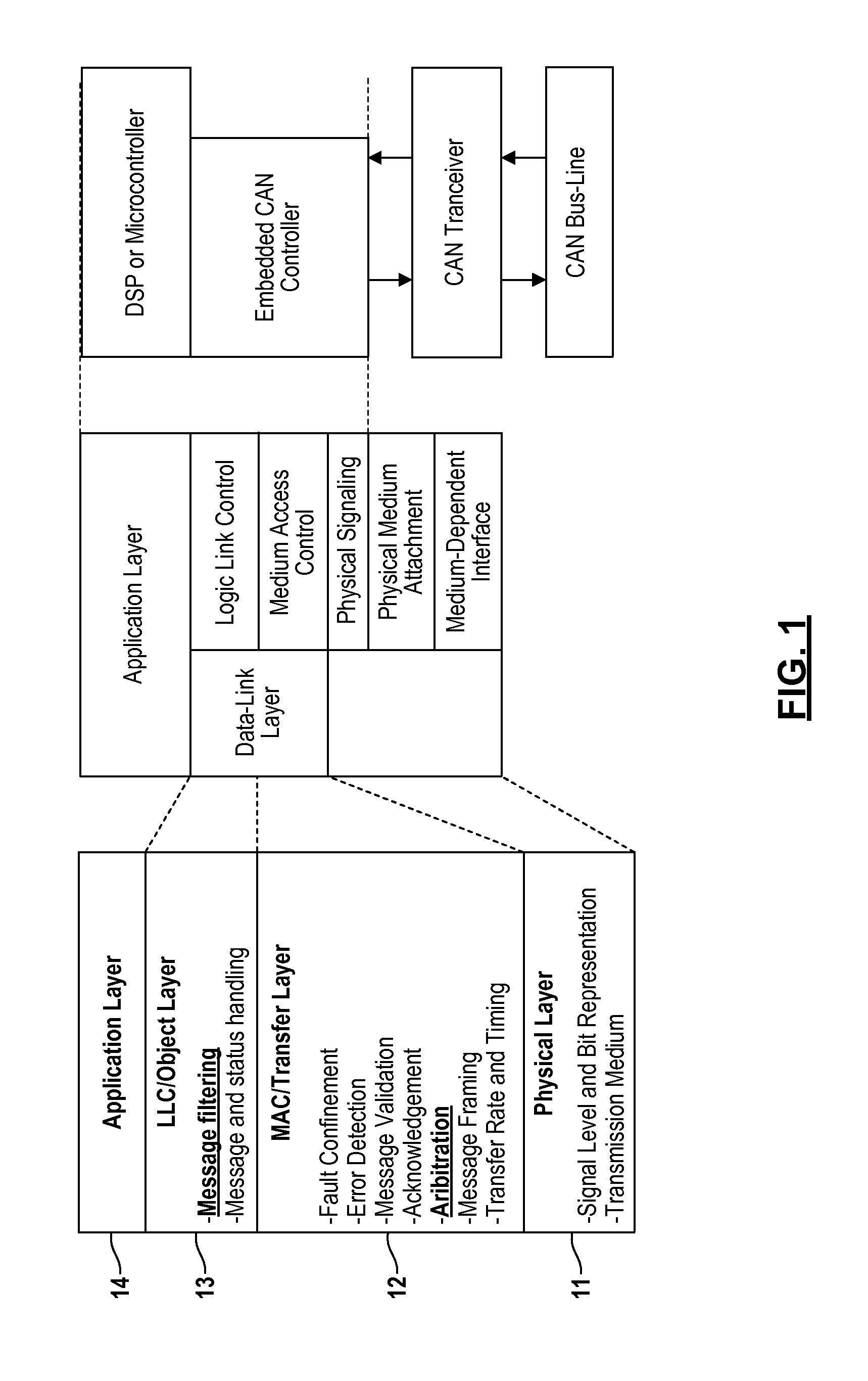
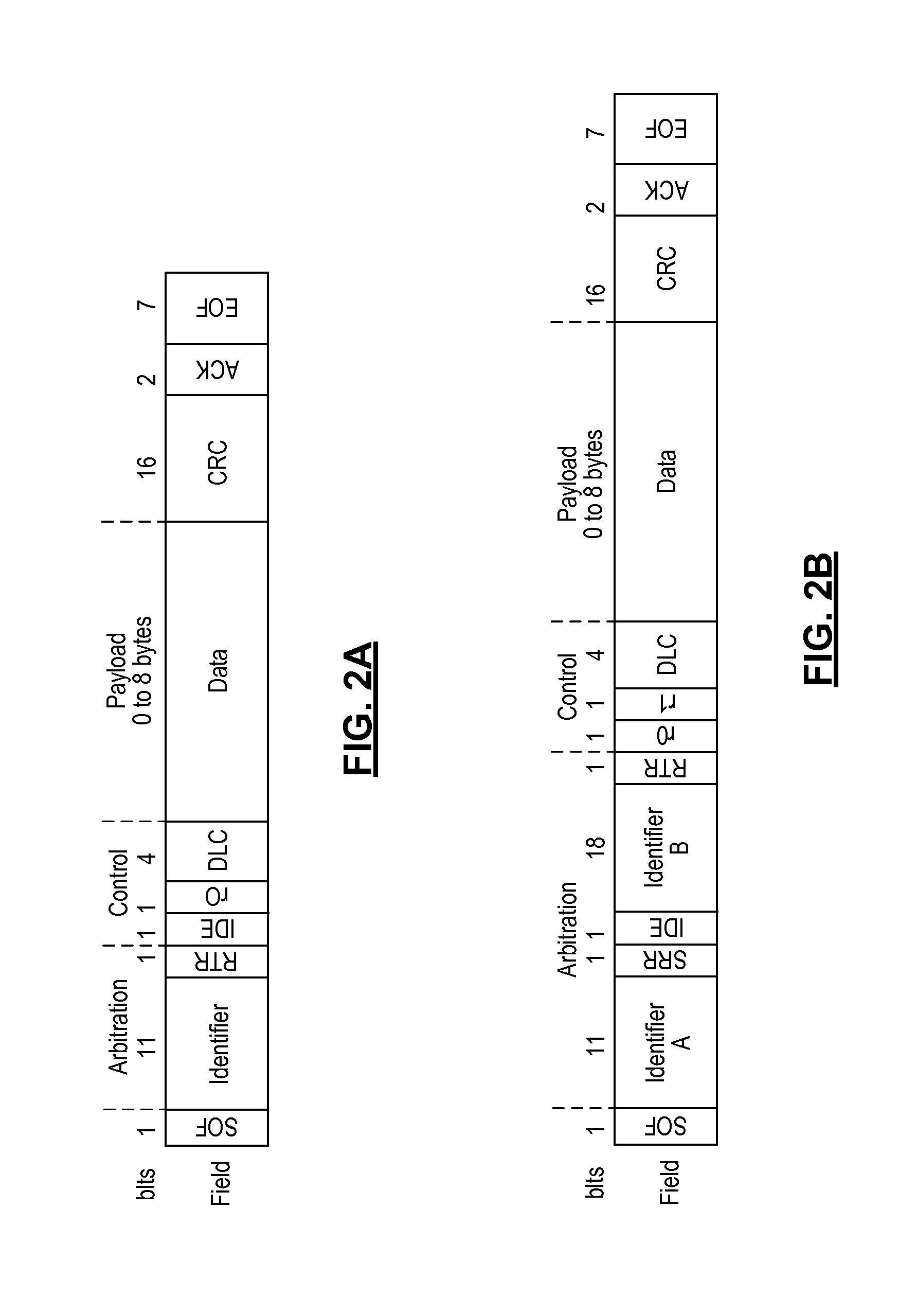
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1300 results about "Authentication protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
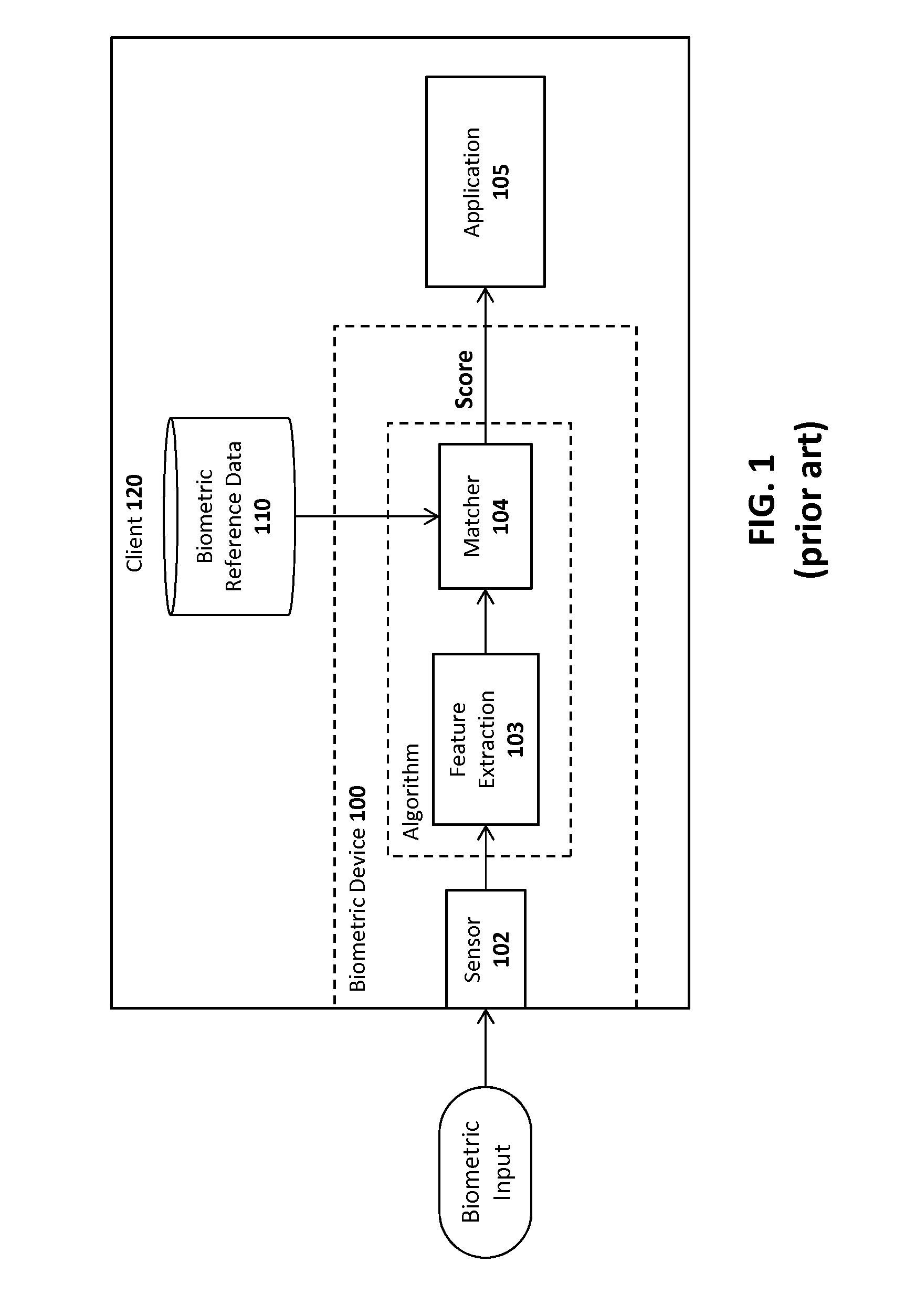
An authentication protocol is a type of computer communications protocol or cryptographic protocol specifically designed for transfer of authentication data between two entities. It allows the receiving entity to authenticate the connecting entity (e.g. Client connecting to a Server) as well as authenticate itself to the connecting entity (Server to a client) by declaring the type of information needed for authentication as well as syntax. It is the most important layer of protection needed for secure communication within computer networks.
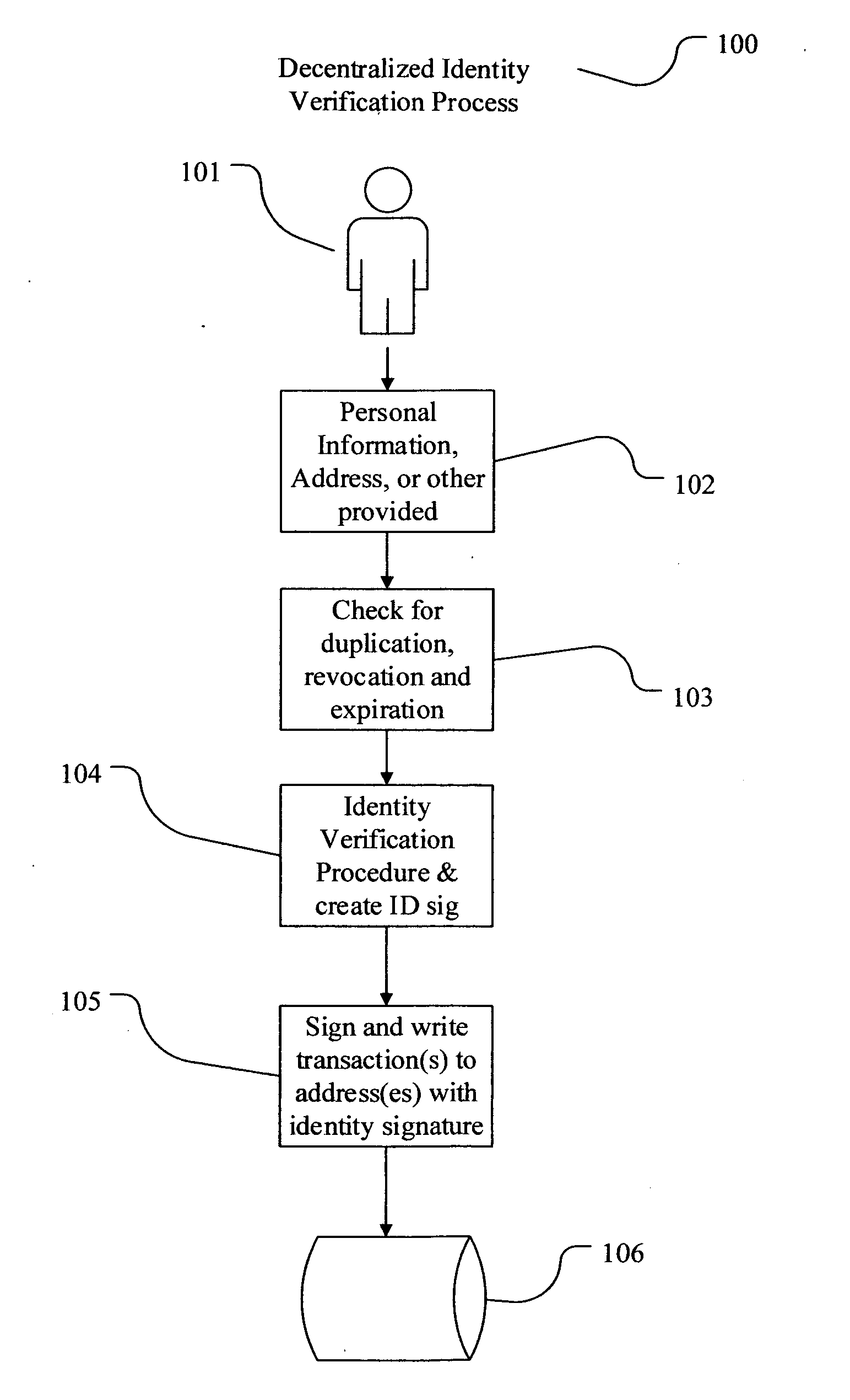
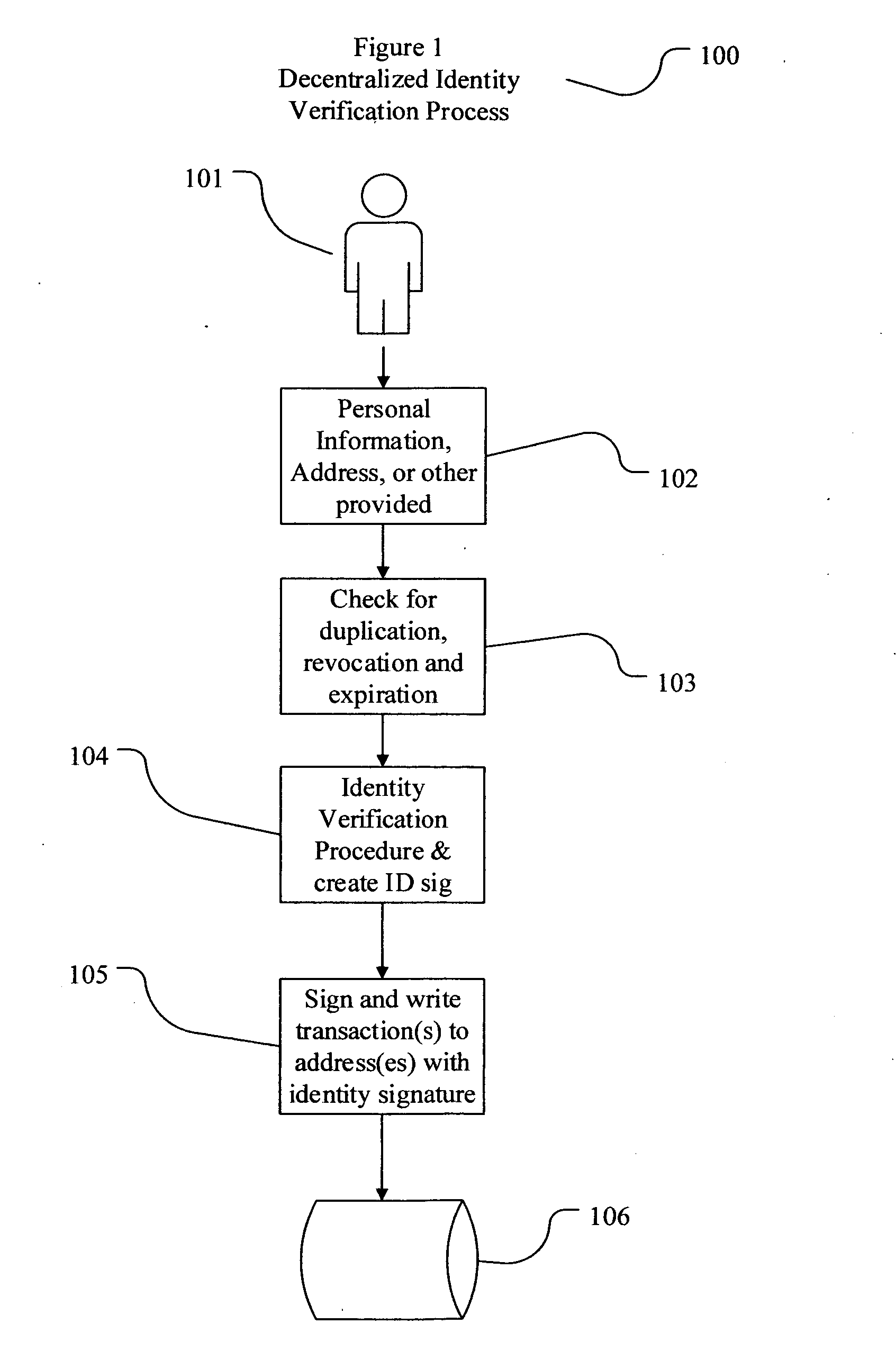
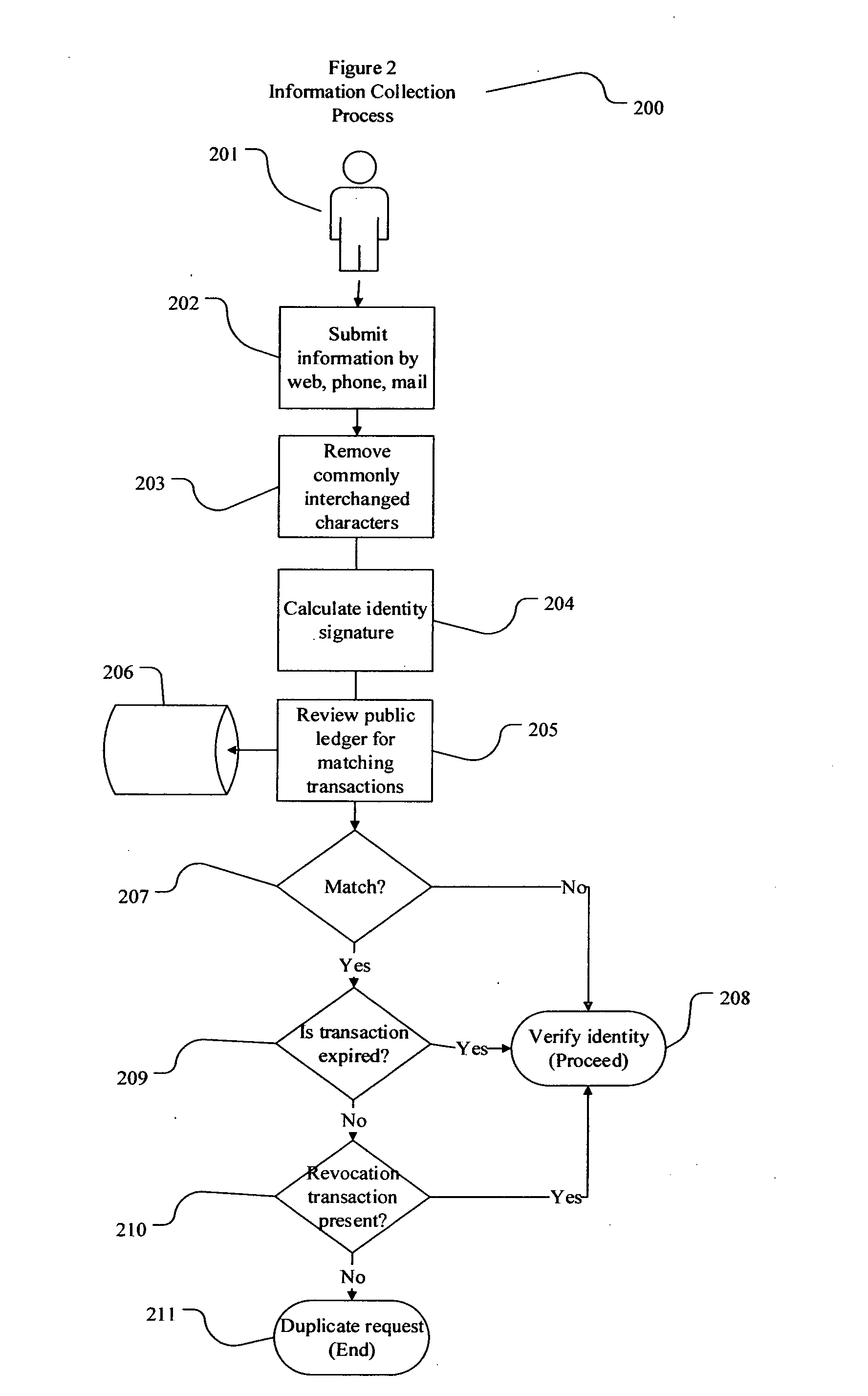
Decentralized identity verification systems and methods
InactiveUS20150356523A1Cryptography processingUser identity/authority verificationRegulatory authorityFinancial transaction
The present invention involves systems and methods that allow participants in cryptocurrency networks to exchange cryptocurrency for traditional currency legally and safely without requiring the use of a traditional exchange or online brokerage as a fiduciary. The invention accomplishes this through the use of a decentralized identity verification protocol that allows a service provider to verify the identity of a participant and then publish an identity signature on the participant's cryptocurrency address or addresses. The invention enables full compliance with Country specific customer identification program and anti-money laundering requirements, and maintains the ability to independently satisfy requests for information or data retention requirements if requested by legally authorized parties, but does not require that the participant store the private keys or access controls to their cryptocurrency on an exchange or brokerage service.The invention serves to verify a participant's identity in full compliance with US Bank Secrecy and Patriot Act provisions or similar regulations where identification may be achieved through non-documentary or documentary identity verification procedures. After passing the applicable verification procedure, the service provider stamps the participant's cryptocurrency address with a transaction containing an identity signature. This identity signature within the transaction consists of a public indicator of the participant's Country and subdivision, a compliance level code, an ID type indicator, and an identity hash. The identity hash is created from the digests of cryptographic hash functions where the participant's personal information is used as an input. The service provider signs the transaction with their authorized private key that corresponds to their publicly accessible public key. This serves as a publicly verifiable confirmation that the identity associated with the address in question was validated by the service provider authorized to act on behalf of the regulatory authority.The participant may then purchase and sell cryptographic currency from and to a third party exchange or brokerage service legally and safely when using their verified cryptocurrency address. This is because the third party is able to confirm compliance by openly referencing and verifying the identity verification transaction present on the address. Subsequent transactions where the third party sells or purchases cryptocurrency for the verified participant are similarly stamped with a transaction conforming to the identity verification protocol. This allows the third party interacting with the verified participant's address to observe any regulations limiting the amount or frequency of transactions over a variable period of time. It follows that this address could be used with any third party or participant in the cryptocurrency network that observes the decentralized identity verification protocol, all without requiring the third party or participant to collect and verify personal information redundantly. The ability to verify an identity remotely also eliminates the need for the third party to act as a fiduciary holding the private keys or access controls to the verified address. Lawful requests for information by authorized authorities are served to the service provider as digitally signed transactions that may then be linked to the participant's identity and transactions, allowing the protocol to observe subpoenas or similar lawful requests for information. The encrypted personal information may be held in escrow by the service provider indexed to the verified cryptocurrency address for such purposes. An alternate embodiment would store the encrypted personal information in a decentralized network of other participants, with the information accessible for retrieval using the public key of the verified cryptocurrency address and decryption using the corresponding private key, decentralizing the process entirely except for the identity verification step.
