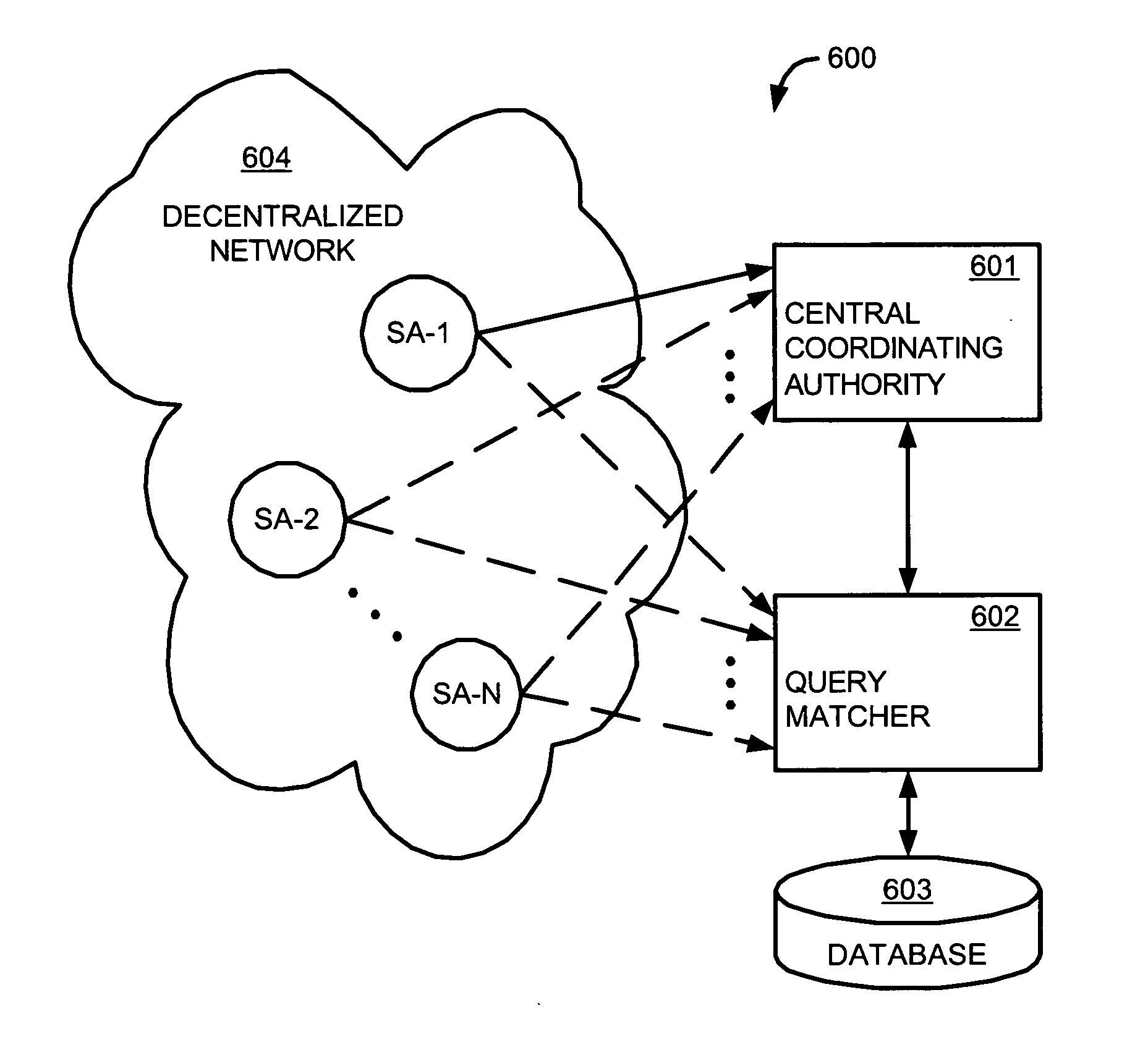
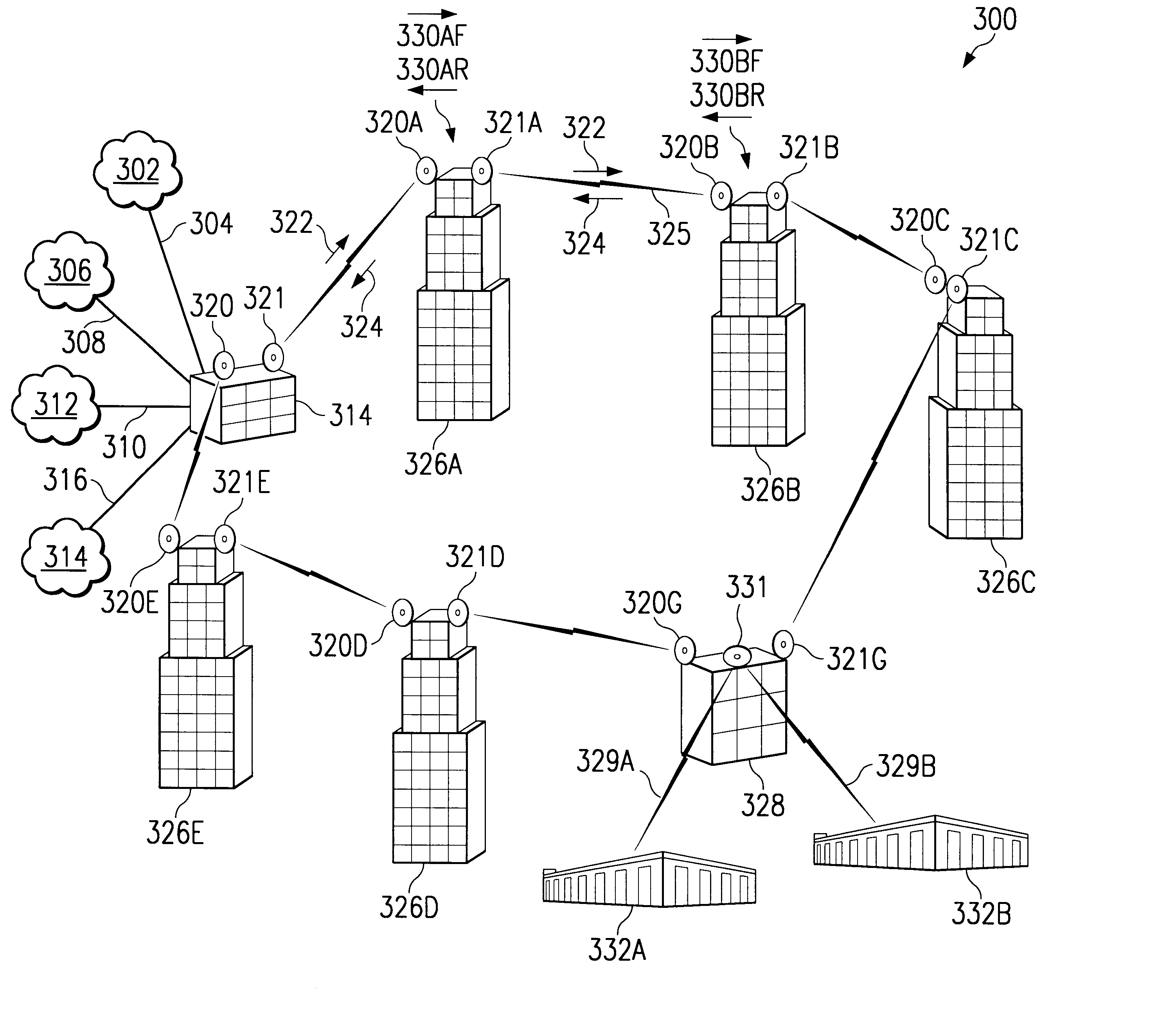
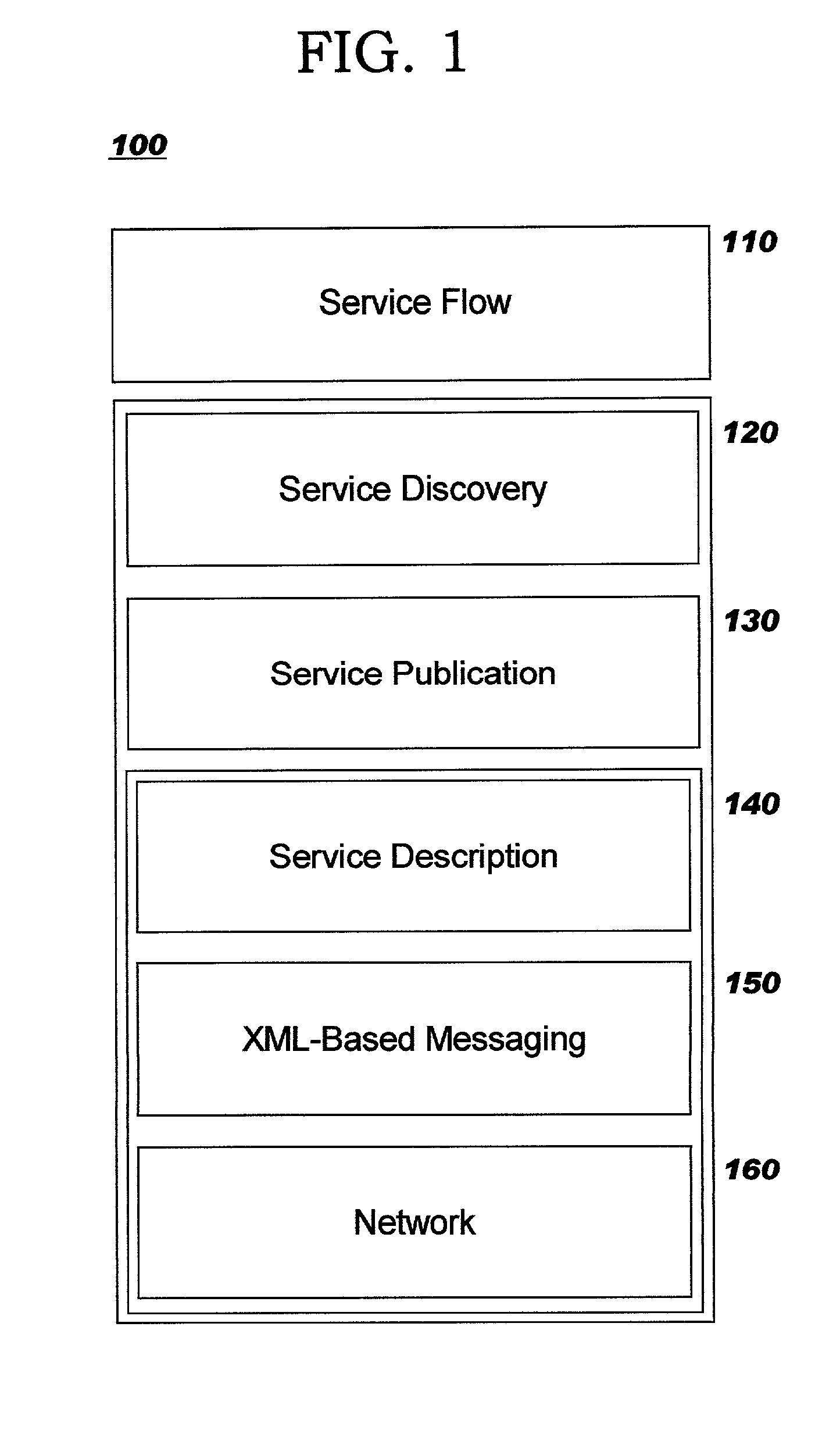
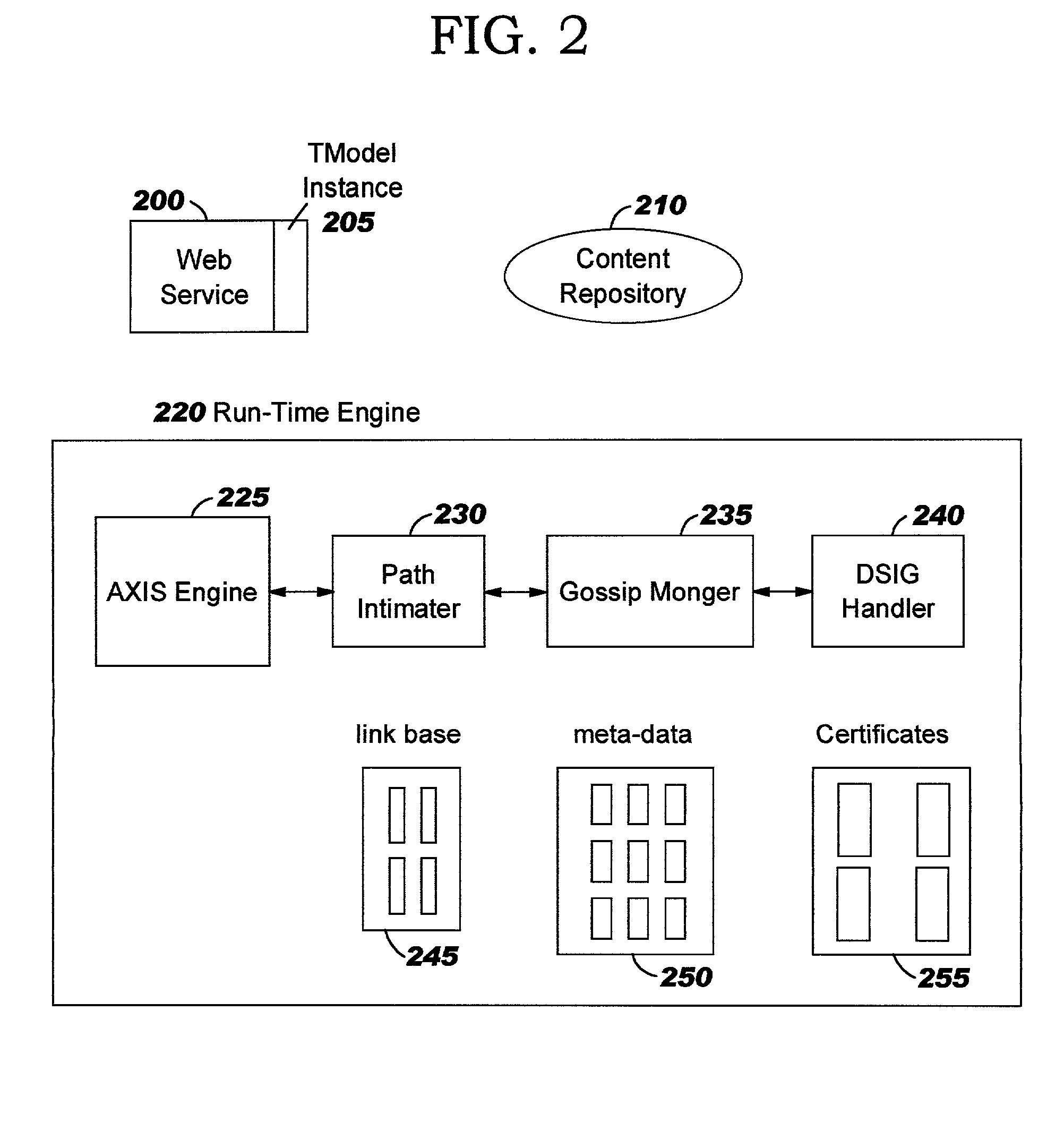
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
167 results about "Decentralized network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A decentralized market is a market structure that consists of a network of various technical devices that enable investors to create a marketplace without a centralized location.
Decentralized identity verification systems and methods
InactiveUS20150356523A1Cryptography processingUser identity/authority verificationRegulatory authorityFinancial transaction
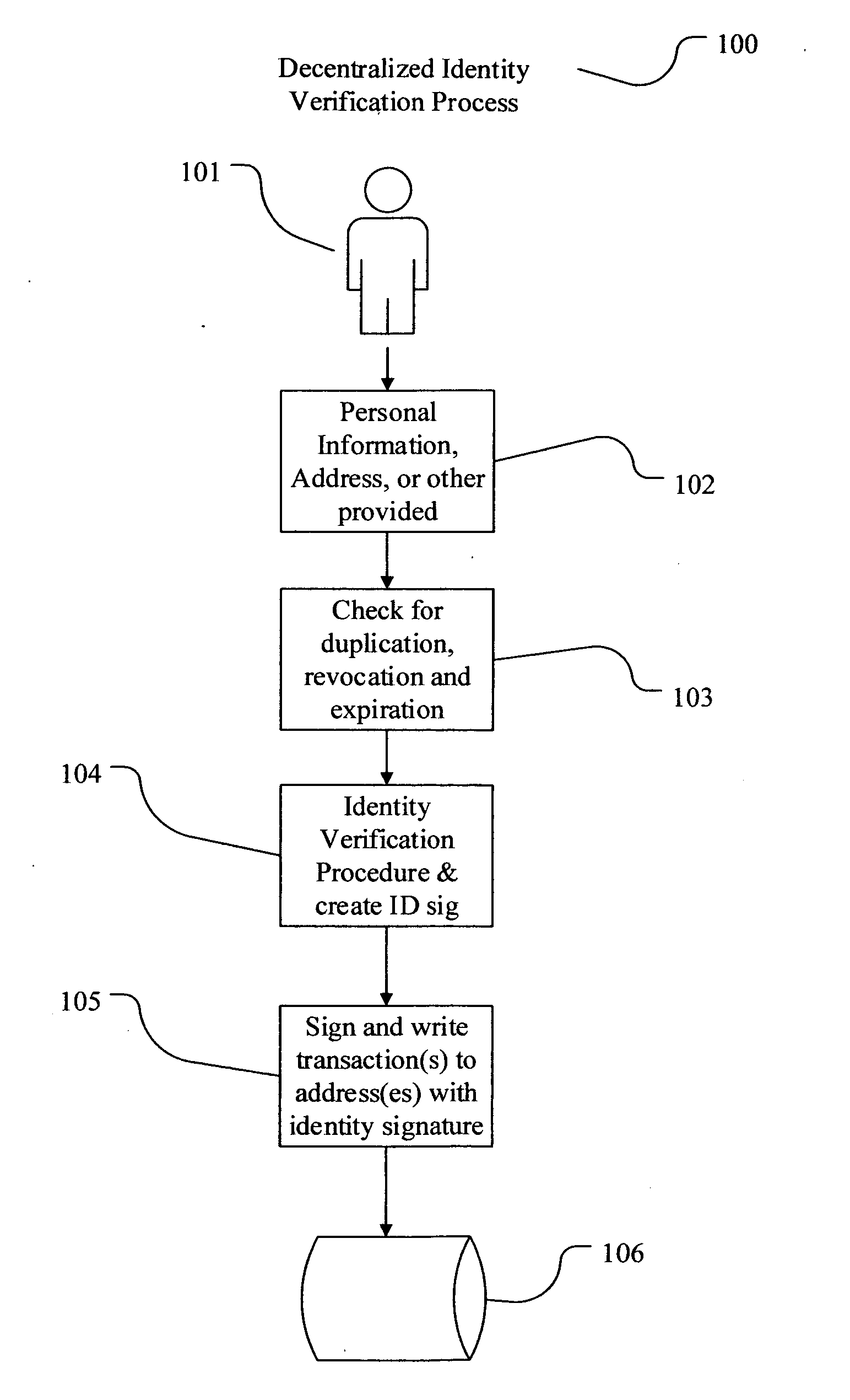
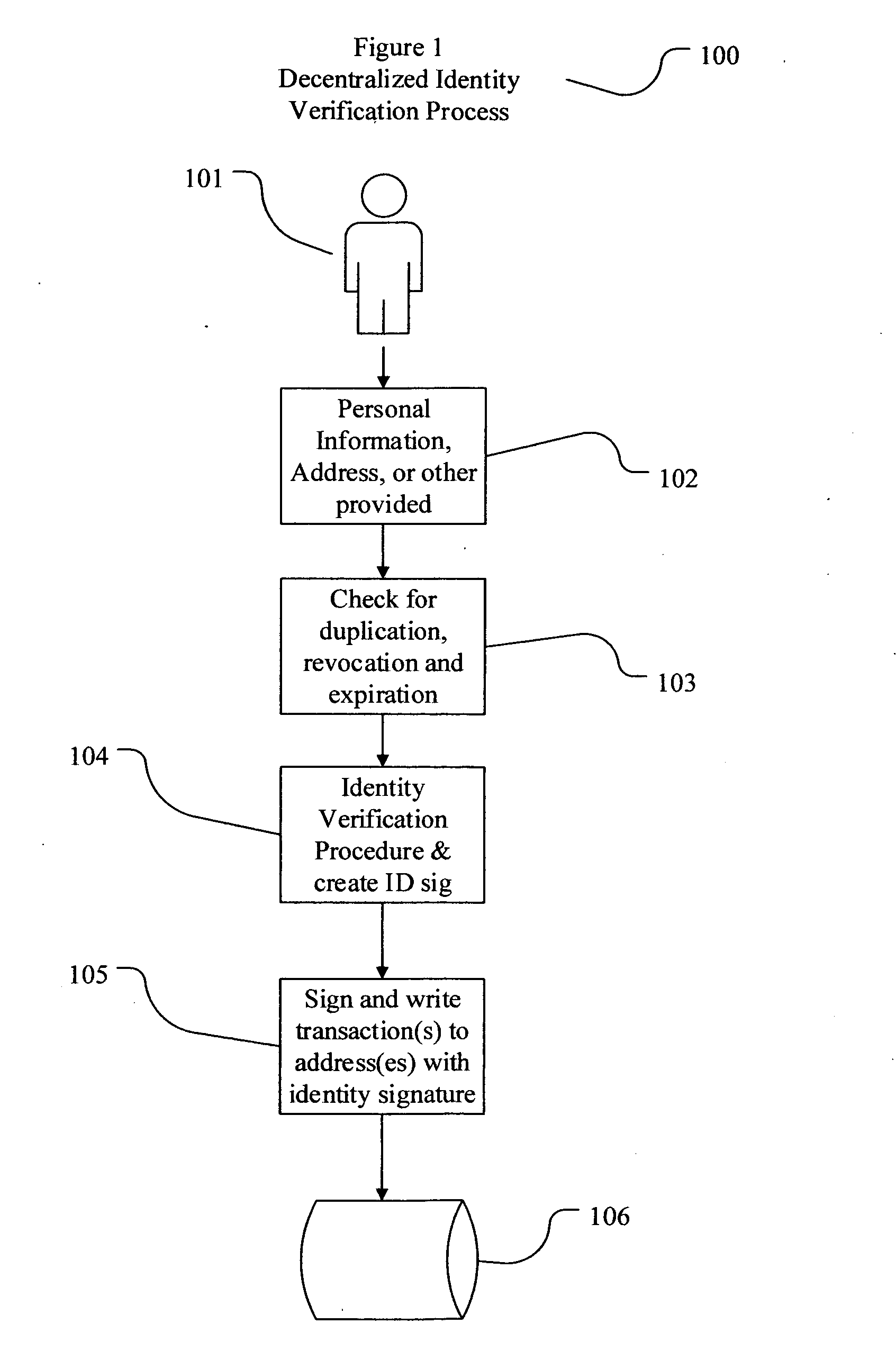
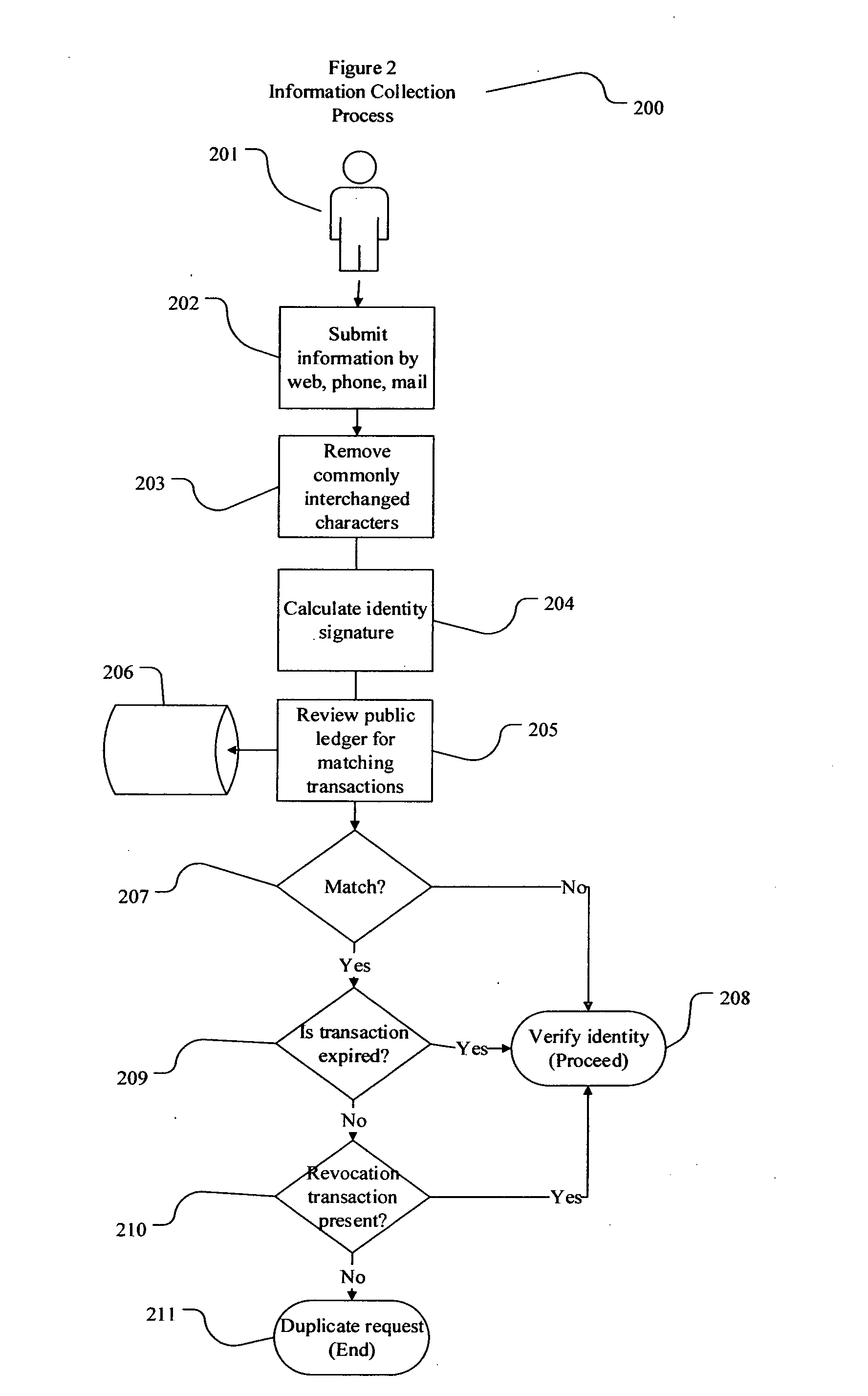
The present invention involves systems and methods that allow participants in cryptocurrency networks to exchange cryptocurrency for traditional currency legally and safely without requiring the use of a traditional exchange or online brokerage as a fiduciary. The invention accomplishes this through the use of a decentralized identity verification protocol that allows a service provider to verify the identity of a participant and then publish an identity signature on the participant's cryptocurrency address or addresses. The invention enables full compliance with Country specific customer identification program and anti-money laundering requirements, and maintains the ability to independently satisfy requests for information or data retention requirements if requested by legally authorized parties, but does not require that the participant store the private keys or access controls to their cryptocurrency on an exchange or brokerage service.The invention serves to verify a participant's identity in full compliance with US Bank Secrecy and Patriot Act provisions or similar regulations where identification may be achieved through non-documentary or documentary identity verification procedures. After passing the applicable verification procedure, the service provider stamps the participant's cryptocurrency address with a transaction containing an identity signature. This identity signature within the transaction consists of a public indicator of the participant's Country and subdivision, a compliance level code, an ID type indicator, and an identity hash. The identity hash is created from the digests of cryptographic hash functions where the participant's personal information is used as an input. The service provider signs the transaction with their authorized private key that corresponds to their publicly accessible public key. This serves as a publicly verifiable confirmation that the identity associated with the address in question was validated by the service provider authorized to act on behalf of the regulatory authority.The participant may then purchase and sell cryptographic currency from and to a third party exchange or brokerage service legally and safely when using their verified cryptocurrency address. This is because the third party