Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
140 results about "Password cracking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptanalysis and computer security, password cracking is the process of recovering passwords from data that have been stored in or transmitted by a computer system. A common approach (brute-force attack) is to repeatedly try guesses for the password and to check them against an available cryptographic hash of the password.
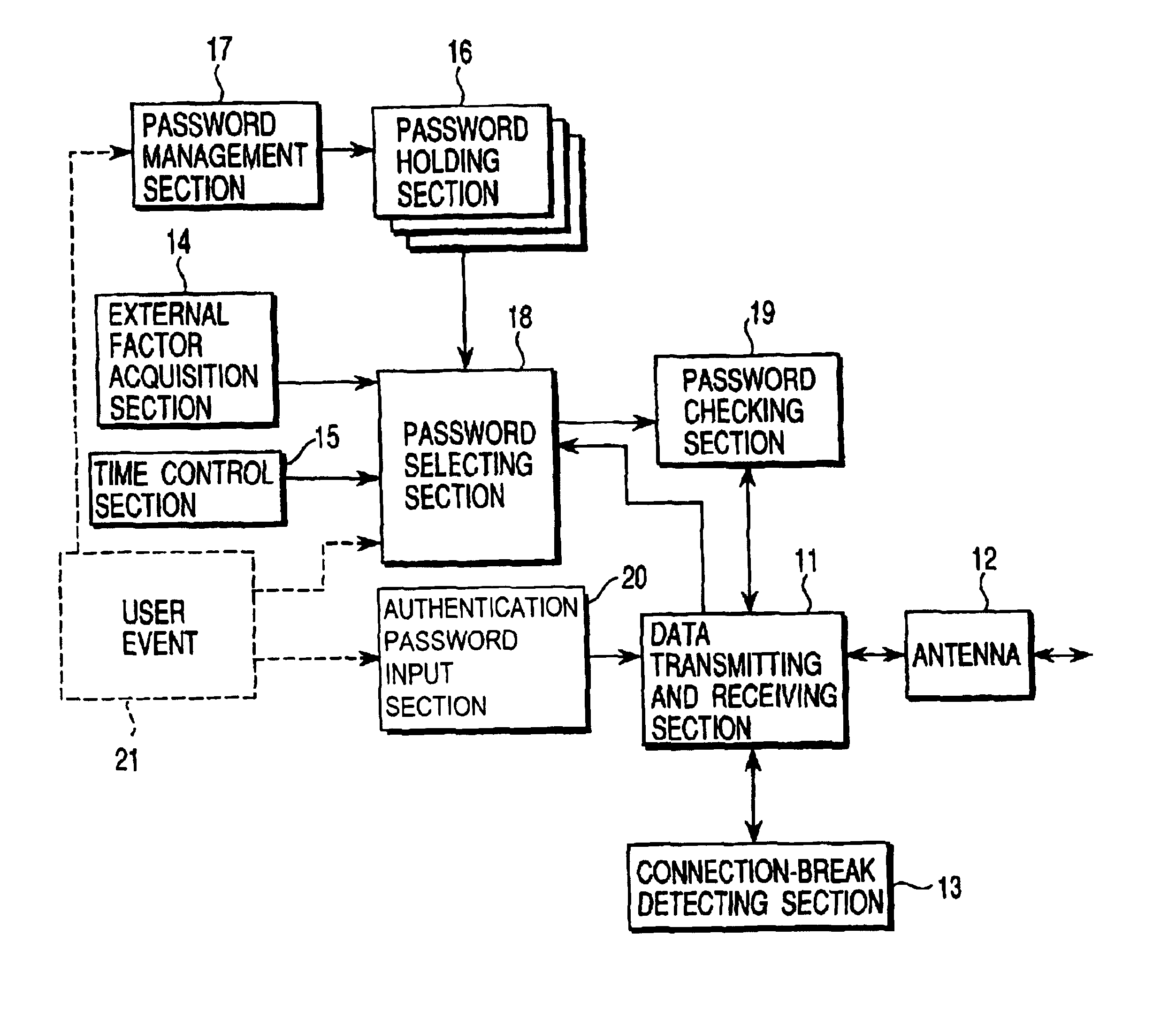
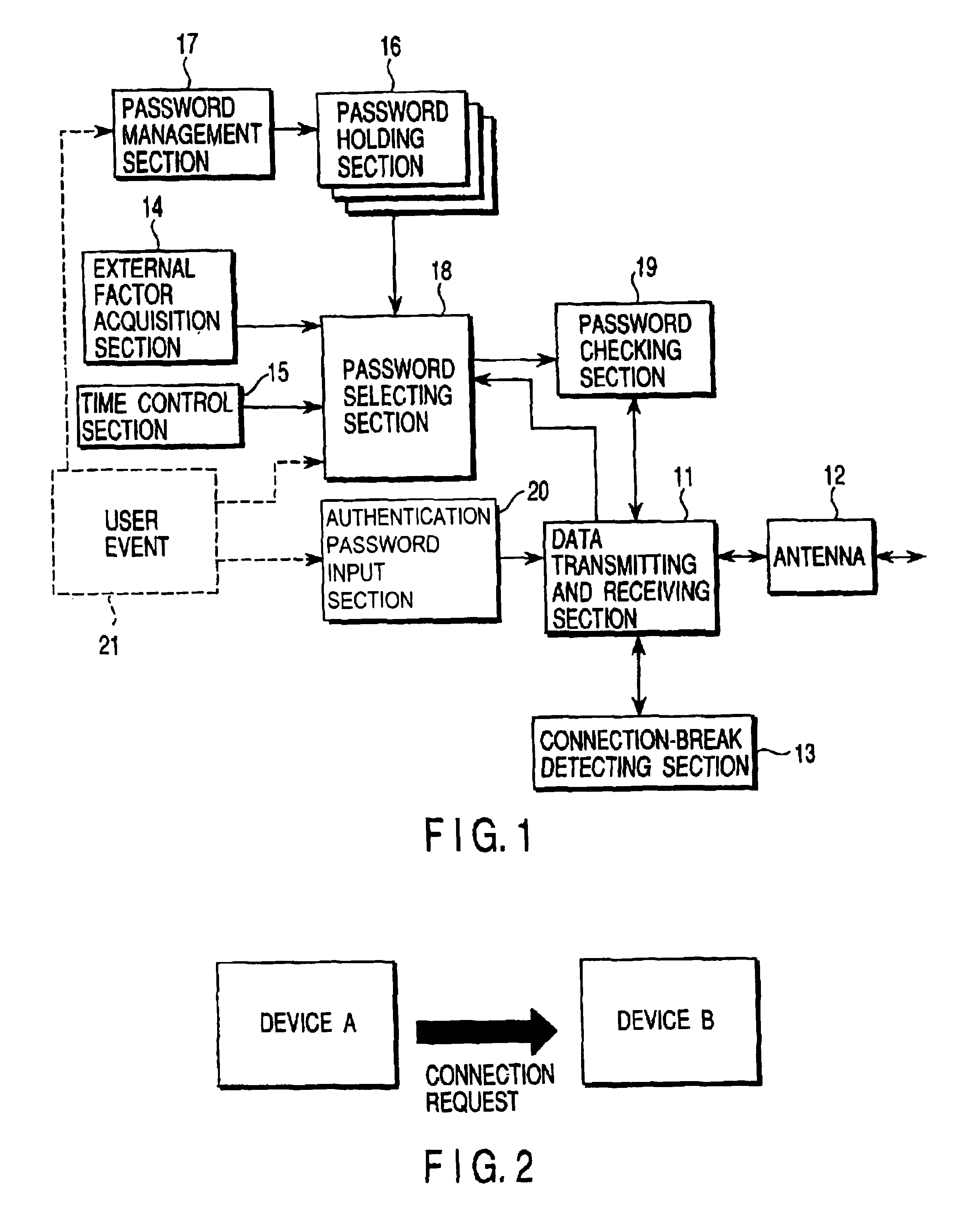
Radio communication device and user authentication method for use therewith
ActiveUS6928166B2Imposing any operating burdenLevel of security can changeMultiple keys/algorithms usageUser identity/authority verificationConfidentialityUser authentication
To allow flexible security level switching according communication situations, a password holding section holds a plurality of device authentication passwords, for example, a temporary password and a private password. The temporary password is valid only under a certain situation and the private password has a high level of confidentiality to increase the device security. A password management section allows the user to add a new password to the password holding section and delete an existing password therefrom. A password selecting section selects the most suitable password for current connection from among passwords in the password holding section according to a user event, information acquired by an external factor acquisition section, and information from a time control section. The selected password is output to a password checking section.
Owner:2BCOM LLC
Method of presenting feedback to user of chances of password cracking, as the password is being created
InactiveUS20080307235A1Improve computerImprove documentUser identity/authority verificationMultiple digital computer combinationsPasswordDocumentation
A method, system and computer program product for automatically displaying the potential risk associated with cracking a password. While creating or modifying a password, feedback is provided describing the risk associated with cracking the password. Risk assessment may be presented as a percentage, accompanied by an explanation of why the value was ascertained. Risk feedback during password creation provides an opportunity to improve computer, document, and file security.
Owner:IBM CORP
System and methods for analyzing and modifying passwords
ActiveUS20140373088A1Increase entropyDigital data protectionDigital data authenticationCode bookPassword
A system for analyzing and modifying passwords in a manner that provides a user with a strong and usable / memorable password. The user would propose a password that has relevance and can be remembered. The invention would evaluate the password to ascertain its strength. The evaluation is based on a probabilistic password cracking system that is trained on sets of revealed passwords and that can generate password guesses in highest probability order. If the user's proposed password is strong enough, the proposed password is accepted. If the user's proposed password is not strong enough, the system will reject it. If the proposed password is rejected, the system modifies the password and suggests one or more stronger passwords. The modified passwords would have limited modifications to the proposed password. Thus, the user has a tested strong and memorable password.
Owner:FLORIDA STATE UNIV RES FOUND INC
Encrypted storage method and encrypted storage device
InactiveCN105721390AIncrease the difficulty of crackingEnsure safetyDigital data protectionSecuring communicationPlaintextComputer hardware
The invention provides an encrypted storage method and an encrypted storage device. The method comprises the steps of calculating the salted Hash value of a plaintext password, combining the salted Hash value and a corresponding random salt value according to a preset rule to get a ciphertext password corresponding to the plaintext password, and storing the ciphertext password. Through the technical scheme of the invention, the difficulty in ciphertext password cracking is improved, and the safety of user accounts is guaranteed.
Owner:ALIBABA GRP HLDG LTD
Access control service and control server
InactiveUS20060224897A1Improve securityPrevent unauthorized accessRandom number generatorsUser identity/authority verificationNetwork linkPassword
To provide an access control service and control server for protecting a computer from an Illegal access such as a password cracking, in a terminal service and other related services. An access server 3 includes an authentication manager 7 for authenticating a user to operate a terminal, and an ACE manager 9 for setting a network link that enables communication between a terminal 1 that the user operates and a specific computer unit 2, to a hub 4 in accordance with a result of the authentication. Information on each user and information on the specific computer unit 2 that the each user can use are associated with each other and registered in the ACE manager 9.
