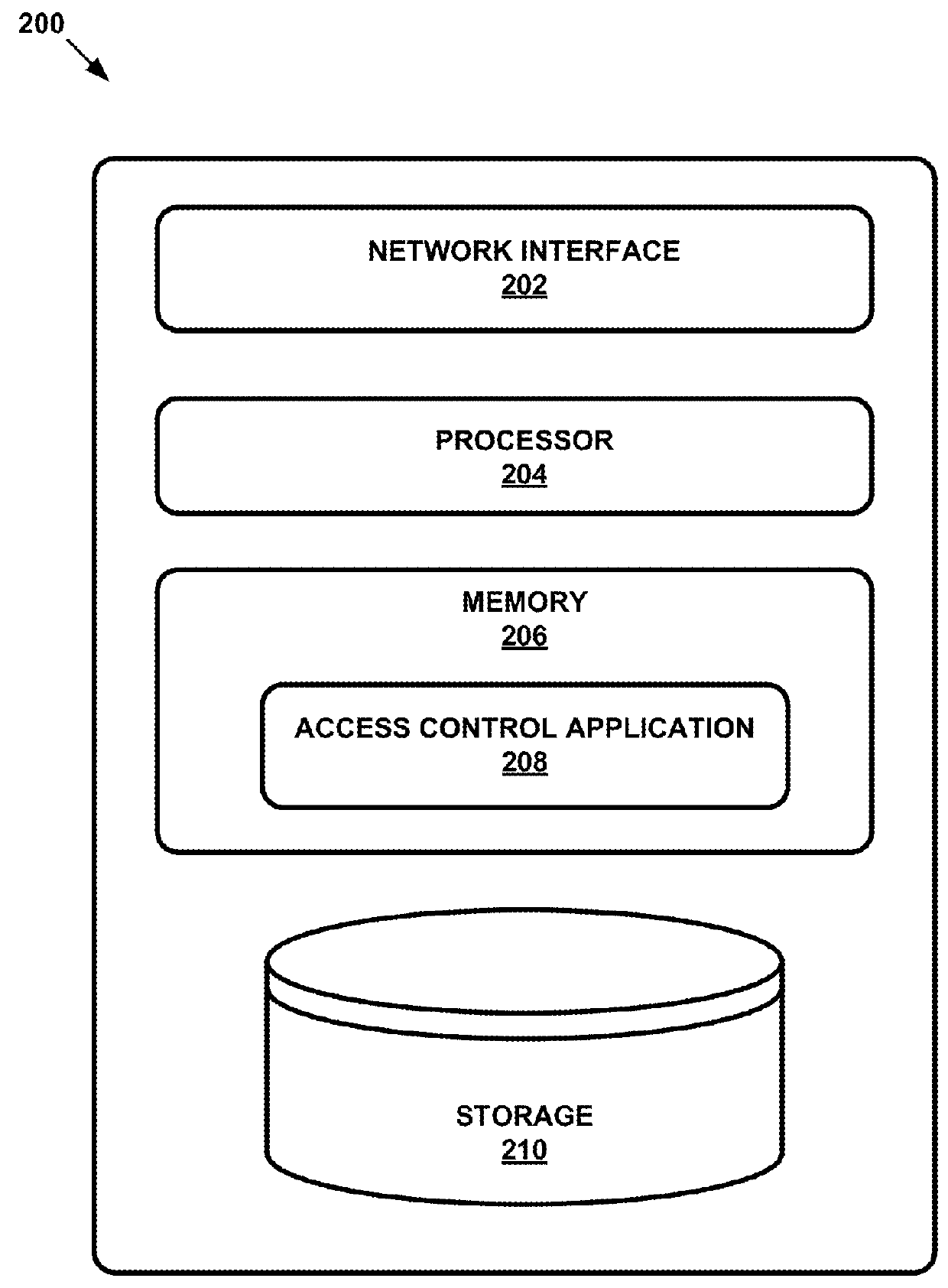
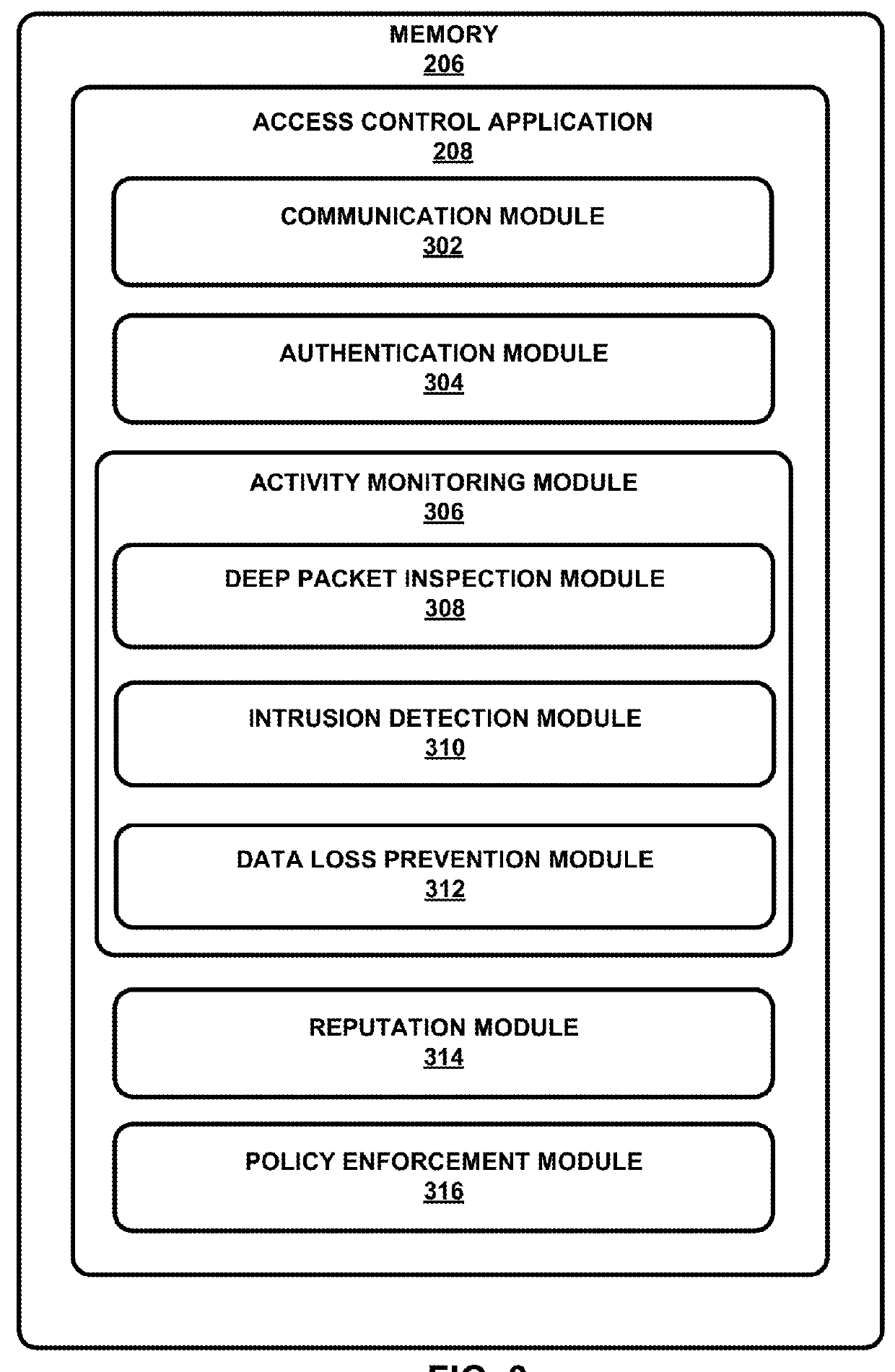
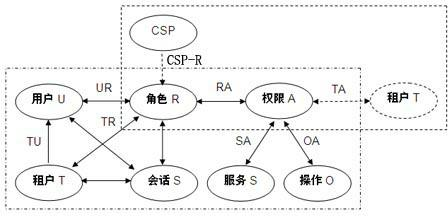
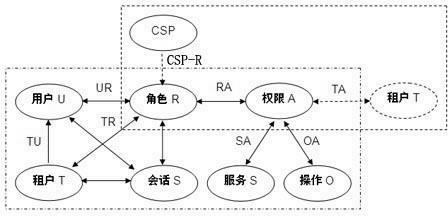
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
151 results about "Role base access control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
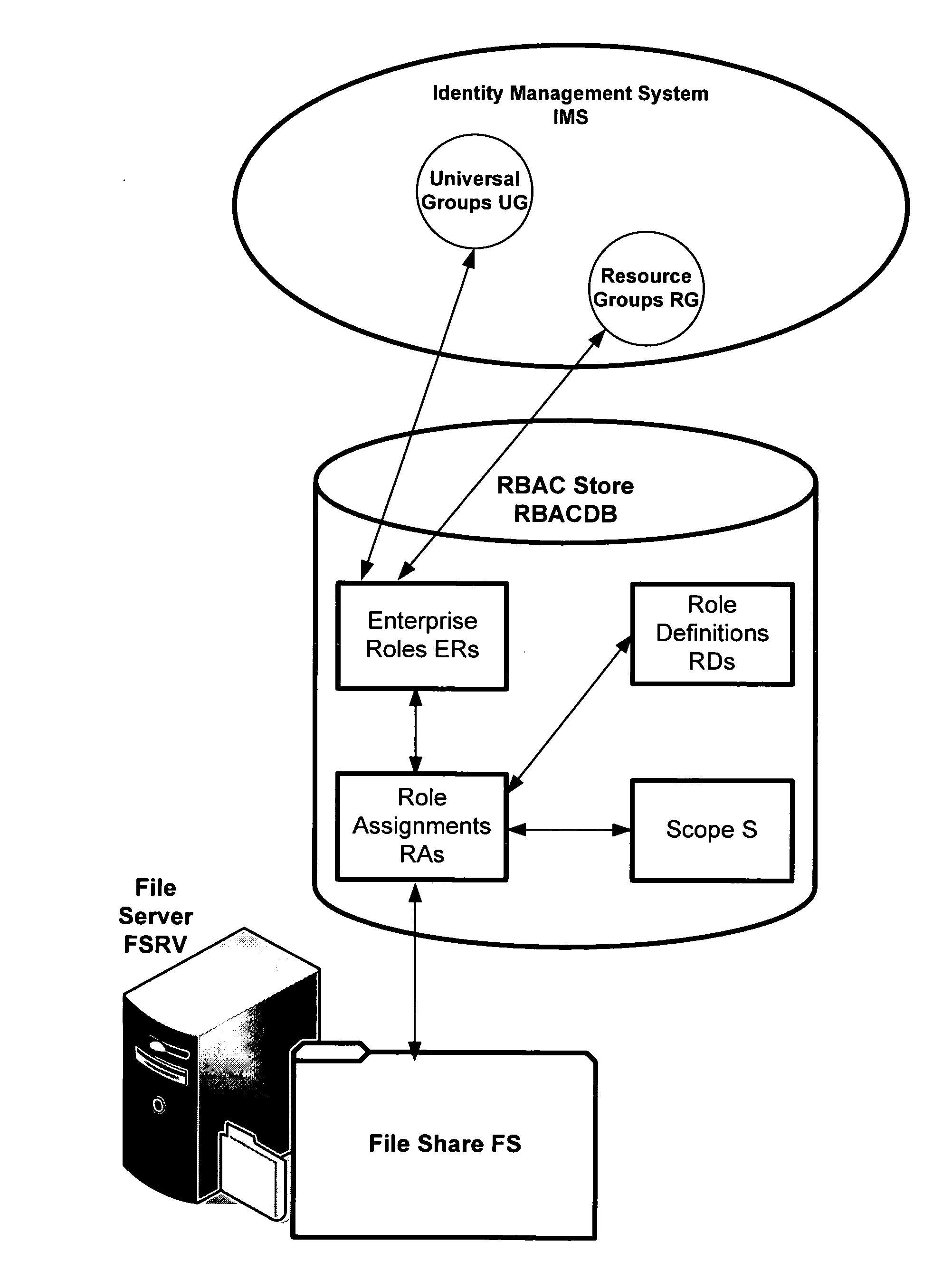
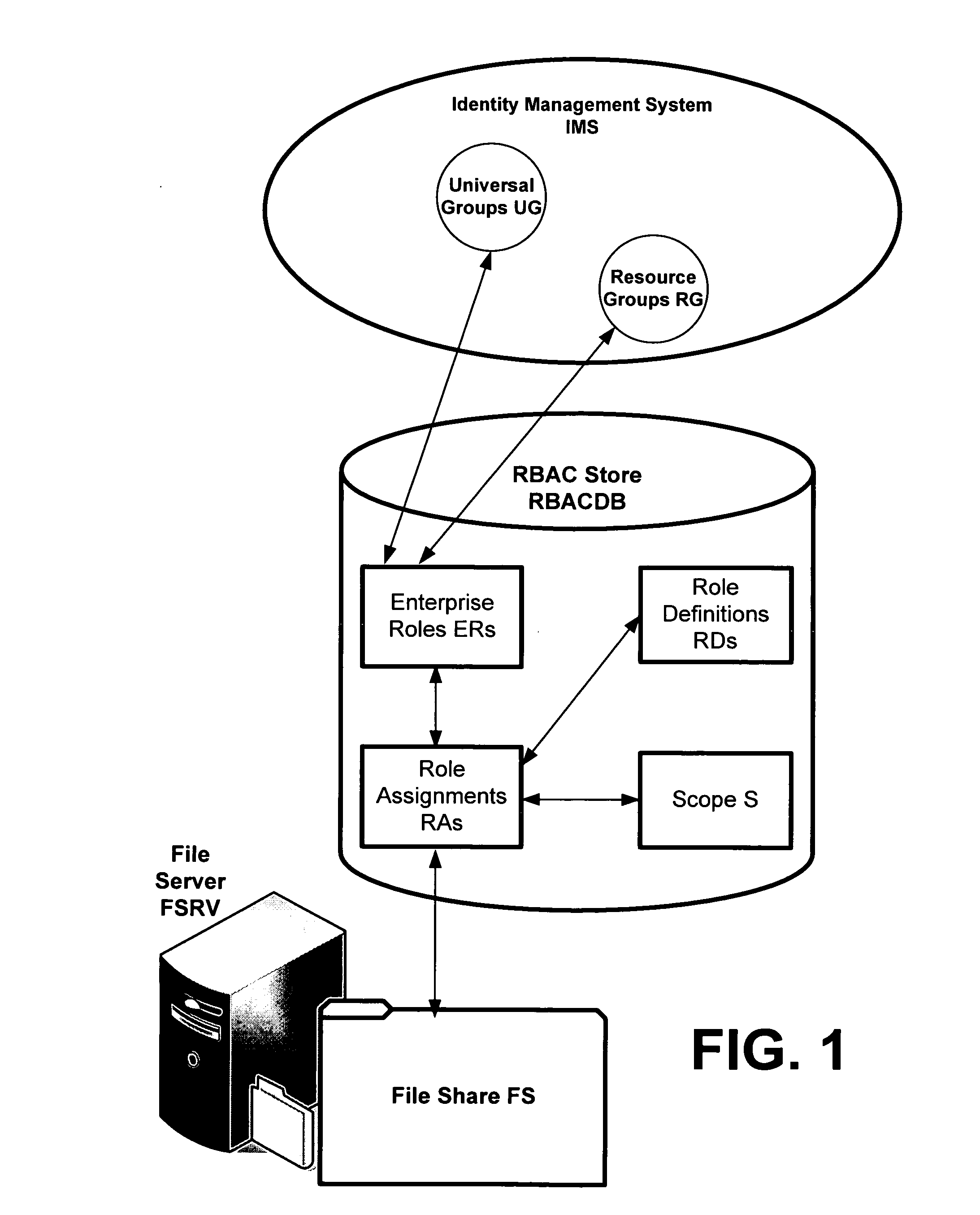
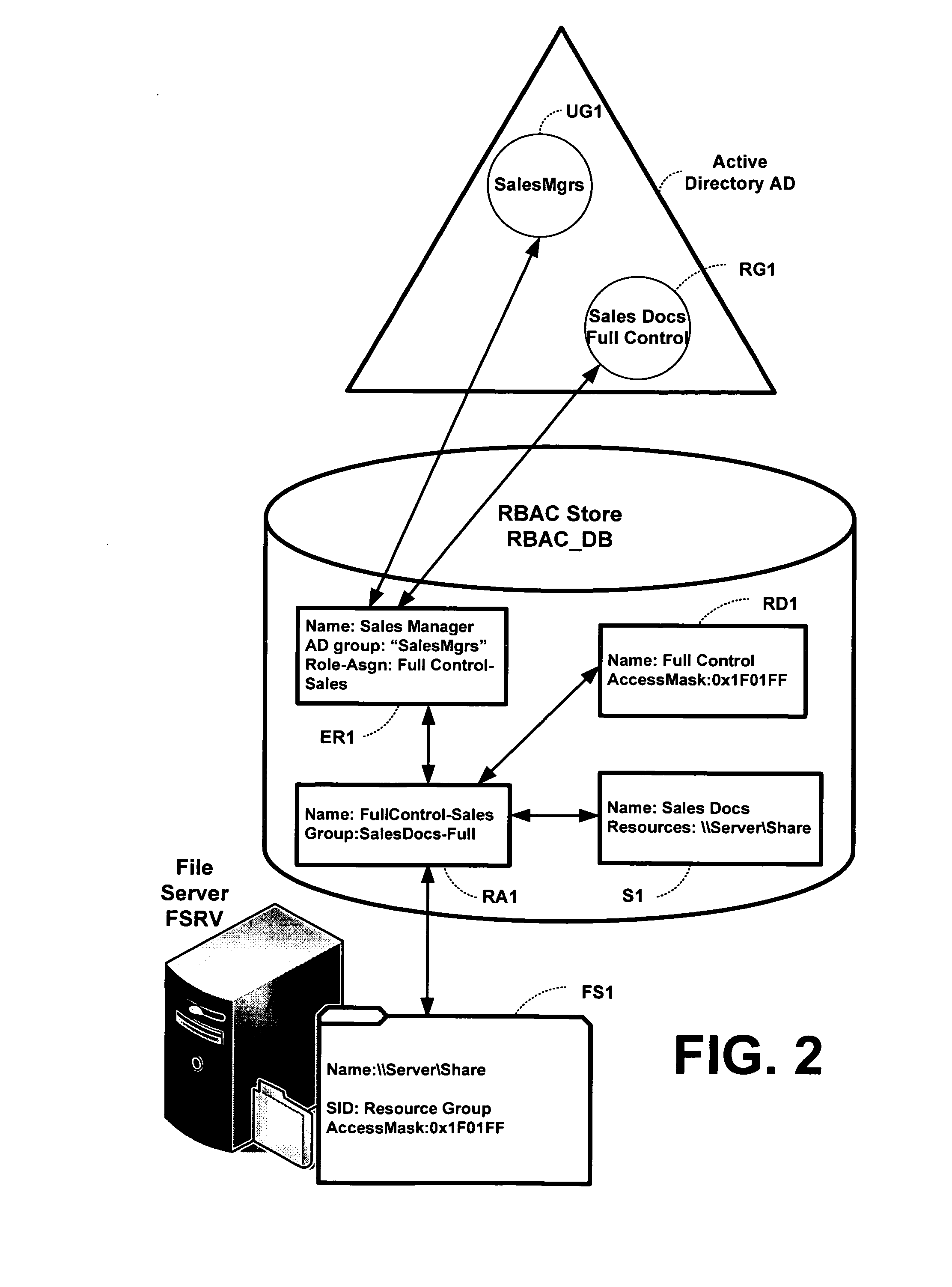
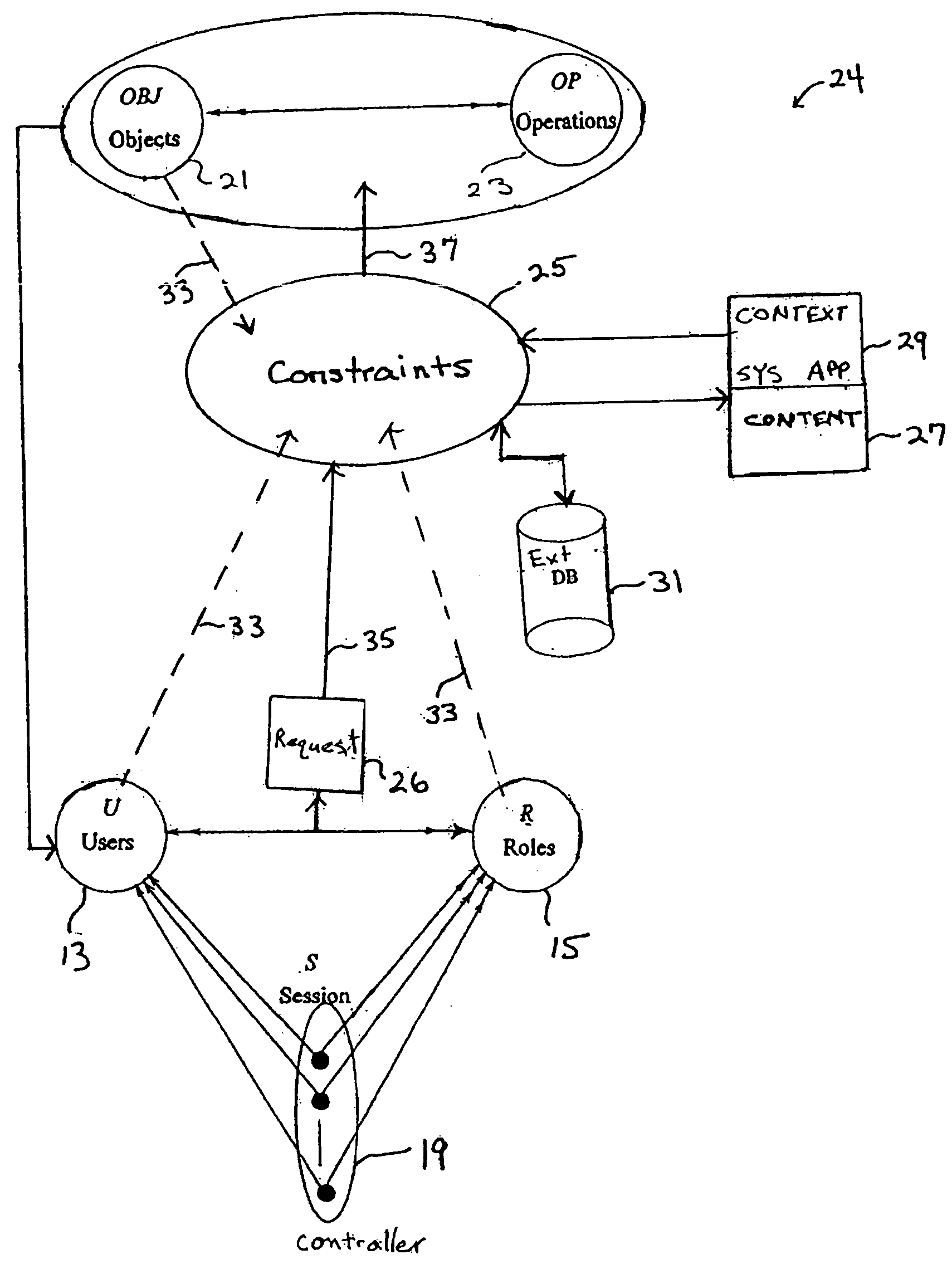
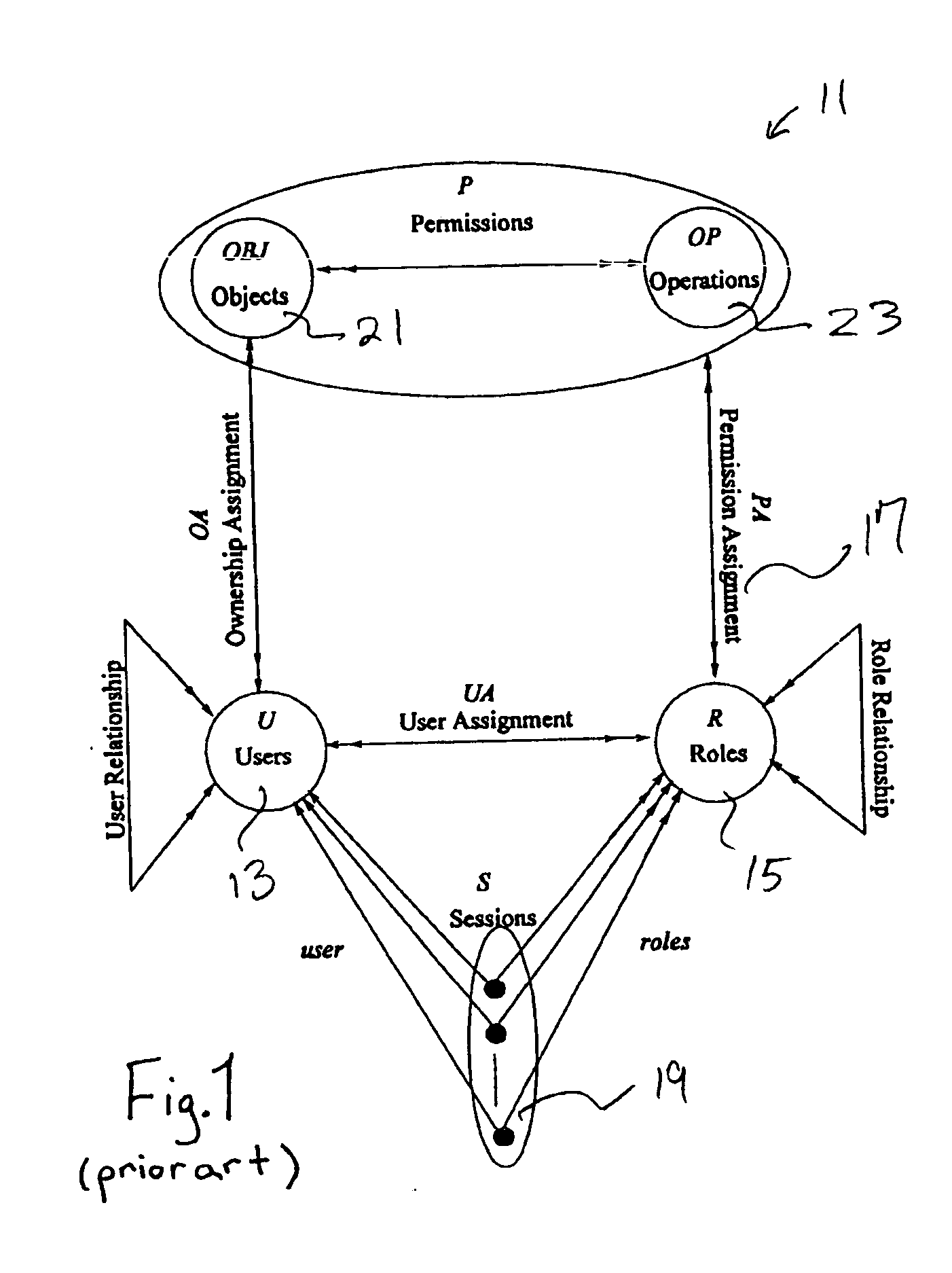
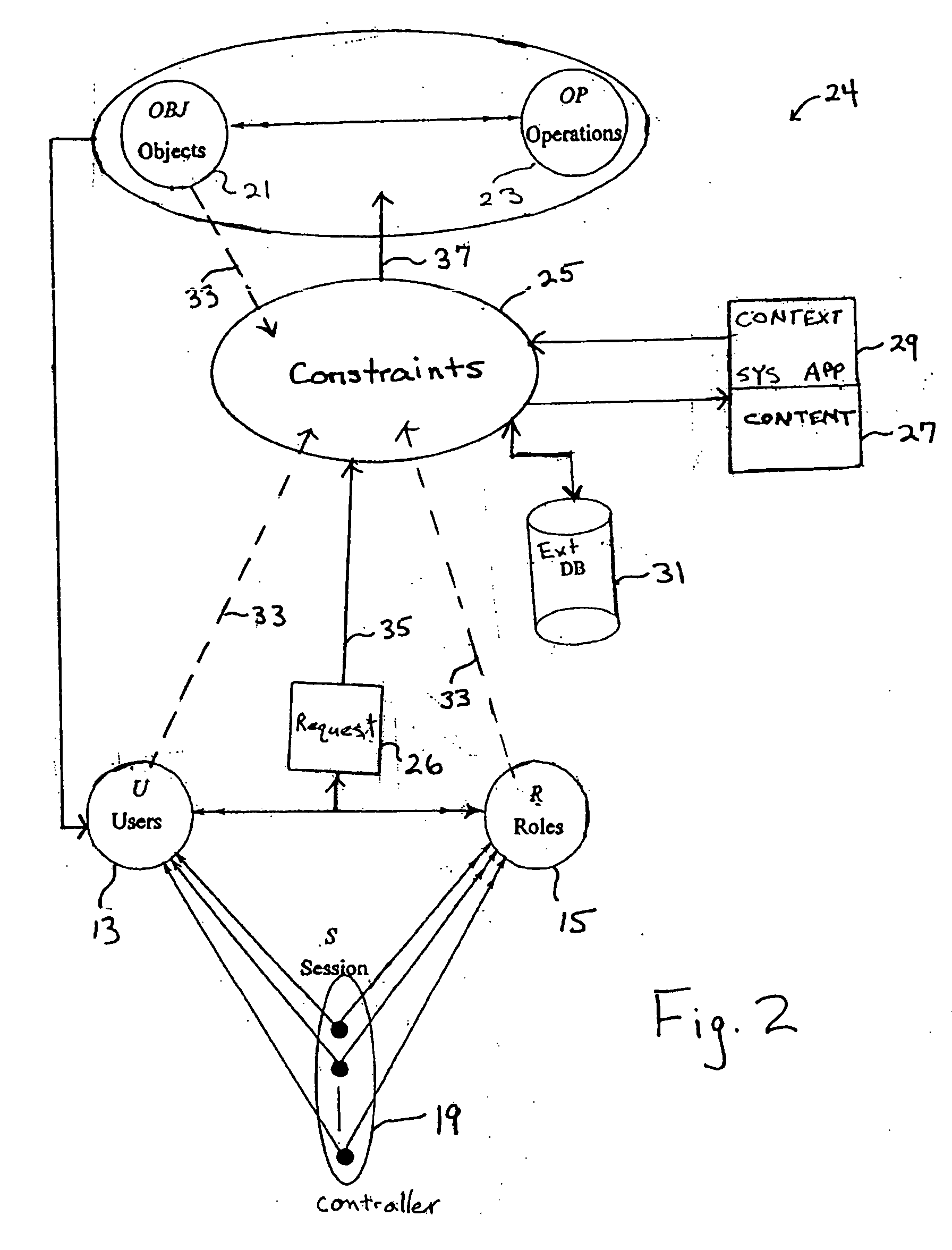
Definition of Role-Based Access Control (RBAC) Role-based access control (RBAC) restricts network access based on a person's role within an organization and has become one of the main methods for advanced access control. The roles in RBAC refer to the levels of access that employees have to the network.
