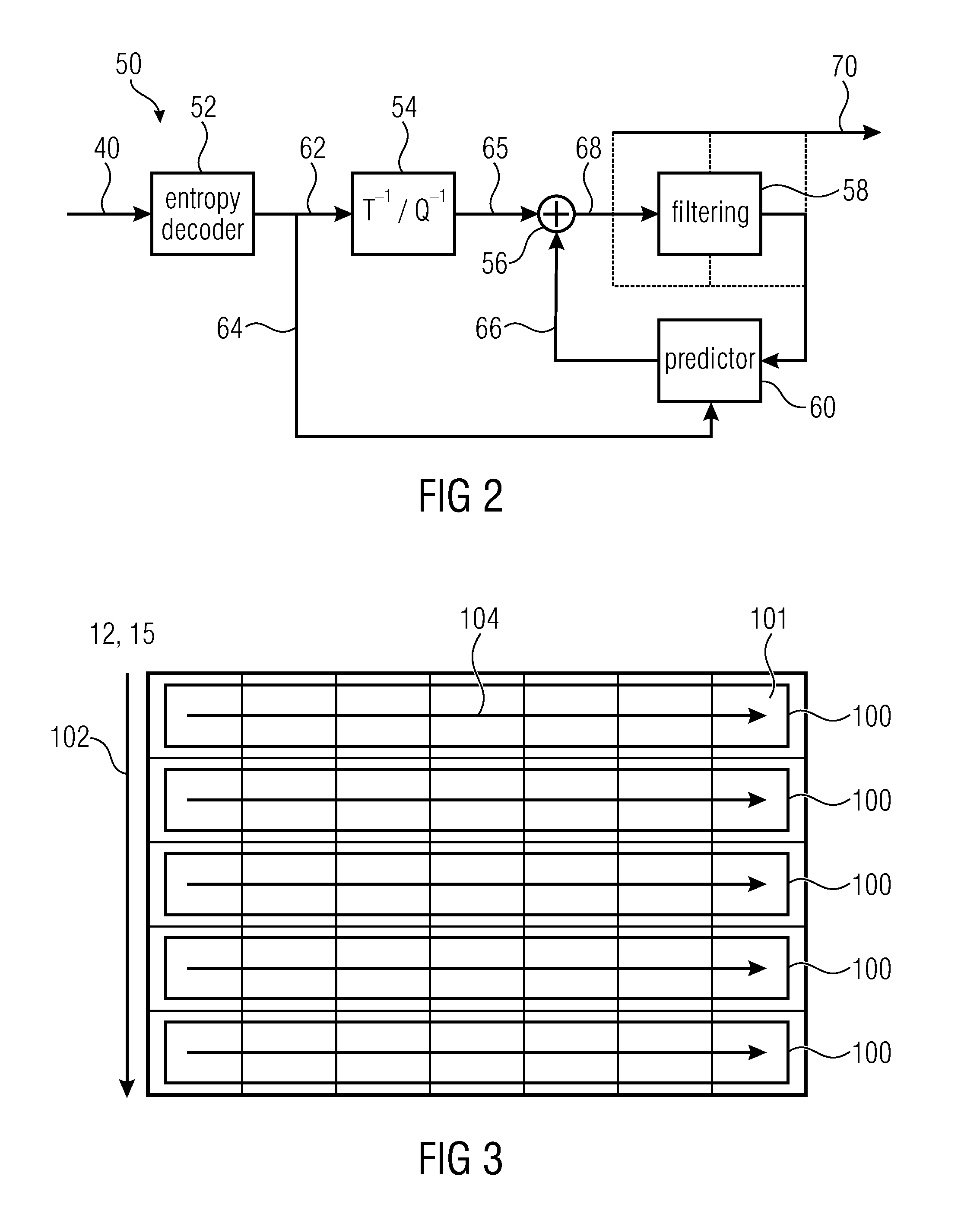
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
123results about How to "Reduce administrative overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
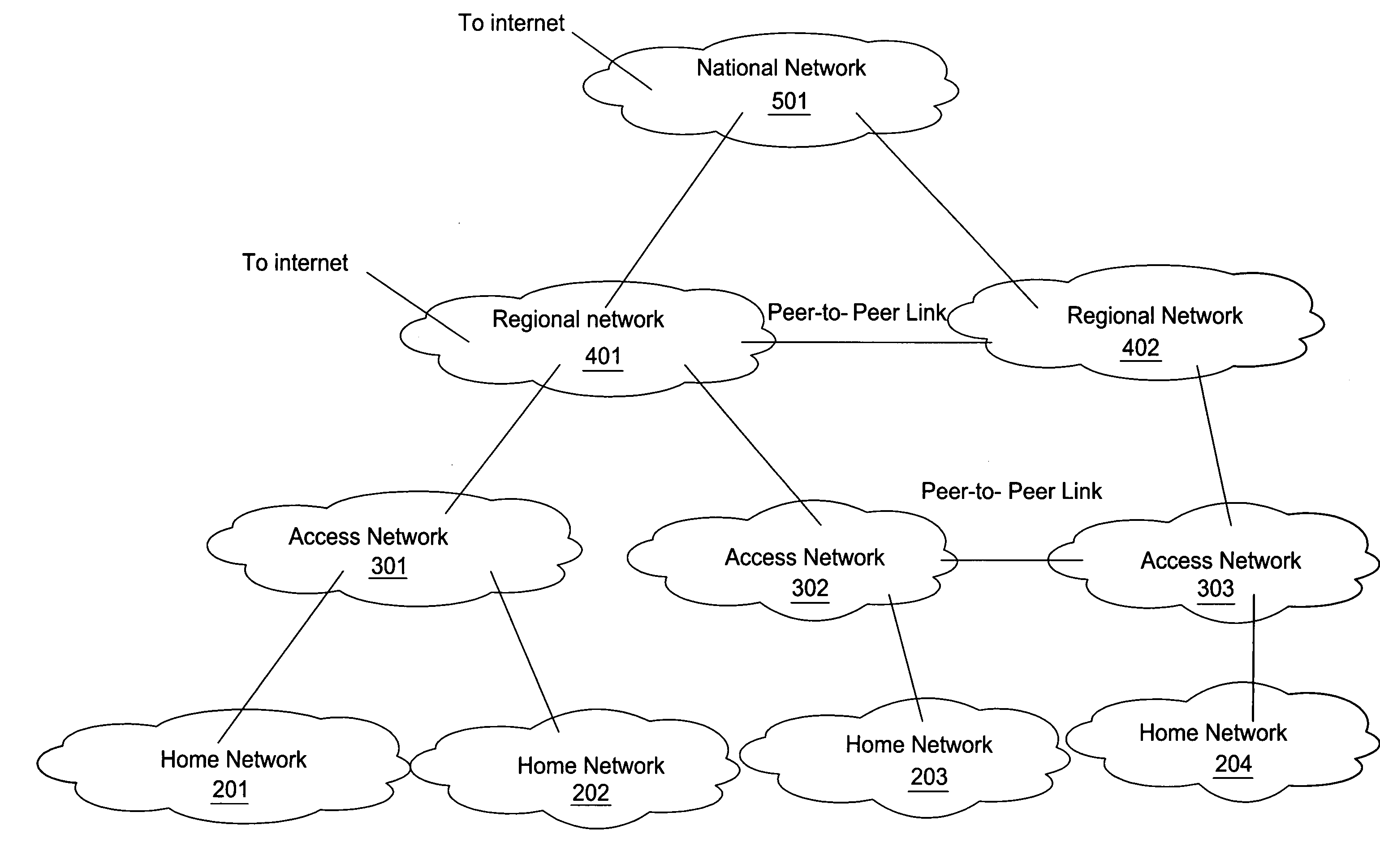
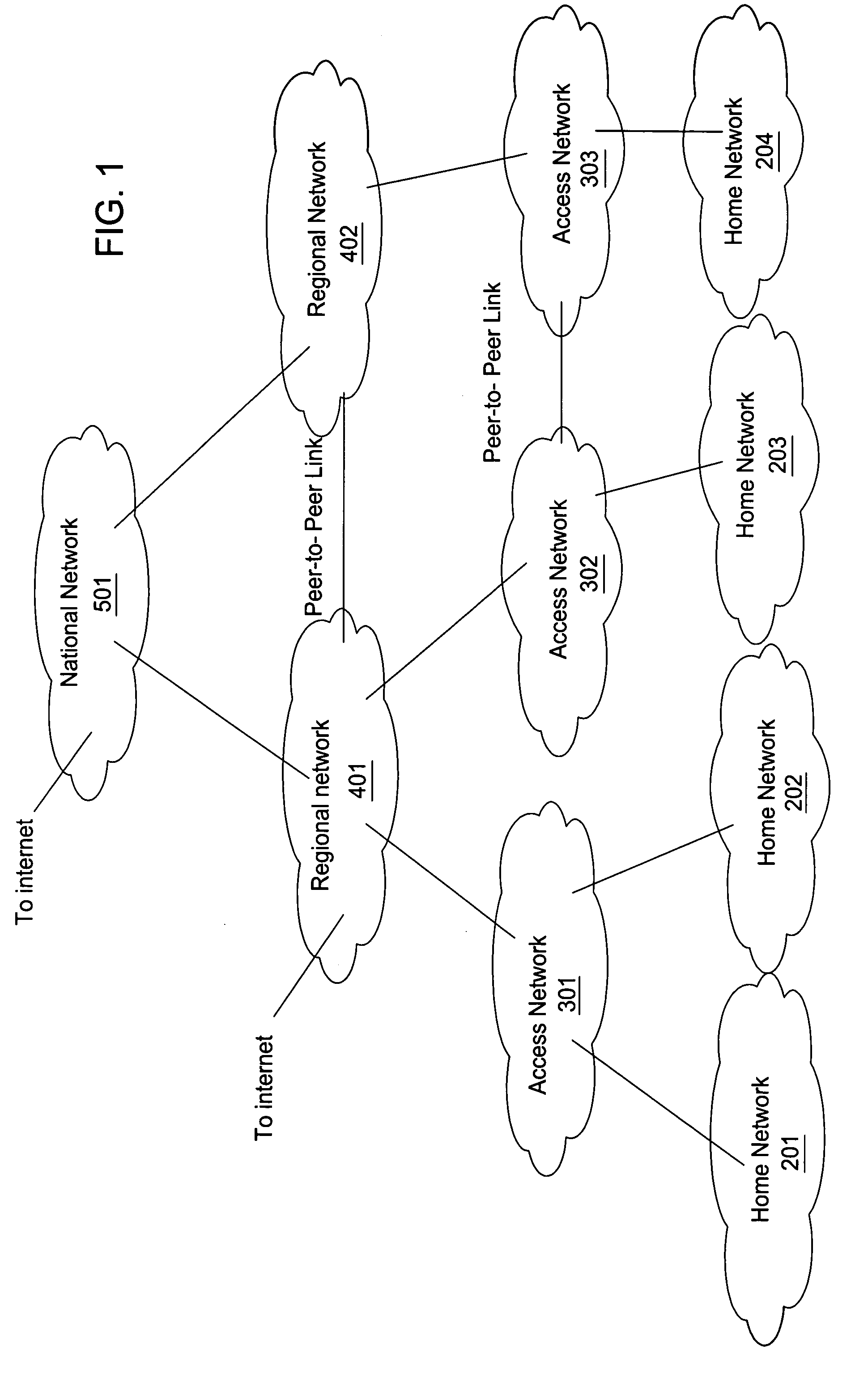
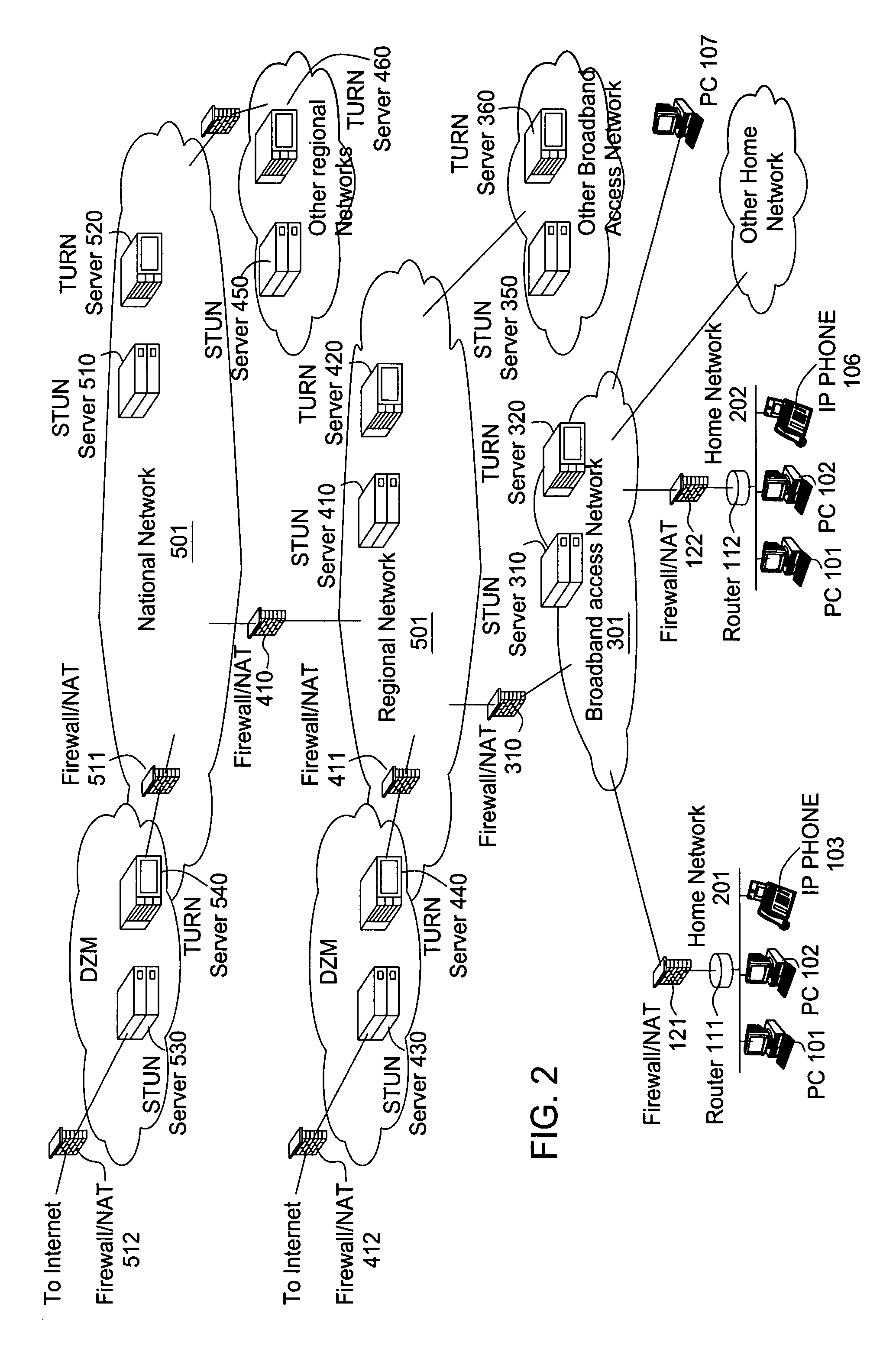
Method for optimal path selection in traversal of packets through network address translators
InactiveUS20050259637A1Reduce administrative overheadFast convergenceMultiplex system selection arrangementsError preventionNetwork addressNetwork address translation
Reduction of administrative overhead in maintaining network information, rapid convergence on an optimal routing path through the data network, and utilization of only required network resources are realized by a novel method for establishing a call path between network users. The method is based upon deployment of a network information server that stores network topology information and that is addressable by each end user. In this method, the network information server receives a request to establish a call path. The request identifies at least the calling party. In response to the request, the network information server determines a network traversal between the calling party and a root network wherein the network traversal includes call path information about the sub-networks between the calling party and the root network. The request for establishing a call path can also identify the called party. Based on the calling and called party identification, the network information server also determines a second network traversal between the called party and the root network. The second network traversal is sent to either the calling party or the called party or to both the calling and called parties. The server can determine an intersection of the traversals and send the intersection information to the parties. The intersection information is known as a merge point and represents an optimal call path between the parties.