Owner:HITACHI LTD
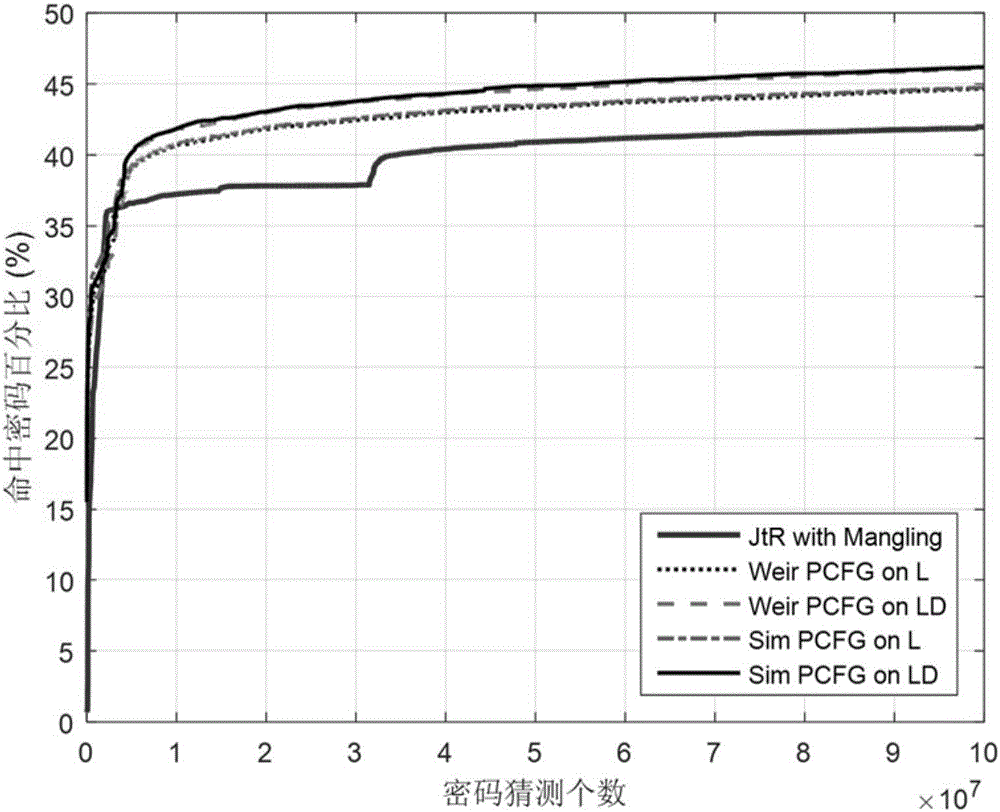
Probabilistic password cracking system
ActiveUS9438419B1Key distribution for secure communicationDigital data authenticationPasswordTheoretical computer science
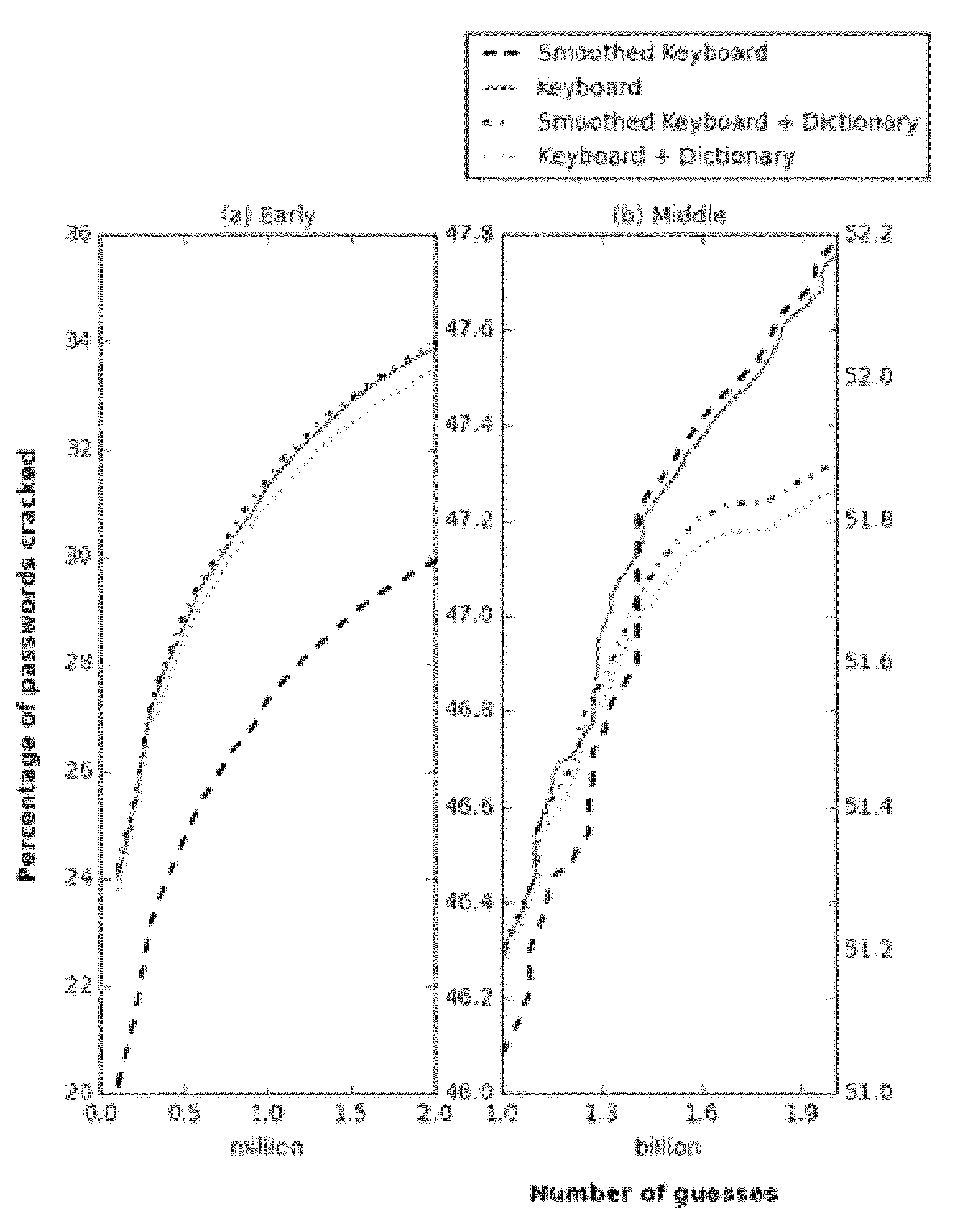
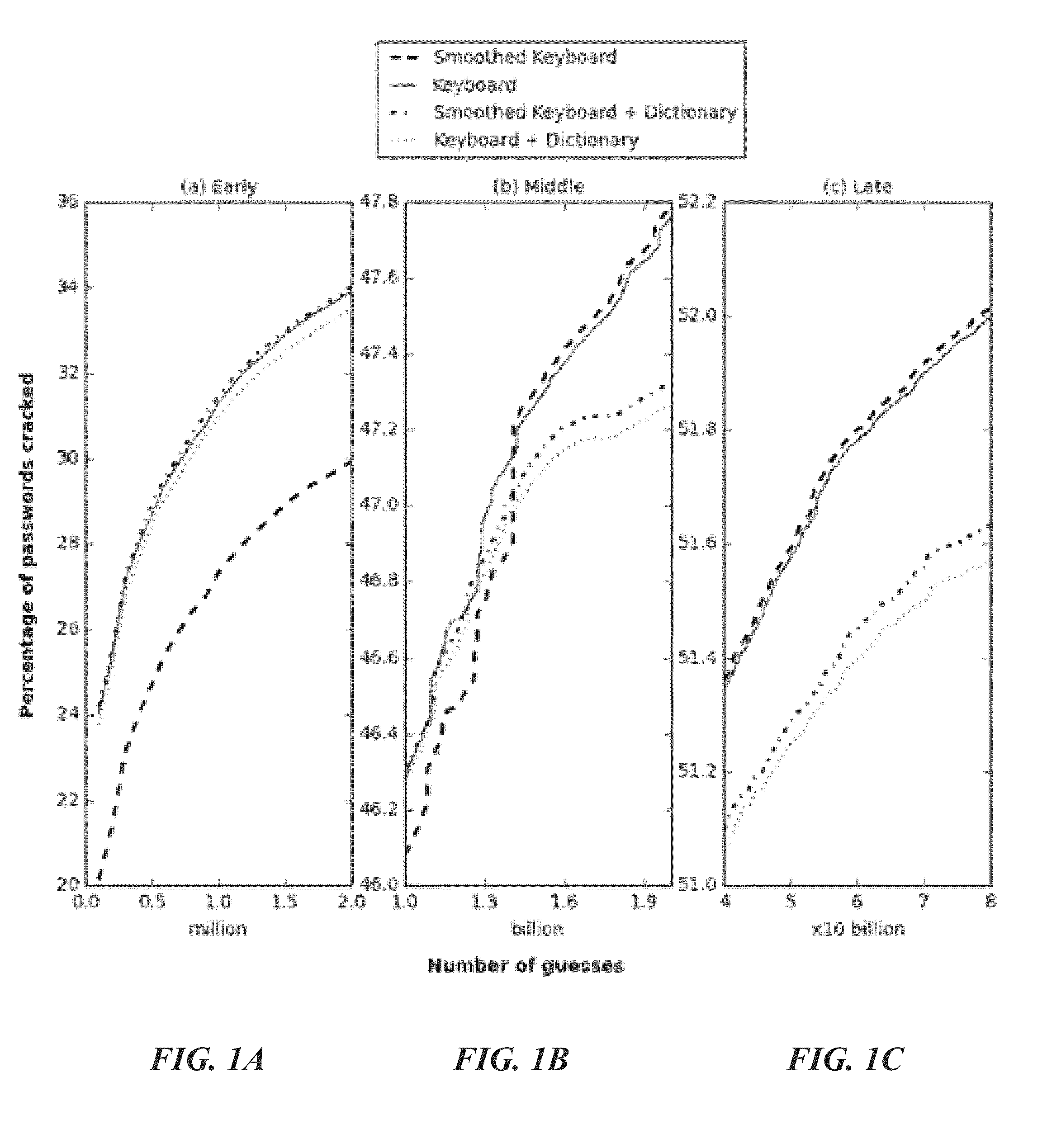
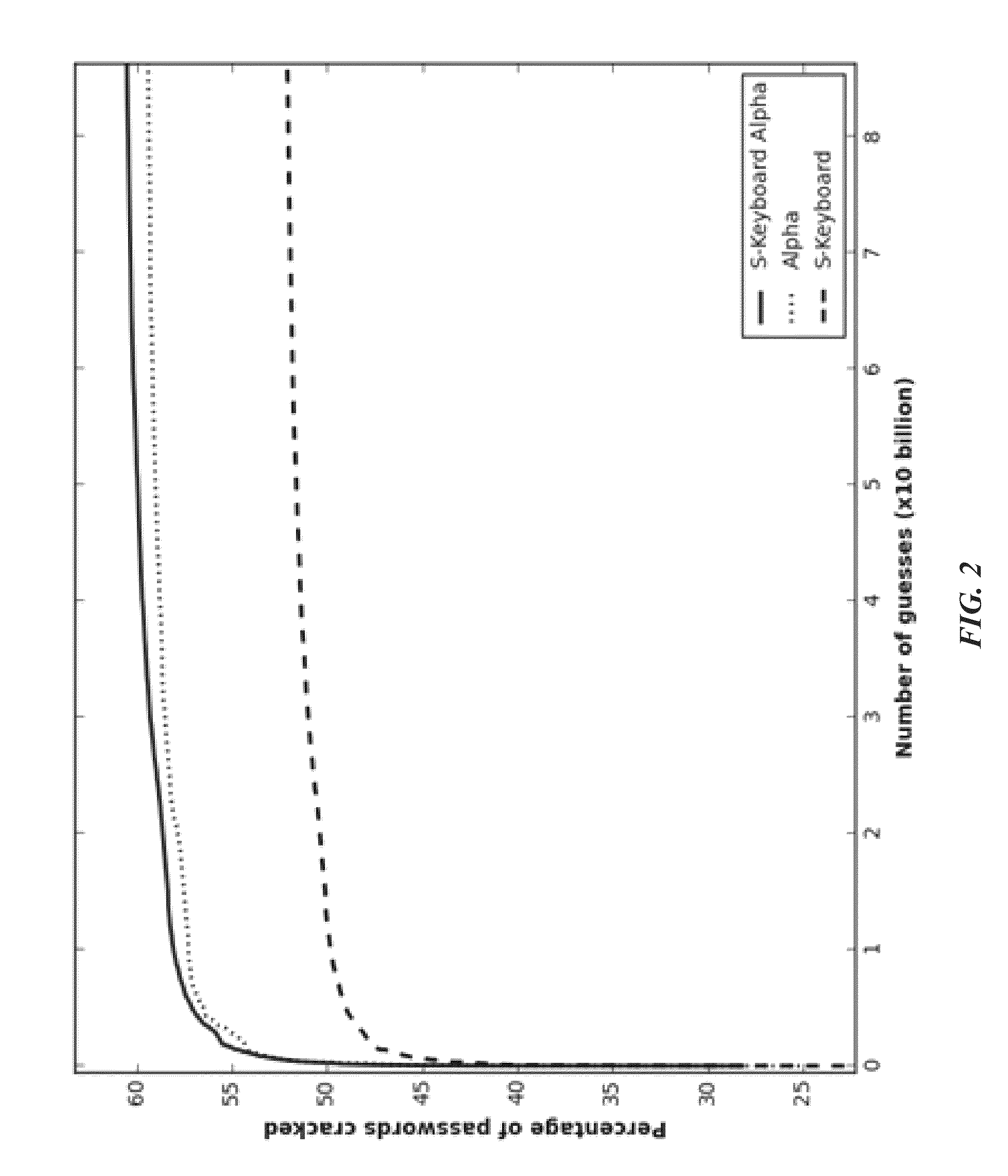
System and methodology that utilizes keyboard patterns and alpha string patterns for password cracking. Keyboard patterns can be used as components of passwords, and the relevant shapes can extracted from these keyboard patterns and passwords. This keyboard information can be used to extend a probabilistic context-free grammar that can then be used to generate guesses containing keyboard patterns. Further, patterns in alpha strings, such as repeated words and multi-words, can be systematically learned using a training dictionary. This information can be used to extend the probabilistic context-free grammars which leads to generation of guesses based on the distribution of these patterns in the alpha strings, Keyboard patterns and alpha string patterns, individually and in combination, are shown herein to be effective for password cracking.
