HDFS access control method based on role and user trust value
A technology of access control and trust value, applied in user identity/authority verification, secure communication devices, digital transmission systems, etc., can solve problems such as non-mandatory access control measures, no security certification, security risks, etc. Behavioural credibility issues, reducing complexity and administrative overhead, and improving the effect of flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
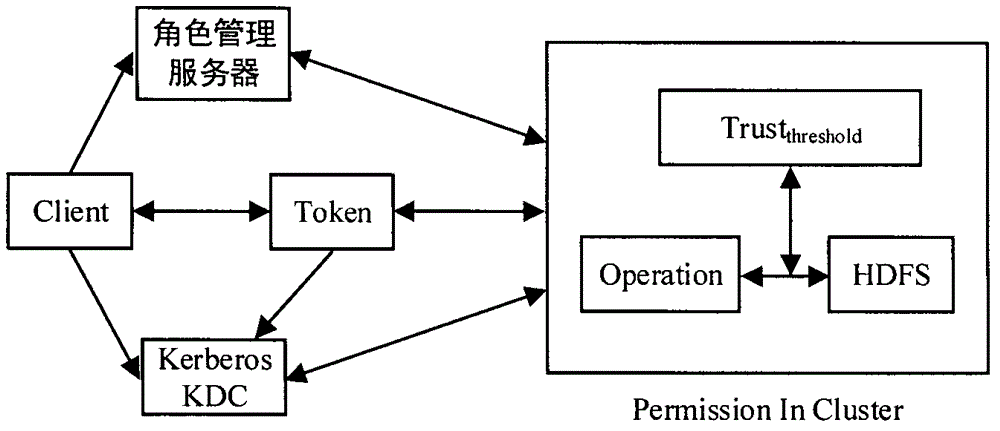
[0034] In order to solve the access control problem of Hadoop distributed file system HDFS, the present invention provides a kind of HDFS access control method based on role and user trust value, specific process is as follows figure 2 As shown, the method includes:
[0035] When a user sends an operation request, the role management server first verifies the integrity of the operation request, and then checks the user's operation authority. After the check is passed, the role management server queries the user and role database according to the user identity, assigns the corresponding role to the user, and The role certificate is sent to the user along with the shared secret.
[0036]The user sends his plaintext user information to the Kerberos key distribution manager (Key Distribution Center, KDC), and the KDC server judges whether the user is in the key database through the authentication server (AS), and if so, generates a ticket authorization ticket ( TGT), and encrypt...
Embodiment 2
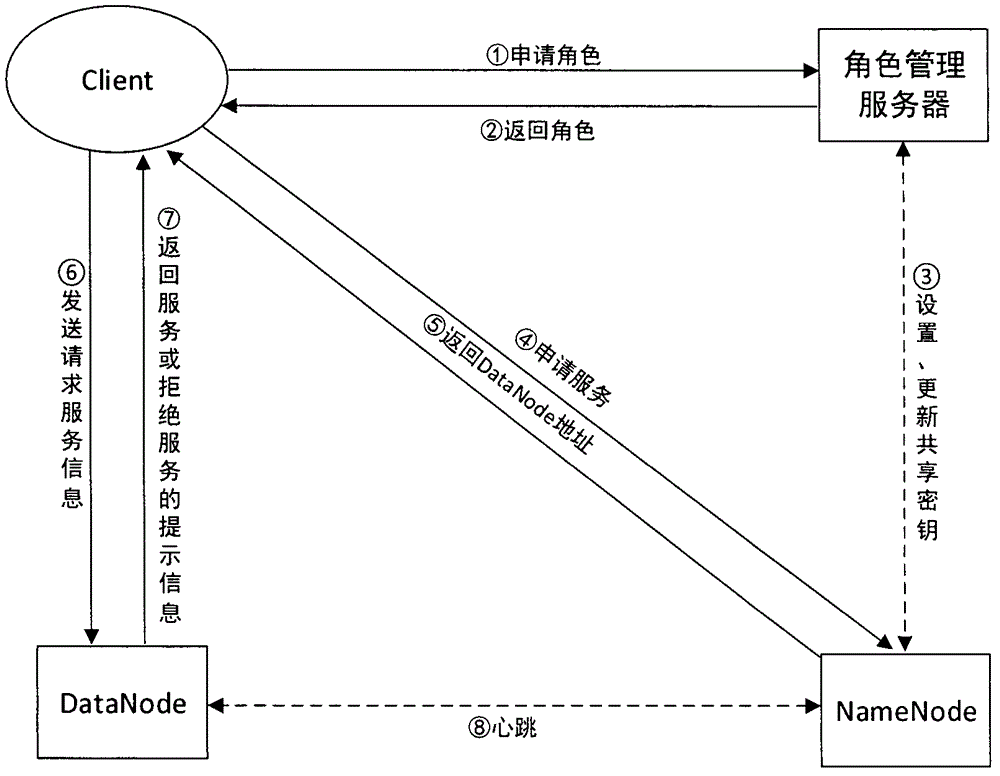
[0039] Embodiment 2 of the present invention provides a role-based HDFS access control method in combination with the traditional role-based access control policy RBAC. The steps of the method are as follows: image 3 shown, including:
[0040] (1) The user Client requests the role management server to assign a role;
[0041] (2) The role management server assigns roles to users, and issues role certificates and shared keys to users;
[0042] (3) Set and update the shared key between the role management server and the Name Node node;
[0043] (4) The user Client accesses the Name Node node with the role certificate and shared key, and applies for access services;
[0044] (5) After the Name Node node verifies that the user's role is legal and the shared key is legal, it returns the best copy address of the data block to the user;
[0045] (6) The user Client requests the required services from all the Data Node nodes notified by the Name Node node;
[0046] (7) After recei...
