Novel authentication mechanism for encrypting vector
A vector and key technology, applied in the field of new vector encryption authentication mechanism, can solve problems such as difficulty in resisting third-party attacks, separation of encryption and authentication, and low implementation efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0159] Embodiment 1, software and hardware hybrid embodiment
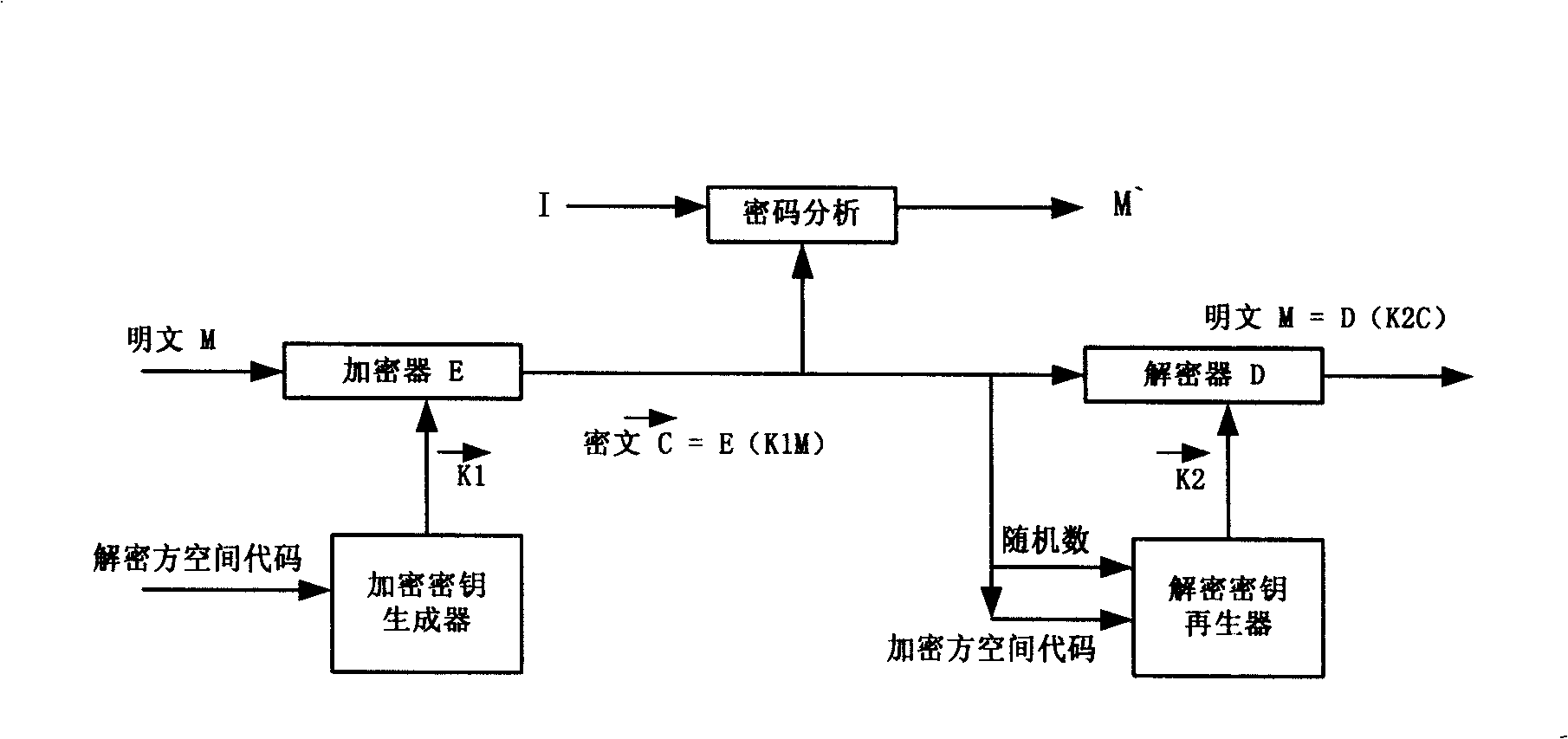
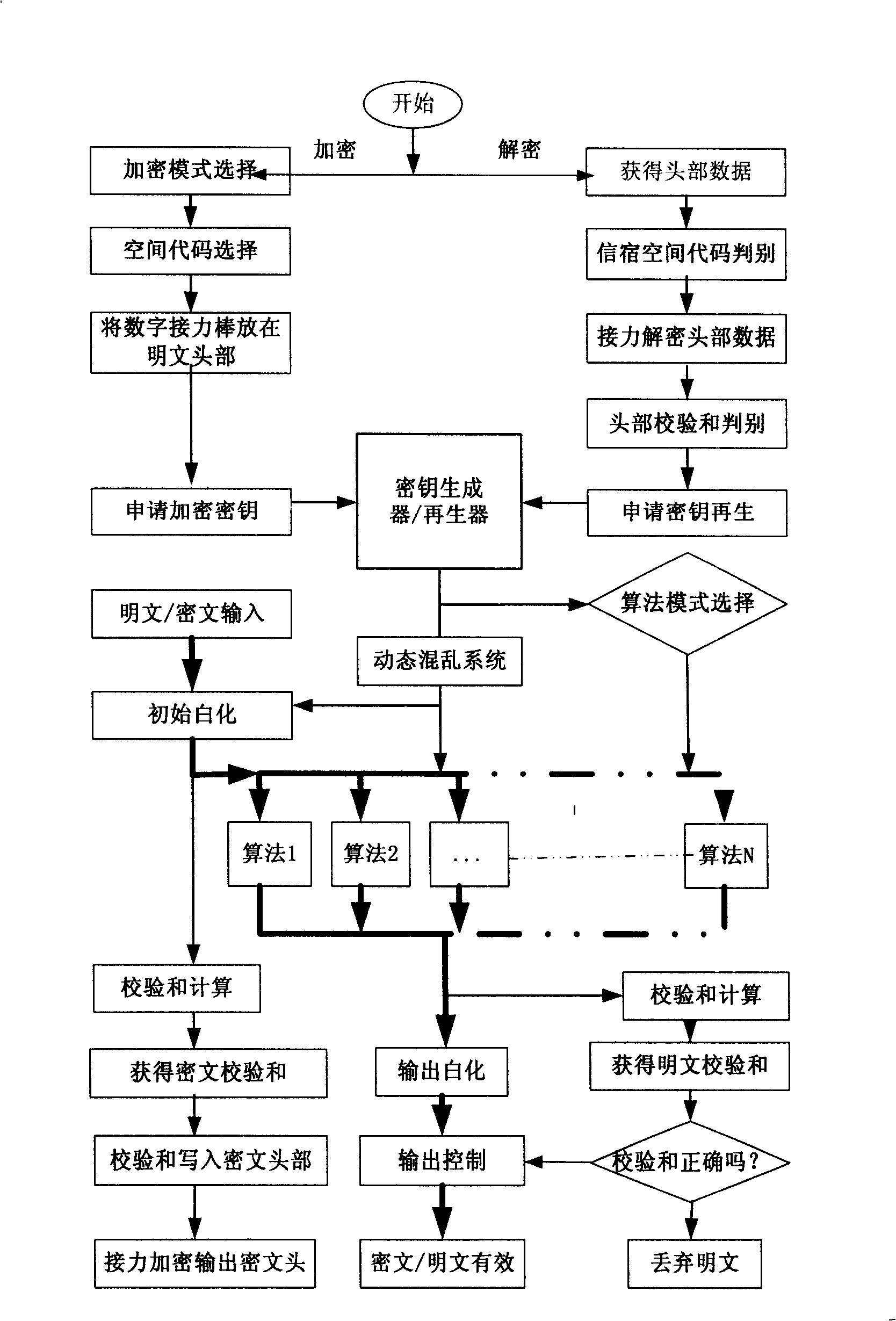
[0160] figure 2 and image 3 It is a preferred software and hardware hybrid embodiment of the present invention, figure 2 The key generation / regenerator is implemented with a digital chip or smart card to form a hardware system, image 3 A software program is used to realize the formation of an encryption authentication software system, and the hardware system and the software system realize information interaction through a USB interface or a sensing interface. Each digital chip or smart card has a globally unique hardware serial number-space code, which determines the range of vector key space that the hardware can generate and reproduce. In practical applications, the serial number must be used by an authoritative third party The user's identity information is bundled with the serial number and made public so that other users can verify their identity and communicate directly with them.
[0161] figure 2...