Owner:FLORIDA STATE UNIV RES FOUND INC
Weak password verification and cracking method and device
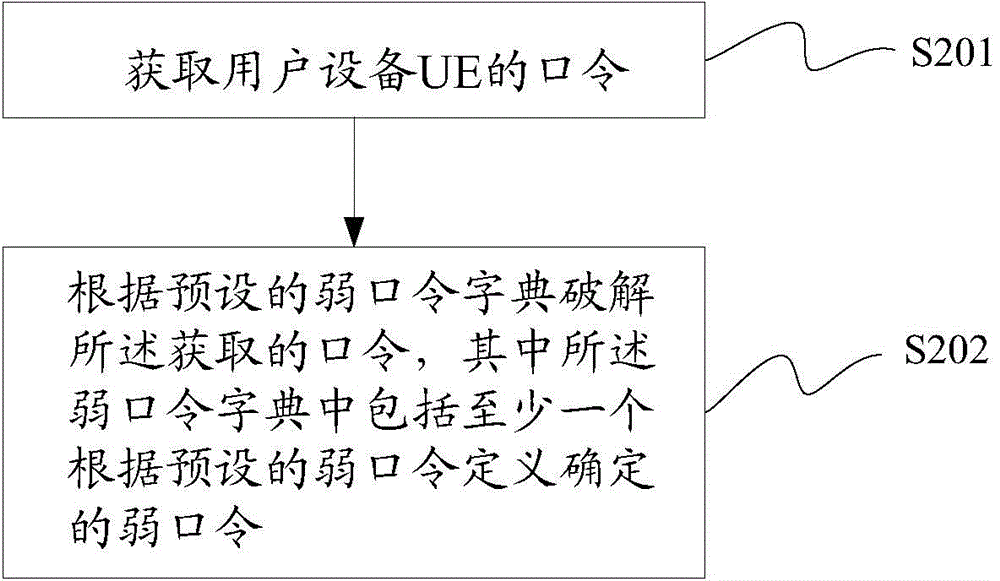
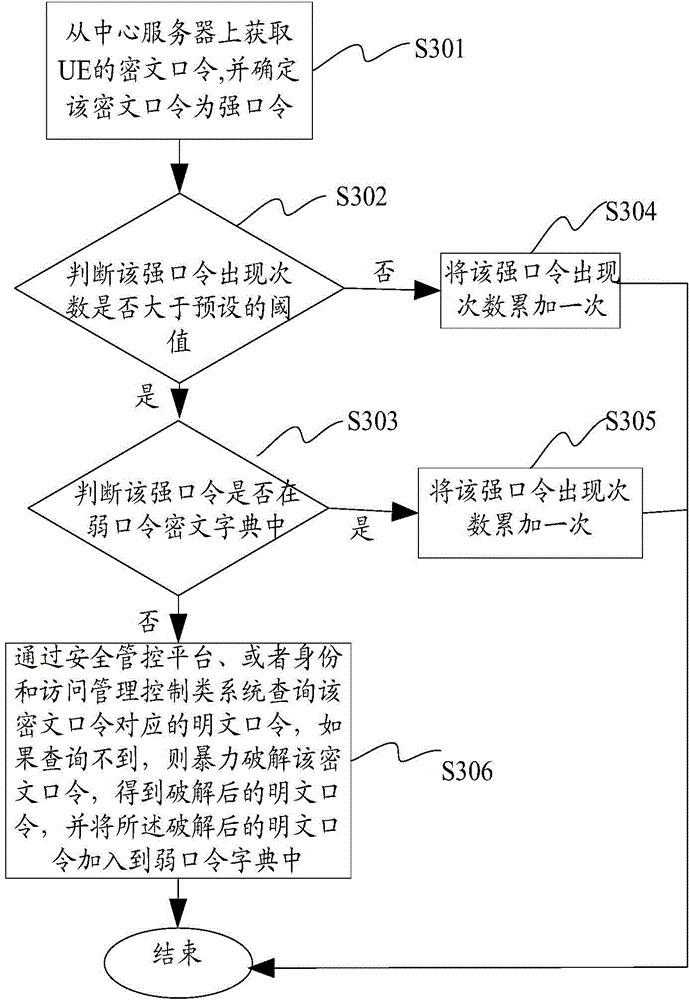
The invention provides a weak password verification and cracking method and device; the method and device can realize central management and optimize a weak password dictionary, thus reducing weak password verification time, improving weak password discovering ability, and improving weak password cracking efficiency; the weak password verification method comprises the following steps: obtaining a use equipment UE password; if the obtained password is a cleartext password, determining whether the obtained password as a weak password or not according to a preset weak password definition; if the obtained password is a weak password and the password is not in the preset weak password dictionary, adding the password into the weak password dictionary.
Owner:中国移动通信集团广西有限公司
Method and apparatus for an access function in network applications
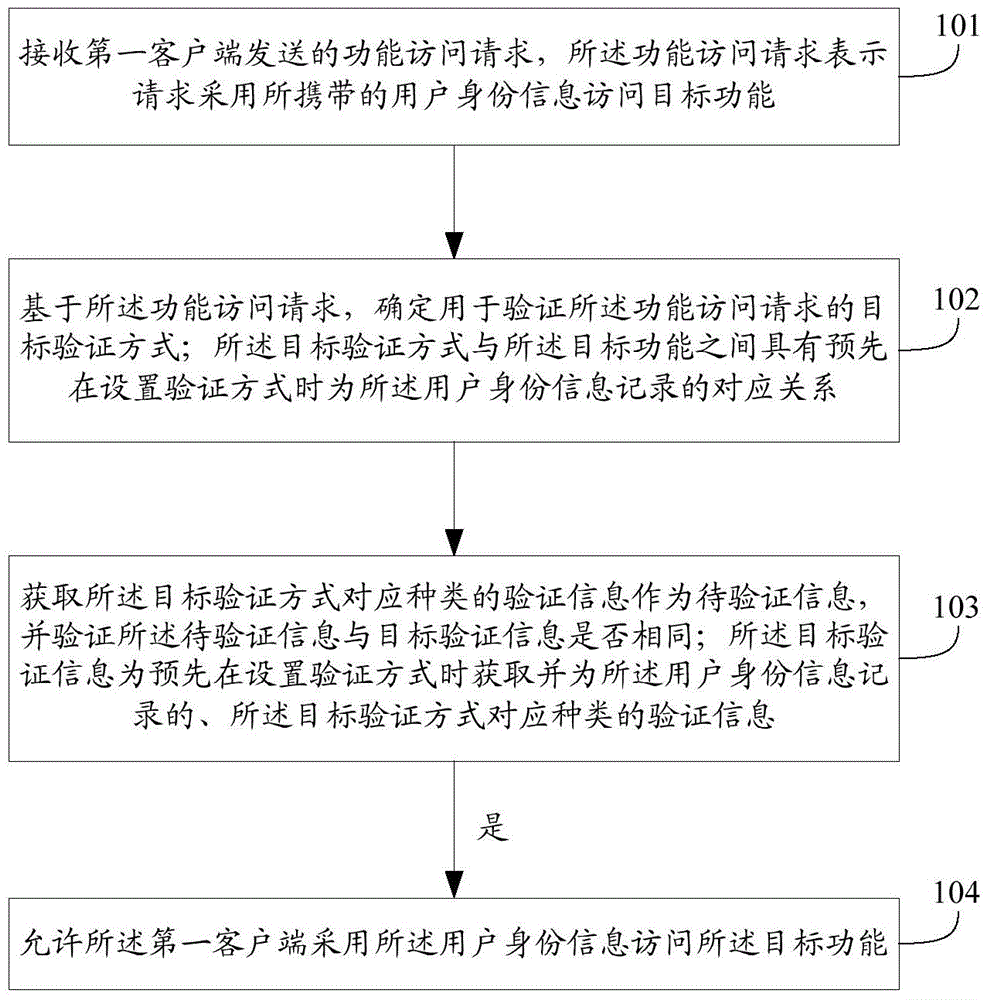
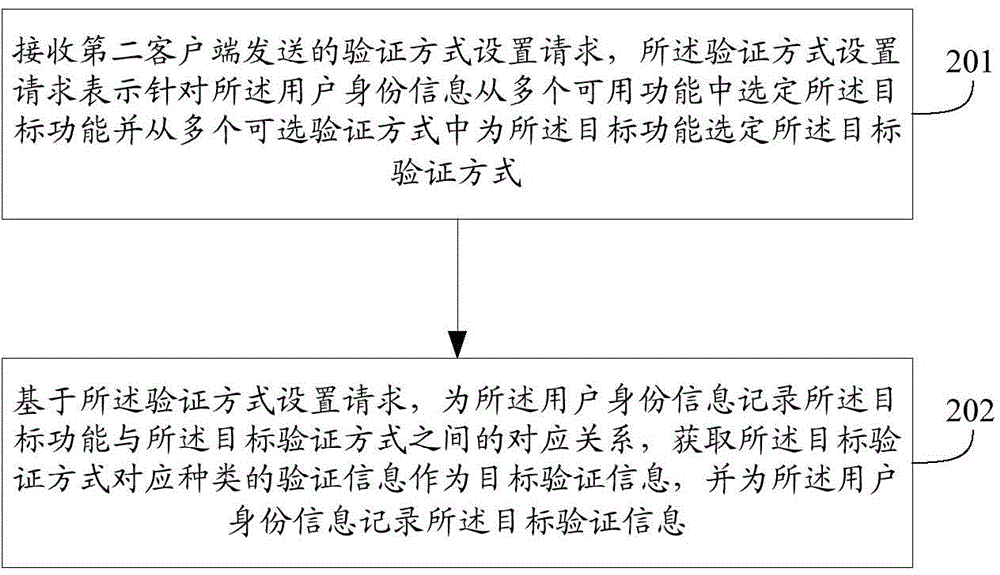
An embodiment of the present invention discloses a method, an apparatus and a system for an access function in network applications. The method includes the steps as follows: receiving a functional access request transmitted by a first client; confirming a target verification mode for verifying the functional access request based on the functional access request; acquiring a kind of verification information as information to be verified, wherein, the verification information corresponds to the target verification mode, and verifying whether the information to be verified and the target verification information are same, if yes, allowing the first client to access the target function by adopting user identity information. According the technical scheme of an embodiment of the present invention, a server pre-records a corresponding relation of the target verification mode and the target function for the user identity information, and the verification modes of various kinds of verification information for various functions are adopted for the user. A problem that a malicious user can maliciously access all functions only needed password cracking is avoided, and thereby increasing a security of the access function in network applications.
