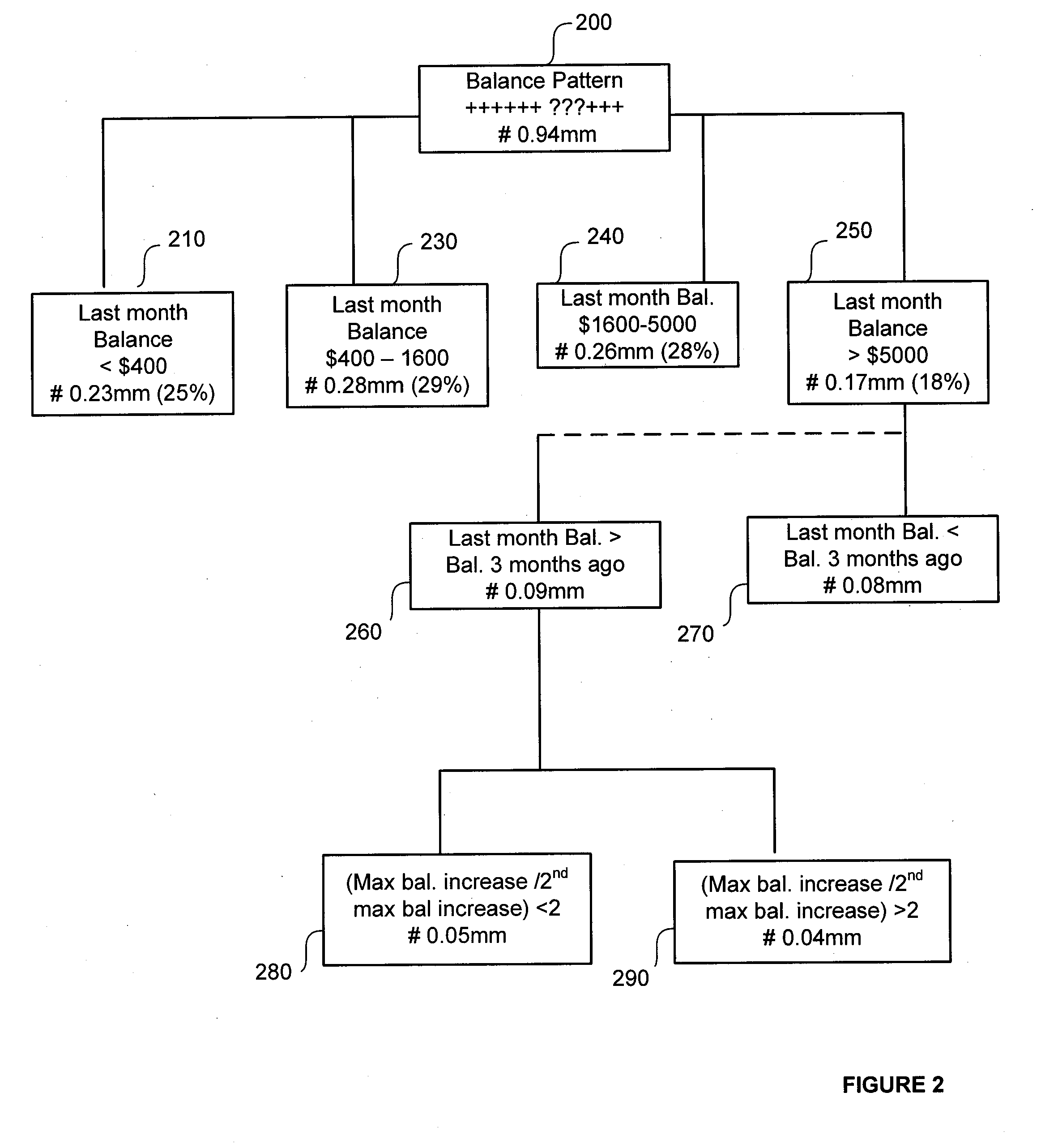
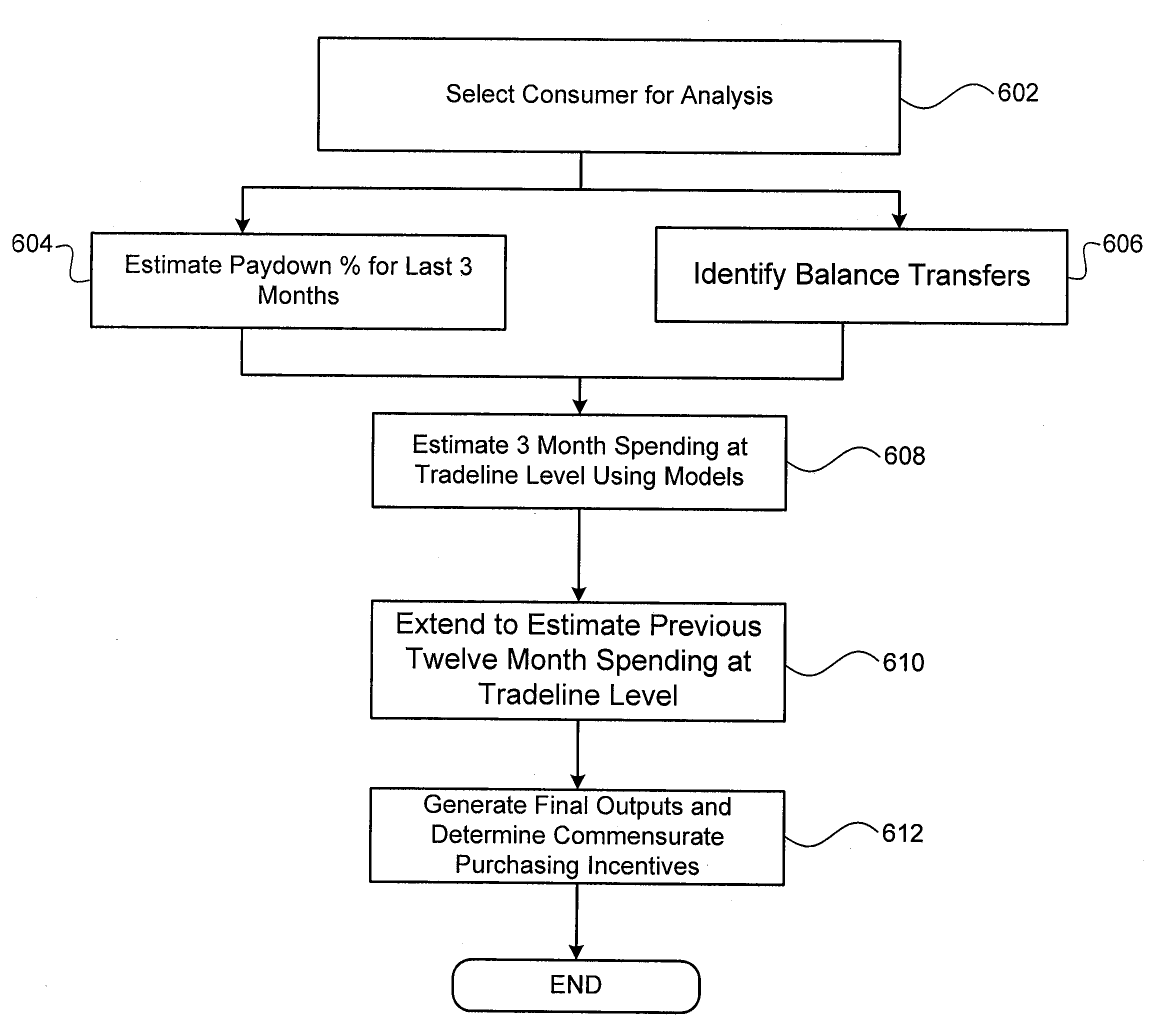
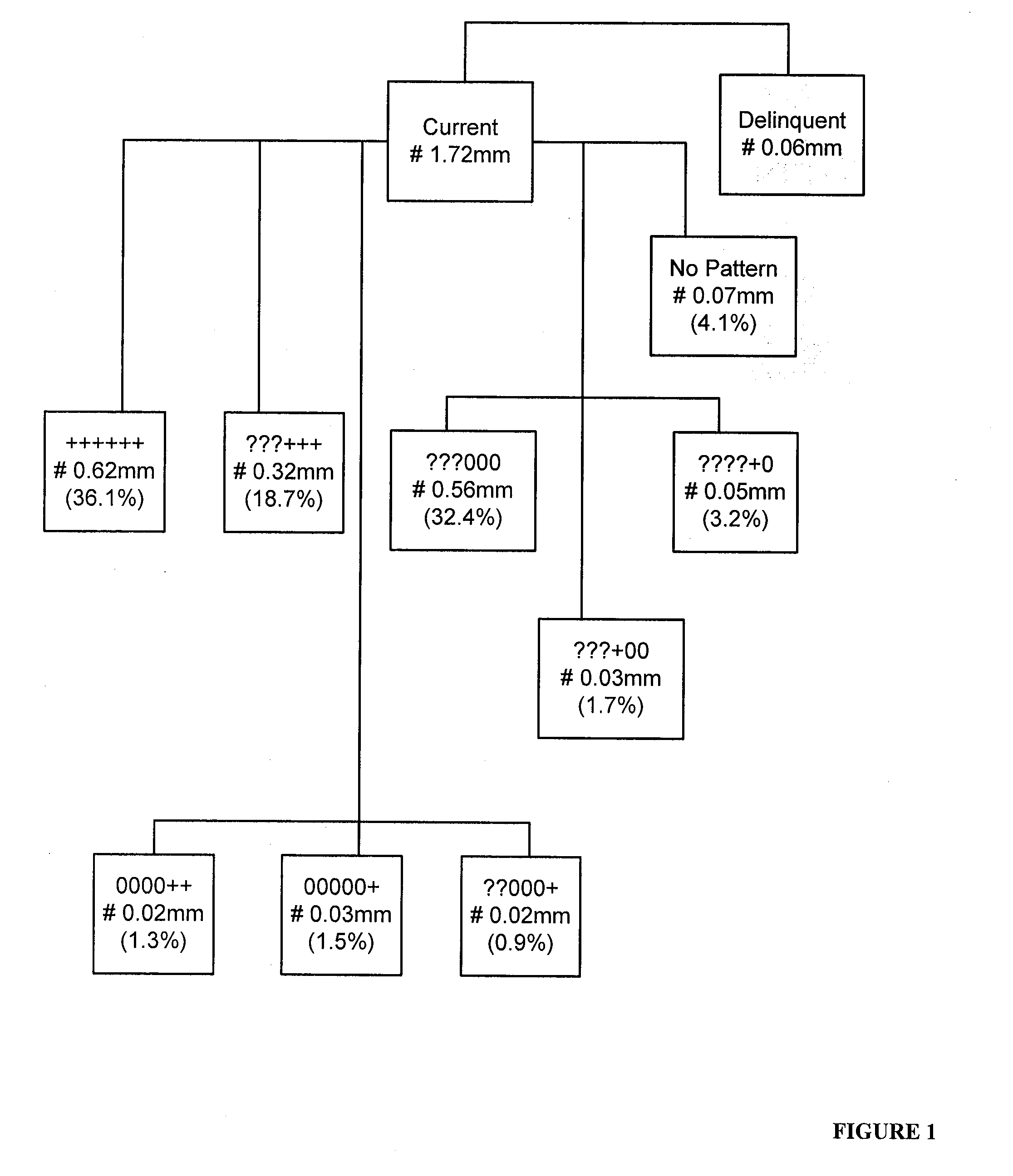
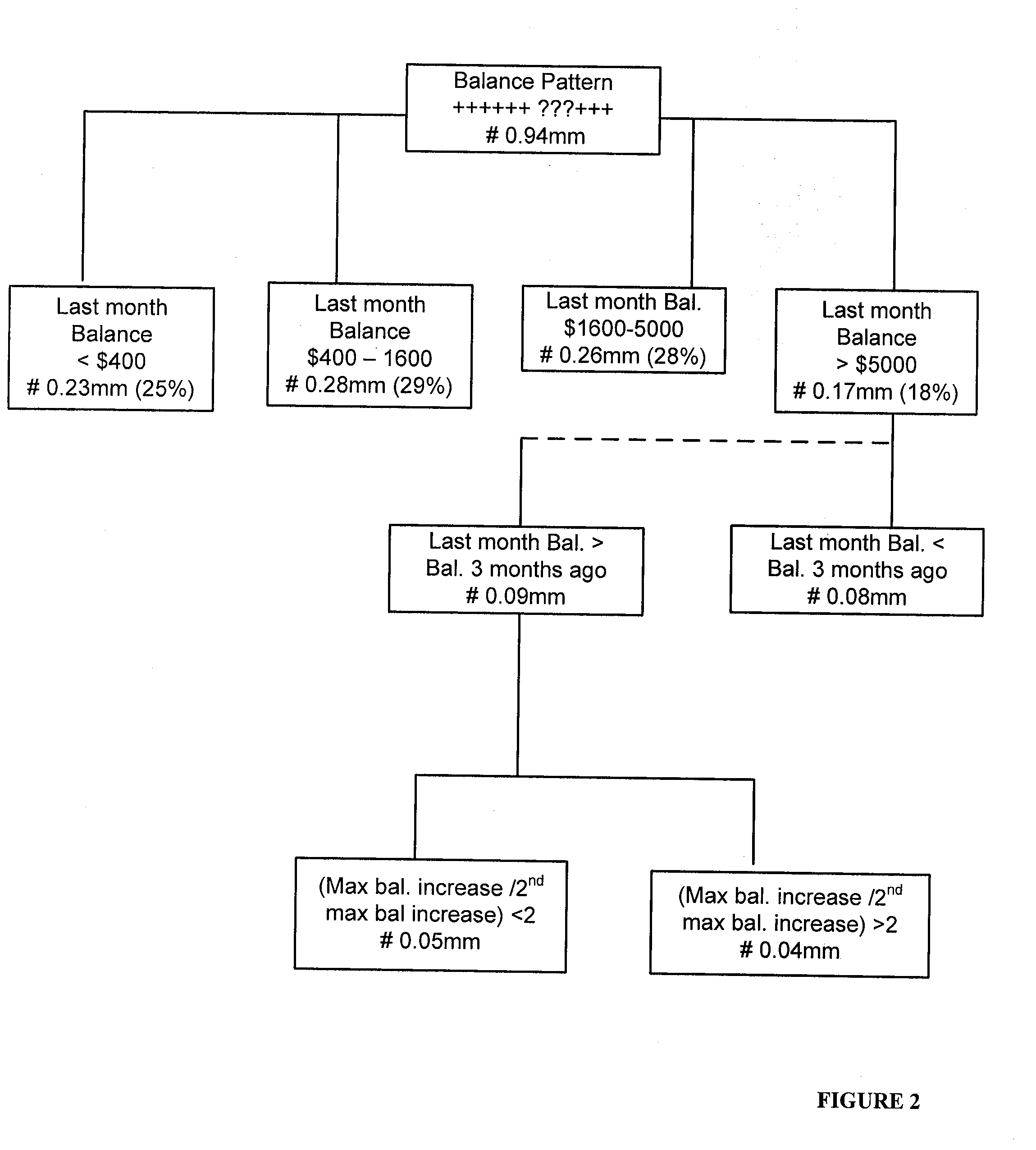
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1059 results about "Behavioral analytics" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Behavioral analytics is a recent advancement in business analytics that reveals new insights into the behavior of consumers on eCommerce platforms, online games, web and mobile applications, and IoT. The rapid increase in the volume of raw event data generated by the digital world enables methods that go beyond typical analysis by demographics and other traditional metrics that tell us what kind of people took what actions in the past. Behavioral analysis focuses on understanding how consumers act and why, enabling accurate predictions about how they are likely to act in the future. It enables marketers to make the right offers to the right consumer segments at the right time.
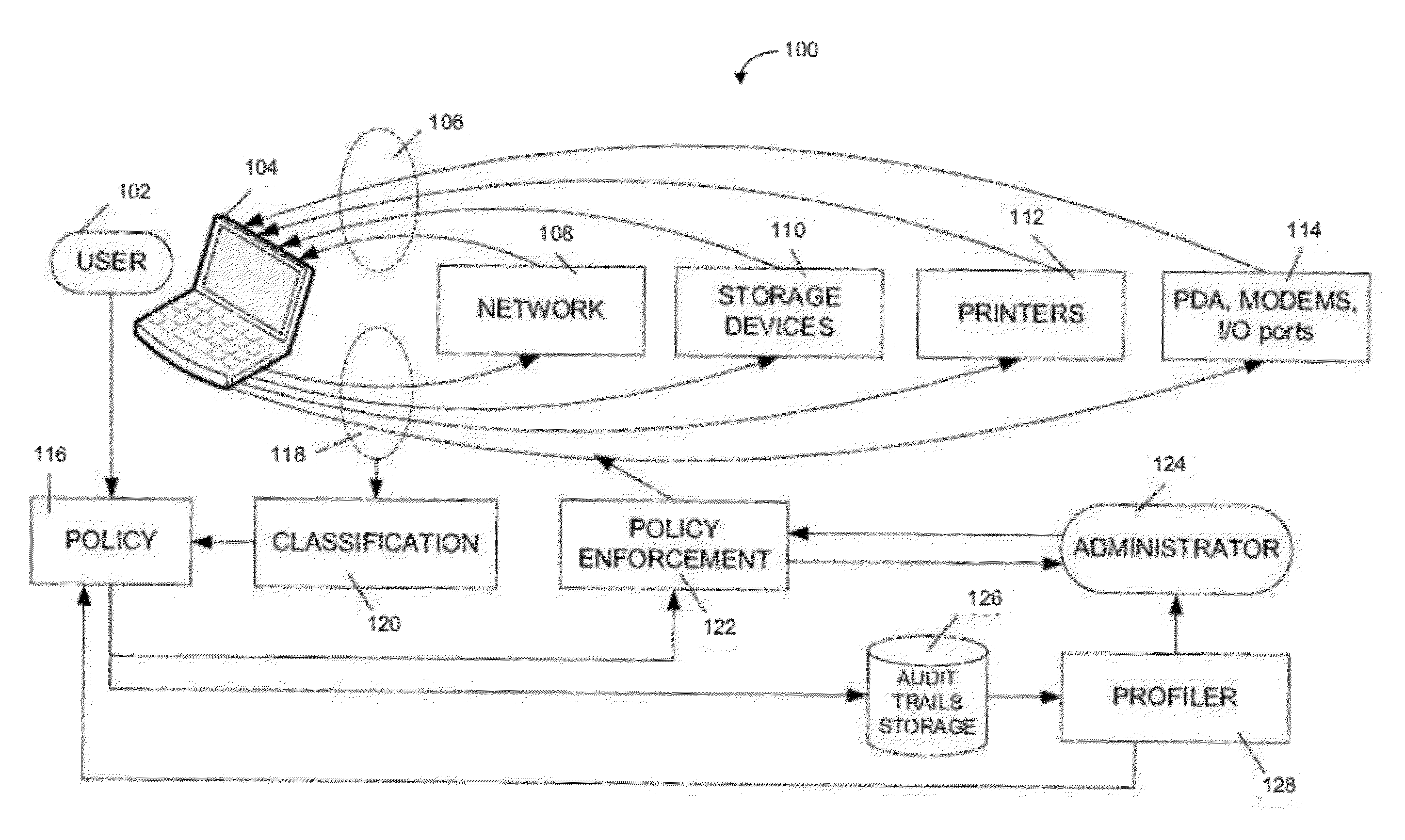
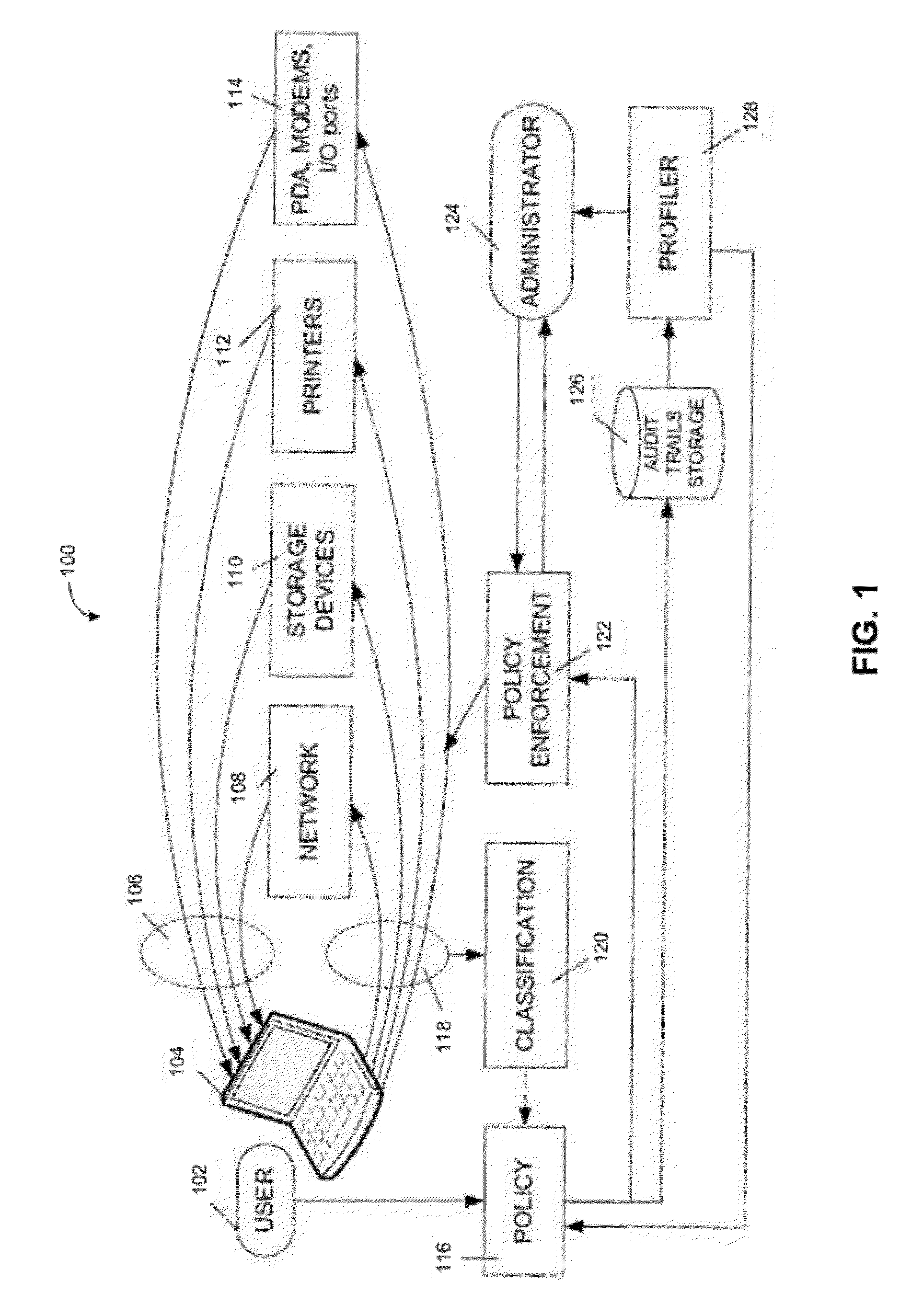
System and method of using two or more multi-factor authentication mechanisms to authenticate online parties
InactiveUS20070136573A1Minimal inconvenienceStrong authenticationDigital data authenticationSecuring communicationUser deviceBehavioral analytics
A system and method for authentication that comprises the use of at least one multiple multi-factor authentication with the optional addition of, mutual (site) authentication, transaction / behavior analysis, that utilizes user-facing geolocation communications and / or information about user device ownership periods, and / or a combination thereof to help prevent fraud.
