Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2036 results about "Risk evaluation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Risk Evaluation Definition. Risk evaluation is defined by the Business Dictionary as: “Determination of risk management priorities through establishment of qualitative and/or quantitative relationships between benefits and associated risks.”.
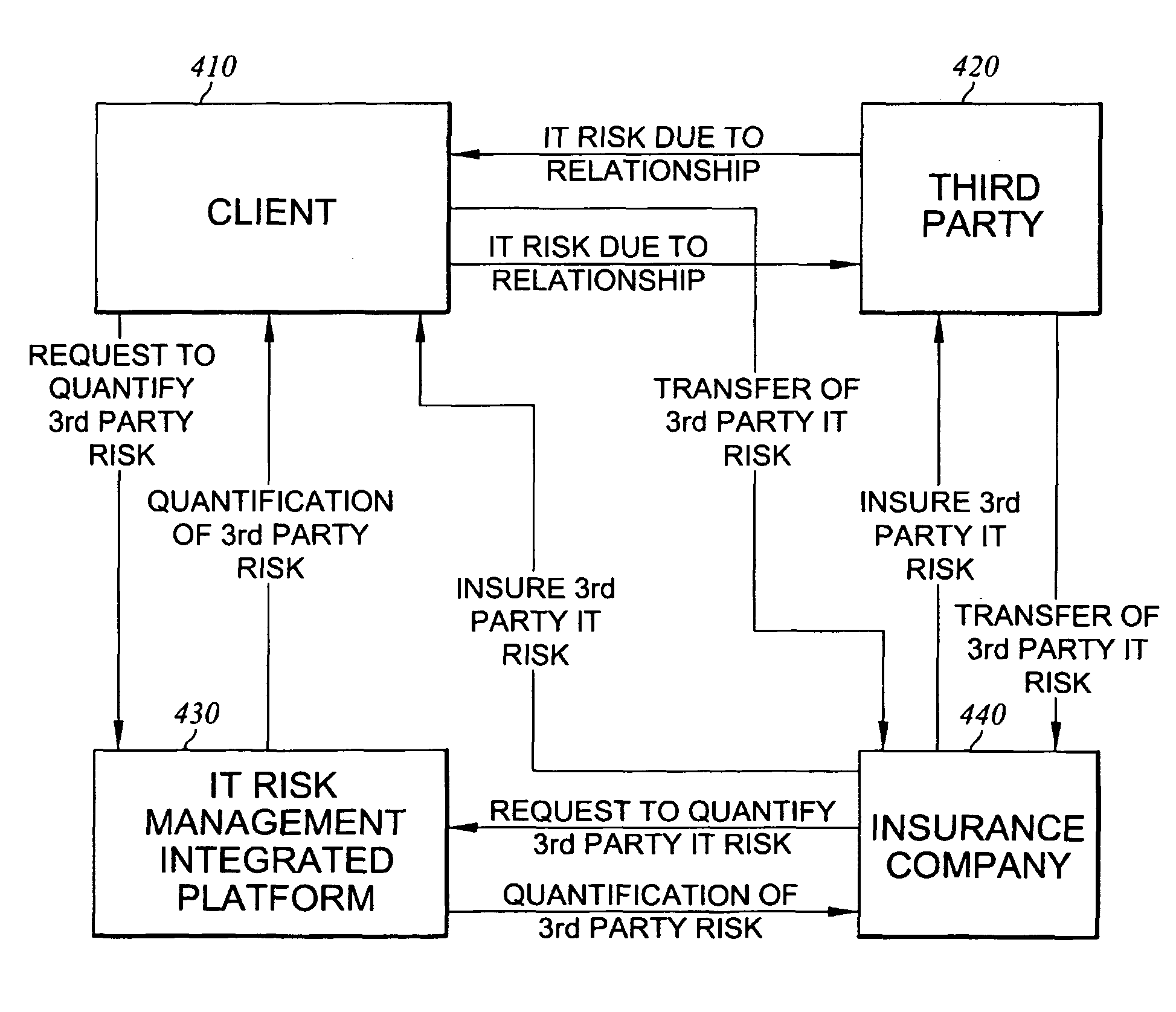
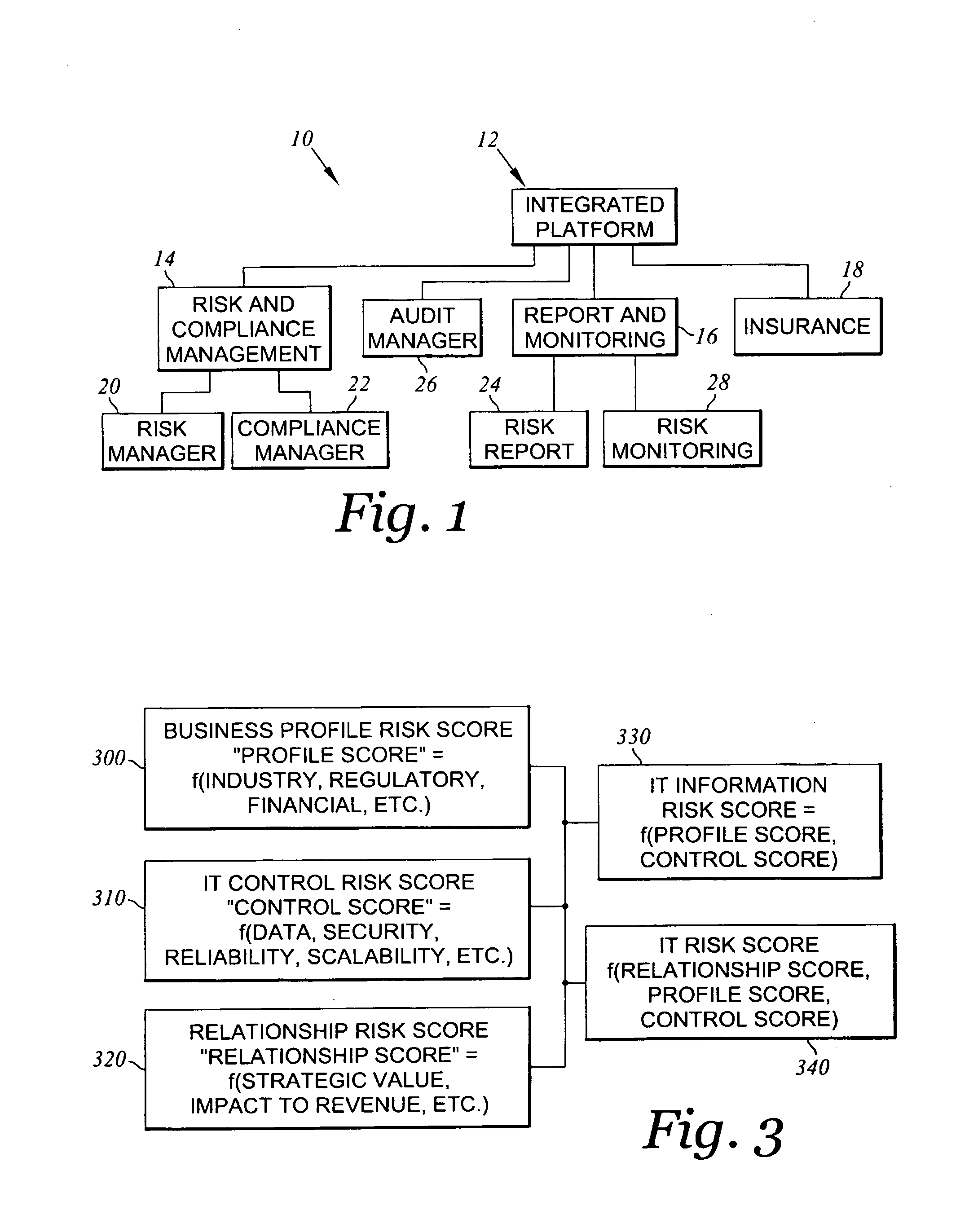
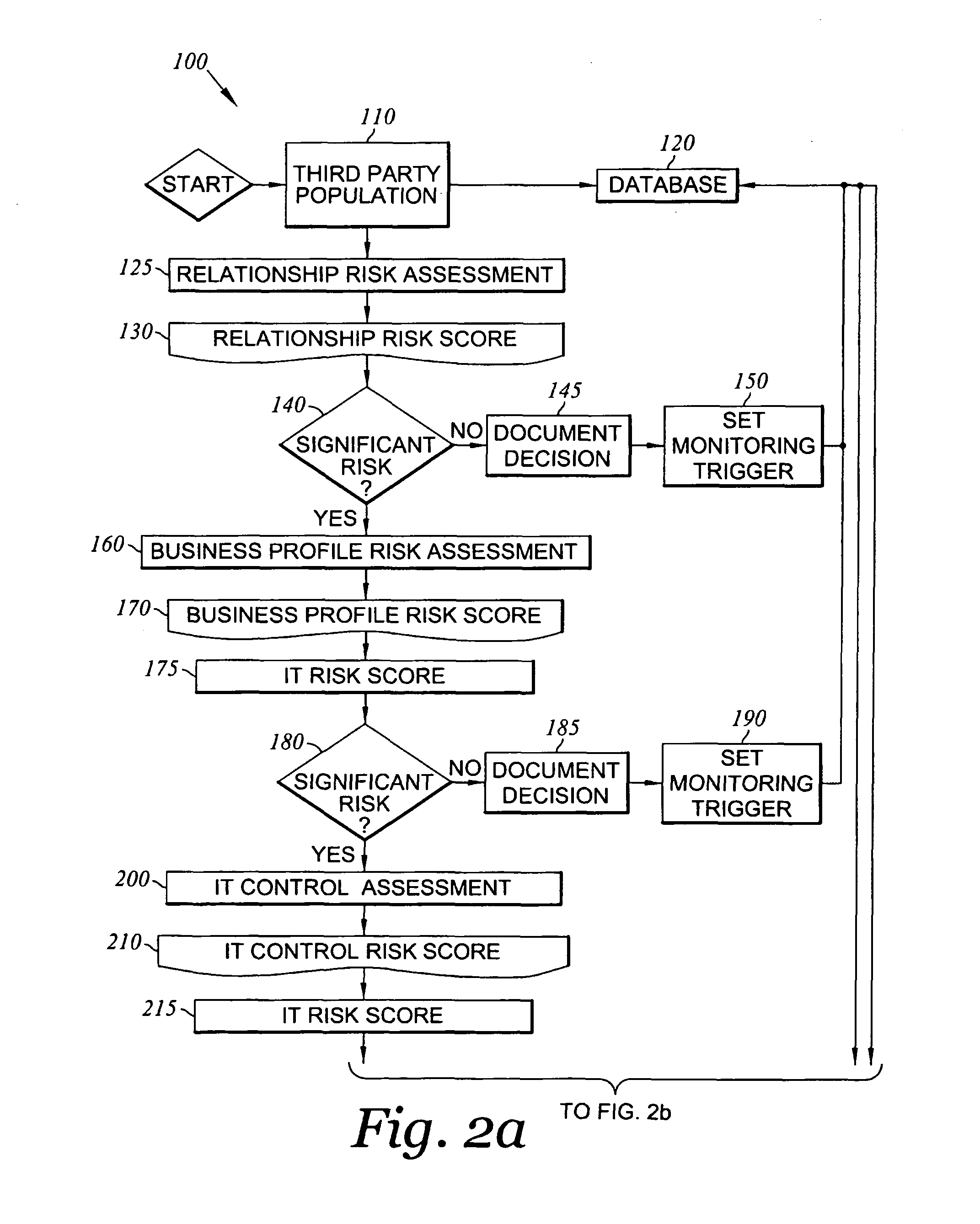
Method and system for assessing, managing, and monitoring information technology risk
A method for information technology (IT) and information asset risk assessment of a business relationship between a client and a third party. The method includes establishing a database. The database includes a plurality of IT information risk factors. The database is configured to receive IT risk information. The IT risk information is associated with the plurality of IT information risk factors. The plurality of IT information risk factors includes a subset of relationship risk factors. The subset of relationship risk factors are utilized for evaluating the business relationship risk between the client and the third party. The method also includes receiving IT risk information corresponding to the subset of relationship risk factors. The method continues with generating a relationship risk score. The relationship risk score is determined in response to evaluating the subset of relationship risk factors using the IT risk information corresponding to the subset of relationship risk factors.
Owner:OPTIV SECURITY INC
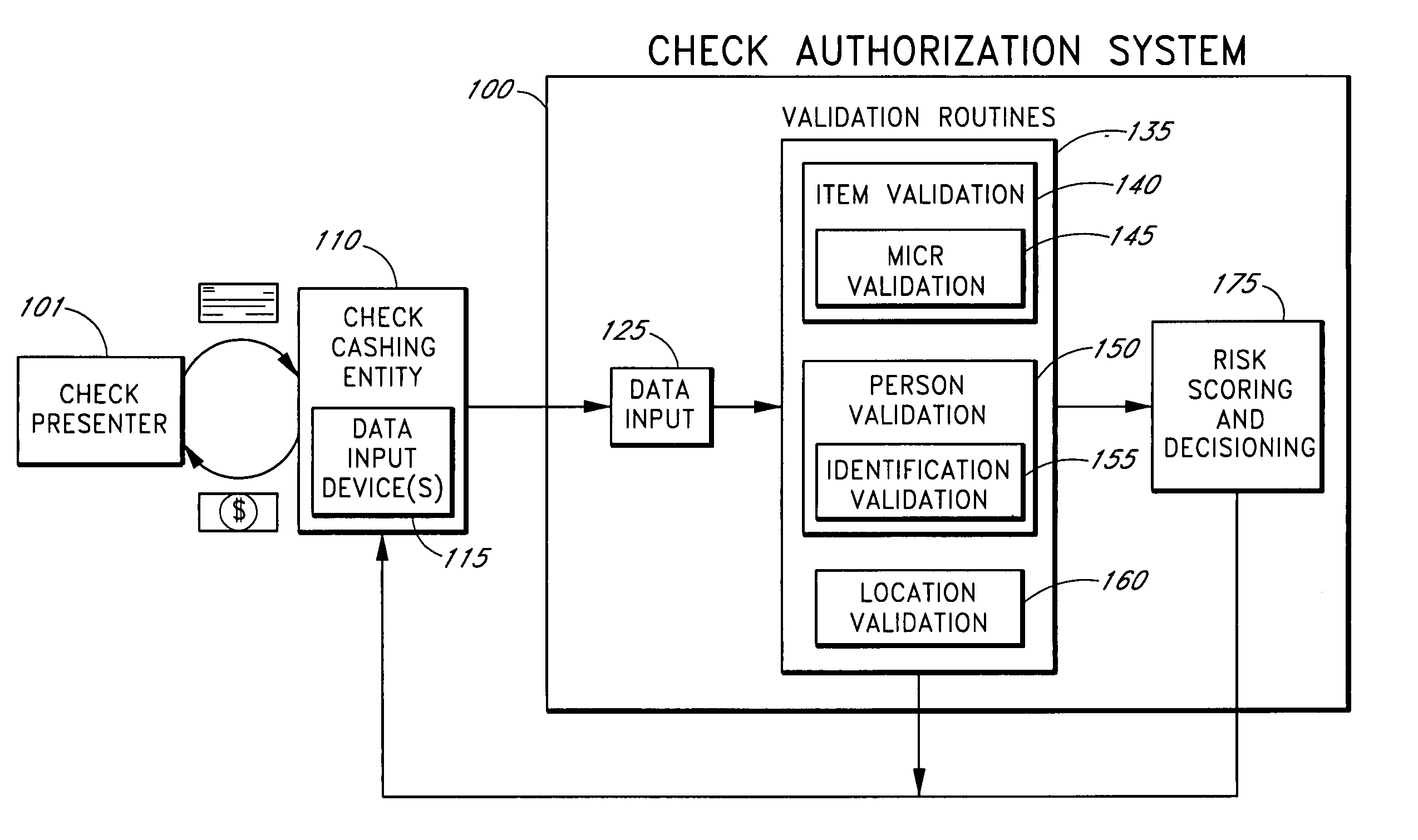
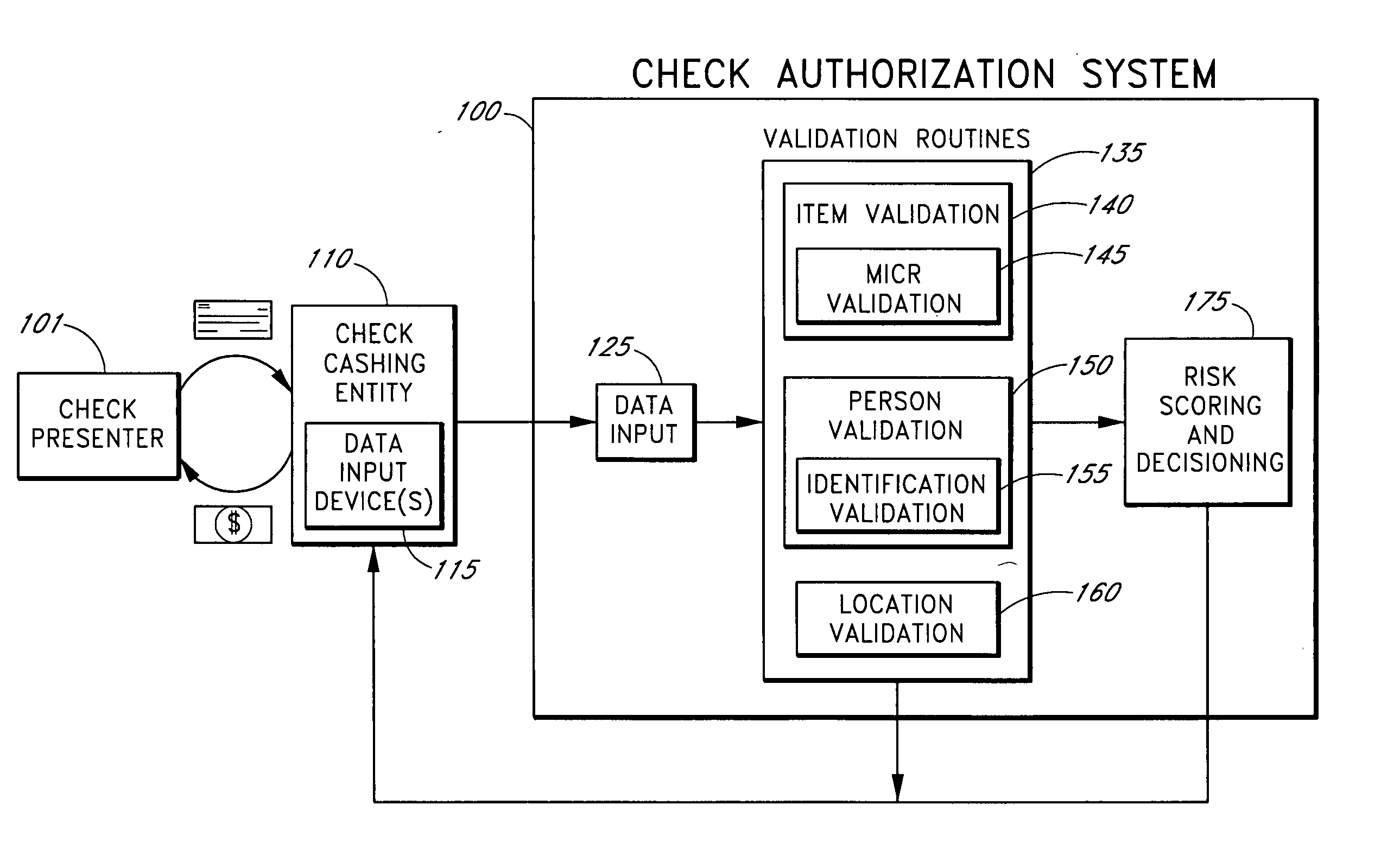
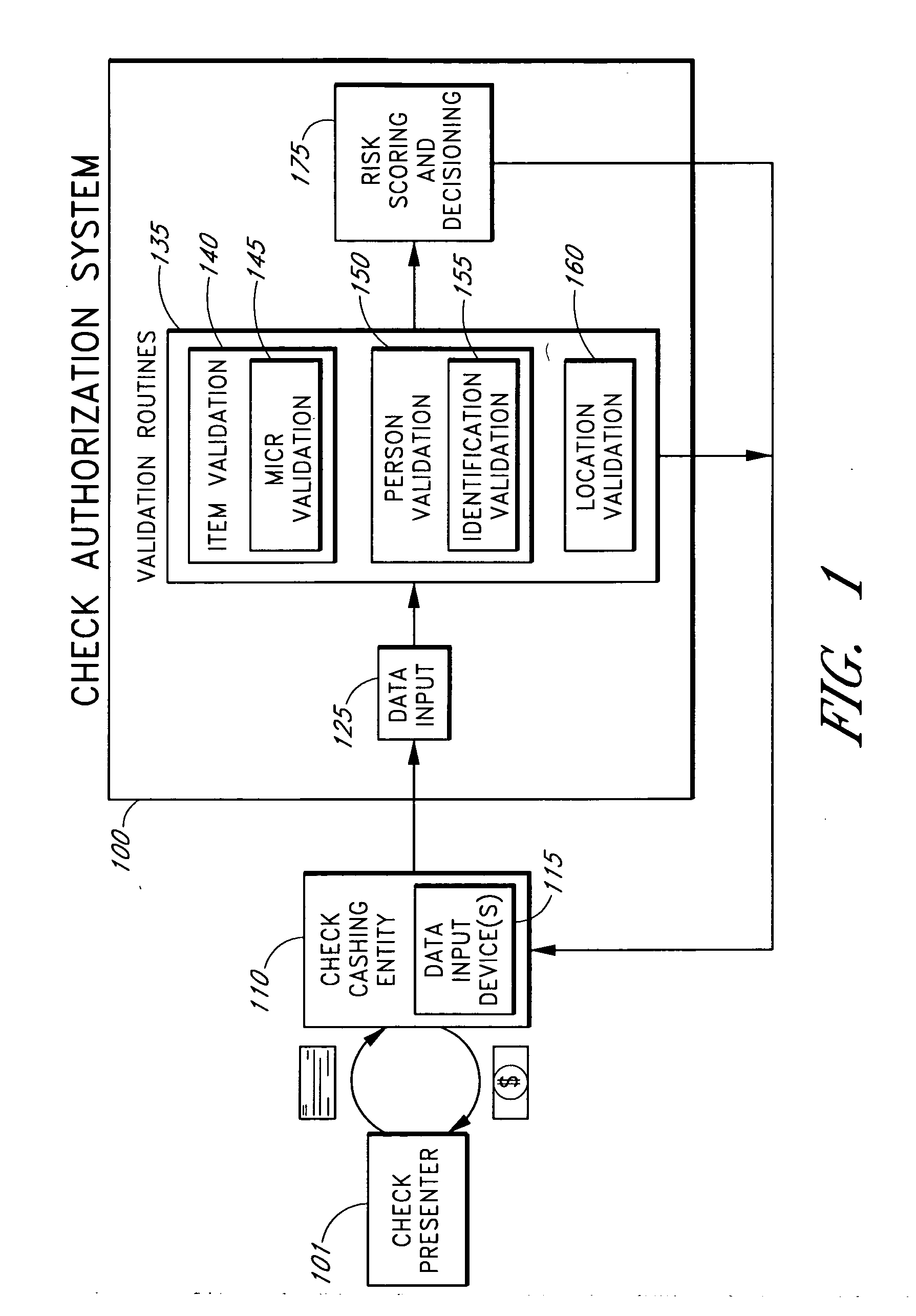
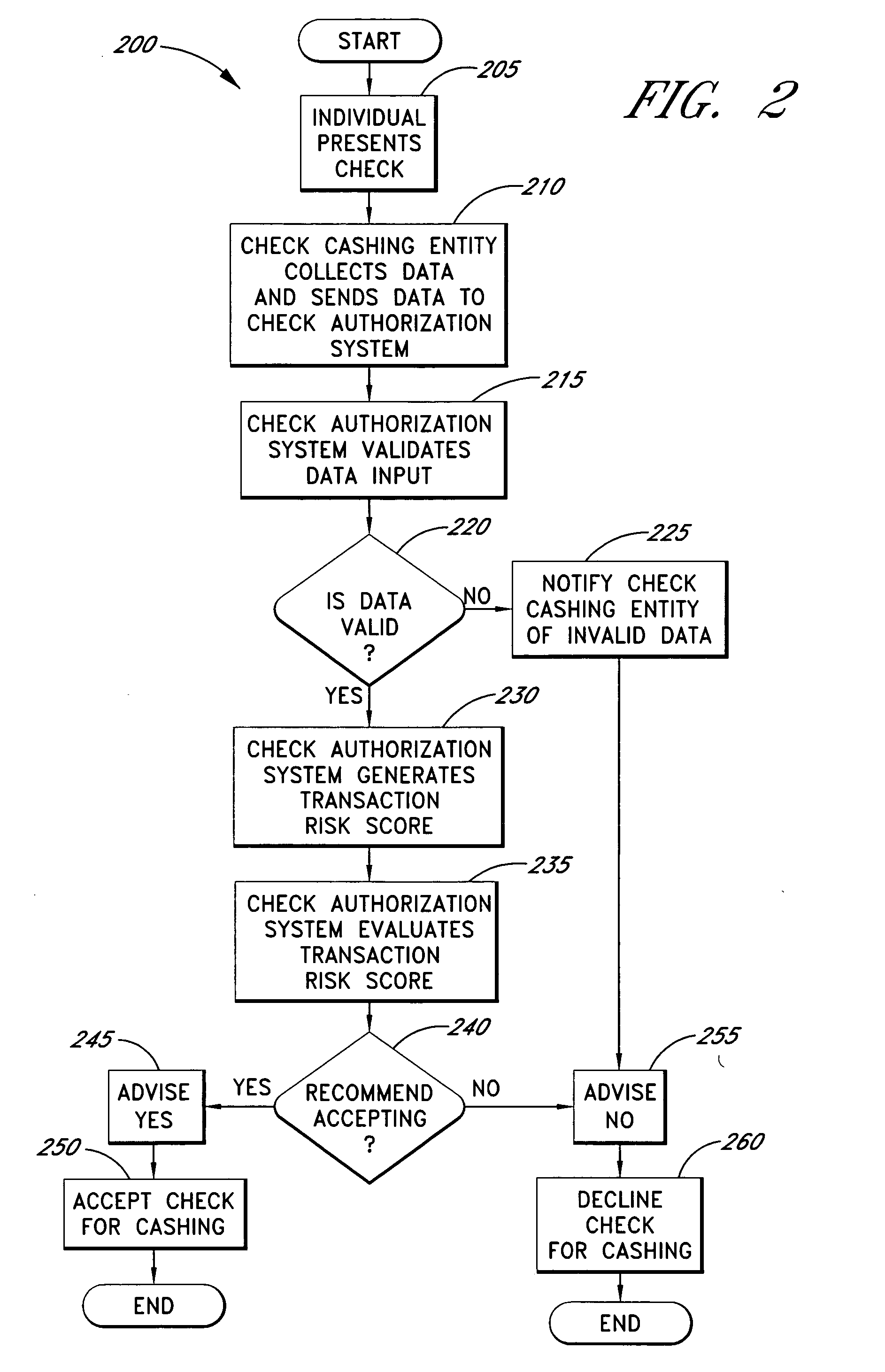
Systems and methods for obtaining authentication marks at a point of sale
InactiveUS20050125360A1Accurate descriptionSlow processPaper-money testing devicesPoint-of-sale network systemsBarcodeCheque
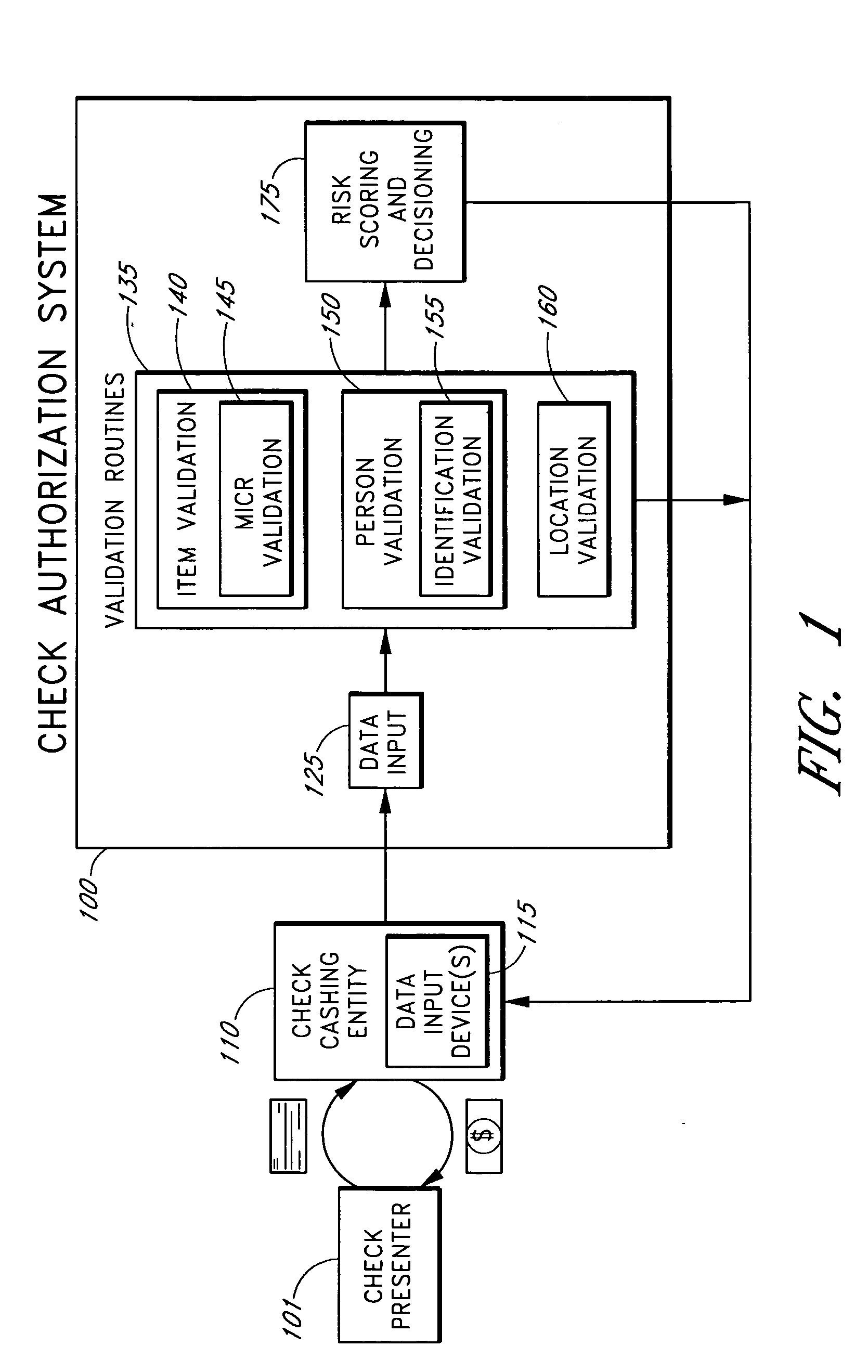
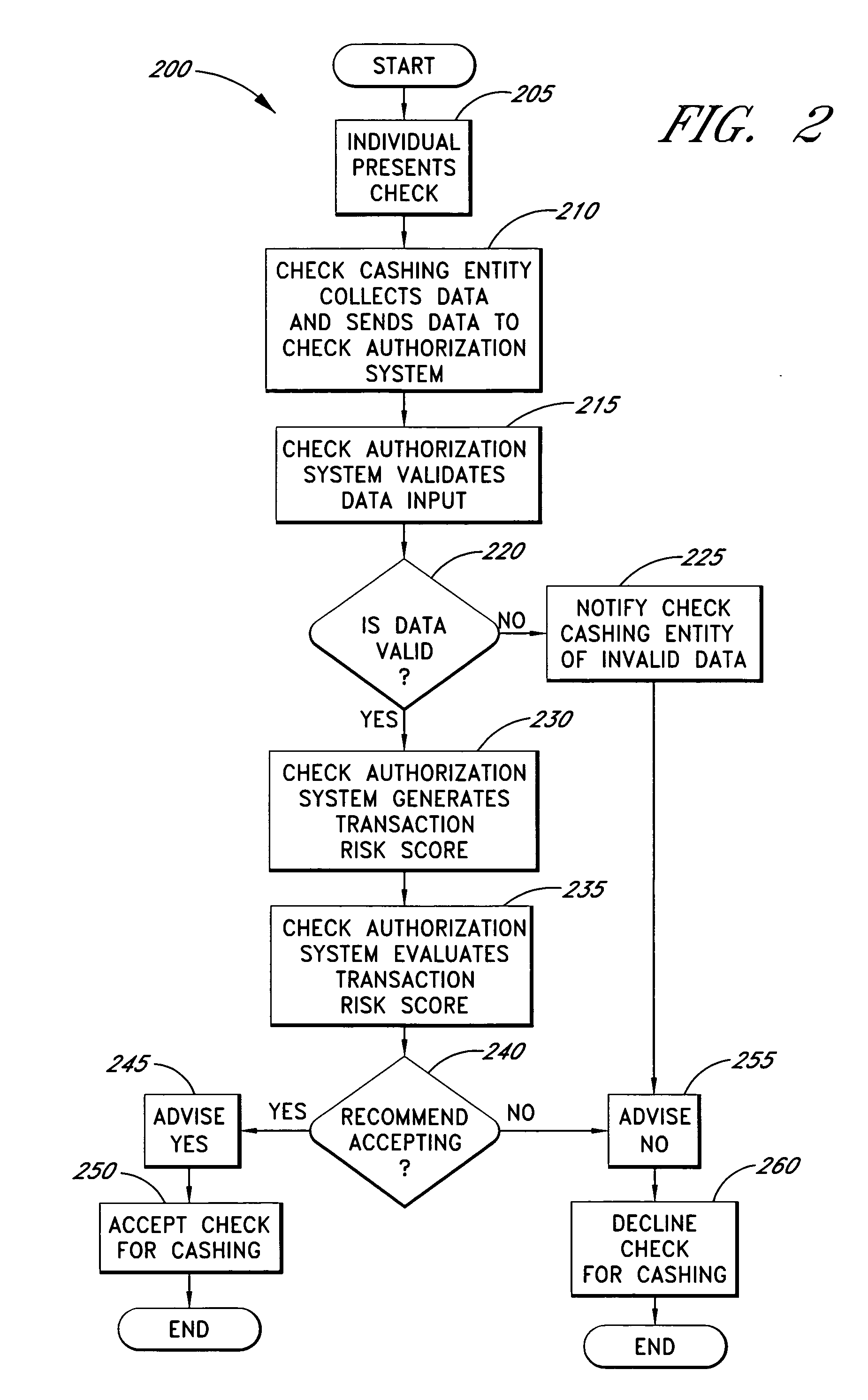
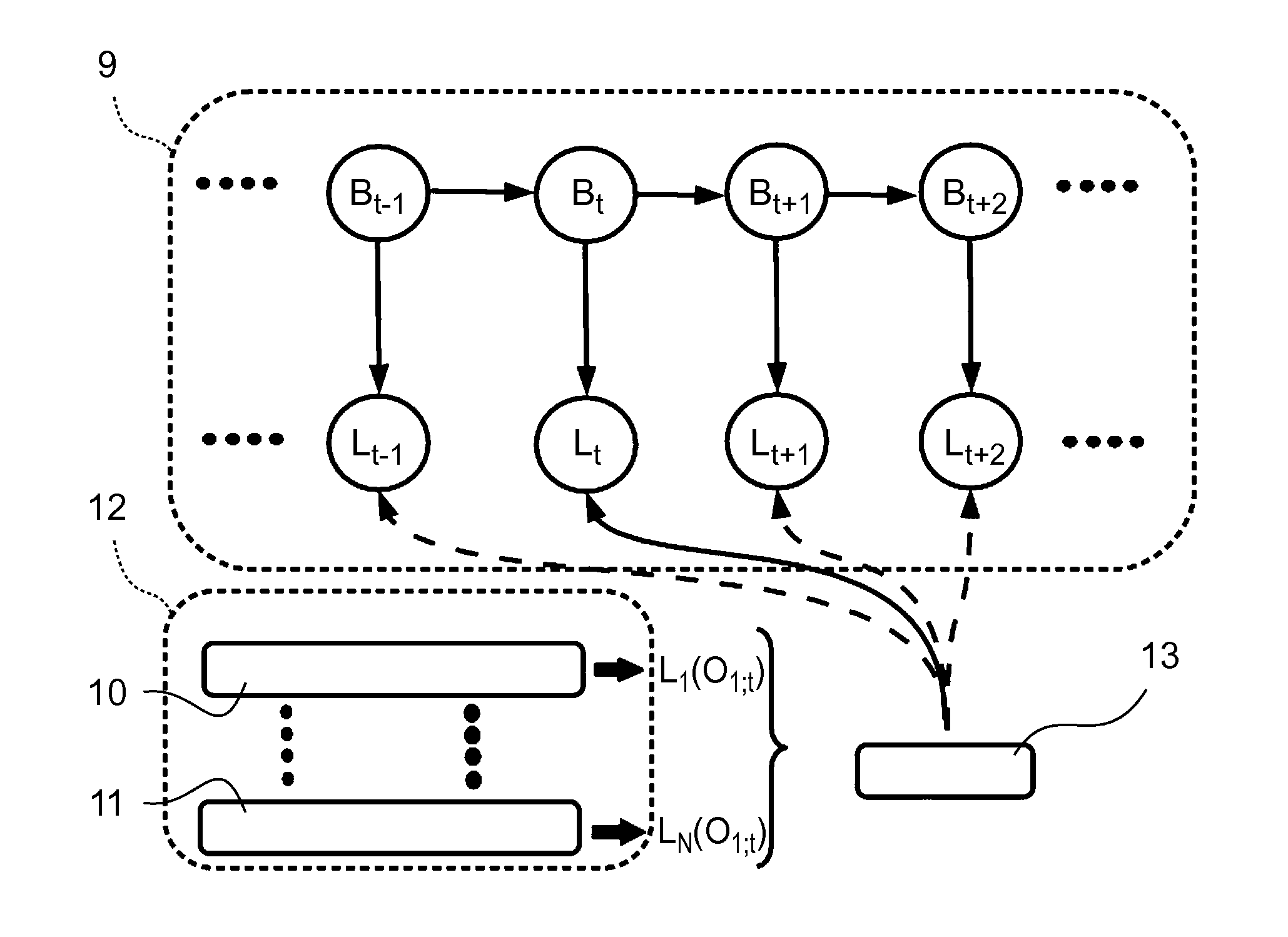
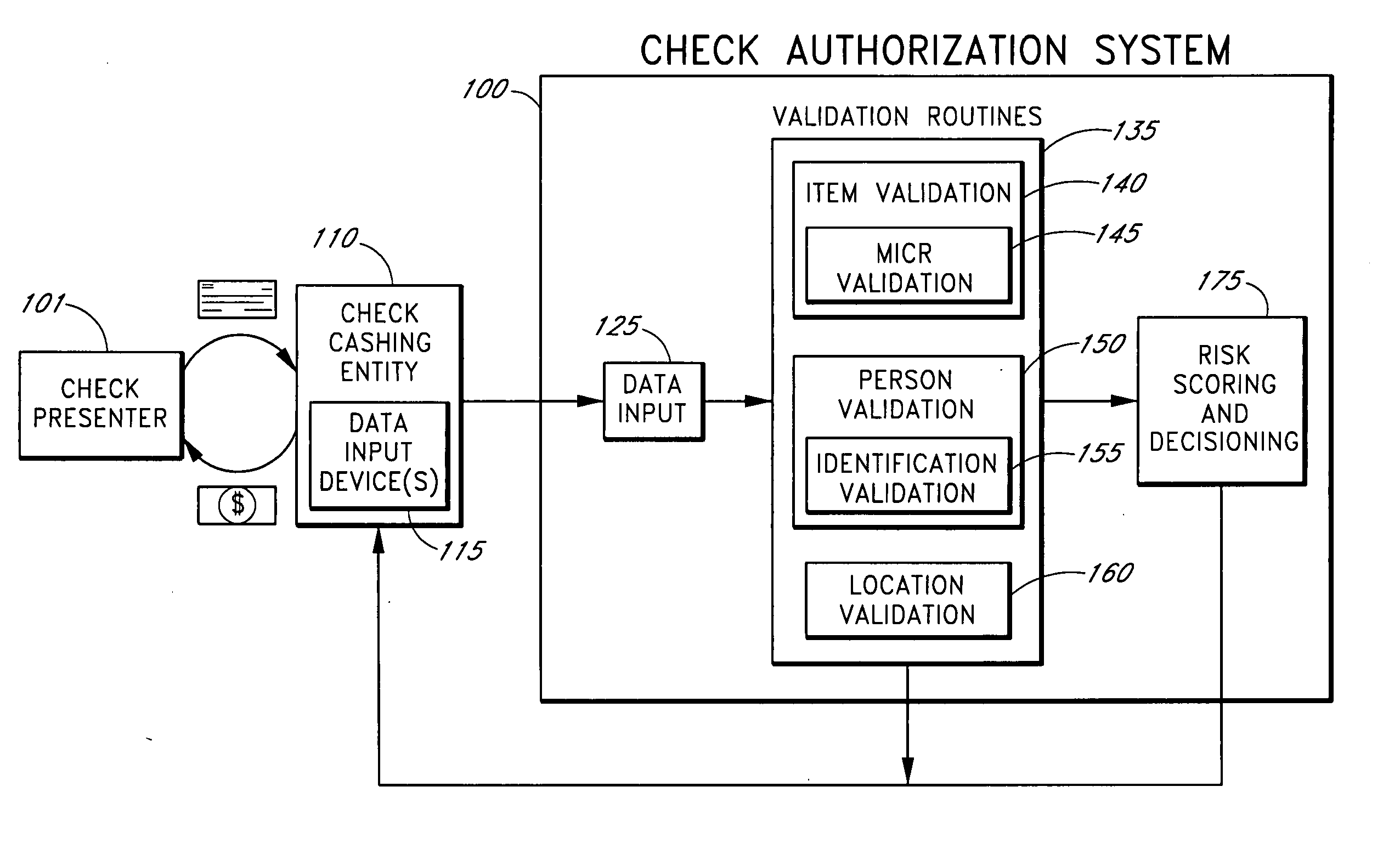
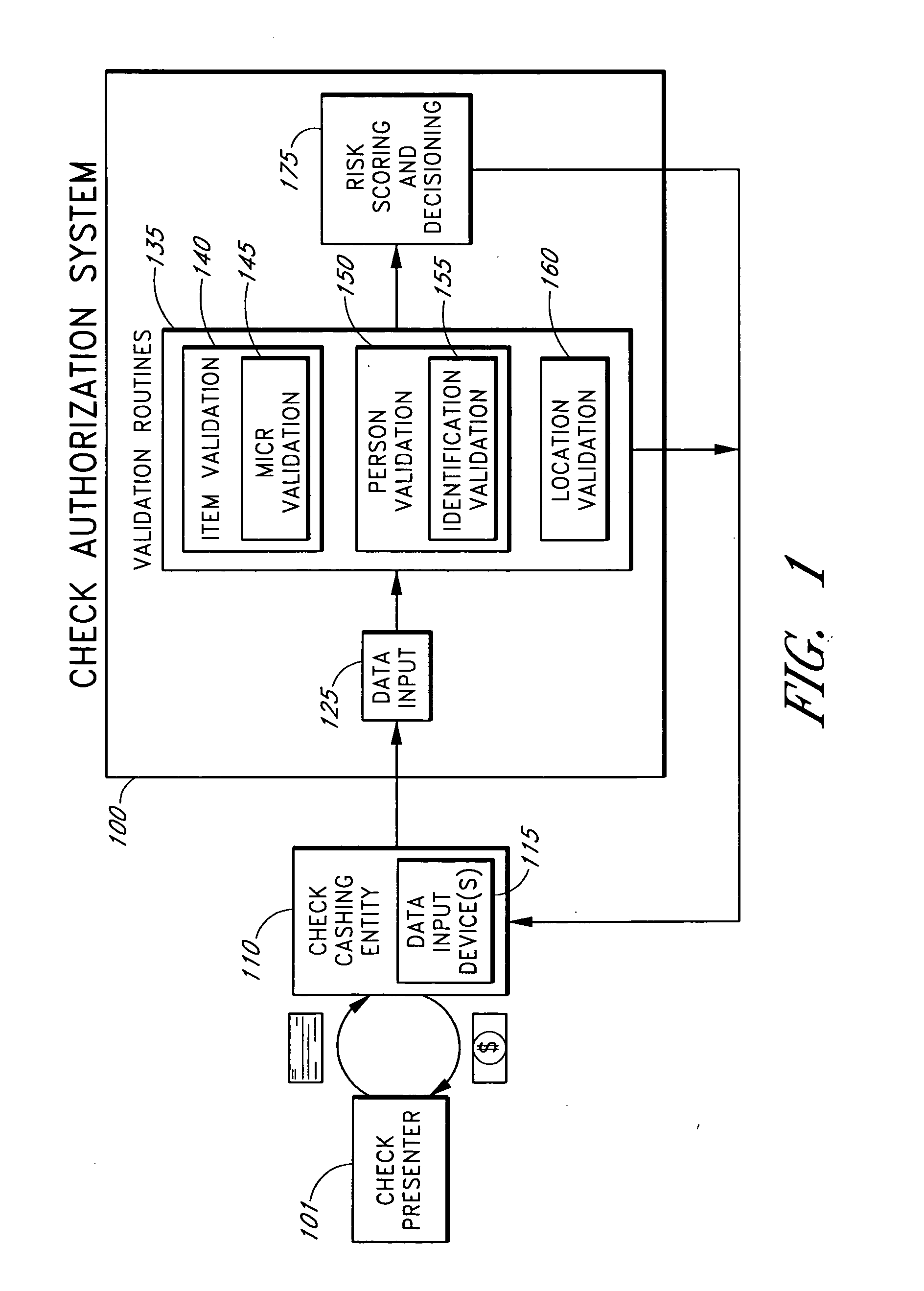
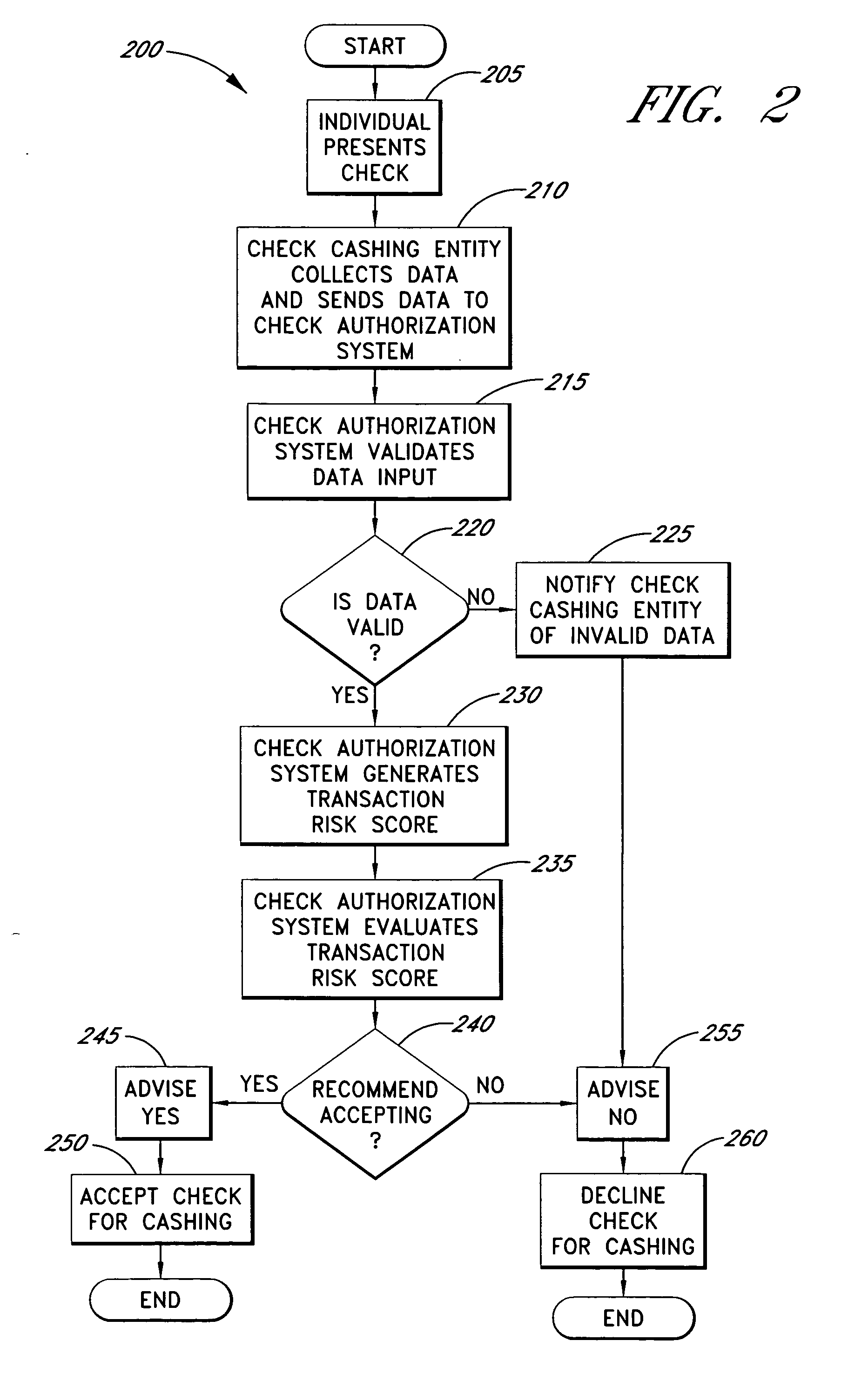