Owner:ADVANCED NEW TECH CO LTD
Data protection device and method, and storage controller
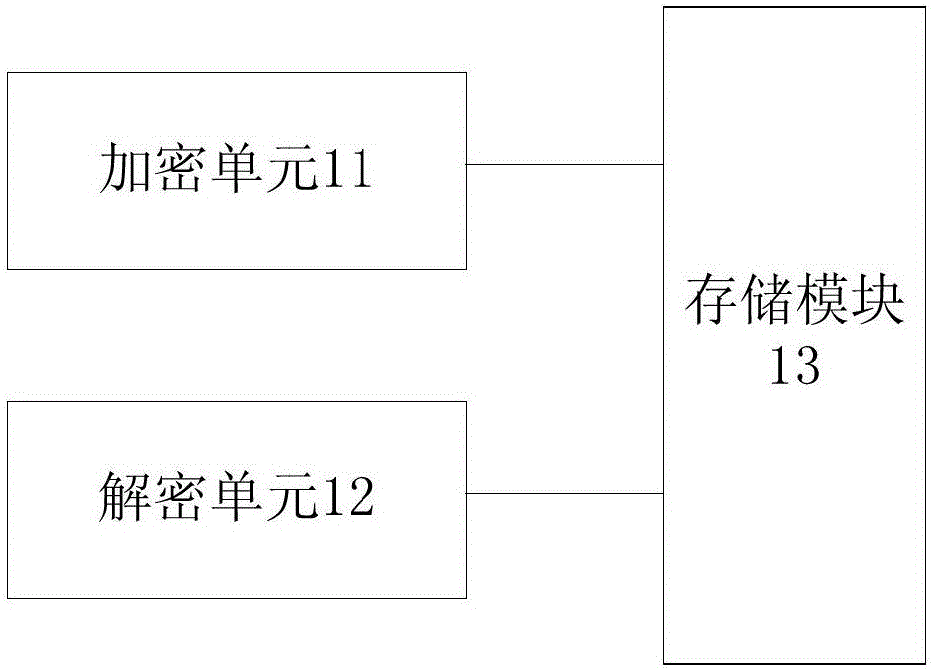
PendingCN106599735AImprove securityAchieve protectionInternal/peripheral component protectionSecuring communicationControl storePassword
The invention discloses a data protection device, a data protection method and a storage controller and relates to the technical field of data protection. The device comprises an encryption unit and a decryption unit, wherein the encryption unit is used for receiving first data of a to-be-written storage module and first storage address information and encrypting the first data based on the first storage address information and characteristic information of a storage module; and the decryption unit is used for reading second data corresponding to second storage address information from the storage module and decrypting the second data based on the second storage address information and the characteristic information. According to the data protection device, the data protection method and the storage controller, write data and read data are encrypted and decrypted based on a storage address and the characteristic information of the storage module, the security of data in the storage module can be improved; after the storage module executes an erasure operation, the read data do not carry information of a decrypted module, the password cracking difficulty can be effectively increased, the content protection is realized; and the data protection device and the data protection method are high in reliability and wide in application range.
Owner:GREE ELECTRIC APPLIANCES INC
Elliptic curve anti-bypass attack method based on randomizing multiplication with symbol scalar
InactiveCN101197668AImprove securityImproving the ability to defend against power consumption attacksPublic key for secure communicationComputations using residue arithmeticPassword crackingSide channel attack
The invention belongs to the information security technical field and provides an elliptical curve bypass attack-proof method based on the randomization tape symbol scalar multiplication. The elliptical curve bypass attack-proof method based on the randomization tape symbol scalar multiplication of the invention comprises the following steps that: firstly, a key in binary system is represented to be a randomization tape symbol binary number; secondly, a finite state machine for realizing the randomization tape symbol scalar product is obtained basing on a randomization addition and subtraction chains of the elliptical curve scalar product; finally, the elliptical curve scalar production operation is completed basing on the finite state machine and the improvement of the ability of the elliptical curve cryptograph to resist the bypass attack is realized. The invention which improves the security of the realization of the method can be applicable to the fields such as the cryptograph theory, the password cracking, the security chip design and the smart card design.
Owner:SHANGHAI JIAO TONG UNIV
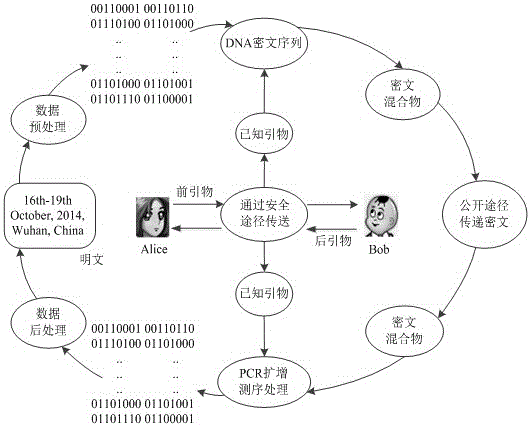
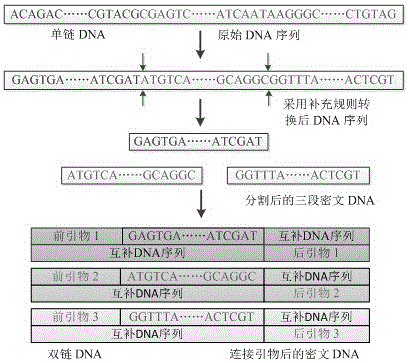
DNA coding based encryption system and encryption method
InactiveCN105119717AIncrease the difficulty of decipheringIncrease the difficulty of crackingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesInformation transmissionPassword
The invention belongs to the technical field of information security in communication transmission, and particularly relates to a DNA encryption system and an encryption method. The system comprises an encryption key, an information conversion portion, an information encryption portion, an information transmission portion, a decryption key and an information decryption portion, wherein the encryption key and the decryption key are primer sequences; and information encryption refers to that information is converted and coded and then corresponds to A, T, C, G bases in DNA in a one-to-one mode according to a predetermined rule. The encryption system and the encryption method provided by the invention can realize automatic operation of corresponding code conversion, encryption and decryption by depending on biological problem setting and biological technology development and by being matched with development of corresponding computer information technologies at the same time, have the characteristics of good compatibility with other encryption methods, high automation degree, simple key, high password cracking difficulty, safer information transmission and the like, has good application values, and can provide better reference for other new encryption systems at the same time.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
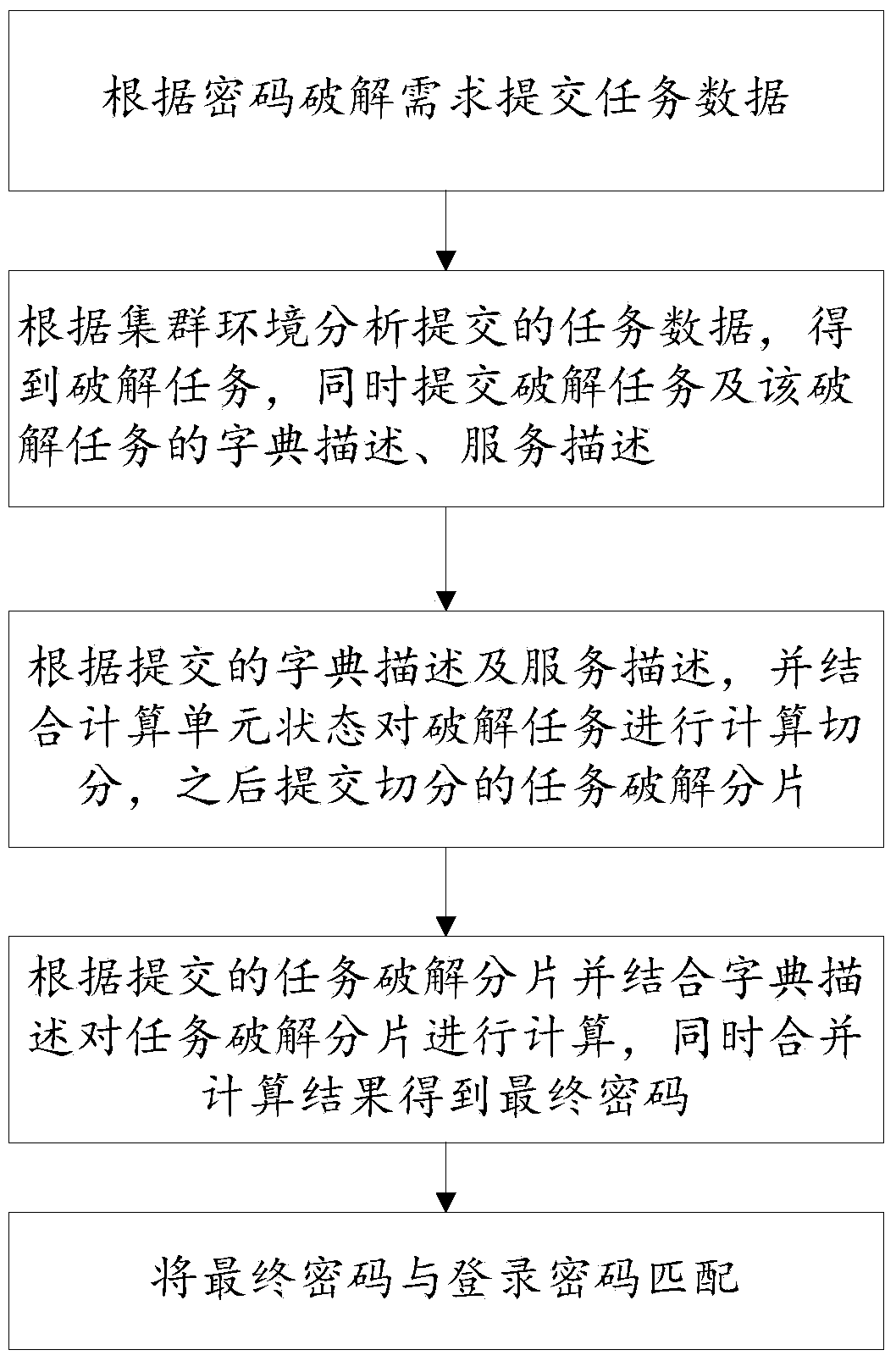
Password cracking system and method
InactiveCN104077542AImprove efficiencyImprove accuracyDigital data protectionPasswordInformation security
The invention provides a password cracking system and method. The method comprises the steps that (1) task data are submitted according to password cracking needs; (2) the submitted task data are analyzed according to a cluster environment, a cracking task is obtained, and meanwhile the cracking task and the dictionary description and service description of the password cracking task are submitted; (3) the cracking task is calculated and segmented by combining a calculating unit state and according to the submitted dictionary description and the submitted service description, and then segmented task cracking segments are submitted; (4) the task cracking segments are calculated according to the submitted task cracking segments and by combining the dictionary description, and meanwhile calculation results are combined to obtain a final password; (5) the final password is matched with a login password. The invention further provides a password cracking system. A network security department can quickly enter an illegal encryption website and collect valuable information to take effectively striking measures subsequently, and important significance on maintenance of national information security is achieved.
Owner:LINEWELL SOFTWARE
Verification method and system
ActiveCN104038346AAvoid insecurityPrevent unfair behaviorUser identity/authority verificationValidation methodsPassword
The invention provides a verification method and a verification system. The verification method includes following steps: a) receiving a web access request and accessory user information, sent by a user; b) confirming a verification code grade provided for the user according to the received user information, wherein the verification code grade is confirmed according to a user experience degree grade and the fact that whether a machine cracking difficulty grade is added; c) obtaining a verification code corresponding to the verification code grade according to the confirmed verification code grade, and sending the verification code to the user; d) receiving a verification code input by the user according to the verification code corresponding to the verification code grade and performing verification; e) returning a verification result to the user. According to the verification method and the verification system, the verification code grade is confirmed based on friendliness of the user and cracking difficulty of a machine, and therefore not only are network insecurity and inequity behaviors such as malicious password cracking, ticket brushing and forum irrigation, but also the common user can obtain good user experience.