Owner:STEINBERG JOSEPH
Method and system for dynamically targeting content based on automatic demographics and behavior analysis
InactiveUS7921036B1Computer security arrangementsPayment architectureBehavioral analyticsComputer graphics (images)
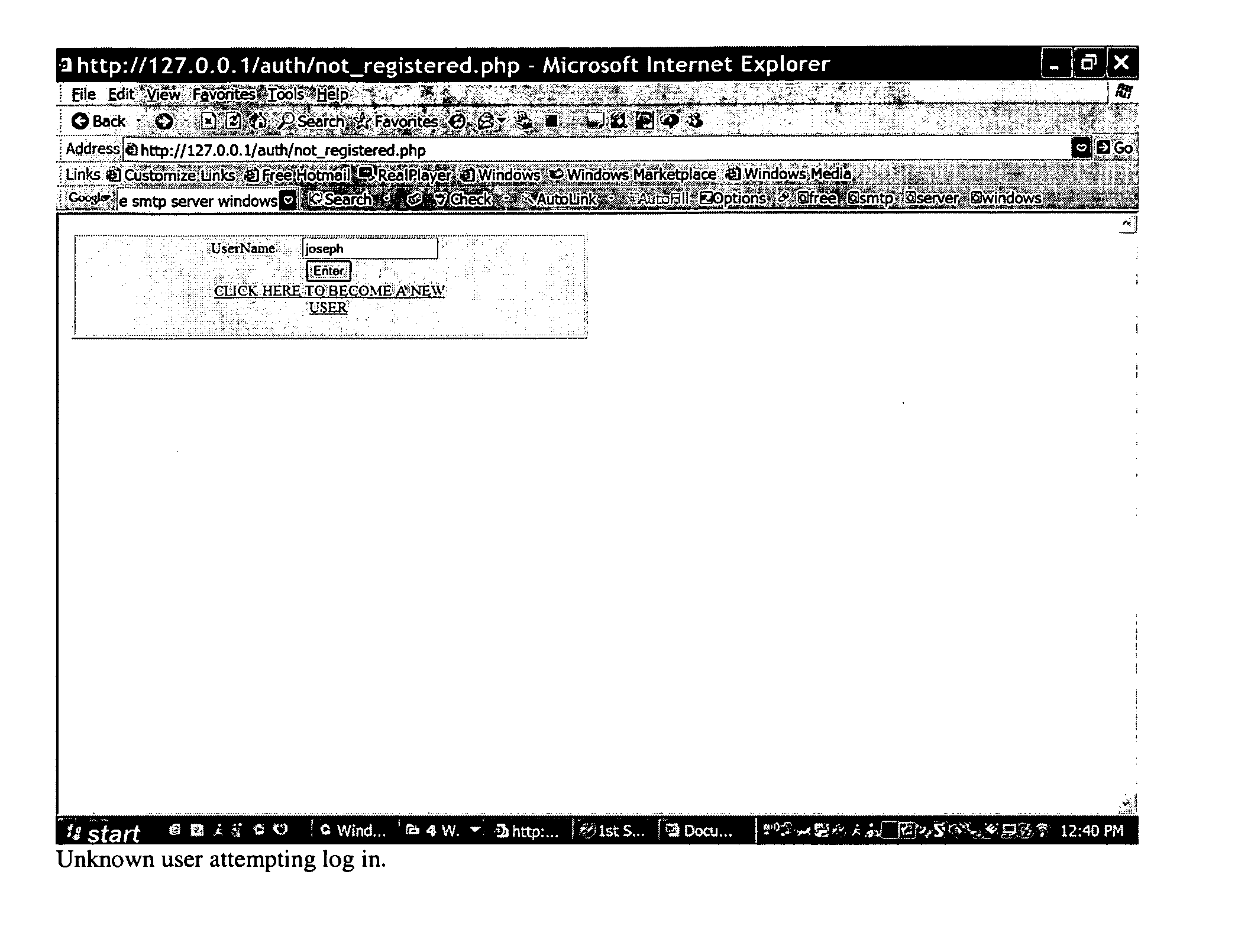
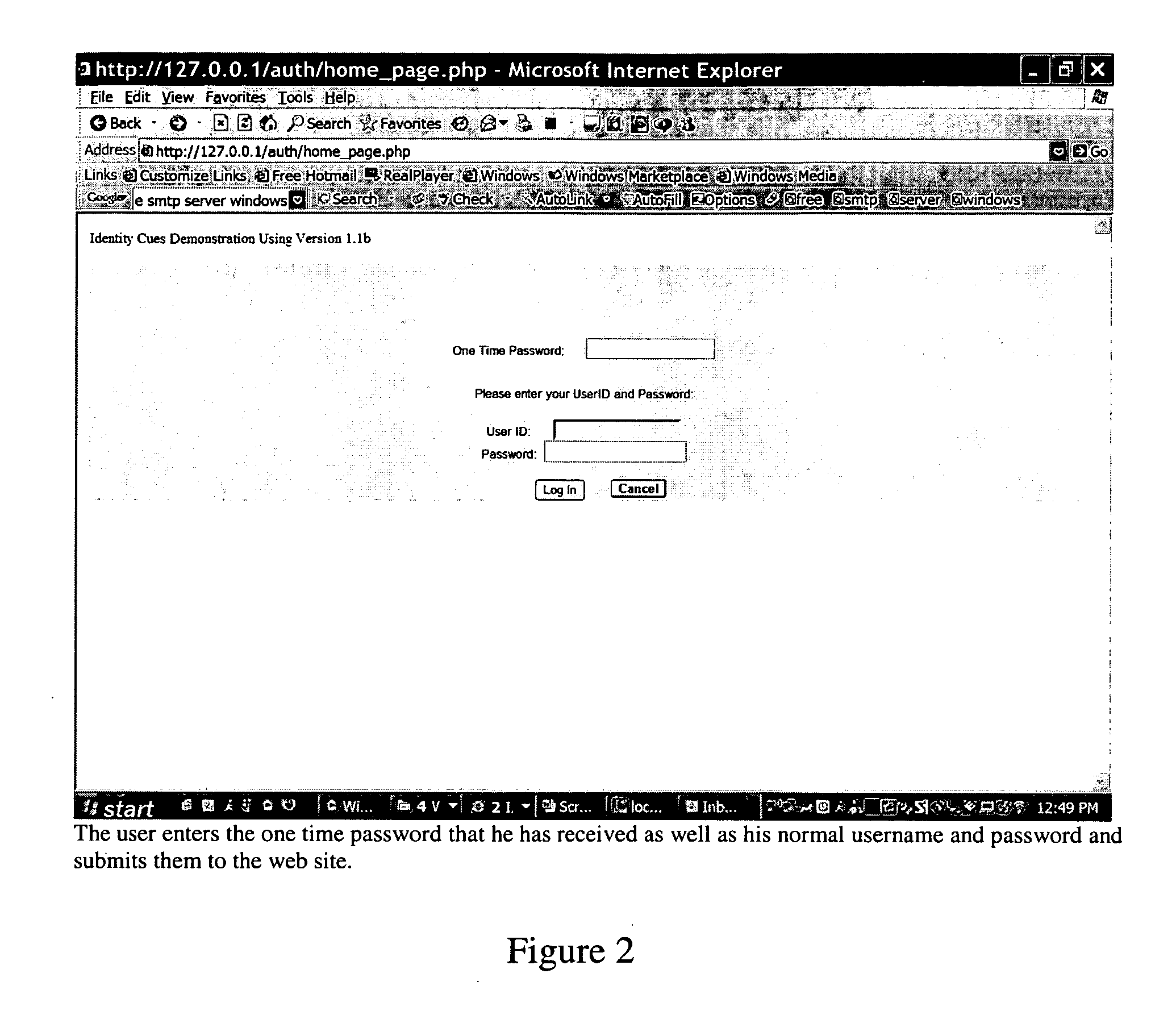
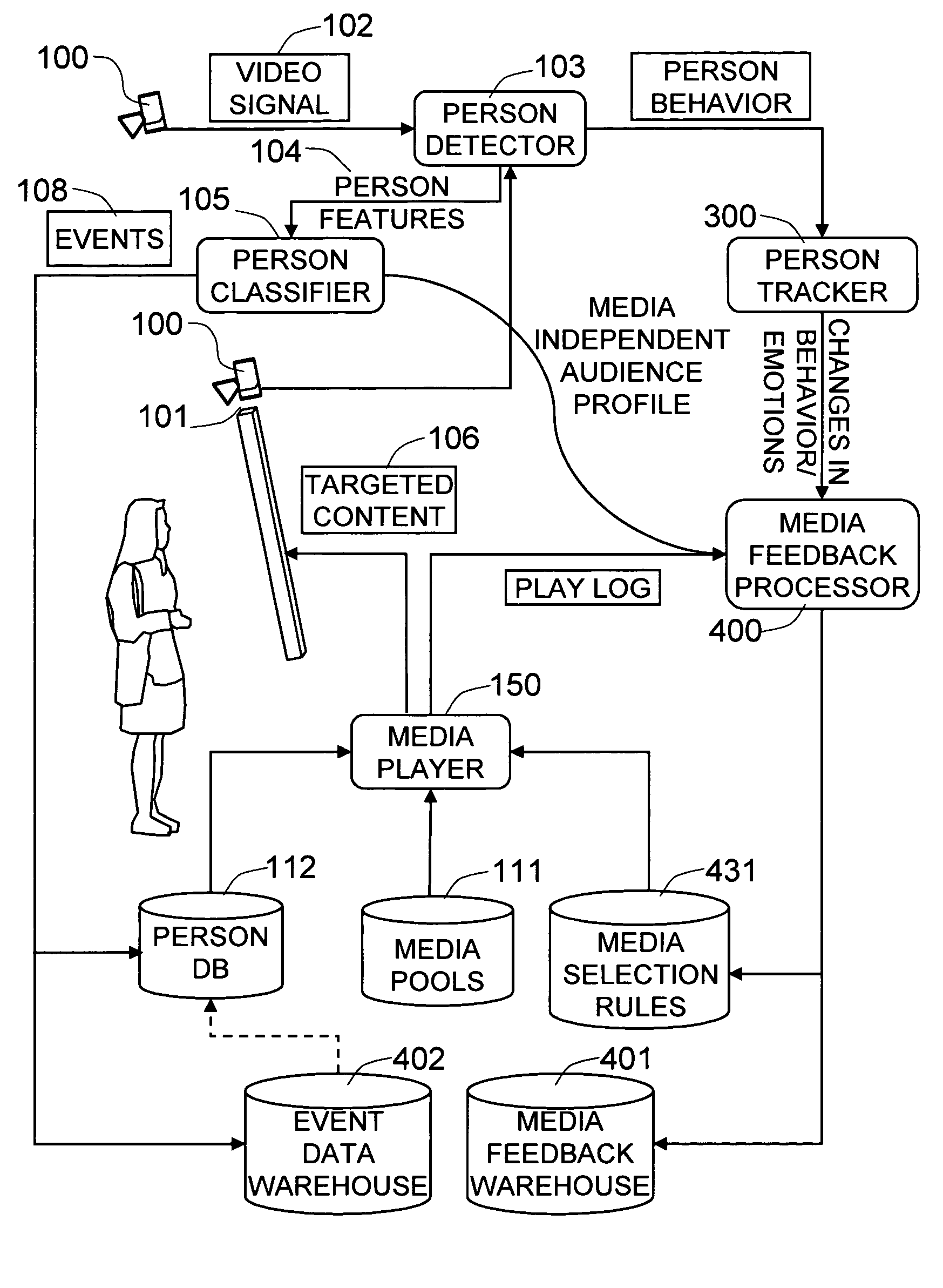
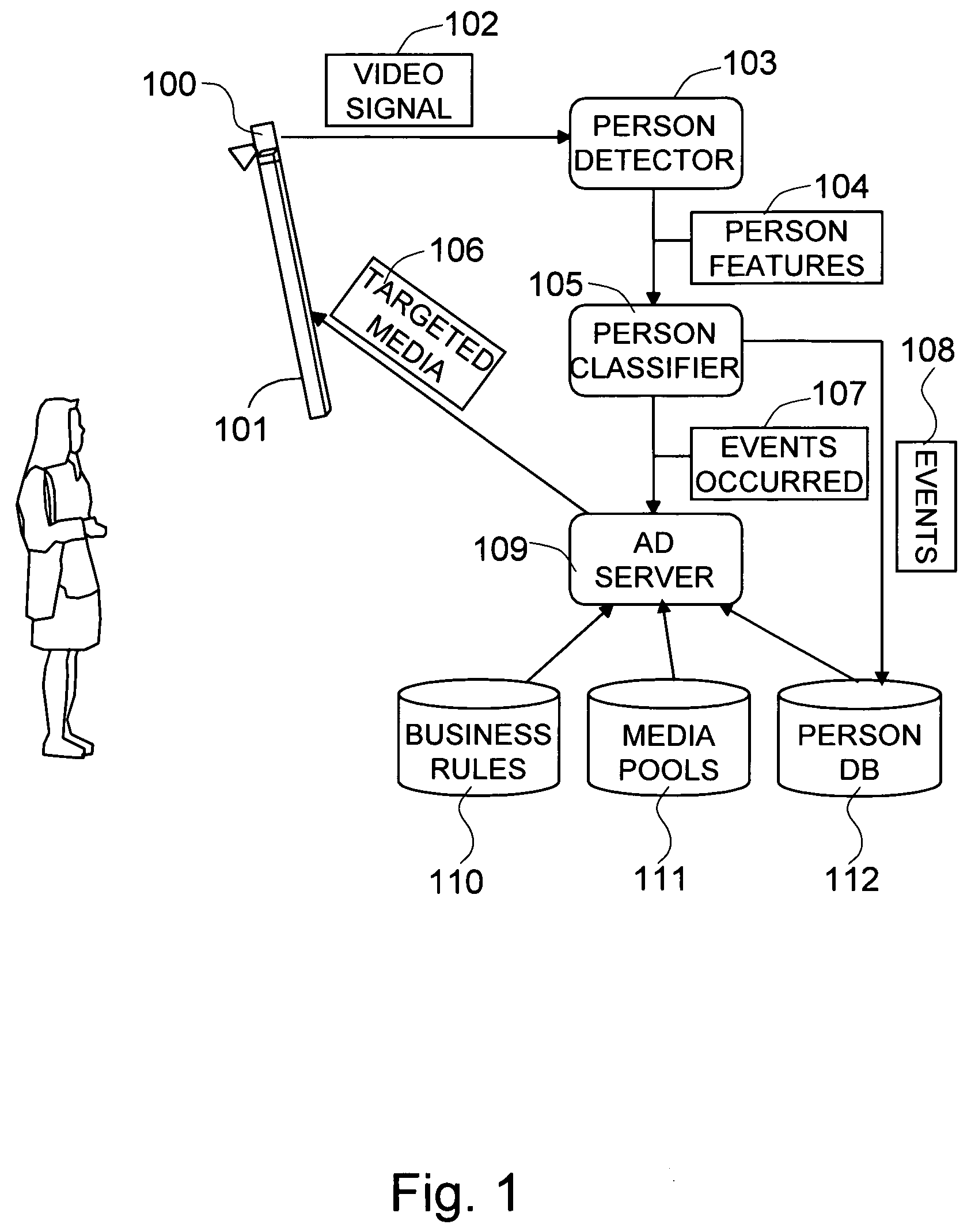
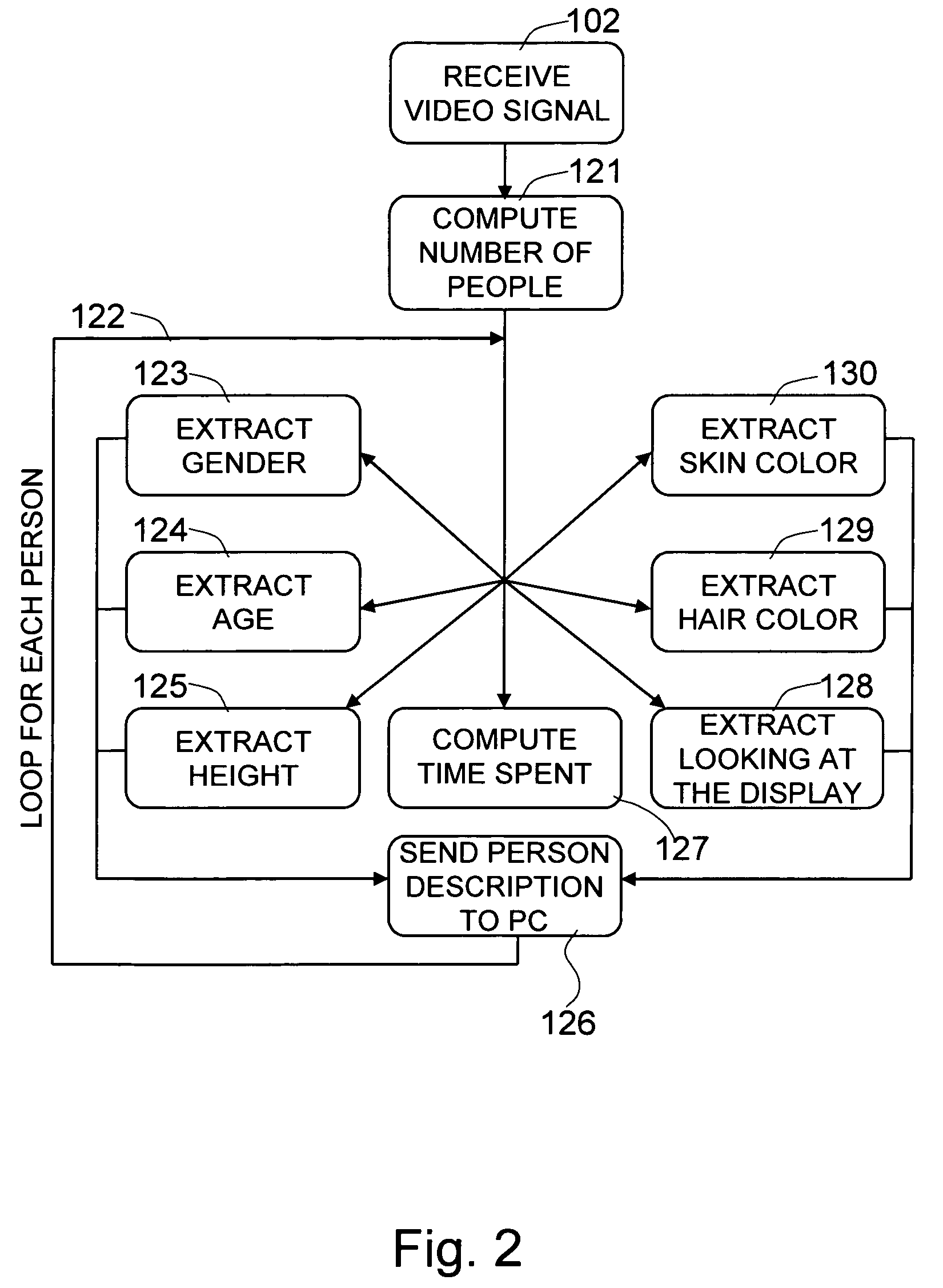
The present invention is a method and system for selectively executing content on a display based on the automatic recognition of predefined characteristics, including visually perceptible attributes, such as the demographic profile of people identified automatically using a sequence of image frames from a video stream. The present invention detects the images of the individual or the people from captured images. The present invention automatically extracts visually perceptible attributes, including demographic information, local behavior analysis, and emotional status, of the individual or the people from the images in real time. The visually perceptible attributes further comprise height, skin color, hair color, the number of people in the scene, time spent by the people, and whether a person looked at the display. A targeted media is selected from a set of media pools, according to the automatically-extracted, visually perceptible attributes and the feedback from the people.
Owner:ACCESSIFY LLC
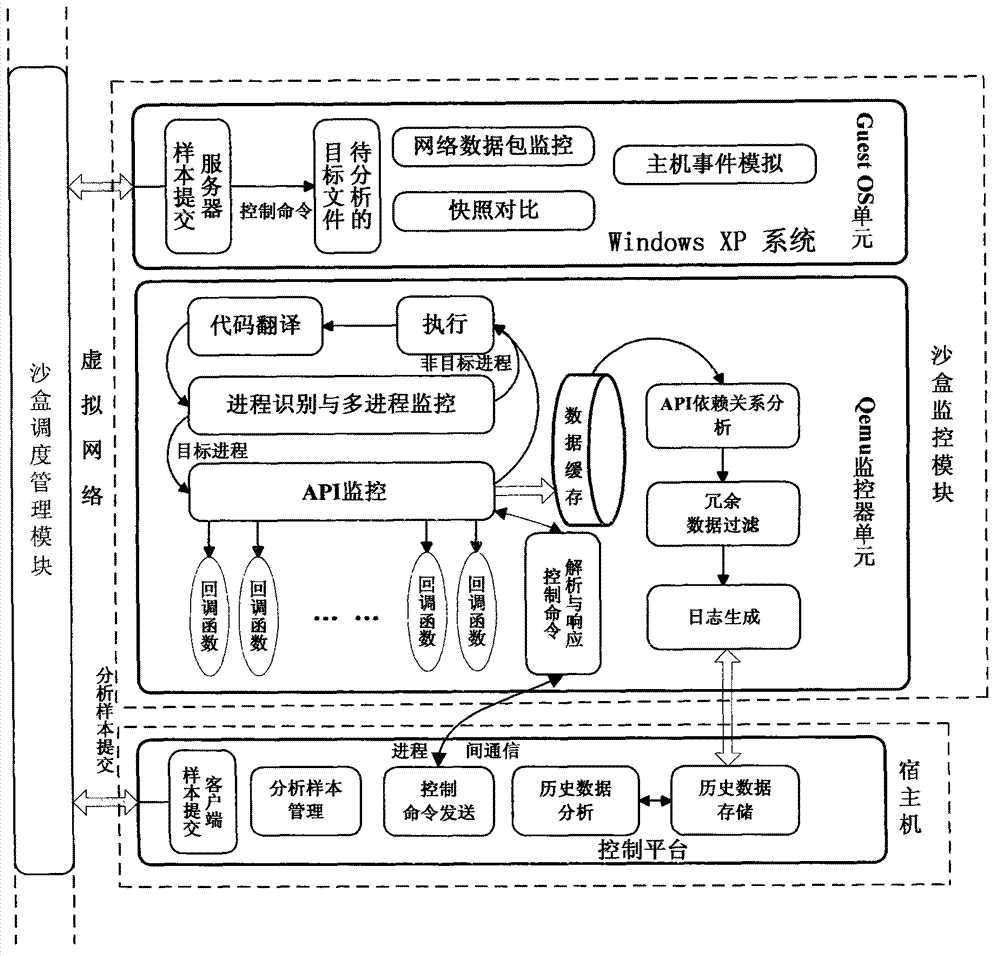
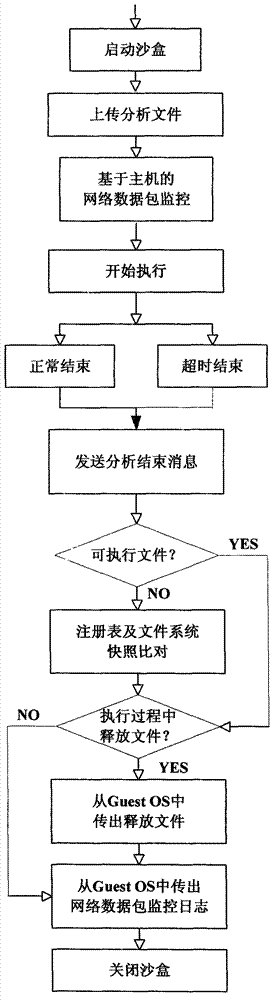
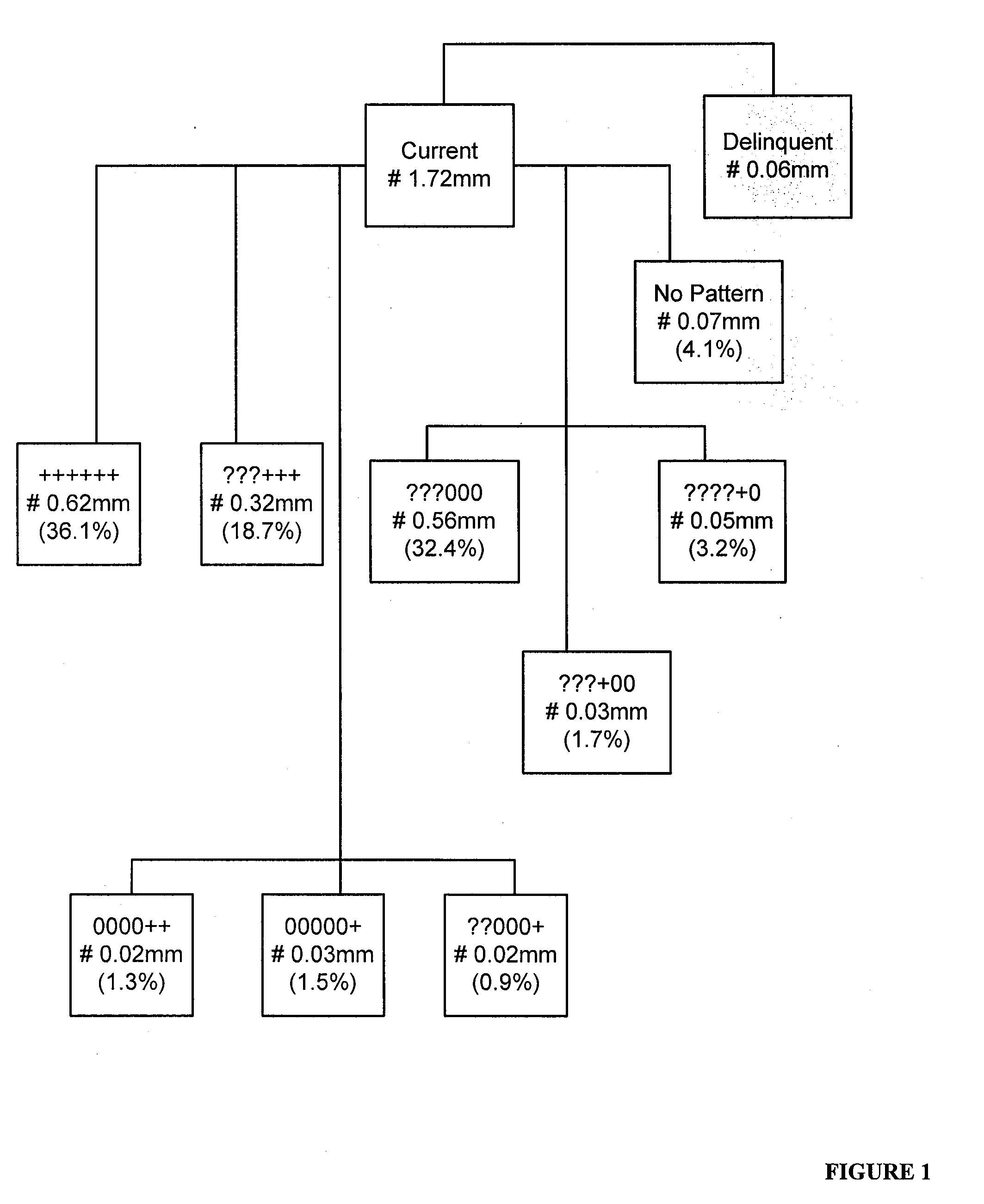
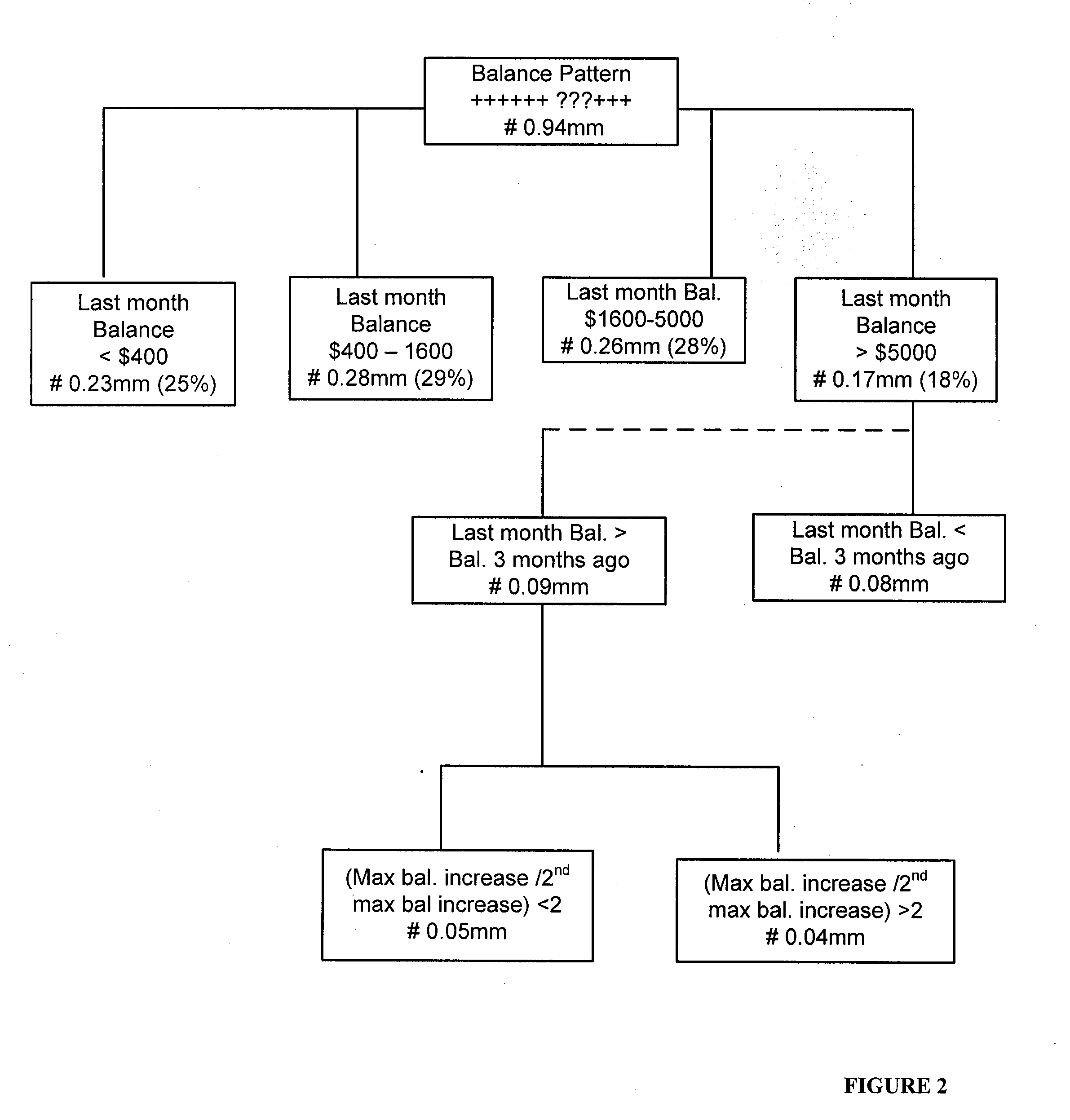
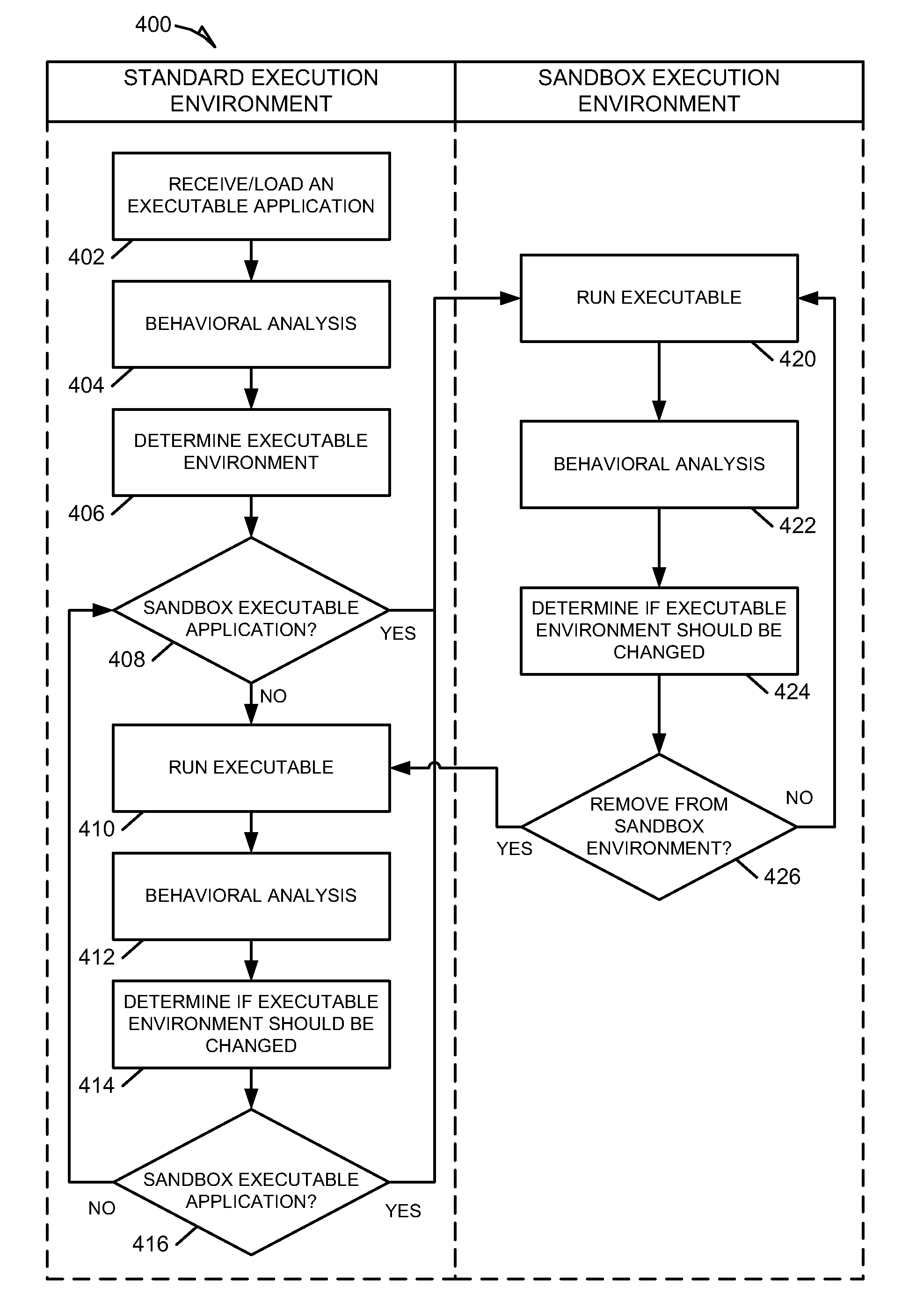
Systems and methods for behavioral sandboxing
ActiveUS20110145926A1Memory loss protectionError detection/correctionBehavioral analyticsApplication software
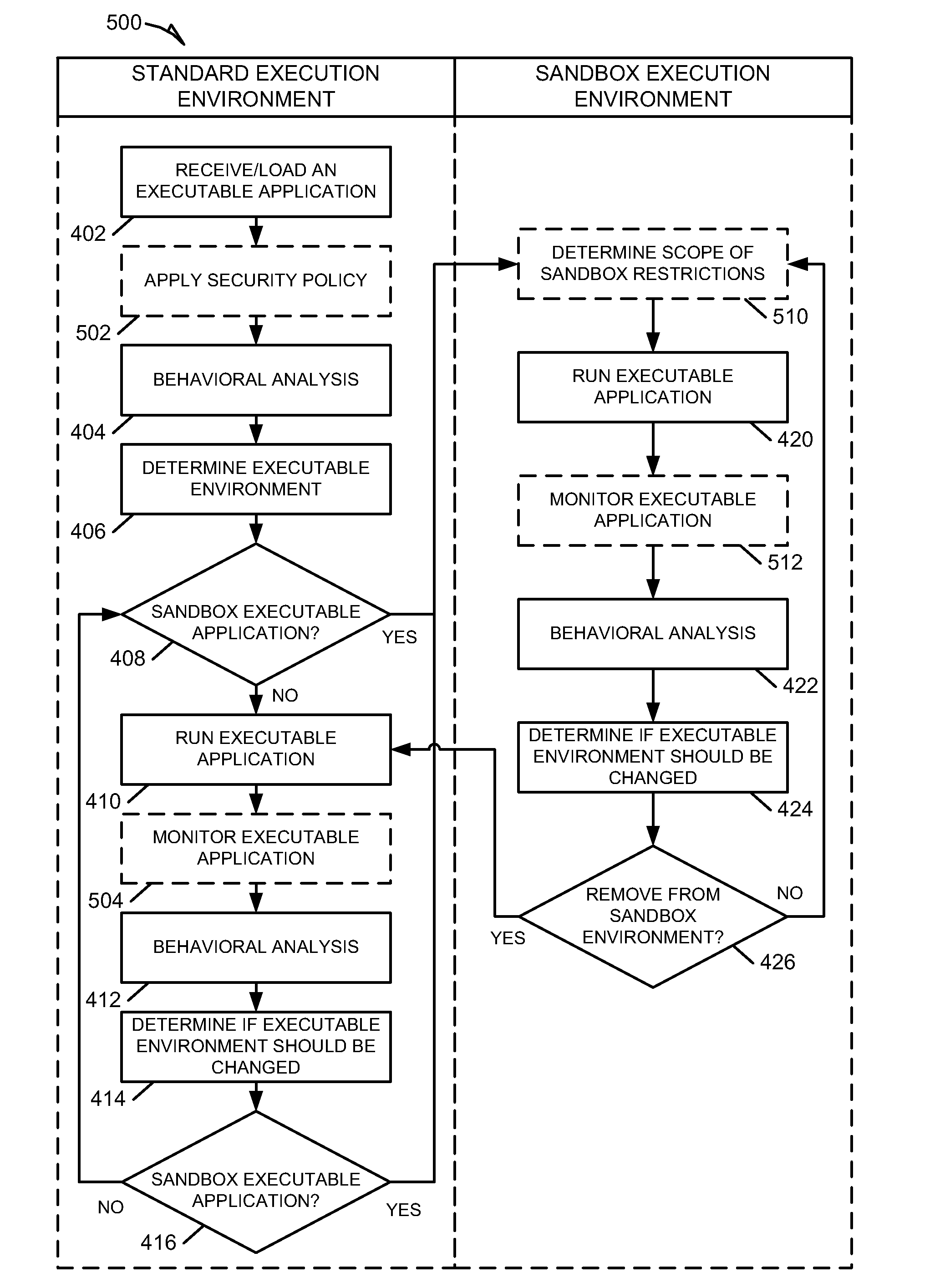
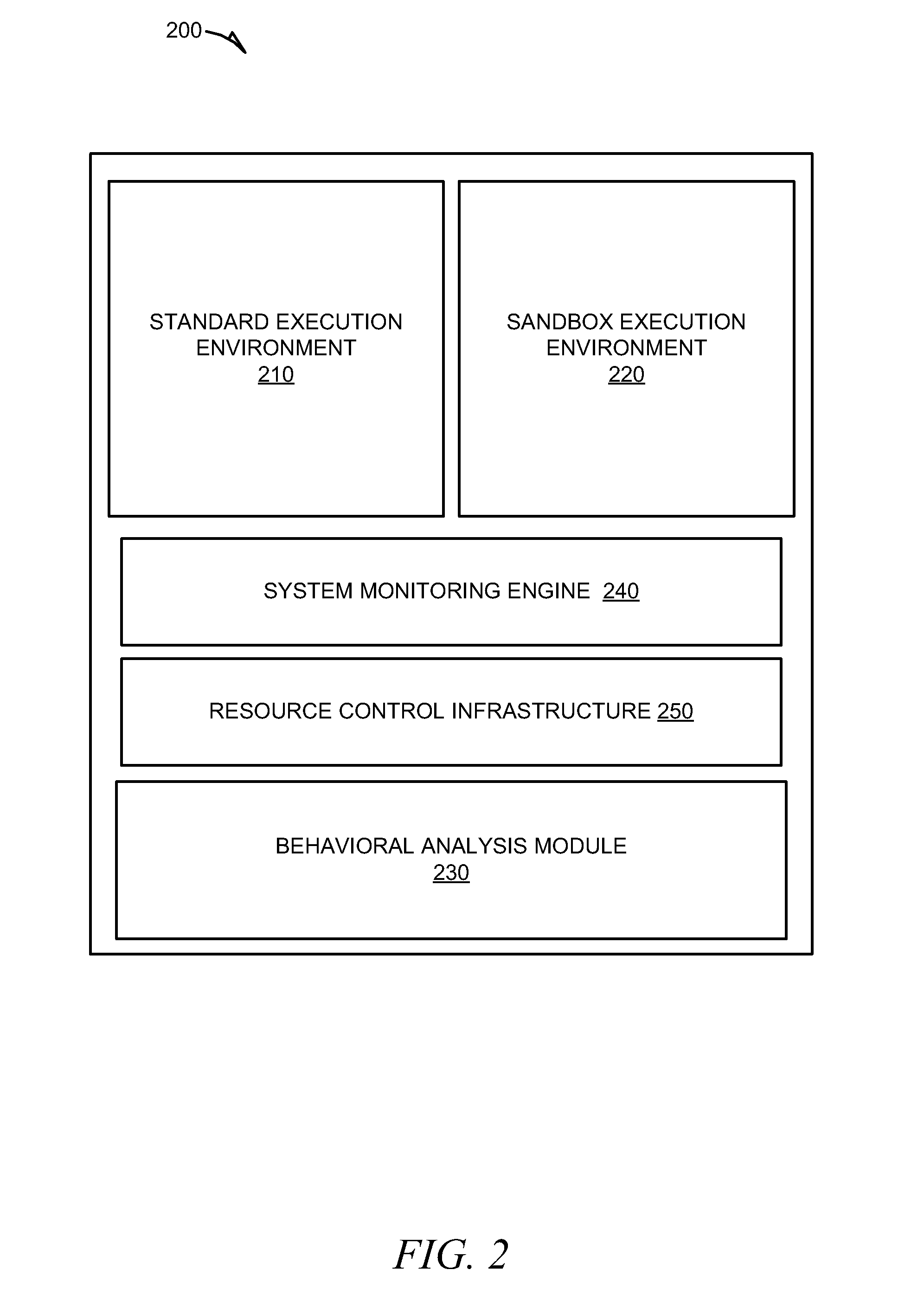
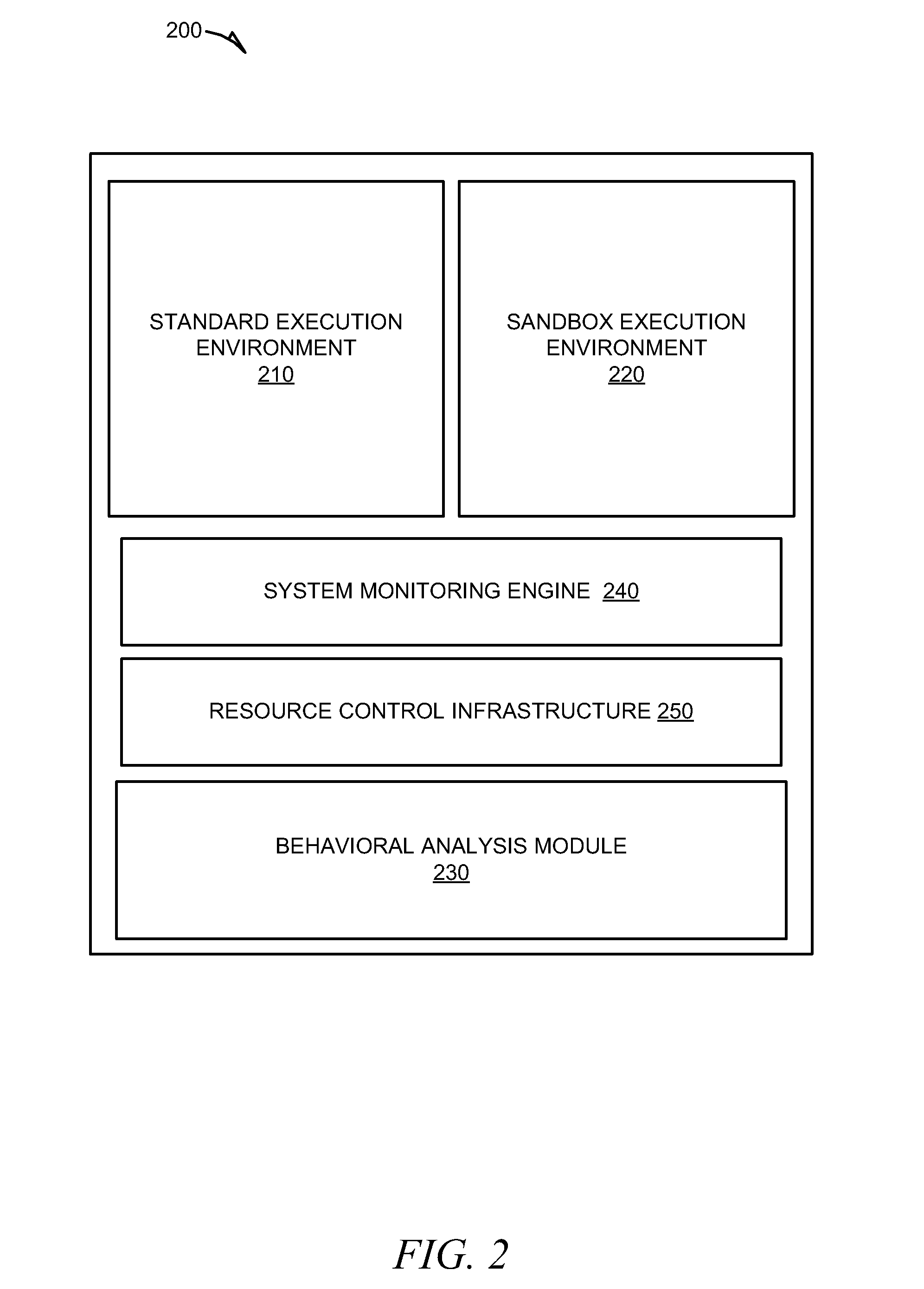
Methods and system for behavioral sandboxing are described. In one example embodiment, a system for behavioral sandboxing can include a network and a computer. The network communicatively coupled to a source of an executable application. The computer communicatively couple to the network and including a behavioral analysis module and a plurality of execution environments. The behavioral analysis module is configured to perform behavioral analysis on the executable application downloaded over the network. The plurality of execution environments including a standard execution environment and a protected execution environment. The behavioral analysis module is configured to evaluate a plurality of behavioral characteristics of the executable application to determine whether the executable application should be executed within the protected execution environment prior to execution of the executable application. The behavioral analysis module also monitors execution of the executable application to determine whether the execution environment can be changed.