is able to confirm compliance by openly referencing and verifying the identity verification transaction present on the address. Subsequent transactions where the third party sells or purchases cryptocurrency for the verified participant are similarly stamped with a transaction conforming to the identity verification protocol. This allows the third party interacting with the verified participant's address to observe any regulations limiting the amount or frequency of transactions over a variable period of time. It follows that this address could be used with any third party or participant in the cryptocurrency network that observes the decentralized identity verification protocol, all without requiring the third party or participant to collect and verify personal information redundantly. The ability to verify an identity remotely also eliminates the need for the third party to act as a fiduciary holding the private keys or access controls to the verified address. Lawful requests for information by authorized authorities are served to the service provider as digitally signed transactions that may then be linked to the participant's identity and transactions, allowing the protocol to observe subpoenas or similar lawful requests for information. The encrypted personal information may be held in escrow by the service provider indexed to the verified cryptocurrency address for such purposes. An alternate embodiment would store the encrypted personal information in a decentralized network of other participants, with the information accessible for retrieval using the public key of the verified cryptocurrency address and decryption using the corresponding private key, decentralizing the process entirely except for the identity verification step.
Owner:CHAINID
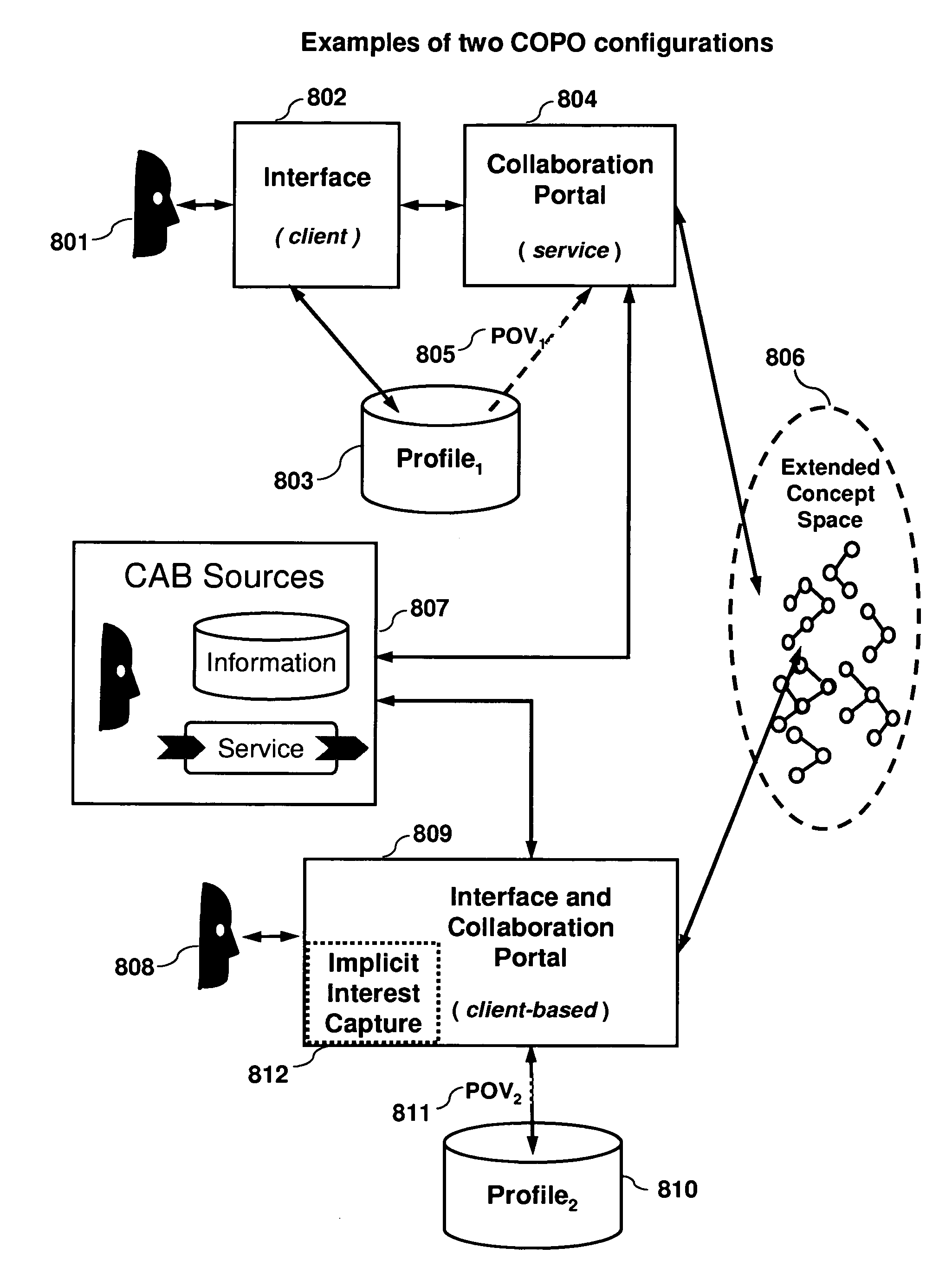
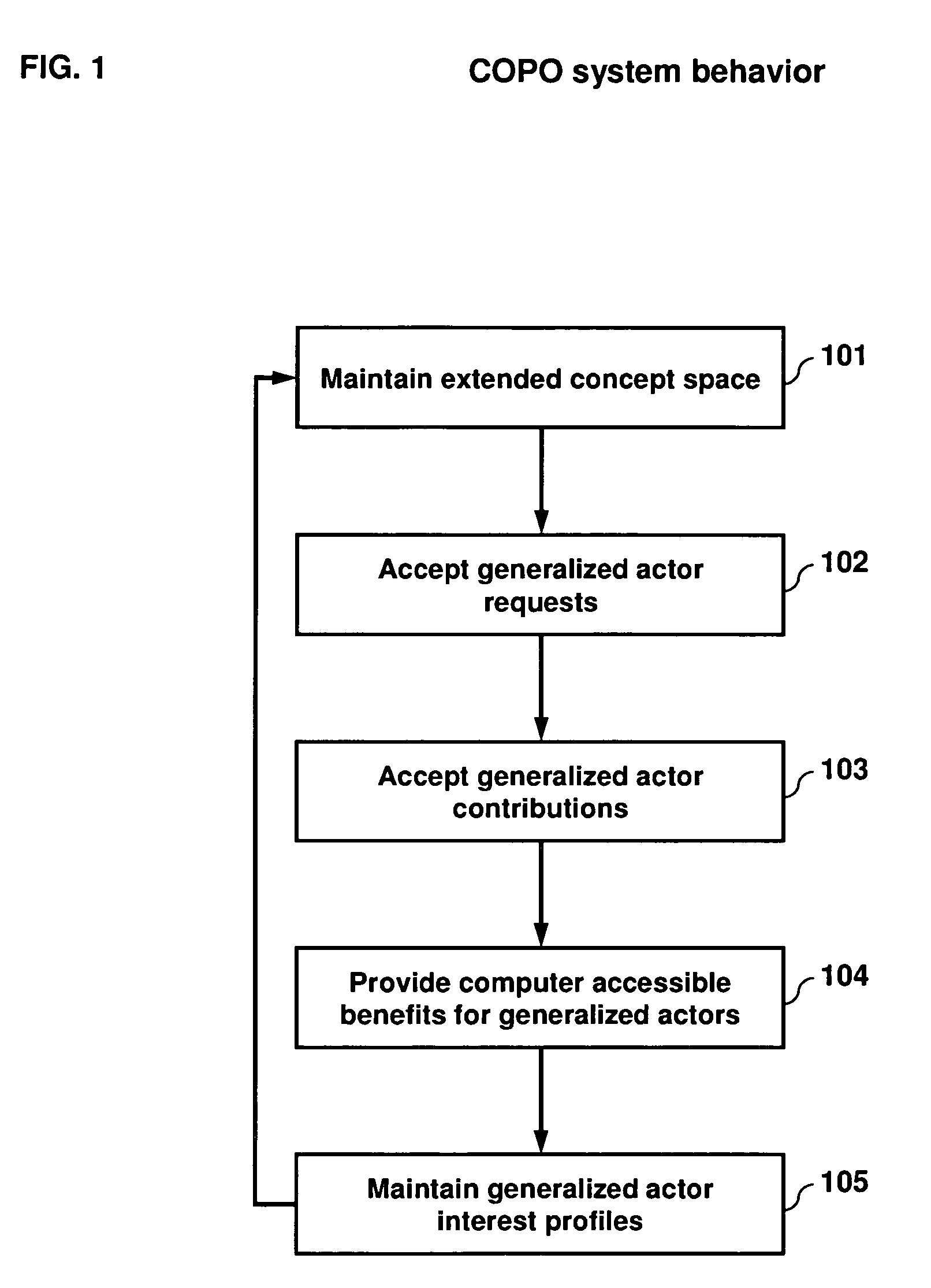
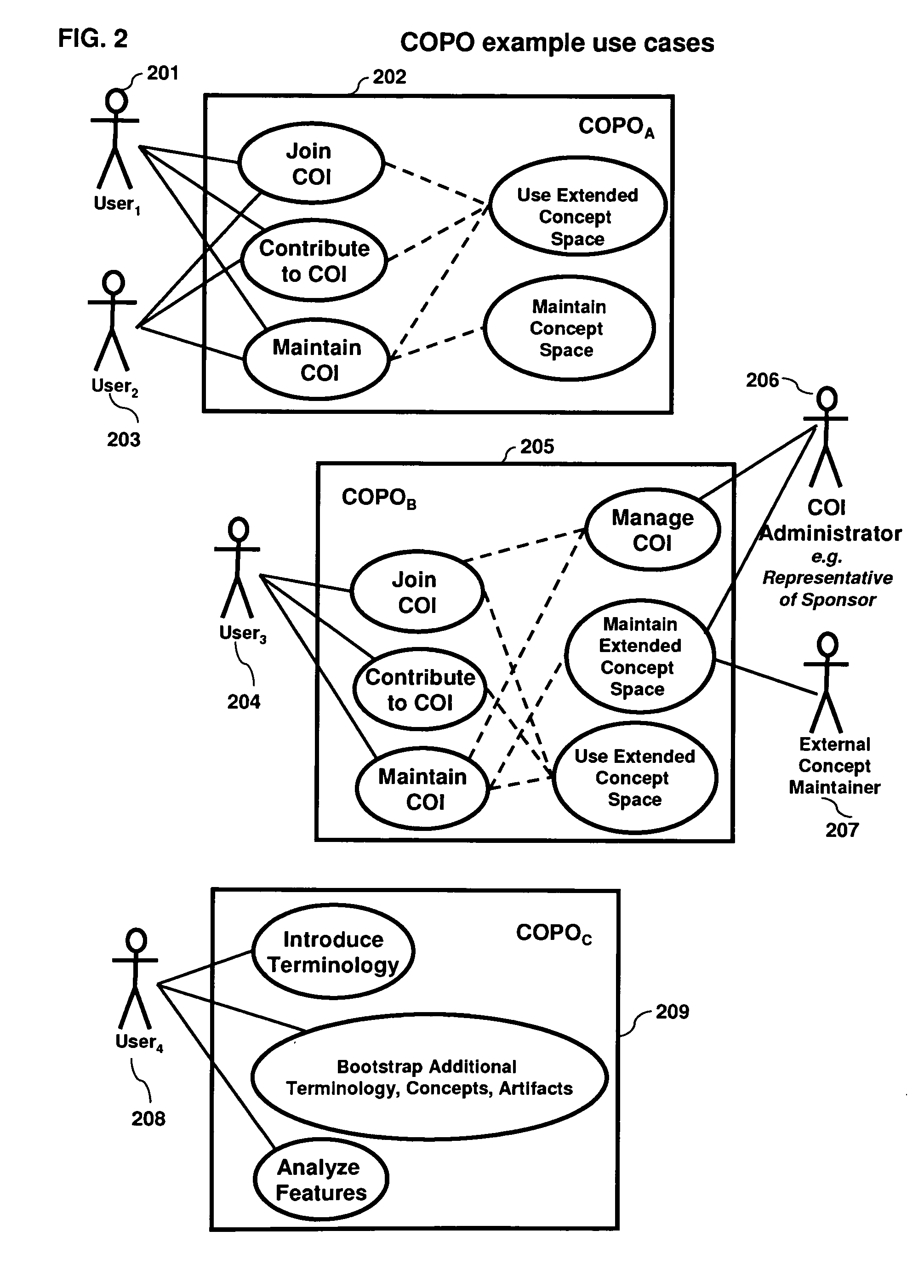
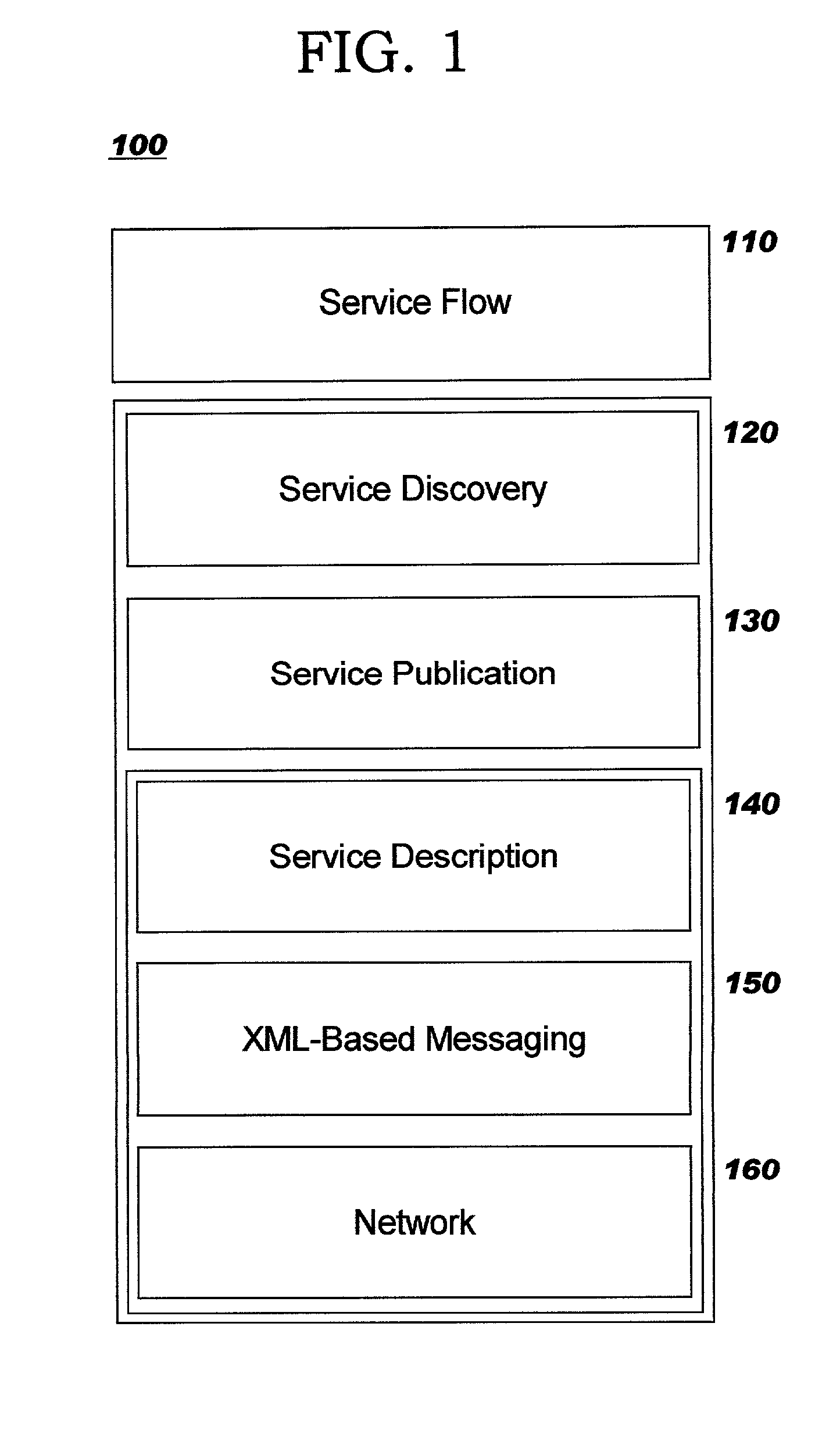
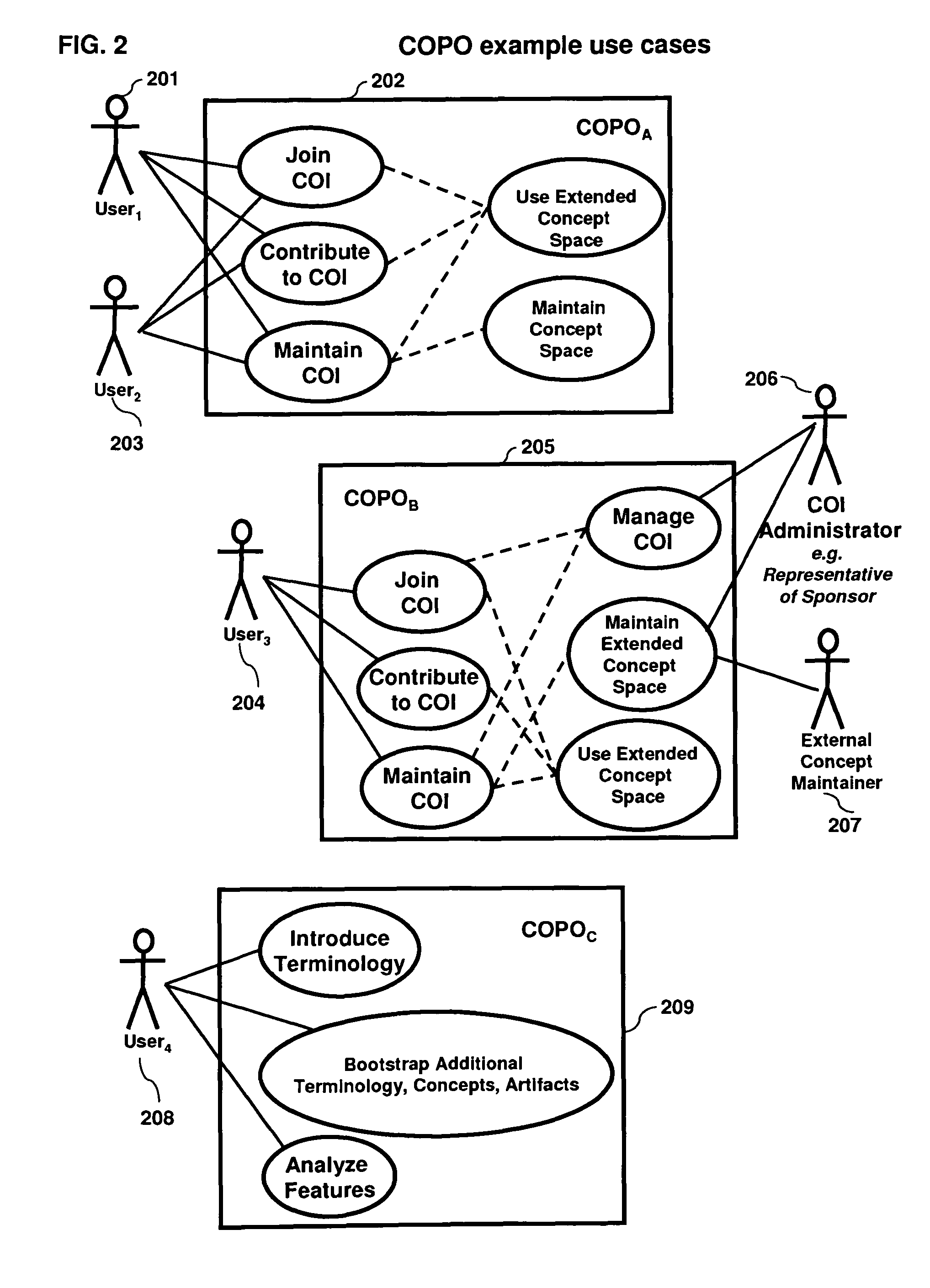
Collaboration portal (COPO) a scaleable method, system, and apparatus for providing computer-accessible benefits to communities of users
InactiveUS20080281915A1Simple indexingAvoid ambiguityDigital data processing detailsMultiple digital computer combinationsData scienceDecentralized network
The present invention, known as The Collaboration Portal (COPO), relates generally to the field of automated entity, data processing, system control, and data communications, and more specifically to an integrated method, system, and apparatus for providing computer-accessible benefits for communities of users. It provides a framework for provisioning computer-accessible benefits for communities of users, and can efficiently and robustly distribute the processing in behalf of those users over a decentralized network of computers. The field of the invention generally encompasses enabling appropriate and desired communication among communities of users and organizations, and providing information, goods, services, a works, opportunities, and connections among users and organizations.
