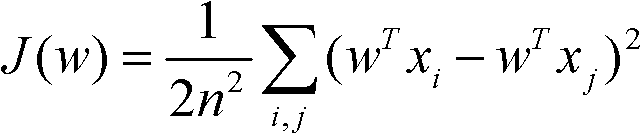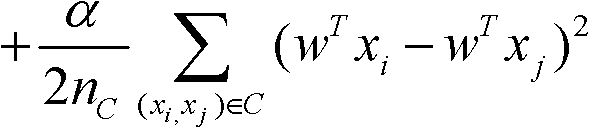Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
218 results about "Program behavior" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
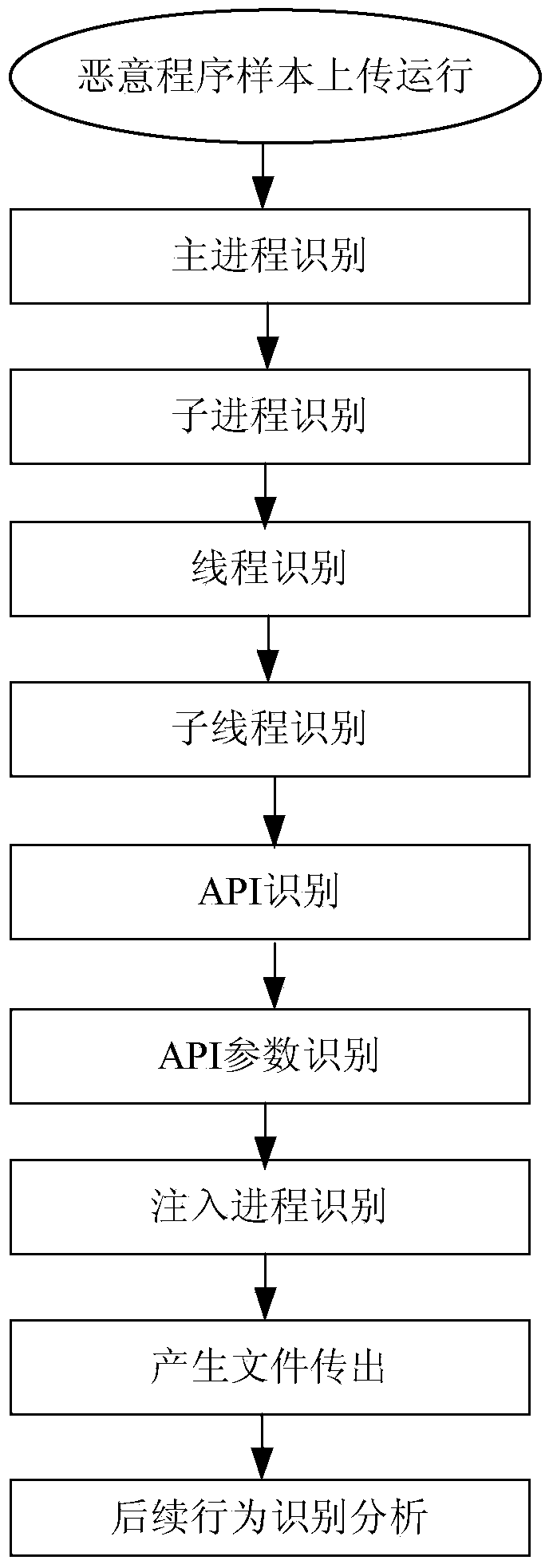
BEHAVIOR - what is the actual behavior that results CONSEQUENCE - what happens in response to the behavior. A behavior program can work on all three of these steps, such as minimizing the triggers for a behavior, shaping more appropriate behavior in the child,...
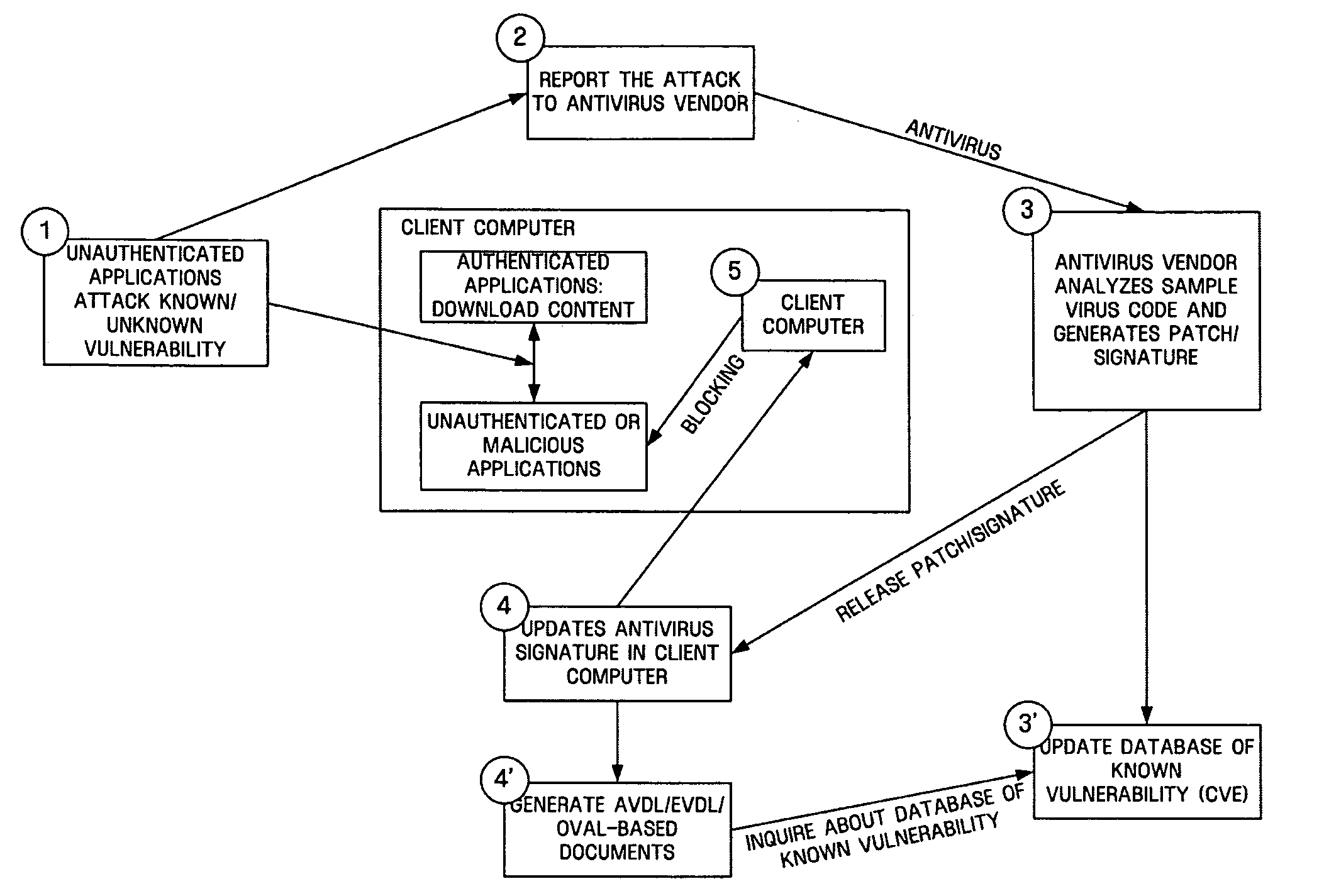
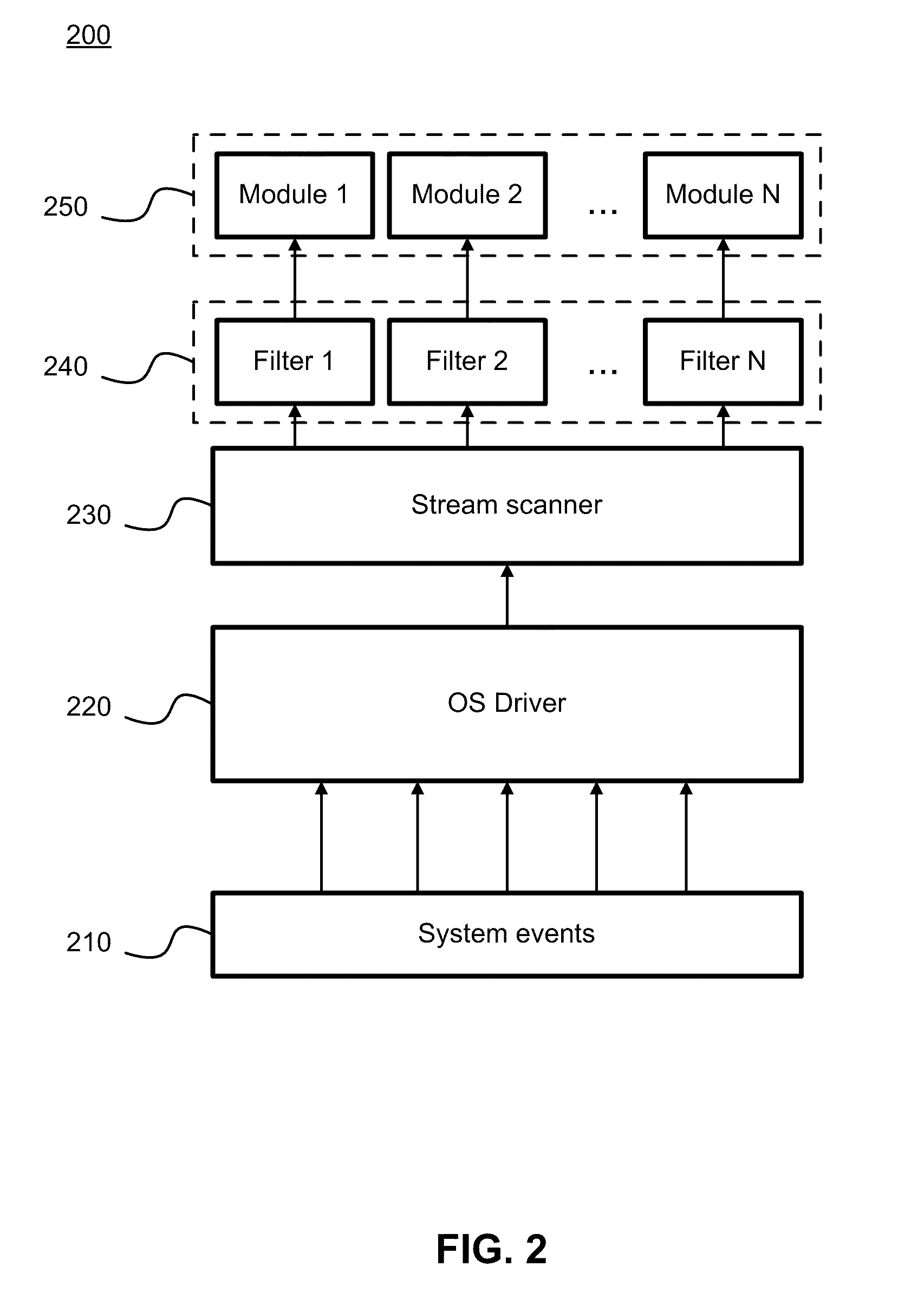
Computer immune system and method for detecting unwanted code in a computer system
InactiveUS7093239B1Memory loss protectionDigital data processing detailsTheoretical computer scienceComputerized system
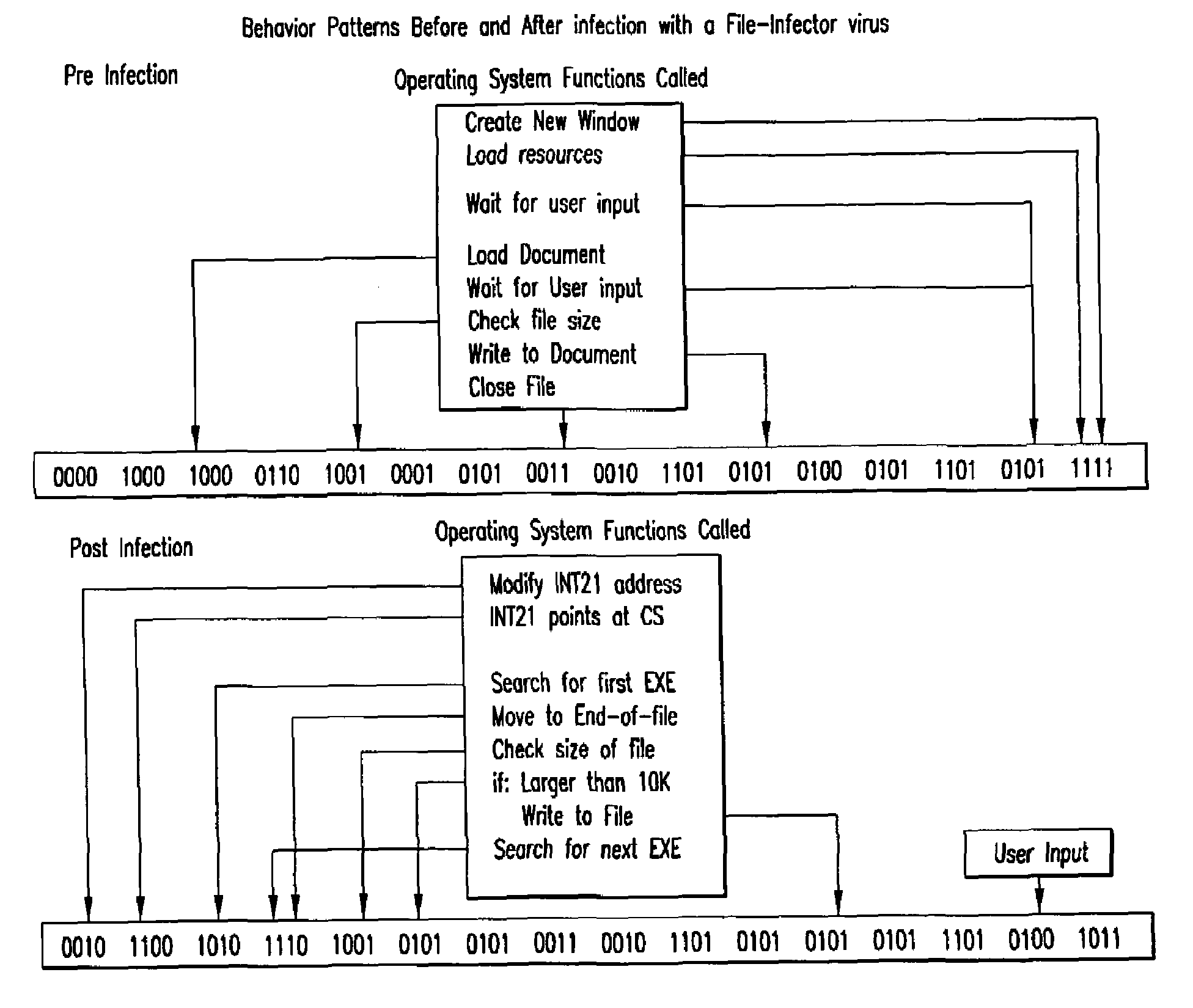
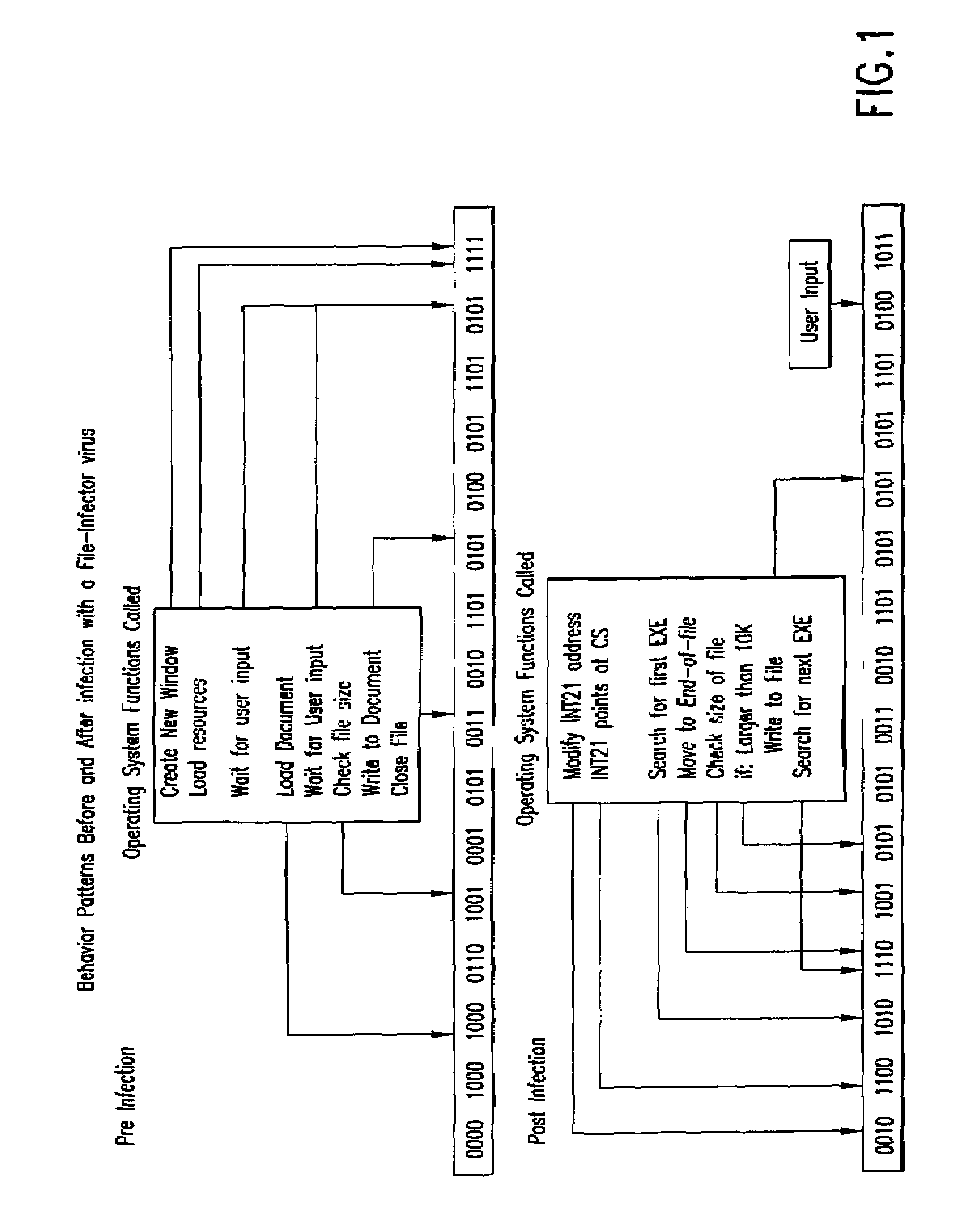
An automated analysis system detects malicious code within a computer system by generating and subsequently analyzing a behavior pattern for each computer program introduced to the computer system. Generation of the behavior pattern is accomplished by a virtual machine invoked within the computer system. An initial analysis may be performed on the behavior pattern to identify infected programs on initial presentation of the program to the computer system. The analysis system also stores behavior patterns and sequences with their corresponding analysis results in a database. Newly infected programs can be detected by analyzing a newly generated behavior pattern for the program with reference to a stored behavior pattern to identify presence of an infection or payload pattern.
Owner:PALO ALTO NETWORKS INC
Antivirus protection system and method for computers
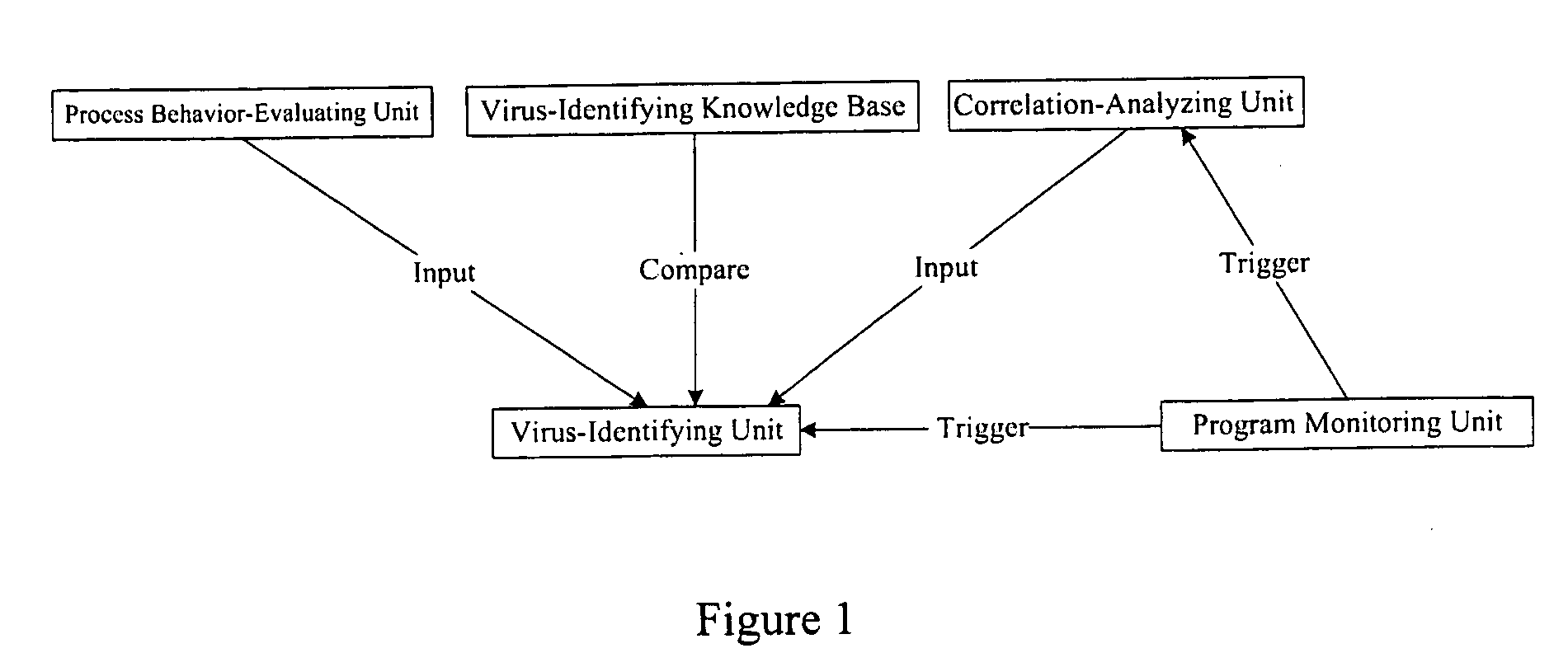
InactiveUS20080066179A1Reduce in quantitySimple methodMemory loss protectionUnauthorized memory use protectionProcess behaviorProgram behavior
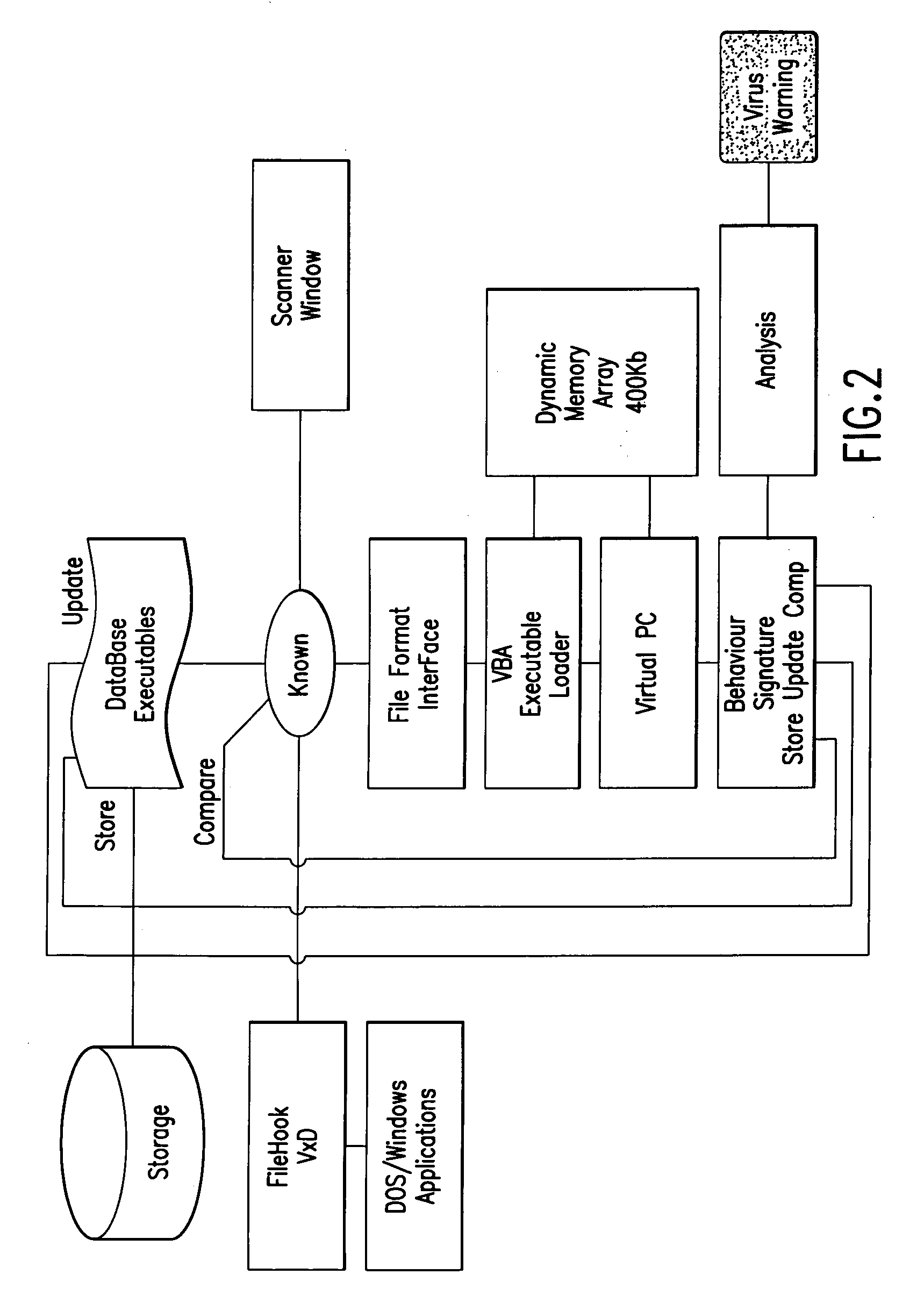
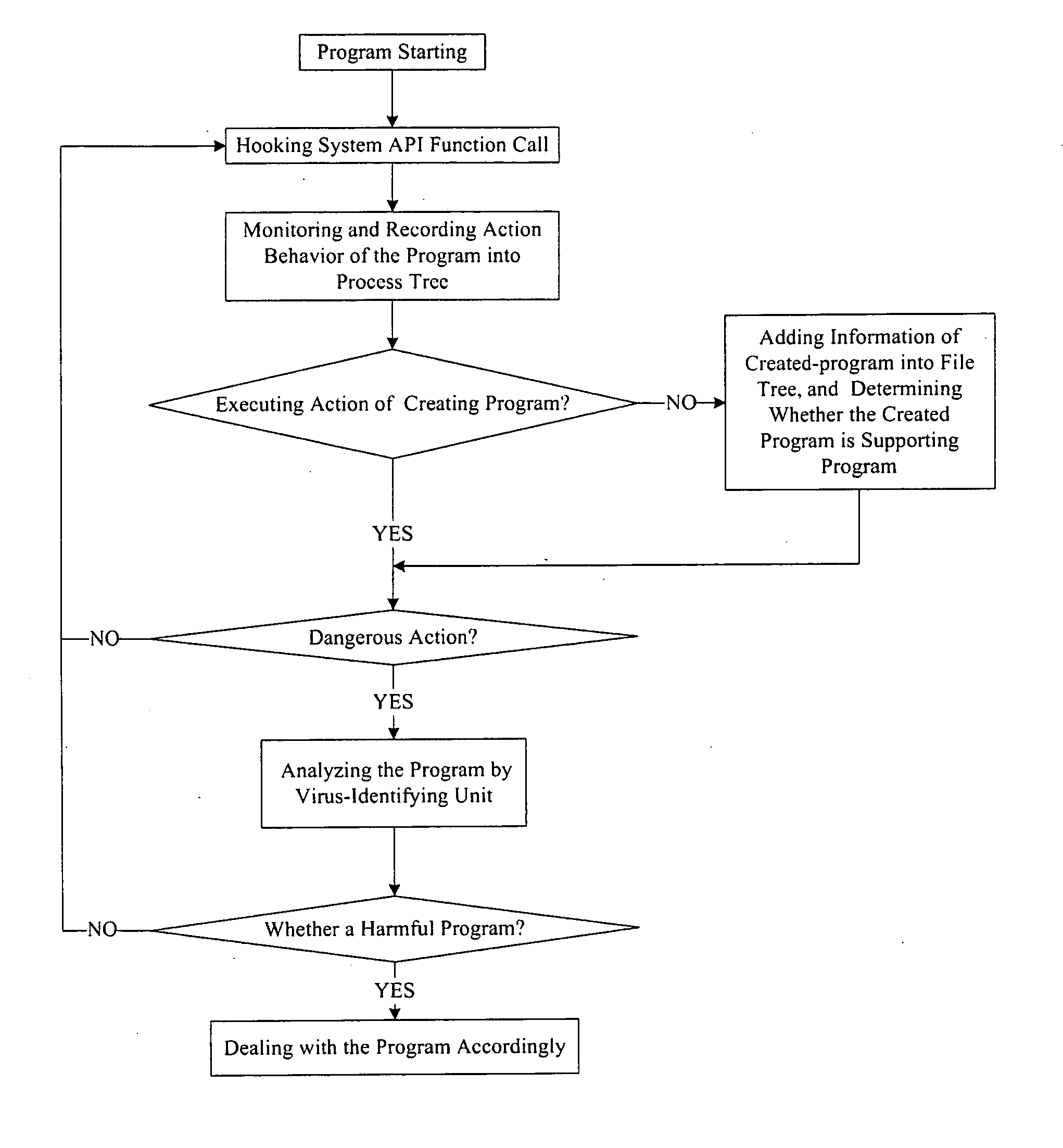
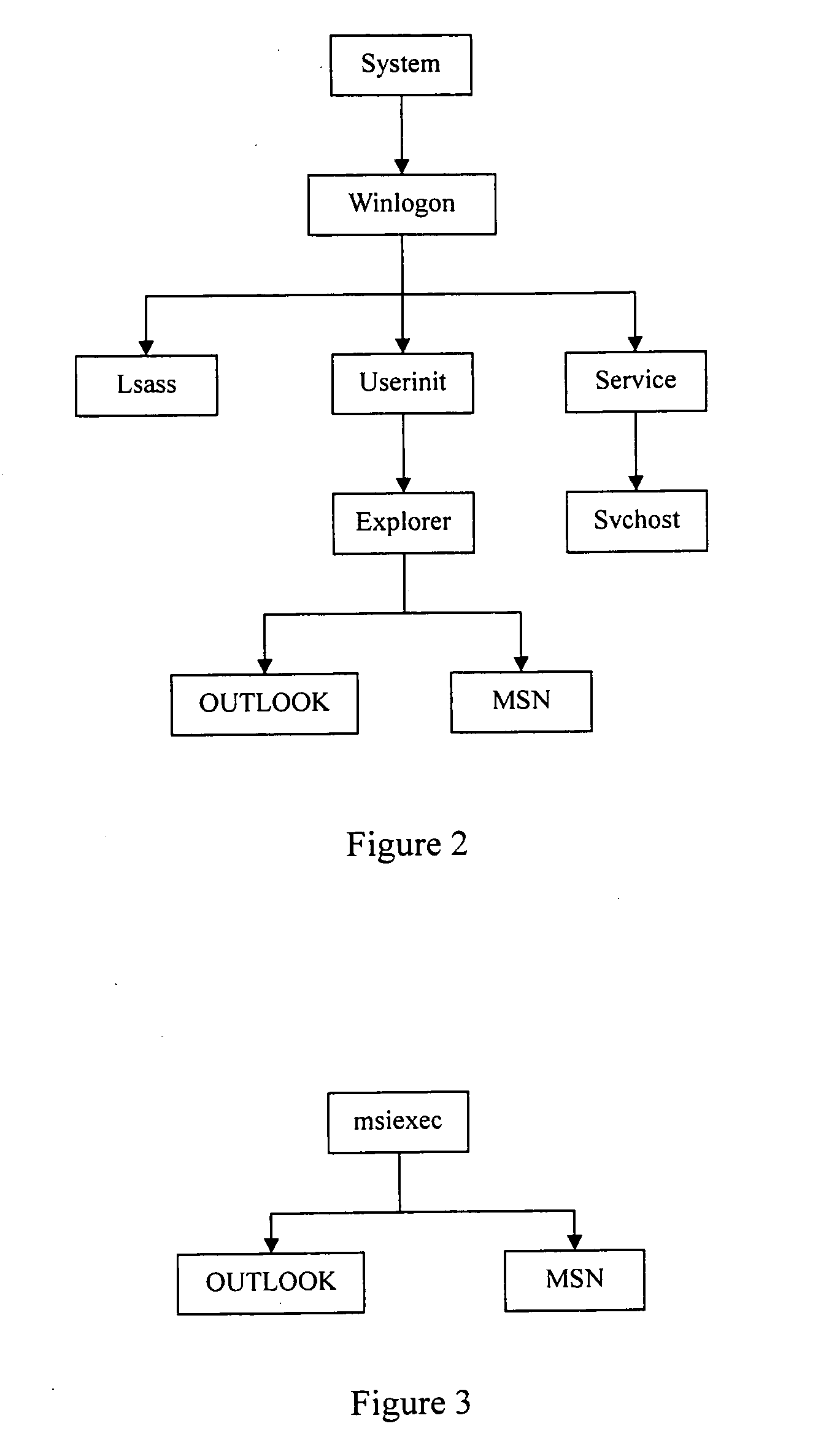
The example embodiments herein relate to an antivirus protection system and method for computers based on program behavior analysis. The antivirus protection system may comprise: a Process Behavior-Evaluating Unit for identifying the programs existing in the user's computers and classifying them into normal programs and suspect programs; a Program-Monitoring Unit for monitoring and recording the actions and / or behaviors of programs; a Correlation-Analyzing Unit for creating correlative trees and analyzing the correlations of actions and / or behaviors of programs, the correlative trees comprising a process tree and a file tree; a Virus-Identifying Knowledge Base, comprising a Program-Behavior Knowledge Base and a Database of Attack-Identifying Rules; a Virus-Identifying Unit for comparing captured actions and / or behaviors to the information in the Virus-Identifying Knowledge Base to determine whether the program is a virus program. With the techniques of certain example embodiments, it may be possible to increase efficiency and reduce the need to upgrade virus codes after viruses become active, while also effectively blocking unknown viruses, Trojans, etc.