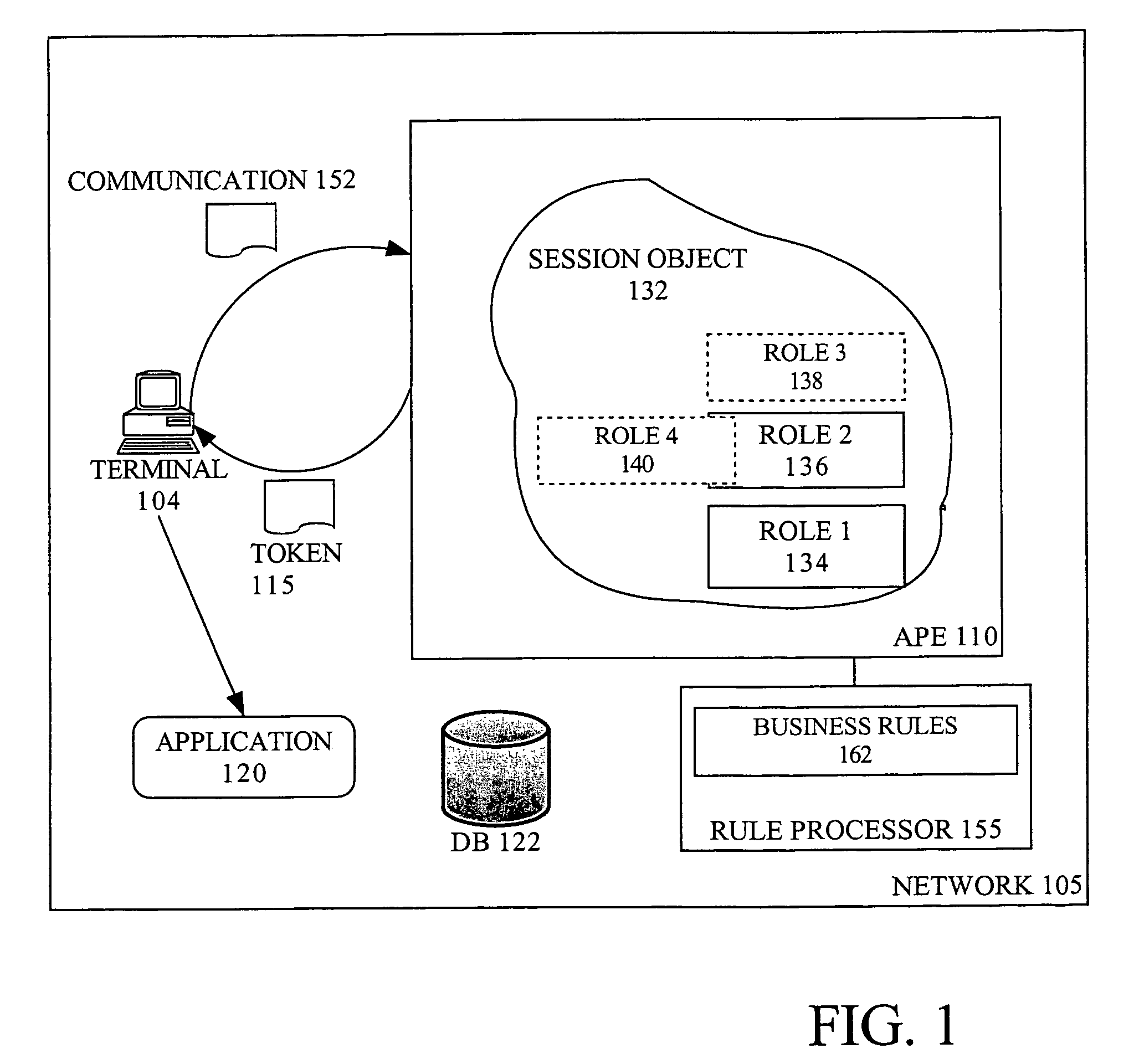
Translating role-based access control policy to resource authorization policy
ActiveUS20070283443A1Program control using stored programsDigital data processing detailsFile systemManaged object
Translation of role-based authoring models for managing RBAC “roles” to resource authorization policy (RAP), such as ACL-based applications, is provided. A generic RBAC system is defined from which mappings to other authorization enforcement mechanism make possible the translation of RBAC “roles” to resource authorization policies applied to resources managed by a resource manager, e.g., a file system resource manager. An implementation is described that uses Windows Authorization Manager as a storage mechanism and object model to manage object types and relationships translated from an RBAC system.
Owner:MICROSOFT TECH LICENSING LLC
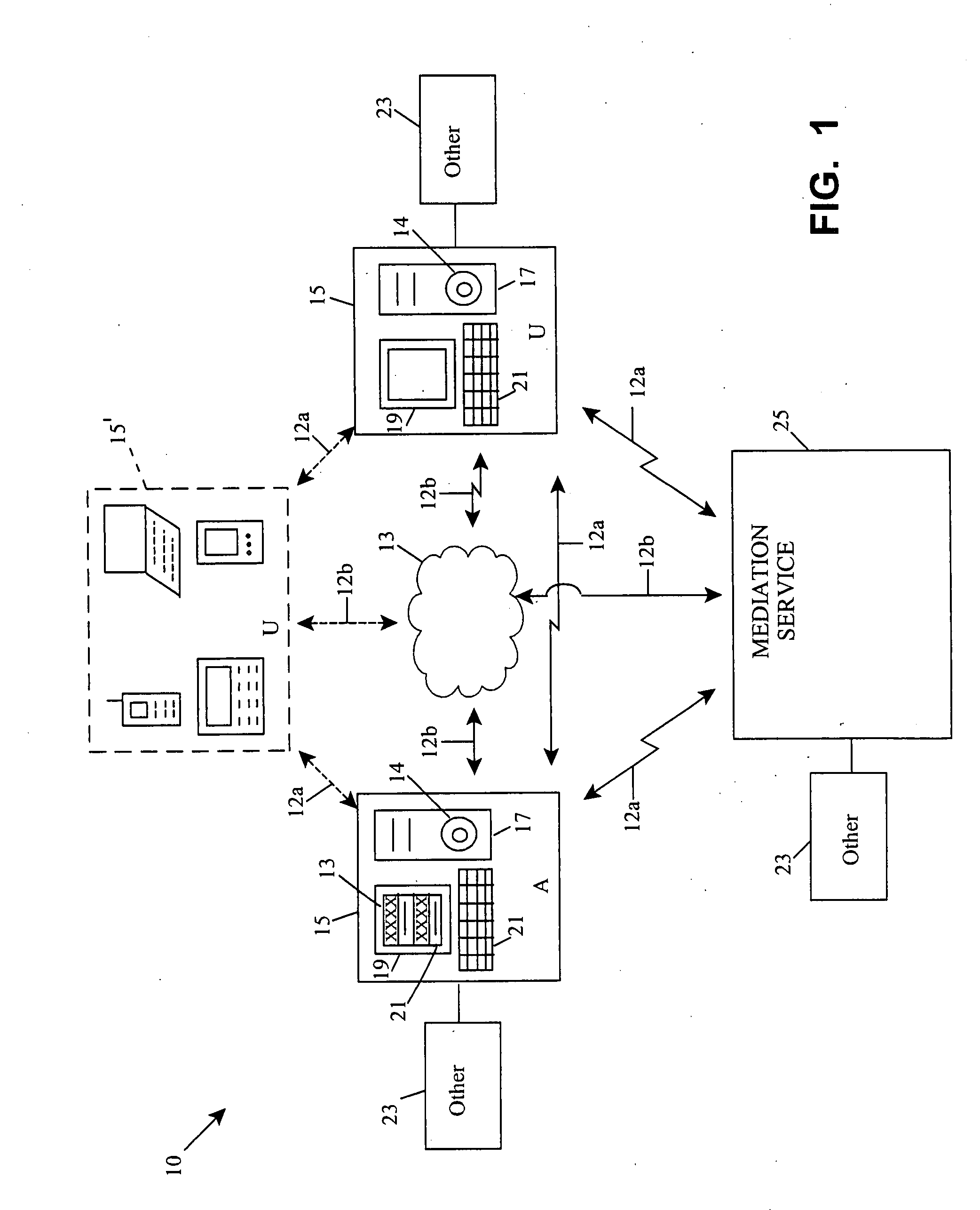
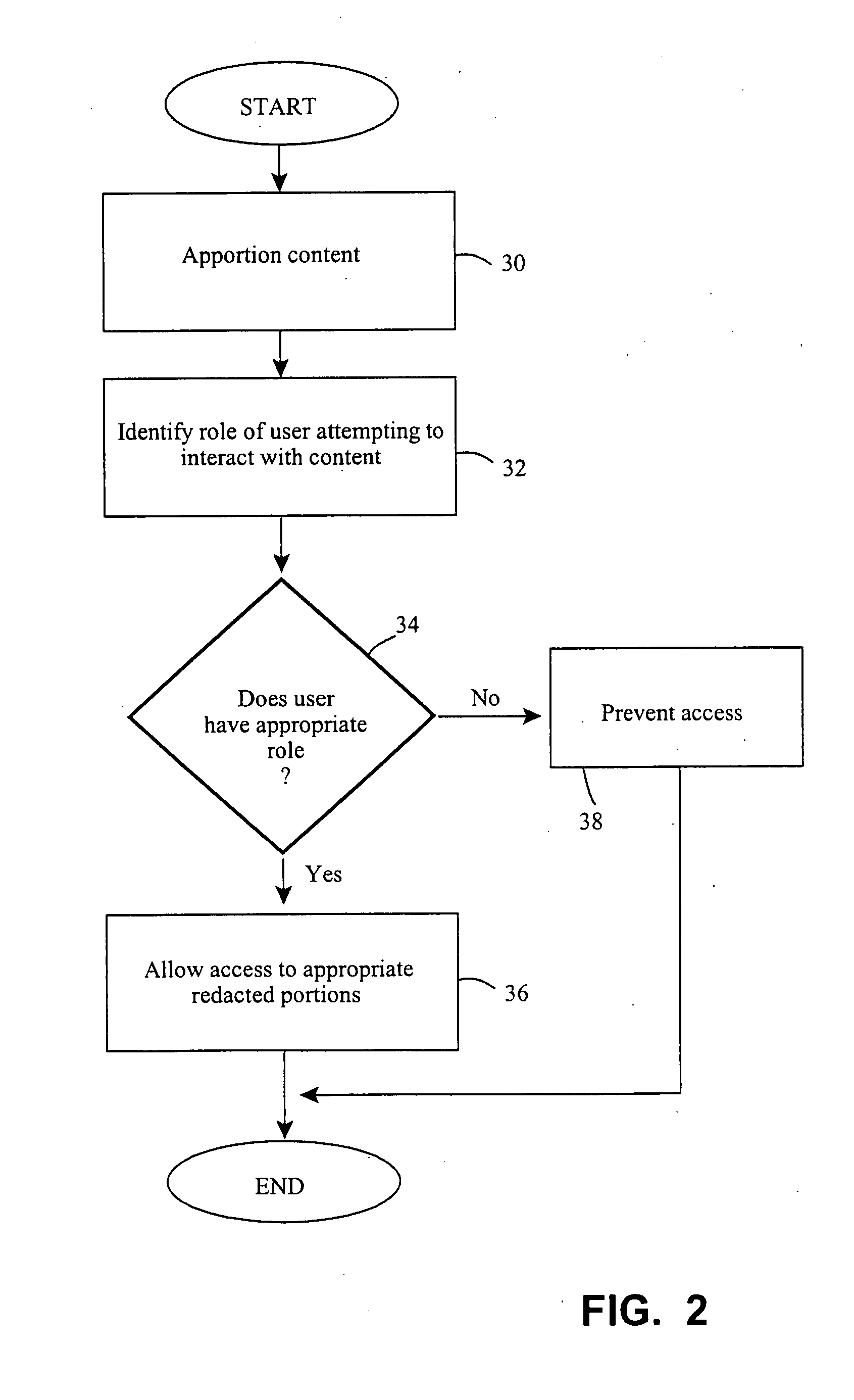
Role-based access control for redacted content
InactiveUS20090025063A1Digital data processing detailsComputer security arrangementsMedia access controlUser interface
Apparatus and methods are described for accessing redacted material based on user roles. An author designates portions of content as to-be-redacted. The author establishes various users roles able to access it and defines attributes or time constraints affecting the viewing / using. Upon electronically saving the content, the to-be-redacted portion is encrypted. An intermediary, such as a keytable service, mediates access between later users and the content. Upon identification of a role of a user attempting to interact with the content, and matching the role to one of the author-established roles, the encrypted redacted portion is decrypted. In this manner, users gain access to content based only on their role. The surrounding events are also loggable, traceable, and verifiable. A monitored connection between the user and the content, as well as various user interface options, are other noteworthy features. Computer program products and computing network interaction are also defined.
Owner:NOVELL INTPROP HLDG
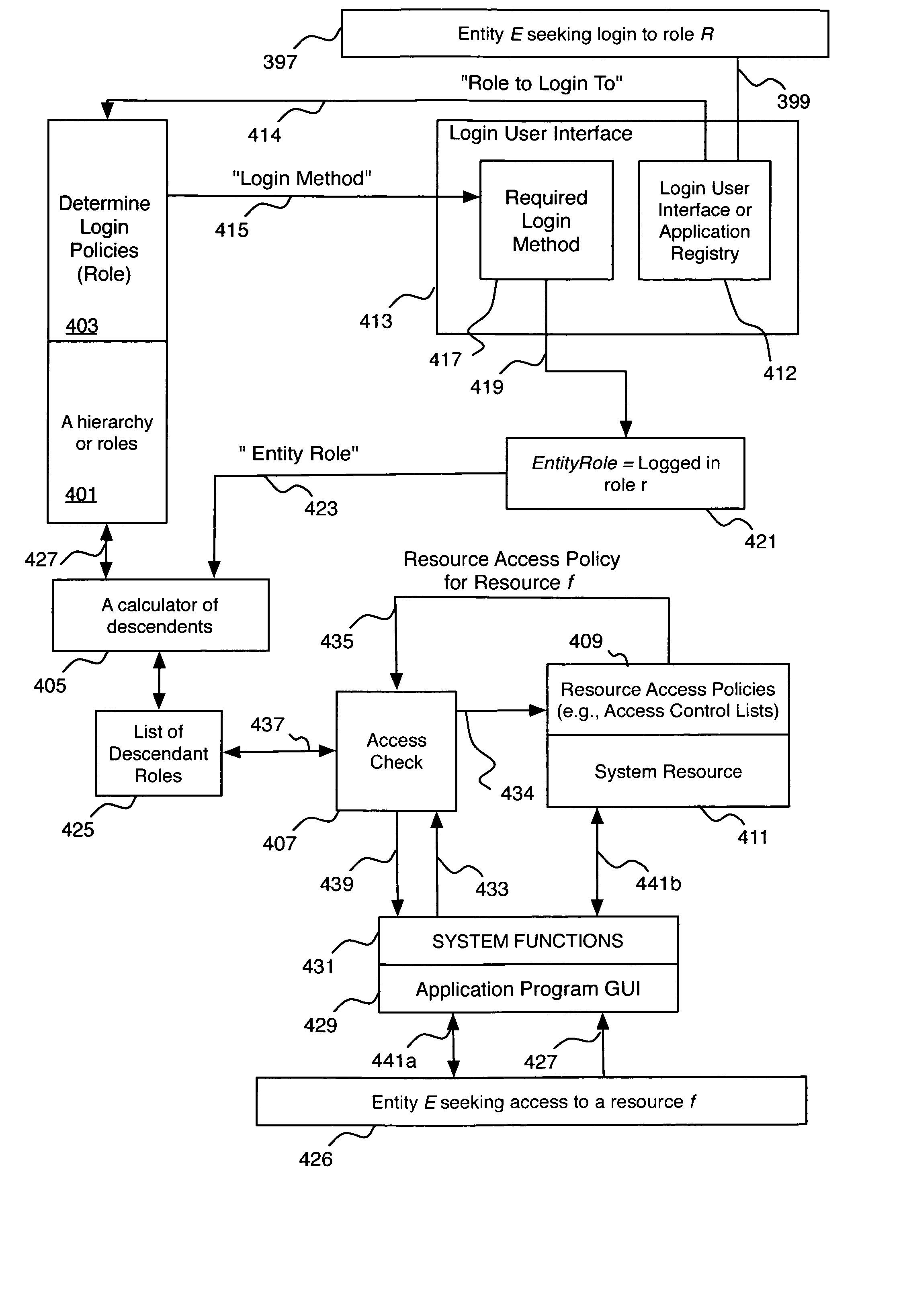
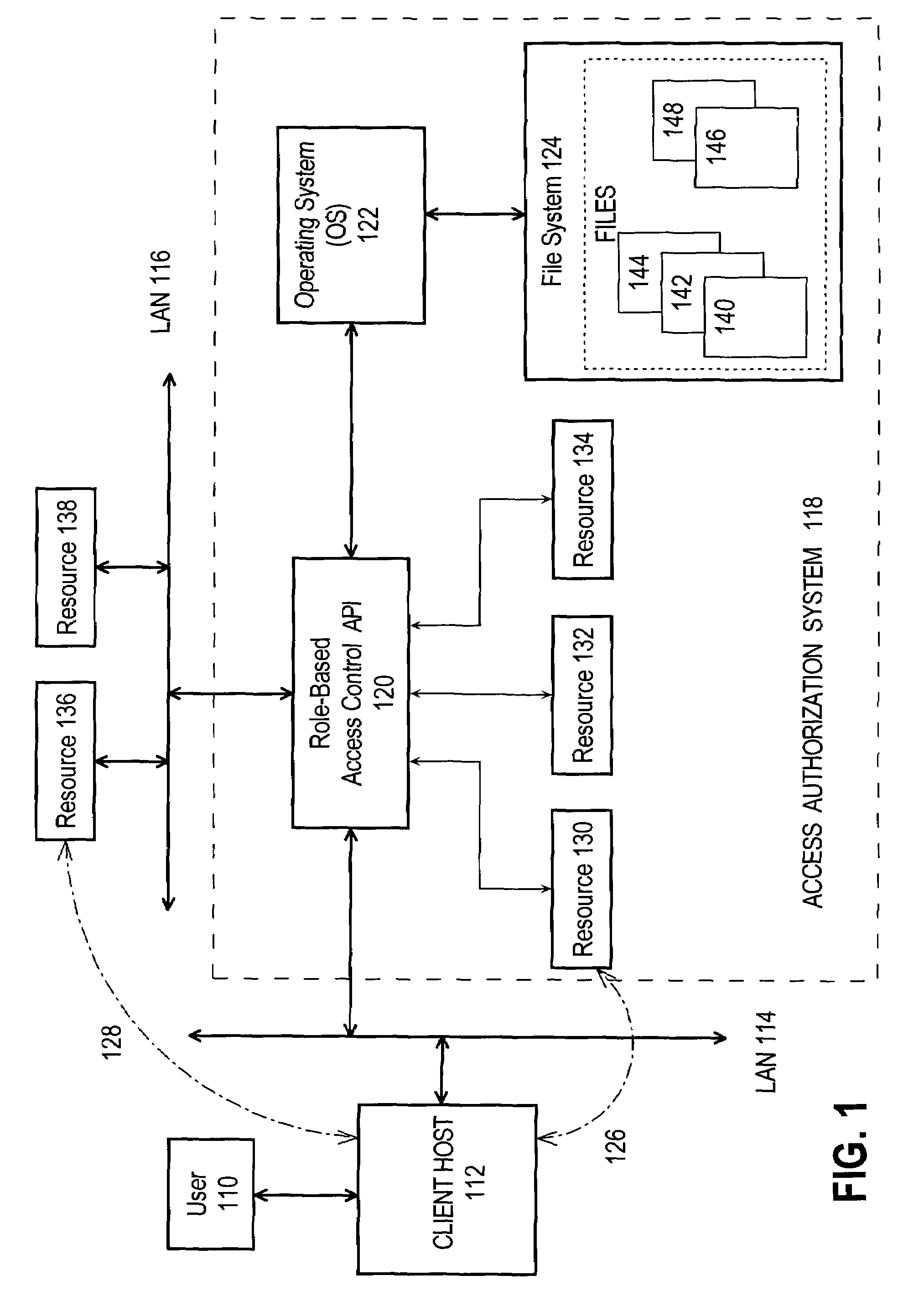
System and method for providing a hierarchical role-based access control
InactiveUS20070214497A1Improve the level ofImprove efficiencyDigital data processing detailsUser identity/authority verificationControl systemWorld Wide Web
Role-based hierarchical access control system and method. A computer system having a data storage capacity and a central processing unit and at least one resource has an access control data structure defining role-based access control lists for the resource, wherein the access control list defines based on the role of a user the types of access that the user may have to the at least one resource. A hierarchy of roles having at least a first role and a second role wherein the second role inherits the permissions granted to the first role for the at least one resource. Access to the resource is determined by comparing roles defined to have access privileges to the resource and the permissions granted to such roles to the role of an entity seeking access to the resource.
Owner:AXALTO INC
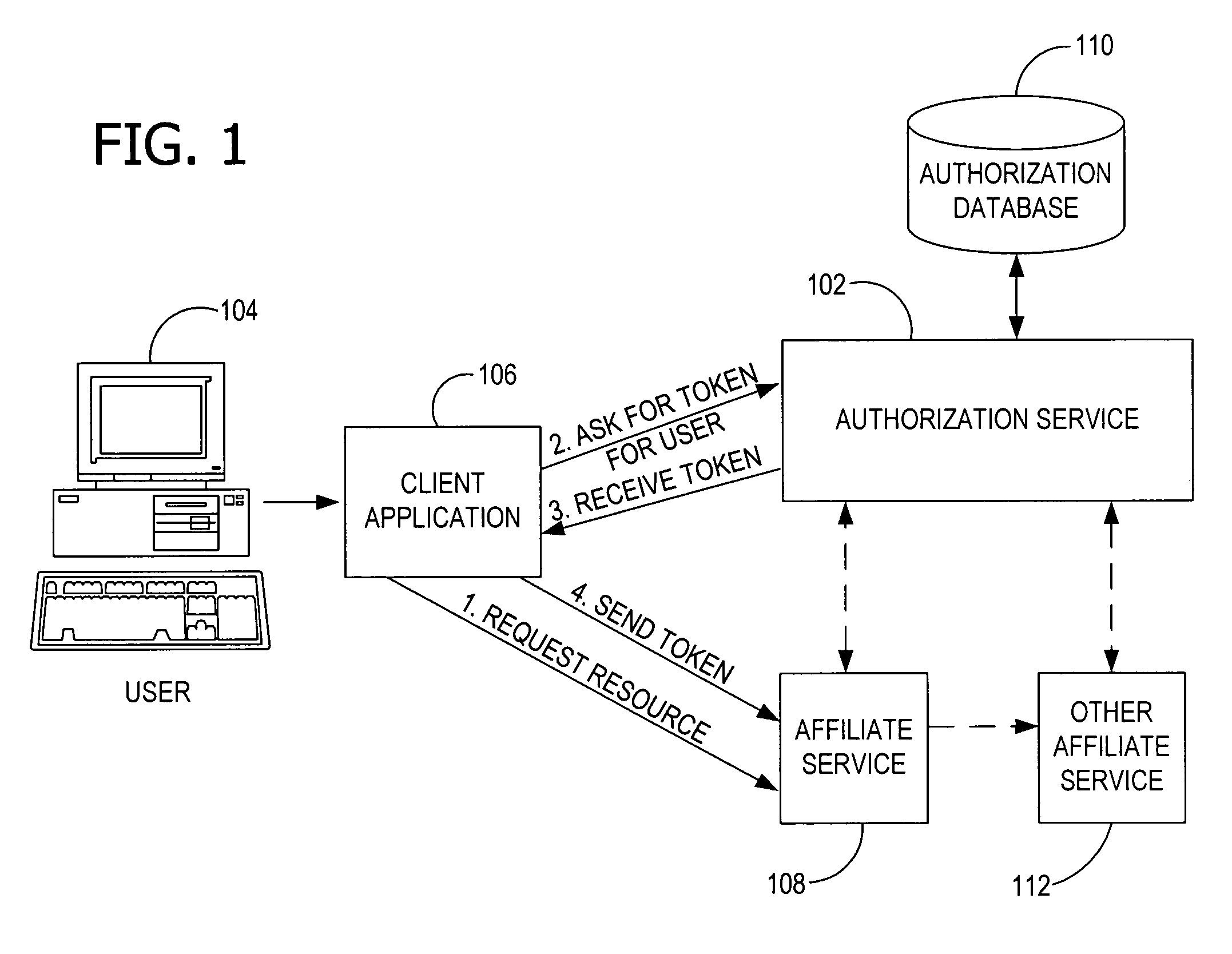
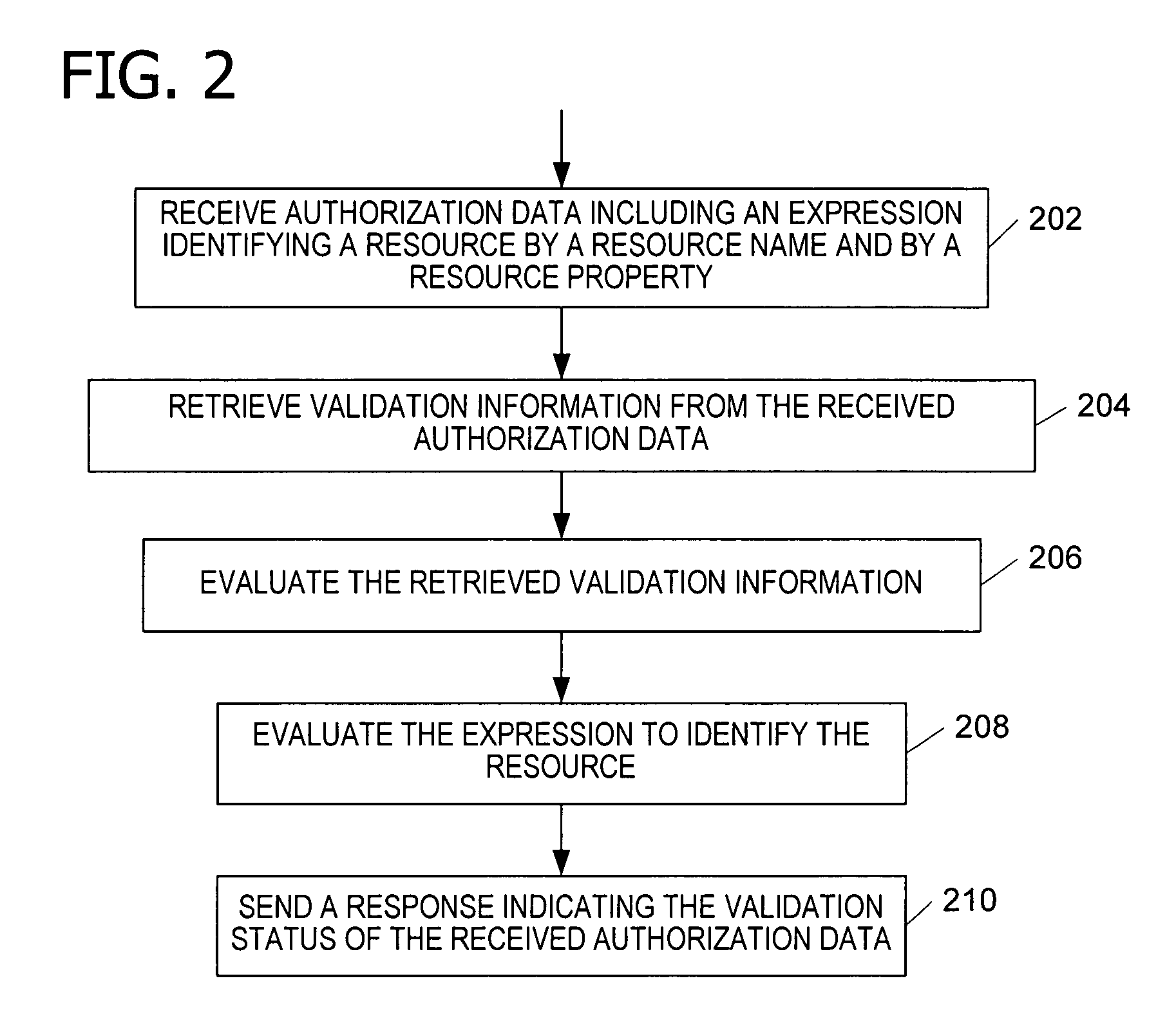
Authorization and access control service for distributed network resources
ActiveUS7685206B1Simplify access control managementEasy to implementDigital data processing detailsTransmissionMulti siteClient-side
Providing access to a resource via authorization data that conditionally defines the access by an expression that identifies the resource by name and by at least one property of the resource. An authorization service issues the authorization data (e.g., as a token) and evaluating authorization data received from a client. The authorization service evaluates the expression in the authorization data to identify the resource and determine the rights associated with the user for the resource. The authorization service implements role-based access control to control access to resources in a distributed, multi-site network.