Owner:QUANTUM LEAP RES
Autonomic provisioning of netowrk-accessible service behaviors within a federted grid infrastructure
InactiveUS20040064548A1Avoiding expensive and inefficient over-commitmentDigital computer detailsMultiprogramming arrangementsService-level agreementAuto-configuration
Methods, systems, computer program products, and a method of doing business are disclosed for autonomically provisioning network-accessible services in a decentralized network having a federated grid infrastructure. Autonomic, grid, and web services-related technologies, standards, and concepts are leveraged. More particularly, web service behaviors (augmented as grid services, according to preferred embodiments) are autonomically provisioned (i.e., dynamically distributed) via a grid of hosting services. In preferred embodiments, this dynamic distribution occurs in response to (and as a function of) external catalysts, such as algorithms that monitor designated resources (e.g., to proactively determine when the commitments in a utility service provider's service level agreements are in jeopardy).
Owner:IBM CORP
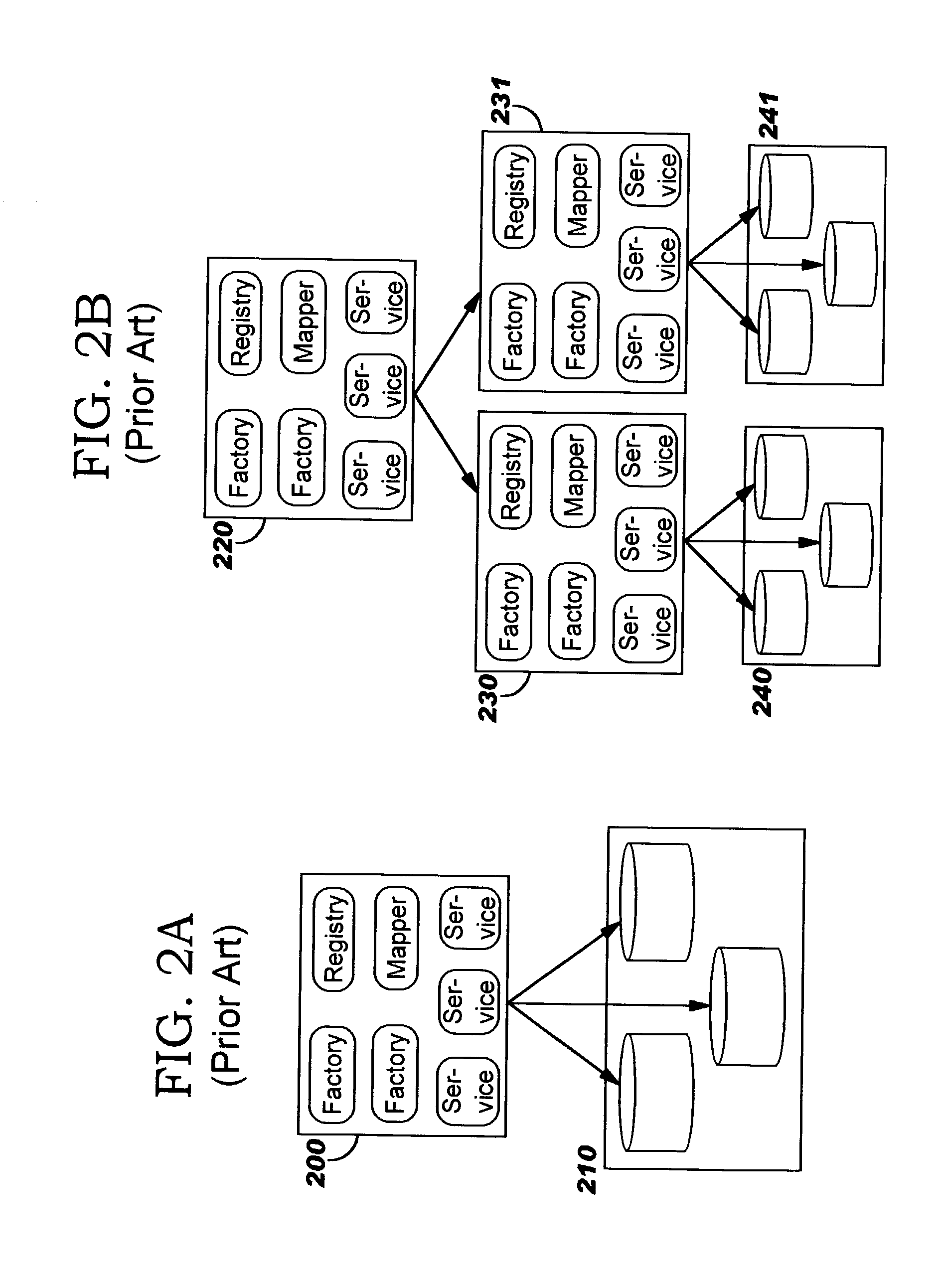
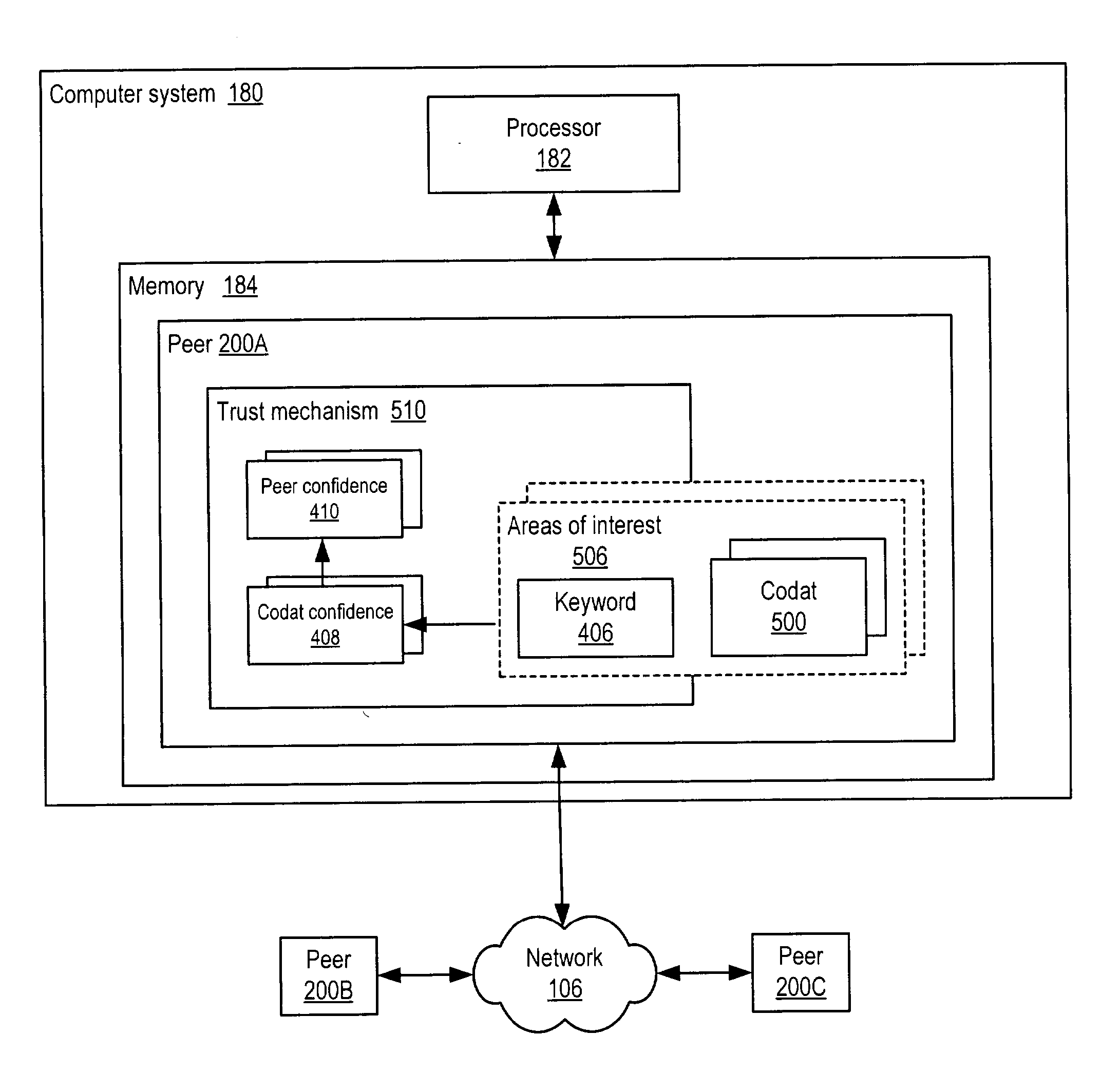
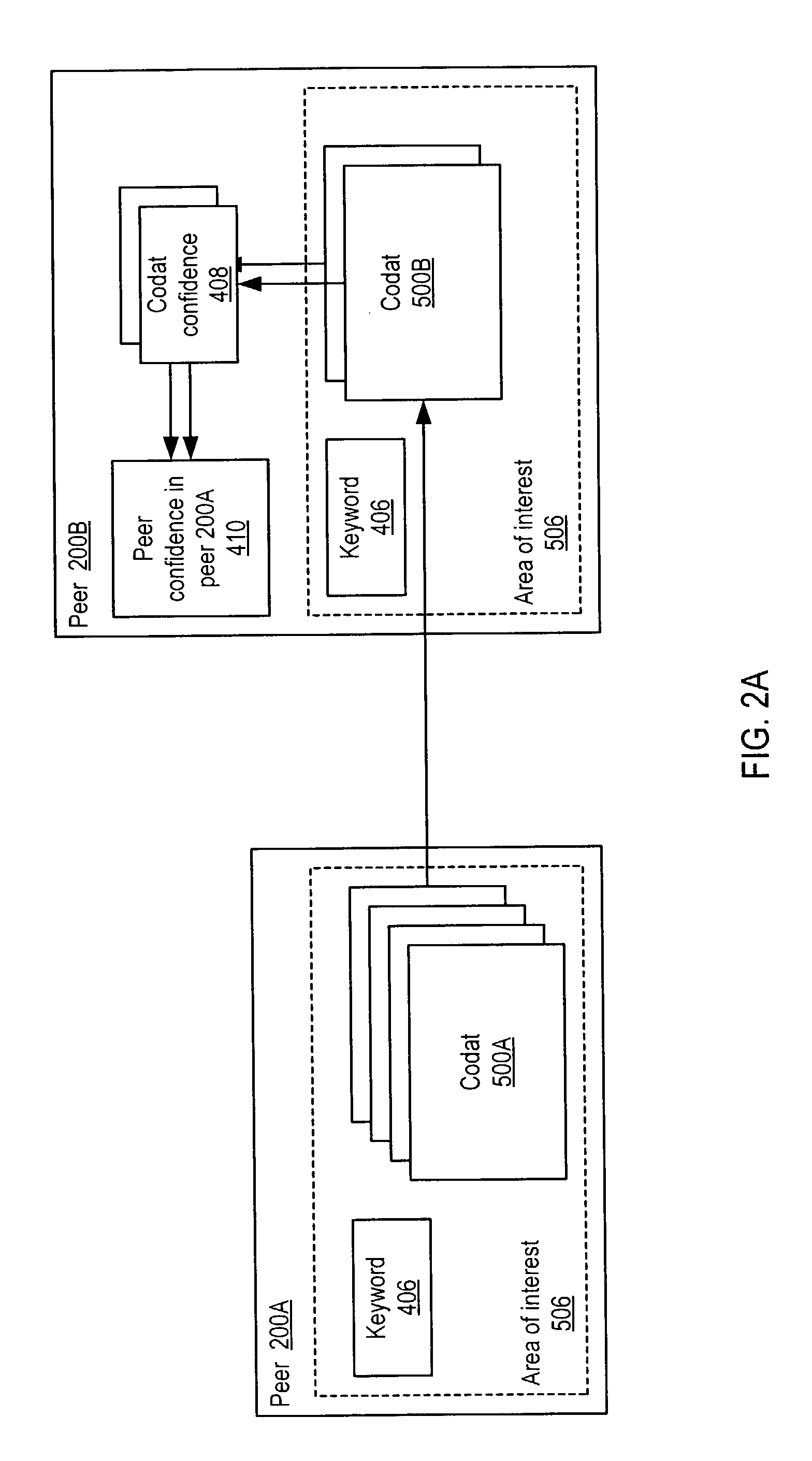
Representing trust in distributed peer-to-peer networks
ActiveUS20030055894A1Multiprogramming arrangementsMultiple digital computer combinationsInformation feedbackPeer-to-peer
Embodiments may provide mechanisms for representing trust between peers or systems in decentralized networking environments including peer-to-peer networking environments. Trust may include both direct trust between two peers and trust in a pipeline of peers along which codat may be passed. Embodiments may provide a mechanism for a peer to represent and rate the trustworthiness of other peers as providers of codat relevant to the peer's interest. To evaluate trust in another peer as a provider of codats in the area of interest, trust may be represented with two components, confidence and risk. Embodiments may provide mechanisms for measuring the components and determining trust from the components. Embodiments may also provide mechanisms for feeding back trust information to the providing peer and for propagating trust information to other peers.
