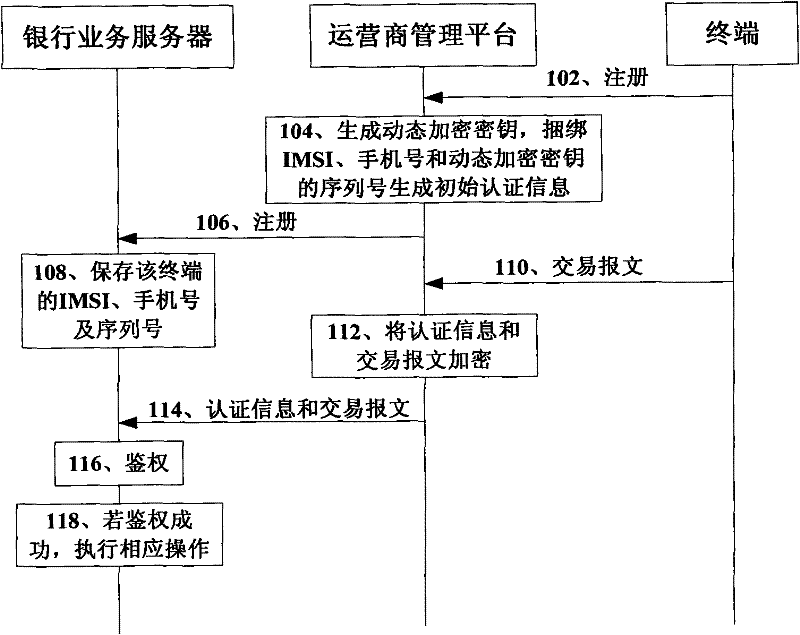
InactiveCN102457842AGuaranteed legalityUser transaction securityPayment architectureSecurity arrangementInternational mobile subscriber identityThird-Party Payments
The invention discloses a method, a device and a system for transaction by a mobile phone. The encryption method for the transaction by the mobile phone comprises the following steps: A, an operator side binds the international mobile subscriber identity (IMSI) and the mobile phone number of a terminal, and then, generates authentication information, the operator side receives a transaction message sent by the terminal, then, encrypts the transaction message and the authentication information by using pre-generated dynamic encryption keys, and sends the encrypted transaction message and authentication information to a bank side; and B, the bank side decrypts the received encrypted transaction message and authentication information, carries out authentication by using the authentication information, and executes corresponding operation according to the transaction message after the authentication is successful. With the adoption of the method, the device and the system for the transaction by the mobile phone, the transactions of users can be safer and more reliable; and the whole transaction process does not need a third-party payment platform actually, so that the transaction process can be simpler and safer and is convenient to maintain.
Owner:中国移动通信集团宁夏有限公司
Payment terminal, payment tool, payment server, payment system and payment processing method
