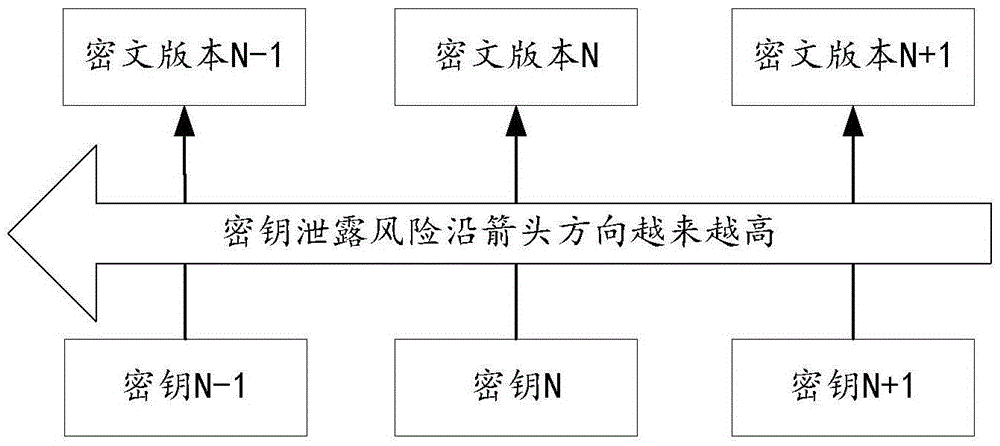
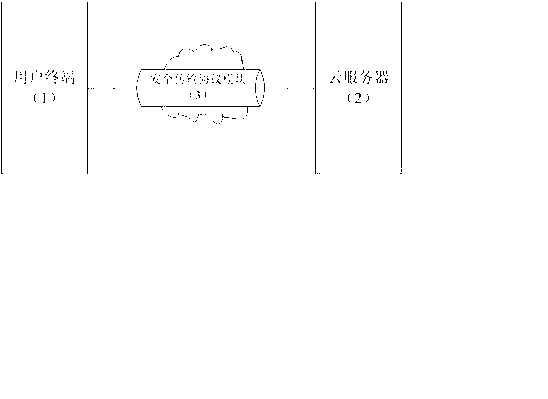Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
858results about How to "Increase the difficulty of cracking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
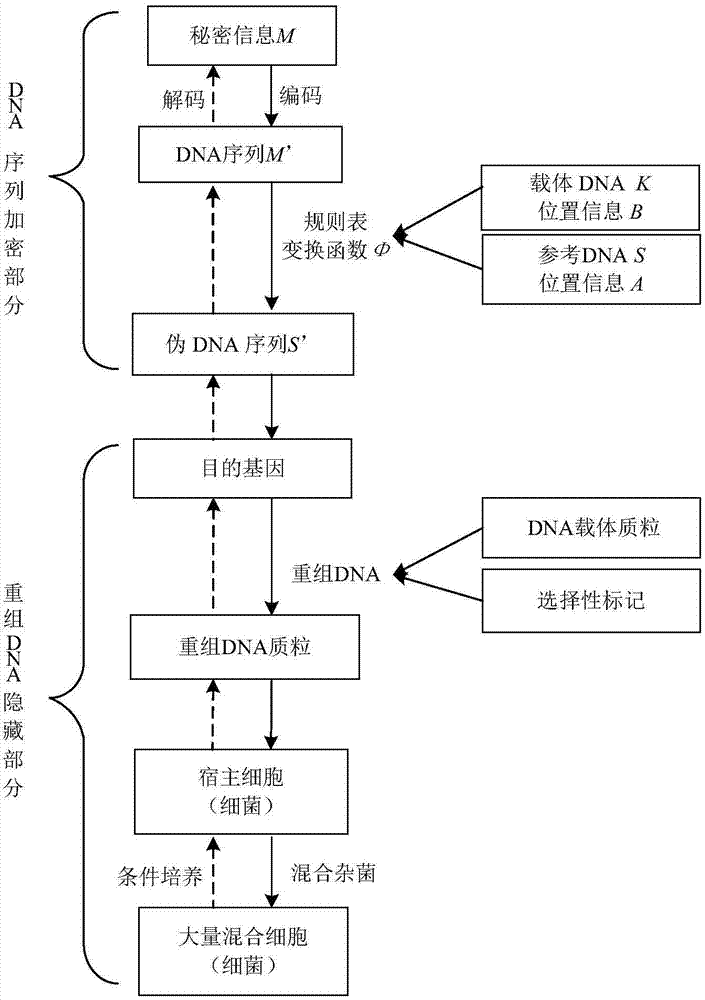
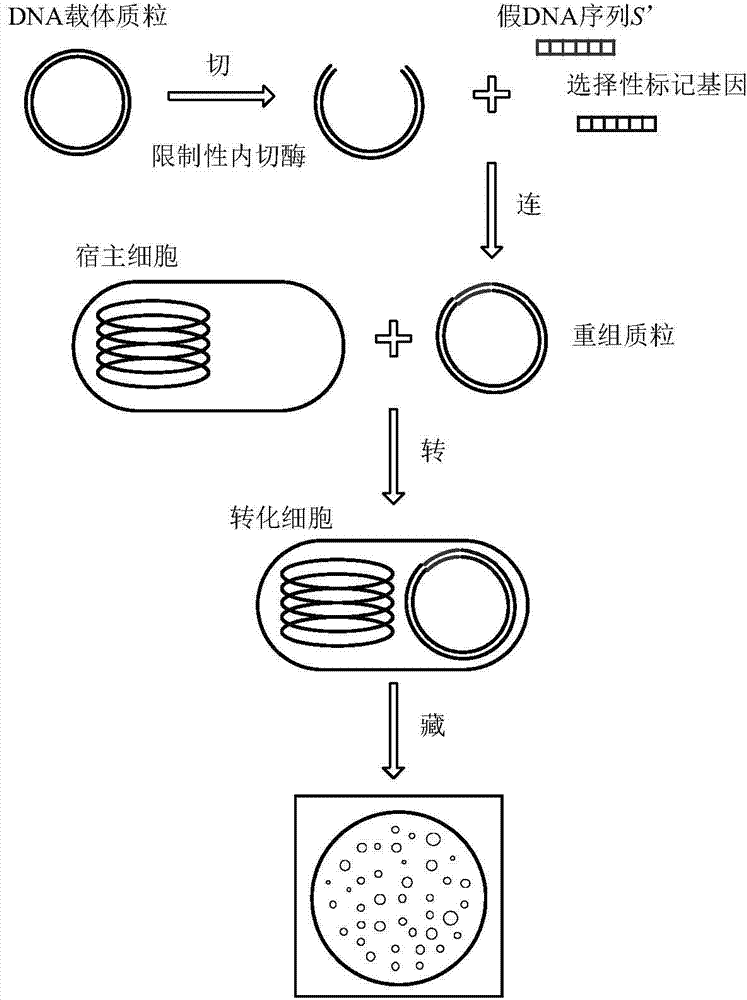
Recombinant DNA technology based information encrypting and hiding method and application
InactiveCN104734848AMeet safety requirementsIncrease the difficulty of crackingVector-based foreign material introductionSecuring communicationPlasmid VectorDNA fragmentation
The invention provides a recombinant DNA technology based information encrypting and hiding method and an application. Firstly, a plain text is coded into a DNA sequence, preprocessing is carried out on the DNA sequence by adopting the encryption algorithm, and a pseudo-DNA segment is generated; and then the pseudo-DNA segment and a marker gene segment are connected to a DNA plasmid vector by using the restriction enzyme and the ligase, and an obtained recombinant plasmid is further hided into a germ body; finally, a cell which contains confidential information is hided into a large number of irrelevant pseudo-cells, and the hided cells can be screened out by the selective cultivation. The encrypting and hiding method is applied to the authentication and signature technology. Encrypting, hiding and transmitting of the confidential information are achieved, and the cracking difficulty of a system is enhanced.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
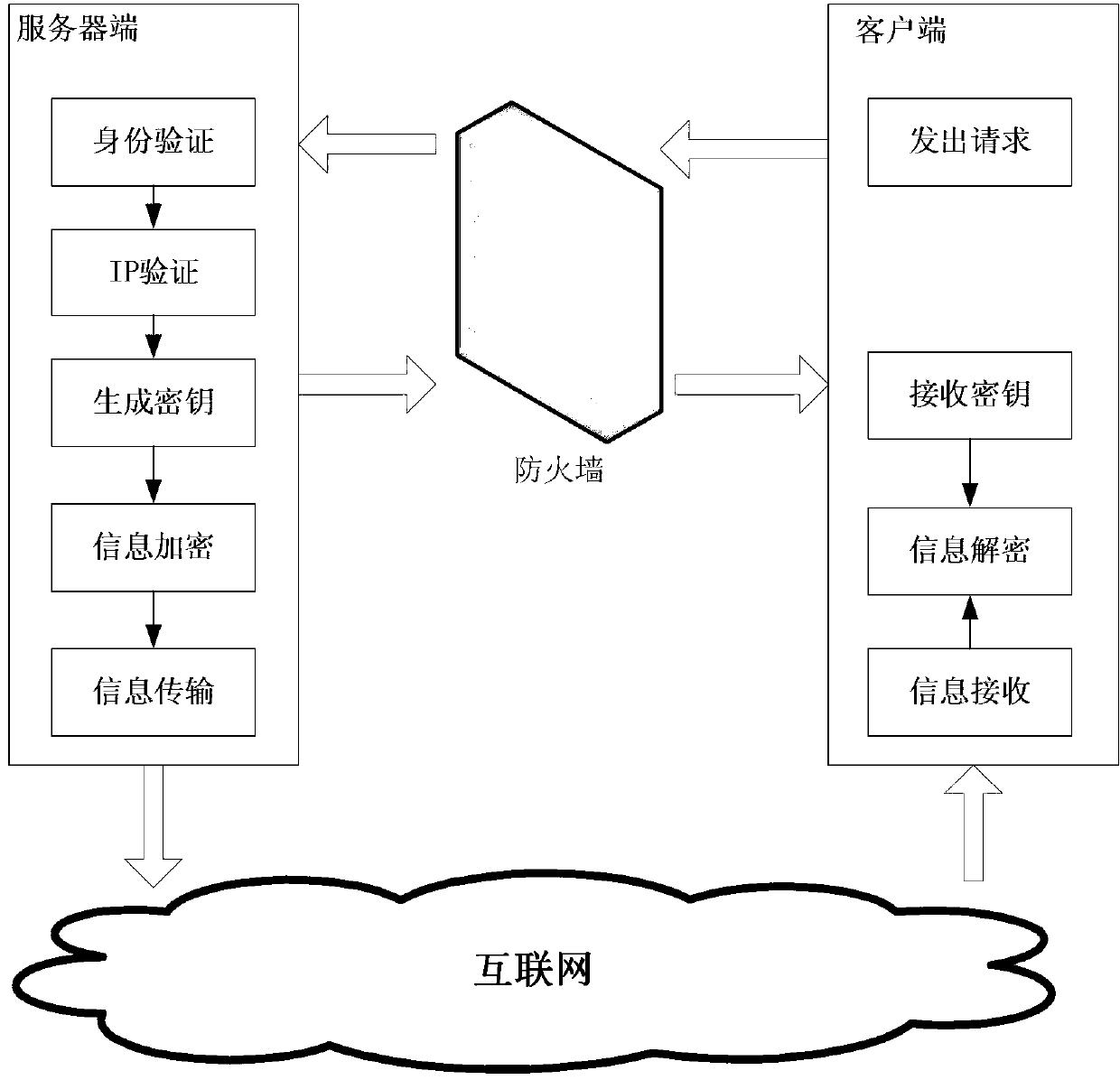
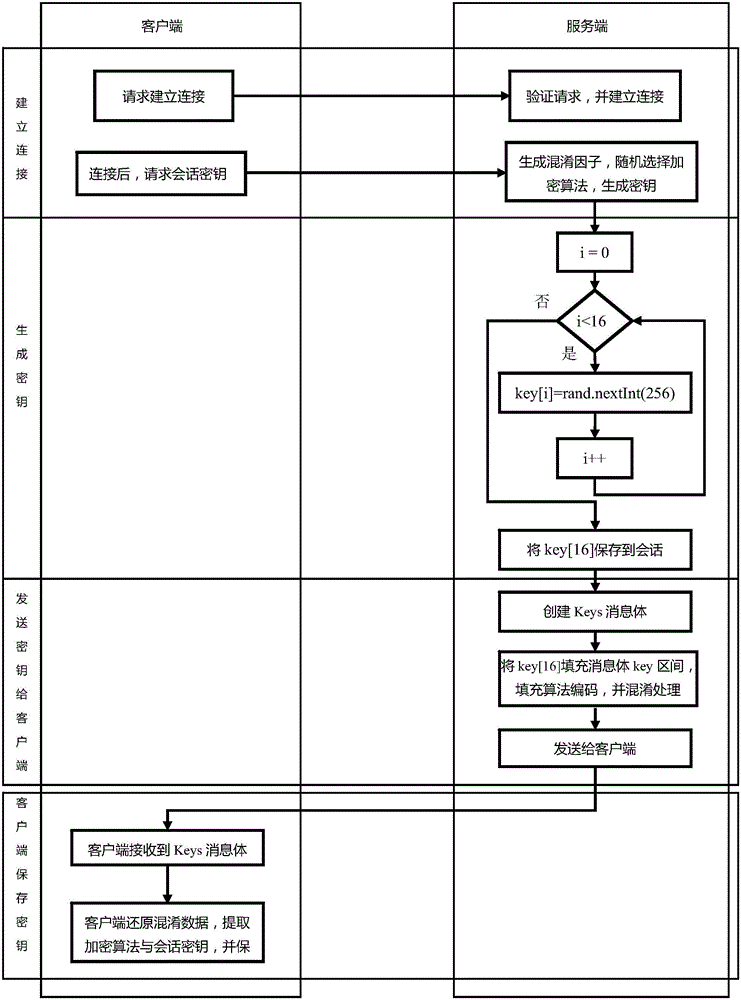
Safe network information transmission method
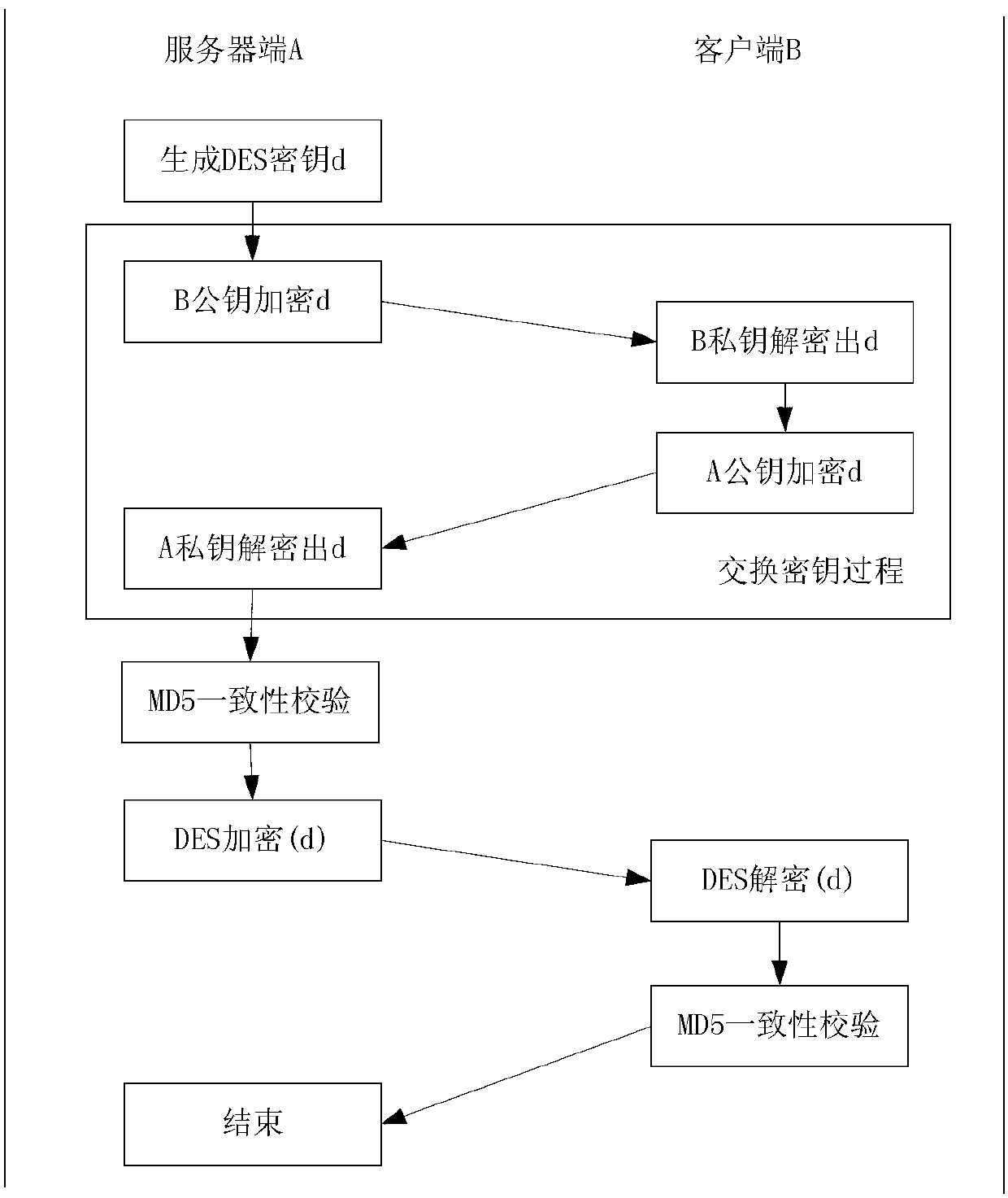
InactiveCN103001976AReduce the possibilityEnsure safetyUser identity/authority verificationEngineeringServer-side
The invention discloses a safe network information transmission method. The method includes that a client sends a service request to a server; a server side verifies a user message in the service request and a client internet protocol (IP) address, and the server side establishes a session with the client if the verification passes; the server side generates a secret key, encrypts the secret key through a public key of the client and sends the secret key to the client; the client decrypts secret key information through a private key, encrypts decrypted secret key information through a public key of the server side and sends the secret key information to the server side; the server side performs digital signature to data of the service request, encrypts the data and digital signature information through the secret key and sends the data and the digital signature information to the client; and the client decrypts the data and performs consistent verification, the information which doesn't pass the consistent verification is discarded, the server side is applied for retransmission, and the information which passes the verification is stored into a local data base. By means of the safe network information transmission method, safety of information transmission is greatly improved.