Systems and methods are described for using a point-of-sale device at a check-cashing entity to obtain information about one or more authenticating marks, such as watermarks, bar codes, background patterns, color schemes, insignia, security validation numbers, or the like, from a second-party check or other negotiable instrument presented for a proposed check-cashing transaction. In various embodiments, the authenticating mark information may be compared to stored information about expected configurations of authenticating marks as part of a risk assessment of the check. In various embodiments, the point-of-sale device transmits authenticating mark information to a check authorization system. The point-of-sale device may receive an accept / decline recommendation for the transaction from the check authorization system, based at least in part on the obtained authenticating mark information. The point-of-sale device may display a message about the recommendation to an operator of the device.
Owner:FIRST DATA
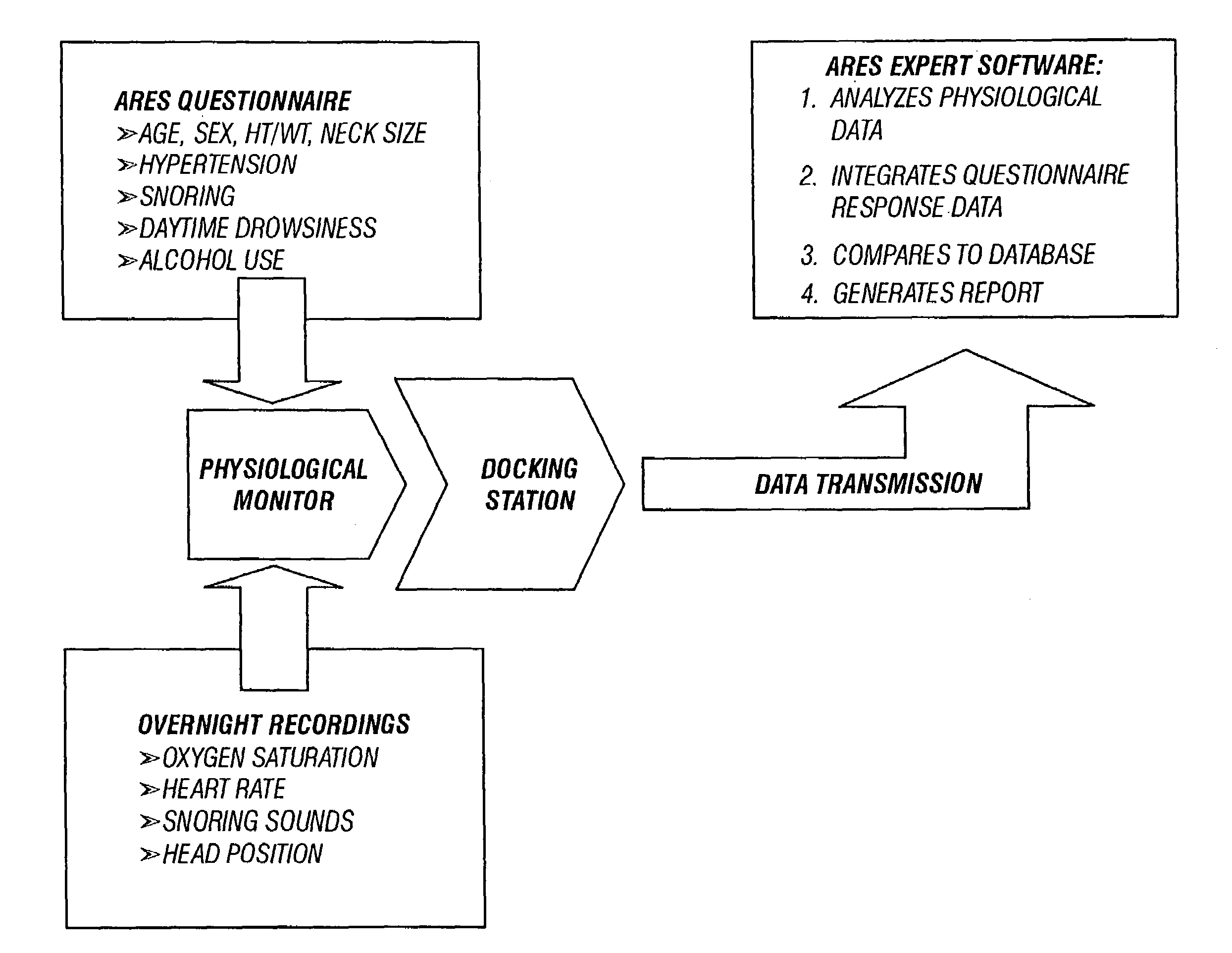
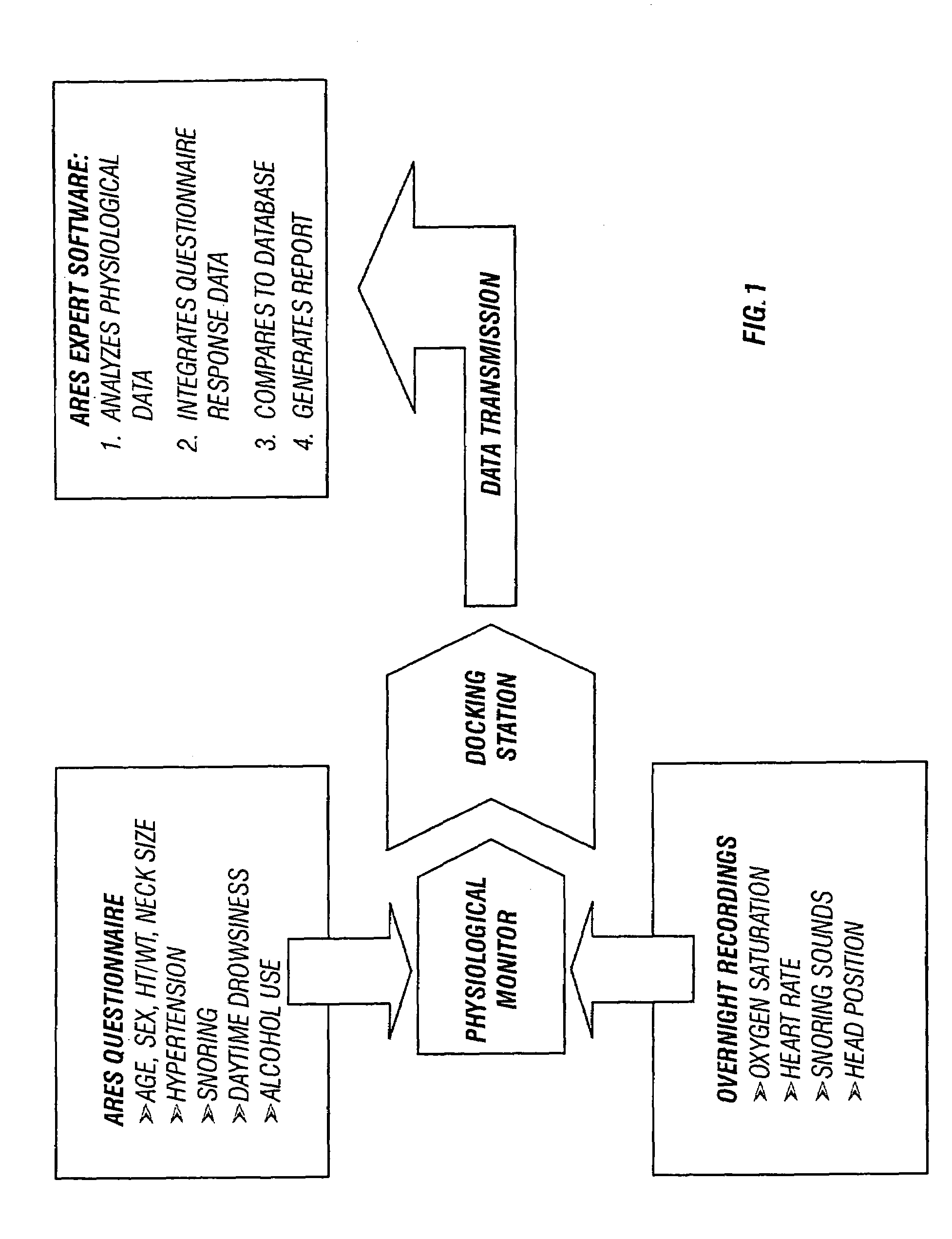
Sleep apnea risk evaluation
InactiveUS20050027207A1Improve accuracyImprove resolutionRespiratorsHealth-index calculationMedicinePulse oximeters
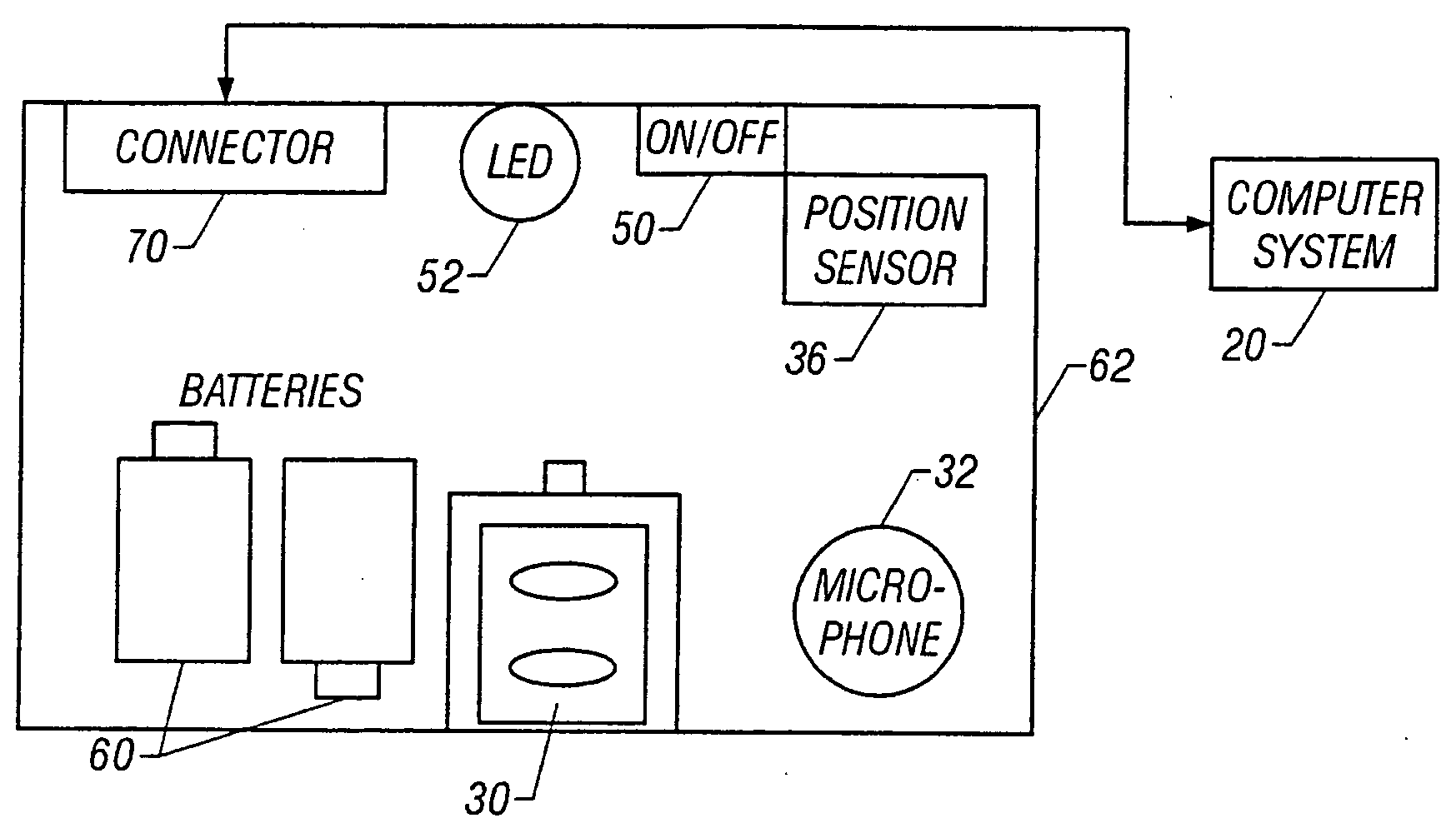
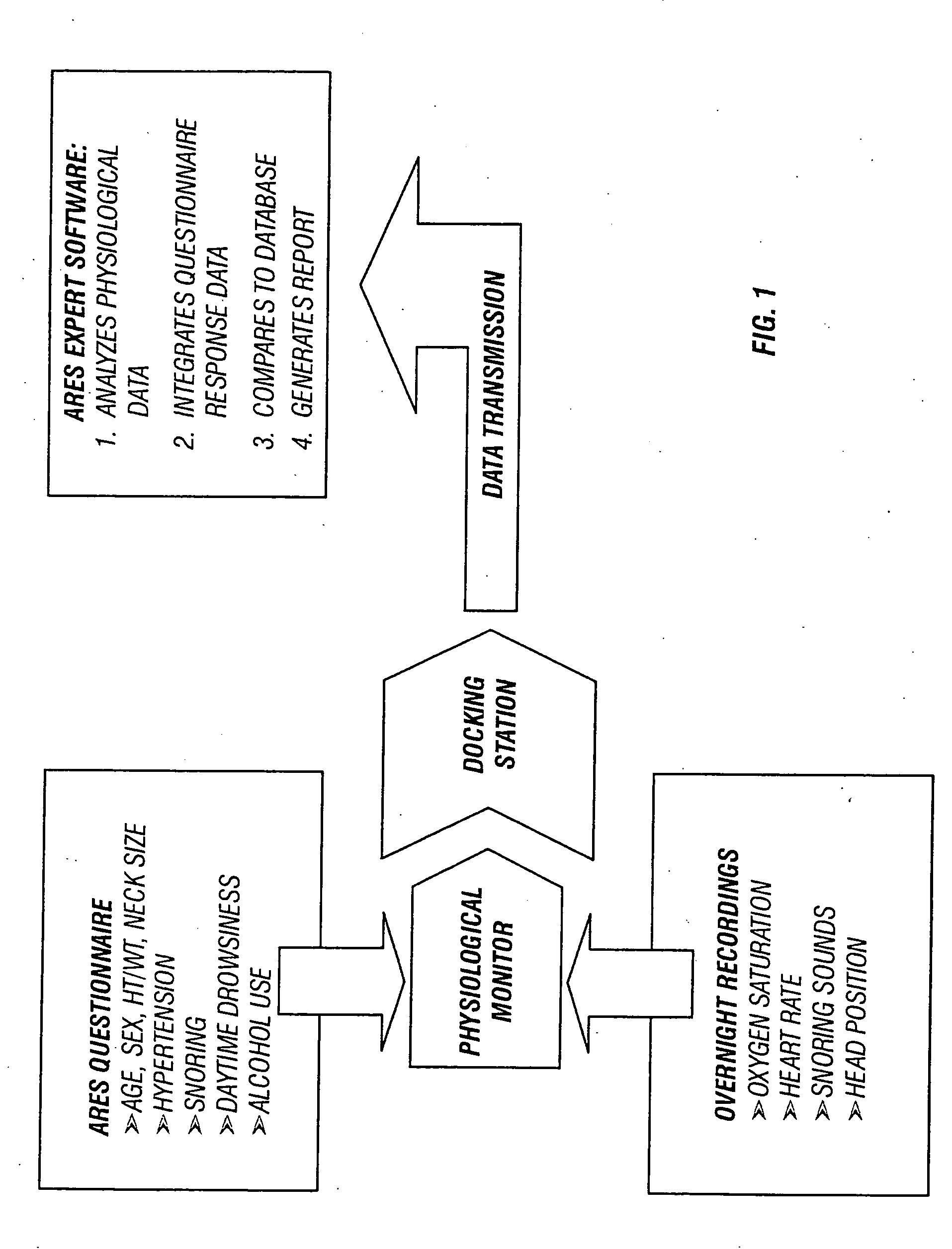
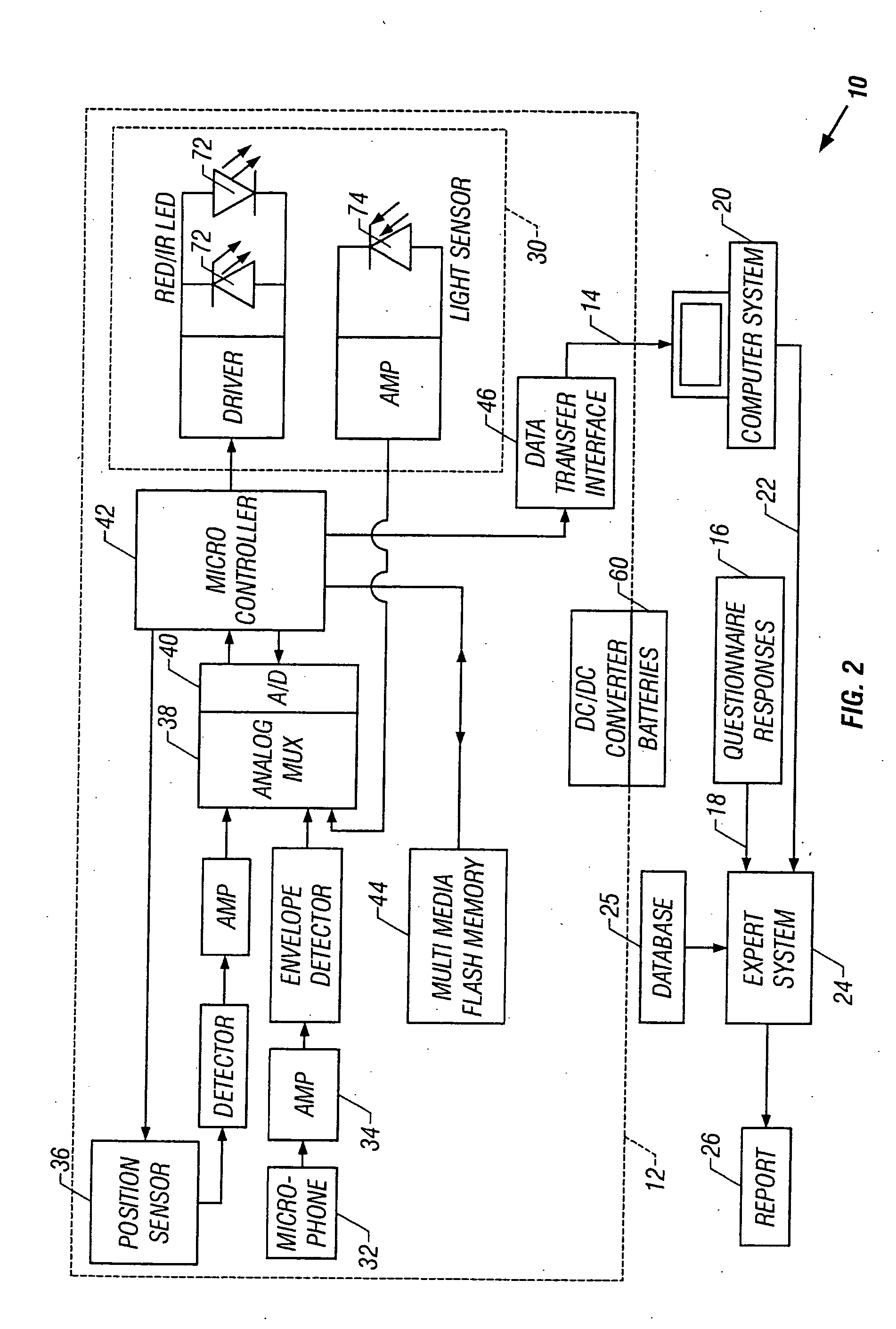
In a technique for collecting and analyzing physiological signals to detect sleep apnea, a small light-weight physiological monitoring system, affixed to a patient's forehead, detects and records the pulse, oximetry, snoring sounds, and head position of a patient to detect a respiratory event, such as sleep apnea. The physiological monitoring system may contain several sensors including a pulse oximeter to detect oximetry and pulse rate, a microphone to detect snoring sounds, and a position sensor to detect head position. The physiological monitoring system also can contain a memory to store or record the signals monitored by the mentioned sensors and a power source. The physiological monitoring system may be held in place by a single elastic strap, thereby enabling a patient to use the system without the assistance of trained technicians.