Owner:ORACLE INT CORP
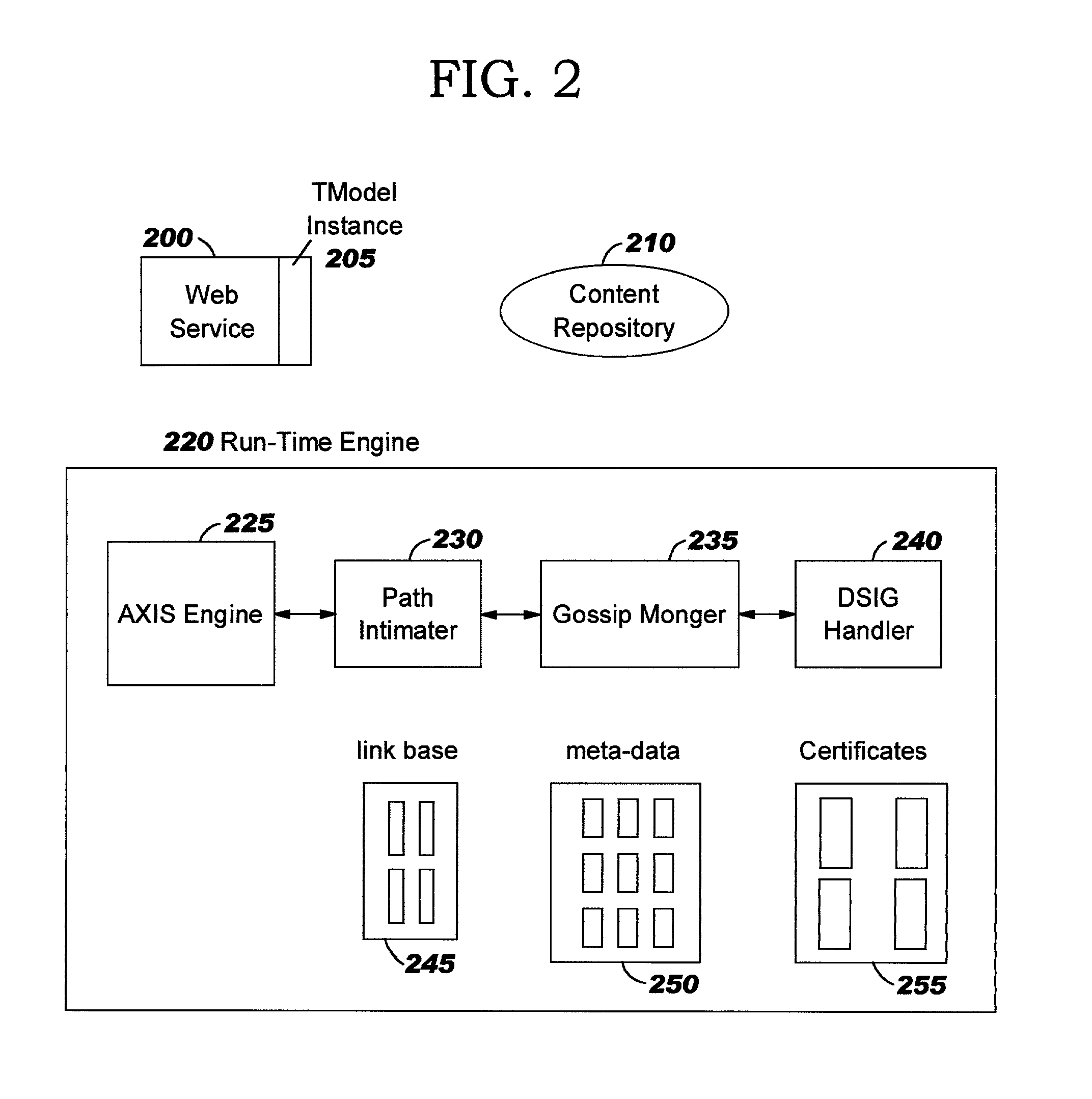
Managing storage resources in decentralized networks
InactiveUS7251689B2Avoiding drawback and limitationMultiple digital computer combinationsSecuring communicationPersistent identifierWeb service
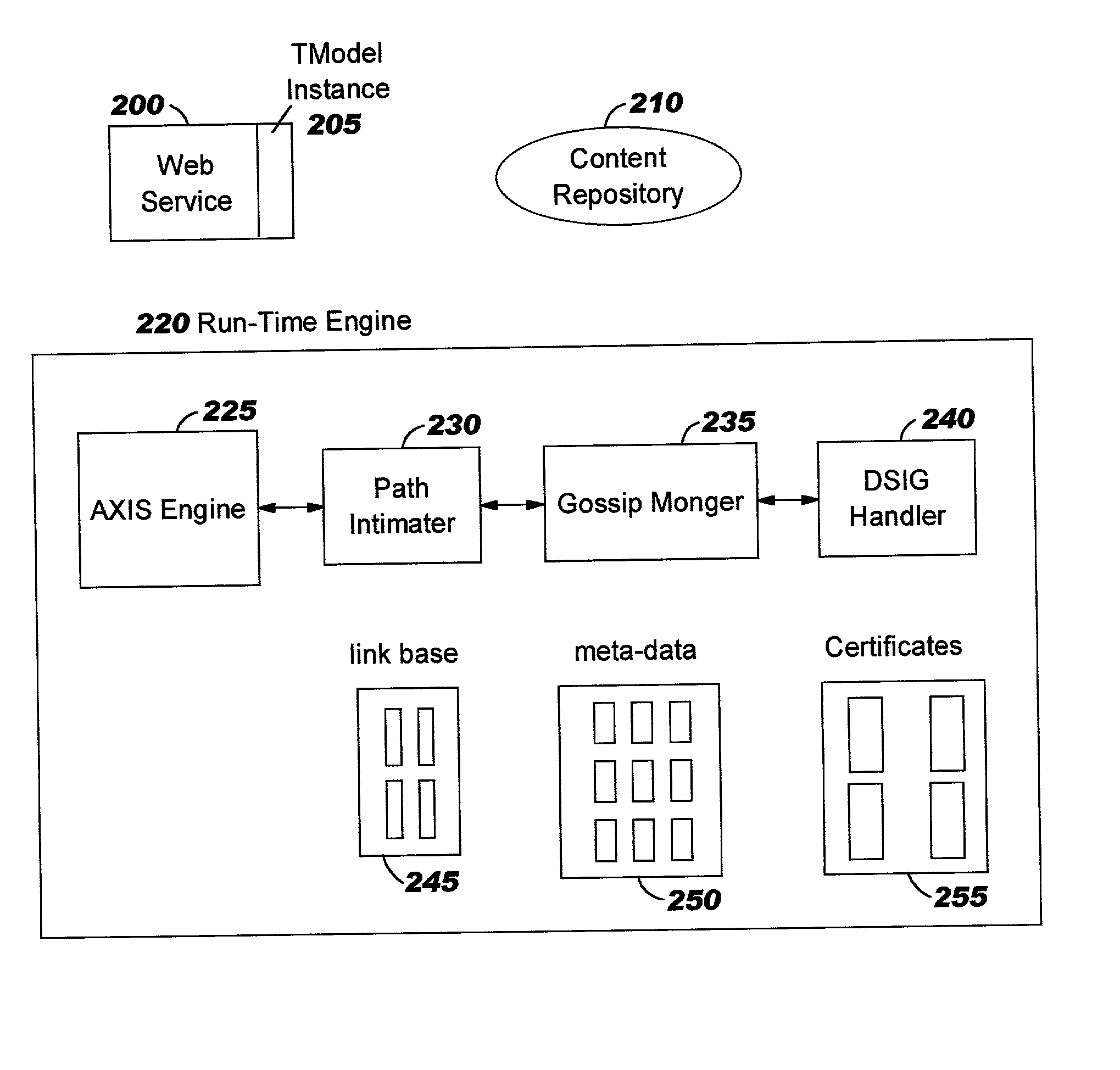
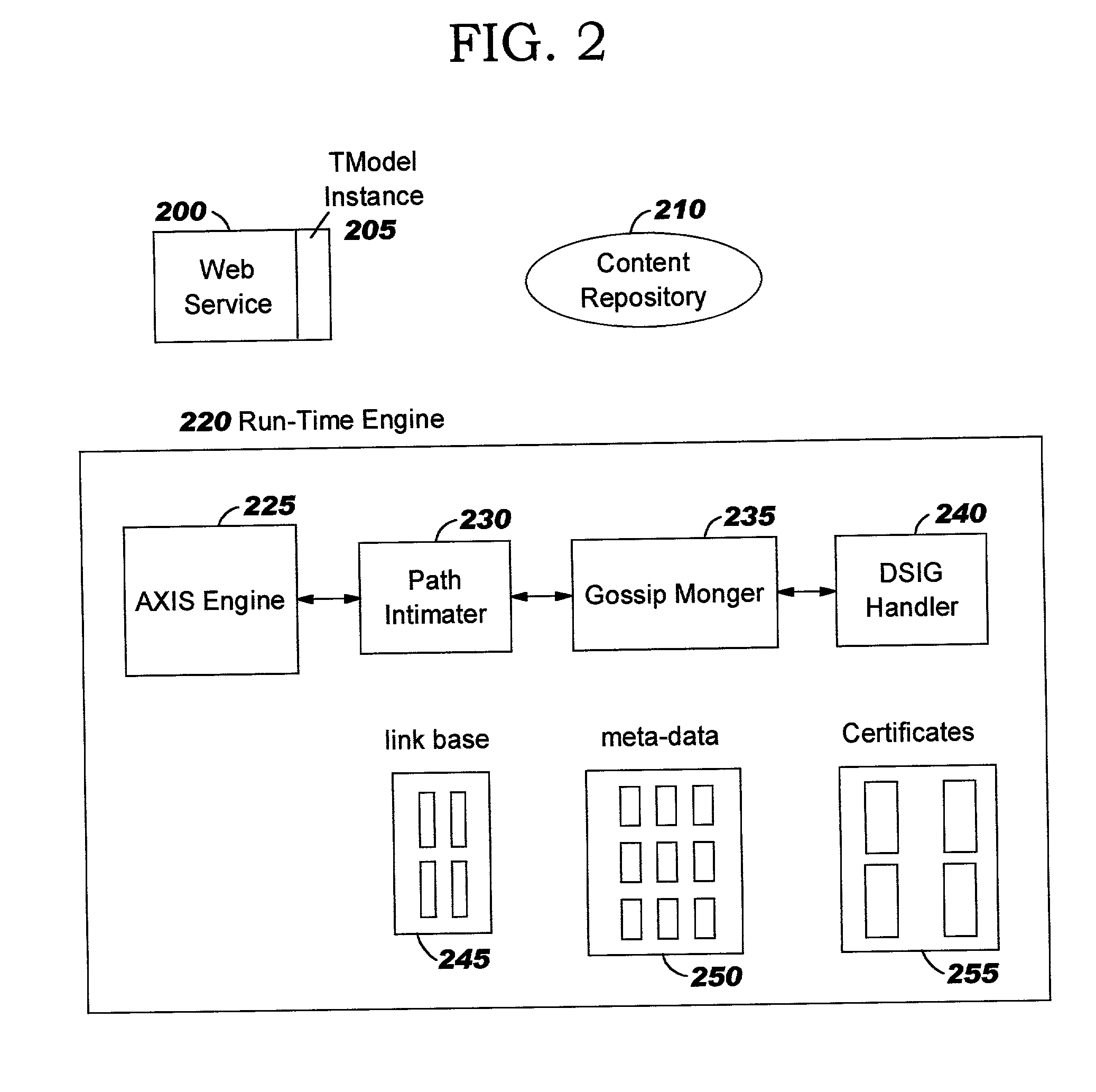
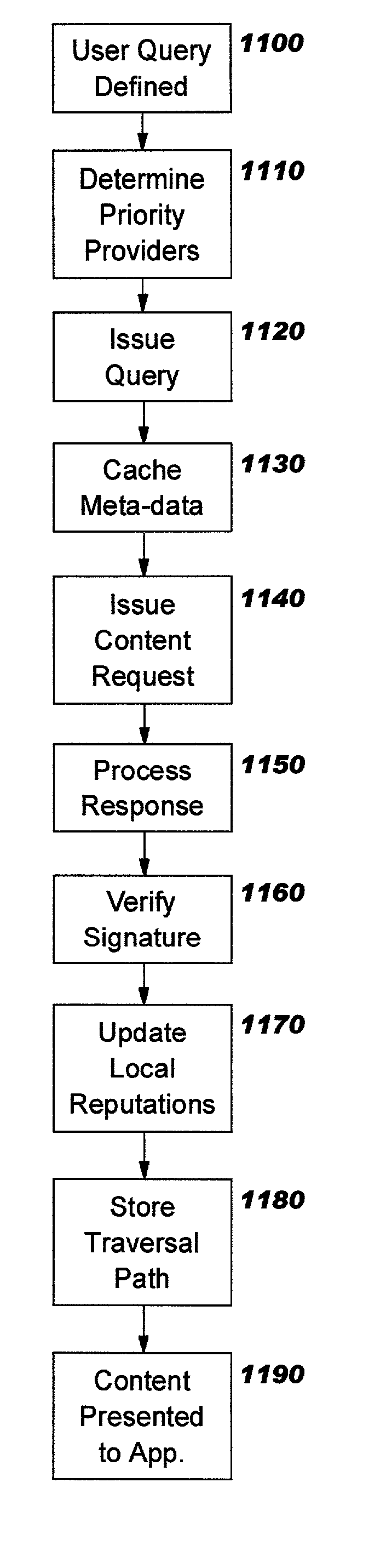
Methods, systems, and computer program products are disclosed for managing storage resources in decentralized networks. Persistent identifiers are defined for nodes, allowing nodes to be identified across sessions and invocations, even though they re-enter the network with a different network address. Paths taken by content resources as they traverse the network (e.g. which nodes forwarded the content) are persisted, along with reputation information about nodes (e.g. indicating how successful they are at answering queries from peers). Trust relationships can be derived using the persisted information. A tiered broadcast strategy is defined for reducing the number of messages exchanged. Preferred embodiments leverage a web services implementation model.
Owner:IBM CORP
Providing management functions in decentralized networks
InactiveUS7039701B2Avoiding drawback and limitationMultiple digital computer combinationsSecuring communicationPersistent identifierWeb service
Methods, systems, and computer program products are disclosed for providing management functions in decentralized networks. Persistent identifiers are defined for nodes, allowing nodes to be identified across sessions and invocations, even though they re-enter the network with a different network address. Paths taken by content resources as they traverse the network (e.g. which nodes forwarded the content) are persisted, along with reputation information about nodes (e.g. indicating how successful they are at answering queries from peers). Trust relationships can be derived using the persisted information. A tiered broadcast strategy is defined for reducing the number of messages exchanged. Preferred embodiments leverage a web services implementation model.
Owner:IBM CORP
Device reporting and protection systems and methods using a secure distributed transactional ledger
ActiveUS20160259937A1Digital data protectionInternal/peripheral component protectionNetwork connectionProtection system
Aspects of the present invention provide systems and methods that allow for a generic, decentralized system that is independent of a centralized resource and allows for the reporting and protecting of all types of smart devices including smart phones, laptop, tablets, or smart packages, and the like. In embodiments, the device comprises a security module or modules that interface with a decentralized network that maintains a secure distributed transactional ledger, or block chain, in order to send and / or receive data via the block chain. In embodiments, the device may not operate when its ability to access a communication channel provided via secure distributed transactional ledger has been impeded or otherwise hindered.
Owner:DELL PROD LP
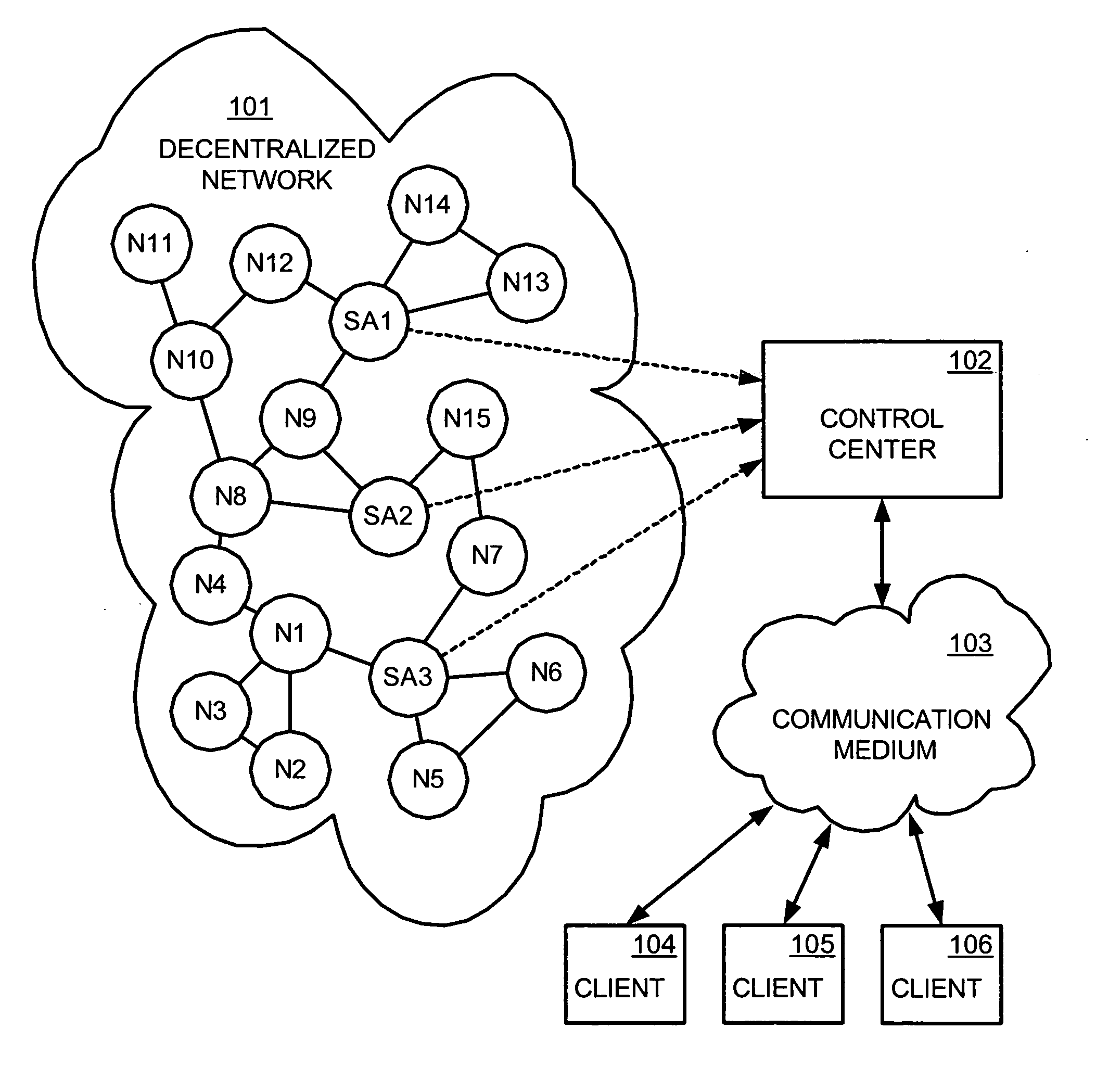
Demand based method for interdiction of unauthorized copying in a decentralized network
InactiveUS20050114709A1Digital data processing detailsUnauthorized memory use protectionDecoyNetwork communication
A multi-level and / or demand based method and apparatus for interdicting unauthorized copying in a decentralized network are described. In their preferred embodiments, the method and apparatus start out by performing search result manipulation to interdict unauthorized copying of protected files. If a trigger event is detected in network communications, however, such as a threshold number of requests being exceeded for a protected file by a network node, then the method floods that node with decoys of the protected file to enhance interdiction efforts.
Owner:MACROVISION CORP
Service tariffing based on usage indicators in a radio based network
InactiveUS6618355B1Improve efficiencyLow costMetering/charging/biilling arrangementsAccounting/billing servicesTraffic capacityRadio networks
The system provides a distributed decentralized network architecture. Network routing is performed at each node in the network, as opposed to the centralized architecture's single POP. Each node is typically an access point to the network, and it collects the relevant traffic statistics for subscribers connecting at that node. This is accomplished by a network switching / control element contained within the (Invisible Fiber Unit) IFU. The information is collected from the switching / control element contained within the IFU. The information is collected from the switching element by the IFU's CPU. This information can then be pre-processed locally, or sent directly to a central billing facility, for further processing, eventually resulting in the creation of the subscriber's bill. Essentially, it is only billing information that flows back to a central point, rather than the data traffic itself.
Owner:TRITON NETWORK SYST
Providing management functions in decentralized networks
InactiveUS20030188019A1Multiple digital computer combinationsSecuring communicationPersistent identifierWeb service
Methods, systems, and computer program products are disclosed for providing management functions in decentralized networks. Persistent identifiers are defined for nodes, allowing nodes to be identified across sessions and invocations, even though they re-enter the network with a different network address. Paths taken by content resources as they traverse the network (e.g. which nodes forwarded the content) are persisted, along with reputation information about nodes (e.g. indicating how successful they are at answering queries from peers). Trust relationships can be derived using the persisted information. A tiered broadcast strategy is defined for reducing the number of messages exchanged. Preferred embodiments leverage a web services implementation model.
Owner:IBM CORP
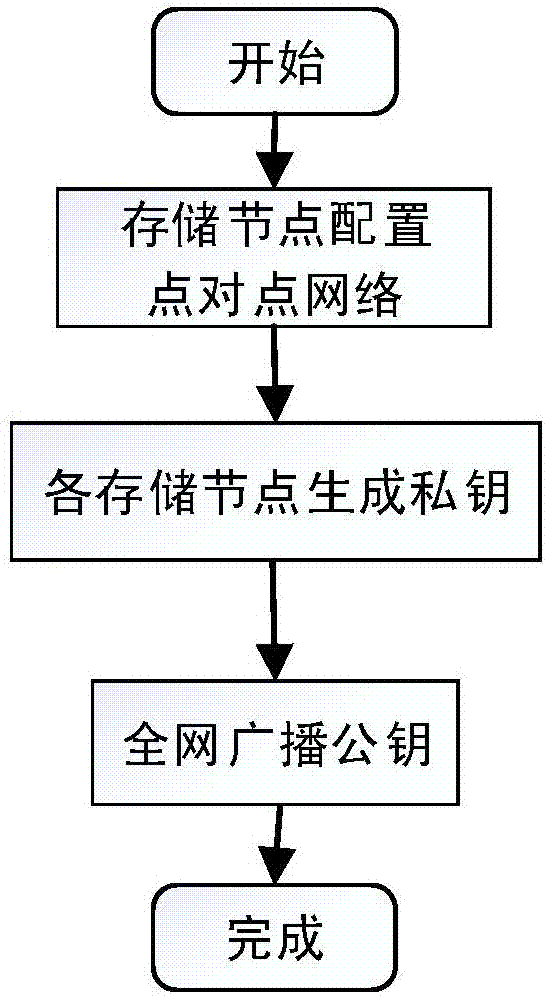
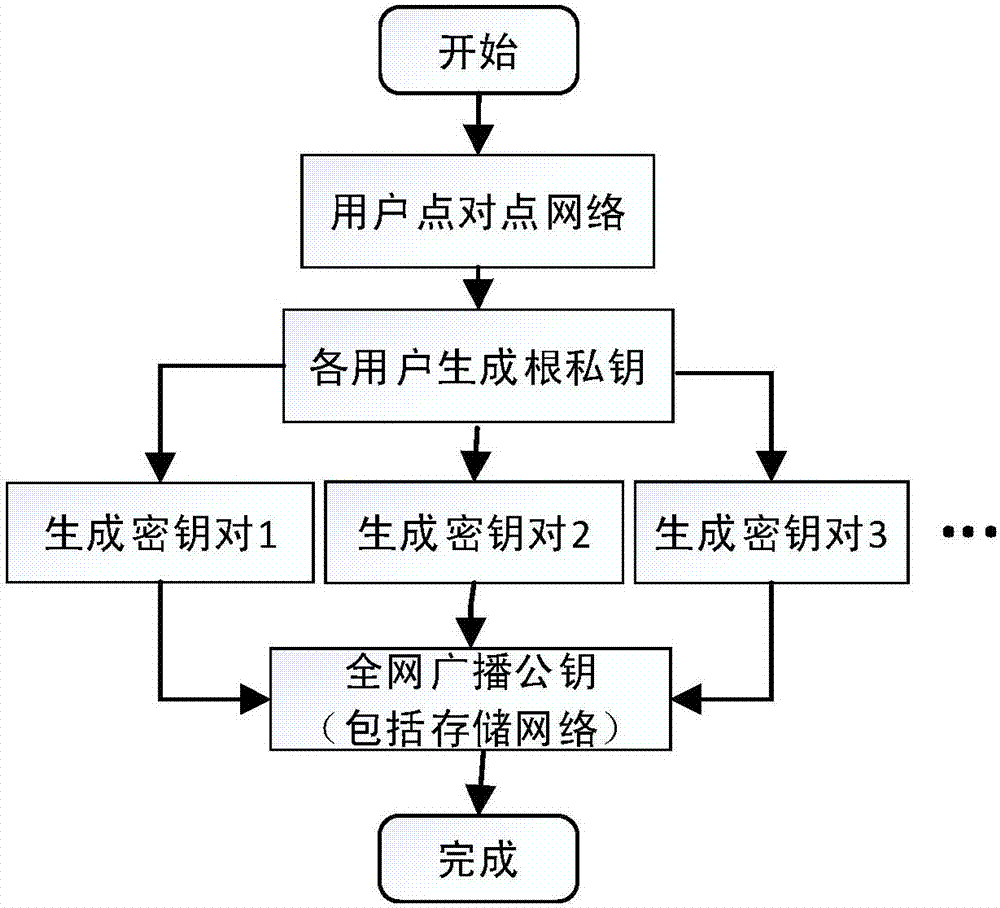
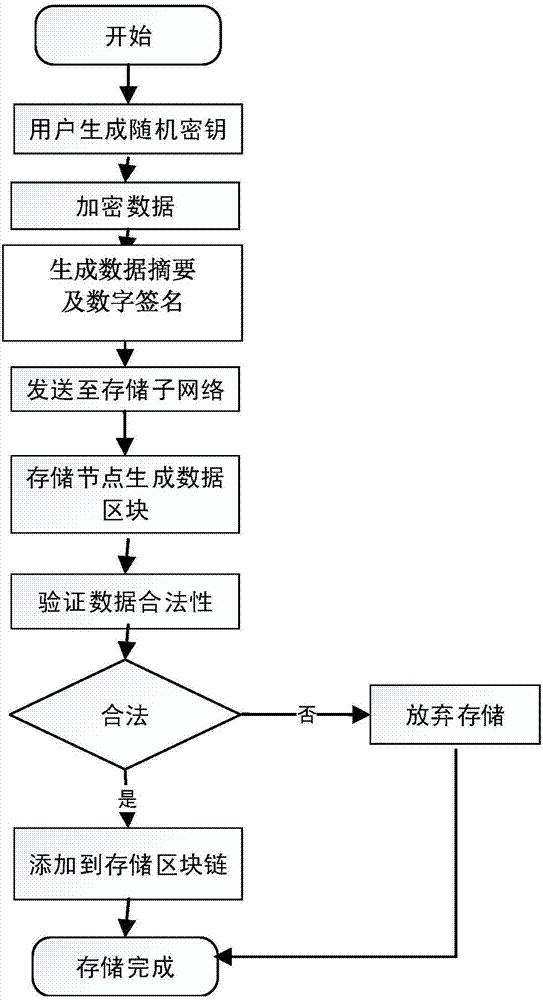
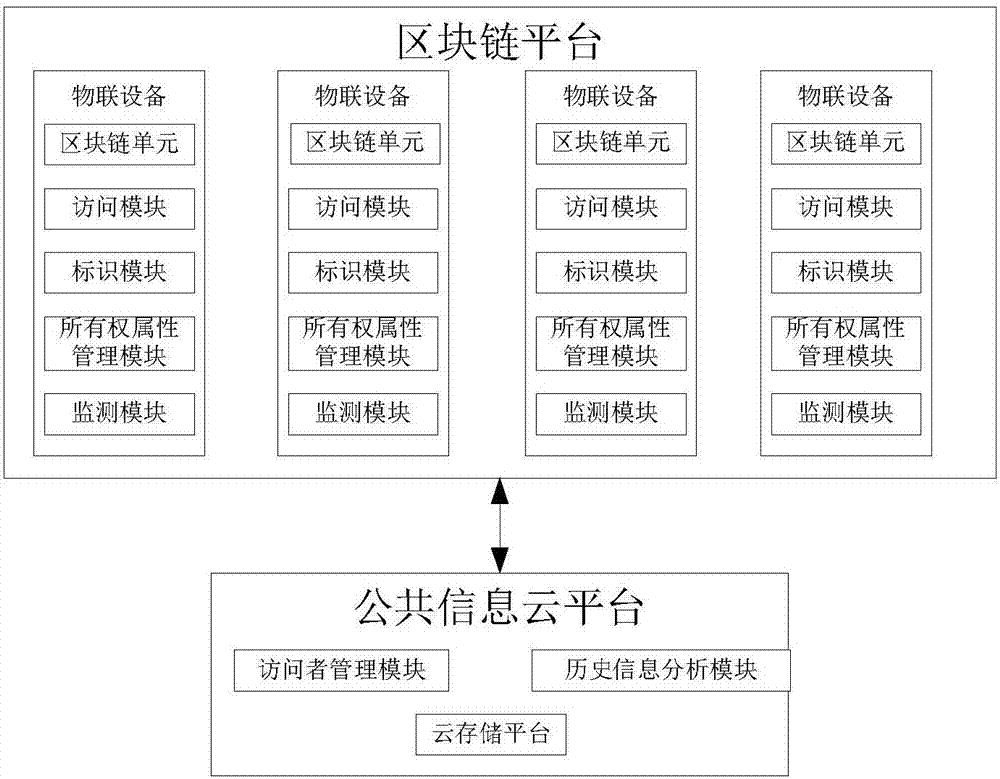
Routing position data secrecy storing and sharing method based on block chain
ActiveCN107181599AGood data protectionSolve workload bottlenecksKey distribution for secure communicationUser identity/authority verificationByzantine fault toleranceOriginal data
Provided is a routing position data secrecy storing and sharing method based on block chains. The routing position data secrecy storing and sharing method includes a data storing method and a data sharing method. The data storing method includes the steps of node configuration, data encryption sending, storage subnetwork verification storing, etc. The data sharing method includes the steps of demand generation, demand response, sharing achievement and the like. The effects of the invention are as follows: through a block chain technology, data sharing is realized through data encryption storage and a decentralized network to solve the problems that data storage parties have no right to use data and users do not have channels to selectively enable personal data to be accessed; local encryption sending is adopted during data storage, service parties store encrypted data, the users themselves save decryption secret keys, and the service parties have no access to original data, so a better data protection effect is achieved; and the block chain technology is adopted during storage, commonly recognized storage is realized through a practical Byzantine fault-tolerant algorithm, workload bottleneck problems of centralized storage are solved, and data is prevented from being tampered.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
Transference tracking
PendingUS20190188706A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationCentralized databaseCentral authority
Systems and methods are disclosed that provide for a blockchain-based transference tracking system to authenticate and register electronic transaction records. The transference tracking system, in one embodiment, is a permissioned, peer-to-peer, decentralized network containing an authorized, verifiable ledger of electronic transaction records that can be shared amongst authenticated actors. The decentralized ledger can be used as a substitute for a centralized database and enables automated tracking and reporting of electronic transaction records to an authoritative, but non-central authority using the blockchain of the transference tracking system.