Owner:FUJIAN EASTERN MICROPOINT INFO TECH
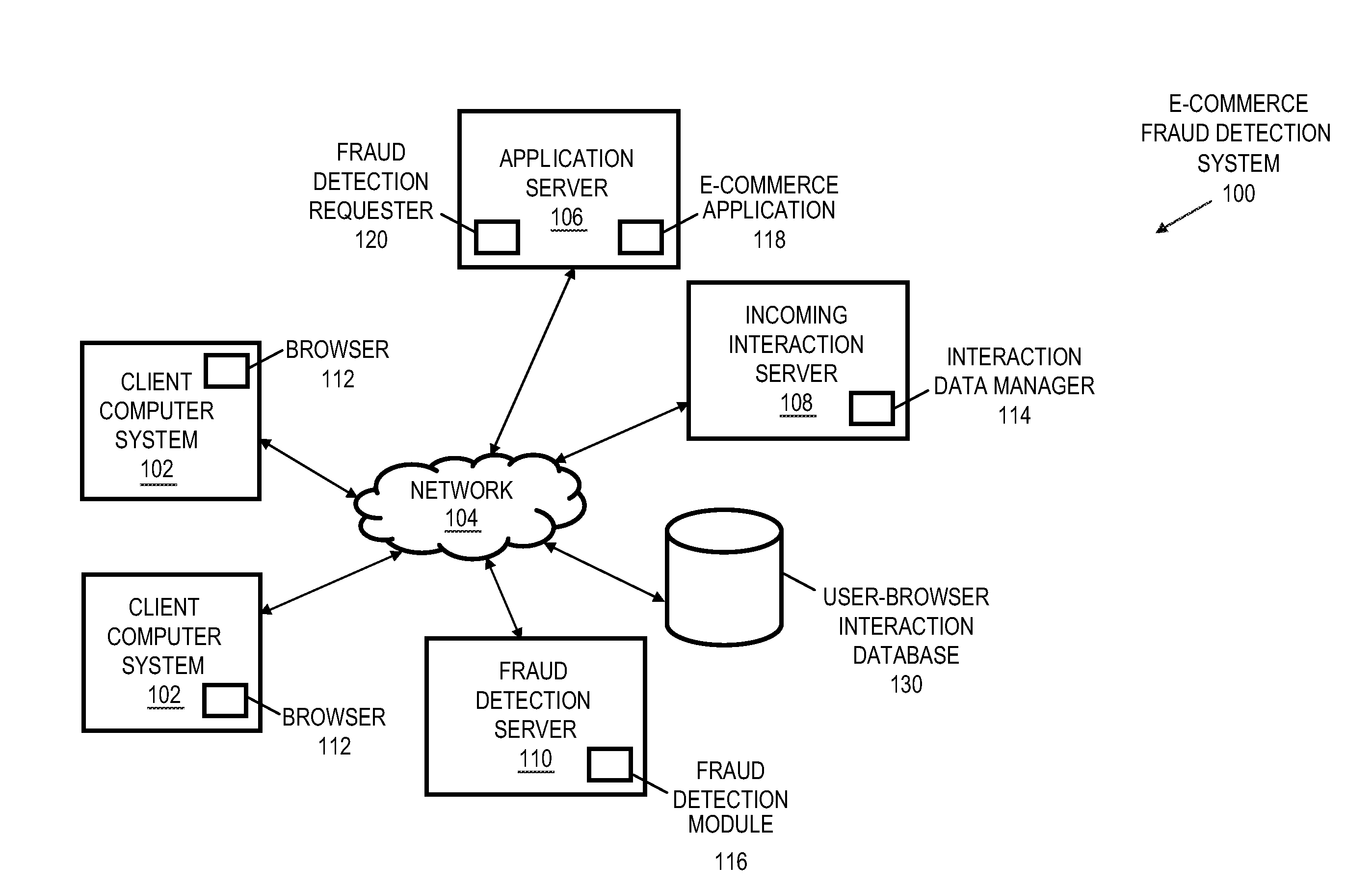
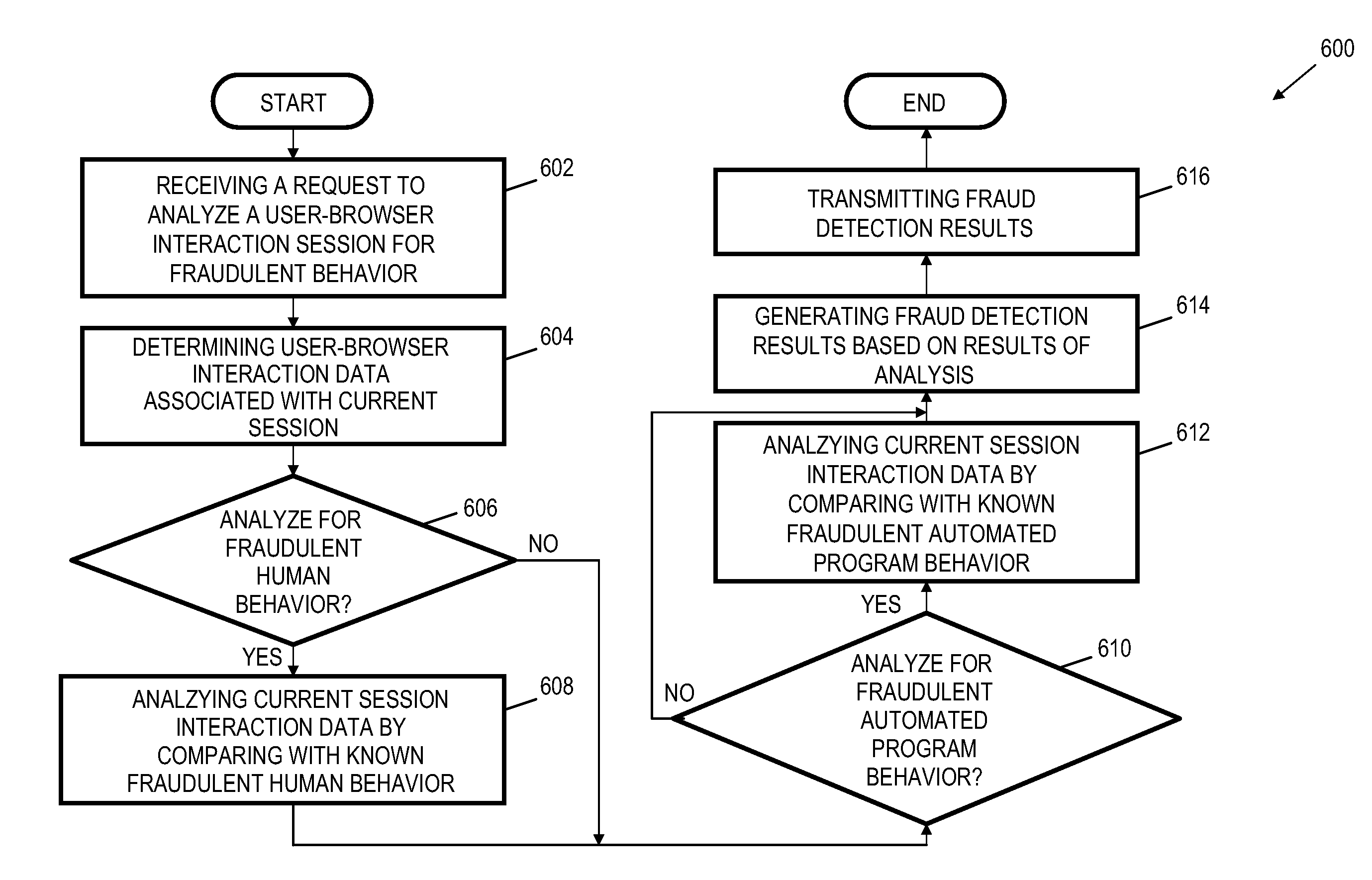
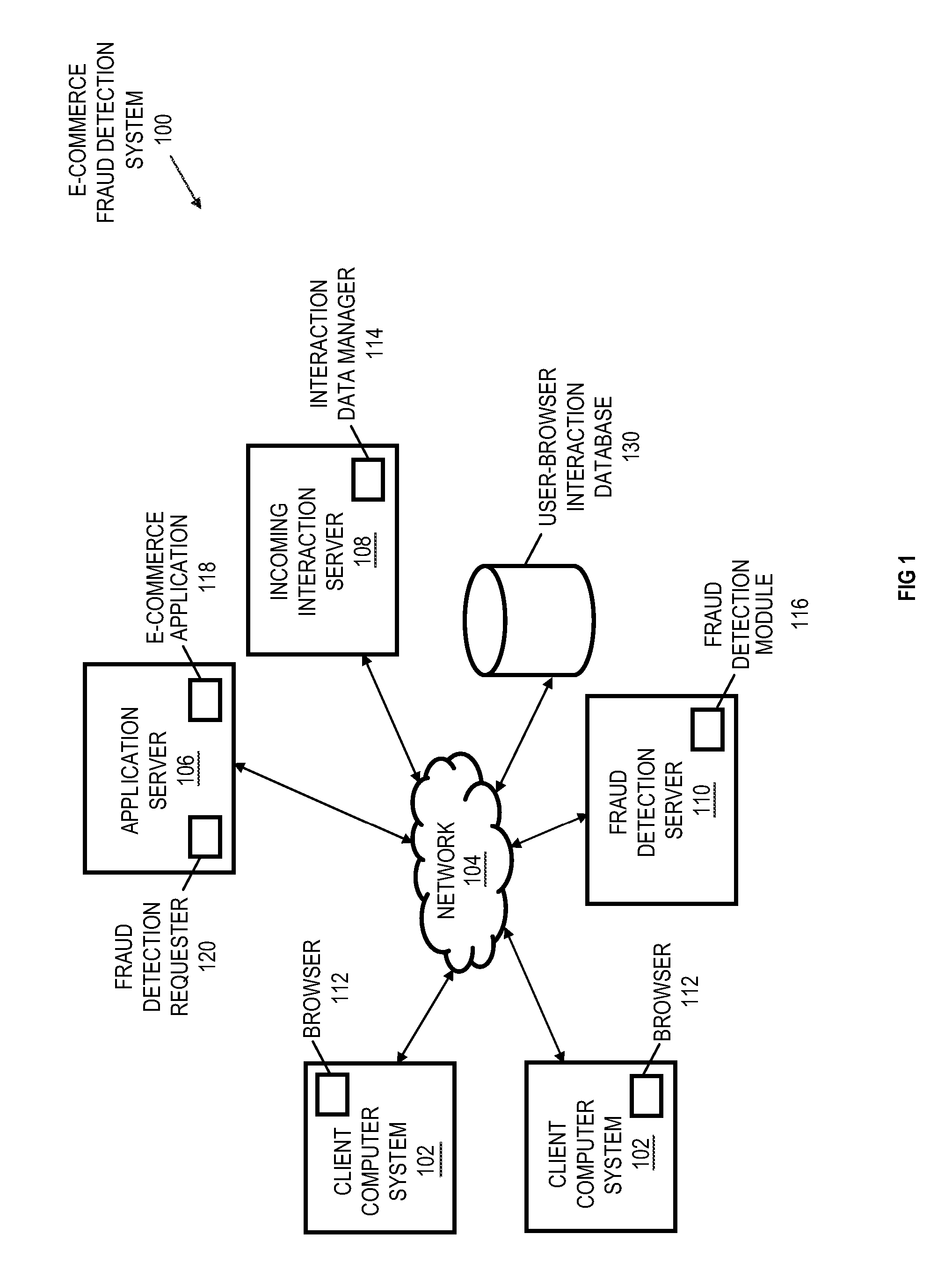
User-browser interaction-based fraud detection system
InactiveUS20070239604A1Payment architecturePlatform integrity maintainanceRequest - actionInternet privacy
Systems, methods and media for detecting fraudulent behavior during an Internet commerce session are disclosed. Embodiments of a method may include establishing an e-commerce session with a user and requesting fraud detection analysis of user-browser interaction during the e-commerce session. Embodiments may also include receiving fraud detection results for the e-commerce session, where the fraud detection results may provide an indication of a comparison between the user's interaction with a browser during the e-commerce session and known fraudulent behavior. Embodiments may also include performing an action based on the fraud detection results. Determining the fraud detection results may include determining user-browser interaction data associated with the session and comparing the user-browser interaction data to known fraudulent human or automated program behavior. Performing the action based on fraud detection results may include one or more of completing an e-commerce transaction, requesting additional authentication, denying the requested action, etc.
Owner:IBM CORP
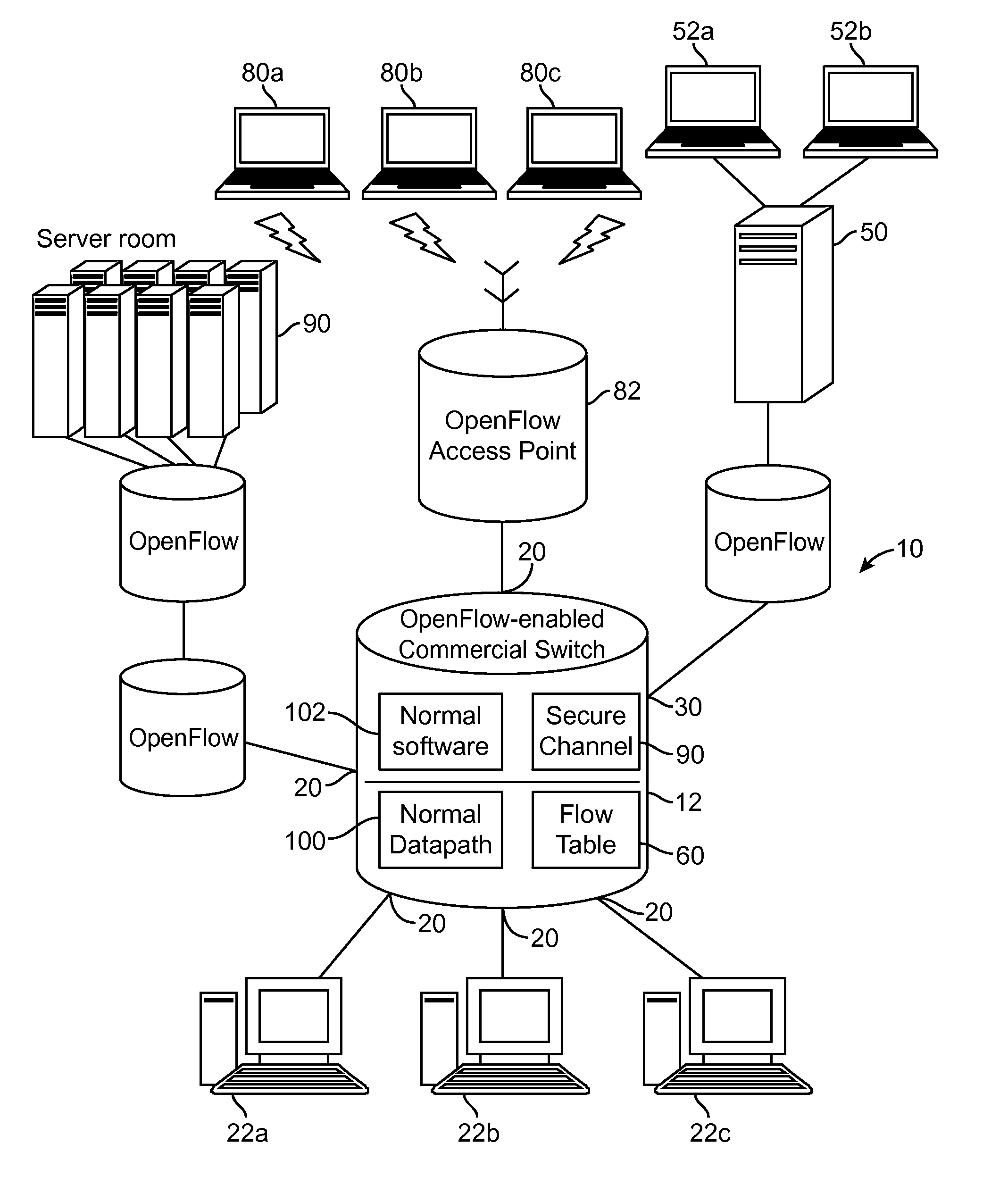
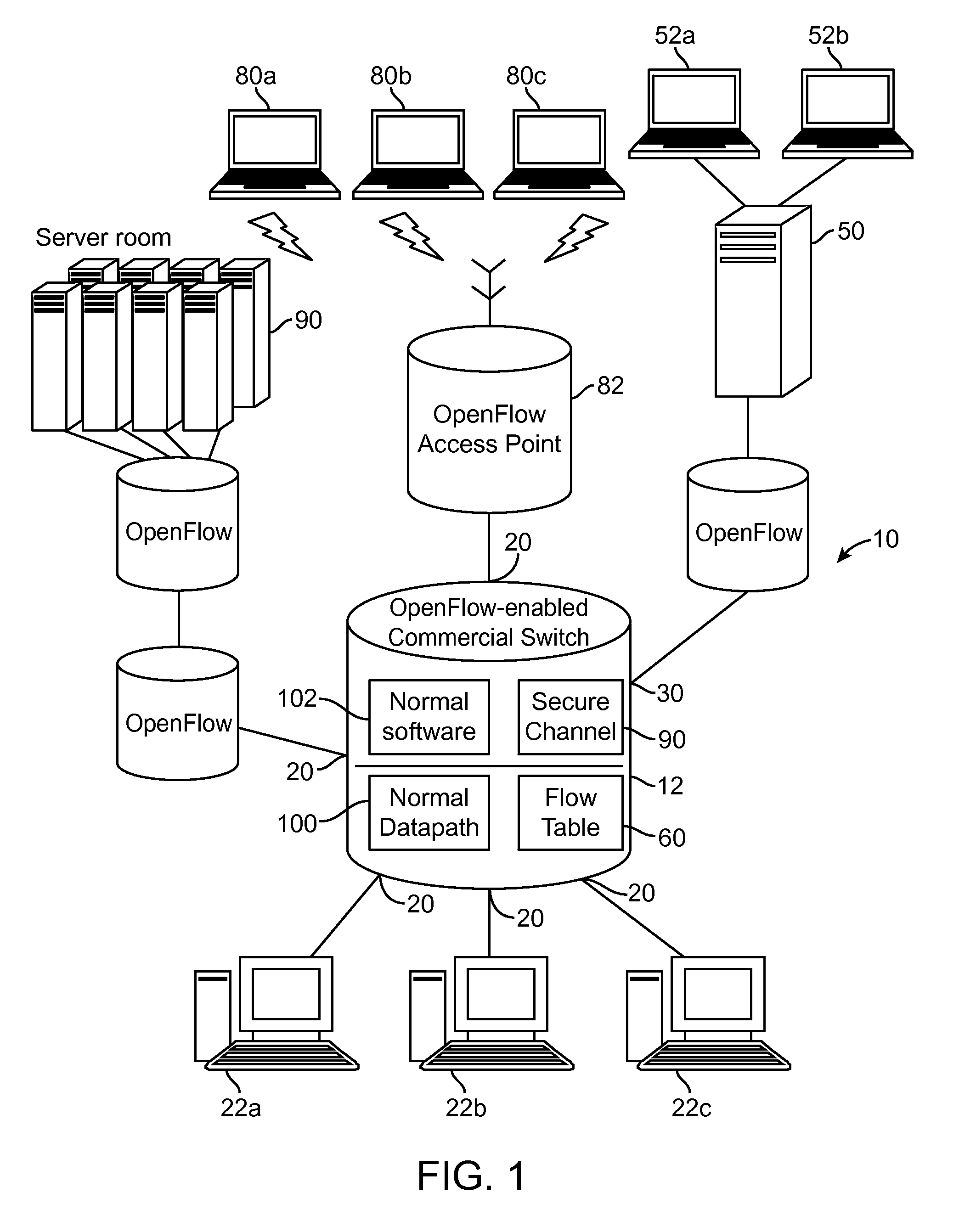
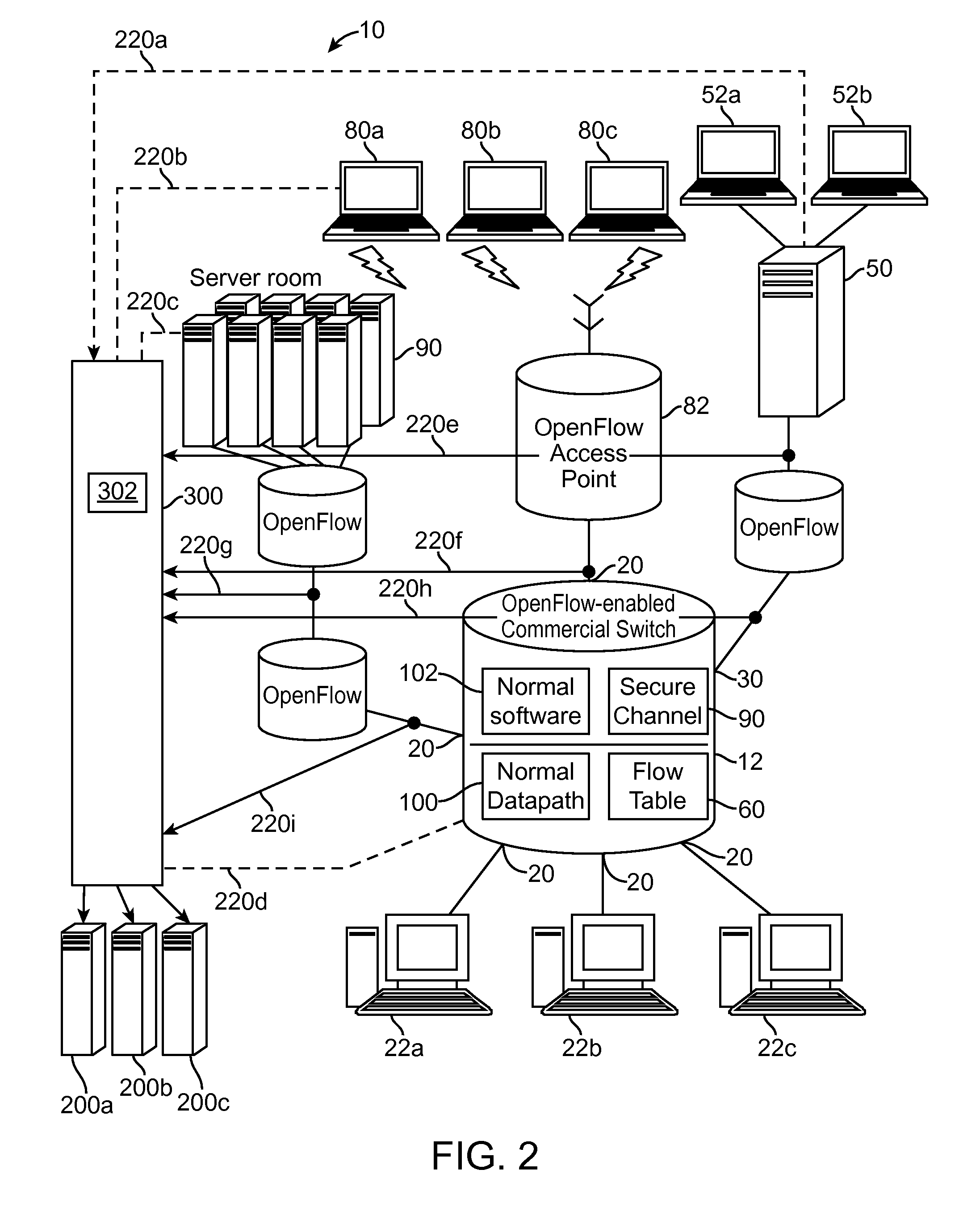
Traffic visibility in an open networking environment
A method of monitoring network traffic includes accessing a network that includes a controller and a switch device having a flow table, wherein the controller is communicatively coupled to the switch device, and is configured to program a behavior of the switch device through an openflow protocol, and obtaining information regarding the programmed behavior of the switch device, wherein the act of obtaining the information is performed by a network appliance that is communicatively coupled to the network. An apparatus communicatively coupled to a network, includes a processor configured for accessing the network that includes a controller and a switch device having a flow table, wherein the controller is communicatively coupled to the switch device, and is configured to program a behavior of the switch device through an openflow protocol, and obtaining information regarding the programmed behavior of the switch device.
