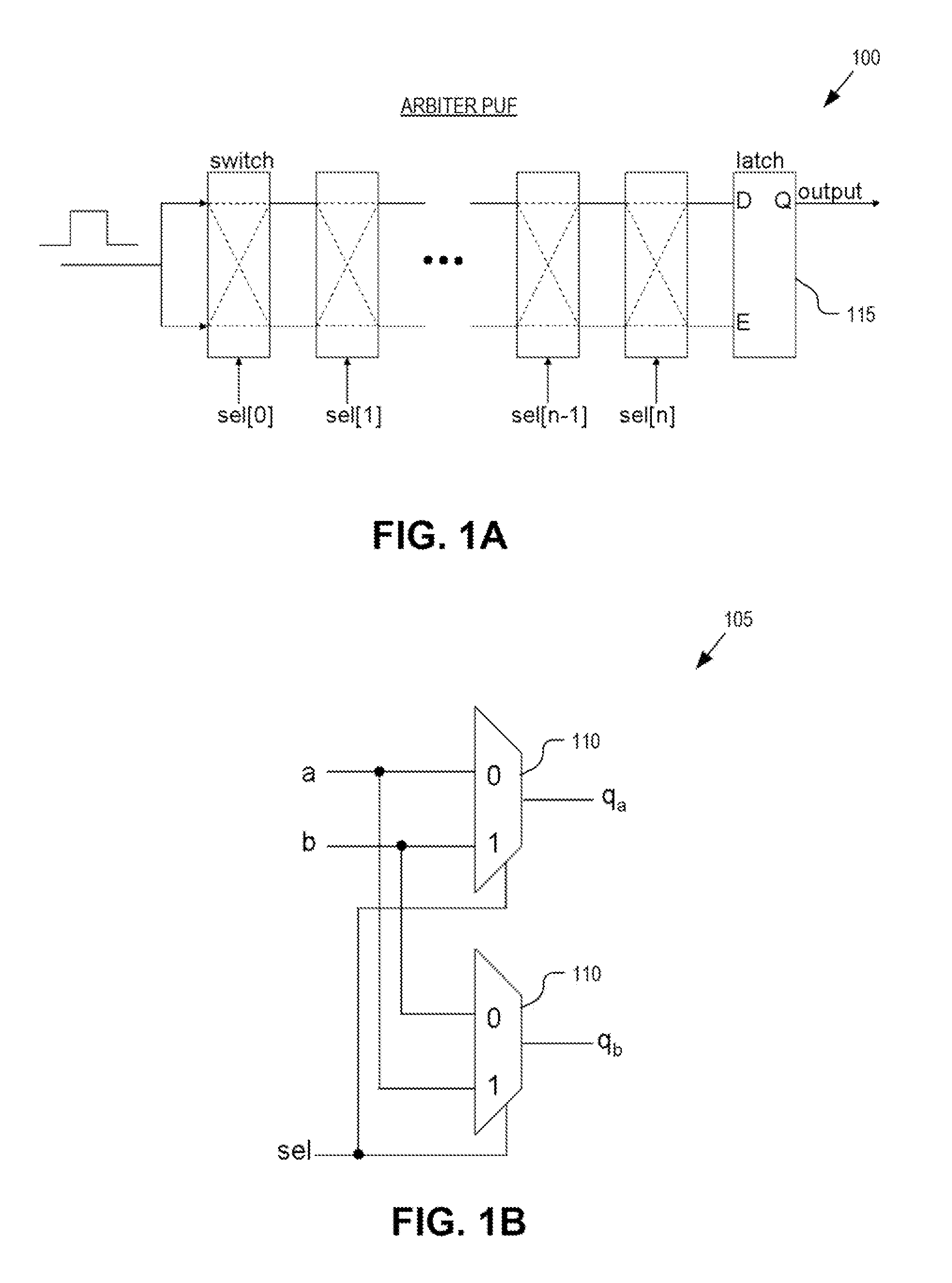
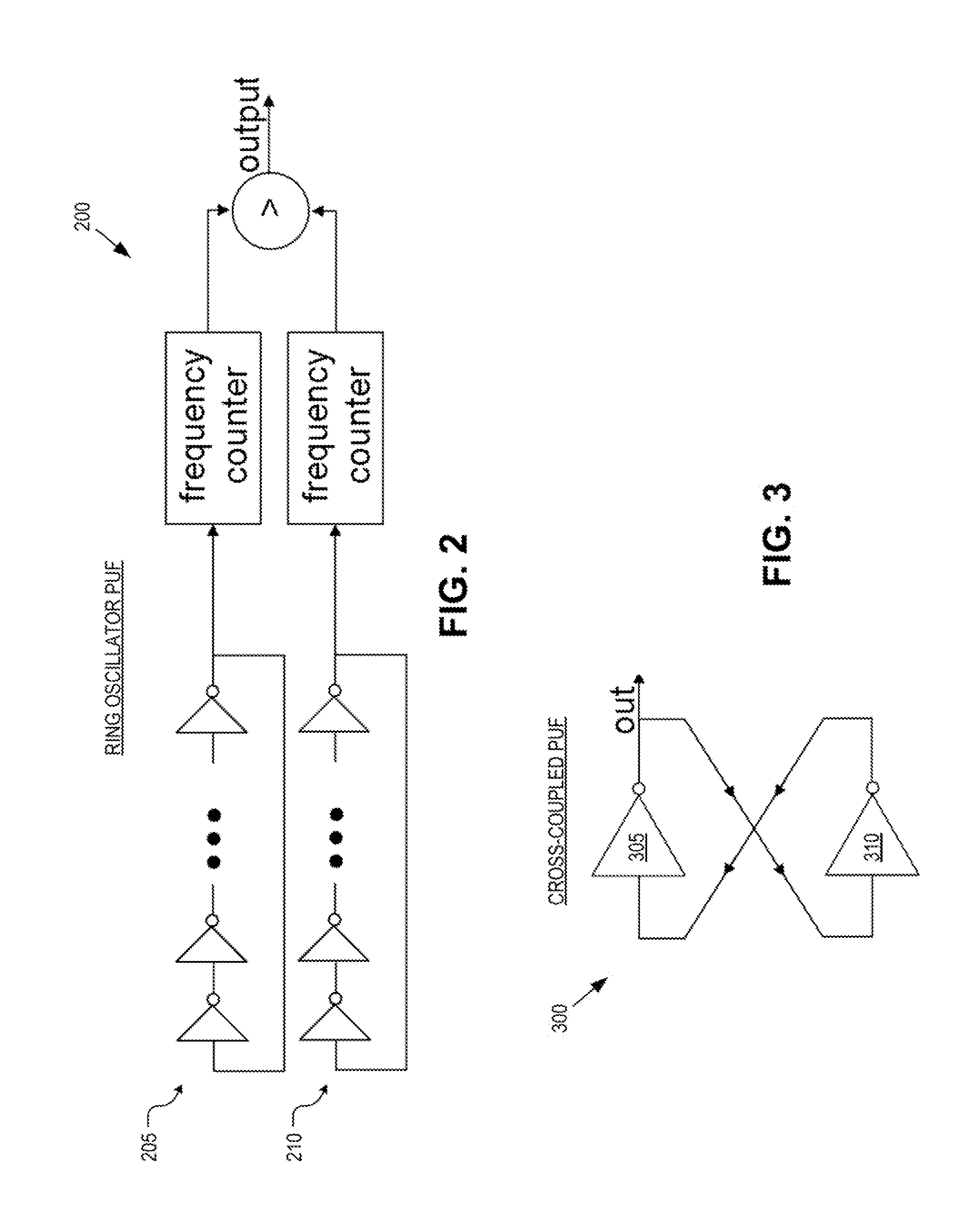
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
645 results about "Physical unclonable function" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
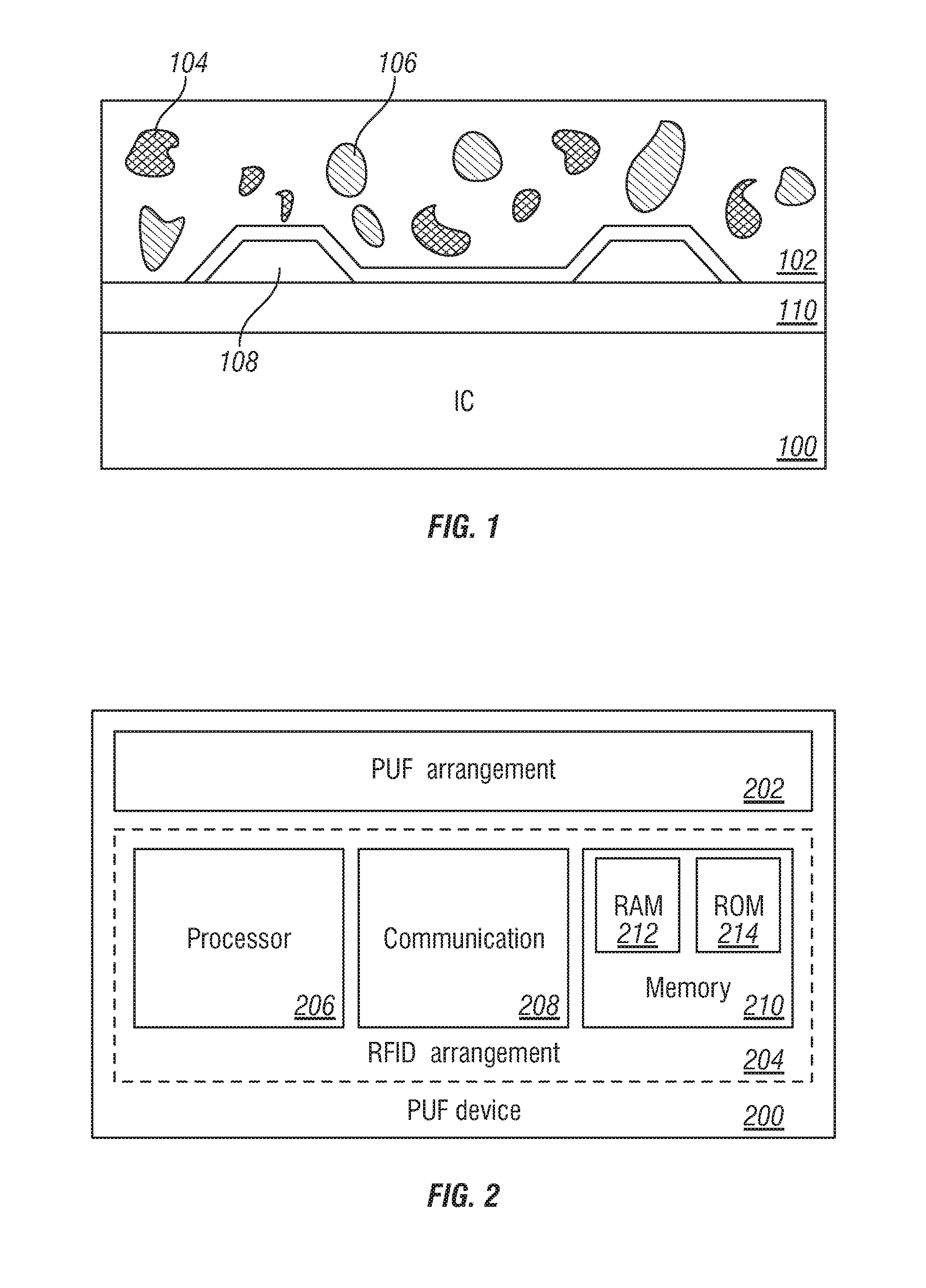
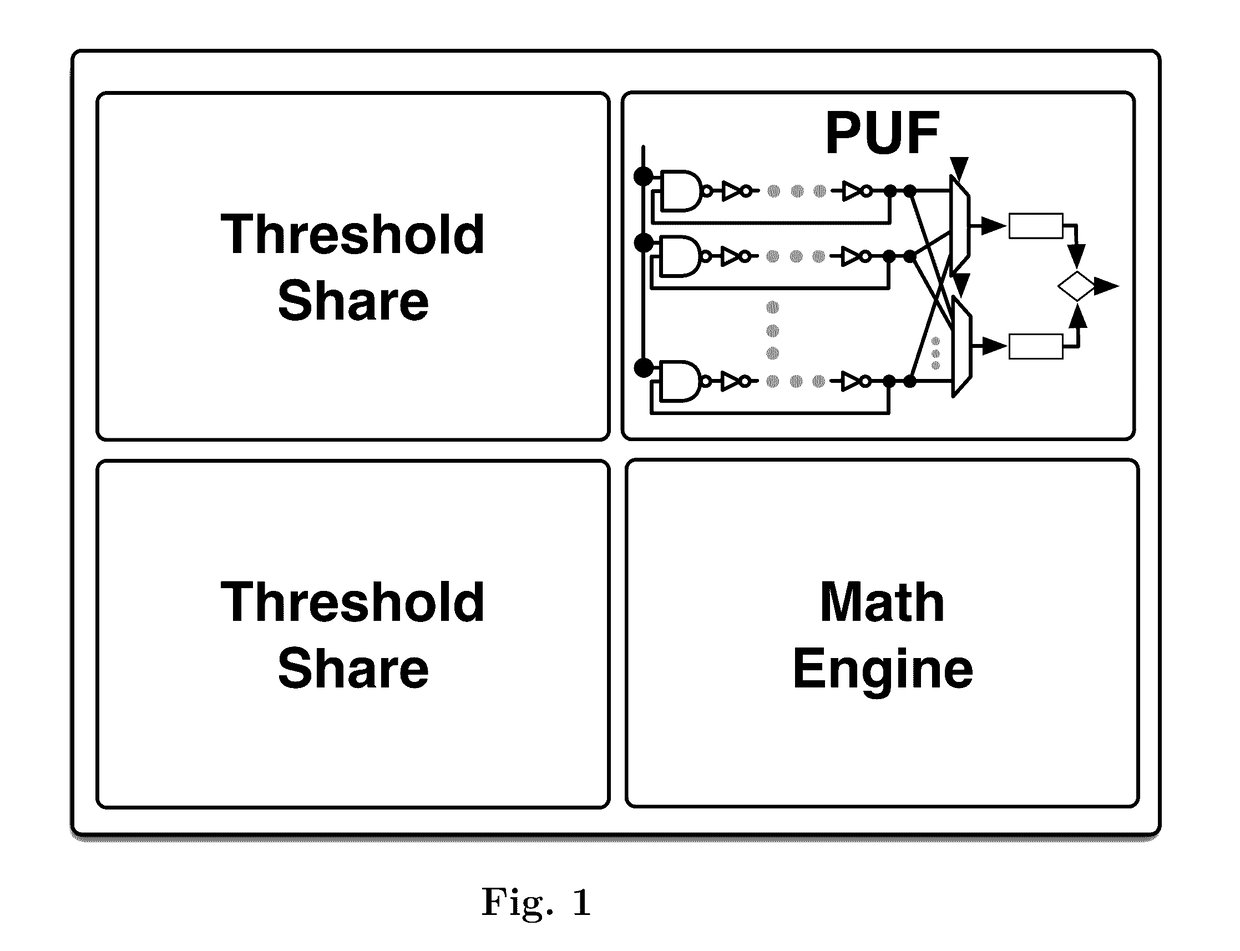
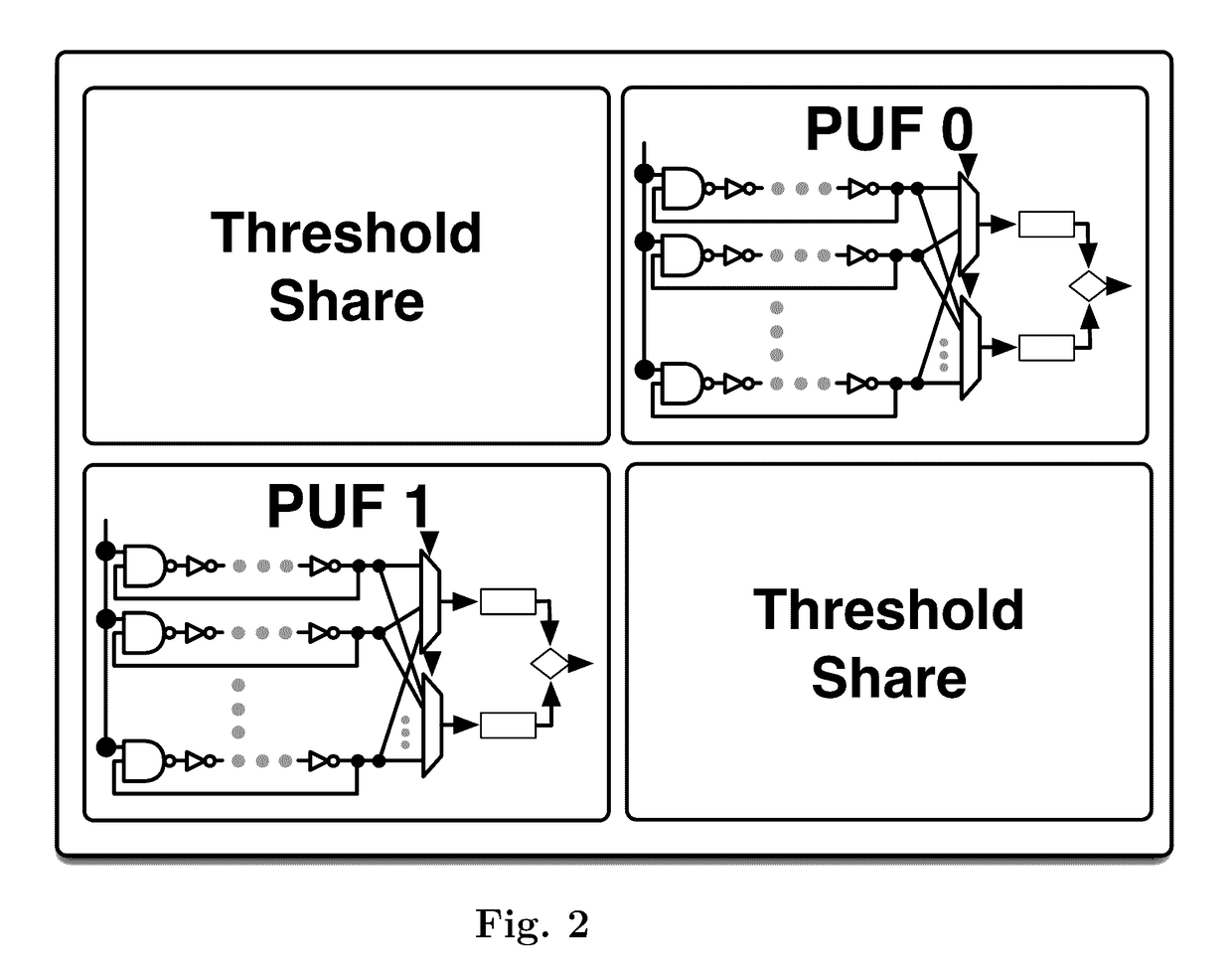
A physical unclonable function (sometimes also called physically unclonable function), or PUF, is a physically-defined "digital fingerprint" that serves as a unique identifier for a semiconductor device such as a microprocessor. They are based on unique physical variations which occur naturally during semiconductor manufacturing. A PUF is a physical entity embodied in a physical structure. Today, PUFs are usually implemented in integrated circuits and are typically used in applications with high security requirements, more specifically cryptography.
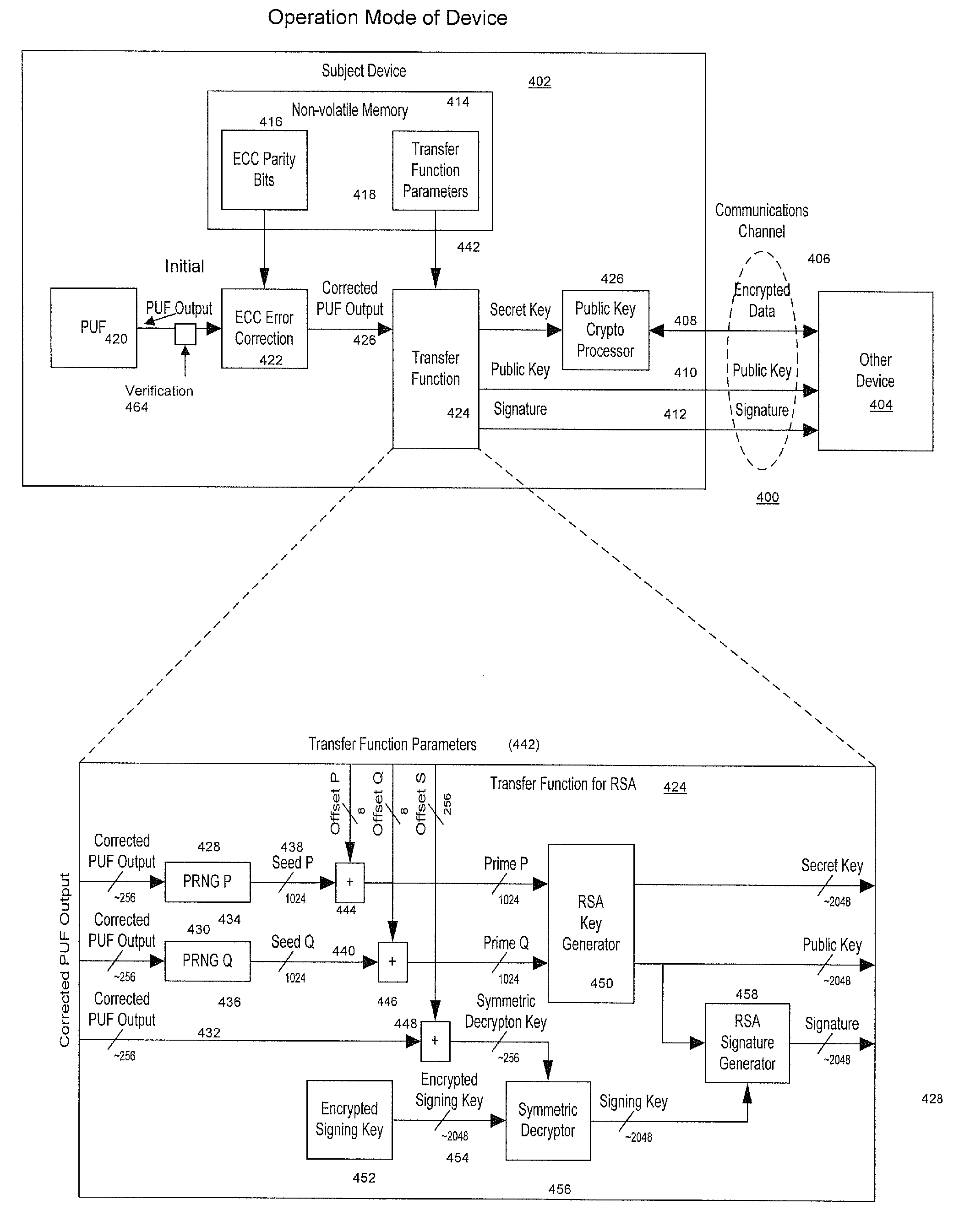
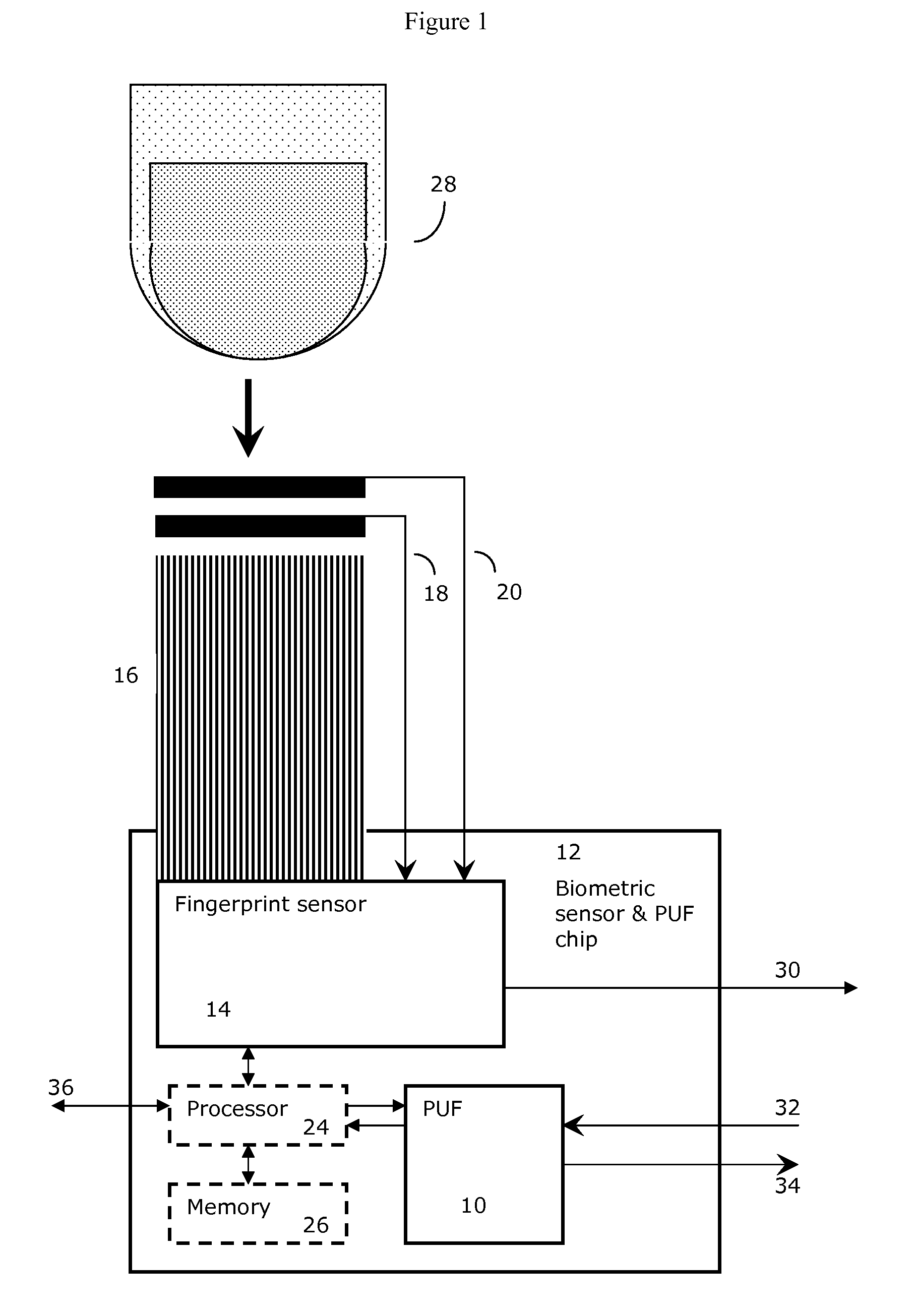
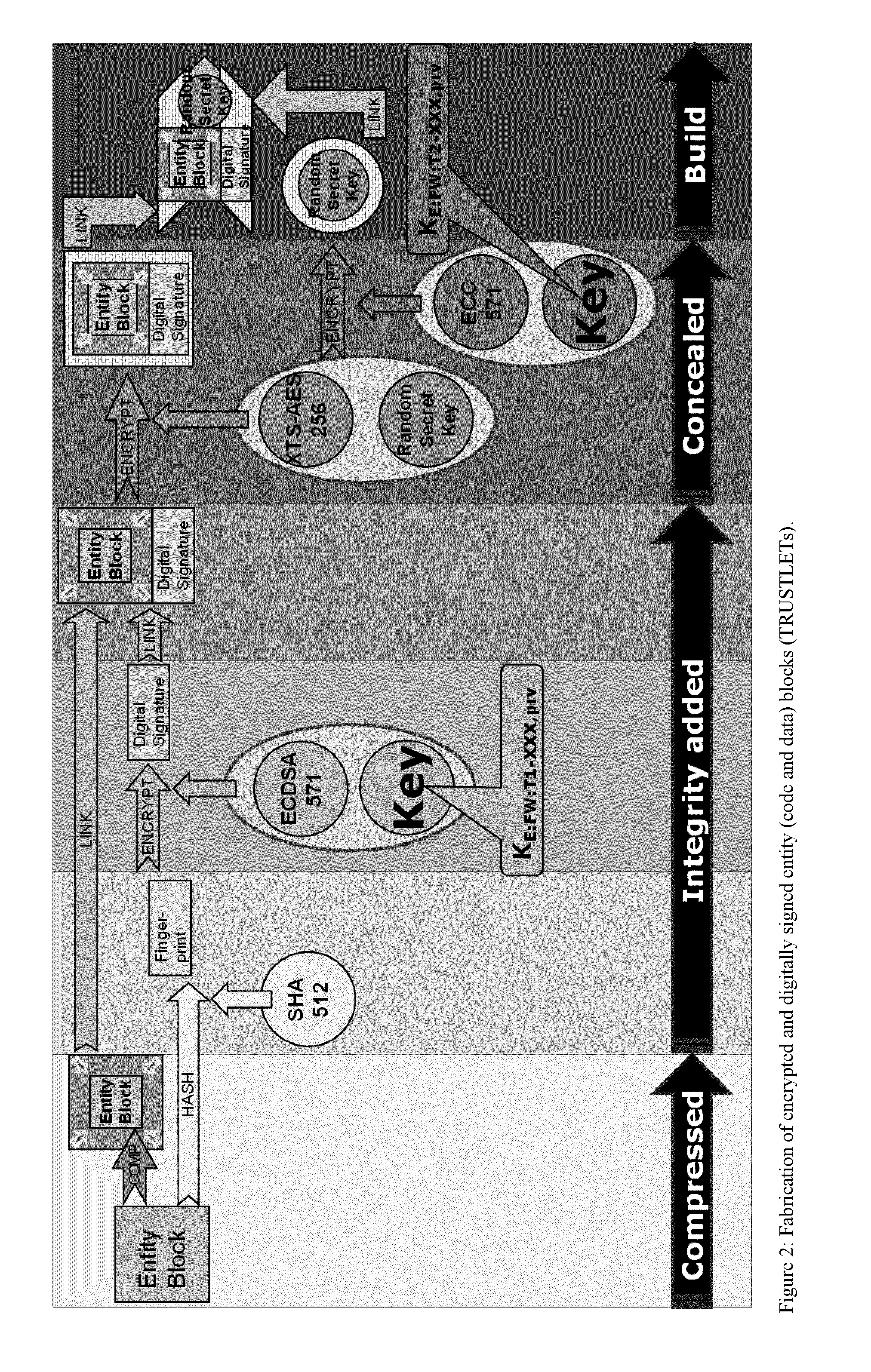
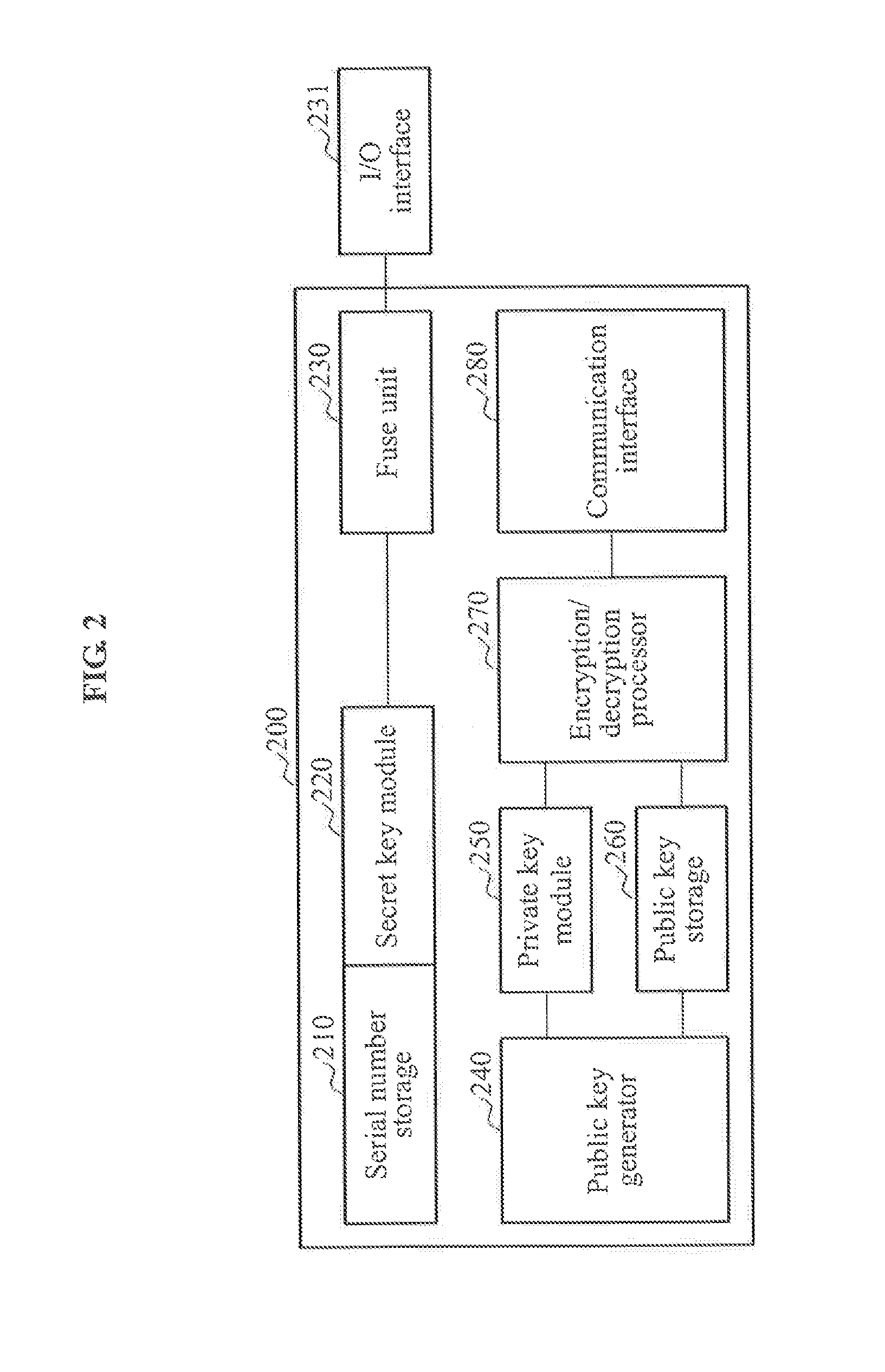
Method and System for Electronically Securing an Electronic Biometric Device Using Physically Unclonable Functions
InactiveUS20110002461A1Consume minimalCost of producingKey distribution for secure communicationElectric signal transmission systemsPhysical unclonable functionSecurity validation
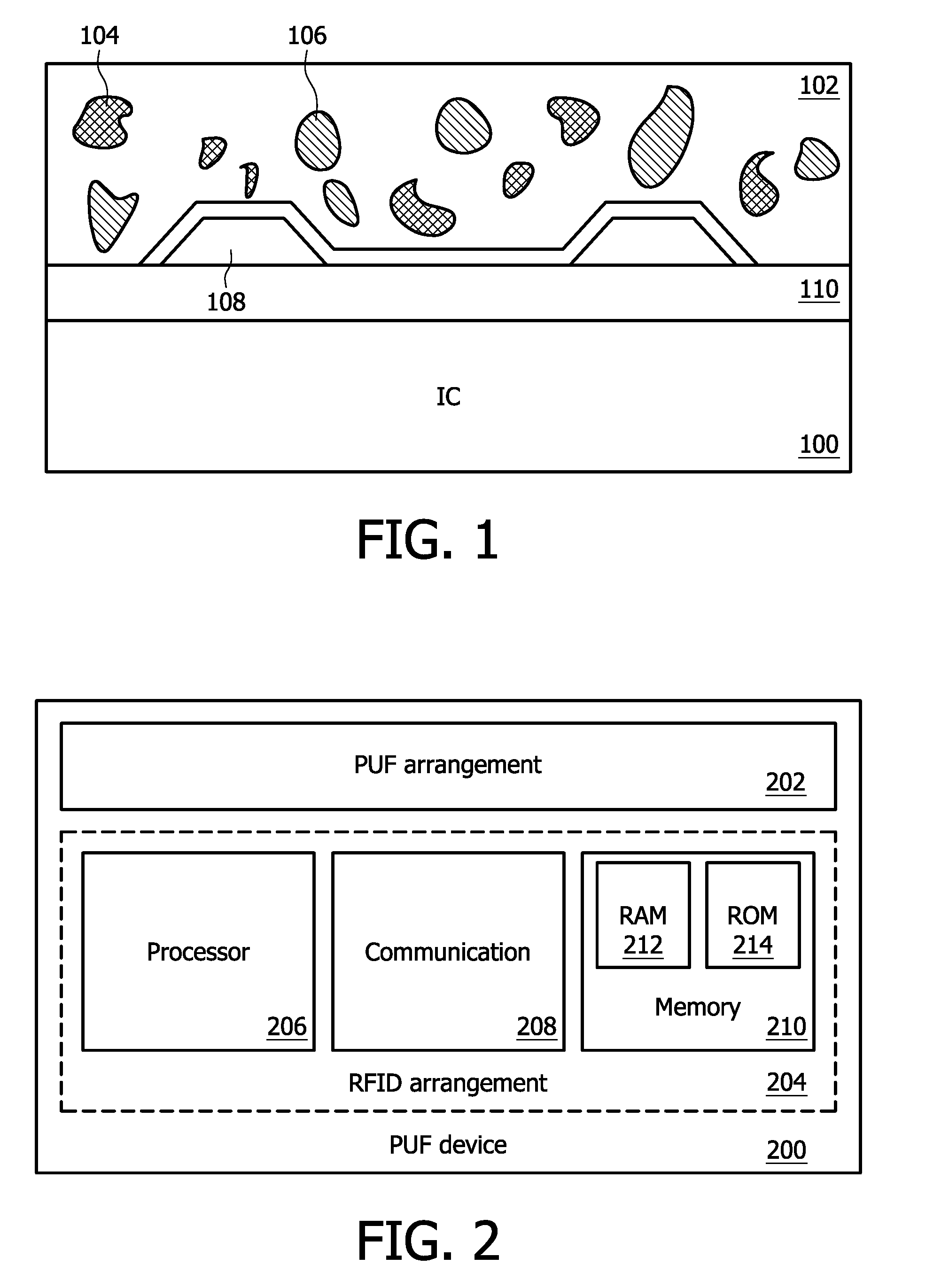
A system for securing an integrated circuit chip used for biometric sensors, or other electronic devices, by utilizing a physically unclonable function (PUF) circuit. These PUF functions are in turn used to generate security words and keys, such as an