Owner:APPLE INC
Broadcast tiers in decentralized networks
InactiveUS20030187974A1Reduce traffic problemsSpecial service provision for substationNetwork traffic/resource managementTraffic capacityPersistent identifier
Methods, systems, and computer program products are disclosed for classifying nodes into broadcast tiers to reduce traffic in decentralized networks. Persistent identifiers are defined for nodes, allowing nodes to be identified across sessions and invocations, even though they re-enter the network with a different network address. Paths taken by content resources as they traverse the network (e.g. which nodes forwarded the content) are persisted, along with reputation information about nodes (e.g. indicating how successful they are at answering queries from peers). Trust relationships can be derived using the persisted information. Preferred embodiments leverage a web services implementation model.
Owner:IBM CORP
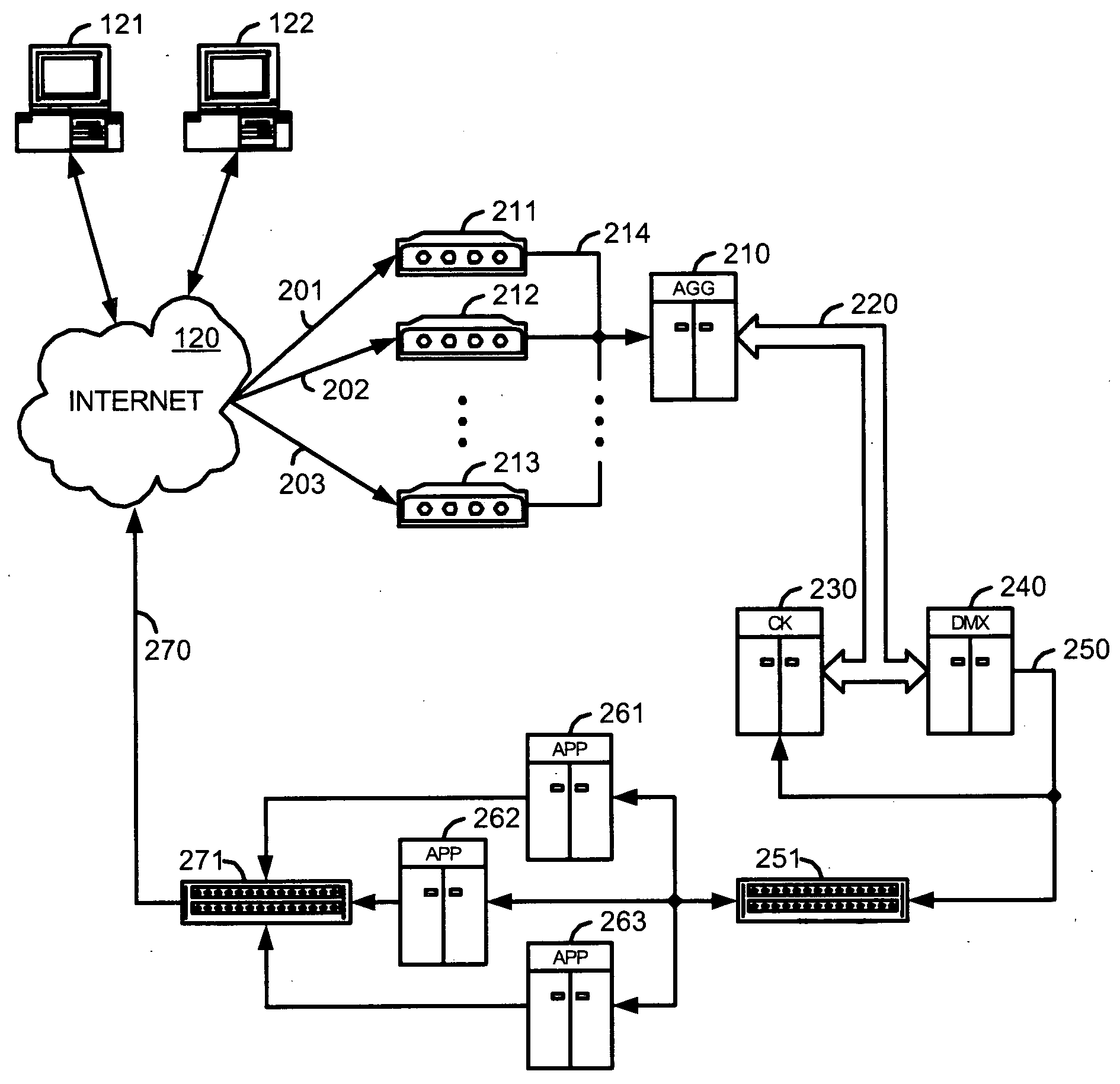
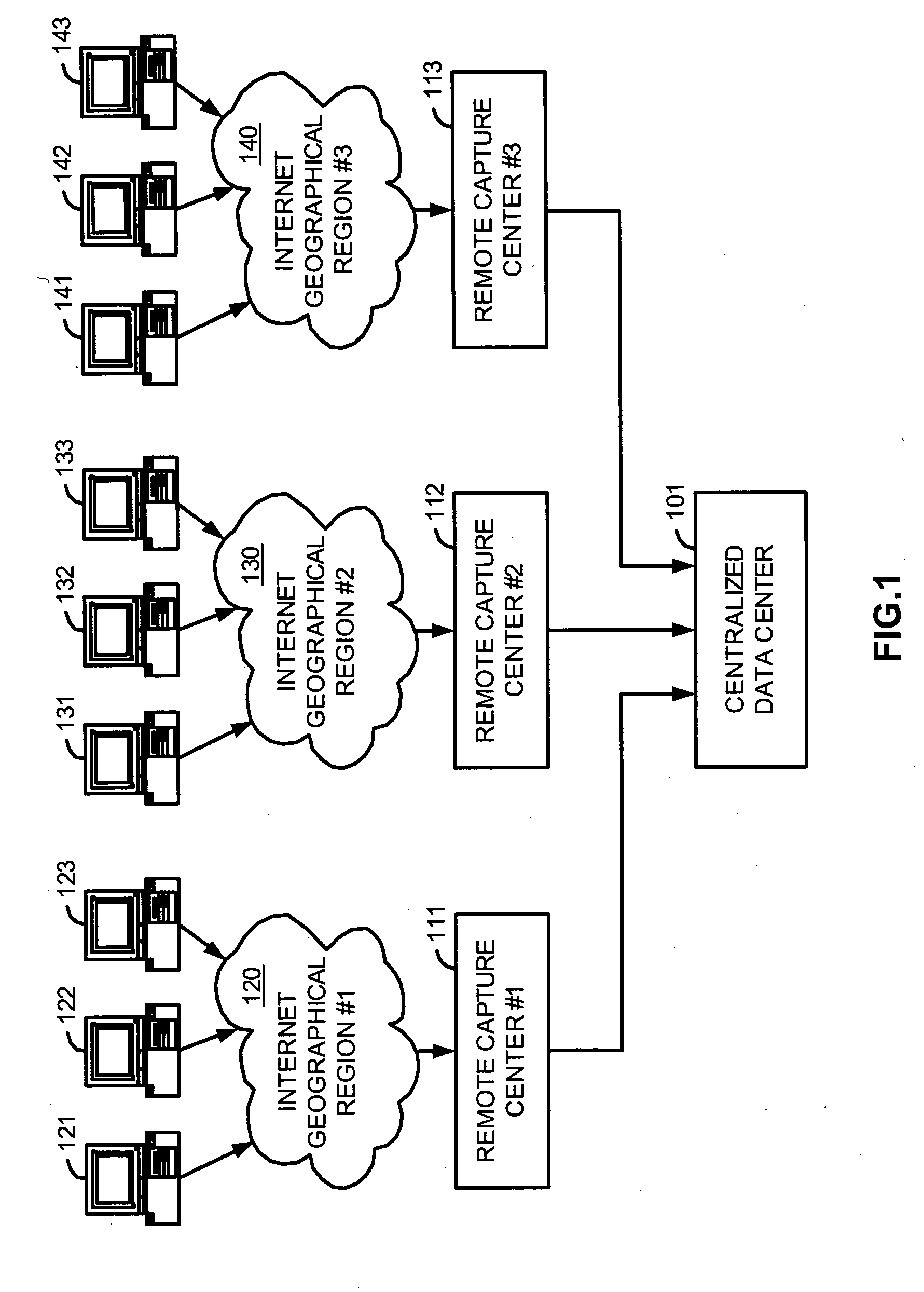
System and methods for communicating over the internet with geographically distributed devices of a decentralized network using transparent asymetric return paths
InactiveUS20050089014A1Easy maintenanceLow implementation costNetworks interconnectionData centerThe Internet
A system and methods for communicating over the Internet with devices of a decentralized network using transparent asymmetric return paths are described. Remote capture centers are geographically distributed so as to communicate with devices of a decentralized network that reside in diverse geographical locations. A centralized data center communicates with the remote capture centers so as to generate processed information in the form of reply packets from information received at the remote capture centers from the devices, and transmit the processed information back to the devices in a manner so that the processed information appears to have been transmitted from the remote capture centers.
Owner:MACROVISION CORP
Method and Apparatus for Medium Access Control for a Decentralized Network with Adapted Beamforming and Power Control
InactiveUS20070002734A1Improve throughputReduce transmit powerError preventionFrequency-division multiplex detailsTransmitted powerPhysical layer
A method and apparatus for medium access control in a wireless ad hoc network is disclosed that takes advantage of physical layer properties to jointly and collectively optimize in a distributed fashion transmission parameters such as beam-patterns and transmit powers of all active links in the network. To resolve signal transmission contention, each potential link is associated with a persistence parameter and the persistence parameter is adapted locally, with no central control, to provide medium access for transmissions. Where a node contending for a transmission slot is unable to optimize its transmission parameters due to an invalidity condition or infeasibility condition, the persistence parameter is updated, preferably so as to reduce the probability of such conditions.
Owner:NEC CORP
Managing storage resources in decentralized networks
InactiveUS20030187973A1Multiple digital computer combinationsElectric digital data processingPersistent identifierWeb service
Methods, systems, and computer program products are disclosed for managing storage resources in decentralized networks. Persistent identifiers are defined for nodes, allowing nodes to be identified across sessions and invocations, even though they re-enter the network with a different network address. Paths taken by content resources as they traverse the network (e.g. which nodes forwarded the content) are persisted, along with reputation information about nodes (e.g. indicating how successful they are at answering queries from peers). Trust relationships can be derived using the persisted information. A tiered broadcast strategy is defined for reducing the number of messages exchanged. Preferred embodiments leverage a web services implementation model.
Owner:IBM CORP
Broadcast tiers in decentralized networks
InactiveUS7143139B2Avoiding drawback and limitationReduce traffic problemsSpecial service provision for substationNetwork traffic/resource managementTraffic capacityPersistent identifier
Owner:INT BUSINESS MASCH CORP
Collaboration portal (COPO) a scaleable method, system, and apparatus for providing computer-accessible benefits to communities of users
InactiveUS7890549B2Simple indexingAvoid ambiguityDigital data processing detailsOffice automationData scienceDecentralized network
The present invention, known as The Collaboration Portal (COPO), relates generally to the field of automated entity, data processing, system control, and data communications, and more specifically to an integrated method, system, and apparatus for providing computer-accessible benefits for communities of users. It provides a framework for provisioning computer-accessible benefits for communities of users, and can efficiently and robustly distribute the processing in behalf of those users over a decentralized network of computers. The field of the invention generally encompasses enabling appropriate and desired communication among communities of users and organizations, and providing information, goods, services, a works, opportunities, and connections among users and organizations.
Owner:QUANTUM LEAP RES
Autonomic provisioning of network-accessible service behaviors within a federated grid infrastructure
InactiveUS7200657B2Effective resourcesEfficient leveragingDigital computer detailsMultiprogramming arrangementsService-level agreementAuto-configuration
Methods, systems, computer program products, and a method of doing business are disclosed for autonomically provisioning network-accessible services in a decentralized network having a federated grid infrastructure. Autonomic, grid, and web services-related technologies, standards, and concepts are leveraged. More particularly, web service behaviors (augmented as grid services, according to preferred embodiments) are autonomically provisioned (i.e., dynamically distributed) via a grid of hosting services. In preferred embodiments, this dynamic distribution occurs in response to (and as a function of) external catalysts, such as algorithms that monitor designated resources (e.g., to proactively determine when the commitments in a utility service provider's service level agreements are in jeopardy).
Owner:IBM CORP
Block chain-based industrial digital information networked platform
InactiveCN107426250ARealize intelligent manufacturingEfficient implementation of the manufacturing processUser identity/authority verificationInformatizationIntellectual property
The invention provides a block chain-based industrial digital information networked platform. An enterprise digital informatization process is built based on a block chain so as to realize a decentralized network system of an enterprise. Industrial manufacture is widely fused with ubiquitous sensors and computing capability, so as to reshape the manufacture industry mode to help enterprises to realize intelligent manufacture. The platform can help manage distributed supply chains in industrial manufacture, can change a product factor instantaneously, can realize a manufacture process efficiently, can prevent risks caused by unauthorized data acquisition, can provide permanent, traceable and tamper-resisting trace record, can help enterprises to find the problem, search the reason and solve the problem so as to upgrade the system, makes management of manufacture more intelligent, improves security and reliability of manufacture, prevents various network risks and protects intellectual property.
Owner:大唐互联科技(武汉)有限公司
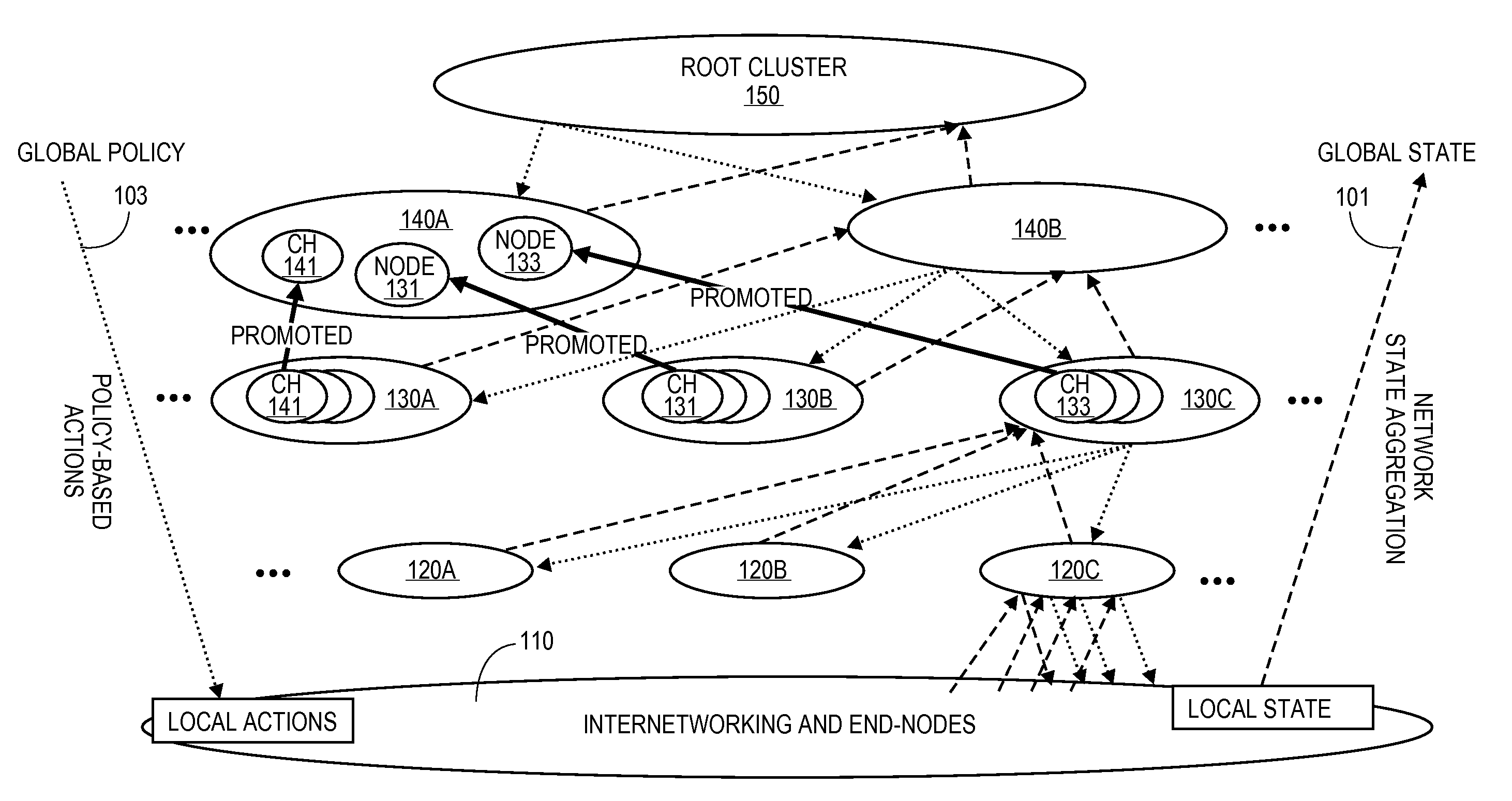
Virtual clustering for scalable network control and management
In some embodiments, the invention involves a system and method relating to a framework to build a new class of network control (policy) and (state) management services. The framework may be used to build a number of self-management services to support decentralized (mesh) networks. In at least one embodiment, the present invention is intended to hybridize centralized and decentralized network models to generate a more stable and robust network environment using clustering. Other embodiments are described and claimed.
