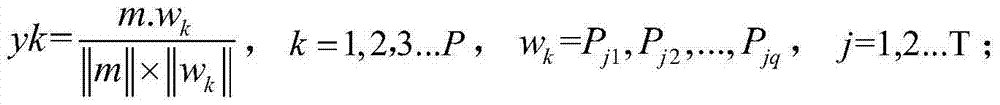Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
122results about How to "Prevent crime" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method and apparatus for providing a safe taxi service
A management server authenticates taxi drivers, searches for taxis near a taxi user, calls a taxi, searches for and tracks a taxi upon an emergency call from a taxi user, and updates assessment information about the services provided by taxi drivers. A taxi driver may undergo authentication on the taxi driver himself and his taxi before driving the taxi by putting his mobile terminal on a terminal holder mounted in the taxi upon a ride in the taxi. Before taking a ride in a taxi, a taxi user may receive driver information about taxis from the management server using a mobile terminal, and select a taxi after checking the received driver information.
Owner:SAMSUNG ELECTRONICS CO LTD
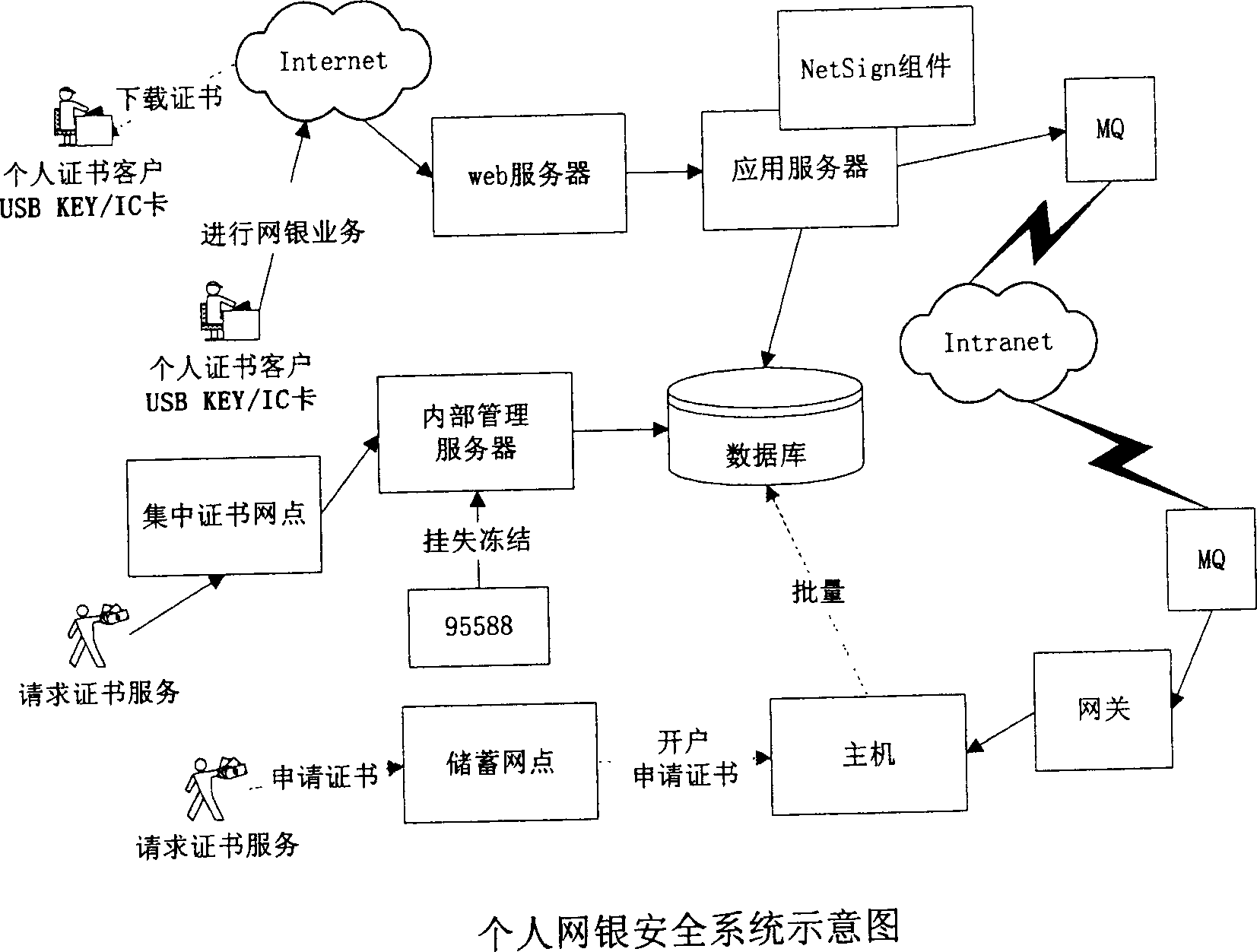
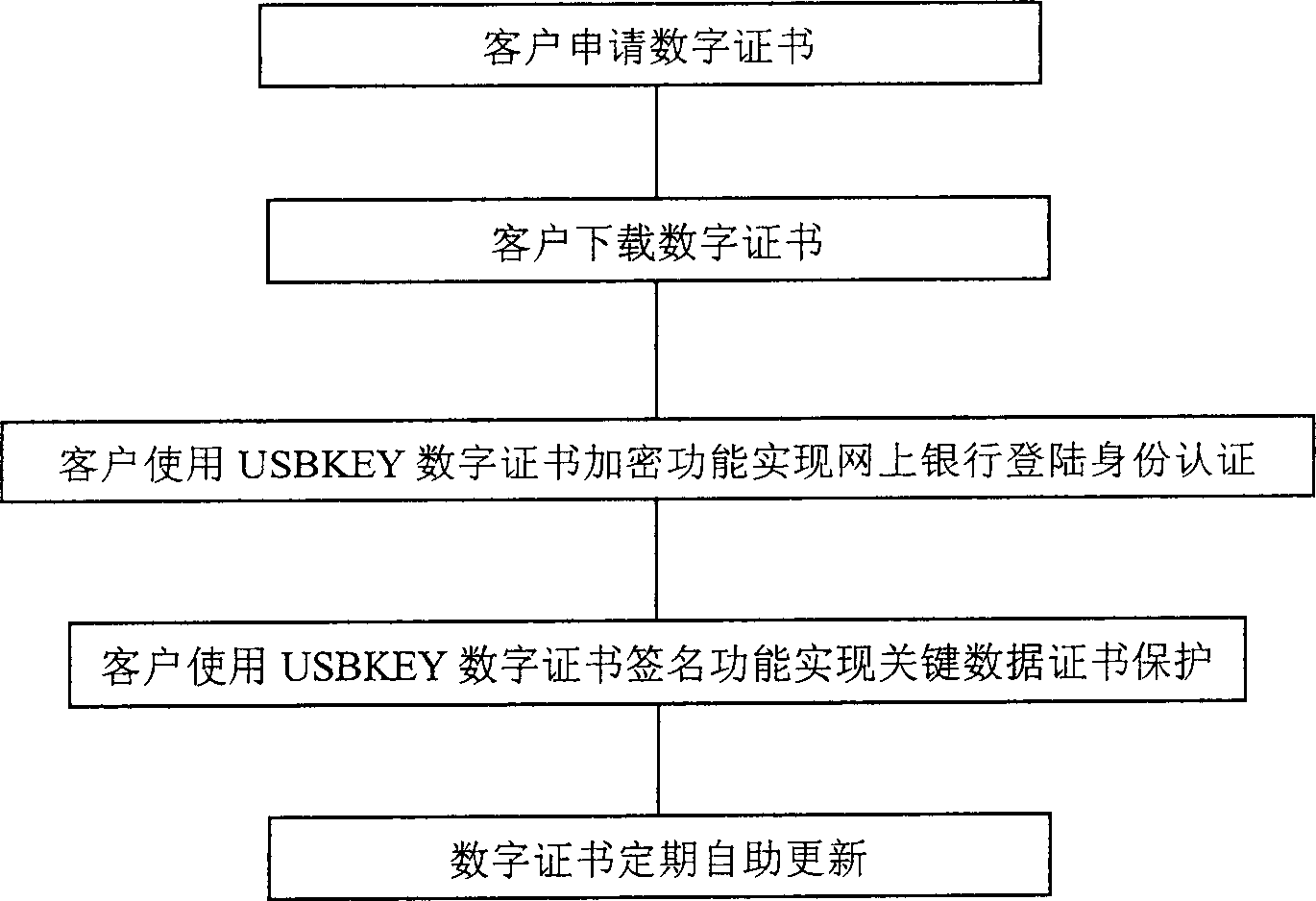
Device and method for proceeding encryption and identification of network bank data
ActiveCN1556449AGuarantee the security of transactionsRealize self-service downloadDigital data processing detailsSpecial data processing applicationsInternal memoryDigital signature
The invention discloses a method of encrypting and certificating network bank data by using a USB KEY, and its characteristics: it includes the steps: a), according to the user information, generating a digital certificate corresponding to the use; b), storing the digital certificate in a USB to be allocated to the user; c), when the user makes a login with the network bank for processing data, it confirms the user ID or digital signature by the USB KEY. It also discloses an implementing device of encrypting and certificating network bank data by using the USB KEY and because every USB KEY has an only serial number and the private key can not leave the internal memory, and it can not make network transaction until the user ID is confirmed, it has high secrecy and safety.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
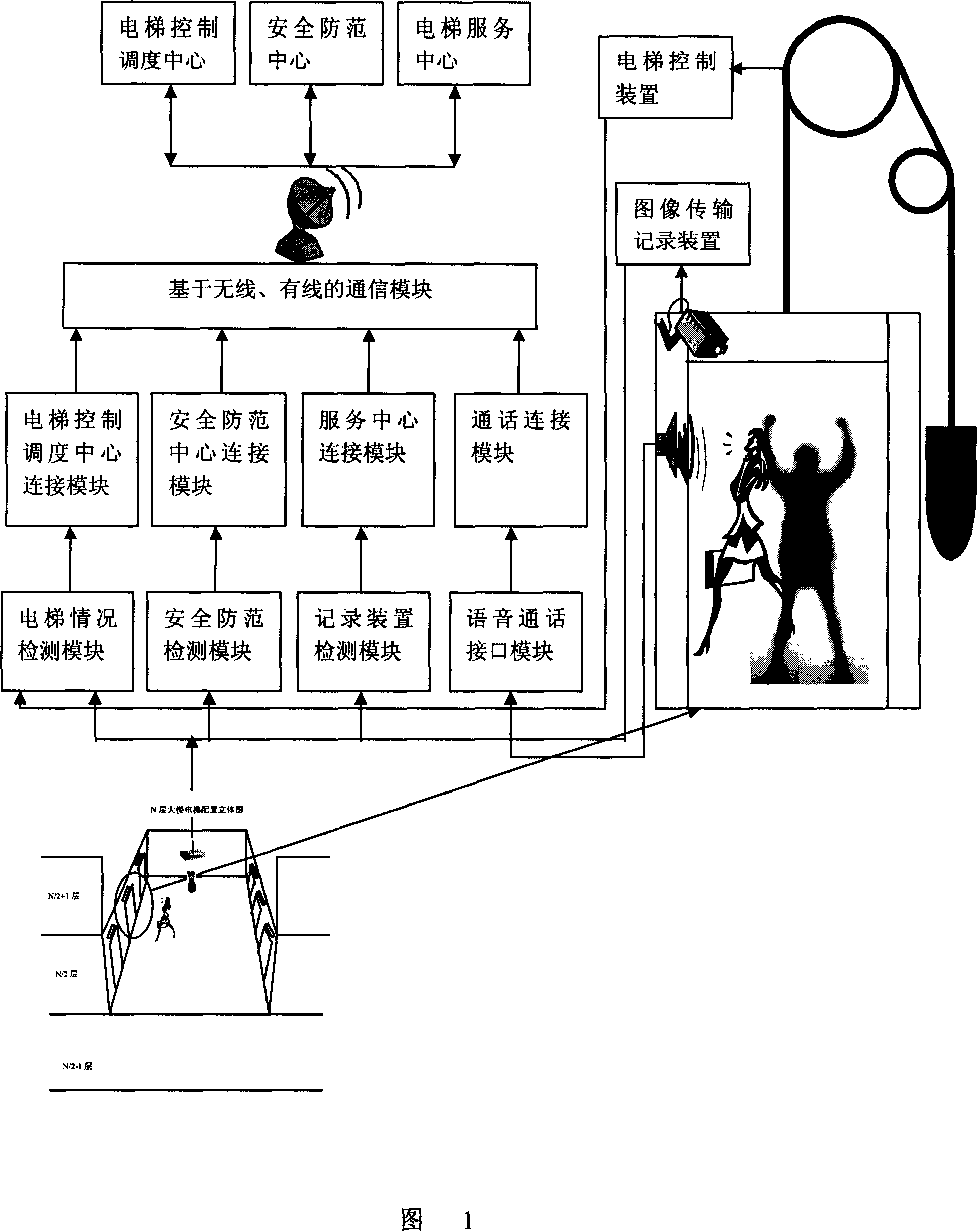
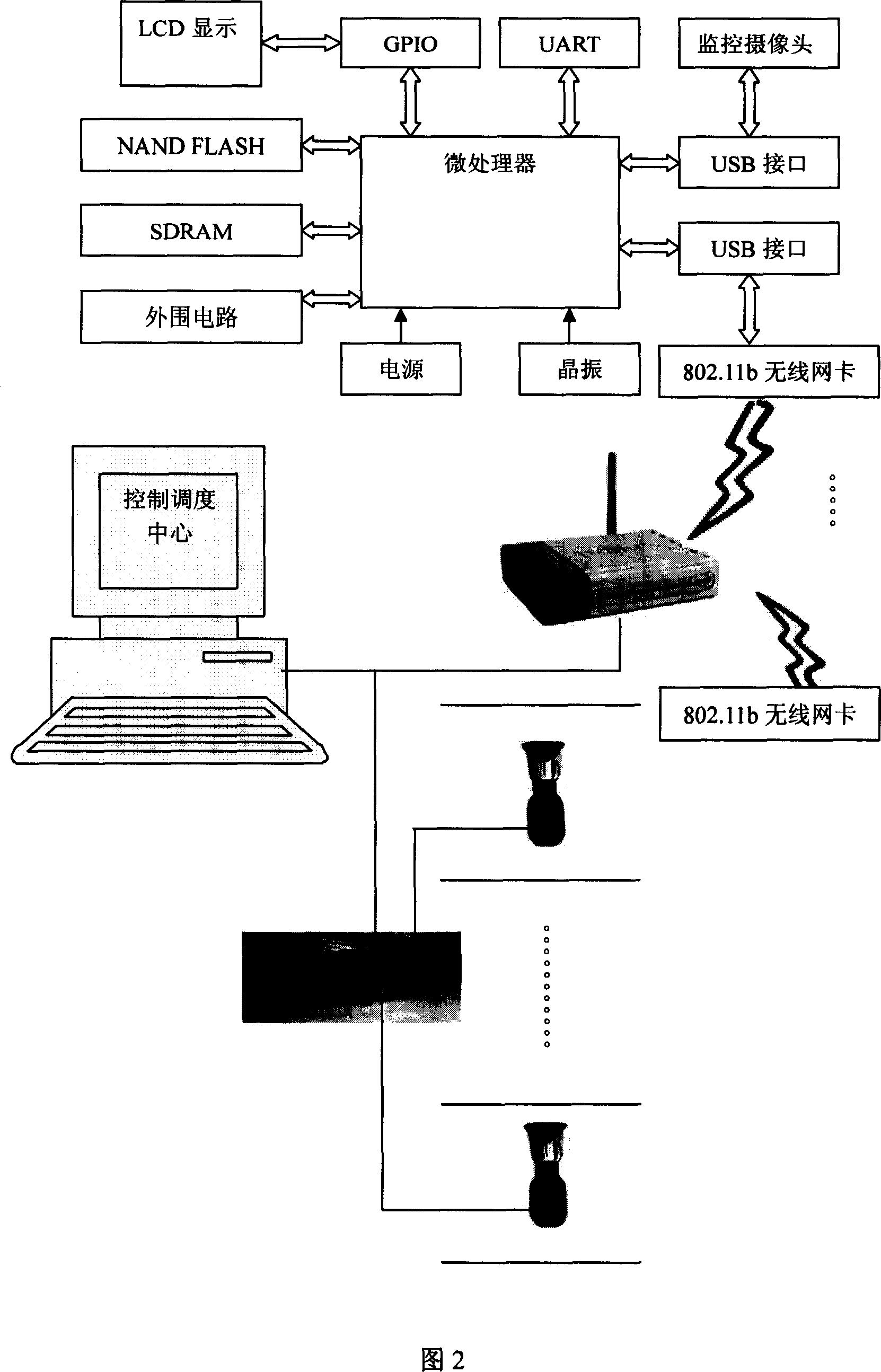
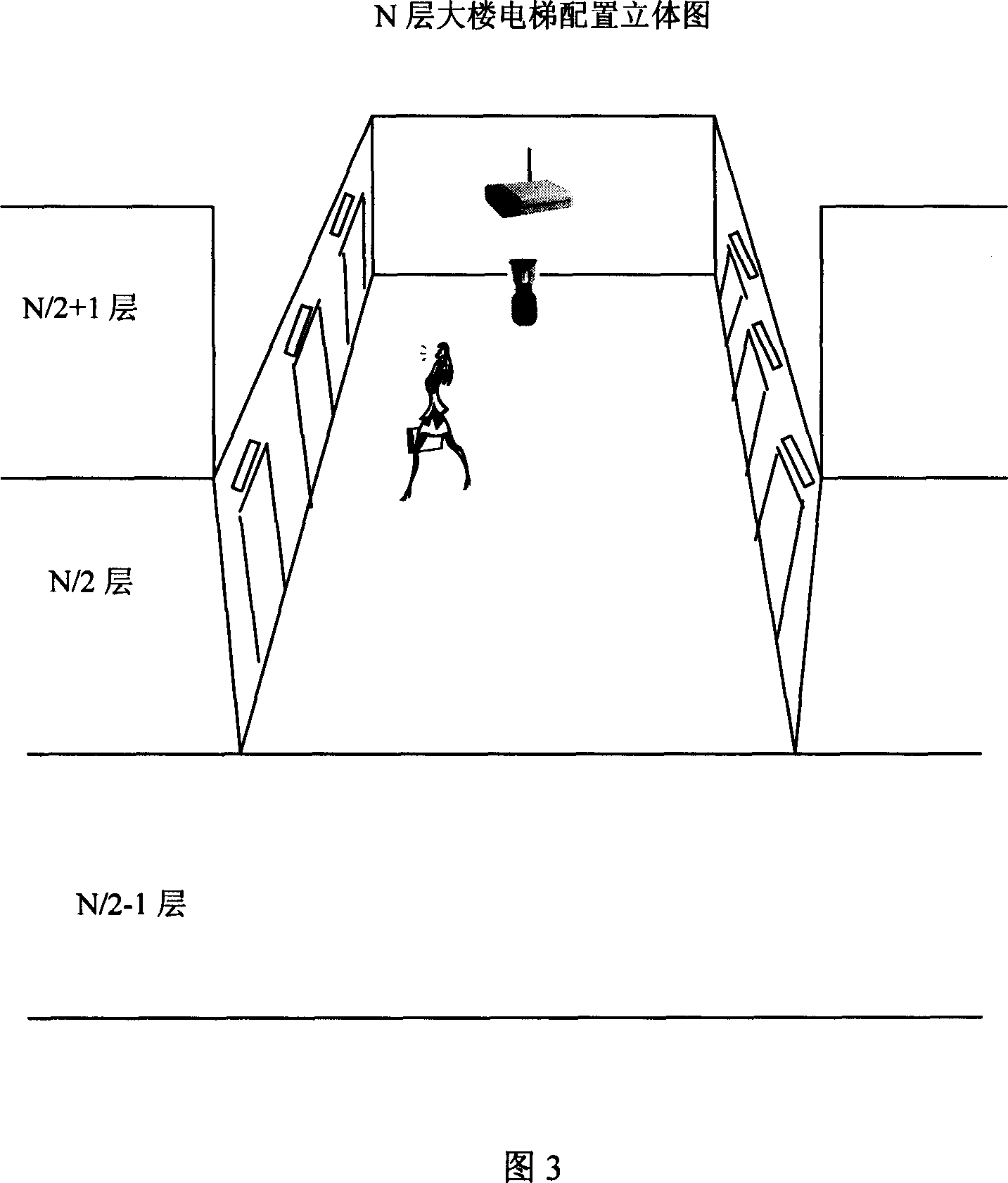
Elevator inner violence-proof apparatus based on image and speech recognition technique
The invention discloses an elevator inner-brute force device based on image and voice recognizing technology, which comprises the following parts: video sensor, voice receiver and monitor central computer to monitor elevator, wherein the video sensor and voice receiver connects monitor center computer through wireless network equipment, which contains display mode to display real-time elevator video data, the video sensor connects monitor central computer through wireless network exchanging equipment, which is warless LAN center, the computer contains microprocessor with image reading mode, image variation calculating mode, connecting area calculating mode, judging mode in the elevator to judge whether the accident occurs.