RSA public or private key. Such a system can be used to protect biometric security sensors and IC chips, such as fingerprint sensors and sensor driver chips, from attack or spoofing. The system may also be used in an efficient method to produce unique device set-up or power-up authentication security keys. These keys can be generated on a low frequency basis, and then frequently reused for later security verification purposes. In operation, the stored keys can be used to efficiently authenticate the device without the need to frequently run burdensome security key generation processes each time, while maintaining good device security.
Owner:SYNAPTICS INC
Tamper-protected hardware and method for using same
ActiveUS20140108786A1Execution of malicious code is preventedPreventing executionKey distribution for secure communicationMultiple keys/algorithms usageTamper proof hardwareComputer module
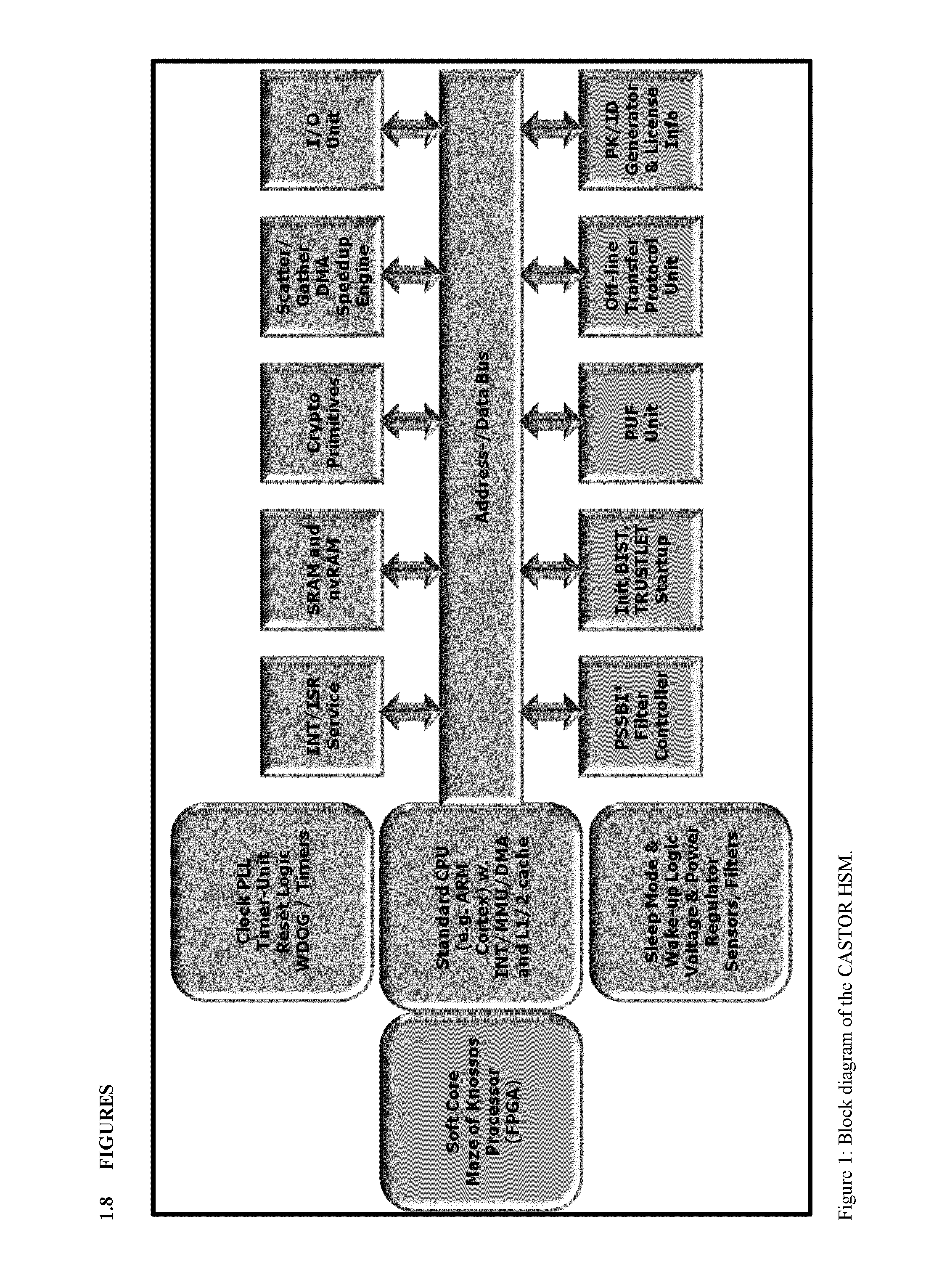
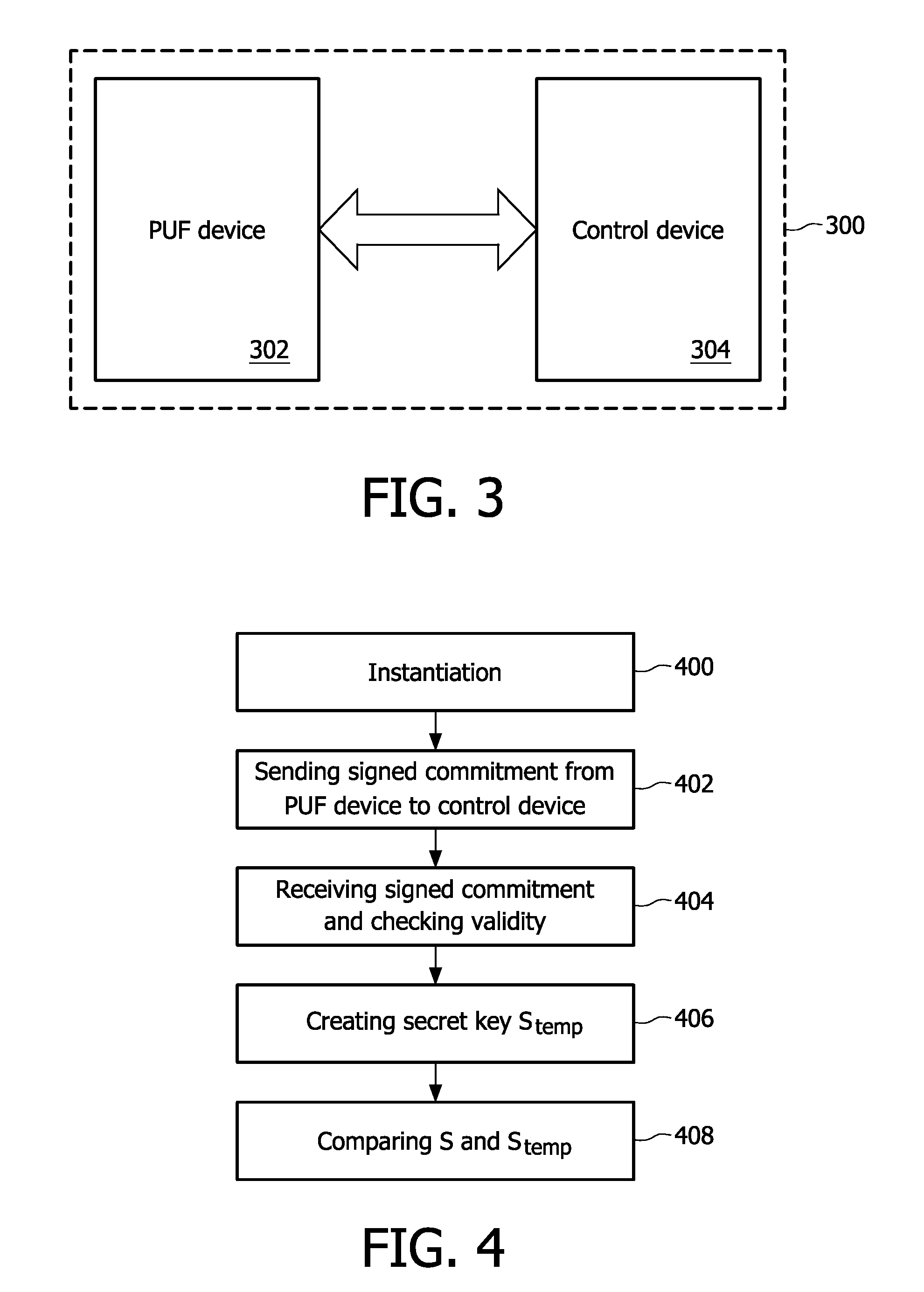
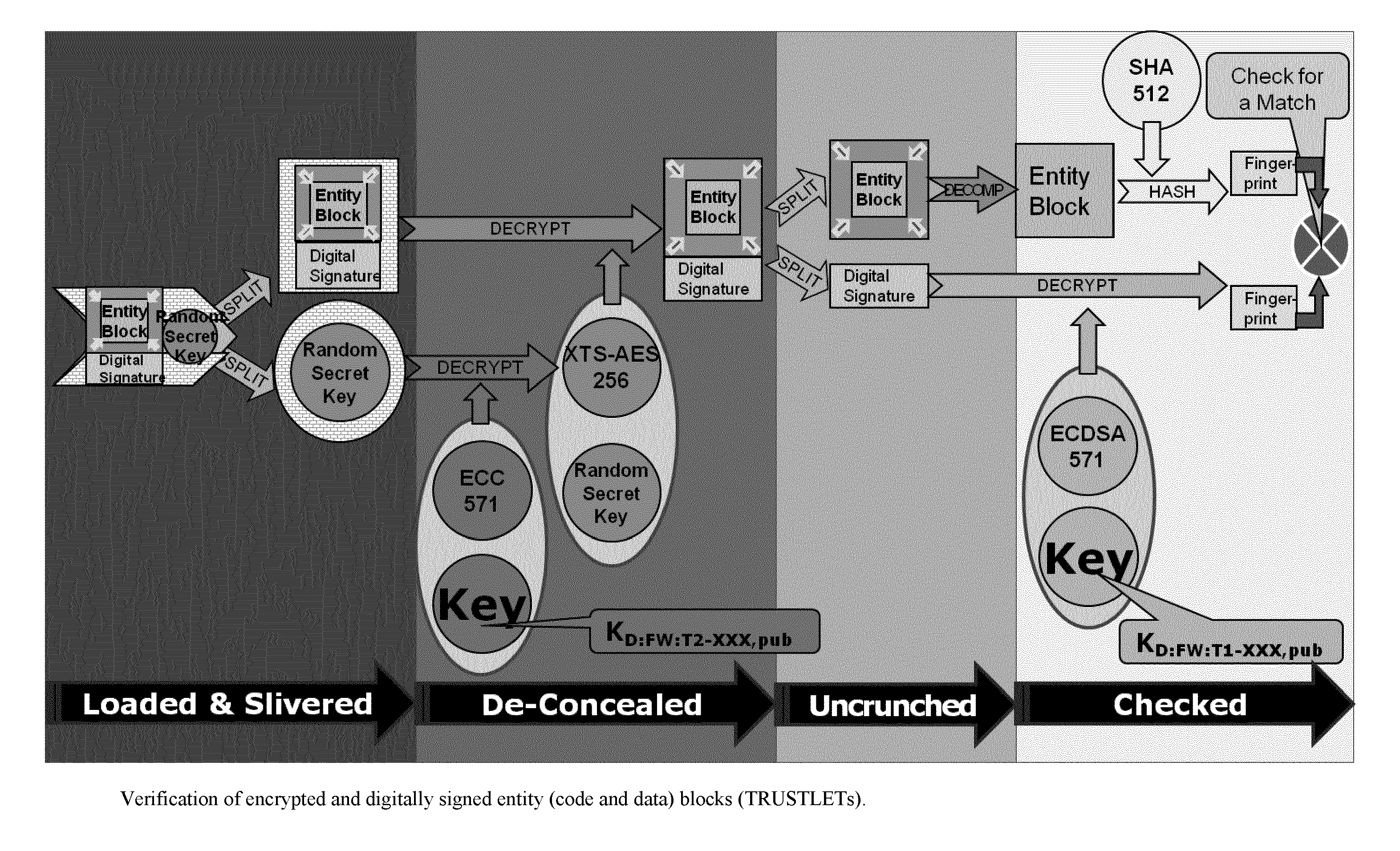
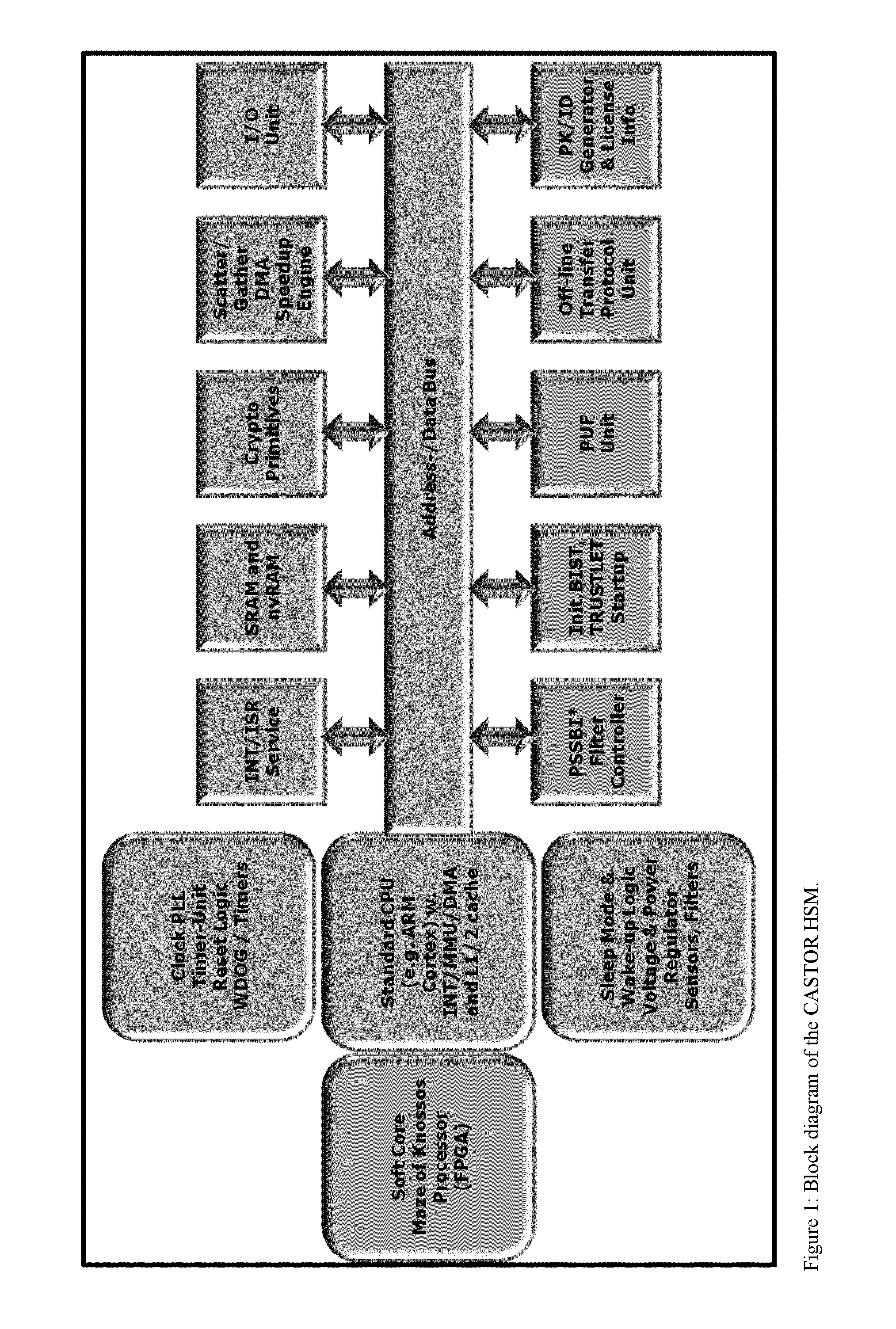
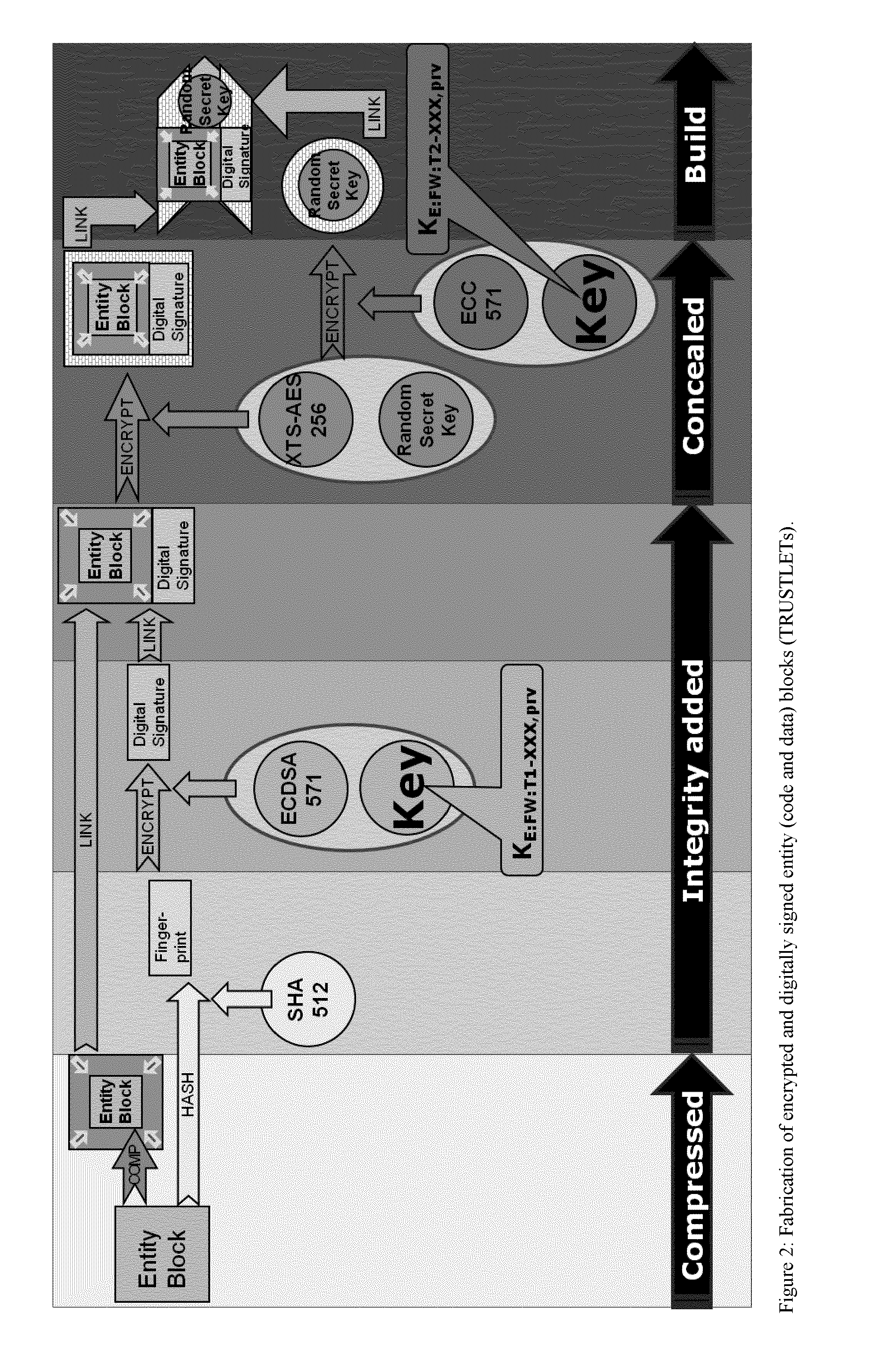
One of the various aspects of the invention is related to suggesting various techniques for improving the tamper-resistibility of hardware. The tamper-resistant hardware may be advantageously used in a transaction system that provides the off-line transaction protocol. Amongst these techniques for improving the tamper-resistibility are trusted bootstrapping by means of secure software entity modules, a new use of hardware providing a Physical Unclonable Function, and the use of a configuration fingerprint of a FPGA used within the tamper-resistant hardware.
