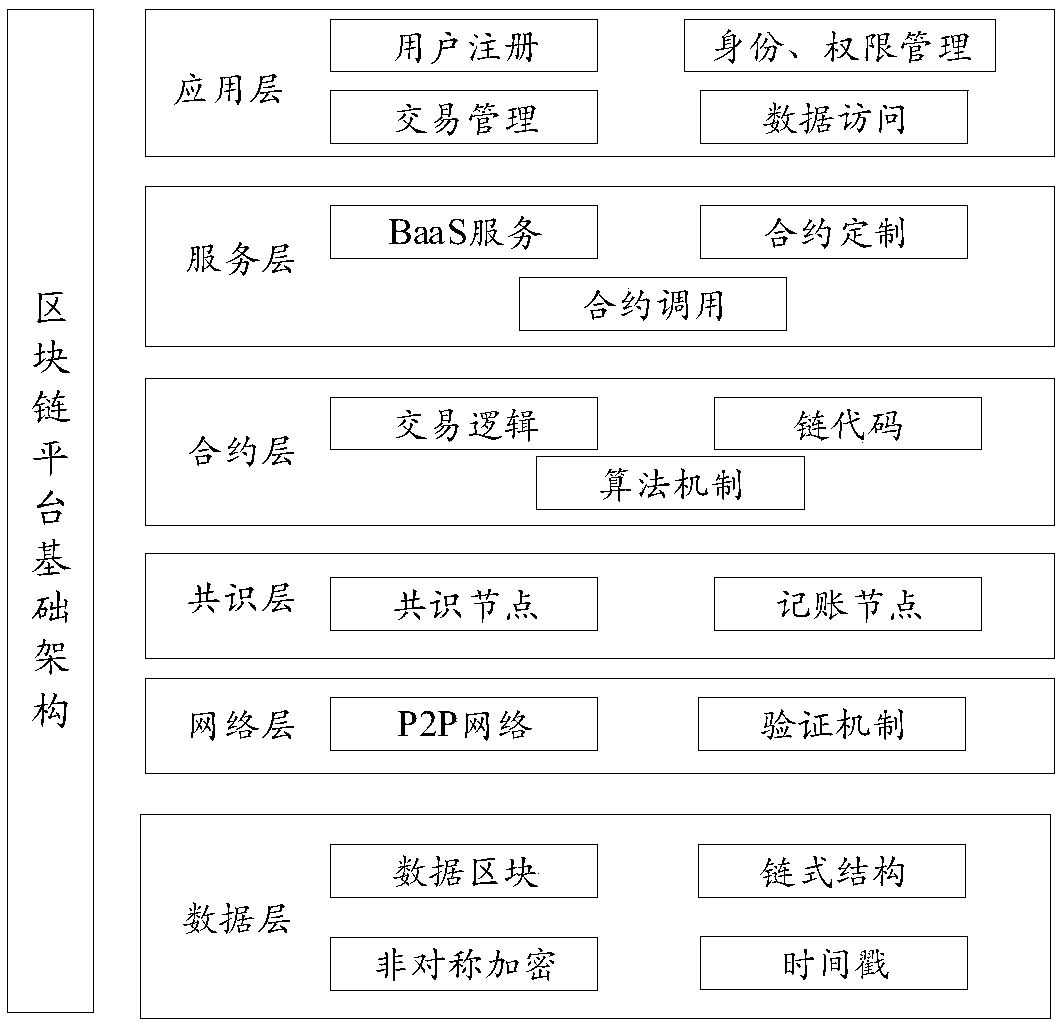
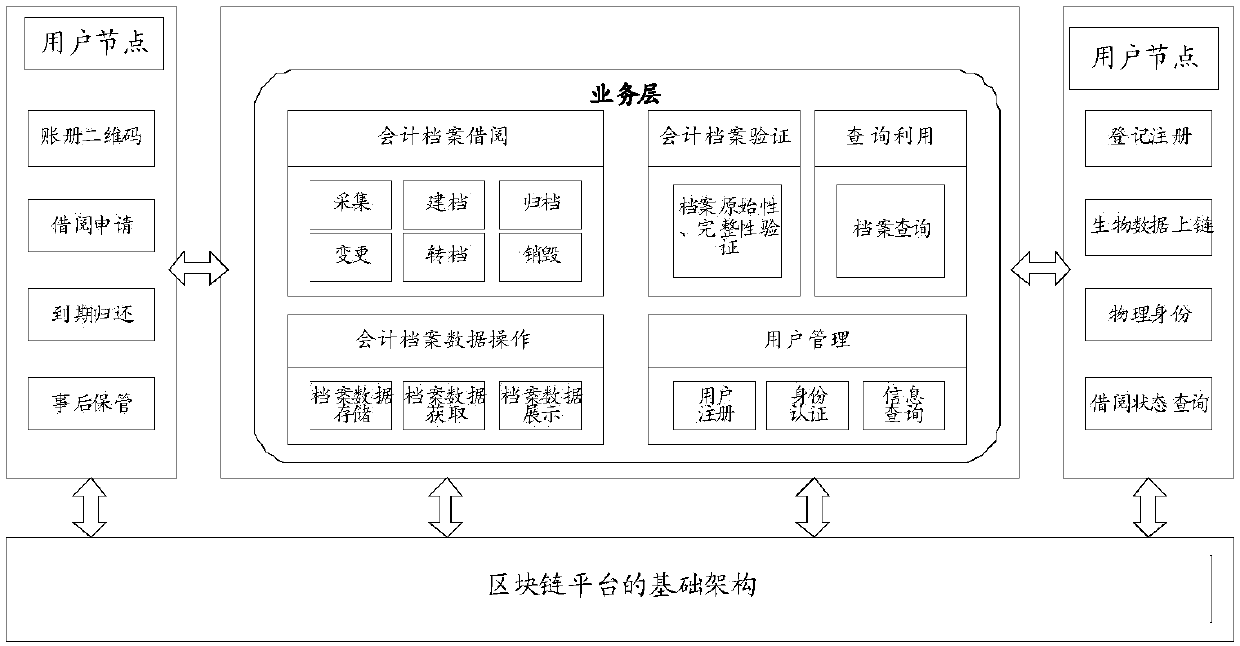
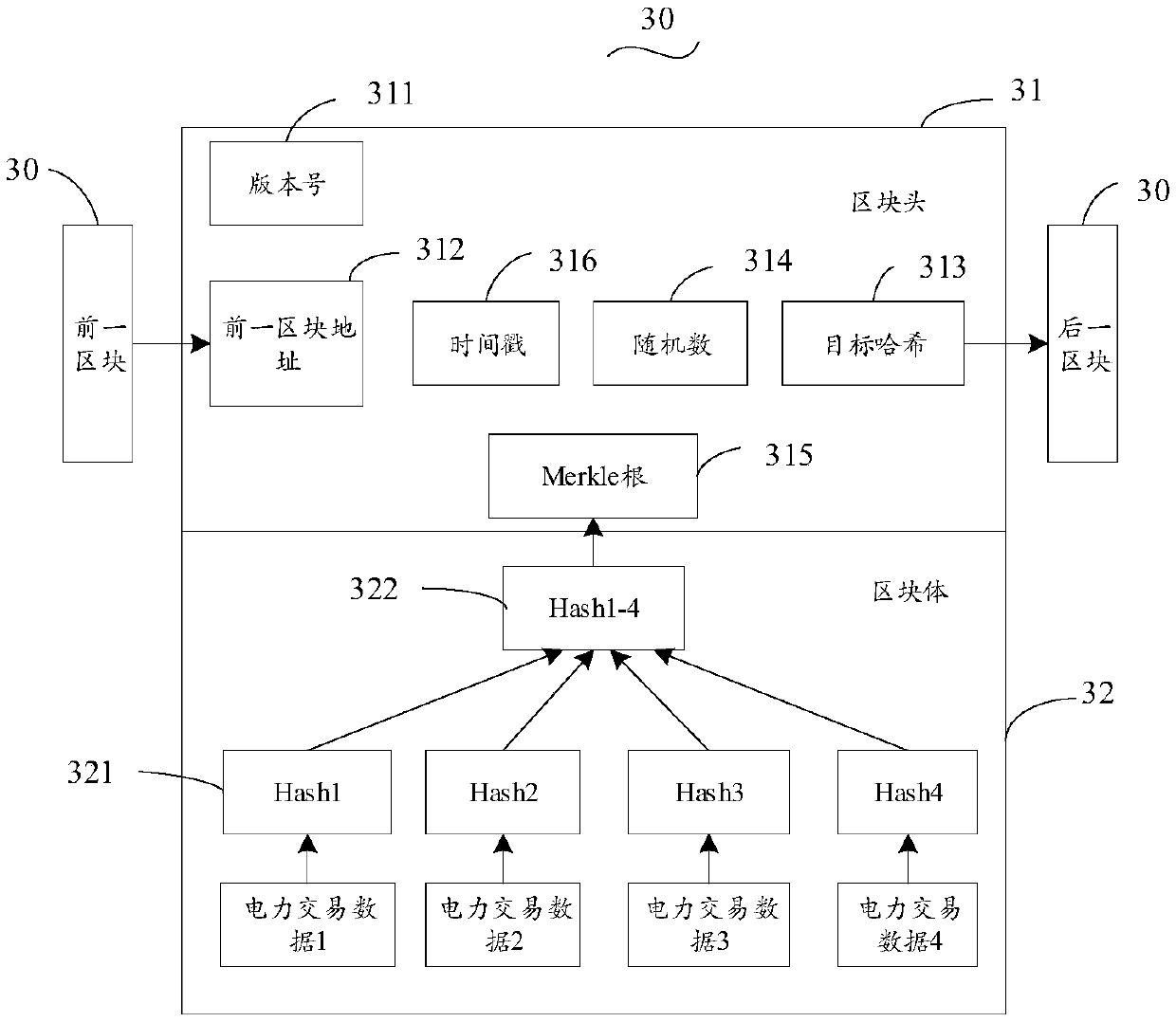
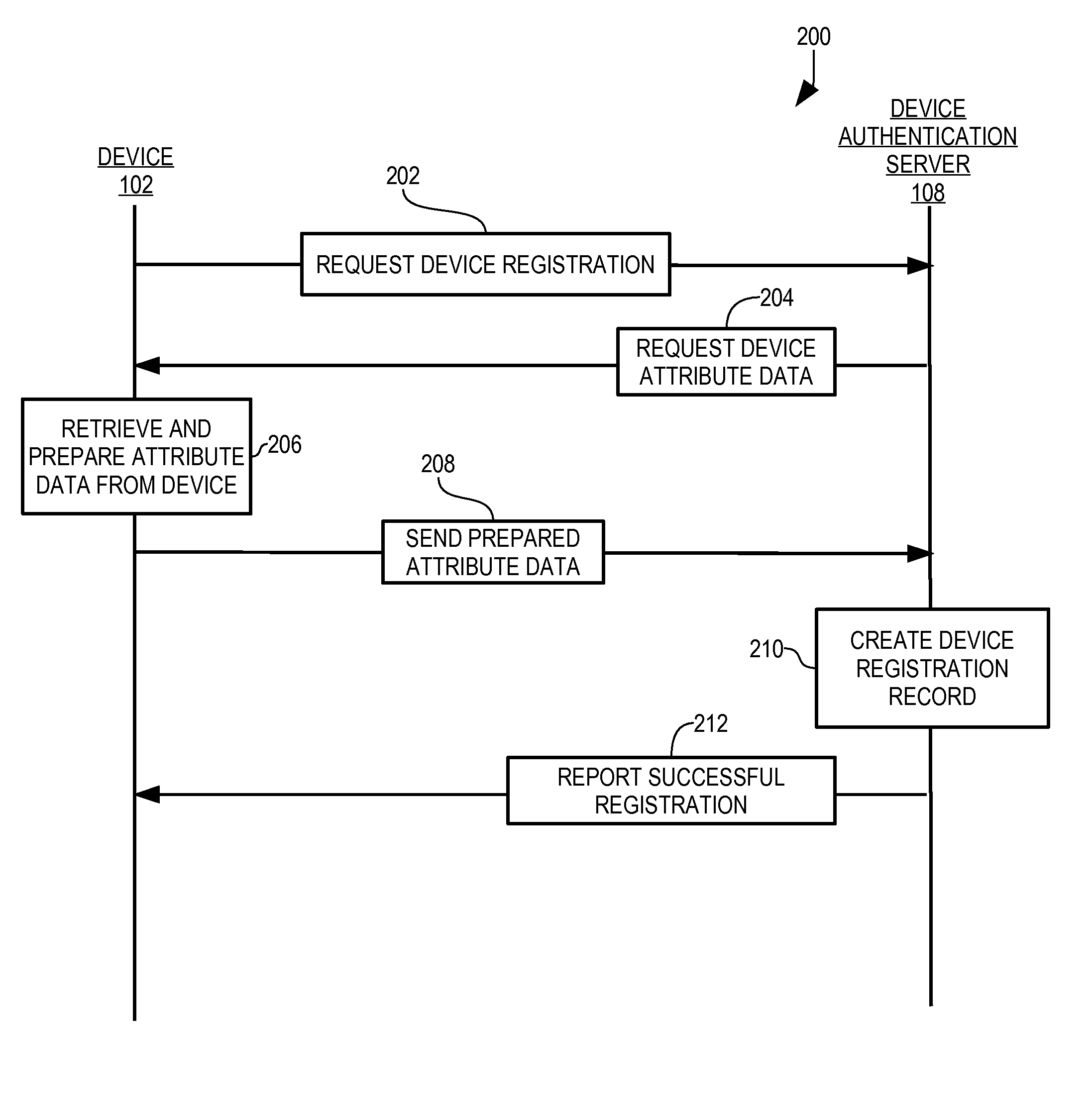
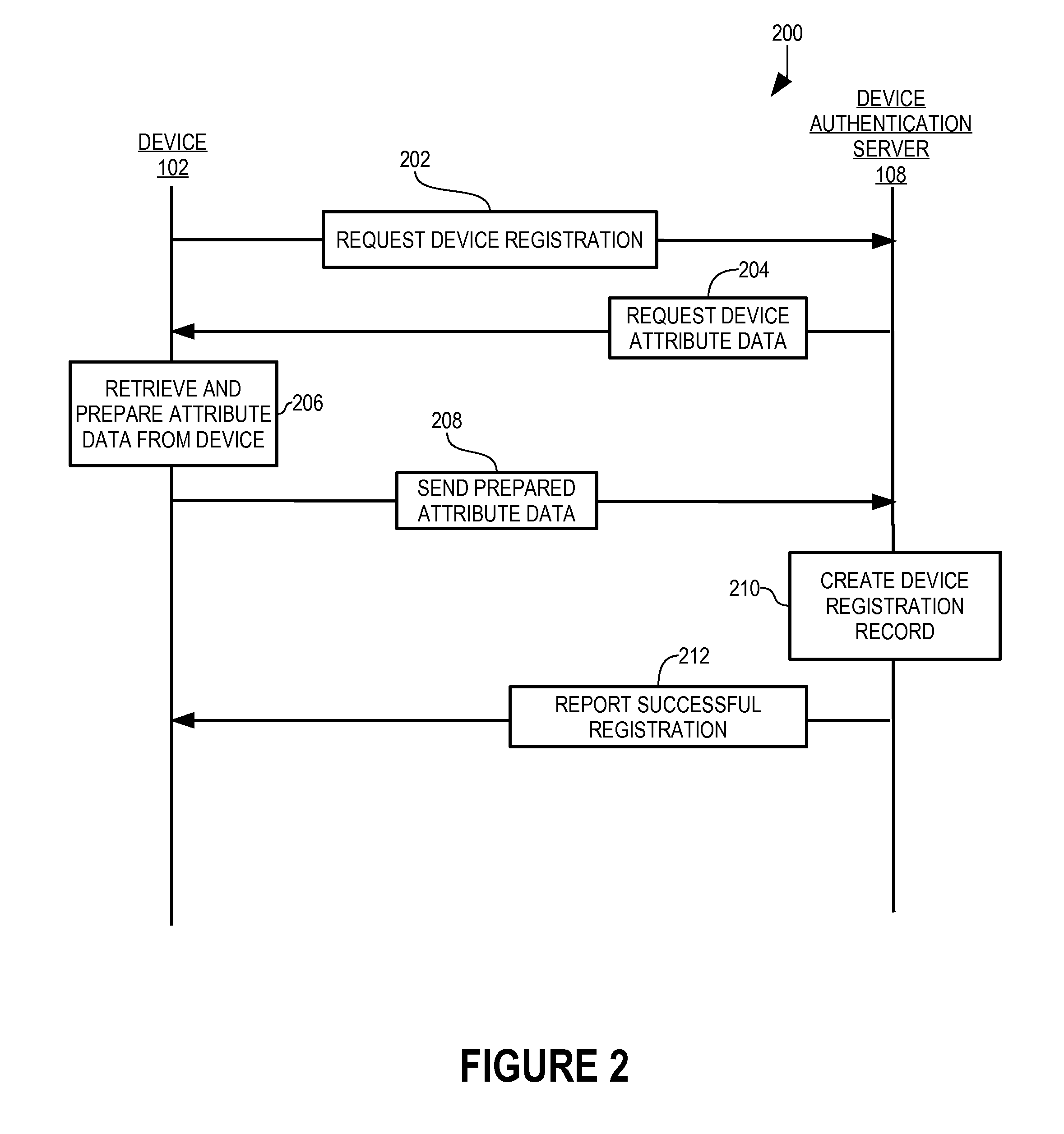
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
147results about How to "Accurate authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Random biometric authentication utilizing unique biometric signatures
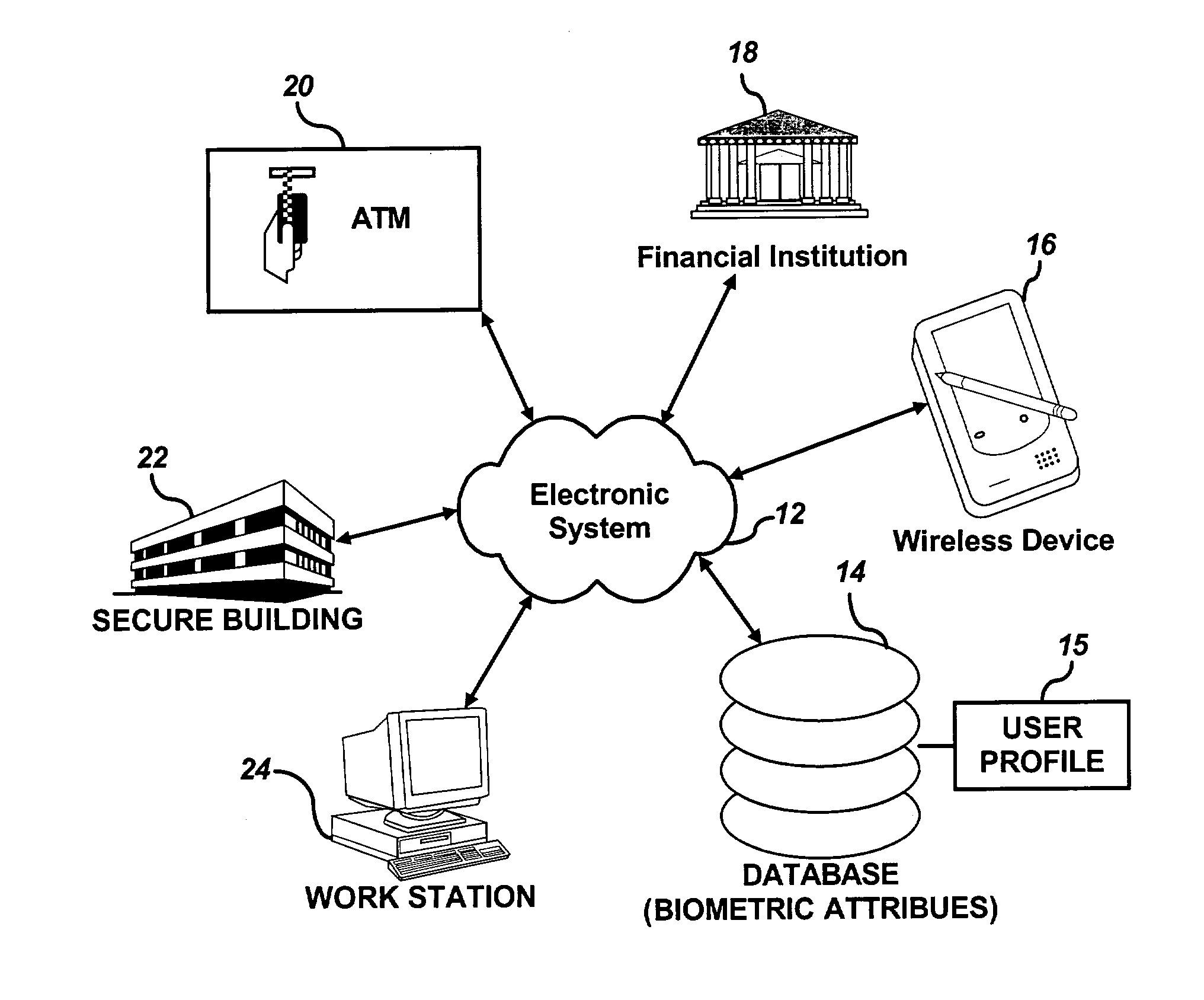
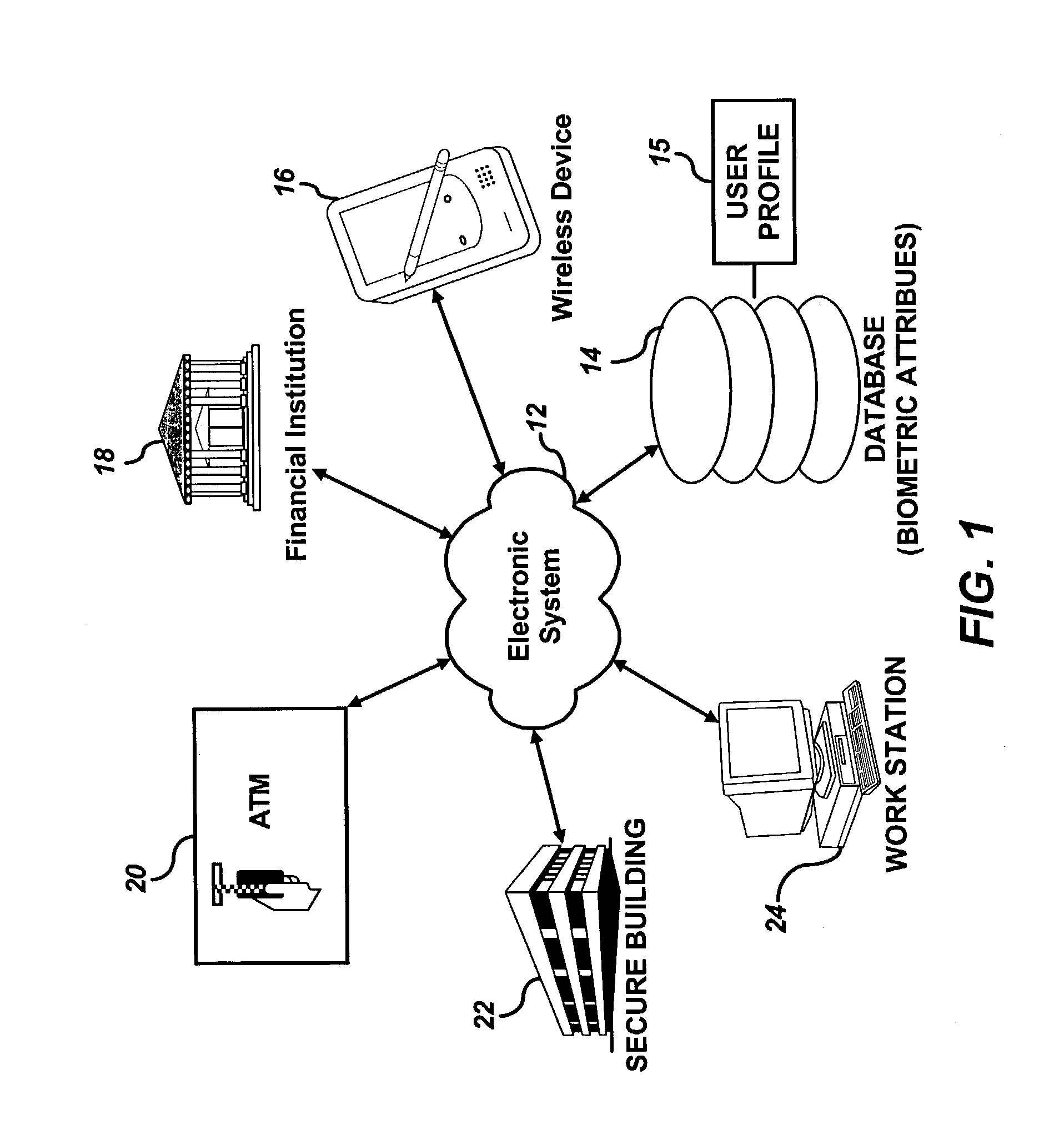
InactiveUS20030163710A1Accurate authenticationSecure user accessDigital data processing detailsUser identity/authority verificationUser inputLayer thickness
A user can be challenged to provide at least one randomly selected biometric attribute. The randomly selected biometric attribute input by the user is automatically compared to a plurality of biometric attributes of the user contained in a user profile. The user can then be authenticated if the randomly selected biometric attribute input by the user matches at least one of the plurality of biometric attributes of the user contained in the user profile. Biometric attributes analyzed according to the methods and systems of the present invention, include, but are not limited to, for example, fingerprints, iris, retina, and / or tissue characteristics, such as skin morphology, skin layer thickness, collage density and orientation, tissue hydration, optical patent length differences, etc.
Owner:IP VENUE LLC
Biometric data card and authentication method
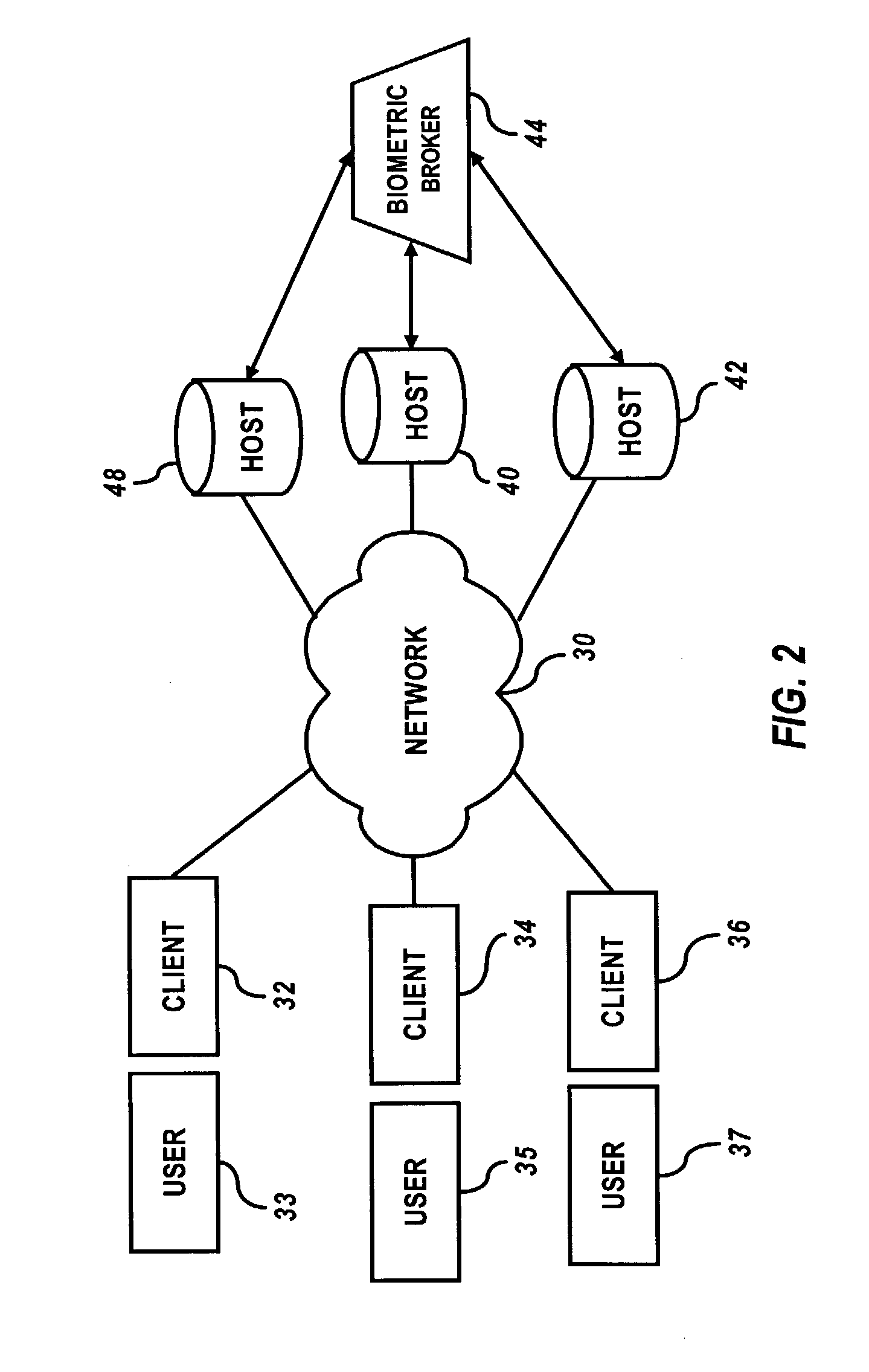
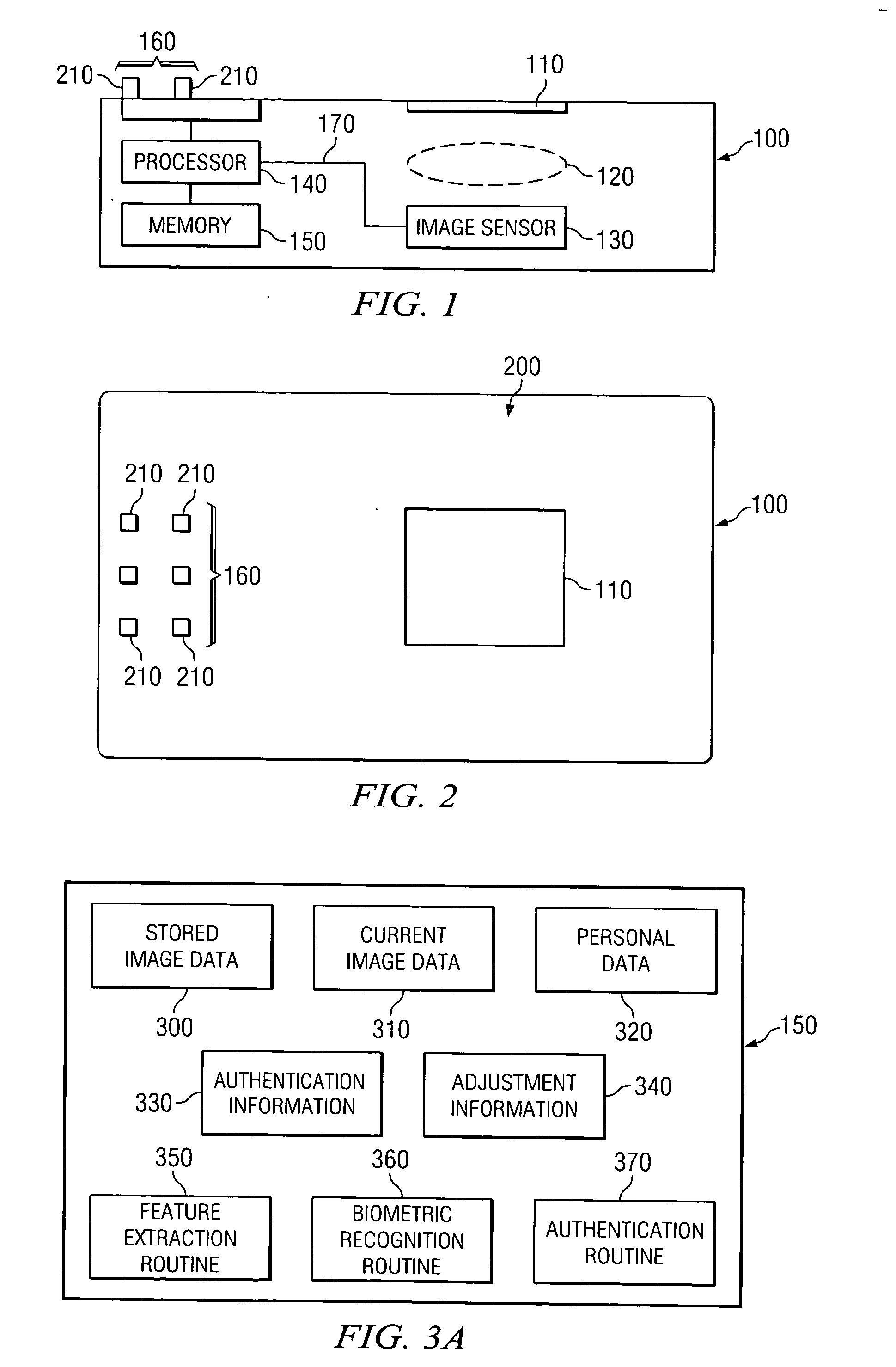
InactiveUS20050232471A1Accurate authenticationResist attackImage analysisBathroom accessoriesComputer hardwareBiometric data
A biometric data card includes an image sensor for capturing an image of a biometric feature of a user of the biometric data card and producing first image data representing the image. The biometric data card compares the first image data to second image data stored within the biometric data card to authenticate the user. The biometric data card is usable with a terminal including a slot for receiving the biometric data card. The terminal can further include an optical element optically coupled to direct the image onto the image sensor of the biometric data card.
