Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
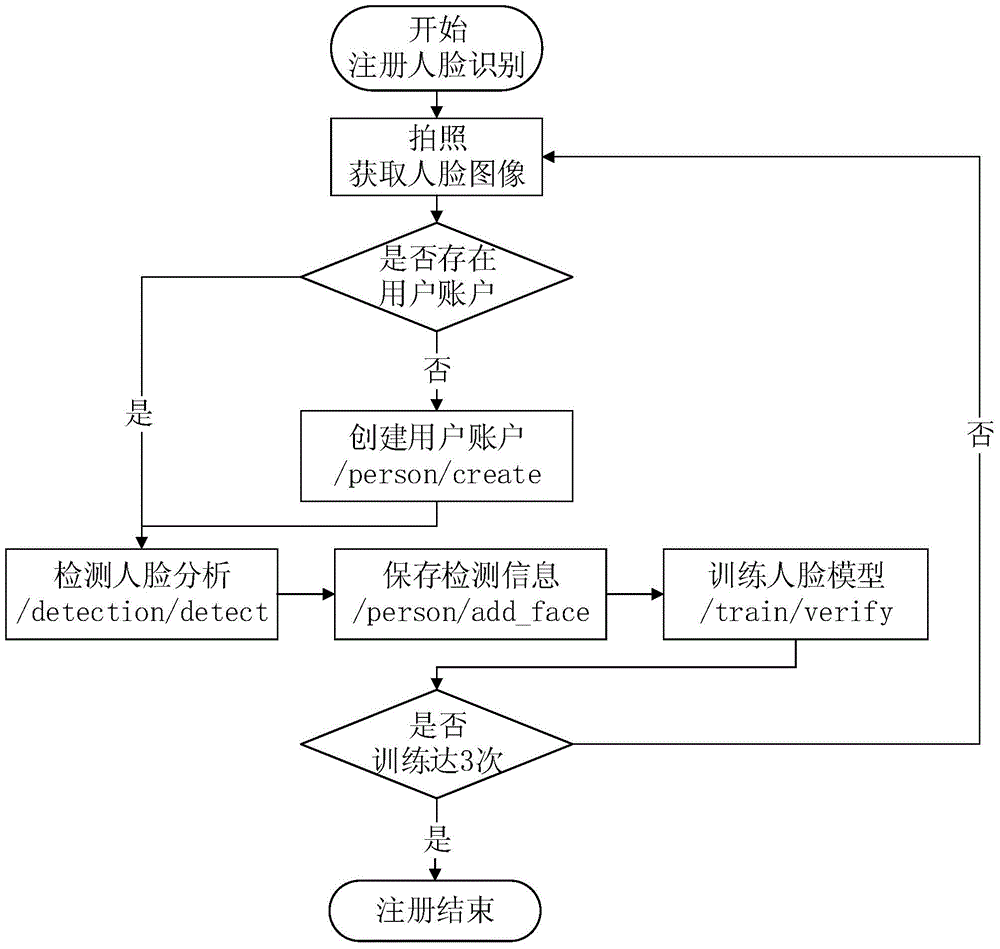
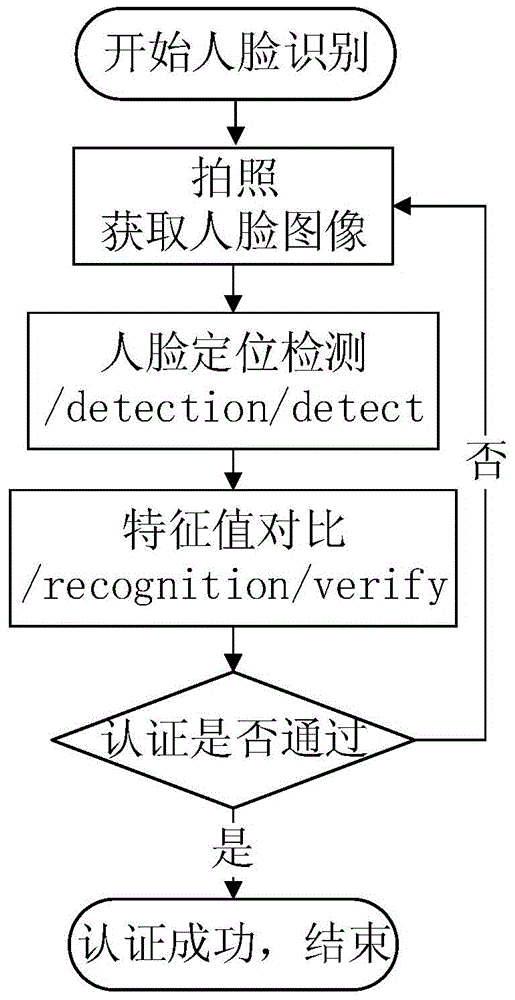
43 results about "Keystroke logging" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
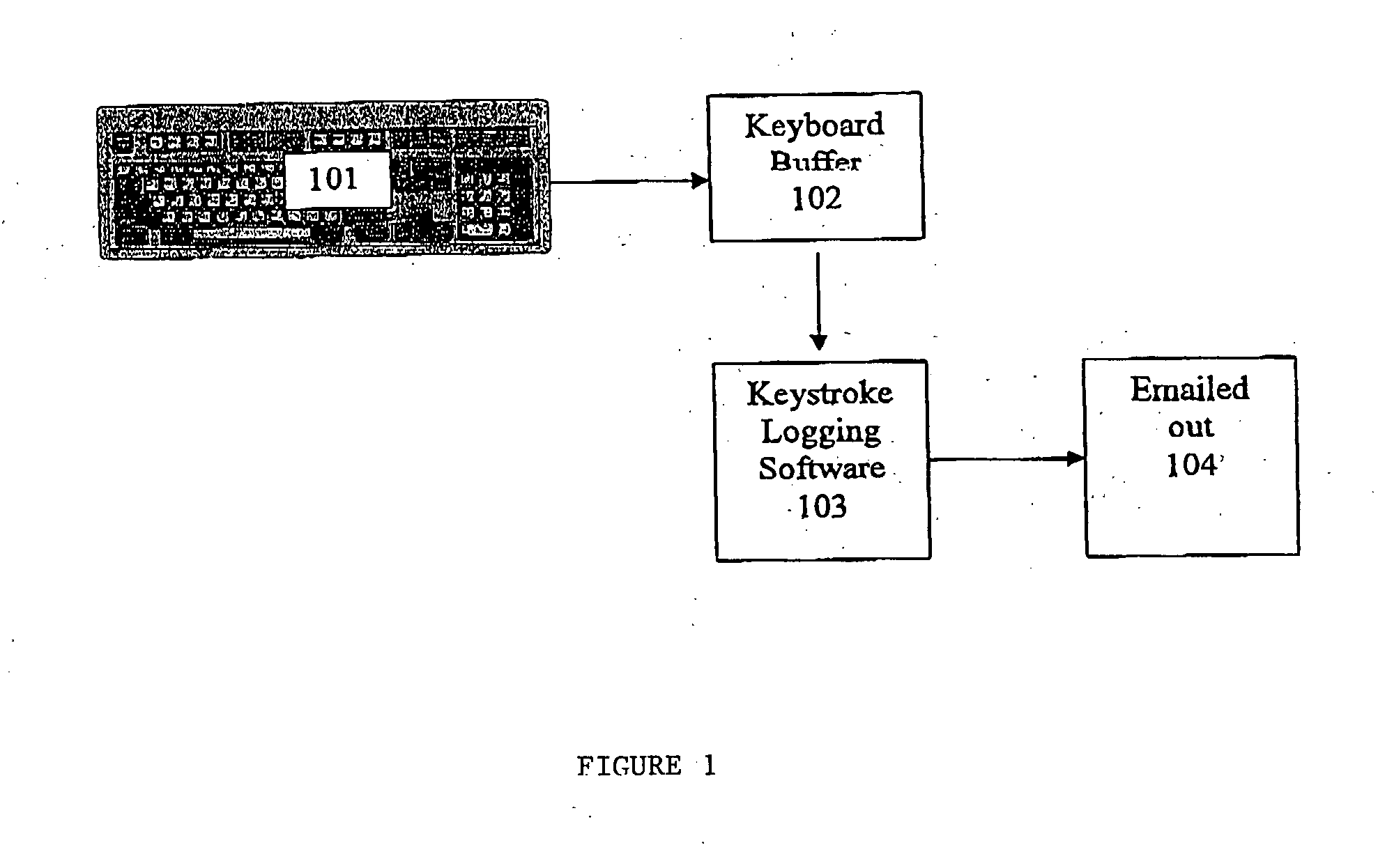
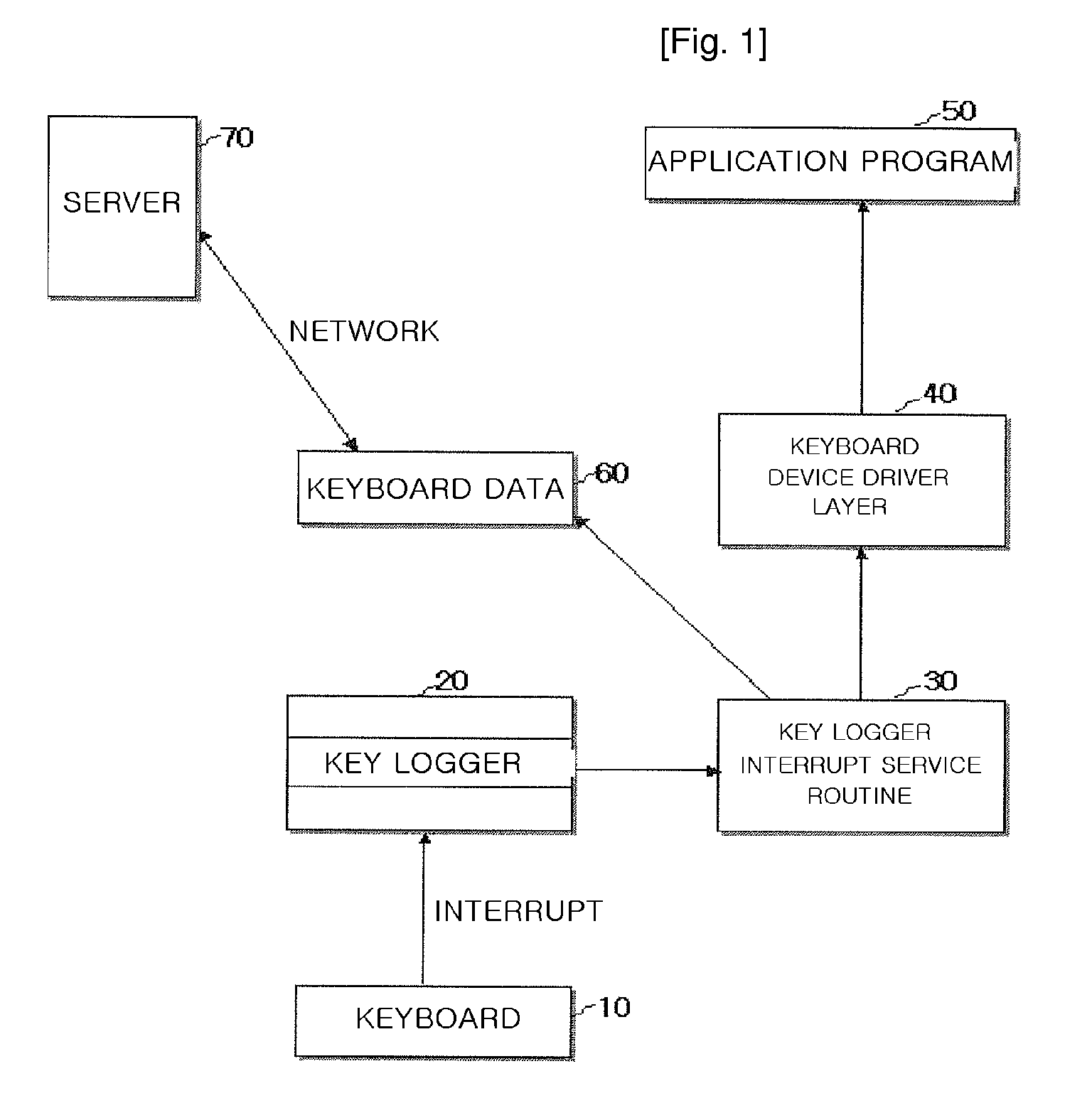
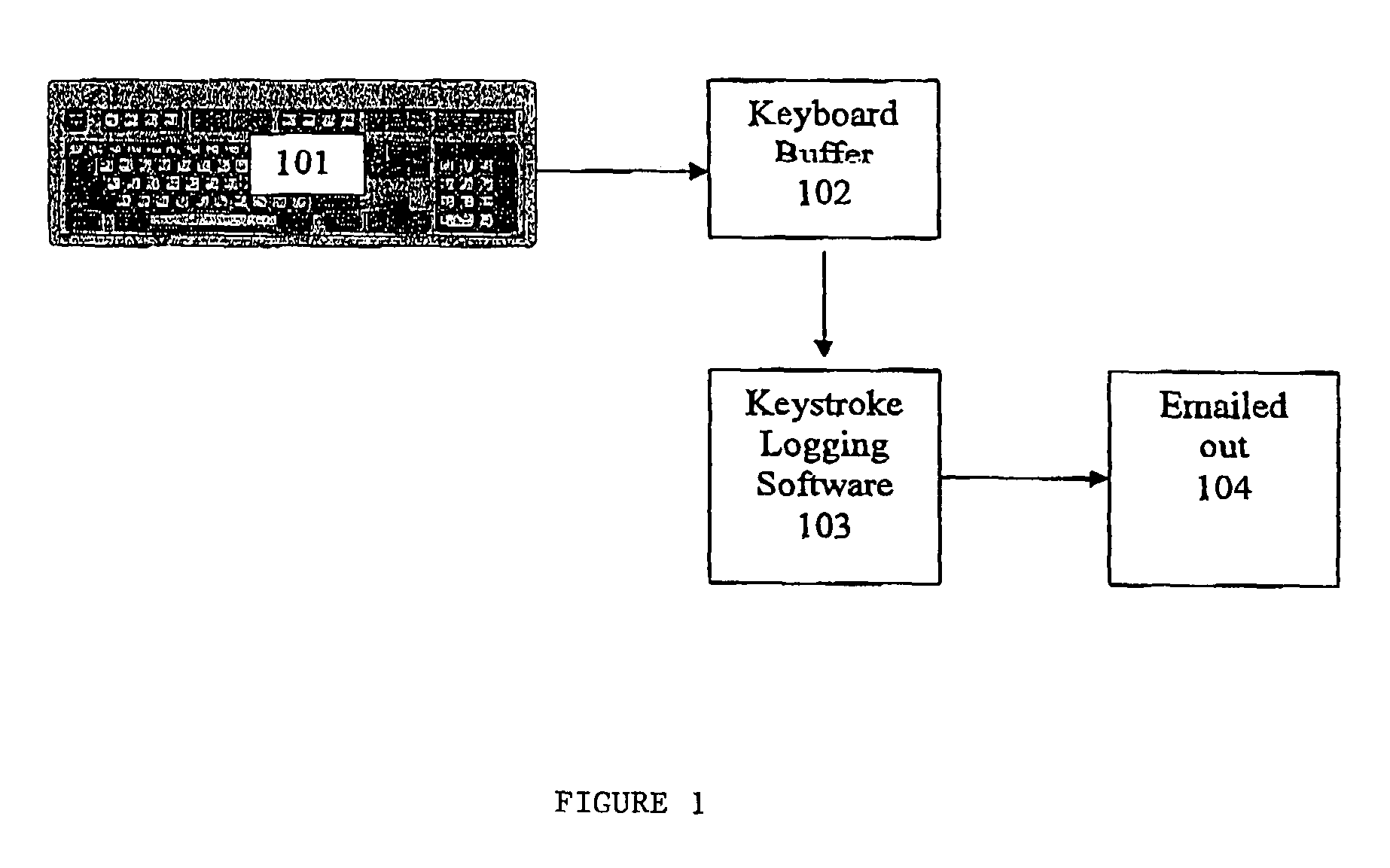
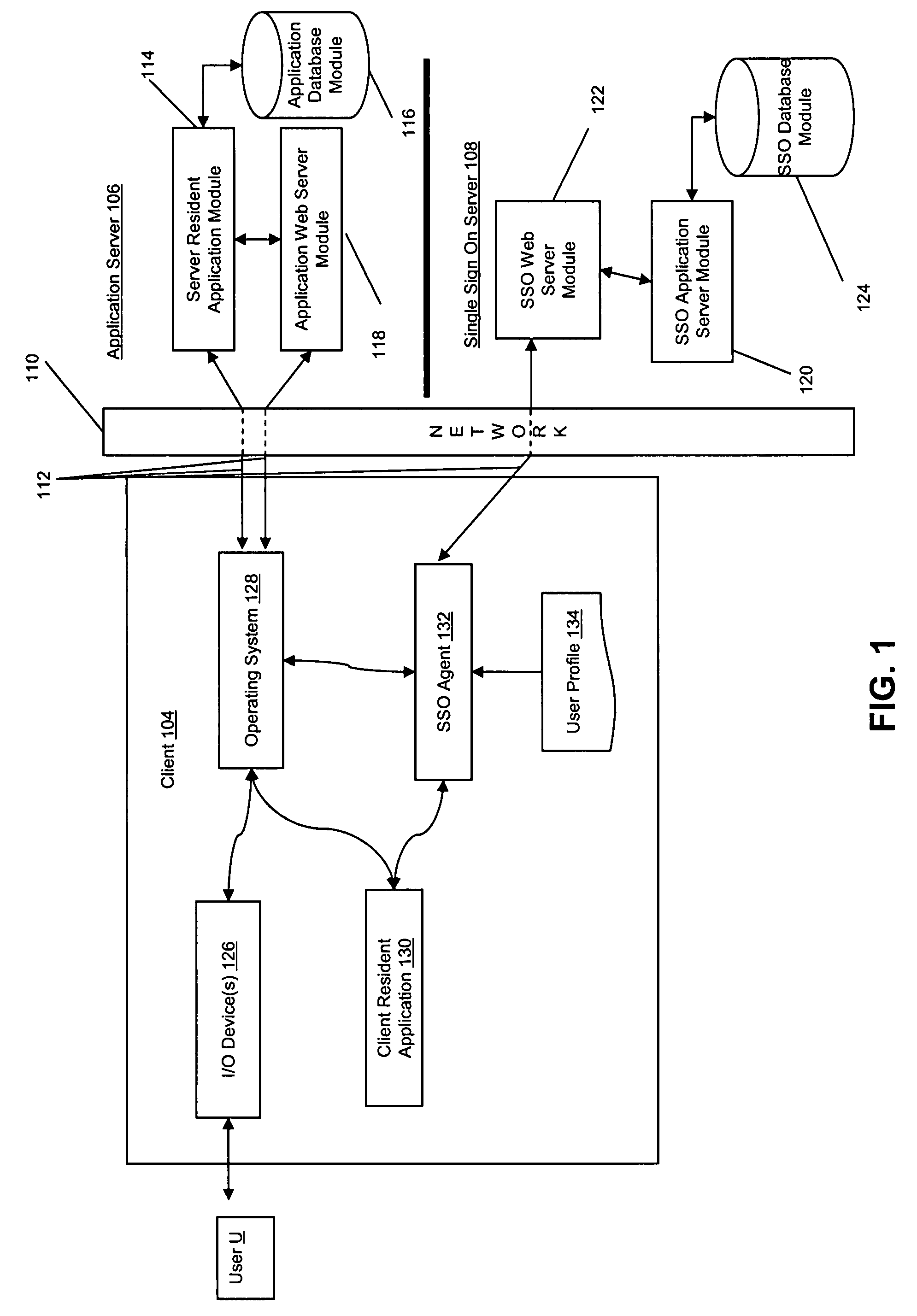
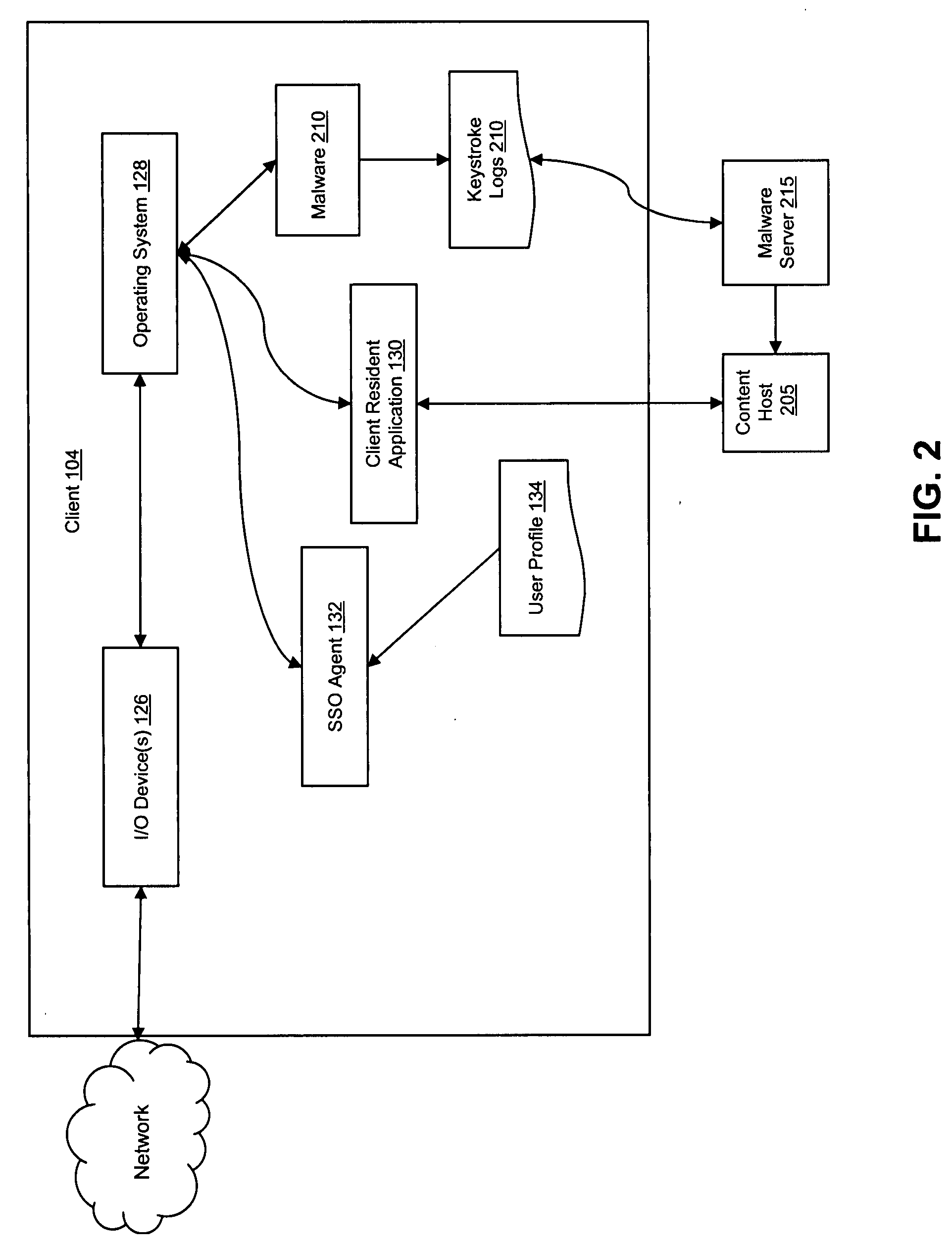
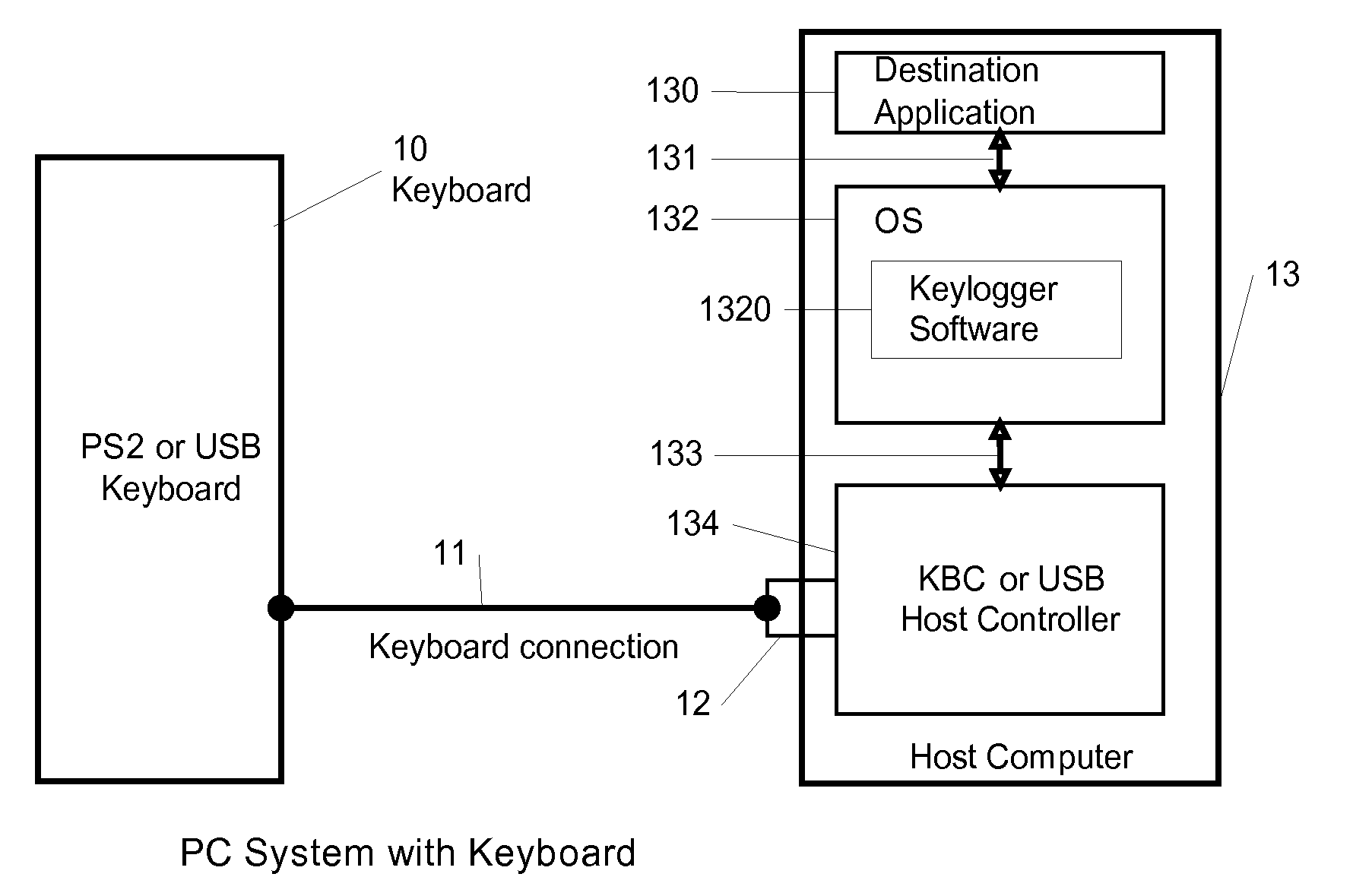
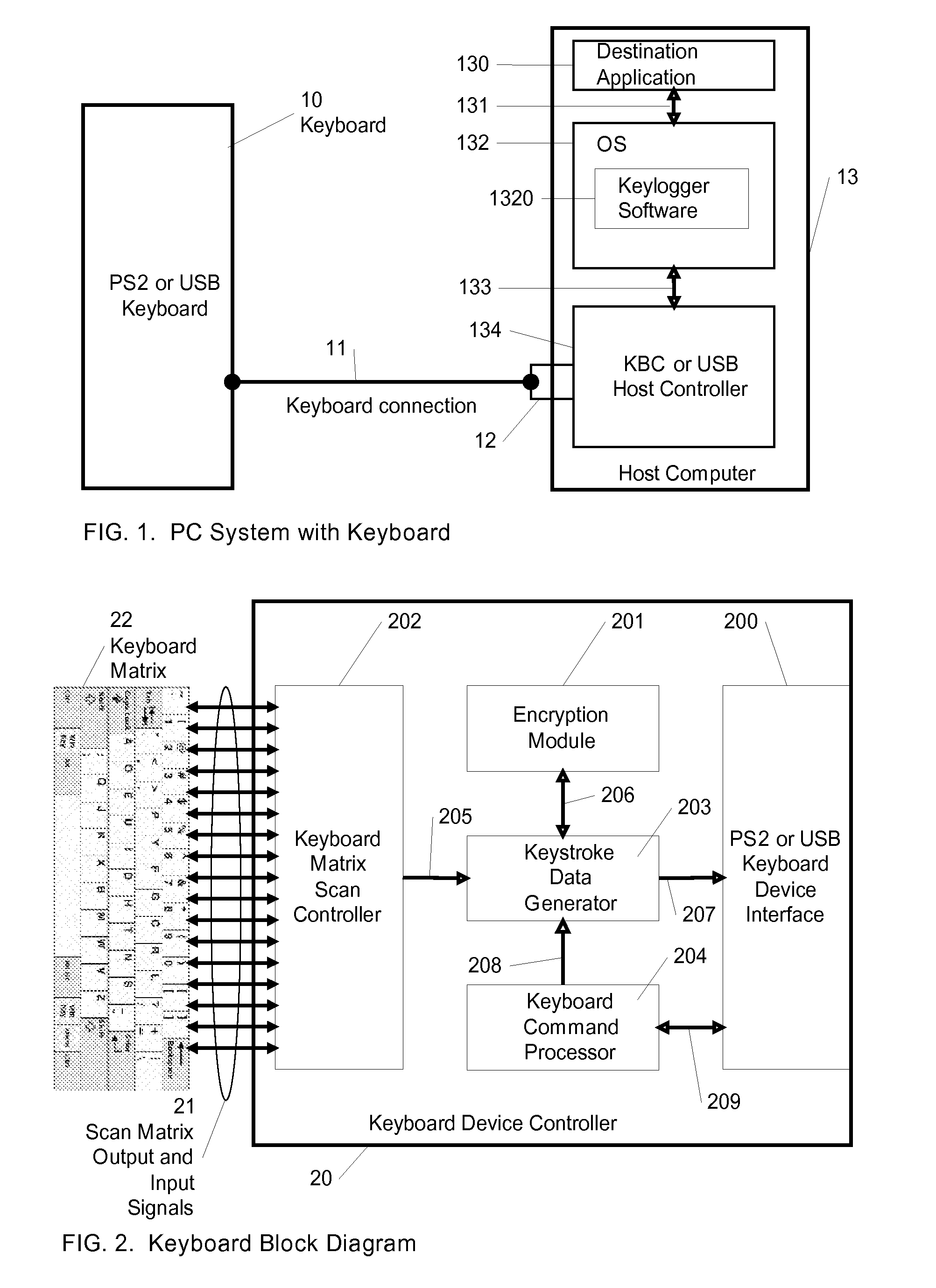
Keystroke logging, often referred to as keylogging or keyboard capturing, is the action of recording (logging) the keys struck on a keyboard, typically covertly, so that person using the keyboard is unaware that their actions are being monitored. Data can then be retrieved by the person operating the logging program. A keylogger can be either software or hardware.