Owner:ALCATEL-LUCENT USA INC
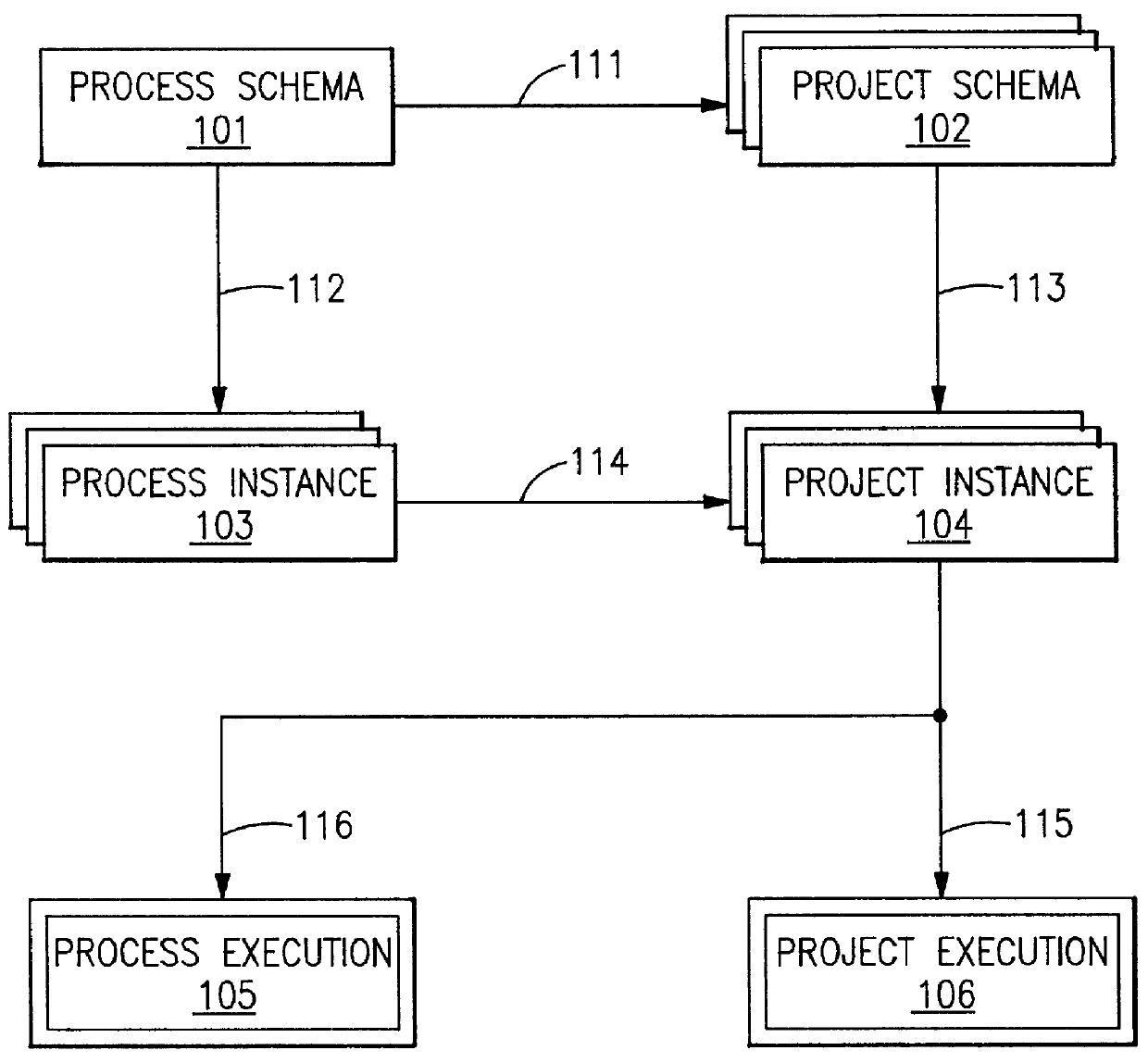
Method and apparatus for a process and project management computer system
InactiveUS6023702AReduce storageImprove performanceProgram control using stored programsResourcesDigital dataModularity
PCT No. PCT / EP95 / 03289 Sec. 371 Date Dec. 10, 1998 Sec. 102(e) Date Dec. 10, 1998 PCT Filed Aug. 18, 1995 PCT Pub. No. WO97 / 07472 PCT Pub. Date Feb. 27, 1997The inventive concept comprises a system platform for a synergistic, role modular work process environment. A work process object (WPO) (1001) is created, residing in a data base, and stored in a memory of the process and project management computer system (1030). All data concerning the process and project management are reported to said work process object (WPO) (1001) and said work process object (WPO) (1001) is used as a common data base. According to the inventive concept, each view must be supported by a specific workplace, represented by digital data and enforcing the rules for the specific role. A work process information model supports the dynamic definition and use of a data base object representing a work process, boch in its process and project planning modes and its execution. According to the inventive concept, one object supports simultaneously all modes delimited by dynamically moving boundaries. Workplace implementation enforces over-all rules for each role in the inventive system.
Owner:IBM CORP
Method and apparatus for managing secure collaborative transactions
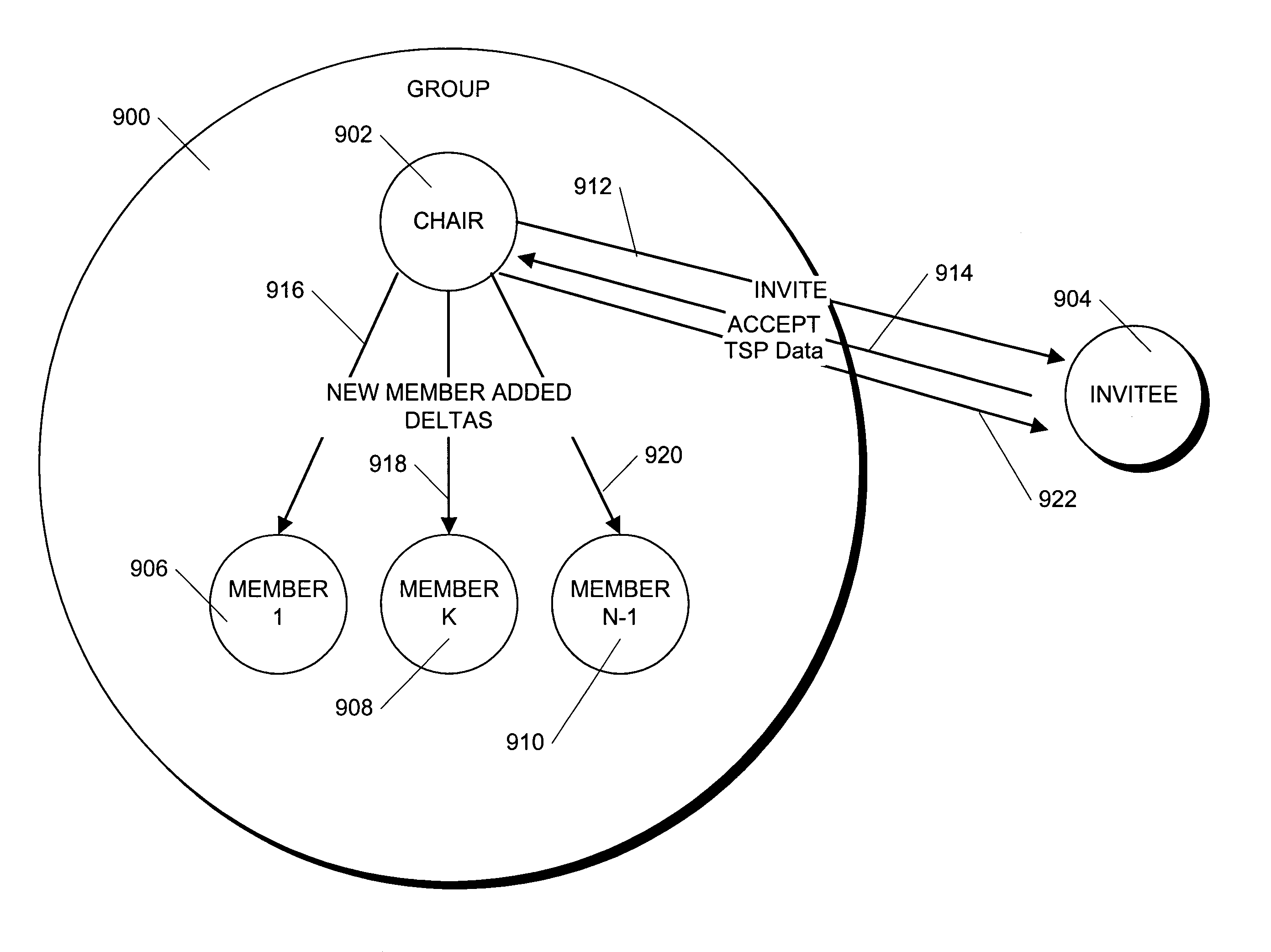
InactiveUS6986046B1Reduce key management overheadReduce administrative overheadKey distribution for secure communicationUser identity/authority verificationPlaintextSecurity level
Different levels of security are provided in a security system so that users can decide the security level of their own communications. Users can choose a low level of security and maintain the security overhead as low as possible. Alternatively, they can choose higher levels of security with attendant increases in security overhead. The different levels of security are created by the use of one or more of two keys: an encryption key is used to encrypt plaintext data in a delta and a message authentication key is used to authenticate and insure integrity of the data. Two keys are used to avoid re-encrypting the encrypted data for each member of the telespace. In one embodiment, the security level is determined when a telespace is created and remains fixed through out the life of the telespace. For a telespace, the security level may range from no security at all to security between the members of the telespace and outsiders to security between pairs of members of the telespace. In another embodiment, subgroups called “tribes” can be formed within a telespace and each tribe adopts the security level of the telespace in which it resides.