Owner:WATERMARK MEDICAL
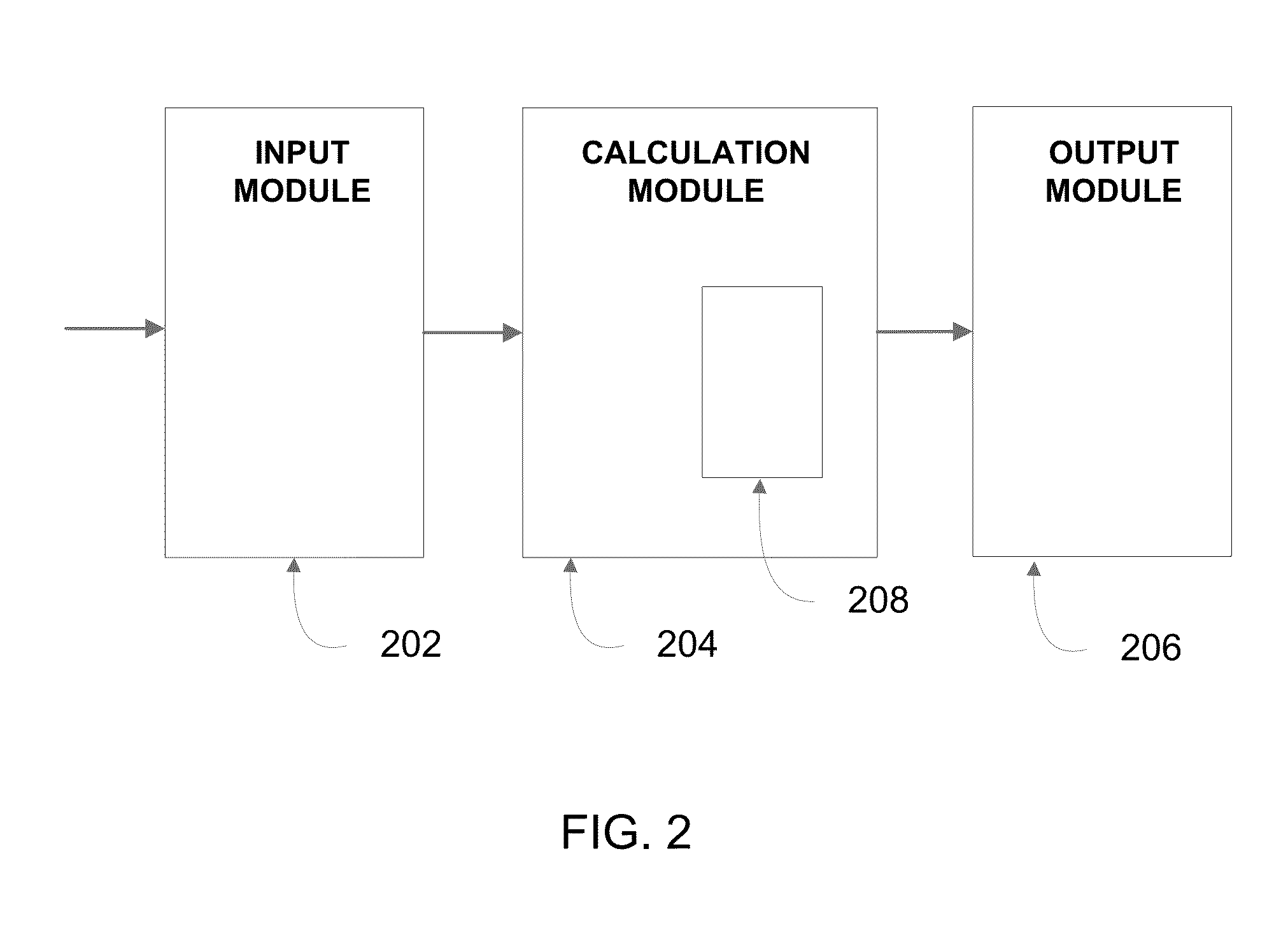
Credit risk evaluation with responsibility factors
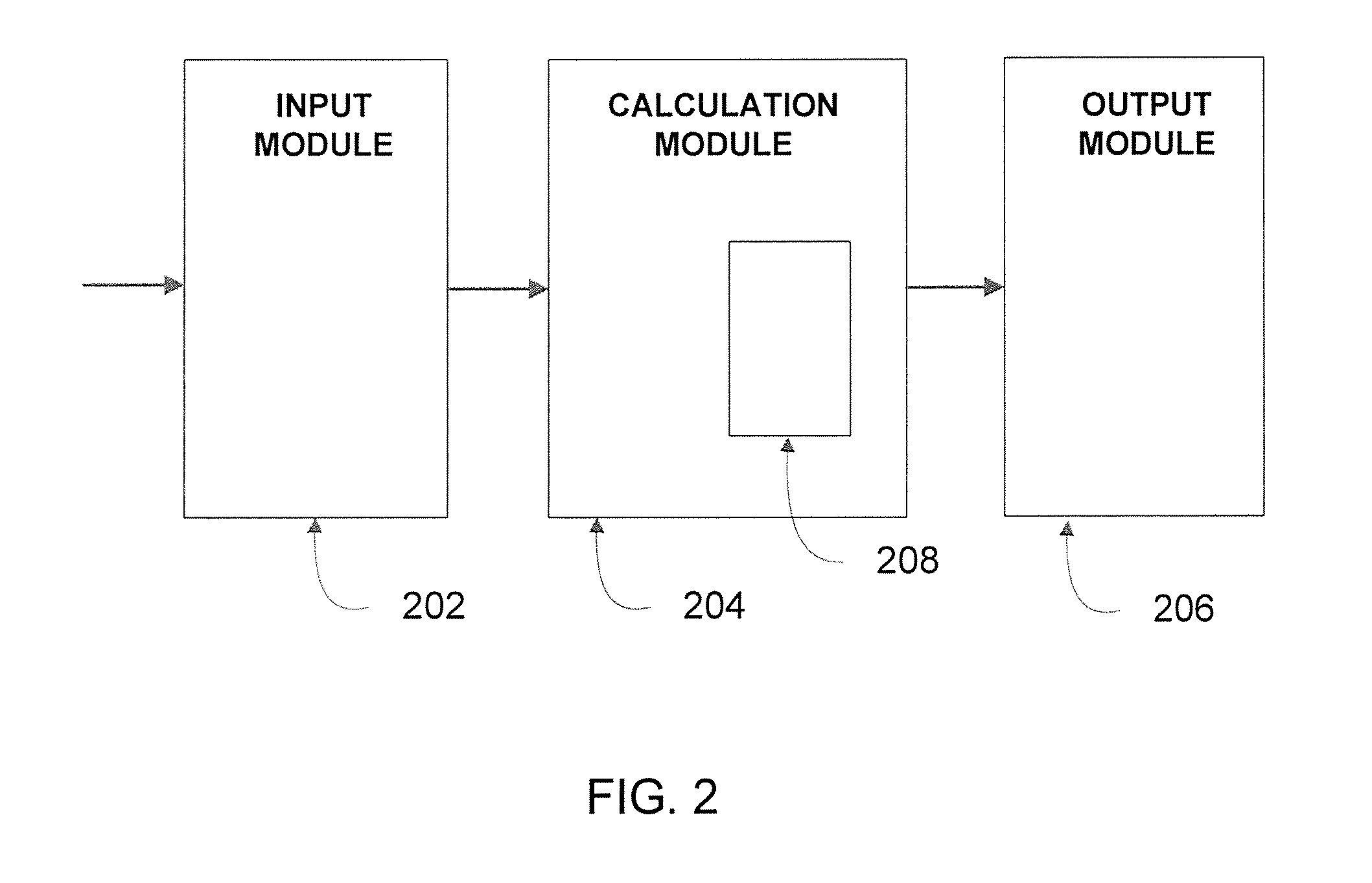
A system, device, and method for calculating an enhanced credit score using insurance rating information, individual rating factors, interaction rating factors, geographic rating factors, vehicle monitoring rating factors, and / or credit risk information is disclosed. Insurance rating information, individual rating factors, interaction rating factors, geographic rating factors, and vehicle monitoring rating factors, either individually or in combinations, may be used as inputs to a novel credit-scoring model to calculate an enhanced or improved credit score for an individual or other type of credit user. The novel credit-scoring model may be implemented in a computer-readable medium comprising computer-executable instructions for causing a computing device to calculate an enhanced credit score. The computer-executable instructions may be arranged into an input module, output module, and calculation module. The modules may be used to calculate an enhanced credit score that may be used by lending institutions and others to determine the terms of a financing agreement with a user.
Owner:ALLSTATE INSURANCE
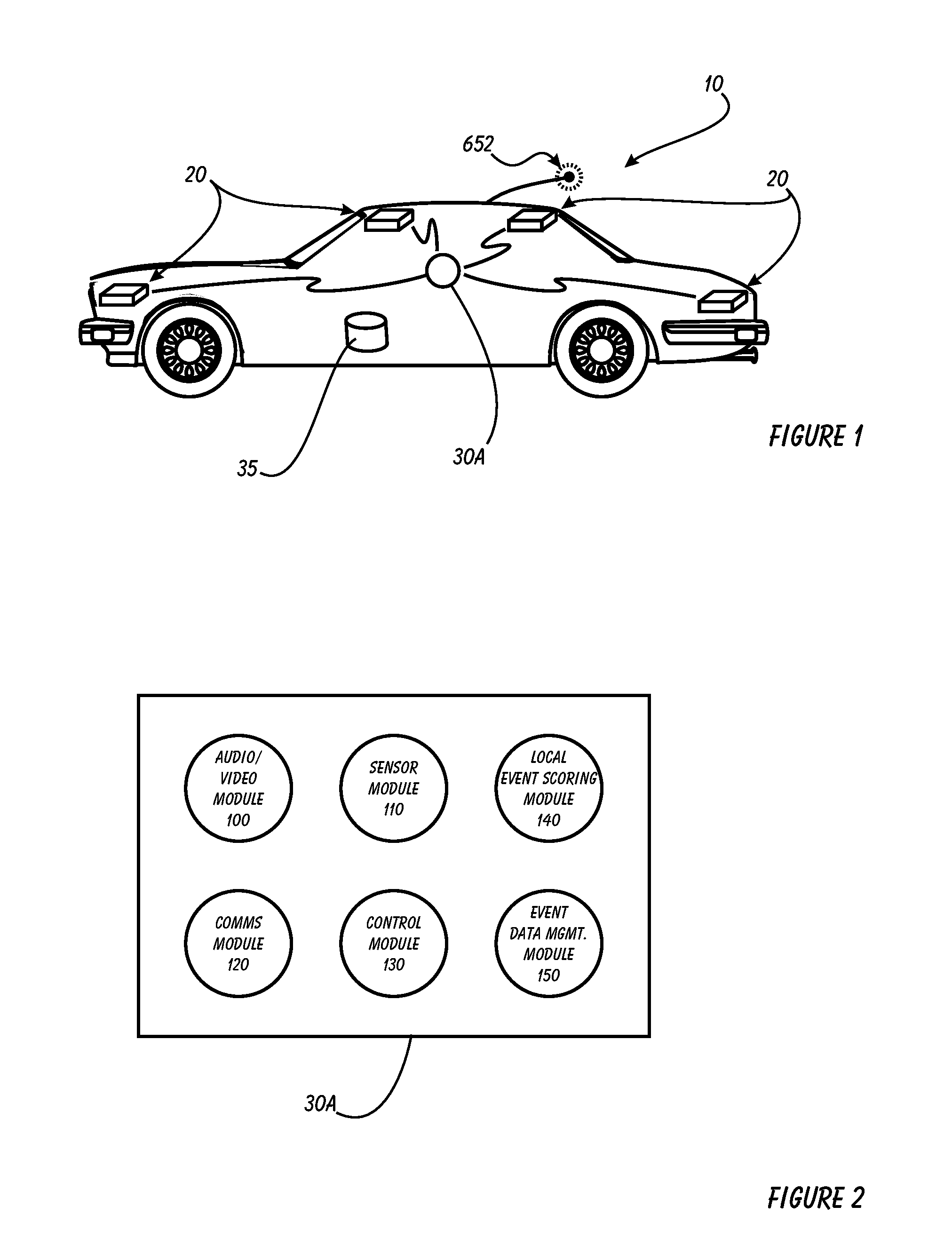
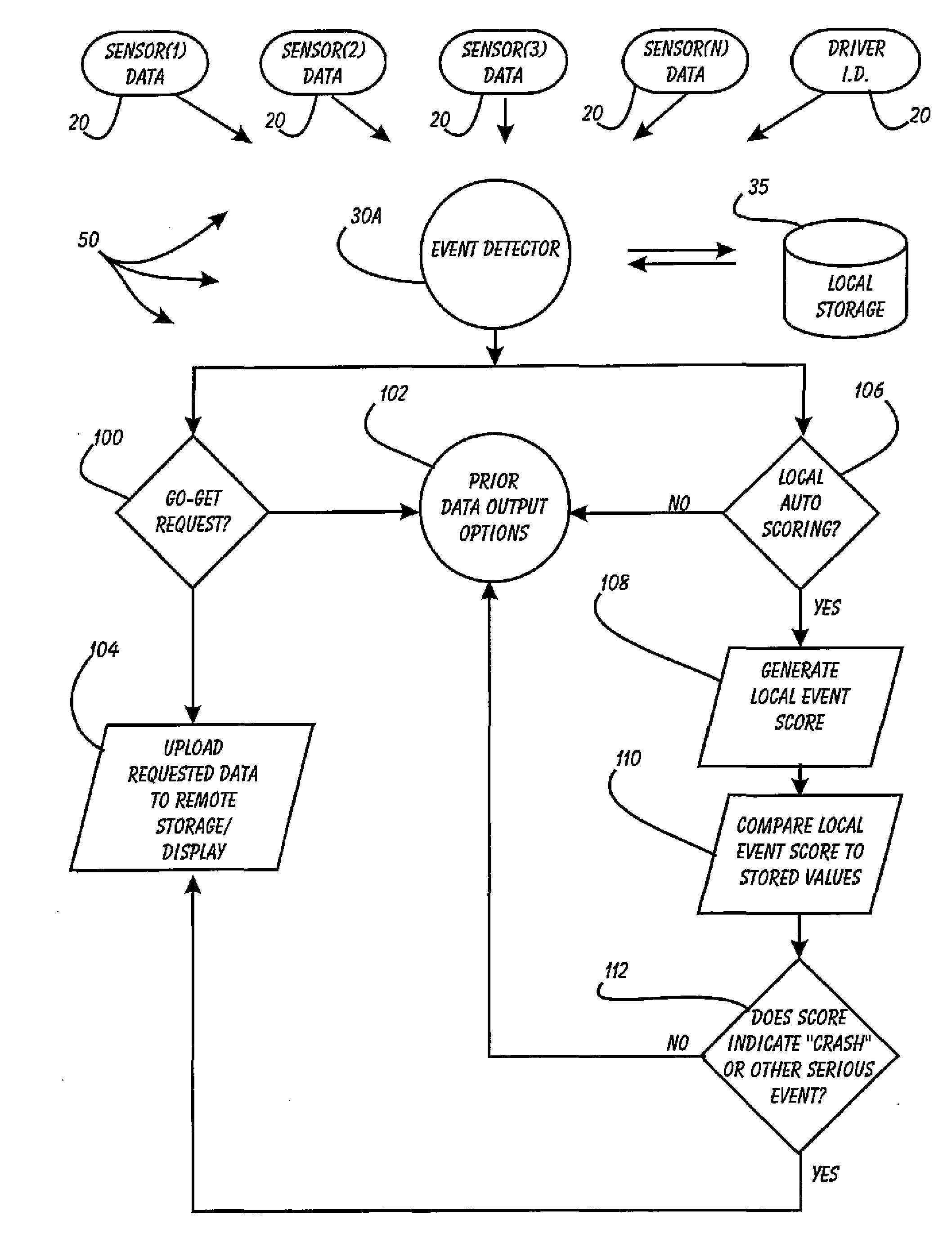
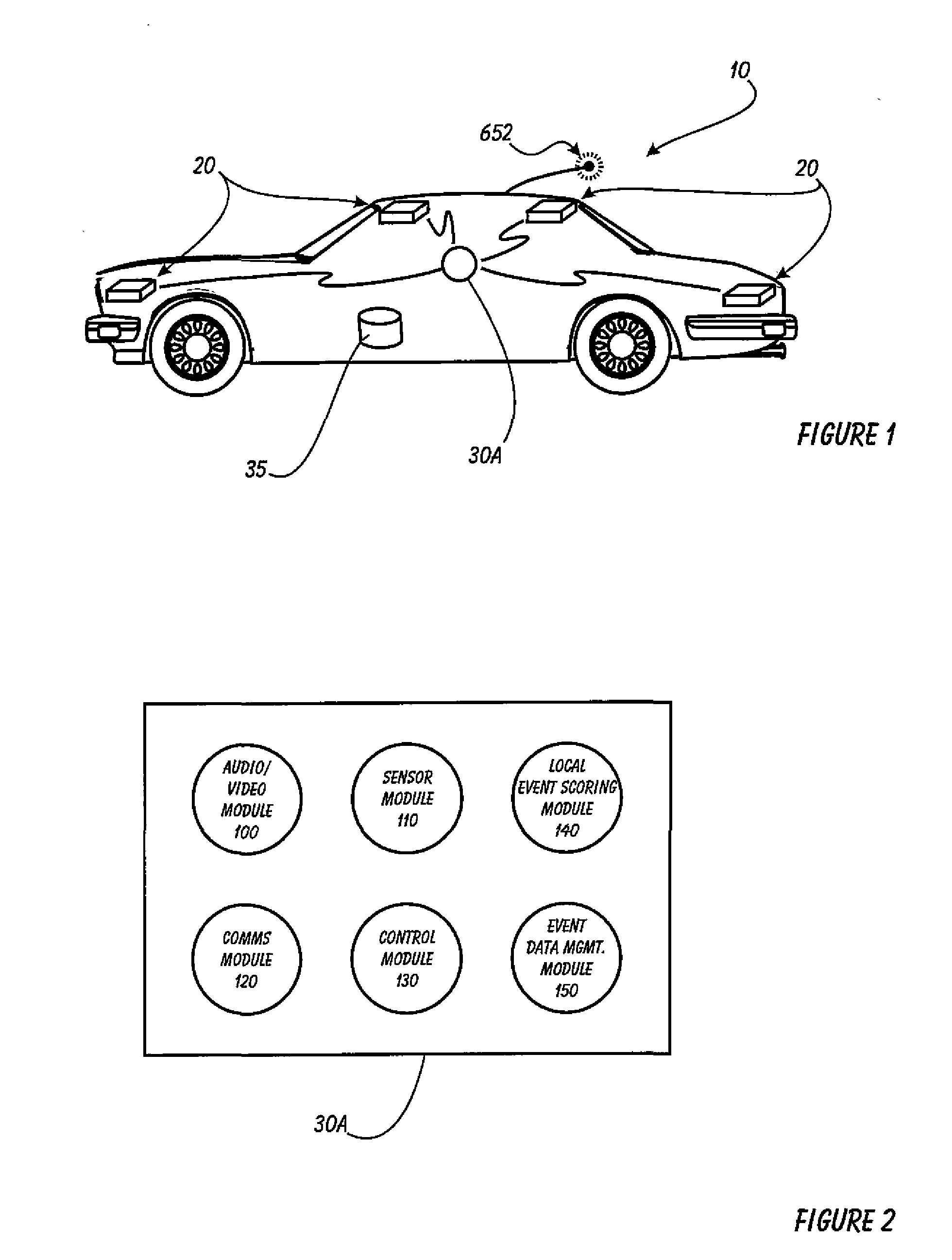
Driver Risk Assessment System and Method Having Calibrating Automatic Event Scoring
ActiveUS20100250021A1Robust and reliable event scoringRobust and reliable and reportingFinanceRegistering/indicating working of vehiclesDriver/operatorDependability
The system and method provides robust and reliable event scoring and reporting, while also optimizing data transmission bandwidth. The system includes onboard vehicular driving event detectors that record data related to detected driving events, selectively store or transfer data related to said detected driving events. If elected, the onboard vehicular system will score a detected driving event, compare the local score to historical values previously stored within the onboard system, and upload selective data or data types to a remote server or user if the system concludes that a serious driving event has occurred. Importantly, the onboard event scoring system, if enabled, will continuously evolve and improve in its reliability by being periodically re-calibrated the ongoing reliability results of manual human review of automated predictive event reports. The system may further respond to independent user requests by transferring select data to said user at a variety of locations and formats.
Owner:DRIVECAM
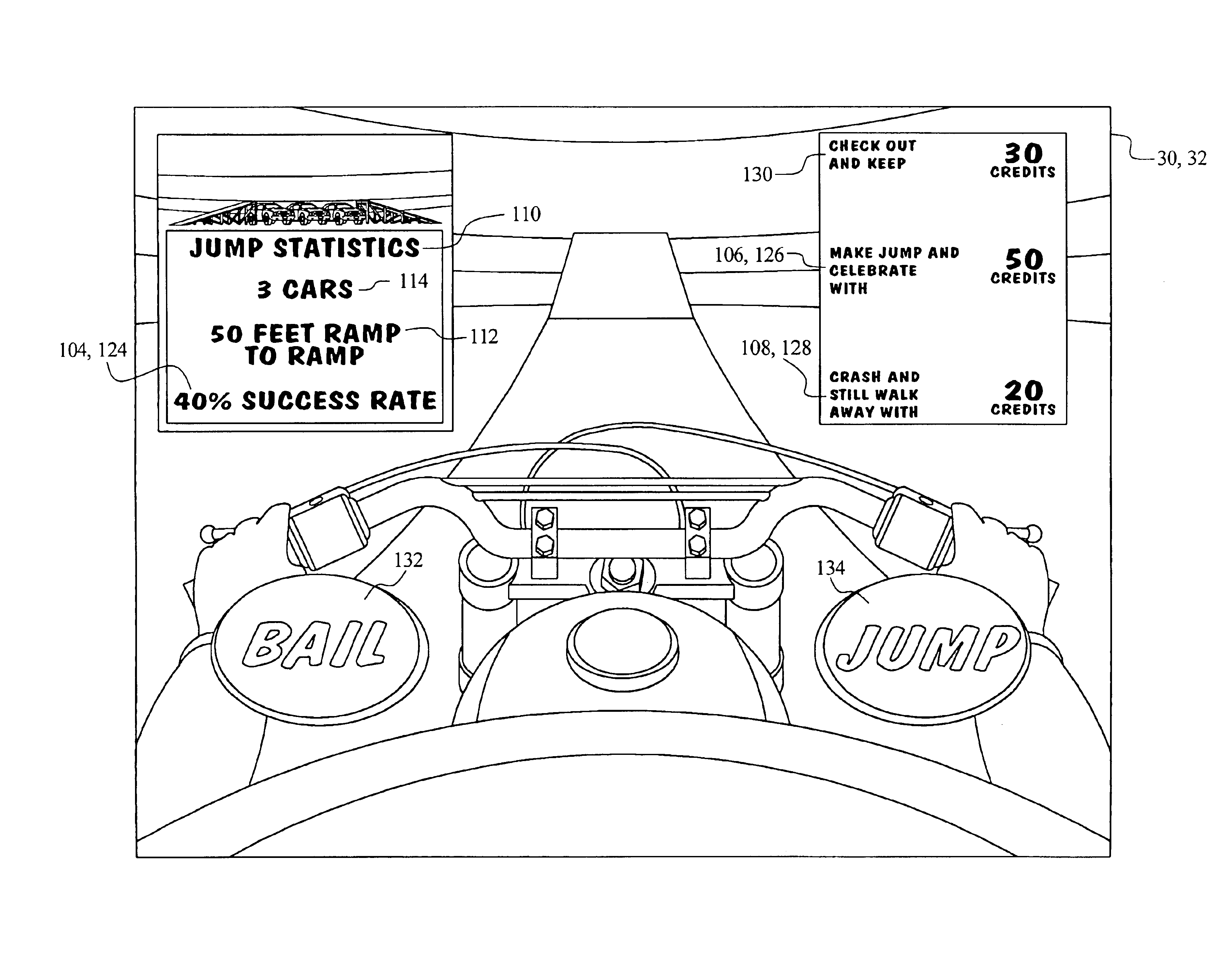
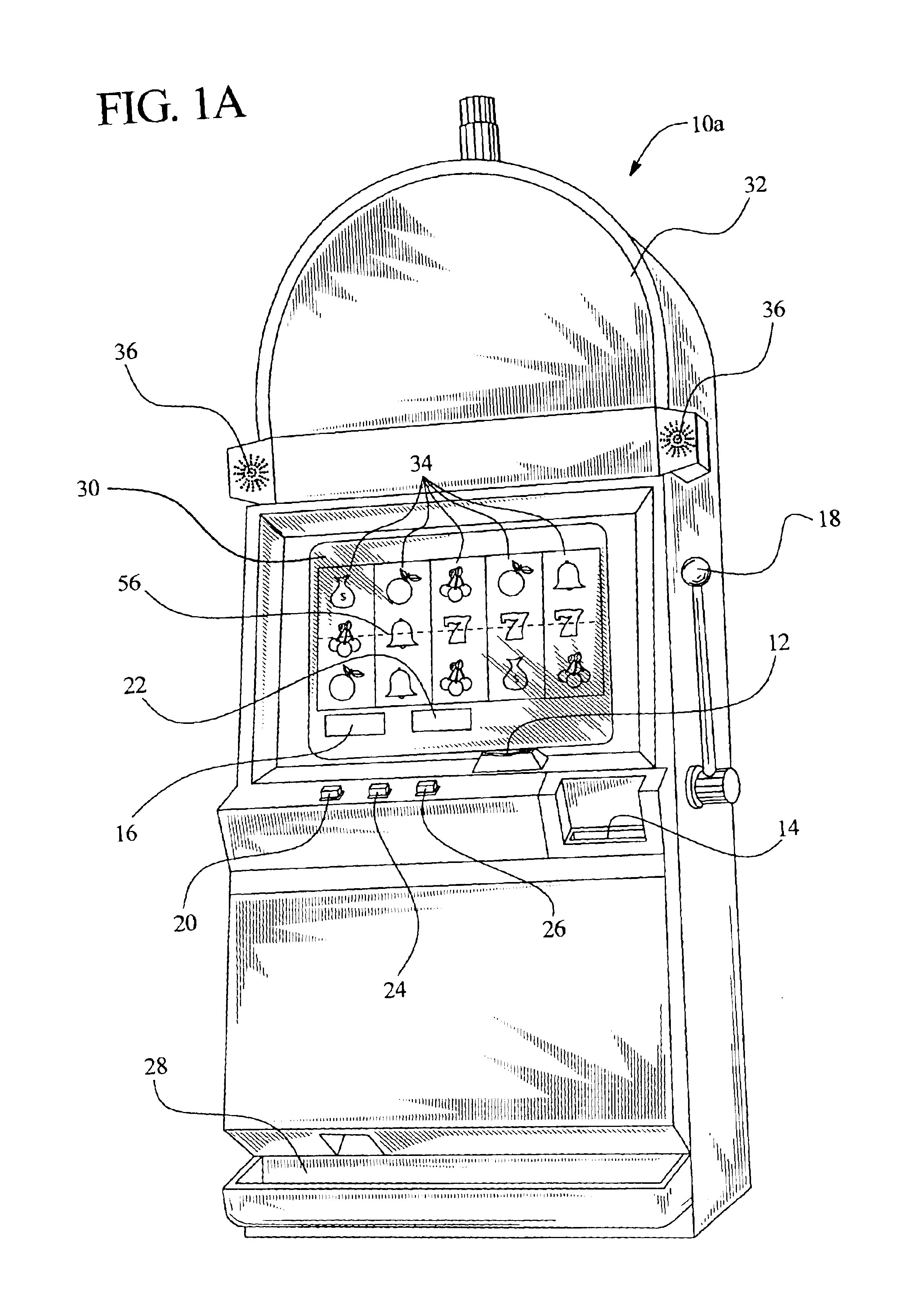
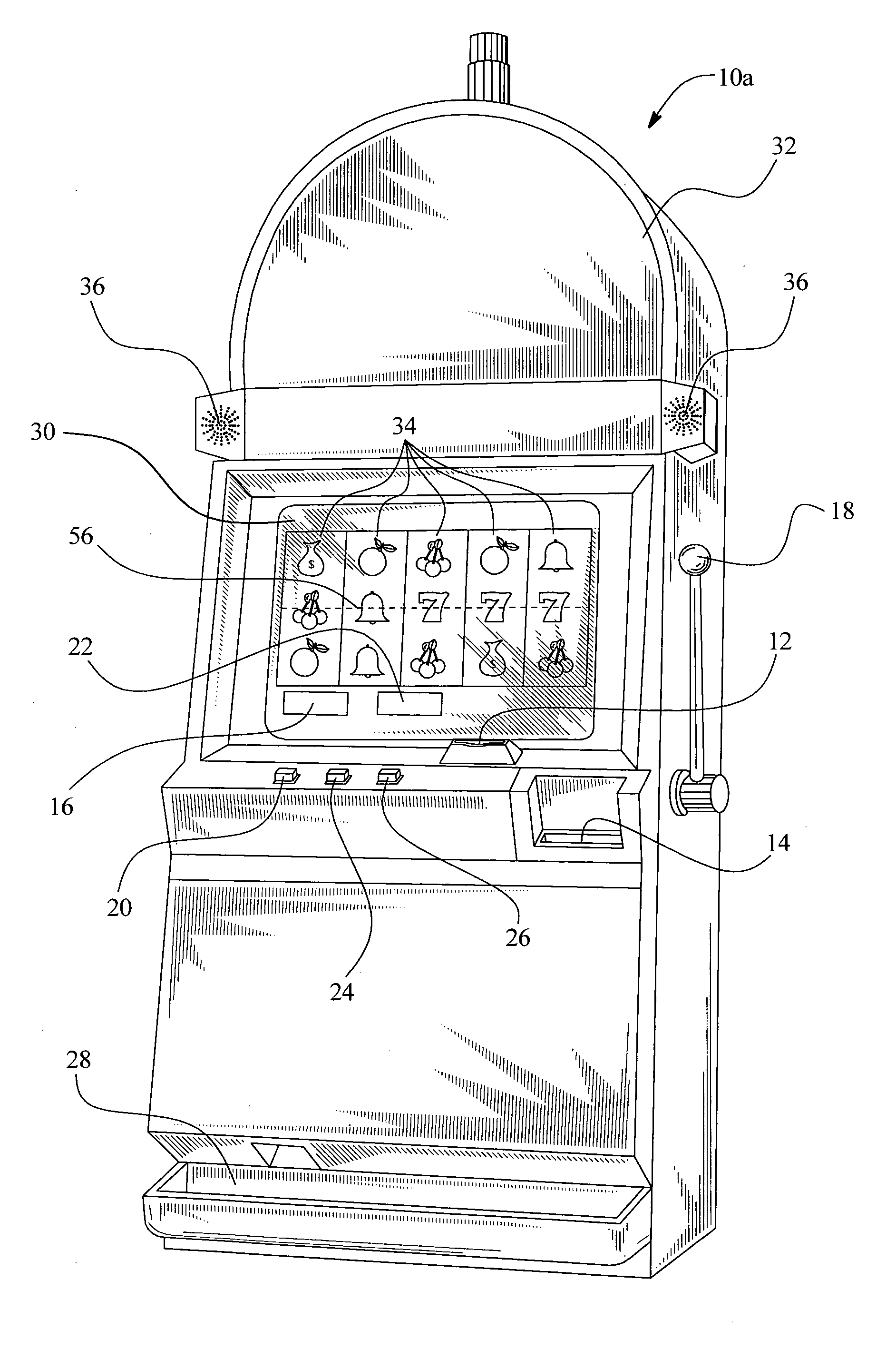
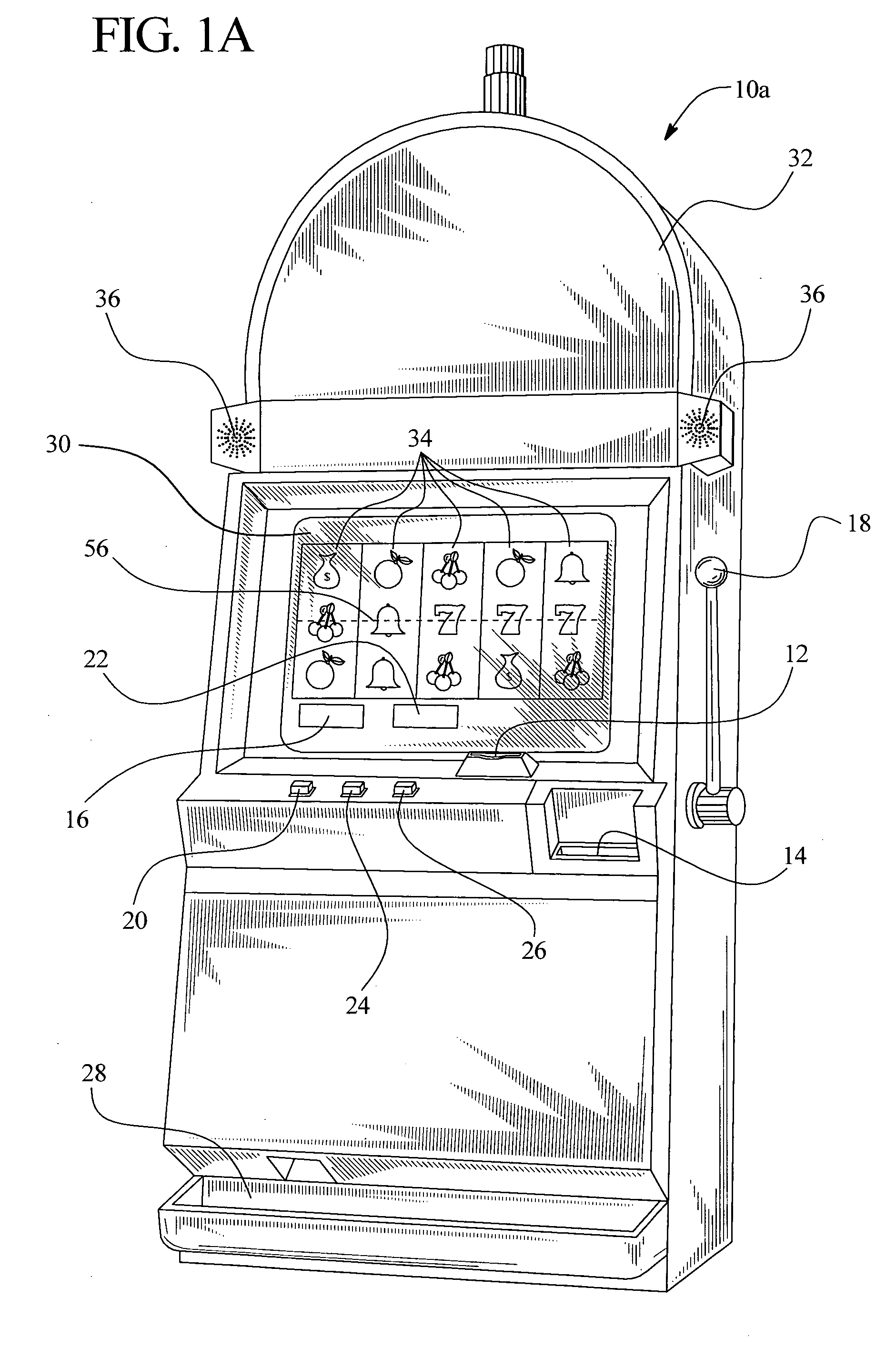
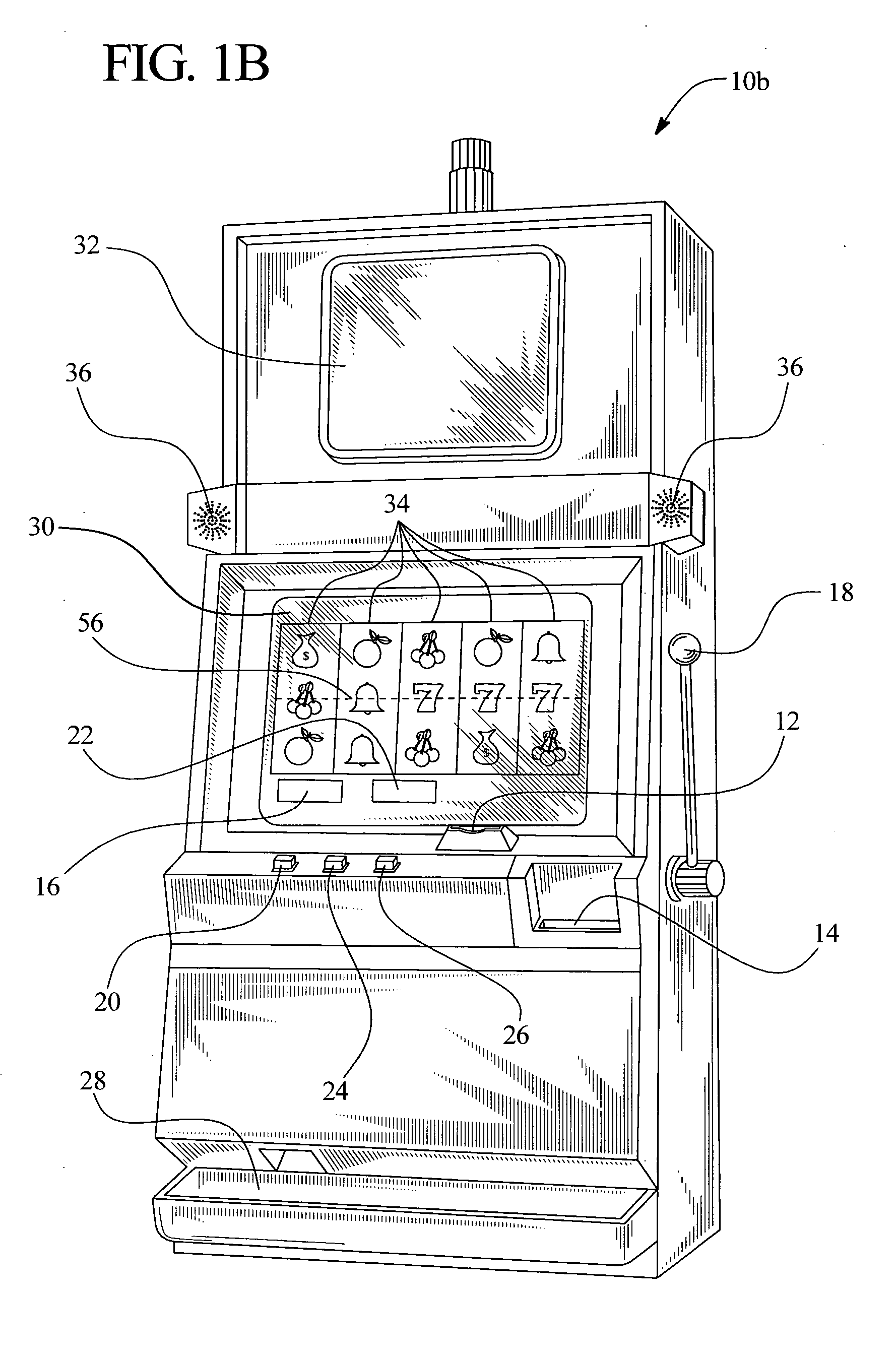
Gaming device having risk evaluation bonus round
InactiveUS6852030B2Increase valueCard gamesApparatus for meter-controlled dispensingEngineeringRisk evaluation
Owner:IGT
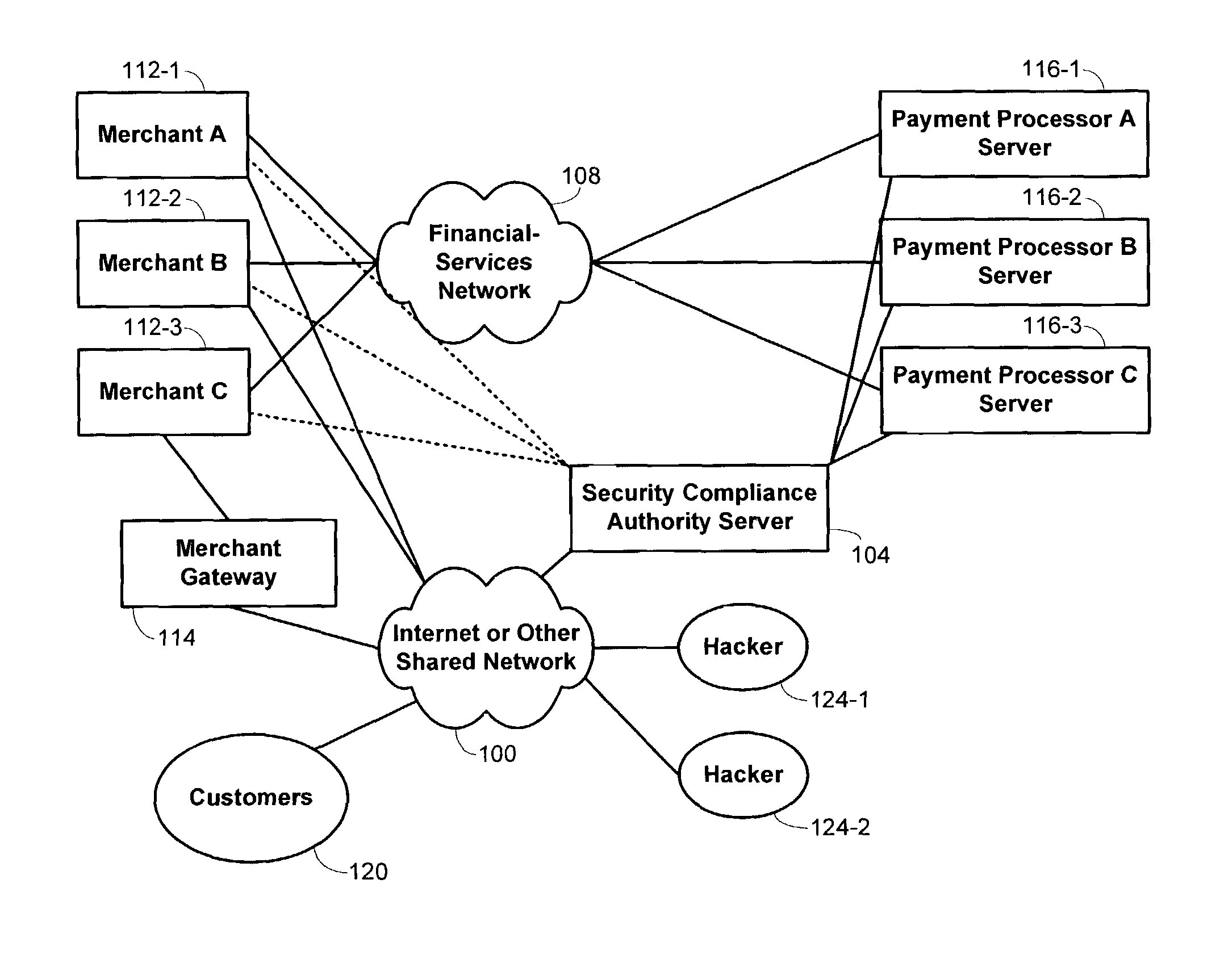
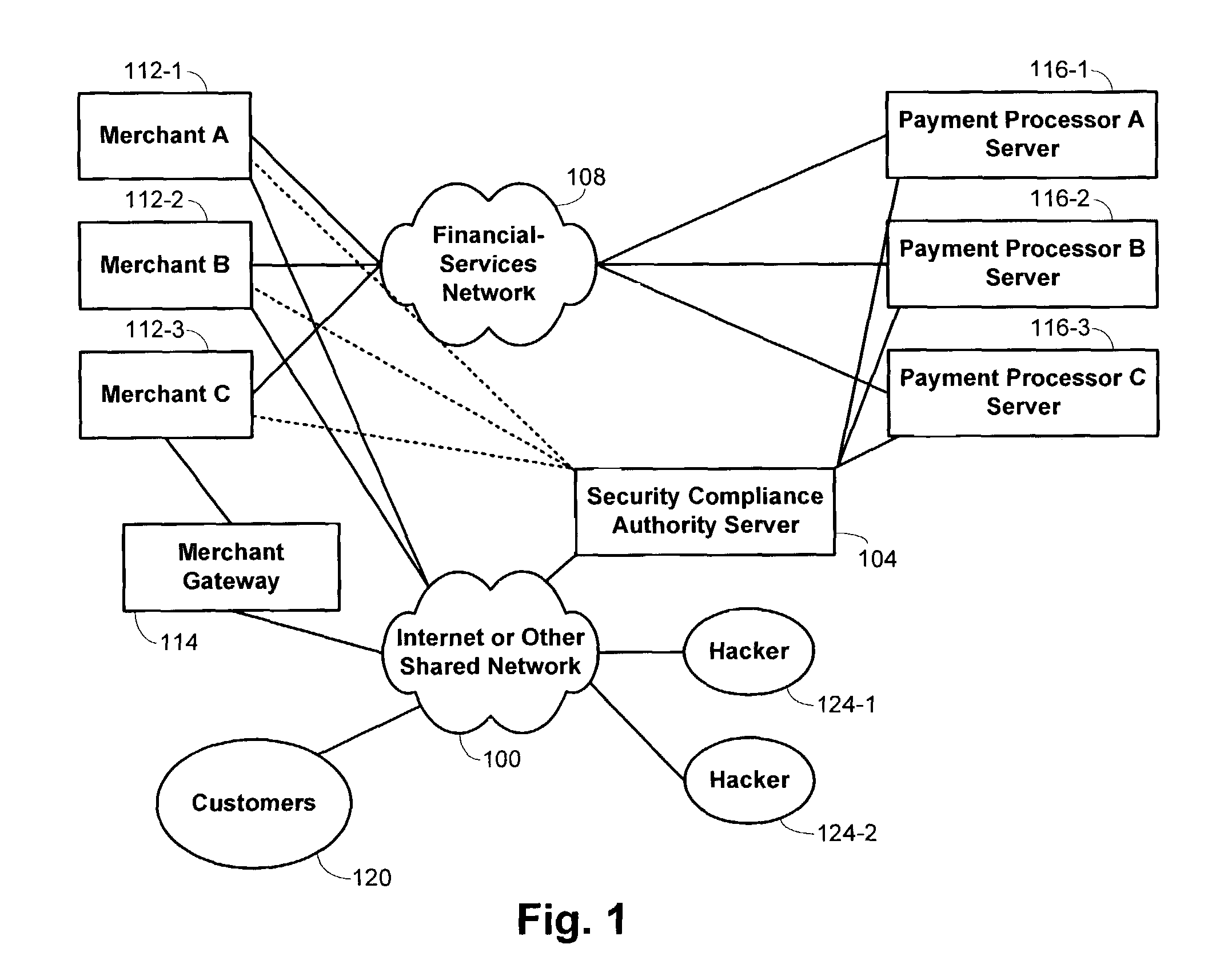