Owner:BEIJING 58 INFORMATION TECH
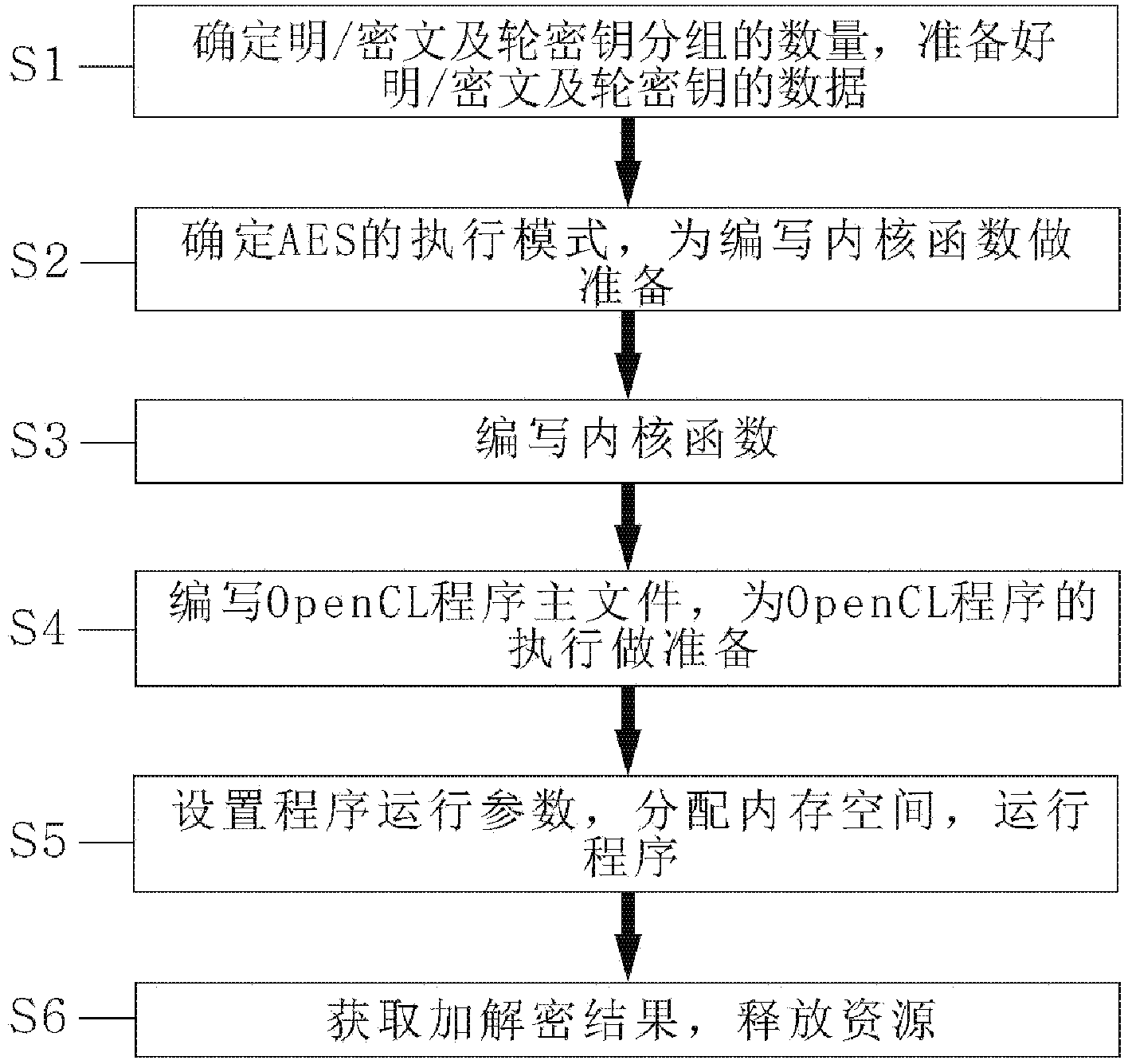
AES parallel implementation method based on OpenCL
ActiveCN103973431AHigh-speed programmingImprove matchEncryption apparatus with shift registers/memoriesConcurrent instruction executionPassword crackingComputer hardware
The invention discloses an AES parallel implementation method based on OpenCL. According to the scheme, when an AES performs parallel running on an AMD GPU based on OpenCL, optimum performance can be achieved. The method includes the following steps that first, the number of plaintext / ciphertext and the number of round key groups are determined, and plaintext / ciphertext and round key data are prepared; second, an executing mode of the AES is determined, and preparation is made for writing of a KiReadyThread; third, the KiReadyThread is written; fourth, a master OpenCL program file is written, and preparation is made for execution of an OpenCL program; fifth, program running parameters are set, memory space is allocated, and the program runs; sixth, the encryption and decryption result is acquired, and resources are released. According to the method, in parallel running process of the AES, data are reasonably allocated in a memory and parallel granularity is reasonably selected so that running performance can be improved, and the method can be used for fast encryption and decryption or password cracking machines.
Owner:SOUTH CHINA NORMAL UNIVERSITY
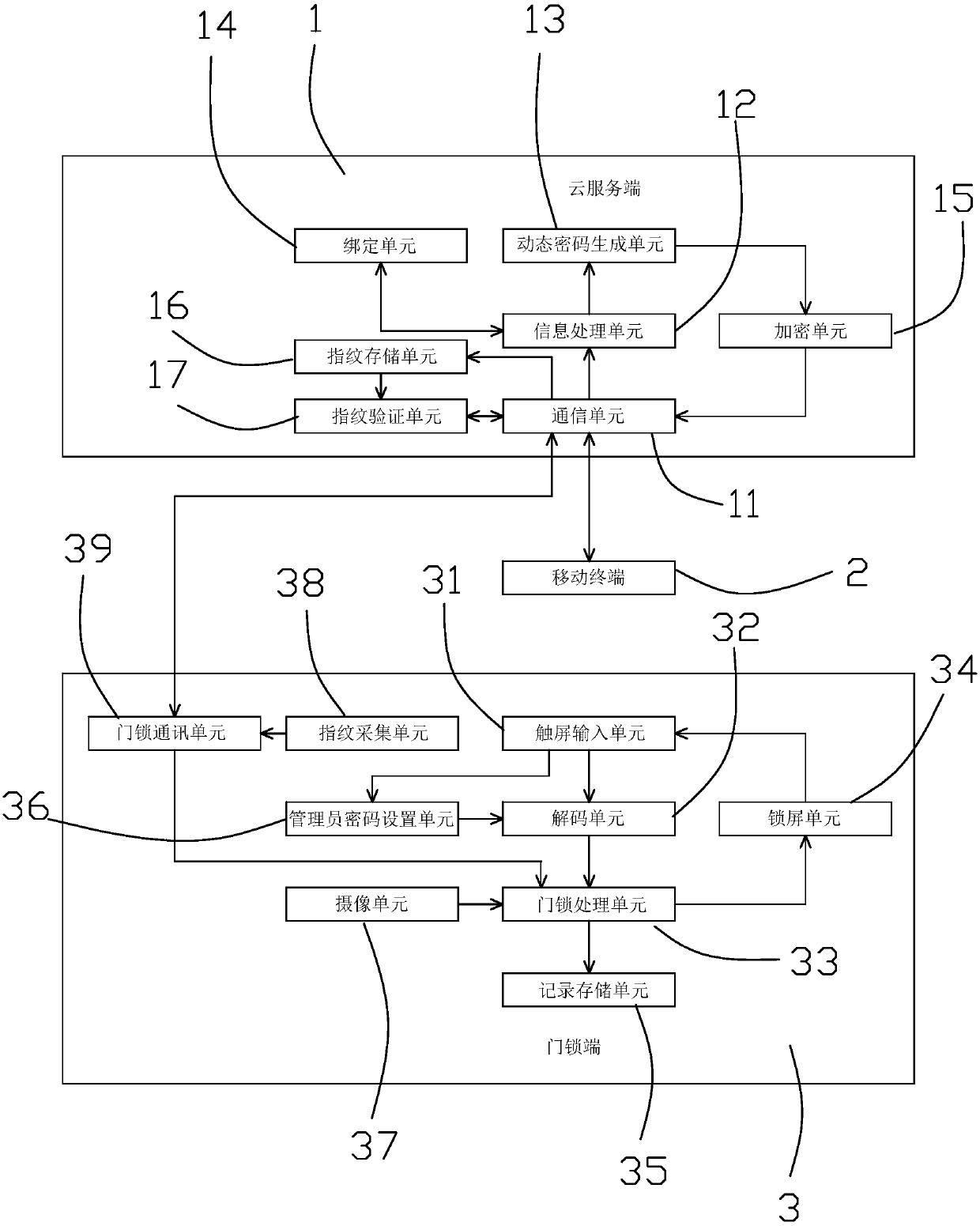
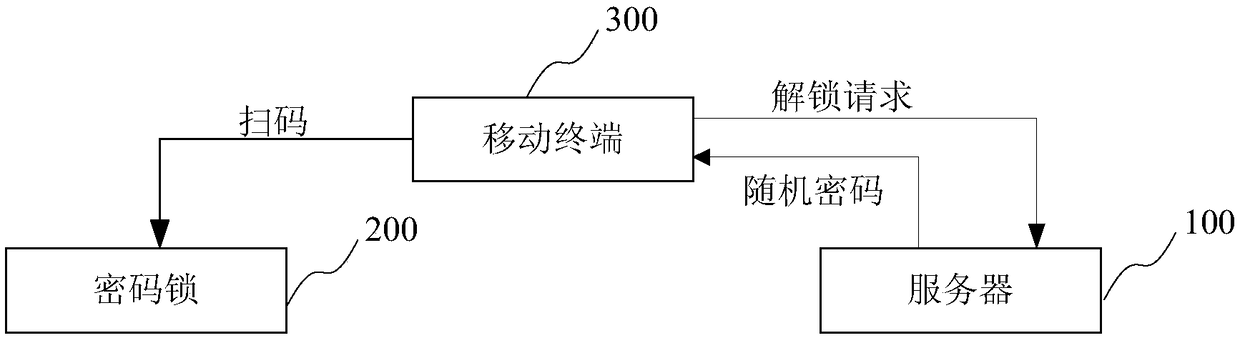
Intelligent door lock system and control method
InactiveCN107893583AReduce consumptionReduce the chance of being crackedElectric permutation locksIndividual entry/exit registersInformation processingCommunication unit
The invention relates to an intelligent door lock system and a control method and aims to solve the problems that an intelligent door lock in the prior art is easy to monitor, filch and falsify when adopting Bluetooth and WIFI to control unlocking. The intelligent door lock system comprises a door lock terminal, a mobile terminal and a cloud service terminal, wherein the cloud service terminal comprises a communication unit, an information processing unit, a binding unit and a dynamic password generation unit; the door lock terminal comprises a touch screen input unit, a decoding unit, a doorlock processing unit, a manager code setting unit and a screen locking unit. According to the intelligent door lock system, a manager password is set at the door lock terminal, the binding relationship between a user, the door lock terminal and the cloud service terminal is set up at the mobile terminal, the user can unlock the door after receiving the generated dynamic security password from themobile terminal, and the mobile terminal needs not to be connected with the door lock terminal, so the probability of password cracking is reduced, and energy consumption of the door lock terminal isreduced as well.