Owner:ZHEJIANG UNIV OF TECH
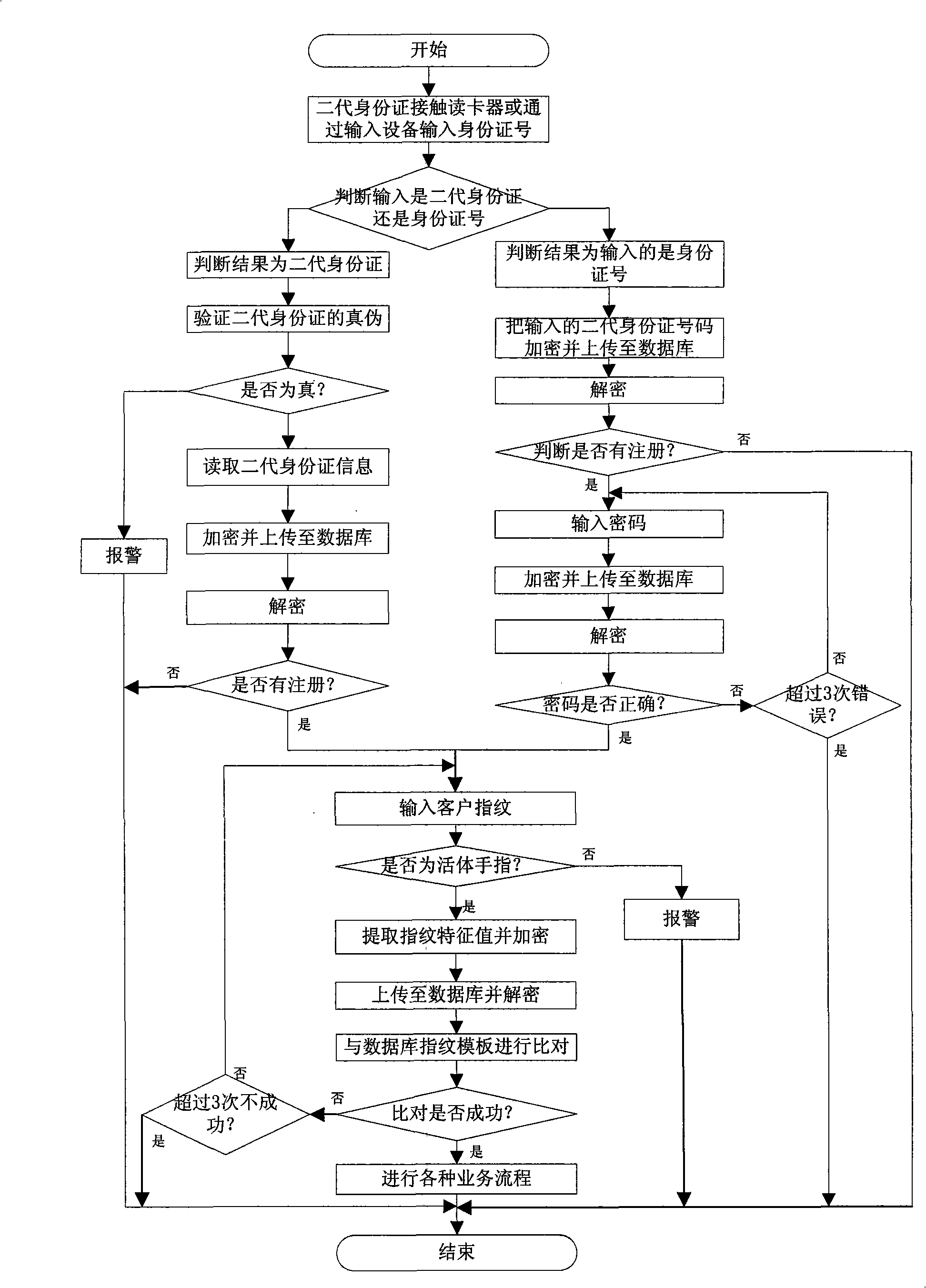
Method utilizing ID card number as bank account number and adopting fingerprint for ID authentication
InactiveCN101540083AImprove securityAvoid the Fake Finger CrimeComplete banking machinesFinanceFingerprintLiving body
The invention relates to a method which uses an ID card number as a bank account number and a living body fingerprint as a necessary authentication method so as to ensure that the information of a second-generation identity card can be read in by a card reader and then be bound with the bank account when people apply for registering bank accounts. Various banking practices can be easily handled and consumption can be paid for by the steps of inputting the ID card number by input equipment and carrying out the simultaneous authentication of passwords and the living body fingerprint, or by the steps of swiping the second-generation identity card and carrying out the fingerprint authentication. The method has the advantages that: the living body fingerprint is utilized as the necessary mode of authentication, and therefore the method is safe and reliable and prevents people from worrying about forgetting the passwords; the ID card number is used as the passwords of the account, so that the cost of a bank can be reduced and customers do not need to take a plurality of bank cards during transaction; and the illegal criminal activity which utilizes the capitation accounts to launder money can be prevented, and abnormal cash flow can be conveniently and effectively supervised.
Owner:CHENGDU FINCHOS ELECTRONICS
Network attacker behavior analyzing method based on attack graph
The invention discloses a network attacker behavior analyzing method based on an attack graph. The method comprises the steps of establishing a network attacker behavior analyzing model and attracting attacks of attackers; carrying out comprehensive capturing on attack data through a data capturing mechanism; and generating an attack state transfer graph through combination of a finite-state machine and analyzing behaviors of the attackers according to possibility indexes of attack behaviors, skill level indexes of the attackers and destination indexes of the attackers. According to the network attacker behavior analyzing method based on the attack graph provided by the invention, the good foundation can be laid for design of an active defense system, the network attacks can be defended, the attacks can be prevented before the network attacks occur, one part of the attacks are screened, a cybercrime can be effectively prevented, the defense efficiency is improved, and the defense cost is reduced.
Owner:HANGZHOU SUNYARD DIGITAL SCI
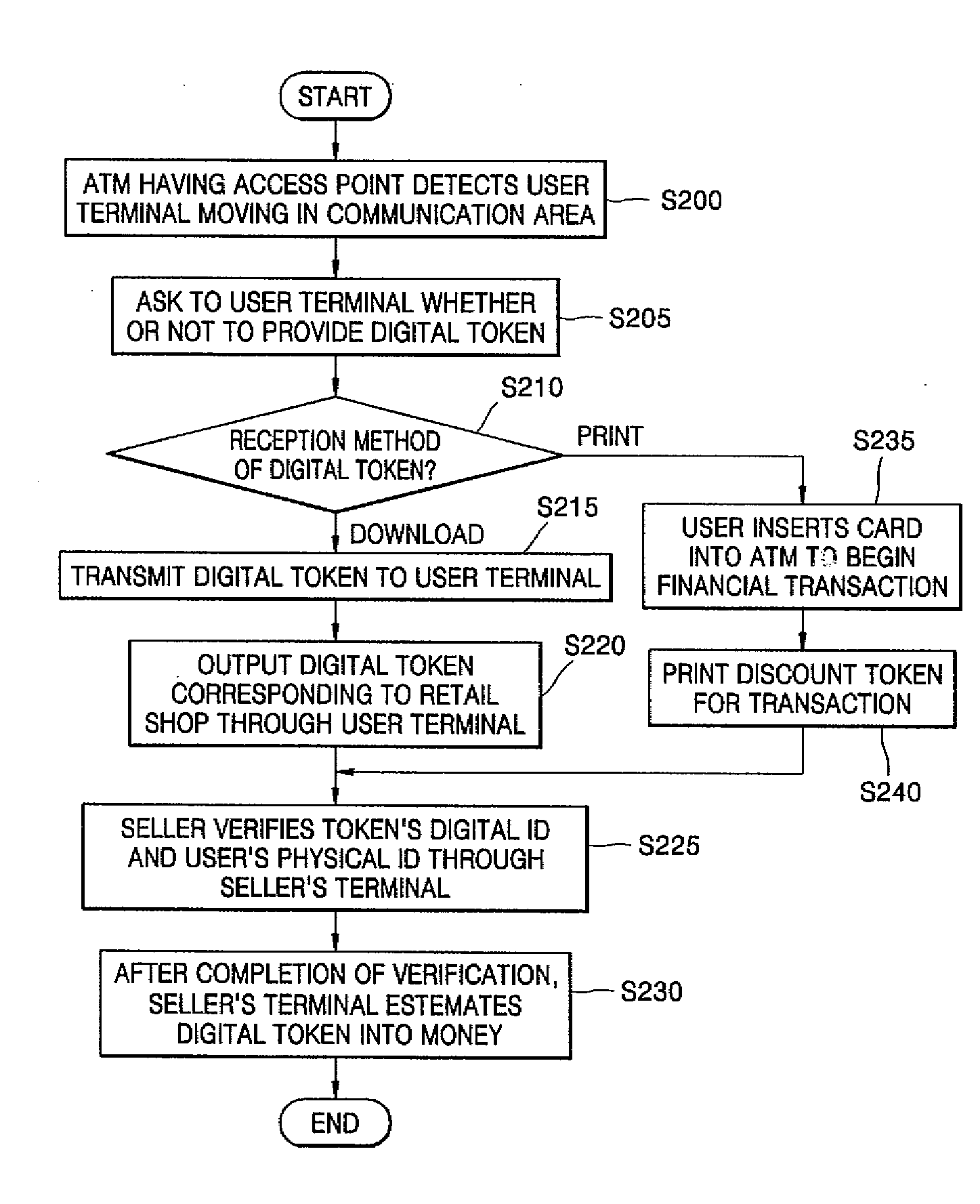
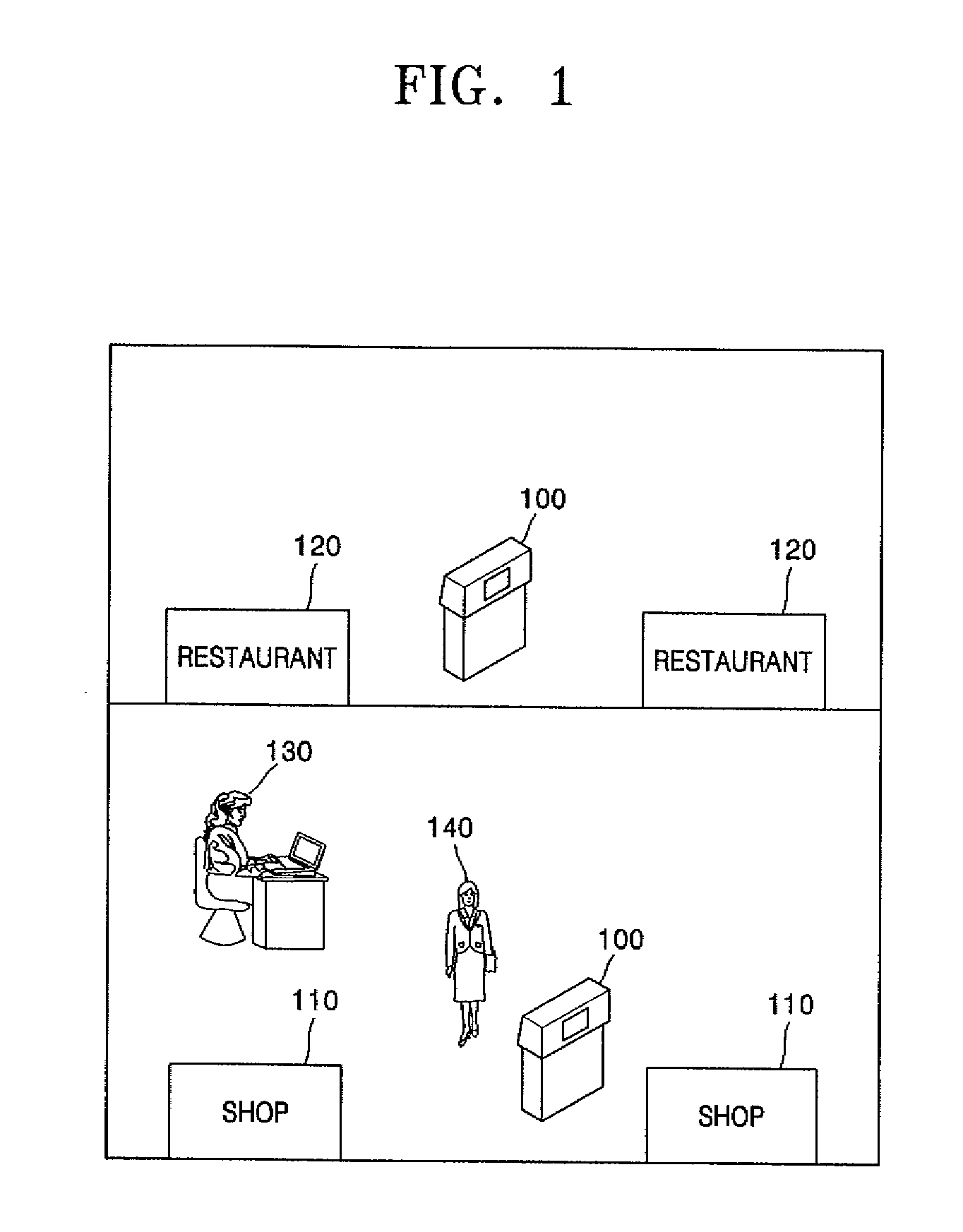
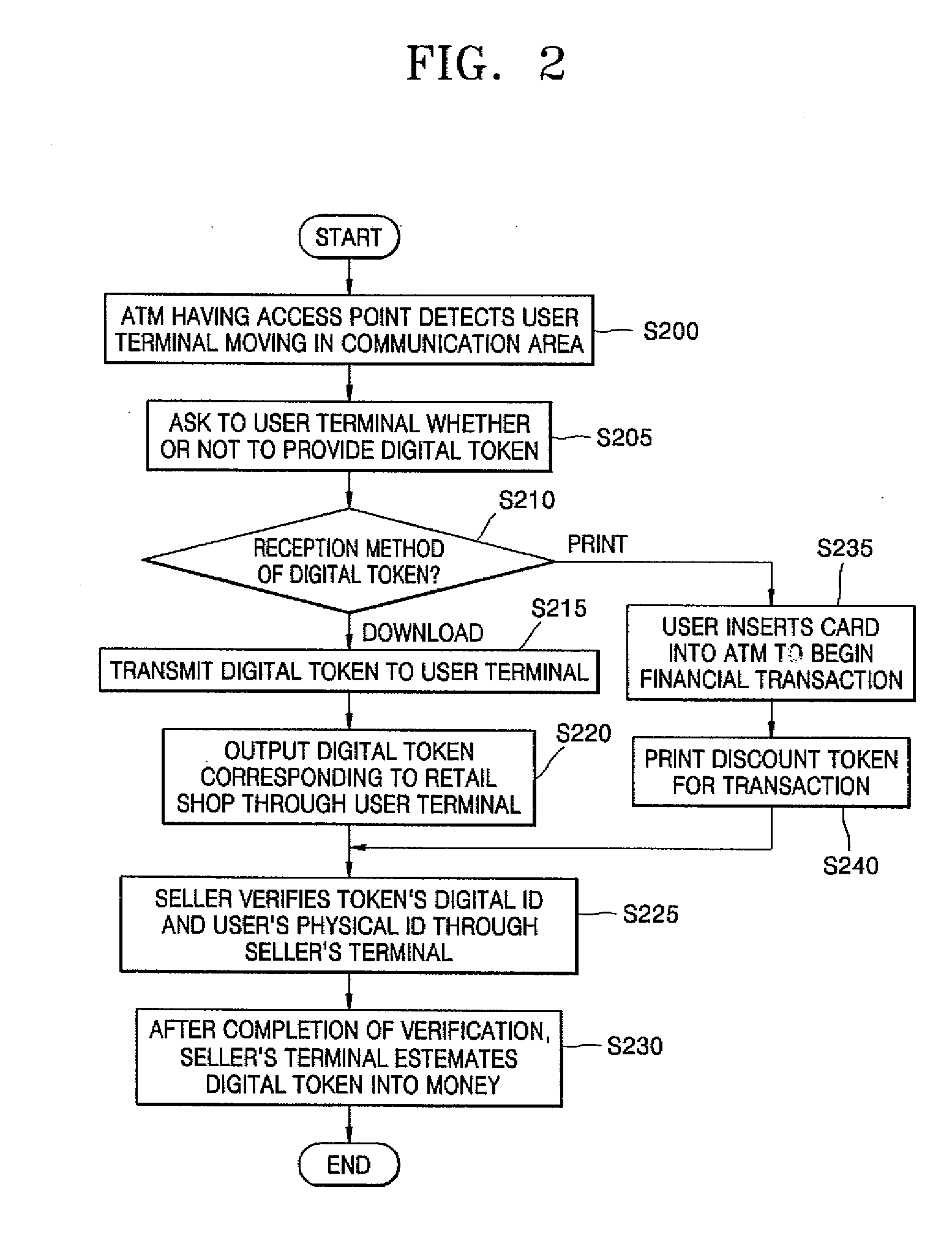
Automated teller machine having access point and method for providing financial service using the same
InactiveUS20080313087A1Promoting Internet useCheap expenseFinanceUser identity/authority verificationComputer terminalOutput device
An automated teller machine (ATM) having a wireless network access apparatus and a method for providing financial services using the ATM are provided. The ATM includes a user interface unit, a first financial processing unit, a first network access unit, a second network access unit, and a second financial service unit. The user interface unit performs data communication with a storage medium on which information is recorded, and outputs information to a user through an output apparatus. The first financial processing unit provides financial services including account inquiry, deposit, and withdrawal, by performing data communication processes with a recognized storage medium. The first network access unit is connected to an ATM network connected to a financial institution server, transmits data obtained as a result of performing financial services, to the financial institution server, and receives processed data from the financial institution server. The second network access unit is connected to an access point establishing a communication path for a wireless communication terminal of the user traveling in a predetermined communication area, and activating wireless communication. The second financial service unit performs data communication with the wireless communication terminal of the user through the access point, and provides at least one or more of financial services, digital token delivery service, and V2oIP service.