Owner:AGILENT TECH INC
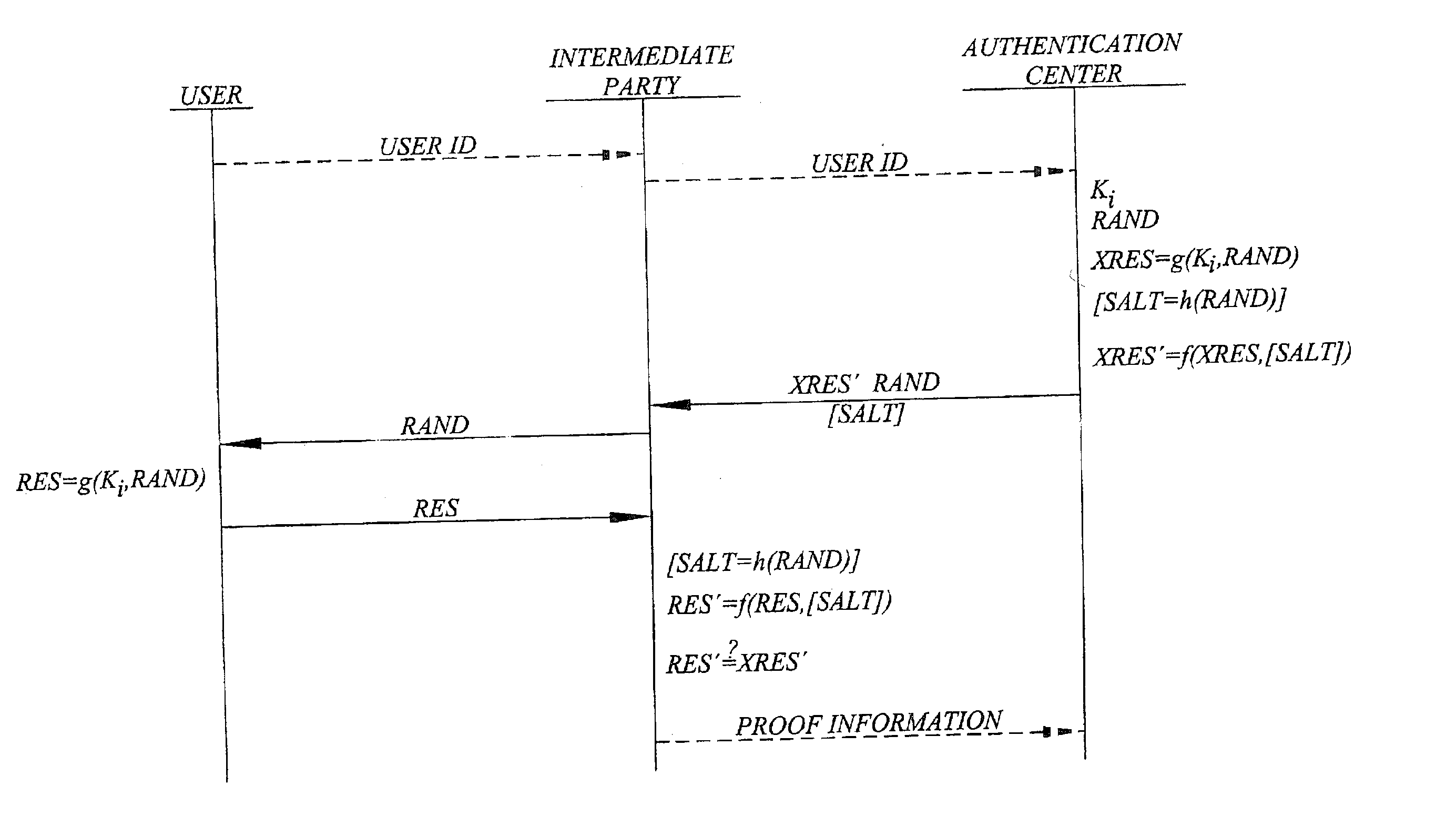
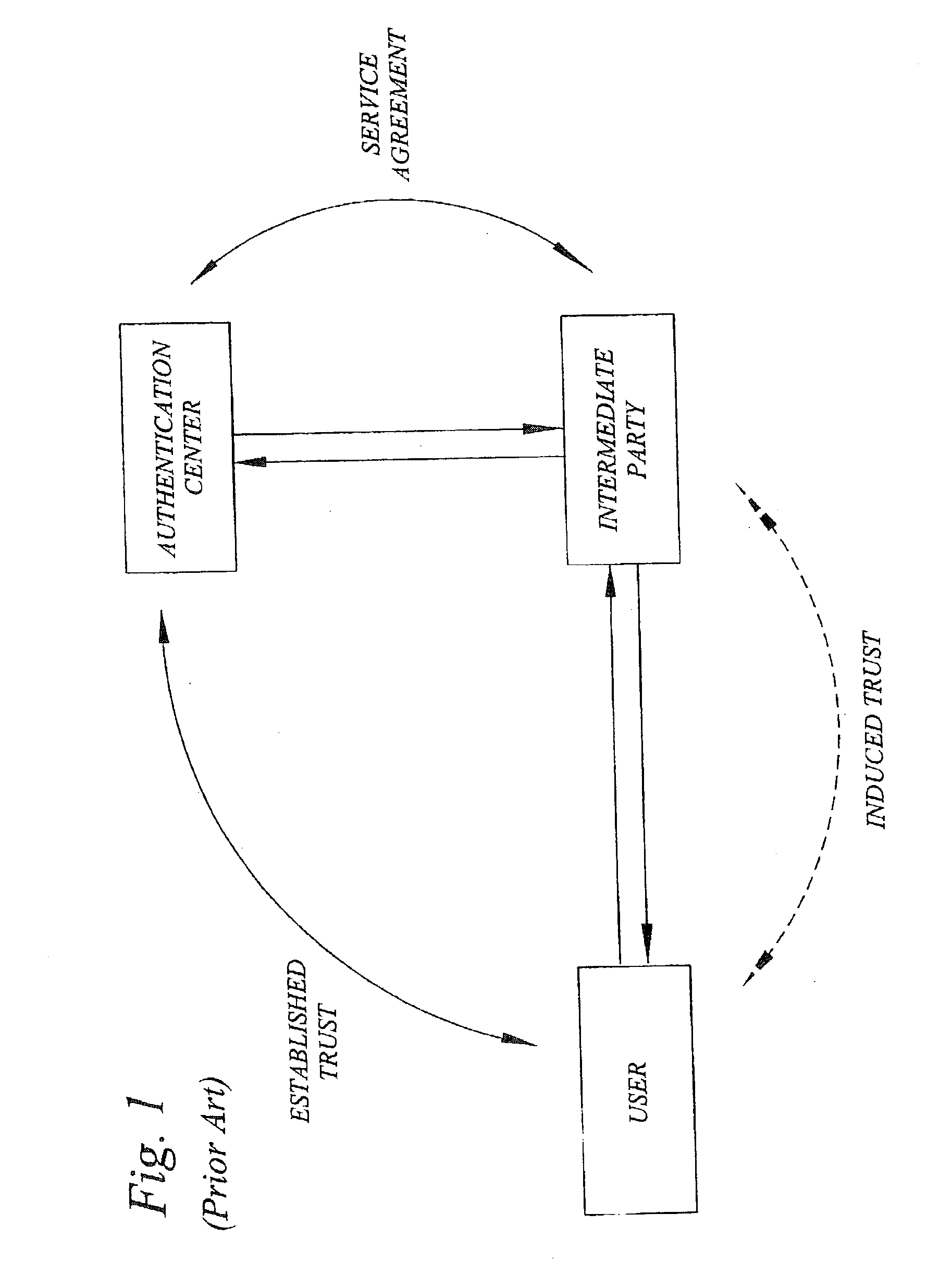
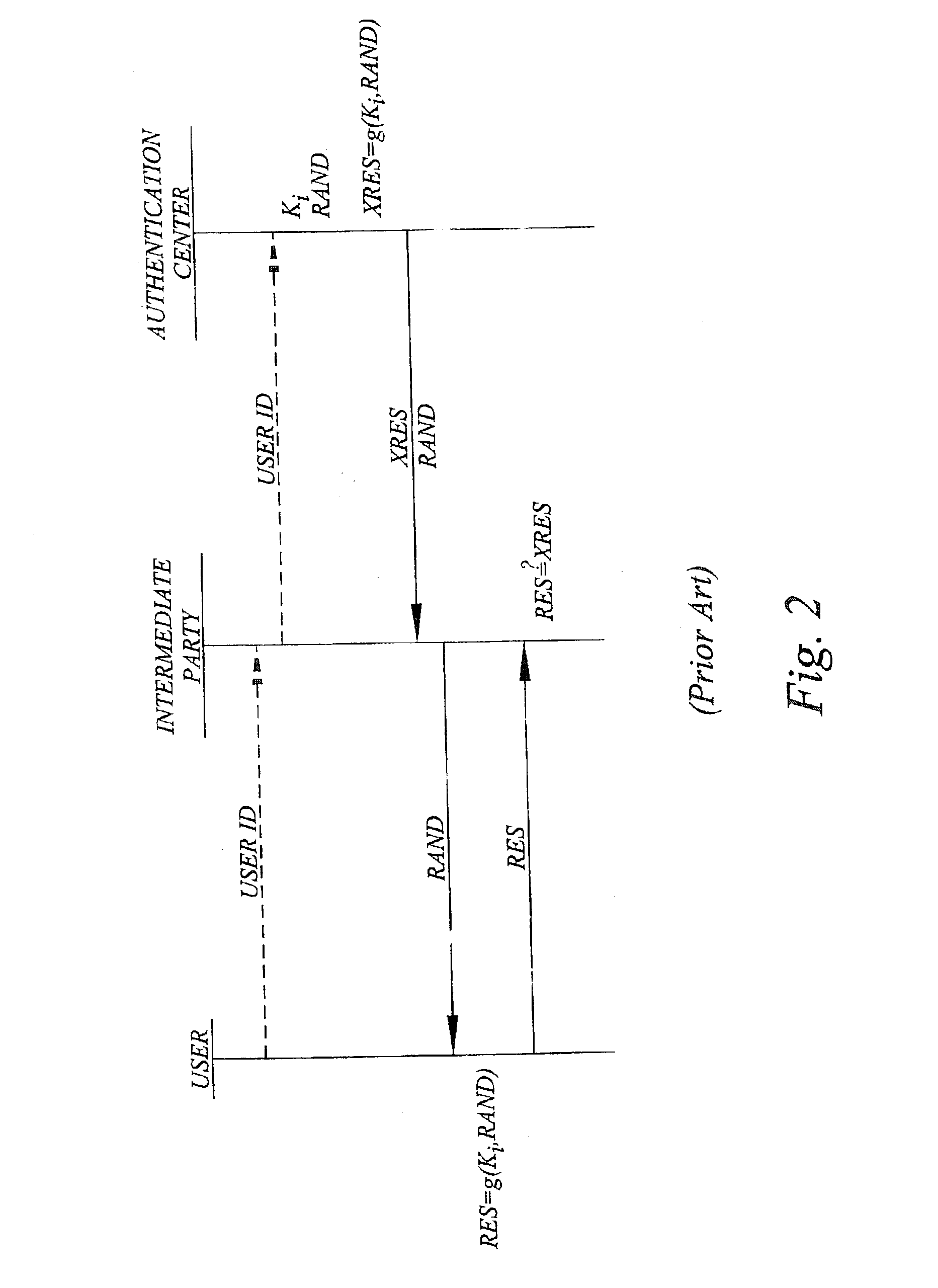
Challenge-response user authentication
ActiveUS20030233546A1Easy to migrateAvoid attackUser identity/authority verificationDigital data authenticationInternet privacyUser authentication
A challenge-response authentication procedure includes masking of the expected response (XRES) generated by an authentication center by means of a masking function (f), and transmission of the masked expected response (XRES'), instead of the expected response itself, to an intermediate party at which the actual user authentication takes place. The intermediate party also receives a user response (RES) from the user and generates a masked user response (RES') using the same masking function (f) as the authentication center did. In order to authenticate the user, the intermediate party then verifies that the masked user response (RES') corresponds to the masked expected response (XRES') received from the authentication center. The above procedure enables the intermediate party to prove that user authentication has taken place, keeping in mind that only the legitimate user knows the response beforehand.
Owner:TELEFON AB LM ERICSSON (PUBL)
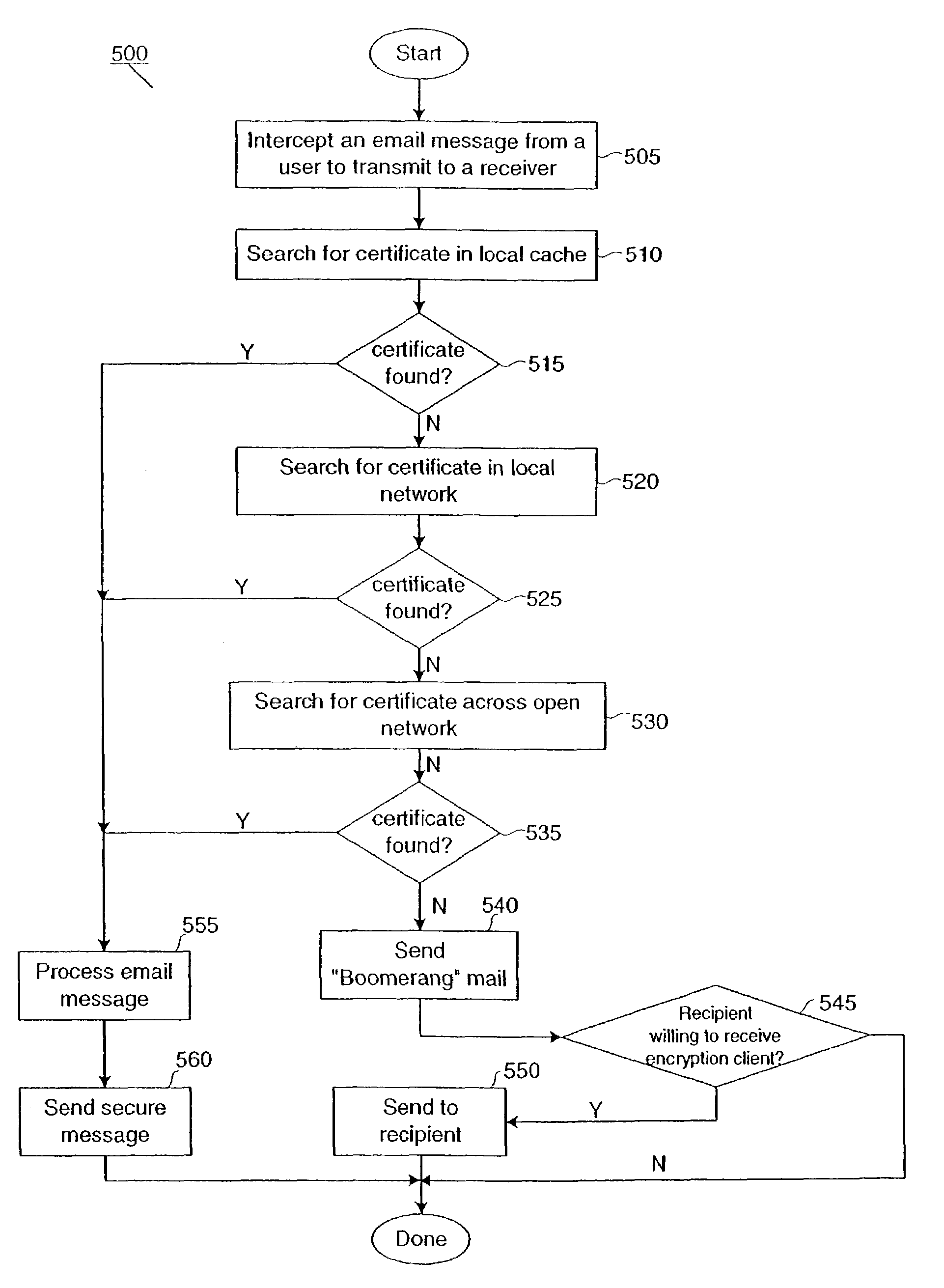
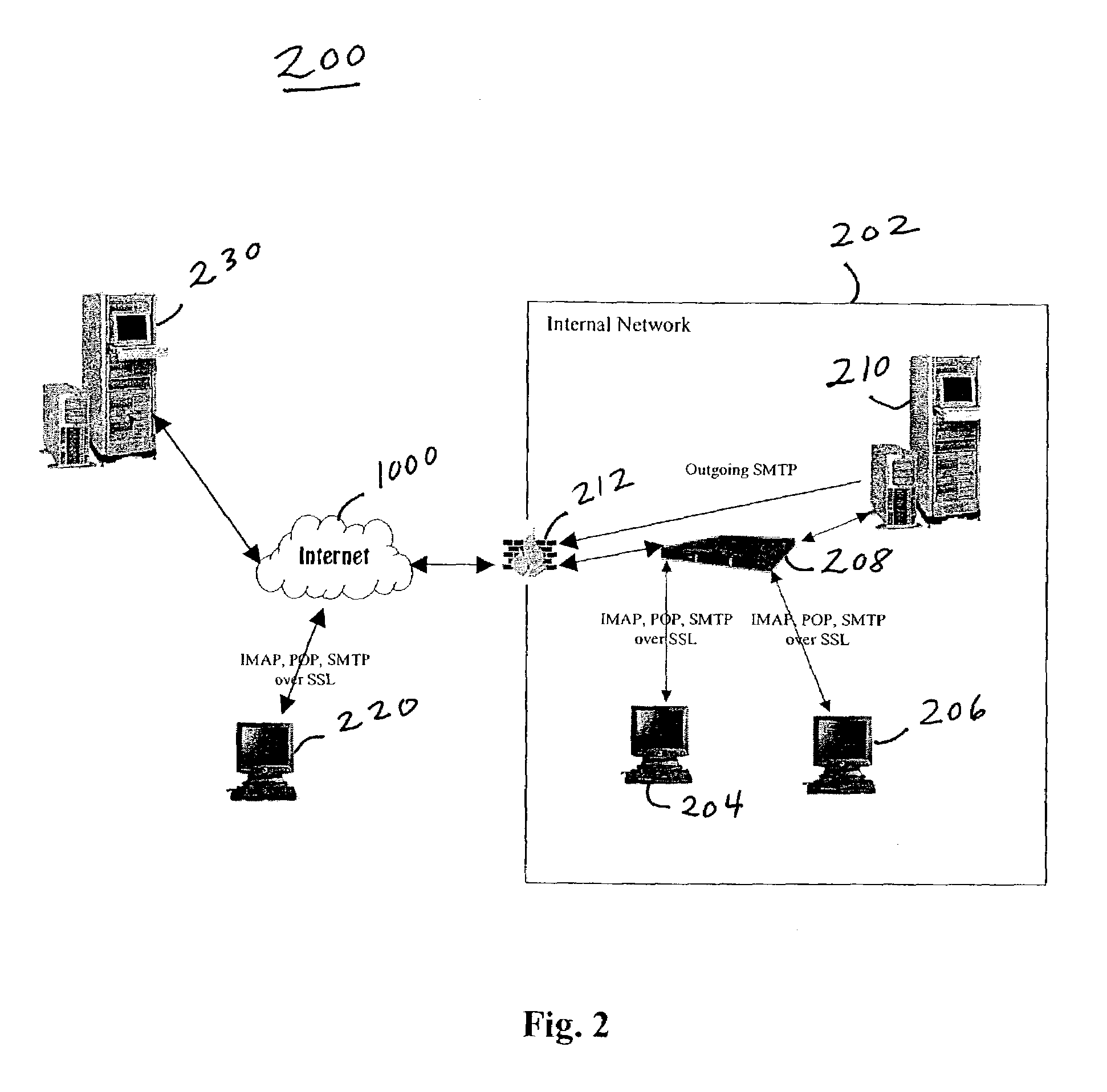
System and method for secure electronic communication in a partially keyless environment
InactiveUS7640427B2Reduce the burden onImprove securityPublic key for secure communicationMultiple digital computer combinationsDigital identityPlaintext
This present invention provides users with secure transparent electronic communication, allowing them to send and receive encrypted and / or signed messages with little or no user involvement. In various embodiments, the present invention provides a user with e-mail security via automated hierarchical techniques for transparently sending and receiving secure messages, and lowers the burden on administrators. Such a system can also manage cryptographic keys and certificates for the users, and creates such keys and certificates for the users when necessary. A server according to the present invention can intercept unsecured messages from a user, automatically transform those messages into secured messages, and transmit those secure messages to the intended recipients. The server can also automatically transform messages after the recipient sends a digital identity to the server and downloads the software necessary for transforming the secured messages back into readable messages (i.e., from ciphertext into plaintext). The server can further intercept an unsecured message from a user, search for a digital identity of the intended recipient, secure the unsecured message upon finding such a digital identity, and transparently send the secured message to the intended recipient.
Owner:CA TECH INC
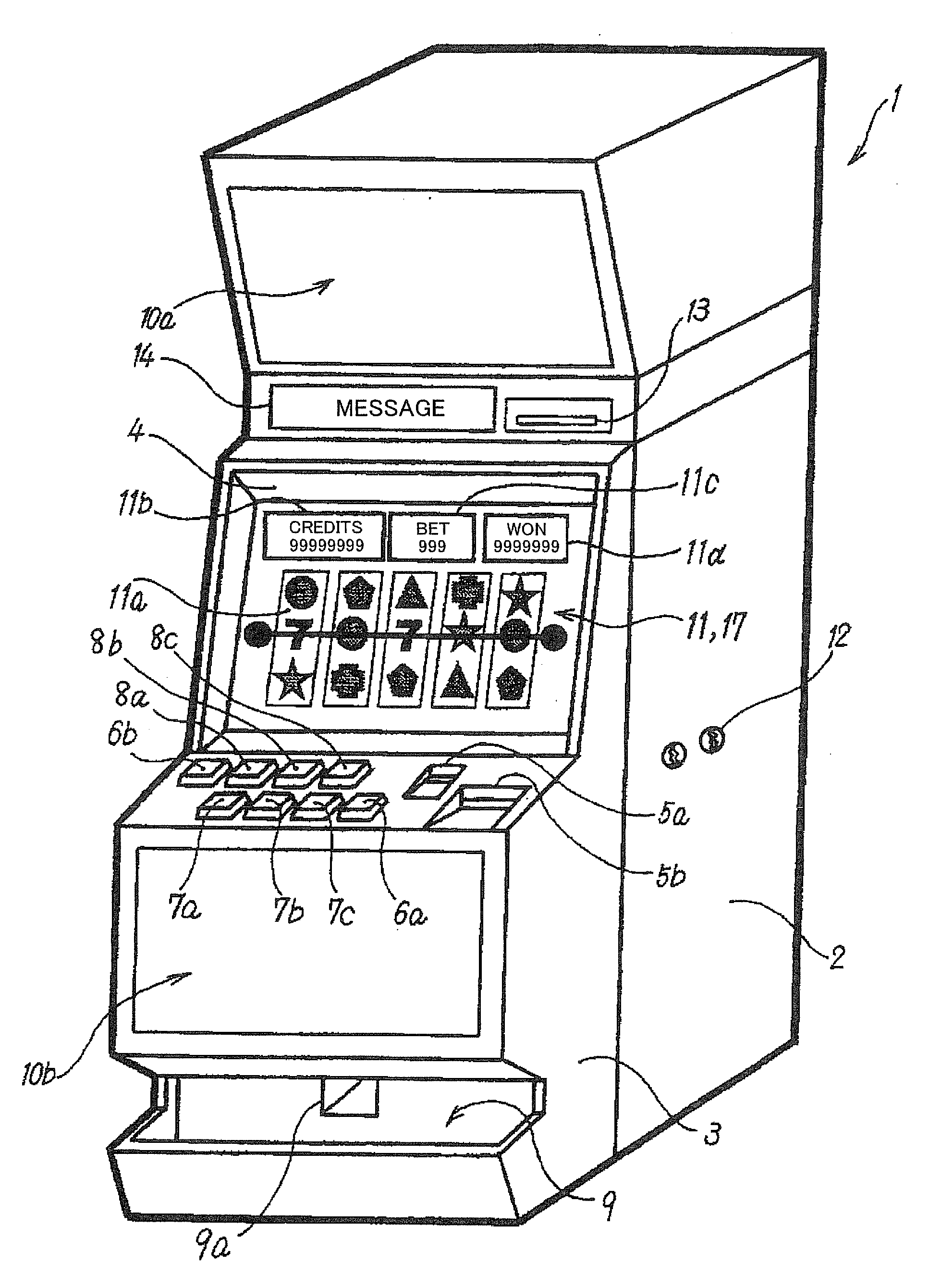
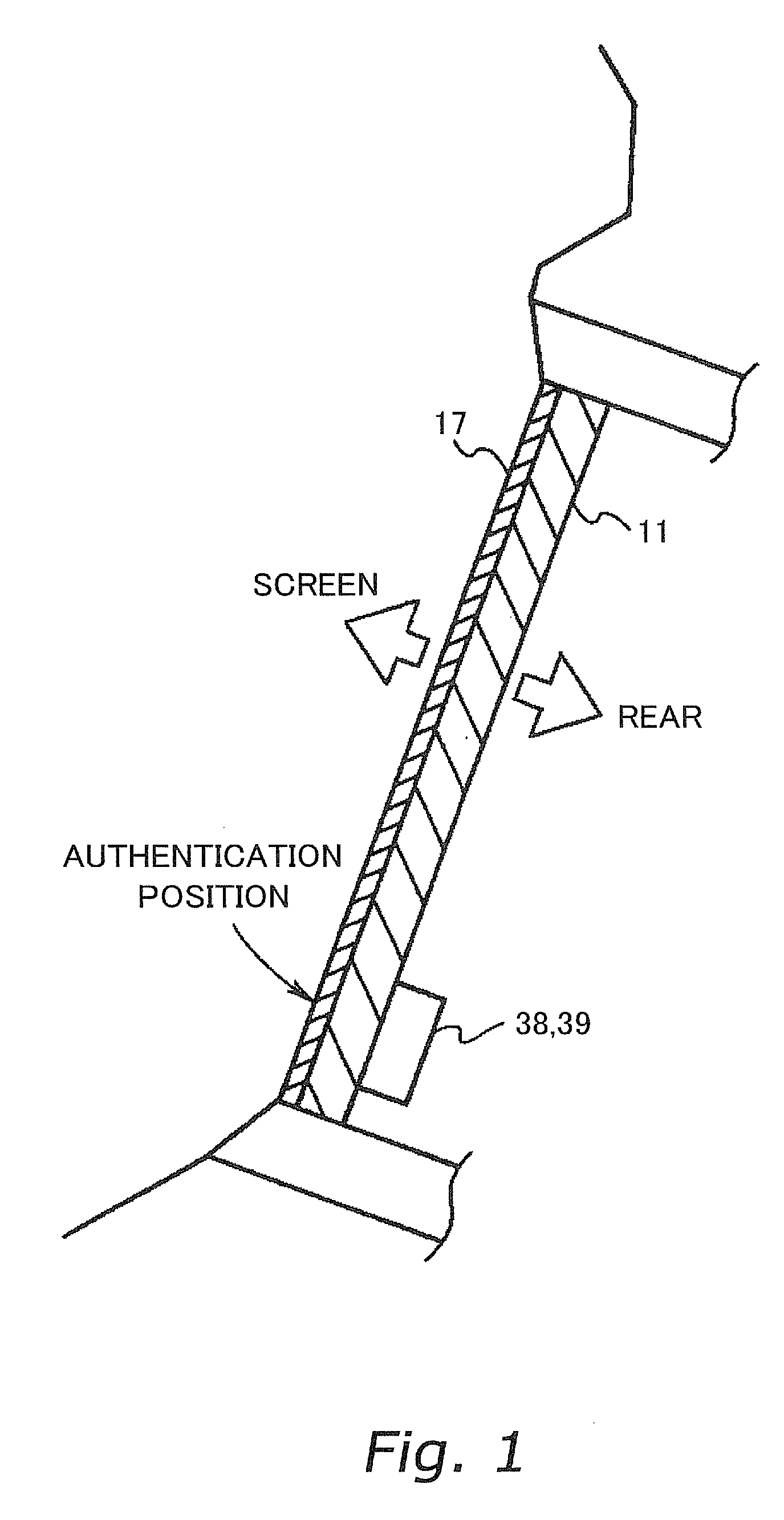
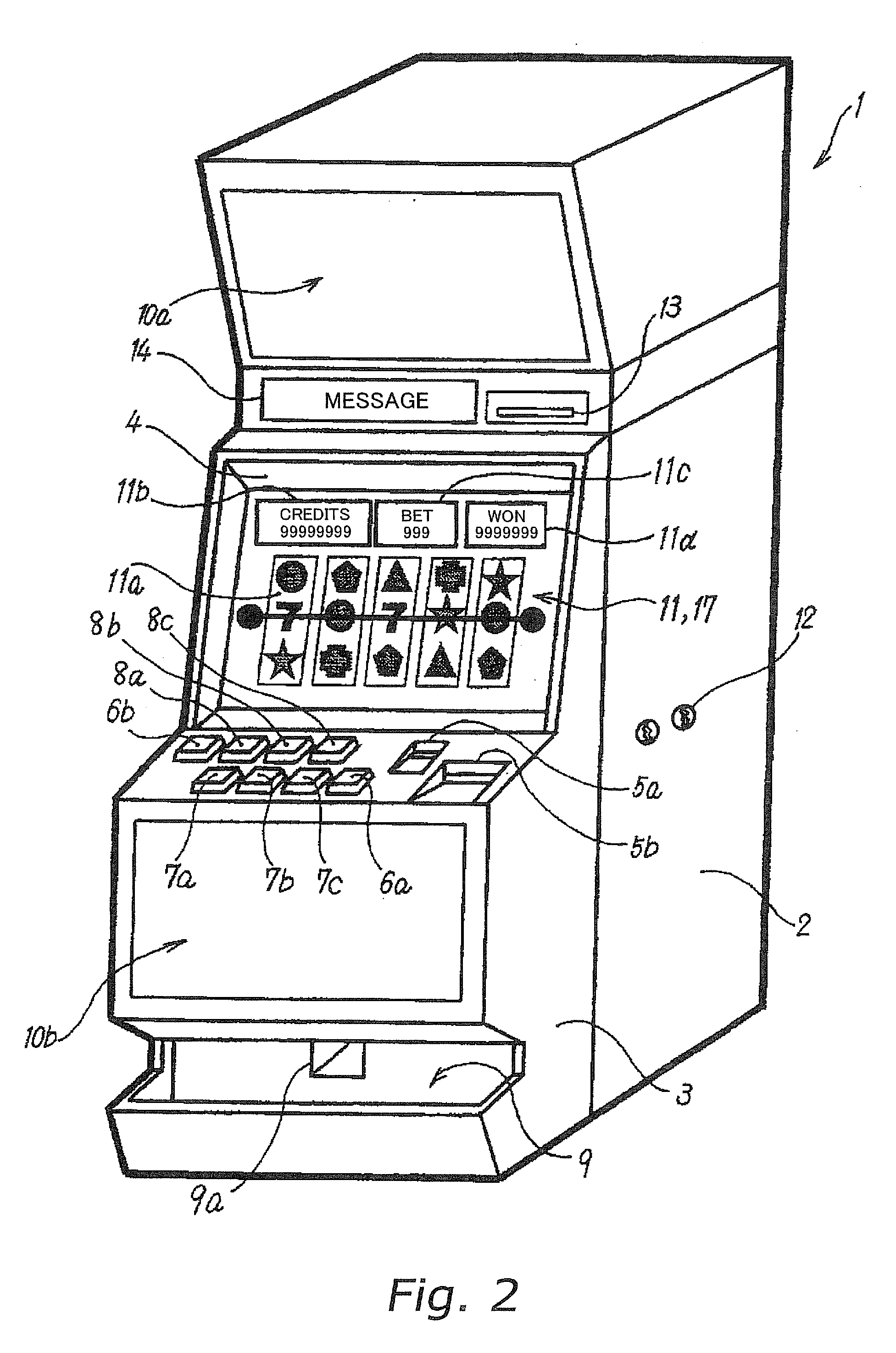
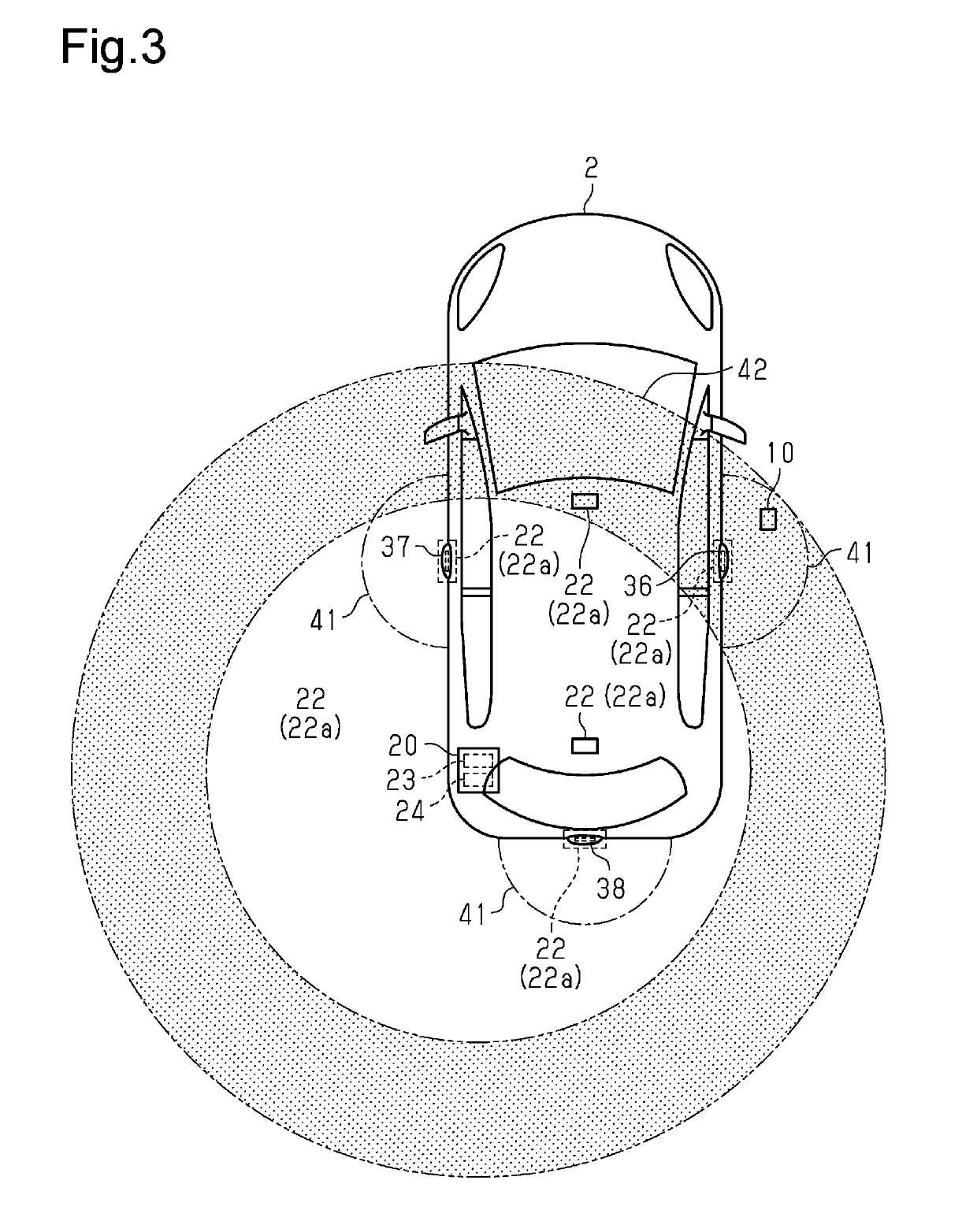
Authentication device and gaming machine equipped with the same
InactiveUS20070021194A1Save energyPrecise positioningImage analysisDigital data processing detailsAuthenticationFingerprint
An authentication device according to the present invention is preferably installed in a gaming machine. In this authentication device, in particular, an authentication data input unit is located on the rear side of a display unit. Furthermore, the screen of the display unit includes an authentication position where an authentication object (for example, a player's finger) is to approach or touch the screen. The authentication data input unit reads the authentication data (for example, fingerprint pattern data) through the screen from the authentication object approaching or touching the screen of the display unit.