Owner:MICROSOFT TECH LICENSING LLC
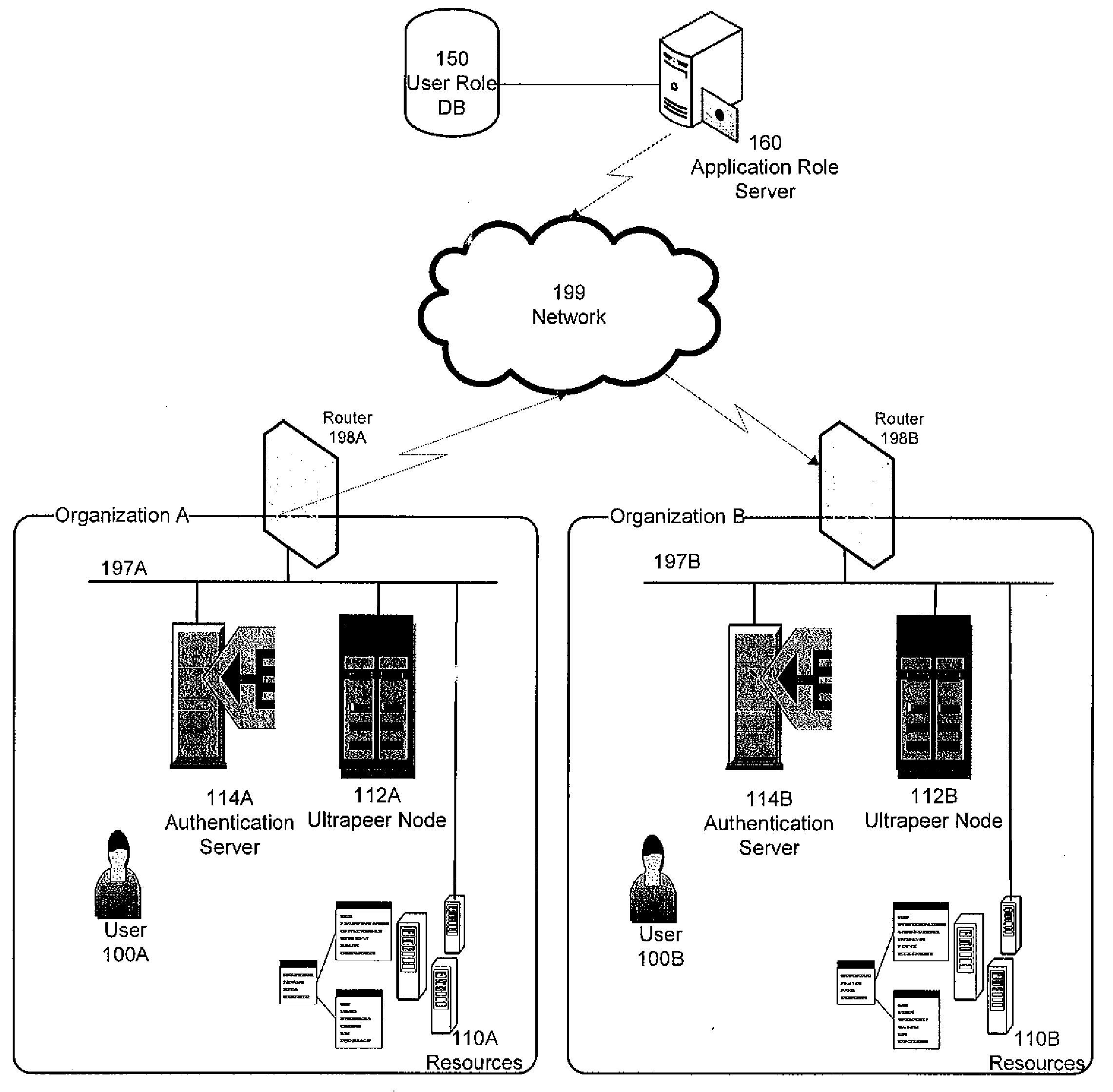
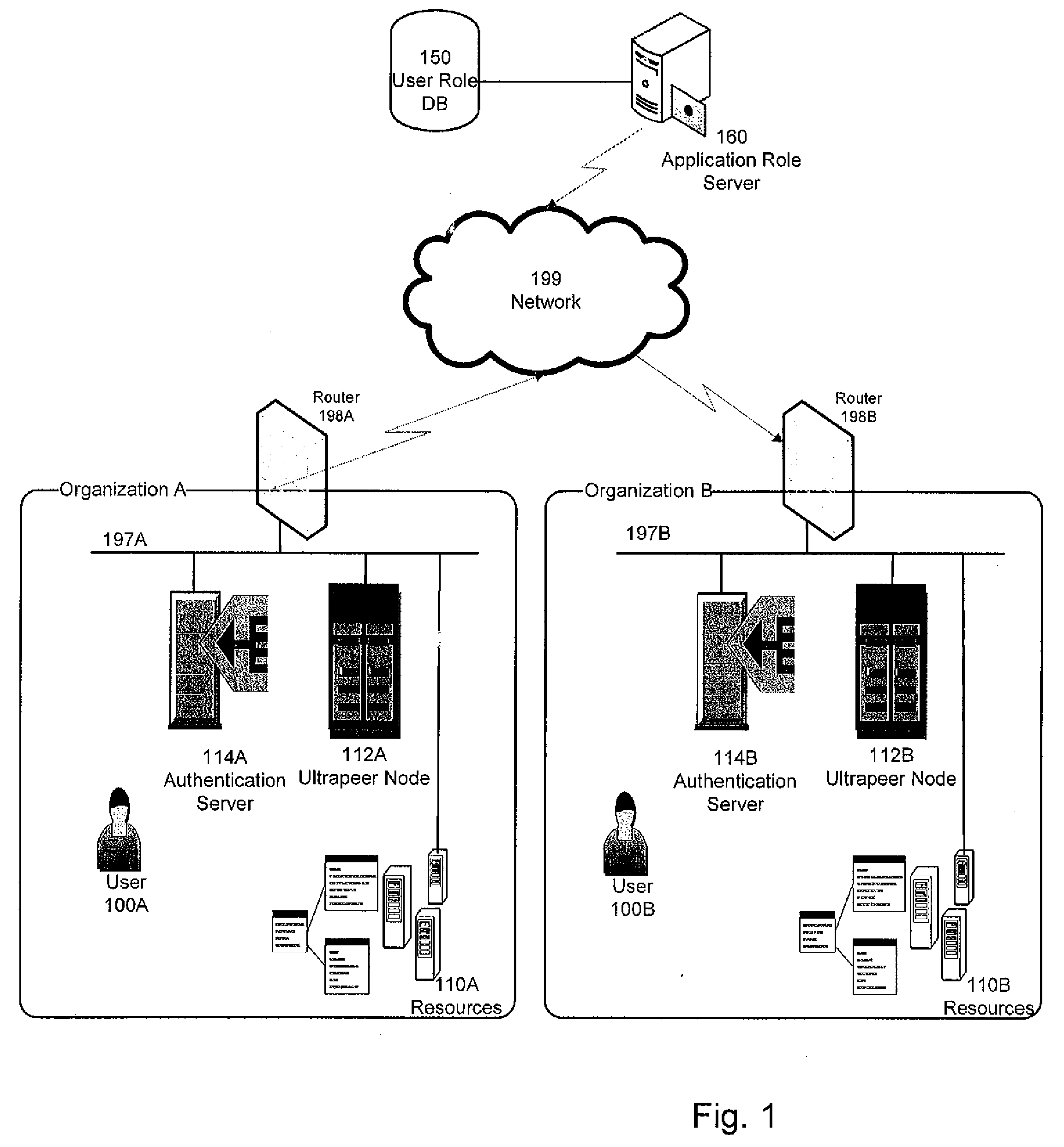
Role-based access control to computing resources in an inter-organizational community
ActiveUS20080313716A1Digital data processing detailsComputer security arrangementsDistributed Computing EnvironmentInter organizational
A method for controlling access to a plurality of computing resources in a distributed computing environment can comprise the steps of: an application role server, responsive to receiving a certificate request, authenticating the requester and issuing a digital certificate to the requester; an access control node, responsive to receiving a resource access request, granting access to the computing resource to the requester upon ascertaining the requestor's access privileges, or forwarding the resource access request to another access control node.
Owner:SYRACUSE UNIVERSITY
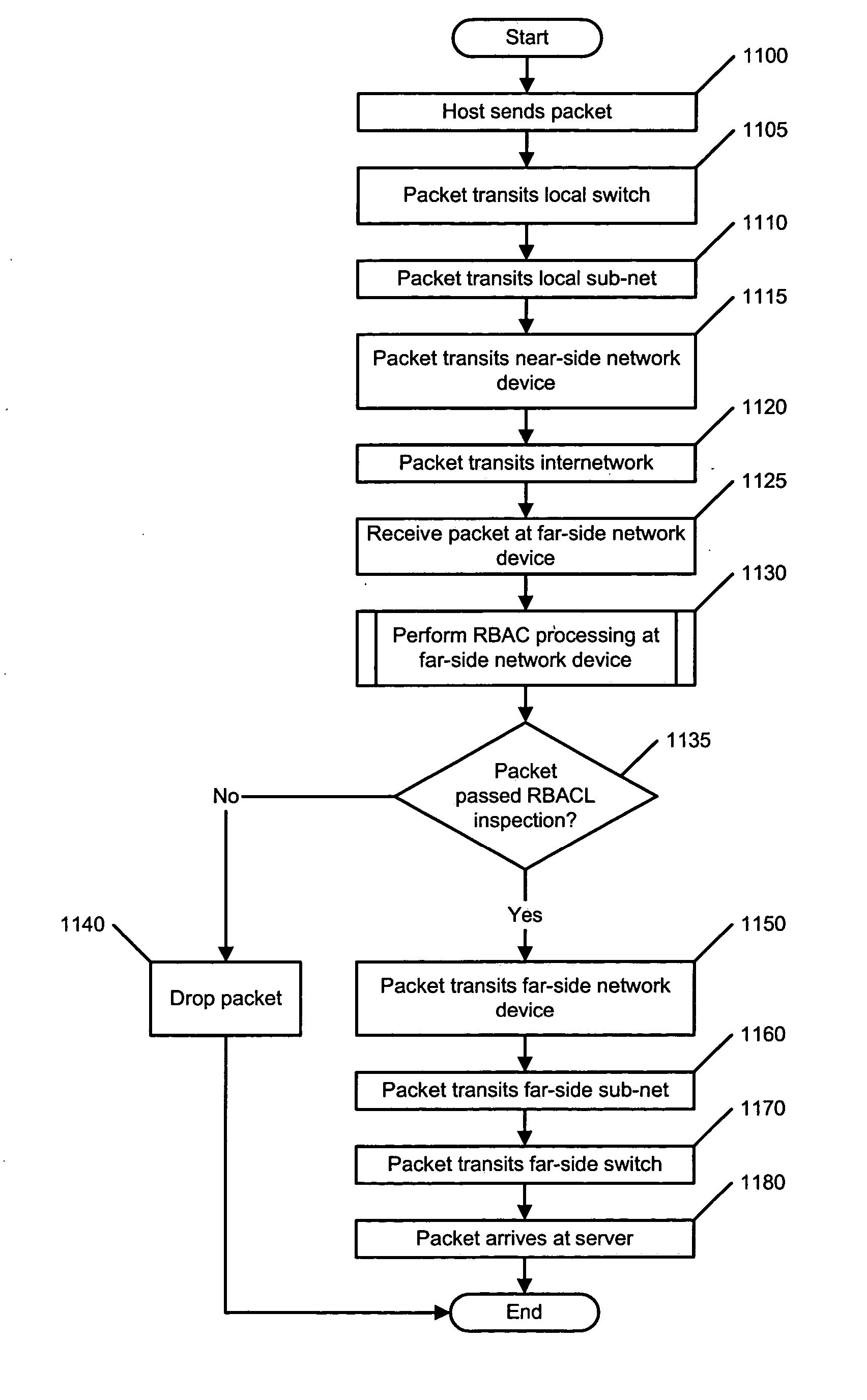
Method and apparatus for providing network security using role-based access control
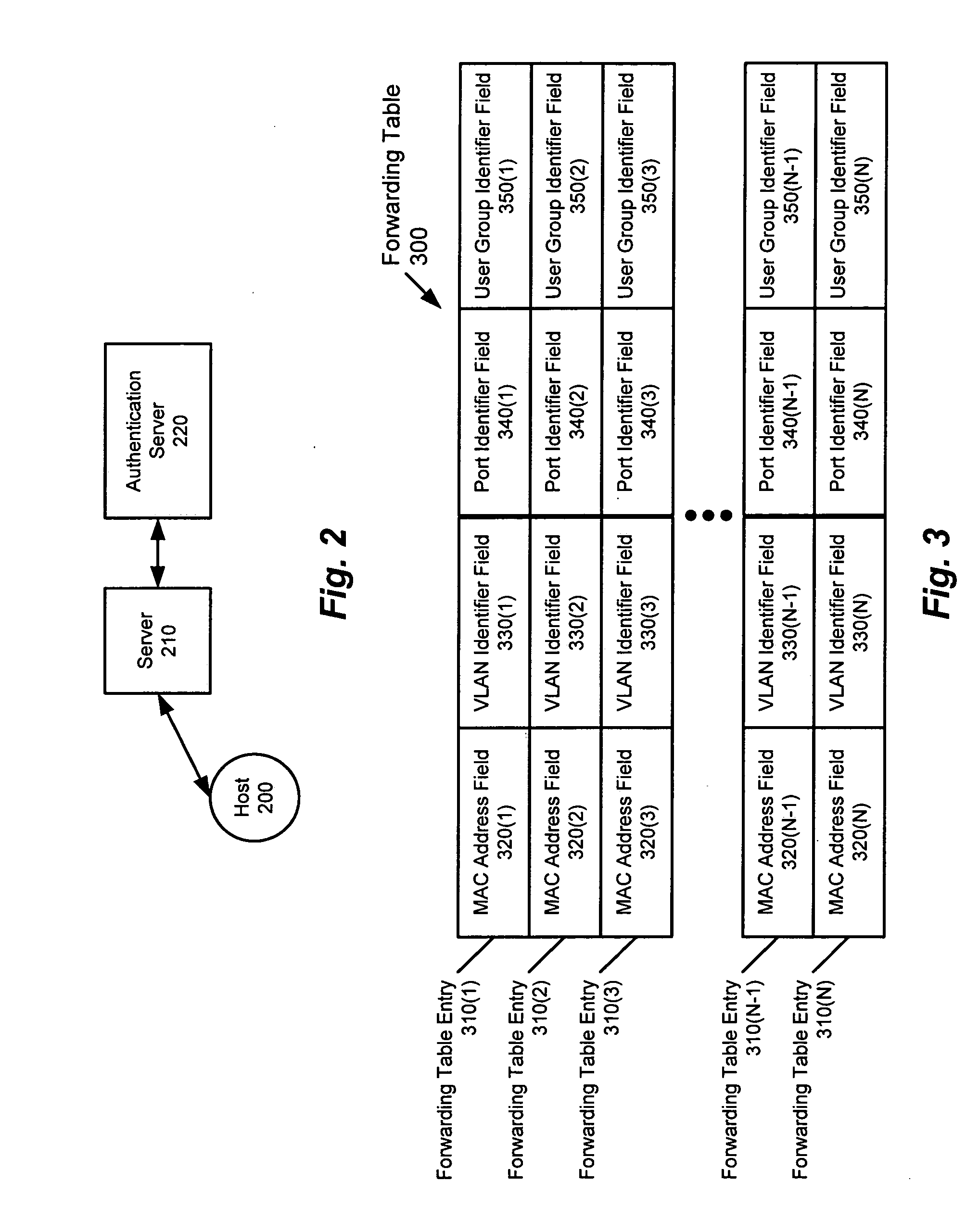
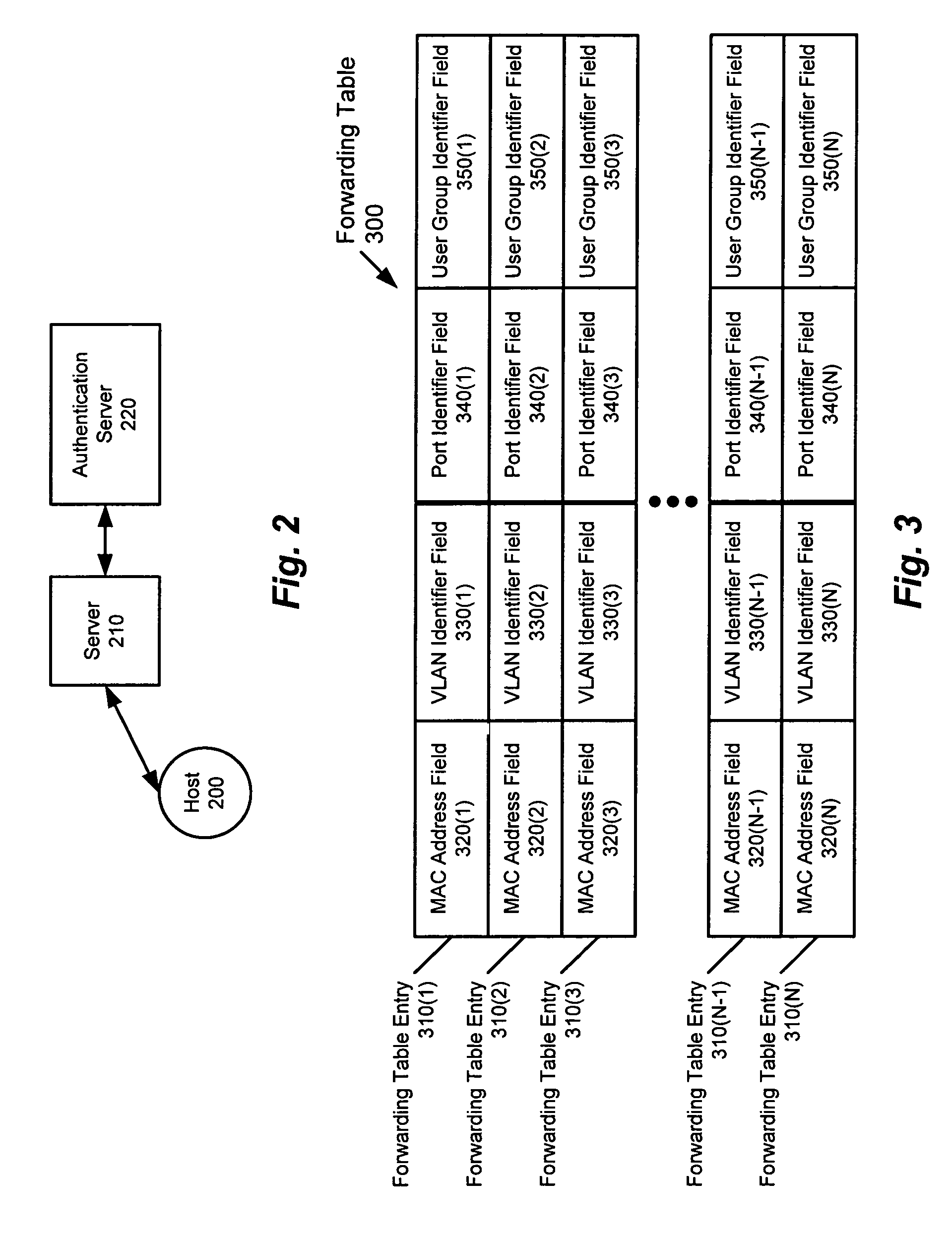
ActiveUS20050055573A1Small sizeImprove performanceDigital data processing detailsAnalogue secracy/subscription systemsAccess control listUser group
A method and apparatus for providing network security using role-based access control is disclosed. A network device implementing such a method can include, for example, an access control list. Such an access control list includes an access control list entry, which, in turn, includes a user group field. Alternatively, a network device implementing such a method can include, for example, a forwarding table that includes a plurality of forwarding table entries. In such a case, at least one of the forwarding table entries includes a user group field.
Owner:CISCO TECH INC
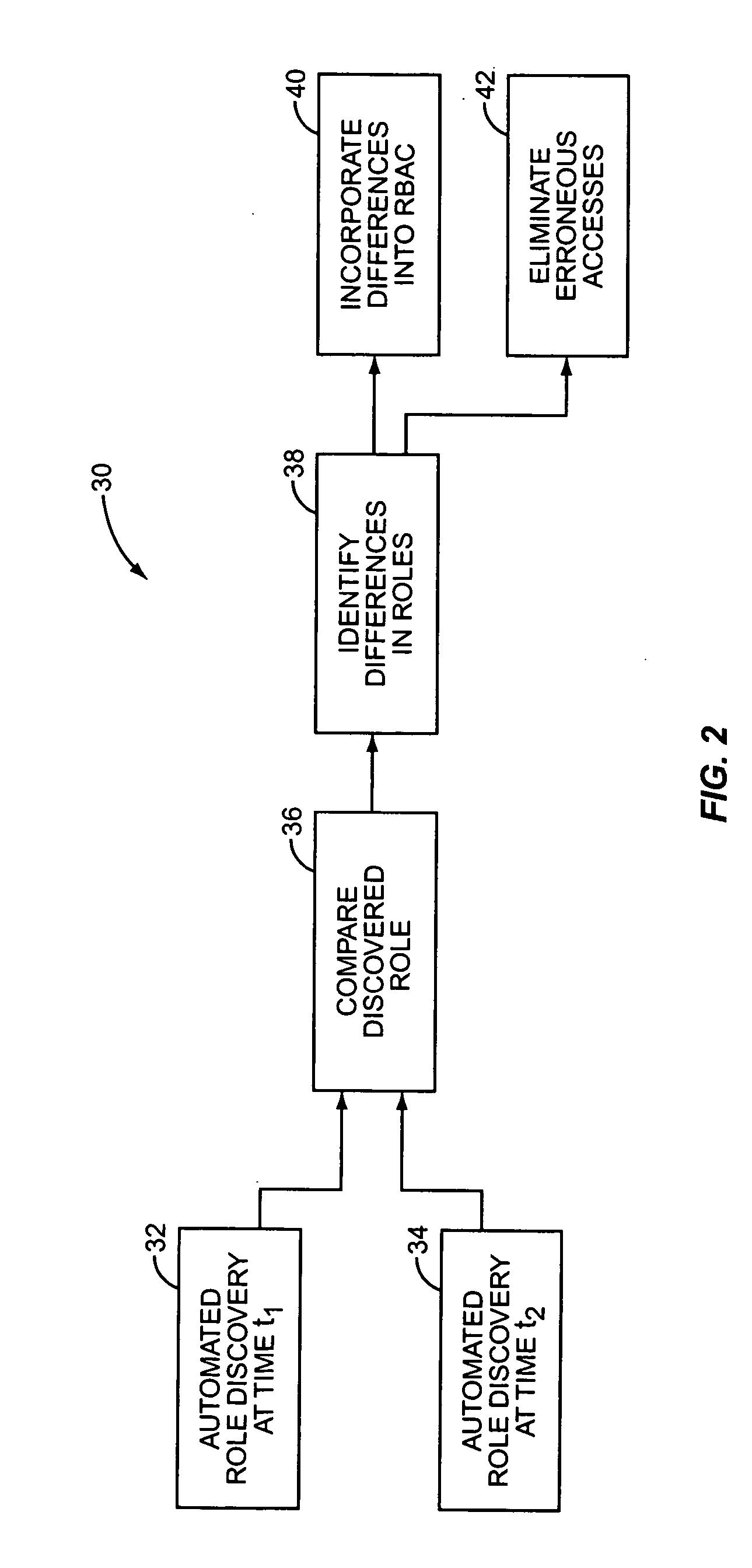
Automated role discovery
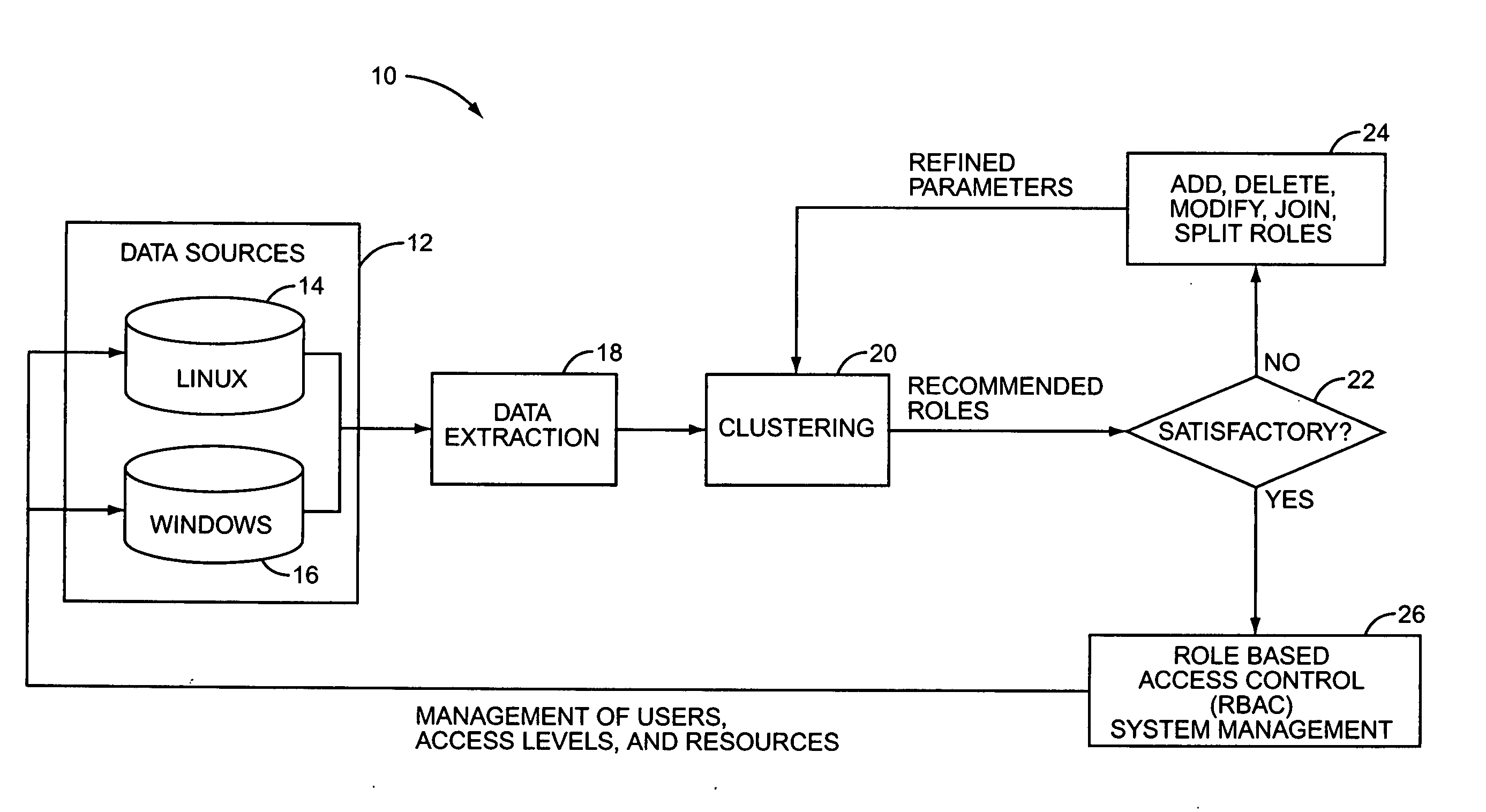
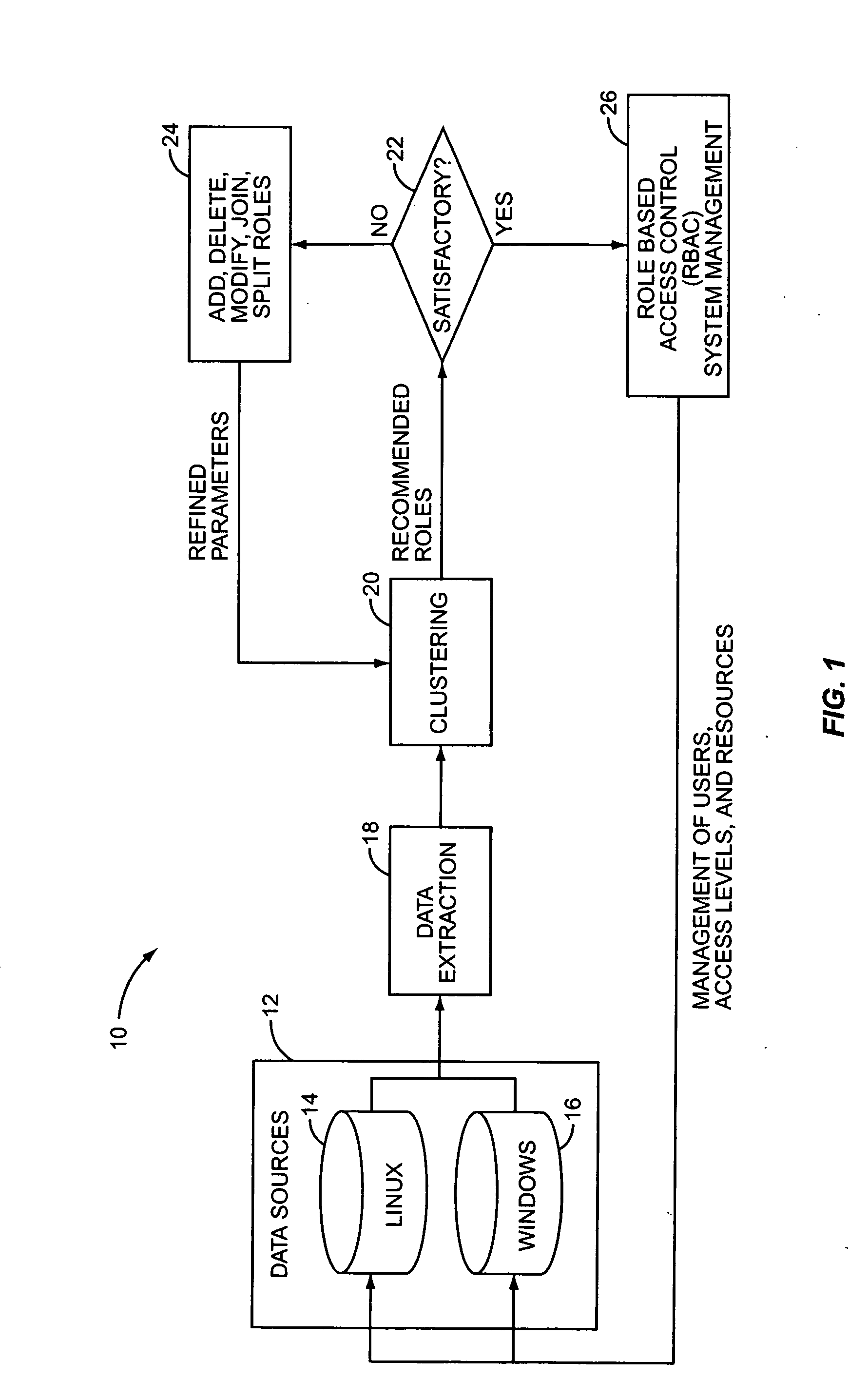
InactiveUS20050138419A1Digital data processing detailsUser identity/authority verificationControl systemData source
An automated, bottom-up role discovery method for a role based control system includes automatically extracting identities and attributes from data sources and automatically clustering the identities based on the attributes to form recommended roles. The recommended roles may be modified by intervention of an administrator. Additionally, the recommended roles may be aggregated by defining the role definition as an attribute of each constituent identity, and re-clustering the identities to generate refined roles. The recommended, modified, and / or refined roles may then be utilized in a role based control system, such as a role based access control system. Periodically performing the role discovery process provides a means to audit a role based access control system.