Owner:MCAFEE LLC
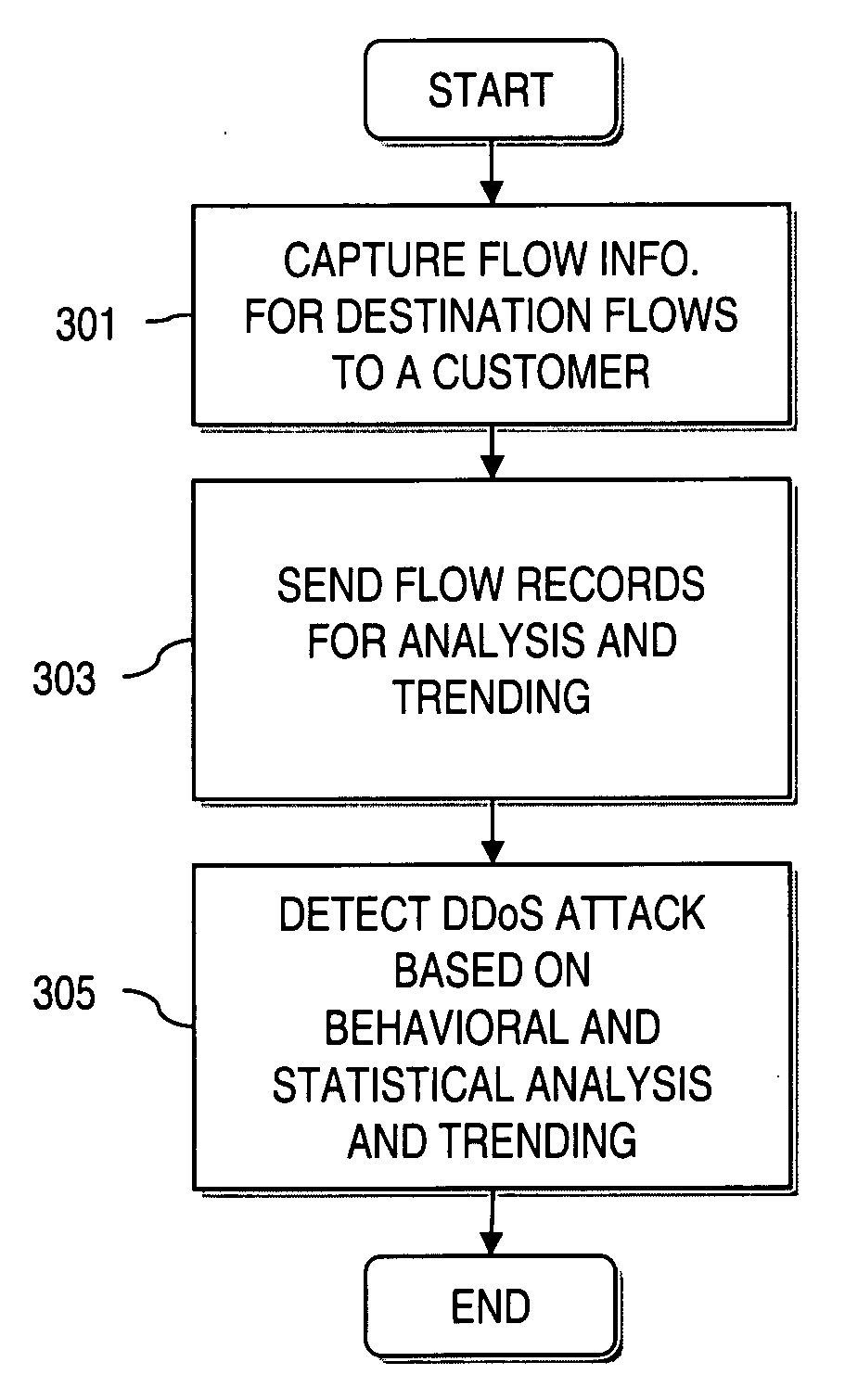
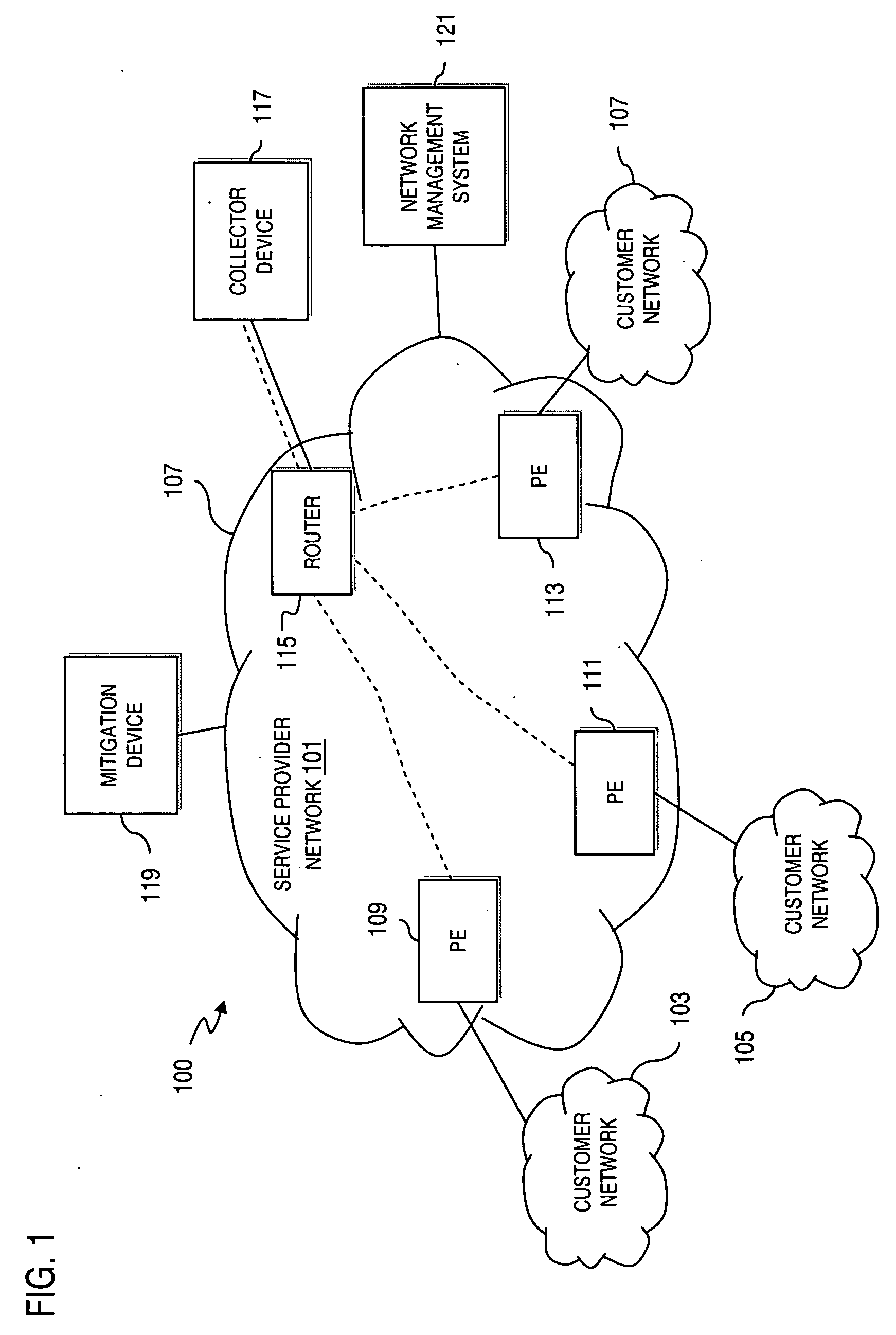
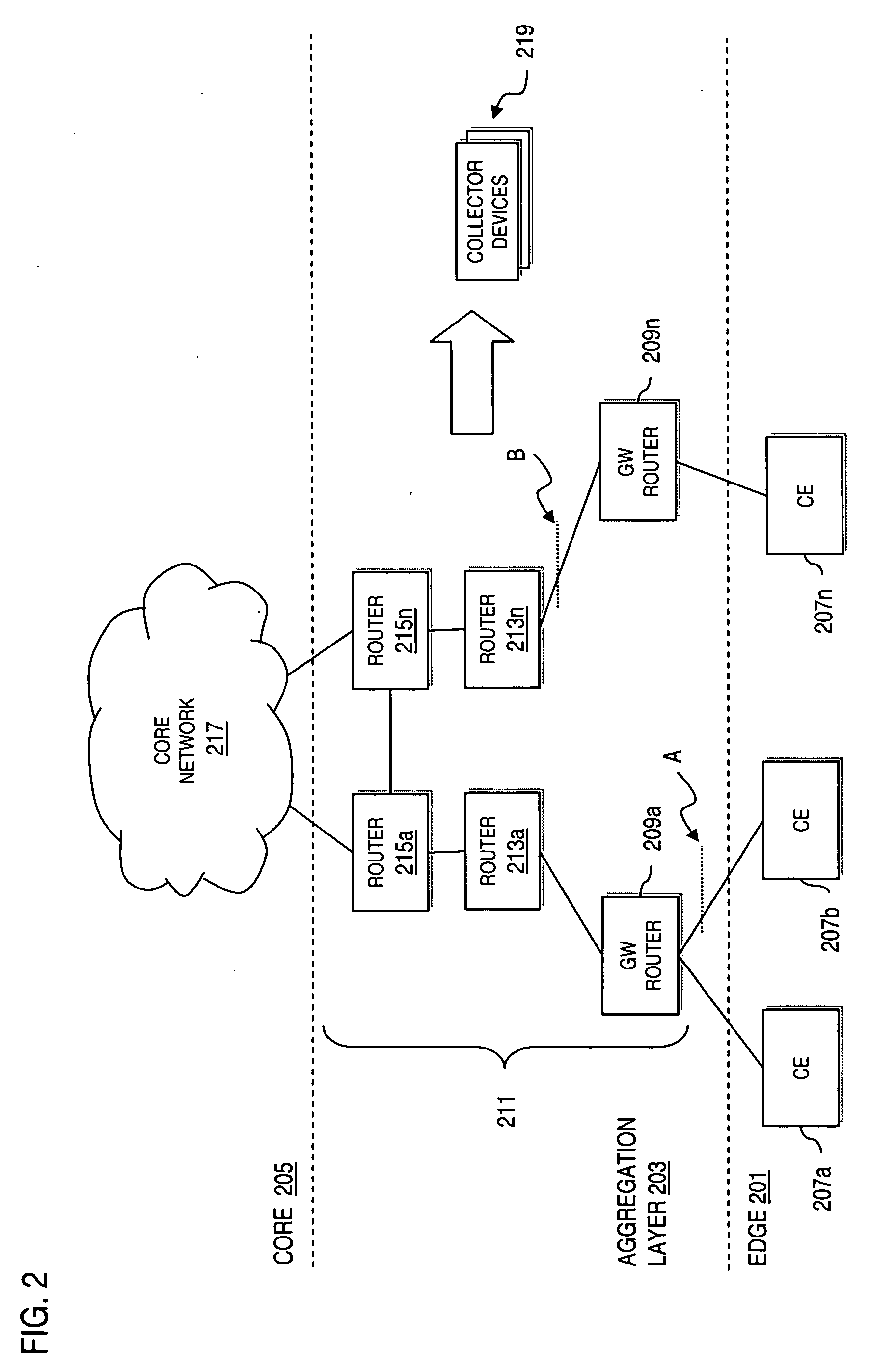
Method and apparatus for detecting denial of service attacks
InactiveUS20060272018A1Memory loss protectionError detection/correctionBehavioral analyticsData stream
An approach is provided for supporting network security. A dataflow destined for an end user network is received. The dataflow is sampled according to a predetermined sampling rate. Flow information is generated from the sampled dataflow. The flow information is forwarded to a collector device for remote behavioral analysis to determine a behavioral profile indicative of a Denial of Service (DoS) attack (e.g., distributed Denial of Service (DDOS) attack) of the end user network.
Owner:VERIZON PATENT & LICENSING INC
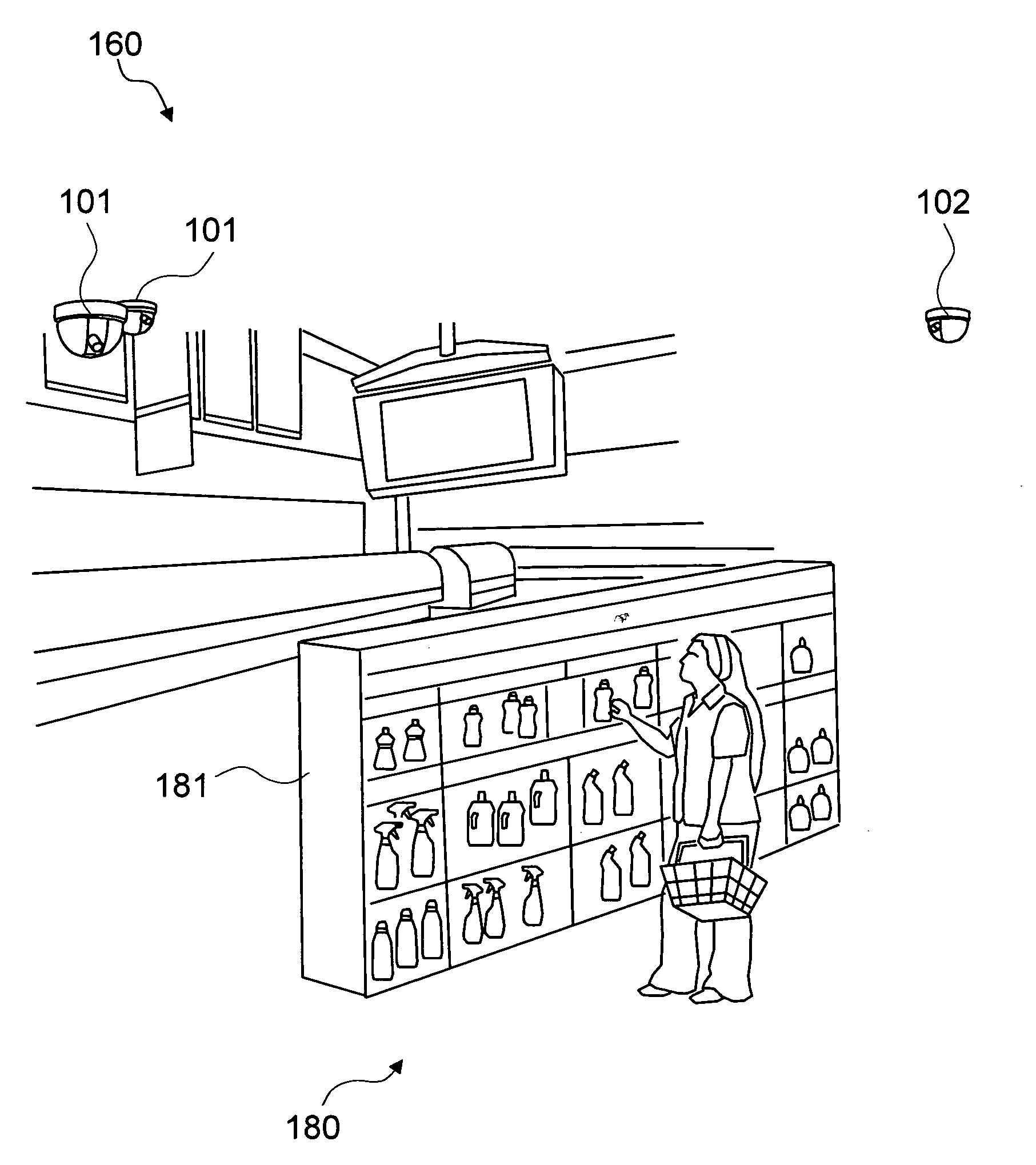
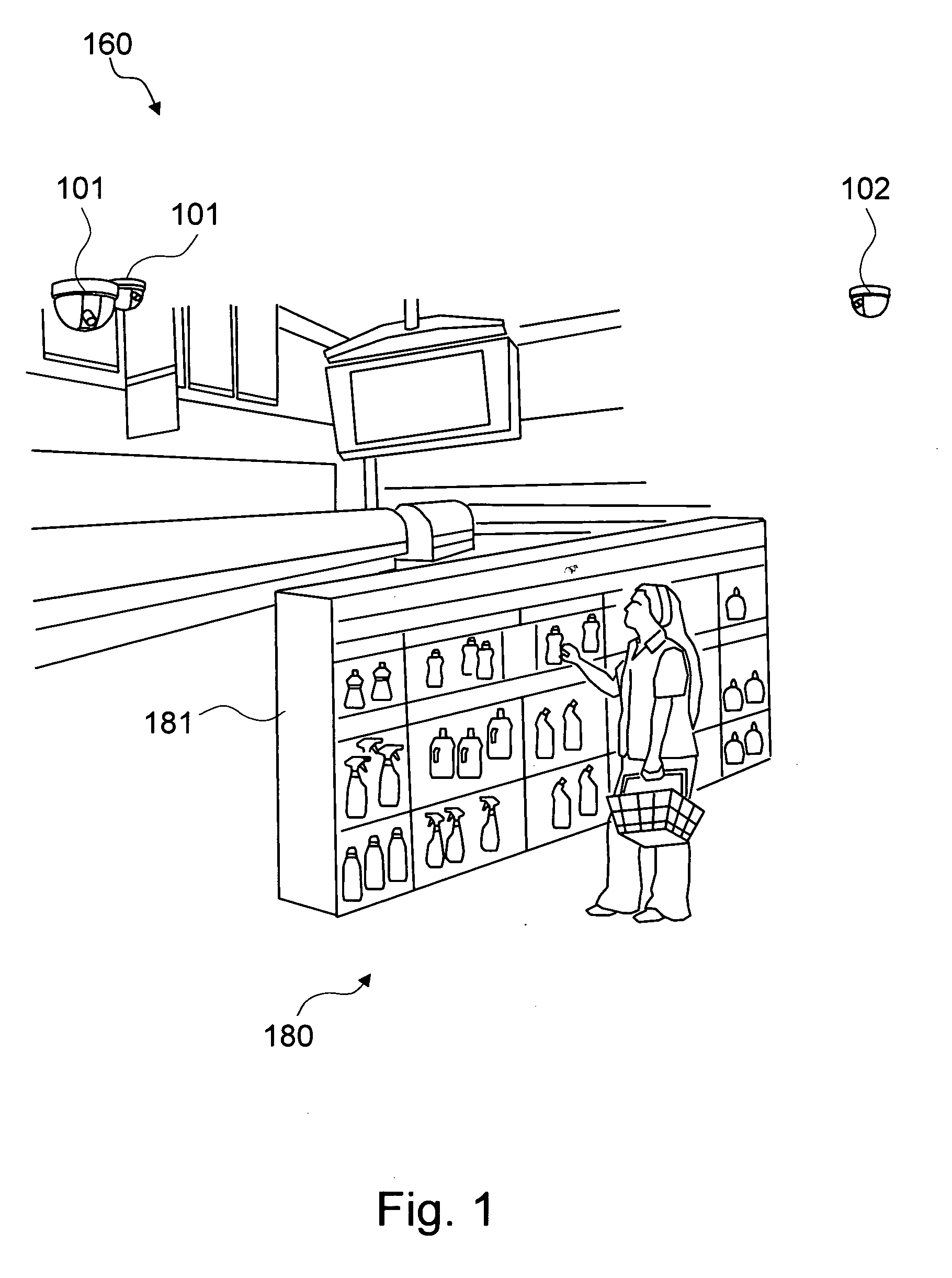
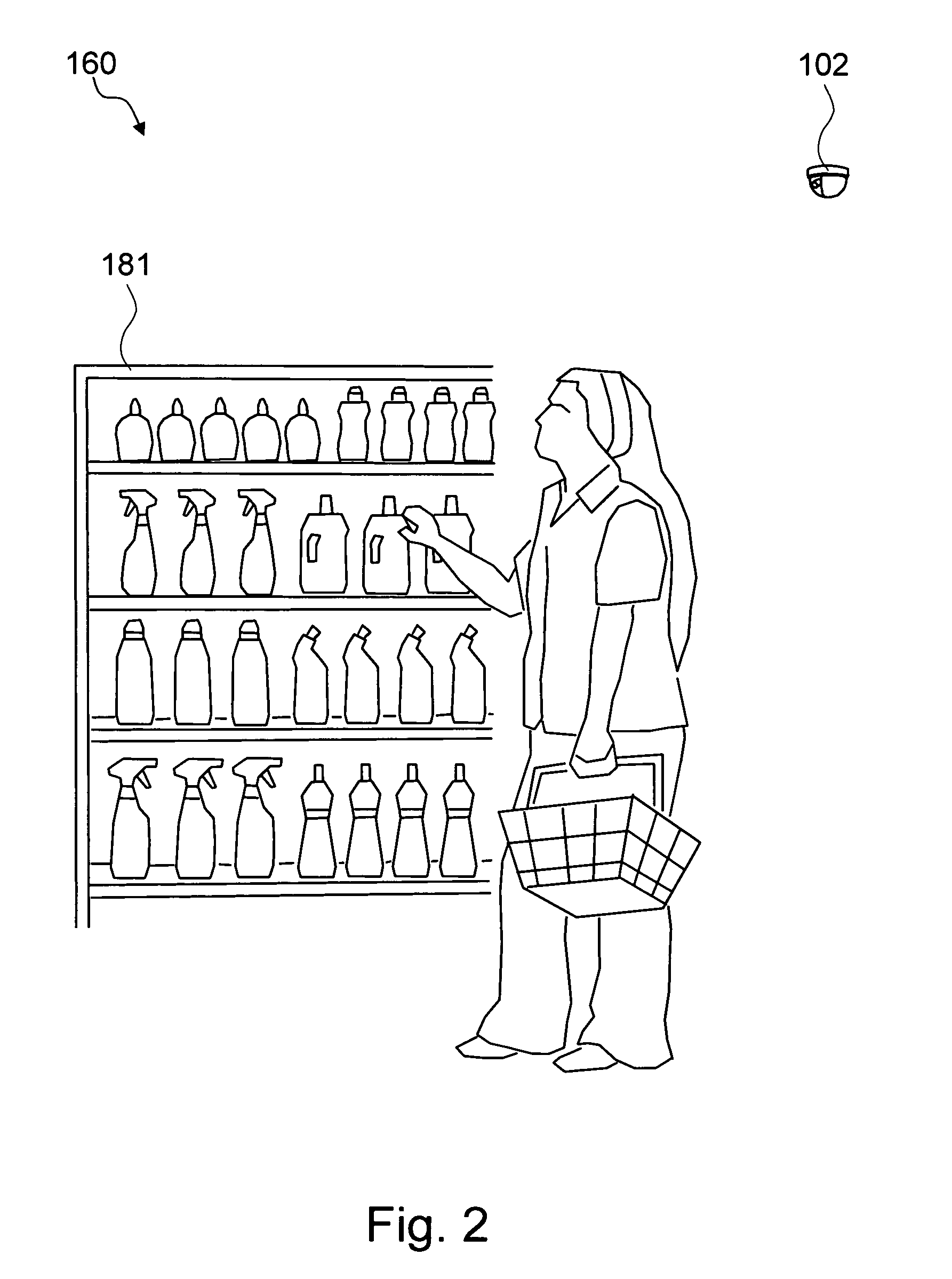
Method and system for automatically analyzing categories in a physical space based on the visual characterization of people
ActiveUS20080159634A1Minimizing number of productMinimizing shelf spaceCharacter and pattern recognitionVisual technologyPhysical space
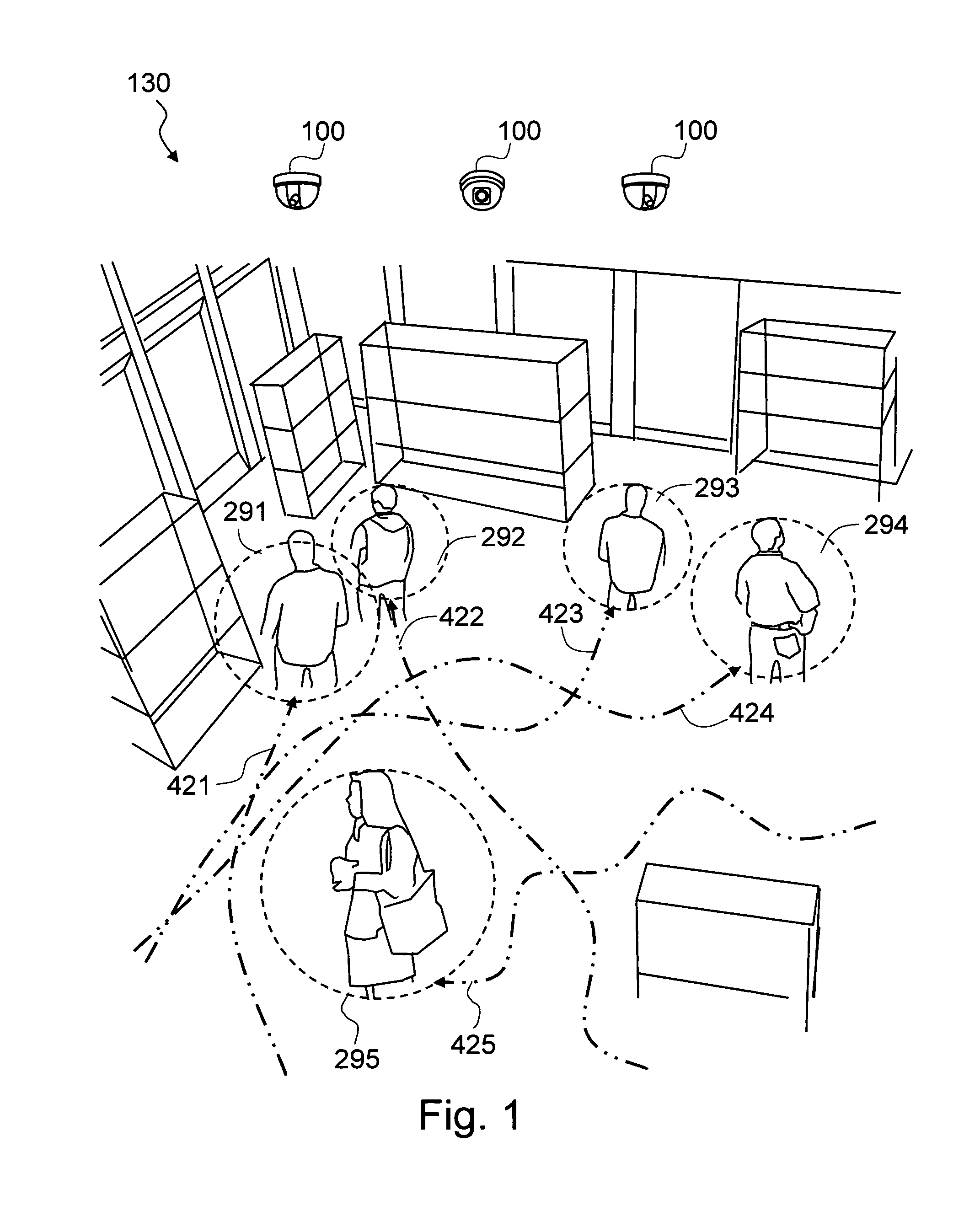
The present invention is a method and system for automatically analyzing a category in a plurality of the categories in a physical space based on the visual characterization, such as behavior analysis or segmentation, of the persons with regard to the category. The present invention captures a plurality of input images of the persons in the category by a plurality of means for capturing images. The present invention processes the plurality of input images in order to understand the shopping behavior of the persons with the sub-categories of the category and analyzes the level of engagement and decision process at the sub-category level. The processes are based on a novel usage of a plurality of computer vision technologies to analyze the visual characterization of the persons from the plurality of input images. The physical space may be a retail space, and the persons may be customers in the retail space.
