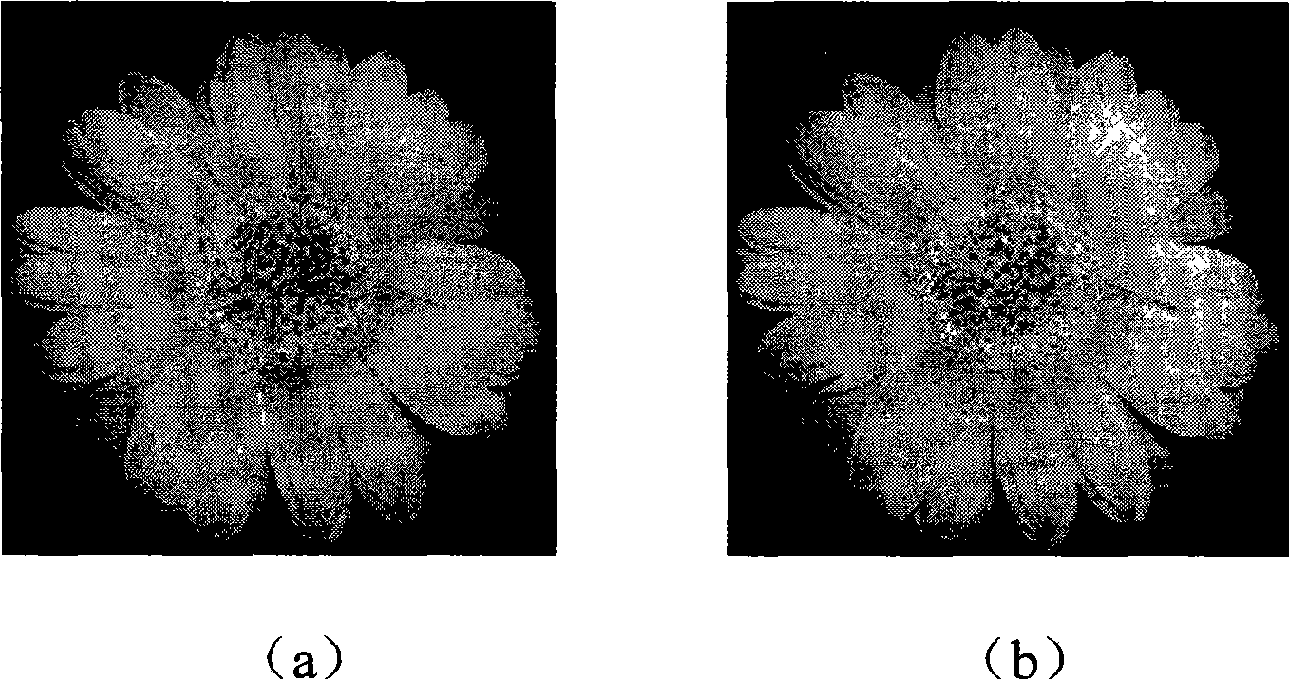Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
116results about How to "Guaranteed Data Integrity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
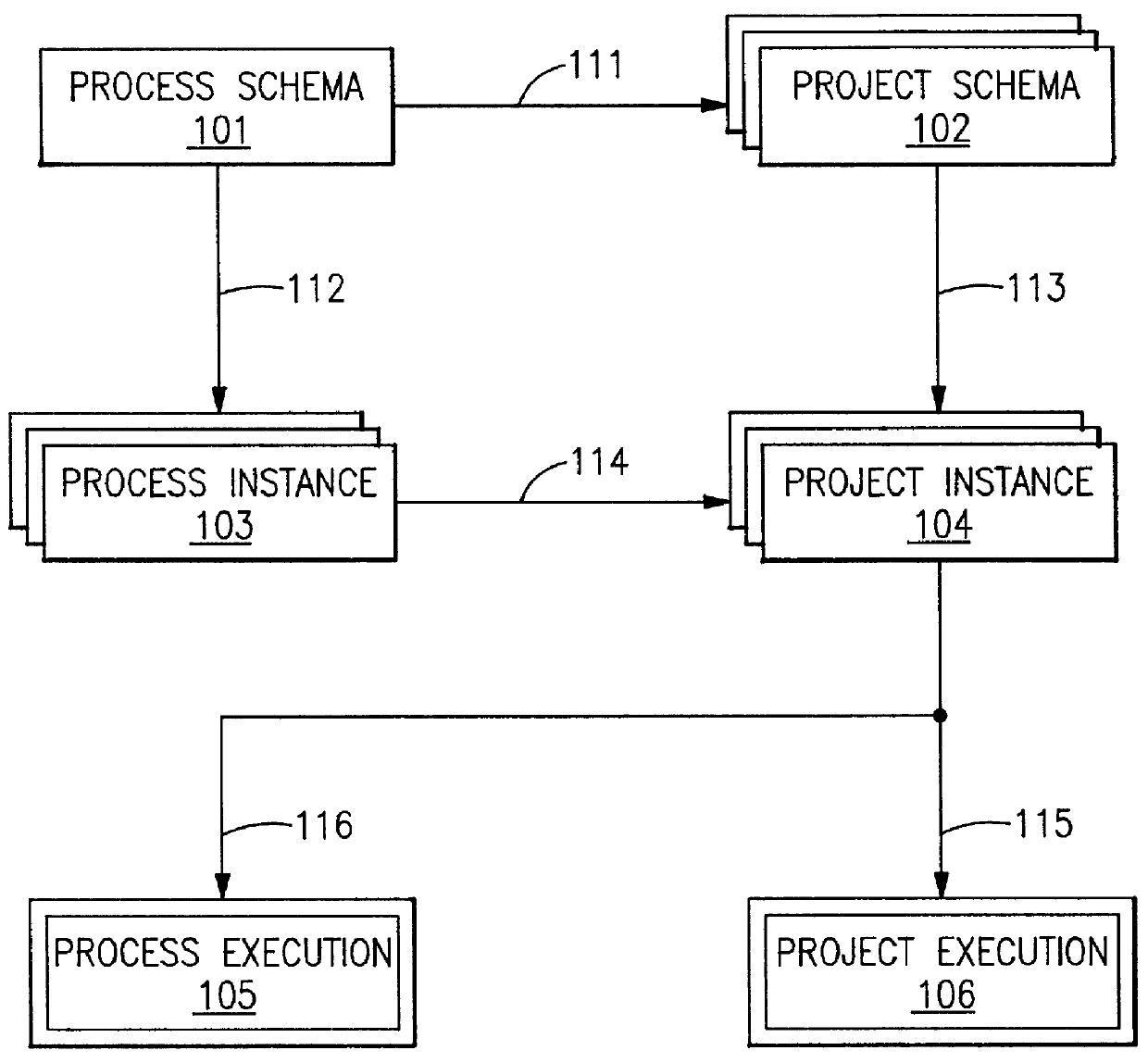
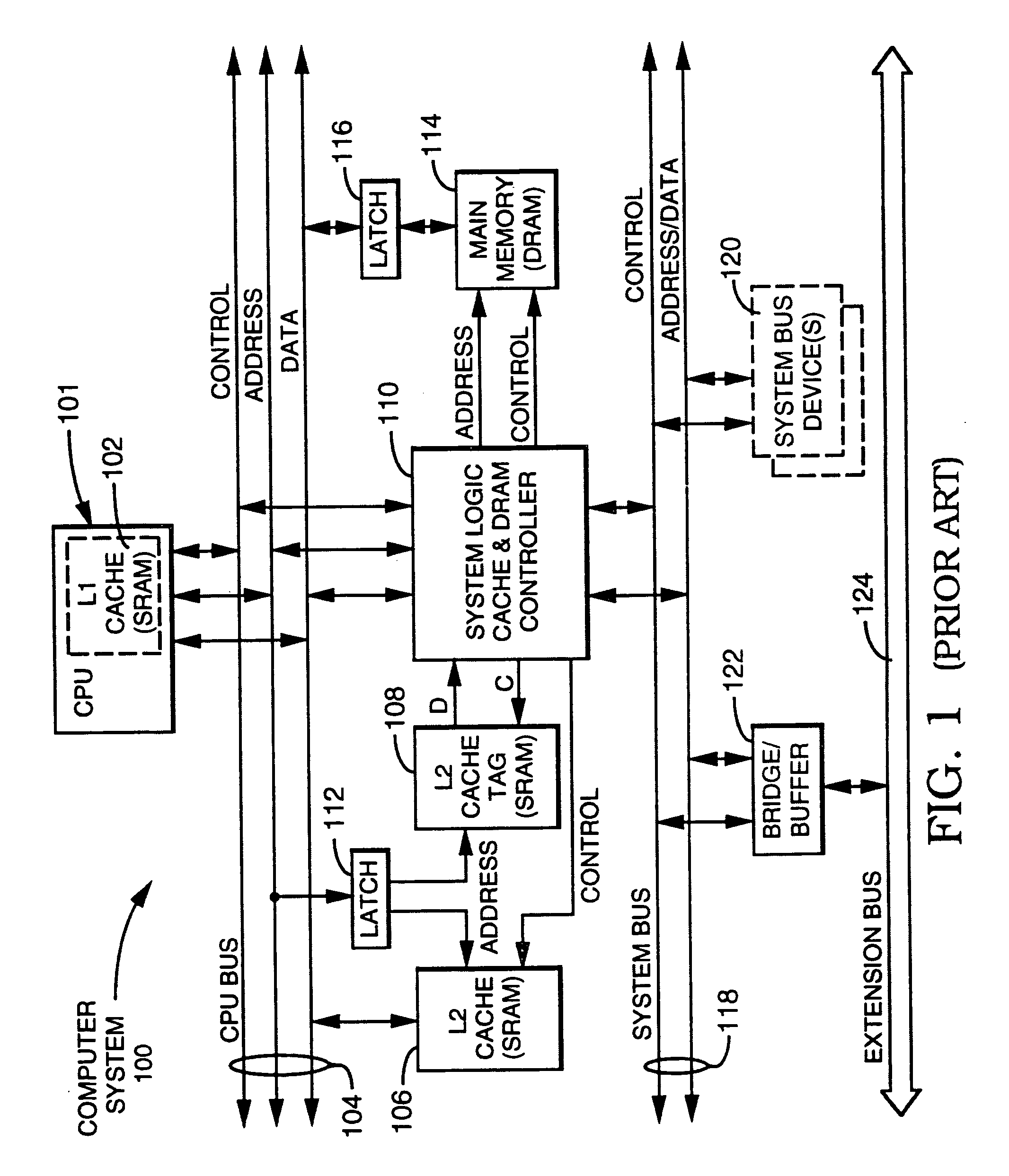
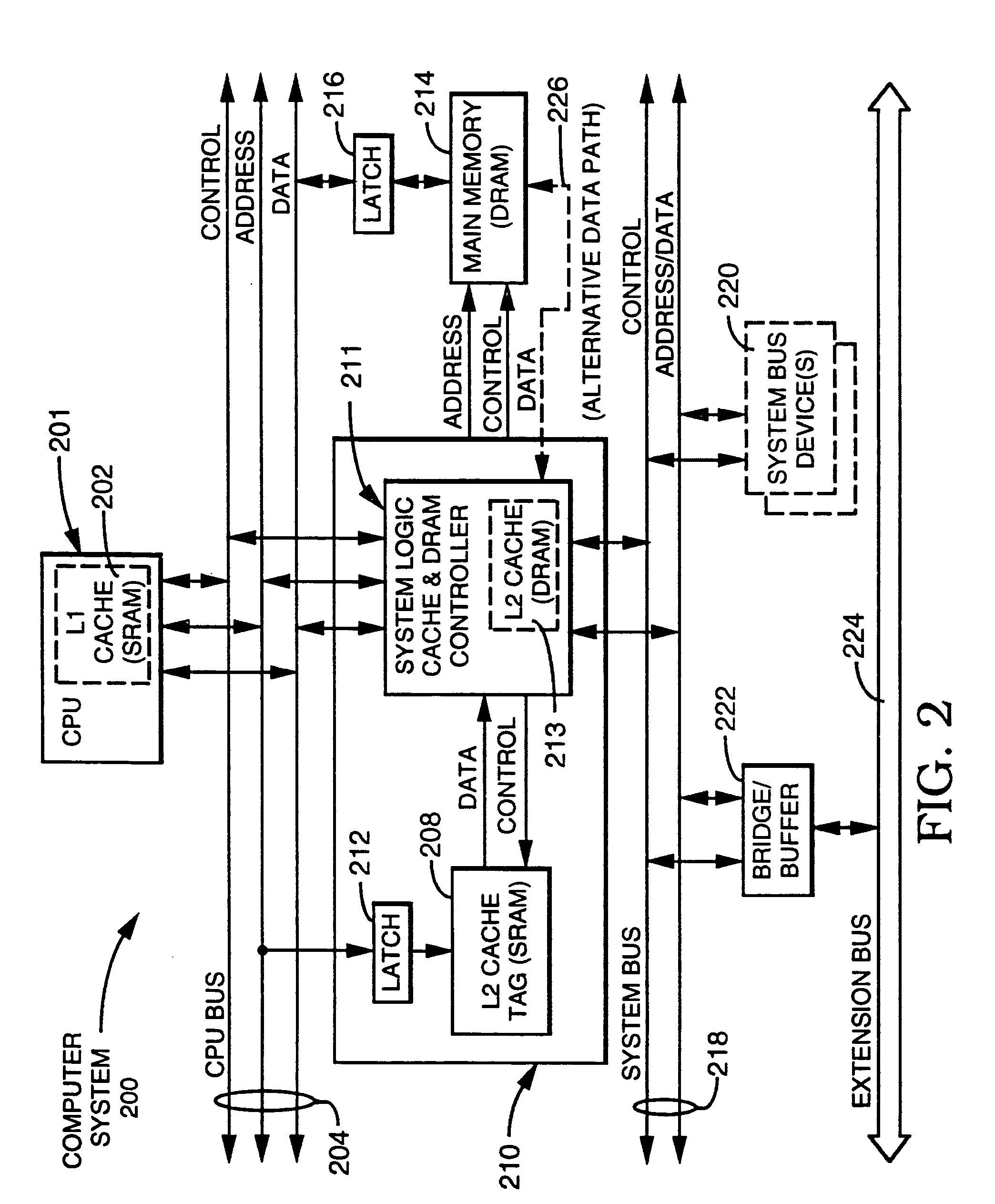
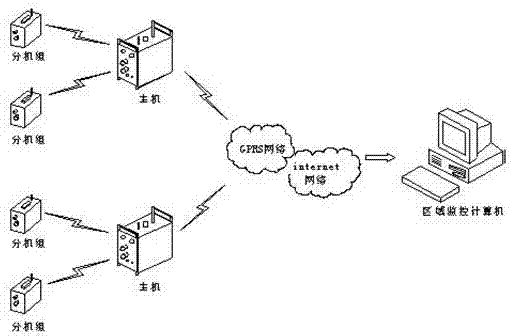
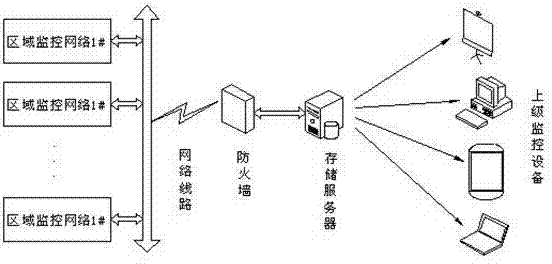
Method and apparatus for a process and project management computer system
InactiveUS6023702AReduce storageImprove performanceProgram control using stored programsResourcesDigital dataModularity
PCT No. PCT / EP95 / 03289 Sec. 371 Date Dec. 10, 1998 Sec. 102(e) Date Dec. 10, 1998 PCT Filed Aug. 18, 1995 PCT Pub. No. WO97 / 07472 PCT Pub. Date Feb. 27, 1997The inventive concept comprises a system platform for a synergistic, role modular work process environment. A work process object (WPO) (1001) is created, residing in a data base, and stored in a memory of the process and project management computer system (1030). All data concerning the process and project management are reported to said work process object (WPO) (1001) and said work process object (WPO) (1001) is used as a common data base. According to the inventive concept, each view must be supported by a specific workplace, represented by digital data and enforcing the rules for the specific role. A work process information model supports the dynamic definition and use of a data base object representing a work process, boch in its process and project planning modes and its execution. According to the inventive concept, one object supports simultaneously all modes delimited by dynamically moving boundaries. Workplace implementation enforces over-all rules for each role in the inventive system.