Owner:JOSEPH VINOD CHERIAN +3
Realm name certification system and method based on biological feature recognition
InactiveCN103036680AReal-name requirements are strictPrevent crimeUser identity/authority verificationDigital data authenticationDomain nameDomain Name System
The invention provides a realm name certification system and method based on biometric feature recognition. The system comprises a biological feature gathering installion, a realm name register server, an authoritative institution database and the like. First, the biological feature information of users is gathered by the biological feature gathering installion. Then, the realm name register server acquires the previously gathered user information from the authoritative institution database and the biological feature information can be in authenticating. After that, the authenticated user information can be in real-named register of the realm name and the register information can be stored in the realm name registration database. The realm name certification system and method introduces a biological feature automatic identification technology into the realm name system, and the check and certification of real-name system can be achieved quickly. The information safety and realm name safety can be guaranteed. The realm name certification system and method can be used for realm name recording automation, reliable website information automatic validation and the like.
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
Authentication method and system for screening network caller ID spoofs and malicious phone calls
ActiveUS9264539B2Crime of fraudulent telephone calling can be effectively reducedReduce crimeSpecial service for subscribersCalled number recording/indicationCode moduleData access
An authentication method and system for screening network caller ID spoofs and malicious phone calls includes a screening authentication system with a server that includes a login register interface, a data accessing interface, a data searching and comparing program, a data searching database, a labeling indication program, a registry coding module and a data searching coding module. Authentication data is generated by the registry coding module from a caller telephone number and caller login identification data input during registration. Corresponding authentication data contained in a network calling signal from a caller sending device is generated by a data searching coding module. A data searching and comparing program compares the authentication data and, if any discrepancy is found, a labeling indication program sends a “failed authentication” signal to the target network receiving callee so that a fraudulent call is detected.
Owner:LIN CHUNG YU
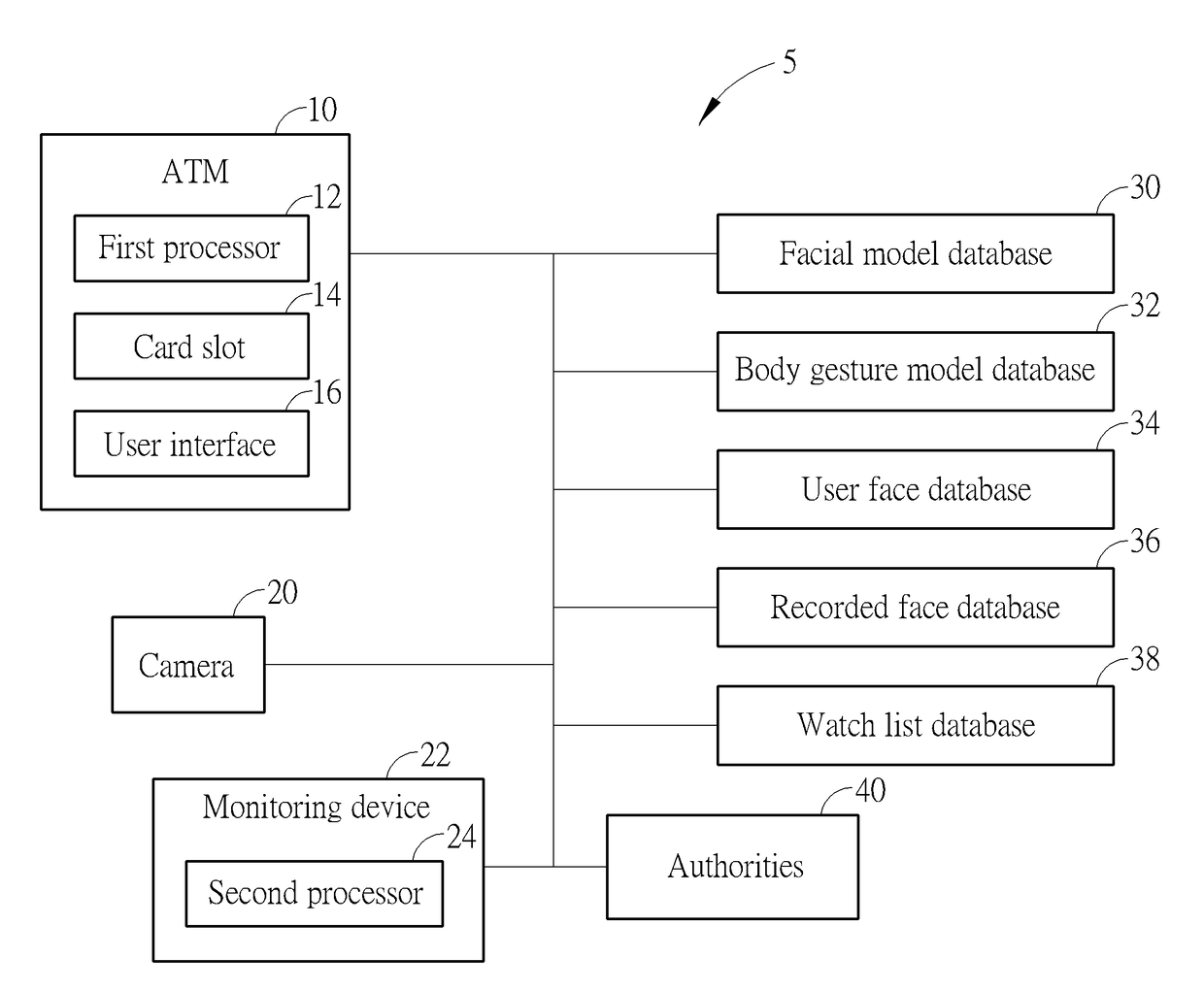
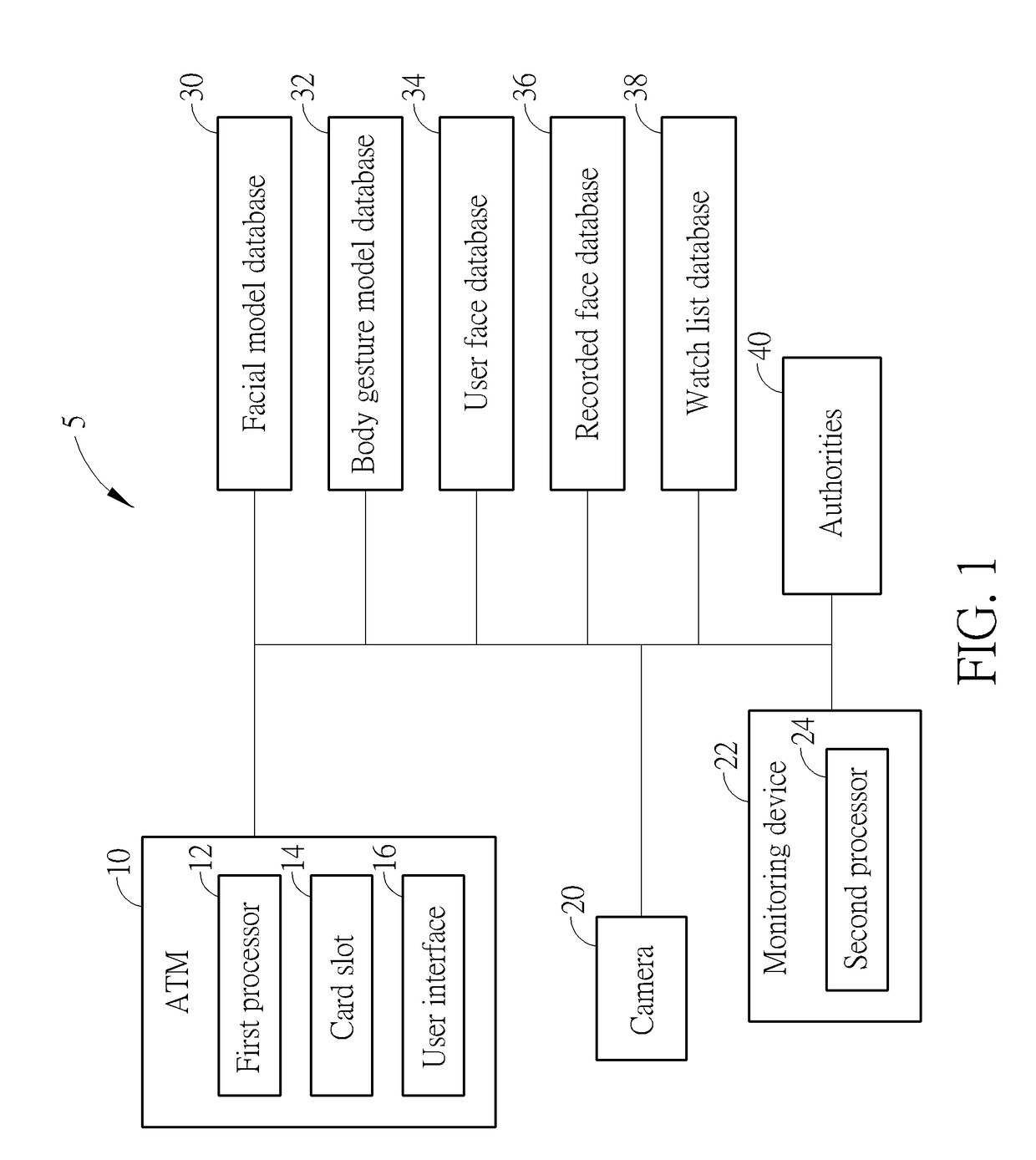
Method of Preventing Fraud and Theft during Automated Teller Machine Transactions and Related System
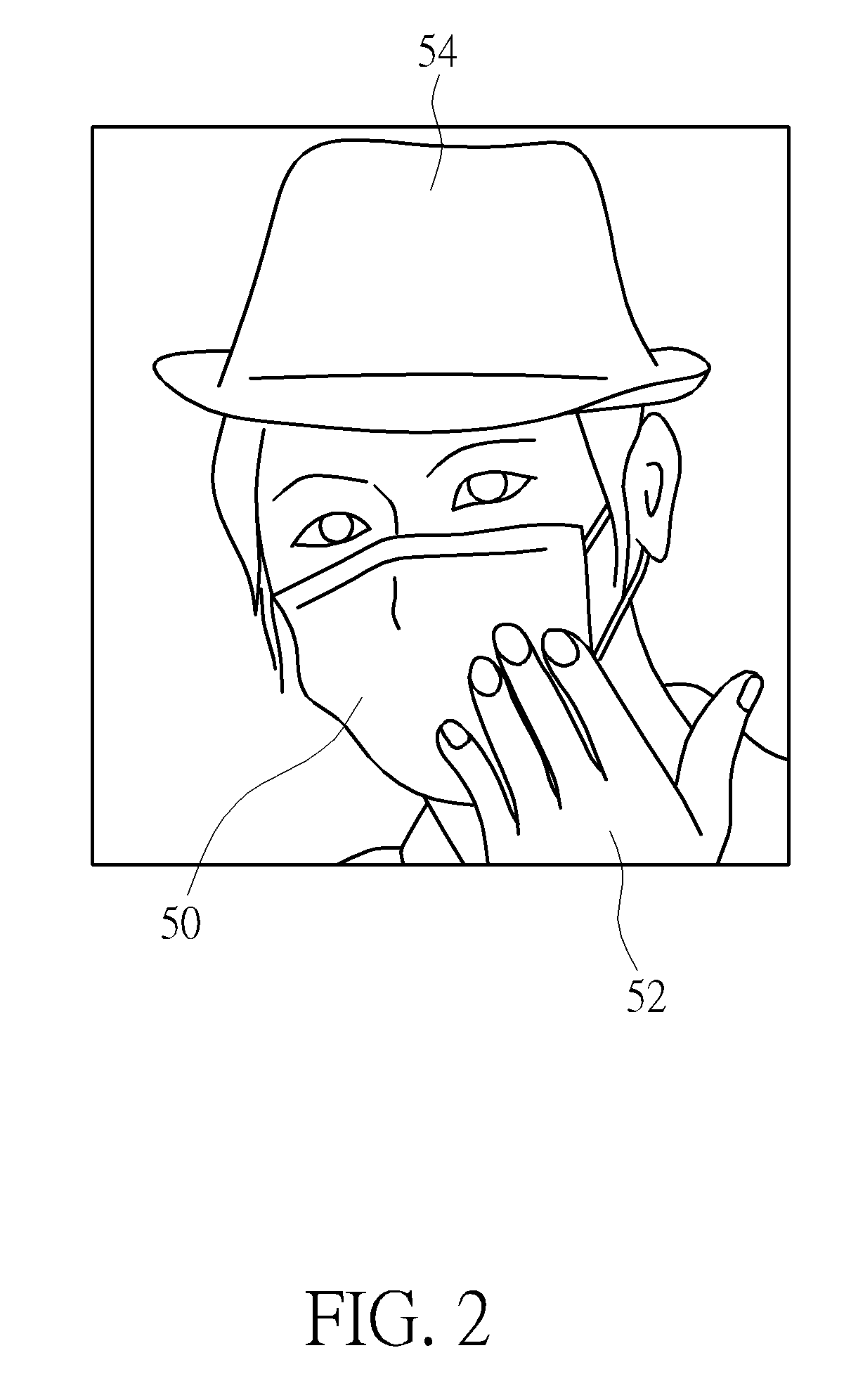
ActiveUS20170352015A1Automatic detectionPrevent crimeCharacter and pattern recognitionClosed circuit television systemsComputer graphics (images)Image capture
A method of preventing fraud and theft during automated teller machine (ATM) transactions includes recording a video stream using a camera mounted on or near the ATM, the camera being positioned to record the face of a user of the ATM and a background behind the user, providing a facial model database containing images of a large number of people taken from different angles, the facial model database containing images of unobscured faces as well as obscured faces, and receiving insertion of a bank card into the ATM. The method further includes comparing images captured from the recorded video stream with images contained in the facial model database, and producing a corresponding first face comparison result, and issuing a notice for the user to uncover the user's face when the first face comparison result indicates that the user's face is obscured.
Owner:ARCSOFT MULTIMEDIA TECH LTD
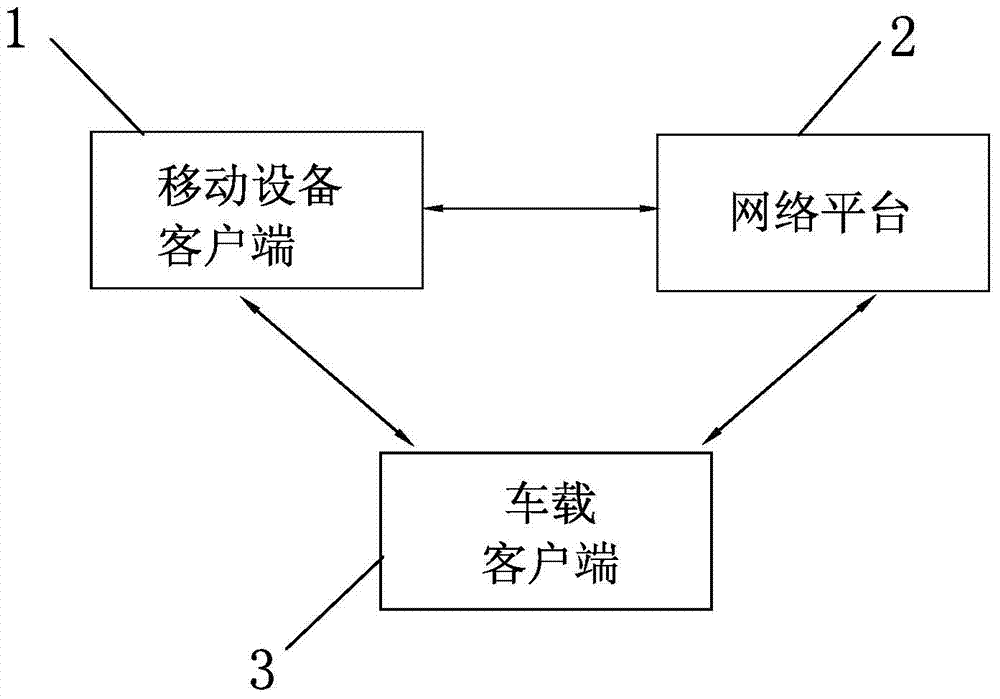
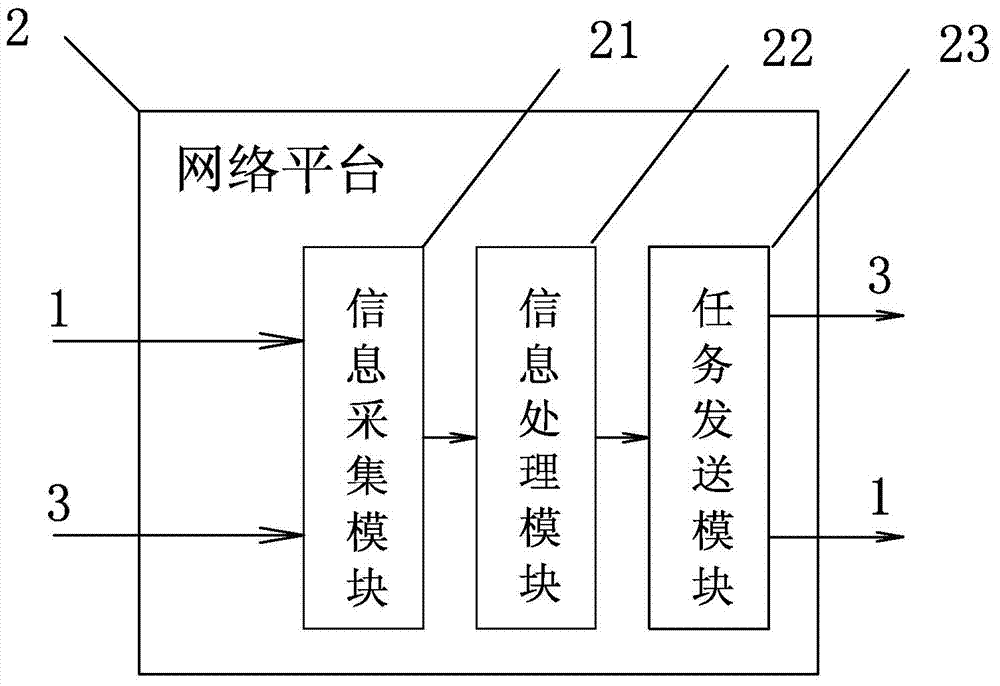
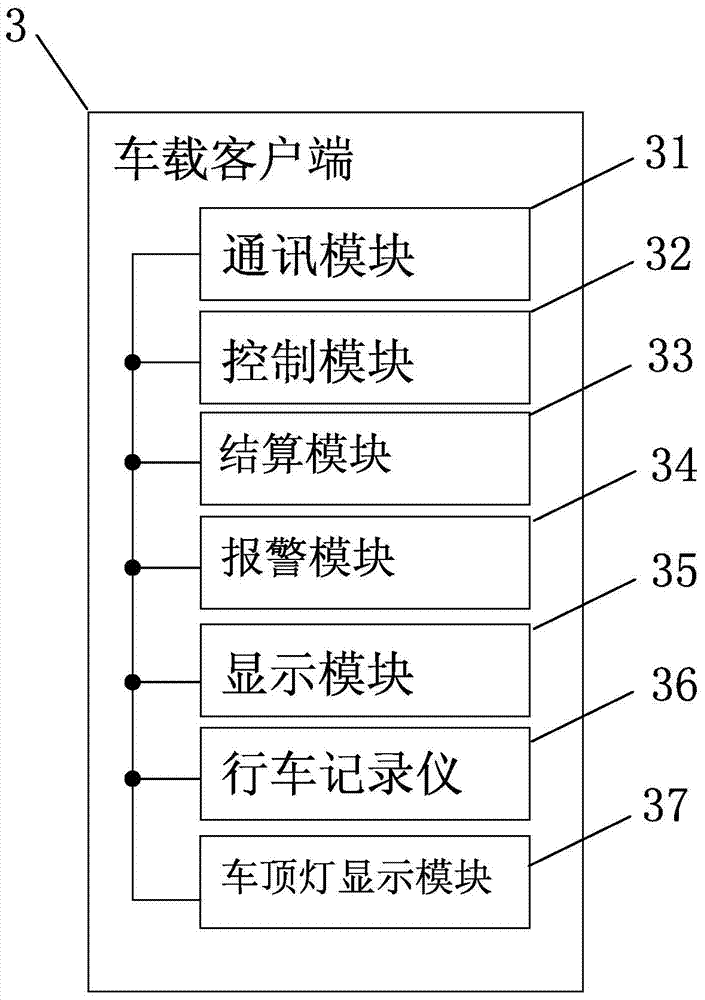
Taxi calling management settlement system and method
InactiveCN104123834AEasy to manageEasy to recordRoad vehicles traffic controlTransmissionPasswordComputer module
The invention discloses a taxi calling management settlement system which comprises a mobile device client, a network platform and a vehicle-mounted client. The network platform is connected with the mobile device client and the vehicle-mounted client through a communication network or a computer network. The mobile device client transmits a taxi calling request to a taxi calling server. The network platform transmits a car distributing command to taxis meeting the condition. The vehicle-mounted client comprises a communication module, a control module, a settlement module and an alarm module. The settlement module comprises a bank card settlement unit and a password and fingerprint input unit. A taxi calling management settlement method is further provided. The system and method integrates taxi calling, taxi distributing, security check, alarming and settlement process, greatly facilitates quick and safe trip of passengers, has good humanized management on the taxis and overcomes the shortcomings in the prior art in the field.
