Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
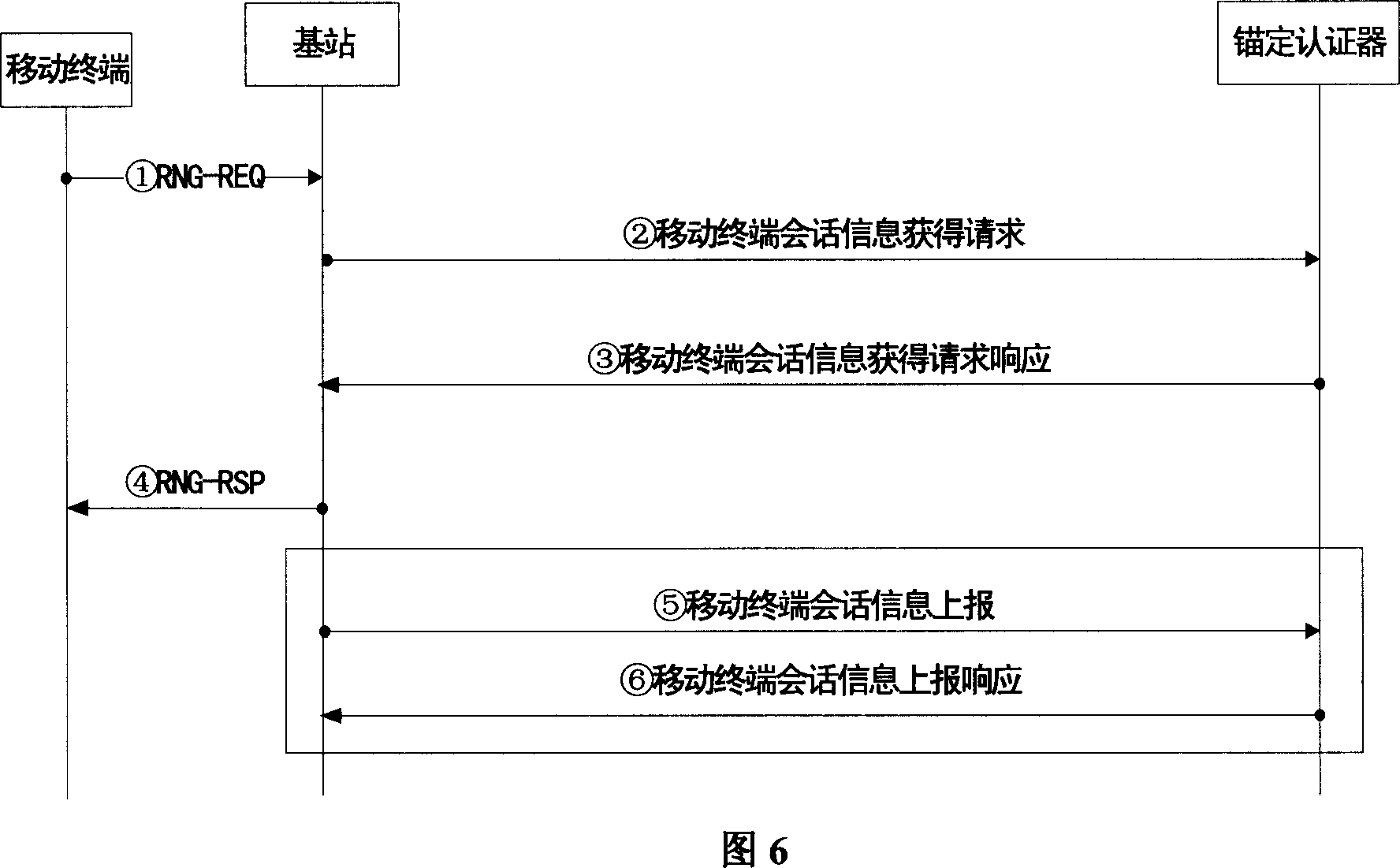
80 results about "Anti-replay" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
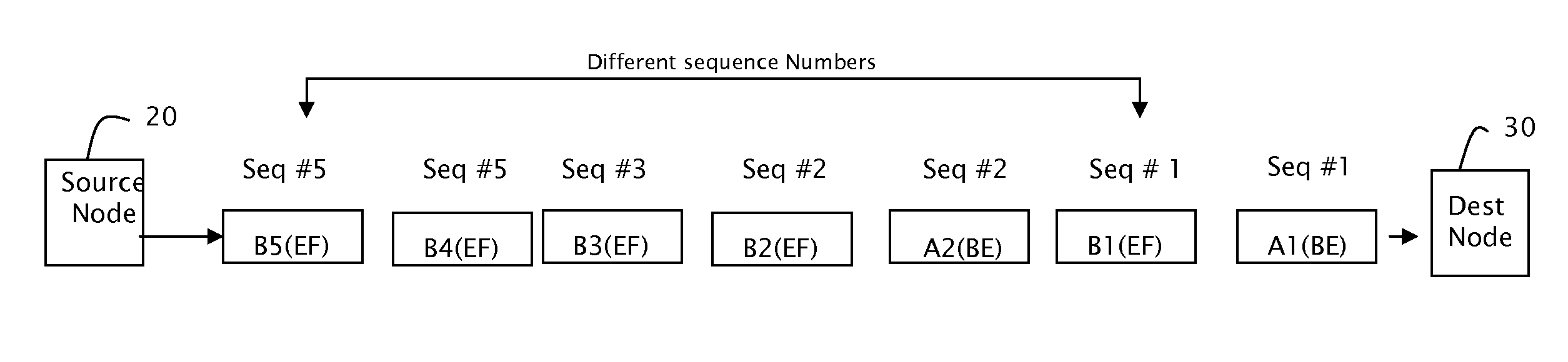
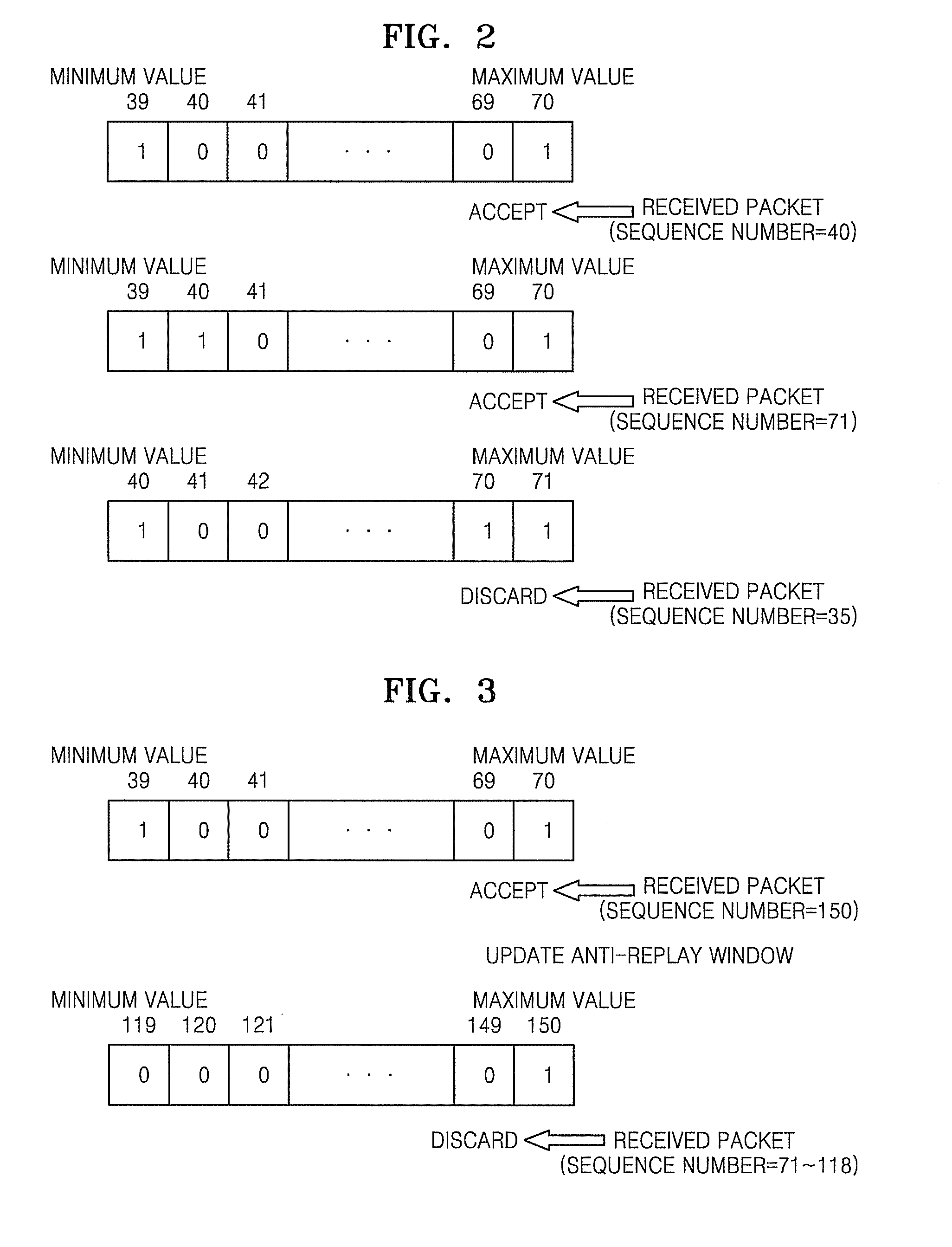
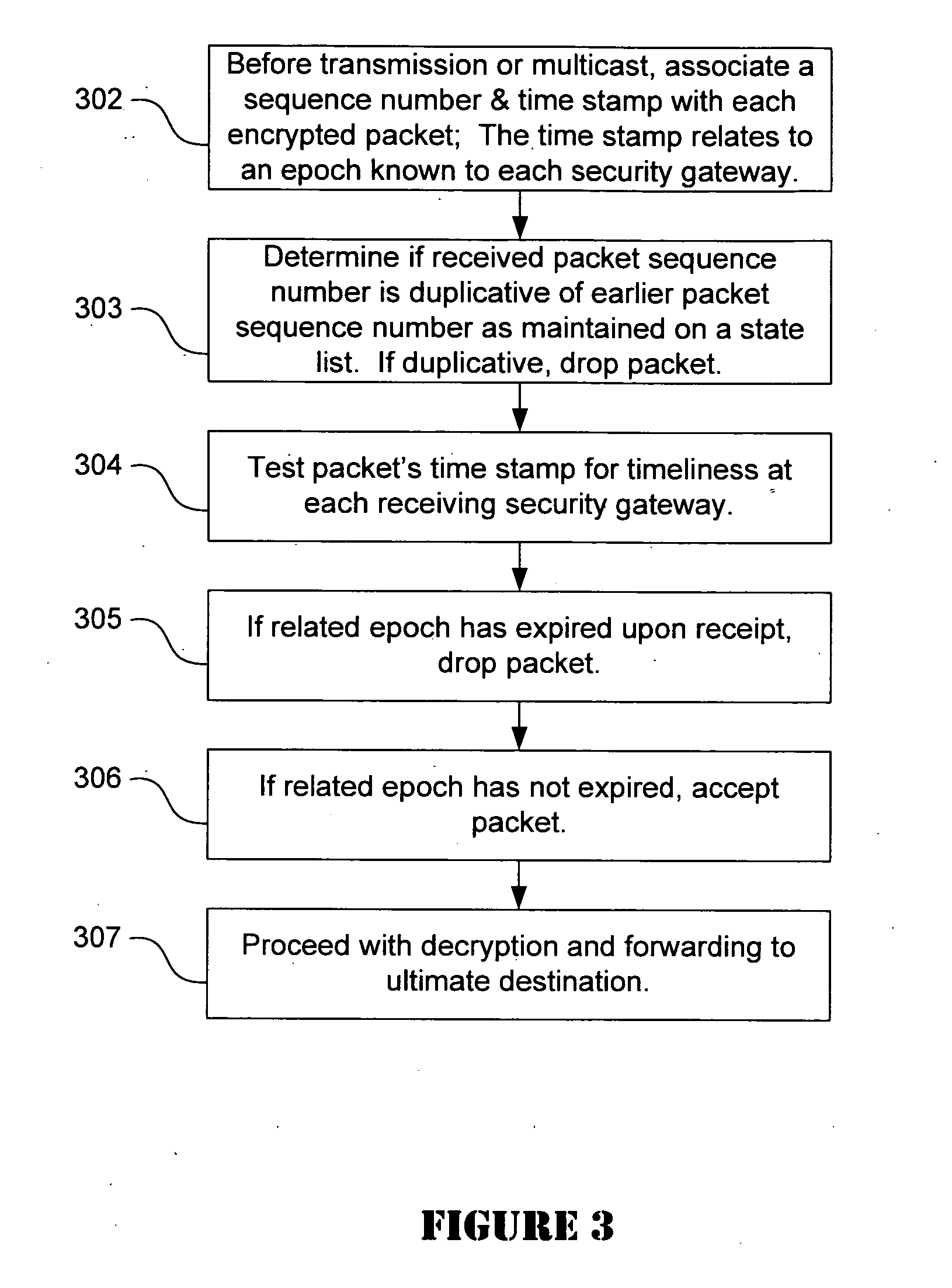
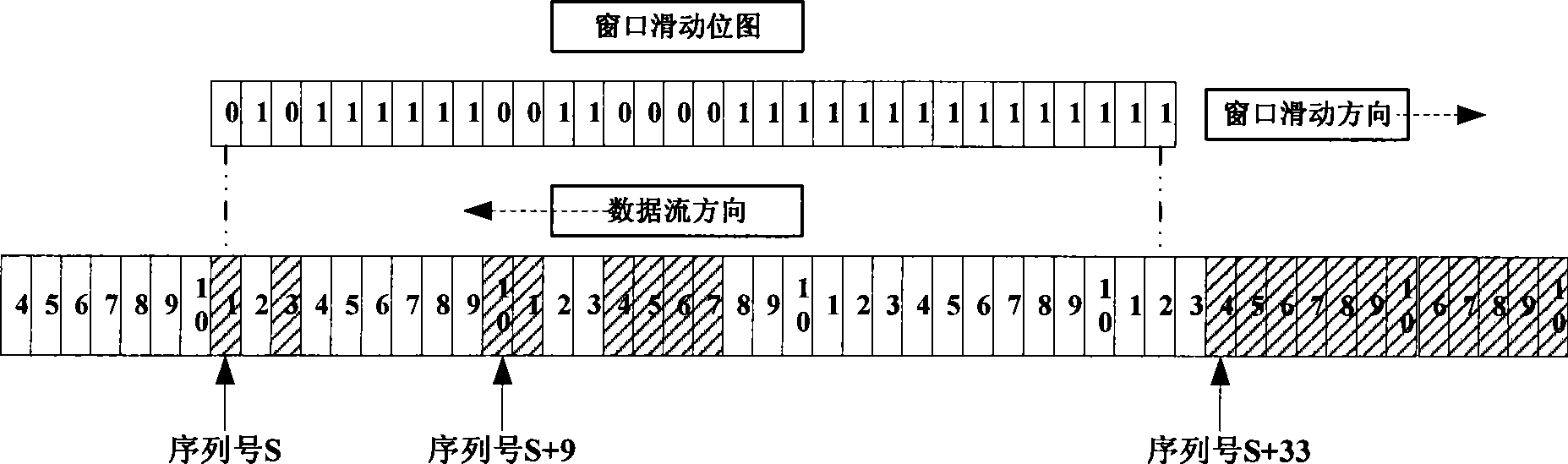
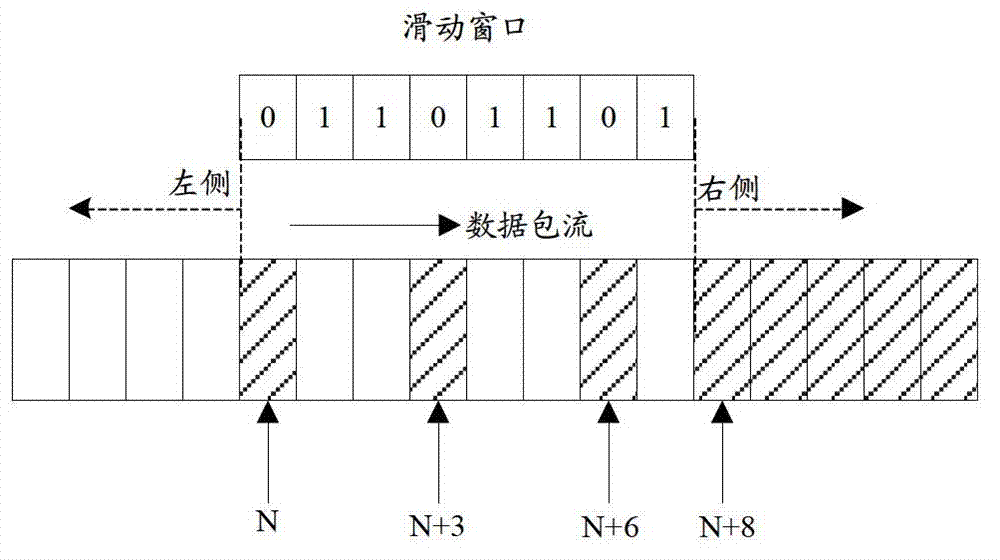
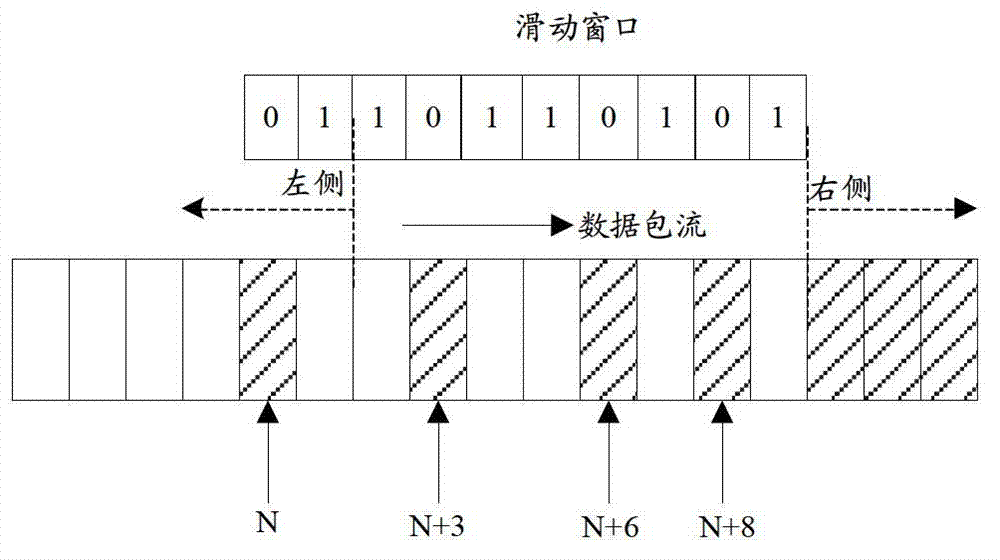
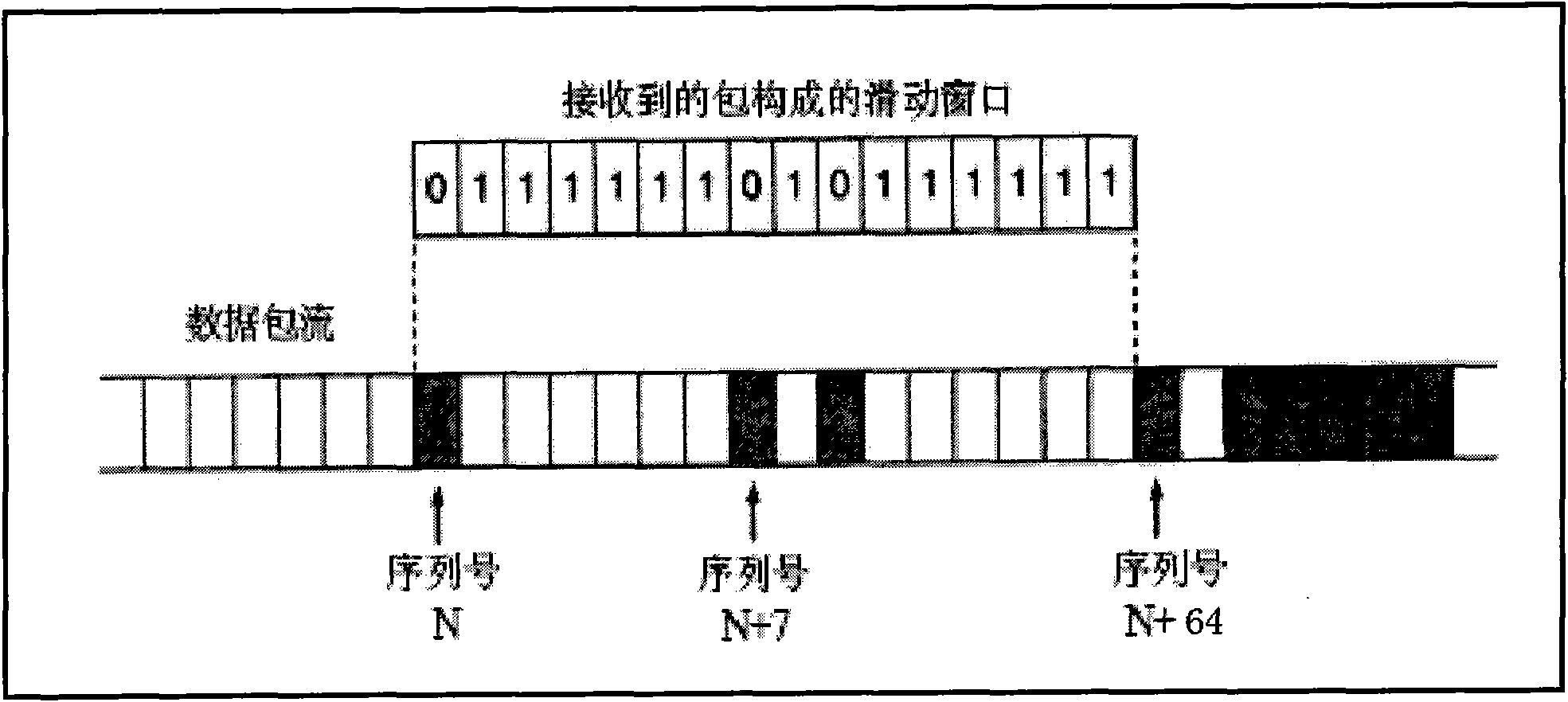
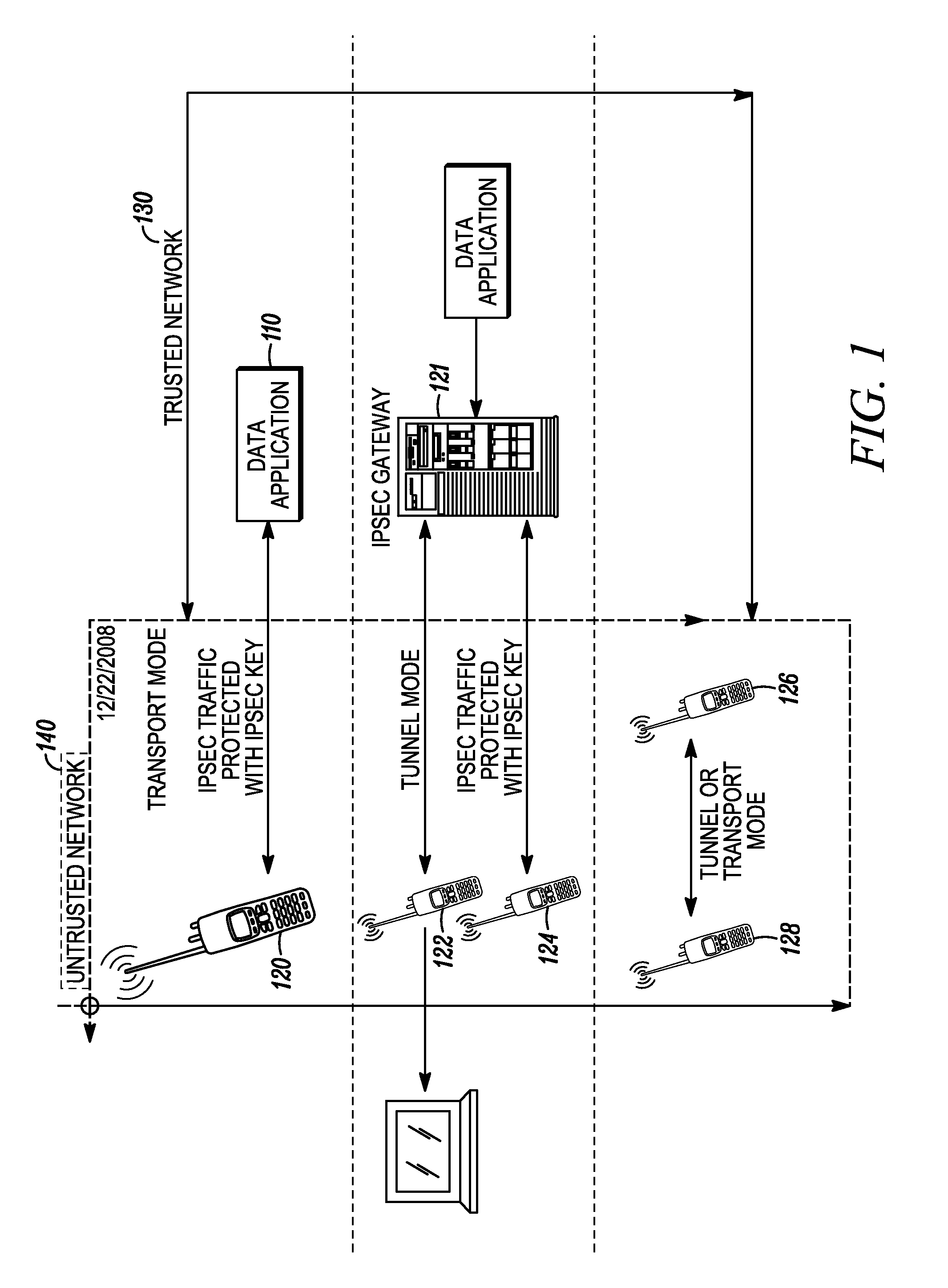
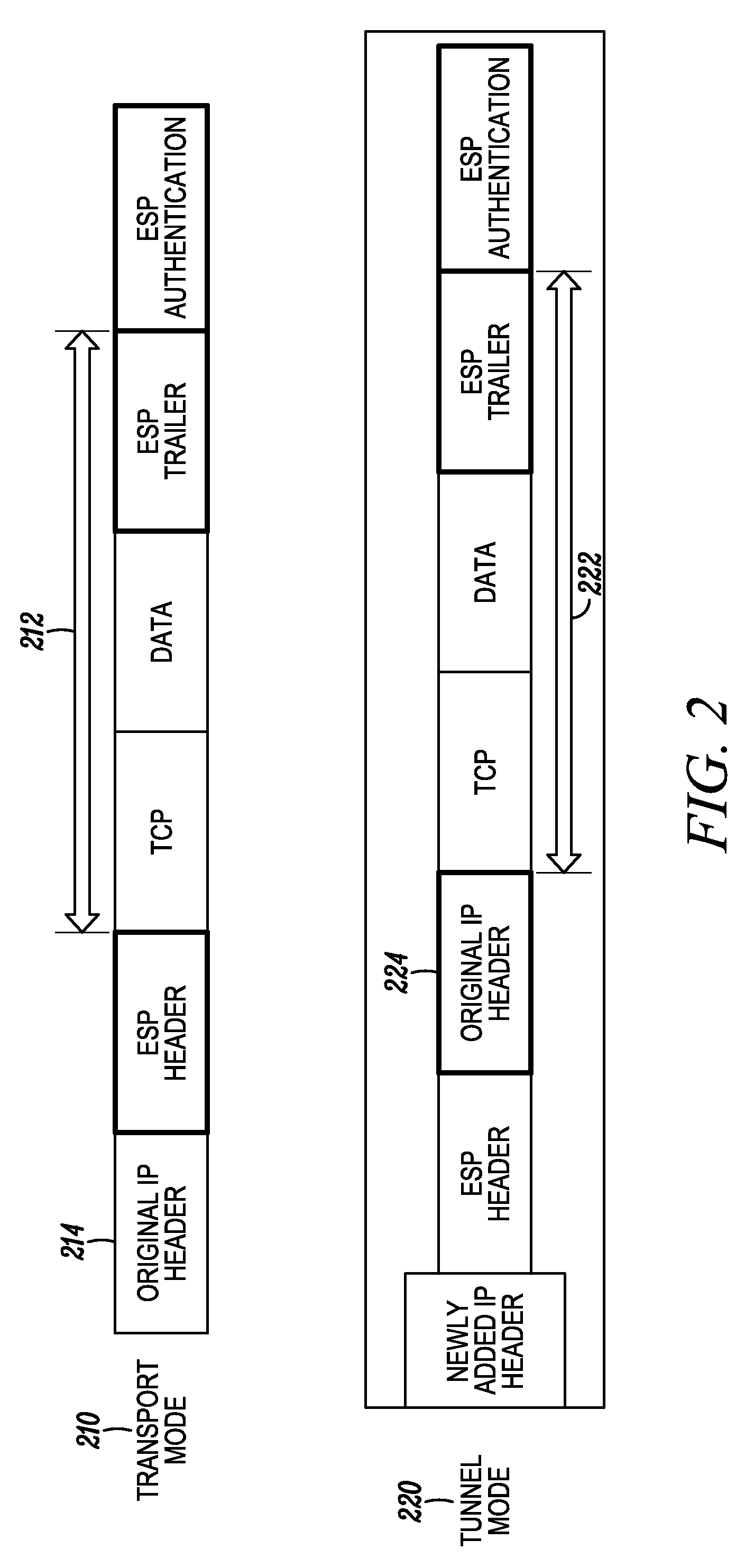
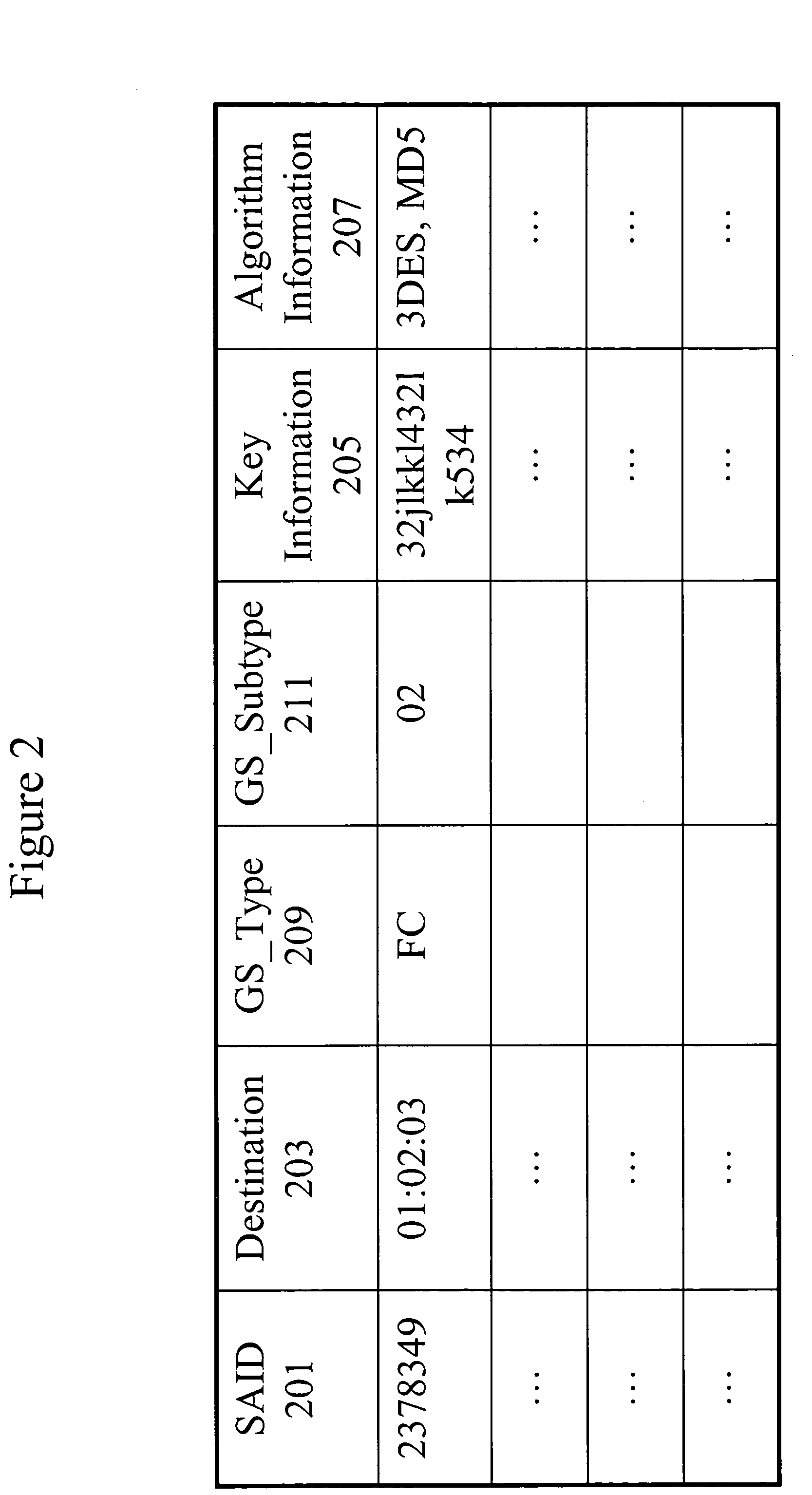
Anti-replay is a sub-protocol of IPsec that is part of Internet Engineering Task Force (IETF). The main goal of anti-replay is to avoid hackers injecting or making changes in packets that travel from a source to a destination. Anti-replay protocol uses a unidirectional security association in order to establish a secure connection between two nodes in the network. Once a secure connection is established, the anti-replay protocol uses packet sequence numbers to defeat replay attacks as follows: When the source sends a message, it adds a sequence number to its packet; the sequence number starts at 0 and is incremented by 1 for each subsequent packet. The destination maintains a 'sliding window' record of the sequence numbers of validated received packets; it rejects all packets which have a sequence number which is lower than the lowest in the sliding window (i.e. too old) or already appears in the sliding window (i.e. duplicates/replays). Accepted packets, once validated, update the sliding window (displacing the lowest sequence number out of the window if it was already full).
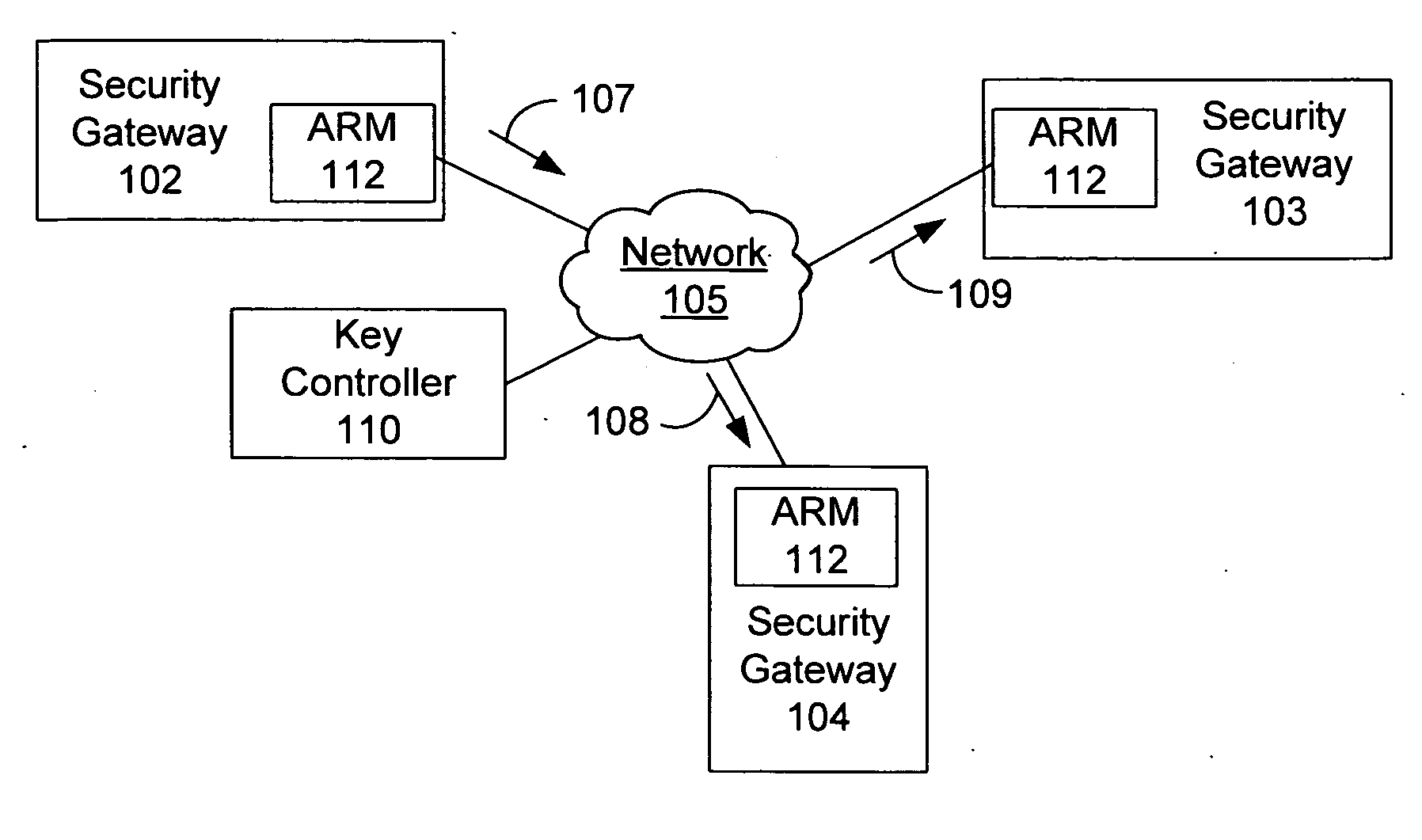
Method and apparatus for preserving data in a system implementing Diffserv and IPsec protocol
InactiveUS7746781B1Reduce the possibilityTransmission systemsFrequency-division multiplex detailsTraffic capacityDifferentiated services
An improved method is described for providing Differentiated Services (Diffserv) traffic to a node in a network that implements a security method that discards duplicate packets received at the node. The method includes the step of identifying at least two service levels to be provided to received traffic and assigning separate sequential sequence numbers and different anti-replay bitmasks to each of the service levels. The anti-replay bitmask indicates the sequence numbers of packets that have been previously received at the node that should be compared against a received packet to determine whether a duplicate packet has been received. Such an arrangement reduces the possibility that traffic having lower priority is dropped as a security measure.
