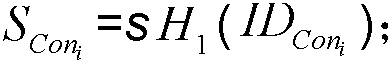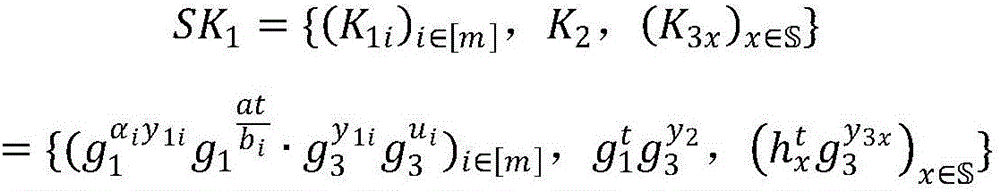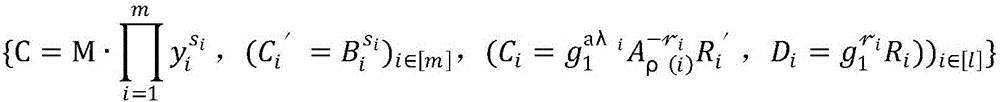Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
228results about How to "Improve security strength" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
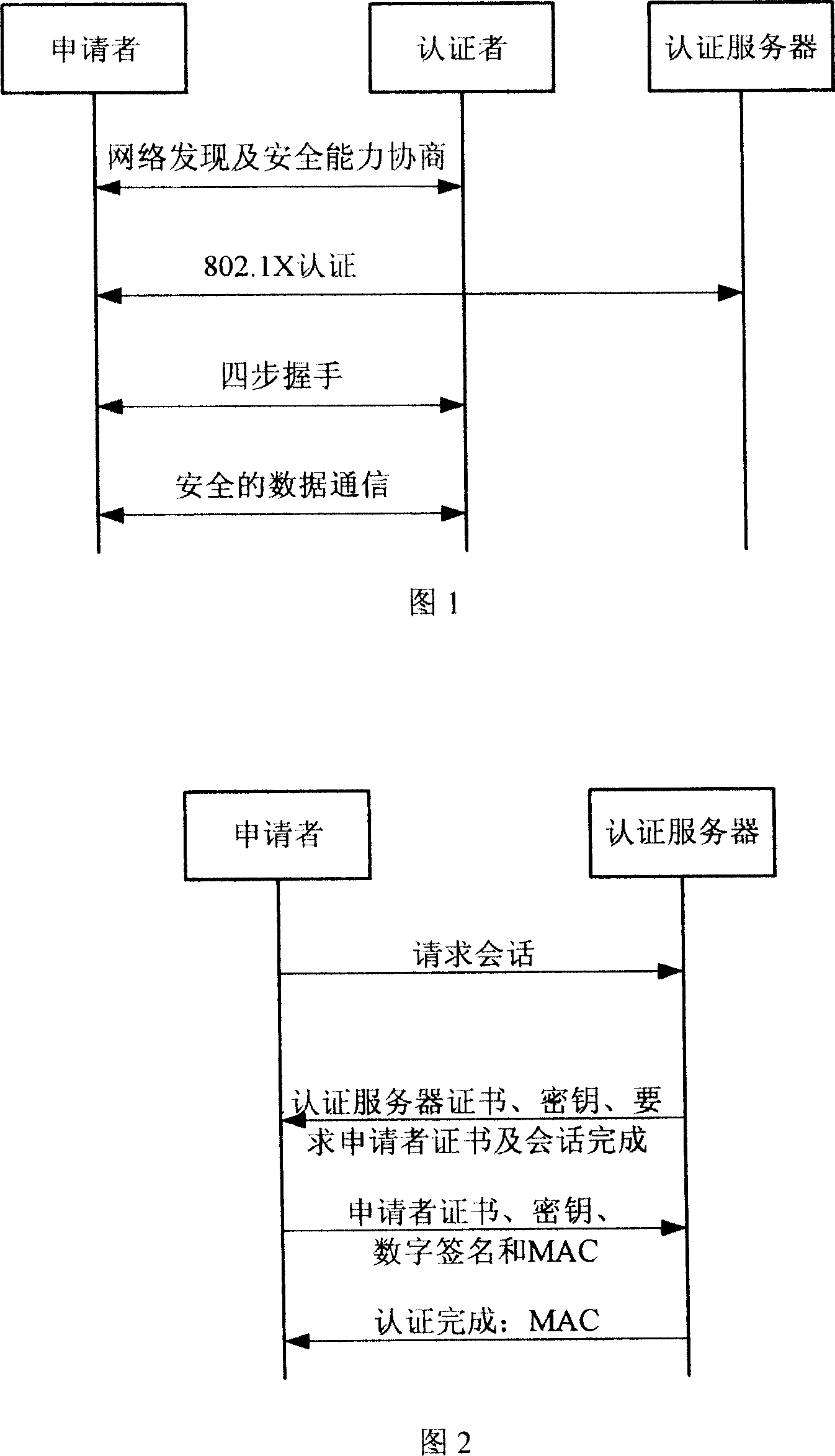
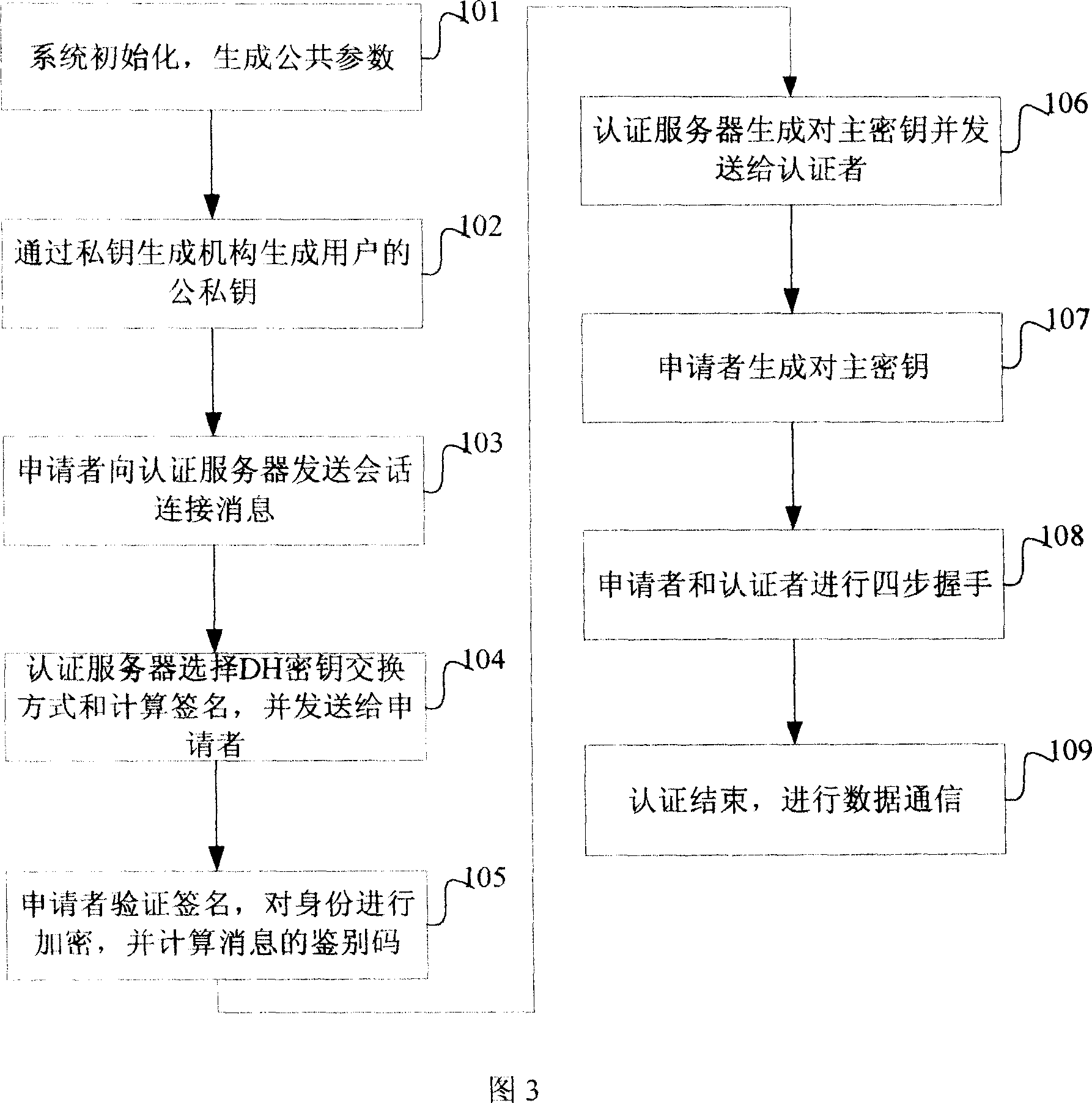
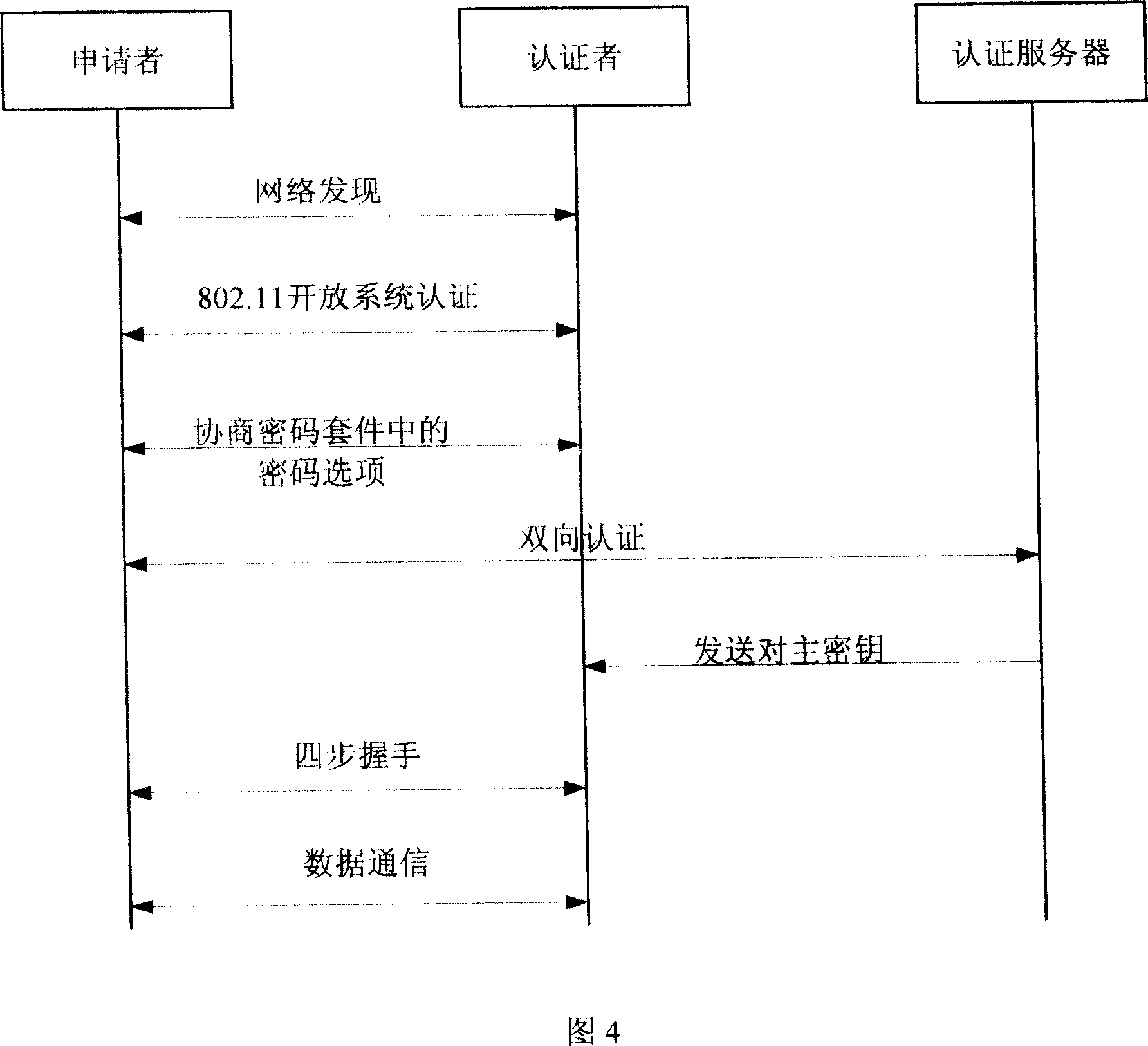
Bidirectional identification method and system
InactiveCN101119196AEffective calculationImprove security strengthUser identity/authority verificationHand shakesNetwork communication
The present invention provides a bi-direction authentication method and system which belongs to the field of network communication. The present invention aims at solving the problems that certificate management in present private key authority technology is complex and the certificate management can not protect the identity of the users. The present invention provides a bi-direction authority method. The present invention includes the procedures of the system initialization and generating system parameters, an applicant initializing a dialogue request to establish connection with an authorization server, the applicant and the authorization server mutually check identity and generate a pair of main key which is used for the four-procedure-hand-shaking. The present invention also provides a bi-direction authorization system. The system includes a parameter initialization module, an establishing dialogue connecting module, a server identity verification module and an applicant identify verification. Applications of the technical proposal of the present invention can reduce the establishing and maintenance cost of the system, to enhance the running efficiency of the system, and to realize the target of protecting applicants.
Owner:XIDIAN UNIV +1
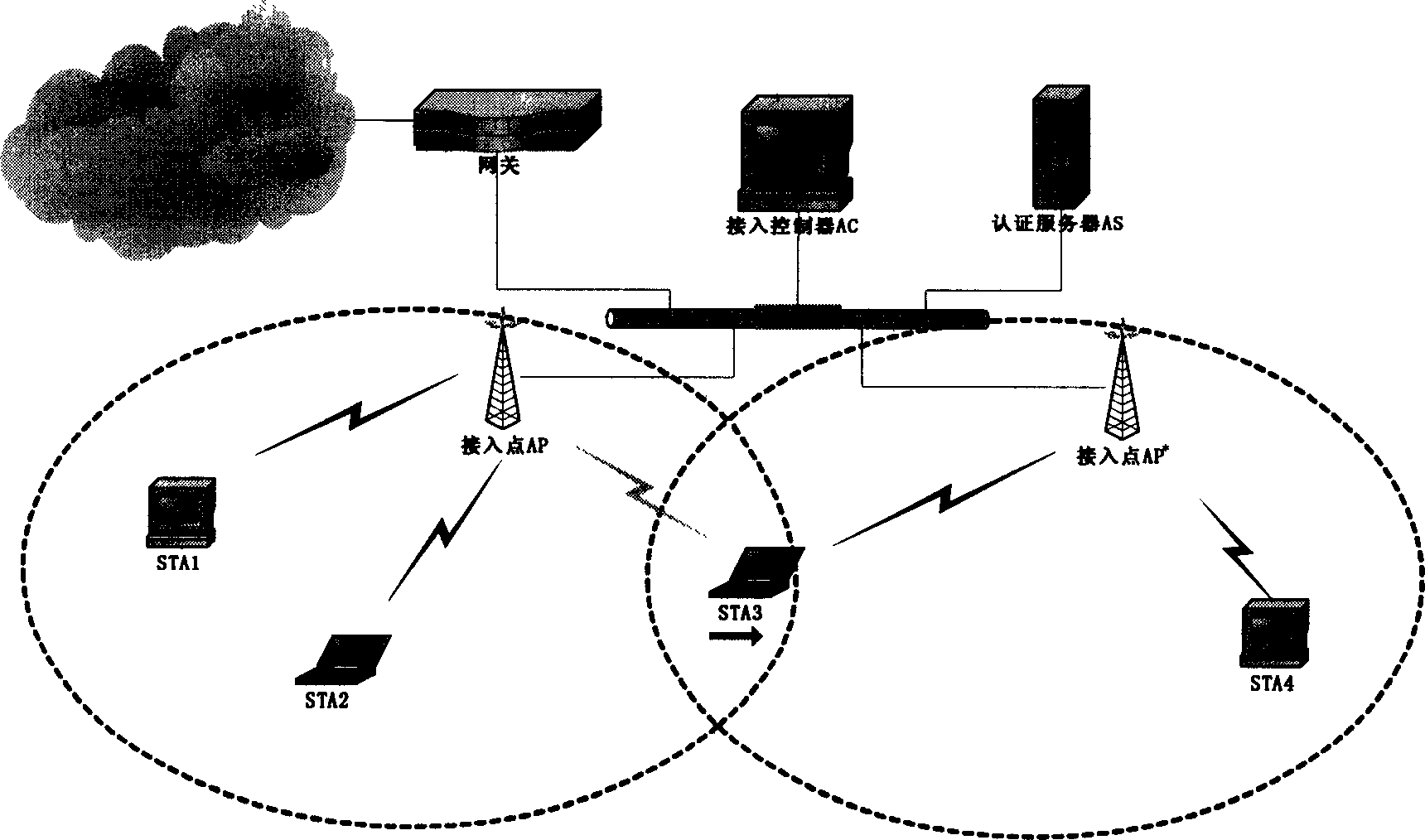
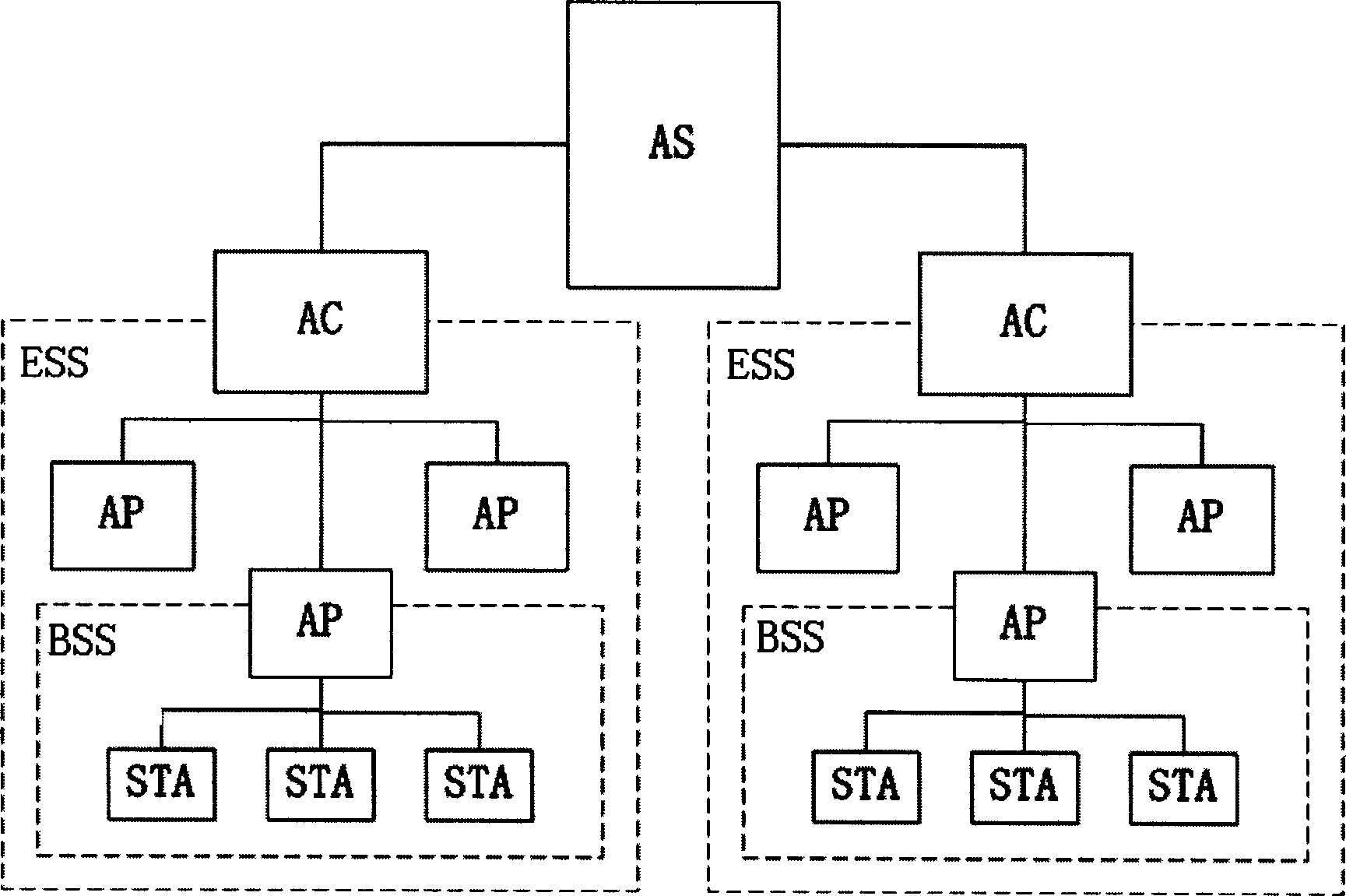
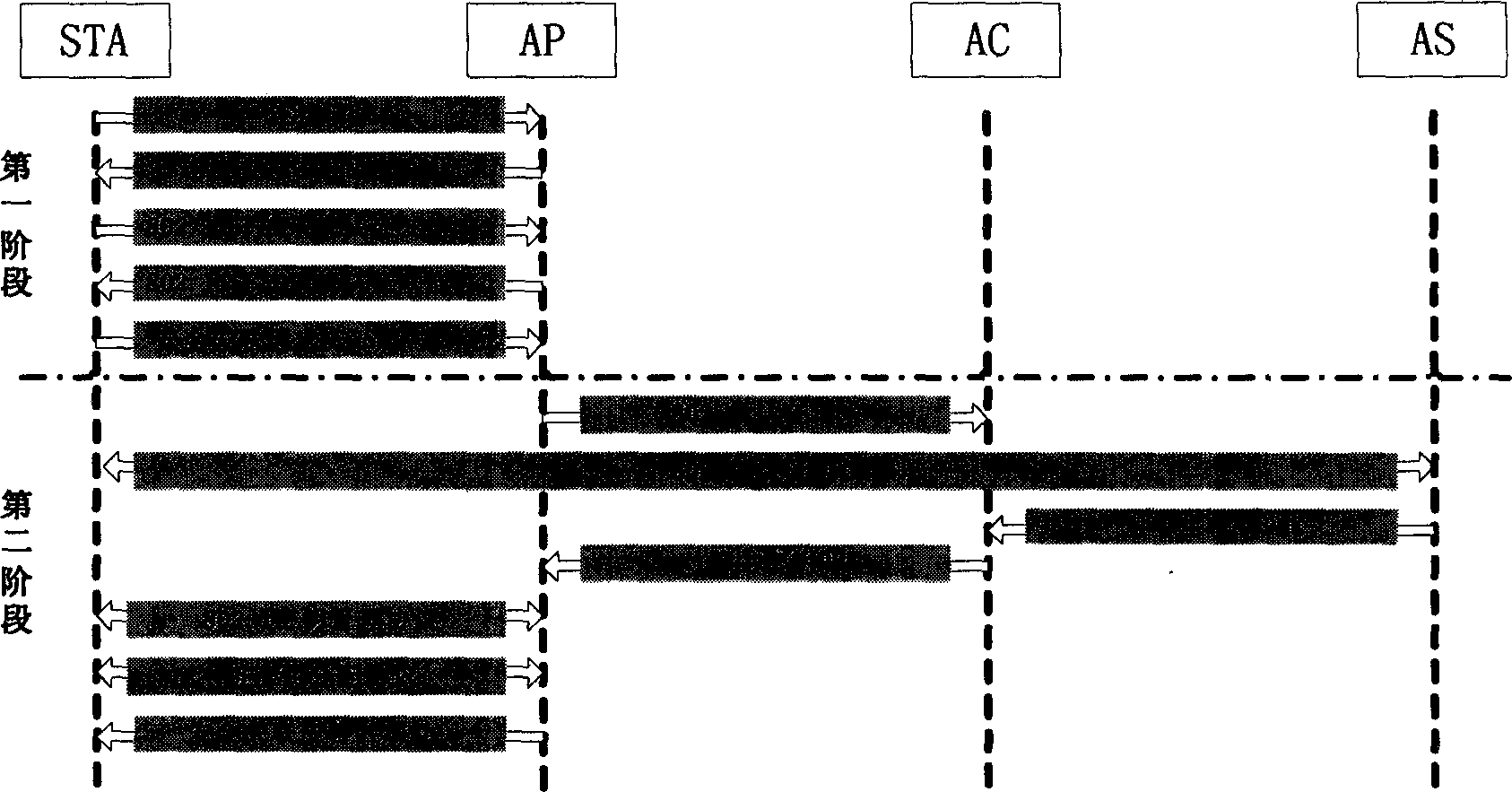
Wireless LAN safety connecting-in control method
InactiveCN1455556AReduce hardware complexityImprove security strengthMultiple keys/algorithms usageUser identity/authority verificationTelecommunicationsThree stage
The control course includes three stages: setting up connection and safety performance bargin as broadcasting connection request by STA and all AP at the area to send connection response message declaring all data protective method to STA; setting up safe correlation a sending 802.1x authentication request message to AC by AP after STA safe correlation request received to request AC to use 802.1x authentication protocol to make authentication for STA by AS; resetting up safe correlation as switching the correlative switch in point from one area to another by STA as well as setting up connection and bargaining safety performance by STA and AP* as per steps in the first stage under the roaming condition with AP* service range being entered by STA.
Owner:SOUTHEAST UNIV
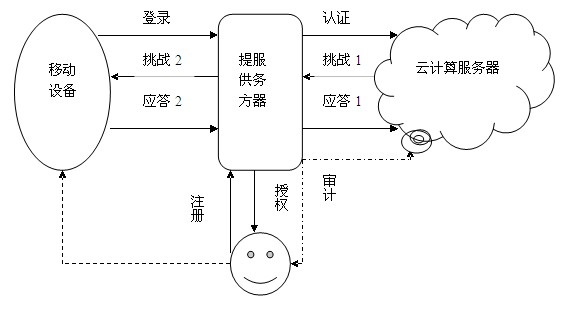
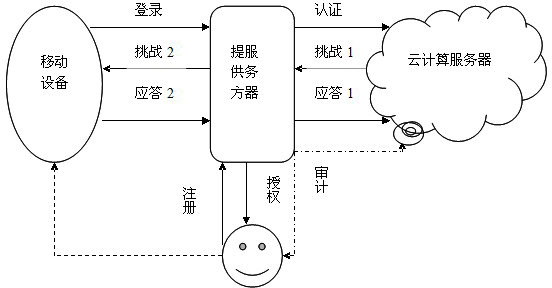
Identity authentication method based on biological feature encryption and homomorphic algorithm
InactiveCN102664885AImprove privacyAvoid crackingUser identity/authority verificationTimestampAlgorithm
The invention discloses an identity authentication method based on biological feature encryption and a homomorphic algorithm. The method is quicker than a normal password method by using biological features of users as passwords to log in a system through a mobile device, using an encrypted biological template is safer, and privacy of the users can be guaranteed as information is transmitted in a ciphertext form. By adding factors such as timestamps, tri-party authentication among the users, a provider server and a cloud computing server is realized, and reliability among the three parties is enhanced. Legal users can be prevented from using resources in the cloud computing environment illegally to better manage the resources by means of user authentication operation according to attribution predicate encryption and real-time updating of permission information. Operation without encryption can be realized by the aid of the homomorphic algorithm, same effects as decrypting before operation can be achieved, time and space expenses can be saved, system efficiency is greatly improved, and the identity authentication method has high safety and efficiency.