Embodiment 2
[0169] Embodiment 2, identity-based trusted computing module PTM
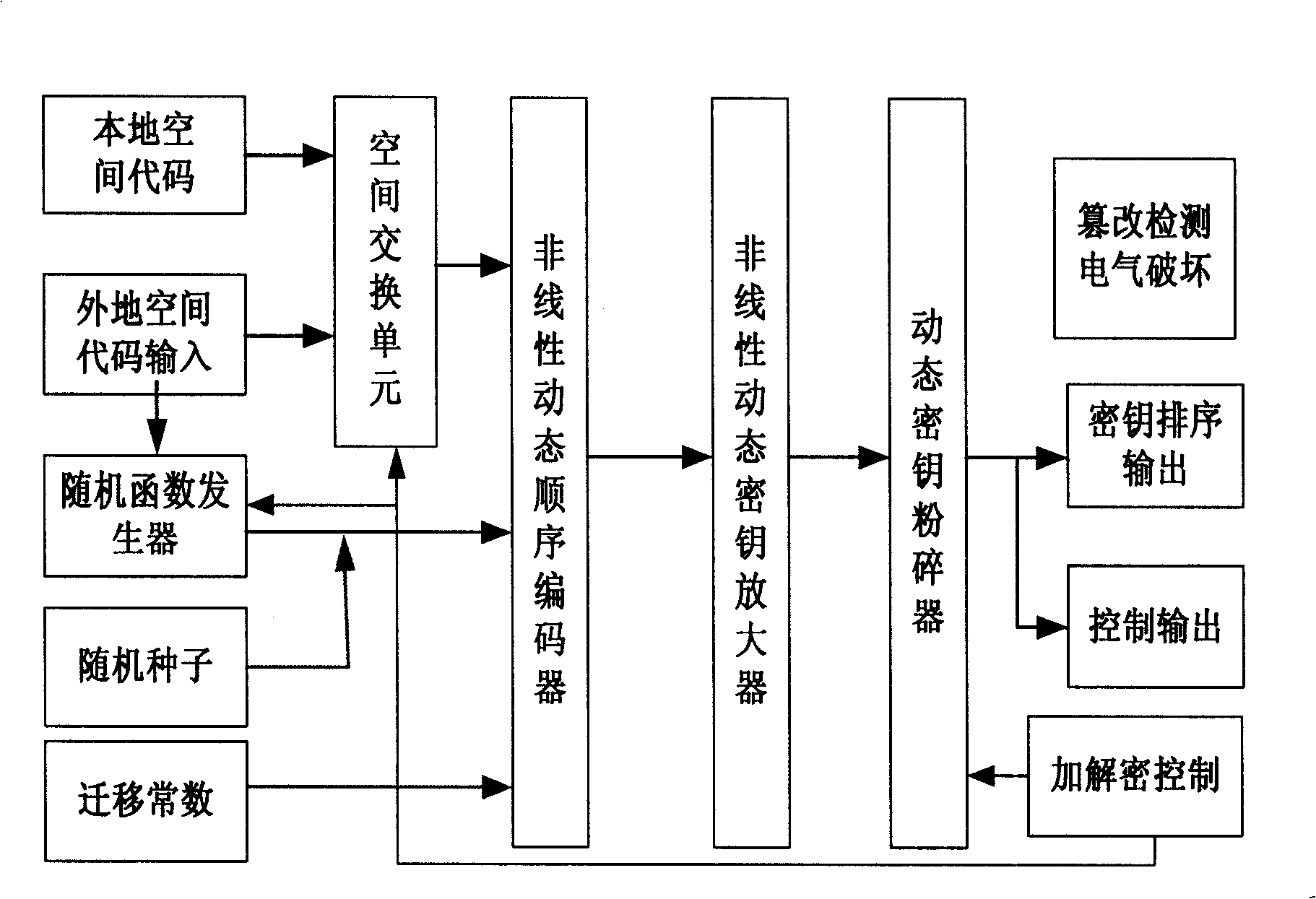
[0170] Such as Figure 4 Shown is the trusted computing platform core module that utilizes the method and system of the present invention to realize by means of hardware——PTM encryption authentication module, in this implementation method, key generation / regenerator of the present invention and encryption authentication algorithm are made in On the same digital chip, it is connected with a terminal such as a computer through a parallel interface to form a trusted terminal. Figure 4 Among them, the local space code unit, key generation / regeneration unit, random number generator unit and tamper detection electrical destruction unit constitute as figure 2 In the shown key generation / regeneration part of the present invention, the local space code is a globally unique production serial number assigned by each PTM module, which determines the encryption key space range used by each PTM module, and the local space...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com