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
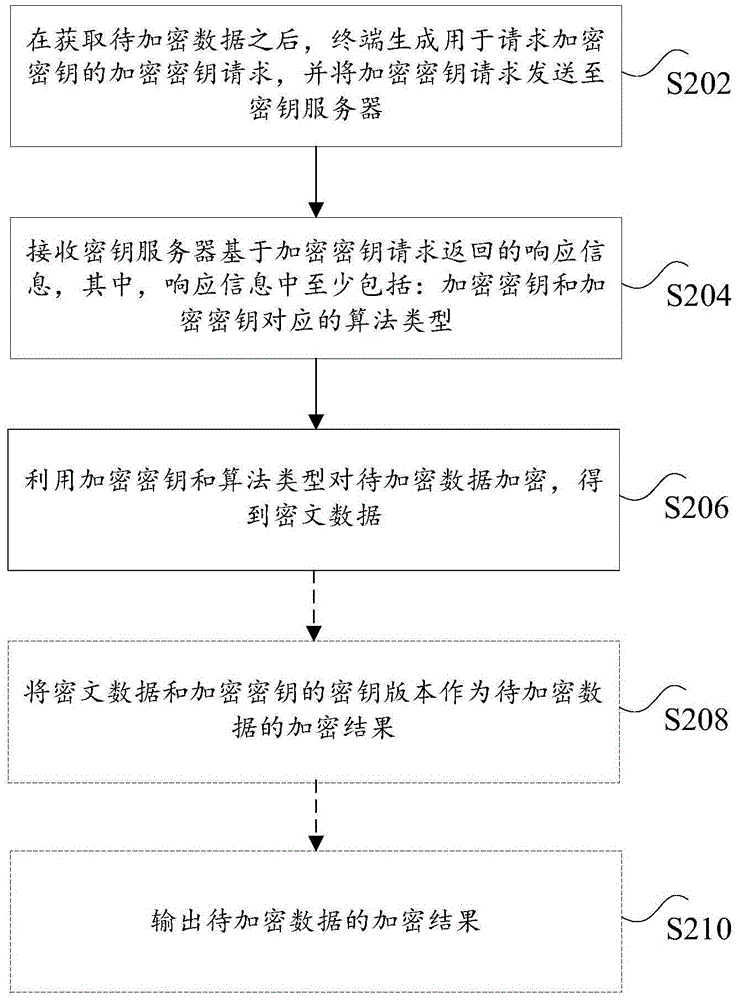
Methods and apparatuses for data encryption and decryption, method and apparatus for processing secret key request, and data encryption and decryption system
The application discloses methods and apparatuses for data encryption and decryption, a method and apparatus for processing a secret key request, and a data encryption and decryption system. The data encryption method includes: after to-be-encrypted data is obtained, a terminal generates an encryption key request used for requesting an encryption key and sends the encryption key request to a secret key server; response information returned by the secret key server based on the encryption key request is received, wherein the response information at least comprises the encryption key and the algorithm type corresponding to the encryption key; and the to-be-encrypted encryption data is encrypted by employing the encryption key and the algorithm type to obtain encrypted data. According to the method, the technical problem of high leakage risk of sensitive data of the encryption method is solved.
Owner:ALIBABA GRP HLDG LTD
Data encryption and decryption method and apparatus thereof, and communication system
InactiveCN105763315AImprove securityIncrease the difficulty of crackingEncryption apparatus with shift registers/memoriesComputer hardwareCommunications system
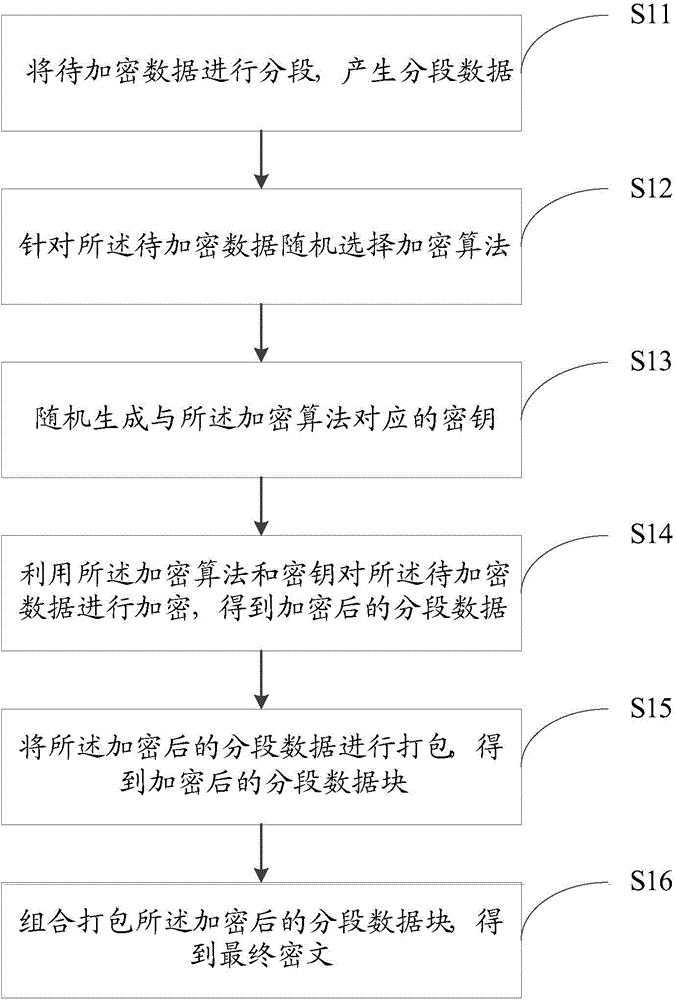
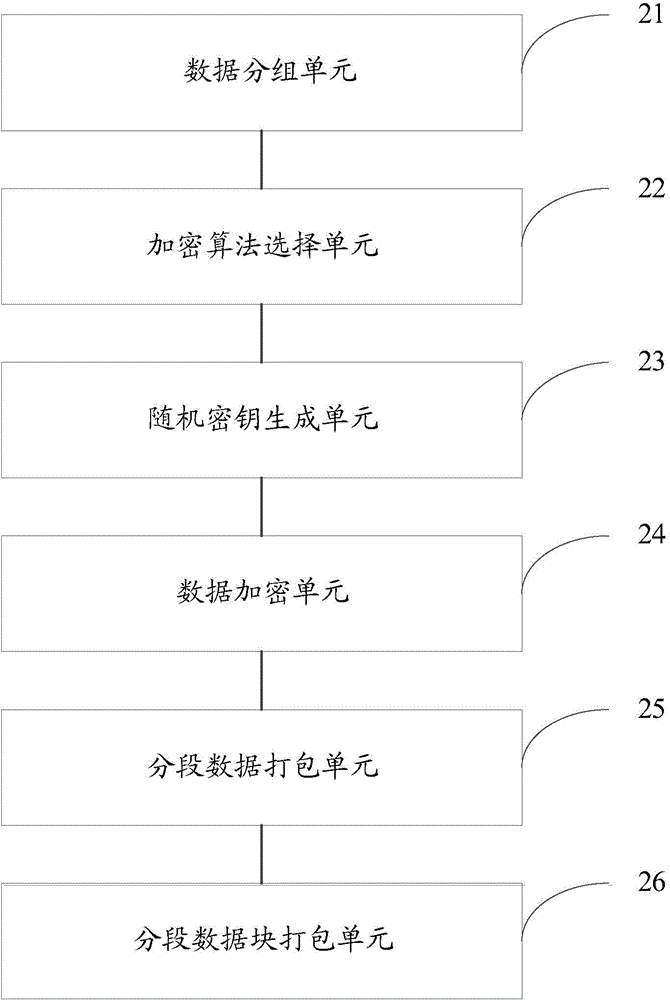
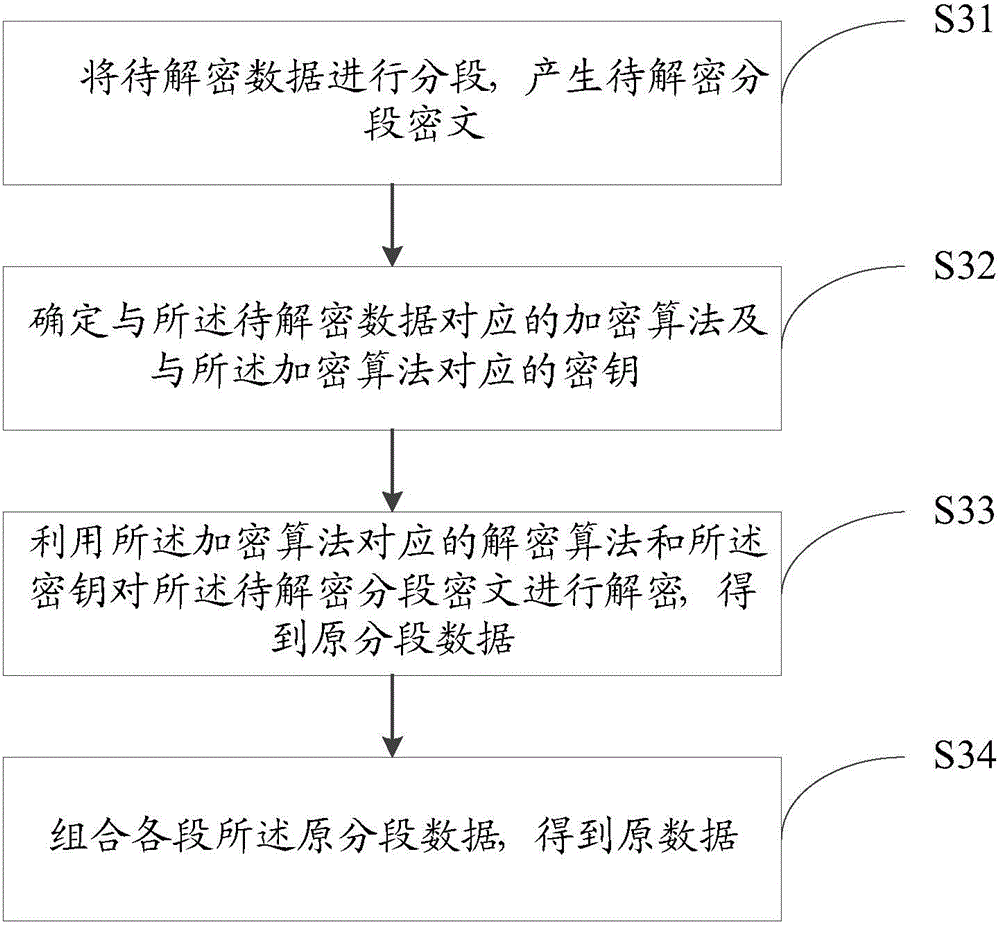
A data encryption and decryption method and an apparatus thereof, and a communication system are disclosed. The data encryption method comprises the following steps of segmenting data to be encrypted and generating a segmented data; aiming at the data to be encrypted, randomly selecting an encryption algorithm; randomly generating a secret key corresponding to the encryption algorithm; using the encryption algorithm and the secret key to encrypt the data to be encrypted so as to acquire the encrypted segmented data; packing the encrypted segmented data to acquire an encrypted segmented data block; and combining and packing the encrypted segmented data block to acquire a final cryptograph. By using the encryption method, cracking difficulty is increased and safety of the data encryption method is increased.
Owner:SPREADTRUM COMM SHENZHEN CO LTD
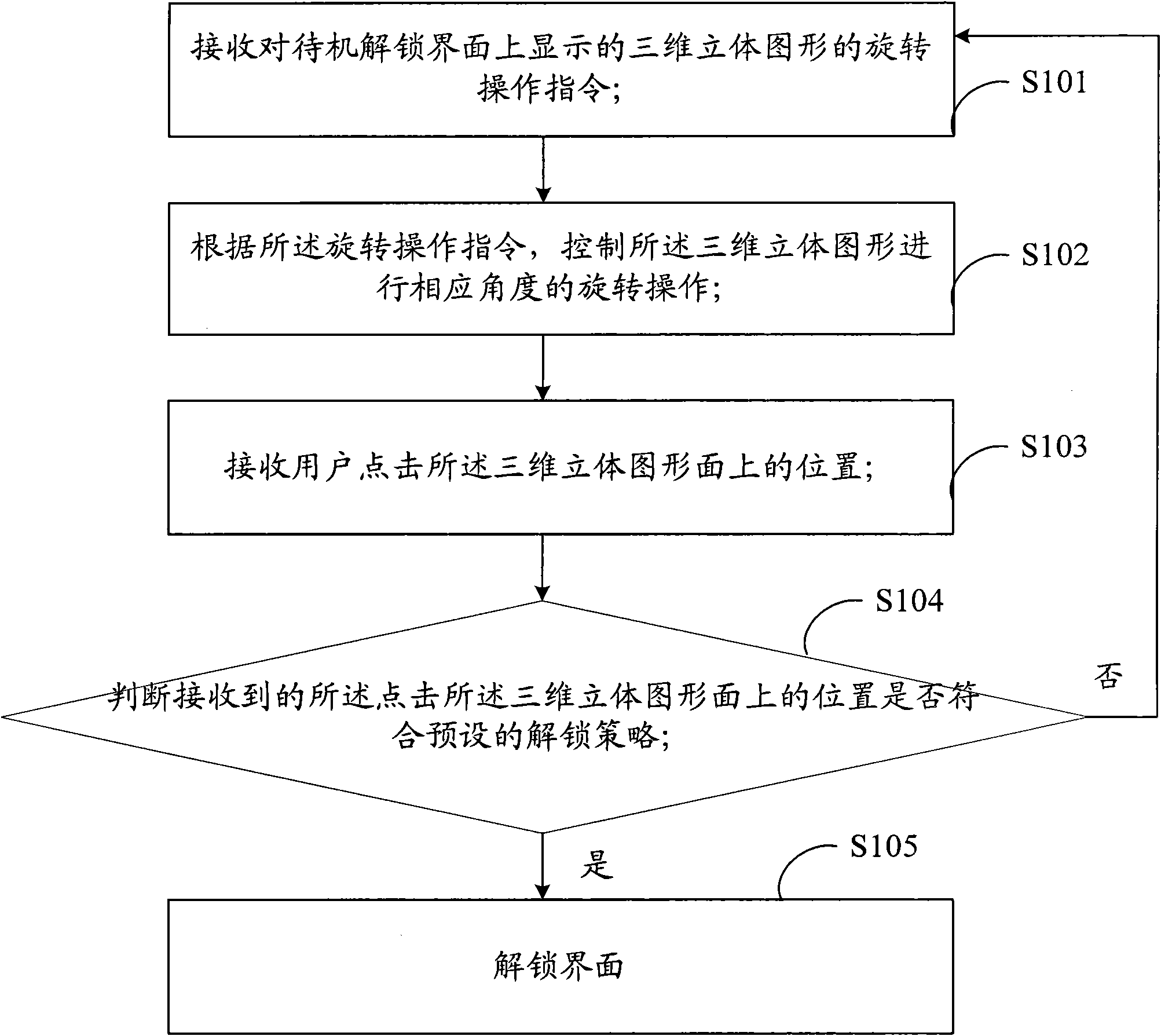
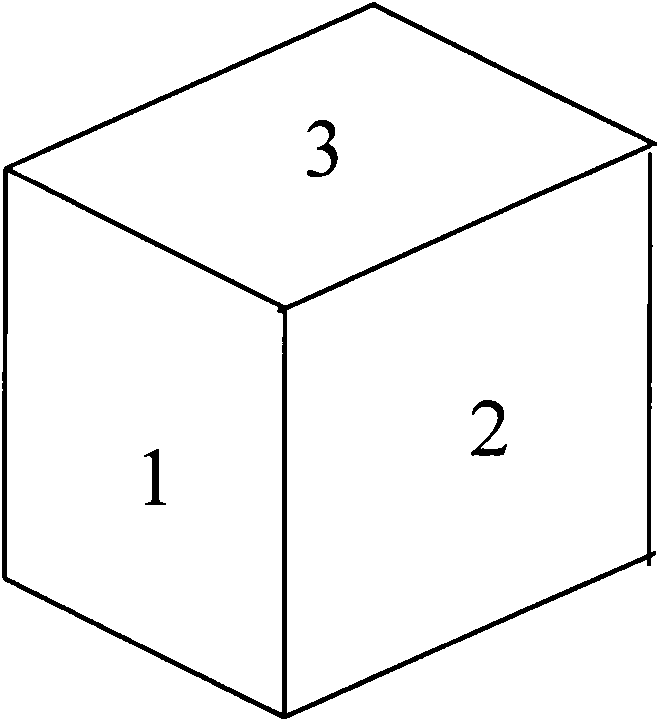
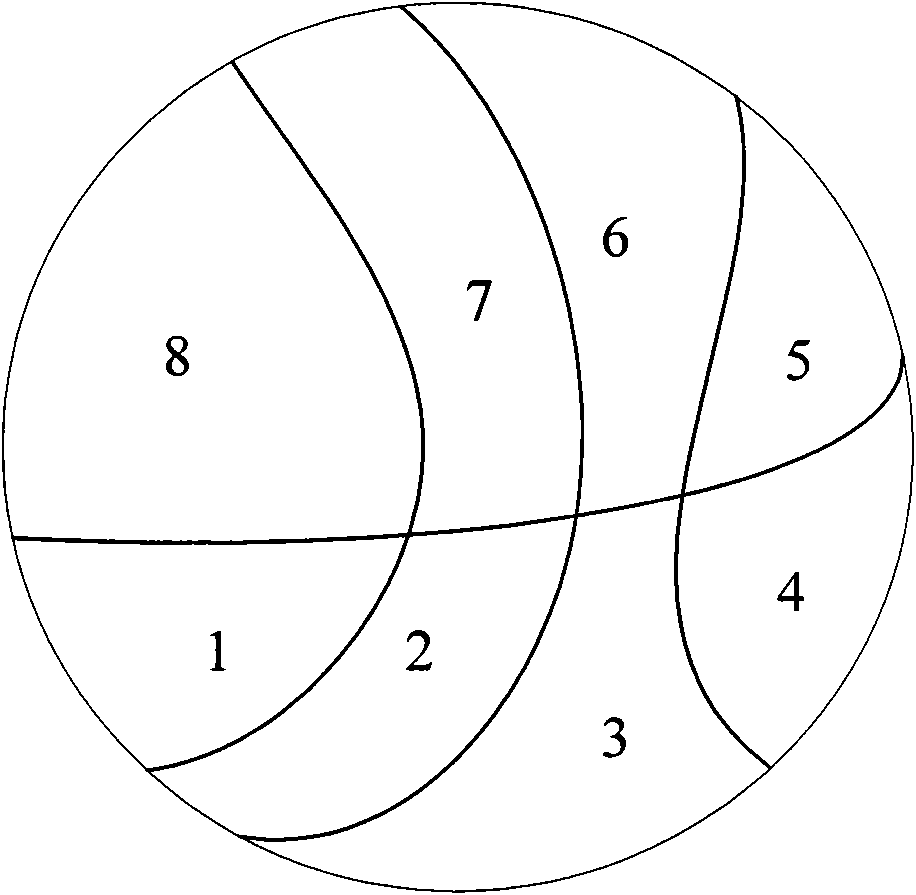
Method, system and touch terminal for unlocking touch terminal interface
ActiveCN101957715AIncrease the difficulty of crackingInput/output processes for data processingVisual spaceGraphics
The invention is suitable for the field of touch technology, and provides a unlocking method, a system and a touch terminal for touch terminal interfaces. The method comprises the following steps: receiving a rotary operation command of a three-dimensional graph displayed on a standby unlocking interface; controlling the three-dimensional graph to perform rotary operation in corresponding angle according to the rotary operation command; receiving the position clicked by a user on the three-dimensional graph; and judging whether the position clicked on the three-dimensional graph conforms to the preset unlocking strategy or not, if so, the interface is unlocked. In the scheme for unlocking the multi-dimensional visual space interface in a single-face touch screen, the invention provides brand new operation experience and the unlocking scheme for multi-dimensional visual space interface for users, and the password setting is improved to a brand new breaking difficulty.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
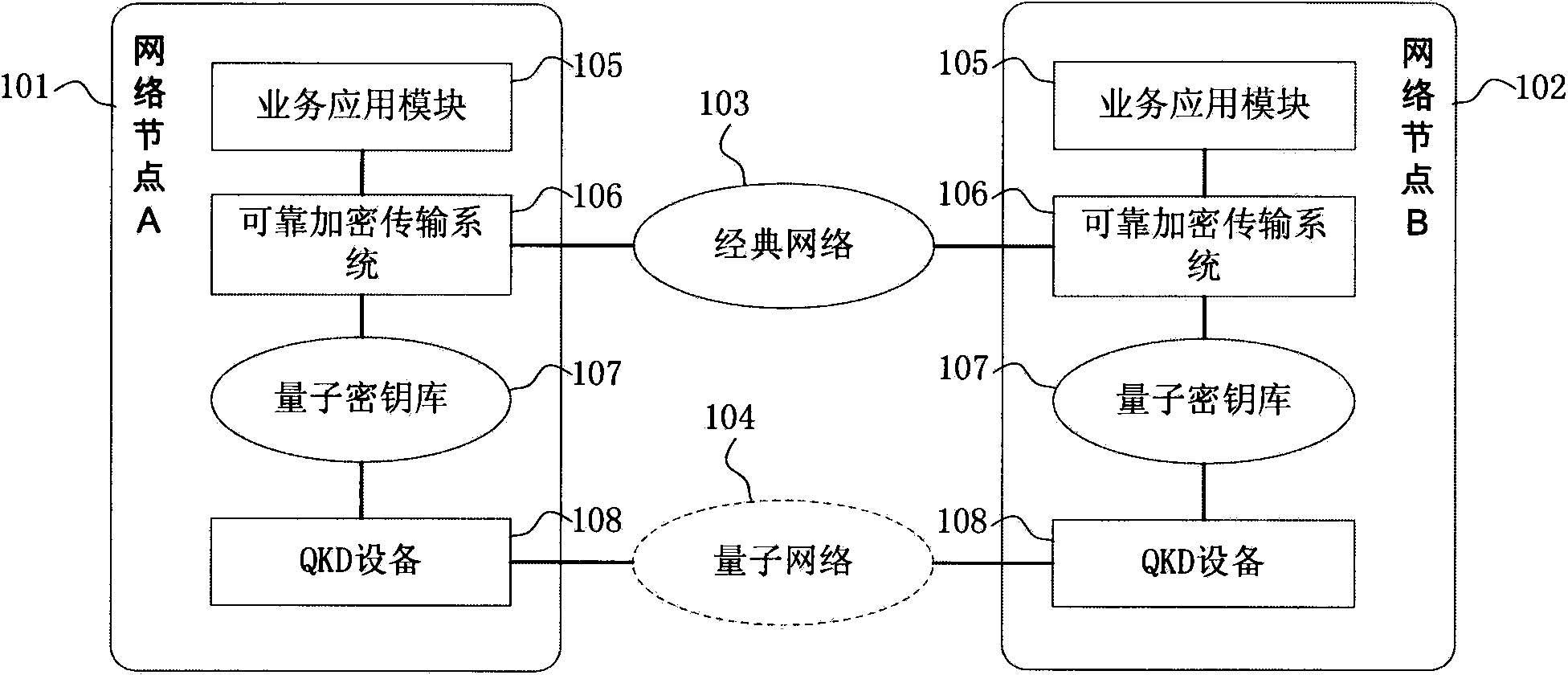
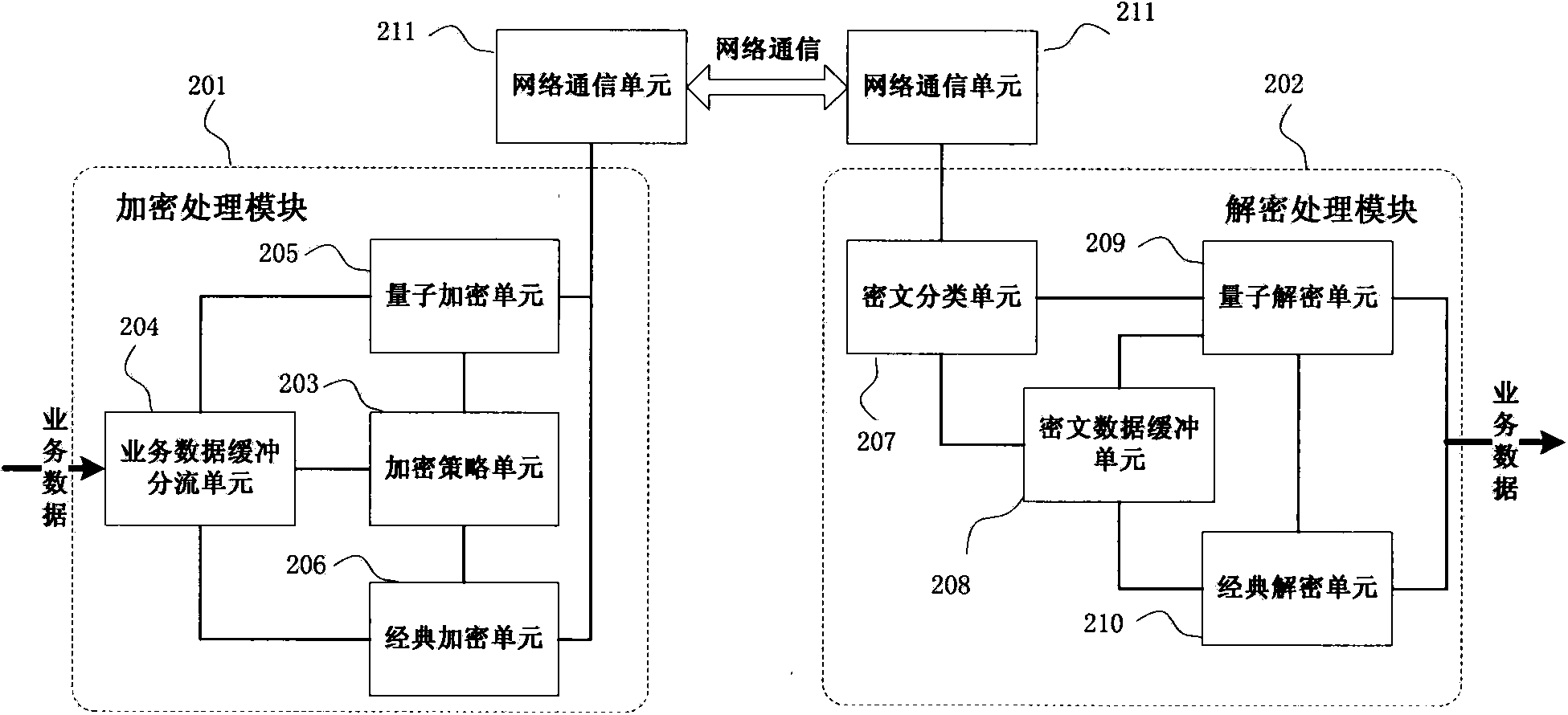
Reliable encryption transmission system and method of quantum cryptography network
ActiveCN103840936AImprove continuityImprove reliabilityKey distribution for secure communicationSynchronising transmission/receiving encryption devicesCiphertextDependability