Owner:CHAINID
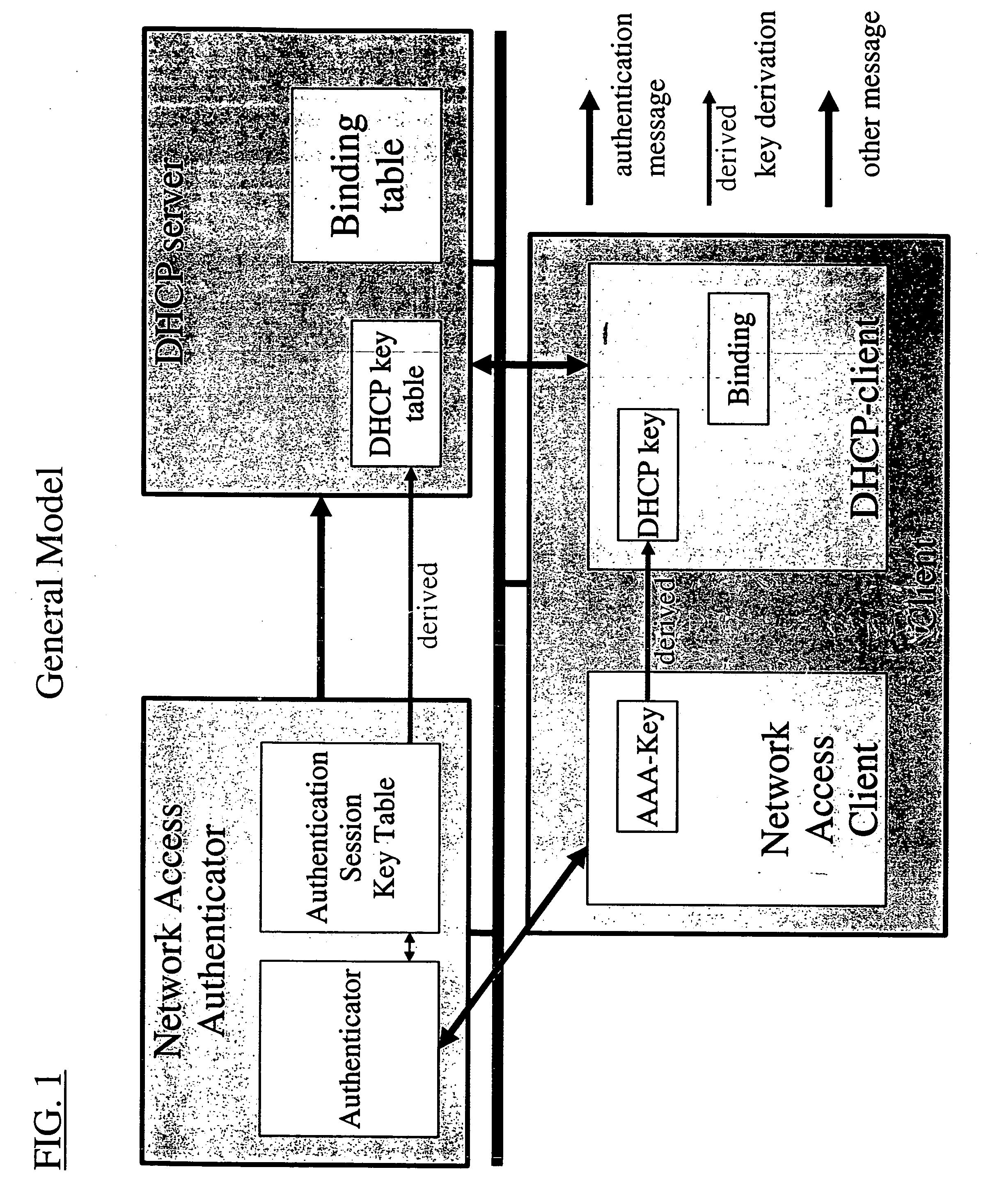
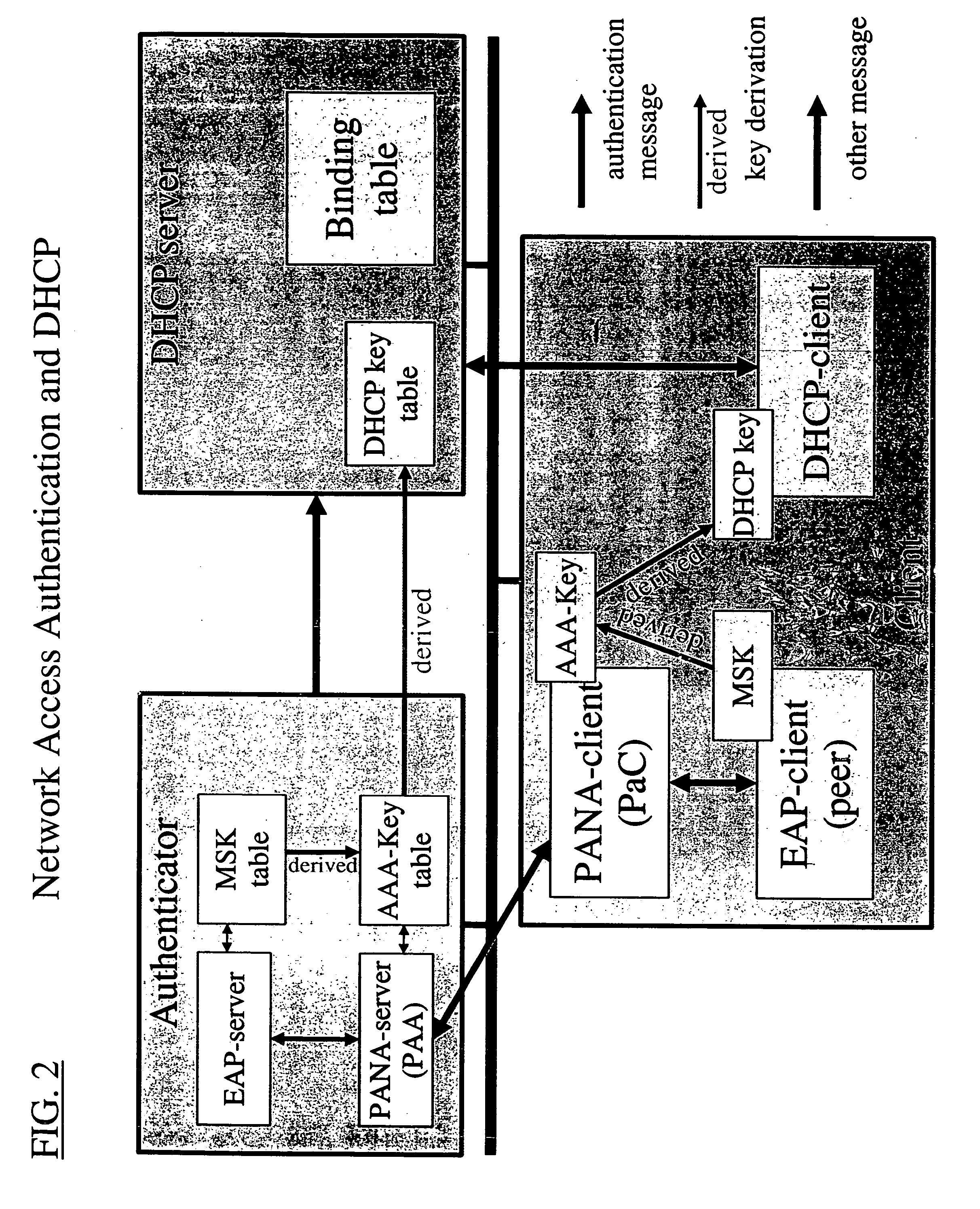
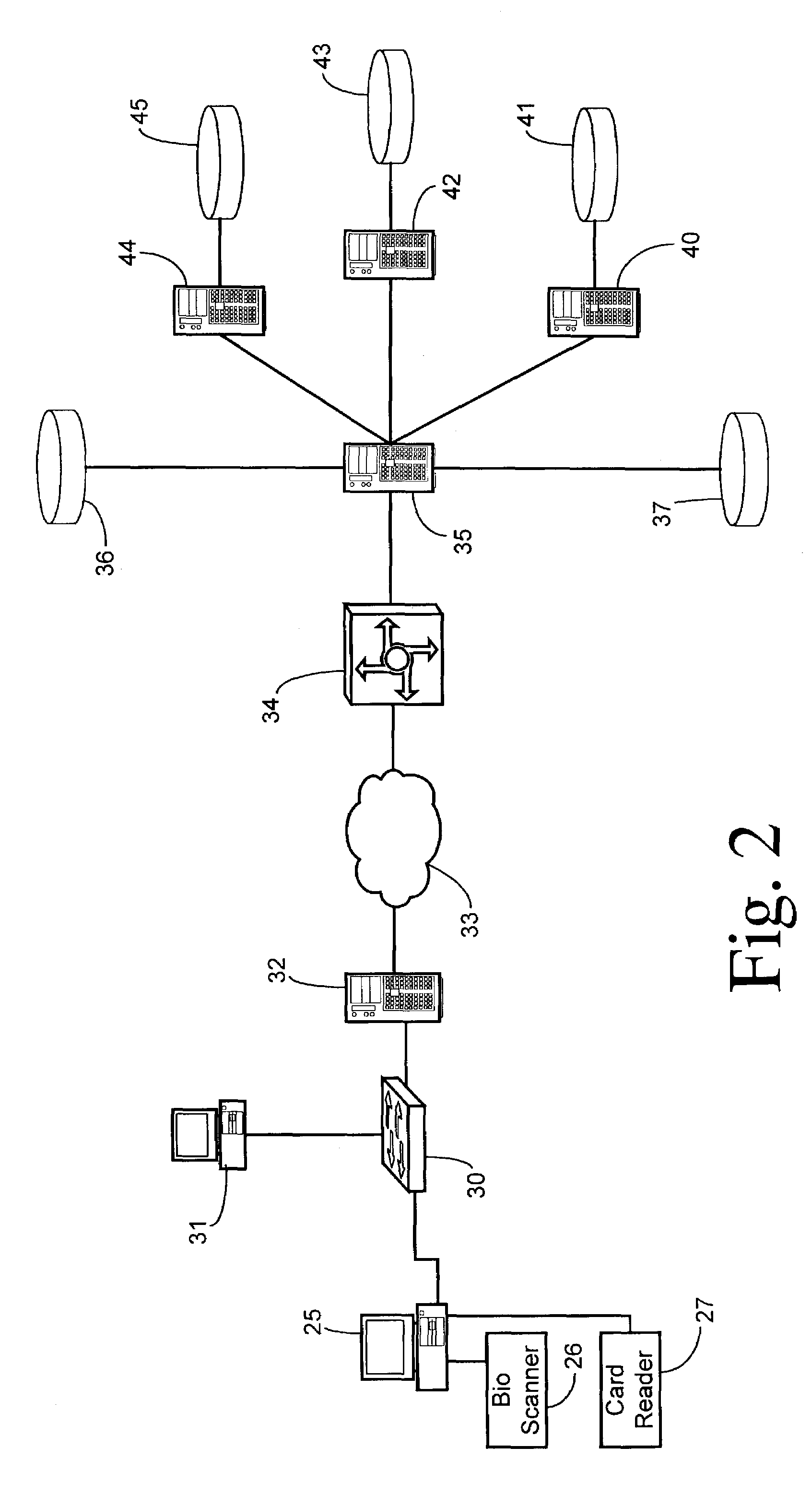
Dynamic host configuration and network access authentication
InactiveUS20060036733A1Digital computer detailsTransmissionIP multicastProtocol for Carrying Authentication for Network Access
Owner:FOUR BATONS WIRELESS LLC
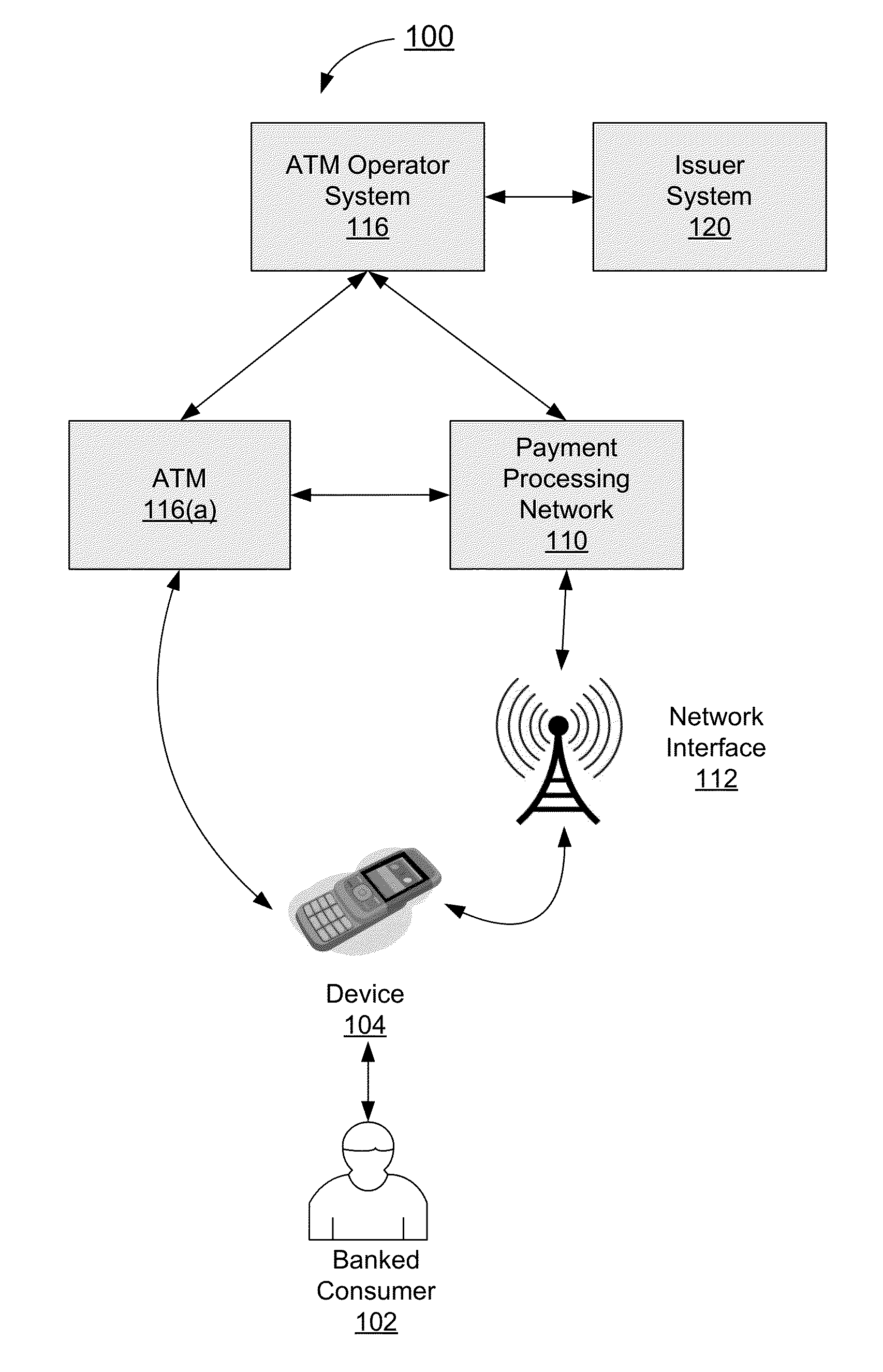
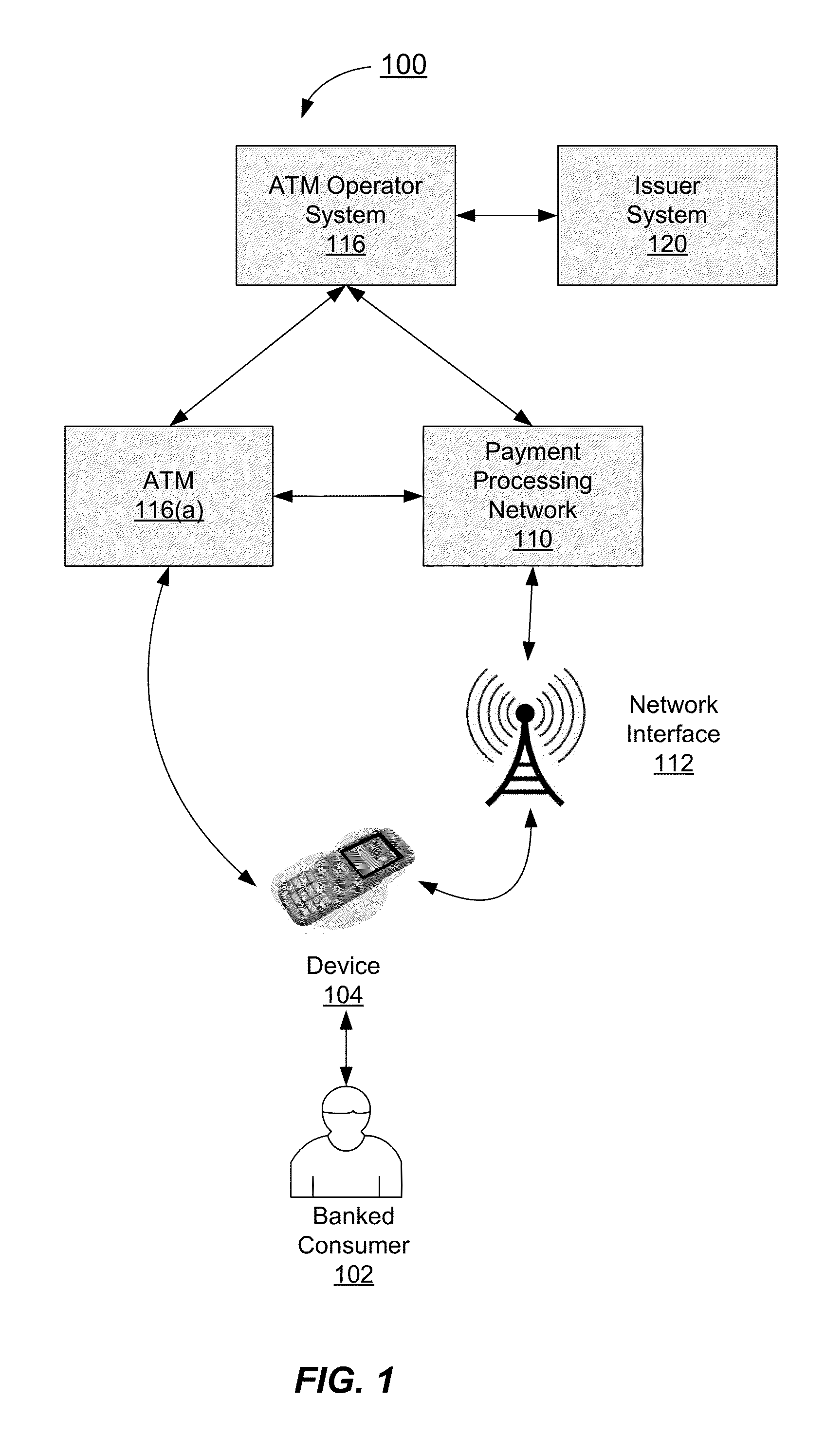
Authentication process for value transfer machine
InactiveUS20130226799A1Prolong transaction processComplete banking machinesFinanceComputer hardwareMessage authentication code
Embodiments of the invention are directed towards improved transaction processing methods and systems with transaction apparatuses, including a value transfer machine, using a device identifier instead of a value transfer machine card to process a transaction. One embodiment of the transaction may be directed to a transaction apparatus and a method including receiving an authentication code from a consumer, sending the authentication code to a first server computer, wherein if the received authentication code matches a generated authentication code, the first server sends a confirmation message. The method continues by receiving the confirmation message from the first server, receiving a secret token from the consumer, and sending an authorization request message to a second server computer. Thereafter, the transaction apparatus receives an authorization response message from the second server, indicating whether the secret token matches an expected token. Other embodiments are directed to first and second servers and corresponding methods.
Owner:VISA INT SERVICE ASSOC
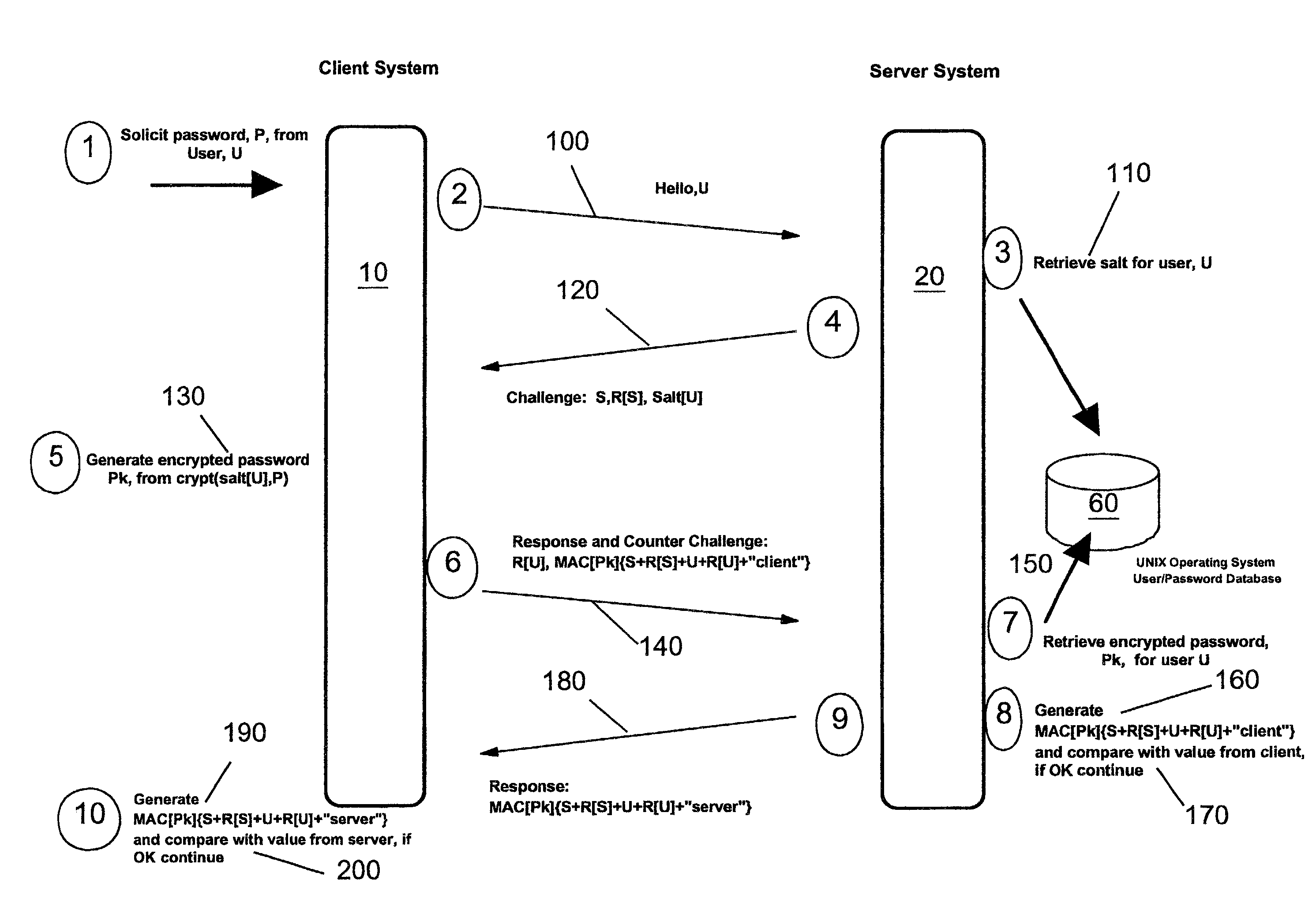
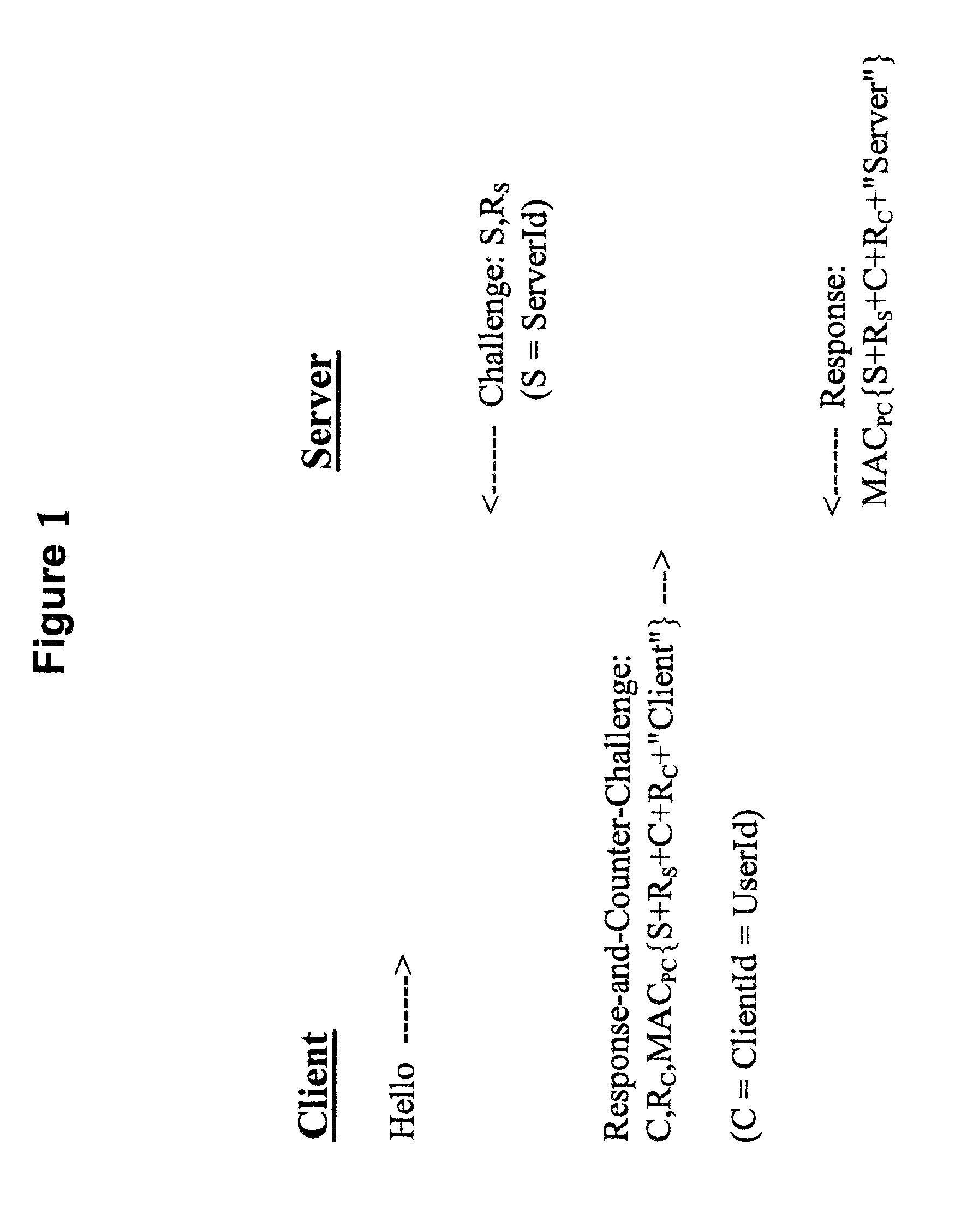
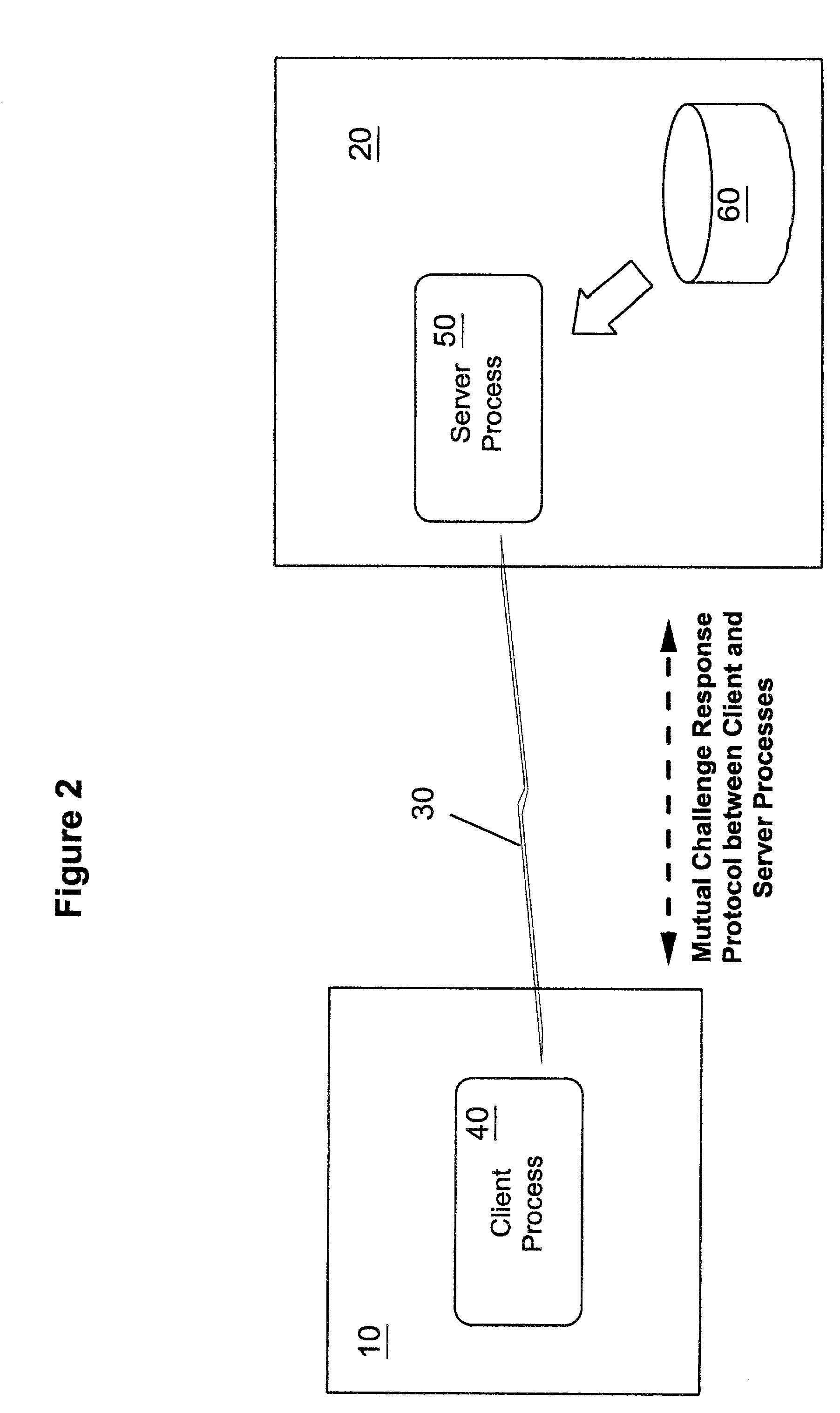
Methods, apparatus and computer programs performing a mutual challenge-response authentication protocol using operating system capabilities
InactiveUS20030093680A1Avoids security exposureMeet growth requirementsKey distribution for secure communicationDigital data processing detailsOperational systemCrypt
A client-server authentication method for use where a server process has access to a repository storing cipher-protected client passwords. The method includes applying the same cipher function to the client's copy of its password as was previously applied to generate the stored cipher-protected client passwords. This ensures that both the client and server have access to an equivalent cipher-protected client password-providing a shared secret for driving a mutual challenge-response authentication protocol without having to convert the password into cleartext at the server. The invention can be implemented without significant additional software infrastructure in a UNIX environment. Client passwords are typically stored in the UNIX password repository under the protection of the crypt( ) function applied to the combination of the password and a random number (a "salt'). By sending the salt to the client system together with the server's initial challenge of the authentication protocol, a process at the client is able to apply the crypt( ) function to the client password with the same salt such that the client and server have a shared secret for use as, or to generate, a common session key for the authentication.
Owner:IBM CORP
Secure authentication systems and methods
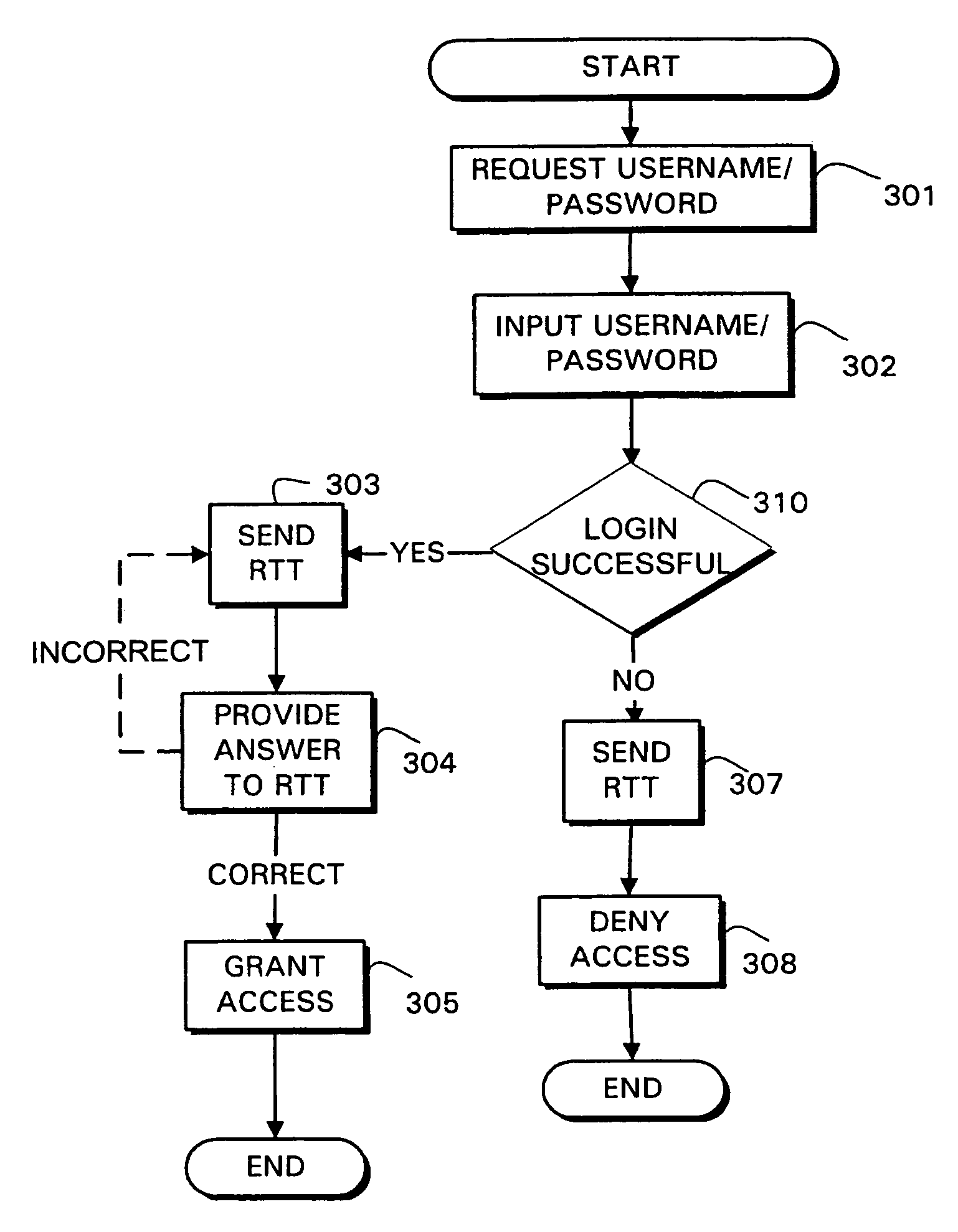
InactiveUS7383570B2Digital data processing detailsUser identity/authority verificationBrute forcePassword
Systems and methods are provided for authentication by combining a Reverse Turing Test (RTT) with password-based user authentication protocols to provide improved resistance to brute force attacks. In accordance with one embodiment of the invention, a method is provided for user authentication, the method including receiving a username / password pair associated with a user; requesting one or more responses to a first Reverse Turing Test (RTT); and granting access to the user if a valid response to the first RTT is received and the username / password pair is valid.
Owner:INTERTRUST TECH CORP
Real-Time Frame Authentication Using ID Anonymization In Automotive Networks
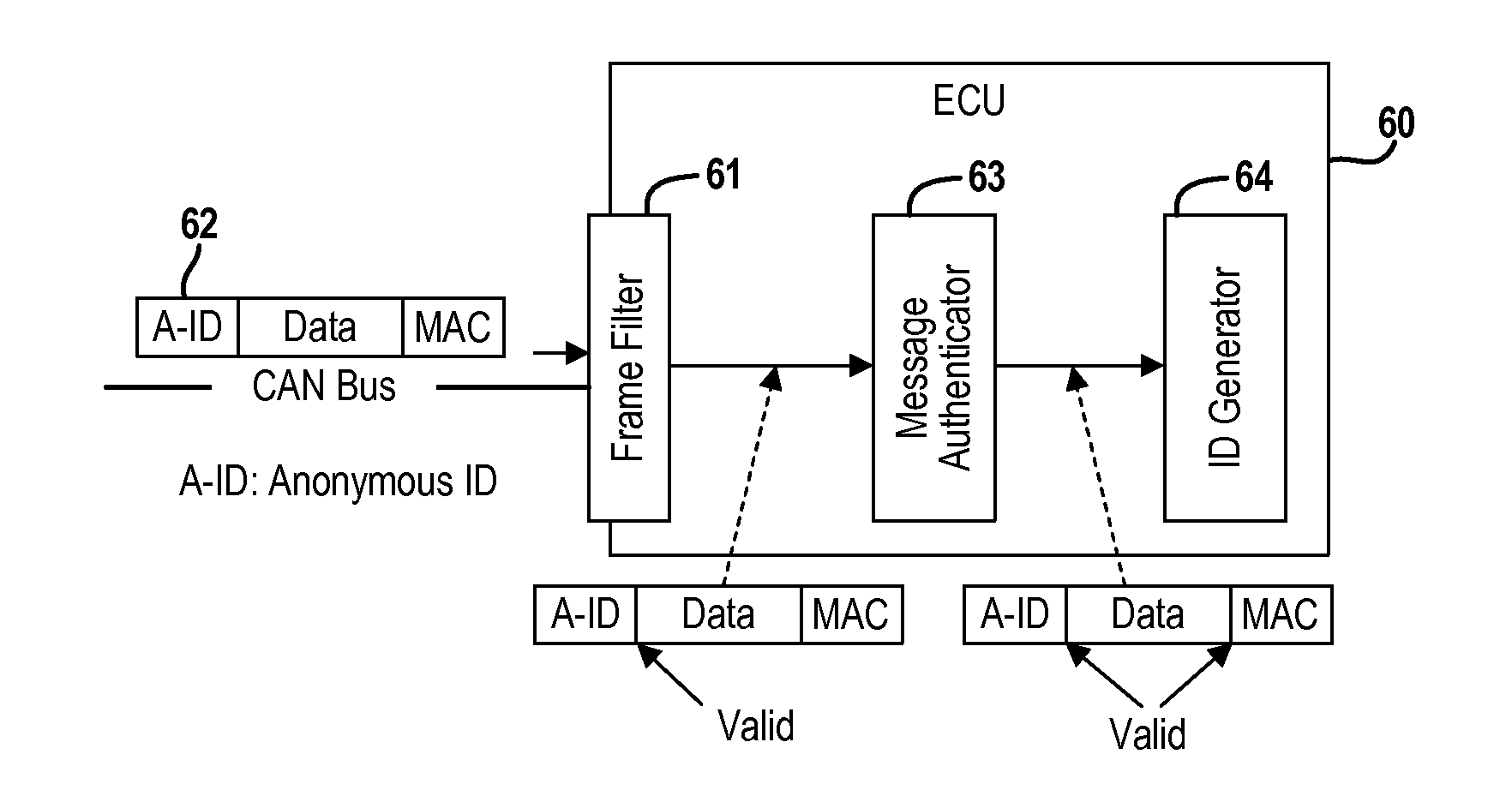
ActiveUS20150089236A1Reduce message authentication delay tmReduce delaysKey distribution for secure communicationSynchronising transmission/receiving encryption devicesComputer networkData integrity
A real-time frame authentication protocol is presented for in-vehicle networks. A frame identifier is made anonymous to unauthorized entities but identifiable by the authorized entities. Anonymous identifiers are generated on a per-frame basis and embedded into each data frame transmitted by a sending ECU. Receiving ECUs use the anonymous identifiers to filter incoming data frames before verifying data integrity. Invalid data frame are filtered without requiring any additional run-time computations.
