Method for role-based access control model with precise access control strategy
An access control strategy and access control technology, applied in the field of security authorization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
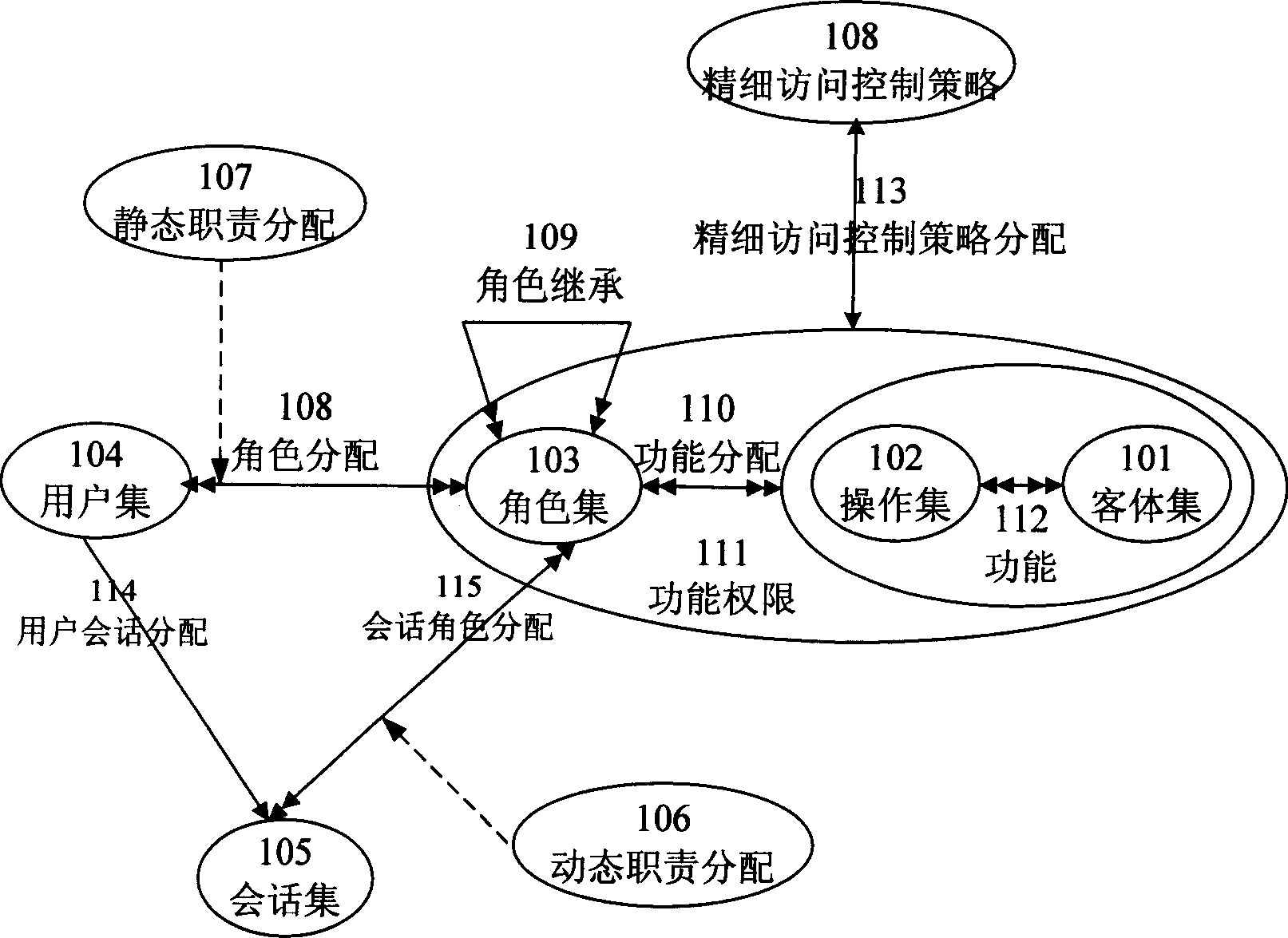
[0110] Example 2 as figure 2 Shown: the user is usually a system user, and the object is usually a database table, but not limited to this, the user can be a program, and the object can also be a data file, an XML file, or any computer resource, and the operations are not limited to the listed ones. It can be expanded arbitrarily according to the actual application system needs.