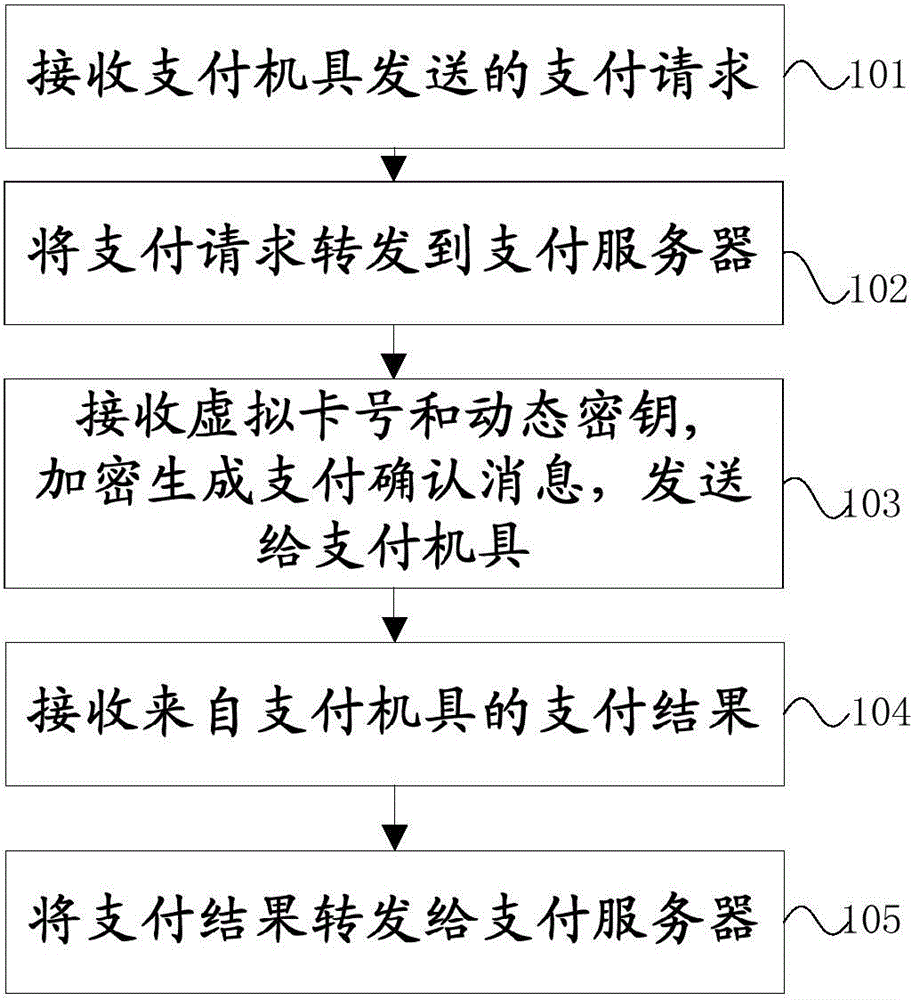
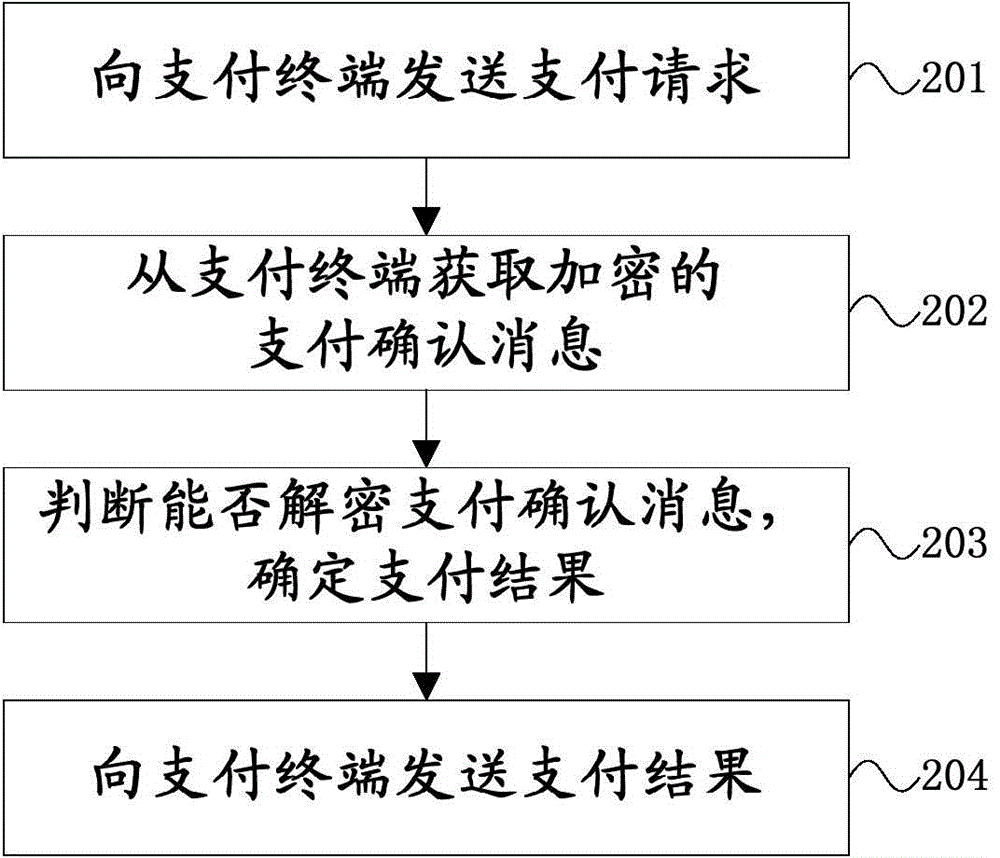
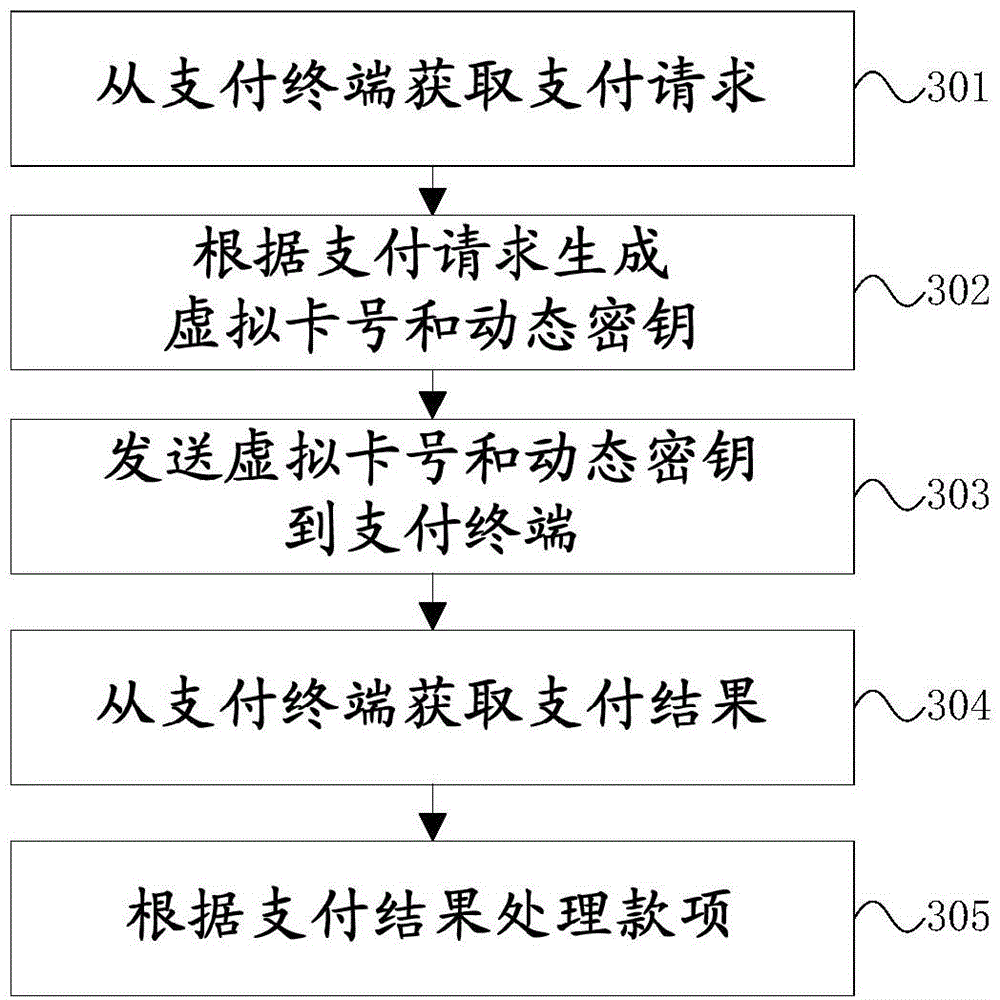
ActiveCN106157013ASafety of tradementUser identity/authority verificationPayment protocolsComputer terminalPayment order
The invention provides a payment terminal, a payment tool, a payment server, a payment system and a payment processing method, and relates to the field of mobile payment. The payment method provided by the invention comprises that the payment terminal receives a payment request which is sent by the payment tool and comprises a payment tool number, payment time and payment amount, the payment request is forwarded to the payment server, and the payment server generates a virtual card number and a dynamic key according to the payment tool number, the payment time and the payment amount; the payment terminal generates a payment confirmation message in an encrypted manner by using the virtual card number and the dynamic key, and sends the payment confirmation message to the payment tool; the payment terminal receives a payment result from the payment tool; and the payment terminal forwards the payment result to the payment server, and the payment server processes the payment according to the payment result. Through the method provided by the invention, a unique virtual card number and a unique dynamic key can be generated, so that the risk caused by circumstances that the payment terminal is intruded and data is stolen is effectively avoided, and safe payment of the payment tool at an off-line state is realized.
