Cloud security access control model
A security access control and access control technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve data security and privacy concerns, user file leakage, security accidents, etc., to achieve small size, Easy-to-use, easy-to-process effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
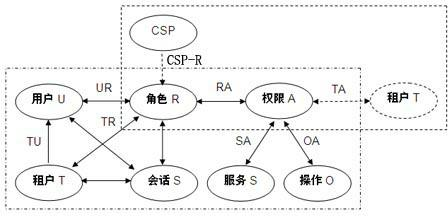
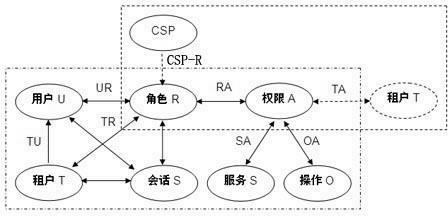
[0069] (1) Tenant access control modeling
[0070] The cloud service provider Cloud provides customer relationship management CRM services externally. According to its business needs and business functions, it defines the roles (including functions and positions) and permissions of cloud service managers, and gives each cloud service management Personnel are assigned corresponding roles, responsible for managing and maintaining a certain number of tenants, so as to complete the internal access control modeling with the service provider Cloud;
[0071] (2) Registration
[0072] Enterprise tenant A plans to use the customer relationship management (CRM) service provided by cloud service provider Cloud. First, enterprise tenant A applies to the cloud service provider Cloud through the registration process, and registers tenant information, including enterprise name, address, contact number, province and city, and other basic enterprise information; then provides tena...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com