Owner:IBM CORP
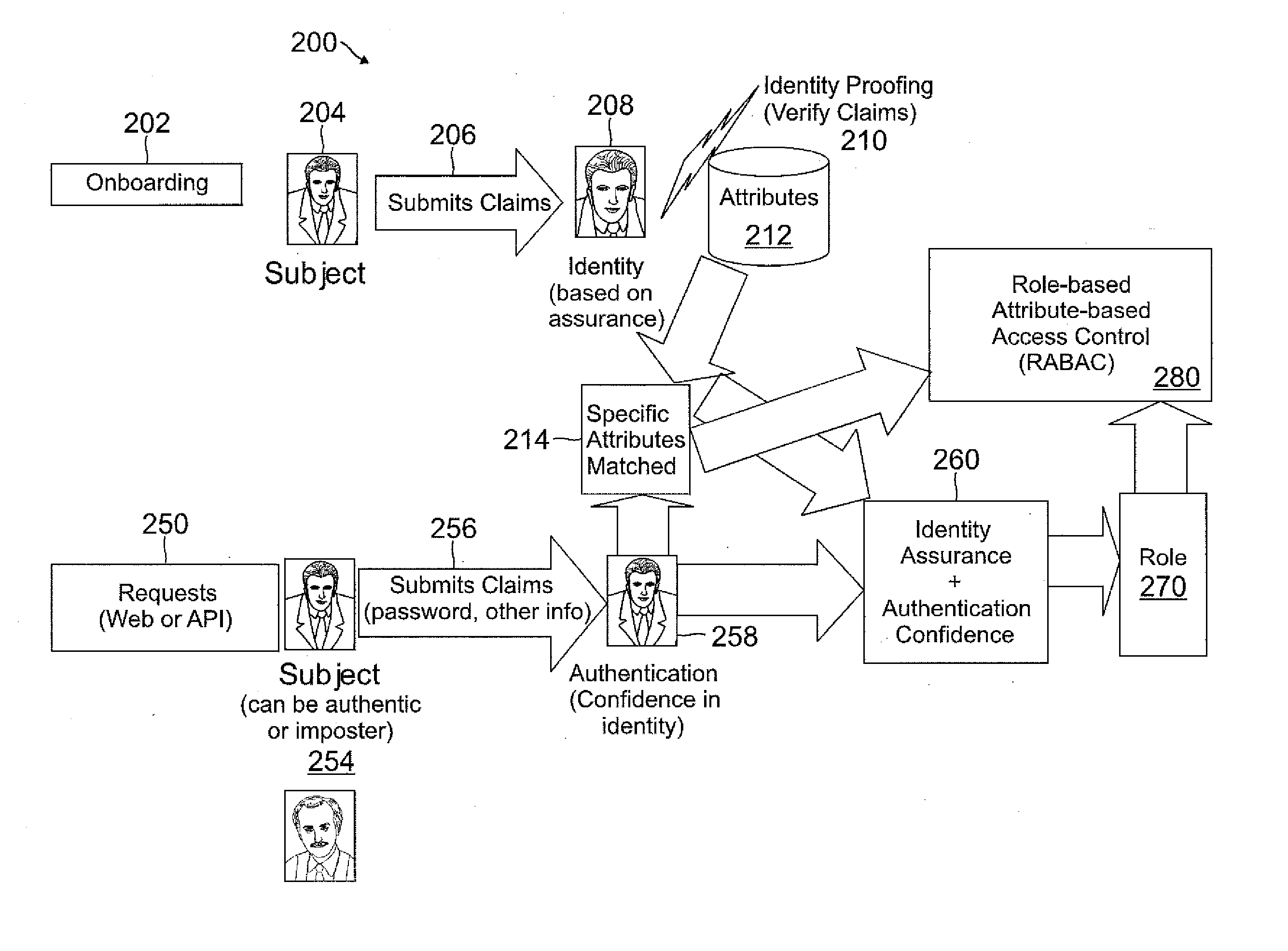
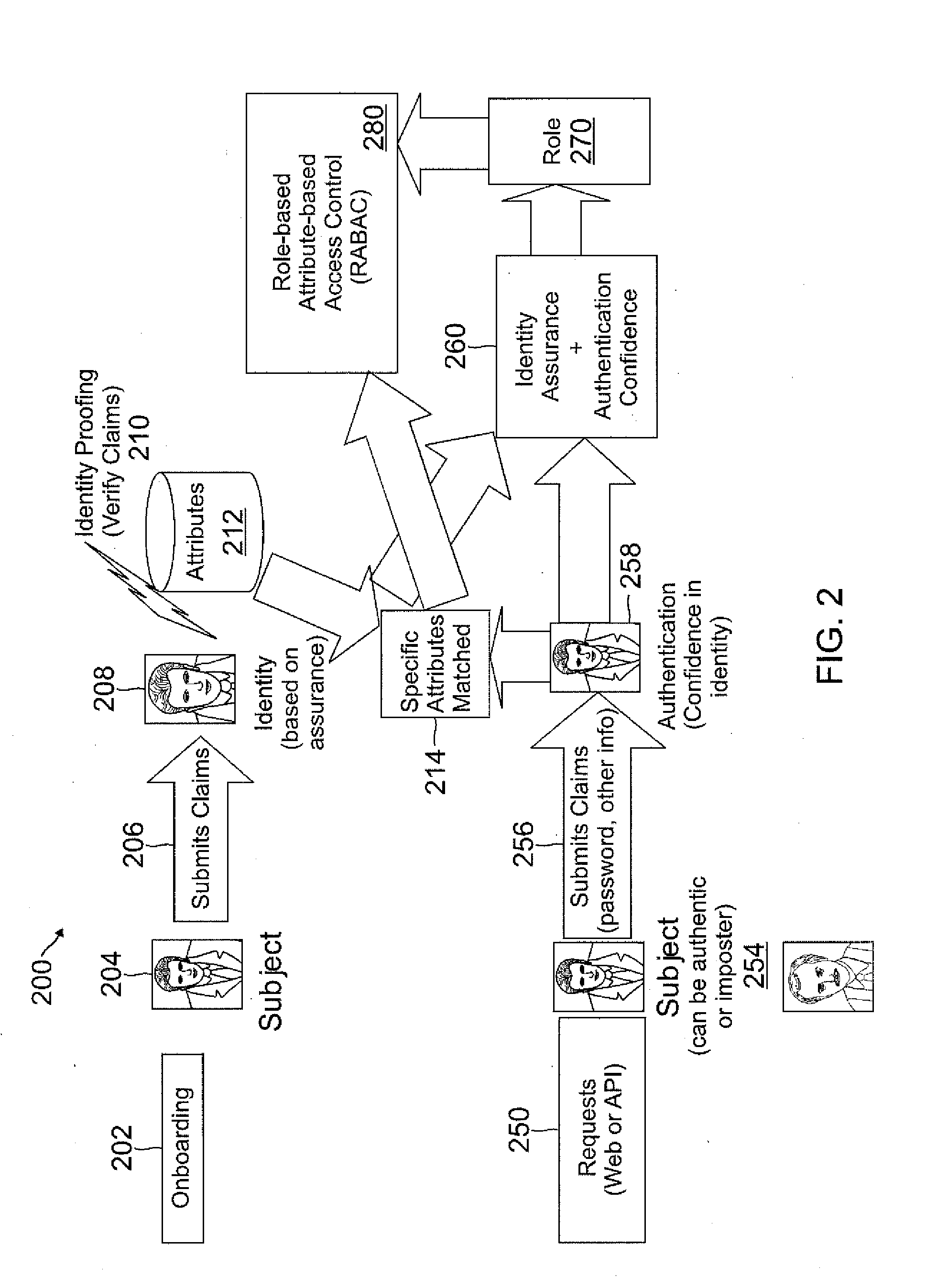
Role-based attribute based access control (RABAC)
ActiveUS20120060207A1Enhanced access control securityConvenient access controlDigital data processing detailsDigital data protectionUser deviceMedia access control
Systems and methods are disclosed for receiving an access request from a user device, the access request including an identity claim for a user; evaluating a risk of access based on matching an attribute of the user device with attributes stored in a user information database; authenticating the access request based on the identity claim and the risk evaluation to determine an authentication confidence level; generating a token based on the confidence level and the attribute matched; producing an authorization response based on inputs from the token, a risk based access control, a role based access control, and an attribute based access control, in which the authorization response determines whether to allow access to a system, deny access to the system, or request additional input from the user device.
Owner:PAYPAL INC
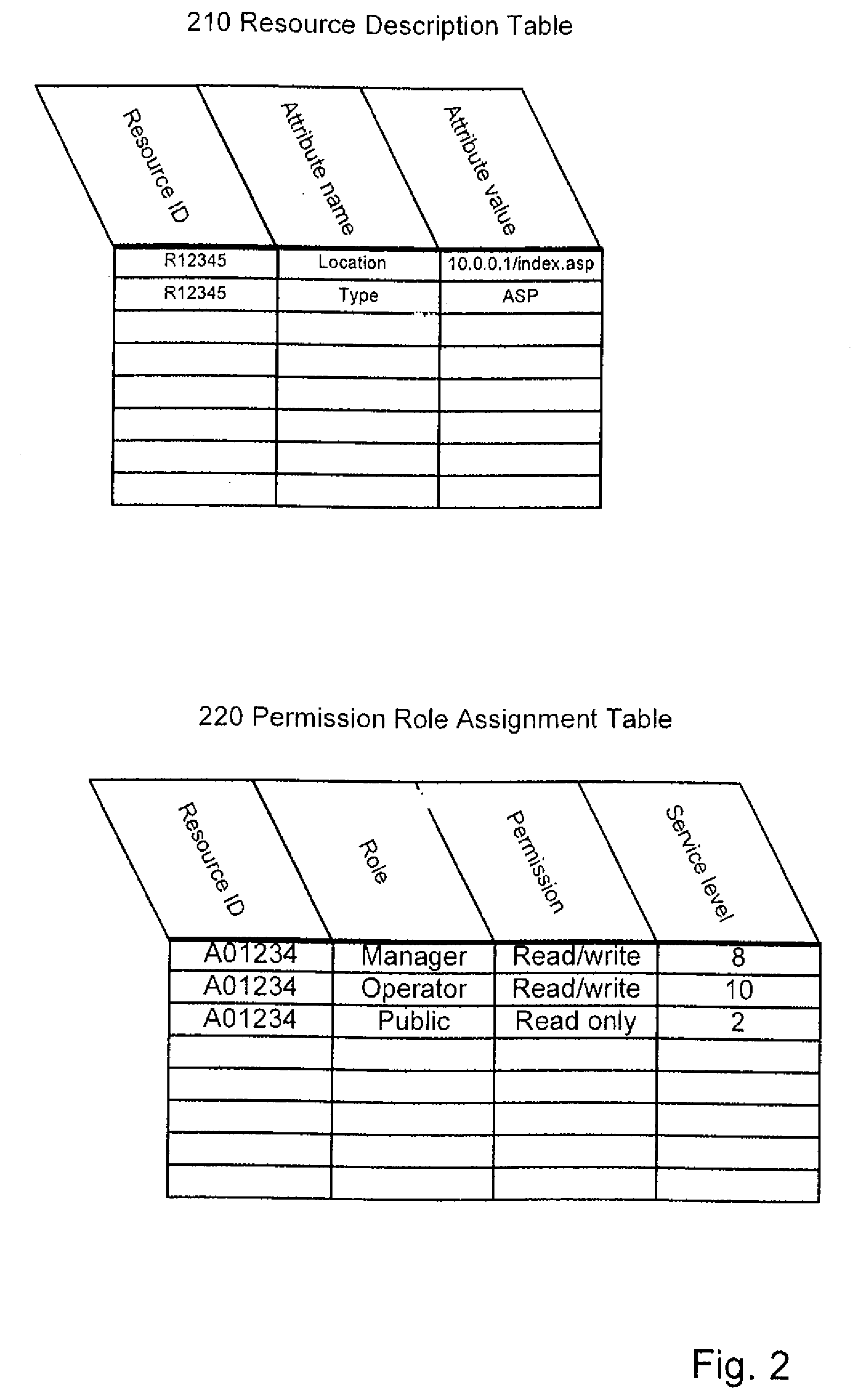
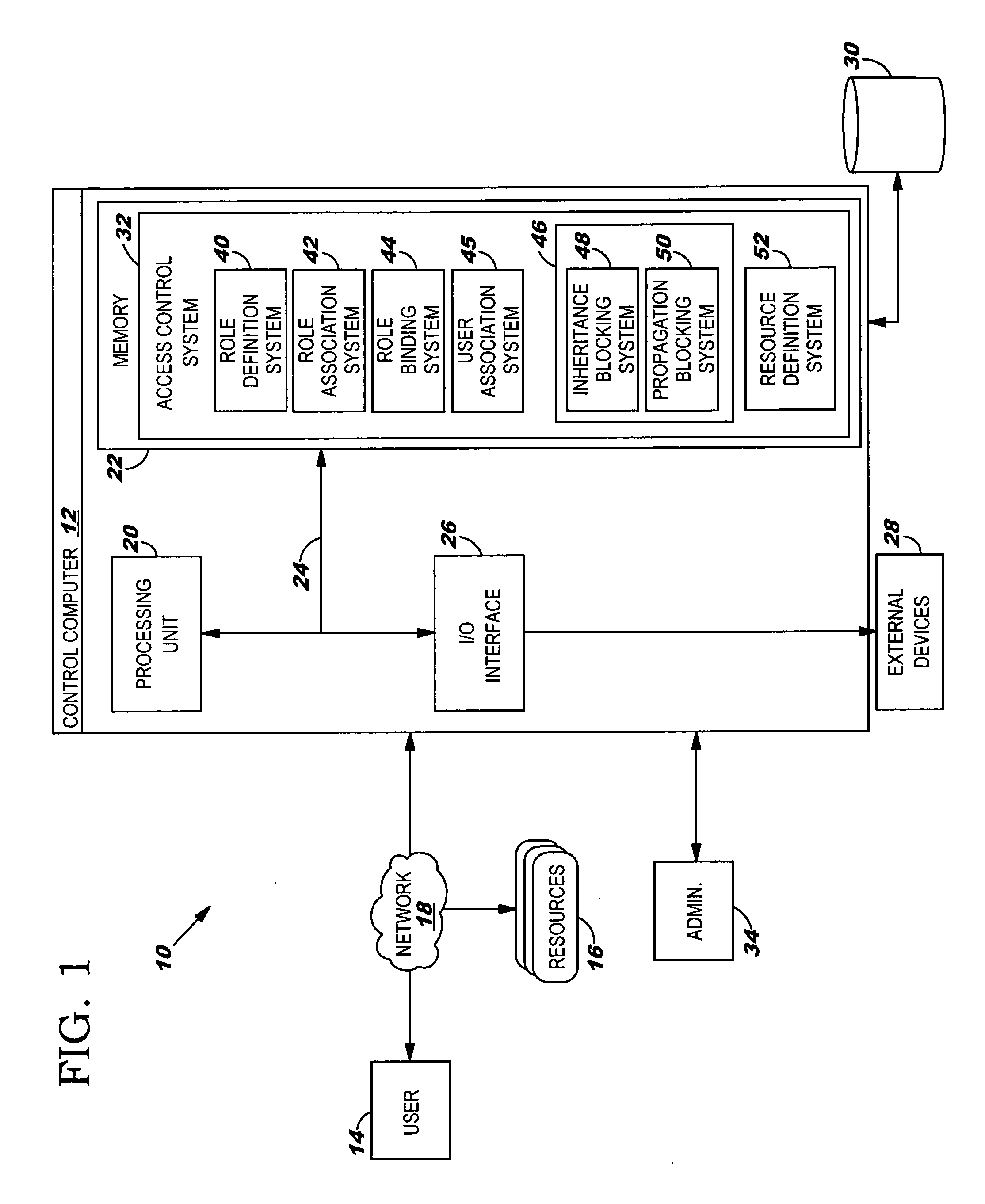
Role-based access control system, method and computer program product
ActiveUS20060089932A1Simplifies consistent dynamic bindingLow costComputer security arrangementsTransmissionControl systemWorld Wide Web
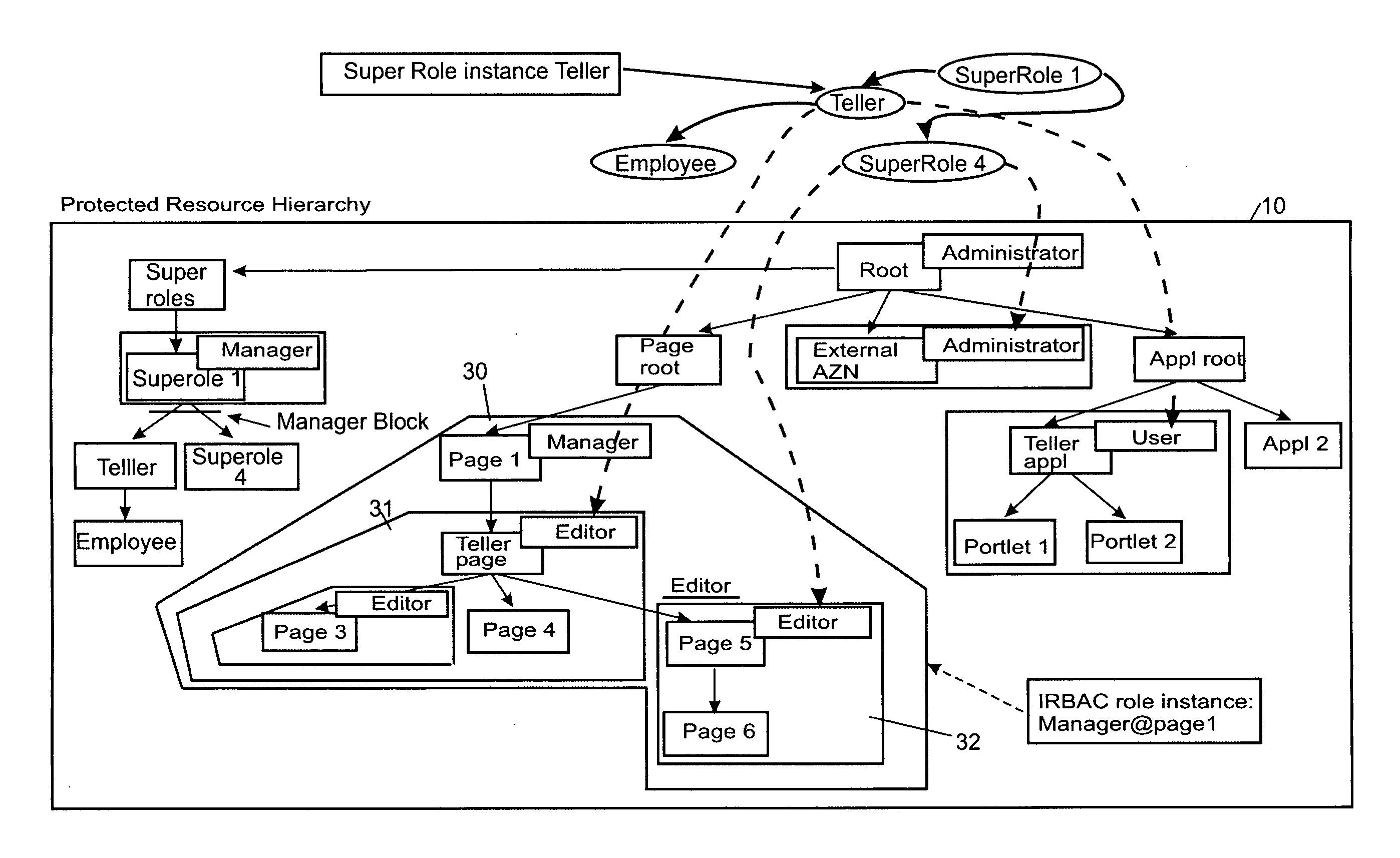
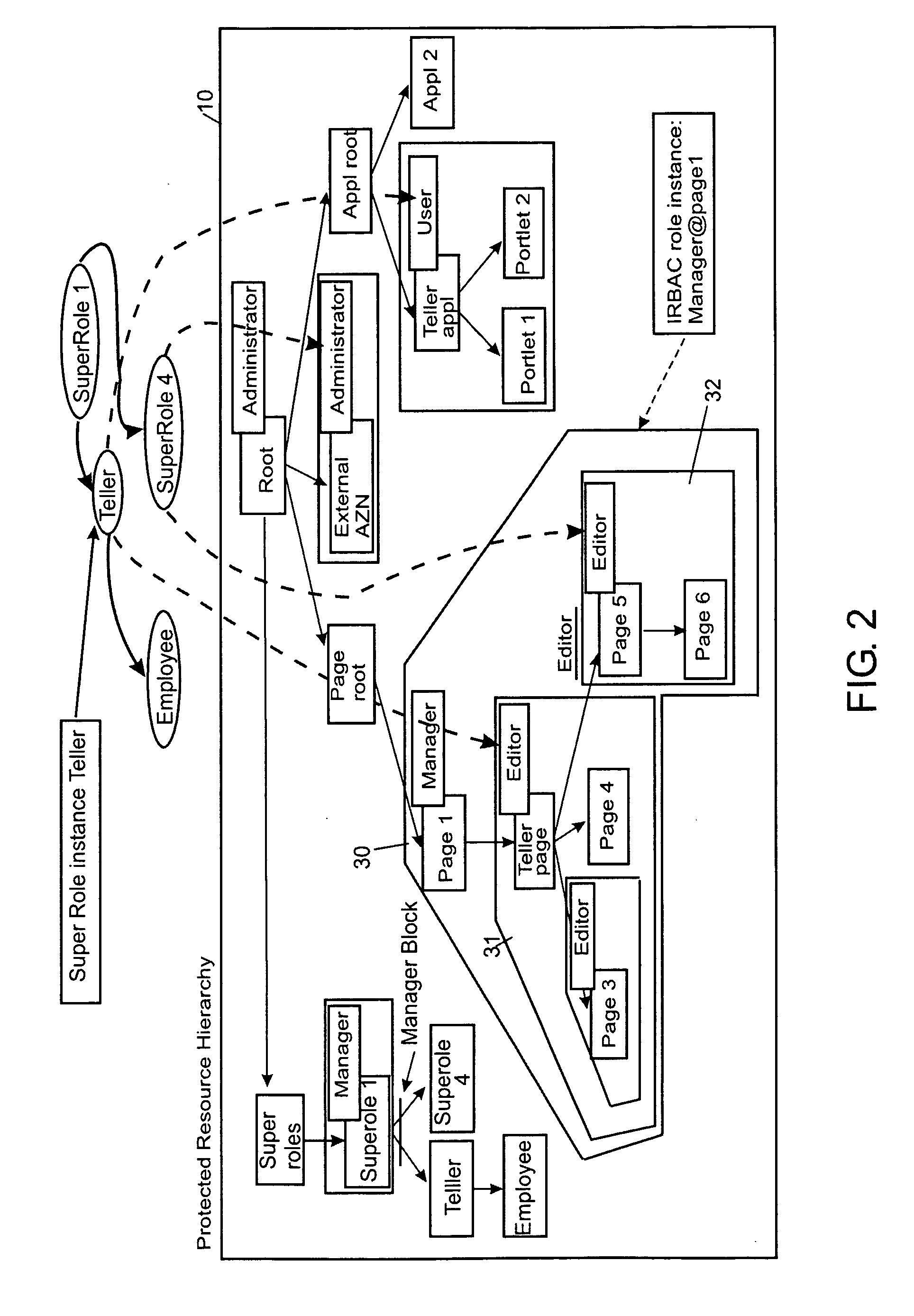
The invention relates to a role-based access control system, including a role definition system for defining roles to be sets of permissions on individual resources thus forming role instances, respectively; and a super role definition system for defining at least one super role by grouping a set of role instances into one super role, wherein the one super role contains all permissions contained in the grouped resource instances. Furthermore, the present invention deals with an appropriate method, a computer program and a computer program product.
Owner:DAEDALUS BLUE LLC
Client Reputation Driven Role-Based Access Control
The present disclosure discloses a system and method for dynamically modifying role based access control for a client based on the activity. Generally, a client device is granted access to a network resource based on a first reputation score assigned to the client device. The activity of the client device is monitored. Responsive to monitoring the activity of the client device, a second reputation score is determined for the client device based on the activity. The access by the client device to the network resource is then modified to be granted based on the second reputation score.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Cloud security access control model
InactiveCN102571821AReasonable designSimple structureData switching networksData access controlMedia access control
The invention discloses a cloud security access control model. The model is characterized in that: aiming at the multi-tenant architecture characteristic of cloud computing, by combining a role-based access control (RBAC) model, a tenant concept and a cloud service provider concept are introduced to an access control model, and a uniform tenant access control model and a user access control model are formed by defining model elements and formally describing model functions. The cloud security access control model can adapt to the characteristic of multi-tenant of the cloud computing, improves the flexibility of user authority management in a cloud computing environment, can reduce the complexity of authorization management and management overhead, and can effectively ensure the security and integrity of user data in the cloud computing environment.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Policy-driven approach to managing privileged/shared identity in an enterprise
ActiveUS20130232541A1Authentication is convenientDigital data processing detailsUser identity/authority verificationInternet privacyContext-based access control
Owner:IBM CORP
Organizational role-based controlled access management system
InactiveUS20060218394A1Easy to manageManagement becomes complicatedDigital data processing detailsUser identity/authority verificationSystems analysisPersonal computer
An Organizational Role-based Access Controlled Management System capable of controlling role-based access within an organization allows system analysts or managers to build and control access roles for the various application systems within an organization. This system can also allow an end-user to choose the functions of the application systems and logon rights associated with the role. The system includes one or more personal computers and a server based on an event-driven mechanism. System analysts and end-users access synchronized data to manage the end-users' access roles. This system allows a system analyst to build and limit “set and set” relationships, as well as “member and set” relationships to pass information and manage organizational networks, roles, functions, privileges, etc. Different roles under various application systems can have different access rights and functions assigned. This system breaks away from the limitation of the conventional RBAC (Role Based Access Control) and allows system analysts to manage and adapt access roles according to the practical needs of different users and their complicated relationships to the organization and one another.