Owner:INTEL CORP
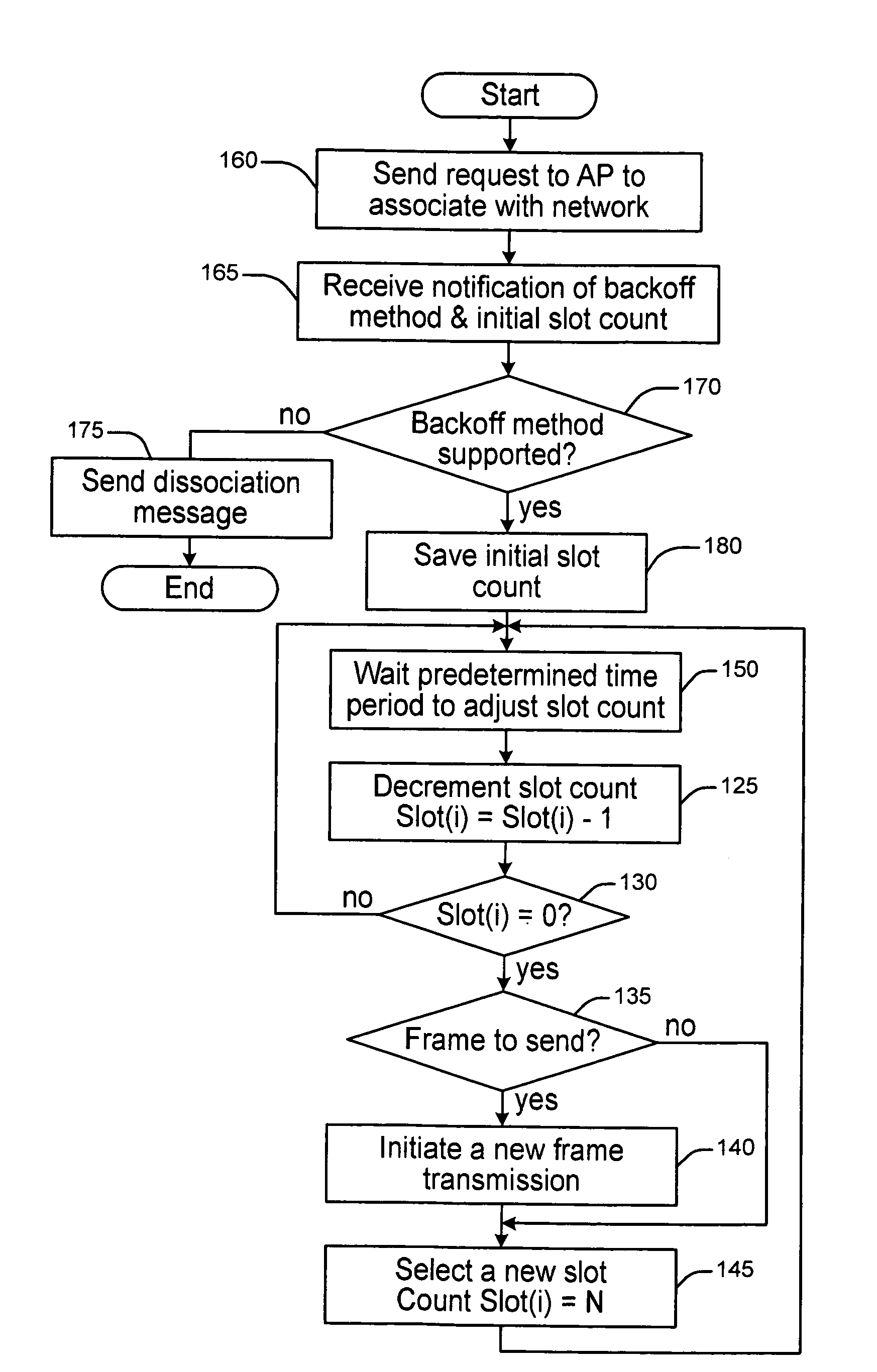
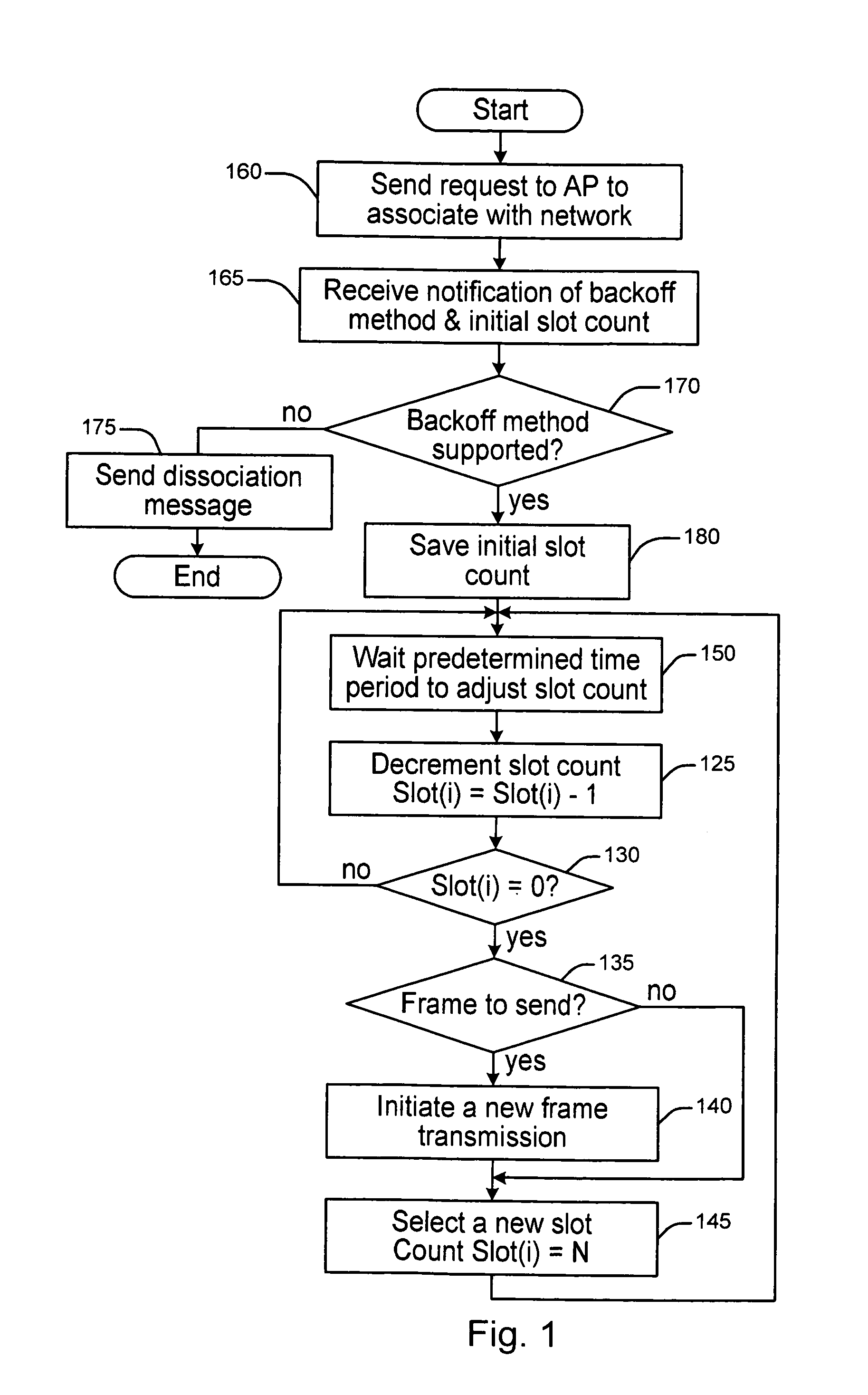
Deterministic back-off method and apparatus for peer-to-peer communications
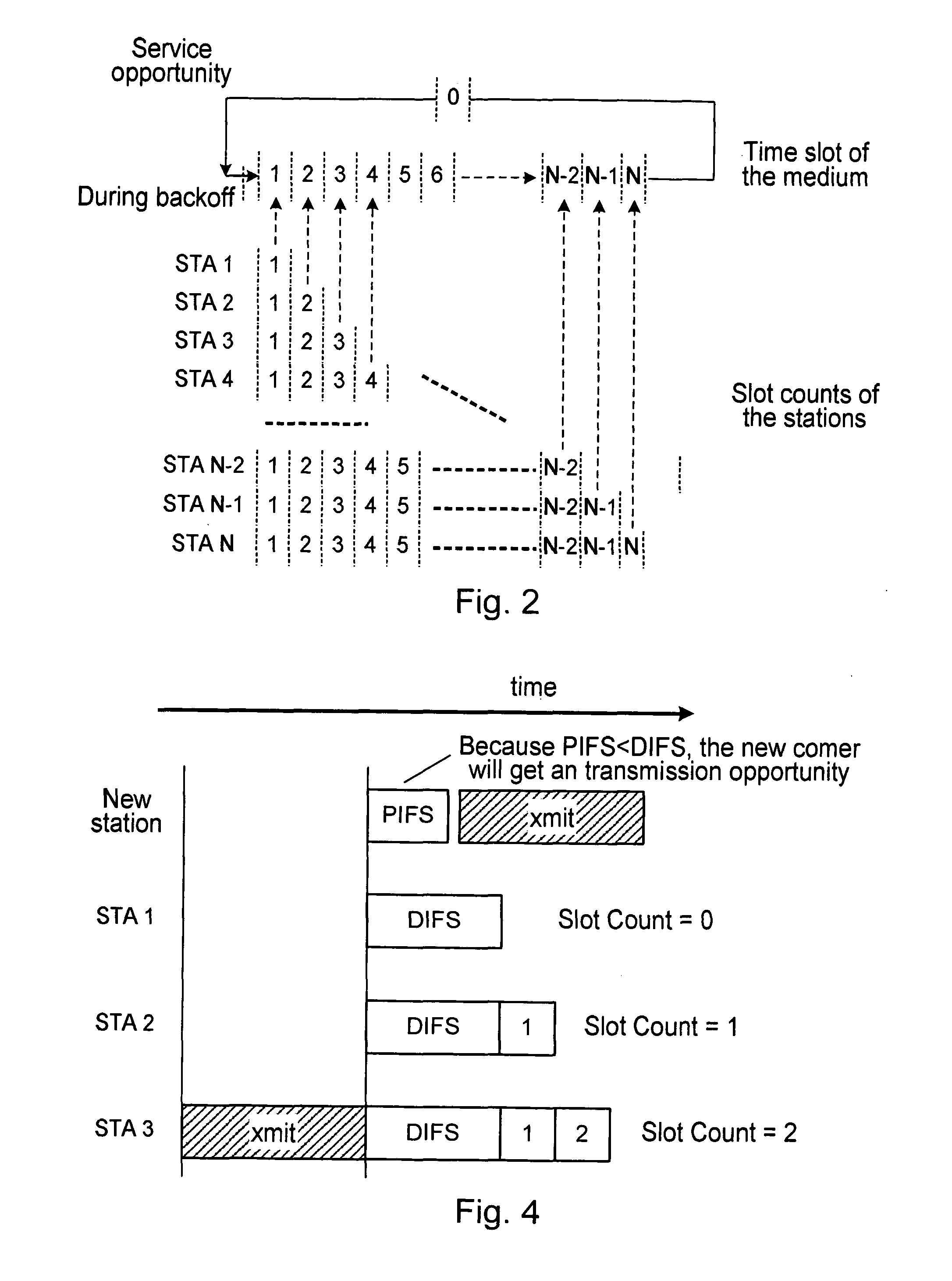
A method and apparatus are described including identifying a channel that a decentralized network is using for communications and identifying a station that is a member of the decentralized network to monitor data transmission activity over the identified channel. Also described are a method and apparatus for a station to transmit data over a communication medium of a decentralized network including monitoring the communication medium, determining if the communication medium is idle, transmitting data if the communication medium is idle and if the station has a data to transmit and adjusting a slot count and a service ring configuration if the medium is busy. Further described are a method and apparatus including monitoring a communication channel used by a decentralized network, determining a number of available idle time slots between two successive frame transmissions initiated by different stations, updating a service ring, adjusting a number of stations and adjusting a slot count.
Owner:INTERDIGITAL CE PATENT HLDG
Dispersed storage network for managing data deletion
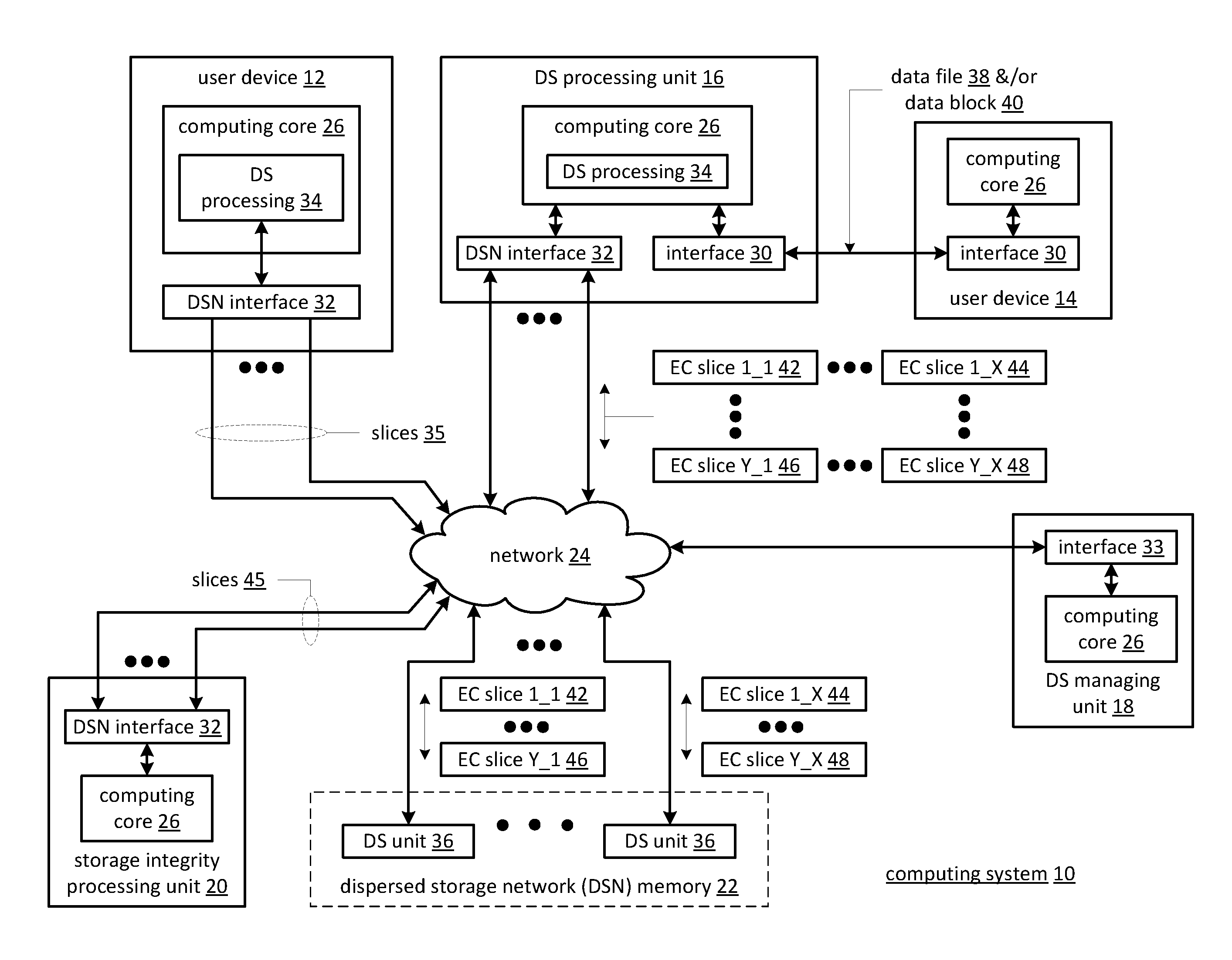
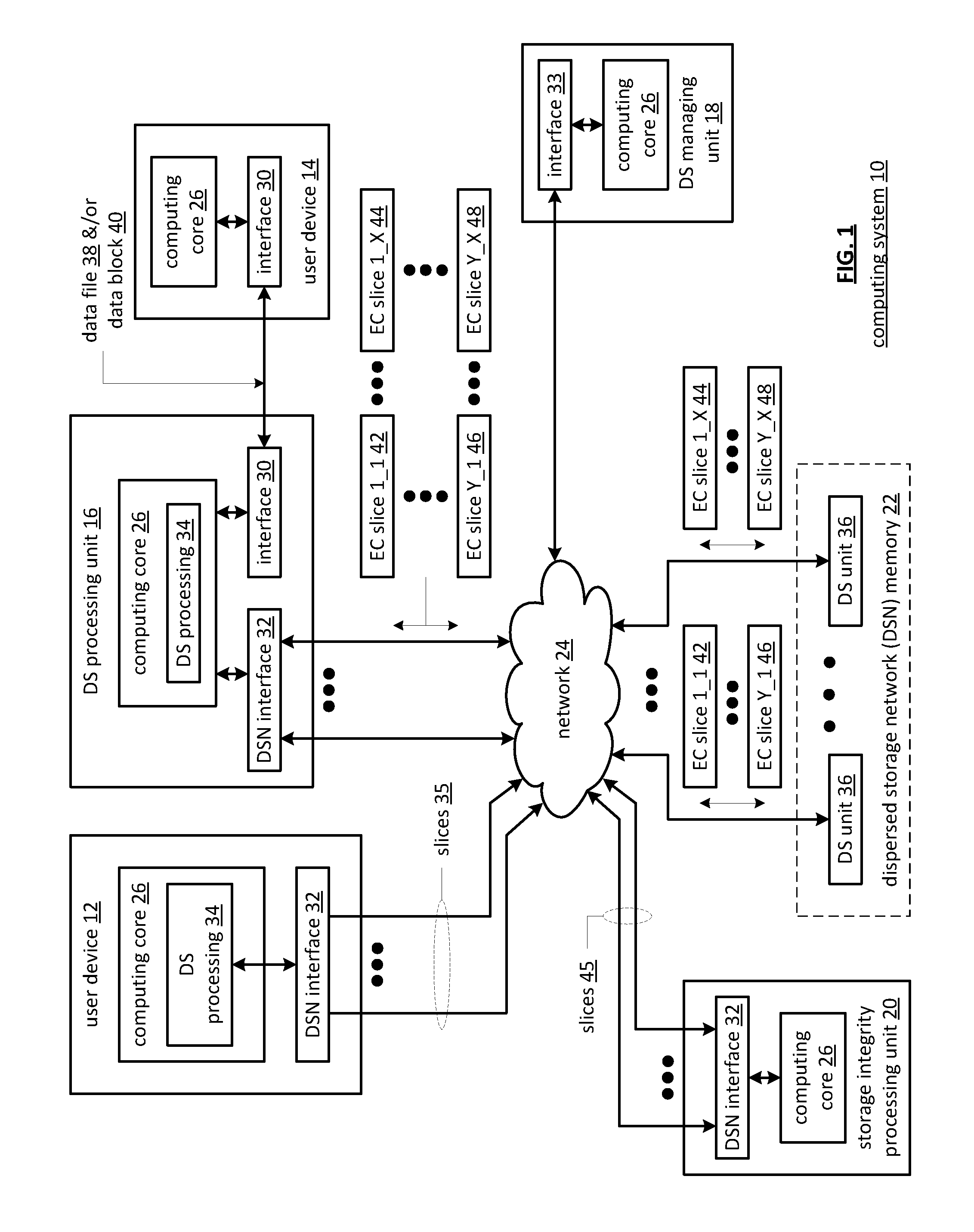
ActiveUS20110225361A1Digital data information retrievalMemory loss protectionStorage area networkObject store
A dispersed storage device manages deletion of data objects stored within a dispersed storage network by receiving a data delete request to delete a data object stored throughout a set of dispersed storage units within a dispersed network memory of the dispersed storage network, determining a deletion policy for the data object and selectively generating and transmitting, based on the deletion policy, a delete command to the set of dispersed storage units.