Owner:南京邦普信息科技有限公司
Key protection method and safety chip based on physical no-cloning function
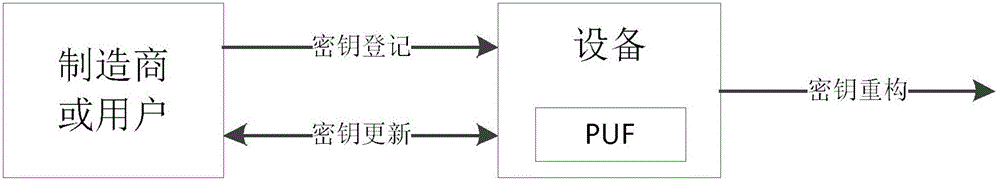
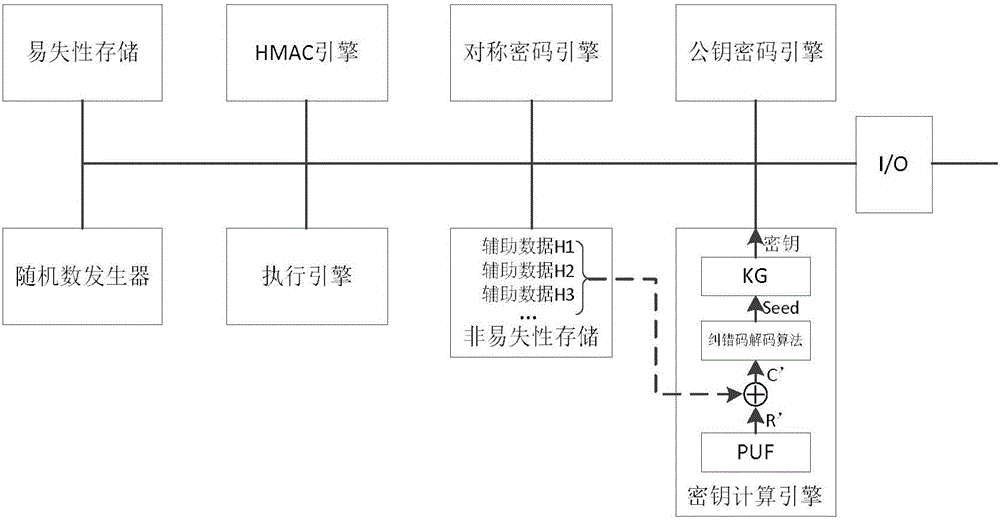
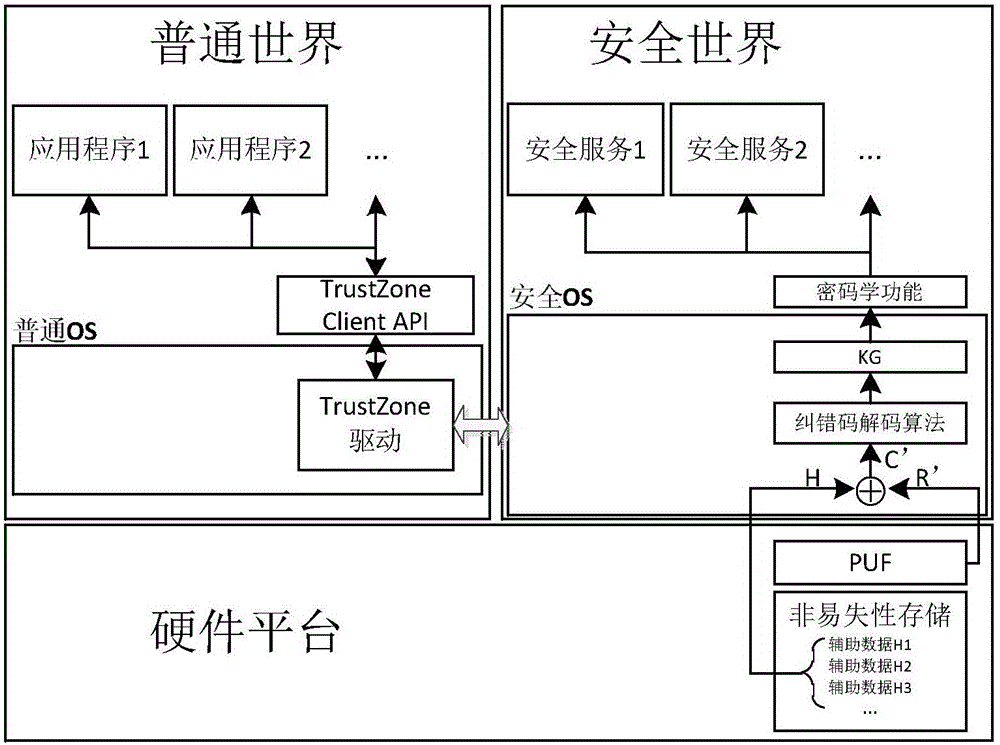
ActiveCN105007285AImprove security strengthProtection securityKey distribution for secure communicationUser identity/authority verificationComputer hardwareChanging equipment
The present invention discloses a key protection method based on a physical no-cloning function. The method comprises a key registration phase and a key reconstruction phase. The key registration phase is generally in an equipment manufacturing stage and is used for using the physical no-cloning function on equipment and binding equipment key to the equipment. The key reconstruction phase is in an equipment using stage and is used for calculating the key bound on the equipment in the registration phase. The method also comprises a key updating phase for updating the equipment key. According to the method and the safety chip, a plurality of keys can be safely bound for the equipment, and the safety of other keys is not affected by the leakage of one key. In addition, the invention provides a key updating mechanism, and the equipment key is updated in the condition of not replacing equipment hardware.
Owner:NANJING WANDAO ELECTRONICS TECH CO LTD
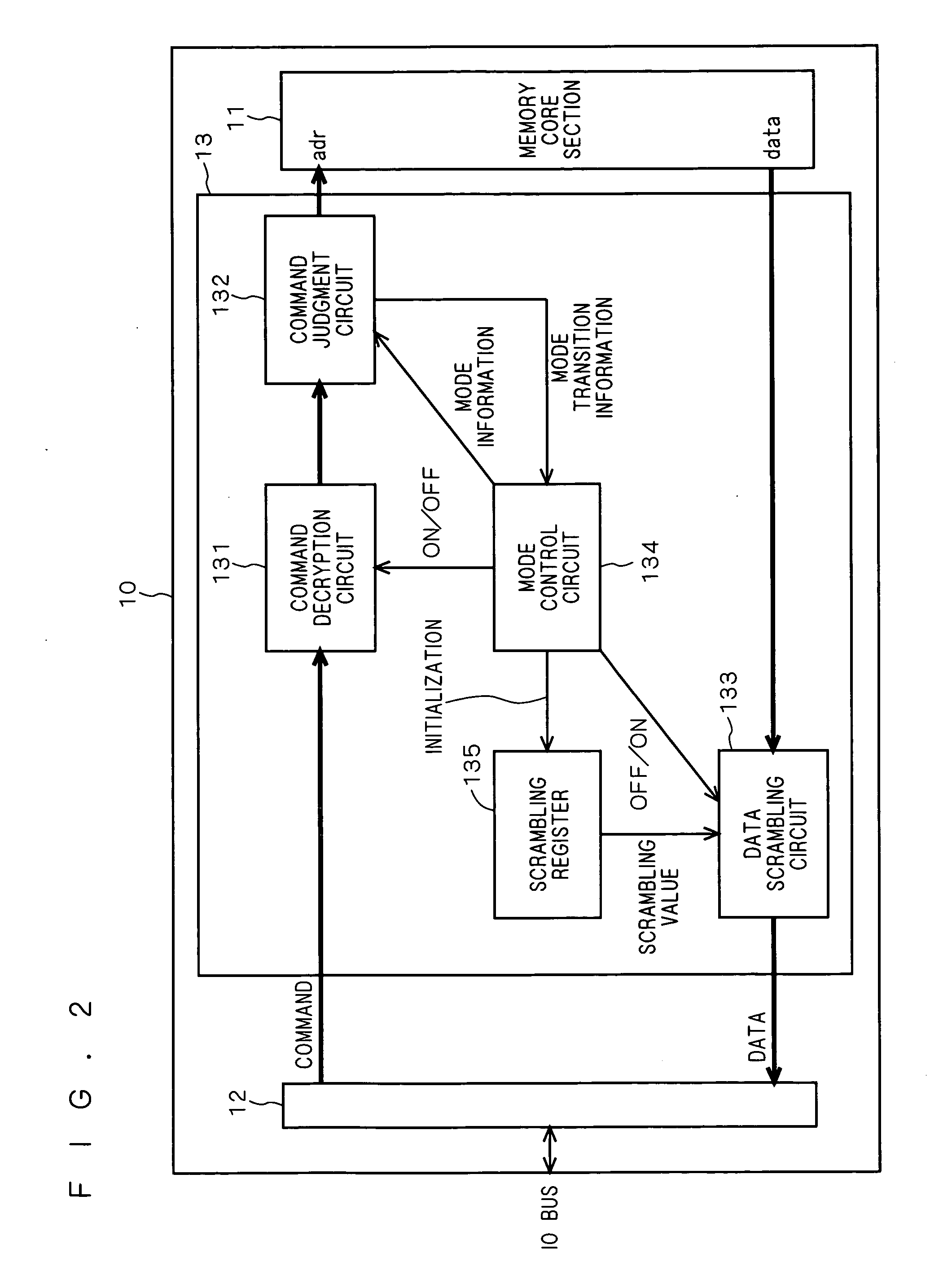
Semiconductor memory device
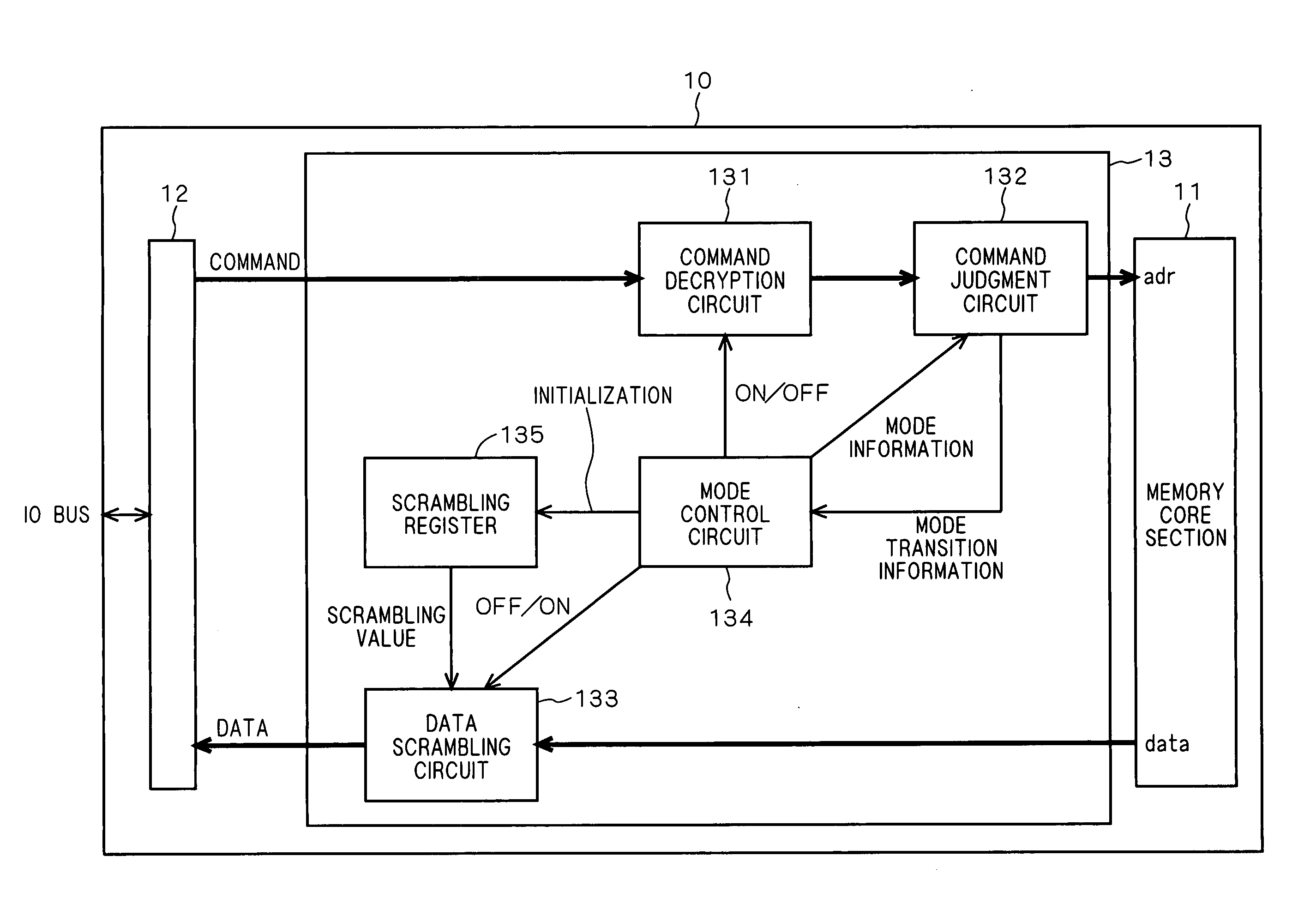
ActiveUS20060107072A1Improve security strengthImprove reading effectDigital data processing detailsUnauthorized memory use protectionInformation processingOperation mode
A semiconductor memory includes a memory control section and a memory core section. A command judgment circuit in the memory control section changes the operating mode of the semiconductor memory in response to a command sent from a controller of an information processing apparatus. In a first mode, a decryption process is performed in a command decryption circuit, and data outputted from the memory core section is not scrambled. In a second mode, the decryption process is not performed in the command decryption circuit, and the command outputted from the memory core section is scrambled.
Owner:NINTENDO CO LTD +1
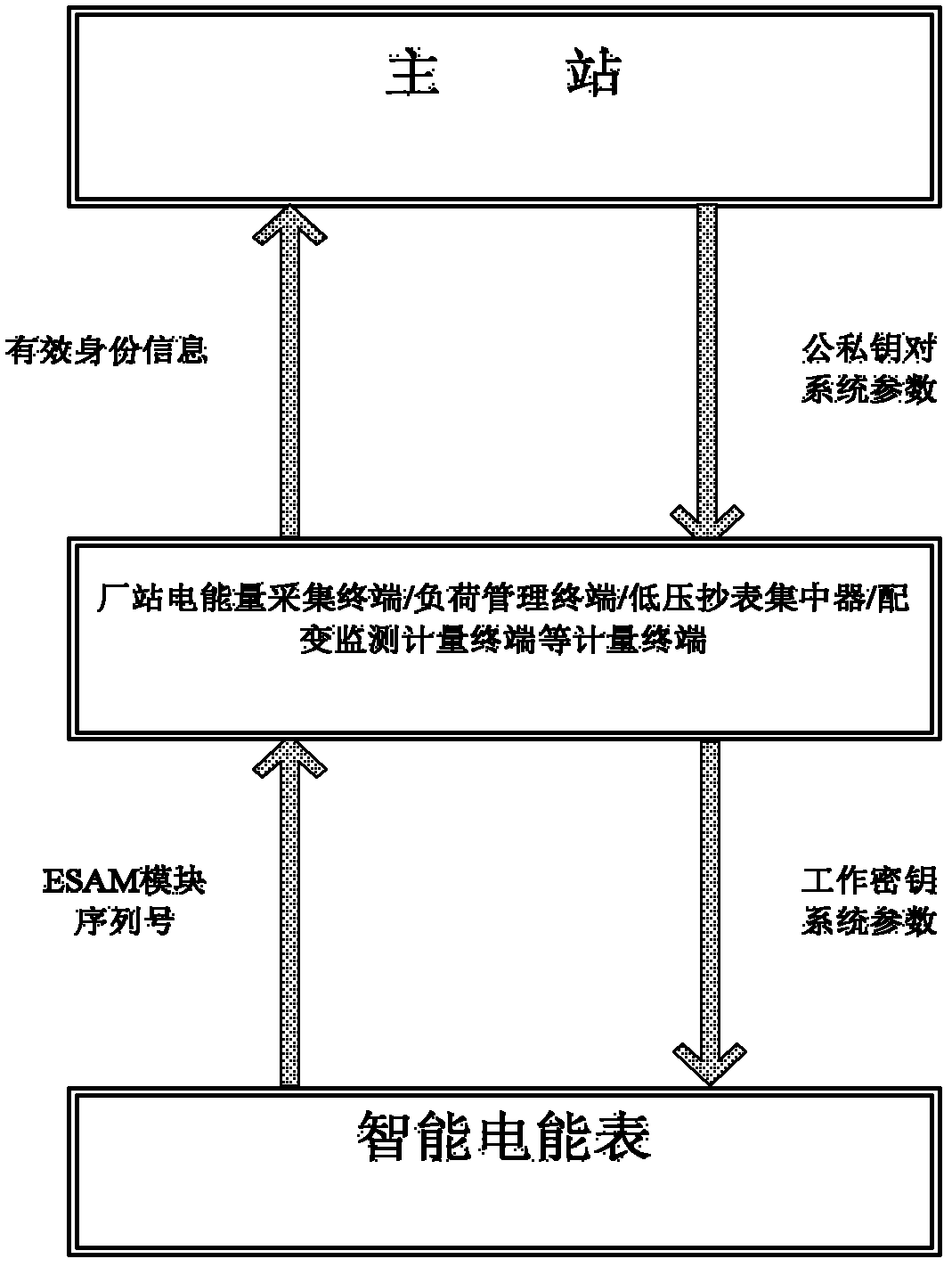
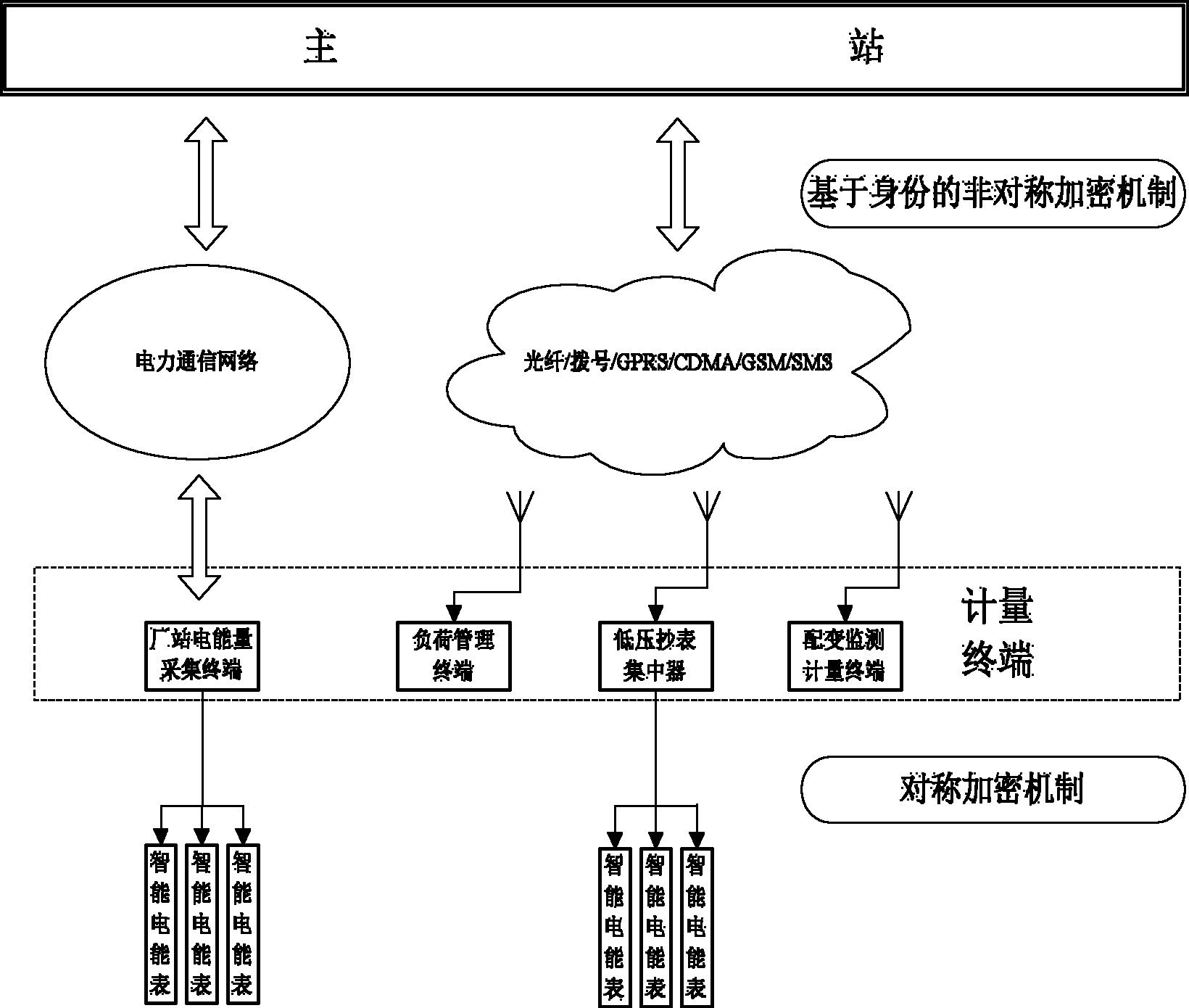
Metering data transmission system based on identity encryption and data transmission method
ActiveCN102685114AReduce computing loadImprove securityUser identity/authority verificationPlaintextPrimary station
The invention discloses a metering data transmission system based on identity encryption, which comprises a host station, a metering terminal and an intelligent electric energy meter, wherein the intelligent electric energy meter encrypts metering data by adopting a working key and sends the metering data to the metering terminal; the metering terminal performs decryption by adopting the working key of the intelligent electric energy meter, then encrypts the metering data to form a ciphertext by using a public key of the metering terminal, generates a signature for the ciphertext, and sends the metering data and ciphertext information to the host station together; the host station verifies the signature by using the public key of the metering terminal, a private key of the metering terminal is generated after the signature is authenticated, and decryption for ciphertext information is performed so as to obtain an information plaintext; the host station generates a control command according to data processing results and encrypts the control command by adopting system sharing parameters and the public key of the metering terminal so as to generate the ciphertext, the ciphertext is sent to the metering terminal after the signature is generated, the metering terminal verifies the signature and the signature is authenticated, and the control command aiming at the intelligent electric energy meter is generated after the private key is adopted to decode the ciphertext and the control command is read; and in addition, the control command aiming at the intelligent electric energy meter is encrypted through the working key of the intelligent electric energy meter and then is sent to the intelligent electric energy meter. The metering data transmission system improves the security for data transmission, and reduces the calculating load of the host station.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID +1
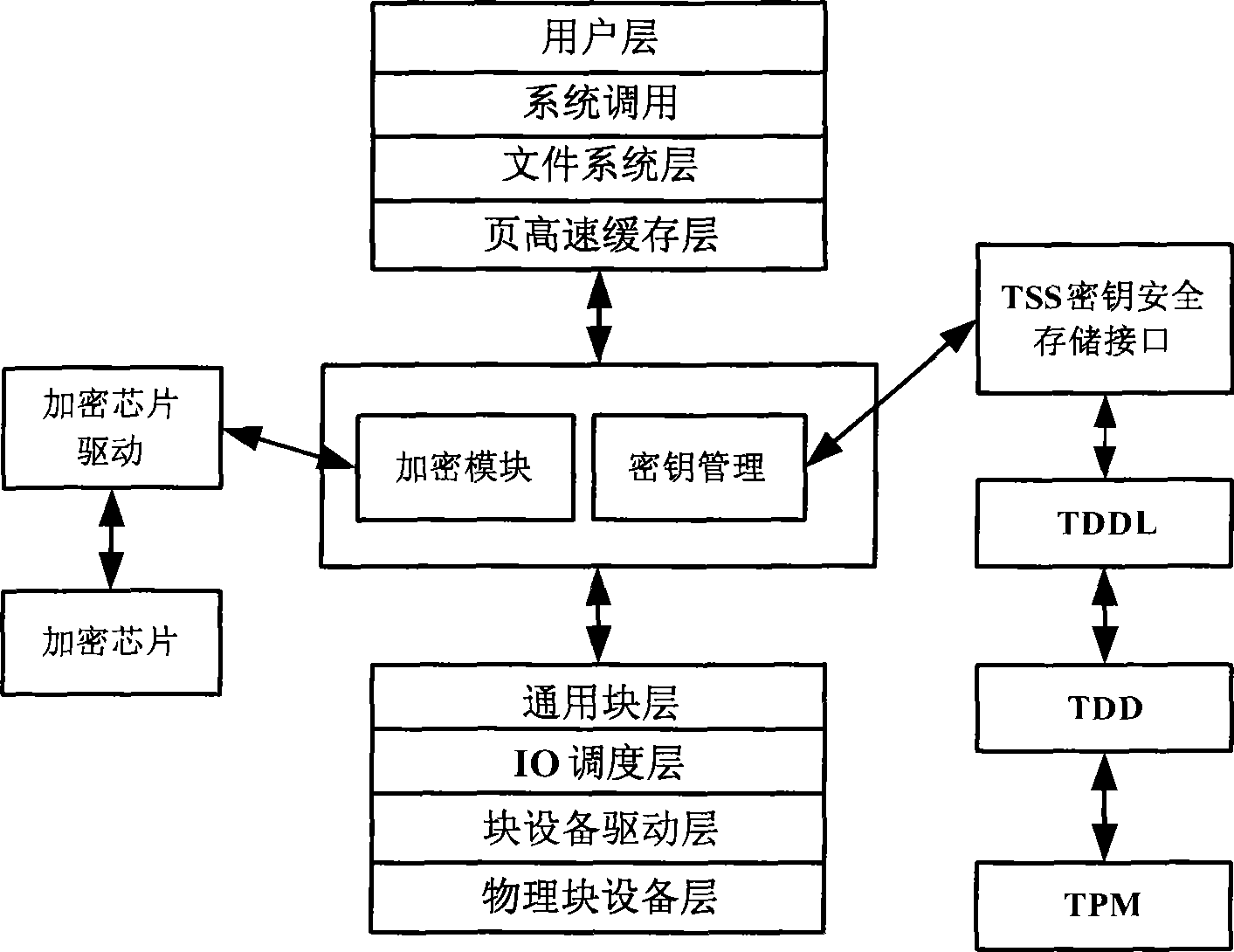
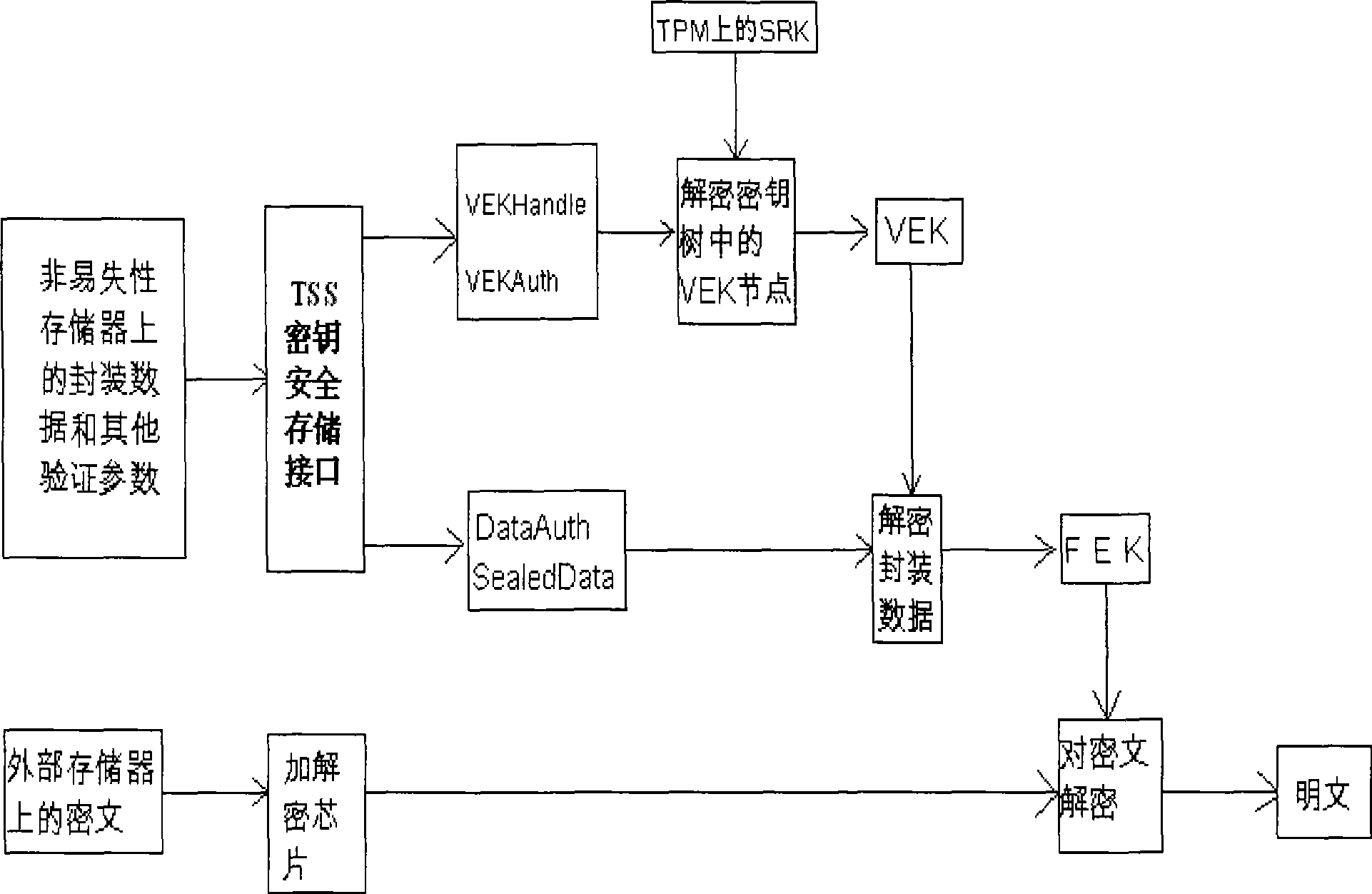
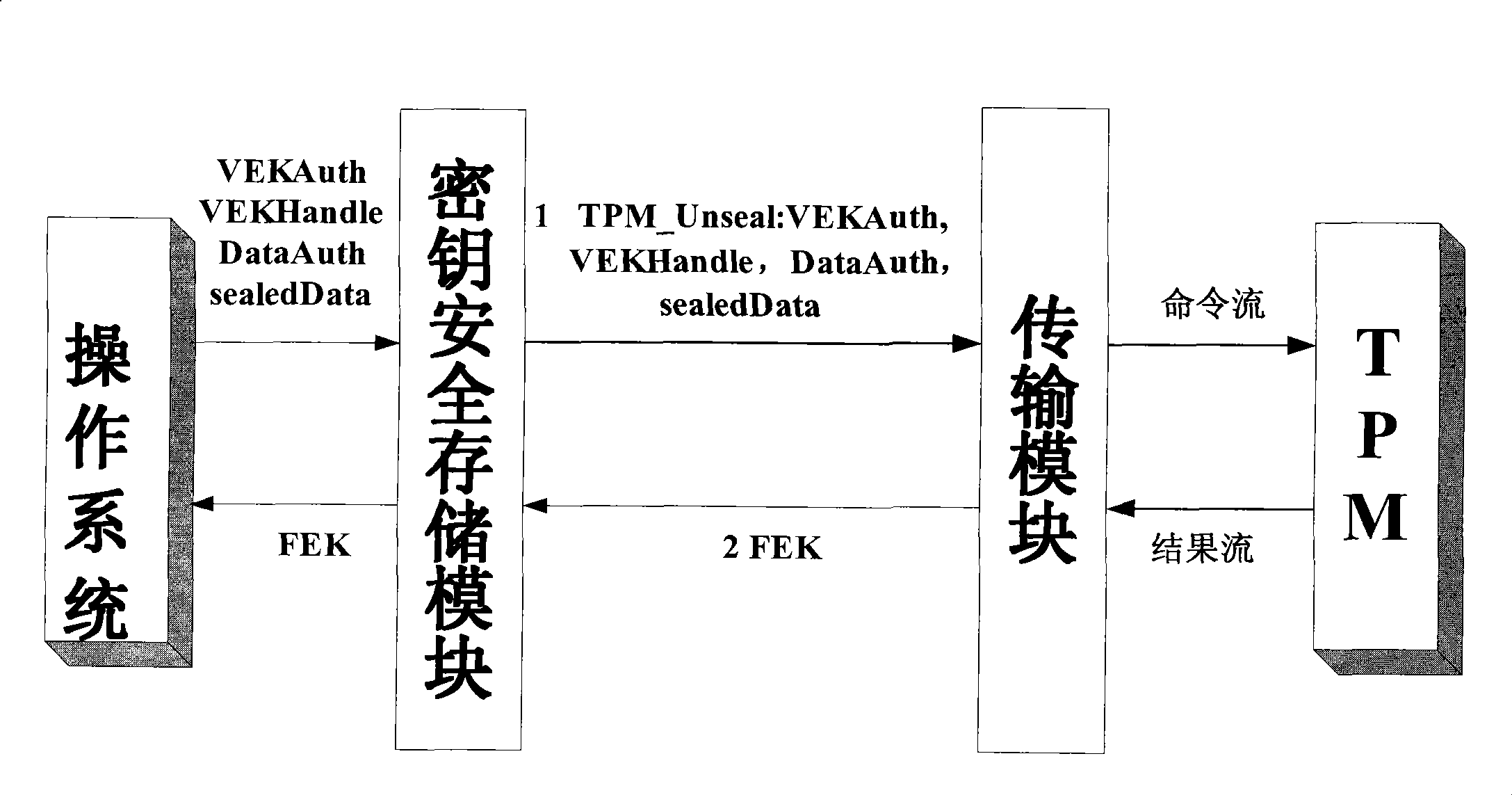
Movable equipment based on credible embedded platform and its security storage method
InactiveCN101430747AImprove securityImprove security strengthDigital data protectionMobile deviceEmbedded system
The invention provides a mobile device based on a trustable embedded platform and a safe storage method thereof. The mobile device comprises an embedded platform, an encrypt / decrypt chip and a TPM module, wherein, the embedded platform, the TPM module and the encrypt / decrypt chip are connected with a high speed bus. In the device and the storage method, according to the characteristics of an embedded system, the embedded platform, the TPM trustable platform module and the hardware encrypt / decrypt chip together are combined, thereby effectively solving the problem of key safe storage, breaking through bottleneck of transmission speed of an embedded system and an encryption engine, and ensuring a reliable environment for encrypt / decrypt operation.