Owner:RGT UNIV OF MICHIGAN
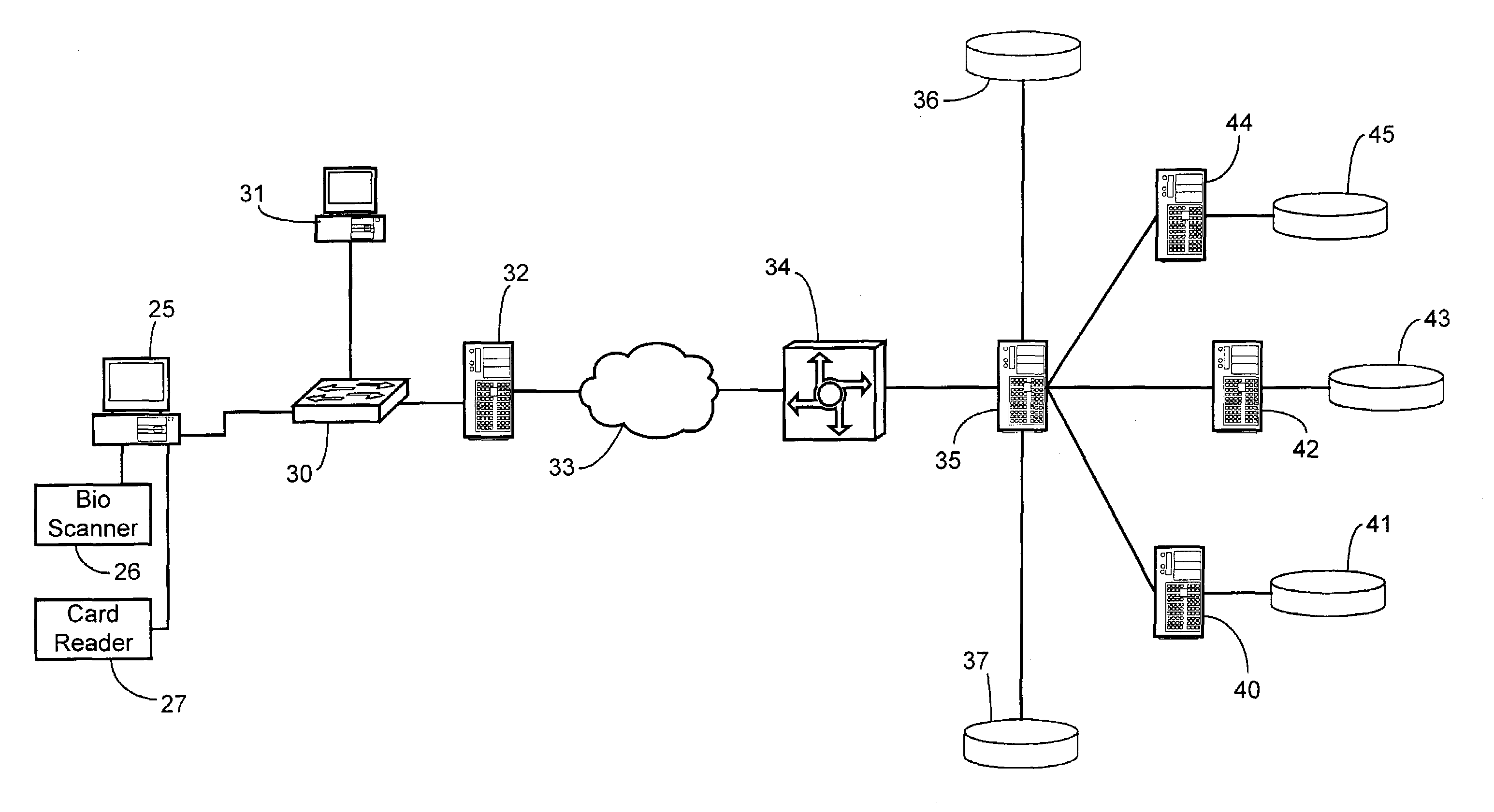
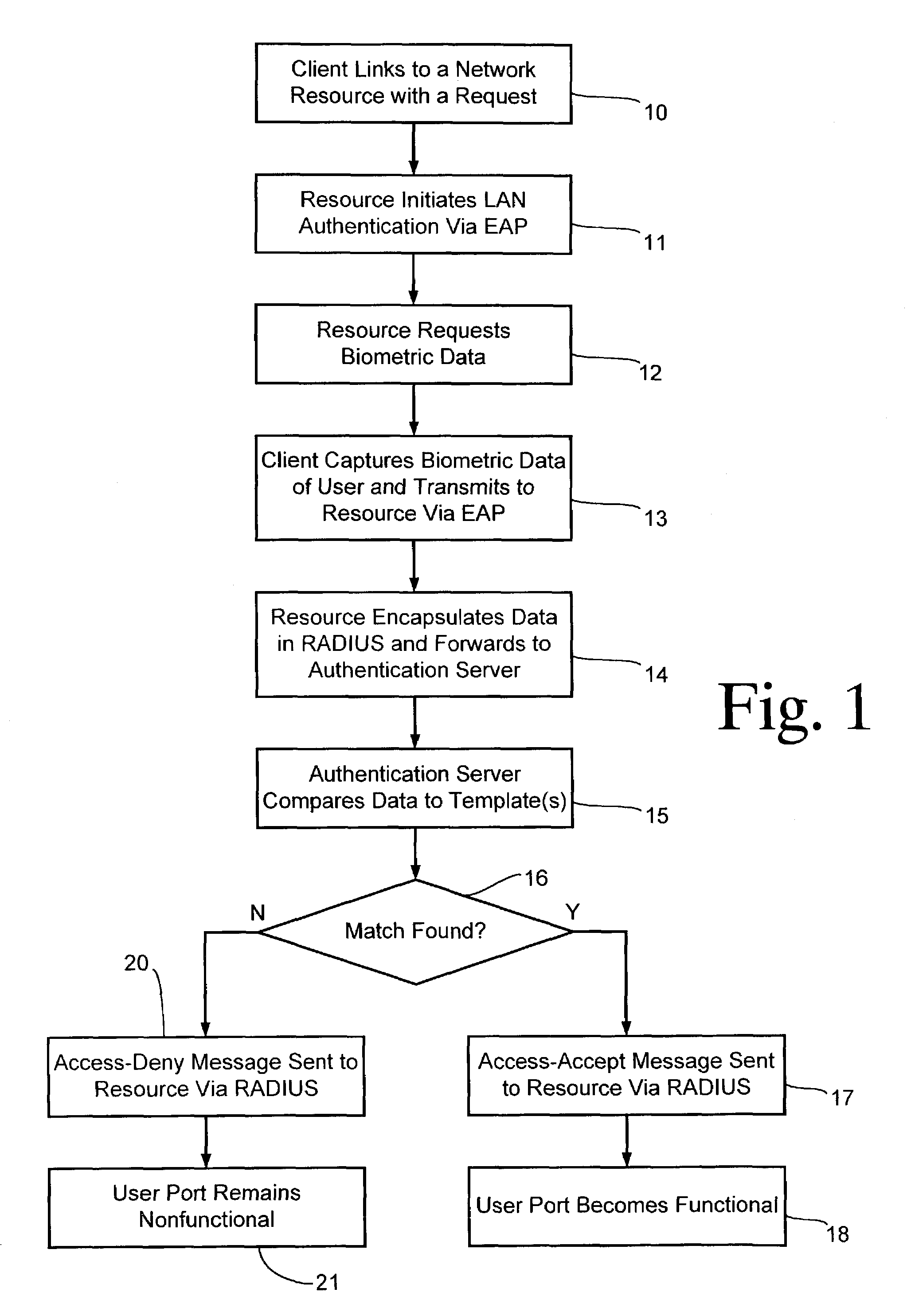
Biometric authentication of a client network connection
InactiveUS7249177B1Low costDigital data processing detailsUnauthorized memory use protectionBiometric dataNetwork connection
A client is authenticated to a network resource wherein the client is coupled to a biometric sensor. The client signals a request to the network resource (e.g., by connecting to an access point). The network resource initiates a point-to-point LAN authentication protocol between the network resource and the client. The network resource requests biometric data from the client via the LAN authentication protocol (optionally either before or after authenticating with other credentials). The client captures biometric data of an attendant user of the client. The client transmits the captured biometric data to the network resource via the LAN authentication protocol. The network resource encapsulates the biometric data in the LAN authentication protocol into an authentication server protocol and forwards the encapsulated biometric data to an authentication server. The authentication server compares the biometric data to a biometric template stored in conjunction with the authentication server for making a determination whether the attendant user should be granted access to the network resource. The authentication server sends either an access-accept message or an access-deny message in the authentication server protocol to the network resource in response to the determination. The network resource grants access to the client only after receiving an access-accept message.
Owner:SPRINT CORPORATION
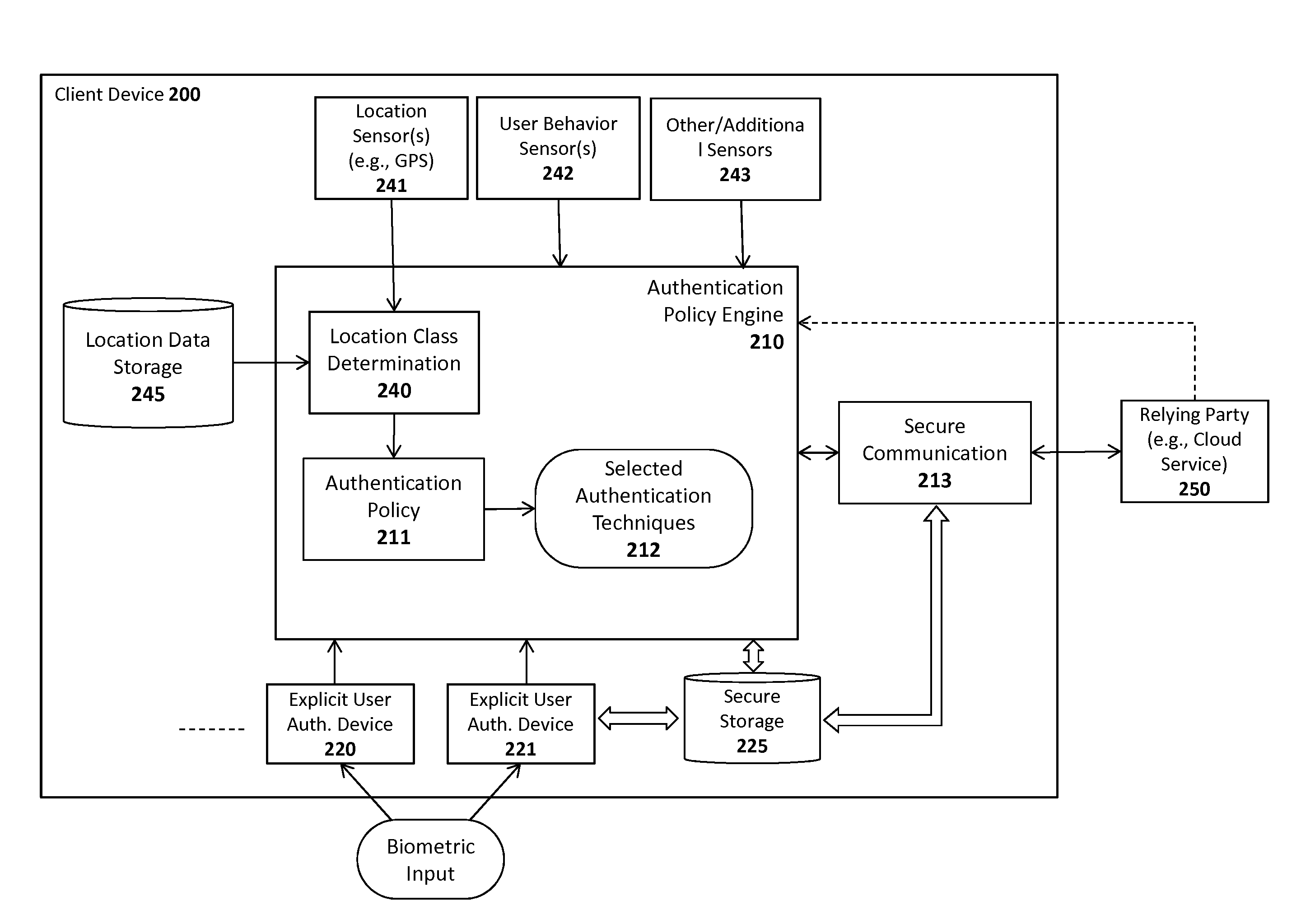
System and method for adaptive application of authentication policies
ActiveUS20140289790A1Payment architectureDigital data authenticationClient-sideHuman–computer interaction
A system, apparatus, method, and machine readable medium are described for adaptively implementing an authentication policy. For example, one embodiment of a method comprises: detecting a user of a client attempting to perform a current interaction with a relying party; and responsively identifying a first interaction class for the current interaction based on variables associated with the current interaction and implementing a set of one or more authentication rules associated with the first interaction class.
Owner:NOK NOK LABS
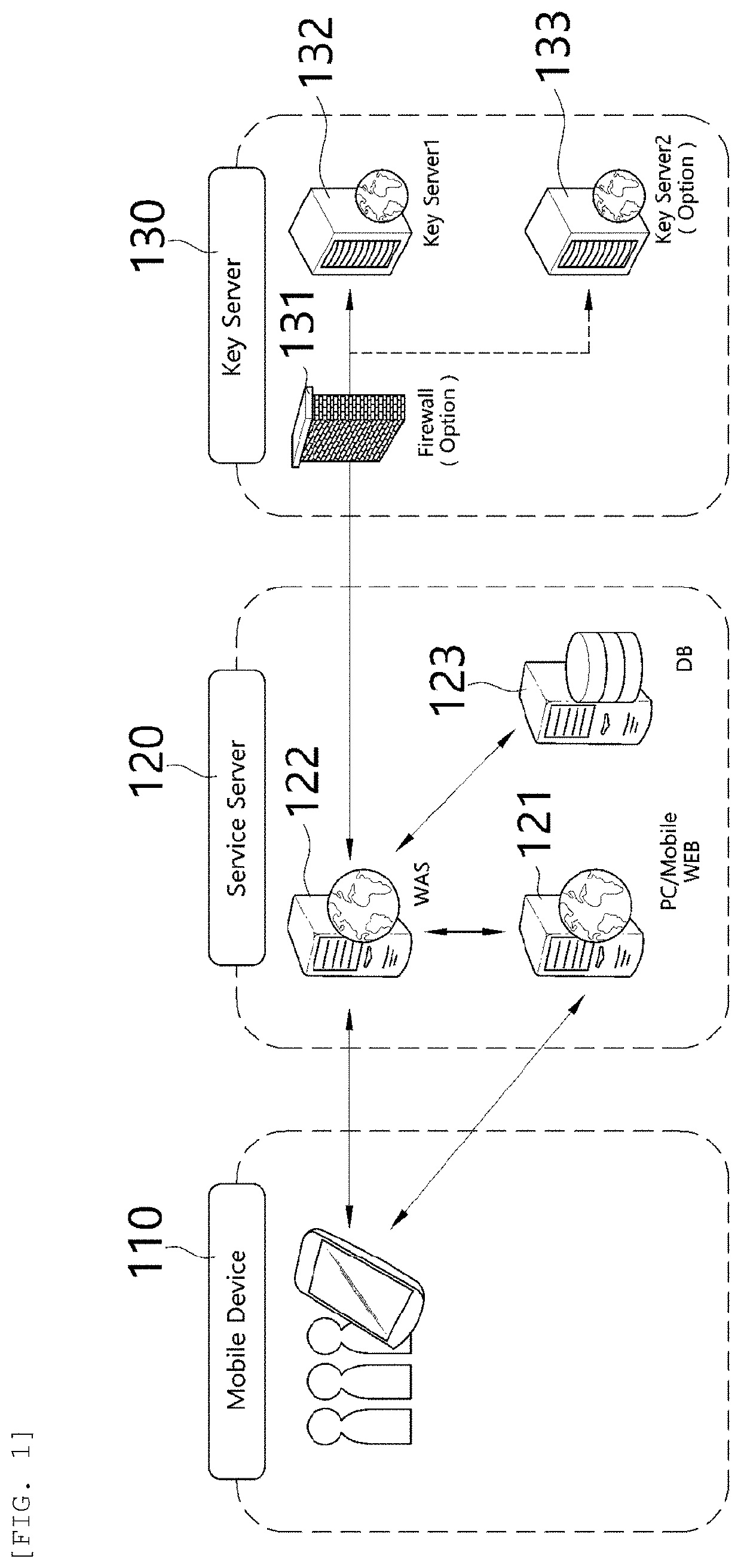
Method and system for protecting personal information infringement using division of authentication process and biometric authentication
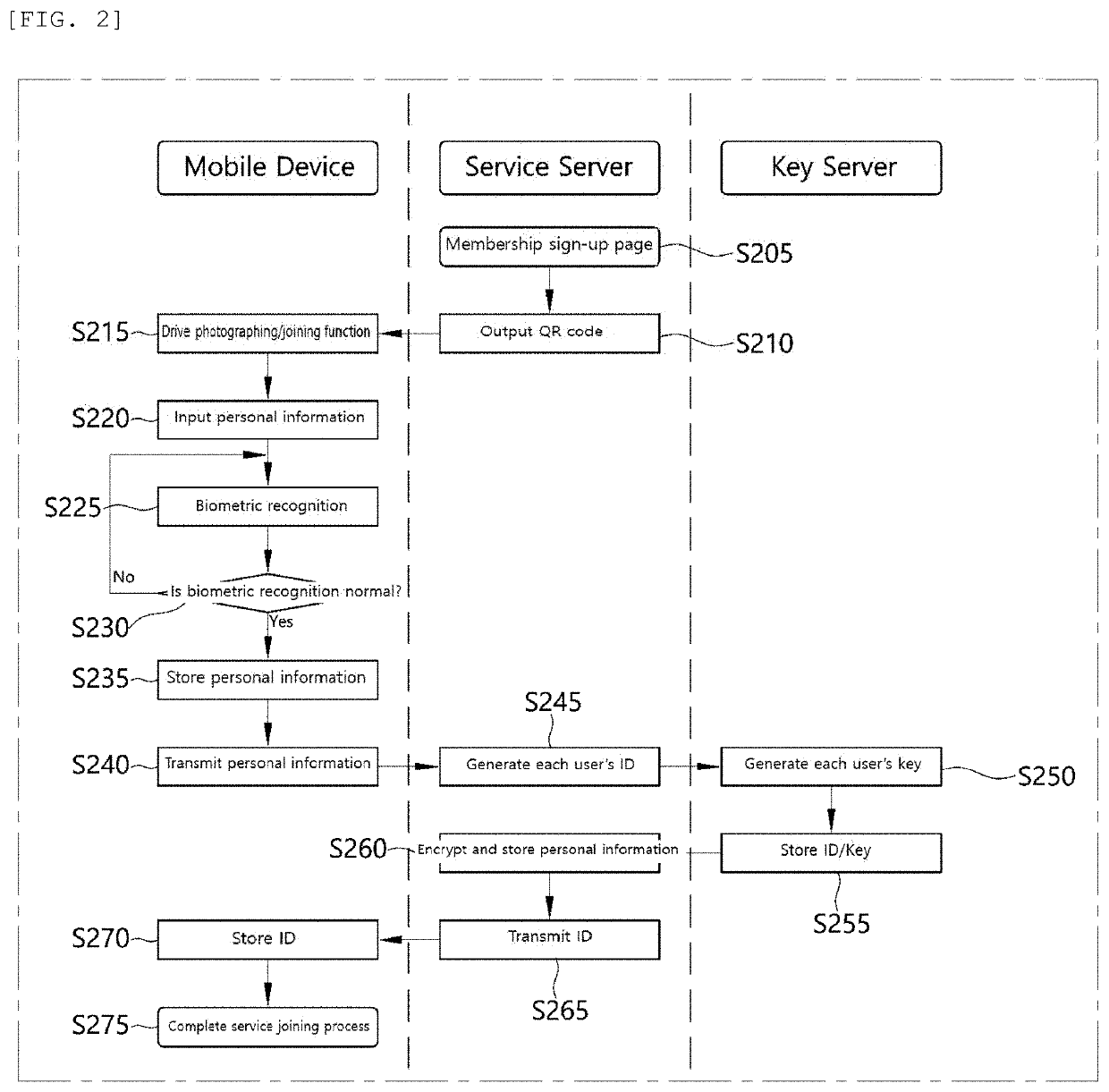
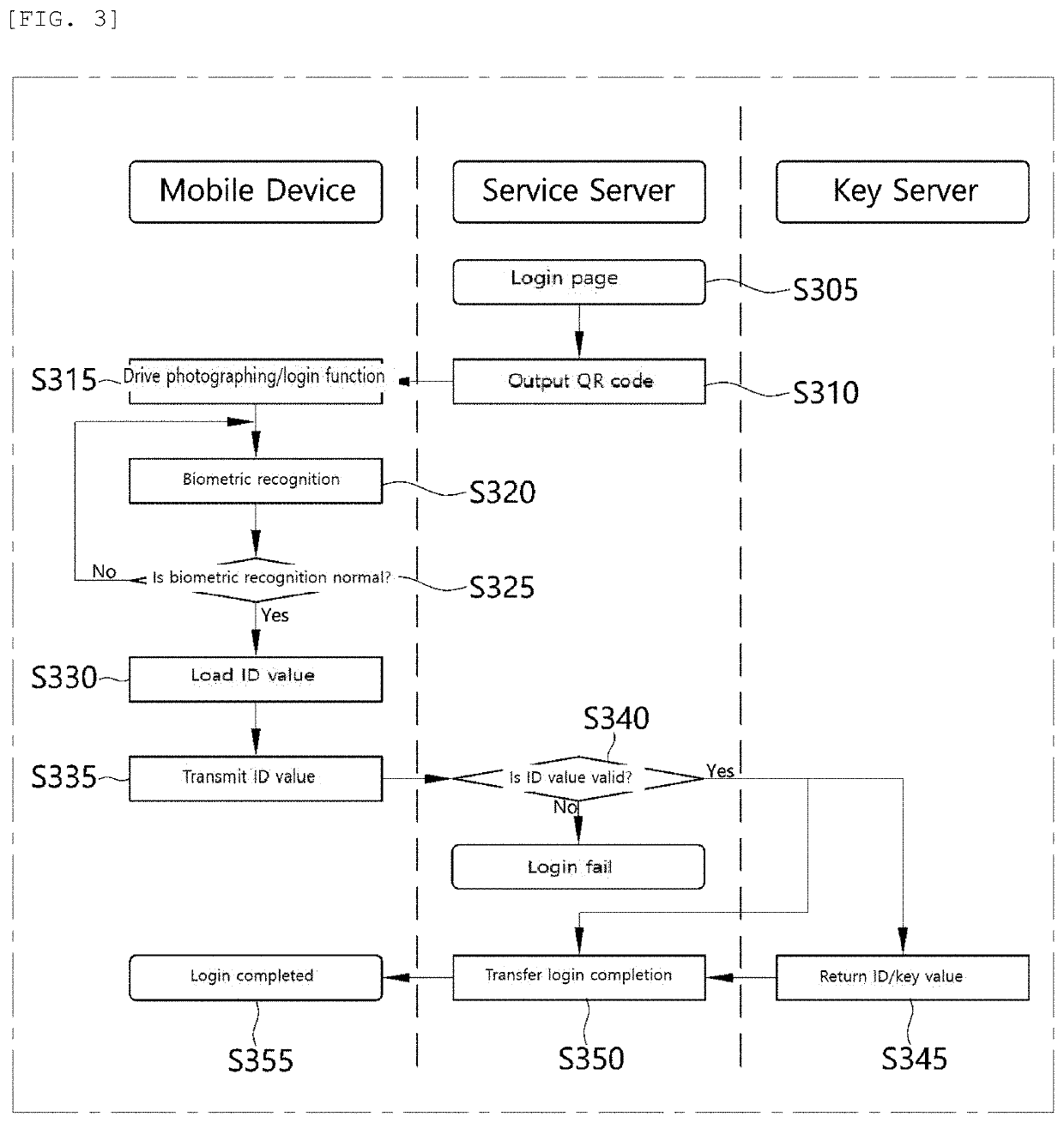
InactiveUS20190384934A1Eliminate chancePreventing situationKey distribution for secure communicationUser identity/authority verificationComputer terminalBiometrics
A personal information infringement protection system, includes: a portable terminal having an application installed therein to photograph a QR code and recognize biometrics; a service server for storing the encrypted personal information, and generating an ID of a user and transmitting the ID to the portable terminal to be stored therein or informing the portable terminal of login completion when the ID received from the portable terminal is a valid ID; and a key server for generating a key value for encryption and decryption of the personal information, classifying and storing the key value by user, and providing the key value to the service server.
Owner:RENOMEDIA CO LTD
Query string processing
ActiveUS20020099671A1Easy mappingData processing applicationsDigital data processing detailsData matchingQuery string
A system is disclosed that is used to provide access management for resources on a network. The system makes use of query data from a URL (or another identification or request) to identify the appropriate access rule. Examples of an access rule include an authentication rule, an authorization rule, or an audit rule. The system can be configured to require the query data to match order dependent variables or order independent variables. In one option, the system can include two levels of rules and the query data can be used to identify first level rules, second level rules or both.
Owner:ORACLE INT CORP
Single sign-on in multi-tenant environments
ActiveUS20140090037A1Digital data processing detailsMultiple digital computer combinationsInternet privacySystem usage
The disclosed embodiments provide a system that authenticates a user. During operation, the system identifies a first tenant associated with a first request for a first resource from the user and obtains an authentication policy for the first tenant. Next, the system uses an authentication mechanism associated with the authentication policy to authenticate the user. Upon authenticating the user, the system provides a first security token for enabling access to the first resource by the user.
Owner:INTUIT INC
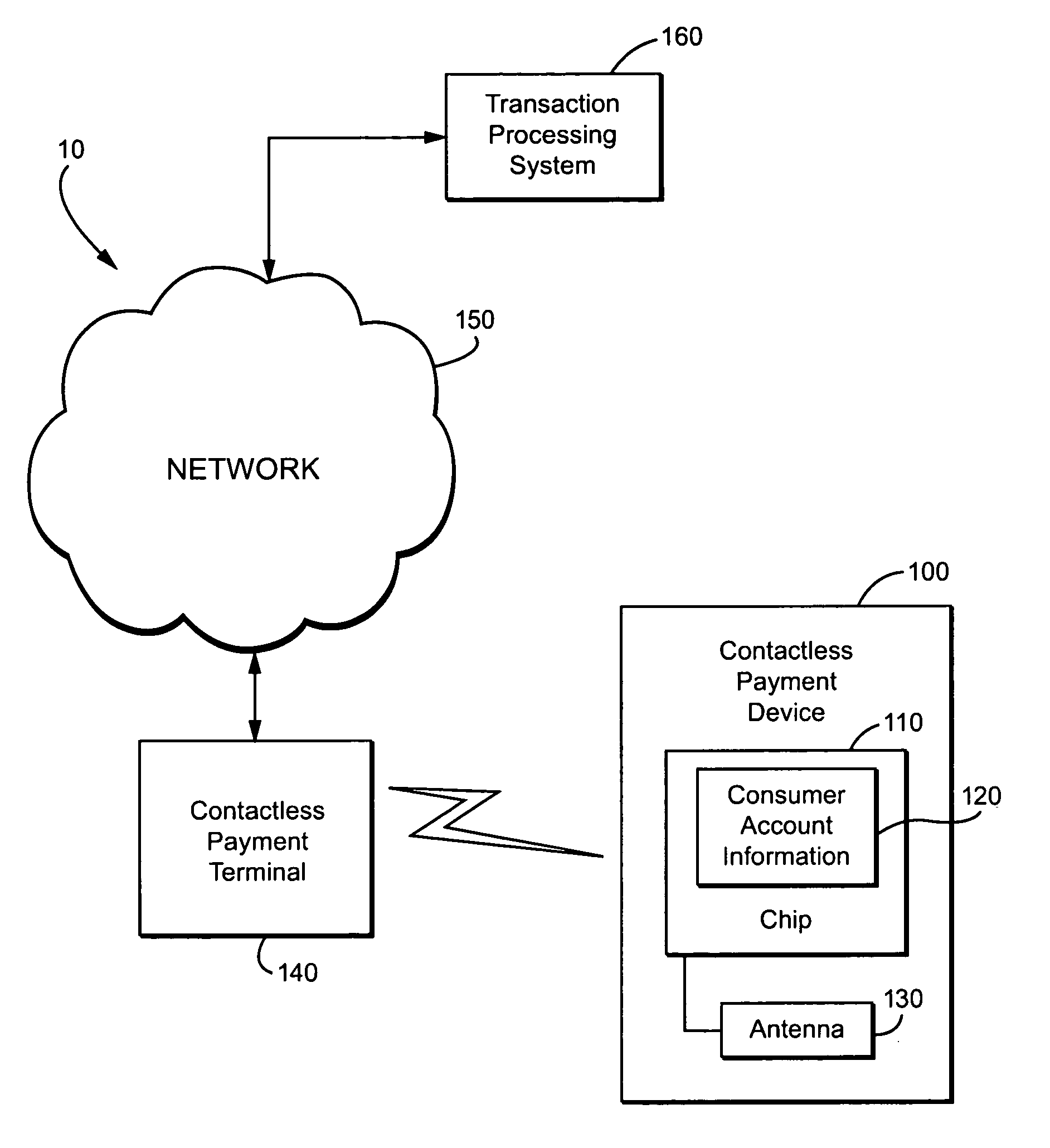
Method and apparatus for contactless payment authentication
ActiveUS20070152035A1Efficient and accurate and easy to implementMaintain conveniencePayment architectureSensing record carriersPaymentPassword protection
The present disclosure relates generally to the authentication of contactless payments attempted by a device having embedded contactless payment functionality. In particular, the disclosure is directed to systems and methods that utilize authentication schemes that already exist on a device in which the contactless payment functionality is embedded. One example of such authentication schemes is the use of password protection to lock or unlock the device in which the contactless payment functionality is embedded. Using the password protection functionality may provide varying levels of authentication protection based on the desires of the user. A number of exemplary uses of such a method and apparatus are disclosed herein.
Owner:MALIKIE INNOVATIONS LTD
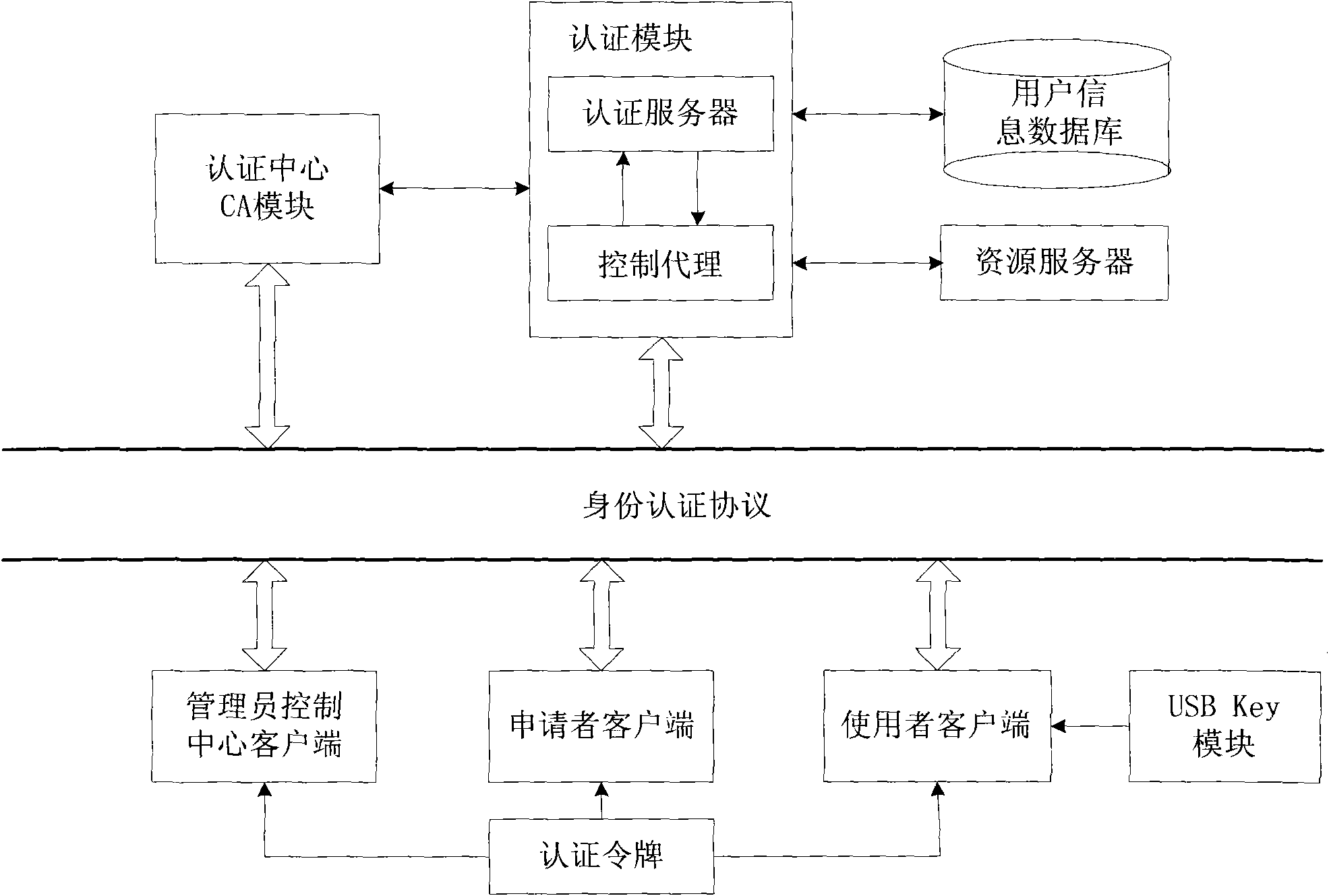
Network identity authentication system and method
InactiveCN101674304AEnsure safetyAchieve separationUser identity/authority verificationConfidentialityAuthentication server
The invention relates to an identity authentication system and an authentication method. The identity authentication system comprises an authentication center CA module, an authentication module, a client side and a USB Key module, wherein the authentication center CA module is responsible for the functions of application, examination and approval, issuing, updating and revocation of a certificate; the authentication module respectively carries out the generation of a digital envelope and the authentication of a digital certificate to the client side and a server side; the client side mainly realizes the management of the system and the clients; and the USB Key module mainly provides a medium for storing the digital certificate and a user private key to the user. The invention adopts a digital envelope technology, and can meet the high-confidentiality requirement of data transmission; an authentication token is used for sending a request to the authentication server by the client sidefor authentication and realizing the security of the authentication process; and the client side and the authentication server respectively carry out the generation of the digital envelope and the digital certificate, thus being capable of realizing the mutual authentication between the client side and the authentication server.