Embodiment 3
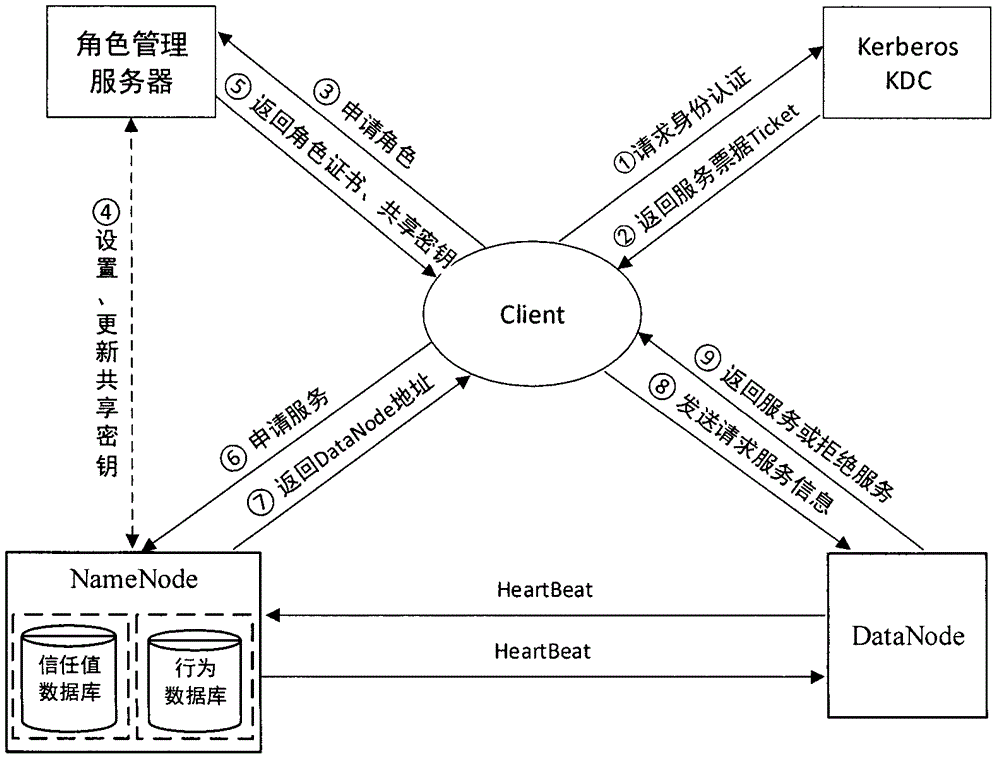
[0049] Embodiment 3 of the present invention combines the concepts of Kerberos and user trust value to provide a HDFS access control method based on user trust value. The steps of the method are as follows Figure 4 shown, including:
[0050] (1) Client encrypts its identity authentication information with K1 and sends it to KDC to request identity authentication;
[0051] (2) KDC verifies that the client's identity is legal and valid, issues a ticket authorization ticket TGT, and encrypts it with K1 and sends it back to the client;
[0052] (3) Client sends a service request to KDC with TGT, and the request content is encrypted with K1;
[0053] (4) KDC receives the request and generates a service ticket Ticket={K3, username, IP, address, service name, validity period, time stamp};
[0054] (5) KDC encrypts K3 with K1, encrypts Ticket with K2 and sends it back to Client;
[0055] (6) Client decrypts and obtains the session key K3 with the Name Node node, and generates Auth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com