Owner:EMSYCON
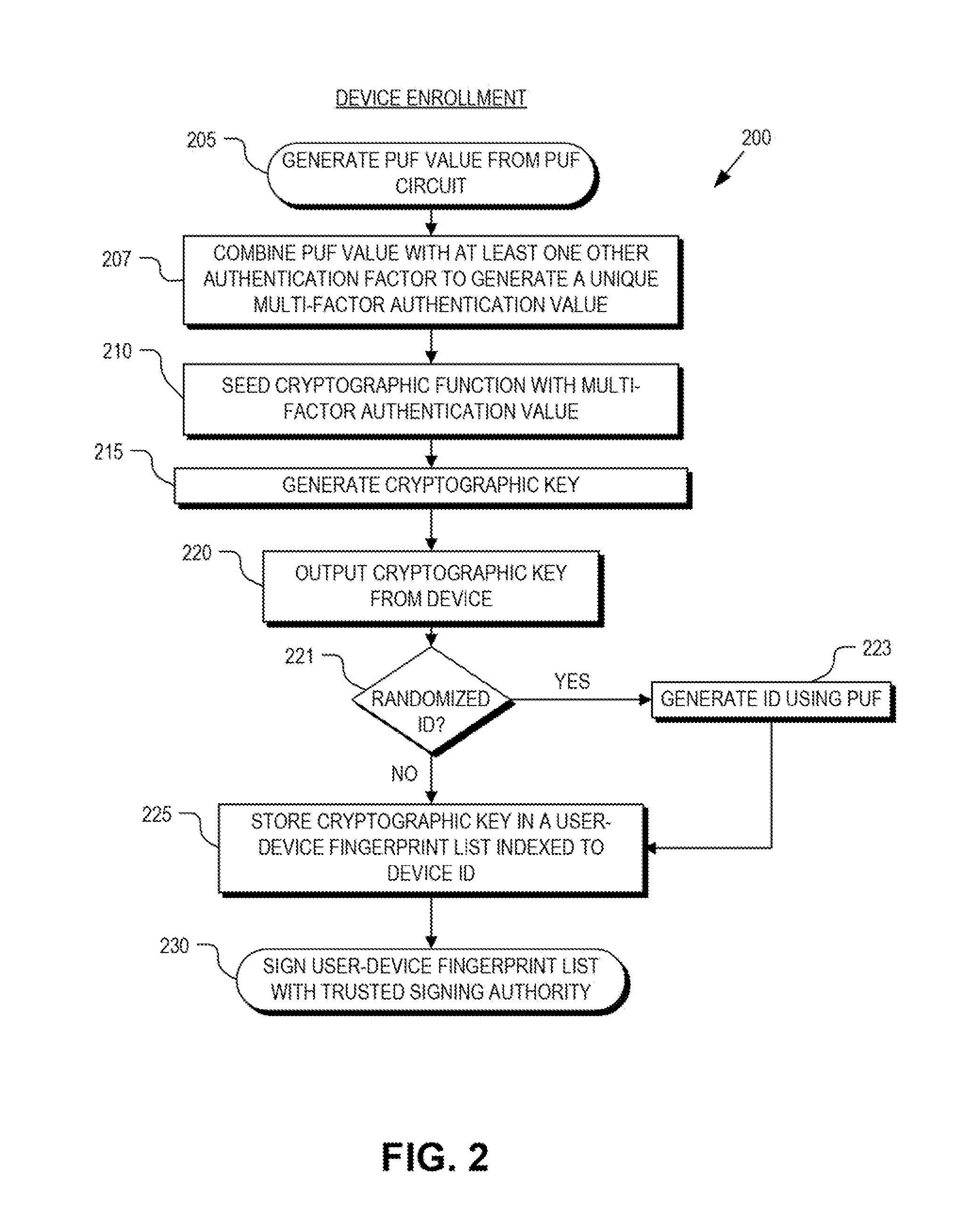
Multi-factor authentication
ActiveUS8868923B1Reliability increasing modificationsElectric signal transmission systemsPhysical unclonable functionUser authentication
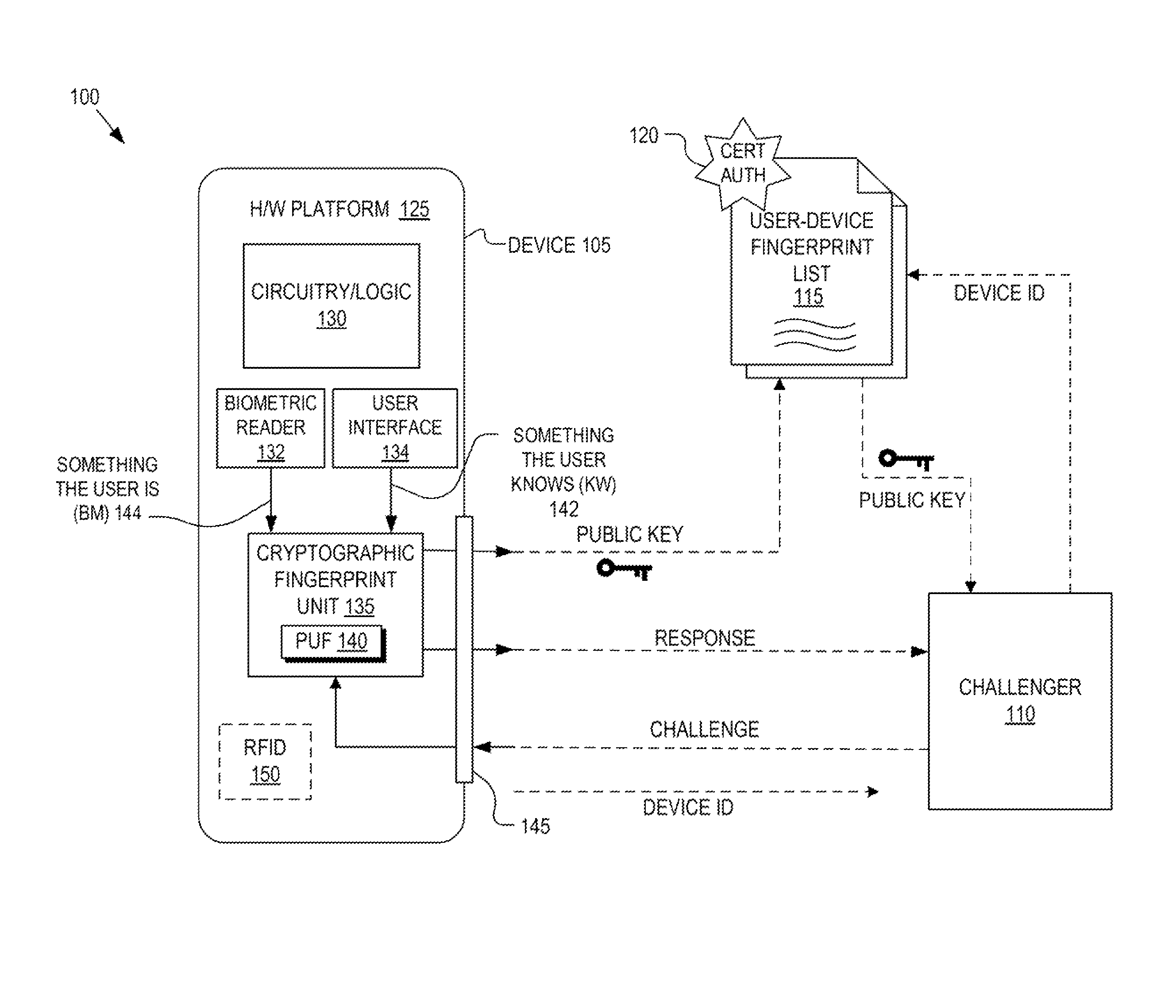
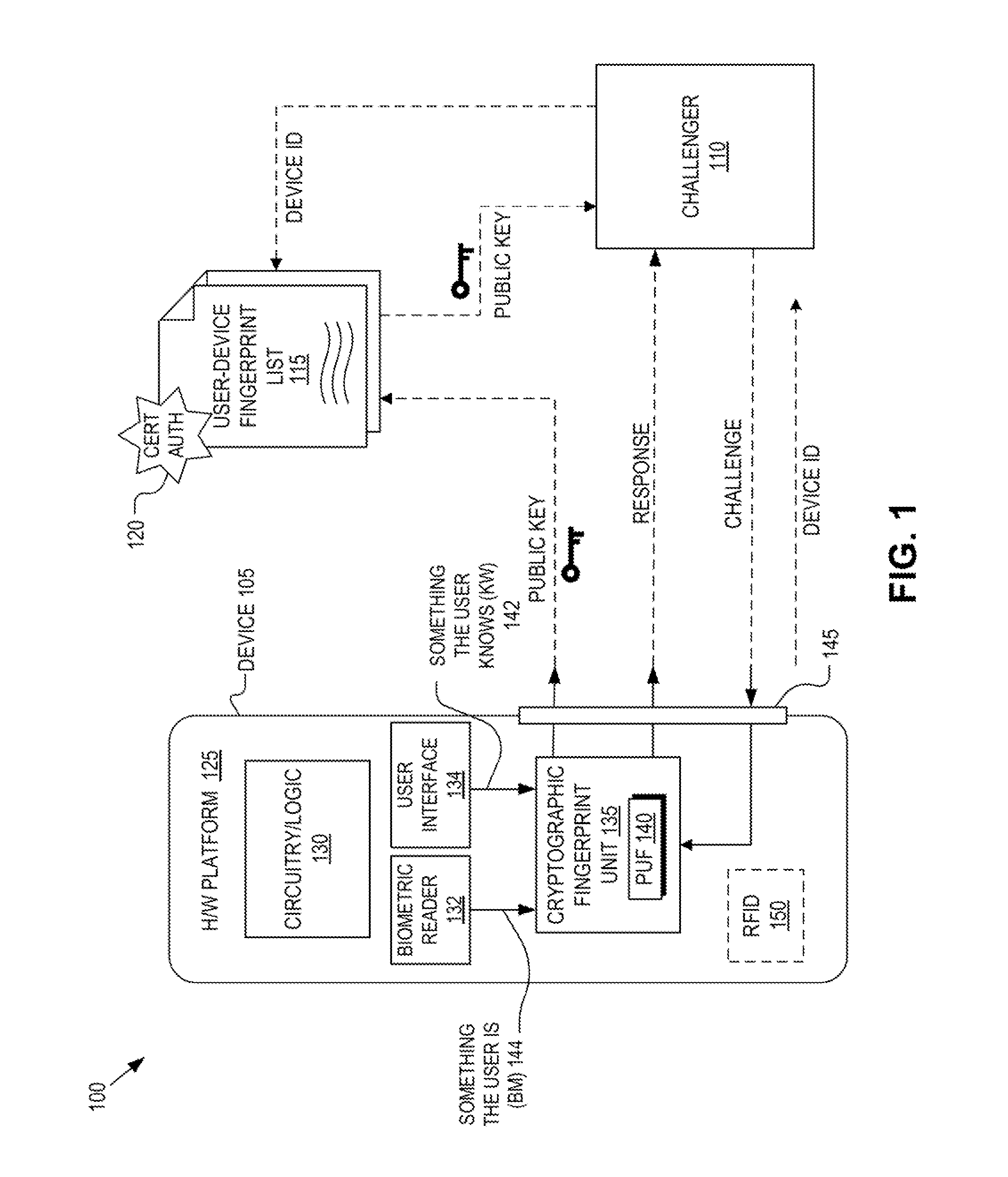
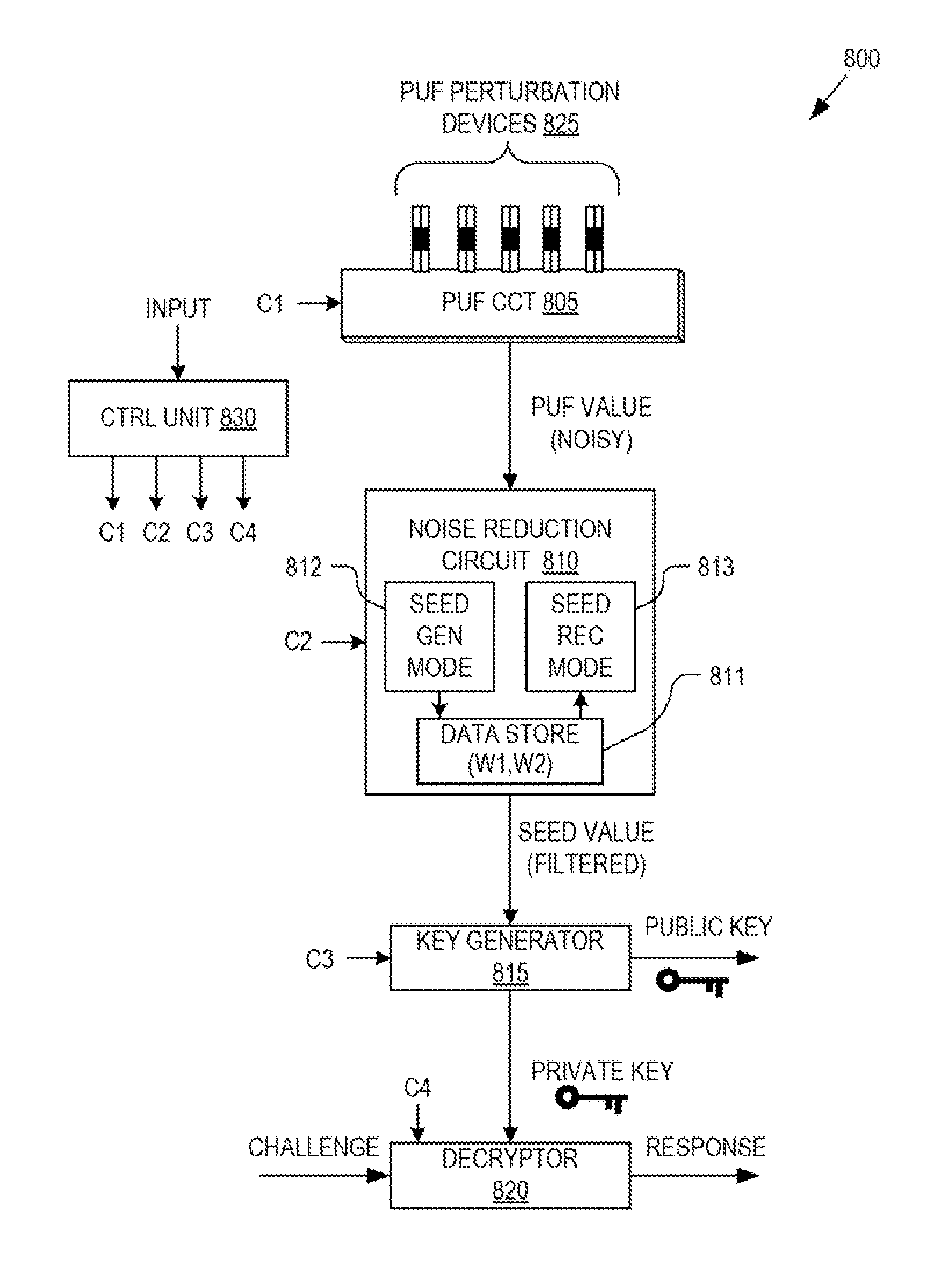
Detection and deterrence of spoofing of user authentication may be achieved by including a cryptographic fingerprint unit within a hardware device for authenticating a user of the hardware device. The cryptographic fingerprint unit includes an internal physically unclonable function (“PUF”) circuit disposed in or on the hardware device, which generates a PUF value. Combining logic is coupled to receive the PUF value, combines the PUF value with one or more other authentication factors to generate a multi-factor authentication value. A key generator is coupled to generate a private key and a public key based on the multi-factor authentication value while a decryptor is coupled to receive an authentication challenge posed to the hardware device and encrypted with the public key and coupled to output a response to the authentication challenge decrypted with the private key.
Owner:NAT TECH & ENG SOLUTIONS OF SANDIA LLC
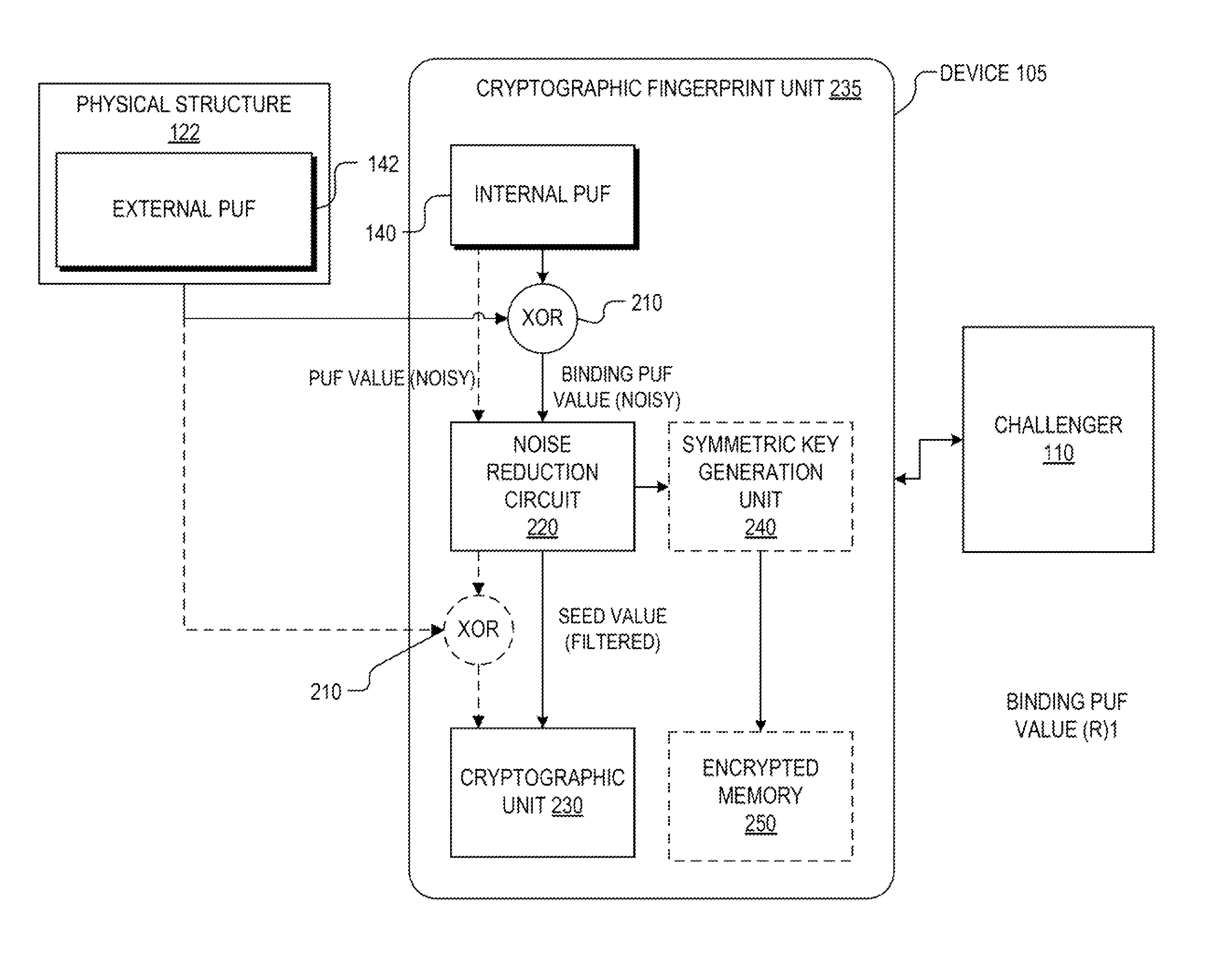
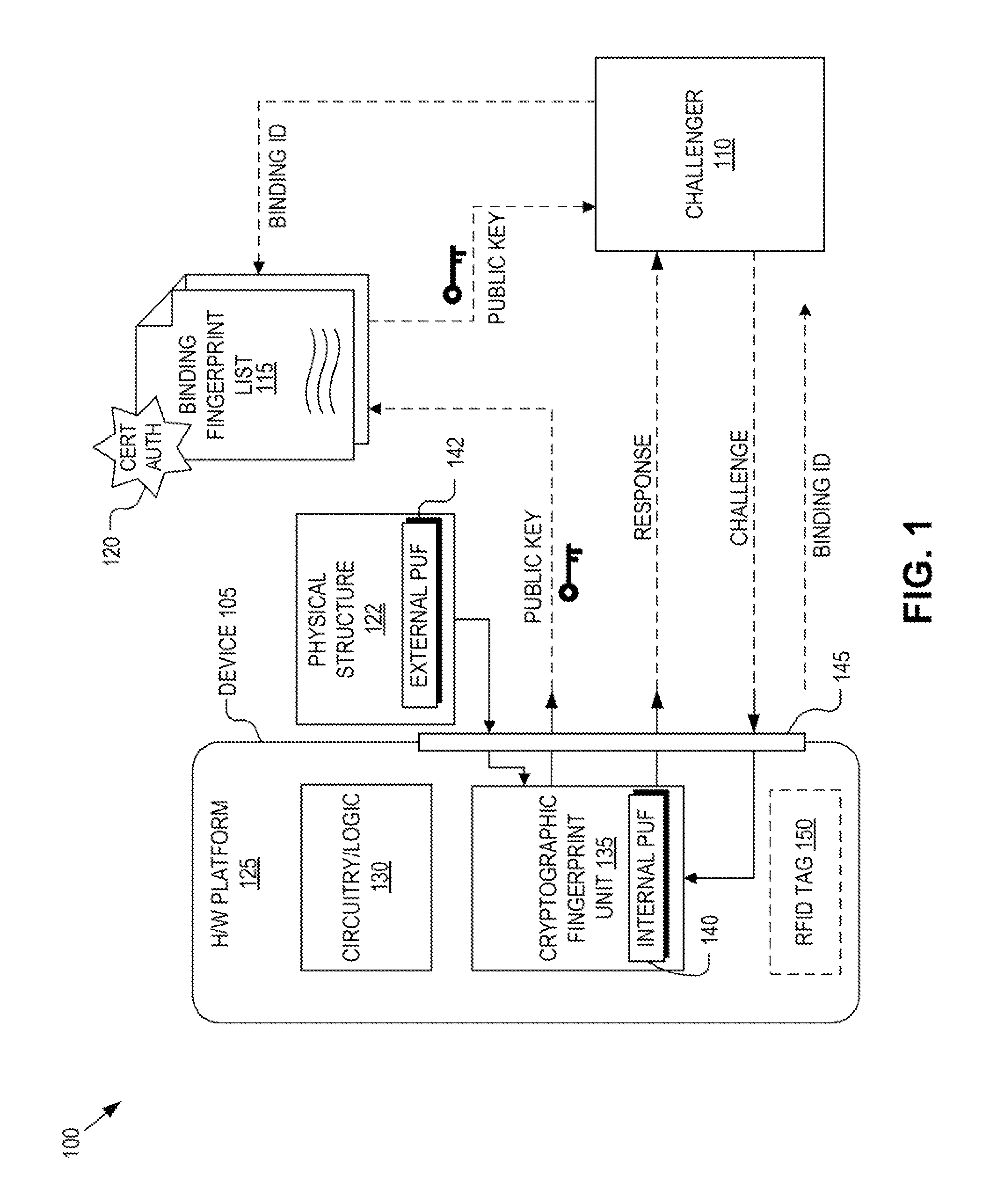
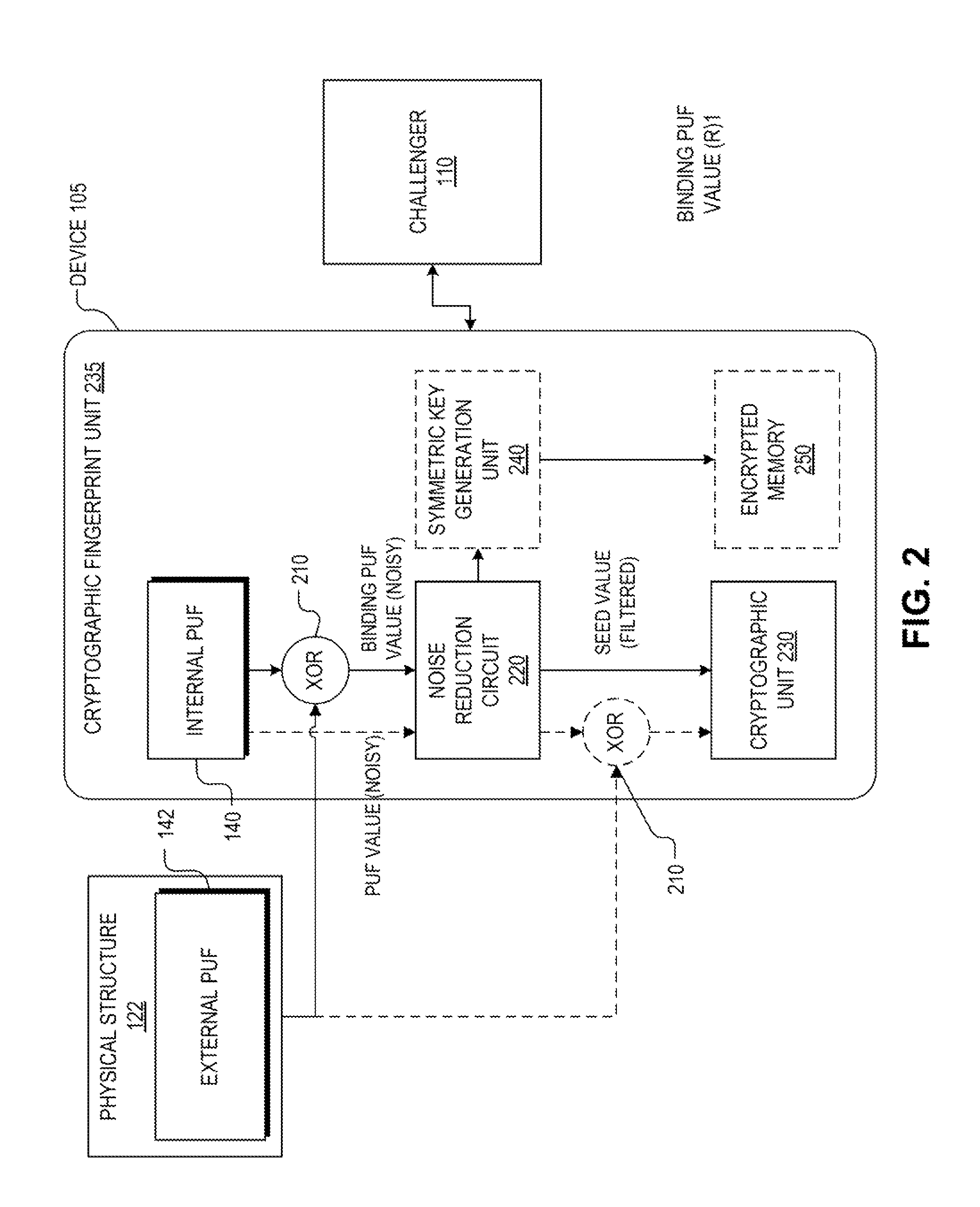
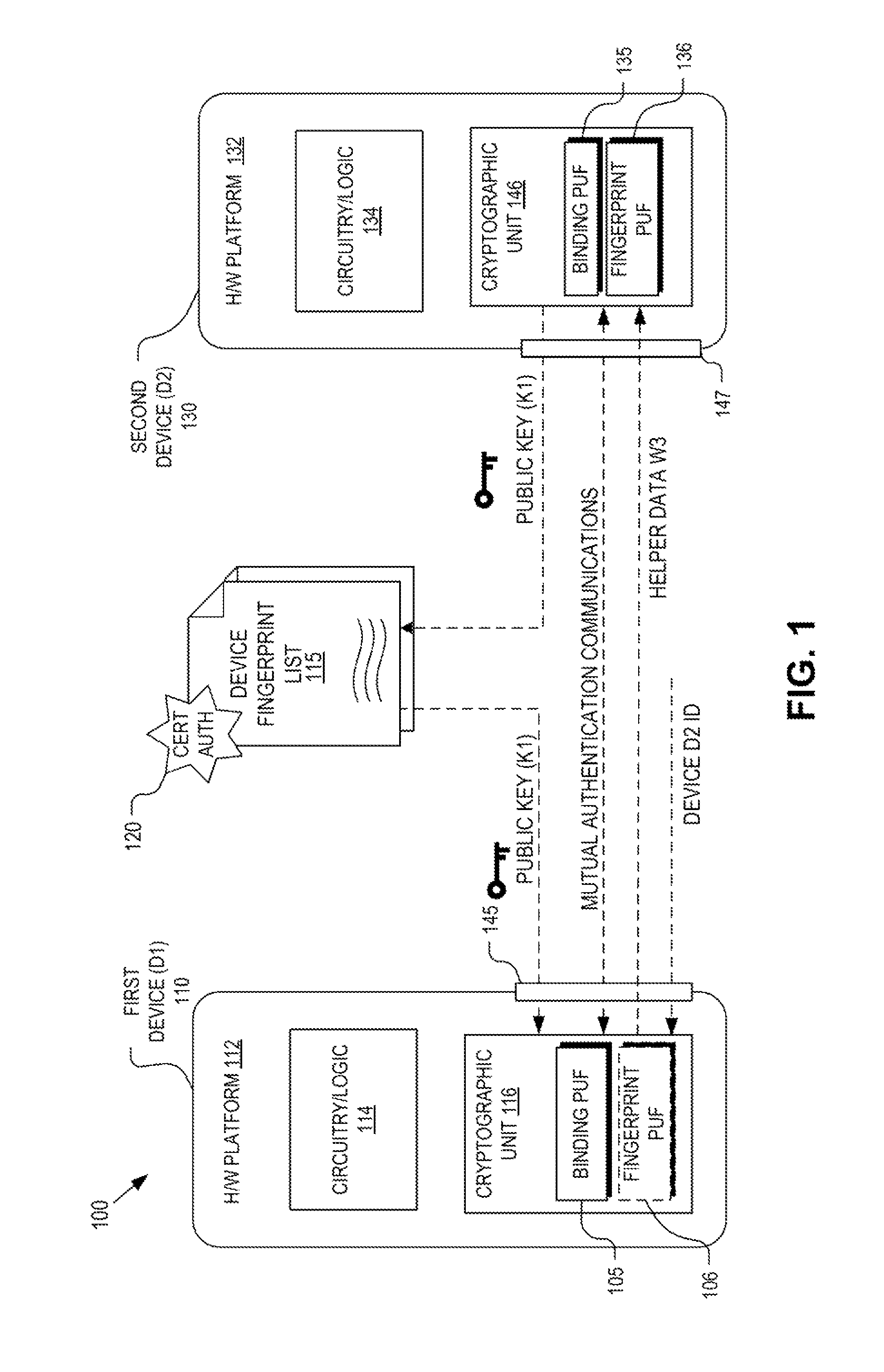
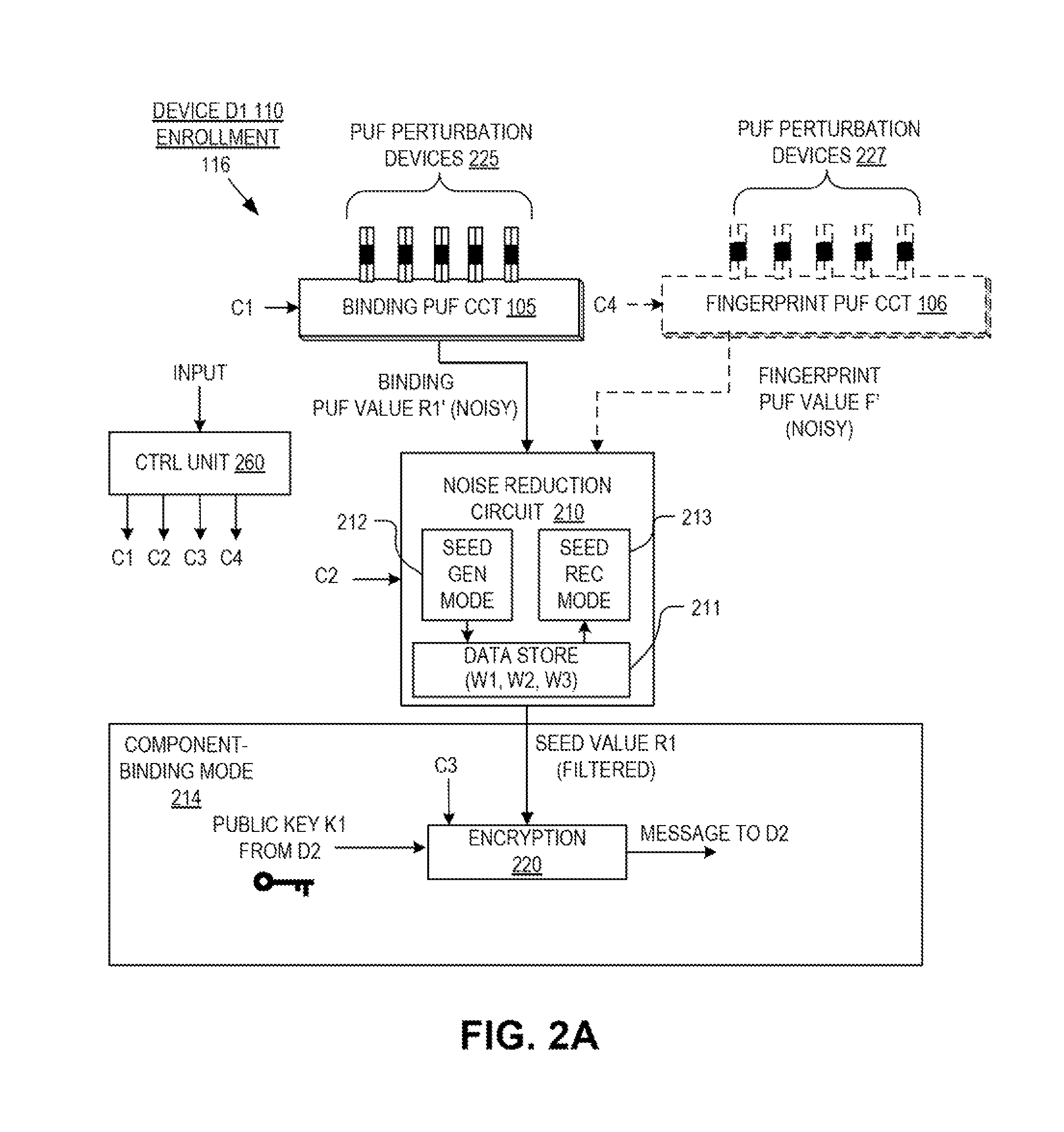
Hardware device to physical structure binding and authentication
ActiveUS8516269B1Electric signal transmission systemsDigital data processing detailsComputer hardwarePhysical unclonable function
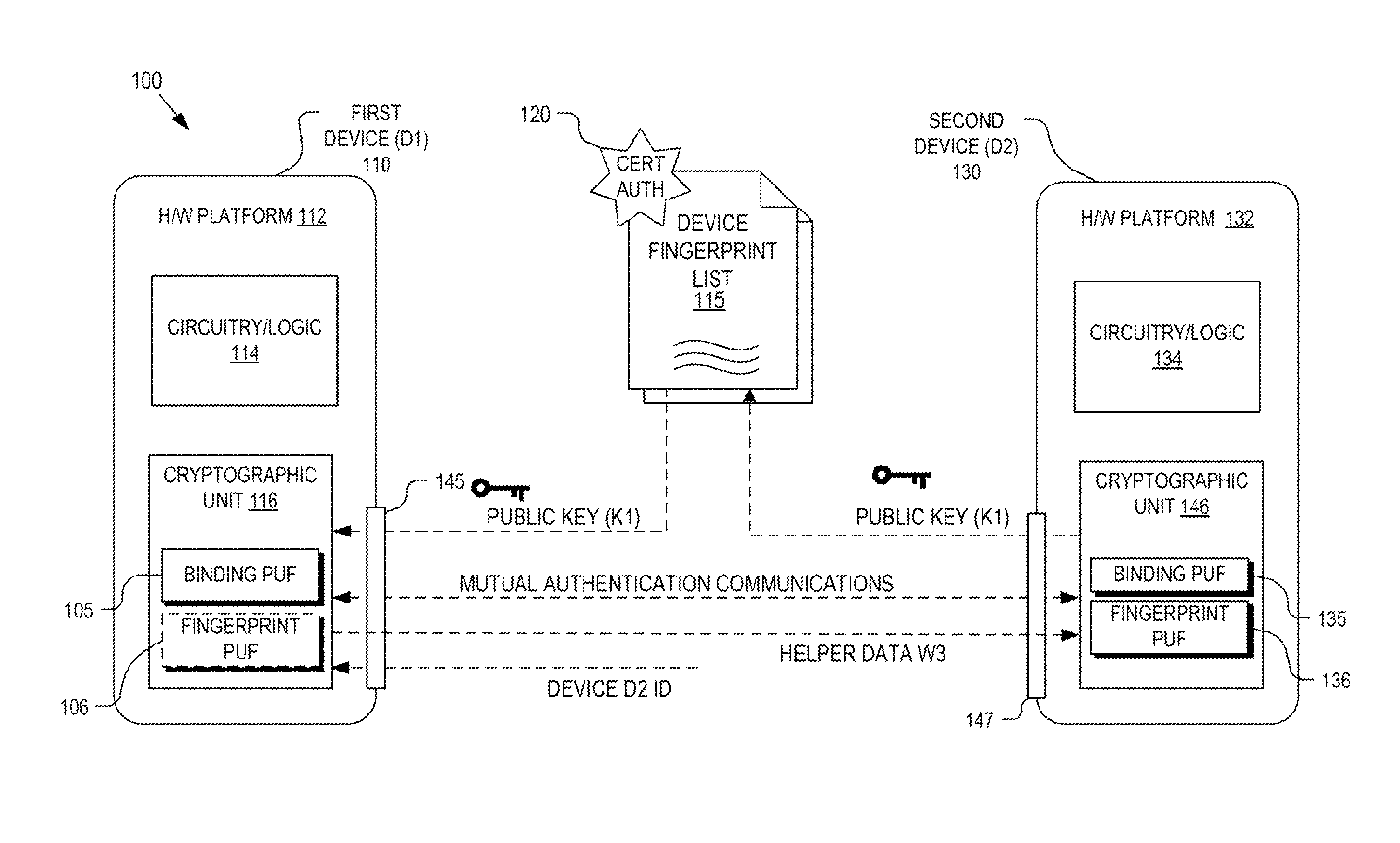