Owner:ZHEJIANG NORMAL UNIVERSITY
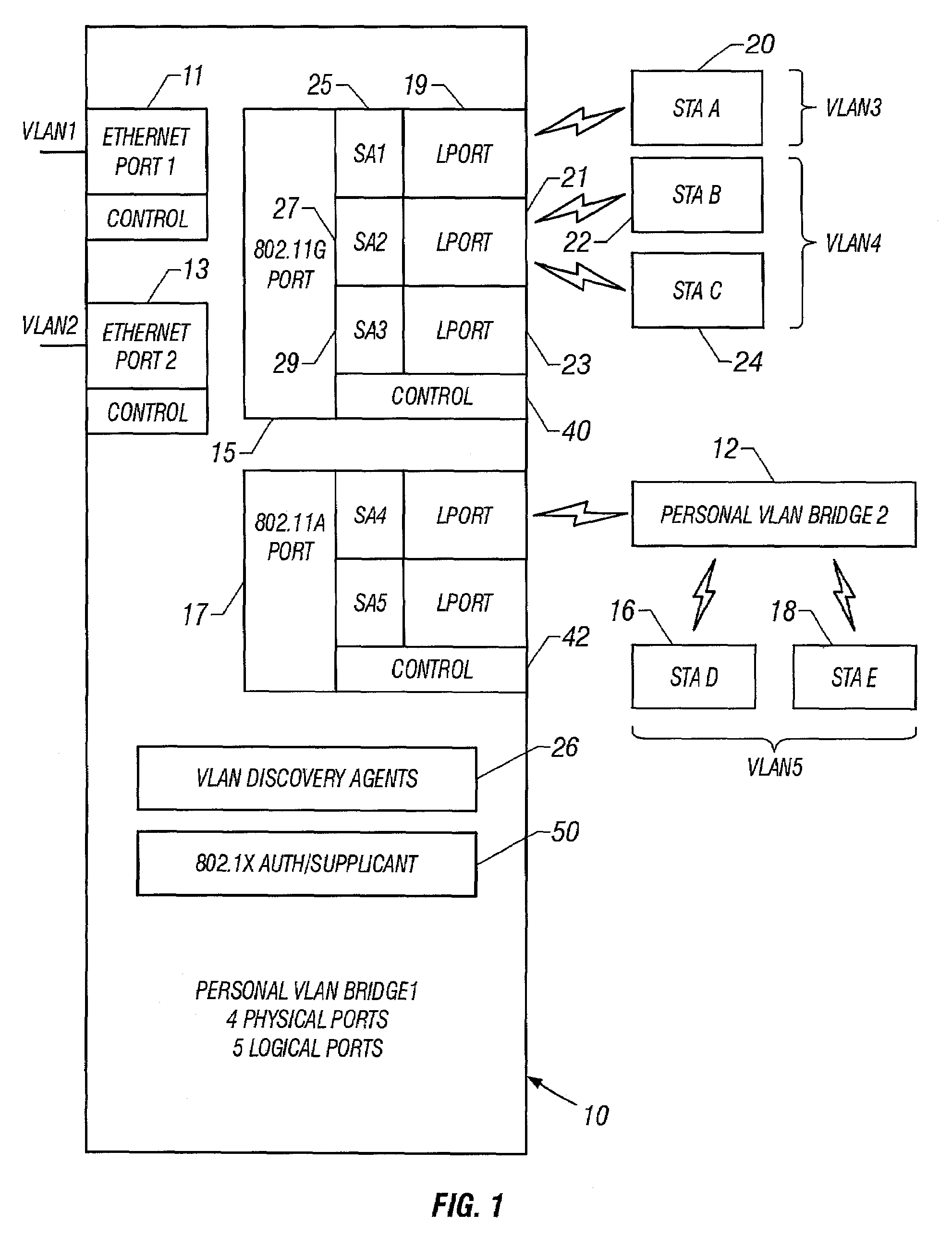
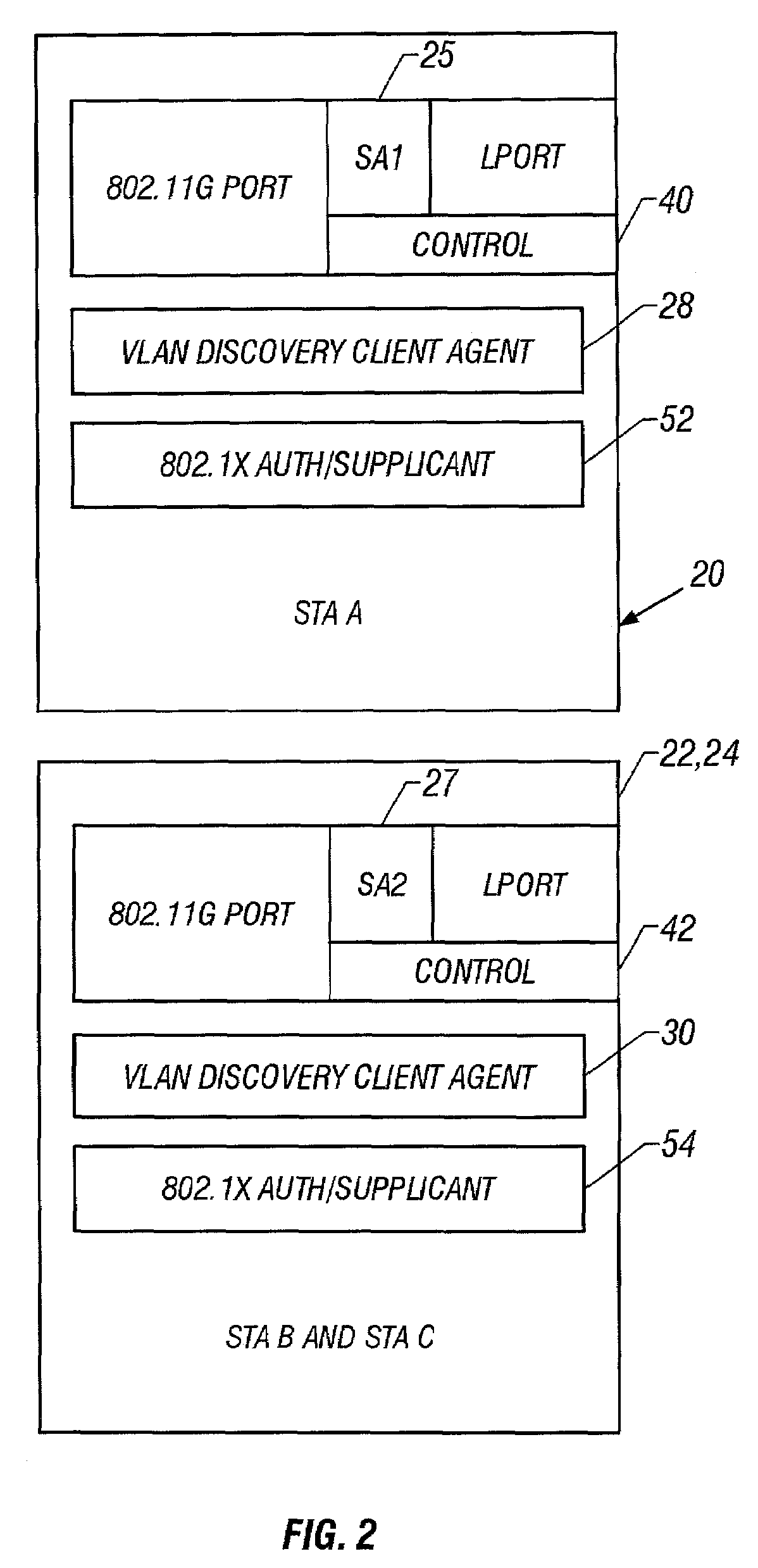
Personal virtual bridged local area networks
InactiveUS7188364B2Multiplex communicationUser identity/authority verificationProtocol for Carrying Authentication for Network AccessBridging model
A mechanism for segregating traffic amongst STAs that are associated with a bridge, referred to herein as the personal virtual bridged local area network (personal VLAN), is based upon the use of a VLAN to segregate traffic. The IEEE 802.1Q-1998 (virtual bridged LANs) protocol provides a mechanism that is extended by the invention to partition a LAN segment logically into multiple VLANs. In the preferred embodiment, a VLAN bridge forwards unicast and group frames only to those ports that serve the VLAN to which the frames belong. One embodiment of the invention extends the standard VLAN bridge model to provide a mechanism that is suitable for use within an AP. In a preferred embodiment, the Personal VLAN bridge extends the standard VLAN bridge in at least any of the following ways: VLAN discovery in which a personal VLAN bridge provides a protocol for VLAN discovery; VLAN extension in which a Personal VLAN allows a station to create a new port that serves a new VLAN, or to join an existing VLAN via an authentication protocol; Logical ports in which a Personal VLAN bridge can maintain more than one logical port per physical port, and bridges between ports of any kind; and cryptographic VLAN separation.
Owner:MICROSOFT TECH LICENSING LLC
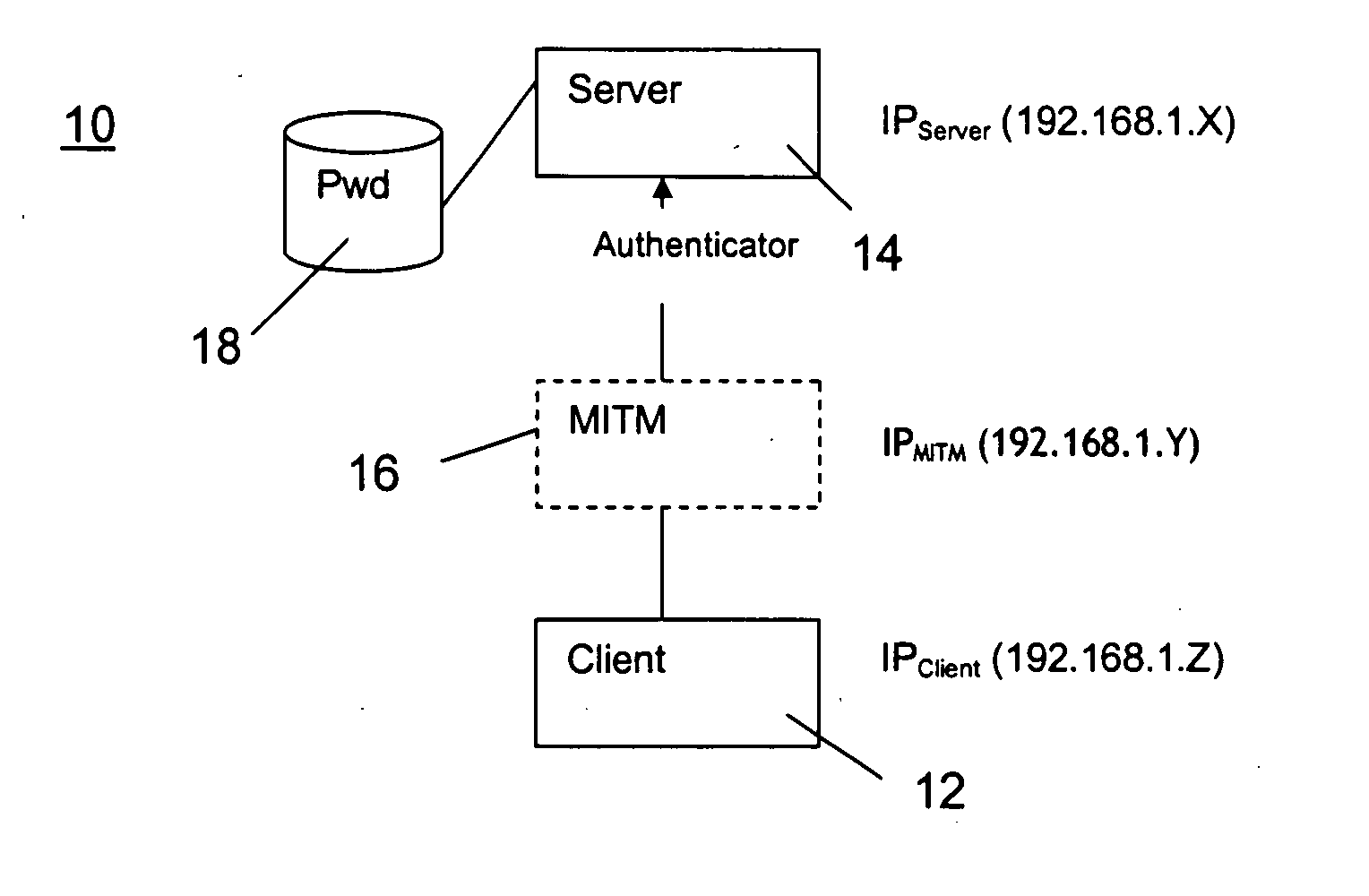
Authentication protocol
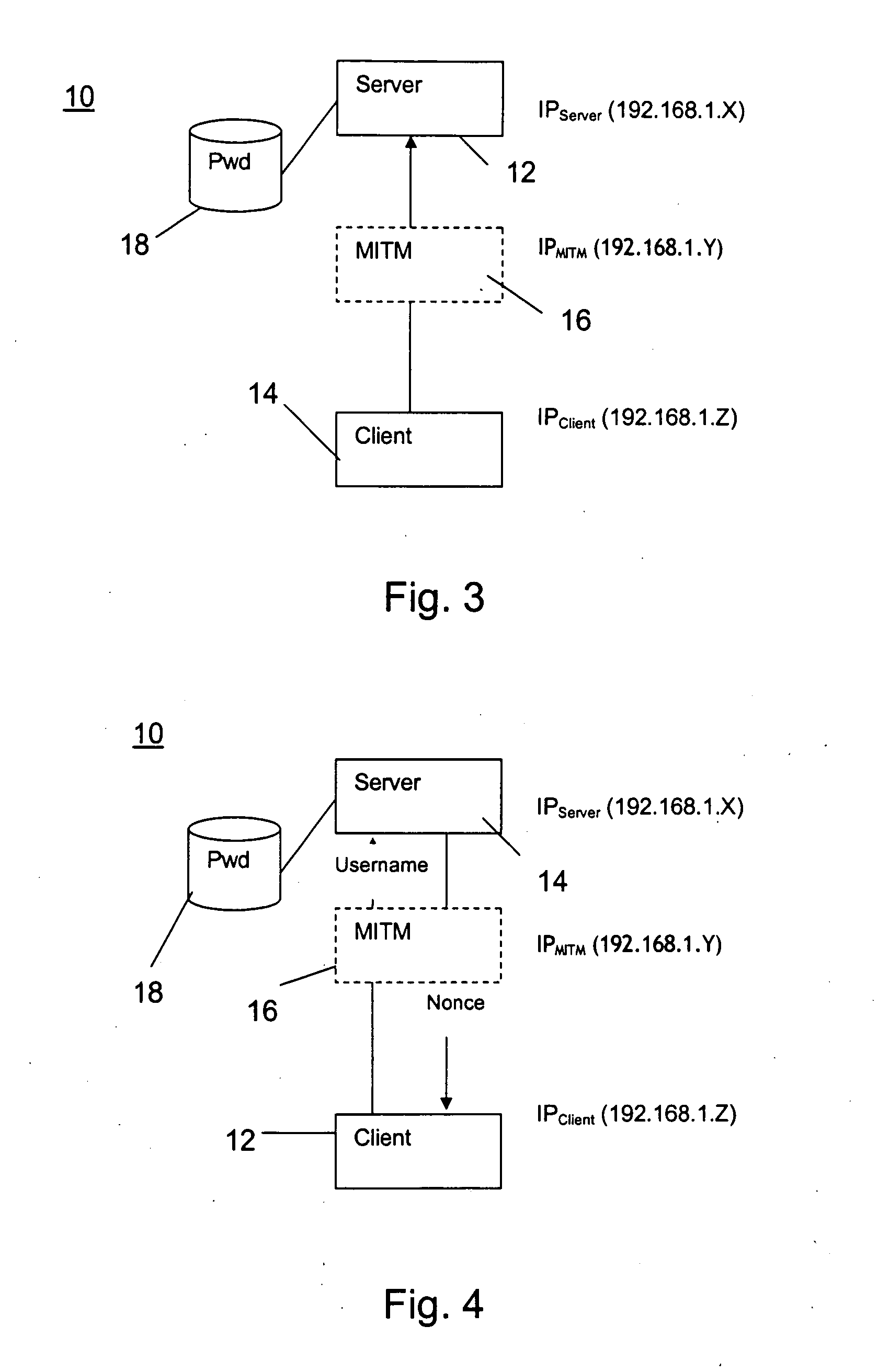
InactiveUS20050022020A1Improve securityDigital data processing detailsUser identity/authority verificationPasswordIp address
The invention relates to an authentication protocol for increasing safety against a man-in-the-middle (MITM) access attack for point-to-point communication (10), between client computer (12) and server (14), to services. The server (14) responds with an N byte nonce value and the client computer (12) utilizes a hash algorithm to compute a hash value of the parameters clients' password, client computer unique IP address, server IP address, and the nonce value. The hash value is transmitted through the client computer (12) as an authenticator for accessing the services, whereby the server (14) reproduces the authenticator by utilizing the same hash algorithm and parameters. A compare between the reproduction and the transmitted authenticator is accomplished. If they match, the grant of an access to the server (14) and services is authorized. By utilizing the client computer (12) unique IP address in the authenticator it prevents a MITM computer (16), having a different IP address, from addressing the server with a matching authenticator. The present invention also comprises an authenticator signal and a medium for carrying the signal.
Owner:CINNOBER FINANCIAL TECH
Monitoring of Authorization-Exceeding Activity in Distributed Networks
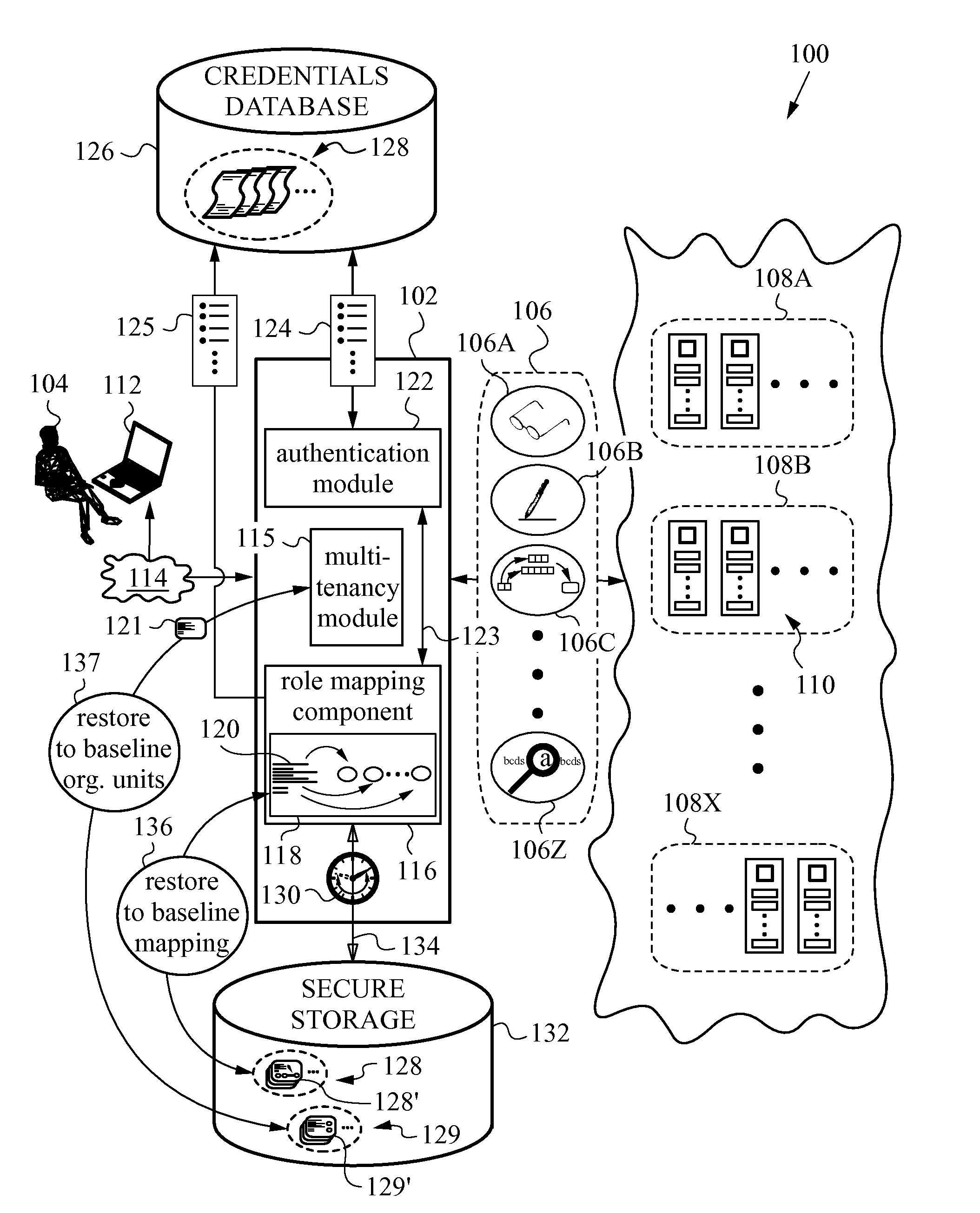
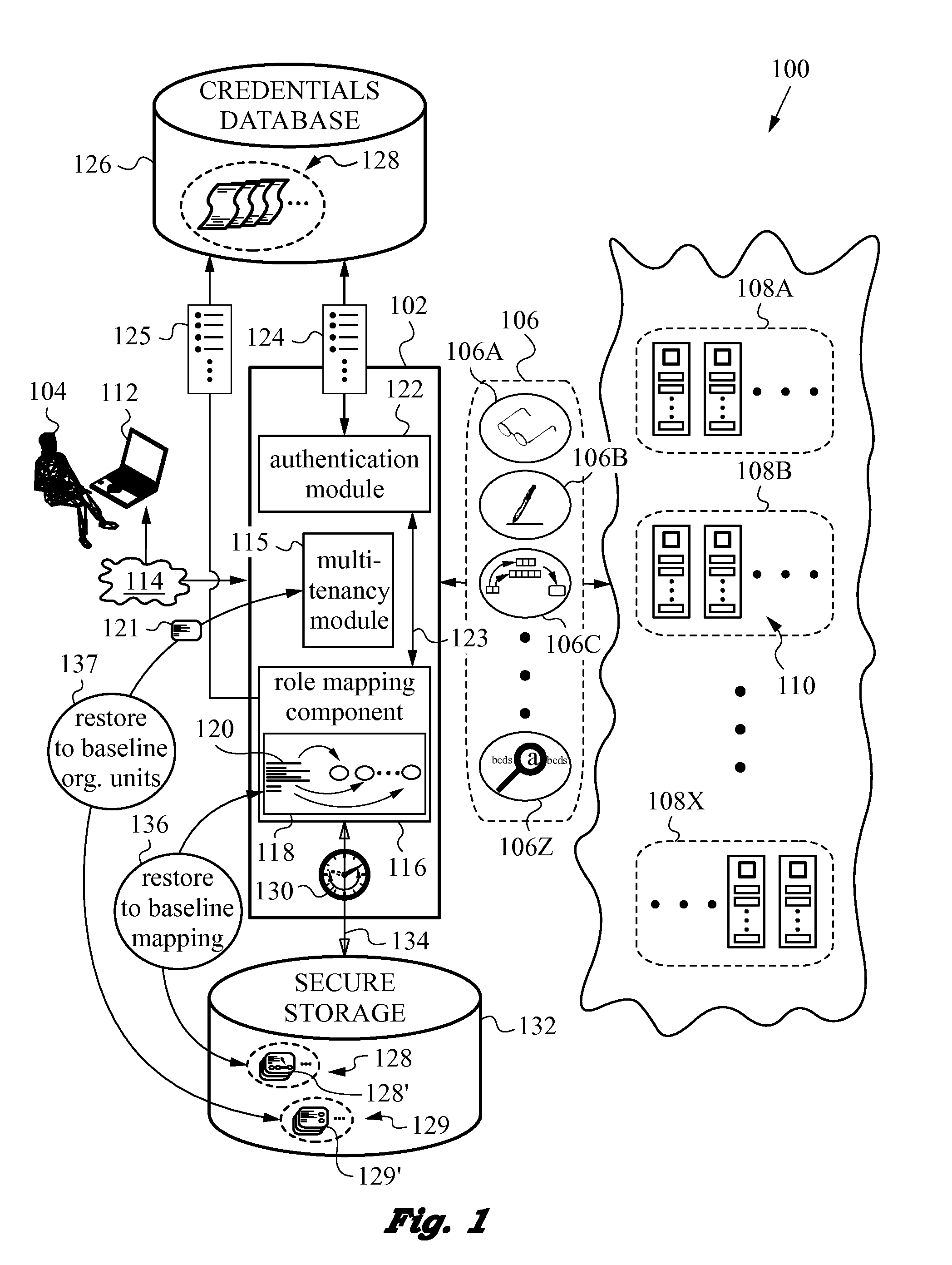
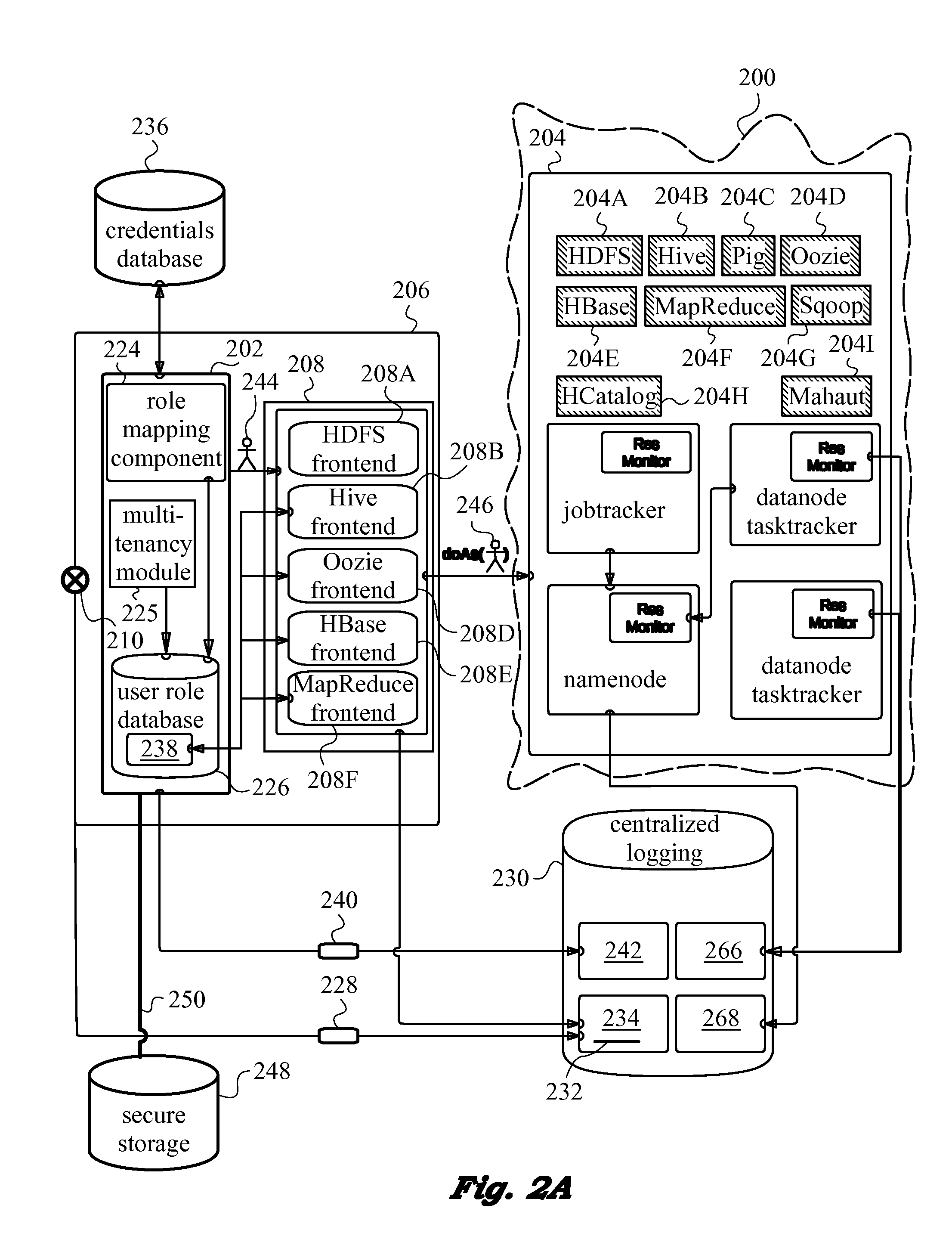
ActiveUS20140196115A1Minimal disruptionProvide supportDigital data processing detailsComputer security arrangementsUser authenticationOnline identity
A network security layer with a role mapping component with a current role mapping between services and access permissions is provided between a user and the services. A multi-tenancy module with current membership mapping is also provided. The security layer has a network authentication protocol for user authentication at log-in. Snapshots of a baseline role mapping between services and permissions are taken at certain times. The role mapping component verifies snapshots at set intervals, and when the user performs certain actions, the current role mapping is compared with the baseline role mapping. Upon discrepancy, the role mapping component executes a set of rules, including forceful log-out to prevent system intrusion. Comparison of current membership mapping with a baseline membership mapping can also be applied. The security layer can thus monitor authorization-exceeding modifications to baseline policies attempted by logged-in and initially authorized users.
Owner:ZETTASET
Systems and methods for enhancing security of communication over a public network
InactiveUS20050120214A1Improve securityDigital data processing detailsUser identity/authority verificationCommunications securityPublic network
An authentication protocol is disclosed for use in enhancing the security of communications between software applications and Internet-based service providers. The protocol incorporates a two level authentication model based on a distribution of authentication responsibilities, wherein the application authenticates users and the service provider authenticates the application. Embodiments of the protocol incorporate public key infrastructure and digital certificate technology. Other embodiments of the present invention pertain to applying a corresponding protocol to peer-to-peer communication scenarios.
Owner:MICROSOFT TECH LICENSING LLC
Access Control System and Method for Operating Said System
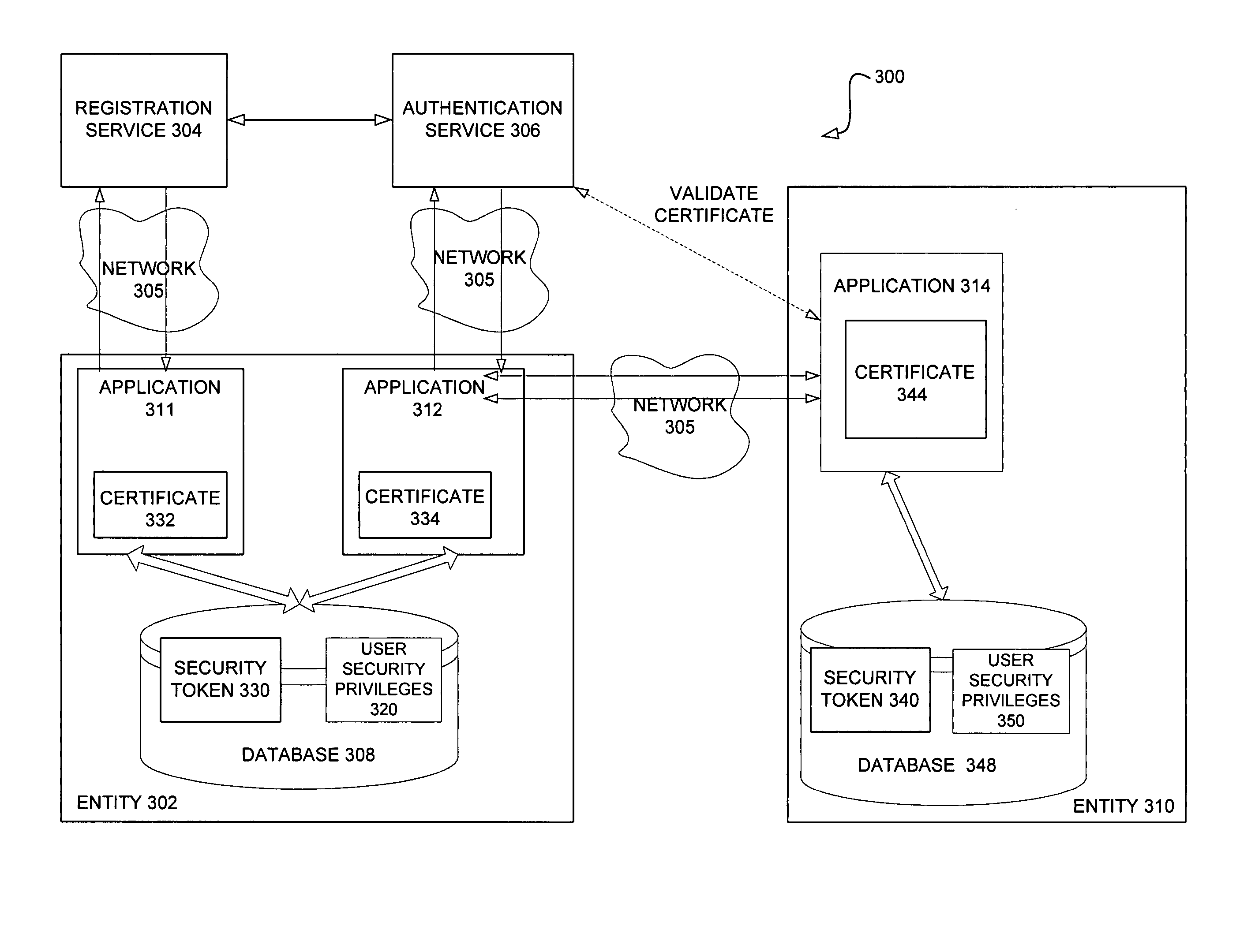
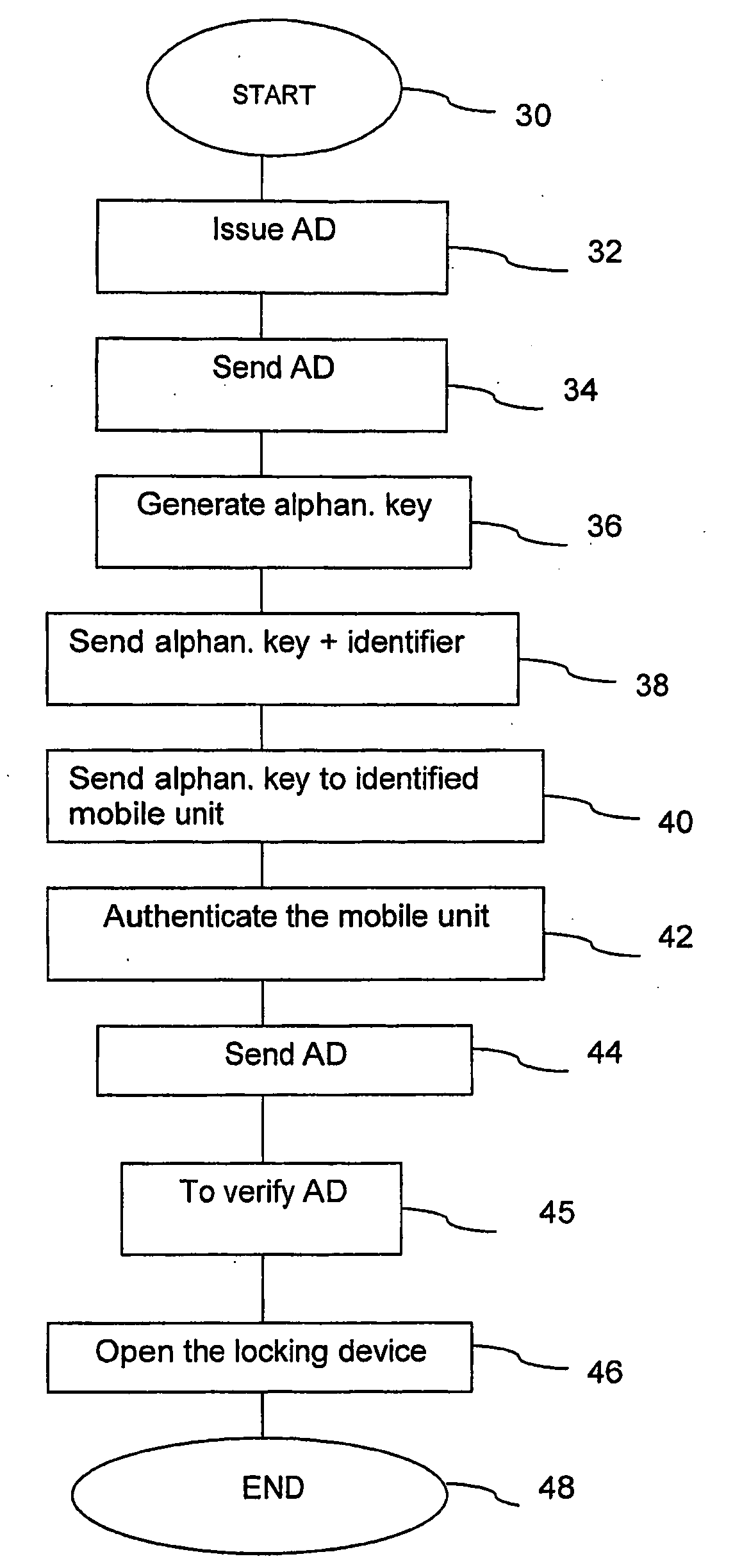
InactiveUS20090183541A1Electric signal transmission systemsMultiple keys/algorithms usageAuthentication protocolUnique identifier
The present invention relates to a system (10) operable to control access to different physical spaces, each provided with an electrical locking device (121, . . . , 12n), with the aid of a programmable, mobile unit (14). The system (10) comprises an authority means (16) operable to issue access rights connected to the programmable, mobile unit (14) in the form of an authorizing data (AD), which authorizing data (AD) is sent to an authorization means (18) connected to the authority means (16), and operable to generate an alpha-numerical key for the mobile unit (14), and to send the alpha-numerical key and a unique identifier of the mobile unit (14) to an operator (20), which is connected to the authorization means (18). The operator (20) is operable to send the alpha-numerical key to the mobile unit (14) identified by the unique identifier. An electrical locking device (12i), wherein 1≦i≦n, and the mobile unit (14) uses an authentication protocol with the alpha-numerical key to authenticate the mobile unit (14), wherein the mobile unit, if it has been authenticated, sends the authorizing data (AD) to the electrical locking device (12i), and if the authorizing data (AD) comprises an identifier of the electrical locking device (12i), the mobile unit (14) is able to open the electrical locking device (12n) with the aid of a communication means (22) comprised in the mobile unit (14) for communication in the near field.