Owner:MICROSOFT TECH LICENSING LLC
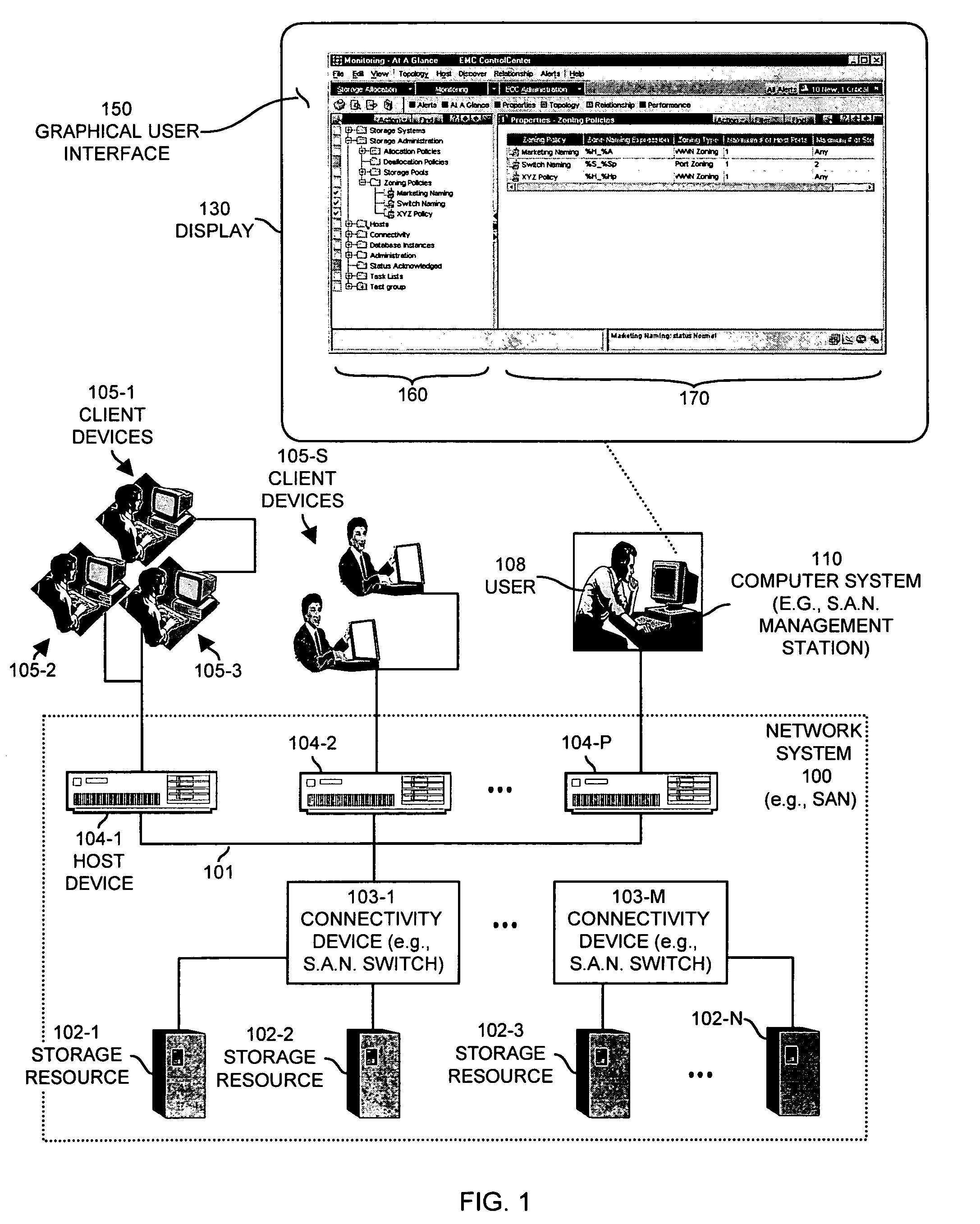
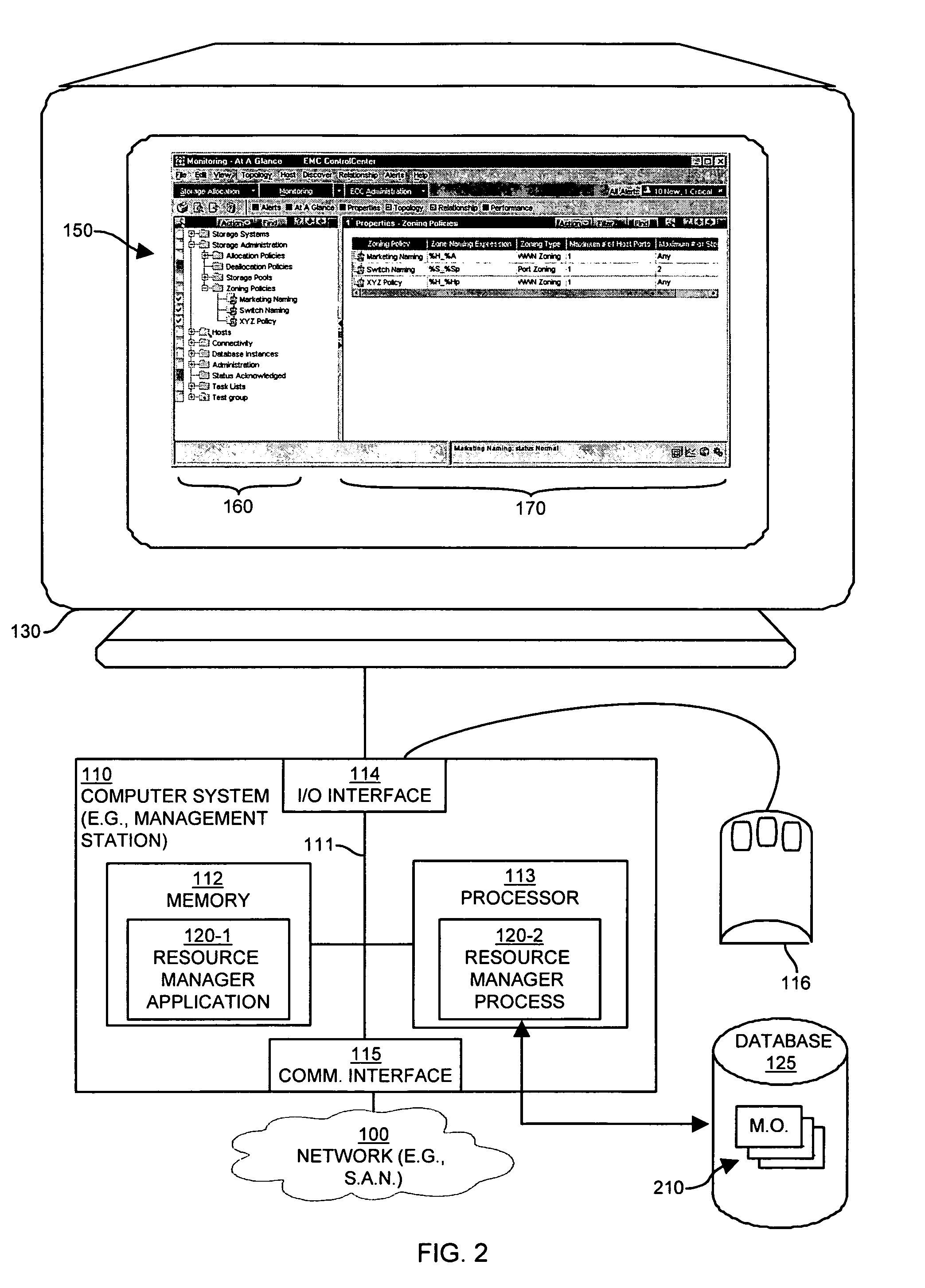
Methods and apparatus for naming resources
ActiveUS7454437B1Reduce effortOvercome deficienciesData processing applicationsDigital data processing detailsStorage area networkEngineering
A software process receives a command initiating creation of a zone naming policy for automatically generating zone names in a storage area network. During creation of a zone naming policy, the software process receives selection of one or more format elements to be used in the zone naming policy. The one or more format elements each identify which corresponding at least one type of characteristic associated with a given zone in the storage area network shall be used to automatically generate a respective zone name for the given zone. For example, the format elements in a zone policy may identify how to generate a respective zone name using identifiers associated with resources associated with the zone. Accordingly, a network manager can create a zone naming policy for automatically generating zone names in a storage area network rather than having to manually create zone names for each created zone.
Owner:EMC IP HLDG CO LLC
Efficient scalable coding concept
ActiveUS20150304667A1Alleviate decoder 's burdenReduce the numberColor television with pulse code modulationColor television with bandwidth reductionOverlayData stream
Scalable coding concepts are described. One aspect improves parallel decoding of inter-dependent layers of a multi-layer video data stream by introducing a long-term syntax element structure for guaranteeing that during a predetermined time period the pictures of the dependent layer are subdivided so that borders of the spatial segments of the pictures of the second layer and the spatial segments of the first layer overlay. Another aspect concerns upsampling from base layer to enhancement layer. Another aspect introduces a long-term syntax element structure allowing the decoder to determine the inter-layer offset for a predetermined time period. Another aspect introduces a type indicator field changing a way a layer indicator field within the NAL unit headers is to be interpreted. Another aspect allows different codecs / standards to be used for the different layers. Another aspect concerns a syntax element structure which indicates the inter-layer offset in units of the base layer blocks.
Owner:GE VIDEO COMPRESSION LLC
System and method for automated patient history intake
InactiveUS20110166884A1Prevent unauthorized accessLimit disruptionFinancePatient personal data managementMedication informationMedicine
A system of automated patient history intake including a retrieval system for retrieving pharmaceutical information specific to a patient, a display system for displaying the pharmaceutical information, and a reconciliation system for reconciling the pharmaceutical information using visual data. A system for automated patient check-in including a retrieval system for retrieving pharmaceutical information specific to a patient, a display system for displaying the pharmaceutical information, and a reconciliation system for reconciling the pharmaceutical information using visual data.
Owner:THE GOVERNMENT OF THE UNITED STATES OF AMERICA AS REPRESENTED BY THE DEPT OF VETERANS AFFAIRS
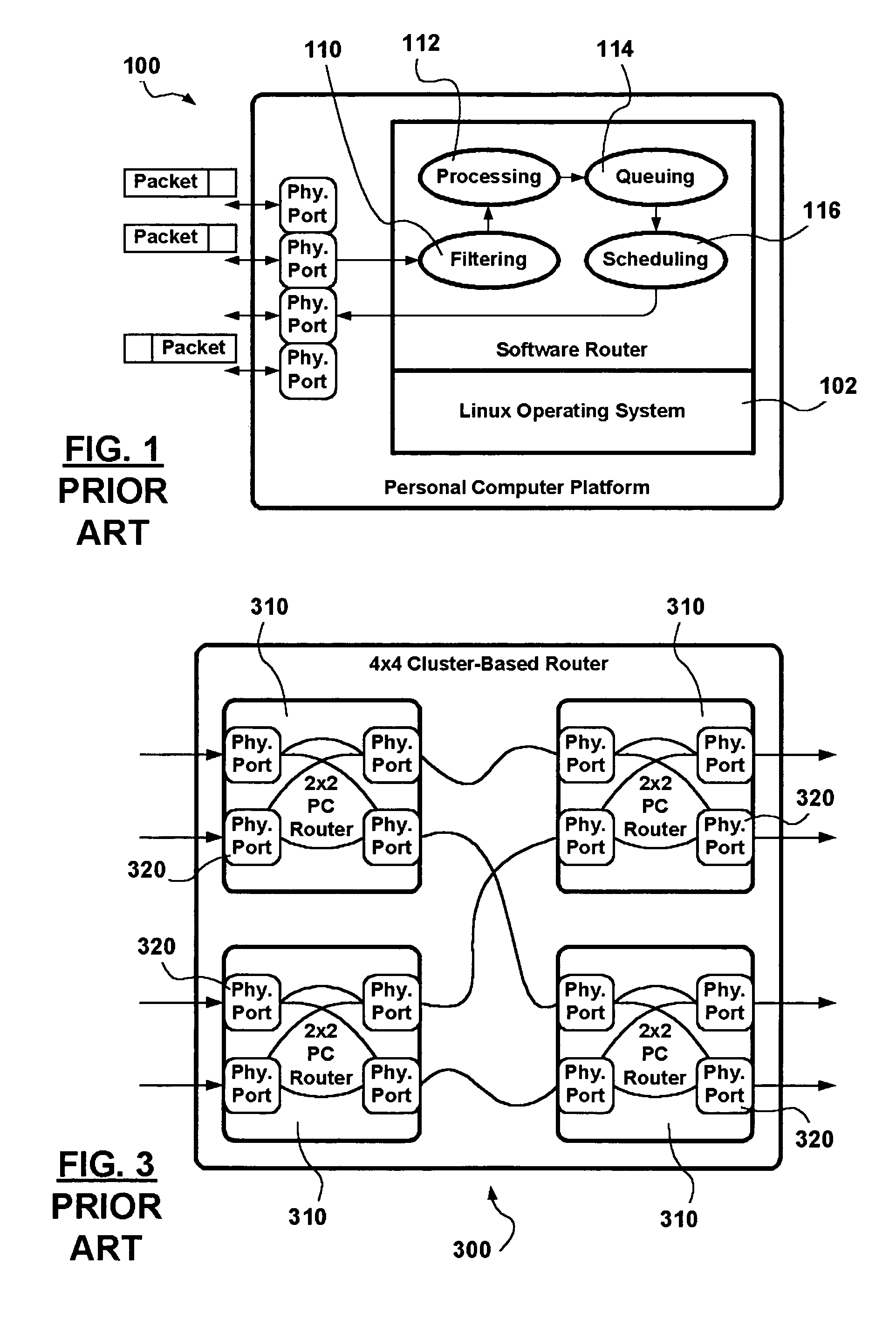
Software configurable cluster-based router using heterogeneous nodes as cluster nodes
ActiveUS20050108425A1Large capacityIncrease diversityError preventionTransmission systemsOff the shelfCluster based
A cluster router architecture and methods for performing distributed routing are presented. The cluster router architecture includes off-the shelf Personal Computer (PC) hardware-based router cluster nodes interconnected in an intra-connection network in multiple dimensions. Each PC-based router cluster node is provided with the same routing functionality and a router-cluster-node-centric configuration enabling each router cluster node by itself or multiple router cluster nodes in the cluster router to provide routing responses for packets pending processing. Optimized packet processing in respect of specific functionality is provided via special purpose router cluster nodes not necessarily PC-based taking part as cluster nodes in the cluster router lattice. The method divides packet processing into entry packet processing and routing response processing; special processing; and exit processing. Entry packet processing and routing response processing is performed by router cluster nodes receiving packets from communication networks in which the cluster router participates. Exit packet processing is performed by router cluster nodes transmitting packets into communication networks in which the cluster router participates. Packet processing in accordance with the router-cluster-node-centric specification is interrupted on determining that special processing is required in respect of a packet, and the packet is handed over to a corresponding special purpose router cluster node. Advantages are derived from: a configurable, and scalable cluster router design providing a re-configurable high routing capacity using cost effective stock PC hardware; from the intra-connection network which provides a high degree of diversity ensuring resilience to equipment failure; from the use of a star topology with respect to management links which reduces management overheads in the intra-connection network; and from the ability to forward packets to designated special purpose router cluster nodes optimized to provide specific packet processing functionality.