Detection and deterrence of device tampering and subversion may be achieved by including a cryptographic fingerprint unit within a hardware device for authenticating a binding of the hardware device and a physical structure. The cryptographic fingerprint unit includes an internal physically unclonable function (“PUF”) circuit disposed in or on the hardware device, which generate an internal PUF value. Binding logic is coupled to receive the internal PUF value, as well as an external PUF value associated with the physical structure, and generates a binding PUF value, which represents the binding of the hardware device and the physical structure. The cryptographic fingerprint unit also includes a cryptographic unit that uses the binding PUF value to allow a challenger to authenticate the binding.
Owner:NAT TECH & ENG SOLUTIONS OF SANDIA LLC
Physically Unclonable Function Implemented Through Threshold Voltage Comparison
InactiveUS20110317829A1Increase the output voltageKey distribution for secure communicationInternal/peripheral component protectionPhysical unclonable functionEngineering
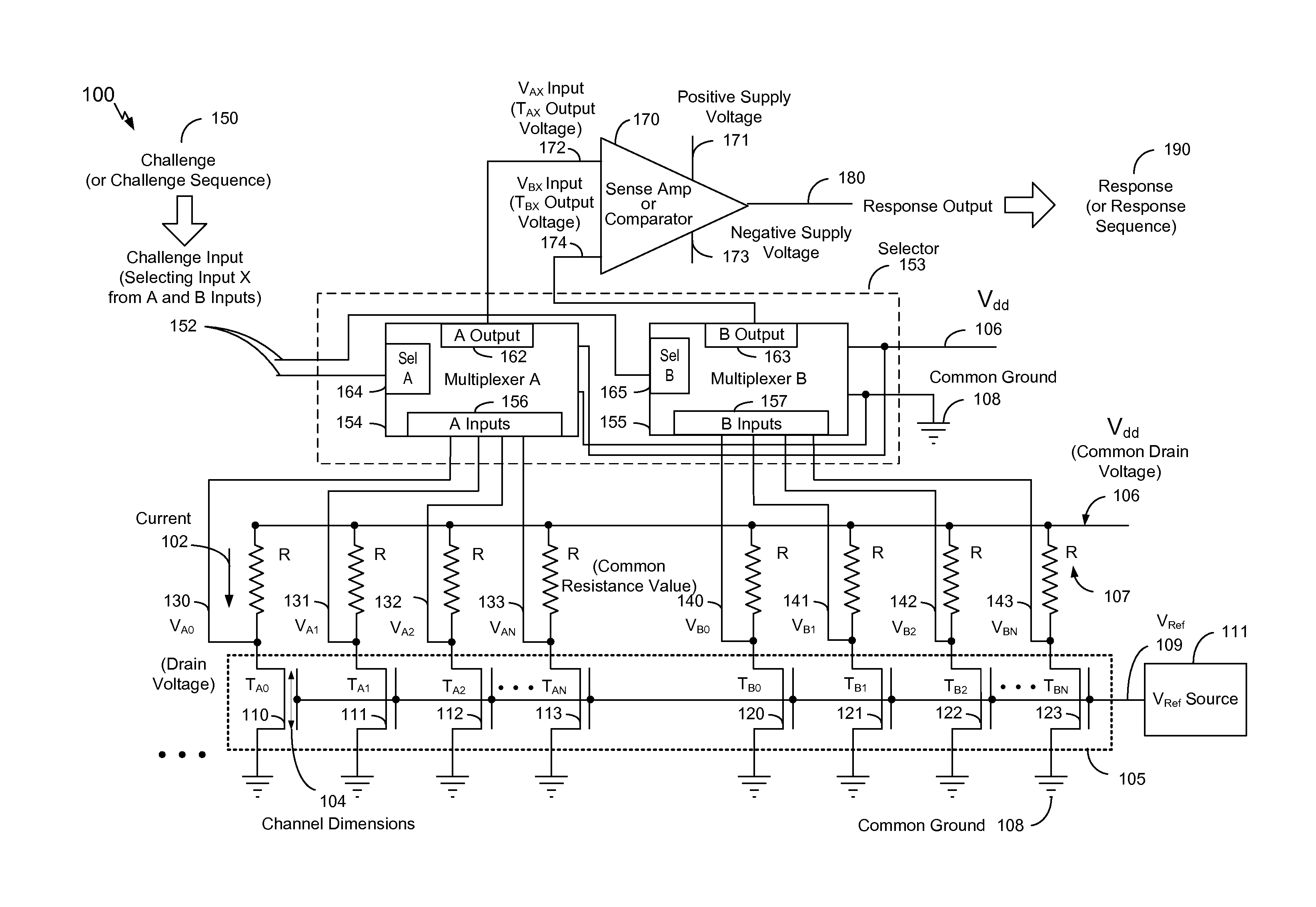
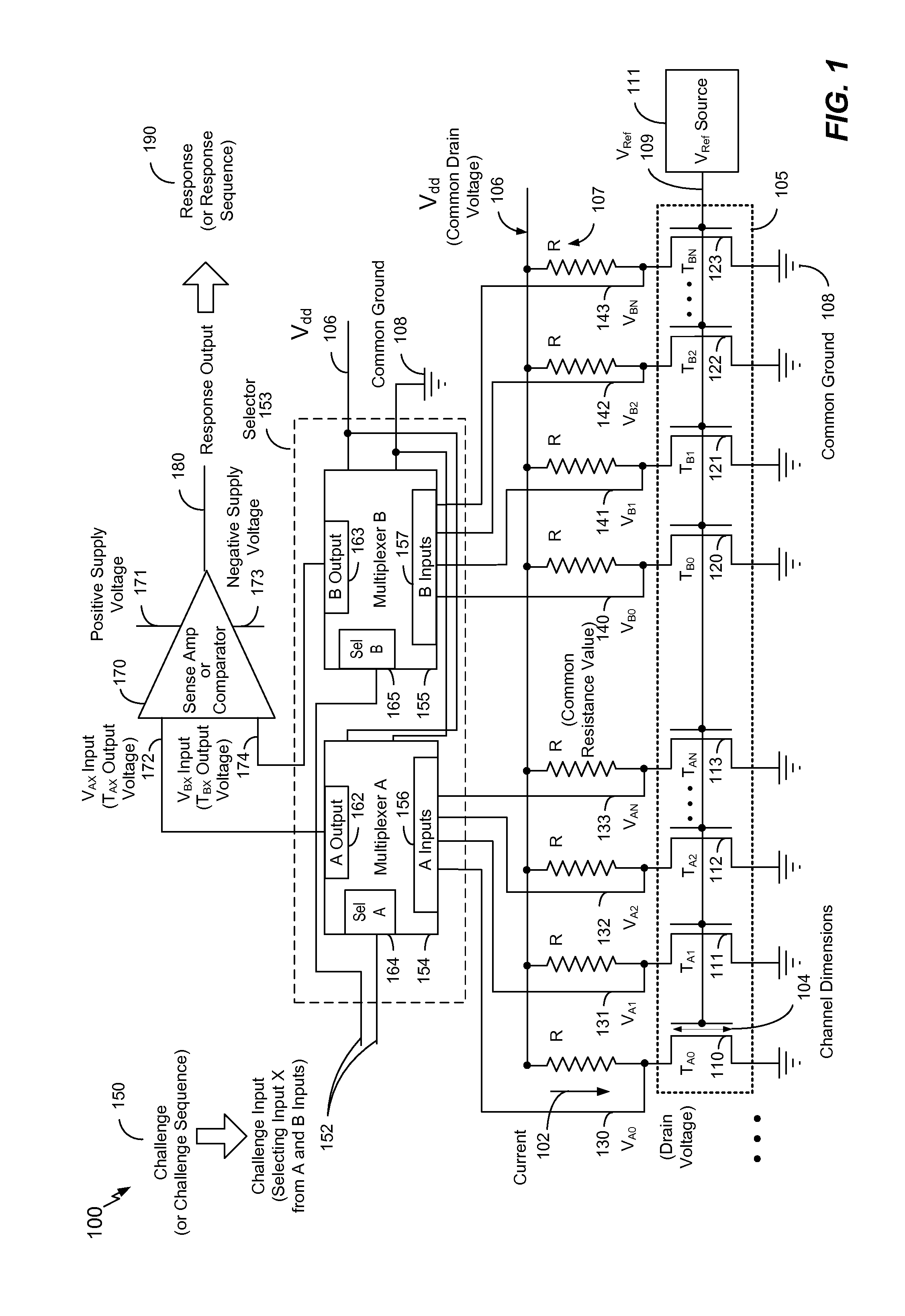
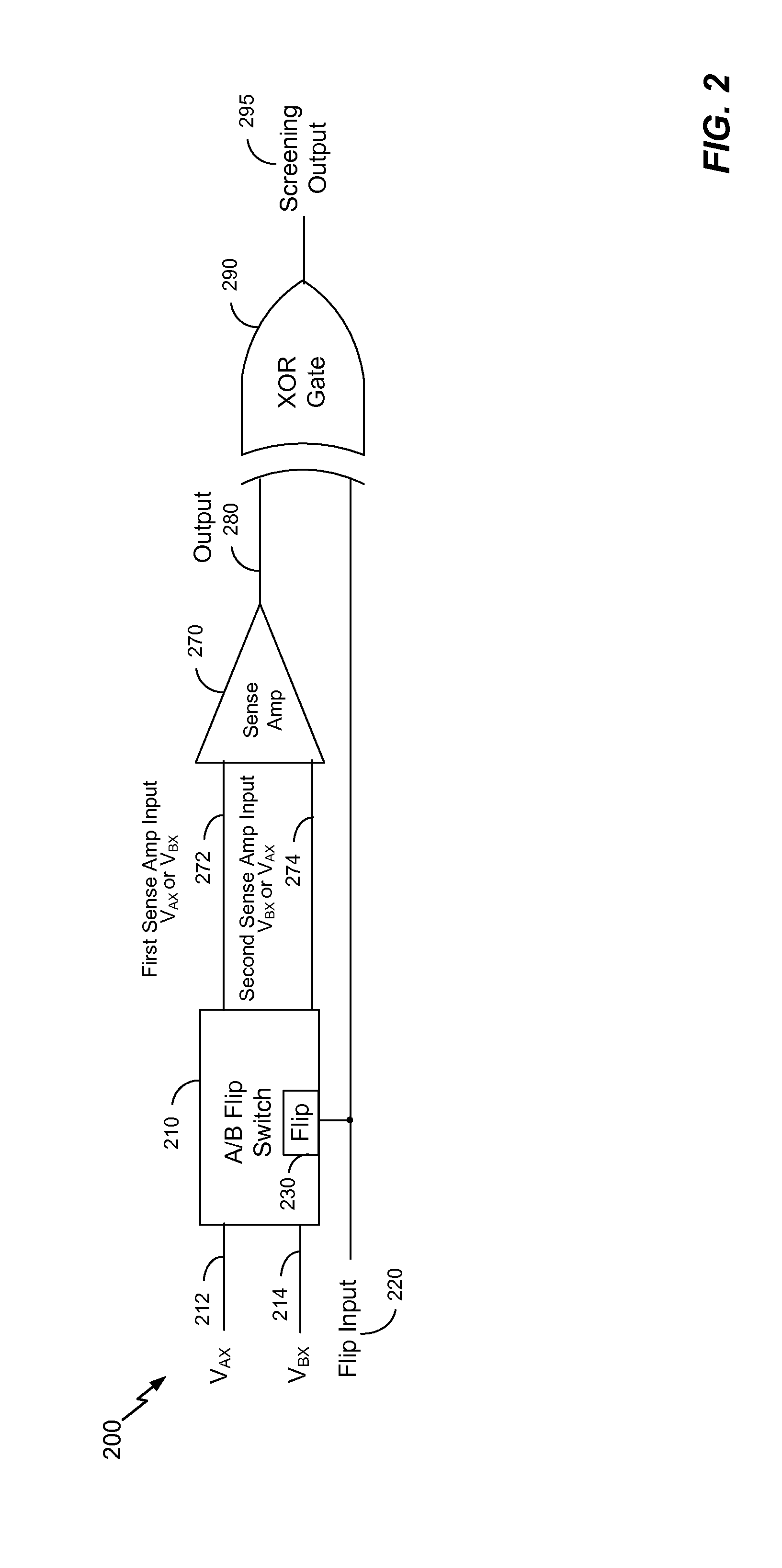
Electronic devices and methods are disclosed to provide and to test a physically unclonable function (PUF) based on relative threshold voltages of one or more pairs of transistors. In a particular embodiment, an electronic device is operable to generate a response to a challenge. The electronic device includes a plurality of transistors, with each of the plurality of transistors having a threshold voltage substantially equal to an intended threshold voltage. The electronic device includes a challenge input configured to receive the challenge. The challenge input includes one or more bits that are used to individually select each of a pair of transistors of the plurality of transistors. The electronic device also includes a comparator to receive an output voltage from each of the pair of transistors and to generate a response indicating which of the pair of transistors has the higher output voltage. The output voltage of each of the pair of transistors varies based on the threshold voltage of each of the pair of transistors.