Owner:北京艾亿沃德电子有限公司 +1
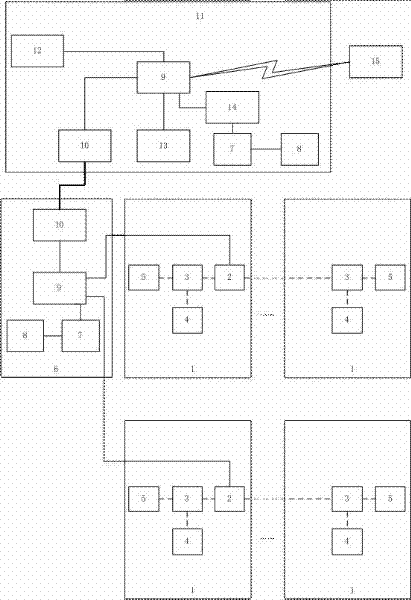
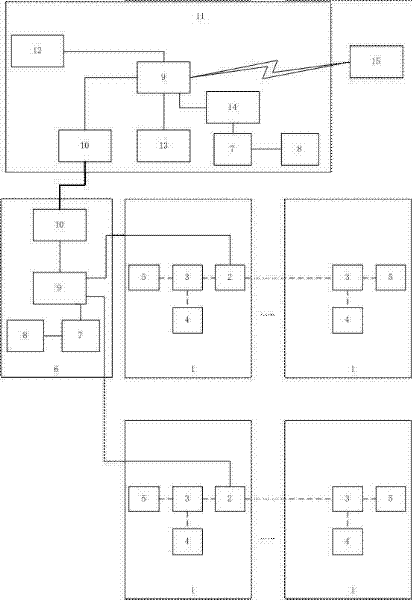
Community population security surveillance system
InactiveCN102521903ASolve difficultySolve \"technical issues\" that are prone to law and order problemsData switching by path configurationIndividual entry/exit registersTransceiverCommunity population
The invention discloses a community population security surveillance system and relates to the technical field of security and protection systems. The community population security surveillance system comprises a plurality of district security and protection nodes and a community central monitoring point respectively connected with the district security and protection nodes, wherein, the district security and protection nodes comprise district gate control nodes and cell gate access control systems, the cell gate access control systems and the district gate control nodes form a local area network, and each district gate control node comprises a switchboard receiving information of the access control systems, and a transceiver, an information reader-writer and a camera respectively connected with the switchboard. The system provided in the invention can monitor access situation of floating population in all the districts and discards the conventional management mode that considerable manpower and material resources are employed for extensive patrol, which enables manpower and material resources to be saved and targeted monitoring and arresting to be realized, thereby improving case handling efficiency.
Owner:成都川大科鸿新技术研究所
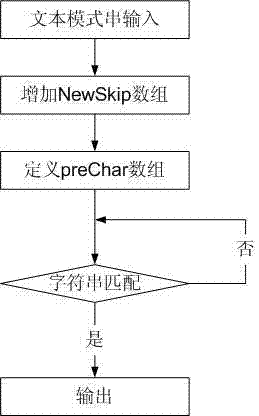
Character string matching method and system
PendingCN107239500ASimple algorithmSave space resourcesSpecial data processing applicationsArray data structureAlgorithm
The invention discloses a character string matching method and system, and relates to the field of character matching. The character string matching method comprises the following steps of: inputting text character strings: setting the input lengths of all the text character strings as n; inputting mode strings: setting the input lengths of the mode strings to be matched with the text character strings as m, wherein m is smaller than or equal to n; defining arrays; and matching the character strings. The character string matching system is characterized by comprising a man-machine interaction module, a character string input module, an array definition module, a character string matching module and an output and display module, wherein the man-machine interaction module is connected with the character string input module; the character string input module is connected with the array definition module; the array definition module is connected with the character string matching module; and the character string matching module is connected with the output and display module. According to the method and system, an algorithm is simpler, the space resources required by the algorithm are less and the calculation speed is higher.
Owner:CHENGDU GOLDTEL IND GROUP
Dumbwaiter system
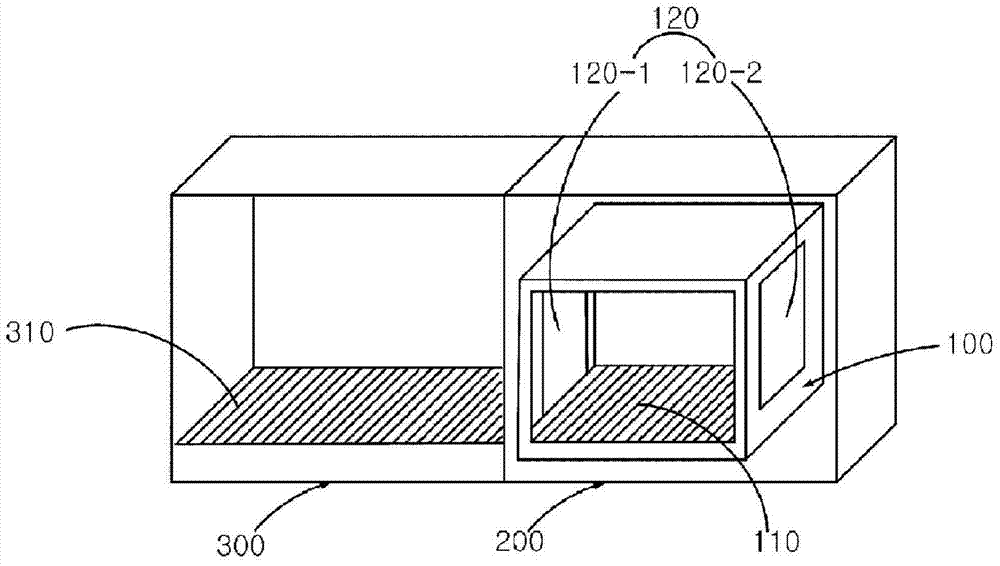
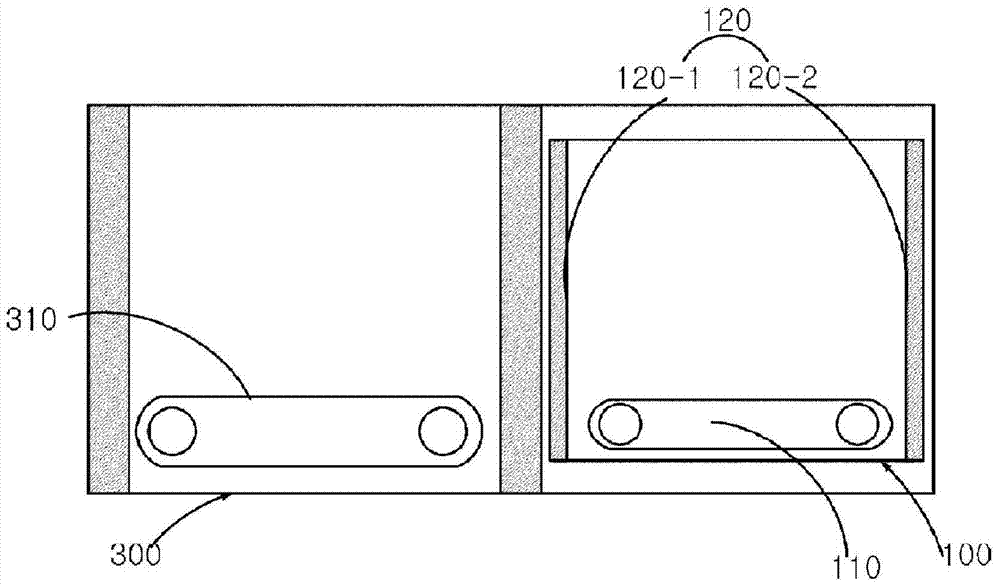
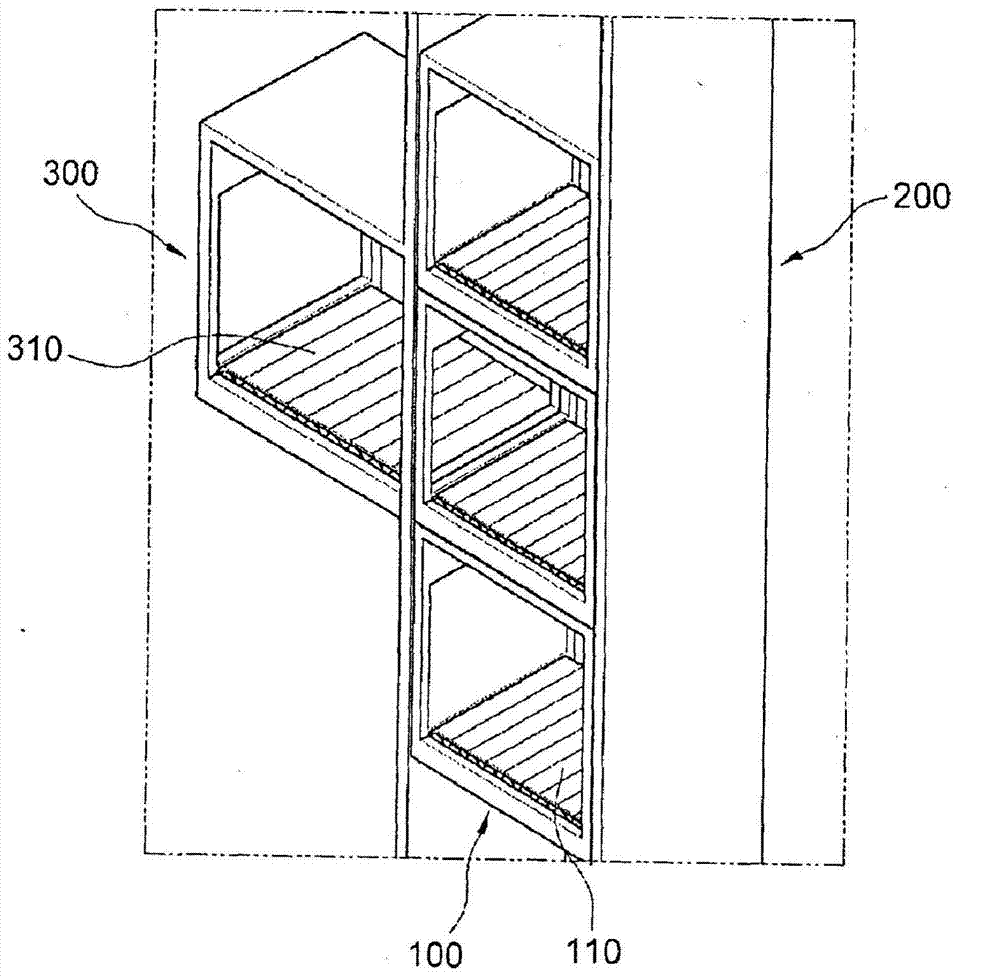
The present invention relates to a dumbwaiter system which is capable of enabling users to automatically purchase and received goods in a residential area by being installed in a multi-dwelling building, and ensures the safety of the users by reducing contact with strangers and preventing crimes. To this end, a multi-stage dumbwaiter system, according to one embodiment of the present invention, comprises: a dumbwaiter having a body of which the inside is vacant the sides can be opened, and a horizontal movement device for carrying an object inside or outside; and a home case disposed on one side of the dumbwaiter, and having a body of which the inside is vacant and the sides can be opened and a home case movement device for carrying an object inside or outside, wherein the dumbwaiter delivers an object to the home case or receives an object from the home case.
Owner:MU
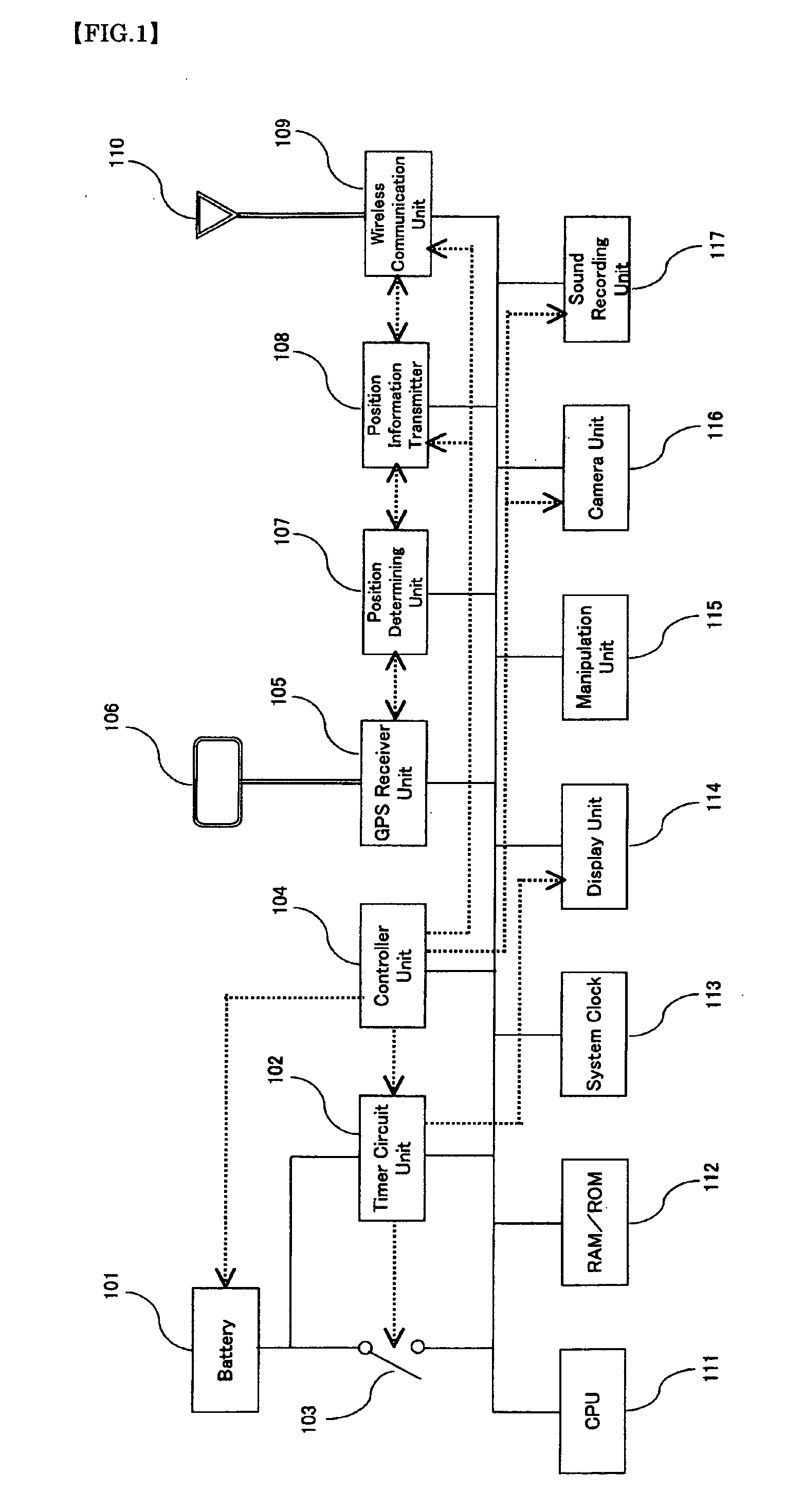
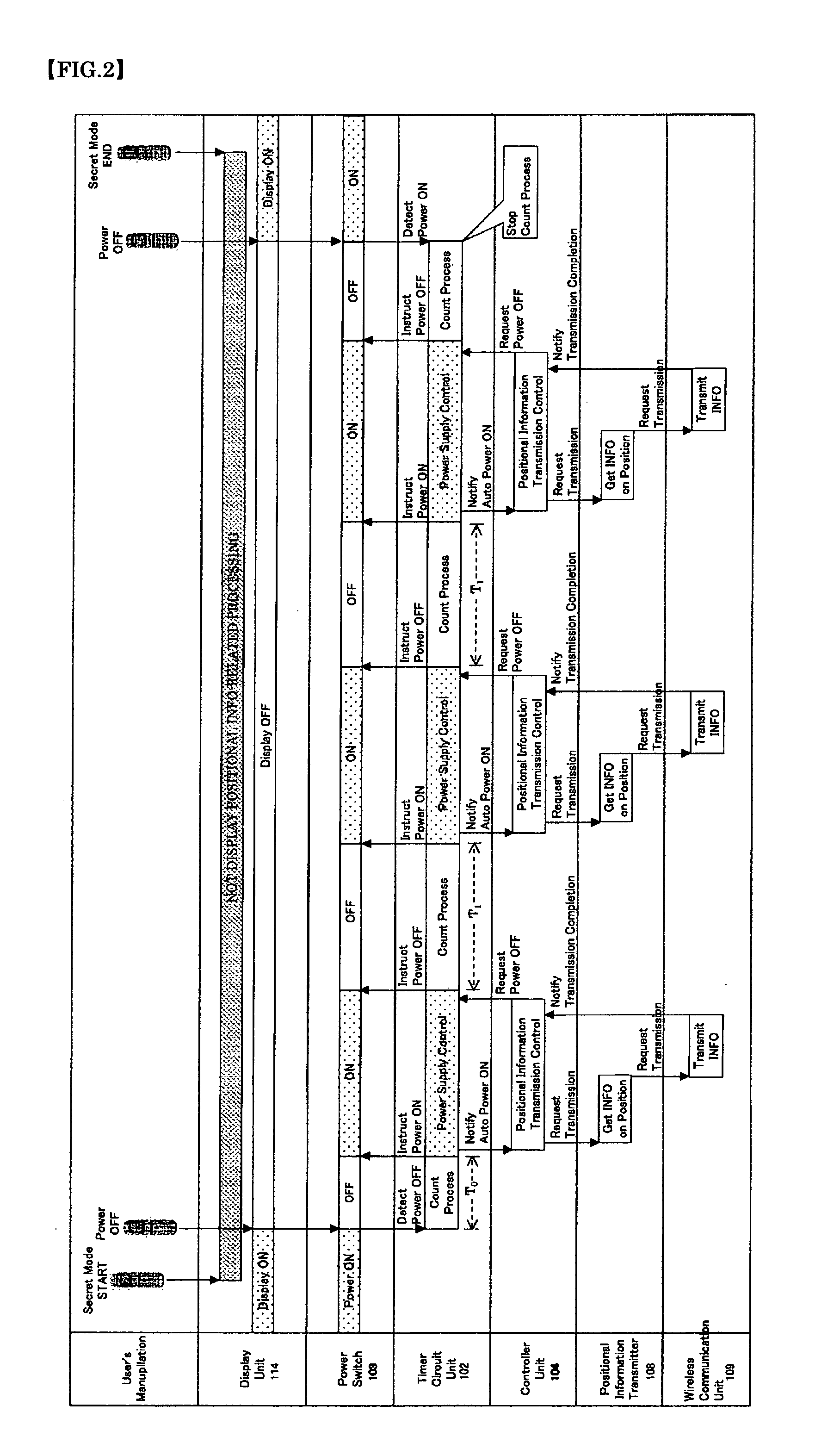
Portable communication terminal with gps function
ActiveUS20090322595A1Quick fixPrevent crimeDevices with GPS signal receiverPosition fixationGps satellitesSatellite
This invention aims to provide a Mobile Communications Terminal (MCT) equipped with a GPS function that automatically transmits the information on the current position of the MCT after the power of the MCT is turned off. The MCT comprises a GPS Receiver Unit 105 for receiving signal data from a GPS satellite, a Position Determining Unit 107 for determining a current position of the MCT based on the aforesaid signal data, a Positional Information Transmitter Unit 108 for automatically transmitting information on the position obtained by the Position Determining Unit 107 and other information, a Controller Unit 104 for sending a request command to the Positional Information Transmitter Unit 108, and a Timer Circuit Unit 102 for turning on the MCT at a predetermined time interval, after power of the MCT is turned off.This invention enables the MCT to automatically transmit the information on the position information and other information of the MCT at a predetermined time interval while the power of the MCT is on, and automatically transmit the information on the position information and other information of the MCT at the a predetermined time interval after the power of the MCT is turned off.