Owner:GALAXY SOFTWARE SERVICES LTD
Cryptographically enforced, multiple-role, policy-enabled object dissemination control mechanism
ActiveUS20050193196A1Reduce administrative expensesReduce expensesDigital data processing detailsUnauthorized memory use protectionRole managementSecret code
An apparatus to implement role based access control which reduces administrative expenses associated with managing access in accordance with policies and roles. The apparatus includes a memory storing a first role based access control condition associated with an action and a subsystem executing an enforcement entity and a decision entity. In one preferred form, the two entities are independent entities. The enforcement entity receives a request for the action from a requestor with a role. Additionally, the enforcement entity communicates the role and the request to the decision entity for the decision entity's decision of whether the role satisfies the first condition. The decision entity then communicates the decision to the enforcement entity. Accordingly, the enforcement entity allows or denies the requestor the action based on the decision made by the decision entity.
Owner:THE BOEING CO
Automated role and entitlements mining using network observations
ActiveUS20140109168A1Computer security arrangementsTransmissionNetwork intelligenceApplication software
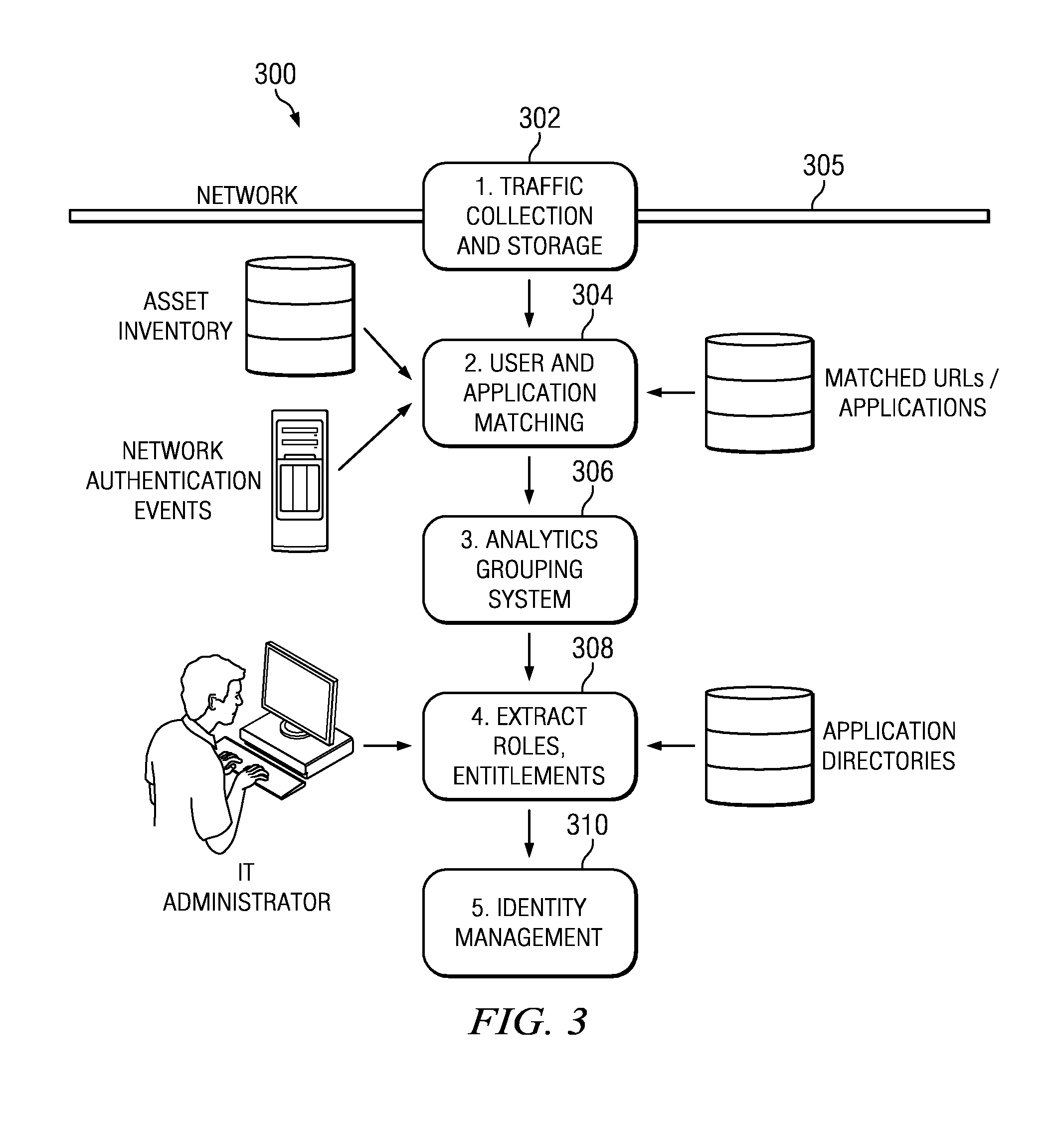
A role and entitlements mining system uses network intelligence to facilitate role definition. The system records traffic on a network. The traffic is analyzed to identify the user and application involved. The matched data is then provided to an analytics engine, which analyzes that data to attempt to derive an initial set of one or more roles and the application entitlements for each role. Each role derived by the analytics engine identifies one or more users who are identified as belonging to the role, as well as one or more application entitlements. Preferably, one or more directory services are then interrogated for known group and user relationships to detect whether the roles identified by the analytics engine can be modified or enriched. Evaluation of the known group and user relationships provides a way to identify a more granular set of role definitions. A role-based access control policy is then generated.
Owner:IBM CORP
Method and apparatus for using a role based access control system on a network
ActiveUS7568217B1Digital data processing detailsComputer security arrangementsControl systemMedia access control
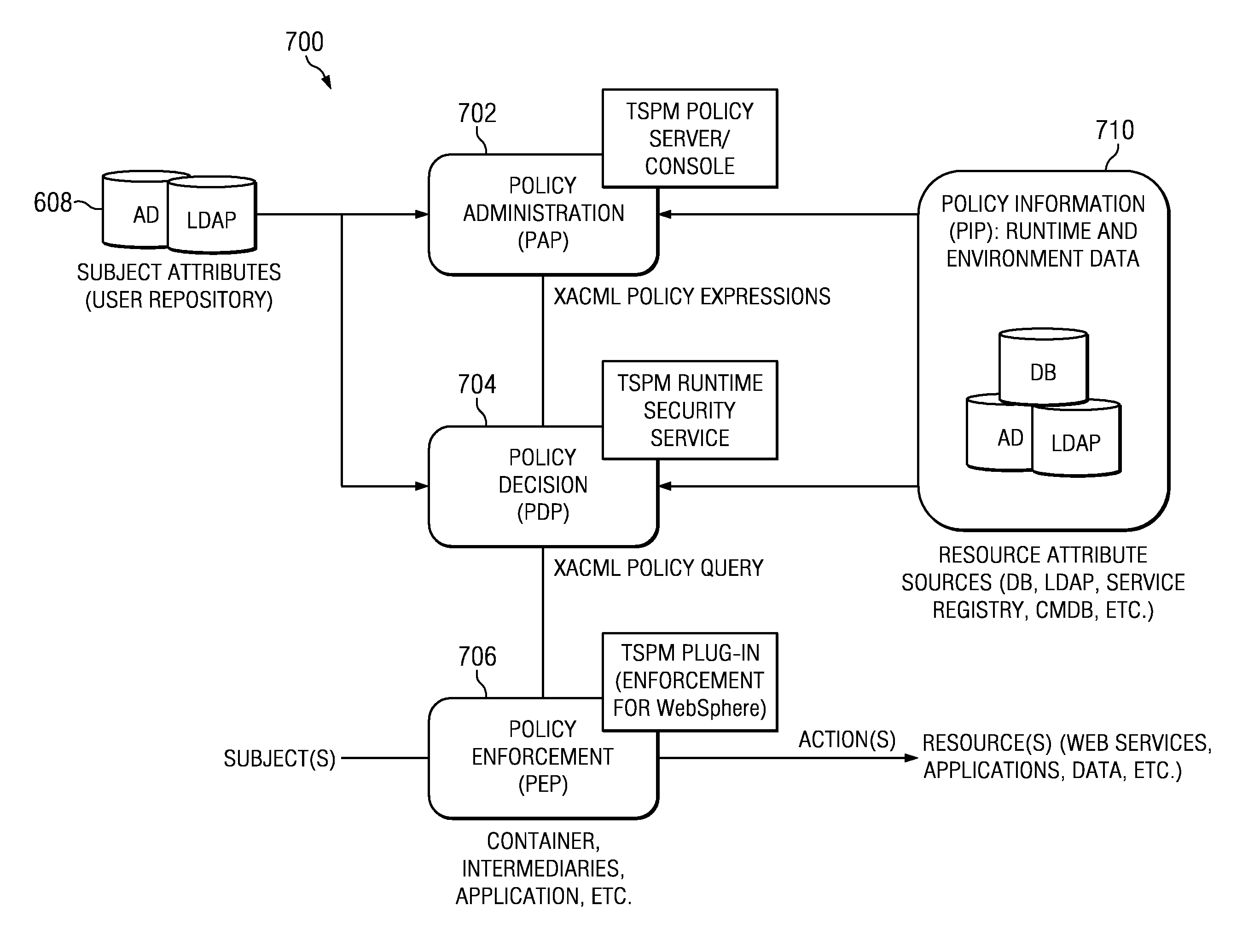
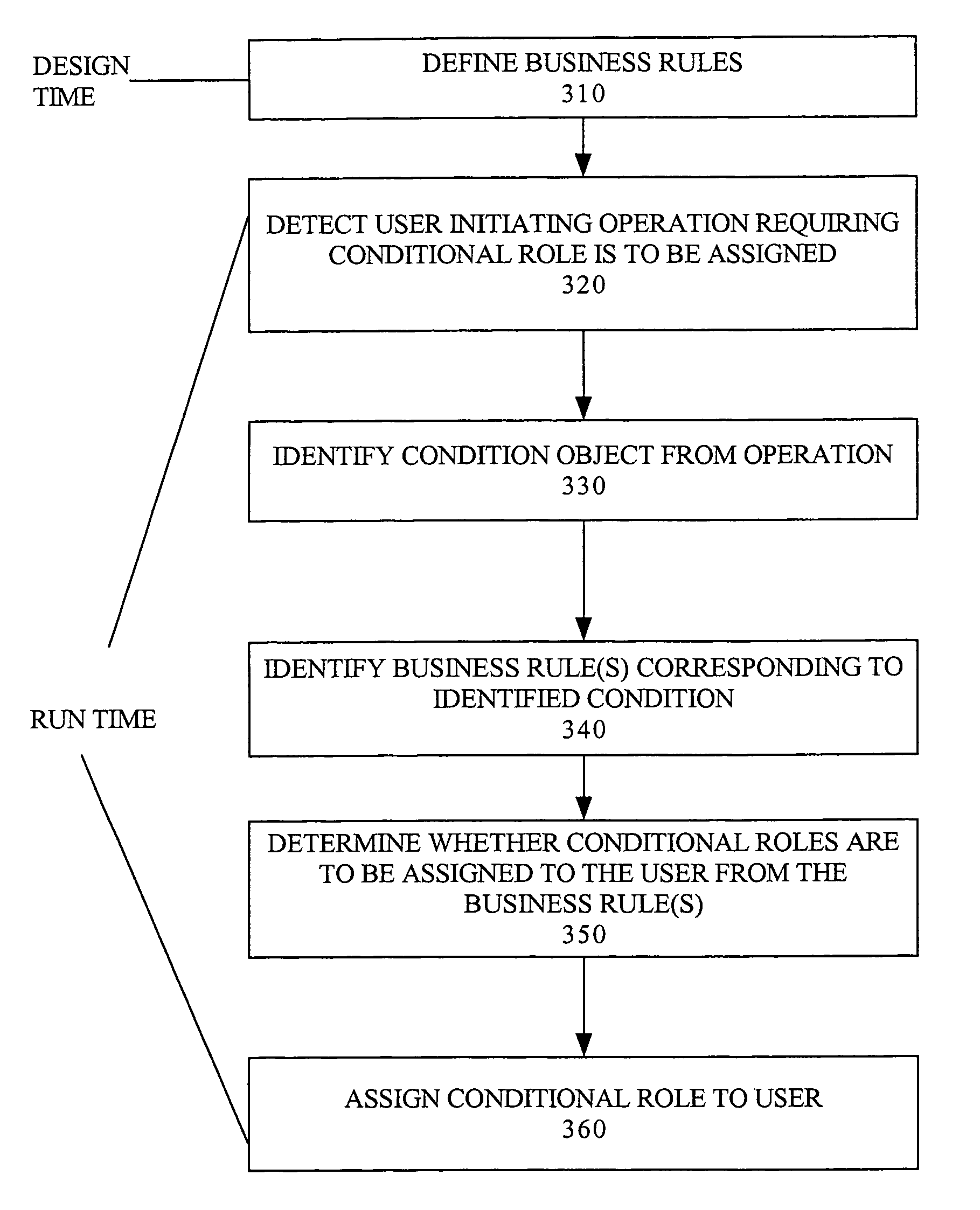
A role based access control system is described that assigns roles, which otherwise are mutually exclusive, to users based on detecting designated conditions when the user initiates actions or operations on the network. The assignment of the role to a particular user may be conditional upon one or more such designated conditions occurring. In particular, two roles that are mutually exclusive of one another may be occupied by one user for purpose of performing specified operations upon designated conditions being detected when the user initiates one or more of the specified operations. Business rules specify conditions for assigning the conditional roles.
Owner:CISCO TECH INC
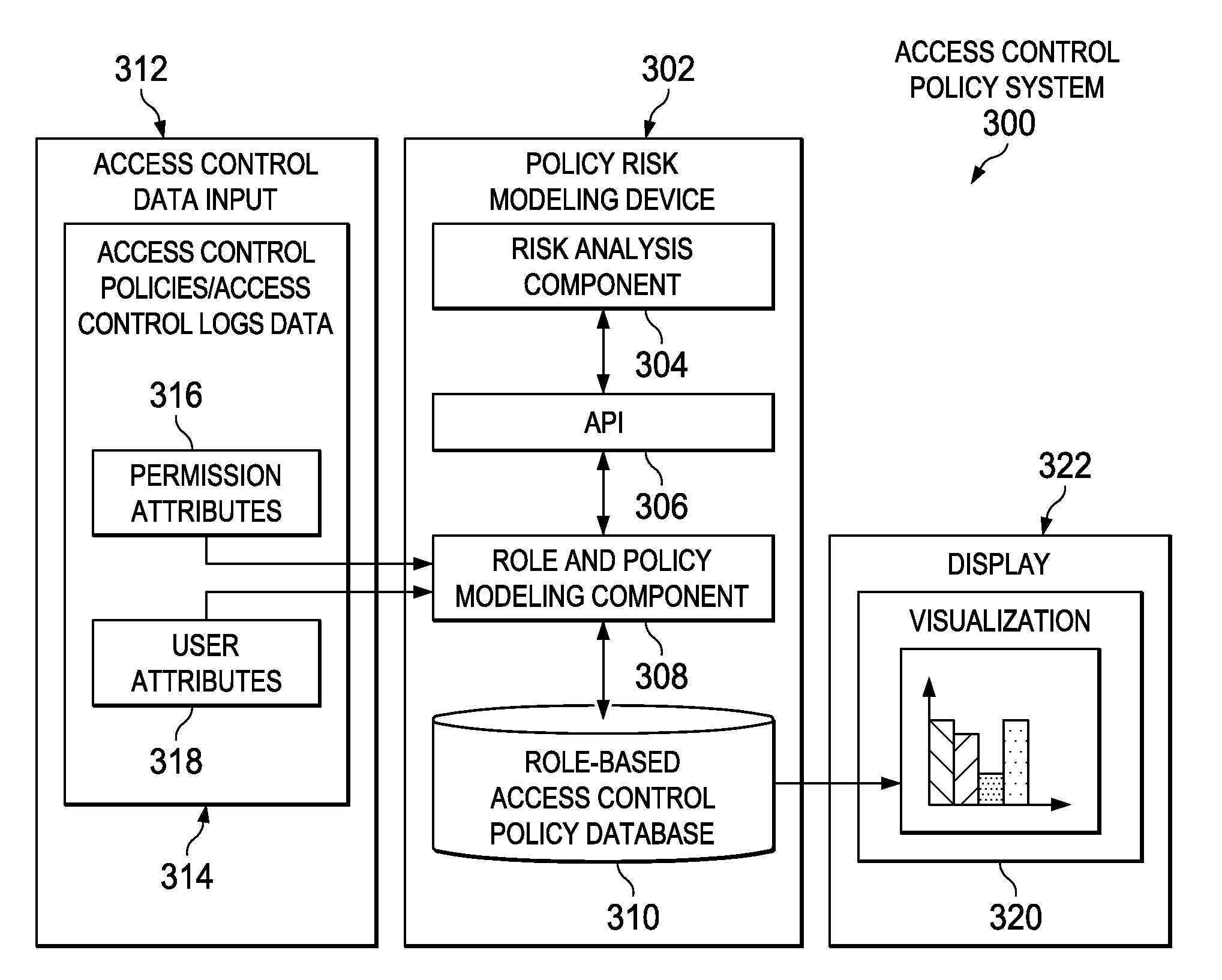
Generating role-based access control policies based on discovered risk-averse roles
InactiveUS20140196104A1Minimize risk profileMinimizes risk profileTransmissionSpecial data processing applicationsUser PrivilegeRisk profiling
Generating role-based access control policies is provided. A user-permission relation is generated by extracting users and permissions assigned to each of the users from a stored access control policy. A user-attribute relation is generated by mapping the users to attributes describing the users. A permission-attribute relation is generated by mapping the permissions to attributes describing the permissions. The set of risk-averse roles, assignment of the set of risk-averse roles to the users, and assignment of the permissions to the set of risk-averse roles are determined based on applying a risk-optimization function to the generated user-permission relation, the generated user-attribute relation, and the generated permission-attribute relation. A role-based access control policy that minimizes a risk profile of the set of risk-averse roles, the assignment of the set of risk-averse roles to the users, and the assignment of the permissions to the set of risk-averse roles is generated.
Owner:IBM CORP
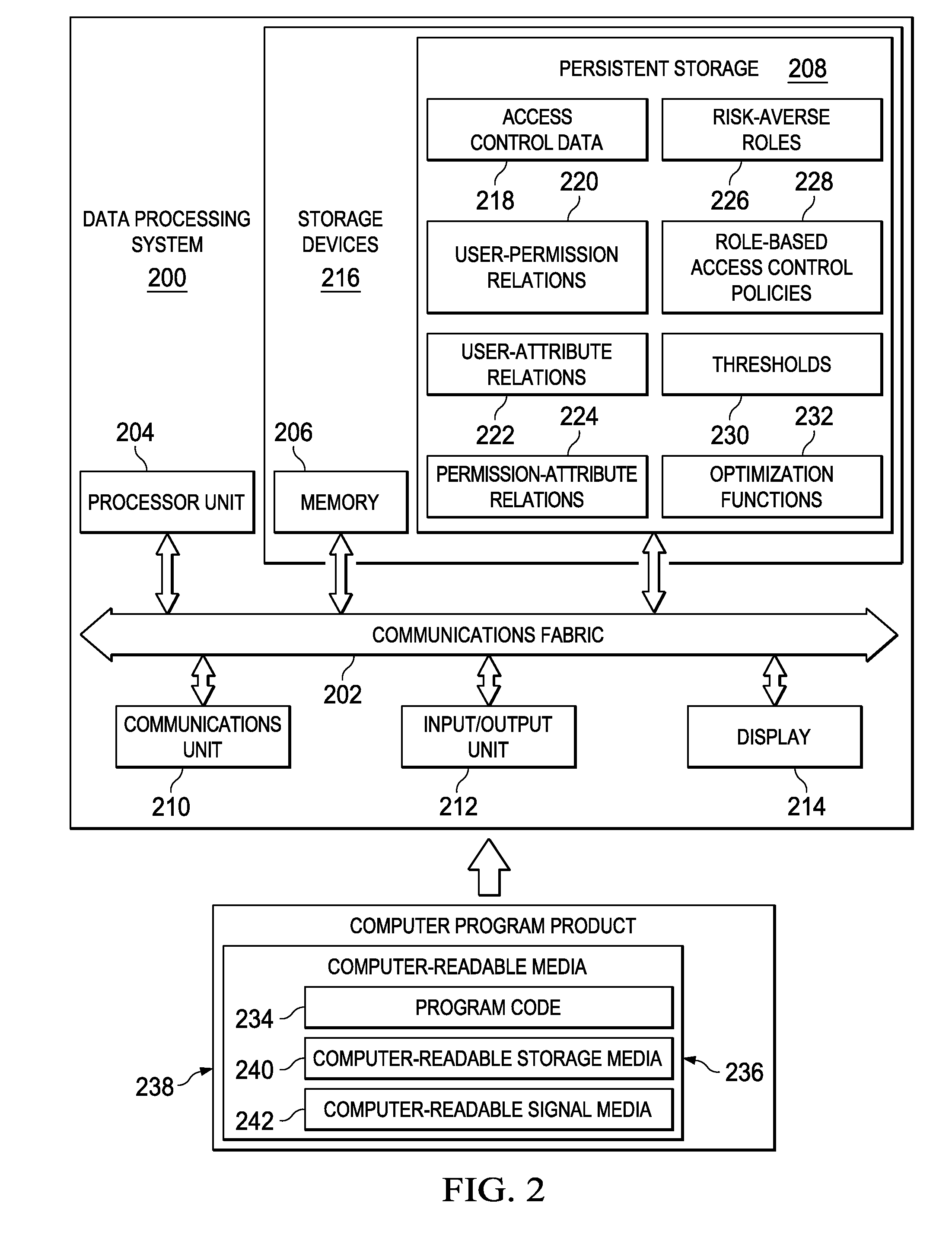
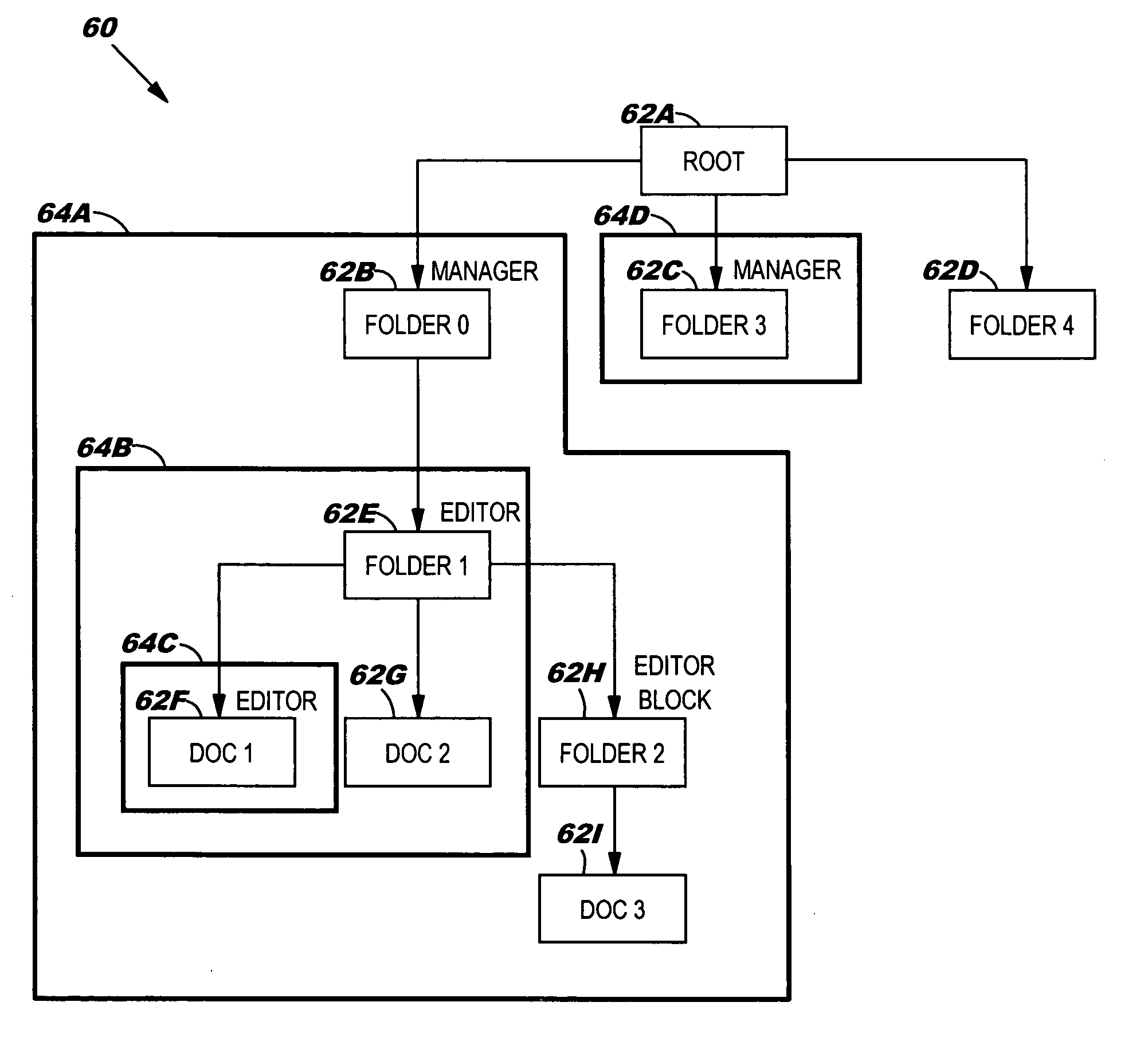
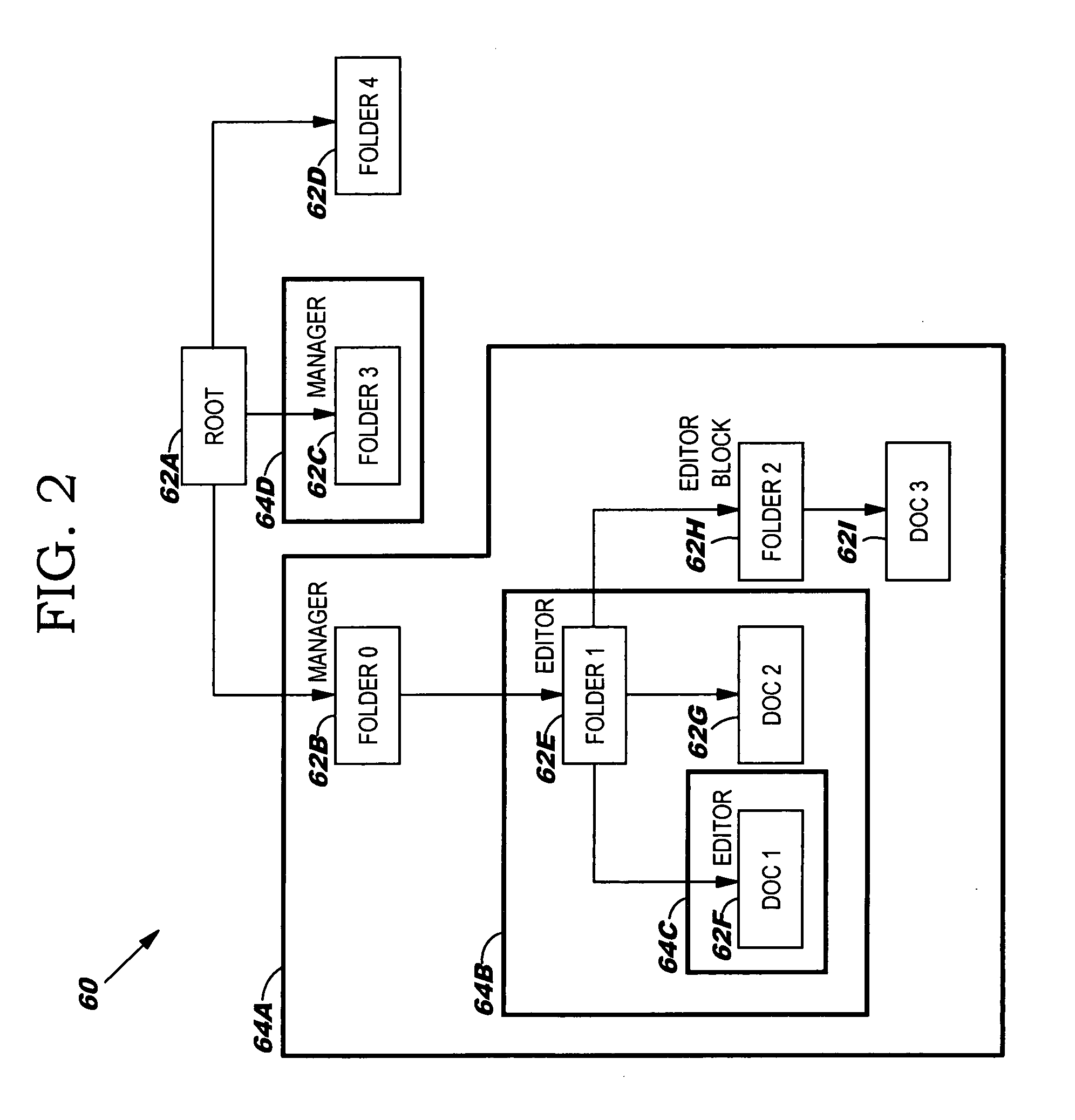
Inherited role-based access control system, method and program product
InactiveUS20060010483A1Digital data processing detailsAnalogue secracy/subscription systemsProgramming languageControl system
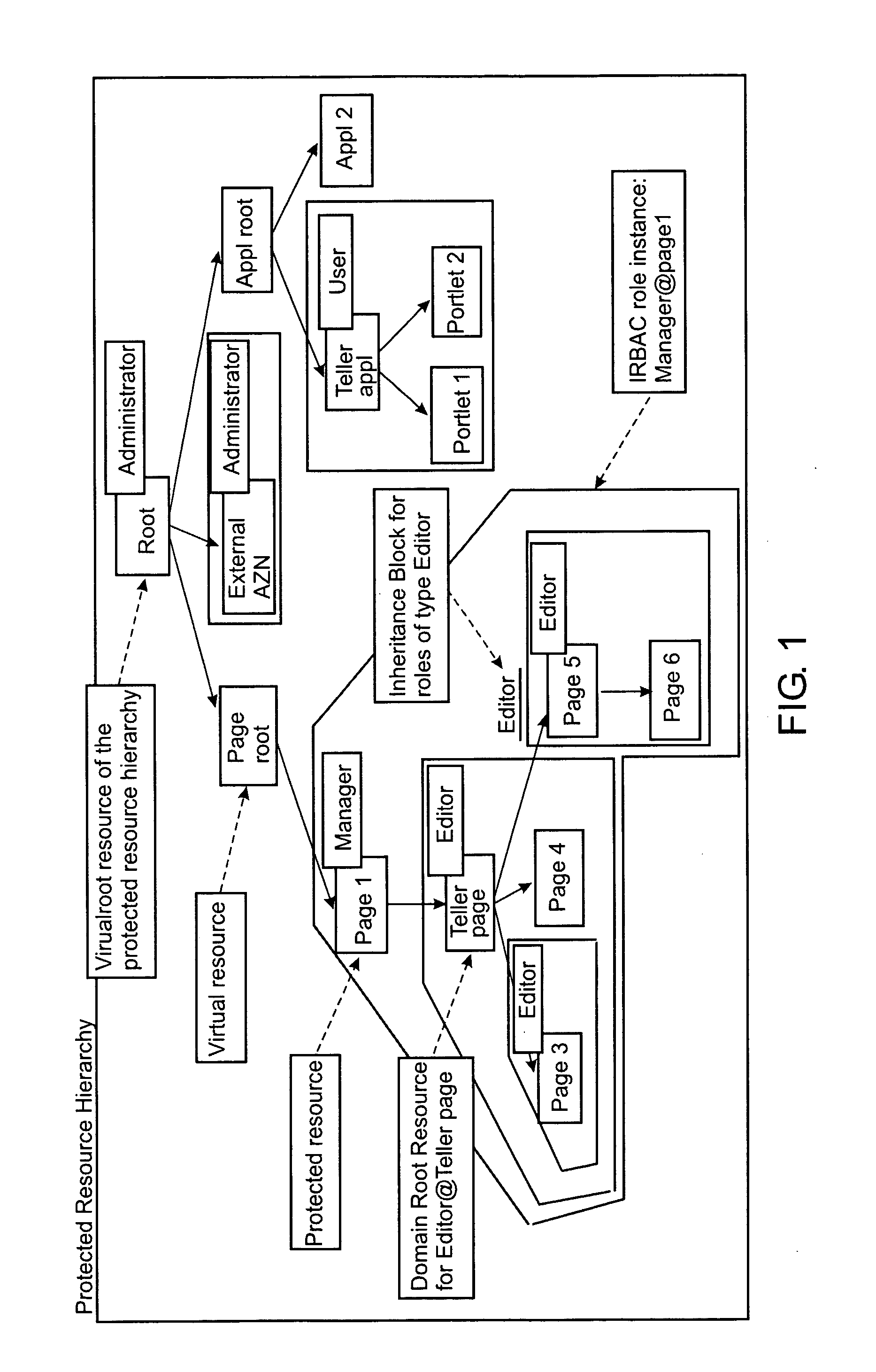
Under the present invention, role types are defined by association with certain permissible actions. Once defined in this manner, a role type can then be bound to “nodes” of a hierarchical tree that represent computer-based resources such as dynamic object spaces. Once bound to a node, instances of this role type are created that will be inherited by hierarchical descendants of that node unless a role type block (e.g., inheritance or propagation) has been established for the corresponding role type. The present invention also allows the computer-based resources to be defined as virtual or private. Virtual resources represent general protected concepts in the system instead of computer-based resources and are subject to be bound with roles, while private resources are not. That is, the private resources remain the “property” of the creating user or group.