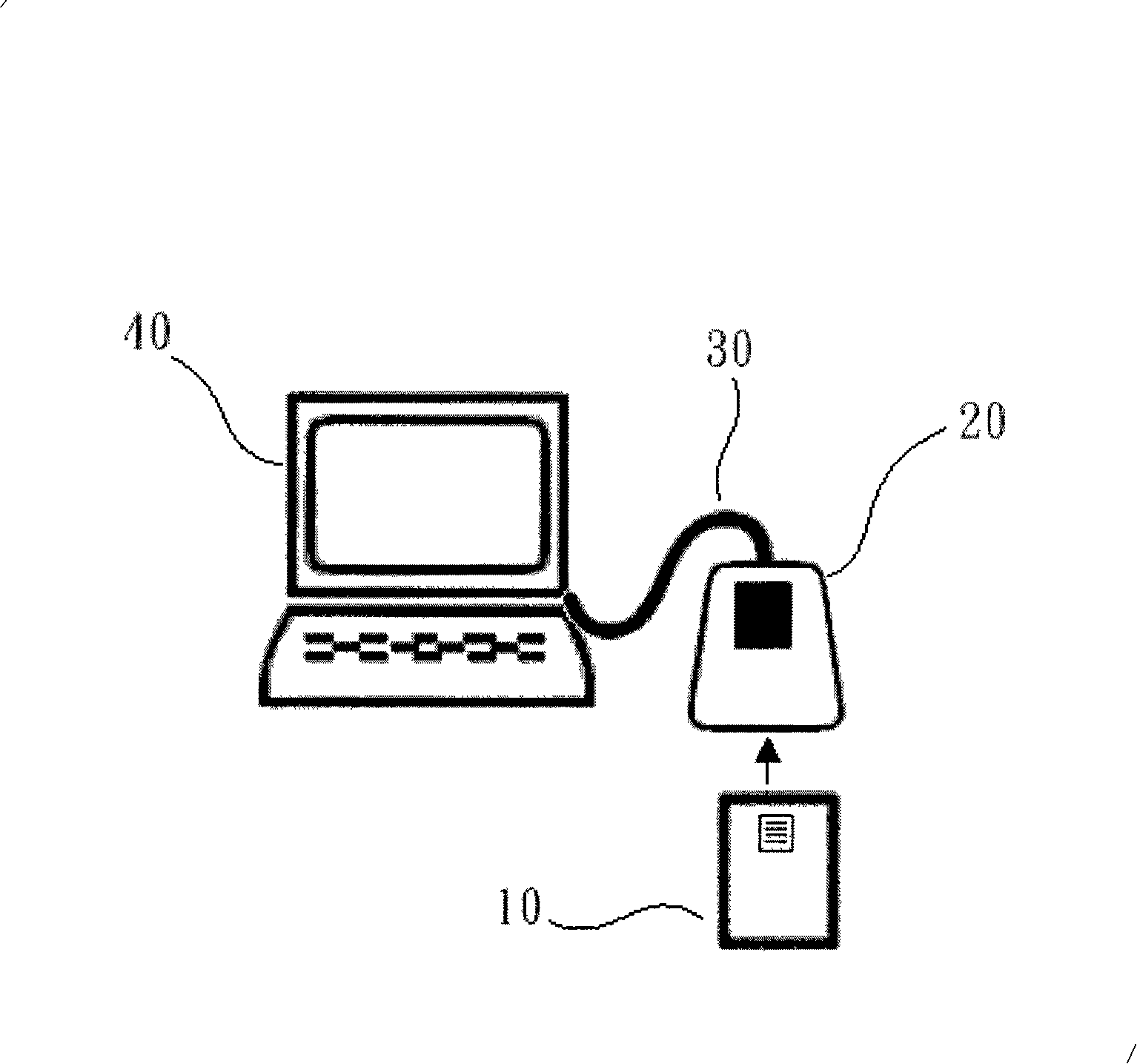
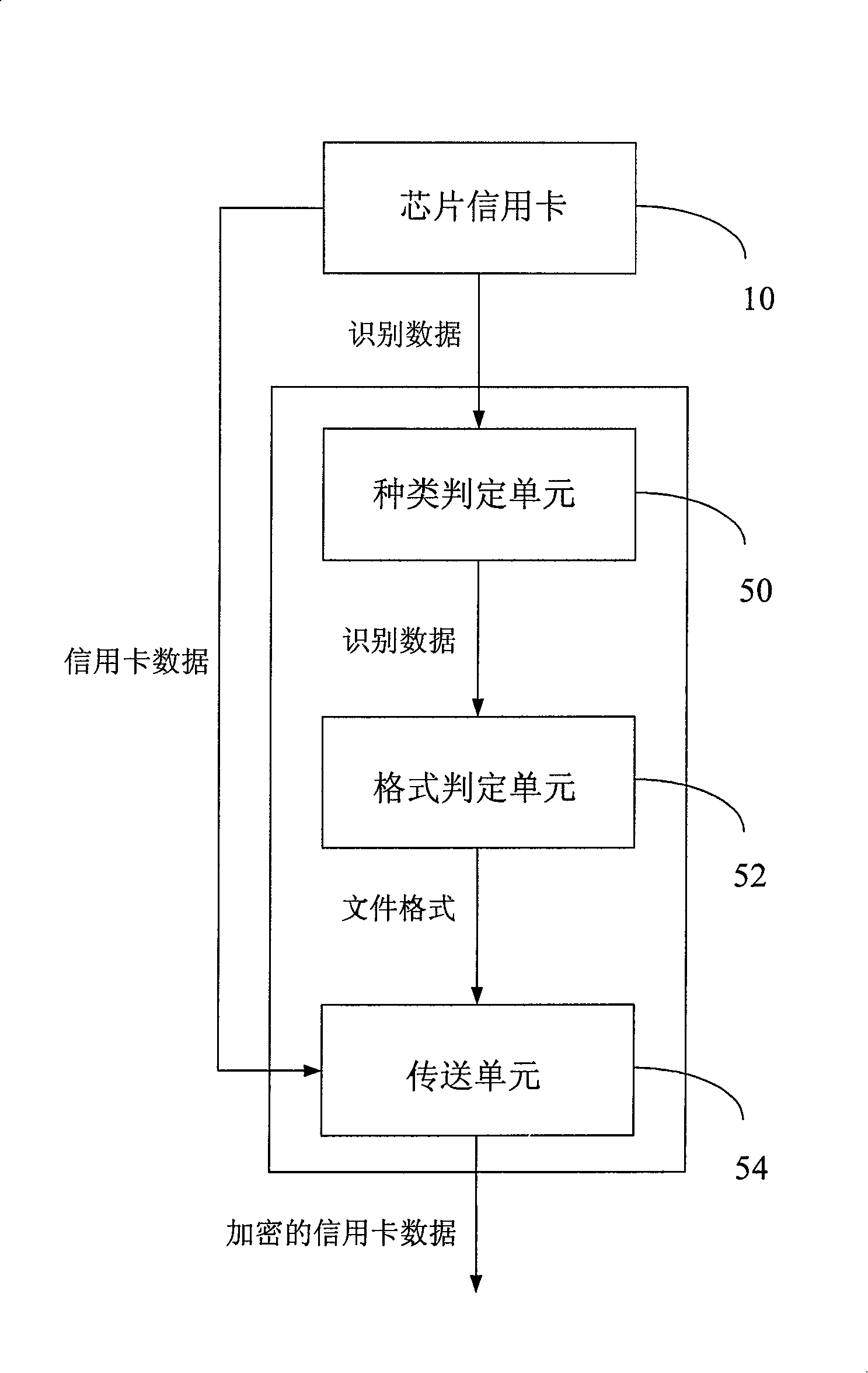
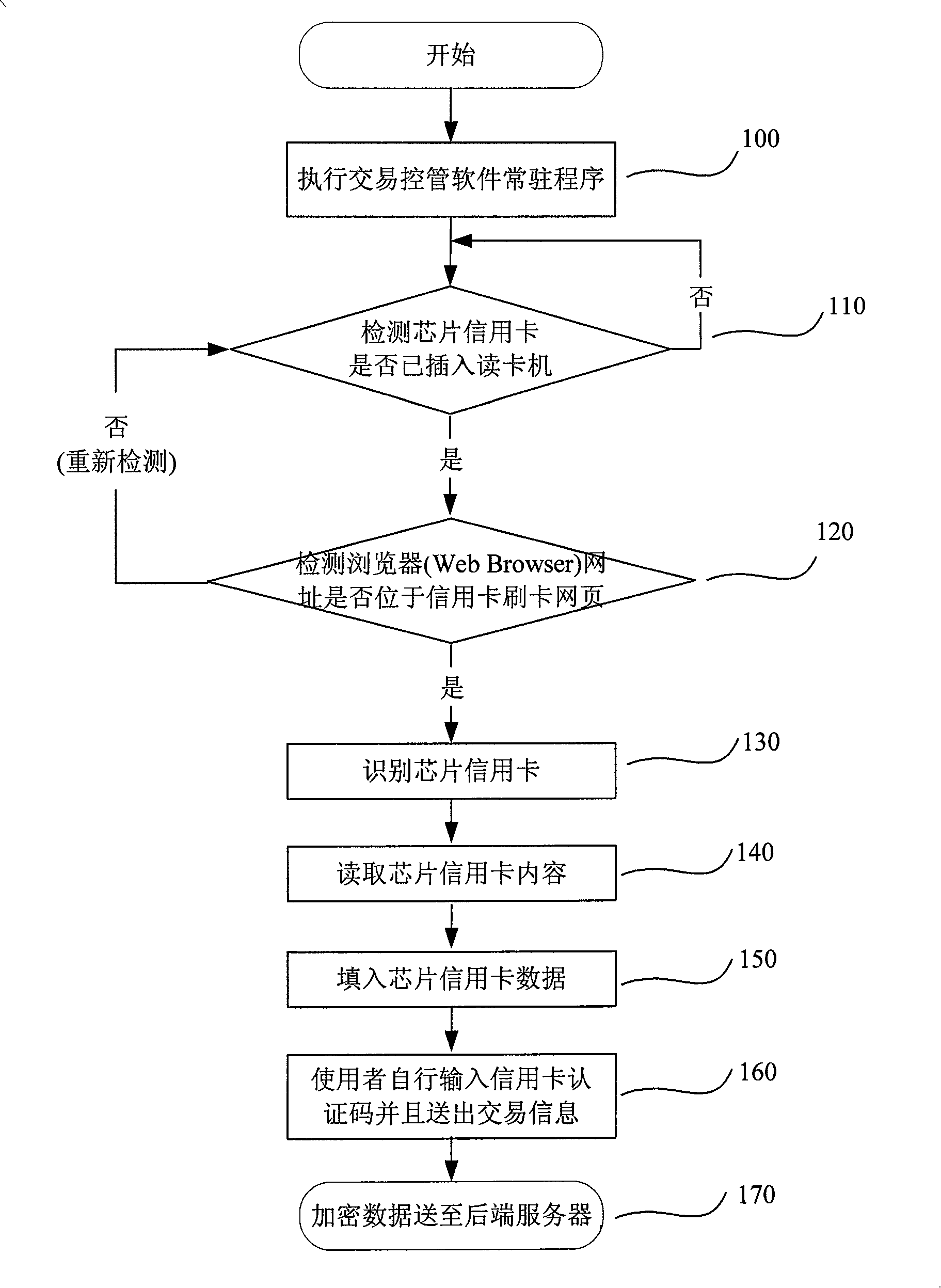
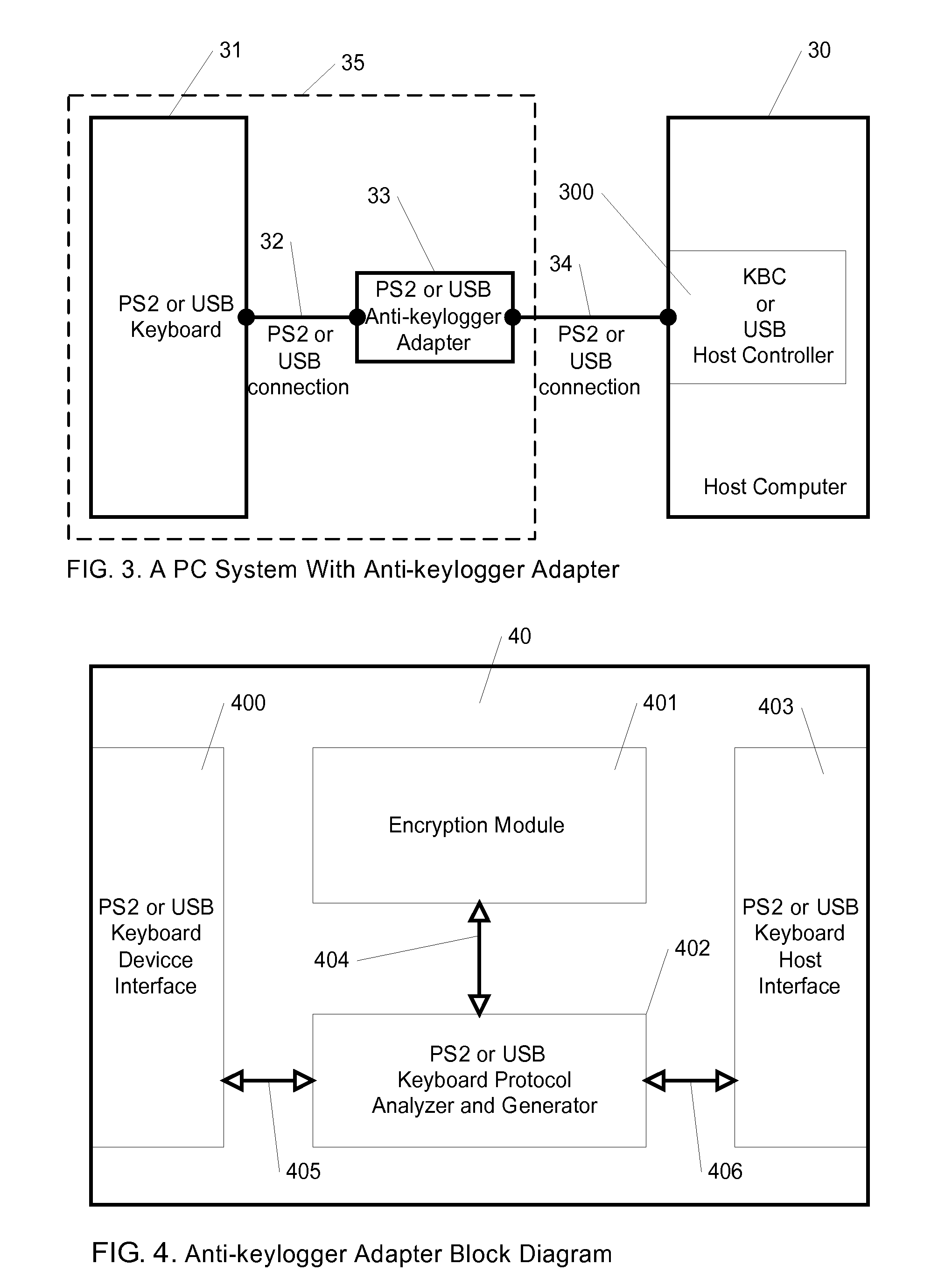
Chip credit card network transaction system and method
The invention provides a network exchanging system and a method of chip credit card, when the chip credit card is inserted into a card reader, the card reader transfers a control signal to a computer, after a controlling and managing module for exchanging executed on the computer detects the control signal transferred from the card reader, the identification data on the chip credit card can be read through the card reader so as to identify the type of the chip credit card, after the database is compared, a card number, an expiry date and a data required for the network exchanging can be acquired from the chip credit card, the controlling and managing module for exchanging can be automatically filled into a credit card data column on the exchanging web page by an encrypting method so as to complete the exchanging operation of the credit card. User does not have to type the card number and other confidential data on the exchanging web page to avoid a Trojan program from recording such as keyboard recording and image recording as well as to prevent the credit card data from leaking.
Owner:INFOTHINK TECH
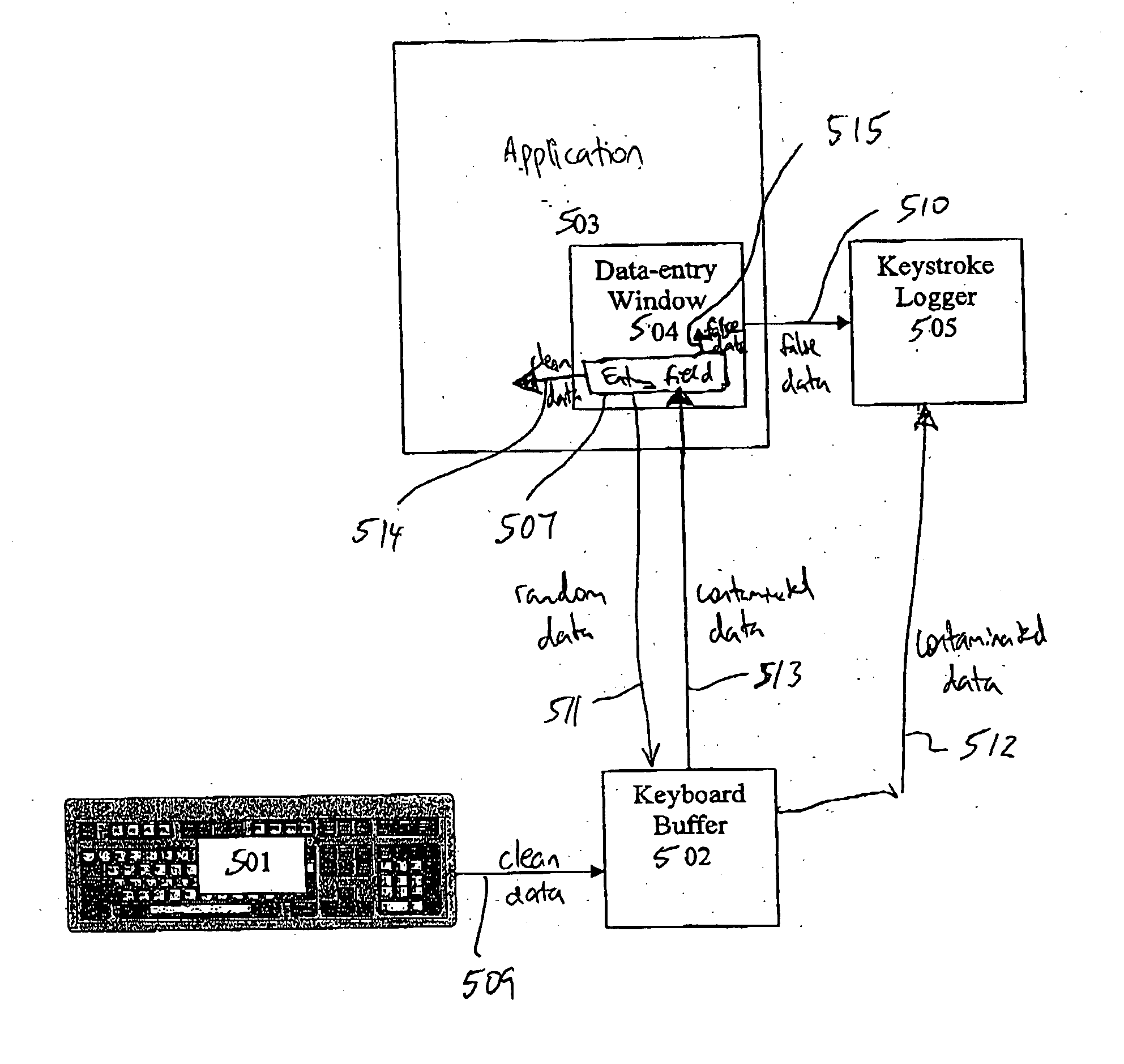
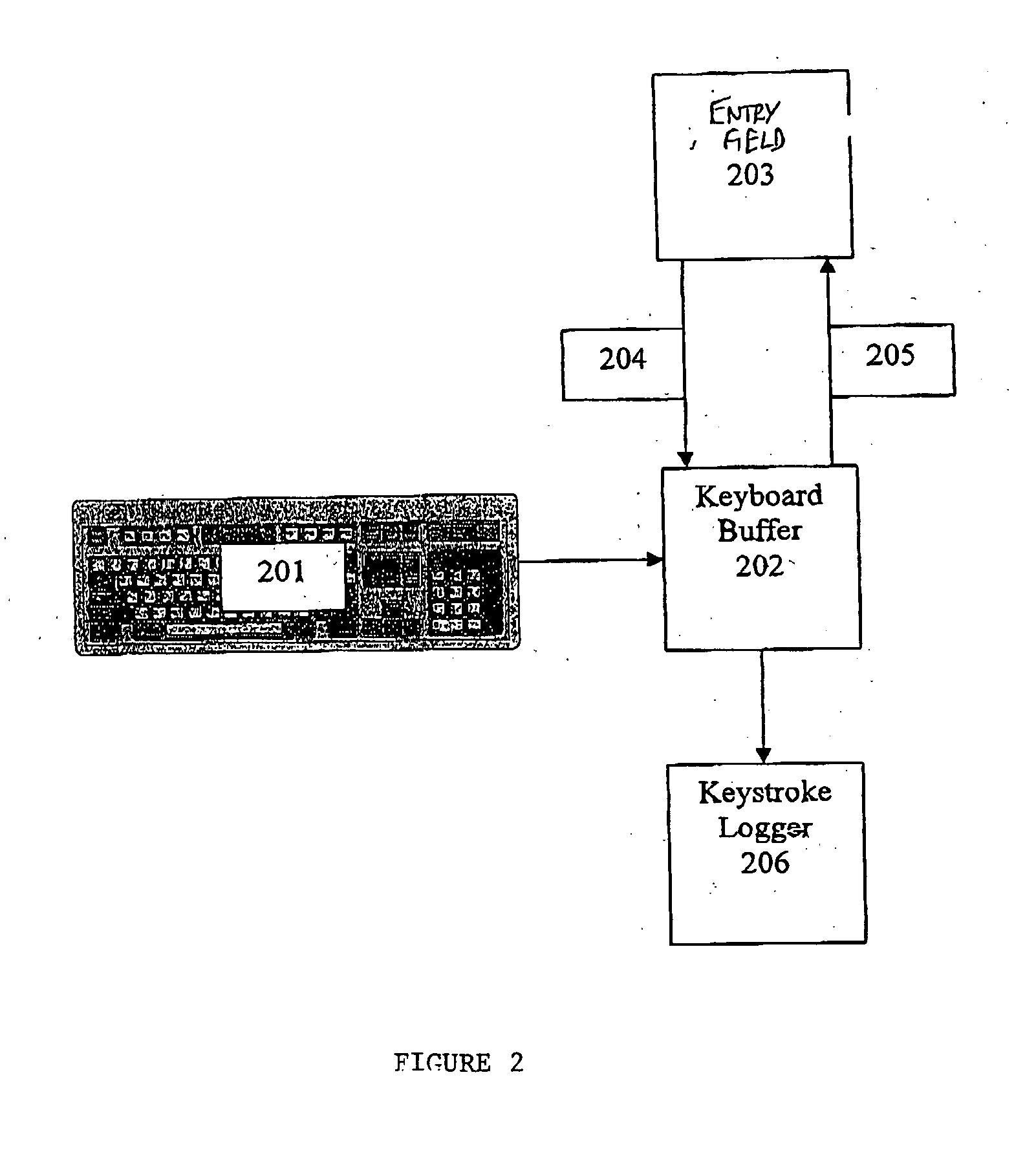
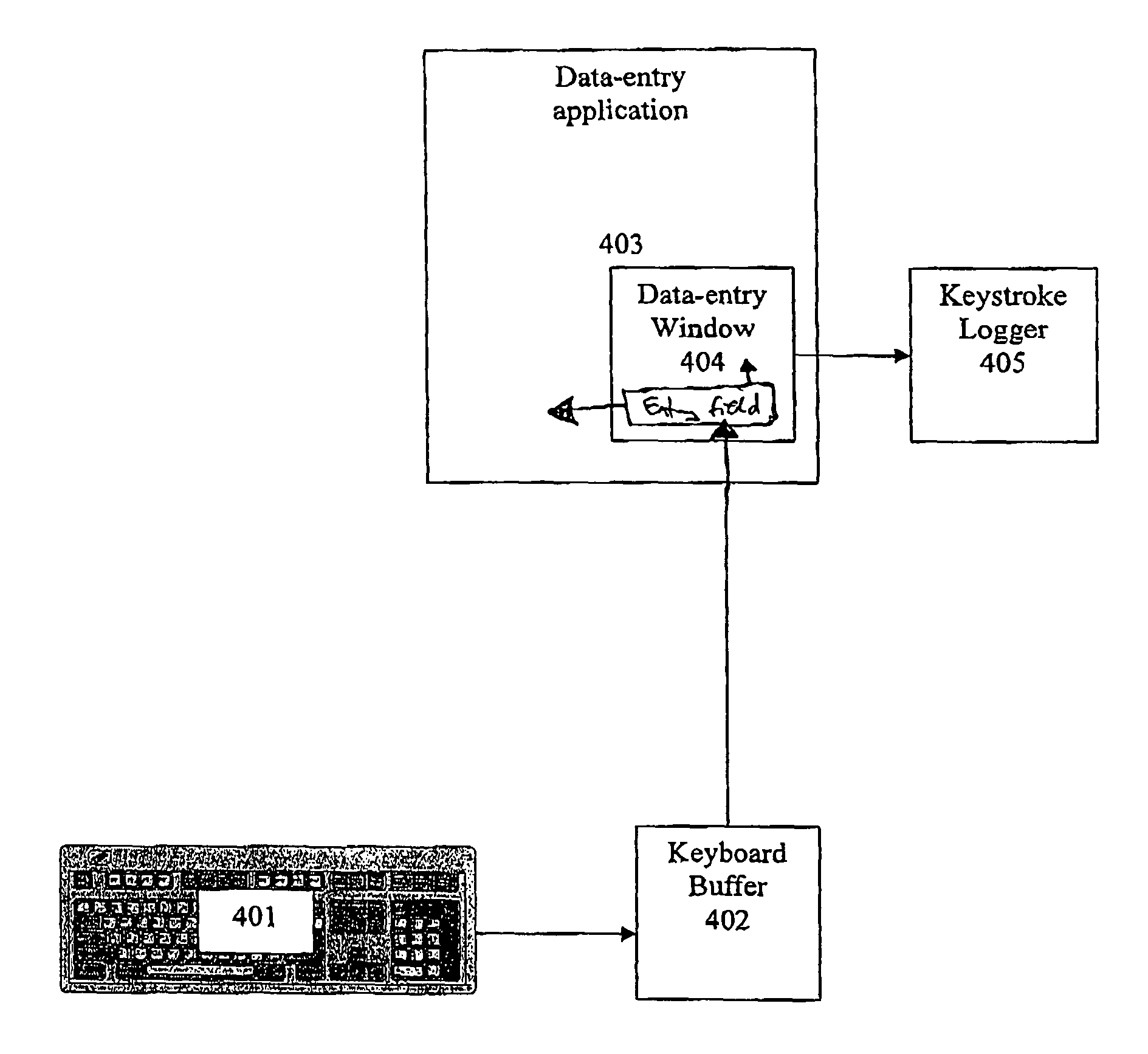
System for preventing keystroke logging software from accessing or identifying keystrokes
ActiveUS20060101128A1Invade privacySecurity threatMemory loss protectionDigital data processing detailsOperational systemUser input
A computer program is adapted for securing user entry data against keyboard login attempts. The program masks user input data, either insulating the data from vulnerable parts of the operating system or application, or contaminating user data that is supplied to those vulnerable parts of the operating system or application. The program securely stores data, either intercepted prior to reaching the vulnerable parts of the operating system or extracted from the contaminated data, and securely provides the data directly to a verified application.