Owner:RPX CLEARINGHOUSE
Method and Apparatus for Updating Anti-Replay Window in Ipsec
InactiveUS20080295163A1Error prevention/detection by using return channelData taking preventionIPsecComputer science
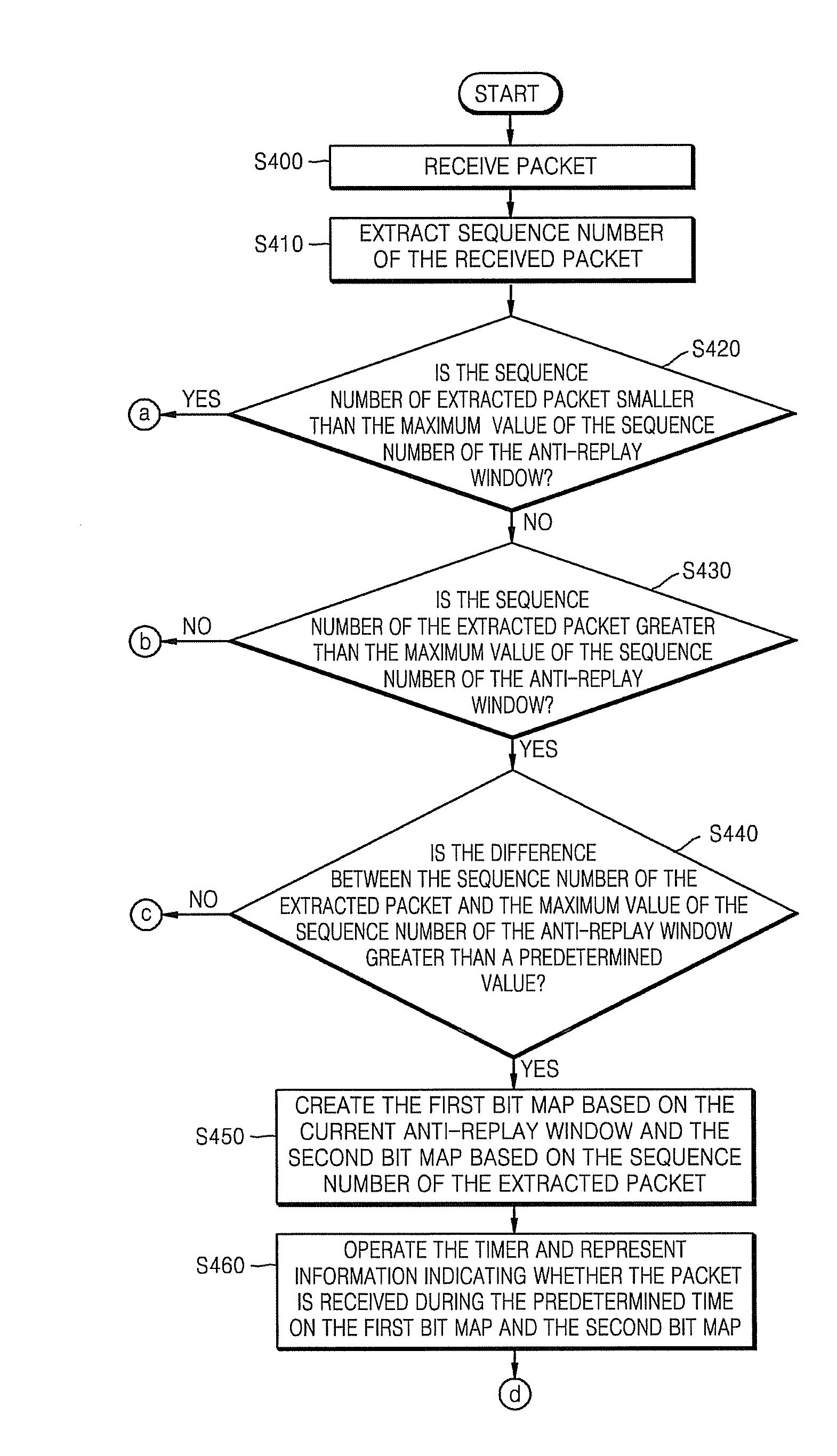
A method and apparatus for updating an anti-replay window in Internet Protocol Security (IPSec). The method includes determining whether a difference between a sequence number extracted from a received packet and a maximum value of a sequence number of an anti-replay window is greater than a predetermined value; if it is determined that the difference is greater than the predetermined value, creating a first bit map based on a size of the anti-replay window and a second bit map based on the sequence number extracted from the received packet, respectively; comparing the number of bit values in the first bit map of packets received during a predetermined time with the number of bit values in the second bit map of packets received during the predetermined time, and updating the anti-replay window.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for routing data over an internet protocol security network
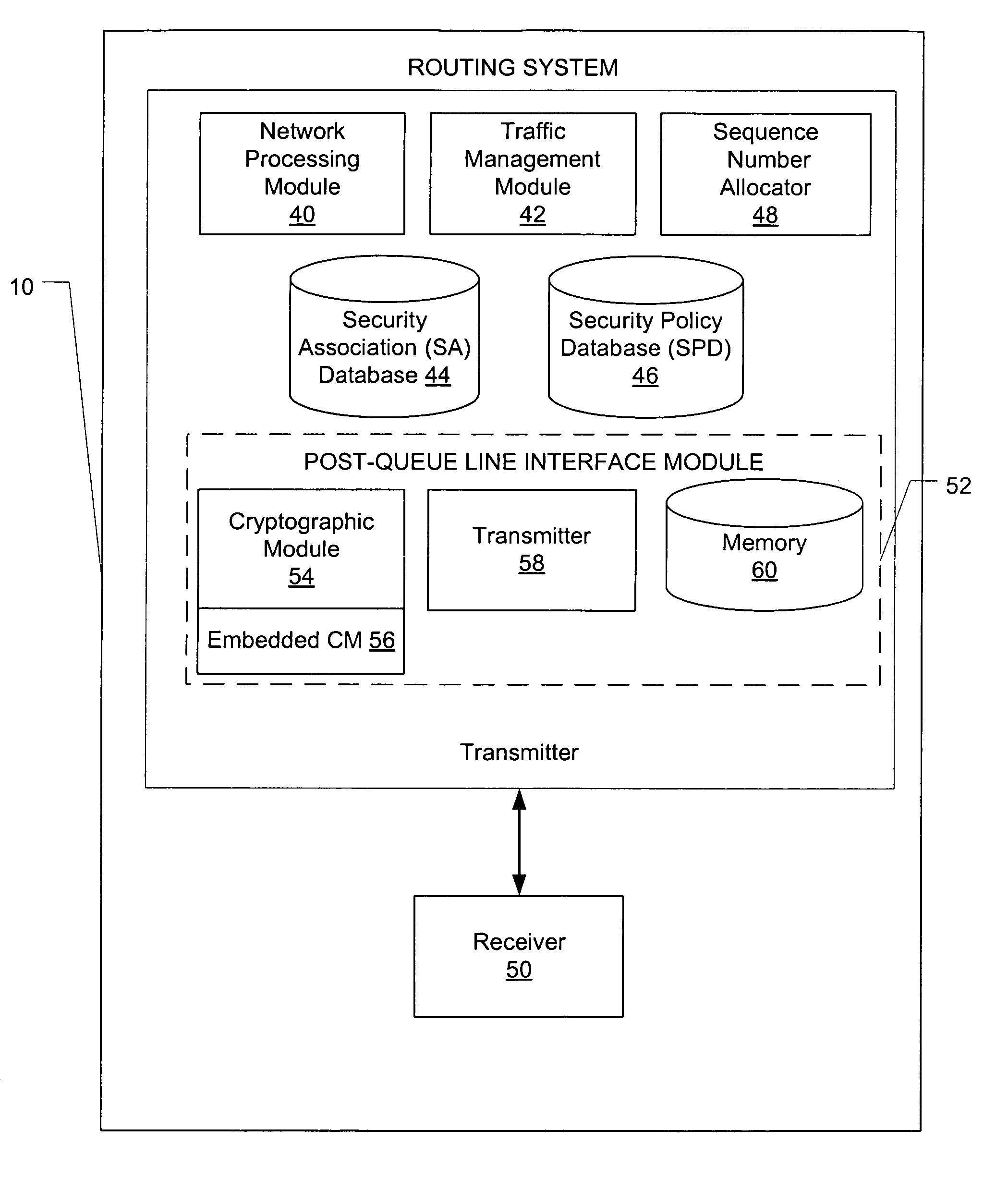
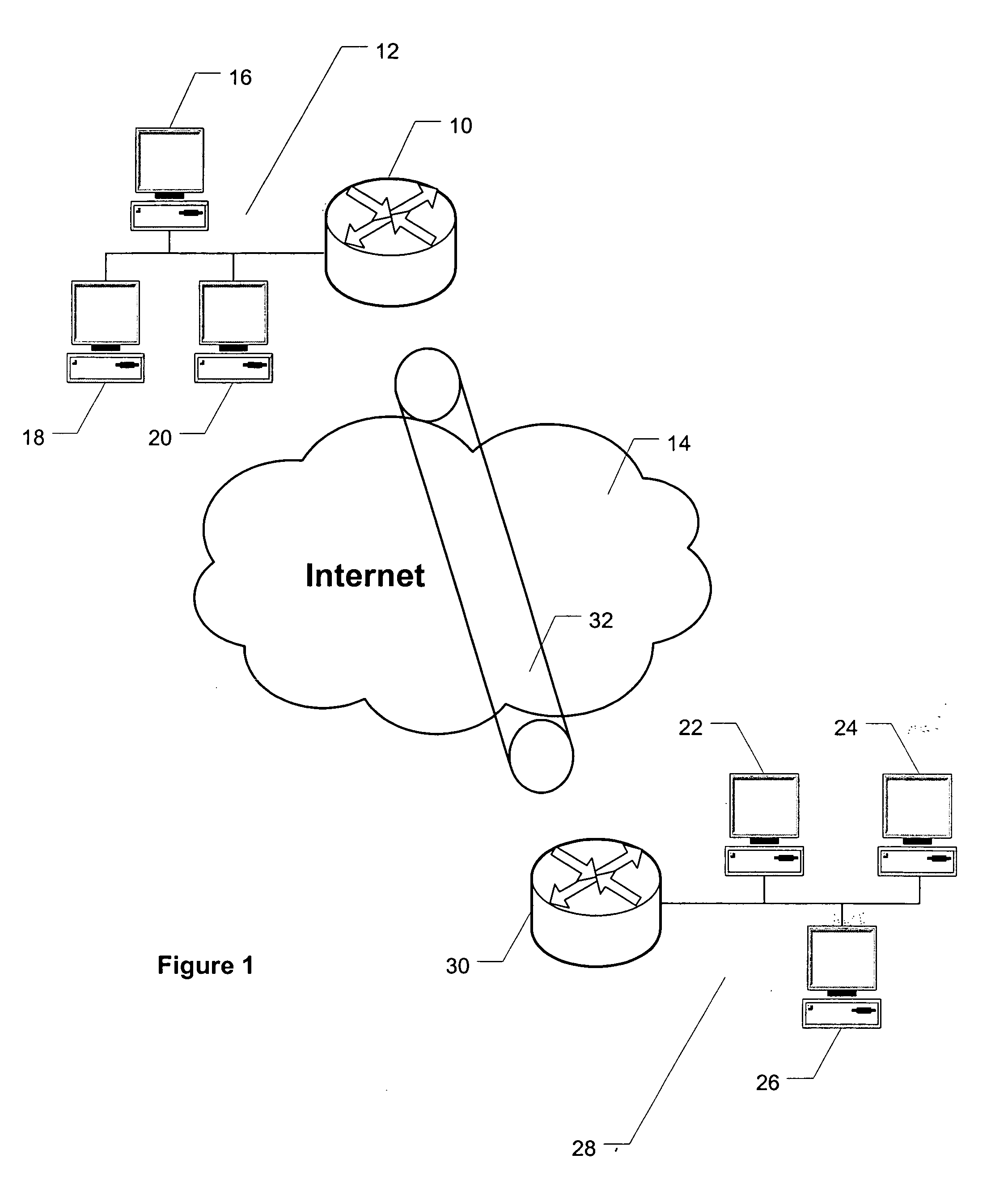
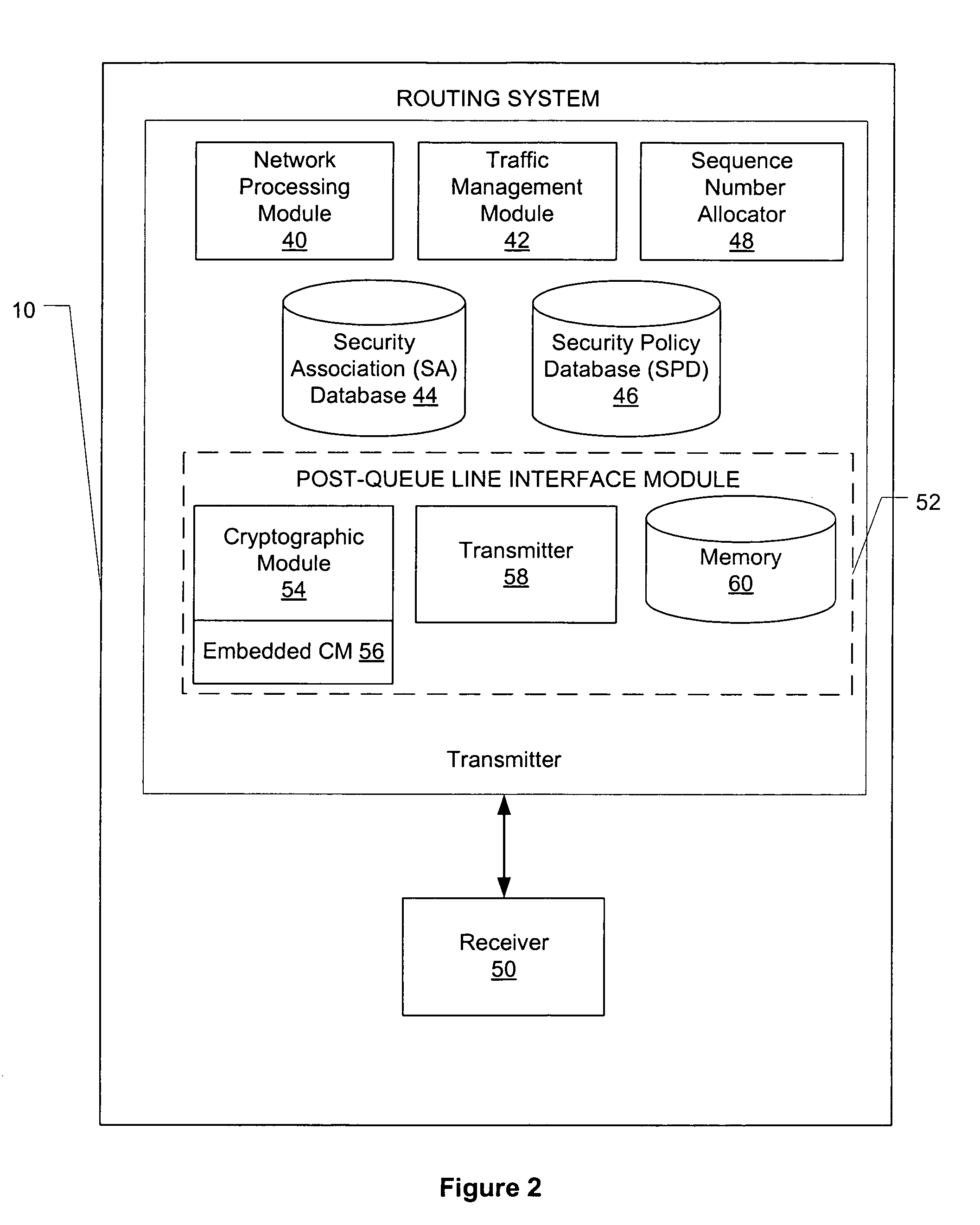
A method of routing data over an Internet Protocol security (IPSec) network, the method comprising: receiving packets for transmission over the IPSec network, controlling the order of processing of the packets, determining whether each packet requires security features, feeding of the packets to a post-queue line interface module according to the order of processing the packets and allocating a sequence number to each packet in the order of feeding of packets to the post-queue line interface module. A packet requiring security features are provided with such features, which may be AH or ESP protocol, before it is transmitted over the Internet Protocol security network. As the queueing of the packet is done before the packet is provided with security features, the quality of service of the IPSec network is improved with the packets being received at the anti-replay window according to the order of the allocated sequence numbers.