Owner:GIGAMON
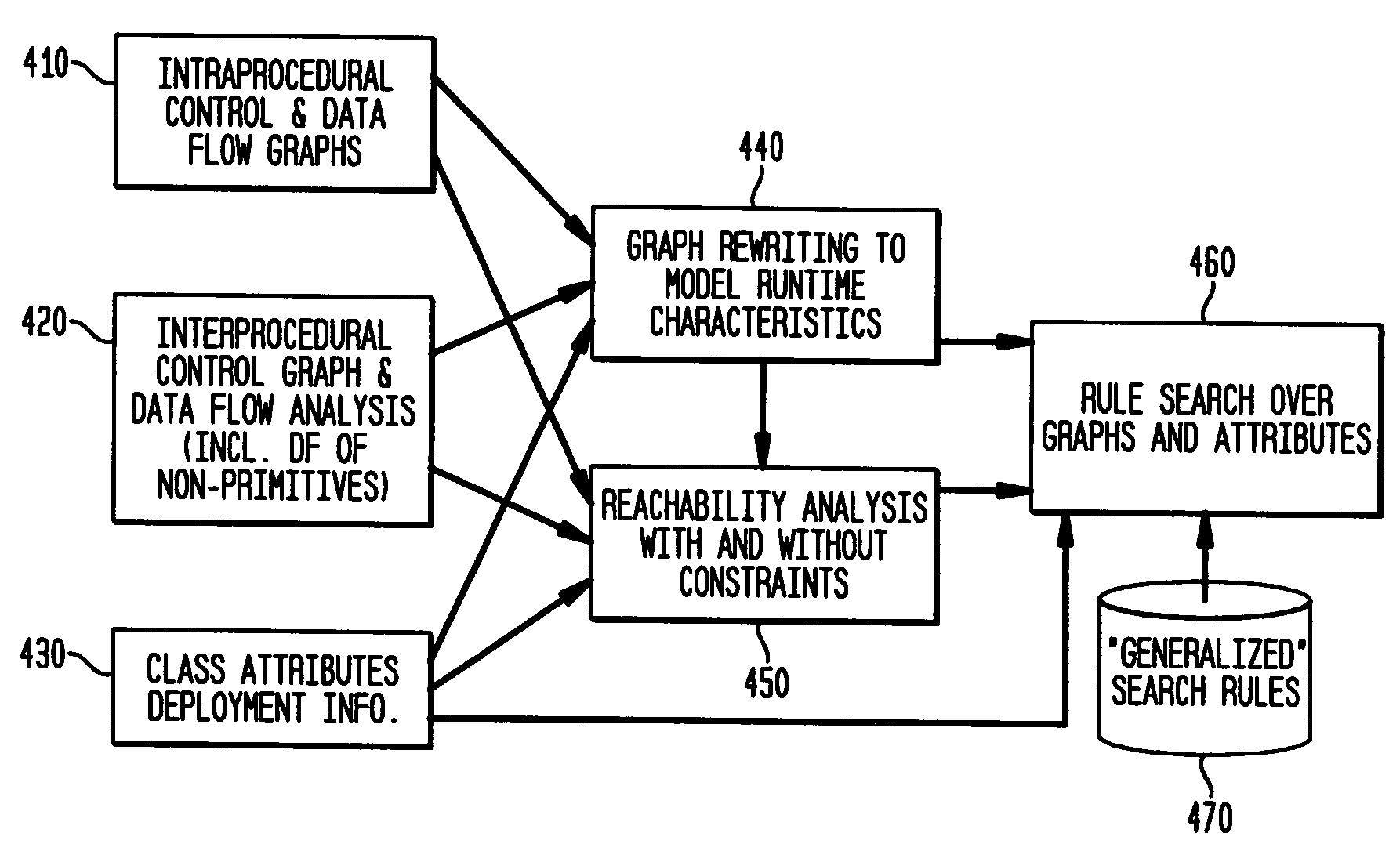
Static analysis based error reduction for software applications
InactiveUS20050015752A1Easy to liftSimple technologyError detection/correctionSpecific program execution arrangementsError reductionMaintainability
A system and method for providing “static analysis” of programs to aid in improving runtime performance, stability, security and privacy characteristics of deployed application code. The method includes performing a set of analyses that sifts through the program code and identifies programming security and / or privacy model coding errors. In particular the invention focuses on identifying coding errors that cause loss of correctness, performance degradation, security, privacy and maintainability vulnerabilities. A deep analysis of the program is performed using detailed control and data flow analyses. These deeper analyses provide a much better perspective of the overall application behavior. This deep analysis is in contrast to shallow analyses in current industry tools, which inspect or model a single or a few classes at a time.
Owner:IBM CORP
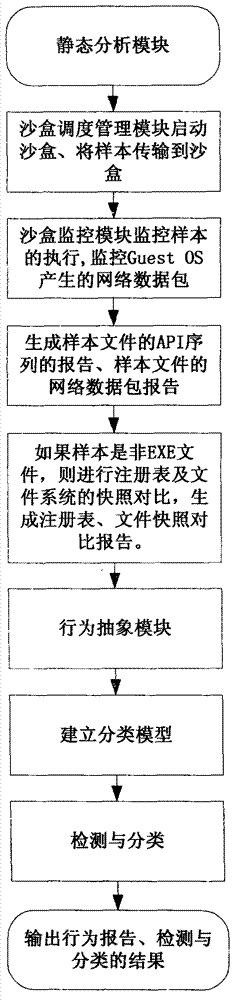
System and method for automatically analyzing, detecting and classifying malicious program behavior
ActiveCN102930210ACause damageOvercome shortcomings such as inability to perform adequatelyPlatform integrity maintainanceSpecial data processing applicationsDomain nameNetwork behavior
The invention discloses a system and a method for automatically analyzing, detecting and classifying a malicious program behavior. The system comprises a static analysis module, a sandbox dispatching management module, a sandbox monitoring module, a behavior abstraction module and a detection and classification module. Compared with the prior art, the system has the advantages that 1, the system is based on a behavior monitoring technology in an instruction set simulation environment; and 2, a virtual Internet is established in a sandbox through means of environment configuration, server program modification and the like, and a common network service is simulated, so that operations such as domain name server (DNS) resolution, http access, file download, Email login and mailing initiated by a malicious program can be successfully executed, the malicious program is inveigled to generate a malicious network behavior, the network behaviors are prevented from damaging a host machine and a real network, and the defects that the malicious program network behavior cannot be fully expressed during dynamic behavior analysis of a malicious program and the like are overcome.
Owner:JIANGSU JINLING TECH GRP CORP
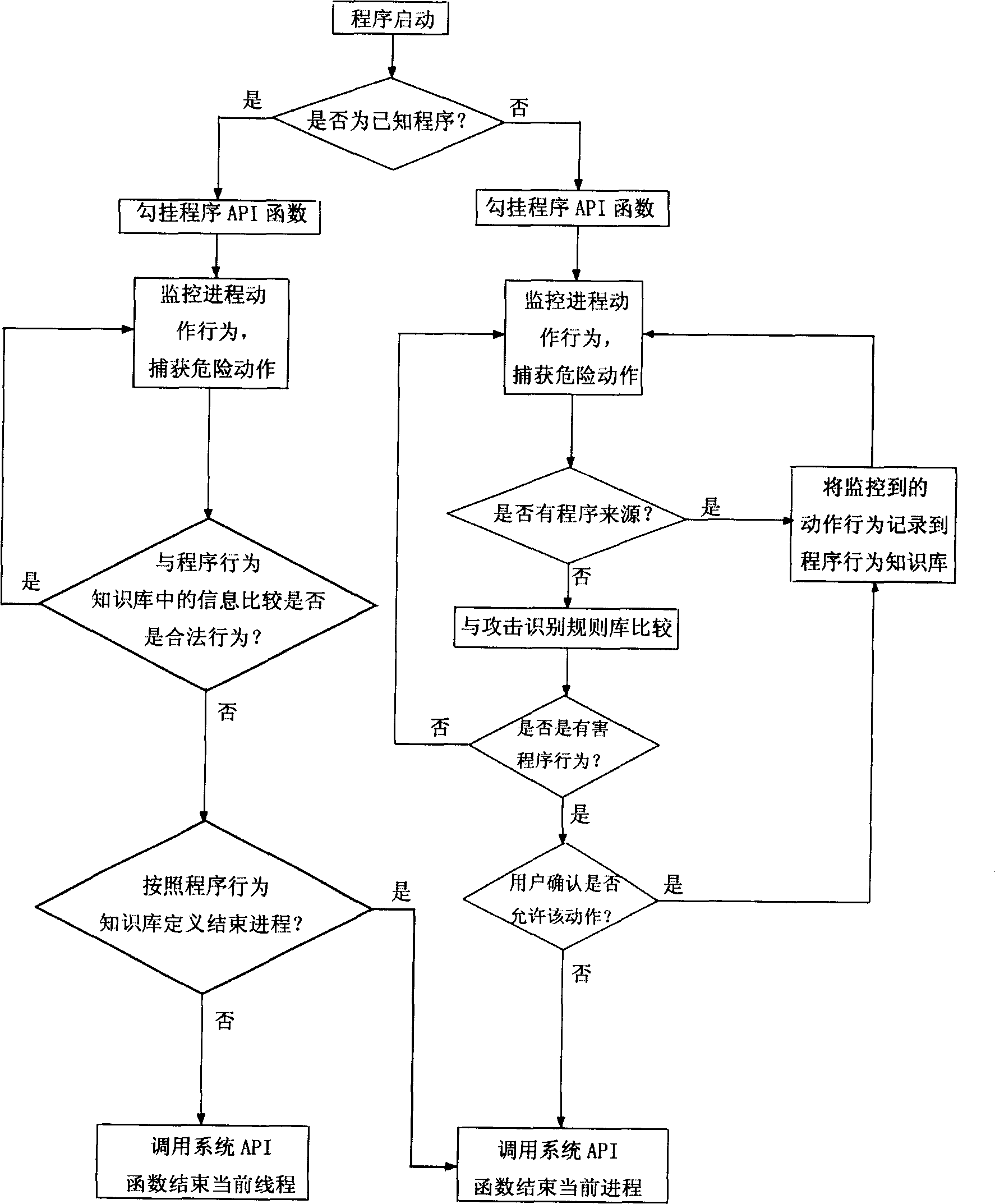
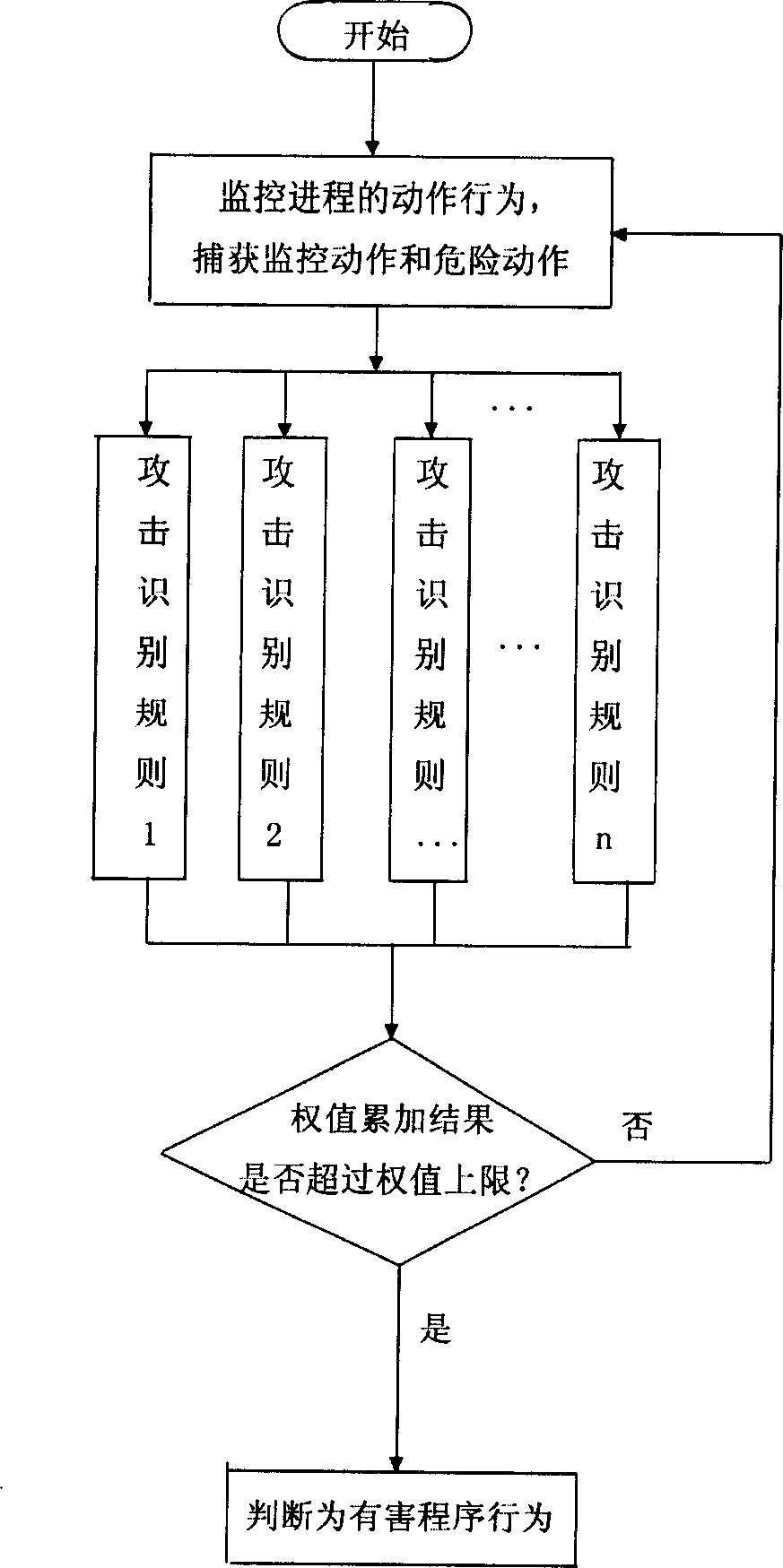
Computer protecting method based on programm behaviour analysis
ActiveCN1818823AEasy to useDigital data processing detailsTransmissionUnknown procedureProgram behavior
A computer protection method based on program behavior analysis includes monitoring its actuation behavior and comparing it with its legal actuation behavior stored in program behavior knowledge bank then judging whether known program is attacked illegally or not for known program; monitoring its actuation behavior and comparing it with attack identification rule stored in attack identification rule bank then judging whether it is harmful program or not for unknown program.
Owner:北京东方微点信息技术有限责任公司
Application instrumentation and monitoring
ActiveUS20060123101A1Cost effectiveAvoid the needDigital computer detailsComputer security arrangementsApplication softwareData store
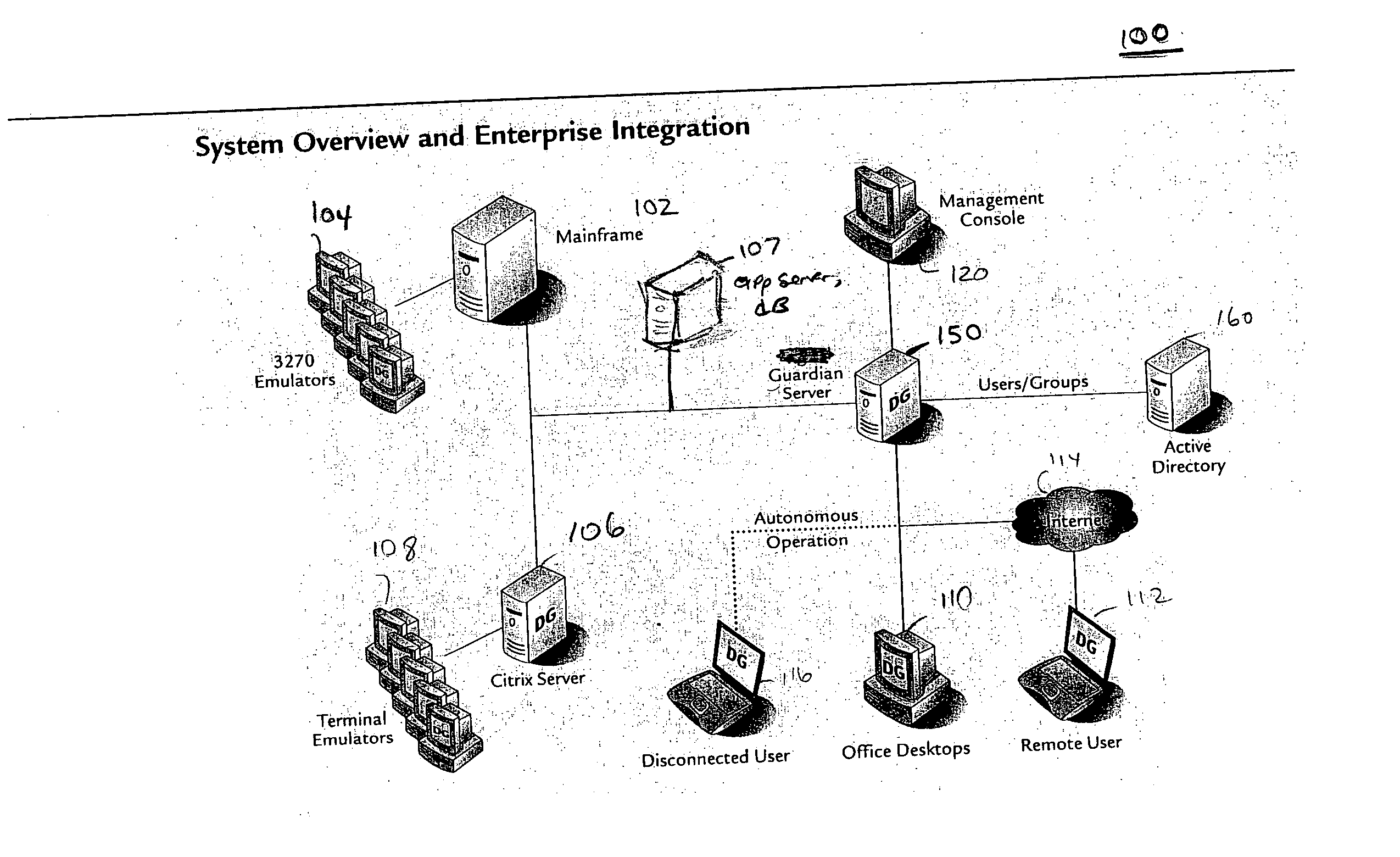
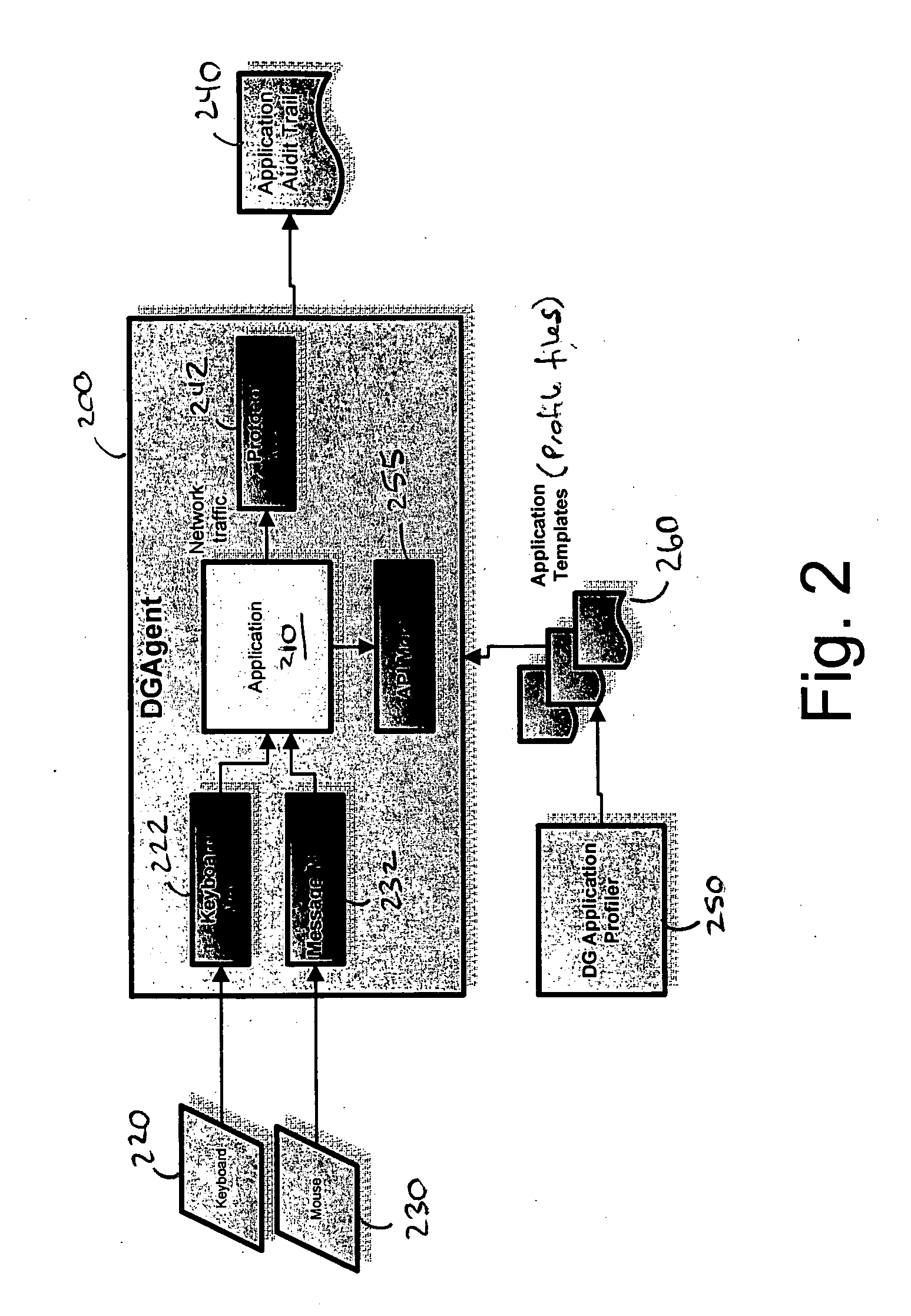
A data processing application logging, recording, and reporting process and infrastructure. Compliance with regulatory directives such as HIPAA, internal organizational and corporate, personal information privacy, and other security policies can thus be enforced without the need to recode legacy application software. In one preferred embodiment, a core agent process provides “listener” functionality that captures user input events, such as keyboard and mouse interactions, between a user and a legacy application of interest. The agent obtains instructions for how to deal with such events, accessing information that describes the application's behavior as already captured by an application profiler tool. Keyboard and mouse data entry sequences, screen controls and fields of interest are tagged during application profiling process. This data is stored in application profile developed for each mode of a legacy application. The technique can be implemented in various Information Technology (IT) environments including mainframe / terminal applications and / or client / server applications. Thus, full coverage of “fat” client, “thin” client, and legacy “mainframe” applications can be provided with a common approach across an enterprise.
Owner:DIGITAL GUARDIAN LLC
Method and system for establishing normal software system behavior and departures from normal behavior
InactiveUS7185367B2Memory loss protectionDigital data processing detailsStatistical analysisSoftware system
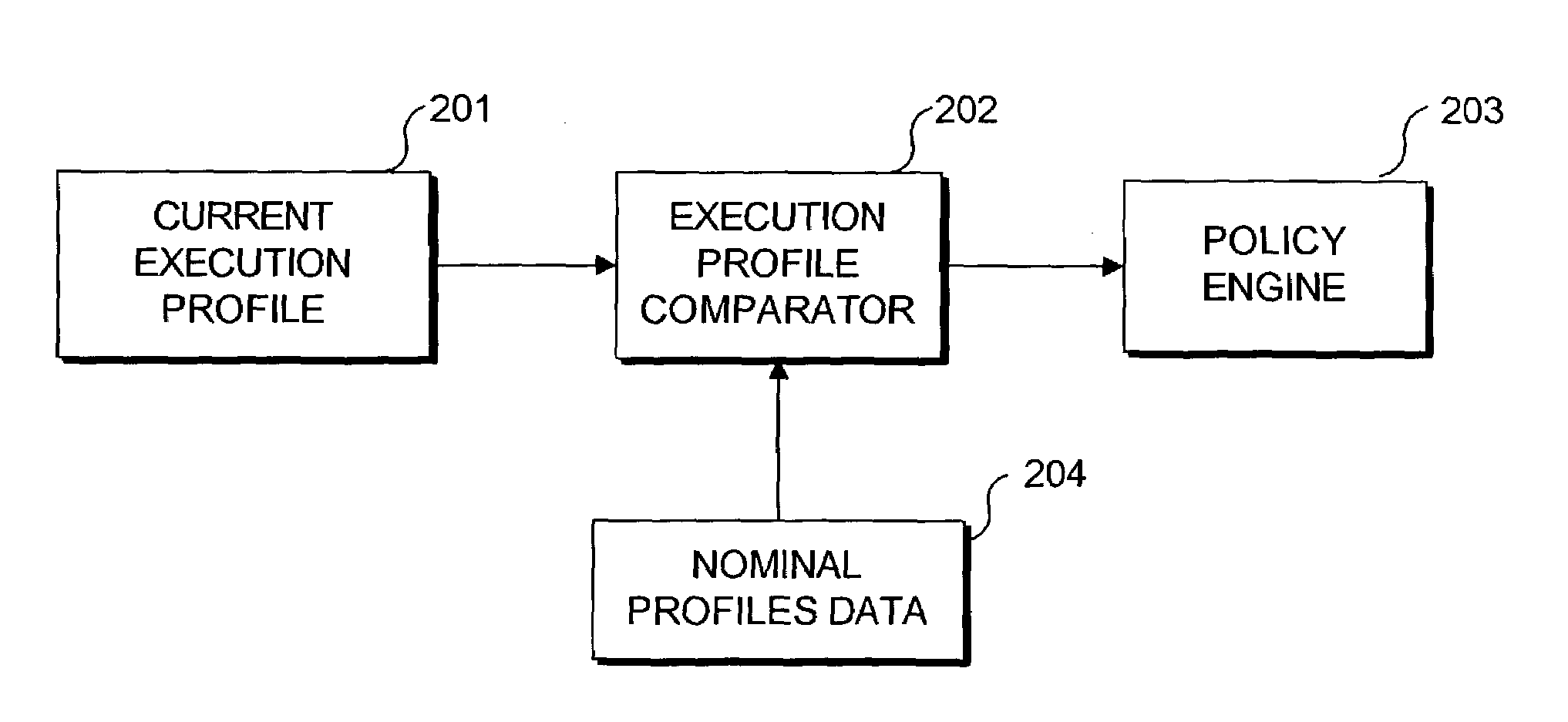
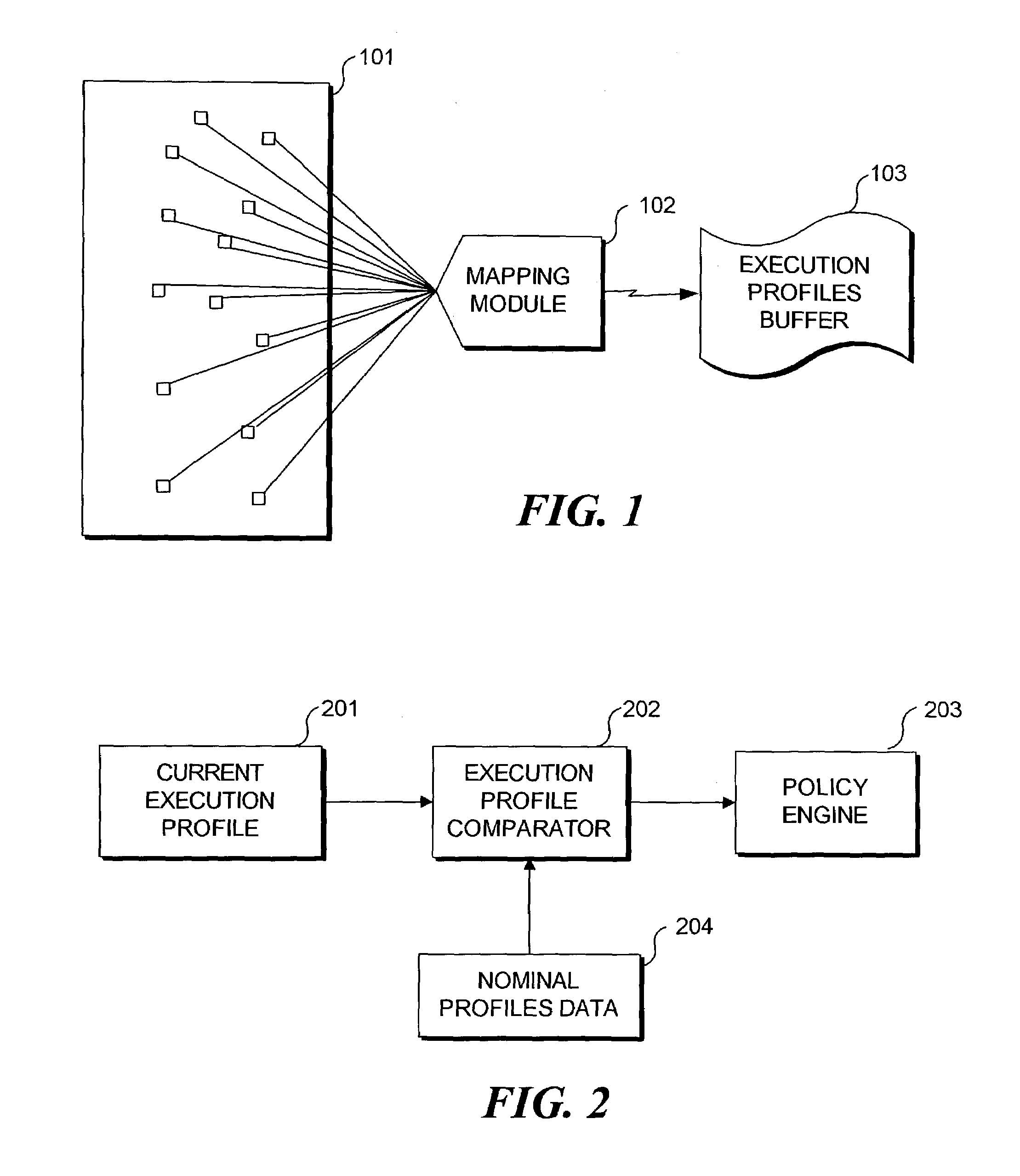
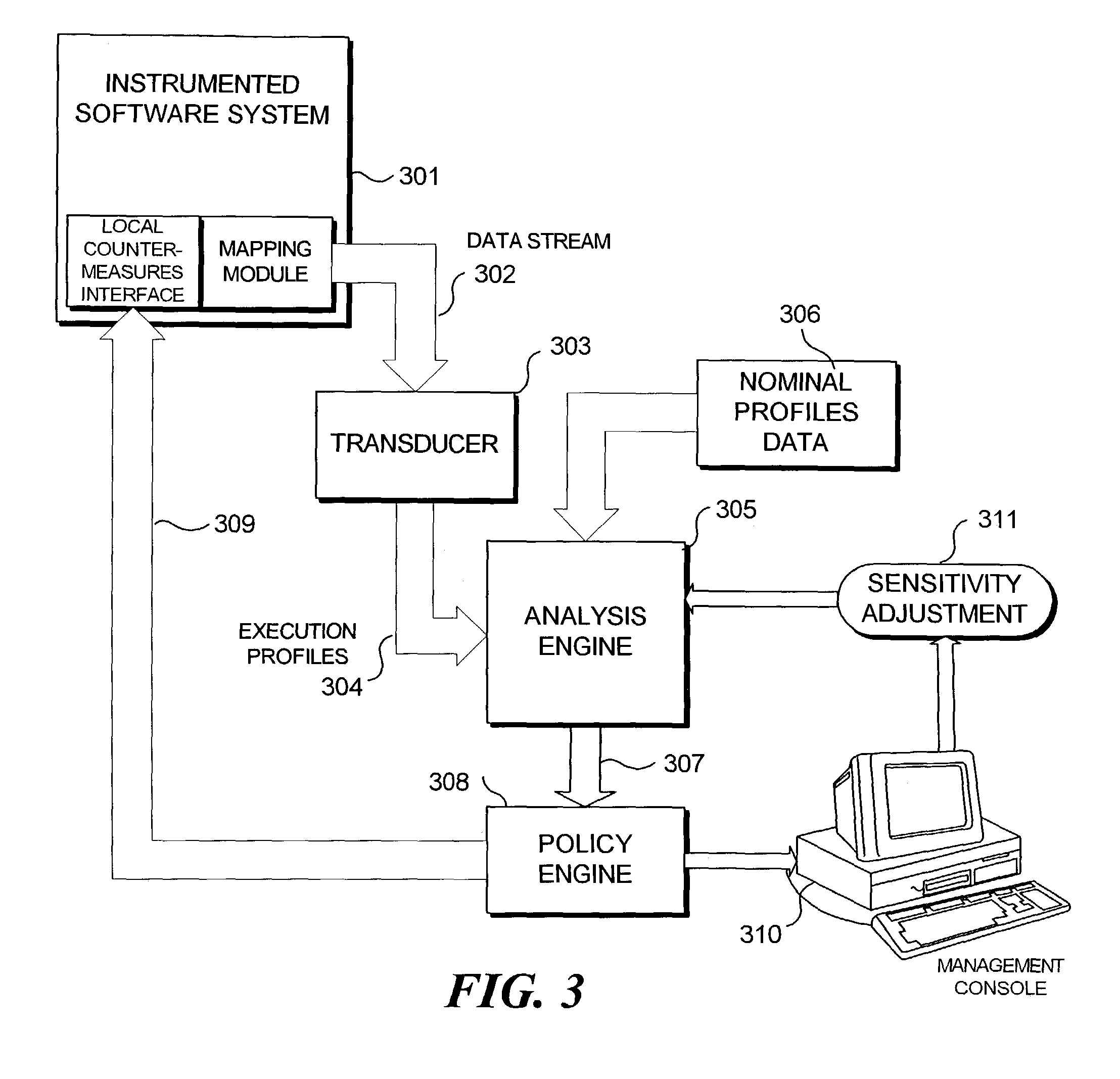
Detecting abnormal activity of a software system is based on behavioral information obtained from an instrumented computer program while it executes. As the program executes, it expresses information about the sequence and frequency with which program modules are called. Over time, this sequence and frequency defines the normal behavior of the program, and the information expressed on any given run is compared to this normal behavior. Statistical analysis of the differences between the normal behavior and the current run can be used to detect unauthorized or abusive use of the program. Program modules whose behavior is highly correlated can be grouped into a smaller number of virtual modules. Comparison between current and normal program behavior can then be made on the (smaller number of) virtual modules, thereby reducing the dimensionality of the problem of analyzing the differences between current and normal program behavior.