Owner:WUHAN UNIV
A secure communication method between nodes in vehicular network
InactiveCN101262333APrevent counterfeitingImprove security strengthKey distribution for secure communicationParticular environment based servicesKey exchangeSecure communication
The invention discloses a safe communication method between nodes in a vehicular network. The method provides a disperse trust and security system based on elliptic curves. Before communicating, communication nodes are two-way indentified by a (t, n) threshold authentication proposal to prevent hostile nodes from personating legal nodes and t-1 members in a network from counterfeiting certificates. Meanwhile, a key exchange based on password authentication is carried out to ensure that all conventioneers consult about a key by a safe approach, and therefore, a strong session key is generated to provide message discrimination, confidentiality and integrality for communication nodes in a vehicular network. The method of the invention adopts an elliptic curve encryption scheme and the (t, n) threshold authentication proposal, thereby being characterized by small calculated amount, low complexity, high safety, small key space, high speed, needing no authentic certificate authority and having great application value in vehicular networks.
Owner:SHANGHAI UNIV
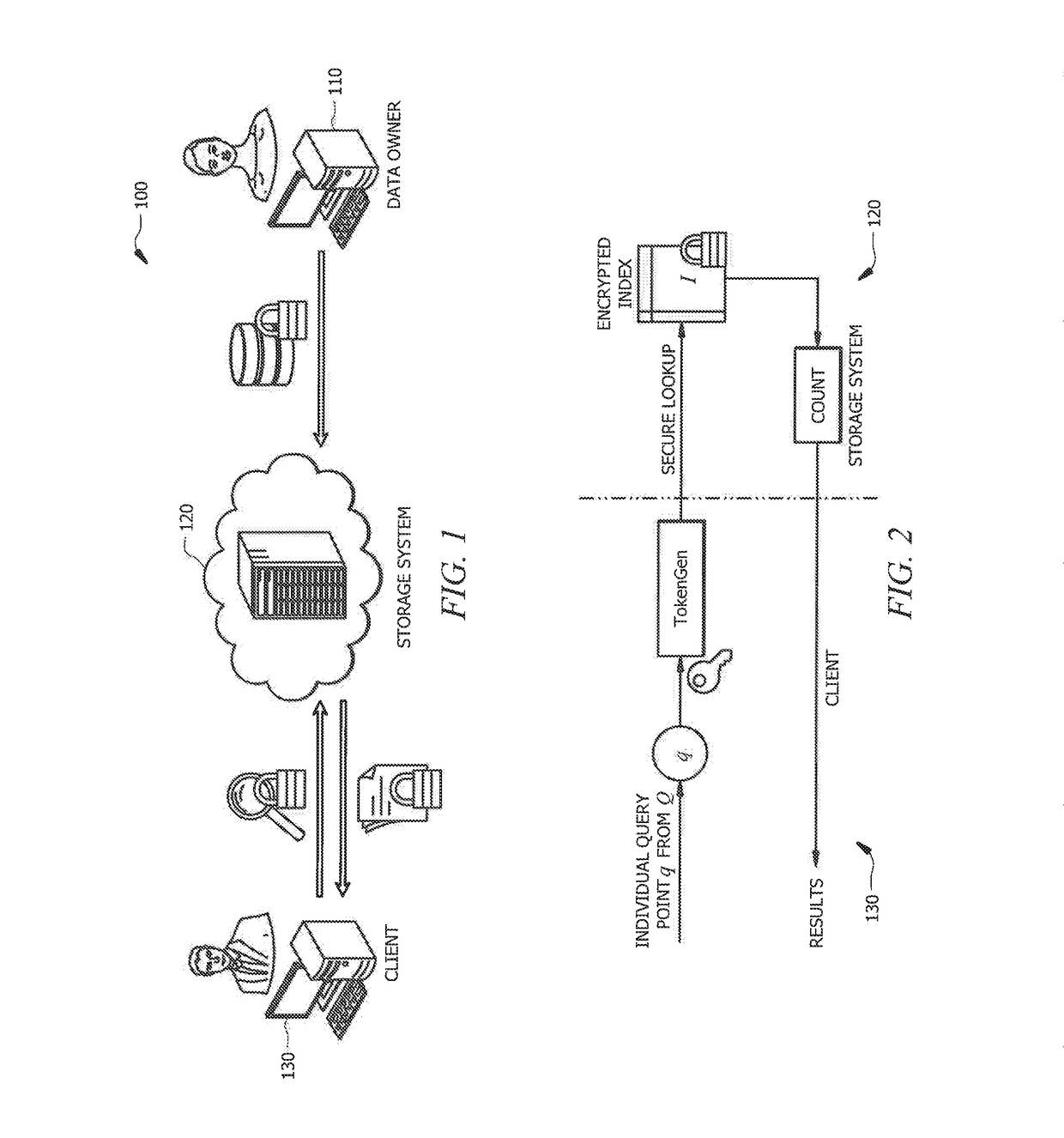
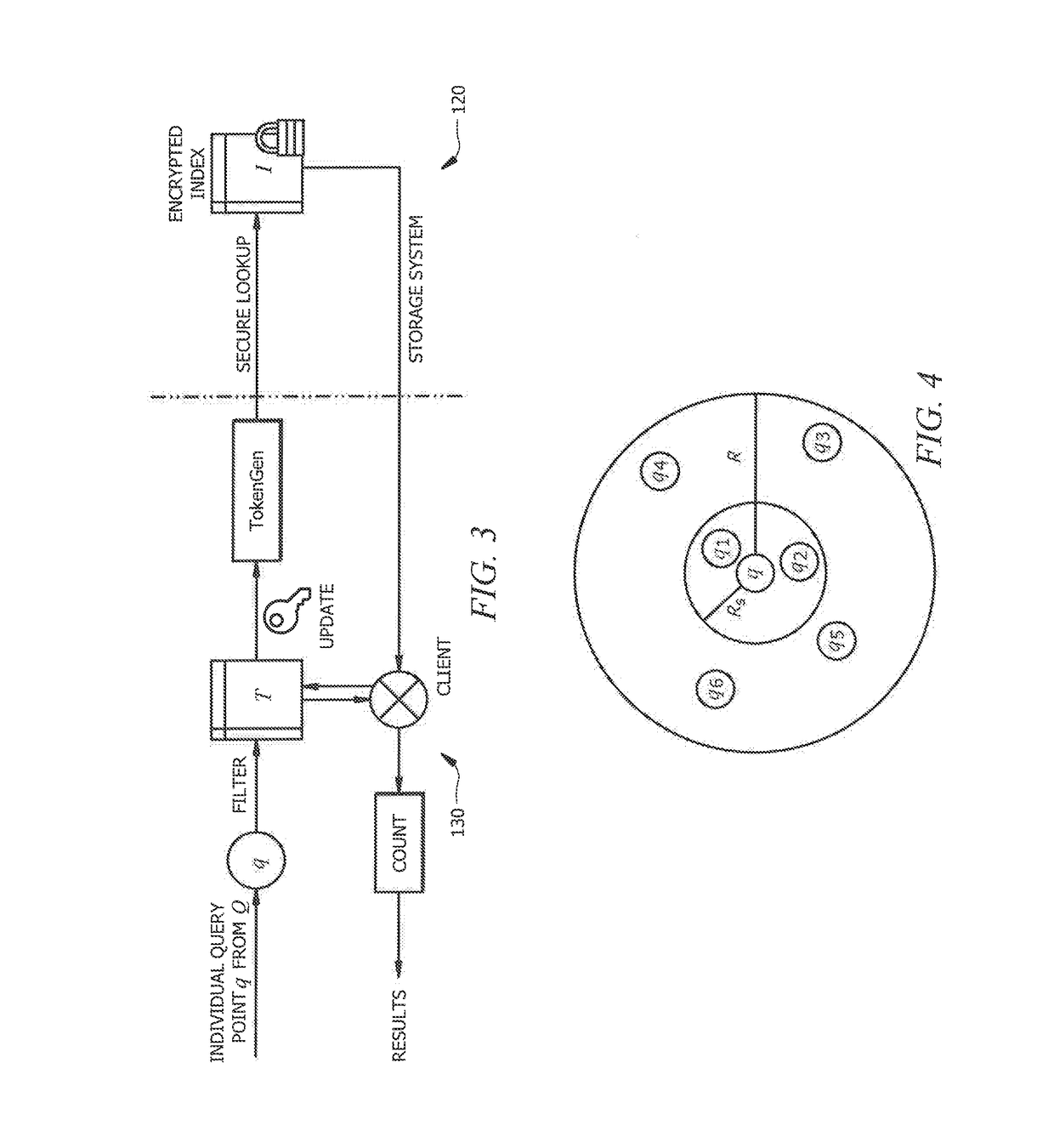
Systems and methods for privacy-assured similarity joins over encrypted datasets
ActiveUS20180157703A1Strong data protectionReduce query latencyMemory architecture accessing/allocationMultiple keys/algorithms usageData setSimilarity query
Systems and methods which provide secure queries with respect to encrypted datasets are described. Embodiments provide privacy-assured similarity join techniques operable with large-scale encrypted datasets. A privacy-assured similarity join technique of embodiments enables a storage system to answer similarity join queries without learning the content of the query dataset and the target dataset. One or more secure query schemes may be implemented in accordance with a privacy-assured similarity join technique herein. For example, embodiments may utilize an individual similarity query scheme, a frequency hiding query scheme, and / or a result sharing query scheme. A particular secure query scheme of the foregoing secure query schemes may be utilized to address different considerations with respect to security, efficiency, and deployability with respect to various applications and scenarios with different requirements.
Owner:CITY UNIVERSITY OF HONG KONG
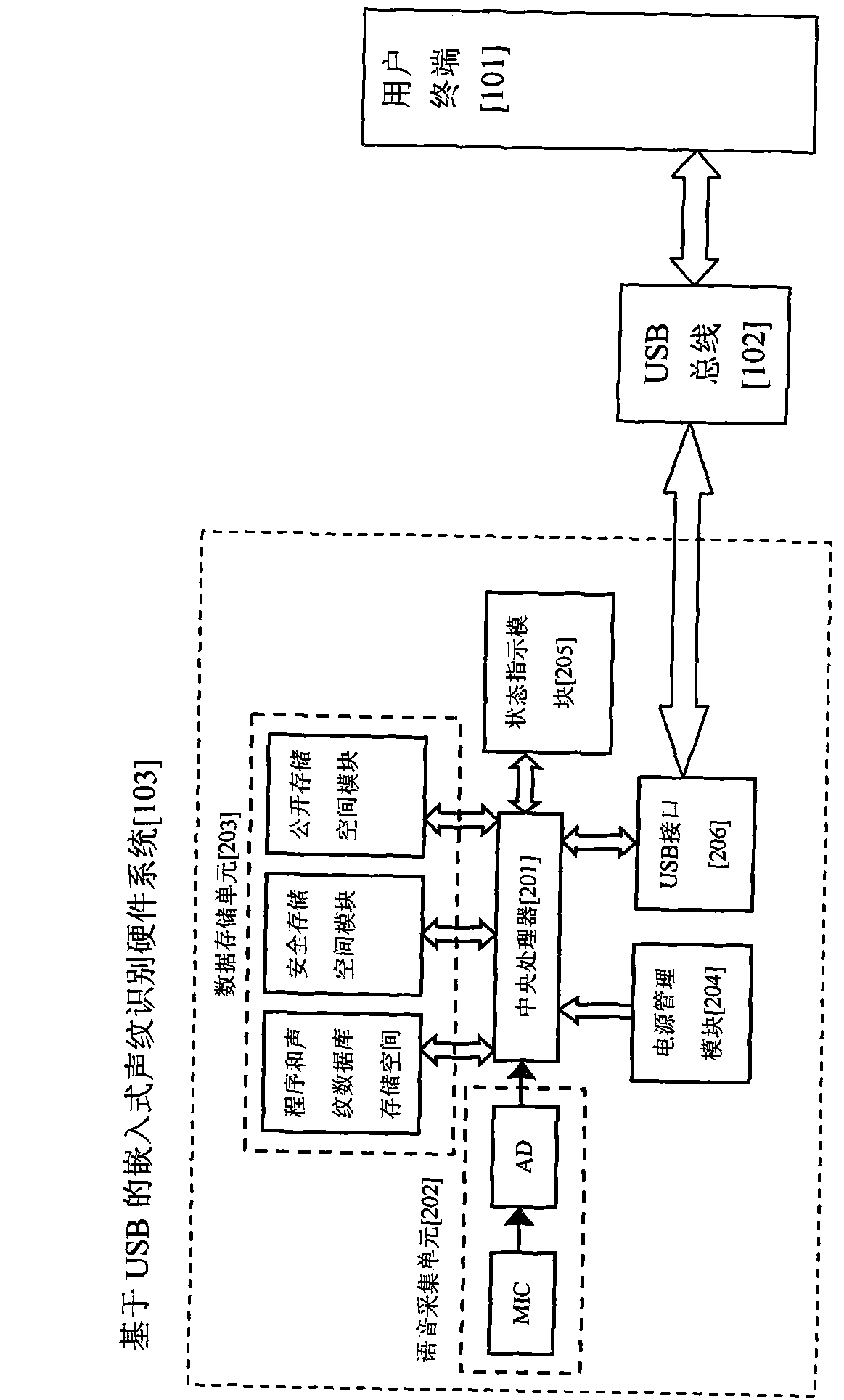
USB (universal serial bus) identity authentication method based on voiceprint recognition and system thereof
InactiveCN101997689APrevent recordingAccurate identificationUser identity/authority verificationSpeech recognitionInternet bankThird party
The invention relates to a USB (universal serial bus) identity authentication method based on voiceprint recognition and a system thereof, belonging to the technical field of computer information safety. The system comprises a user terminal and an embedded voiceprint recognition hardware system based on USB, wherein the user terminal and the embedded voiceprint recognition hardware system based on USB are connected by a USB bus; the embedded voiceprint recognition hardware system based on USB comprises a central processing unit for finishing authenticated voiceprint recognition operation, and the central processing unit is respectively connected with a voice acquisition unit, a data storage unit, a power supply management module, a state indication module and a USB interface used for connecting the user terminal. The invention has the advantage of higher safety. The invention also can provide third-party application and service voiceprint certification interface, and can expand to fields, such as internet banks, e-commerce, e-government affairs and the like.
Owner:JILIN UNIV
Multi-protocol industrial communication safety gateway and communication method with gateway applied
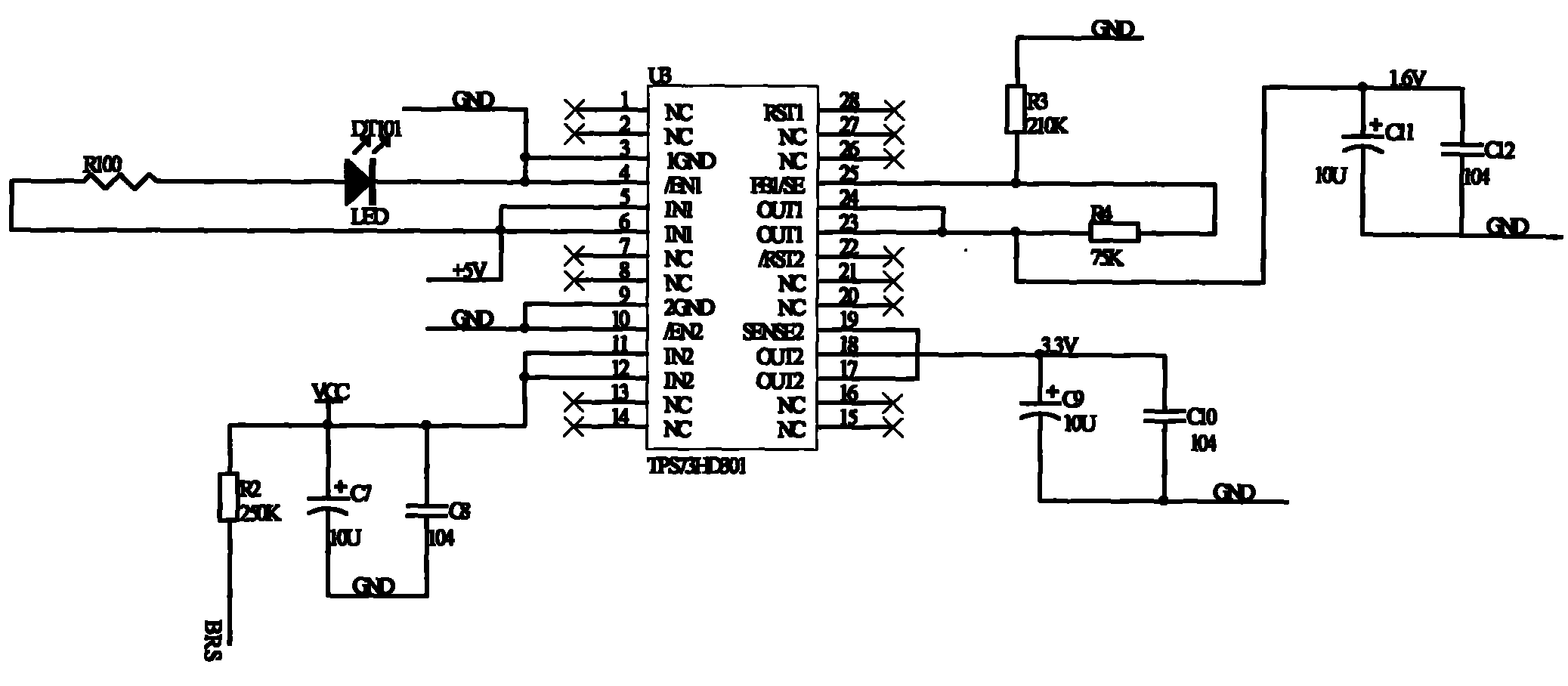
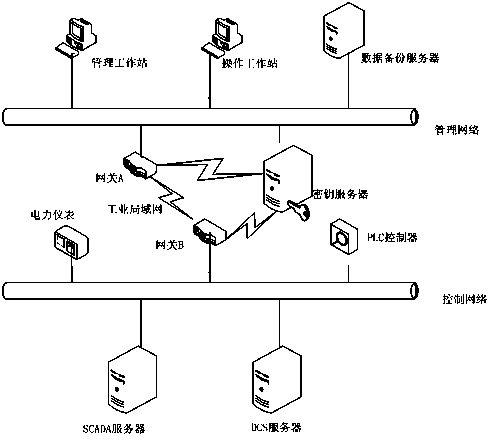
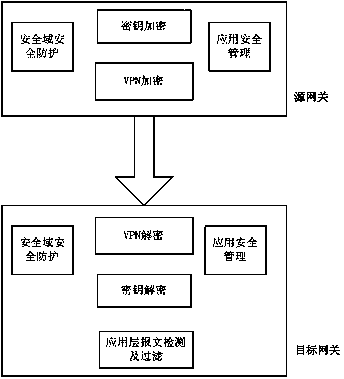
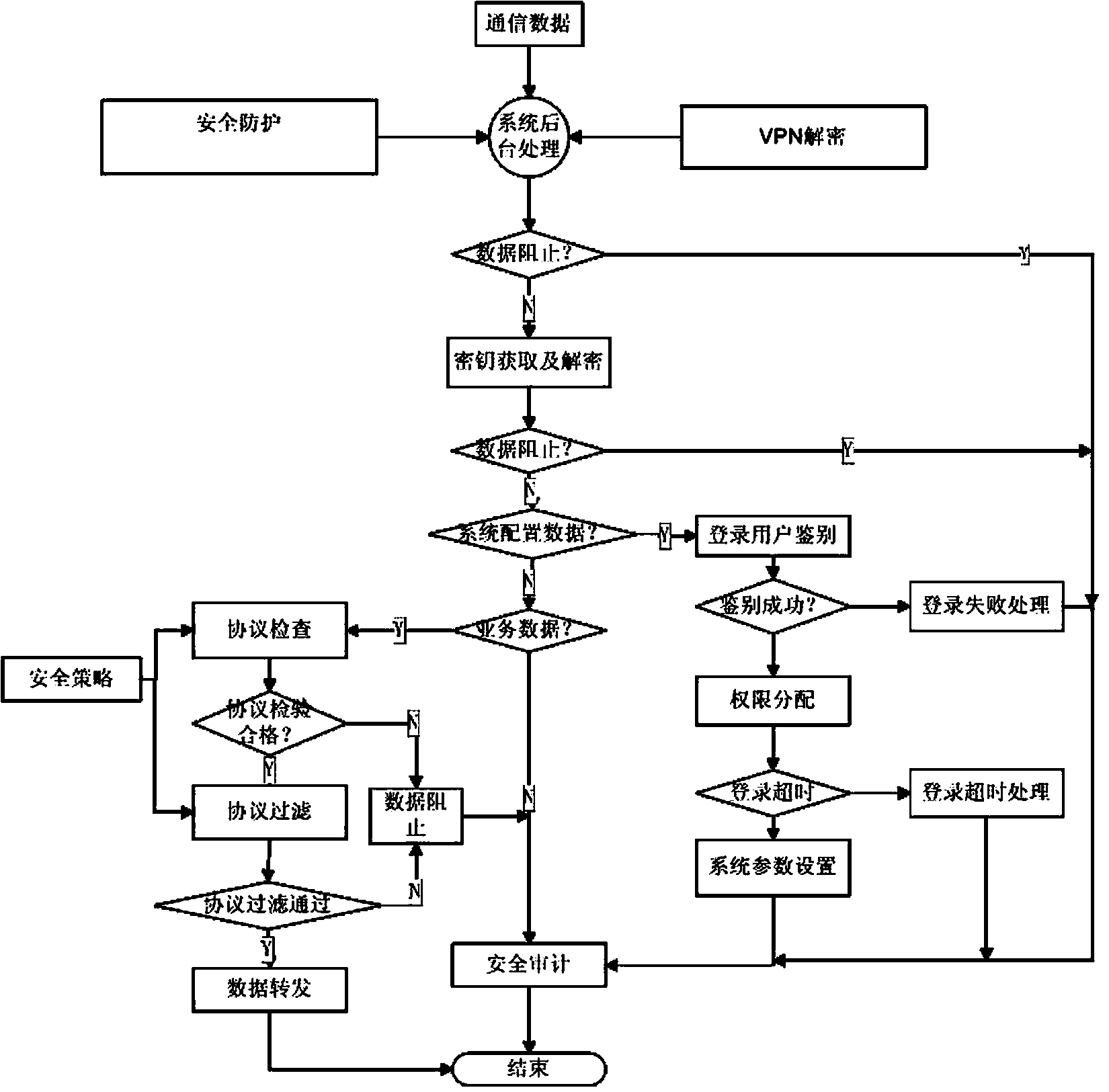
InactiveCN104320332AEnsure safetyImprove forwarding speedNetworks interconnectionNetwork connectionsCommunications securityMulti protocol
The invention relates to a multi-protocol industrial communication safety gateway and a communication method with the gateway applied. In the data communication process, a source gateway encrypts data through a secret key management mechanism module and a VPN encryption and decryption module and then sends the data to a target gateway. The target gateway decrypts the data through the VPN encryption and decryption module, and provides safe detection and control service for data communication through a safety domain safety protection module; if the data are safe, secret key decryption is carried out on application layer data, the types of the application layer data are judged, an application management safety module is used for management if the application layer data are application management data, and an application layer message detecting and filtering module is called for detecting and filtering messages if the application layer data are application layer messages. The mode of combination of the VPN encryption and decryption, the secret key encryption and decryption, and the application layer message detecting and filtering is adopted for communication safety assurance; the safety domain safety protection and the application safety management are adopted for gateway application safety assurance.
