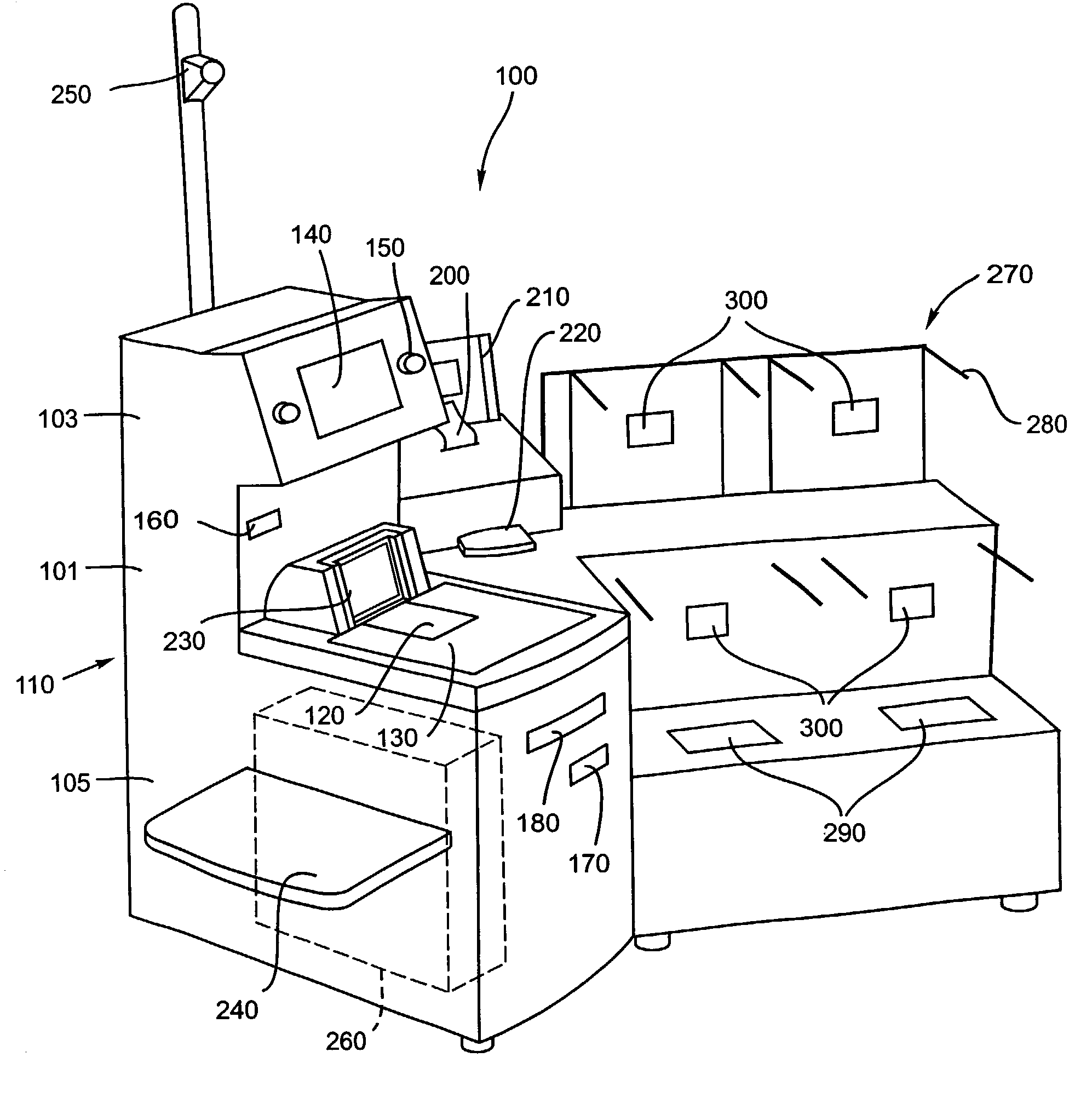
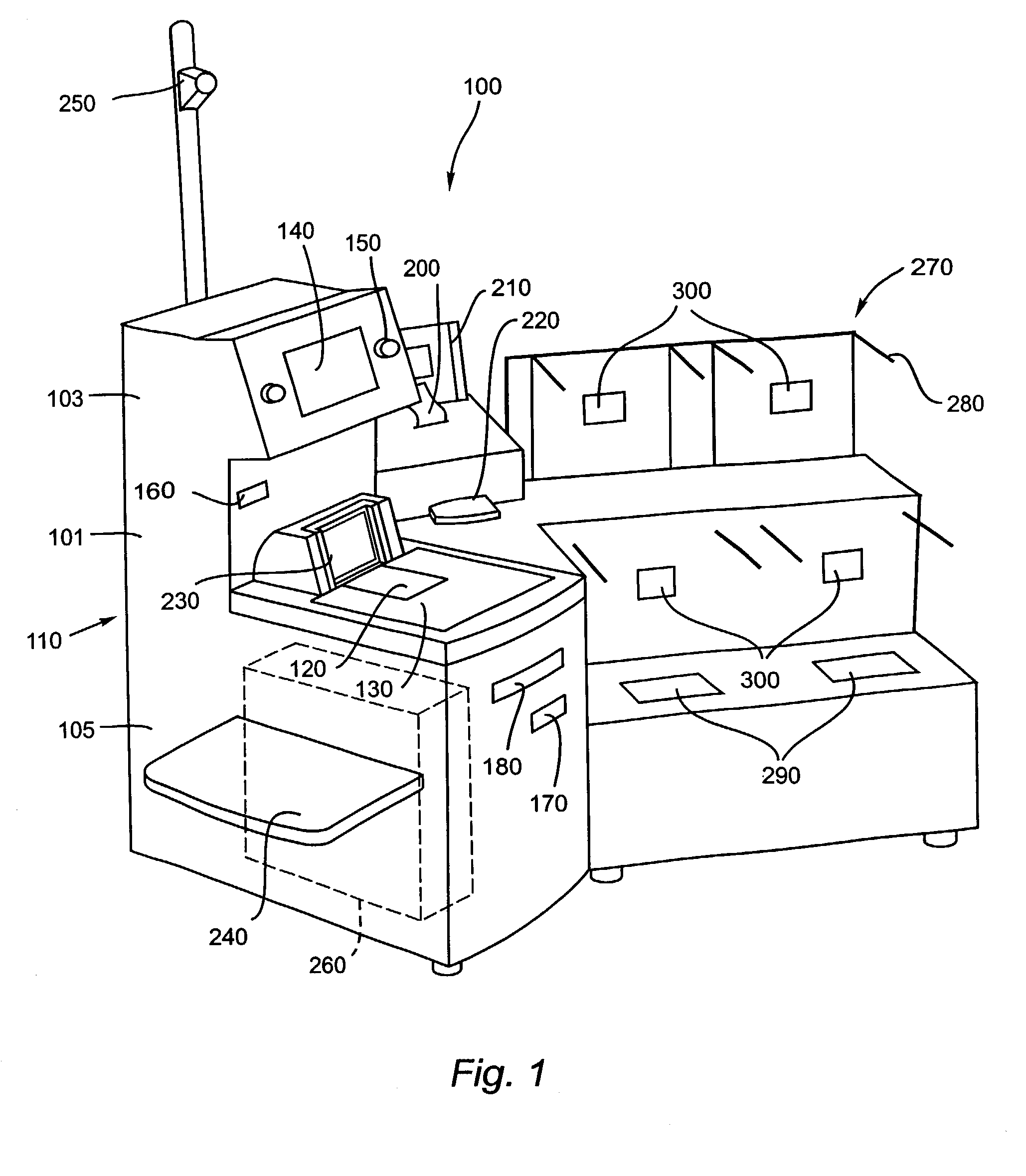
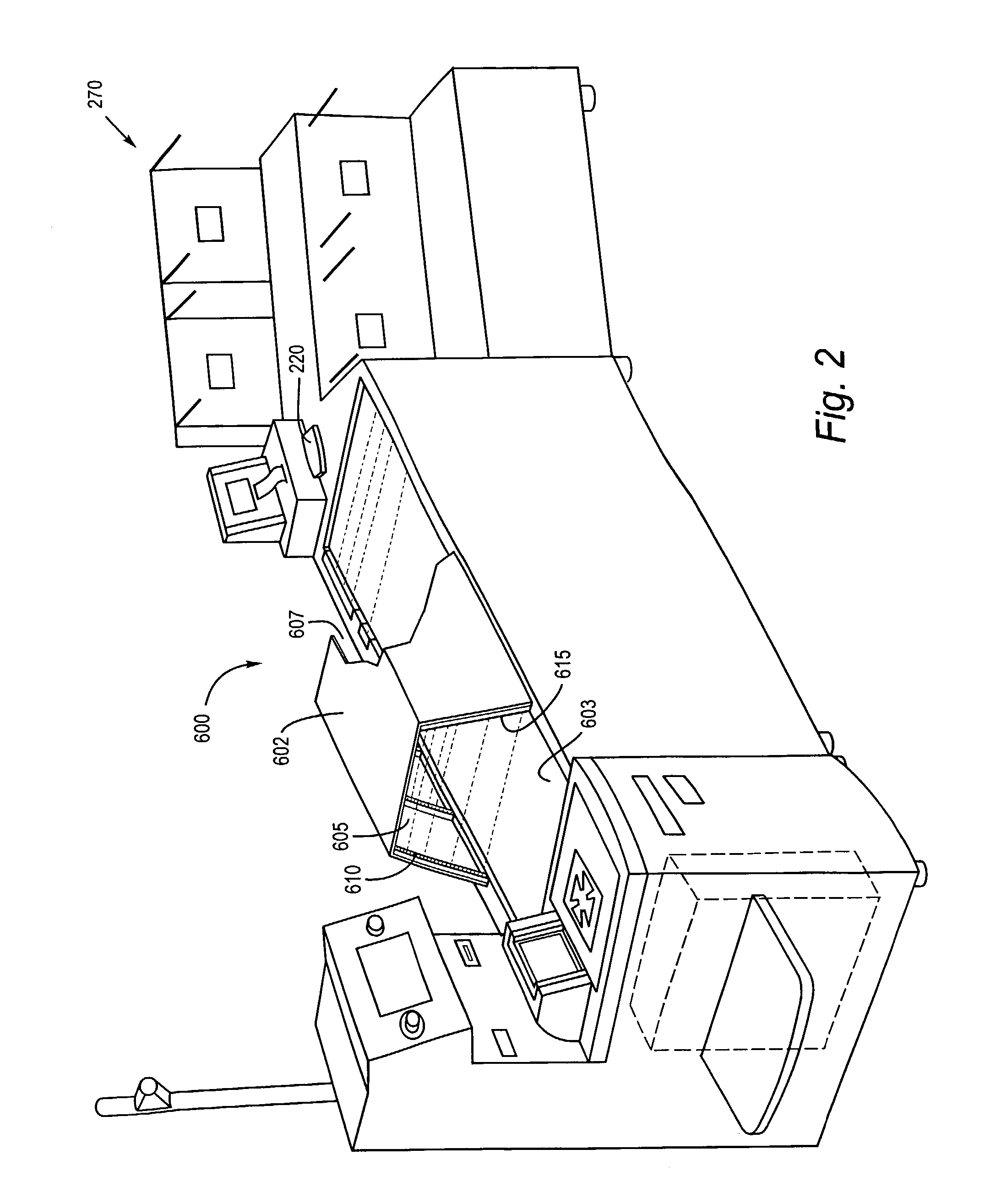
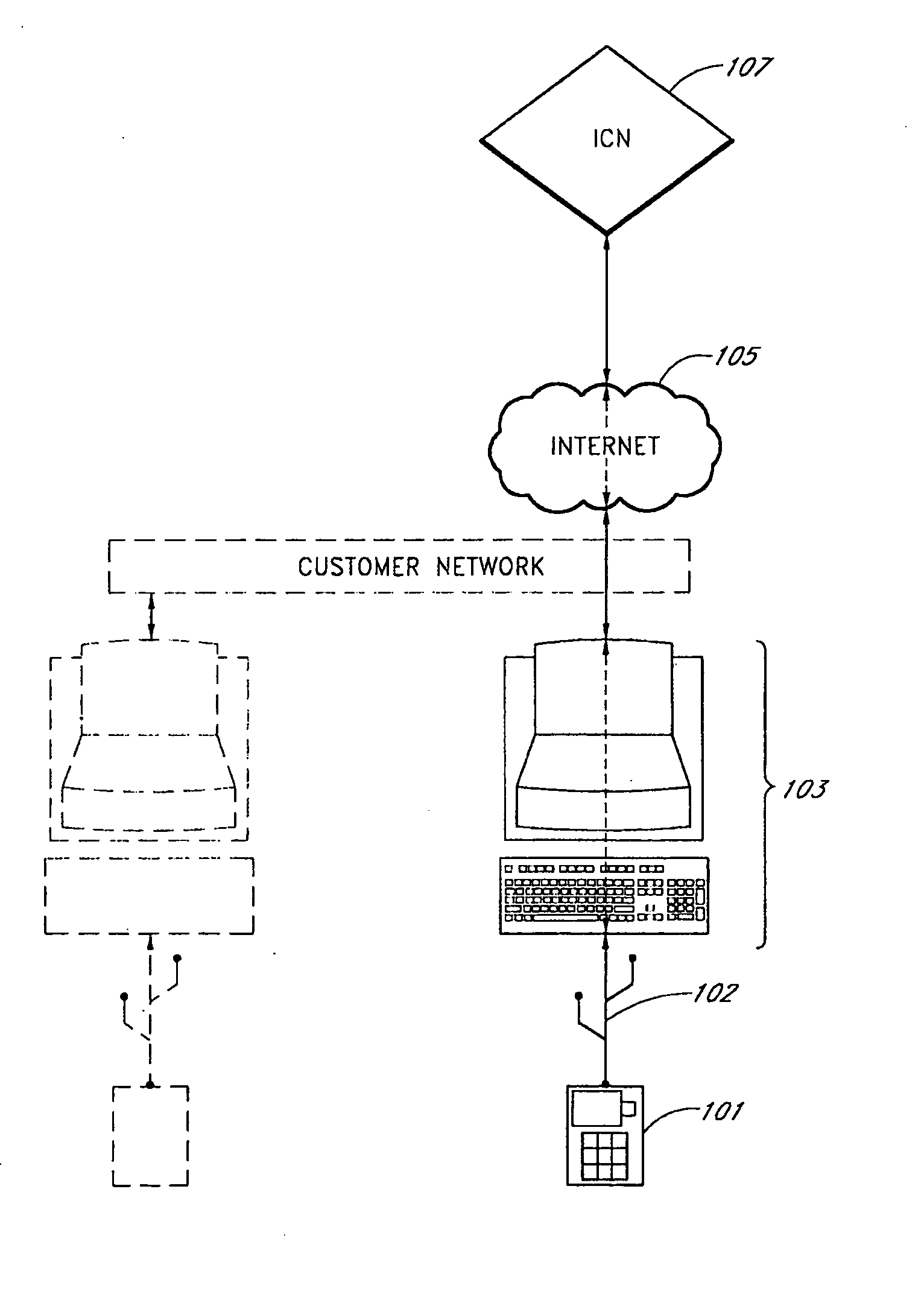
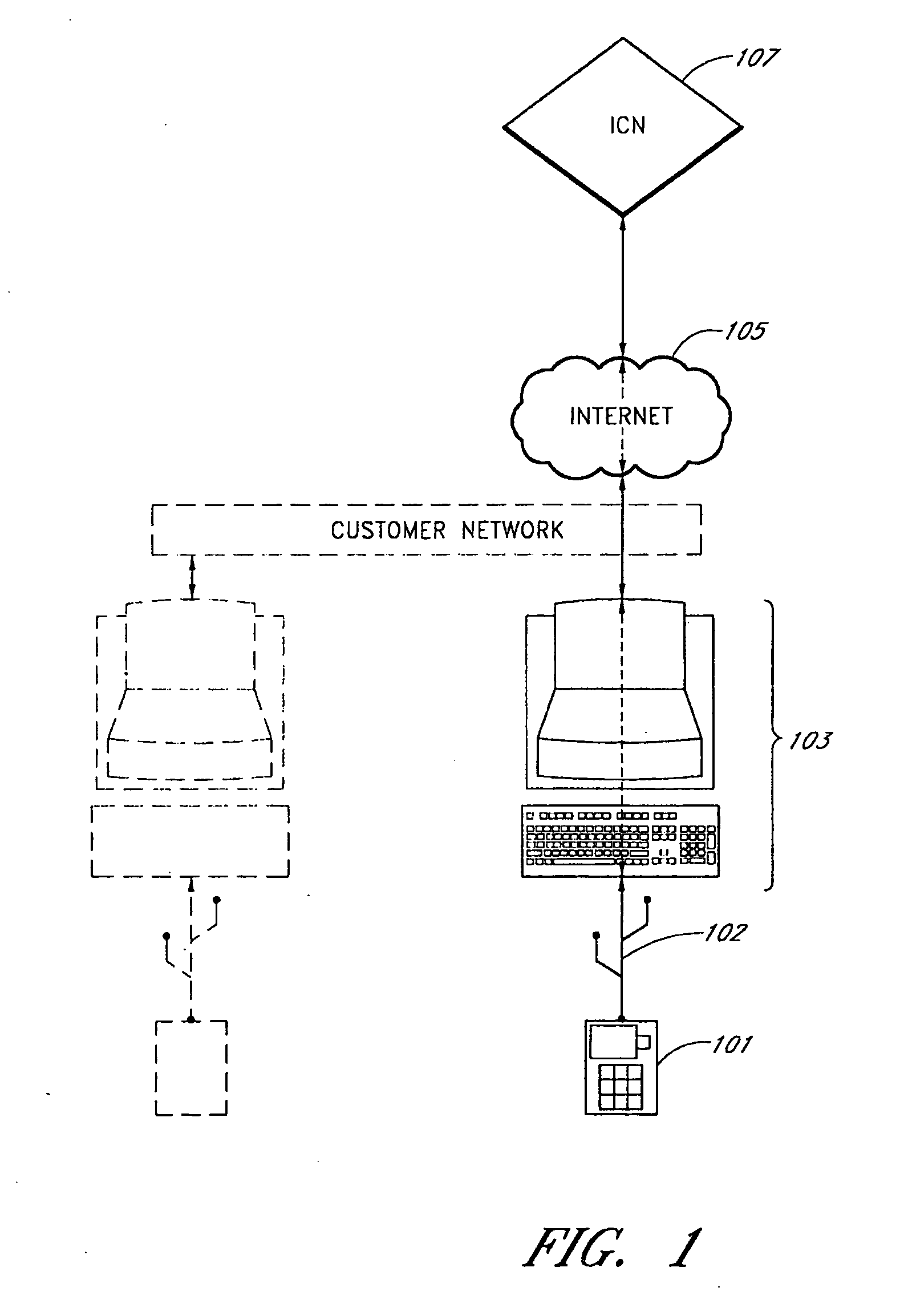
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
991 results about "Security validation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
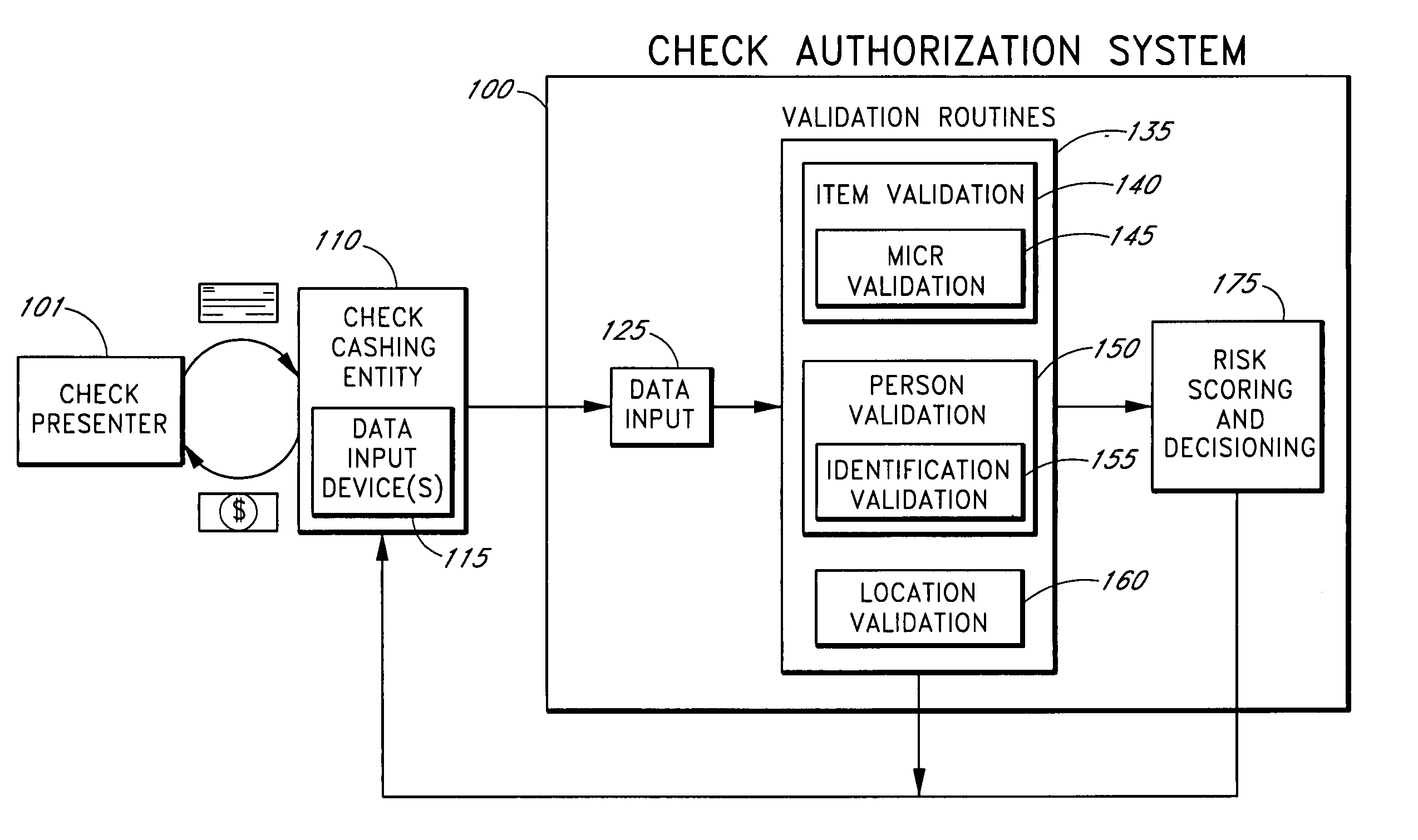
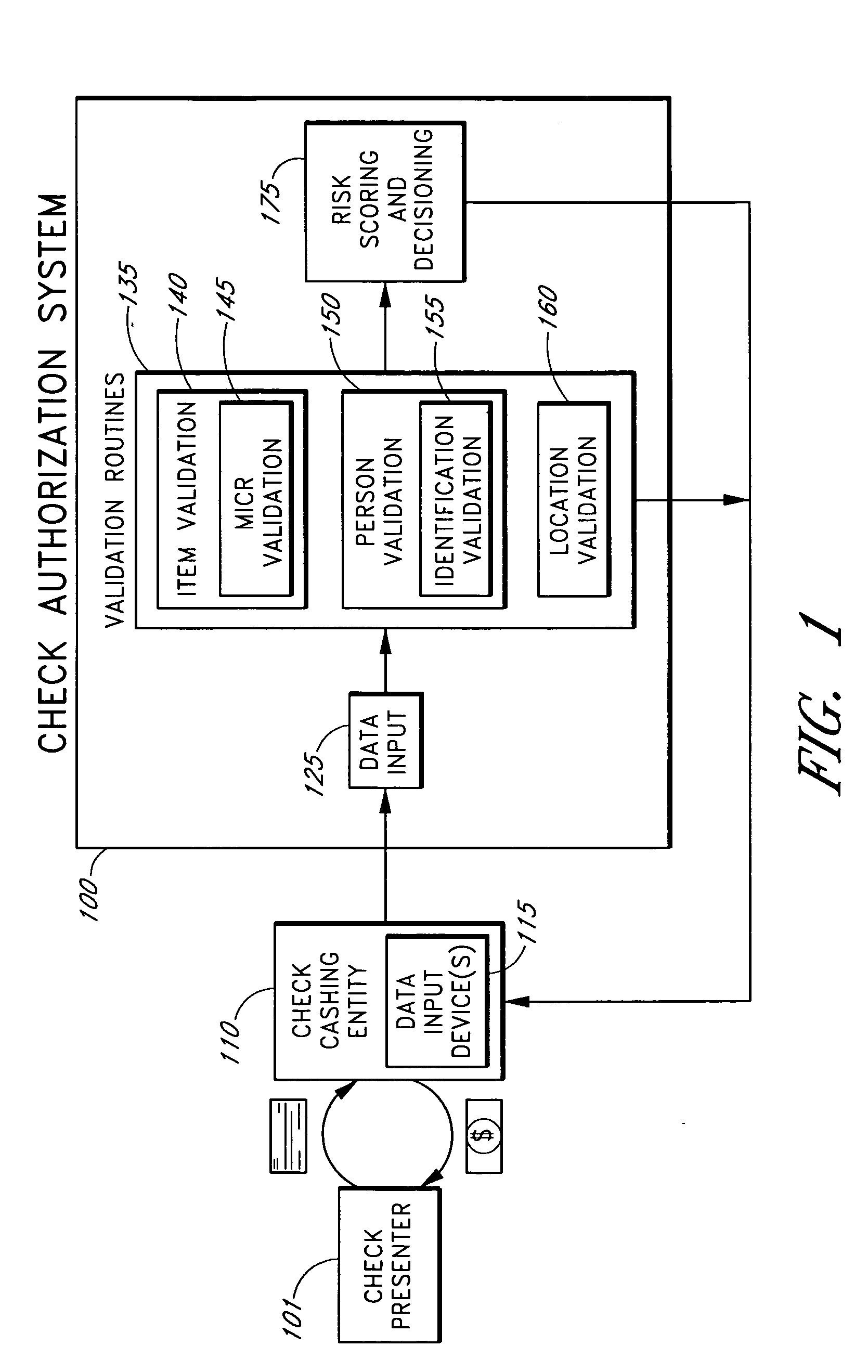
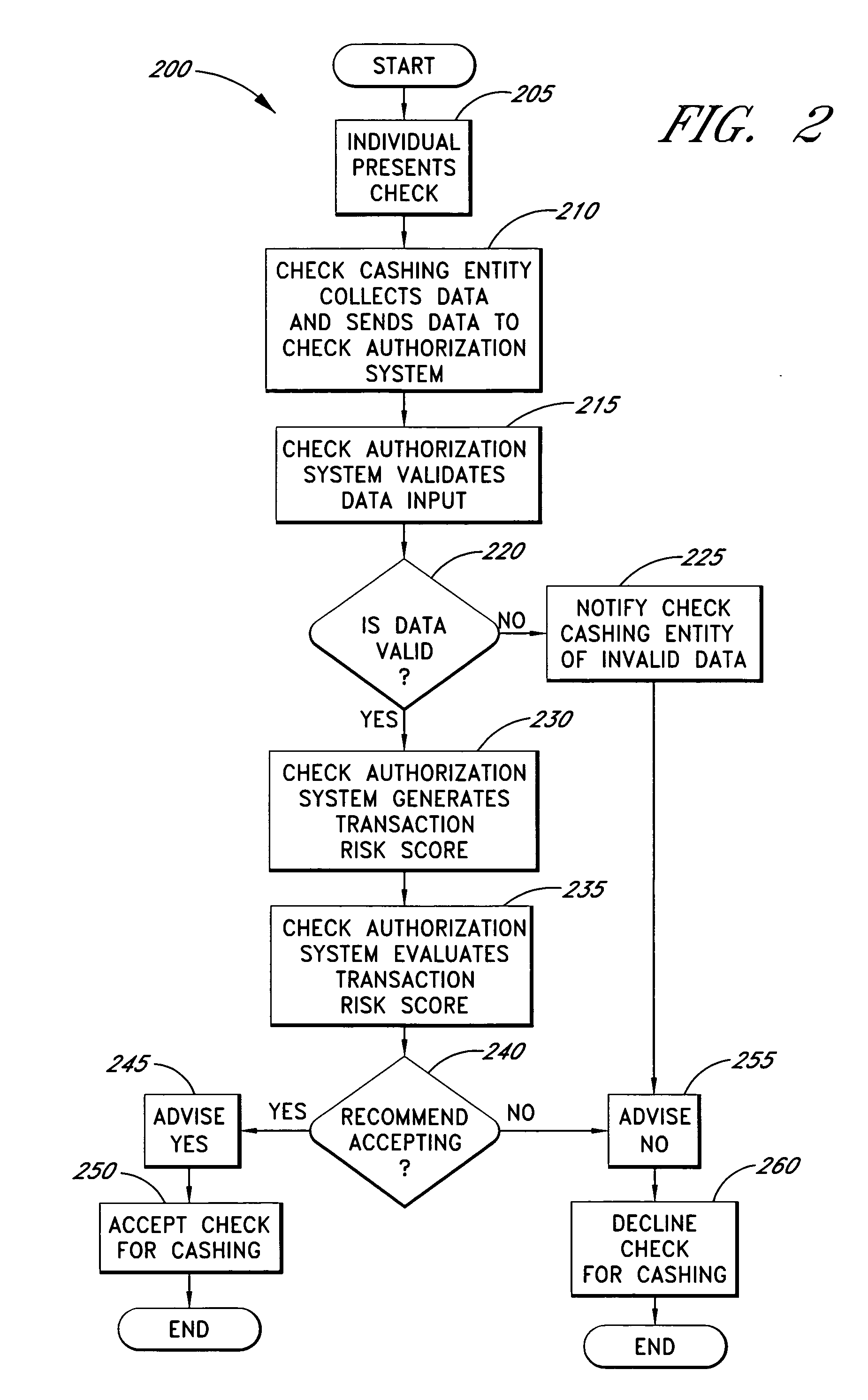
Systems and methods for obtaining authentication marks at a point of sale
InactiveUS20050125360A1Accurate descriptionSlow processPaper-money testing devicesPoint-of-sale network systemsBarcodeCheque
Systems and methods are described for using a point-of-sale device at a check-cashing entity to obtain information about one or more authenticating marks, such as watermarks, bar codes, background patterns, color schemes, insignia, security validation numbers, or the like, from a second-party check or other negotiable instrument presented for a proposed check-cashing transaction. In various embodiments, the authenticating mark information may be compared to stored information about expected configurations of authenticating marks as part of a risk assessment of the check. In various embodiments, the point-of-sale device transmits authenticating mark information to a check authorization system. The point-of-sale device may receive an accept / decline recommendation for the transaction from the check authorization system, based at least in part on the obtained authenticating mark information. The point-of-sale device may display a message about the recommendation to an operator of the device.