Owner:CHINA TELECOM CORP LTD
Method for network on-line payment double authentication by telephone and identifying card
InactiveCN101291329APrevent crimeSafety of tradementFinanceUser identity/authority verificationIssuing bankCredit card
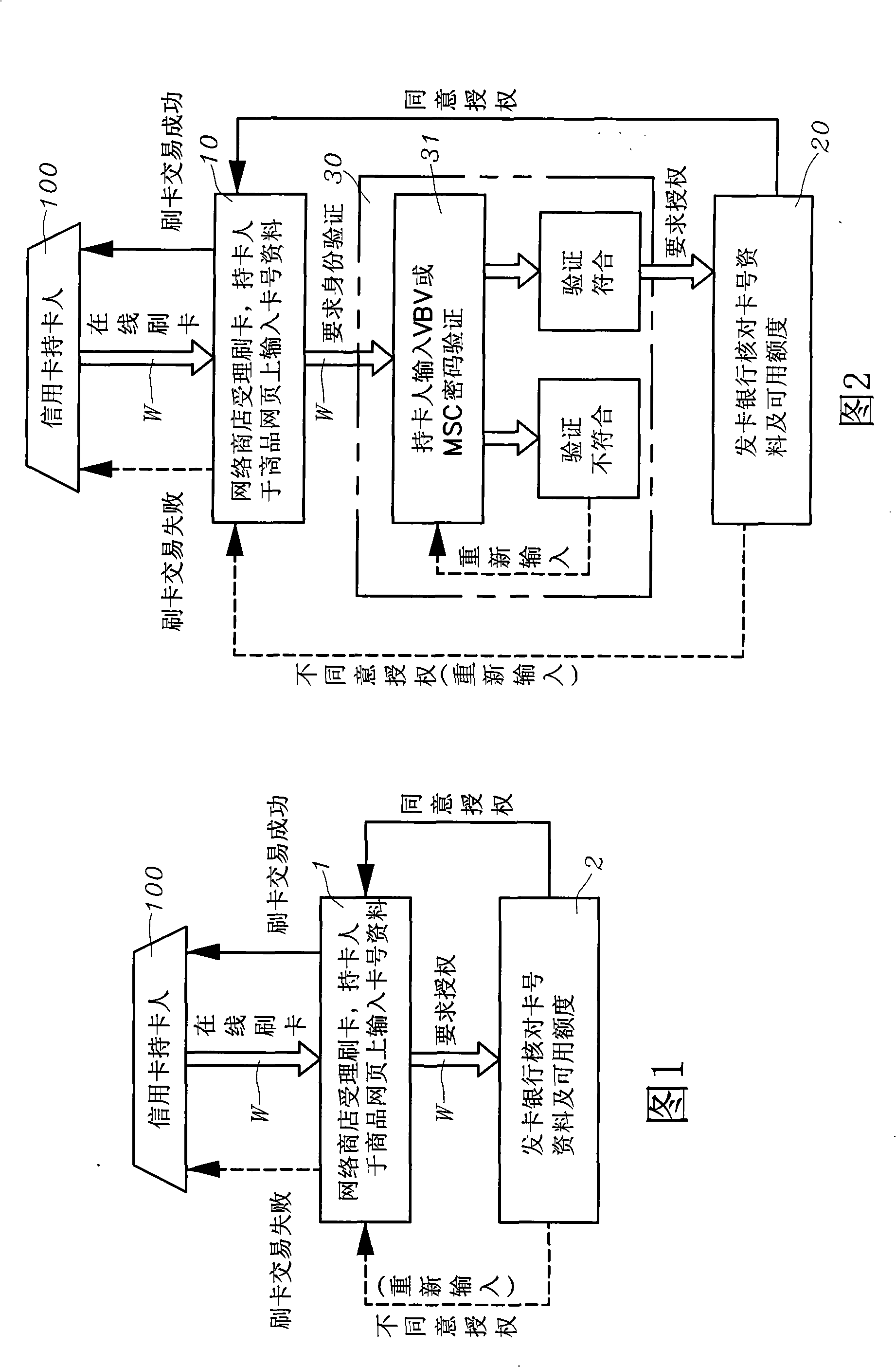
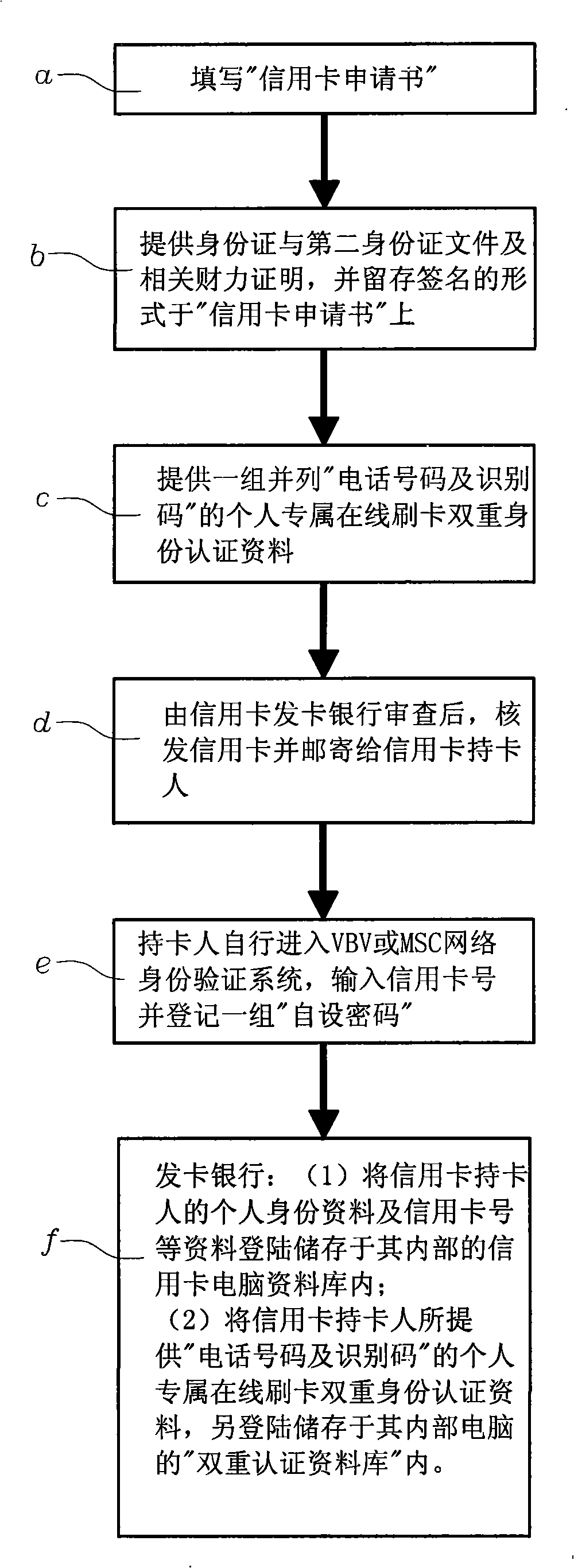
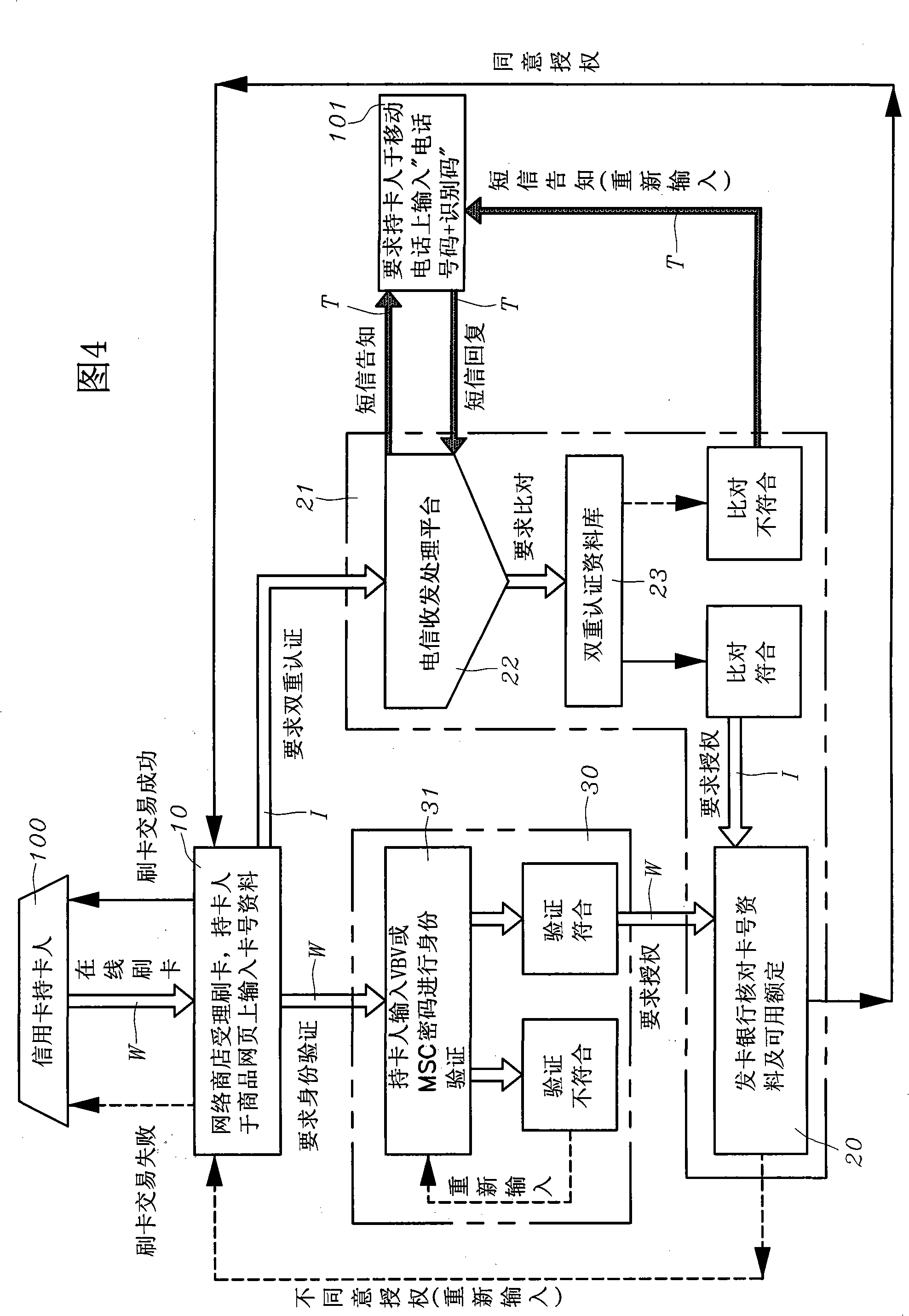
The invention uses the phone number and the identifying codes as the network online dual authentication method. The card holder of the credit card registers the VBV or MSC network identity checking ''self-setting password'' to the card-issuing bank, the holder also provides a group of ''phone number and the identifying codes'' personal special online dual identity authentication data to the card-issuing bank; the data login is stored in the ''dual authentication database'' of the ''credit card dual authentication computer system'' of the card-issuing bank; while the card-issuing bank is processing the online card slotting, the bank informs the card holder in the short message way besides the ''self-setting password'' of the VBV or MSC network identity checking for the card holder; requiring to respond to the personal special online identity authentication data of the ''phone number and the identifying codes''; comparing to the ''phone number and the identifying codes'' in the ''dual authentication database'' as the card slotting transaction on the network for the card holder for the dual rechecking to confirm whether the invention is the network credit card transaction under the entitlement.