Owner:VIDEOMINING CORP
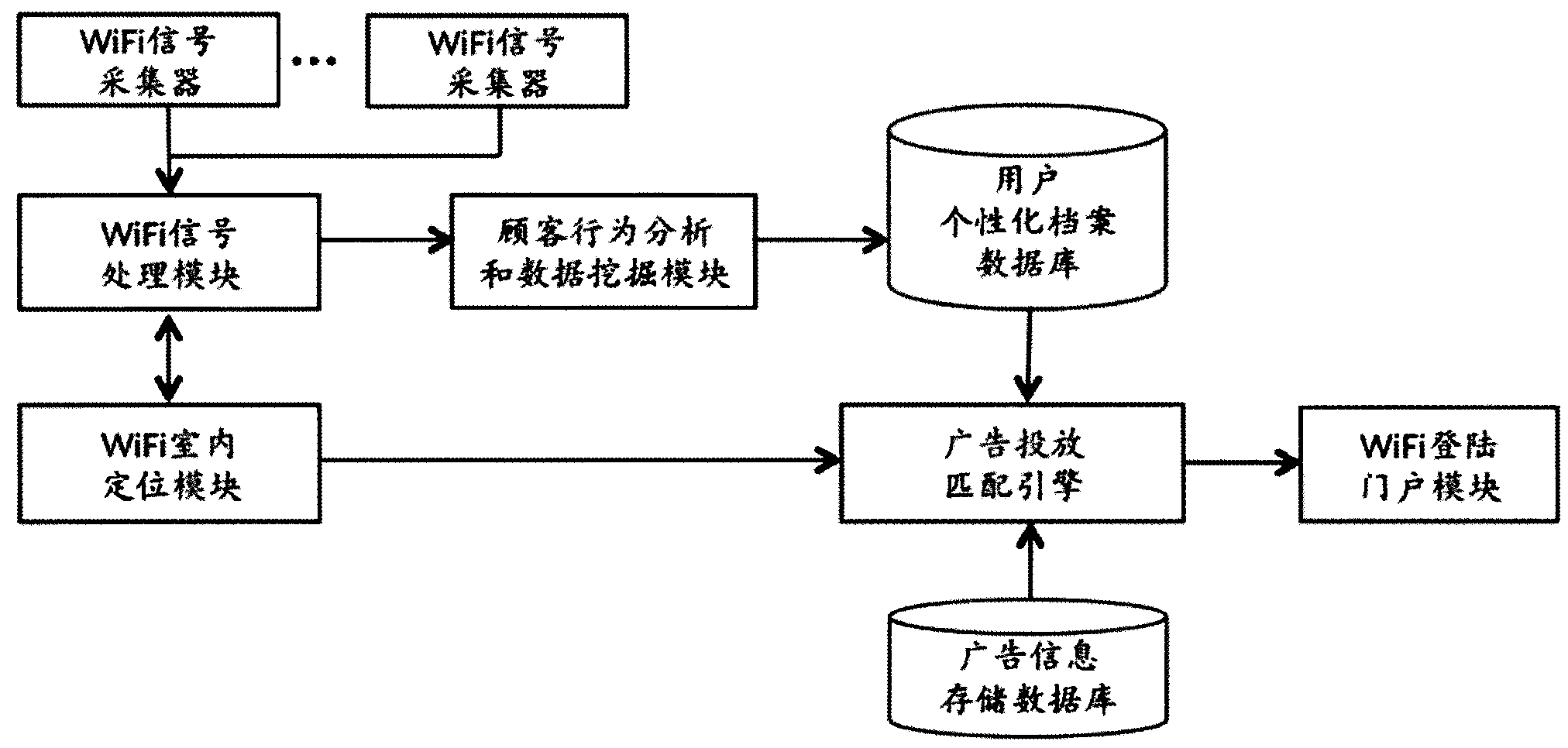
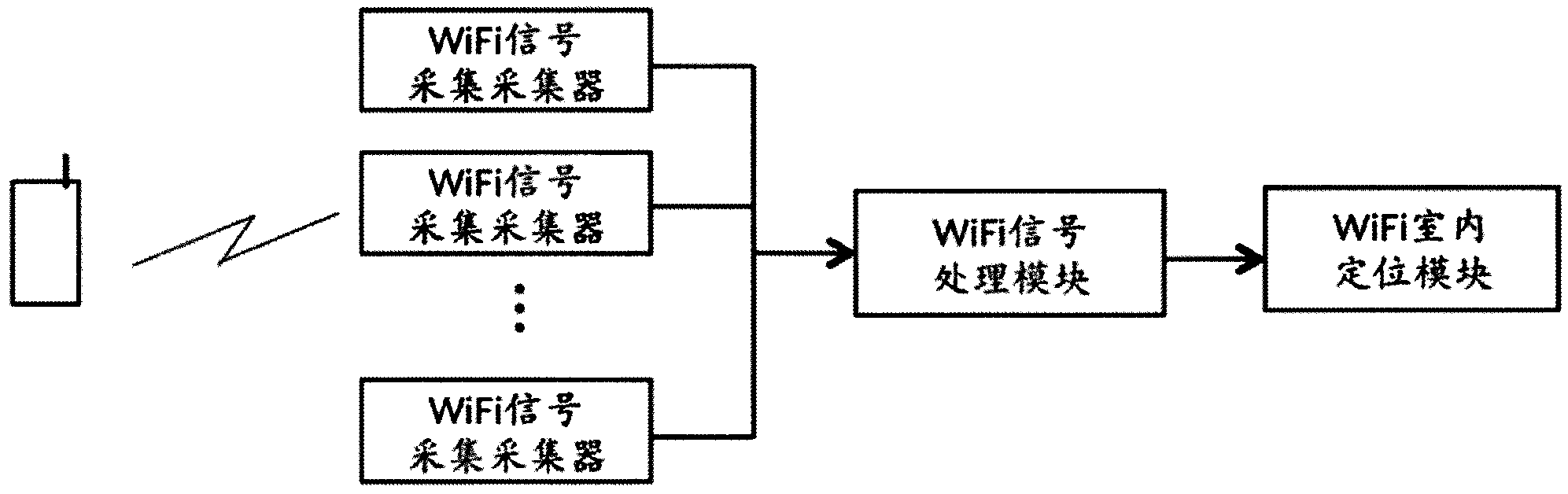
Information pushing system of WiFi (wireless fidelity) terminal and implementation method thereof
ActiveCN103402177AImprove experienceReal-time field precision marketingBroadcast service distributionMessaging/mailboxes/announcementsPersonalizationBehavioral analytics
The invention discloses an information pushing system of a WiFi (wireless fidelity) terminal and an implementation method thereof. The system comprises a WiFi signal collector, a WiFi signal processing module, a WiFi indoor positioning module, a customer activity analyzing and data mining module, a user personality file database, an advertisement information storage database, an advertisement putting and matching engine and a WiFi logging portal module. The system is suitable for all terminals with the WiFi function, such as mobile phones, PADs (personal access device) and PCs (personal computer), and different software platforms, such as Andriod, wP, iOS, Windows, MAC OS and Linux, the WiFi terminals do not need any software modification and updating, and the applicable range is wide. The possible hobby of a consumer is judged through data analysis and mining, and the real-time and on-site precise marketing is realized for target users, so on one hand, the experience of the user consuming in business places is improved, and on the other hand, the commercial value of sellers and factories is improved.
Owner:江苏数原信息技术有限公司
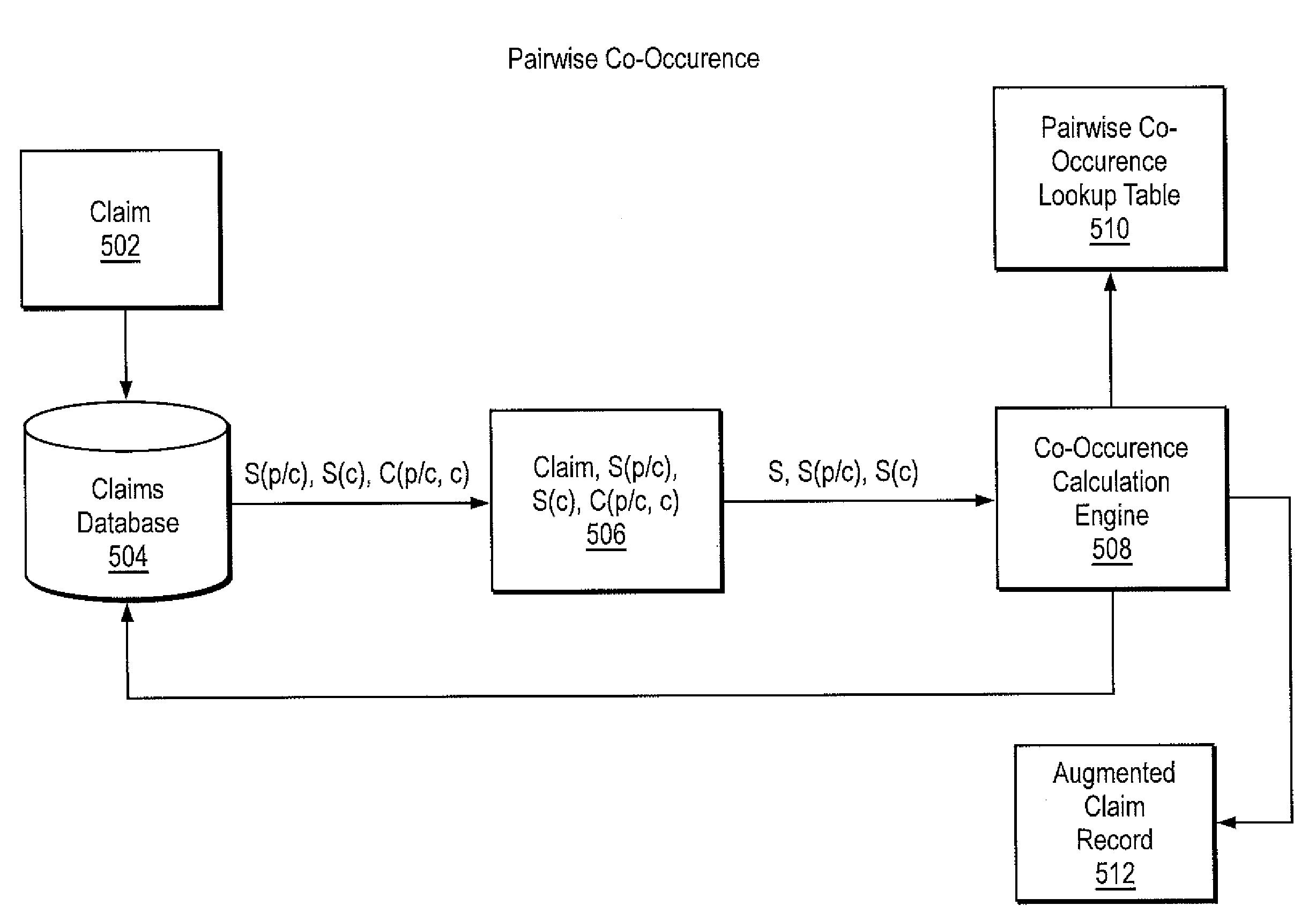
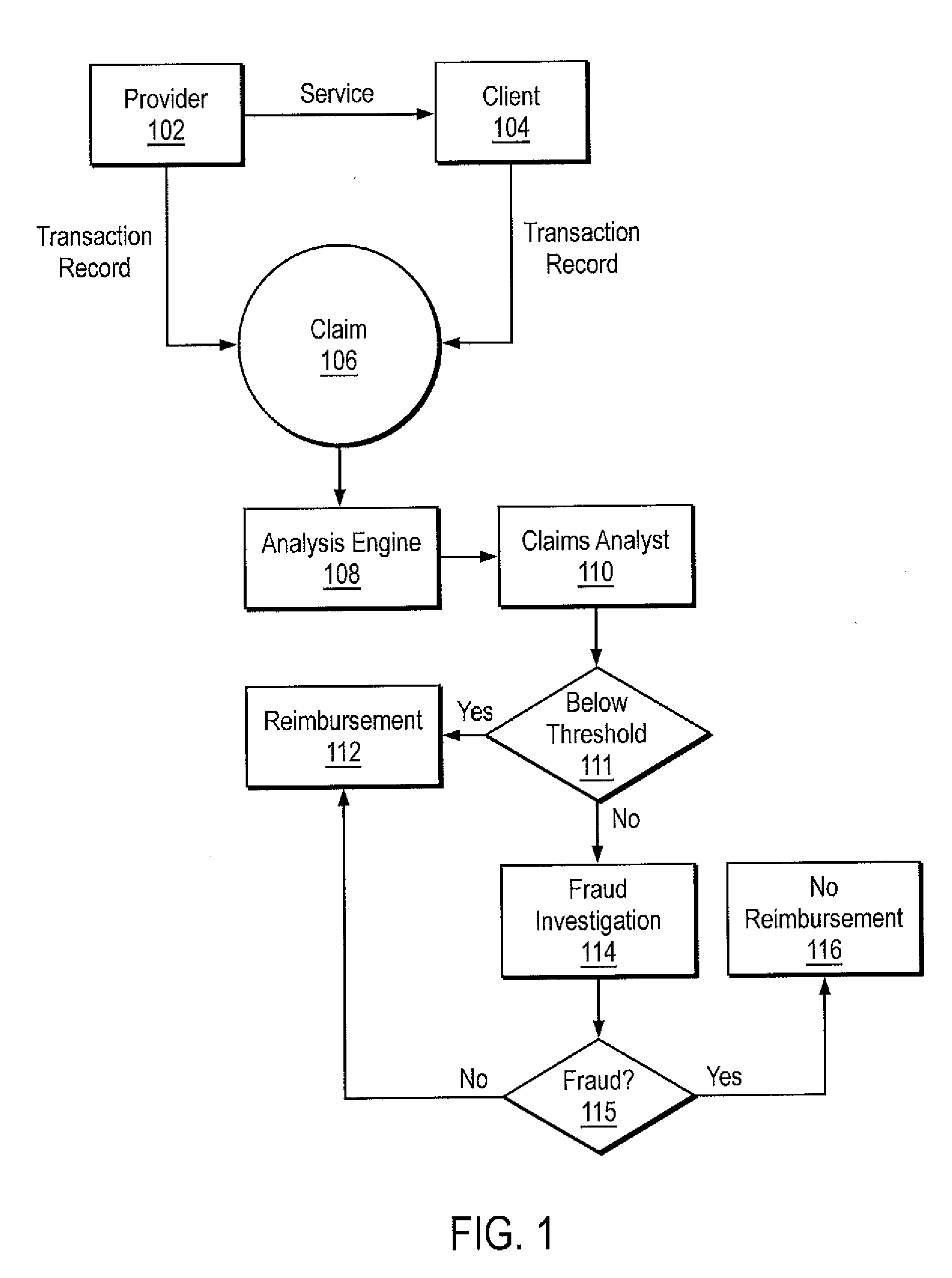
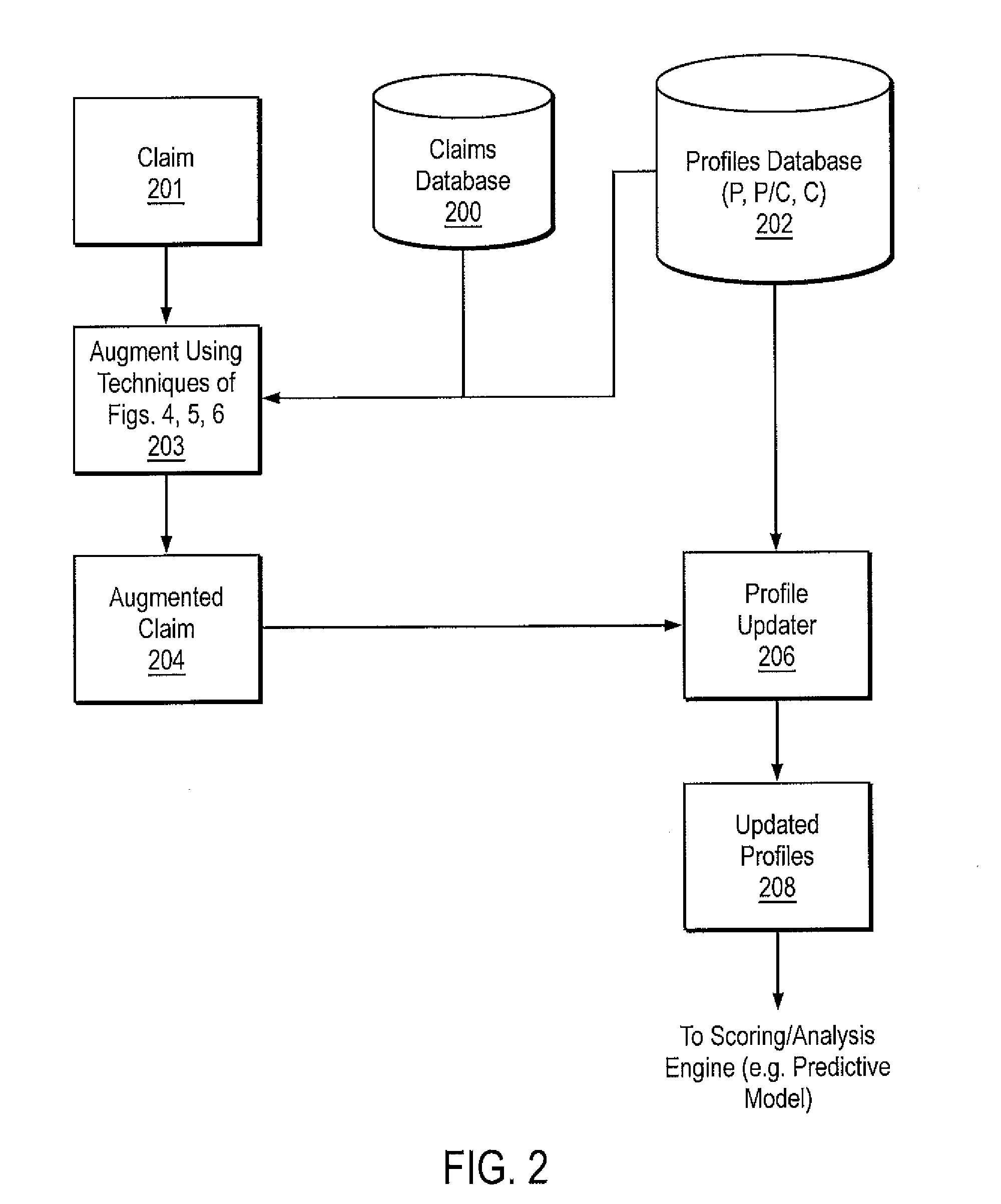
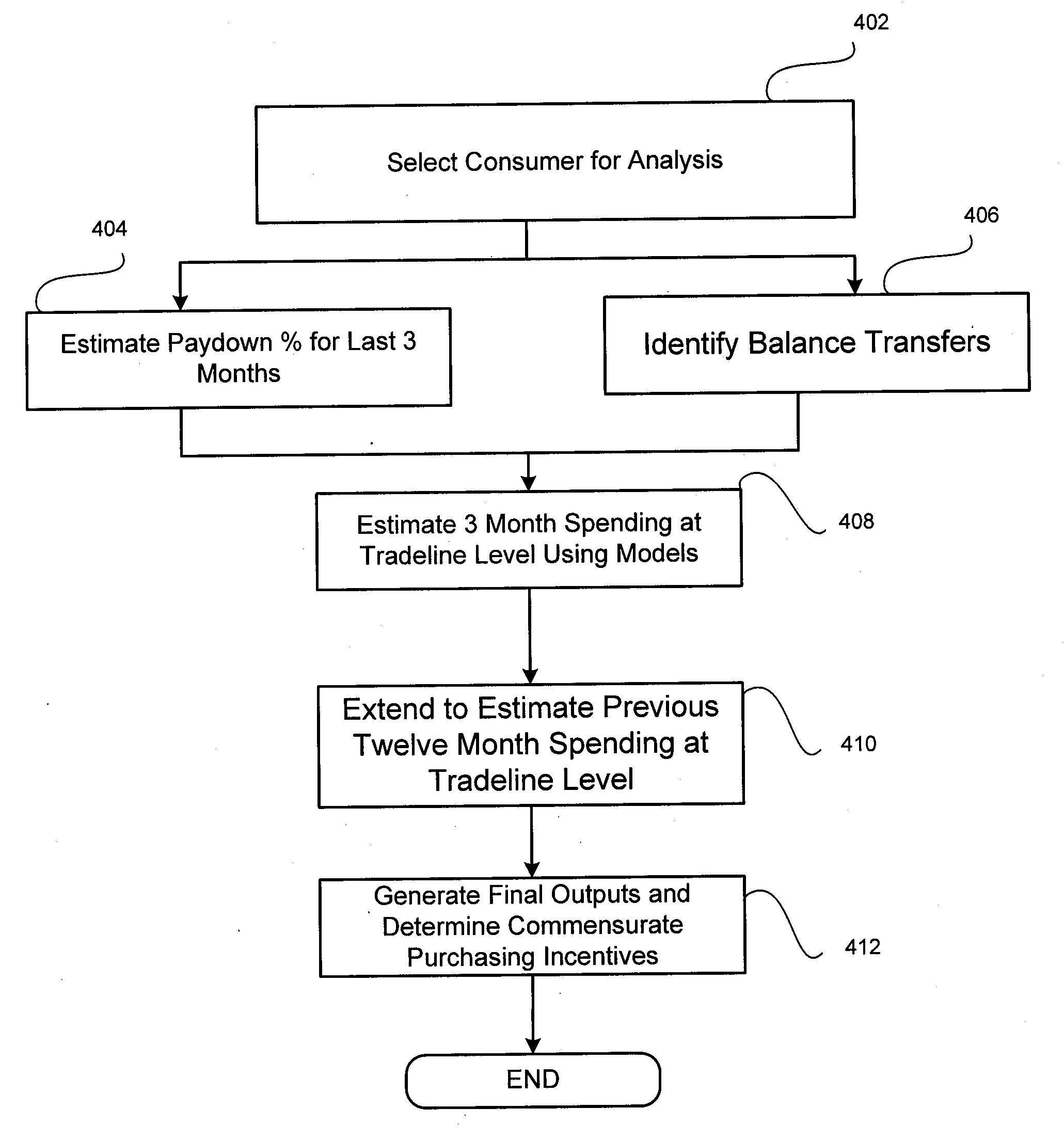
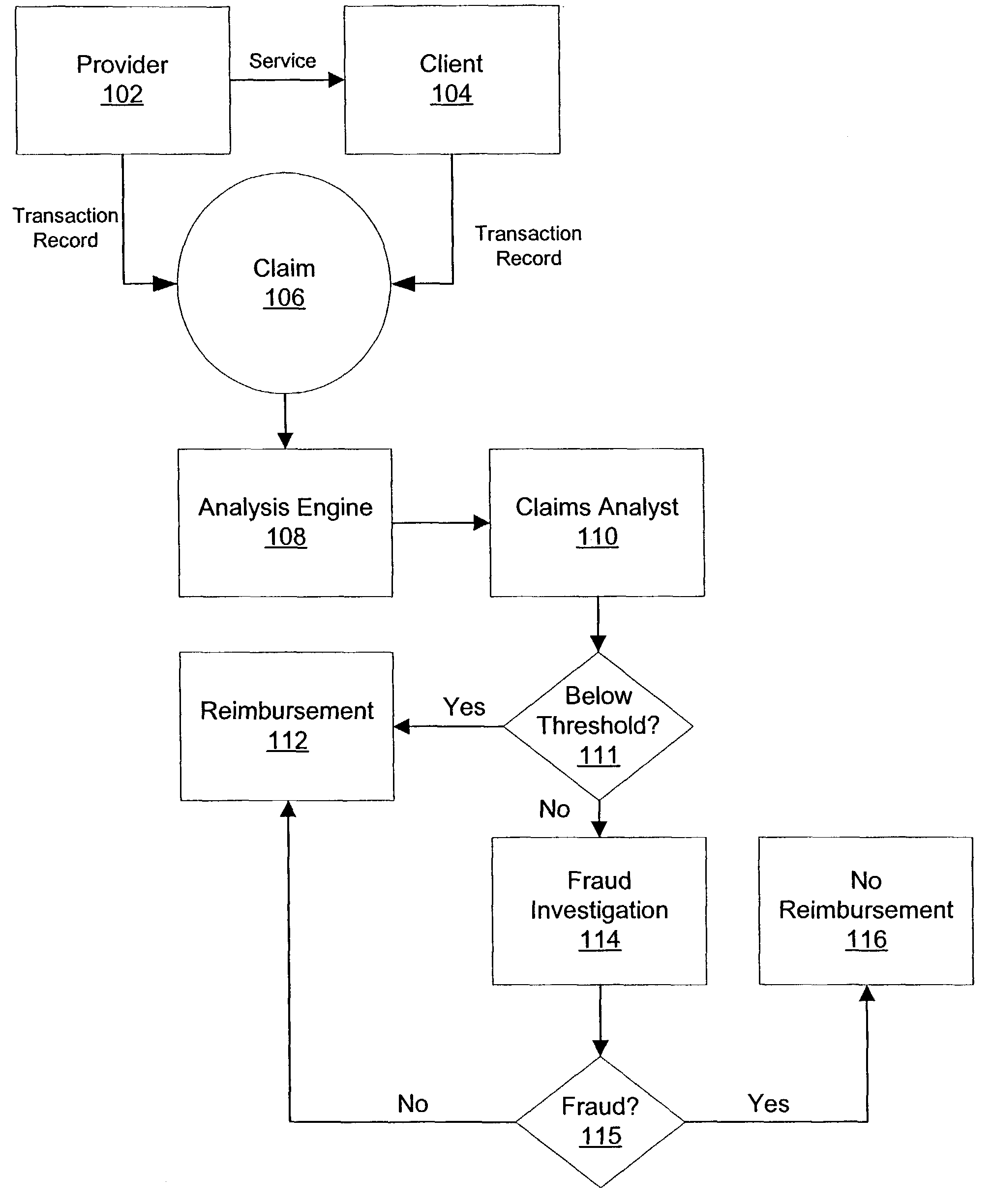
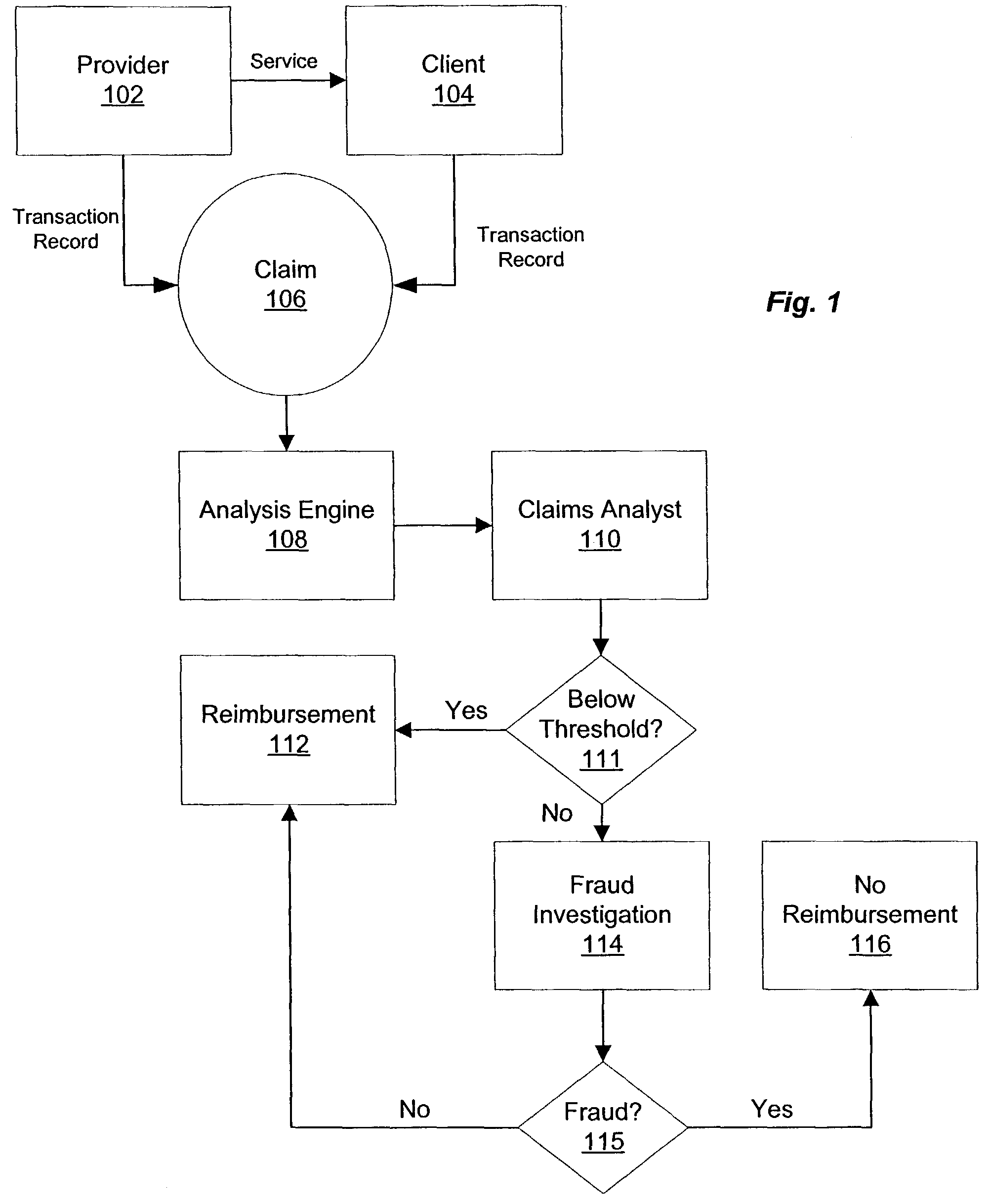
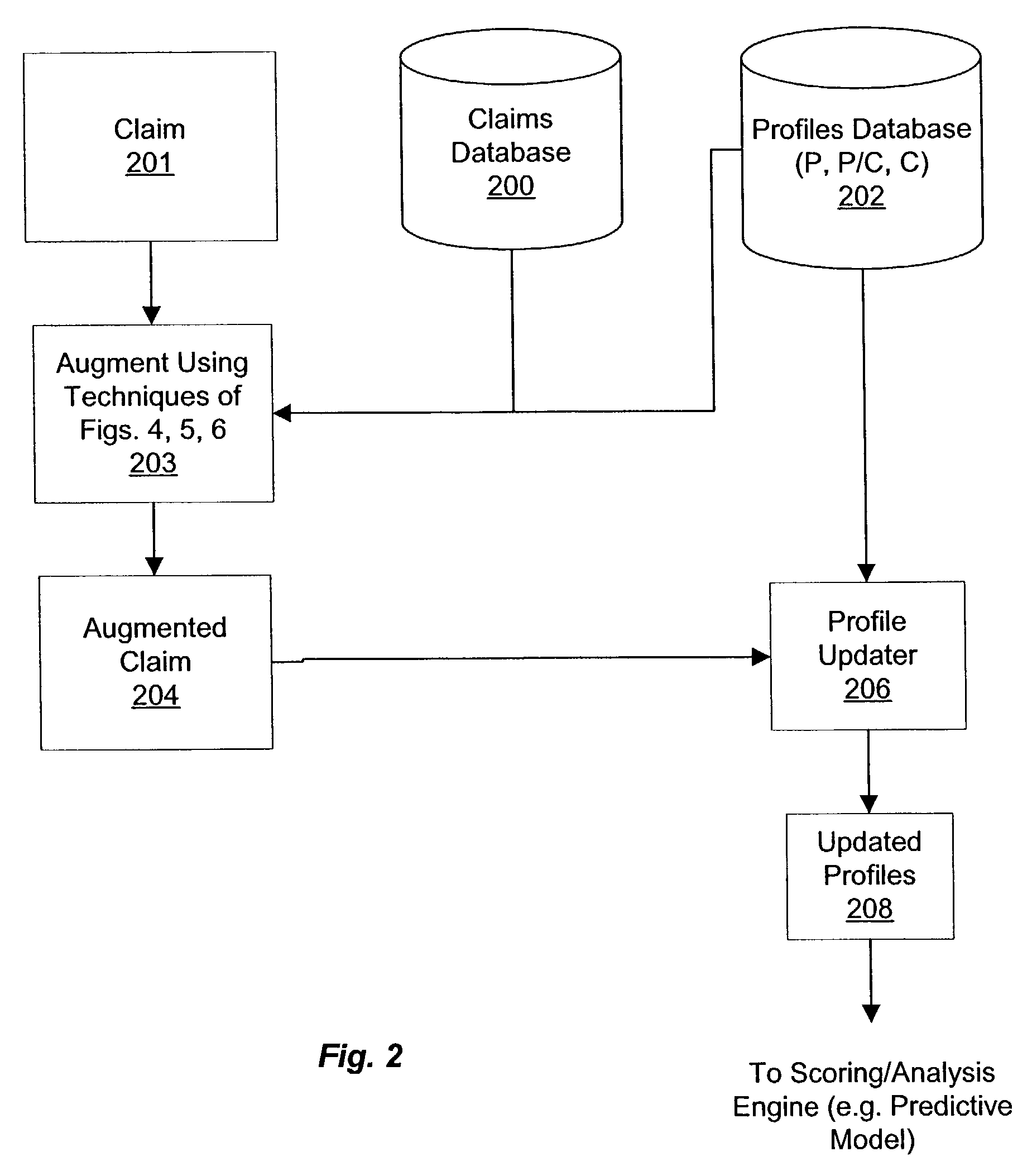
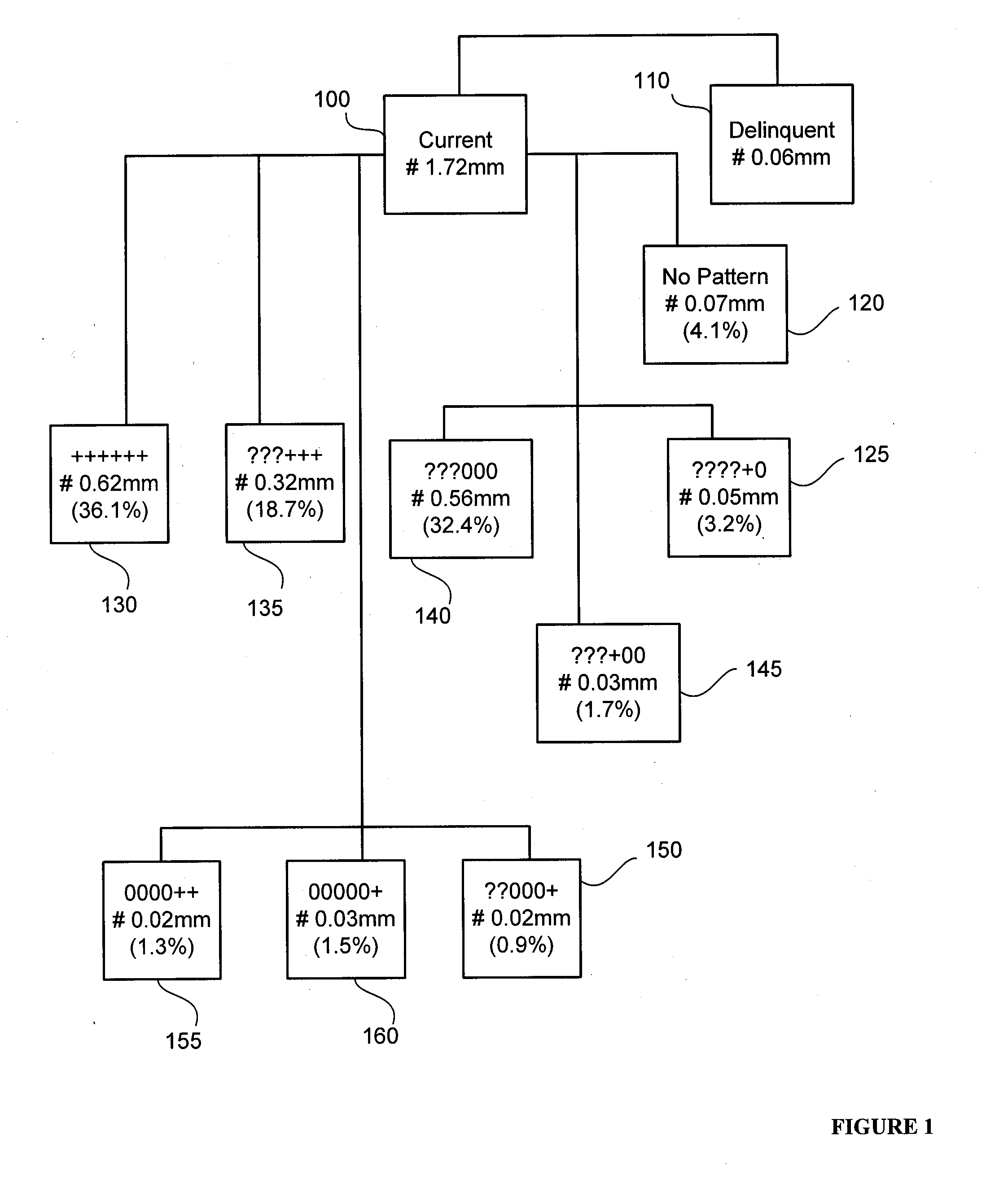
Consistency modeling of healthcare claims to detect fraud and abuse
InactiveUS20080249820A1Accurate pictureEasy to detectComplete banking machinesMedical data miningData dredgingPredictive modelling
Transaction-based behavioral profiling, whereby the entity to be profiled is represented by a stream of transactions, is required in a variety of data mining and predictive modeling applications. An approach is described for assessing inconsistency in the activity of an entity, as a way of detecting fraud and abuse, using service-code information available on each transaction. Inconsistency is based on the concept that certain service-codes naturally co-occur more than do others. An assessment is made of activity consistency looking at the overall activity of an individual entity, as well as looking at the interaction of entities. Several approaches for measuring consistency are provided, including one inspired by latent semantic analysis as used in text analysis. While the description is in the context of fraud detection in healthcare, the techniques are relevant to application in other industries and for purposes other than fraud detection.
Owner:FAIR ISAAC & CO INC
Driver safety program based on behavioral profiling
InactiveUS20100143872A1Cosmonautic condition simulationsSimulatorsBehavioral analyticsDriver/operator
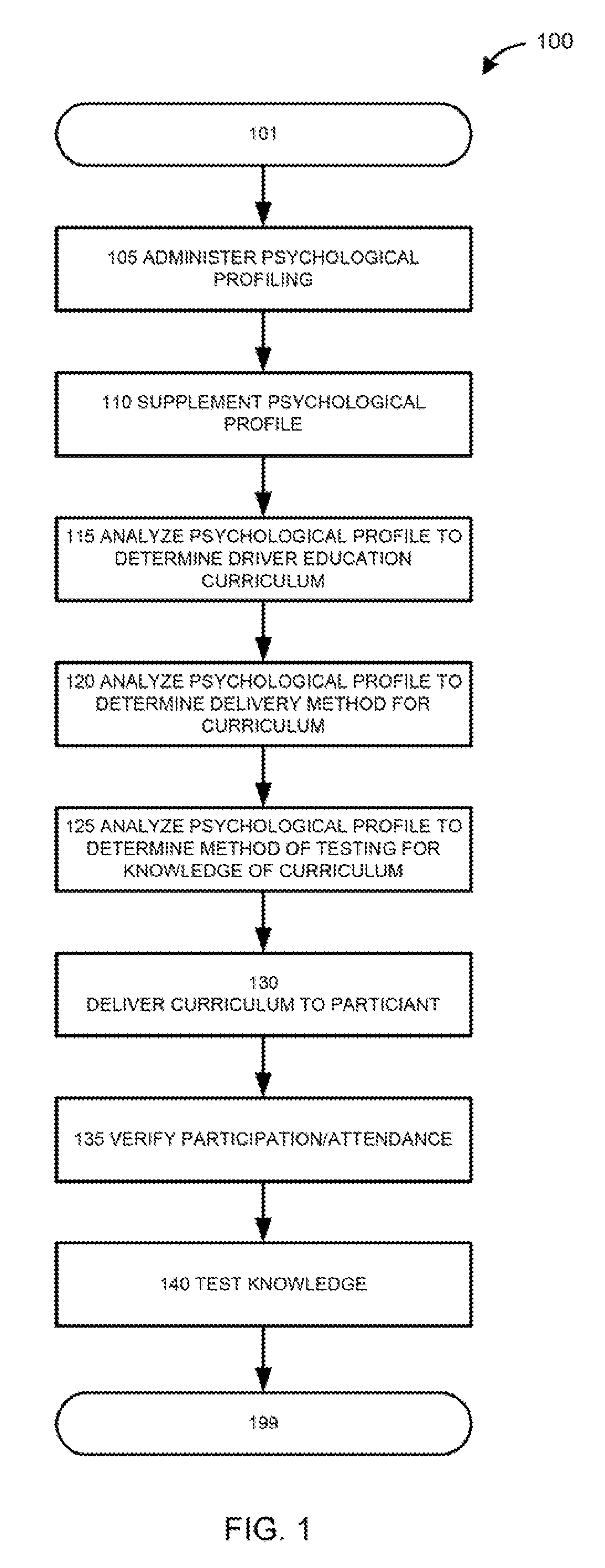
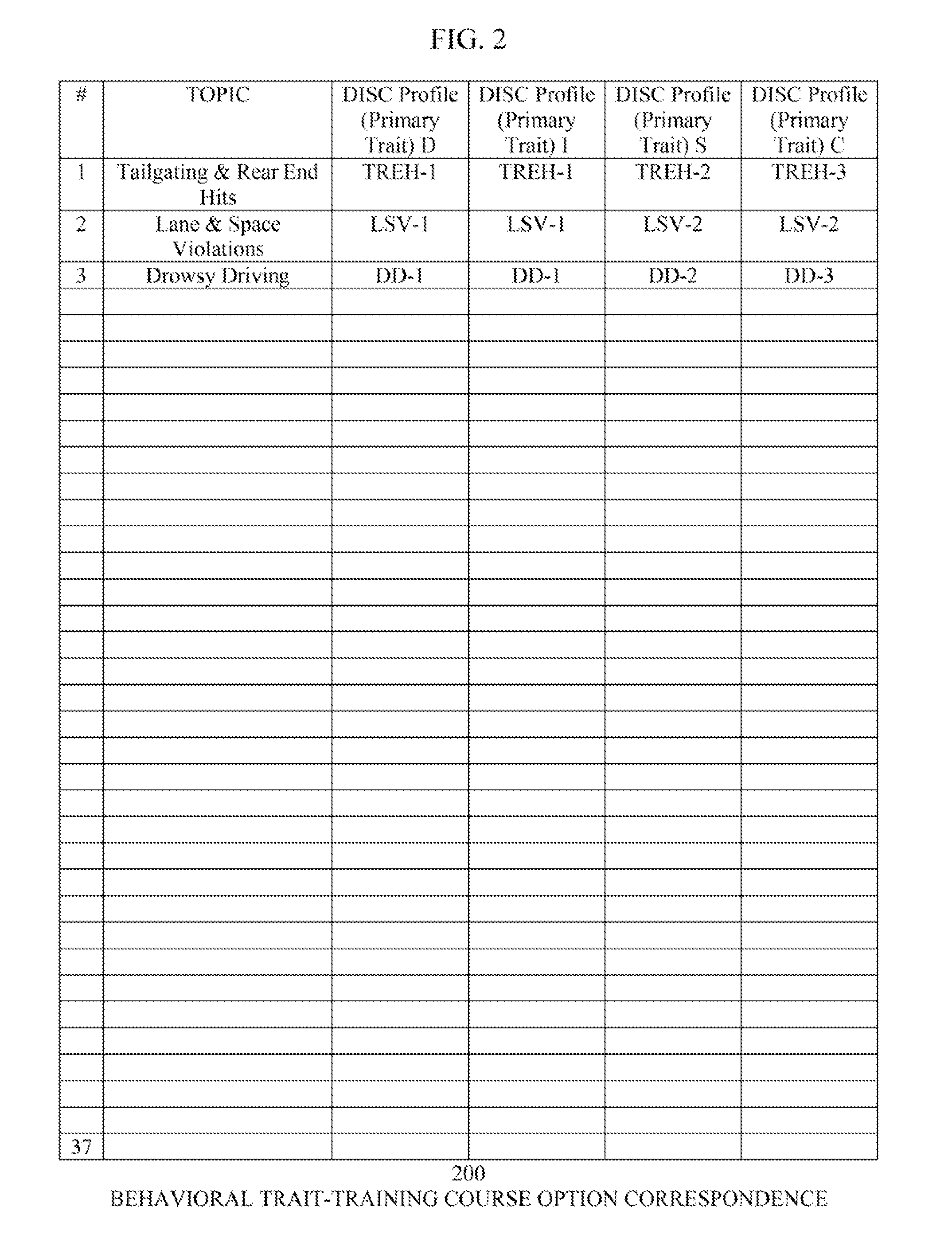
A computer system is configured to administer a psychological profiling test to a participant in a driver education program, or receive such profile from another source; to determine the participant's psychological profile. The system then selects a driver education program for the participant based on the profile. The system also selects a method of delivering the curriculum to the participant based on the profile. The system further selects a method of testing the participant's comprehension and retention of the curriculum material, also based on the profile. The system delivers the selected curriculum to the participant using the selected delivery method, verifies attendance or participation, and tests the participant's comprehension and retention of the curriculum material using the selected testing method.
Owner:GOLD CROSS BENEFITS CORP
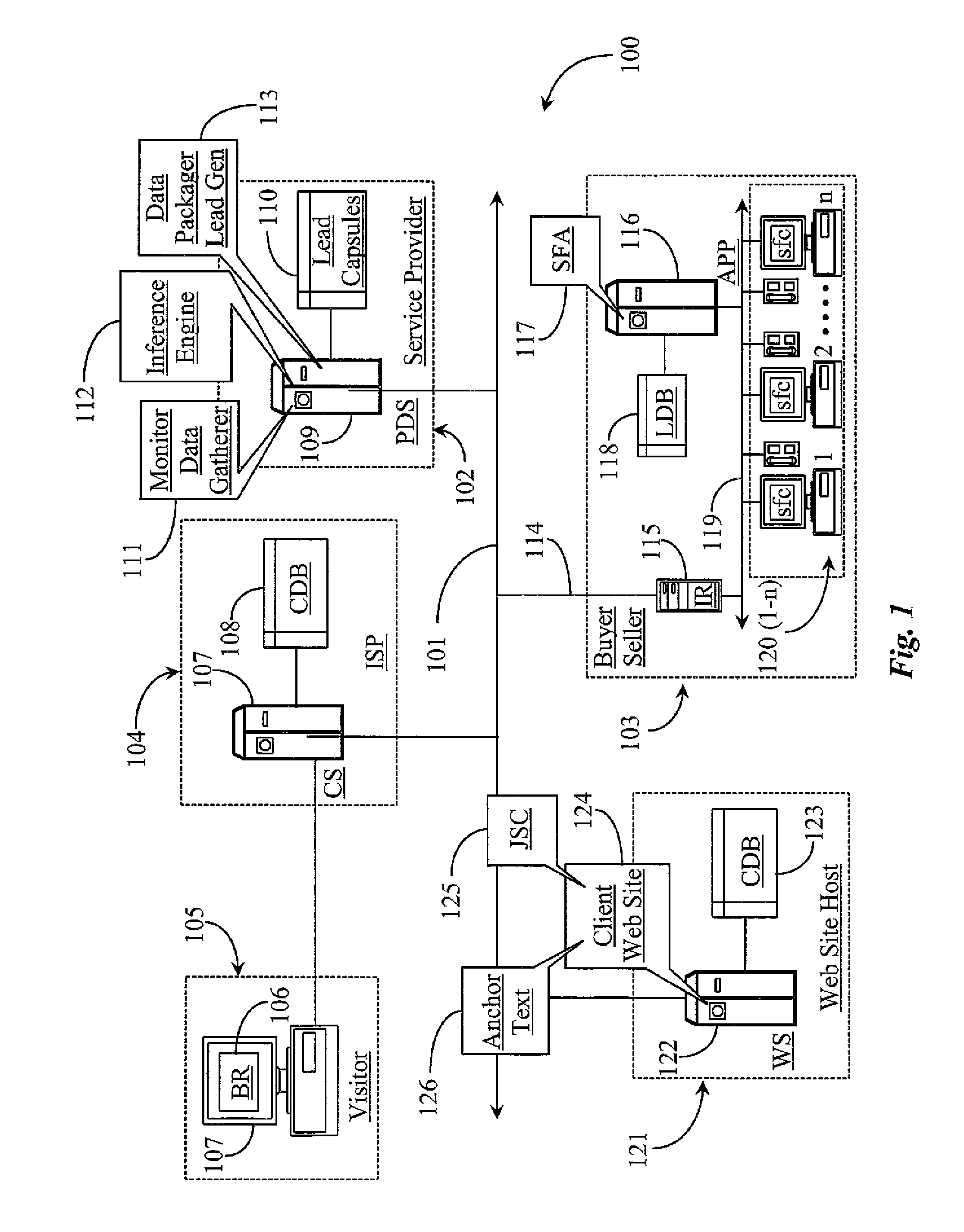
System and methods for inferring intent of website visitors and generating and packaging visitor information for distribution as sales leads or market intelligence
ActiveUS20100131835A1Without ambiguityInterprogram communicationCommerceWeb siteBehavioral analytics