Owner:GLOBALFOUNDRIES INC
Hardware device binding and mutual authentication
ActiveUS8667265B1Digital data authenticationSecuring communicationComputer hardwarePhysical unclonable function
Detection and deterrence of device tampering and subversion by substitution may be achieved by including a cryptographic unit within a computing device for binding multiple hardware devices and mutually authenticating the devices. The cryptographic unit includes a physically unclonable function (“PUF”) circuit disposed in or on the hardware device, which generates a binding PUF value. The cryptographic unit uses the binding PUF value during an enrollment phase and subsequent authentication phases. During a subsequent authentication phase, the cryptographic unit uses the binding PUF values of the multiple hardware devices to generate a challenge to send to the other device, and to verify a challenge received from the other device to mutually authenticate the hardware devices.
Owner:NAT TECH & ENG SOLUTIONS OF SANDIA LLC
Reliable physical unclonable function for device authentication
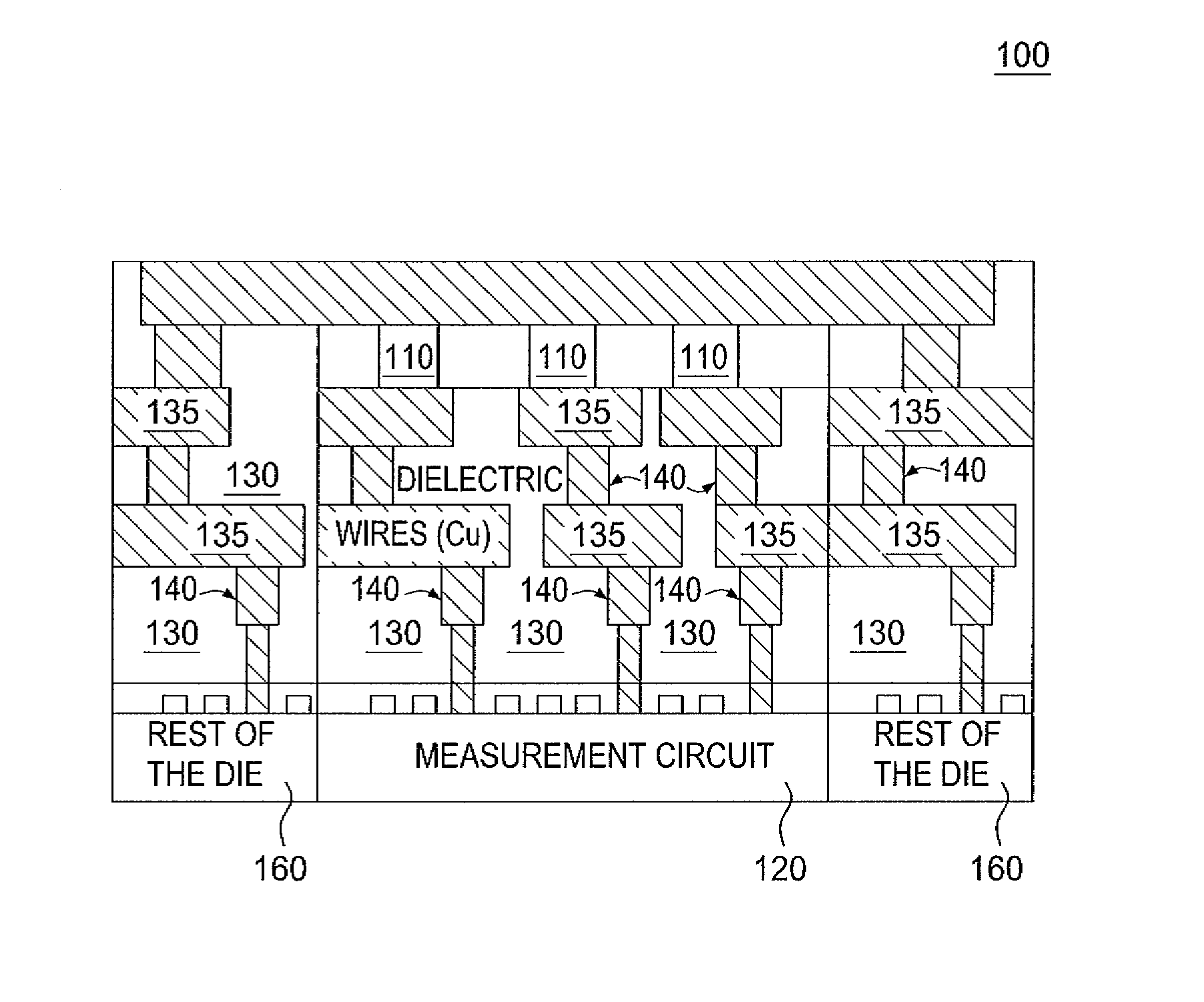
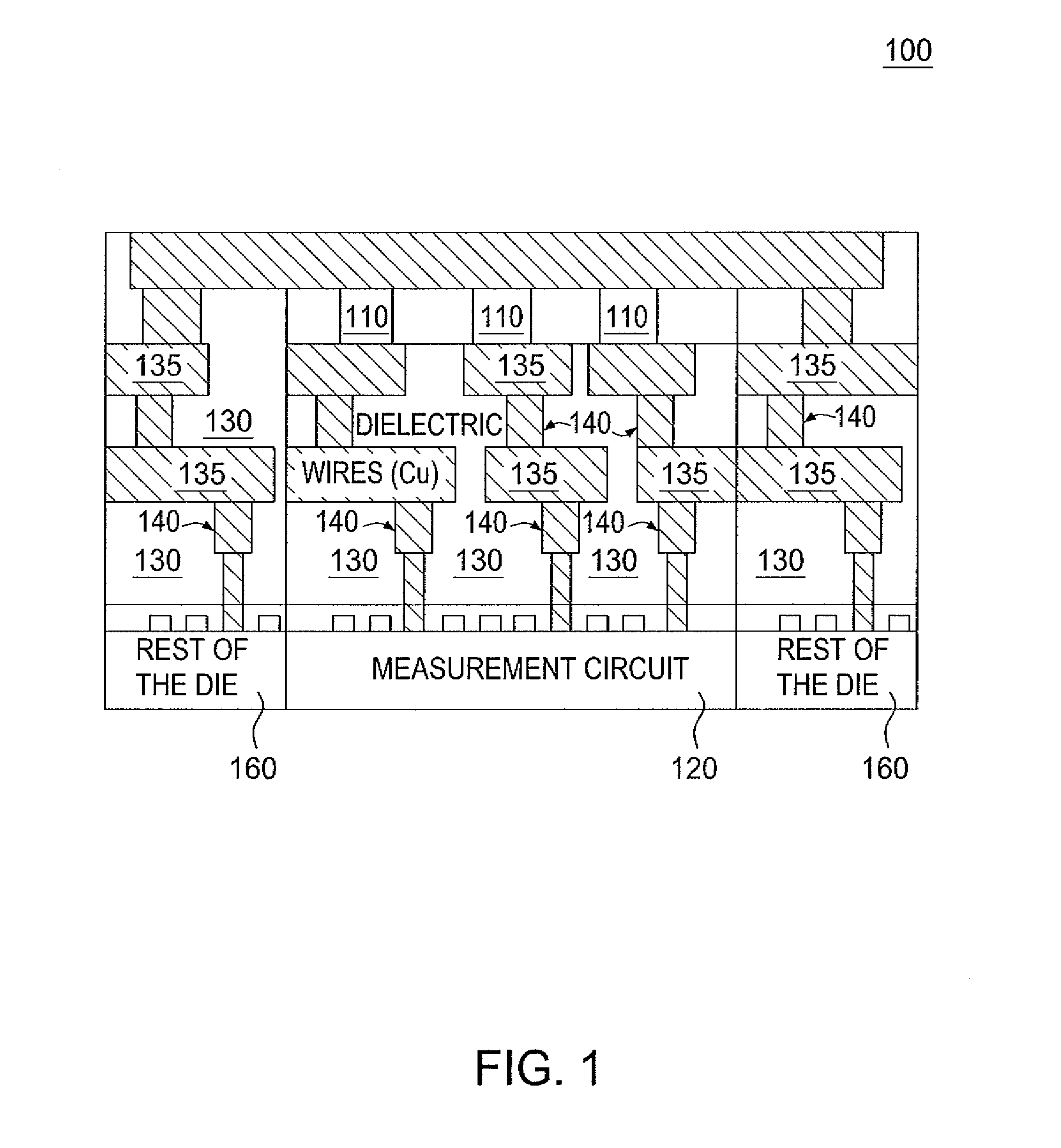
ActiveUS8525169B1Semiconductor/solid-state device testing/measurementSemiconductor/solid-state device detailsComputer hardwareSemiconductor materials
The present disclosure relates to a secure device having a physical unclonable function. The device includes an integrated circuit having a semiconducting material in at least one via in a backend of the integrated circuit. The present disclosure also relates to a method for manufacturing a secure device having a physical unclonable function. The method includes providing an integrated circuit and adding a semiconducting material to at least one via in a backend of the integrated circuit. In some instances a property of the semiconducting material in the at least one via is measured to derive a signature.
Owner:GLOBALFOUNDRIES US INC
Secure provisioning of secret keys during integrated circuit manufacturing
ActiveUS20140093074A1Internal/peripheral component protectionSecuring communicationComputer hardwareIntegrated circuit manufacturing
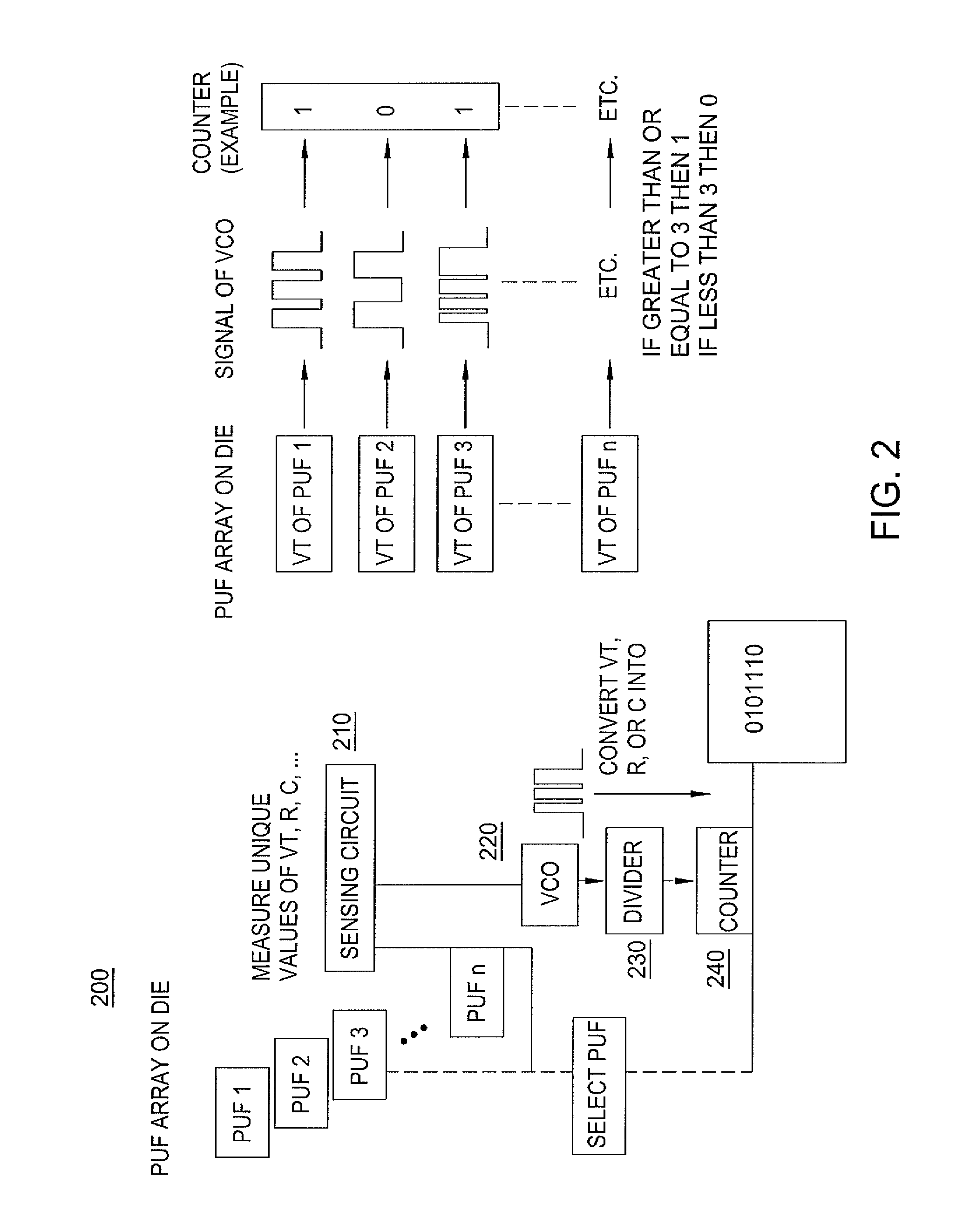
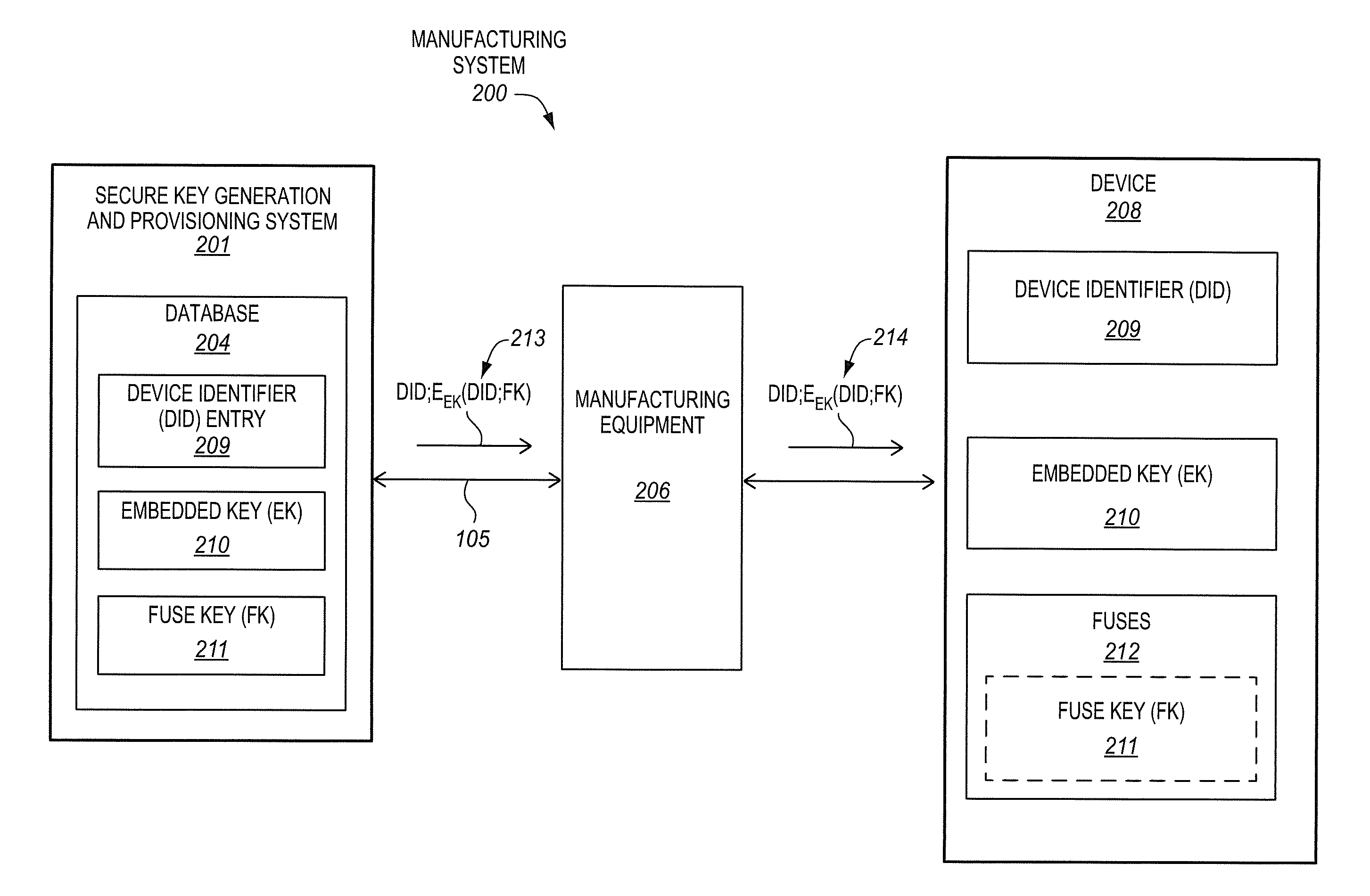
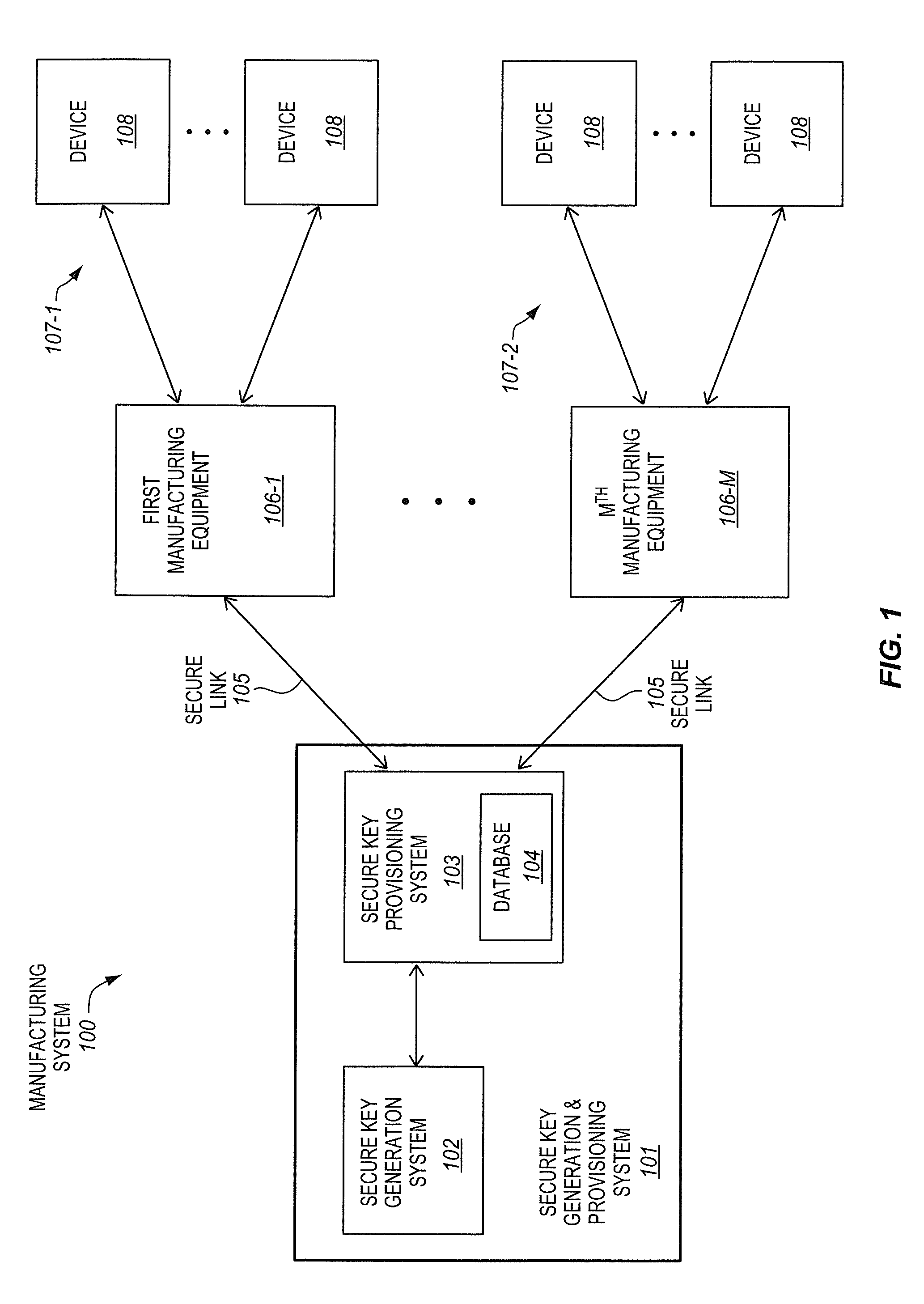
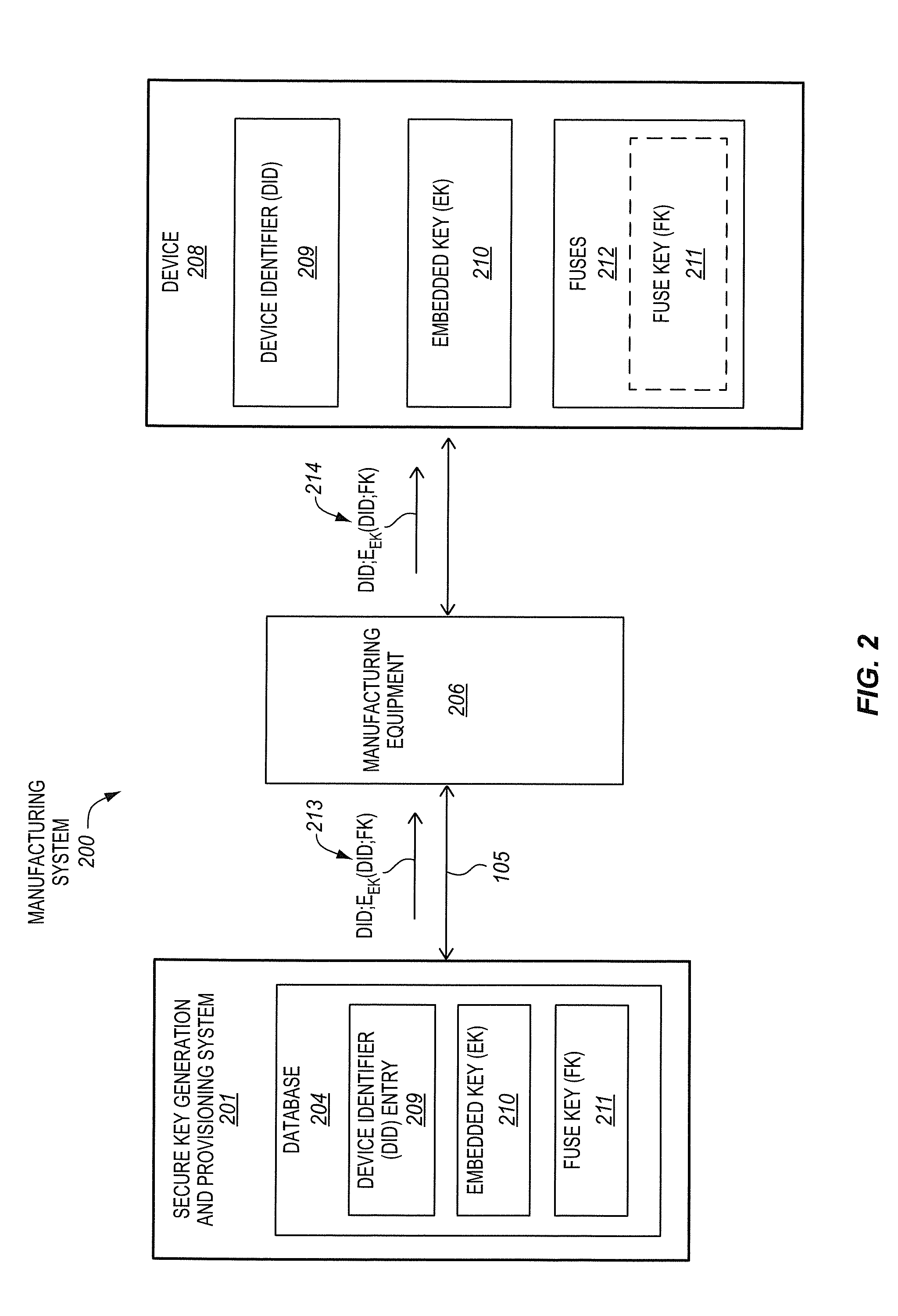
A method, of an aspect, includes challenging a set of Physically Unclonable Function (PUF) cells, of an integrated circuit device, and receiving a set of PUF bits from the PUF cells in response. A PUF key is generated based on the set of PUF bits. An encryption of the PUF key with an embedded key is output from the integrated circuit device. The integrated circuit device receives an encryption of a fuse key with the PUF key. Fuses of the integrated circuit device are programmed with at least one of the fuse key and the received encryption of the fuse key with the PUF key. Other methods, apparatus, and systems are also disclosed.