Owner:SENTRYBAY
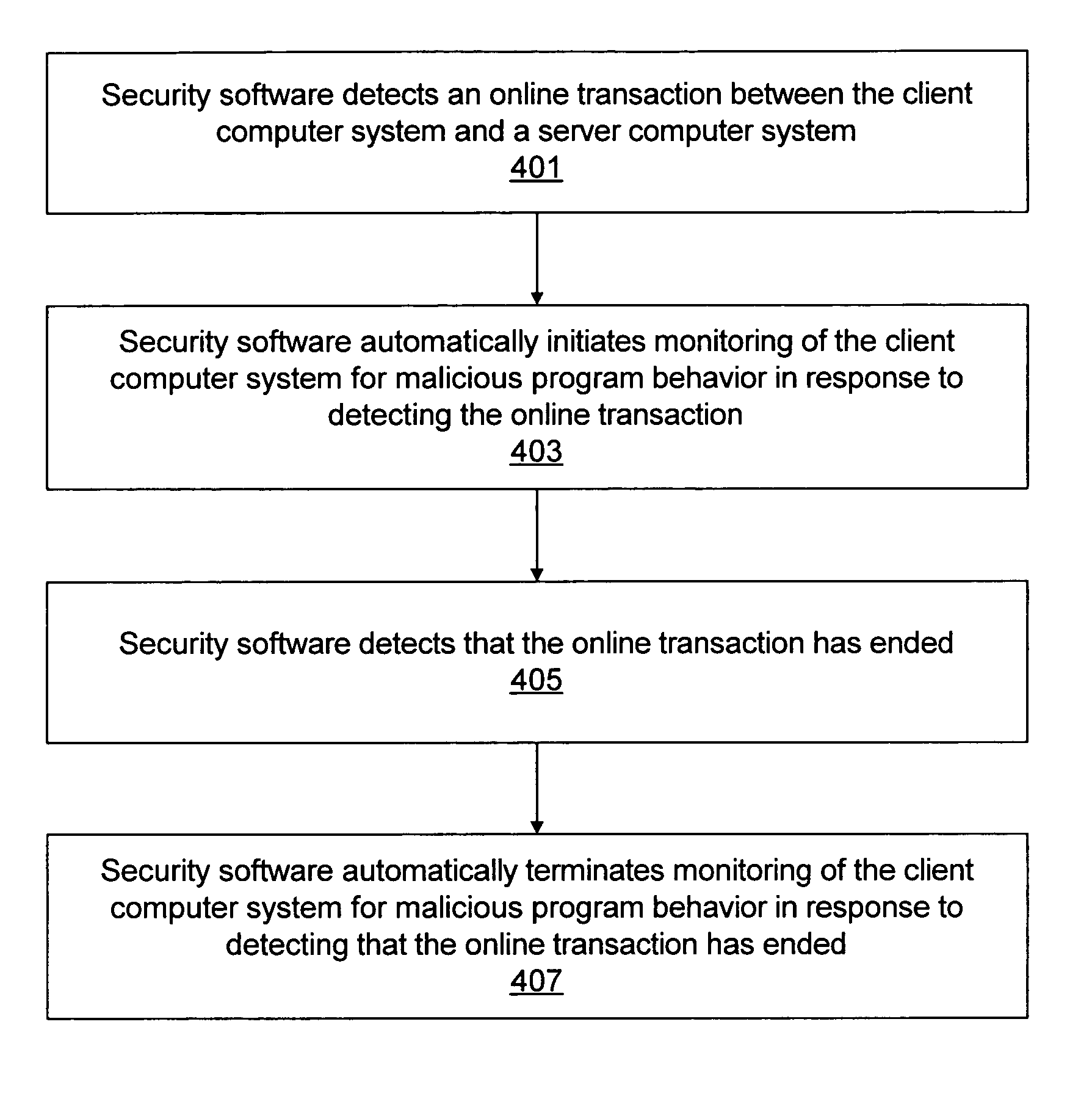
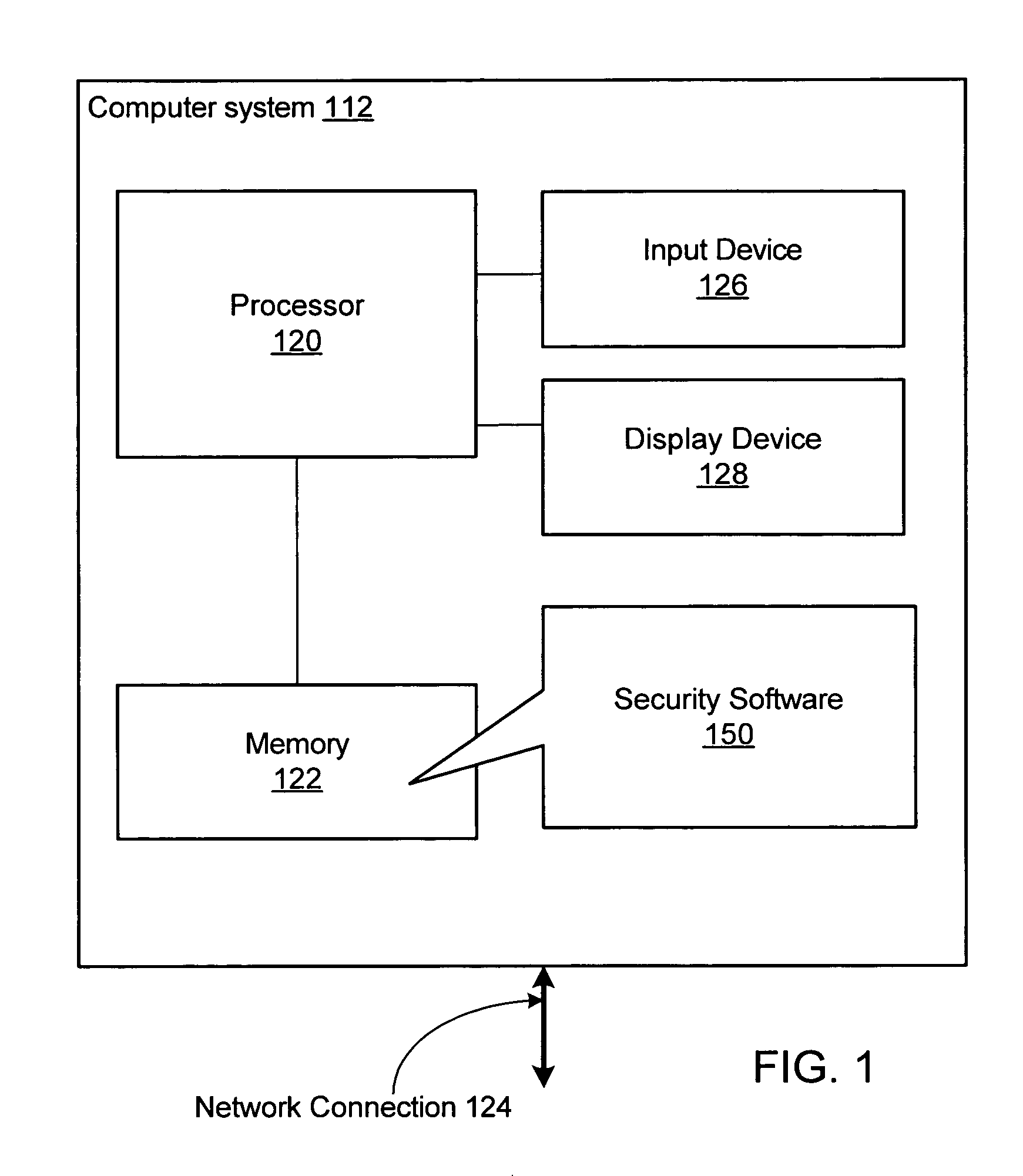
Method, system, and computer program product for blocking malicious program behaviors
InactiveUS7818800B1Memory loss protectionError detection/correctionSecurity softwareComputerized system
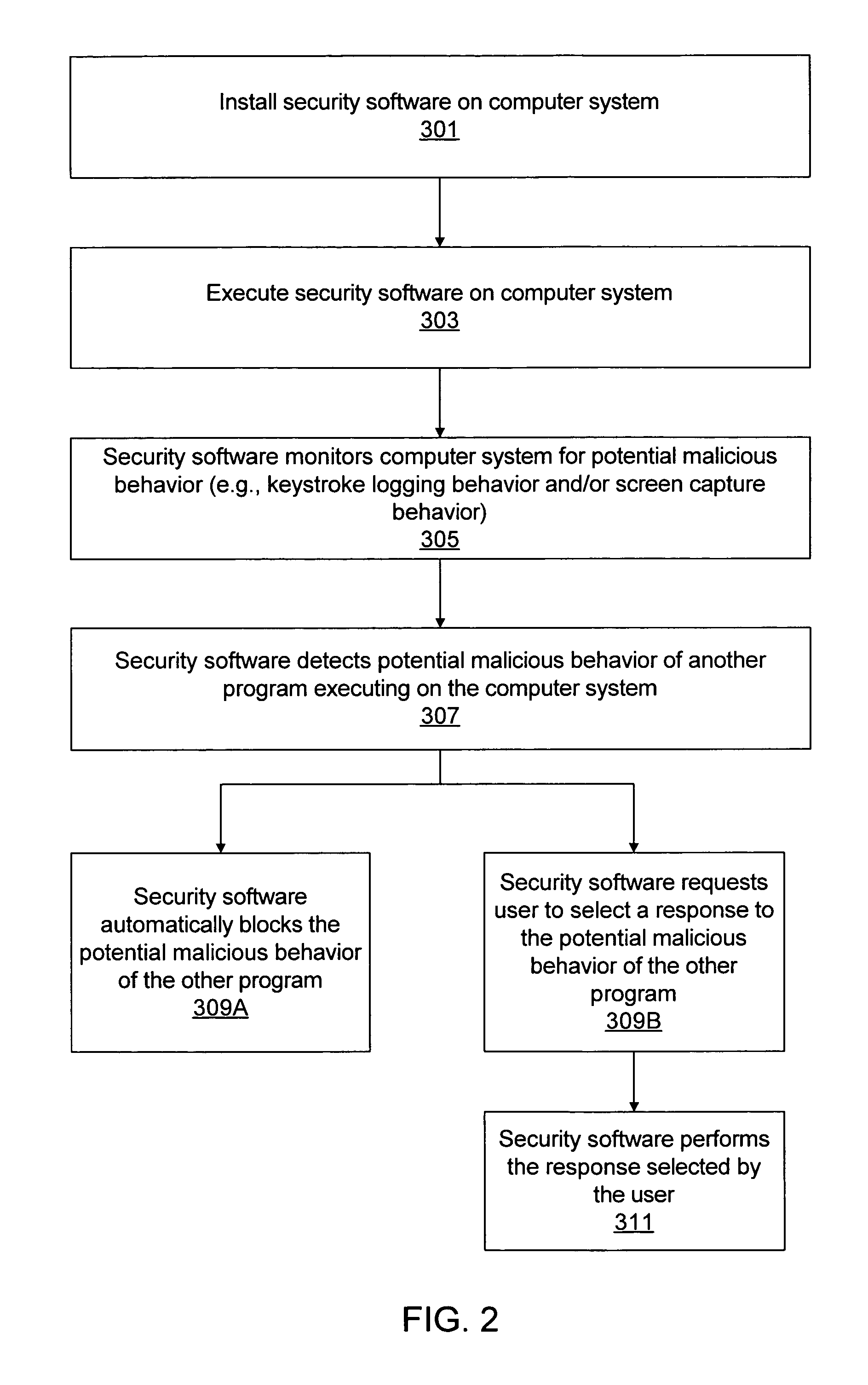
Various embodiments of a system and method for blocking malicious program behaviors, such as keystroke logging behavior or screen capture behavior, are disclosed. Security software may execute on a computer system, where the security software is operable to monitor the computer system to detect malicious program behavior. In response to detecting a first condition indicating that monitoring of the computer system to detect malicious program behavior should be initiated, the security software automatically initiates monitoring of the computer system to detect malicious program behavior. After initiating the monitoring for malicious program behavior, the security software may detect malicious program behavior of a second program executing on the computer system and block the malicious program behavior of the second program.
Owner:CA TECH INC
Method For Preventing Key Logger From Hacking Data Typed on Keyboard Through Autorization of Keyboard Data
ActiveUS20080189790A1Prevent hackingPreventing a key logger from hackingInput/output for user-computer interactionMemory loss protectionComputer hardwareEvent data
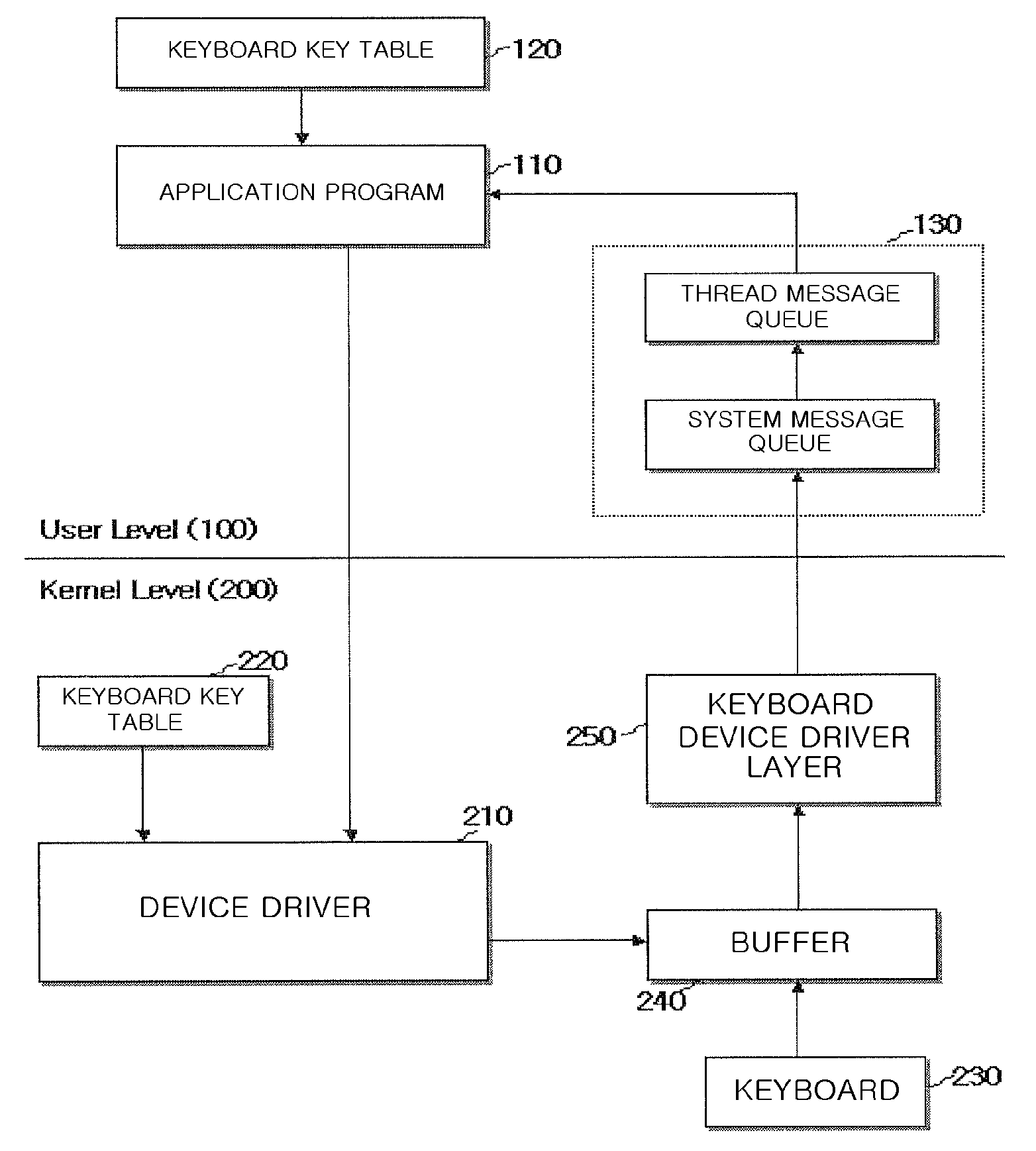
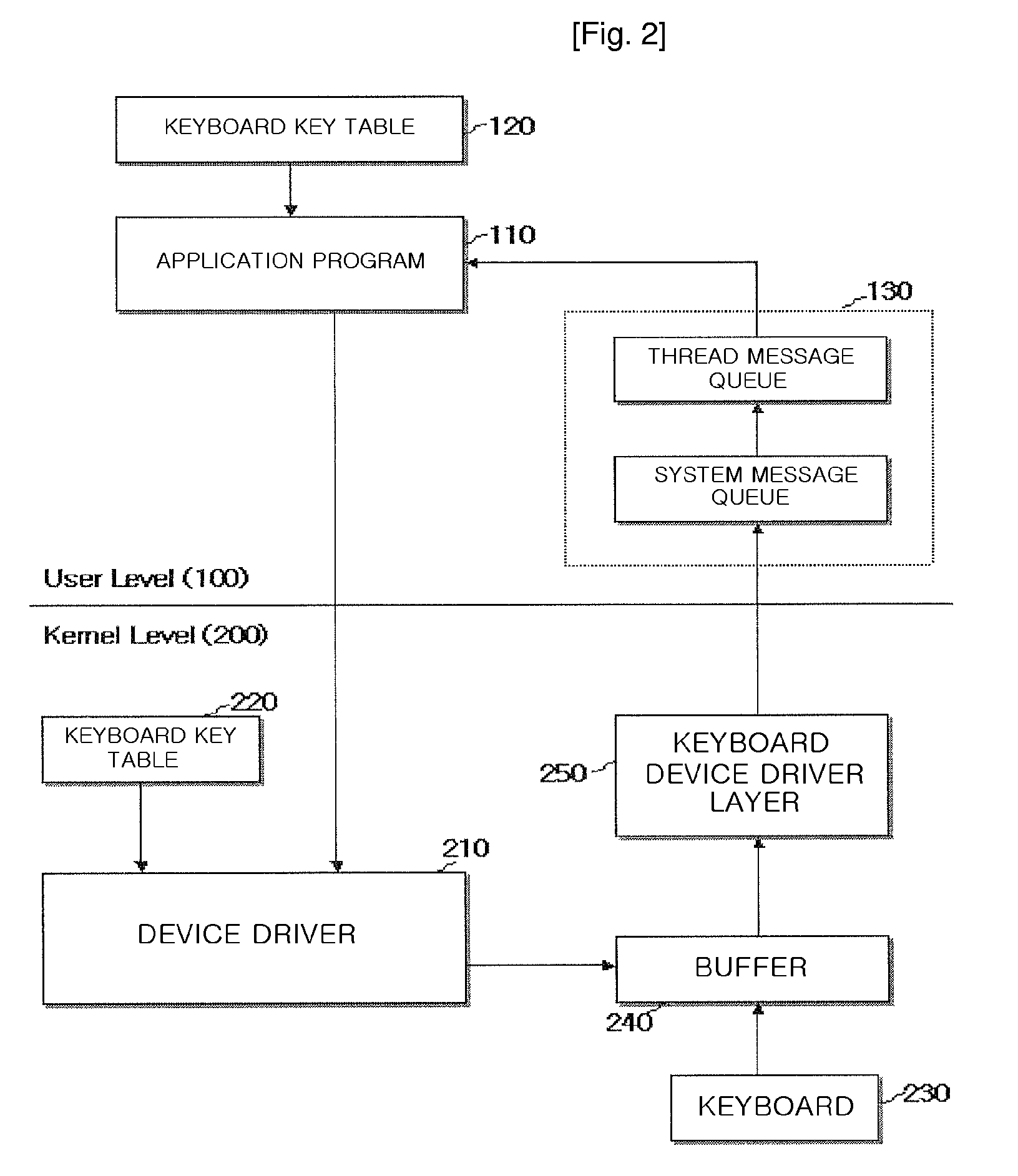
A method for preventing a key logger from hacking the keyboard data typed on keyboard through authorization of keyboard data according to the present invention comprises the steps of: transmitting a seed and hash counter, which were created according to a ready-to-input signal in an application program to be protected from hacking, to a device driver; creating a first key data on the basis of the seed and hash counter or a keyboard data created by a keyboard interrupt created from outside in the device driver; creating a second key data on the basis of the seed and hash counter when the application program receives the first key data or an keyboard event data equivalent to the keyboard data; comparing the keyboard event data with the second key data; and receiving the keyboard event data as the data typed on keyboard when the keyboard event data is not identical with the second key data according to the result of the comparison of the prior step.
Owner:AHNLAB INC
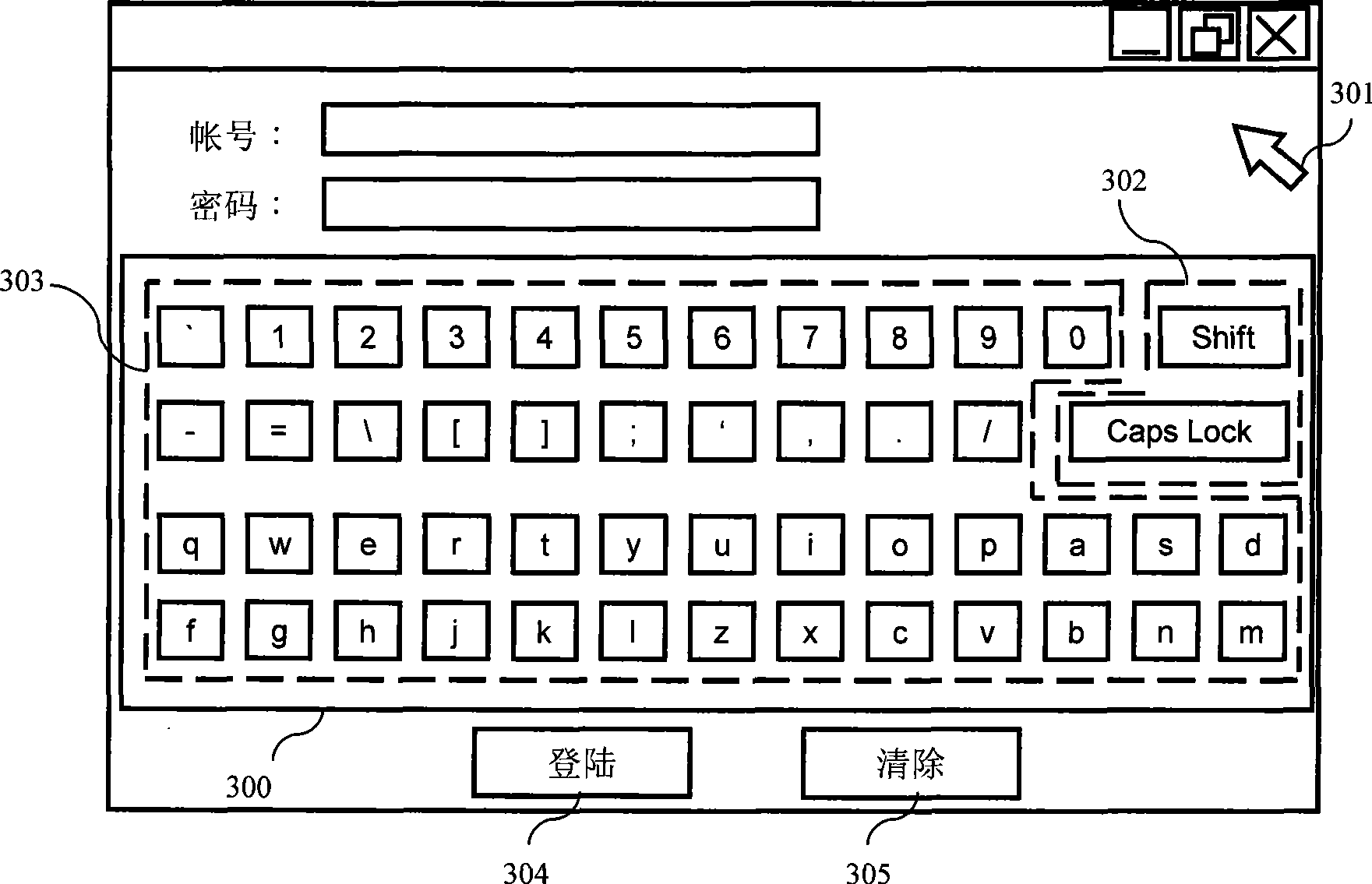
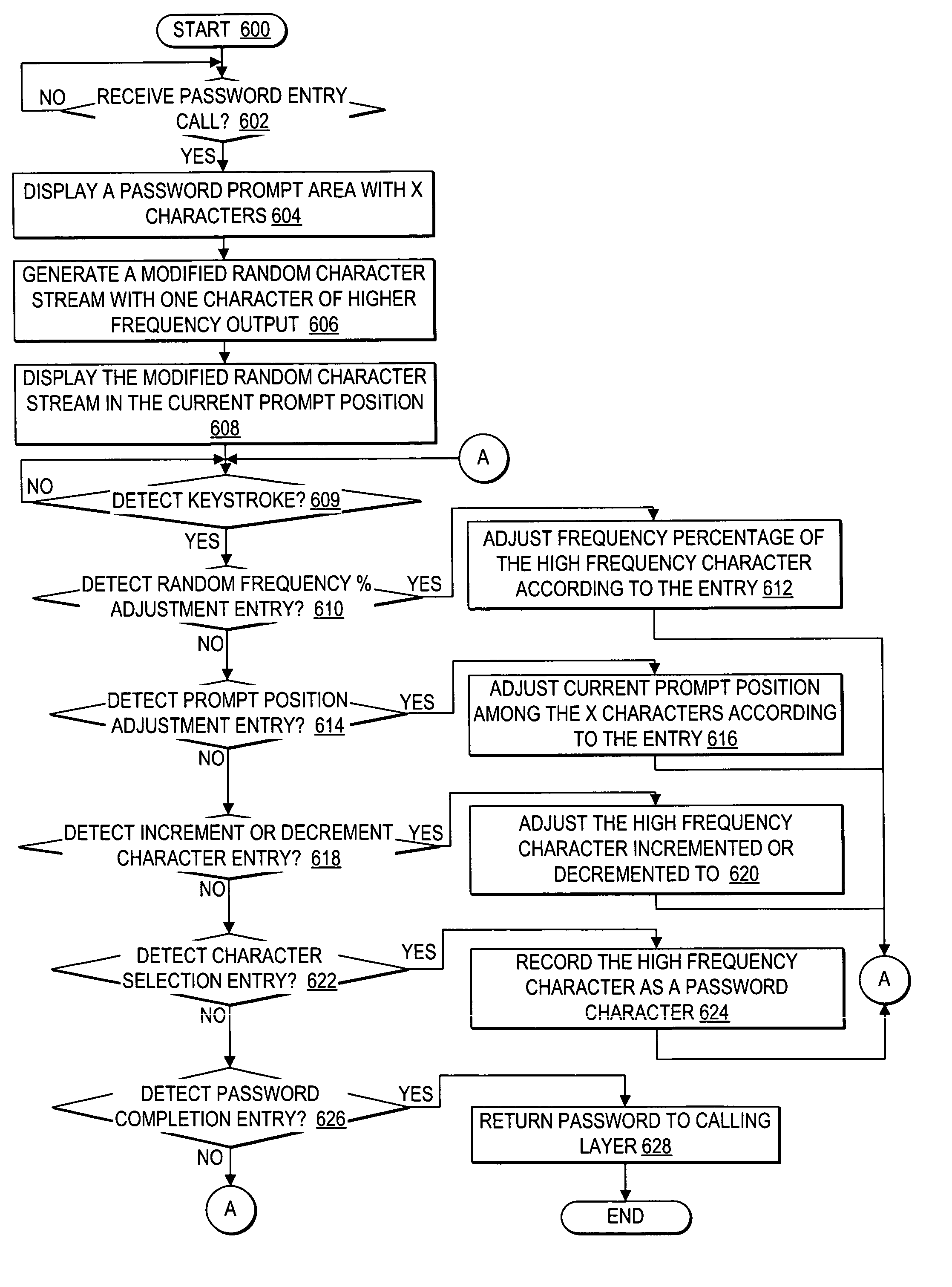
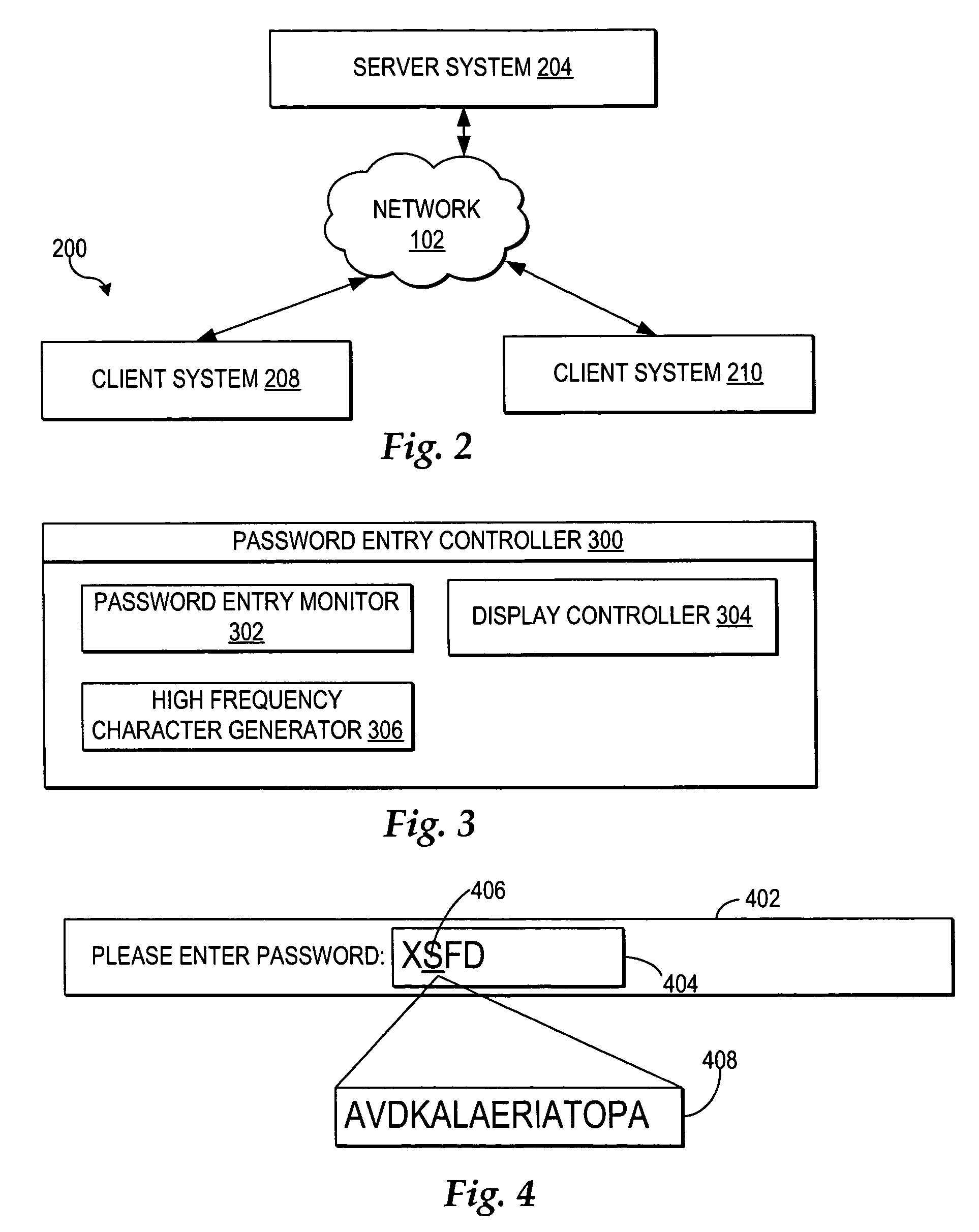
Secure password entry
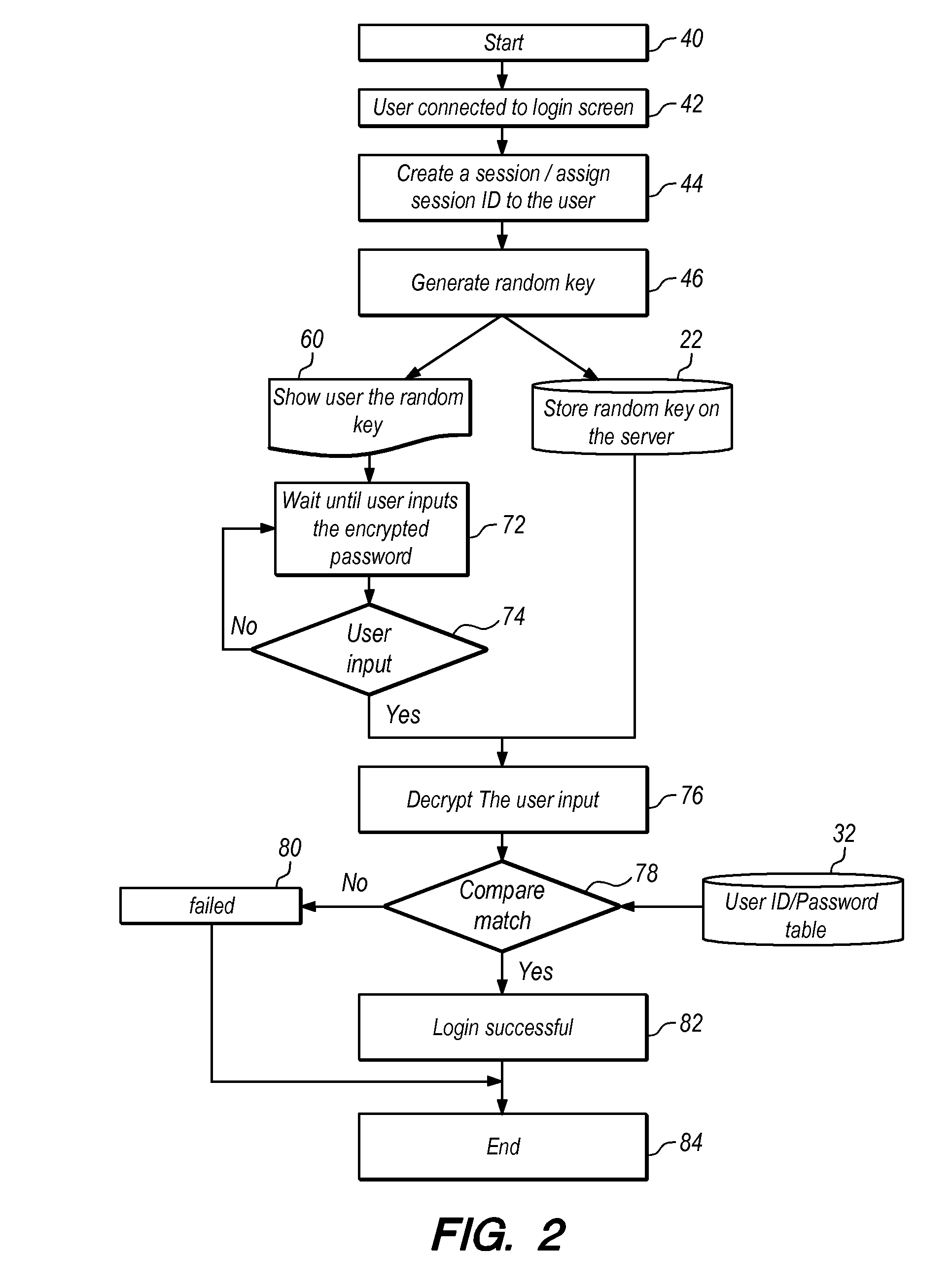
InactiveUS20050262555A1Improve securityPrevent and defeat unauthorized keystroke logging aimedDigital data processing detailsUnauthorized memory use protectionPasswordUser input
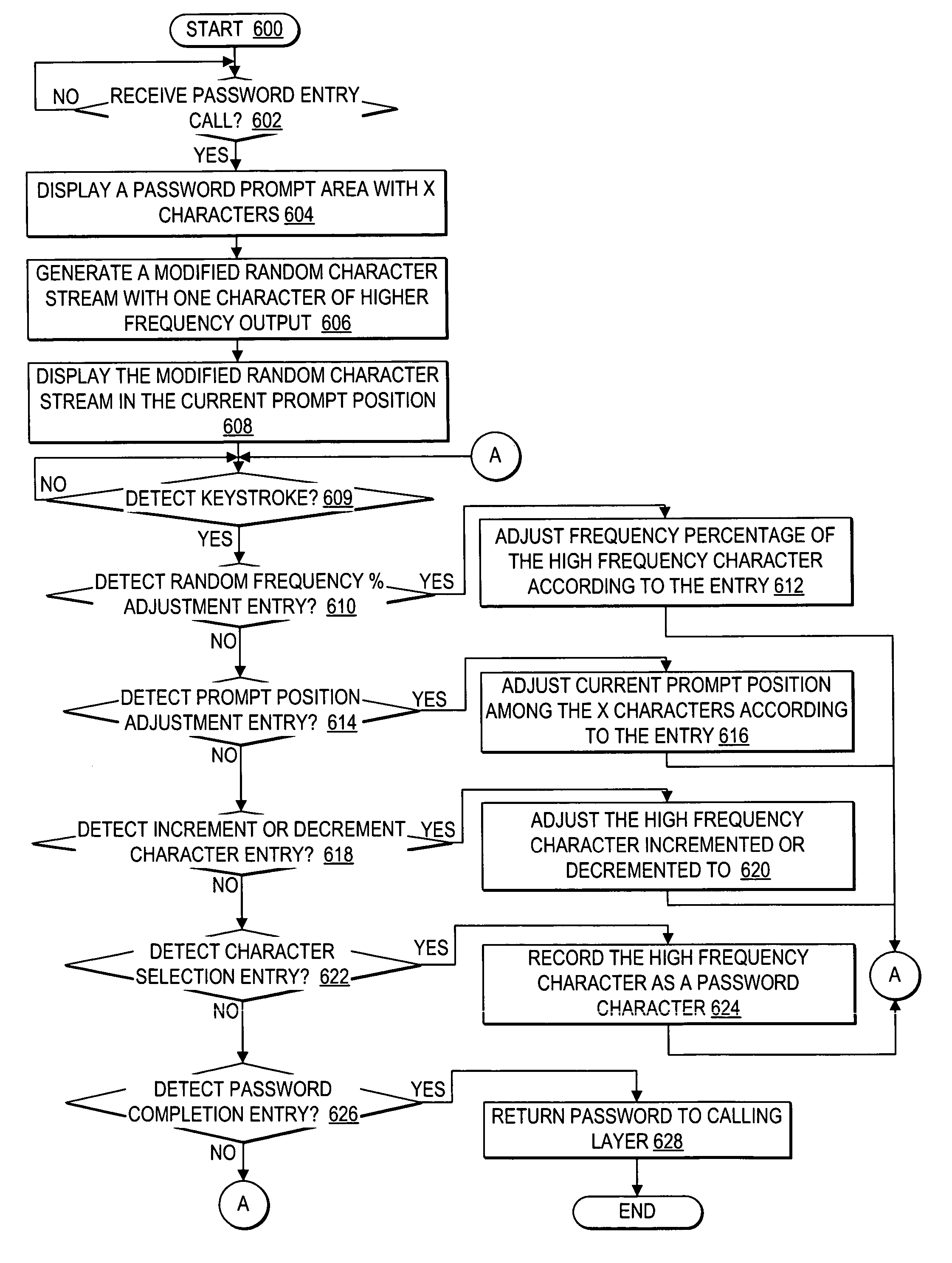
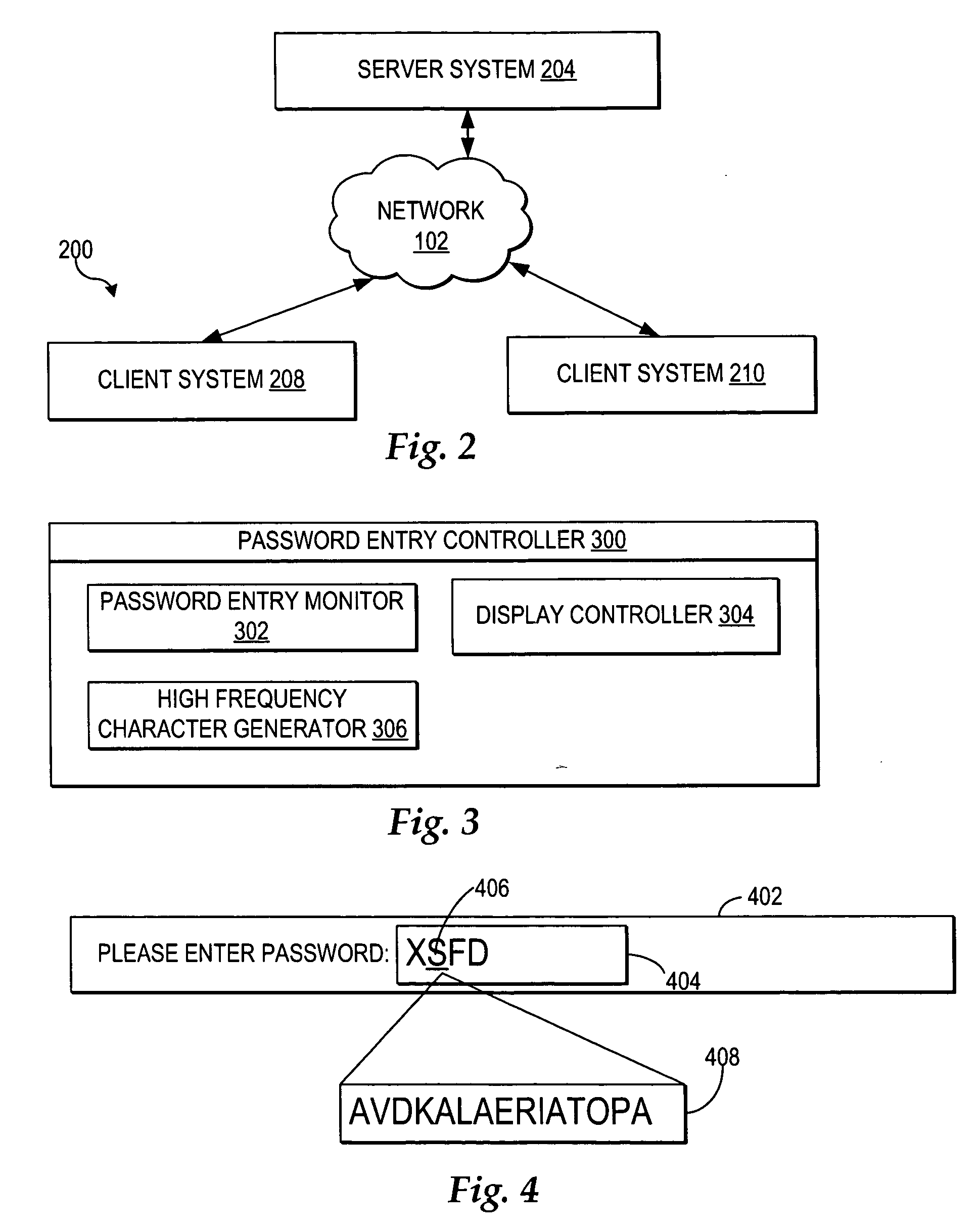
A method, system, and program defeating unauthorized keystroke logging during password entry are provided. Secure password entry is facilitated by displaying a password prompt comprising a changing stream of random characters, where a particular character within the stream of random characters is displayed at a visibly detectable higher frequency. A user selects a password character by entering input to increment or decrement the particular high frequency character to reach the password character, such that any unauthorized keystroke logging to detect said password is ineffective. Once the user reaches the password character, the user provides another input indicating a selection of the current high frequency character as the password character. Once the user has selected all the characters of the password, the user enters an input indicating the password is complete and the password entry controller then passes the password to the calling layer.
Owner:IBM CORP
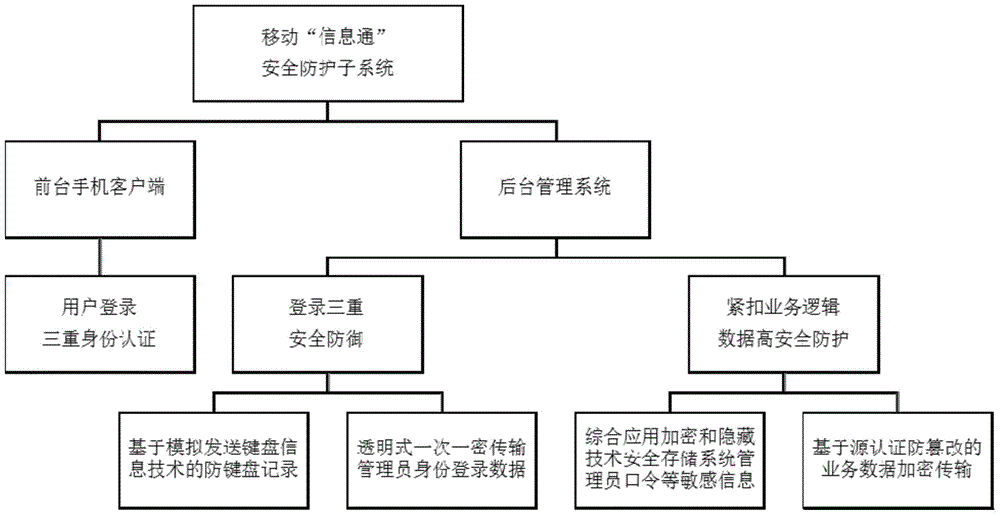
Implementation method for integrated security protection subsystem of mobile office system
ActiveCN104469767AImprove data securityRealize multi-factor authentication security defenseTransmissionSecurity arrangementInformation securityOne-time pad