Owner:FIRST DATA
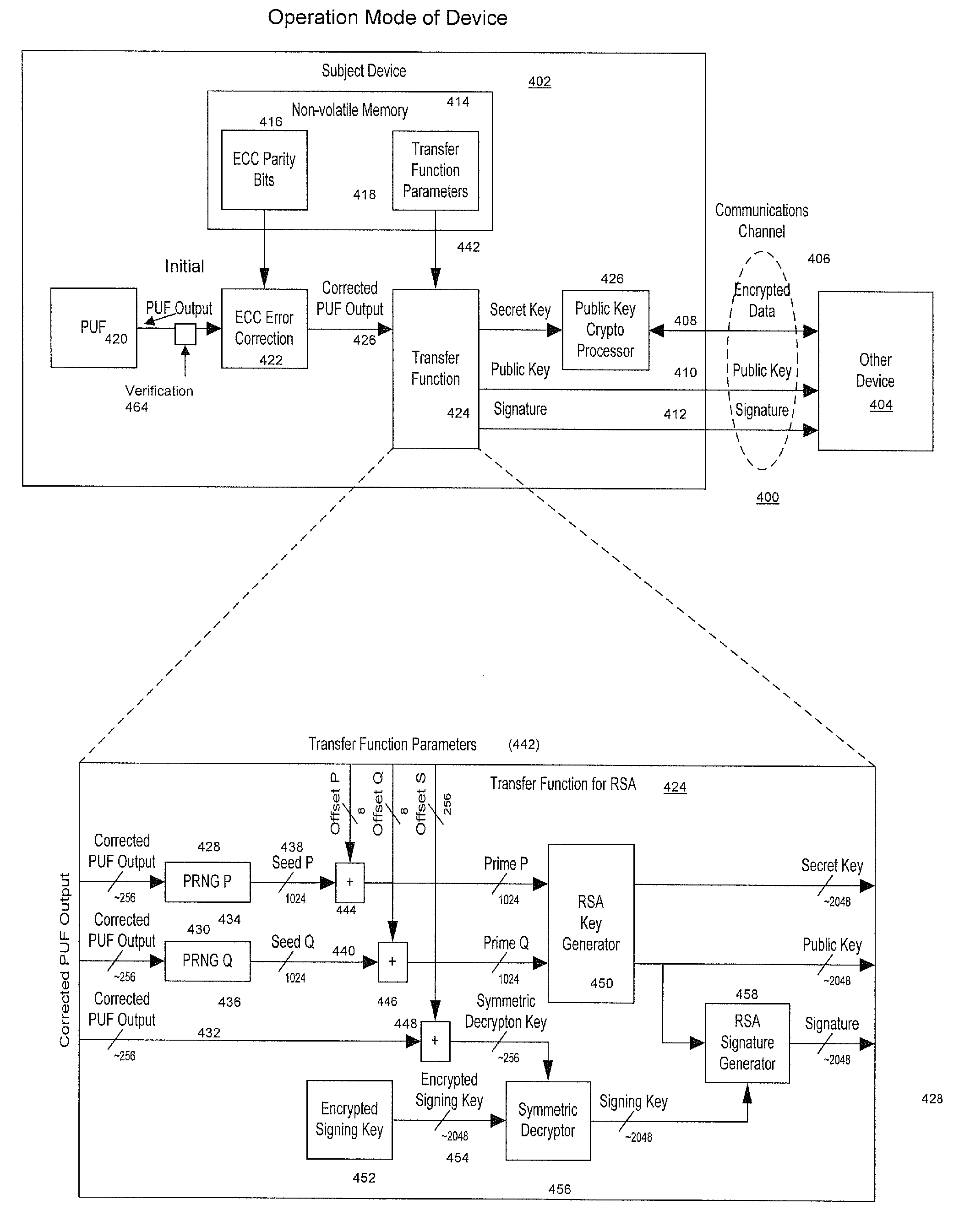
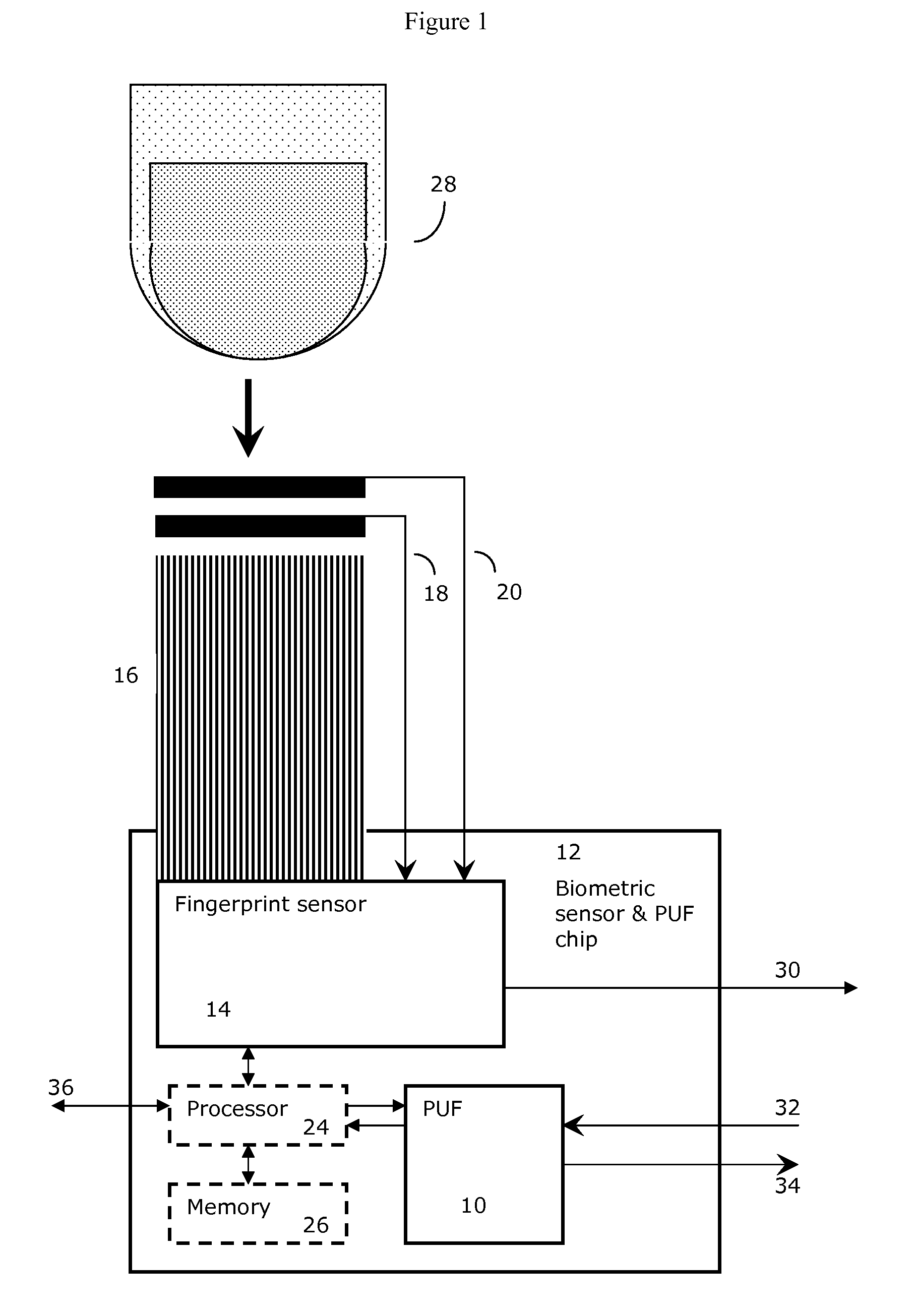
Method and System for Electronically Securing an Electronic Biometric Device Using Physically Unclonable Functions
InactiveUS20110002461A1Consume minimalCost of producingKey distribution for secure communicationElectric signal transmission systemsPhysical unclonable functionSecurity validation
A system for securing an integrated circuit chip used for biometric sensors, or other electronic devices, by utilizing a physically unclonable function (PUF) circuit. These PUF functions are in turn used to generate security words and keys, such as an RSA public or private key. Such a system can be used to protect biometric security sensors and IC chips, such as fingerprint sensors and sensor driver chips, from attack or spoofing. The system may also be used in an efficient method to produce unique device set-up or power-up authentication security keys. These keys can be generated on a low frequency basis, and then frequently reused for later security verification purposes. In operation, the stored keys can be used to efficiently authenticate the device without the need to frequently run burdensome security key generation processes each time, while maintaining good device security.