A system for inferring intent of visitors to a Website has a visitor-tracking application executing from a digital medium coupled to a server hosting the Website, the server connected to a repository adapted to store data about visitor behavior, and an inference engine for processing the data to infer the intent of visitors. Visitor behavior relative to links is tracked, and intent of a visitor is inferred from one or both, or a combination of analysis of the behavior and deducing meaning for anchor text of links selected.
Owner:CALLIDUS SOFTWARE
Total structural risk model
ActiveUS20090222379A1Improve business satisfactionFinancePayment architectureFinancial data processingBehavioral analytics
The present invention generally relates to financial data processing, and in particular it relates to credit scoring, consumer profiling, consumer behavior analysis and modeling. More specifically, it relates to risk modeling using the inputs of credit bureau data, size of wallet data, and, optionally, internal data.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
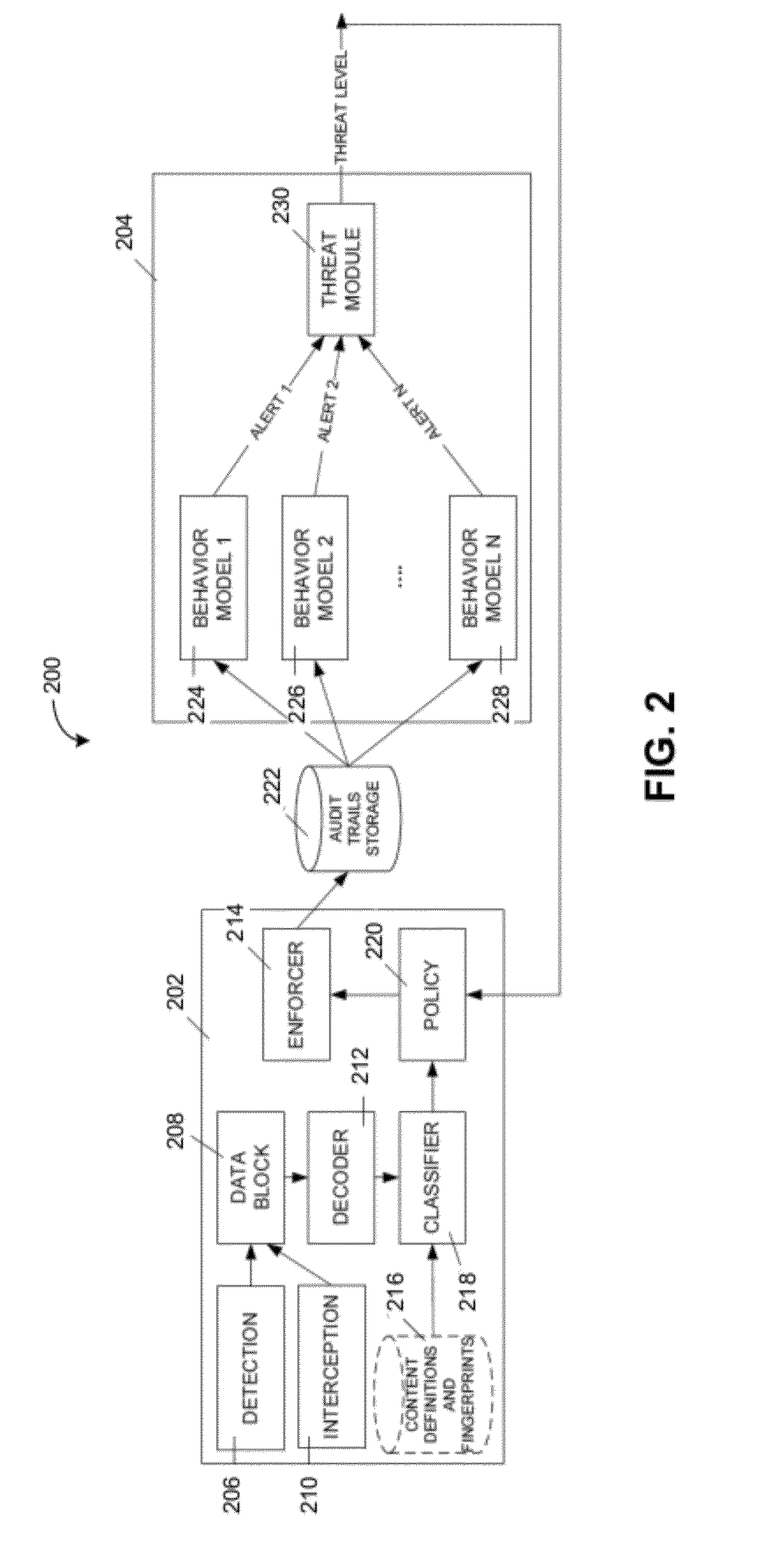
System and method for detecting or preventing data leakage using behavior profiling
InactiveUS20120210388A1Avoid data breachesComputer security arrangementsTransmissionBehavioral analyticsComputer users
Various embodiments provide systems and methods for preventing or detecting data leakage. For example, systems and methods may prevent or detect data leakage by profiling the behavior of computer users, computer programs, or computer systems. Systems and methods may use a behavior model in monitoring or verifying computer activity executed by a particular computer user, group of computer users, computer program, group of computer programs, computer system, or group of computer systems, and detect or prevent the computer activity when such computer activity deviates from standard behavior. Depending on the embodiment, standard behavior may be established on past computer activity executed by the computer user, or past computer activity executed by a group of computer users.
Owner:BEYONDTRUST SOFTWARE
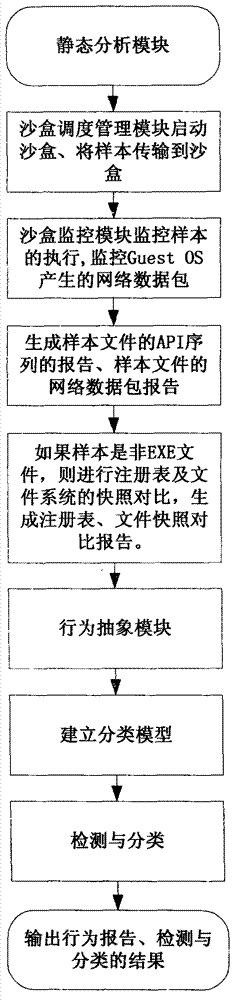
System and method for automatically analyzing, detecting and classifying malicious program behavior
ActiveCN102930210ACause damageOvercome shortcomings such as inability to perform adequatelyPlatform integrity maintainanceSpecial data processing applicationsDomain nameNetwork behavior
The invention discloses a system and a method for automatically analyzing, detecting and classifying a malicious program behavior. The system comprises a static analysis module, a sandbox dispatching management module, a sandbox monitoring module, a behavior abstraction module and a detection and classification module. Compared with the prior art, the system has the advantages that 1, the system is based on a behavior monitoring technology in an instruction set simulation environment; and 2, a virtual Internet is established in a sandbox through means of environment configuration, server program modification and the like, and a common network service is simulated, so that operations such as domain name server (DNS) resolution, http access, file download, Email login and mailing initiated by a malicious program can be successfully executed, the malicious program is inveigled to generate a malicious network behavior, the network behaviors are prevented from damaging a host machine and a real network, and the defects that the malicious program network behavior cannot be fully expressed during dynamic behavior analysis of a malicious program and the like are overcome.
Owner:JIANGSU JINLING TECH GRP CORP
System and Method for Predicting Impending Cyber Security Events Using Multi Channel Behavioral Analysis in a Distributed Computing Environment
InactiveUS20160028758A1Parts stableImprove throughputDigital data information retrievalMemory loss protectionEarly warning systemBehavioral analytics
Multi channel distributed behavioral analysis architecture provides a software solution to the major operational challenges faced with providing an early warning system for impending cyber security events. Most cyber security events are premeditated. However, many current cyber security defense technologies only address the real-time detection of a software vulnerability, the presence of malware (known or unknown “zero day”), anomalies from pre-established data points, or the signature of an active security event. The system and method of the multi channel distributed behavioral analysis architecture introduces a technique which provides the data collection, assessment, and alerting ability prior to the occurrence of an event based on threat actor behavior.