Owner:IBM CORP
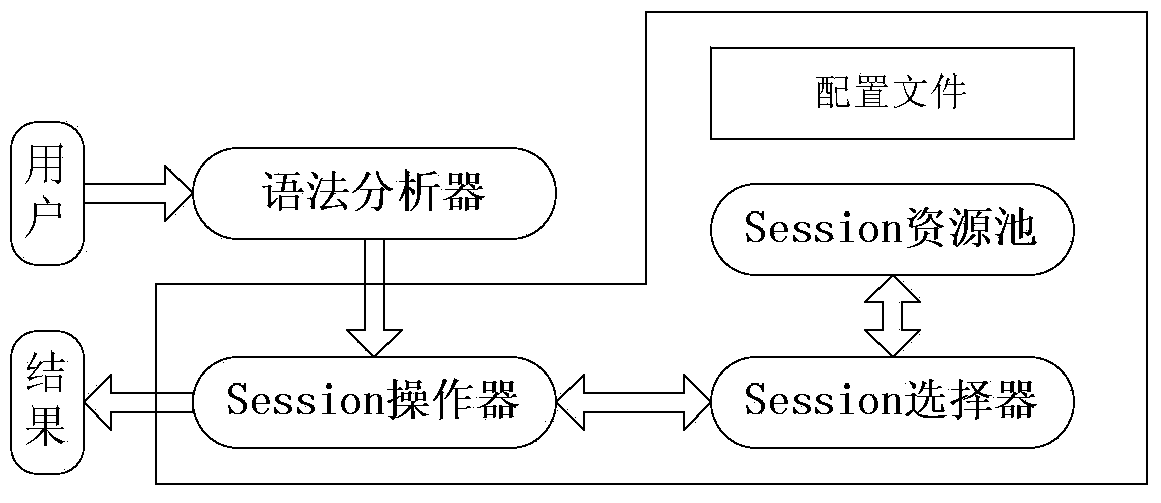
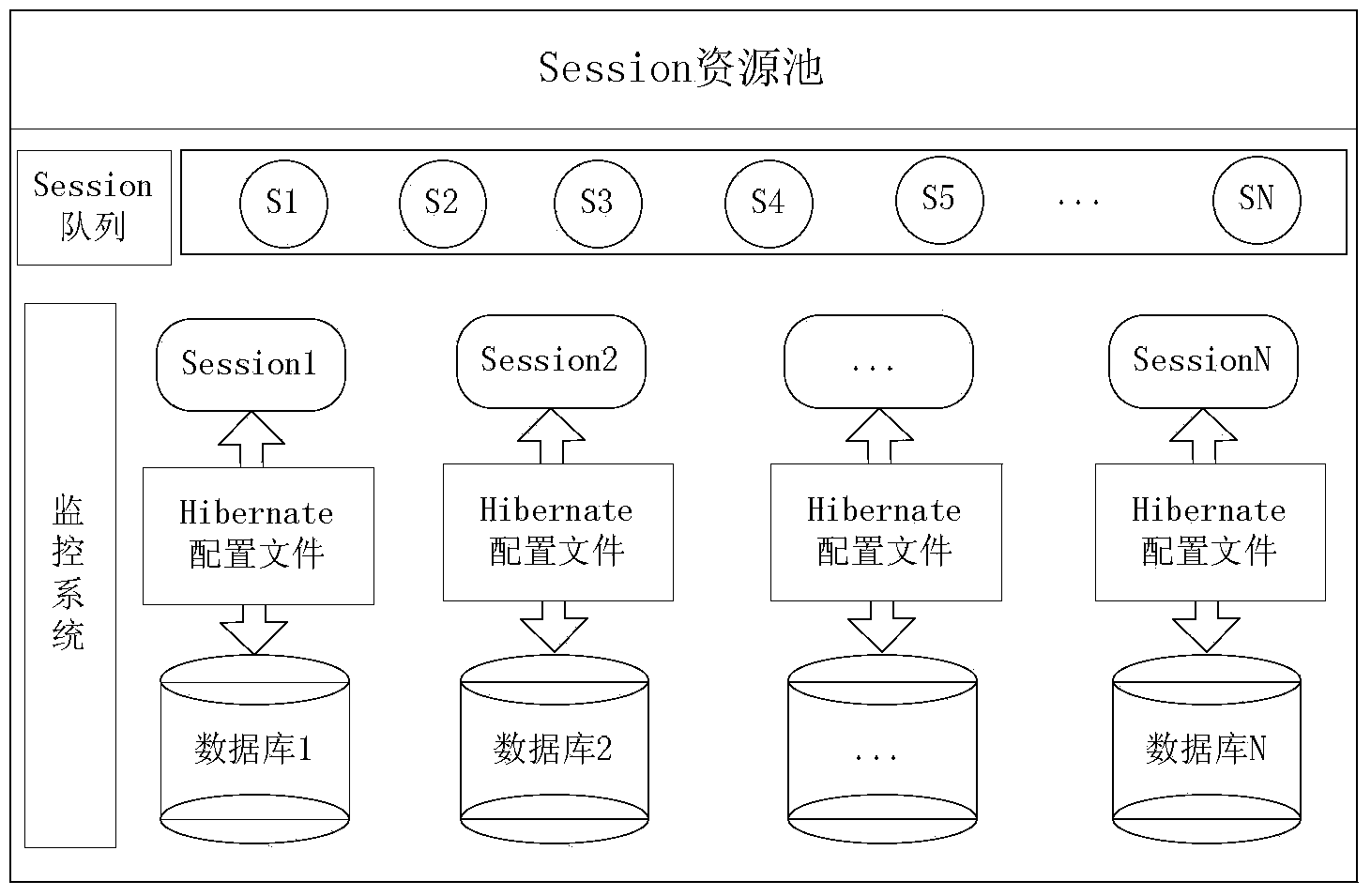
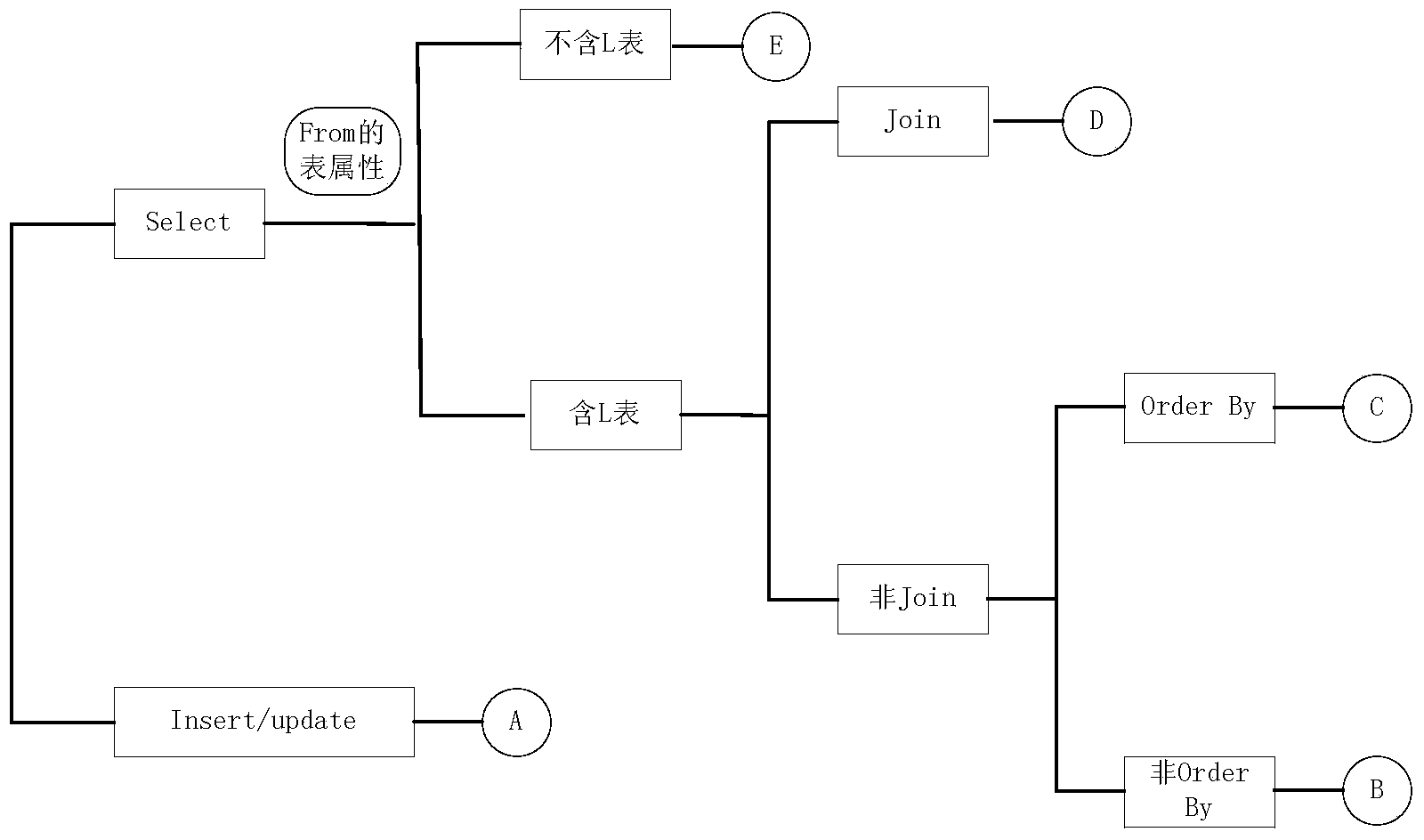
Large data inquiring method based on distribution relation-object mapping processing
ActiveCN103678609AGuaranteed Data IntegrityGuaranteed query efficiencyRelational databasesSpecial data processing applicationsData processingData mining
The invention discloses a large data inquiring method based on distribution relation-object mapping processing. The method includes the following steps that firstly, m data processing nodes are selected, a Hibernate Session object is constructed for each data processing node, a distributed Hibernate framework is obtained and a Session resource queue is generated; secondly, a configuration file is set, a storage strategy and a routing strategy corresponding to a list of each type are set, an S list with a data volume is backed up at each data processing node, and an L list with a large data volume is stored to the m data processing nodes in a blocking mode; thirdly, an input inquiring request is analyzed and a corresponding processor is selected according to the type of the inquiring request; fourthly, the selected processor selects the corresponding node from the resource queue to process the inquiring request according to the inquiring request, the corresponding routing strategy, and a processing result is protocoled. The large data inquiring method based on distribution relation-object mapping processing can obviously improve the rate of inquiring large data lists.
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
Network data aggregation method for wireless sensor
InactiveCN104967517AGuaranteed confidentialityGuaranteed Data IntegrityUser identity/authority verificationSpecial data processing applicationsData integrityConfidentiality
The invention belongs to the technical field of wireless communication, and specifically relates to a network data aggregation method for a wireless sensor. The method is based on an elliptical curve homomorphic encryption algorithm, a safety outsourcing algorithm and an aggregation signature algorithm based on identity, and is a verifiable wireless sensor network data safety aggregation method. The beneficial effects of the invention are that the method employs the elliptical curve homomorphic encryption algorithm, the aggregation signature algorithm based on identity and the safety outsourcing algorithm to enable a semi-credible aggregator to work in a more severe network environment so as to obtain needed aggregation statistic data; moreover, the method can achieve the functions of confidentiality guarantee, data integrity guarantee, data source authentication guarantee, and replay attack resistance, so the method is better in prospect of actual application.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
APK signature authentication method and APK signature authentication system
ActiveCN105391717AReduce maintenance costsEasy to installUser identity/authority verificationAuthentication system
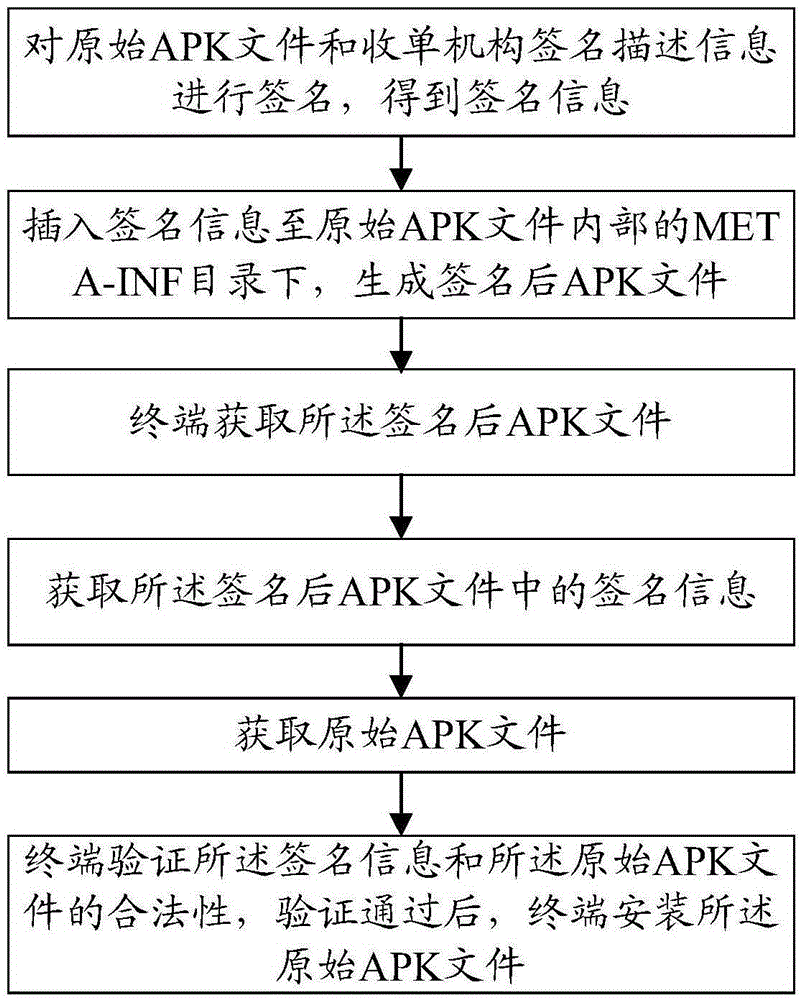
The invention provides an APK signature authentication method and an APK signature authentication system. The method comprises the following steps: an original APK file and an acquiring mechanism are signed based on signing description information to get signature information; the signature information is inserted under an META-INF directory inside the original APK file, and a signed APK file is generated; a terminal acquires the signed APK file; the terminal acquires the signature information in the signed APK file; the terminal acquires the original APK file; and the terminal verifies whether the signature information and the original APK file are legitimate, and the terminal installs the original APK file after the signature information and the original APK file pass verification. The signed file is stored under the META-INF directory, the original APK file is restored when a manufacturer verifies the signed APK file, and thus, the APK file passes verification of the manufacturer. Meanwhile, a native signature verification mechanism of a terminal operating system for the original APK file is not affected, unified APK signature is realized, and the compatibility of the terminal operating system is improved.
Owner:FUJIAN LANDI COMML TECH CO LTD
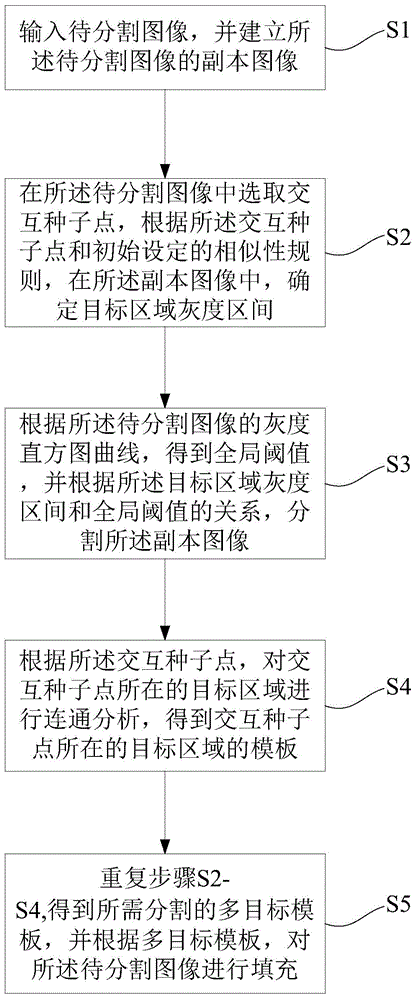
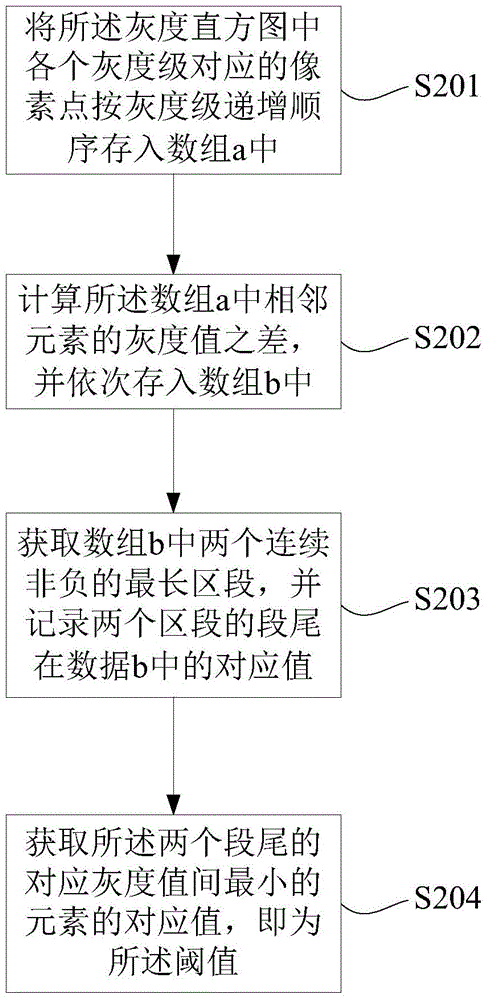
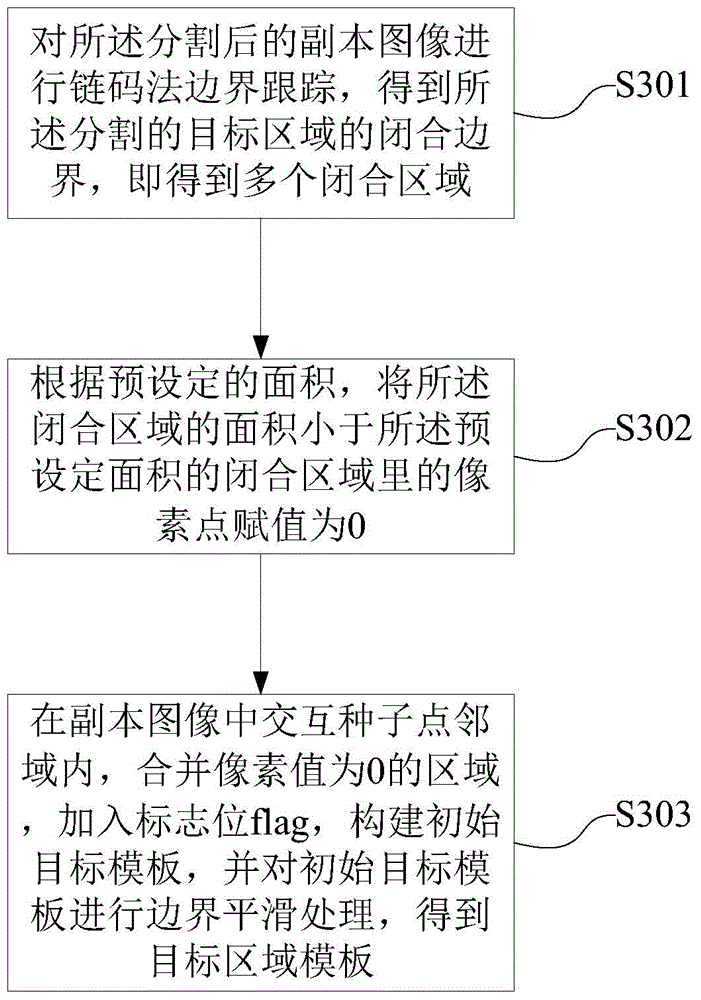
Multi-target interactive image segmentation method and device
The invention provides a multi-target interactive image segmentation method and device. The method comprises the following steps that (1) an image to be segmented is inputted, and a duplicate image of the image to be segmented is established; (2) an interactive seed point is selected in the image to be segmented, and a target area gray scale section is confirmed according to the interactive seed point and the initially set similarity rule; (3) a global threshold is obtained according to the gray scale histogram curve of the image to be segmented, and the duplicate image is segmented according to the relation between the target area gray scale section and the global threshold; (4) connection analysis is performed on a target area in which the interactive seed point is positioned according to the interactive seed point so that a target area template in which the interactive seed point is positioned is obtained; and (5) the steps (2)-(4) are repeated so that the required segmented multi-target template is obtained, and the image to be segmented is filled according to the multi-target template. Reliable segmentation of the target area can be guaranteed by the technical scheme, and interactive multi-target combined segmentation and management can also be realized.