The invention discloses an implementation method for an integrated security protection subsystem of a mobile office system. The implementation method includes the steps of triple mobile phone client identity authentication, triple background management system login security defense and tight service logic data security protection. The step of triple mobile phone client identity authentication includes password authentication, face recognition authentication and pattern password authentication. The step of triple background management system login security defense includes keyboard record prevention based on the simulative transmission keyboard information technology, a transparent one-time pad administrator login identity information encryption transmission mode based on RSA, and a double-factor authentication mode based on cloud pushing and combining dynamic passwords with static user names / passwords. Various kinds of security technology is transparently adopted, the data security is improved, multi-identity-authentication security defense is achieved, the access control capacity is enhanced, and notice announcement and news browsing of enterprises are safe and efficient through the integrated information security protection subsystem.
Owner:杭州安新立行网络科技有限公司
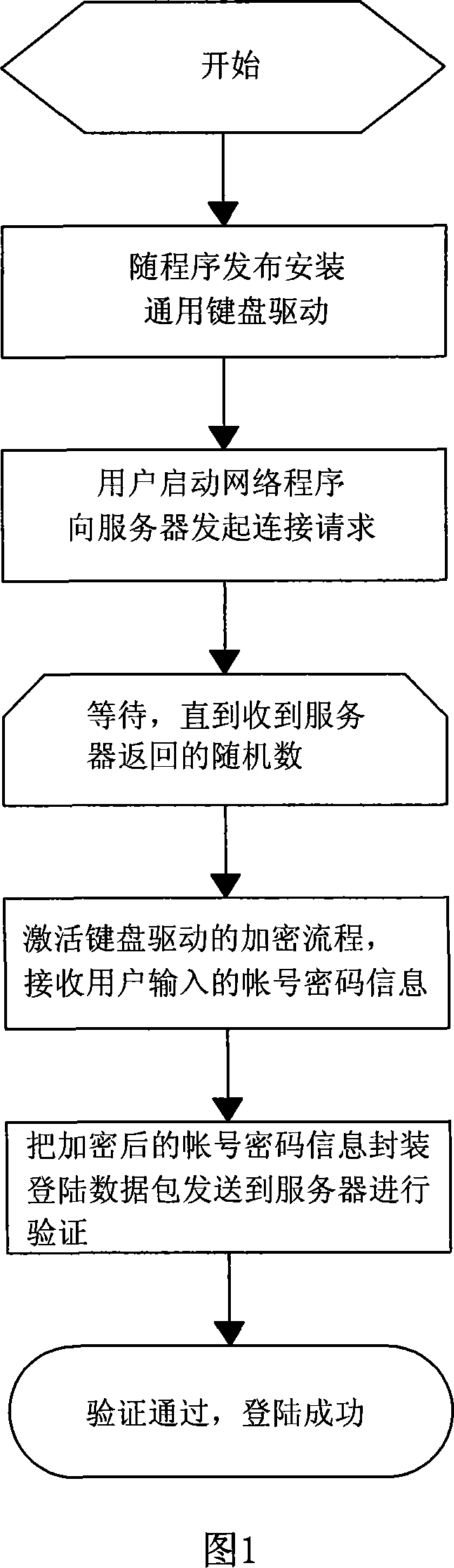
Method for landing by account number cipher for protecting network application sequence
ActiveCN101051904APrevent theftAvoid interceptionUser identity/authority verificationComputer hardwareOperational system
Through client end to input cipher, then the method carries out log on through authentication at server end. Characters are that universal keyboard drive program is setup at client end, encrypted private key and module for encrypting private key are preset inside the keyboard drive program; at same time, being identical to those setup at client end, the encrypted private key and module for encrypting private key are also setup at server end. The invention can prevent wooden horse virus process possessing function of recording keyboard and running at application layer on operation system from stealing account cipher input by user effectively as well as prevent network monitor tool (NMT) from intercepting log on data packet containing information of user account cipher etc, and prevent NMT implements chicaning log on through software method.
Owner:成都金山互动娱乐科技有限公司
Extensible Ubiquitous Secure Operating Environment
InactiveUS20080244689A1Secures user session activityPlatform integrity maintainanceSpecial data processing applicationsOperational systemSecure state
The present invention provides a portable and secure computer operating system, and applications that can be used securely on virtually any computer system regardless of its security state (i.e., regardless of the presence of computer viruses, Trojan code, keylogging software, or any other malicious mobile code that may exist on host computer system). The present invention is embodied within three (3) components including 1) the client desktop or server software, 2) the appliance-based management server, and 3) the media (i.e., including but not limited to USB thumb drive or CDROM) on which the client desktop or server software is installed.
Owner:DALTON CURTIS EVERETT
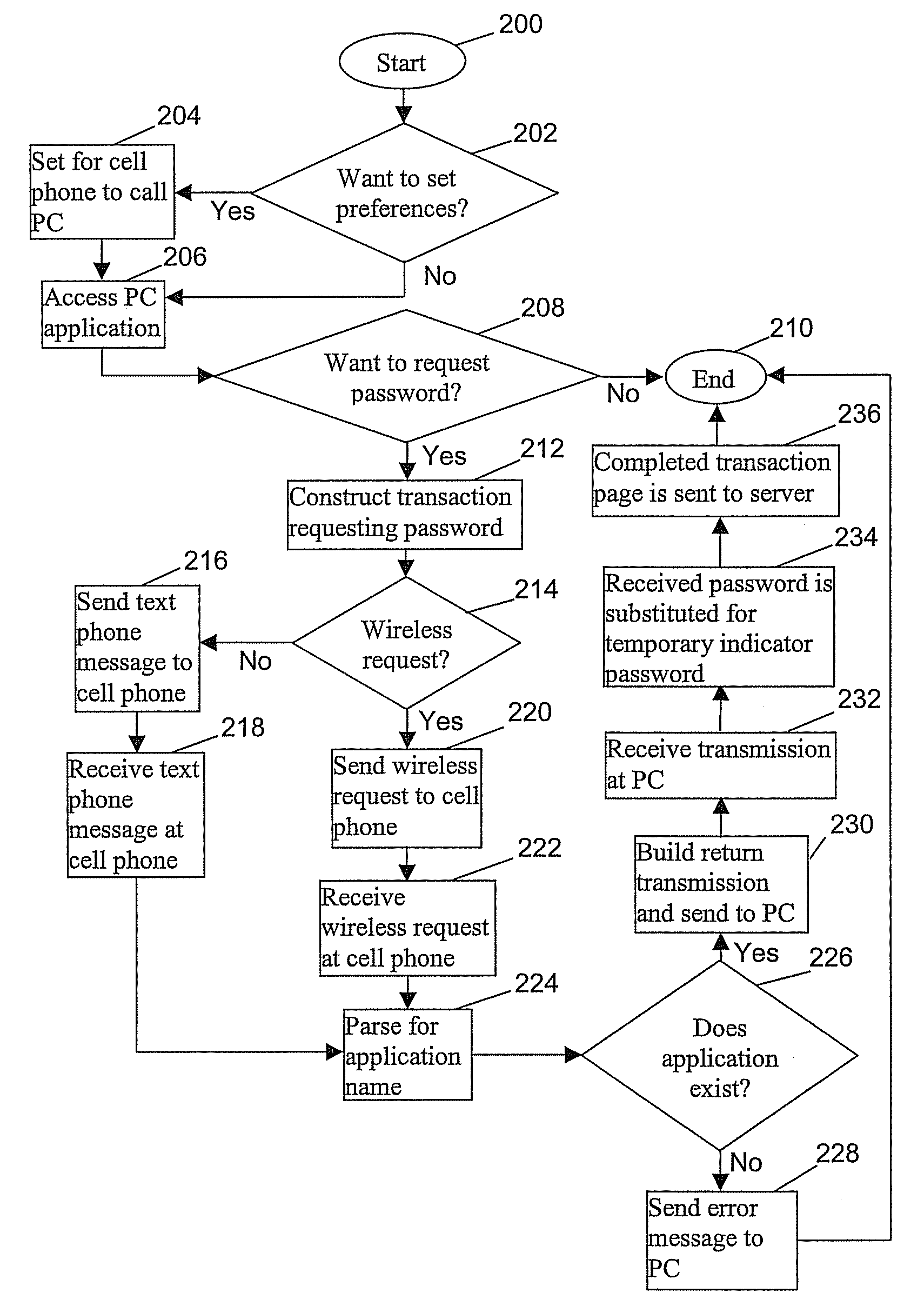
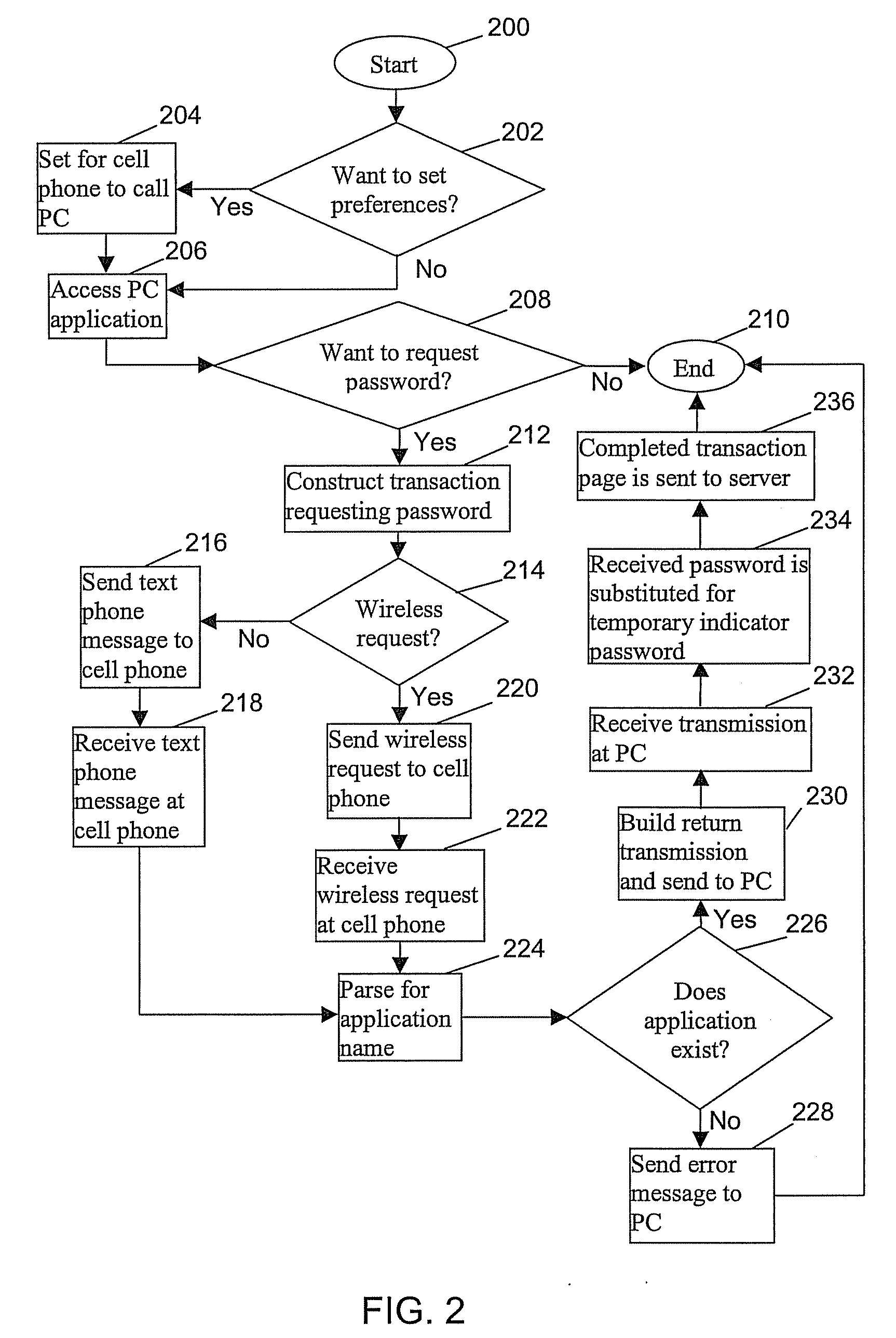
Method for protecting against keylogging of user information via an alternative input device
InactiveUS20090125993A1Digital data processing detailsUser identity/authority verificationPasswordSecret code
A method for protecting against keylogging, the method includes: detecting from a host browser application, a request for a password input by a user of an alphanumeric input device in an entry field of a transaction; inserting a temporary indicator password in the entry field; sending an identifier of the host application with the temporary indicator password to an alternative device; retrieving a user assigned password stored in a table in the alternative device in response to matching the identifier of the host application and the temporary indicator password; sending the user assigned password to the host application; inserting the user assigned password in place of the temporary indicator password in the entry field; and sending the transaction to a server for verification and further processing.