Owner:STRATACLOUD
Methods for analyzing dynamic program behavior using user-defined classifications of an execution trace
InactiveUS6557011B1Data processing applicationsError detection/correctionTheoretical computer scienceSingle type
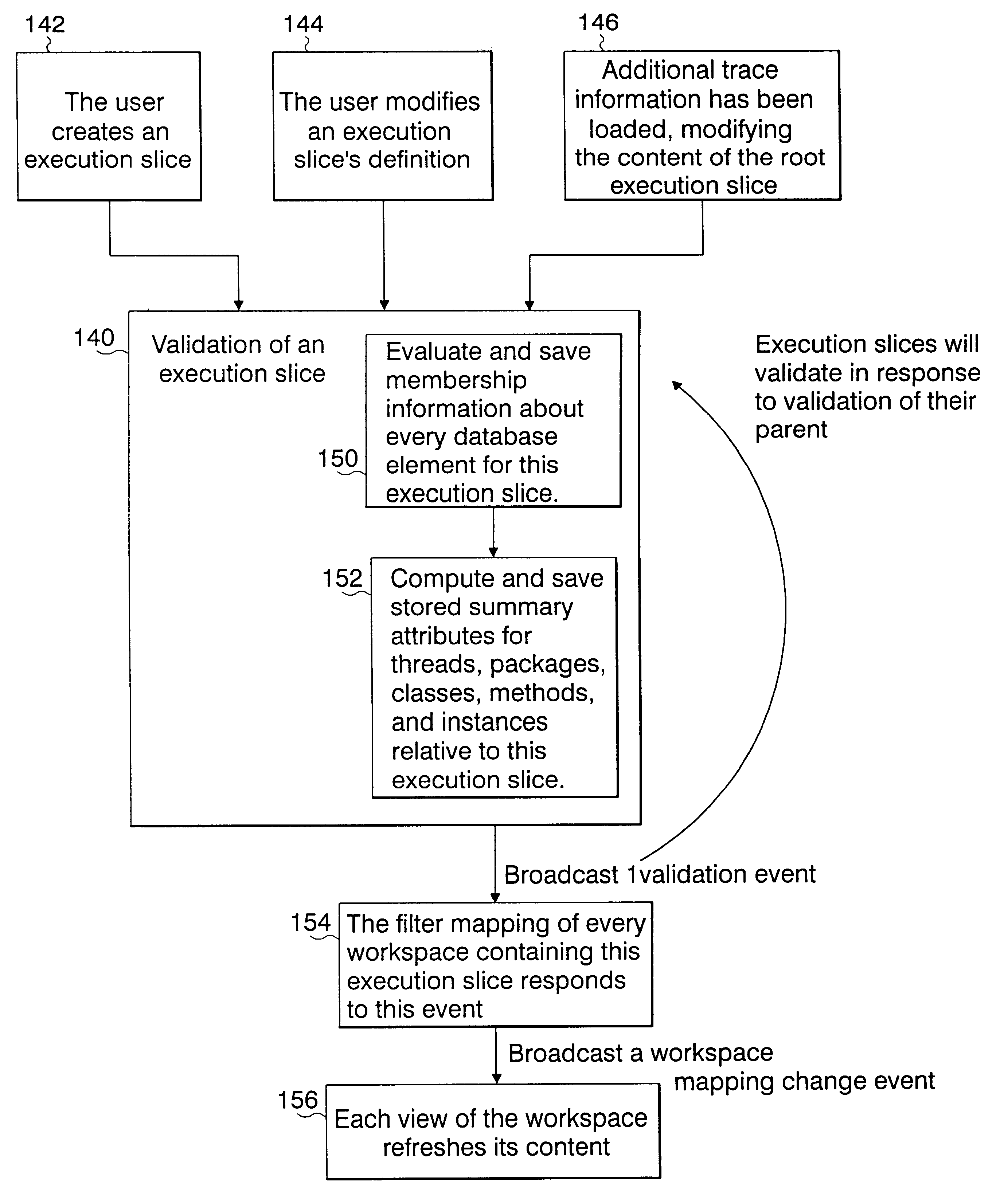
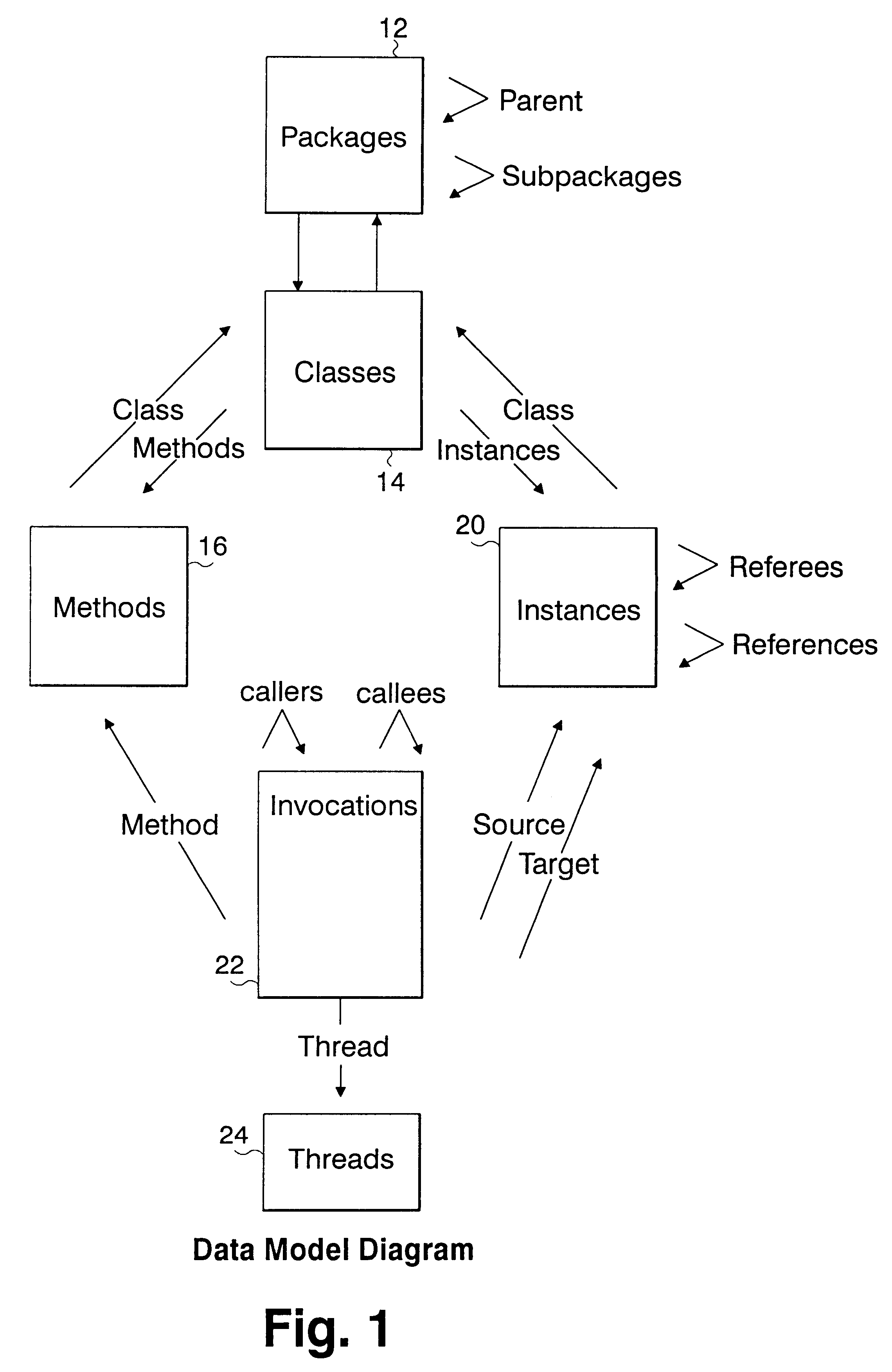
A method and system for analyzing dynamic behavior of a computer program using user-defined classifications of an execution trace. The method comprises the step of forming a database describing the executions of the program. The database includes static information obtained from the program source, and dynamic information describing particular executions of the program. The database is structured into entities, and each of the entities is comprised of a single type of information about the program execution. Each entity is comprised of elements representing individual program elements of said single type, and each element has attributes with values describing the element. The database is augmented by classifying every element of the database as a member of zero or more user defined execution slices; and dynamic behavior of the program is analyzed using the execution slices.
Owner:IBM CORP
Tree-based thread management
ActiveUS20150205607A1Increase speedAvoid bad consequencesDigital computer detailsSpecific program execution arrangementsMulti processorParallel computing
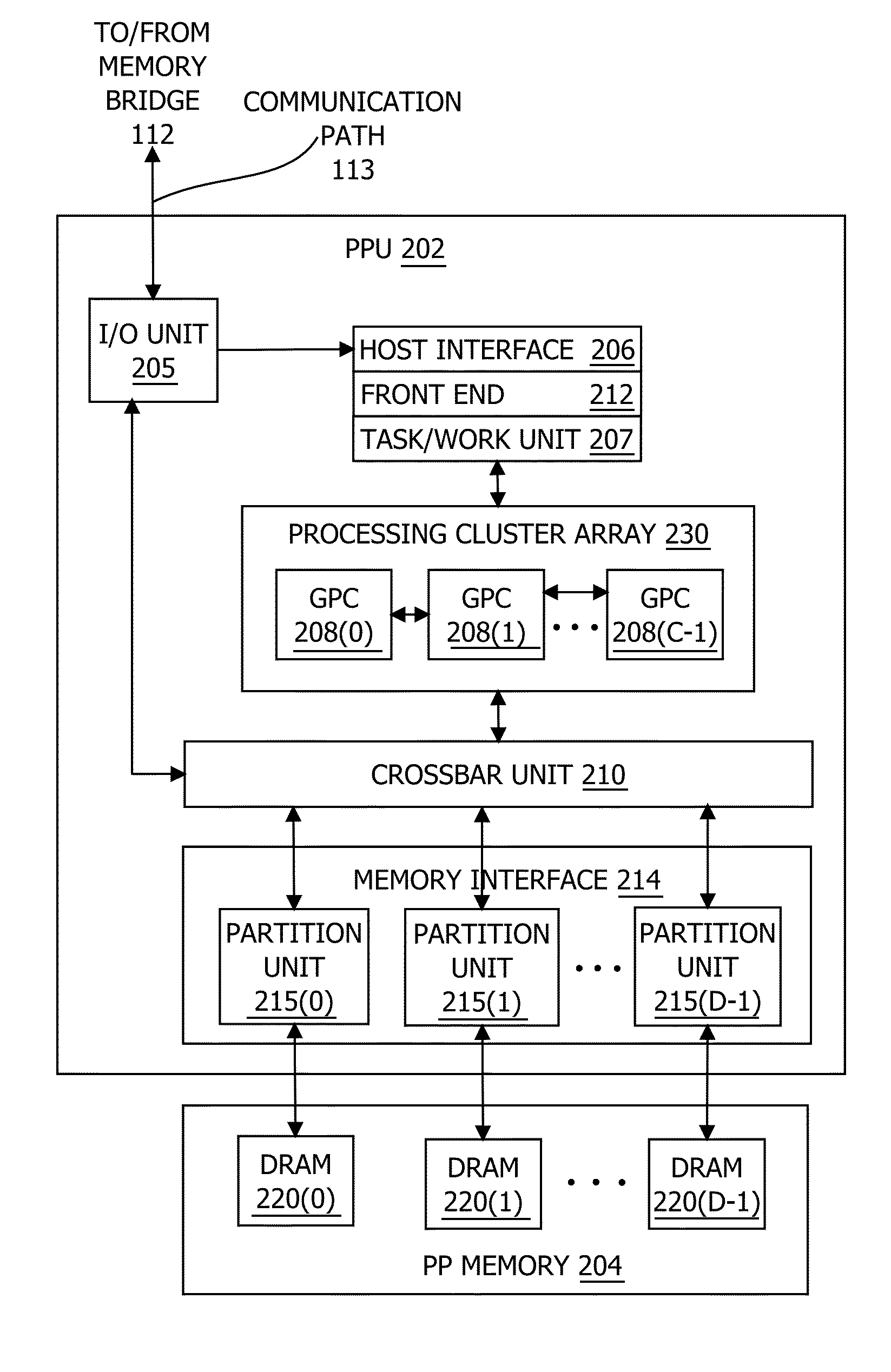
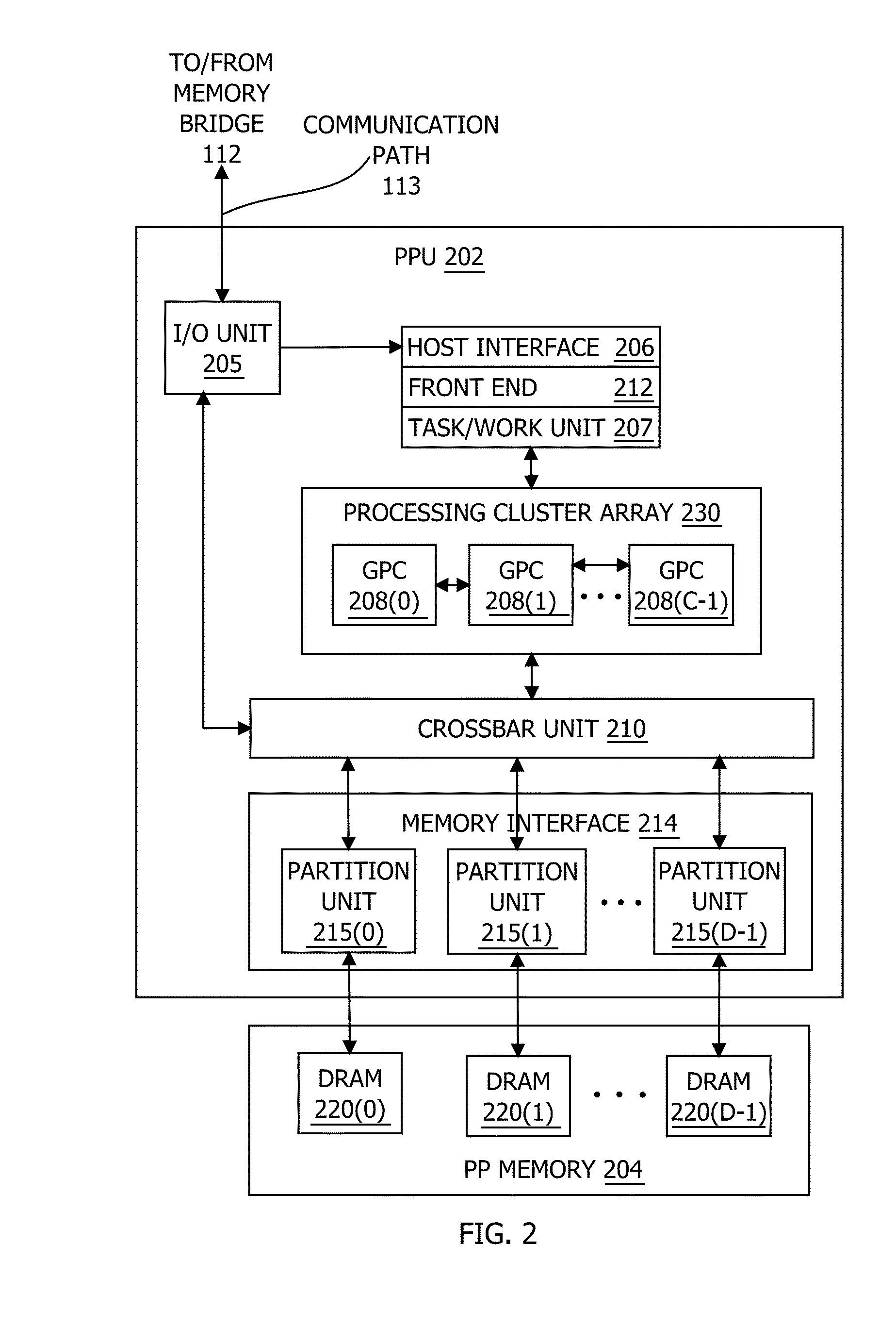
In one embodiment of the present invention, a streaming multiprocessor (SM) uses a tree of nodes to manage threads. Each node specifies a set of active threads and a program counter. Upon encountering a conditional instruction that causes an execution path to diverge, the SM creates child nodes corresponding to each of the divergent execution paths. Based on the conditional instruction, the SM assigns each active thread included in the parent node to at most one child node, and the SM temporarily discontinues executing instructions specified by the parent node. Instead, the SM concurrently executes instructions specified by the child nodes. After all the divergent paths reconverge to the parent path, the SM resumes executing instructions specified by the parent node. Advantageously, the disclosed techniques enable the SM to execute divergent paths in parallel, thereby reducing undesirable program behavior associated with conventional techniques that serialize divergent paths across thread groups.
Owner:NVIDIA CORP
Apparatus and method for using information on malicious application behaviors among devices
InactiveUS20070192866A1Memory loss protectionError detection/correctionPaper documentDocument preparation
A device for using information on malicious application behaviors is provided. The device includes a capability-monitoring unit that monitors application capabilities, a behavior-monitoring unit that monitors application behaviors, an mBDL-generating unit that generates a document in a formal language specifying the application capabilities and the application behaviors, and a controlling unit that controls execution of application using the formal language.
Owner:SAMSUNG ELECTRONICS CO LTD
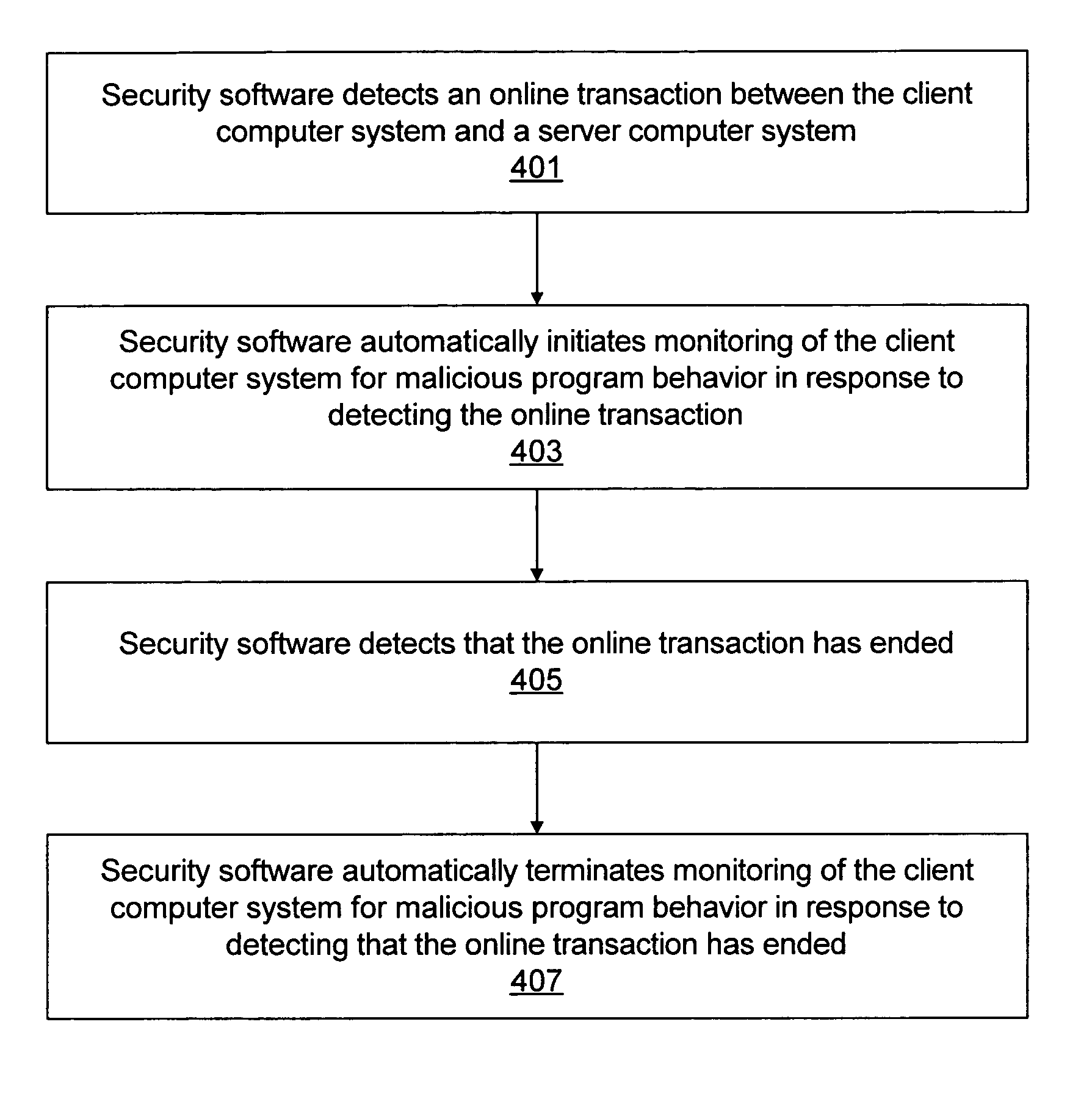
Method, system, and computer program product for blocking malicious program behaviors
InactiveUS7818800B1Memory loss protectionError detection/correctionSecurity softwareComputerized system
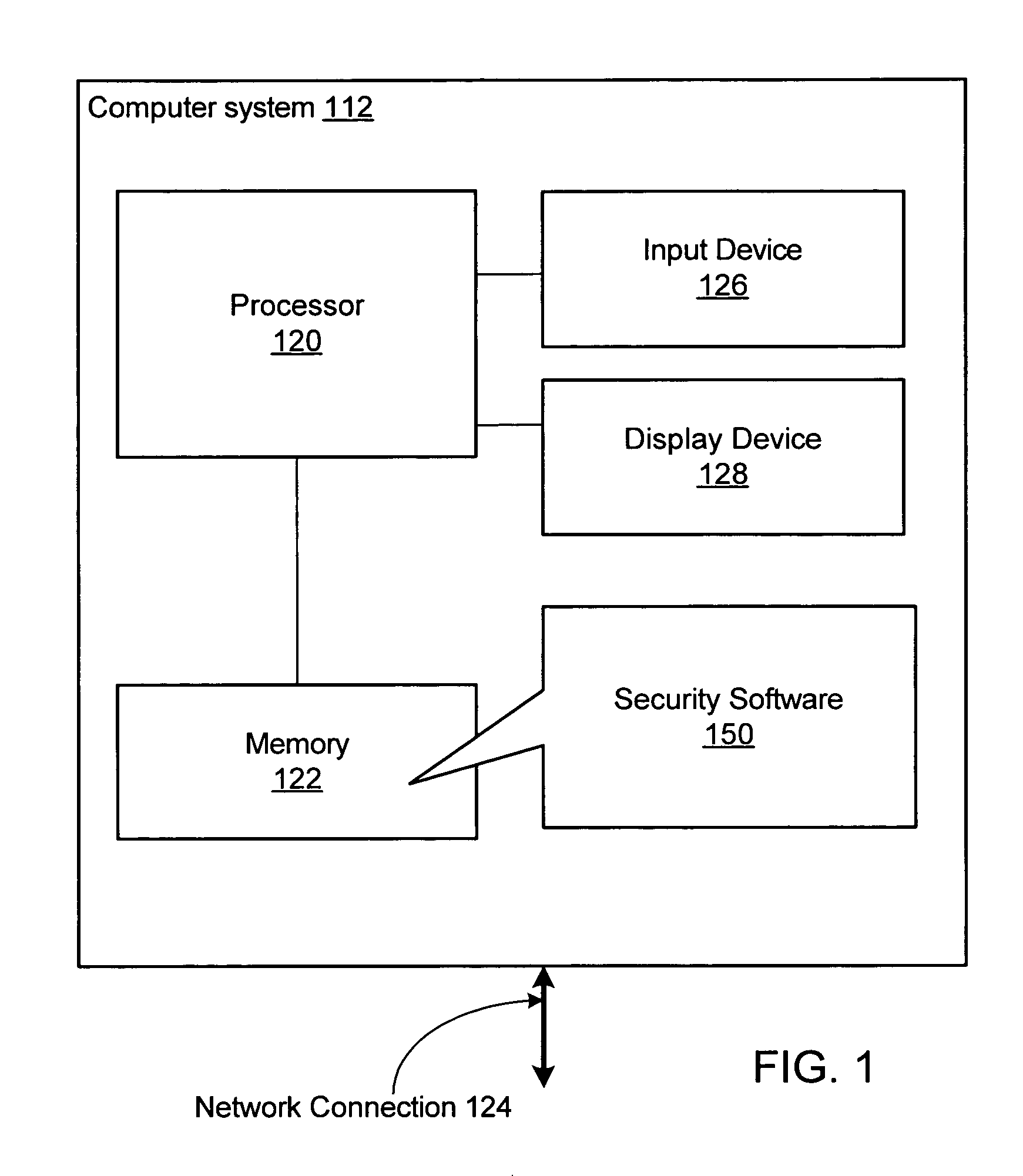
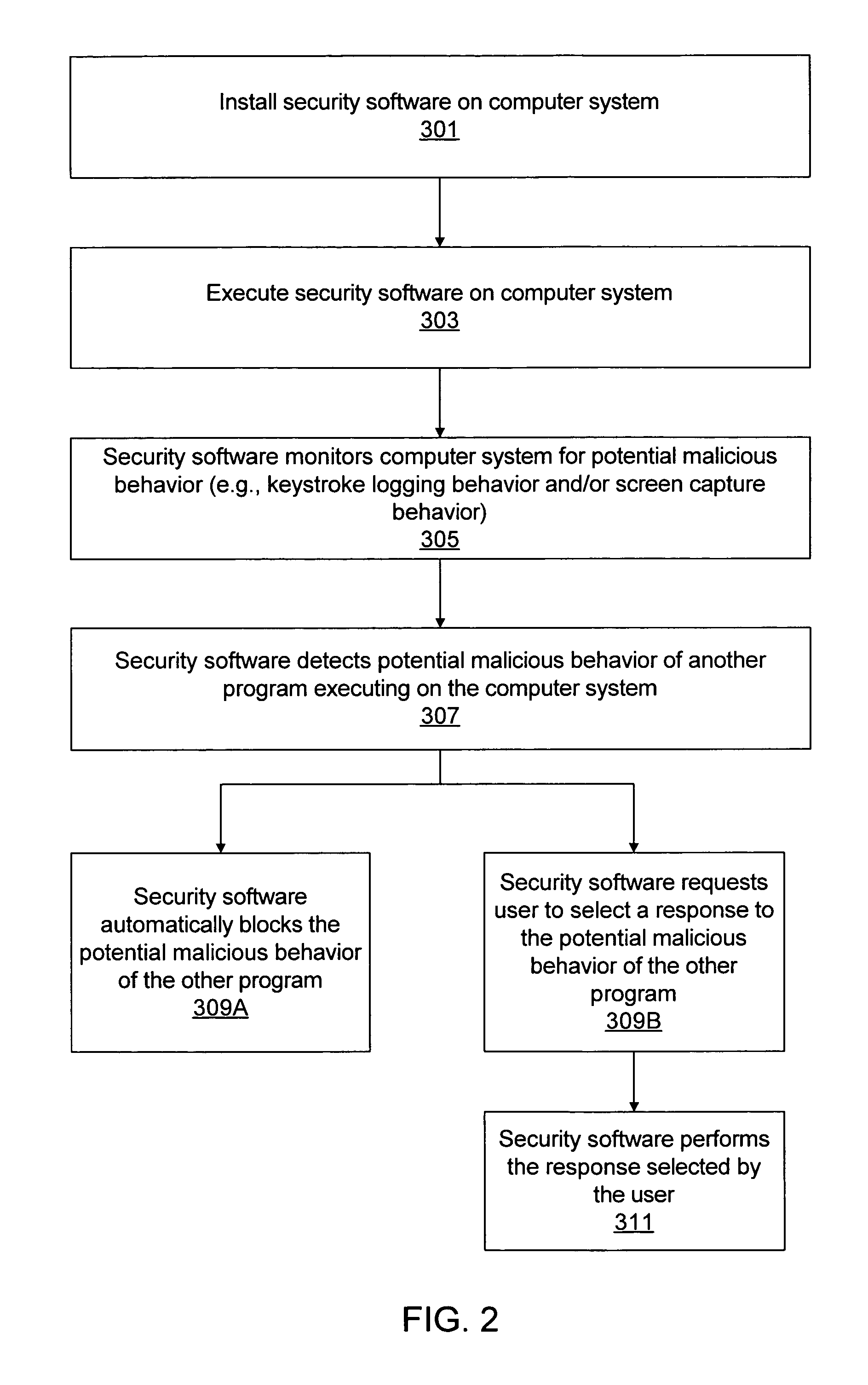
Various embodiments of a system and method for blocking malicious program behaviors, such as keystroke logging behavior or screen capture behavior, are disclosed. Security software may execute on a computer system, where the security software is operable to monitor the computer system to detect malicious program behavior. In response to detecting a first condition indicating that monitoring of the computer system to detect malicious program behavior should be initiated, the security software automatically initiates monitoring of the computer system to detect malicious program behavior. After initiating the monitoring for malicious program behavior, the security software may detect malicious program behavior of a second program executing on the computer system and block the malicious program behavior of the second program.