Owner:INTEL CORP
Physically unclonable function with tamper prevention and Anti-aging system
ActiveUS20120179952A1Avoids freezing attackReduce the impactMemory adressing/allocation/relocationInternal/peripheral component protectionComputer hardwarePhysical unclonable function
Owner:INTRINSIC ID
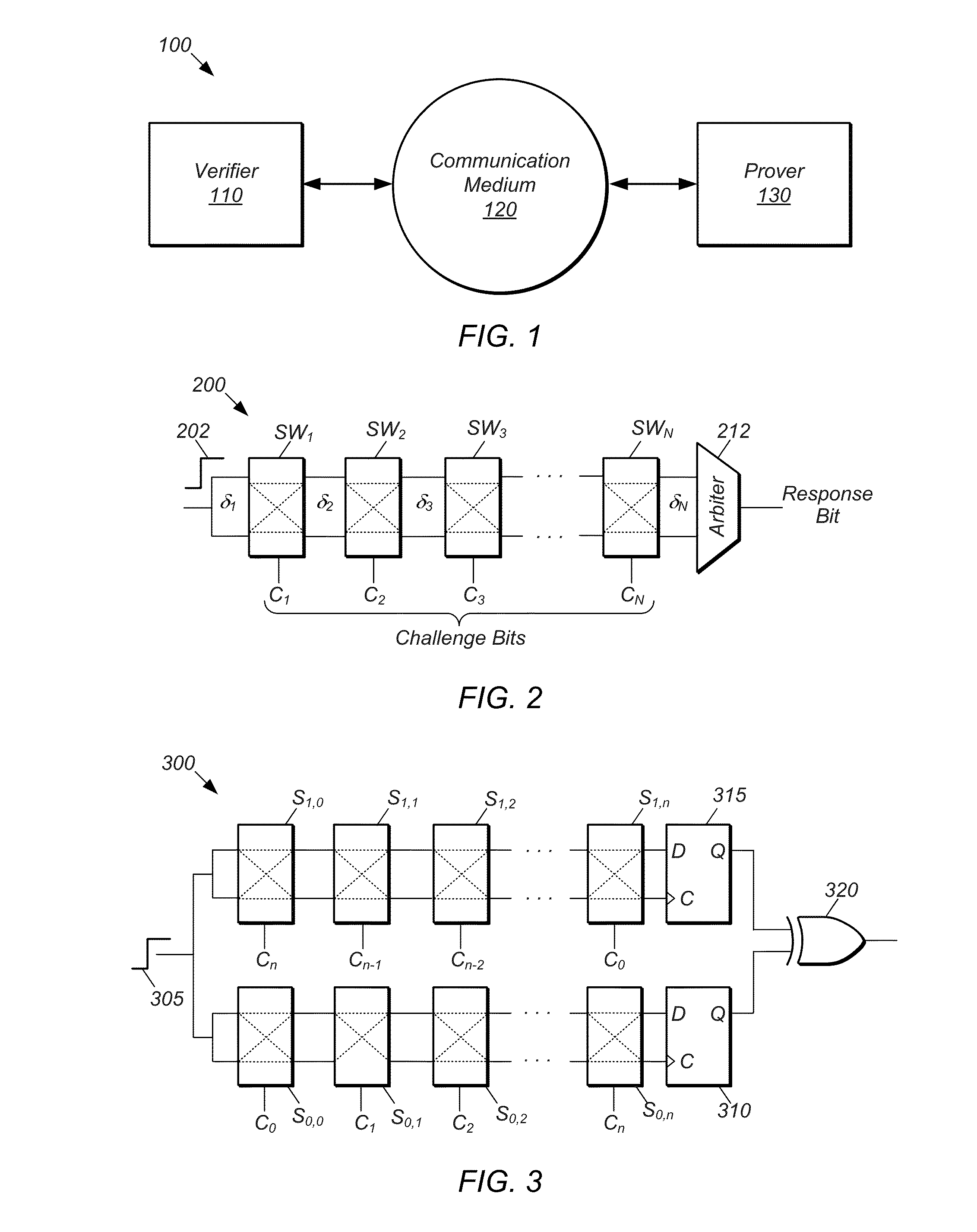
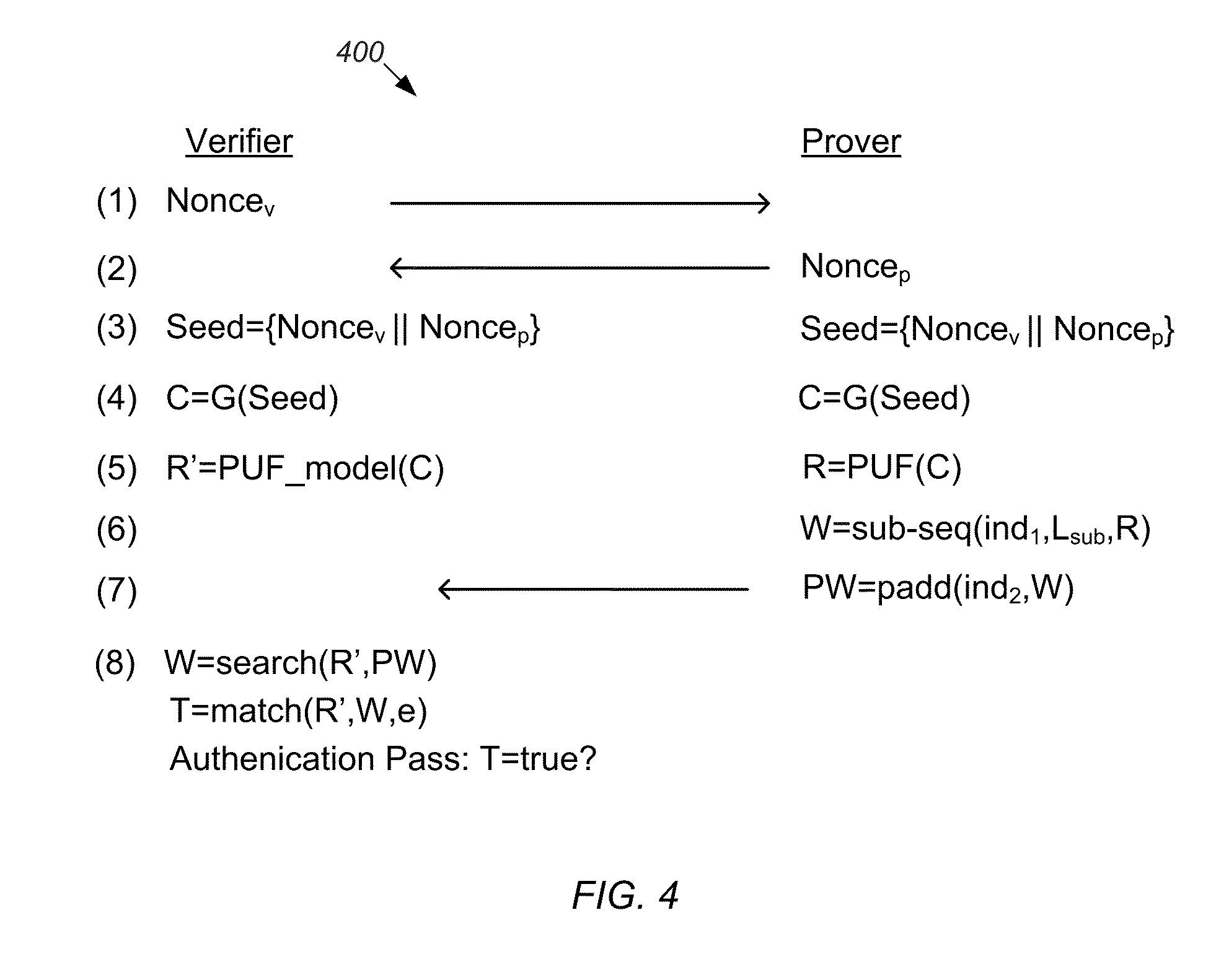
PUF Authentication and Key-Exchange by Substring Matching
ActiveUS20150195088A1Key distribution for secure communicationSecret communicationKey exchangeComputational model
Mechanisms for operating a prover device and a verifier device so that the verifier device can verify the authenticity of the prover device. The prover device generates a data string by: (a) submitting a challenge to a physical unclonable function (PUF) to obtain a response string, (b) selecting a substring from the response string, (c) injecting the selected substring into the data string, and (d) injecting random bits into bit positions of the data string not assigned to the selected substring. The verifier: (e) generates an estimated response string by evaluating a computational model of the PUF based on the challenge; (f) performs a search process to identify the selected substring within the data string using the estimated response string; and (g) determines whether the prover device is authentic based on a measure of similarity between the identified substring and a corresponding substring of the estimated response string.
Owner:RICE UNIV +1
System for establishing a cryptographic key depending on a physical system
ActiveUS20120072737A1Reduction of informationReduce decreaseKey distribution for secure communicationDigital data processing detailsComputer hardwareCryptographic nonce
In systems for establishing a cryptographic key depending on a physical uncloneable function (PUF) it may be a problem that internal information correlated with the cryptographic key is leaked to the outside of the system via a side-channel. To mitigate this problem a cryptographic system for reproducibly establishing a cryptographic key is presented. The system comprises a physical system comprising a physical, at least partially random, configuration of components from which an initial bit-string is derived. An error corrector corrects deviations occurring in the initial bit-string. Through the use of randomization the error corrector operates on a randomized data. Information leaking through a side channel is thereby reduced. After error correction a cryptographic key may be derived from the initial bit-string.
Owner:INTRINSIC ID
Device, System and Method for Determining Authenticity of an Item
ActiveUS20080256600A1Less computationMultiple keys/algorithms usageDigital data processing detailsPhysical unclonable functionComputer science
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Deterrence of device counterfeiting, cloning, and subversion by substitution using hardware fingerprinting
ActiveUS8848905B1Digital data processing detailsUser identity/authority verificationPhysical unclonable functionKey generator
Deterrence of device subversion by substitution may be achieved by including a cryptographic fingerprint unit within a computing device for authenticating a hardware platform of the computing device. The cryptographic fingerprint unit includes a physically unclonable function (“PUF”) circuit disposed in or on the hardware platform. The PUF circuit is used to generate a PUF value. A key generator is coupled to generate a private key and a public key based on the PUF value while a decryptor is coupled to receive an authentication challenge posed to the computing device and encrypted with the public key and coupled to output a response to the authentication challenge decrypted with the private key.
Owner:UT BATTELLE LLC +1
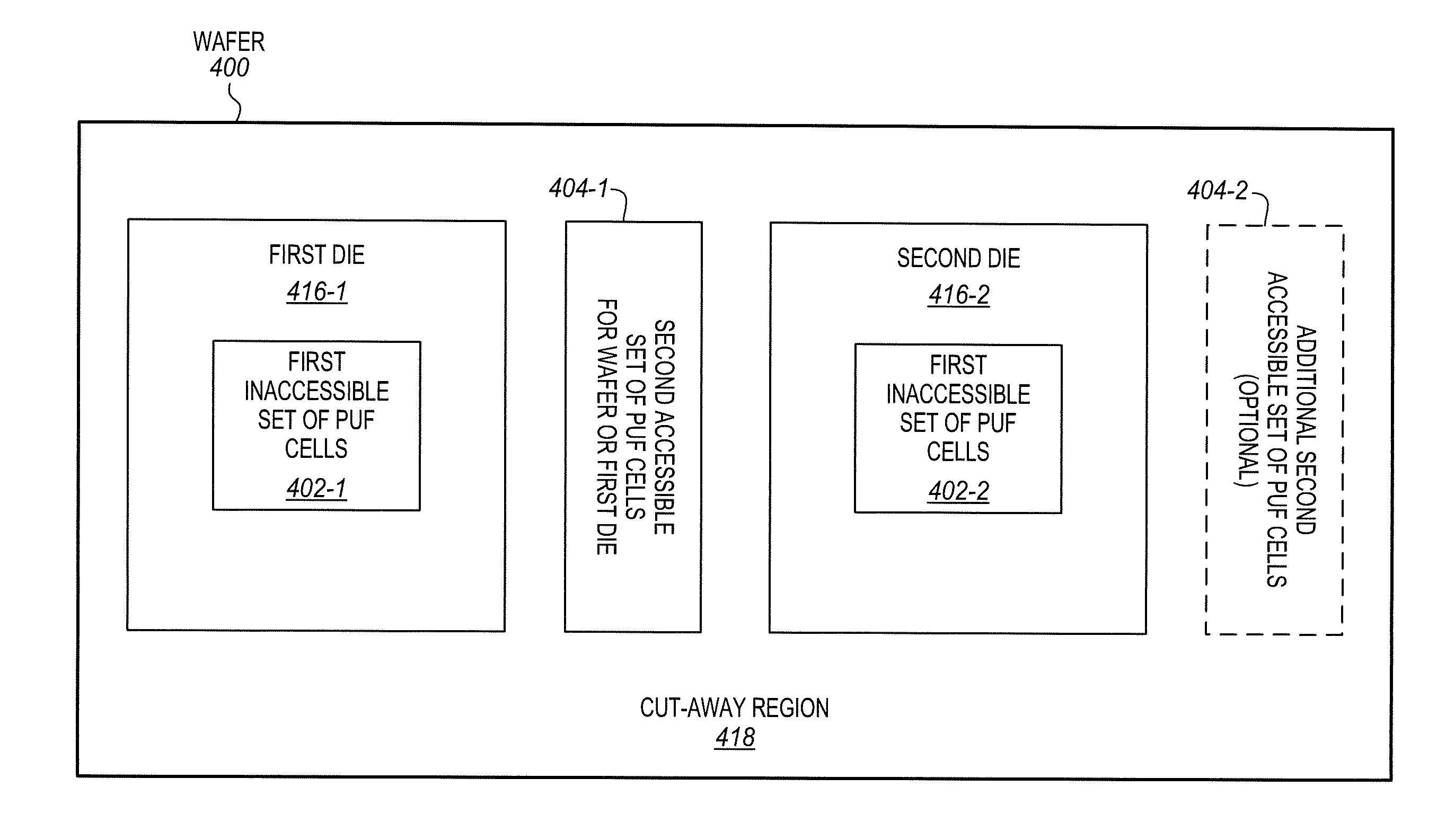
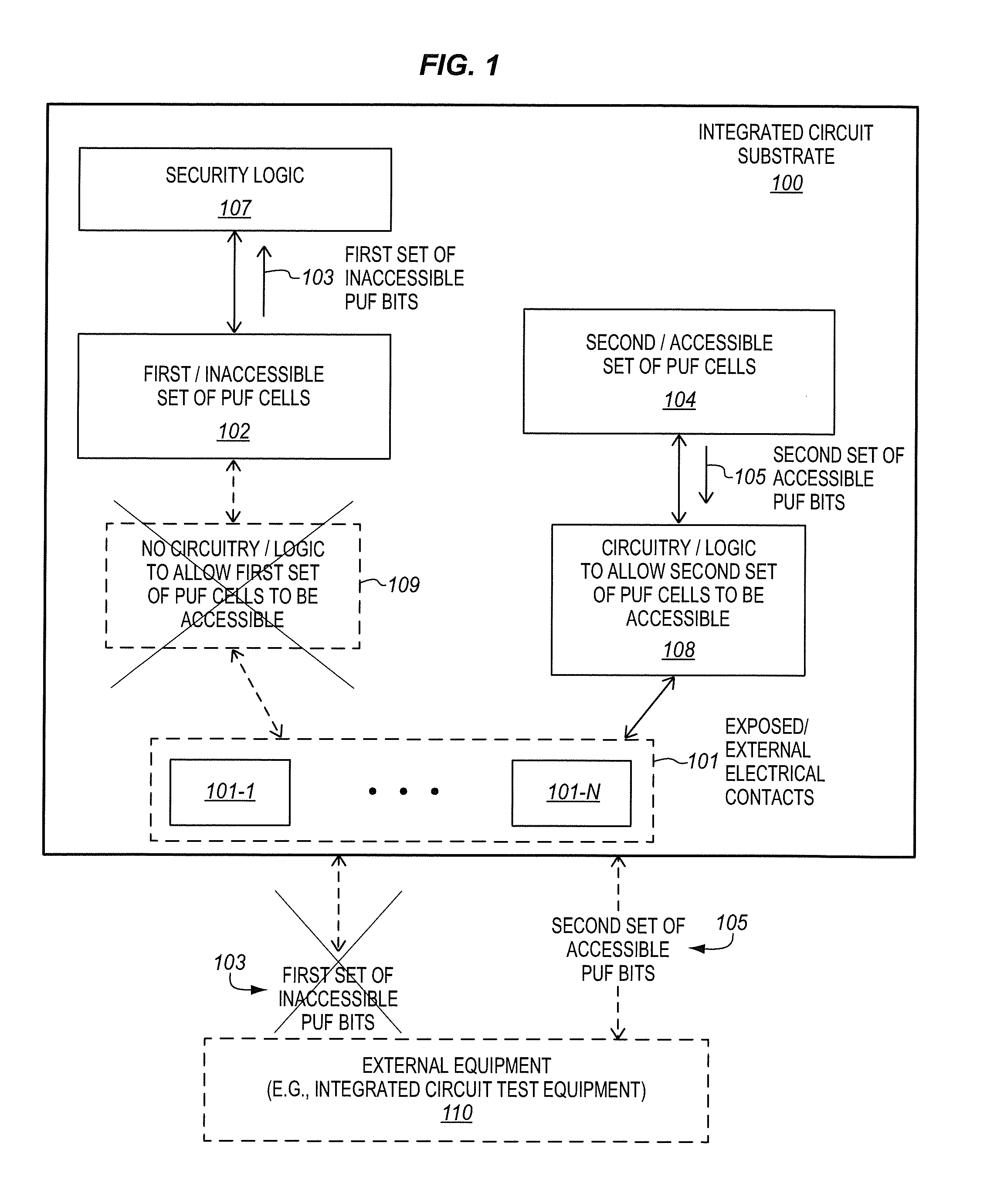
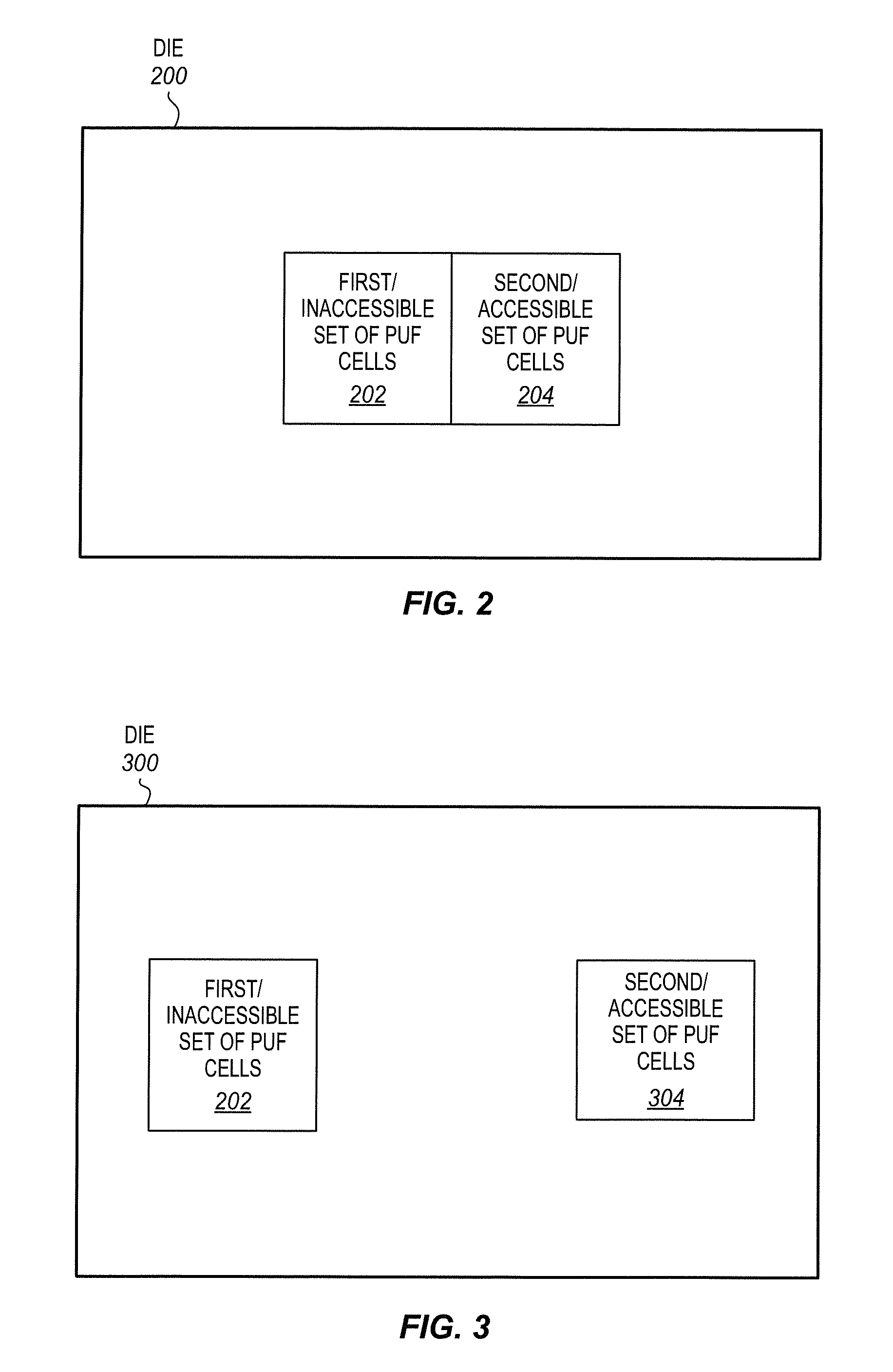
Integrated circuits having accessible and inaccessible physically unclonable functions
ActiveUS20140091832A1Reliability increasing modificationsSemiconductor/solid-state device testing/measurementPhysical unclonable functionIntegrated circuit
An integrated circuit substrate of an aspect includes a plurality of exposed electrical contacts. The integrated circuit substrate also includes an inaccessible set of Physically Unclonable Function (PUF) cells to generate an inaccessible set of PUF bits that are not accessible through the exposed electrical contacts. The integrated circuit substrate also includes an accessible set of PUF cells to generate an accessible set of PUF bits that are accessible through the exposed electrical contacts. Other apparatus, methods, and systems are also disclosed.
Owner:INTEL CORP
System and device binding metadata with hardware intrinsic properties
ActiveUS20150318994A1User identity/authority verificationDigital data authenticationComputer hardwareHash function
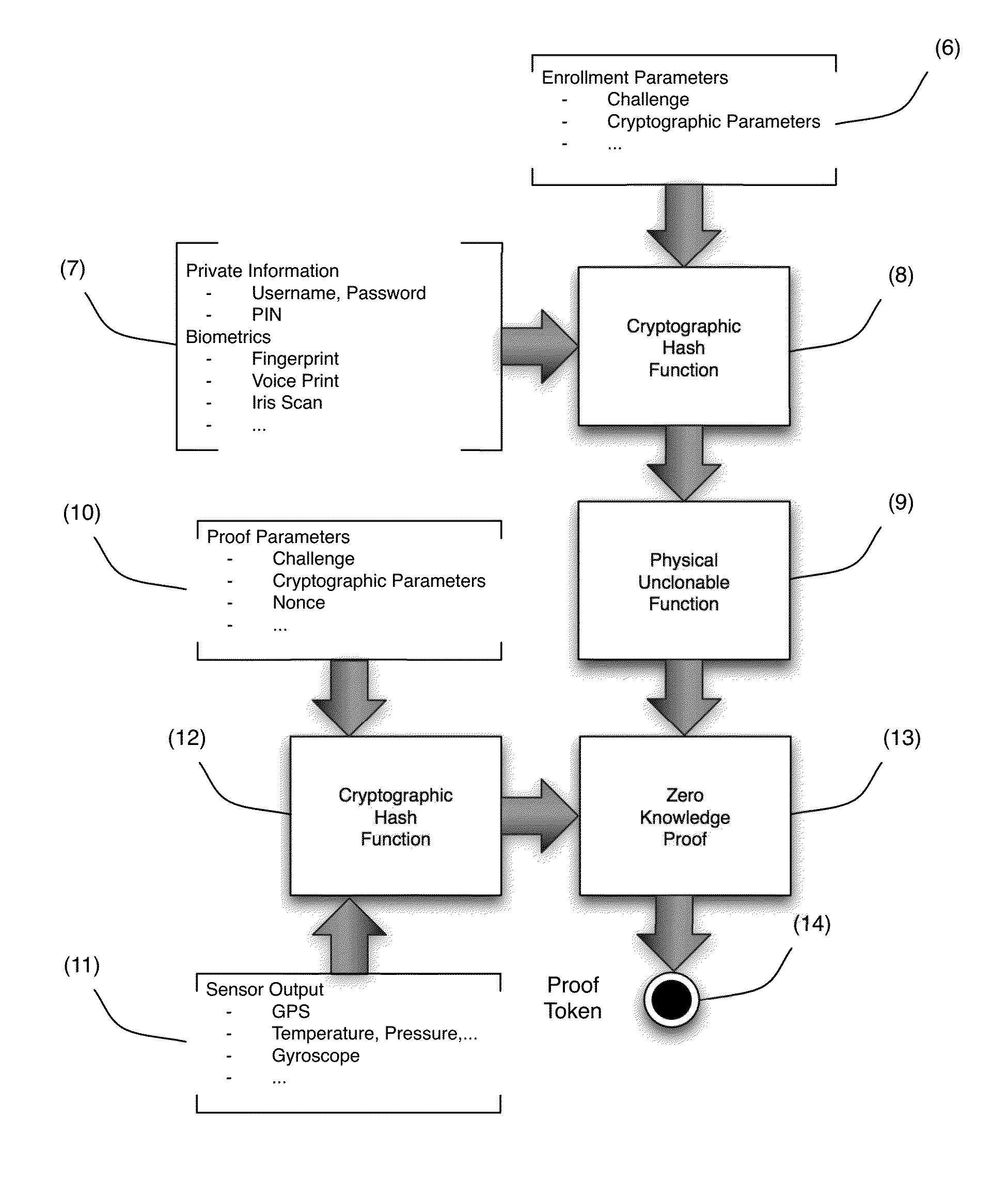
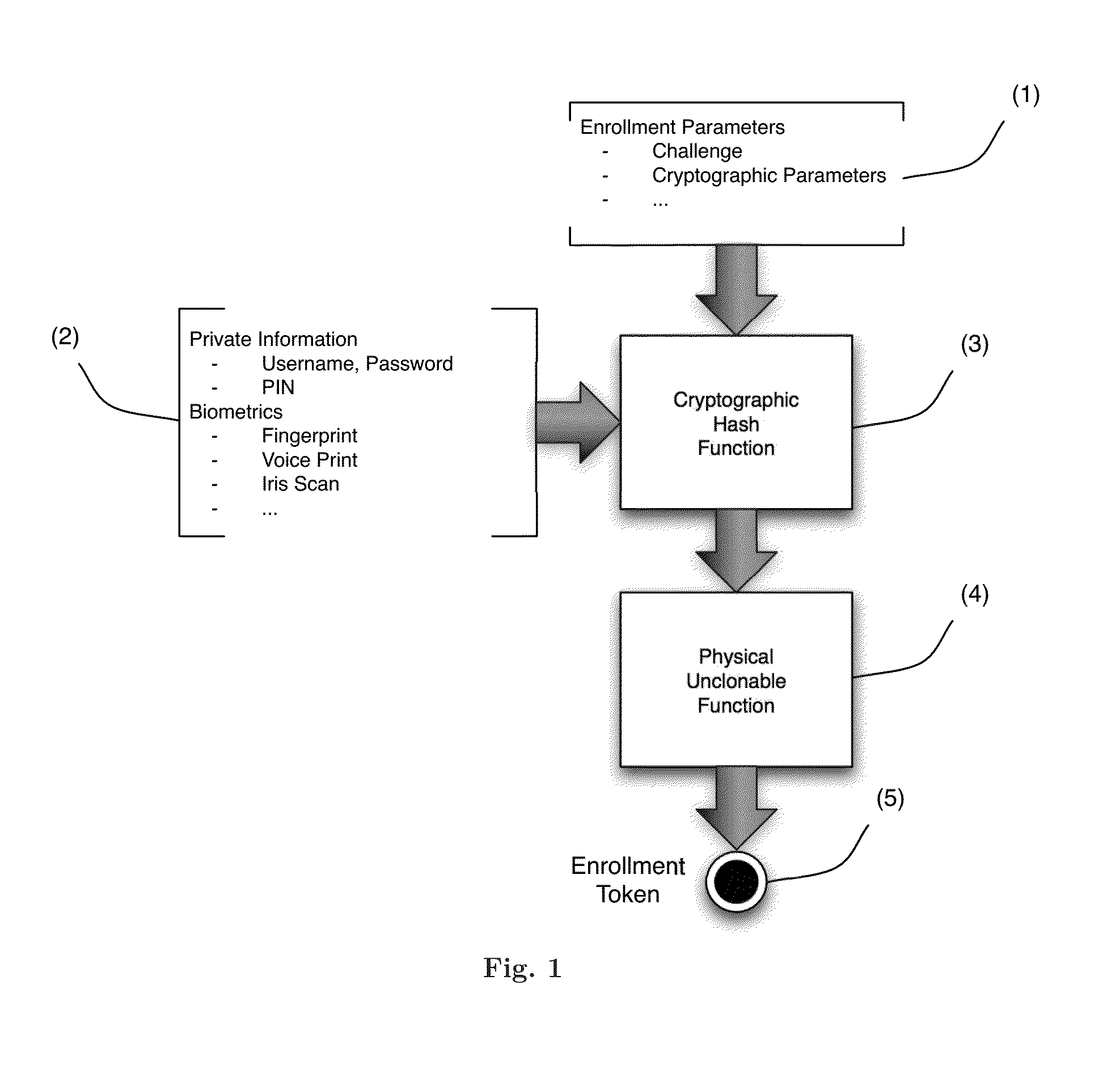
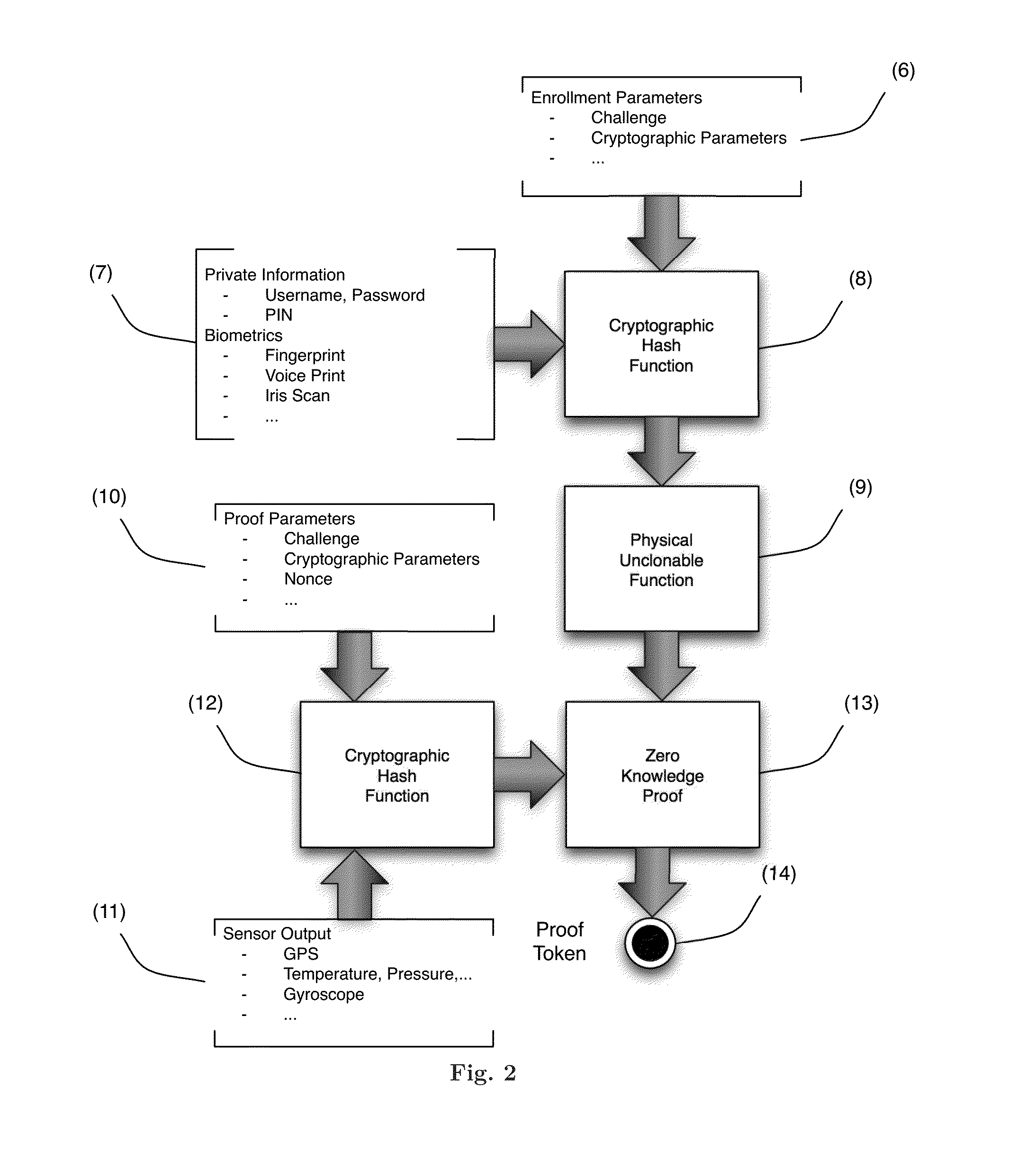
A system, device, and method for binding metadata, such as information derived from the output of a biometric sensor, to hardware intrinsic properties by obtaining authentication-related metadata and combining it with information pertaining to a root of trust, such as a physical unclonable function. The metadata may be derived from a sensor such as a biometric sensor, the root of trust may be a physical unclonable function, the combination of the metadata and root of trust information may employ a hash function, and output from such a hash process may be used as an input to the root of trust. The combined information can be used in interactive or non-interactive authentication.