Owner:ZITOVAULT
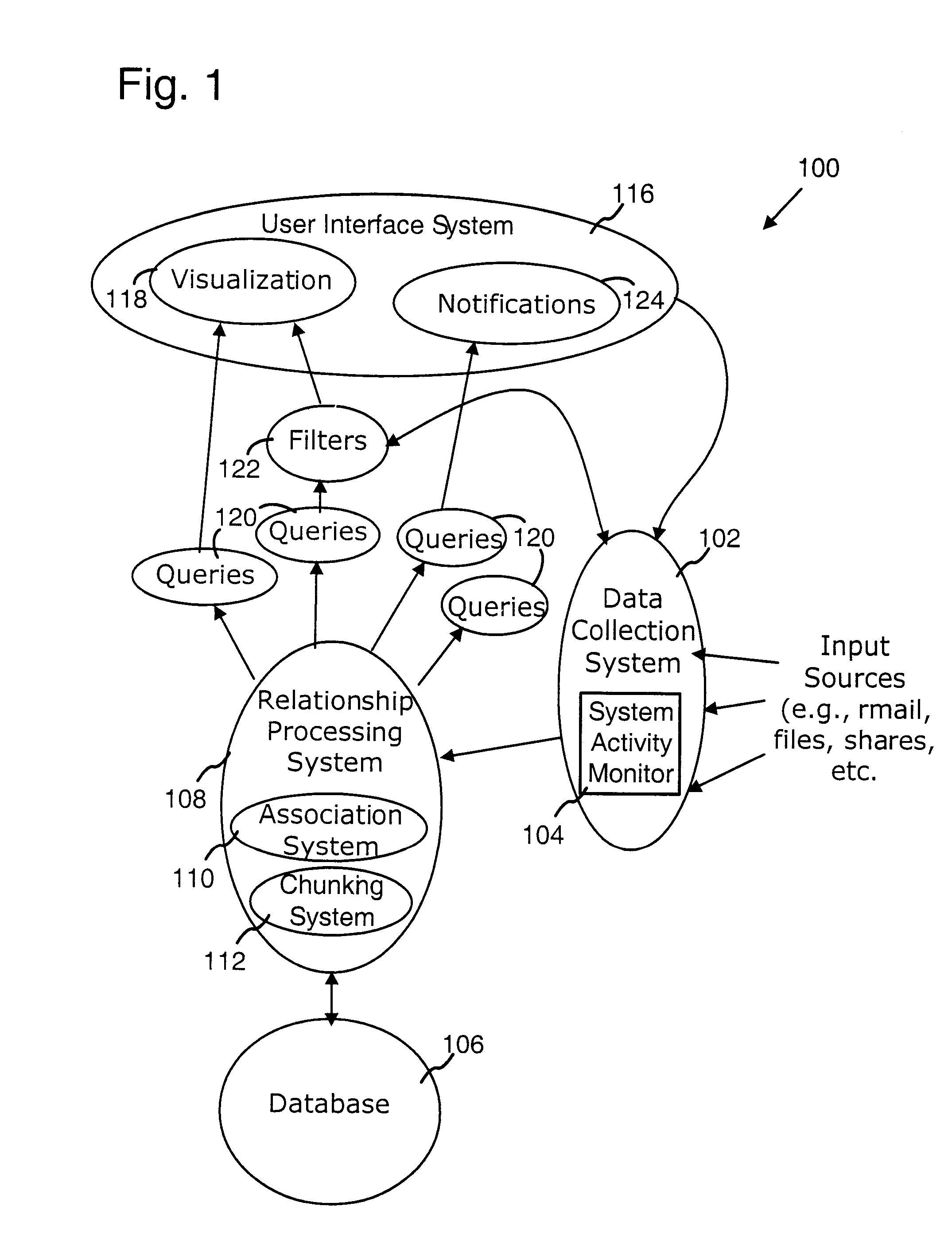
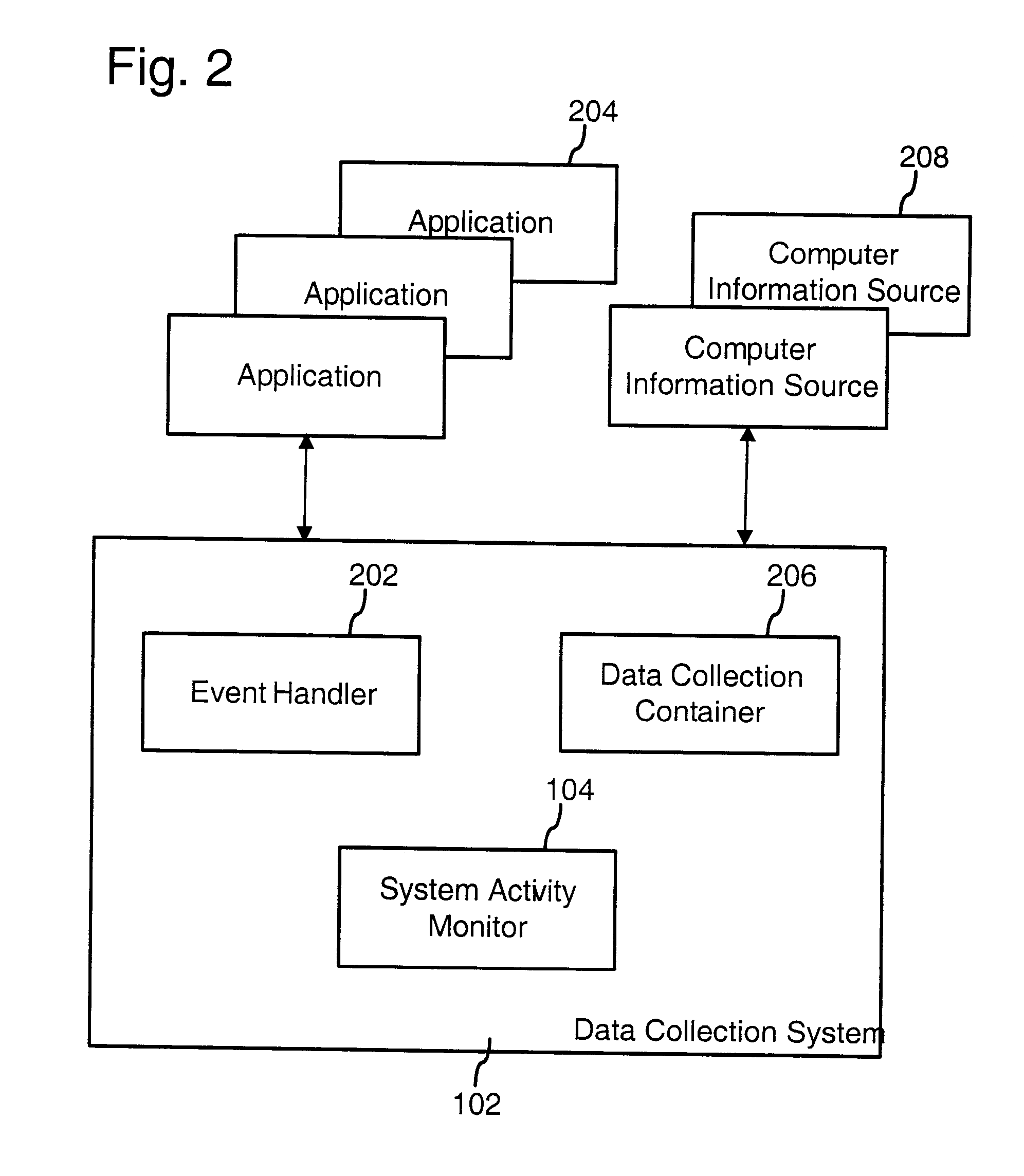
Computer system architecture for automatic context associations
InactiveUS20080222170A1Digital data processing detailsOffice automationComputer usersBehavioral analytics
A computer system models human memory by deriving associations between objects, events, and the context of the computer user or users. These associations can be dynamically generated, changing depending on the behavior of the user and context. Examples of areas in which this system can be used include time management (e.g., a calendar that presents time-based groupings of objects), people management (e.g., use analysis of user communications to rank importance of people to the user, groupings, and associations between people / groups and other objects such as documents, email), and general computer management (e.g., use analysis of user behavior to identify important objects and objects that are related to a current focus and context of the computer user).
Owner:MICROSOFT TECH LICENSING LLC
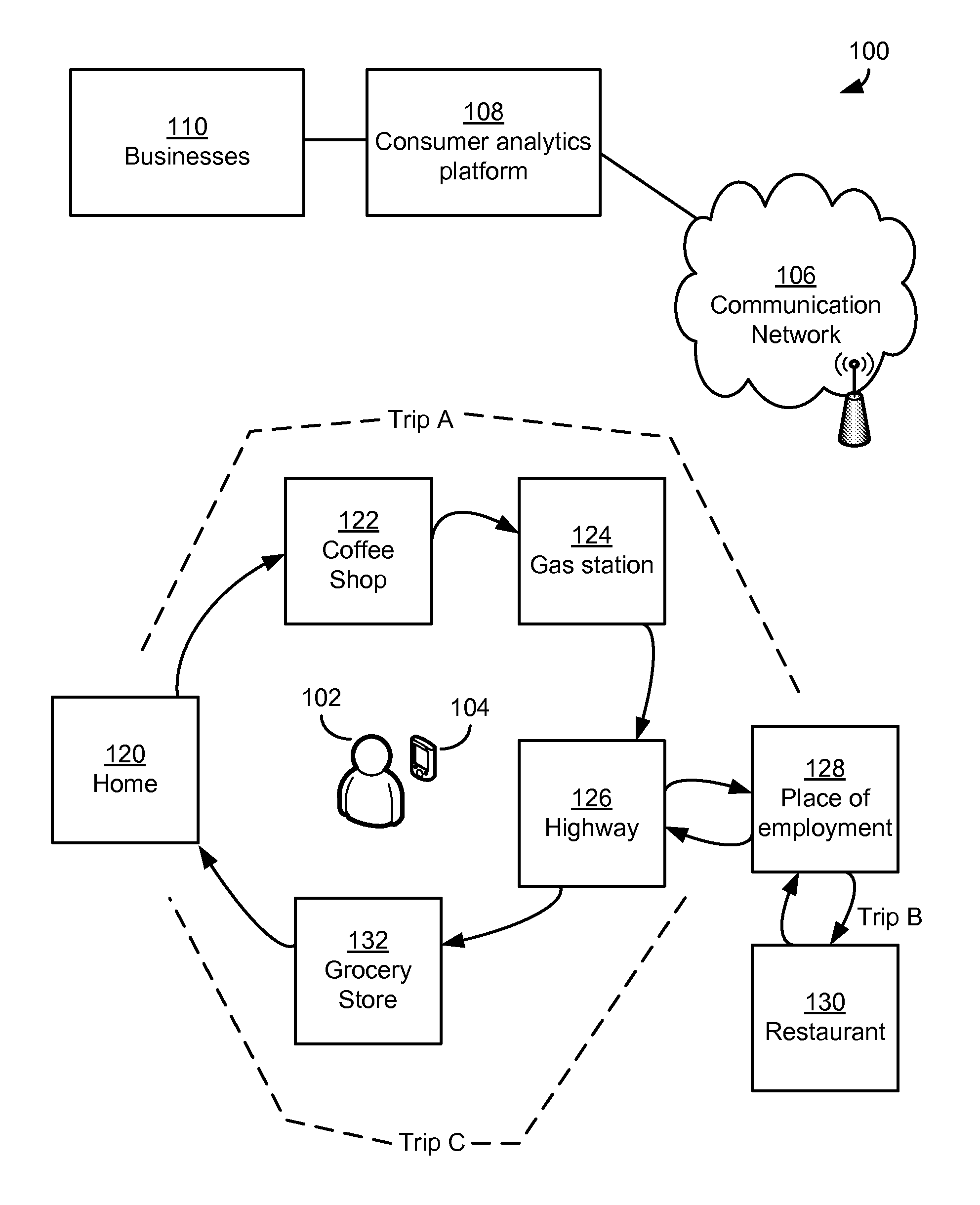
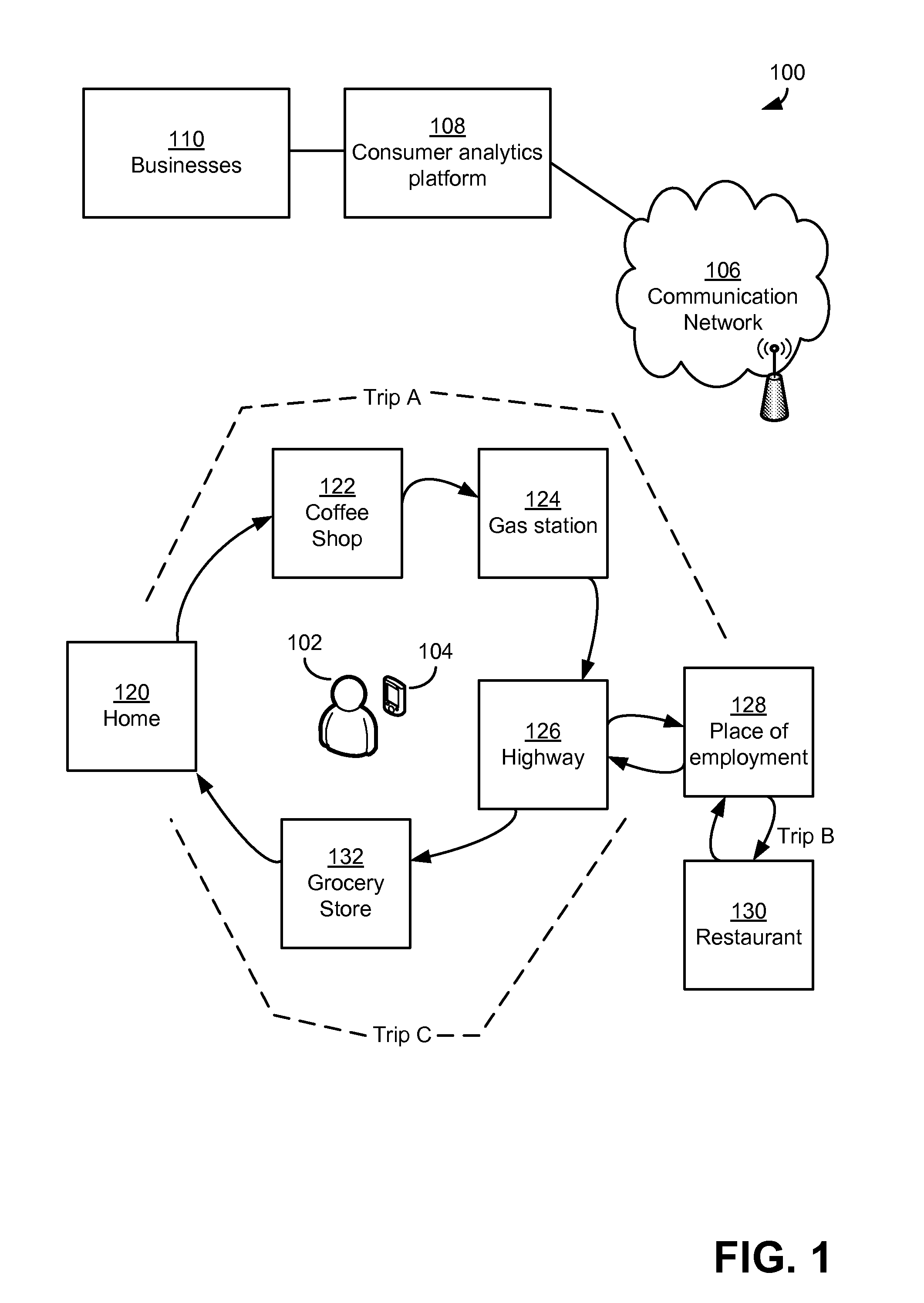
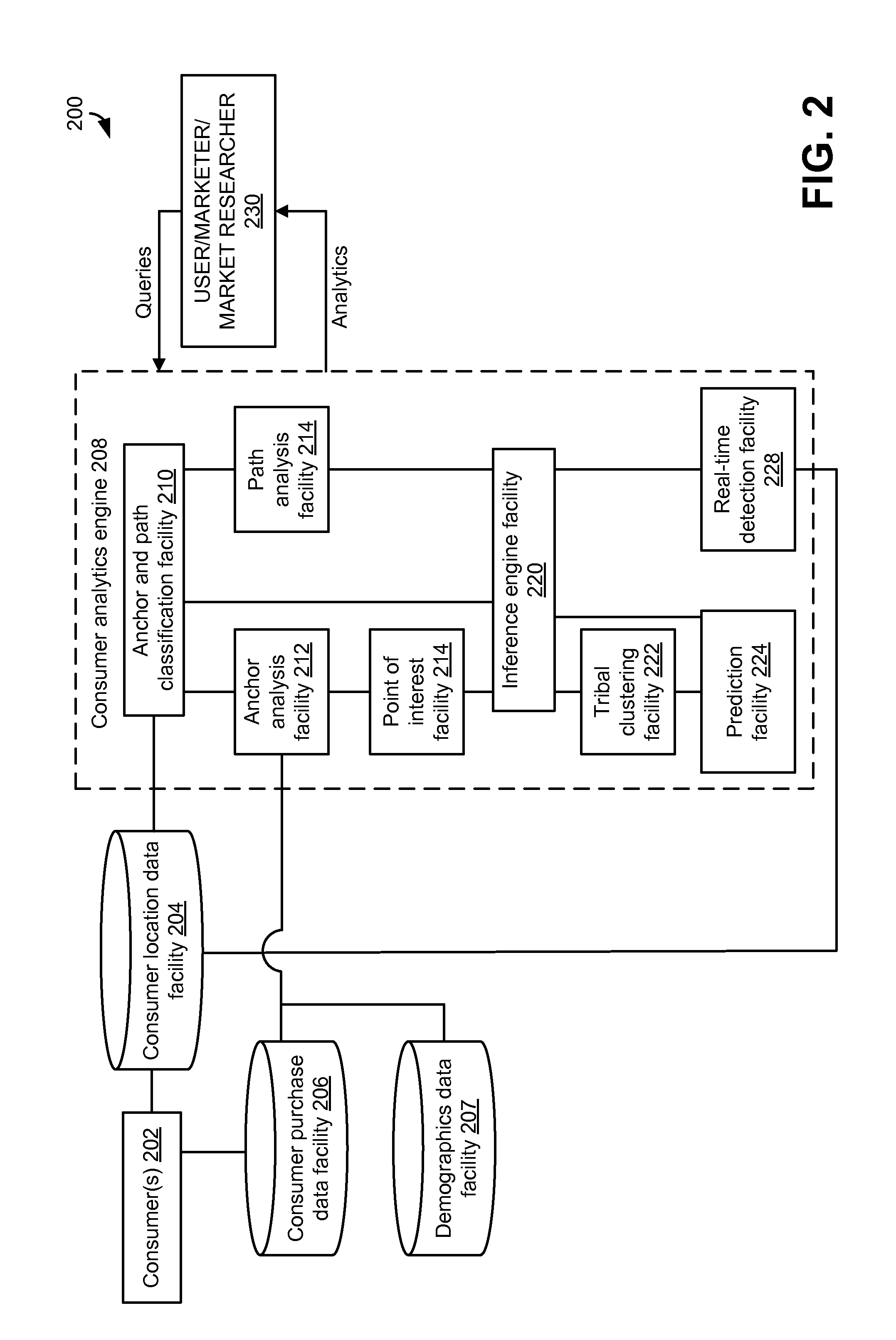
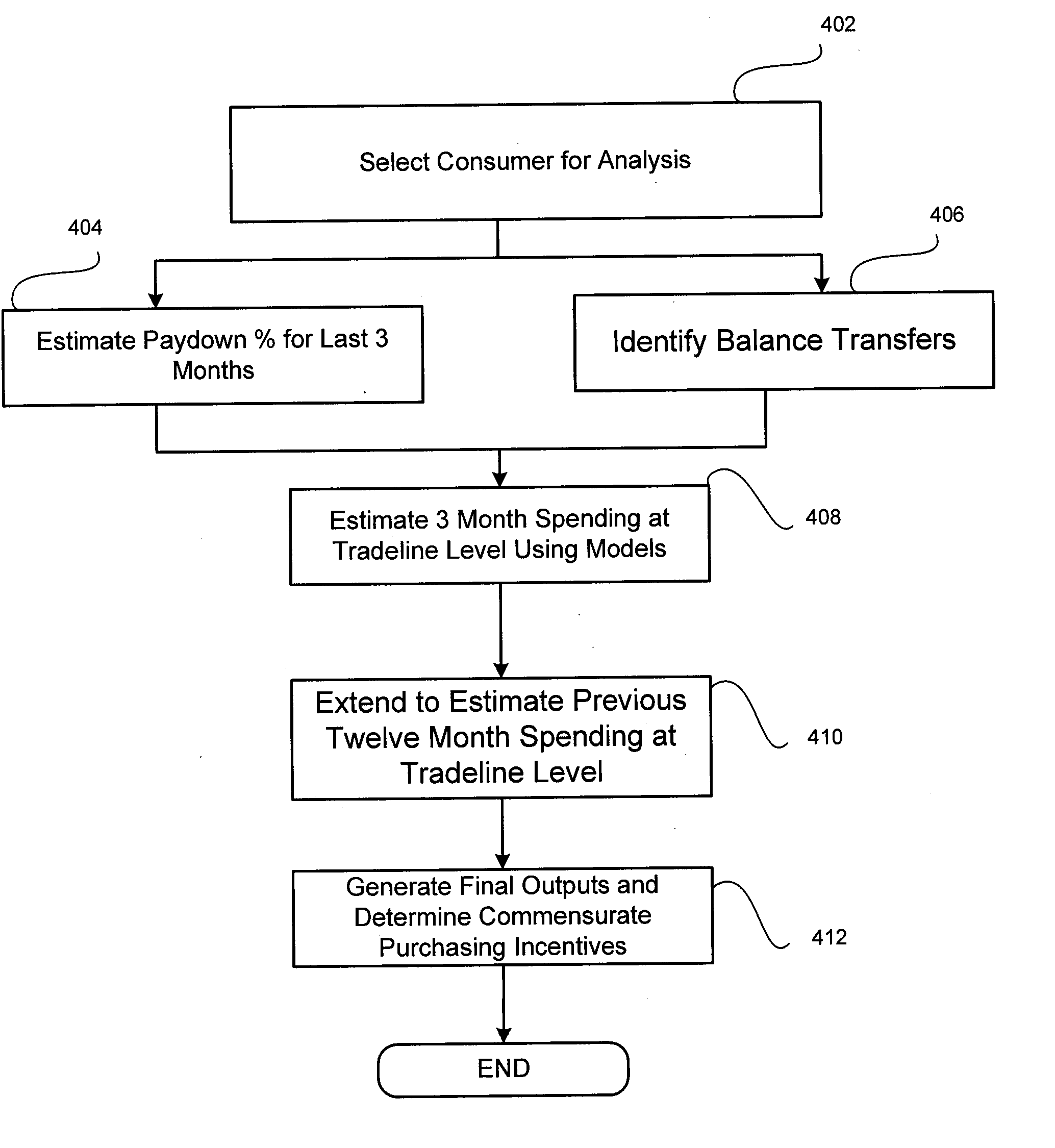
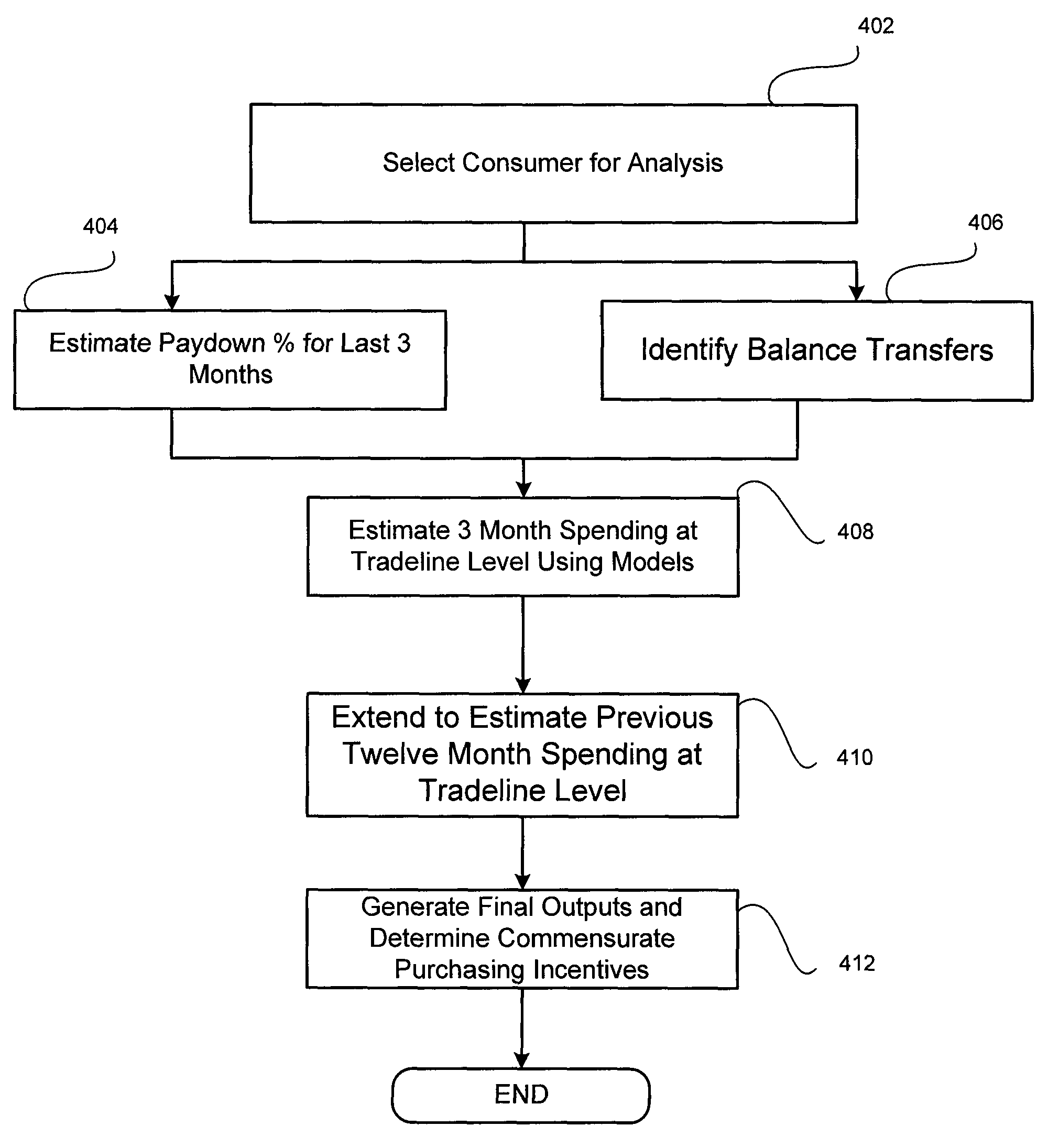
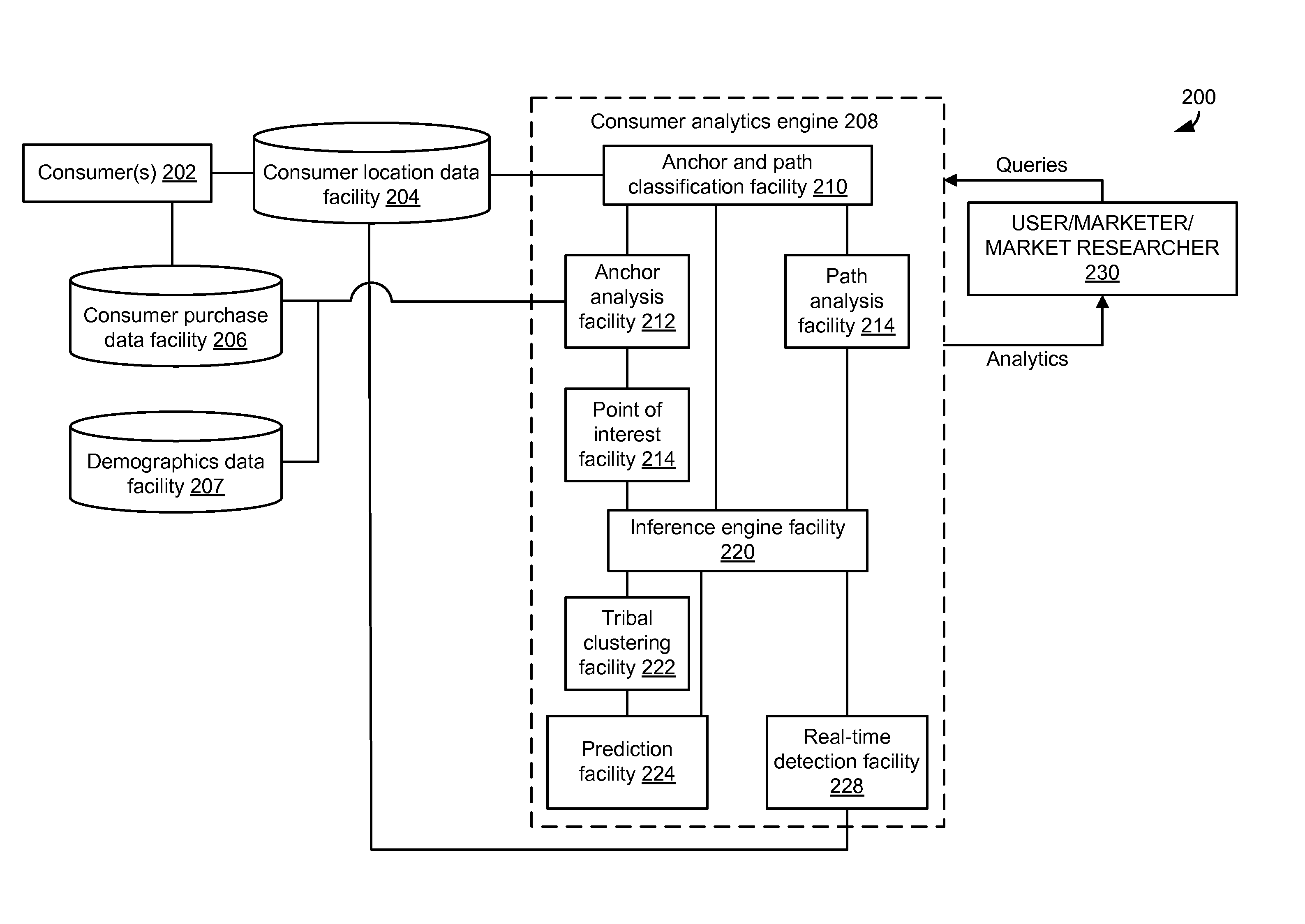
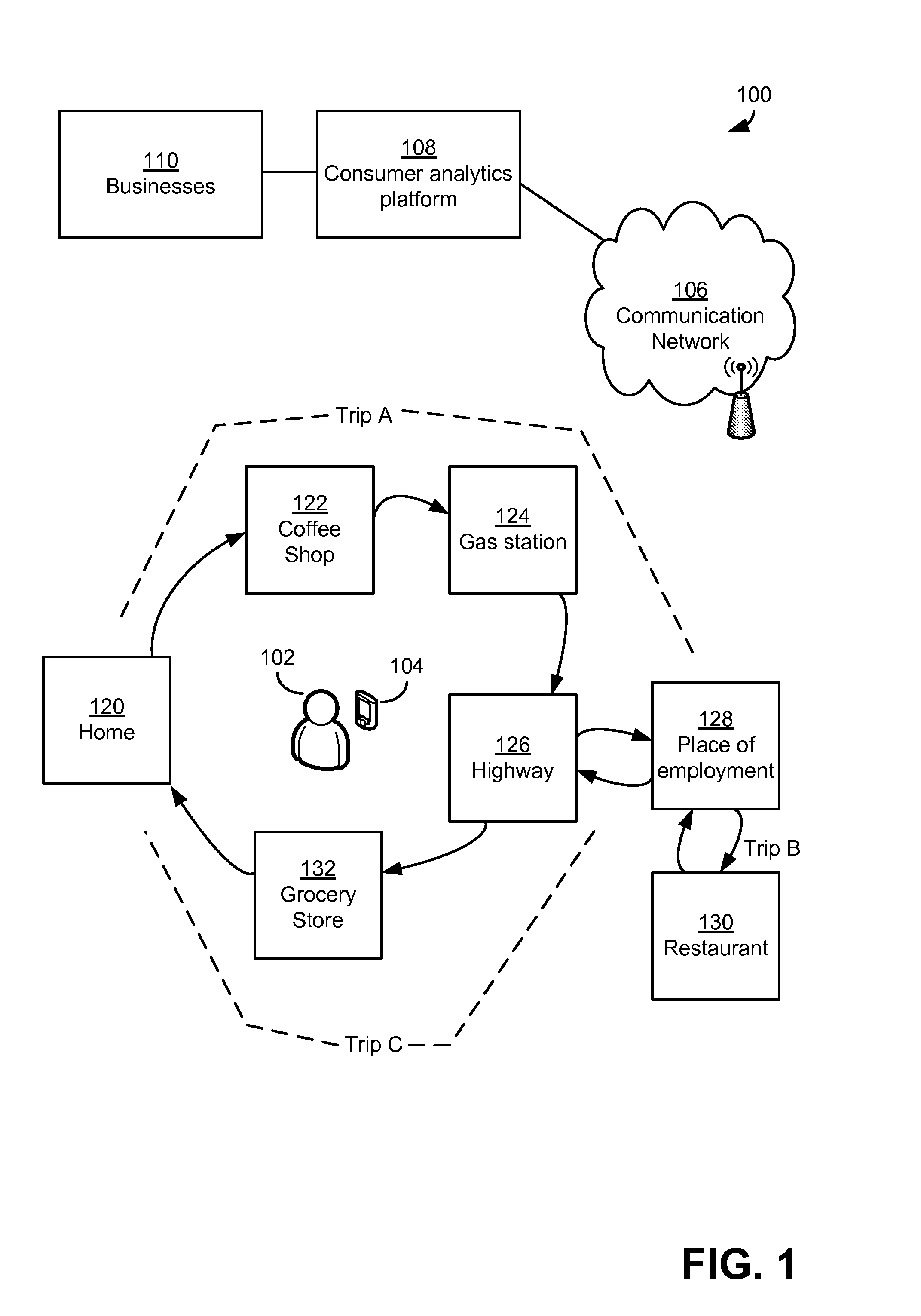
Electronically capturing consumer location data for analyzing consumer behavior
In embodiments, methods and systems for electronically capturing consumer location data for consumer behavior analysis may be provided. The location data may be gathered for one or more consumers from any suitable source. In some cases, the location data may be gathered using electronic devices associated with consumers, such as mobile phones. The gathered data may be analyzed to determine behavior patterns or other characteristics of the one or more consumers. Further, inferences or predictions about consumers may be derived based on the characteristics. The inferences and predictions may be the basis of consumer analytics supplied to a business or other entity.