Owner:CA TECH INC
Asynchronous processing of events for malware detection
ActiveUS20110083176A1Easy to handleIncrease probabilityMemory loss protectionDigital data processing detailsWeb siteBehavioral analytics
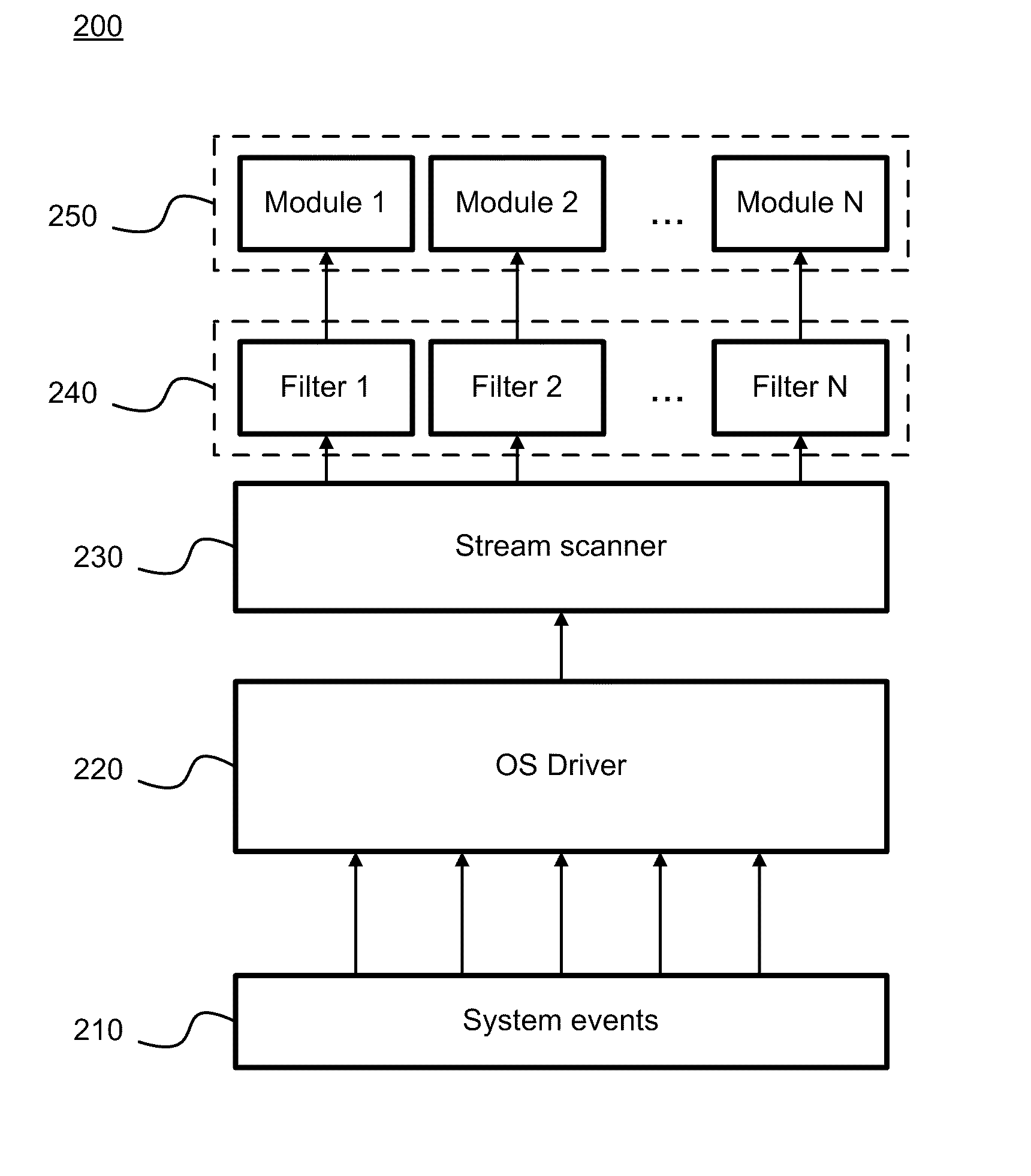
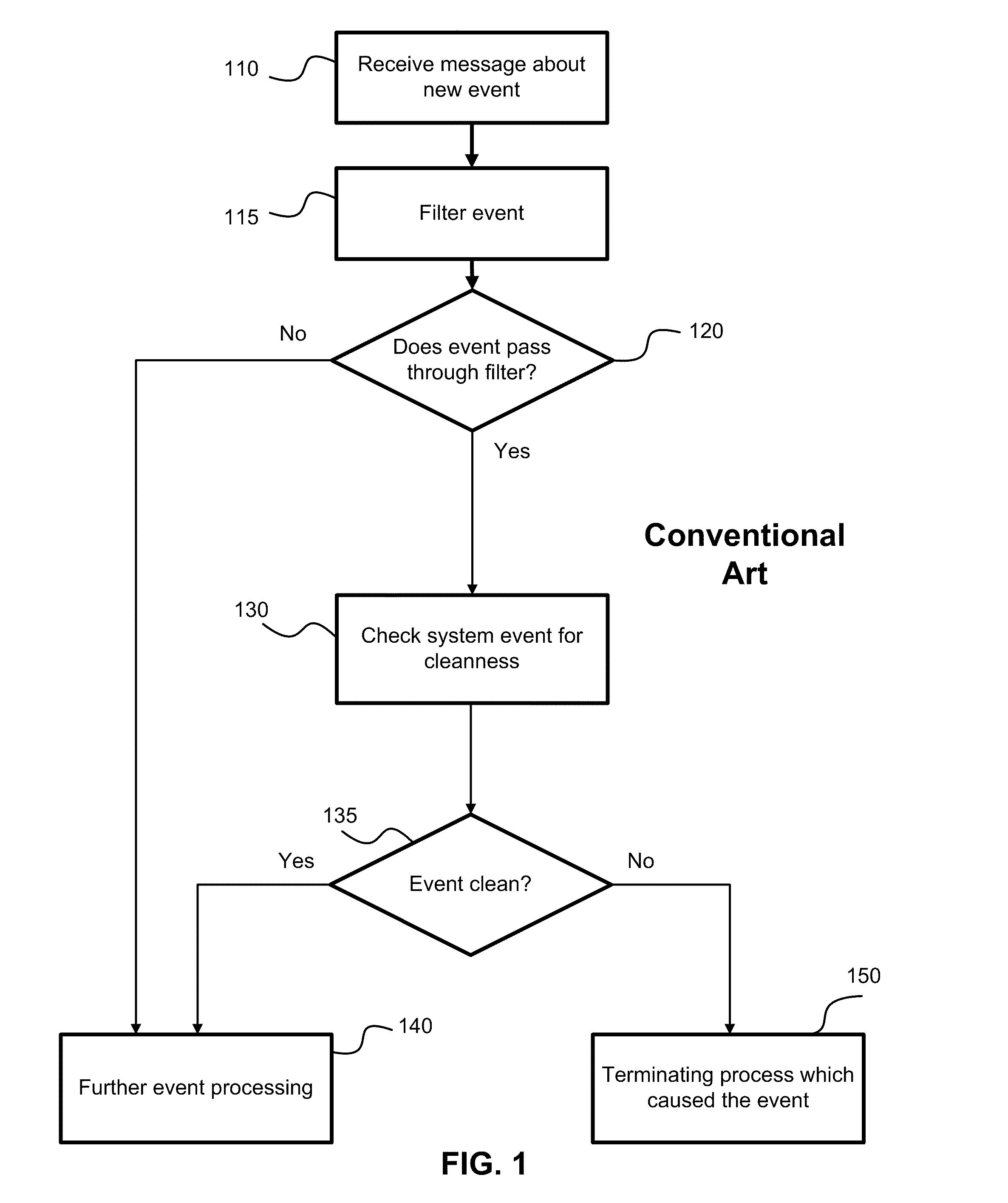
A system, method and computer program product for malware detection based on the behavior of applications running on a computer system, including: asynchronous processing of system events for malware threat analyses using application filters; analyzing events using heuristic and signature data; analyzing applications behavior and detecting abnormal behavior of “clean” applications; automatically classifying applications (i.e., detecting new versions) based on behavior analysis; automatically analyzing the reliability of web sites based on behavior triggered by the web site accesses; in enterprise networks, detecting abnormalities in configuration of user computer systems; recognizing a user by his behavior profile and using the profile for an automatic configuration of user applications.
Owner:AO KASPERSKY LAB
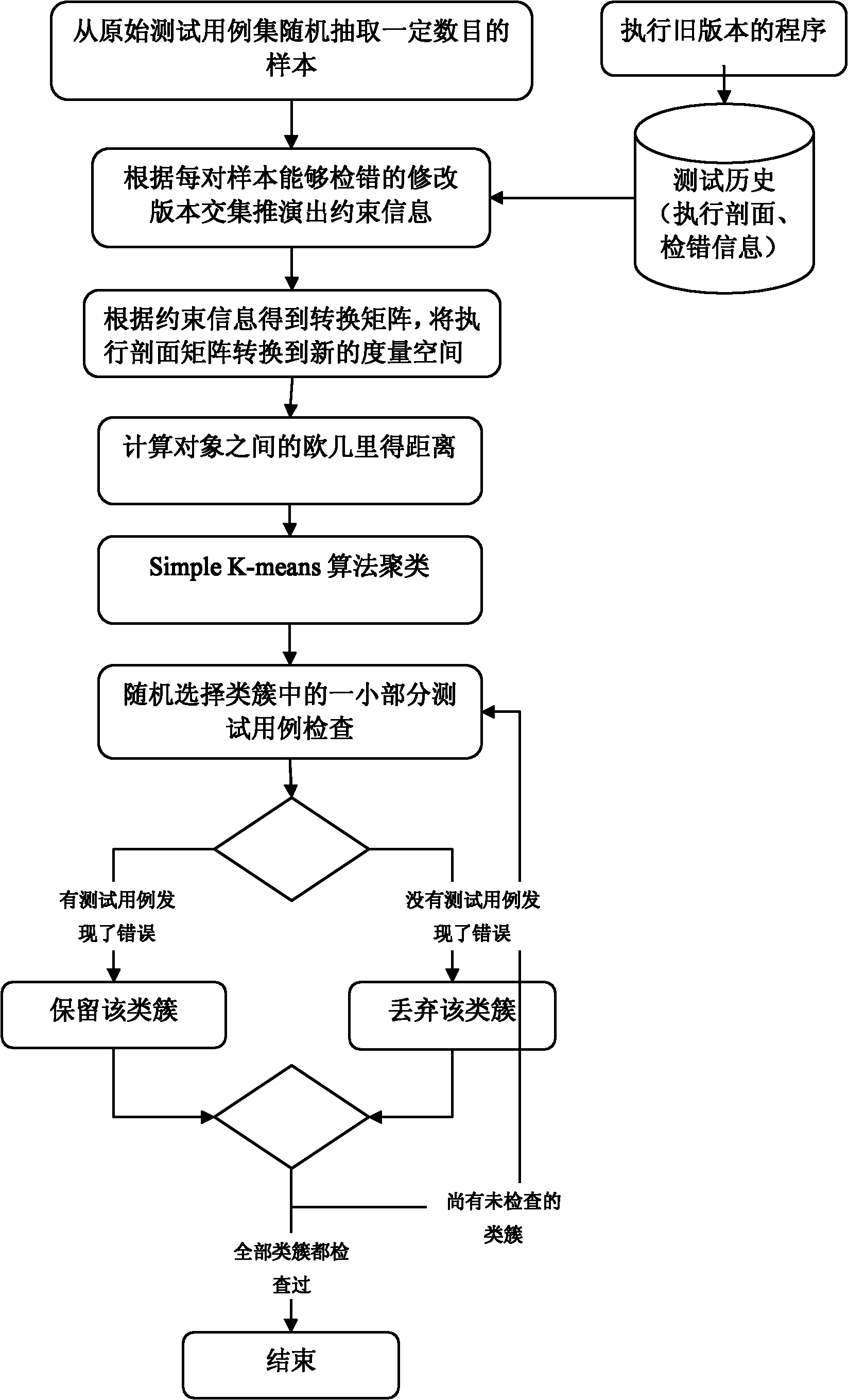
Method for selecting regression test case for clustering with semi-supervised information
InactiveCN102063374AEasy to useImprove efficiencySoftware testing/debuggingCluster algorithmData dredging
The invention discloses a method for selecting a regression test case for clustering with semi-supervised information. The method comprises the following steps: recording the execution overage information of the test case, generating a function execution profile, and representing the test case in a quantitative form; analyzing the historical test results to obtain the constraint relationship among test cases; and analyzing the test cases with a semi-supervised clustering algorithm to obtain similarities and differences of the execution conditions of the test cases, understand the relation between program behaviors and the test cases, effectively reduce the number of test cases in the regression test stage and maintaining enough high error detection capability. According to the invention, the program is understood according to the internal relation of the program behaviors revealed by the test cases based on the data mining technology so that the selection of the test cases is easier and more automatic, the tests cases can be used more effectively in regression tests, the test case selection accuracy is promoted, and the regression test efficiency is improved.
Owner:NANJING UNIV
User-browser interaction-based fraud detection system
InactiveUS8650080B2Payment architecturePlatform integrity maintainanceRequest - actionInternet privacy
Systems, methods and media for detecting fraudulent behavior during an Internet commerce session are disclosed. Embodiments of a method may include establishing an e-commerce session with a user and requesting fraud detection analysis of user-browser interaction during the e-commerce session. Embodiments may also include receiving fraud detection results for the e-commerce session, where the fraud detection results may provide an indication of a comparison between the user's interaction with a browser during the e-commerce session and known fraudulent behavior. Embodiments may also include performing an action based on the fraud detection results. Determining the fraud detection results may include determining user-browser interaction data associated with the session and comparing the user-browser interaction data to known fraudulent human or automated program behavior. Performing the action based on fraud detection results may include one or more of completing an e-commerce transaction, requesting additional authentication, denying the requested action, etc.
Owner:IBM CORP
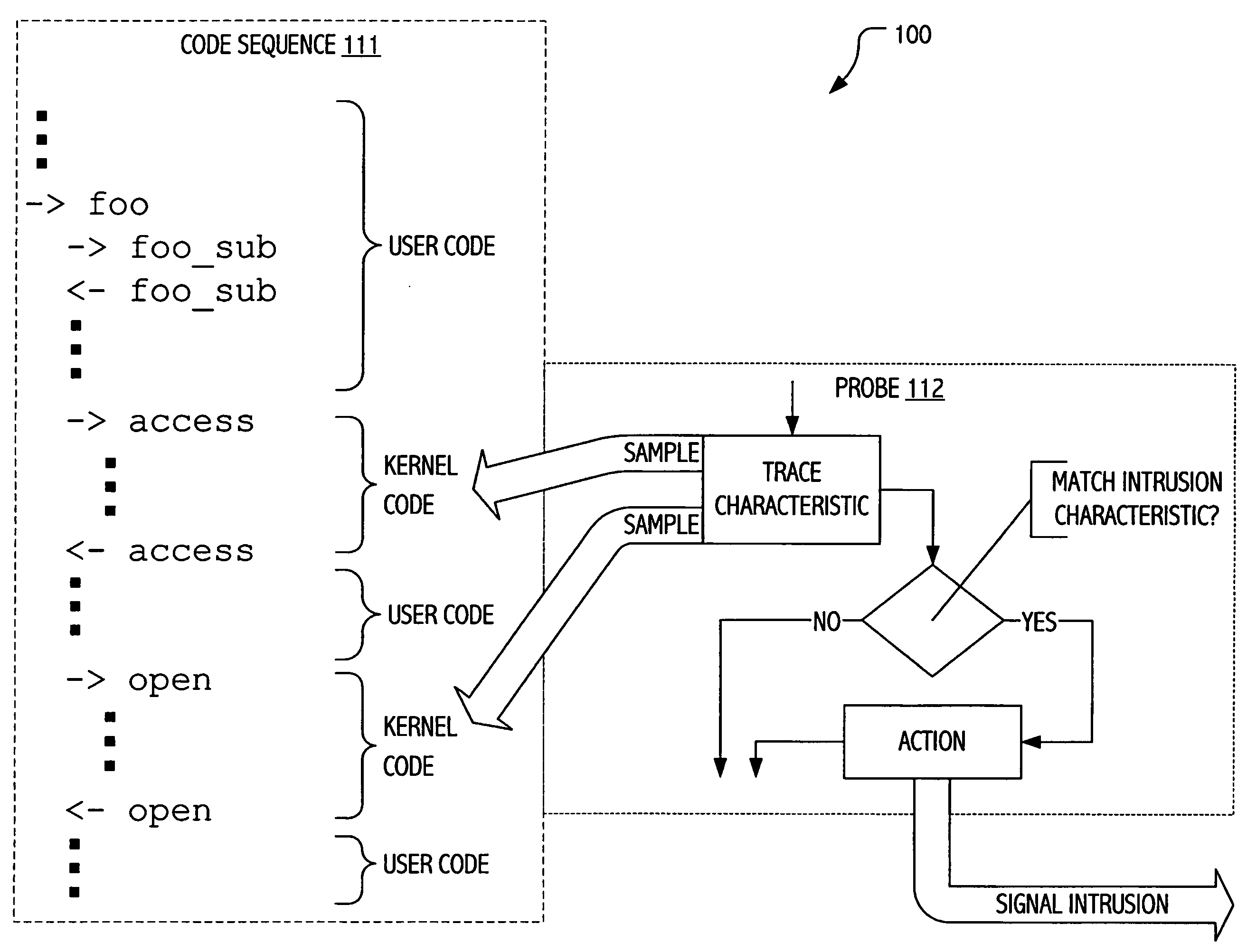
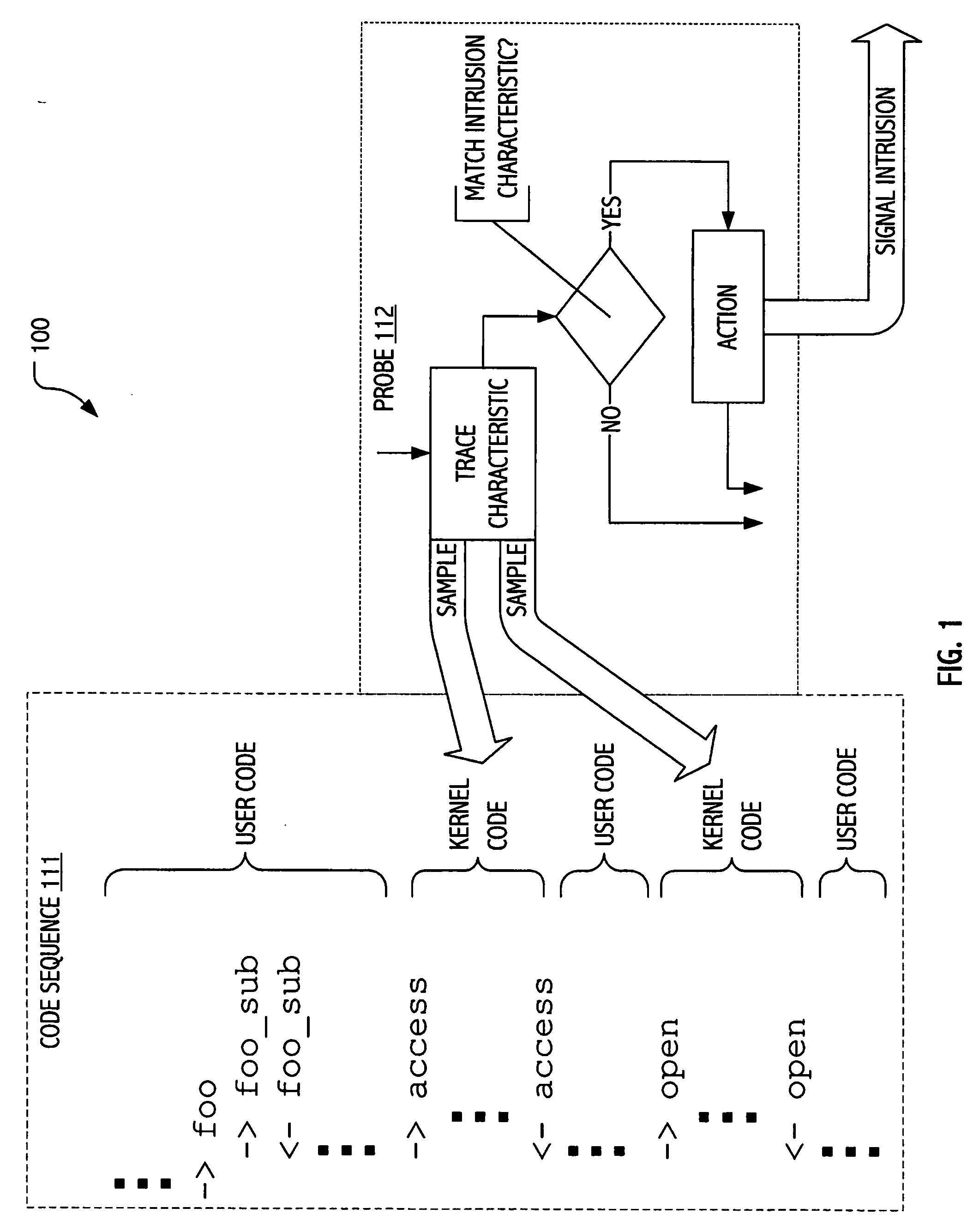
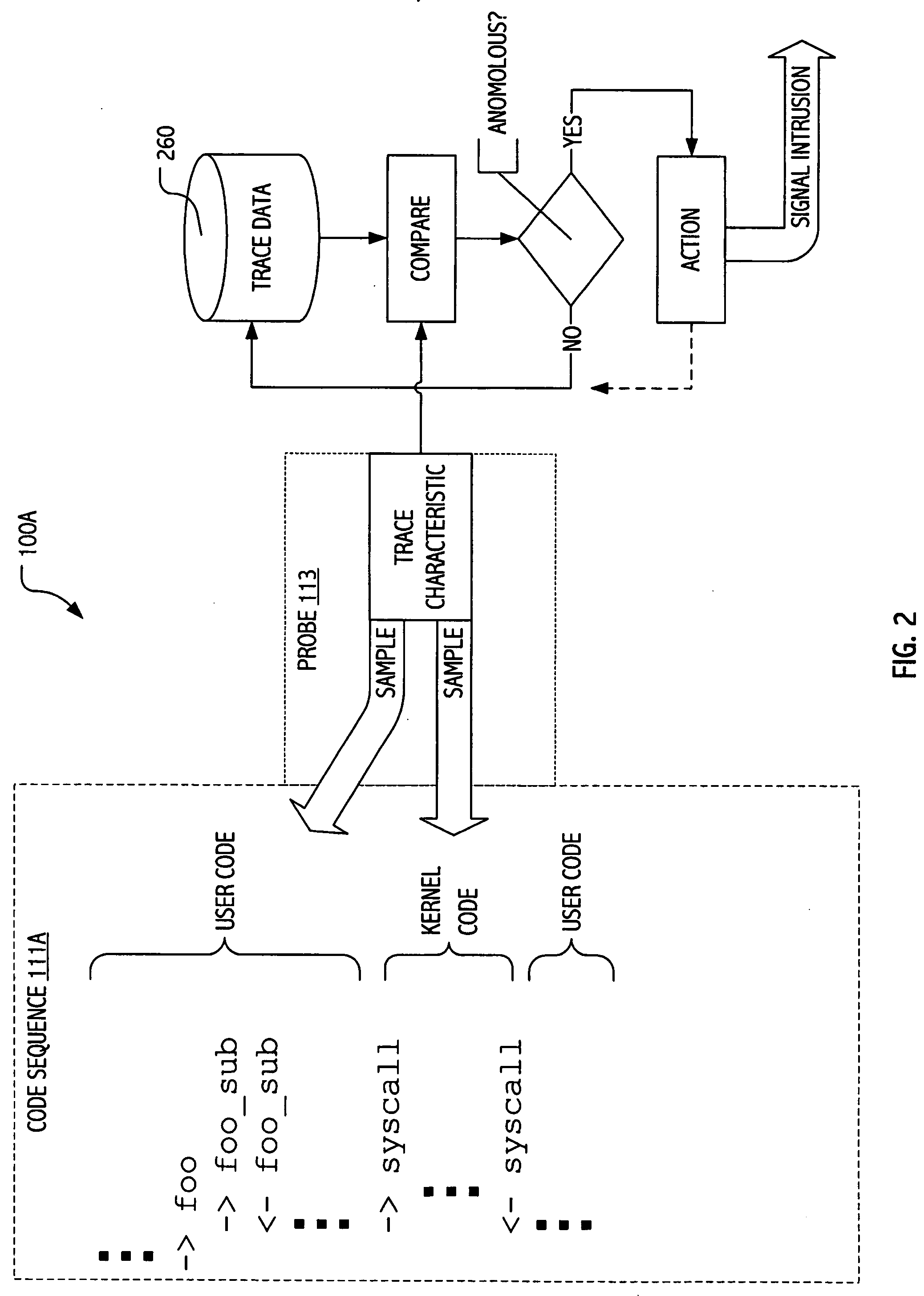
Intrusion detection using dynamic tracing
ActiveUS20070107058A1Reduce overheadPractical limitationMemory loss protectionError detection/correctionTime informationParallel computing
Techniques have been developed whereby dynamic kernel / user-level tracing may be employed to efficiently characterize runtime behavior of production code. Using dynamic tracing techniques, user space or kernel instruction sequences between system calls may be instrumented without access to source code. In some realizations, instrumentation may be interactively specified on a host system. In some realizations, instrumentation specifications may be supplied as functional definitions (e.g., as scripts and / or probe definitions) for installation on a host system. Using the developed techniques, data states, parameters passed and / or timing information may be sampled to provide more detailed insight into actual program behavior. In signature-oriented exploitations, more powerful intrusion signatures are possible. In anomaly-oriented exploitations, a more detailed “sense of self” may be developed to discriminate between normal and anomalous program behavior.