Owner:SYNAPTICS INC
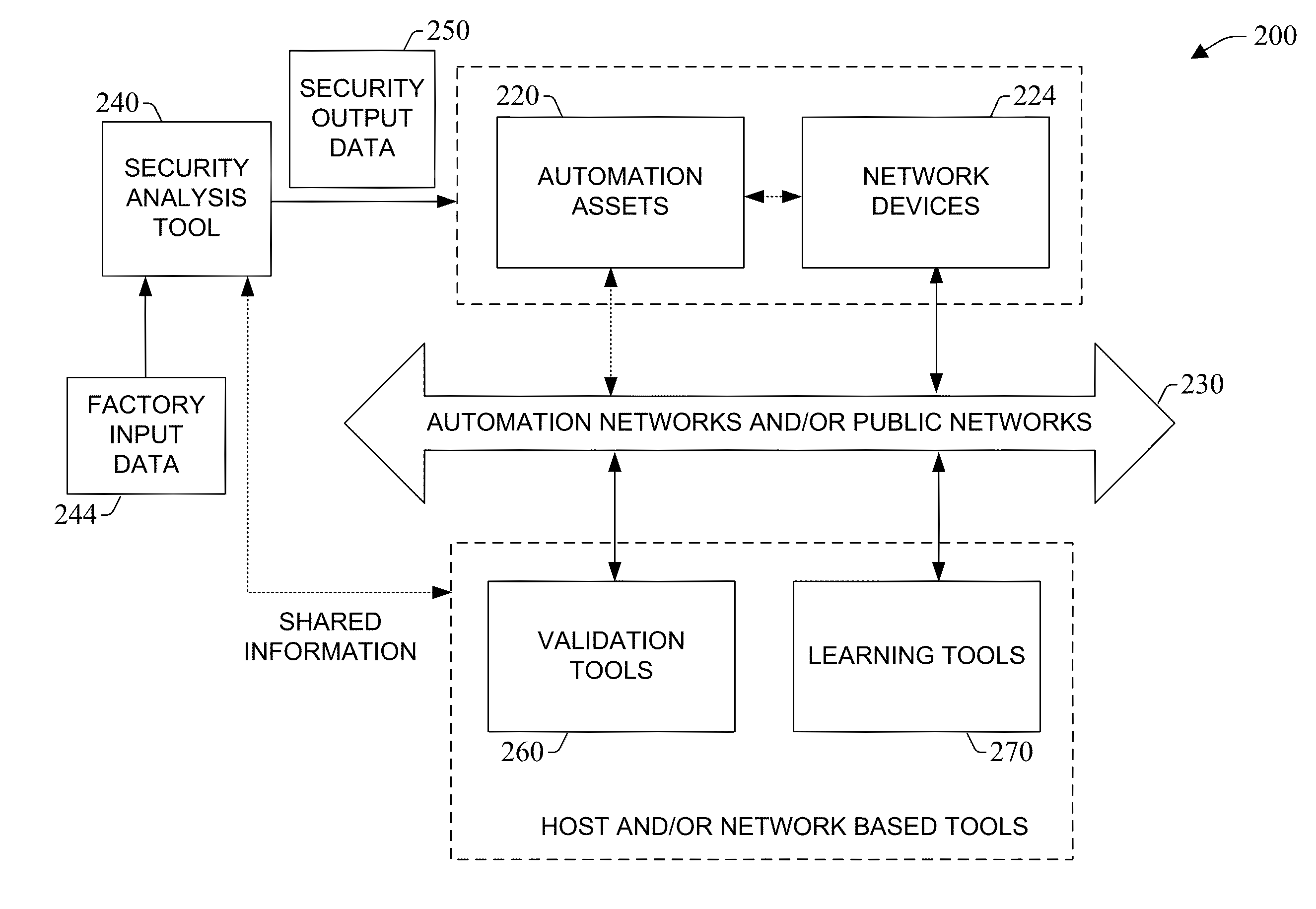
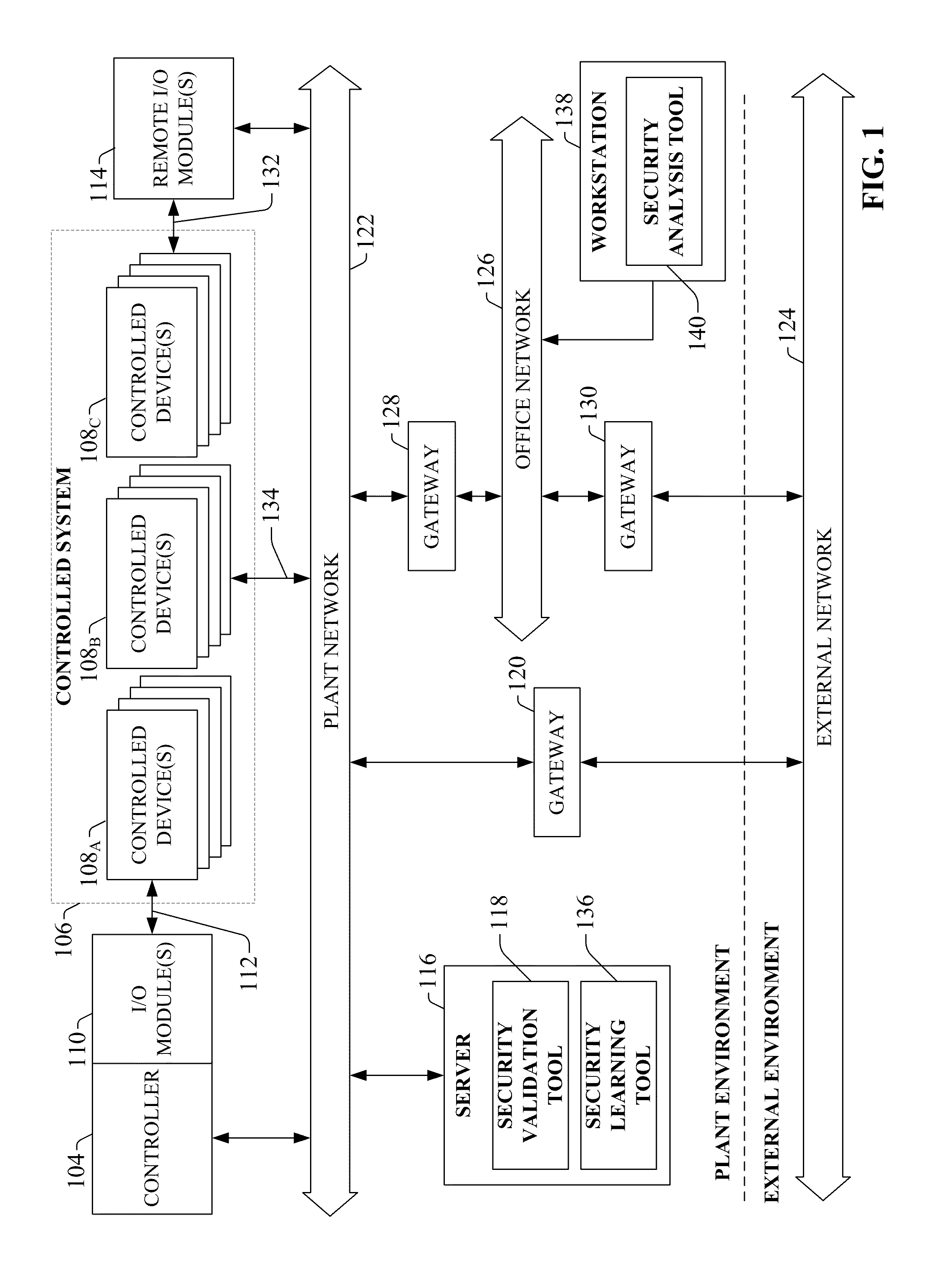
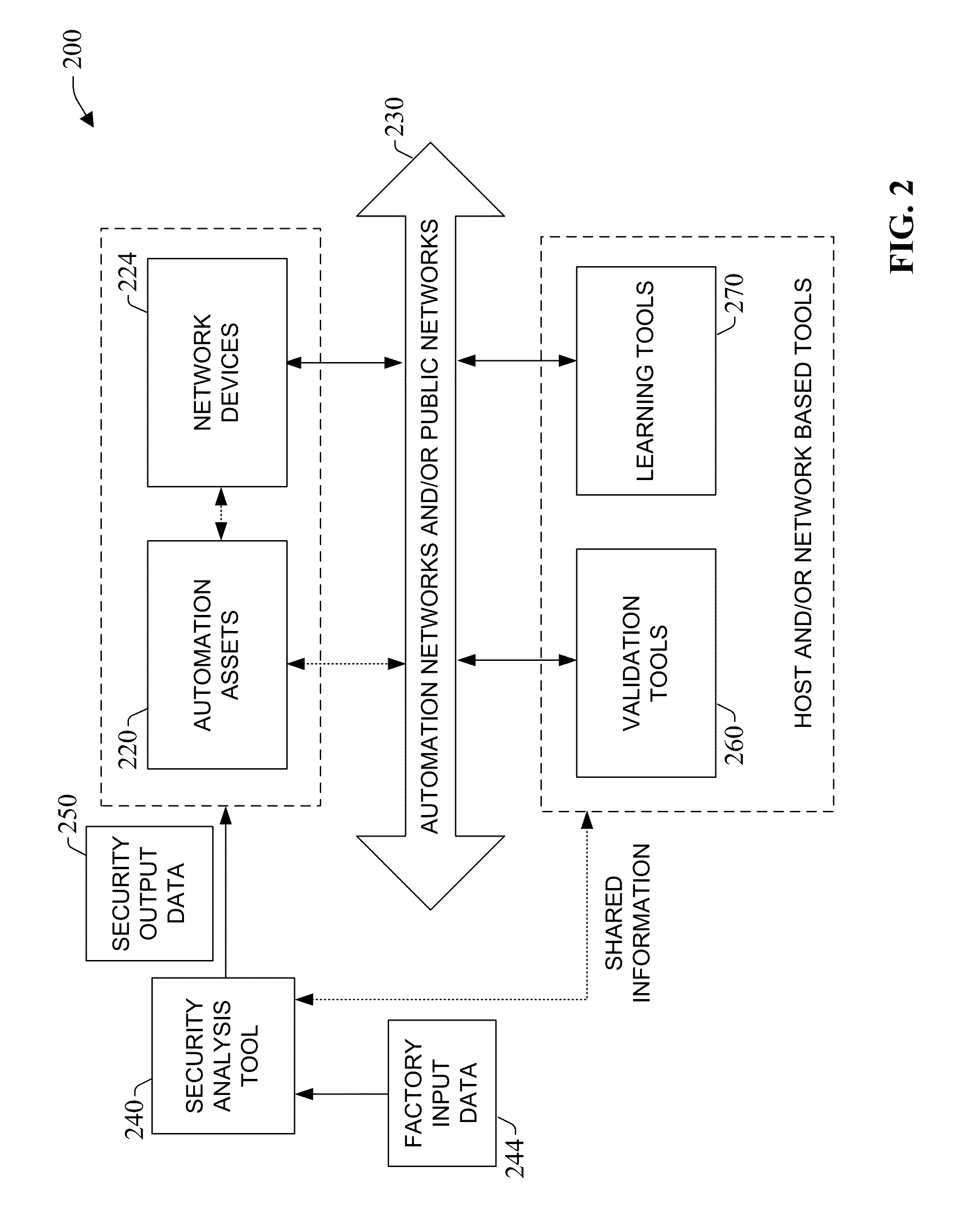
System and methodology providing automation security analysis and network intrusion protection in an industrial environment
ActiveUS20130031037A1Improve integrityFacilitate privacyProgramme controlComputer controlGuidelineEngineering
The present invention relates to a system and methodology facilitating automation security in a networked-based industrial controller environment. Various components, systems and methodologies are provided to facilitate varying levels of automation security in accordance with security analysis tools, security validation tools and / or security learning systems. The security analysis tool receives abstract factory models or descriptions for input and generates an output that can include security guidelines, components, topologies, procedures, rules, policies, and the like for deployment in an automation security network. The validation tools are operative in the automation security network, wherein the tools perform security checking and / or auditing functions, for example, to determine if security components are in place and / or in suitable working order. The security learning system monitors / learns network traffic patterns during a learning phase, fires alarms or events based upon detected deviations from the learned patterns, and / or causes other automated actions to occur.
Owner:ROCKWELL AUTOMATION TECH
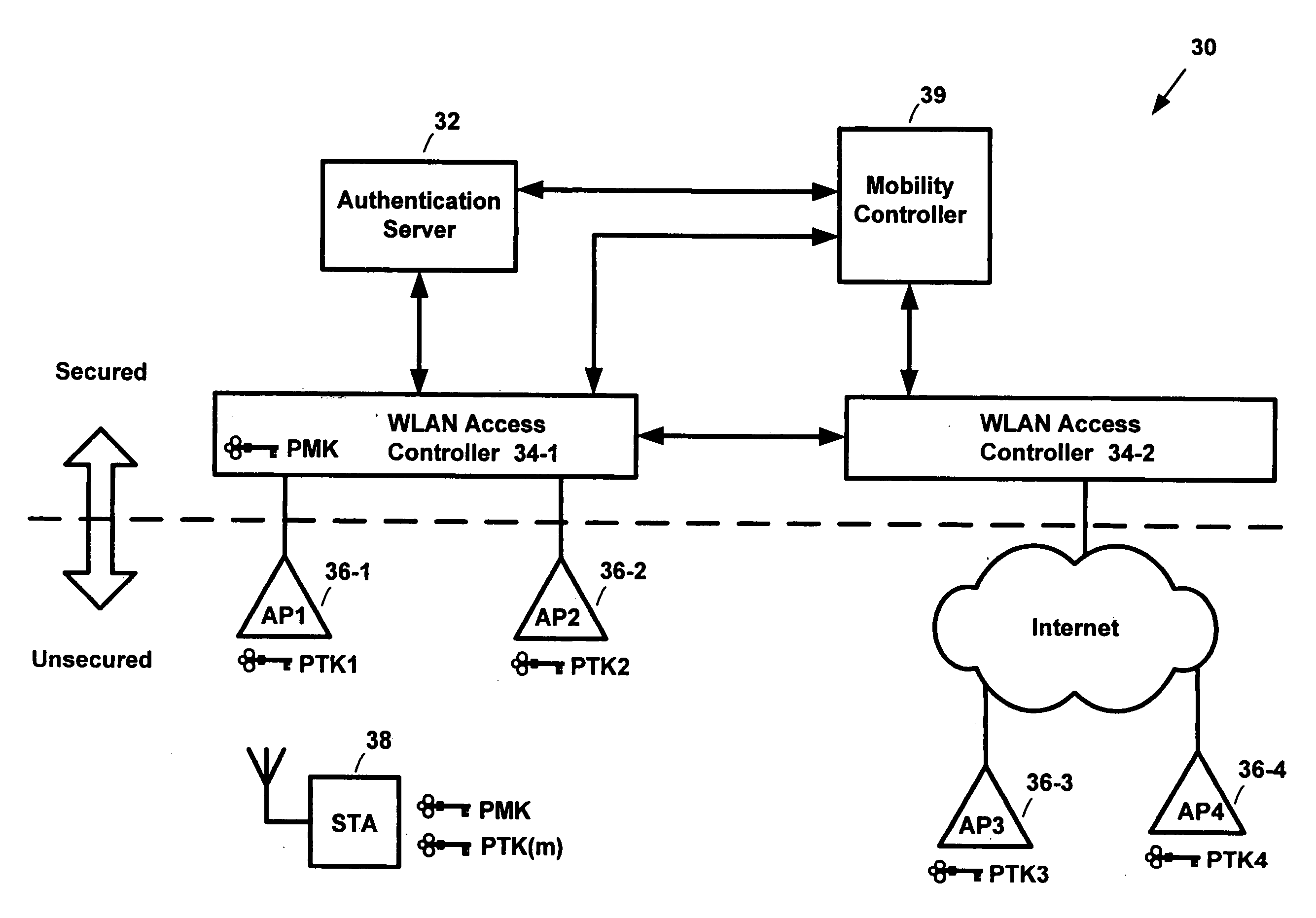
Pre-authentication of mobile clients by sharing a master key among secured authenticators
InactiveUS20050254653A1Key distribution for secure communicationUser identity/authority verificationAuthentication serverClient-side
Systems and methods for pre-authenticating a mobile client in a wireless network. Authenticators in a secured section of the wireless network share a master key generated during an authentication session between a mobile client and an authentication server. The shared master key is not allowed to reside on any devices located outside the secured section of the network. Accordingly, the likelihood that the master key may be hijacked is essentially eliminated. A first session encryption key is derived from the master key and used by the mobile client and a first access point during a first communications session. When the mobile client roams to a second access point, a fast authentication process is performed. The fast authentication process retrieves the shared master key and generates a second session encryption key. A full authentication process between the authentication server and the mobile client is not required. The second session encryption key is used by the mobile client and a second access point during a second communications session.
Owner:MOTOROLA INC
Checkout system with a flexible security verification system
InactiveUS7044370B2Verify securityCash registersAlarm indicatorsSecurity validationVerification system
A method and system for self-checkout of items from a retail or non-retail establishment is disclosed. The system verifies security by comparing a measured physical characteristic of an item with the stored security characteristic for that item and determining if the measured physical characteristic is within an operator-modifiable tolerance range. The operator-modifiable tolerance range is different for different of items in the store. Moreover, a stored security characteristic of an item can be updated automatically. In addition, the system includes a dynamic-weight scale that reports a measured weight before the scale settles.
Owner:ECR SOFTWARE CORP
System and method for user identification and authentication
InactiveUS20070192601A1Improve security levelGuaranteed growthUser identity/authority verificationDigital data authenticationSecurity validationAuthorization
A user identification and authentication device provides a secure computing platform and a secure computing path for communication with a secure remote host. The device is coupled to an unsecure PC but provides for secure verification of a user's identity and authorization in participating in a transaction.
Owner:SPAIN JOHN D R +4
Microprocessor-controlled field device for connection to a field bus system
InactiveUS7337369B2Low costIntegration of a safety layer is relatively simpleError detection/correctionTotal factory controlActuatorSecurity validation
A microprocessor-controlled standard field device, such as a measuring sensor or an actuator, is connected to a field bus system that, in turn, is connected to, for example, a freely programmable controller. The field device is equipped with a security layer for carrying out a security proven communication. A secure and simultaneously cost-effective communication with a control device via a field bus system is made possible by implementing a security layer in, e.g., a conventional operationally proven or redundant standard field device.