The invention provides a reliable encryption transmission system of a quantum cryptography network. The reliable encryption transmission system comprises an encryption processing module and a decryption processing module, the encryption processing module is composed of an encryption strategy unit, a service data buffering shunt unit, a classic encryption unit and a quantum encryption unit, and the decryption processing module is composed of a cryptograph classification unit, a cryptograph data buffering unit, a classic decryption unit and a quantum decryption unit. Meanwhile, the invention further provides a reliable encryption transmission method of the quantum cryptography network. The classic encryption mode and the quantum one-time pad encryption mode are adopted for transmitting service data in a shunt mode, the shunt proportion of the service data can be timely and correspondingly changed according to changes of the quantum secret key supply-demand relationship, on the basis that the safety is guaranteed, the continuity of service data encryption transmission is improved, and the reliability of service data encryption transmission is improved. Meanwhile, the consumption of quantum secret key data is reduced, quantum secret key generation loads of the quantum cryptography network are reduced, and the cost of service data encryption transmission of the quantum cryptography network is reduced.
Owner:SHANDONG INST OF QUANTUM SCI & TECH
Data encryption, decryption and transmission methods and systems
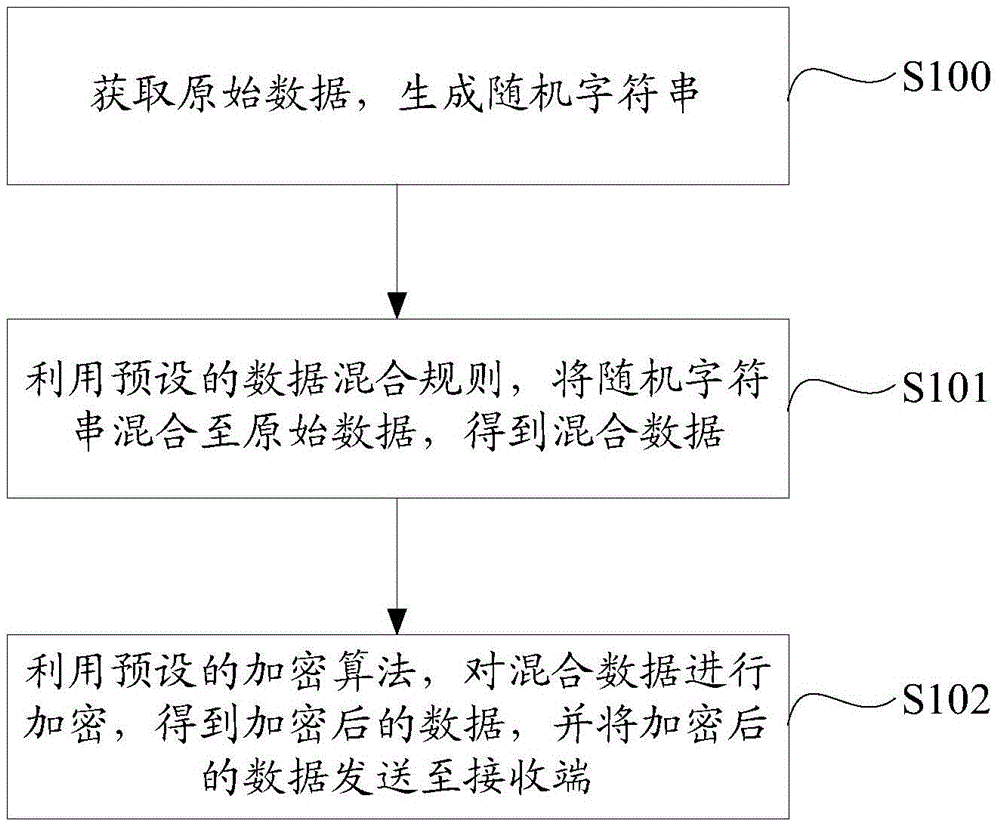
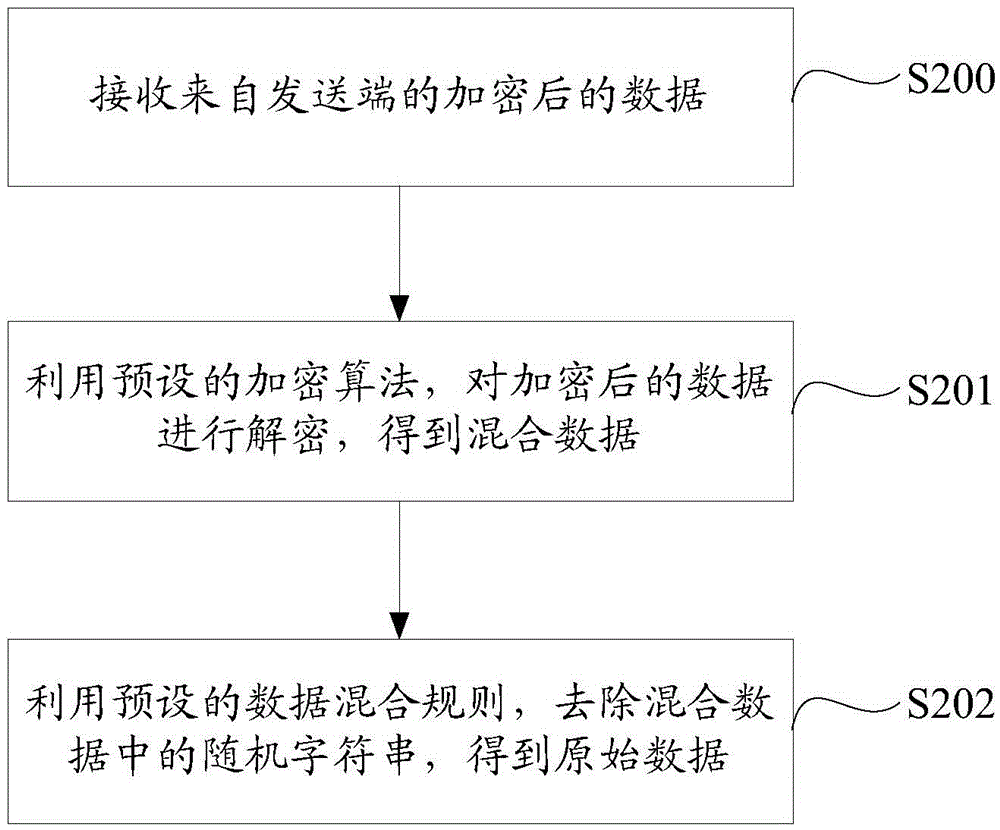
InactiveCN105591737AIncrease the difficulty of crackingImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareOriginal data
The invention discloses data encryption, decryption and transmission methods and systems. The data encryption method comprises the steps of: obtaining original data, and generating a random character string; utilizing a preset data mixing rule, mixing the random character string to the original data, and obtaining mixed data; and utilizing a preset encryption algorithm to encrypt the mixed data, obtaining encrypted data, and sending the encrypted data to a receiving end. According to the invention, for either a symmetric encryption mode or an asymmetric encryption mode, dual insurance by the random character string and an encryption key exists, and even if the same secret key is used to encrypt the same original data, different encrypted data is obtained because of the adding of the random character string, so that the decryption difficulty of the encrypted data is enhanced, and the safety of the encrypted data is further improved.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
Method for realizing locking of user number by wireless terminal device, unlocking method and device
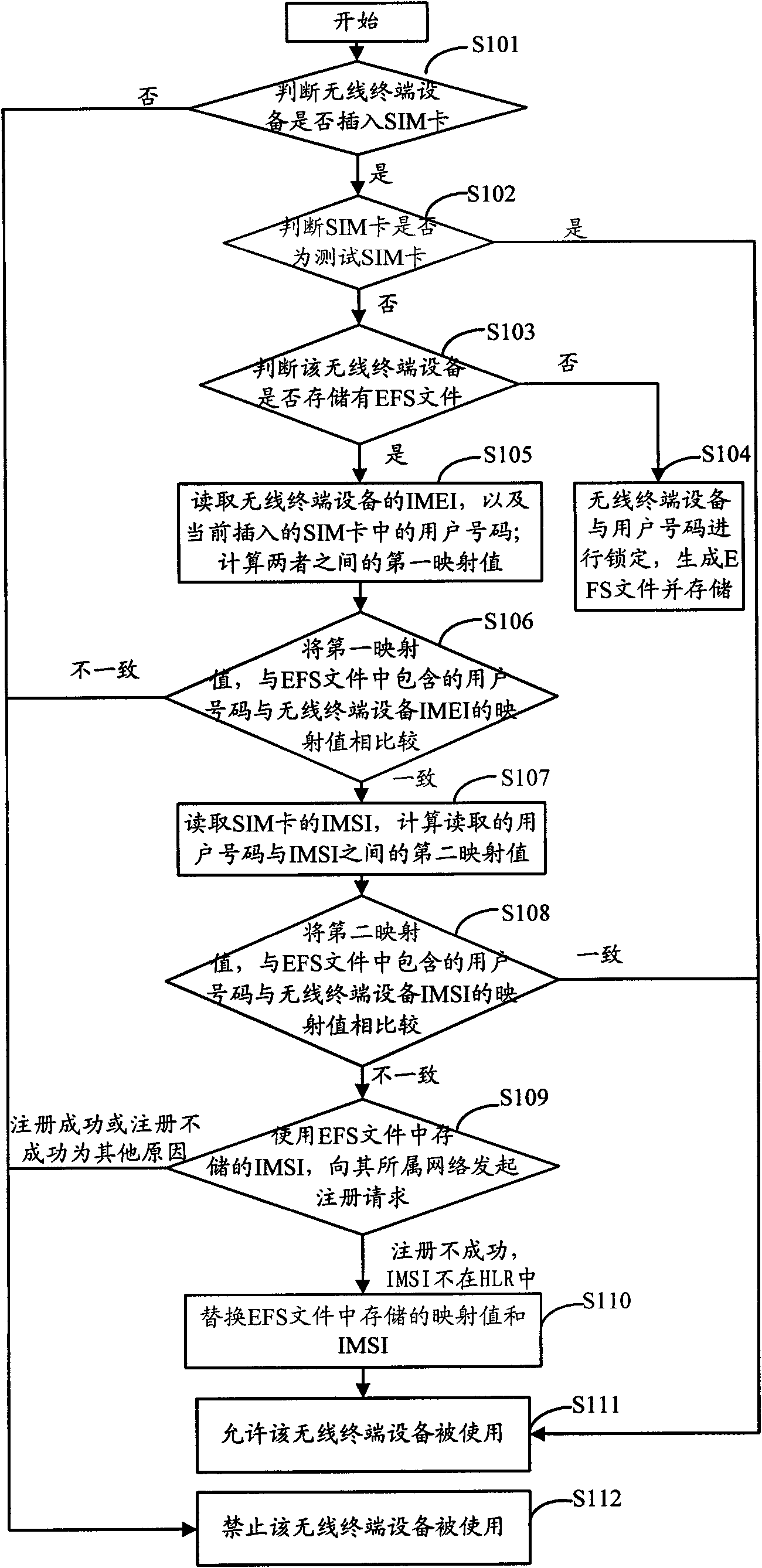
InactiveCN101616401AStrong implementation flexibilityThe unlocking process is simple and convenientSecurity arrangementNetwork data managementTerminal equipmentComputer science
The invention discloses a method for realizing locking of a user number by a wireless terminal device, an unlocking method and a device. The method for realizing the locking of the user number by the wireless terminal device comprises the following steps: reading IMEI of the wireless terminal device and the current user number which is stored in an inserted SIM card and pre-distributed to the wireless terminal device; calculating a first mapped value between the IMEI and the user number; reading IMSI of the SIM card, and calculating a second mapped value between the user number and the IMSI; comparing the calculated first mapped value and the second mapped value, the mapped value between the IMEI pre-stored by the wireless terminal device and the user number and the mapped value between the IMSI and the user number; and when the comparison results are consistent, permitting the wireless terminal device to be used. The invention establishes a binding relation between the wireless terminal device and the user number, has high safety, and is simple and convenient to use.
Owner:ZTE CORP
Encrypted storage method and encrypted storage device
InactiveCN105721390AIncrease the difficulty of crackingEnsure safetyDigital data protectionSecuring communicationPlaintextComputer hardware
The invention provides an encrypted storage method and an encrypted storage device. The method comprises the steps of calculating the salted Hash value of a plaintext password, combining the salted Hash value and a corresponding random salt value according to a preset rule to get a ciphertext password corresponding to the plaintext password, and storing the ciphertext password. Through the technical scheme of the invention, the difficulty in ciphertext password cracking is improved, and the safety of user accounts is guaranteed.