Owner:林仲宇
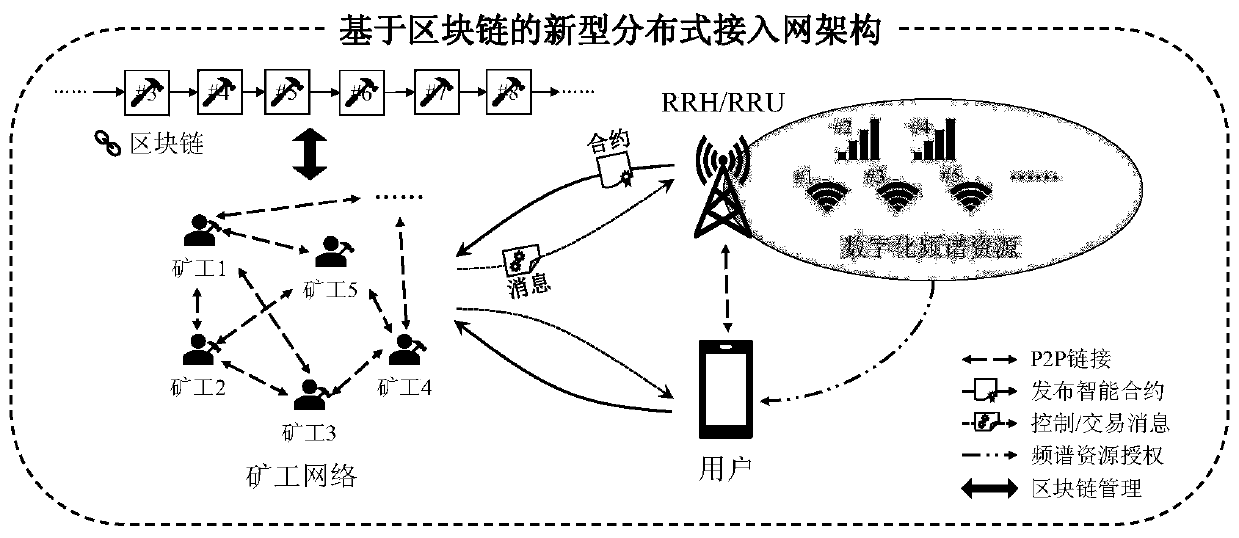
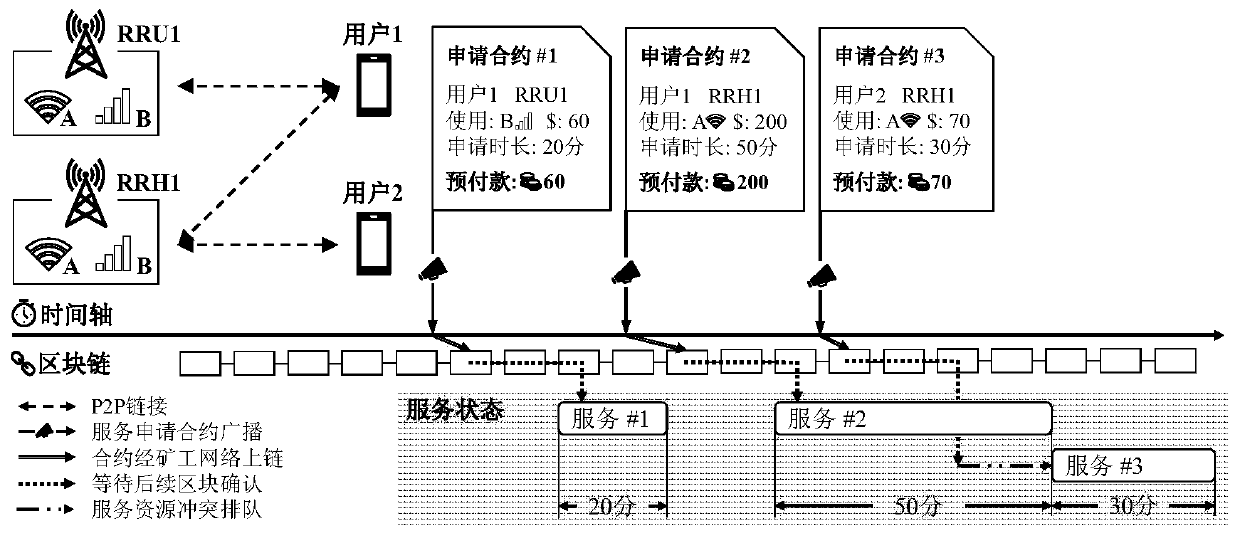
Novel distributed access network architecture based on block chain
ActiveCN110035440AIncrease varietyIncrease profitAssess restrictionTransmissionAccess networkFrequency spectrum
The invention discloses a novel distributed access network architecture based on a block chain. The architecture comprises RRH and RRU used as access points in a wireless radio frequency communicationsystem, a user, digital spectrum resources managed by the RRH and the RRU respectively, a miner network formed by miners for maintaining a block chain, and a novel distributed mechanism used for managing sharing and access of the wireless spectrum resources. And the RRH and the RRU equipment provide wireless spectrum resource sharing and access services for the user, and the service process is controlled by a novel distributed mechanism for managing network access. The invention provides a novel distributed access network architecture based on a block chain. The RRH or the RRU in the architecture and a user can perform safe and reliable spectrum resource transaction in an untrusted environment.