Owner:山东华汉电子有限公司
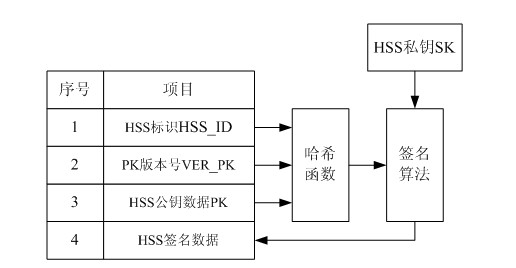
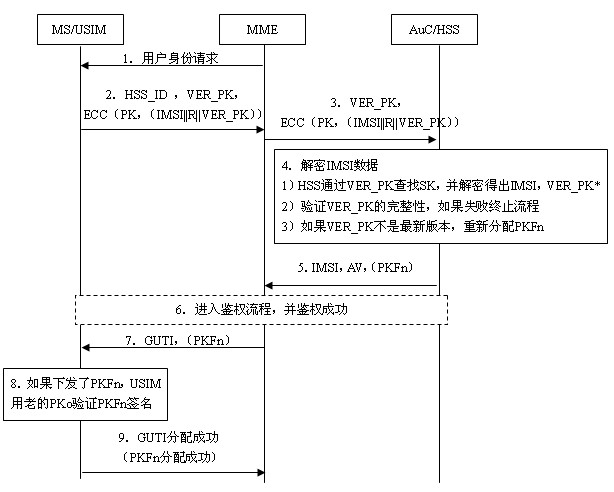
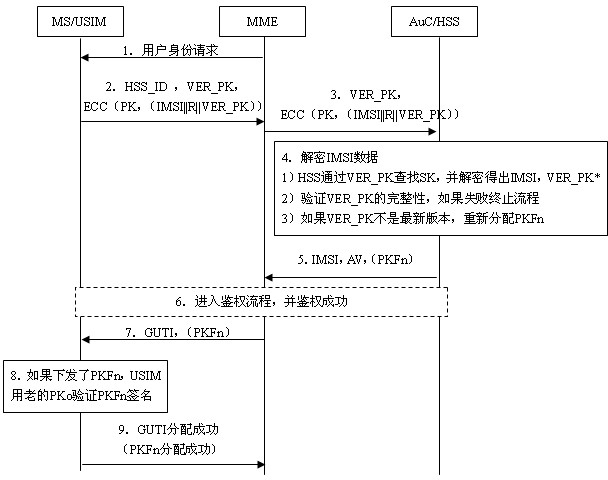
User identity protection method based on public-key mechanism
ActiveCN102026178AIncrease the difficulty of decipheringIntegrity guaranteedSecurity arrangementInternet privacyEngineering
The invention relates to the secret communication field of mobile communication technologies, and discloses a user identity protection method based on a public-key mechanism. The method comprises the following steps: an HSS (hierarchical service system) produces a pair of keys, namely, a public key PK and a secret key SK, then the public key PK is preset to a USIM (universal subscriber identity module) card of UE (user equipment) belonging to the public key PK in the form of a public key file PKF, and the secret key SK is stored in the HSS; a mobile phone sends the following information to anMME (mobility management entity), including HSS identification: HSS_ID, public-key PK version number: VER_PK; and data (IMSI || R|| VER_PK) encrypted by using an asymmetric encryption algorithm; after receiving the information, the MME sends the VER_PK and the (IMSI || R|| VER_PK) to the HSS according to the HSS_ID; and the HSS decrypts the VER_PK and the (IMSI || R|| VER_PK) by using the secret key SK. Because attackers do not know the secret key SK of the HSS, the attackers can not decrypt the (IMSI || R|| VER_PK).
Owner:成都三零瑞通移动通信有限公司
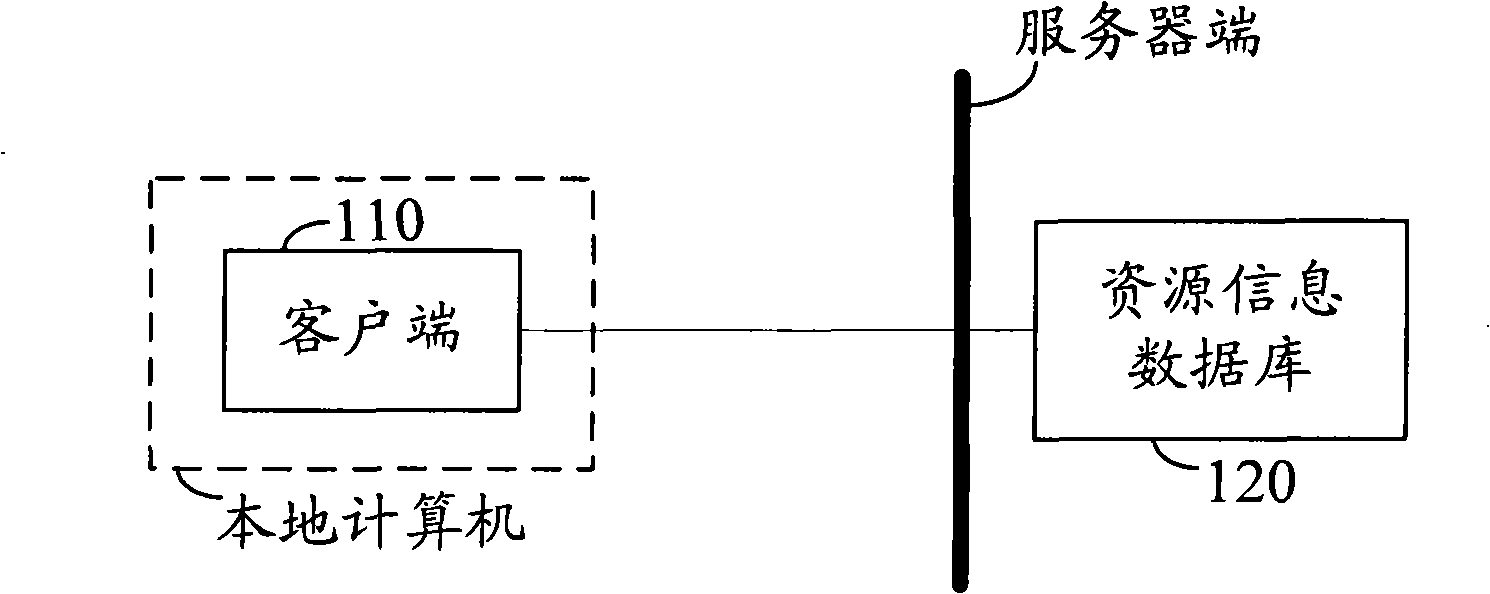
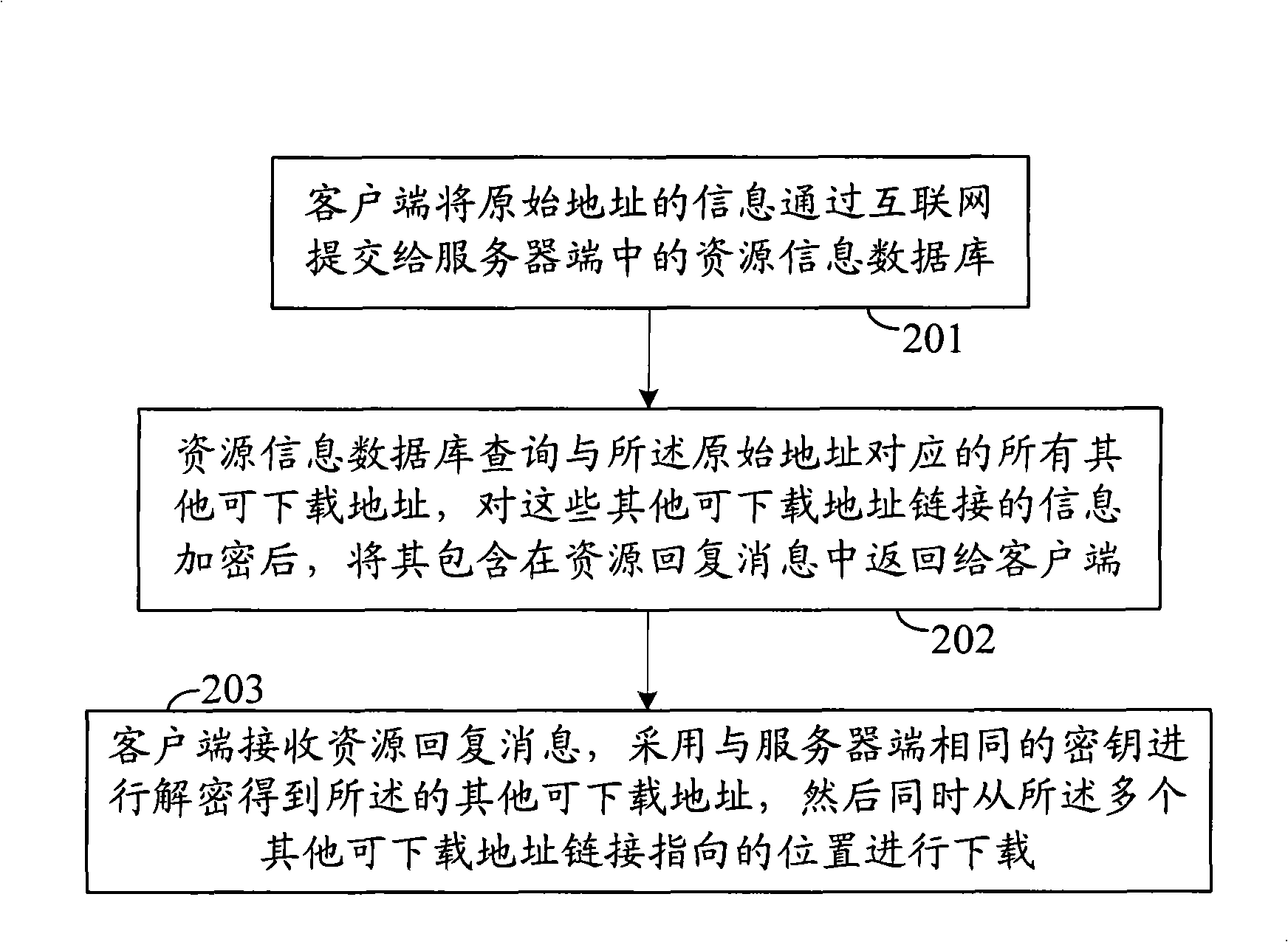
Network resource query method and system
ActiveCN101404576APrevent illegal theftImprove security strengthKey distribution for secure communicationUser identity/authority verificationResource informationClient-side
The invention discloses a network resources inquiry method. A client side and a server side are equipped with the same security policy which is an algorithm used in the whole identity authentication process. The method comprises the following steps: the client side sends a resource inquiry request to the server side, and the server side indicates the client side to authenticate identity after receiving the resources inquiry request; after the identity authentication is passed, the server side inquires resources to obtain a resources inquiry result, and sends back the resources inquiry result to the client side. The invention also further provides a network resources inquiry system. The network resource inquiry method and the system ensure that the valid client side can successfully pass the identity authentication and obtain the resources inquiry result, avoid hackers or rivals from illegally stealing information in the resource information database, and greatly enhances the information security in the resource information database.
Owner:SHENZHEN THUNDER NETWORK TECH
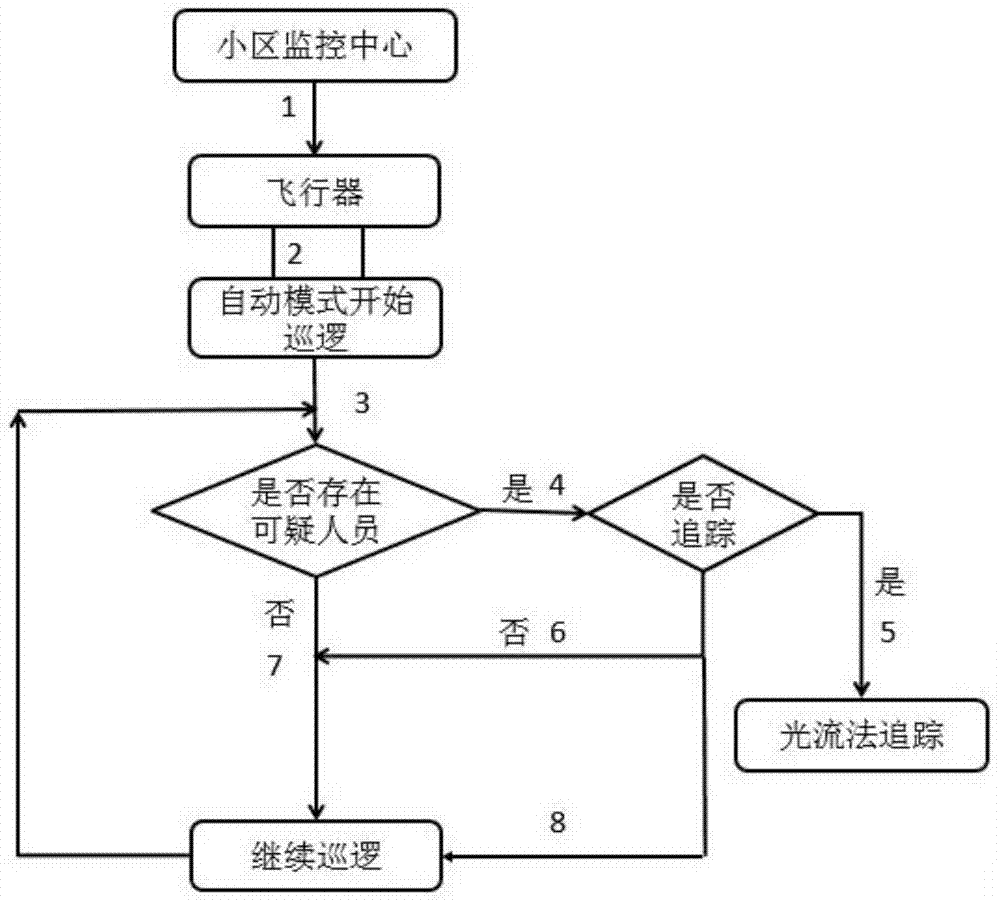
Aircraft platform-based intelligent district safety protection system and intelligent district safety protection method
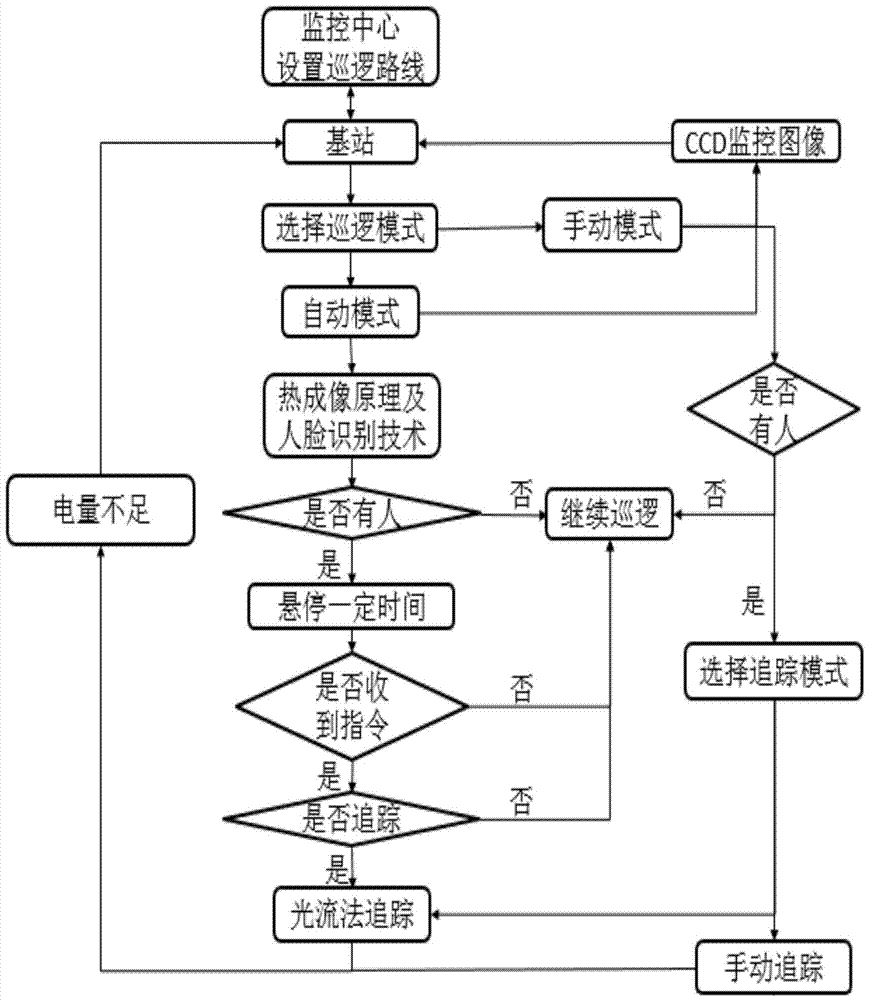
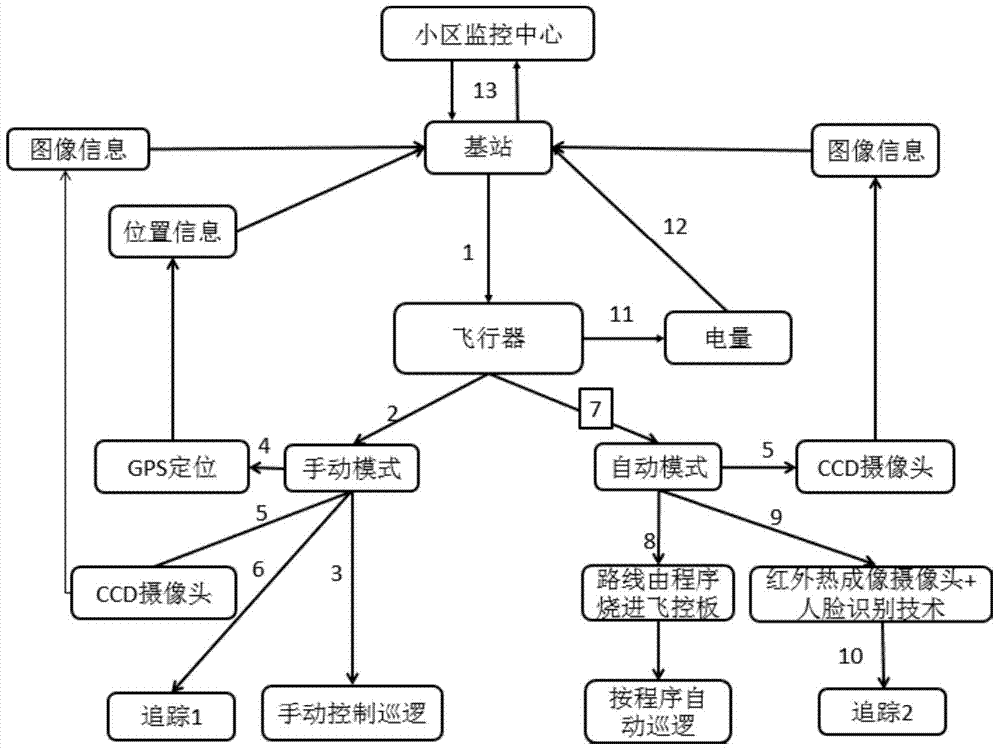
InactiveCN104853167AExpand the range of patrolsImprove security strengthClosed circuit television systemsCcd cameraProtection system
The invention discloses an aircraft platform-based intelligent district safety protection method, which comprises step: according to distribution of monitoring blind areas in the district, a monitoring center sets a patrol route of the aircraft; when the aircraft works in an automatic mode, the monitoring center controls the aircraft to fly via a base station, images of the district are monitored via a CCD camera of the aircraft along the set patrol route, and the images obtained through monitoring of the CCD camera are transmitted in real time to the monitoring center via the base station; the aircraft uses the equipped infrared camera thermal imaging principle and adopts the face recognition technology to judge whether a person exists in the patrol route, if yes, the aircraft stops in the air for a certain time and transmits an announcement instruction to the monitoring center via the base station, and if not, patrol operation is continued. Monitoring can be executed on places at which no one can arrive via the CCD camera, and the safety protection range is increased; and through the thermal imaging principle of the infrared camera and the face recognition technology, the district safety protection strength is enhanced.
Owner:HUAZHONG UNIV OF SCI & TECH
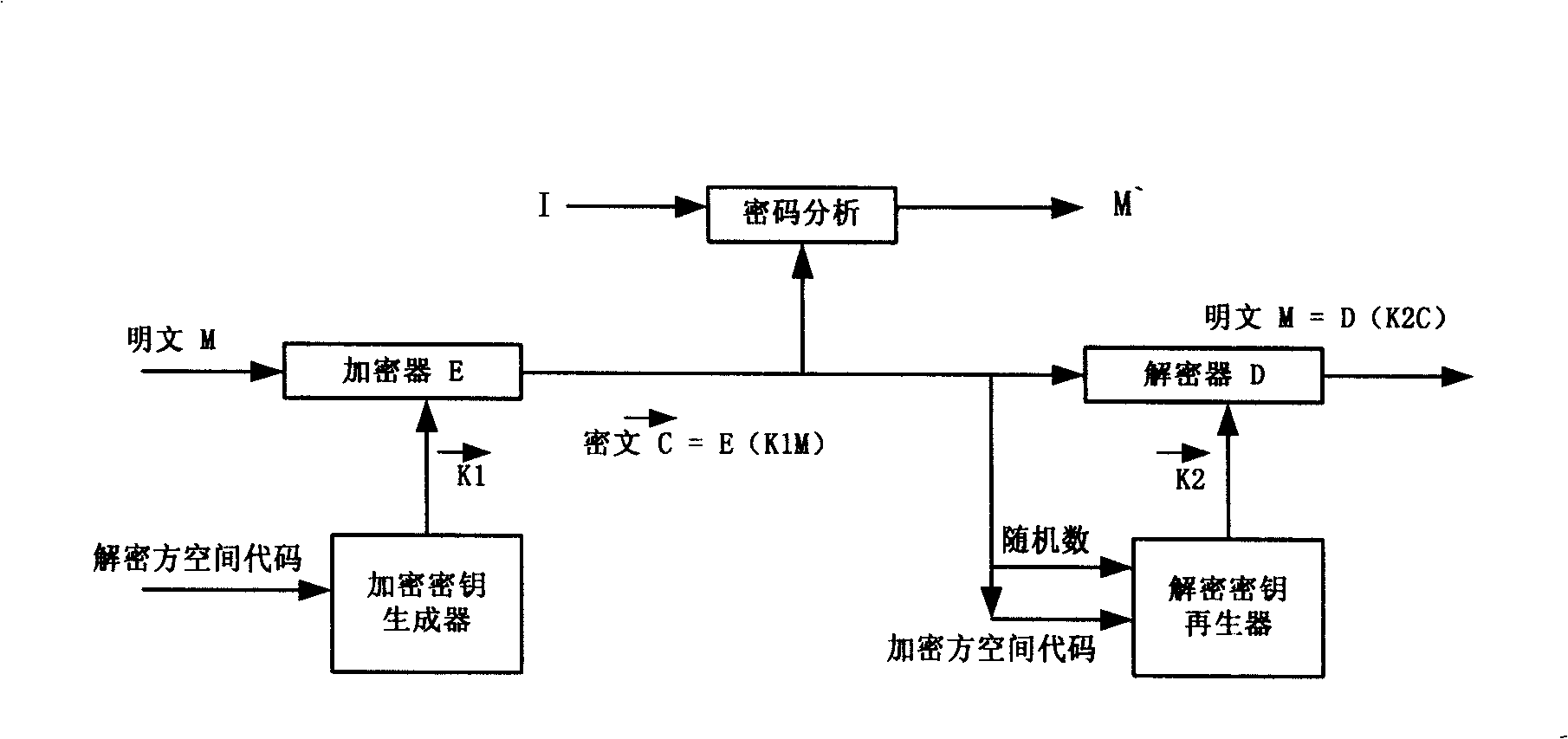
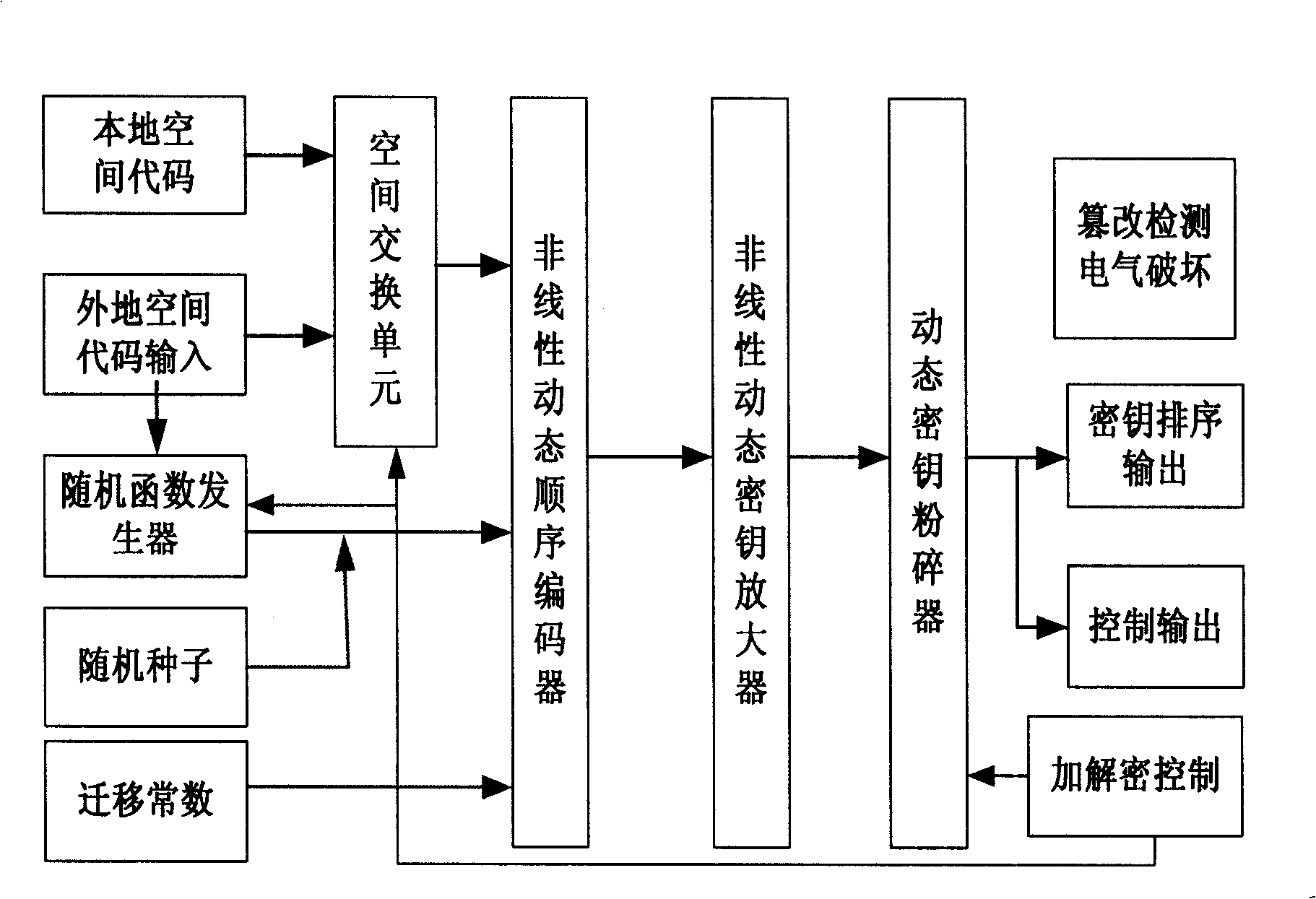
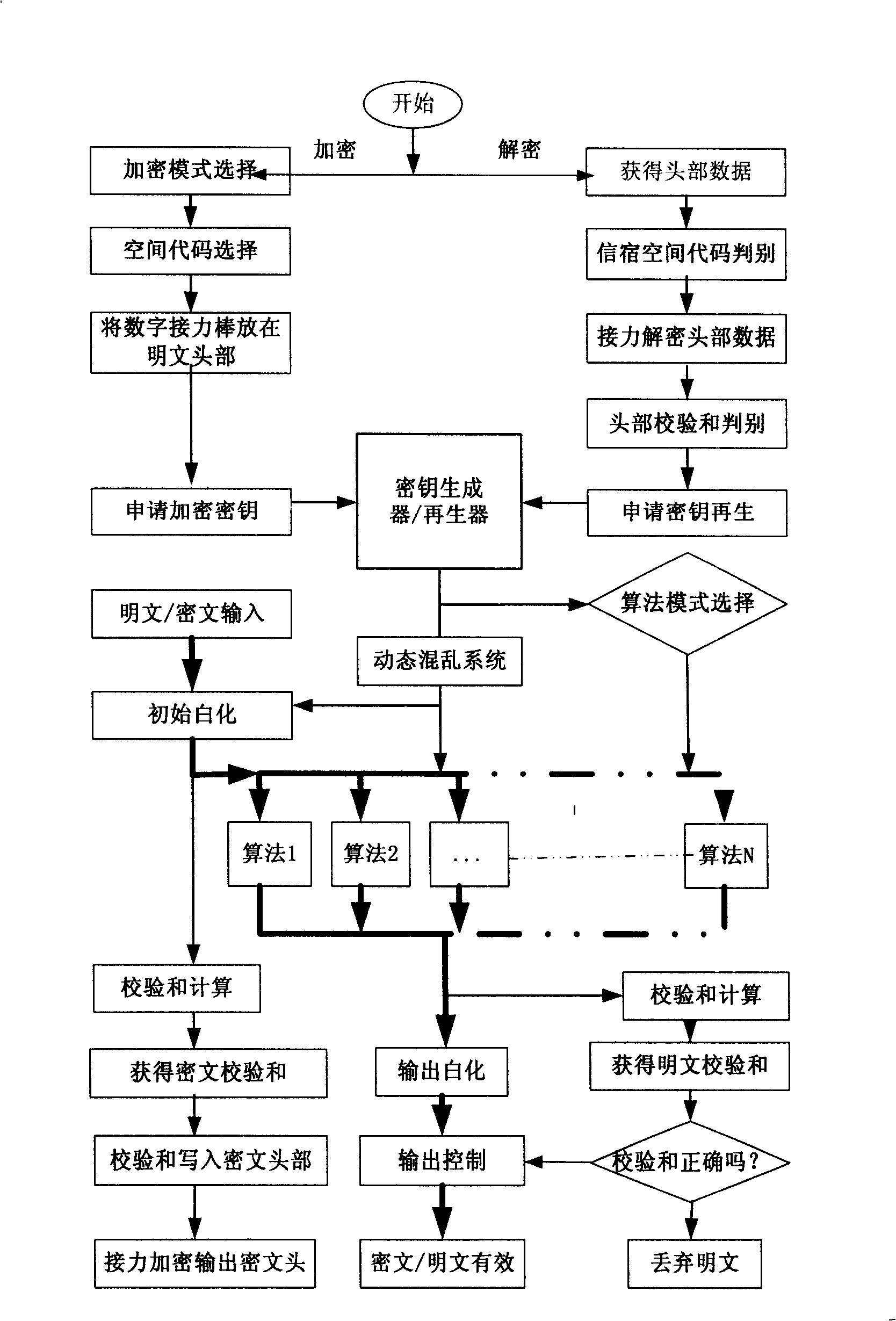
Novel authentication mechanism for encrypting vector
InactiveCN101355422AObvious superiorityImmune to cryptographic attack methodsPublic key for secure communicationUser identity/authority verificationCryptosystemKey generation
The invention discloses a novel vector encryption authentication mechanism and relates to a vector cryptography method, belonging to the technical field of information security. The method comprises the following steps: a cipher system selects a large number encryption key space M which is twice divided into 2*2 encryption key subspaces which are provided with 2 vectors with different orientations in order that each cipher system of the system possesses a unique encryption key subspace and a unique decryption key subspace; according to the method, the novel vector encryption authentication mechanism can be constructed; the mechanism adopts a hardware tamperproof encryption key generation / regeneration technology to realize the secondary division of the large number encryption key space and endow the encryption key with vector property; and the mechanism adopts a dissymmetrical symmetric algorithm array for encryption / decryption, thereby realizing high strength security, anti-replay, integral control, identity authentication and digital signature and having no problem of the management of the encryption key.