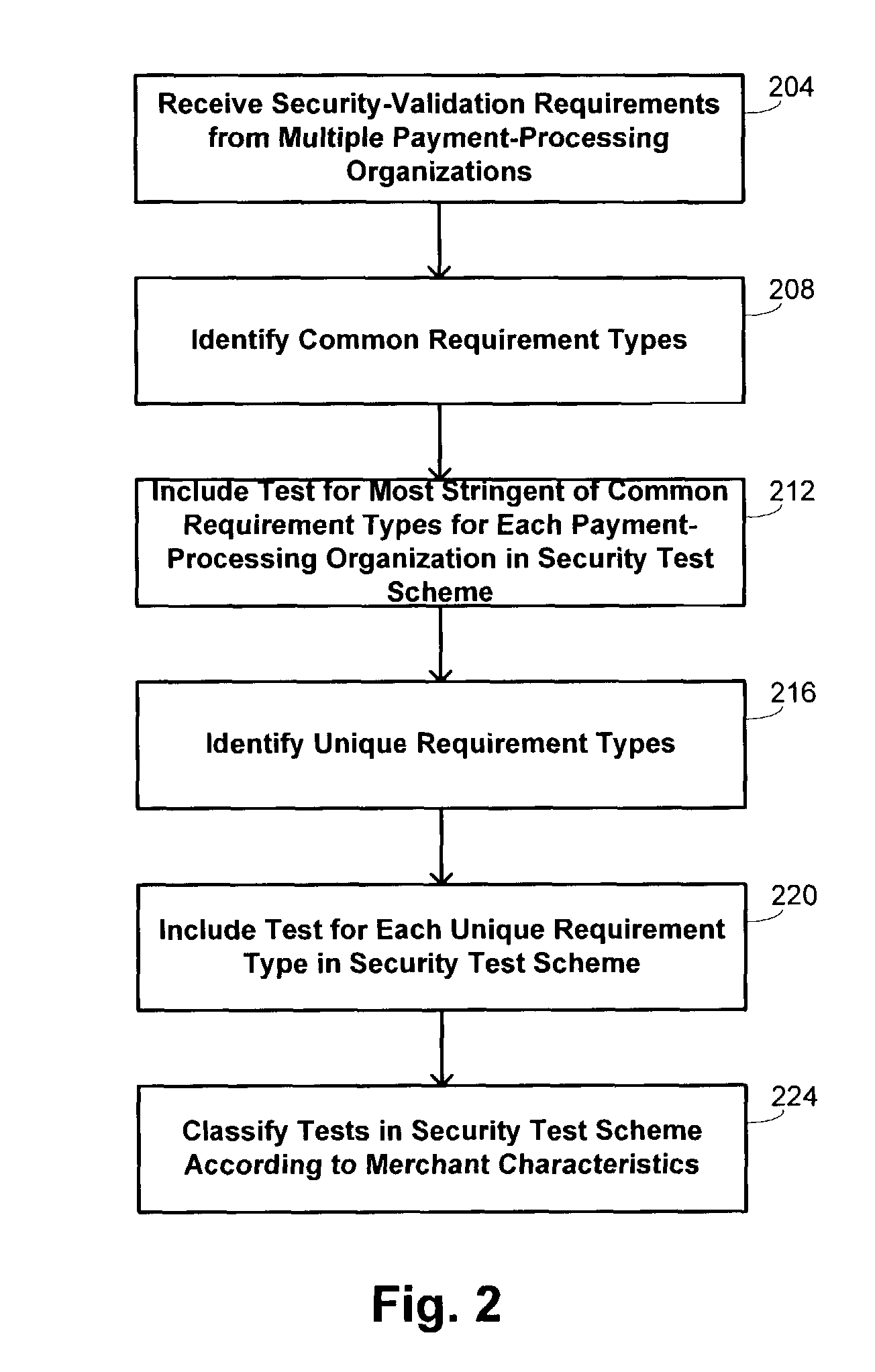
Methods and systems for performing security risk assessments of internet merchant entities
ActiveUS7930753B2Simplify complianceDigital data processing detailsAnalogue secracy/subscription systemsPaymentSecurity compliance
Methods and systems are provided for assessing a security risk for a merchant entity having connectivity to a shared network. Information describing characteristics of the merchant entity are received from the merchant entity. A determination is made which test requirements of a security test scheme are to be used in assessing the security risk for the merchant entity. The security test scheme includes a set of test requirements whose satisfaction by the merchant entity is sufficient to ensure compliance with a multiple sets of security requirements defined by multiple payment-processing organizations. The security test scheme is executed with a security compliance authority server in accordance with the determined test requirements.
Owner:FIRST DATA
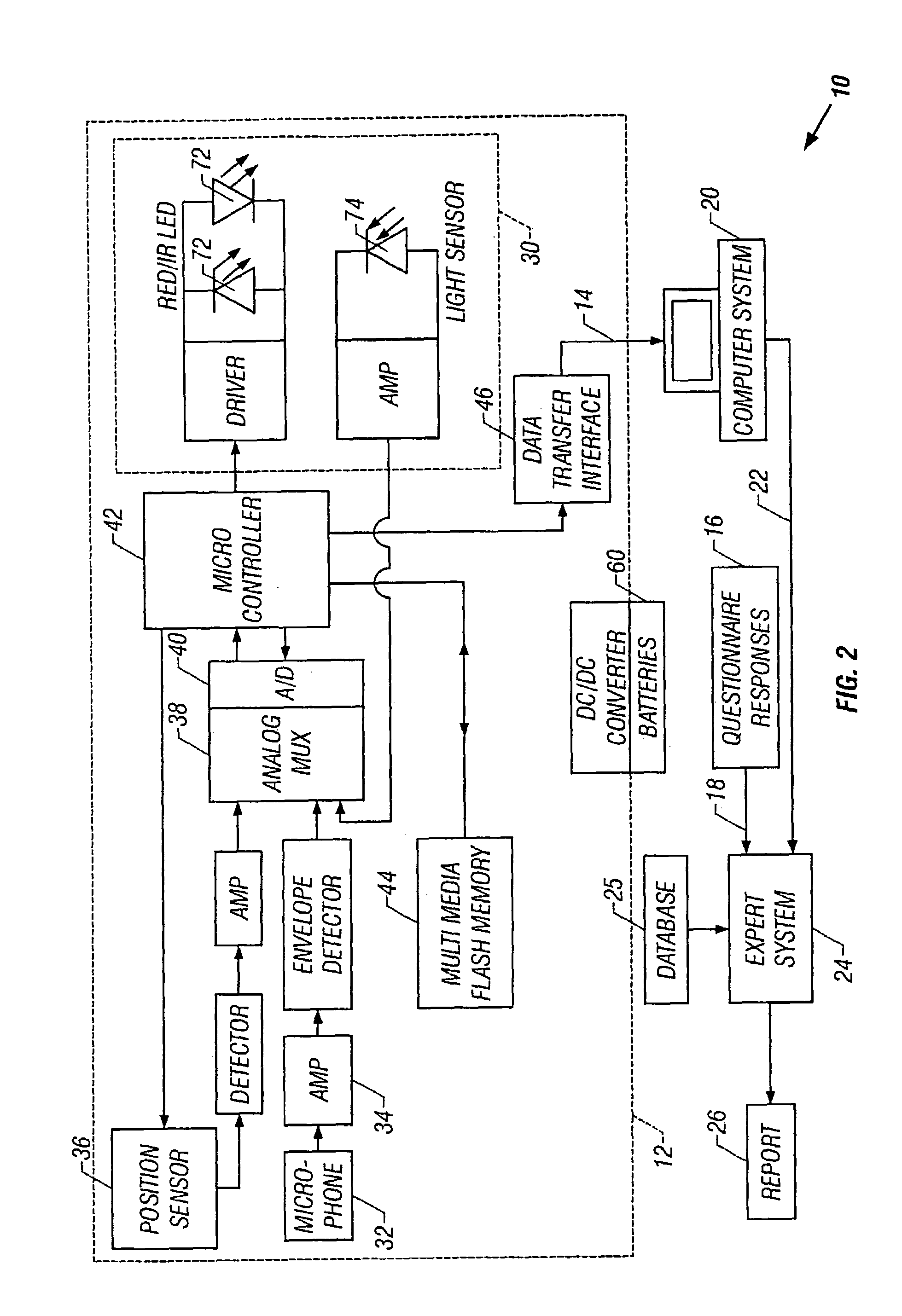
Sleep apnea risk evaluation
InactiveUS7297119B2Improve accuracyImprove resolutionHealth-index calculationSurgeryPulse oximetersLate apnea
In a technique for collecting and analyzing physiological signals to detect sleep apnea, a small light-weight physiological monitoring system, affixed to a patient's forehead, detects and records the pulse, oximetry, snoring sounds, and head position of a patient to detect a respiratory event, such as sleep apnea. The physiological monitoring system may contain several sensors including a pulse oximeter to detect oximetry and pulse rate, a microphone to detect snoring sounds, and a position sensor to detect head position. The physiological monitoring system also can contain a memory to store or record the signals monitored by the mentioned sensors and a power source. The physiological monitoring system may be held in place by a single elastic strap, thereby enabling a patient to use the system without the assistance of trained technicians.
Owner:WATERMARK MEDICAL
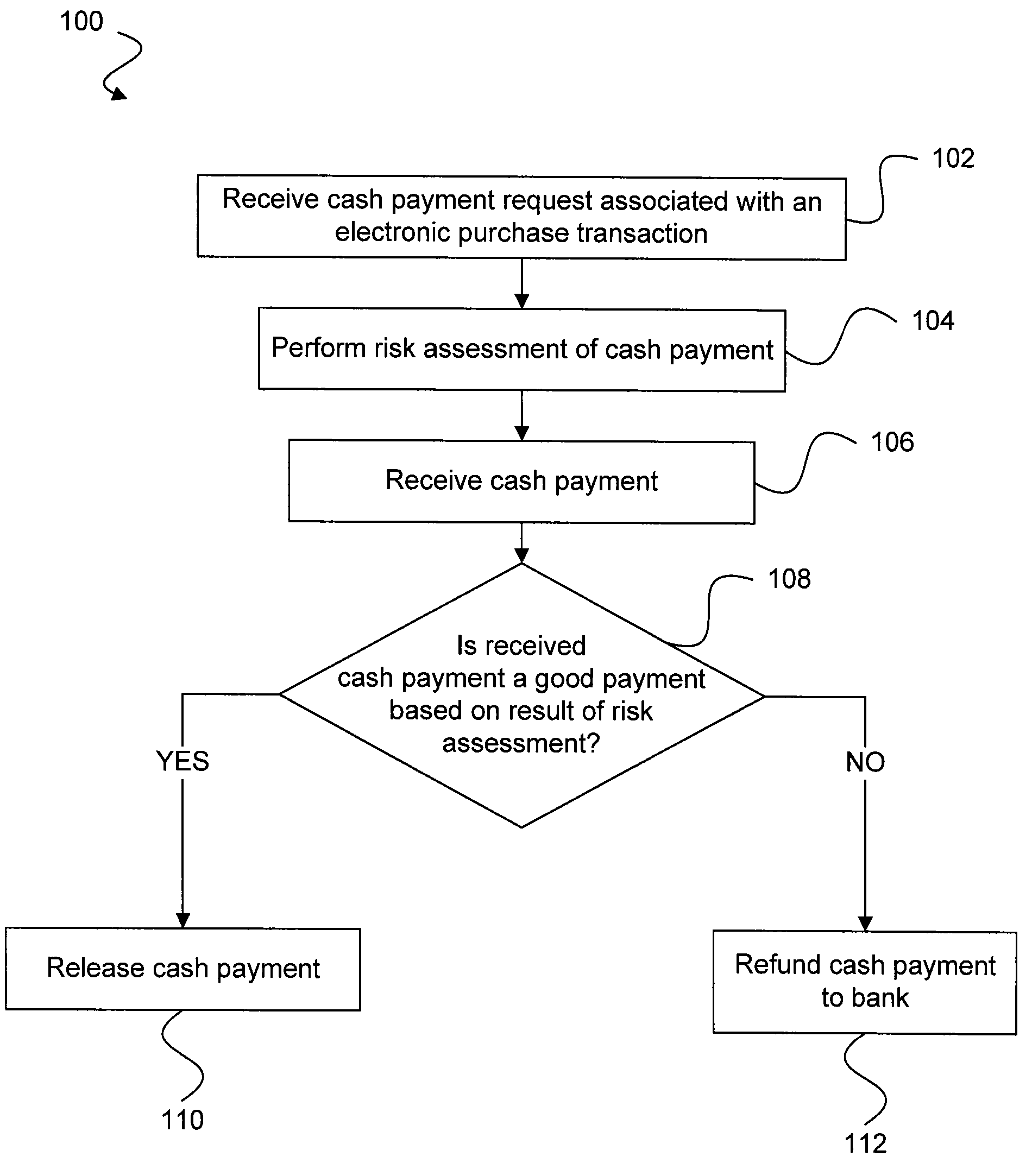
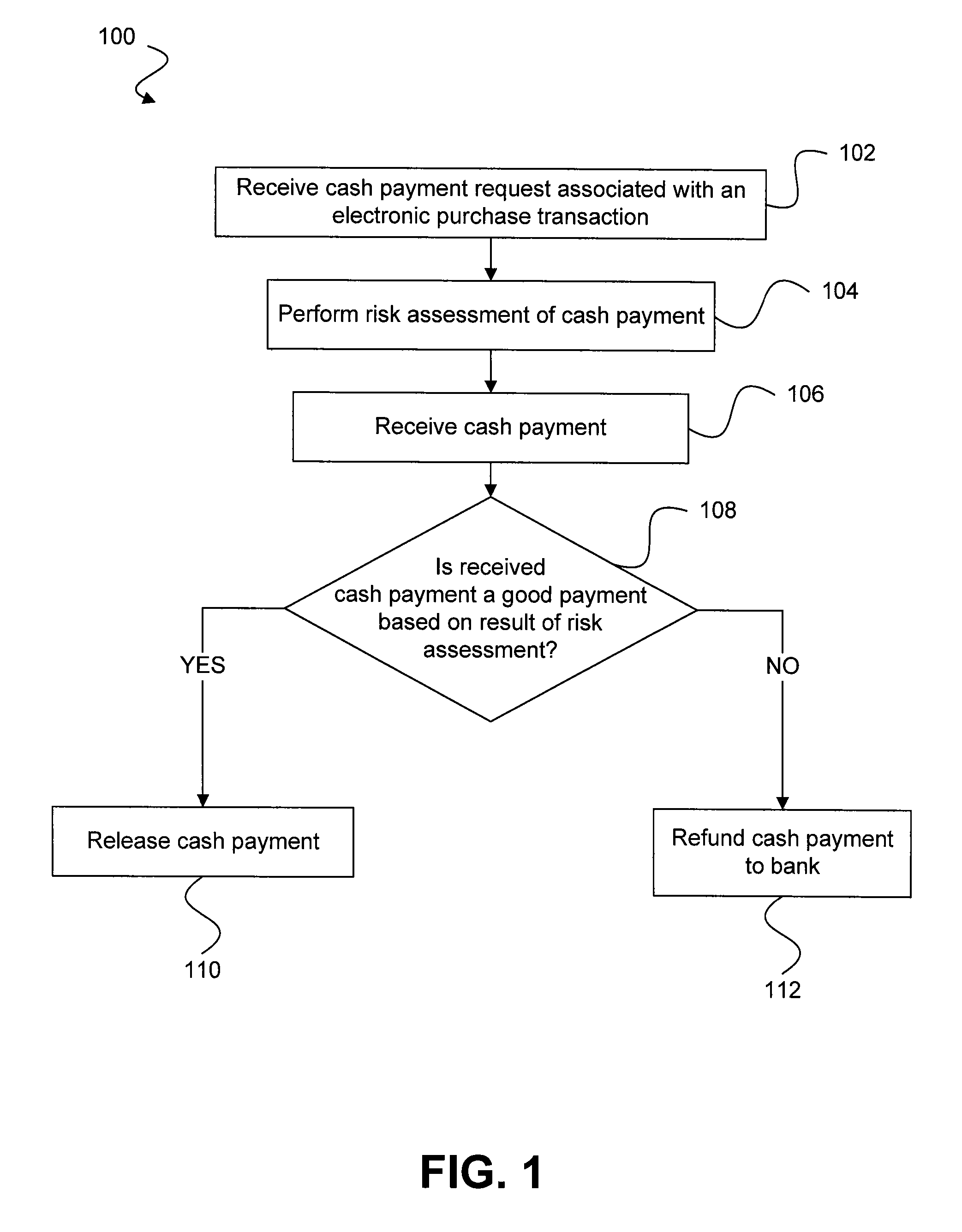
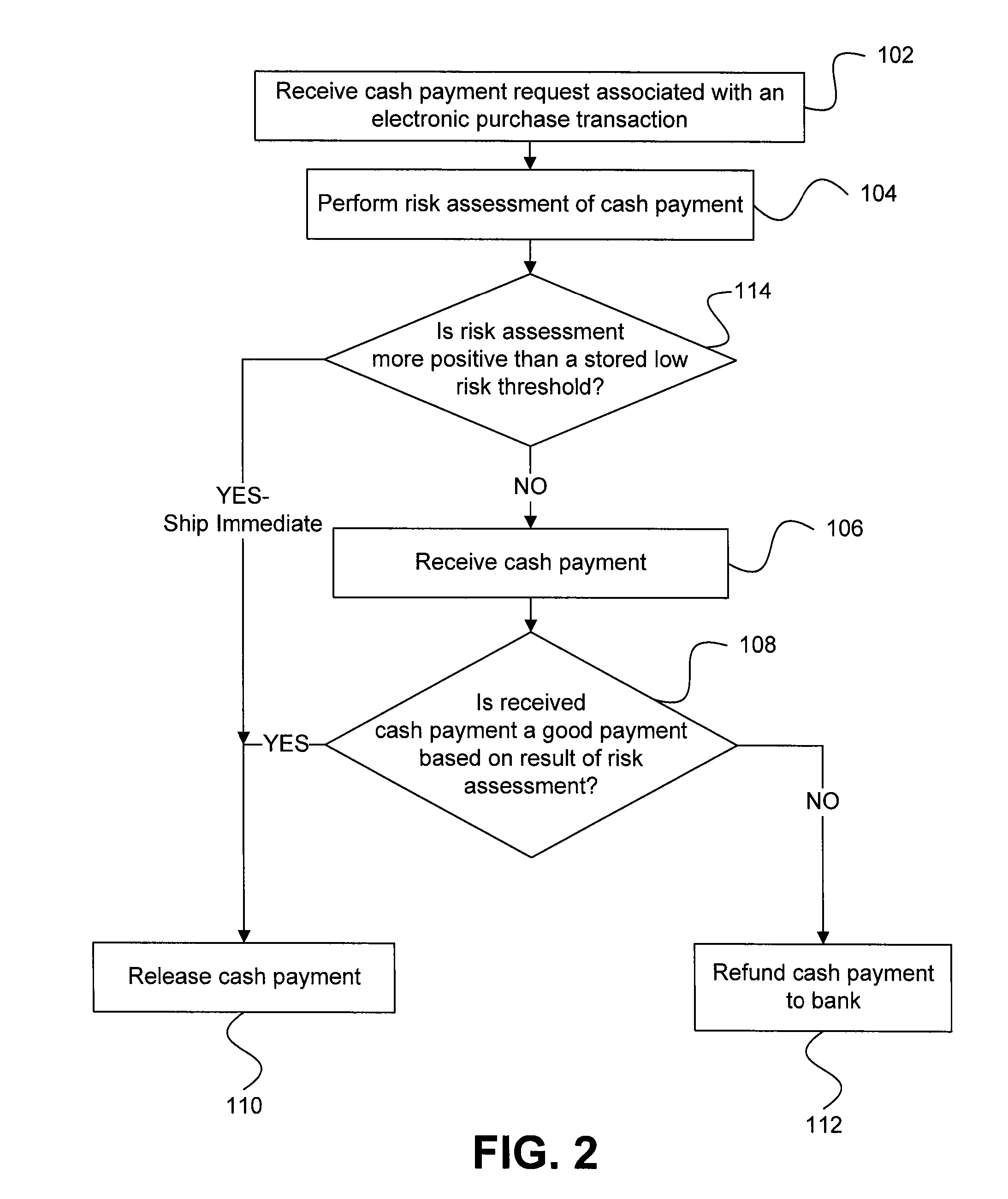
Risk detection and assessment of cash payment for electronic purchase transactions
A system and methods are provided which allow consumers to pay for ecommerce transactions through online bill payment and for merchants to determine that payments are not fraudulent. The system and methods do not rely on personal or confidential customer information relating to credit-cards and / or bank account routing information, date of birth and / or social security number. A risk manager can perform risk assessment for the cash payment based on order information and non-confidential purchaser information included in a cash payment request. In response to receiving an indication of the cash payment from the purchaser, a determination is made whether the cash payment is a good payment based on the risk assessment. The cash payment is released to a merchant in response to a determination that the cash payment is a good payment.