Owner:杭州软库科技有限公司
WPA shared key cracking system based on GPU cluster
ActiveCN103684754AGood cracking effectReliable Task Scheduling SystemKey distribution for secure communicationPassphraseComputer architecture
The invention relates to the technical field of password cracking, and discloses a WPA shared key cracking system based on a GPU cluster. The WPA shared key cracking system based on the GPU cluster specifically comprises a control node and a plurality of GPU computational nodes. The control node intercepts and obtains a WPA data package, a characteristic value extracting module extracts cracking characteristic values, and a user interaction module of the control node receives a password cracking range defined by a user; a password space partition module partitions password sections of certain ranges to all GPU computational nodes, and sends the password sections to all the corresponding GPU computational nodes; the GPU computational nodes calculate and obtain temporary verification parameters MIC_TMP, a breaking password passphrase is regarded as the shared key when the temporary verification parameters MIC_TMP are identical with a verification parameter MIC value, and password cracking is completed. According to the WPA shared key cracking system based on the GPU cluster, the GPU cluster is adopted to crack a password of a WPA / WPA2-PSK, multi-node GPU clusters are supported, expansion can be carried out properly according to needs, and cracking performance is improved well. Meanwhile, oriented to the heterogeneous characteristic of the GPU clusters, a reliable task dispatching system is designed, load balancing is achieved, and cracking speed is improved.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
User authentication method and device
InactiveCN107026731AAvoid interferenceReduce experienceUser identity/authority verificationThird partyData ingestion
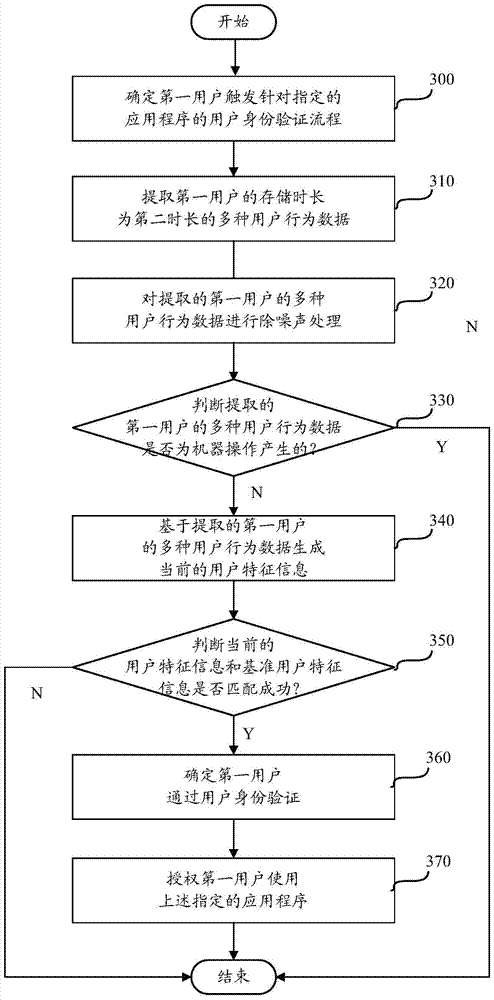
The application relates to a computer technology, and discloses a user authentication method and device aiming at ensuring the accuracy of authentication while reducing the operation complexity of a verification process. The method comprises the following step: a user authentication device real-timely collects and stores a plurality of user behavior data of a first user through a plurality of sensors, separately generates corresponding user characteristic information based on two segments of user behavior data with different storage time, and then matches the two pieces of user characteristic information, and judges that the user is successfully authenticated when a successful match is determined. Thereby, according to a method for authenticating the user by using the user characteristic information extracted based on the user behavior data, the information leakage can be effectively avoided, the difficulty of password cracking can be increased, the possibility of stealing or copying passwords by third parties can be effectively reduced, the accuracy of authentication can be ensured, and the security of the system can be enhanced.
Owner:ALIBABA GRP HLDG LTD
Gesture-based digital password input method and system thereof
InactiveCN106503620AImprove input securityReduce sensitivityComplete banking machinesCharacter and pattern recognitionHand partsComputer graphics (images)
The present invention discloses a gesture-based digital password input method and a system thereof. The system comprises the steps of S1, inputting a gesture in a collection darkroom and acquiring a depth image containing a hand area; S2, preprocessing the acquired depth image and segmenting a hand part to obtain the depth image of the palm of the hand part; S3, subjecting the depth image of the palm to gesture modeling to obtain a gesture model according to a predefined gesture category; S4, identifying the gesture model according to a mapping relationship between the predefined gesture category and digitals, and converting to obtain a corresponding digital code string. According to the technical scheme of the invention, the peeping phenomenon during the inputting process of passwords can be avoided. Meanwhile, no personal information including fingerprints and the like, which might be acquired by a lawless person, is left. Therefore, during the entire inputting process, no information is left, and the information leakage is avoided. The password cracking risk is small and the password inputting security is high.
Owner:SHENZHEN ORBBEC CO LTD
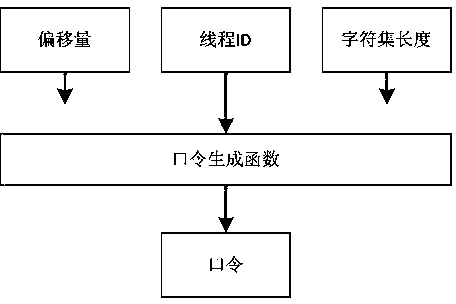
A dynamic password generation and verification method
The invention provides a dynamic password generation verification method, which involves the following parts: original prime number library, dynamic password group generation, dynamic password traversal sequence generation, dynamic password verification and redundancy processing. The dynamic password group is generated by the original prime number library through a randomization algorithm, including n 128-bit dynamic passwords; the dynamic password traversal sequence is a pseudo-random sequence generated by UID (Unique User ID); the dynamic password is triggered by the system clock according to a certain clock frequency The pointer is dynamically generated by traversing the dynamic cipher group according to the dynamic traversal sequence; the dynamic password verification is verified by matching the decrypted result of the encrypted dynamic cipher at the current moment with the redundant password in the dynamic cipher group, and at the same time adjusting the traversal pointer to avoid system errors. After the dynamic password group is generated, it is stored locally in encrypted mode. Two mechanisms are used for dynamic password group generation and dynamic password traversal sequence generation to minimize the possibility of password cracking.
Owner:LIAONING GOETHINK TECH
Method and apparatus for setting keyboard
InactiveUS20150309724A1Avoid crackingValue can be obtainedDigital data authenticationInput/output processes for data processingPasswordComputer science
The disclosure discloses a method and apparatus for setting a virtual keyboard which may adjust individual buttons in the virtual keyboard to prevent password cracking software from cracking a password by the approach of continuously trying to input a command sequence. The method comprises: in a current keyboard layout, receiving a character string constituted by selected button key values for password check; when it is detected that the character string matches a preset password, passing the password check of the character string; when it is detected that the character string does not match the preset password, resetting the keyboard layout, and changing the button positions corresponding to the button key values in the virtual keyboard; and in the reset keyboard layout, receiving the character string constituted by selected button key values to continue to perform the password check.
Owner:BEIJING QIHOO TECH CO LTD
Identity authentication system and method thereof
InactiveCN104778390AIncrease the difficultyReduced risk of crackingDigital data authenticationImaging processingHash-based message authentication code
The invention discloses an identity authentication system and a method thereof. The identity authentication system comprises an image processing module, a verification database and a processing unit. An image acquisition device is used for obtaining images of a plurality of users. The verification database stores a biological characteristic template and an action message authentication code. The processing unit is coupled to between the image acquisition device and the verification database, analyzes images of the users in order to generate a biological characteristic and a face dynamic message, and generates an action message code in dependence on the face dynamic message. If the biological characteristic accords with the biological characteristic template, the processing unit compares the action message code with the action message authentication code. If the action message code accords with the action message authentication code, the identity of the user is verified successfully. According to the invention, a multiple authentication manner is employed, the difficulty degree of password cracking is greatly improved, and the risk that the password is cracked is reduced.
Owner:UTECHZONE CO LTD
Password lock unlocking method, system and server, equipment and password lock
InactiveCN109102607AGuarantee the stability of useImprove work efficiencyIndividual entry/exit registersPasswordSecret code
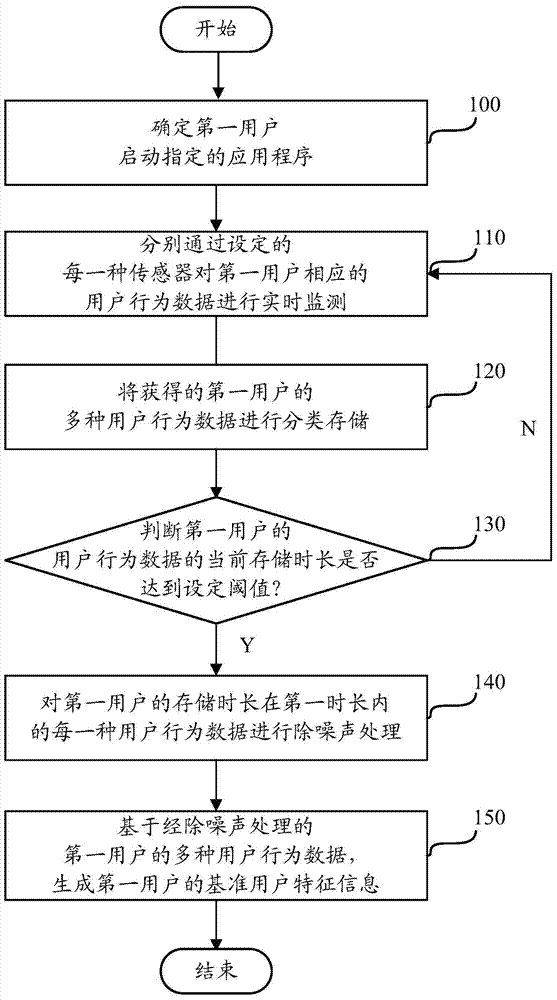
The invention provides a password lock unlocking method, system and server, equipment and a password lock. The server comprises a receiving module, a synchronization time module, a password generatorand a transmission module, wherein the receiving module is used for receiving an unlocking request; the synchronization time module is used for acquiring synchronization time of time synchronization with a password generator in the password lock; the password generator is used for generating a random password according to the unlocking request and the synchronization time; and the transmission module is used for sending a random password to a mobile terminal. The password lock comprises a lock body, a password generator, a password receiving module, a password comparator and an unlocking control module, wherein the password generator is used for synchronously generating a random password identical to the random password generated in the server; the password receiving module is used for receiving an input unlocking password; the password comparator is used for comparing whether the received unlocking password is identical to the generated random password or not; and the unlocking control module is used for controlling the lock body to be opened or keep closed. Through adoption of the password lock unlocking method, system and server, a series of network problems caused by unlockingby means of network communication are solved, and the risk of password reusing and equipment password cracking is also avoided.
Owner:上海幸卓智能科技有限公司
Password guessing set generating method and password cracking method based on user name information
InactiveCN106803035AImprove cracking efficiencyHigh guessing success rateDigital data protectionDigital data authenticationPasswordLabelling
The invention discloses a password guessing set generating method and a password cracking method based on user name information. The password cracking method comprises the steps of: 1) labelling user names and passwords of a data training set leaked according to word segmentations and semantic structures, calculating the semantic similarity of the user names and passwords, wherein the semantic similarity comprises semantic structure similarity and semantic portion similarity; 2) applying the semantic similarity to PCFGs grammar, in another word, PCFGs grammar is built based on the semantic similarity; 3) building PCFGs grammar according to step 2), generating a password guessing set according to the probability of descending; 4) cracking the password according to the password guessing set. The password guessing set generating method and password cracking method have the advantages of utilizing the portion similarity and the structure similarity of the usernames and passwords, understanding the constitution semantic of the password, generating the password guessing set, and improving the password cracking efficiency.