Owner:冯振周
Method for binding/recovering key using fingerprint details
InactiveCN101013943AImprove security strengthUser identity/authority verificationCharacter and pattern recognitionTheoretical computer scienceUltimate tensile strength
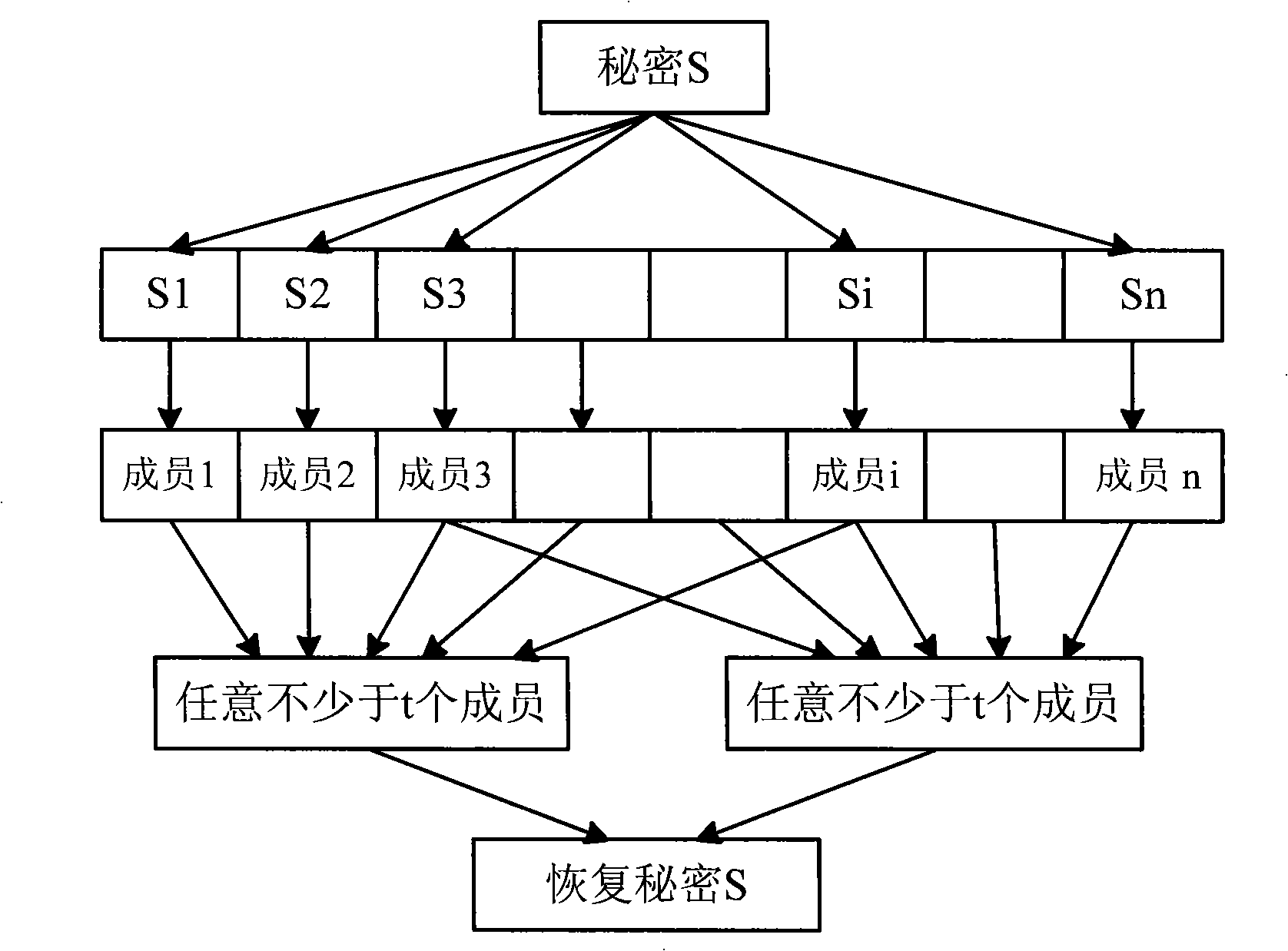
The invention provides one method to bind and restore key by use of print details, which adopts multiple formula to bind one set of random bit and finger print detail property and needing match detail number to determinate random number; using several parameters of random number to generate one key to protect keys S to realize print detail property points and key binding. Due to key S indirectly and multiple formula binding, its design has no protection of length limits.
Owner:BEIJING UNIV OF POSTS & TELECOMM
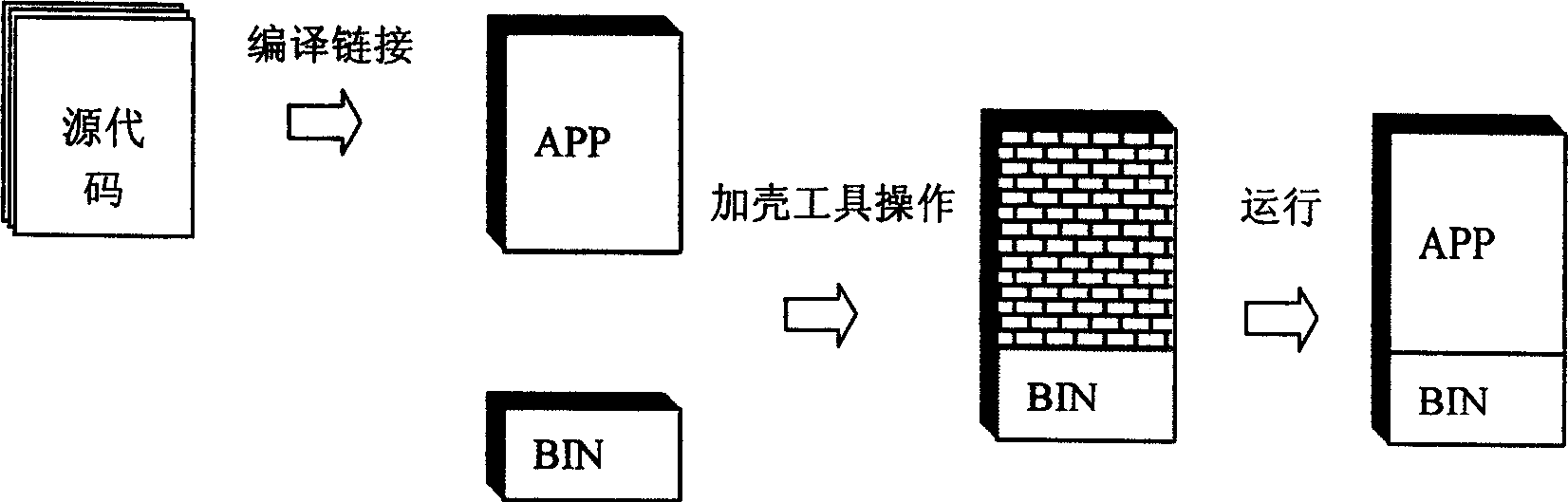
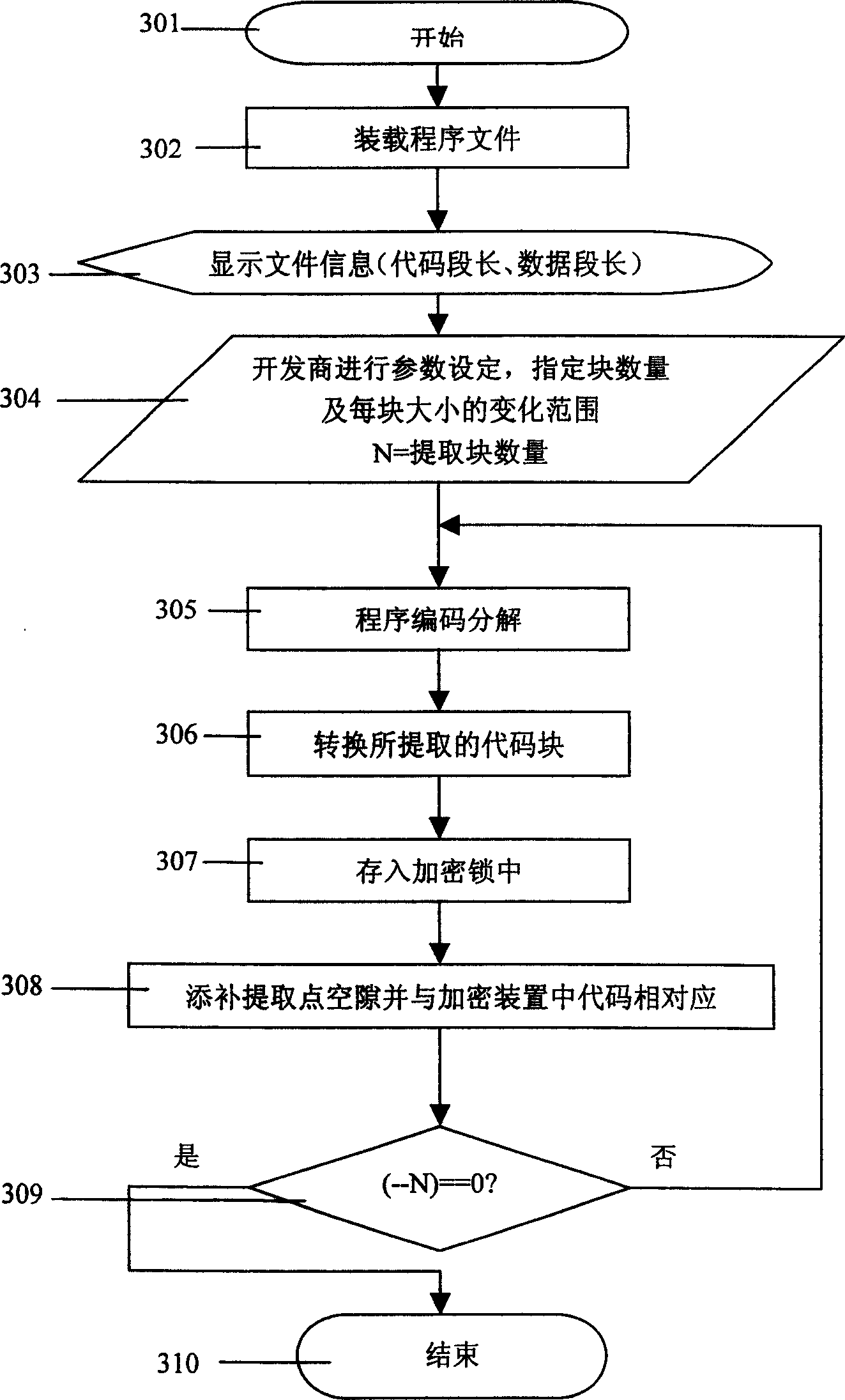
Software copy right protecting method for extracting partial code to enciphed device from software
ActiveCN1749915AIncrease the difficulty of crackingNo burdenDigital data processing detailsSoftware engineeringSoftware development
The present invention relates to software copyright protecting method, and is especially software copyright protecting method by extracting partial codes from program file to the enciphering device. The compiled program file has its codes decomposed into partial codes running in the enciphering device and the other in the computer, and this makes it possible for the software developer to raise the enciphering safety degree without increasing load in developing software protecting functional module. The software copyright protecting method is superior to traditional shell enciphering method.
Owner:北京坚石诚信科技有限公司
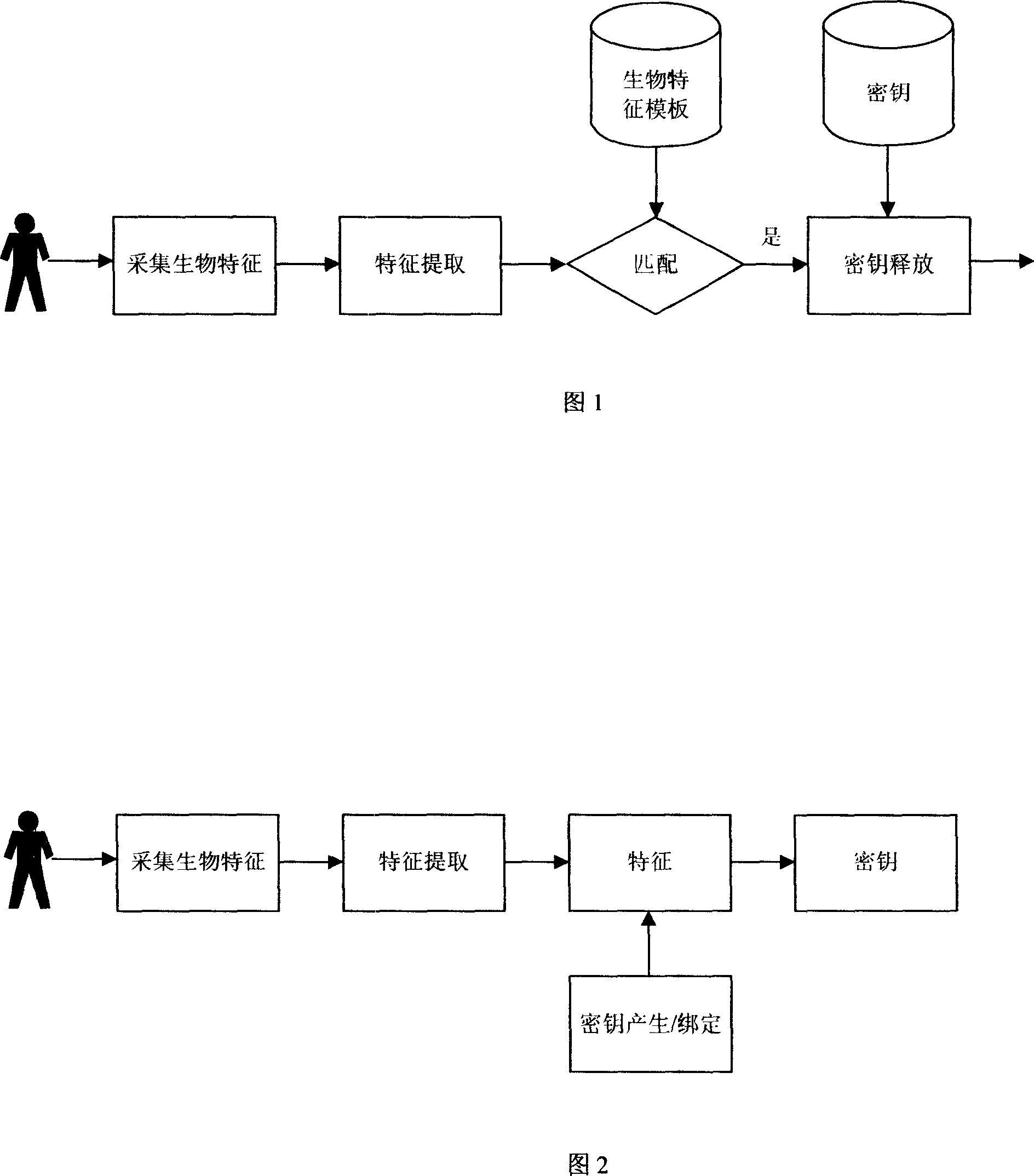
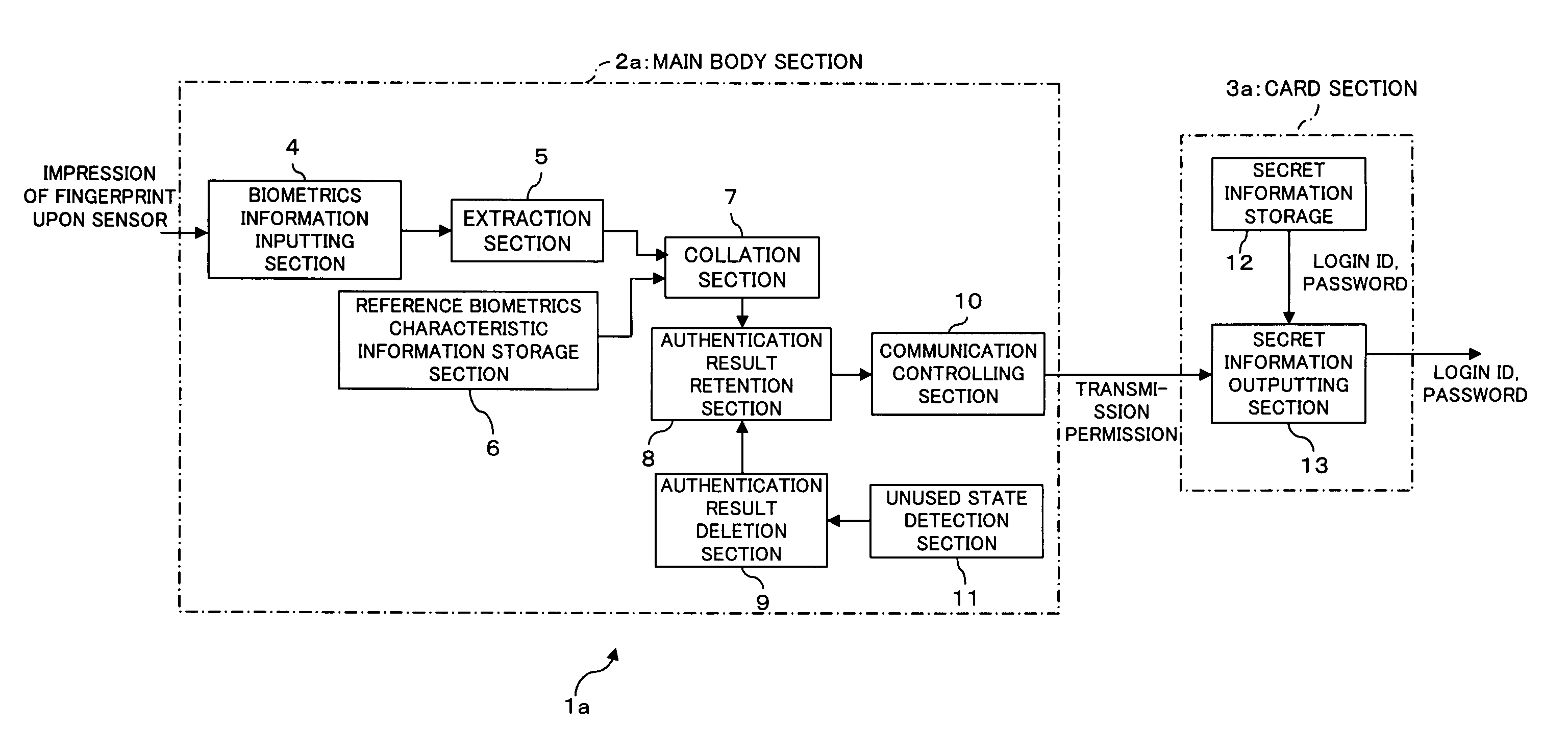
Electronic storage apparatus, authentication apparatus and authentication method
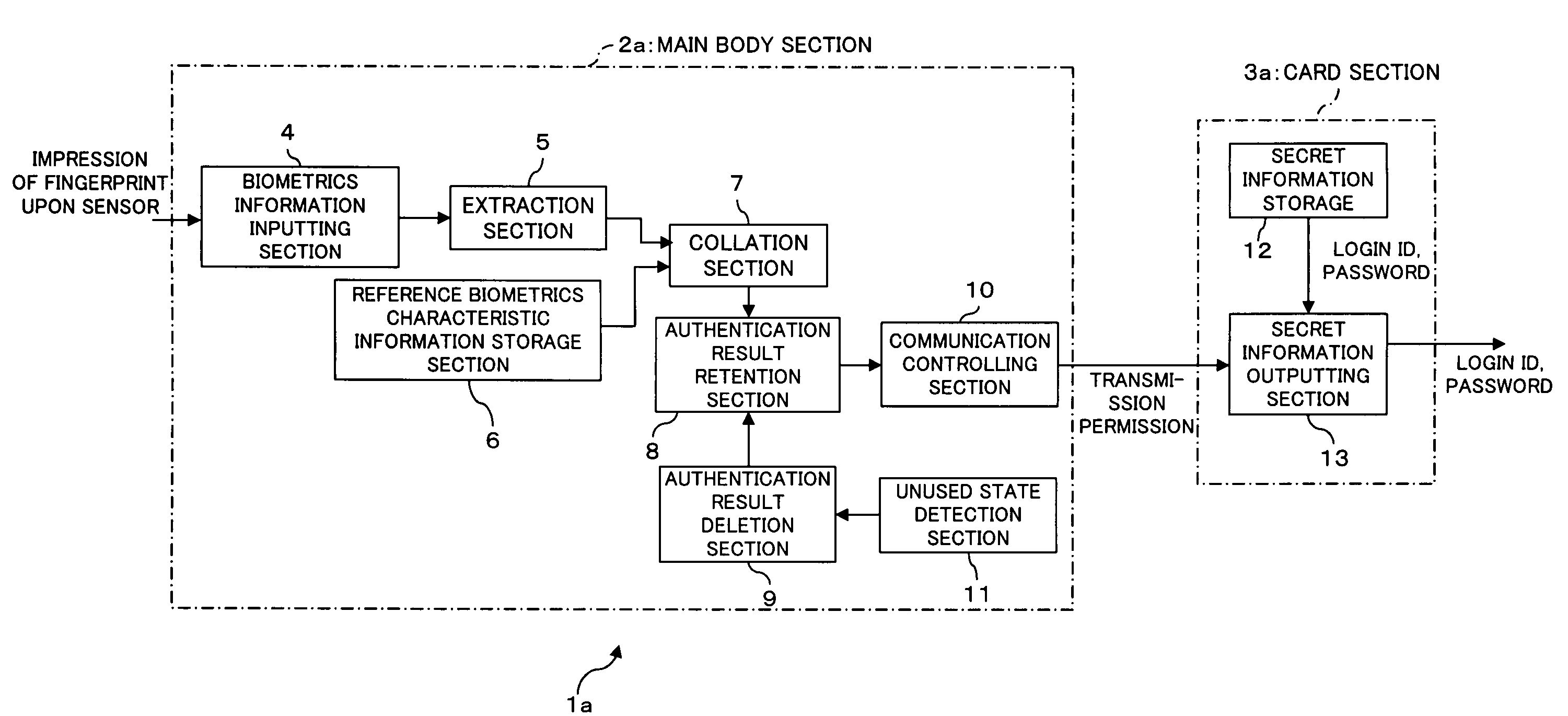
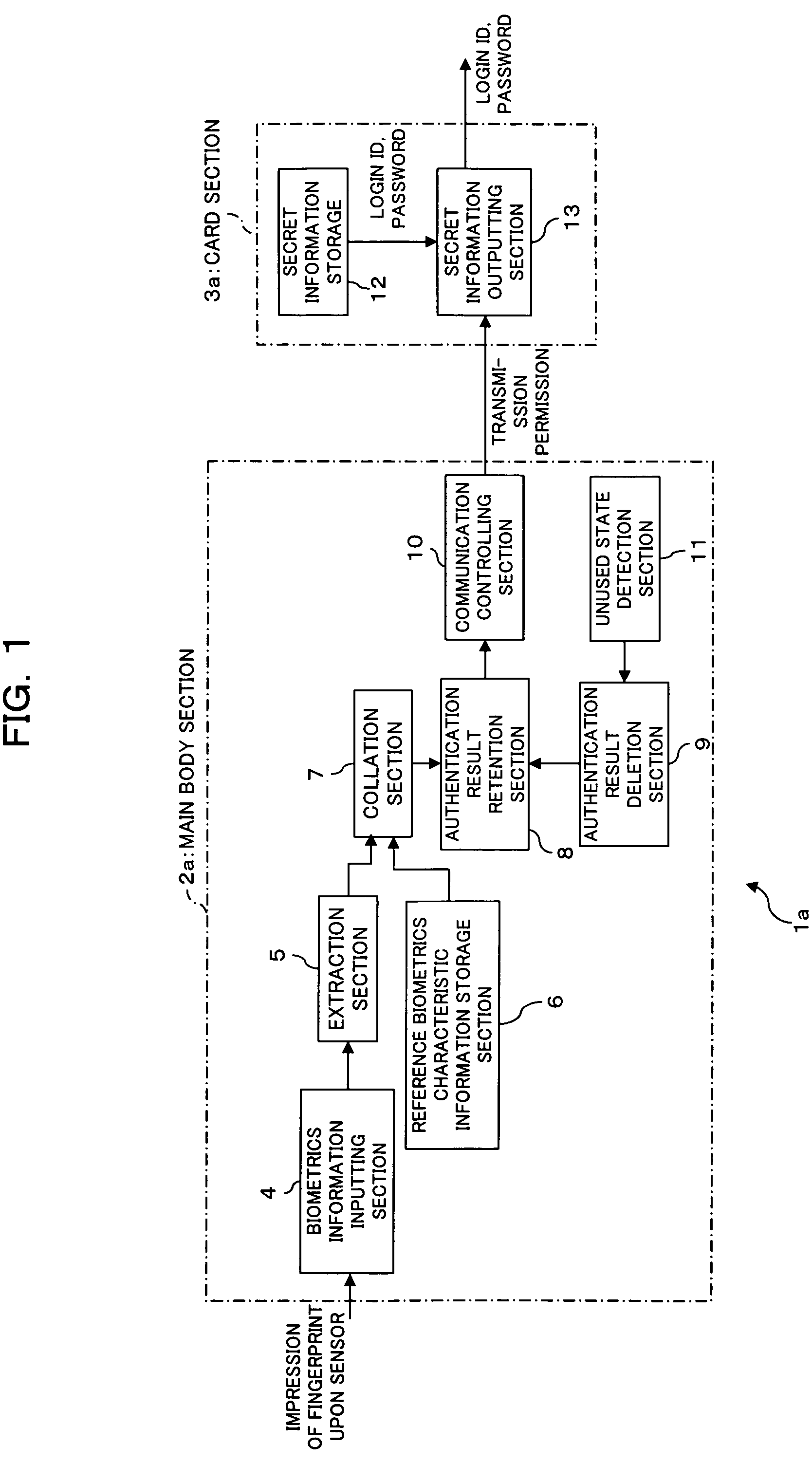
InactiveUS20050144354A1Simple configurationImprove authentication strengthDigital data processing detailsUser identity/authority verificationBiometricsCollation
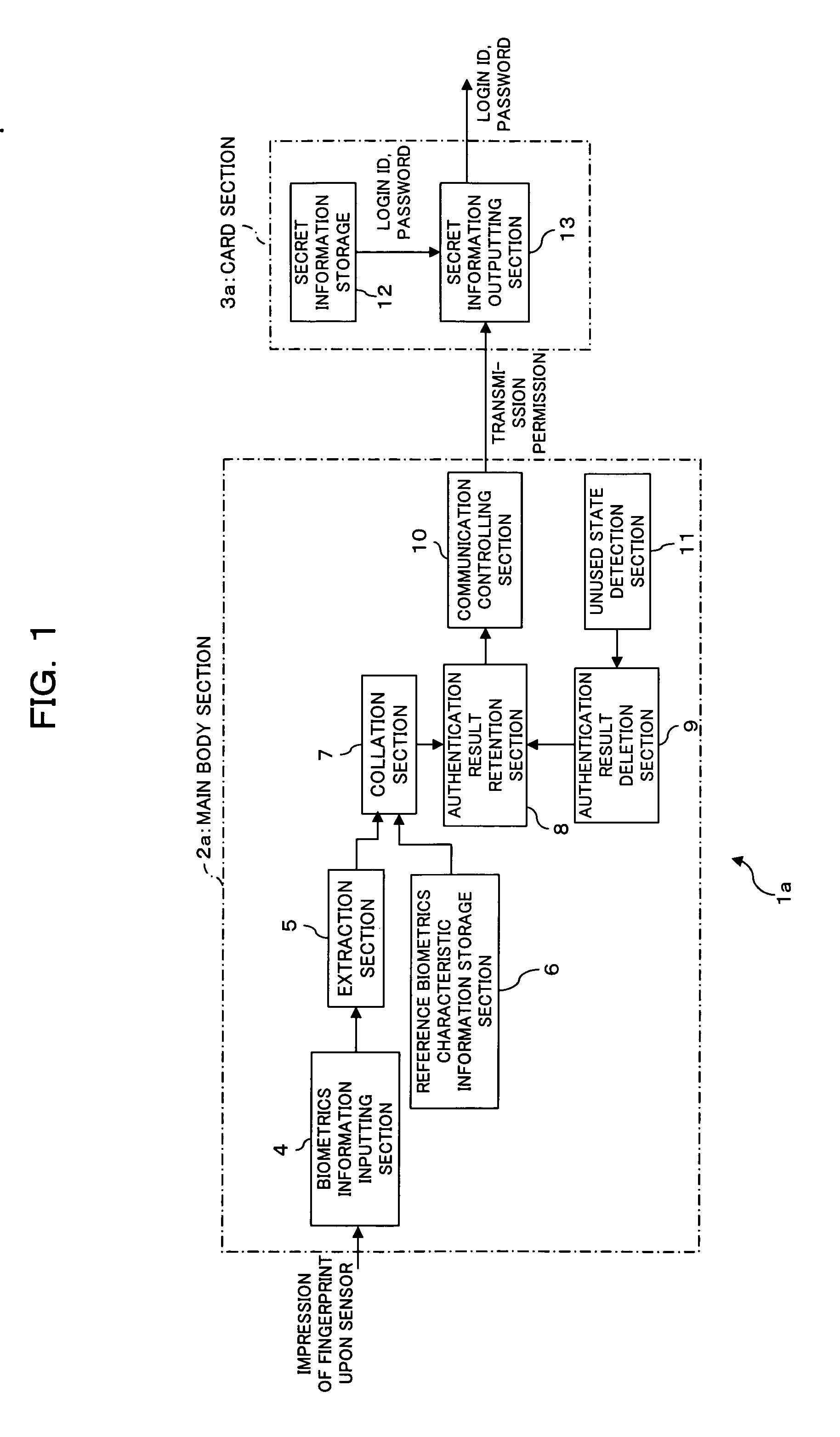
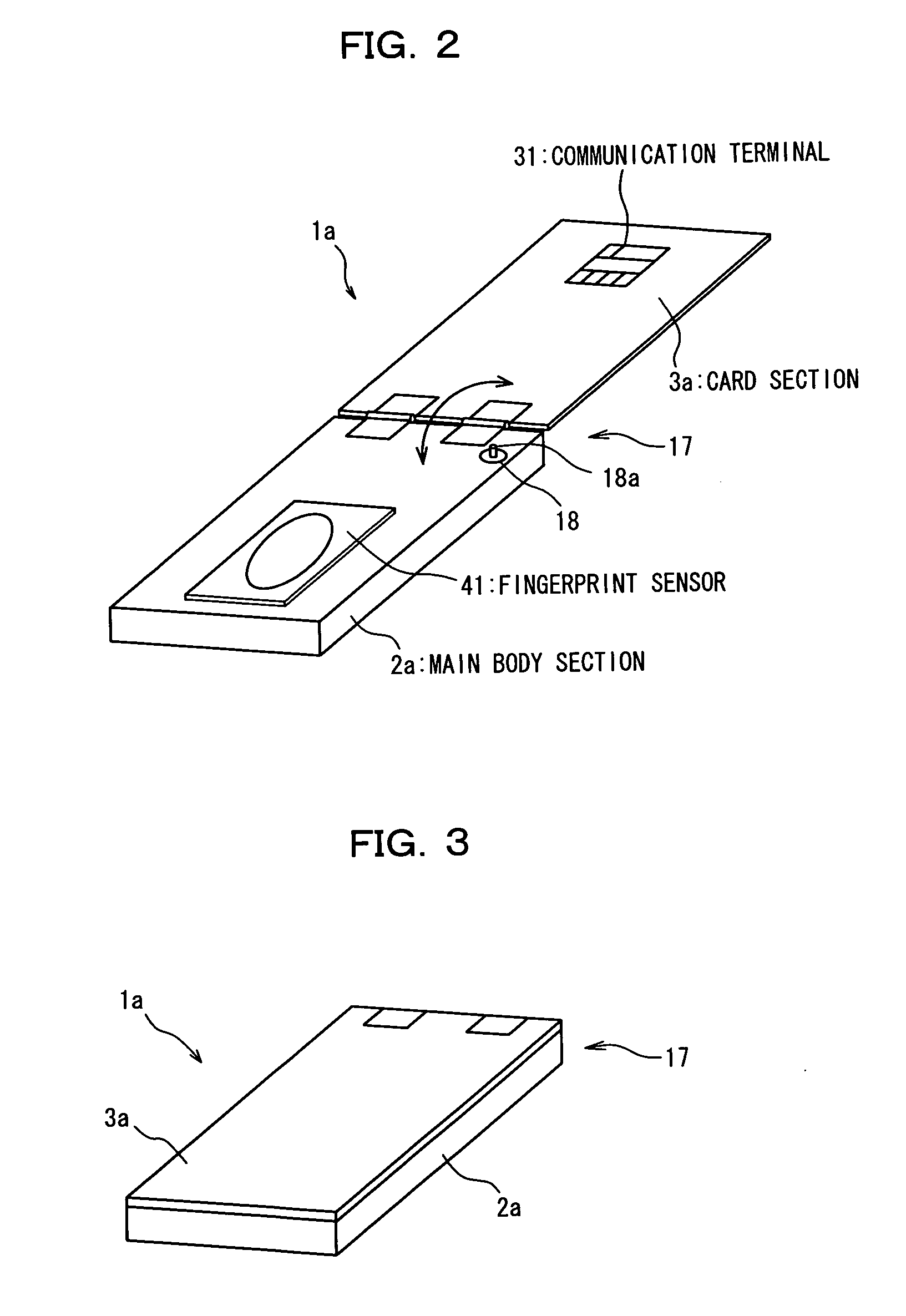