Owner:WESTERN UNION FINANCIAL SERVICES
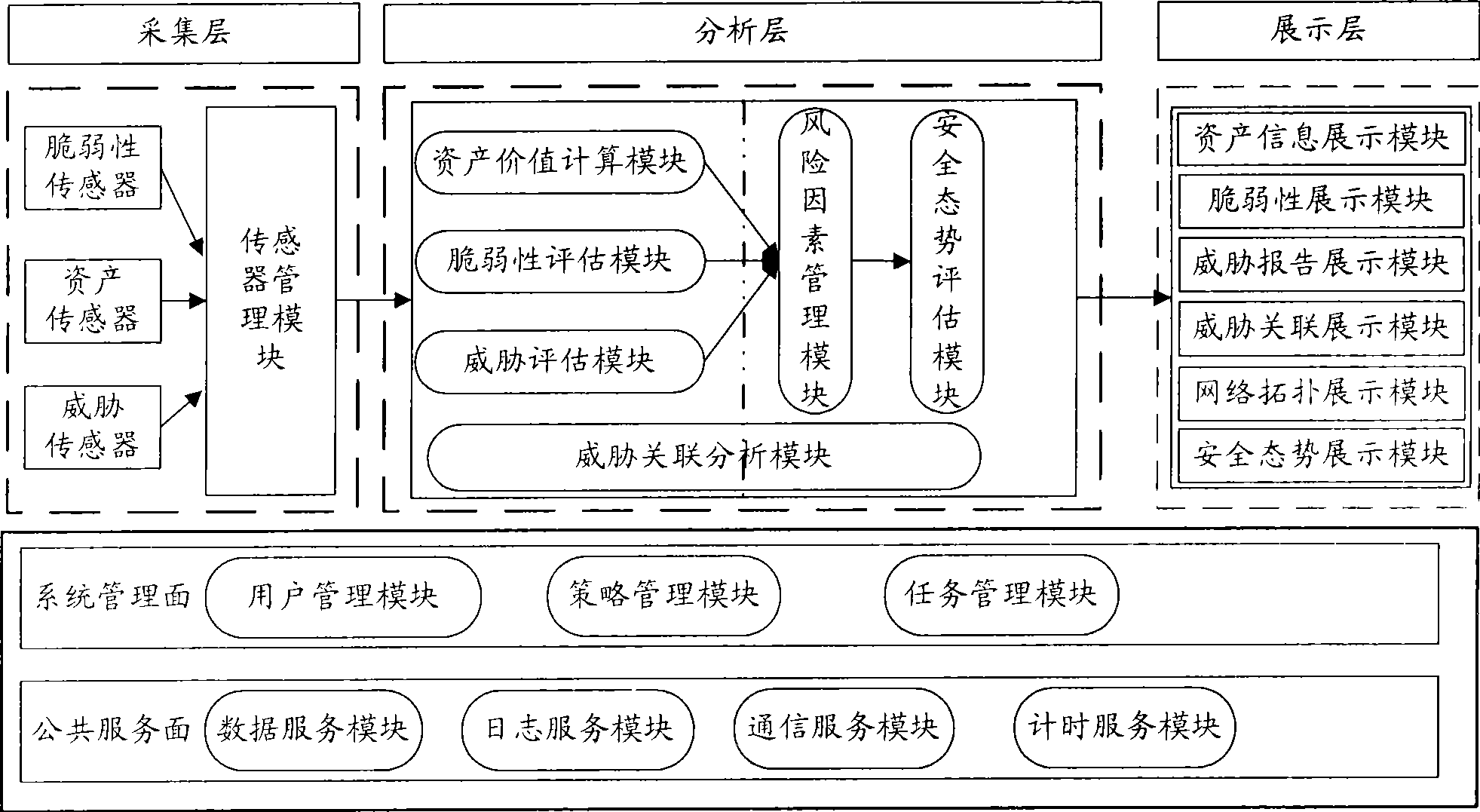
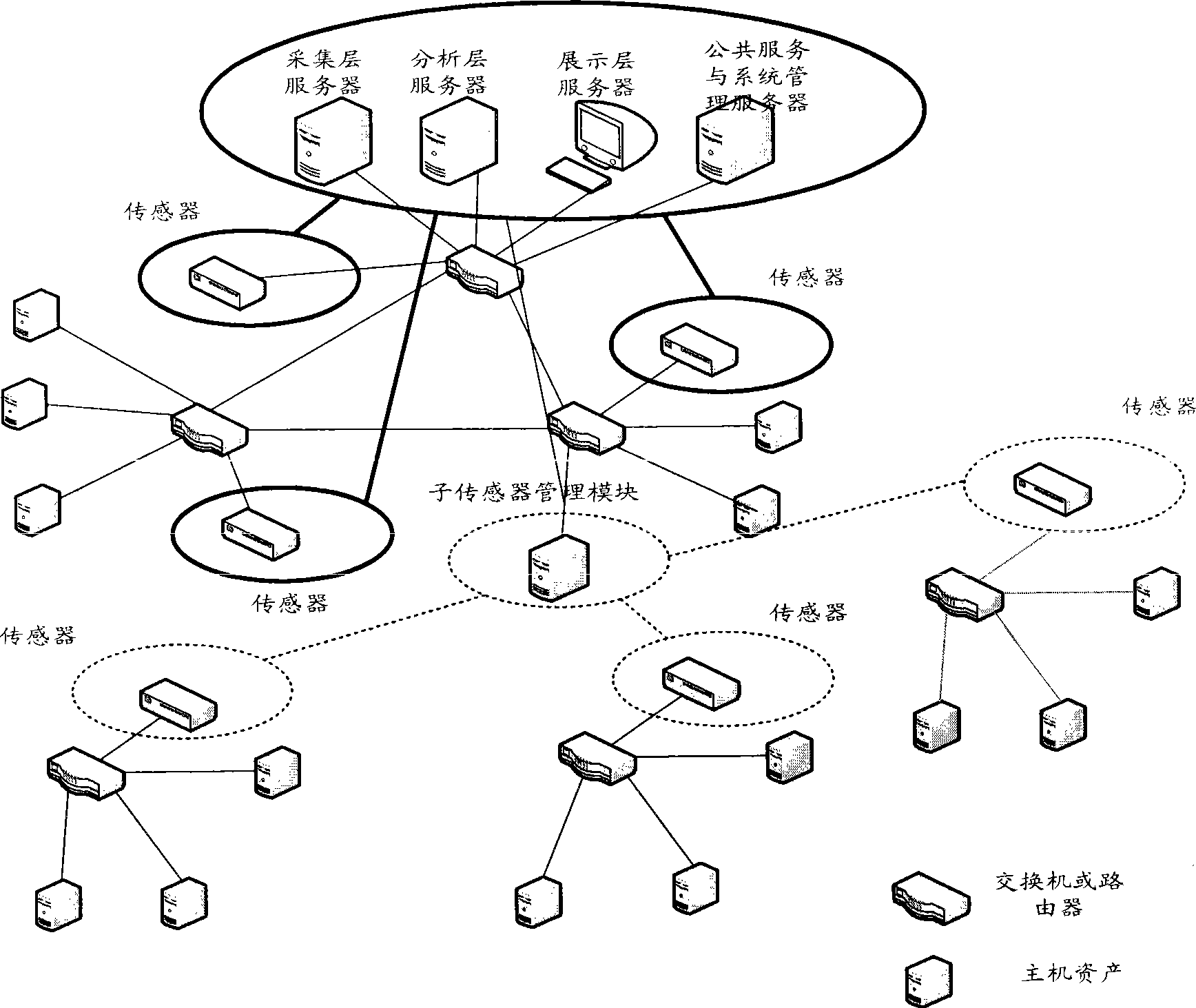
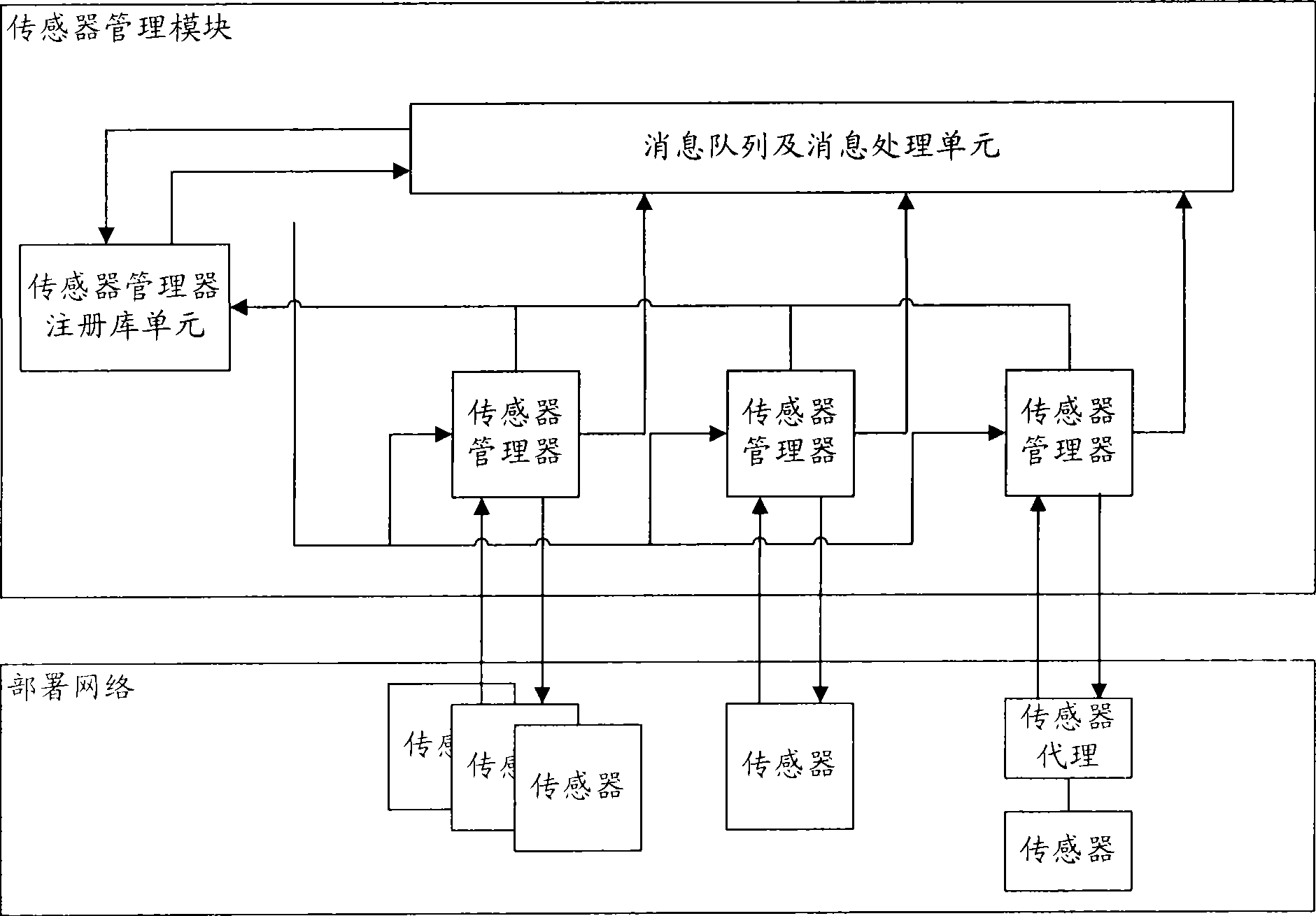
Method and system for evaluating network safety situation
InactiveCN101436967AEasy to operateImprove securityData switching networksThree levelSecurity solution
The invention relates to a method for evaluating the security situation of a network and a system thereof. The system has a two-surface three-level framework and is provided with a public service surface and a service management surface for executing uniform coordinated management on each functional module of the system; according to a service logic processing flow, the system is divided into three levels: an acquisition level, an analysis level and an exhibition level for completing four evaluating operations of assets, frangibility, threat and security situation; the invention is based on the characteristic of service operation in the network, combines the prior risk evaluation method, the prior flow and the prior security detection tool and provides a set of a novel dynamic real-time evaluation method. The system can analyze the assets and service of the network and the risk of the whole network and carries out the evaluation of the security situation. The system can provide the security state of the whole network in macroscopy, can deepen to specific service and assets and know the specific security problem, thereby effectively helping network security personnel to analyze the root of the security problem and assisting to provide a security solution proposal and implement a defense measure.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method and system to edit and analyze longitudinal personal health data using a web-based application
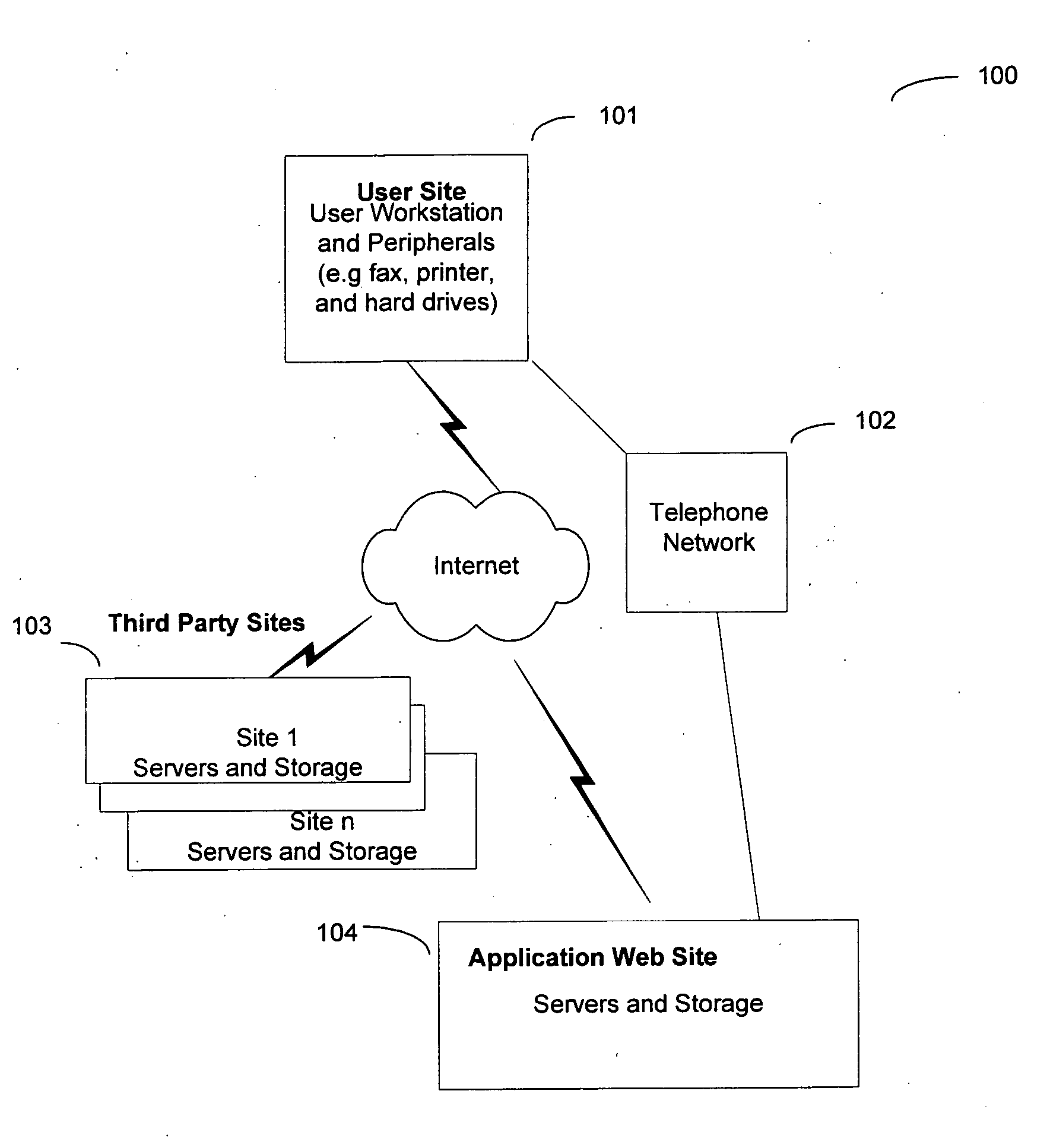
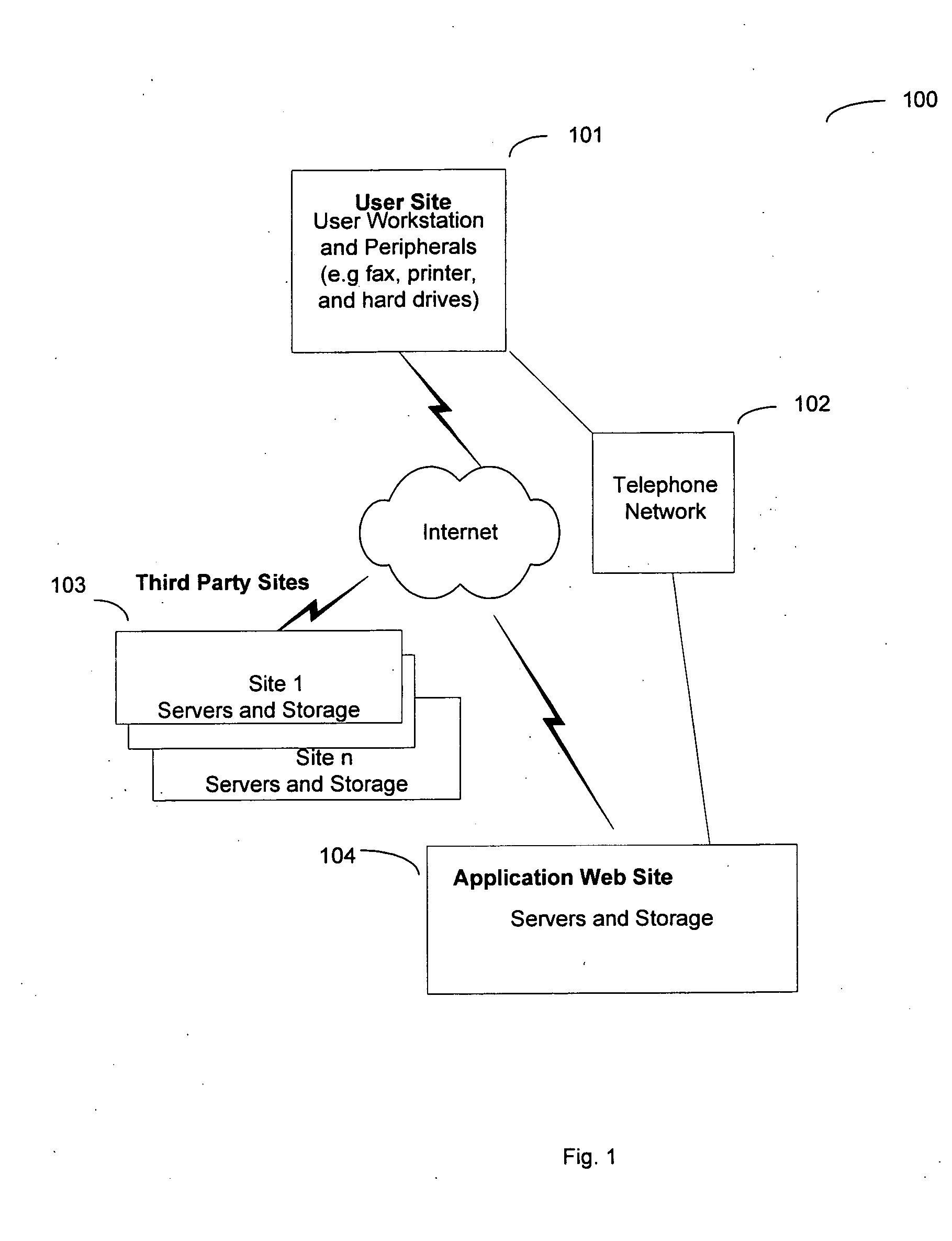
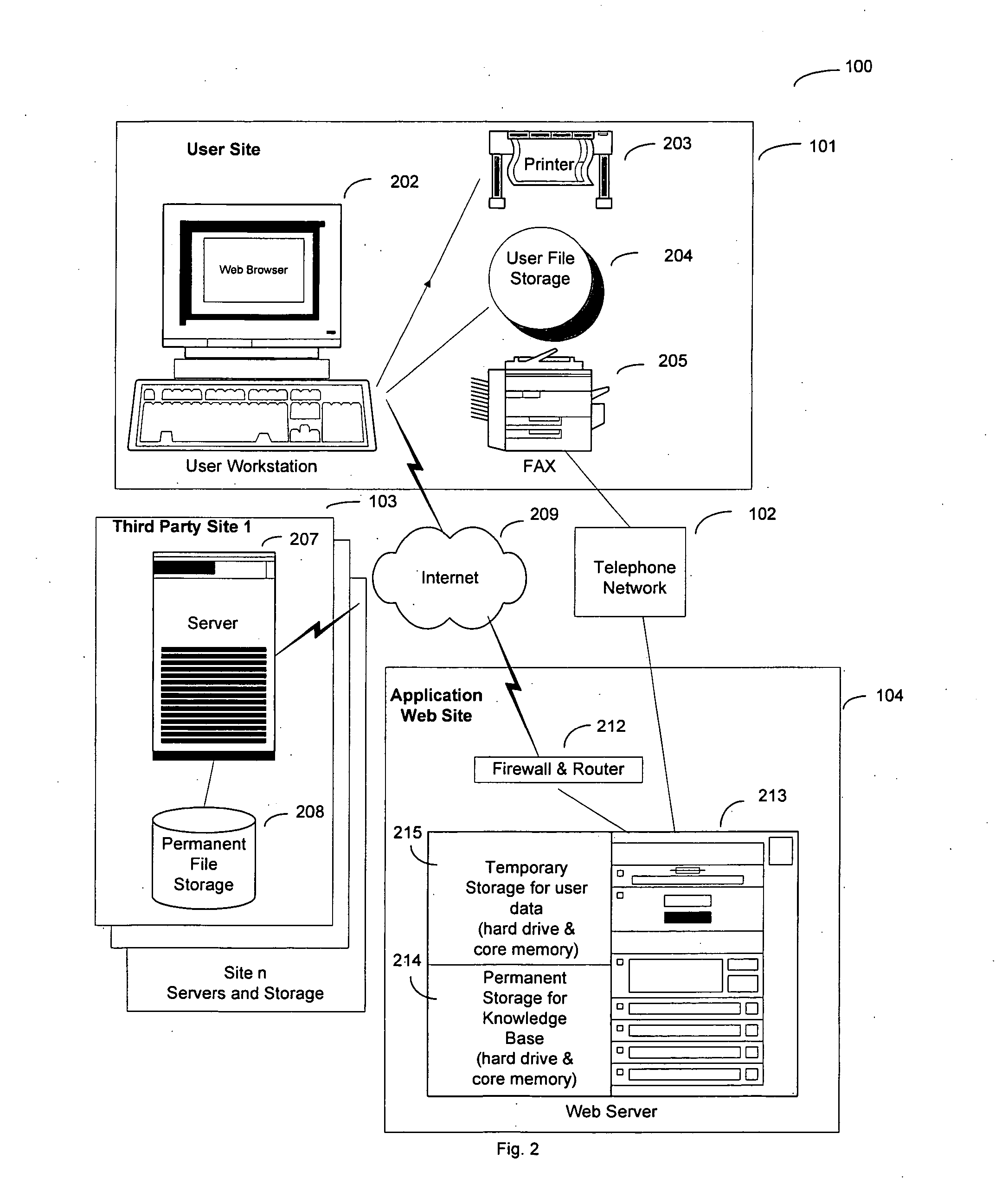
In a global computer network, a system for processing personal health records is disclosed. The system includes a web-based application providing an application web server that does not store personal data. A user starts a new session using the application web site and begins entering medical data. During the session, with the user's data in transient storage, the application web site can perform health risk assessments and search other databases to provide information relevant to the user's health. At the end of the session, the user downloads a file that saves all of the data. Next, the application web site erases the user's data from the web site. The user continues data entry in the future by uploading the saved file. Since the user keeps the data, no identification of the user is necessary and privacy is preserved.
Owner:WU HARRY C
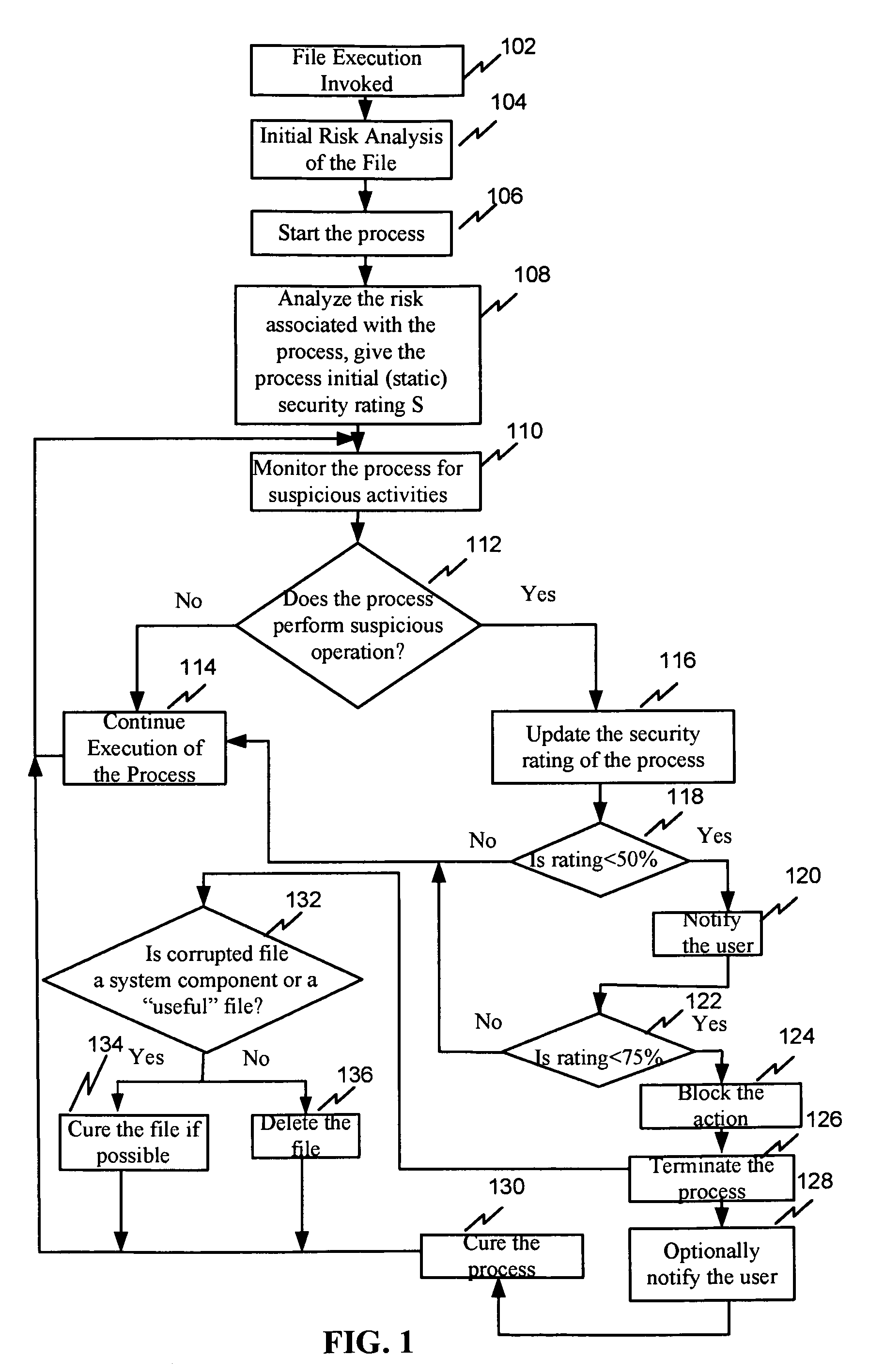
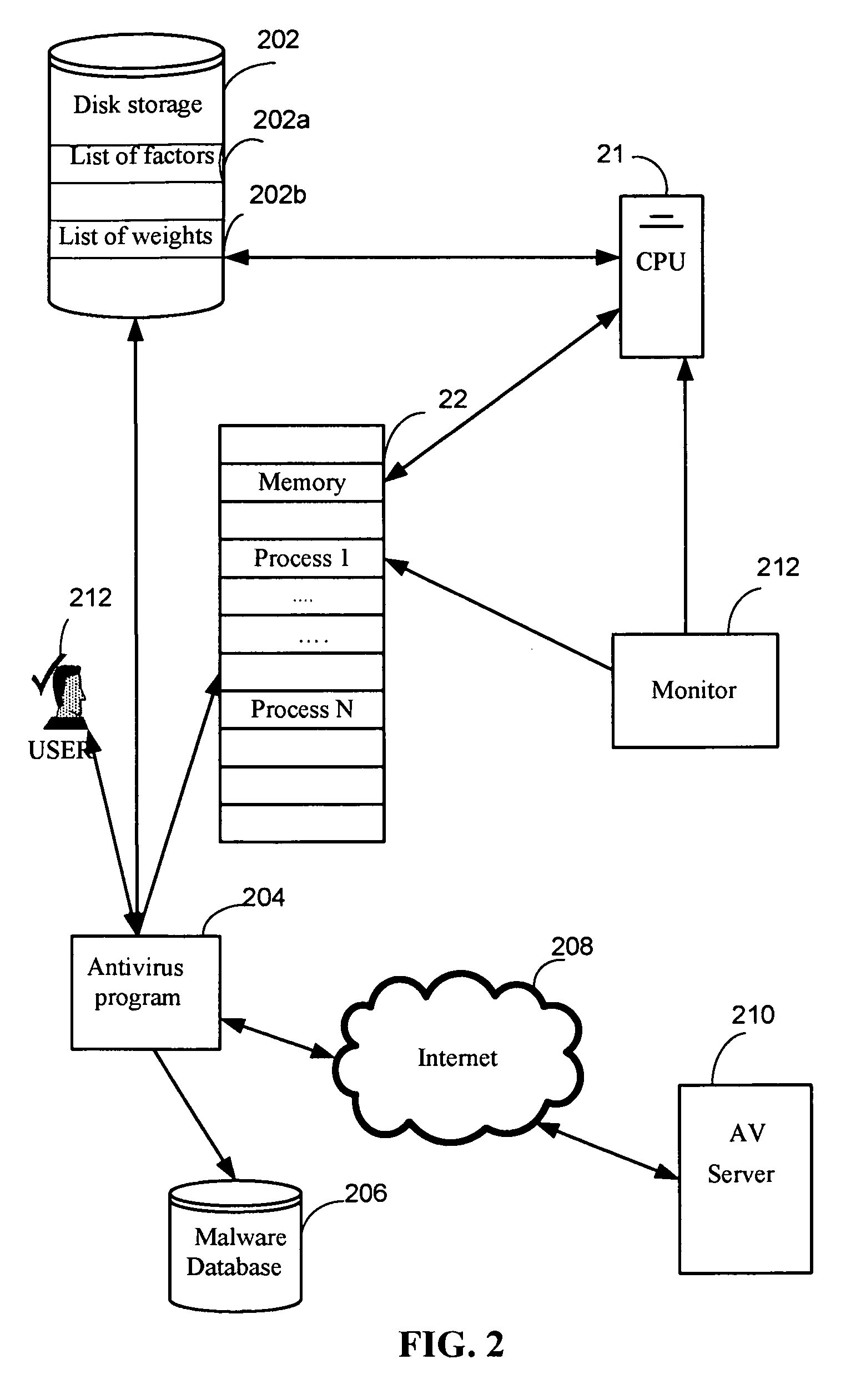
System and method for security rating of computer processes
ActiveUS7530106B1Eliminate disadvantagesMemory loss protectionUnauthorized memory use protectionMalwareRisk evaluation
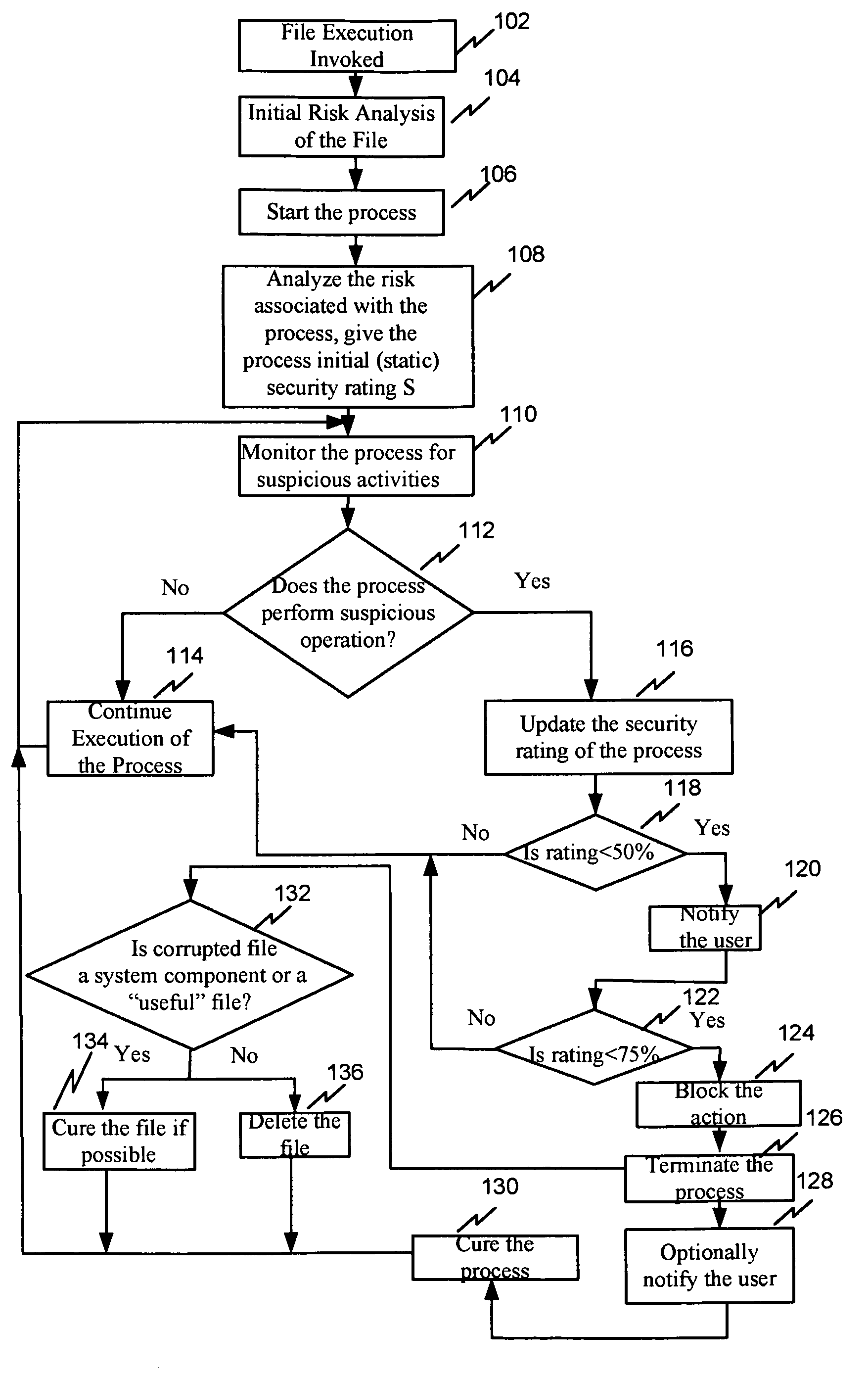
A system, method, and computer program product for secure rating of processes in an executable file for malware presence comprising: (a) detecting an attempt to execute a file on a computer; (b) performing an initial risk assessment of the file; (c) starting a process from code in the file; (d) analyzing an initial risk pertaining to the process and assigning an initial security rating to the process; (e) monitoring the process for the suspicious activities; (f) updating the security rating of the process when the process attempts to perform the suspicious activity; (g) if the updated security rating exceeds a first threshold, notifying a user and continuing execution of the process; and (h) if the updated security rating exceeds a second threshold, blocking the action and terminating the process.