Owner:KONAMI GAMING
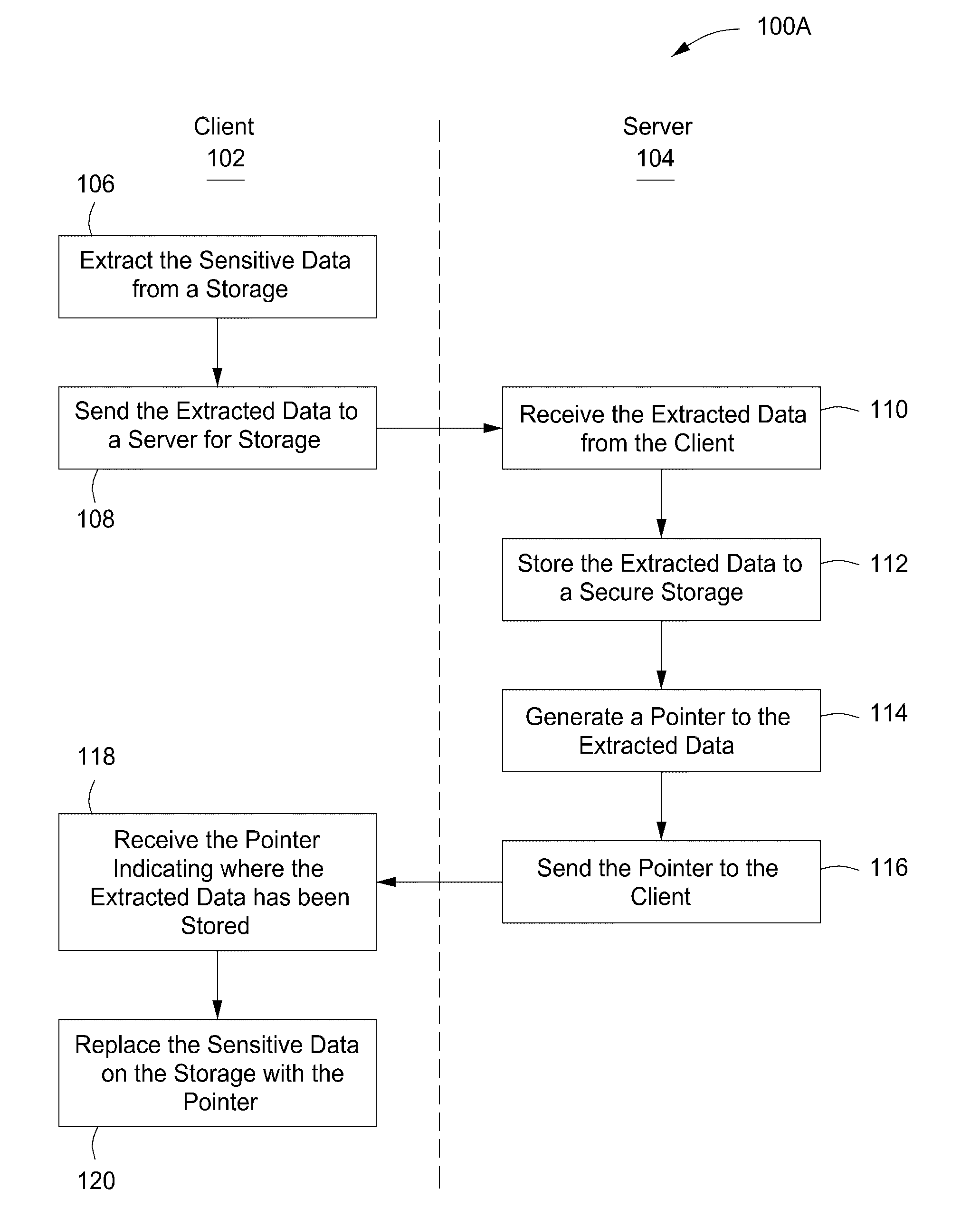
System, method and apparatus for electronically protecting data and digital content
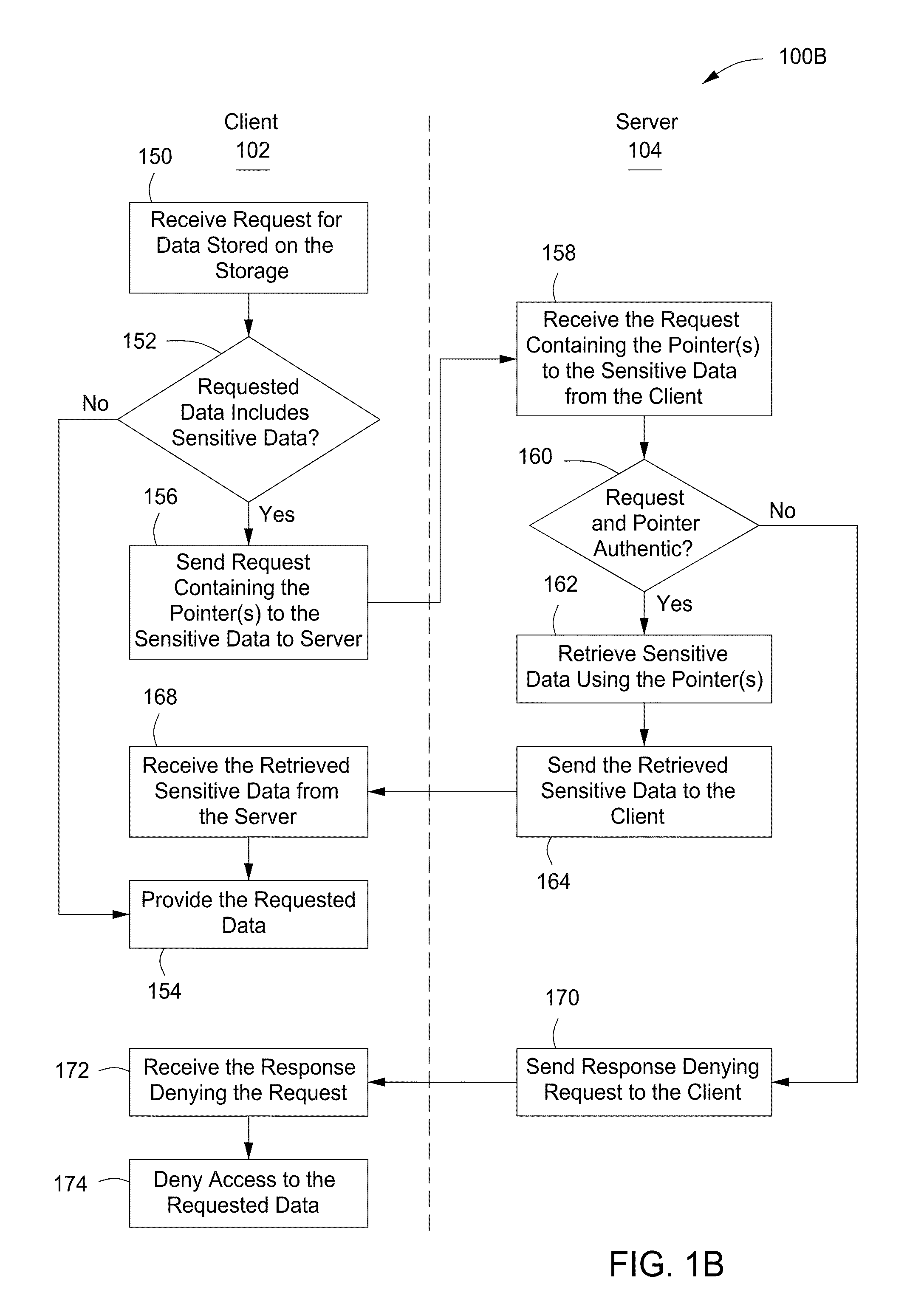
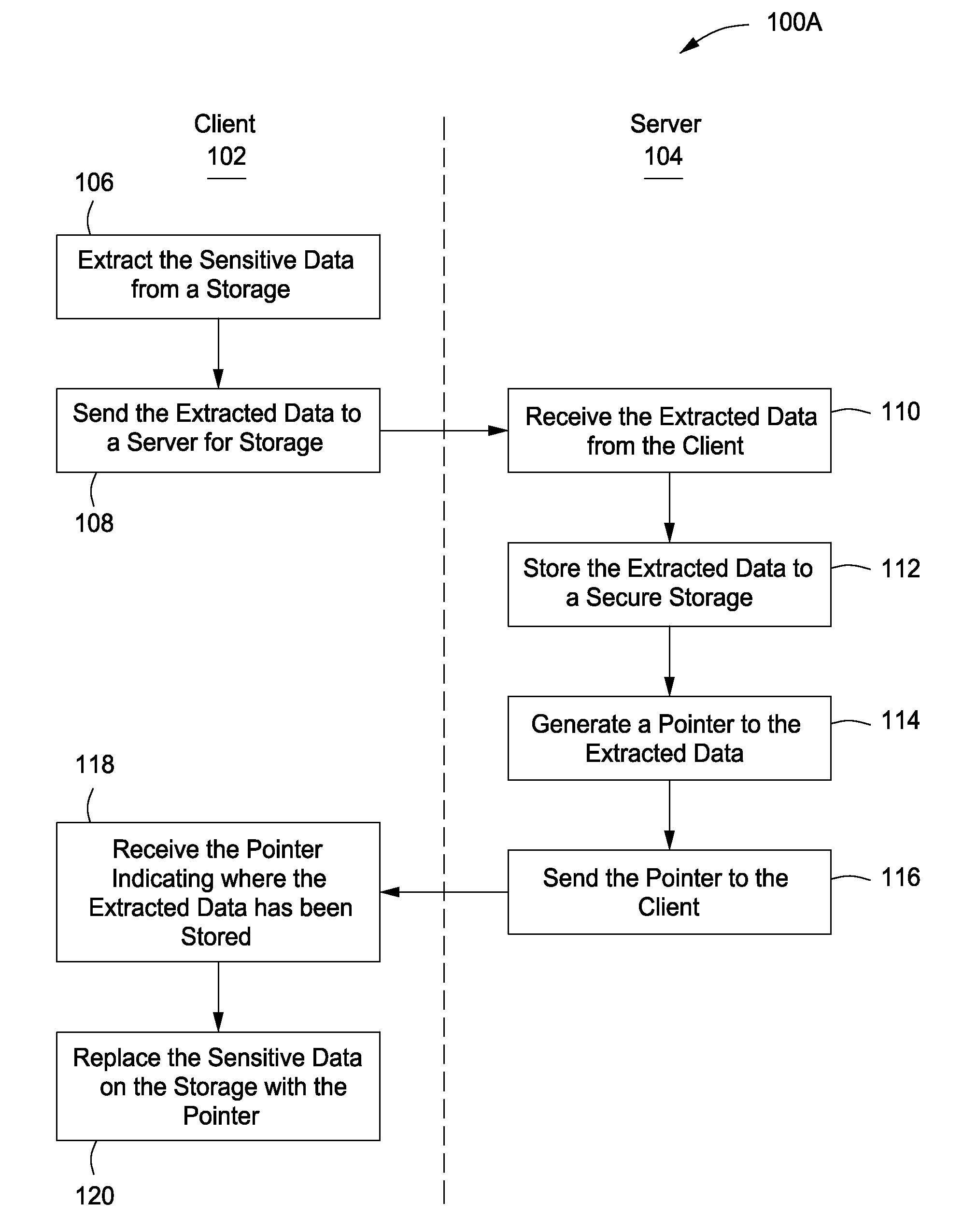
InactiveUS20100005509A1Existing technologyAccurate authenticationDigital data processing detailsMultiple digital computer combinationsClient-sideContent management
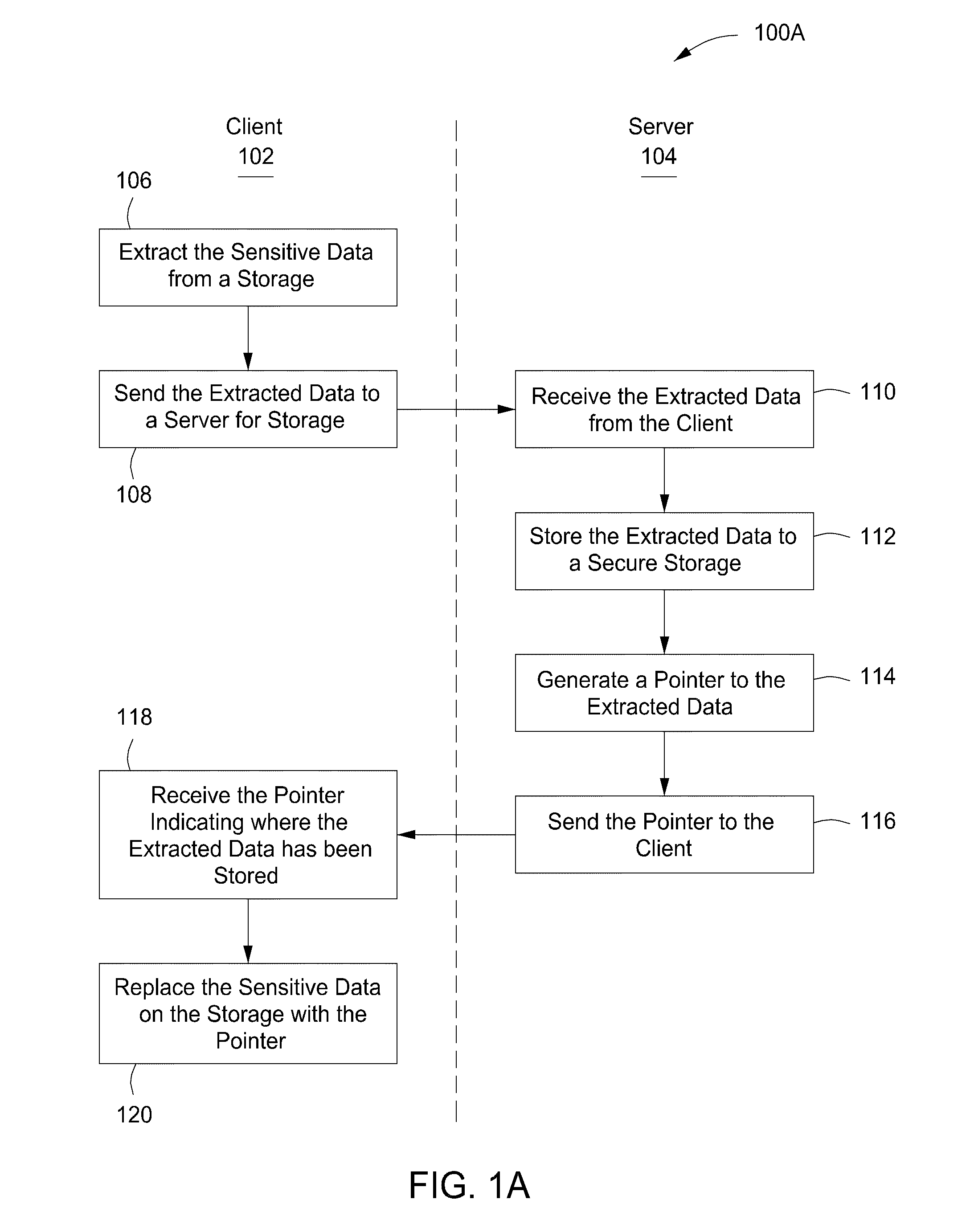
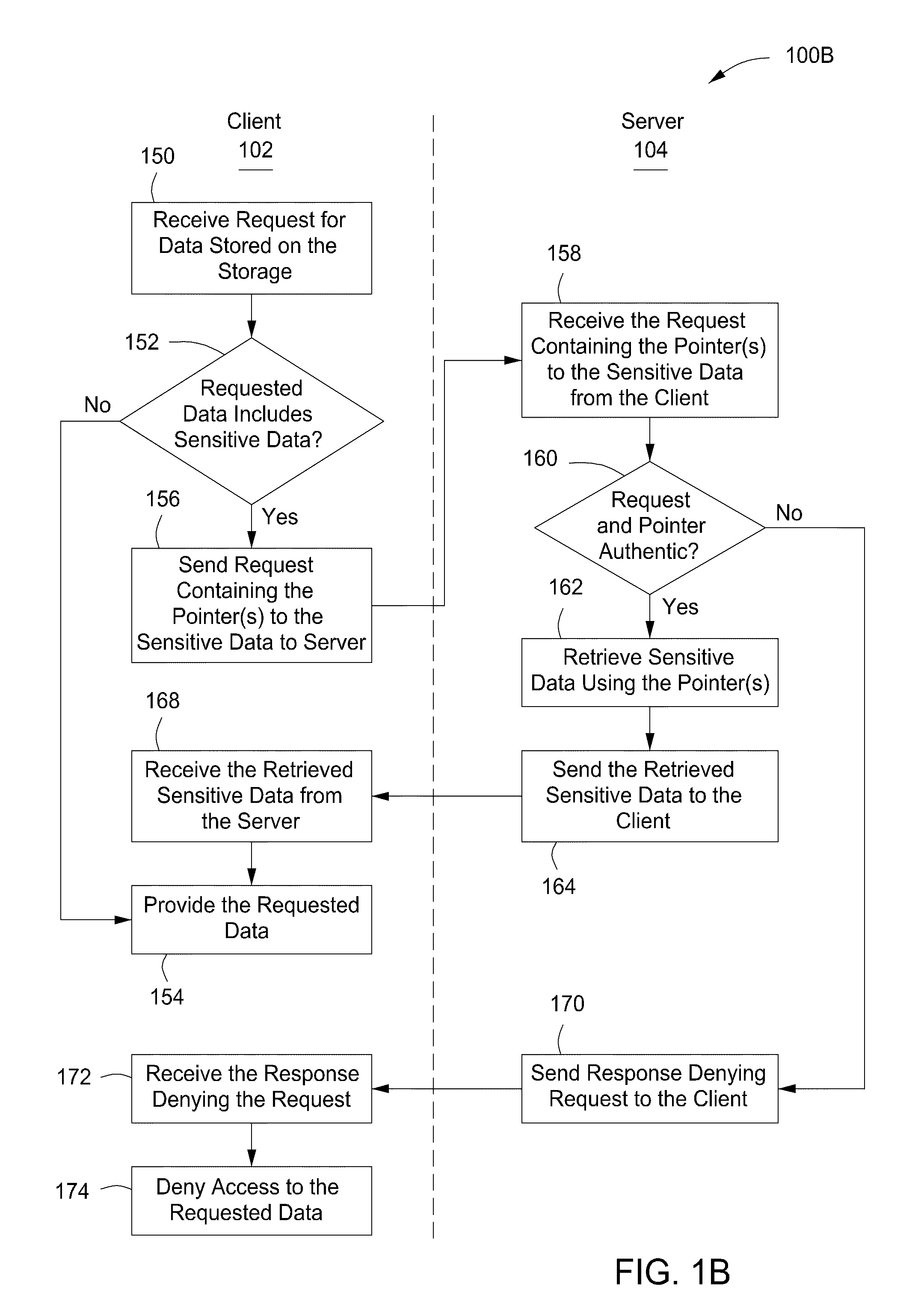
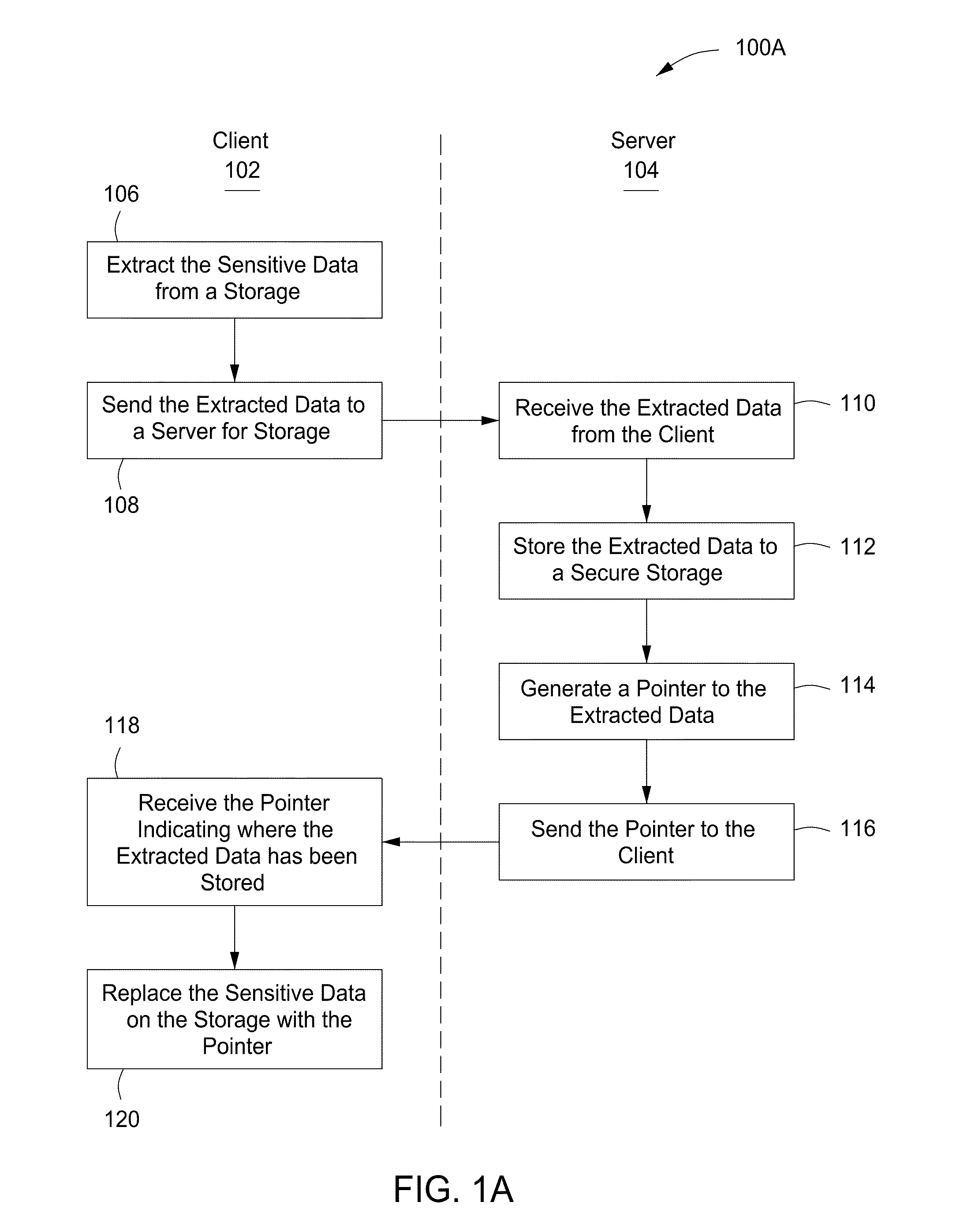
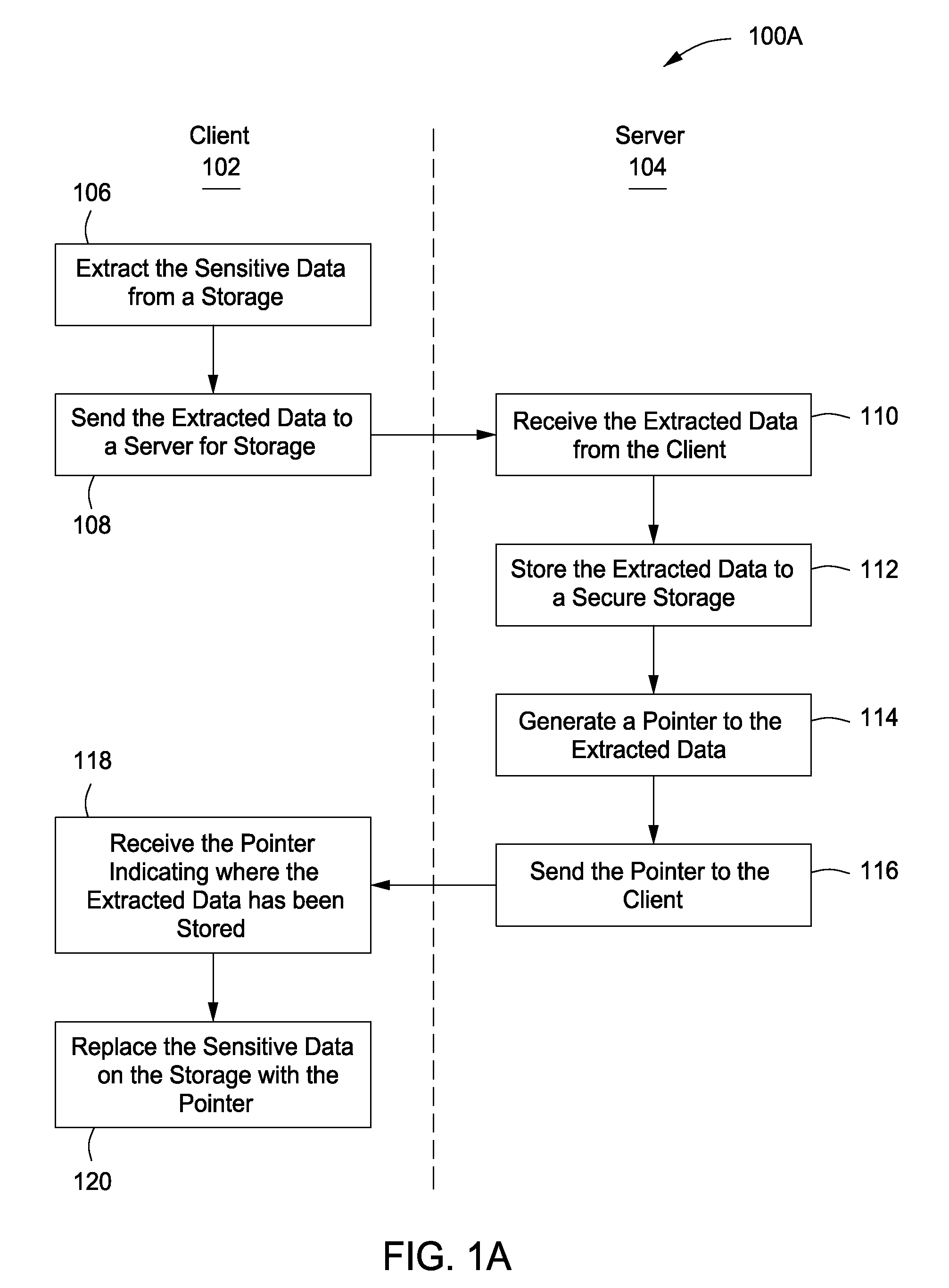
The present invention provides a system, apparatus and method for protecting sensitive data can be provided using a pre-content manager and a post-content manager. The pre-content manager extracts sensitive or non-sensitive data from a data storage on a client, sends the extracted sensitive data to a server for storage, receives a pointer indicating where the extracted sensitive data has been stored and replaces the sensitive data on the data storage on the client with the pointer. The post content manager receives the sensitive data from the pre-content manager and transmits the sensitive data to one or more media devices. The foregoing can be implemented as a computer program embodied on a computer readable medium wherein the steps are executed by one or more code segments.
Owner:DT LABS INC
System and Method for Customer Authentication of an Item
ActiveUS20100106645A1Existing technologyAccurate authenticationDigital data processing detailsMultiple digital computer combinationsClient dataClient-side
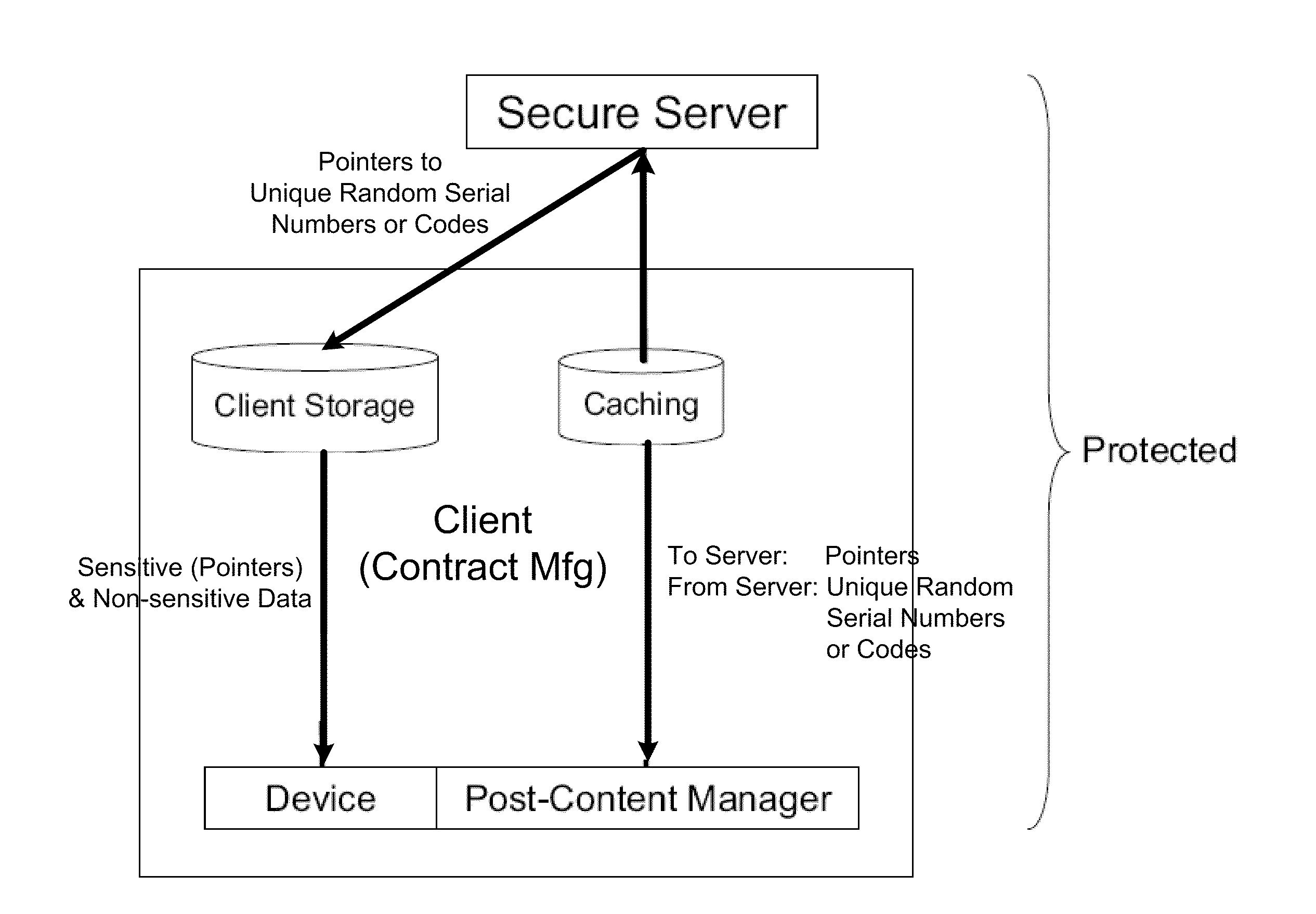
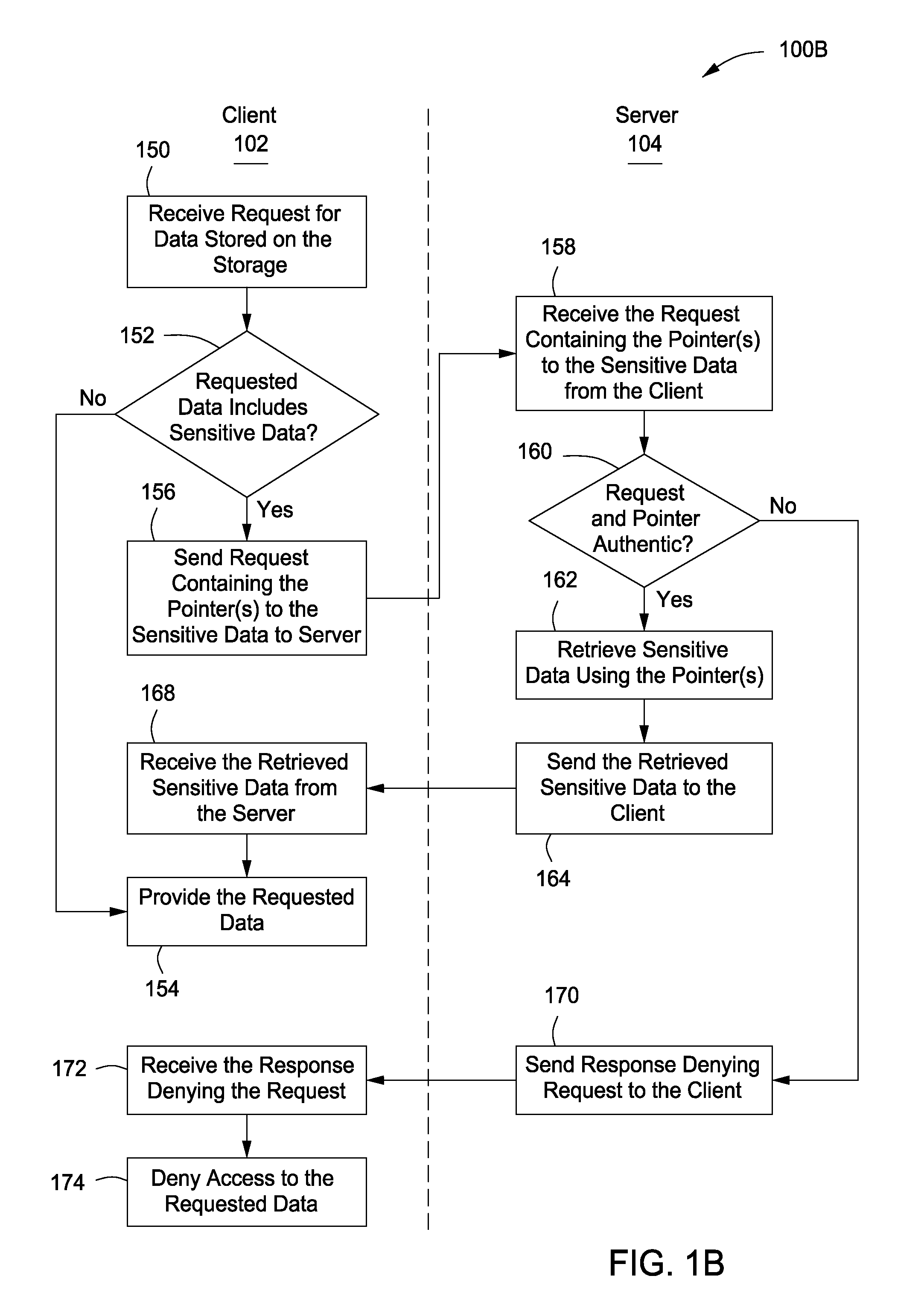
A system, apparatus and method is provided for authentication of an item or a label by storing unique random serial numbers or codes in a remote secure storage that can be used to authenticate the item or the label, generating a pointer to each stored unique random serial number / code and storing the generated pointer(s) in a client data storage. During or prior to a production run of the item(s) or label(s): the generated point(s) are sent from the client data storage to one or more media devices, the generated pointer(s) are obtained from the media device using a post-content manager, the unique random serial number(s) / code(s) are obtained from the server via the post-content manager using the generated pointer(s), the obtained unique random serial number(s) / code(s) are sent to the media device, and the received unique random serial number(s) / code(s) are imprinted on the item(s) or the label(s) using the media device.
Owner:KLOKE LLC
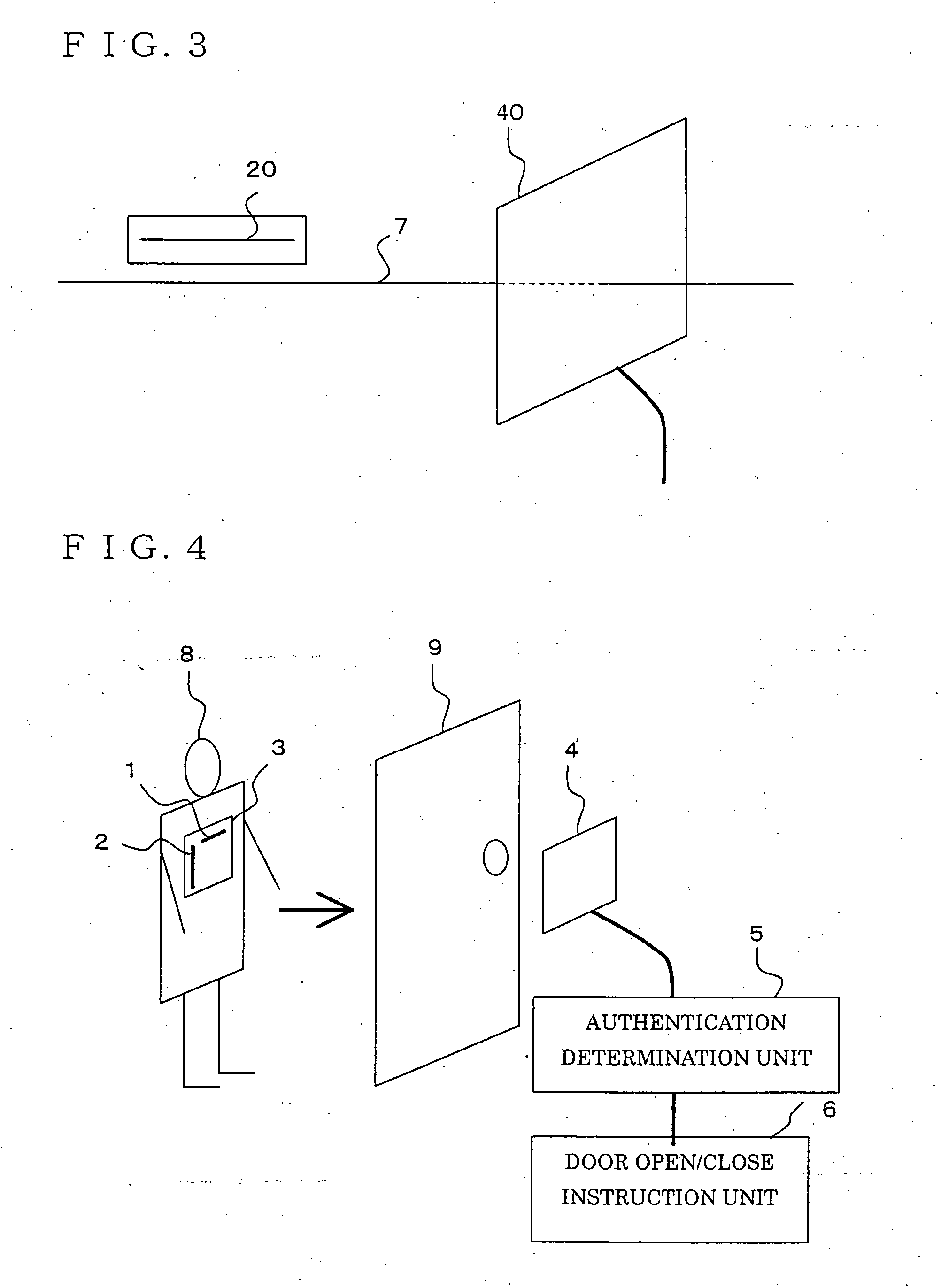
System and method for authenticating an element in a network environment
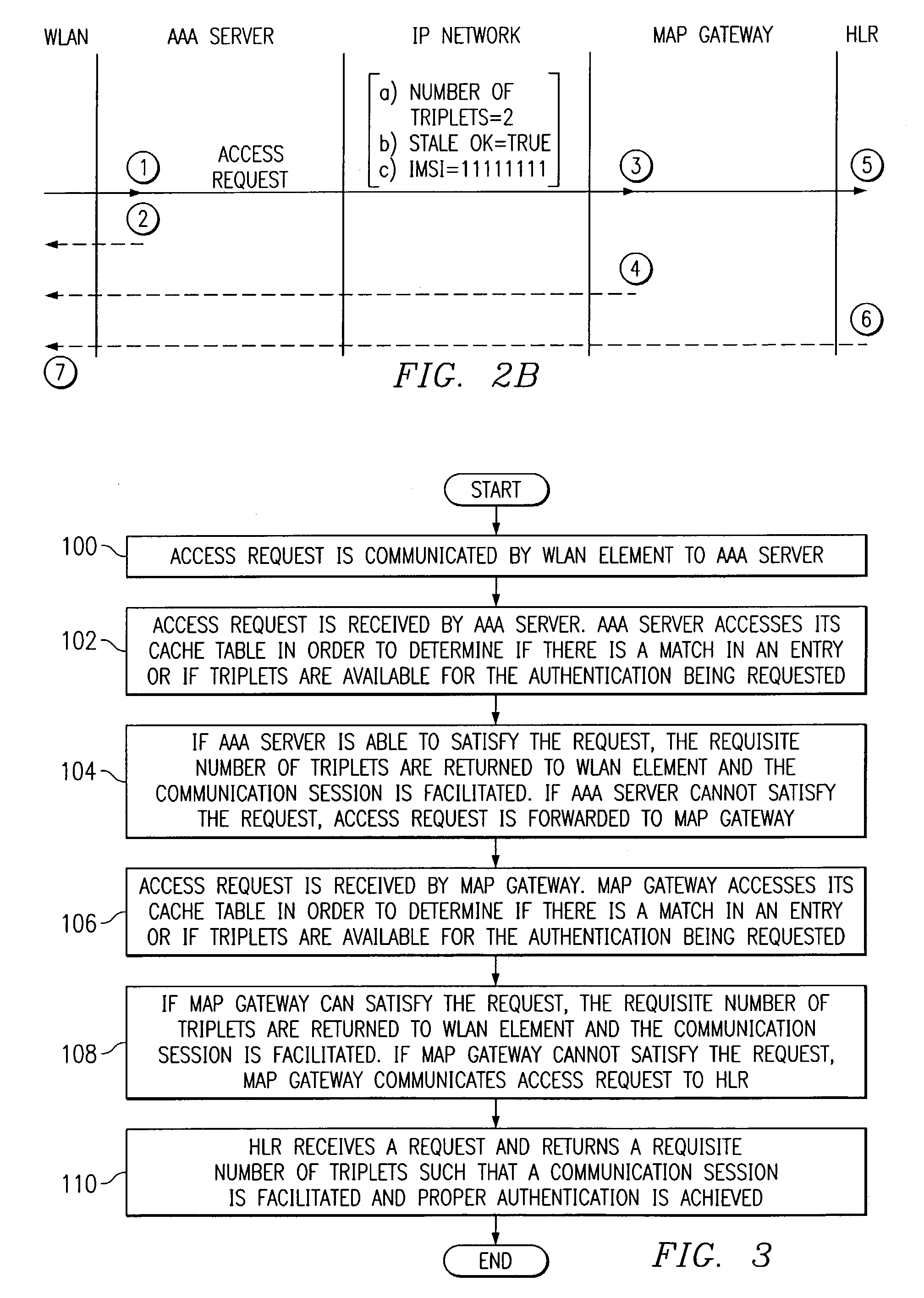
ActiveUS7310307B1Facilitate communication sessionAvoid excessive trafficError preventionFrequency-division multiplex detailsNetwork Communication ProtocolsWeb environment
A method for authenticating an element in a network environment is provided that includes receiving a request for one or more triplets. One or more of the triplets may be associated with an authentication communications protocol that may be executed in order to facilitate a communication session. The method further includes returning one or more of the triplets in response to the request and initiating the communication session in response to the triplets after proper authentication of an entity associated with the request.