Owner:ORACLE INT CORP
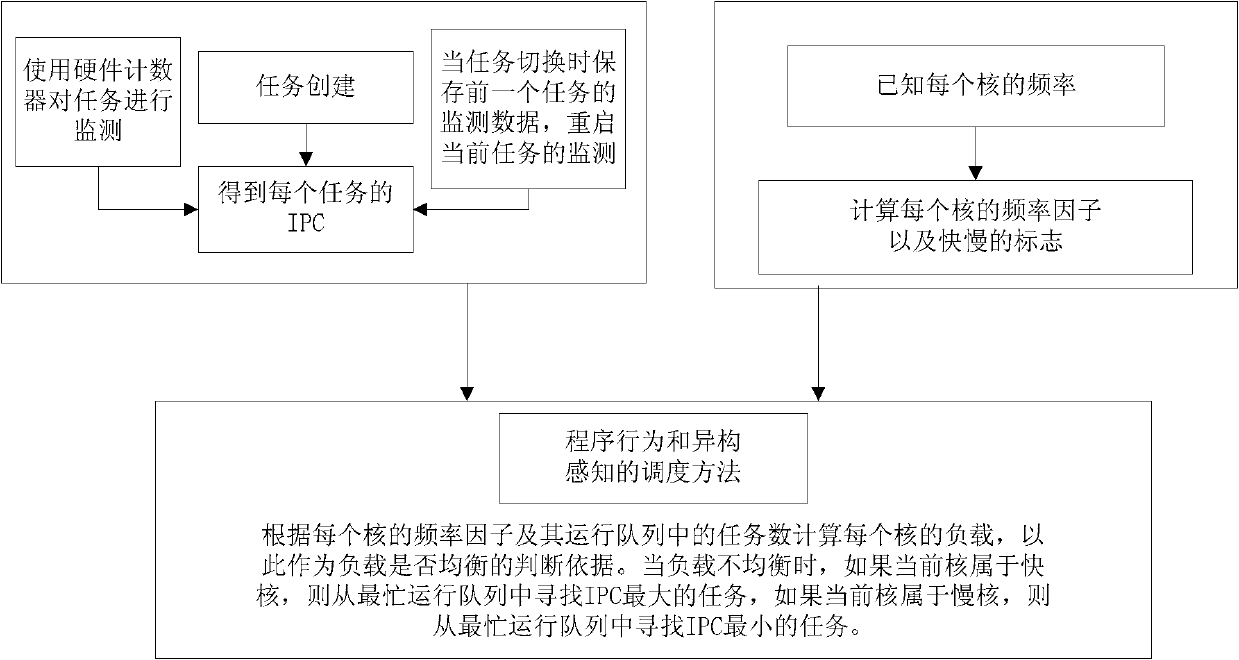
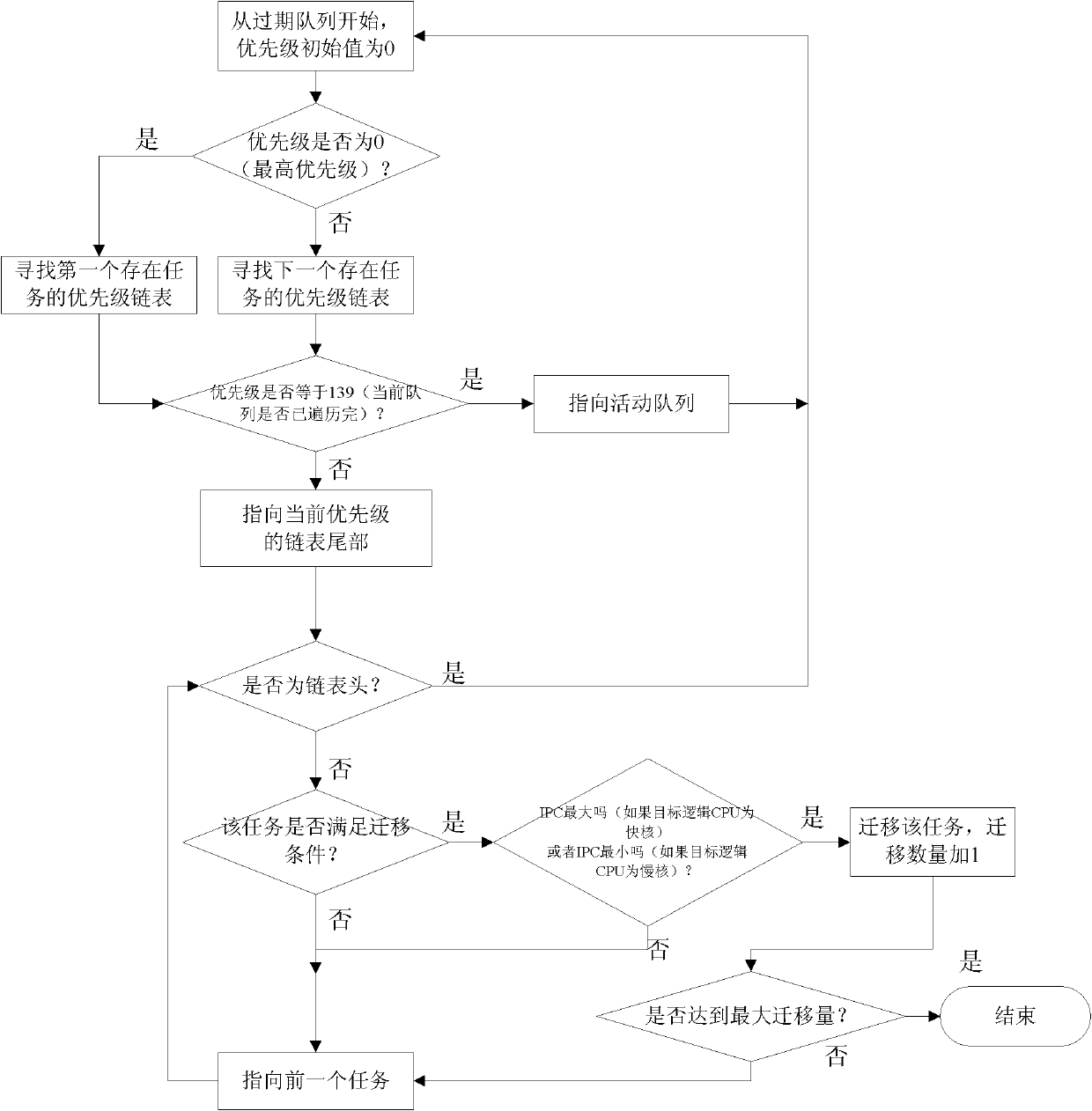
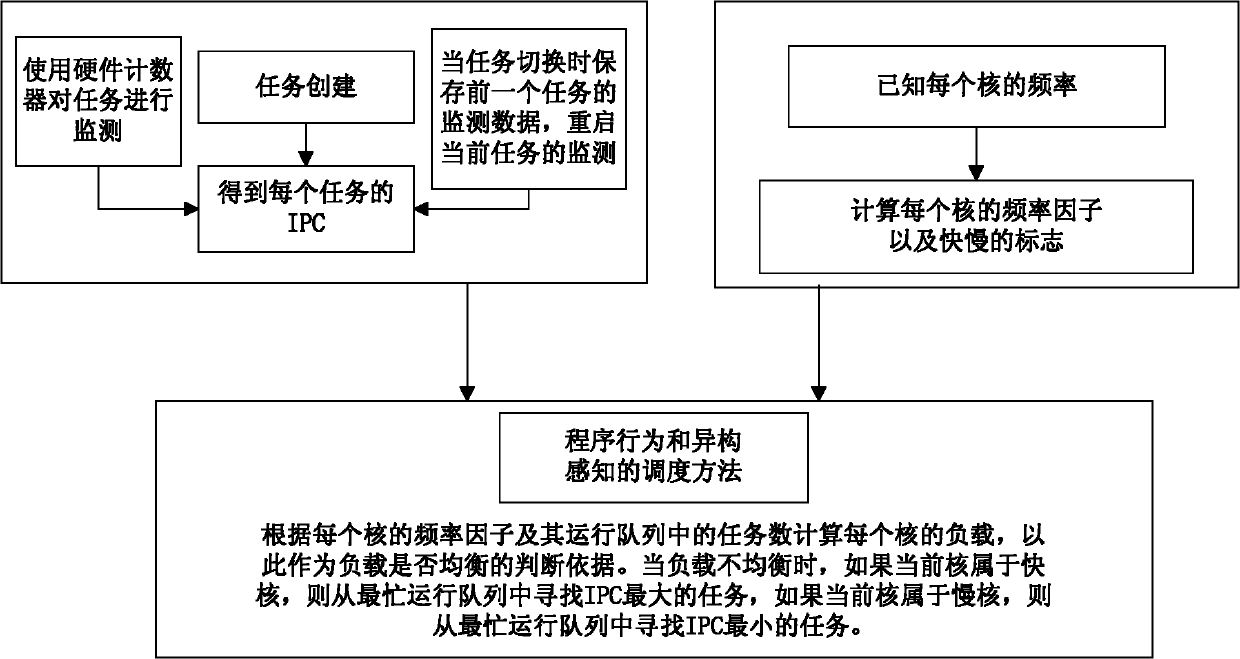
Load balancing method based on program behaviour online analysis under heterogeneous multi-core environment
InactiveCN102184125AHigh frequencyBear moreResource allocationMultiple digital computer combinationsDomain modelOperational system
The invention discloses a load balancing method based on program behaviour online analysis under a heterogeneous multi-core environment, which comprises the steps of: being compatible with a heterogeneous multi-core environment of the traditional scheduling domain model, dynamically monitoring task characteristics, calculating a logic CPU load, and balancing loads of program behaviour perception. The load balancing method is completely compatible with the traditional operating system scheduling strategy, is simple and efficient, and is suitable for popularization; and an algorithm is tested on an actual software and hardware platform.
Owner:CAPITAL NORMAL UNIVERSITY
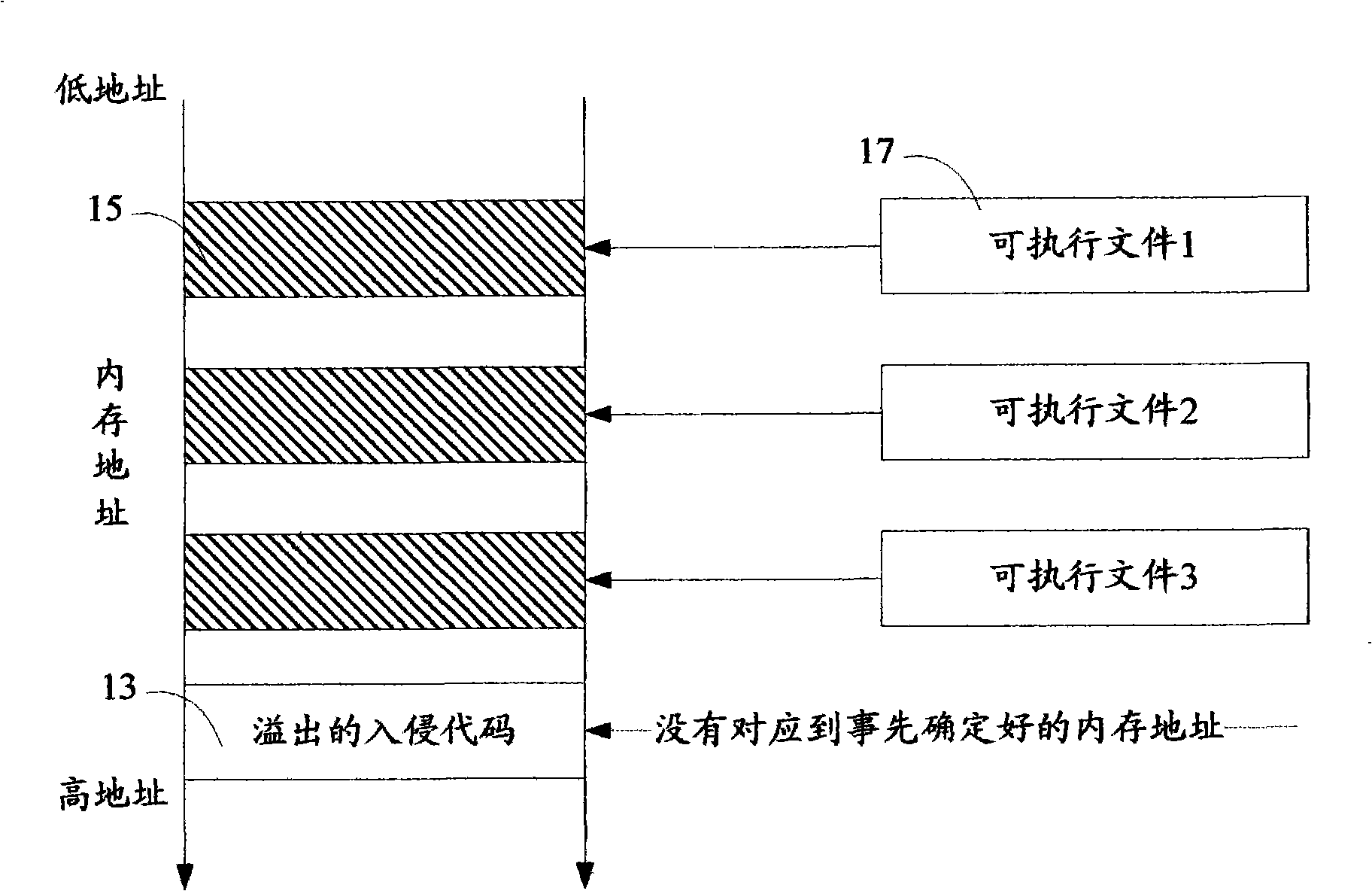
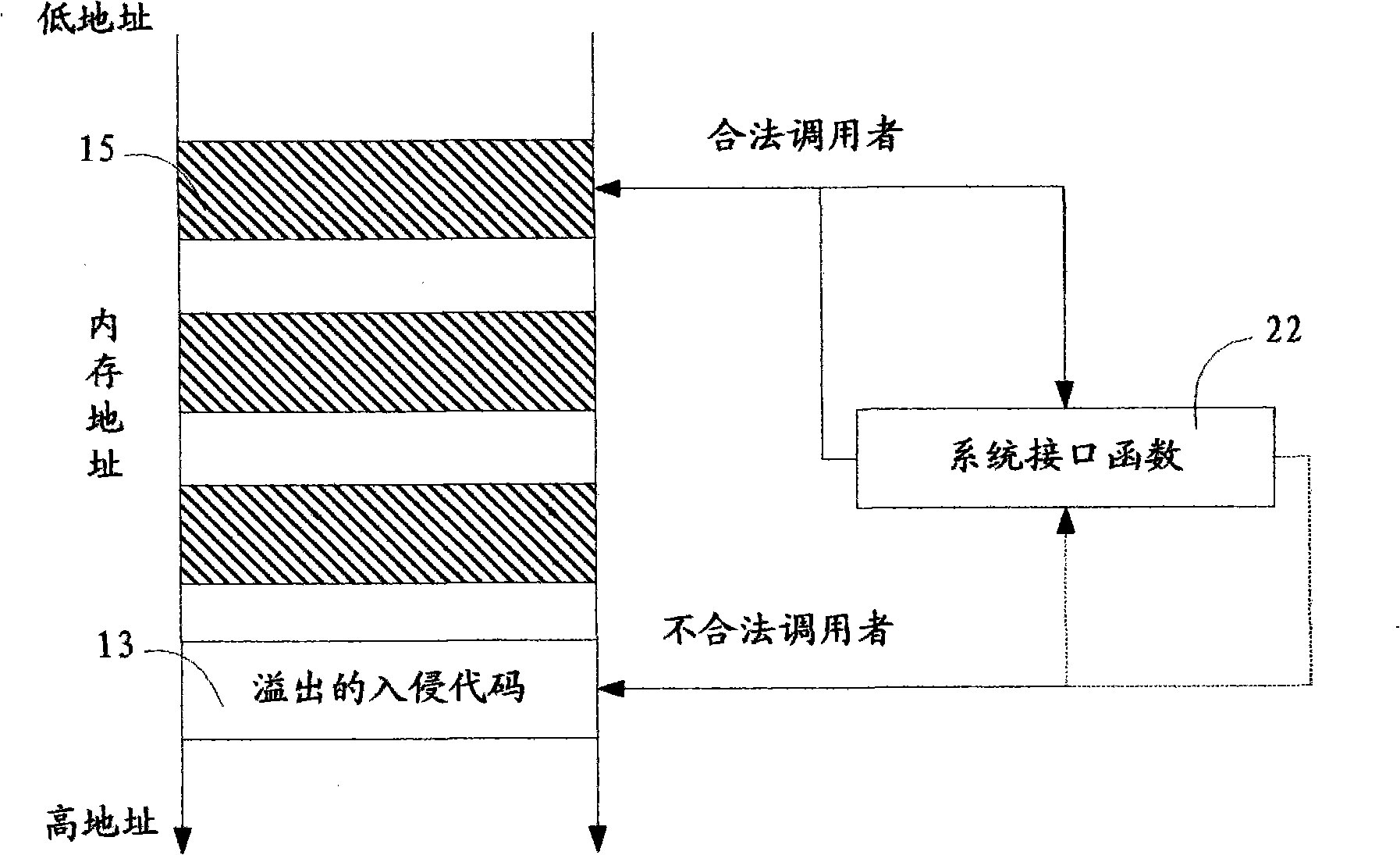
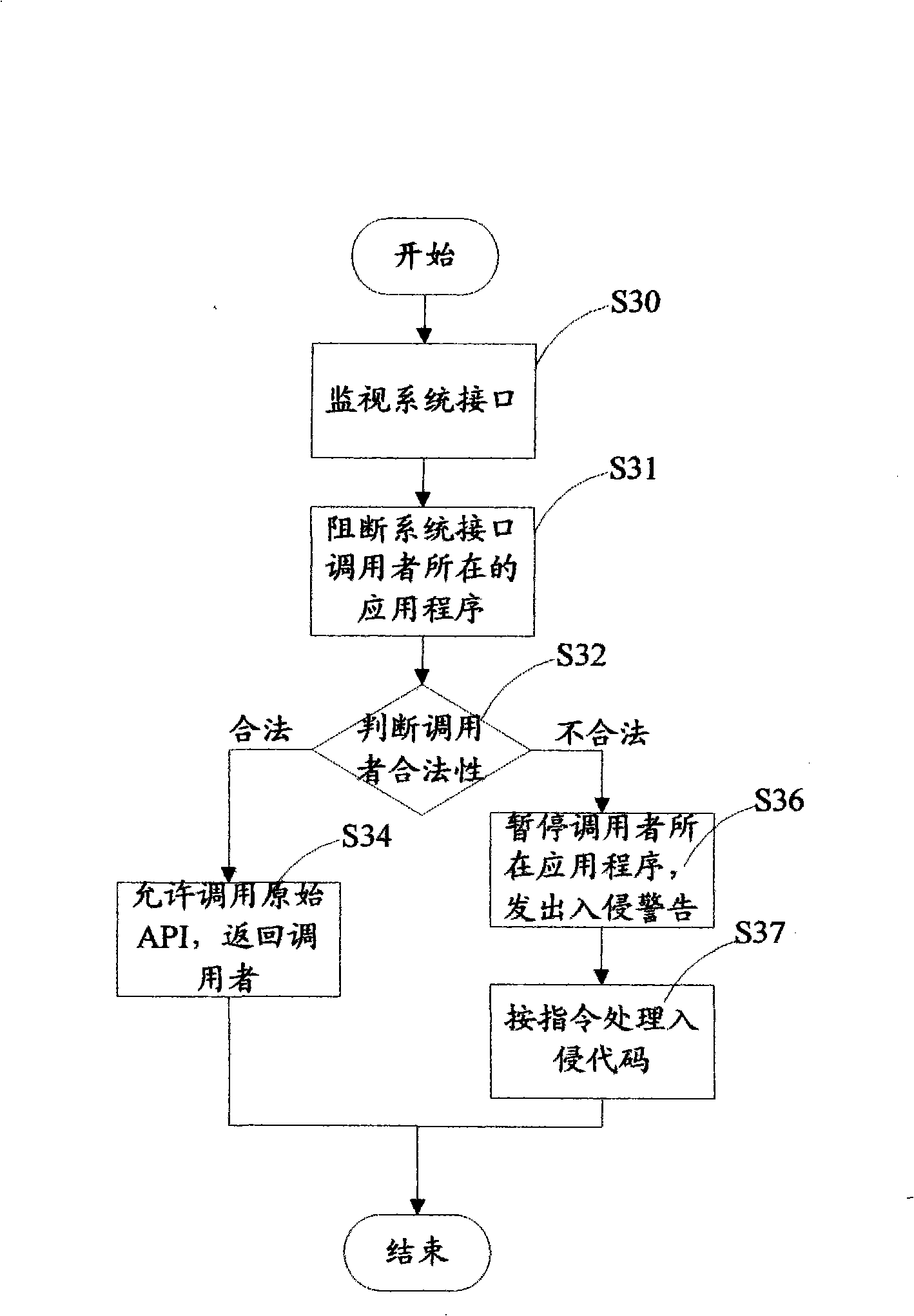
Method and system for detecting application program behavior legality
InactiveCN101408917AReduce false alarm rateImprove recognition ratePlatform integrity maintainanceBehavioral analyticsMonitoring system
A method for detecting the legitimacy of an application program behavior comprises the following steps: monitoring one or more system interfaces of a computer to cause the monitored system interfaces to jump to a monitoring module for execution when the monitoring system interfaces receive a call; blocking the application program of a caller and judging the validity of the caller: permitting the caller to call an interface function and continuously perform the application program of the caller if the caller is legal; and, pausing the behavior of the application program of the caller and issuing an intrusion alarm if the caller is illegal. The detection method finds out whether an executor of the application program behavior is legal or not by monitoring the system interfaces of the computer so as to intercept the program behavior executed by illegal executors and give an alarm. Compared with the existing fuzzier behavioral analysis technology, the detection method has the advantages of low false alarm rate, high recognition rate and the like, especially has good defense effect against the intrusion behavior due to overflow vulnerability, so the detection method is an effective supplement to the existing behavior analysis defense technology.
Owner:厦门市美亚柏科资讯科技有限公司
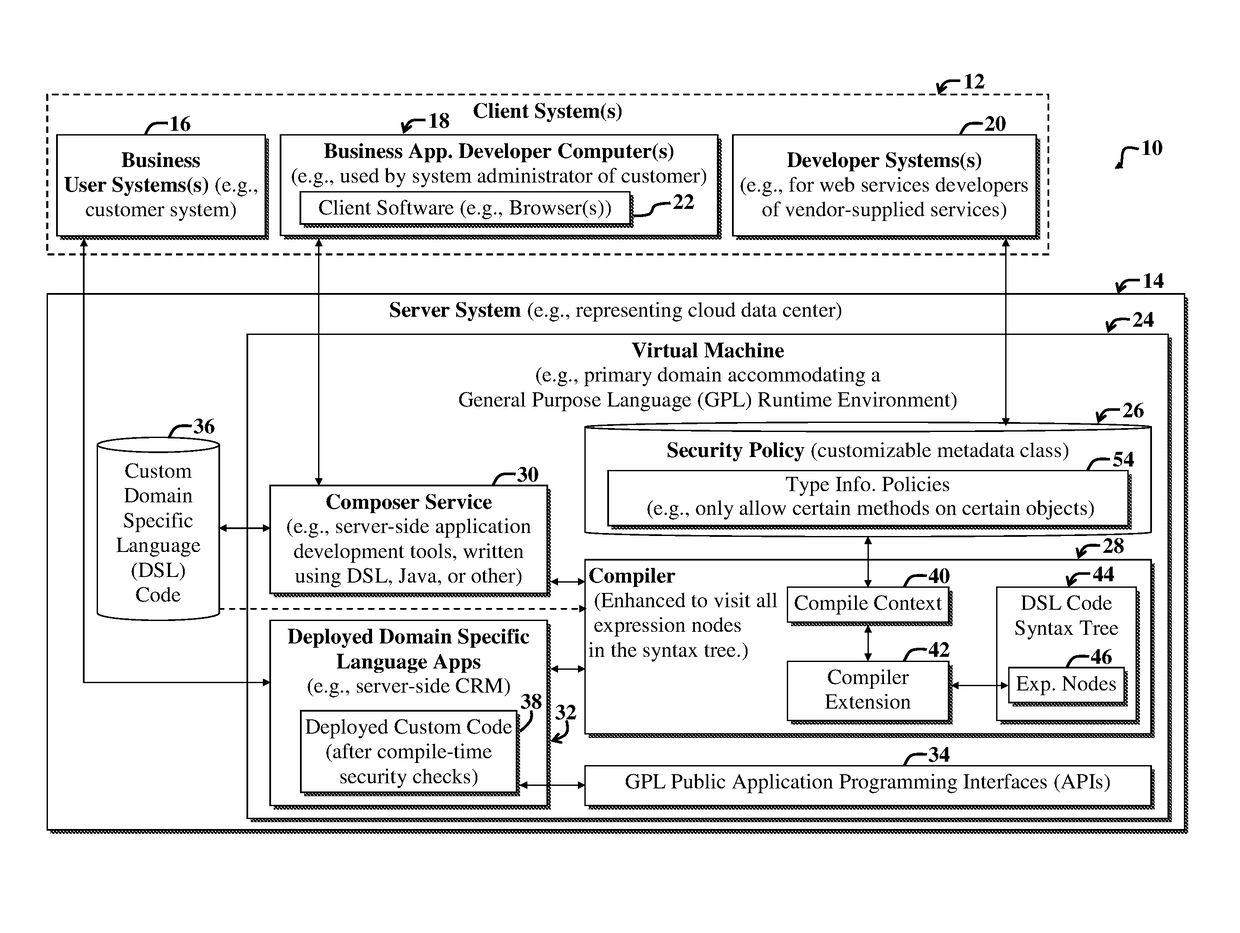
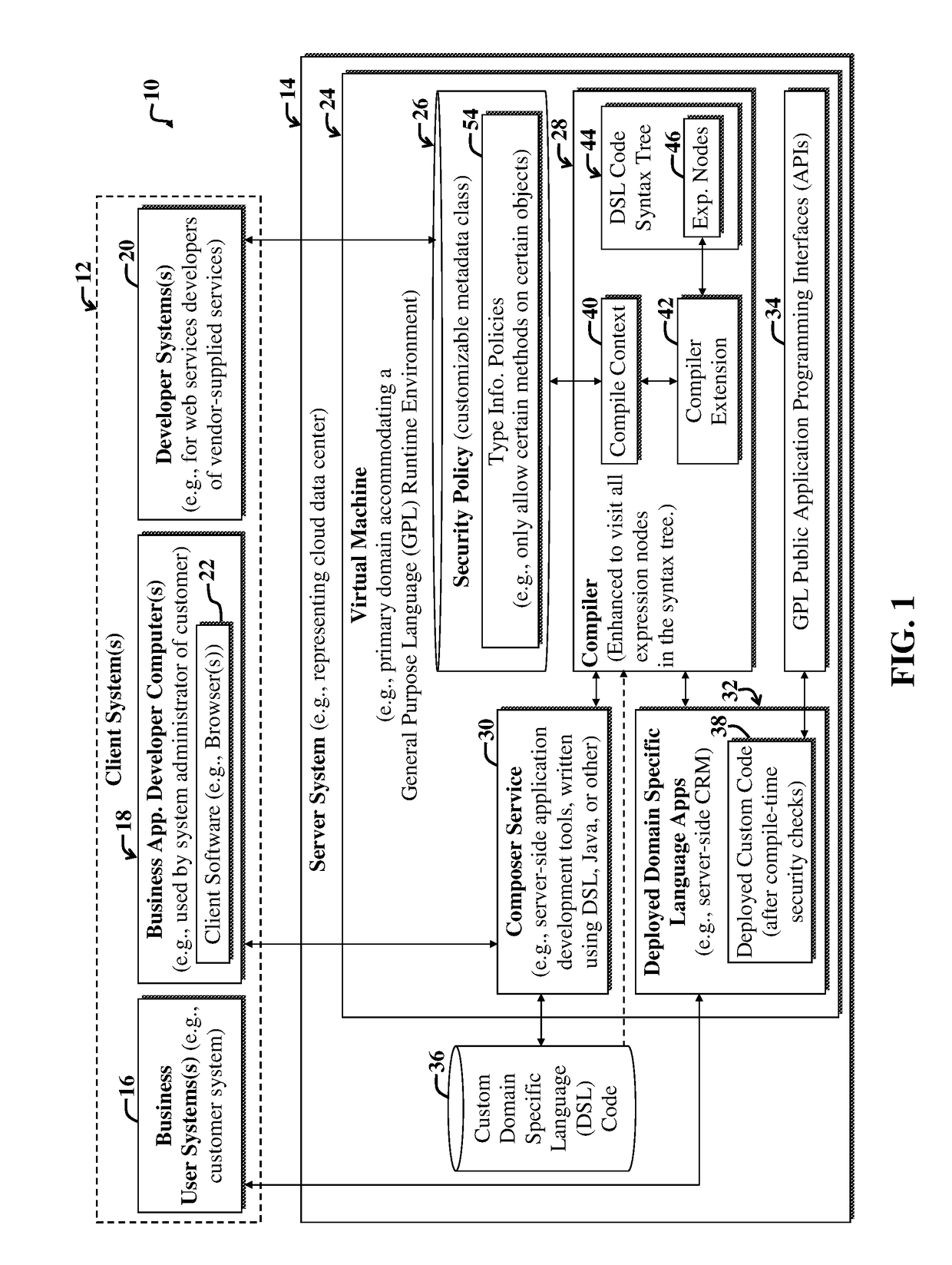
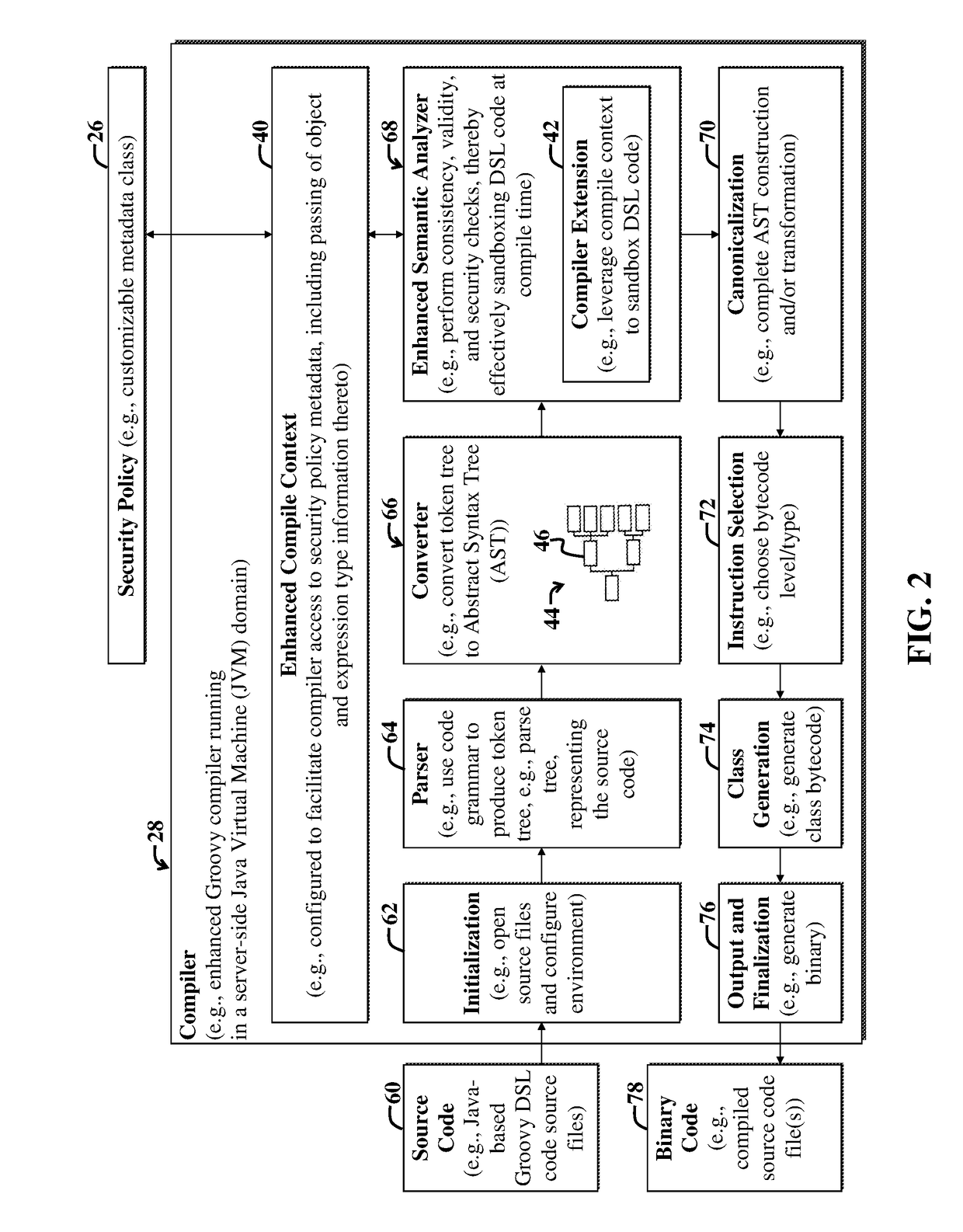
Method for static security enforcement of a DSL
ActiveUS20170249130A1Improve protectionImprove securityDigital data protectionReverse engineeringSecurity policyProgram behavior
An example system and method for securing computer code of a dynamic Domain Specific Language (DSL) that leverages a General Purpose Language (GPL). An example method includes enhancing compile-time security enforcement functionality for computer code written using the DSL, in part by using a compiler to perform static analysis on the DSL computer code. The static analysis includes referencing a security policy defining one or more unacceptable program behaviors; and indicating when execution of the computer code would result in performance of the one or more unacceptable program behaviors based on results of the static analysis.