Owner:WUHAN UNITED IMAGING HEALTHCARE CO LTD +1
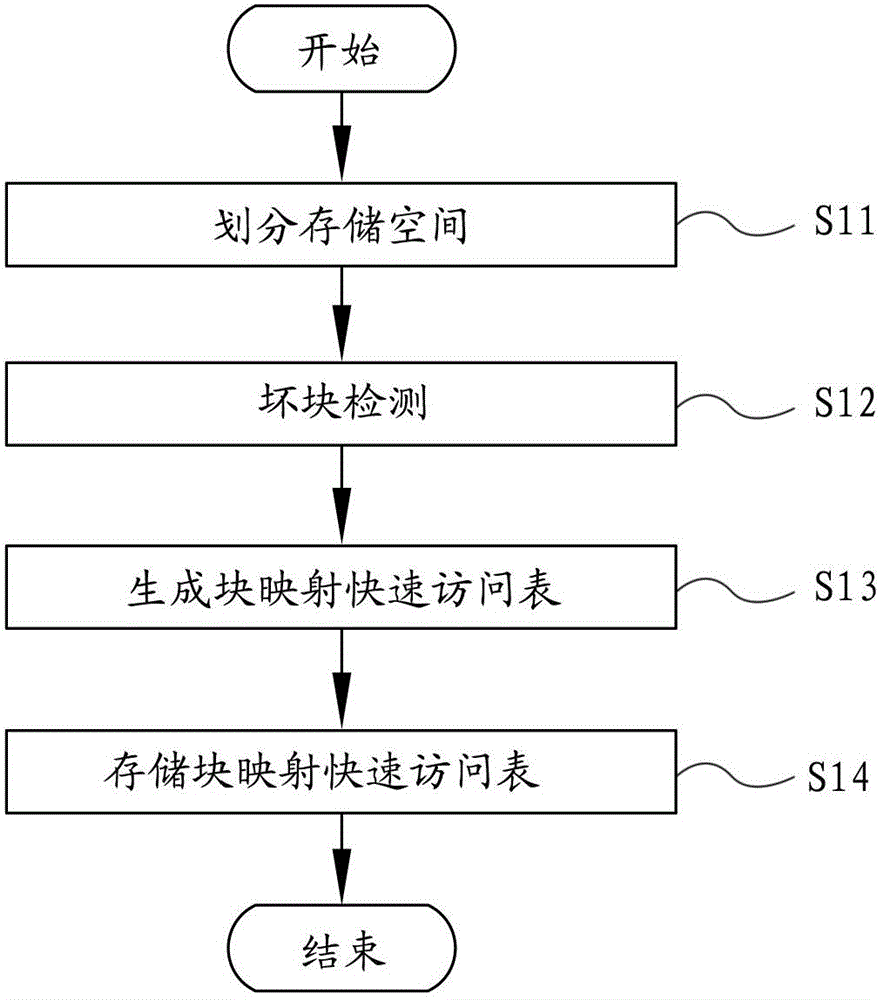
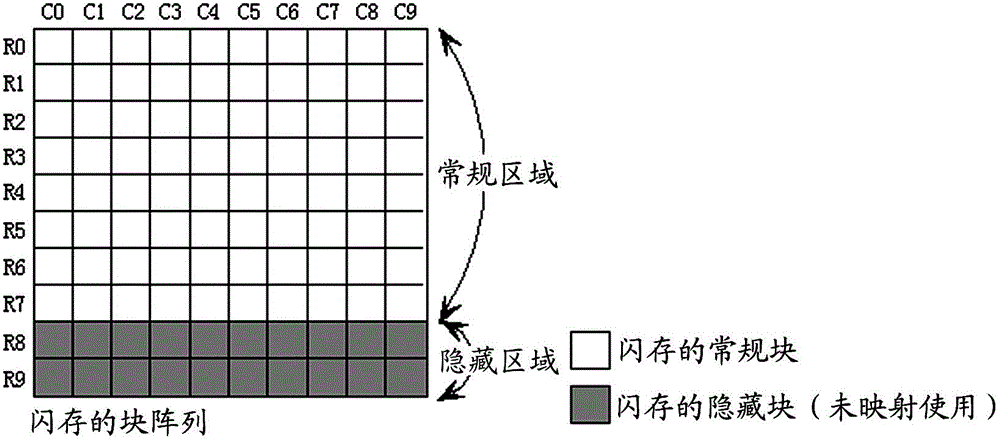
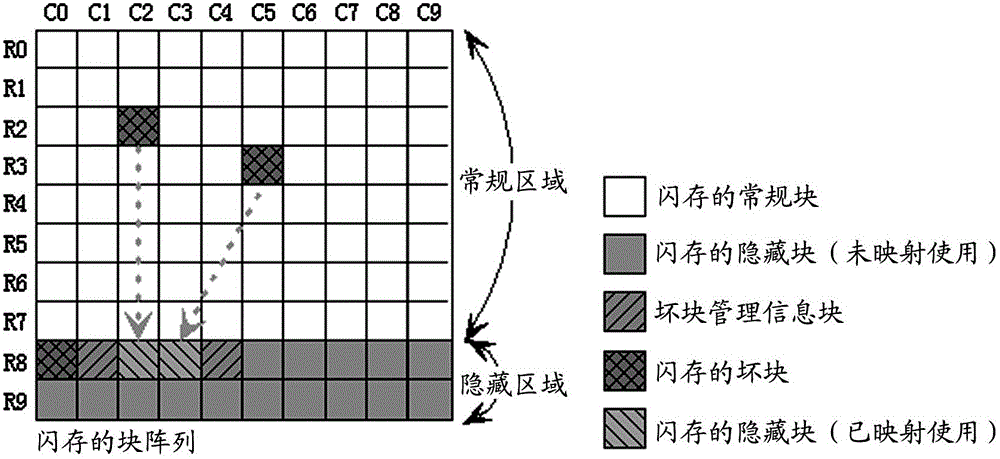
Bad block management method for flash memory
ActiveCN102722443AGuaranteed reliabilityAvoid destructionMemory adressing/allocation/relocationBlock detectionSpace partitioning
The invention provides a bad block management method for a flash memory. The method comprises the following steps of: dividing the storage space of the flash memory into a first area comprising a plurality of blocks and a second area comprising a plurality of blocks; performing bad block detection on the flash memory to acquire information about bad blocks; establishing a mapping relation between the bad blocks in the first area and normal blocks in the second area according to the acquired information about the bad blocks, and generating a block mapping quick access table comprising the information about the established mapping relation; and respectively storing the generated block mapping quick access table into a plurality of bad block management information blocks in the second area, wherein a plurality of bad block management information blocks are any normal blocks which are positioned in the second area and do not have the mapping relation with the bad blocks in the first area.
Owner:SAMSUNG SEMICON CHINA RES & DEV +1
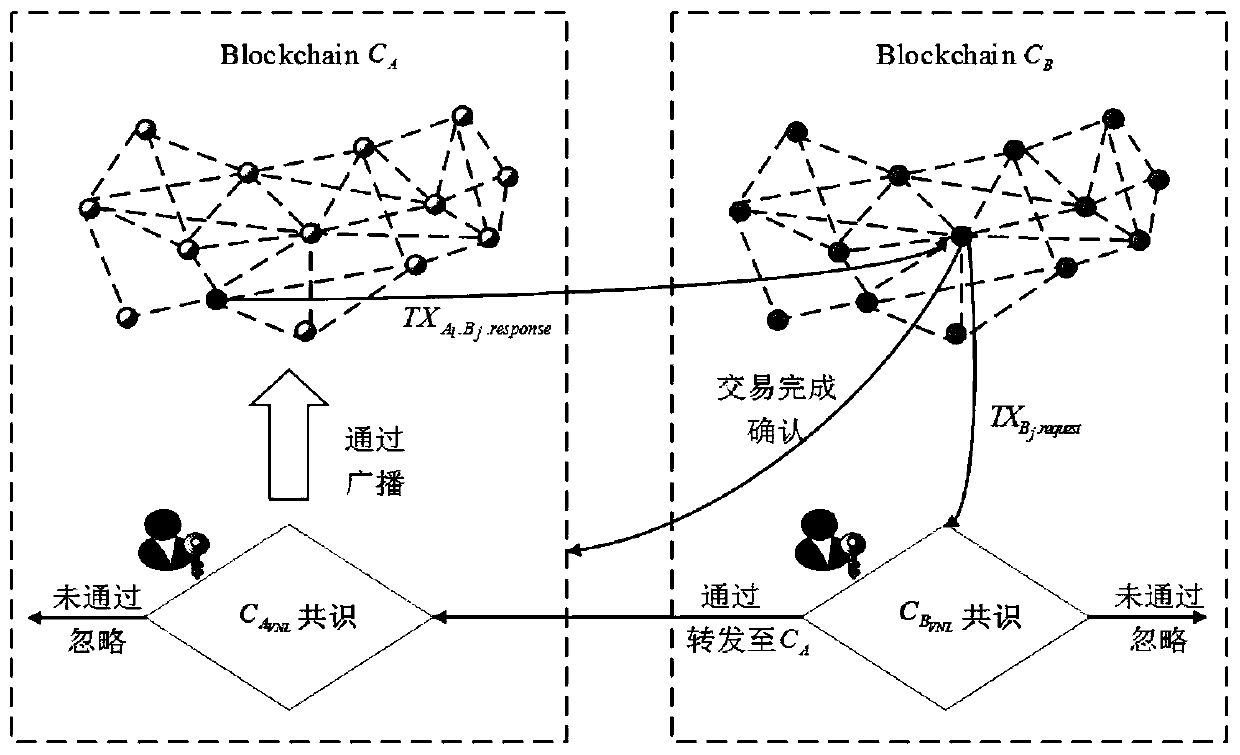
Medical alliance chain lightweight dynamic autonomous cross-chain interaction method
ActiveCN110993044AGuaranteed Data IntegrityGuarantee data reliabilityDigital data protectionPatient-specific dataDigital signatureSmart contract
The invention belongs to the technical field of medical alliance chains, and discloses a medical alliance chain lightweight dynamic autonomous cross-chain interaction method. The method comprises thesteps: constructing a cross-chain consensus mechanism based on a threshold digital signature; constructing a cross-chain path certification signature, including group key generation and sharing, threshold subgroup signature generation and path certification updating; and realizing the value transfer among different alliance chain nodes. According to the method, the inter-node communication topology of a medical alliance chain is simplified, a node cross-chain communication model based on an intelligent contract state period and a node cross-chain communication identity credibility path provingconstruction rule are given, and dynamic construction and verification of inter-chain transaction interactive credible path proving are carried out; the consensus process of cross-chain transactionsby a plurality of alliance chain verification node lists is modeled into a threshold digital signature process with a plurality of privilege subgroups, so the alliance chain internal consensus based on the verification node lists is expanded into the inter-alliance chain cross-chain consensus on the premise of not increasing the computational complexity.
Owner:ZHOUKOU NORMAL UNIV
Data synchronization method and device, electronic device and storage medium
ActiveCN107590277AGuaranteed Data IntegrityAchieve synchronizationSpecial data processing applicationsData synchronizationData integrity
The embodiment of the invention provides a data synchronization method and device, an electronic device and a storage medium, and relates to the technical field of computers. The data synchronizationmethod includes the steps of monitoring data operation events occurring in a source database by a trigger arranged in the source database, generating corresponding data operation records based on themonitored data operation events, and synchronizing the source database with a target database according to the data operation records. According to the technical scheme, various data operation eventsoccurring in the source database can be monitored, and meanwhile the synchronization between the source database and the target database can be achieved under the precondition of maintaining data integrity.
Owner:TAIKANG LIFE INSURANCE CO LTD +1
A method of traceability information security of agricultural products based on block chain technology
InactiveCN109146524ARealize distributed accountingGuaranteed Data IntegrityFinanceUser identity/authority verificationProduct traceabilityProduct base
The invention relates to the technical field of traceability information security of agricultural products, in particular to a traceability information security solution of agricultural products adopting block chain technology. The method comprises the following steps: an improved consensus mechanism being obtained, wherein the improved consensus mechanism is that when all entity terminals hold blocks to be submitted for verification, in order to maximize their own benefits, no entity terminal can change the verification result of blocks generated by packaging other entity terminals; conducting multi-level traceability information verification; using multi-private-key rules to control access rights; through the improved consensus mechanism, multi-level traceability information verificationand multi-private key rules for access control, distributed bookkeeping being realized. The invention solves the data storage safety problem existing in the agricultural product traceability system.
Owner:ZHOUKOU NORMAL UNIV
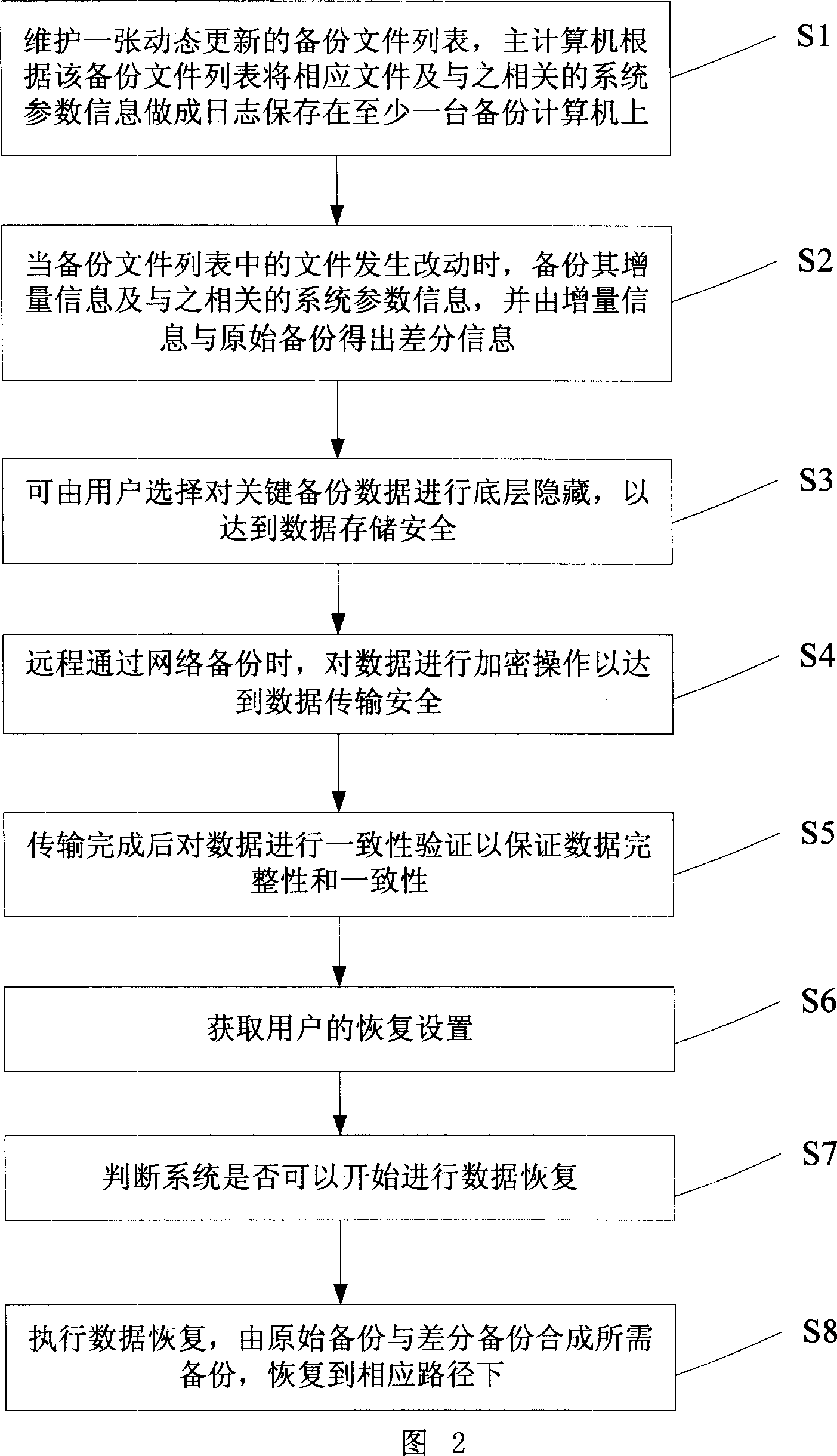
Computer network datarecovering method
InactiveCN1975683ASmall amount of data backupGuaranteed Data IntegrityTransmissionRedundant operation error correctionInformation technologyData transmission
The invention is a data backup method in computer networks, which belongs to the area of network information technology. The steps are: (1) maintain a backup files list which is dynamically updated; (2) Incremental backup information as well as related system parameters when files in the backup file list are changed, and obtain the difference information with the incremental information and original backup information; (3) bottom hide critical data selected by users; (4) encrypt data when they are remotely backup through network; (5) conduct consistency validation after the data transmission; (6) Get user's configuration for recovery; (7) judge whether system can start the data recovery; (8) conduct data recovery. Get the needed data from the original backup and incremental backup information and recover them to the corresponding paths.