Owner:CISCO TECH INC
Strong anti-replay protection for IP traffic sent point to point or multi-cast to large groups
Owner:CISCO TECH INC
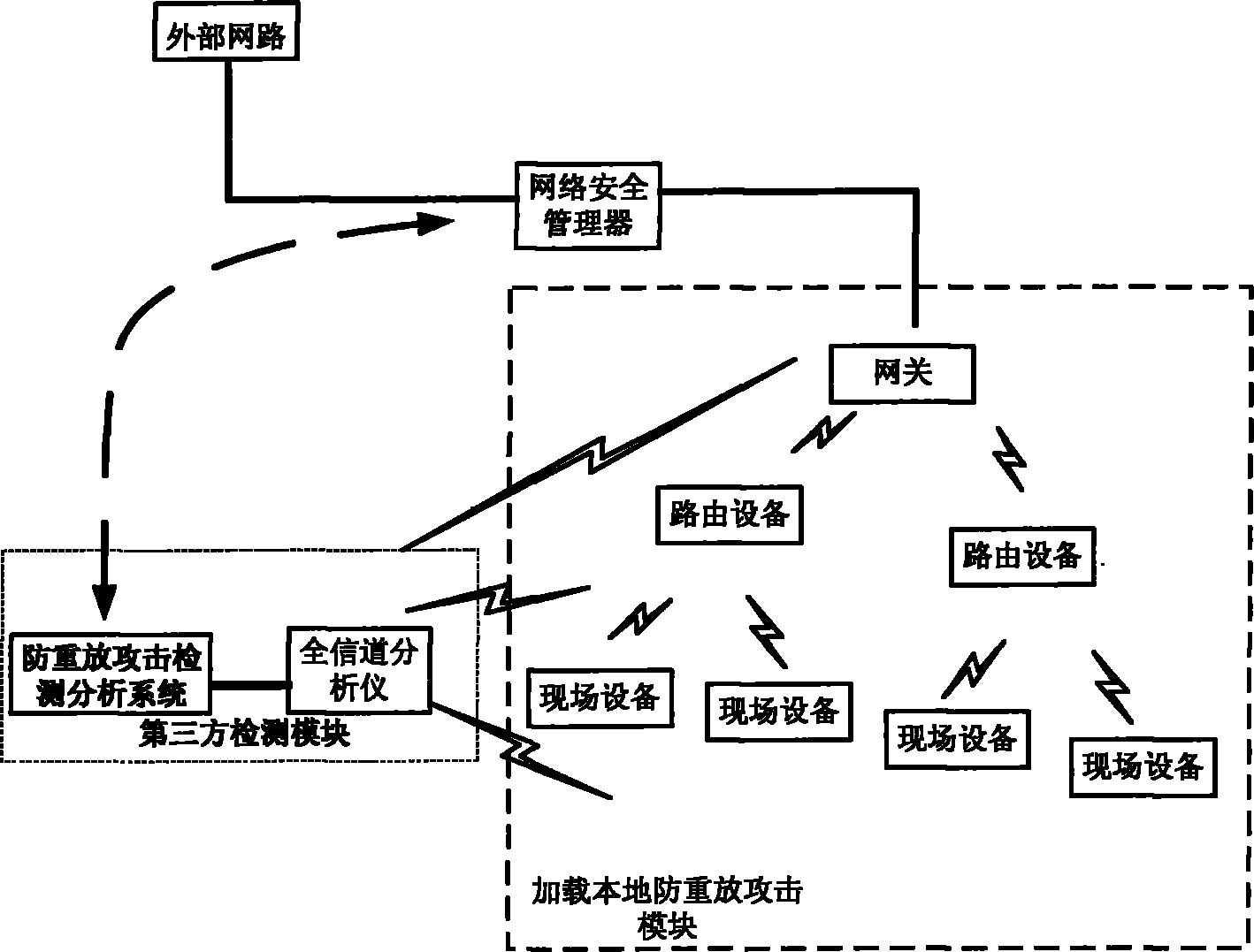
Anti-replay-attack system for industrial wireless network
InactiveCN101800989AReduce consumptionAvoid consumptionNetwork traffic/resource managementSecurity arrangementThird partyResource consumption
The invention provides an anti-replay-attack system for an industrial wireless network, which introduces a third-party detection mechanism in order to reduce system resource consumption. The industrial wireless network comprises a gateway, a router, field equipment and network security manager. The anti-replay-attack system for the industrial wireless network comprises a third-party detection module used for detecting whether intrusion data packets and replay attack data packets exist in the industrial wireless network or not and sending detection results to the network security manager, and the network security manager compares the system resource consumption caused by replay attacks with resource consumption brought by using an anti-replay-attack means to determine whether the anti-replay-attack means is used, thereby effectively preventing the anti-replay-attack means from bringing more system resource consumption than the replay attacks, and two time stamps of creation time and sending time are added in the data packet by a sender, so that the certainty and uniqueness of messages can be ensured; a receiver detection mechanism is adopted, and the data packets of the replay attacks are judged and discarded by a receiver so as to solve the problems of ID authentication and the like.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
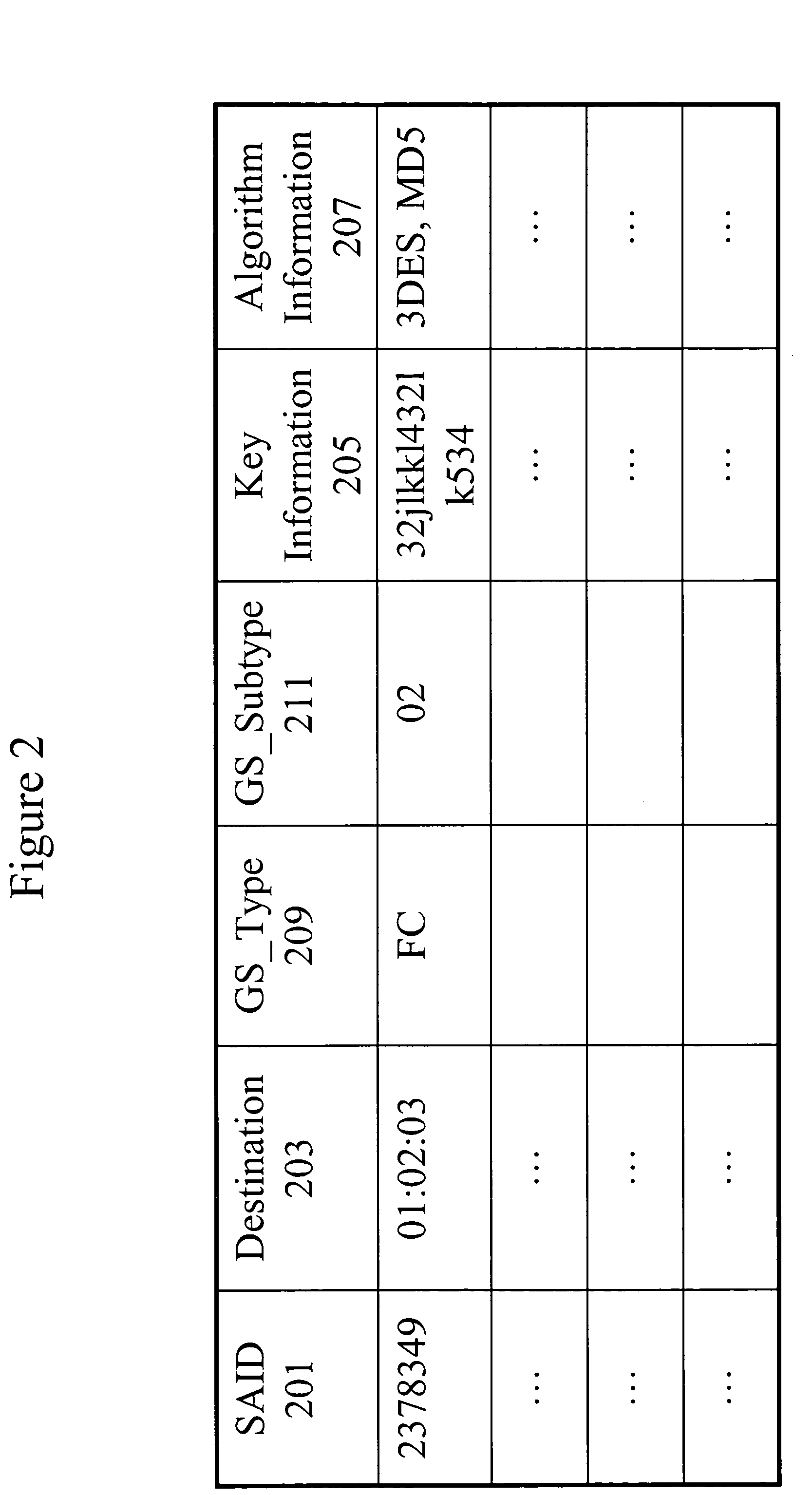
Method for implementing IPSEC resistance of replay aggression
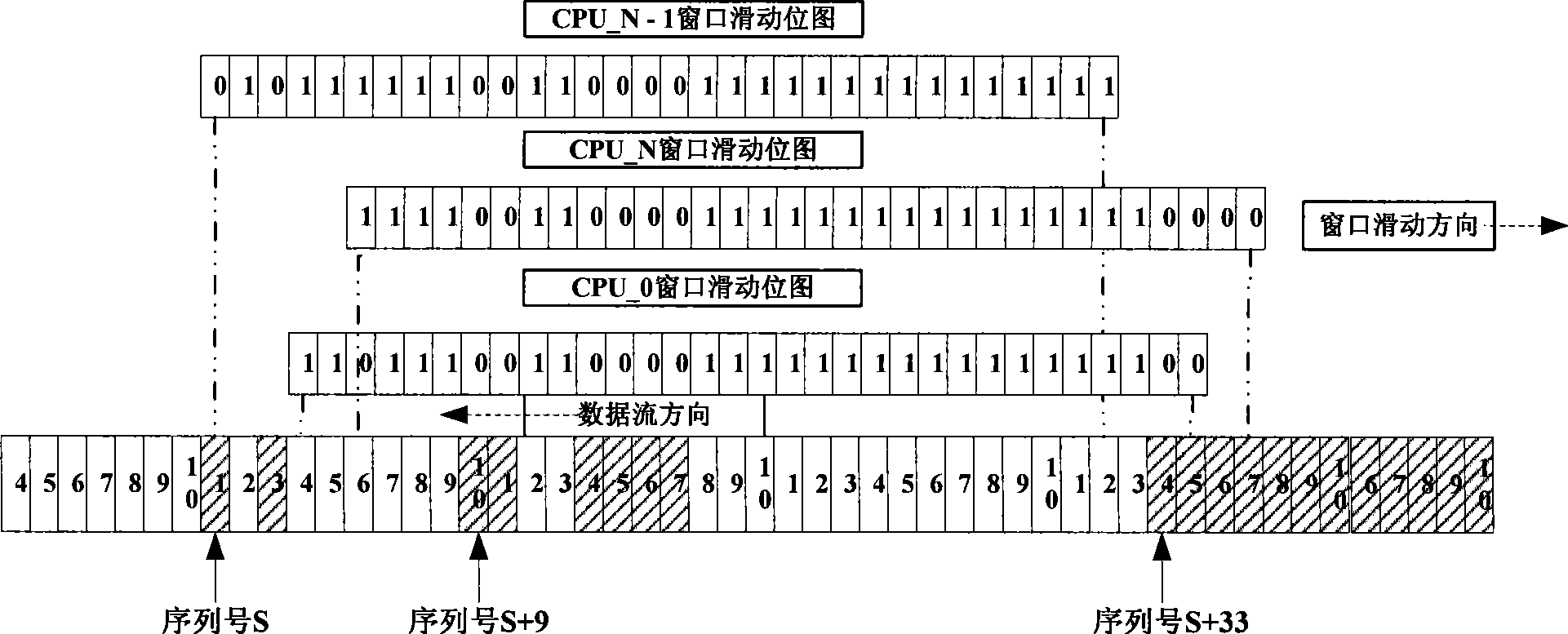
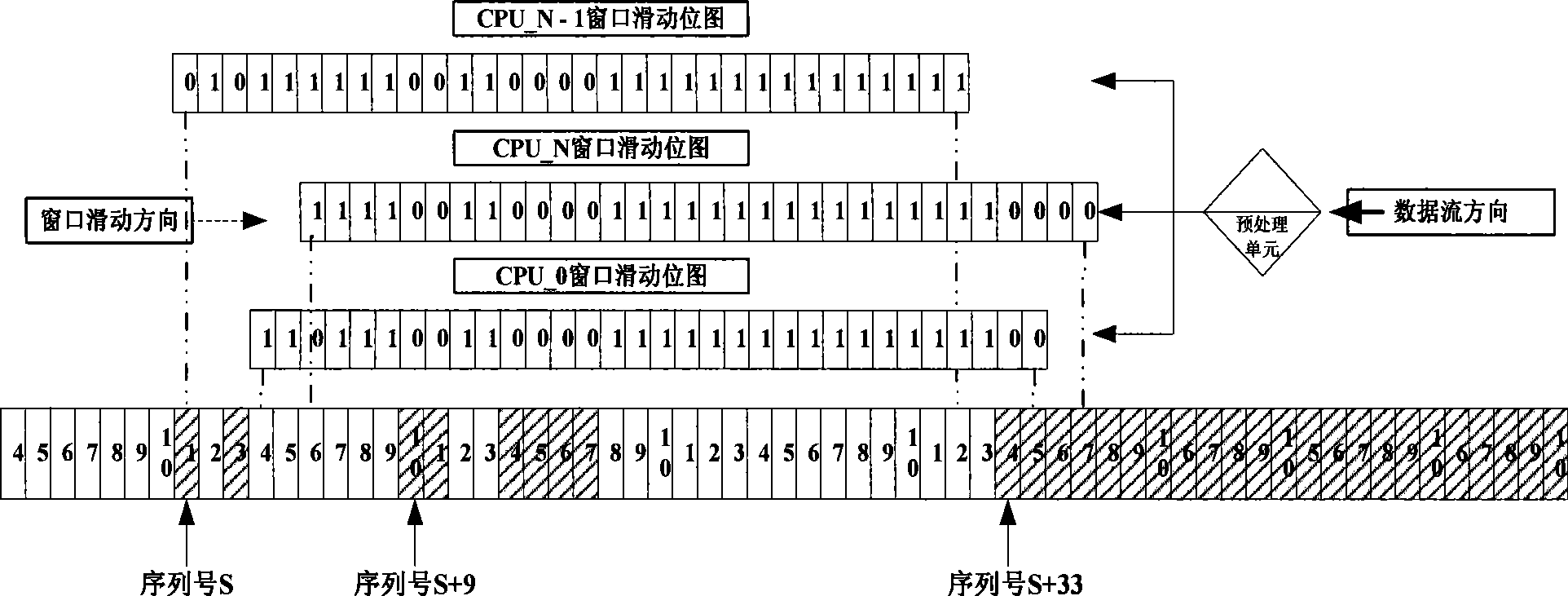
ActiveCN101471784APerfect anti-replay attack functionAvoid technical difficulties that severely degrade performanceSecuring communicationSlide windowLocking mechanism
The invention provides a method for realizing IPSec anti-replay attack, wherein, a plurality of sliding-windows are utilized to distinguish whether a received message is new in a system providing the IPSec service. For a multi-core architecture, the IPSec anti-replay attack function is perfected by utilizing the multi-sliding window technique, thereby avoiding the technical problem that system performance decreases badly caused by single sliding windows and lock mechanism. In the method, the message with specific type is dispatched to an appointed IPSec processing unit through a pretreatment module according to a plaintext serial-number on an IPSec message header, thereby leading the anti-replay attack detection to be more accurate.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH
Message anti-replay method, message anti-replay device and network device
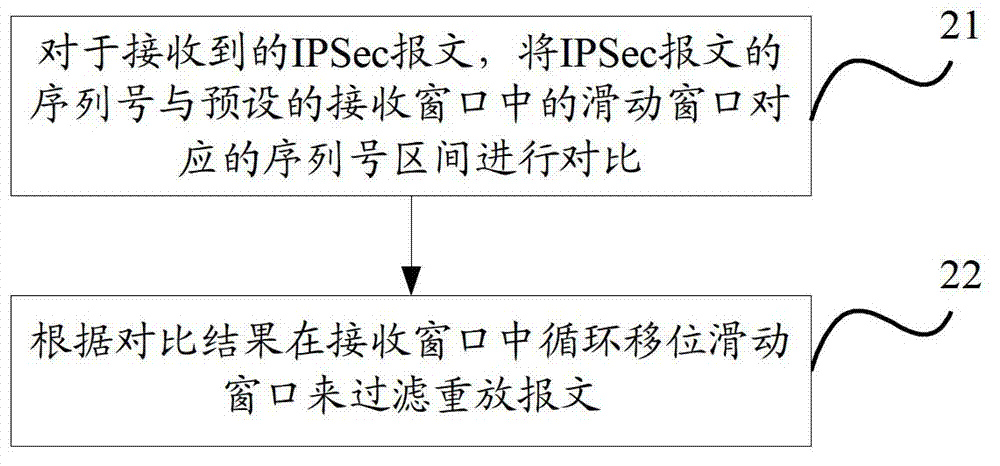
ActiveCN102769572AAddressing ComplexitySolve processing efficiencyData switching networksSlide windowIPsec
The invention discloses a message anti-replay method, a message anti-replay device and a network device which are based on IPSec (internet protocol security). The method includes: comparing a serial number of an IPSec message with a preset serial number range corresponding to a sliding window in a receiving window, and filtering the replay message by means of cyclic shift of the sliding window in the receiving window according to a comparison result. Sliding shift of the sliding window can be achieved only by cyclic shift of the sliding window in the receiving window, and the replay message can be filtered by means of cyclic shift of the sliding window, so that processing complexity of shift of the sliding window can be lowered, system overhead is reduced, and processing efficiency is improved. Therefore, the problems of processing complexity and low processing efficiency due to the fact that message anti-replay processing is performed by shifting the sliding window by means of sequential shift in the prior art are solved.