Owner:SIEMENS AG
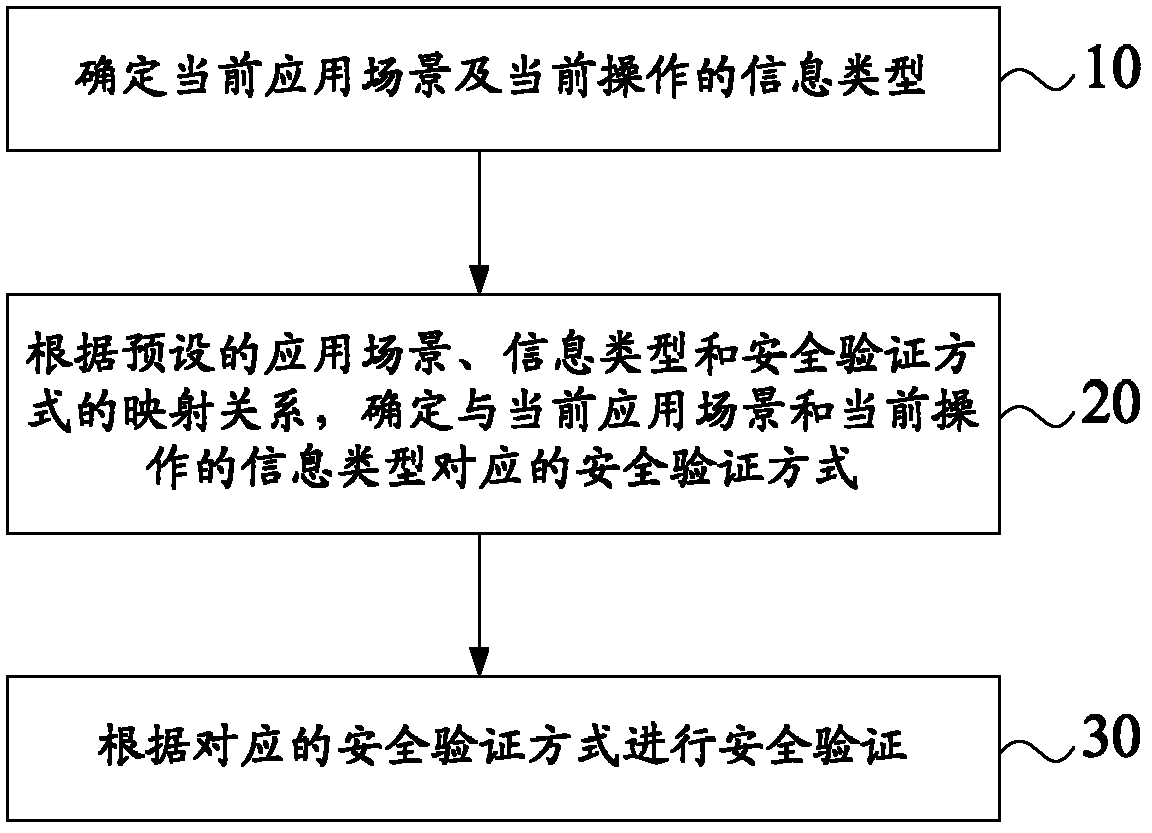
Safety verification method and equipment
InactiveCN102685106AImprove operational convenienceProtection securityUser identity/authority verificationSpeech analysisInformation typeUnsafe environment
The invention provides a safety verification method and equipment. The safety verification method comprises the following steps of: determining a current application scene and an information type of current operation; determining a safety verification mode corresponding to the current application scene and the information type of the current operation according to a mapping relation among the pre-supposed application scene, the information type and the safety verification mode; and performing safety verification according to the corresponding safety verification mode. By adopting the technical scheme, the pre-supposed safety verification mode matched with the current application scene is selected according to the application scene in which a user is located. According to the dynamic safety verification mode, the operation convenience of the user in a safe environment can be enhanced, and the safety of private information and data of the user in an unsafe environment can also be protected as far as possible.
Owner:BEIJING BENY WAVE SCI & TECH
Systems and methods for security verification in electronic learning systems and other systems
ActiveUS9396327B2Digital data processing detailsDigital data protectionSecurity validationVerification system
The embodiments described herein relate to security verification systems and methods. In some aspects, there is provided a security verification server comprising a server processor. The server processor is adapted to provide at least one account identifier, receive at least one command for execution, determine whether to activate one or more available additional permission sets to execute the received command, and if it is determined that one or more additional permission sets should be activated to execute the received command, activate those permission sets by executing the security verification processes associated therewith.
Owner:DESIRE2LEARN
Method for Monitoring the Safety of Travelers
ActiveUS20110018709A1Ensure safetyElectric lighting sourcesVisible signalling systemsEngineeringSecurity validation
A method is provided for monitoring the present location of a traveler at time t1, predicting a location at which the traveler is expected to arrive by time t2, and verifying the safety of the traveler. The safety verification is conducted if the traveler has not reached the expected location at time t2, if signal from the traveler is lost or if a message from the traveler is not received within a predetermined time period. In some embodiments of the present invention, verifying the safety of the traveler involves contacting the traveler at one or more telecommunications devices which the traveler is known to carry, contacting another person that is known to be accompanying the traveler, and if all else fails—alerting the local emergency response team.
Owner:AVAYA INC
Method and apparatus for real-time security verification of on-line services
A unique combination of several functions achieves a system by which consumers can validate the actual security status of a website before they decide to trust it, and therefore transact with it. In one example implementation, a security system includes a scanning engine that periodically and thoroughly scans the network and connected components of an on-line service such as a website. The results are stored and perhaps reported back to the service via alerts and the like. The website includes a “bug” which visitors can click on. The visual appearance of the “bug” can be altered (e.g. made invisible) in accordance with a determined level of security for the website. By clicking on the “bug,” the visitors can also be displayed web pages showing the security status of the website. Based on their review of such web pages, visitors can then decide whether to trust the website for further transactions.
Owner:MCAFEE LLC
Cryptographic methods and apparatus for secure authentication
ActiveUS7725730B2Readily apparentDigital data processing detailsAnalogue secracy/subscription systemsCommunications systemInternet privacy
Secure authentication protocols, particularly well-suited for use in authenticating mobile communications devices having limited computational resources, are disclosed. In an illustrative embodiment, a network-based communication system includes a client device and at least two servers. First and second shares are generated from a first password associated with the client device, and stored in respective first and second servers. The client device submits additional information associated therewith to at least one of the first and second servers. Each of the first and second shares has the property that it is infeasible to determine solely therefrom correspondence of the additional information with the first password. The first and second servers then utilize the respective first and second shares to collectively determine said correspondence of the additional information with the first password.
Owner:EMC IP HLDG CO LLC
Security verification method and device
InactiveUS20050144475A1Rigorously verifying security settingRigorously verifying security settingsDigital data processing detailsDigital computer detailsData transmissionSecurity validation
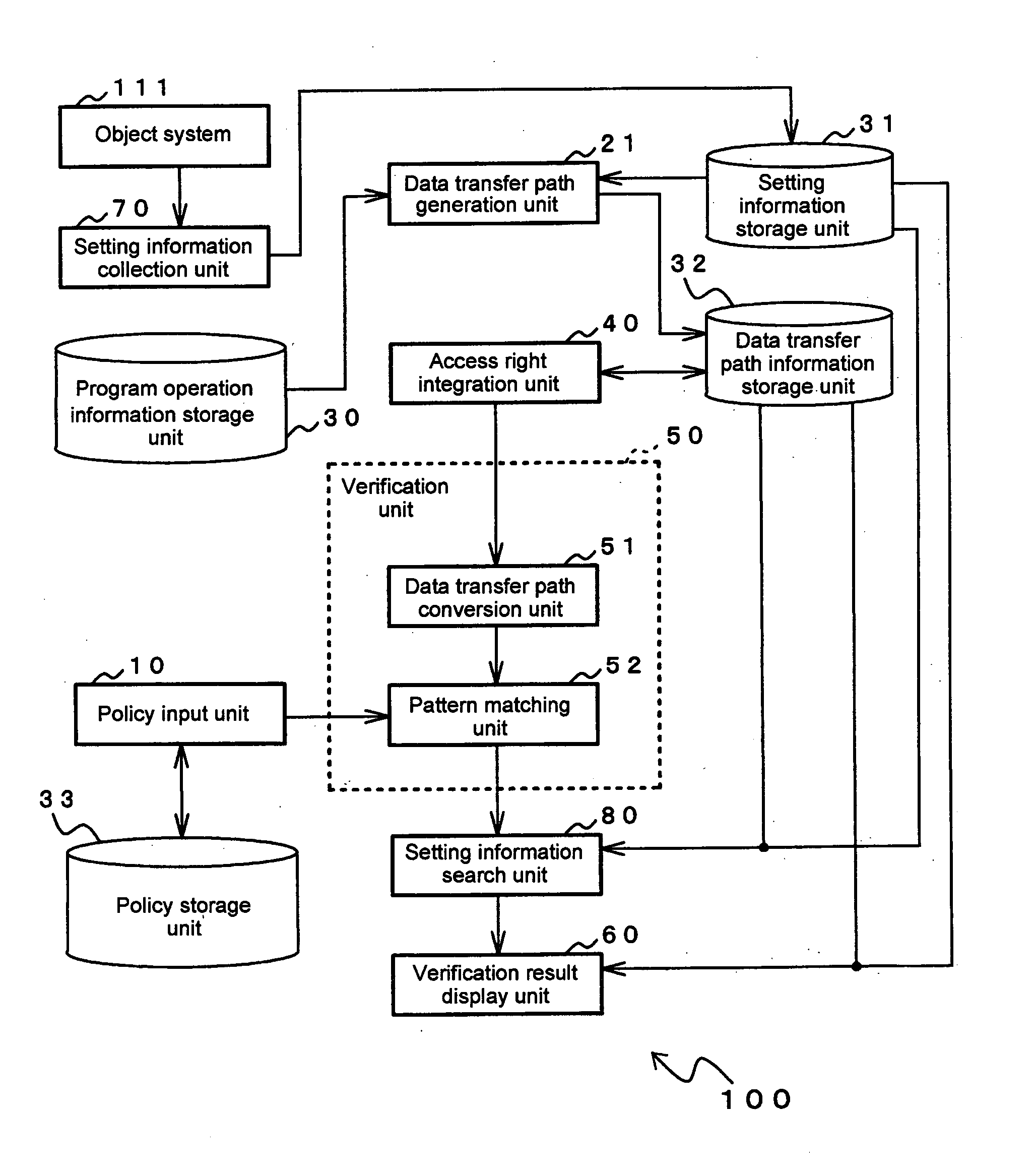
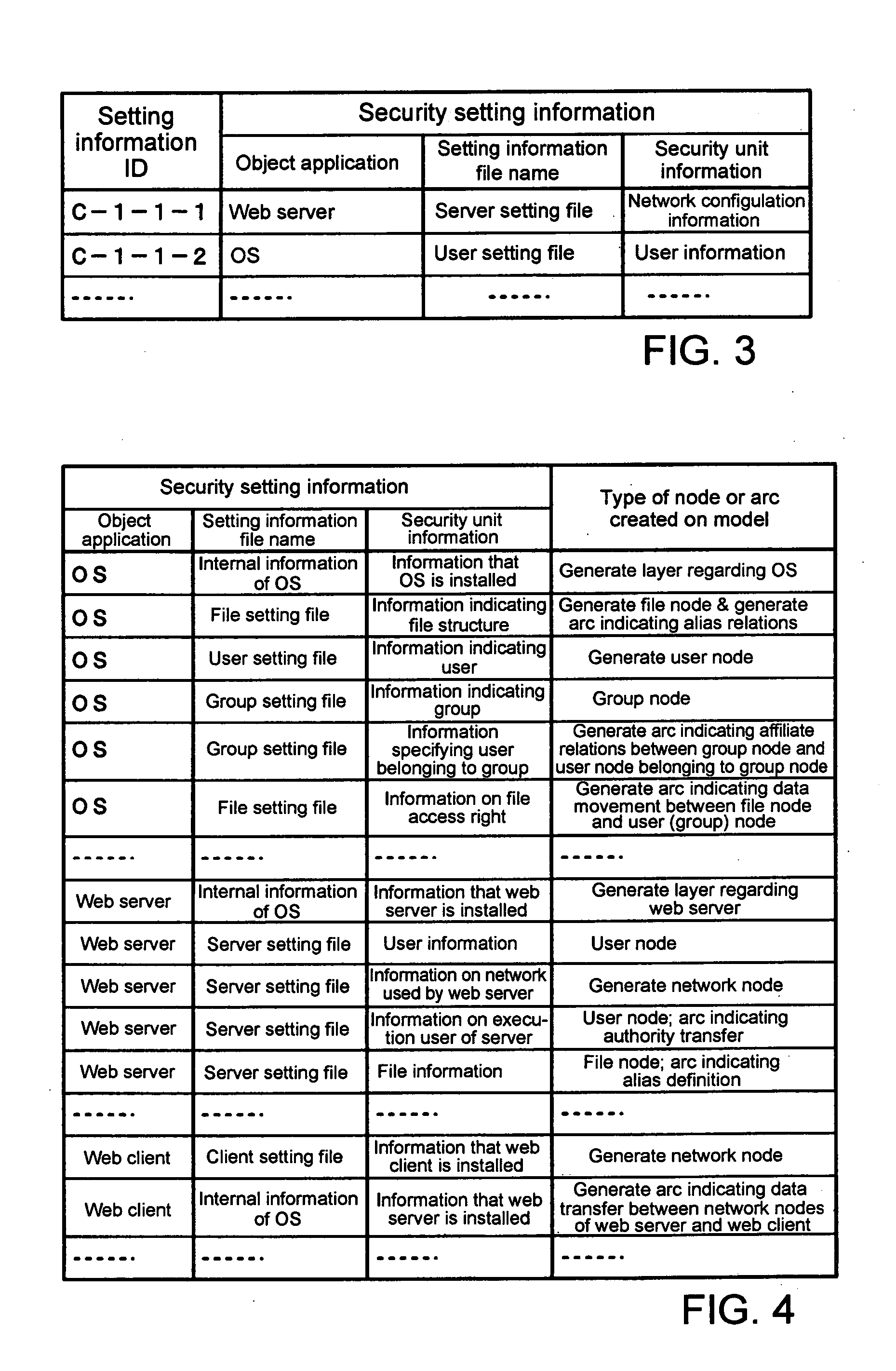
A security verification method for verifying whether improper settings that indicate composite errors of security settings exist in an object system, which is an object of examination, includes steps of: reading data transfer paths that represent data movement in the object system and that are generated based on program operation information that describes operations of a program that is used in the object system, integrating the access rights of data transfer paths that have been read; and searching for improper paths among the data transfer paths for which access rights have been integrated based on security verification policies in which improper paths, which are paths of data movement that are improper from the standpoint of security, have been set in advance.