Owner:SHANGHAI JIAO TONG UNIV
RFID (Radio Frequency Identification) system capable of ensuring confidentiality and data integrity and implementation method thereof
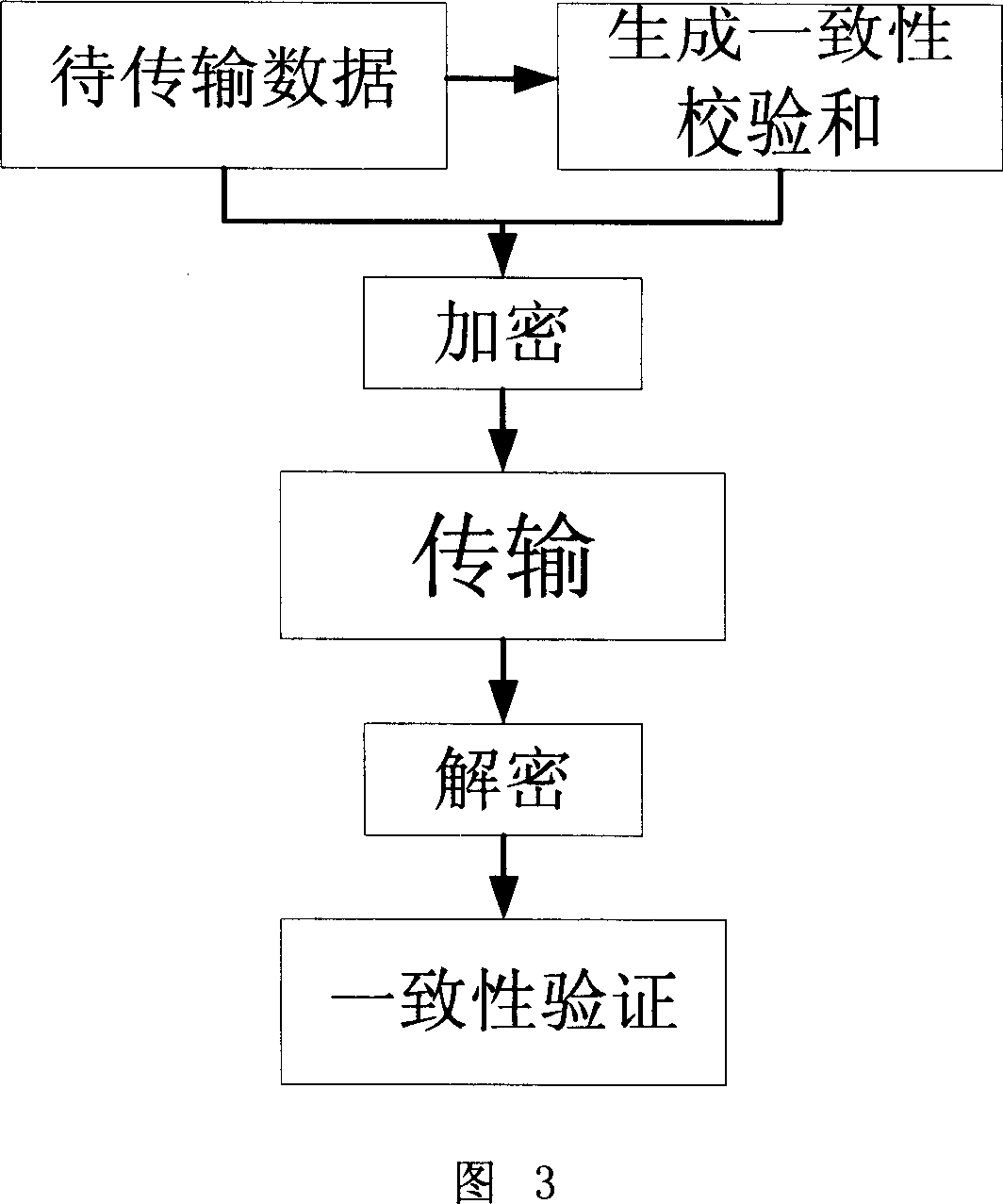
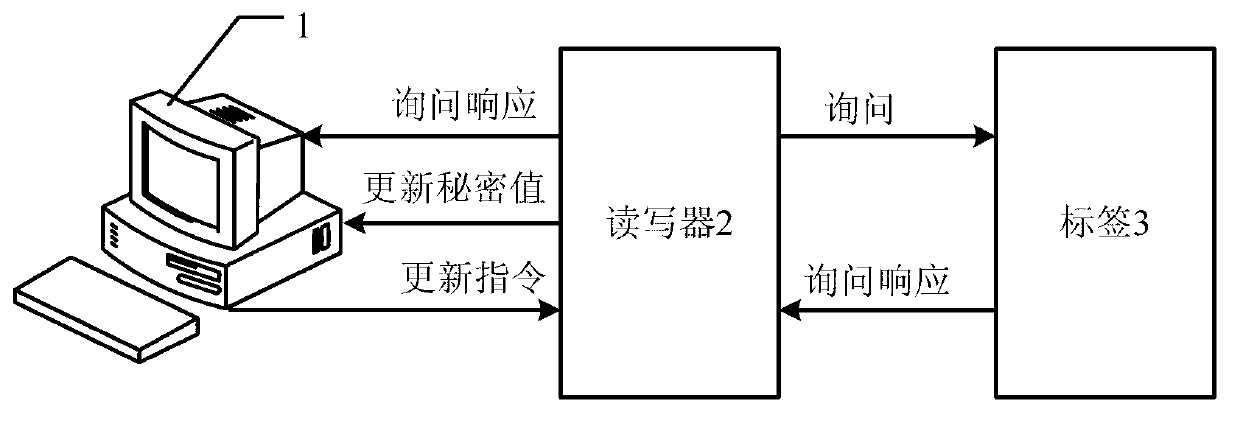
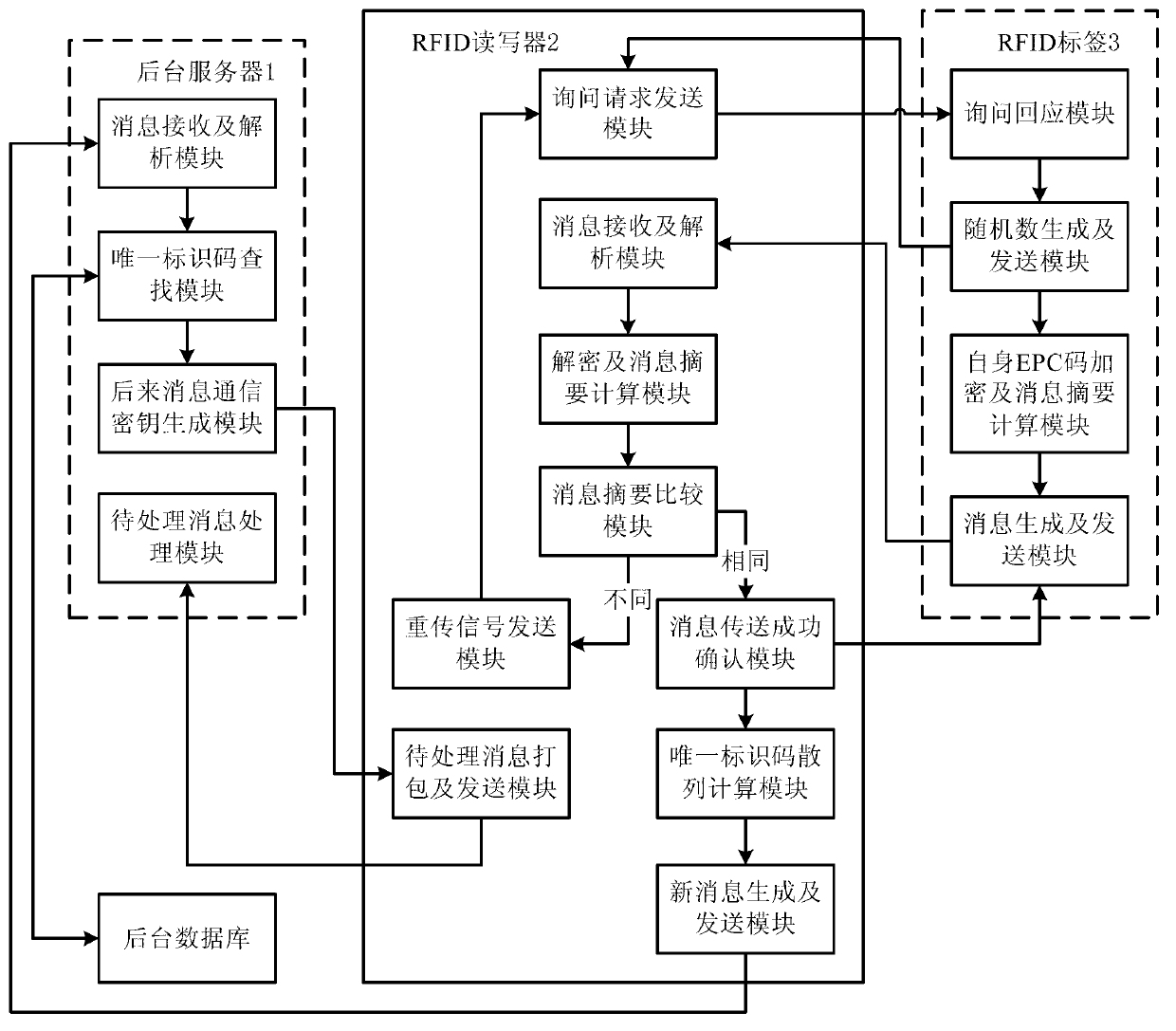
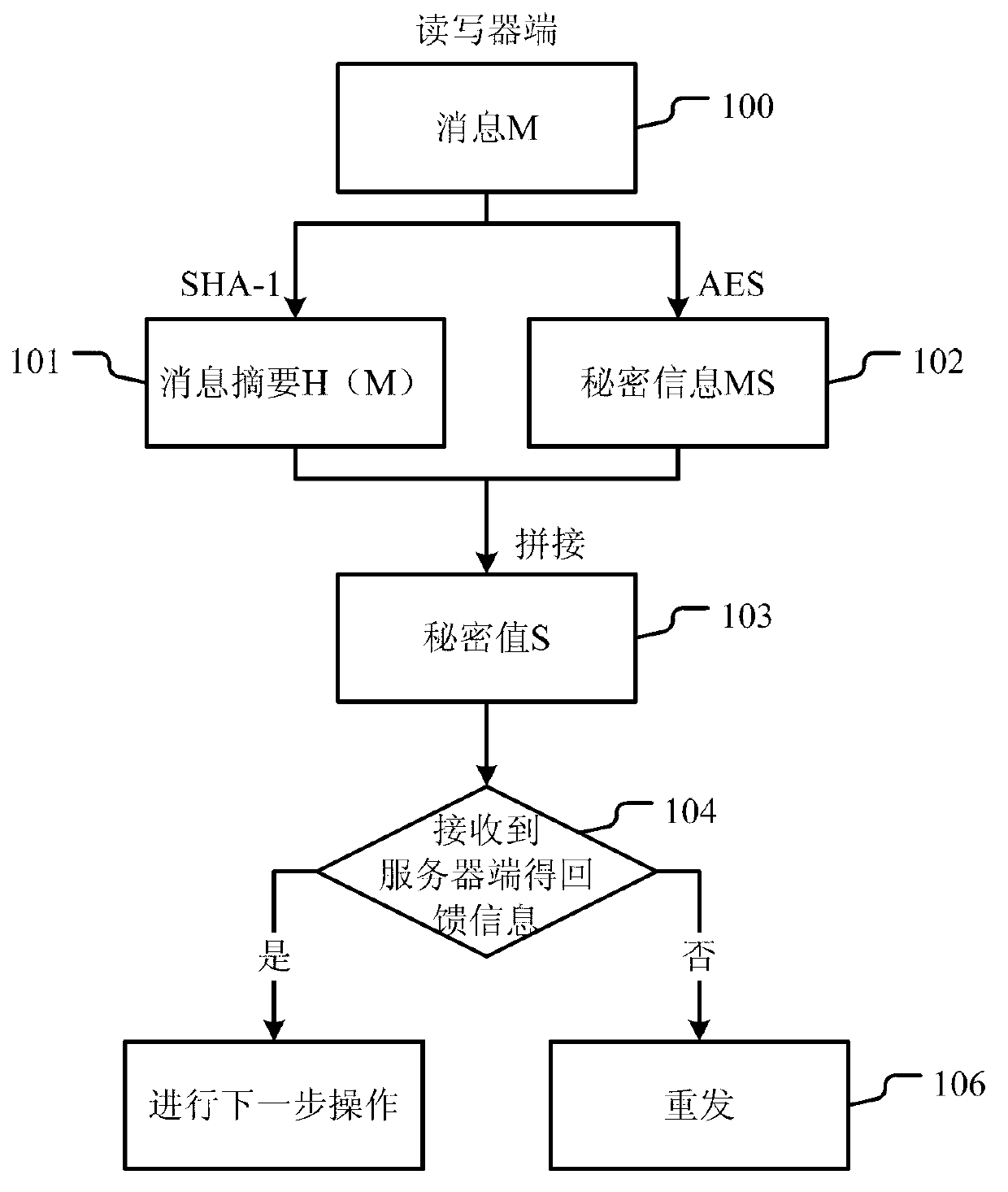
ActiveCN103279775ASolve potential safety hazardsGuaranteed confidentialityCo-operative working arrangementsDigital data protectionComputer hardwareData integrity
The invention discloses an RFID (Radio Frequency Identification) system capable of ensuring confidentiality and data integrity and an implementation method thereof. The system comprises an RFID tag, an RFID reading-writing module and a background service module, wherein the RFID reading-writing module is used for obtaining a communication key from the RFID tag and carrying out secret data interaction with the RFID tag based on the communication key, and the background service module is used for providing data storage and secret interaction service for the data interaction between the RFID tag and the RFID reading-writing module; and the background service module, the RFID reading-writing module and the RFID tag are sequentially connected. The RFID system capable of ensuring confidentiality and data integrity and the implementation method thereof provided by the invention can overcome the defects of poor security, easiness in failure, poor reliability and the like in the prior art so as to realize the advantages of good security, non-easiness in failure and good reliability.
Owner:CHENGDU HONGFU RADIO TECH
Electronic evidence storage method based on block chain smart contract
ActiveCN110223068ARealize the core logic functionTransparent deposit processElectronic credentialsTransmissionTamper resistanceEvidence analysis
The invention requests to protect an electronic evidence storage method based on a block chain smart contract, and the method comprises the steps: carrying out the evidence storage through the smart contract by a evidence storage person, carrying out the query of evidence information through the smart contract by a verification person, carrying out the evidence downloading through the smart contract by a researcher, and carrying out the uploading of an evidence analysis result through the smart contract. The smart contract is a key logic module for realizing the method and exchanges data withthe block chain, so that the integrity, the verifiability and the tamper resistance of the electronic evidence are ensured. And meanwhile, all data operations are recorded on the block chain, so thatthe traceability of the electronic evidence is realized.
Owner:广东灏昌商业保理有限公司
Testament management system and method based on block chain technology
PendingCN110287167ABest buildTrusted Will AppData processing applicationsUser identity/authority verificationData integrityData-driven
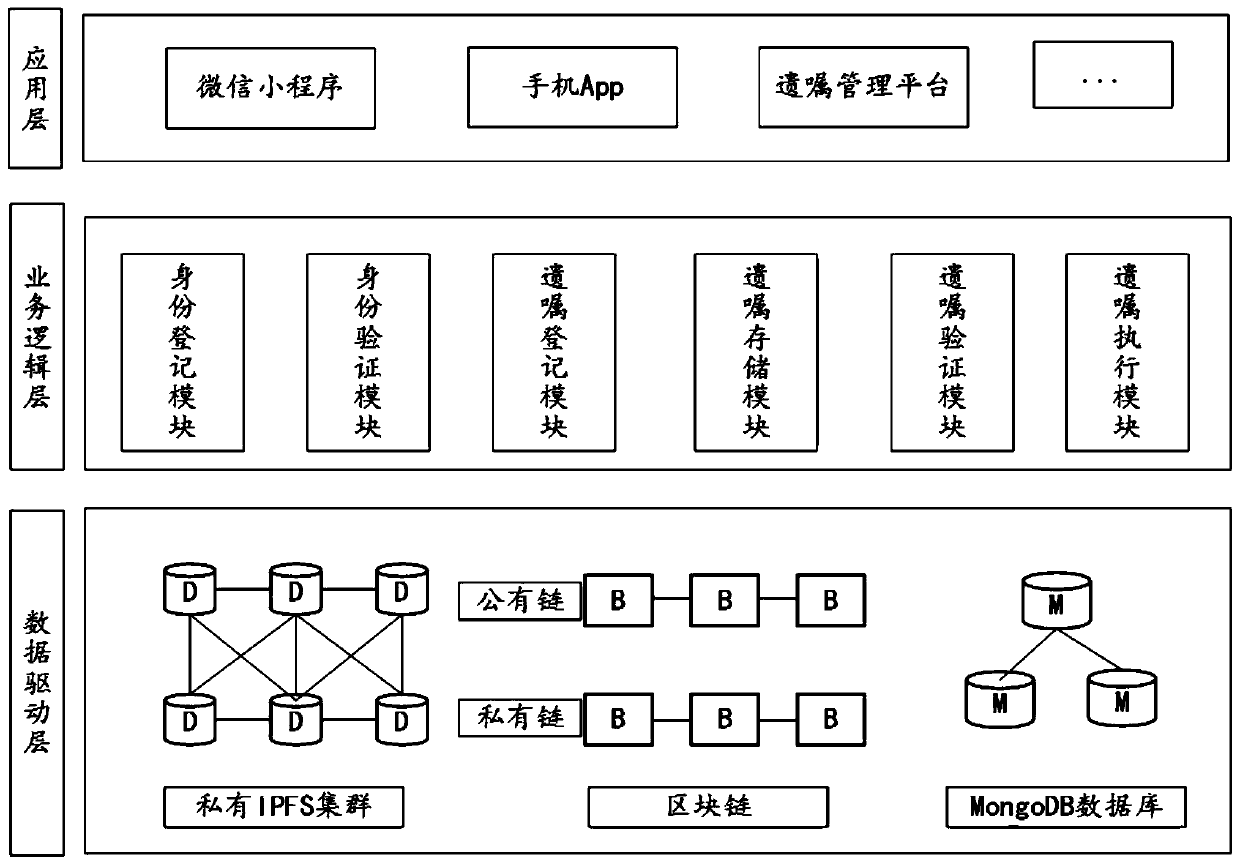
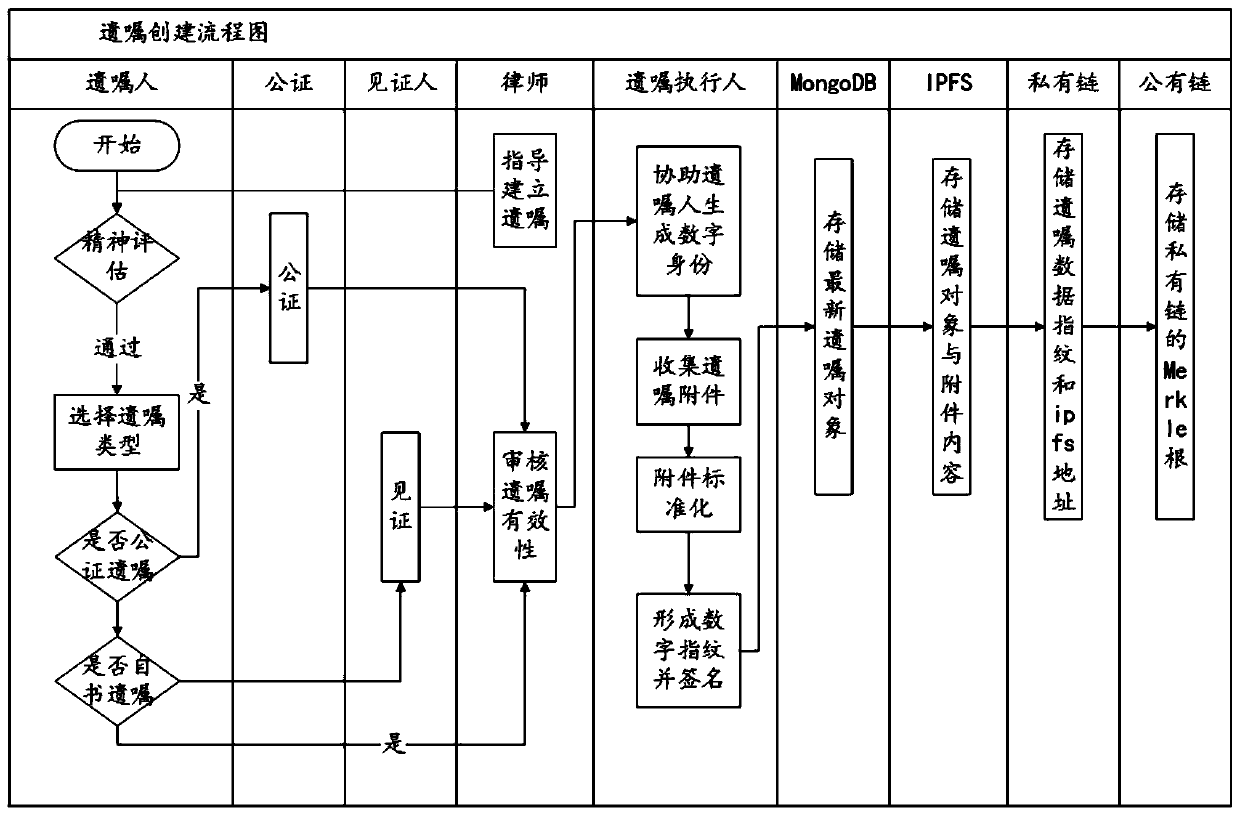
The invention relates to the technical field of data storage technologies and information security, in particular to a testament management system and method based on a block chain technology. The testament management system comprises a data driving layer, a business logic layer and an application layer, the data driving layer is used for providing the underlying technical support, the business logic layer is used for dividing the business scenes, and the application layer is used for providing the use interfaces. The testament management method is realized based on the testament management system. By the testament management system, the defects of a traditional testament management technology can be better overcome, and the data integrity of the testament customizing, storing, updating, verifying and other processes can be effectively guaranteed through the block chain technology.