Owner:PURE STORAGE
Method and a system for secure execution of workflow tasks in a distributed workflow management system within a decentralized network system
ActiveUS20090077376A1Key distribution for secure communicationPublic key for secure communicationWorkflow management systemNetworked system
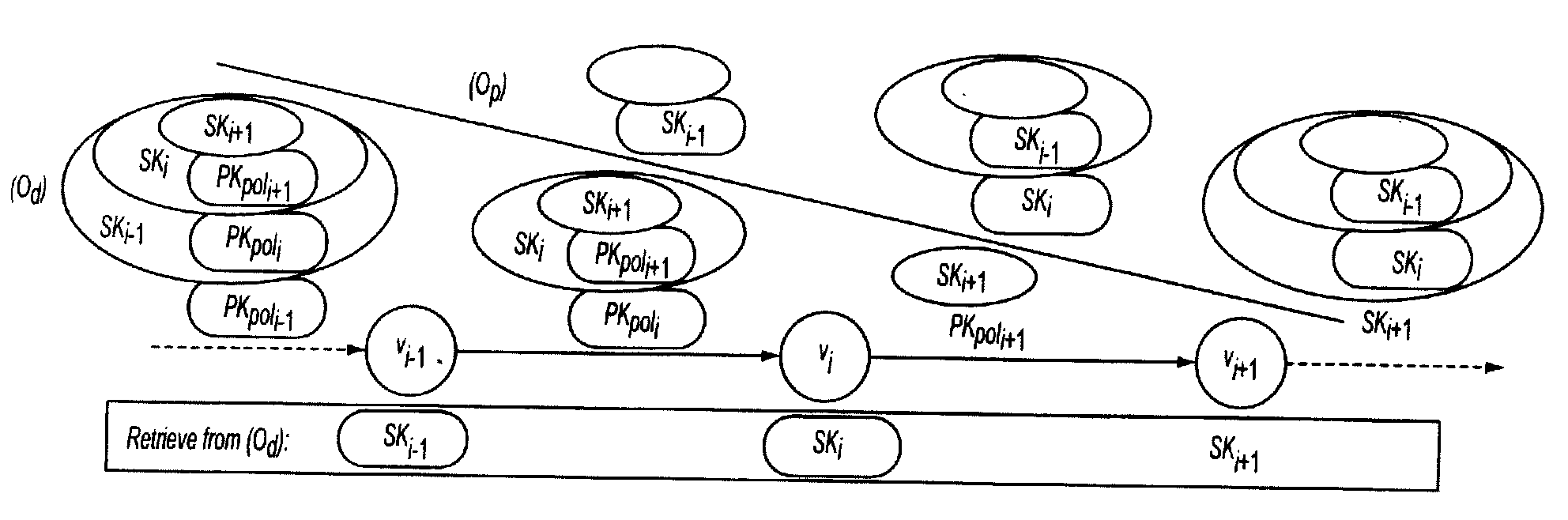
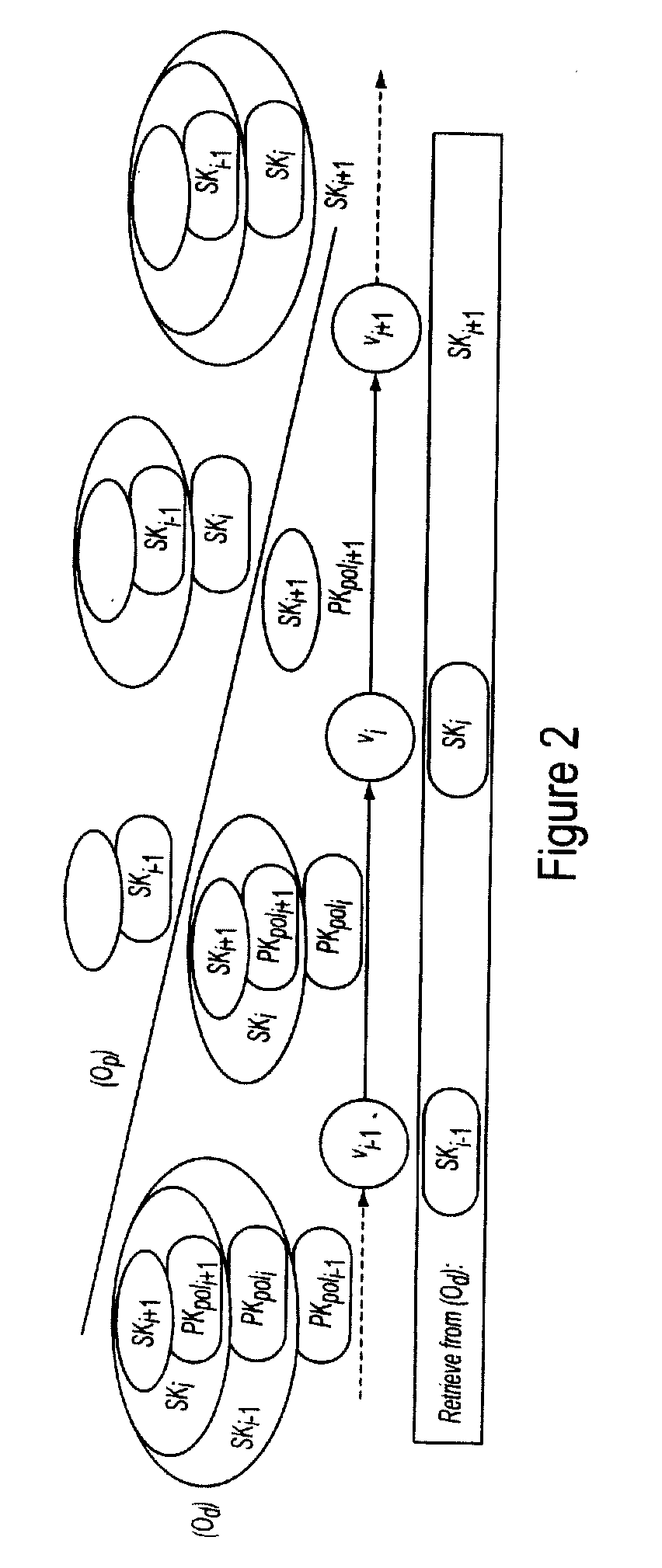
There are provided a method, a system and an initiator server for a secure execution of workflow tasks of a workflow to be executed according to a given execution pattern in a distributed workflow management system within a decentralized network system with a plurality of servers (b0, b1, . . . , bn) including at least an initiator server and at least a number of groups of servers of the plurality of servers. Each group satisfies a policy (poli) of a vertex, and thus, knows a corresponding policy key pair including a policy private key (SKpoli) and a policy public key (PKpoli), respectively. Each vertex denotes a set of workflow tasks to be executed in accord with the execution pattern and is assigned a vertex key pair including a vertex private key and a vertex public key. The vertex private keys and the policy public keys are jointly encrypted within a first onion structure, the first onion structure being built up of a number of onion layers representing the execution pattern which defines a succession of vertices such that each layer is decryptable by using the policy private key of exactly one vertex thus revealing the corresponding vertex private key.
Owner:SAP AG
Method, device and system for managing file copies
InactiveCN101909068AReduce administrative overheadLoad balancingTransmissionService conditionComputer science
The invention relates to a method, a device and a system for managing file copies. The method comprises the following specific steps of: in a distributed storage network, selecting a source node for diffusing or transferring the file copies according to idle resources of nodes; and selecting a target node for receiving the file copies by the source node according to the idle resources of relevant nodes. Therefore, in the embodiment of the invention, the nodes with higher resource idle rate can be selected according the current service condition of the resources in a network to transfer and diffuse the copies, so the cost of transferring and diffusing the copies is reduced greatly; and the load pressure of the network is dispersed to save the expenditure of managing the copies, equalize network loads and greatly improve the service performance of the network.
Owner:HUAWEI TECH CO LTD
Overhead message update with decentralized control
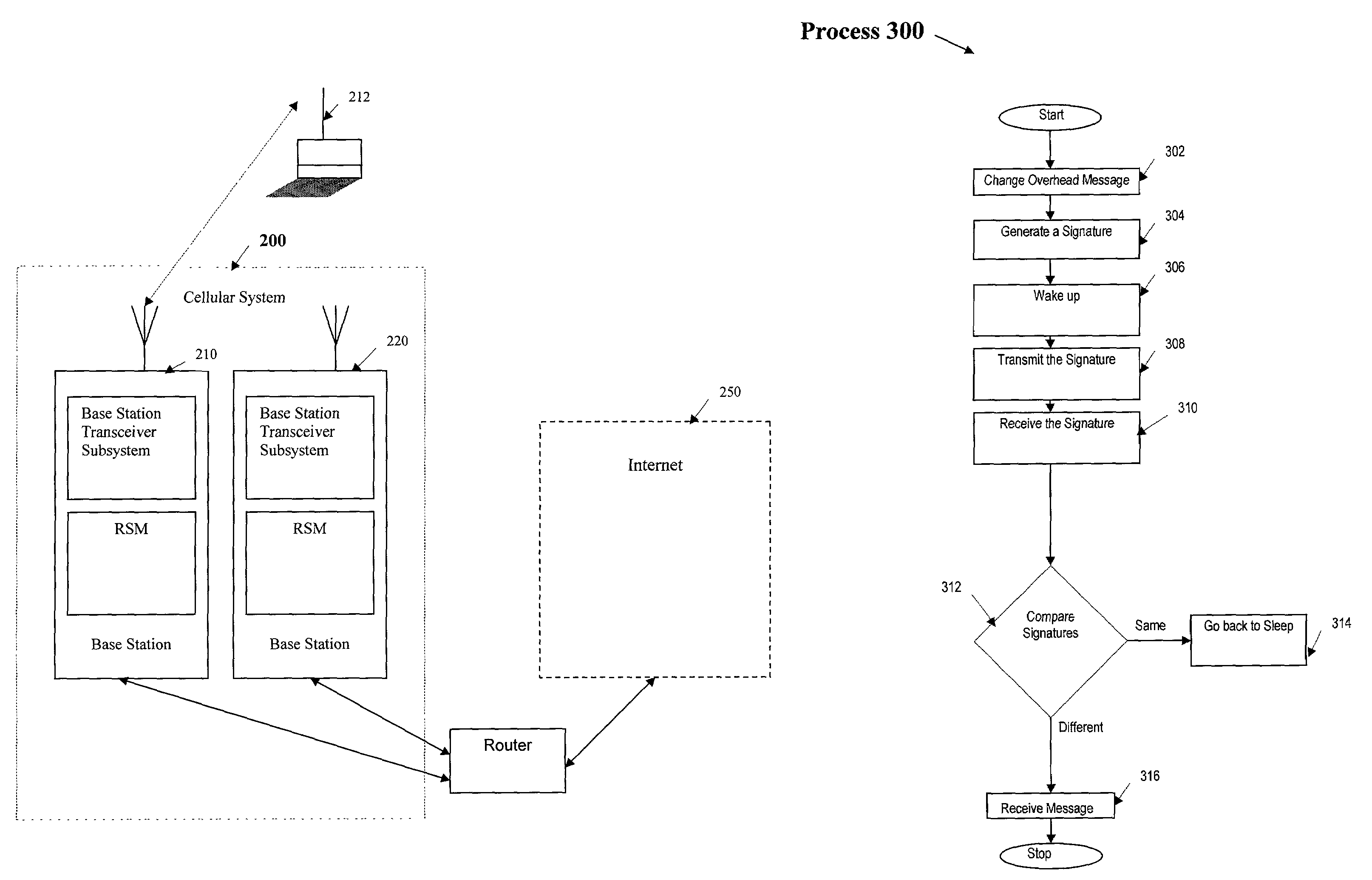
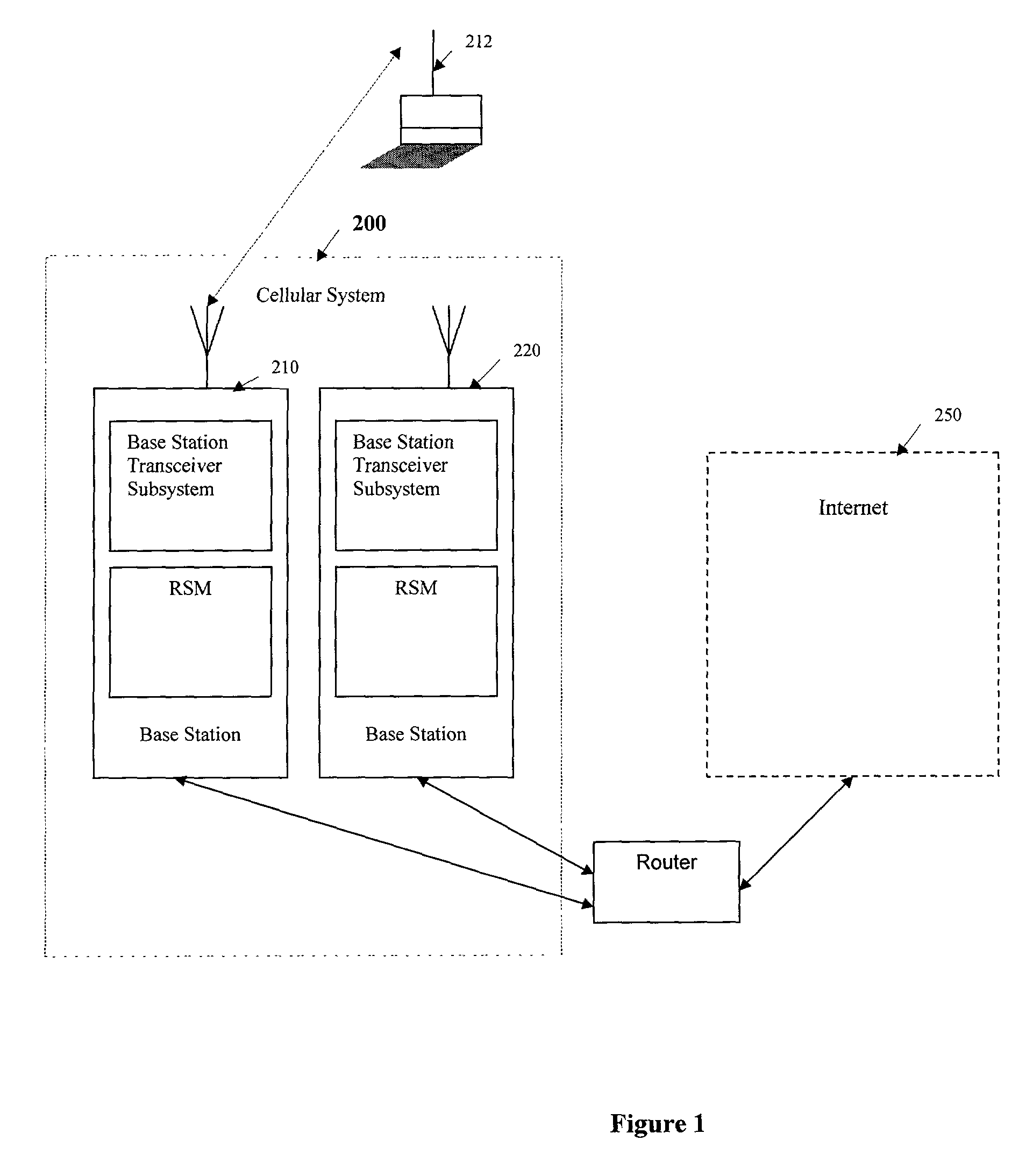
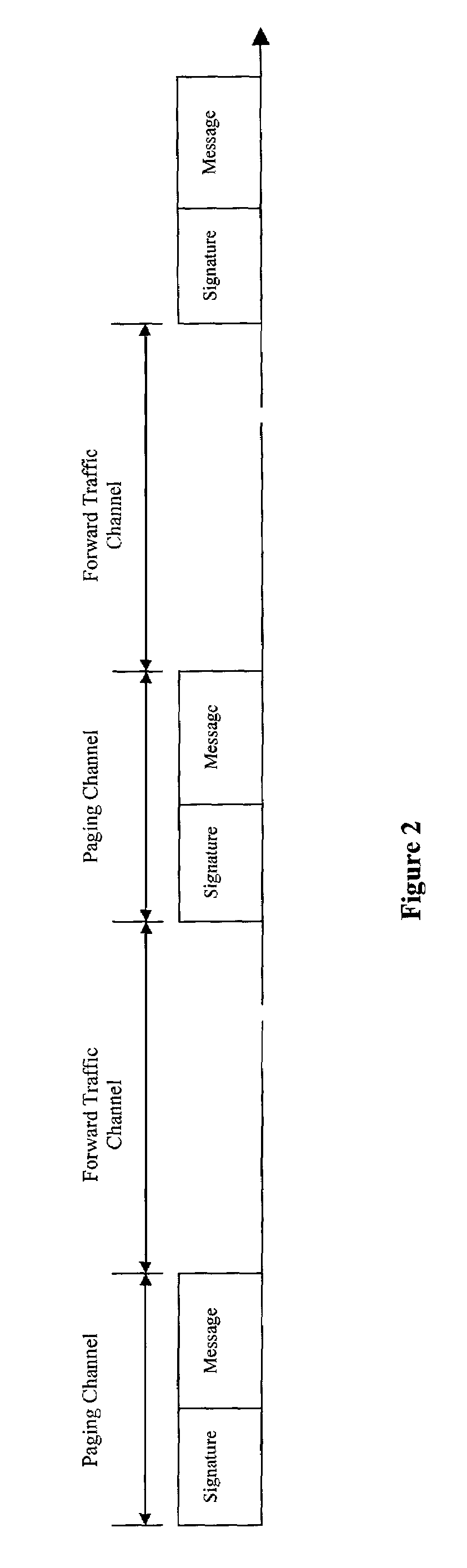
InactiveUS7483699B2Minimize power consumptionSave bandwidthEnergy efficient ICTPower managementCommunications systemDecentralized network
A system and method for providing a simple, but effective technique for communicating overhead messages in a wireless communication system providing access to a decentralized network, while achieving bandwidth savings as well as minimizing power consumption. In one embodiment, a wireless base station which is connected to a decentralized network transmits a sequence of signatures for overhead messages to a mobile unit. The mobile unit wakes up receives the signatures and compares them to signatures stored at the mobile unit. If the signatures received by the mobile unit are different from the signatures stored at the mobile unit, the mobile unit stays awake to receive the overhead messages to be transmitted by the wireless base station. If the signatures received by the mobile unit are the same as the signatures stored at the mobile unit, the mobile unit may go back to sleep.
Owner:QUALCOMM INC
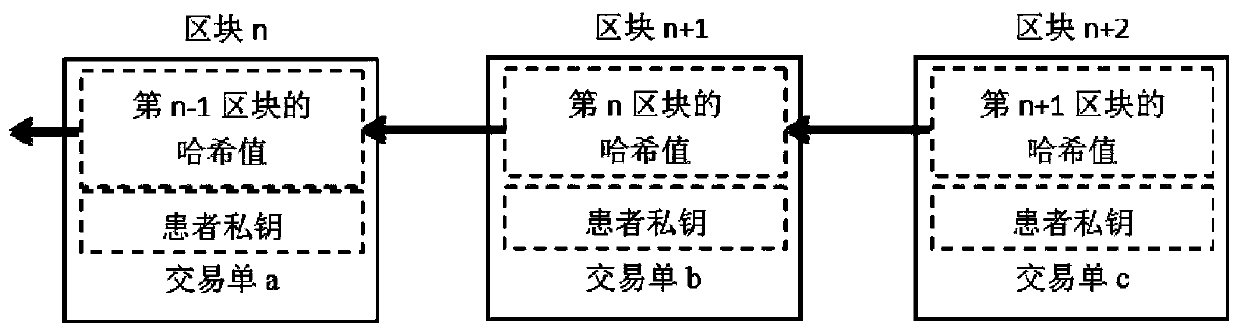
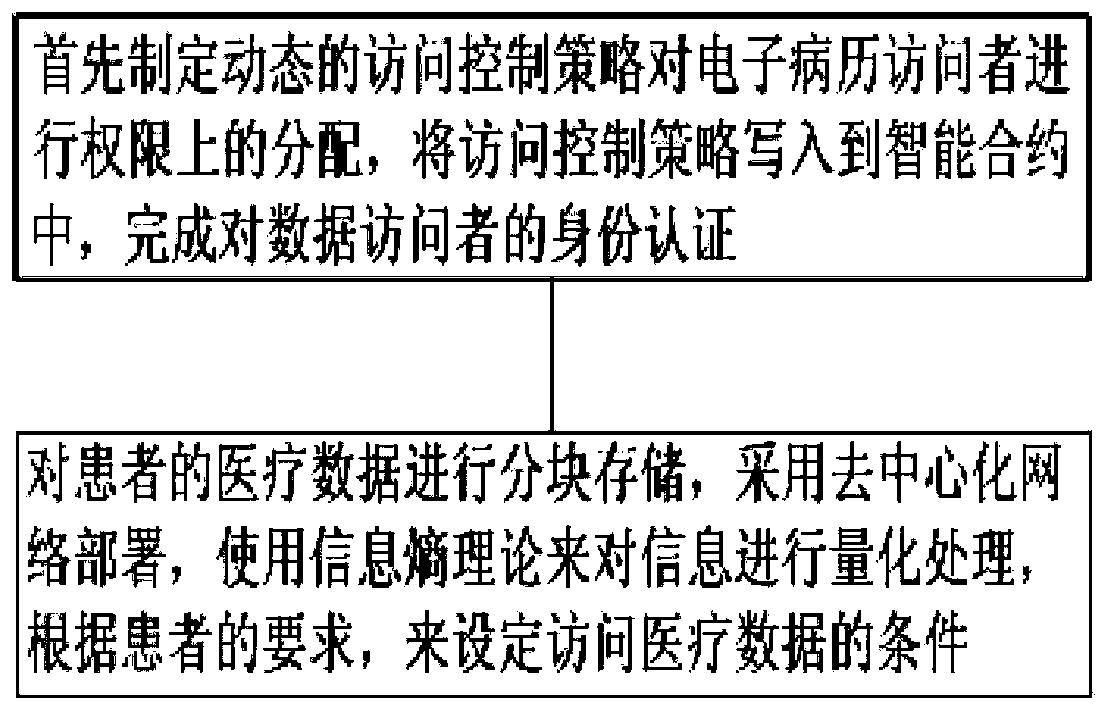
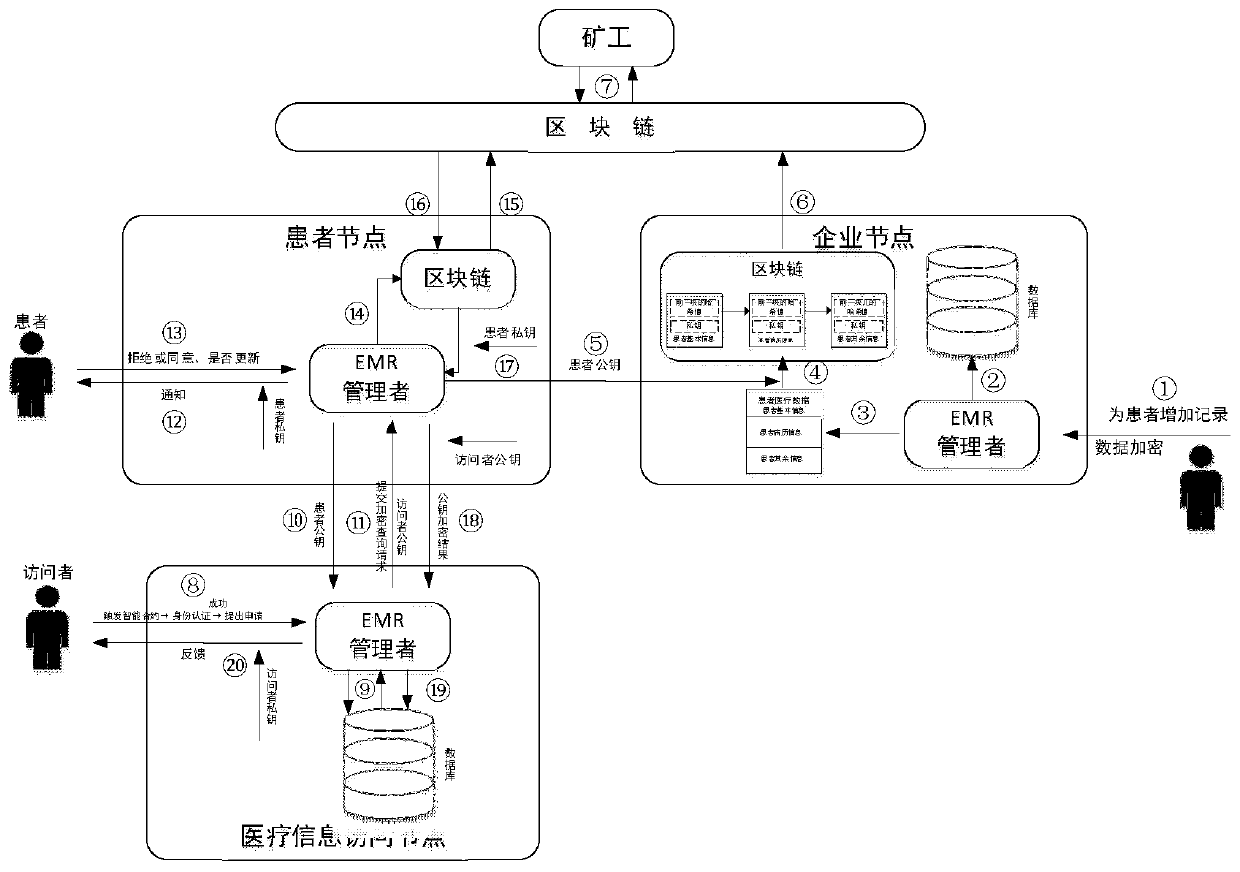
Electronic medical record access control method based on block chain
ActiveCN110321721AFix the leakAchieve protectionDigital data protectionPatient-specific dataMedical recordData access
The invention discloses an electronic medical record access control method based on a block chain, and relates to the technical field of medical data sharing methods. The method comprises the following steps: firstly, formulating a dynamic access control strategy to carry out authority distribution on an electronic medical record visitor, and writing the access control strategy into an intelligentcontract to complete identity authentication on a data visitor; storing medical data of a patient in blocks, adopting decentralized network deployment, using an information entropy theory for carrying out quantitative processing on information, and setting conditions for accessing the medical data according to the requirements of the patient. According to the method, the medical privacy information protection of the user in the service process can be realized, the patient can autonomously manage own medical data, and the privacy protection method under medical data sharing is favorably realized.