Owner:NEC CORP
Method for fast configuring remote video monitoring system
InactiveCN103414881AEasy to deployEasy to set upClosed circuit television systemsTransmissionVideo monitoringPassword
The invention discloses a method for fast configuring a remote video monitoring system. The method comprises the steps that (1) a wireless network access module is arranged on a monitoring camera; (2) currently available wireless networks are scanned by a monitoring client, a wireless network is selected and a wireless network password is input; (3) after receiving authentication information of the monitoring client, a monitoring server sends a safety verification code to the monitoring client; (4) the monitoring client converts an access point name, the password, the safety verification code and the authentication information to a two-dimension code picture, and the two-dimension code picture is placed in a shooting area of the monitoring camera; (5) the two-dimension code picture is shot through the monitoring camera and is analyzed, the monitoring camera has access to the wireless network, and an equipment serial number, the safety verification code and the authentication information of the monitoring camera are then sent to the monitoring server; (6) authentication is conducted on the monitoring client by the monitoring server according to information sent by the monitoring camera, and when the certification is passed, the monitoring camera and the monitoring client are bound to enter a monitoring module.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI +1
System and Method for Providing Symbolic Execution Engine for Validating Web Applications
InactiveUS20090089759A1Eliminates and reduces of disadvantageEliminates and reduces of and problemError detection/correctionSpecific program execution arrangementsWeb applicationApplication software
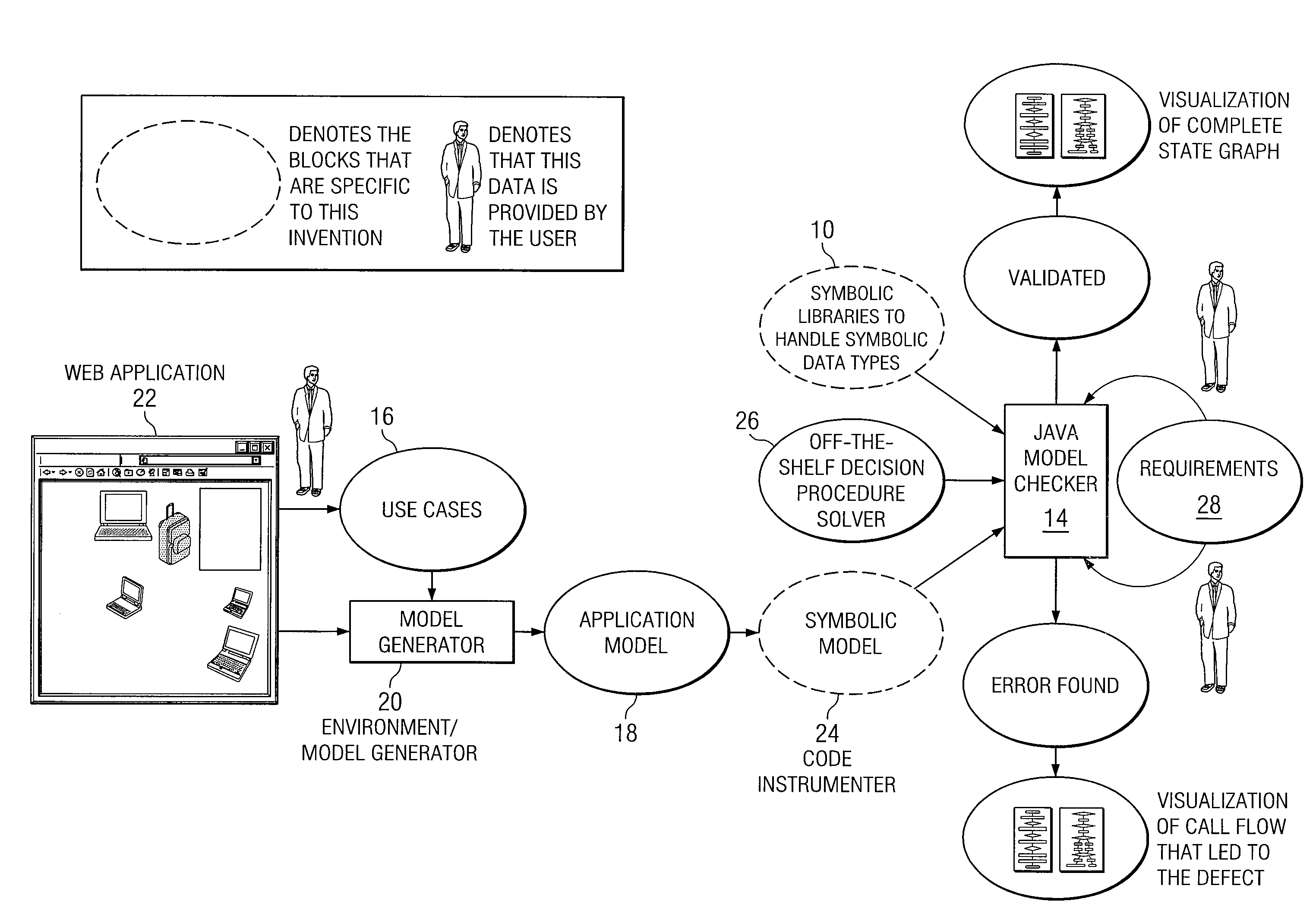
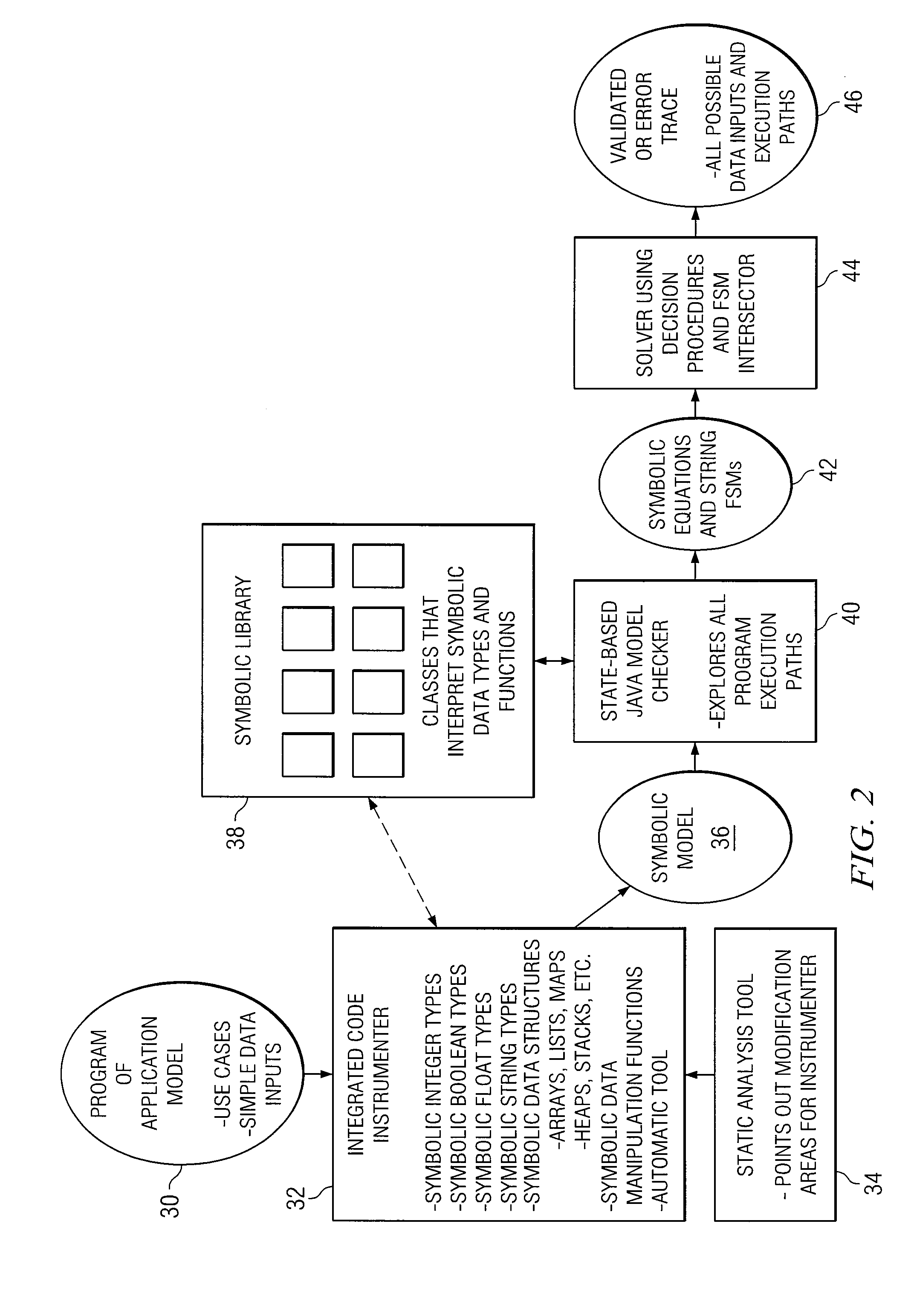
In accordance with a particular embodiment of the present invention, a method is offered that includes generating a symbolic string manipulation class library for one or more web applications. The manipulations are generalized into a string manipulation symbolic algebra. The method also includes performing symbolic execution for one or more web applications. Typically, a Java model checker is augmented to check for certain types of requirements or properties in performing the symbolic execution. If an error scenario exists, a solution to a set of symbolic constraints is obtained, and the solution is mapped back to a source code to obtain an error trace and a test case. In still other specific embodiments, requirements or properties are encoded through templates and checked using public domain decision procedures. The properties or requirements can relate to security validation. The symbolic execution can be customized and tuned for Java-based web applications.
Owner:FUJITSU LTD
Generating security validation code automatically
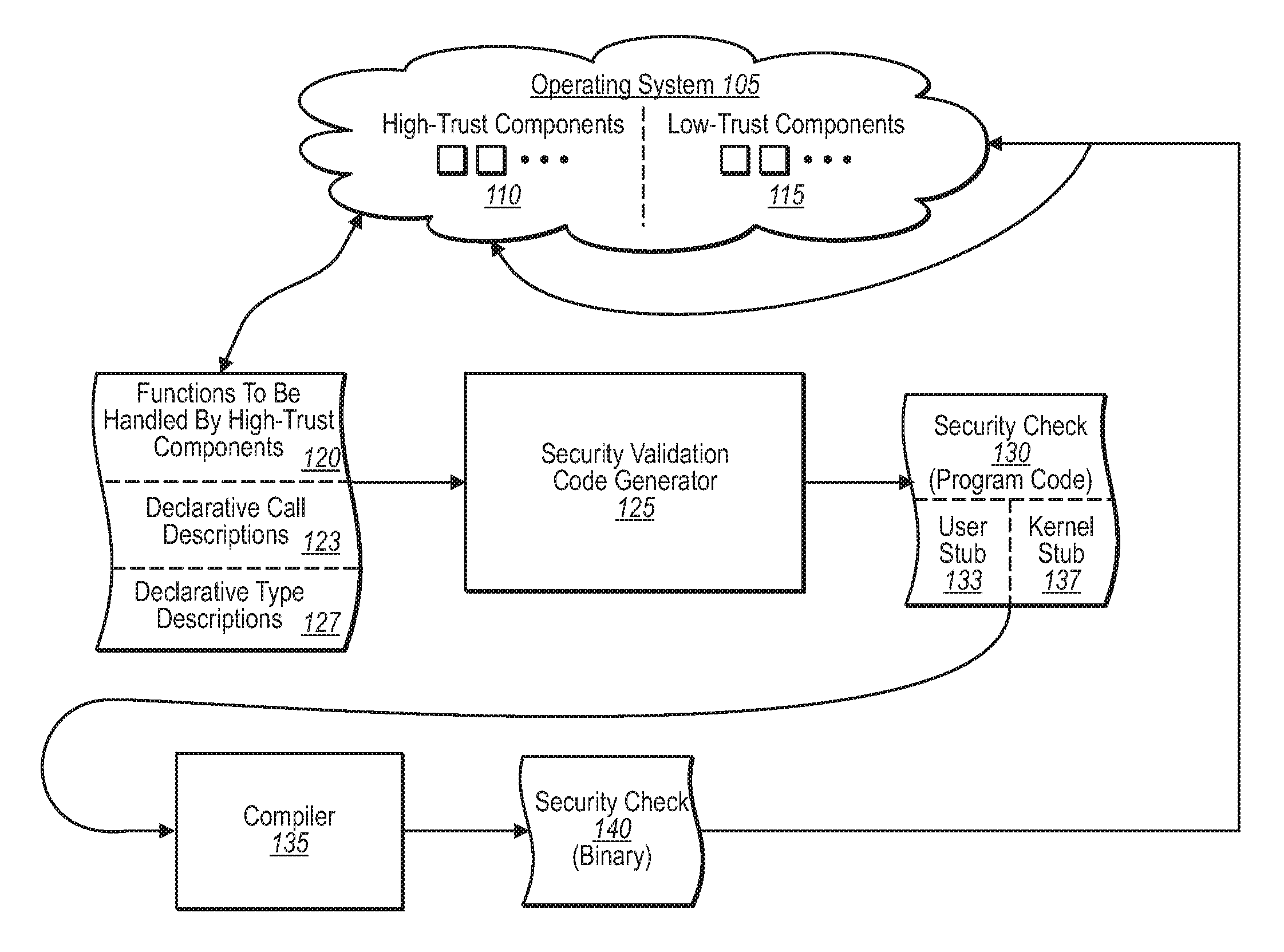
InactiveUS20080127303A1Memory loss protectionSoftware engineeringProgramming languageOperational system
A security program code generator is configured to automatically generate program code used to perform one or more validation checks of components operating in user mode. In one implementation, for example, the program code generator receives one or more files that include declarative values and parameters regarding one or more function calls made by any user mode component. The program code generator then takes the file of declarative call descriptions and automatically generates a user mode stub and a kernel mode stub for each function call of interest to be handled by a kernel mode component. The file(s) that include the user mode stub and the kernel mode stub can then be compiled and linked into the operating system components.