Owner:安徽中科晶格技术有限公司
Method for avoiding data loss in switching process
ActiveCN1992971AAvoid data lossGuaranteed Data IntegrityRadio/inductive link selection arrangementsWireless communicationTime delaysData transmission
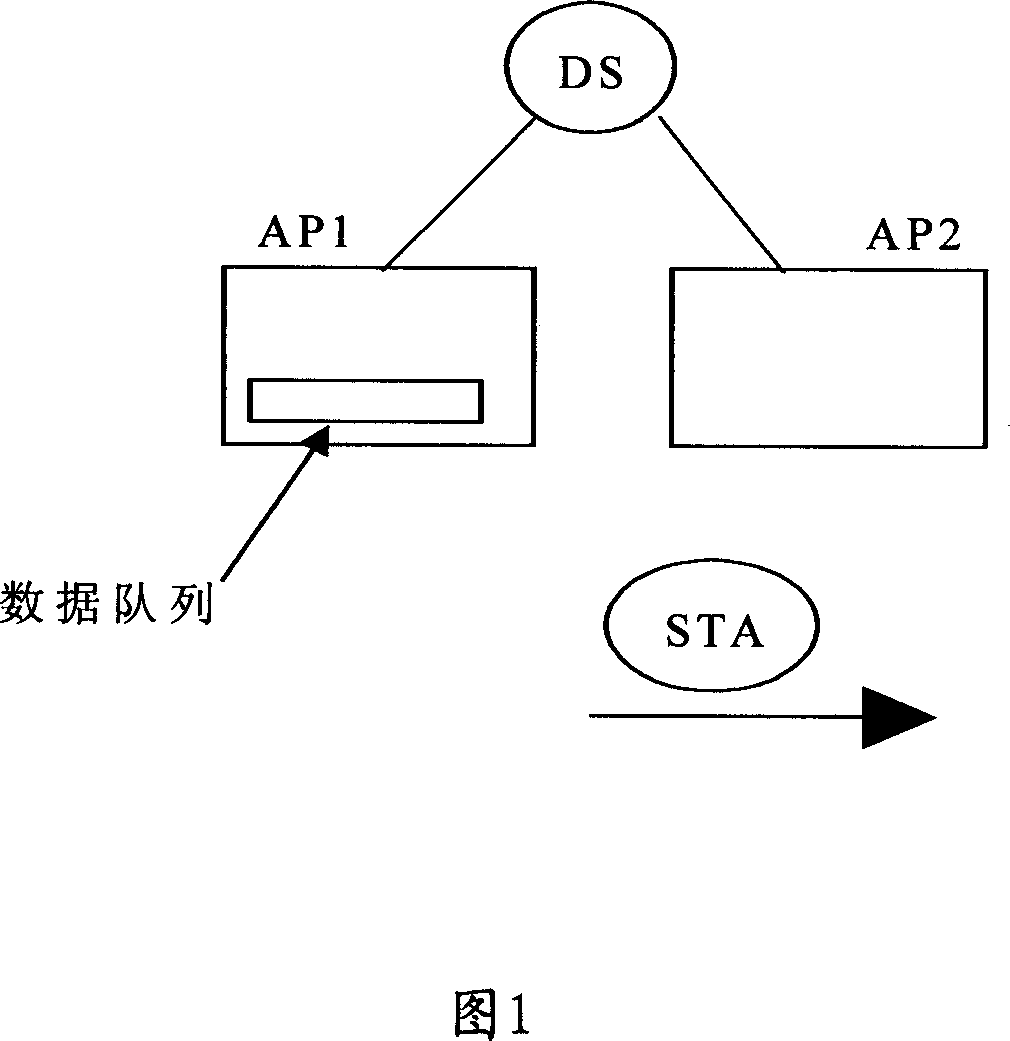
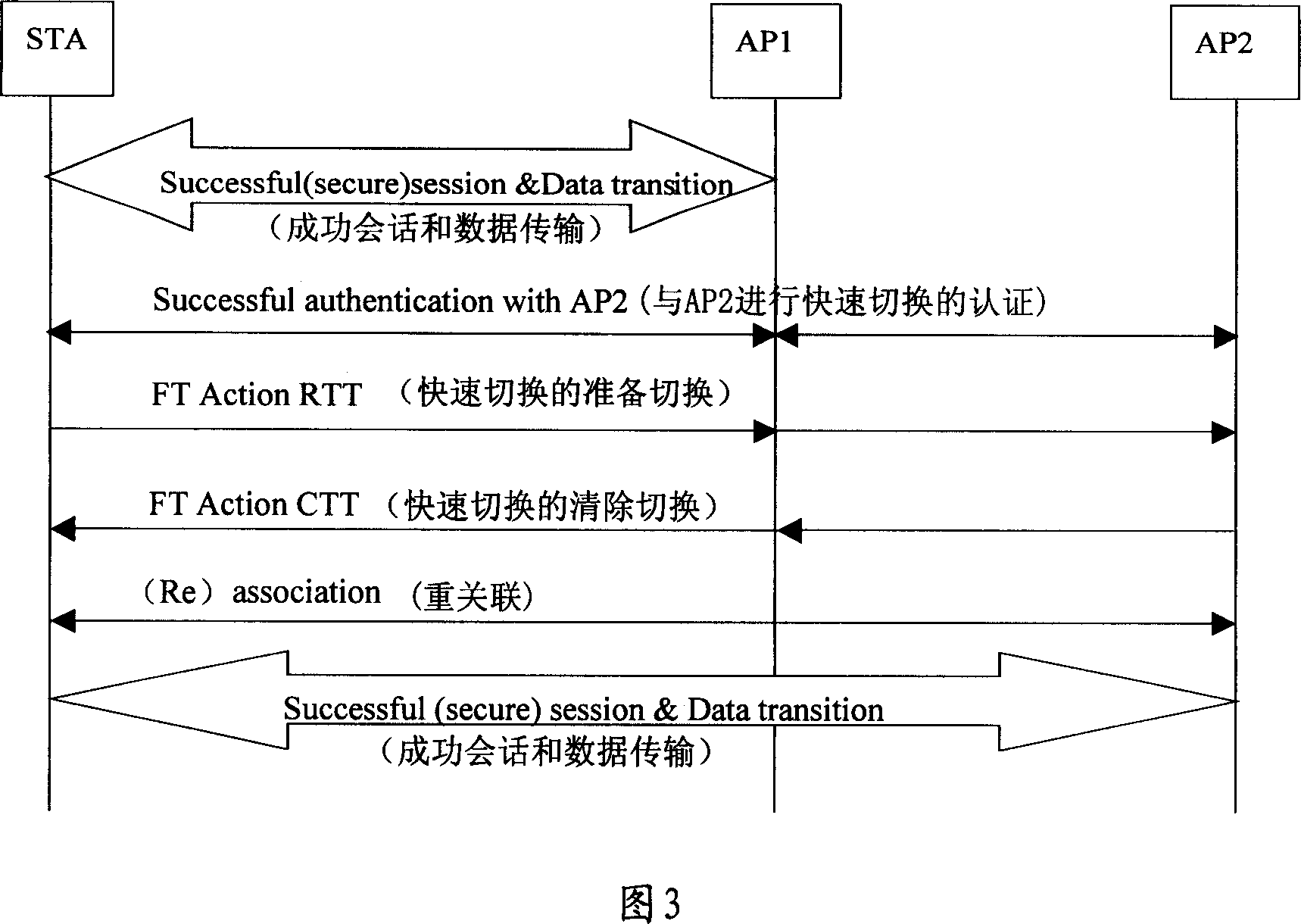
The invention relates to a method for avoiding losing data in switch process, wherein it is characterized in that: when receiver switches from local wireless access point AP into target AP, it will send buffer information to wireless access point AP; AP based on buffer information processes the data sent to the receiver, via the target AP sends processed data to the receiver. The invention can avoid losing data, confirm data integrality. And receiver STA can switch without complete data transmission by AP, to reduce time delay.
Owner:XFUSION DIGITAL TECH CO LTD
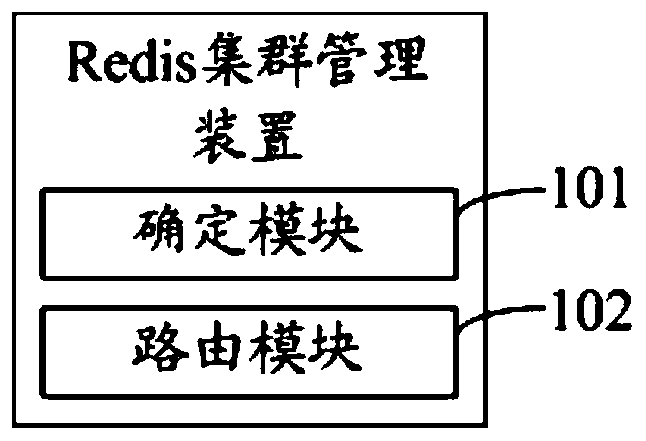
Redis cluster management method, device and equipment and readable storage medium
The invention discloses a Redis cluster management method, which comprises the following steps of: when a data access request is monitored, determining a target data partition which is not downtime through a Redis cluster agent component and a data key value in the data access request; routing the data access request to the target data partition, and processing the data key value to obtain a hashslot number; and routing the data access request to a Redis node corresponding to the hash slot number in the target data partition. The invention also discloses a Redis cluster management device, equipment and a readable storage medium. According to the invention, the data integrity and high availability of the Redis cluster can be effectively ensured.
Owner:WEBANK (CHINA)
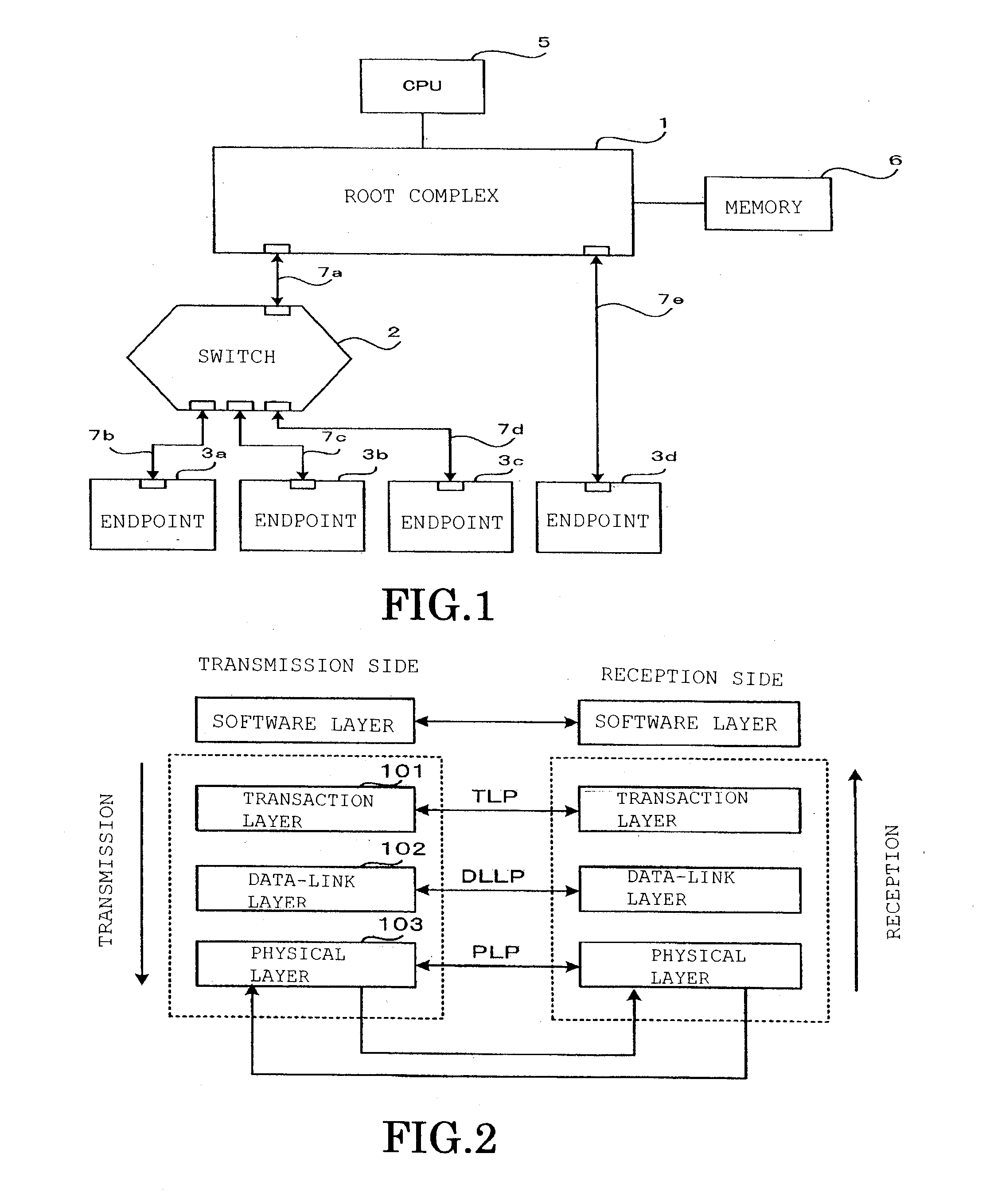
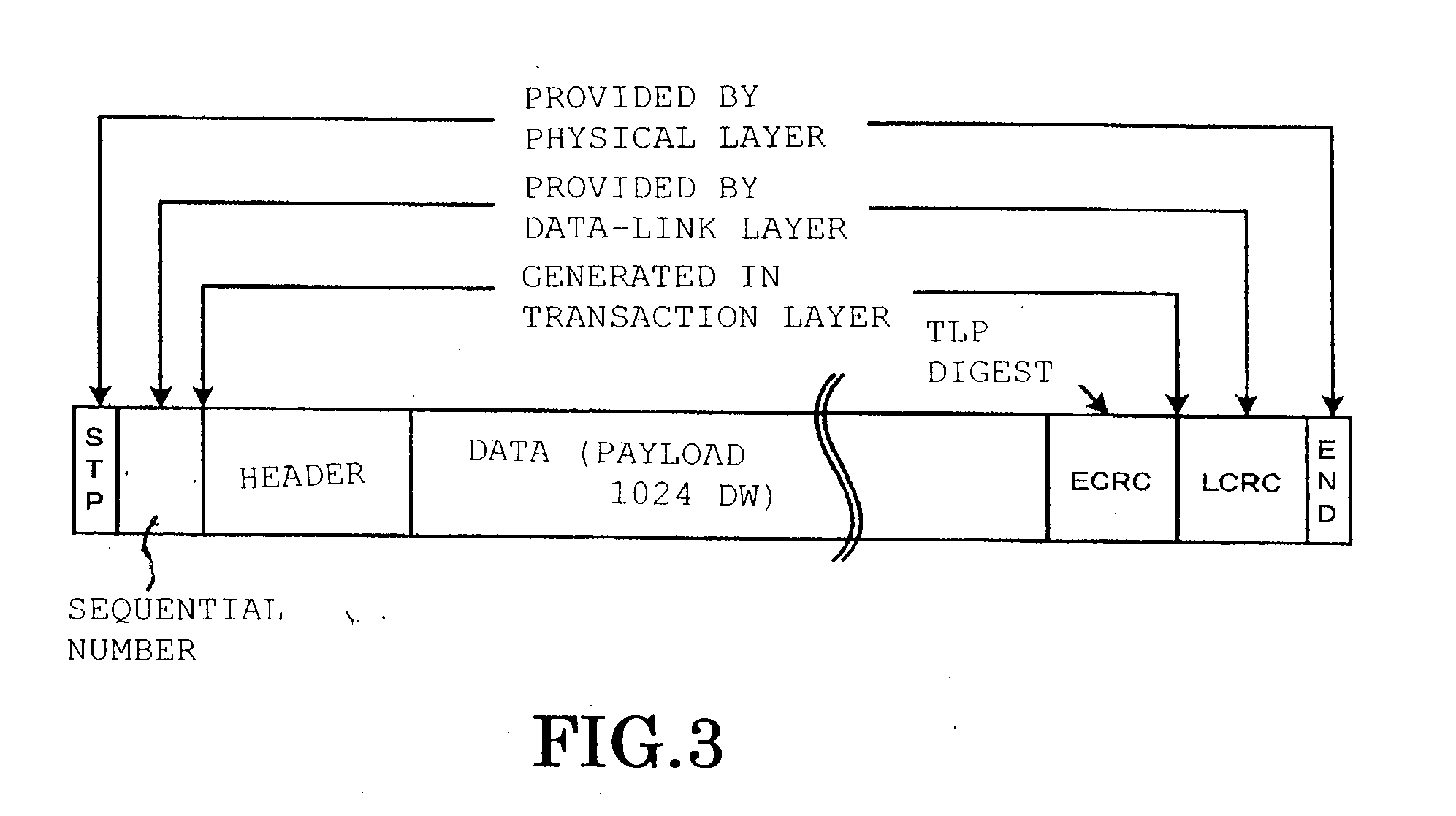
PCI express tlp processing circuit and relay device provided with this
InactiveUS20120030402A1Guaranteed Data IntegrityElectric digital data processingTransmission link error control systemData integrityMultiplexer
A PCI Express TLP processing circuit (10) comprises: a plurality of reception processing sections (2a1); a transmission processing section (2b); and a multiplexer (2c1) that performs transmission to the transmission processing section, selecting one of the reception processing sections; and at least a reception processing section comprises: a redundancy code generating circuit (12); an LCRC / sequential number detection circuit (13); a buffer memory (14); a packet control circuit section (16) that controls transmission for normal transmission to the transmission destination of the TLP in question or for nullifying transmission; and the transmission processing section comprises: a sequential number generating circuit (19); an LCRC generating circuit (20) and a relay circuit error detection circuit (21), whereby data integrity of the transmitted TLP can be guaranteed.
Owner:KK TOSHIBA
Clustered storage system with external storage systems
InactiveUS20060179188A1Guaranteed Data IntegrityError detection/correctionTransmissionData storage systemStorage cell
A data storage system comprises a first platform storage system including a first network interface to communicate with a host computer, a first storage unit to provide storage volumes, a first storage controller to control the first storage unit, and a first memory to store a first control program to process an input / output (I / O) request received by the first platform storage system. A second platform storage system includes a second network to communicate with the host computer, a second storage unit to provide storage volumes, a second storage controller to control the second storage unit, and a second memory to store a second control program to process an I / O request received by the second platform storage system. An external storage system is coupled to the first and second platform storage systems, the external storage system including a third storage unit to provide storage volumes and a third storage controller to control the third storage unit. The first and second platform storage systems are configured to present the storage volumes of the external storage system to the host computer, so that the host computer can access the storage volumes of the external storage system via one of the first and second platform storage systems if the host computer is unable to access the storage volumes of the external storage system via the other platform storage system.
Owner:HITACHI LTD
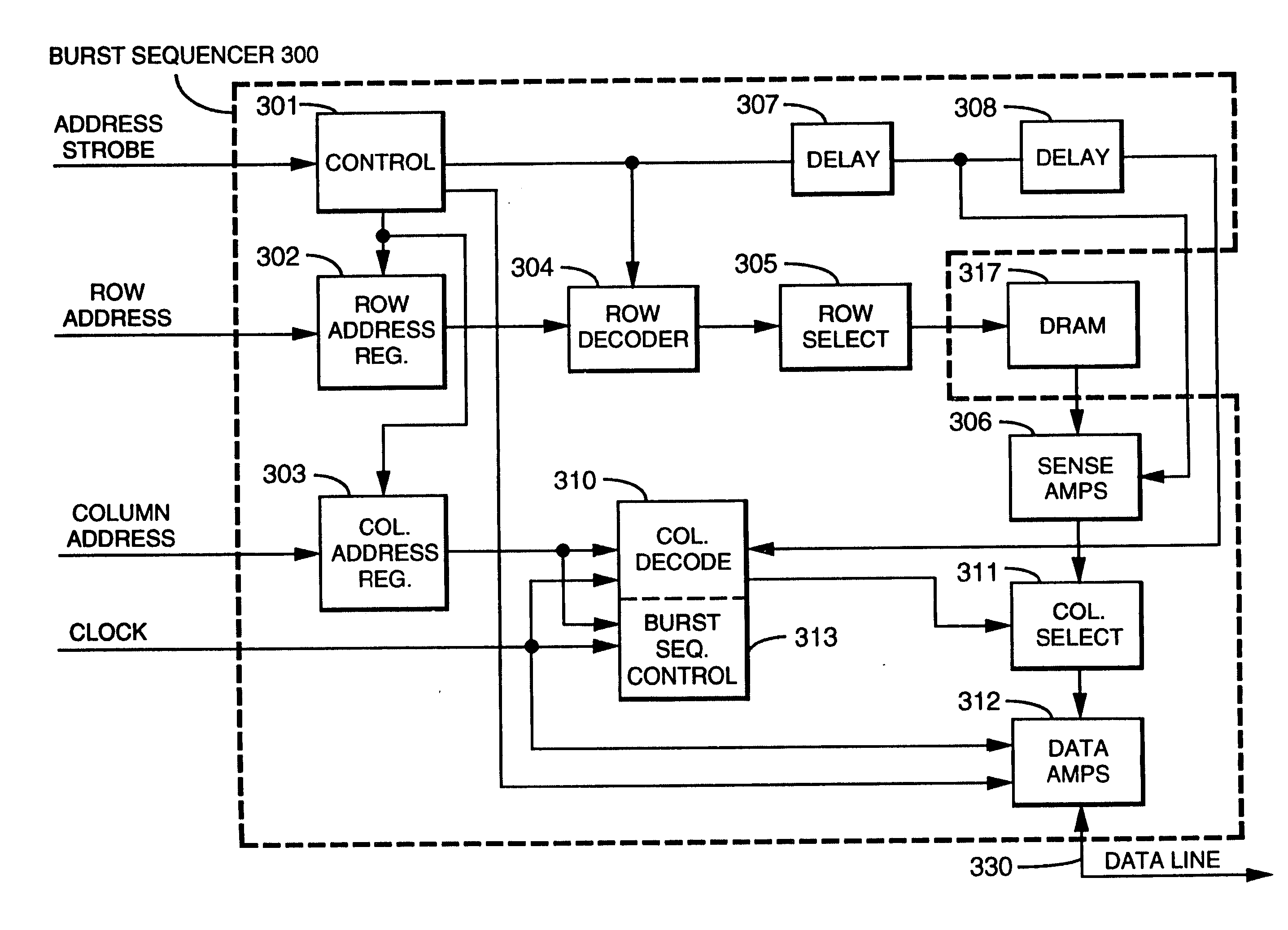
High speed memory system
InactiveUS20050027929A1Prevent incorrect and delayed operationMaximum compatibilityMemory adressing/allocation/relocationDigital storageHigh speed memoryDram memory
A method and structure for implementing a DRAM memory array as a second level cache memory in a computer system. The computer system includes a central processing unit (CPU), a first level SRAM cache memory, a CPU bus coupled to the CPU, and second level cache memory which includes a DRAM array coupled to the CPU bus. When accessing the DRAM array, row access and column decoding operations are performed in a self-timed asynchronous manner. Predetermined sequences of column select operations are then performed in a synchronous manner with respect to a clock signal. A widened data path is provided to the DRAM array, effectively increasing the data rate of the DRAM array. By operating the DRAM array at a higher data rate than the CPU bus, additional time is provided for precharging the DRAM array. As a result, precharging of the DRAM array is transparent to the CPU bus.