Owner:SERVICE MANAGEMENT GRP LLC
Total structural risk model
InactiveUS20090222380A1Improve business satisfactionFinanceFinancial data processingBehavioral analytics
The present invention generally relates to financial data processing, and in particular it relates to credit scoring, consumer profiling, consumer behavior analysis and modeling. More specifically, it relates to risk modeling using the inputs of credit bureau data, size of wallet data, and, optionally, internal data.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
Systems and methods for behavioral sandboxing
ActiveUS8479286B2Memory loss protectionDigital data processing detailsBehavioral analyticsOperating system
Methods and system for behavioral sandboxing are described. In one example embodiment, a system for behavioral sandboxing can include a network and a computer. The network communicatively coupled to a source of an executable application. The computer communicatively couple to the network and including a behavioral analysis module and a plurality of execution environments. The behavioral analysis module is configured to perform behavioral analysis on the executable application downloaded over the network. The plurality of execution environments including a standard execution environment and a protected execution environment. The behavioral analysis module is configured to evaluate a plurality of behavioral characteristics of the executable application to determine whether the executable application should be executed within the protected execution environment prior to execution of the executable application. The behavioral analysis module also monitors execution of the executable application to determine whether the execution environment can be changed.
Owner:MCAFEE LLC
Method and system for segmenting people in a physical space based on automatic behavior analysis
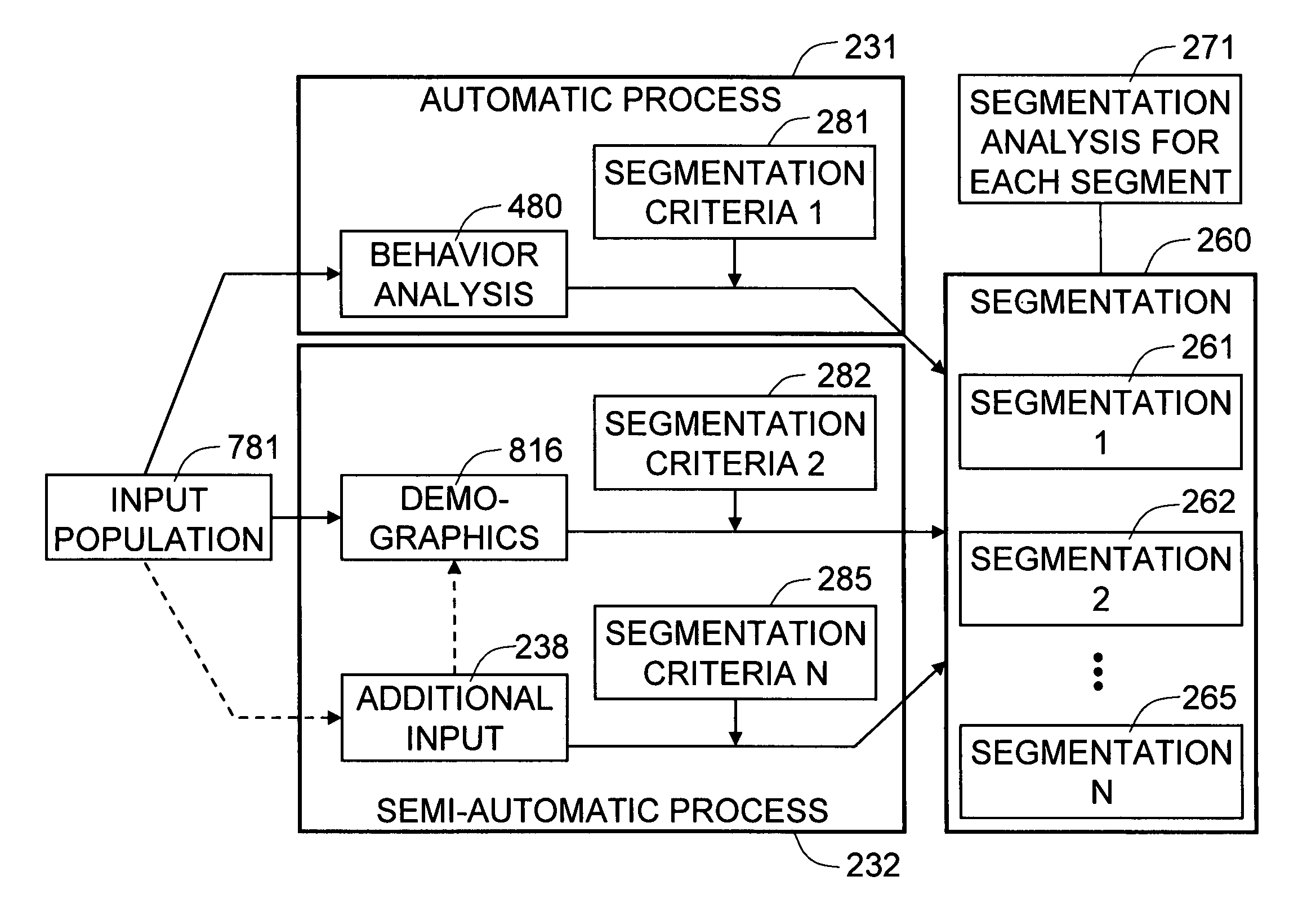
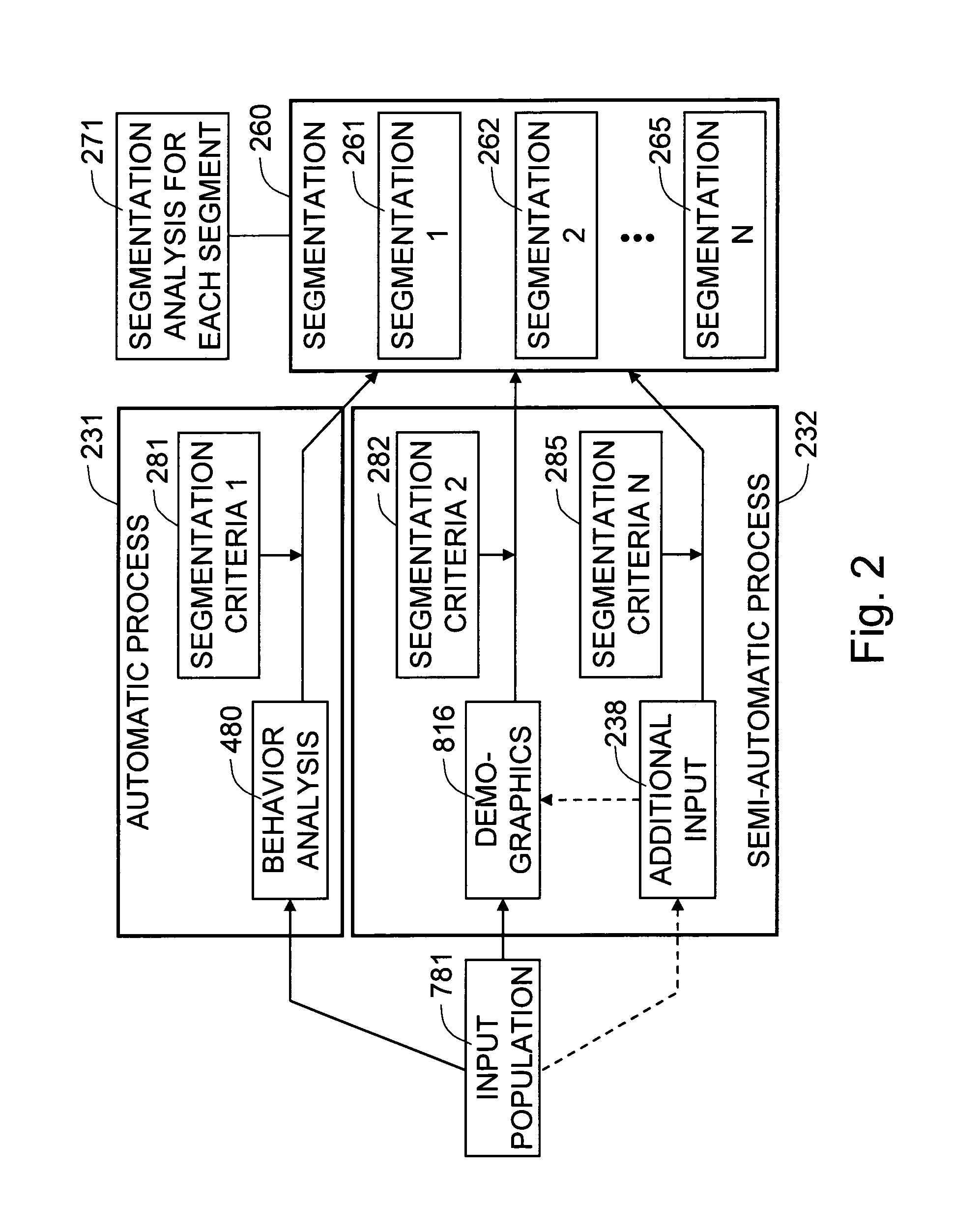
The present invention is a method and system for segmenting a plurality of persons in a physical space based on automatic behavior analysis of the persons in a preferred embodiment. The behavior analysis can comprise a path analysis as one of the characterization methods. The present invention applies segmentation criteria to the output of the video-based behavior analysis and assigns segmentation label to each of the persons during a predefined window of time. In addition to the behavioral characteristics, the present invention can also utilize other types of visual characterization, such as demographic analysis, or additional input sources, such as sales data, to segment the plurality of persons in another exemplary embodiment. The present invention captures a plurality of input images of the persons in the physical space by a plurality of means for capturing images. The present invention processes the plurality of input images in order to understand the behavioral characteristics, such as shopping behavior, of the persons for the segmentation purpose. The processes are based on a novel usage of a plurality of computer vision technologies to analyze the visual characterization of the persons from the plurality of input images. The physical space may be a retail space, and the persons may be customers in the retail space.
Owner:VIDEOMINING CORP
Total structural risk model
ActiveUS20090222377A1Improve business satisfactionFinanceDigital data processing detailsFinancial data processingBehavioral analytics
The present invention generally relates to financial data processing, and in particular it relates to credit scoring, consumer profiling, consumer behavior analysis and modeling. More specifically, it relates to risk modeling using the inputs of credit bureau data, size of wallet data, and, optionally, internal data.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
Consistency modeling of healthcare claims to detect fraud and abuse
InactiveUS7813937B1Accurate pictureEasy to detectMedical data miningFinanceData dredgingPredictive modelling
Transaction-based behavioral profiling, whereby the entity to be profiled is represented by a stream of transactions, is required in a variety of data mining and predictive modeling applications. An approach is described for assessing inconsistency in the activity of an entity, as a way of detecting fraud and abuse, using service-code information available on each transaction. Inconsistency is based on the concept that certain service-codes naturally co-occur more than do others. An assessment is made of activity consistency looking at the overall activity of an individual entity, as well as looking at the interaction of entities. Several approaches for measuring consistency are provided, including one inspired by latent semantic analysis as used in text analysis. While the description is in the context of fraud detection in healthcare, the techniques are relevant to application in other industries and for purposes other than fraud detection.
Owner:FAIR ISAAC & CO INC
Total structural risk model
ActiveUS20090222374A1Improve business satisfactionFinanceFinancial data processingBehavioral analytics
The present invention generally relates to financial data processing, and in particular it relates to credit scoring, consumer profiling, consumer behavior analysis and modeling. More specifically, it relates to risk modeling using the inputs of credit bureau data, size of wallet data, and, optionally, internal data.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
Total structural risk model
InactiveUS20090222378A1Improve business satisfactionFinanceFinancial data processingBehavioral analytics
The present invention generally relates to financial data processing, and in particular it relates to credit scoring, consumer profiling, consumer behavior analysis and modeling. More specifically, it relates to risk modeling using the inputs of credit bureau data, size of wallet data, and, optionally, internal data.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
Total structural risk model
The present invention generally relates to financial data processing, and in particular it relates to credit scoring, consumer profiling, consumer behavior analysis and modeling. More specifically, it relates to risk modeling using the inputs of credit bureau data, size of wallet data, and, optionally, internal data.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
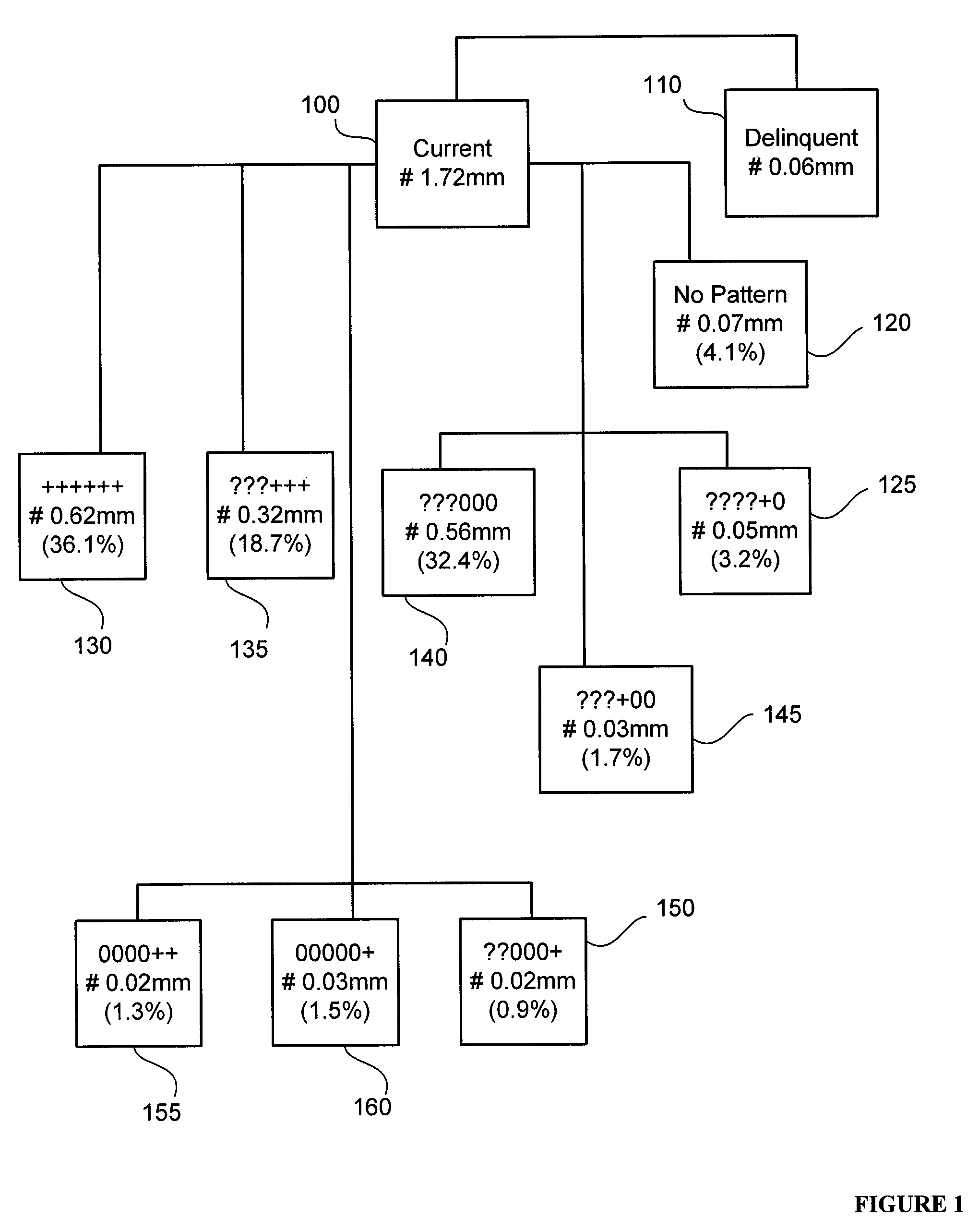
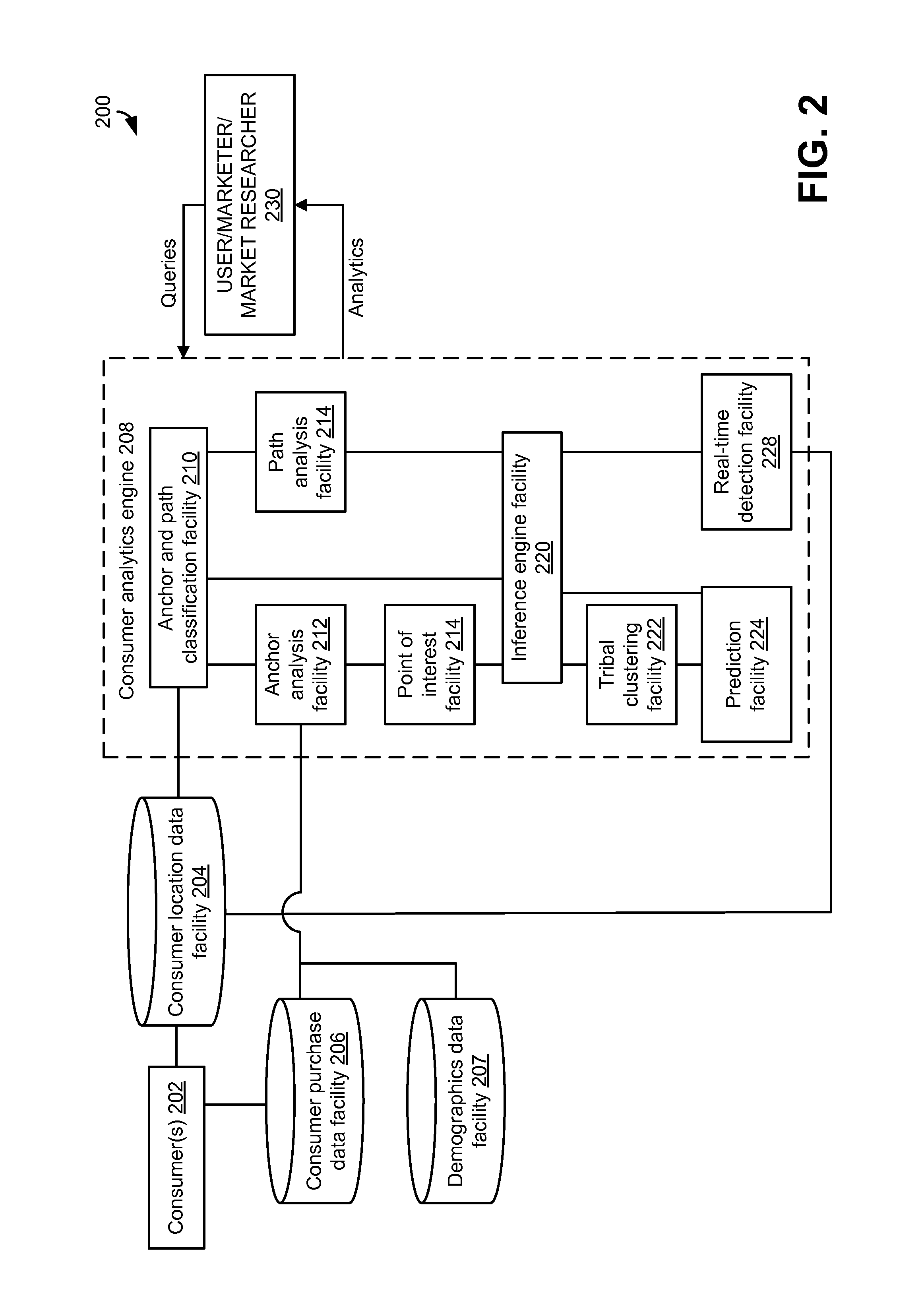
Analyzing consumer behavior using electronically-captured consumer location data
ActiveUS20110099046A1Location information based serviceMarketingBehavioral analyticsBehaviour pattern
In embodiments, methods and systems for consumer behavior analysis using electronically-captured consumer location data may be provided. The location data may be gathered for one or more consumers. The gathered data may be analyzed to determine behavior patterns or other characteristics of the one or more consumers. Further, inferences or predictions about consumers may be derived based on the characteristics. The inferences and predictions may be the basis of consumer analytics supplied to a business or other entity.
Owner:SERVICE MANAGEMENT GRP LLC
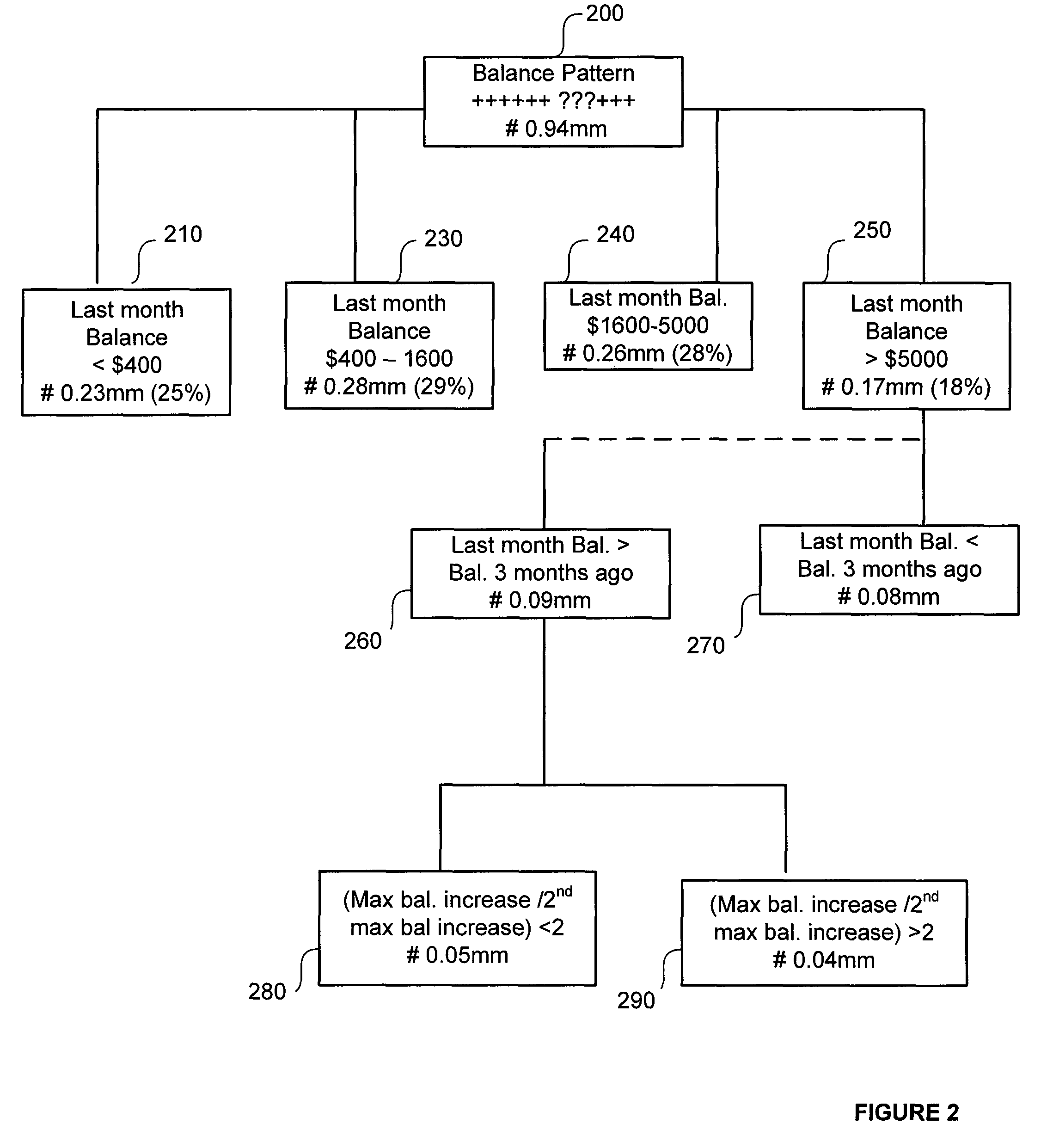
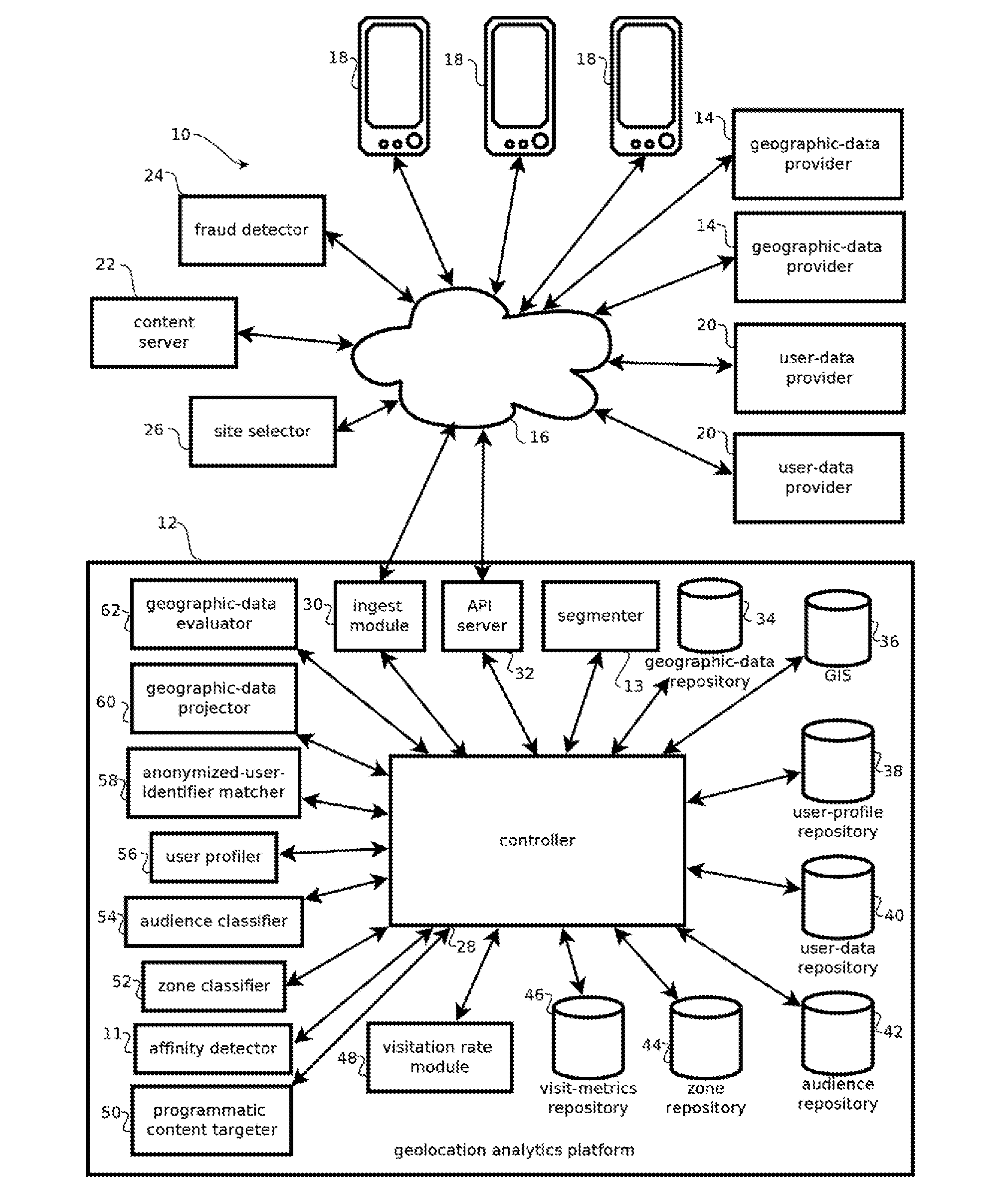
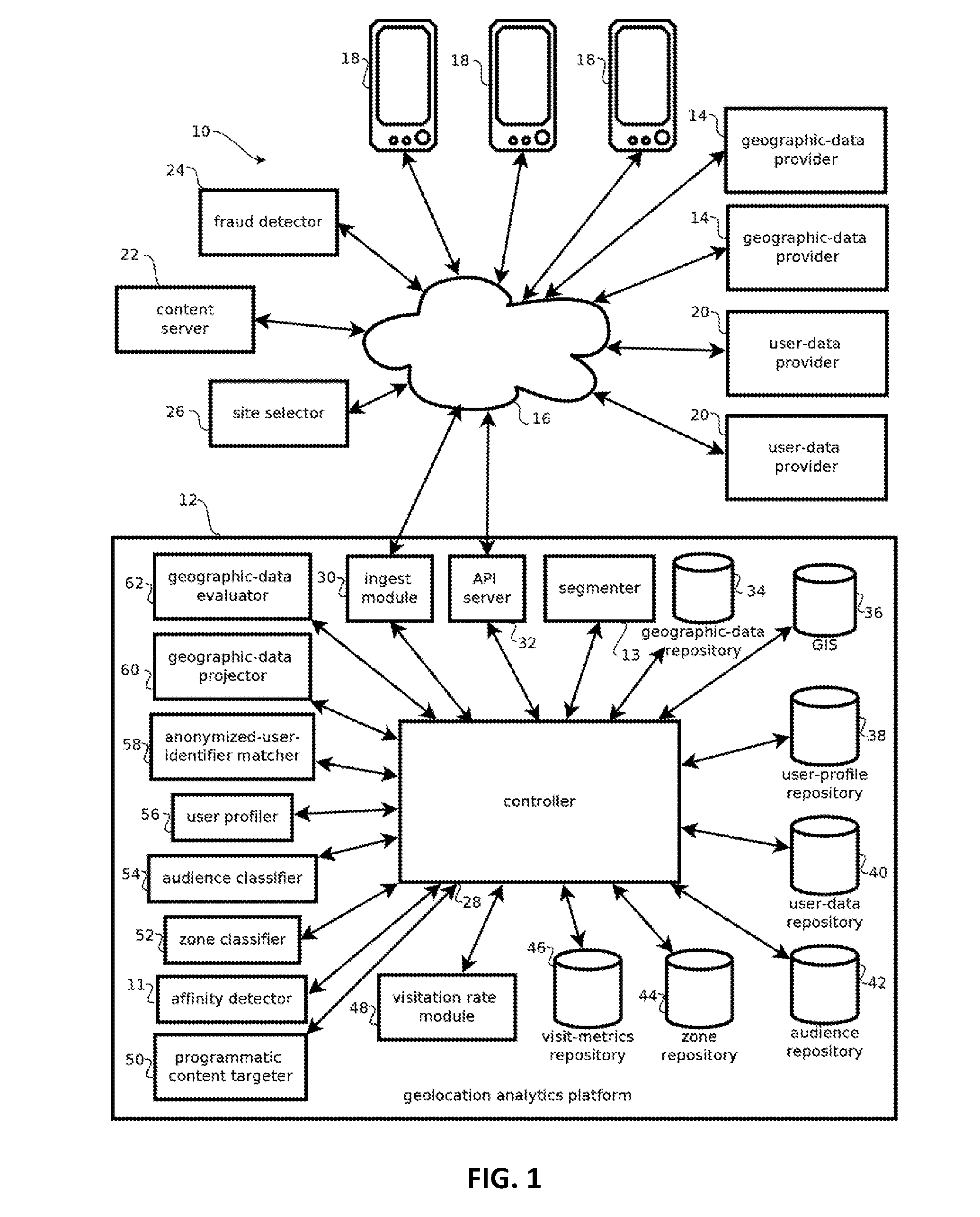
Analyzing consumer behavior based on location visitation
ActiveUS20160247175A1Geographical information databasesLocation information based serviceBehavioral analyticsGeolocation
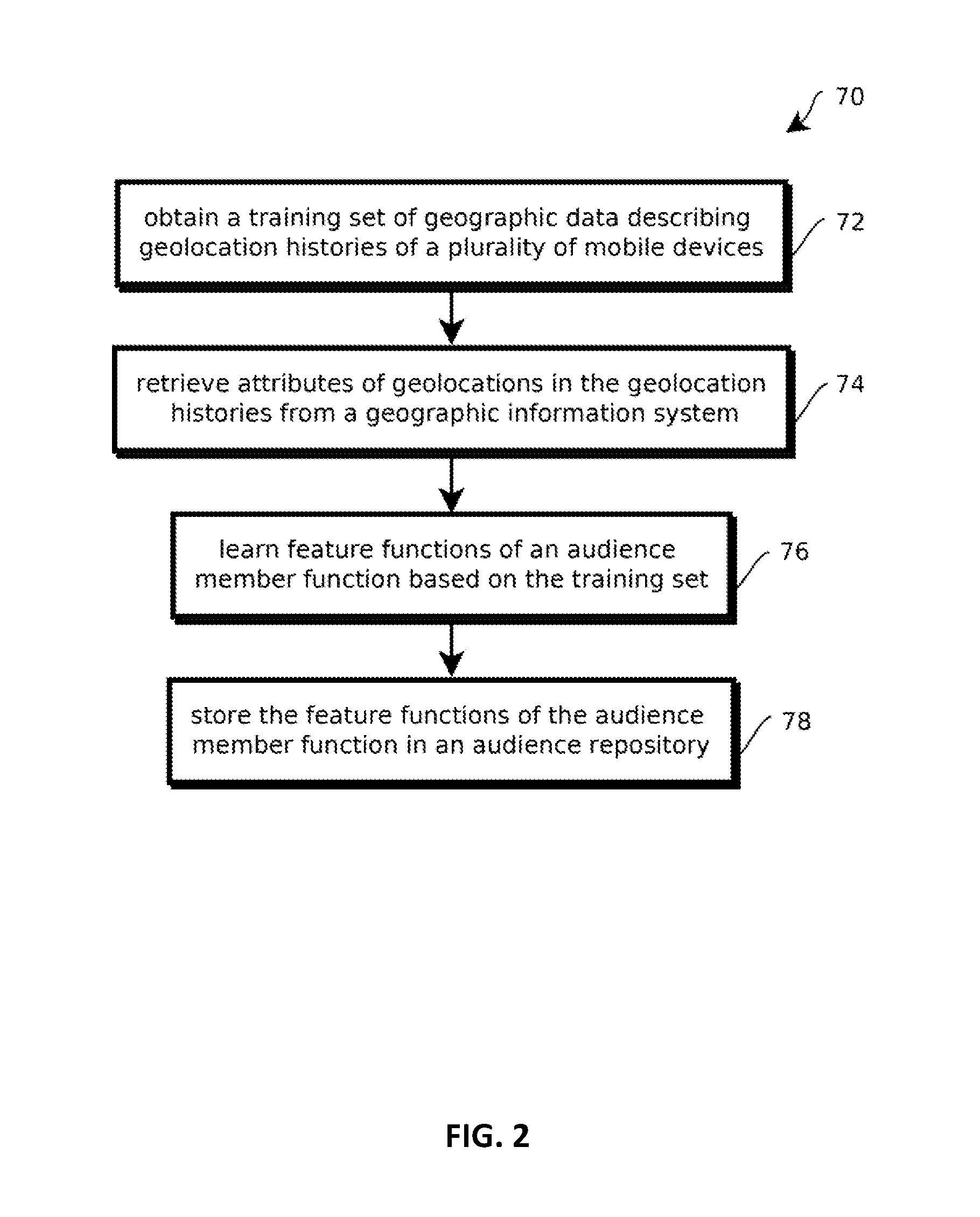
Provided is a process, including: obtaining geolocations histories of computing devices; assigning different subsets of the location histories to different computing devices in a compute cluster; querying a geographic information system (GIS) with geolocations in the geolocations histories to obtain identifiers of chain retail establishments; determining visit graphs for the individuals; and determining, for a given retail chain and a given individual, a score indicative of an affinity of the given individual to the given retail chain based on the visit graphs for more than 100 individuals including the given individual.