An electronic storage apparatus comprises a biometrics information inputting section, a collation section for comparing and collating collation biometrics characteristic information and reference biometrics characteristic information with each other, an authentication result retention section for retaining, where it is recognized that the collation biometrics characteristic information is that of an owner, the result of the authentication, a secret information outputting section capable of outputting secret information of the owner stored in a secret information storage section to the outside, and an authentication result deletion section for deleting, when an unused state detection section detect that the secret information outputting section is in an unused state, the result of authentication retained by the authentication result retention section, whereby the security strength of a card type storage medium is raised and the electronic storage apparatus can be used more easily by a user.
Owner:FUJITSU LTD
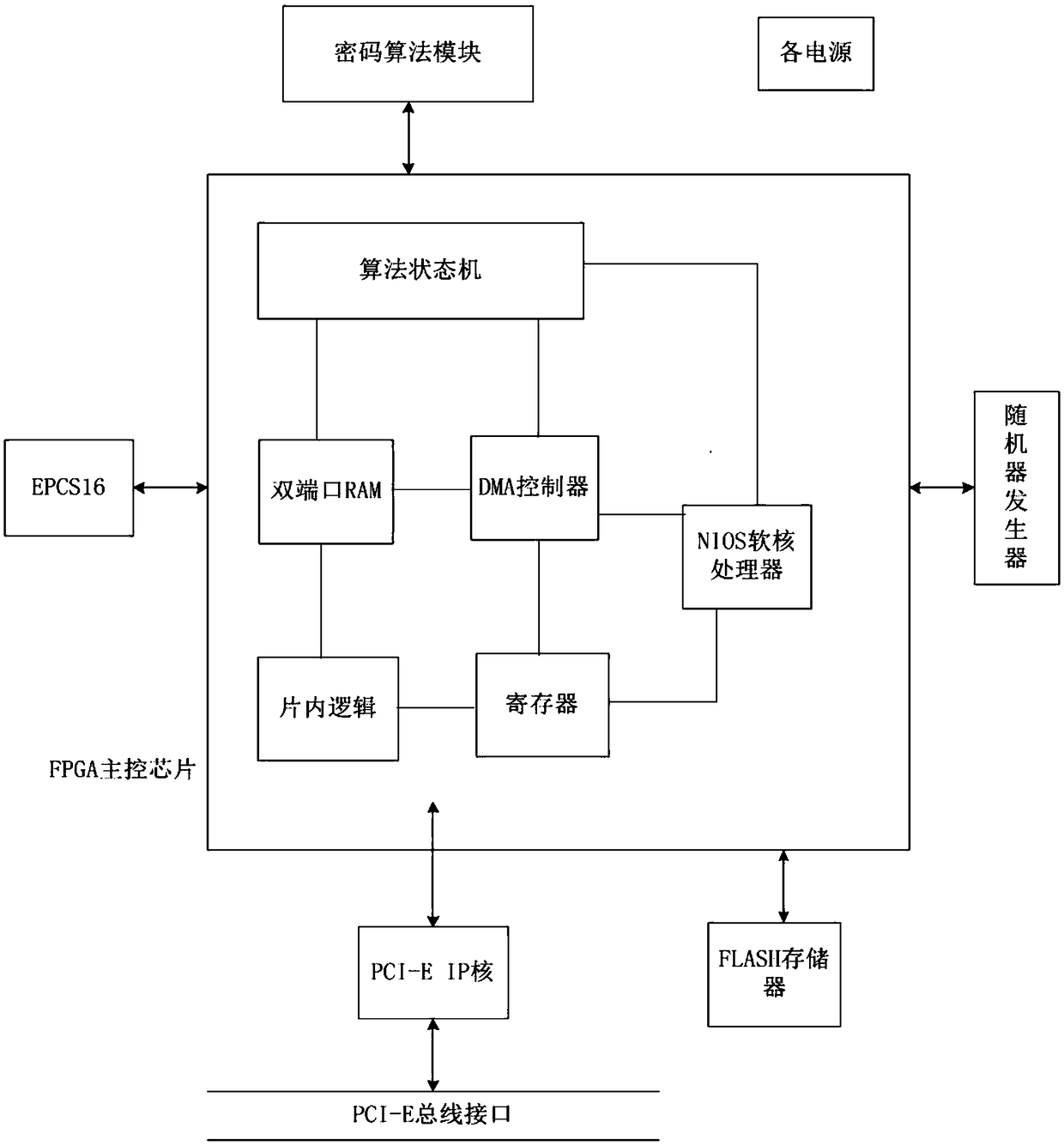
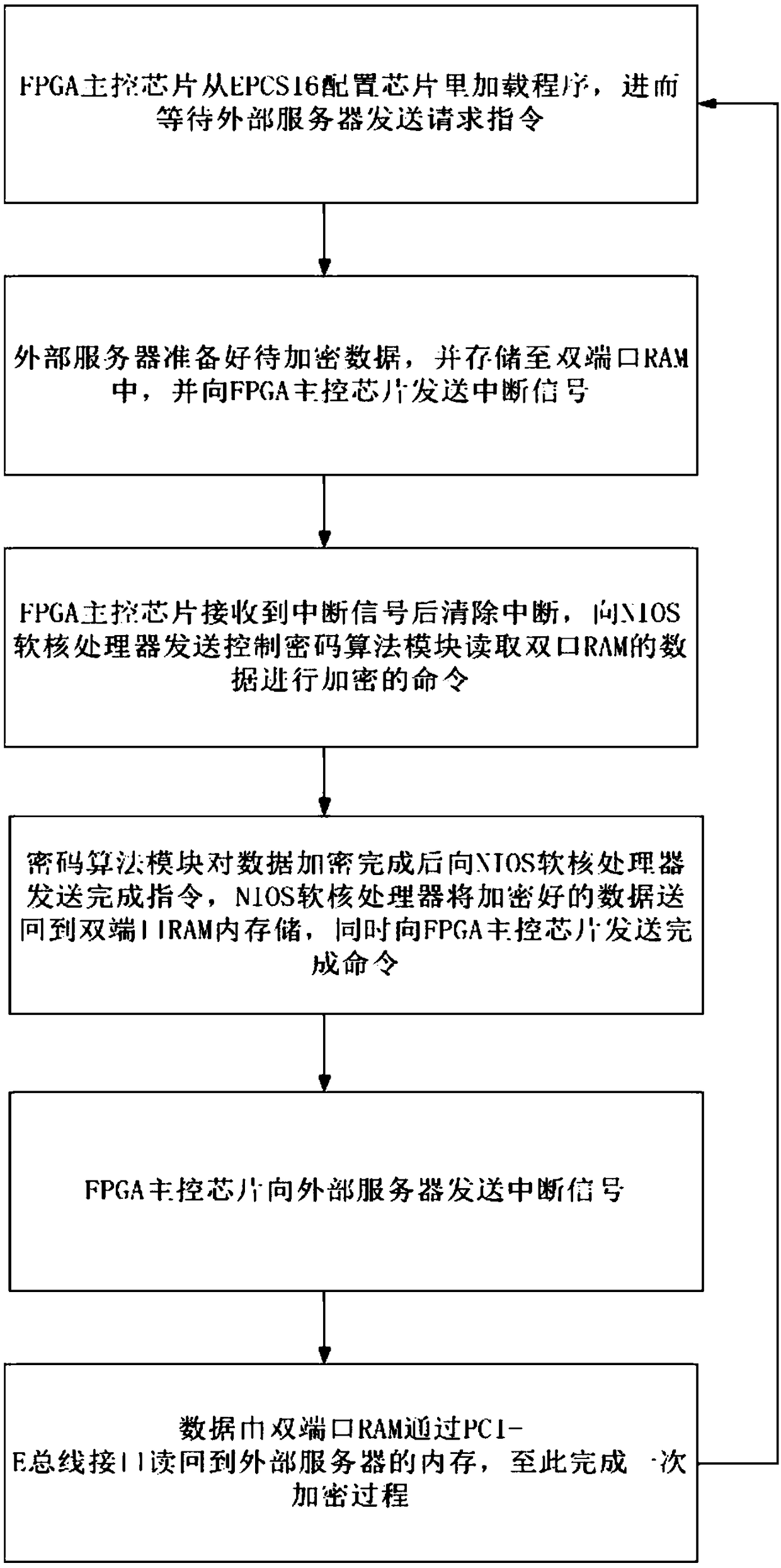
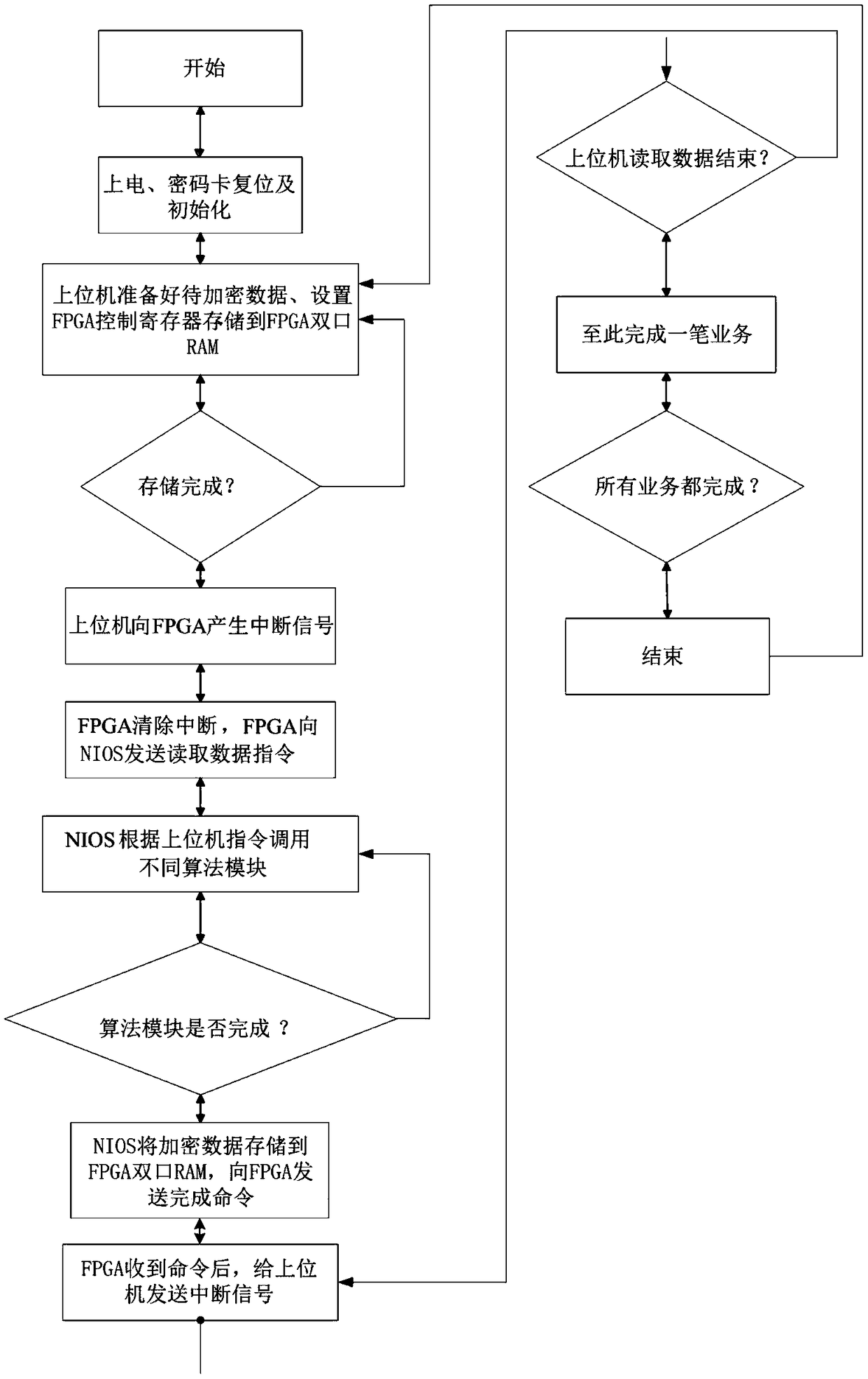
A full algorithm cryptographic card based on PCI-E interface and an encryption method thereof
InactiveCN109145568AImprove security strengthImprove securityDigital data authenticationEnergy efficient computingAlgorithmic State MachineSERCOS interface
The invention discloses a method based on PCI-E interface full algorithm cryptographic card, including: a cryptographic algorithm module, a FLASH memory, a PCI-E bus interface, a random numb generator, and an FPGA master control chip with NIOS soft core processor, wherein a PCI-E IP core and an algorithm state machine are integrated in the FPGA master control chip. The cryptographic algorithm module comprises a symmetric key encryption SM4 algorithm chip, a symmetric key encryption SM1 algorithm chip and an asymmetric key encryption SM2 algorithm chip. The invention also discloses an encryption method of the cipher card. The invention provides a high-performance full-algorithm cryptographic card, which simultaneously reduces the complexity of hardware circuit and energy consumption, improves the key operation speed, and the cryptographic card adopts a home-made cryptographic algorithm, so that the user's key is most securely protected.