Owner:ALIBABA GRP HLDG LTD
Optical-fiber secret communication device and data encryption method thereof
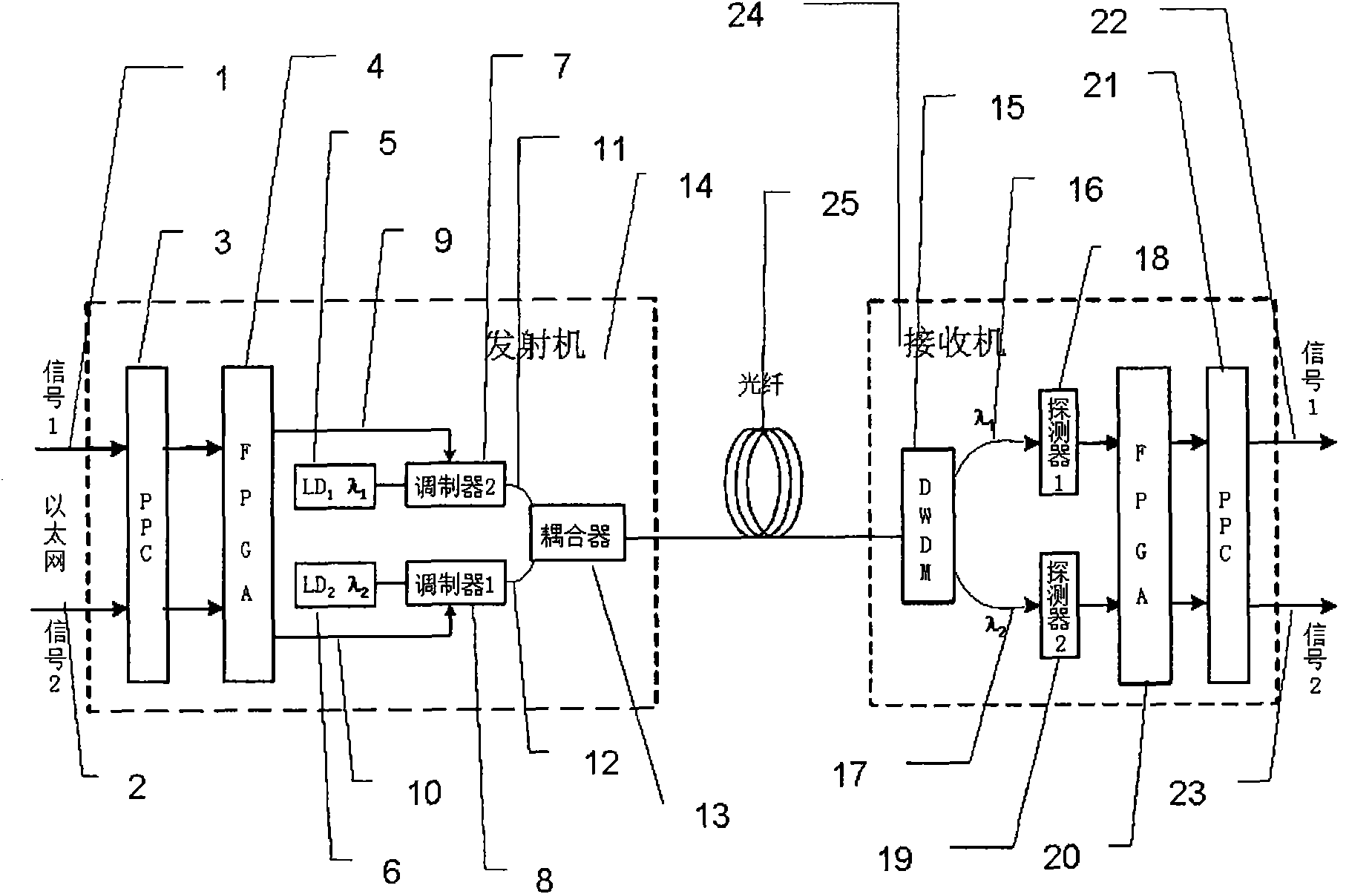
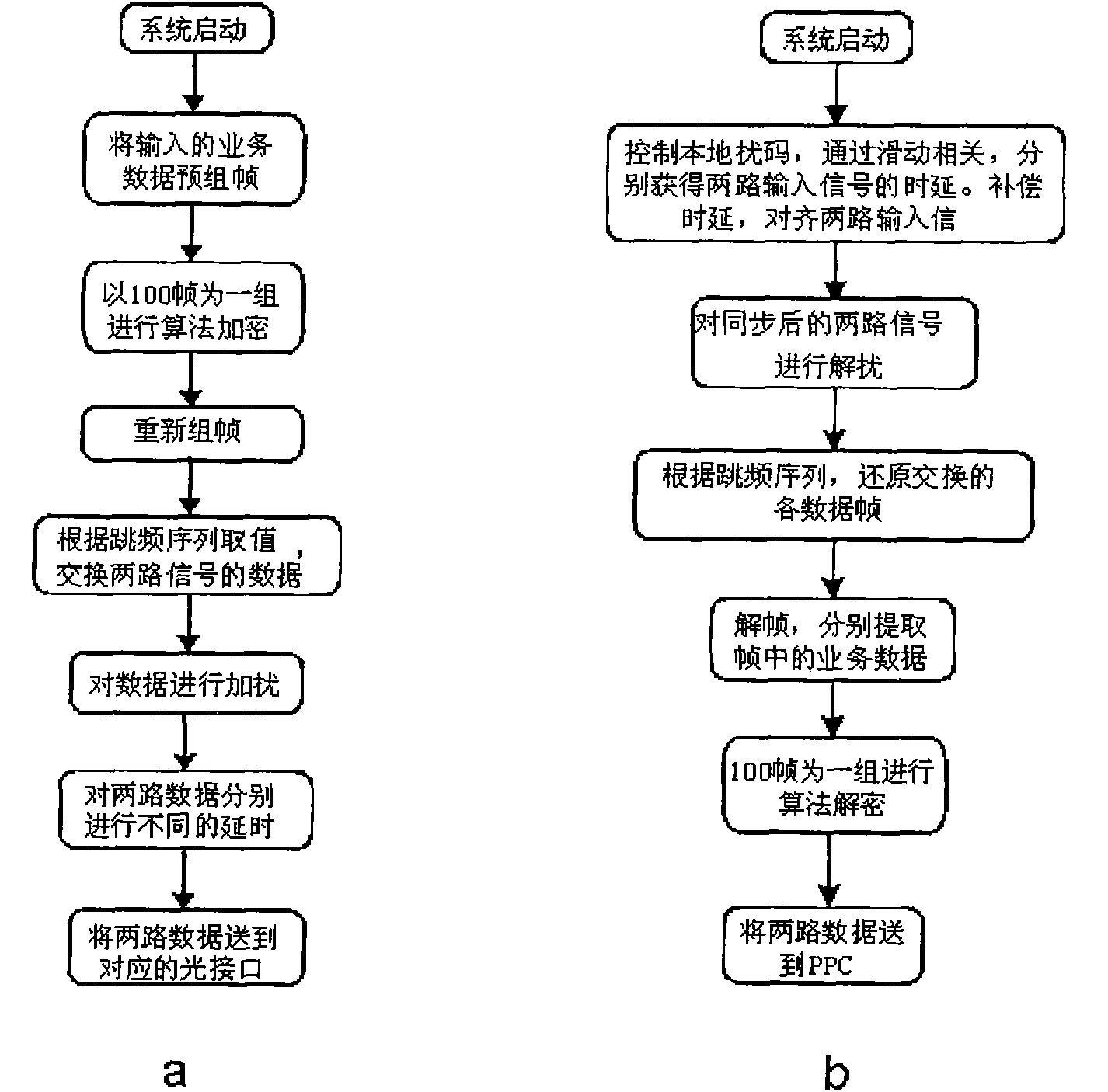
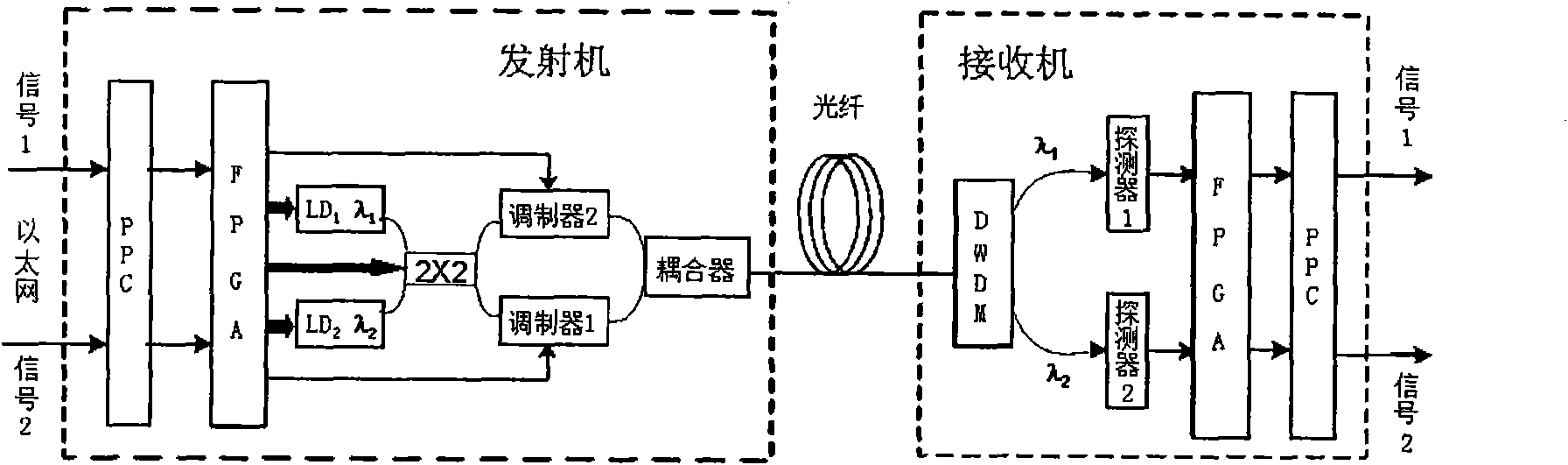
ActiveCN102055584AContinuous reductionIncrease the difficulty of crackingEncryption apparatus with shift registers/memoriesElectromagnetic transmission optical aspectsOptical fiber couplerField-programmable gate array
The invention discloses an optical-fiber secret communication device and a data encryption method thereof. The device is formed by connecting a transmitter and a receiver through an optical fiber. The transmitter comprises a PPC power PC) processor unit, a field-programmable gate array testing plate, a light-transmitting module, an optical-fiber coupler and a connecting optical fiber; and the receiver comprises a wavelength division multiplexer, a connecting optical fiber, a light detector, a field-programmable gate array testing plate, a PPC processor unit and a signal output interface. At atransmitting end, two paths or multiple paths of input data are retransmitted through a PPC and then sent to the light-transmitting module with two or multiple wavelengths after the encryption processing by an FPGA (Field-Programmable Gate Array) to convert electrical signals into light signals. At a receiving end, two- or multi-wavelength signals respectively enter the light detector to be converted into electrical signals and then retransmitted and output after the encryption by the FPGA by the PPC. By utilizing the invention, the secrecy of transmitted data is improved, and the data decryption difficulty is improved.
Owner:INST OF SEMICONDUCTORS - CHINESE ACAD OF SCI
Protecting method and running method and device and system for Android platform application program
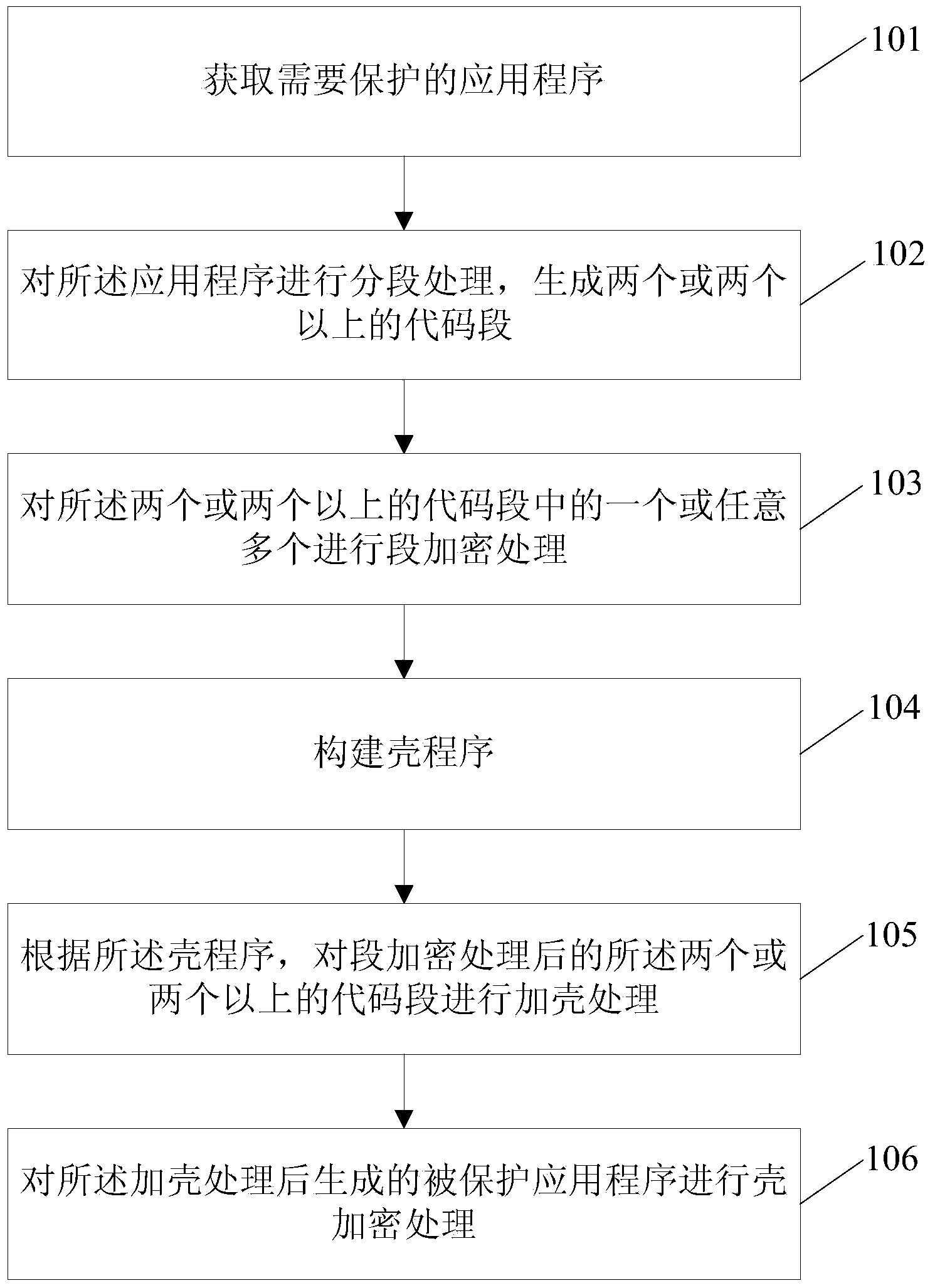
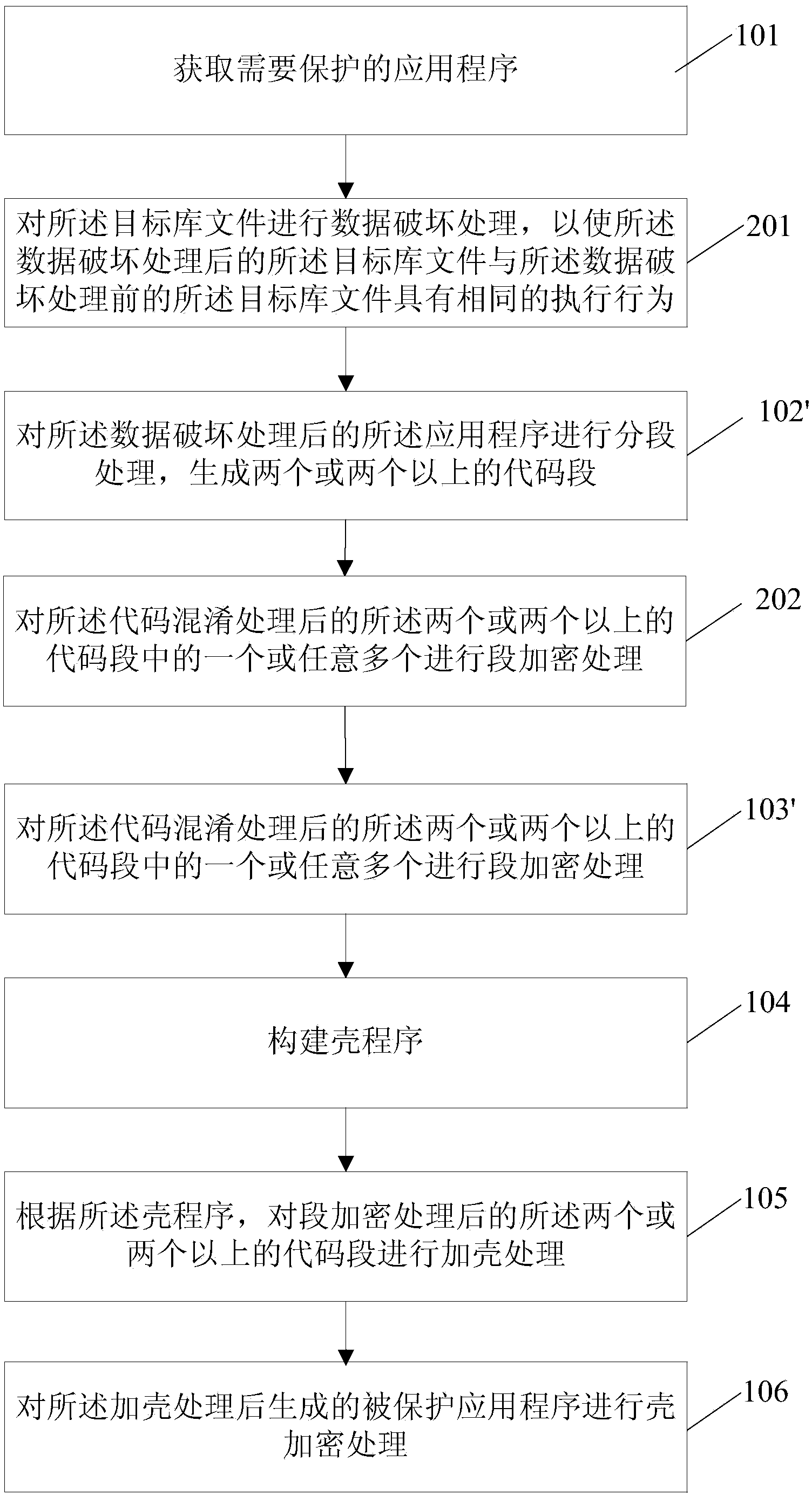
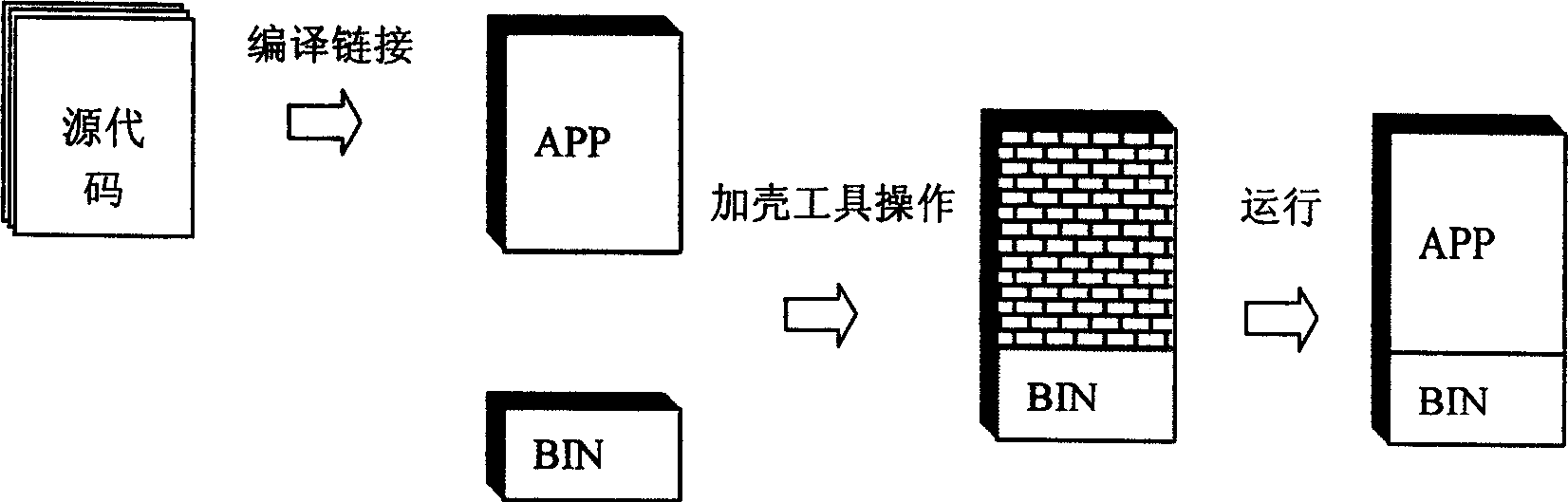
InactiveCN104102860AIncrease the difficulty of crackingImprove protection strengthProgram/content distribution protectionApplication softwareCode segment
The invention relates to a protecting method and a running method and device and system for an Android platform application program. The protecting method comprises the steps of obtaining an application program needing to be protected; performing segment handling on the application program and generating two or more code segments; performing segment encryption processing on one or random more of the two or more code segments; constructing a shell procedure; according to the shell procedure, performing shell adding processing on the two or more code segments having undergone segment encryption processing, and performing shell encryption processing on the protected application program generated after the shell adding processing. According to the technical scheme, the solving difficulty of the application program is increased, and protecting strength of the application program is further improved.