Owner:MIZUKAMI TOSHIHIKO
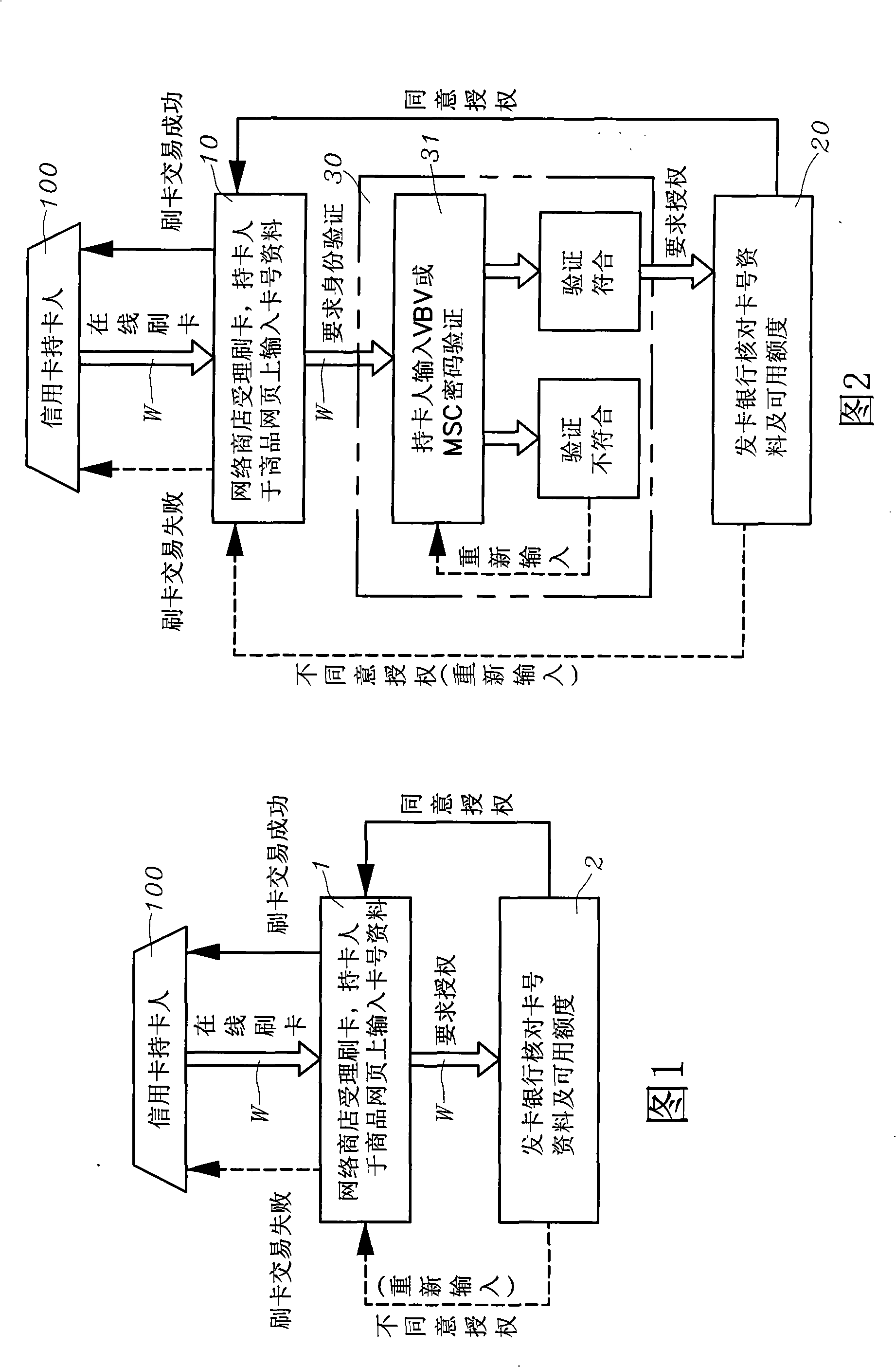
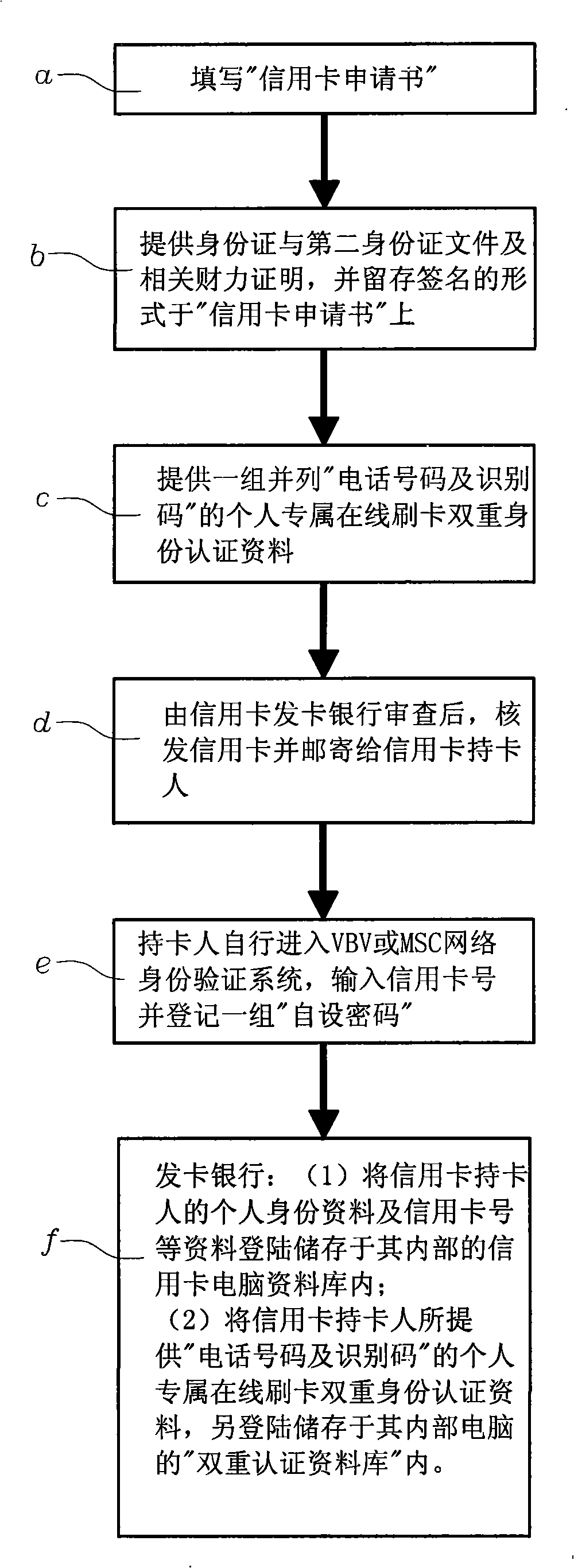
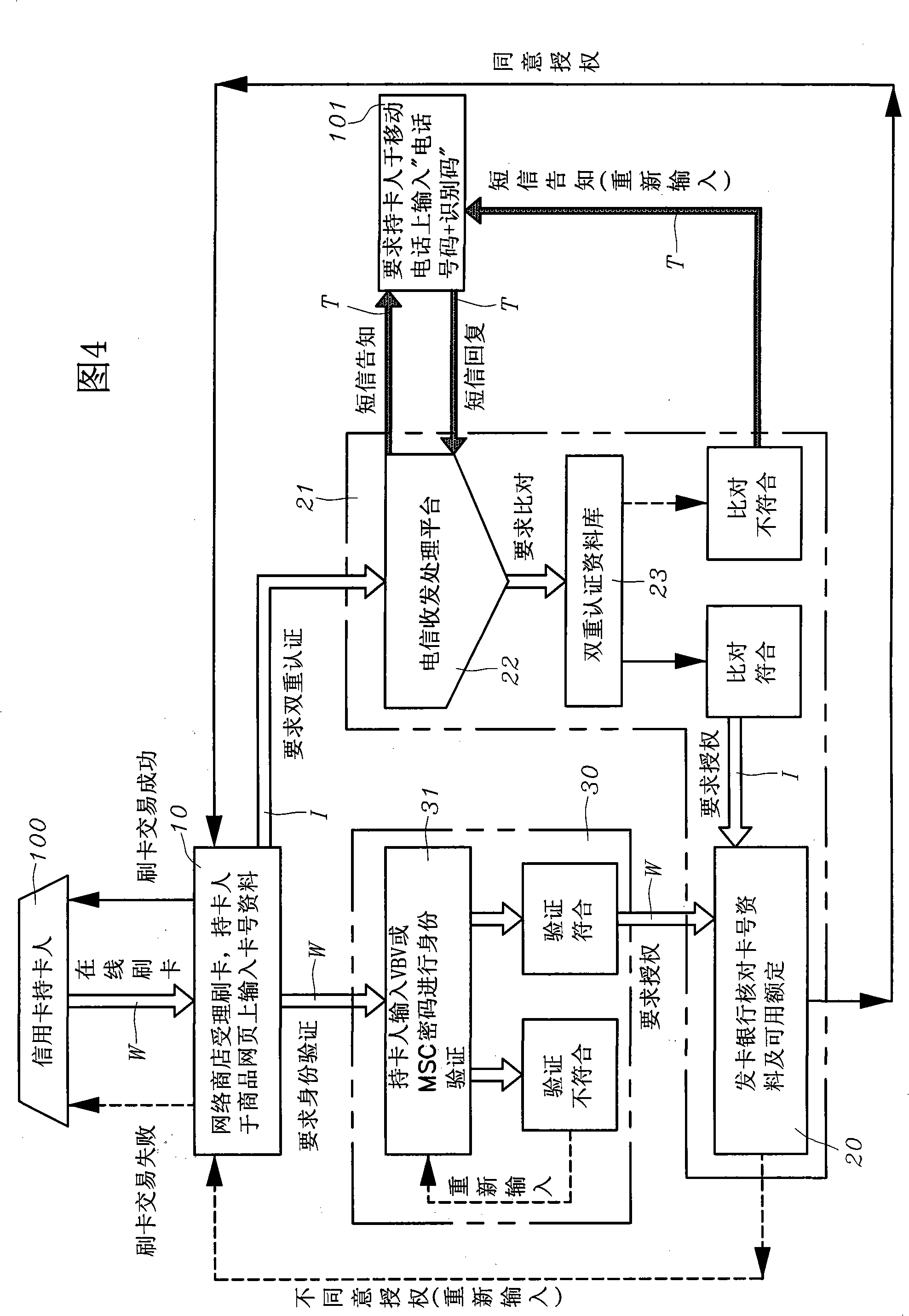
Method for network on-line payment double authentication by telephone and identifying card
InactiveCN101291329APrevent crimeSafety of tradementFinanceUser identity/authority verificationIssuing bankCredit card
The invention uses the phone number and the identifying codes as the network online dual authentication method. The card holder of the credit card registers the VBV or MSC network identity checking ''self-setting password'' to the card-issuing bank, the holder also provides a group of ''phone number and the identifying codes'' personal special online dual identity authentication data to the card-issuing bank; the data login is stored in the ''dual authentication database'' of the ''credit card dual authentication computer system'' of the card-issuing bank; while the card-issuing bank is processing the online card slotting, the bank informs the card holder in the short message way besides the ''self-setting password'' of the VBV or MSC network identity checking for the card holder; requiring to respond to the personal special online identity authentication data of the ''phone number and the identifying codes''; comparing to the ''phone number and the identifying codes'' in the ''dual authentication database'' as the card slotting transaction on the network for the card holder for the dual rechecking to confirm whether the invention is the network credit card transaction under the entitlement.
Owner:林仲宇
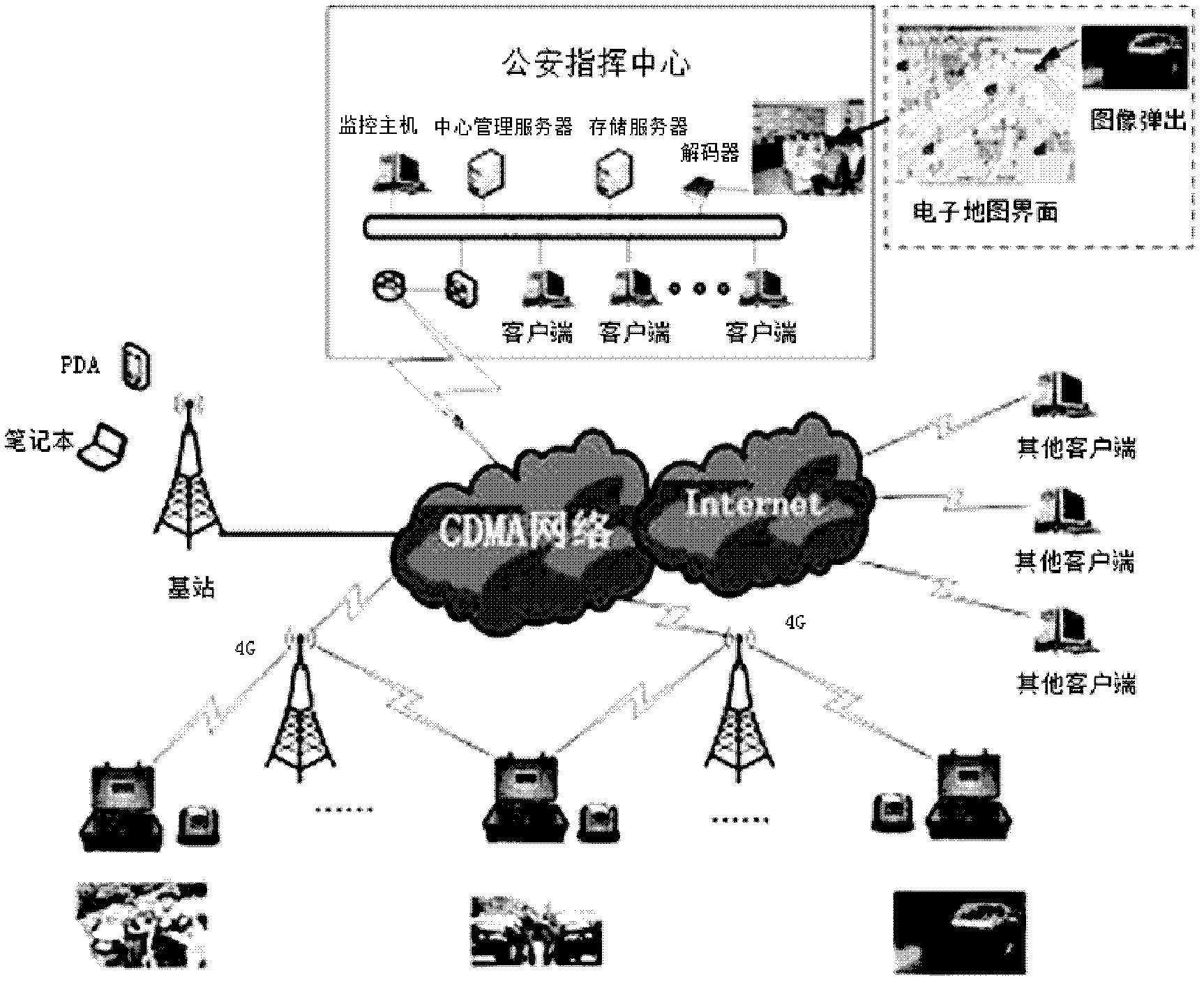
Police escort 4G video transmission system
InactiveCN102611876AEnsure safetyStrengthen security managementClosed circuit television systemsWireless commuication servicesInformatizationTransport system
The invention discloses a police escort 4G (4-Generation) video transmission system comprising a command center platform and a client, wherein the client is capable of inquiring about the information of an escort vehicle in the command center platform, wherein the command center platform is composed of a monitoring center, a center management server, a memory server and a decoder, and wherein the center management server obtains the real time image, voice information and position of the escort vehicle through a 4G network, and stores the information in the memory server; the monitoring center monitors the real time image, voice information and position of the escort vehicle obtained by the center management server, and processes problems encountered in the running process of the vehicle immediately; and the decoder decodes the information of the escort vehicle obtained by the center management server, converts the information into information that the client can recognize, and then provides the information for the client through a router for use. The police escort 4G video transmission system is capable of further enhancing the security management of the escort vehicle and improving holistic management efficiency and informatization degree.