Owner:CISCO TECH INC
User information management method based on block chain, electronic equipment and storage medium
ActiveCN109639632AAccurate authenticationPrevent leakageFinanceUser identity/authority verificationInternet privacyChain network
The application discloses a user information management method based on a block chain, electronic equipment and a storage medium. The user information management method comprises the following steps:acquiring a registration biological characteristic entered by a user through a user node, performing Hash computation on the registration biological characteristic to obtain corresponding registrationdigital fingerprint; acquiring registration identity information entered by the user; associating the registration digital fingerprint with the registration identity information, and storing in a block chain network, thereby enabling an accounting node of the block chain network to account the registration digital fingerprint and the registration identity information to accomplish the identity registration on the block chain network by the user. Through the method disclosed by the application, the digital fingerprint of the user and the identity information are associated and chained, therebyguaranteeing that the privacy of the user is hard to leak, and the identity authentication on the user can be more accurately performed when the user performs the related transaction by subsequentlyutilizing the block chain network, the identity authentication error is reduced.
Owner:YGSOFT INC
Method and system for user authentication
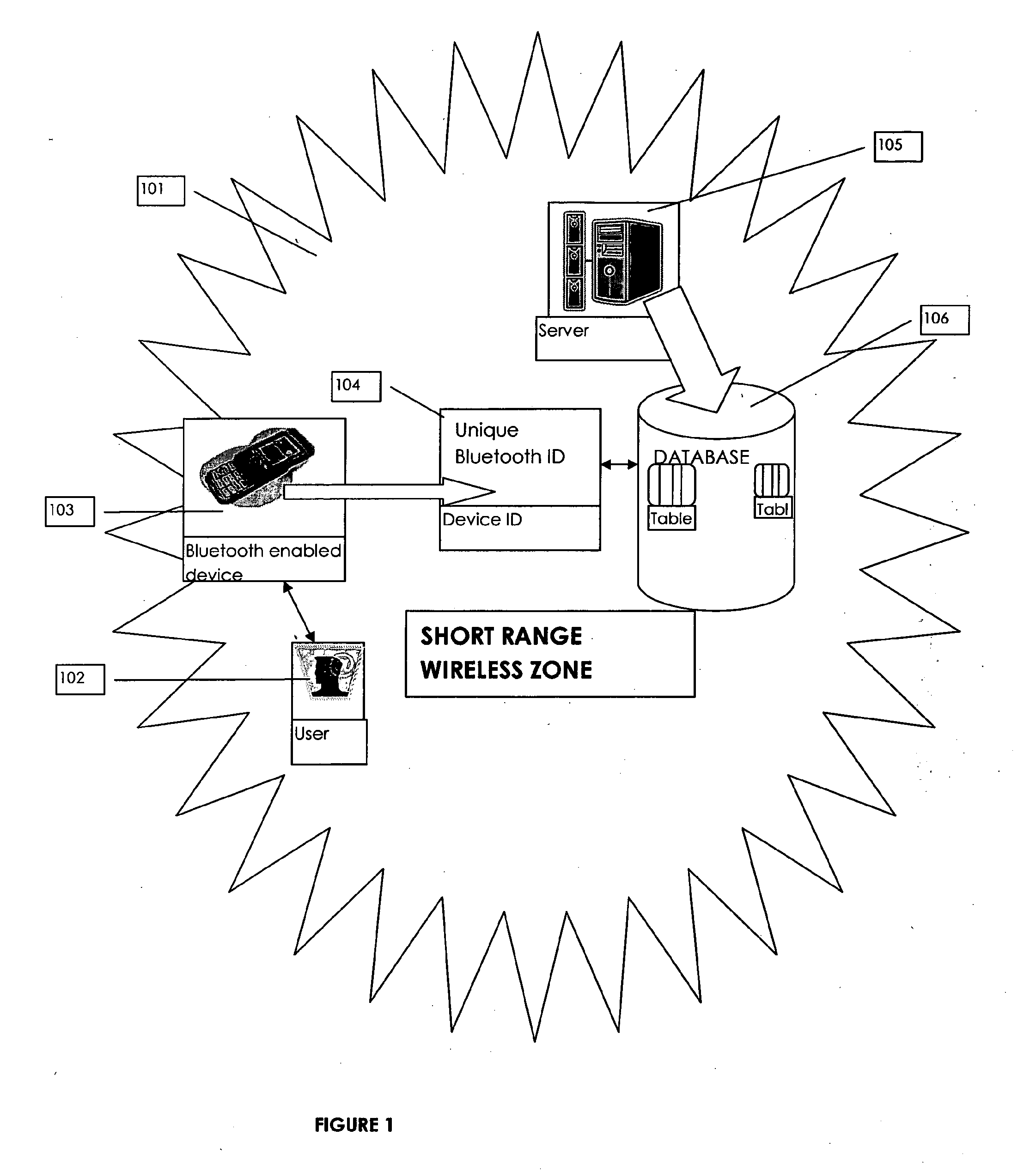
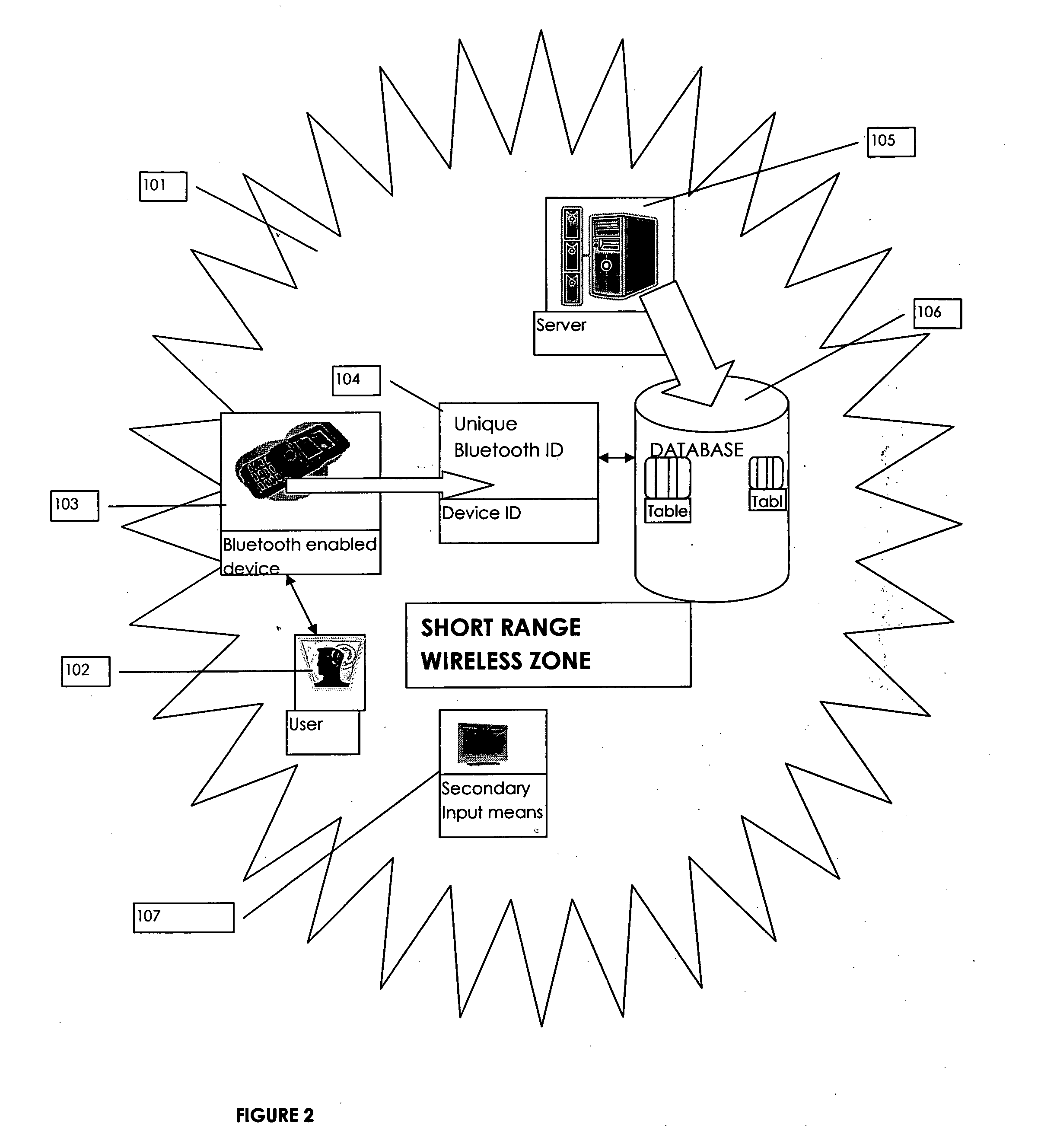
ActiveUS20110154460A1Improve protectionImprove securityDigital data processing detailsNetwork topologiesUser inputUser authentication
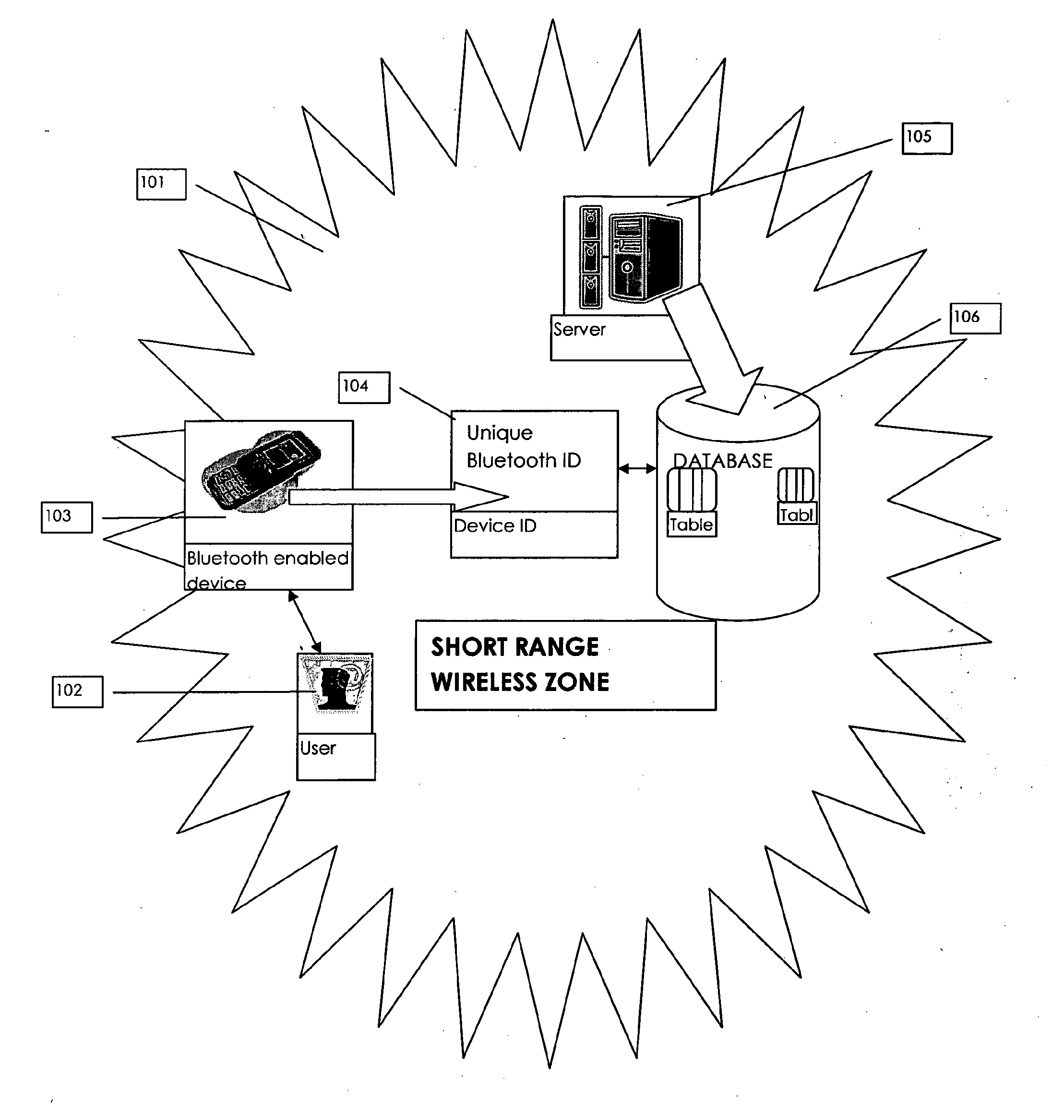
Method and system for user authentication using one or more unique ID's associated with one or more electronic devices connected in a communication network, more specifically in short range radio communication network. the method comprising the steps of polling and detection of a short range wireless electronic device within a short range radio communication network, establishing a connection between such short range wireless electronic device with a centralized server, authenticating the short range wireless device ID, requesting further the user to feed a pre-determined authentication code, verifying the fed authentication code with corresponding entries in the database of the central server, establishing an encrypted channel if authentication code found in such database, receiving a user authentication certificate from the wireless electronic device.
Owner:INDUSEDGE INNOVATIONS PRIVATE
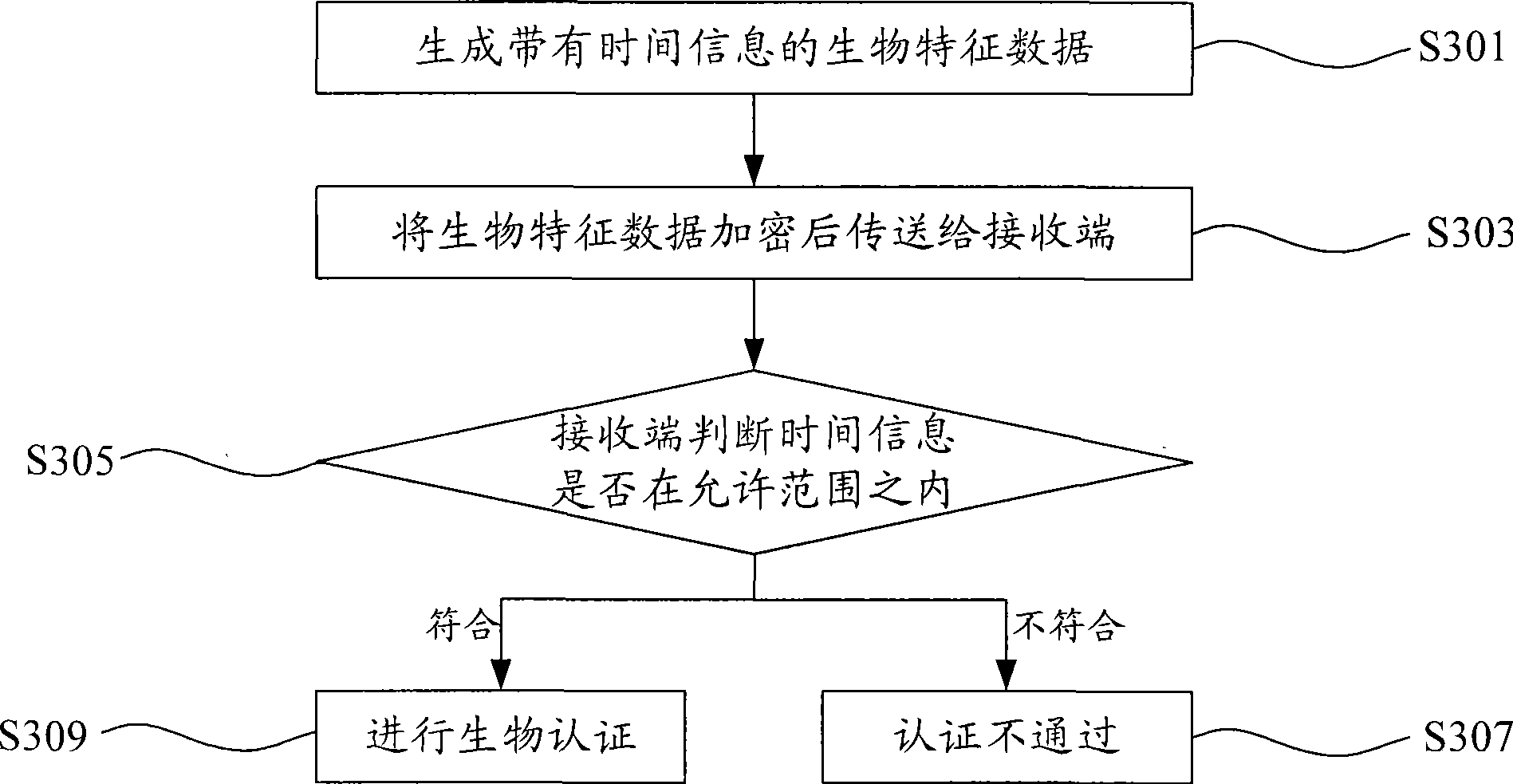
Method and system for identification authentication using biology characteristics
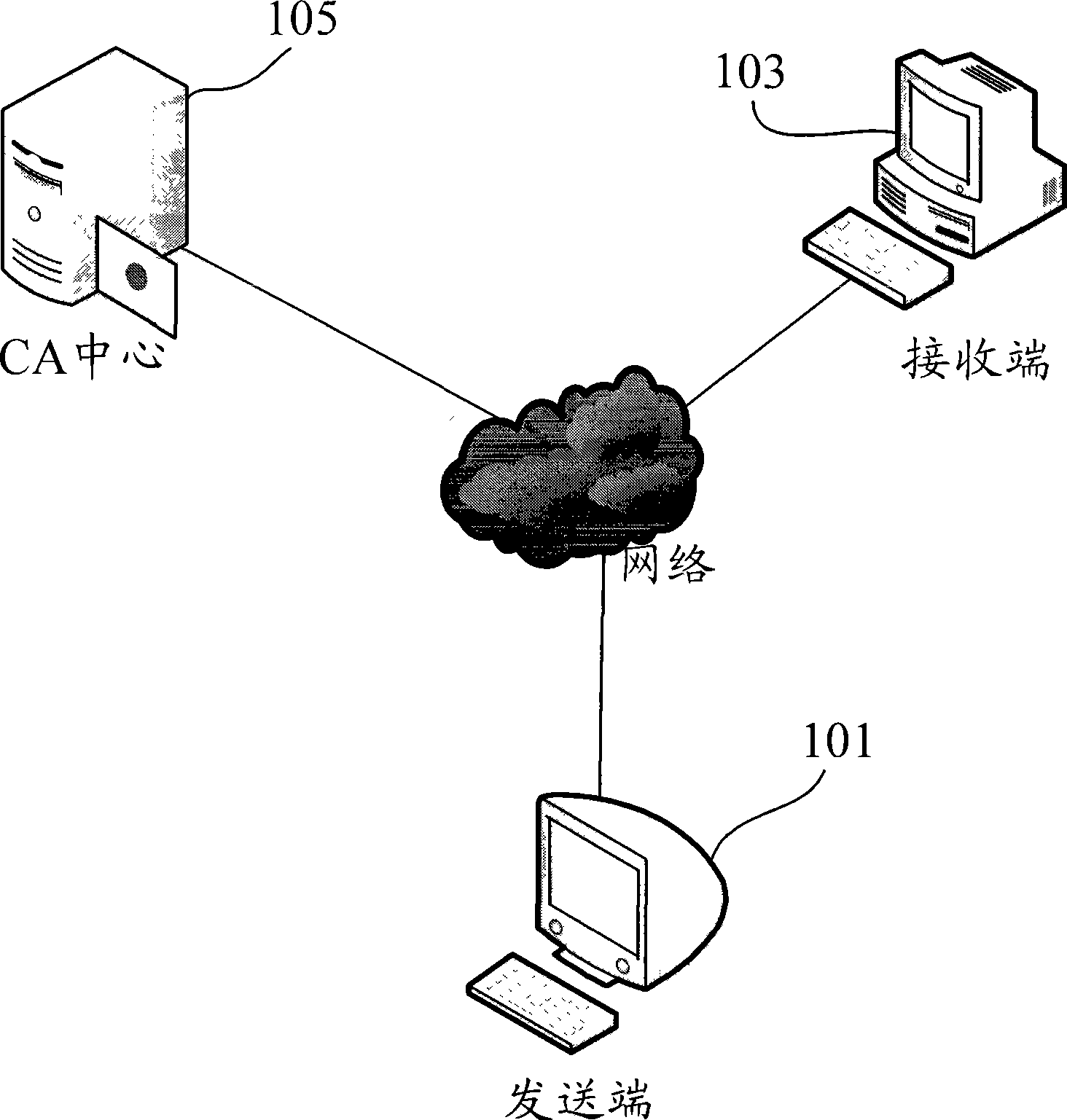
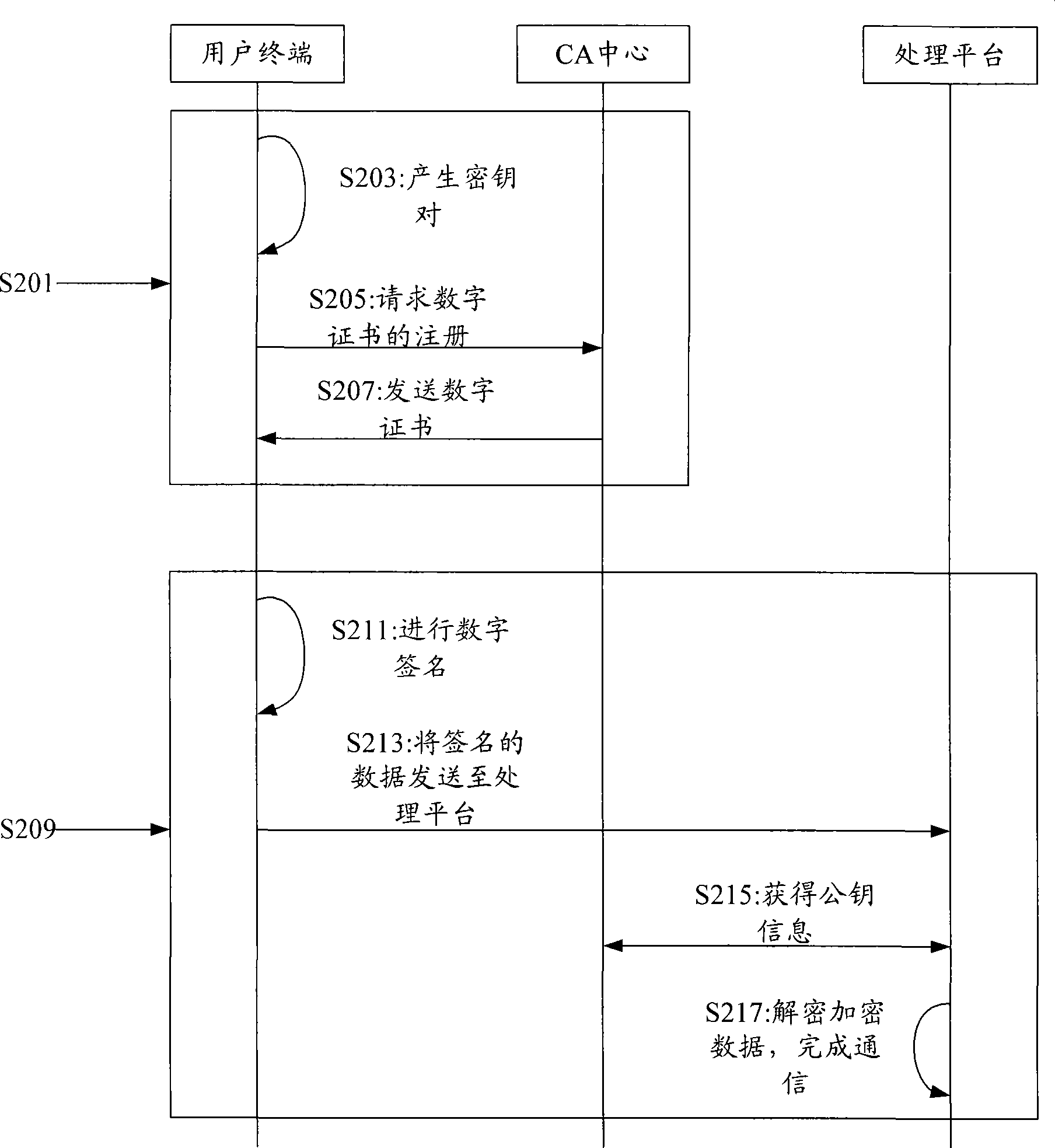
ActiveCN101442407AImprove securityTime constraintsPublic key for secure communicationUser identity/authority verificationBiological specificityBiometric trait
The invention provides a method for authenticating identification by biological specificity. The method comprises the following steps: firstly, a transmitting end generates a biological specificity digital certificate, wherein generation of the biological specificity digital certificate comprises the following steps: generating a public and private key pair; extracting biological specificity point information, transmitting the public key in the public and private key pair, the biological specificity point information and personal register information to a CA center, and signing and generating the biological specificity digital certificate by the CA center; secondly, time of two communication parties are synchronized, and during communication, a current time stamp of the transmitting end is extracted, the time stamp is loaded into the biological specificity digital certificate, and the biological specificity digital certificate is signed by the private key corresponding to the public key and is transmitted to a receiving end; and finally, the receiving end decrypts the biological specificity digital certificate by the public key, and determines whether the identification passes the authentication or not according to the time stamp in the biological specificity digital certificate and the biological specificity point information. The invention makes identification authentication more secure and more reliable.
Owner:ZHEJIANG MIAXIS TECH CO LTD
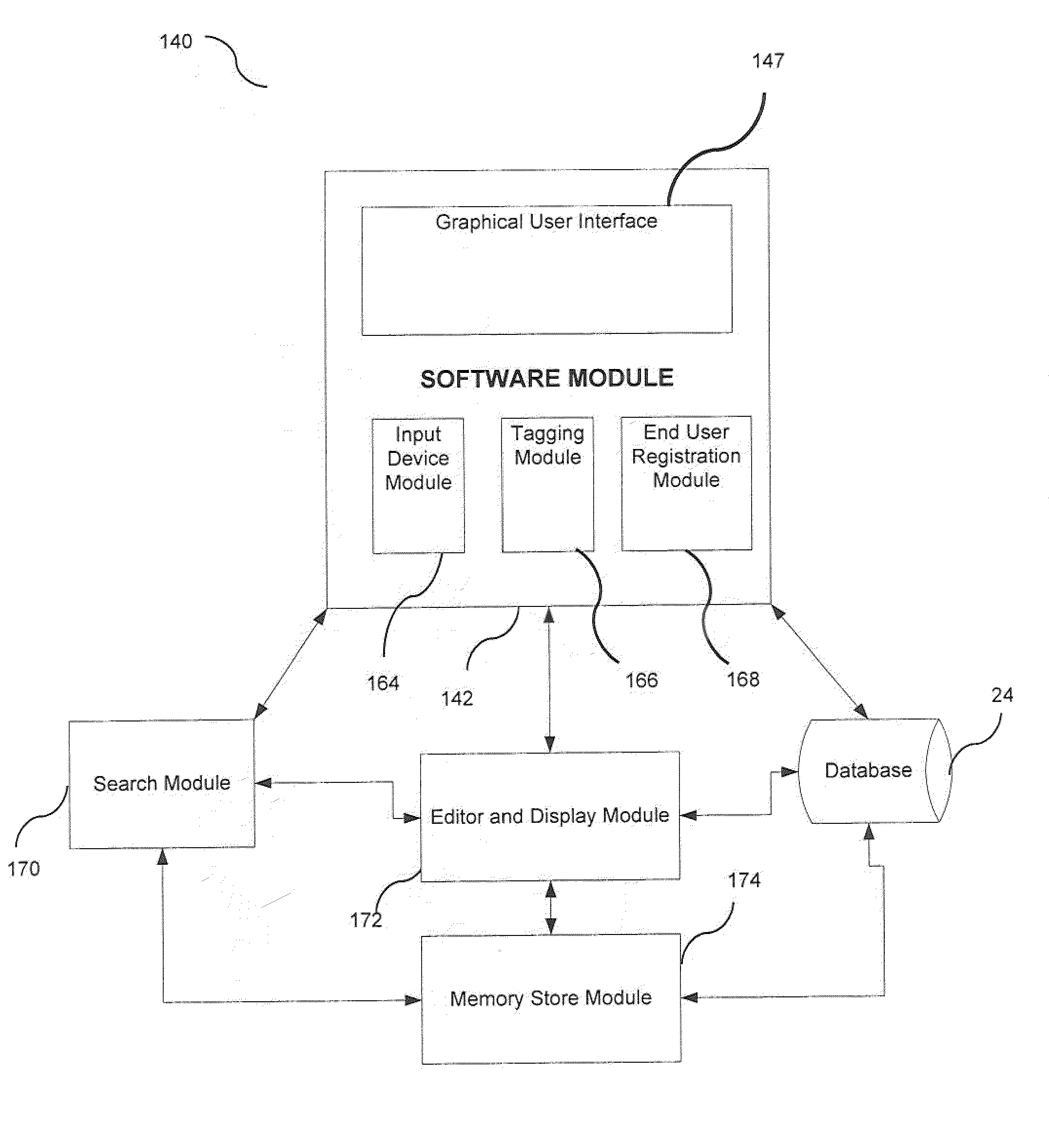
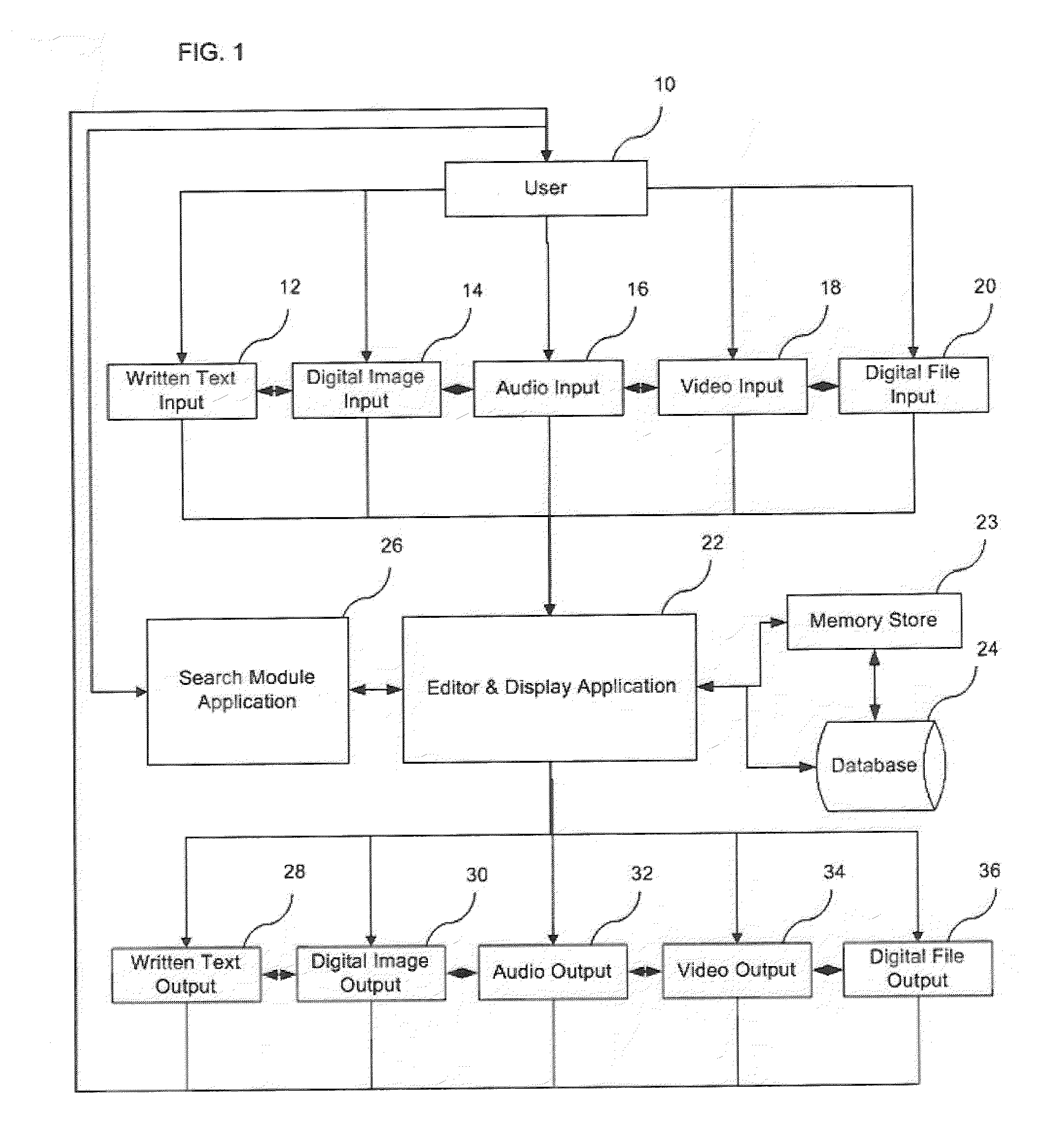
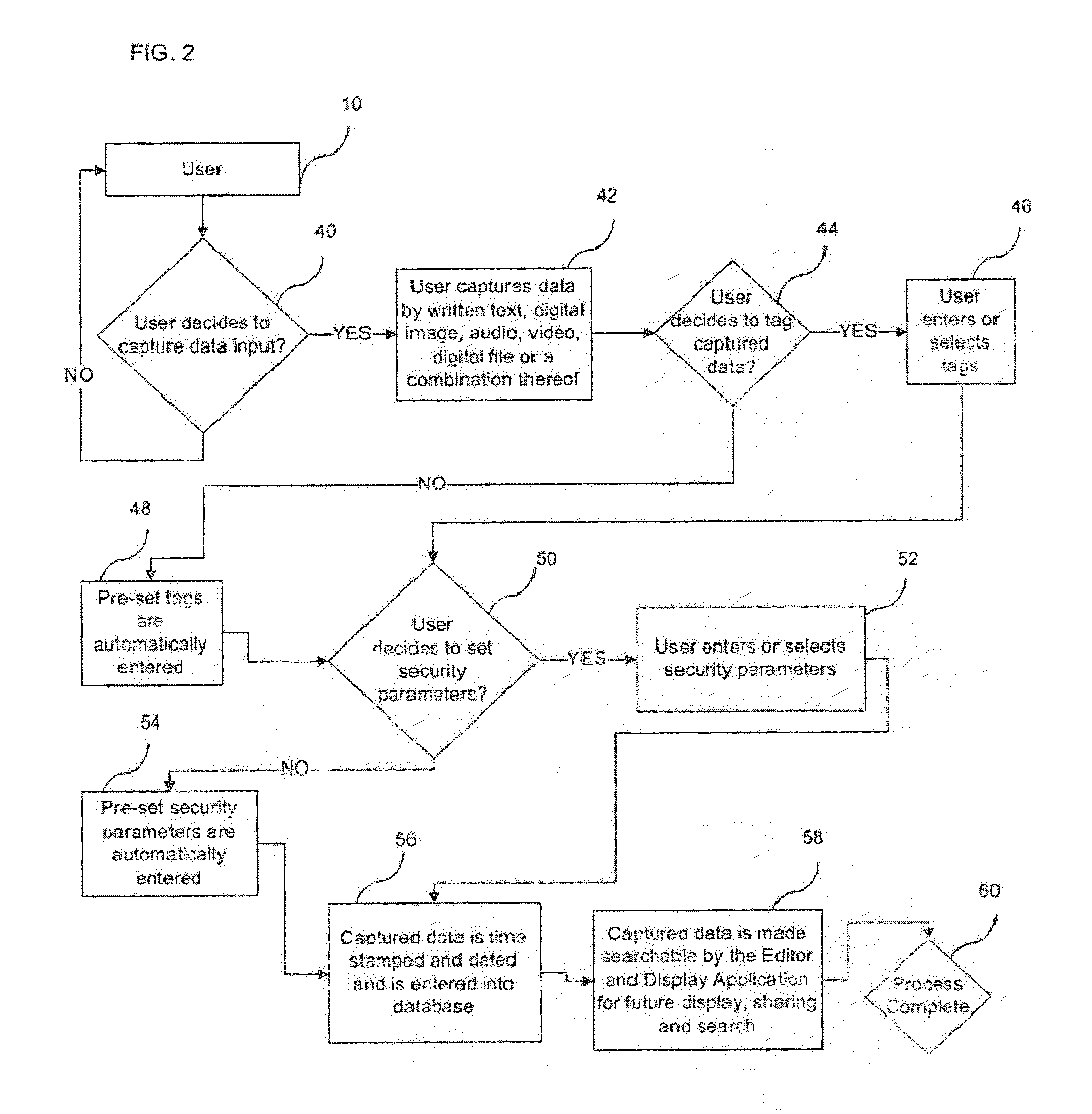
System, Method, and Apparatus for Capturing, Securing, Sharing, Retrieving, and Searching Data
InactiveUS20100333194A1Accurate authenticationImprove abilitiesDigital data processing detailsUnauthorized memory use protectionApplication softwareLabeled data
This present invention relates to a system, method and apparatus for scientists and researchers and others to capture, secure, share, retrieve and search captured data. Said system and method is able to: fully-integrate hardware and software, required to seamlessly capture data inputs; combine edit and display functions from devices into one single edit and display platform; compile captured inputs from devices into text-searchable and tag-able data that can be displayed, edited and searched on one platform; compile captured inputs from devices into text-searchable and tag-able data that can be searchable by using free-text search, advanced search modules, or a combination thereof; provide advanced search modules that can search based on embedded text in files, tags tied to images or files, parallel image search and other intelligent parameter-based search formats; and can be provided as a hosted application, available via a wire line or wireless on-demand service, also referred to as Software as a Service (SaaS) delivery method.