Owner:BEIJING QIHOO TECH CO LTD +1
File encryption method
InactiveCN103279693AIncrease the difficulty of crackingIncrease the difficultyProgram/content distribution protectionComputer hardwareEncryption
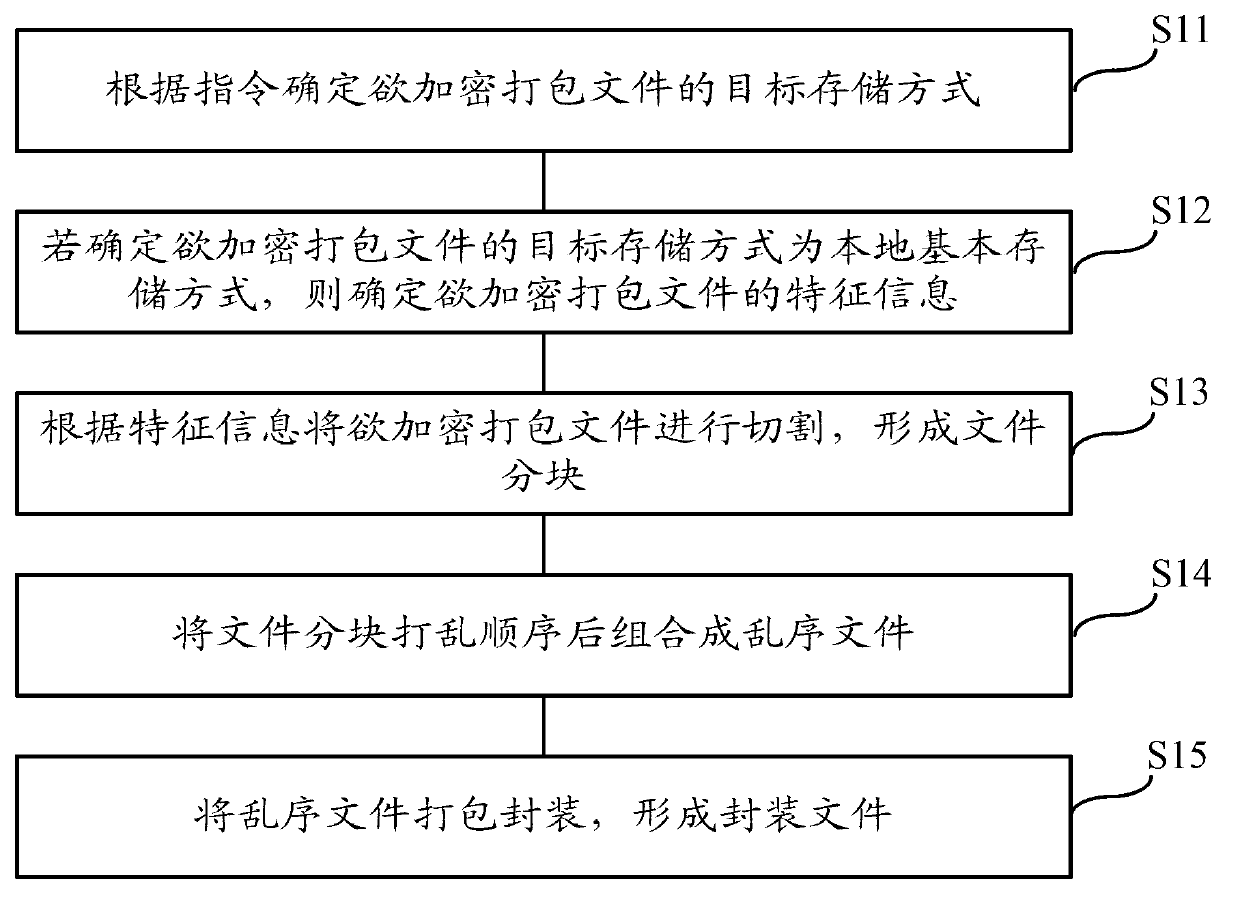
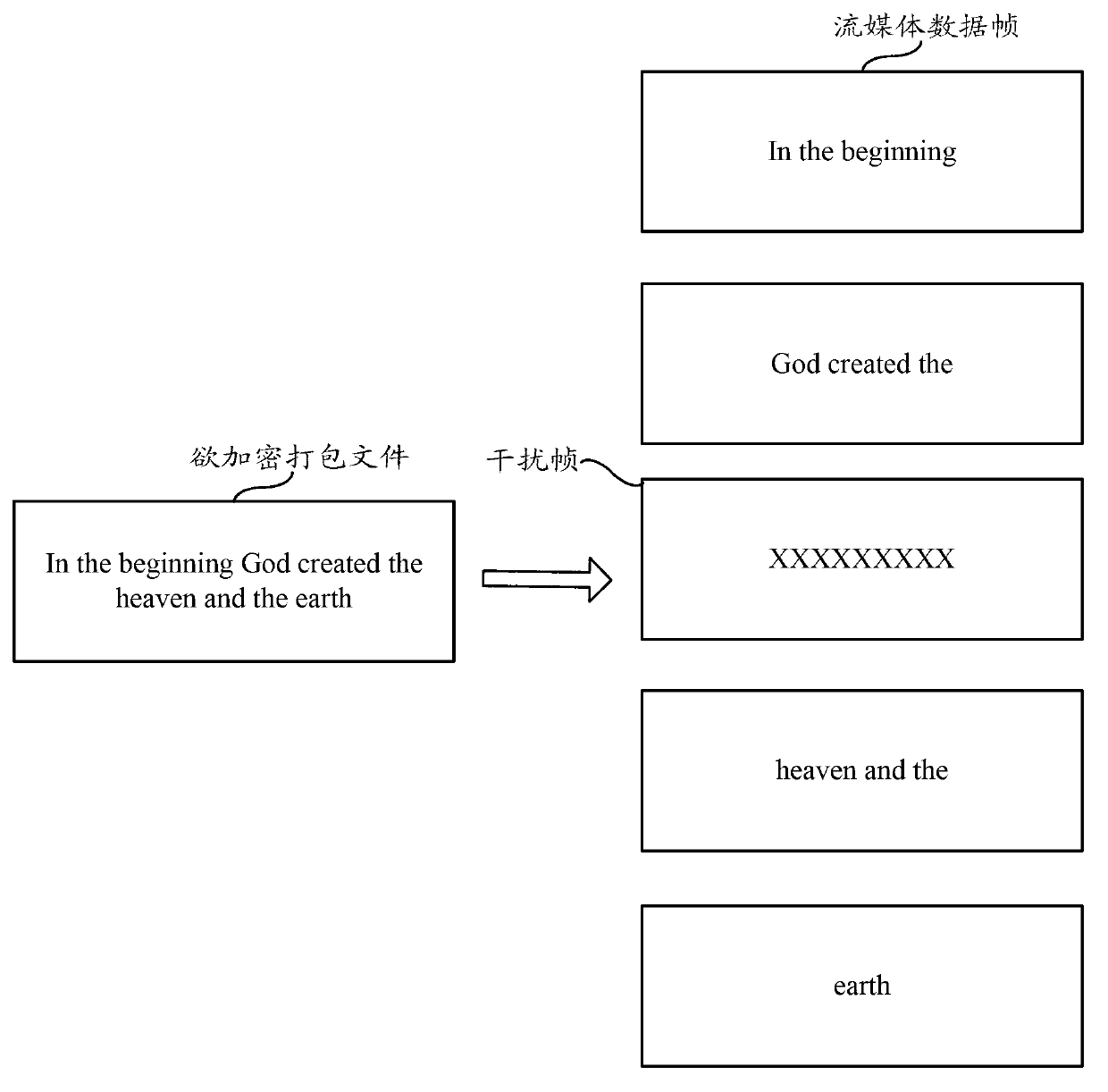
The invention relates to the technical field of encryption, in particular to a file encryption method which comprises the steps that a target storing mode of a packed file to be encrypted is determined according to an instruction; if the determined target storing mode of the packed file to be encrypted is a local basic storing mode, the feature information of the packed file to be encrypted is determined; the packed file to be encrypted is cut according to the feature information to form file blocks; the sequence of the file blocks is disorganized, then the file blocks form an out-of-order file; the out-of-order file is packed and packaged to form a packaged file. According to the file encryption method, obtaining the packed file to be encrypted in the packaged file is complex, the difficult of the process of obtaining file content in the packaged file is increased, and accordingly safety and reliability of encryption of the encrypted packaged file can be improved.
Owner:HUBEI NORMAL UNIV
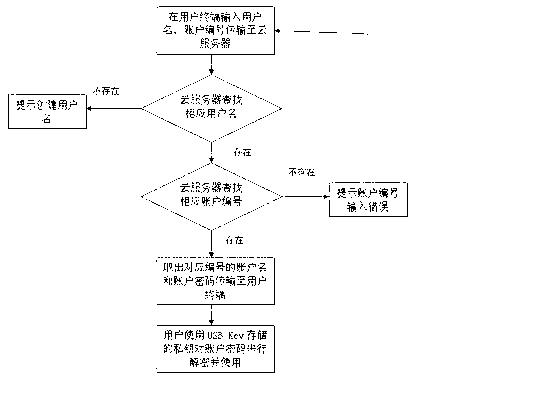
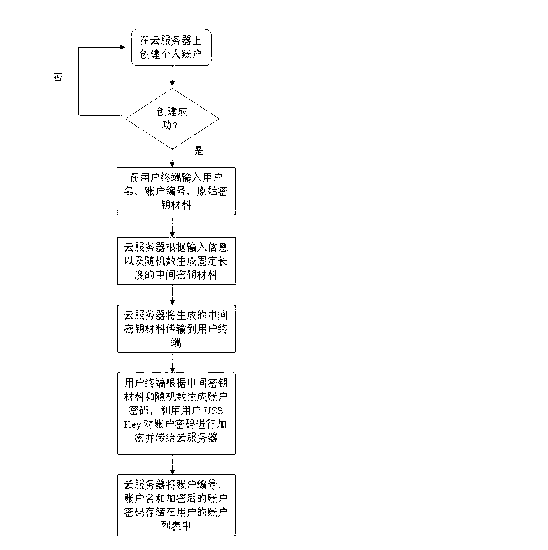
Account management system and account management method based on cloud service
ActiveCN102843422AIncreased complexityImprove securityUser identity/authority verificationResourcesUser needsSecure transmission
The invention relates to an account management system and an account management method based on cloud service. The account management system comprises a user terminal, a cloud server, and a secure transport protocol module connected between the user terminal and the cloud server. The account password is generated at the client side by executing the Hash algorithm twice according to the account number provided by the user, the original key material, a random number generated by a cloud server and the random number generated by a user side USB (Universal Serial Bus) Key, and the account password is stored in the cloud server after being encrypted by the user side USBKey, and when the user needs the account information, the user can read the account password information stored in the cloud server by inputting the account name and the account number. According to the method and the system provided by the invention, the account password with fixed length is generated by two times of execution of Hash algorithm, thus, the account password cannot be decrypted easily; the account password encrypted by the USBKey is stored in the cloud server, so that the security of the account password is ensured; and when the user needs the password, the user can directly read the password without memorizing the password, so that the password management is convenient and easy to carry out.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
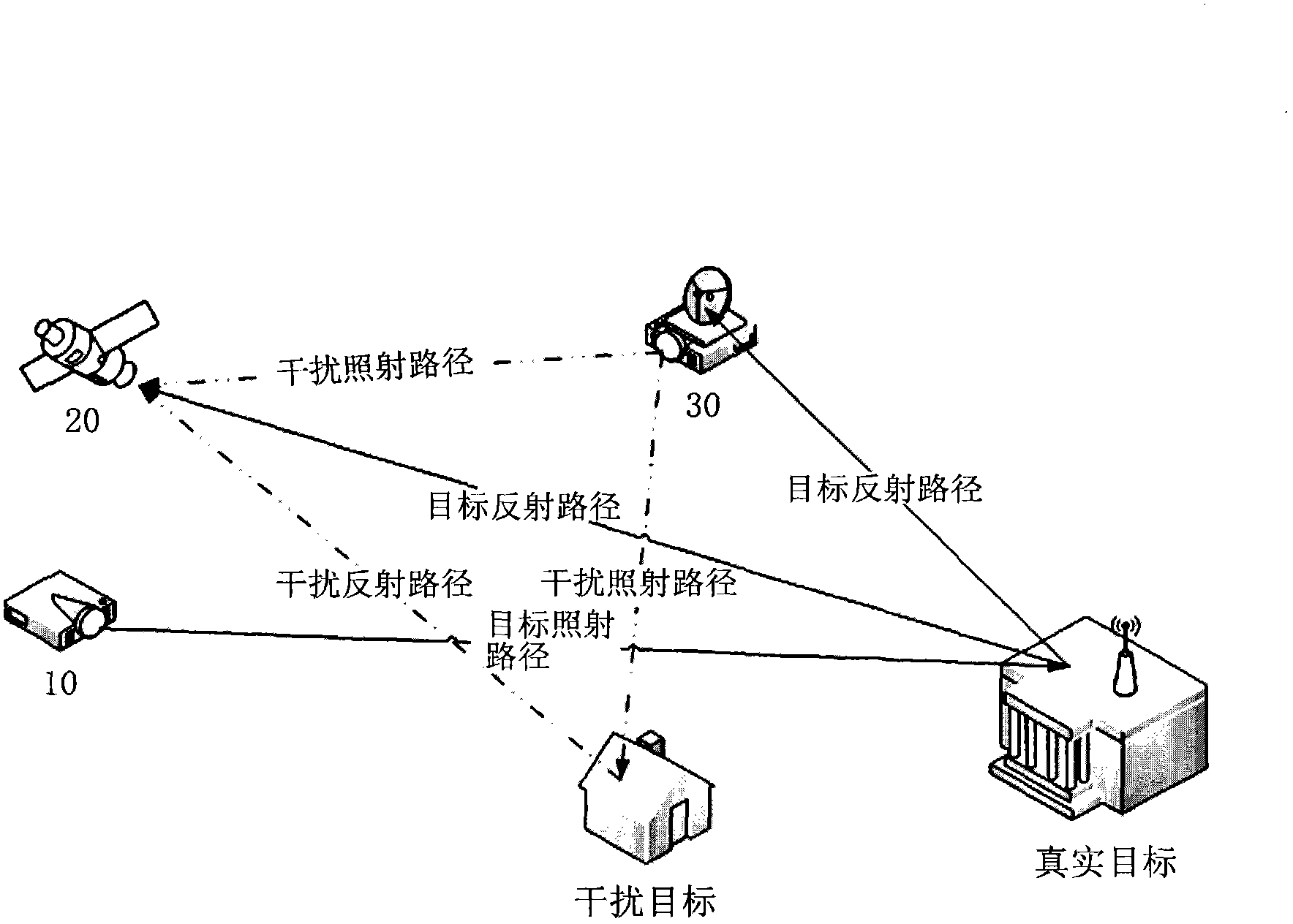
Confrontation method for laser active jamming
InactiveCN103675793AIncreased complexityImprove concealmentWave based measurement systemsPhase shiftedImage resolution
The invention discloses a confrontation method for laser active jamming. A laser locating and tracking system comprises an emitter and a receiver; the method comprises the following steps: the emitter encodes laser detecting signals according to the finite random cycle encoding mode, so that intervals of all laser detecting pulses in one encoding cycle are changed randomly; the emitter introduces the random phase shift Delta i on the all laser detecting pulses, so that the laser detecting pulses have variable phase differences, wherein one random phase shift value is distributed to each laser detecting pulse from the random phase shift sequence; any random phase shift value in the random phase shift sequence is greater than or equal to the time resolution of the receiver, and is smaller than the predetermined minimum period t0 of interference pulses. The confrontation method and system for the laser active jamming of the laser locating and tracking system, disclosed by the embodiment of the invention, both have excellent confrontation effect on the present common three laser active jamming modes and complex jamming modes thereof.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
User verification processing method, user device and server
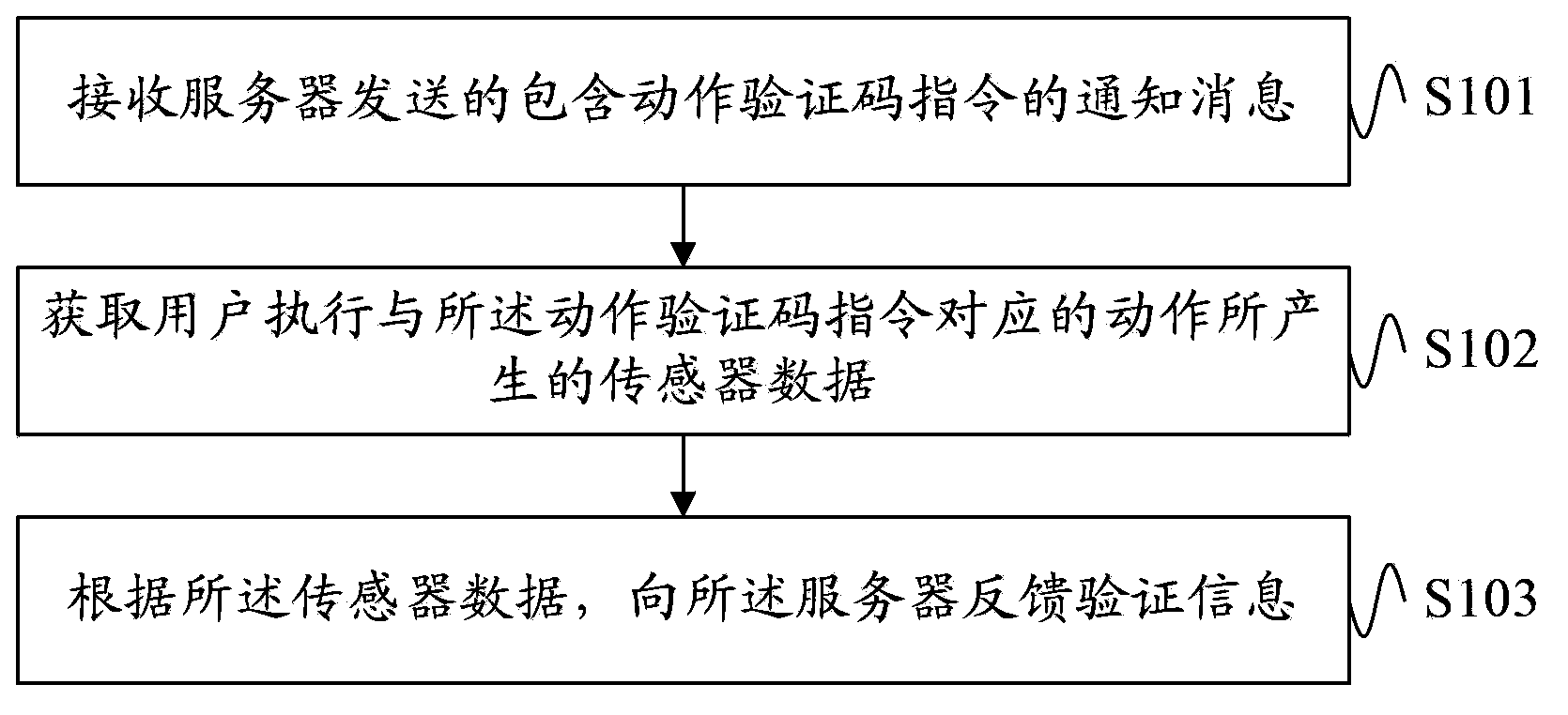
InactiveCN103685195AAvoid crackingIncrease the difficulty of crackingParticular environment based servicesUser identity/authority verificationUser verificationUser equipment
Owner:HUAWEI TECH CO LTD
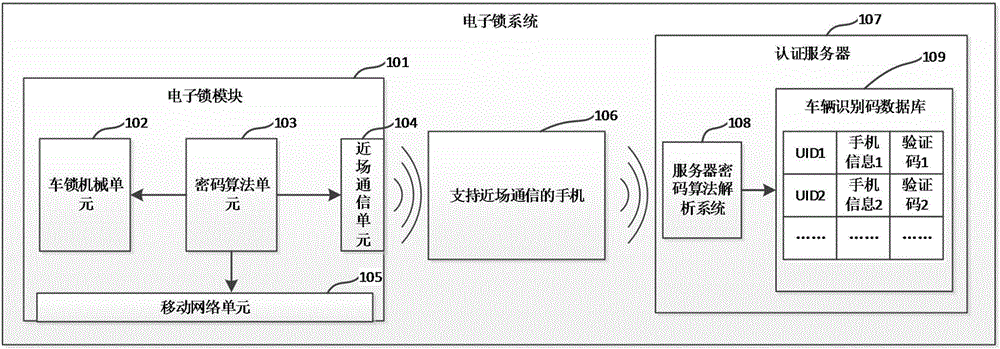
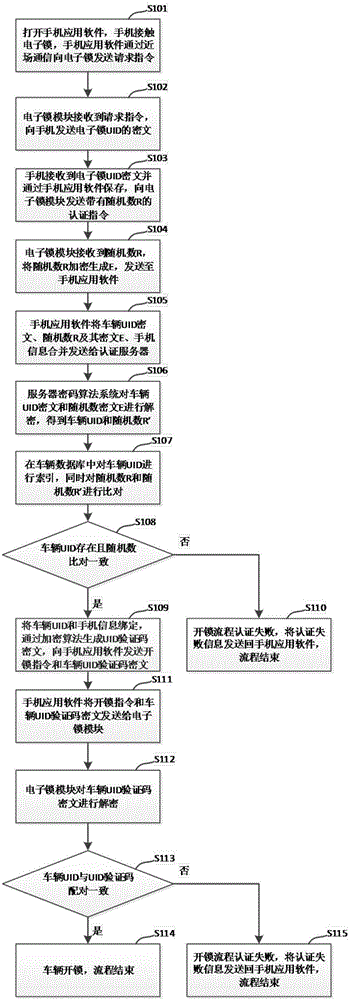
Shared bike electronic lock system and unlocking method thereof
InactiveCN107181742ASolve the problem of being easily copied and forgedSolve the defect of defacementMetering/charging/biilling arrangementsAnti-theft cycle devicesBike sharingComputer module
The invention discloses a shared bike electronic lock system and an unlocking method thereof. The electronic lock system comprises an electronic lock module, a mobile phone supporting near-field communication and an authentication server. The electronic lock module is an electronic lock supporting the near-field communication and the mobile communication modes and having a cipher algorithm. The mobile phone supporting the near-field communication is a smart phone with the near-field communication technology. The authentication server comprises a cipher algorithm analysis system and a vehicle identification code database. According to the invention, by use of the near-field communication technology, encrypted message interaction between the electronic lock and the authentication server is improved; user experience is improved; and information safety is ensured.