Owner:IBM CORP
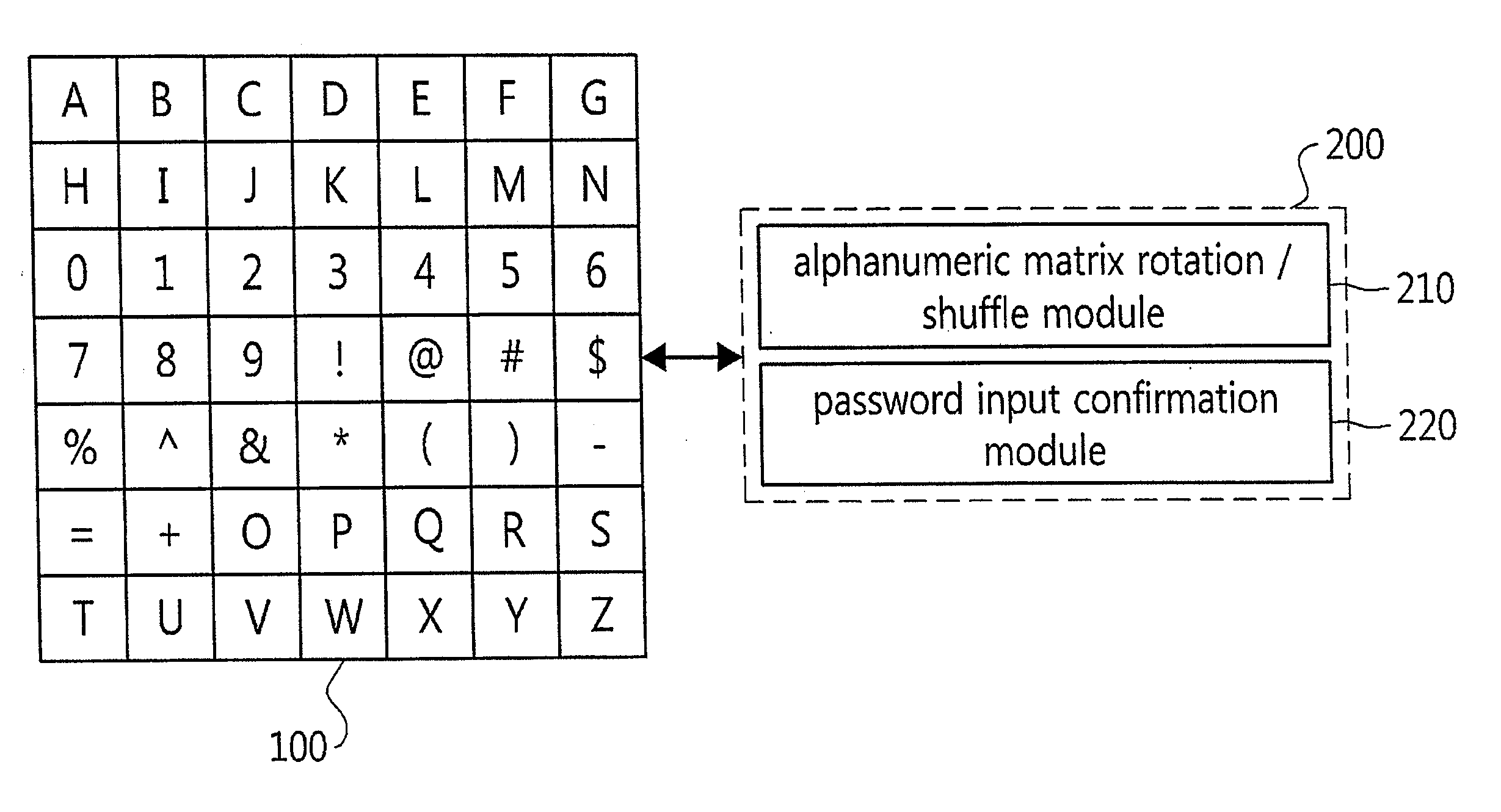
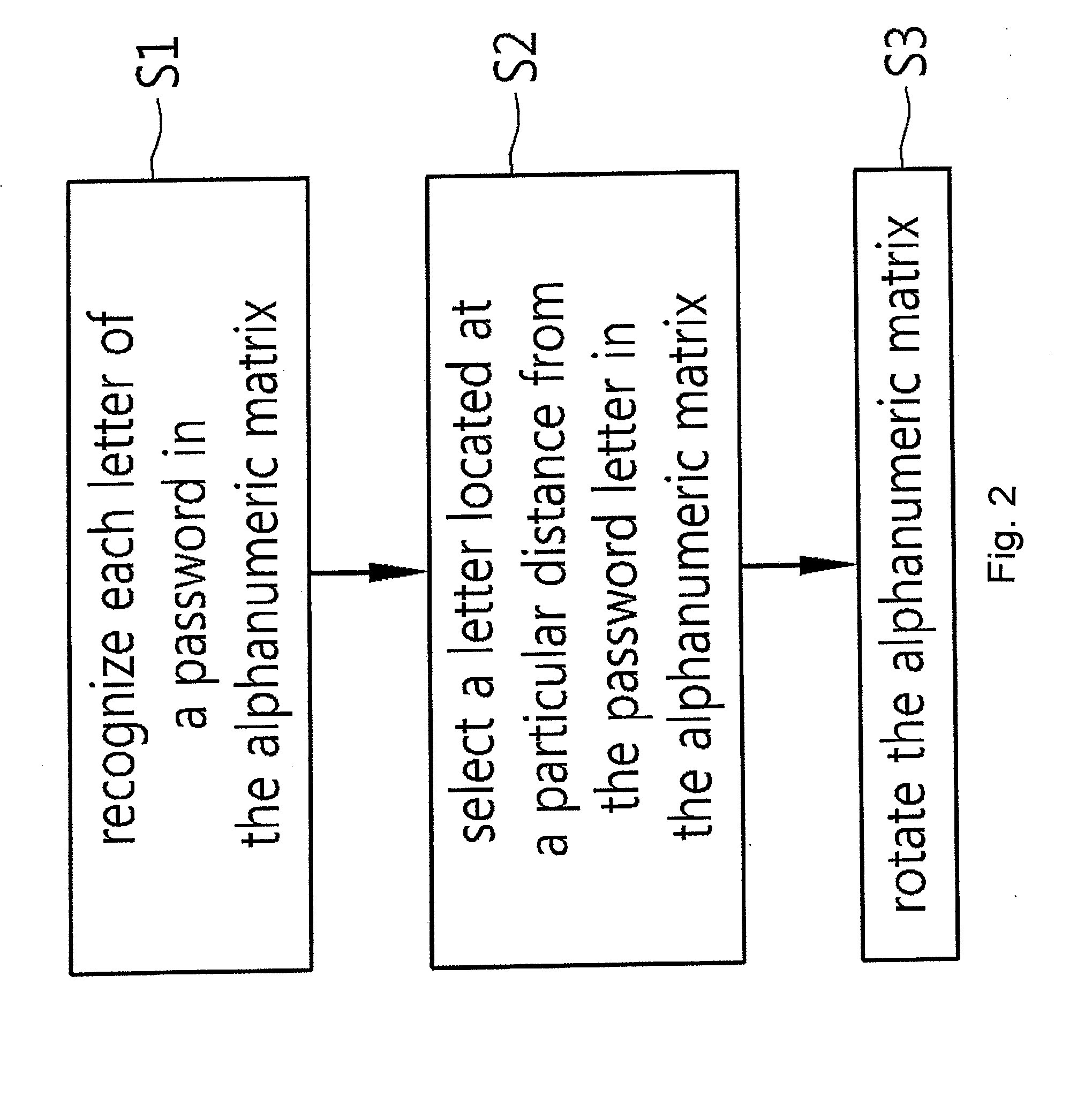
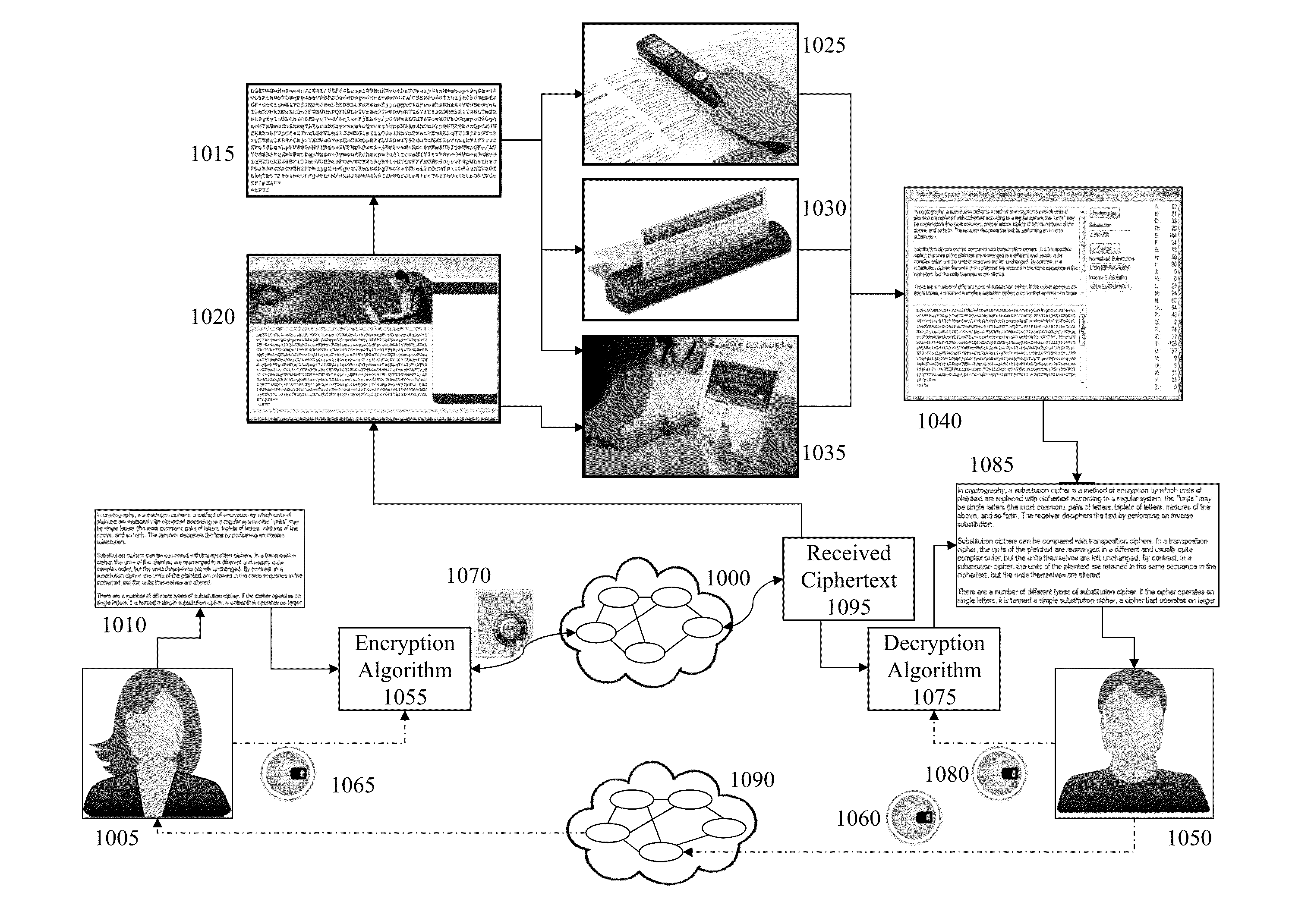
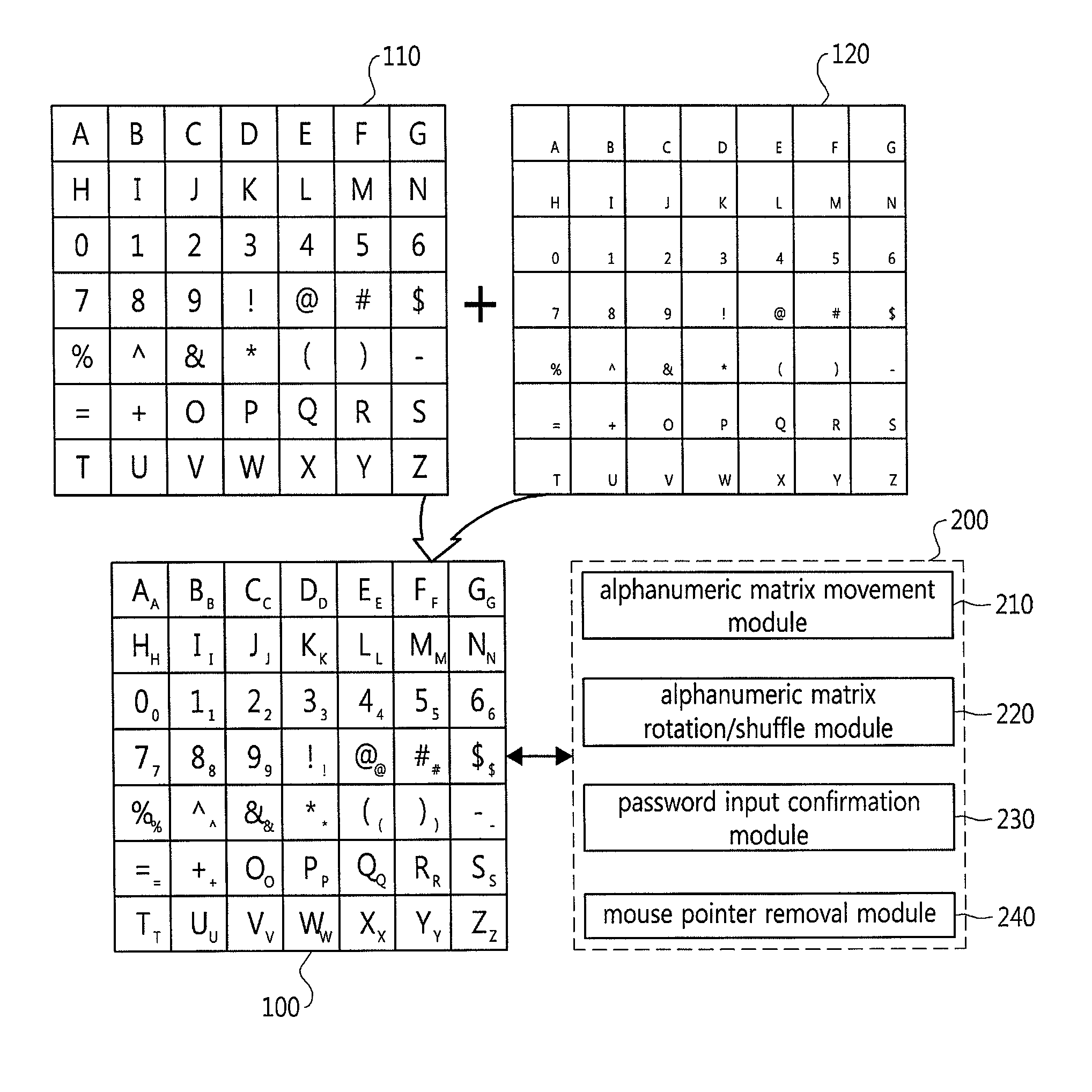
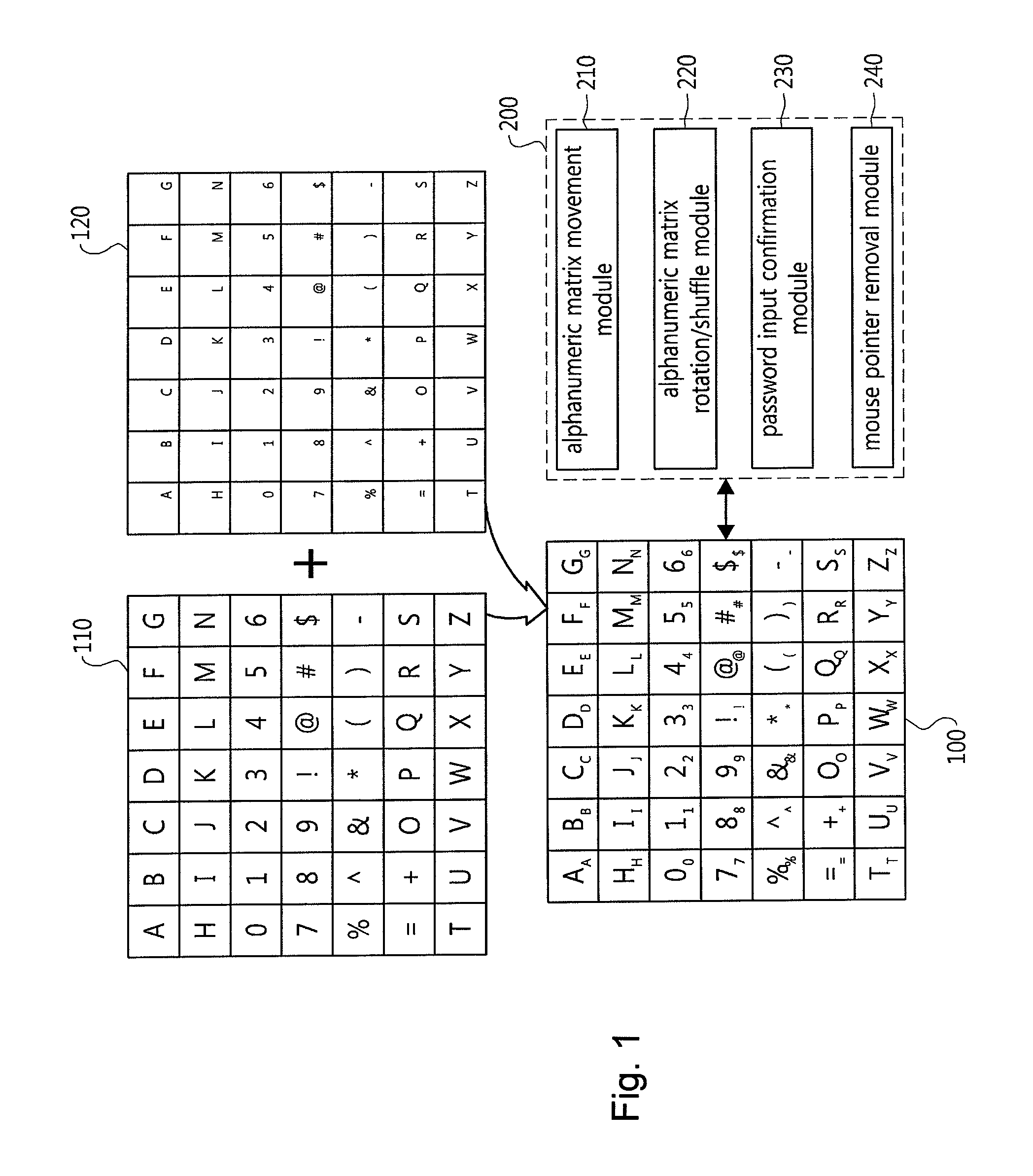
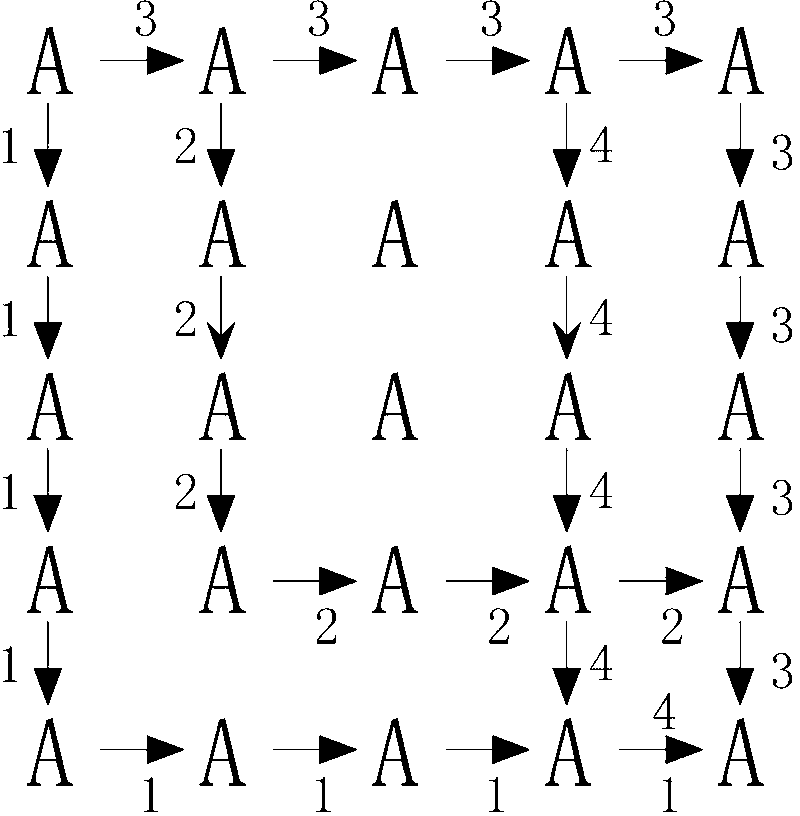
Password input system using an alphanumeric matrix and password input method using the same
InactiveUS20110004769A1Increase probabilityDigital data authenticationInput/output processes for data processingPasswordShoulder surfing attack
The present invention relates to a password input algorithm, more particularly to a password input system and method using an alphanumeric matrix. An aspect of the invention can provide a password input system and method that can defend against keylogging attacks and shoulder surfing attacks, by having the final password inputted by way of certain alphanumeric matrix letters which are separated by a particular distance from the letters forming the password in the alphanumeric matrix. Also, an aspect of the invention can provide a password input system and method that can further increase the probability of defending against keylogging attacks and shoulder surfing attacks, by having the final password inputted by way of certain alphanumeric matrix letters which are separated by a particular distance from the letters forming the password in the alphanumeric matrix, but with the alphanumeric matrix rotated every time a letter is inputted.
Owner:KOREA INTERNET & SECURITY AGENCY
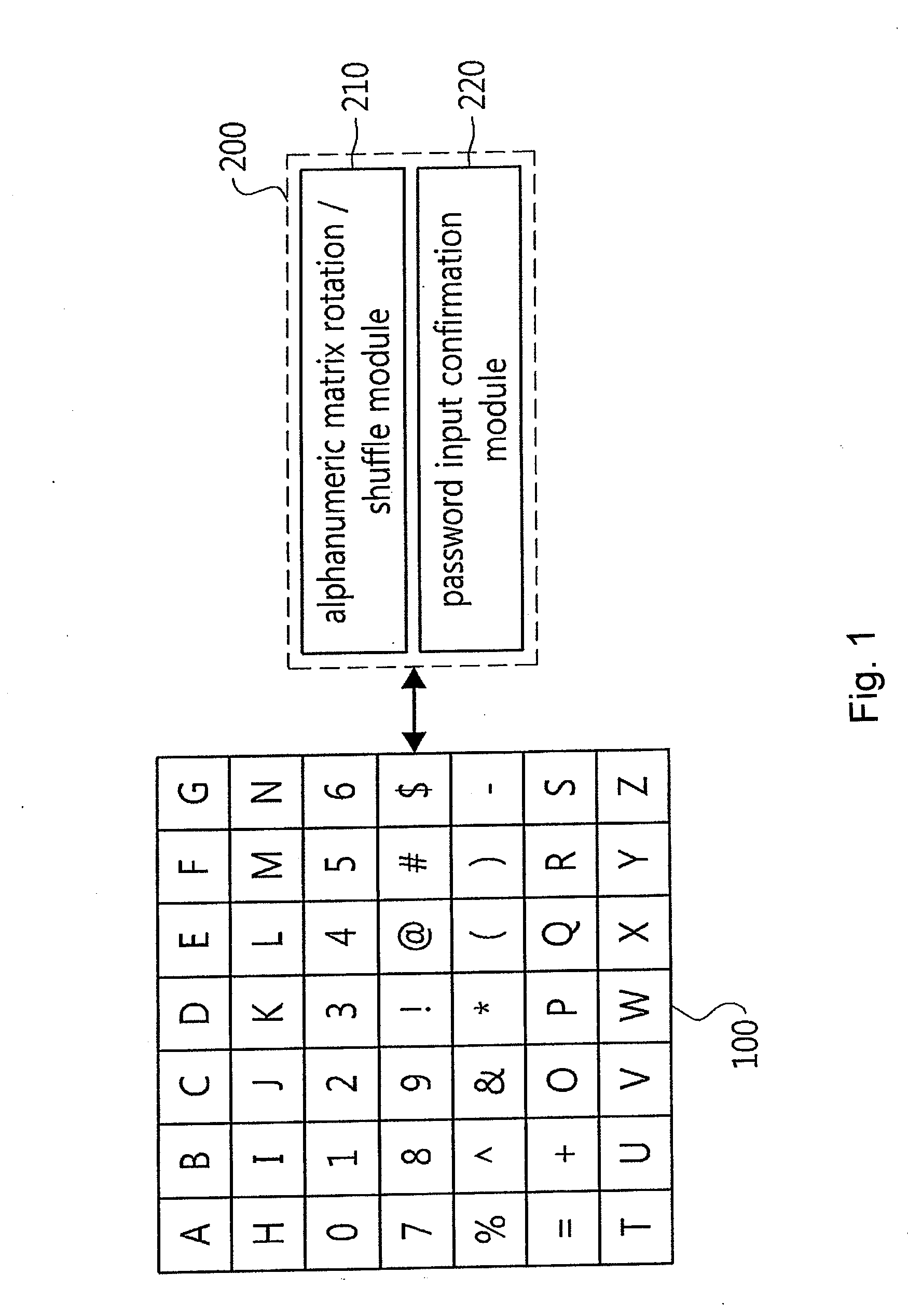
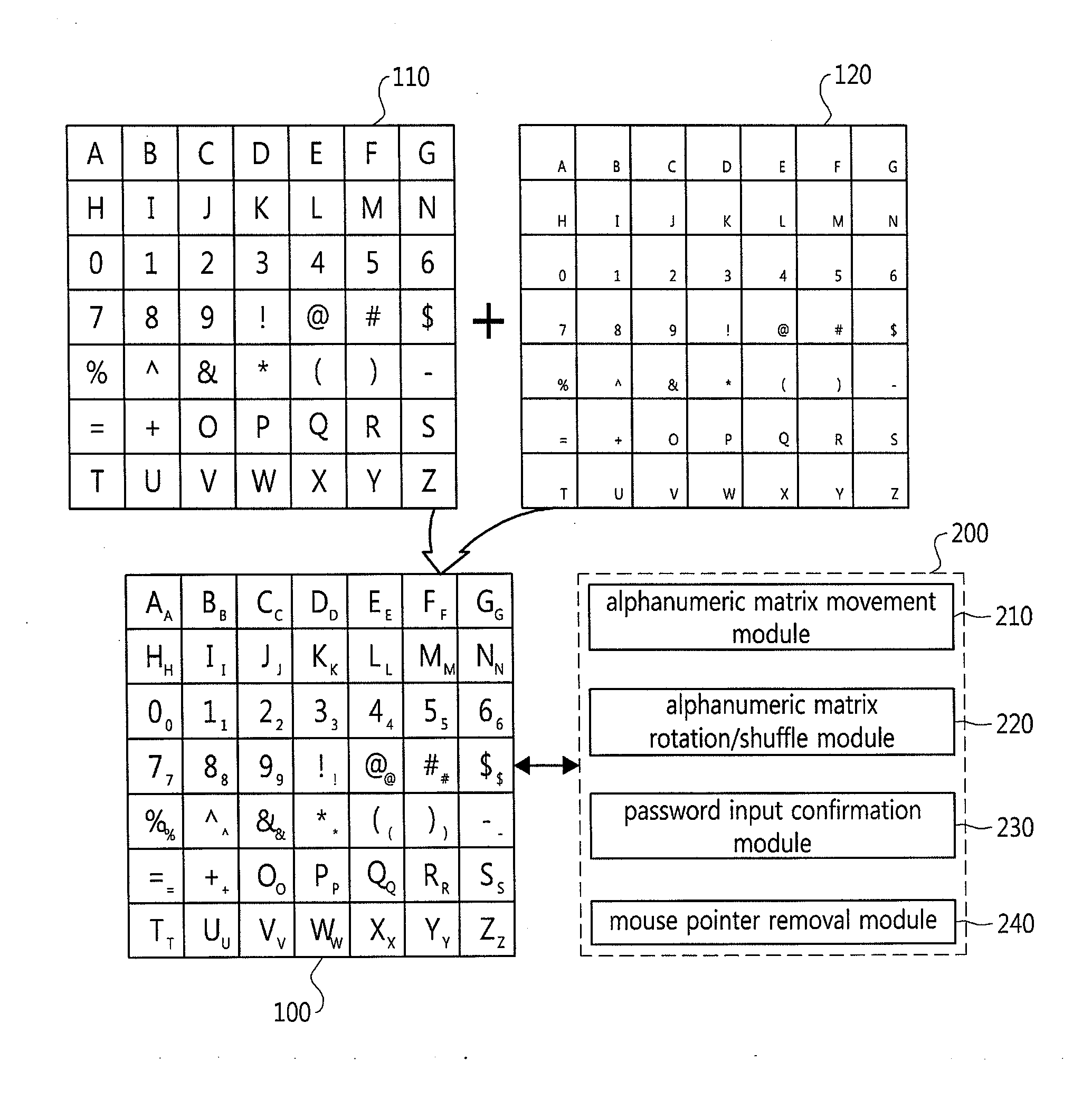
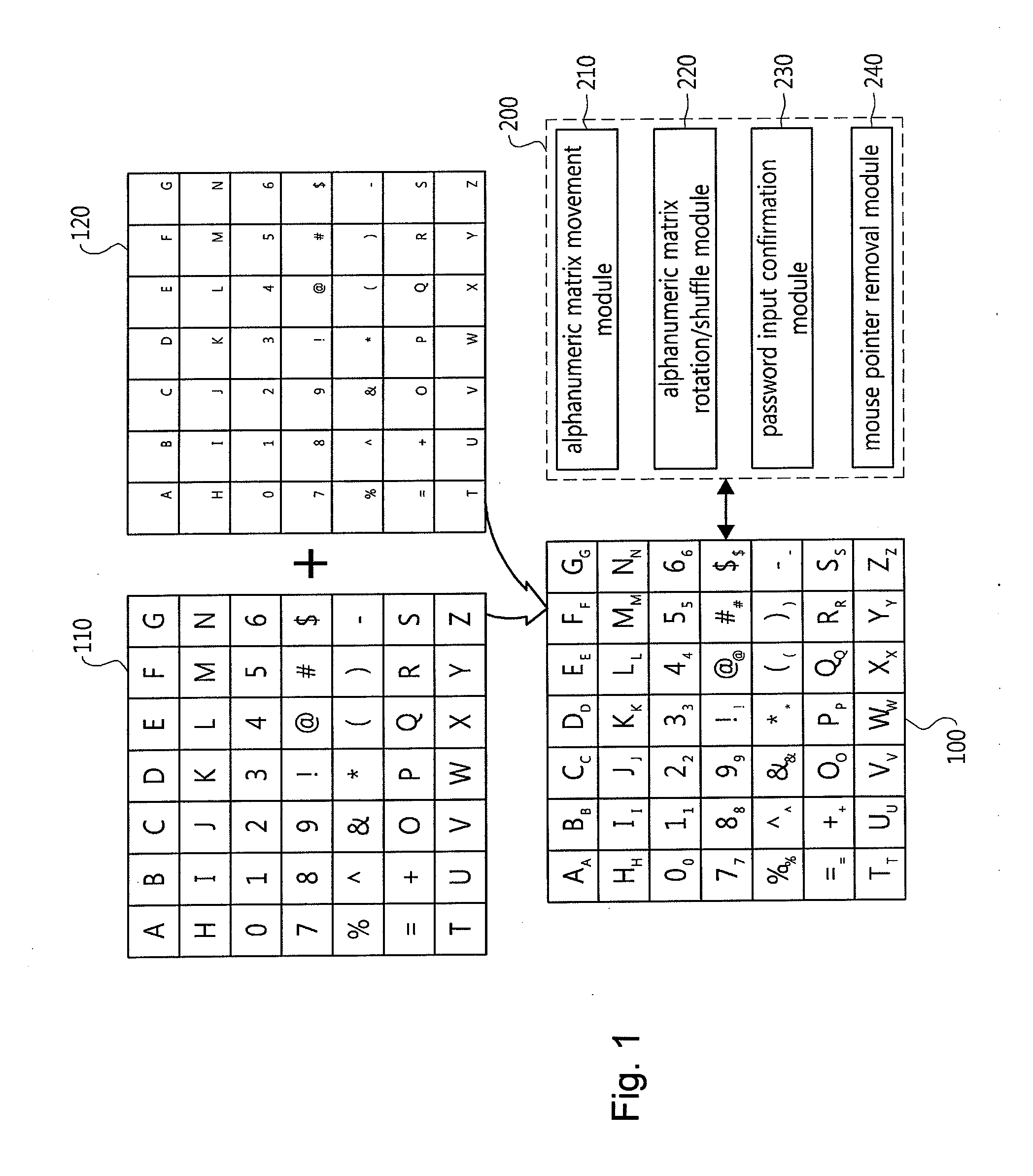
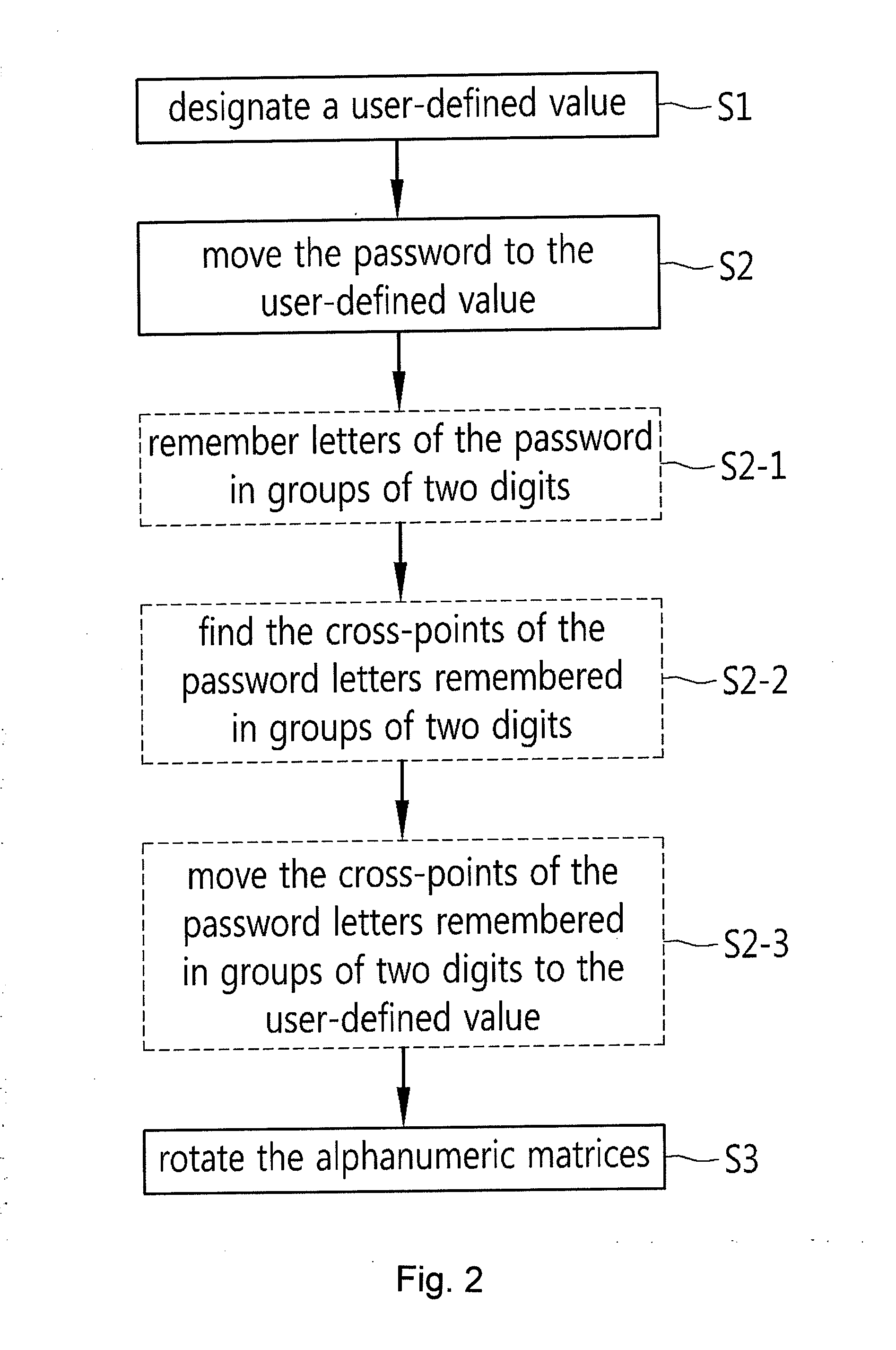
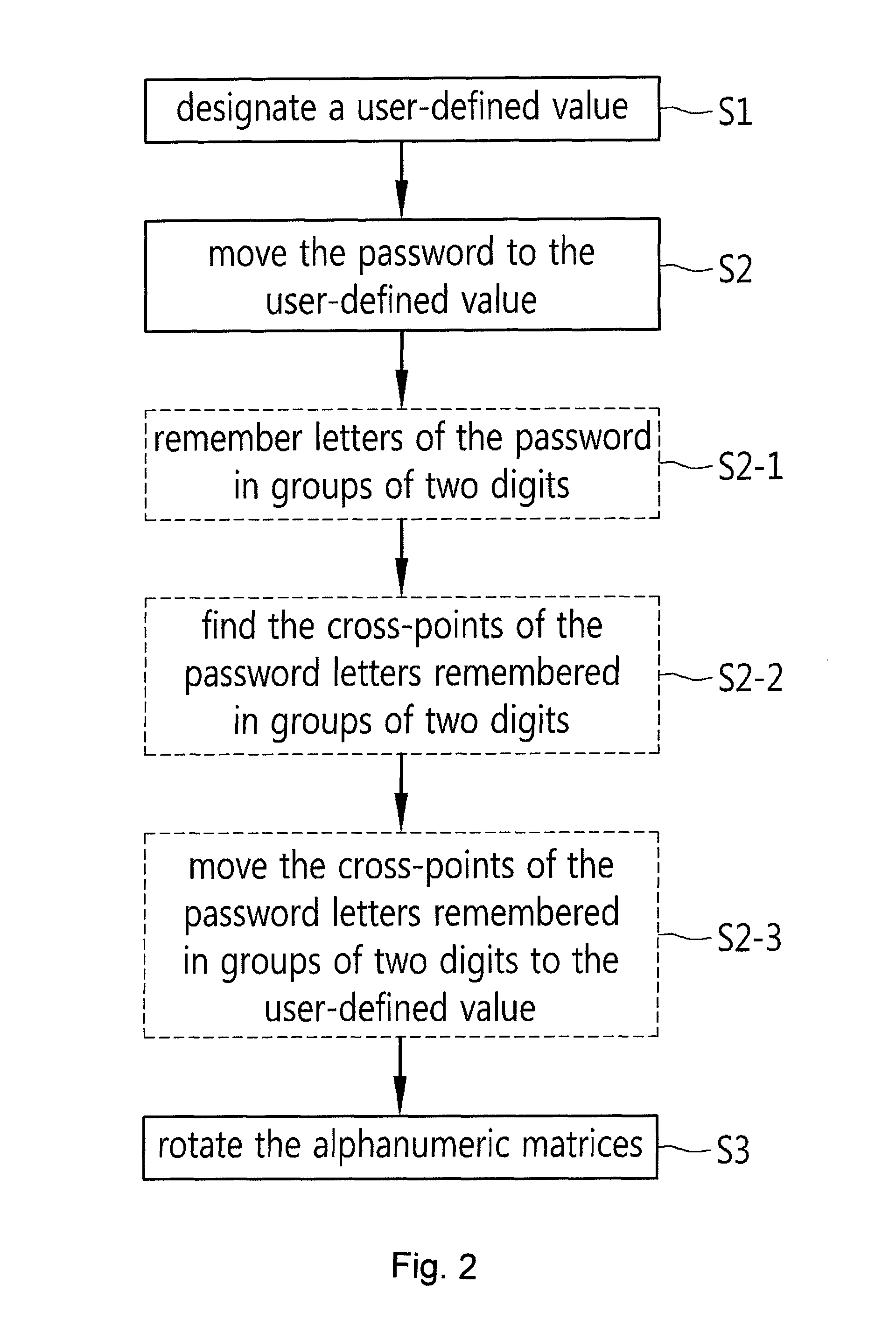
Password input system using alphanumeric matrices and password input method using the same
InactiveUS20110004928A1Digital data processing detailsUser identity/authority verificationPasswordShoulder surfing attack
The present invention relates to a password input algorithm, more particularly to a password input system and method using alphanumeric matrices. An aspect of the invention can provide a password input system and method using alphanumeric matrices that can defend against keylogging attacks and shoulder surfing attacks by including a movable second alphanumeric matrix and a fixed first alphanumeric matrix and enabling a user to input a password by moving the password letters of the second alphanumeric matrix to the user-defined value of the first alphanumeric matrix. Another aspect of the invention can provide a password input system and method using alphanumeric matrices that can defend against shoulder surfing attacks by enabling a user to input a password by dividing the password by every two digits and moving the cross-points for the two digits, respectively, to the user-defined value of the first alphanumeric matrix.