Owner:ORACLE INT CORP
System and method for characterizing program behavior by sampling at selected program points
InactiveUS7103877B1Reduce overheadError detection/correctionSpecific program execution arrangementsRelevant informationTheoretical computer science
A system and method for characterizing runtime behavior of a computer program executing in an execution environment, the method comprising: identifying one or more instances of yield points in a program to be executed, each yield point indicating a potential sampling operation during program execution; during program execution, in response to an identified yield point instance, ascertaining a state of the execution environment for indicating whether a sampling operation is to be performed; and, when the state of the execution environment indicates a sampling operation, recording relevant information for characterizing behavior of the execution environment. Relevant information for characterizing program behavior includes frequencies of methods executed in the program, and calling context associated with methods called by the program. Different mechanisms are provided for determining the sampling condition including the setting of a trigger bit by a runtime system, or, determining a sampling operations based on a fixed percentage of all executed yield points taken.
Owner:LINKEDIN
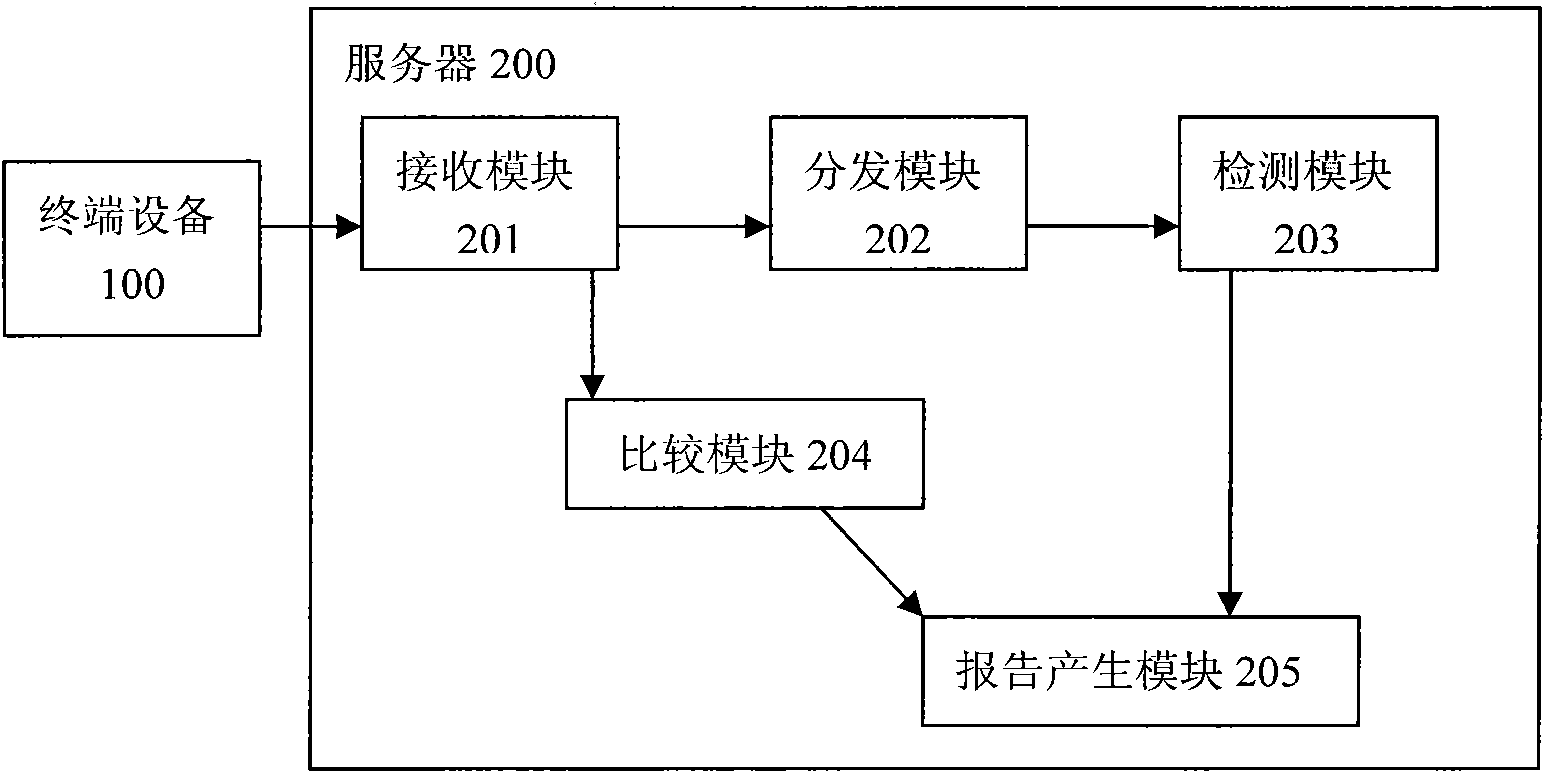
Behavior-based mobile terminal security protection system and method
InactiveCN102082802APrevent installationImprove detection efficiencyPlatform integrity maintainanceTransmissionTerminal equipmentSoftware engineering
The invention provides a program behavior-based mobile equipment security protection system and a program behavior-based mobile equipment security protection method. The program behavior-based mobile equipment security protection system comprises terminal equipment and a server, wherein the server comprises a receiving module, a distribution module, a detection module and a report generation module; the receiving module is used for receiving a software program from the terminal equipment; the distribution module is used for distributing the received software program to a simulator in cloud consisting of processors; the detection module is used for detecting and recording the execution behaviors of the software program or other files run in an hourglass model of the server; and the report generation module is used for evaluating the friendliness or hazard level of the software program or the other files according to the execution behaviors of the software program in the hourglass model, and providing an analysis report for the terminal equipment.
Owner:BEIJING BANGCLE TECH CO LTD
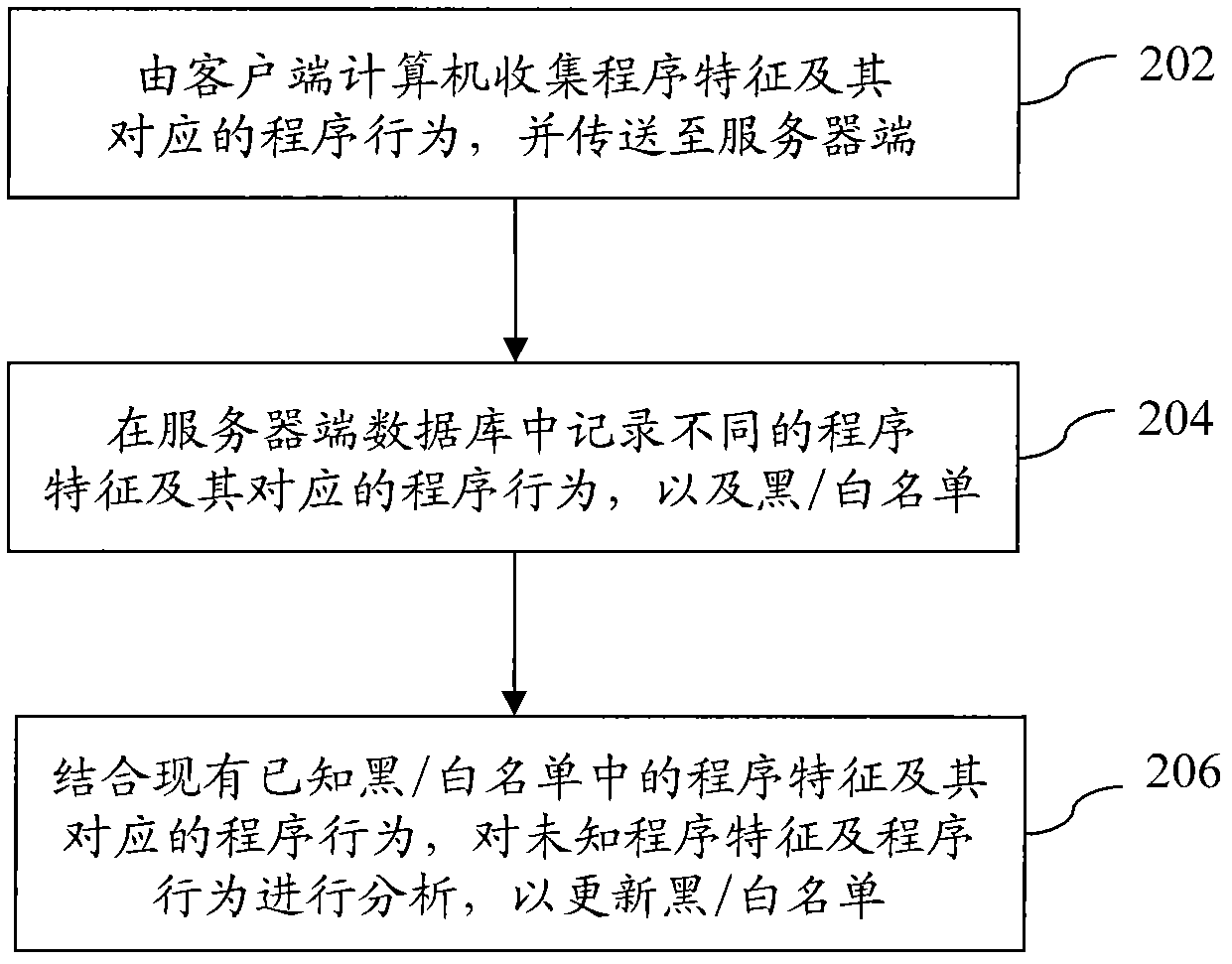
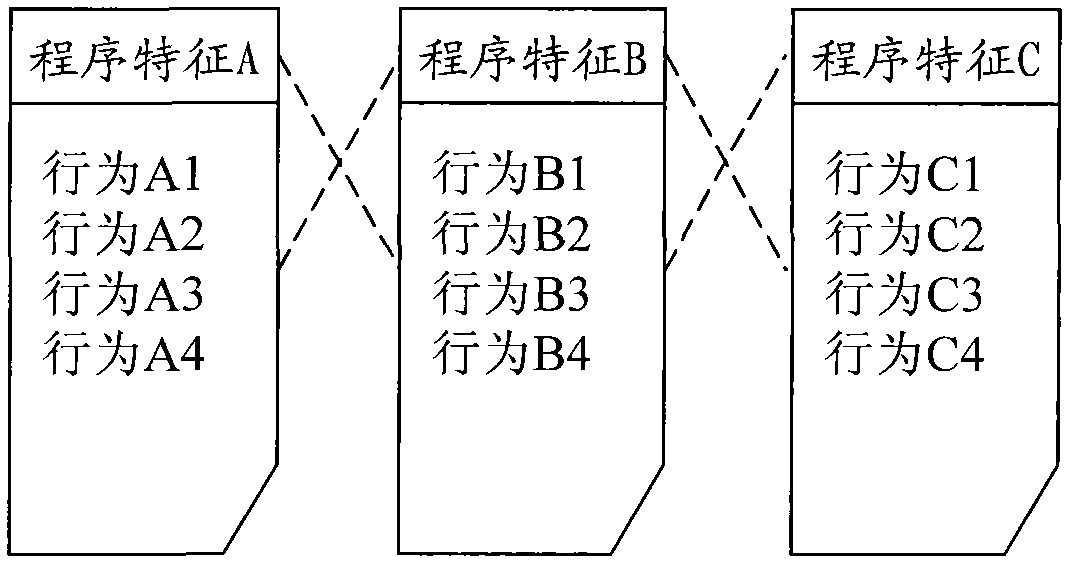
Cloud-based sample database dynamic maintaining method
The invention provides a cloud-based sample database dynamic maintaining method comprising the following steps of: firstly, collecting program characteristics and program behaviors corresponding to the program characteristics and transmitting the program characteristics and the program behaviors corresponding to the program characteristics to a server end by a client computer; secondly, recordingdifferent program characteristics and the program behaviors corresponding to the program characteristics in a server end database and a black / white list; and finally analyzing unknown program characteristics and the program behaviors by combining with the program characteristics and the program behaviors corresponding to the program characteristics in the existing black / white list so as to updatethe black / white list. By collecting the program behaviors and linking to the program characteristics through a client, the invention can be used for recording the program characteristics and the program behaviors corresponding to the program characteristics in the database, analyzing and inducting a sample in the database according to the linking relationship between the collected program behaviors and the program characteristics, thereby being beneficial to classifying and discriminating black software or programs from white software or programs. In addition, the invention can be used for formulating corresponding clearing or restoring measures aiming at malicious software in a blacklist.
Owner:BEIJING QIHOO TECH CO LTD
System and method for software testing with extensible markup language and extensible stylesheet language
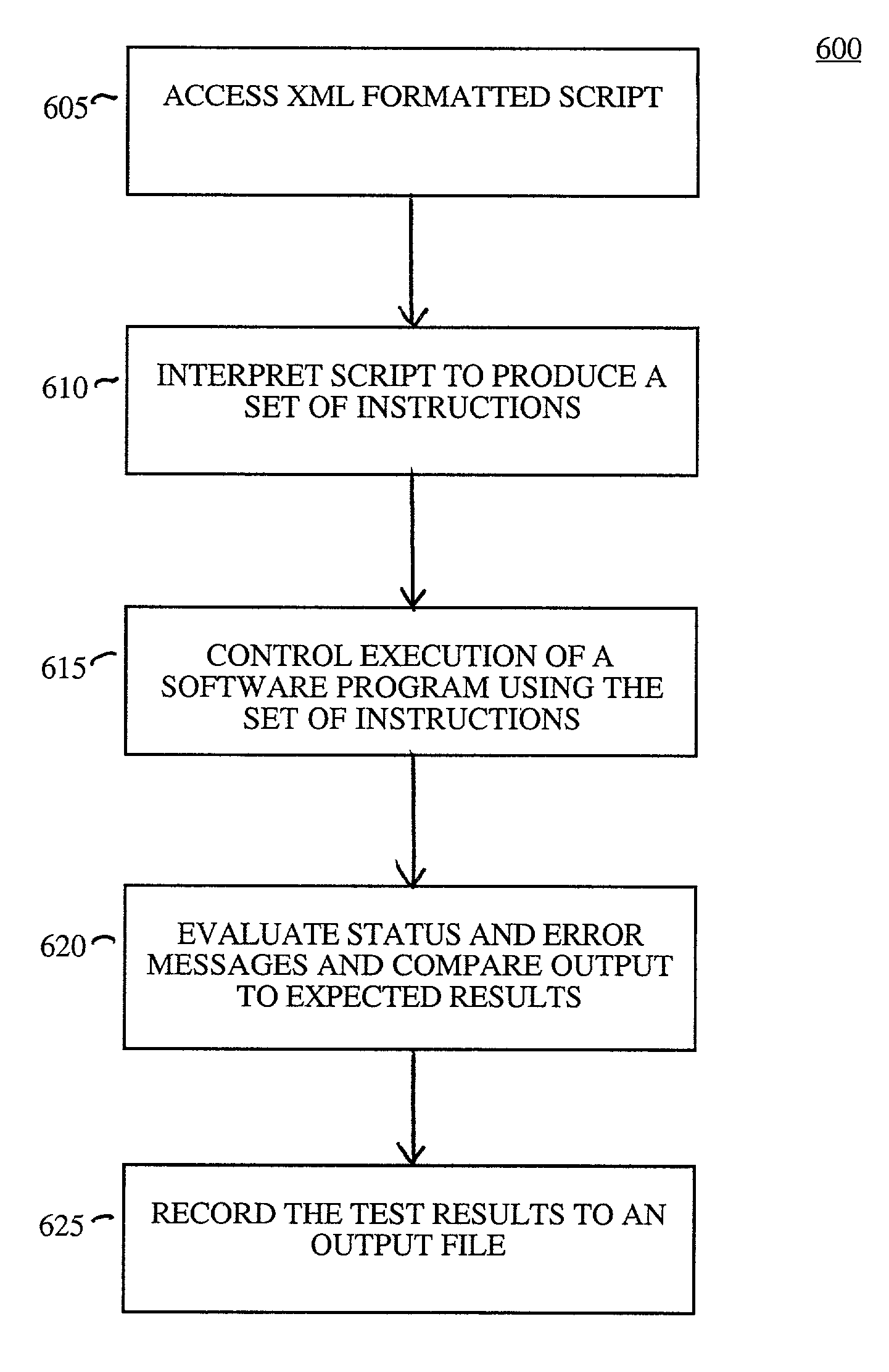
ActiveUS7127641B1Error detection/correctionSpecific program execution arrangementsScripting languageSoftware engineering
A system and method for using Extensible Markup Language (XML) as a scripting language to drive testing of a software program. XML is used to define a markup language in a script that provides commands that are interpreted by a test control processor. The test control processor includes an XML processor for processing the script. Using the script, the test control processor submits instructions to a software program and extracts the behavior of the software program. The software program behavior is tested by submitting multiple sets of instructions and comparing the results. Information regarding the software program behavior and test results is written to an output log file by the test control processor.
Owner:INTELLECTUAL VENTURES II
Memory access monitoring
InactiveUS20080034355A1Error detection/correctionSoftware engineeringDynamic compilationParallel computing
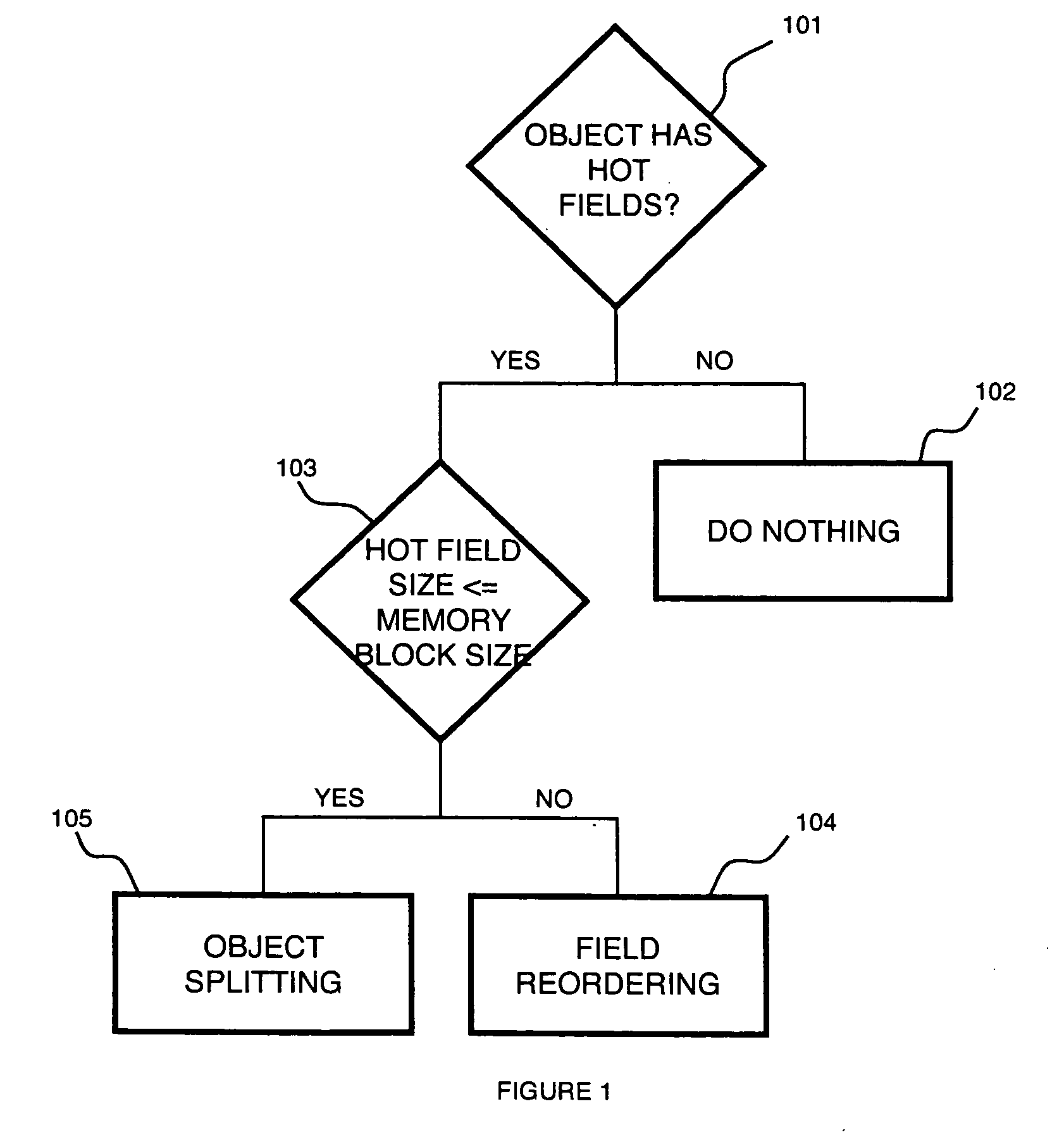
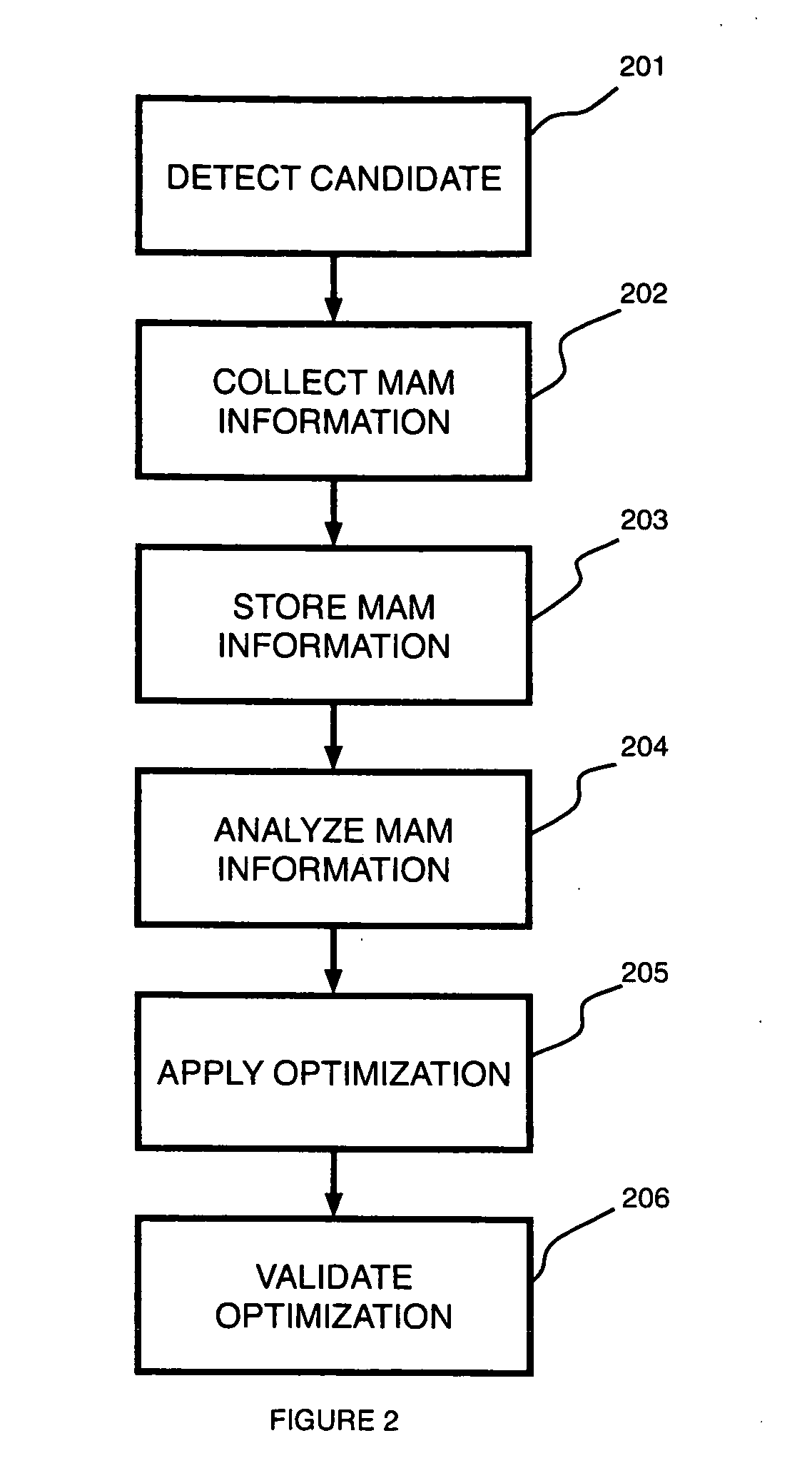
A computer-implemented method for memory access monitoring, implemented by a managed runtime environment computer system including a controller that monitors application behavior and determines actions to be taken to change a behavior of an application, and a runtime, dynamic compiler that analyzes the application and generates code sequences to access a memory access monitoring (MAM) mechanism, includes determining monitor information of a plurality of fields of a memory block to drive an optimization of the application.