Owner:ANALOG DEVICES INC
Tamper-protected hardware and method for using same
ActiveUS9071446B2Improve robustnessSuitable for useKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareTamper proof hardware
Owner:EMSYCON
Device, system and method for verifying the authenticity integrity and/or physical condition of an item
ActiveUS20110099117A1Improve the situationInternal/peripheral component protectionDigital data authenticationPhysical unclonable functionComputer science
A physical uncloneable function (PUF) pattern is used for verifying a physical condition of an item. The PUF pattern is arranged to be damaged in the event that said item is exposed to a predetermined environmental condition. Verification of the physical condition of the item, is carried out by obtaining a measured response from the PUF pattern, and comparing the measured response with a stored response in respect of the PUF.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
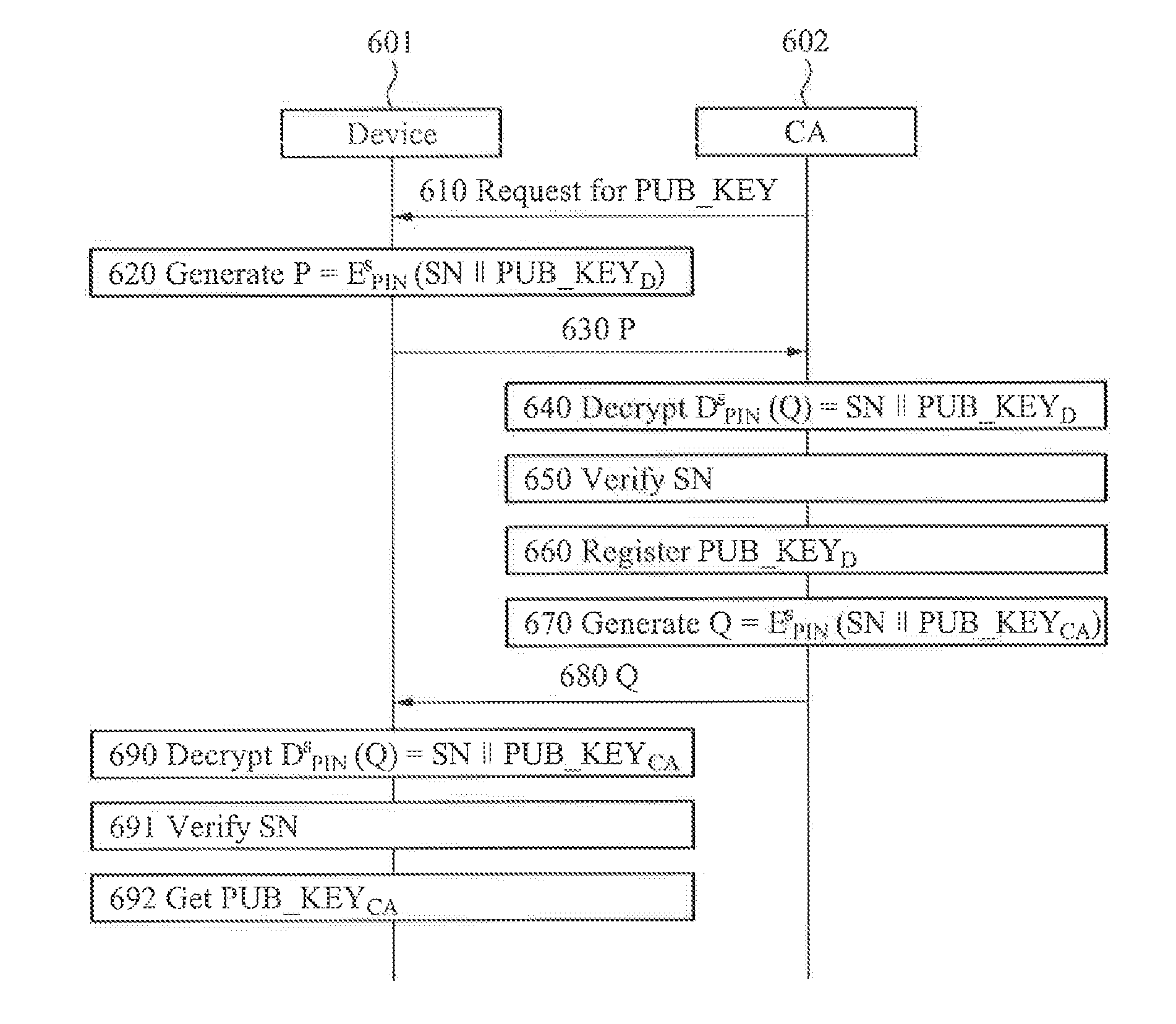
Apparatus and method for authentication between devices based on puf over machine-to-machine communications
ActiveUS20140310515A1Authentication securityGuaranteed reliabilityMultiple keys/algorithms usagePublic key for secure communicationPasswordSecret code
Terminal devices that perform machine-to-machine (M2M) communication may autonomously perform password authentication by autonomously generating a personal identity number (PIN) value, which is not exposed externally, using a physical unclonable function (PUF). A terminal apparatus that performs M2M communication may include a PUF embedded in the terminal apparatus to generate an authentication key for password authentication associated with the terminal apparatus, and an authentication unit to perform the password authentication associated with the terminal apparatus using the authentication key generated by the PUF.
Owner:ICTK
Physical structure for use in a physical unclonable
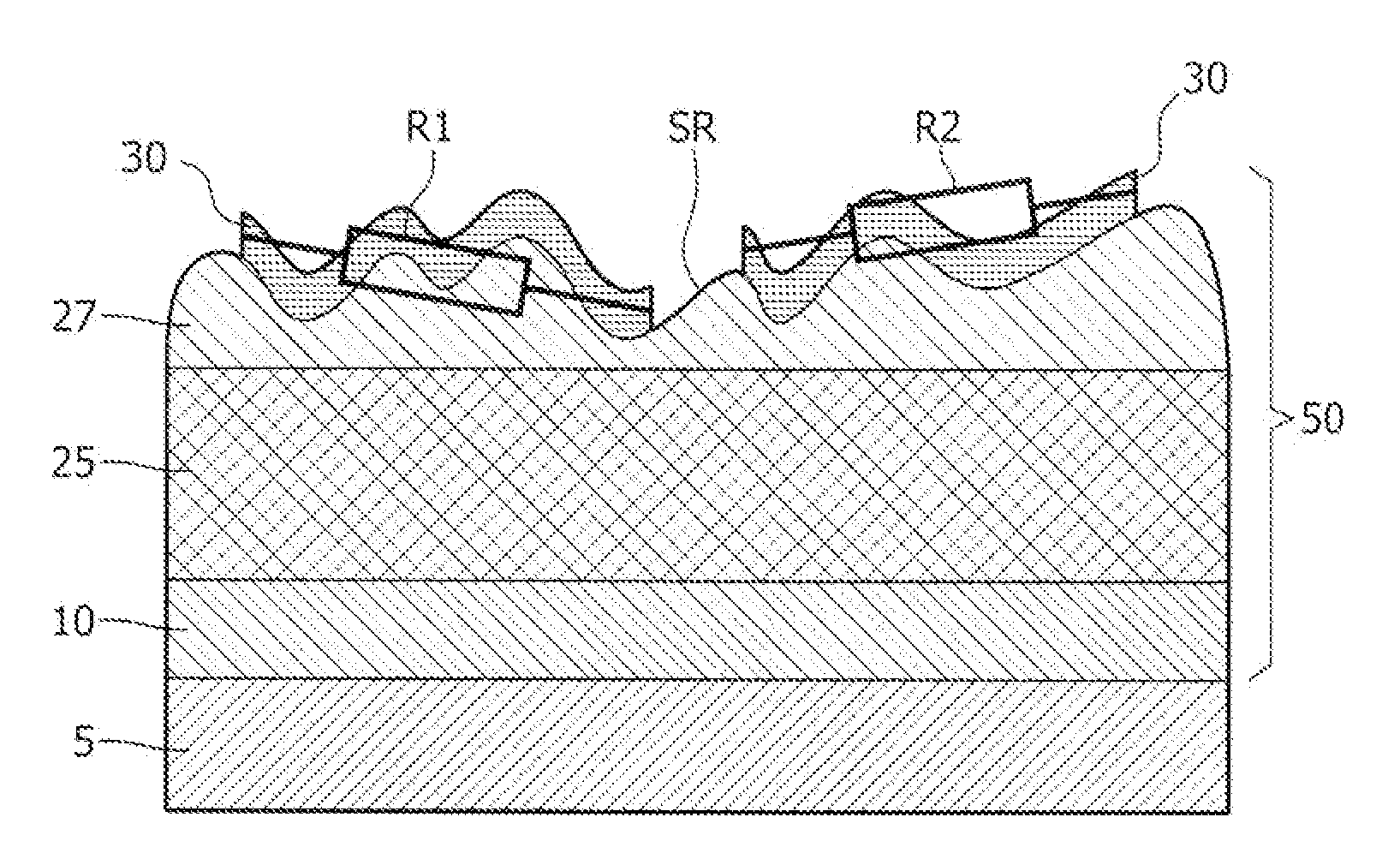
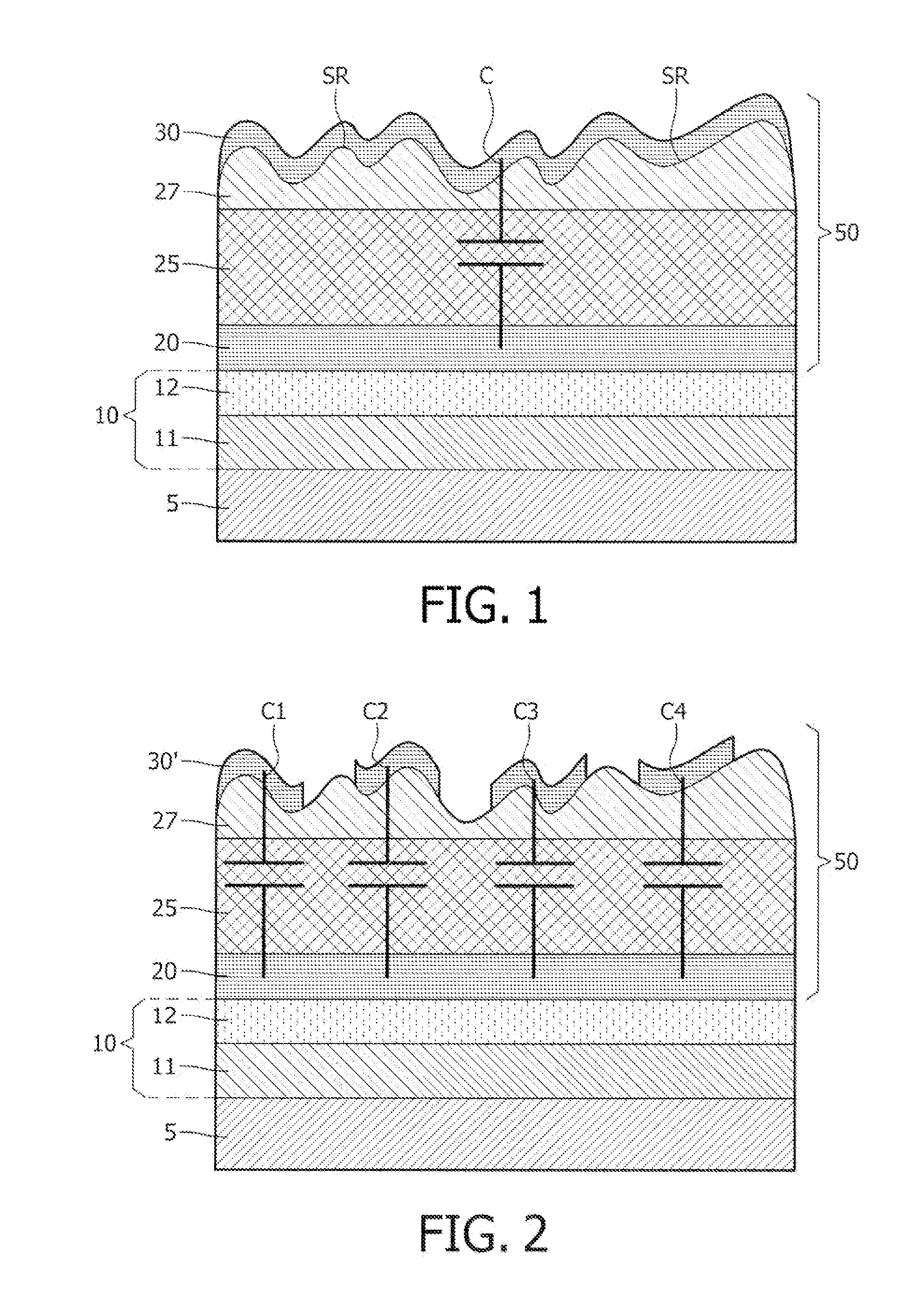
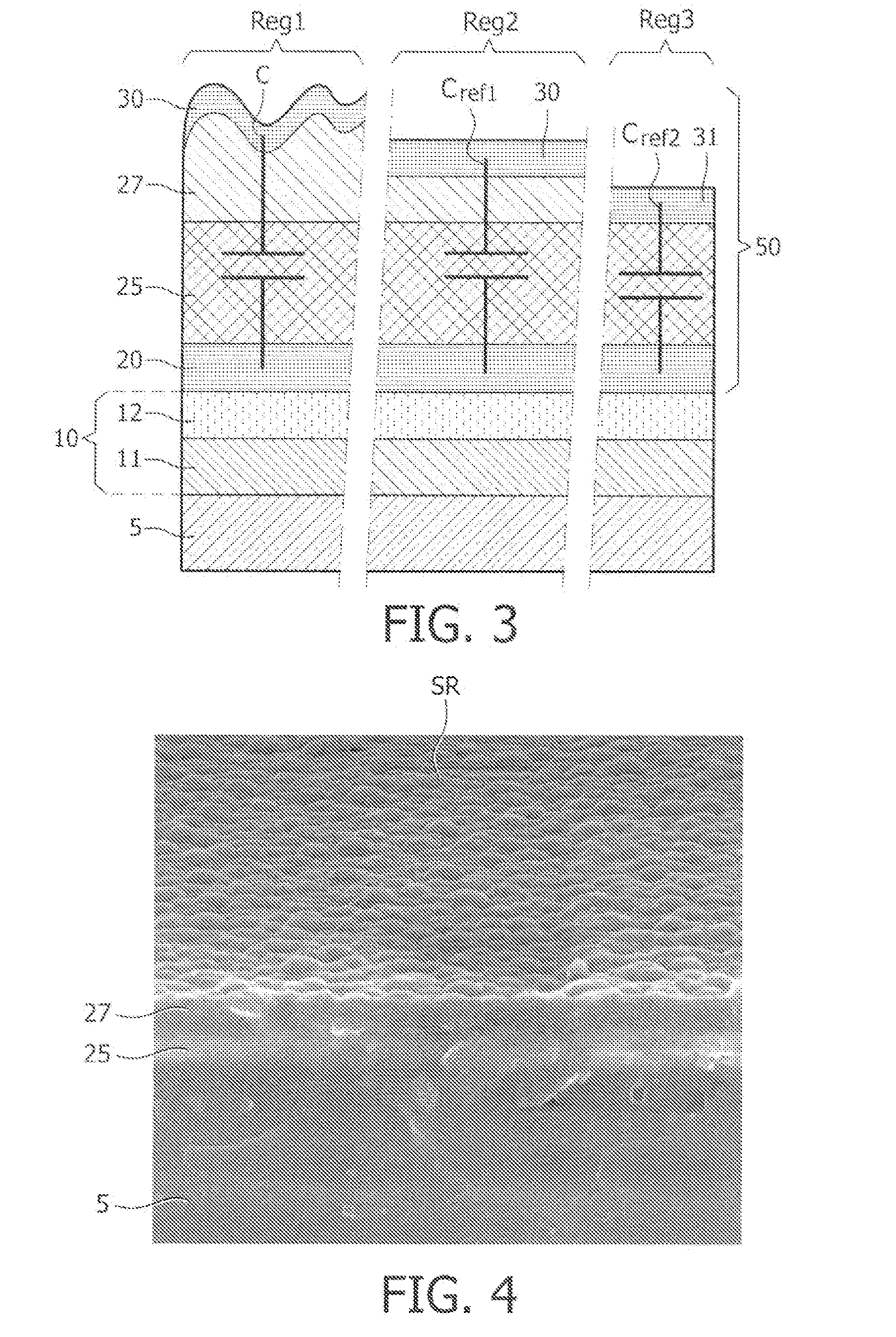
InactiveUS20110254141A1Rough surfaceConfidenceSemiconductor/solid-state device detailsSolid-state devicesCapacitancePhysical unclonable function
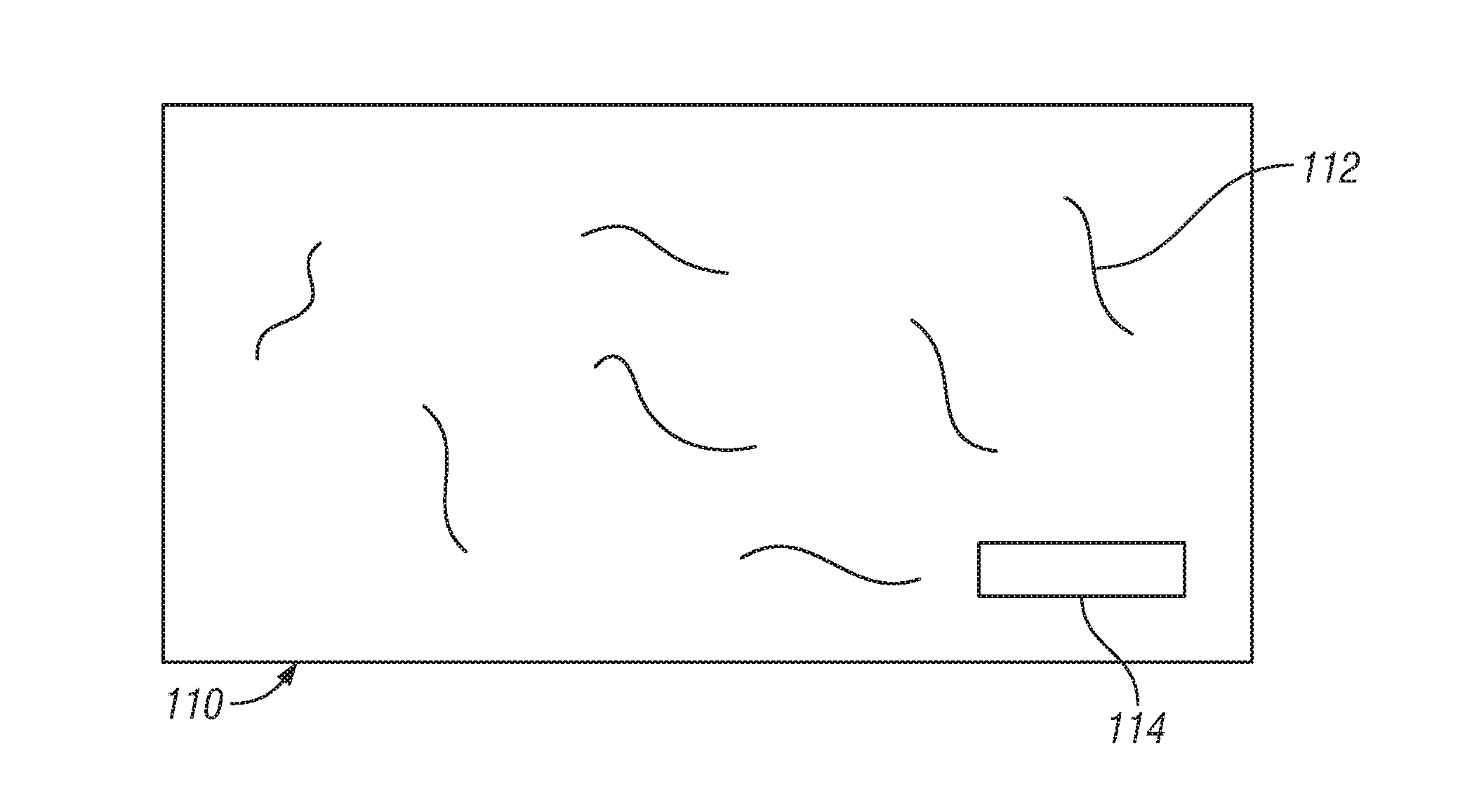
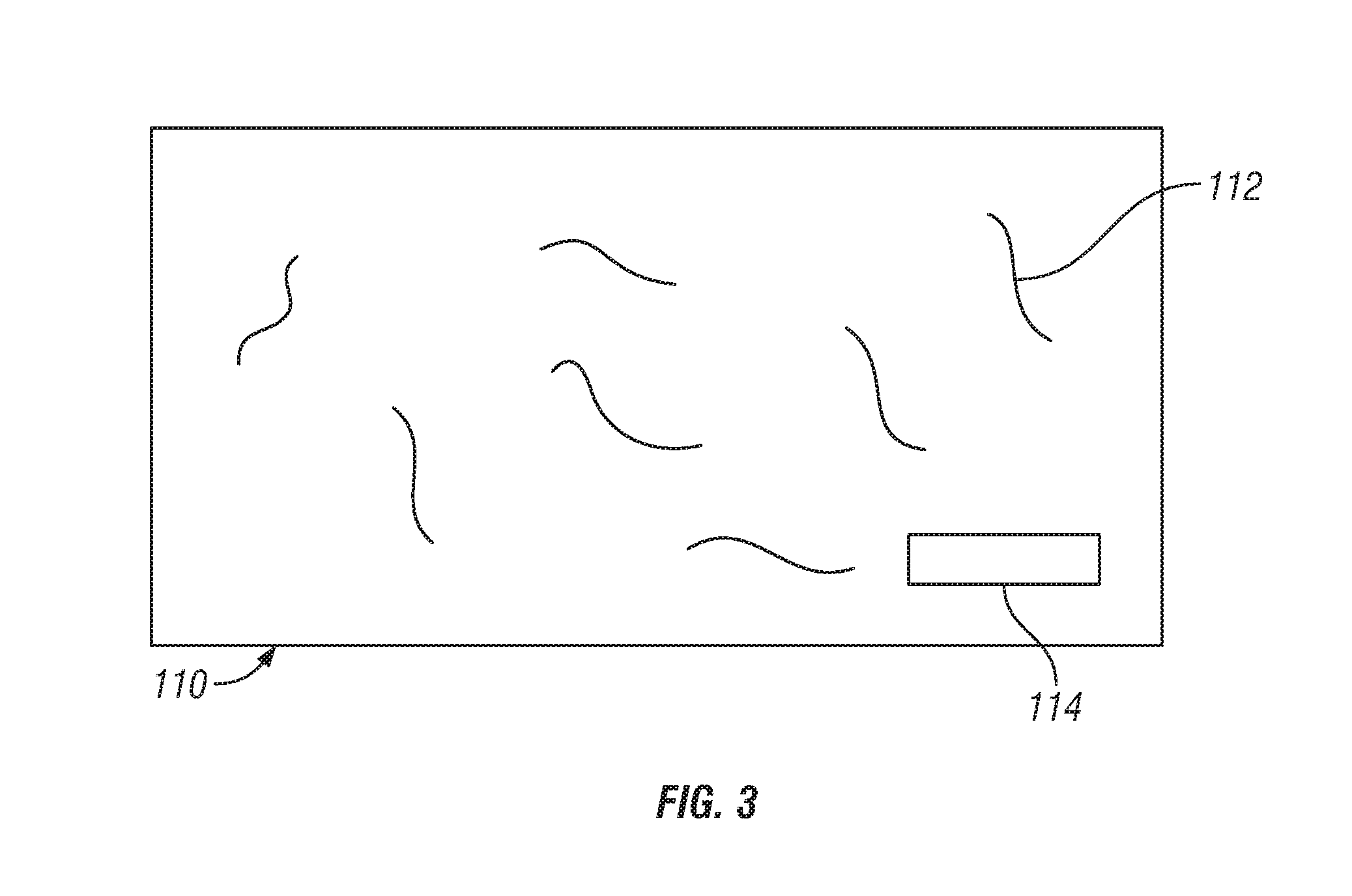
The invention relates to a semiconductor device comprising a physical structure (50) for use in a physical unclonable function, wherein the physical structure (50) comprises a lead-zirconium titanate layer (25), and a silicon-comprising dielectric layer (27) deposited on the lead-zirconium-titanate layer (25), wherein the silicon-comprising dielectric layer (27) has a rough surface (SR), the physical structure (50) further comprising a conductive layer (30) provided on the rough surface (SR) of the silicon-comprising dielectric layer (27). The invention further relates to a method of manufacturing such semiconductor device. The invention also relates to a card, such as a smartcard, and to a RFID tag comprising such semiconductor device. The inventors have found that depositing of a silicon- comprising dielectric layer (27) on a lead-zirconium titanate layer (25) using vapor deposition results in a silicon-comprising dielectric layer (27) having a rough surface (SR). This rough surface (SR) can be used in a PUF to make a resistor (R) with a variable random value by depositing a conductive layer (30) on the rough surface (SR). Alternatively, the combination of both layers (25, 27) can be used in a PUF as composite dielectric to make a capacitor (C) with a variable random capacitance value.