Owner:KOREA INTERNET & SECURITY AGENCY
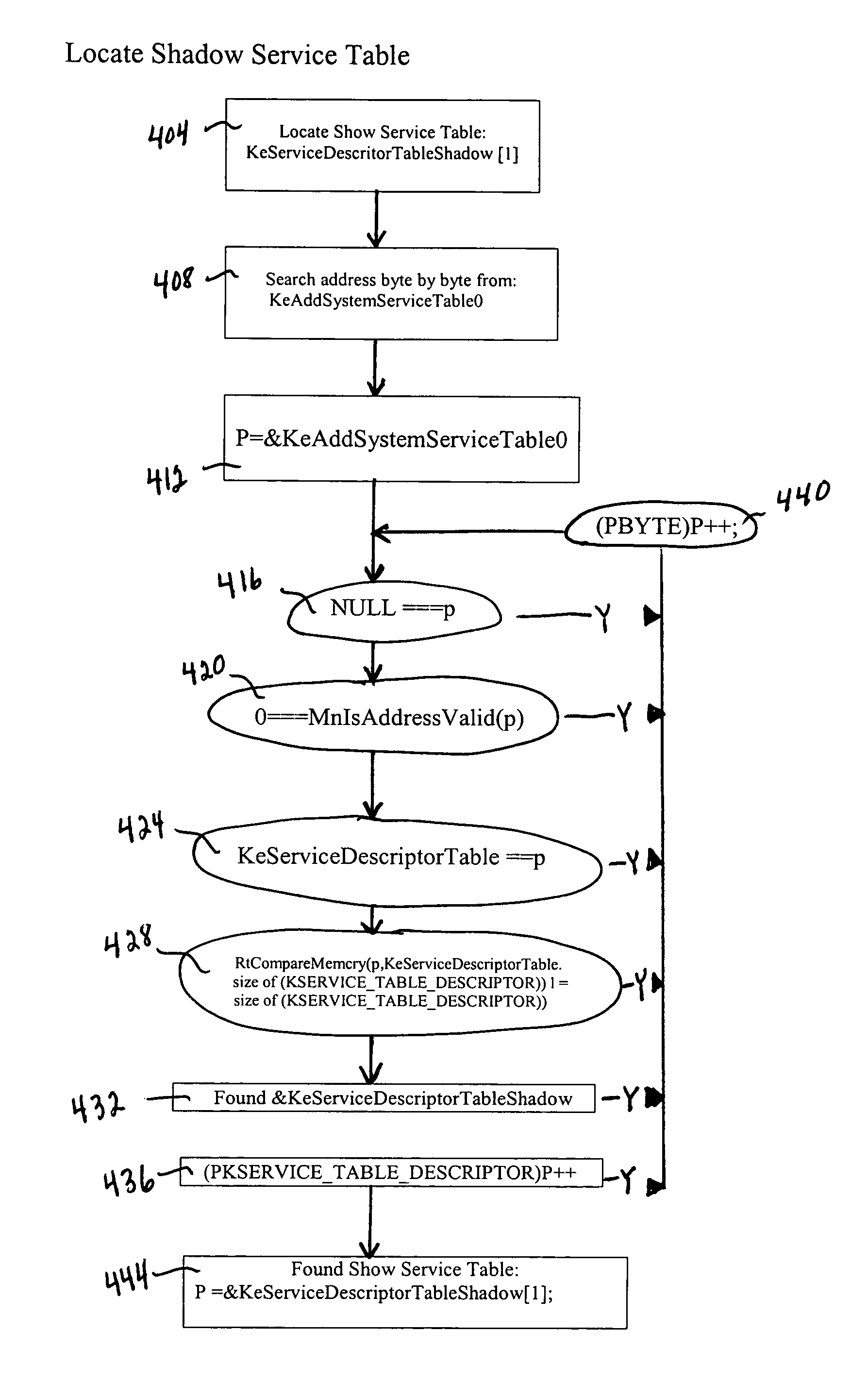
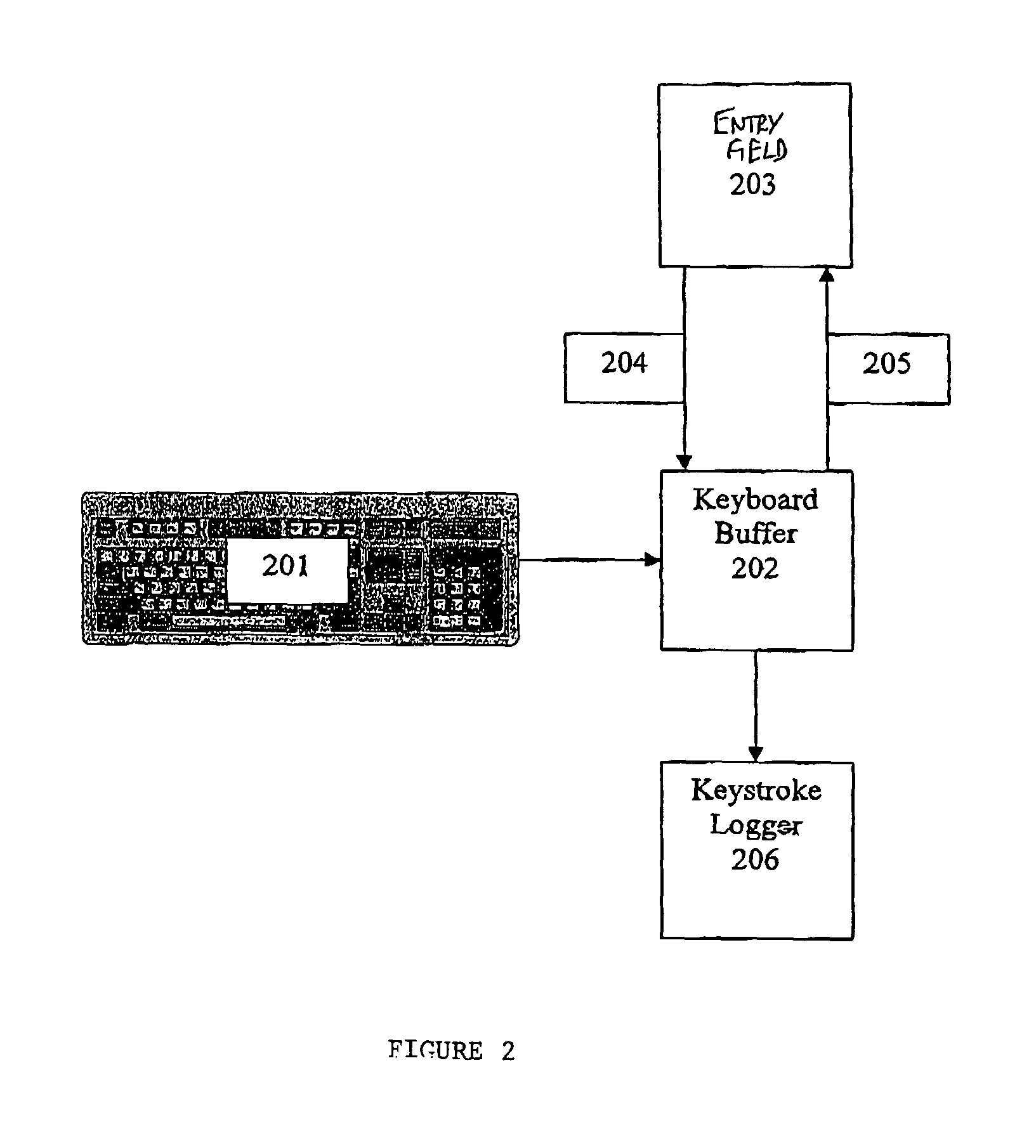
Detection of key logging software
Installing a detection hook function aids in the detection of keylogger software on a computer. A request to install a hook procedure via the system service function is intercepted by the detection hook function. The detection hook function determines whether the request indicates that the hook procedure is keylogger software. If so, an action is taken such as denying the request or alerting the user. A detection hook function also intercepts a request to remove a hook procedure. A dynamic detection function intercepts a call to a hook chain function attempting to pass an event to a hook procedure.
Owner:TREND MICRO INC
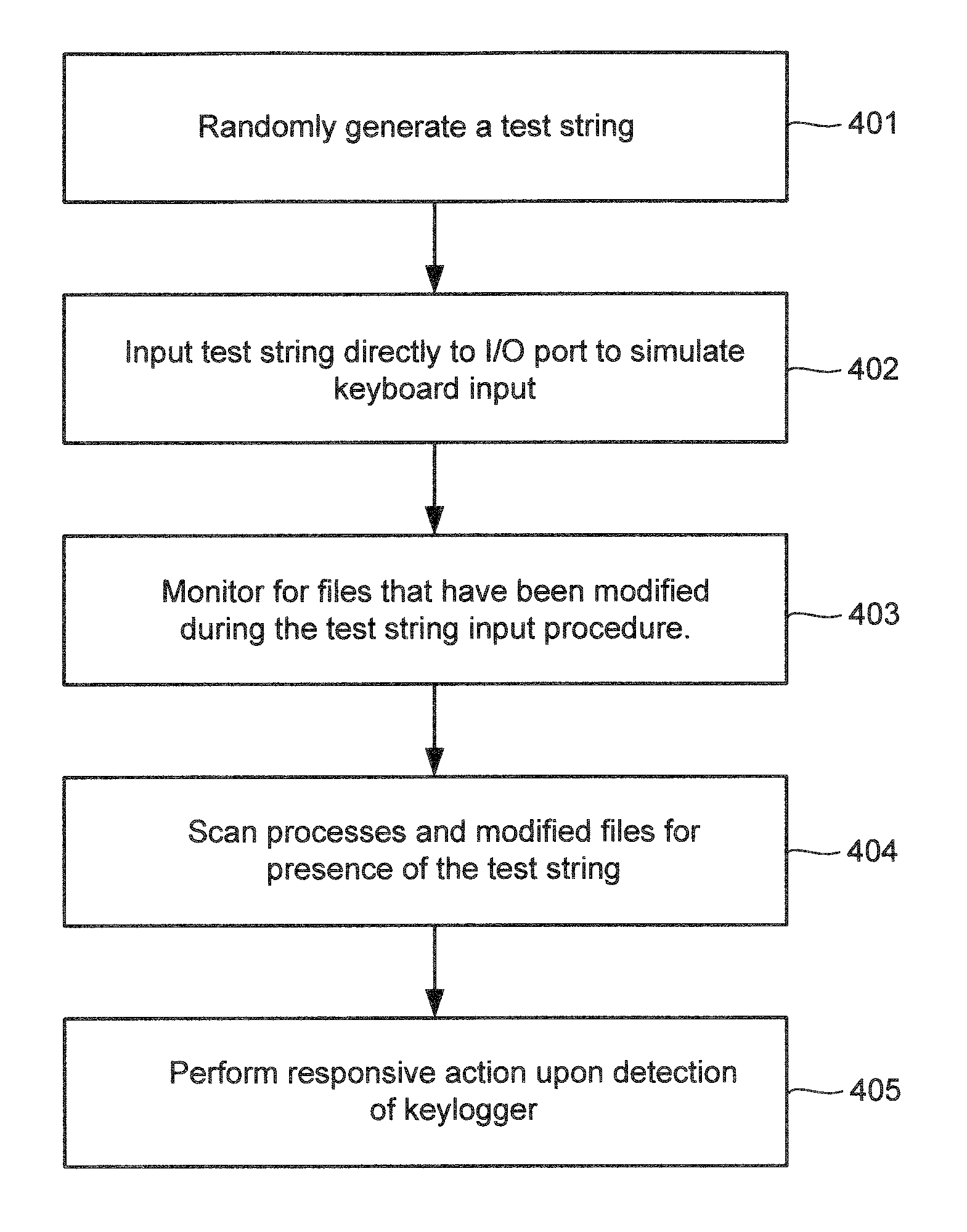
Techniques for detecting keyloggers in computer systems
ActiveUS8707437B1Memory loss protectionError detection/correctionComputer hardwareApplication software
Keyloggers are detected in a computer. A test string is generated in the computer. Keyboard input is simulated using the test string. The test string may be input to a hidden browser connected to a sensitive site or a hidden application program, for example. Files modified during the input procedure are detected. Processes running in memory and modified files are scanned for presence of the test string to detect keyloggers.
Owner:TREND MICRO INC
System for preventing keystroke logging software from accessing or identifying keystrokes
Owner:SENTRYBAY
Method and system for handling keystroke commands
InactiveUS20080301816A1Improve confidentialitySafeguard keystrokeDigital data processing detailsAnalogue secracy/subscription systemsMalwareKeystroke logging
Keystroke commands are safeguarded from keyboard logging malware based on a destination application's memory address.
Owner:IMPRIVATA
Method For Anit-Keylogger
InactiveUS20090144558A1Easy to fixImprove securityUnauthorized memory use protectionHardware monitoringComputer usersComputer science
A method for preventing keyloggers from logging text data, that is outputted by a computer user data input device. By encrypting the text data of the user data input device, the keyloggers cannot understand the text data of the user data input device in a computer.
Owner:WANG CHI PEI
Budget tracking calculator system and method
Owner:BUDGET TRACKING SOLUTIONS
Secure content and encryption methods and techniques
In order to capture electronic information provided by a user to another user different third parties seek to download tracking software, viruses etc. to the user's computer systems. These may include, but are not limited to, message intercepting, email logging, hacking, spamming, phishing, spyware, malware, keyloggers, screen capturing, Trojan horses, WWW robots (BOTs or bots), IP spoofing, man-in-the-middle attacks, worms and viruses. Whilst within the prior art methodologies exist to protect the message by converting the plaintext at the sender's terminal to ciphertext for transmission before it is re-converted to plaintext at the receiver's (or recipient's) terminal once decrypted the message content, now in plaintext is accessible to malware, Trojan horse software, etc. upon the recipient's terminal allowing its contents to be acquired and transmitted without the recipient's and / or sender's knowledge. Accordingly, it would be beneficial to provide users with methods and systems enabling secure messaging to be undertaken as well as secure document transmission and viewing that overcomes the limitations within the prior art. Accordingly, beneficially embodiments of the invention provide secure messaging and secure document transmission even upon potentially compromised desktop computers.
Owner:BLULNK LTD
Password input system using alphanumeric matrices and password input method using the same
InactiveUS8375428B2Digital data processing detailsUser identity/authority verificationPasswordShoulder surfing attack
The present invention relates to a password input algorithm, more particularly to a password input system and method using alphanumeric matrices. An aspect of the invention can provide a password input system and method using alphanumeric matrices that can defend against keylogging attacks and shoulder surfing attacks by including a movable second alphanumeric matrix and a fixed first alphanumeric matrix and enabling a user to input a password by moving the password letters of the second alphanumeric matrix to the user-defined value of the first alphanumeric matrix. Another aspect of the invention can provide a password input system and method using alphanumeric matrices that can defend against shoulder surfing attacks by enabling a user to input a password by dividing the password by every two digits and moving the cross-points for the two digits, respectively, to the user-defined value of the first alphanumeric matrix.
Owner:KOREA INTERNET & SECURITY AGENCY
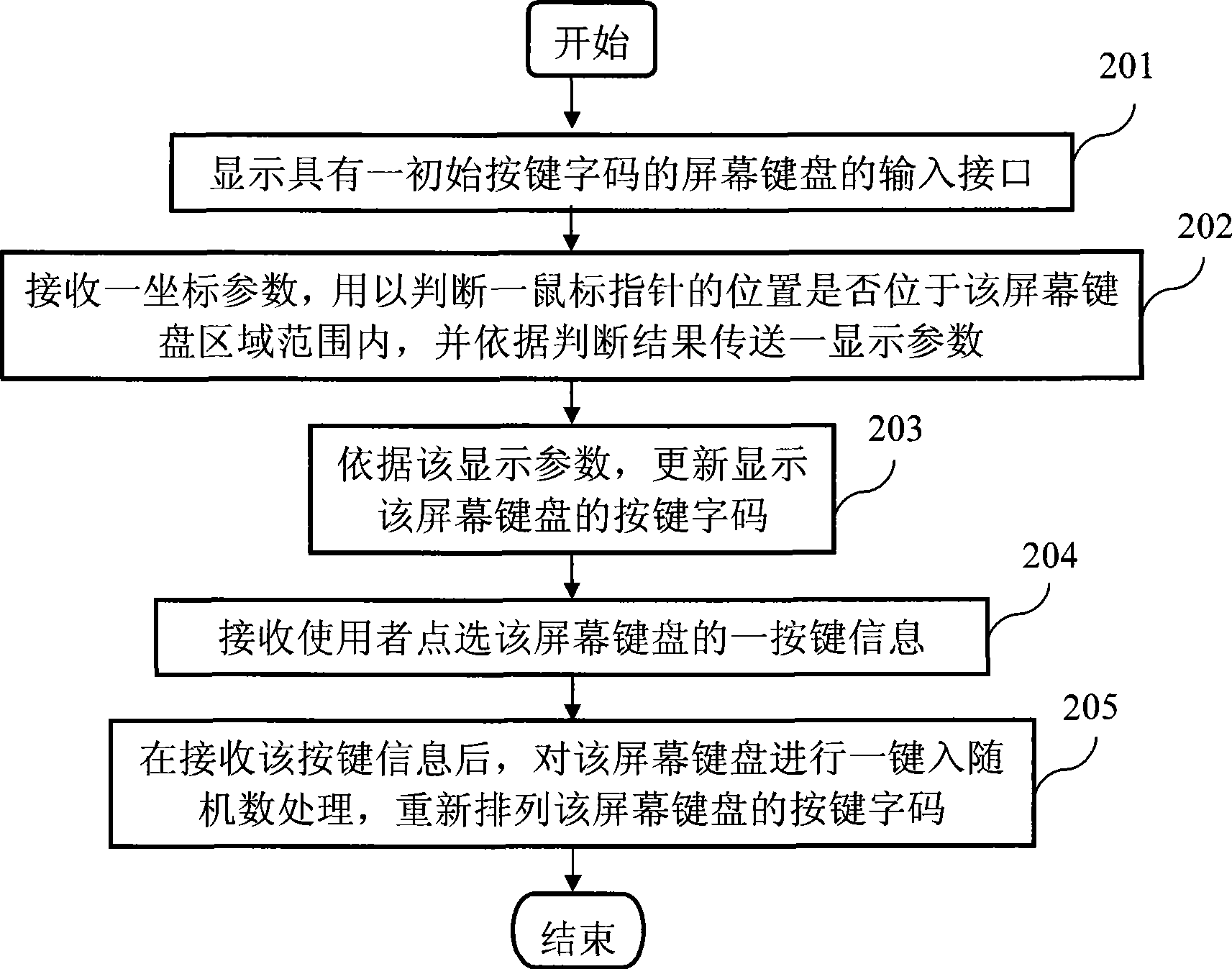
Screen key entry system for preventing trojan program and method thereof
The invention discloses an on-screen keyboard input system for preventing Trojan programs and a method thereof, which aims to solve the problem of keystroke logging easily by the Trojan programs when inputting confidential and private data. By allocating with random numbers and performing the process of hide display via keys of the on-screen keyboard, the method is used to prevent Trojan programs with functions of logging keystrokes and image acquisition.
Owner:INVENTEC CORP
Secure password entry
InactiveUS7539874B2Improve securityPrevent and defeat unauthorized keystroke logging aimedDigital data processing detailsUnauthorized memory use protectionKey pressingUser input
A method, system, and program defeating unauthorized keystroke logging during password entry are provided. Secure password entry is facilitated by displaying a password prompt comprising a changing stream of random characters, where a particular character within the stream of random characters is displayed at a visibly detectable higher frequency. A user selects a password character by entering input to increment or decrement the particular high frequency character to reach the password character, such that any unauthorized keystroke logging to detect said password is ineffective. Once the user reaches the password character, the user provides another input indicating a selection of the current high frequency character as the password character. Once the user has selected all the characters of the password, the user enters an input indicating the password is complete and the password entry controller then passes the password to the calling layer.