Owner:RICORDI CAMILLO +3
System and method for secure self registration with an insurance portal
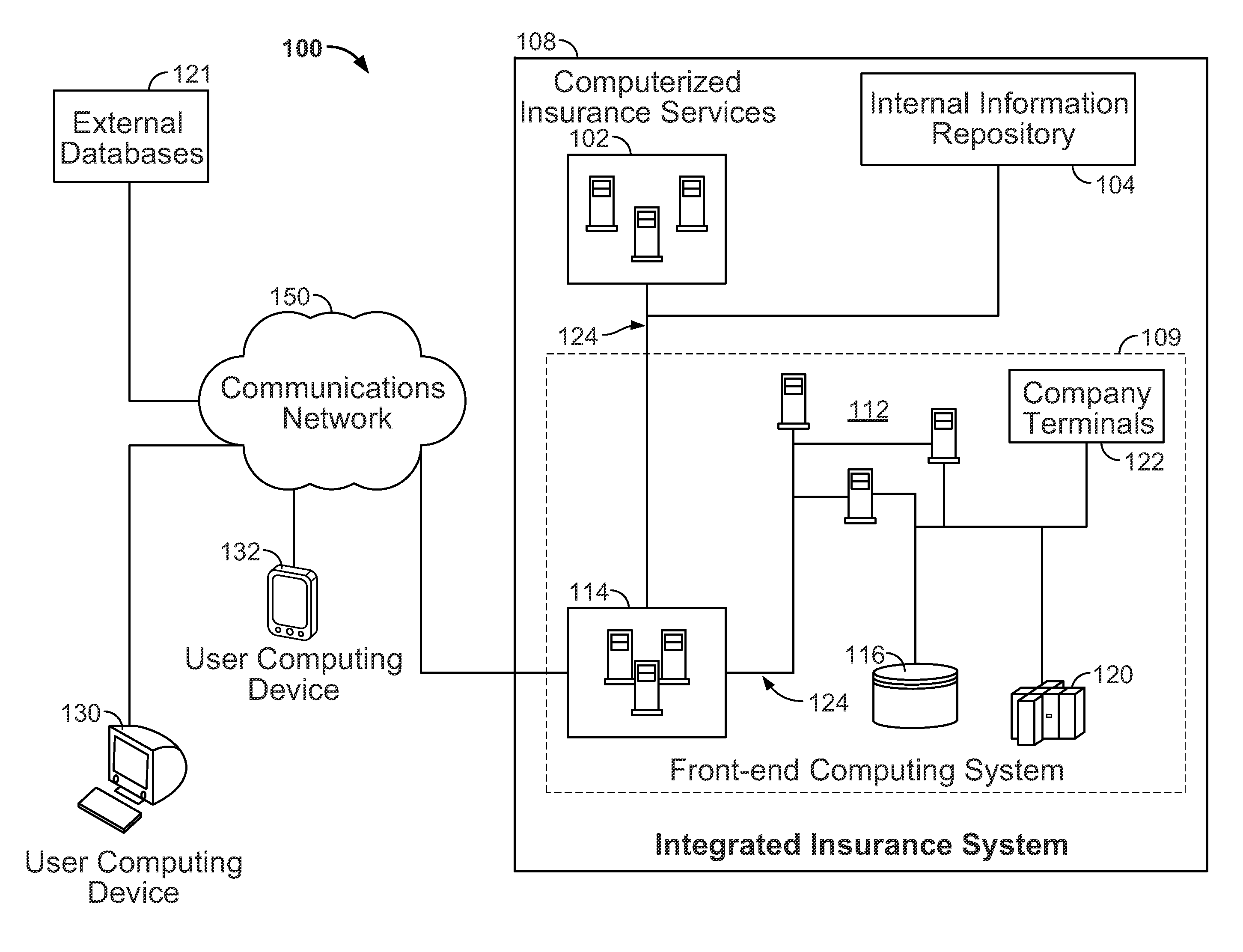
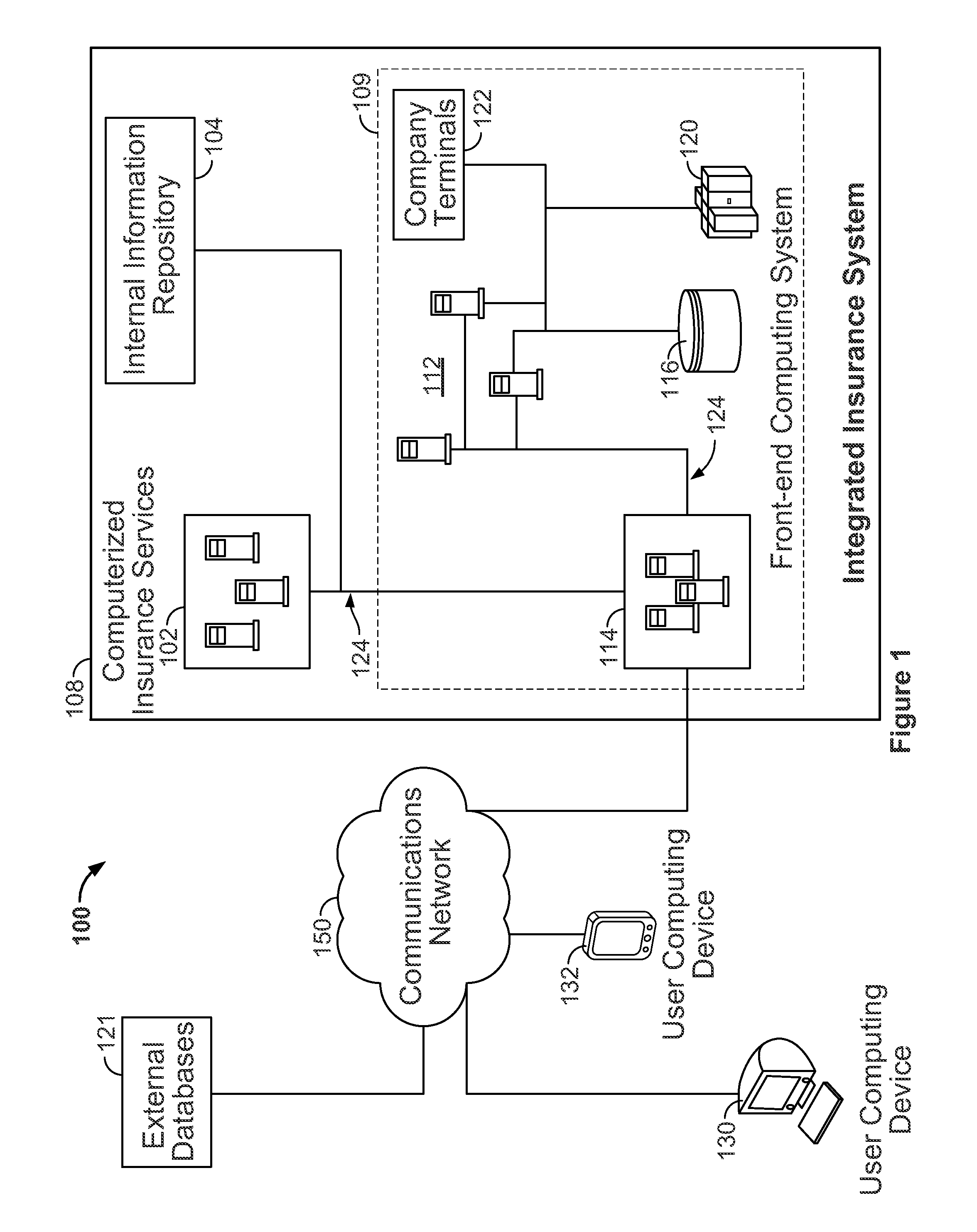
InactiveUS20130124229A1Simpler and more flexible interfaceAccurate authenticationFinanceSecurity informationInternet privacy
Systems and methods are disclosed herein for processing a first-time registration request for electronic access to a plurality of computerized insurance services. A network interface is configured to communicate with the plurality of computerized insurance services by interfacing with a plurality of disparate information platforms and communicating with a user computing device. A memory stores a portal module, a profile module, and a security module, each in the form of computer executable instructions, which, when executed by a processor, cause the system to receive a user identity, a first-time registration request of the user identity, and one or more secure information items associated with the user identity from the user computing device, determine a verification score for the user identity based on the one or more secure information items, and selectively register the user identity with a plurality of the computerized insurance services based on the verification score.
Owner:HARTFORD FIRE INSURANCE
Apparatus for customer authentication of an item
ActiveUS20130097085A1Existing technologyAccurate authenticationInternal/peripheral component protectionTransmissionClient dataClient-side
An apparatus is provided for authentication of an item or a label by storing unique random serial numbers or codes in a remote secure storage that can be used to authenticate the item or the label, generating a pointer to each stored unique random serial number / code and storing the generated pointer(s) in a client data storage. During or prior to a production run of the item(s) or label(s): the generated pointer(s) are sent from the client data storage to one or more media devices, the generated pointer(s) are obtained from the media device using a post-content manager, the unique random serial number(s) / code(s) are obtained from the server via the post-content manager using the generated pointer(s), the obtained unique random serial number(s) / code(s) are sent to the media device, and the received unique random serial number(s) / code(s) are imprinted on the item(s) or the label(s) using the media device.
Owner:KLOKE LLC
User authentication system and room entry/exit management system
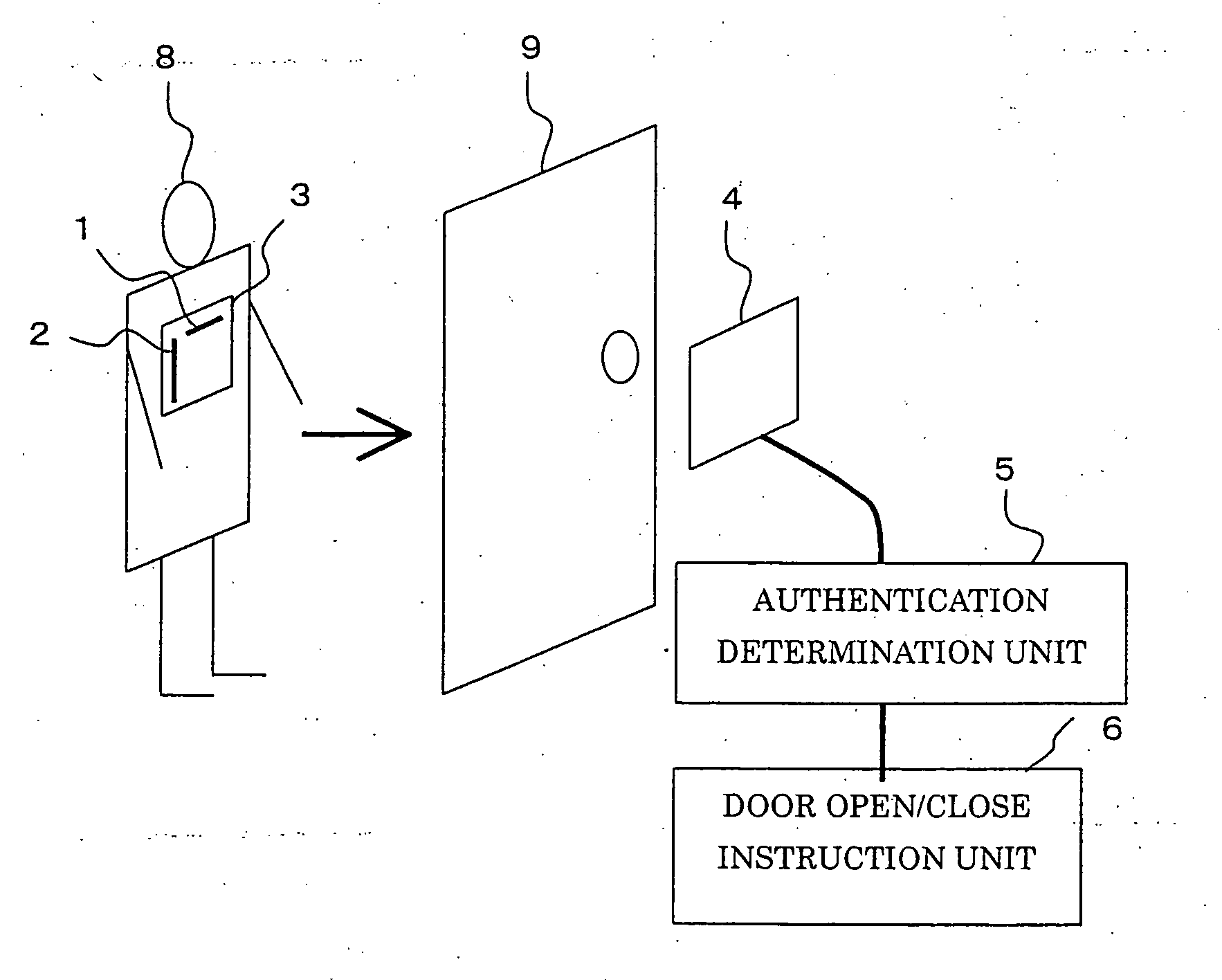
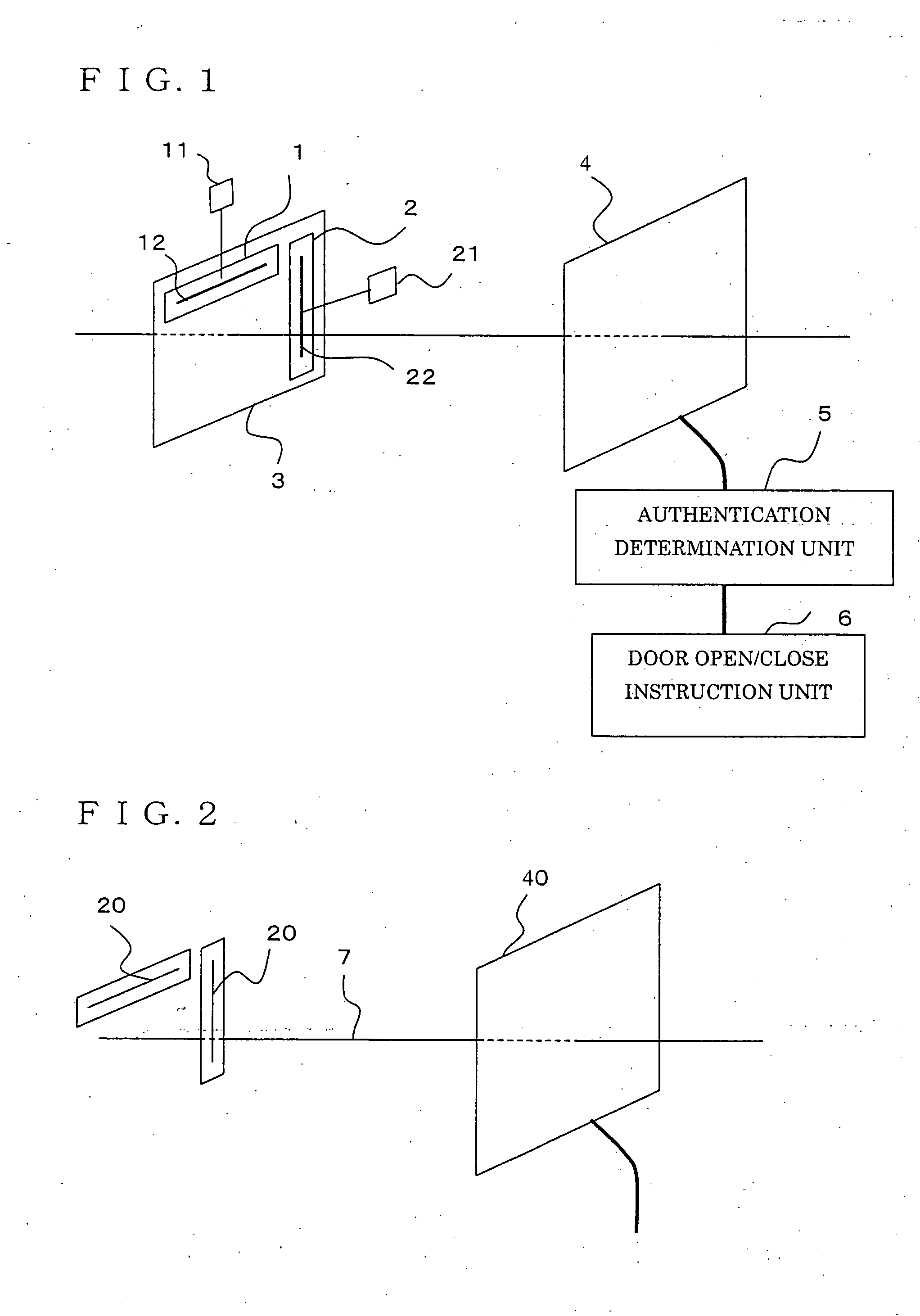
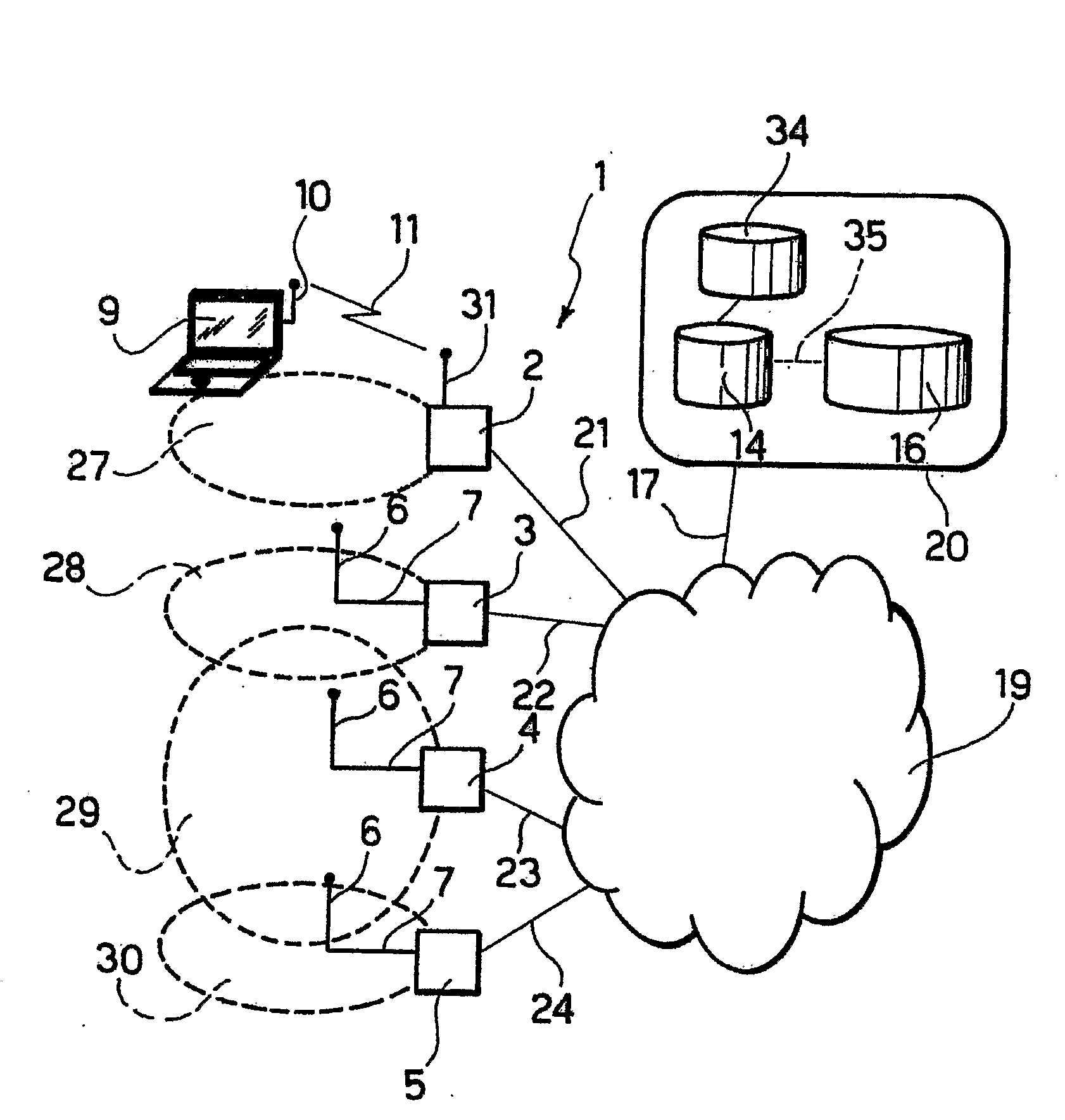
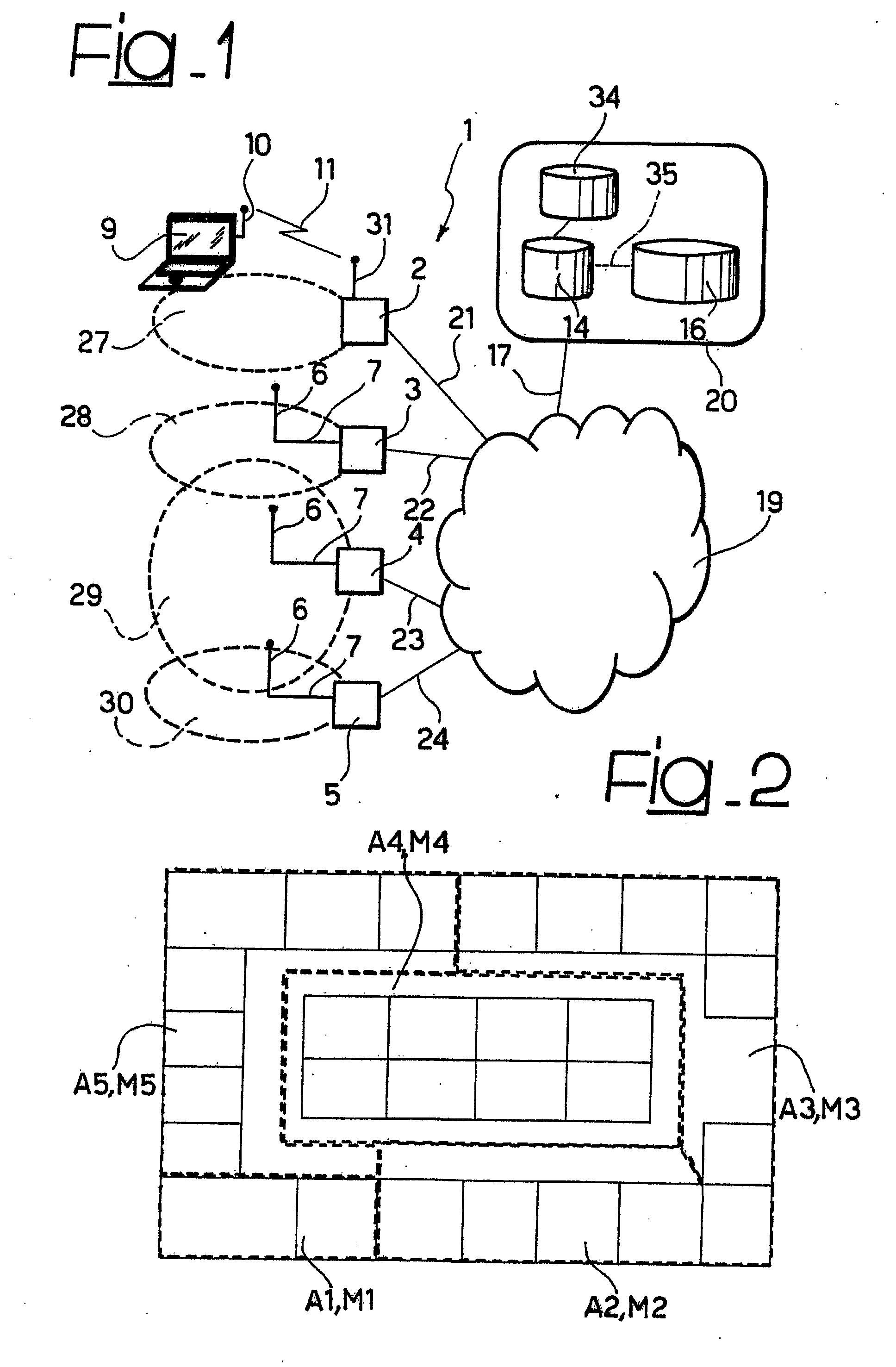
InactiveUS20060119469A1User authenticationEnsure correct executionElectric signal transmission systemsDigital data processing detailsUser authenticationComputer science
A user authentication system of the present invention includes: a first wireless tag having first ID data about a user and a first antenna for transmitting the first ID data; a second wireless tag having second ID data different from the first ID data, and a second antenna, perpendicular to the first antenna, for transmitting the second ID data; a wireless-tag receiver for receiving the first ID data transmitted from the first antenna and the second ID data transmitted from the second antenna; and a use-permission determining apparatus for determining whether the ID data received by the receiver matches pre-registered ID data, and for determining, based on timing of or counts of receptions of the first ID data and the second ID data received during a predetermined period of time, whether use is permitted.
Owner:MITSUBISHI ELECTRIC CORP
System and Method for Authenticating an Element in a Network Environment
ActiveUS20080081592A1Eliminate and greatly reduce disadvantageEliminate and greatly reduce and problemError preventionFrequency-division multiplex detailsNetwork Communication ProtocolsAuthentication
A method for authenticating an element in a network environment is provided that includes receiving a request for one or more triplets. One or more of the triplets may be associated with an authentication communications protocol that may be executed in order to facilitate a communication session. The method further includes returning one or more of the triplets in response to the request and initiating the communication session in response to the triplets after proper authentication of an entity associated with the request.
Owner:CISCO TECH INC
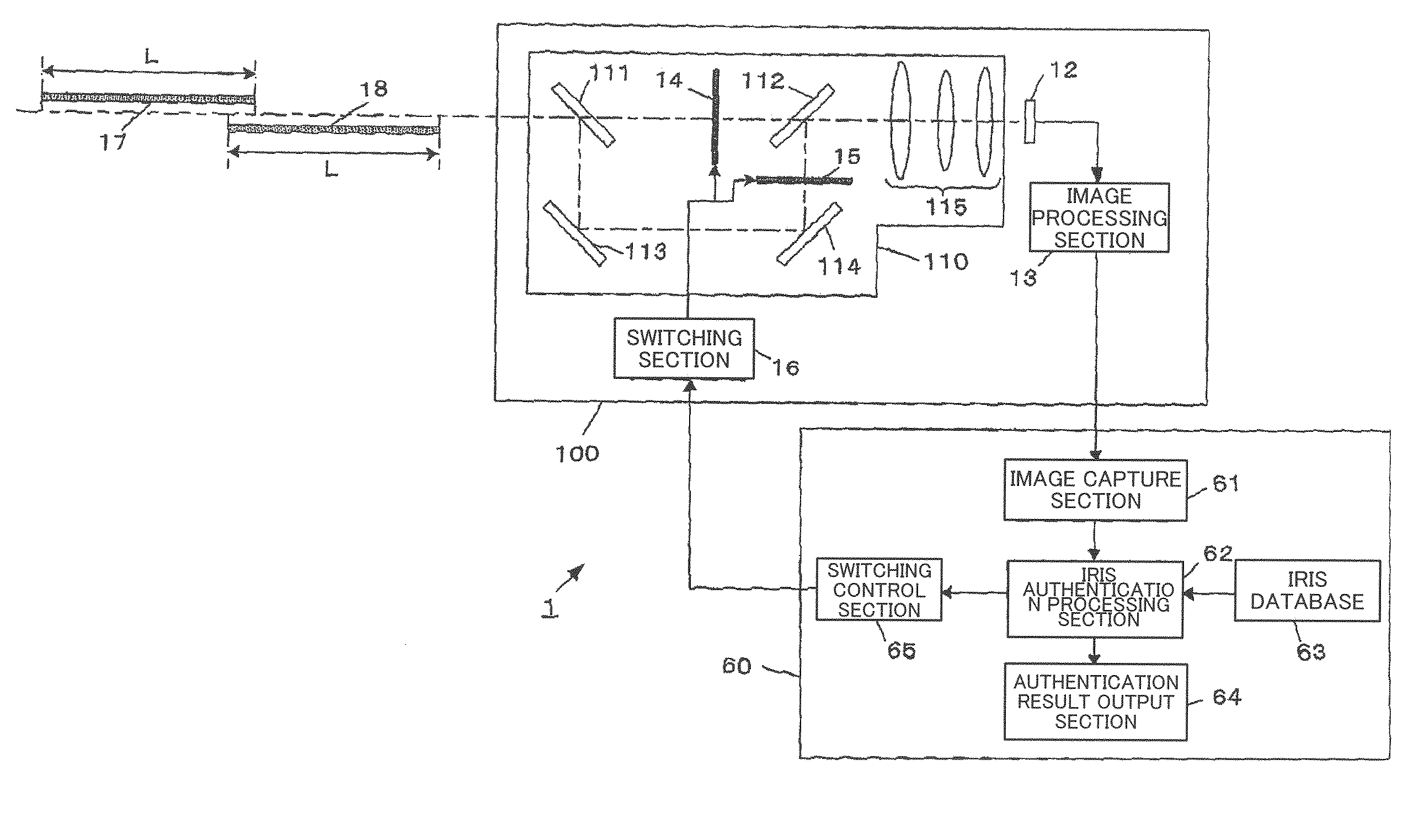
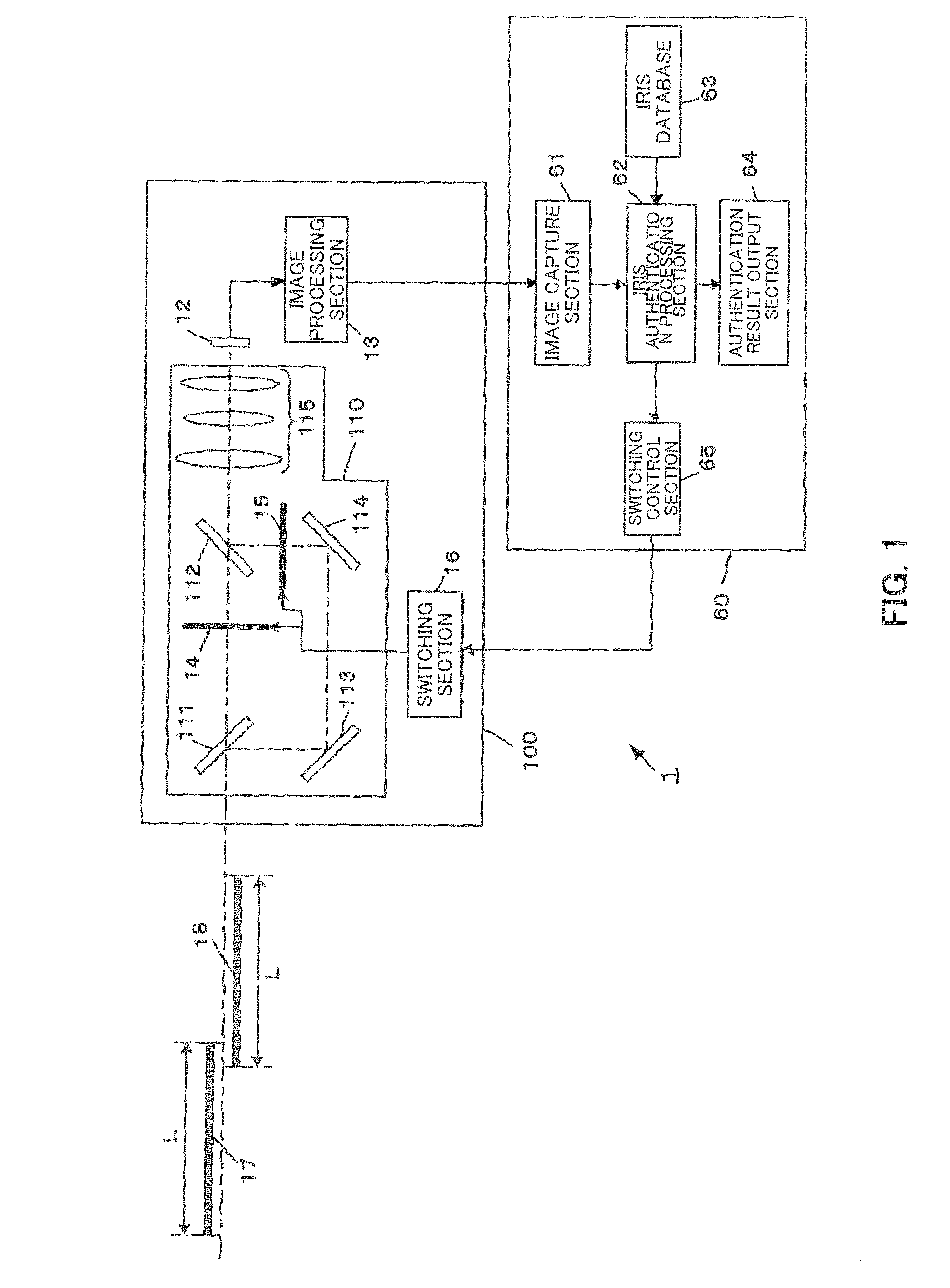
Iris image pickup camera and iris authentication system
InactiveUS20070160265A1Simple configurationEasy accessAcquiring/recognising eyesEye diagnosticsPhysicsAuthentication system
An imaging optical system 110 of an iris image pickup camera 100 has a common light axis in a region where an iris as an object is situated, and has first and second branch light axes branched from the common light axes. The imaging optical system 110 further has focusing ranges displaced from each other on the common axis for each of first and second branch light paths which passes through each of the first and second branch light axes. An imaging element 12 and an image processing section 13 generate image data of an iris image formed through the first and second branch light paths. Thus, an iris image pickup camera can be provided, which can promptly take an iris image for iris authentication in a simple configuration and without bothering a person to be authenticated.