Owner:WSOU INVESTMENTS LLC
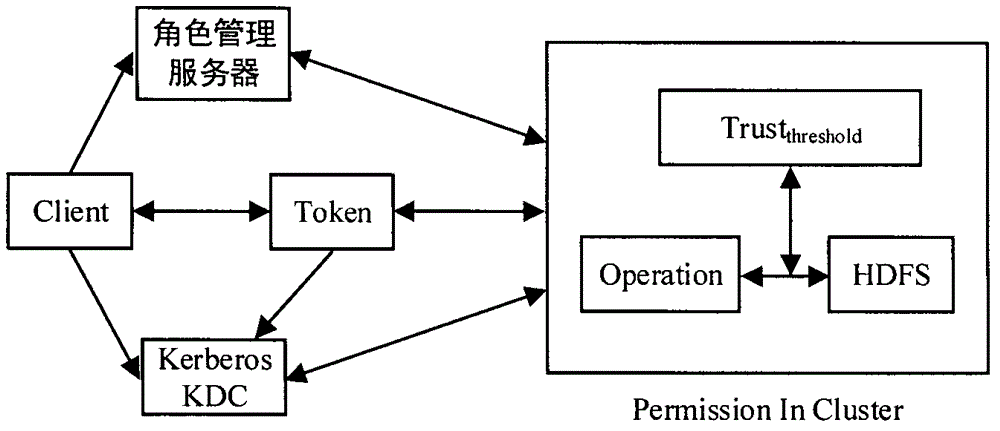
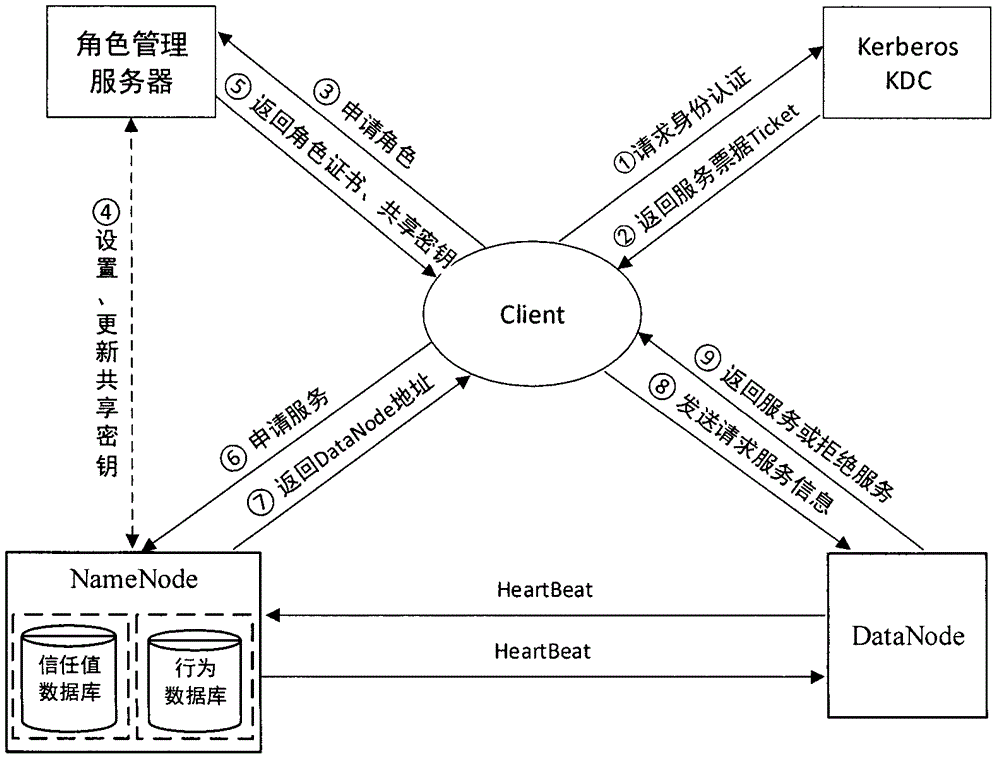
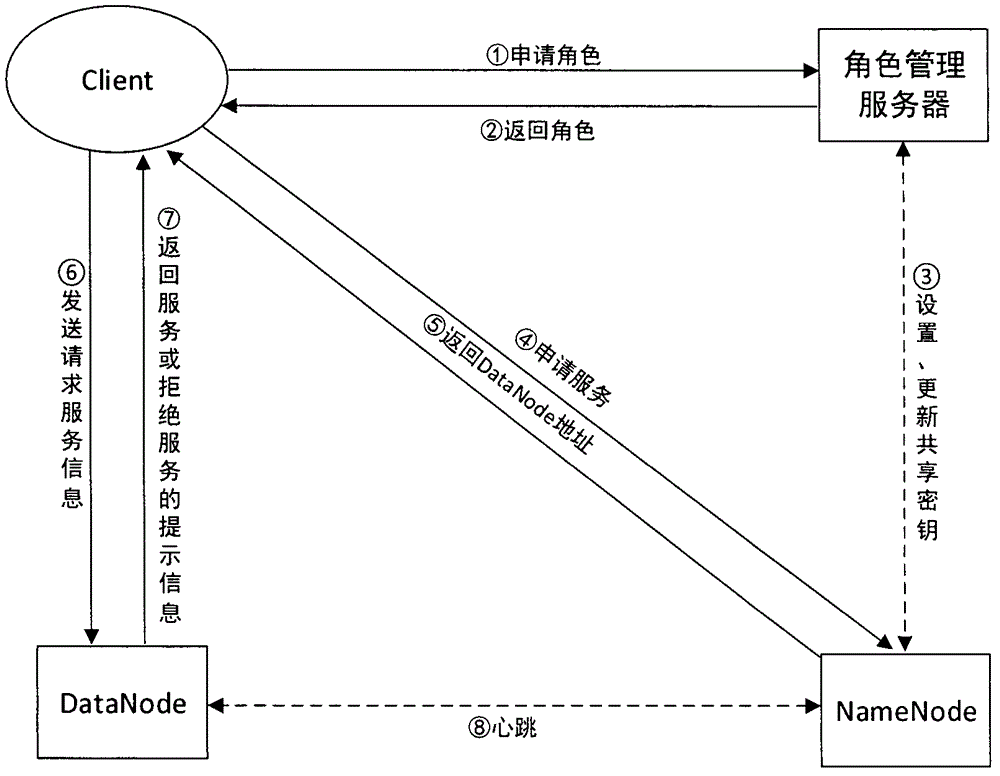
HDFS access control method based on role and user trust value
InactiveCN104935590AReduce complexityReduce administrative overheadUser identity/authority verificationCloud storageDiscretionary access control
The invention provides an HDFS access control method based on a role and a user trust value and belongs to the field of computer cloud storage access control. The HDFS access control method of the invention firstly combines with a role-based access control policy RBAC to replace a discretionary access control policy of an HDFS, thereby reducing complexity and management expenditure of HDFS authorization management and improving flexibility of the authorization management. When a user accesses the HDFS for the first time, a role is granted to the user, so that users are isolated from authorization through roles, and the management is facilitated. On this basis, the HDFS access control method of the invention further introduces a concept of the user trust value and sets one trust value for each user so that different users with the same role could obtain different access permissions because of their different trust values, and the trust value of the user is dynamically updated according to the later behavior of the user, thereby dynamically and effectively controlling the access of the user to a resource in the HDFS.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Software configurable cluster-based router using stock personal computers as cluster nodes
InactiveUS20050018665A1Increase capacityIncrease diversityMultiplex system selection arrangementsCircuit switching systemsData packCost effectiveness
A cluster router architecture and methods for performing distributed routing is presented. Implementations include off-the shelf Personal Computer (PC) hardware. The cluster router architecture includes PC-based router cluster nodes toroidally interconnected in an intra-connection network in multiple dimensions. The cluster router may further make use of a management node. Each router cluster node is provided with the same routing functionality and a node centric configuration enabling each router cluster node by itself or multiple router cluster nodes in the cluster router to provide routing responses for packets pending processing. The method divides packet processing into entry packet processing and routing response processing; and exit processing. Entry packet processing and routing response processing is performed by router cluster nodes receiving packets from communication networks in which the cluster router participates. Exit packet processing is performed by router cluster nodes transmitting packets into communication networks in which the cluster router participates. Advantages are derived from: a configurable, and scalable cluster router design providing a high routing capacity using cost effective stock PC hardware; from the toroidal topology of the intra-connection network which provides a high degree of diversity ensuring resilience to equipment failure, and from the use of the star topology of the management links which reduces management overheads in the intra-connection network.
Owner:WSOU INVESTMENTS LLC
Unmanned ship device and sampling method for automatic sampling of water quality
PendingCN107585266AAutomatic sampling facilitatesAutomatic sampling fastWaterborne vesselsWithdrawing sample devicesMarine engineeringWork cycle
The invention relates to an unmanned ship device and sampling method for automatic sampling of the water quality. The unmanned ship device comprises an unmanned ship body, an energy and control unit arranged in a bin of the unmanned ship body, and an automatic water quality sampling unit. The automatic water quality sampling unit comprises a sampling bottle, a supporting body mechanism for installation of the sampling bottle, a sampling pump arranged on the outer side of the unmanned ship body, a sample hose connected with the sampling pump, and an oscillating arm water-fetching mechanism forcontrolling the sampling hose to rotate. The oscillating arm water-fetching mechanism comprises a hollow pipe nested on the outer side of the tail section of the sampling hose, and a first stepping motor connected with the end, close to the sampling pump, of the hollow pipe. By means of the unmanned ship device and sampling method for automatic sampling of the water quality, water quality samplesof multiple sampling sites can be collected sequentially in a working cycle, the samples can be analyzed synchronously after being sent back, the sampling efficiency is further improved, and water quality samples of different areas or watersheds can be conveniently, quickly and automatically collected.
Owner:BEIJING ORIENT LANDSCAPE
Large scale resource memory managing method based on network under SAN environment
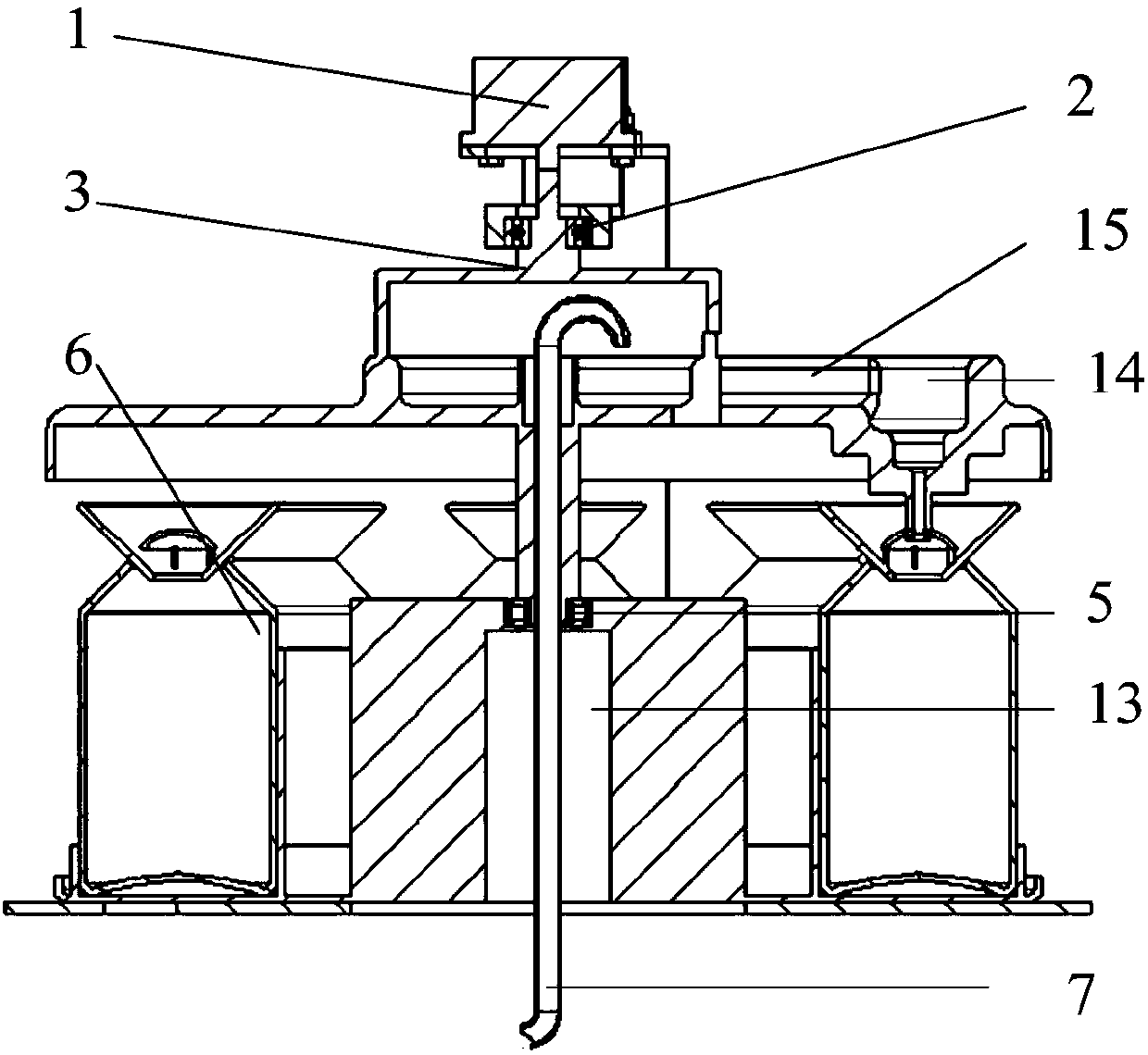
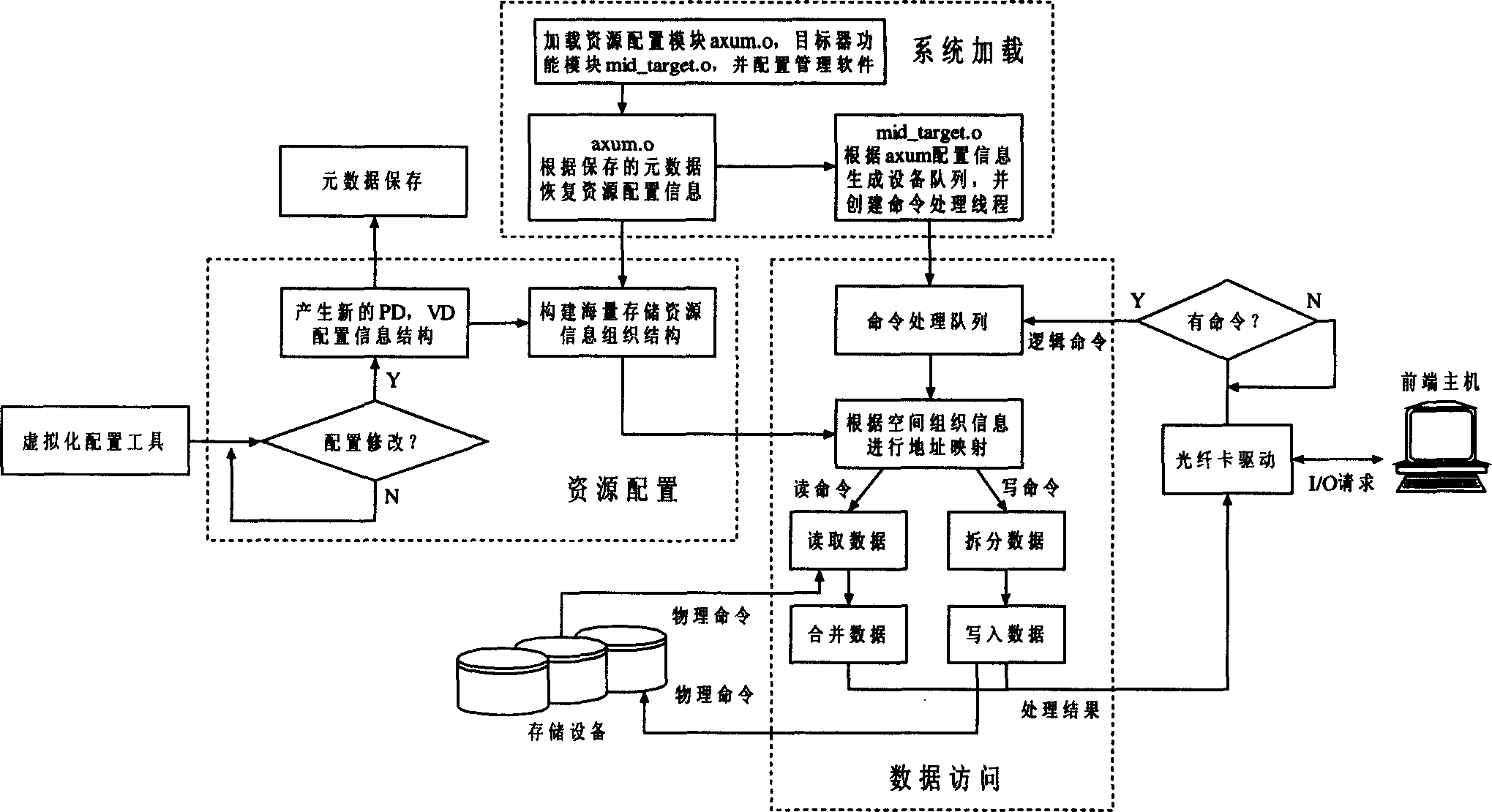
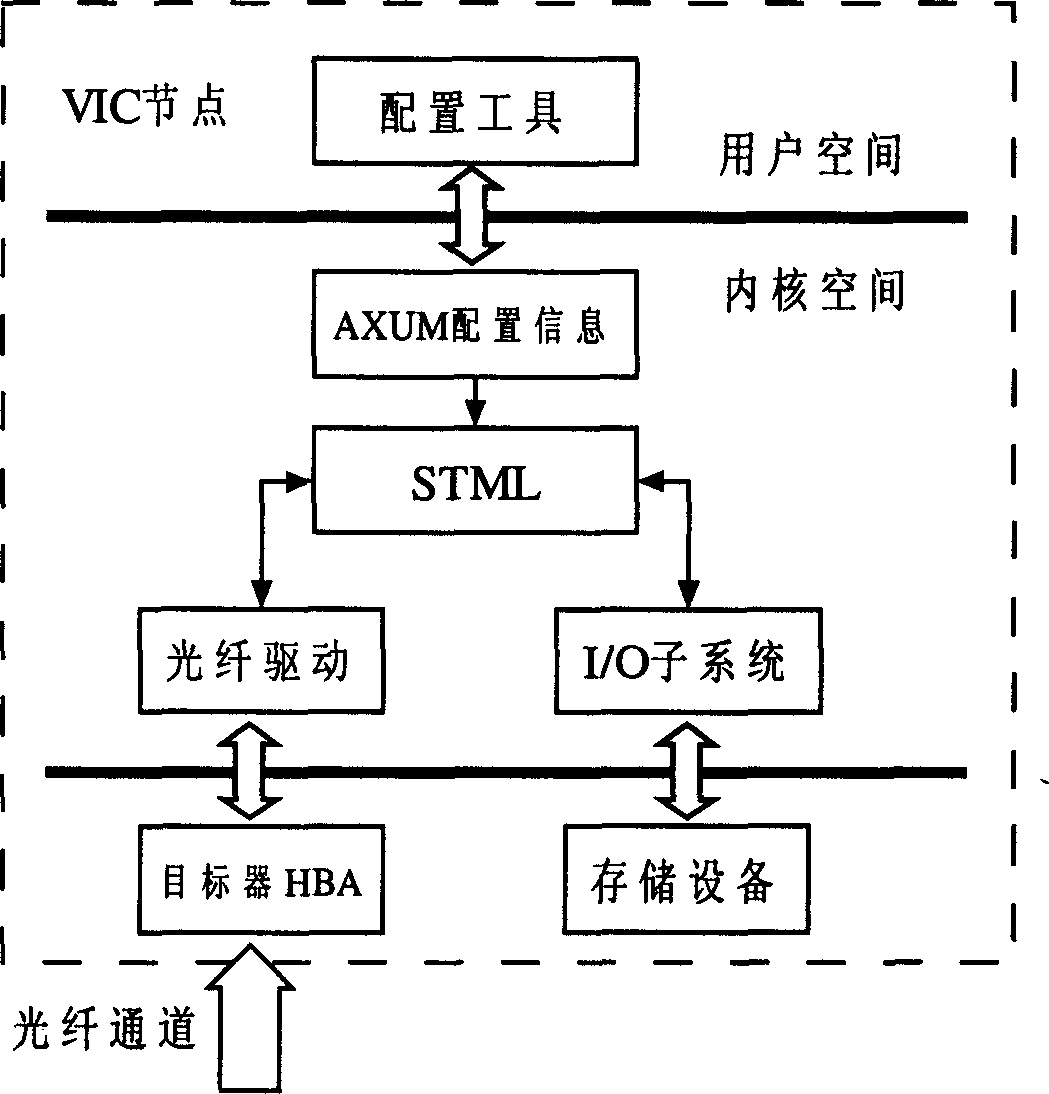
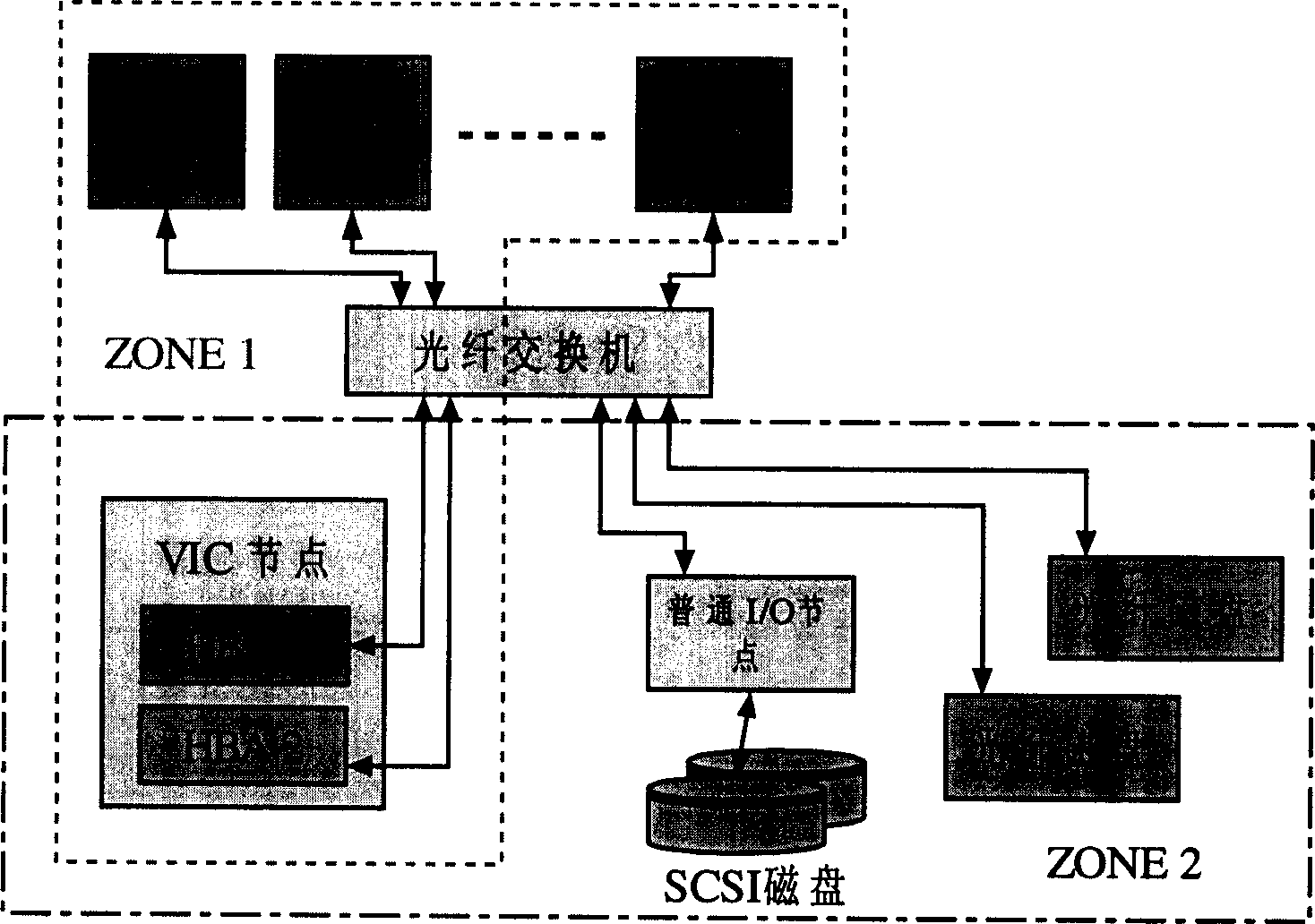
InactiveCN1645342AEasy to manageSmall space requirementMetering/charging/biilling arrangementsMemory adressing/allocation/relocationVirtualizationSCSI