Owner:RUIJIE NETWORKS CO LTD
Security protocol processing for Anti-replay protection
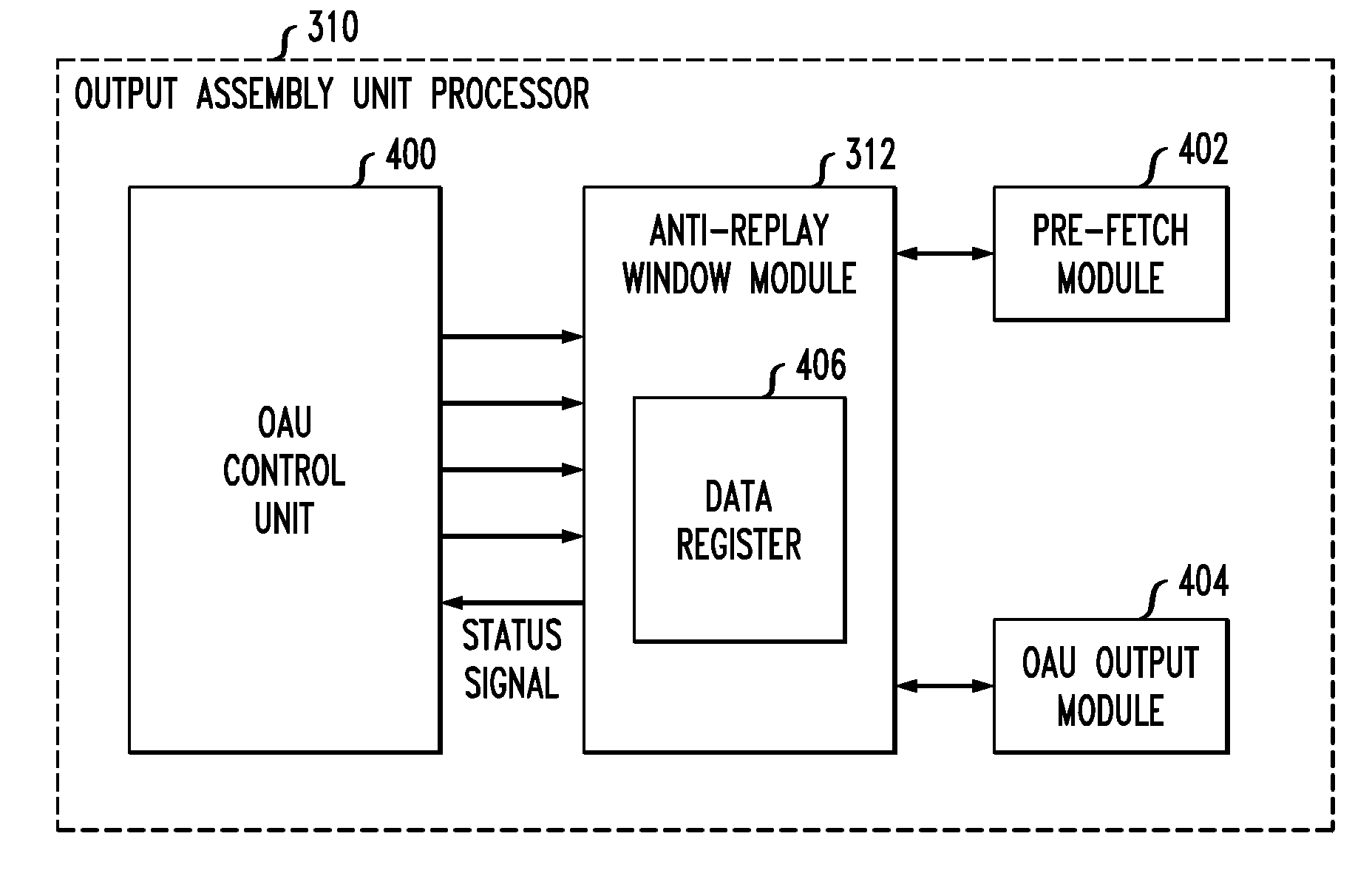
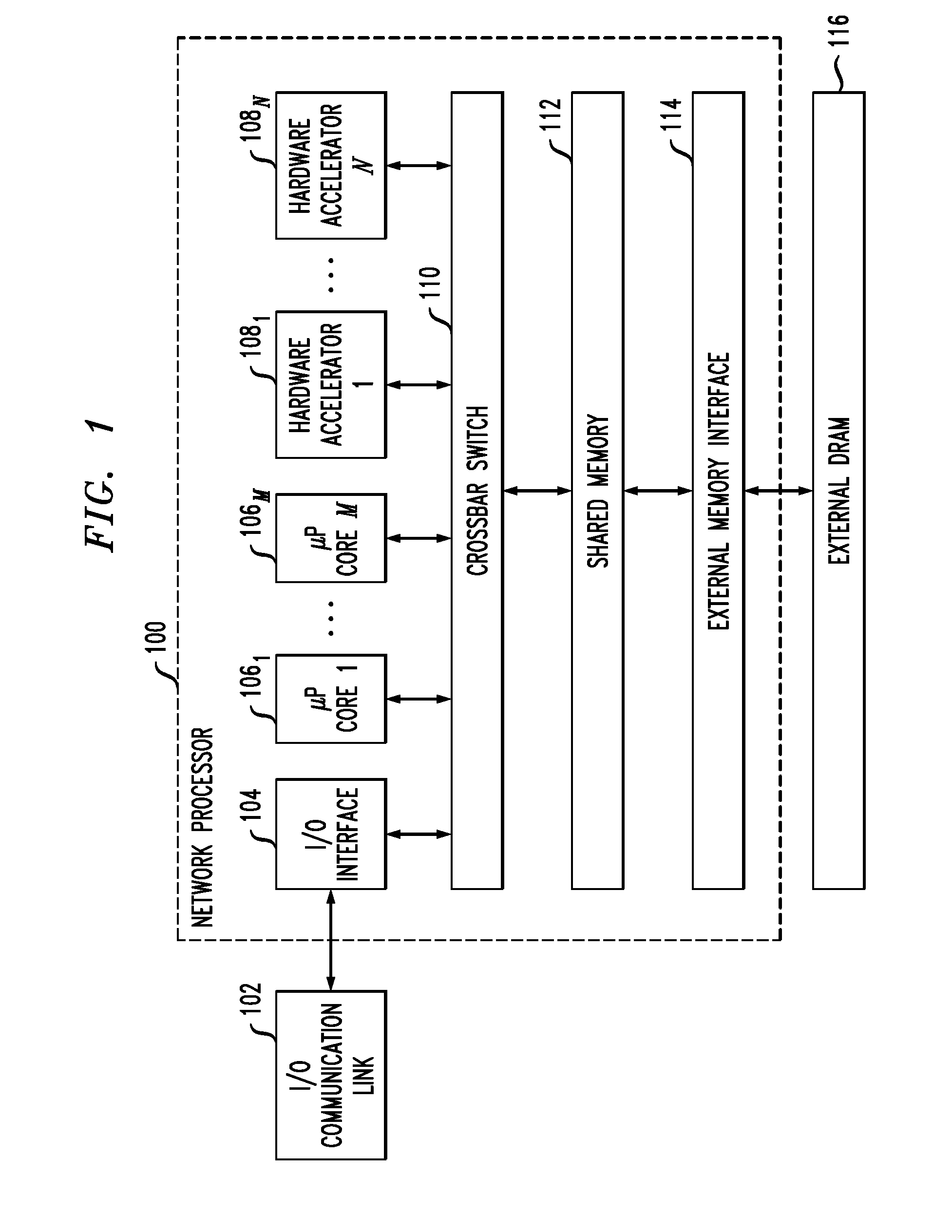
InactiveUS20120174216A1Well formedPrevent replay attacksMemory loss protectionUnauthorized memory use protectionProtocol processingData stream
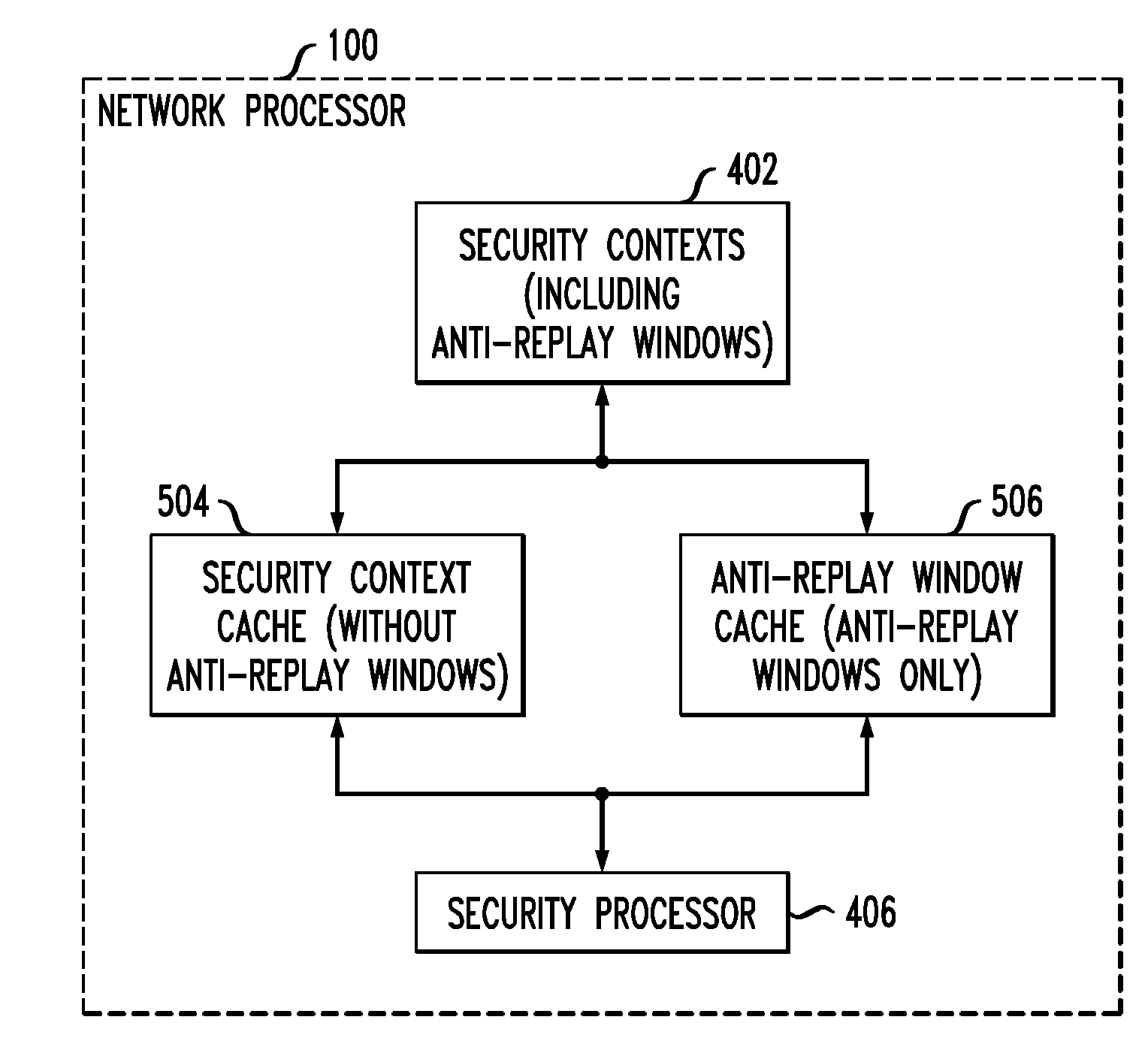
Described embodiments provide a network processor that includes a security protocol processor to prevent replay attacks on the network processor. A memory stores security associations for anti-replay operations. A pre-fetch module retrieves an anti-replay window corresponding to a data stream of the network processor. The anti-replay window has a range of sequence numbers. When the network processor receives a data packet, the security hardware accelerator determines a value of the received sequence number with respect to minimum and maximum values of a sequence number range of the anti-replay window. Depending on the value, the data packet is either received or accepted. The anti-replay window might be updated to reflect the receipt of the most recent data packet.
Owner:INTEL CORP
Packet sequence number tracking for an Anti-replay window
InactiveUS20120042096A1Prevent replay attacksMultiple digital computer combinationsStore-and-forward switching systemsData packData stream
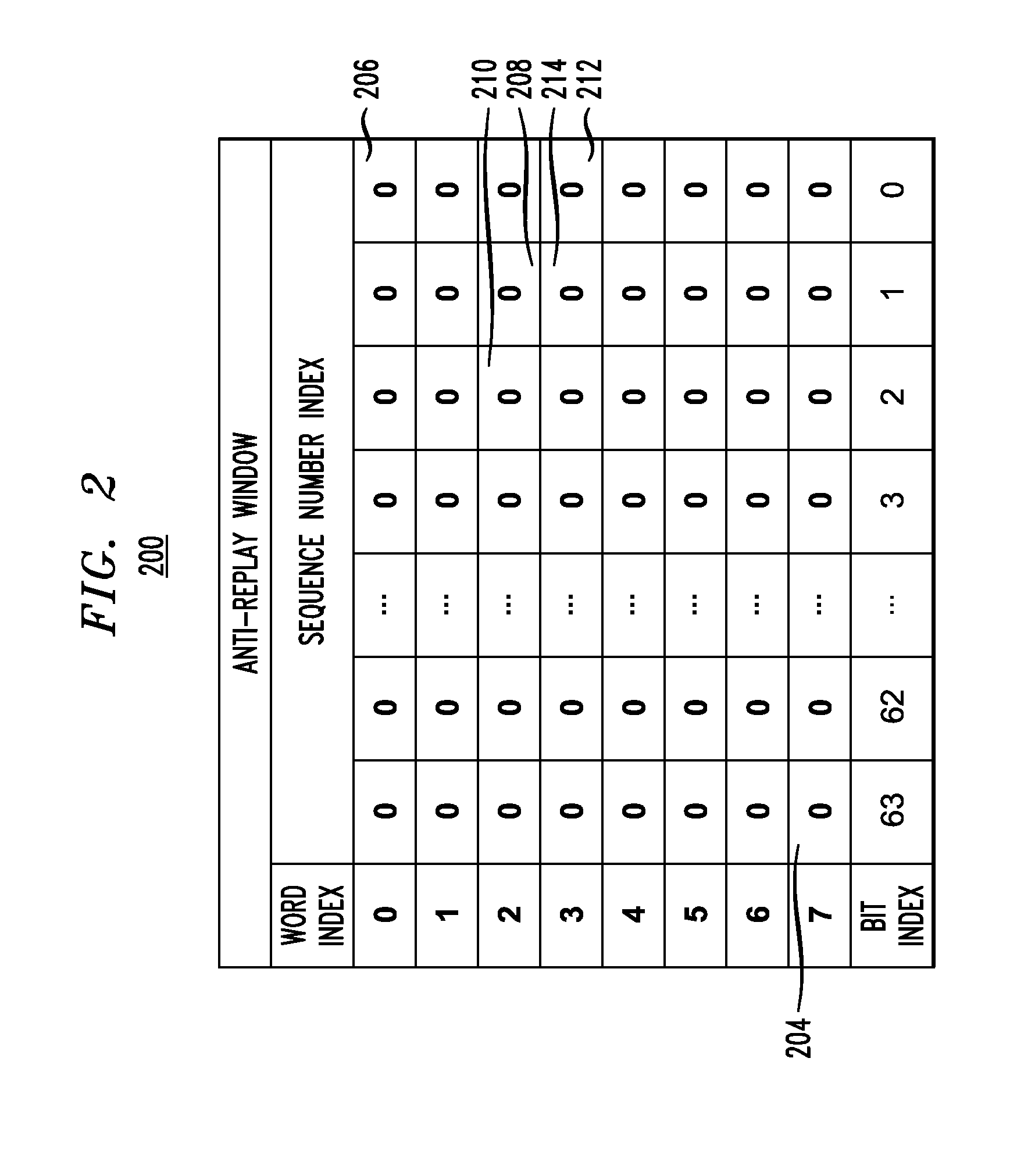
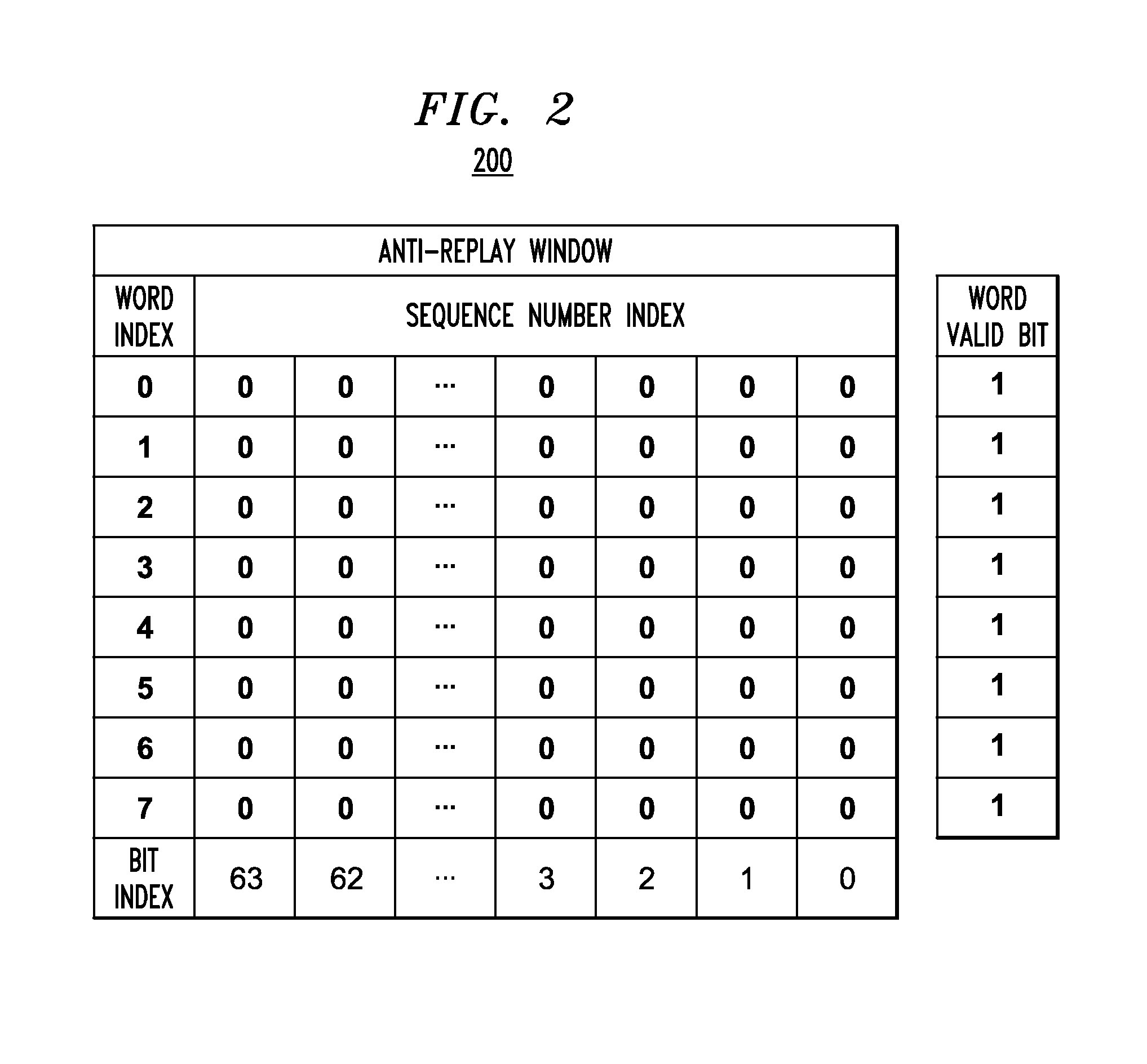
Described embodiments provide a network processor that includes a security sub-processor to prevent replay attacks on the network processor. A memory stores an anti-replay window corresponding to a data stream of the network processor. The anti-replay window has N bits initialized to correspond to data packet sequence numbers in the range 1 to N. The anti-replay memory is stored in a plurality of data words. A plurality of flip-flops store word valid bits corresponding to each of the data words. A multiplexer selects the word valid bit corresponding to a data word requested by the security processor, and an AND gate performs a bitwise AND operation between the selected data word and word valid bit. When the network processor receives a data packet, the security sub-processor determines a value of the received sequence number with respect to minimum and maximum values of a sequence number range of the anti-replay window.
Owner:INTEL CORP
Live nv replay for enabling high performance and efficient takeover in multi-node storage cluster
ActiveUS20150261633A1TransmissionRedundant hardware error correctionHigh availabilityNon-volatile random-access memory
A live non-volatile (NV) replay technique enables a partner node to efficiently takeover a failed node of a high-availability pair in a multi-node storage cluster by dynamically replaying operations synchronously logged in a non-volatile random access memory (NVRAM) of the partner node, while also providing high performance during normal operation. Dynamic live replay may be effected through interpretation of metadata describing the logged operations. The metadata may specify a location and type of each logged operation within a partner portion of the NVRAM, as well as any dependency among the logged operation and any other logged operations that would impose an ordering constraint. During normal operation, the partner node may consult the metadata to identify dependent logged operations and dynamically replay those operations to satisfy one or more requests. Upon failure of the node, the partner node may replay, in parallel, those logged operations having no imposed ordering constraint, thereby reducing time needed to complete takeover of the failed node.