Owner:TELCRED
Identity-based-encryption system with district policy information
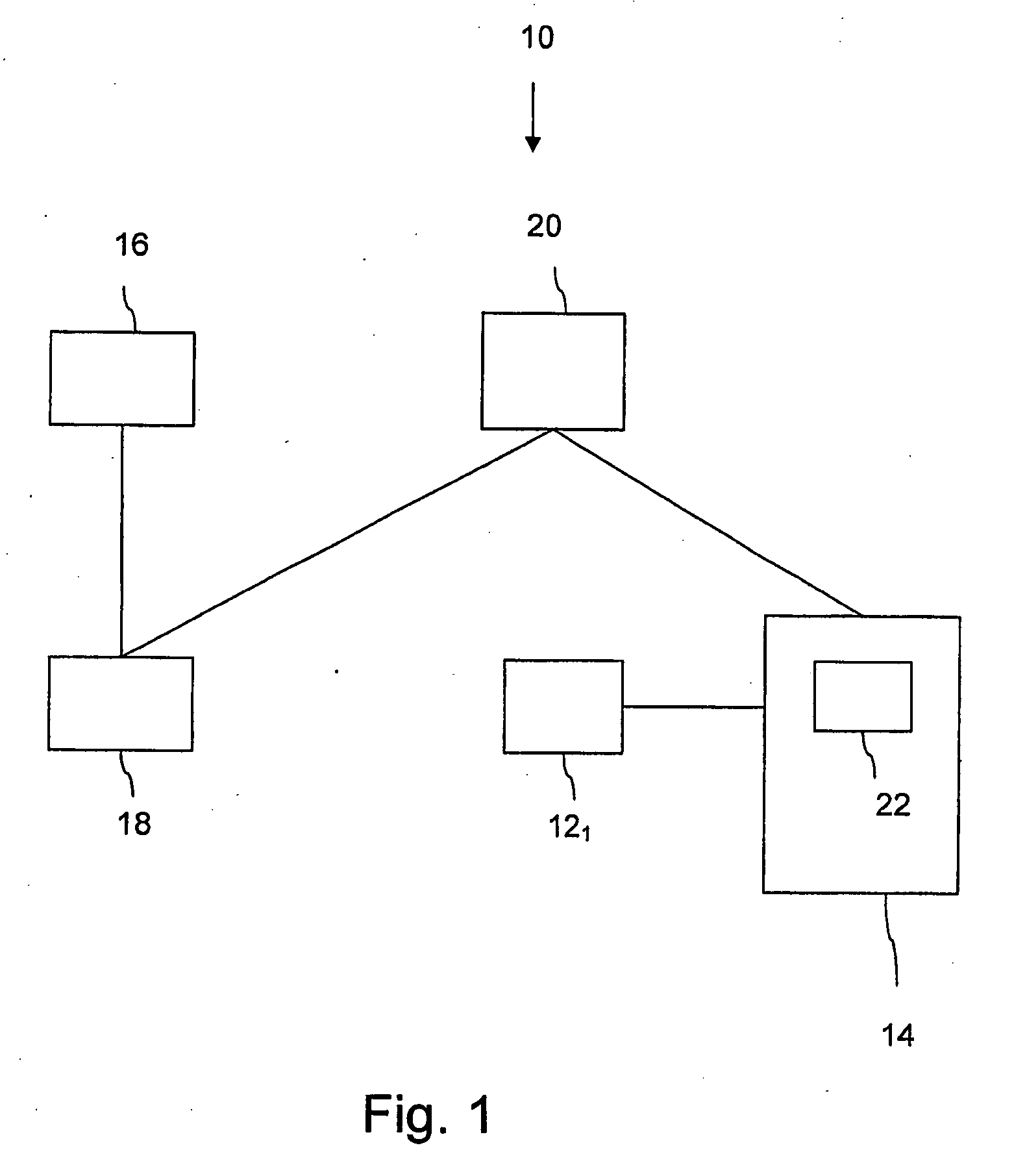
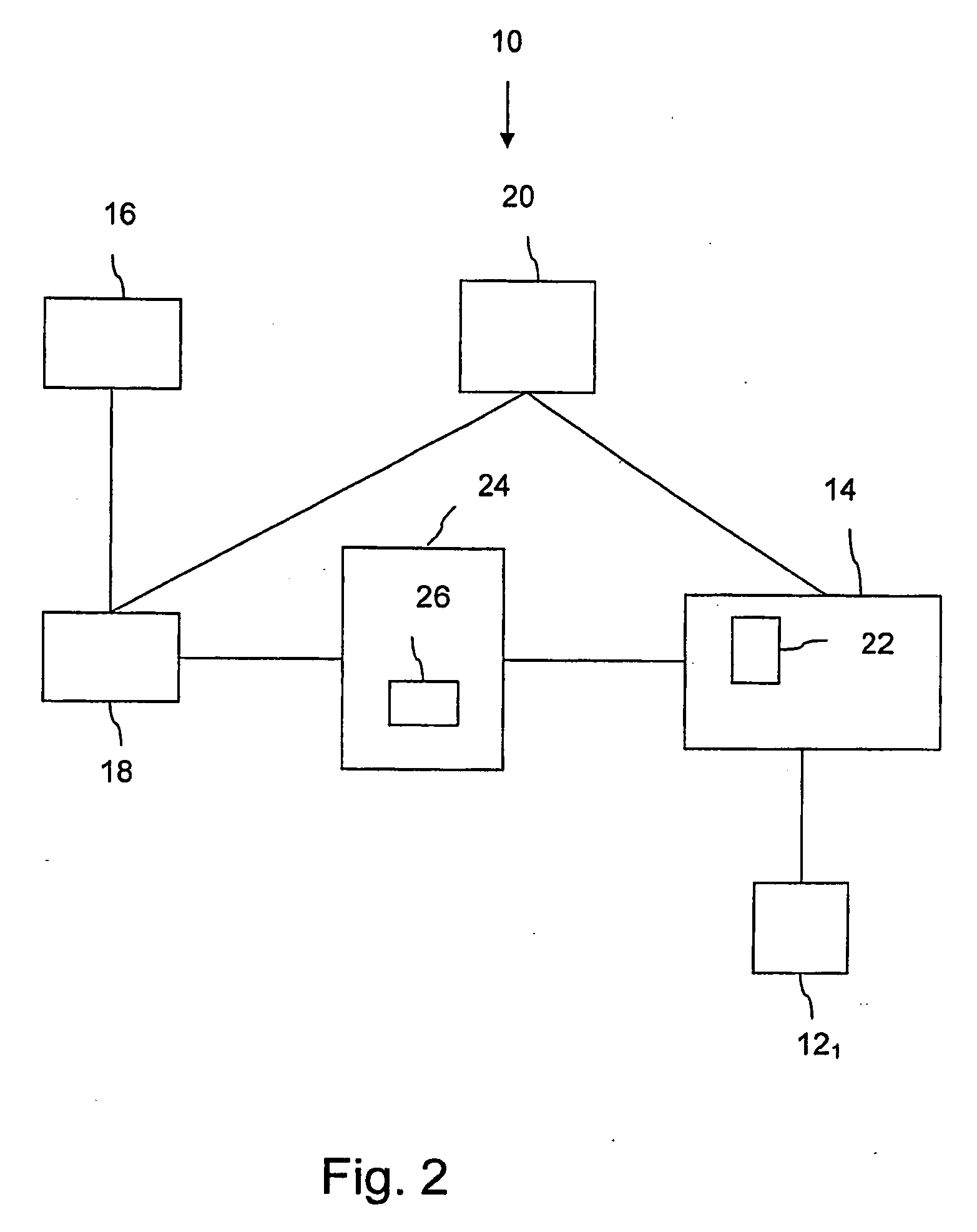
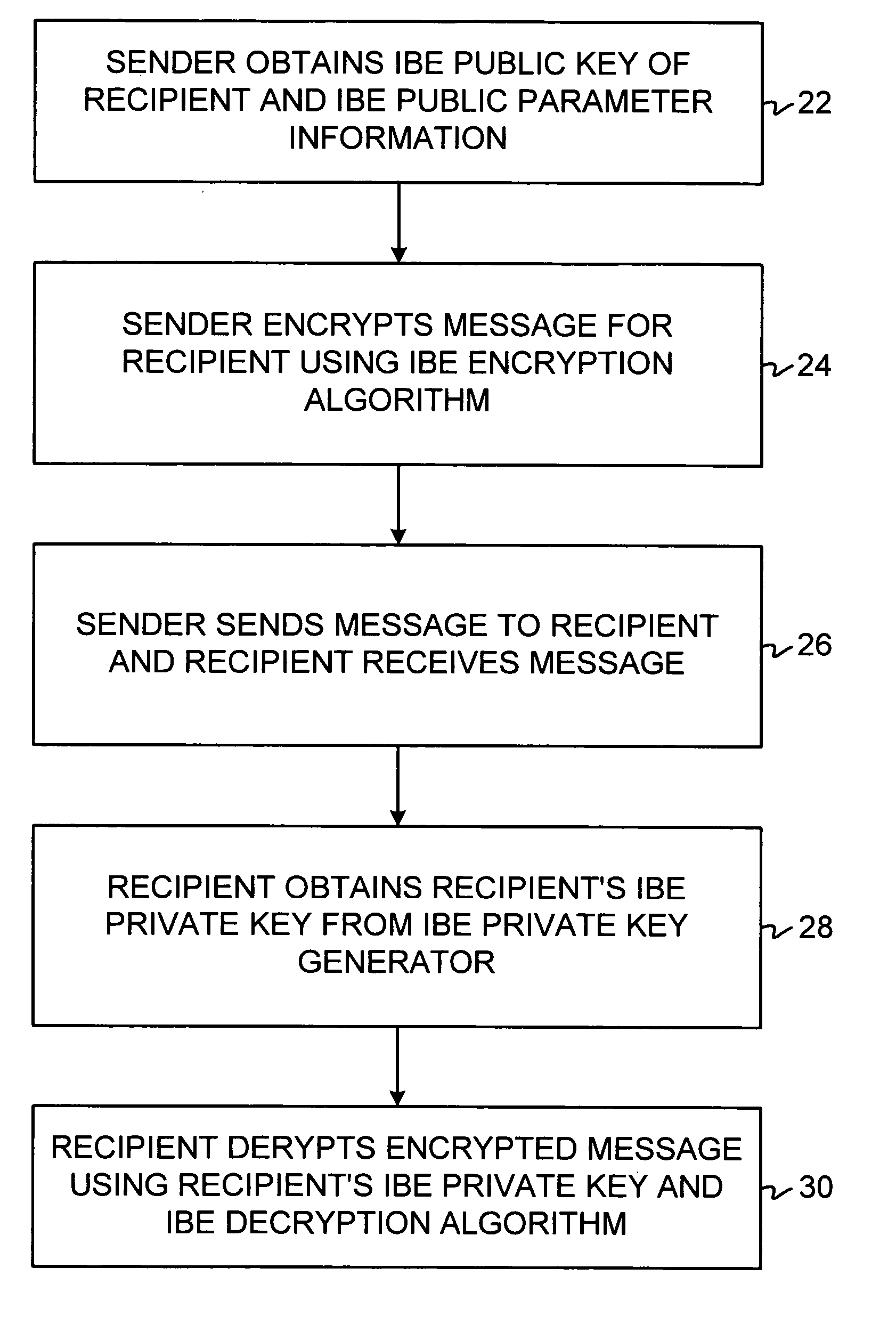
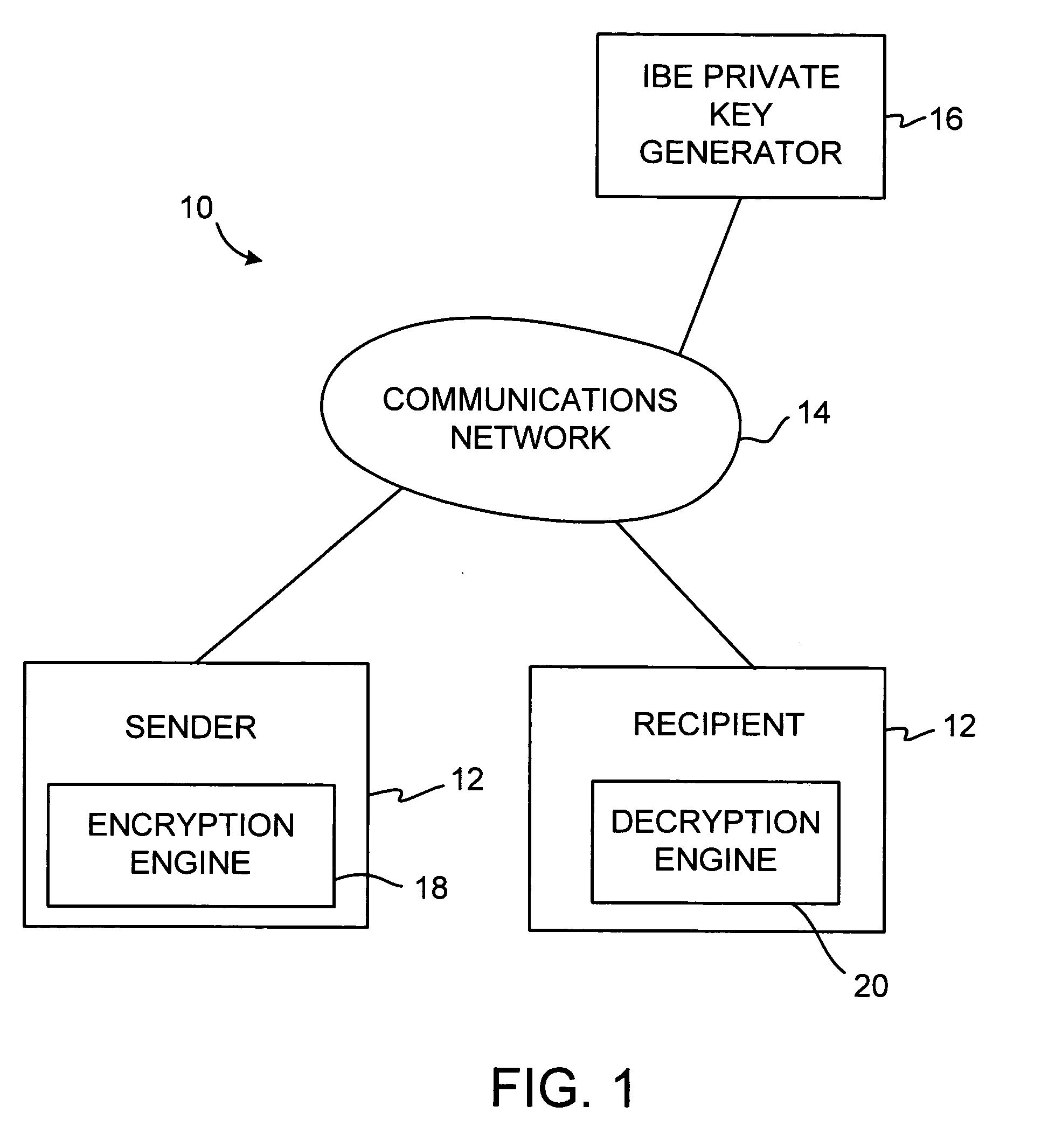
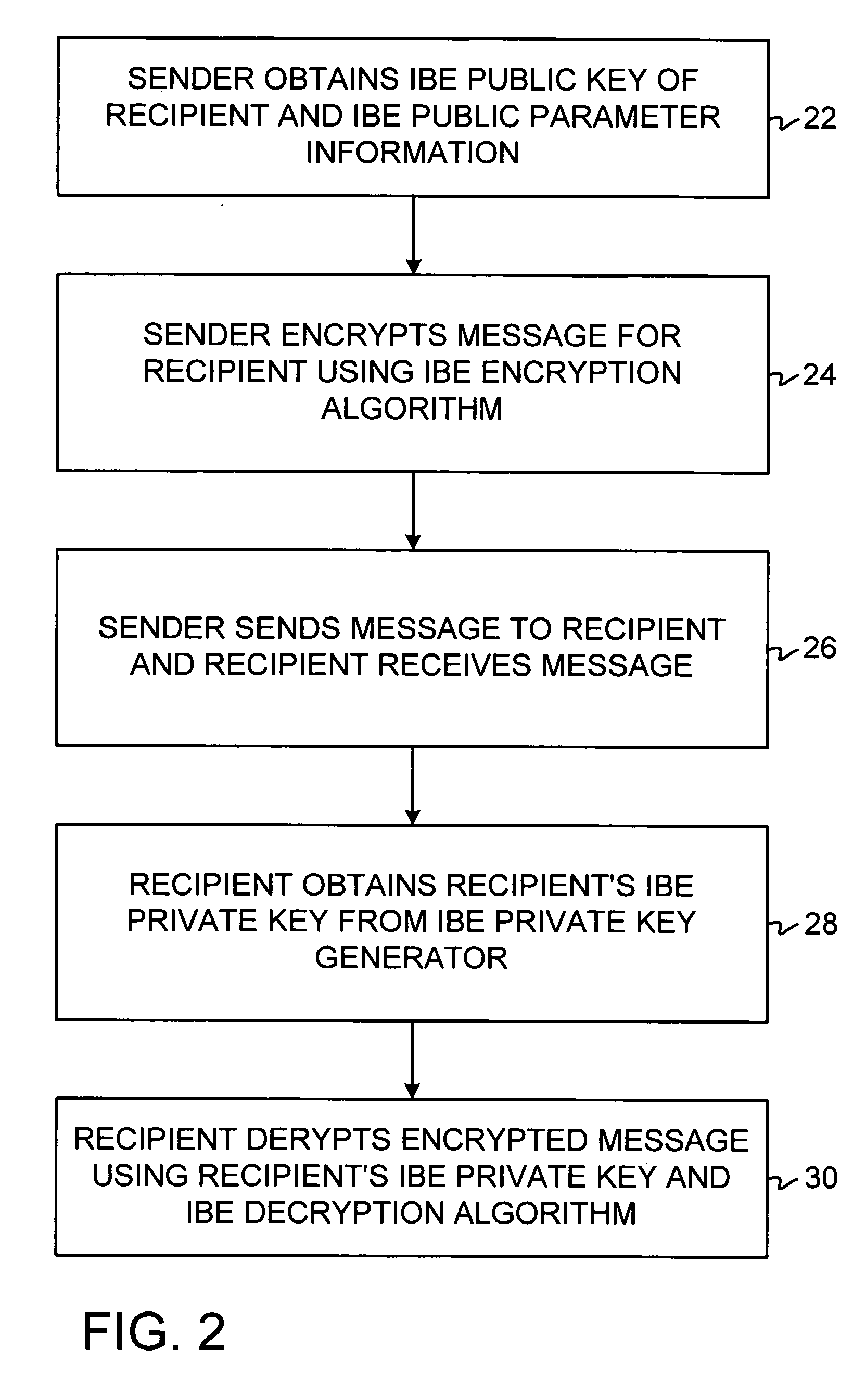
ActiveUS20050084100A1Public key for secure communicationSecret communicationNetwork Communication ProtocolsInformation security
A system is provided that uses identity-based encryption (IBE) to allow a sender to securely convey information in a message to a recipient over a communications network. IBE public key information may be used to encrypt messages and corresponding IBE private key information may be used to decrypt messages. The IBE private keys may be provided to message recipients by an IBE private key generator. The IBE private key generator and the recipients who obtain their IBE private keys from that generator form a district. District policy information may be provided by the IBE private key generator that specifies which encryption and communications protocols are used by the district. The district policy information may also specify which authentication protocols are used by the district and may set forth how content-based protocols are implemented. This information may be used by senders in sending messages to recipients.
Owner:MICRO FOCUS LLC
Pluggable authentication and access control for a messaging system
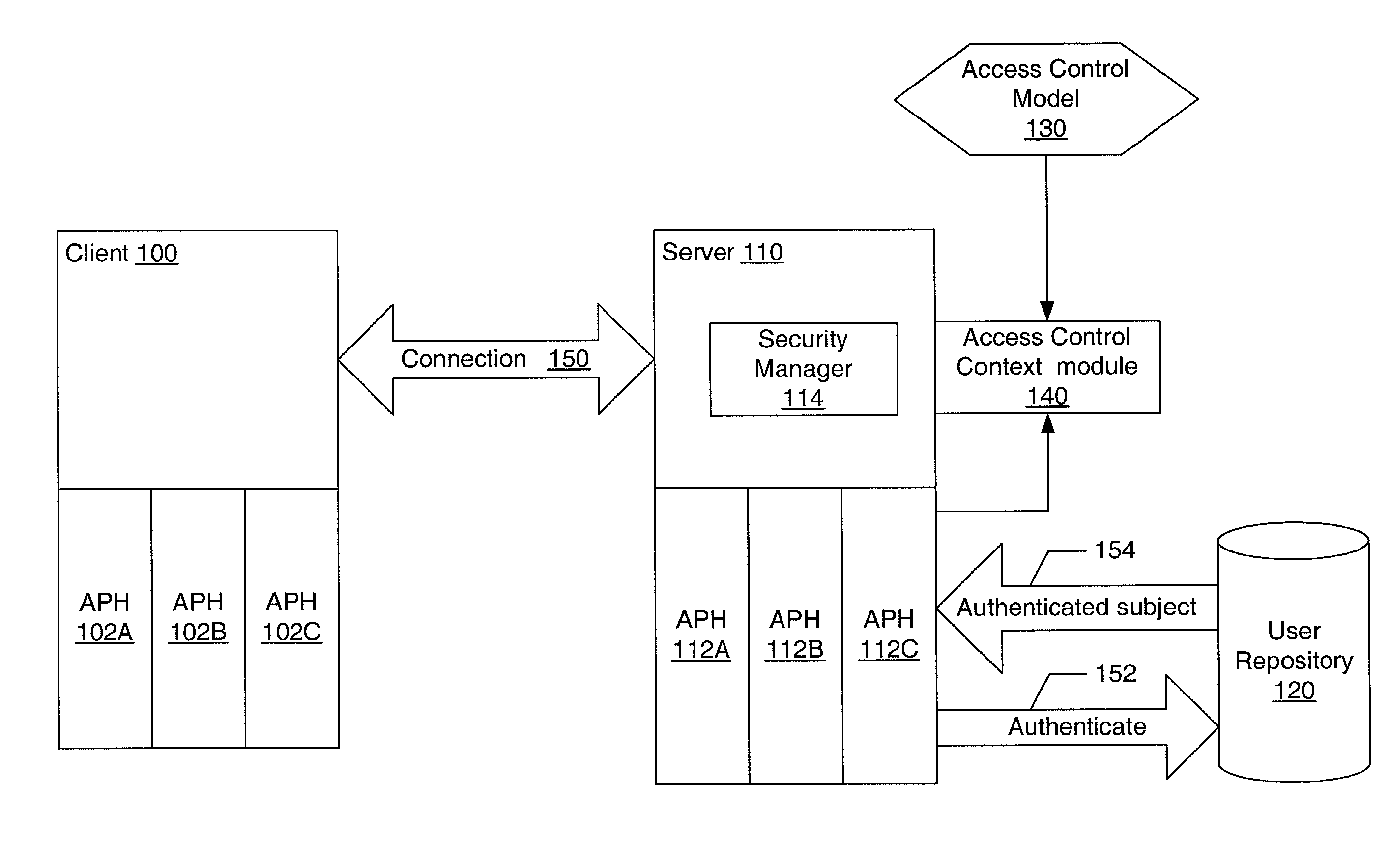
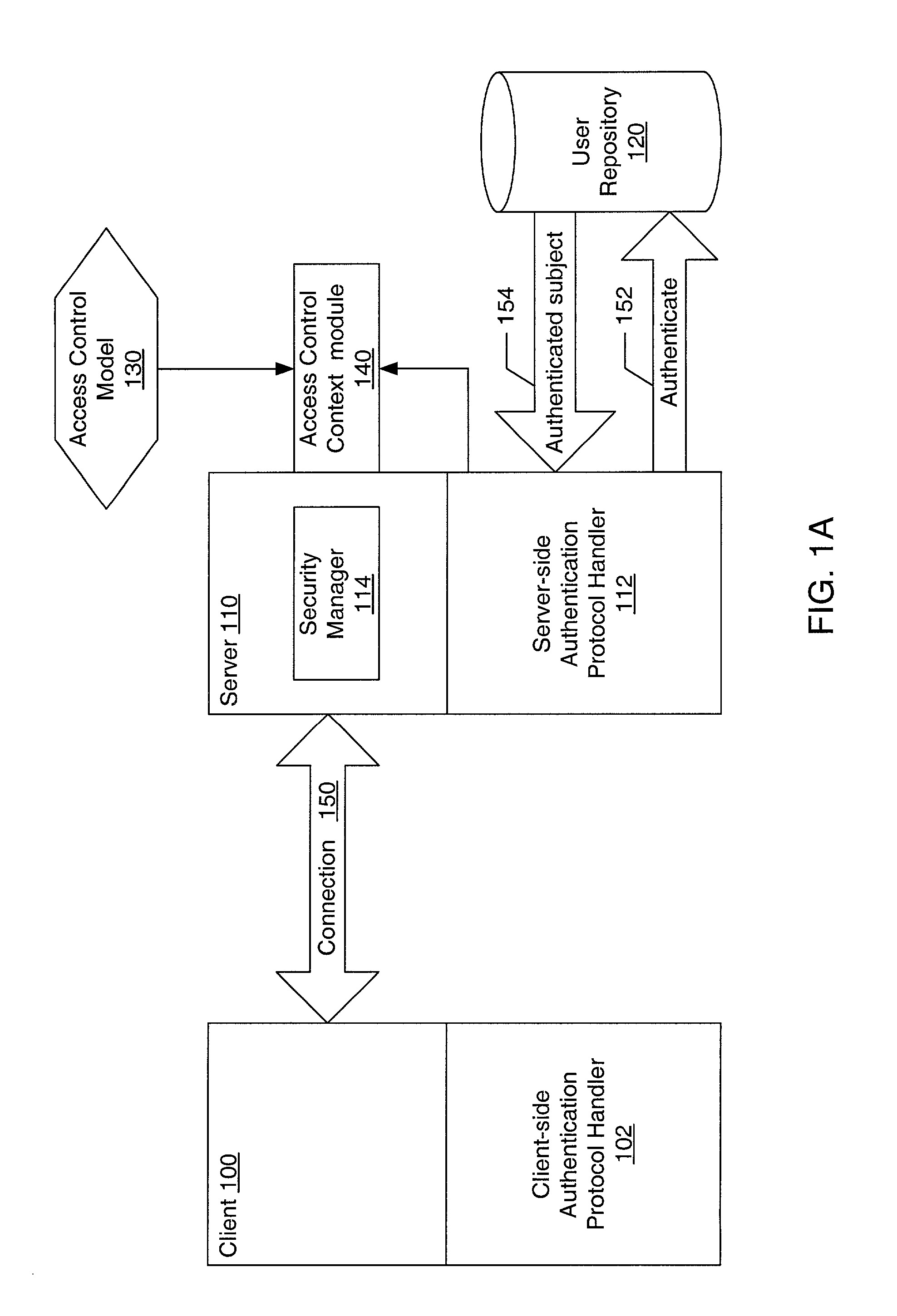
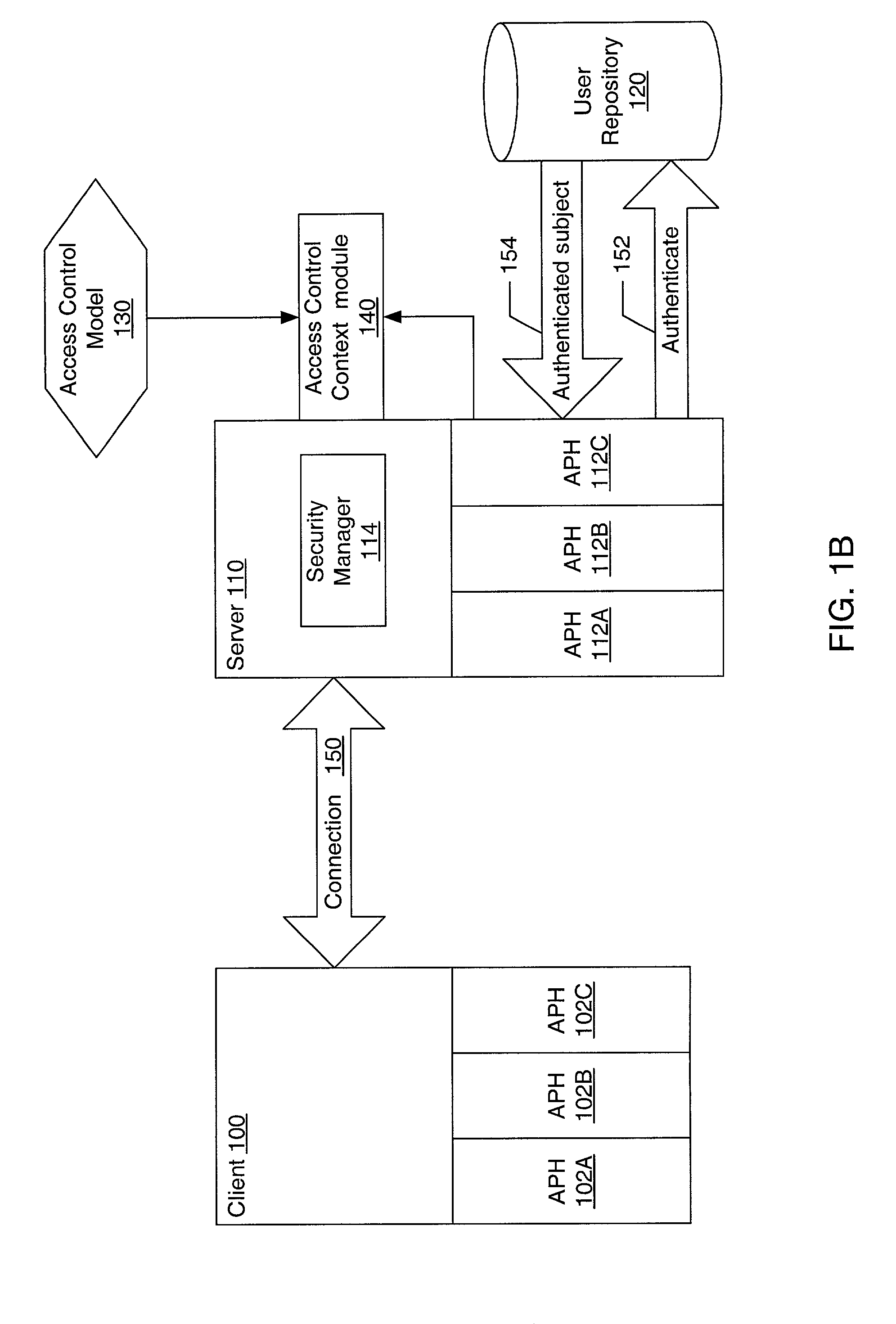
ActiveUS20030005117A1Memory loss protectionError detection/correctionData access controlComputerized system
A system and method for providing pluggable authentication and access control in computer systems and services are described. The authentication and access control process may be categorized into three components: an authentication protocol, a user repository and an access control model. In one embodiment, the authentication and access control mechanism may be implemented as three pluggable modules: an authentication protocol handler module for the authenticator side, an authentication protocol handler for the side to be authenticated, and an access control context module on the authenticator side. The pluggable modules may be exchangeable to support a variety of authentication types, user repositories, and access control models. The authentication protocol handlers provide symmetrical methods to handle requests and responses in the authentication process that reflect the symmetrical nature of the authentication process.