Owner:MICROSOFT TECH LICENSING LLC
Multi-account security verification system with a virtual account and linked multiple real accounts
InactiveUS20070185820A1Easy to useInexpensive to produceAcutation objectsFinanceVerification systemSecurity validation
A multi account security verification system, which consists off a virtual account card and a central authentication enterprise. The cardholder is able to select one of the real accounts belonging to the account owner by adding control digits to the virtual account number. The real account is retrieved from the Central Authentication Enterprise by accessing the virtual account number record stored in a system database thereby retrieving the selected real account number associated with the control digits and the virtual account number. The database may also store a plurality of secret keys or public / private key sets associated with the virtual account number in addition to optional BIO information, which can be used for authentication and authorization
Owner:TALKER ALBERT I
System and methodology providing automation security analysis, validation, and learning in an industrial controller environment
ActiveUS8909926B2Improve integrityFacilitate privacyComputer controlUser identity/authority verificationGuidelineEngineering
The present invention relates to a system and methodology facilitating automation security in a networked-based industrial controller environment. Various components, systems and methodologies are provided to facilitate varying levels of automation security in accordance with security analysis tools, security validation tools and / or security learning systems. The security analysis tool receives abstract factory models or descriptions for input and generates an output that can include security guidelines, components, topologies, procedures, rules, policies, and the like for deployment in an automation security network. The validation tools are operative in the automation security network, wherein the tools perform security checking and / or auditing functions, for example, to determine if security components are in place and / or in suitable working order. The security learning system monitors / learns network traffic patterns during a learning phase, fires alarms or events based upon detected deviations from the learned patterns, and / or causes other automated actions to occur.
Owner:ROCKWELL AUTOMATION TECH
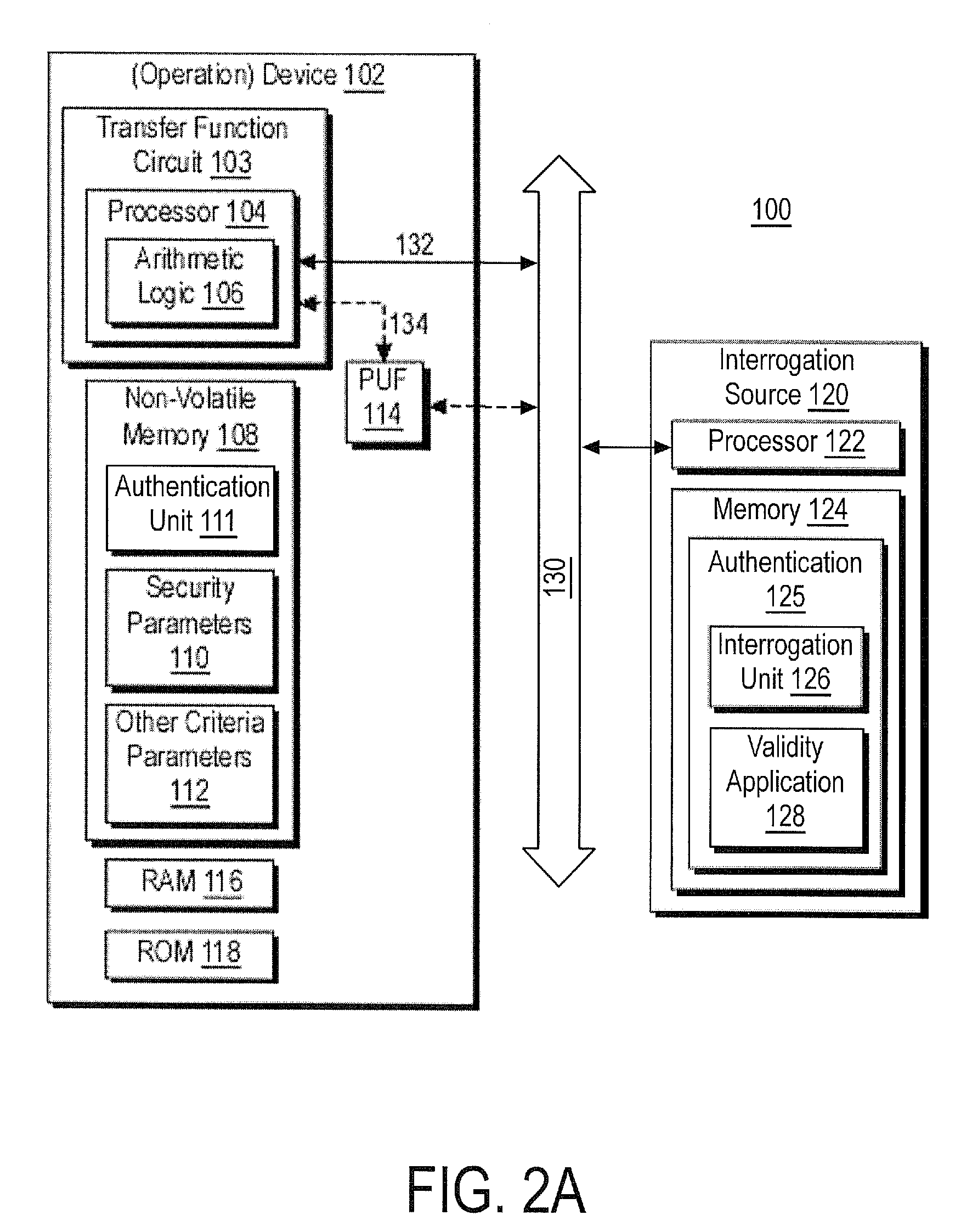
Apparatus and method for unilaterally loading a secure operating system within a multiprocessor environment
InactiveUS7024555B2Memory loss protectionVolume/mass flow measurementInformation repositoryOperational system
An apparatus and method for unilaterally loading a secure operating system within a multiprocessor environment are described. The method includes disregarding a received load secure region instruction when a currently active load secure region operation is detected. Otherwise, a memory protection element is directed, in response to the received load secure region instruction, to form a secure memory environment. Once directed, unauthorized read / write access to one or more protected memory regions are prohibited. Finally, a cryptographic hash value of the one or more protected memory regions is stored within a digest information repository as a secure software identification value. Once stored, outside agents may request access to a digitally signed software identification value in order to establish security verification of secure software within the secure memory environment.
Owner:INTEL CORP
Method and system for creating receipt on paper with embedded RFID tags therein
A central information processing system and method that issues receipts or tickets that can be securely validated at points of redemption. The method and system couple a client system with a server system and also couple at least one Radio Frequency IDentification (RFID) reader to the client system. The method and system read at least one identifier from a sheet with a RFID tag embedded therein with the RFID reader. The method and system also send the at least one identifier from the client system to the server system and receive from the server system at least one receipt image for printing on the paper with the RFID tag embedded therein. The method and system also print, at the client system, a receipt containing ticket information received from the server system. The server system further accepts at least one identifier that was read from a Radio Frequency Identification tag that was read from a sheet at the client system, records the at least one identifier, sends to the client system, in response to the accepting, at least one receipt image. Validation of the receipt or ticket includes reading, at a point of delivery, the at least one identifier from the Radio Frequency Identification tag and providing, in response to reading the at least one identifier, at least one of a good and a service.
Owner:FARRELL DAVID +2
System and methodology providing automation security analysis, validation, and learning in an industrial controller environment
InactiveUS20150067844A1Improve integrityFacilitate privacyMemory loss protectionComputer controlGuidelineEngineering
The present invention relates to a system and methodology facilitating automation security in a networked-based industrial controller environment. Various components, systems and methodologies are provided to facilitate varying levels of automation security in accordance with security analysis tools, security validation tools and / or security learning systems. The security analysis tool receives abstract factory models or descriptions for input and generates an output that can include security guidelines, components, topologies, procedures, rules, policies, and the like for deployment in an automation security network. The validation tools are operative in the automation security network, wherein the tools perform security checking and / or auditing functions, for example, to determine if security components are in place and / or in suitable working order. The security learning system monitors / learns network traffic patterns during a learning phase, fires alarms or events based upon detected deviations from the learned patterns, and / or causes other automated actions to occur.
Owner:ROCKWELL AUTOMATION TECH
Real-time security verification for banking cards
Embodiments of the invention provide a means for verifying that a person using a bank card at a point-of-sale merchant location is in fact a person authorized to use the bank card. In one embodiment of the invention, verification may involve communicating with the mobile device 103 associated with the person authorized to use the bank card. The person authorized to use the bank card may be required to send verification data to the bank card verification system via the mobile device to confirm a purchase. The bank card verification system may not authorize the purchase if the proper verification data is not received from the mobile device. In another embodiment, the bank card verification system may be configured to determine a proximity of the mobile device to the merchant point-of-sale location to verify the purchase.
Owner:IBM CORP
Method and system for security verification of data among non-contact equipments
InactiveCN101202621AImprove securityKey distribution for secure communicationThird partyShortest distance
The invention discloses a method and a system for carrying through security authentication on data among non-contact devices. The invention includes the steps of transmitting a data voucher form a first movable device to a second movable device by a short distance communicating mode; launching an authentication request of the data voucher to a third party from the second movable device through a safe data transmission channel; the third party carries through authentication on the data voucher by utilizing the key information shared by the first movable device based on the authentication request; transmitting a data access description to the second movable device through the safe data transmission channel under the situation that the authentication result of the data voucher carried out by the third party is positive; and the second movable device acquires safe data corresponding to the data voucher through the data access description. By utilizing the invention, the security for carrying through data transmission among the non-contact devices can be improved.
Owner:LENOVO (BEIJING) CO LTD
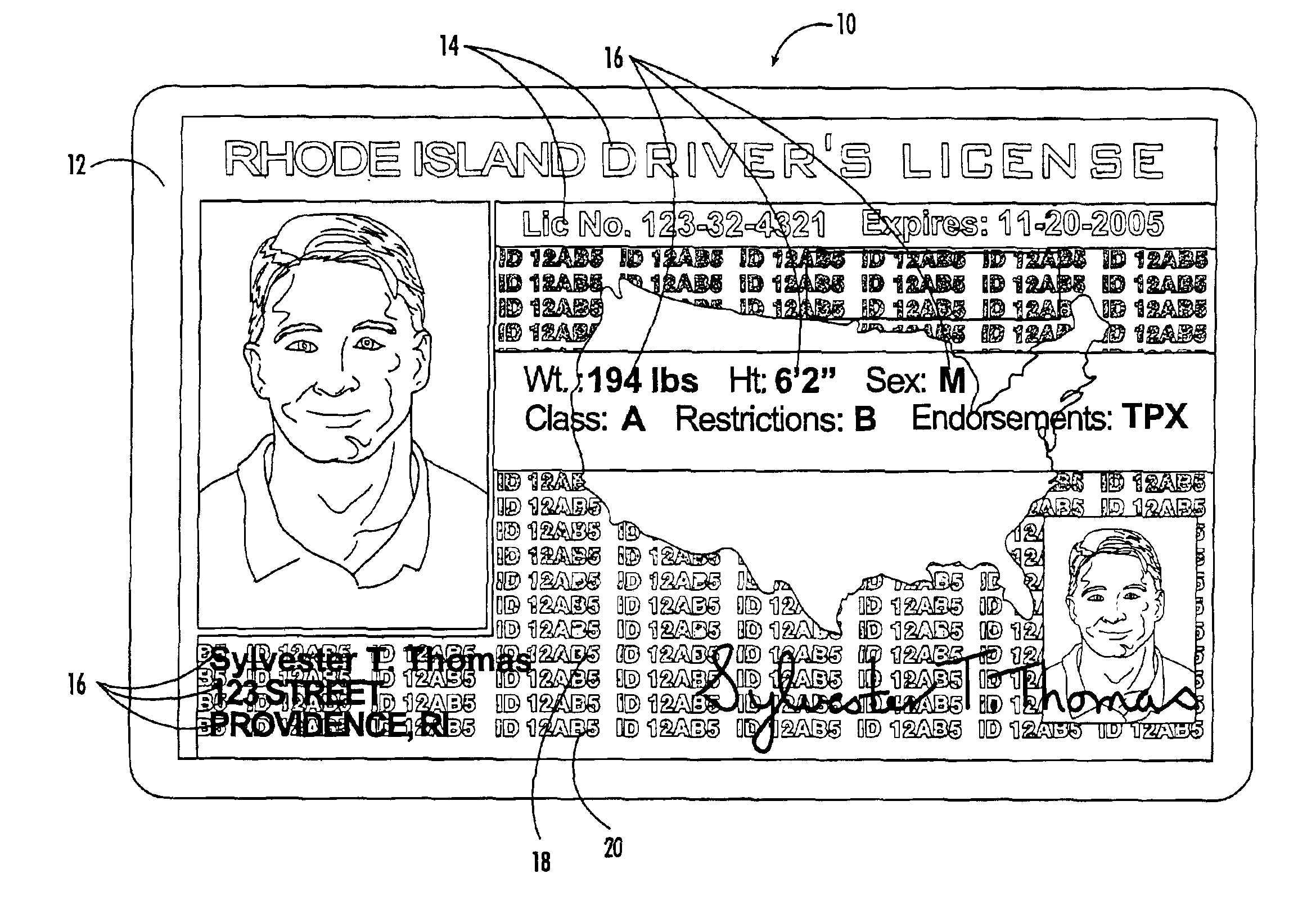
Printer driver log security verification for identification cards
InactiveUS6929413B2Reduce capacityQuality improvementOther printing matterCharacter and pattern recognitionCentral databaseSecurity validation
The present invention provides a counterfeit resistant ID card where a printed security feature is applied to the ID card at the issuance location at the time the card is issued. Specifically, the present invention provides for a process of producing an ID card having a unique imbedded security code that is generated and specifically matched to the particular ID card being printed and is applied at the time and place that the card is issued thereby providing a code by which the authenticity of the ID card can be cross verified. Verification is completed by comparing the code on the ID card to the date stamped log of all ID cards printed by the printer at the issuance location. Each entry in the log is encoded with a unique code number that corresponds to the specific print job and more importantly to the specific ID card printed. The present invention provides for the recording of this print log code into a central database to be maintained with the records corresponding to the particular ID card that was printed.