Owner:INST OF INFORMATION ENG CAS
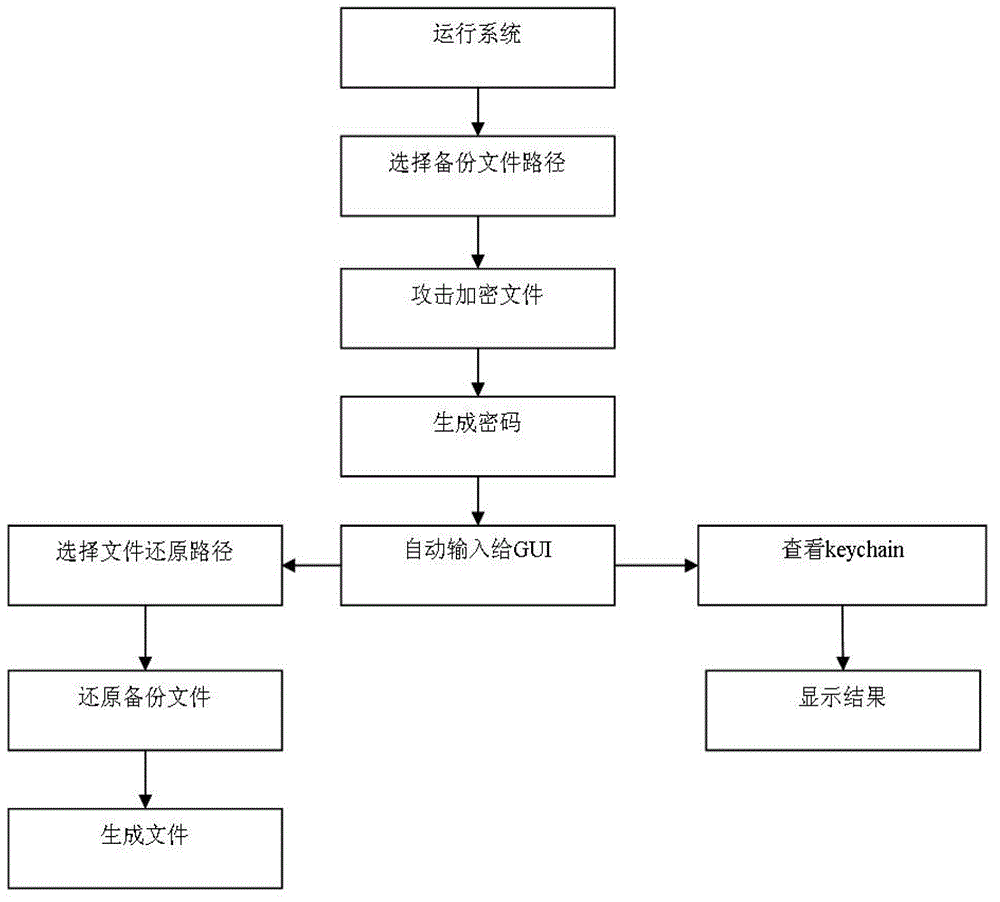
System for cracking and restoring iPhone encrypted backup files
InactiveCN102750495AEasy to collect evidenceEasy detectionComputer security arrangementsSubstation equipmentGraphicsGraphical user interface
The invention provides a system for cracking and restoring iPhone encrypted backup files. The system comprises a graphical user interface (GUI) module, a password cracking module, a backup file restoring module and a keychain checking module. The GUI module is used for interactive operation between a user and a device; the password cracking module is connected with the GUI module and used for cracking encrypted files to obtain cracking passwords; the backup file restoring module receives the cracking passwords to restore encrypted backup files; and the keychain checking module receives the cracking passwords to check data stored in the keychain. According to the system for cracking and restoring encrypted backup files, the iPhone encrypted backup files are restored directly through the encrypted passwords, so that data in the iPhone are obtained, and the inside of existing mobile phone forensic systems can be integrated, and evidence obtaining and case detecting of office departments are facilitated.
Owner:RUN TECH CO LTD BEIJING
Cloud platform based human health detection system and method
InactiveCN103646163AAvoid distressing situationsHigh strengthDigital data authenticationDiagnostic recording/measuringPasswordHuman health
The invention discloses a cloud platform based human health detection system and method. The system comprises a collector, a cloud server and a health management center. The collector and the health management center are connected with the cloud server through a network respectively. A recognition module is a fingerprint recognition module, and a display module is a touch display screen. According to the system and the method, human fingerprints are used as user login passwords, so that the password strength is improved, and disturbance caused to users due to password cracking is prevented; the whole system is simple in structure and high in practicality.
Owner:CHENGDU BOYUE CHUANGXIN TECH
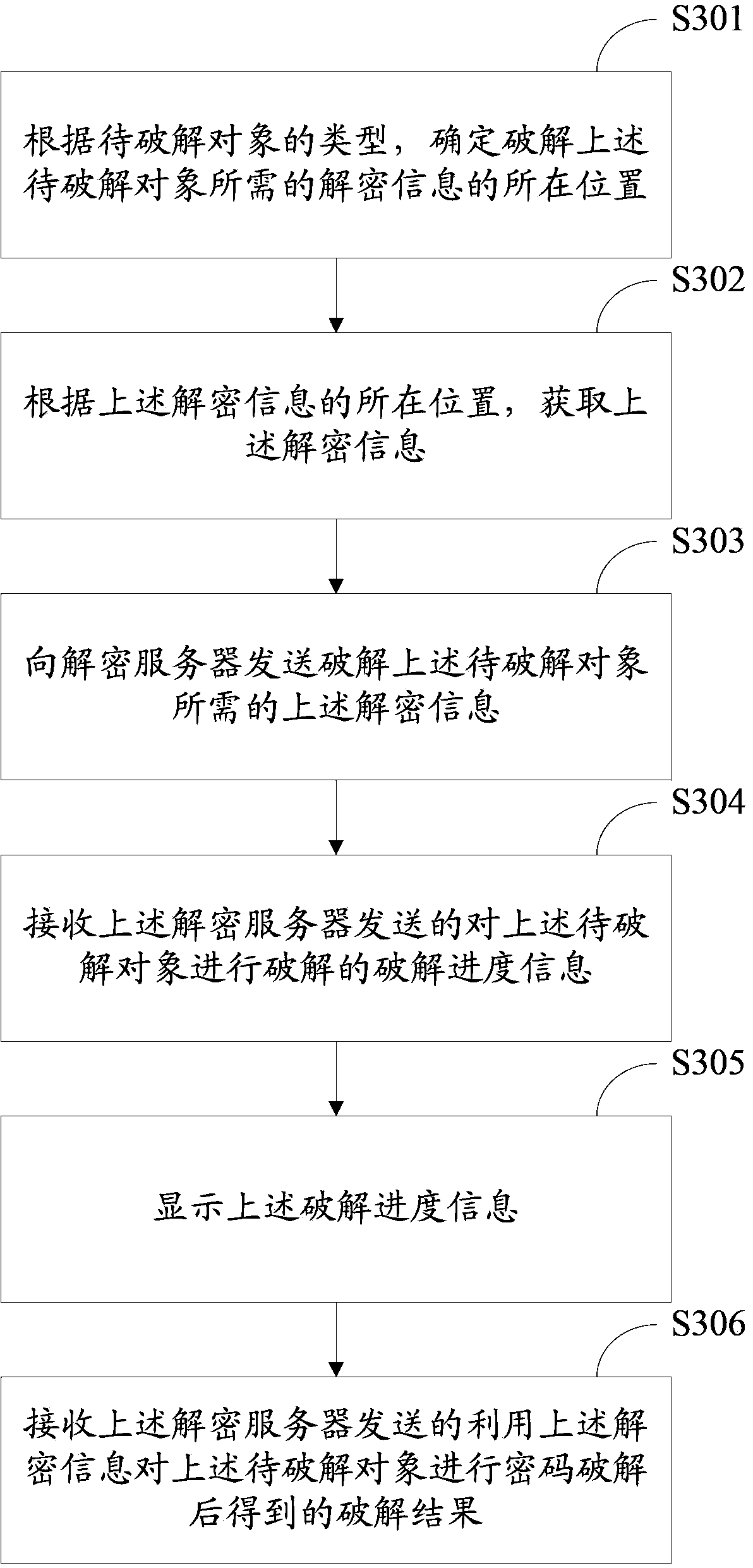
Password cracking method, device and system
The embodiment of the invention provides a password cracking method, device and system, and relates to the field of information security. According to the password cracking method, a client side determines the position of decryption information needed for cracking an object to be cracked according to the type of the object to be cracked; according to the position of the decryption information, the decryption information is obtained; the decryption information needed for cracking the object to be cracked is sent to a decryption server; the decryption server receives the decryption information needed for cracking the object to be cracked from the client side; password cracking is carried out on the object to be cracked through the decryption information, and an obtained cracking result is sent to the client side; the client side receives the cracking result from the decryption server. The password cracking method, device and system solve the problem that in the prior art, password cracking can not be carried out on an object to be cracked closely related to the site environment and an object to be cracked which is high in requirement for password cracking real-time performance and depends on hardware equipment.