Owner:ORACLE INT CORP
Secure item identification and authentication system and method based on unclonable features
ActiveUS20110096955A1Improve efficiencyEasy to usePaper-money testing devicesCharacter and pattern recognitionKey exchangeDistributed source
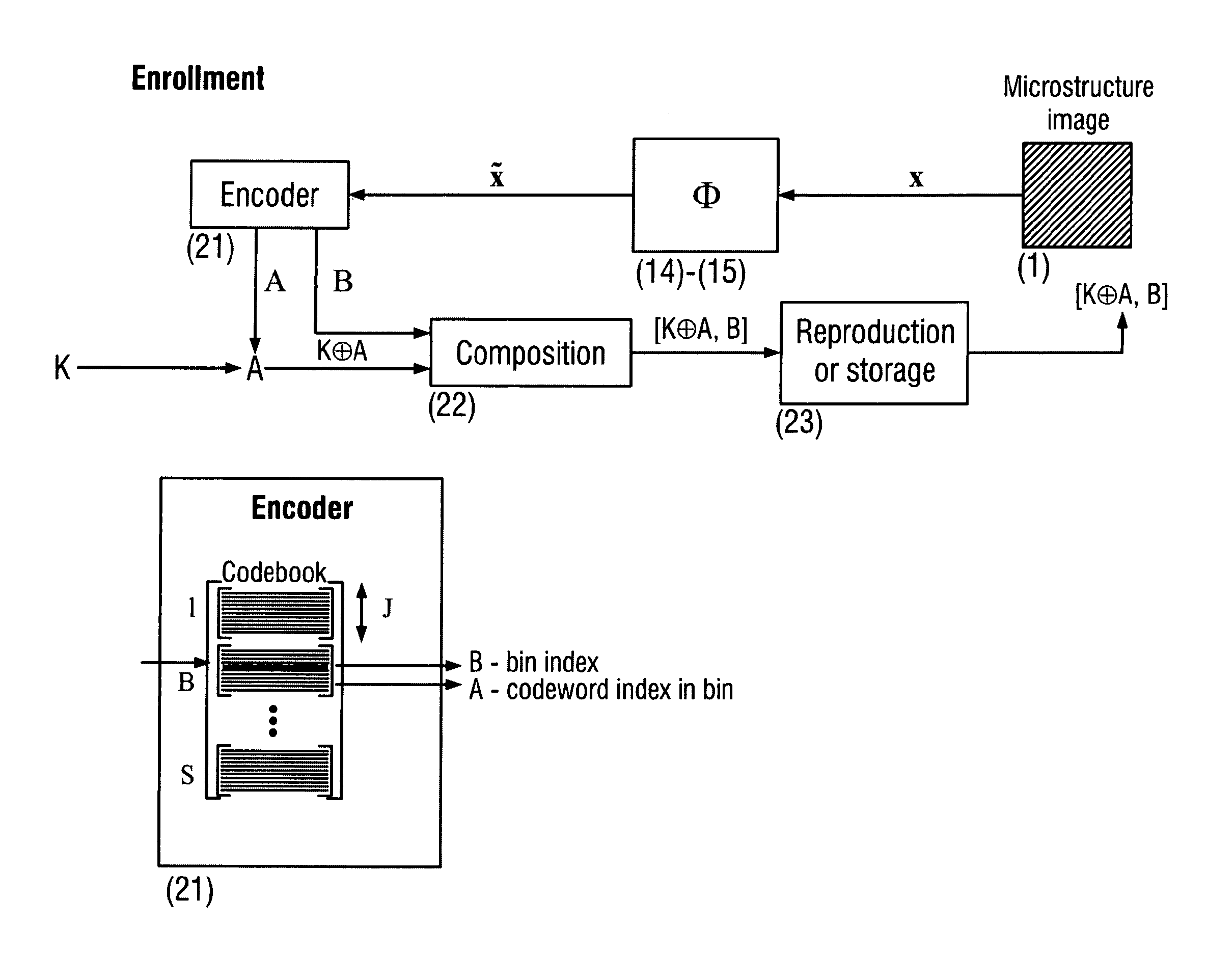
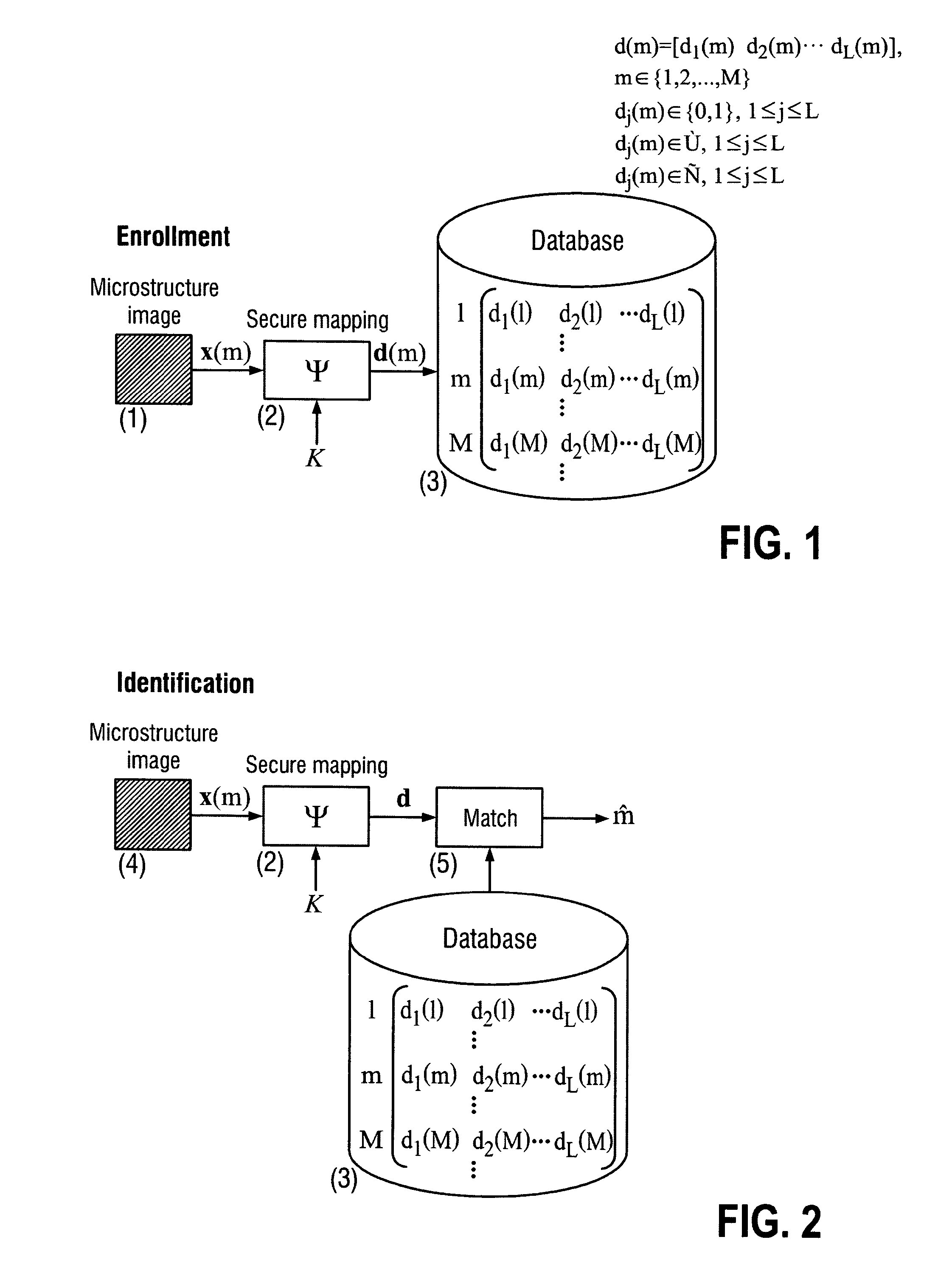
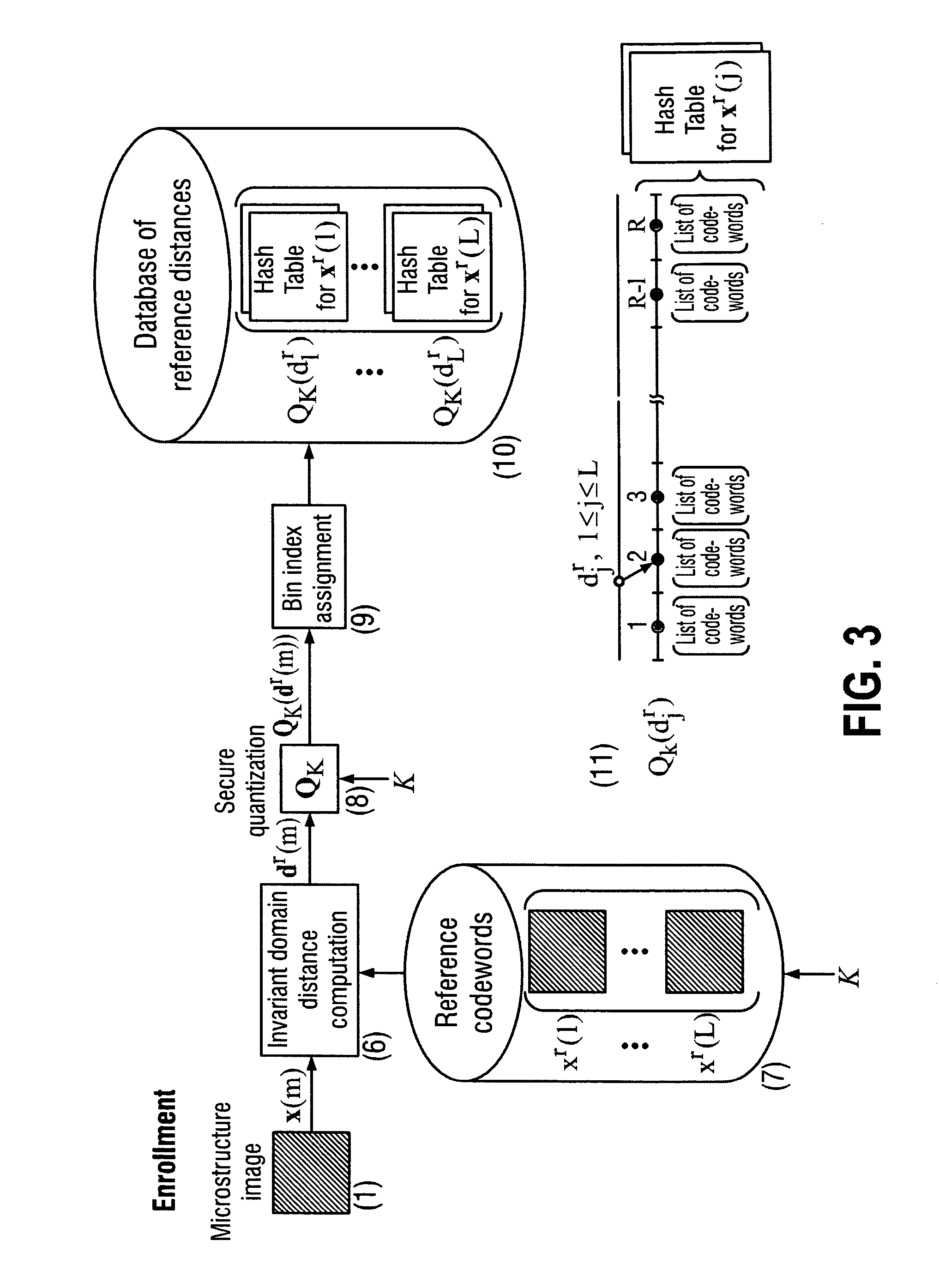
The present invention is a method and apparatus for protection of various items against counterfeiting using physical unclonable features of item microstructure images. The protection is based on the proposed identification and authentication protocols coupled with portable devices. In both cases a special transform is applied to data that provides a unique representation in the secure key-dependent domain of reduced dimensionality that also simultaneously resolves performance-security-complexity and memory storage requirement trade-offs. The enrolled database needed for the identification can be stored in the public domain without any risk to be used by the counterfeiters. Additionally, it can be easily transportable to various portable devices due to its small size. Notably, the proposed transformations are chosen in such a way to guarantee the best possible performance in terms of identification accuracy with respect to the identification in the raw data domain. The authentication protocol is based on the proposed transform jointly with the distributed source coding. Finally, the extensions of the described techniques to the protection of artworks and secure key exchange and extraction are disclosed in the invention.
Owner:UNIVERSITY OF GENEVA
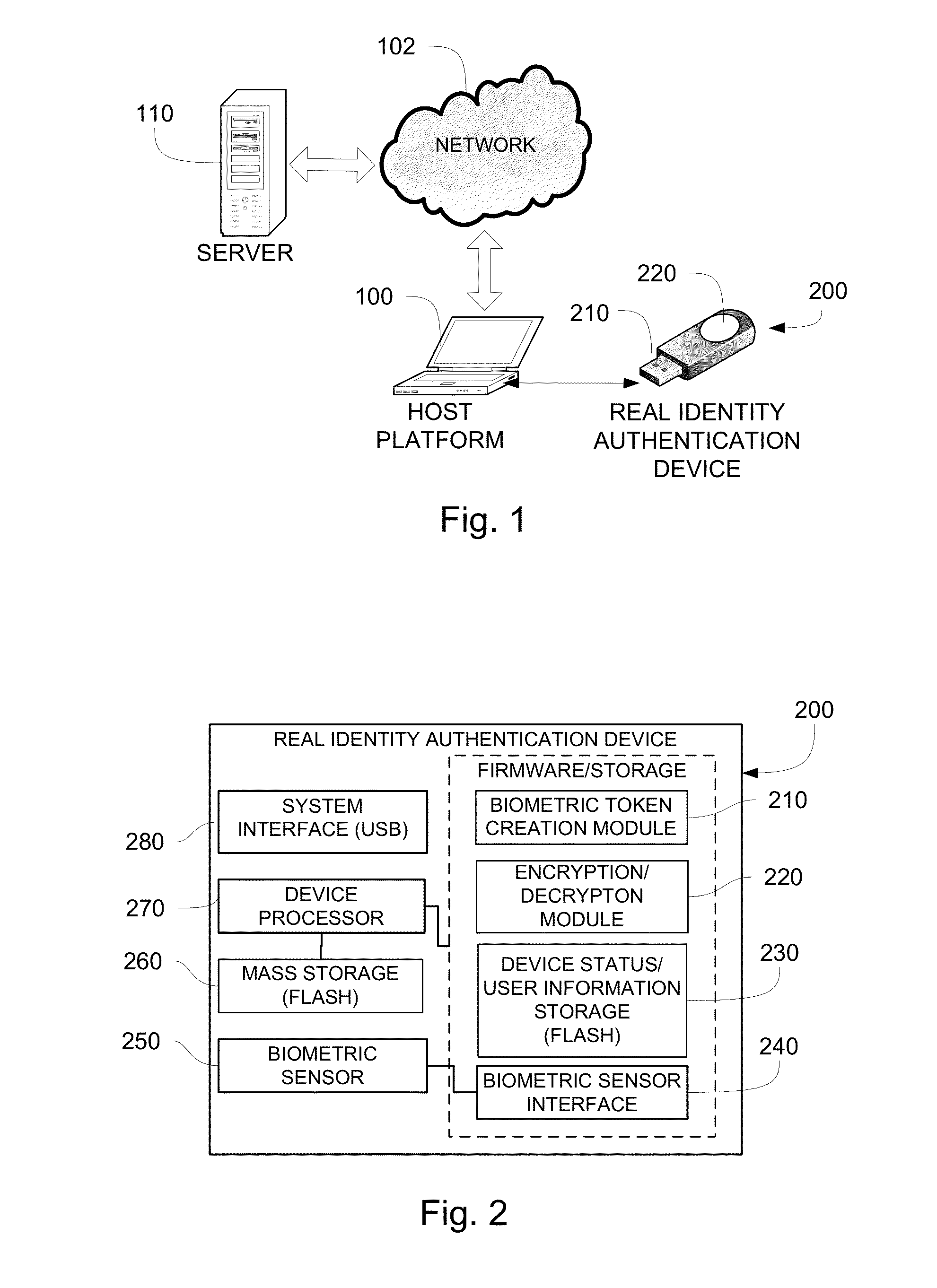
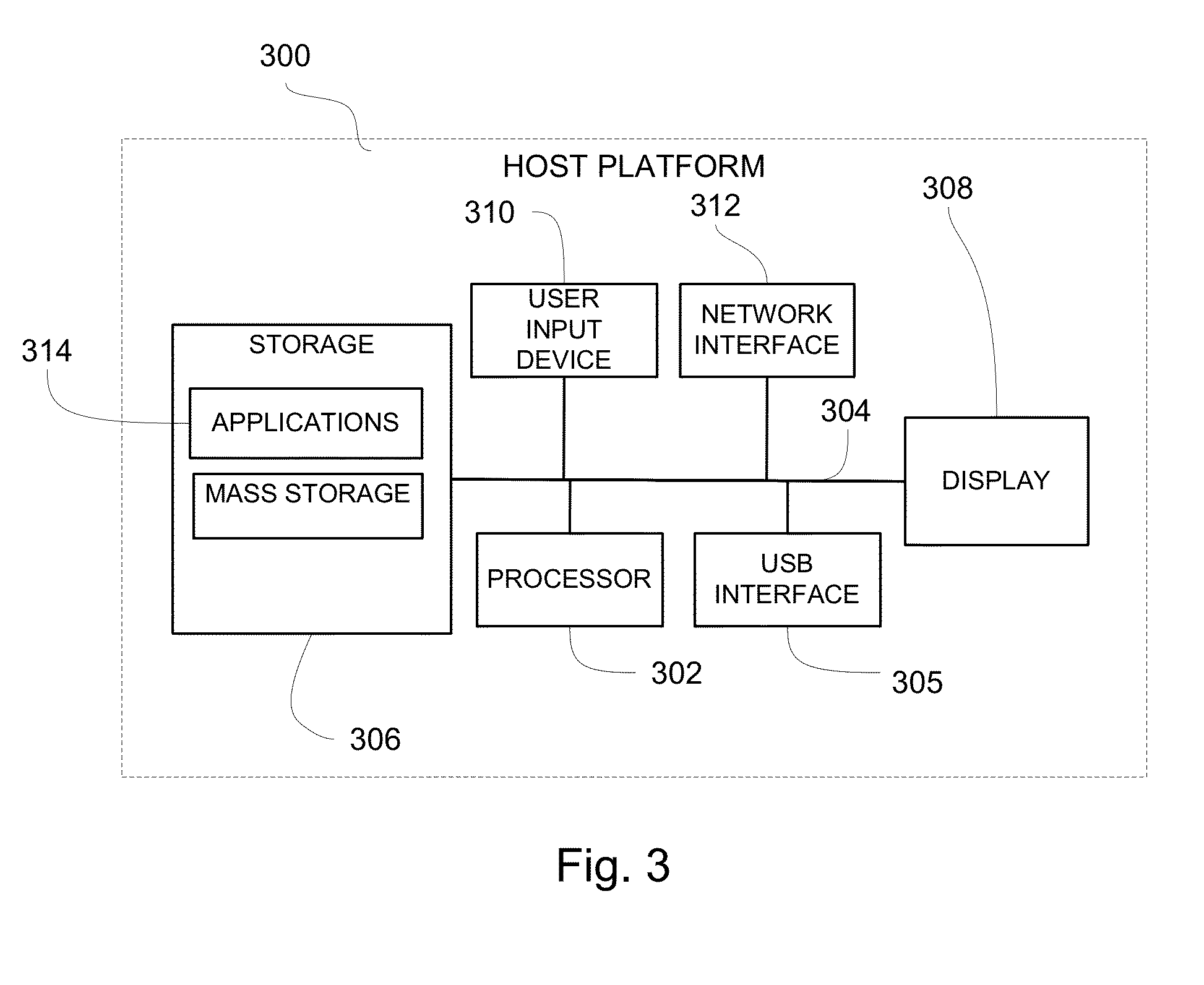
Real identity authentication
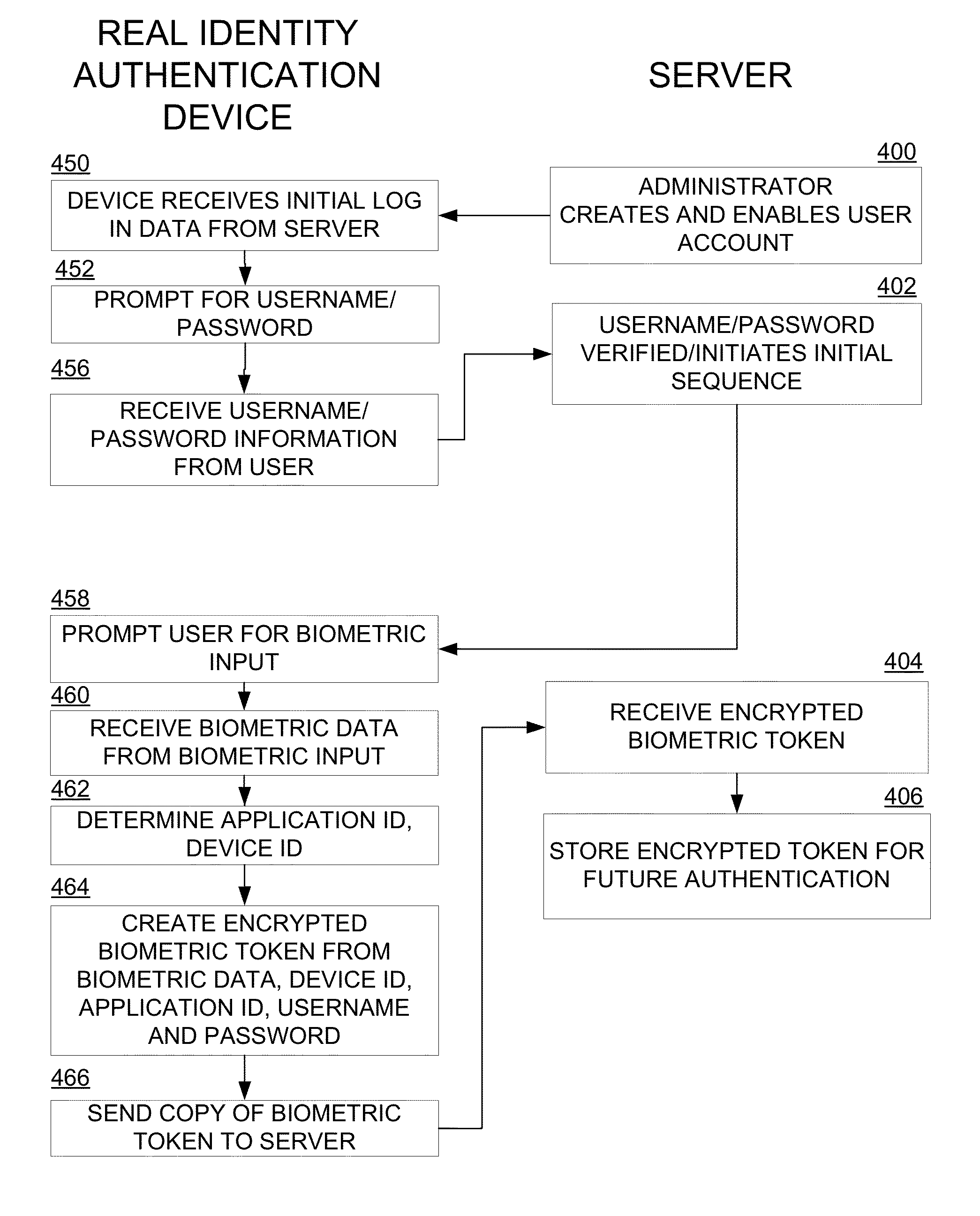
InactiveUS20140101453A1Eliminate potential safety hazardsReducing and eliminating riskUser identity/authority verificationDigital data authenticationData matchingBiometric data
A real identity biometric authentication device includes a USB thumb drive form factor, with a biometric sensor and designated device processor and stored instructions in firmware which perform authentication in a secure manner, independent of processing and storage resources on a host platform. The device and authentication process require biometric data and are secured against effects of malware or other security risks presented by applications running on the host platform. During an enrollment process, a unique encrypted enrollment biometric token is created using biometric data and uploaded securely to an authentication server. During an authentication process, the encrypted enrollment biometric token is downloaded to the real identity authentication device firmware and is decrypted on the device. The biometric data obtained from the decrypted data and is compared with live, real-time biometric data obtained from the user, for example, by a real-time fingerprint scan. If the real-time biometric data and the enrolled, decrypted biometric data match, the user is authenticated.
Owner:LAW OFFICE OF JOHN F ROLLINS
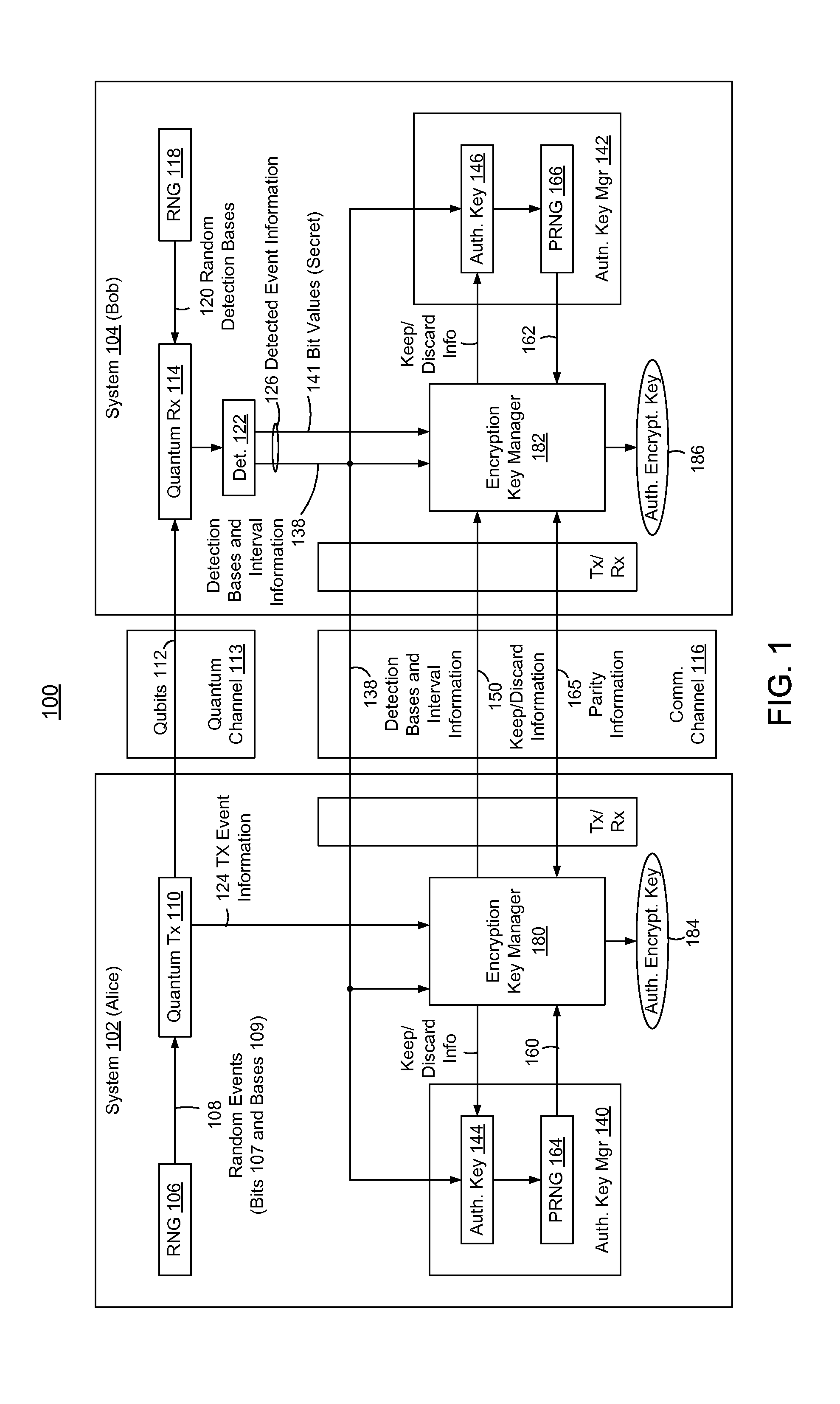
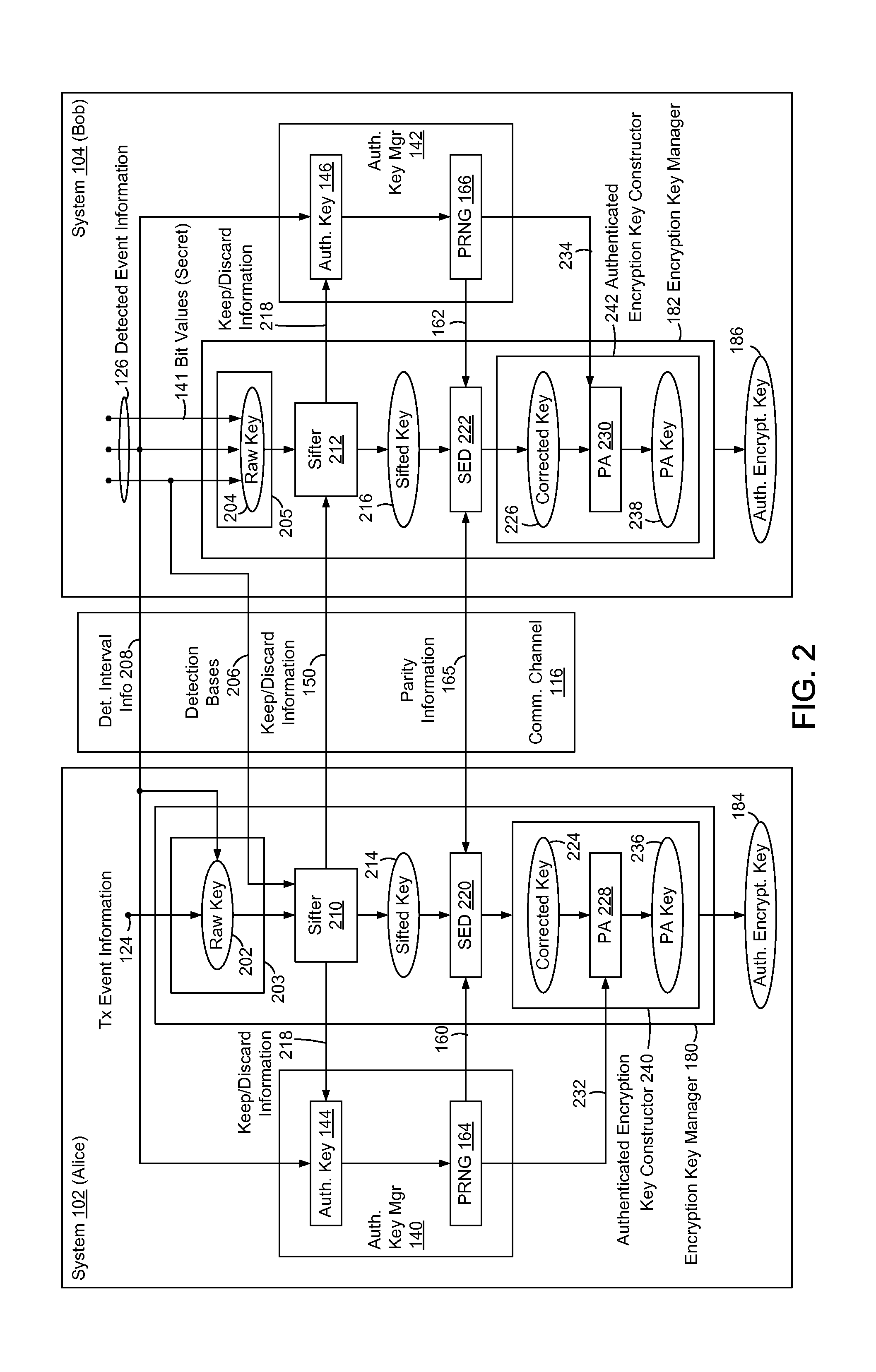
Embedded Authentication Protocol for Quantum Key Distribution Systems
ActiveUS20130315395A1Reduction of informationReduce overheadKey distribution for secure communicationAuthenticated encryptionQuantum key distribution
In methods and systems to authenticate systems in a quantum key distribution environment based on limited disclosures and identical, re-usable, pre-provisioned authentication keys, each system constructs an encryption key based on a corresponding one of transmitted events and detected events. Basis-sifting, error detection, error correction, and / or privacy amplification (PA) may be performed on the encryption keys based on limited disclosures (e.g., detection interval information, basis-sifting information, associated detection basis information, and / or parity measures). The authenticated keys may be modified based on disclosed detection information. Error detection and / or PA may be performed with identical pre-provisioned algorithms and pseudo-random values generated from the authenticated keys or modified authenticated keys. Final authenticated encryption keys are selectively constructed depending upon an extent of detected errors. Construction of authenticated encryption keys indicates authentication of the systems. None of the pre-provisioned authentication keys or modified authentication keys is disclosed and may thus be reused.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
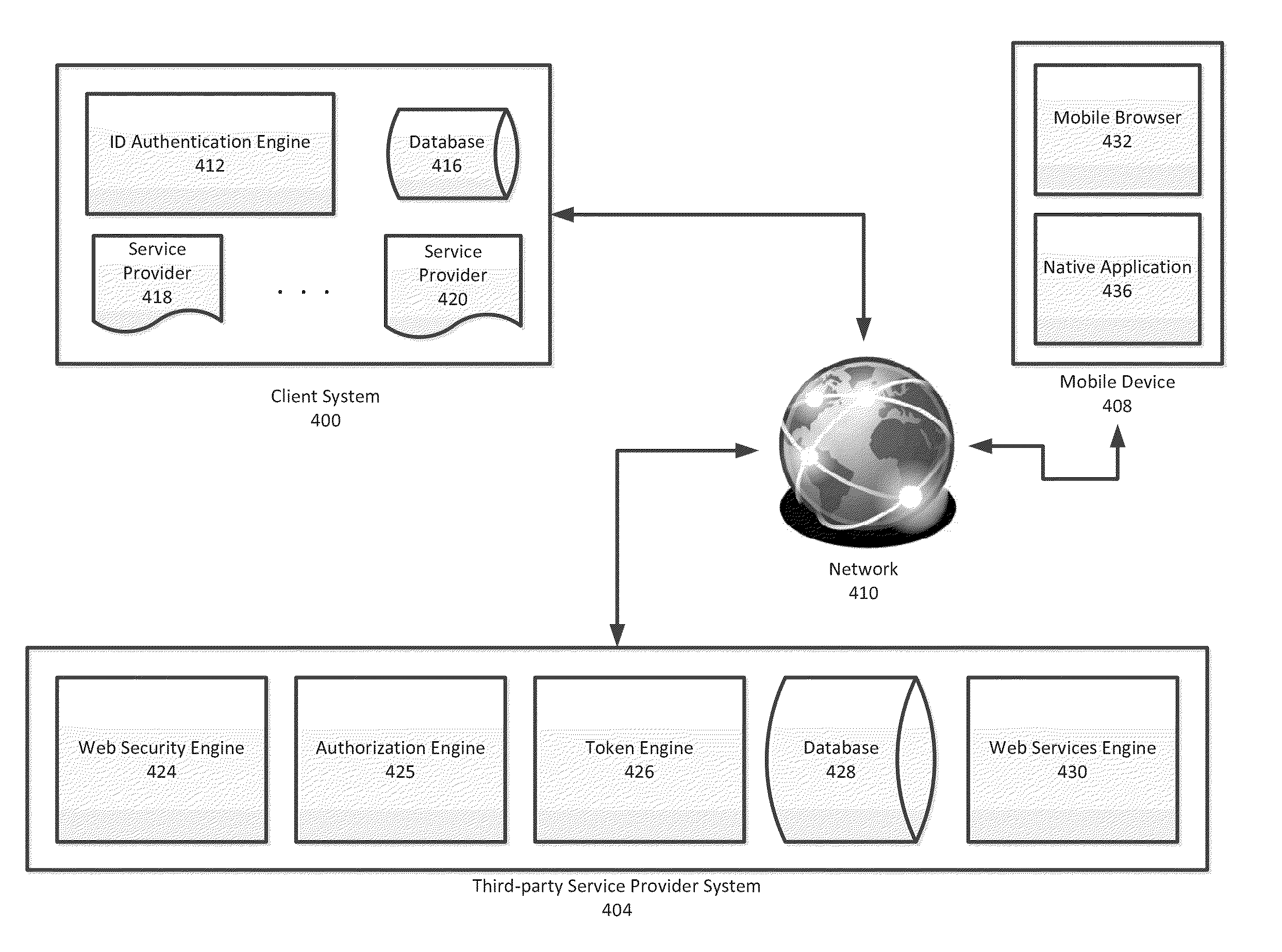
System and Method for Mobile Single Sign-On Integration
ActiveUS20140310792A1Digital data processing detailsMultiple digital computer combinationsWeb serviceApplication software
Improved methods and systems for integrating client-side single sign-on (SSO) authentication security infrastructure with a mobile authorization protocol are disclosed that provide clients with secured SSO mobile access to third-party services. Embodiments of the present invention leverage SSO authentication protocols that are utilized at many client-side systems already and integrate these SSO authentication protocols with a mobile SSO authorization protocol, thereby effectively extending the SSO framework to mobile service requests of web services at third-party service provider systems. Embodiments of the present invention provide a secure and automated solution which may be implemented in any existing client-side SSO frameworks with minimum cost and time, while providing a lightweight and secure solution that provides users using either native applications or mobile web application to access third-party web services.