Owner:NETWORK APPLIANCE INC
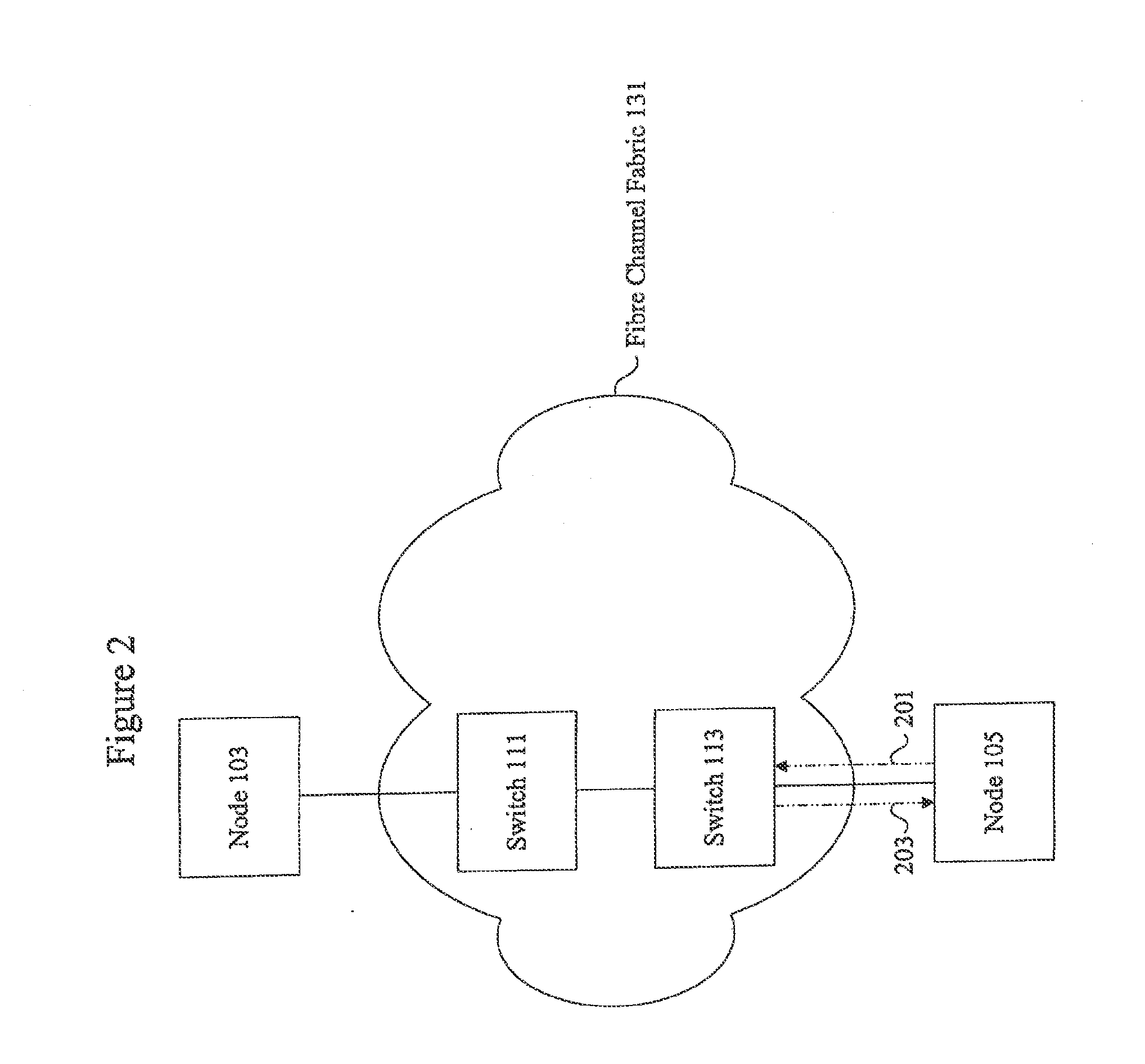
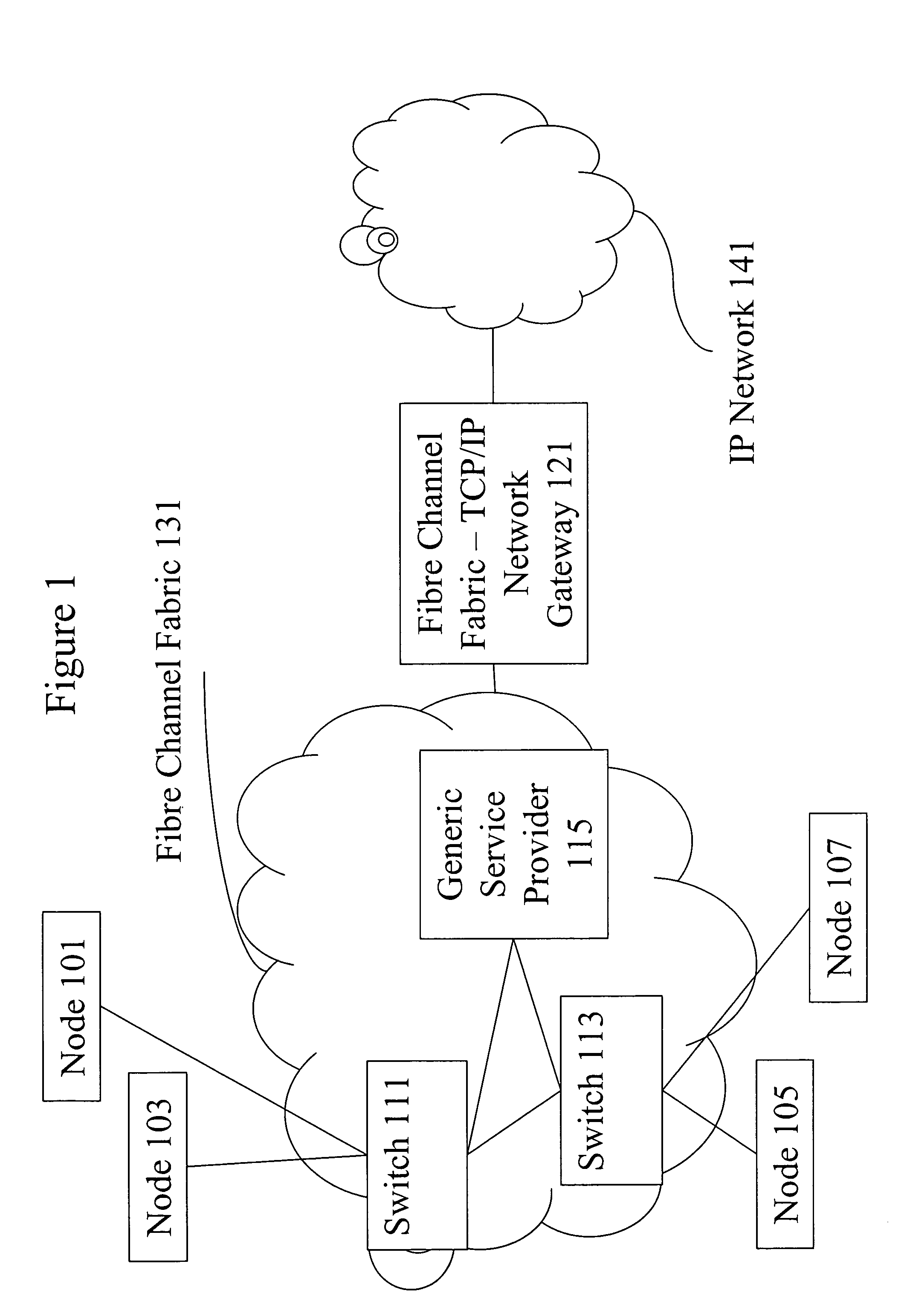
Methods and apparatus for security over fibre channel
InactiveUS20110219438A1Improve securityDigital data processing detailsComputer security arrangementsKey exchangeFiber
Owner:CISCO TECH INC
Anti-replay attack method, and related apparatuses
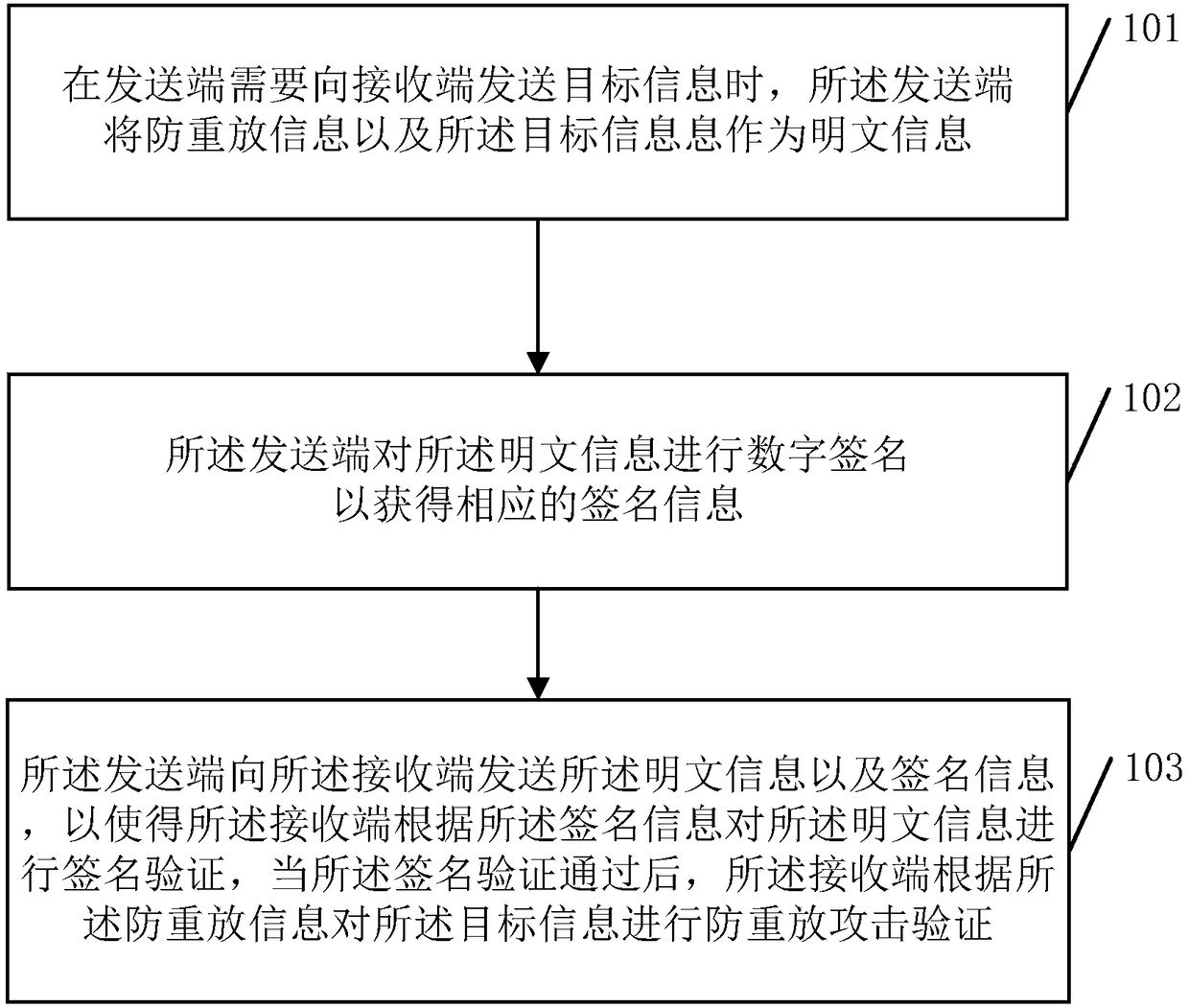
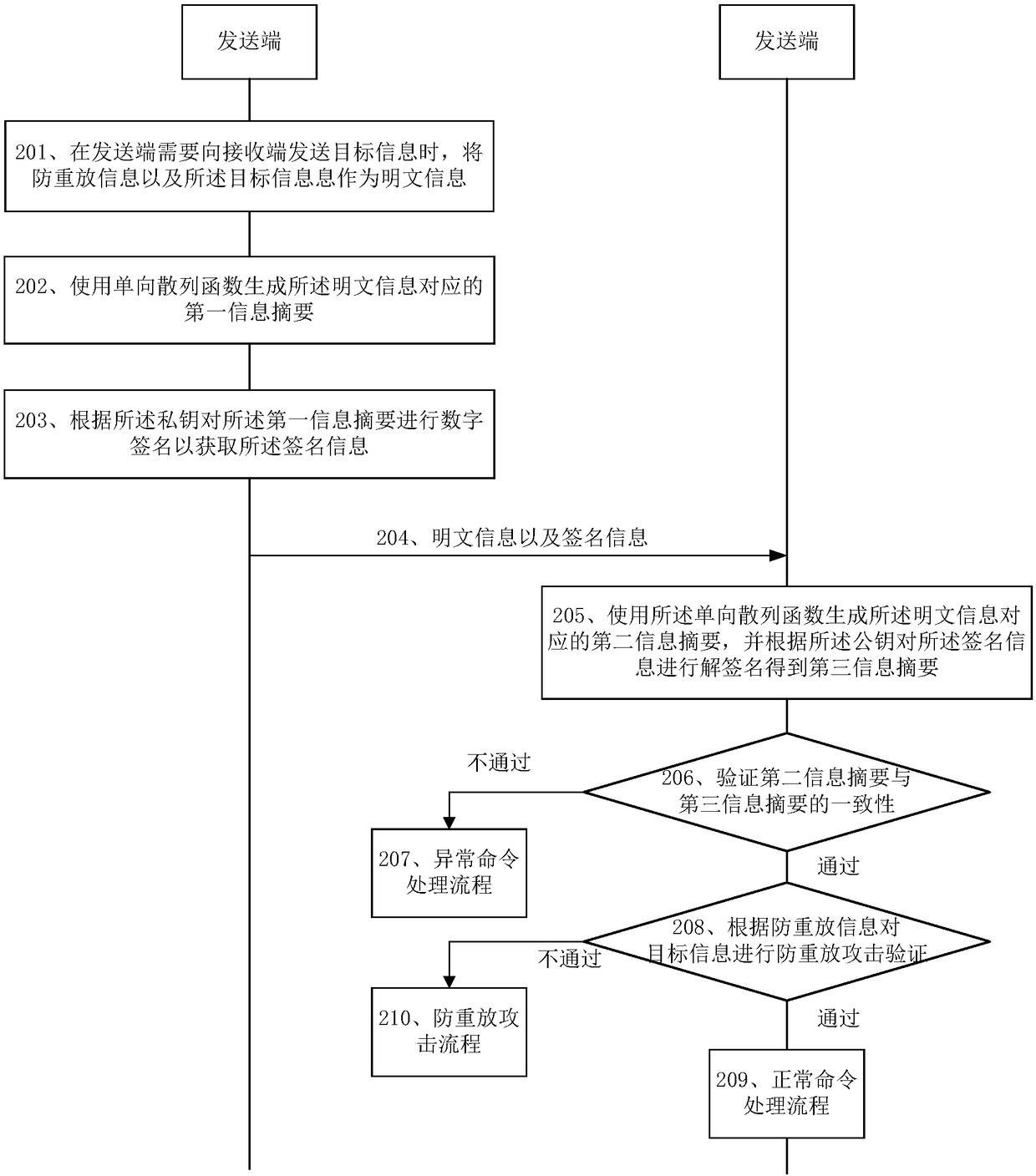
InactiveCN108512848AAccurate authenticationGood anti-replay attack effectUser identity/authority verificationDigital signatureAnti-replay
The embodiment of the invention discloses an anti-replay attack method, a sending end, a receiving end, a corresponding computer device and a program product. The method disclosed by the embodiment ofthe invention comprises the following steps: when the sending end needs to send target information to the receiving end, the sending end uses anti-replay information and the target information as plaintext information, wherein the anti-replay information is applied to anti-replay attack verification; the sending end performs digital signature on the plaintext information to obtain corresponding signature information; and the sending end sends the plaintext information and the signature information to the receiving end, so that the receiving end performs signature verification on the plaintextinformation according to the signature information, and after the signature verification is passed, the receiving end performs anti-replay attack verification on the target information according to the anti-replay information.
Owner:SHENZHEN DAPU MICROELECTRONICS CO LTD
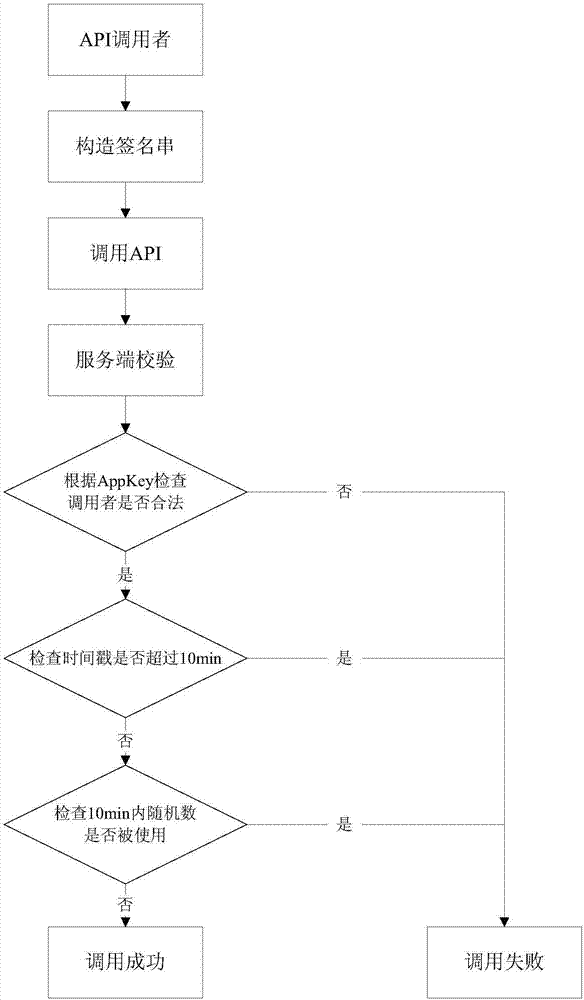
Anti-tamper and anti-replay method in support of REST API
InactiveCN107453878ASolve malicious tampering request parametersSolve the problem of using the stolen API to perform replay attacksKey distribution for secure communicationUser identity/authority verificationTimestampAnti-replay
The invention discloses an anti-tamper and anti-replay method in support of REST API. The method includes the following steps: 1. an API invocation end applying access authority and secret key for performing signing to an API server; 2. the API invocation end generating invocation timestamp and random number, ranking request parameters in a lexicographic order, in combination with system request headers, performing signing with the applied secret key; 3. the server detecting the identity of the API invocation person, determining whether the API invocation person has invocation authority; 4. the server using the same secret key to sign request parameters and system request headers in accordance with same rules, comparing whether the signatures are the same, and preventing the parameters from being tampered; 5. the server determining the API invocation timestamp, and determining timeout; and 6. the server re-determining random number. According to the invention, the API invocation person only needs to strictly save the secret key, and attacker does not need to forge the signature and the parameters in the request process are unable to be tampered, thus achieving safe access to API.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Method and equipment for updating anti-replay parameter during master and slave switching
The invention discloses a method and equipment for updating an anti-replay parameter during master and slave switching. During master and slave switching, new master equipment sets IPSec SA to be invalid, acquires an anti-replay window and an anti-replay sequence number from opposite-end equipment of an IPSec tunnel to update the anti-replay window and the anti-replay sequence number of the IPSec SA per se, and sets the corresponding IPSec SA to be valid after the update is finished to process data so that the new master equipment can acquire the real and reliable anti-replay window and anti-replay sequence number and the security of data transmission is ensured.
Owner:NEW H3C TECH CO LTD
Gaming network
InactiveUS20070054734A1Reduce the possibilityReduce successDigital data processing detailsUser identity/authority verificationConfidentialityAnomalous behavior
The gaming network described herein includes network security features, host security features, audit protocols, and design architecture approaches to reduce the possibility of network attacks. The gaming network provides for traffic confidentiality, encryption, message authentication, secure authentication mechanisms, anti-replay protection of traffic, key management mechanisms, robust network availability, misrouting and redirection protection and prevention, rejection of external traffic, and a high entry-barrier to device addition to the network. The host protection and security includes secure host initialization, disabling unneeded components, download verification, disabling of unused IP ports, discarding traffic, strong passwords, dynamic one-time passwords for remote login, disabling default accounts, and appropriate “least-level” device privileges. Audit requirements include integrity protection of audit logs, appropriate definition of auditable events, auditing of anomalous behavior, chain of evidence preservation, shutdown if audit disabled, full log entry audit, personal ID and time access audit trail, and auditing of internal user actions.
Owner:BALLY GAMING INC
Anti-replay method for unicast and multicast ipsec
InactiveUS20100165839A1Error preventionNetwork traffic/resource managementCommunications systemIPsec
A method for managing a packet in a communication system between two or more endpoints, a sender and one or more recipients, comprises receiving a first packet comprising a source identifier that uniquely identifies a sender of the first packet and a current source time assigned to the first packet by the sender, determining a received time for the first packet, retrieving a cached source time assigned by the sender to a second packet that was received prior to receiving the first packet, and determining whether to discard or process the first packet based on the current source time, the received time, and the cached source time. The current source time, the received time, and the cached time, in addition to predetermined parameters such as a maximum age and an anti-replay window allows a recipient to determine whether to process or discard a packet.
Owner:MOTOROLA SOLUTIONS INC
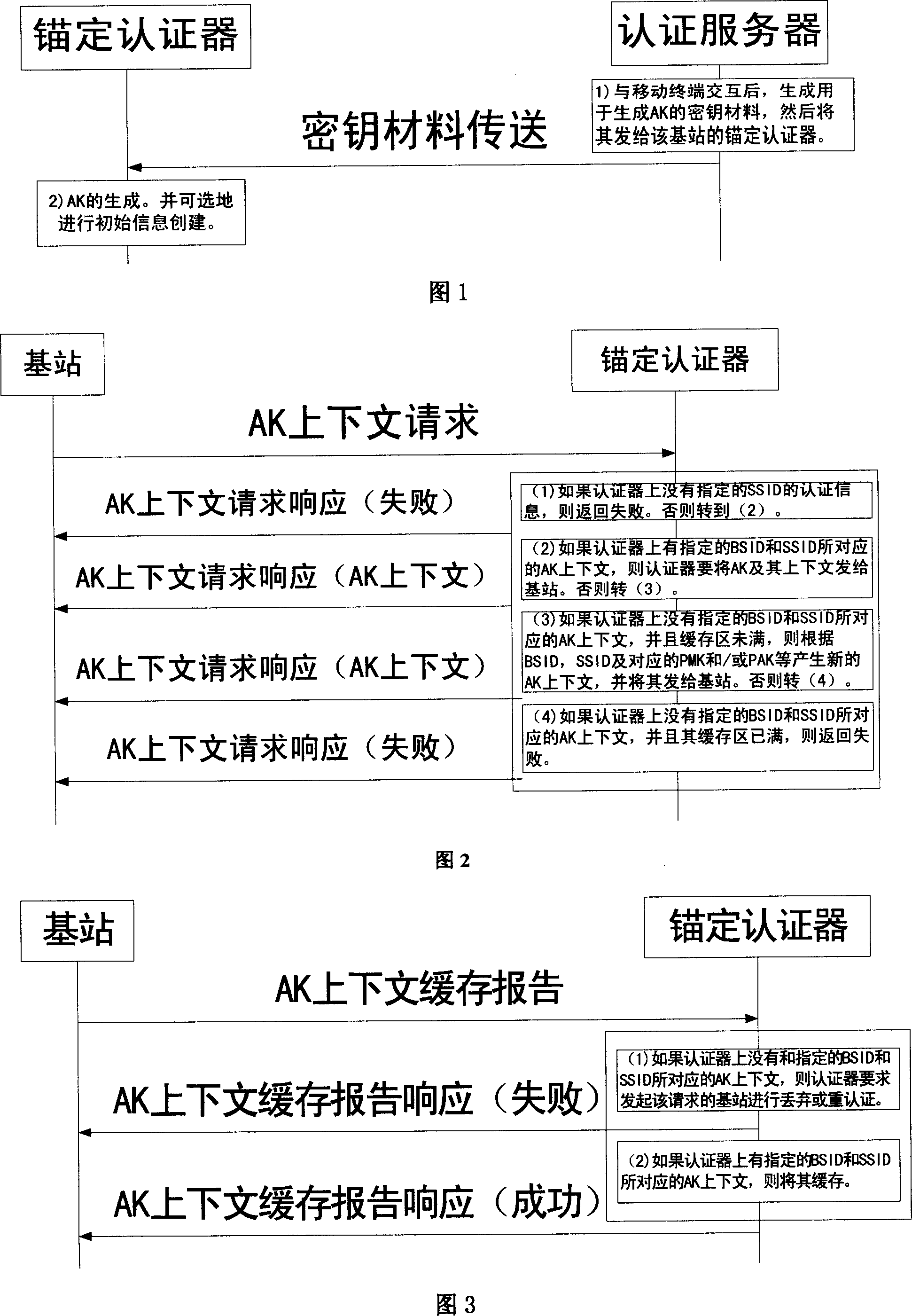
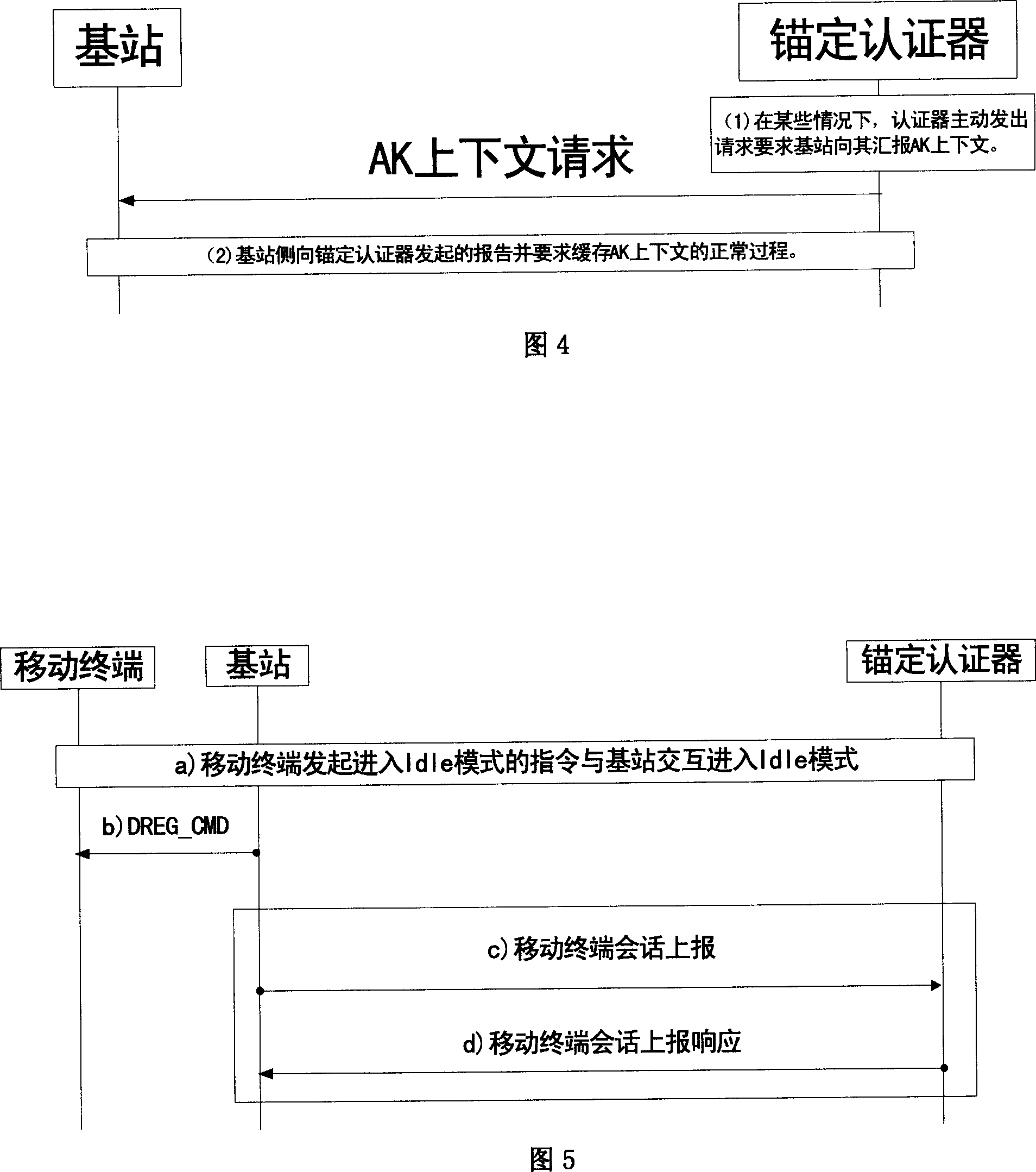
AK context cache method for wireless communication system
InactiveCN101026866AImprove performancePrevent replay attacksKey distribution for secure communicationRadio/inductive link selection arrangementsCommunications systemAnti-replay
Through AK context is buffered on mobile terminal, and authenticator, when moving to different base stations, mobile terminal can store AK context within its lifetime. At the same time, when moving back to the base station, which obtained and buffered the AK context effective till now, mobile terminal can continues using the AK context (mainly, packet sequence number of anti replay attack of up / down going link message) without need of authenticating again. The invention also raises efficiency of switching and moving system greatly, improves seamless communication performance between different sectors provided by system.