A management method of large scale storage resource includes maintaining a set of storage resouce disposal information by node machine of special processor to manage different storage device resource in storage network so as to provide virtual storage service for front end host by carrying out process of command analysis with interface middle layer of small computer interface. The node machine with information list and software target machine can convert virtual access to be access of physical device.
Owner:TSINGHUA UNIV
Software configurable cluster-based router using heterogeneous nodes as cluster nodes
ActiveUS7483998B2Increase capacityIncrease diversityError preventionFrequency-division multiplex detailsOff the shelfHeterogeneous network
A cluster router architecture and methods for performing distributed routing are presented. The cluster router architecture includes off-the shelf Personal Computer (PC) hardware-based router cluster nodes interconnected in an intra-connection network in multiple dimensions. Each PC-based router cluster node is provided with the same routing functionality and a router-cluster-node-centric configuration enabling each router cluster node to provide routing responses for packets pending processing. Packet processing is divided into entry packet processing and routing response processing; special processing; and exit processing. Exit packet processing is performed by router cluster nodes transmitting packets into communication networks in which the cluster router participates. Packet processing is interrupted on determining that special processing is required in respect of a packet, and the packet is handed over to a corresponding special purpose router cluster node.
Owner:WSOU INVESTMENTS LLC
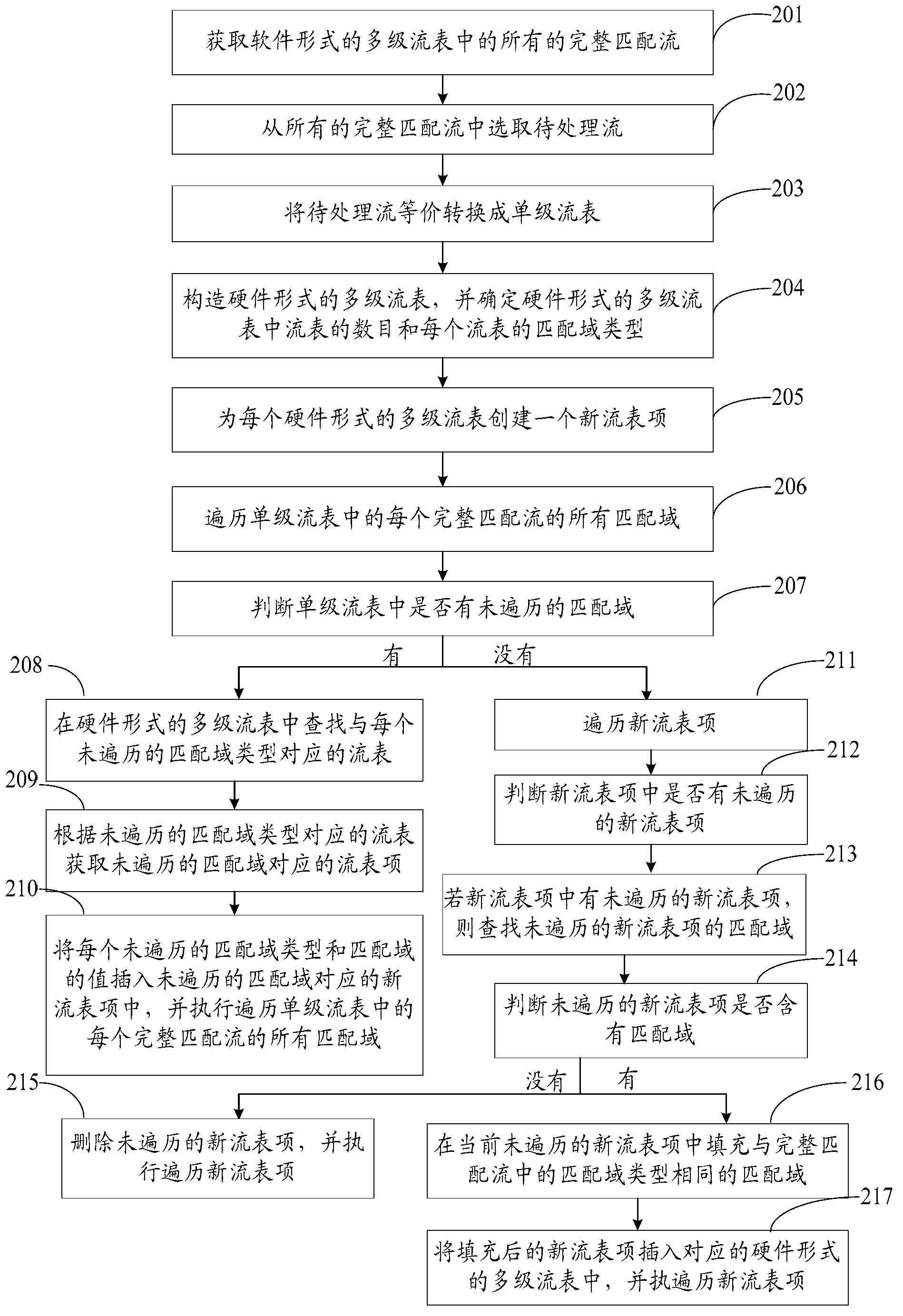
Flow table conversion method and device
ActiveCN103259718AReduce the burden onReduce administrative overheadData switching networksSingle stageSoftware engineering
The invention provides a flow table conversion method and device and relates to the technical field of networks. According to the flow table conversion method and device, in the achievement process from software to hardware, a controller does not need to fit in with an issuing rule of the hardware, and therefore burden of the controller and management expense are reduced. The flow table conversion method includes the following steps of converting a software-type multistage flow table into a software-type single-stage flow table in network equipment architecture with detached control and transmission in an equivalent mode, wherein the single-stage flow table is single-table multi-domain, and dividing the single-stage flow table into corresponding multi-stage flow tables of a hardware type based on the multi-stage flow table achieved by the hardware. The flow table conversion method and device is applied to flow table conversion.
Owner:罗三杰
Method for restricting access to a web site by remote users
ActiveUS7249262B2Simplifies useReduce administrative overheadDigital data processing detailsComputer security arrangementsWeb sitePassword
A method of restricting access to data maintained on a server computer by one or more authorized, networked client machines includes the step of installing a client-side software program on the client machine for generating a client machine-specific identifier determined by particular characteristics of the client machine. The machine-specific identifier is used by the server administrator to generate a unique password, which the user enters into the client-side software program. Server-side software is embedded on protected Web pages of the server computer that hosts the protected Web site. When a user desires access to protected content, the client-side software is prompted to re-generate its machine-specific identifier and valid client password list for comparison with the password previously entered by the user. Access is granted if they correspond, and denied if they do not. If the client machine is recognized as being authorized to access data on the protected Web site during a first access request, then the current session identifier is saved in a temporary storage table remote from the client machine for indicating current working sessions of authorized client machines. The client machine returns such session identifier with each additional request for access, and the temporary storage table is consulted to search for such session identifier before granting access.
Owner:BROWSERKEY
Method, device and system for managing file copies
InactiveCN101909068AReduce administrative overheadLoad balancingTransmissionService conditionComputer science
The invention relates to a method, a device and a system for managing file copies. The method comprises the following specific steps of: in a distributed storage network, selecting a source node for diffusing or transferring the file copies according to idle resources of nodes; and selecting a target node for receiving the file copies by the source node according to the idle resources of relevant nodes. Therefore, in the embodiment of the invention, the nodes with higher resource idle rate can be selected according the current service condition of the resources in a network to transfer and diffuse the copies, so the cost of transferring and diffusing the copies is reduced greatly; and the load pressure of the network is dispersed to save the expenditure of managing the copies, equalize network loads and greatly improve the service performance of the network.