Owner:上海信力唐电子信息科技有限公司
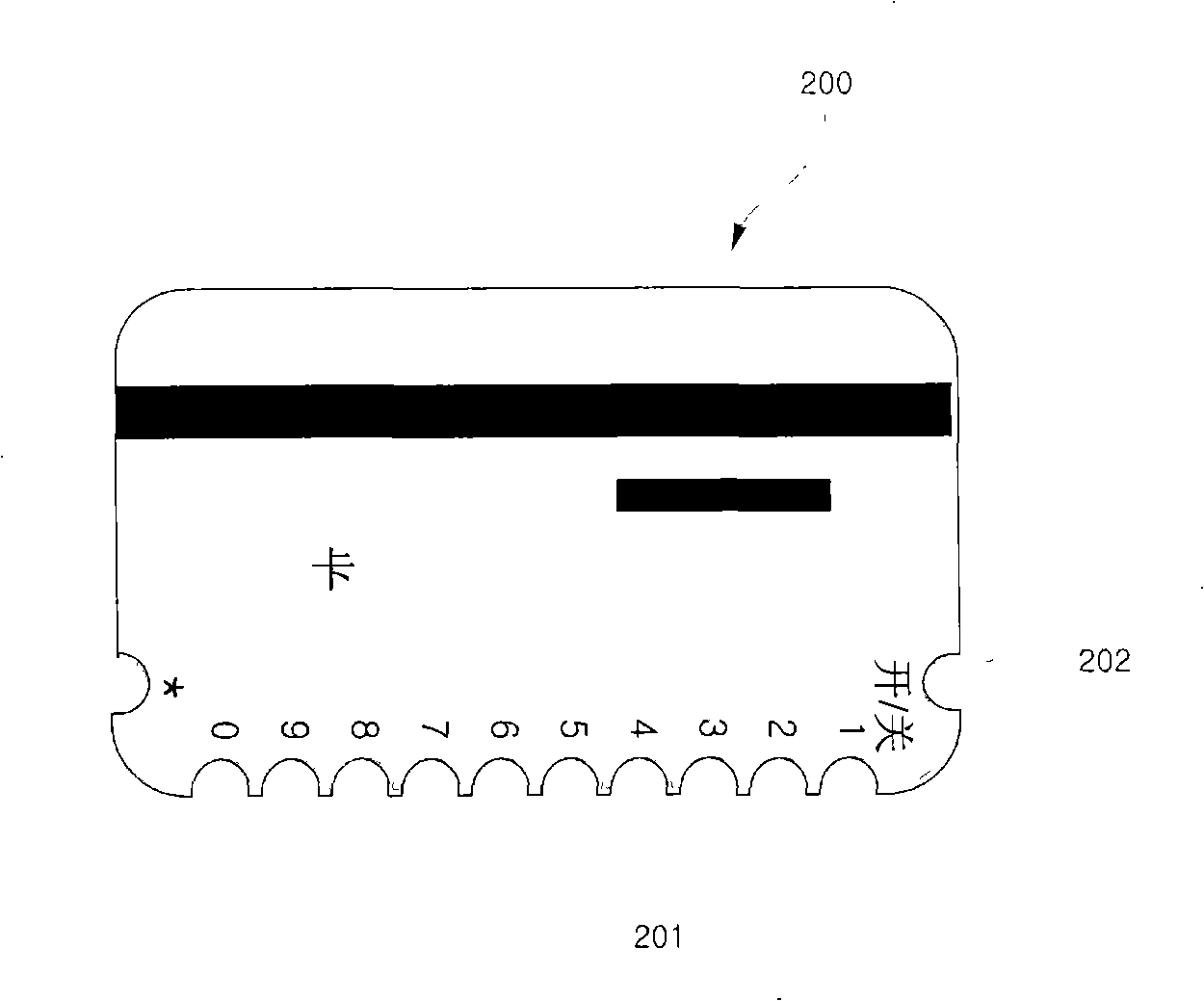
Card having password input key
InactiveCN101322143AAvoid damageReduce defectsAcutation objectsDigital data authenticationCredit cardThird party
Owner:朴正雄
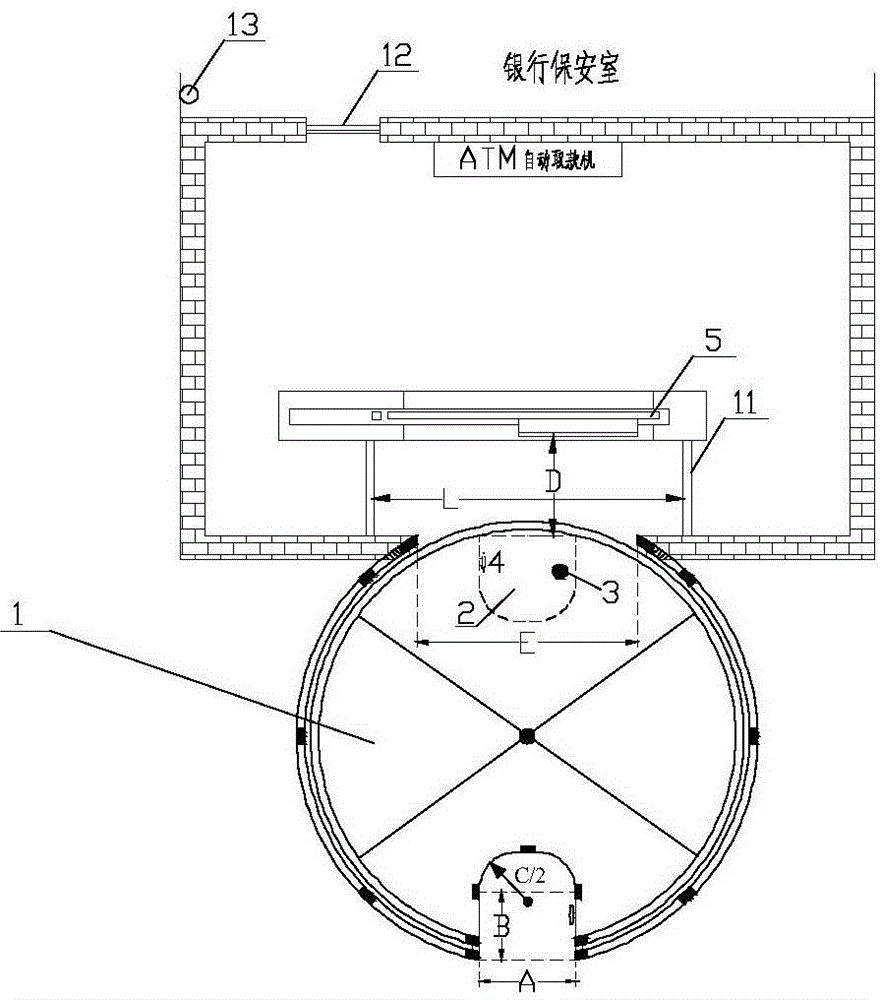
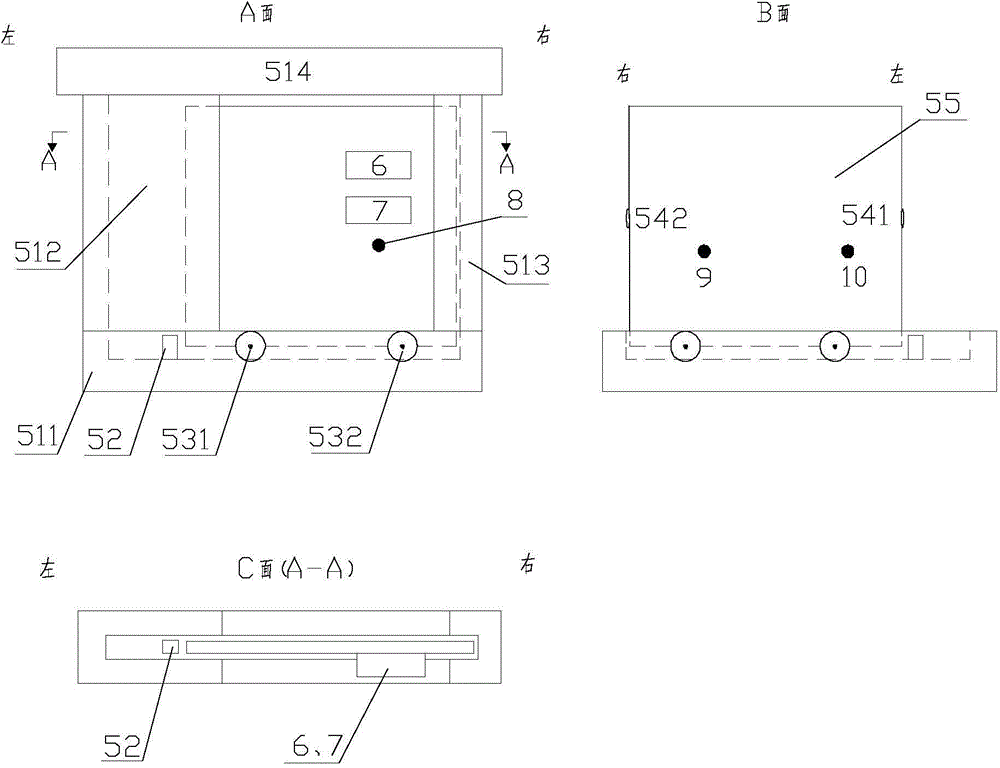
ATM (automatic teller machine) automatic safety device and method for implementing protection measures of ATM automatic safety device
ActiveCN104574694APrevent crimeCrime eliminationComplete banking machinesAuthorizationComputer science
The invention provides an ATM (automatic teller machine) automatic safety device and a method for implementing protection measures of the ATM automatic safety device. The ATM automatic safety device comprises an operation room surrounded by a rotating door, a safety door and connecting walls; and an identity recognizer and a visual checking device are arranged in the operation room. The method comprises the following steps of recording videos and checking authorization by using the visual checking device after a doer enters the operation room through the rotating door; leaving information of an identity card, fingerprints or iris of the doer by using the identity recognizer so that initial verification on legality of the doer is finished; judging legality of a card inserting behavior of the doer according to the information of a bank card and the information obtained before the doer enters the ATM room after the doer inserts the bank card in an ATM successfully; and whether an alarming behavior is carried out or not is judged according to a judgment result. By the ATM automatic safety device and the method for implementing the protection measures of the ATM automatic safety device, confirmation on the identities of actual users of bank cards is strengthened effectively, most of criminal behaviors about the bank cards can be actively prevented and stopped, and legal interests of legal holders of the bank cards can be protected. The ATM automatic safety device and the method for implementing the protection measures of the ATM automatic safety device have the advantages of convenience in use, safety, reliability and the like.
Owner:临沂高新区金蓝领劳务有限公司
Multi-service management system
InactiveCN102446290AImprove service levelConvenient and convenientSpecial data processing applicationsM-governmentIT service management
The invention discloses a multi-service management system comprising a plurality of service management terminals, a data receiving and authenticating platform, a plurality of demand processing platforms and a financial service platform. According to the invention, the government, the publication of public information and the like, various public services, communication services, financial services and the like are integrated; the service level is improved through the cooperative work of integration platforms; better convenience and efficiency are provided; and a mass of resources are saved in the meantime.
Owner:KINGBIRD COMP SOFTWARE
Kindergarten access control system and method based on cloud computing
InactiveCN107845174AEnsure personal safetyEffective controlIndividual entry/exit registersTransmissionCloud data centerData library
The invention provides a kindergarten access control system and method based on cloud computing. The method comprises the steps of carrying out face recognition on user groups, sending results to a cloud computing platform, carrying out comparison and verification, controlling the access control system by virtue of the cloud computing platform so as to open and close access control, recording datain a cloud server, and carrying out statistics and pre-warning in the system, so as to finish the access control of entry and exit of infants. According to the method, the infants can safely enter and exit a kindergarten under the guarantee of parents, the operation can be convenient, rapidly and accurately realized, and the access control management can be effectively controlled, so that the personal safety of the infants can be guaranteed; and suspicious information can be recorded into a big database in a cloud data center for comparison, so that the criminal case can be prevented.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Method and device for intelligently monitoring and identifying surrounding environment of payee, and medium
ActiveCN112528966AReal time monitoringFacilitate face recognitionCharacter and pattern recognitionPayment architectureVideo monitoringHuman body
The invention discloses an intelligent monitoring and recognition method and device for the surrounding environment of a payee, and a medium. The method comprises the steps of video monitoring, targettracking, and interactive behavior detection and recognition. The target tracking comprises the following steps: when the video monitors that someone enters the periphery of the ATM, performing multi-target tracking by taking a human body in the monitoring video as a target by adopting Markov Monte Carlo to obtain a tracking video comprising a multi-target tracking track; the interactive behaviordetection comprises the steps of extracting features from a tracking video and constructing combined features to judge a face portrait and feature points thereof of a human body target through a convolutional neural network algorithm so as to judge whether a head posture and a sight angle are abnormal or not, and carrying out interactive behavior detection on the abnormal situation; the interactive behavior recognition is to further judge the type of the interactive behavior if the interactive behavior exists. According to the invention, people and objects in the withdrawal area can be monitored in real time, and the behaviors of people can be automatically detected and identified.
Owner:EAST CHINA JIAOTONG UNIVERSITY
Linkage bill processing and pre-warning system
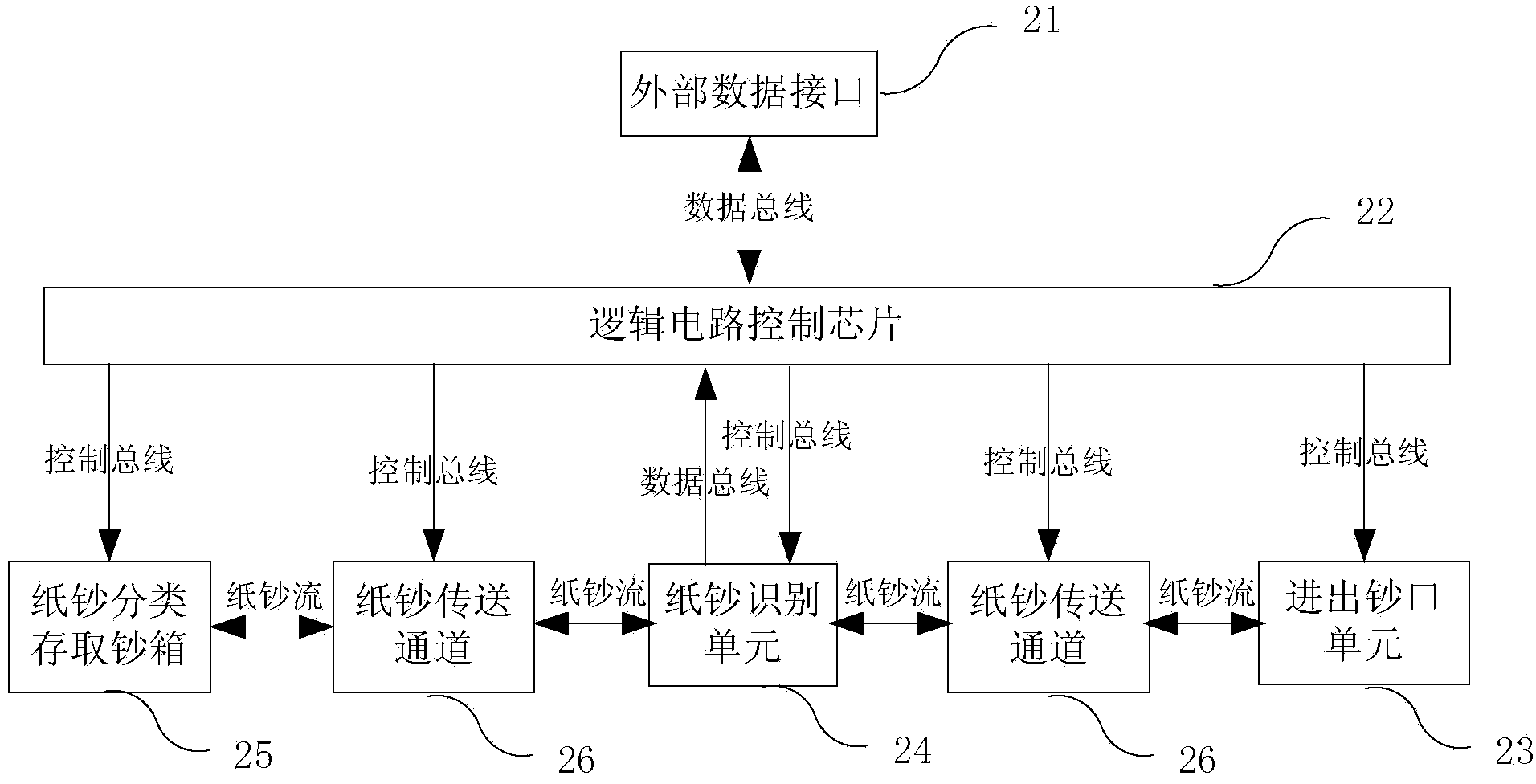
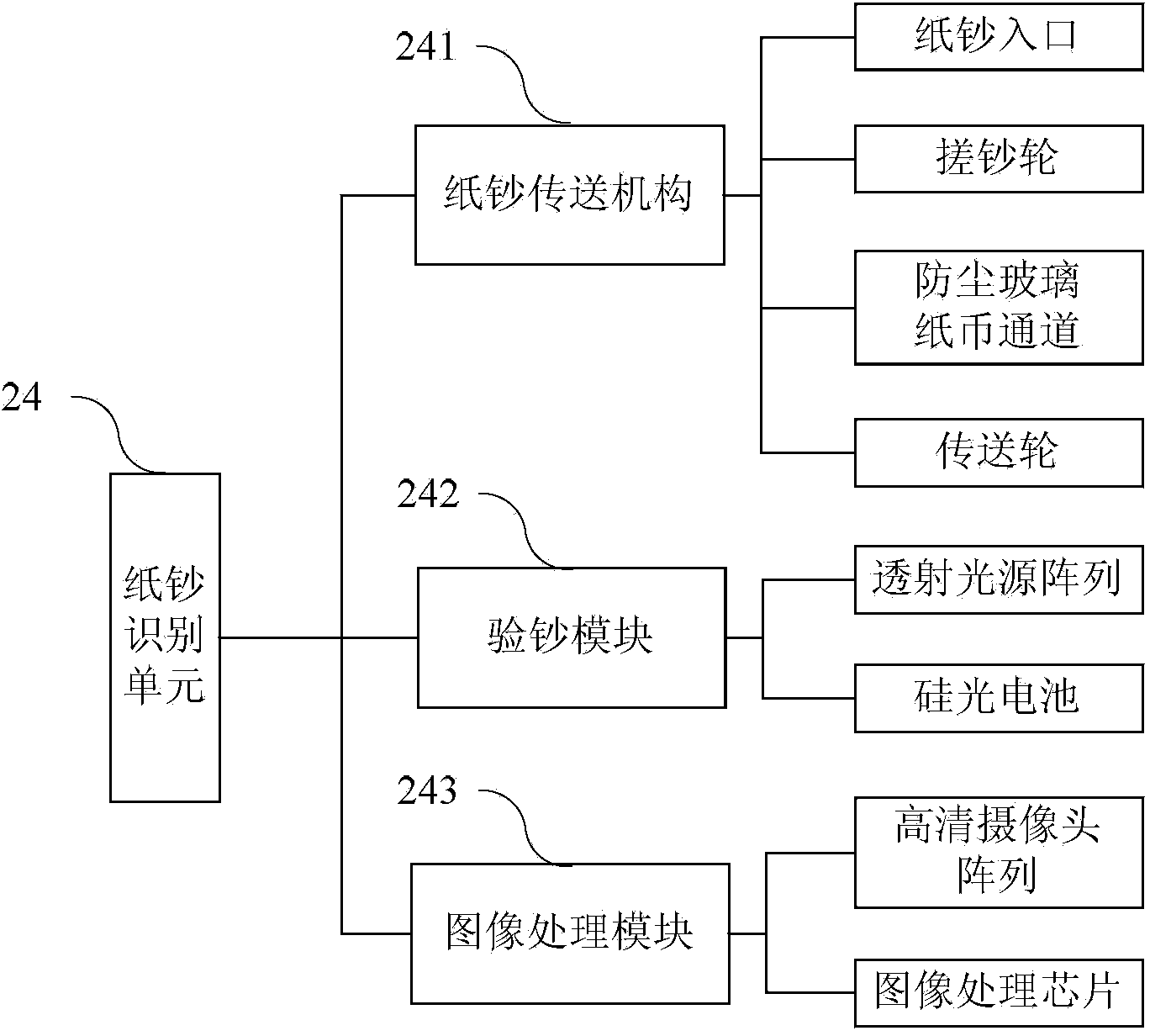
ActiveCN103955996ARealize information transmissionImprove securityCoin/paper handlersInformation transmissionExternal data
The invention provides a linkage bill processing and pre-warning system. The linkage bill processing and pre-warning system comprises a teller transaction terminal, a bill processing device, a host server and a pre-warning server, wherein the teller transaction terminal comprises a transaction processing module and a drive module; the bill processing device comprises an external data interface, a logic circuit control chip, a bill mouth unit, a bill recognition unit, a bill classification storing and taking bill box and a bill conveying channel; the pre-warning server comprises a bill data storage module, a sensitive data storage module and a pre-warning module. The linkage bill processing and pre-warning system achieves information transmission between bill processing equipment and a transaction data processing terminal, achieves a pre-warning function for bills with the sensitive number, is beneficial for finding forged bills on suspicion of crime and recycling the bills in specific types timely, facilitates tracking of the bills having problems, and improves safety of cash processing.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Method of generating bill for protecting user access privacy in network service
InactiveCN103281180AProtect access privacyAchieving non-connectabilityKey distribution for secure communicationUser identity/authority verificationInternet privacySecurity parameter
The invention discloses a method of generating a bill for protecting user access privacy in network service. The method comprises the following steps: (1) performing system initiation, namely generating a system public parameter pps according to the input system security parameter, and respectively generating public key / private key pairs of groups G managed by a management mechanism M, a detection mechanism D and a recognition mechanism O; (2) constructing a group signature key xi by a user Ui and acquiring an authorization certification Ci about the group signature key xi of the user Ui from the management mechanism M; (3) constructing request information of protecting the user access privacy and a group signature thereof according to the request information by the user; (4) identifying the legality of the request information by the recognition mechanism O and determining that the qualification of group members of the user is not repealed; (5) verifying the legality of the information by utilizing the group signature by the detection mechanism D, acquiring legal service types and providing corresponding anonymous service; and (6) generating the service bill for protecting the user access privacy by the recognition mechanism O. The method disclosed by the invention can be used for effectively protecting the user access privacy and has the advantages of low communication cost, high safety and the like.