Owner:KASPERSKY LAB ZAO
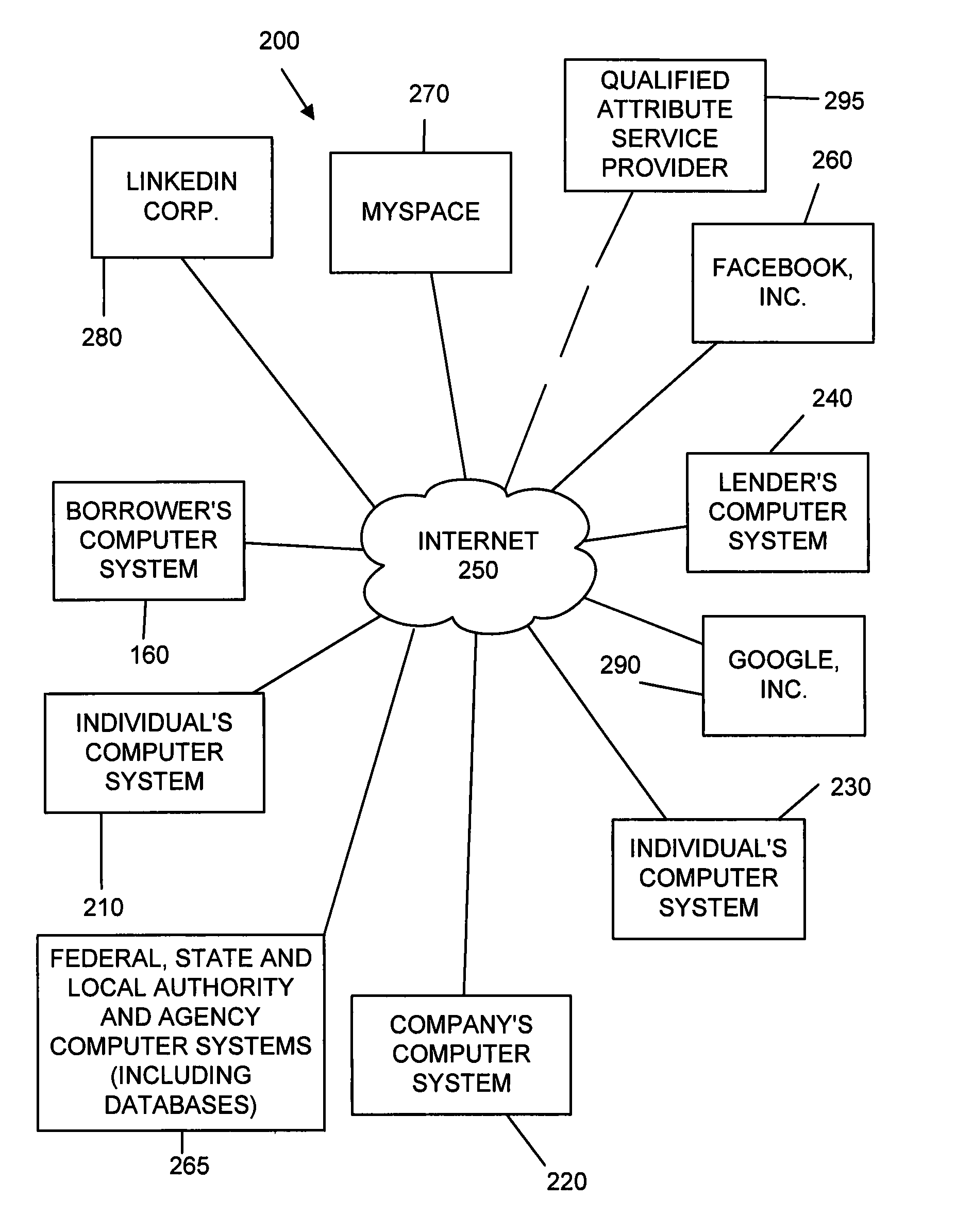
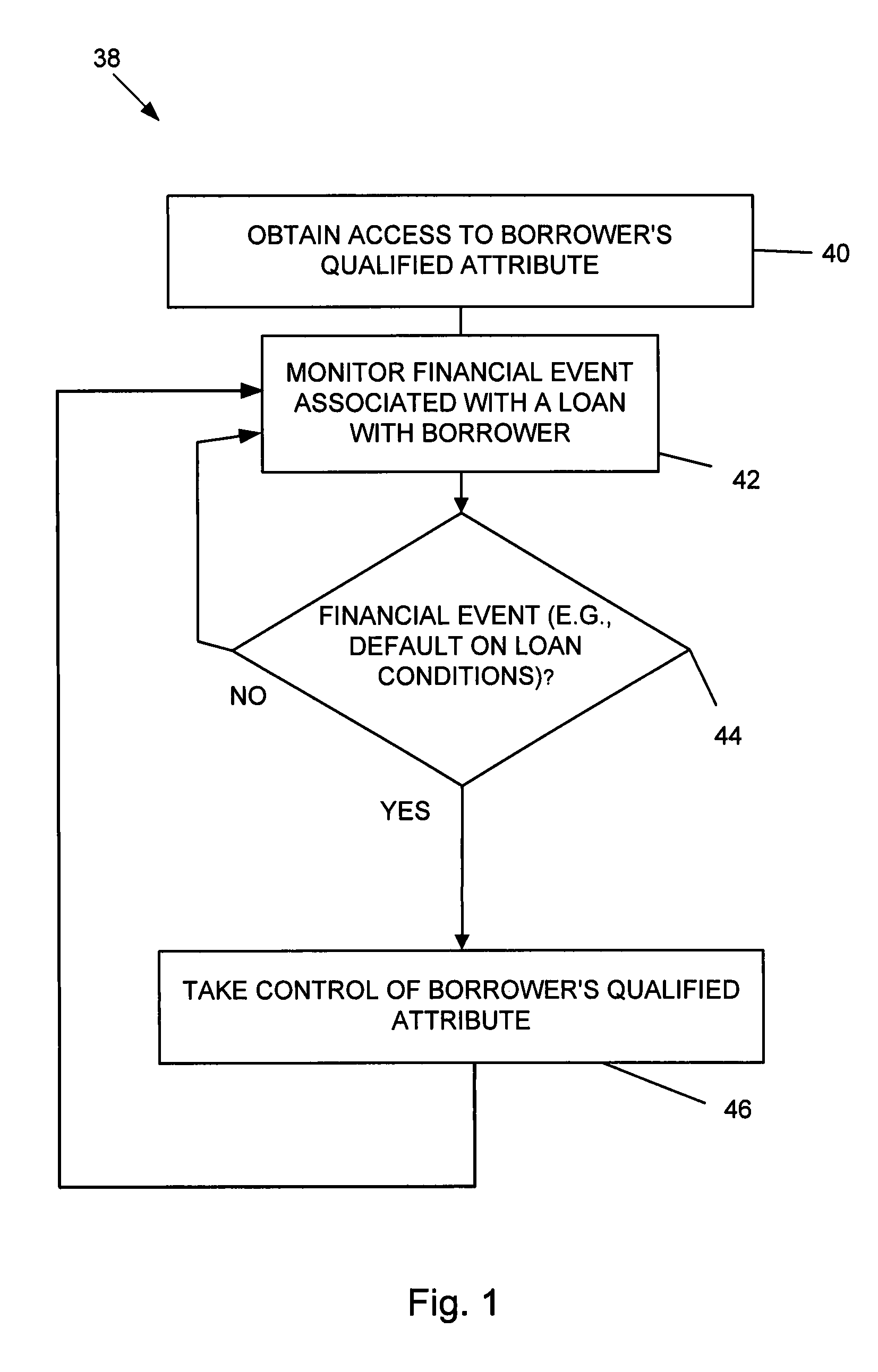
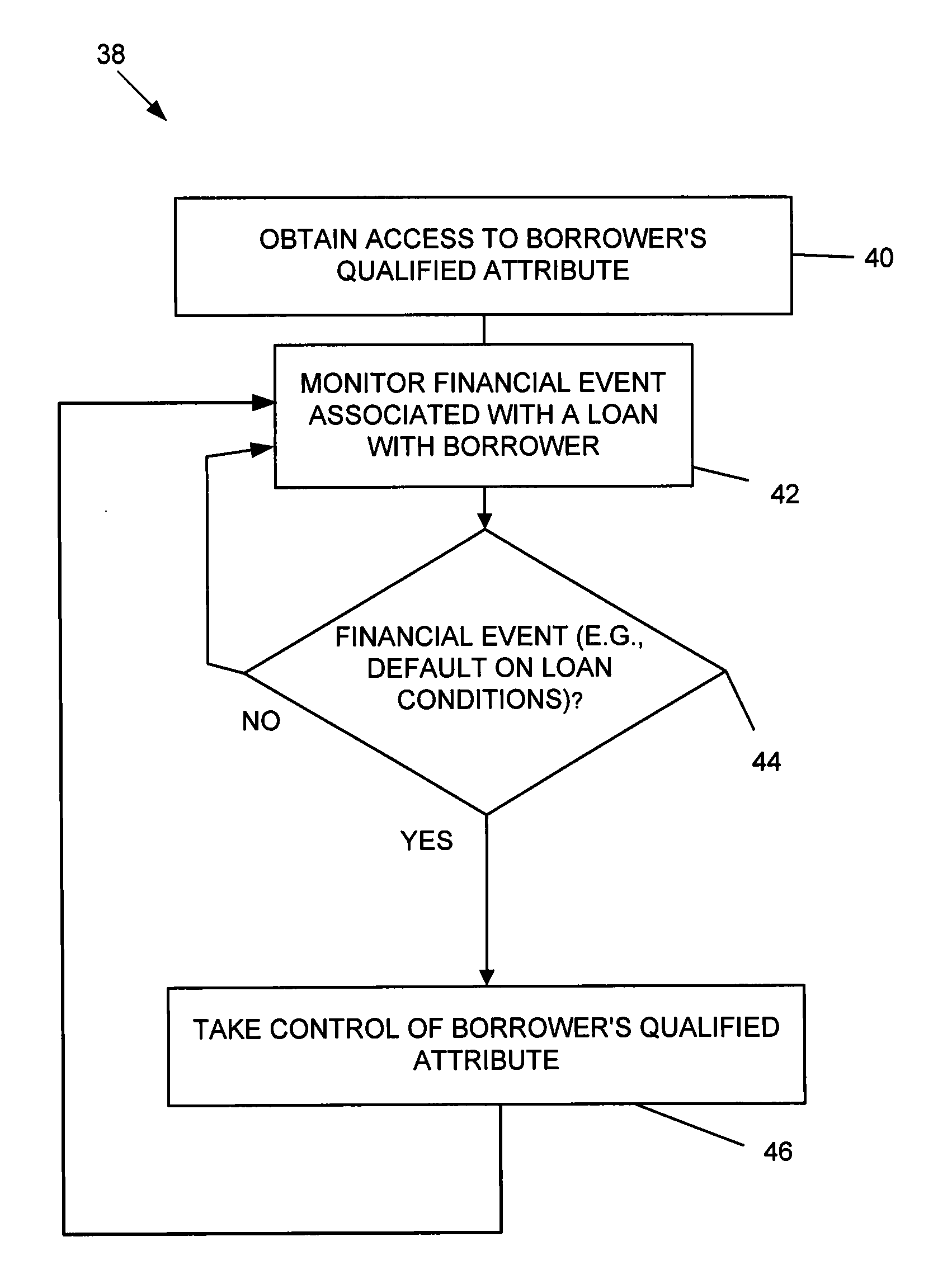
Systems and methods for collateralizing loans
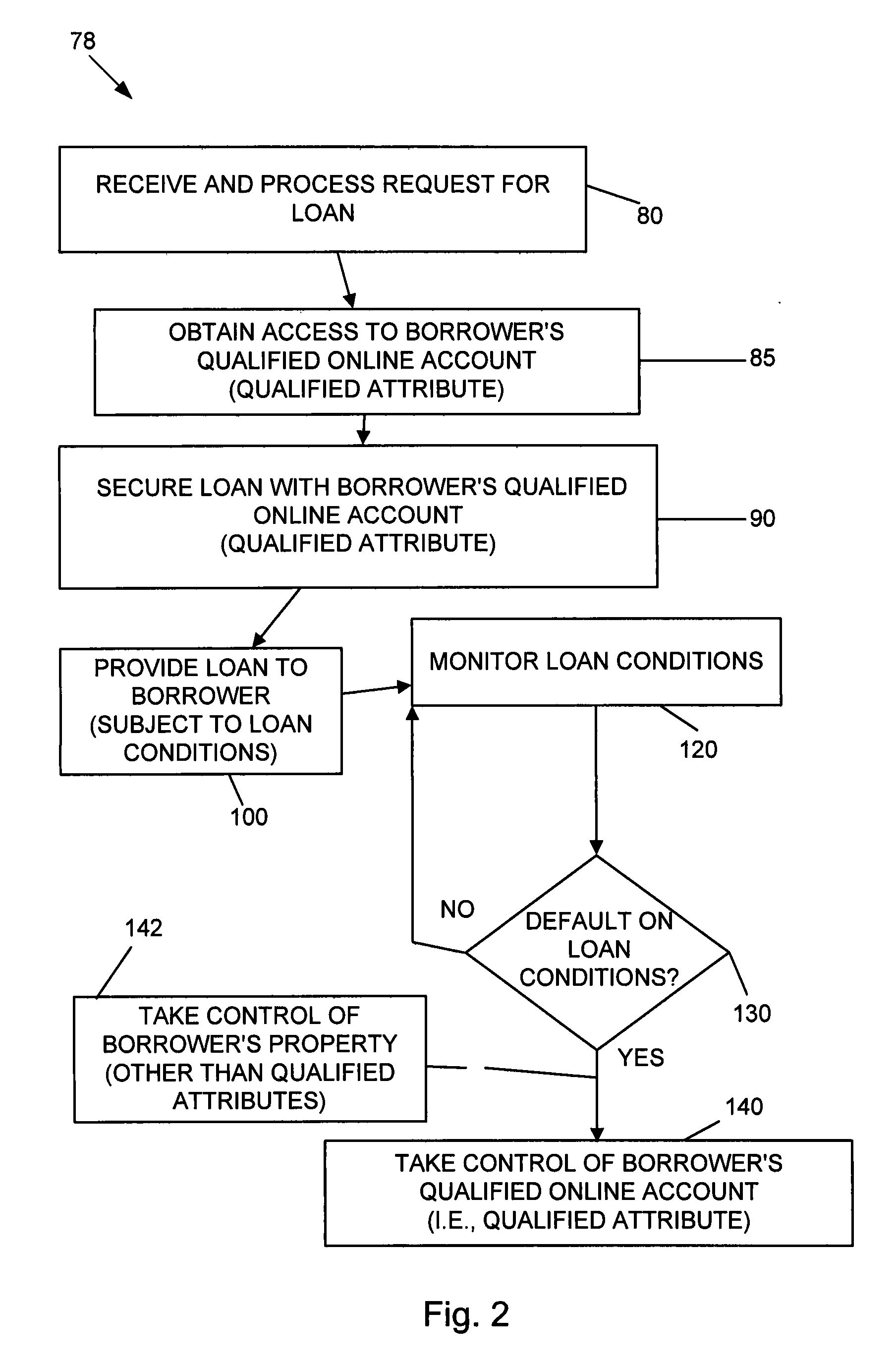
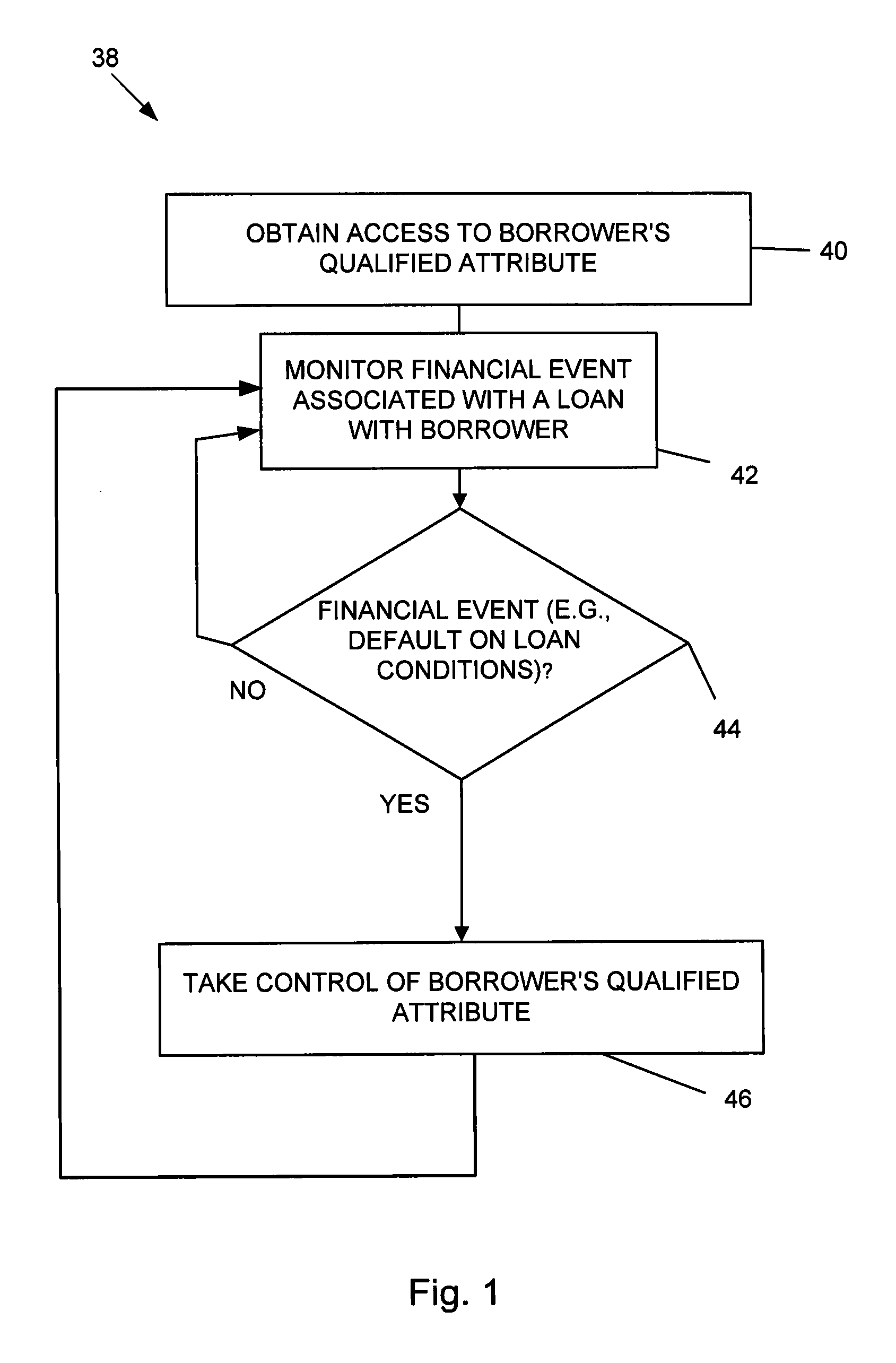
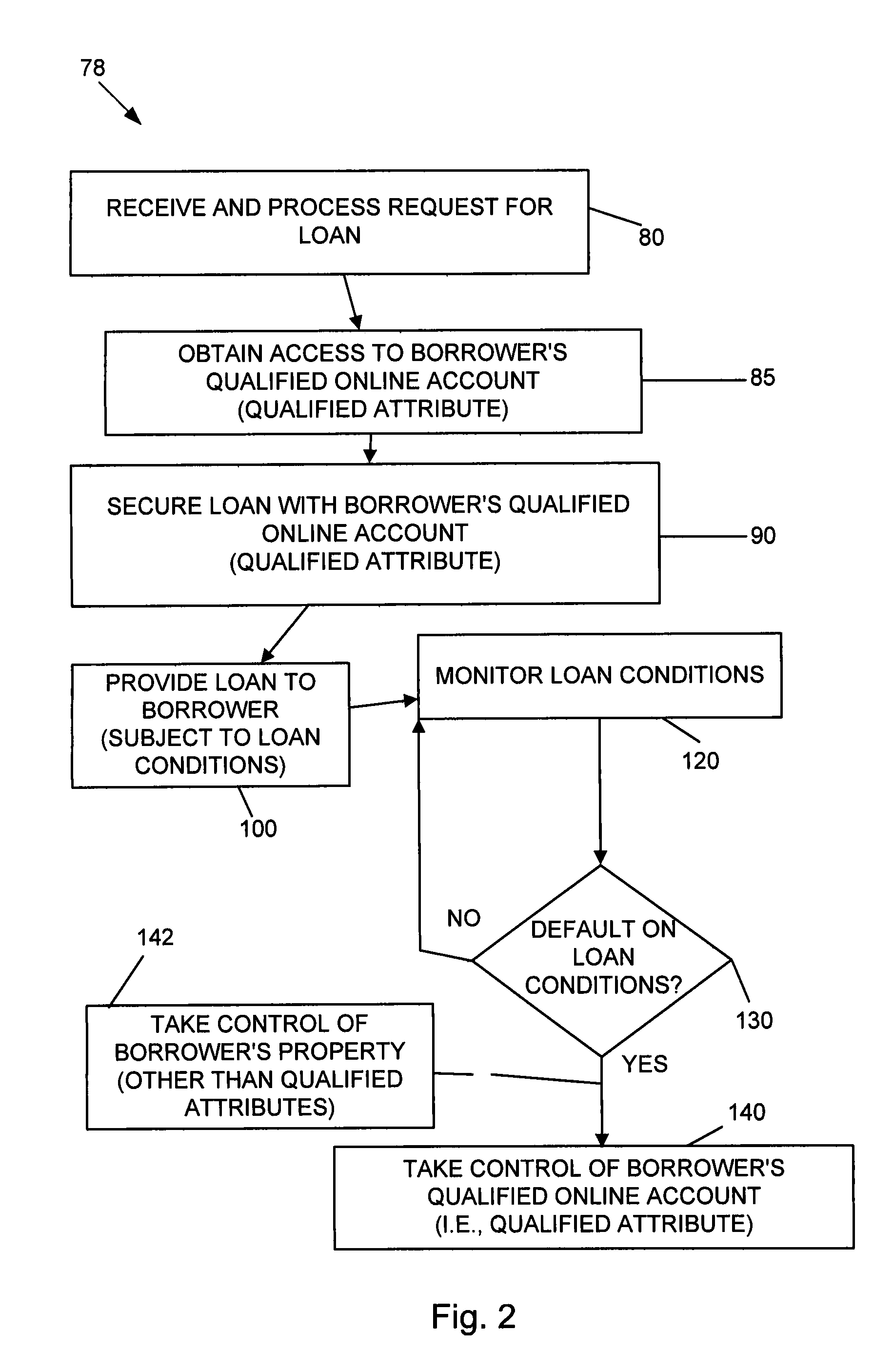
Systems and methods are disclosed for collateralizing loans. Some embodiments increase the likelihood of repayment by obtaining access to a qualified attribute of a borrower by a first computer component, monitoring by a second computer component for a financial event associated with the loan to the borrower, and taking control of the qualified attribute of the borrower by a third computer component. Taking control may include notifying social contacts. Securing the loan by taking various security interests and technical countermeasures against the borrower re-obtaining access or re-taking control are disclosed. Providing loans, receiving loan applications, providing loans proceeds, processing payments, and underwriting criteria are disclosed. Underwriting employing social contacts for recommendations, loan guarantees, social contact credit scores, public repayment promises, loan repayment coaches, fraud criteria, crowdsourced risk evaluation, social graphs, borrower stability factors derived from social graphs, data associated with online information repositories, and efficacy of notification are disclosed.
Owner:SOCIOGRAMICS
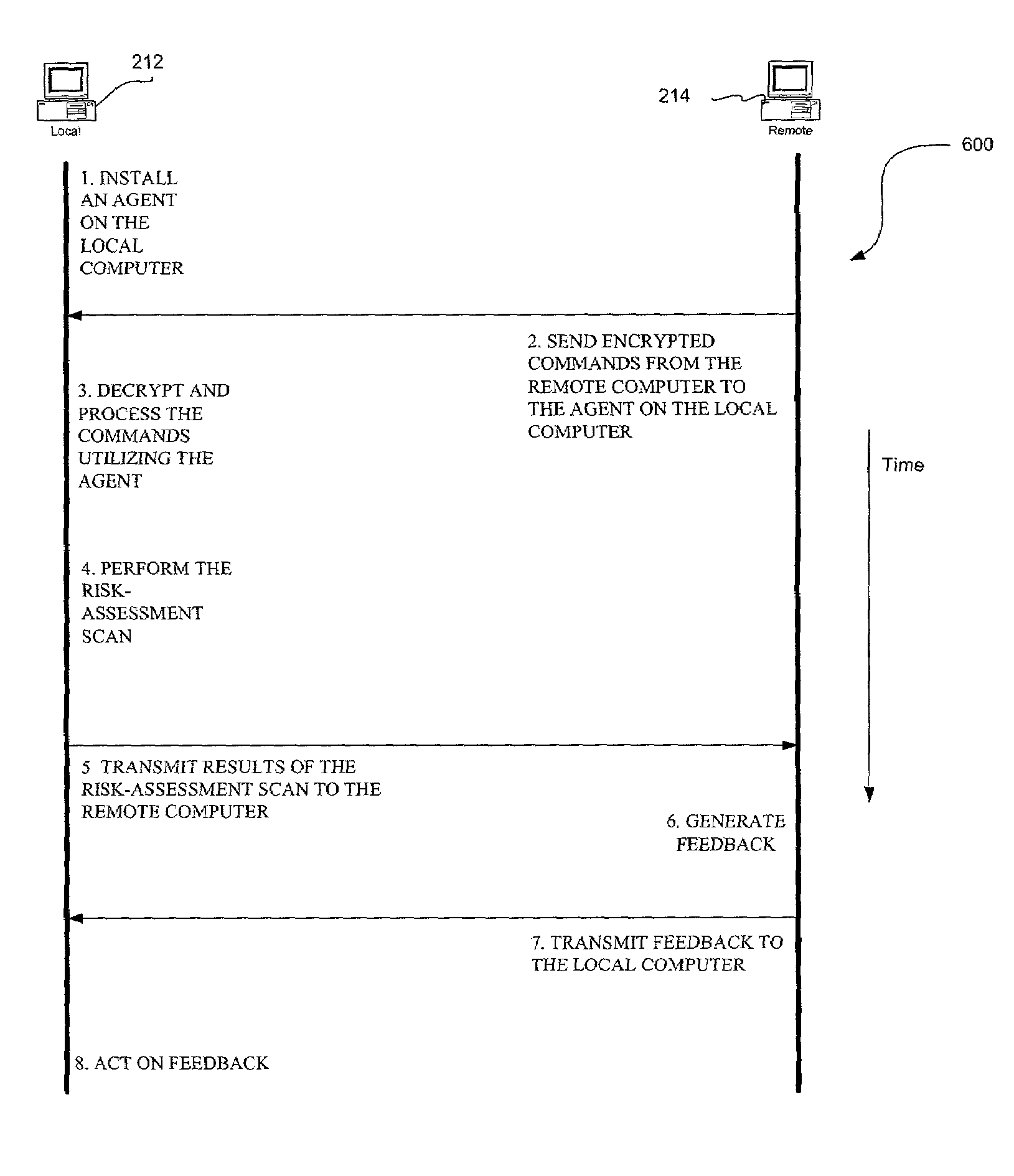
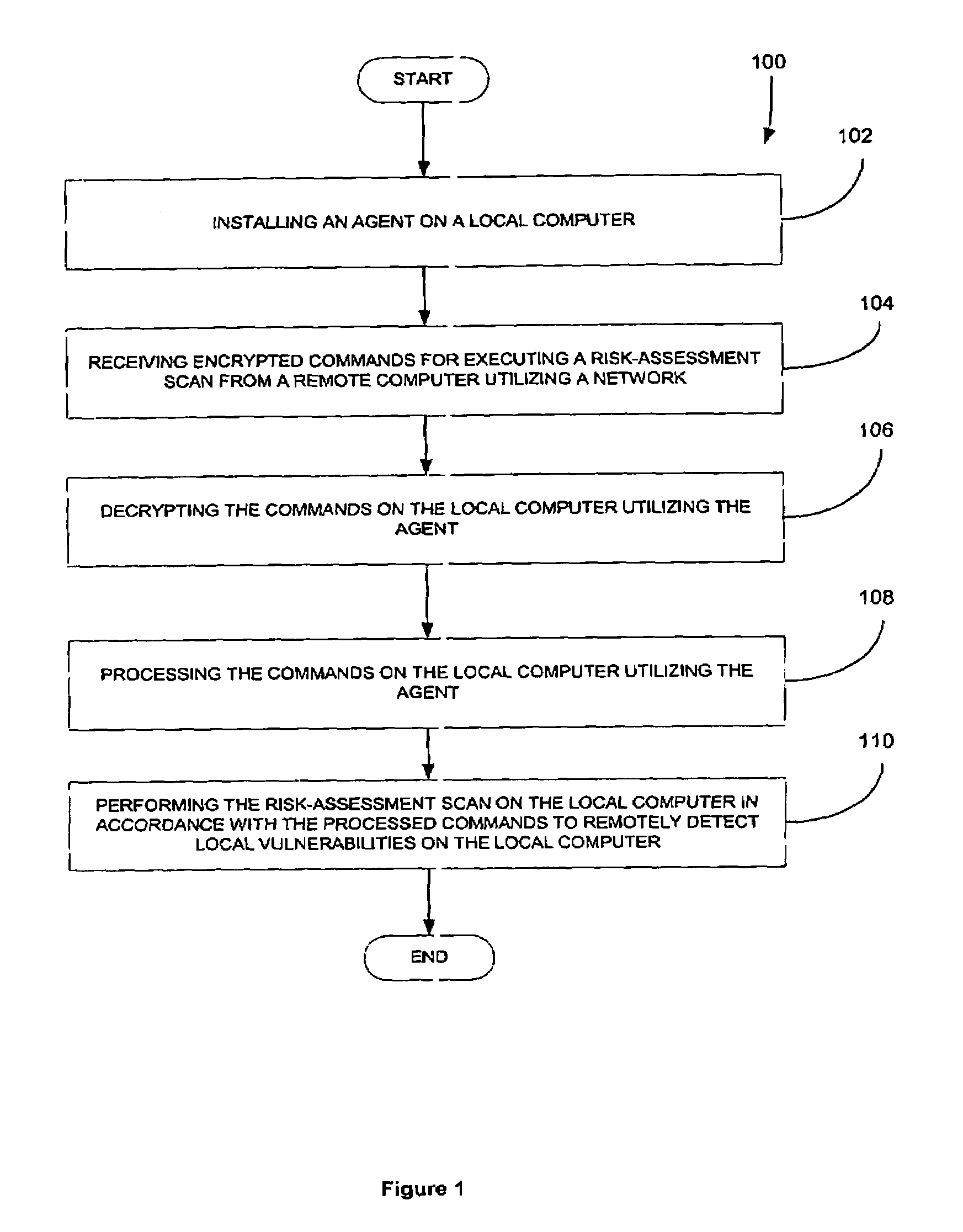
Network-based risk-assessment tool for remotely detecting local computer vulnerabilities
ActiveUS7096503B1Memory loss protectionUnauthorized memory use protectionRemote computerRisk evaluation
A system, method and computer program product are provided for remotely detecting vulnerabilities on a local computer. Initially, an agent is installed on a local computer for receiving encrypted commands from a remote computer utilizing a network. Next, the commands are decrypted and processed on the local computer utilizing the agent. A risk-assessment scan is then performed on the local computer utilizing the agent in accordance with the processed commands for the purpose of remotely detecting local vulnerabilities on the local computer.
Owner:MCAFEE LLC
Systems and methods for obtaining payor information at a point of sale
InactiveUS20050125295A1Slow processKeep their service fees lowPaper-money testing devicesPoint-of-sale network systemsBank accountCheque
Systems and methods are described for using a point-of-sale device to obtain information about a payor of a second-party check or other negotiable instrument presented for a proposed check-cashing transaction. In various embodiments, a keyboard, touchscreen, voice input system or other input system is used to enter information about a payor of a second-party check, which may comprise, for example, payor name, payor bank account identifier, payor location information, and the like. The payor information may be used to determine the proximity of the payor to the location of the proposed check-cashing transaction. In various embodiments, the point-of-sale device transmits the payor information to a check authorization system for a risk assessment of the transaction. In some embodiments, the point-of-sale device may prompt an operator or a check presenter to enter payor information in response to a request from the check authorization system. In various embodiments, the point-of-sale device may receive an accept / decline recommendation for the transaction from the check authorization system, based at least in part on the obtained payor information.
Owner:FIRST DATA
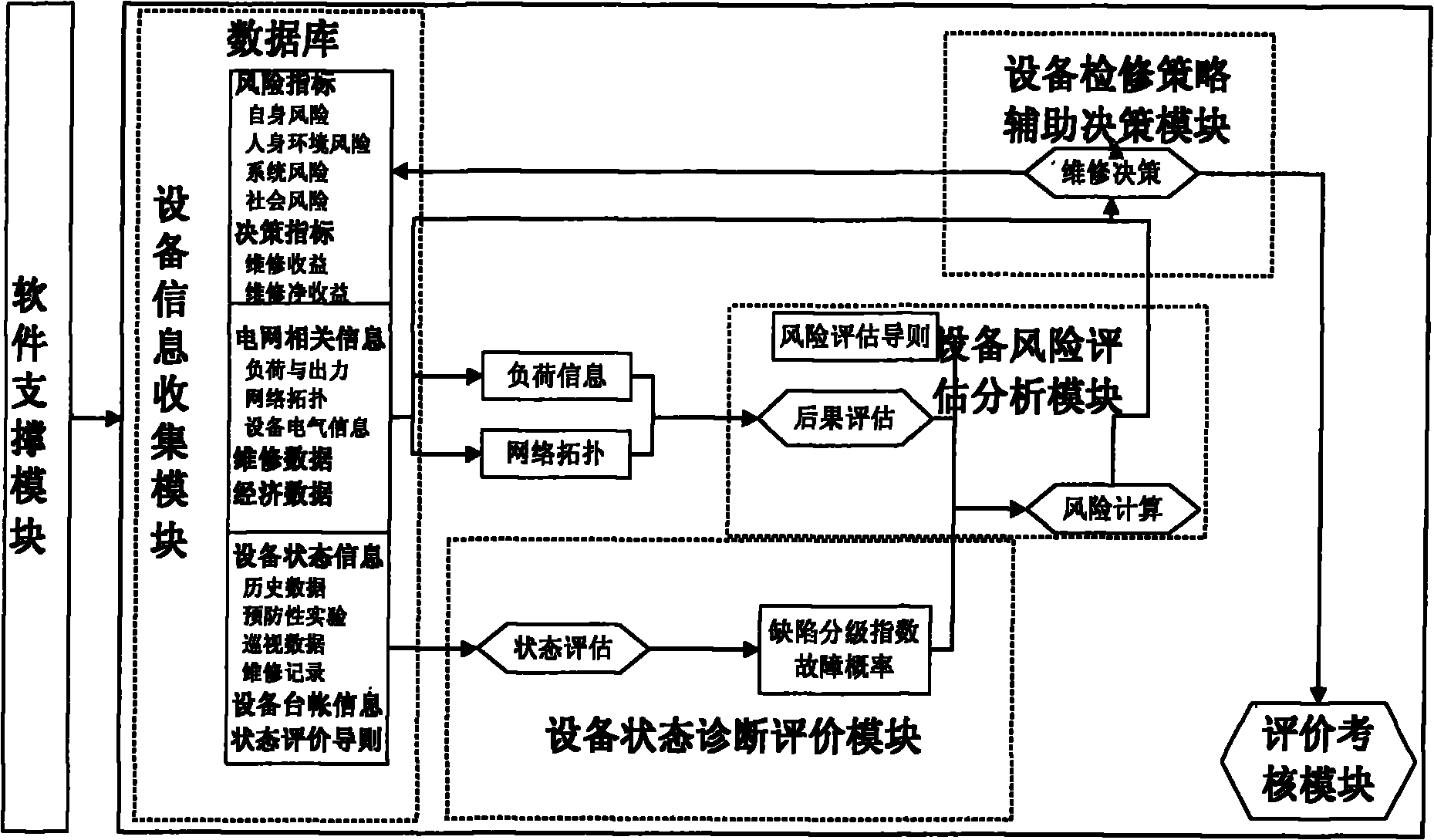
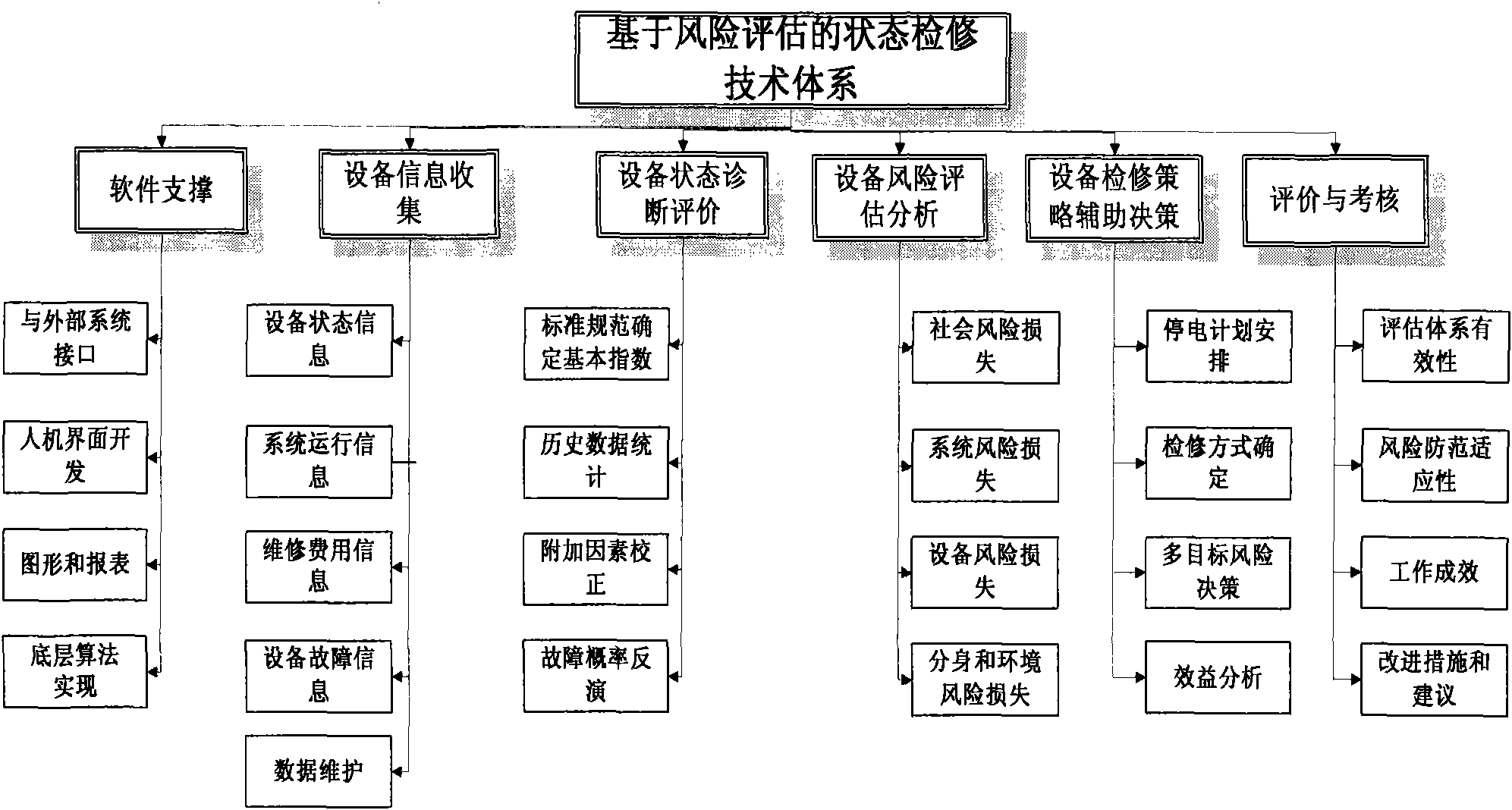
Power transmission and transformation equipment state overhauling system based on risk evaluation
InactiveCN101859409ARealize quantitative scientific evaluationAvoid influenceInstrumentsAc network circuit arrangementsData informationPower grid
The invention discloses a power transmission and transformation equipment state overhauling system based on risk evaluation. The system consists of a software supporting module, an equipment information collecting module, an equipment state diagnosing and evaluating module, an equipment risk evaluating and analyzing module, an equipment overhauling strategy auxiliary decision making module and an evaluating and checking module. The six modules are sequentially connected and mutually supported from bottom to top to form a pyramid type decision making flow path. The invention implements one set of complete system on the data information and equipment maintenance of a power network, makes a dynamic, timely, high-reliability and economic maintenance plan for the power transmission and transformation equipment under the condition of carrying out quantitative calculation on risks, greatly reduces the unnecessary maintenance, decreases the equipment damage caused by maintenance, saves the maintenance and management cost, and enhances the reliability of the power network.