Owner:HUAWEI TECH CO LTD
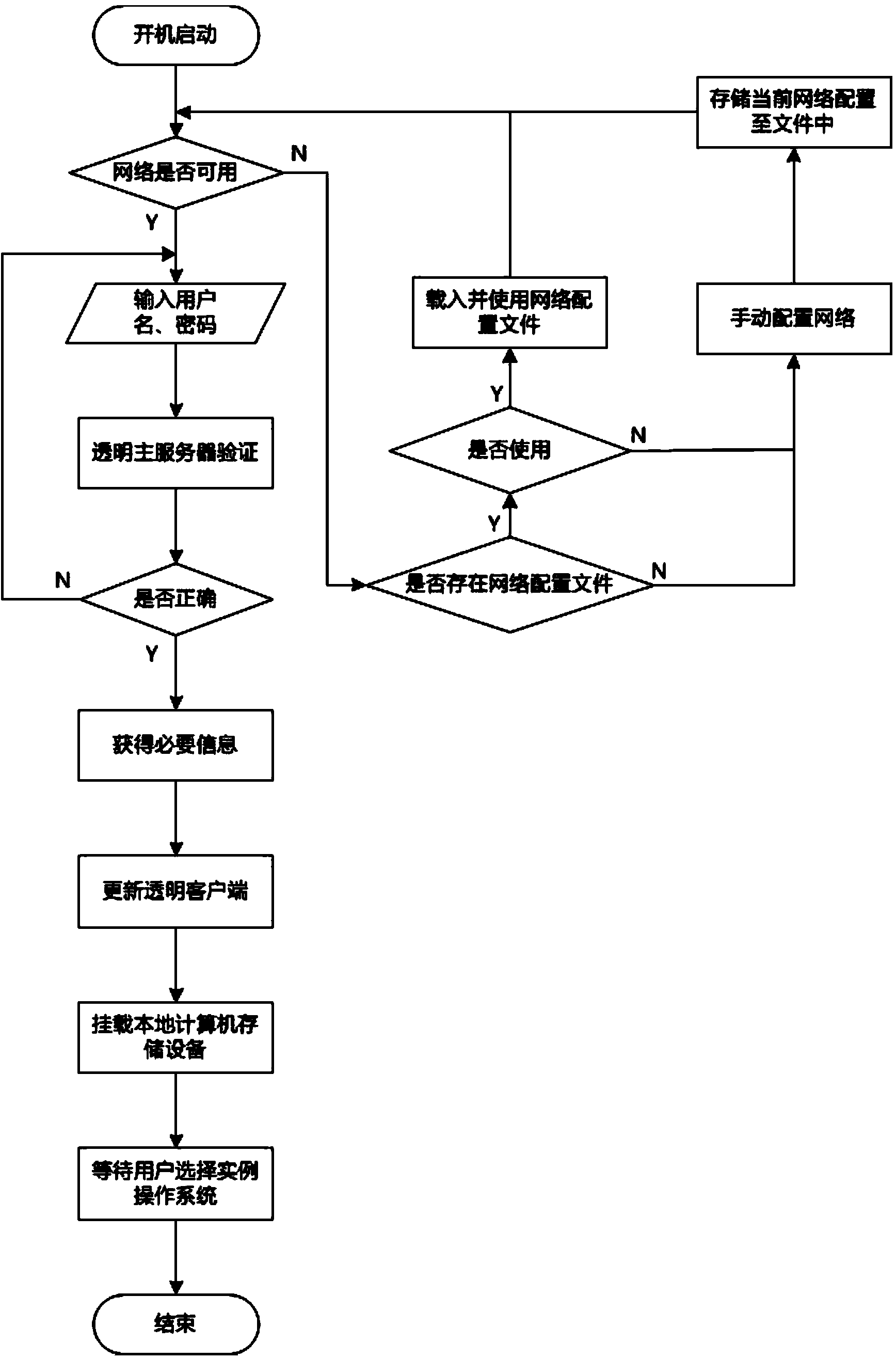
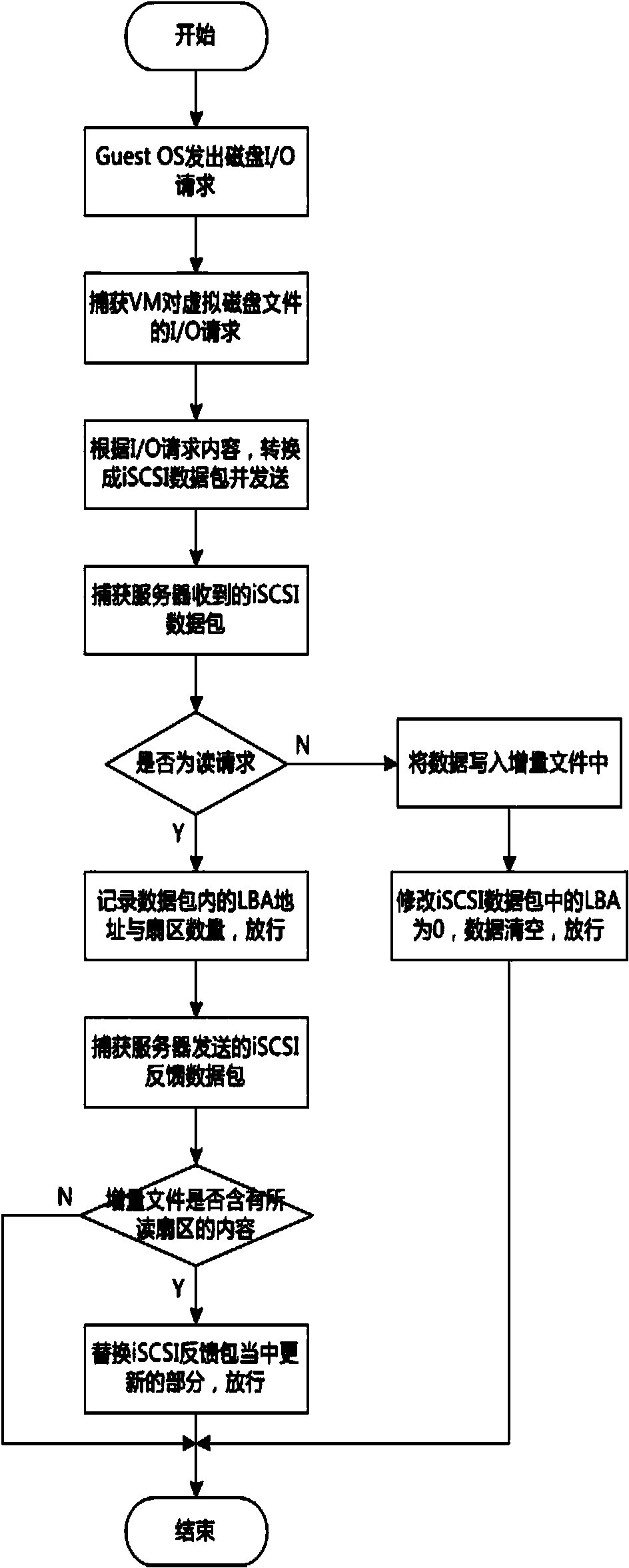
Transparent computing method and transparent computing system based on virtualization technology
ActiveCN104166586AMeeting Mobility NeedsShort startup timeTransmissionSoftware simulation/interpretation/emulationVirtualizationOperational system
The invention discloses a transparent computing method and transparent computing system based on the virtualization technology. Through the virtualization technology, physical differences between different hardware platforms of a client are shielded, wide support for different hardware devices is provided, the mobility requirement of a user is met, application service support across terminal devices and operating systems is provided for the user, and the user does not need to worry about management of computer hardware devices and systems. The scheme is achieved in the transparent computing system based on a wide area network, a request is started by the client in the transparent computing system, legality of the request is confirmed through a management client and a transparent main server of a software resource server, connection of resources is given, instance operating systems stored in the transparent software resource server are loaded remotely and run, needed service is acquired, and the task requirement of the user is completed. The transparent computing method and transparent computing system based on the virtualization technology can adapt to different hardware platforms and operating system platforms, can be started on the wide area network faster, and is higher in safety performance and practicability.
Owner:HUNAN NEW CLOUDNET TECH CO LTD
System and Method for Managing Appointments
InactiveUS20150081327A1Acceptance and/or rejection of appointmentsHandled more quicklyOffice automationHealthcare resources and facilitiesAppointment timeNursing
Systems and methods for managing appointments and, particularly, for managing appointments for patients in healthcare systems that include health care facilities and hospitals. Computer systems can detect geophysical positions of patient devices, such as their smart phones to update likelihood of patients being able to make appointment dates on time during the date of the appointments The computer systems can detect the patients travel locations before the appointment at one or more geo-fences associated with the location of the appointment for determining whether the geographical position is inside or outside the geo-fence to determine likelihood of patient making their appointment ontime, and if time permits registering the patient during their travels to the appointment, and / or sending reminders to the patient of the scheduled appointment time, or determining if the appointment needs to be rescheduled.
Owner:CRANEWARE
Method and apparatus for managing secure collaborative transactions
InactiveUS20060036862A1Reduce administrative overheadKey distribution for secure communicationUser identity/authority verificationPlaintextSecurity level
Different levels of security are provided in a security system so that users can decide the security level of their own communications. Users can choose a low level of security and maintain the security overhead as low as possible. Alternatively, they can choose higher levels of security with attendant increases in security overhead. The different levels of security are created by the use of one or more of two keys: an encryption key is used to encrypt plaintext data in a delta and a message authentication key is used to authenticate and insure integrity of the data. Two keys are used to avoid re-encrypting the encrypted data for each member of the telespace. In one embodiment, the security level is determined when a telespace is created and remains fixed through out the life of the telespace. For a telespace, the security level may range from no security at all to security between the members of the telespace and outsiders to security between pairs of members of the telespace. In another embodiment, subgroups called “tribes” can be formed within a telespace and each tribe adopts the security level of the telespace in which it resides.
Owner:MICROSOFT TECH LICENSING LLC
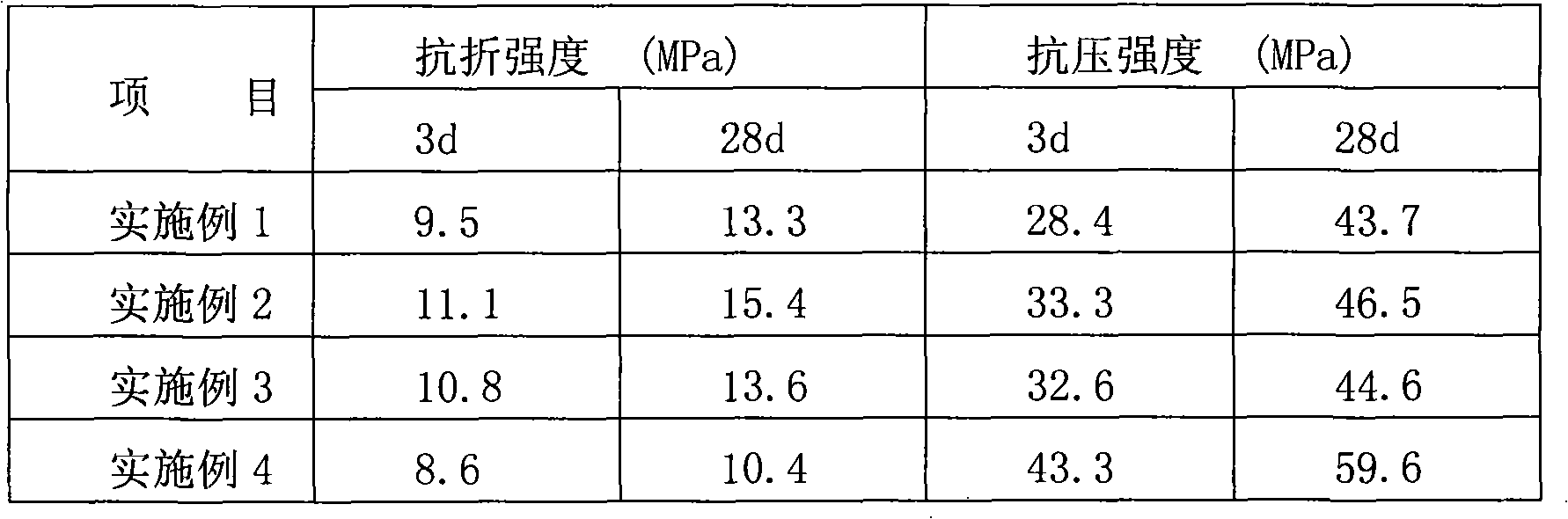
Steel scoria tail mud composite slag micro mist agglutination material
InactiveCN101492261APromote sustainable economic developmentEliminate slag damageSolid waste managementSlagBall mill
The invention relates to a cementing material of steel slag tailings and composite slag micro powder, which comprises the composite slag micro powder and the steel slag tailings, and the weight ratio of the composite slag micro powder to the steel slag tailings is between 1 to 1 and 1 to 3; the specific surface area of the composite slag micro powder is larger than 350 m / kg, the composite slag micro powder comprises a combined material and the slag micro powder, wherein the combined material accounts for 8 to 35 percent of the composite slag micro powder by weight, and the slag micro powder accounts for 65 to 92 percent of the composite slag micro powder by weight; and the combined material comprises gypsum. The cementing material has the advantages that: 1, the method is an effective method utilizing large amount of waste slag; 2, the raw material of the composite slag micro powder has wide source; 3, the steel slag tailings are natural-grade tailings after steel slag wet-type ball milling magnetic separation particles are toughened, and the settled tailings do not need to be dried and are directly used as an auxiliary material; and 4, the steel slag tailings account for large proportion, and can fully utilize waste slag resources.
Owner:武钢集团有限公司
Unmanned ship device and sample reserving method for automatic water sample reserving
PendingCN107560893AEasy accessReduce construction costsWaterborne vesselsWithdrawing sample devicesMarine engineeringFishery
The invention relates to an unmanned ship device and a sample reserving method for automatic water sample reserving. The unmanned ship device comprises an unmanned ship main body, an energy and control unit and an automatic water sample reserving unit arranged in a cabin of the unmanned ship main body and a water multi-parameter monitoring probe arranged on the lower side of the unmanned ship mainbody. The water multi-parameter monitoring probe transmits water parameter data to the energy and control unit through a transmission cable; the automatic water sample reserving unit comprises a sampling bottle, a supporting body mechanism provided with the sampling bottle, a sampling pump arranged on the outer side of the unmanned ship main body, a sampling hose connected to the sampling pump and a swing arm water taking mechanism which controls the sampling hose to rotate. The unmanned ship device has the monitoring and sample reserving functions at the same time, triggers sampling by online monitoring data and preset conditions, and is immediate to reserve samples; the reserved samples are highly consistent to online monitoring objects, so that the follow-up application and analysis application are improved.
Owner:BEIJING ORIENT LANDSCAPE
Orbit and domain partition type double-layer satellite network system and management method
InactiveCN104601363AReduce the numberReduce interactionRadio transmissionData switching networksRouting tableManagement efficiency
The invention provides an orbit and domain partition type double-layer satellite network management system. The orbit and domain partition type double-layer satellite network management system comprises cluster heads and management satellites; when every time slice is started, the link state information is collected by a low-layer satellite and sent to the cluster head corresponding to the time slice; the link state information is gathered through the cluster heads and sent to the management satellites, a routing table is calculated through the management satellites according to the integral network of link state information, and the routing table is issued. The invention also provides an orbit and domain partition type double-layer satellite network management method. According to the orbit and domain partition type double-layer satellite network management method, the orbit partition management is performed on the low-layer satellite through the cluster heads, a domain formed by one or more than one orbit is managed through the management satellites, and accordingly the number of the required management satellites is greatly reduced, the interaction between the management satellites is reduced, and the management efficiency is improved; the management satellites are arranged in the same orbit and accordingly the design complexity of the management on a layer constellation is reduced; the interlayer communication only needs to be performed through cluster heads and the management satellites and accordingly the integral management overhead of the system is reduced.