Owner:HUAWEI TECH CO LTD
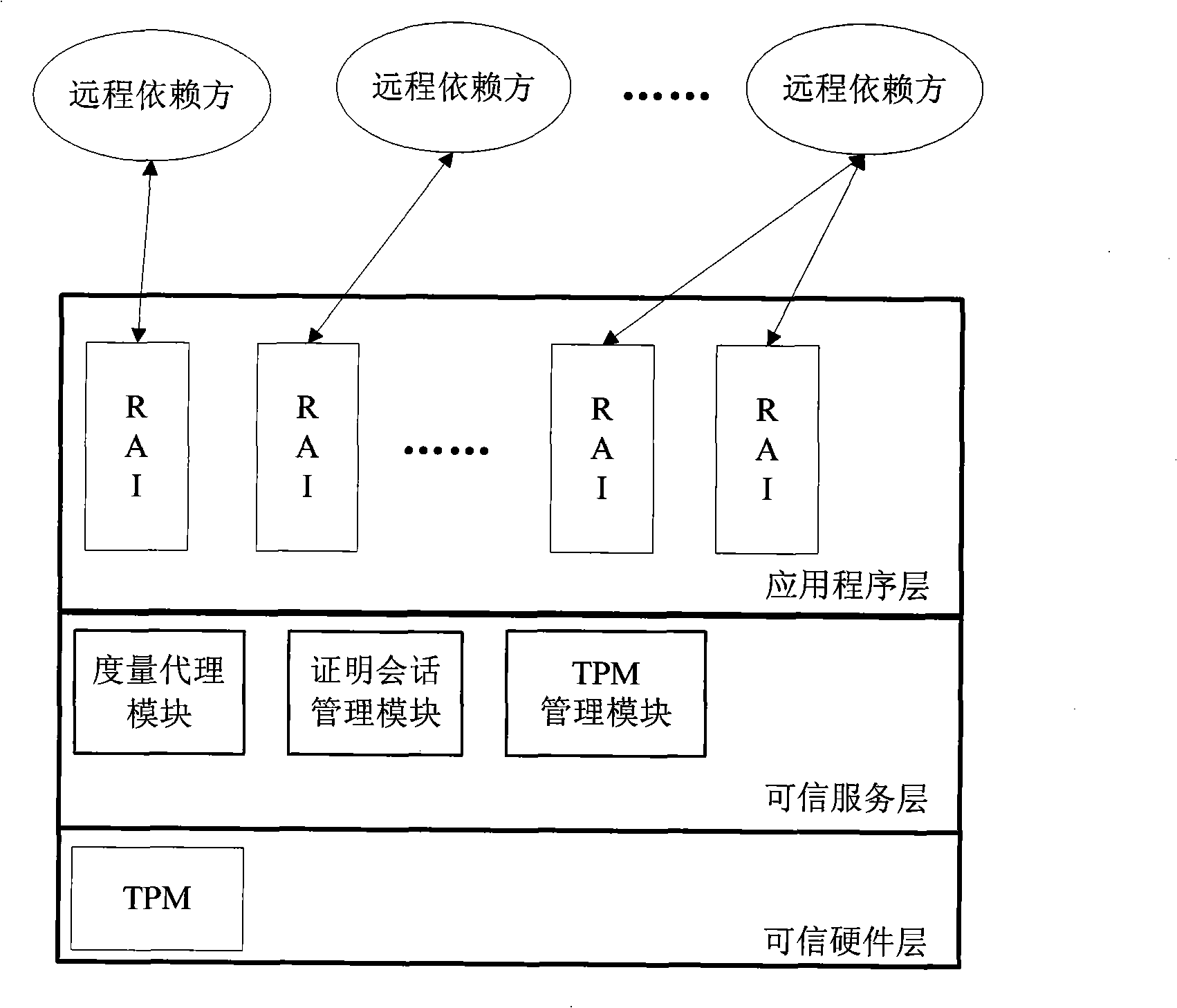
Multi-case dynamic remote certification method based on TPM
InactiveCN101344903AAddress dynamicsResolving State ConsistencyPlatform integrity maintainanceTrusted ComputingInformation security
The invention discloses a TPM-based multi-instance dynamic remote attestation method which belongs to the field of information security technology. The method comprises the steps as follows: a) an RAI instance is started: the TPM measures the RAI instance and issues an initial attestation certificate for the RAI instance; the remote relying party of the RAI instance obtains and authenticates the initial attestation certificate, if the authentication is passed, the link between the RAI instance and the remote relying party of the RAI instance is established; b) if the component of the RAI instance is updated, the TPM re-measures the RAI instance and issues an updating attestation certificate; the remote relying party of the RAI instance obtains and authenticates the updating attestation certificate; if the authentication is passed, the link is maintained; and c) the step b) is repeated until the RAI instance is closed and the link is disconnected; meanwhile, all the attestation steps of a plurality of RAI instances intersperse with each other for forming a TPM attestation chain. Compared with the remote attestation methods of other trusted computing platforms, the method is characterized by the dynamic attestation of platform status, the concurrent attestations of multiple network programs, and anti-replay attack, etc.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
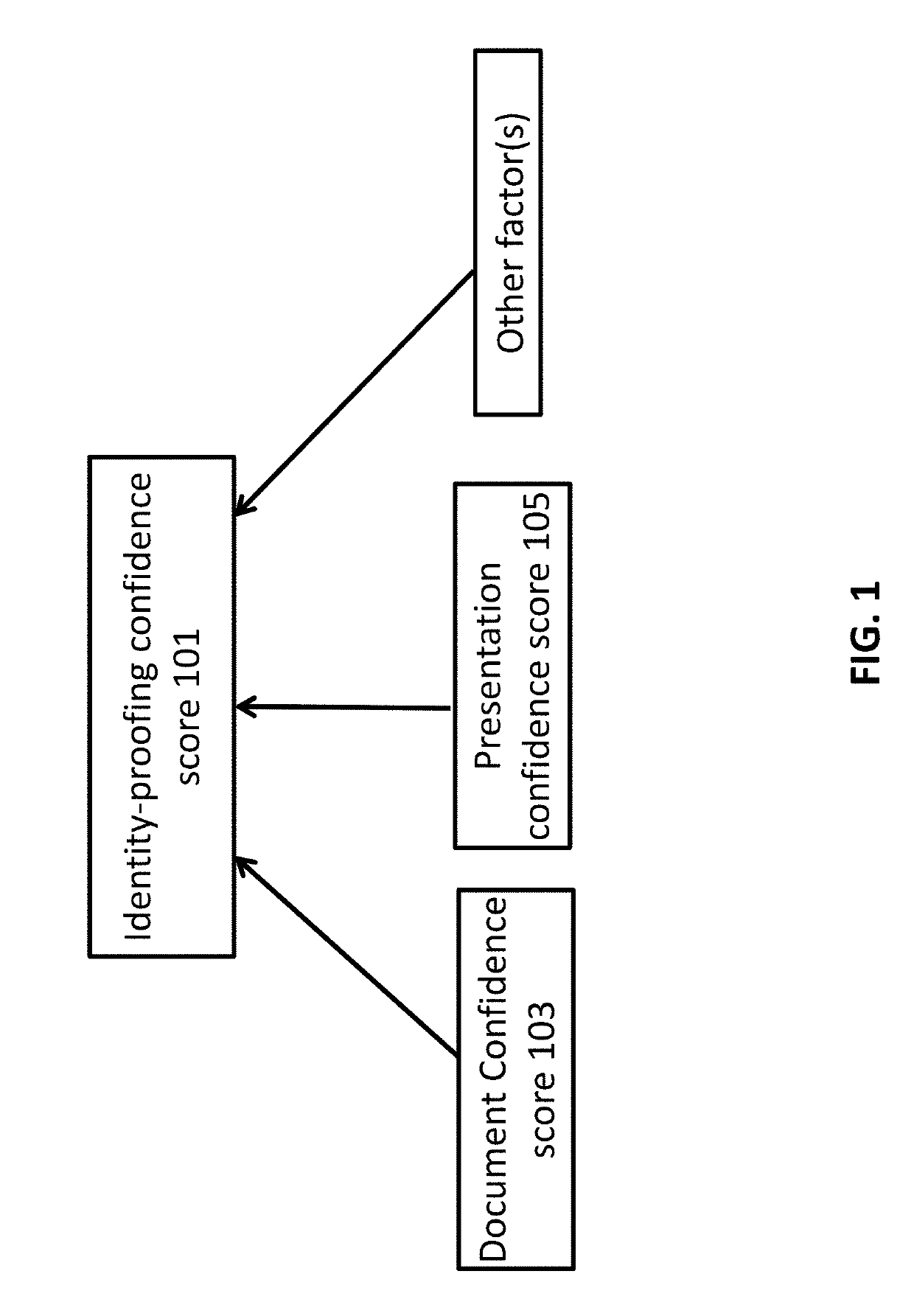
Systems and methods for distribution of selected authentication information for a network of devices
ActiveUS20190281036A1Provide protectionAccurate measurementFinanceDigital data authenticationProgram planningDisplay device
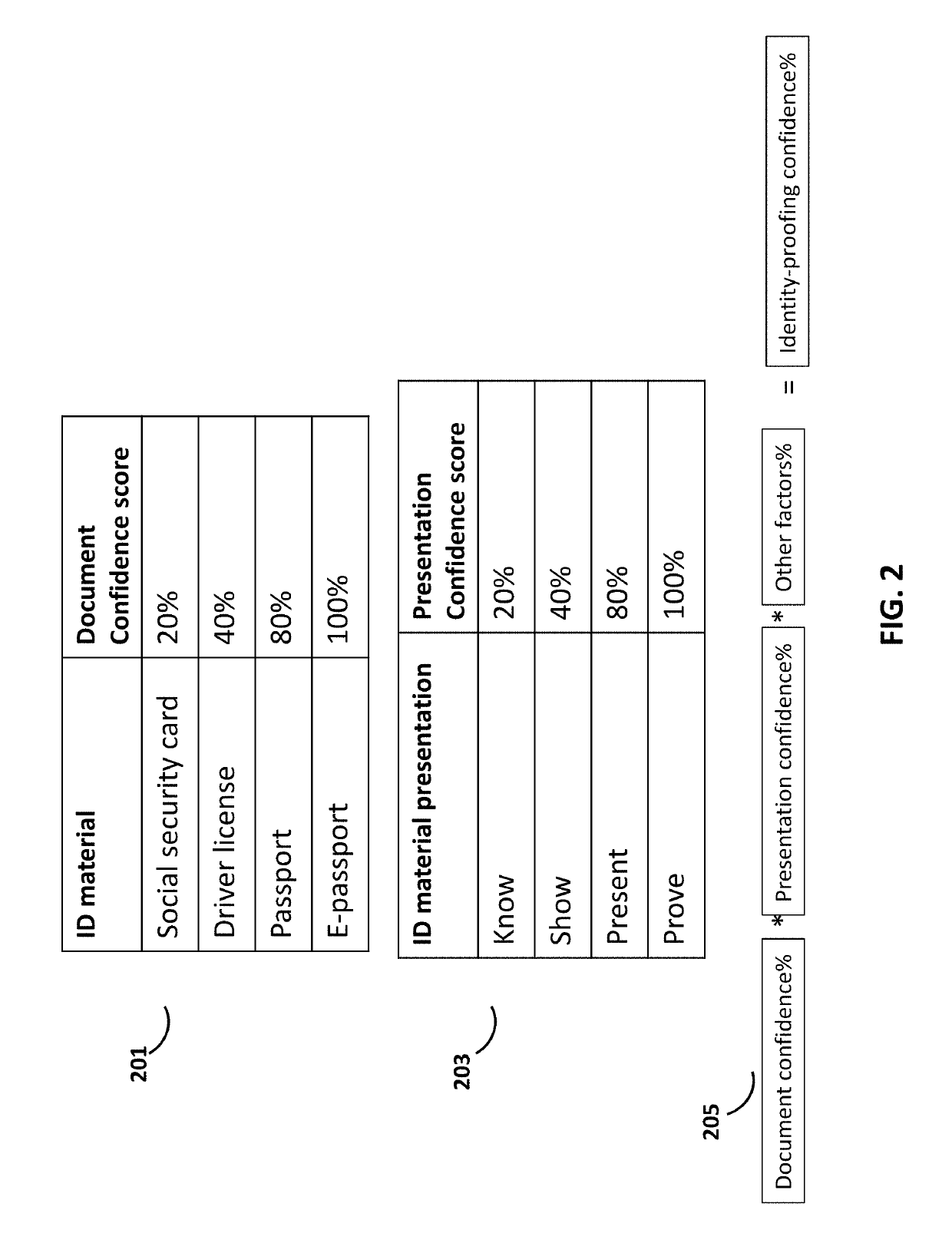
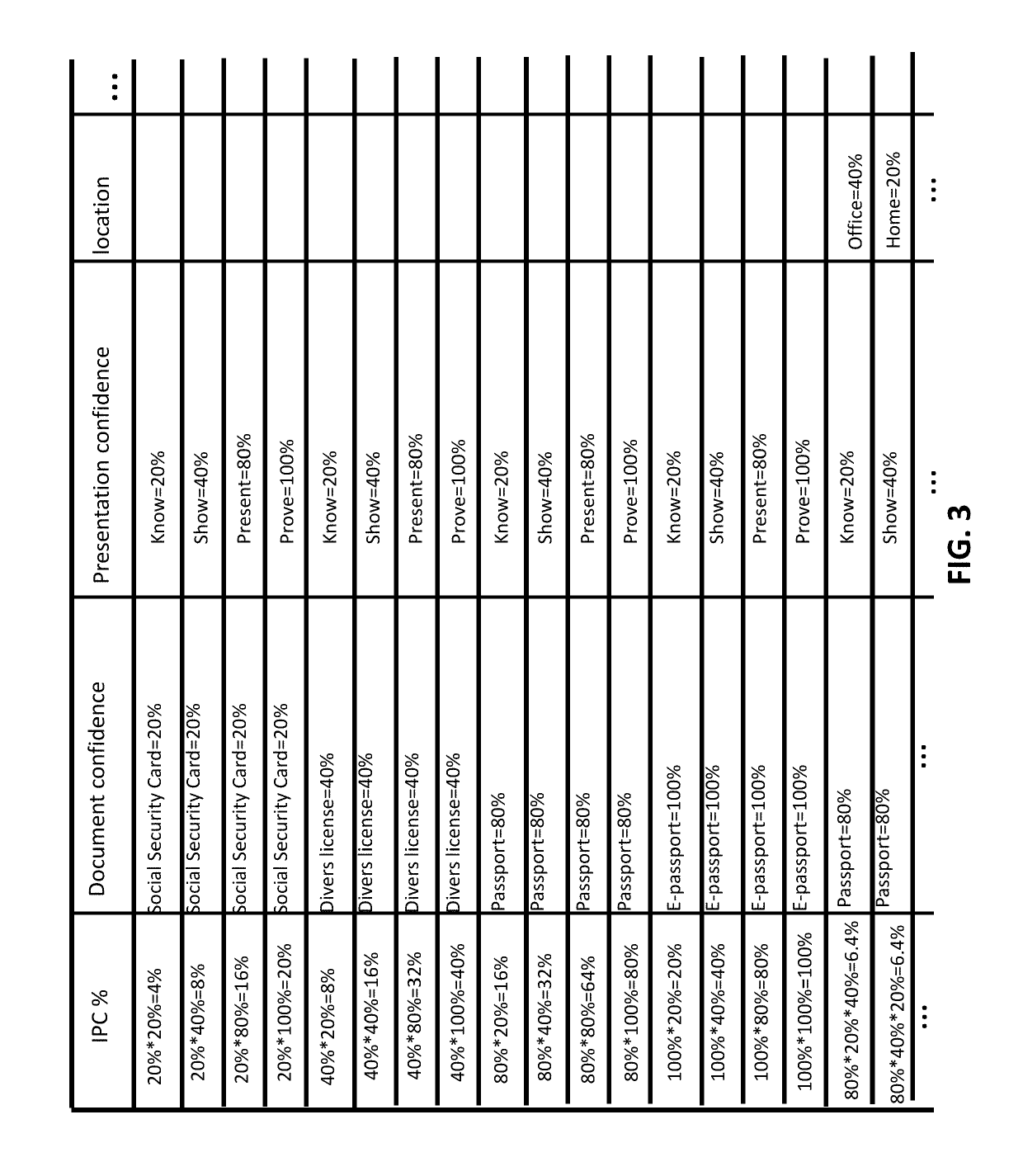
A system for facilitating distribution of authentication information for a network of devices to be authenticated is provided. The system comprises: an authentication module configured to obtain an identity-proofing confidence score, based on data about identity-proofing of a user obtained from an authentication service system, wherein the data about identity-proofing comprises a type of identity document of the user and a presentation method used for verifying the user's identity by the authentication service system; and an insurance module in communication with the authentication module, configured to generate a plurality of security levels for the user, wherein each of the plurality of security levels is generated based on the identity-proofing confidence score and a credential authentication confidence score that is (1) obtained with aid of at least one device from the network of devices, and (2) determined based on a credential to be used for a transaction and a presence of an anti-replay feature about the at least one device, wherein a display is configured to show a plurality of coverage plans associated with the plurality of security levels to the user for selection, such that the authentication service system performed credential authentication according to a selected coverage plan.
Owner:TRUSONA INC
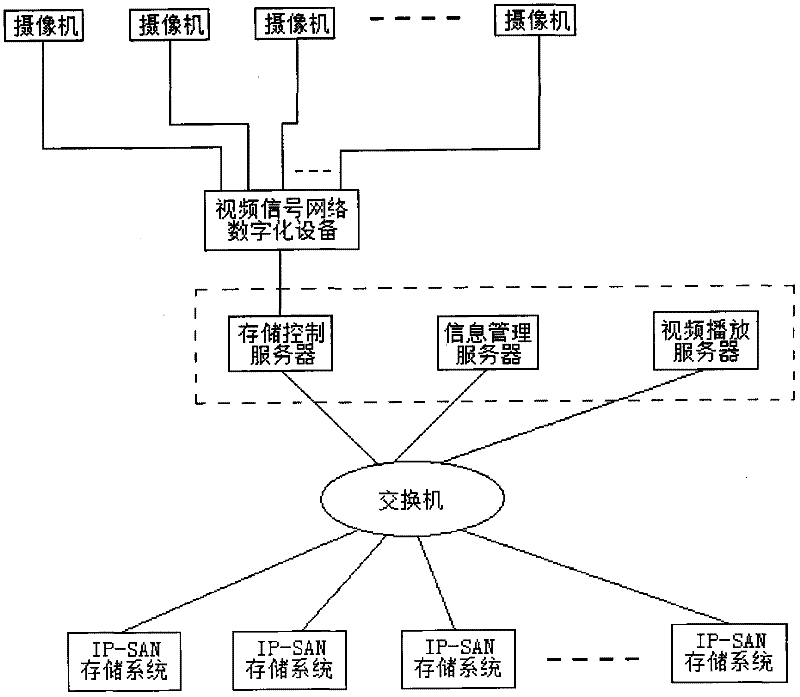
Video storing and instant replay system based on IP (identification of position)-SAN (storage area networking) direct storage technology
InactiveCN102387347AIncrease compensation processingAdd anti-jitter processing technologyTelevision system detailsColor television detailsStorage area networkStructure of Management Information
The invention relates to a video storing and instant replay system based on an IP (identification of position)-SAN (storage area networking) direct storage technology. Video data required to be stored adopts a sequence block storage preferential strategy to be stored into an IP-SAN storage system. When a video is replayed, the video data in the IP-SAN storage system is read by iSCSI (internet Small Computer System Interface) protocol commands so as to carry out replaying after initial addresses of video data blocks in an IP-SAN are obtained. The system can realize automatic retrieval and intelligent identification of specific pictures, is huge in synchronous data processing quantity, approximately realizes a real-time network monitoring function in a way that a non-real-time video is replayed by delaying within one second, eliminates a streaming media server, simplifies a system structure and reduces the management cost of the system.
Owner:何进波 +1
Methods and apparatus for secure communication in a vehicle-based data communication system
ActiveUS20150082380A1Digital data processing detailsTransmissionSecure communicationCommunications system
A method provides secure communication between a first module and a second module within a vehicle communication network. A first anti-replay counter is provided within the first module, and a second anti-replay counter is provided within the second module. A message is transmitted from the first module to the second module over the vehicle communication network. The message includes a partial counter including only a portion of the contents of the first anti-replay counter, and the message is authenticated based on the partial counter.