Owner:西康软件有限责任公司
System, method and client user interface for a copy protection service
ActiveUS20050198535A1Easily interfaceDigital data processing detailsUnauthorized memory use protectionClient-sideCopy protection
A system, method and client user interface for a copy protection service employs software agents masquerading as nodes in decentralized networks for monitoring and interdicting file sharing activities of protected files in the networks. A control center communicates with the software agents and subscriber client computers through user interfaces, so as to provide monitoring information to users of the client computers and control the monitoring and interdiction of protected files according to instructions received from the client computers. A one-click method for requesting protection of a file, providing the terms of such protection, and updating billing information for the user is implemented through the user interface to simplify user interaction with the copy protection service.
Owner:ROVI SOLUTIONS CORP
Trusted device management method based on decentralized network
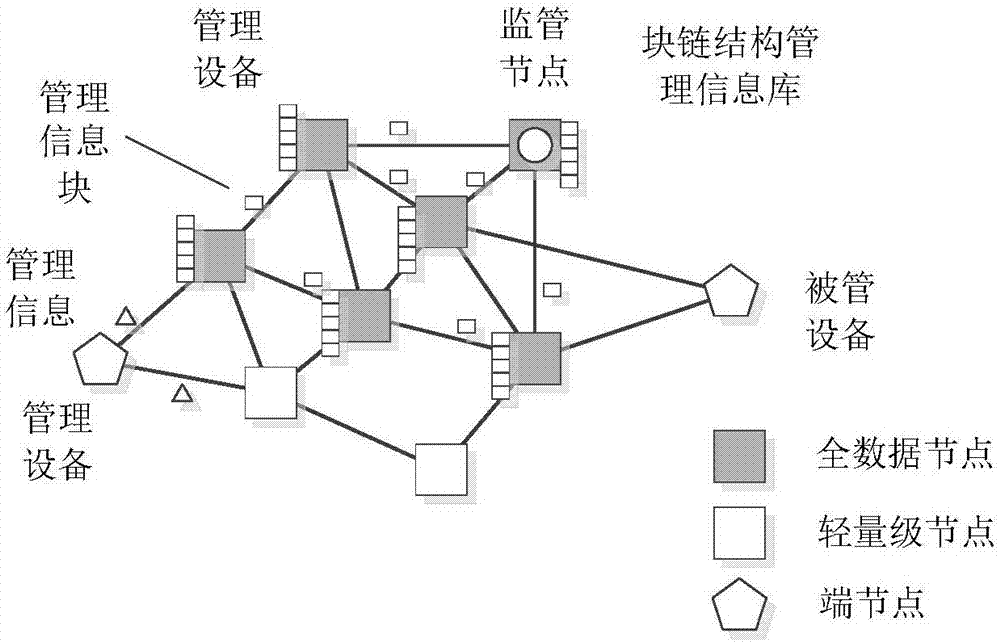
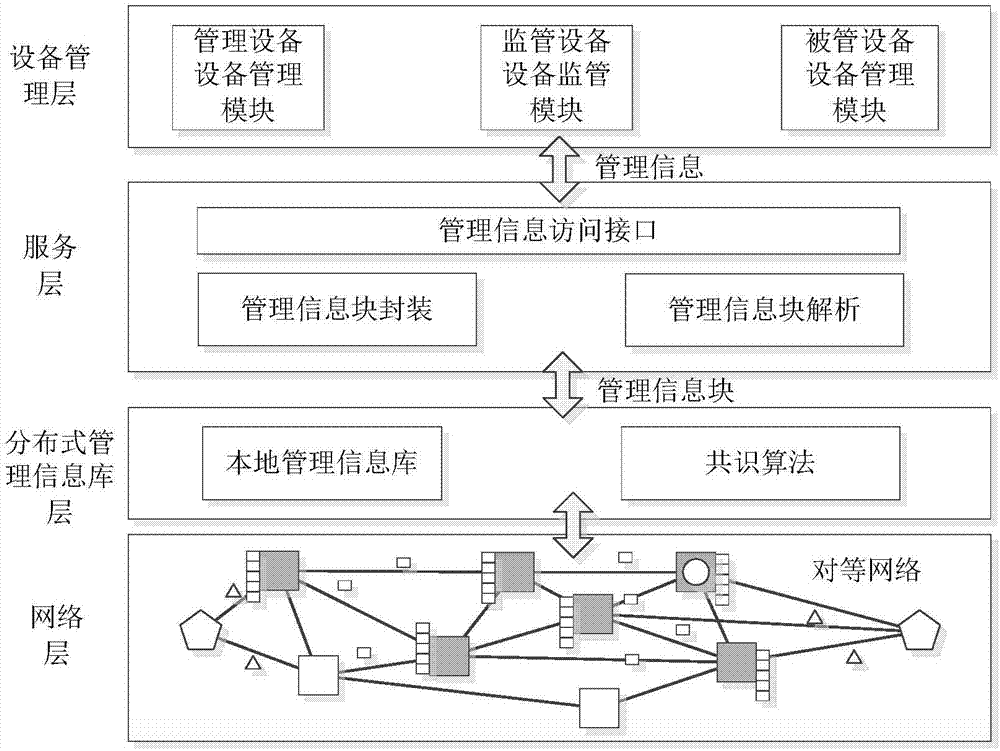
ActiveCN106911513AGuaranteed not to be tampered withSecure tamperingUser identity/authority verificationData switching networksManagement information baseAsynchronous communication
The invention relates to the field of device networking management, and provides a trusted device management method based on a decentralized network. According to the method, a distributed decentralized network is adopted, and coupling between a management device and a managed device is eliminated. Encrypted management commands and management data are utilized. The managed device actively or passively acquires a management instruction from the distributed network, and furthermore feedback information is written, thereby realizing asynchronous communication between the management device and the managed device. A target node according to the invention acquires management information through a lightweight node, wherein the lightweight node filters local node information; the information which matches the address of the target node is forwarded to the target node; and the target node verifies an information signature by means of a source node public key, decrypts a session key through a local private key and decrypts a message, thereby acquiring management information and processing.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
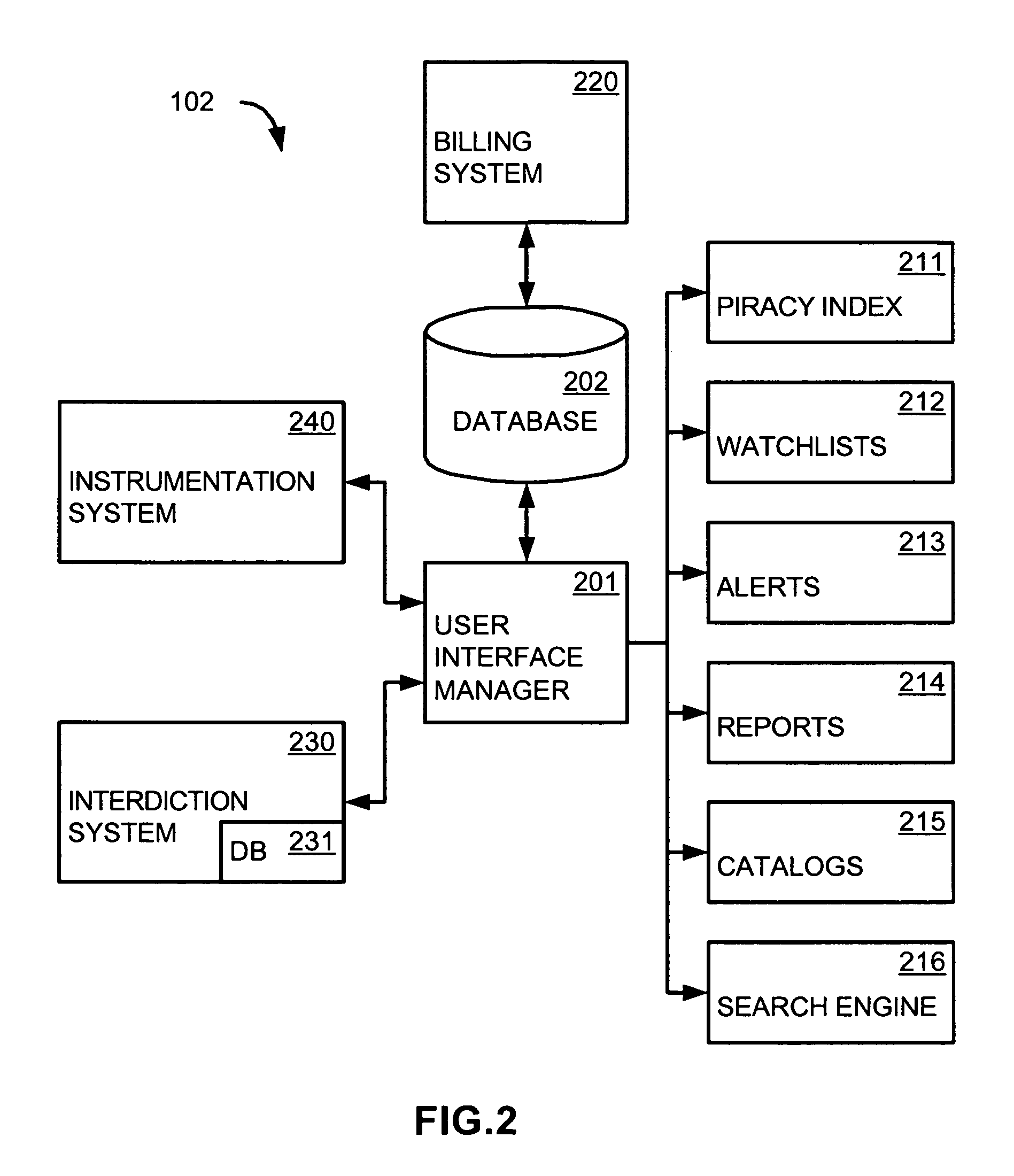
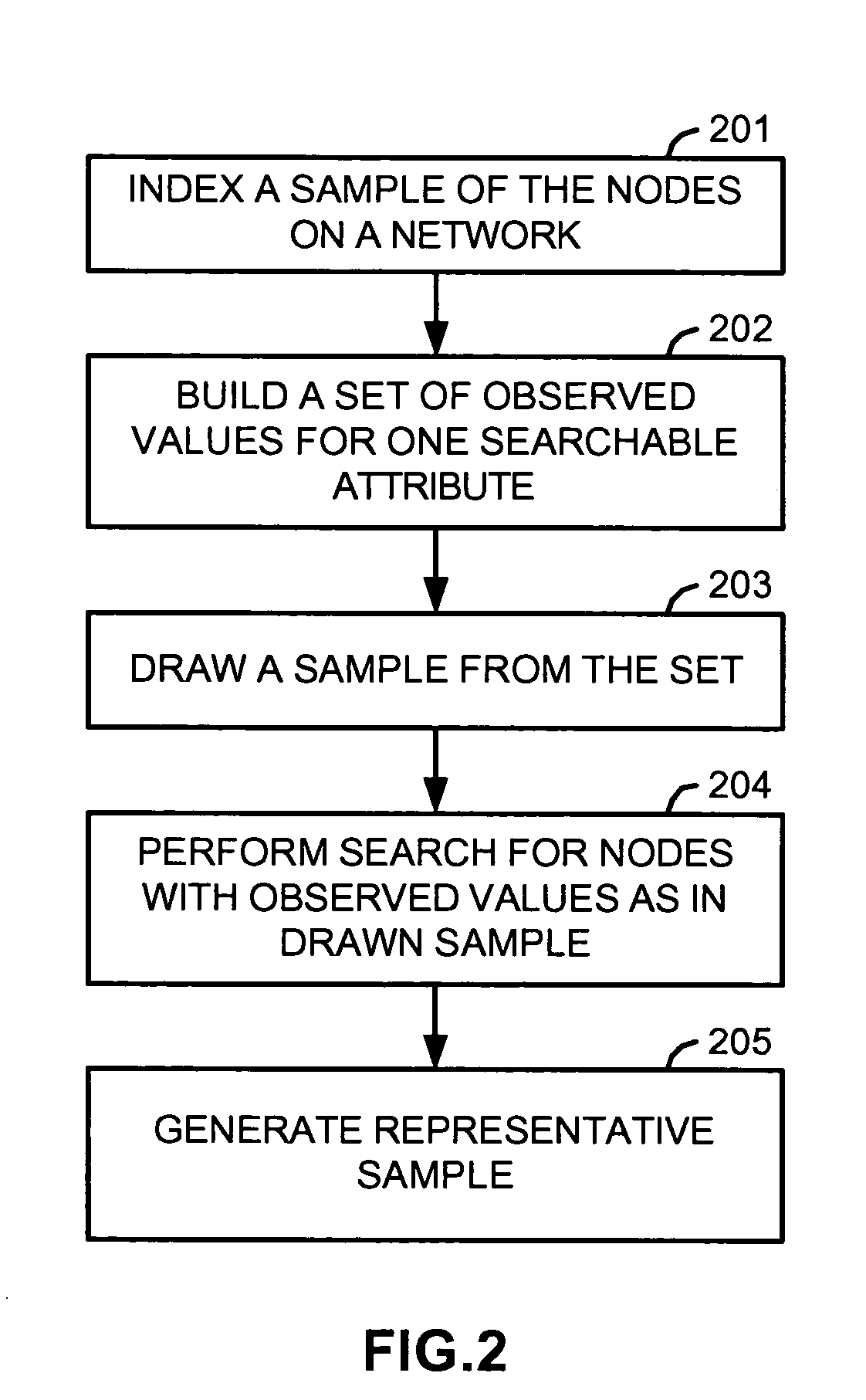
Instrumentation system and methods for estimation of decentralized network characteristics
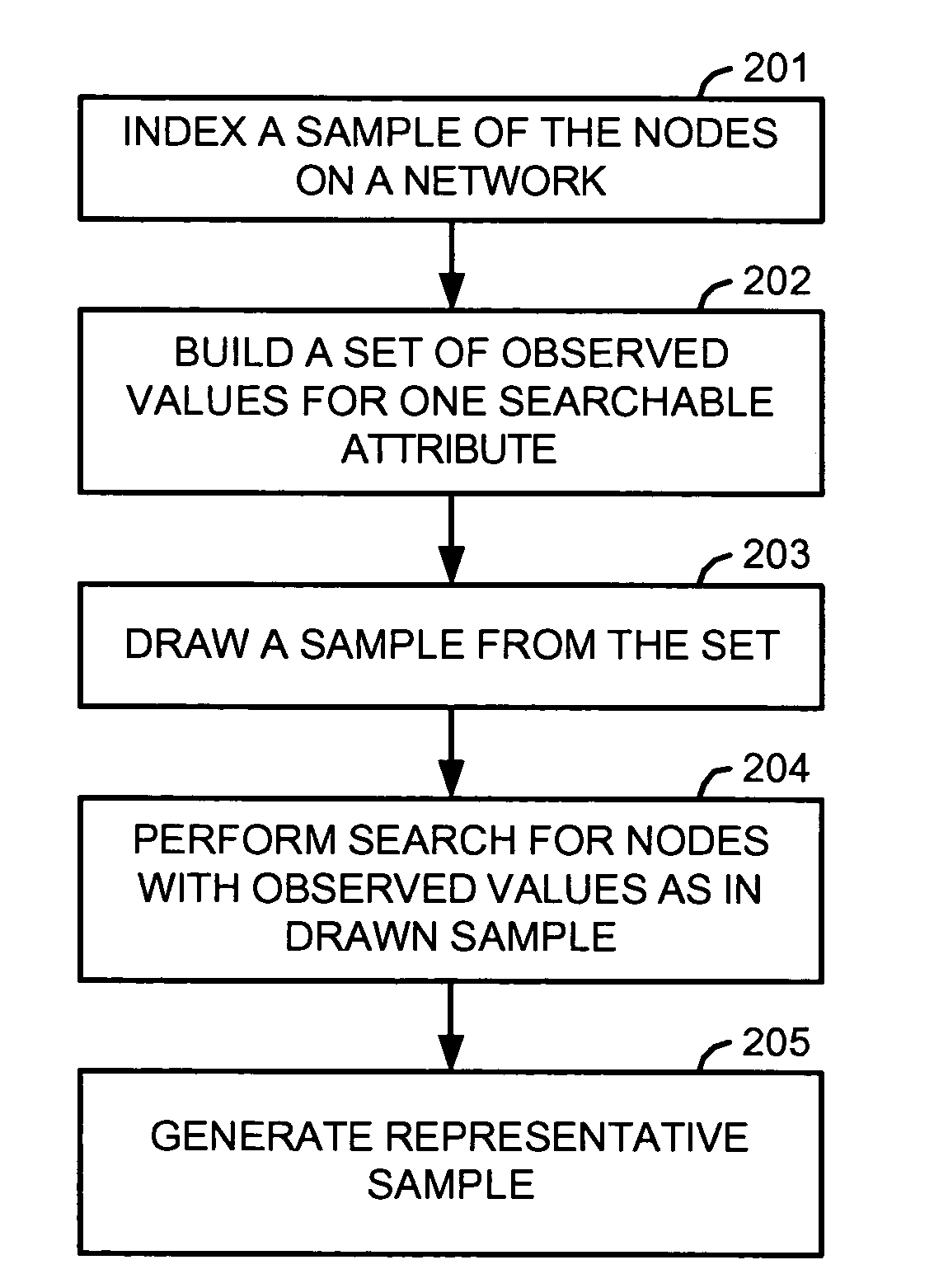
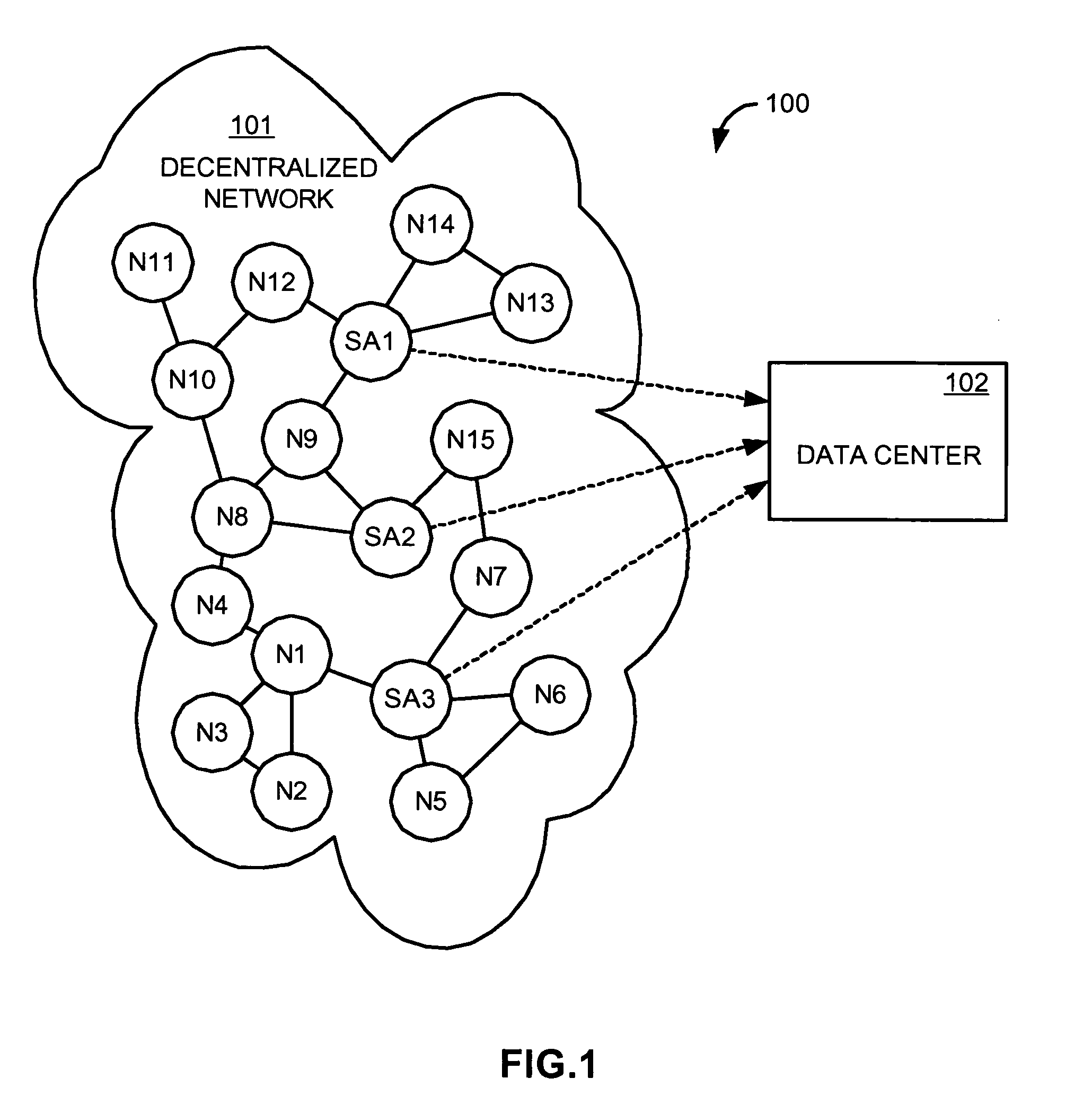
InactiveUS20050108378A1Digital computer detailsData switching networksSoftware agentDistributed computing
An instrumentation system estimates characteristics of a decentralized network, such as: the size, growth rate, and growth acceleration of the network; the number of instances, the rate of propagation, and the acceleration of propagation of a file in the network; and the search and download activities, in the aggregate and for particular files, in the network. A data center in the instrumentation system performs a set of interrelated methods for inferring these and other characteristics of the network. For estimating some characteristics, it identifies and uses a subset of the network, and uses information from the subset to infer or obtain information of the entire network. For estimating other characteristics, it deploys software agents to masquerade as nodes in the network.
Owner:MACROVISION CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com