Owner:INT BUSINESS MASCH CORP
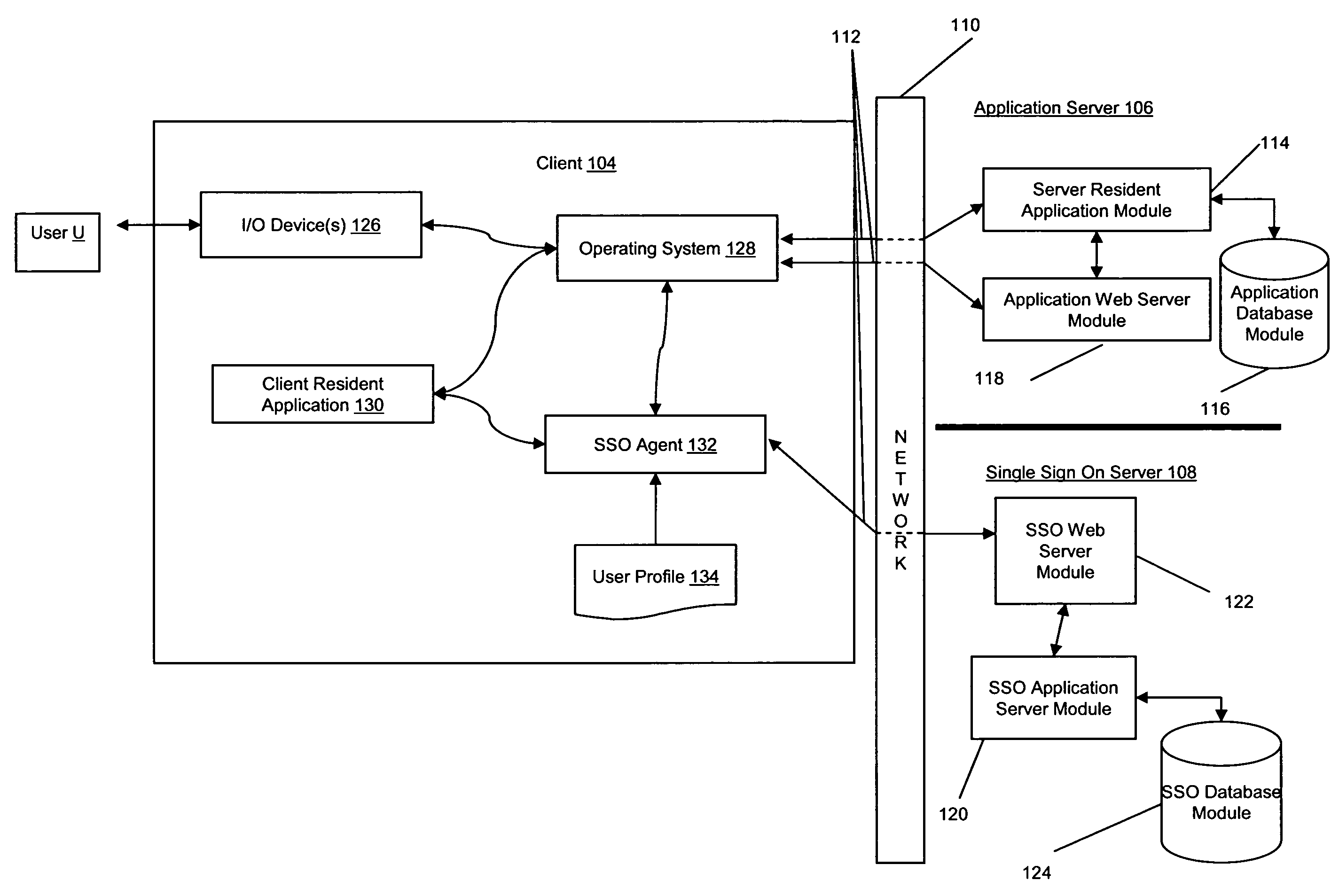
System and method for protecting data accessed through a network connection
ActiveUS8918865B2Facilitate gathering of informationEnhanced interactionMemory loss protectionDigital data processing detailsInternal memoryTelecommunications link
Owner:WONTOK
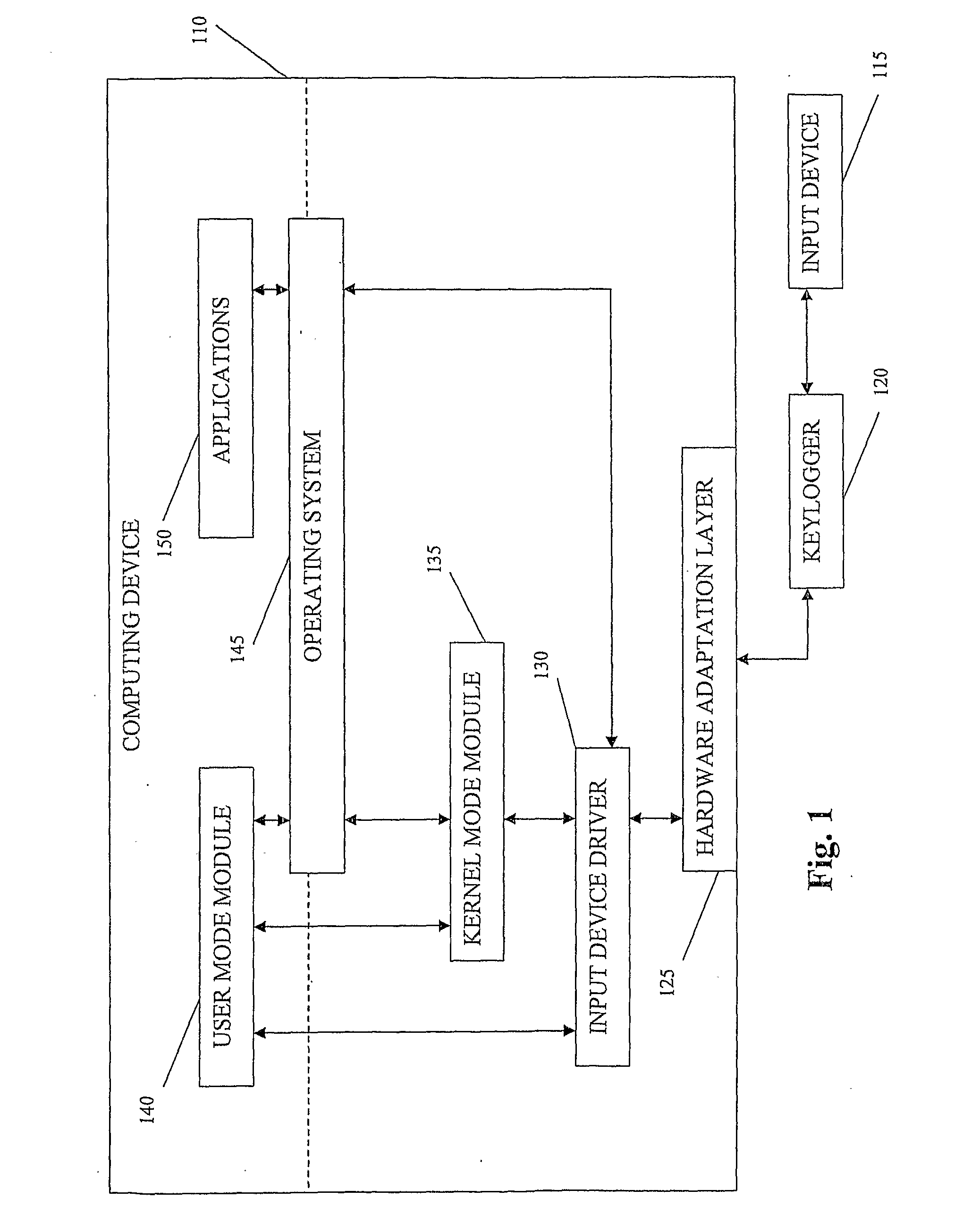
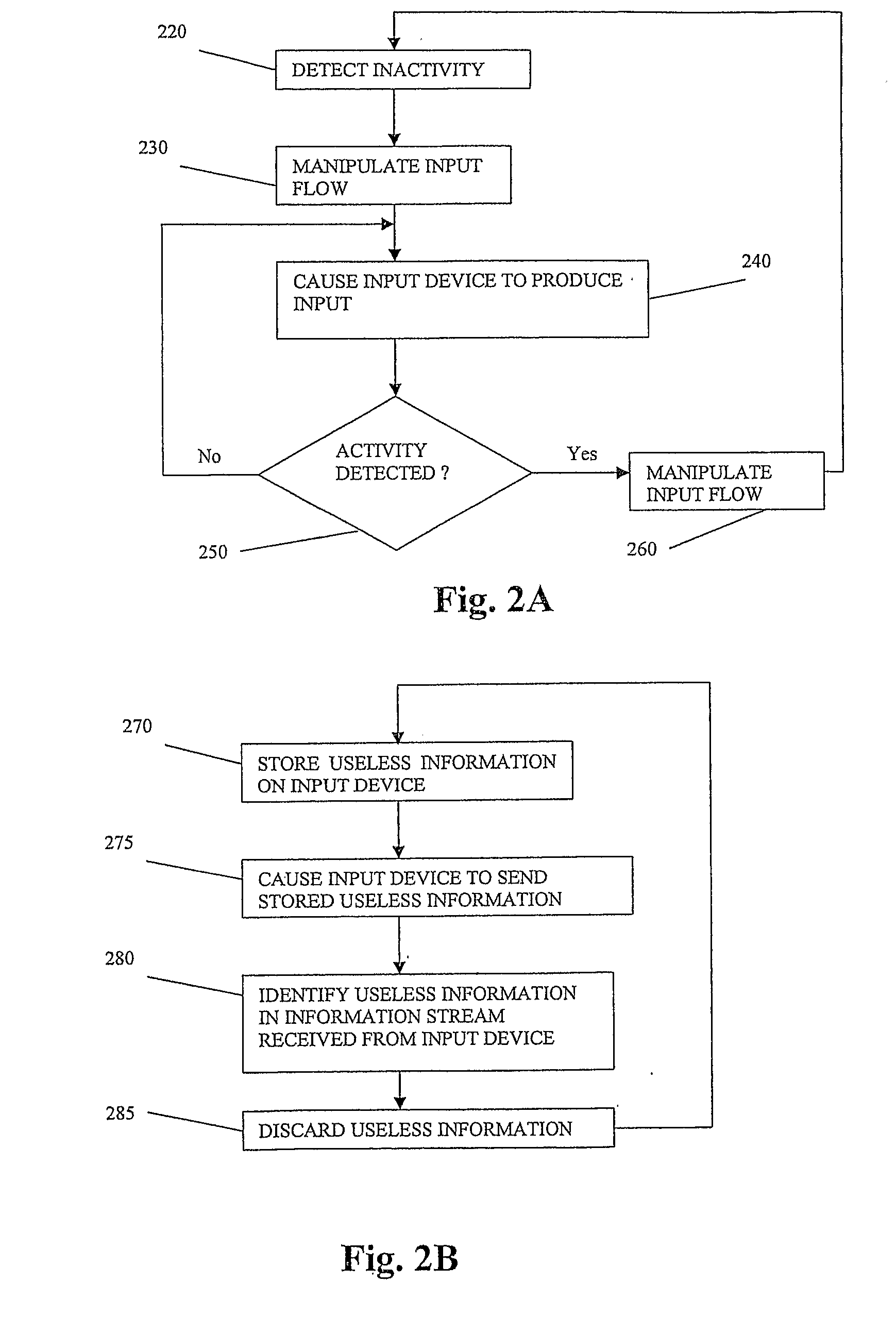
System and method for incapacitating a hardware keylogger
ActiveUS20110219457A1Digital data processing detailsAnalogue secracy/subscription systemsComputer scienceKeystroke logging
A system, device and method for incapacitating a keylogger. An inactivity of an input device may be detected. A flow of information from an input device to a computing device may be manipulated. A keylogger may be caused to store redundant information by causing the input device to produce redundant input. Other embodiments are described and claimed.
Owner:SUPERCOM IP LLC
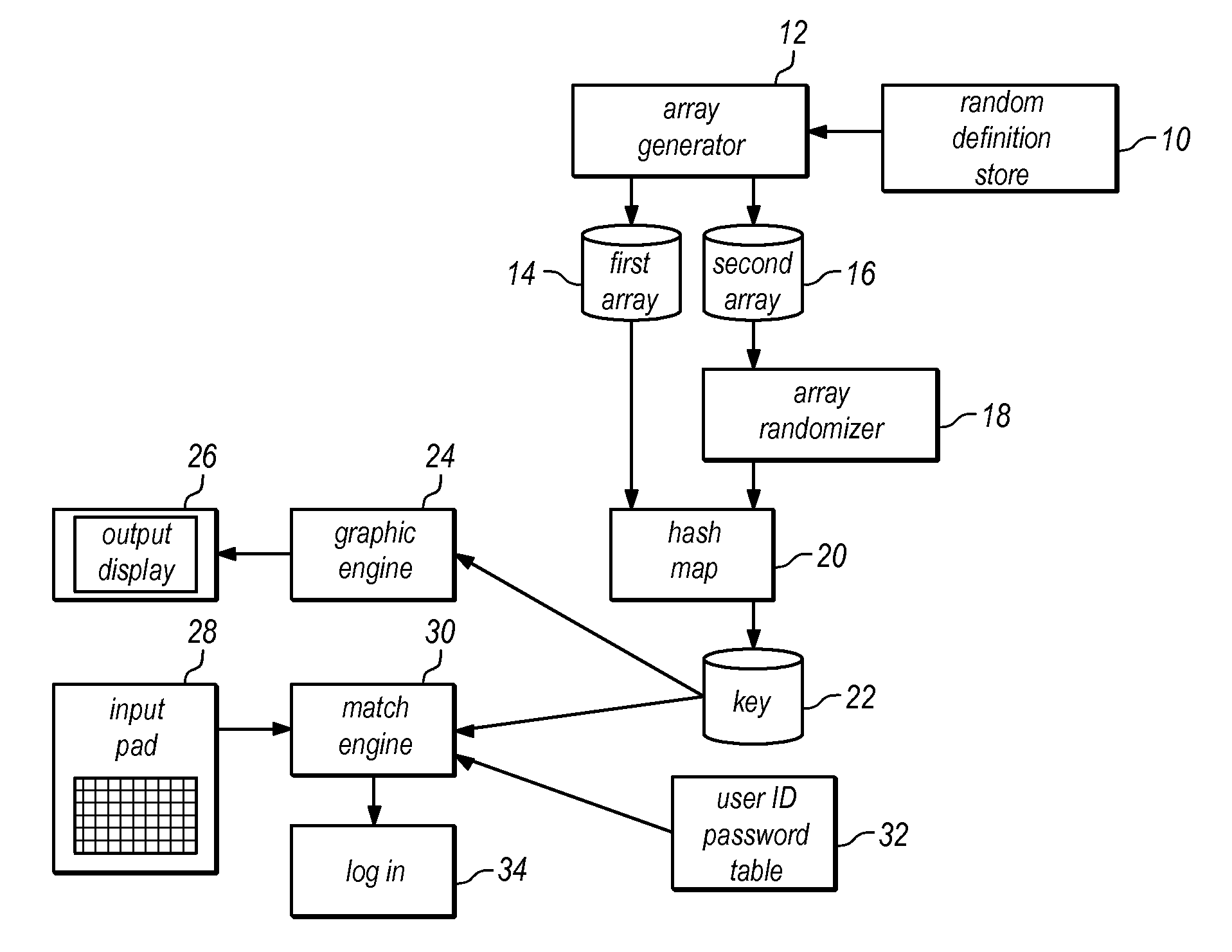
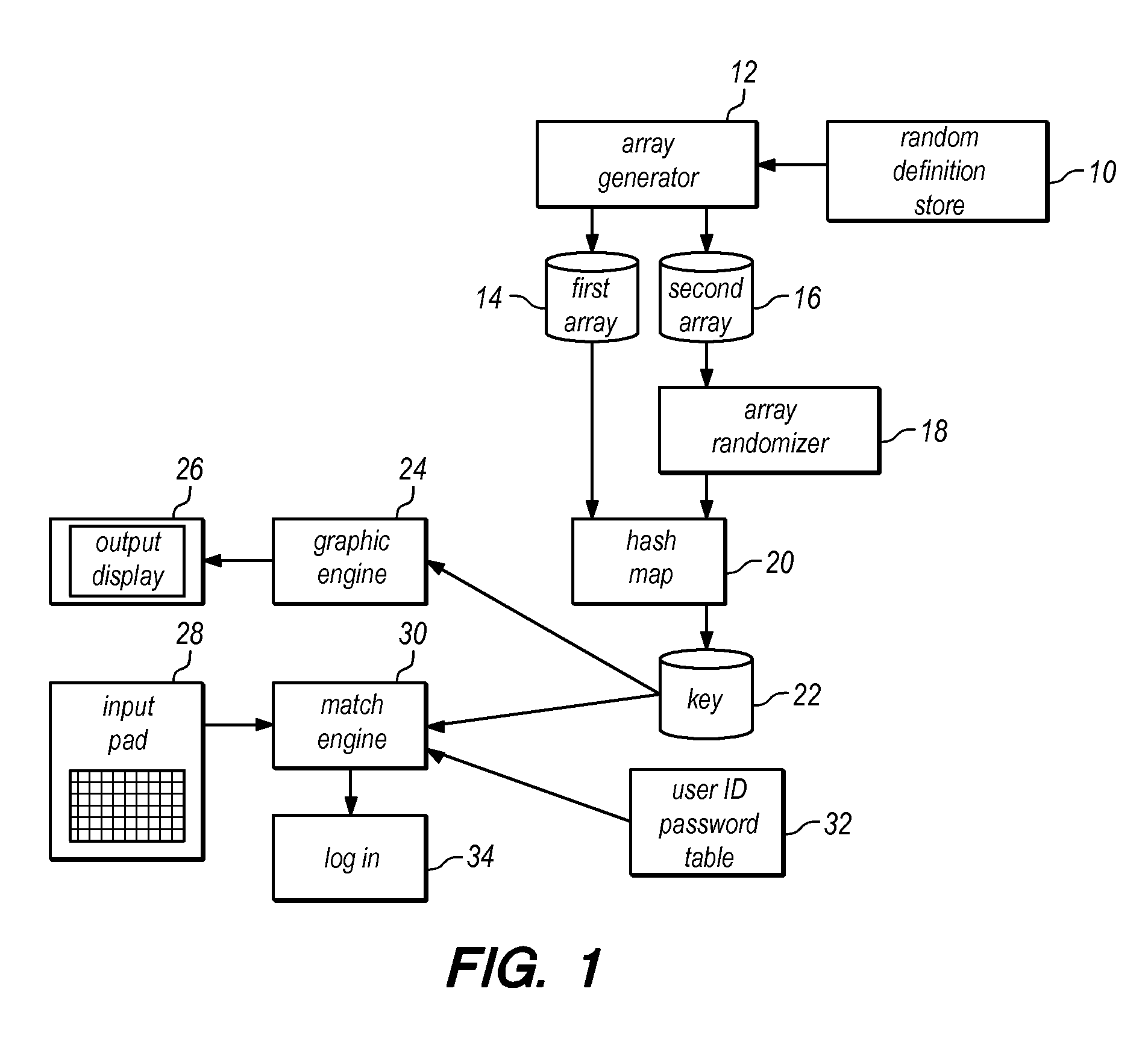
Computer Security System and Method to Protect Against Keystroke Logging
ActiveUS20160117510A1Improve operationImprove efficiencyKey distribution for secure communicationUnauthorized memory use protectionPasswordClient-side
Static security credentials are replaced by pseudonyms and session-specific passwords to increase security associated with user login attempts, and specifically to defeat keylogging attacks. For each login event, the system generates unique, session-specific credentials by randomly replacing characters within a given username and password. The random character generation ensures that system login attempts use different combinations of characters, thereby producing a new username and password for every user session. The client side of the system requires only the capability to display an image file, with specialized software / hardware limited to the server side, thereby facilitating the use of the system by a wide range of client devices.
Owner:LIVERAMP
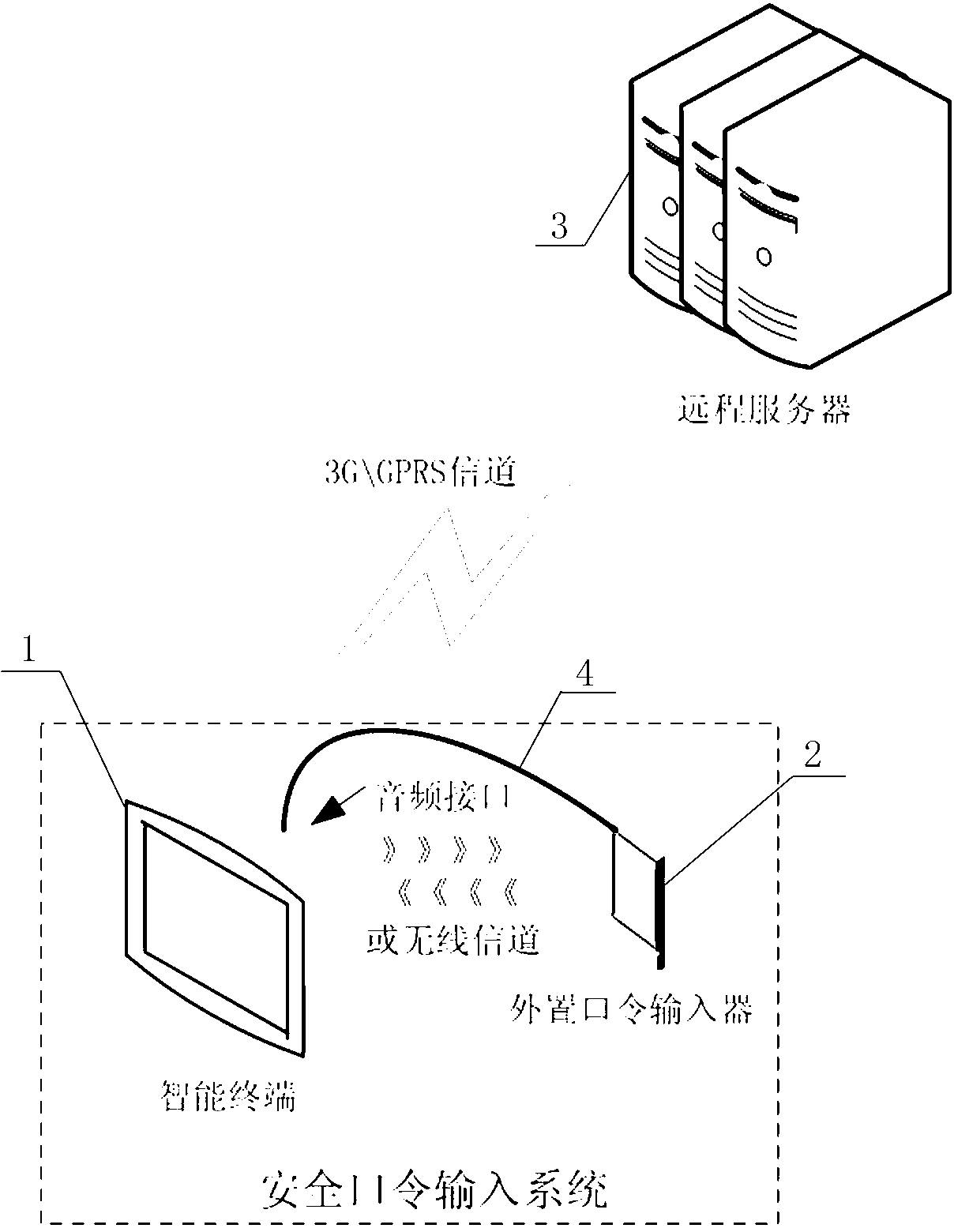
Intelligent terminal oriented security password input system and implementation method
InactiveCN103297240AReduce volumeEasy to carryUser identity/authority verificationComputer security arrangementsGraphicsPassword
The invention discloses an intelligent terminal oriented security password input system which comprises an intelligent terminal, an external password input unit and a remote server. The external password input unit is used for displaying and encrypting graphic information and directed line segment information. An implementation method includes a), enabling the external password input unit to be in communication connection with the intelligent terminal; b), configuring graphic parameters; c), selecting directed line segments; d), encrypting password configuration information; e), transmitting the password configuration information; f), acquiring the password configuration information; g), randomly generating a regular graph; h), encrypting the graphic information; i), transmitting the encrypted graphic information; j), decrypting the graphic information and the directed line segment information; k), enabling the remote server to perform judgment. The intelligent terminal oriented security password input system and the implementation method have the advantages that passwords are configured by the aid of the graph and the directed line segments jointly and accordingly are different from one another; the real passwords of users cannot be detected even if a keyboard recorder is mounted on the intelligent terminal; the intelligent terminal oriented security password input system and the implementation method have wide application space in the field of mobile application and particularly in the field of electronic commerce and electronic governments.
Owner:QILU UNIV OF TECH
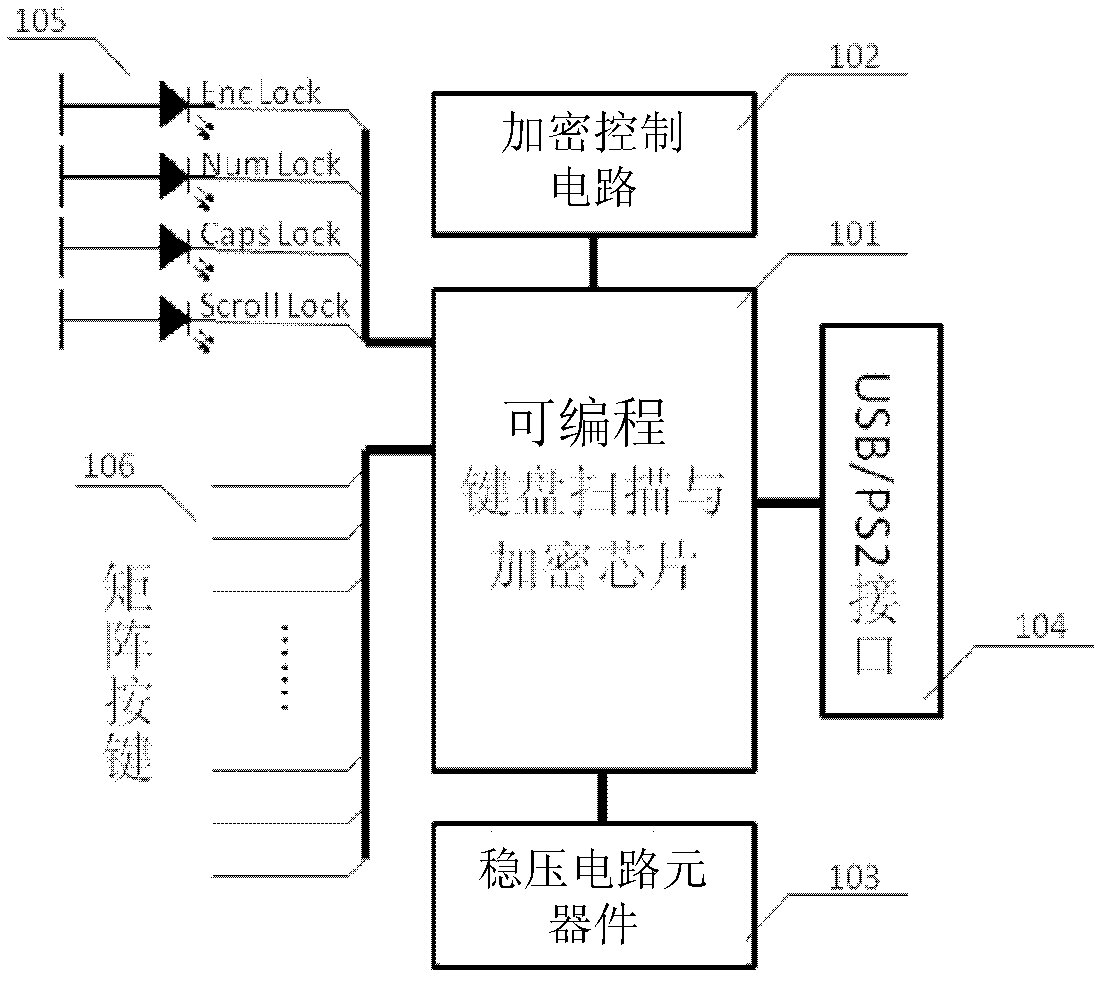
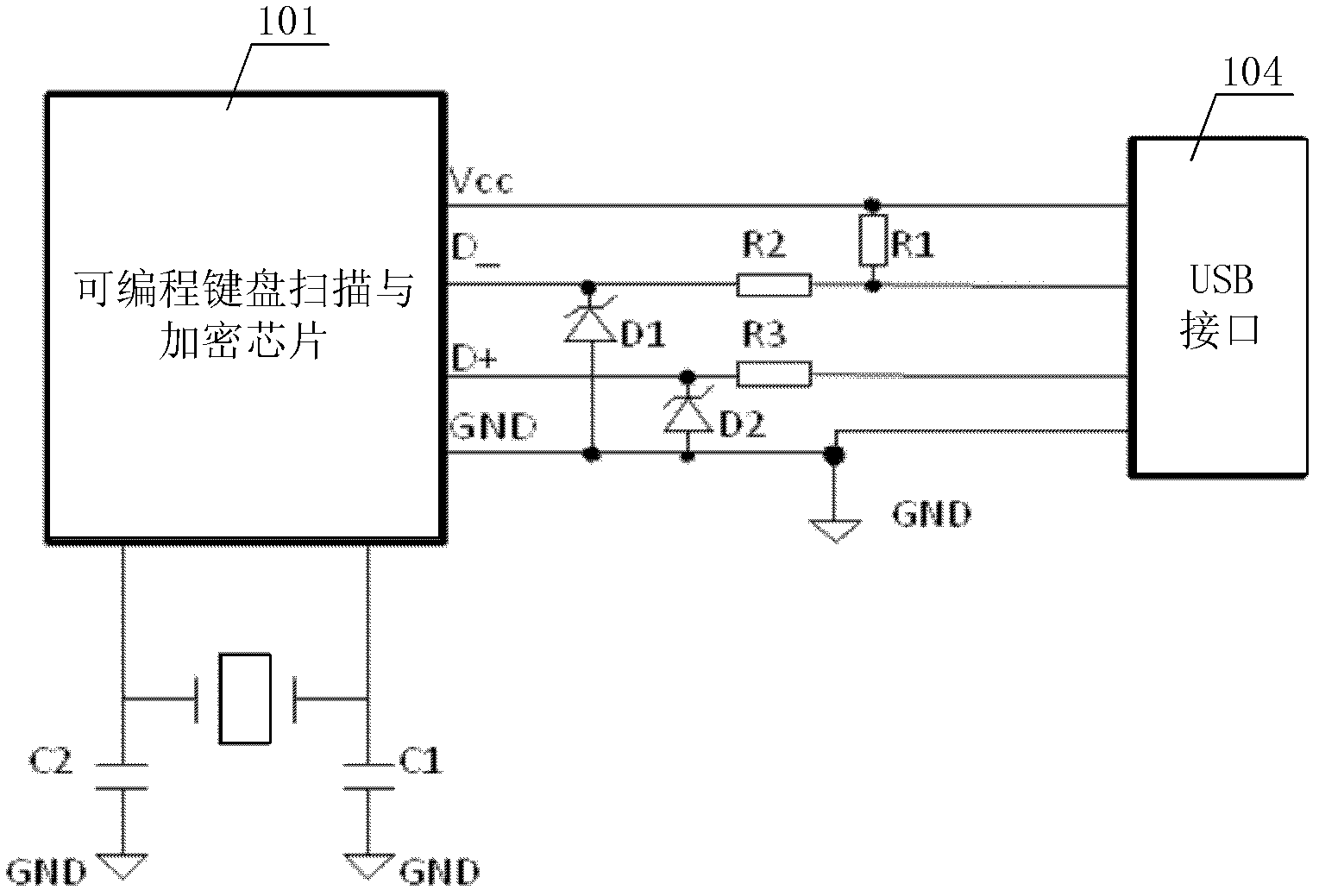
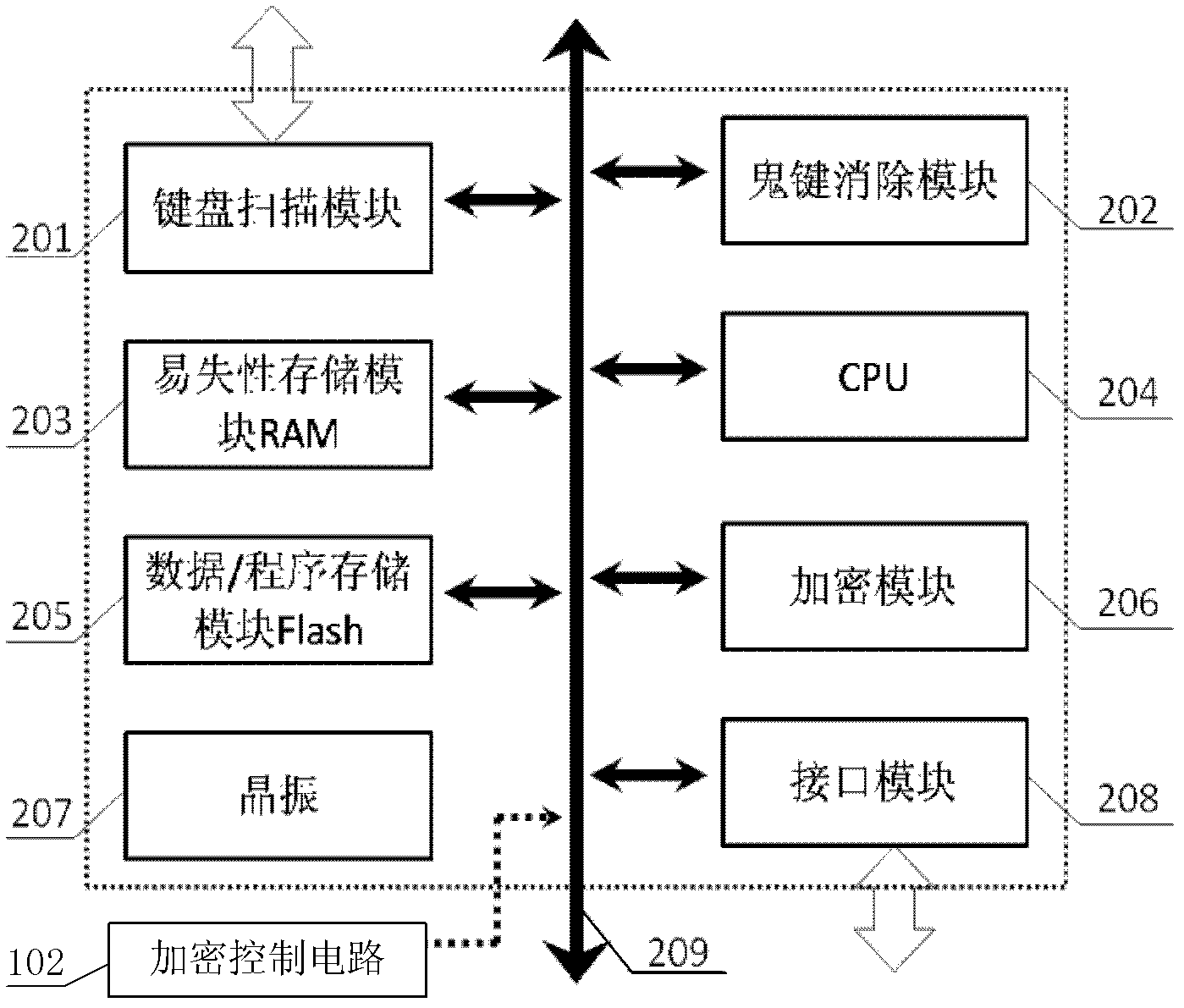
Reusable encryption keyboard circuit and design method thereof
ActiveCN102681672AHigh degree of integrationReasonable control of power consumptionInput/output for user-computer interactionInternal/peripheral component protectionComputer hardwareSecure transmission
The invention provides an anti-bootlegging and anti-attacking reusable encryption keyboard circuit and an encryption method thereof. The reusable encryption keyboard circuit includes a programmable keyboard scanning and encrypting chip and an encryption control circuit. The programmable keyboard scanning and encrypting chip is used for scanning keyboard information, encrypting under control of the encryption control circuit, and inputting the keyboard information to a computer. The reusable encryption method includes: firstly, the keyboard information is scanned to be written in a caching area by a keyboard scanning circuit; secondly, encryption state, encryption manner and replacement of a secret key by the encryption control circuit are controlled so as to realize encryption of the scanned keyboard information; and thirdly, keyboard data enters an encryption mode, and encryption algorithm and the secret key are replaced according to a control instruction, and accordingly safety class of data recorded by the keyboard can be kept high. Data can be encrypted in multiple modes without a redundant hardware circuit by the reusable encryption keyboard circuit and the encryption method thereof compared with the prior art, and accordingly real-time construction of the keyboard information is facilitated, and safe transmission of the keyboard information is achieved.