Owner:SAFE STONE INFORMATION TECHBEIJINGCO +1
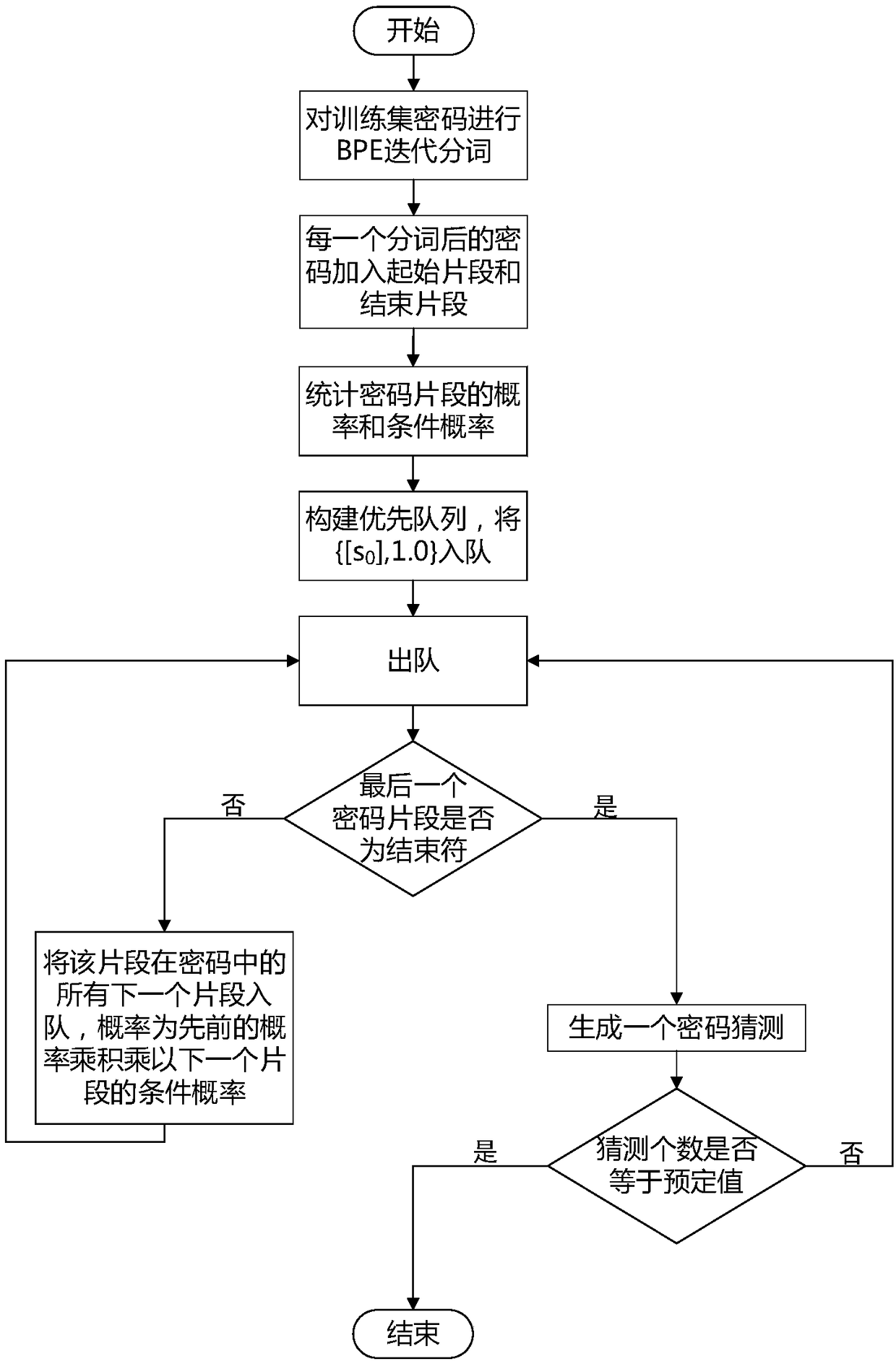
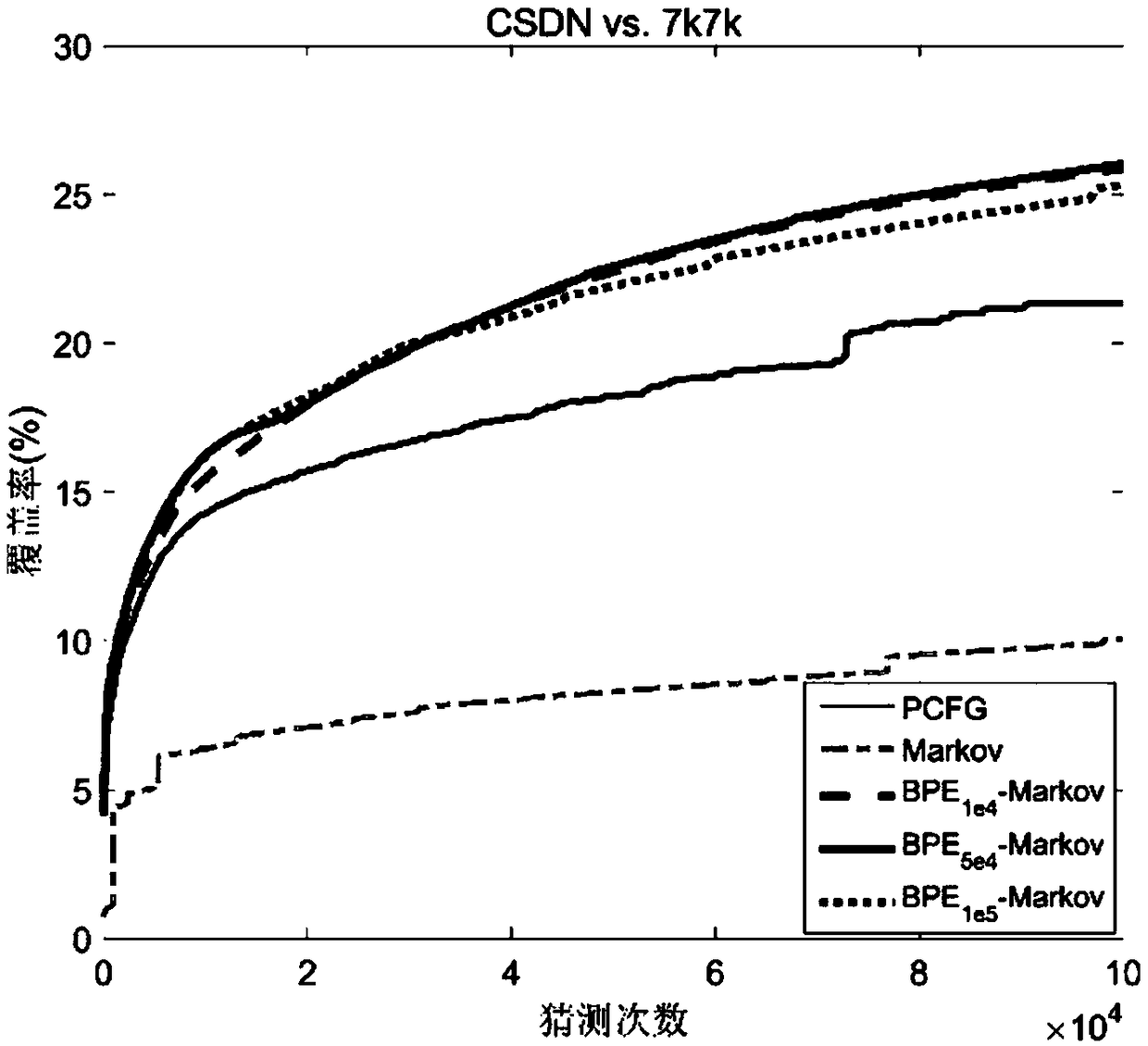
Password guessing set generation method based on byte pair encoding, password cracking method and device
ActiveCN109145582AImprove guessworkImprove efficiencyDigital data protectionDigital data authenticationPlaintextDecoding methods
The invention relates to a password guessing set generation method based on byte pair encoding, a password decoding method and a device. Firstly, byte pair encoding is used to segment the cipher of training set, and then Markov model is used to generate the cipher guess set according to the result of word segmentation. Further, the plaintext password is decoded by string matching using the password guess set. The invention fully utilizes the idea of statistical probability to segment the cipher, and uses Markov model to explore the correlation between the cipher components, thereby improving the cipher guess effect and the cipher decoding efficiency. The password guessing set generated by the invention is directly used for string matching, so that the password guessing set can be better generated and the security strength of the password can be evaluated.
Owner:INST OF INFORMATION ENG CAS
Data transmission encryption method and device, storage medium and server
ActiveCN109921894AEnsure safetyGuaranteed verifiabilityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwarePassword
The invention relates to the technical fields of cryptography, information encryption and decryption and symmetric encryption, and provides a data transmission encryption method, which comprises the following steps of: obtaining a current data storage request, and generating a first token and a first random bit according to the current data storage request; Extracting to-be-stored data contained in the current data storage request, and performing AES encryption on the to-be-stored data based on the first token and the first random bit to obtain a first key; And performing md5 encryption on thefirst key to obtain a ciphertext data packet. When the front end receives the data storage request once, the data needing to be transmitted at the time is encrypted and transmitted to the rear end, the rear end verifies the password of the data transmission, and when the password is incorrect, the rear end refuses the data storage request at the time. And the front end dynamically generates the password through the AES every time, so that the security of data transmission is improved. And through the AES cryptographic algorithm, the adjustment is convenient, the password cracking difficulty is increased, and the data transmission security is improved again.
Owner:PING AN TECH (SHENZHEN) CO LTD
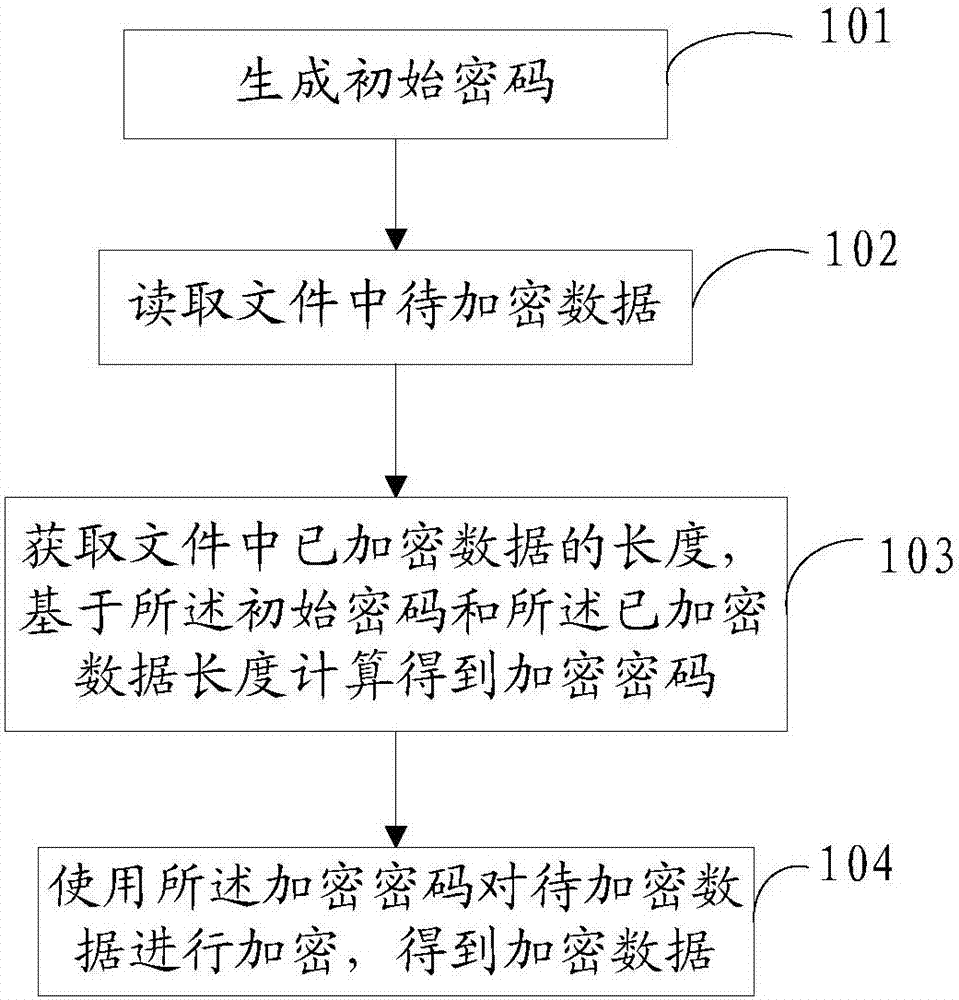
File encryption and decryption method and device
ActiveCN106878013AIncrease the difficultyMeet the needs of technological developmentKey distribution for secure communicationData stream serial/continuous modificationPasswordEncryption decryption
The invention discloses a file encryption method, which comprises the steps of generating an initial password; reading data to be encrypted in a file; acquiring the length of encrypted data in the file, and calculating an encrypted password based on the initial password and the length of the encryption data; and performing encryption on the data to be encrypted by using the encryption password so as to acquire encrypted data. Each byte in the file is encrypted through the encryption password. Compared with a traditional encryption method, the file encryption method disclosed by the invention improves the difficulty of password cracking to a great extent and improves the data security.
Owner:CHINANETCENT TECH
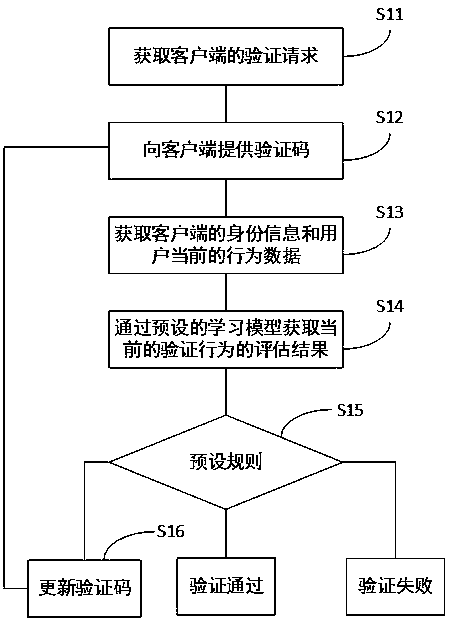
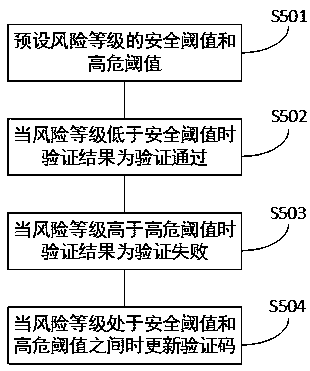
Storage device and verification code application method and device
ActiveCN109600336AQuick and easy verificationImprove user experienceUser identity/authority verificationEvaluation resultComputer security
The invention discloses a storage device and a verification code application method and device. The verification code application method comprises the steps: obtaining a verification request of a client; providing a verification code for the client; obtaining the identity information of the client and current behavior data of a user of the client; taking the identity information and the behavior data as parameters, and obtaining an evaluation result of the current verification behavior through a preset learning model; generating a verification result or updating the verification code accordingto a preset rule; and returning to the step of providing the verification code to the client if the verification code is updated. According to the invention, a real user can conveniently and quicklycomplete verification, high security can be kept while good user experience is ensured for the user, and malicious behaviors such as password cracking, ticket swiping and forum water filling can be effectively avoided.
Owner:WUHAN JIYI NETWORK TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com