Owner:SOUTHEAST UNIV
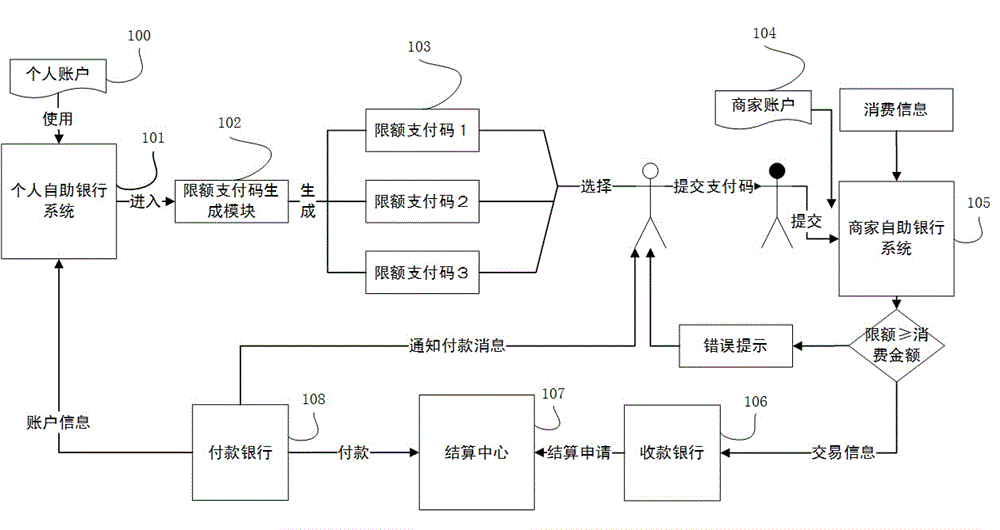
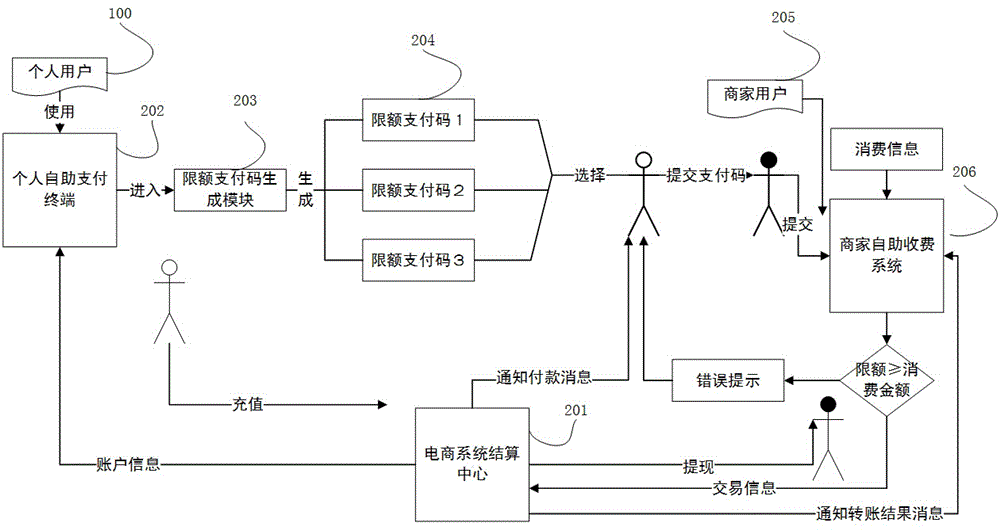
Method for payment with limit code
InactiveCN104657847ASafety of tradementOvercoming the problem of recharging troublePayment schemes/modelsComputer hardwareElectronic communication
The invention discloses a method for payment with a limit code. On the basis of modern electronic equipment and electronic communication, a user generates an information code with the payment limit according to the payment requirement on a certified client side, and a merchant submits the electronic limit code and payment information of the user to a transaction settlement center for decryption, certification and settlement. The method has the characteristics that the user is not required to provide real cards such as bank cards and the like, the user can set the limit code freely, account information is encrypted, the payment limit is set, password inputting can be avoided for micropayment, a payment code is invalid after used once and the like, has the advantage of convenient payment of Quick Pass