Owner:PANASONIC CORP
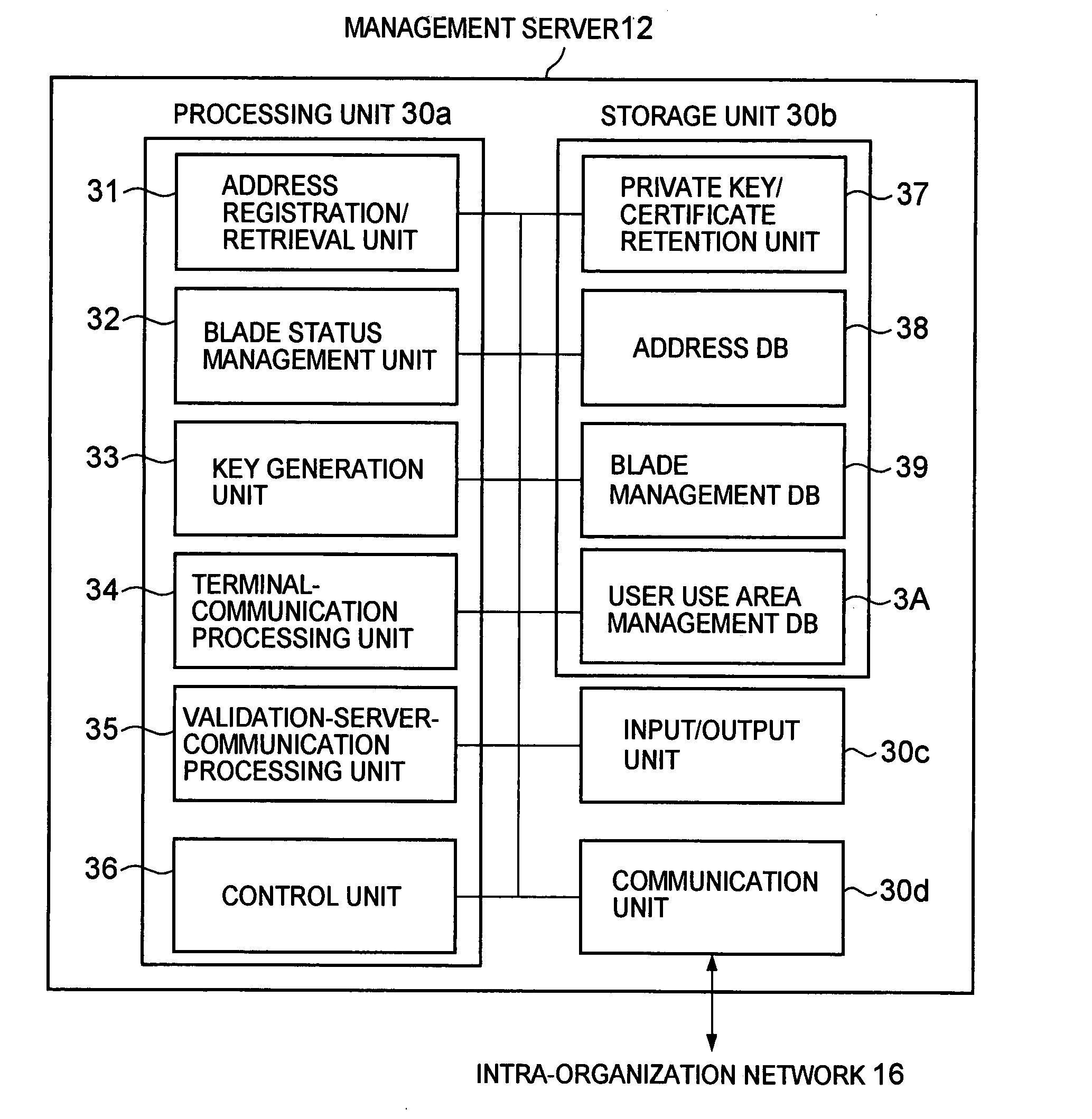
Method for encrypted communication with a computer system and system therefor
InactiveUS20080098221A1Accurate authenticationReduce loadUser identity/authority verificationMultiple digital computer combinationsEnd-to-end encryptionComputer hardware
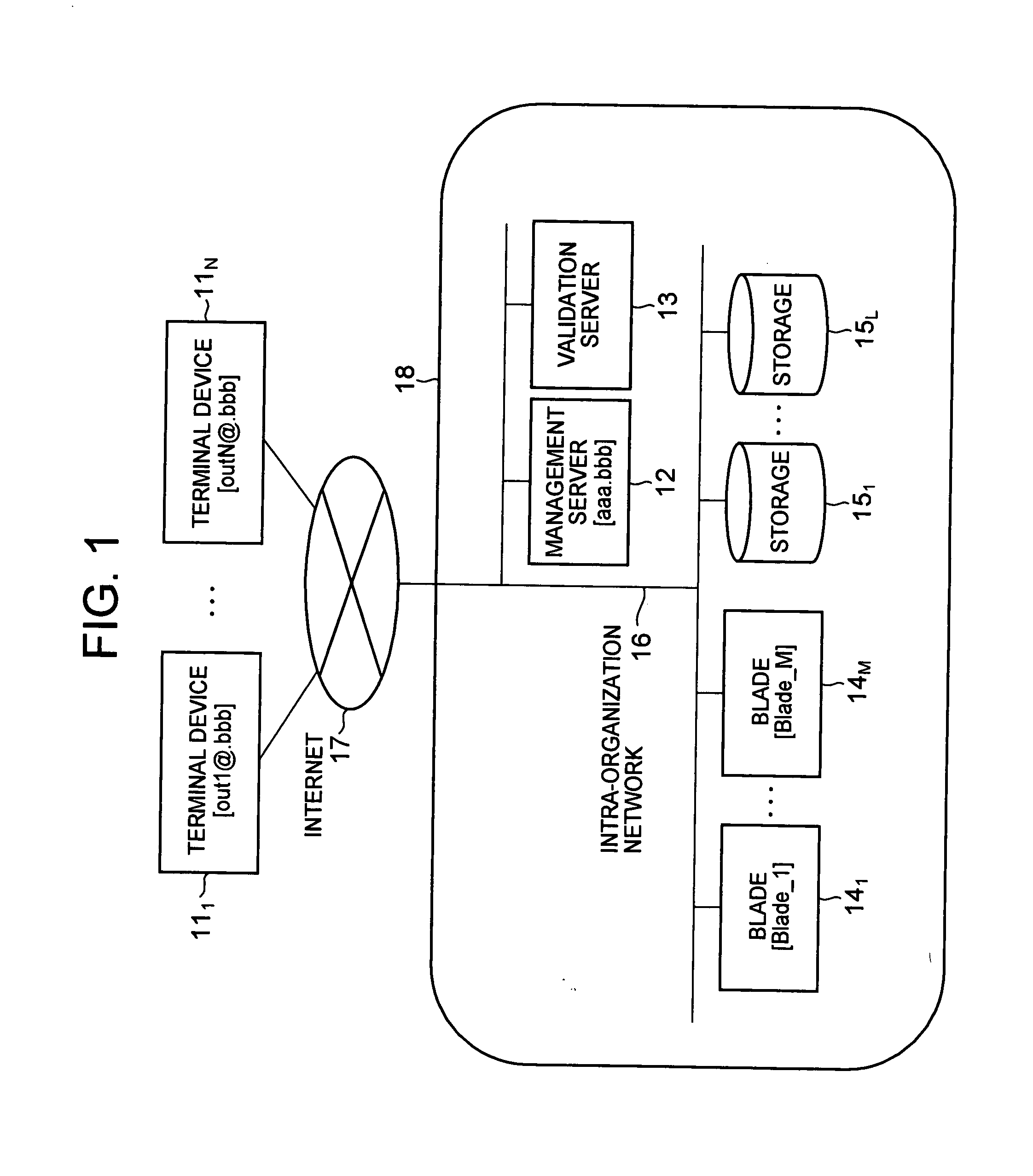
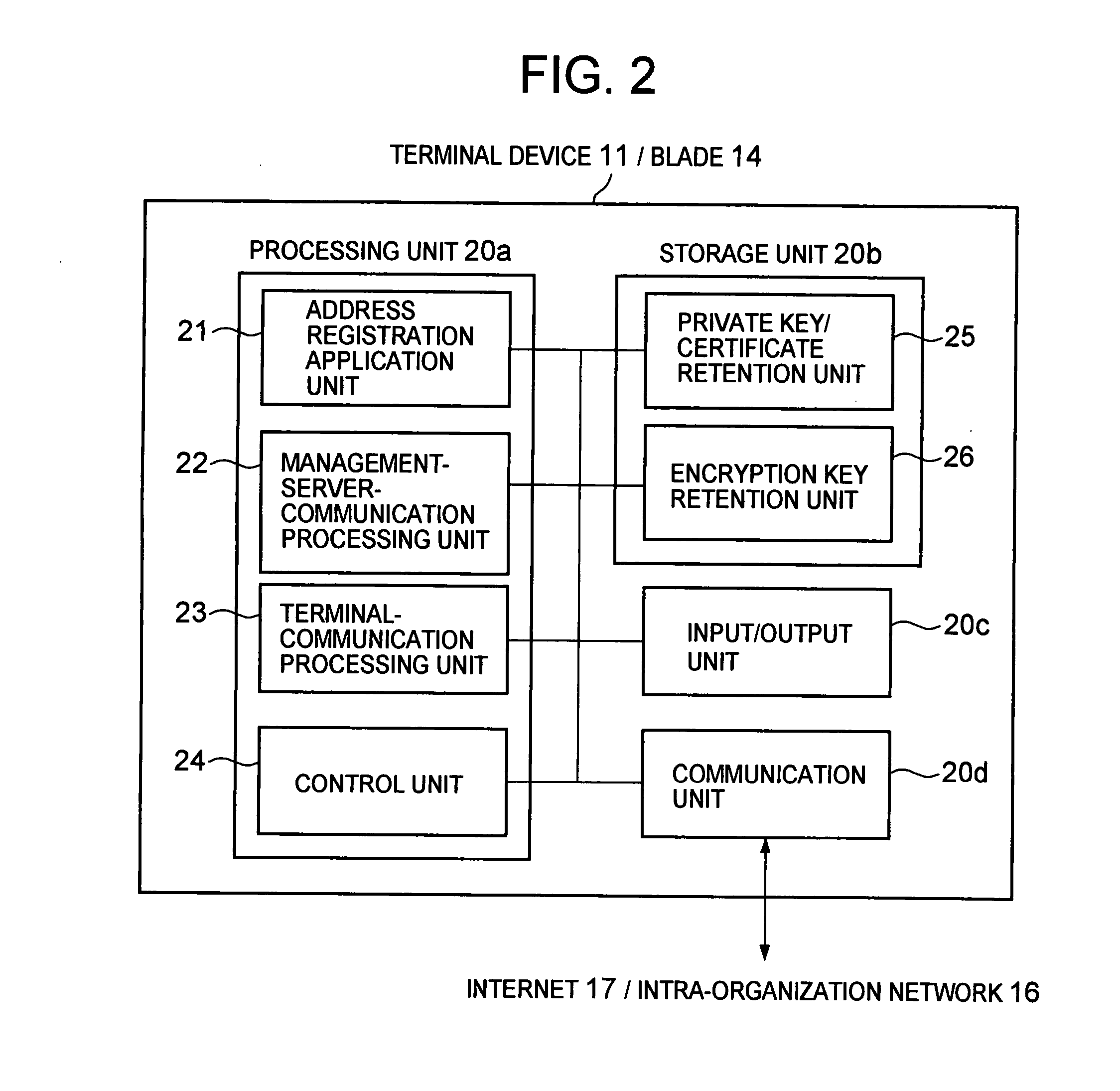
To solve problems in that a load on a VPN device is large in a case where the number of terminal devices increases in encrypted communication using a VPN technique, and that only communication between the terminal device and the VPN device is encrypted, thus disabling end-to-end encrypted communication, a communication system is provided, including: a terminal device; a plurality of blades; and a management server that manages the blades, in which: the management server selects a blade, authenticates the terminal device and the selected blade, and mediates encrypted communication path establishment between the terminal device and the selected blade; the terminal device and the blade perform encrypted communication without the mediation of the management server; and the management server requests a validation server to authenticate each terminal.
Owner:HITACHI LTD
Smart identification terminal system and method based radio-frequency identification and biological characteristic
InactiveCN1979518AAccurate authenticationShorten the timeUser identity/authority verificationCharacter and pattern recognitionOperating instructionData acquisition
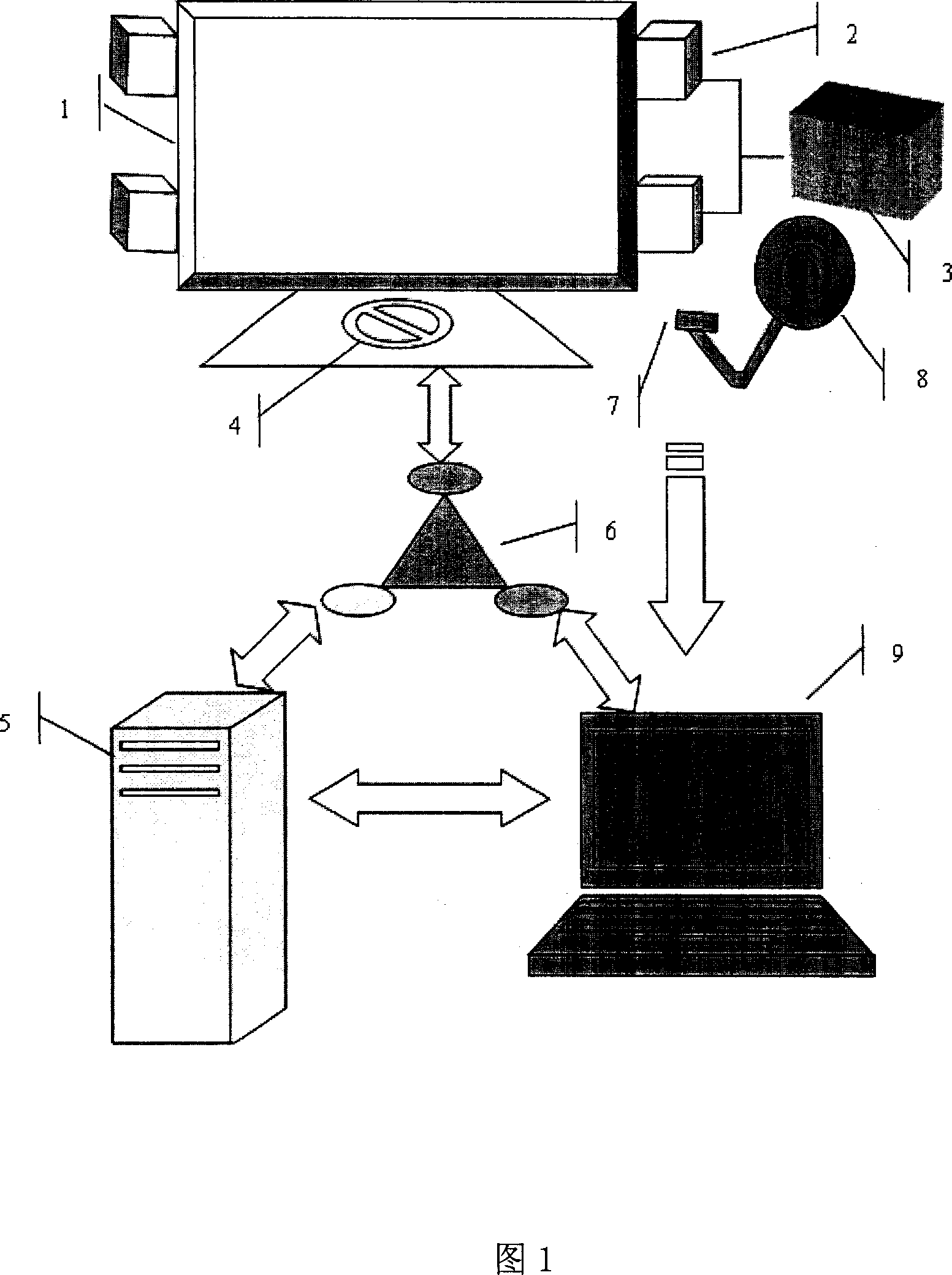
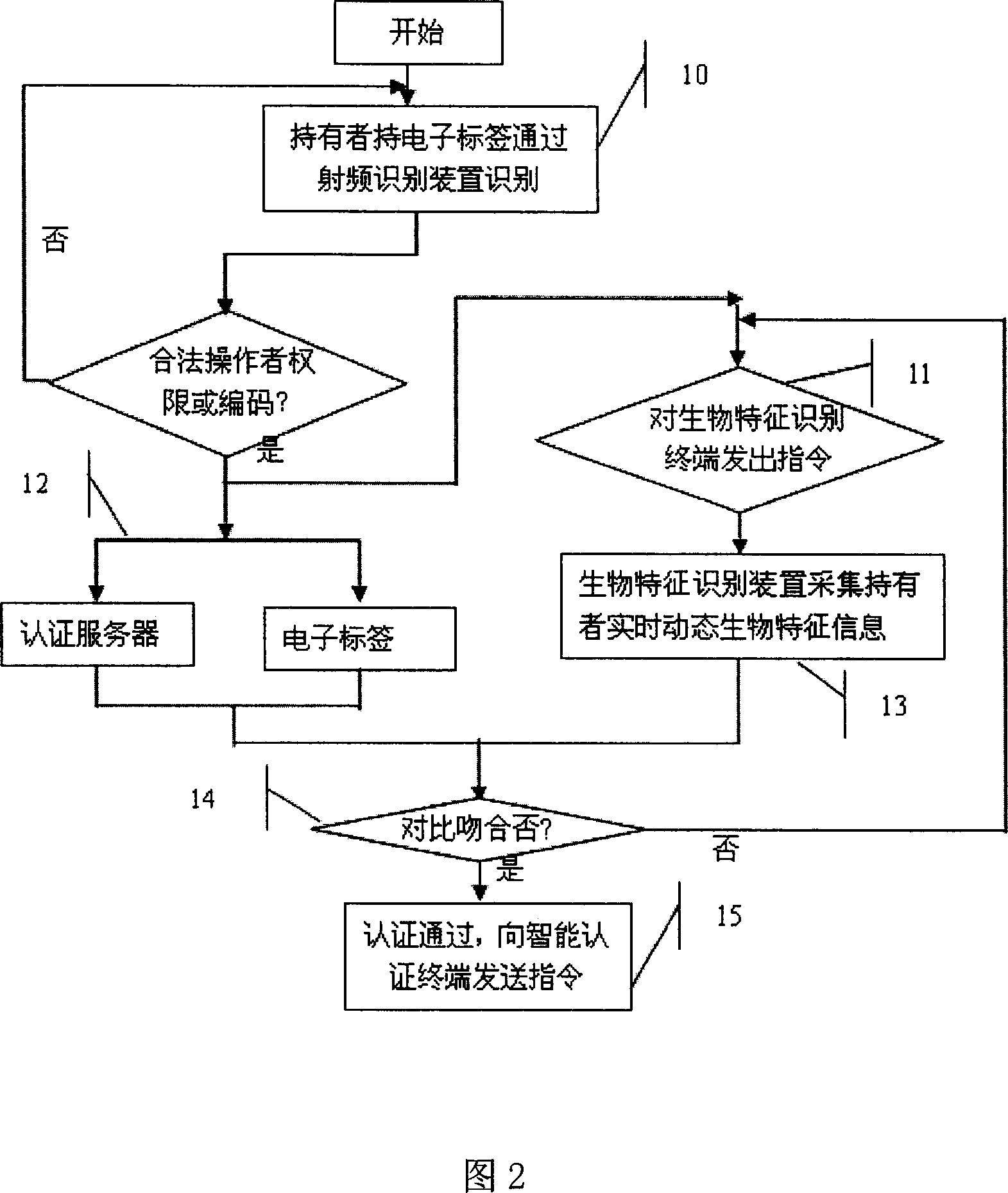
The invention belongs to information electronic field, integrating RFID technique with bio-character recognition technique to implement two authentication mode-complementary intelligent authentication terminal systems and besides, implementing reliable instruction executing operation by the RFID technique and bio-character recognition technique. When an operator holding an electronic tag with right information sends operating instructions to intelligent terminal, a RFID system finds out the right information and bio-character information corresponding to the electronic tag, and makes bio-character recognition on the operator by bio-character recognition data collector, and executes the instruction the operator sends after authentication passes. Thus, the operators with different rights can execute different operations in different read regions by electronic tag, and the authentication course and operation are united in a terminal.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Image processing apparatus, image processing method, program, and recording medium
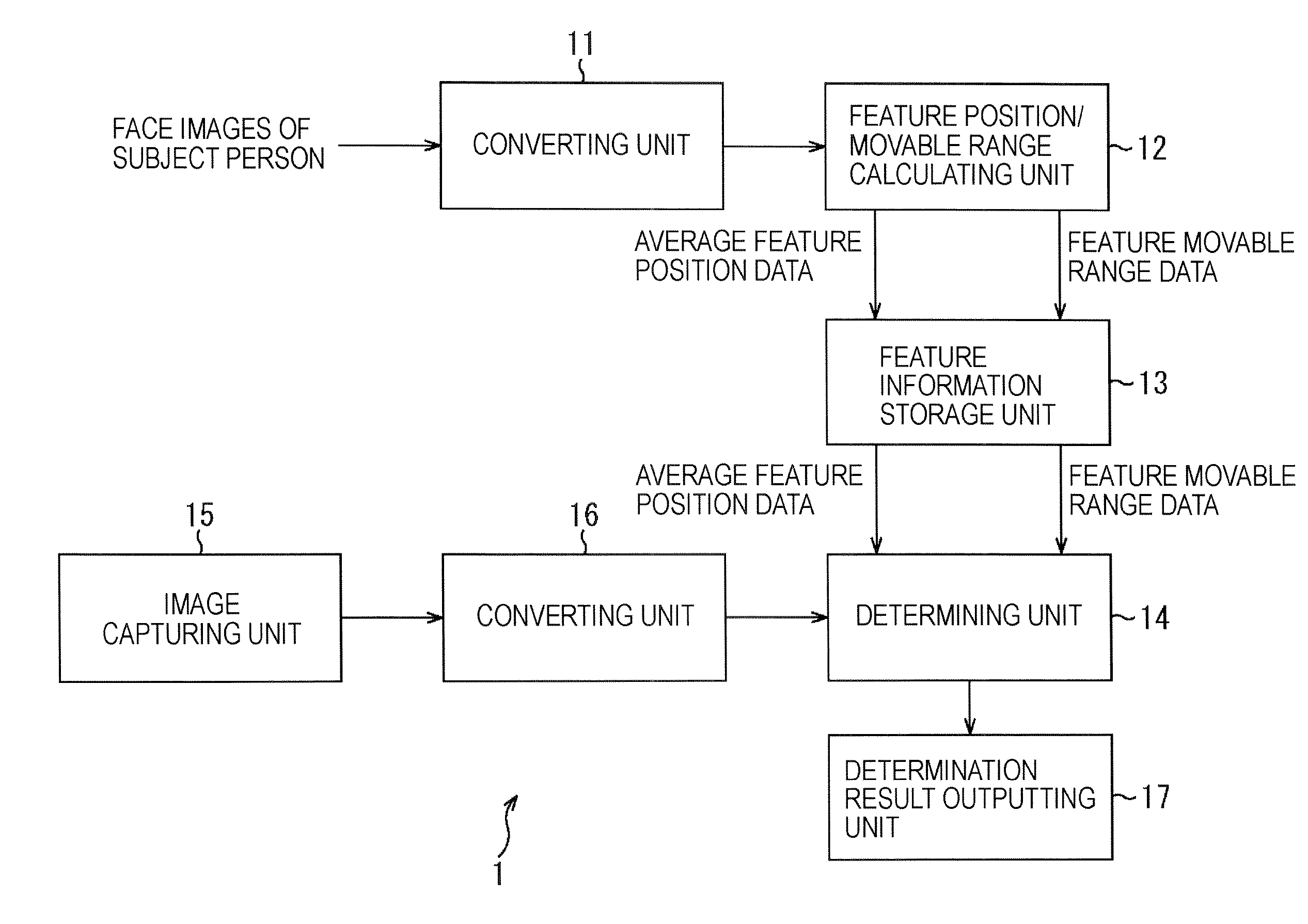
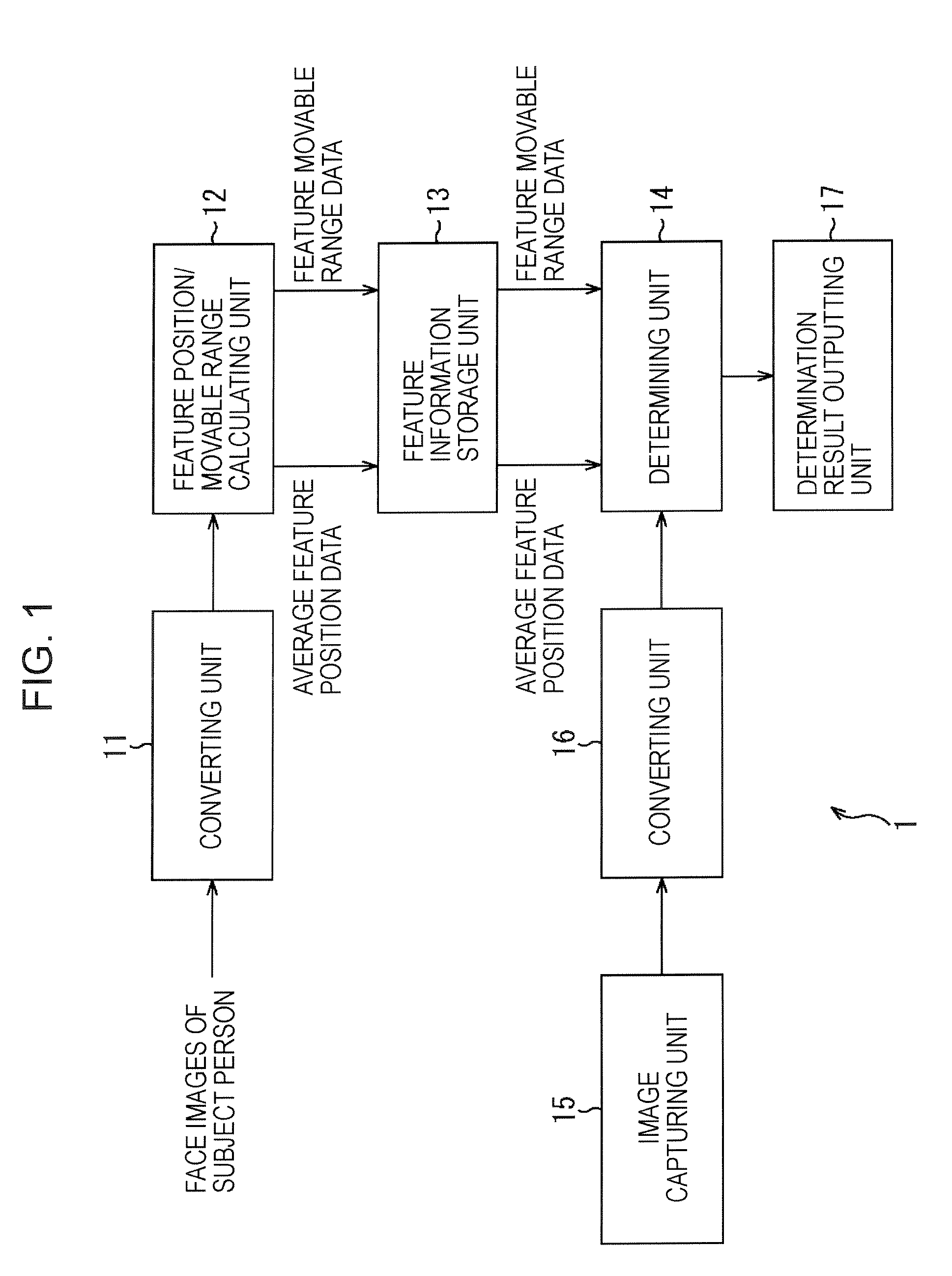
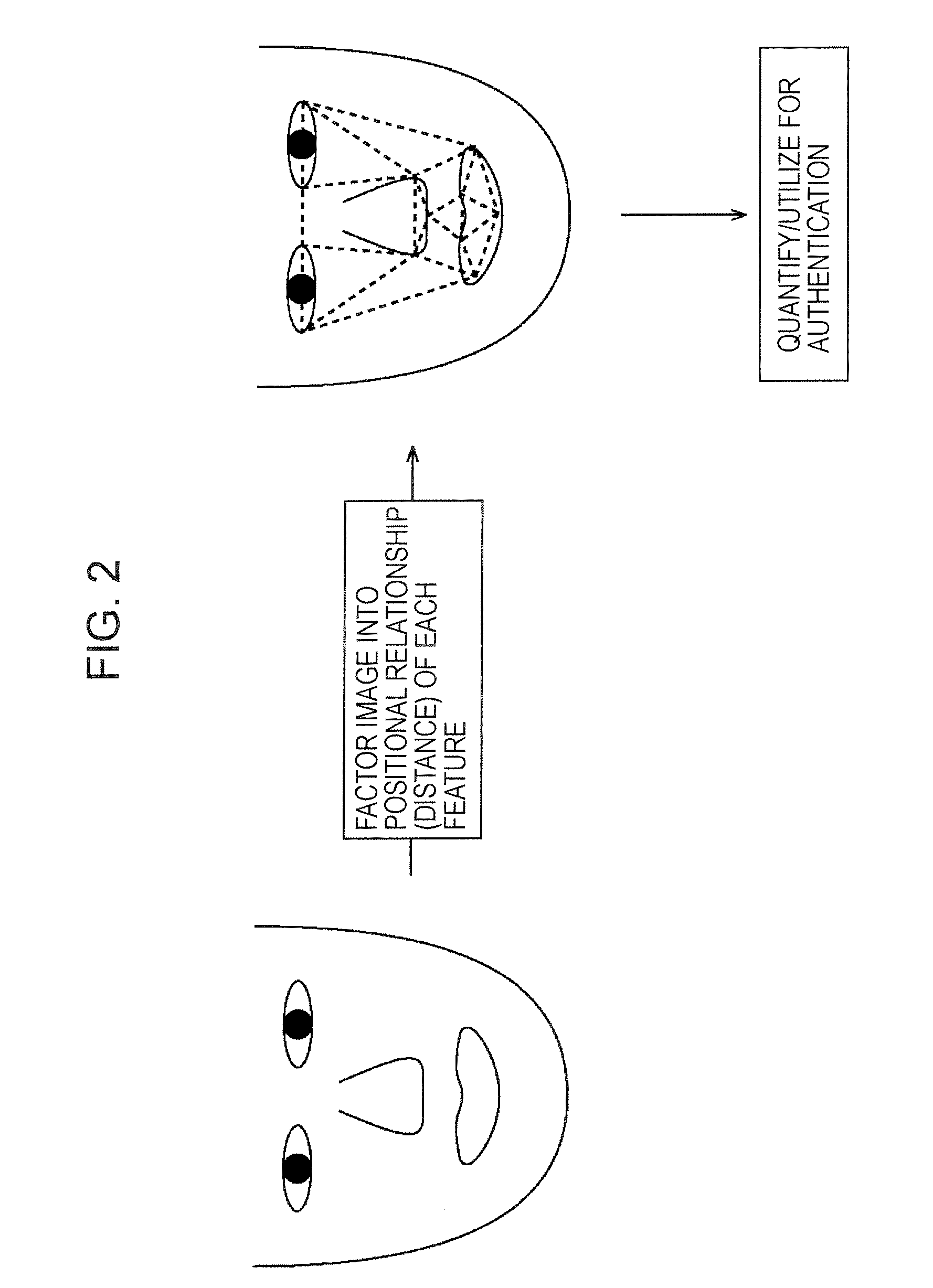
InactiveUS20070127785A1Increase possibilityRaise the possibilityAcquiring/recognising facial featuresImaging processingPrincipal component analysis
An image processing apparatus includes a detecting unit for detecting a position of a facial feature in a face image, a principal component analysis performing unit for performing principal component analysis on the position of the facial feature in a registered image that is a pre-registered face image, a first evaluation value calculating unit for calculating a first evaluation value that is used to evaluate the position of the facial feature in a target image relative to the principal component obtained in the principal component analysis operation, and a first determining unit for determining whether or not the face in the target image matches the face in the registered image by comparing the calculated first evaluation value with a first threshold set based on the position of the facial feature in the registered image relative to the principal component.
Owner:SONY CORP
Dynamic multimedia pairing
ActiveUS20150135049A1Accurate authenticationWider exposureElectronic editing digitised analogue information signalsCarrier indexing/addressing/timing/synchronisingUser definedMultimedia
The present invention generally relates to systems and methods for producing mixed media. Specifically, embodiments of the present invention are configured to provide users the ability to play one or more multimedia files and mix the files in real time (live) according to user manipulation of system controls and or manipulation of user defined presets, thus producing a mixed media mashup. Further embodiments of the present invention are configured to allow users to record, save, replay, and share the mixed media mashup.
Owner:MURPHY TIMOTHY MICHEAL
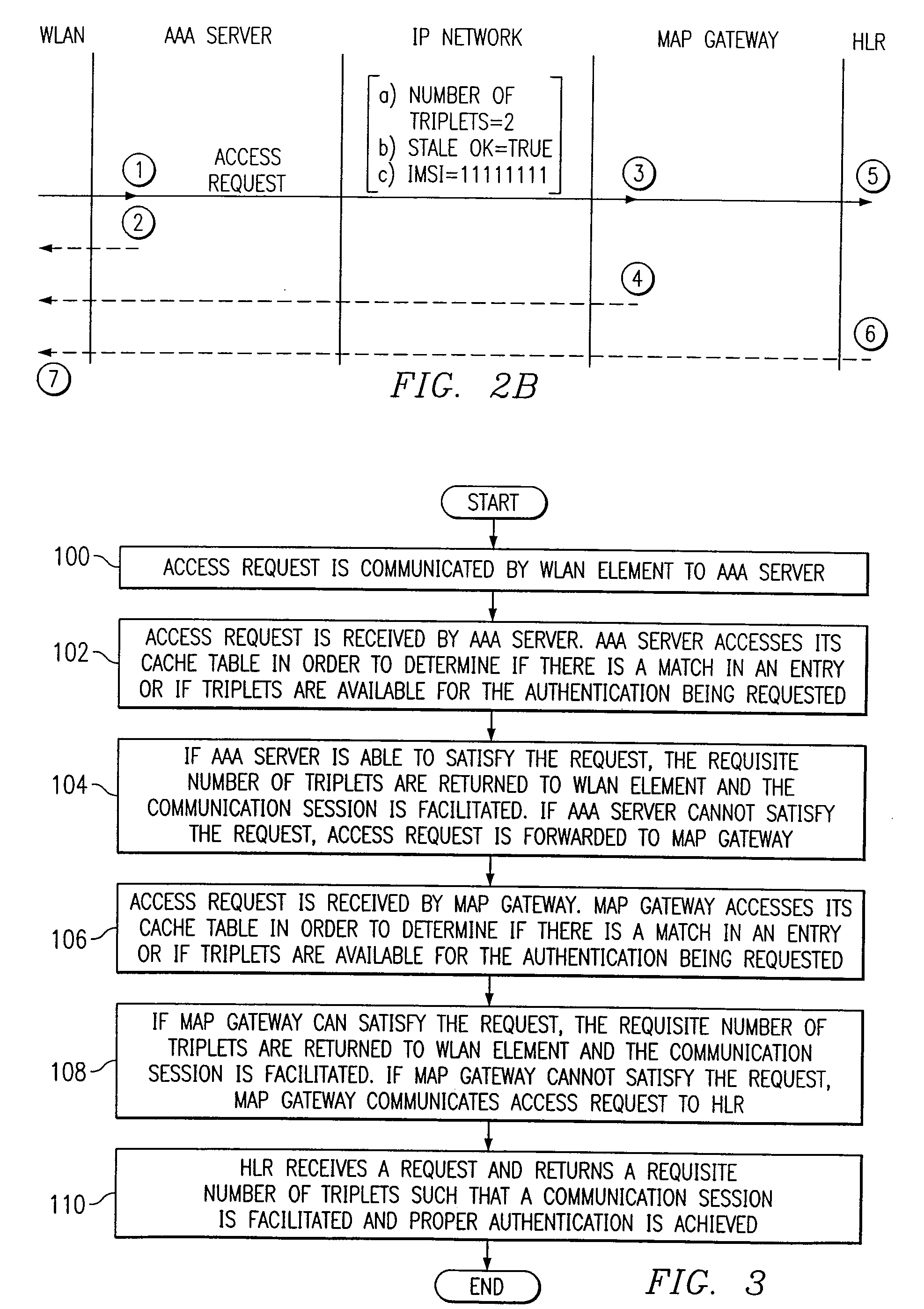
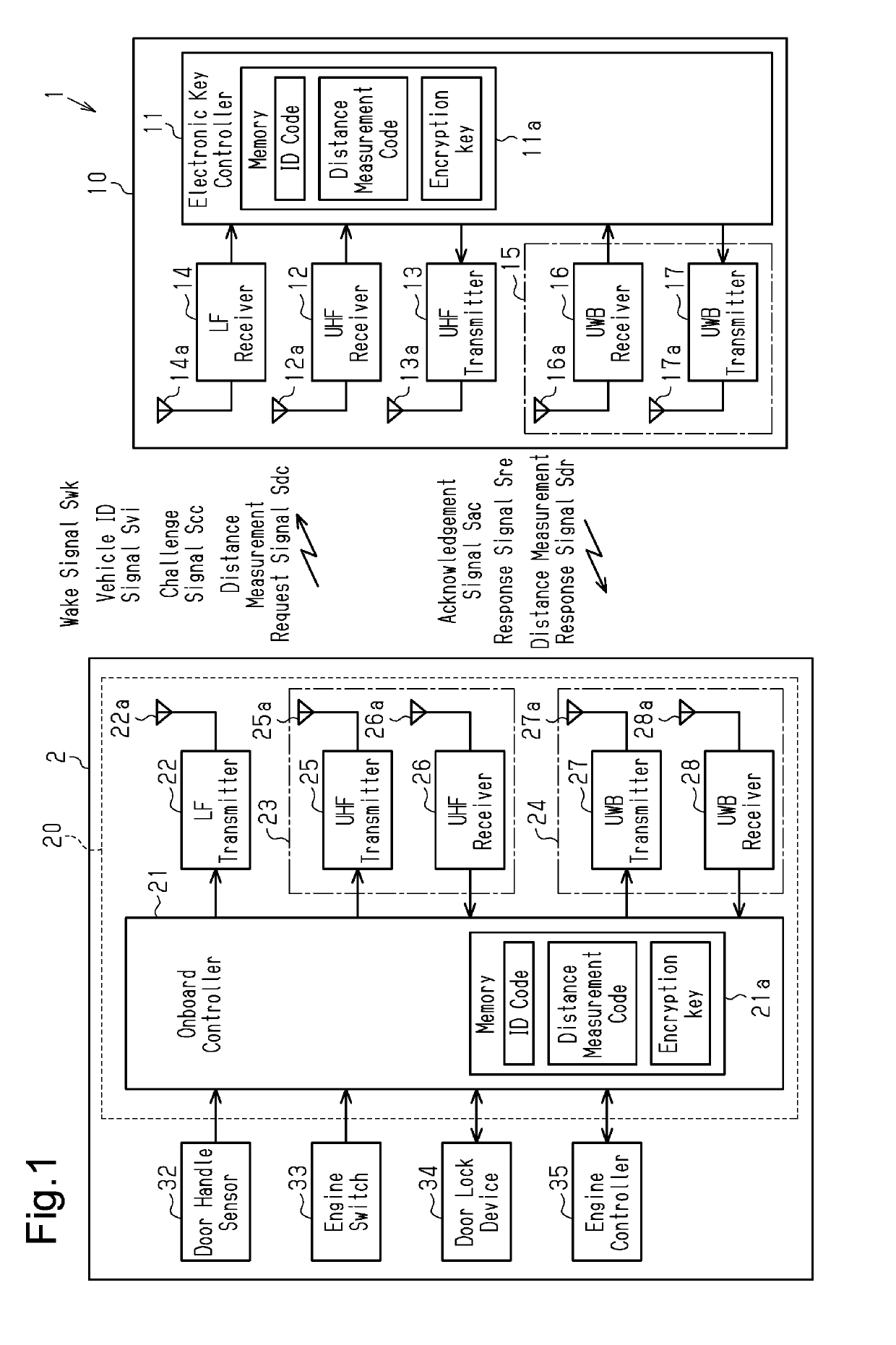
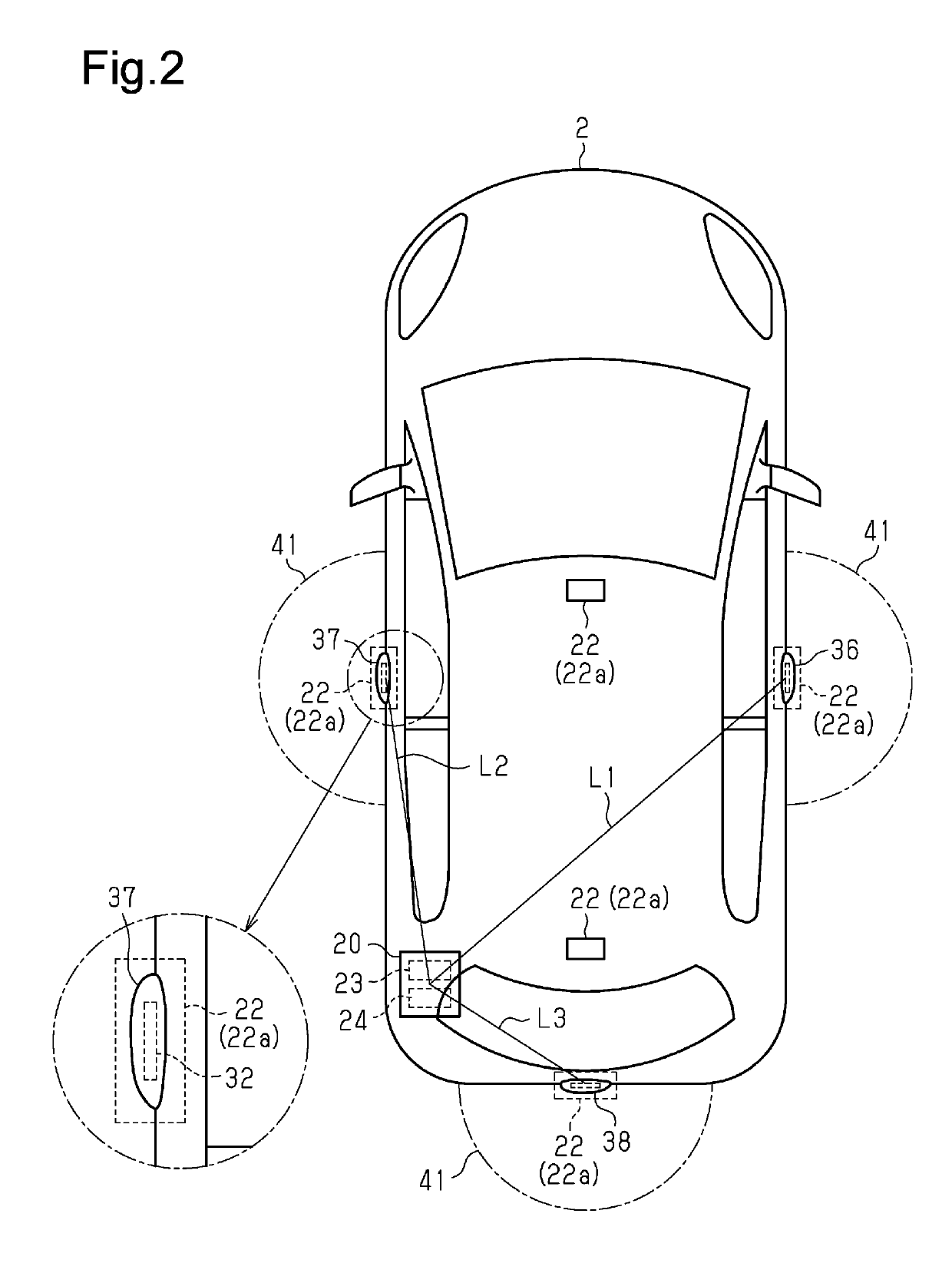
Electronic key system
ActiveUS20190256047A1Avoid communicationAccurate measurementTelemetry/telecontrol selection arrangementsAnti-theft devicesOn boardLocation determination
An electronic key system determines that legitimate communication has been performed on the basis of conditions including that a measured distance from a ranging request unit to a ranging response unit measured on the basis of a ranging request signal and a ranging response signal is within a threshold range that is set on the basis of the distance from a communication area of a transmission antenna where an electronic key is determined to be located by a key location determination unit to one of either the ranging request unit or the ranging response unit that is provided in an on-board device.