Owner:ZHUHAI CRYSTONE TECH CO LTD
Code obfuscation method and code running method and device
InactiveCN107038354AIncrease confusionSolve technical issues with low confusion ratesProgram/content distribution protectionProgramming languageObfuscation
The invention discloses a code obfuscation method and a code running method and device. The method comprises the steps that an object name to be called is acquired through preset static replacement operation, wherein the static replacement operation is a function configured in a first target file of a target application in advance, and the first target file is used for recording installation information of the target application; whether the object name to be called is contained in a preset obfuscation table is judged, wherein the obfuscation table is generated according to the first target file and a second target file and used for indicating the corresponding relation between the object name and an obfuscation name, and the second target file is used for recording declaration information of the target application; and if the object name to be called is contained in the obfuscation table, the obfuscation name corresponding to the object name to be called is searched for in the obfuscation table and output. Through the method, the technical problem that in the prior art, the obfuscation rate of Java layer codes of an application is low is solved.
Owner:ALIBABA GRP HLDG LTD
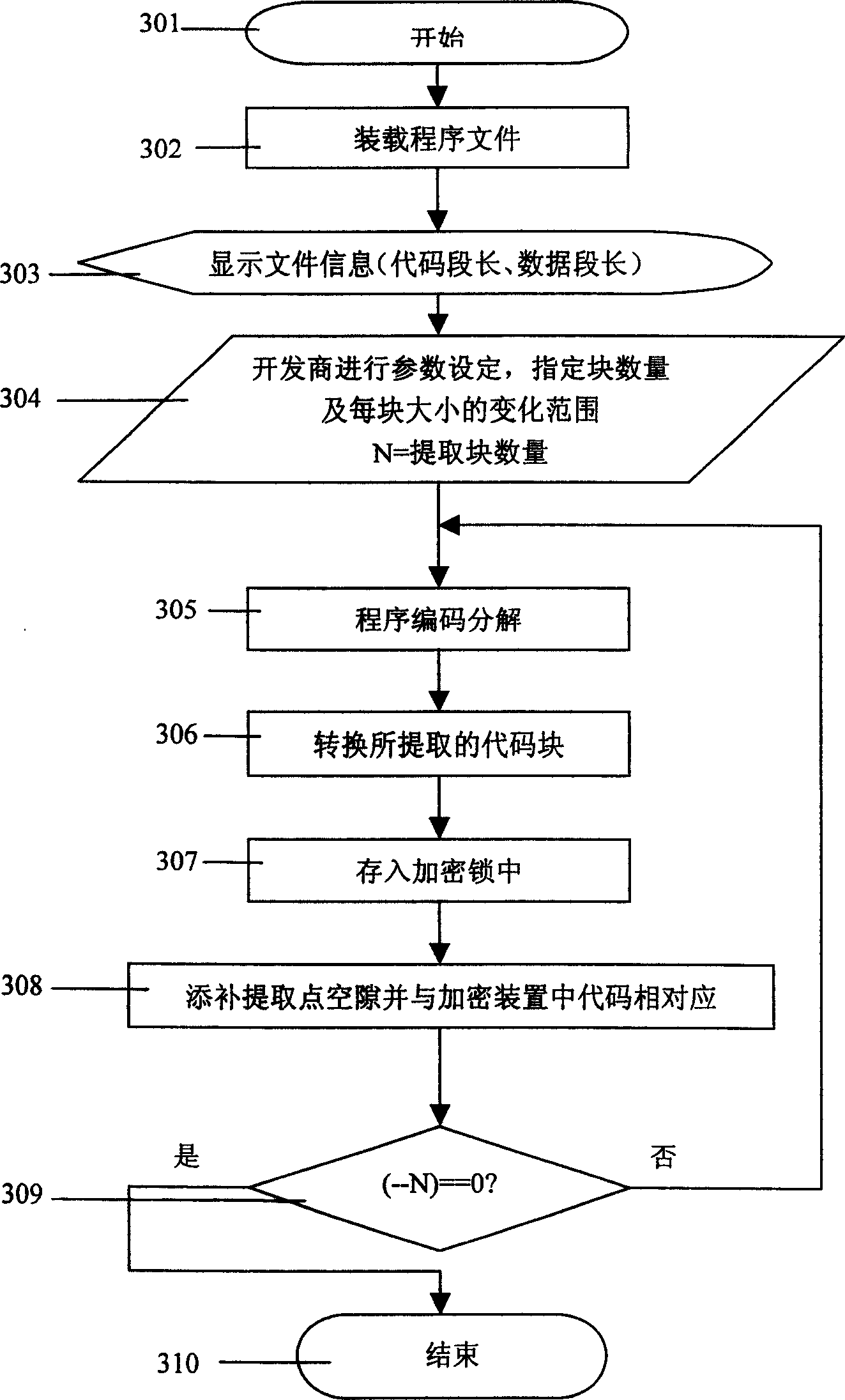
Software copy right protecting method for extracting partial code to enciphed device from software
ActiveCN1749915AIncrease the difficulty of crackingNo burdenDigital data processing detailsSoftware engineeringSoftware development
The present invention relates to software copyright protecting method, and is especially software copyright protecting method by extracting partial codes from program file to the enciphering device. The compiled program file has its codes decomposed into partial codes running in the enciphering device and the other in the computer, and this makes it possible for the software developer to raise the enciphering safety degree without increasing load in developing software protecting functional module. The software copyright protecting method is superior to traditional shell enciphering method.
Owner:北京坚石诚信科技有限公司
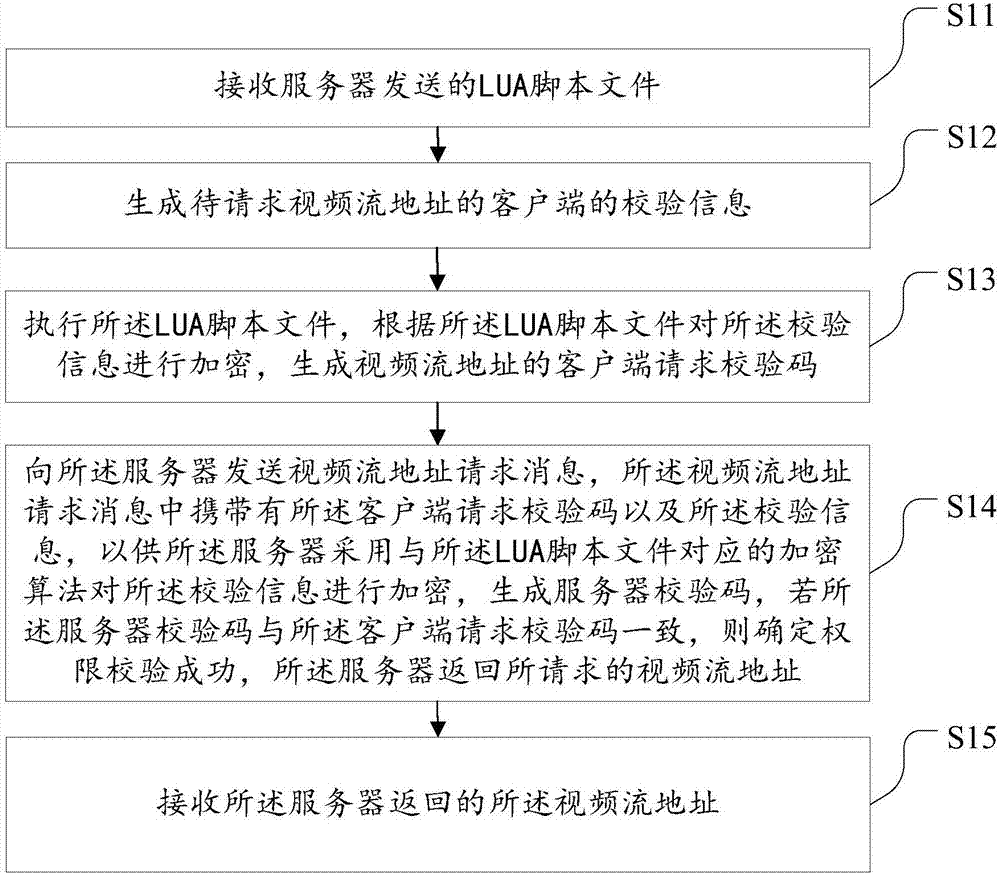
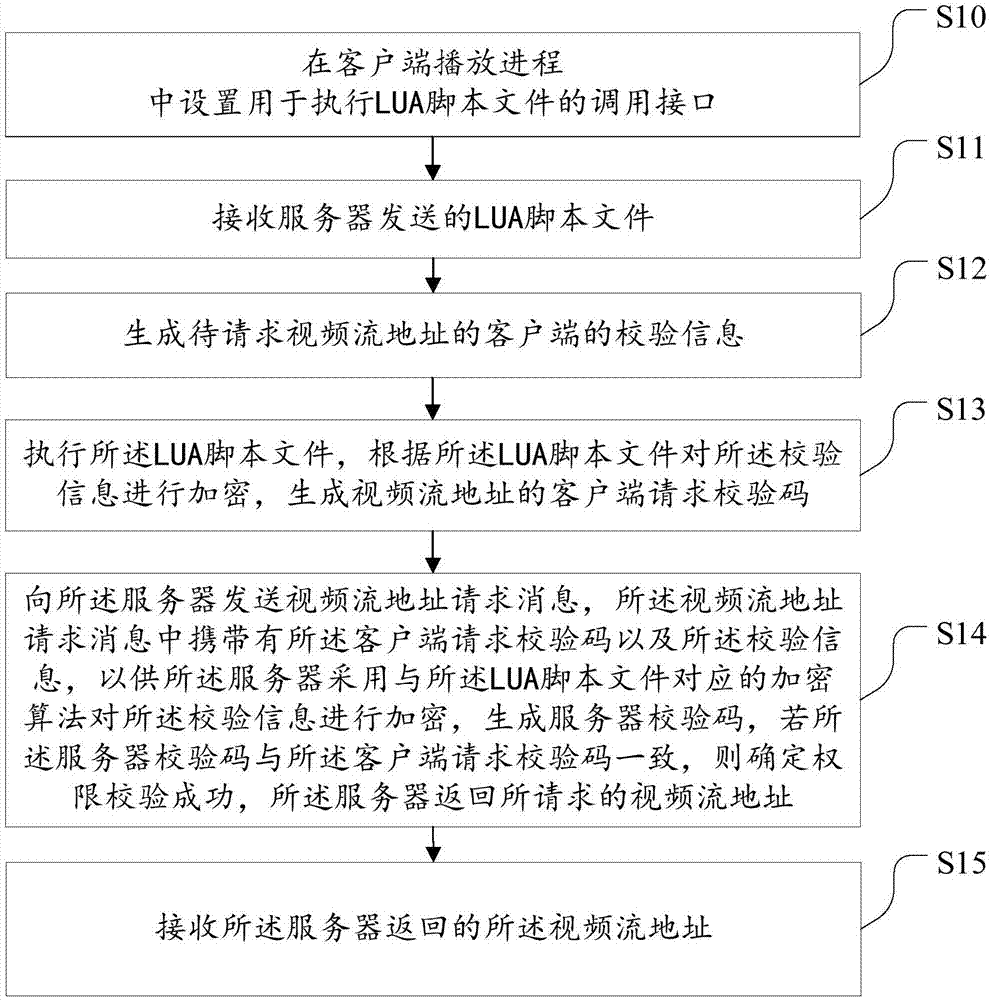
Authority check method and device for video playing
InactiveCN107094261AImplement authentication verificationIncrease the difficulty of crackingSelective content distributionComputer hardwareLive video
Embodiments of the invention disclose an authority check method and device for video playing. The method comprises the following steps of receiving an LUA script file sent by a server; generating check information of a client of a to-be-requested video stream address; executing the LUA script file, encrypting check information according to the LUA script file and generating a client request check code; sending a video stream address request message to the server, wherein the video stream address request message carries the client request check code and the check information, so that the server adopts a corresponding encryption algorithm to encrypt the check information in order to generate a server check code, and if the server check code is consistent to the client request check code, the server returns the requested video stream address; and receiving the video stream address. According to the method and the device, authentication and verification of the video stream address can be effectively realized, the safety of a live video process is improved and the user experience is improved.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Data transmission method and data transmission device
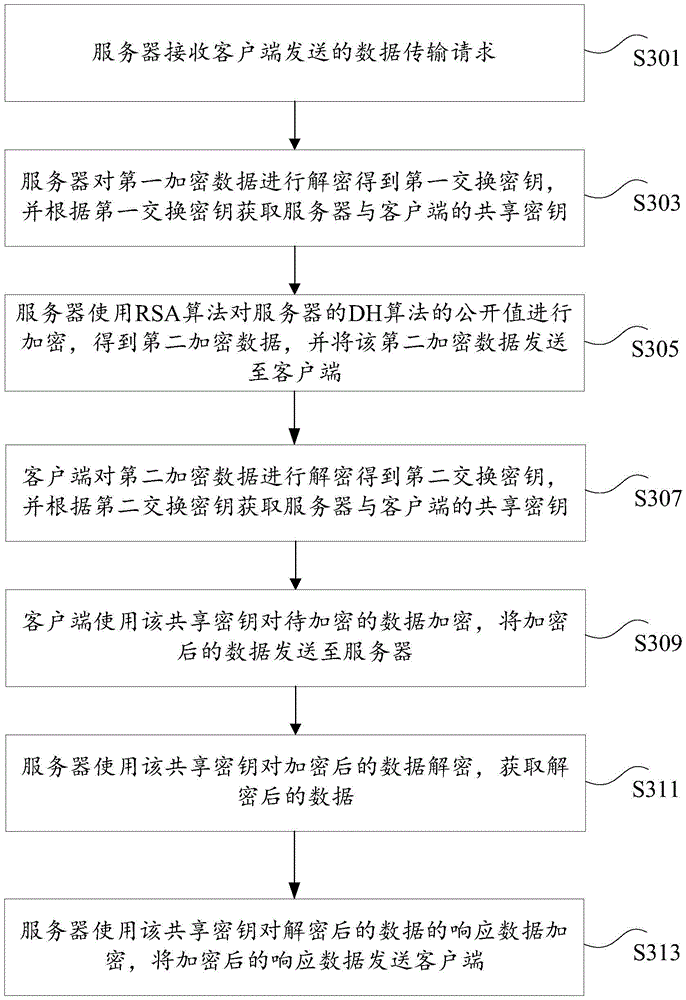
ActiveCN105553951ATroubleshoot technical issues with poor securityIncrease the difficulty of crackingMultiple keys/algorithms usagePublic key for secure communicationComputer terminalData transmission
The invention discloses a data transmission method and a data transmission device. The method comprises the following steps: a first terminal acquires a data transmission request sent by a second terminal, wherein the data transmission request at least carries first encrypted data obtained by using a private key of the second terminal to encrypt a first exchange key of the second terminal; the first terminal uses a public key of the second terminal to decrypt the first encrypted data to get the first exchange key, and acquires a shared key of the first terminal and the second terminal according to the first exchange key; and the first terminal uses the shared key to encrypt to-be-transmitted data to get encrypted transmitted data, and sends the encrypted transmitted data to the second terminal. The technical problem that the existing encryption algorithm is of poor security in data transmission is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
DNA coding based encryption system and encryption method
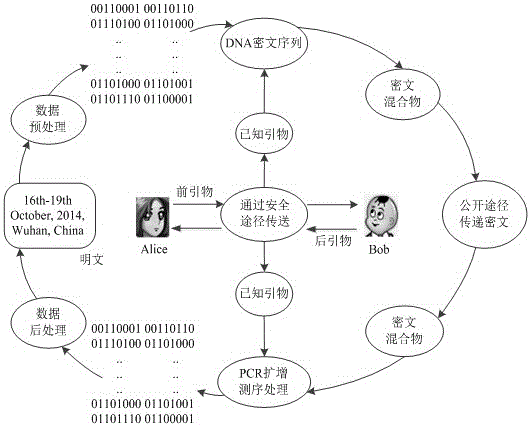
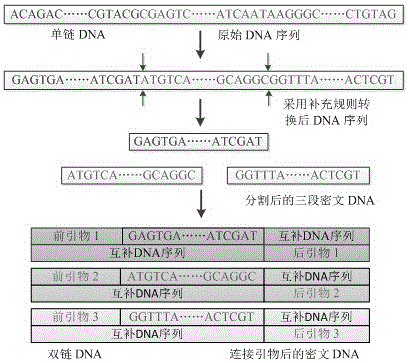
InactiveCN105119717AIncrease the difficulty of decipheringIncrease the difficulty of crackingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesInformation transmissionPassword