Owner:GLOBOFORCE
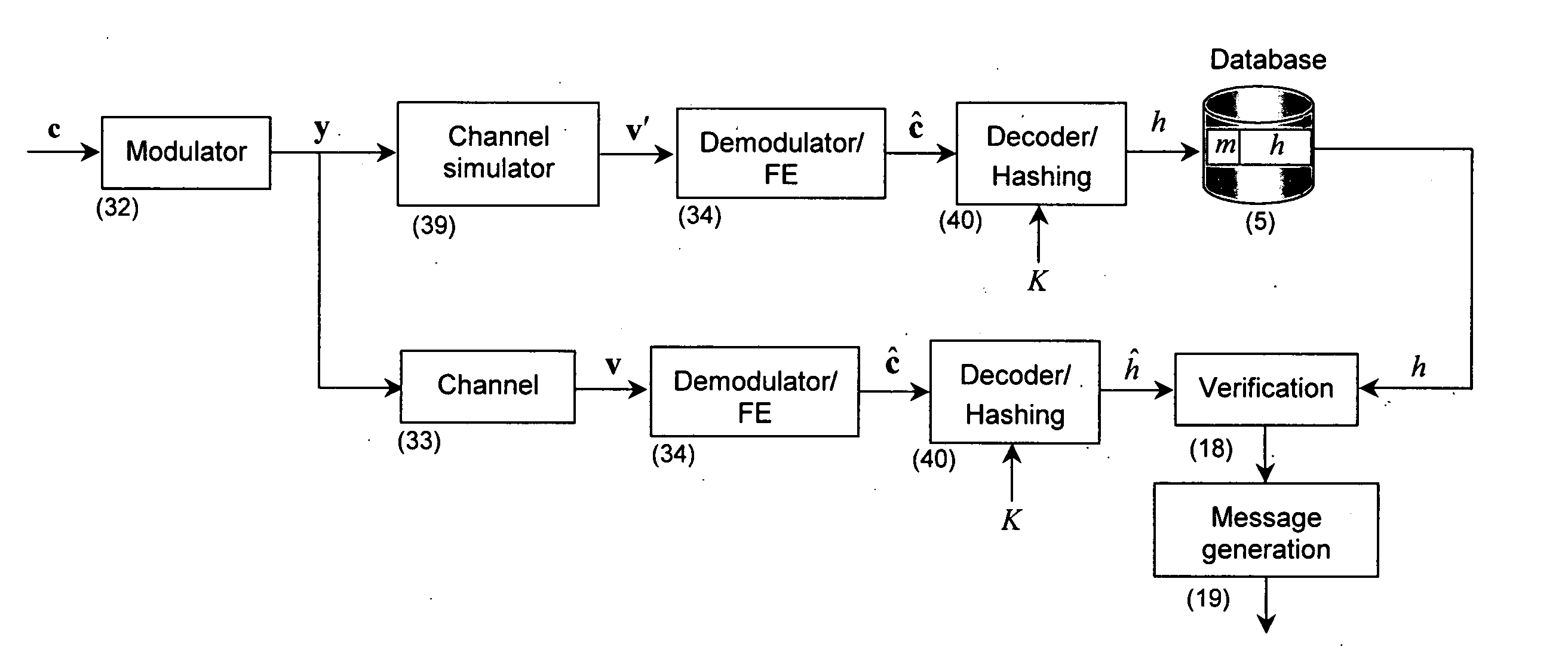
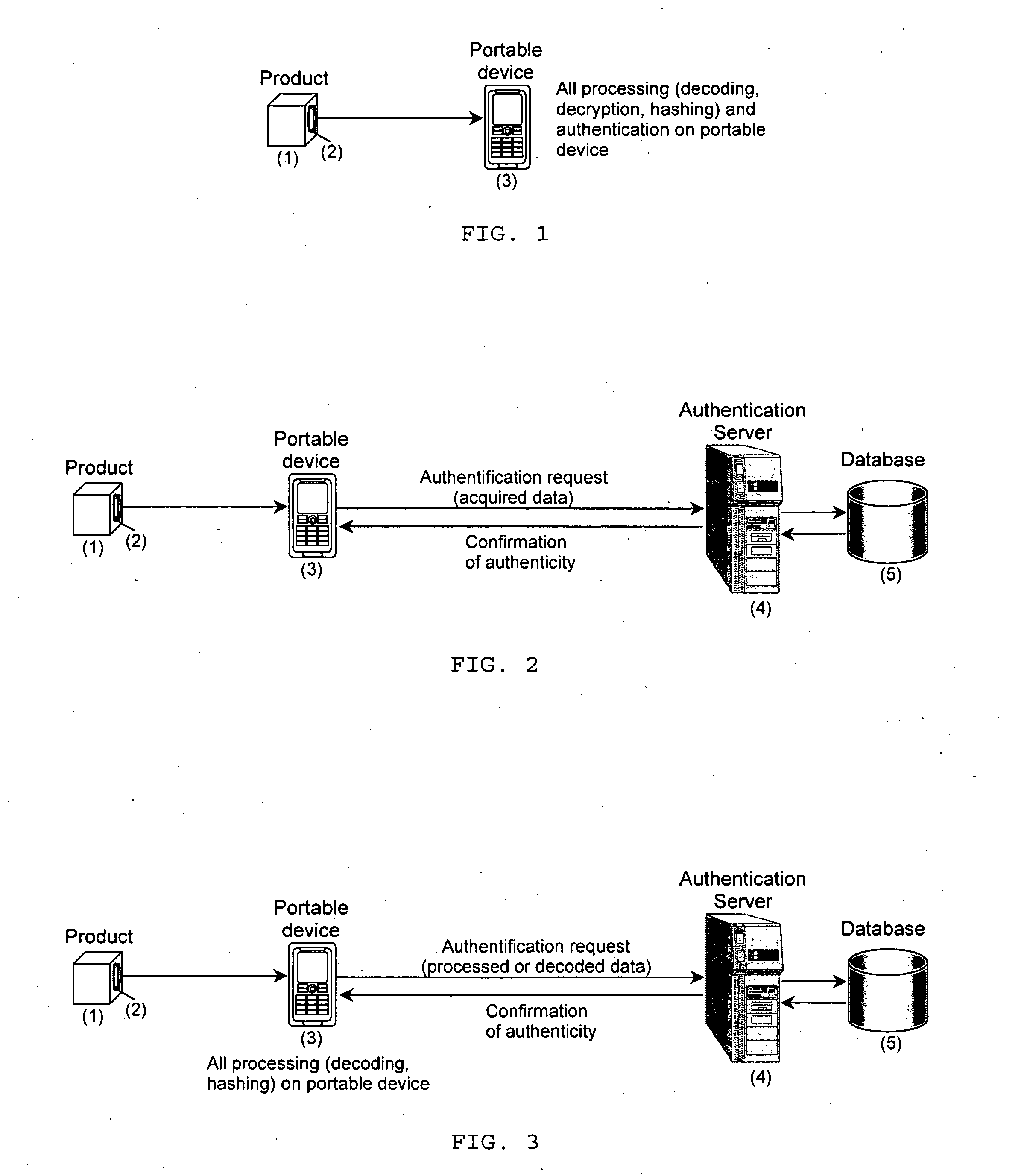
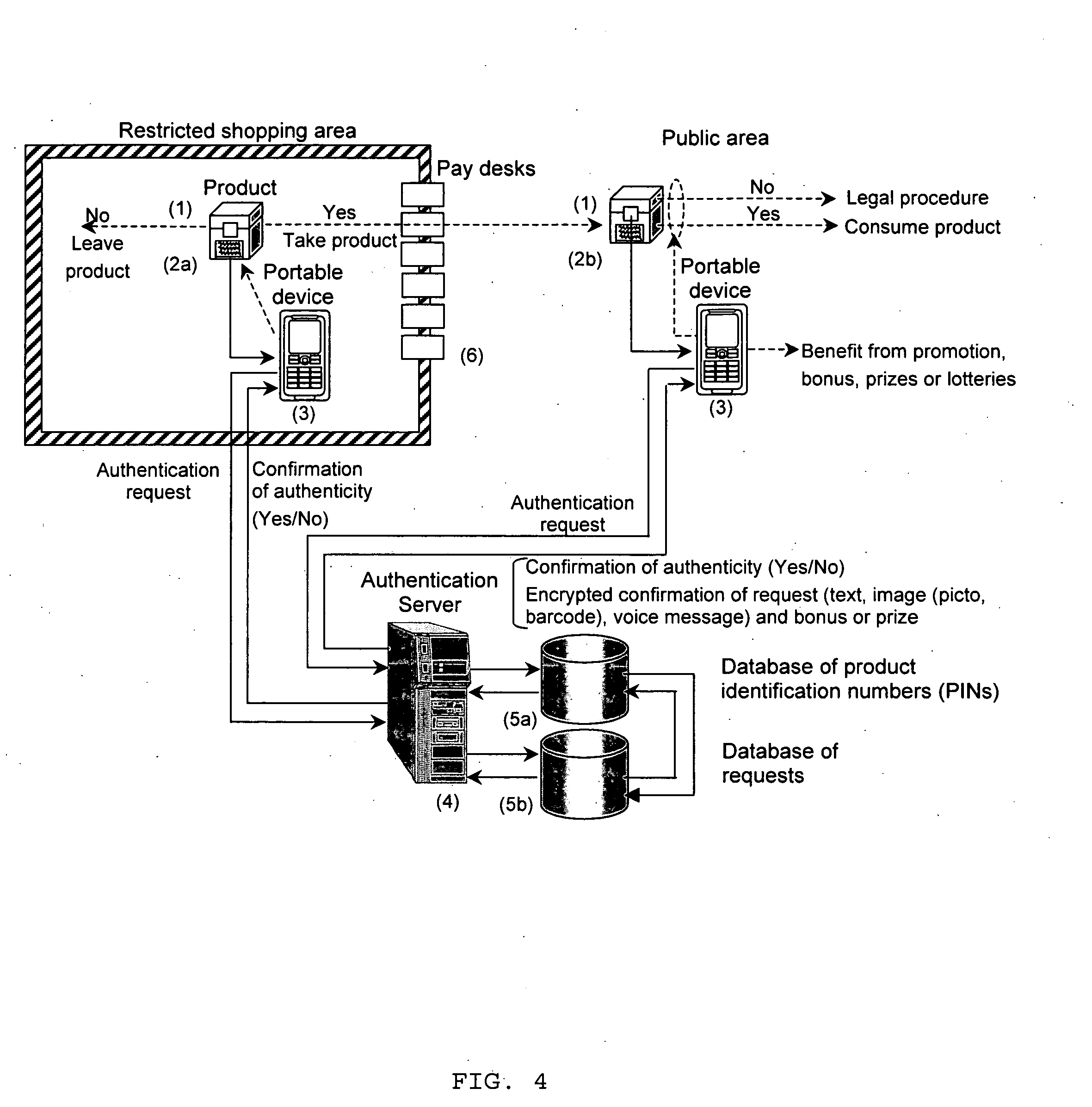
Brand protection and product autentication using portable devices
ActiveUS20080002882A1Easy to applyPreserving product integrityOther printing matterPaper-money testing devicesAuthentication serverOperating system
The present invention is a method and apparatus for protection of products and packaging against counterfeiting using dedicated authentication protocol coupled with portable devices. It is based on the product identification information, i.e., PIN, generated by the product manufacturer, stored in the product database and added to product or packaging in an open and / or a hidden form. The open part is directly available to the consumer before buying, opening or consuming the product or package or damaging its integrity while the hidden part is only revealed after these operations. The hidden information can also be disappearing after a predefined interval of time or number of trials or usages. Both parts are communicated to the authentication server in a predefined order to verify the product or package authenticity. The presence, absence, or multiple requests for the same product PIN, confirm or reject product authenticity or detect attempt at attacking the system or at using counterfeited products.
Owner:UNIVERSITY OF GENEVA
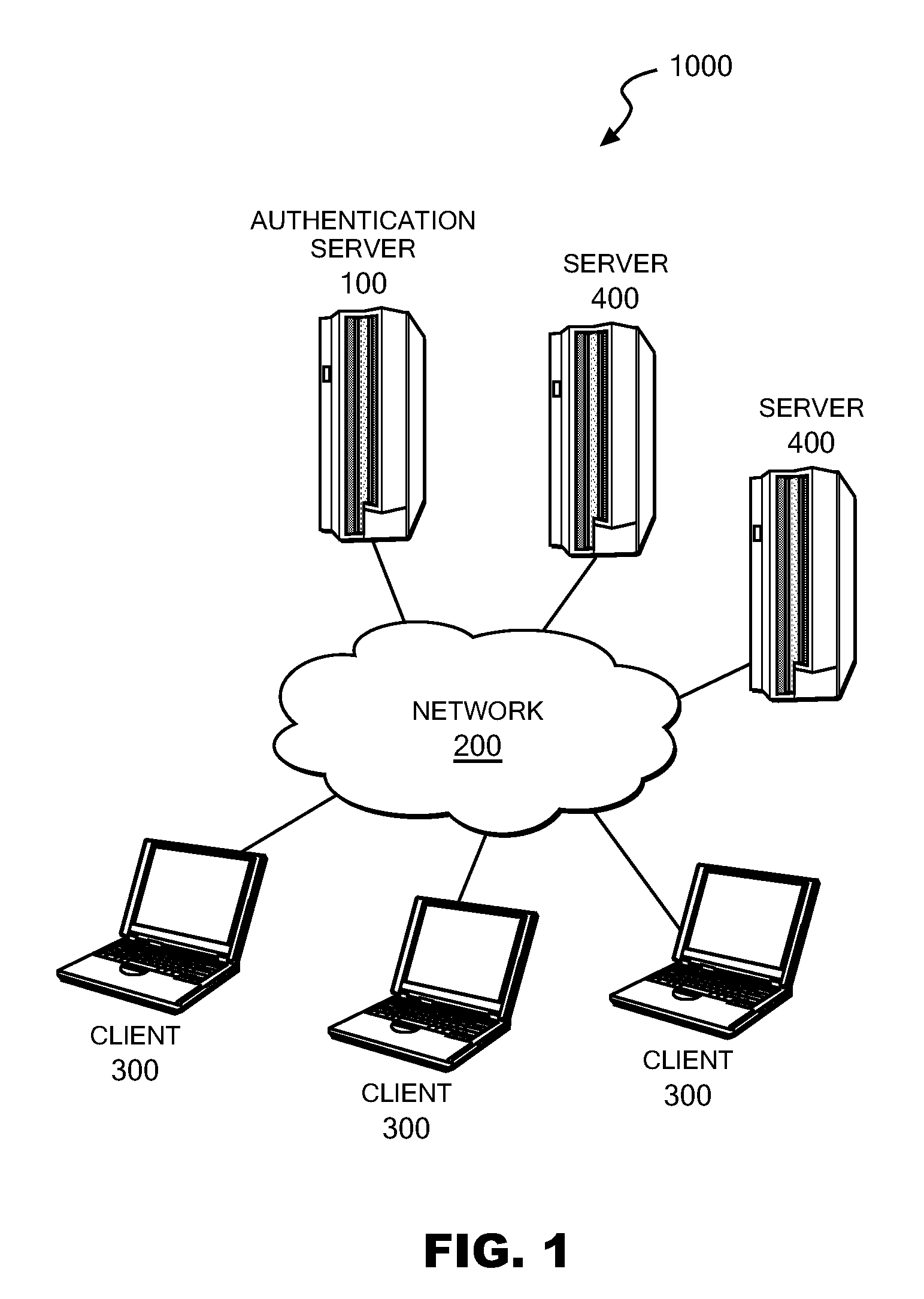
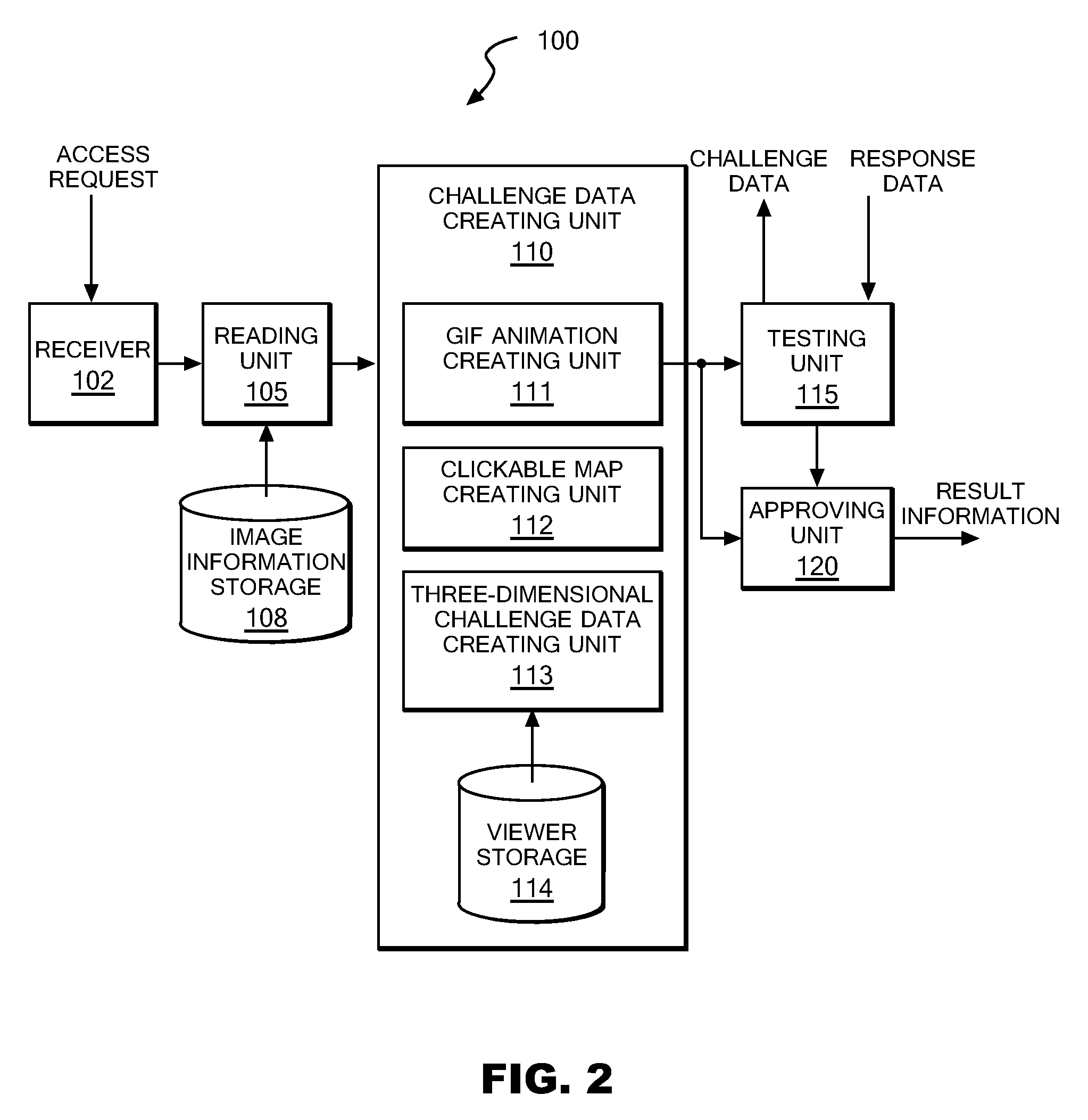
Authentication server, authentication method and authentication program
ActiveUS20090187986A1Digital data processing detailsUser identity/authority verificationUse of servicesAuthentication server
Upon receipt of a service use request from a client, an authentication server device reads one or more image information pieces from an image information storage storing multiple image information pieces each containing one or more known symbols, one or more dummy symbols, or both of them, and thereafter creates challenge data using the one or more read image information pieces so that one or more two-dimensional images each containing one or more of the known symbols and one or more two-dimensional images each containing one or more of the dummy symbols can be presented to the user of the client, one image at a time. Upon receipt of response data, the authentication server device judges whether or not the received response data matches the one or more known symbols contained in the challenge data, and approves the service use of the client device if the match is confirmed.
Owner:IBM CORP
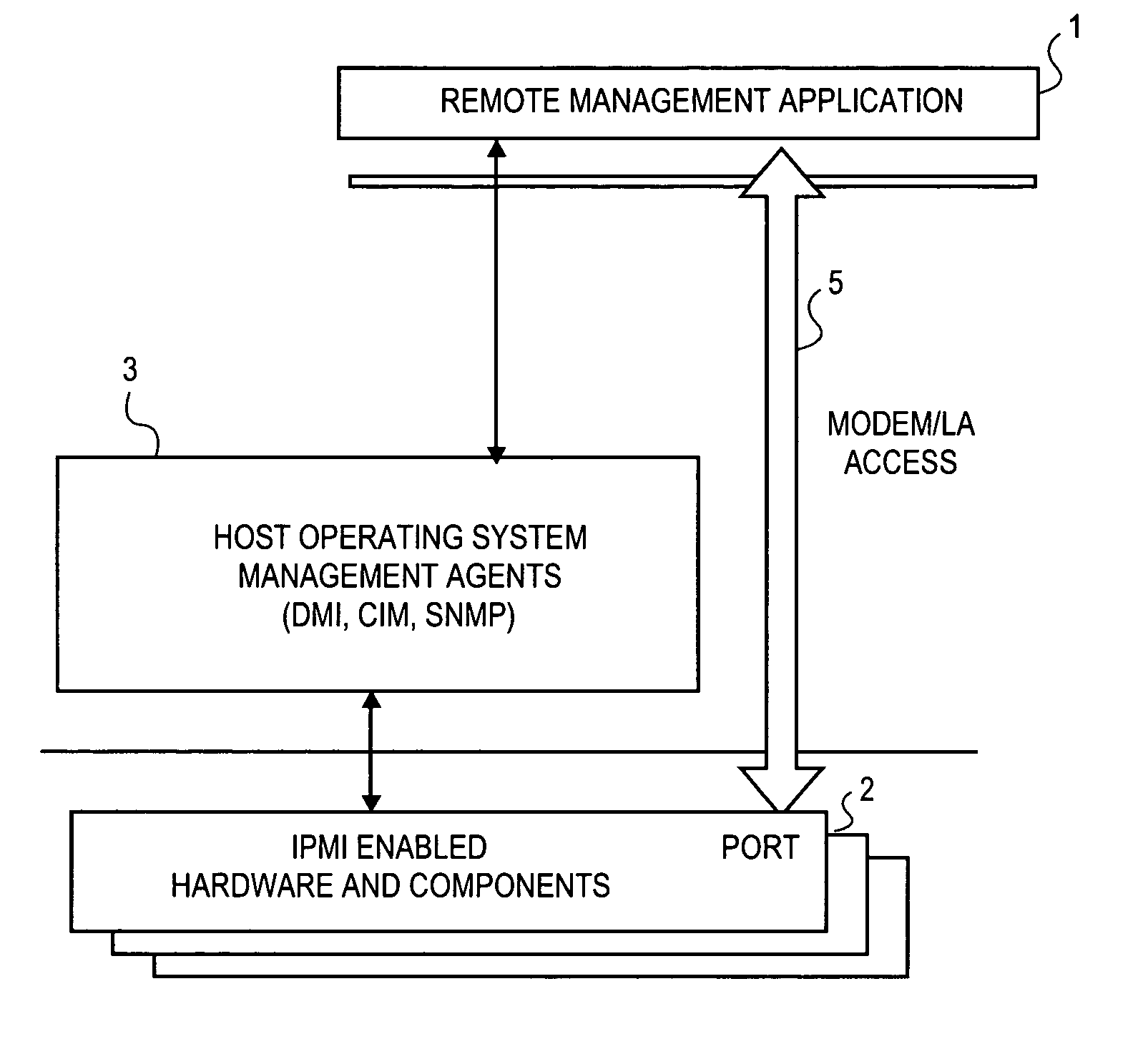
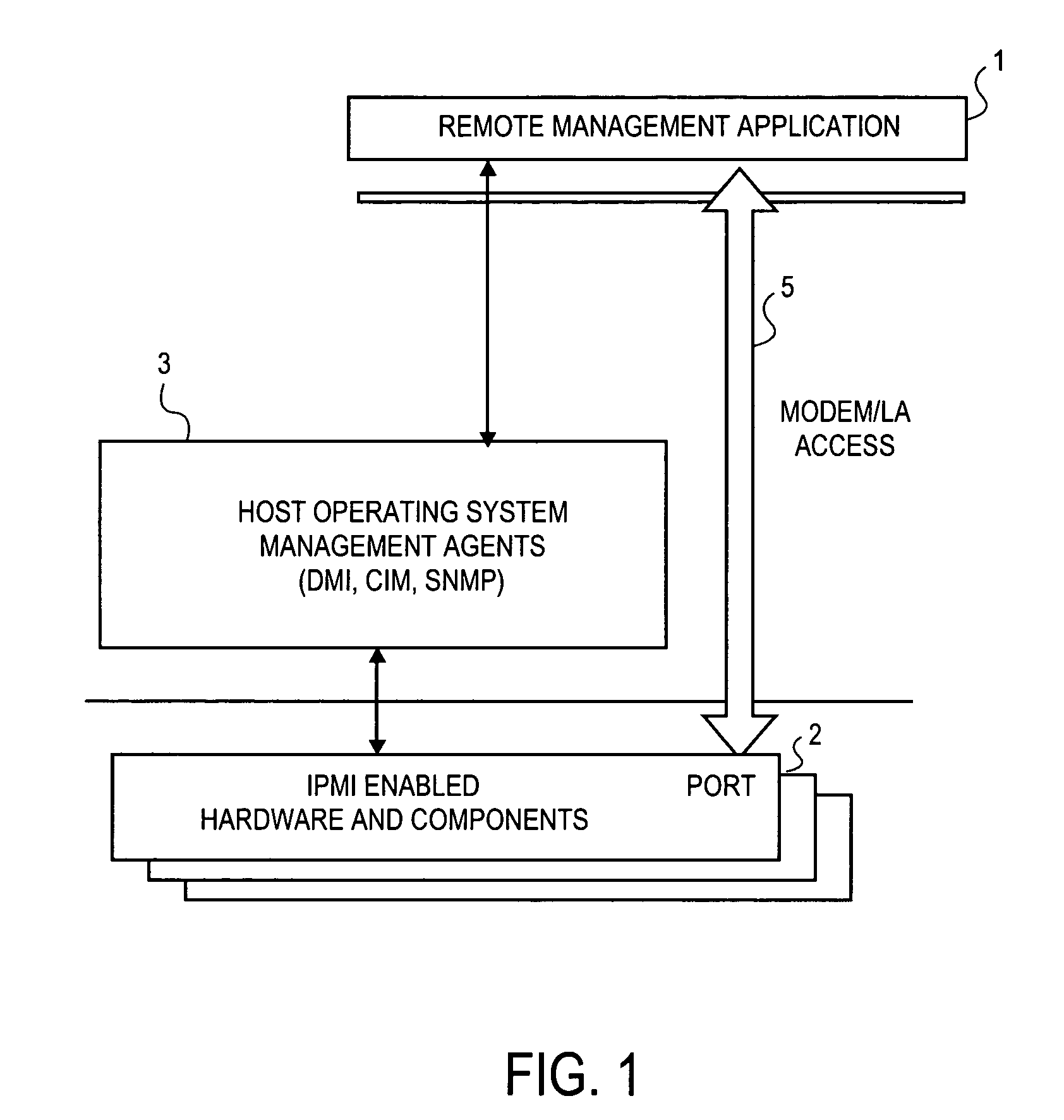
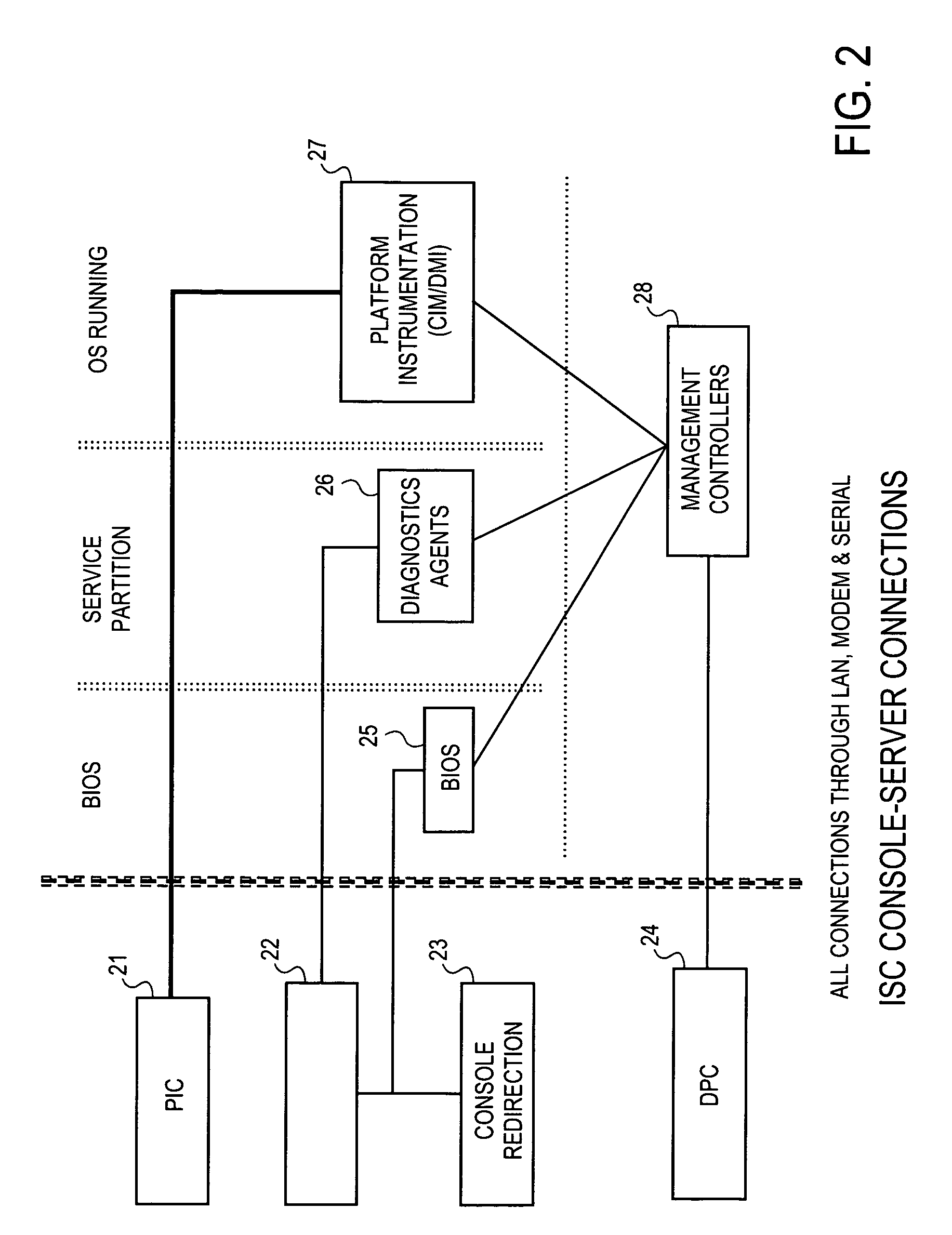
Method and apparatus for secure remote system management
InactiveUS7024695B1Digital data processing detailsAnalogue secracy/subscription systemsComputer hardwareOperational system
To prevent unauthorized access to hardware management information in an out-of-band mode, i.e., when the operating system of the hardware is not executing, a method and apparatus employ an authentication protocol. Upon receiving a request for hardware component information in a service processor that is disposed in a hardware component, which request is received as an open session request and which request passes external to an operating system controlling the hardware component, the service processor transmits a challenge string to the requesting client application. In response to a challenge response received from the requesting client application, the service processor compares the challenge response to an expected response to the challenge. The expected challenge response is calculated by the service processor. Based on the result of the comparison, the service processor transmits an authentication response to the requesting client application indicating success or failure of the authentication process. On the client side, in response to a challenge string from the service processor, the requesting client application transmits to the service processor a challenge response, which includes an sequence number that increments with every new message from the requesting client application. The challenge response also includes a hash number calculated by the requesting client application, which hash number is a function of the challenge string, session identification number, sequence number and / or a password. Each new packet including data and / or commands from the client application includes a similarly calculated hash number.