Owner:INVENSAS CORP
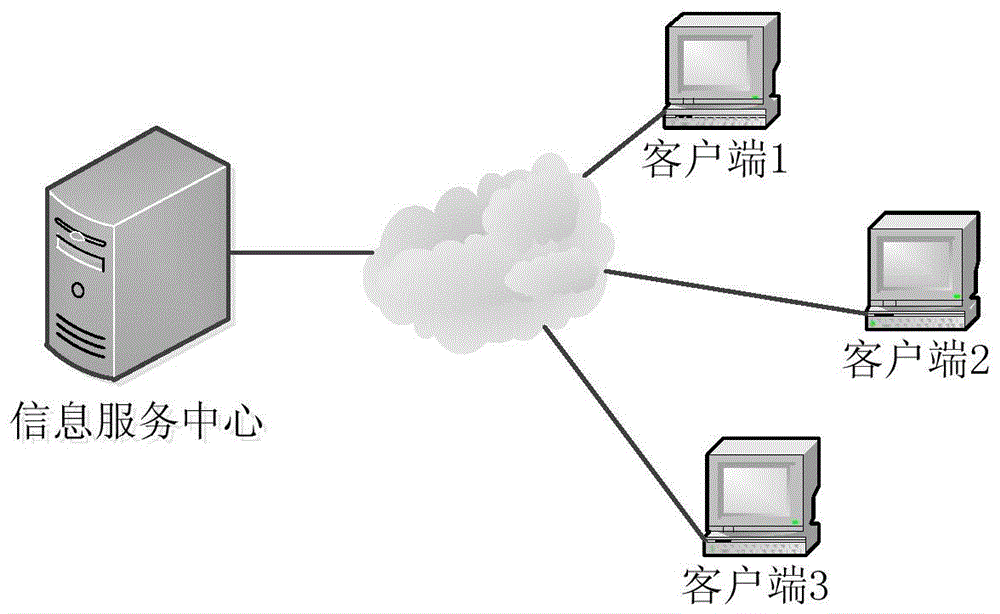
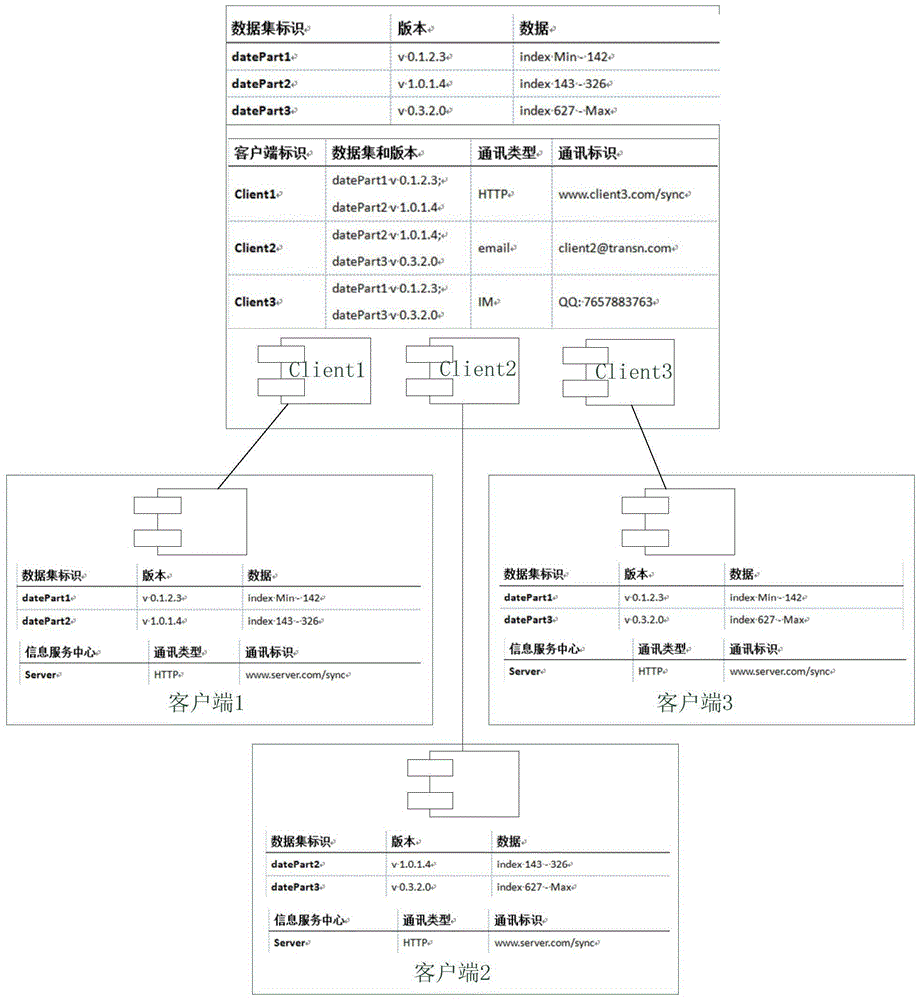
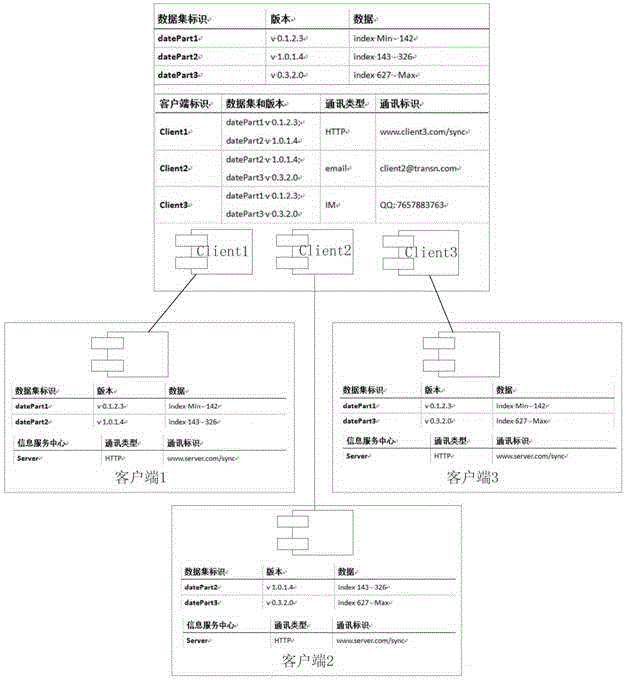
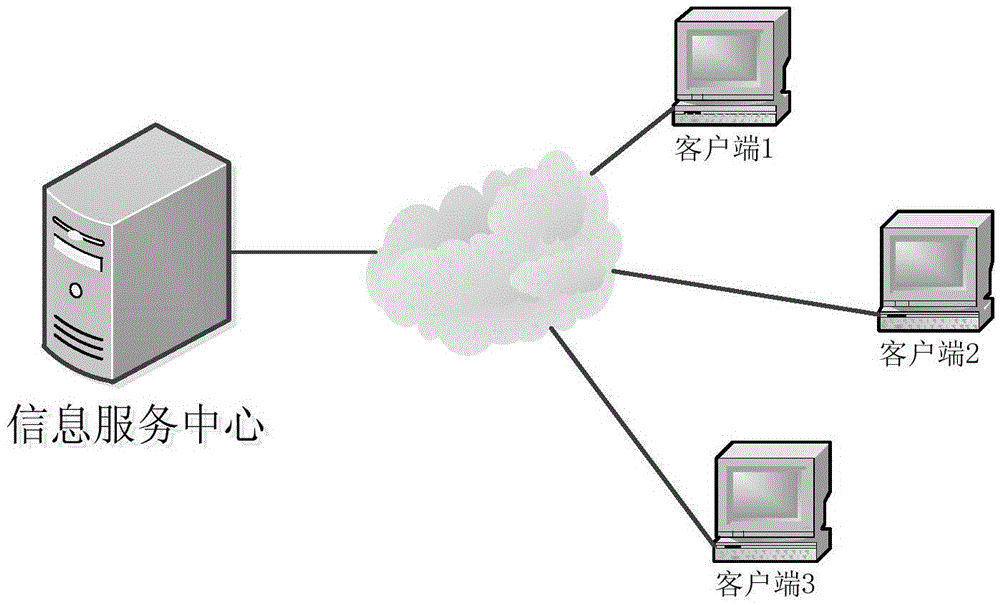
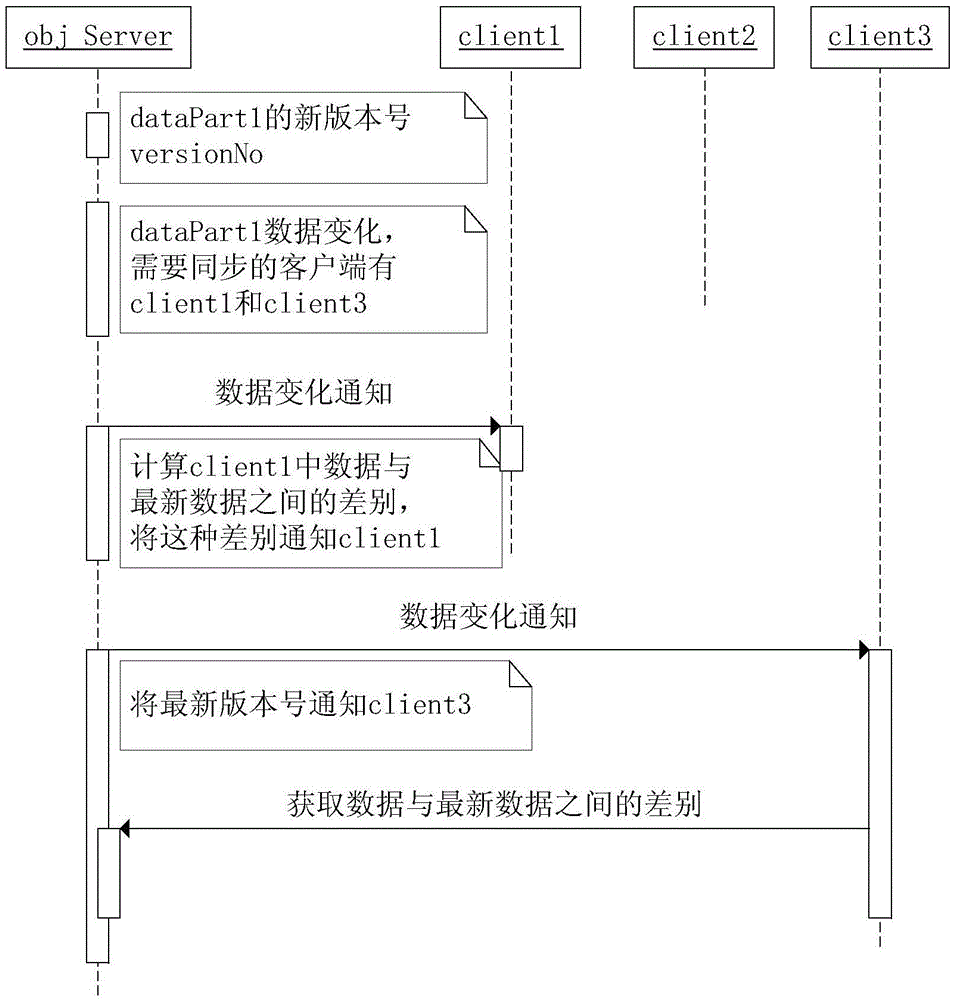
Asynchronous data synchronization method for distributed systems
InactiveCN105743970AThe downside of avoiding wasteReduce occupancyTransmissionData synchronizationData integrity
The invention relates to an asynchronous data synchronization method for distributed systems, comprising an information service center and a plurality of clients. The information service center stores synchronization data, and is provided with a synchronization information table. When the data in the information service center changes, a data update message is transmitted to a target in the synchronization information table. The clients update the synchronization data thereof when receiving the data update message. After data updating, the clients notify the information service center of the latest data version. The information service center updates the synchronization information table after receiving the notice. According to the invention, a data synchronization method characterized in that a synchronous end makes a response asynchronously after one end initiates synchronization is adopted, waste of network resources caused by the existing polling synchronization method is avoided, and the amount of system resources needed for data synchronization is reduced. Moreover, the network communication mode of asynchronous data synchronization is more flexible and adaptive, occupation of the communication network is less, and the data integrity and unity of distributed systems are ensured.
Owner:IOL WUHAN INFORMATION TECH CO LTD
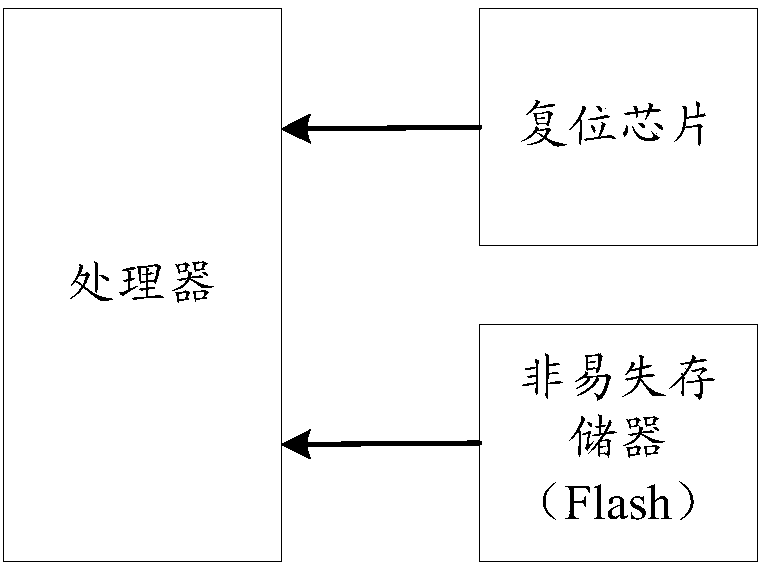
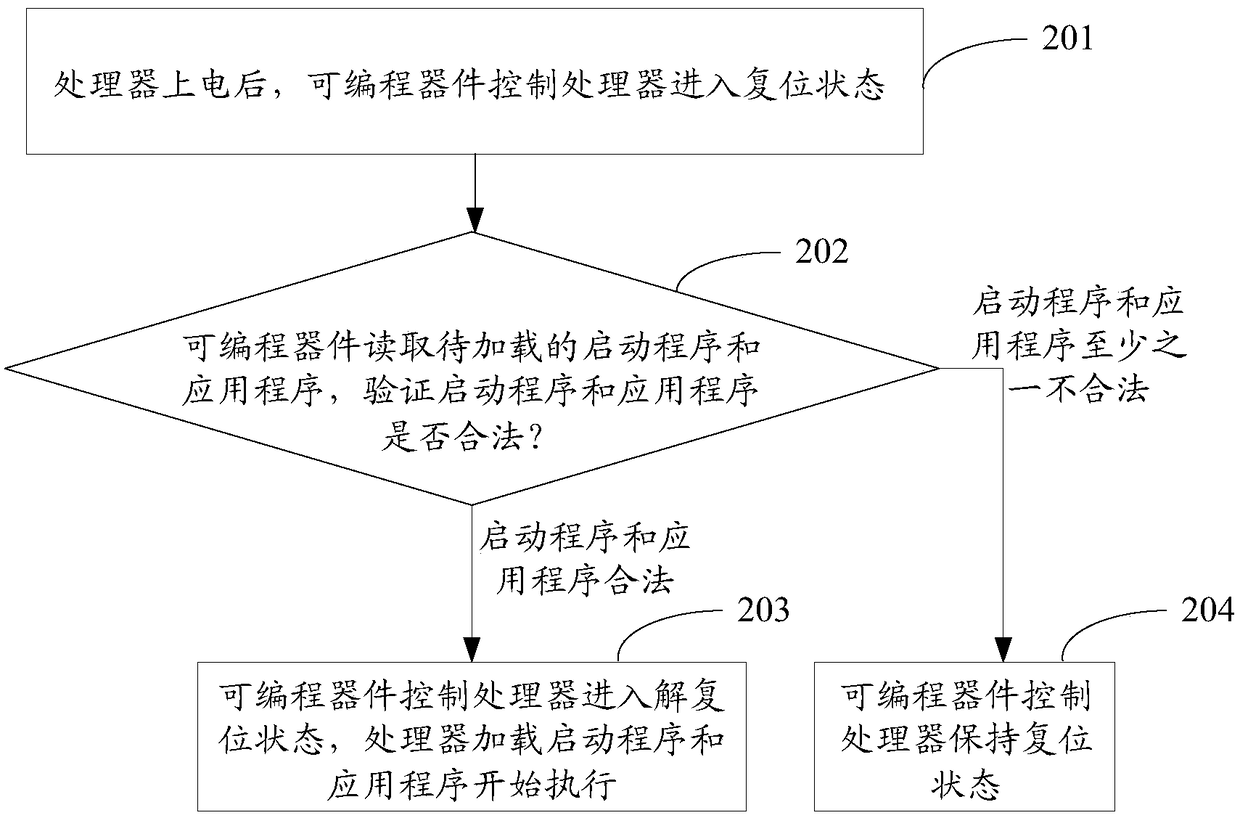
Safe starting method and device and terminal
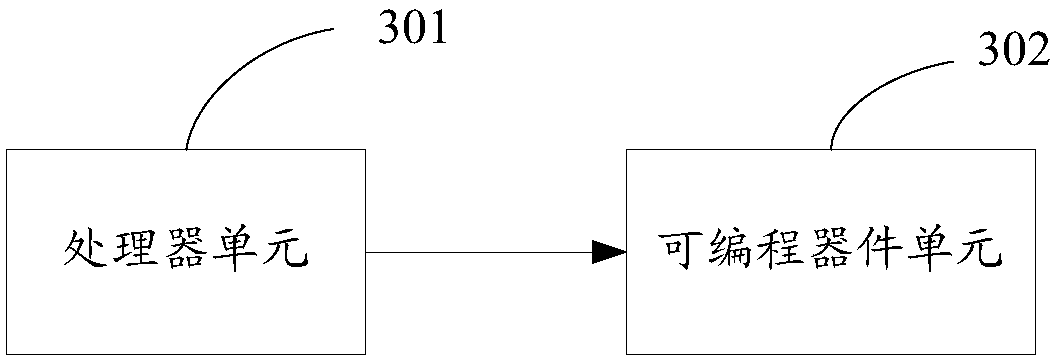
InactiveCN108229132AGuaranteed Data IntegrityEnsure data securityData resettingDigital data protectionData validationElectricity
The invention discloses a safe starting method. The safe starting method comprises the following steps: after a processor is electrified, controlling the processor to enter a resetting state by a programmable device; reading a to-be-loaded starting program and a to-be-loaded application program by the programmable device, and verifying whether the starting program and the application program are legal or not; if the starting program and the application program are legal, controlling the processor to enter a non-resetting state by the programmable device, and loading the starting program and the application program to begin to execute by the processor; and if at least one of the starting program and the application program is not legal, controlling the processor to maintain a resetting state by the programmable device. The invention further discloses a safe starting device and a terminal. The independent programmable device is used for verifying whether the to-be-loaded starting programand the to-be-loaded application program of the processor are legal or not, the verification and execution of codes of the processor are isolated completely, an independent data verifying channel isconstructed, and data integrity and safety in a terminal starting process are ensured.