Owner:ZEBRA TECH CORP
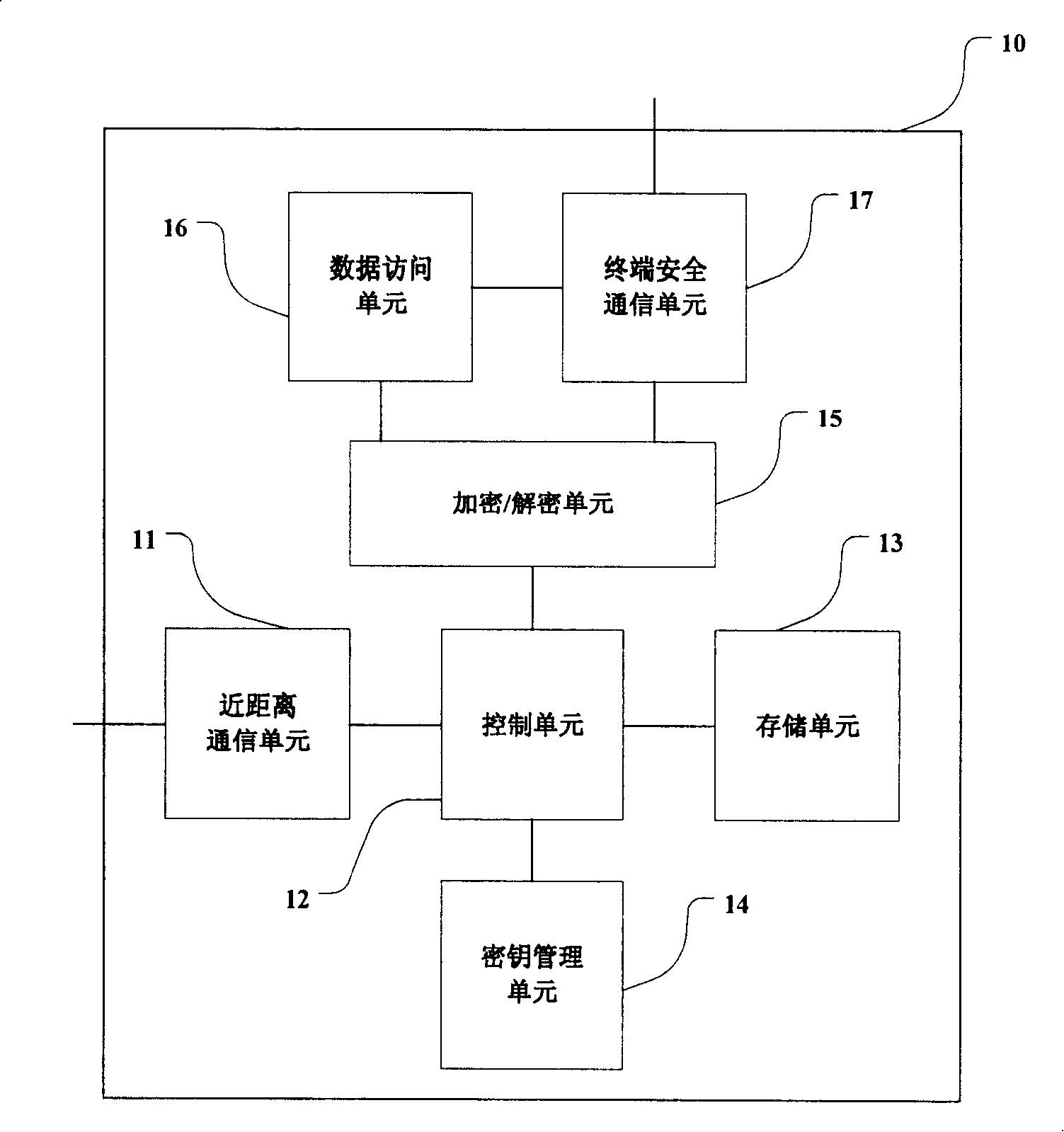
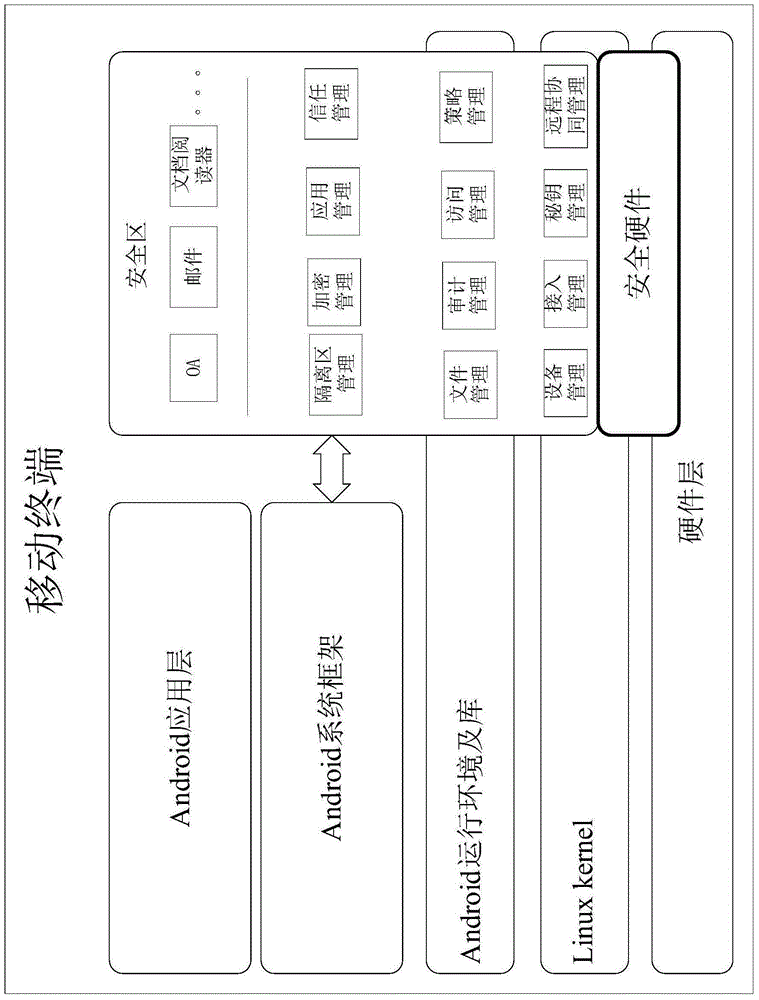
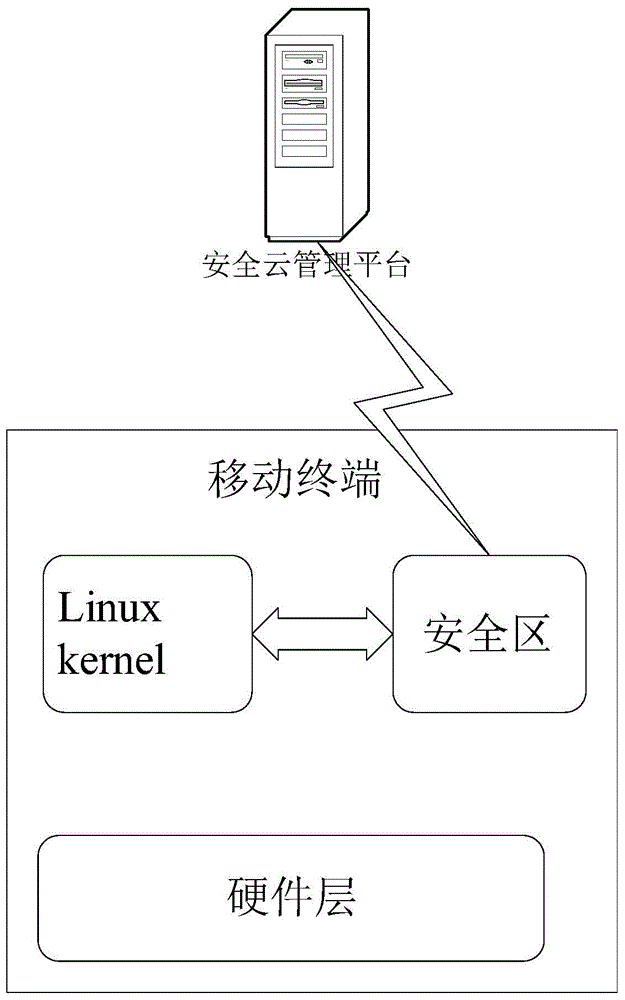
Safety protection method for mobile terminal, mobile terminal, safety system and application method
InactiveCN105205370ARealize active isolation protectionInternal/peripheral component protectionDigital data authenticationThird partySafety zone
The invention relates to a safety protection method for a mobile terminal, a mobile terminal, a safety system and an application method. The safety protection method is used for increasing the safety of the mobile terminal and is easy in operation. According to the safety protection method for the mobile terminal, a separate area is isolated on the mobile terminal and taken as a safety area, a third party application outside the safety area cannot access the application and data in the safety area, and a user is required to pass the safety verification in order to enter into the safety area. The safety system is characterized in that a cloud safety management platform is mainly used for performing mutual collaborative interlocking between the safety area of the mobile terminal, the system kernel of the mobile terminal and the cloud safety management platform, so that the running of the safety area under a safe and reliable environment is ensured, and the safety area is safe. A trust chain is built in the safety area, an application method for realizing the running access management for the application and data on the basis of the trust chain is adopted, and the biometric features recognition is taken as the verification for entering into the safety area, so that the safety is further promoted.
Owner:北京恒信安科技有限公司
Access method for internet, system and mobile terminal
The invention is applicable in the technical field of communication, and provides an access method for internet, a system and a mobile terminal. The method comprises the following steps: when a selection instruction for an internet web in an account management application list pre-collocated by a user is received, outputting a security verification request; receiving and verifying the security verification instruction input by the user; when the security verification instruction is accurate, acquiring an account and a password corresponding to the internet web selected by the selection instruction from the pre-collocated account management application list, and inputting the account and the password to the internet web; and receiving login instruction of the user, wherein a control link enters the internet web corresponding to the account and the password, thereby effectively protecting account information and registration information of the internet web, assisting the user to memorize the account and the password, prevent the trouble when the user forgets the login account or password and facilitate the usage of the user.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Portal for secure validation of parking and integrated services
An interface to a parking application, such as a web portal, is provided over a secure network connection to tenants for managing parking validation services as well as related parking services and other integrated building services. An authenticated user may provide information for authorizing full, partial, or subsidized payment for a use of a parking facility, such as a use by a guest. The information may be provided by way of a personal computer, a mobile device, a special-purpose terminal, or the like. If the guest then presents a ticket at a separate attended or unattended exit terminal or point-of-sale device to complete the parking transaction, the transaction is processed in accordance with the provided information. According to other aspects of the invention, techniques for enabling configurable event notifications for events associated with validation services, and techniques for associating parking events with video and / or photographic image data are provided.
Owner:LANG DARIN R +3
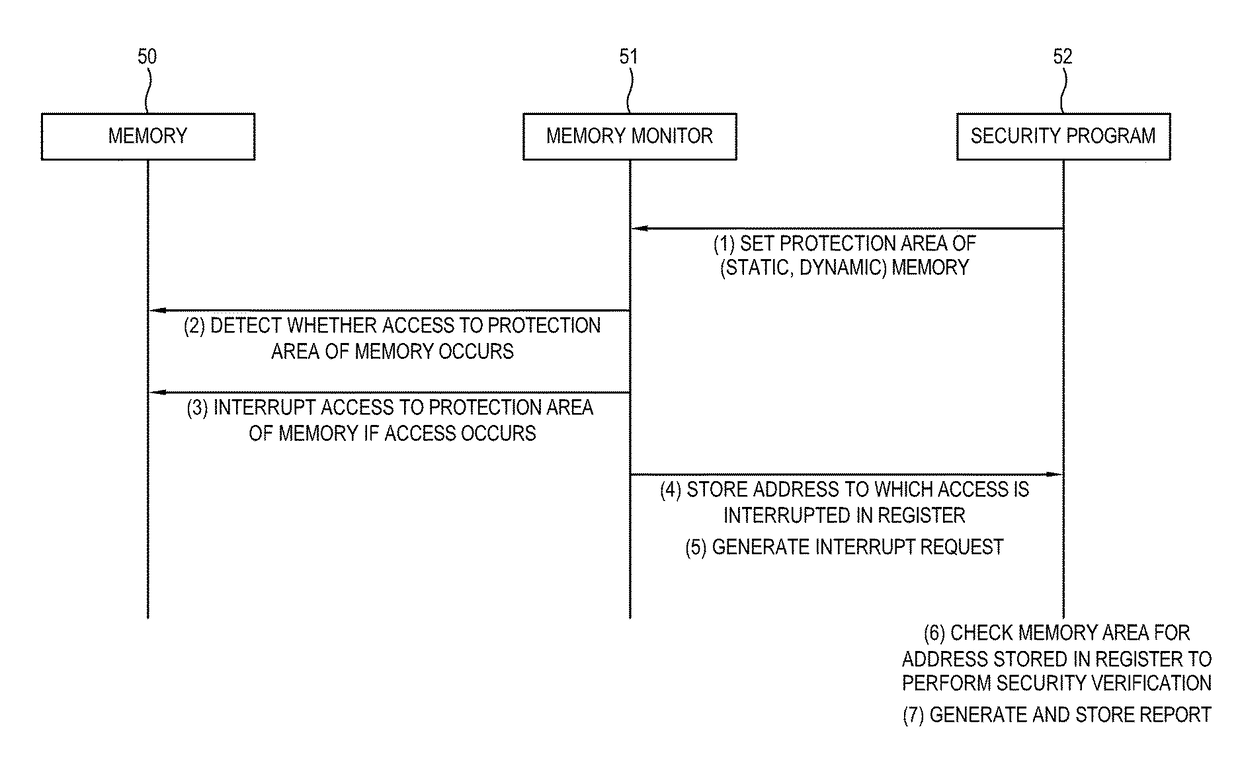
Electronic apparatus and control method thereof
InactiveUS20170262383A1Reduce riskImprove integrityMemory architecture accessing/allocationUnauthorized memory use protectionOperational systemData storing
An electronic apparatus and a control method thereof are provided. The electronic apparatus includes a memory having a protection area and storing data of a first operating system (OS) and at least one first program involved with first OS in the protection area; at least one processor configured to execute the at least one first program and at least one second program involved with a second OS having an authority higher than the first OS; and a memory monitor comprising circuitry configured to detect whether an access to the protection area of the memory occurs, to interrupt the access if the access occurs, and to perform a security verification of the data stored in the protection area. The electronic apparatus may guarantee and / or improve integrity thereof using a hardware device, which can directly monitor the memory at a CPU environment in which a security area and a general area are separated.
Owner:SAMSUNG ELECTRONICS CO LTD
Custom communication channels for application deployment
ActiveUS20160344798A1Program loading/initiatingTransmissionSoftware engineeringApplication procedure
An application deployment service (ADS) component receives a request to establish a communication channel for clients to submit deployment artifacts associated with an application. A set of endpoints are created for the channel. In response to receiving a message via one of the endpoints, the ADS determines that additional security verification operations are to be performed before a deployment task indicated in the message can be performed. After the security verification operations are completed, the task is implemented.
Owner:AMAZON TECH INC
Executing Trusted Applications with Reduced Trusted Computing Base
ActiveUS20110154500A1Digital data processing detailsAnalogue secracy/subscription systemsTrusted ComputingApplication software
A system for executing trusted applications with a reduced trusted computing base. In one embodiment, the system includes a processor to dynamically instantiate an application protection module in response to a request by a program to be executed under a trusted mode. The system further includes memory to store the program which is capable of interacting with a remote service for security verification. In one embodiment, the application protection module includes a processor-measured application protection service (P-MAPS) operable to measure and to provide protection to the application.
Owner:INTEL CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com