Owner:西安得安信息技术有限公司
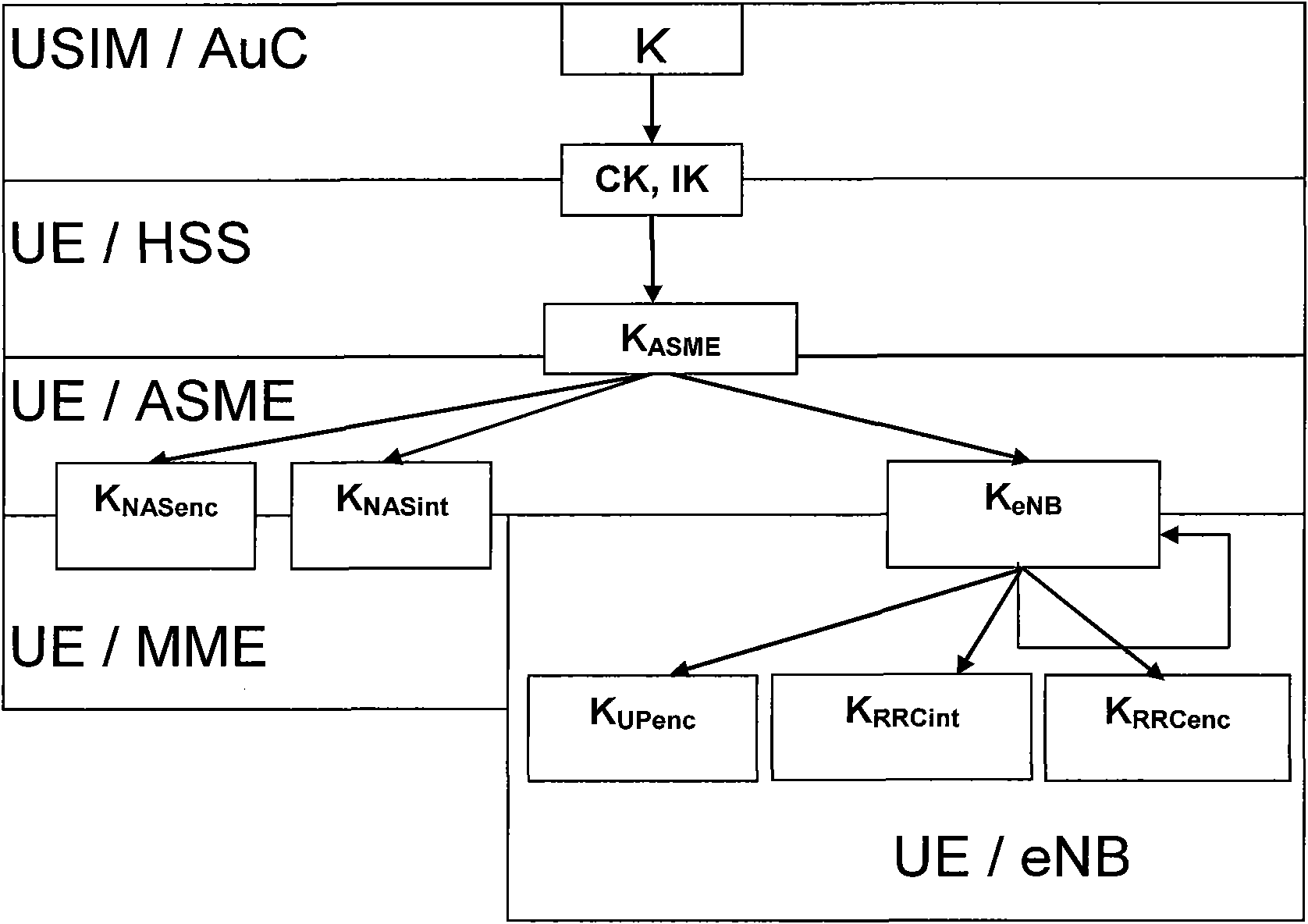
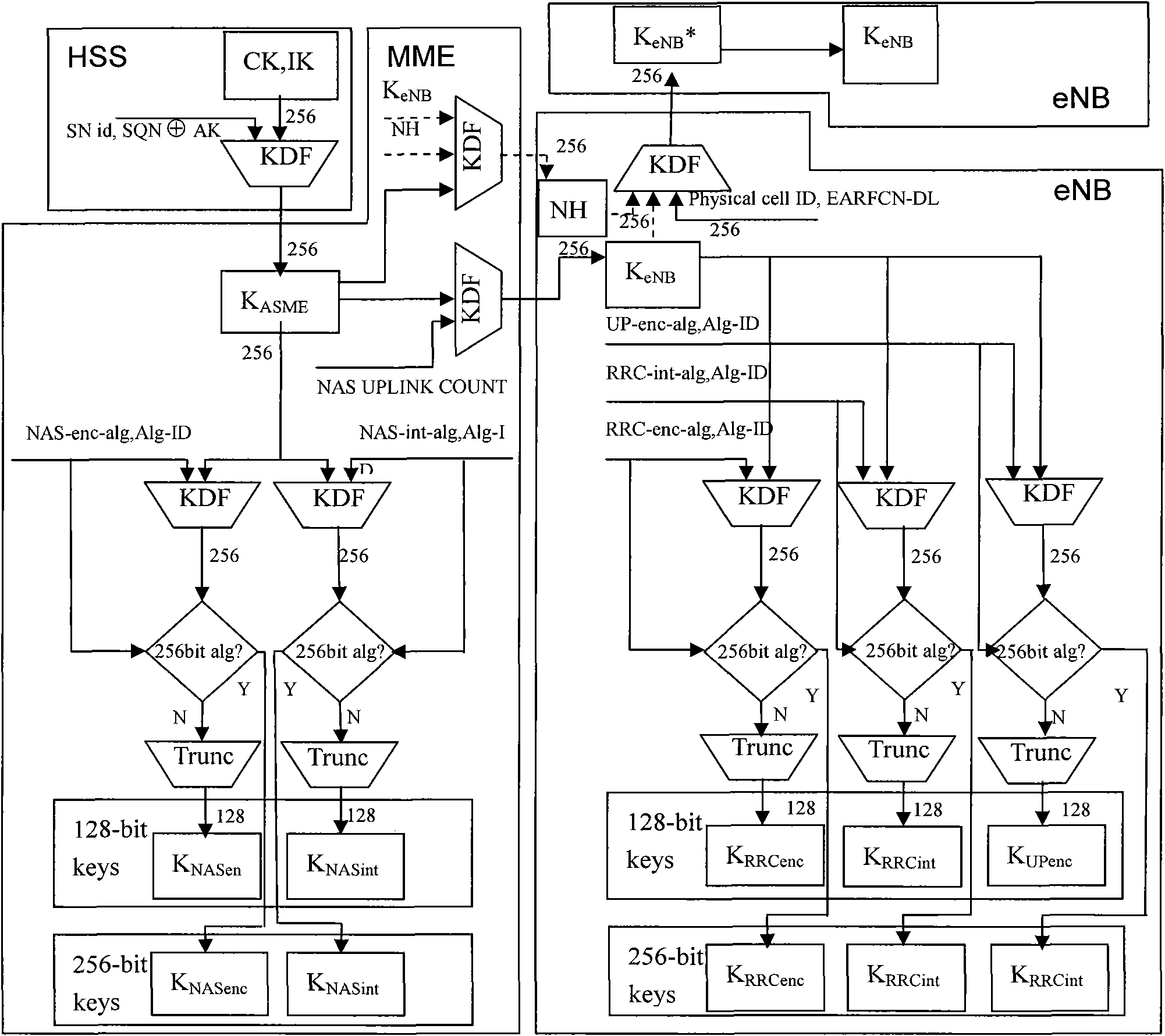
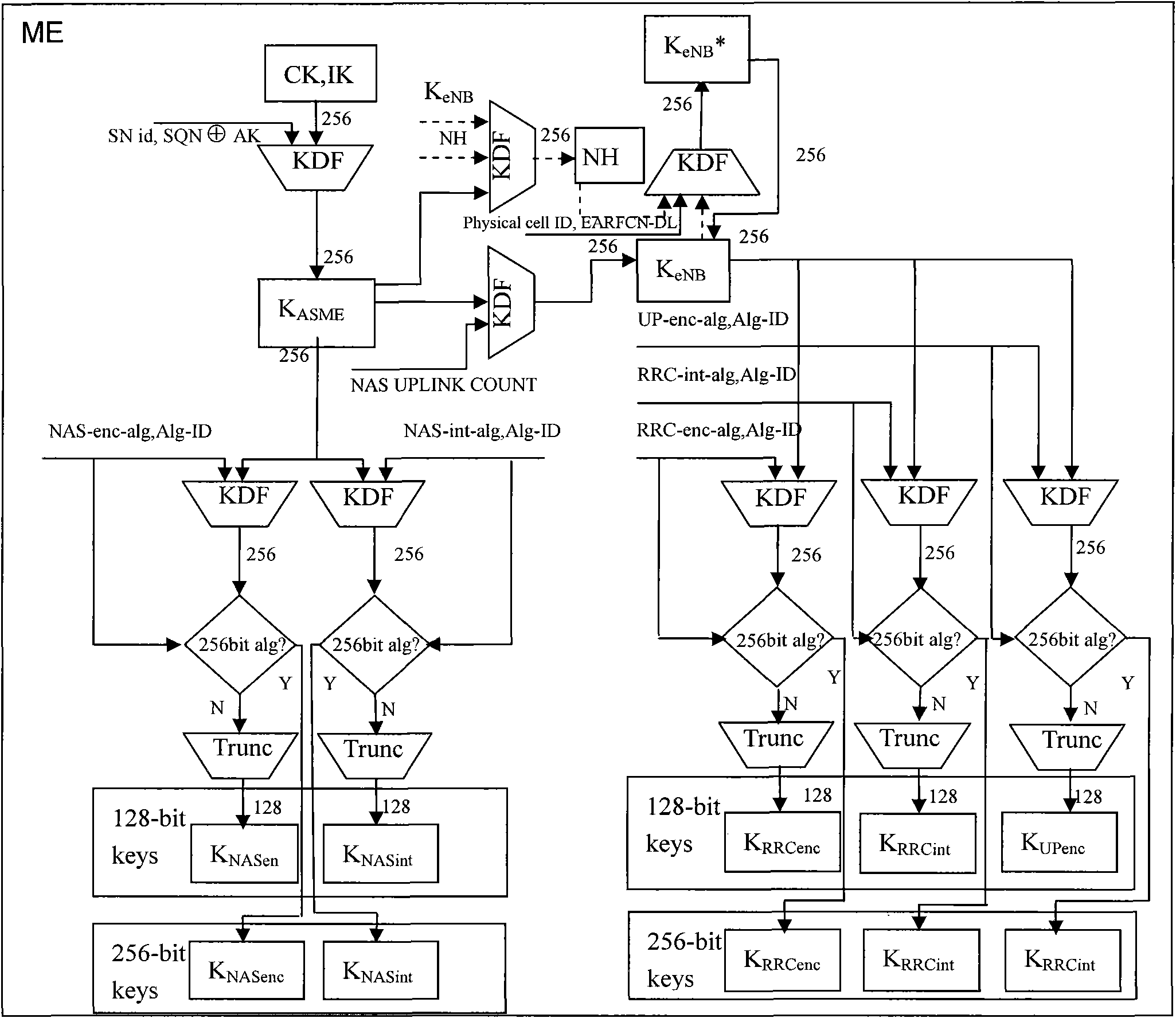
Enhanced encryption and integrity protection method
The invention discloses an enhanced encryption and integrity protection method, and belongs to the field of network communication. The method comprises the following steps of: 1) allocating a 4-bit algorithm identifier to each algorithm supported by an LTE / SAE system in advance, wherein the algorithm identifier comprises a key length of the highest bit identification algorithm; 2) performing algorithm negotiation on a key negotiation layer to determine an algorithm used for communication between entities, wherein the entities comprise user equipment, an access network and a core network; 3) calculating a communication key by using the entities according to the negotiated algorithm and a permanent key, and determining the length of the exported key according to the algorithm identifier in the calculation process; and 4) in the communication process, performing encryption or integrity protection on messages according to the negotiated algorithm and the exported key. Compared with the prior art, the method improves the strength of algorithms supported by the system and the flexibility of an encryption and integrity protection mechanism.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Motorcade safety management system and method based on ring signature and vehicle management platform
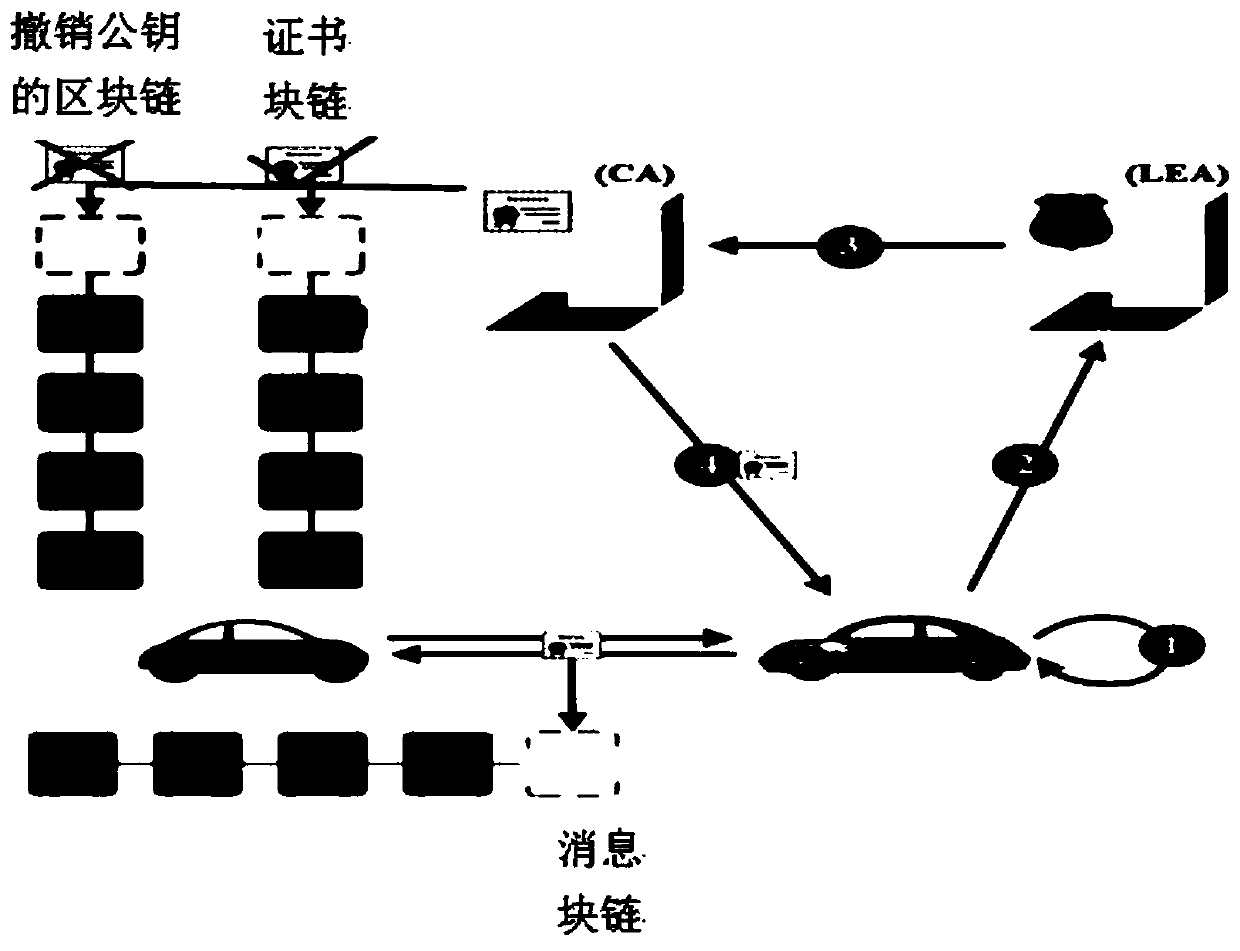
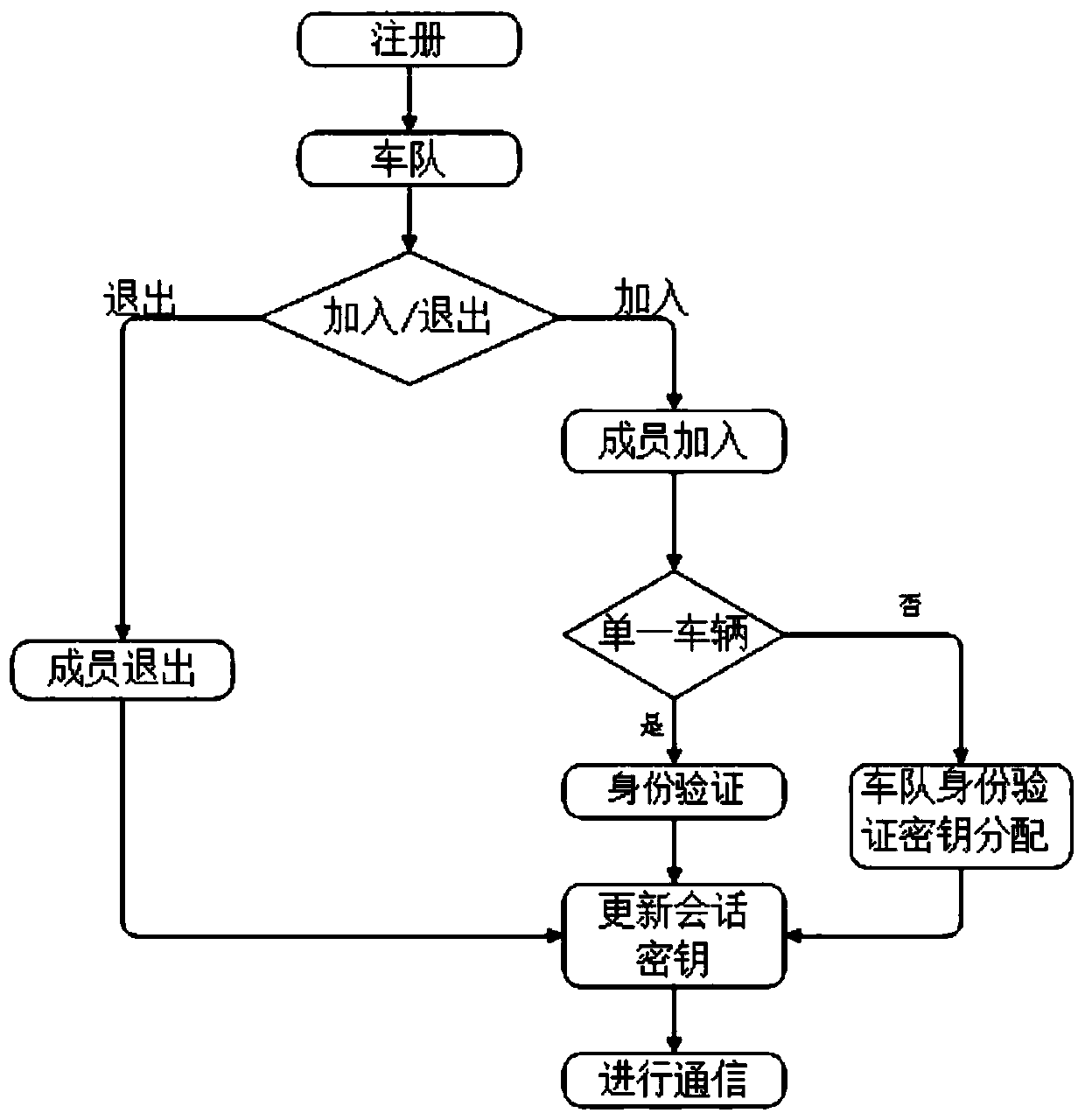
ActiveCN109698754AEnsure safetyPrevent leakageKey distribution for secure communicationPublic key for secure communicationSafety management systemsRing signature
The invention belongs to the technical field of Internet of Vehicles, and discloses a motorcade safety management system and method based on ring signatures, and a vehicle management platform. identity-based ring signatures are performed on the identities of motorcade members on the basis of an elliptic curve. Hiding and public key updating are conducted on identities of motorcade members throughthe elliptic curve, the block chain and the ring signatures, the identities of the message senders are authenticated, and session keys are updated; the block chain is utilized to publish a public keycertificate and a reputation value of the vehicle; The vehicle inquires the public key, the public key validity and the current reputation value of the surrounding vehicles through the roadside unit,so that the addition of malicious vehicles is avoided; Updating of the public key can prevent information from being intercepted and tampered by malicious vehicles when the private key of the user issubjected to security threats. The privacy of registered users and the privacy of motorcade members are effectively prevented from being leaked, and the communication safety of the members in the motorcade is ensured.
Owner:XIAN UNIV OF POSTS & TELECOMM
Networked transaction certification system and method
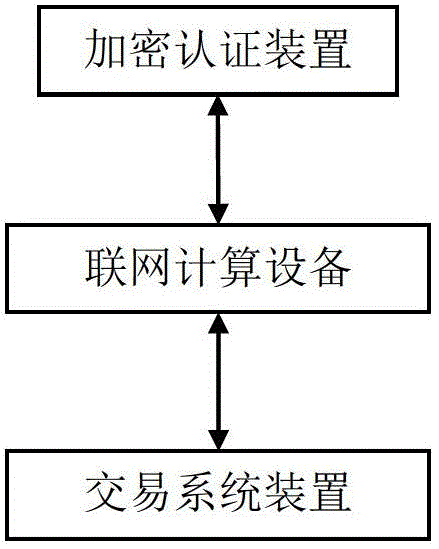
ActiveCN102868531AImprove security strengthAvoid transaction hijackingUser identity/authority verificationPayment architectureCiphertextPassword
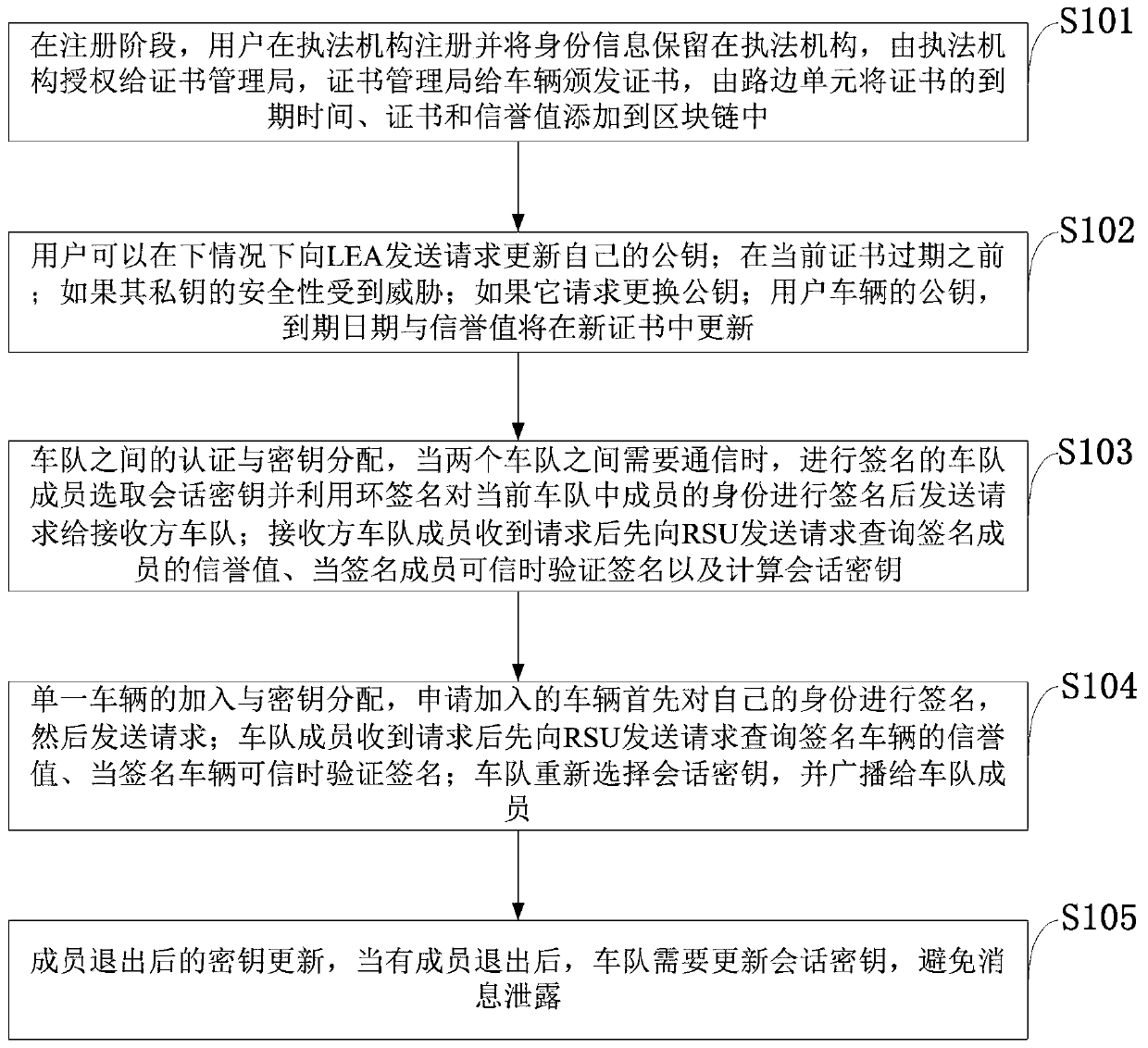
The invention discloses a networked transaction certification system which comprises an encryption authentication device, a networked computing device and a transaction system device, wherein the encryption authentication device is connected with the transaction system device through the networked computing device, the networked computing device is used for receiving request transaction information submitted by a user, and transmitting the request transaction information to a transaction system device; the transaction system device is used for generating a random code according to the request transaction information, and searching an elliptic curve password public key corresponding to the user in a user database, and the transaction system device is also used for encrypting request transaction information and a random code by using the elliptic curve password public key, transmitting the encrypted ciphertext to the networked computing device, and storing the request transaction information and the random code into a transaction information database. The invention can realize confidentiality and integrity of a message, authenticity of a transaction entity and non-repudiation of transaction, and has the characteristics of high safety, capability of avoiding transaction hijacking, transaction falsification and remote control.
Owner:北京信安世纪科技股份有限公司 +1
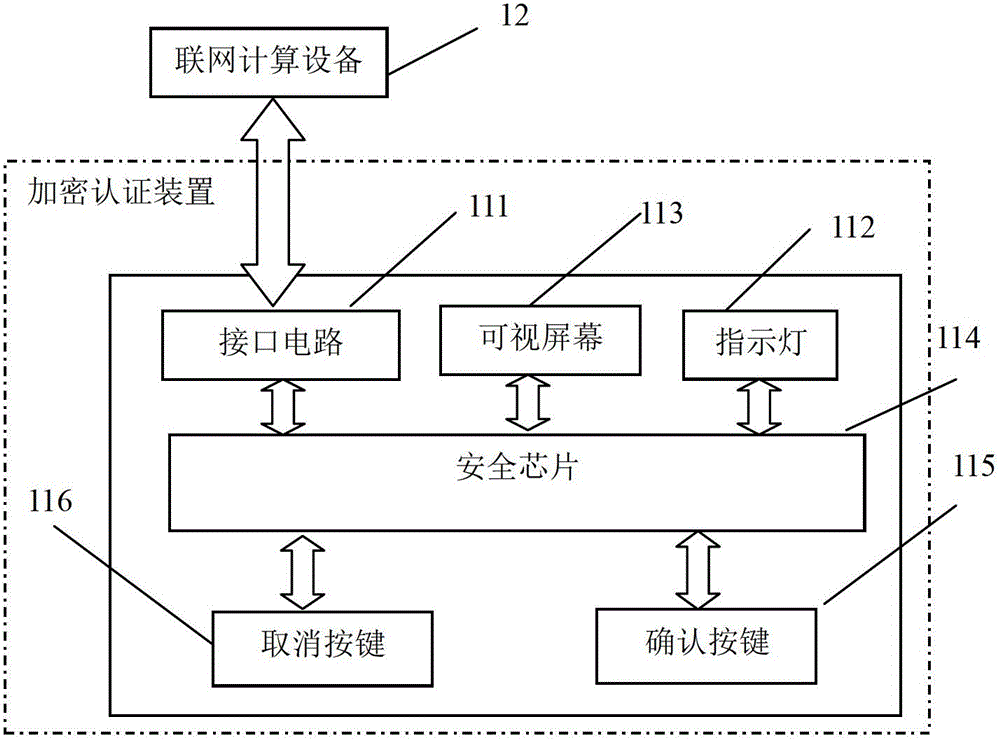
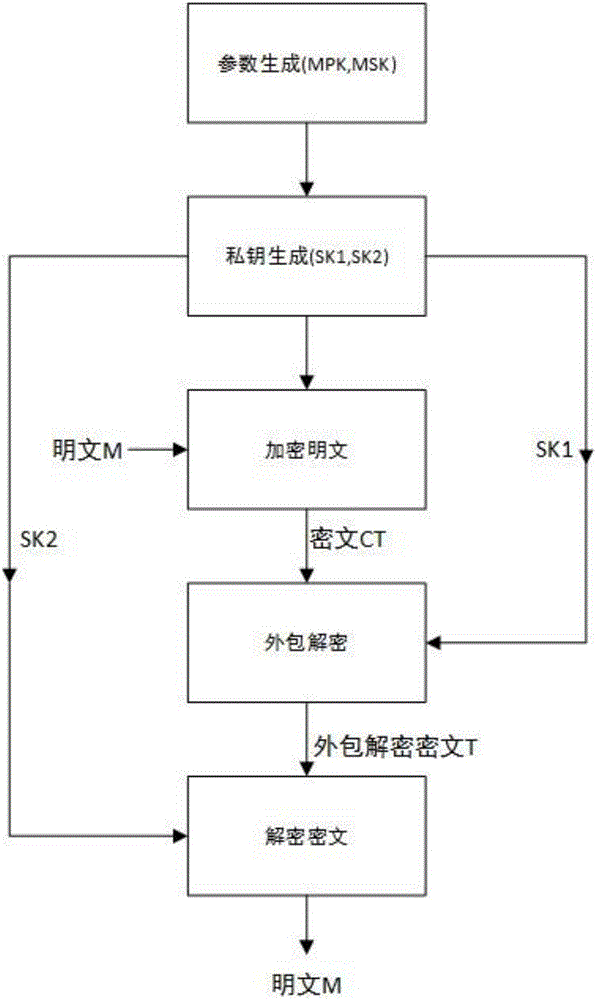
Anti-leakage CP-ABE method under strategy hiding and outsourcing decryption
ActiveCN107181590AReach the hidden functionPrevent leakageKey distribution for secure communicationThird partyComposite number
The invention discloses an anti-leakage CP-ABE (Ciphertext Policy-Attribute-Based Encryption) method under strategy hiding and outsourcing decryption. The anti-leakage CP-ABE method under strategy hiding and outsourcing decryption mainly realizes a CP-ABE scheme with three characteristics: leakage resistance, strategy hiding and outsourcing decryption, and belongs to the information safety field. The anti-leakage CP-ABE method under strategy hiding and outsourcing decryption utilizes a composite number order bilinear group to construct parameters, and adds the elements in a sub group Gp2 of the composite number order bilinear group in the main public key and the encryption algorithm to achieve the effect of hiding the access strategy. Besides, the algorithm decomposes the decryption process and adds an outsourcing decryption algorithm, and at the same time utilizes a double key system to enable the third party to be unable to completely decrypt the cryptograph, thus reducing the computing cost and guaranteeing safety of the user private key and the cryptograph. Compared with traditional anti-leakage scheme, the anti-leakage CP-ABE method under strategy hiding and outsourcing decryption has the advantages of leakage resistance, strategy hiding, outsourcing decryption, and higher safety, and greatly reduces the computing cost for decryption for the user.