Owner:JINAN UNIVERSITY
Multifunctional vehicle-mounted intelligent password safe
InactiveCN103419751ASolve self-protection problemsImprove anti-theftAnti-theft devicesChannel state informationPassword
The invention discloses a multifunctional vehicle-mounted intelligent password safe, which comprises a safe having a password unlocking function, wherein a vehicle-mounted electronic anti-theft device is further arranged in the safe; the vehicle-mounted electronic anti-theft device comprises a state detection module for automatically detecting the state of a vehicle and converting the state into vehicle state information, a control module for receiving the vehicle state information of the state detection module, processing the vehicle state information and generating a control command, and a GSM (Global System for Mobile) communication module for transmitting the vehicle state information to a user mobile phone in response to the control command; the state detection module is connected with the control module; the control module is connected with the GSM communication module. The vehicle-mounted electronic anti-theft device is arranged in the safe, so that the vehicle-mounted electronic anti-theft device is protected in the safe; meanwhile the state detection module is used for automatically detecting the vehicle state, so that invasion of automobiles by lawbreakers can be found in time, a user is informed via the GSM communication module, and the safety performance of theft prevention, damage prevention, detachment prevention, shielding prevention and the like is enhanced remarkably.
Owner:惠州诺盾高科电子有限公司
Sheet glass laminate structure and multiple sheet glass laminate structure
InactiveCN101516798AImpact resistantThermal shock resistantGlass/slag layered productsWoven fabricsEngineeringElectrical and Electronics engineering
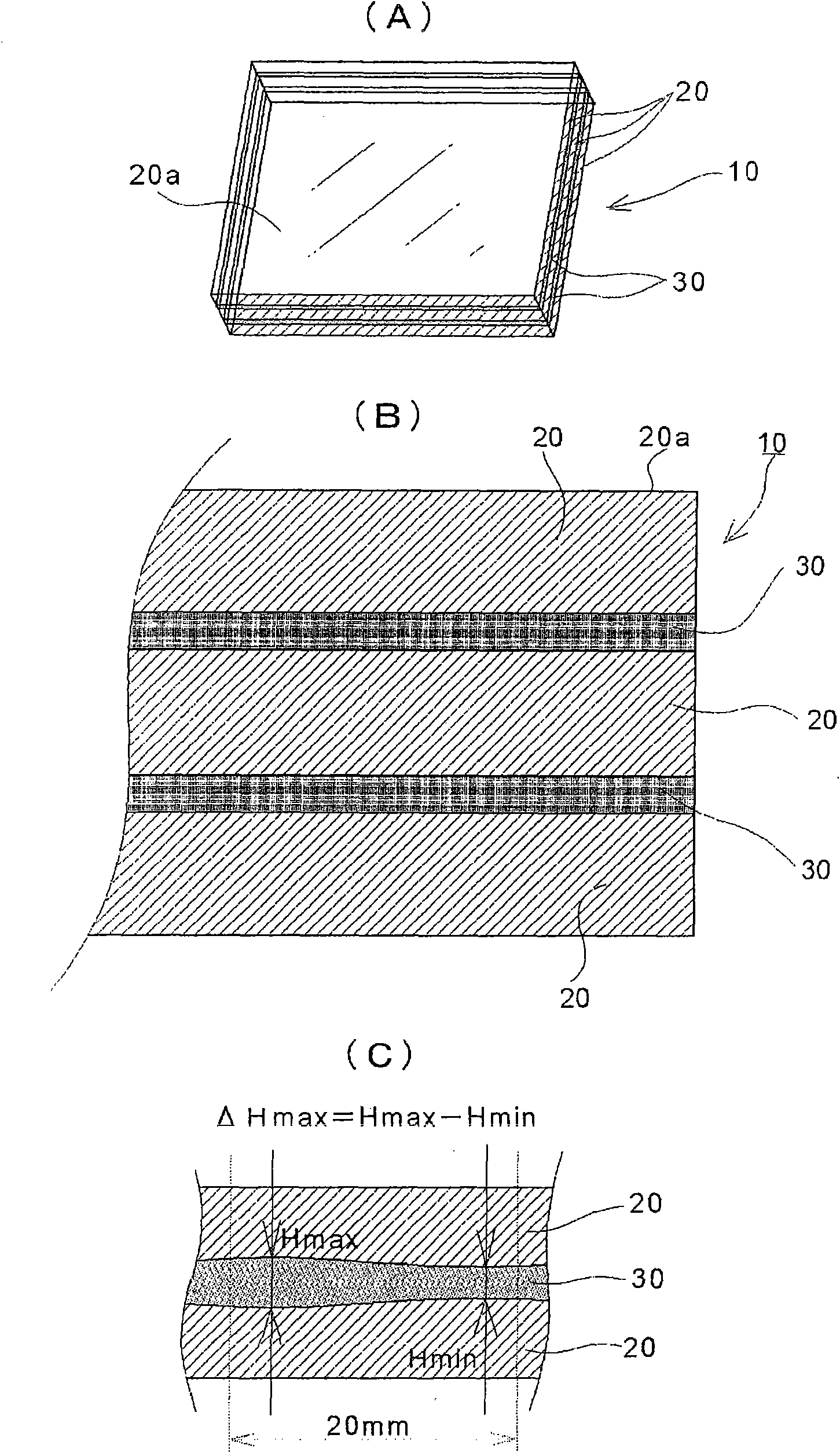
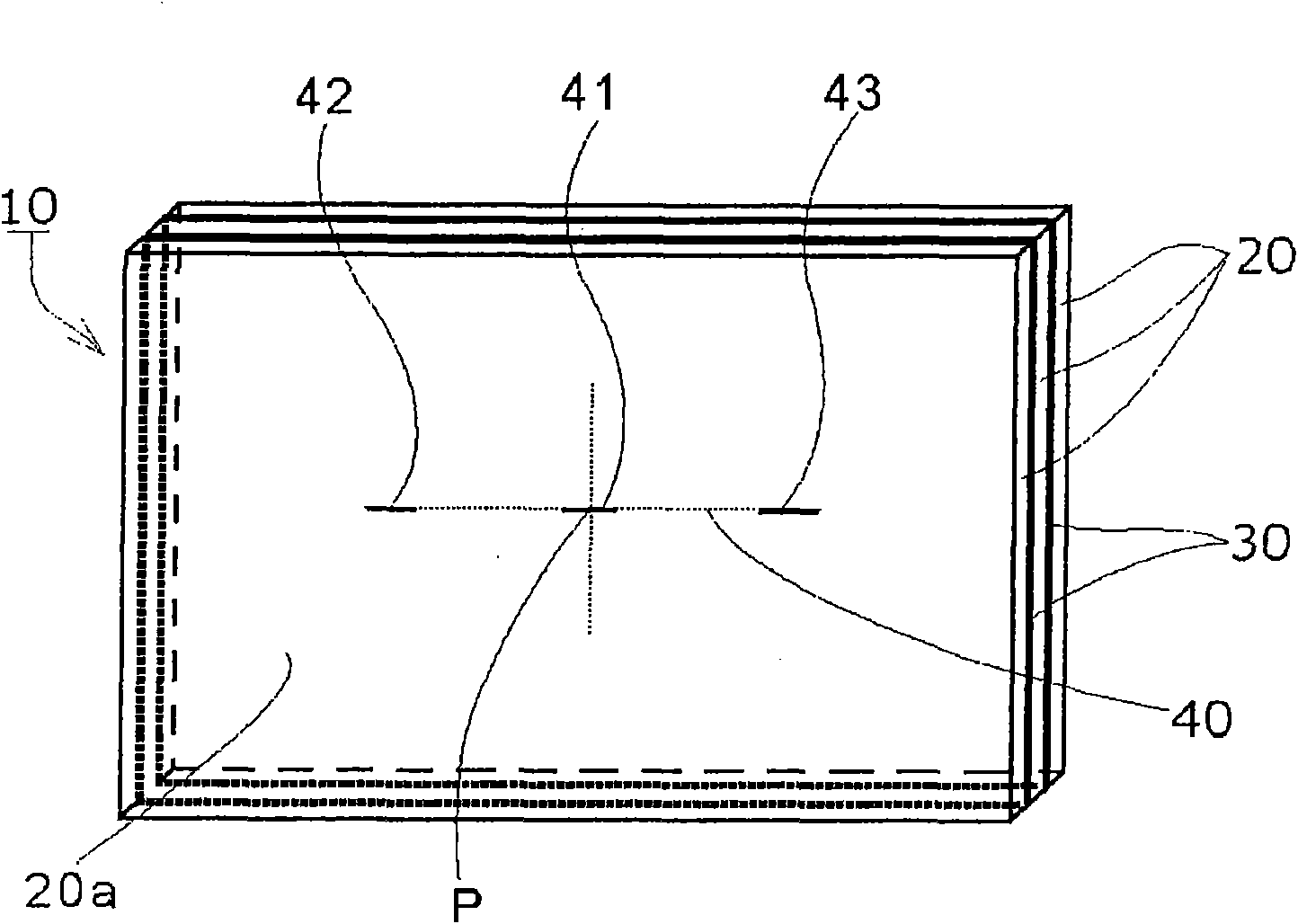
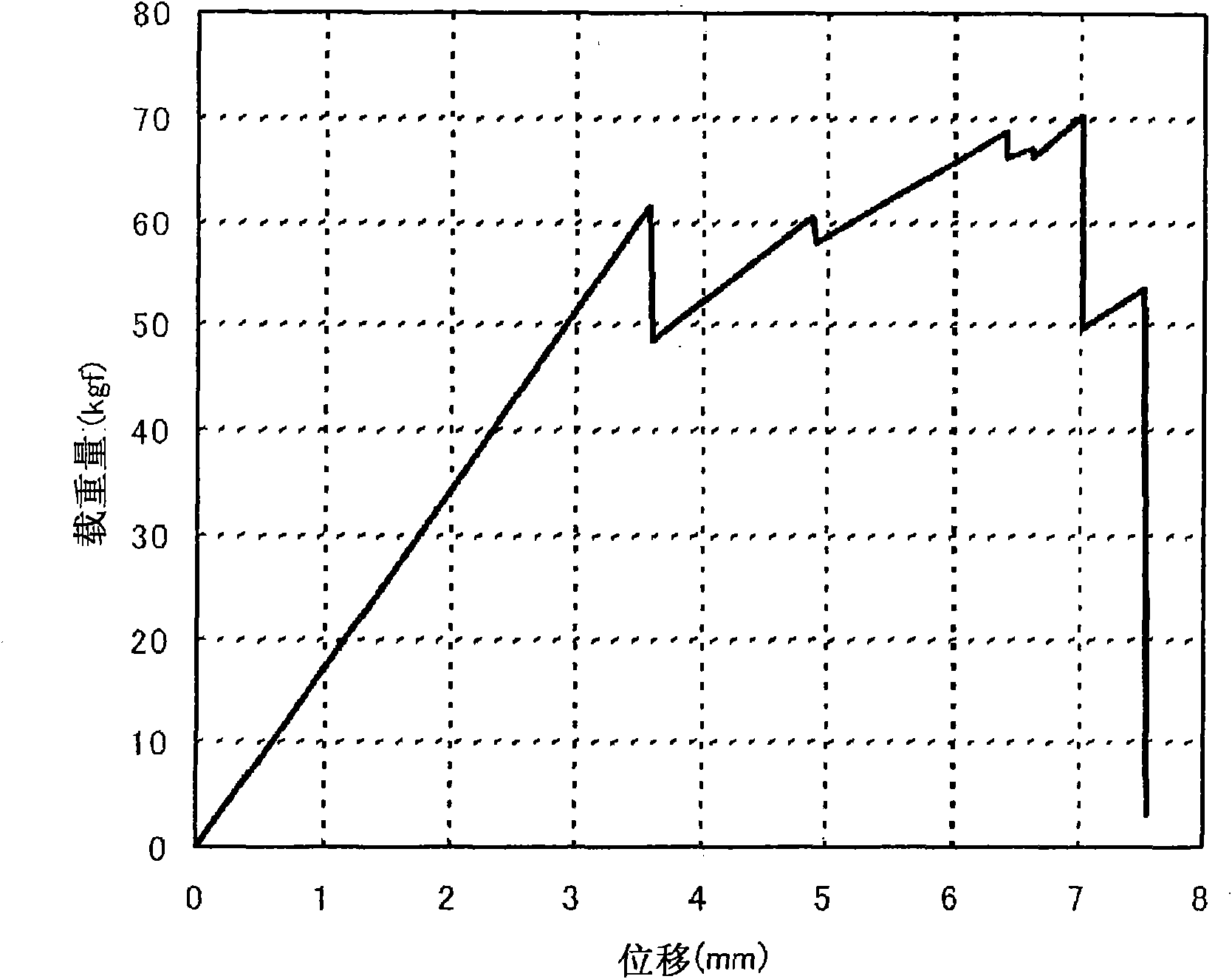
The present invention provides a sheet glass laminate structure excellent in penetration resistance (bulletproof nature), crime prevention nature, heat shock resistance, translucency and airtightness. The sheet glass laminate structure (10) is produced by laminating at least three sheets of sheet glass (20) each having a sheet thickness of less than 1 mm with intermediate layers (30) interposed between them. When a central portion 20 mm in length including the middle point of a virtual line and opposite end portions respectively being 20 mm long from the opposite ends of the virtual line are set on the virtual line having a length equal to 50% of the maximum overall dimension of the translucent surface of the sheet glass (20) and extending in parallel with the direction of maximum overall dimension with the center of the translucent surface as its middle point, maximum variation DeltaHmax of the interval H between sheets of sheet glass opposing across the intermediate layer in connection with the central portion and the opposite end portions satisfies the following relation; 0[mu]m<DeltaHmax<20[mu]m.
Owner:NIPPON ELECTRIC GLASS CO LTD
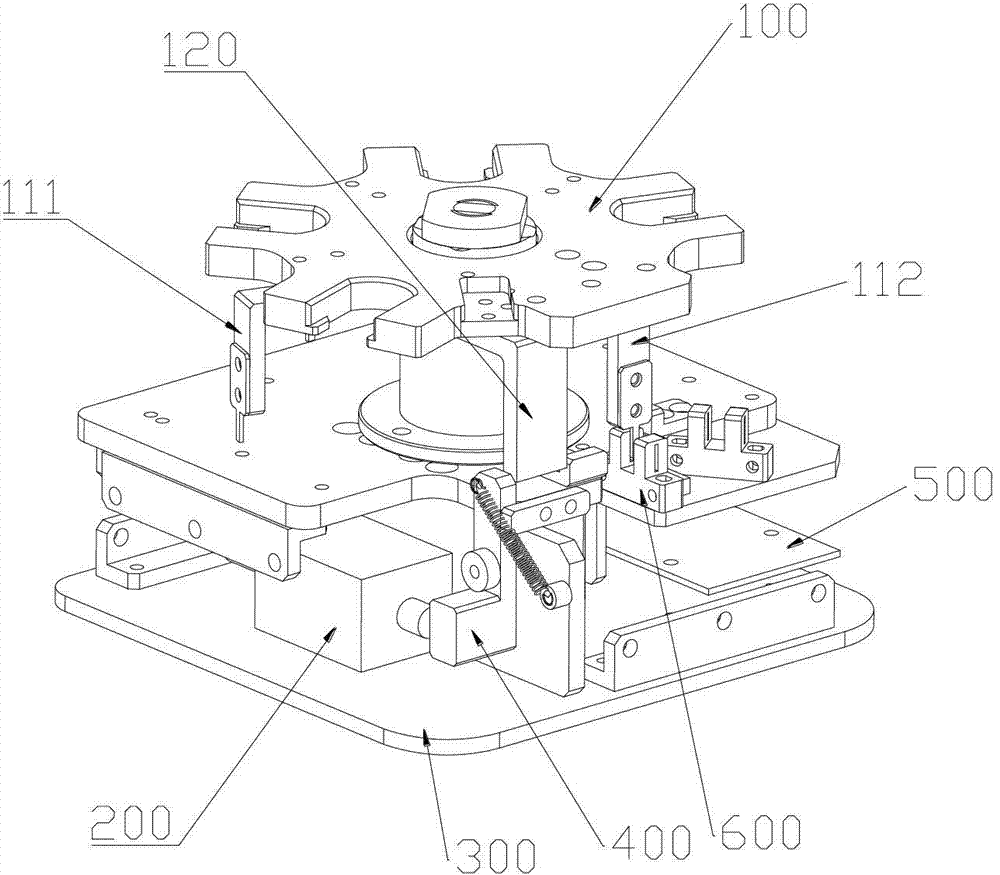
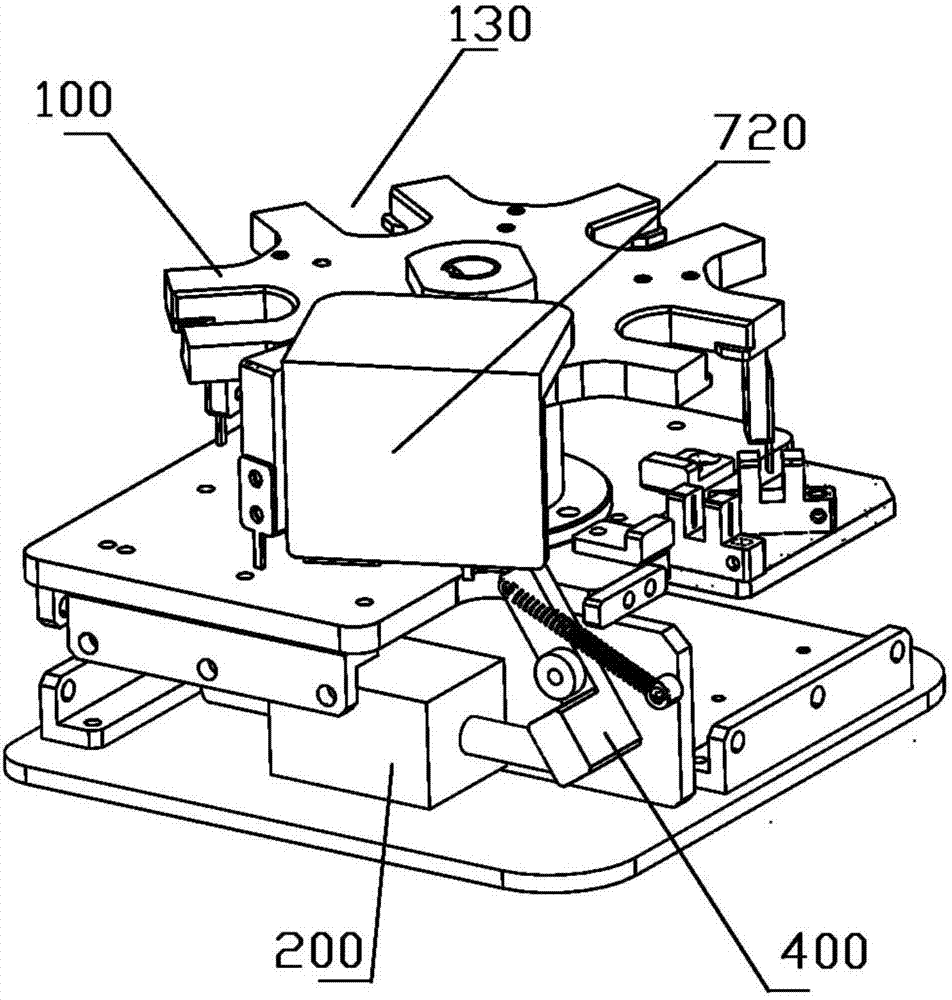
Seal taking and placing device and method
A seal taking and placing device comprises a seal locking case and a seal taking module arranged in the seal locking case, wherein a seal outlet for taking and placing seals is opened on the seal locking module; the seal taking module comprises a base board and a spindle with one end connected onto the base board, the other end of the spindle is sleeved with a seal taking rotary table capable of rotating around the spindle, and the seal taking rotary table is provided with snapping positions for accommodating the seals and fixedly connected with a baffle; and when the seal taking rotary table rotates, the baffle or the snapping position corresponds to the seal outlet. By means of the seal taking and pacing device, safety protection can be performed on the seals inside, abuse of the seals due to ineffective storage can be prevented, and criminal behaviors of seal sealing and forgery of bills and documents can be eradiated completely; when the seals are needed to be taken or placed, the device can rapidly position to the required snapping position for taking and placing of the seals, and therefore the using efficiency of the seals is improved; and a control circuit is used for controlling the rotary table, so that taken and placed seals can not be mixed up, and the using accuracy of the seals is improved.