cards, and solves problems that the Quick Pass cards of banks are troublesome to recharge, the bank cards are stolen easily, unauthorized swiping and excessive swiping can occur, information is copied and the like. Thus, the method has very high value in aspect of convenient transaction payment as well as protection of user account and bank card security. The method is applicable to quick financial payment and settlement for on-the-spot transactions in fields such as supermarkets, shopping malls, traffic, parking lots and the like.
Owner:吴勇
Method for consuming electronic wallet
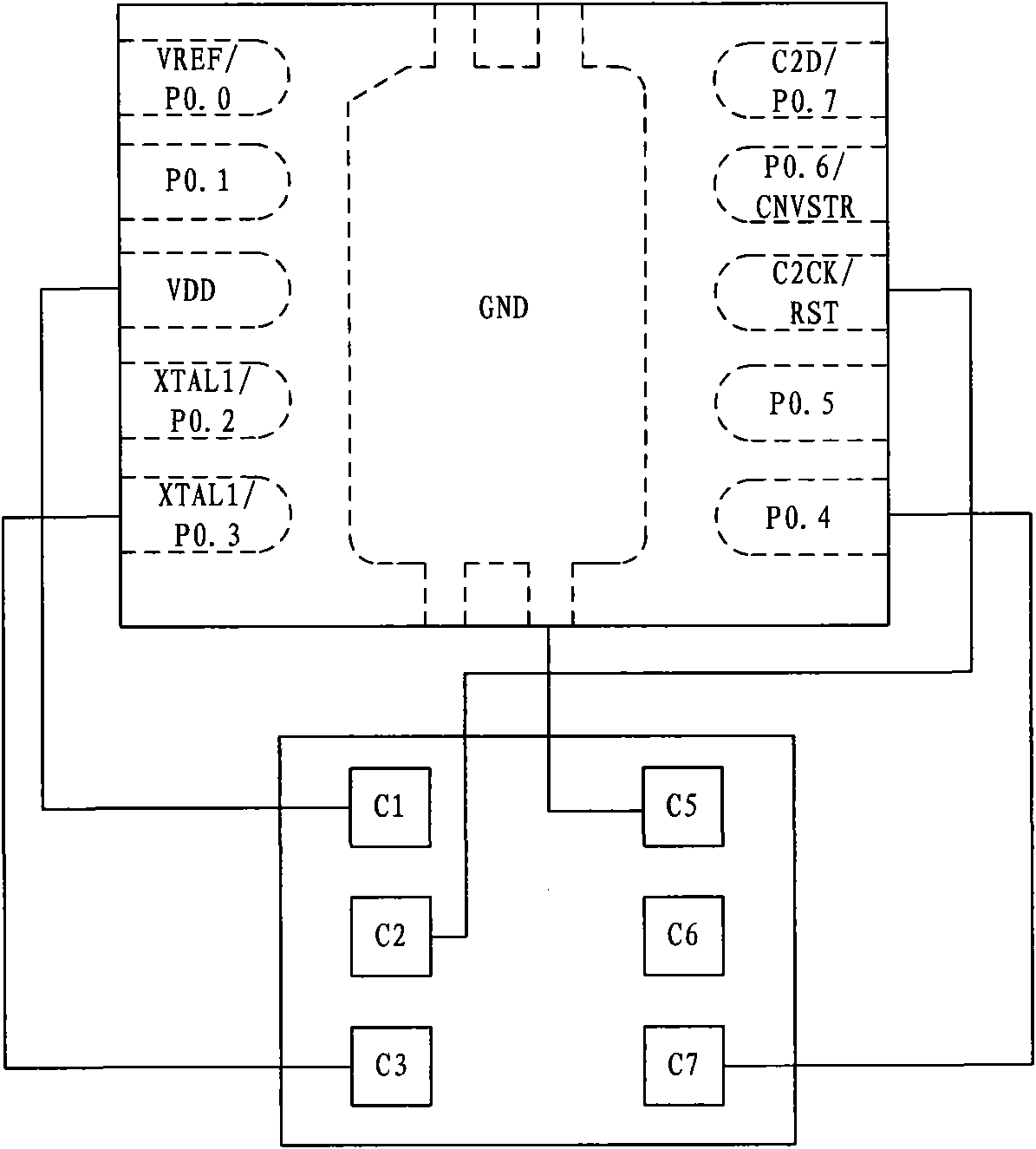
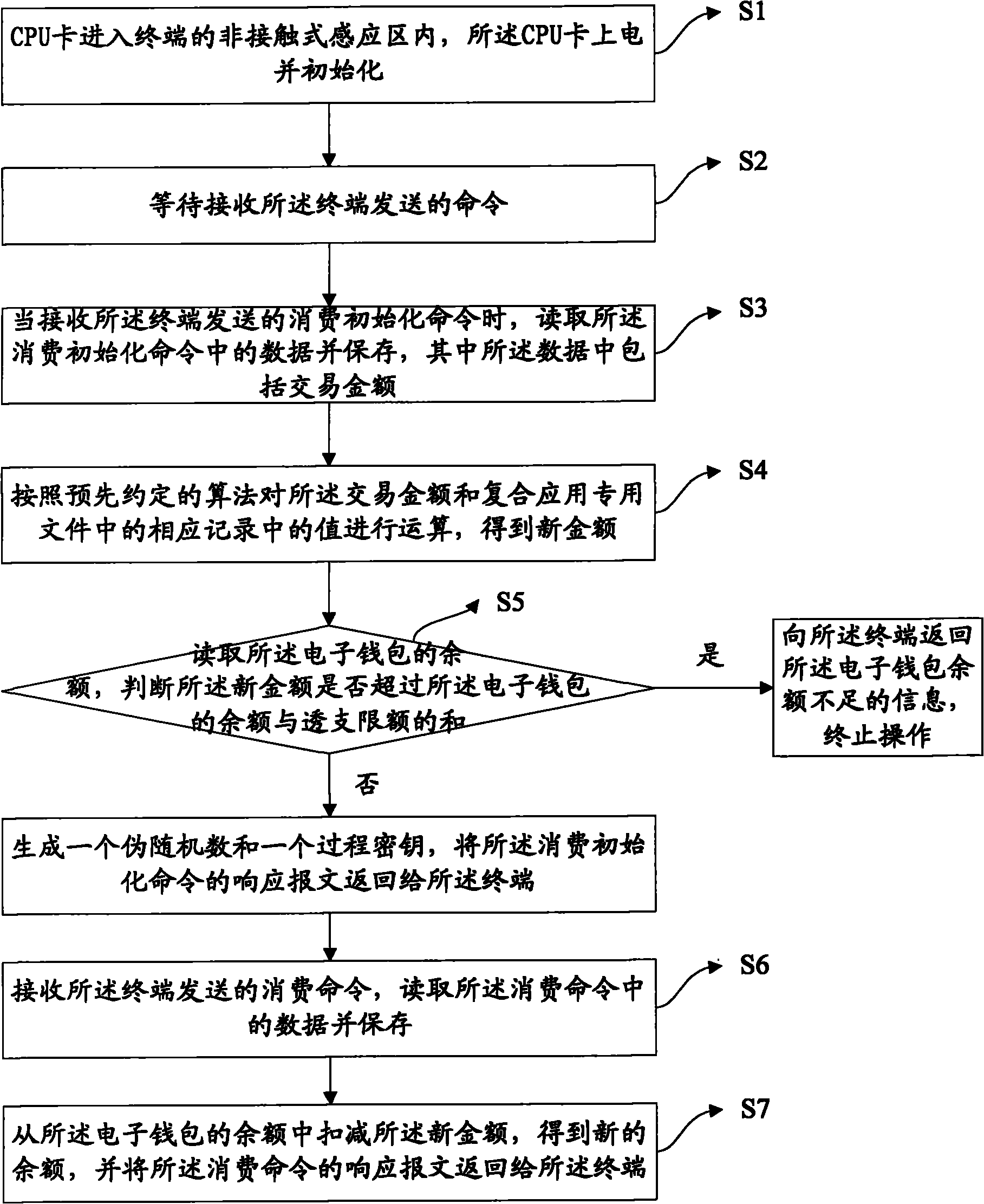
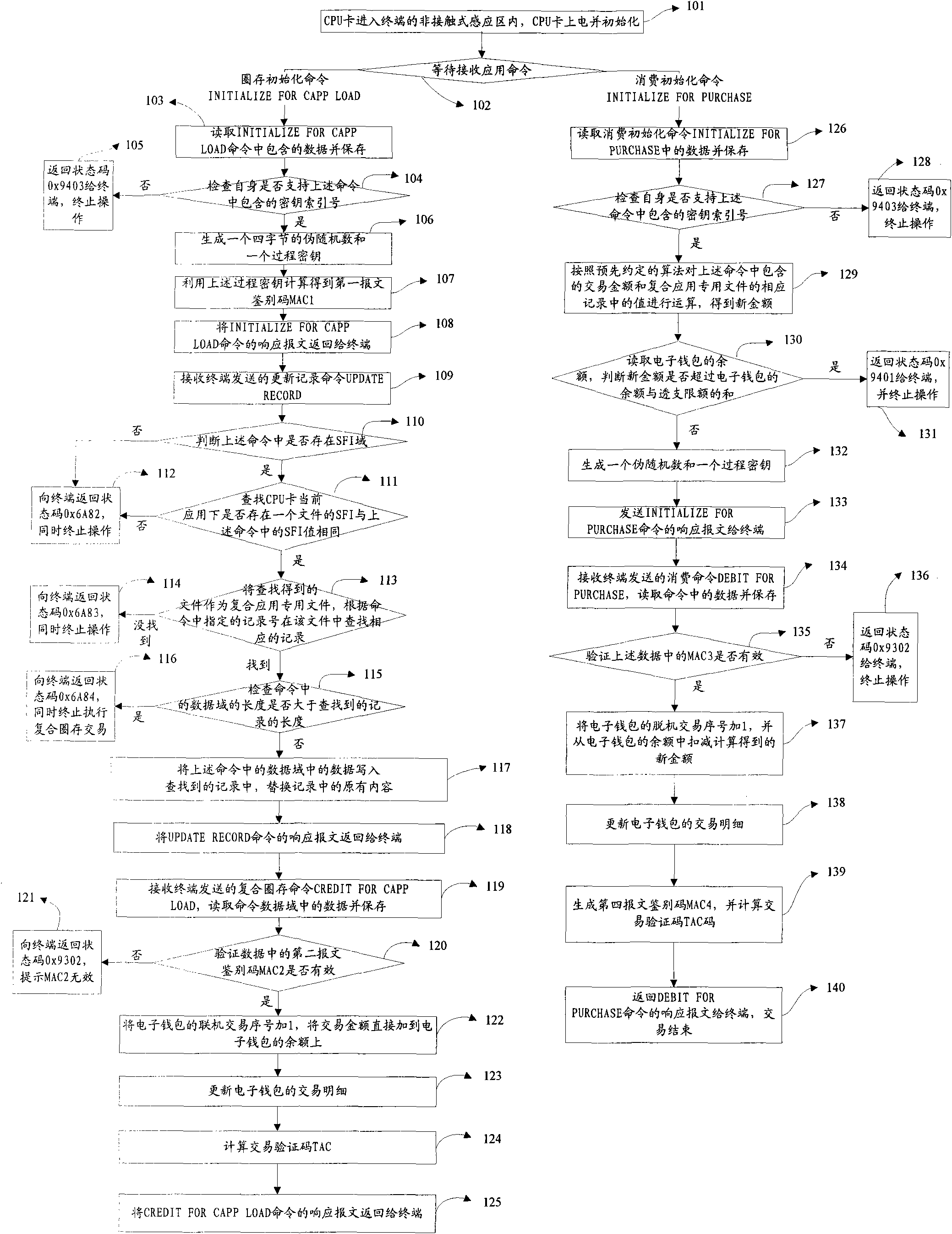
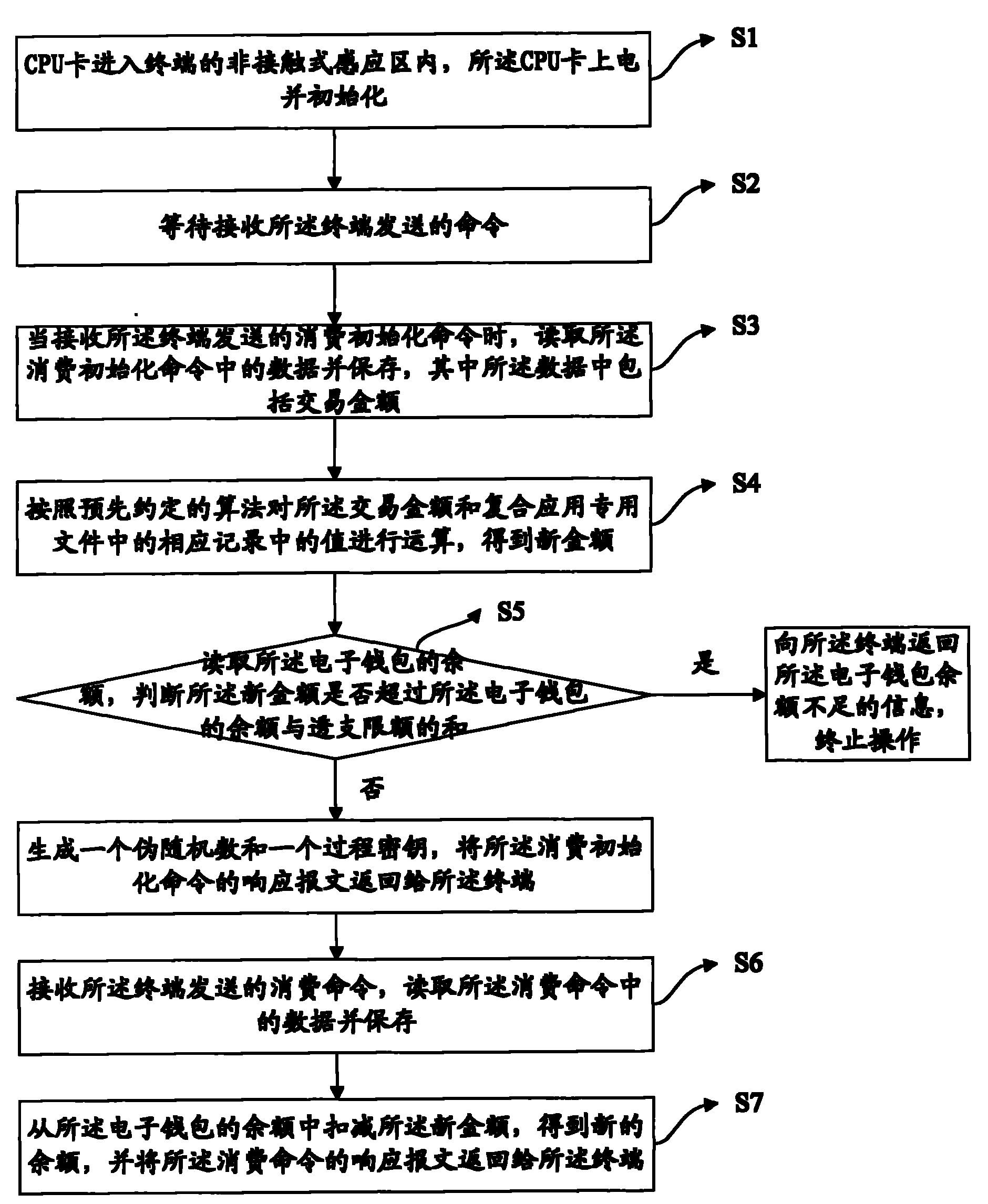
ActiveCN102044114ATransaction process securityEasy to implementComplete banking machinesCoded identity card or credit card actuationComposite applicationElectronic purse
The invention discloses a method for consuming an electronic wallet, and belongs to the field of information safety. The method comprises the following steps that: a central processing unit (CPU) card enters a non-contact induction area of a terminal, is electrified and initialized, reads data in a consumption initialization command when receiving the consumption initialization command sent by the terminal and stores the data, wherein the data comprises transaction amount; the CPU card operates the transaction amount and a value in a corresponding record in a composite application dedicated file according to a predetermined algorithm to obtain new amount, reads the balance of the electronic wallet, and judging whether the new amount exceeds the sum of the balance and limit of overdrawn account of the electronic wallet or not, if so, the CPU card stops operating, and otherwise, the CPU card generates a pseudo-random number and a process key and returns a response message of the consumption initialization command to the terminal; and the CPU card receives a consumption command sent by the terminal, deducts the new amount from the balance of the electronic wallet to obtain new balance, and returns a response message of the consumption command to the terminal.
Owner:FEITIAN TECHNOLOGIES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com