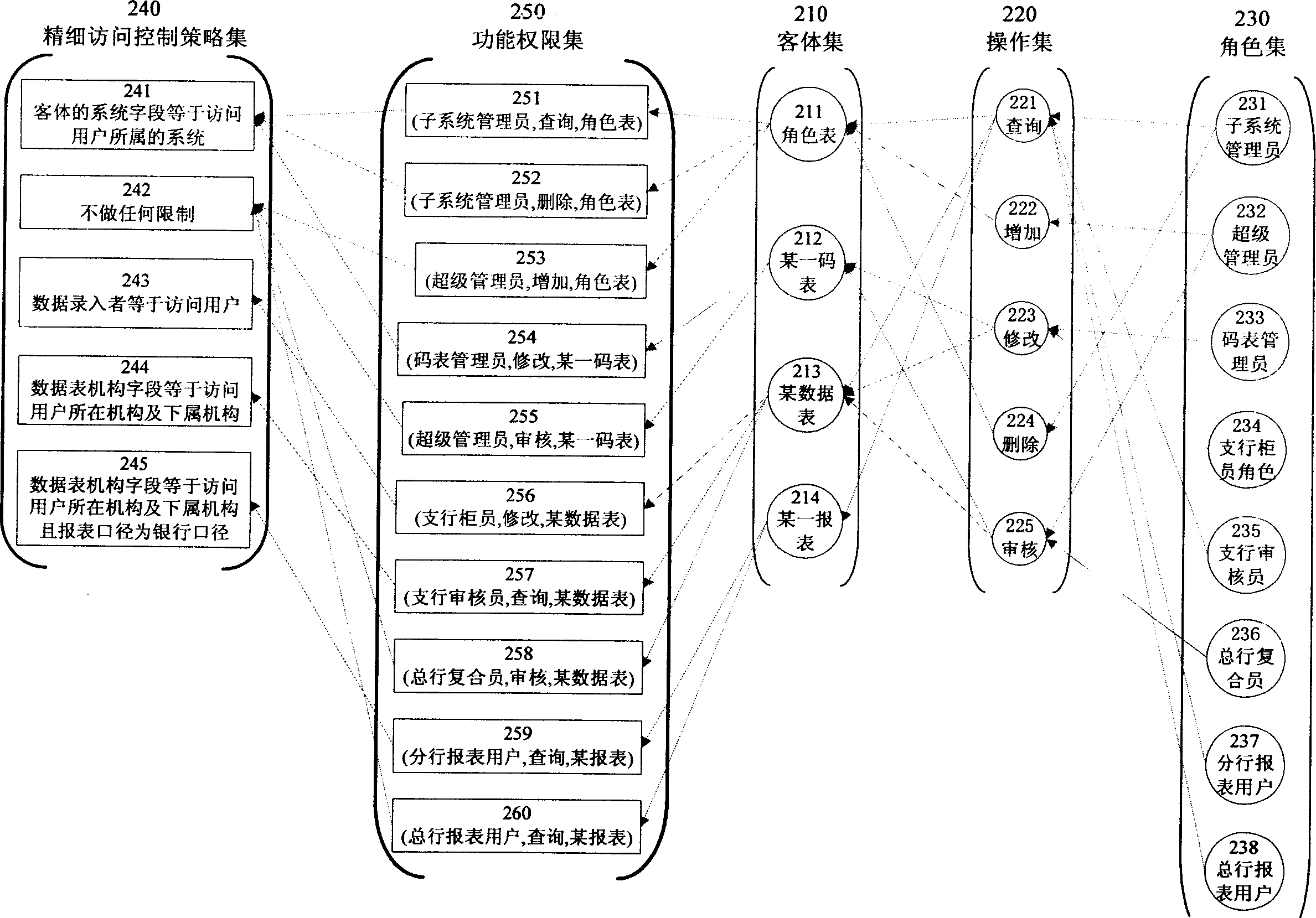
[0111] For example, in the management information system, the functional items are divided into four categories according to the coarse-grained division: system management, code table management, data processing and report query. Generally, it corresponds to four types of roles, namely, roles related to system management, roles related to computer management, roles related to data processing and roles related to report query.
[0112] System management is used for adding, changing, reviewing, querying, system log monitoring, user locking and unlocking, etc. for users using the system. The roles in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com