Software copy right protecting method for extracting partial code to enciphed device from software
A technology of encryption device and extraction part, applied in digital data processing parts, instruments, electrical digital data processing and other directions, can solve the problems of low controllability of protection strength, recurrence, long development cycle, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
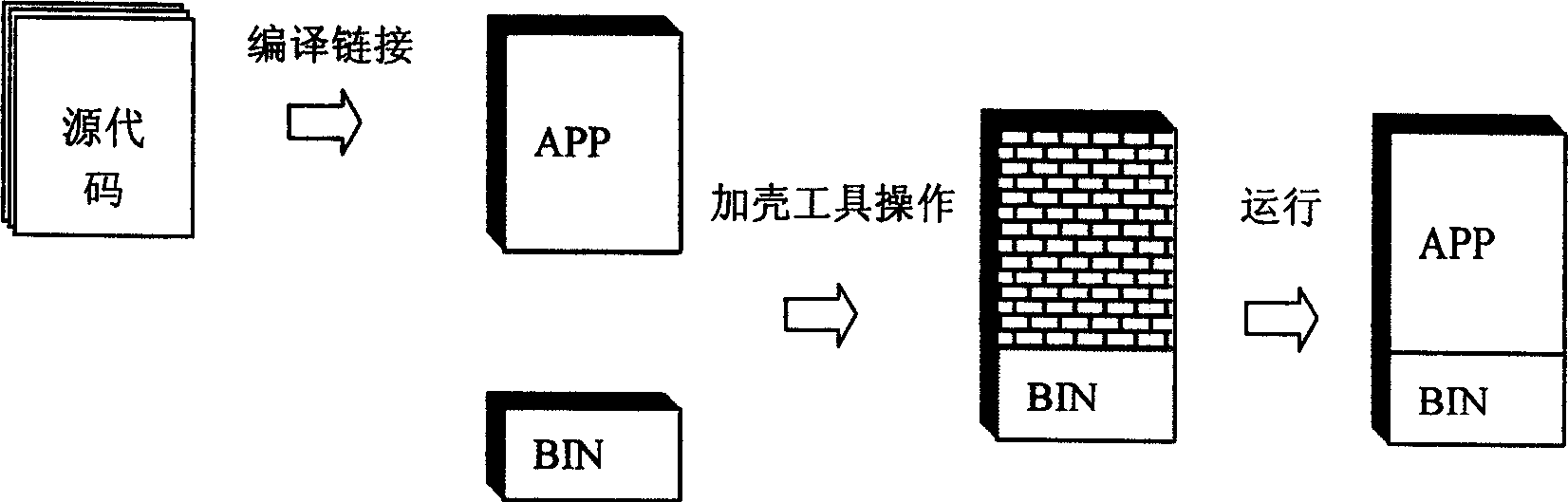
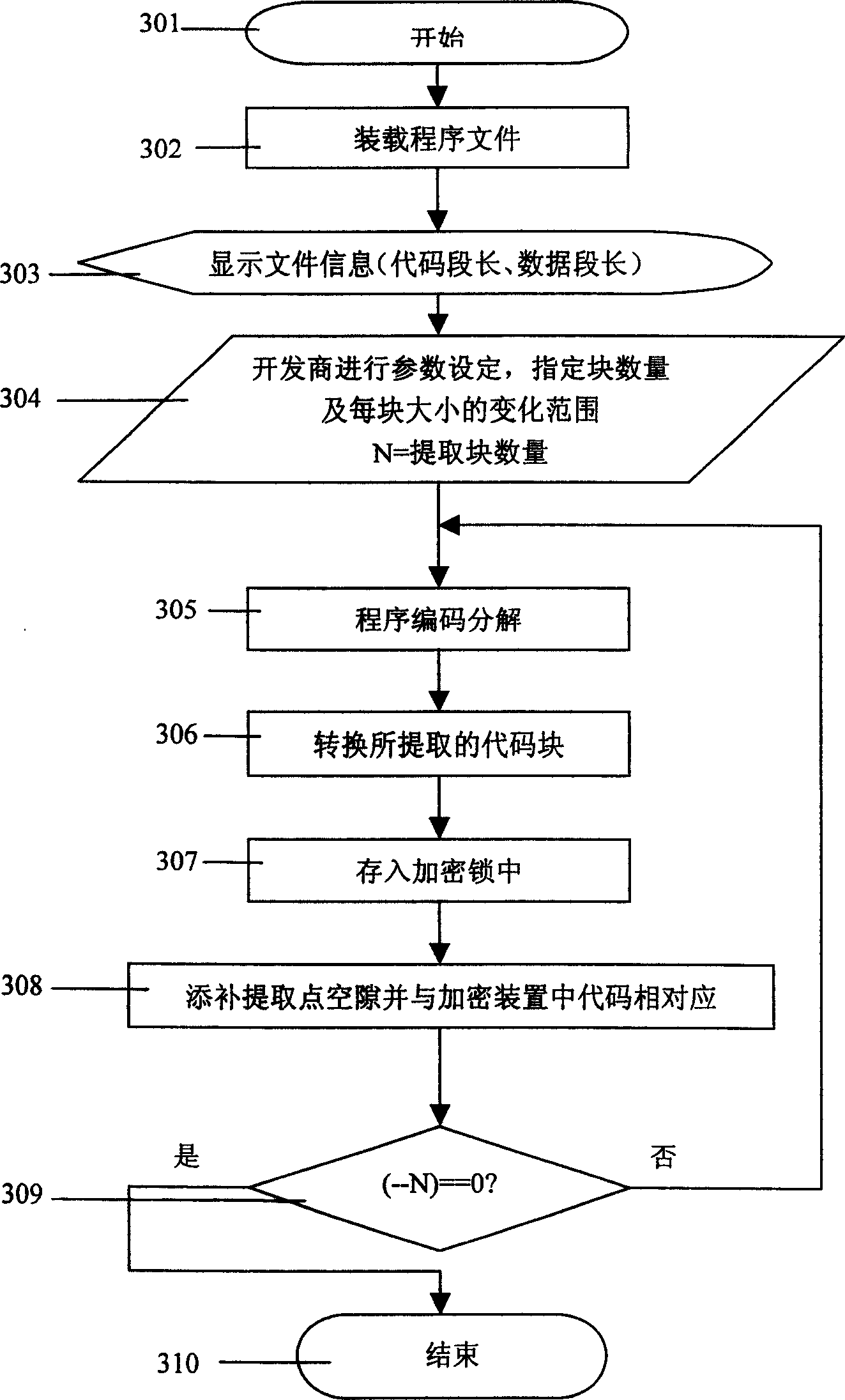
[0047] The present invention decomposes the instruction code information of the application program file to be protected according to the principles of cryptography, and extracts a relatively suitable ratio of instruction code into the encryption device, destroying the visual integrity of the code information in the program file to be protected in the computer sex. It is necessary to ensure that the amount of code information is not too large and does not exceed the processing capacity of the encryption device, and at the same time, it must be ensured that the decomposed and extracted data information will not be reversely deduced by the decryptor using the remaining code information after extraction. When encrypting the same program file, the larger each code block extracted is, and the greater the number of code blocks extracted each time, the higher the security will be. As for the specific size of each code block, the range of variation, and the random value of the number ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com