Owner:北京和利时控制技术有限公司
Distributed cloud navigation system and method based on ROS2
InactiveCN110427039AMake up for deficienciesLow costTotal factory controlProgramme total factory controlData spaceInteraction device
The invention provides a distributed cloud navigation system and method based on ROS2. The system comprises a bottom layer, global data space, a cloud server and a management layer, wherein the bottomlayer comprises at least one robot, a sensor module is mounted on each robot, and each sensor module is used for collecting environmental data and own motion state data of the corresponding robot; each robot and an interactive device thereof are taken as nodes respectively to form an ROS network; the global data space as a network layer is used for achieving intercommunication between each robotand the cloud server and receiving related data of topic publication or topic subscription issued by each node in the ROS network; the cloud server is configured to receive the environmental data andown motion state data which are uploaded by each robot, calculate control information of the corresponding robot and conduct positioning and route planning on the corresponding robot, so that the corresponding robot moves to reach a designated position; the management layer is configured to communicate with each node in the ROS network for monitoring a running state of the distributed cloud navigation system.
Owner:SHANDONG UNIV
Verification method, equipment and system of increment provable data integrity (IPDI)
InactiveCN101729250AGuaranteed Data IntegrityIntegrity guaranteedKey distribution for secure communicationPublic key for secure communicationThird partyData integrity
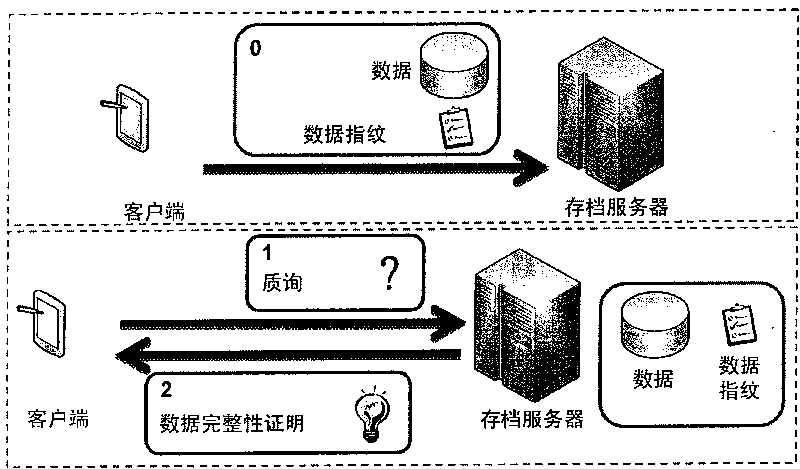
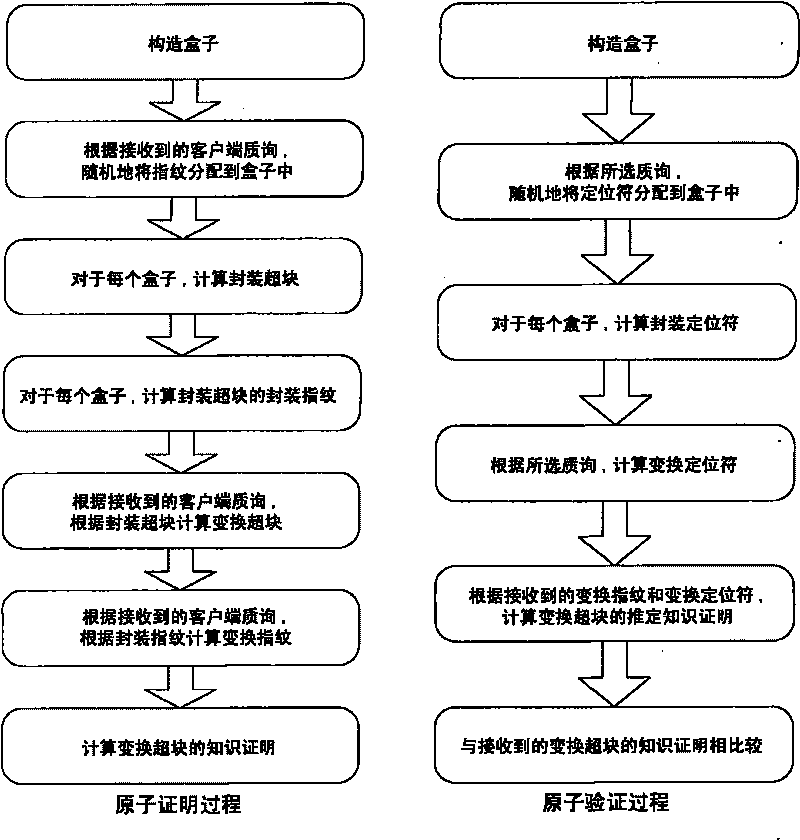
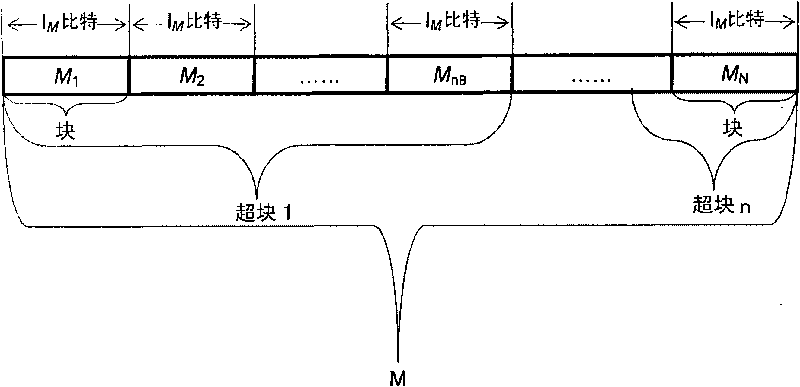
The invention provides a verification method of increment provable data integrity (IPDI), which comprises the following steps: firstly, generating digital fingerprints of data at a client, and sending the fingerprints and the data together to an archive server; when necessary, sending an 'inquiry' to the archive server by the client or a third party verifier to determine the integrity of the data, and proving the integrity of the data through the archive server by using the received fingerprints; and finally, verifying the integrity of the data by the client or the third party verifier according to the output for responding to the 'inquiry' from the archive server. In addition, the IPDI scheme securely realizes the purpose of adding incremental data into a data file which already generates fingerprints and is outsourced.
Owner:NEC (CHINA) CO LTD
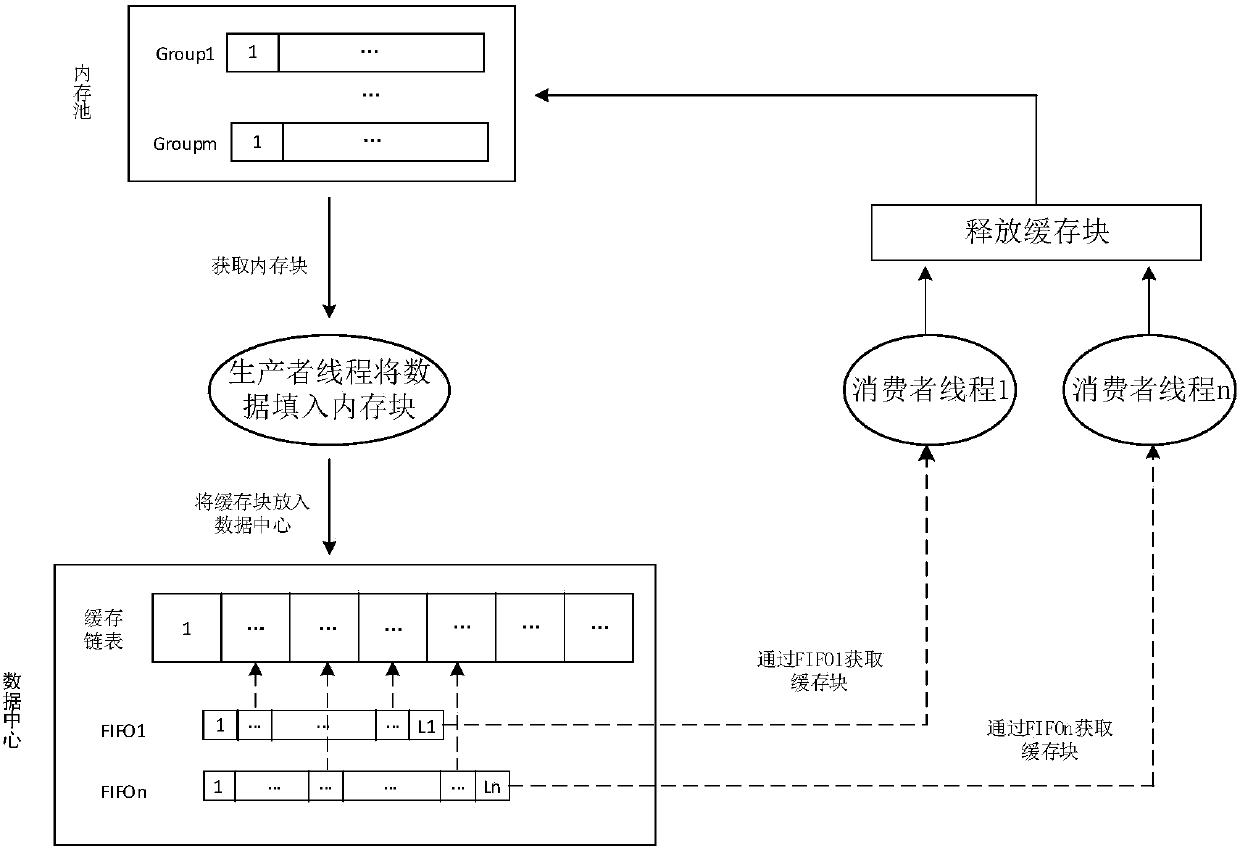
Video stream cache distribution method and device
ActiveCN107864391AGuaranteed smoothnessGuaranteed Data IntegrityVideo data indexingClosed circuit television systemsData centerDistribution method
The invention belongs to the field of video processing and particularly relates to a video stream cache distribution method and device. The invention aims to solve problems of the waste of a memory space, easy data loss and increased system overhead caused by a fixed length of a cache queue in the prior art. The video stream cache distribution method provided by the invention comprises a step of distributing a memory block containing video data as a cache block and storing the memory block into the cache block, a step of storing the cache block into a data center and storing an address of thecache block into a first address queue, and a step of obtaining the cache block, distributing data in the cache block to a corresponding client, and releasing the cache block. According to the video stream cache distribution method, the memory space can be fully utilized, and the smoothness and integrity of a video are ensured. The invention also provides the video stream cache distribution device, a storage device and a processing device with the above effects.
Owner:BEIJING DIGIBIRD TECH CO LTD
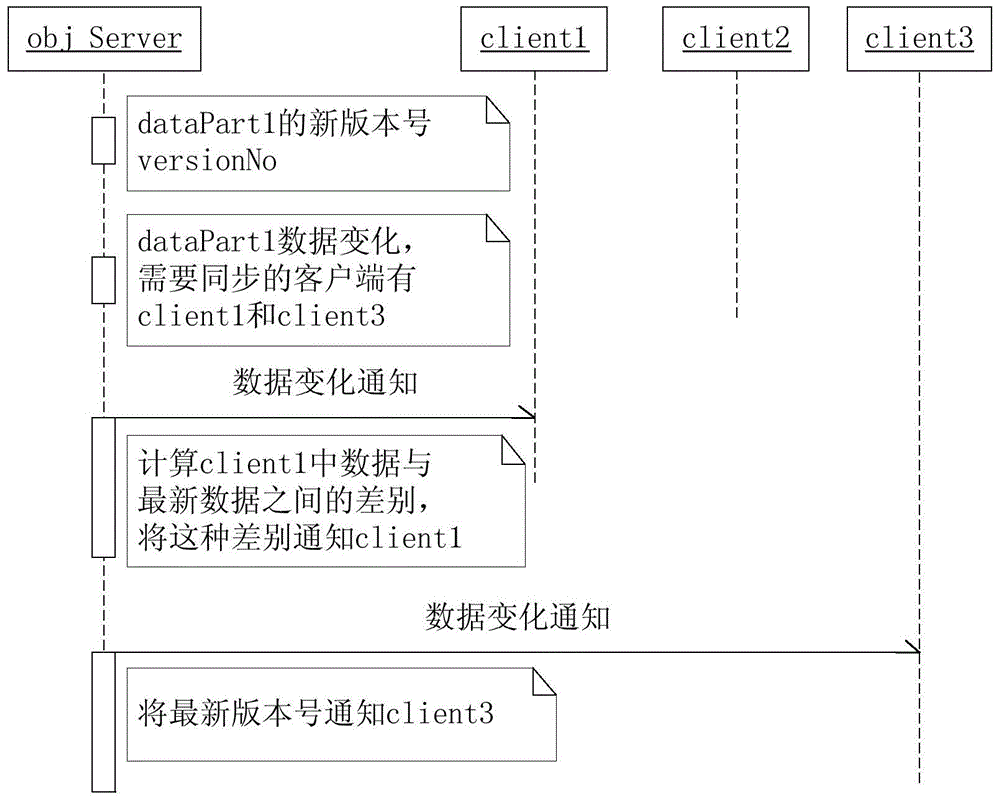
Method for synchronous data synchronization of distributed system
InactiveCN105635286AThe downside of avoiding wasteGuaranteed Data IntegrityTransmissionData synchronizationData integrity
The invention relates to a method for information synchronization in a distributed system. The method comprises an information service center and a plurality of clients. Synchronous data are stored in an information service center. Synchronous data are stored into the information service center and a synchronization information table is set; when data of the information service center change, a data updating message is transmitted to a target client; after one client receives one data updating message, synchronous data are updated according to data difference information, and an information synchronization completion signal is sent to the information service center after updating; and after the information service center receives the synchronization completion signal, the synchronization information table is updated and then the data synchronization task is completed. According to the invention, a method for data synchronization by initiating synchronization by one terminal and carrying out responding synchronously by a synchronization terminal is employed, so that a defect of network resource wasting existing in the existing polling synchronization way can be overcome; and the system resource quantity needed for data synchronization can be reduced. Moreover, the data synchronization updating can be carried out timely and data integrity and uniformity of the distributed system can be guaranteed.
Owner:IOL WUHAN INFORMATION TECH CO LTD
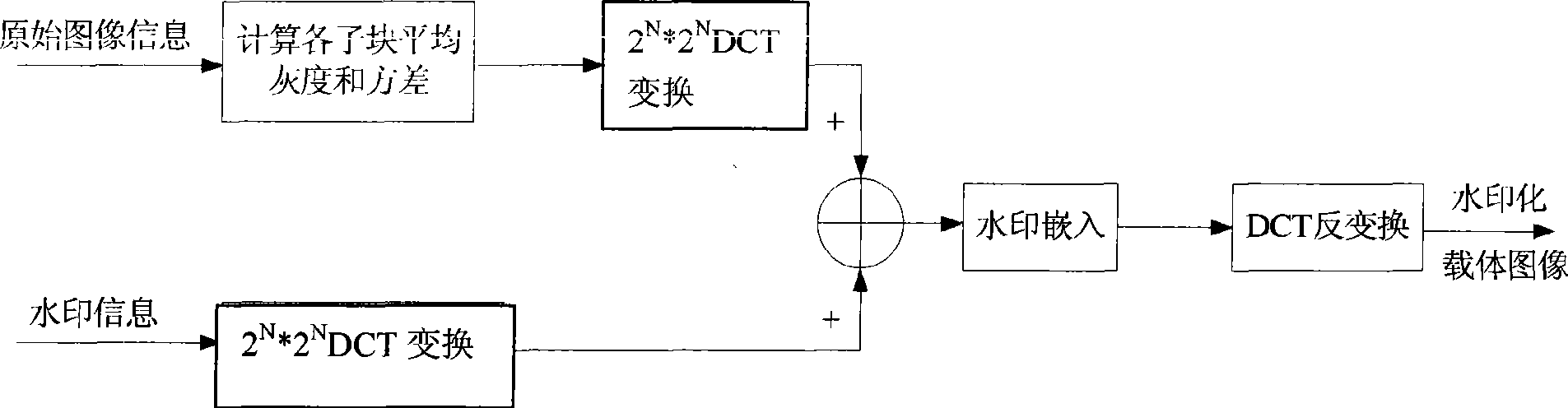
Digital image watermark imbedding method based on DCT algorithm
InactiveCN101504758AAnti-counterfeitingTamper proofImage codingImage data processing detailsComputer visionDigital image watermarking
The invention discloses a DCT algorithm-based method for digital image watermark embedment, which comprises: a first step of reading an original public image and a light and shade watermark image into two-dimensional arrays I and W respectively; a step two of dividing the original public image I and the watermark image W into 2*2 image blocks which do not cover each other respectively, computing the average gray m and a variance sigma of the sub blocks, and performing the DCT conversion of the sub blocks of the public image; a step three of embedding one element W(p,q) in the light and shade watermark in a sub block with a complex texture; a step four of performing the inverse DCT conversion of image blocks embedded with watermark information; and a step five of combining image the image blocks to obtain an image embedded with the light and shade watermark. The method is characterized by counterfeit prevention, falsification prevention, verification, and data security and integrity guarantee.
Owner:SHAANXI UNIV OF SCI & TECH
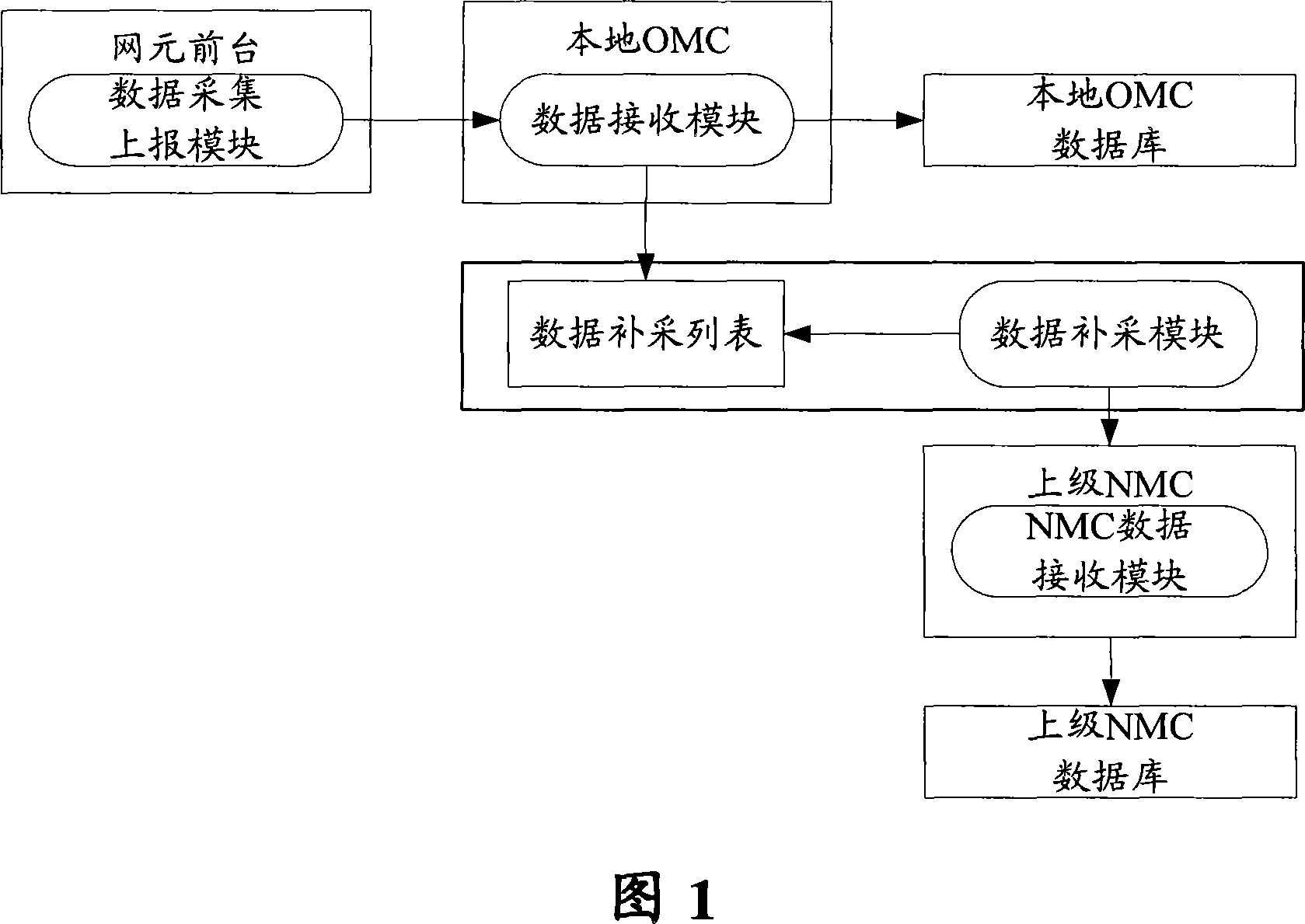
Method and system for supplementary reporting of performance data
InactiveCN101227326AGuaranteed Data IntegrityStore-and-forward switching systemsNetwork managementData acquisition module
The invention discloses a method and a system for complementarily reporting performance data, wherein the method comprises: storing the performance data which is collected into a local operation and maintenance center by a data collecting module, reporting a data transmitting module to transmit the performance data from the local operation and maintenance center to a high authority network management center, selecting part of or whole performance data from the performance data by the data transmitting module, transmitting the part of or whole performance data to an appointed position when the part of or whole performance data can not be transmitted to the high authority network management center, obtaining the part of or whole performance data from the appointed position by a data complement sampling module when the part of or whole performance data can be transmitted to the high authority network management center, and transmitting the part of or whole performance data to the high authority network management center.