Owner:PLACEIQ
Total structural risk model
InactiveUS20090222373A1Improve business satisfactionFinanceFinancial data processingBehavioral analytics
The present invention generally relates to financial data processing, and in particular it relates to credit scoring, consumer profiling, consumer behavior analysis and modeling. More specifically, it relates to risk modeling using the inputs of credit bureau data, size of wallet data, and, optionally, internal data.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
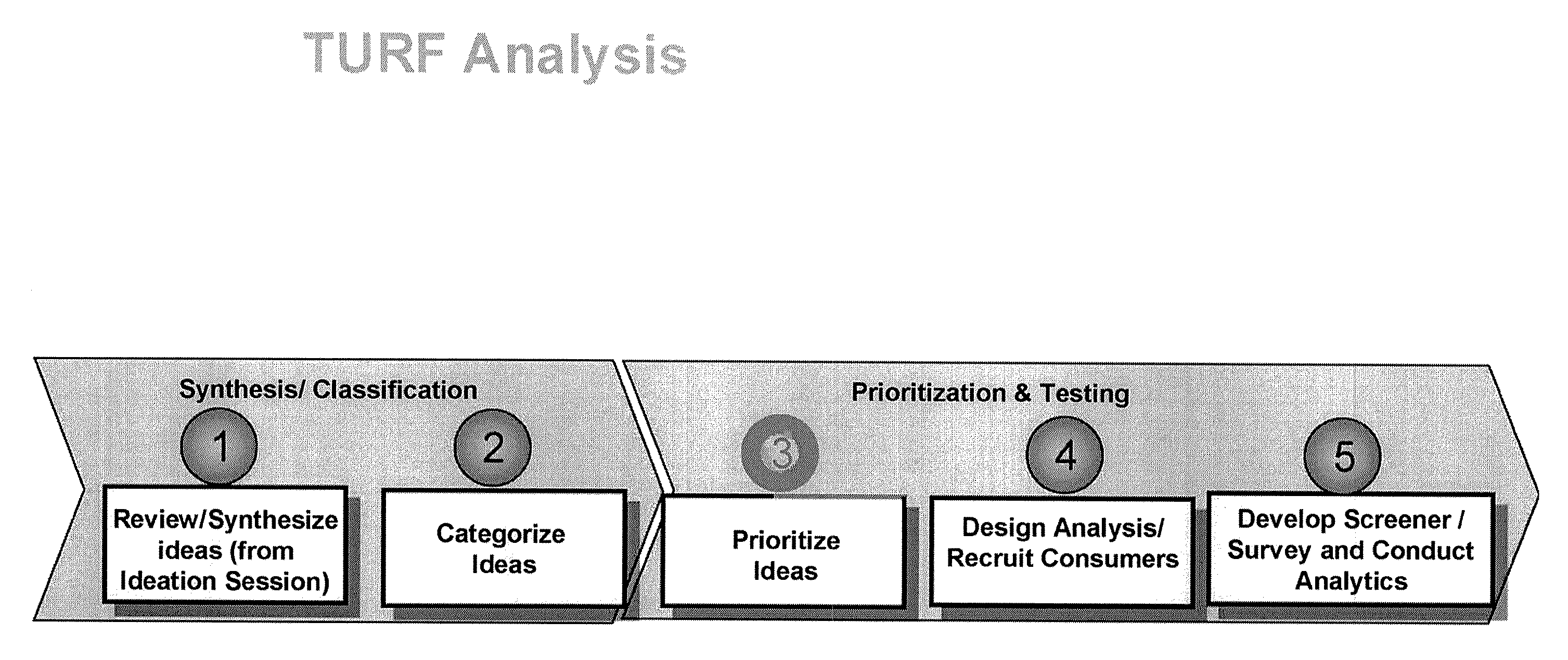
Systems And Methods For Segment-Based Payment Card Solutions
A payment card product targeted to specific consumer market segments is provided. The payment card product has features, benefits and functions that are responsive to consumer needs, aspirations and habits, which evolve over time and across consumer market segments. The consumer market segments are comprehensively characterized using a combination of demographic, attitudinal and behavioral analyses and research. Consumer ideation processes used in product design ensure that the card features, benefits and functions are relevant to consumers. Quantitative methods are used to optimize the product design with respect to consumer market segment characteristics.
Owner:MASTERCARD INT INC
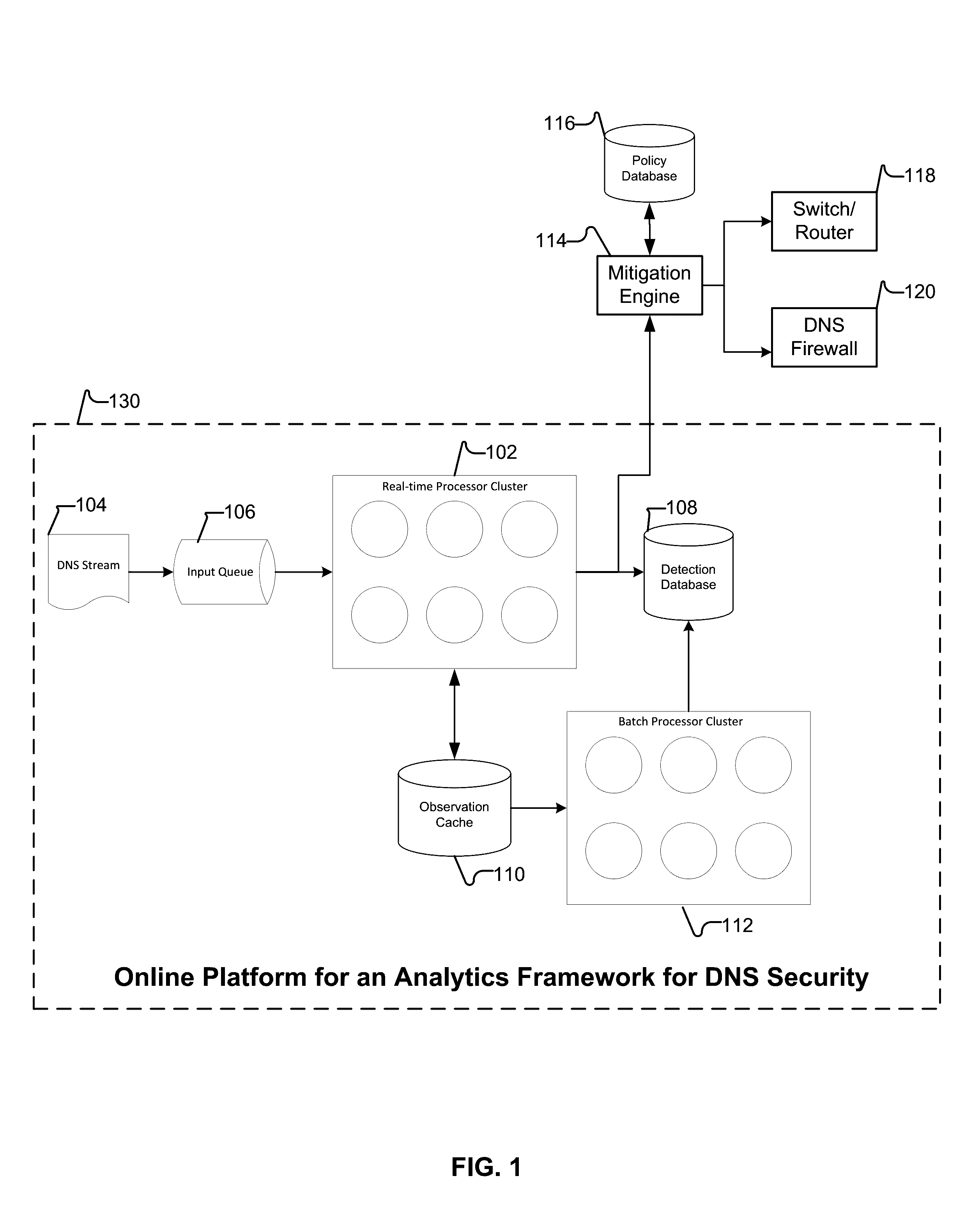
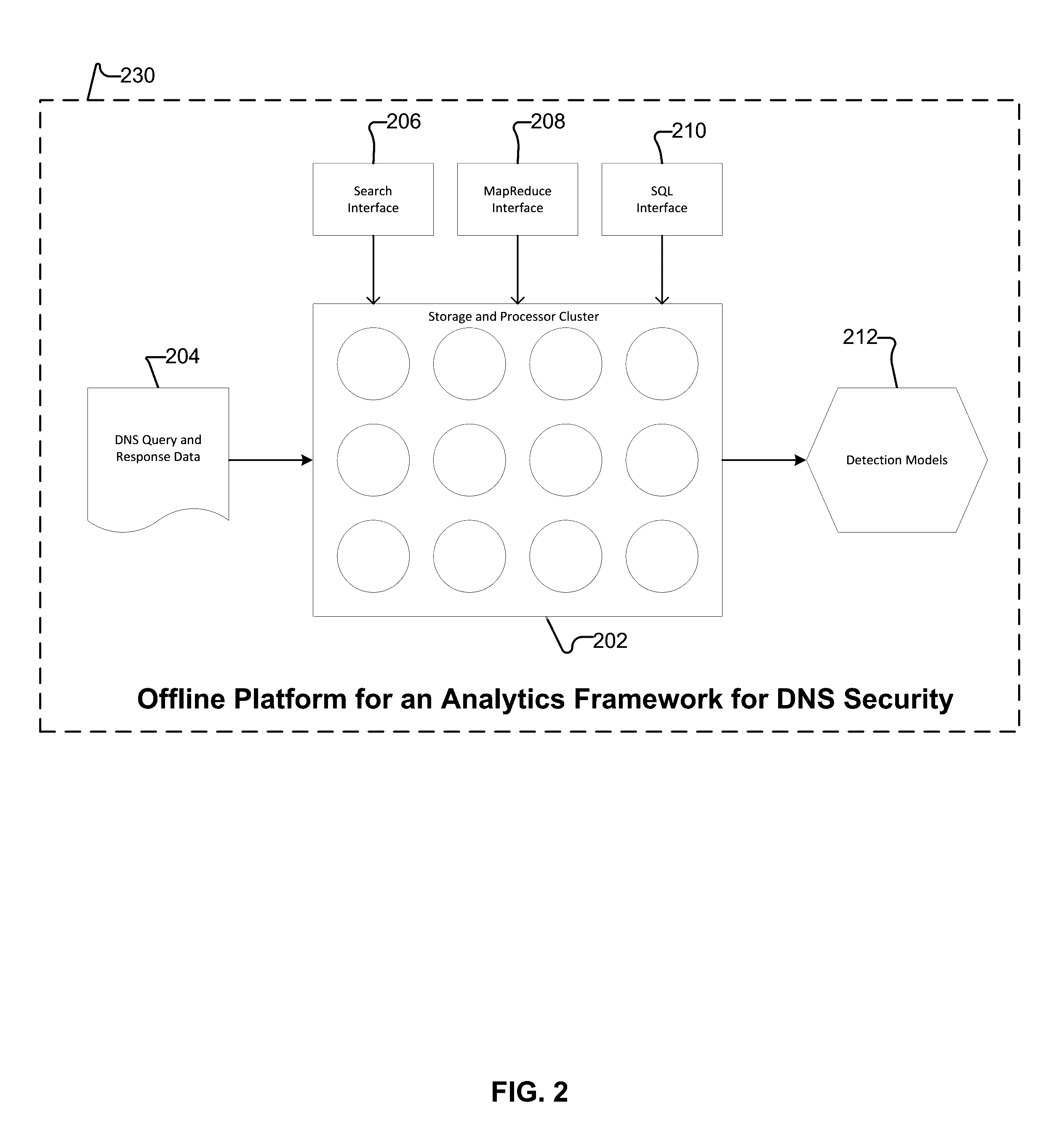
Behavior analysis based DNS tunneling detection and classification framework for network security
New and improved techniques for a behavior analysis based DNS tunneling detection and classification framework for network security are disclosed. In some embodiments, a platform implementing an analytics framework for DNS security is provided for facilitating DNS tunneling detection. For example, an online platform can implement an analytics framework for DNS security based on passive DNS traffic analysis.
Owner:INFOBLOX
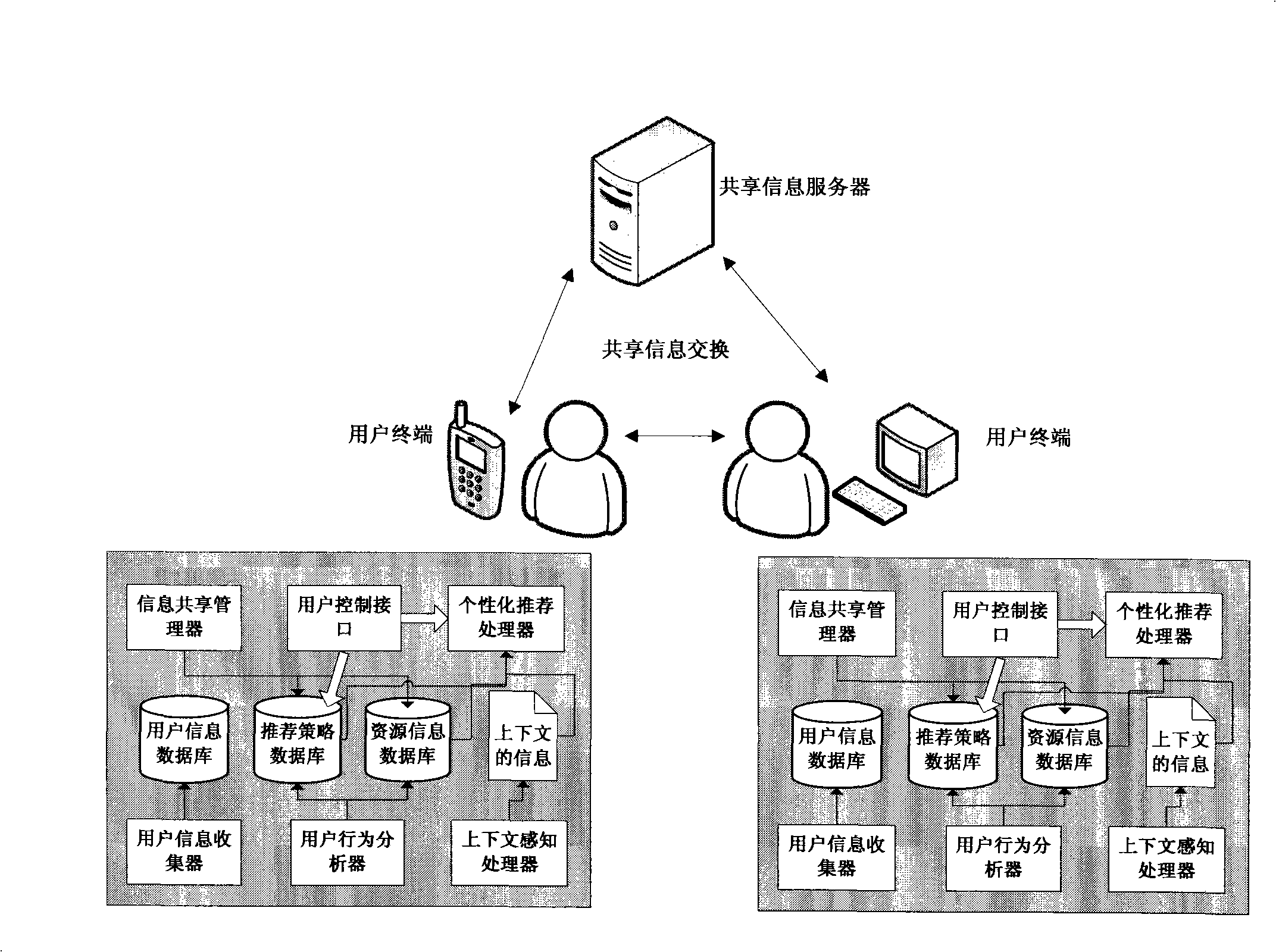
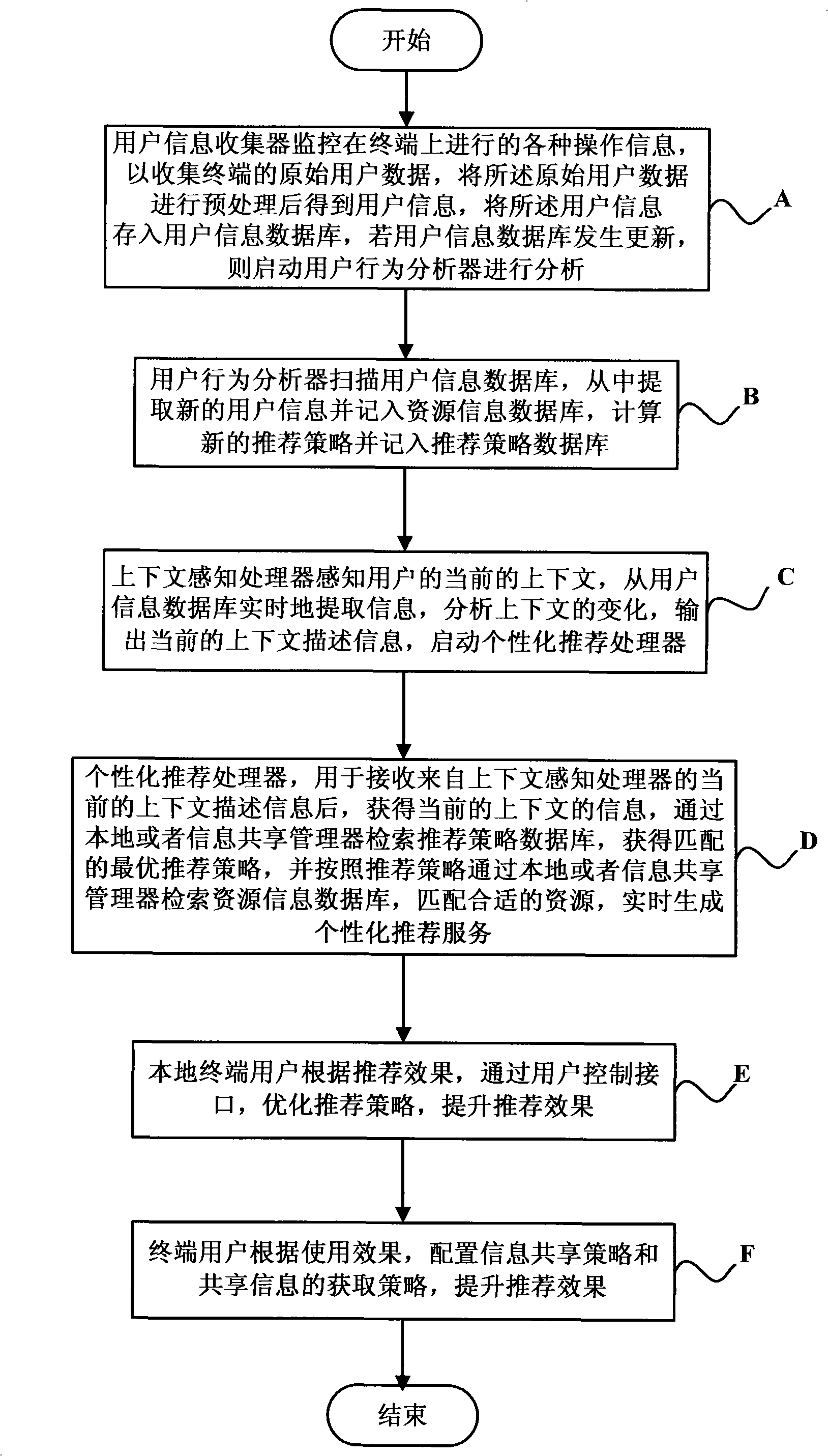
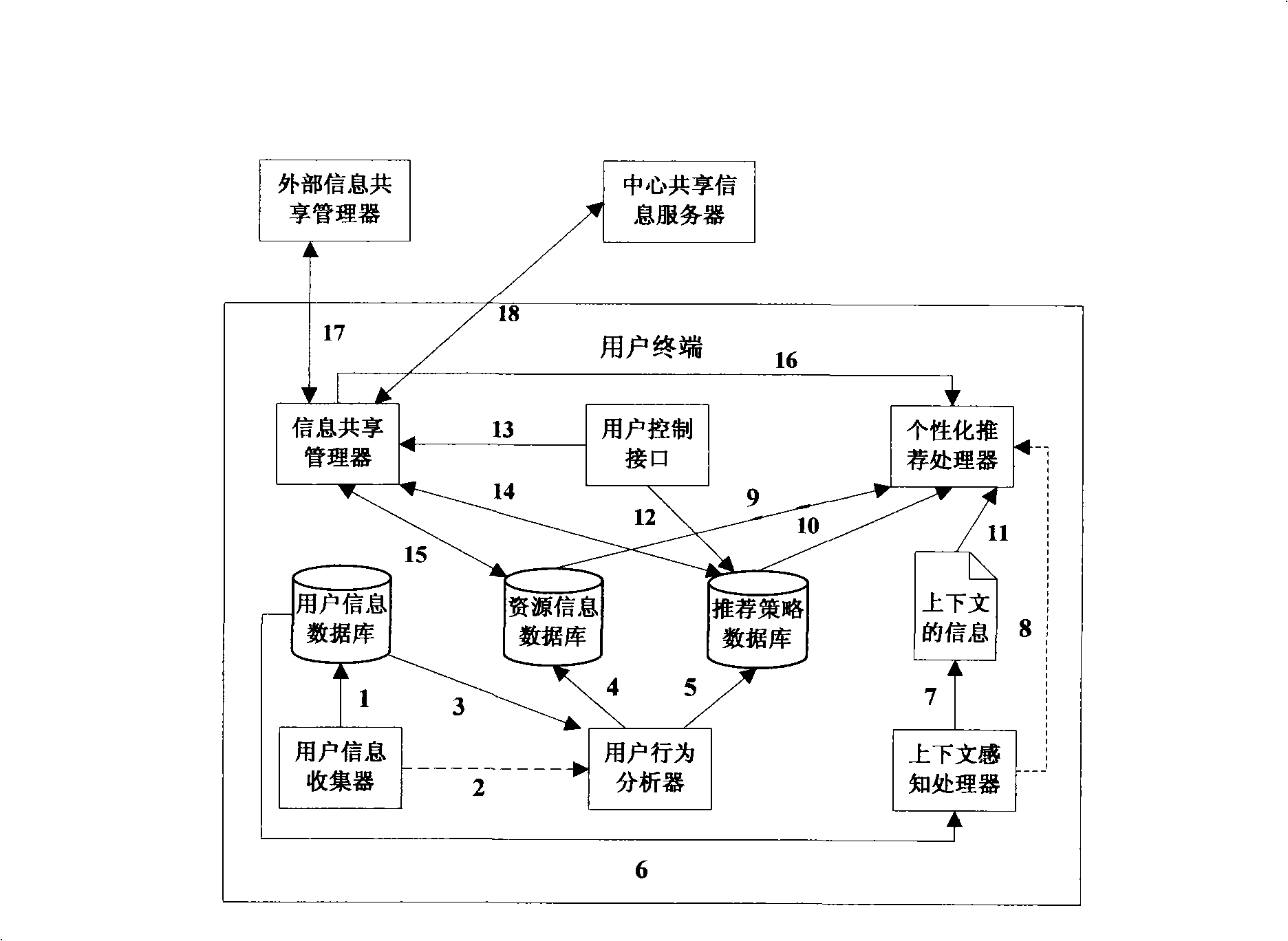
Personalized service recommendation system and method
ActiveCN101334792AUse without any restrictionsEffective protectionSpecial data processing applicationsBehavioral analyticsContext sensing
The invention discloses an individualized service recommendation system and a corresponding method including the following steps: various operation information existing on a terminal is monitored by a user information collector and after a pre-processing the operation information is stored in a user information database; and if the user information database is updated, a user behavior analyzer is started for analysis; the user behavior analyzer scans the user information database and extracts the new user information and stores the new information in a resource information database, and then new recommendation strategies are computed and stored in a recommendation strategy database; a context sensing processor senses the present context of the user and sends out the present context description information and an individualized recommendation processor is started; the individualized recommendation processor acquires the present context information after receiving the information from the context sensing processor and also acquires a matched optimal recommendation strategy by searching the recommendation strategy database and then matches the proper resource information according to the optimal recommendation strategy and by searching the resource information database so as to generate the individualized recommendation service in real time.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Total structural risk model
InactiveUS20090222376A1Improve business satisfactionFinanceFinancial data processingBehavioral analytics
The present invention generally relates to financial data processing, and in particular it relates to credit scoring, consumer profiling, consumer behavior analysis and modeling. More specifically, it relates to risk modeling using the inputs of credit bureau data, size of wallet data, and, optionally, internal data.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com