Owner:NANJING UNIV OF POSTS & TELECOMM
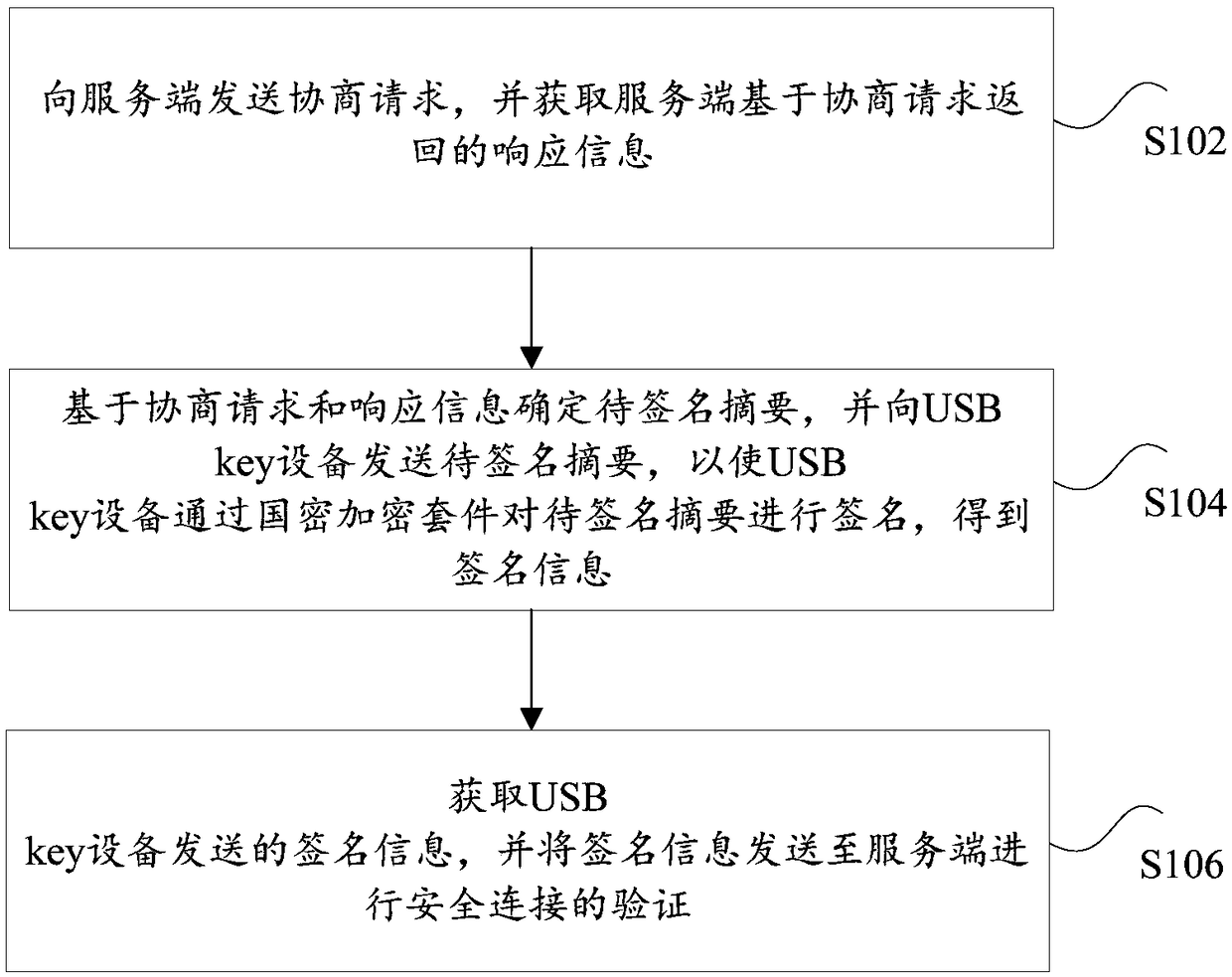
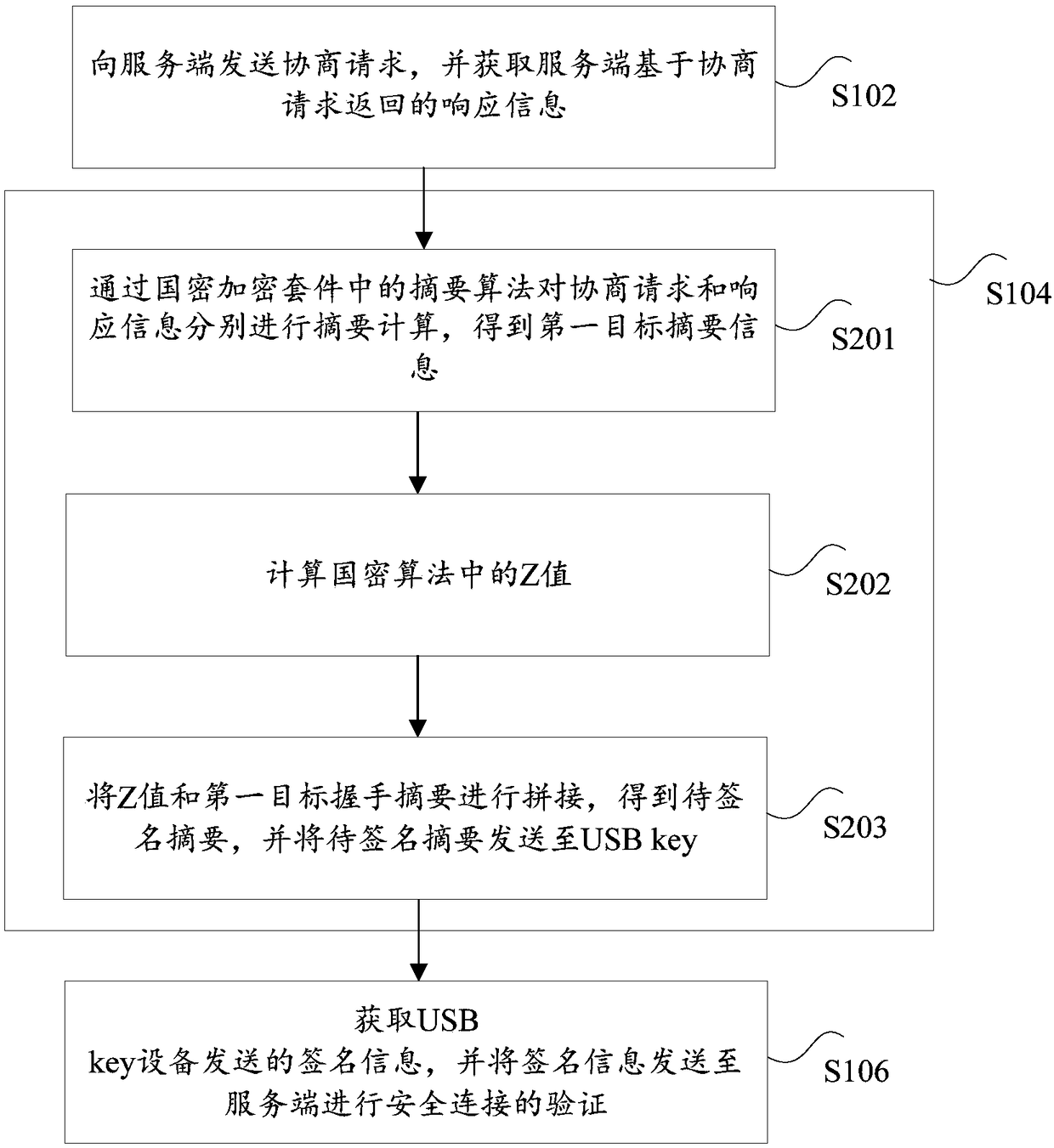
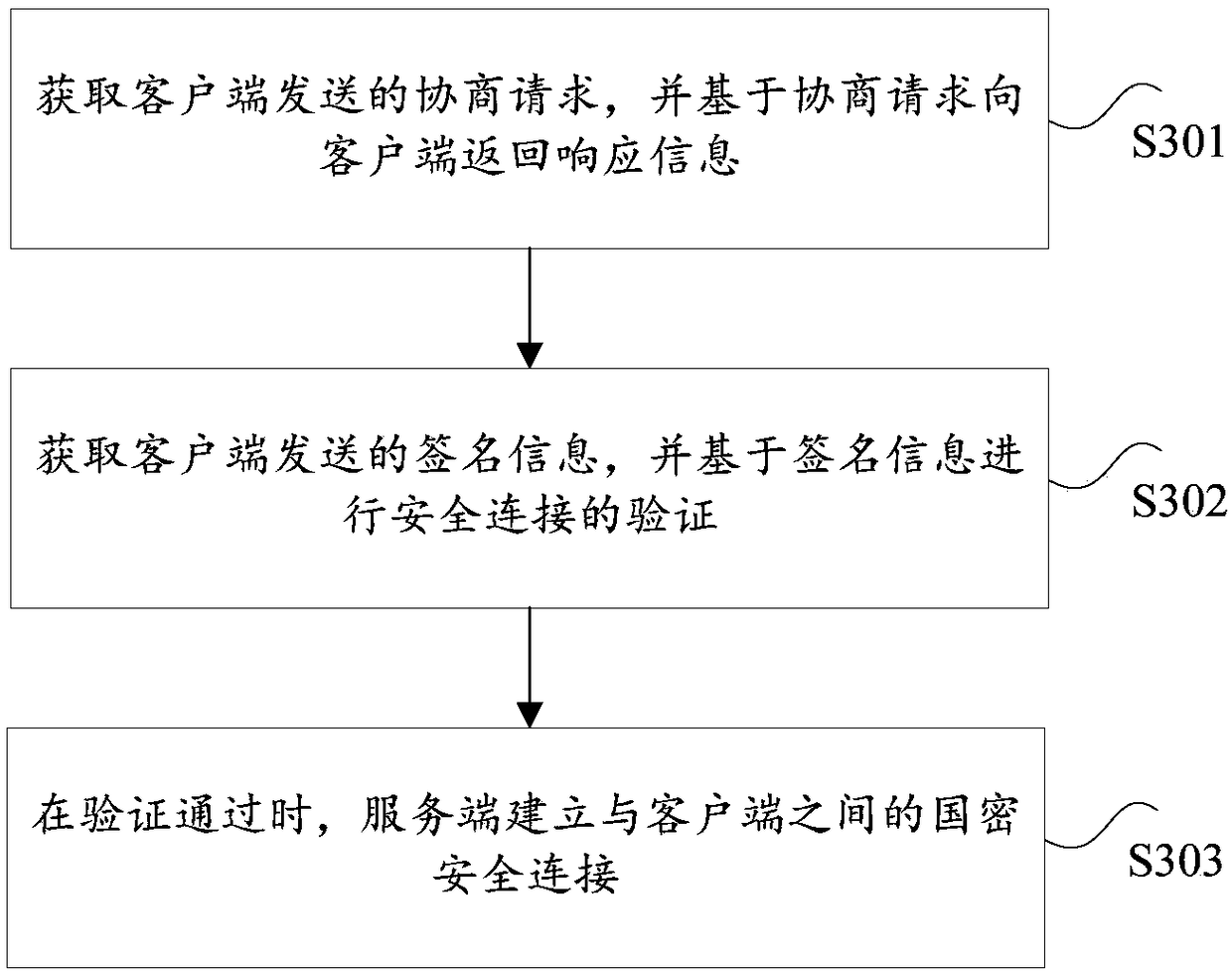
Safe connection establishing method, safe connection establishing system, client, and server
ActiveCN108429620AImprove security strengthMitigate less secure technical issuesUser identity/authority verificationRelevant informationClient-side
The invention provides a safe connection establishing method, a safe connection establishing system, a client, and a server. The safe connection establishing method comprises steps that a negotiationrequest is transmitted to the server, and response information returned by the server based on the negotiation request is acquired, and comprises related information of commercial cipher code encryption suite used for safe connection verification; a to-be-signed abstract is determined based on the negotiation request and the response information, and is transmitted to USB key equipment, and thenthe USB key equipment is used to sign the to-be-signed abstract by the commercial cipher code encryption suite to acquire signature information; the signature information transmitted by the USB key equipment is acquired, and is transmitted to the server for the verification of the safe connection, and when the verification is passed, the commercial cipher code safe connection between the client and the server is established. According to the invention, a technical problem of low data safety performance of conventional safe connection ways used for establishing the safe connection for the dataexchange is solved.
Owner:NEW H3C TECH CO LTD
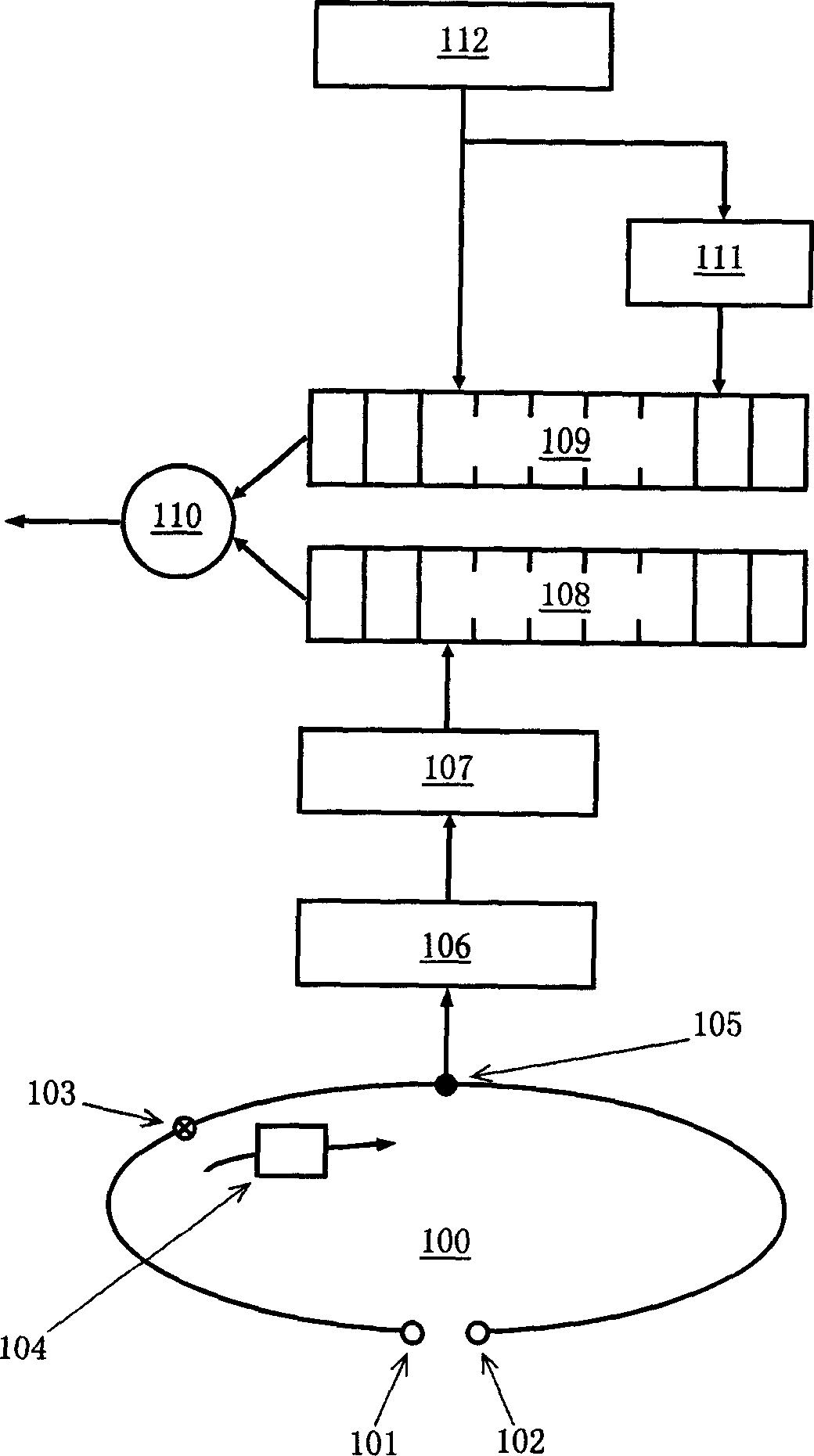
Image processing apparatus, controlling method of image processing apparatus, program and storage medium
InactiveUS20080285069A1Improve security strengthImprove securityDigitally marking record carriersTelephonic communicationDigital dataImaging processing
The present invention provides an image processing apparatus, a method of controlling the image processing apparatus, a program and a storage medium that can increase security strength of encoded data, printed on a recording medium. According to an embodiment of the present invention, an image to be a document is read and is subjected to image processing, and thereby digital data is acquired. Next, the above-described digital data is encoded to generate a first encoded data. Next, information on a process of decoding the digital data from the first encoded data is encoded to generate second encoded data.
Owner:CANON KK
Data security authentication method between cloud and edge node
ActiveCN111294352ASmall sizeSmall system parametersKey distribution for secure communicationPublic key for secure communicationKey sizeTimestamp
The invention provides a data security authentication method between a cloud and an edge node, and the method provides a bidirectional identity authentication protocol between the edge node and the cloud, can guarantee the authenticity and effectiveness of the identities of the cloud and the edge node, prevents malicious attacks from permeating into a core network, and greatly guarantees the industrial Internet security. According to the method, an elliptic curve cryptographic algorithm is introduced to encrypt key data in an authentication process; the algorithm key size, the system parameters and the storage space are relatively small; operation speed is high, the highest safety intensity per bit is realized; the method is suitable for an authentication environment of edge computing nodes with limited computing resources and storage resources. According to the method, the data plaintext transmission leakage risk is avoided, the replay attack is avoided through the timestamp, the hashiterative operation of the one-time password authentication protocol is simplified, compared with the original authentication protocol, the security is higher, the operation efficiency is also improved, and the authentication security requirement can be met under the environment that the edge node resources are limited.
Owner:国家工业信息安全发展研究中心
Distribution network embedded telecontrol communication security gateway
InactiveCN102307161AResolve conflicts in constructionSolve the real problemNetwork connectionsCommunications securityGeneral Packet Radio Service
The invention discloses a novel secure wireless data communication device, which realizes a remote distribution automation control function in a public network on the premise of ensuring the secure and effective transmission of distribution network data. A distribution network embedded telecontrol communication security gateway is classified into a calling distribution network embedded telecontrol communication security gateway and a called distribution network embedded telecontrol communication security gateway, and comprises a main board (1). A central processing unit (2), at least one read only memory (ROM) module (3), a FLASH module (4), a general packet radio service (GPRS) module (5), a hardware encryption module (6) comprising a digital certificate, a serial interface (7), a power interface (8), a subscriber identity module (SIM) card interface (9) and an antenna (10) are integrated on the main board. The gateway further comprises a management and configuration module, a network access module, an authentication module, a virtual private network (VPN) module, a firewall module and a network serial port conversion module. The gateway can be widely applied in the field of distribution network communication construction.
Owner:ZHUHAI POWER SUPPLY BUREAU GUANGDONG POWER GIRD CO +1
Deterministic key pre-distribution and operational key management for moblie body sensor networks
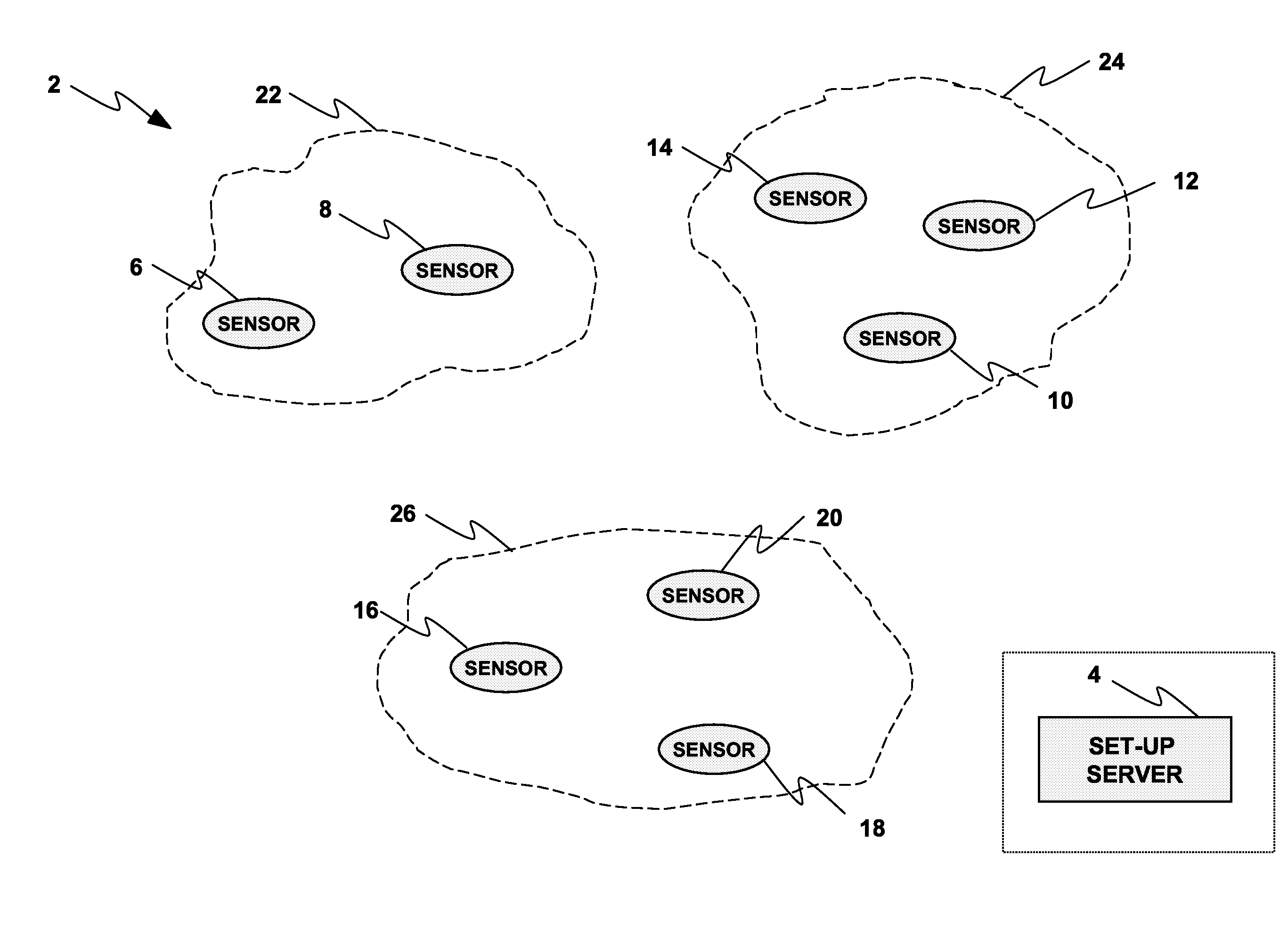
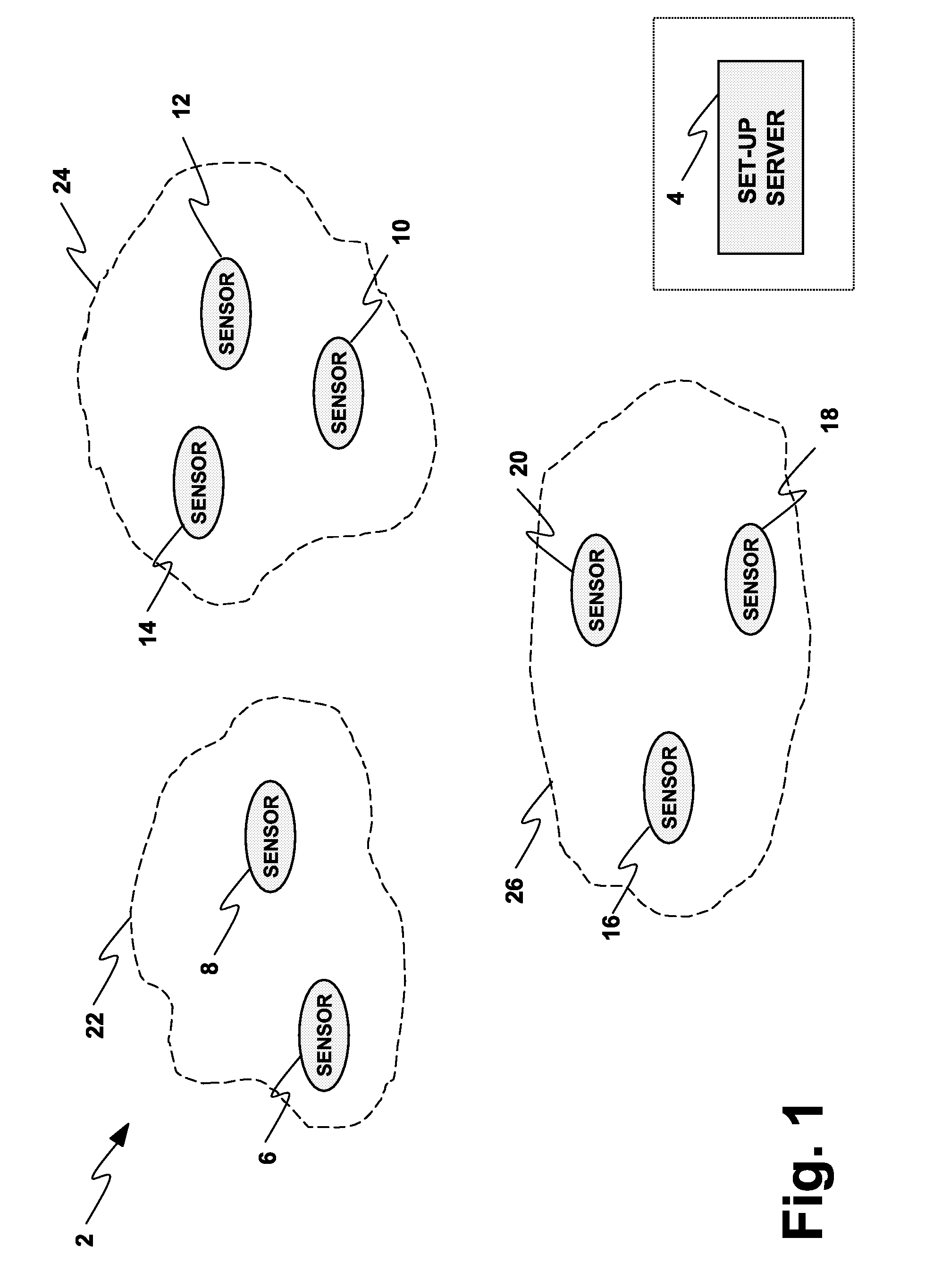
InactiveUS7999685B2Facilitate communicationImprove security strengthError preventionFrequency-division multiplex detailsLine sensorBody sensors
A wireless network (2, 150) for monitoring a patient includes a body sensor network (22, 24, 26, 172, 174, 176) that includes one or more wireless sensors (6, 8, 10, 12, 14, 16, 18, 20, 156, 158, 160, 162, 164, 166, 168, 170) operatively connected to the patient that collect and transfer information related to the patient's health to the wireless network (2, 150). A set-up server (4, 154) configures the one or more wireless sensors (6, 8, 10, 12, 14, 16, 18, 20, 156, 158, 160, 162, 164, 166, 168, 170) with keying material before the one or more sensors (6, 8, 10, 12, 14, 16, 18, 20, 156, 158, 160, 162, 164, 166, 168, 170) are deployed to the wireless network (2, 150). A base station (178, 180) distributes a key certificate to the one or more sensors (6, 8, 10, 12, 14, 16, 18, 20, 156, 158, 160, 162, 164, 166, 168, 170) associated with the body sensor network (22, 24, 26, 172, 174, 176), such that two sensors generate a unique pairwise key based at least in part upon the pre-distributed keying material and the key certificate distributed by the base station (178, 180).
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Electronic storage apparatus, authentication apparatus and authentication method
InactiveUS7404081B2Improve authentication strengthImprove security strengthDigital data processing detailsUser identity/authority verificationComputer hardwareBiometrics
Owner:FUJITSU LTD
Method and device for constructing sequential cipher
InactiveCN1694397AImprove security strengthSecuring communicationKey spaceTheoretical computer science
This invention relates to a method for setting up sequence ciphers and a device, the main content is how to generate the cryptographic key sequence including the following steps: appointing a large enough root cryptographic key space to select seeds secretly and appointing steps to determine the current root cryptographic key as the new seed value. A single-way hash transformation is carried out to the current root cryptographic key to get the current frame cryptographic key, the process of generating said key is repeated to get the necessary key sequence and further enhance the randomness of said generated key sequence.
Owner:侯方勇
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com