Owner:IBM CORP
Context-aware role-based access control system and control method thereof
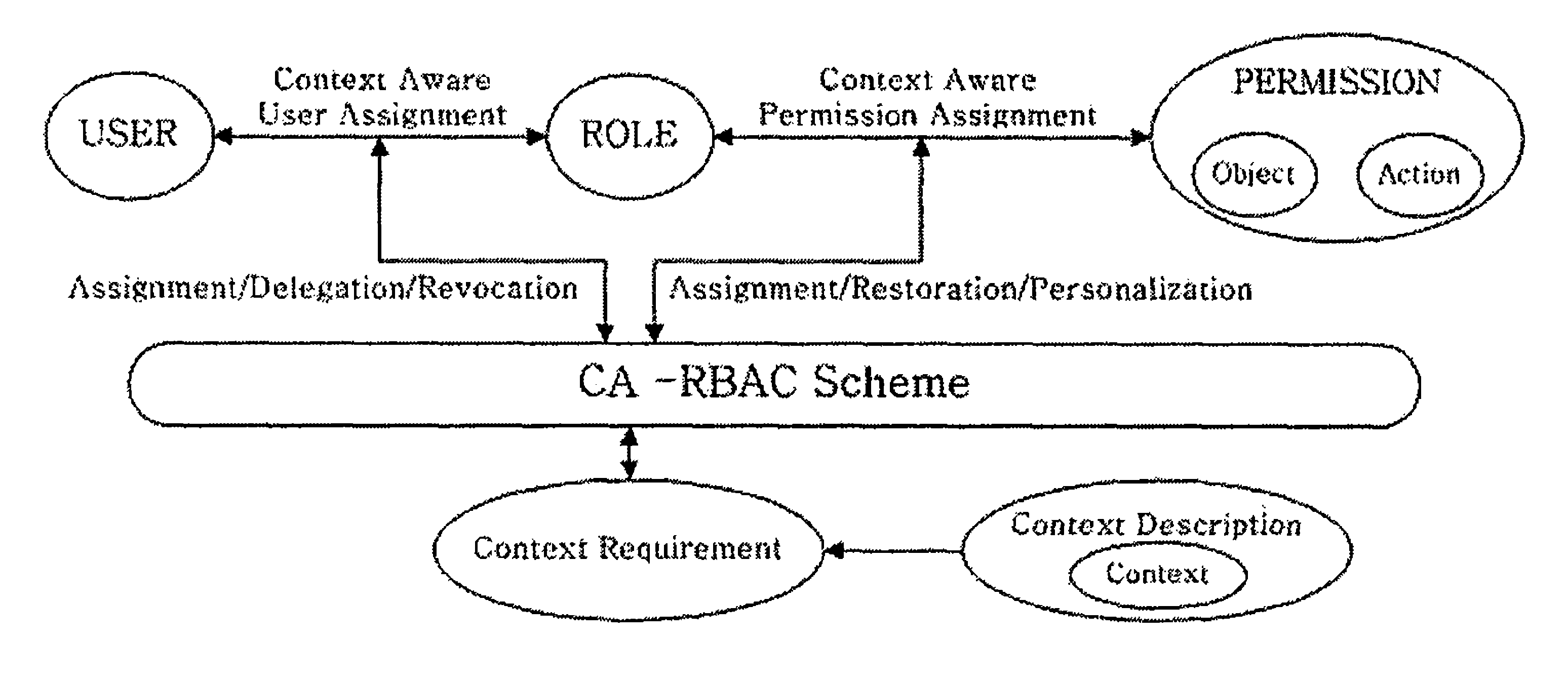
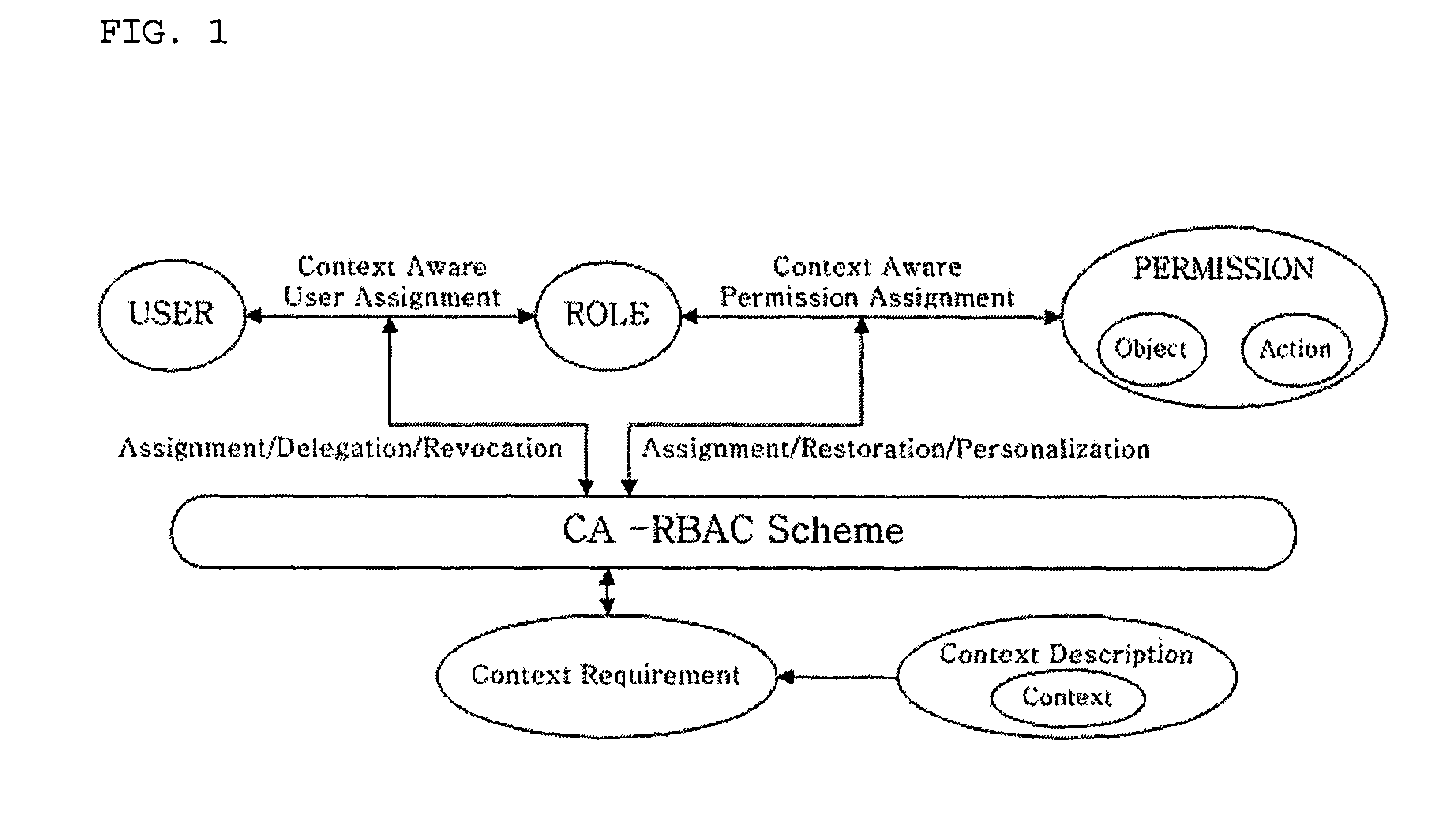
ActiveUS8387117B2Efficient expressionEffective controlDigital data processing detailsUser identity/authority verificationPersonalizationInformation repository
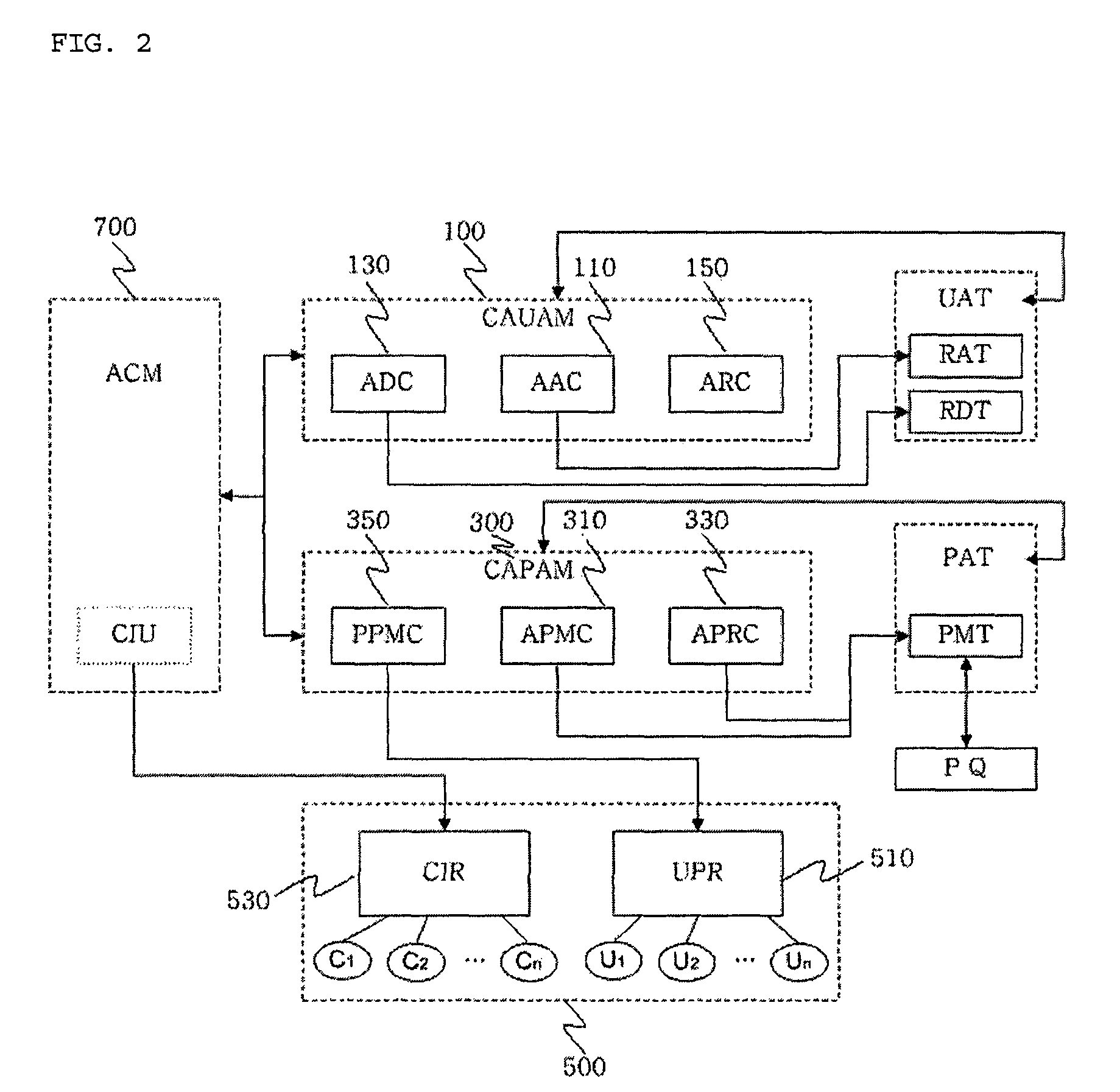
A context-aware role-based access control system and a control method thereof. The context-aware role-based access control system includes: a context-aware user assignment manager (CAUAM) for performing a role assignment function, a role delegation function, or a role revocation function for a user according to a context of the user, based on a preset context request condition; a context-aware permission assignment manager (CAPAM) for performing a permission modification, a permission restoration, and a personalized permission modification for a permission, which the role has, according to changes in the context of the user; an information repository for storing a user profile and context information; and an access control manager (ACM) for controlling the context-aware user assignment manager, the context-aware permission assignment manager, and the information repository, and processing an access control request. Accordingly, more efficient access control can be achieved in ubiquitous environments where the context of the user dynamically changes.
Owner:INTELLECTUAL DISCOVERY CO LTD
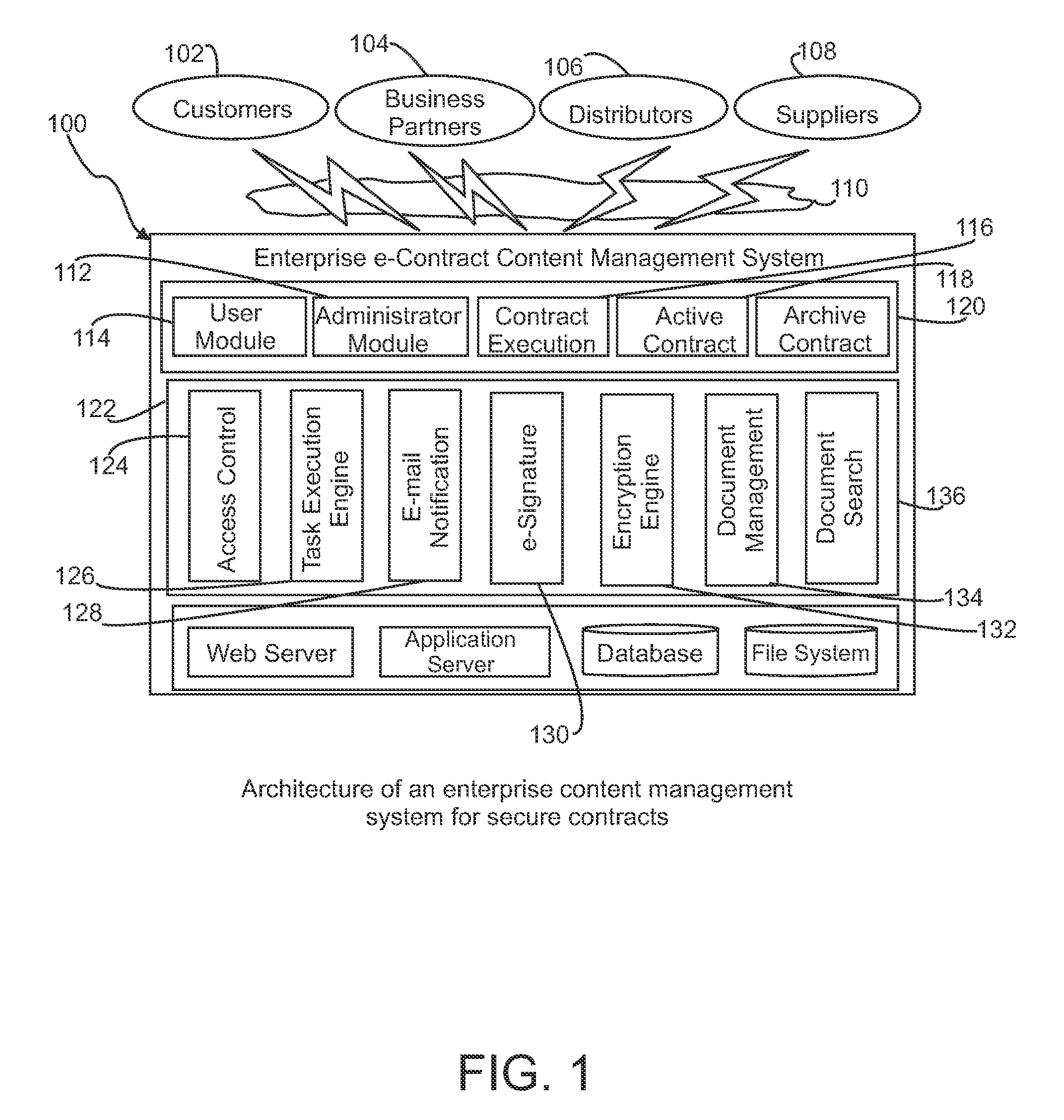
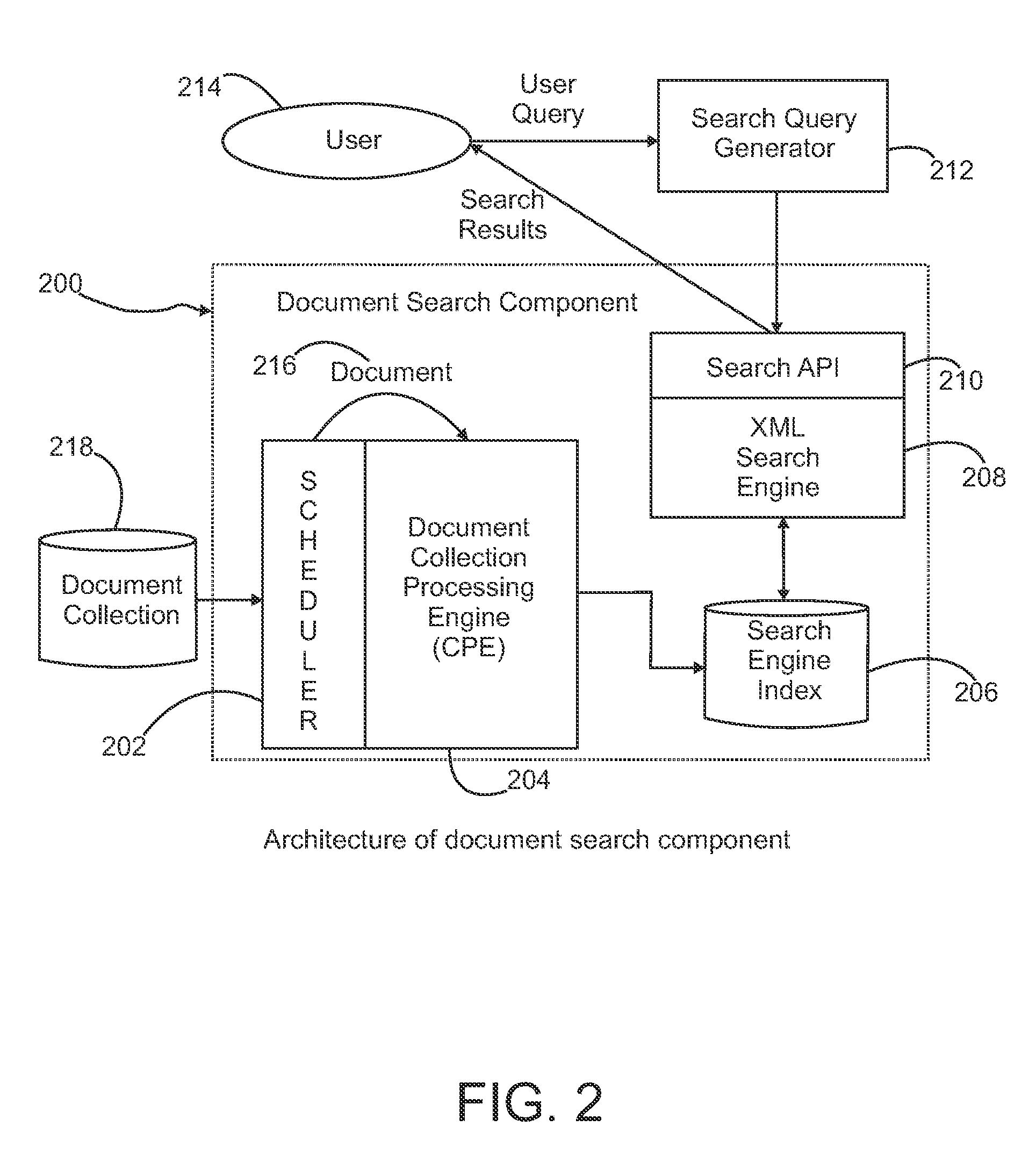
Secure search of private documents in an enterprise content management system
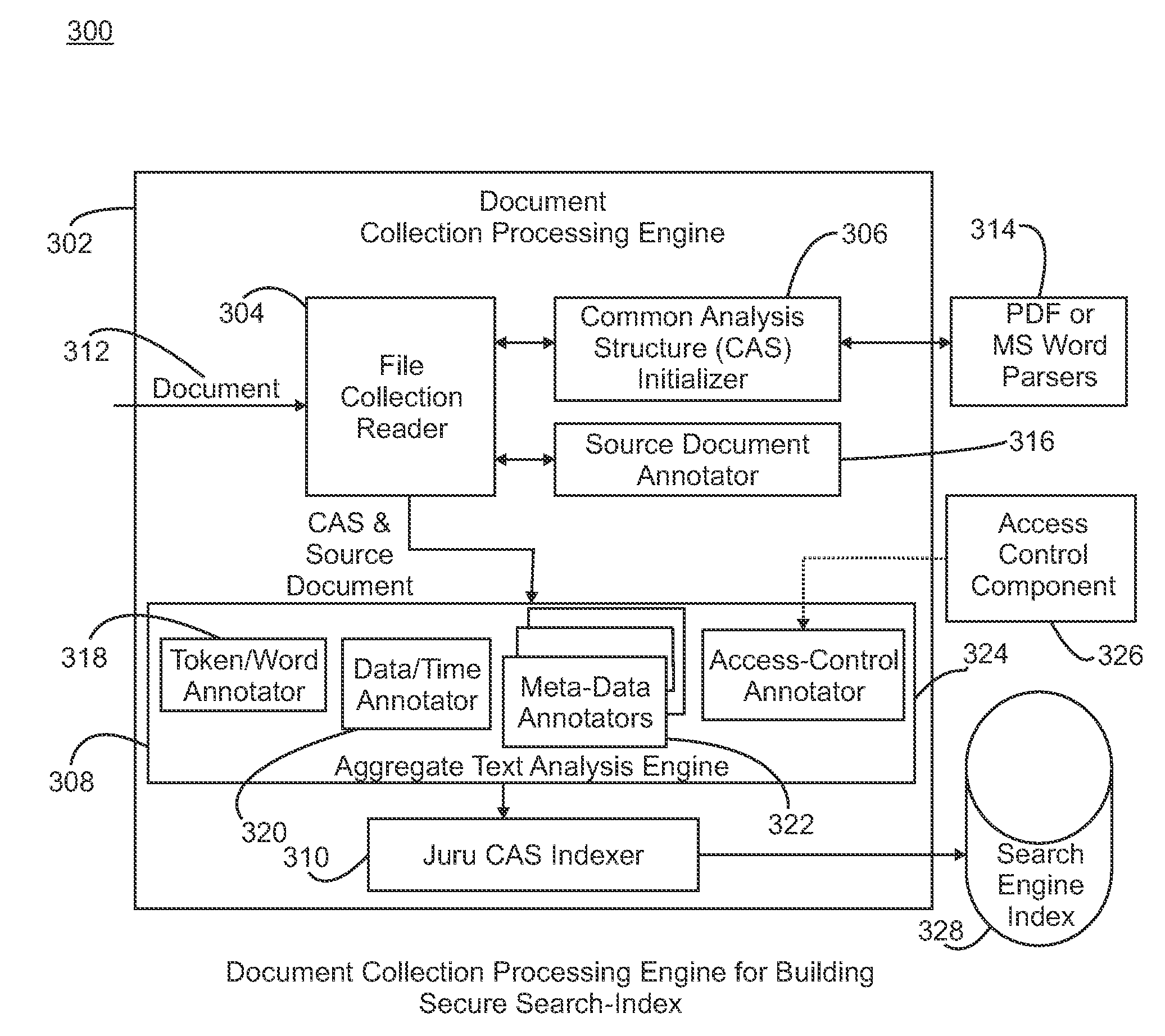
InactiveUS20090106271A1Efficient use ofEfficient retrievalText database queryingSpecial data processing applicationsDocument analysisEnterprise content management
An enterprise content management system such as an electronic contract system manages a large number of secure documents for many organizations. The search of these private documents for different organizational users with role-based access control is a challenging task. A content-based extensible mark-up language (XML)-annotated secure-index search mechanism is provided that provides an effective search and retrieval of private documents with document-level security. The search mechanism includes a document analysis framework for text analysis and annotation, a search indexer to build and incorporate document access control information directly into a search index, an XML-based search engine, and a compound query generation technique to join user role and organization information into search query. By incorporating document access information directly into the search index and combining user information in the search query, search and retrieval of private contract documents can be achieved very effectively and securely with high performance.