Owner:ELECTRIC POWER RES INST OF GUANGXI POWER GRID CO LTD +1
Driver Risk Assessment System and Method Employing Selectively Automatic Event Scoring
ActiveUS20100191411A1Robust and reliable event scoringRobust and reliable and reportingVehicle testingRegistering/indicating working of vehiclesDriver/operatorEngineering
A Driver Risk Assessment System and Method Employing Selectively Automatic Event Scoring. The system and method provides robust and reliable event scoring and reporting, while also optimizing data transmission bandwidth. The system includes onboard vehicular driving event detectors that record data related to detected driving events, selectively store or transfer data related to said detected driving events. If elected, the onboard vehicular system will score a detected driving event, compare the local score to historical values previously stored within the onboard system, and upload selective data or data types to a remote server or user if the system concludes that a serious driving event has occurred. The system may further respond to independent user requests by transferring select data to said user at a variety of locations and formats.
Owner:DRIVECAM
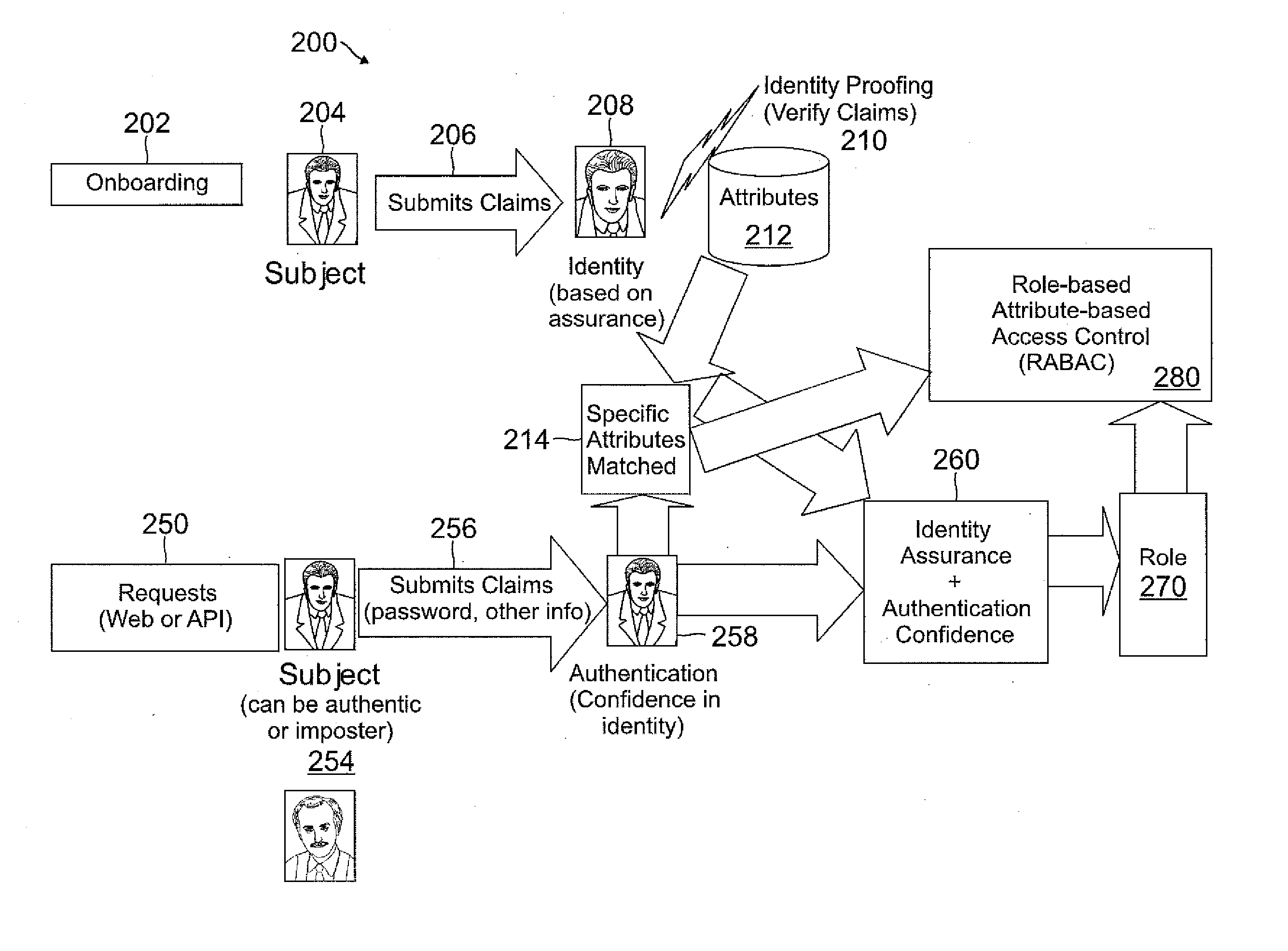
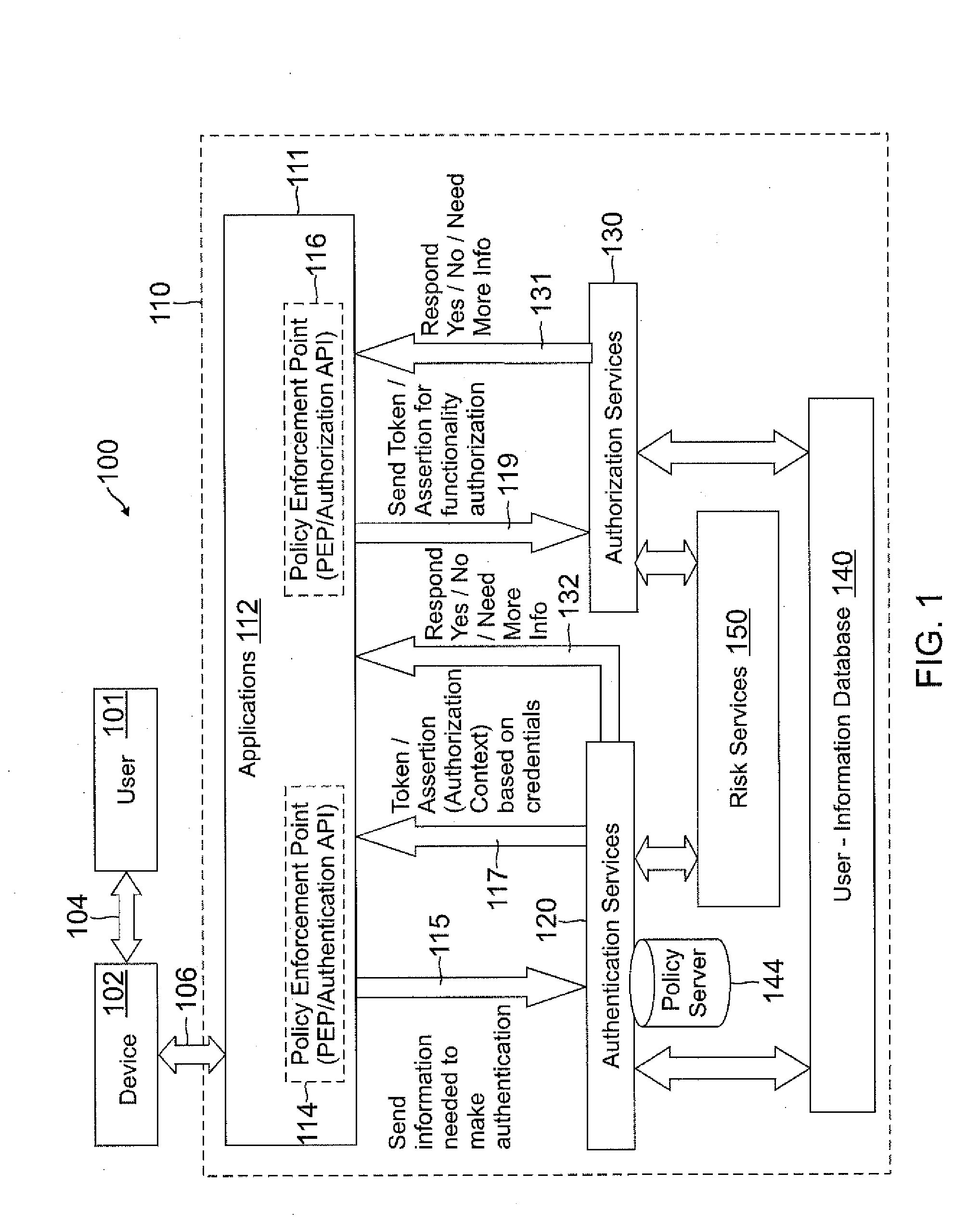
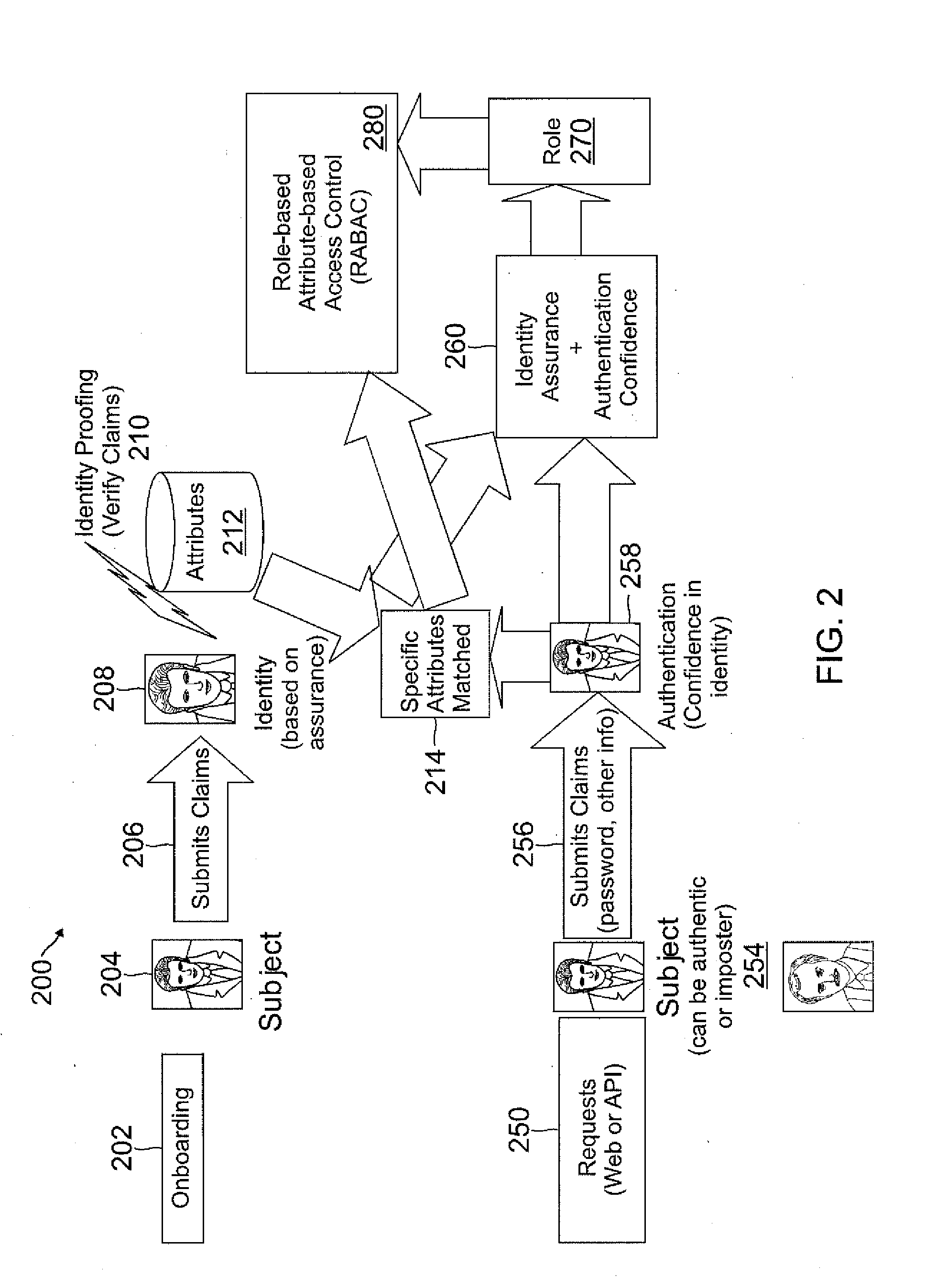
Role-based attribute based access control (RABAC)
ActiveUS20120060207A1Enhanced access control securityConvenient access controlDigital data processing detailsDigital data protectionUser deviceMedia access control
Systems and methods are disclosed for receiving an access request from a user device, the access request including an identity claim for a user; evaluating a risk of access based on matching an attribute of the user device with attributes stored in a user information database; authenticating the access request based on the identity claim and the risk evaluation to determine an authentication confidence level; generating a token based on the confidence level and the attribute matched; producing an authorization response based on inputs from the token, a risk based access control, a role based access control, and an attribute based access control, in which the authorization response determines whether to allow access to a system, deny access to the system, or request additional input from the user device.
Owner:PAYPAL INC
Gaming device having risk evaluation bonus round
InactiveUS20050130729A1Increase valueCard gamesApparatus for meter-controlled dispensingEngineeringRisk evaluation
Owner:IGT
Systems and methods for underwriting loans
Systems and methods are disclosed for underwriting loans. Some embodiments increase the likelihood of repayment by obtaining access to a qualified attribute of a borrower by a first computer component, monitoring by a second computer component for a financial event associated with the loan to the borrower, and taking control of the qualified attribute of the borrower by a third computer component. Taking control may include notifying social contacts. Securing the loan by taking various security interests and technical countermeasures against the borrower re-obtaining access or re-taking control are disclosed. Providing loans, receiving loan applications, providing loans proceeds, processing payments, and underwriting criteria are disclosed. Underwriting employing social contacts for recommendations, loan guarantees, social contact credit scores, public repayment promises, loan repayment coaches, fraud criteria, crowdsourced risk evaluation, social graphs, borrower stability factors derived from social graphs, data associated with online information repositories, and efficacy of notification are disclosed.
Owner:SOCIOGRAMICS
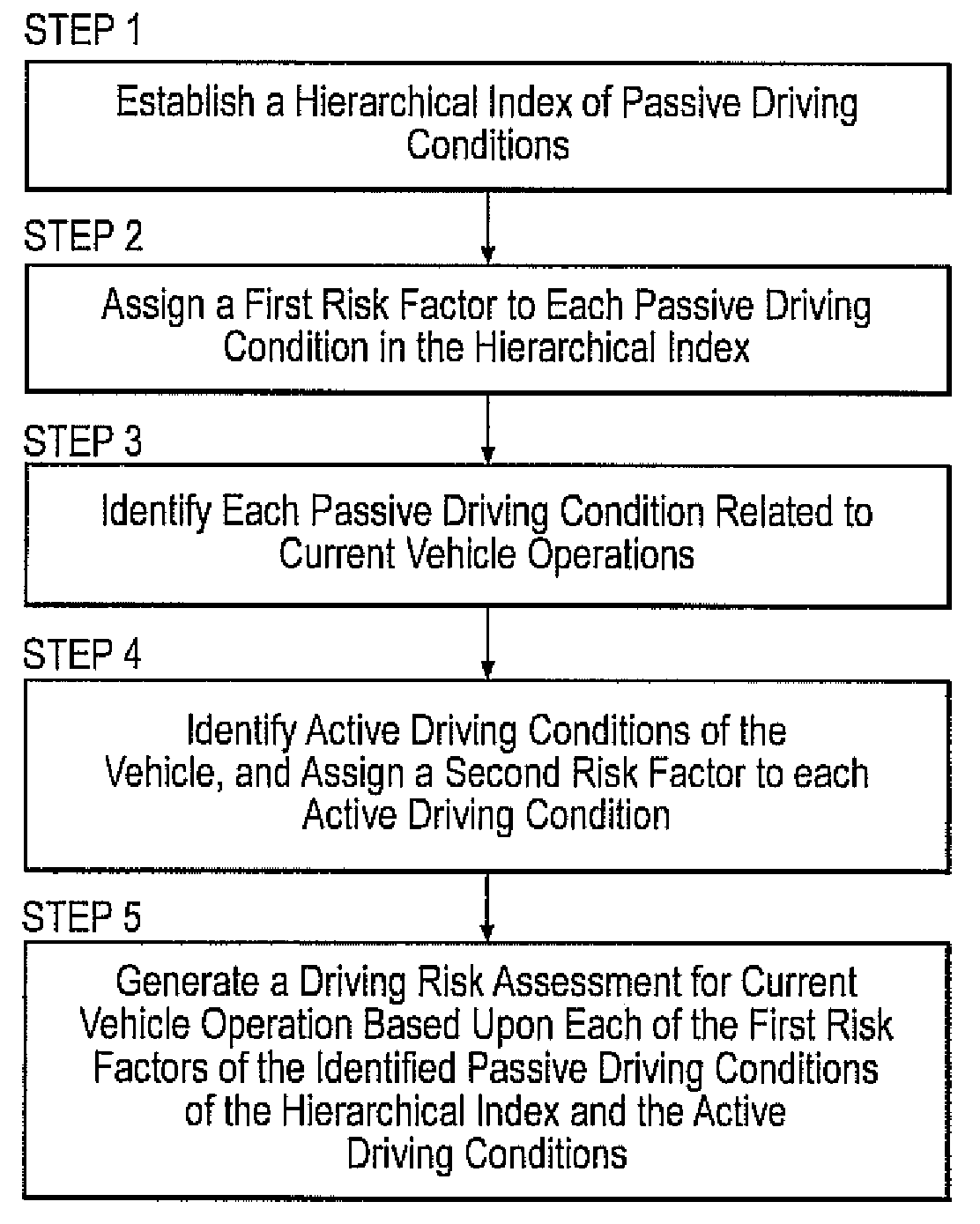
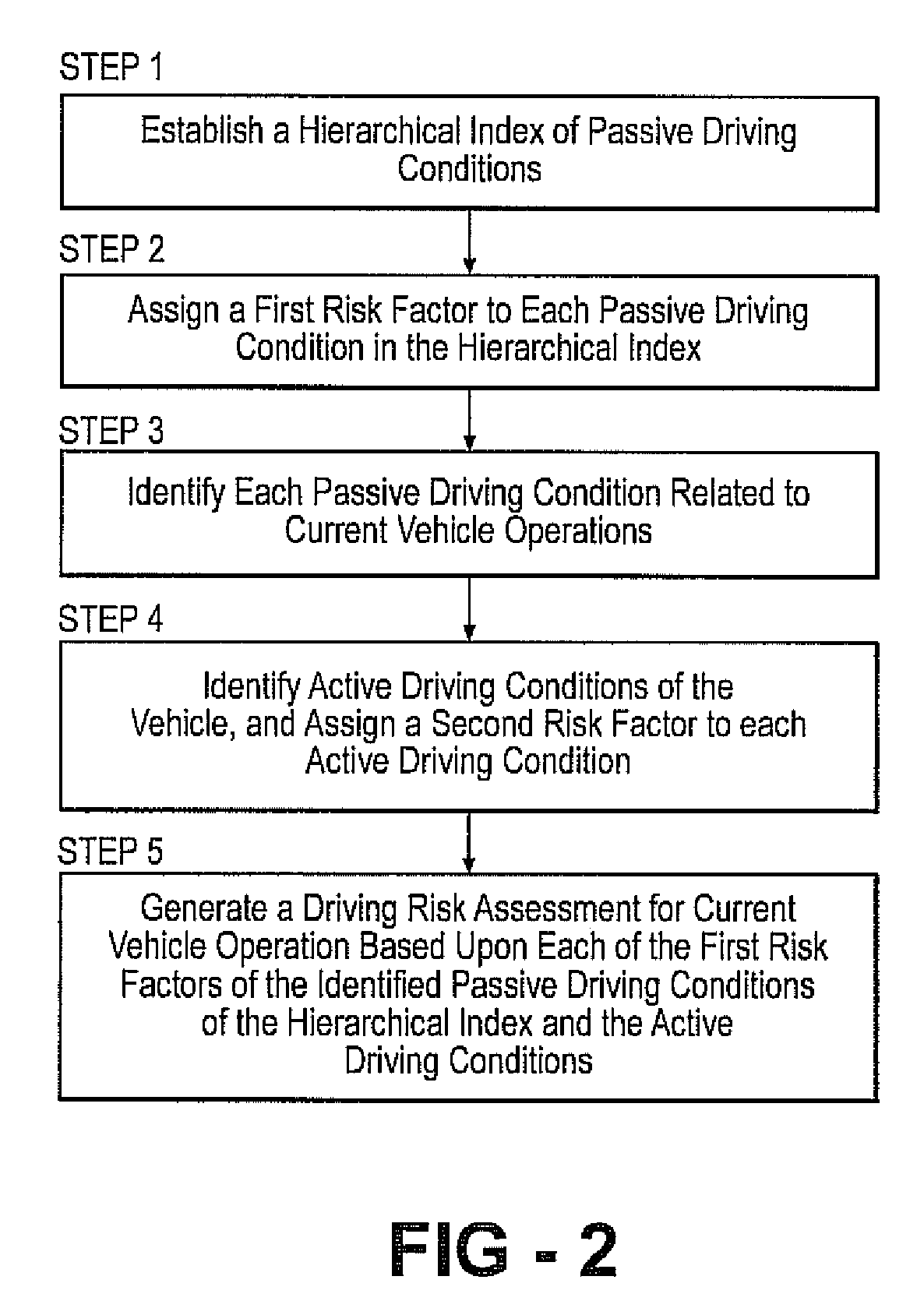
Method and system to estimate driving risk based on a heirarchical index of driving
A system and method for providing driving risk assessment for a host vehicle equipped with on-board sensors or vehicle-to-vehicle or infrastructure-to-vehicle systems. The system includes a hierarchical index of passive driving conditions, a means of collecting active driving conditions and a processor whereby the sum of passive driving conditions may be further refined by the active driving conditions The method incorporates a hierarchical index of risks associated with passive driving conditions, and refining said risks with active driving conditions of the vehicle to generating a driving risk assessment for current vehicle operation.
Owner:TOYOTA MOTOR CO LTD
Method and apparatus for obtaining data from vendors in real time
InactiveUS6584467B1FinanceMultiple digital computer combinationsComputer networkApplication software
A system and method of controlling a computer network to obtain information needed to render risk evaluative decisions from vendors in real time. The information may be obtained for agents preparing insurance applications or for an automated application processing system. Agents or automated application processing systems require access to an external vendor to obtain information about a customer, such as car accident or credit records. The request for data must be formatted to be read by the vendor system, which sends the responding data in real time. This responding data is forwarded to the requesting party for further processing of the application.
Owner:ALLSTATE INSURANCE
Internet security dynamics assessment system, program product, and related methods
ActiveUS20100100962A1Prevent malicious attacksLimited accessMemory loss protectionDigital data processing detailsIp addressThe Internet
Systems, program product, and methods related to dynamic Internet security and risk assessment and management, are provided. For example, a system, program product, and method of identifying and servicing actual customer requests to a defended or protected computer or server can include the steps / operations of receiving by the defended computer, a service request from each of a plurality of IP addresses associated with a separate one of a plurality of service requesting computers, sending an inspection code adapted to perform a virtual attack on each existing service requesting computers at each respective associated IP address, and restricting provision of services from the defended computer to a subset of the service requesting computers identified for restriction when a security feature of the respective service requesting computer is determined to have been defeated by the virtual attack.
Owner:LOCKHEED MARTIN CORP
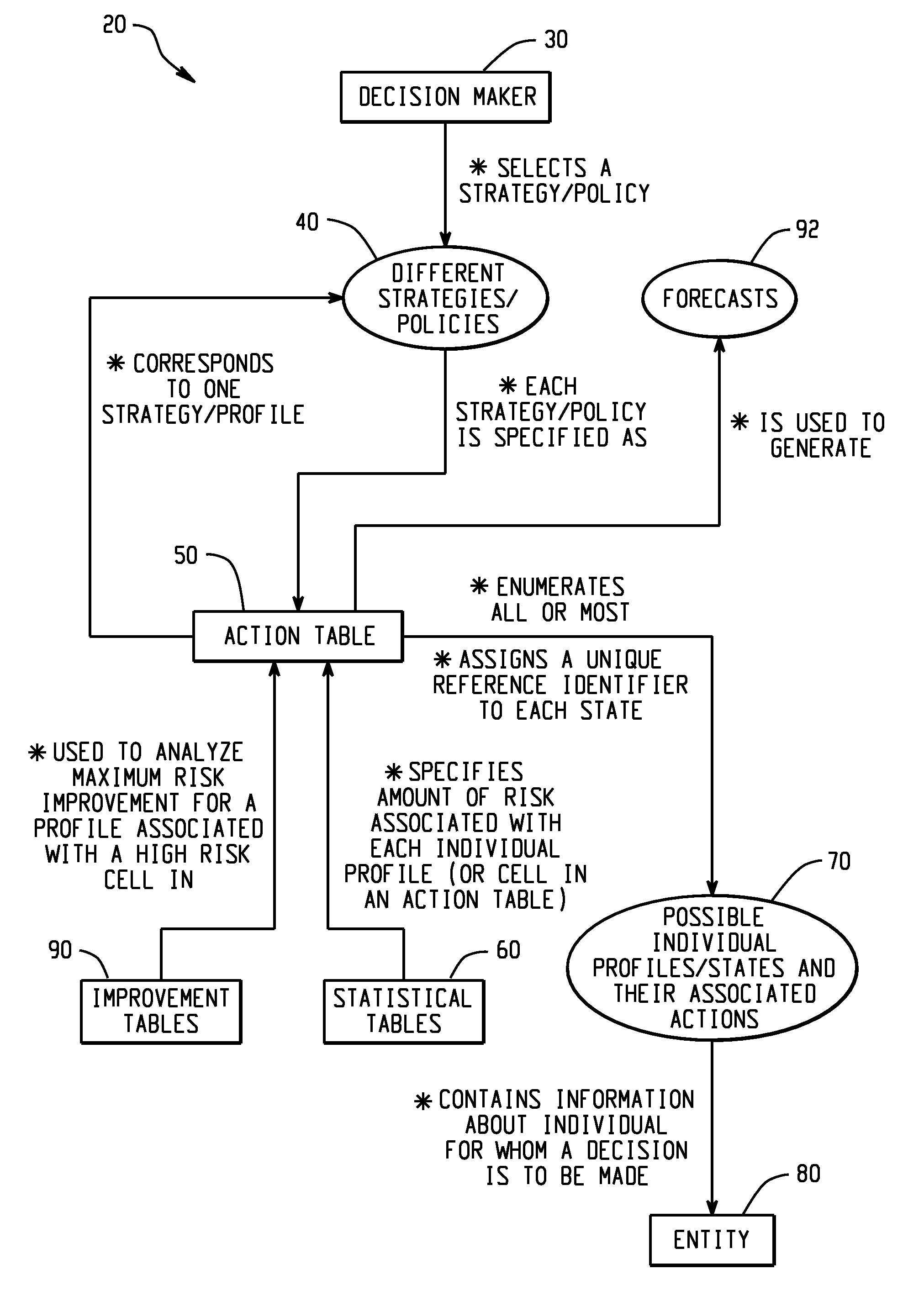
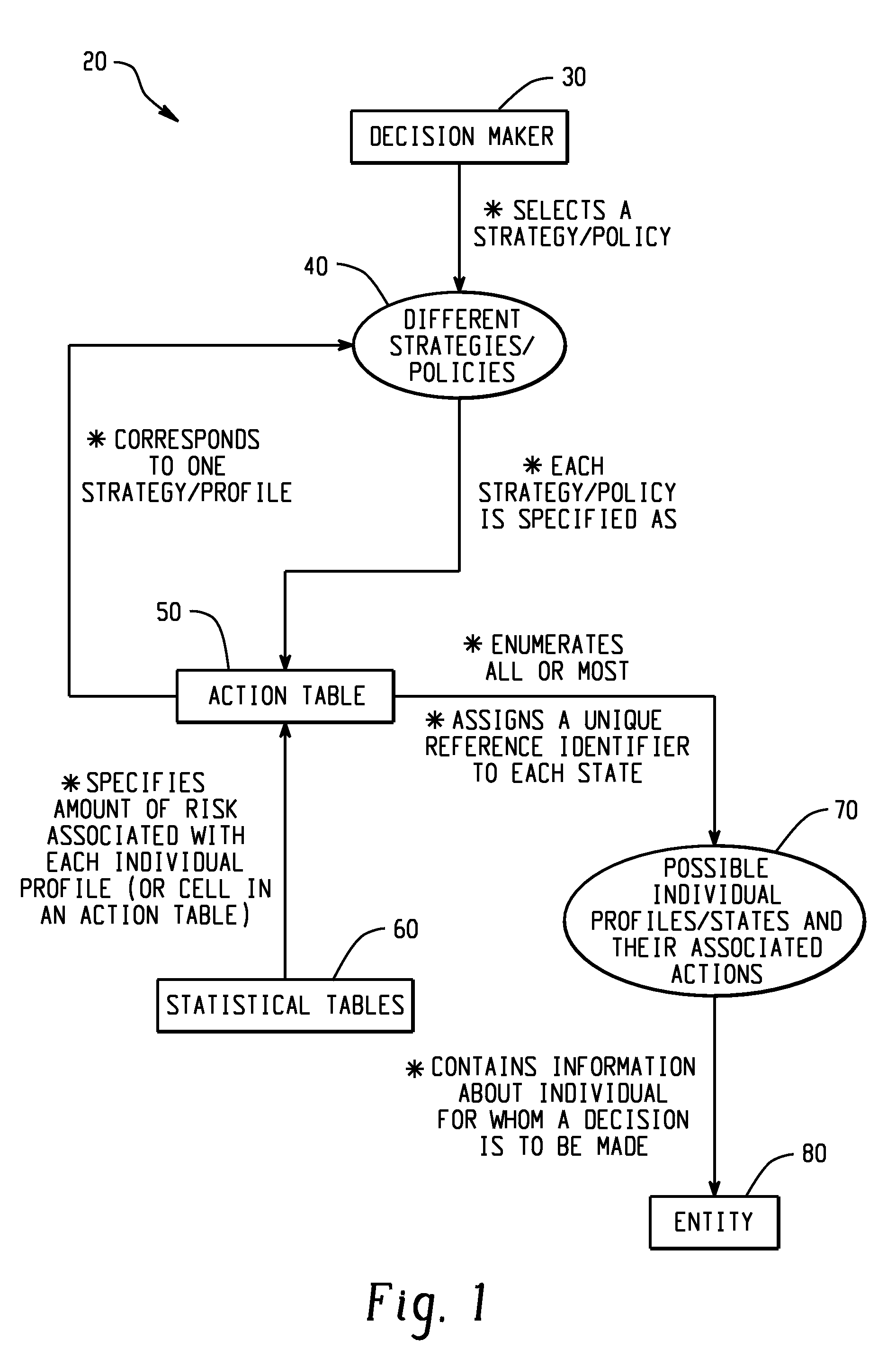
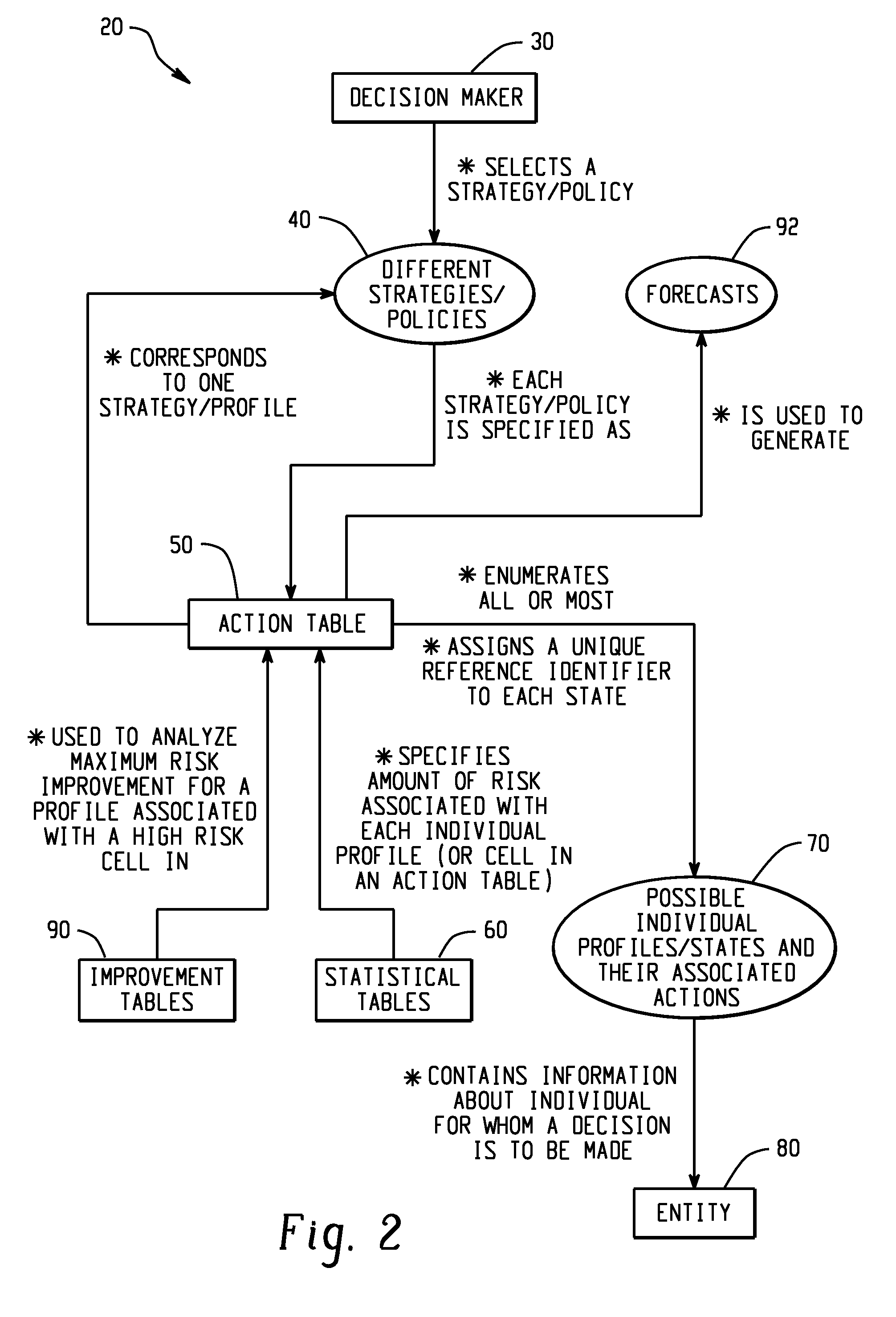
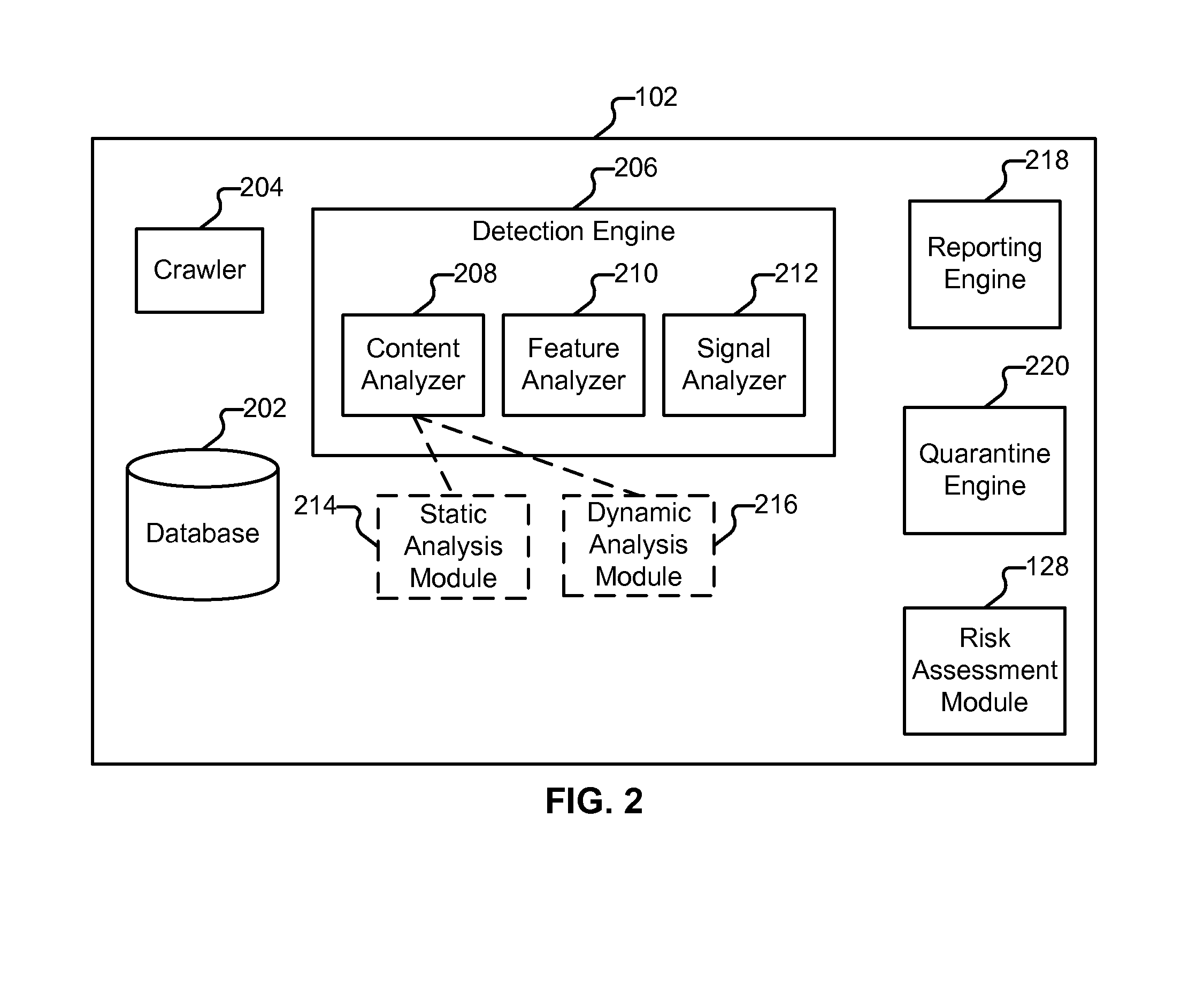
Computer-implemented risk evaluation systems and methods
Computer-implemented systems and methods are disclosed herein that relate to processes, which construct an empirically derived and statistically based risk evaluation and policy formulation system. For example, a process can be configured so as to accept as input an information base in computer readable form and produce either a single or multistage system composed of alternative decision making strategies.