Owner:SHENZHEN DELUX IND
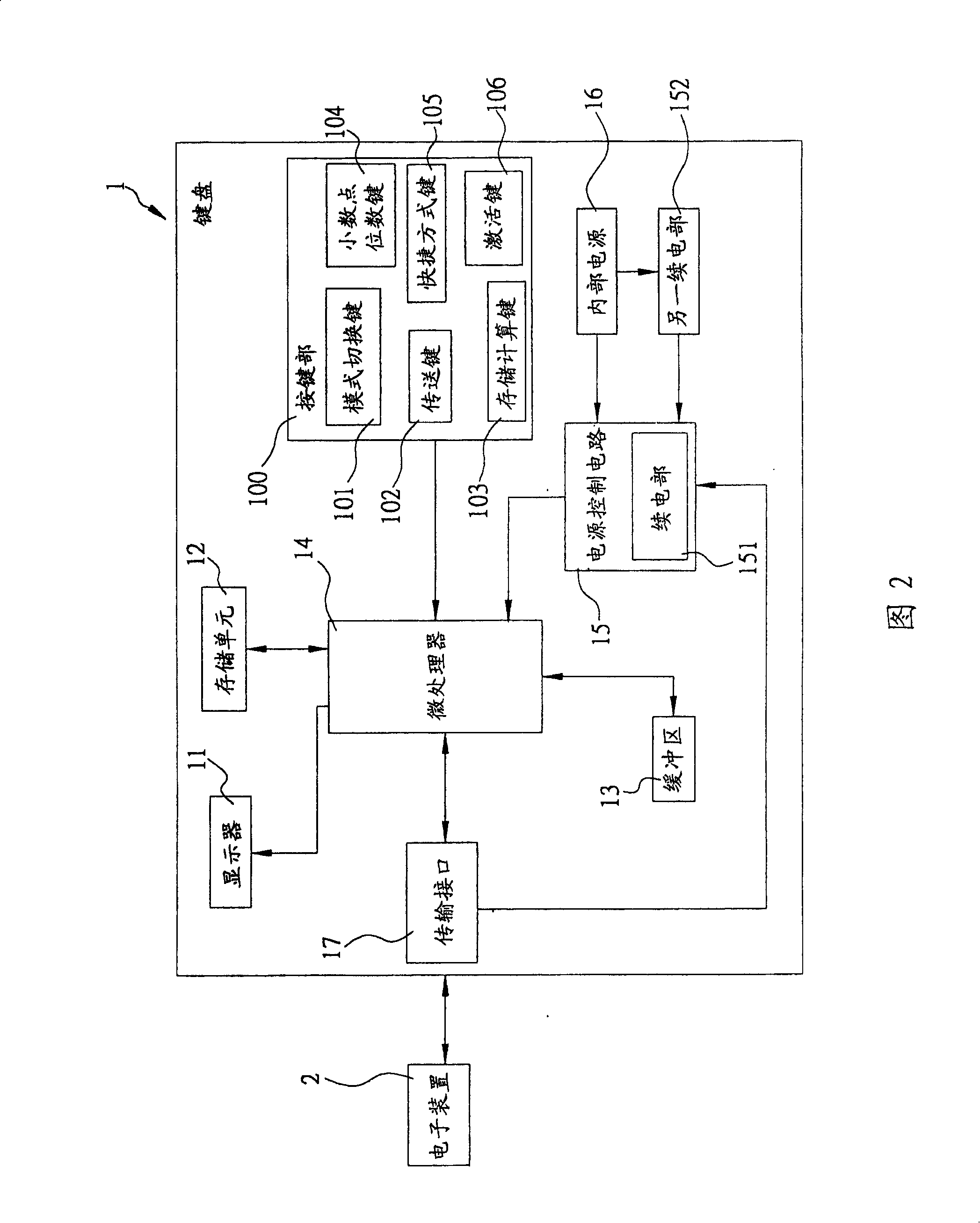
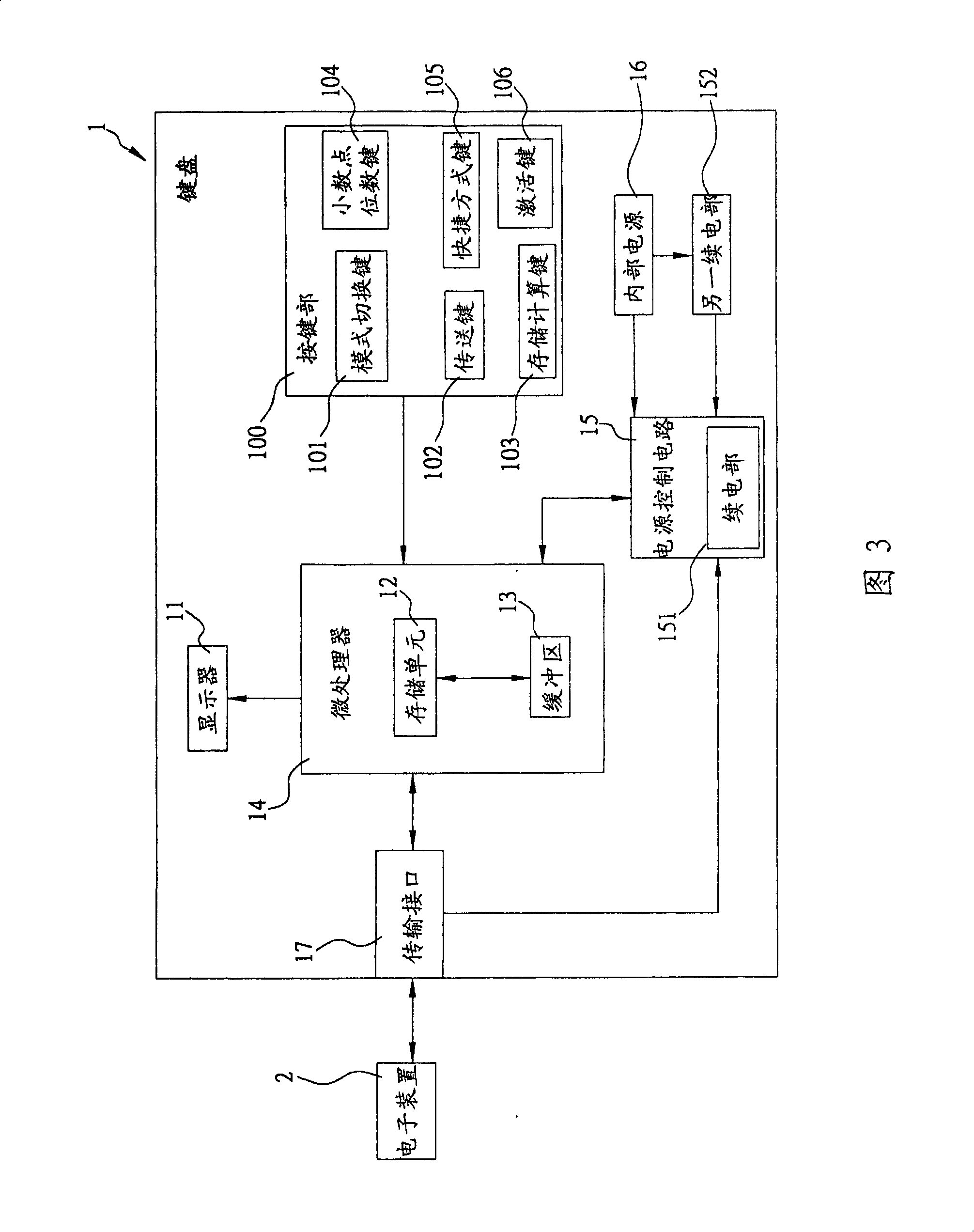
Keyboard and information saving method thereof
InactiveCN101206527AVolume/mass flow measurementPower supply for data processingElectricityDigital data
The present invention relates to a keyboard and the information saving method thereof. The keyboard is pressed and then can generate various input signals; the input signals represent at least one mode data and digital data; the keyboard outputs a picture to a display according to each of the mode data and the digital data; when the keyboard is not operated for some time, the display is turned off after the keyboard records the mode data and the digital data, and if an activation signal is received in the meanwhile, the keyboard reads each of the mode data and the digital data, recovers to the usage pattern before entering the electricity saving state, and outputs the picture before entering the electricity saving state on the display. The present invention effectively solves the disadvantages that: the prior keyboard cannot be in dormant state and leads users to calculate anew if users continue to calculate or record the calculation data after automatic power-down or mode switching, which causes time waste trouble and operation trouble and so on.
Owner:ORTEK TECH
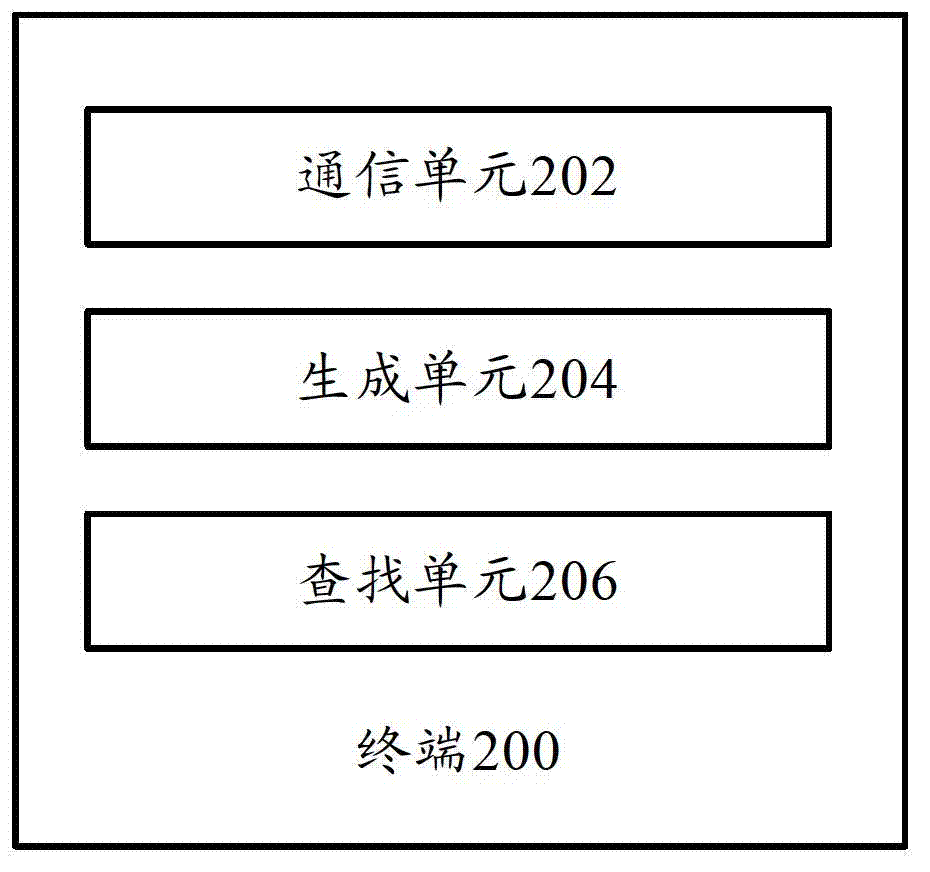
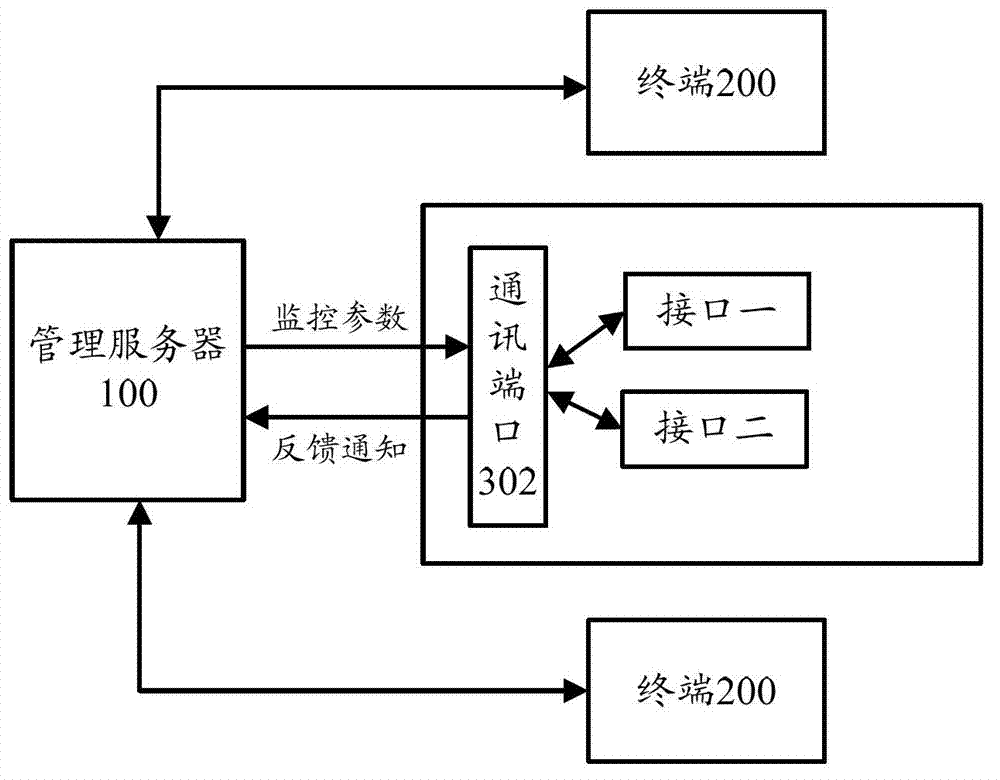
Management server, terminal and keyboard recording method
InactiveCN102932433ARealize Simultaneous MonitoringRealize remote controlHardware monitoringTransmissionComputer hardwareComputer science
The invention discloses a management server connected to at least one terminal. The management server comprises a transceiving unit for transmitting monitoring parameters to the at least one terminal and receiving feedback notifications and keyboard recording files from the at least one terminal. Correspondingly, the invention provides a terminal and a keyboard recording method. According to the technical scheme, a plurality of terminals can be managed and monitored remotely, and keyboard recording information corresponding to different users can be recorded on one terminal to generate the different keyboard recording files.
Owner:ZICT TECH CO LTD
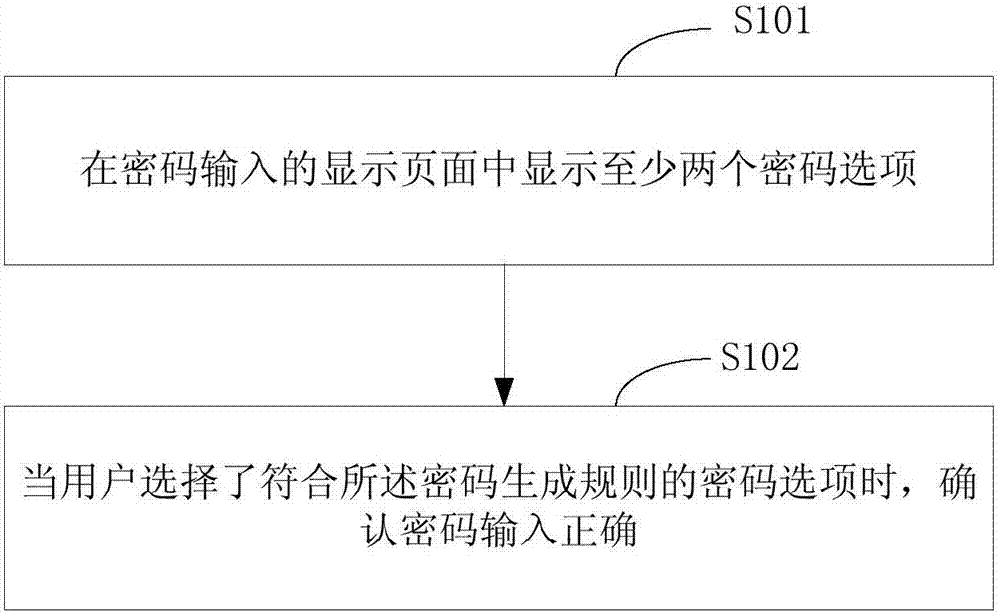
Password input method and apparatus
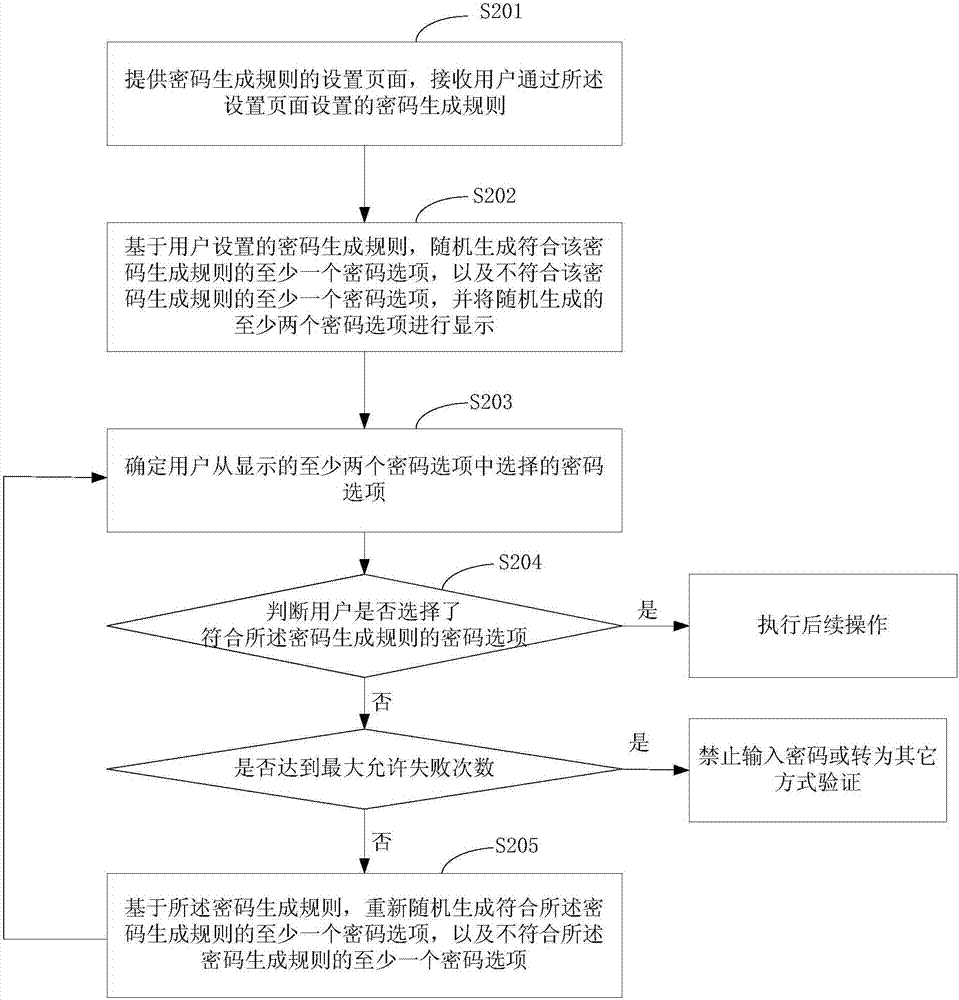
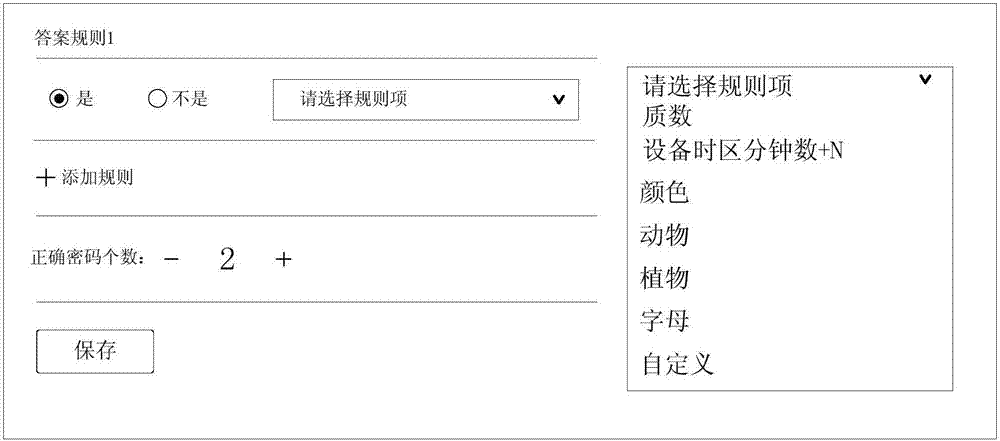
InactiveCN107423589AAvoid crackingAvoid uncertaintyDigital data authenticationPasswordKeystroke logging
Embodiments of the invention provide a password input method and apparatus, which is used for solving the problems that the requirements on equipment hardware conditions are high and a password is easily recorded to be cracked in the prior art. The password input method provided by the embodiment of the invention comprises the steps of displaying at least two password options in a display page, wherein the at least two password options include at least one password option meeting a password generation rule, and the password generation rule is pre-confirmed by a user; and when the user selects the password option meeting the password generation rule, confirming that password input is right. According to the mode, the requirements on the equipment hardware conditions are relatively low, and illegal personnel are prevented from cracking the password by using a keyboard recorder and the like; relatively high exposability and relatively high security are achieved; and in addition, the displayed right password has uncertainty, so that the password cracking difficulty is increased.
Owner:ALIBABA GRP HLDG LTD
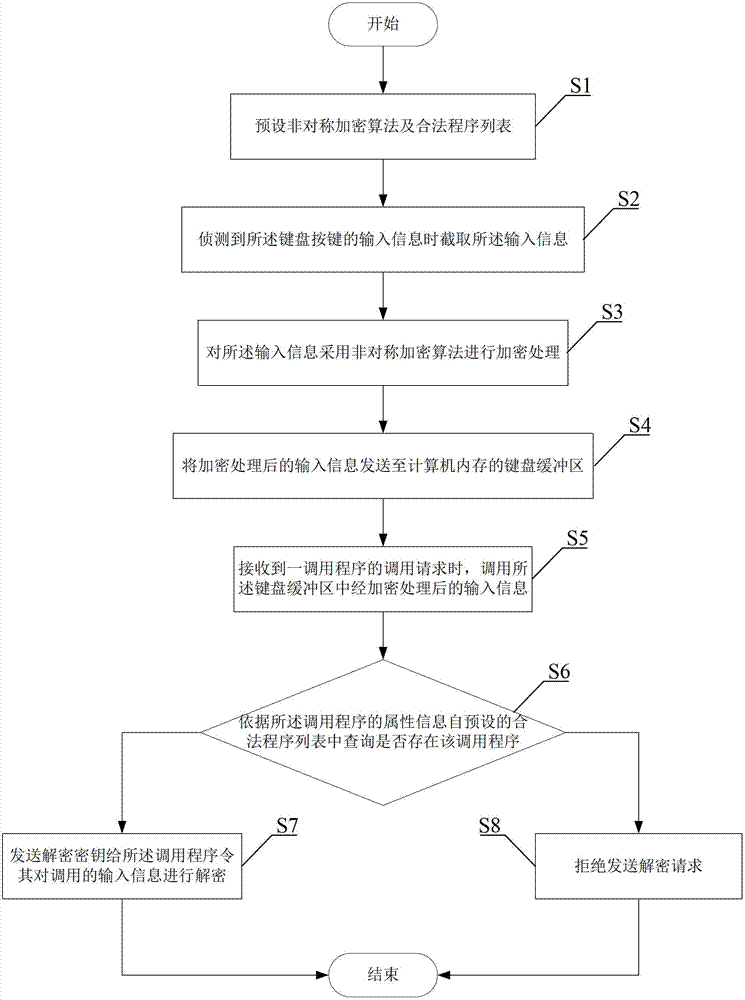
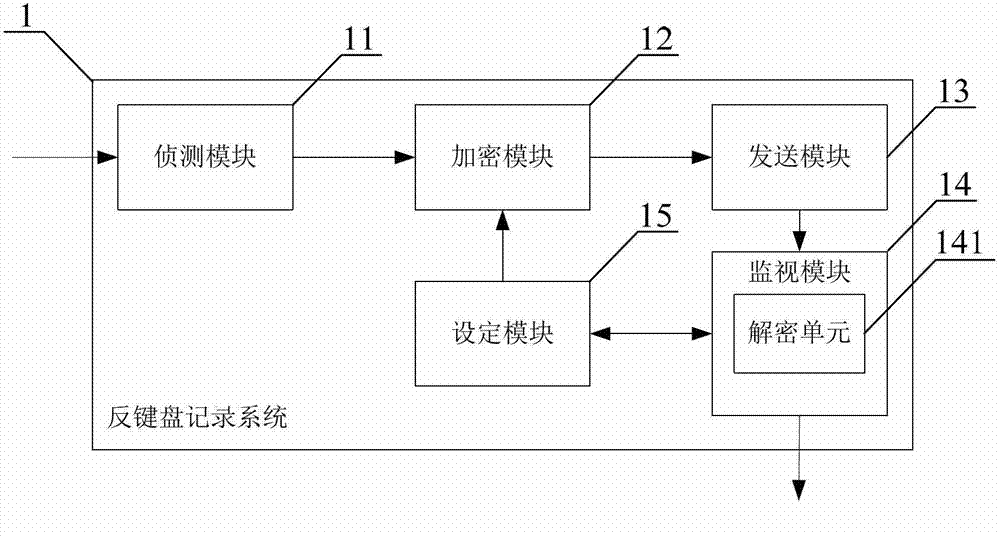
Key-defending recording method and system
The invention provides a key-defending recording method and a key-defending recording system which are applied to a computer with a keyboard. The method comprises the following steps of: when input information of keys of a keyboard is detected, intercepting the input information; encrypting the input information by adopting an asymmetric cryptographic algorithm; sending the encrypted input information to a keyboard buffer area of a computer memory; calling the encrypted input information in the keyboard buffer area, monitoring and analyzing the keyboard buffer area to judge whether the calling is legal or not; and when the calling is judged to be legal, decrypting the called input information, and when the calling is judged to be abnormal, refusing to send a decryption request. Therefore, by the method and the system, the aim of protecting keyboard input is fulfilled, so that the safety of the keyboard input for users can be ensured to a large extent.
Owner:江苏华御威盾网络科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com