Owner:IBM CORP
Refined permission constraints using internal and external data extraction in a role-based access control system
ActiveUS20060047657A1Enhance content availableIncrease profitDigital data processing detailsComputer security arrangementsExternal dataControl system
The present invention can enable increasing refinement of role-based permission to access data within a Role Based Access Control (RBAC) controlled computer system by enabling constraints to be written on the role-based permissions. The constraints may utilize each and every type or combination of subject, object, or environment information extracted from sources internal or external to the controlled computer system and may evaluate the content or context of the information extracted to enable refined and dynamic access after the role permission assignment and immediately before every access grant without the reassignment of roles.
Owner:ILLINOIS INSTITUTE OF TECHNOLOGY
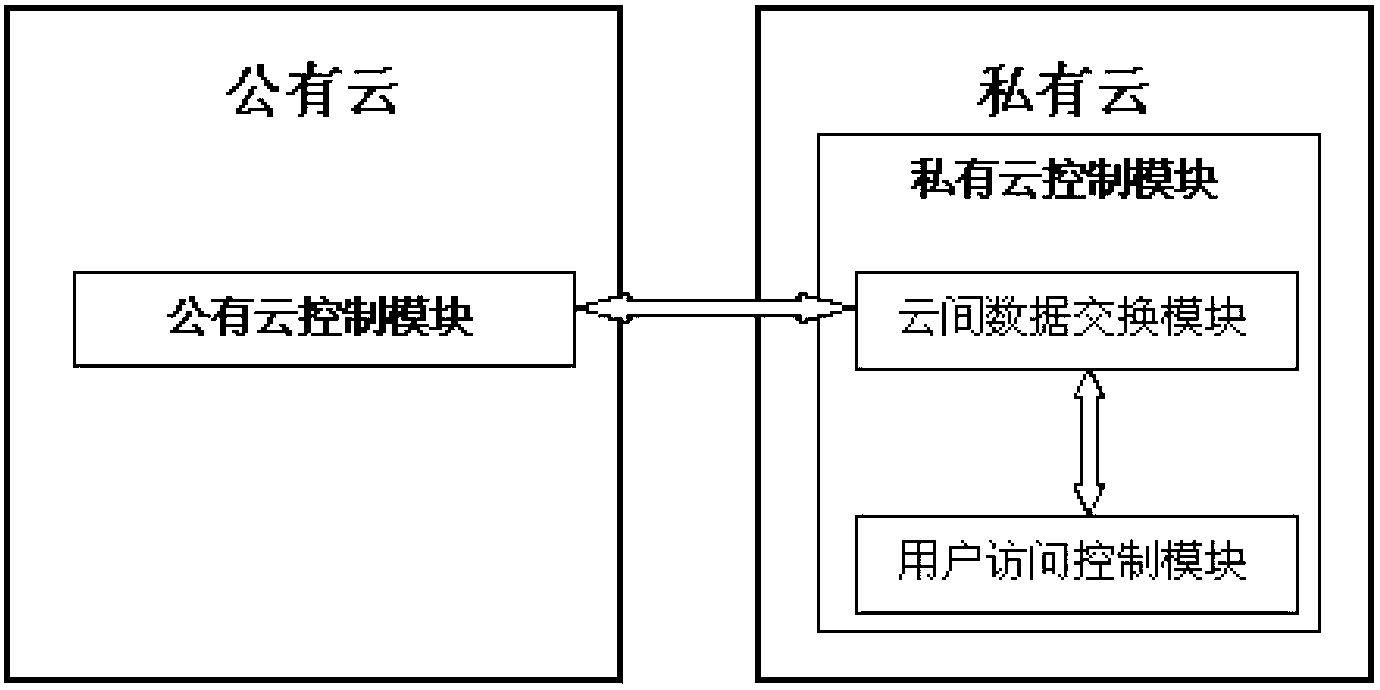
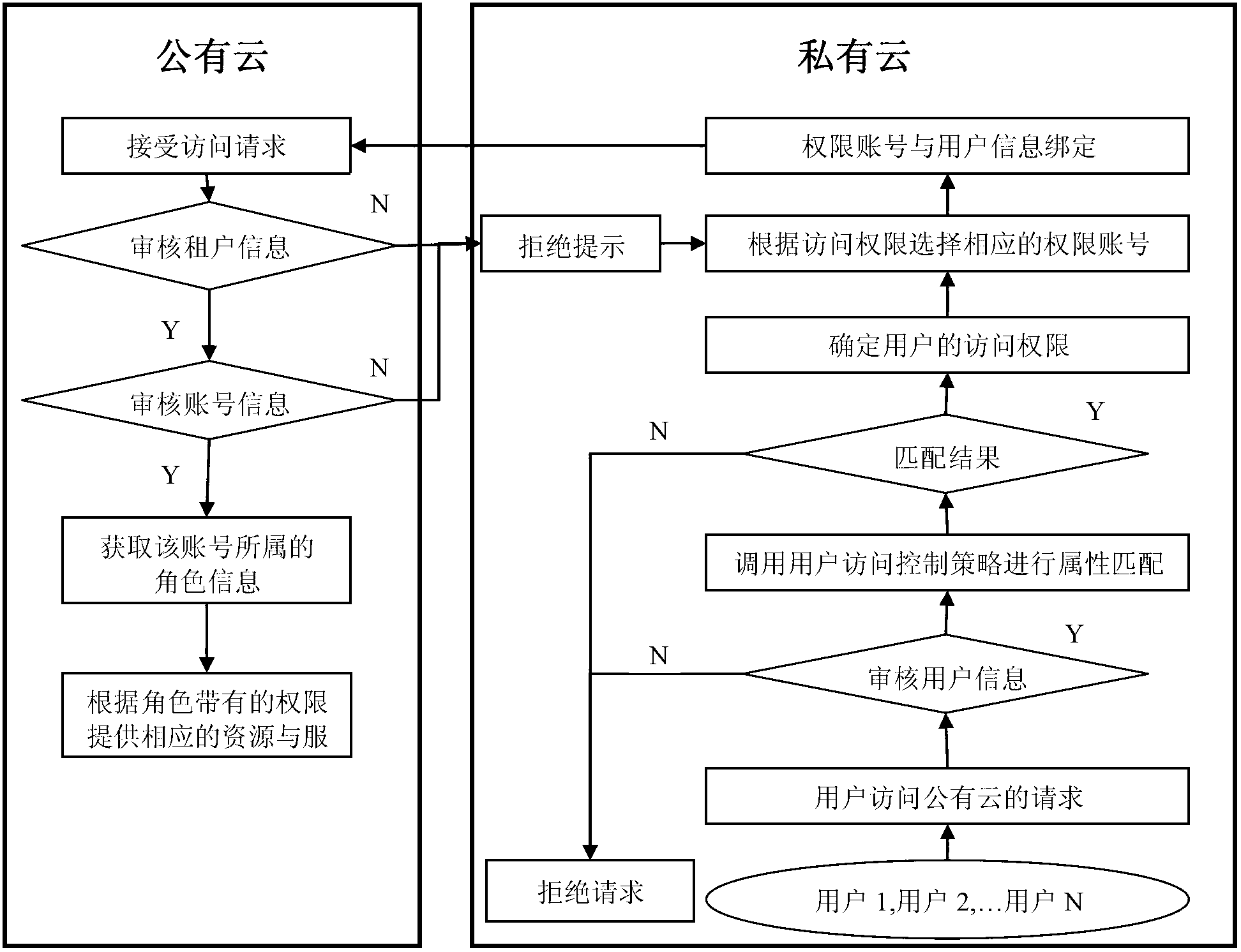
Access control system and access control method between public cloud and private cloud
ActiveCN103067406AControl Access Request ManagementEnsure safetyTransmissionControl systemCloud data
The invention discloses an access control system and an access control method between a public cloud and a private cloud. The access control system includes a private cloud control module at a private cloud end, and a public cloud control module at a public cloud end. The private cloud control module comprises an inter-cloud data exchange module and a user access control module. The inter-cloud data exchange module is respectively connected with the user access control module and the public cloud control module through a network. The access control method combines role-based access control and attribute-based access control, an attribute-based access control mode is adopted in the private cloud, and a role-based access control mode is adopted when the private cloud accesses the public cloud. Due to the fact that the access control system limits the access right of users of the private cloud to resources or services of the public cloud, the access control system has the advantages of being quite high in inter-cloud data exchange safety.
Owner:JINAN UNIVERSITY
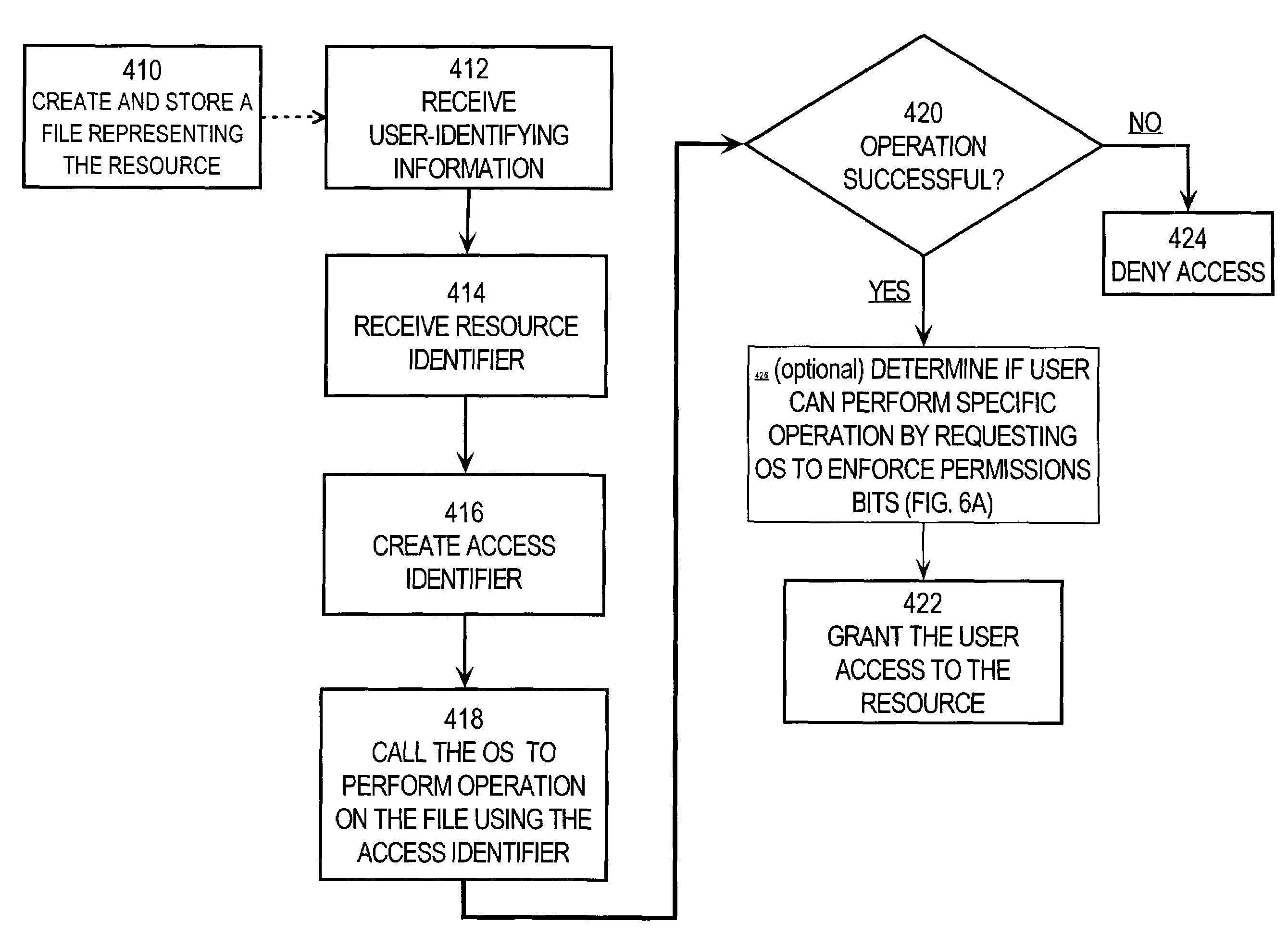
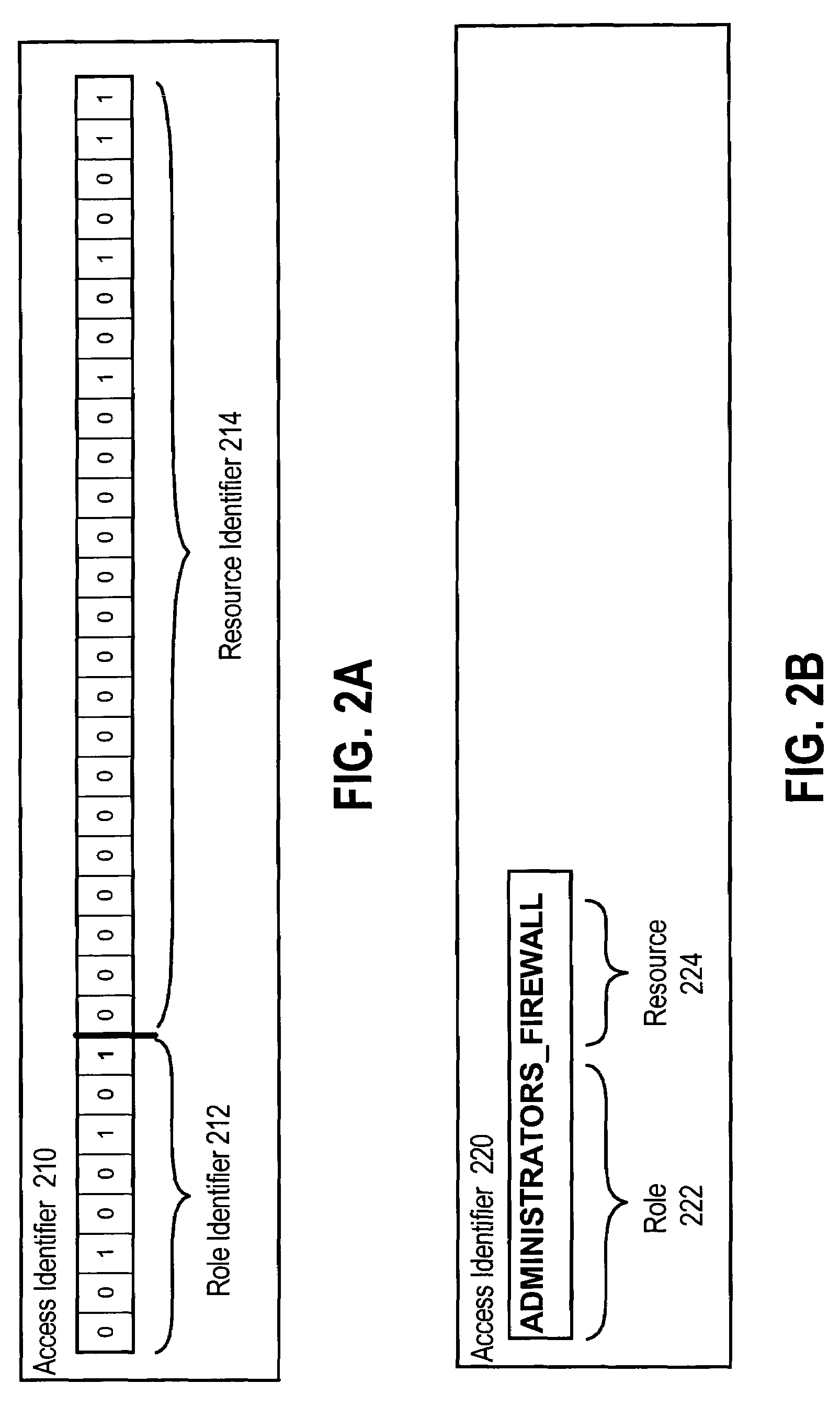
Role-based access control enforced by filesystem of an operating system
InactiveUS7702693B1Digital data processing detailsComputer security arrangementsOperational systemFile system
A method and system for role-based access control enforced by an Operating System filesystem are provided. A file representing a resource is created and stored in the Operating System filesystem. A user requests access to the resource and provides user-identifying information and a resource identifier. An access identifier is created based on the user-identifying information and the resource identifier, and is formatted as the file attribute used by the Operating System to manage file access. A system call to the Operating System is made to perform an operation on the file representing the resource, where the system call uses the access identifier to gain access to the file. The user is granted access to the resource only if the operating system successfully performs the operation on the file representing the resource.
Owner:CISCO TECH INC
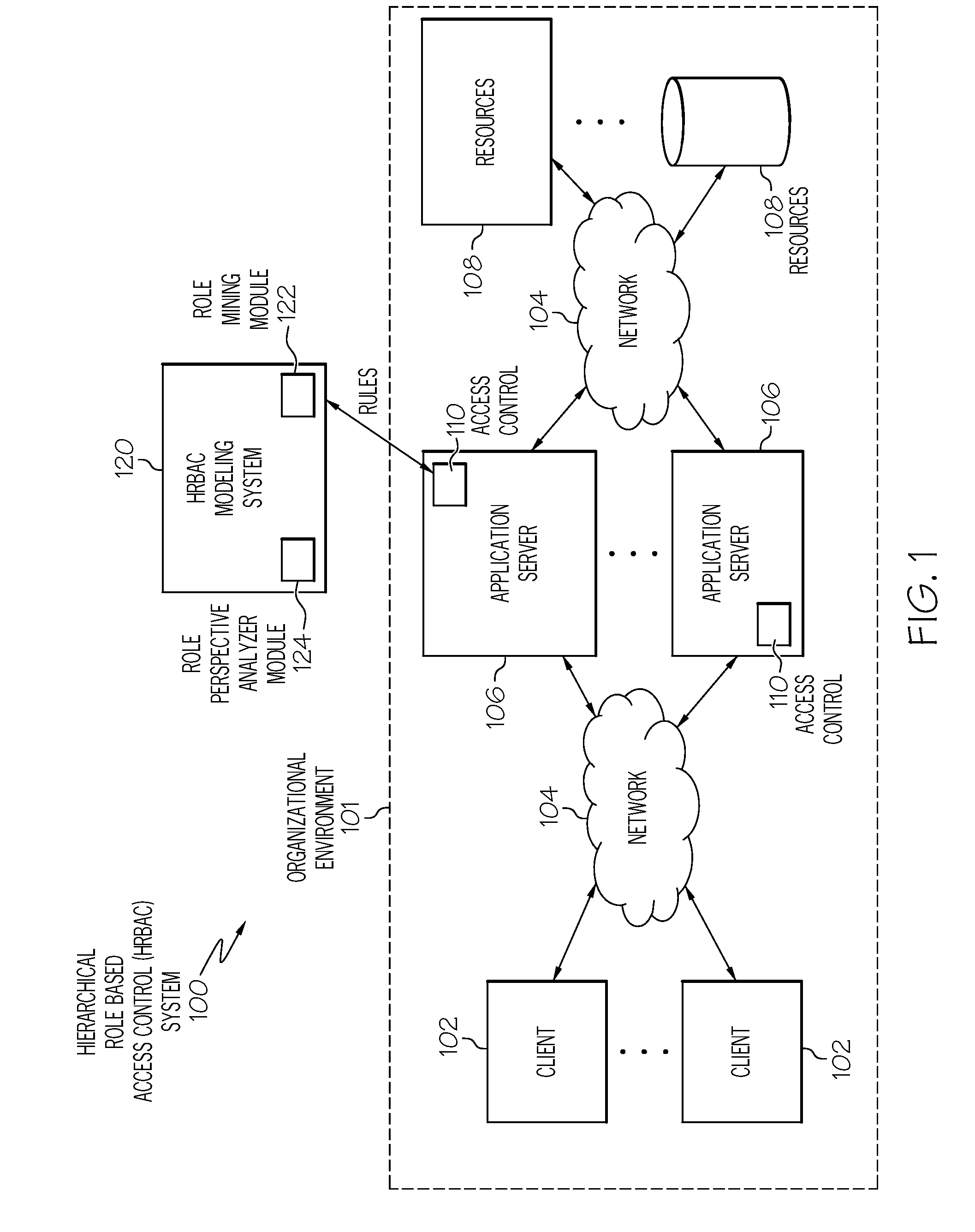
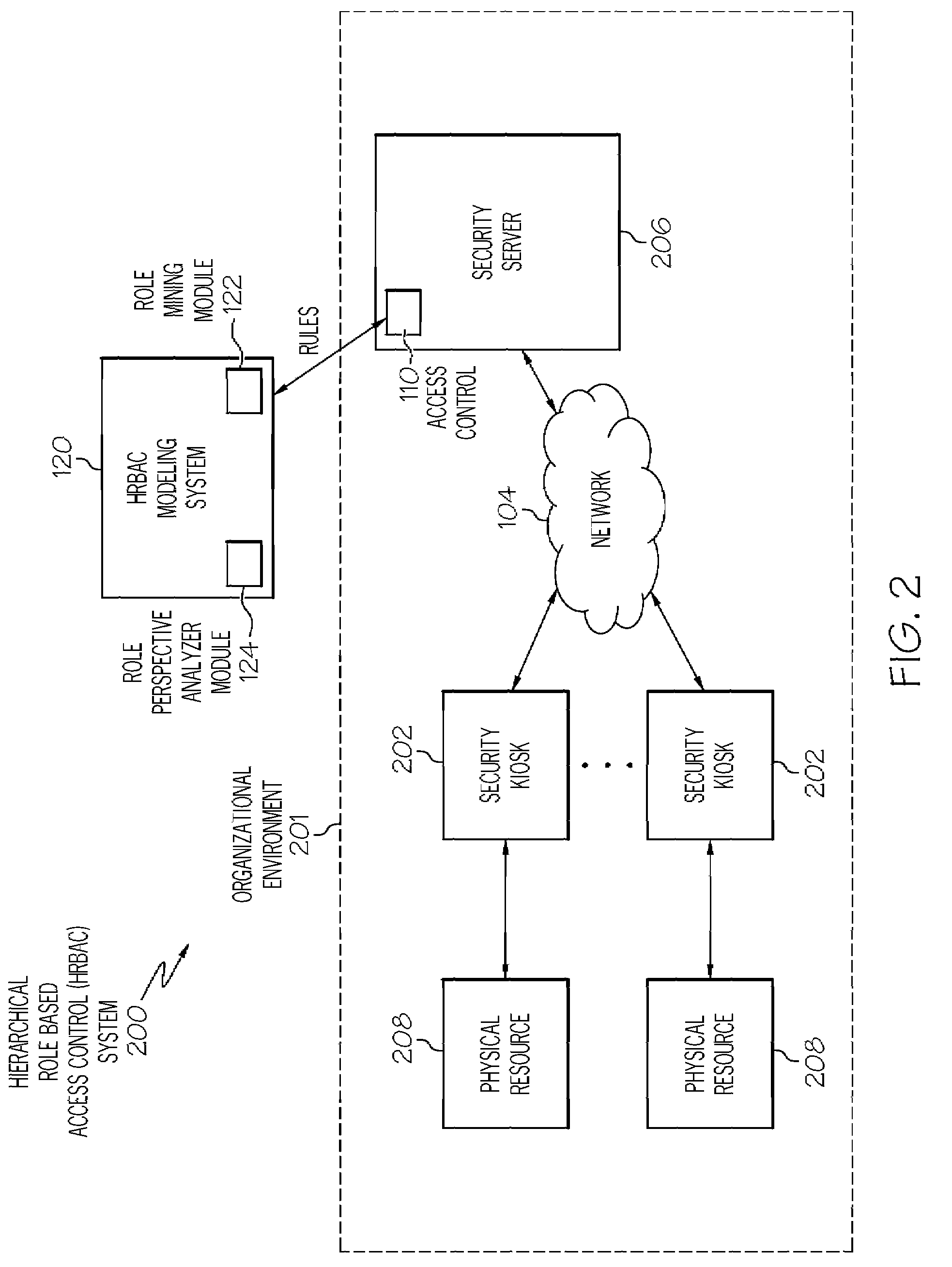
Automated organizational role modeling for role based access controls
ActiveUS7650633B2Digital data processing detailsUnauthorized memory use protectionControl systemMedia access control
Generally speaking, systems, methods and media for automatically generating a role based access control model (RBAC) for an organizational environment with a role based access control system such as a hierarchical RBAC (HRBAC) system are disclosed. Embodiments may include a method for generating an RBAC model. Embodiments of the method may include accessing existing permissions granted to users of an organizational environment and analyzing the permissions to create permission characteristics. Embodiments of the method may also include performing cladistics analysis on the permission characteristics to determine role perspective relationships between individual users of the organizational environment. Embodiments of the method may also include generating an RBAC model based on the determined role perspective relationships between individual users of the organizational environment. Further embodiments of the method may include where generating the RBAC model includes generating a cladogram based on the determined role perspective relationships.