Owner:GM GLOBAL TECH OPERATIONS LLC
Baseband secure boot with remote storage
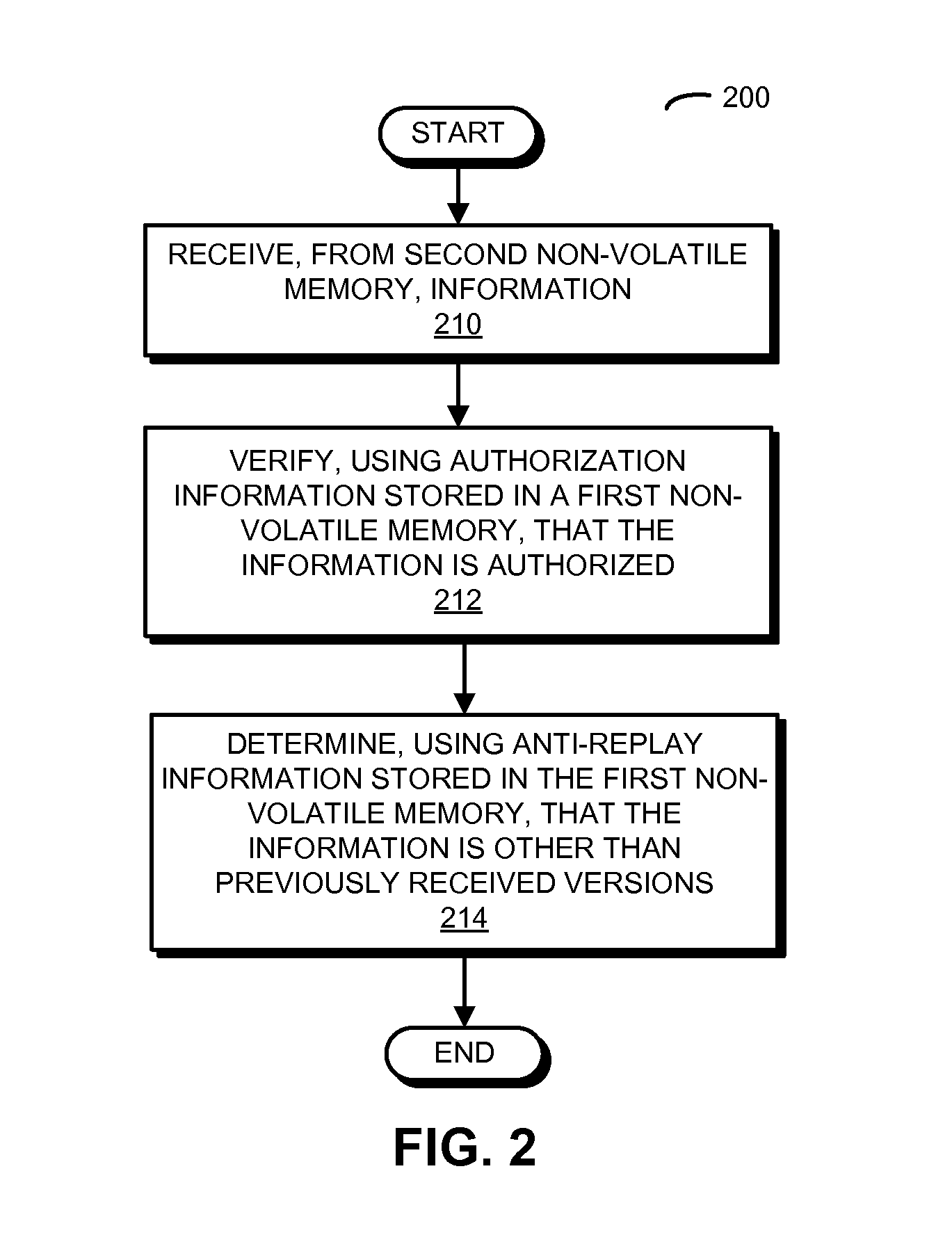
ActiveUS20160232343A1Digital data authenticationBootstrappingOperational systemEmbedded operating system
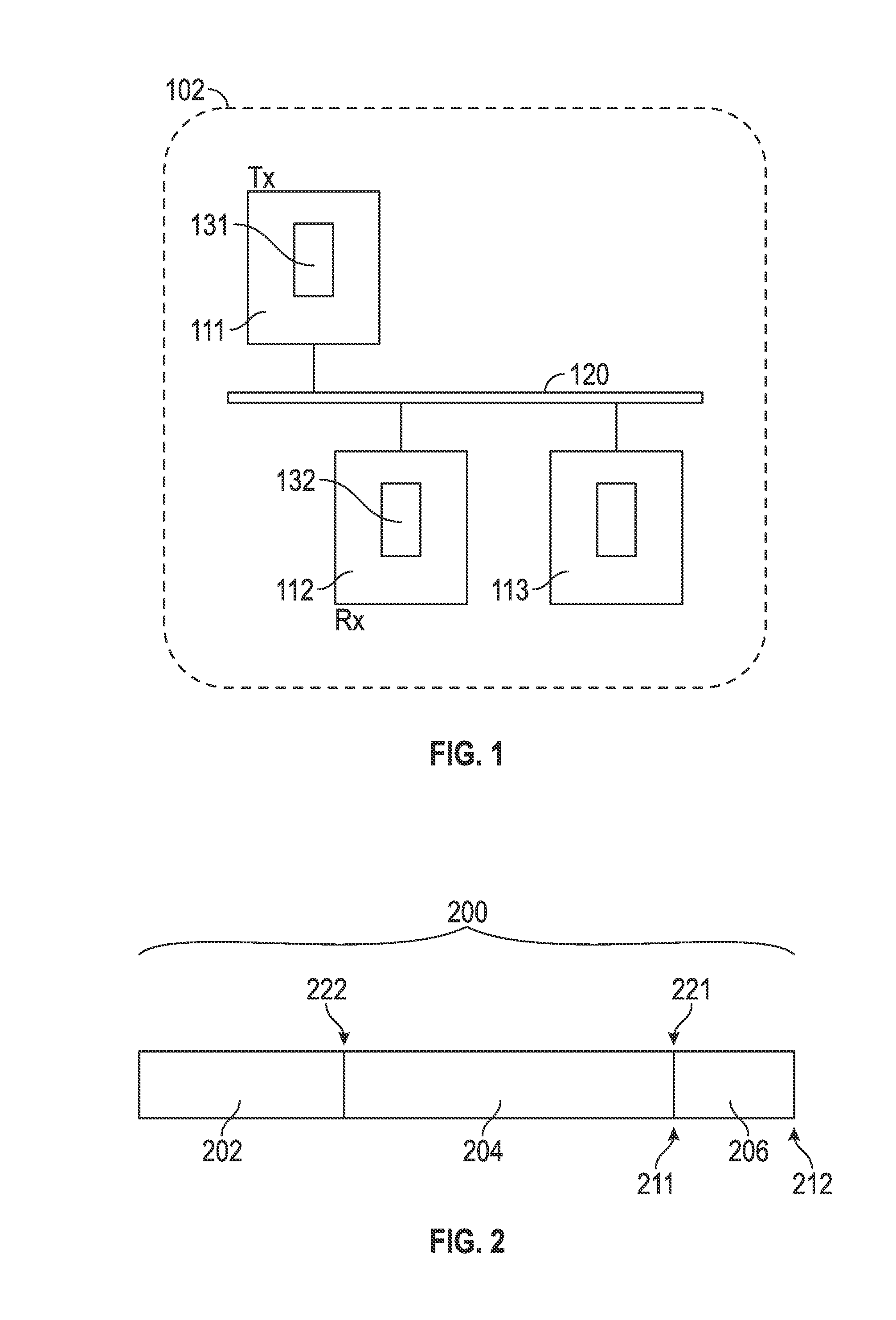
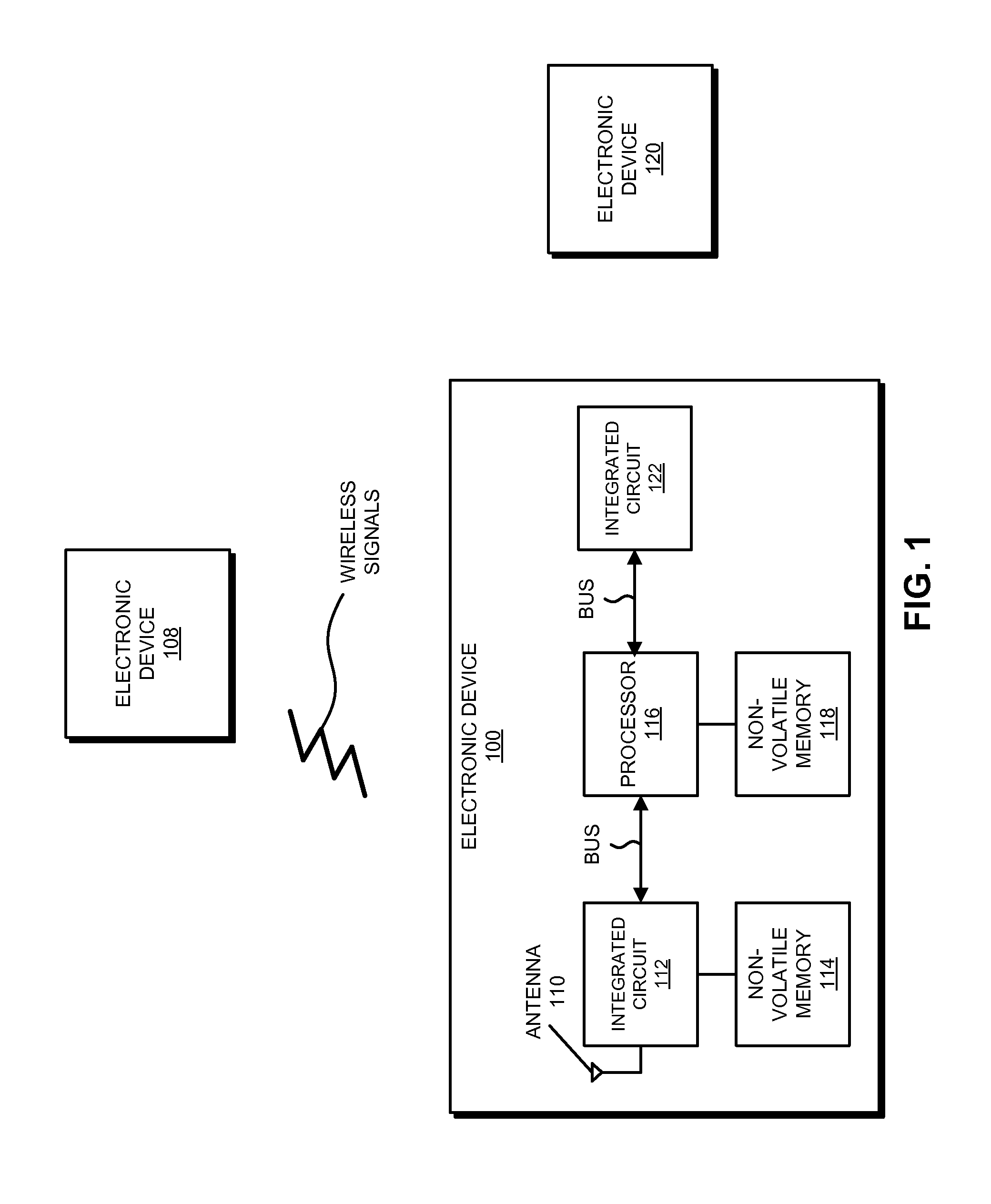
In order to simplify and reduce the cost of an electronic device, the size of a first non-volatile memory associated with an integrated circuit is significantly reduced. Instead of using the first non-volatile memory, a second non-volatile memory associated with a processor in the electronic device is used to store an embedded operating system of the integrated circuit, as well as associated data and a configuration of the integrated circuit. To reduce the security risks associated with using this remote second non-volatile memory, the first non-volatile memory may store authorization information and anti-replay information. During a secure boot of the integrated circuit, the authorization information is used to verify that the embedded operating system, the data and the configuration are authorized. In addition, the anti-replay information is used to determine that the embedded operating system, the data and the configuration are different than previously received versions of these items.
Owner:APPLE INC
Audio data recognition method and human voice anti-replay recognition system
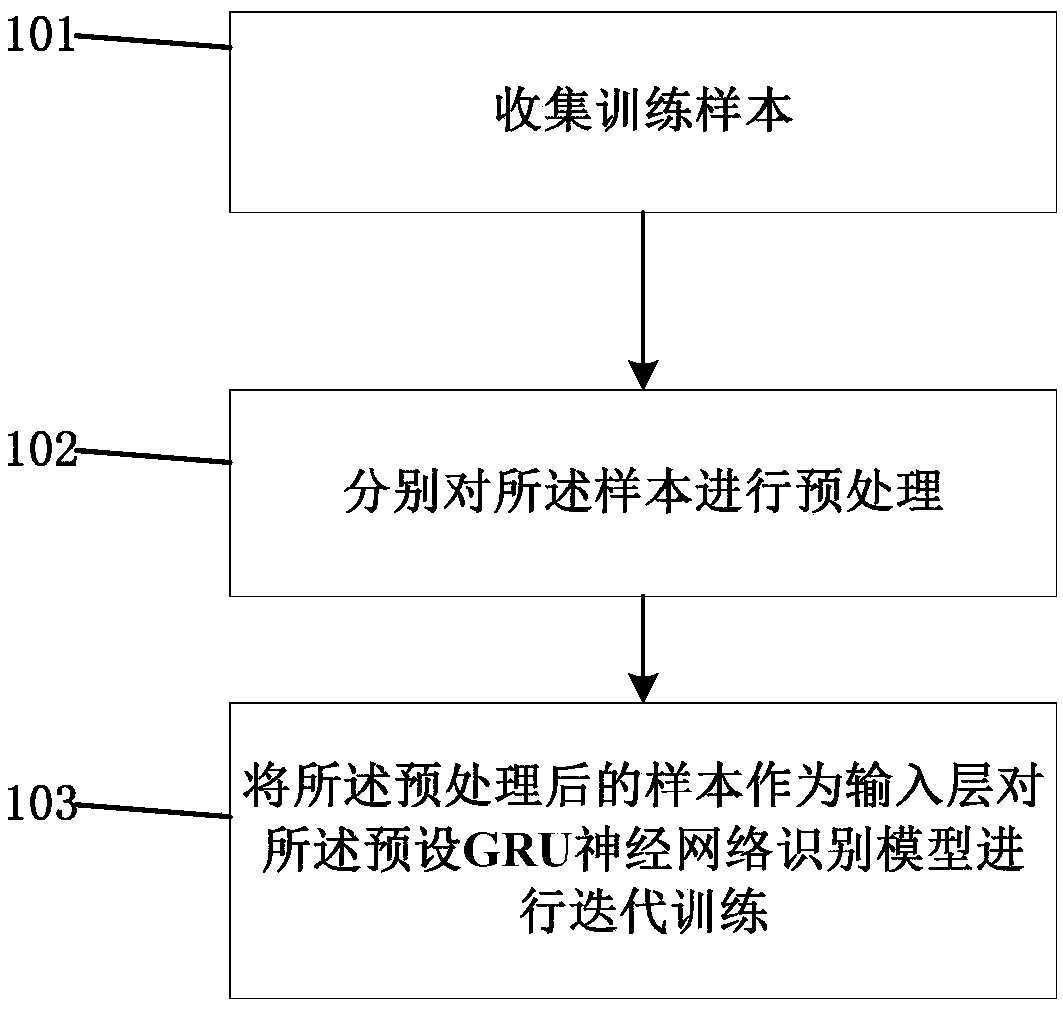
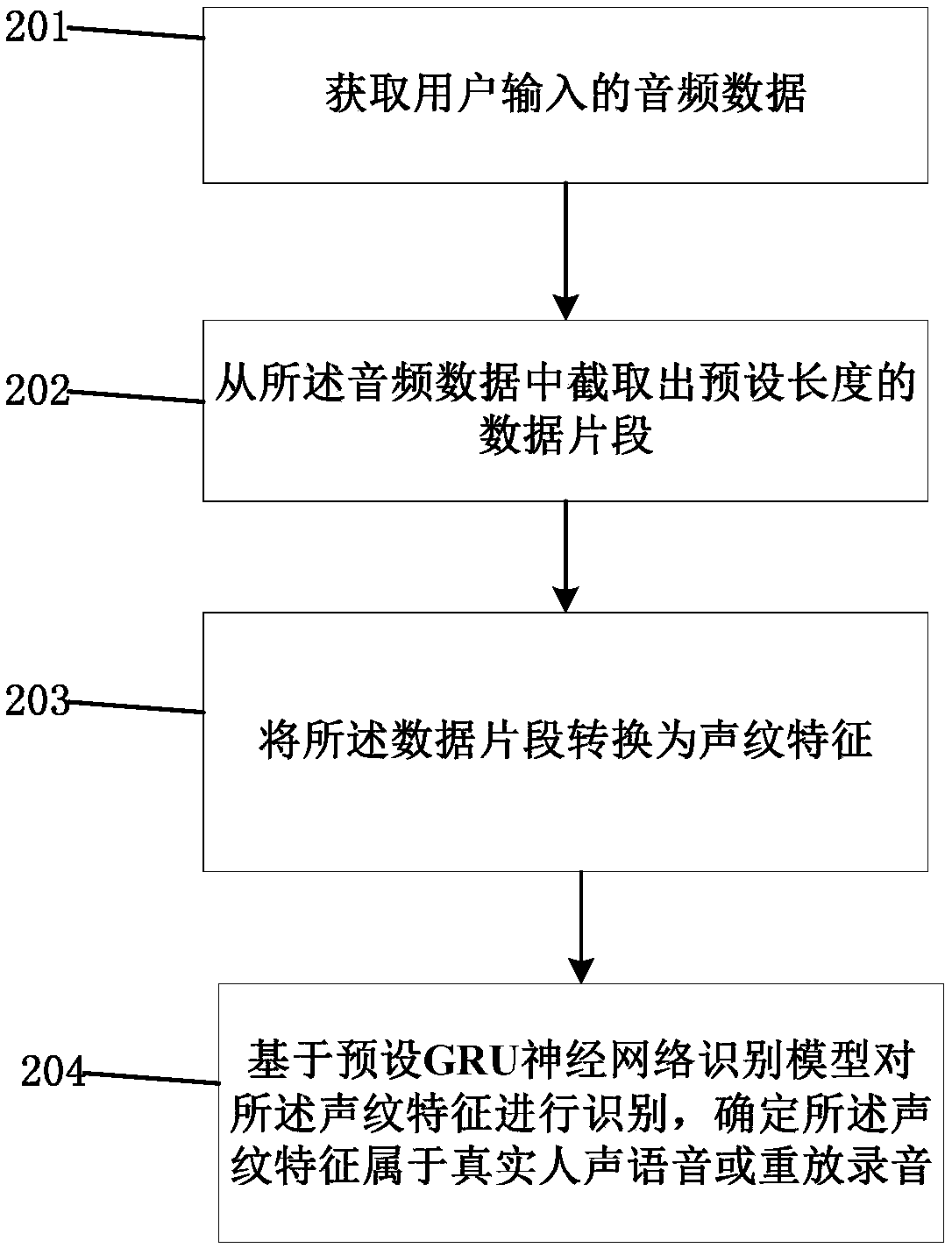
InactiveCN109599117ATake advantage ofMeet the needs of identificationSpeech analysisData segmentUser input
The invention relates to the technical field of voiceprint recognition and provides an audio data recognition method which comprises the following steps: acquiring audio data input by a user; cuttinga data segment of a preset length from the audio data; converting the data segment into voiceprint characteristics; on the basis of a preset GRU (Gated Recurrent Unit) neural network recognition model, recognizing the voiceprint characteristics, and confirming that the voiceprint characteristics belong to real human voice or replayed recorded voice. By adopting the method provided by the invention, real human voice or replayed recorded voice can be accurately recognized, anti-replay recognition on audio data input by a user can be achieved, and hostile attack can be prevented. In addition, theinvention further provides a human voice anti-replay recognition system.
Owner:XIAMEN KUAISHANGTONG INFORMATION TECH CO LTD
Credible inter-domain rapid authentication method on basis of separation mechanism network
InactiveCN102355663AImpossible to decryptImpossible to tamper withSecurity arrangementAnonymityInter-domain
The invention relates to a credible inter-domain rapid authentication method on the basis of a separation mechanism network for solving the problem of rapid authentication when a terminal in the separation mechanism network is subjected to inter-domain switching. In the method, a novel protocol is provided for realizing the rapid authentication when the terminal is subjected to inter-domain switching; and when the identity of a user is authenticated, the identity authentication of a terminal platform and the integrity check of the terminal platform are realized. In the method, when the terminal is subjected to inter-domain switching, an authentication center of a home domain does not need to participate again and an authentication center of a local domain can authenticate the mobile terminal by a Ticket. The method can resist the anti-replay attack, so that the credibility, safety, anonymity, anonymity of the identity of the user and untraceability of the identity of the user of the platform are ensured.
Owner:BEIJING JIAOTONG UNIV
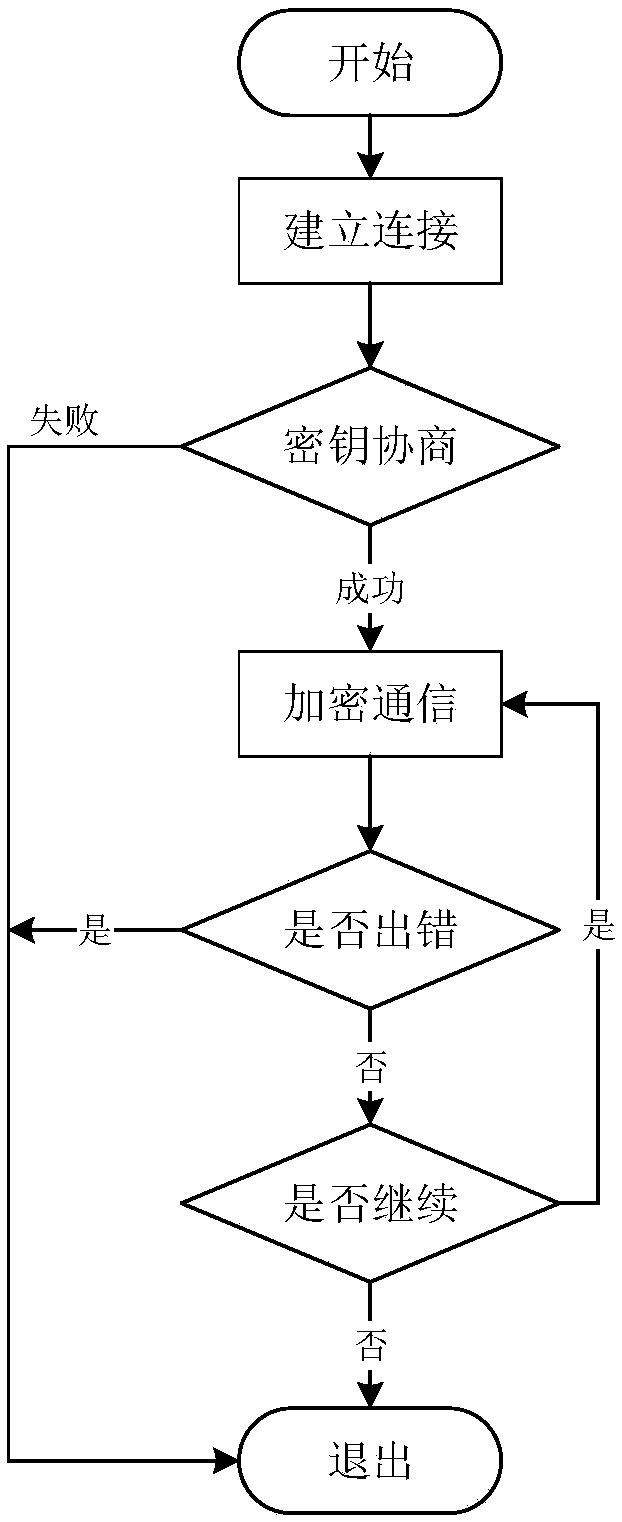
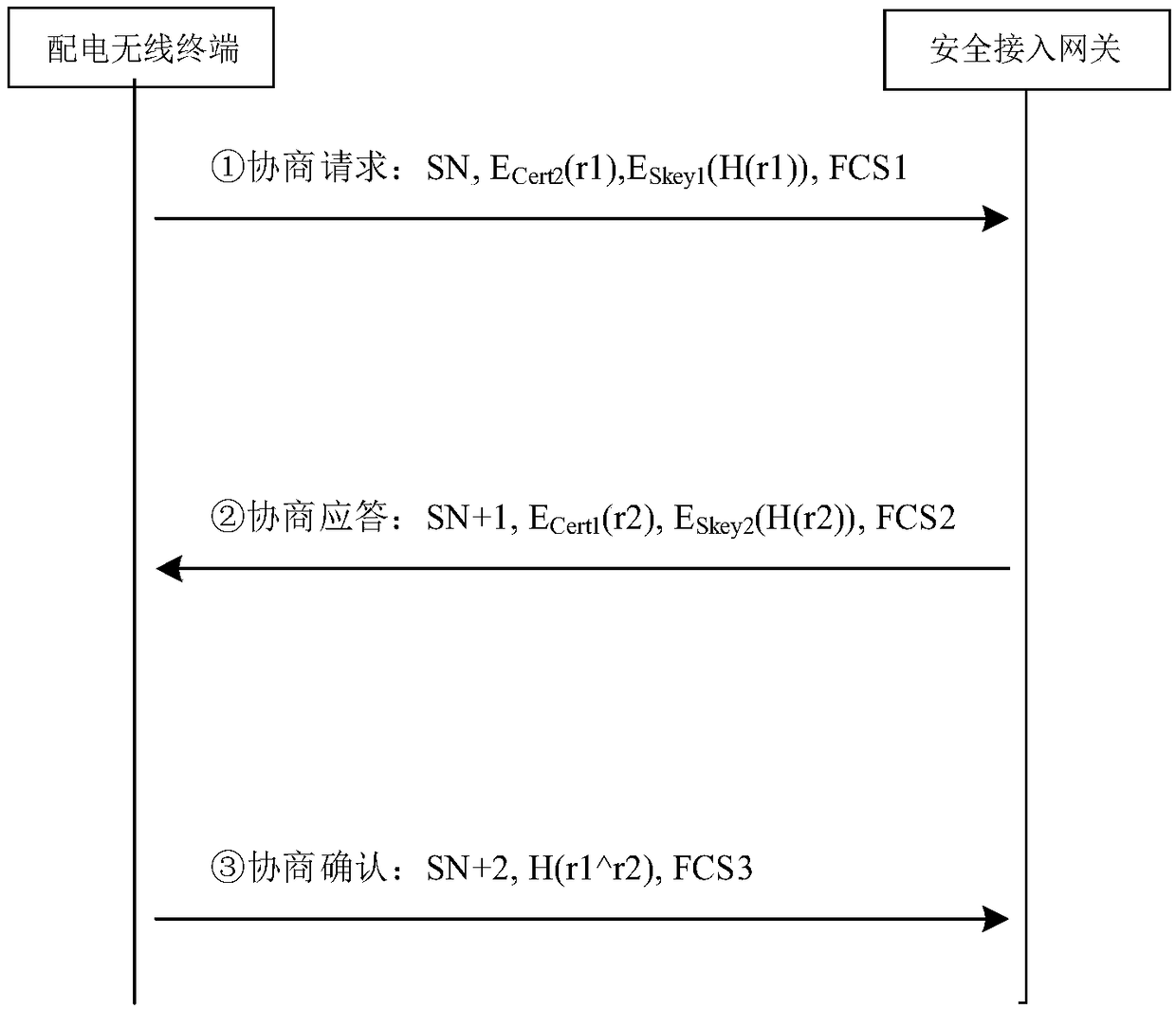
Method of safety access of power distribution wireless terminal
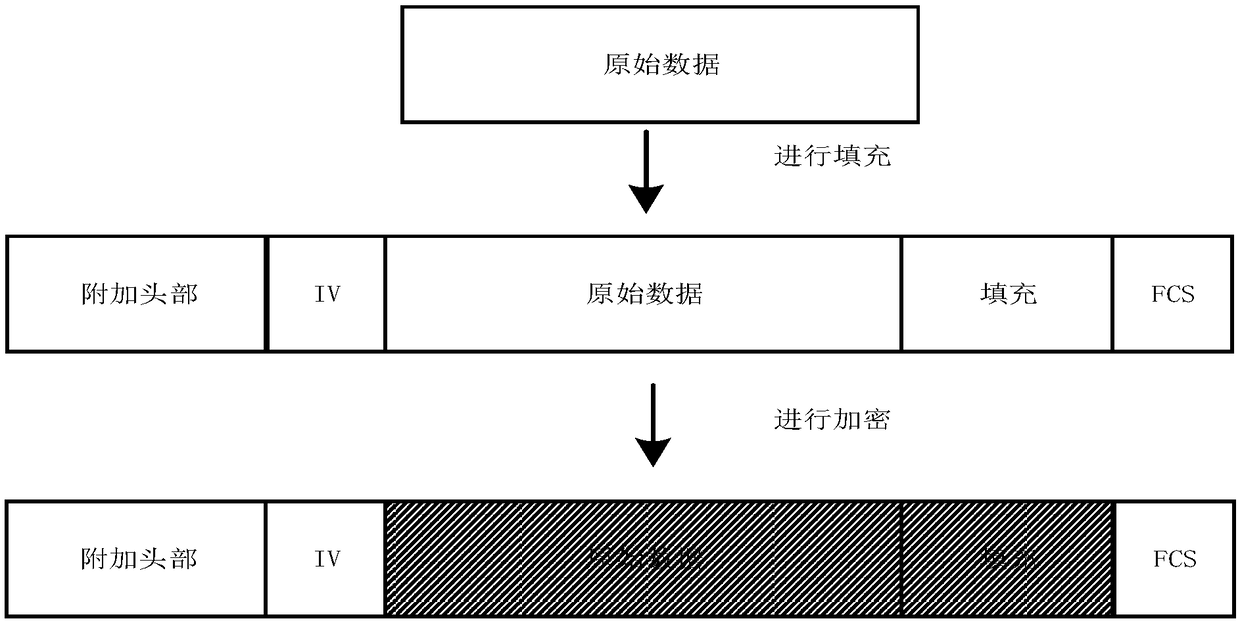
InactiveCN109194656ATo achieve the purpose of anti-replay attackImprove timelinessTransmissionPrimary stationConfidentiality
The present invention discloses a method of safety access of a power distribution wireless terminal based on a domestic commercial cryptographic algorithm. The method comprises the following steps of:1) prior to interaction of a power distribution wireless terminal and safety access data, performing two-way identity authentication and key negotiation; 2) when the power distribution wireless terminal and a safety access gateway perform normal data communication, performing message filling of the original data of the communication, and employing a domestic symmetric encryption algorithm to encrypt the original data and the filled message; and 3) after the encrypted message is received, performing decryption of the ciphertext data based on the domestic symmetric encryption algorithm to checkthe decrypted original data and the filled message. The method of safety access of the power distribution wireless terminal can achieve the purpose of anti-replay attack; attackers cannot obtain symmetrical encryption keys and cannot decrypt the ciphertext transmission data so as not to perform eavesdropping or tampering of the sensitive interaction information between the power distribution wireless terminal and a master station so as to achieve confidentiality and integrity protection of the sensitive interaction information.