Owner:INTEL CORP
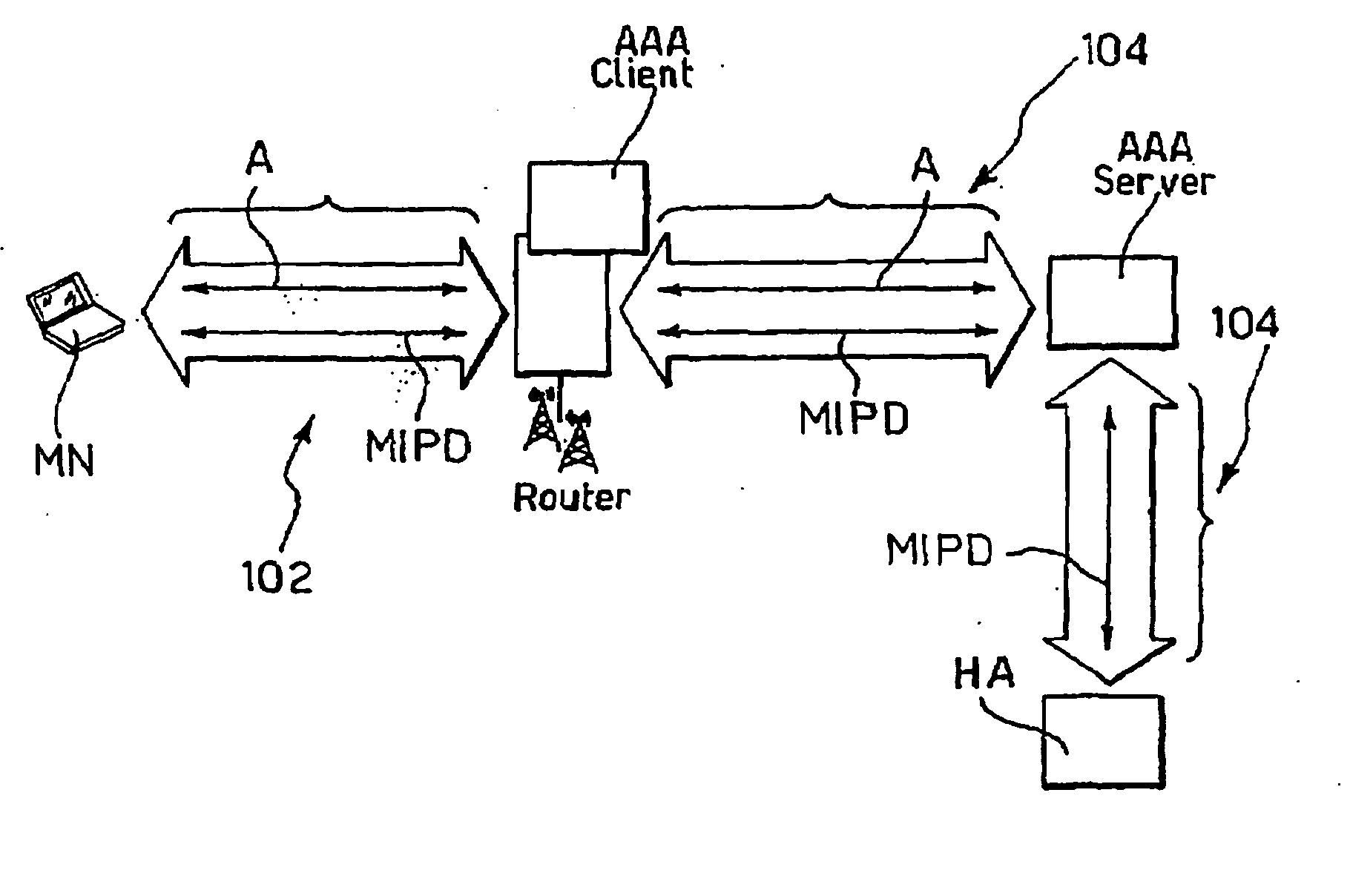
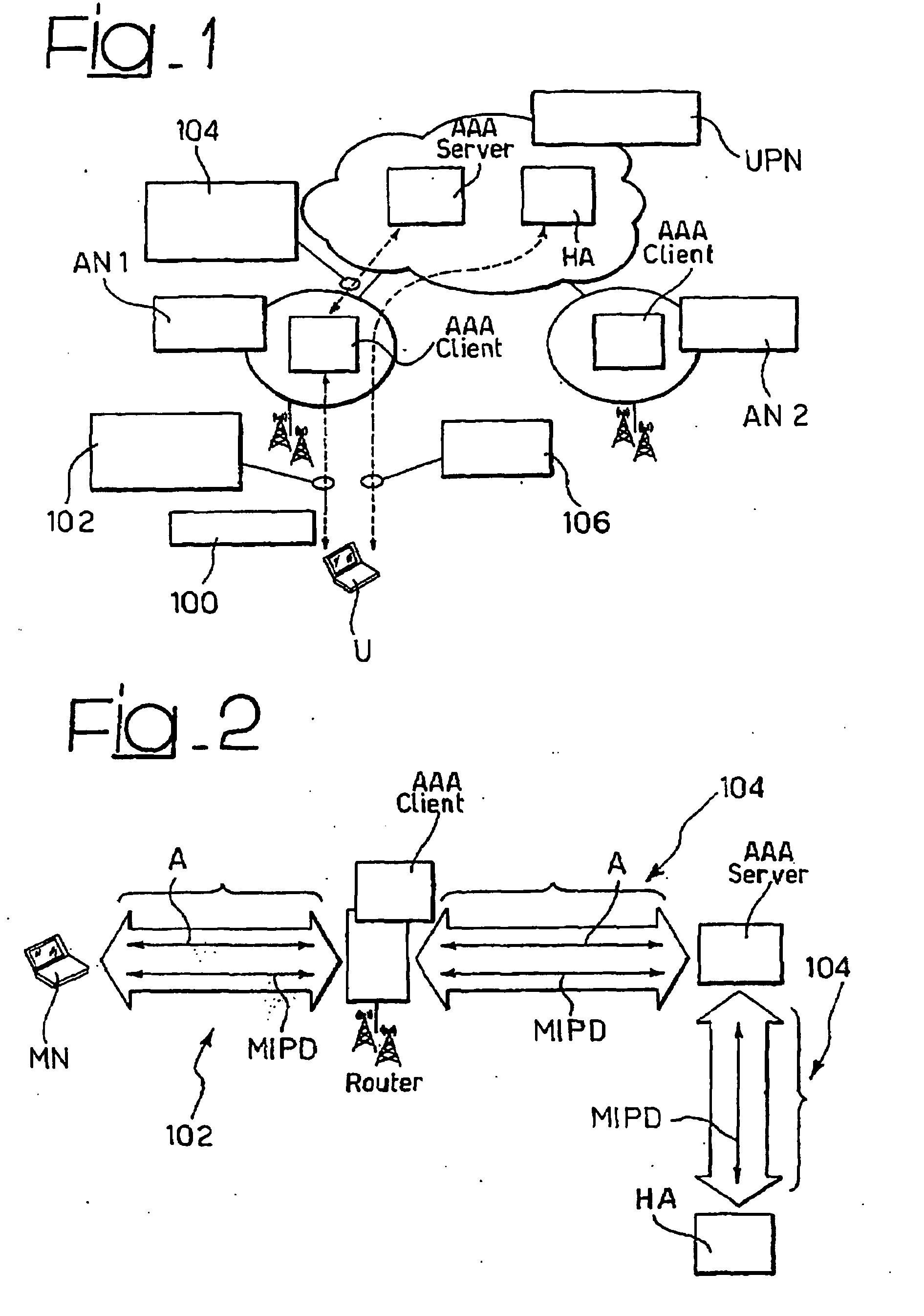
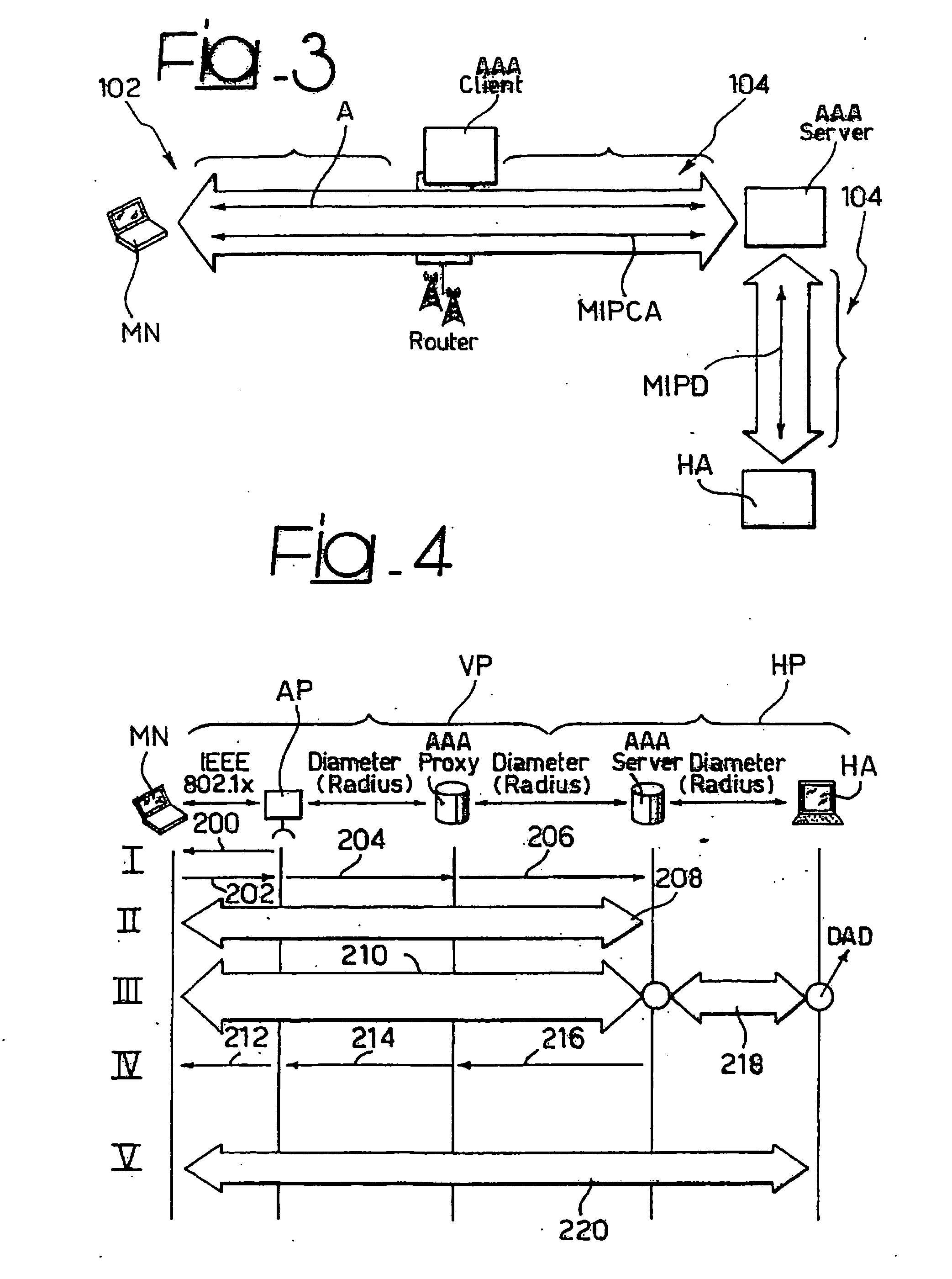
Method and System for the Secure and Transparent Provision of Mobile Ip Services in an Aaa Environment
InactiveUS20070230453A1Easy to useLower deployment costsData switching by path configurationWireless network protocolsMobile serviceMIP protocol
A system for negotiating the provision of a mobile IP service, such as, MIPv4 or MIPv6, between a mobile node and a server in a network includes the steps of providing an authentication protocol establishing a pass-through transport between the mobile node and the server and negotiating the provision of the mobile IP service via the authentication protocol over the pass-through transport.
Owner:TELECOM ITALIA SPA
Variable authentication process and system
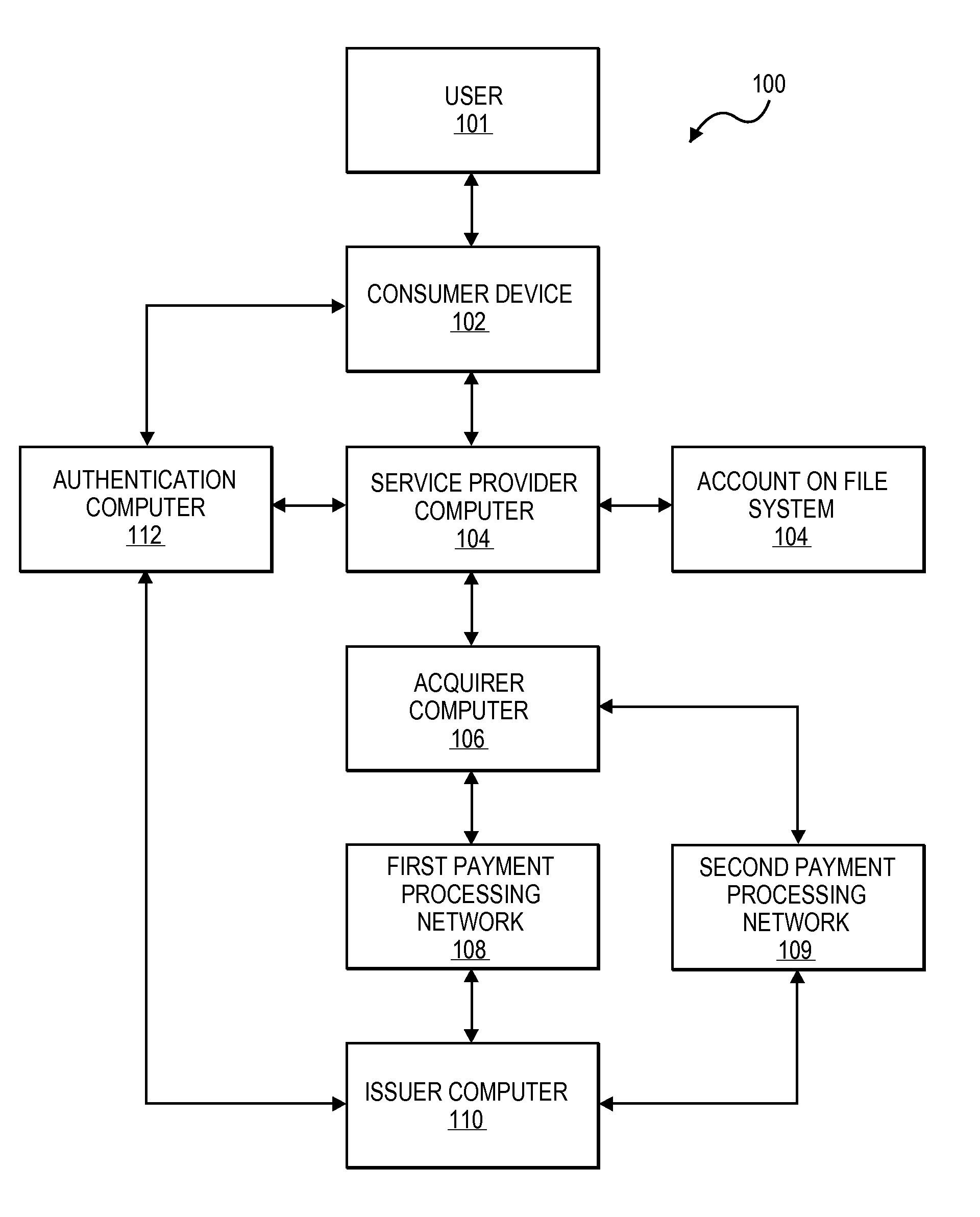
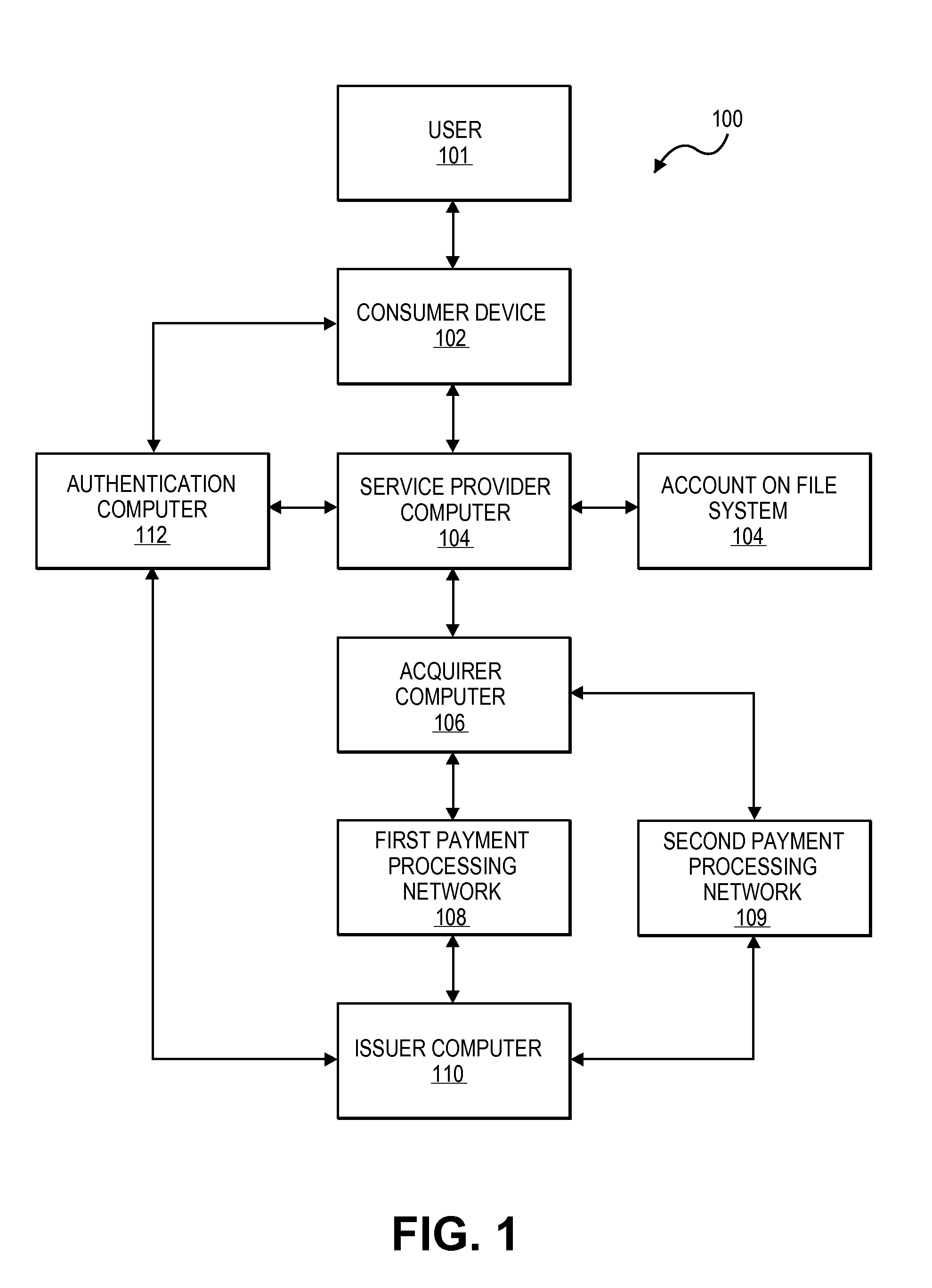
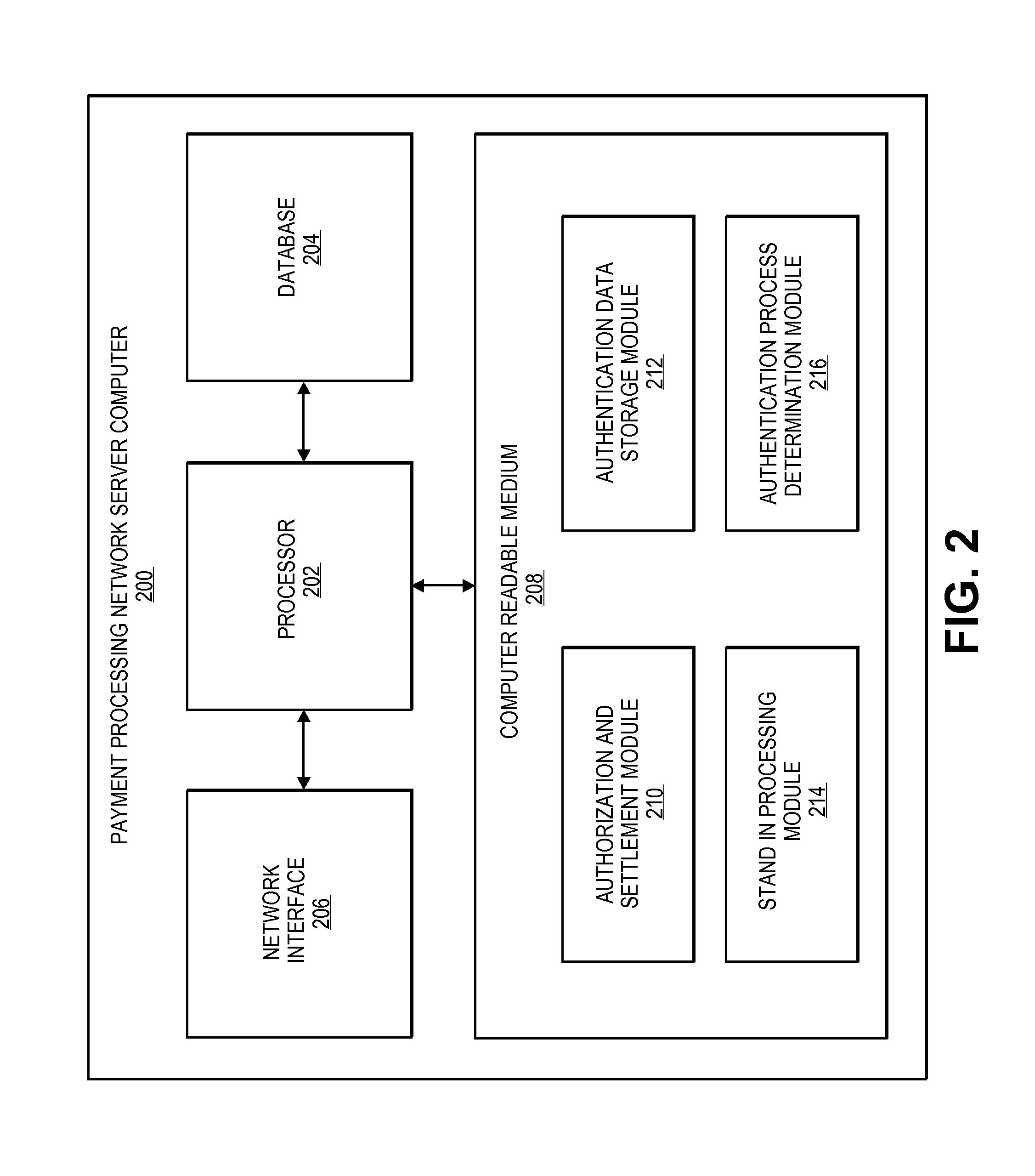
Efficient methods and systems for verifying personal identifiers in transactions such as financial transactions are disclosed. In an exemplary method, an authentication server computer may provide an account number and a personal identifier such as a PIN to a payment processing network server computer. The payment processing network server computer may then determine which of a plurality of authentication processes to initiate.
Owner:VISA INT SERVICE ASSOC
Anti-counterfeiting and authentication system taking block chain background as authentication core
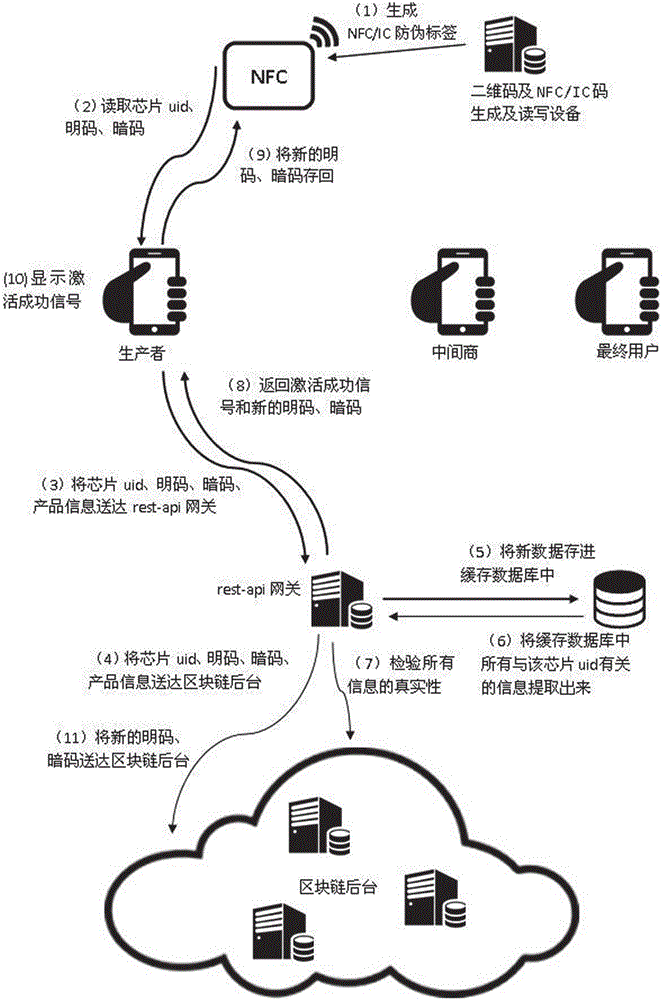
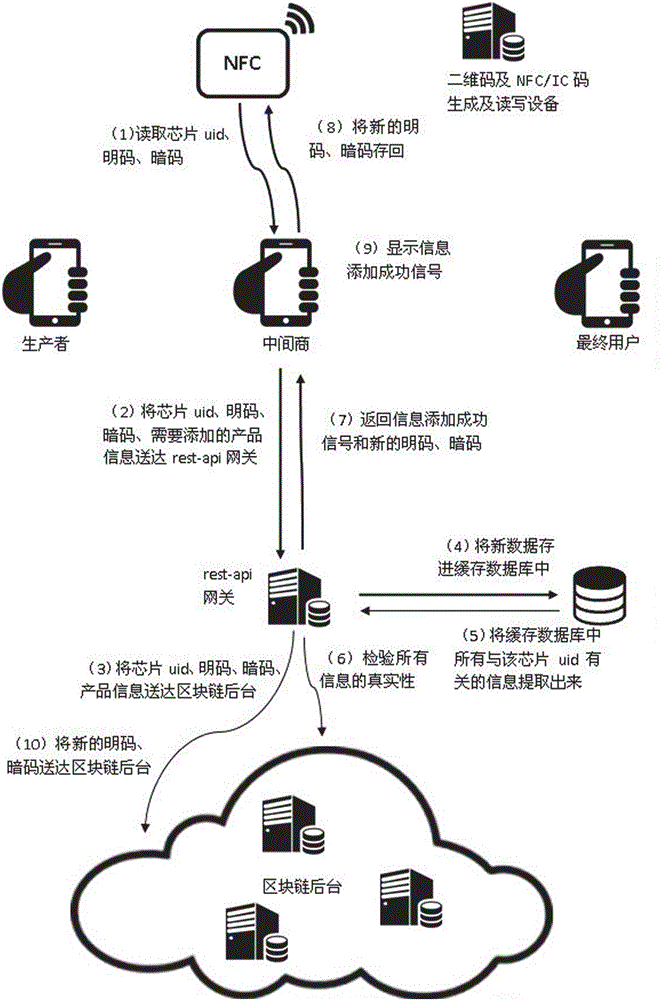
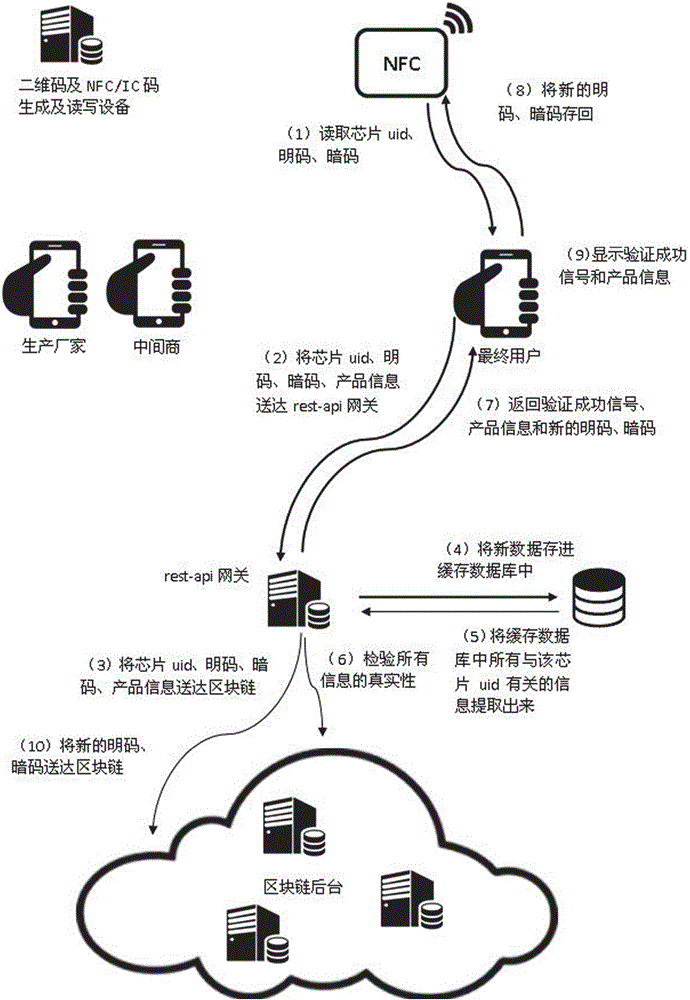
InactiveCN106209877AAchieve traceabilityAvoid self-indulgenceUser identity/authority verificationCo-operative working arrangementsThird partyComputer terminal
The invention discloses an anti-counterfeiting and authentication system taking a block chain background as an authentication core. The anti-counterfeiting and authentication system comprises an anti-counterfeiting label, a verification terminal, a Rest-api gateway, a block chain background and a cache database, wherein producers, middlemen and verification personnel read information in the anti-counterfeiting label through the verification terminal and send the read information to the Rest-api gateway; the Rest-api gateway sends the received information to the block chain background, records the information in the block chain background, also stores new data in the cache database, then extracts all information related to the anti-counterfeiting label in the cache database, and verifies the authenticity of all information of the block chain background according to the extracted information, and if the information is real, the Rest-api gateway returns an operation success signal and / or product information to the verification terminal. The anti-counterfeiting and authentication system disclosed by the invention has the beneficial effects as follows: the problem of dependence on the anti-counterfeiting label trust, node trust and third-party trust can be solved, the problem of dependence on anti-counterfeiting techniques can also be solved, and low anti-counterfeiting and authentication thresholds can be achieved.
Owner:井创(北京)科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com