Owner:SHANGHAI JIAO TONG UNIV
System and method for providing a secure computing environment
ActiveUS20090070576A1Safe storageImprove efficiencyDigital computer detailsData resettingBootingTrusted Computing
A system and method for providing a secure computing environment to untrusted computer systems is described. A carrier media and an interface are provided, the interface being connectable to a computer to enable communication between the computer and the carrier media. The carrier media encodes a secure computing environment and a boot system, upon connection of the system via the interface to a computer system and booting of the computer system, the boot system is operative to take over the boot process of the computer system and to authenticate the user, wherein upon successful authentication, the boot system is arranged to load the secure computing environment on the computer system, the secure computing environment being configured to prevent predetermined interaction from outside the secure computing environment when it is running.
Owner:BECRYPT
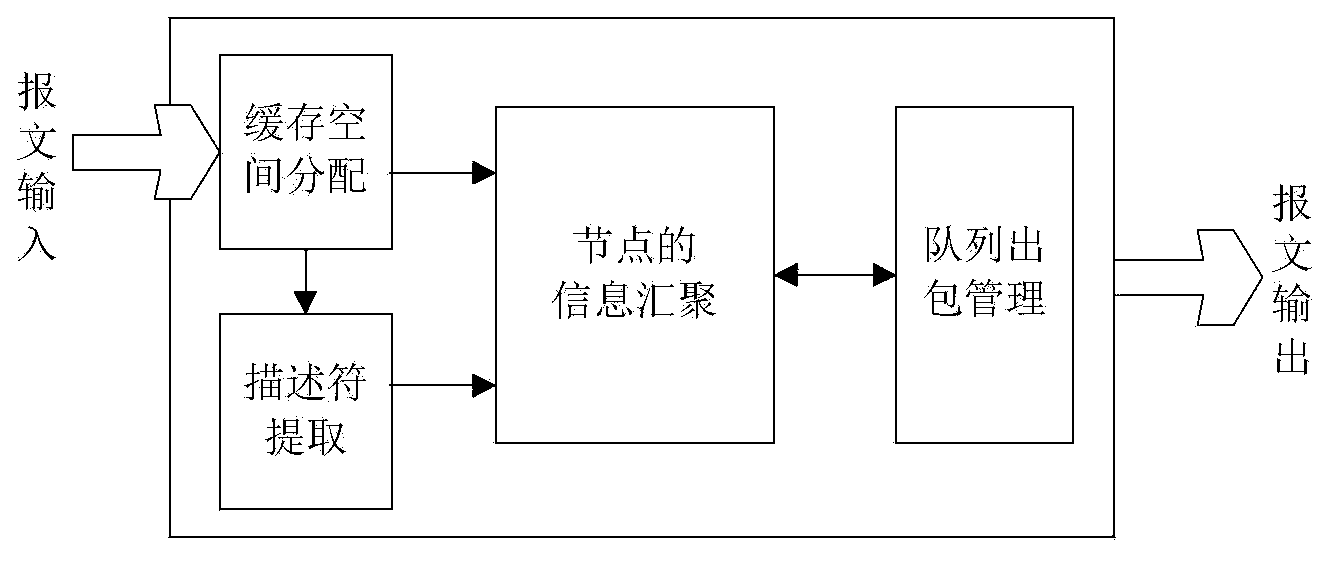
Method and device for processing message
ActiveCN103731368ARealize unified storageReduce administrative overheadSpecial service provision for substationDistributed computingLinked list
The invention provides a method and device for processing a message. The method comprises the steps of distributing a node to the input message in a cache space, storing the message, using the position corresponding to the cache space as index information of a descriptor of the message, extracting information of the descriptor of the message, carrying out framing on the information of the descriptor of the message and information of the node of the message, and storing the result in a node linked list. According to the method and device for processing the message, uniform storage of unicast messages and multicast messages can be achieved, a descriptor linked list corresponds to package entity cache resources, the management overheads of the unicast messages and the multicast messages are remarkably reduced, and the node convergence capacity can be improved.
Owner:SANECHIPS TECH CO LTD
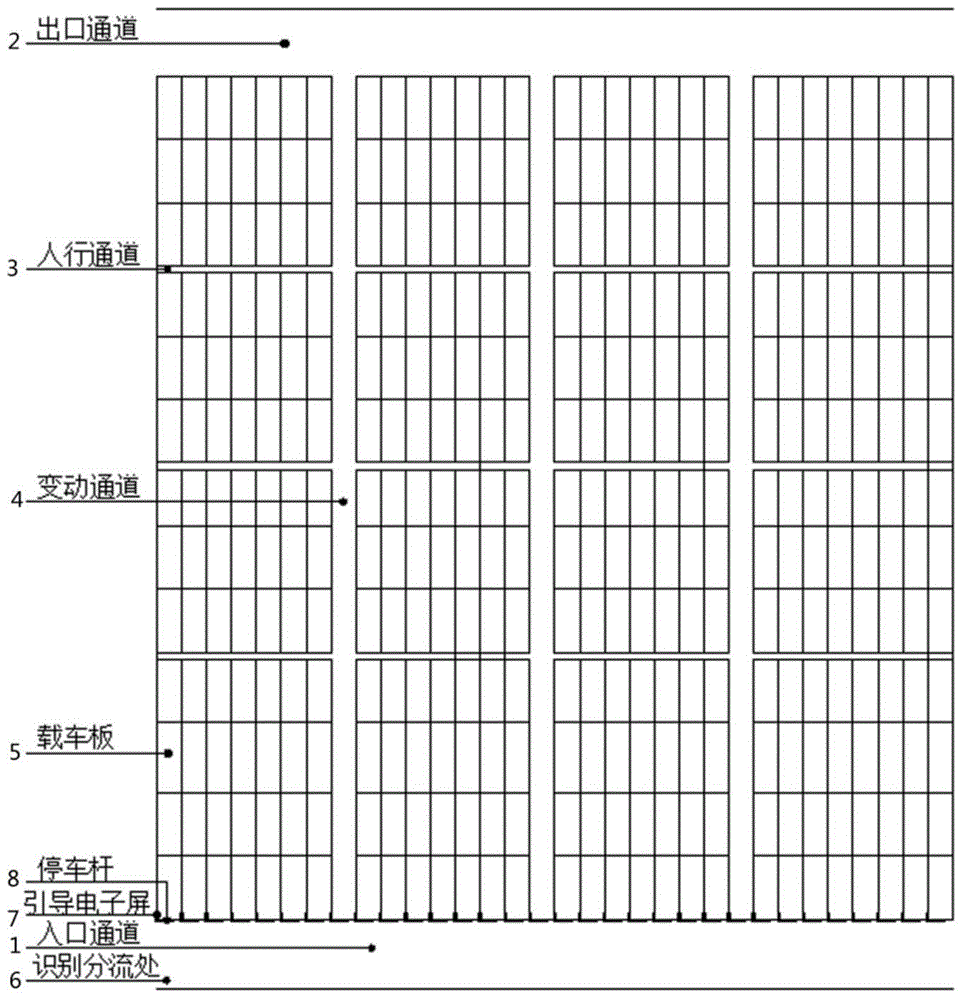
Horizontal-transverse-moving no-fixed-driveway parking system and parking control method based on parking system
The invention discloses a horizontal-transverse-moving no-fixed-driveway parking system and a parking control method based on the parking system and belongs to the technical field of parking equipment. A parking lot structure comprises an entrance passageway and an exit passageway, wherein the entrance passageway and the exit passageway are parallel to each other; tracks are laid in a parking area between the entrance passageway and the exit passageway; a plurality of vehicle carrying boards which can horizontally and transversely move along the tracks are densely laid on the tracks; each vehicle carrying board serves as a parking space, and longitudinal parking columns and transverse parking rows are formed through connecting the densely-laid vehicle carrying boards; a plurality of change lanes, where the vehicle carrying boards are not arranged, are further reserved on the tracks, and the vehicle carrying boards can horizontally and transversely move to the locations of the change lanes; a plurality of pedestrian passageways are further arranged in the parking area and are vertical to the change lanes. According to the parking system, the design is reasonable, the number of parking spaces is increased greatly, the safety is high, the failure rate is low, the operating efficiency is high, the planar high-density parking can be realized, and thus, the time efficiency of a whole parking process is effectively increased.
Owner:西安交投空间科技发展有限公司
Time sharing a single port memory among a plurality of ports
InactiveUS6920510B2Reduce areaReduce in quantityInput/output to record carriersImage codingComputer hardwareControl signal
Owner:AVAGO TECH INT SALES PTE LTD
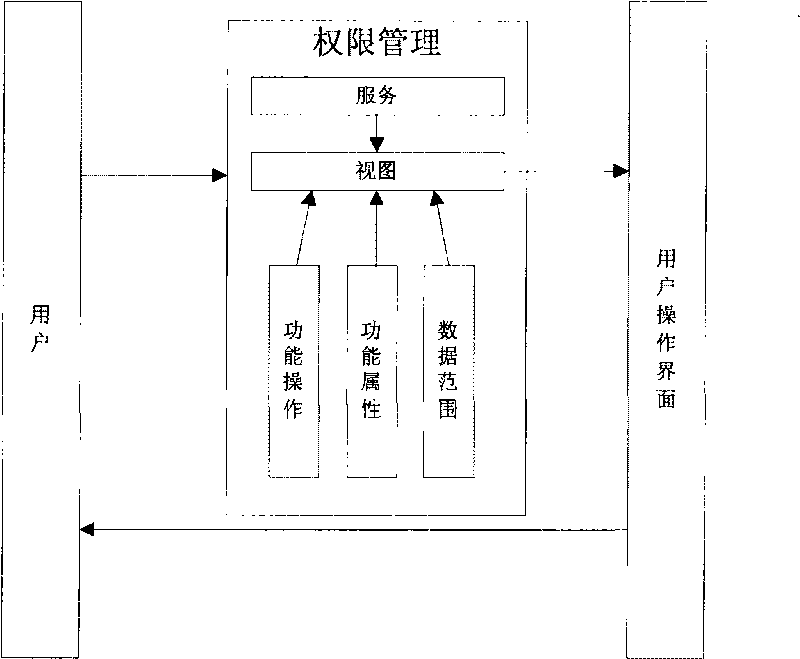
Service system-oriented and oriented object-based rights management method
InactiveCN101739526AReduce complexityFlexible support for security policiesDigital data authenticationVisibilityObject based
The invention discloses a service system-oriented and oriented object-based rights management method, belonging to the technical field of computer security. The method comprises the steps of: identifying the function of an operation system in the form of service; abstracting and organizing open service functions in the form of orienting an object; taking each service function as a rights management object; and enveloping the operation, the attribute and the data range which are contained by the function in the object to identify by being taken as an atomic scale rights management unit. By analyzing the scene, different views are abstracted to be taken as authorization templates of object levels. The function visibility of a user is controlled by ensuring whether the service has been distributed when authorizing, and a more perfect rights management mechanism is provided to an application developer by authorizing the rights management unit of the object level in each authorization template, thereby reducing the complexity of the authorization management and the management cost, flexibly supporting security policies of enterprises, and having great flexibility to the change of the enterprises.
Owner:BEIJING JIAXUN FEIHONG ELECTRIC CO LTD
Key reuse method and multifunctional key
ActiveCN103279203AImprove integrityIncrease flexibilityInput/output processes for data processingCapability managementKey pressing
The invention provides a key reuse method and a multifunctional key. The key reuse method and the multifunctional key resolve the technical problem of shortage of management in the function management process of passive optical network terminal equipment. According to the technical scheme, a timer is arranged through the motion of the functional key, a plurality of different time lengths can be preset on the timer, and different preset functional operations are triggered according to the time length that the functional key keeps closed. The key reuse method and the multifunctional key strengthen the integrality and flexibility of function management of the passive optical network terminal equipment, and strengthen the practicability of the passive optical network terminal equipment, and provide friendlier user experience for users of the passive optical network terminal. Meanwhile, the key reuse method and the multifunctional key are also suitable for coordinated management on the passive optical network terminal equipment among the users of the passive optical network terminal or network administrators, and reduce the management consumption of network operators or the network administrators.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
Method for dynamic information technology infrastructure provisioning
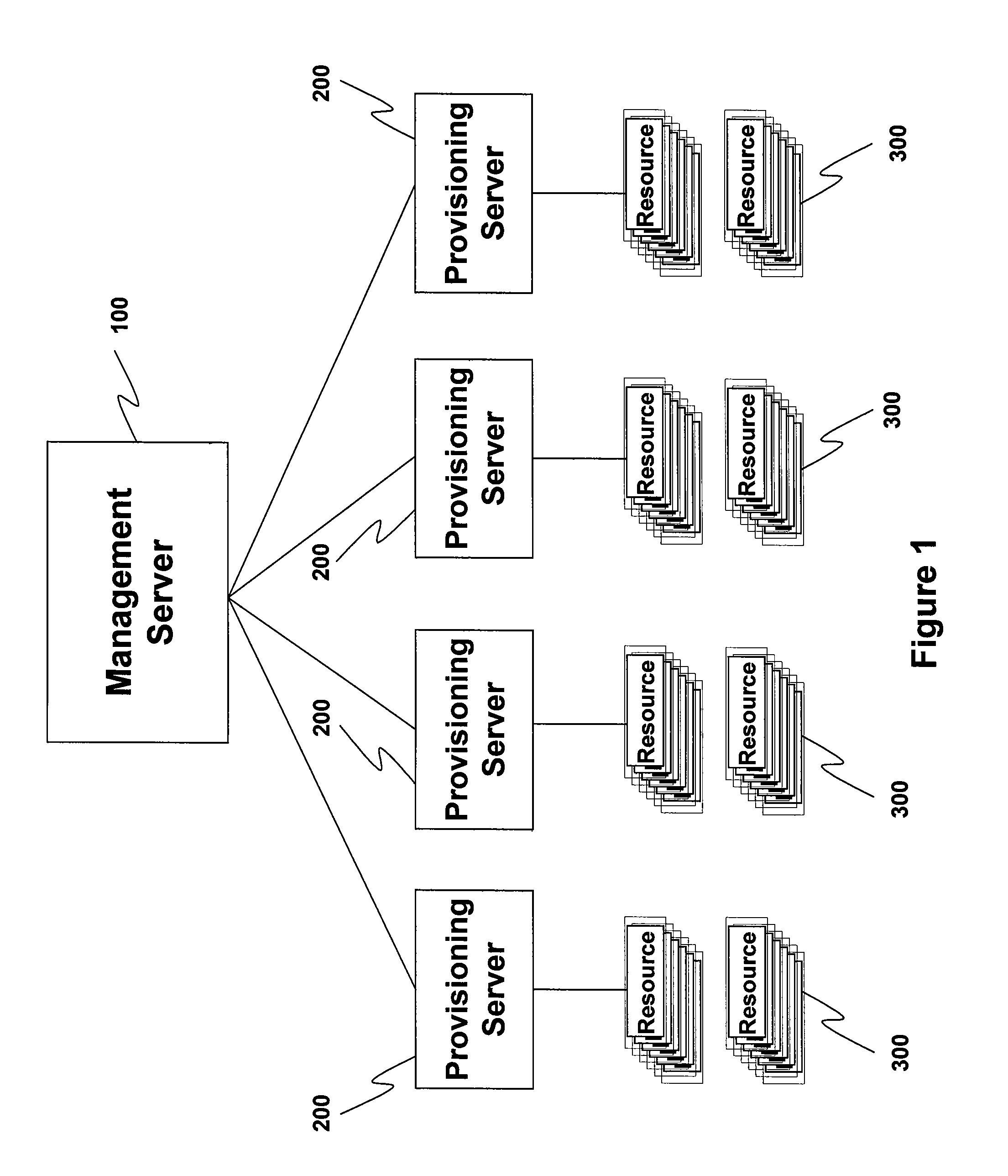
InactiveUS20070294736A1Reduce in quantityMinimal amountData switching by path configurationTwo-way working systemsResource poolNetwork overhead
Provisioning and management resources are drawn from an overall pool of resources. Management and managed resources are then dynamically associated on the network to securely perform requested on-demand management functions. Since the managing system controls the networking between the devices that are managed or provisioned, the linkage of resources incurs a minimal amount of network overhead. Since provisioning resources are themselves dynamically built and automatically associated with the resources being managed, a dramatically reduced management overhead is achieved.