Owner:ZTE CORP
Environmental pollution monitoring and managing system of construction site
InactiveCN103543709AImprove stabilityGuaranteed Data IntegrityTotal factory controlProgramme total factory controlData storage systemMultilayer architecture
The invention discloses an environmental pollution monitoring and managing system of a construction site. The environmental pollution monitoring and managing system comprises a field monitoring system and a remote real-time monitoring system. Field pollution monitoring is a core, the field monitoring system comprises a field monitoring platform of the construction site, the field monitoring platform of the construction site comprises a construction environment comprehensive detector and a data host, the remote monitoring system comprises a management platform, a data storage system and an accident handling system, the system is developed by the aid of a multilayer architecture technology on the basis of a .NET technology of the Microsoft, and a multilayer distribution architecture mainly comprises a presentation layer, a logic layer, a data access layer and a data storage layer.
Owner:SHAANXI MING LU OPTICAL TECH
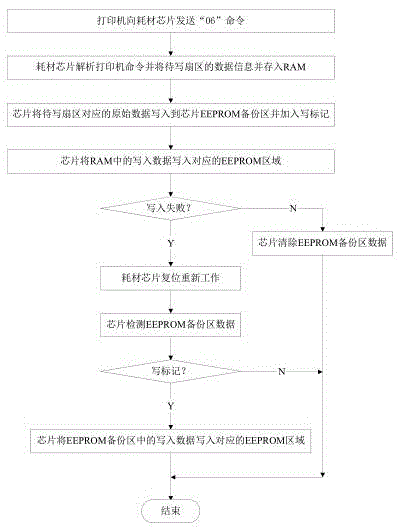
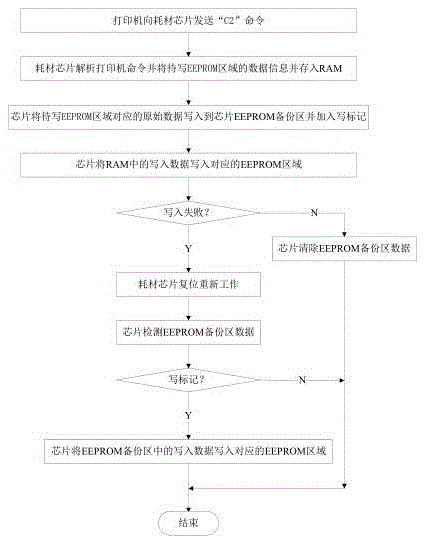
Anti-error consumable chip and control method thereof
ActiveCN105538917AGuaranteed Data IntegrityEnsure data stabilityOther printing apparatusControl circuitTemporary storage
The invention belongs to the field of ink-jet printing and particularly relates to an anti-error consumable chip and a control method thereof. According to the technical scheme, the anti-error consumable chip comprises a chip control circuit and a data storage unit for storing data. The data storage unit comprises an ROM region and an RAM region. The ROM region comprises a main data region and a backup region. The RAM region is used for temporarily storing write-in data transmitted to the anti-error consumable chip by a printer. Initial data is preserved in the main data region. The backup region is used for preserving the initial data. The main data region can receive the write-in data from the RAM region and covering and replacing the initial data with the write-in data. According to the anti-error consumable chip and the control method thereof, even though under certain abnormal conditions, the data storage unit of the consumable chip goes wrong, a system can restore normal data, and normal use of consumables is not affected.
Owner:HANGZHOU CHIPJET TECH
TWS earphone based on monitoring scheme and implementation method thereof
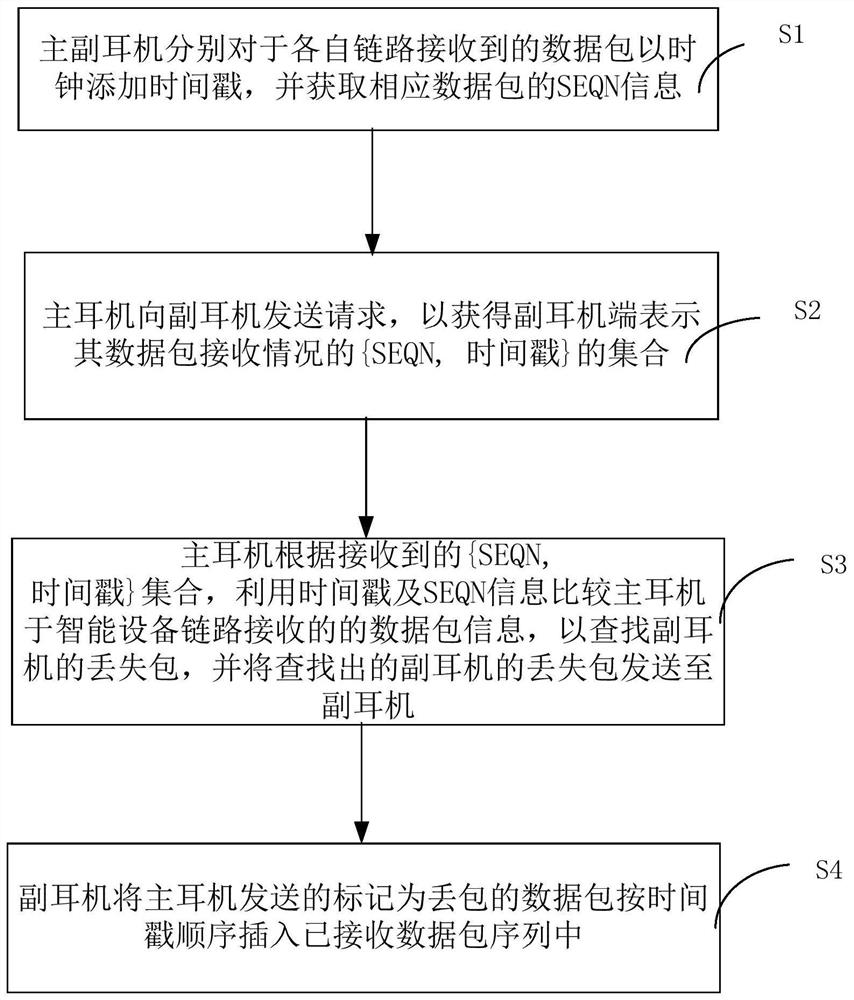
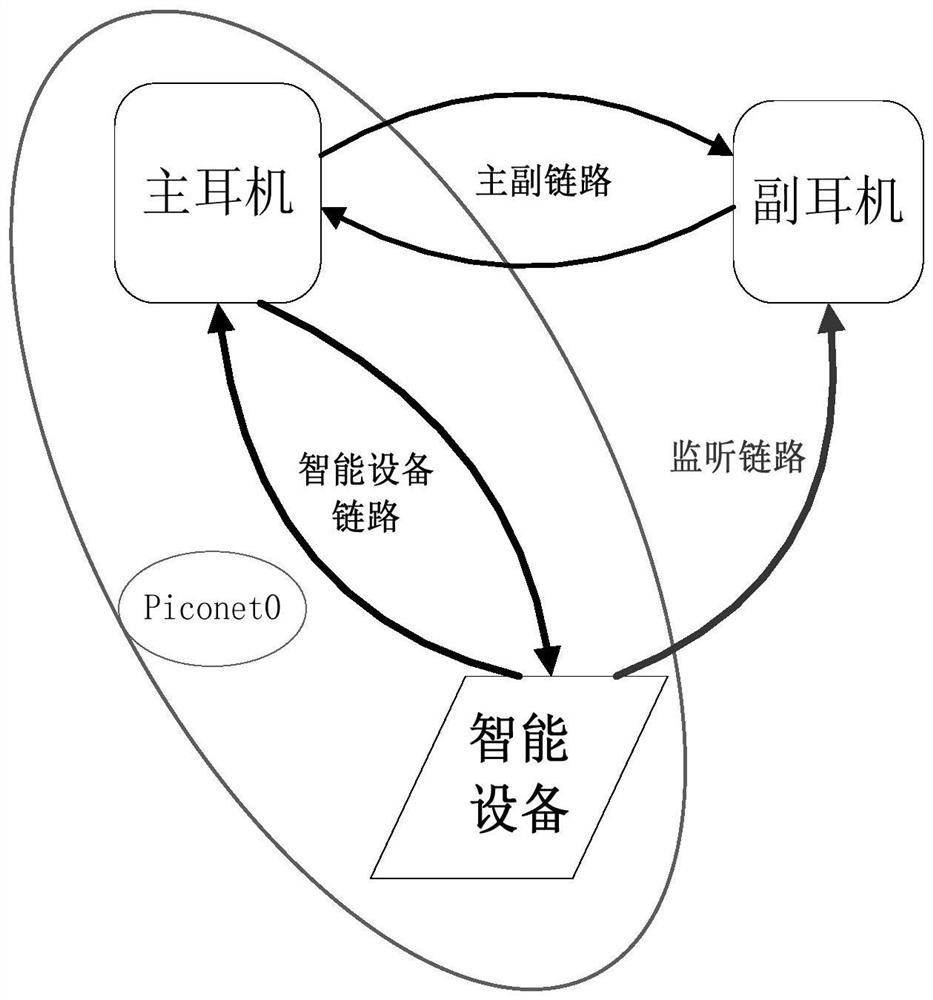
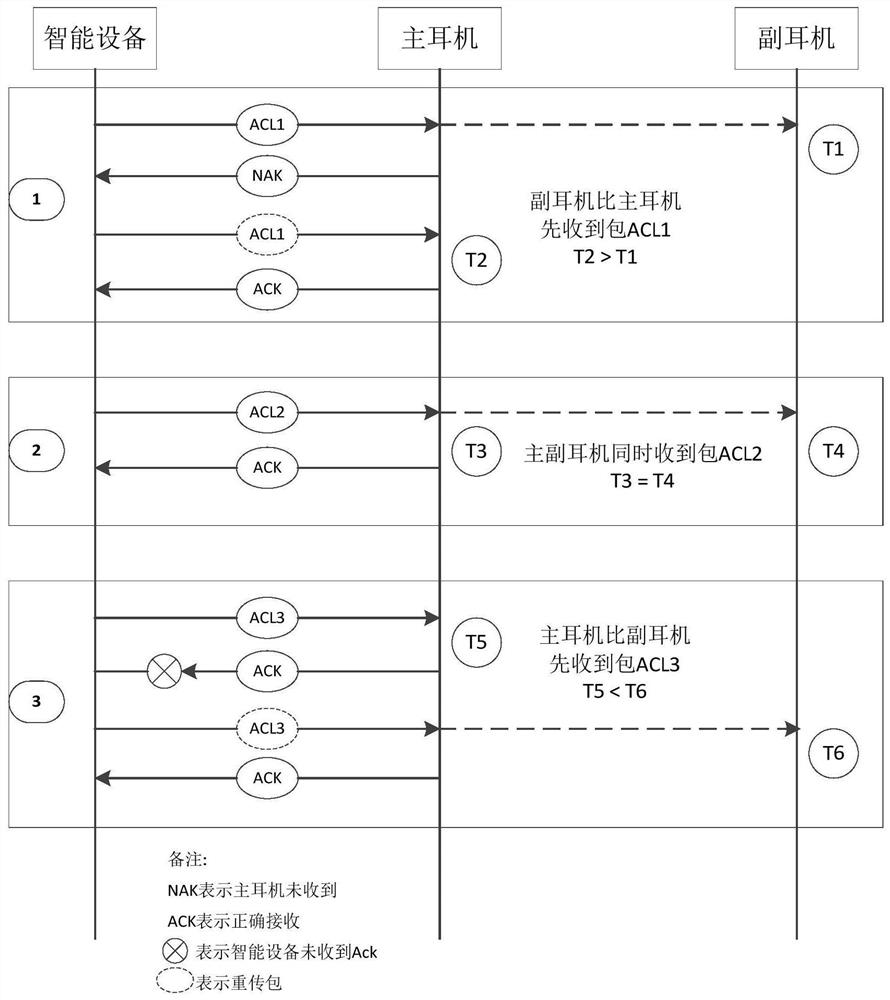
ActiveCN111885555ADecode and play in timeGuaranteed Data IntegritySynchronisation arrangementShort range communication serviceTimestampingHeadphones
The invention discloses a TWS earphone based on a monitoring scheme and an implementation method thereof, and the earphone comprises a main earphone which is in communication connection with an intelligent device, adds a timestamp to a received data packet through a Bluetooth clock, obtains corresponding SEQN information, obtains a set of {SEQN, timestamp} of an auxiliary earphone for representingthe receiving condition of the data packet, and transmits the data packet to the intelligent device according to the set of {SEQN, timestamp}, finds out a lost packet of the auxiliary earphone according to the timestamp and the SEQN information and sends the lost packet to the auxiliary earphone; the auxiliary earphone which is used for adding timestamps to the data packets received in the monitoring link through a Bluetooth clock, obtaining corresponding SEQN information, representing the data packet receiving condition of each received data packet through a set of {SEQN, timestamps}, sending the set of {SEQN, timestamps} to the main earphone after receiving a request of the main earphone, and sending the set of {SEQN, timestamps} to the main earphone; and inserting the lost packet withthe timestamp forwarded by the main earphone into the received data packet sequence when the lost packet with the timestamp forwarded by the main earphone is received.
Owner:ANYKA (GUANGZHOU) MICROELECTRONICS TECH CO LTD
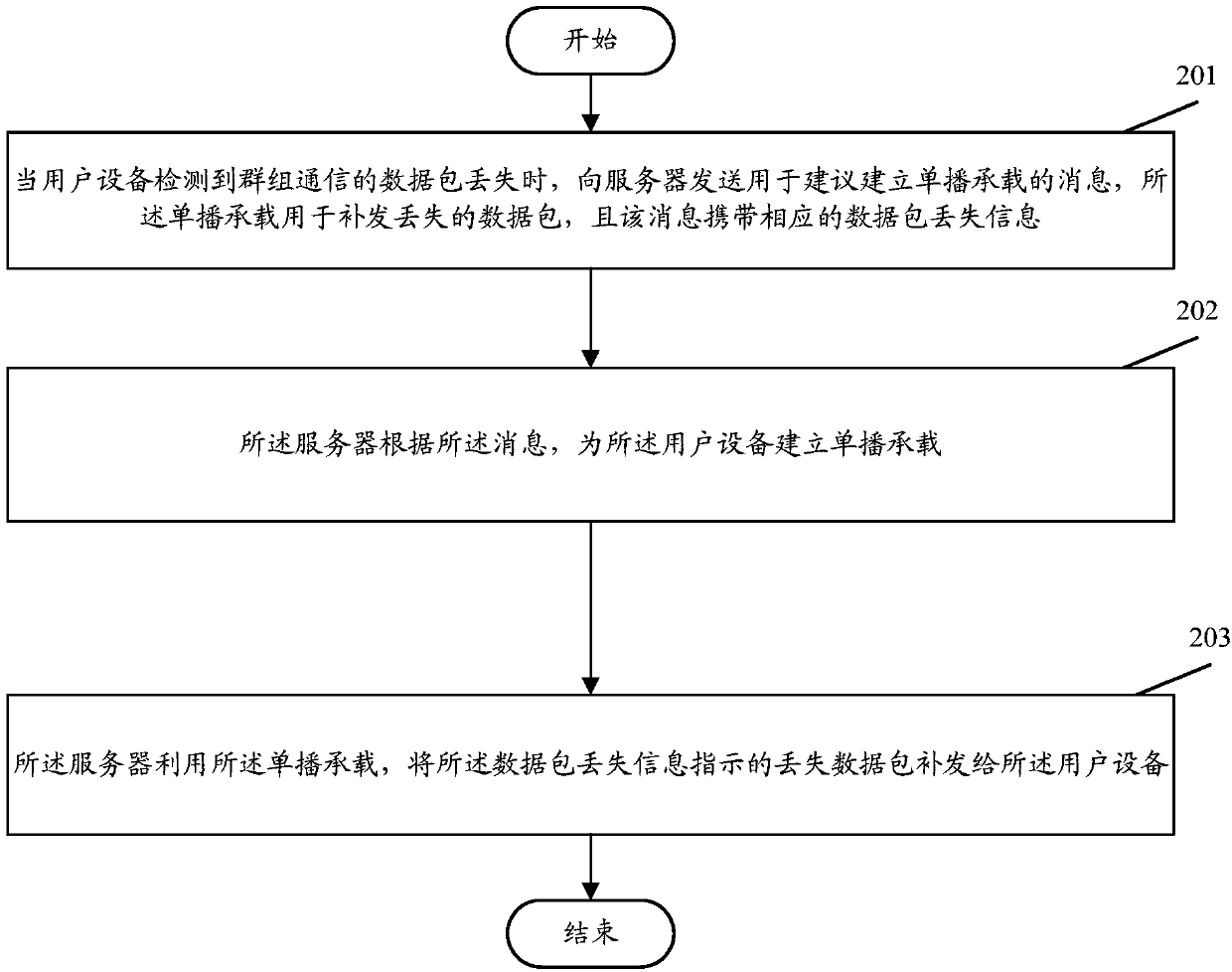
Packet supplementing method and system for group communication
InactiveCN109756846ASolve packet lossGuarantee data integrityError prevention/detection by using return channelBroadcast service distributionUnicastPacket loss
The invention discloses a packet reissuing method and system for group communication, and the method comprises the steps: sending a message which is used for suggesting the establishment of a unicastbearer to a server when user equipment detects the loss of a data packet of the group communication, the unicast bearer being used for reissuing the lost data packet, and the message carrying corresponding data packet loss information; enabling the server to establish a unicast bearer for the user equipment according to the message; and enbaling the server to utilize the unicast bearer to retransmit a lost data packet indicated by the data packet loss information to the user equipment. By adopting the method and the device, the packet loss problem of group communication can be effectively solved, and the data integrity of the group communication is ensured.
Owner:CHENGDU TD TECH LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com