The invention belongs to the technical field of information security in communication transmission, and particularly relates to a DNA encryption system and an encryption method. The system comprises an encryption key, an information conversion portion, an information encryption portion, an information transmission portion, a decryption key and an information decryption portion, wherein the encryption key and the decryption key are primer sequences; and information encryption refers to that information is converted and coded and then corresponds to A, T, C, G bases in DNA in a one-to-one mode according to a predetermined rule. The encryption system and the encryption method provided by the invention can realize automatic operation of corresponding code conversion, encryption and decryption by depending on biological problem setting and biological technology development and by being matched with development of corresponding computer information technologies at the same time, have the characteristics of good compatibility with other encryption methods, high automation degree, simple key, high password cracking difficulty, safer information transmission and the like, has good application values, and can provide better reference for other new encryption systems at the same time.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
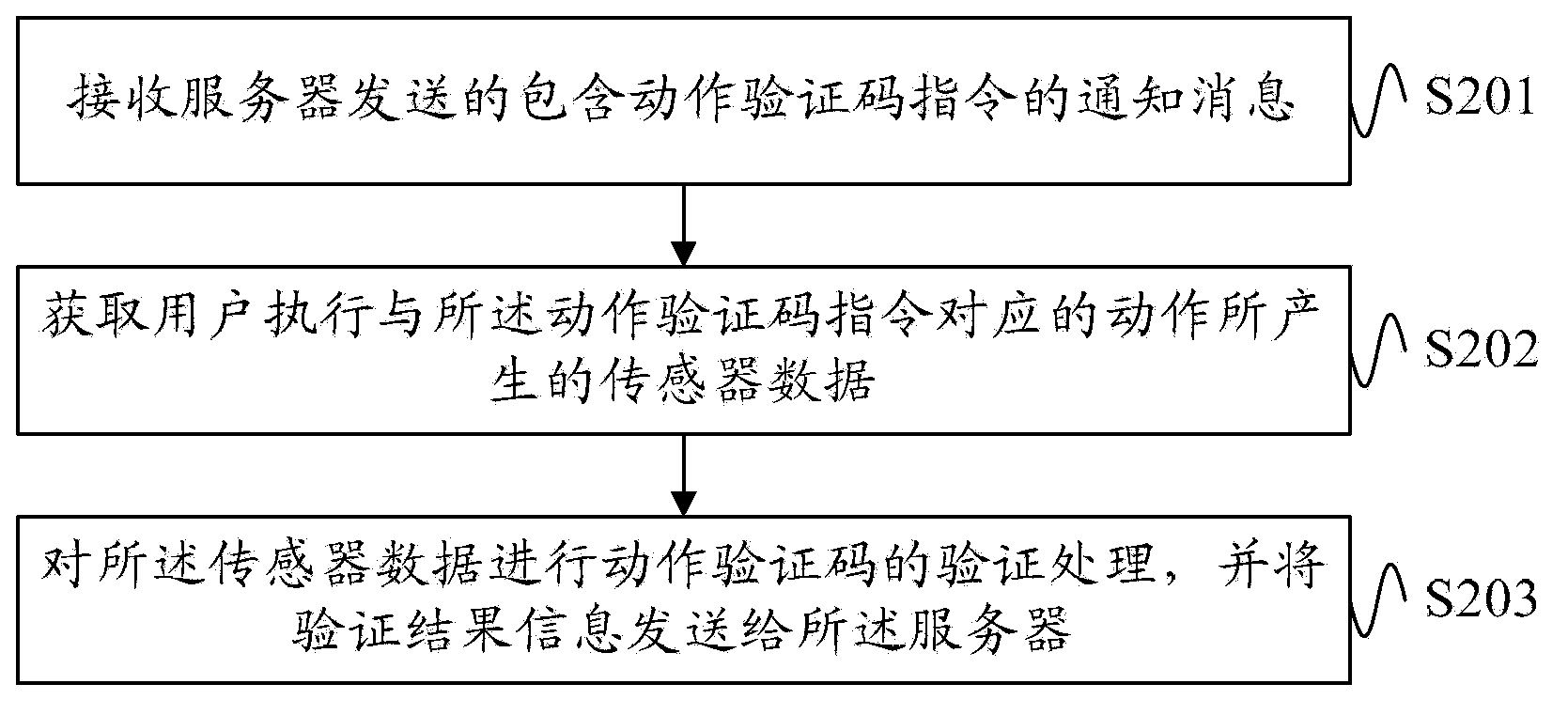
Identity authentication method, identity authentication device and identity authentication system
InactiveCN105323073ATo achieve the purpose of authenticationIncrease the difficulty of crackingUser identity/authority verificationAuthentication systemAuthentication information
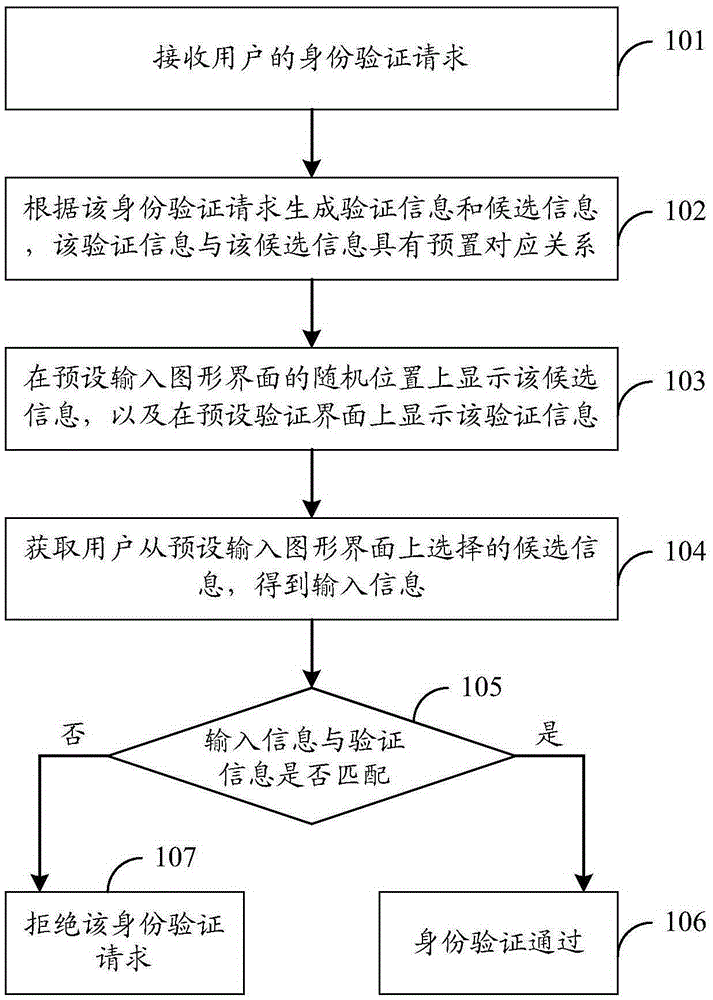
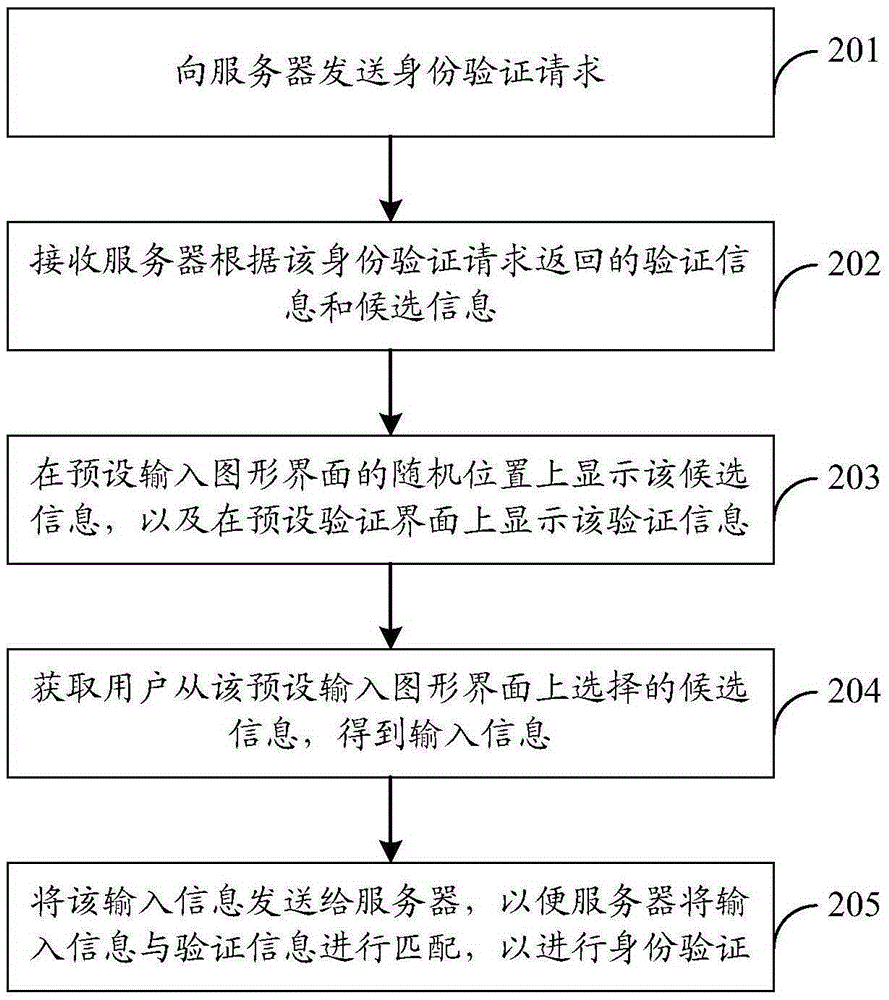
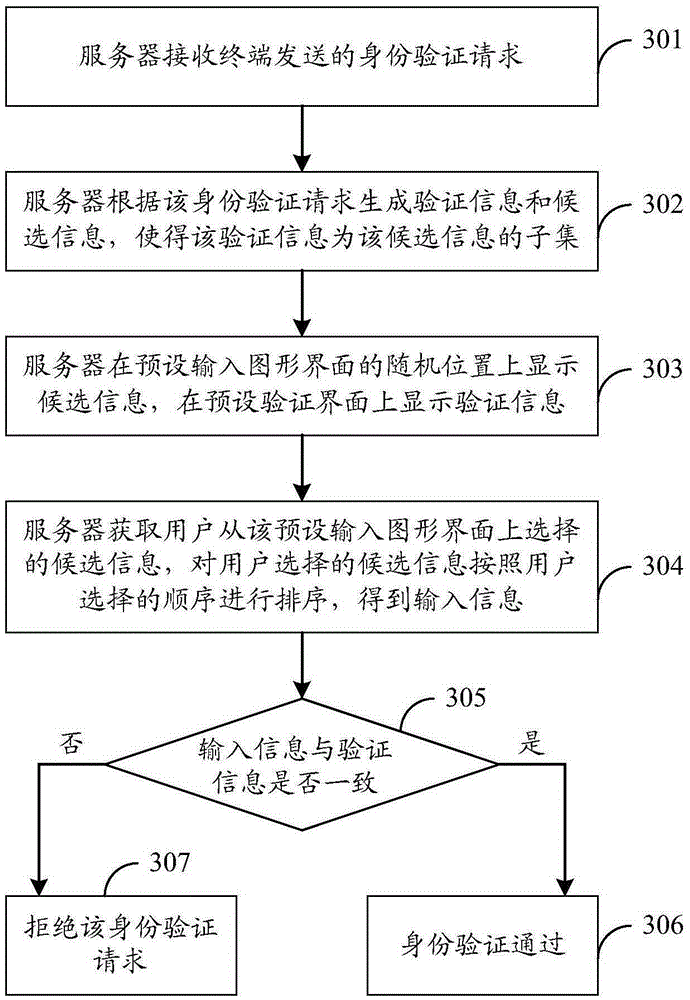
The embodiment of the invention discloses an identity authentication method, an identity authentication device and an identity authentication system. According to the embodiment, the identity authentication method comprises the steps of when the identity authentication request of a user is received, generating authentication information and candidate information based on an identity authentication request; displaying the candidate information at a random position of a preset input graphical interface; displaying the authentication information in a preset authentication interface, wherein the authentication information and the candidate information have a preset corresponding relationship; then obtaining the candidate information selected by the user from the preset input graphical interface so as to obtain an input message; matching the input information with the authentication information; if the input information matches with the authentication information, determining that the identity authentication is successful; otherwise, if the input information does not match with the authentication information, refusing the identity authentication request. The scheme can improve safety.
Owner:TENCENT TECH (SHENZHEN) CO LTD
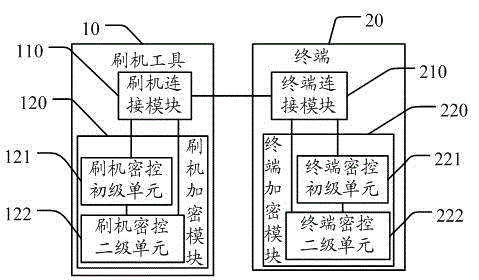
Method and device for improving terminalself-flashing safety through ciphertext handshaking
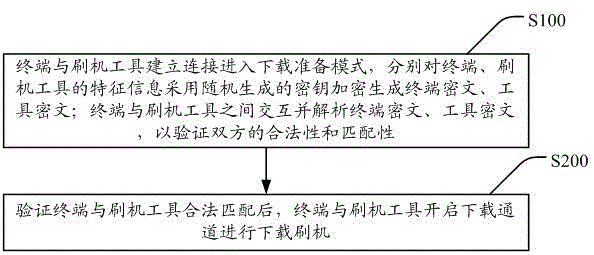
InactiveCN104065482AImprove securityIncrease the difficulty of crackingUser identity/authority verificationProgram loading/initiatingHandshakingCiphertext
The invention discloses a method and device for improving terminal self-flashing safety through ciphertext handshaking. The method includes the steps that A, a terminal is connected with a flashing tool so as to enter a downloading preparation mode, feature information of the terminal and feature information of the flashing tool are respectively encrypted through secret keys randomly generated, and therefore a terminal ciphertext and a tool ciphertext are generated; the terminal and the flashing tool interact, the terminal ciphertext and the tool ciphertext are analyzed, and therefore legality and matching performance of the terminal and the flashing tool are verified; B, after it is verified that the terminal and the flashing tool are legally matched, a downloading channel is started by the terminal and the flashing tool for downloading and flashing. According to the method and device, after it is verified that the terminal and the flashing tool are legal, the terminal and the flashing tool are controlled to start the downloading channel to conduct downloading and flashing; due to the fact that the secret keys used for encryption each time are generated randomly, the deciphering difficulty is greatly increased, and the ciphertexts can be prevented from being deciphered; meanwhile, downloading and flashing can be conducted only after the terminal and the flashing tool are legally matched, so that safety is improved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD +1
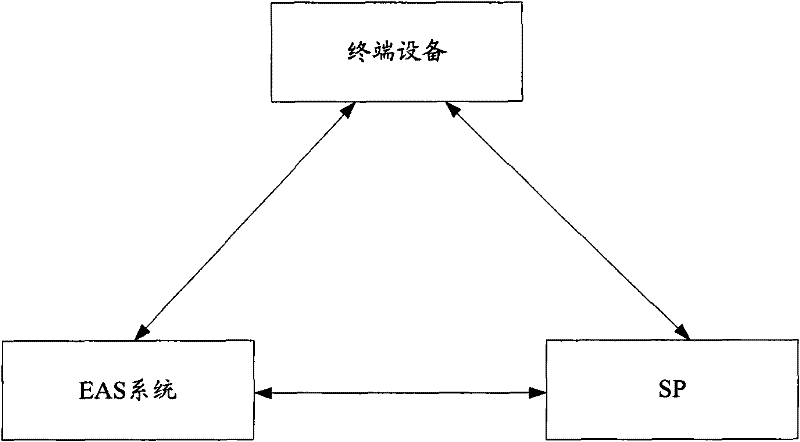
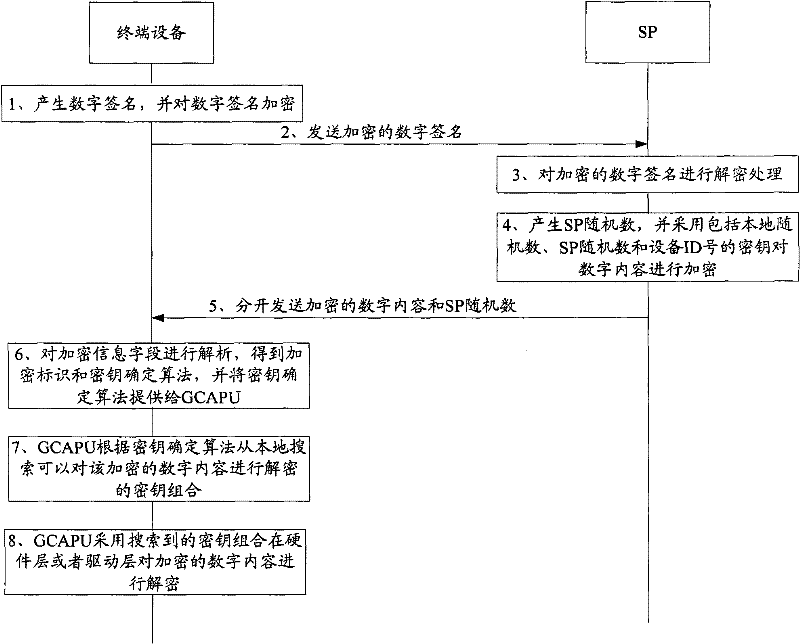
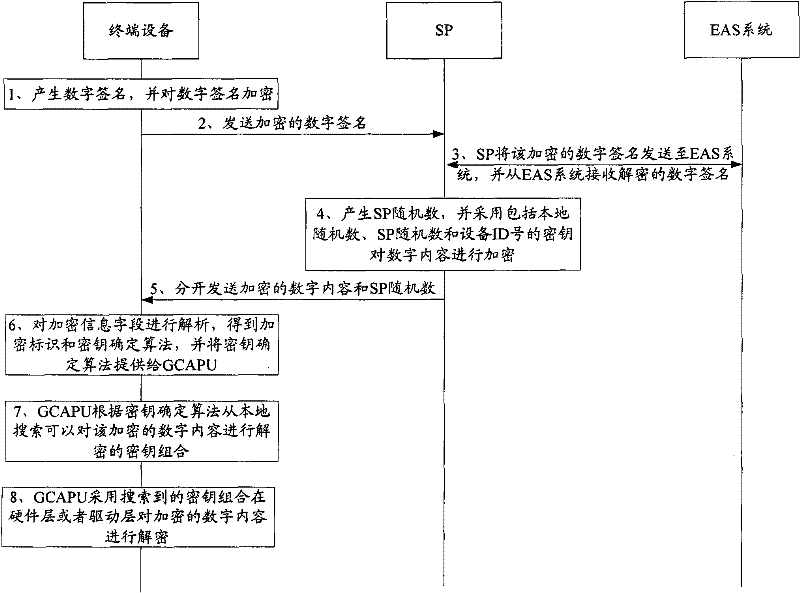
Method and system for protecting digital content
ActiveCN102279908AIncrease the difficulty of crackingImprove securityEncryption apparatus with shift registers/memoriesUser identity/authority verificationDigital signatureDigital content
The invention is suitable for the field of information safety and provides a method for protecting digital contents. The method comprises the following steps: a core processor of terminal equipment generates a digital signature, encrypts the digital signature and transmits the encrypted digital signature to an SP (Service Processor); the SP decrypts the digital signature, generates an SP random number, constitutes a key with an equipment identification number, a local random number and the SP random number, encrypts digital contents, and adds an encrypted information field comprising an encryption identifier and a key determining algorithm to the engaged head part of the digital contents; the SP separately transmits the digital contents to which the encrypted information field is added and the SP random number to the terminal equipment; and the core processor of the mobile equipment locally searches for a key combination which can be used for decrypting the encrypted digital contents according to the key determining algorithm, and decrypts the encrypted digital contents by adopting the key combination. According to the method and the system, the cracking difficulty of encrypted digital contents can be improved, the security of the digital contents is improved, and the aim of protecting the digital contents is fulfilled.