Owner:IBM CORP
Use of iterative learning for resolving scalability issues of bandwidth broker
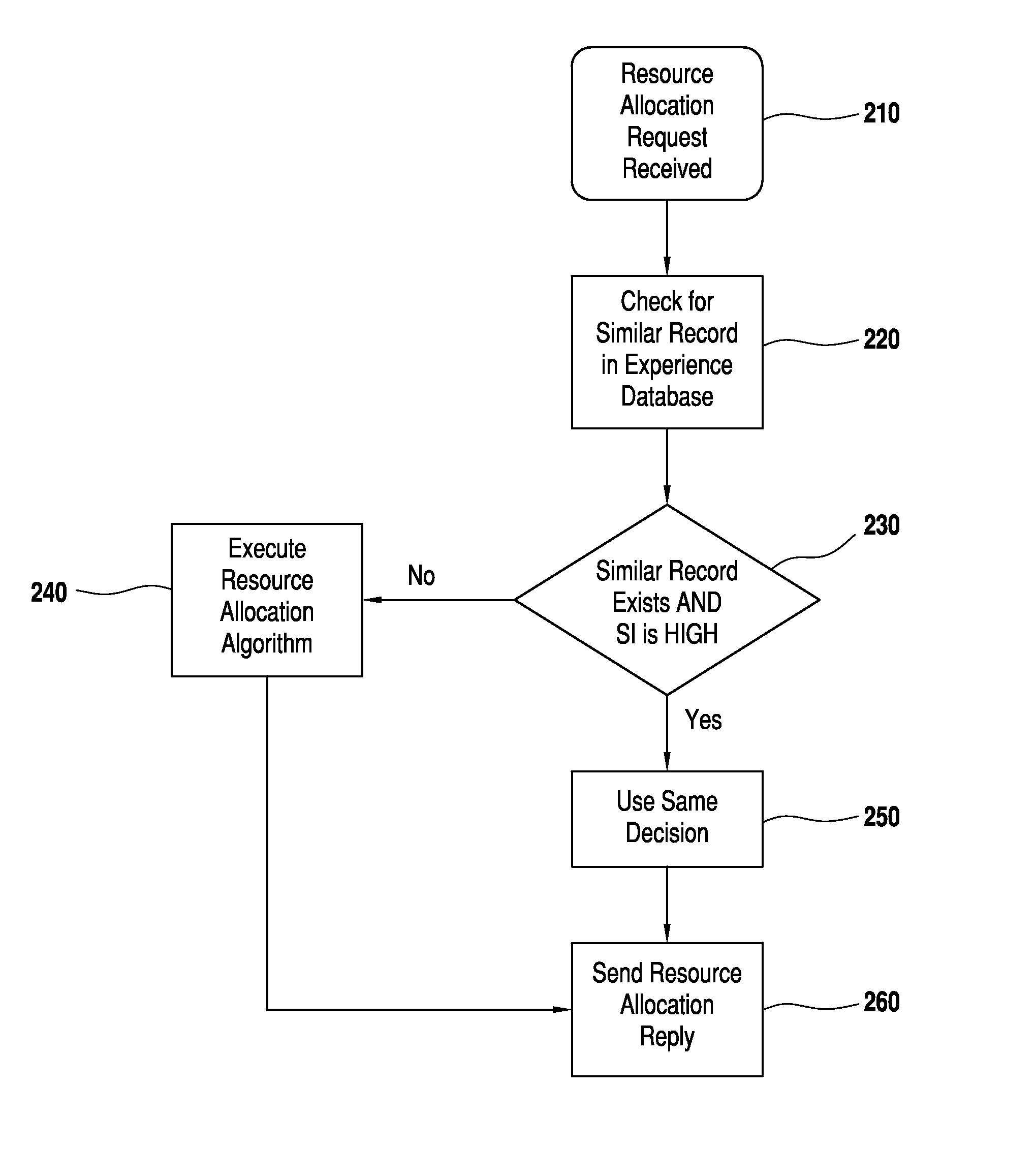
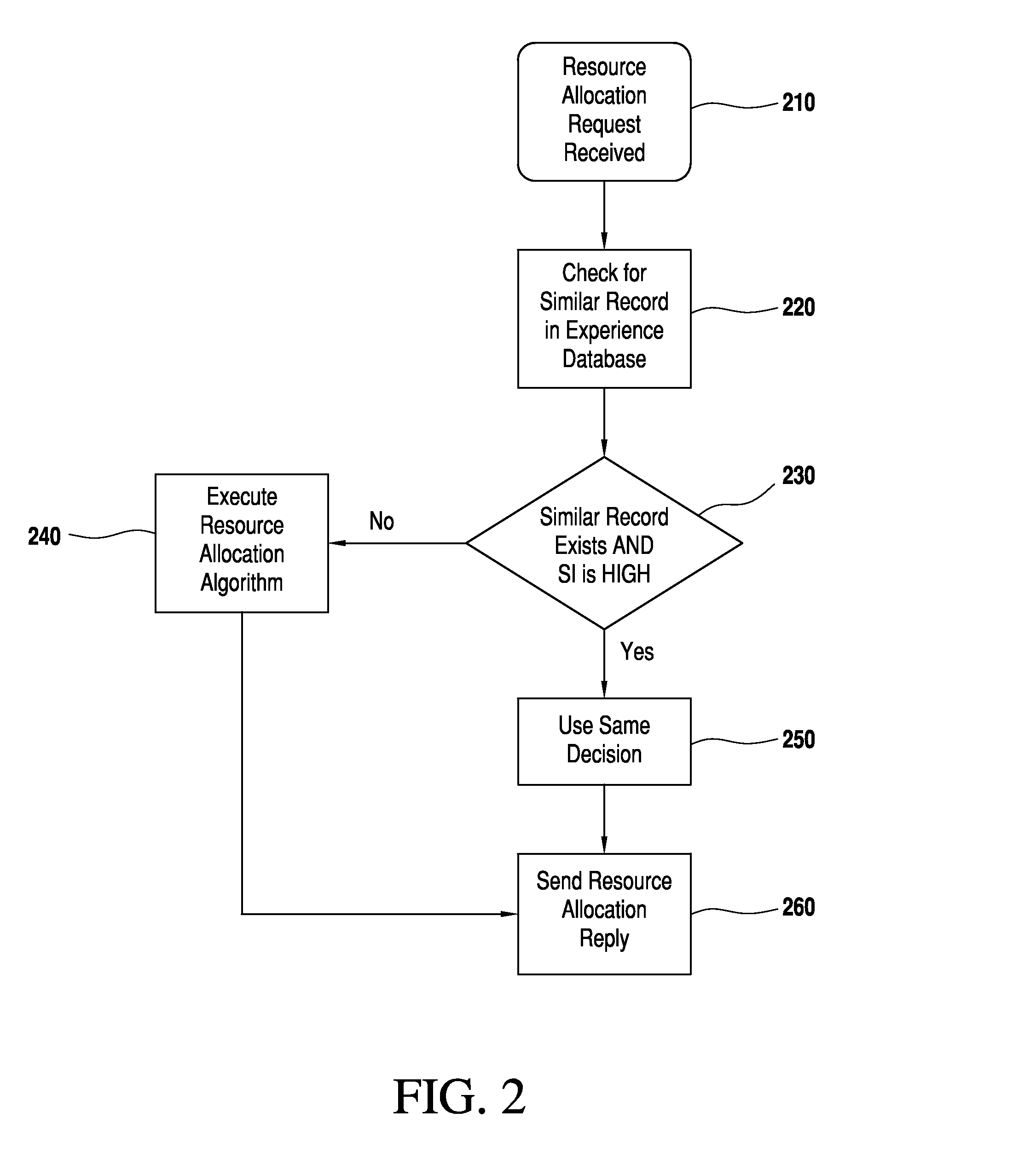
InactiveUS20150100694A1Improve optimalImprove quickDigital computer detailsData switching networksExtensibilityInternet network
A centralized bandwidth broker (a special network server) functioning as a domain manager in an internet network having differentiated services architecture is responsible for receiving and replying to a large number of requests and for performing huge numbers of resource management tasks at the inter- and intra-domain level. Consequently, it can have scalability issues. According to the invention the bandwidth broker maintains an experience database in addition to information about other aspects of the network, and uses iterative learning for solving scalability issues by using information of previous good experiences to take future resource management decisions. Based on similarity with previous network and request conditions, the new decision can be taken without executing resource intensive algorithms. The database of experience is continuously updated for optimized iterative learning. Processing overhead is reduced, enabling a single bandwidth broker to manage big networks with large numbers of users.
Owner:UMM AL QURA UNIVERISTY
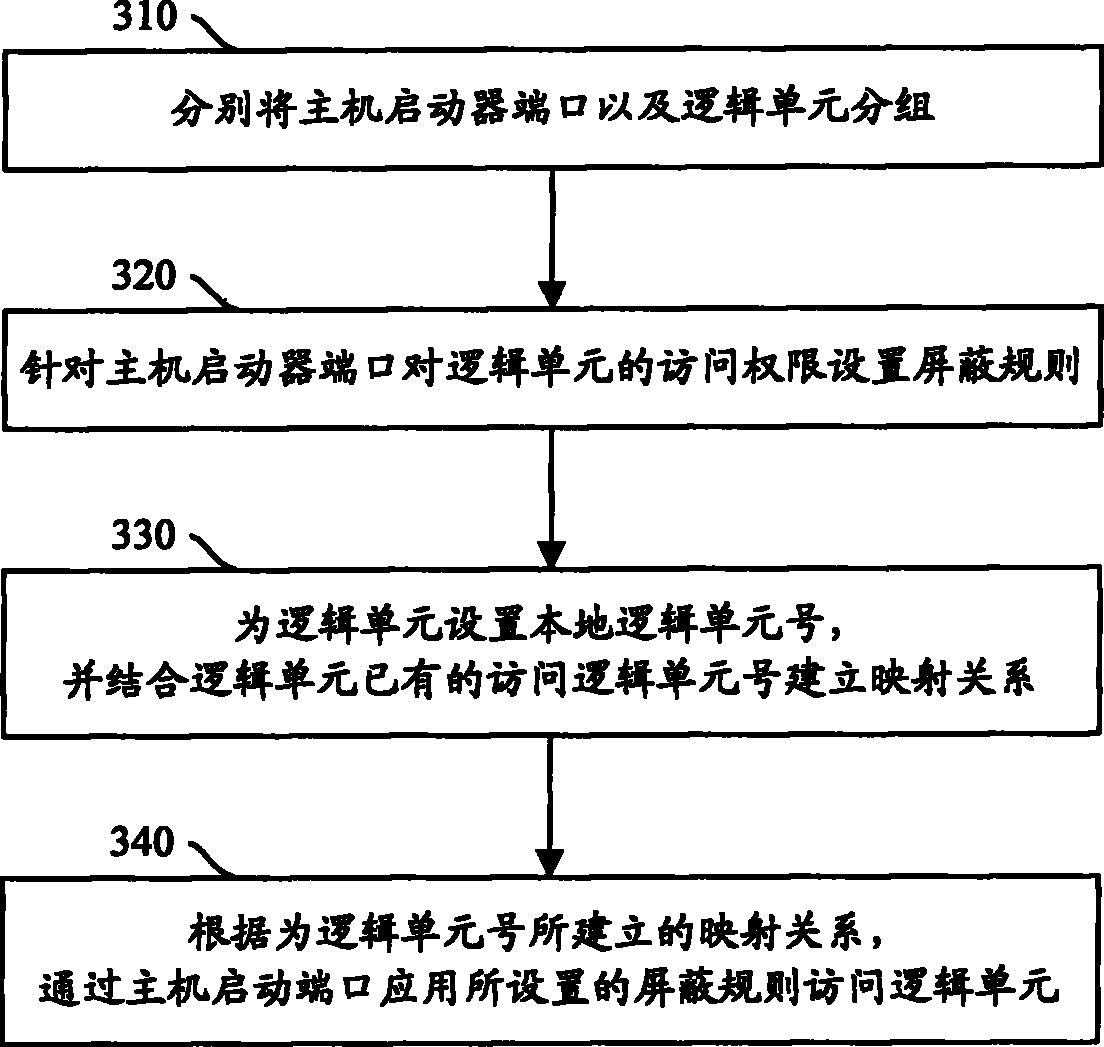
Method and device for realizing access control
InactiveCN101815036AImprove satisfactionReduce administrative overheadData switching networksApplication softwareMedia access control
The invention discloses a method and a device for realizing access control. The method comprises the following steps of: setting a shielding rule for the access authority of logical units aiming at a port of an initiator of a host; setting local logical unit numbers for the logical units, and establishing the mapping relationship between the local logical unit numbers and access logical unit numbers by combining the existing access logical unit numbers of the logical units; and according to the mapping relationship established for the logical unit numbers, accessing the logical units by using the set shielding rule through the an initiating port of the host. By adopting the method and the device of the invention, the access authority still can be limited and the access control is realized based on the access authority under the condition that a special hardware facility or special solidified application software does not need to be added in a network, so that the method and the device reduce management overhead without causing additional network burden; and because the settings of shielding and mapping have flexibility, the flexibility of the change of user requirements can be met, the work efficiency of a system is increased, and user satisfaction is improved.
Owner:GLOBAL INNOVATION AGGREGATORS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com