Owner:KK TOKAI RIKA DENKI SEISAKUSHO
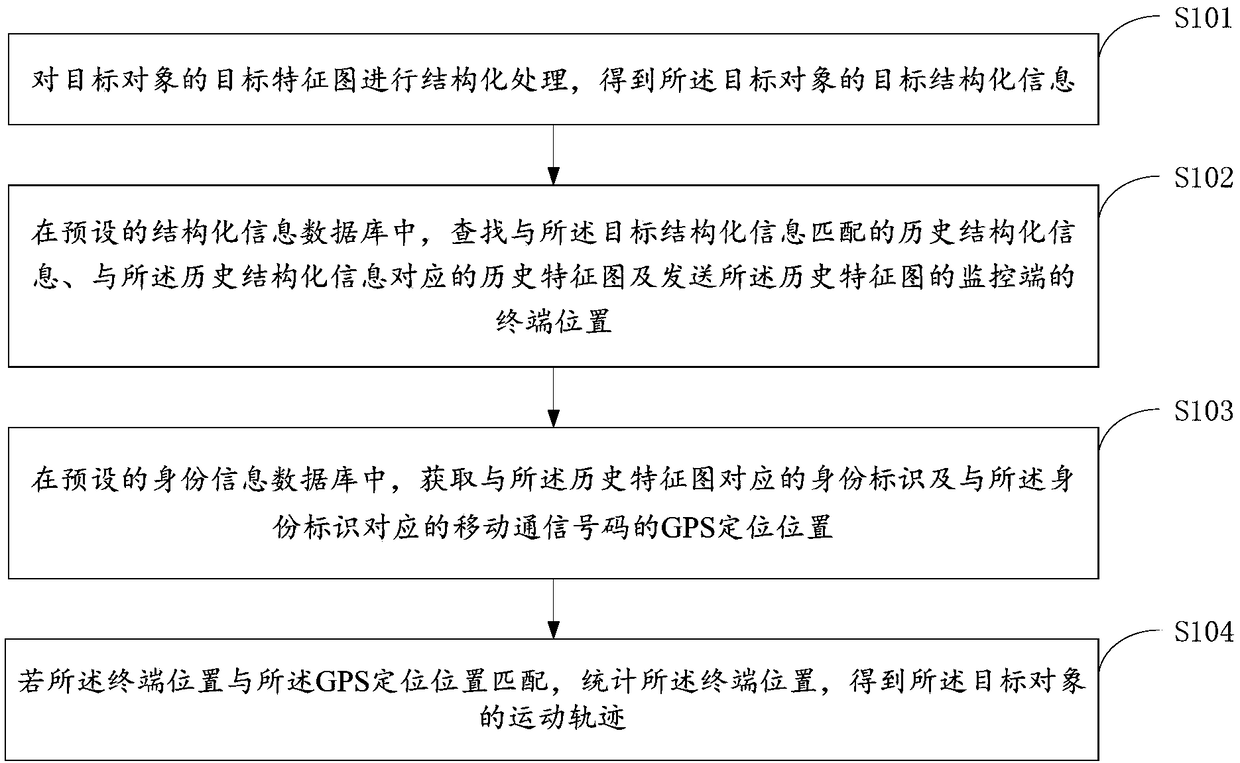
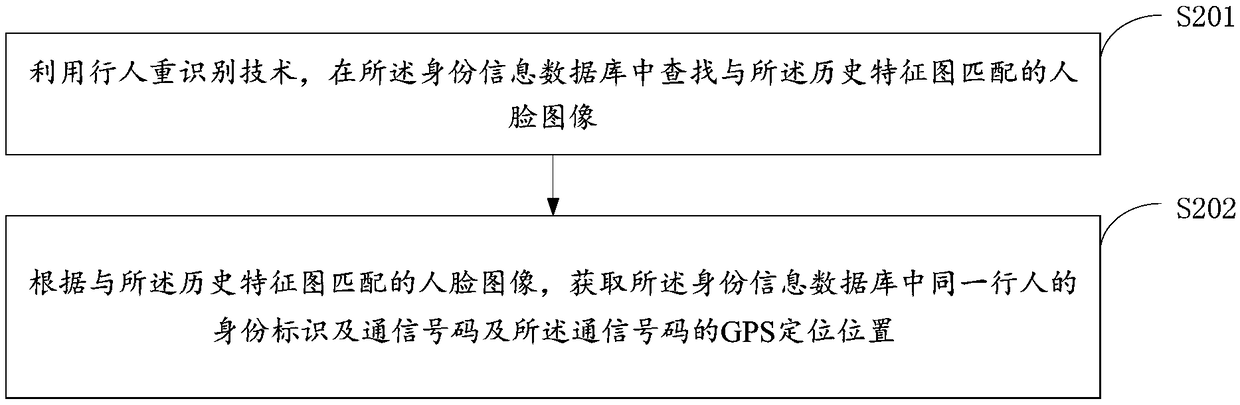
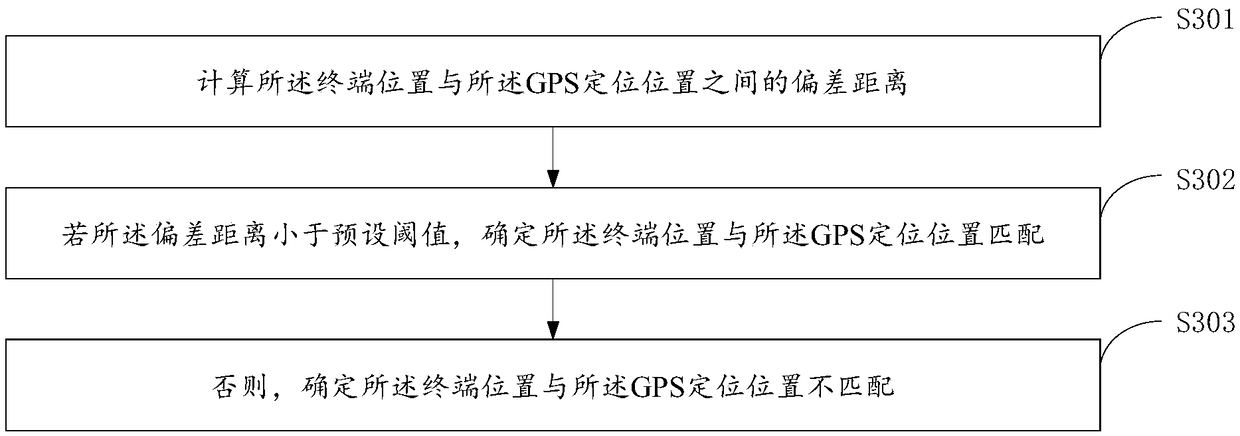
A method and apparatus for trajectory tracking of an object
InactiveCN109102531AEasy to viewAccurate authenticationImage enhancementImage analysisVideo monitoringComputer graphics (images)
The invention provides a target track tracking method and a device, which relate to the technical field of intelligent video surveillance. The target track tracking method comprises the following steps: carrying out structured processing on the target characteristic map of the target object to obtain the target structured information of the target object; in the preset structured information database, history structured information matching the target structured information, history characteristic map corresponding to the history structured information and the terminal position of the monitoring end for sending the history characteristic map are searched; in a preset identity information database, acquiring an identity mark corresponding to a history characteristic map and a GPS positioning position of a mobile communication number corresponding to the identity mark; if the position of the terminal matches the position of the GPS positioning, the movement trajectory of the target object can be obtained by counting the position of the terminal, which achieves the technical effect of determining the identity authentication and trajectory tracking accurately through the mass surveillance video.
Owner:BEIJING SEEMMO TECH CO LTD
Method and System for Managing Authentication of a Mobile Terminal in a Communications Network, Corresponding Network and Computer-Program Product
ActiveUS20090217357A1Ensure safetyAvoid enteringDigital data processing detailsAssess restrictionComputer networkAuthentication server
A terminal is authenticated in view of inclusion in a communication network by an authentication process conditioned upon location information transmitted from the terminal to at least one server in the network. At least one access point for the terminal to the network is configured for allowing a non-authenticated terminal to transmit to an authentication server in the network authentication messages based on a given authentication protocol, such as, e.g., EAP. The terminal is configured for transmitting the location information to the authentication server by conveying it over the authentication protocol. A location system can be integrated in the terminal to generate location information identifying the location of the terminal, and in that case the terminal is configured for transmitting the location information identifying the location of the terminal to authentication server. As an alternative, a location server is associated with the network and the location information is transmitted from the terminal to the location server. On the basis of the location information transmitted from the terminal, the location server generates location information identifying the location of the terminal and sends the information to the authentication server.
Owner:TELECOM ITALIA SPA
Multi-model biological recognition general platform and multi-model biological recognition identity authentication method
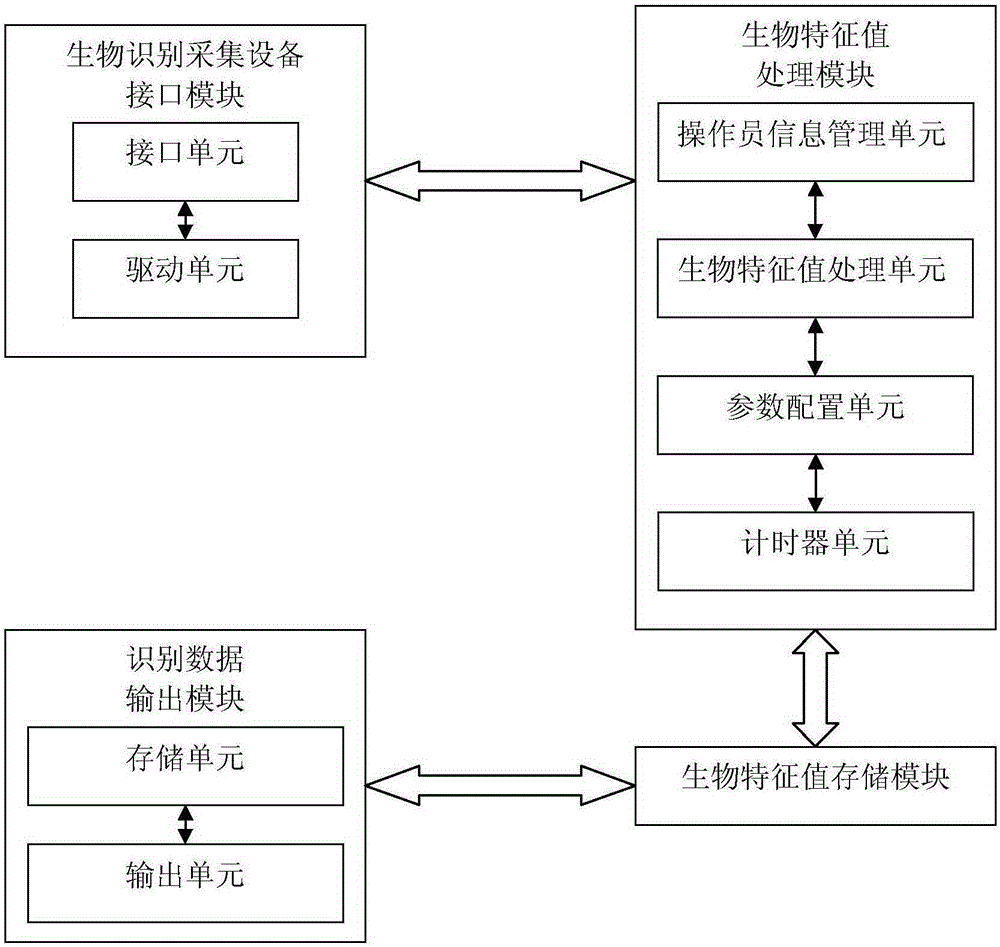
ActiveCN105160302AOvercome the shortcomings of limited applicationOvercome lossAcquiring/recognising eyesDigital data authenticationPattern recognitionComputer module
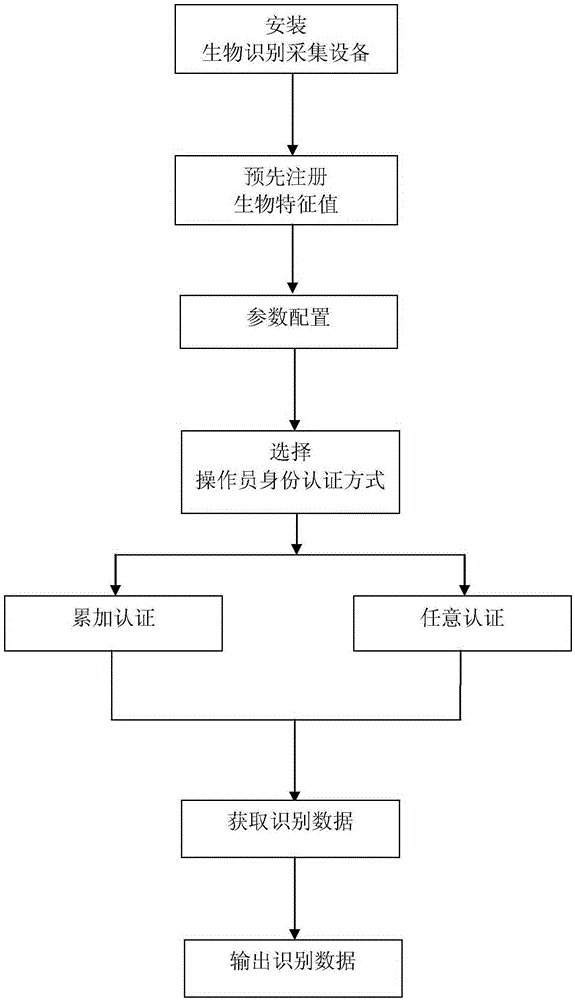
The invention discloses a multi-model biological recognition general platform and a multi-model biological recognition identity authentication method. Highly-integrated middleware technologies are achieved by means of a computer terminal. The platform comprises a biological recognition collection equipment interface module, a biological characteristic value processing module, a biological characteristic value storage module and an identification data output module. The method comprises the following steps of installing biological recognition collection equipment; registering biological characteristic values in advance; performing parameter configuration; selecting an operator identity authentication mode; accumulating authentication; performing random authentication; obtaining identification data; and outputting identification data. The invention collects biological characteristic information with the combination of single-mode or multi-mode biological recognition collection equipment which is widely applied to identity authentication, and can be widely applied to application systems for identity authentication, control, display and alarm, and gather, statistics and analysis.
Owner:西安凯虹电子科技有限公司
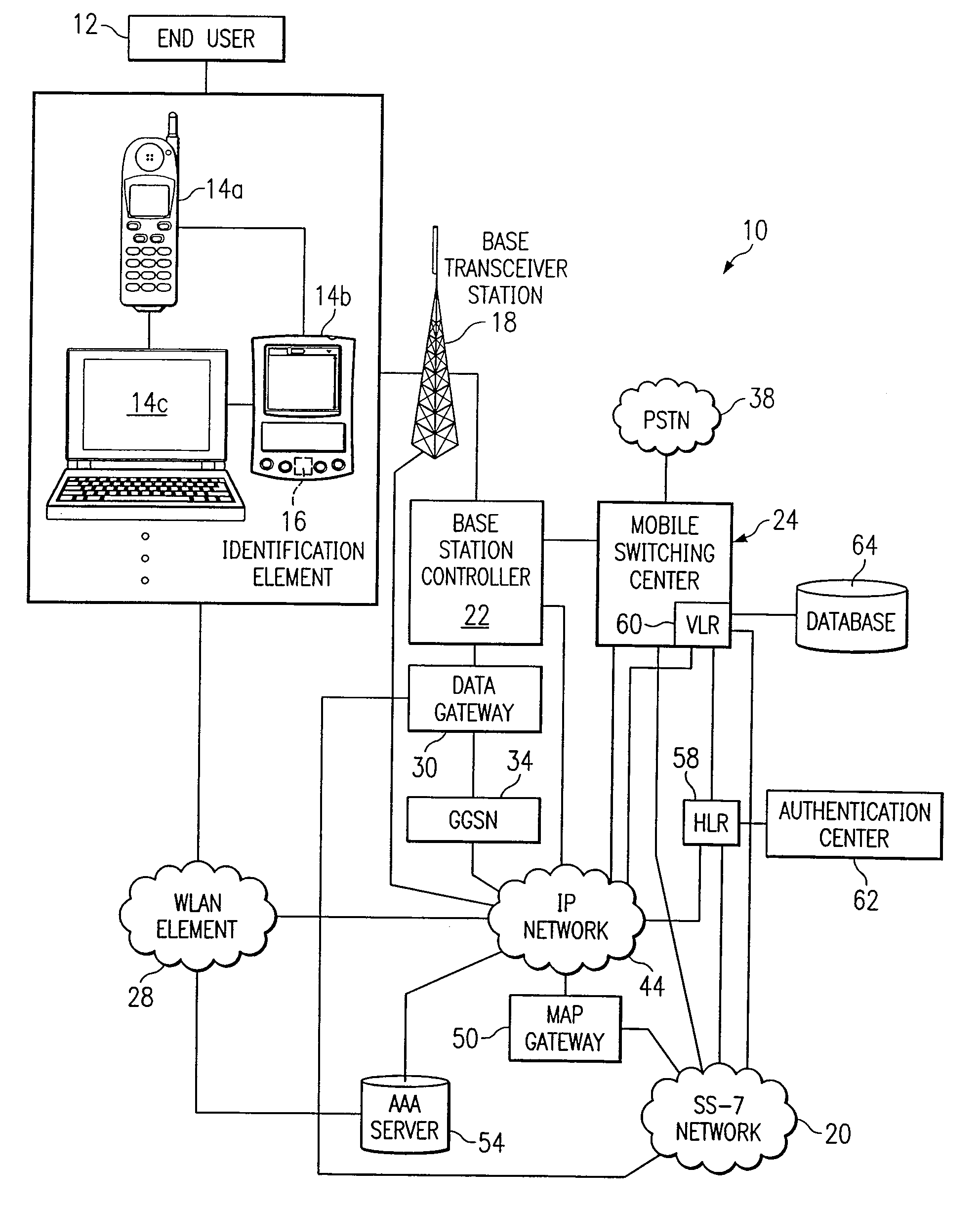
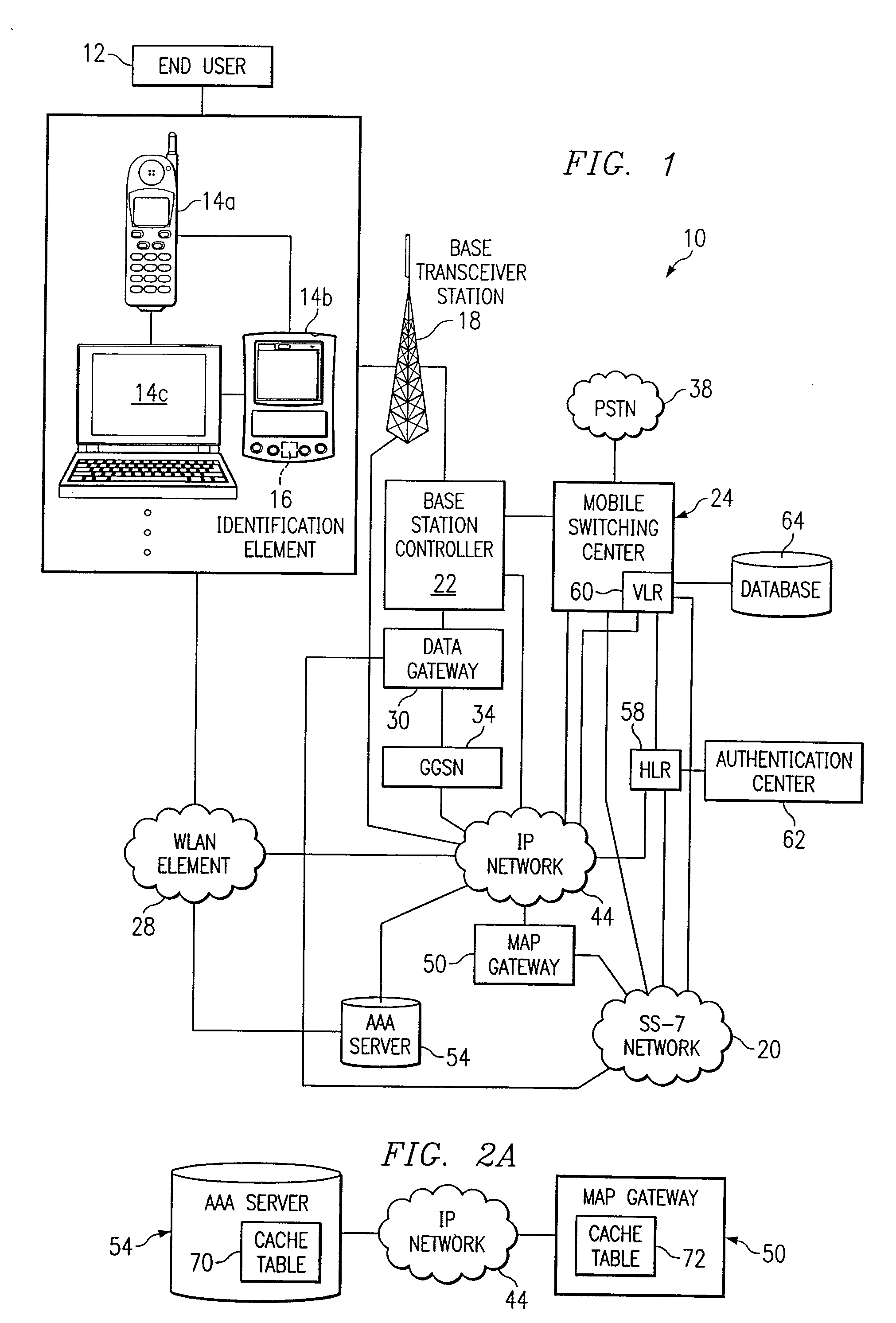
System and method for providing access to a network in a communications environment
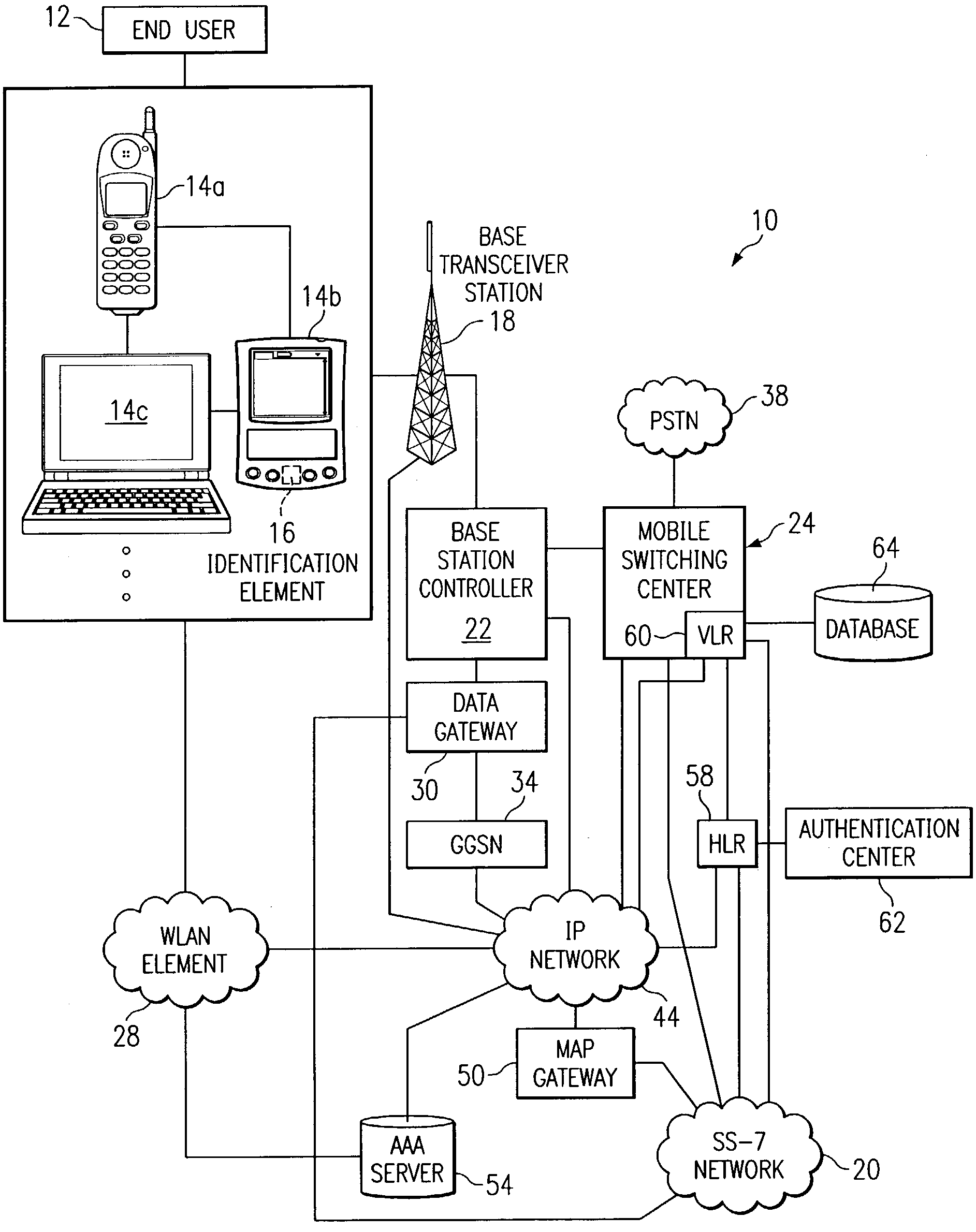
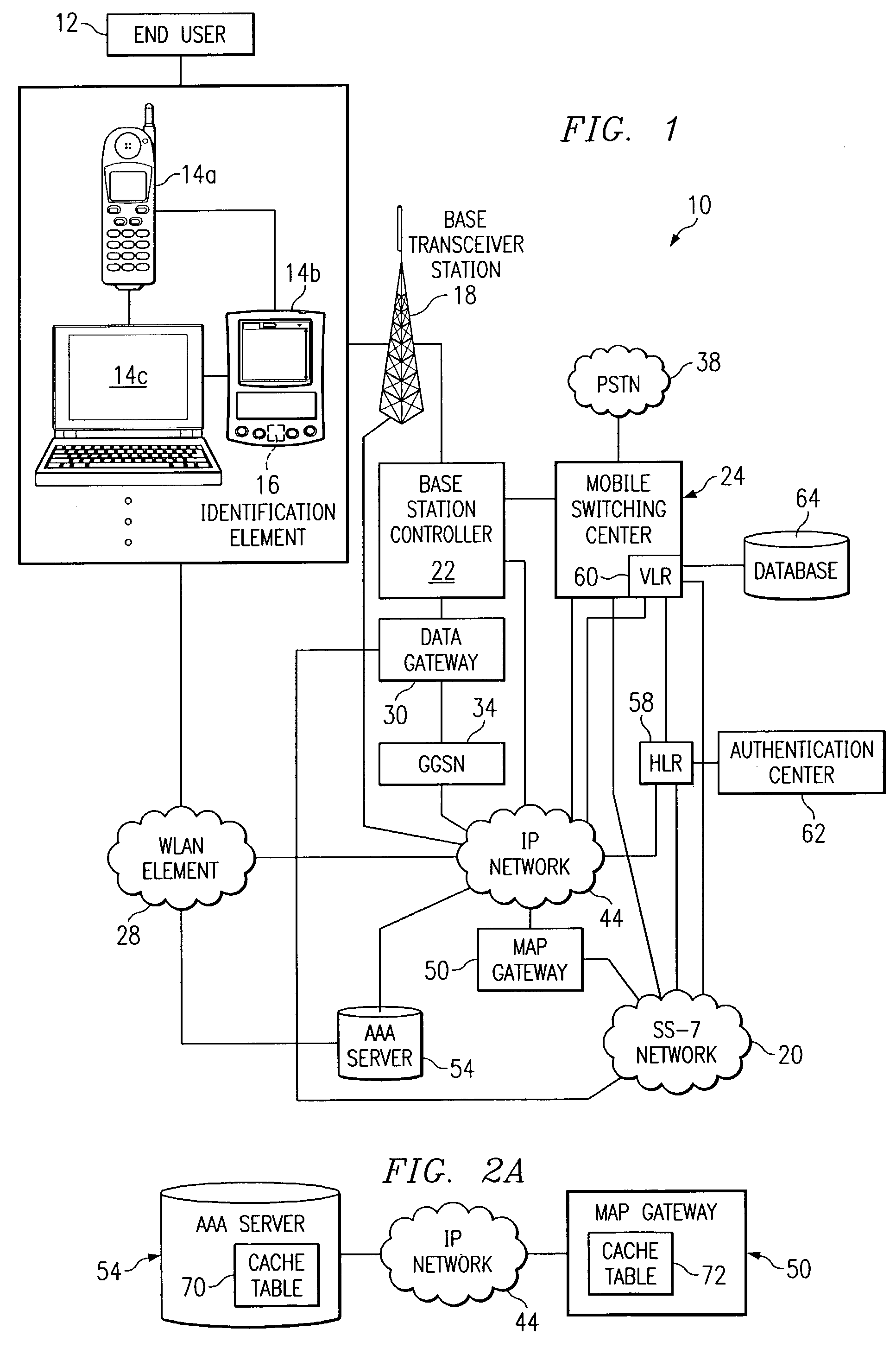
ActiveUS7296152B1Eliminate and greatly reduce disadvantageEliminate and greatly reduce and problemDigital data processing detailsUser identity/authority verificationAccess networkEnd user
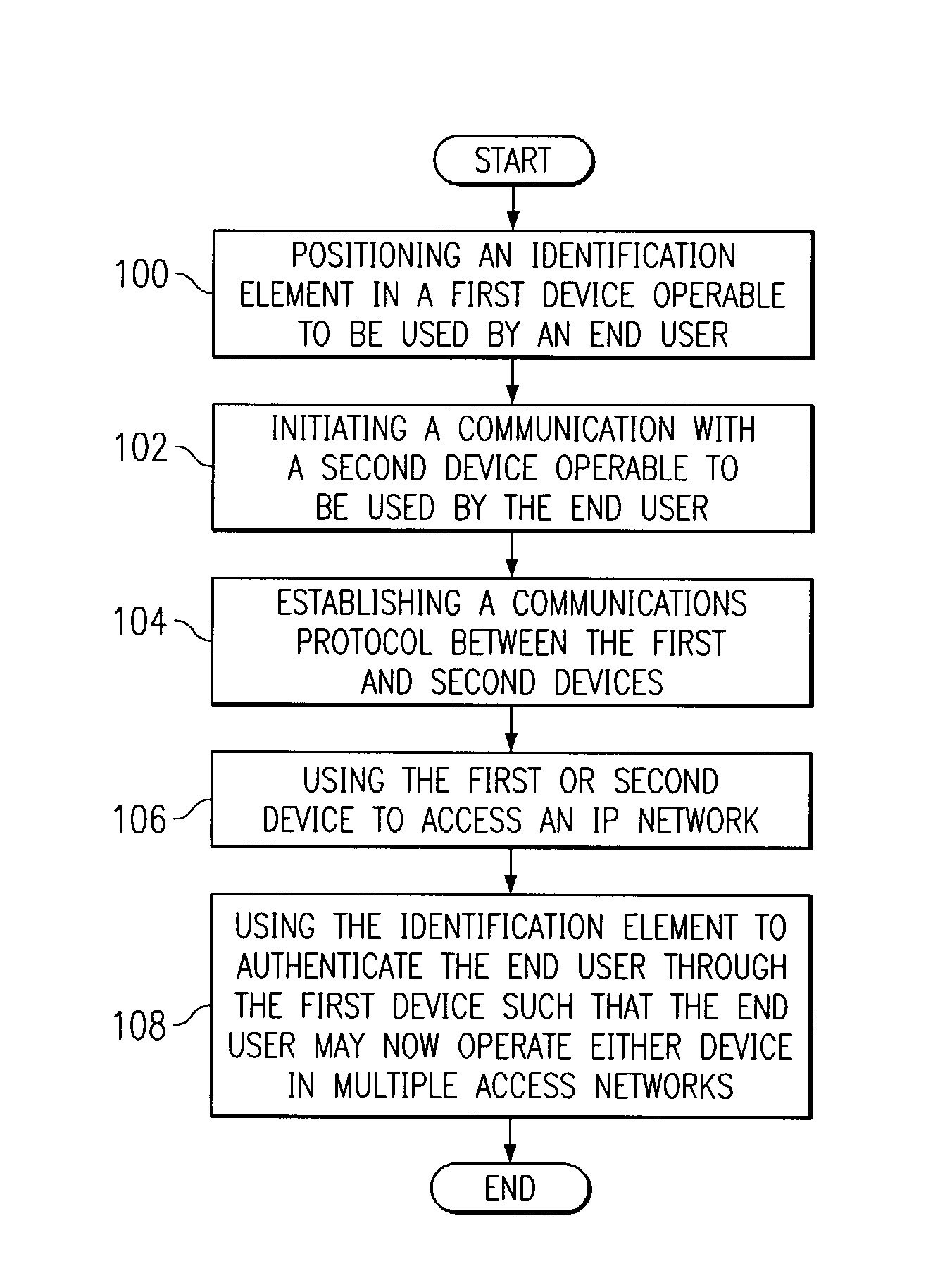
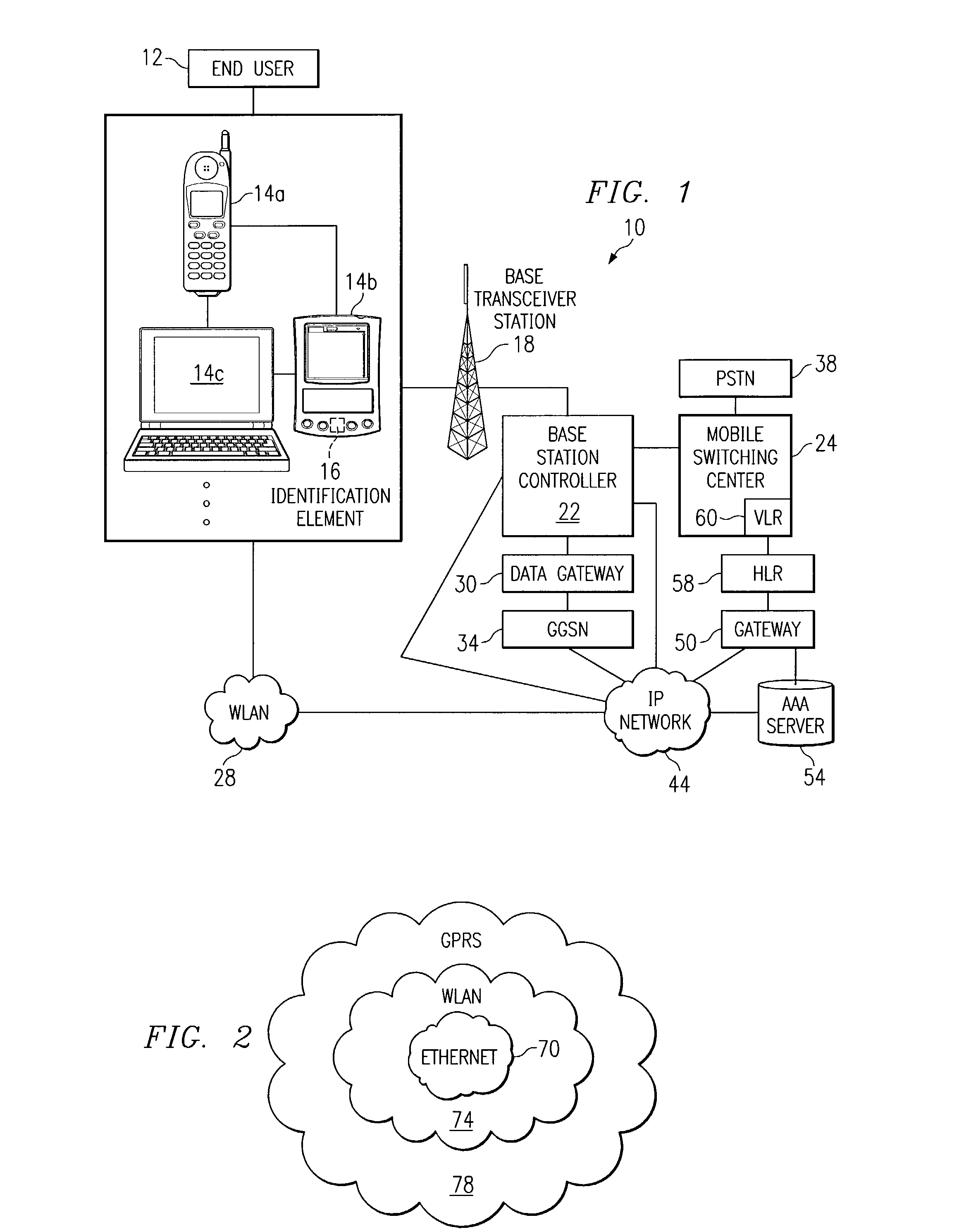
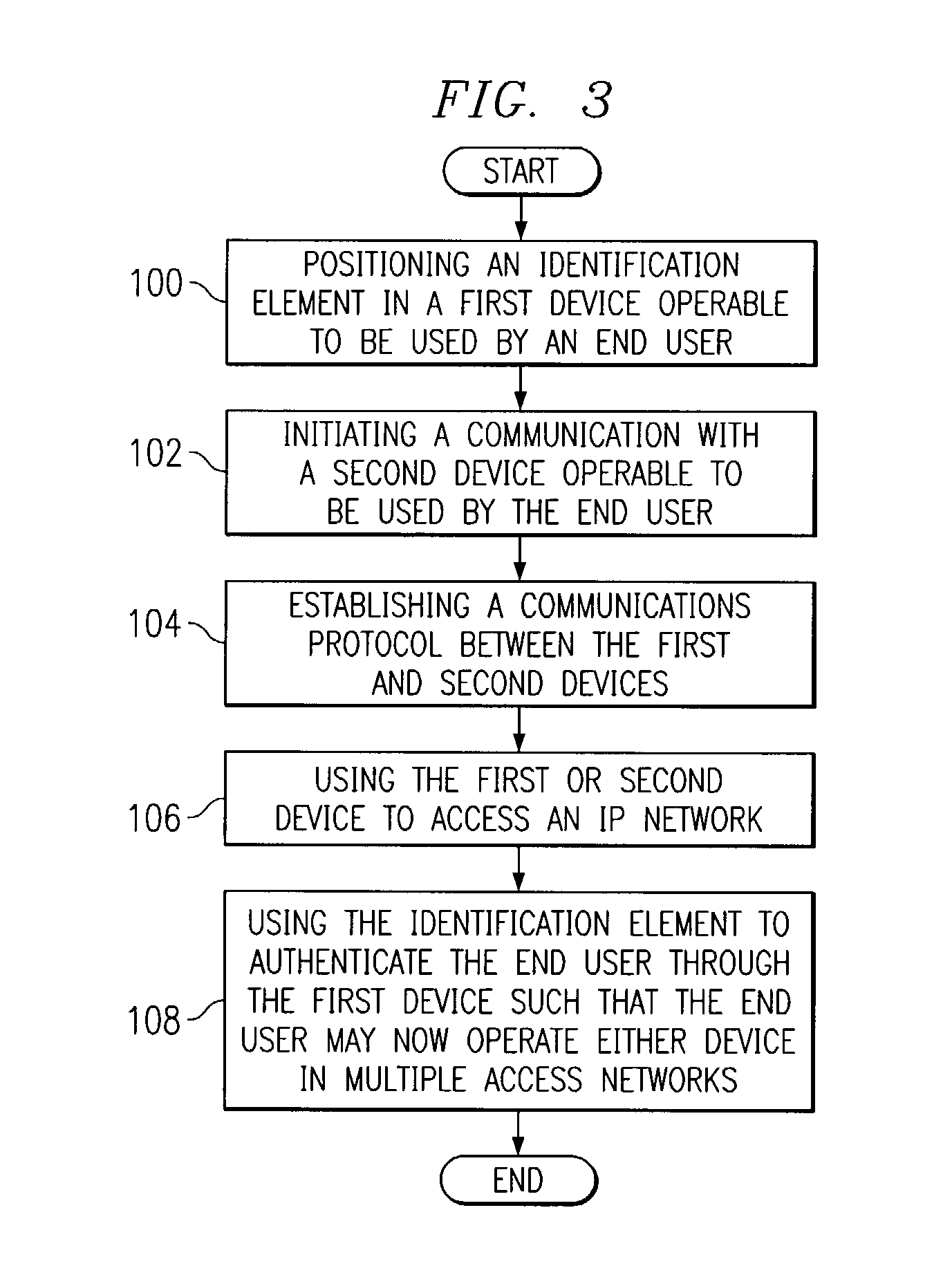
A method for authenticating an end user in a network environment is provided that includes positioning an identification element in a first device that is operable to provide an interface for an end user. The first device is further operable to communicate with an internet protocol (IP) network and with a second device. The end user is then authenticated with a selected one of the first and second devices through the IP network using the identification element such that the end user may operate the first and second devices in multiple access networks that cooperate to provide connectivity to the end user. Each of the access networks is operable to facilitate communications between the end user and the IP network.