Owner:ANYKA (GUANGZHOU) MICROELECTRONICS TECH CO LTD
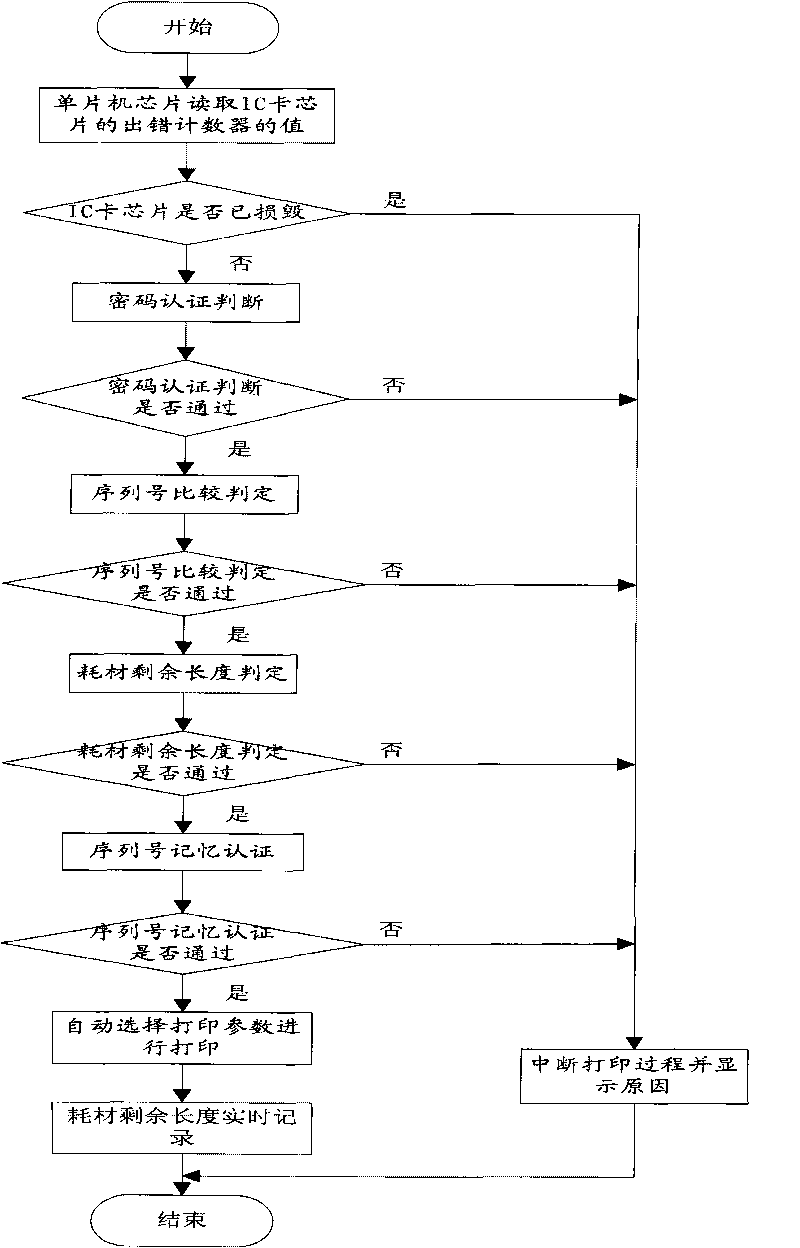
Method for identifying genuine or counterfeit printing consumable material and automatically selecting printing parameters
ActiveCN101746165ALow priceReal-time response remainingInk ribbonsSensing record carriersTime responsePassword protection
The invention discloses a method for identifying a genuine or counterfeit printing consumable material and automatically selecting printing parameters, and the method sequentially comprises the following steps: (1) authenticating and judging a password; (2) comparing and determining a serial number; (3) determining the residual length of the consumable material and recording the process in a real-time manner; (4) memorizing and authenticating the serial number; and (5) automatically selecting the printing parameters for printing; if the judgment in any step of (1), (2), (3) and (4) is no, the printing process is stopped and error information is displayed. Compared with the traditional method for identifying the printing consumable material, the method has the advantages of high imitation cost, large capacity of a storage medium, low device cost, password protection function of information, real-time response of the residual amount of the consumable material and the like.
Owner:上海威侃电子材料有限公司
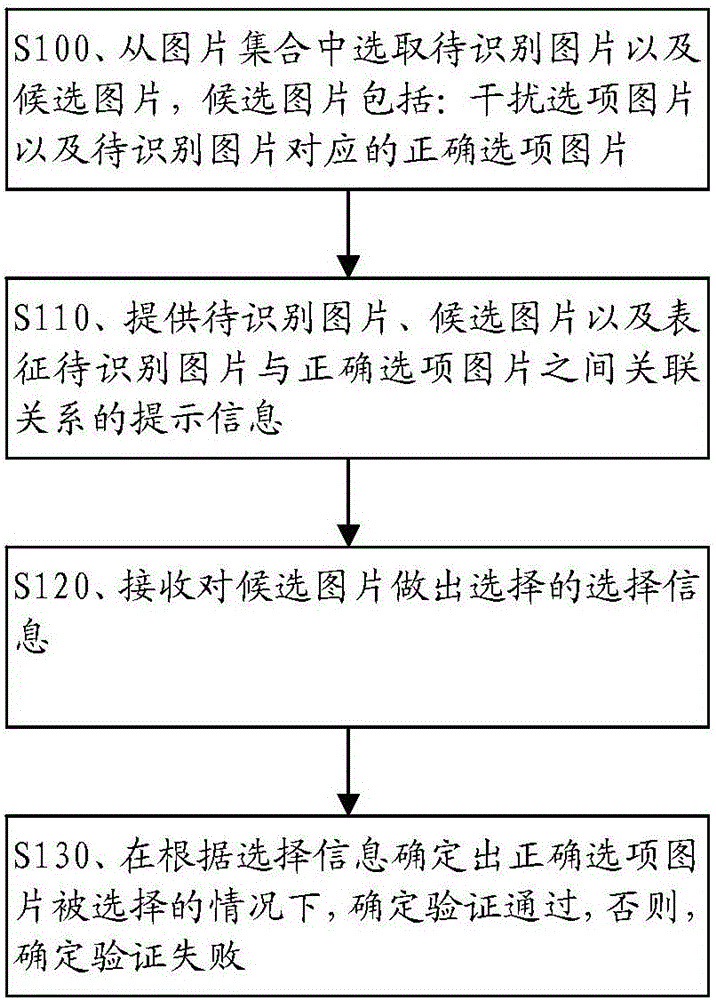
Verification method and apparatus based on image verification codes
InactiveCN106034029AAvoid crackingIncrease the difficulty of crackingUser identity/authority verificationCharacter and pattern recognitionUser inputValidation methods
The present invention provides a verification method and apparatus based on image verification codes. The method comprises selecting an image to be identified and multiple candidate images from an image gallery, wherein the candidate images comprise interference images and correct images corresponding to the image to be identified; providing hint information for the image to be identified, the candidate images, and relationships between the image to be identified and the correct images; receiving selection information of images selected from the candidate images; and determining that the verification passed when the correct images are determined to have been selected based on the selection information or, determining that verification has failed when the correct images are determined not to have been selected based on the selection information. According to technical schemes of the invention, a user is prevented from updating the verification code repeatedly or input the wrong verification code caused by that the verification code is hard to identify; verification technology based on the image verification codes is enriched, the difficulty in declassifying the image verification codes is improved, and the friendly degree and easy use degree are improved in the verification process.
Owner:ALIBABA GRP HLDG LTD
Software encrypting registration piracy-preventing method
InactiveCN101082950AIncrease randomnessIncrease the difficulty of crackingProgram/content distribution protectionSoftwareComputer engineering
The invention discloses a pirate edition resisting method of coded register software, which comprises the following steps: making user end code to generate sequence code with implicit applying software and computer hardware information at the first time; regarding the sequence code as user's mark code to apply for credit to use register code; coding the legal user to generate a new sequence code through credit end; analyzing the implicit limit information of software and user mark code into the information of applying software and computer hardware; feedbacking the information as register code to the user end; using software user end to store the register code to analyze and detect the register code during operating stage; affirming whether the software is stopped. The invention adopts key character list to group, rearrange and repair to code the random number, which increases the decoding difficulty of code to prevent software edition from embezzling.
Owner:侯同济
Data encryption method
InactiveCN106452776AEasy to set upImprove securityEncryption apparatus with shift registers/memoriesUser identity/authority verificationNetwork security policySecurity policy
The invention discloses a data encryption method which comprises the following steps: presetting an algorithm library including a plurality of encryption algorithms; establishing a corresponding security policy according to the user's attribute requirement for the encryption algorithms, wherein the establishment of the corresponding security policy includes selecting the required encryption algorithm from the algorithm library; and encrypting the data to be encrypted according to the security policy. In the embodiment of the invention, when being required to establish a new security policy to improve the security of the data, the user only needs to determine the attribute requirement of the encryption algorithm. Thus, the corresponding security policy can be established so that the appropriate encryption algorithm can be selected to encrypt the data to be encrypted. As a result, it is possible for the user to easily establish or update the security policy, thereby effectively saving the cost of replacing the security policy and changing the encryption and decryption algorithms.
Owner:AEROSPACE INFORMATION
Safe data transmission method based on Real-Time Messaging Protocol (RTMP) connections
ActiveCN105847238AIncrease the difficultyNo significant impact on real-time performanceTransmissionTransmission protocolSecure transmission
The invention discloses a safe data transmission method based on Real-Time Messaging Protocol (RTMP) connections. The method has the advantages that functional extensions of the RTMP are carried out, and through a key negotiation process between a client and a server, an encryption algorithm and a key adopted by each connection are random, so that external cracking analysis of encrypted data is much more difficult; the symmetrical encryption algorithms are adopted for encryption processing, so that the encryption and decryption processing efficiencies are high, real-time performance of data transmission and user experience are not obviously affected, and the effects on the processing load of the server are small; meanwhile, the server can flexibly select an encryption mode, and, according to a user type or a resource type requested by a user, can determine whether encrypted transmission is needed or not or select one specific encryption algorithm and a key length (the keys with a length of 64 bytes or more can be provided, and the number of the encryption algorithms can reach 255).
Owner:HANGZHOU SHISHUO EDUCATION TECH CO LTD
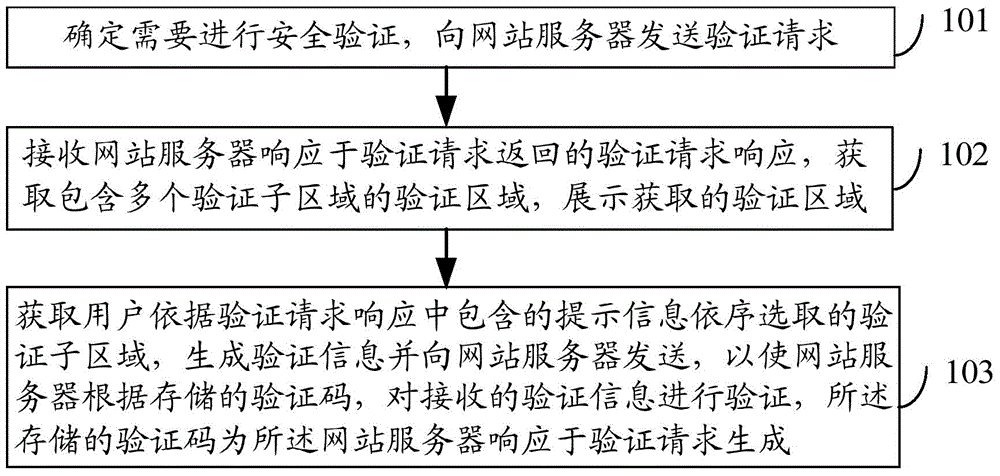
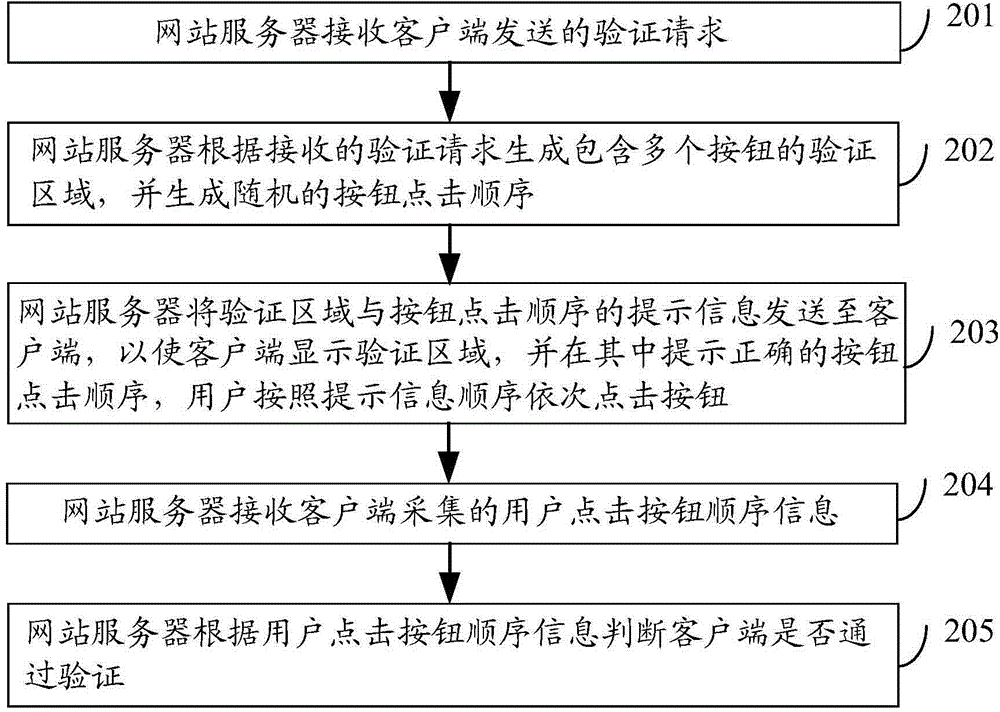
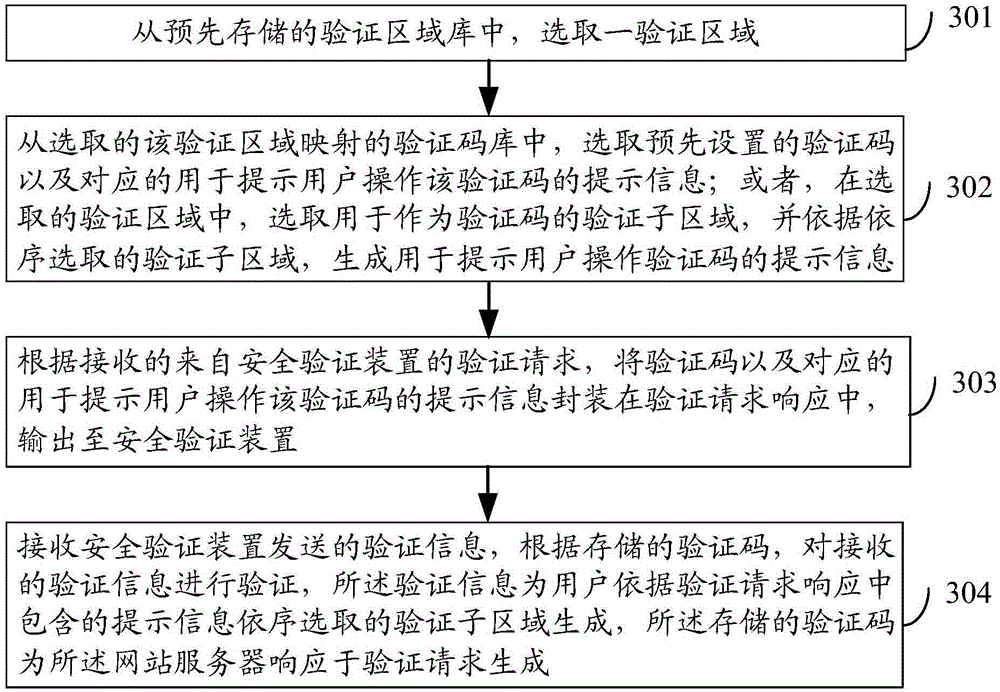
Identifying code generating method, safety identification method, safety identification device and safety identification system
ActiveCN105471808AIncrease the difficulty of crackingImprove user experienceTransmissionIdentification deviceSecure authentication
The invention discloses an identifying code generating method, a safety identification method, a safety identification device and a safety identification system, wherein the safety verification method mainly comprises the steps of determining a fact that safety identification is required, transmitting an identification request to a website server; receiving an identification request response which is returned from the website server, acquiring an identification area which comprises a plurality of identification sub-areas, displaying the acquired identification area; acquiring identification sub-areas which are successively selected according to prompting information contained in the identification request response, generating identification information and transmitting the identification information to the website server, so that the website server identifies the received identification information according to a stored identifying code, wherein the stored identifying code is generated by the website server in response to the identification request. The identifying code generating method, the safety identification method, the safety identification device and the safety identification system provided by the technical solution of the invention have advantages of further reducing time required for safety identification, and improving safety identification efficiency.
Owner:BEIJING SOGOU TECHNOLOGY DEVELOPMENT CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com