Owner:IBM CORP
Method and System for Software System Performance Diagnosis with Kernel Event Feature Guidance
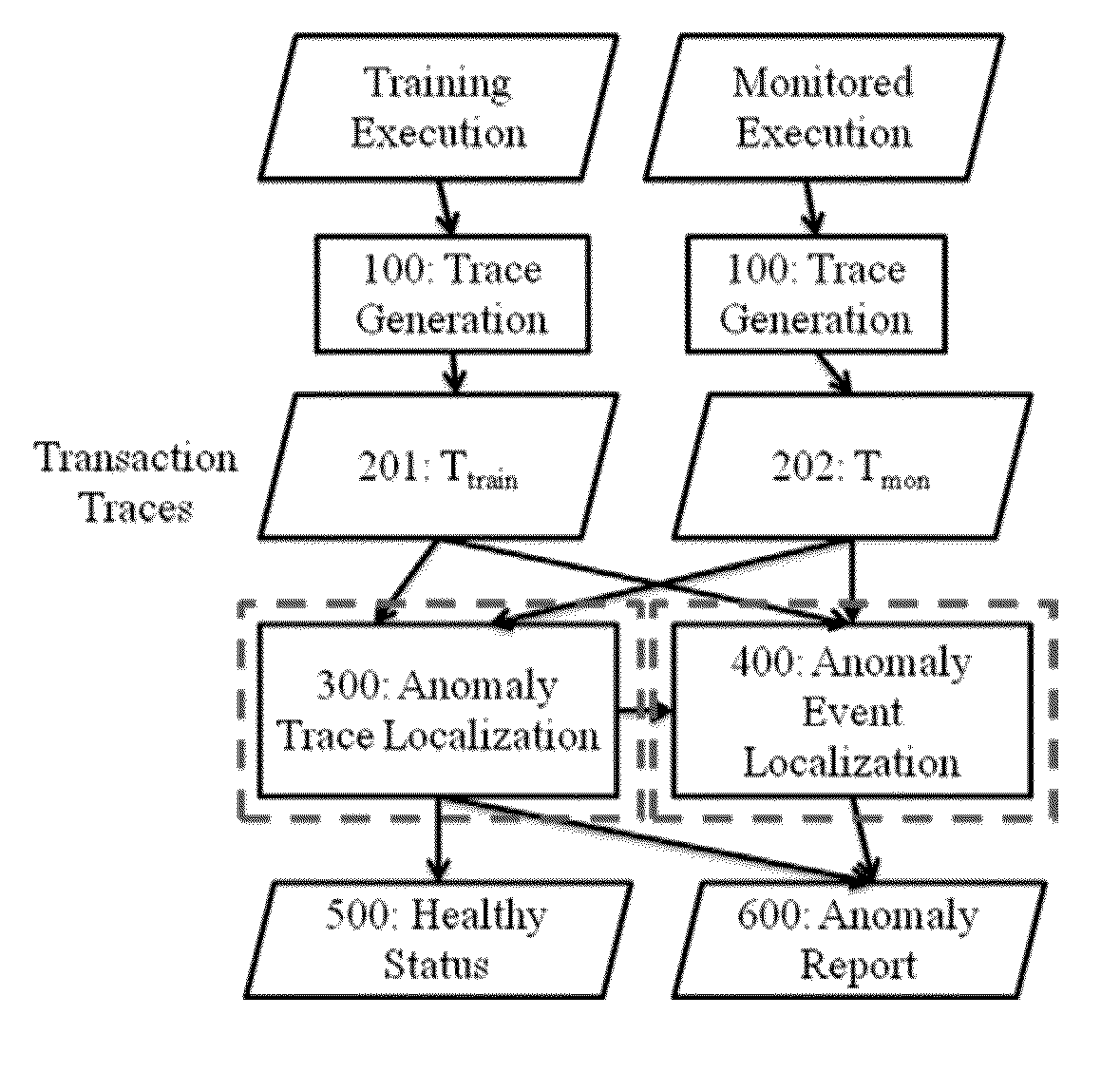
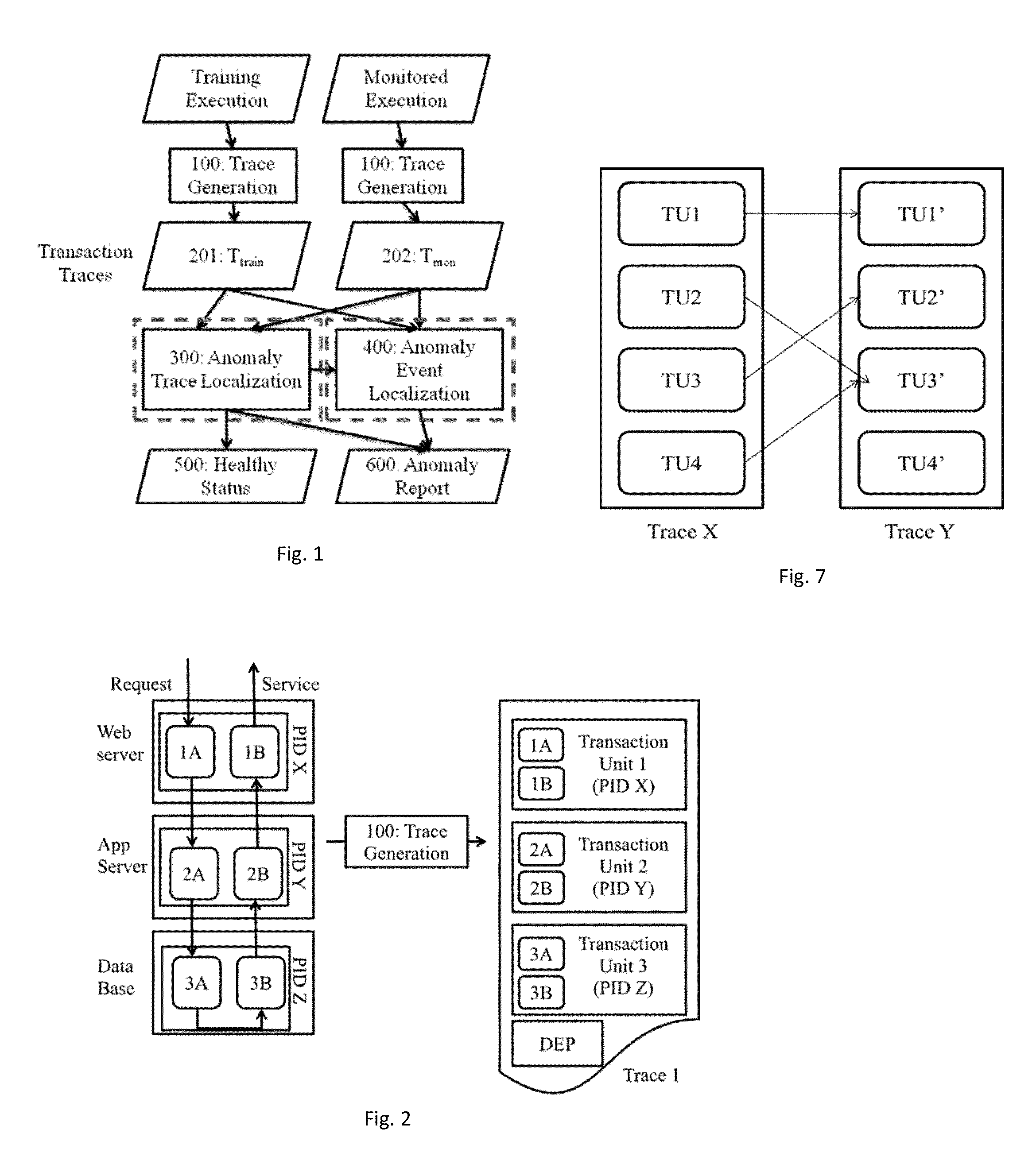
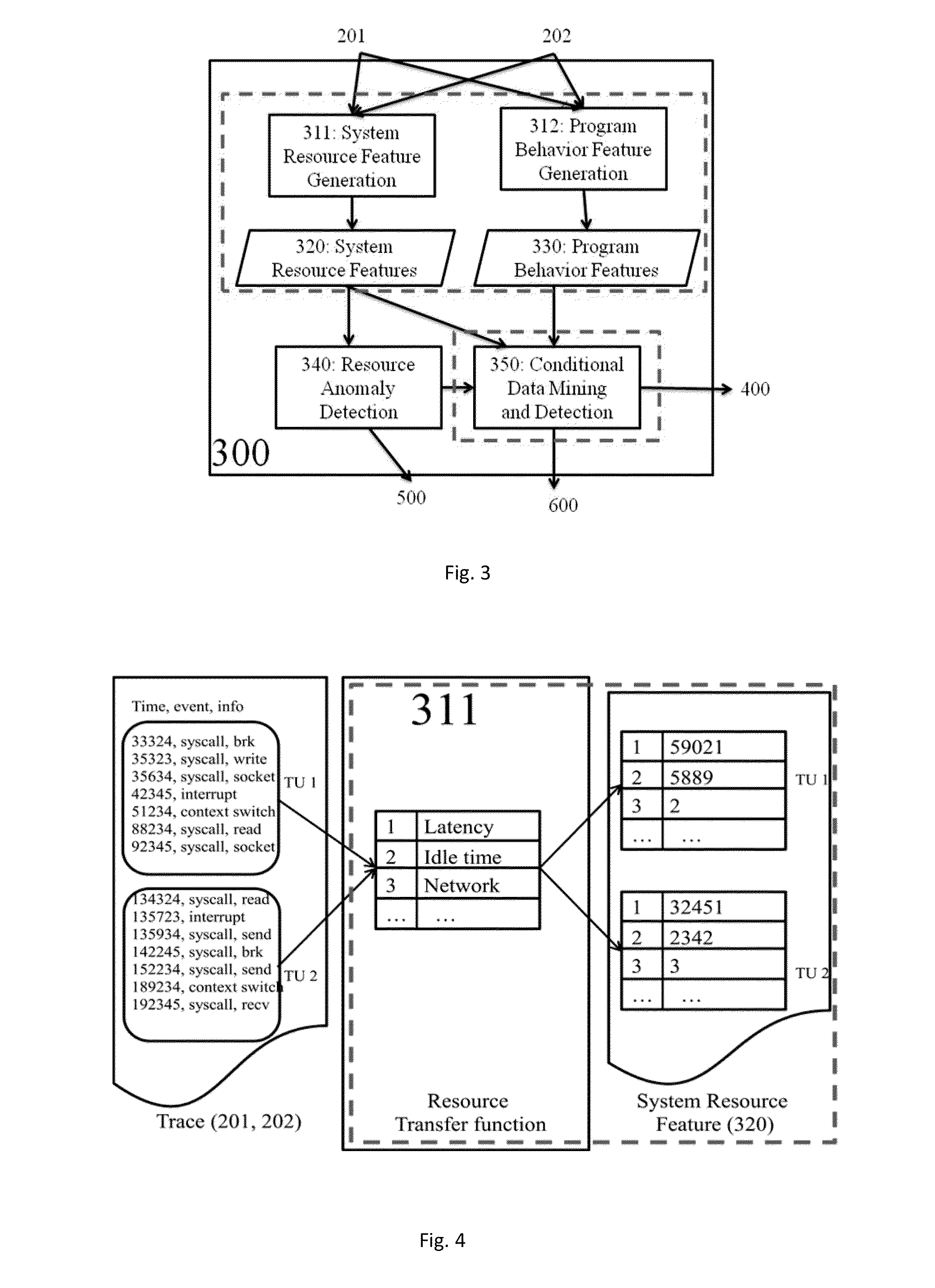
A method includes generating a normal trace in a training stage for the monitored software systems and a monitored trace in the deployment stage for anomaly detection, applying resource transfer functions to traces to convert them to resource features, and system call categorization to traces to convert them to program behavior features, performing anomaly detection in a global scope using the derived resource features and program behavior features, in case the system finds no anomaly, generating no anomaly report, in case the anomaly is found, including the result in an anomaly report; and performing conditional anomaly detection.
Owner:NEC CORP
Generational real-time garbage collection
InactiveUS20060294165A1Improved real-time garbage collectionImprove utilizationSpecial data processing applicationsMemory systemsTime rangeRefuse collection
Disclosed are a partial heap garbage collector, and a partial heap garbage collection method, that during collection checks the time remaining (or equivalently the time taken so far, or the work done so far) to complete the partial heap collection. In a preferred embodiment, the partial heap collection is guaranteed to complete within a fixed time interval. For example, this guarantee may be obtained by applying a worst-case execution time (WCET) and sizing a nursery so that complete evacuation of the nursery can always be achieved on time. As an alternative, a technique, referred to as syncopation, may be used to allow generational collection to be used despite variance in program behavior over the short time scales in which a nursery can be collected. Syncopation may be accomplished via allocation control or via collection control.
Owner:IBM CORP
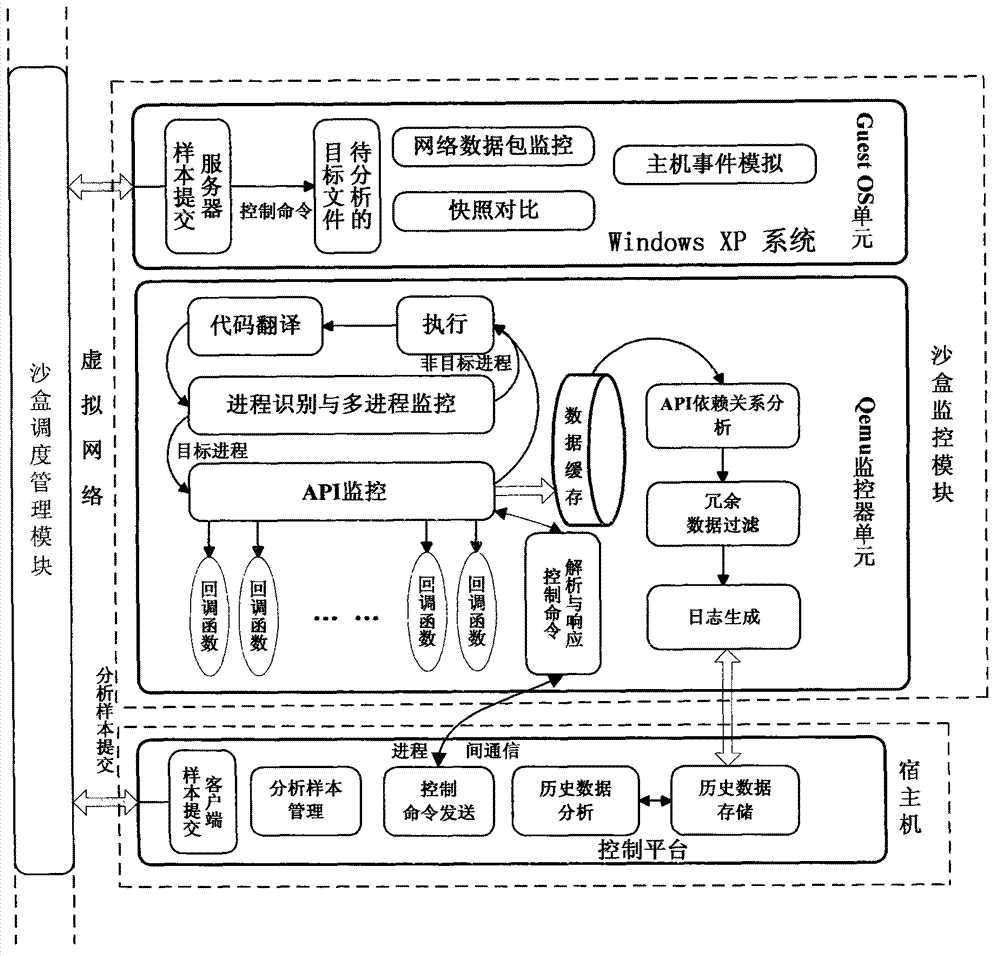
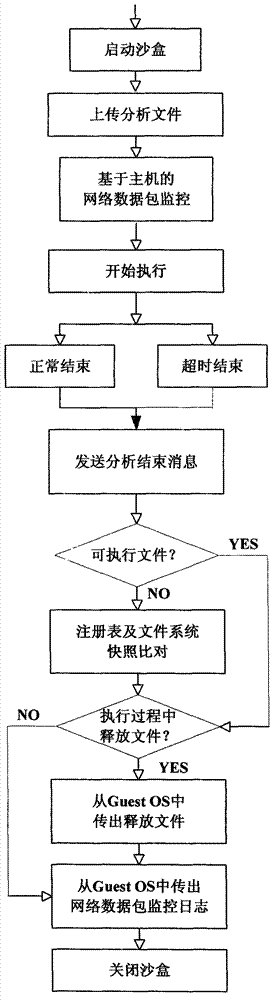
Malicious program behavior capture method based on Qemu
InactiveCN103927484AAchieve captureNo omission semanticsPlatform integrity maintainanceSource codeProgram behavior
The invention relates to a malicious program behavior capture method based on the Qemu. The method is characterized in that a malicious program behavior capture module is directly inserted into a source code of the Qemu, a client operating system is installed on the Qemu, and then behavior capture is carried out on malicious program samples on the client operating system through the malicious program behavior capture module running in the Qemu. The method has the advantages that the malicious program behavior capture module is directly inserted into the source code of the Qemu, completely isolated from the samples running on the client operating system and located on the lower layer of the operating system, and in theory, the malicious program samples can not detect or escape the malicious program behavior capture module easily.
Owner:XIDIAN NINGBO INFORMATION TECH INST
Technique to monitor application behavior and tune replication performance
ActiveUS7334062B1Improve performanceMultiple digital computer combinationsProgram controlGuidelineResource based
A method and mechanism for modifying computing resources in response to application behavior. A computing system includes a replication component configured to replicate data storage from a first data volume to a second data volume. In addition, the replication component is configured to monitor application I / O characteristics and store related statistics. I / O characteristics may include size, concurrency, locality, and frequency. I / O characteristics which are stored, and guidelines for modifying system resources based on those characteristics, may be displayed for use by an administrator in tuning system resources. Periodically, or in response to detecting an event, the replication component may automatically access the statistics and modify the system resources used by the replication system to better accommodate the application's behavior.
Owner:SYMANTEC OPERATING CORP
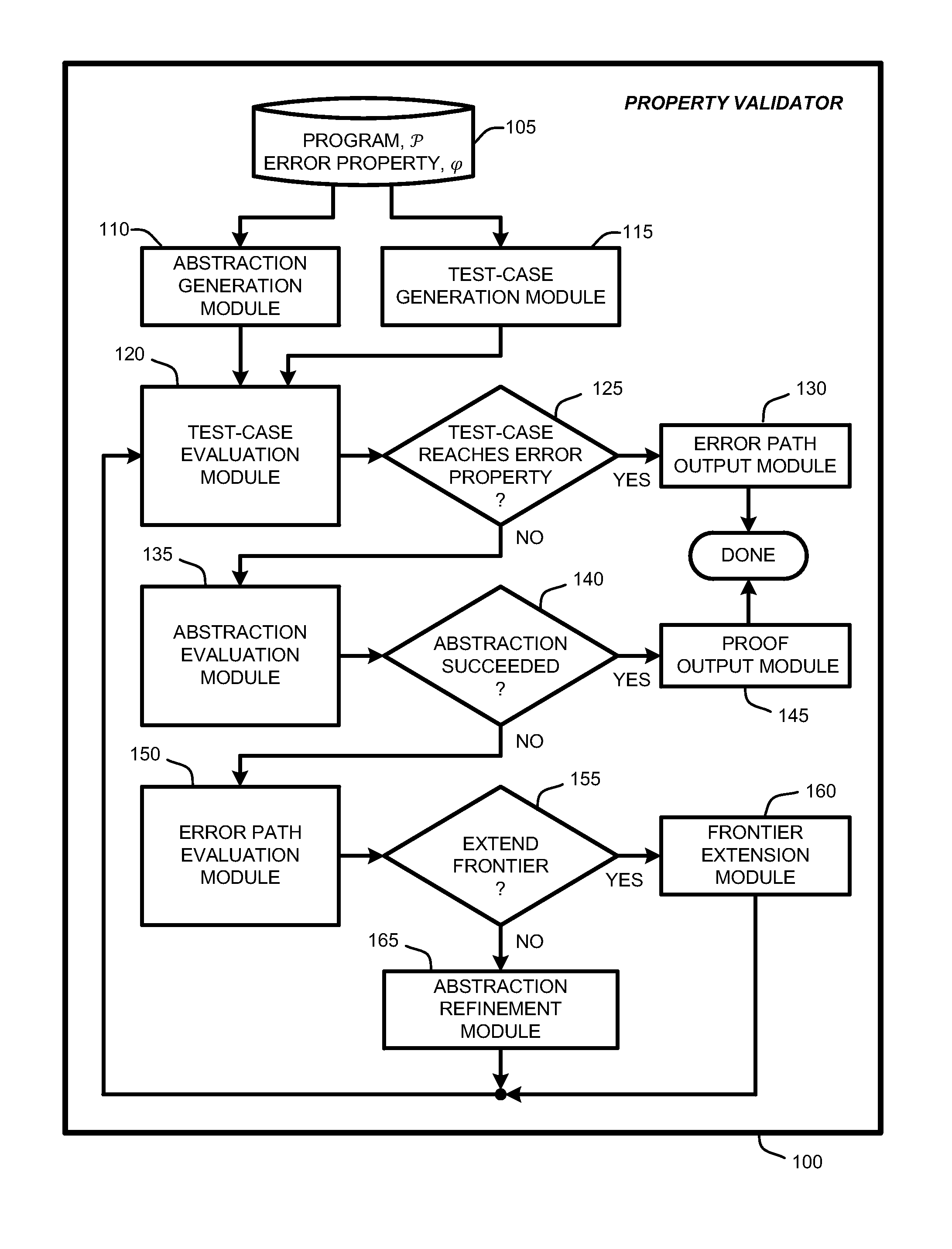
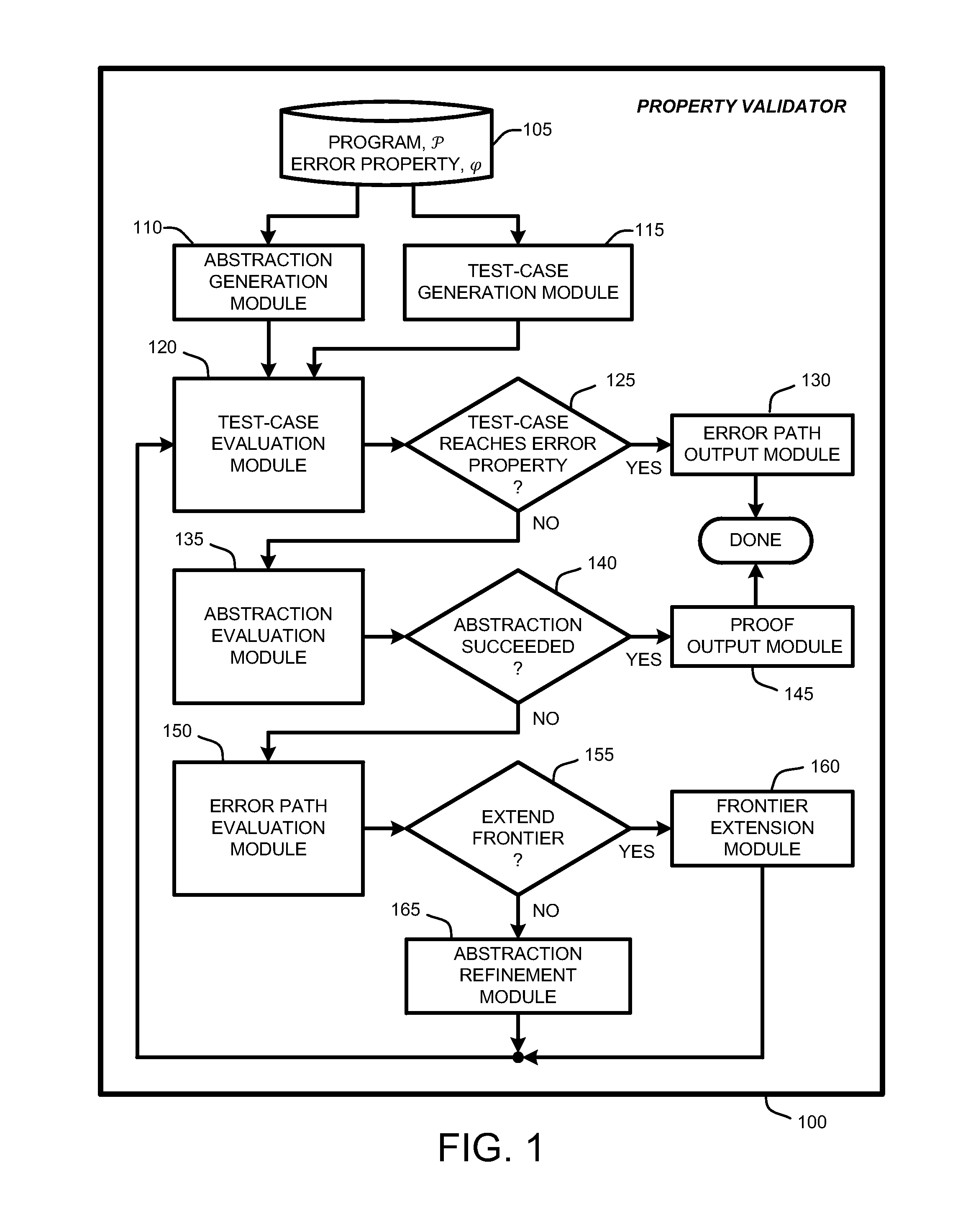
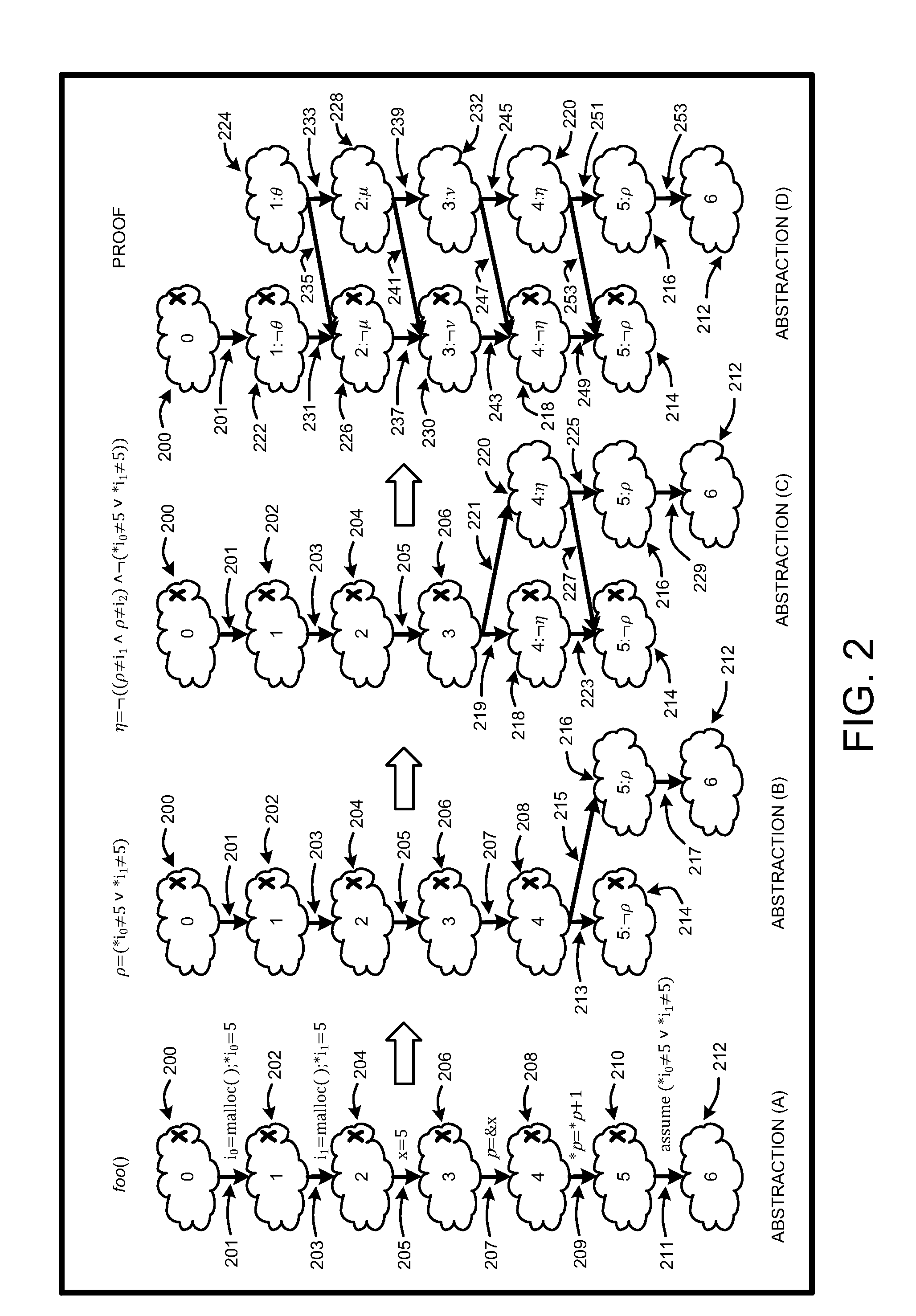
Generation and evaluation of test cases for software validation and proofs
InactiveUS20090282289A1Computationally efficientSoftware testing/debuggingState spaceProgram testing
A “property checker” uses light-weight symbolic execution to prove that software programs satisfy safety properties by simultaneously performing program testing and program abstraction. A simple example of safety properties includes conditions that must be satisfied for proper program execution, such as whether an application properly interfaces with API methods or functions. Program tests are an “under-approximation” of program behavior, and abstractions are an “over-approximation” of the program. This simultaneous testing either finds a test-case that reaches an error state, or finds an abstraction showing that no path in the state space of the program can reach any error state. If a test-case reaches an error state, the property checker has discovered a violation of the safety property. Conversely, if no path in the state space can reach any error state, the property checker has proved that the program satisfies the desired safety property.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com