Owner:CISCO TECH INC
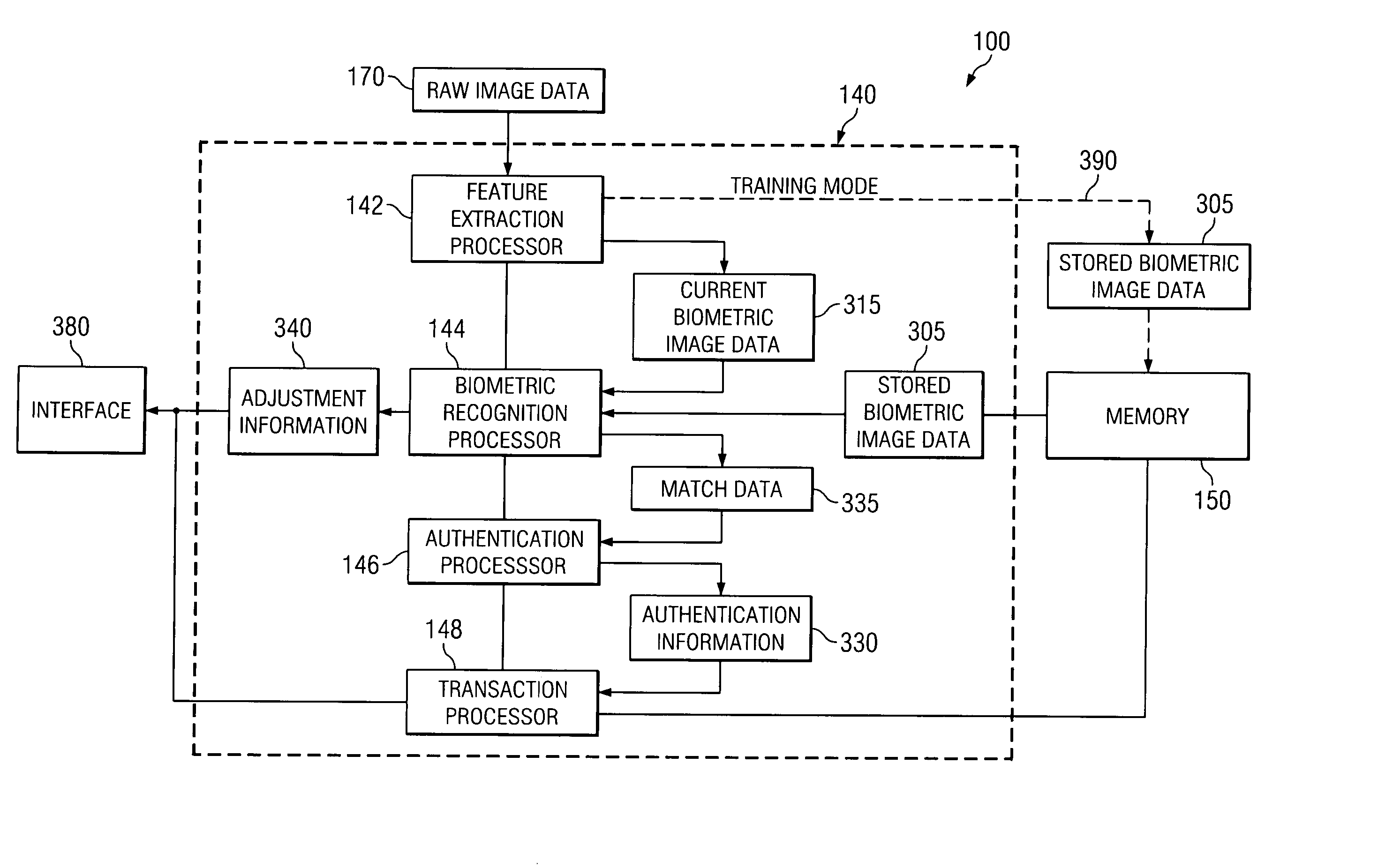
Adaptive device authentication
InactiveUS20140068738A1Accurate authenticationImprove biometric comparisonDigital data processing detailsMultiple digital computer combinationsSystem configurationUser authentication
Device attributes corresponding to hardware and system configuration and characteristics of the user of the device are associated with adjustment logic, e.g., according to various types and classes of attributes. A hierarchical authentication process provides highly detailed and accurate authentication of a device, including device identification, device authentication, user authentication, and attribute adjustment. If the device is not properly identified, authentication fails. Otherwise, device authentication is attempted. If device authentication fails, all authentication fails. Otherwise, the user of the device is authenticated. If user authentication fails, authentication of the device fails. Otherwise, adjustment logic is used to adjust attributes for subsequent authentication.
Owner:DEVICE AUTHORITY LTD
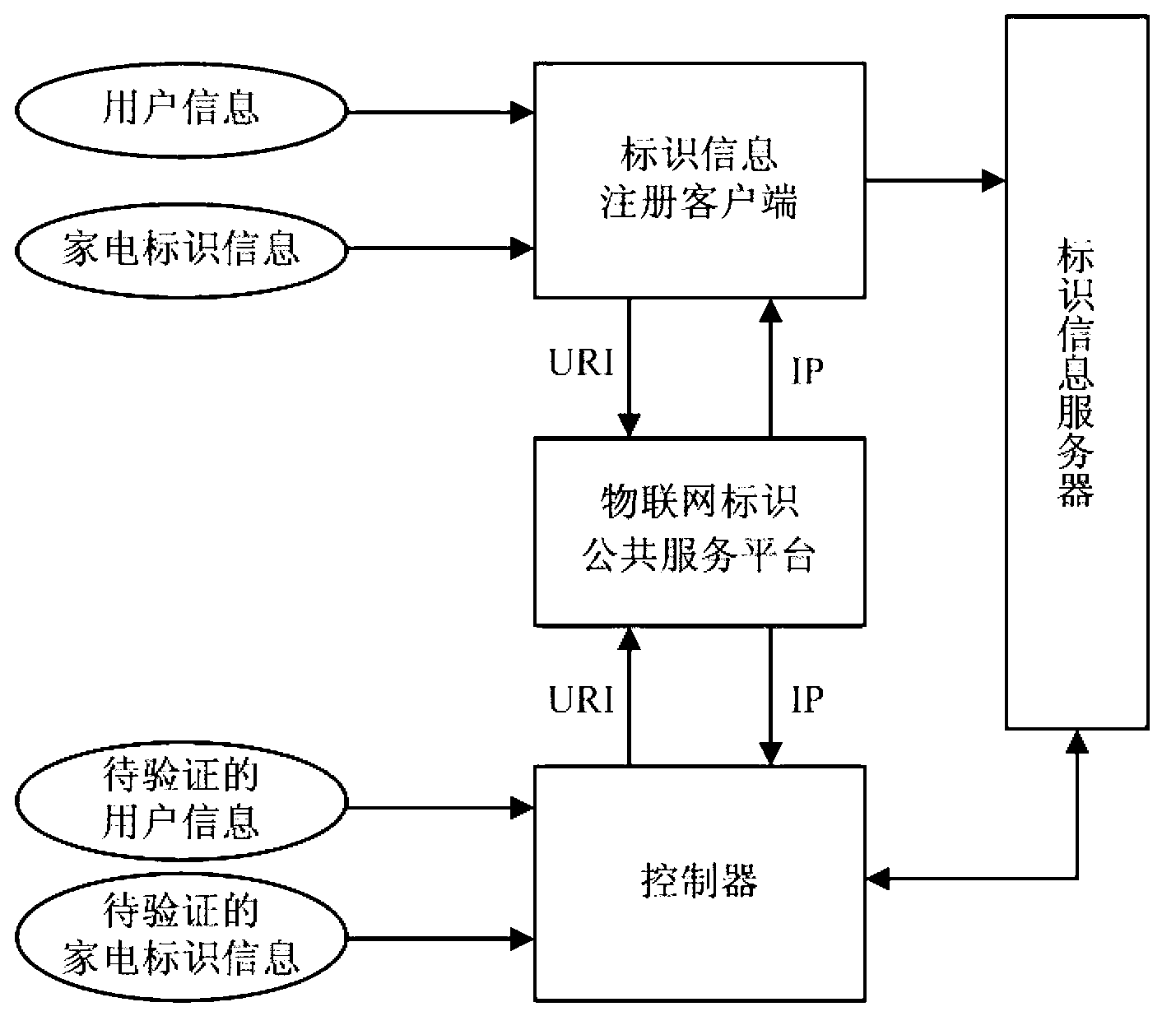
Bidirectional authentication method and system of intelligent equipment
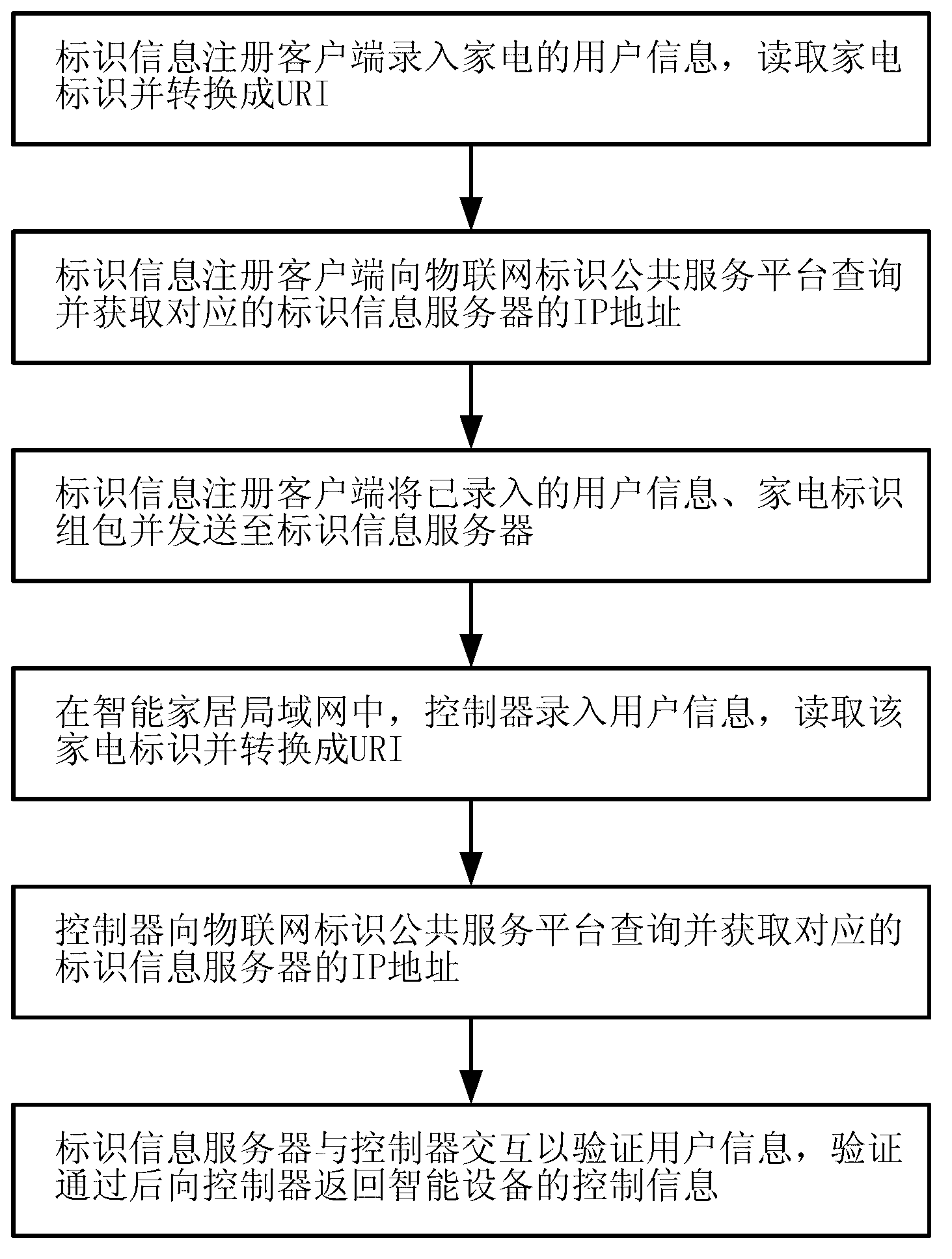
ActiveCN103078875AAccurate authenticationAppliances AccurateTransmissionClient-sideIntelligent equipment
The invention provides a bidirectional authentication method and system of intelligent equipment. The bidirectional authentication method comprises the following steps: establishing an identifier information server, inputting user information and identifier information of the intelligent equipment through an identifier information registration client side when a user purchases the intelligent equipment, and sending the user information and the identifier information to the identifier information server; inputting the user information to be verified into a controller of the intelligent equipment, and identifying the identifier information of the intelligent equipment through the controller; and performing interaction between the controller and the identifier information server to verify the user information, and after a verification success, returning control information of the intelligent equipment to the controller by the identifier information server so as to realize the control over the intelligent equipment by the controller. According to the invention, a bidirectional control function is achieved through the interaction between the controller and the information server, so that the intelligent equipment such as electric appliances can be authenticated accurately and safely on the premise of not increasing the cost of electric appliance products.
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
Wireless network access authentication system and method based on radio frequency fingerprint and biological fingerprint
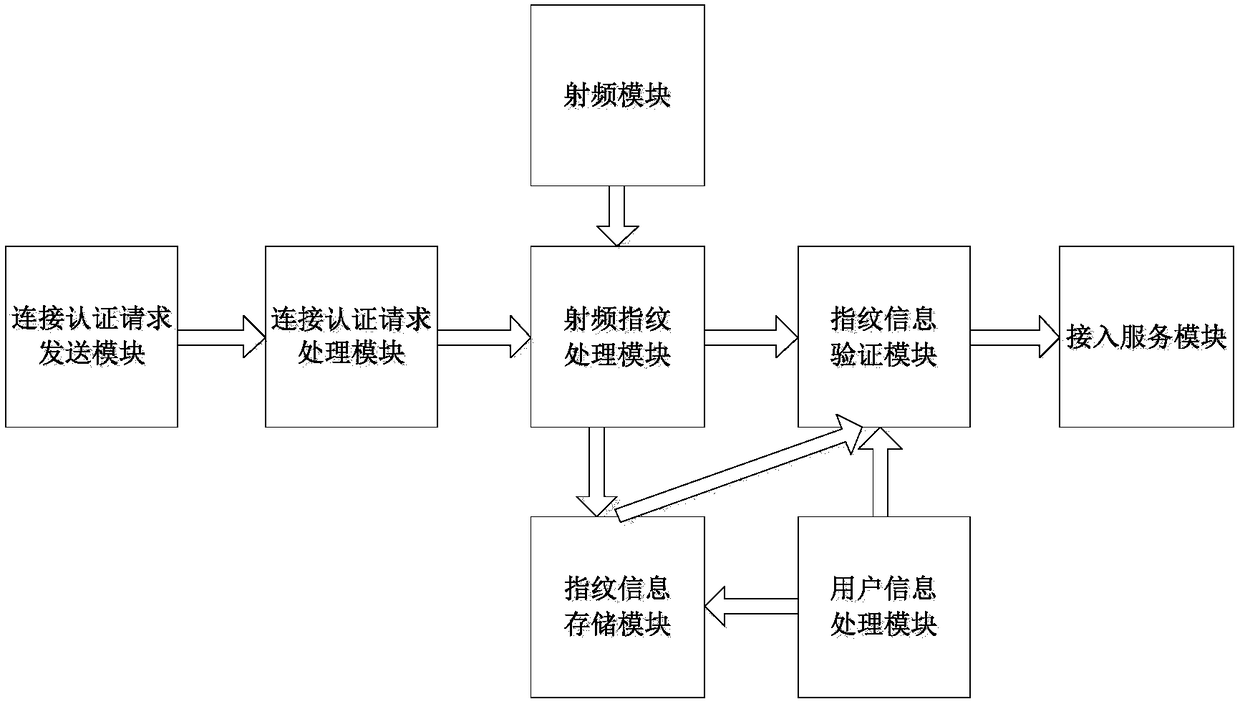
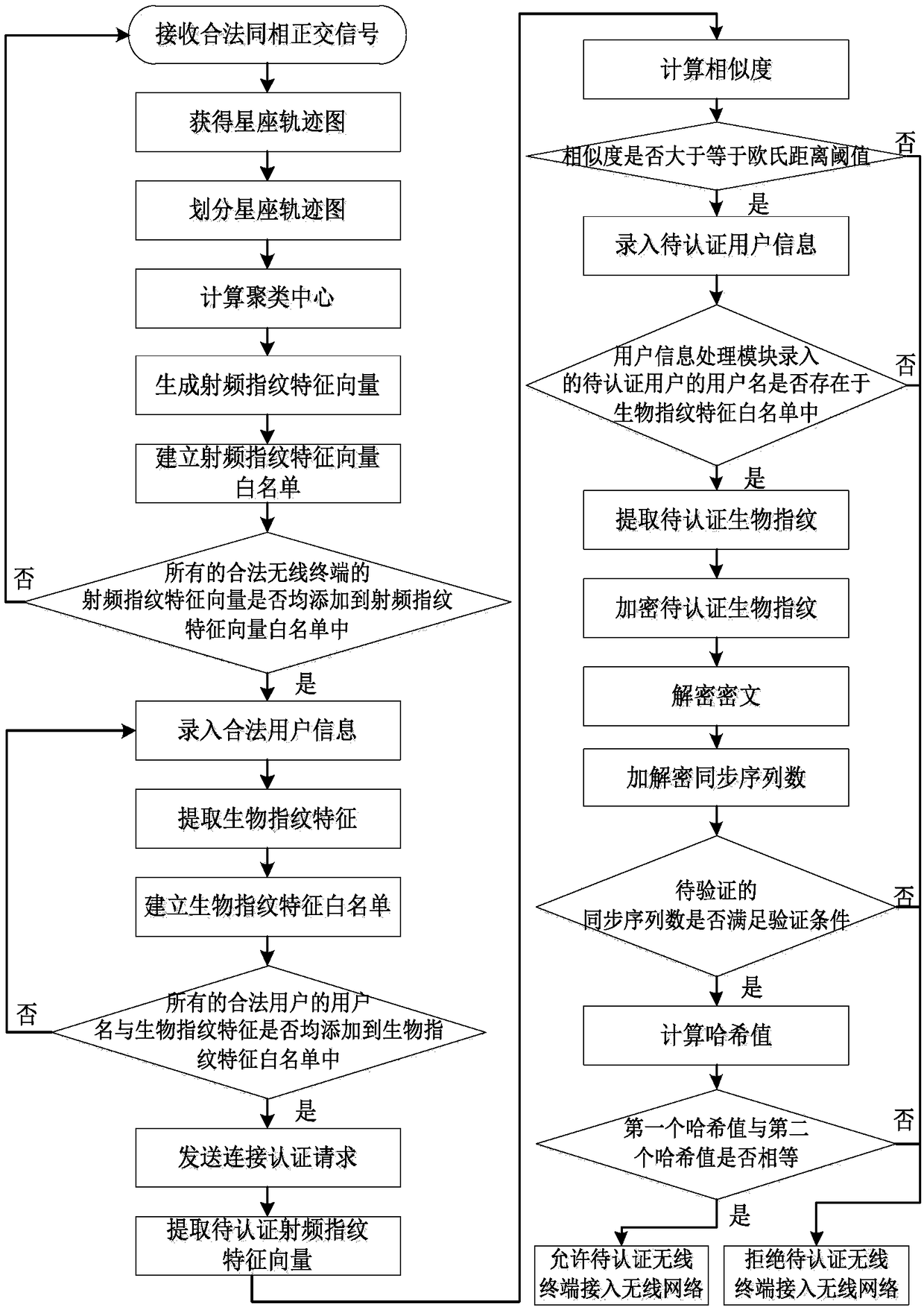
ActiveCN108173871AAchieve authenticationImprove securityTransmissionAuthentication systemRadio frequency
The invention discloses a wireless network access authentication system and a wireless network access authentication method based on a radio frequency fingerprint and a biological fingerprint. The system provided by the invention comprises a radio frequency module, a radio frequency fingerprint processing module, a fingerprint information storage module, a user information processing module, a fingerprint information authentication module, a connection authentication request sending module, a connection authentication request processing module and an access service module. According to the method provided by the invention, the radio frequency fingerprint of a wireless terminal used by a user for applying for accessing a wireless network is authenticated, after the radio frequency fingerprint is authentication, the biological fingerprint of the user using the wireless terminal to access the wireless network is authentication, and after the biological fingerprint of the user is authenticated, the user is allowed to use the wireless terminal to access the wireless network. According to the system and the method provided by the invention, the secure access to the wireless network is achieved through authenticating the wireless terminal and the user applying for using the network.
Owner:XIDIAN UNIV
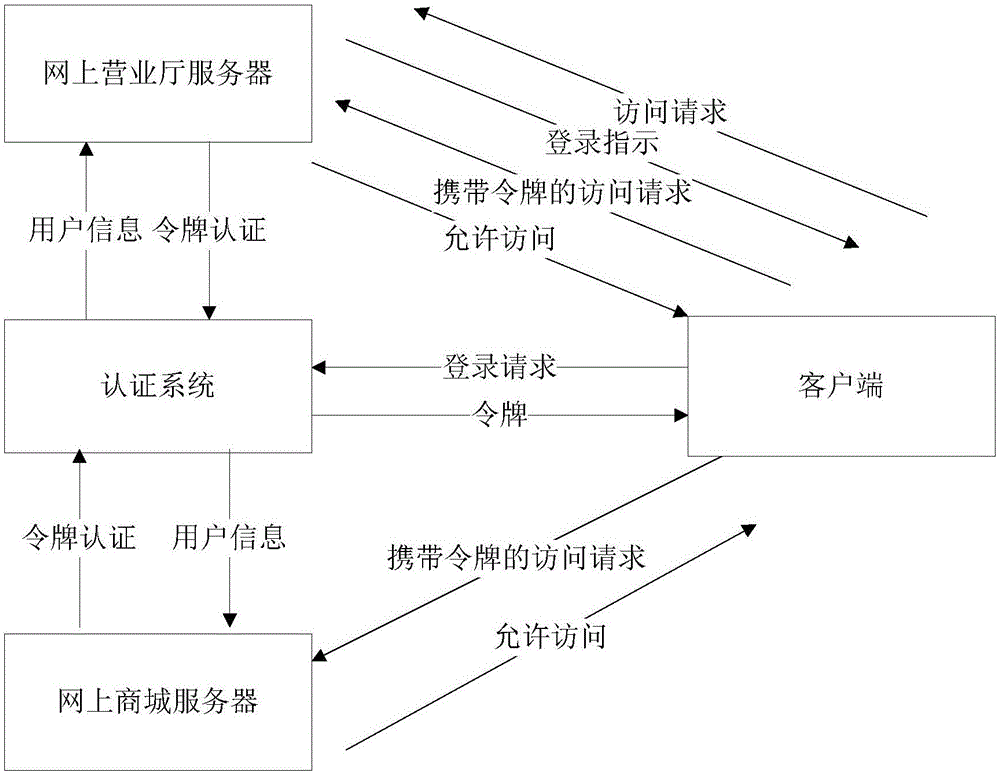
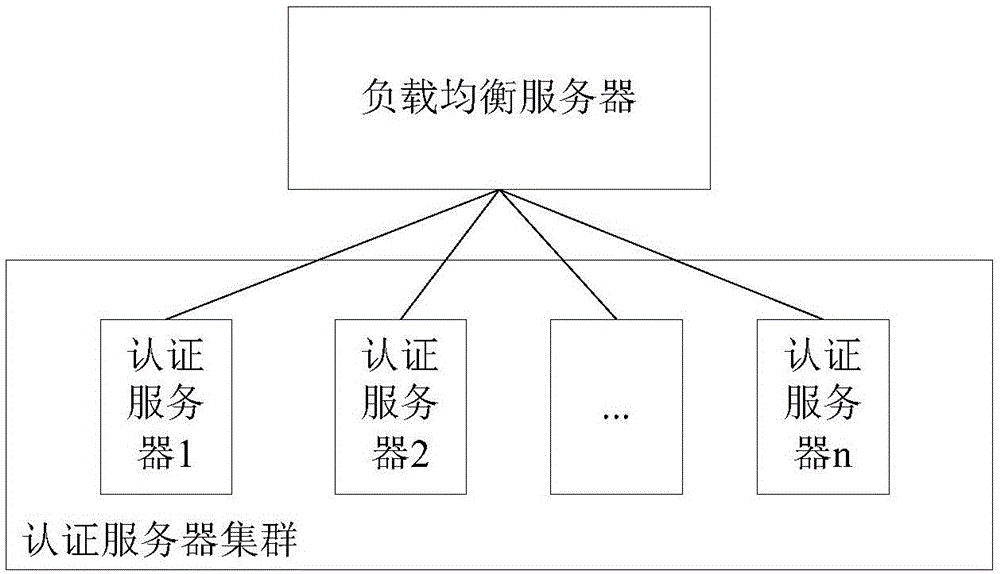
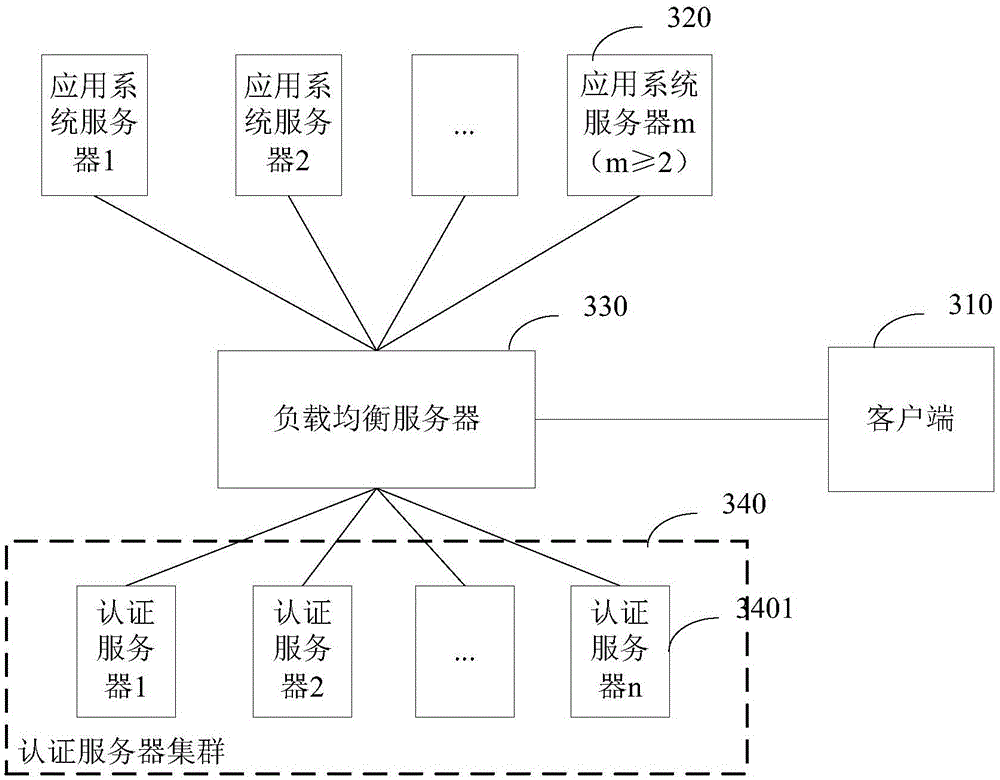
Token generation and authentication method and authentication server
ActiveCN106375270ASave resourcesSave storage resourcesUser identity/authority verificationAuthentication serverData transmission
The embodiment of the invention discloses a token generation and authentication method and an authentication server. The method comprises steps: the first authentication server authenticates a login request of a user; when the first authentication server succeeds in authenticating the login request of the user, a session is built for the user, and a token comprising identifier information and token addressing information is generated for the user, wherein the identifier information is used for identifying the session of the user, and the token addressing information is used for indicating the storage position of the token in an authentication server cluster, and the first authentication server is located in the authentication server cluster. In a condition of correctly authenticating the token, the data transmission resources and the storage resources in the authentication server cluster can be saved.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com