Owner:STATE GRID CORP OF CHINA +3
Methods and apparatus for confidentially protection for Fibre Channel Common Transport
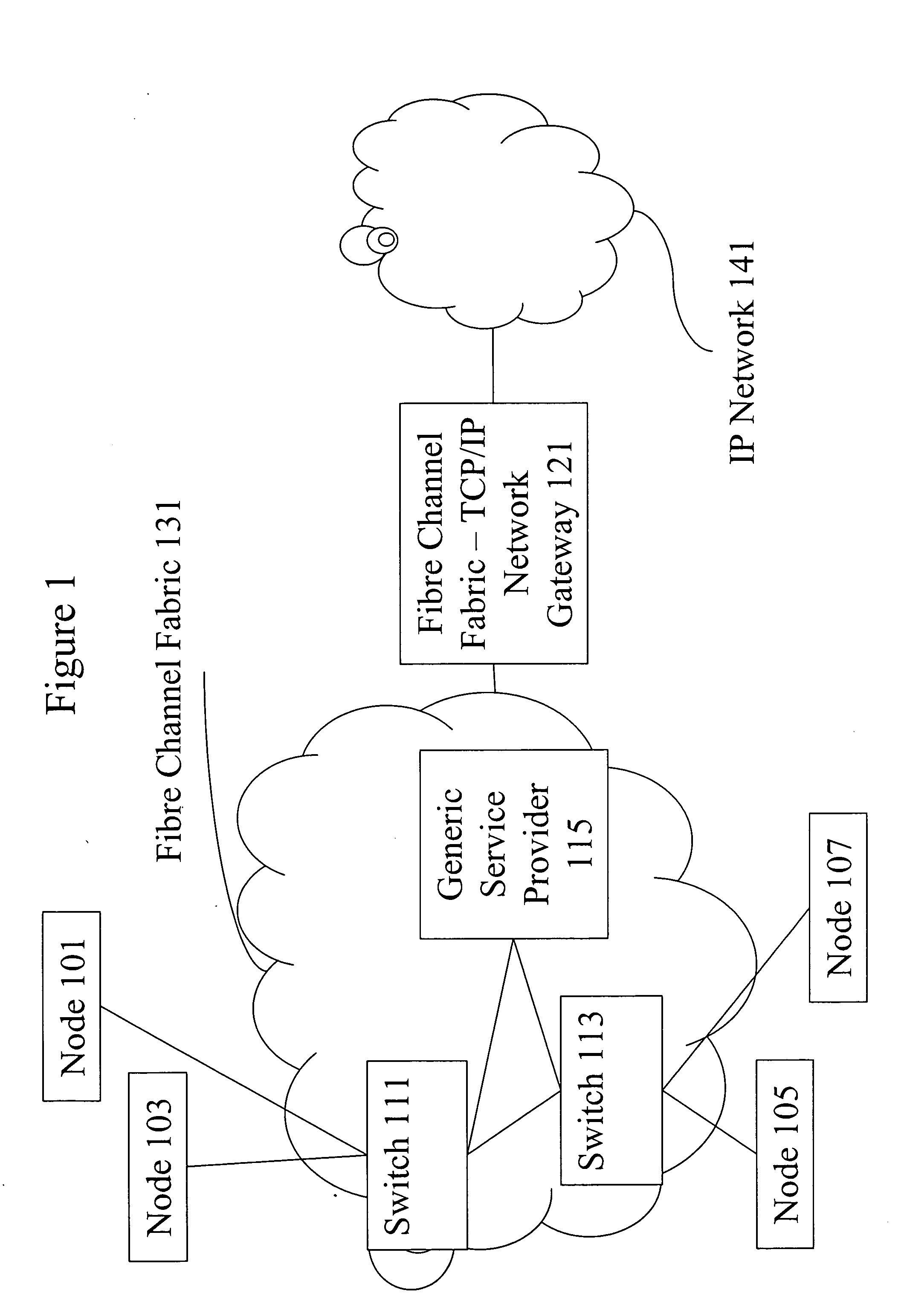
InactiveUS20050207579A1Improve confidentialityKey distribution for secure communicationSecret communicationData OriginFiber
Methods and apparatus are provided for improving message-based security in a Fibre Channel network. More specifically, the present invention relates to methods and apparatus for providing confidentiality for Fibre Channel control messages encapsulated within Common Transport Information Units. Control messages transported with the Fibre Channel Common Transport protocol, and passed between Fibre Channel network entities, can be encrypted providing confidentiality combined with data origin authentication, integrity and anti-replay protection provided by existing Fibre Channel security mechanisms.
Owner:CISCO TECH INC
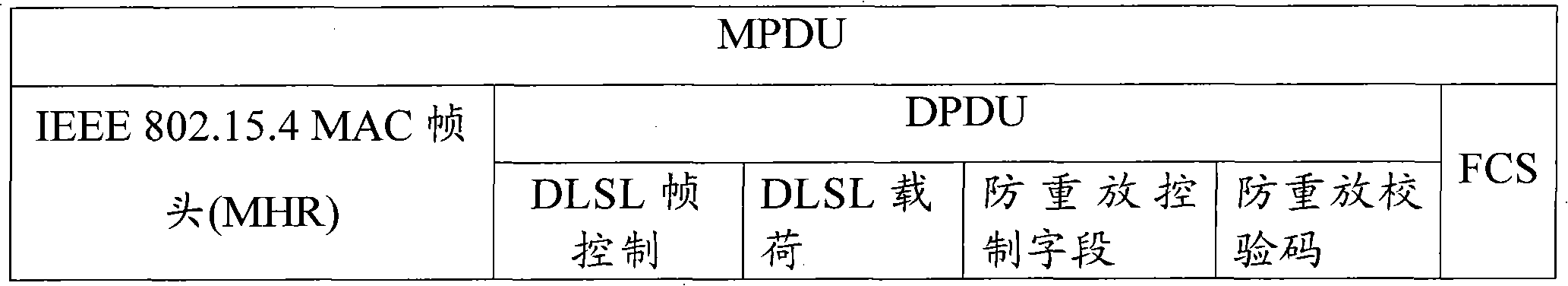
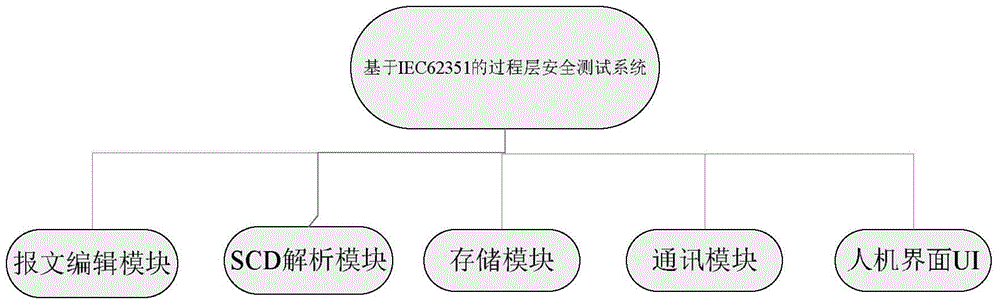
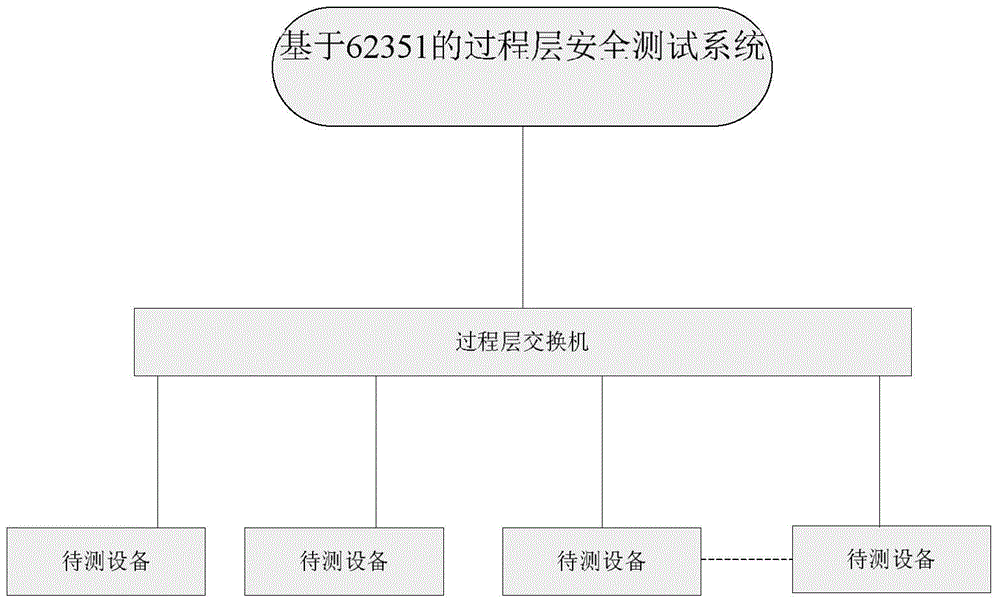
IEC62351 (International Electrotechnical Commission 62351)-based process layer safety test system and method
The invention aims to provide an IEC62351 (International Electrotechnical Commission 62351)-based process layer safety test system which effectively verifies whether process layer network equipment has tamper-proof and anti-replay safety functions. The system consists of the following modules: a human-computer interface UI (User Interface), a message editing module, a storage module, an SCD (namely substation configuration description) analysis module and a communication module. The invention also provides an IEC62351 (International Electrotechnical Commission 62351)-based process layer safety test method. By using the system and the method, an IEC62351 specification-based process layer message can be edited. The EC62351 specification-based process layer message is edited according to the principle that the message check and signature algorithm is increased based on the EC62351 specification-based process layer message, so the message meets the EC62351 specification. Any field of the edited EC62351 specification-based message can be modified. Thus the message tamper attack and message replay attack to to-be-tested equipment can be simulated to verify whether the to-be-tested equipment has defense capacity.
Owner:CHINA SOUTHERN POWER GRID COMPANY
Methods and apparatus for confidentiality protection for Fibre Channel Common Transport
InactiveUS7333612B2Improve confidentialityKey distribution for secure communicationSecret communicationFiberData Origin
Methods and apparatus are provided for improving message-based security in a Fibre Channel network. More specifically, the present invention relates to methods and apparatus for providing confidentiality for Fibre Channel control messages encapsulated within Common Transport Information Units. Control messages transported with the Fibre Channel Common Transport protocol, and passed between Fibre Channel network entities, can be encrypted providing confidentiality combined with data origin authentication, integrity and anti-replay protection provided by existing Fibre Channel security mechanisms.
Owner:CISCO TECH INC
Three-way handshake protocol method
InactiveCN101431519AWith anti-replay functionKey distribution for secure communicationSecurity arrangementComputer hardwareBroadband
The invention relates to a three-step handshake protocol method suitable for ultra wide band network. The method comprises following steps: 1) initiator sends message 1 to responser; 2) the responser sends message 2 to initiator after receiving message 1; 3) initiator sends message 3 to initiator after receiving message 2; 4) the responser sends message 4 to initiator after receiving message 3; 5) after the initiator receives message 4, the initiators each acquires corresponding pair temporary key and key confirmation key. When pair temporary key updates, the transmitter directly sends I-Nonce construction message 1 to responser produced and stored using last pair temporary key negotiation process, the three-step handshake protocol interacted message does not need encryption processing, thereby the invention possesses not only anti-replay function compared with ECMA 386 three-step handshake protocol, and superiority in resource-limited application.
Owner:CHINA IWNCOMM
Empty message sequence processing method and system for mobile terminal switching process
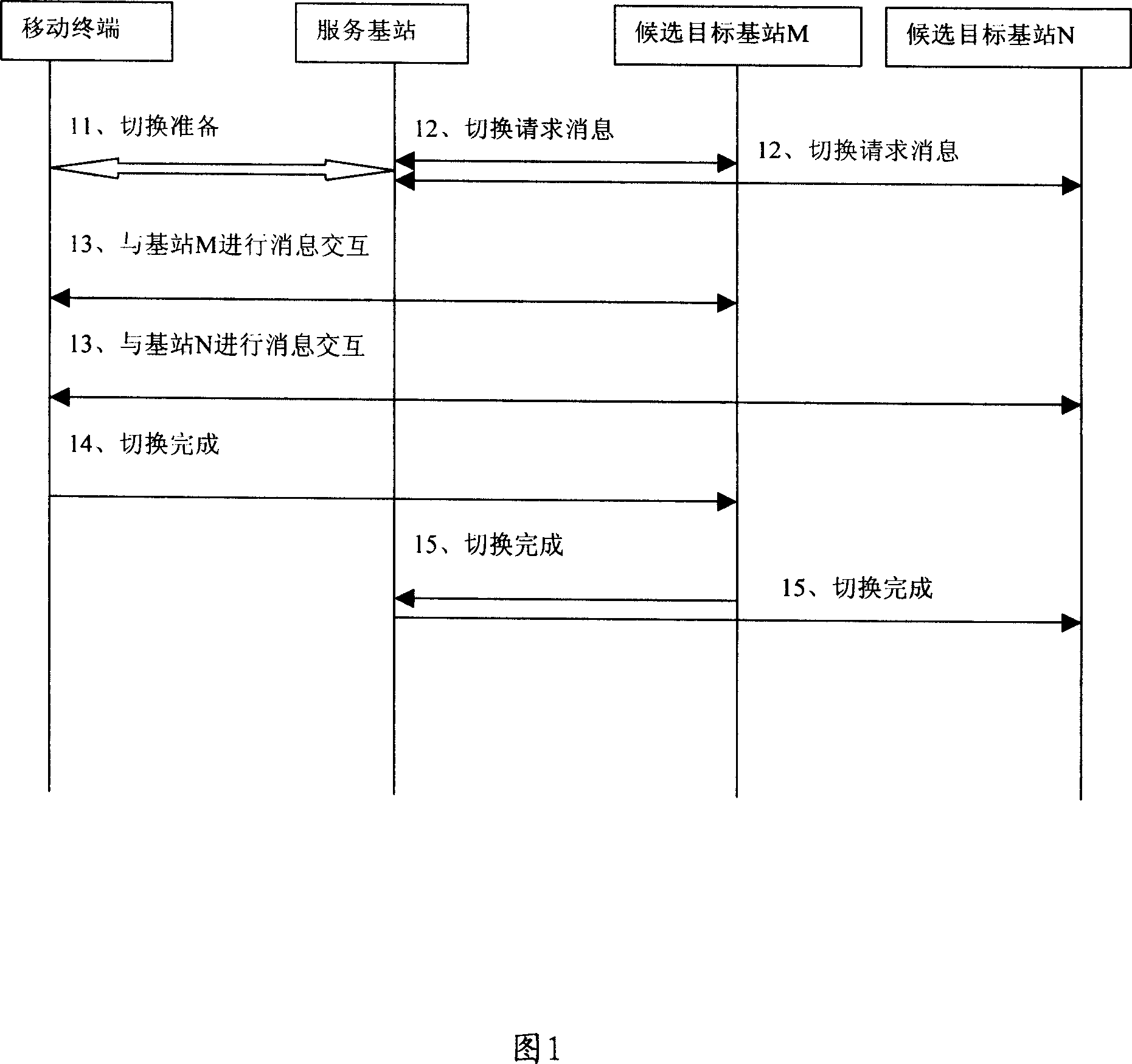
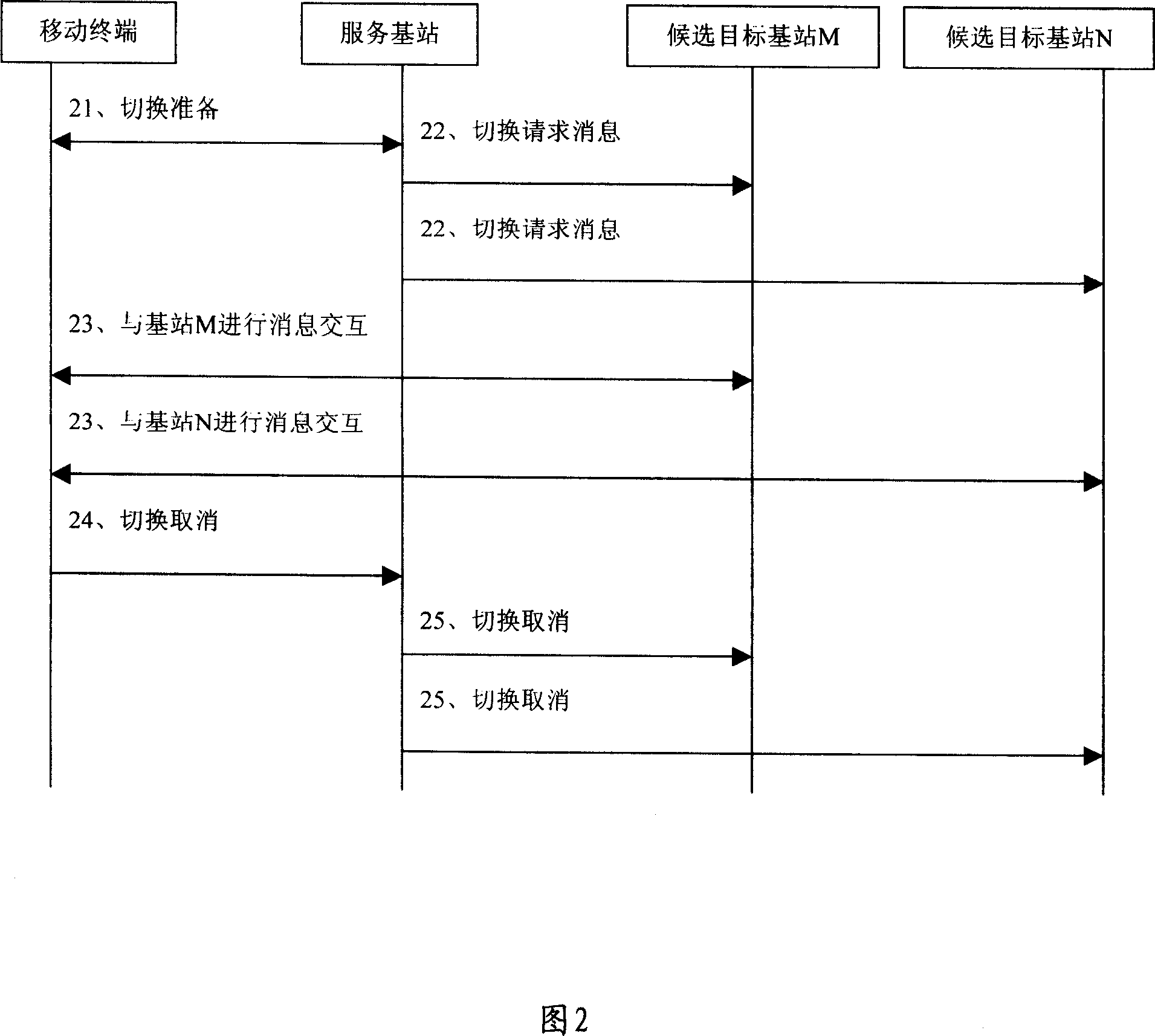
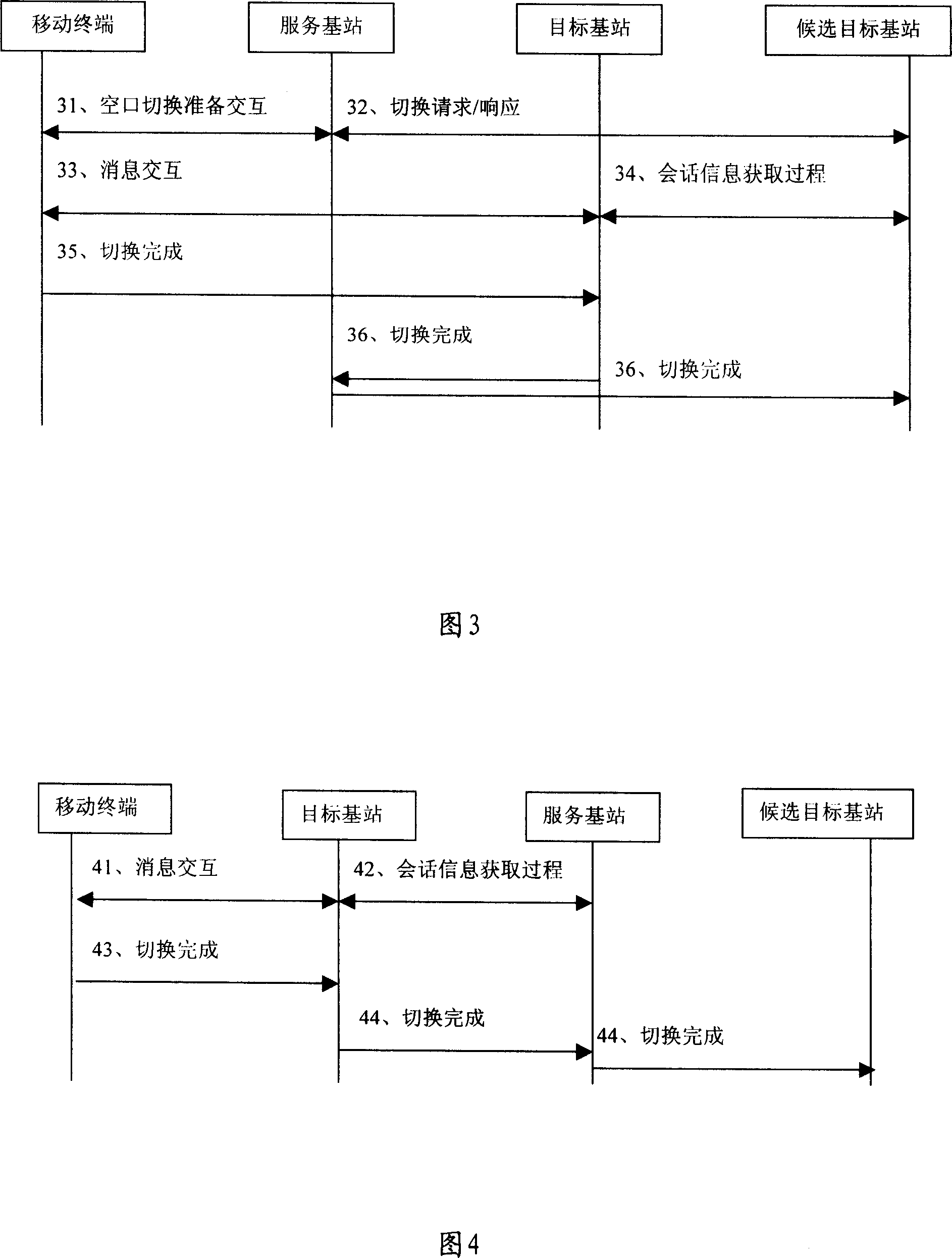
InactiveCN101026856AImprove reliabilityFacilitate anti-replay attack processingRadio/inductive link selection arrangementsWireless communicationSequence processingMobile station
The method includes steps: maintaining mutual independent up and down going aerial port message sequence number (UDAPMSN) for each candidate target base station and service station respectively is setup on mobile terminal to be switched; maintaining UDAPMSN corresponding to the mobile terminal is setup on candidate target base station and service station respectively; after finishing switching, mobile station and final selected base station adjusts obtained each current UDAPMSN based on saved UDAPMSN. The invention guarantees that when mobile terminal has switched, new base station (i.e. target base station) can determine corresponding UDAPMSN correctly. Based on the sequence number, the invention implements anti replay attack process so as to raise reliability of wireless communication.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com