Owner:SHENZHEN INFOTECH TECH
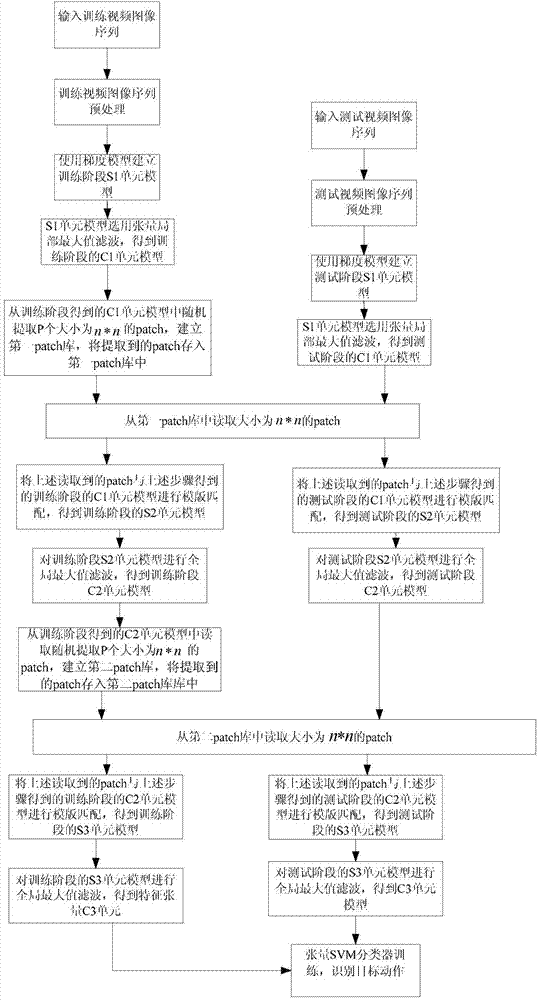
Method for motion recognition for simulating human visual cortex perception mechanism
InactiveCN103761510AEfficient identificationQuick and accurate identificationImage analysisCharacter and pattern recognitionVisual cortexTemplate matching
The invention discloses a method for motion recognition for simulating a human visual cortex perception mechanism. The method comprises the steps that preprocessing is conducted on a video image sequence; feature extraction is conducted, an S1 unit model is established, and tensor local maximum filtering processing is conducted through the S1 unit model so that a C1 unit model can be obtained; a fragment is randomly extracted from the C1 unit model obtained from a training stage, template matching is conducted on the fragment and the C1 unit model so that an S2 unit model can be obtained, global maximum filtering is conducted on the S2 unit model, and therefore a C2 unit model is obtained; a fragment is randomly extracted from the C2 unit model obtained from the training stage and template matching is conducted on the fragment and the C2 unit model so that an S3 unit model can be obtained, global maximum filtering is conducted on the S3 unit model, and therefore a feature tensor C3 unit is obtained; the feature extraction processing is successively conducted on a preprocessed training sample and a preprocessed testing sample, and therefore the feature tensor C3 is obtained; the feature tensor C3 is input into a classifier for classification. The method can effectively, rapidly and accurately identify the action of a movement target.
Owner:SOUTH CHINA UNIV OF TECH
Session identification method and device, control equipment and storage medium
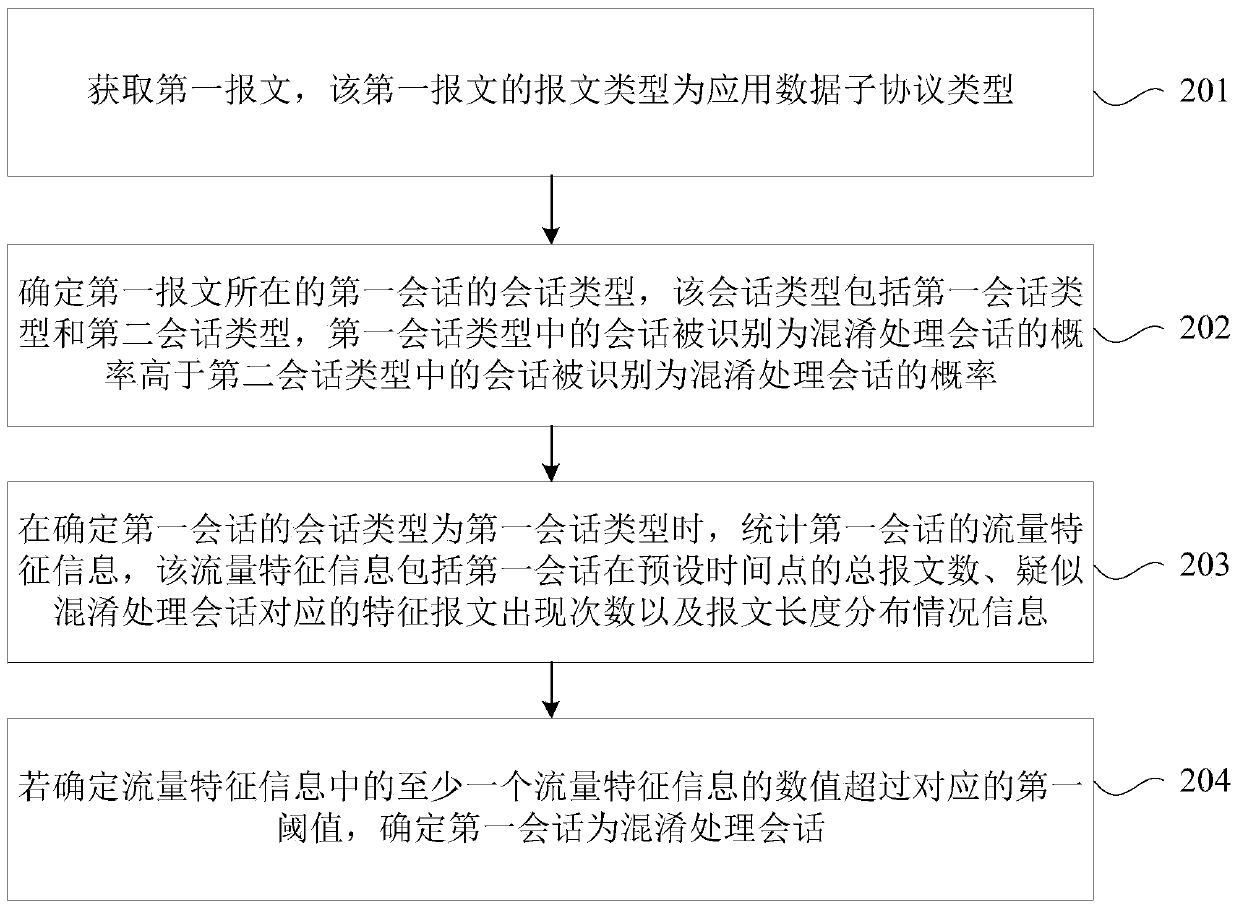
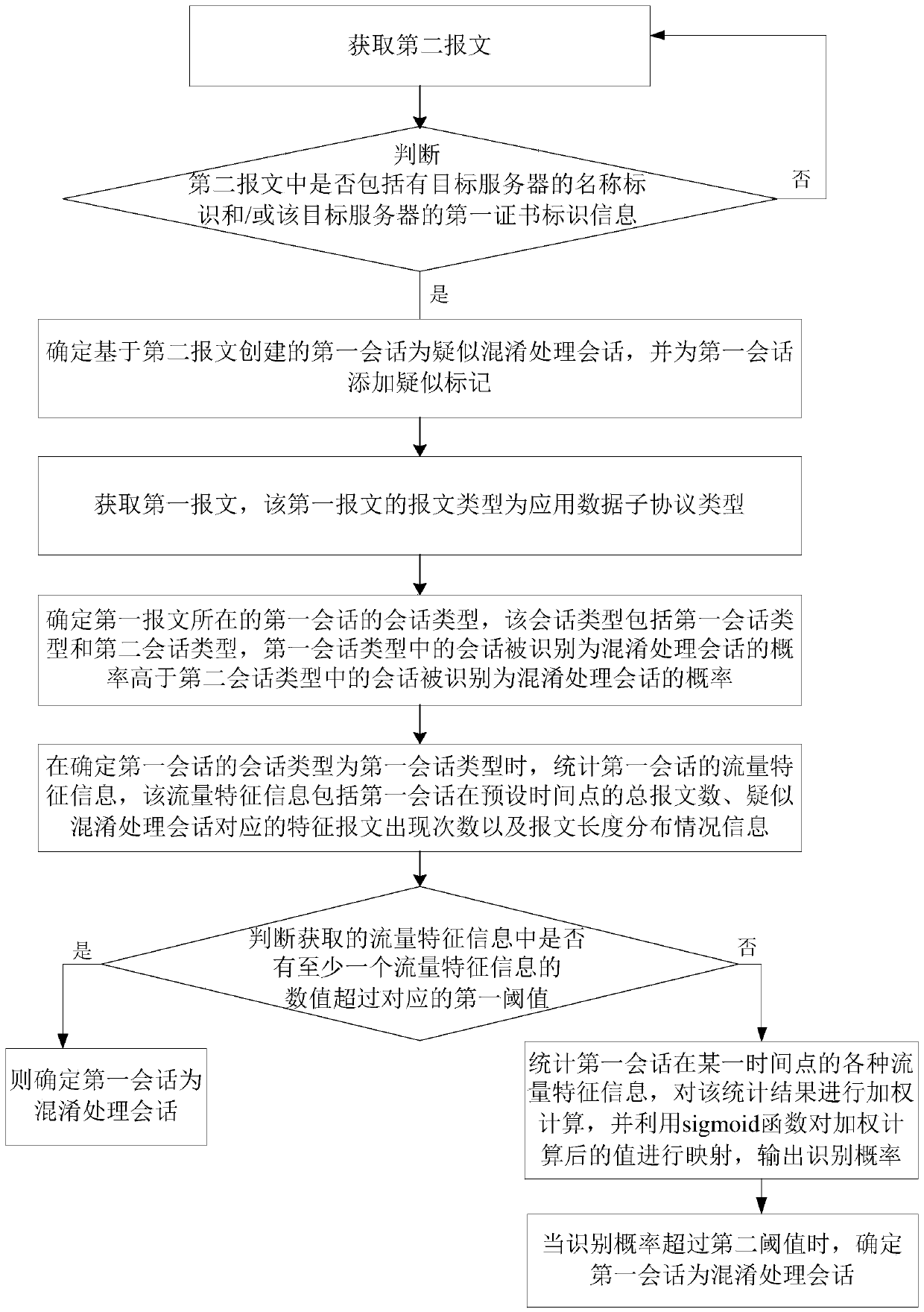
The invention discloses a session identification method and device, control equipment and a storage medium, which are used for identifying Tor flow confused by confused plug-ins. The method comprisesthe steps of acquiring a first message, wherein the message type of the first message is an application data sub-protocol type; determining a session type of a first session corresponding to the firstmessage, with the session type comprising a first session type and a second session type, identifying the probability that the session in the first session type as an with obfuscation processing session being higher than the probability that the session in the second session type is identified as an obfuscation processing session; if the session type of the first session is the first session type, counting flow characteristic information of the first session, with the flow characteristic information representing the total number of messages of the first session at a preset time point, and thenumber of occurrences of characteristic messages corresponding to the suspected obfuscation processing session, and message length distribution condition information; and if determining that the value of at least one piece of traffic feature information in the traffic feature information exceeds a corresponding first threshold, determining that the first session is an obfuscation processing session.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Foreign substance detection device for card reader and card reader socket
InactiveUS8348162B2Avoid lostOvercome influenceComplete banking machinesConveying record carriersForeign matterEngineering
A foreign substance detection device for a card reader includes an emitting module (1), a receiving module (2) and a control processing module (3). The emitting module (1) is embedded on a wall surface of a card reader insertion opening (101) for emitting detection waves to a detection area (103) in front of the card reader insertion opening (101). The receiving module (2) is embedded on the wall surface of the card reader insertion opening (101) for receiving the detection waves emitted by the emitted the emitting module (1). The control processing module (3) identifies whether the receiving module (2) receives the detection wave reflected by the foreign substance in the detection area (103), and determines whether the foreign substance exists in the detection area (103) according to the determination result. A card reader socket which includes a case (100) and the foreign substance detection device is also provided.
Owner:GRG BAKING EQUIP CO LTD
Foldable unmanned home-delivered article storage box
InactiveCN107708501ATake the hassle out of retrieving itemsPrevent crimeKitchen equipmentDomestic articlesSurface plateEngineering
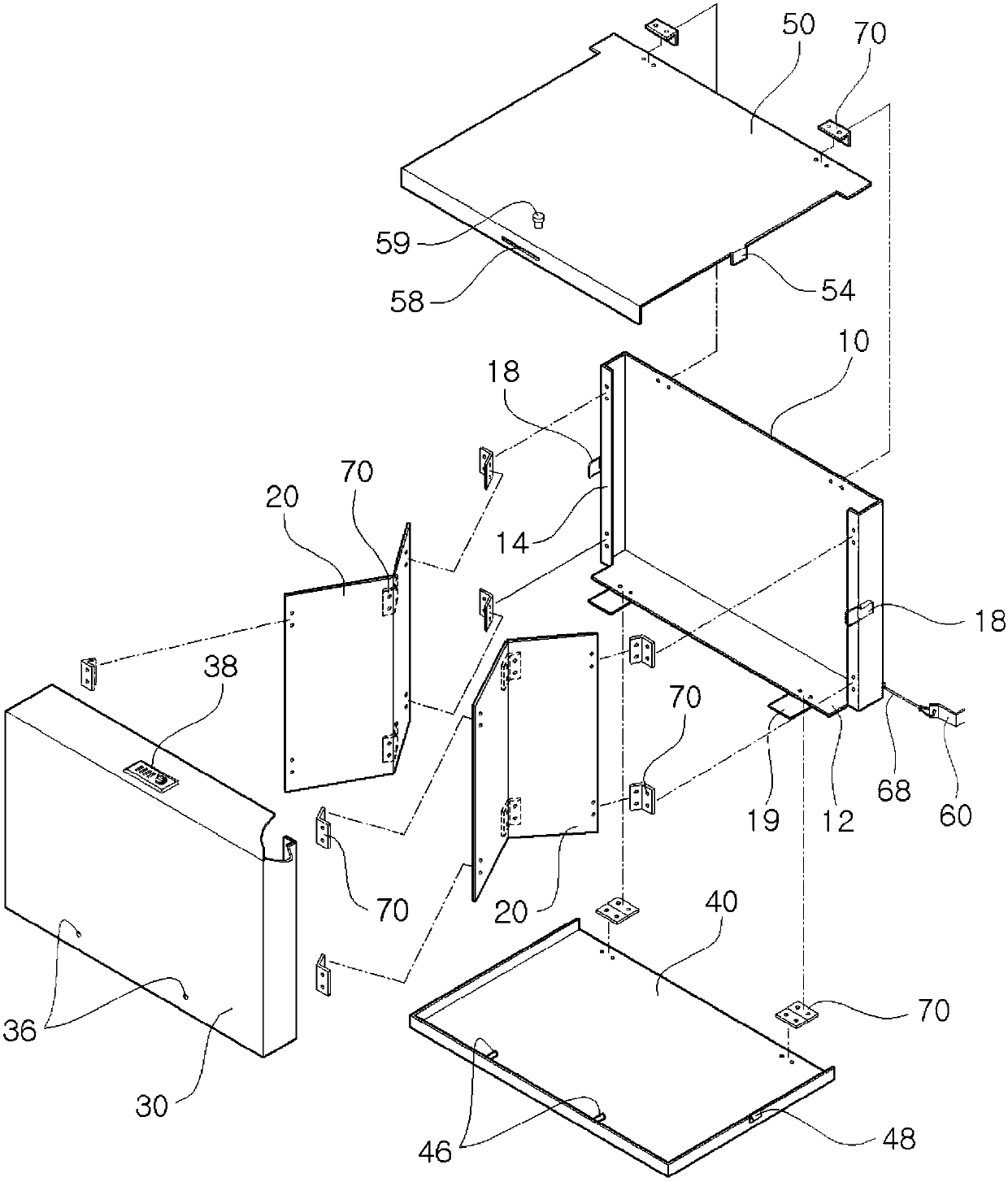
Owner:SHARENS HITECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com