Owner:SAS INSTITUTE
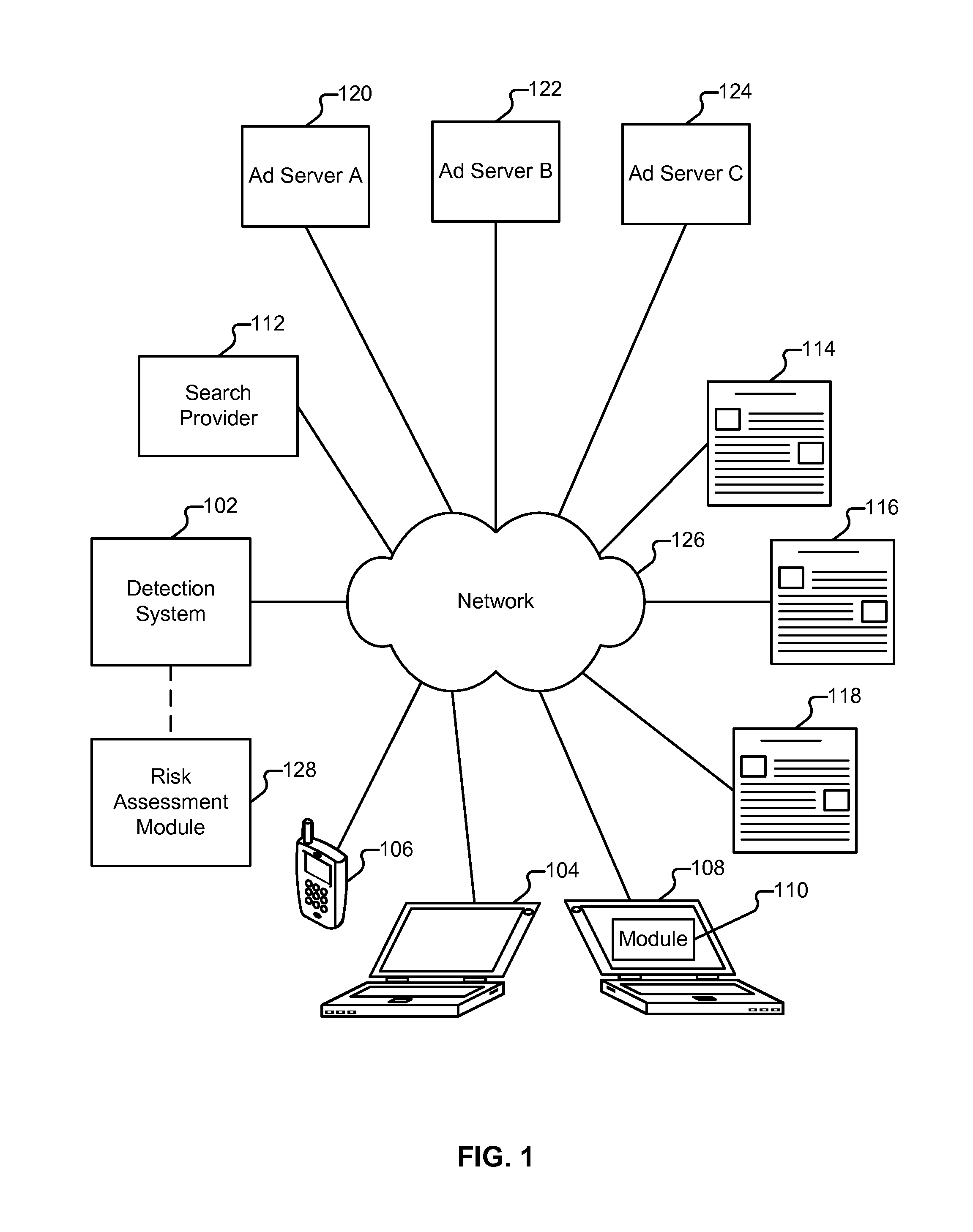
Risk assessment
Performing a risk assessment of a website is disclosed. A plurality of elements included in the website is categorized. The risk posed by the presence of at least some of the plurality of elements is assessed. Example elements include third party content and out-of-date web applications. A risk assessment report is provided as output.
Owner:DASIENT
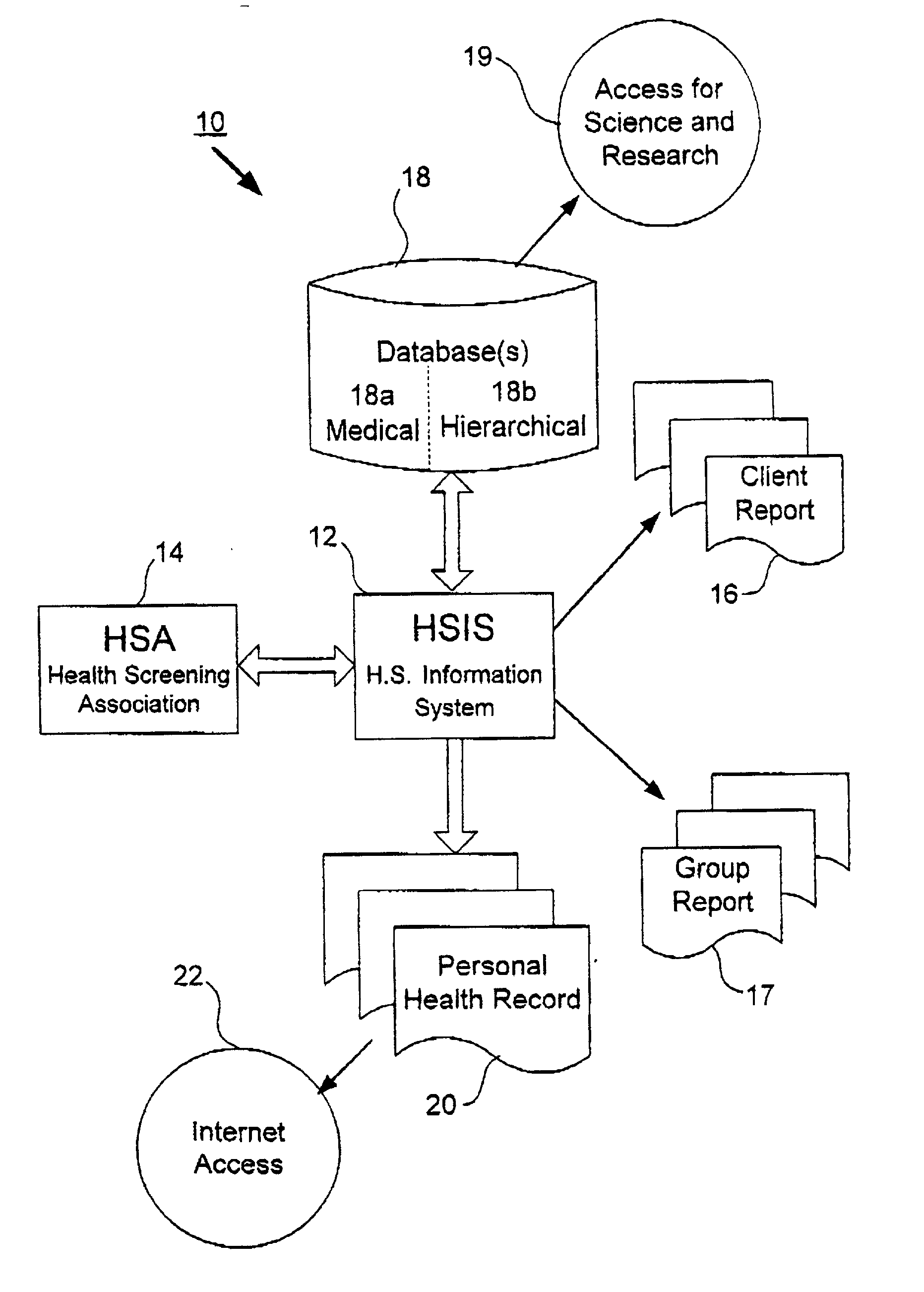
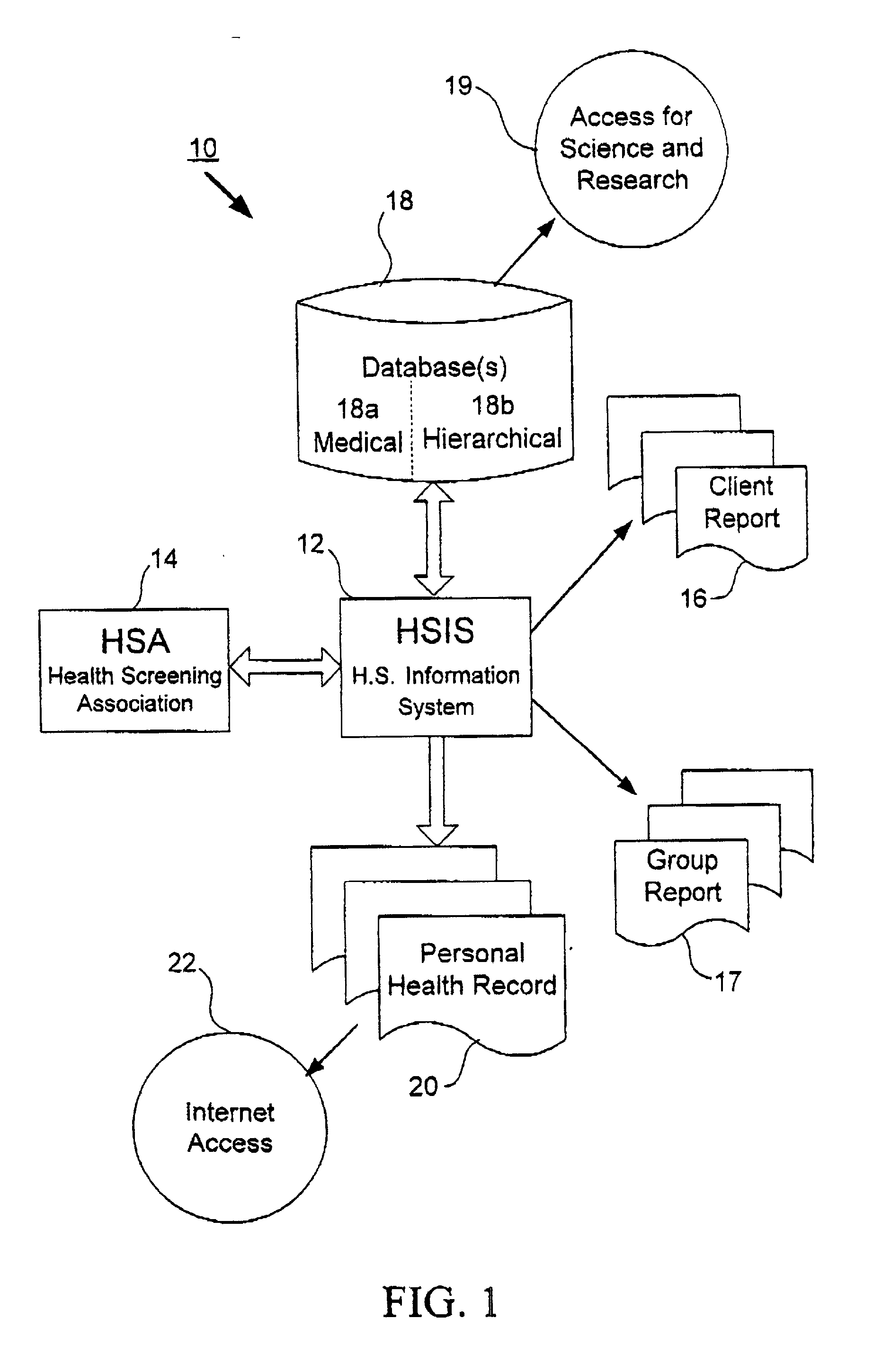
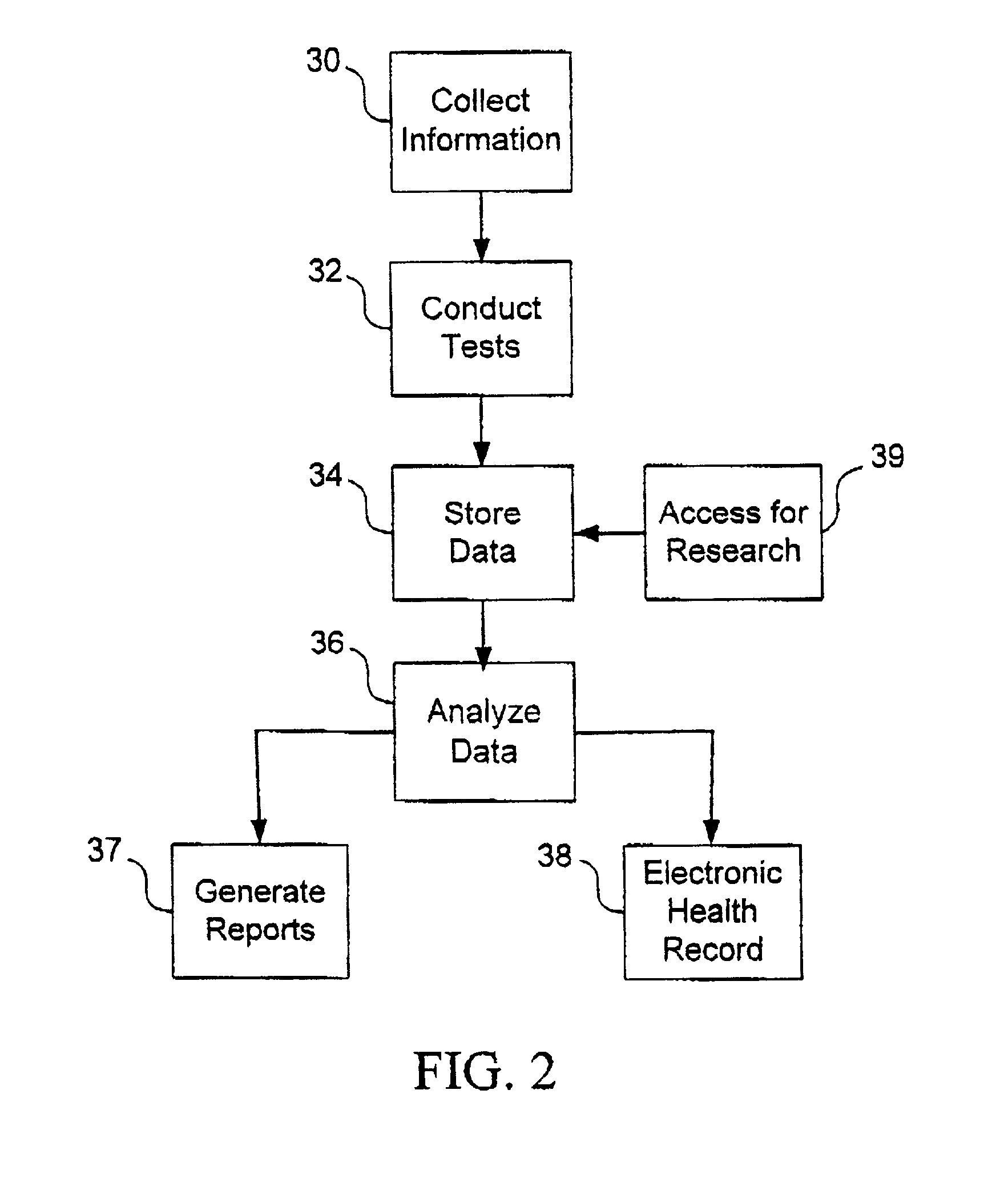
Method, system and computer program for health data collection, analysis, report generation and access
InactiveUS20030187688A1Easy maintenanceData processing applicationsHealth-index calculationClinical studyDemographic data
A health data management system is provided. Specifically, the invention includes a system and method for collecting screening, diagnostic, and demographic data from clients, processing and analyzing health data from health risk assessments and screening tests, generating custom reports, maintaining heath data, pre-populating data into user accessible personal health records and aggregate data for scientific research and clinical studies. The invention can be implemented in numerous ways, including as a system, a device, a method, or a computer readable medium.
Owner:HEALTHSCREEN INT
Credit risk evaluation with responsibility factors
ActiveUS8407139B1Ease of evaluationEasy to calculateFinanceUser identity/authority verificationEngineeringArticles of Agreement
A system, device, and method for calculating an enhanced credit score using insurance rating information, individual rating factors, interaction rating factors, geographic rating factors, vehicle monitoring rating factors, and / or credit risk information is disclosed. Insurance rating information, individual rating factors, interaction rating factors, geographic rating factors, and vehicle monitoring rating factors, either individually or in combinations, may be used as inputs to a novel credit-scoring model to calculate an enhanced or improved credit score. The novel credit-scoring model may be implemented in a computer-readable medium comprising computer-executable instructions for causing a computing device to calculate an enhanced credit score. The computer-executable instructions may be arranged into an input module, output module, and calculation module. The modules may be used to calculate an enhanced credit score that may be used by lending institutions and others to determine the terms of a financing agreement with a user.
Owner:ALLSTATE INSURANCE
Vehicle or traffic control method and system
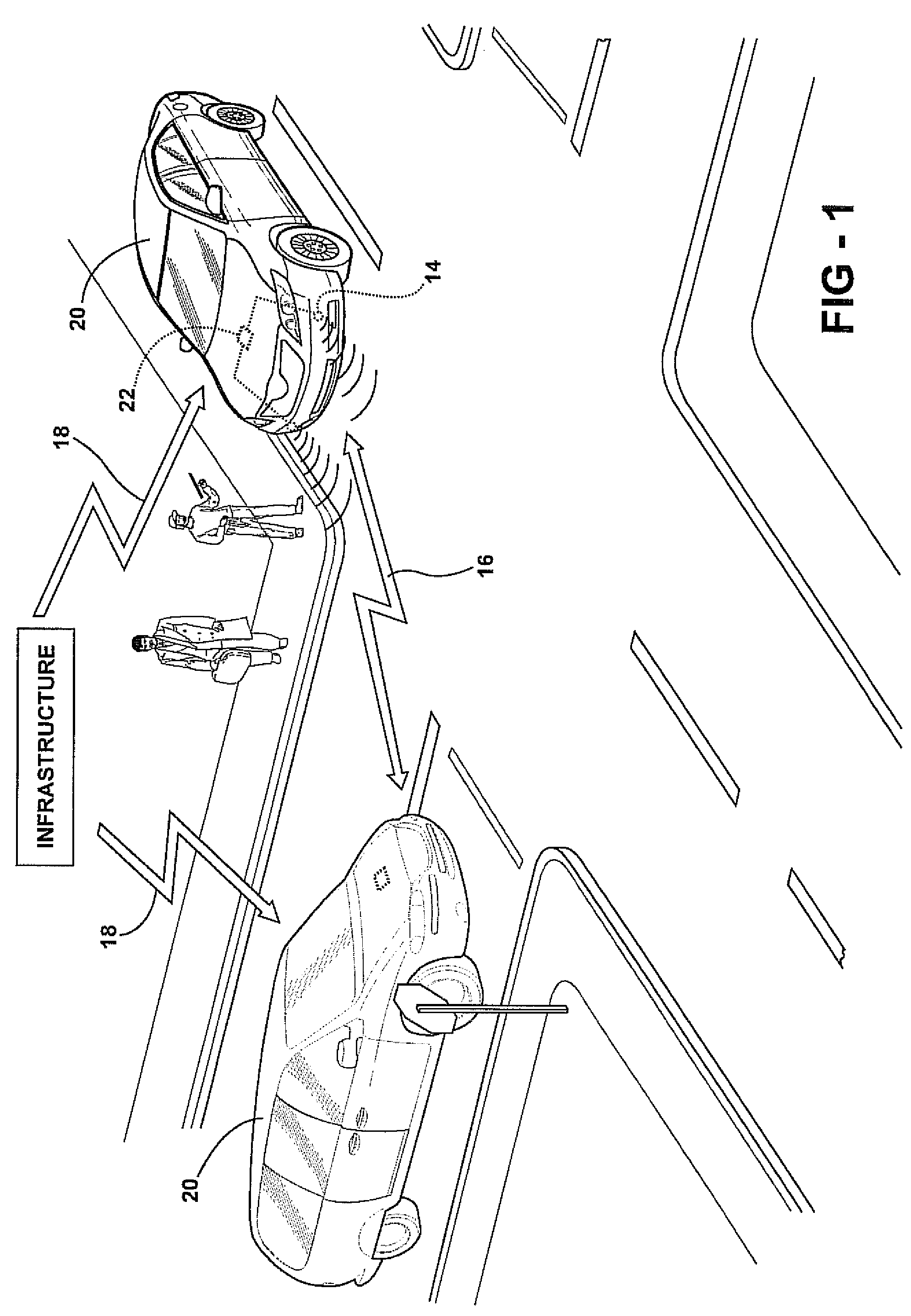
InactiveUS20120143488A1Accurate estimateSimple calculationAnti-collision systemsAutomatic initiationsTraffic capacityTime range
The invention relates to a vehicle or traffic control method and to a vehicle or traffic control system. The vehicle or traffic control method comprises the steps: a) estimating actual and / or future behavior of a first traffic participant and of a second traffic participant, respectively, the second traffic participant being different from the first traffic participant, b) estimating a trajectory to be taken by the first traffic participant and / or a trajectory to be taken by the second traffic participant, c) determining risk of collision of the first traffic participant relative to the second traffic participant by calculating information adapted for risk assessment of collision of the first traffic participant relative to the second traffic participant, and d) controlling the behavior of the first traffic participant based on the information provided after step a), step b) and / or step c). In this way a probability value is determined which indicates the plausibility that a vehicle or traffic participant might enter into collision within a certain time horizon in the future.
Owner:TOYOTA MOTOR EUROPE +1
Systems and methods for obtaining biometric information at a point of sale
InactiveUS20050125296A1Accurate descriptionSlow processPaper-money testing devicesPoint-of-sale network systemsBiometric dataCheque
Systems and methods are described for using a point-of-sale device to obtain biometric information from an individual presenting a second-party check in association with a proposed check-cashing transaction. In various embodiments, a biometric sample is obtained from the check presenter and is compared to stored biometric data in order to enhance an assessment of the correct identification of the check presenter. In various embodiments, the biometric information, along with other transaction-related information, such as information about one or more authentication marks from the check, is transmitted to a check authorization system for a risk assessment of the transaction. In various embodiments, the point-of-sale device may receive an accept / decline recommendation from the check authorization system, based at least in part on the biometric information and may display a message about the recommendation to an operator of the point-of-sale device.
Owner:THE WESTERN UNION CO +1
Price and risk evaluation system for financial product or its derivatives, dealing system, recording medium storing a price and risk evaluation program, and recording medium storing a dealing program
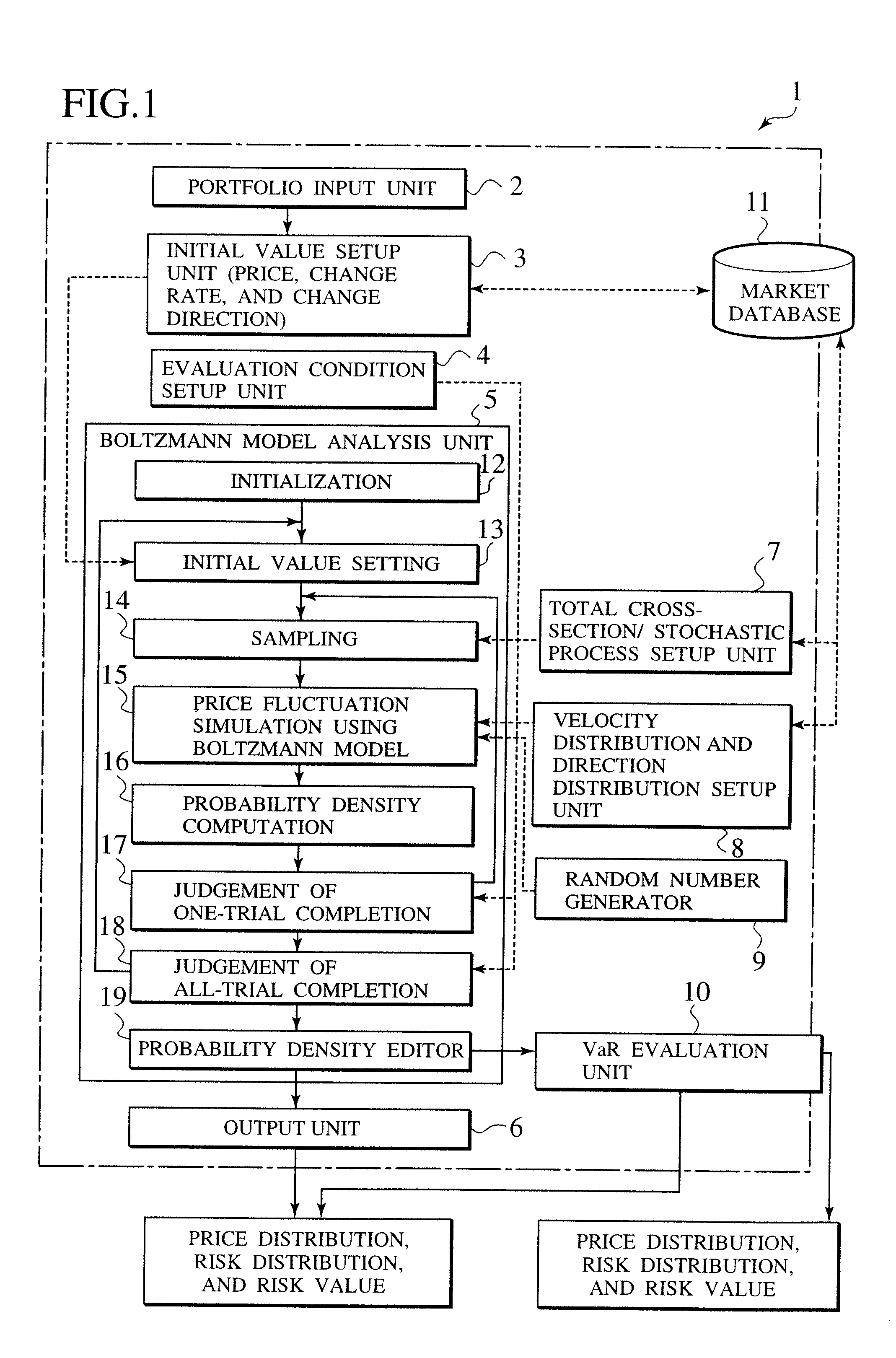
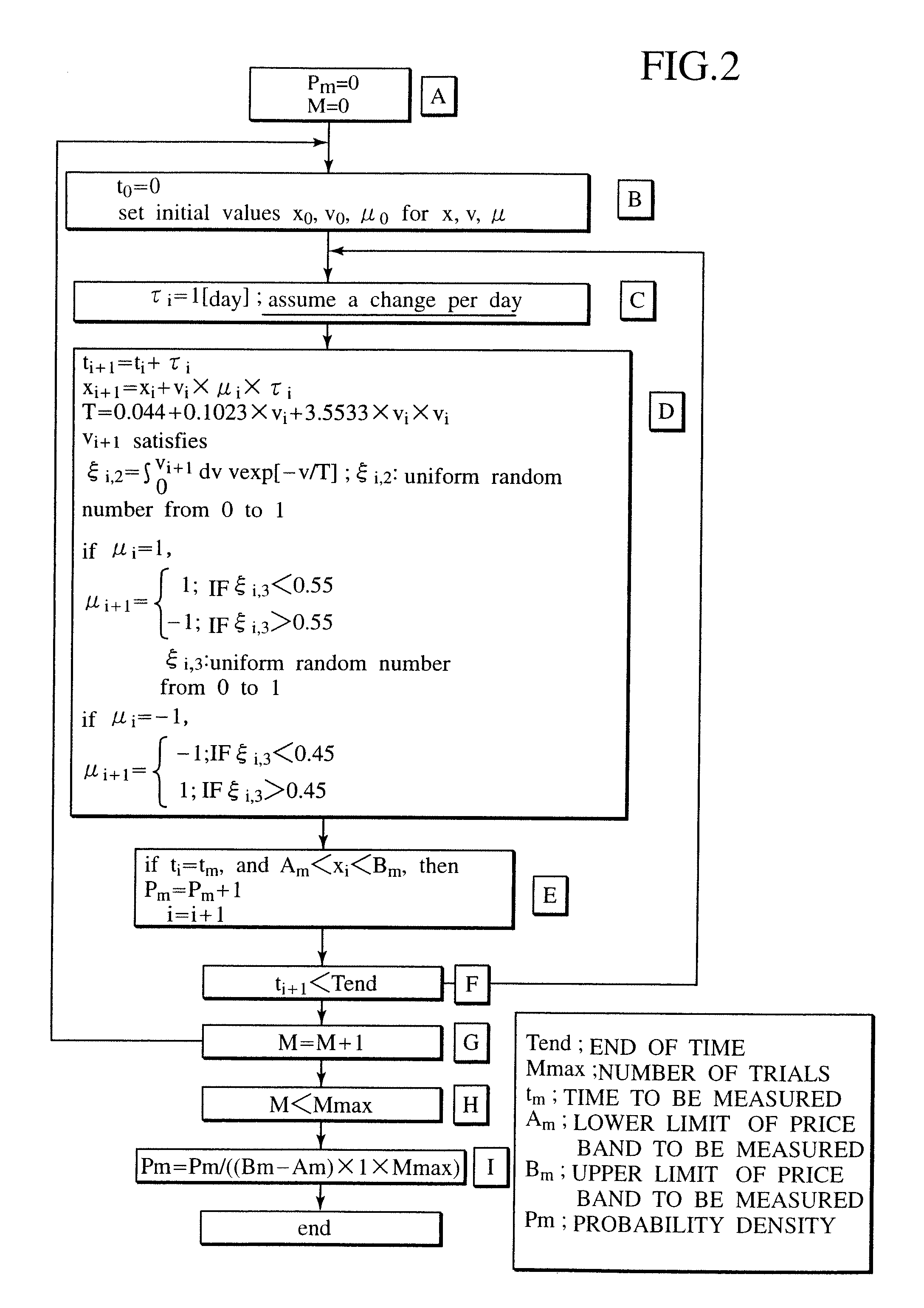
A system for correctly evaluating a price distribution and a risk distribution for a financial product or its derivatives introduces a probability density function generated with a Boltzmann model at a higher accuracy than the Gaussian distribution for a probability density. The system has an initial value setup unit and an evaluation condition setup unit. Initial values include at least one of price, price change rate, and the price change direction of a financial product. The evaluation conditions include at least time steps and the number of trials. The Boltzmann model analysis unit receives the initial values and the evaluation conditions, and repeats simulations of price fluctuation, based on the Boltzmann model using a Monte Carlo method. A velocity / direction distribution setup unit supplies the probability distributions of the price, price change rate, and the price change direction for the financial product to the Boltzmann model analysis unit. A random number generator for a Monte Carlo method employed in the analysis by the Boltzmann model, and an output unit displays the analysis result. A dealing system applies the financial Boltzmann model to option pricing, and reproduces the characteristics of Leptokurcity and Fat-tail by linear Boltzmann equation in order to define risk-neutral and unique probability measures. Consequently, option prices can be evaluated in a risk-neutral and unique manner, taking into account Leptokurcity and Fat-tail of a price change distribution.
Owner:KK TOSHIBA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com