Owner:TWITTER INC
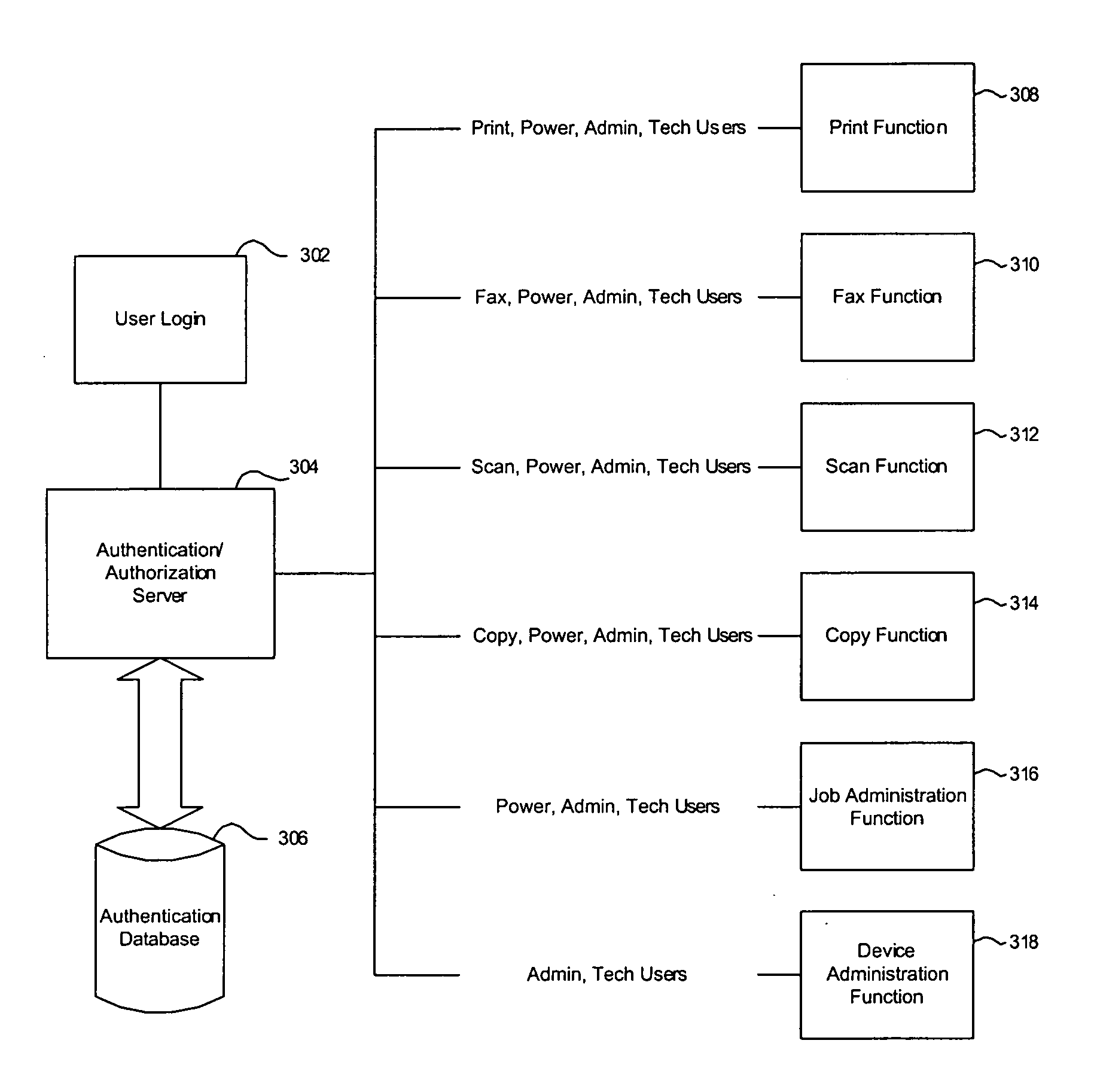
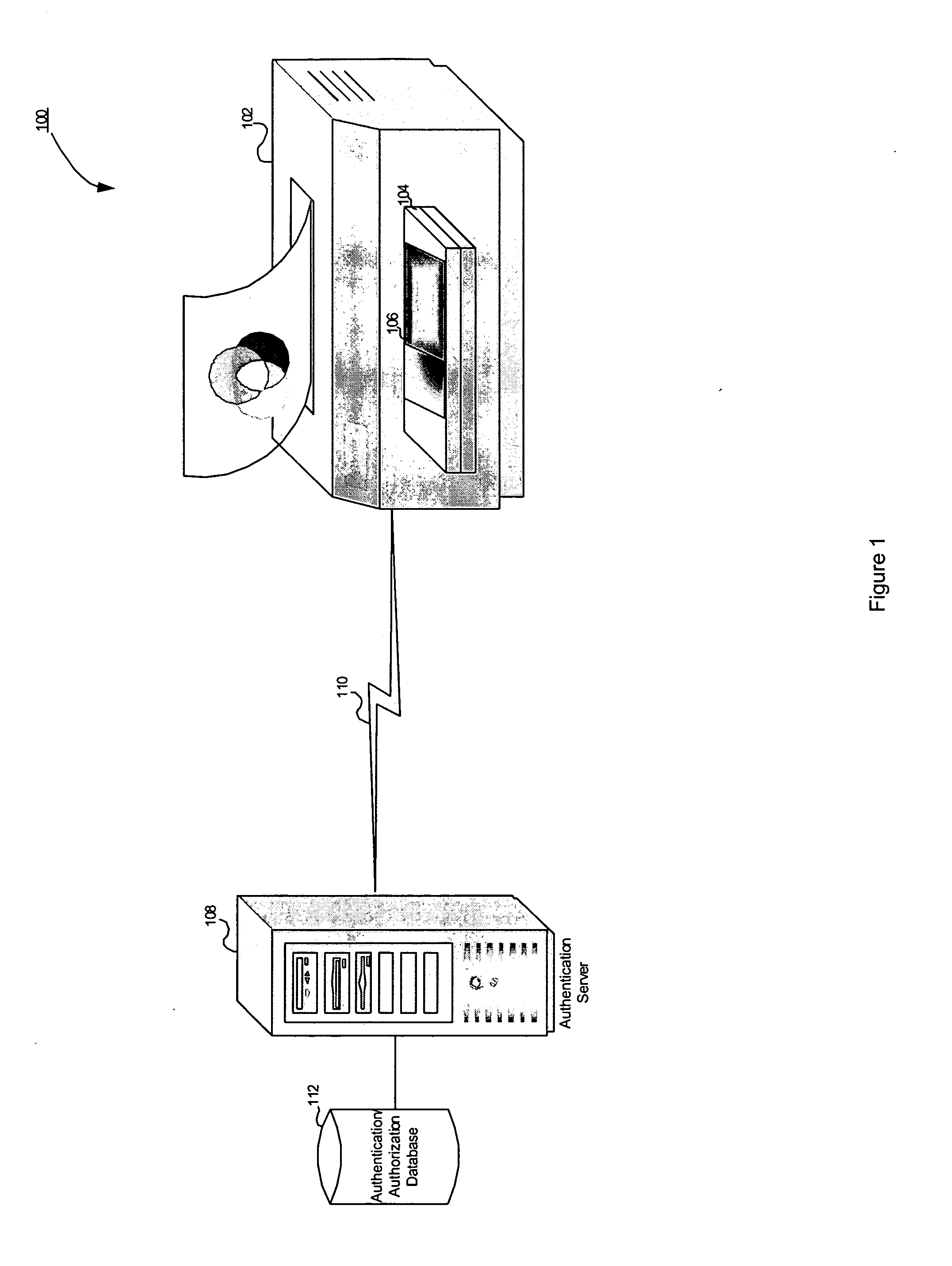
System and method for role based access control of a document processing device
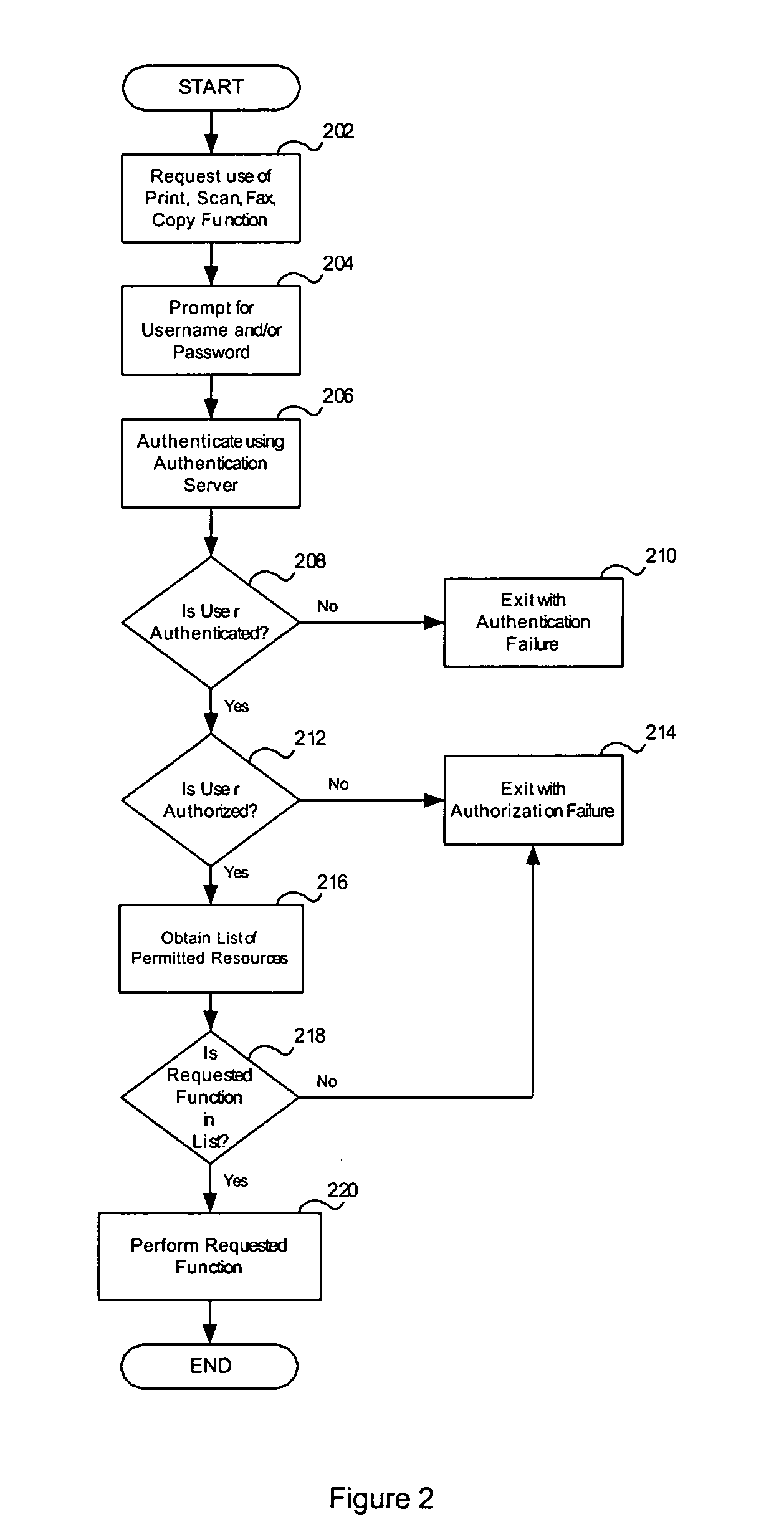
InactiveUS20050172151A1Improve securityDigital data processing detailsUnauthorized memory use protectionRelevant informationPassword
A system and method for controlling access to a document processing device based on roles assigned to user groups. Each group of users has certain functions for which they are authorized to use the document processing device. The device compares a username and password with correlating information stored in an authentication server. The server transmits a list of functions for which the user is authorized to employ the device. The device then compares the requested function with the authorized functions to determine if the user is allowed to utilize the document processing device for the requested function. The document processing device then performs the authorized requested function.
Owner:KK TOSHIBA +1
Method and apparatus for providing network security using role-based access control
ActiveUS7530112B2Small sizeImprove performanceDigital data processing detailsUser identity/authority verificationMedia access controlNetwork security policy
A method and apparatus for providing network security using role-based access control is disclosed. A network device implementing such a method can include, for example, an access control list. Such an access control list includes an access control list entry, which, in turn, includes a user group field. Alternatively, a network device implementing such a method can include, for example, a forwarding table that includes a plurality of forwarding table entries. In such a case, at least one of the forwarding table entries includes a user group field.
Owner:CISCO TECH INC
Defining consistent access control policies
ActiveUS20070056018A1Computer security arrangementsSpecial data processing applicationsControl systemAuthorization
A method of defining policies for controlling access to resources of a system. Authorization requirements for the system are modeled to obtain a model expressing each of a plurality of access control policies as a constraint. From the model is generated a single policy set in an authorization markup language that captures the requirements. This method can be used to define role-based access control policies in a format that can be adapted for input to a variety of access control mechanisms. This generative approach to access control design allows maintenance to be performed at the requirements level.
Owner:THE BOEING CO
Identity context-based access control
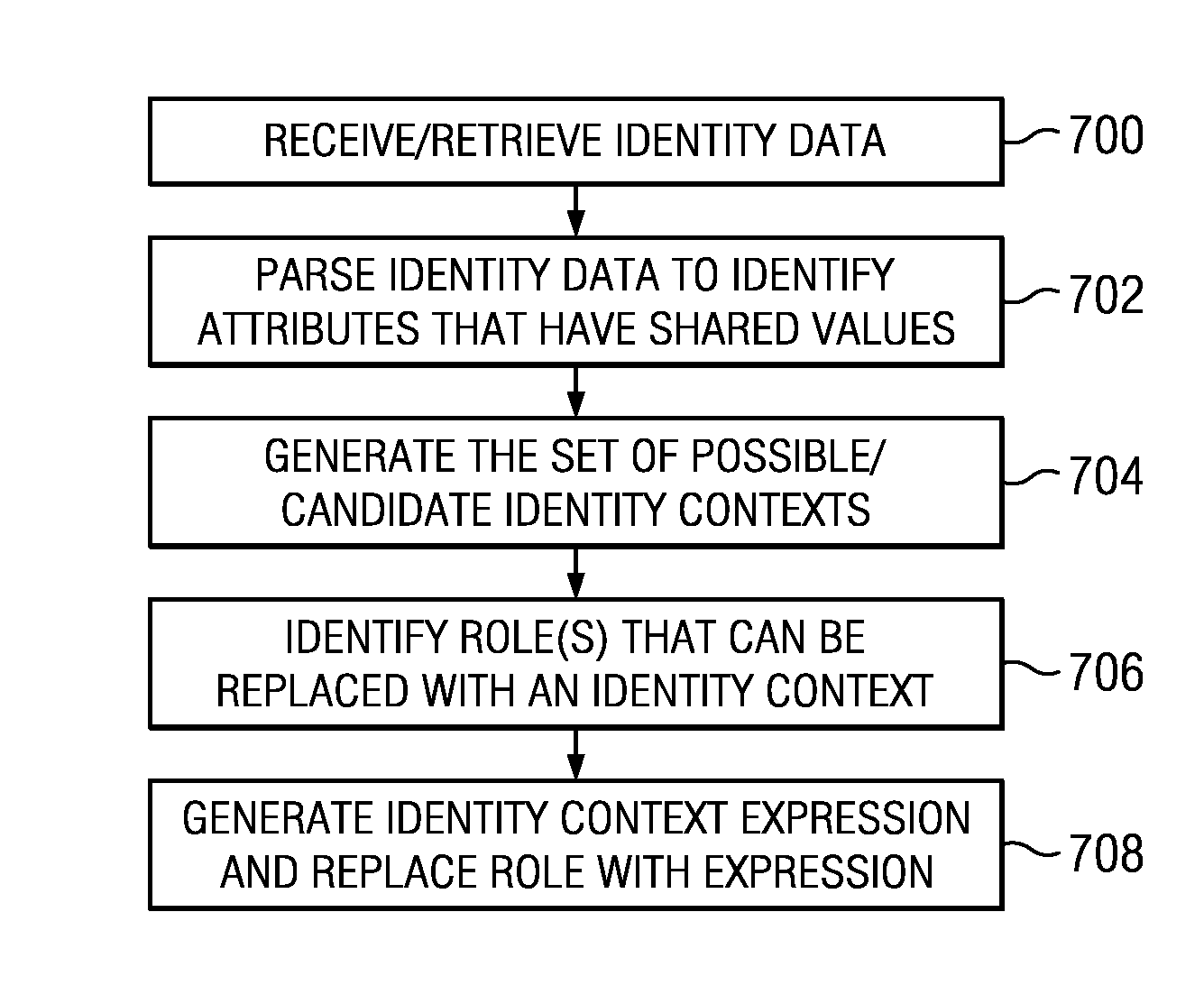
ActiveUS20140075492A1Reduce in quantityComputer security arrangementsTransmissionData access controlMedia access control
Identity context-based access control is implemented by generating an identity context expression from user identity data. In particular, users are clustered based on combinations of one or more attributes. These clusters comprise one or more identity context(s). Preferably, an intersection of attribute sets of each user in the cluster is formed. In addition, an intersection of attribute sets of each user not in the cluster also is formed. If the attribute set that is common across the cluster of users is not a subset of the attribute set that is common across the rest of the users, then the attribute set forms a unique identity context expression. To reduce the number of roles used in role-based access control (RBAC), at least one role is replaced with an identity context expression. Run-time access control is then enabled.
Owner:IBM CORP
Method and apparatus for role-based access control
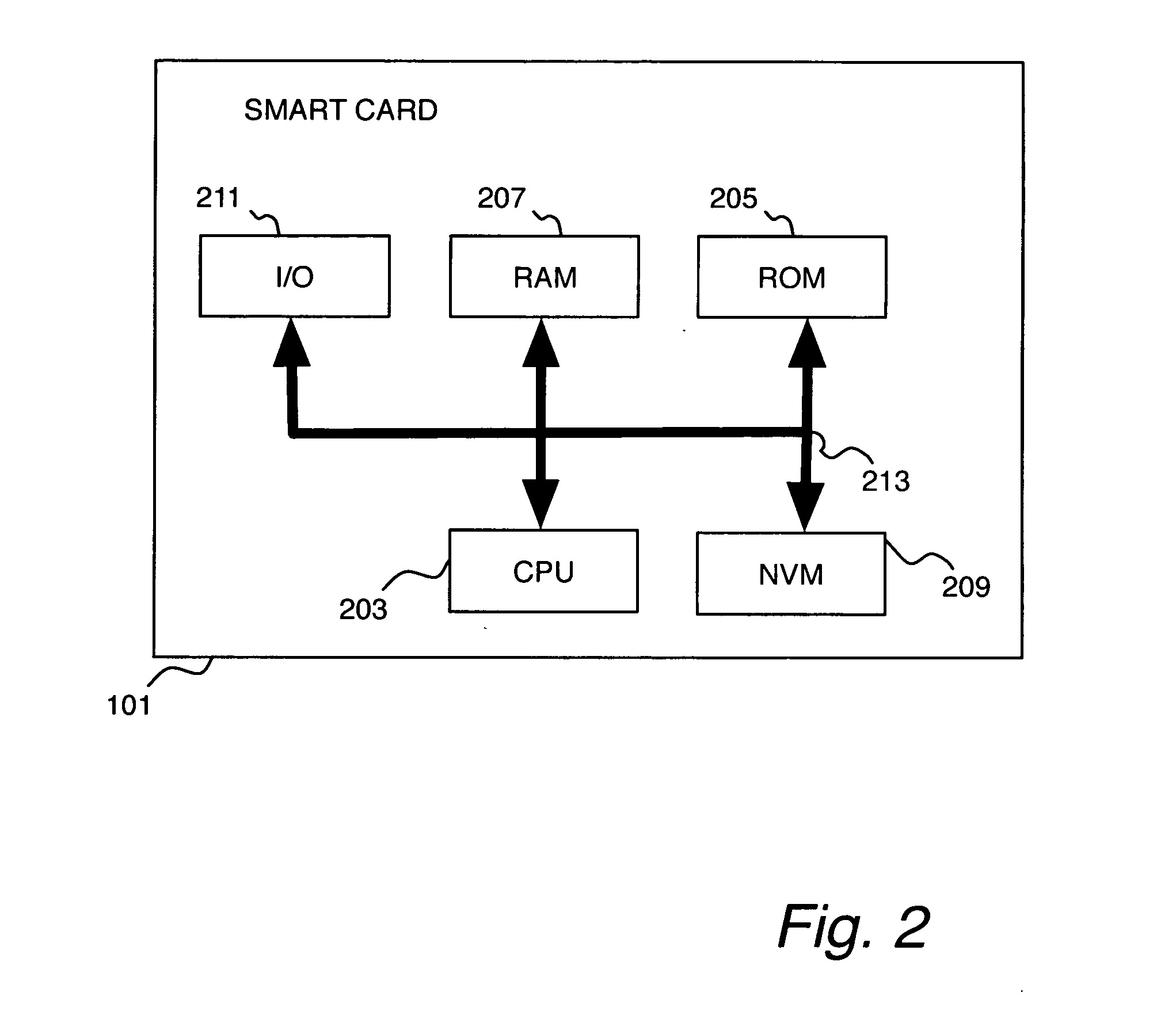
ActiveUS7424533B1Digital computer detailsComputer security arrangementsArea networkStorage area network
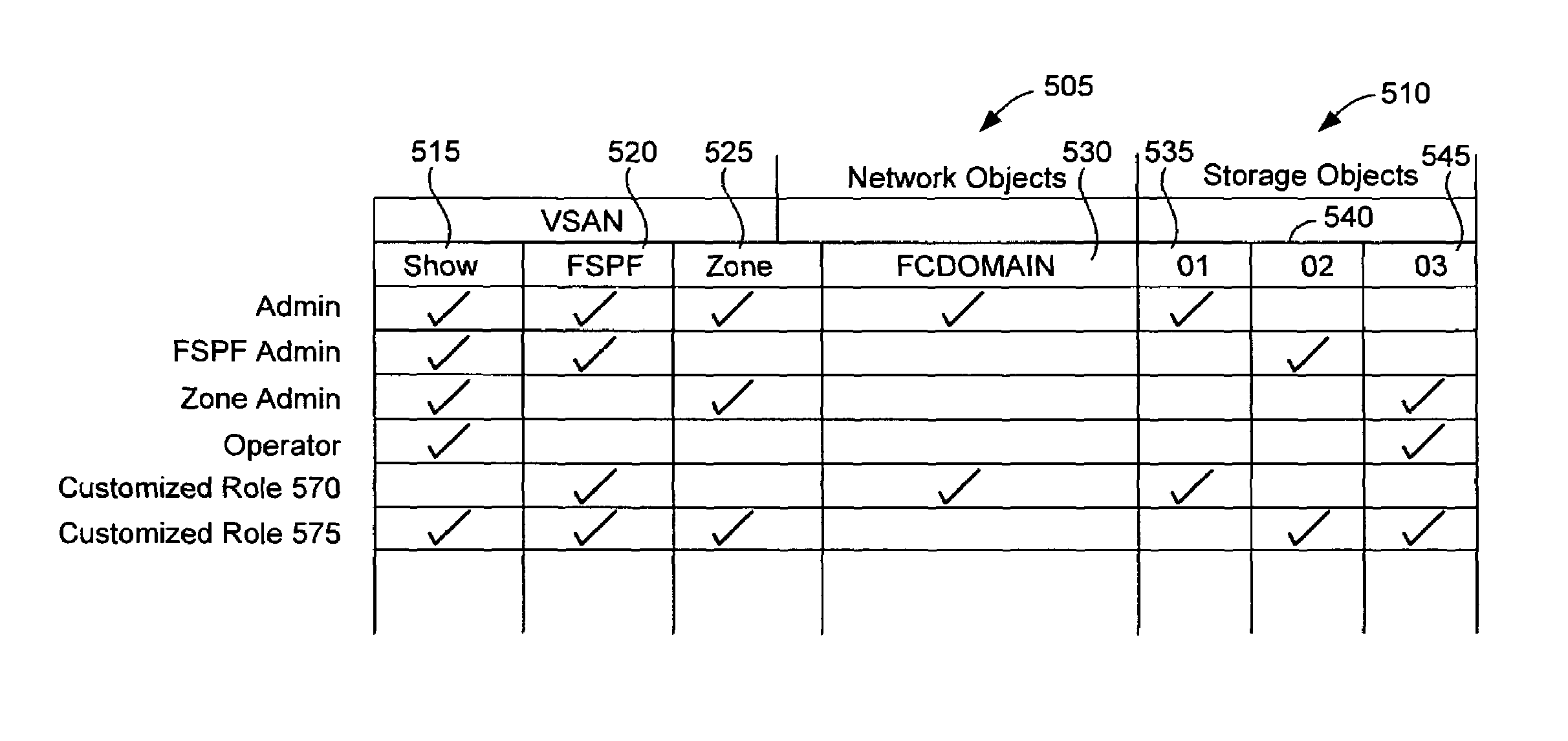
Methods and devices are provided for role-based access control of network devices. The network devices may constitute the fabric of a storage area network (“SAN”) that has been logically partitioned into virtual storage area networks (“VSANs”) that are allocated to various administrators. Roles assigned according to preferred aspects of the invention do not need to be hierarchical, but are customized according to administrators' needs.
Owner:CISCO TECH INC
Method for role-based access control model with precise access control strategy
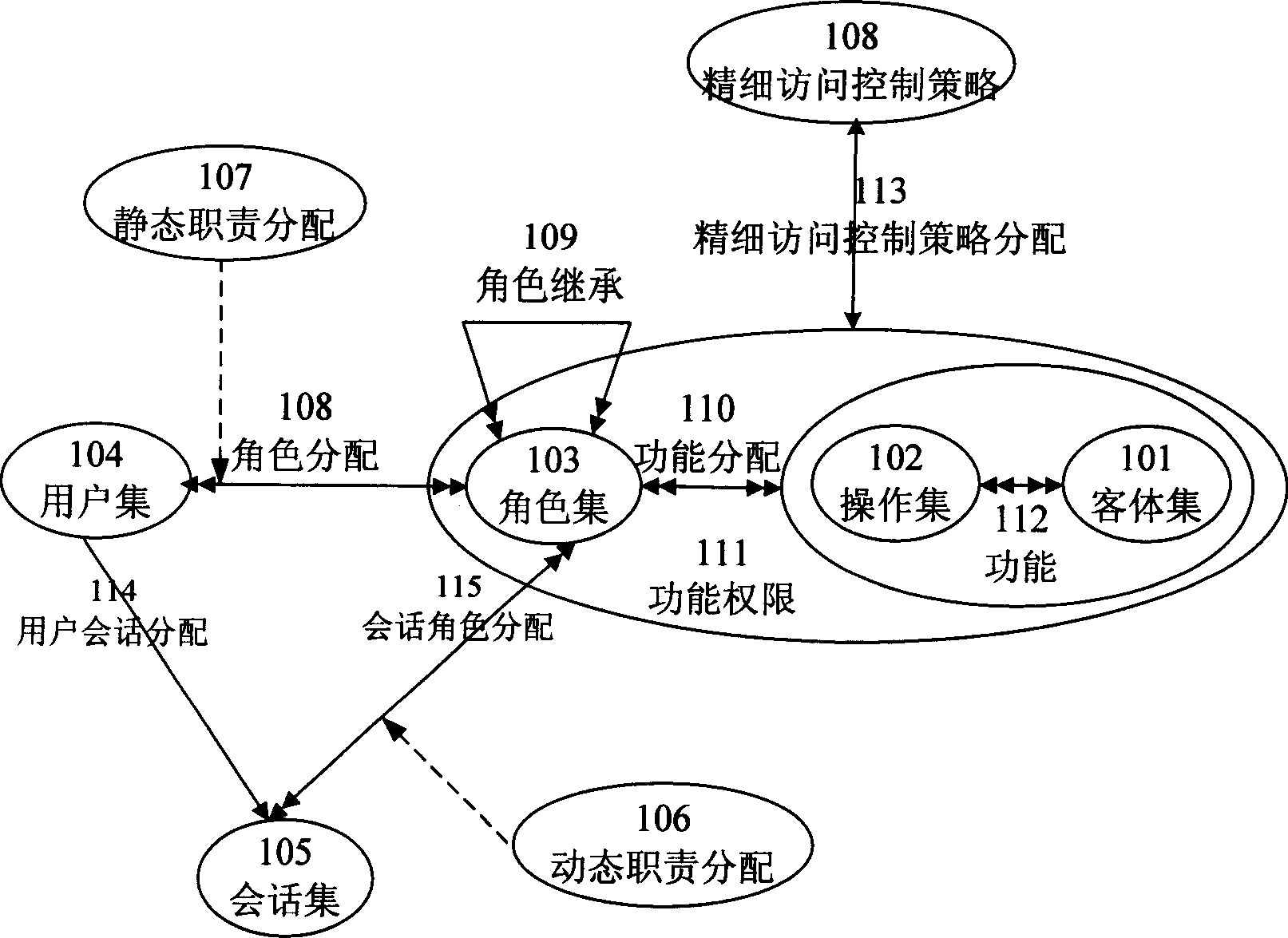
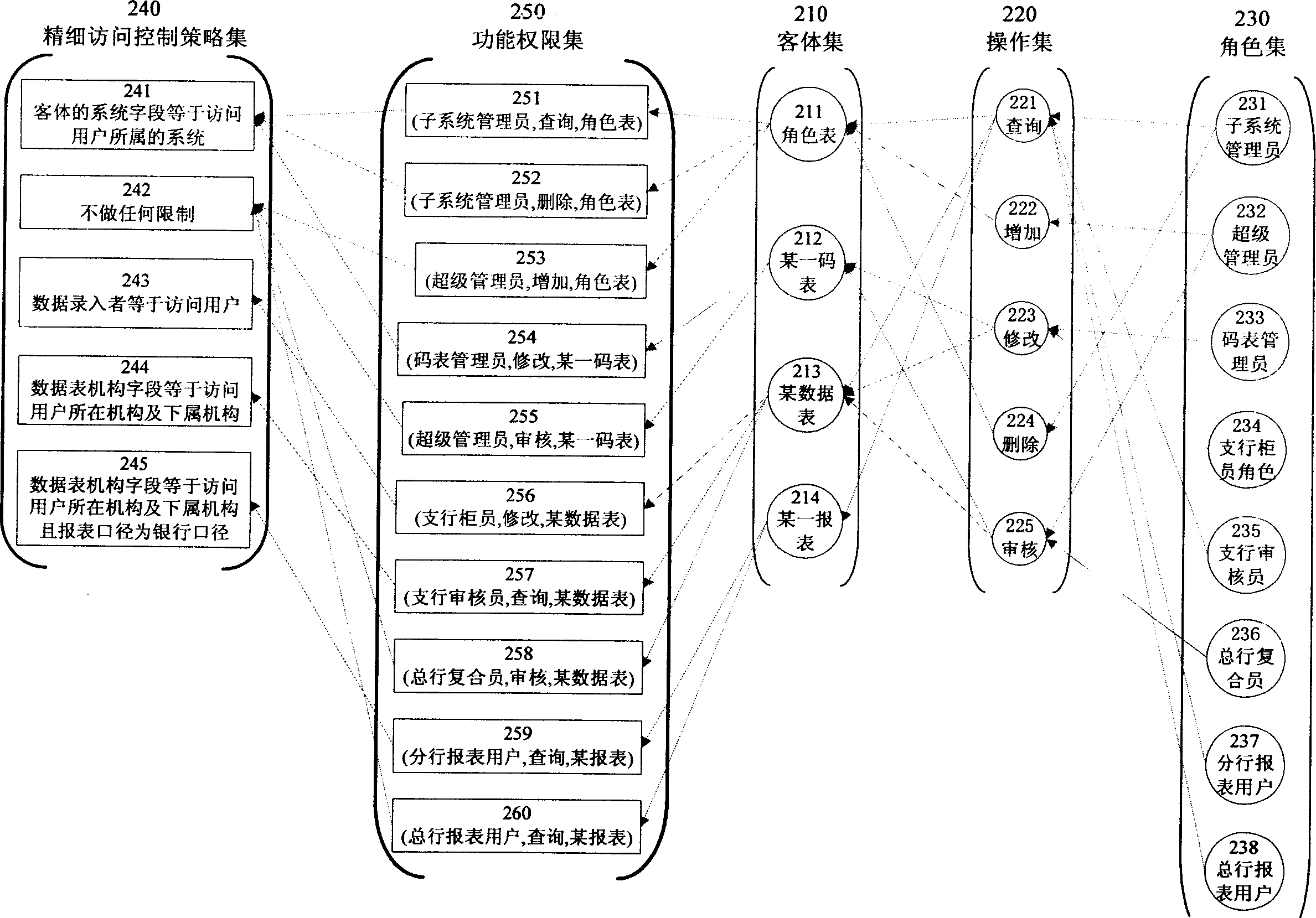
ActiveCN1885297AFunctional permission refinementDigital data authenticationBusiness logicContextual information
The invention relates to a method for accessing control model based on identification, with accurate access control strategy, wherein the method comprises: accurate access control strategy and the projection function between function priority and accurate access control strategy; the control strategy is predefined operation dynamic strategy function, which comprises limit logic demanded by service logic on accurate control and the limit based on external condition and context information. The invention can fine the graininess of access control in the standard access control model.
Owner:HANGYIN CONSUMER FINANCE CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com