Owner:NXP BV
Physical key-protected one time pad
ActiveUS20130243187A1Maximize overlapDetector's pixelsModulated-carrier systemsSecret communicationSpatial light modulatorHemt circuits
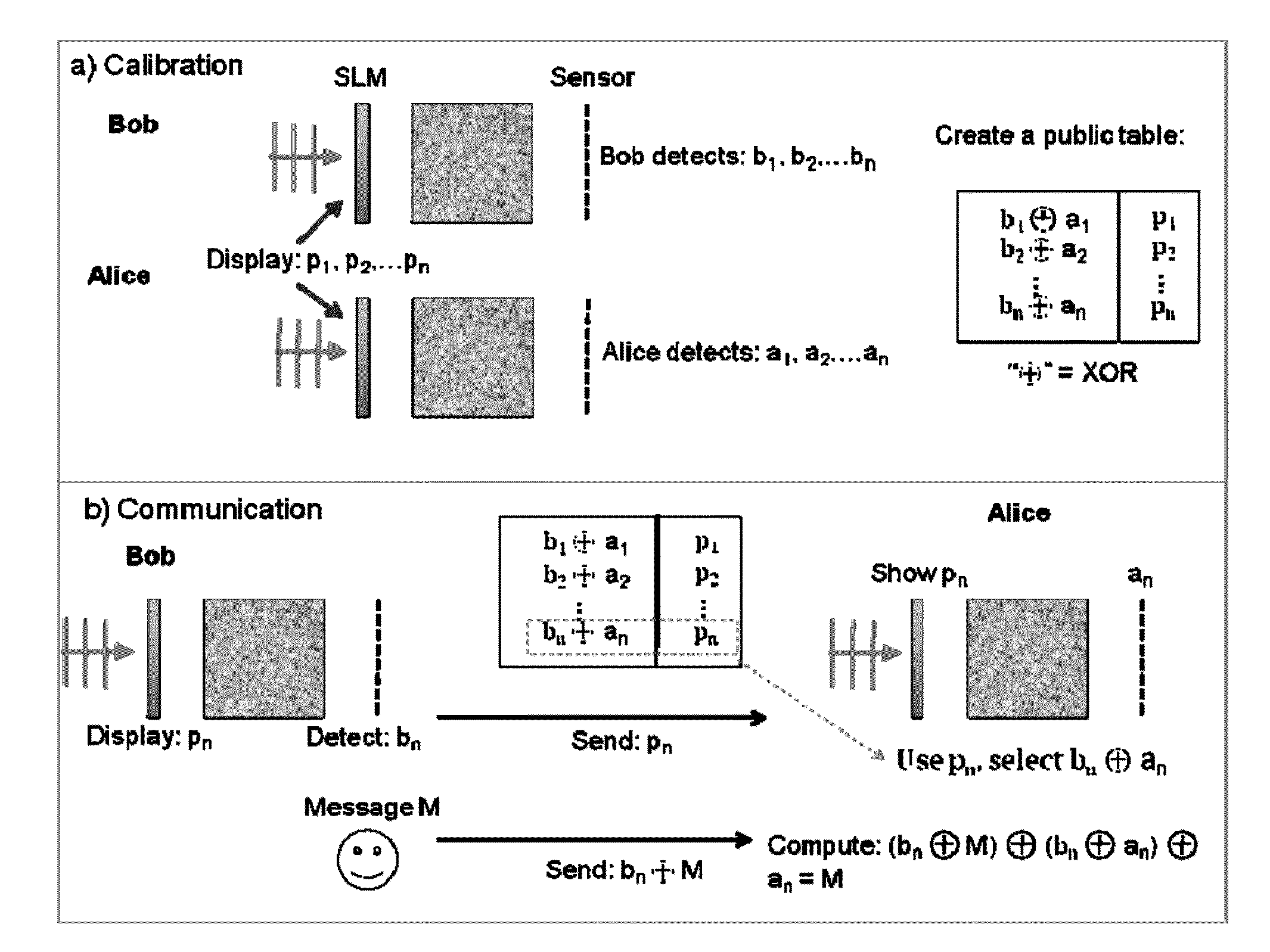
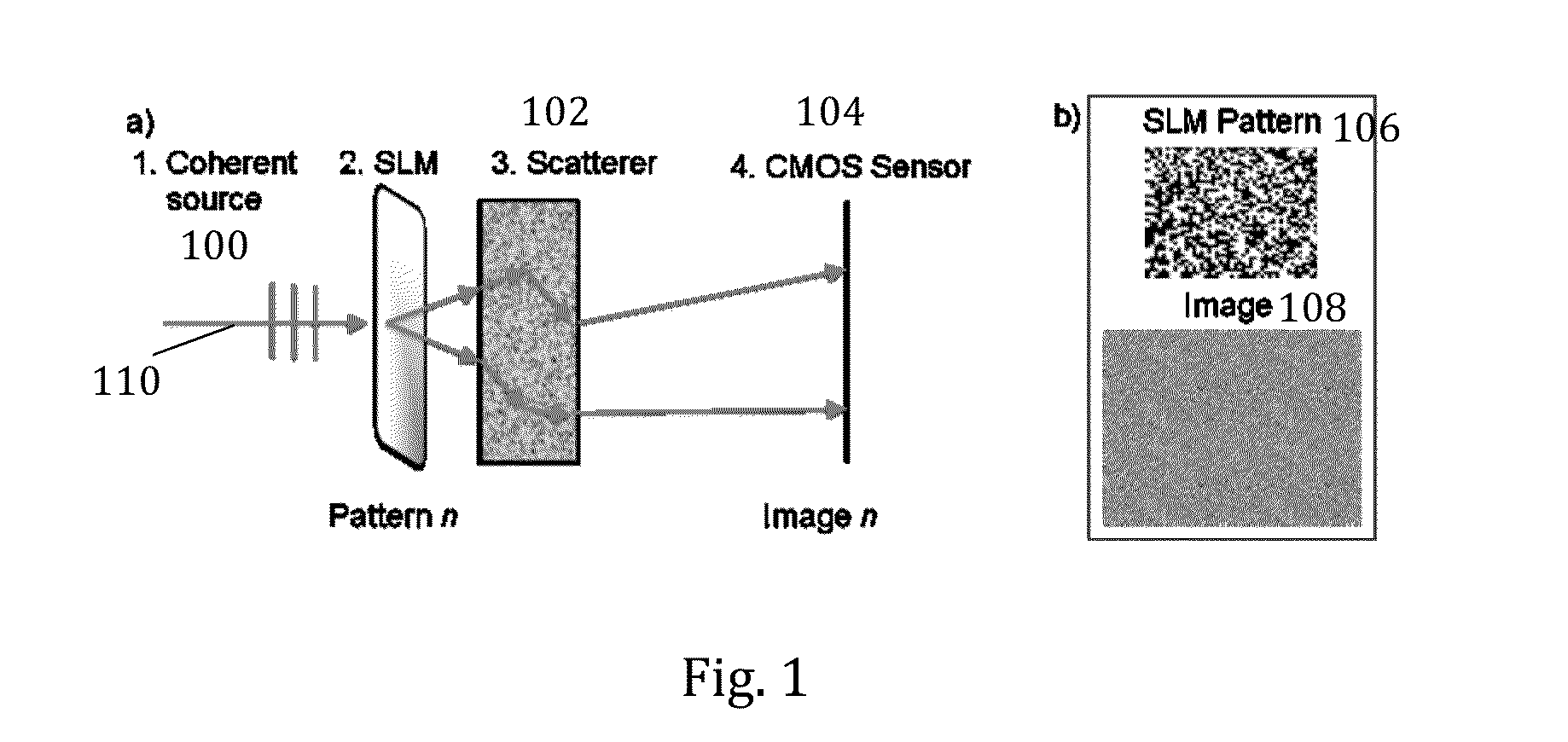
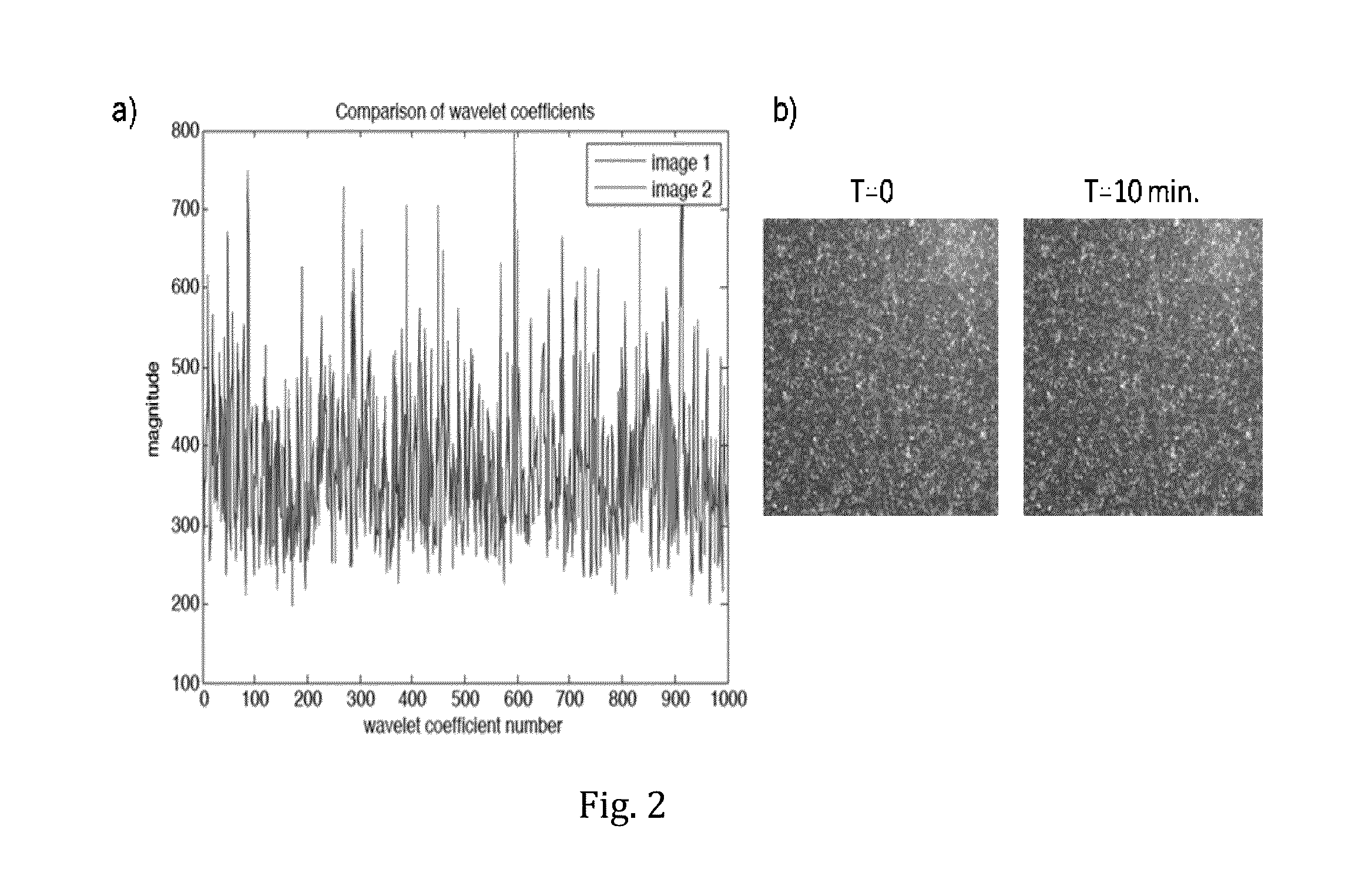
A device, including one or more Communication Physical Unclonable Function (CPUF) and key storage devices, the CPUF devices each comprising: a coherent Electromagnetic (EM) radiation source; a spatial light modulator (SLM) connected to the coherent EM radiation source; a volumetric scattering medium connected to the SLM; a detector connected to the volumetric scattering medium; and one or more processors or circuits connected to the detector and one or more processors or circuits connected to the SLM. A communication protocol is also provided.
Owner:LONDON SCHOOL OF HYGIENE & TROPICAL MEDICINE
Authenticatable device with reconfigurable physical unclonable functions
ActiveUS20170149572A1User identity/authority verificationInternal/peripheral component protectionPhysical unclonable functionComputer science
An authenticatable device according to one embodiment includes a reconfigurable physical unclonable function (‘RPUF’) used with one parameter to recover sensitive values (e.g., a secret or a share of a secret) and a different parameter to encode and store values (e.g., challenge-helper pairs) correlated to the sensitive values. In another embodiment, a pair of RPUFs is used instead of a single PUF, with one RPUF used to recover sensitive values and the other RPUF used to encode and store correlated values. In still another embodiment, the desired expiration of values can be enforced by employing redundant RPUFs; when the device is powered on, one (or more than one, but less than all) of the RPUFs is selected and transitioned to a new configuration, invalidating any correlated values previously constructed using the old configuration, and the RPUF that was not reconfigured is used to recover the sensitive value(s) using the remaining correlated value(s).
Owner:ANALOG DEVICES INC
Distribution system and method for distributing digital information
ActiveUS20120204023A1Improve recoverabilityImprove abilitiesKey distribution for secure communicationUser identity/authority verificationComputer hardwareDistribution system
A distribution system and method for distributing digital information is provided, which has high recoverability from a security breach. The distribution system comprises a server (200) and a computing device (110). During an enrollment phase, the computing device obtains a first response from an integrated physically unclonable function (150) integrated in the computing device. The system comprises an enrollment module (130) for determining helper data from a decryption key and the first response to enable later reconstruction of the decryption key from the helper data and a second response obtained from the physically unclonable function. During a reconstruction phase, which occurs after the enrollment phase and typically after a security breach has occurred that revealed data and / or programming code of the computing device, the server may encrypt digital information using an encryption module (220) with a cryptographic encryption key corresponding to the decryption key. The computing device comprises a decryption module (120) for decrypting the encrypted digital information with the decryption key. The digital information may be used to send an update message to the computing device. Since, the decryption key need only be available at the computing device after the breach, it can recover even if data, such as a cryptographic key, or programming code of the computing device was revealed, and even if an attacker could eavesdrop on the encrypted digital information.
Owner:INTRINSIC ID
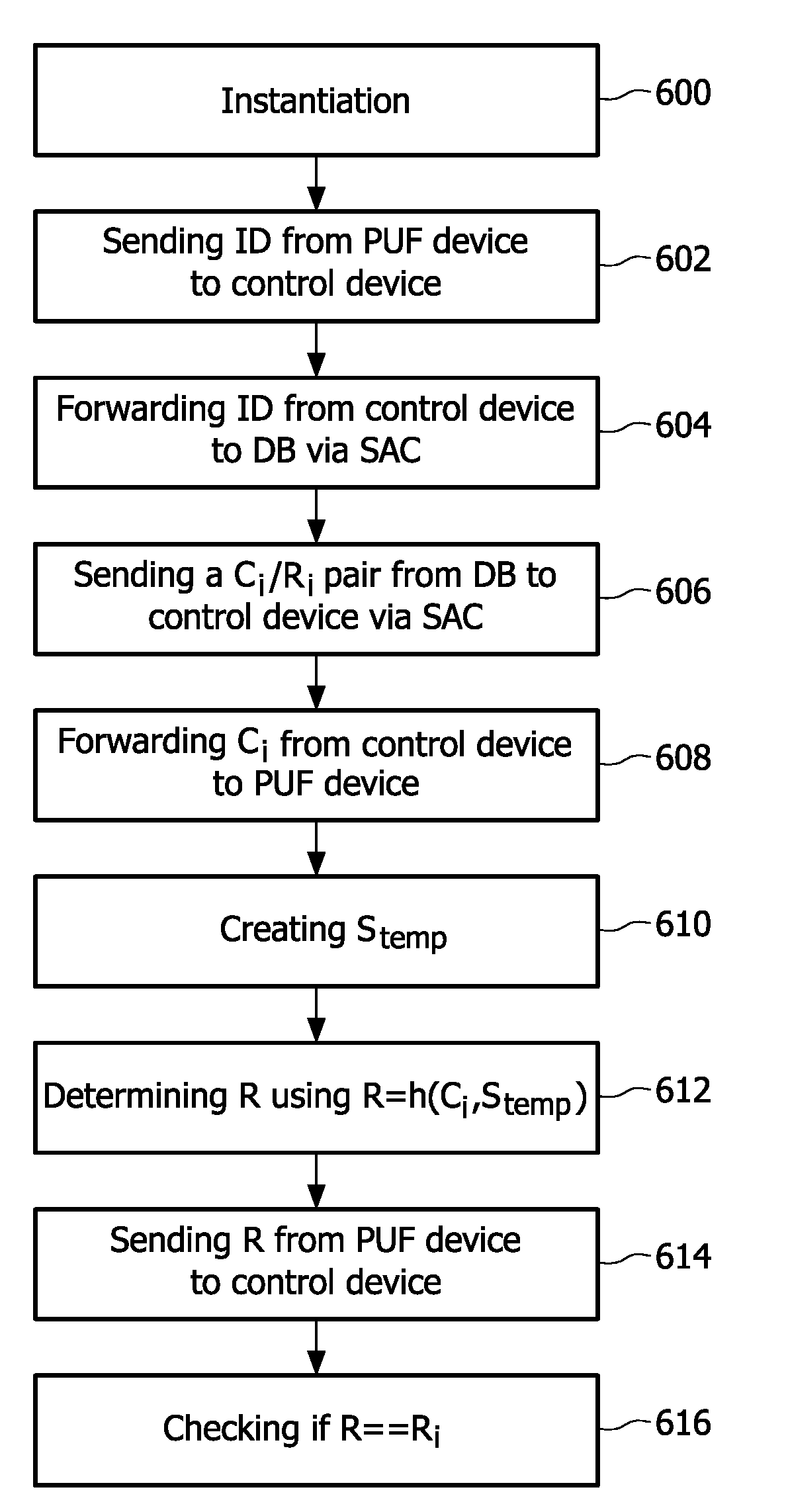
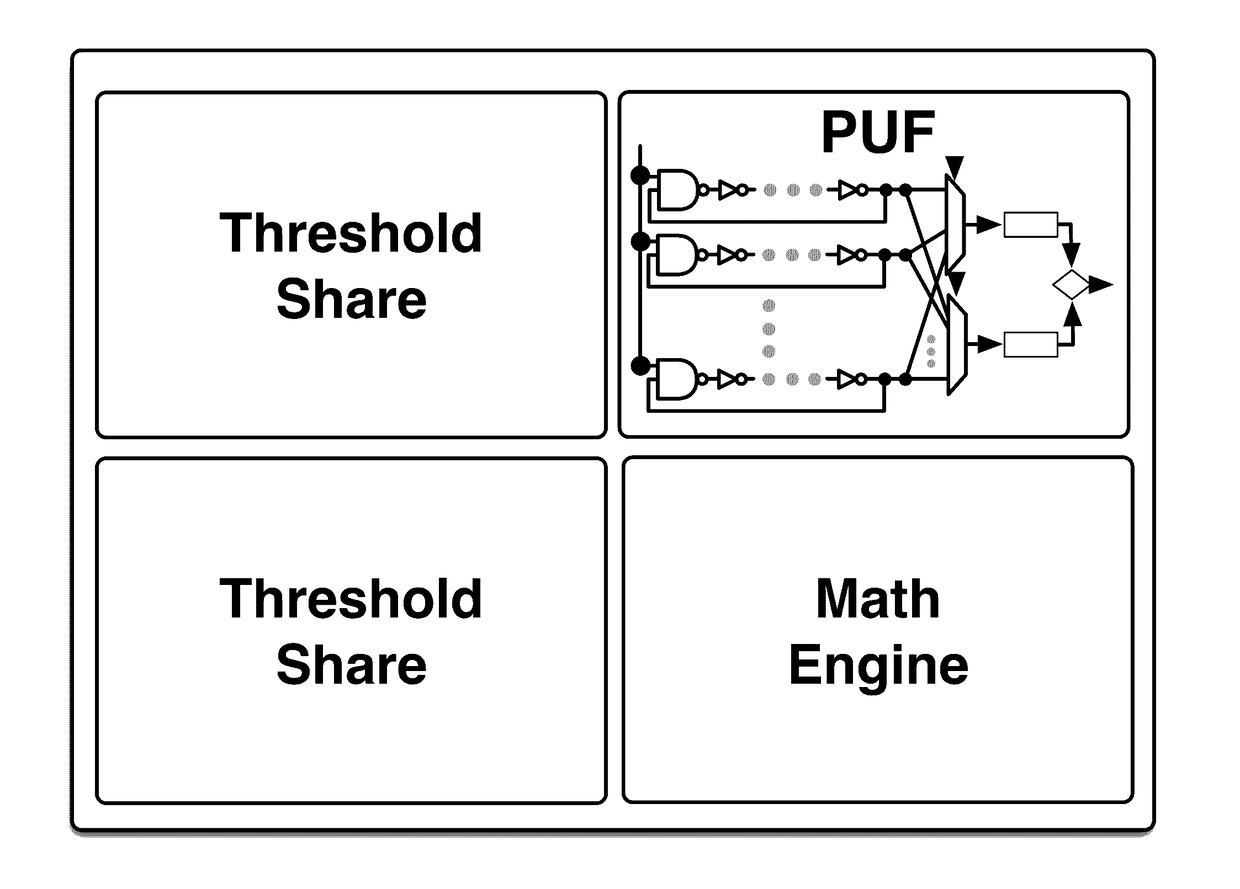
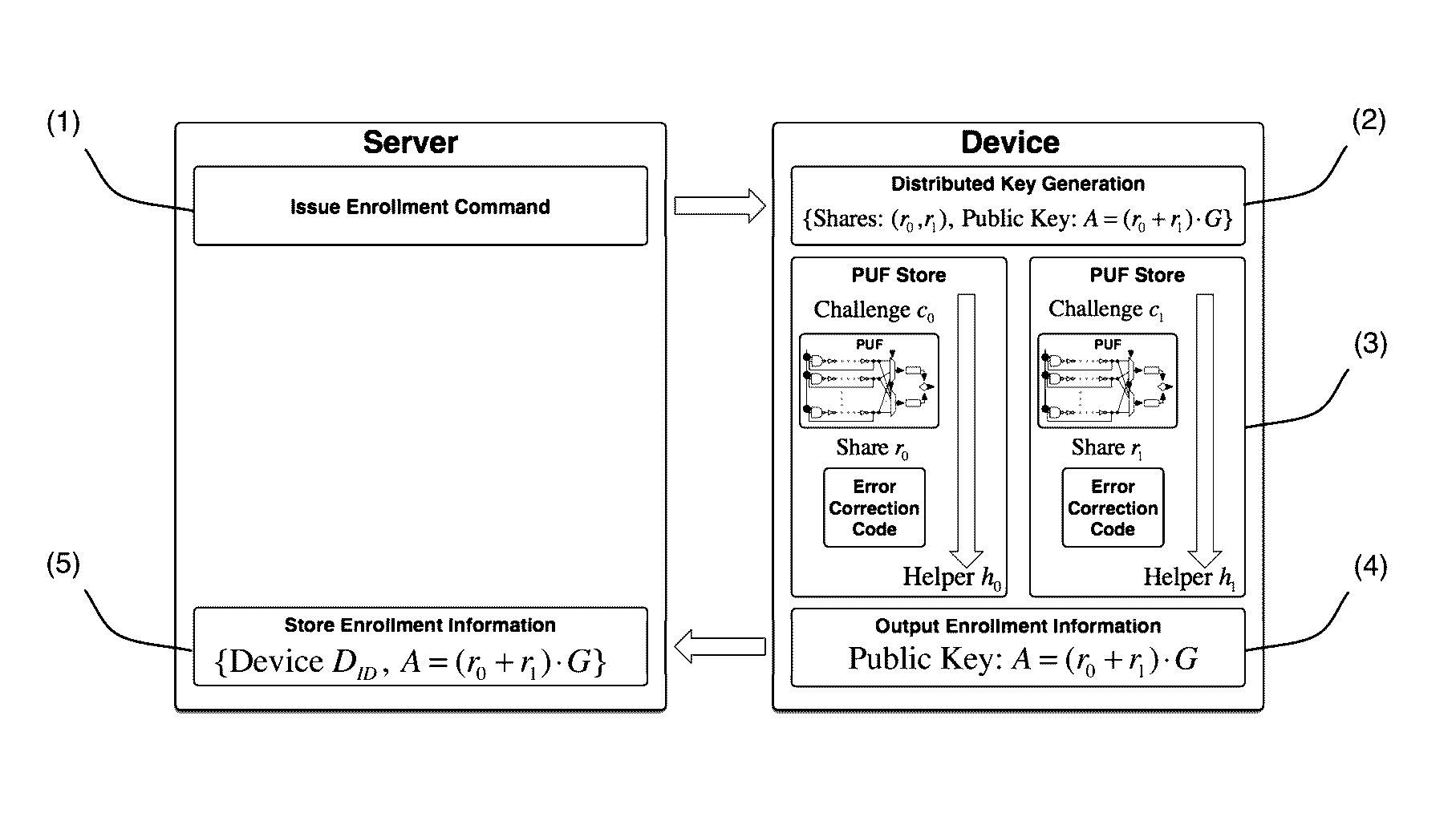
Authentication system and device including physical unclonable function and threshold cryptography
ActiveUS20170063559A1Mitigate side-channel attackEliminate needKey distribution for secure communicationData stream serial/continuous modificationPhysical unclonable functionAuthentication system
An authentication system and device including physical unclonable function (PUF) and threshold cryptography comprising: a PUF device having a PUF input and a PUF output and constructed to generate, in response to the input of a challenge, an output value characteristic to the PUF and the challenge; and a processor having a processor input that is connected to the PUF output, and having a processor output connected to the PUF input, the processor configured to: control the issuance of challenges to the PUF input via the processor output, receive output from the PUF output, combine multiple received PUF output values each corresponding to a share of a private key or secret, and perform threshold cryptographic operations. The system and device may be configured so that shares are refreshable, and may be configured to perform staggered share refreshing.
Owner:ANALOG DEVICES INC
Integrated circuit provisioning using physical unclonable function
InactiveUS20150143130A1Volume/mass flow measurementUnauthorized memory use protectionComputer hardwareIntegrated circuit manufacturing
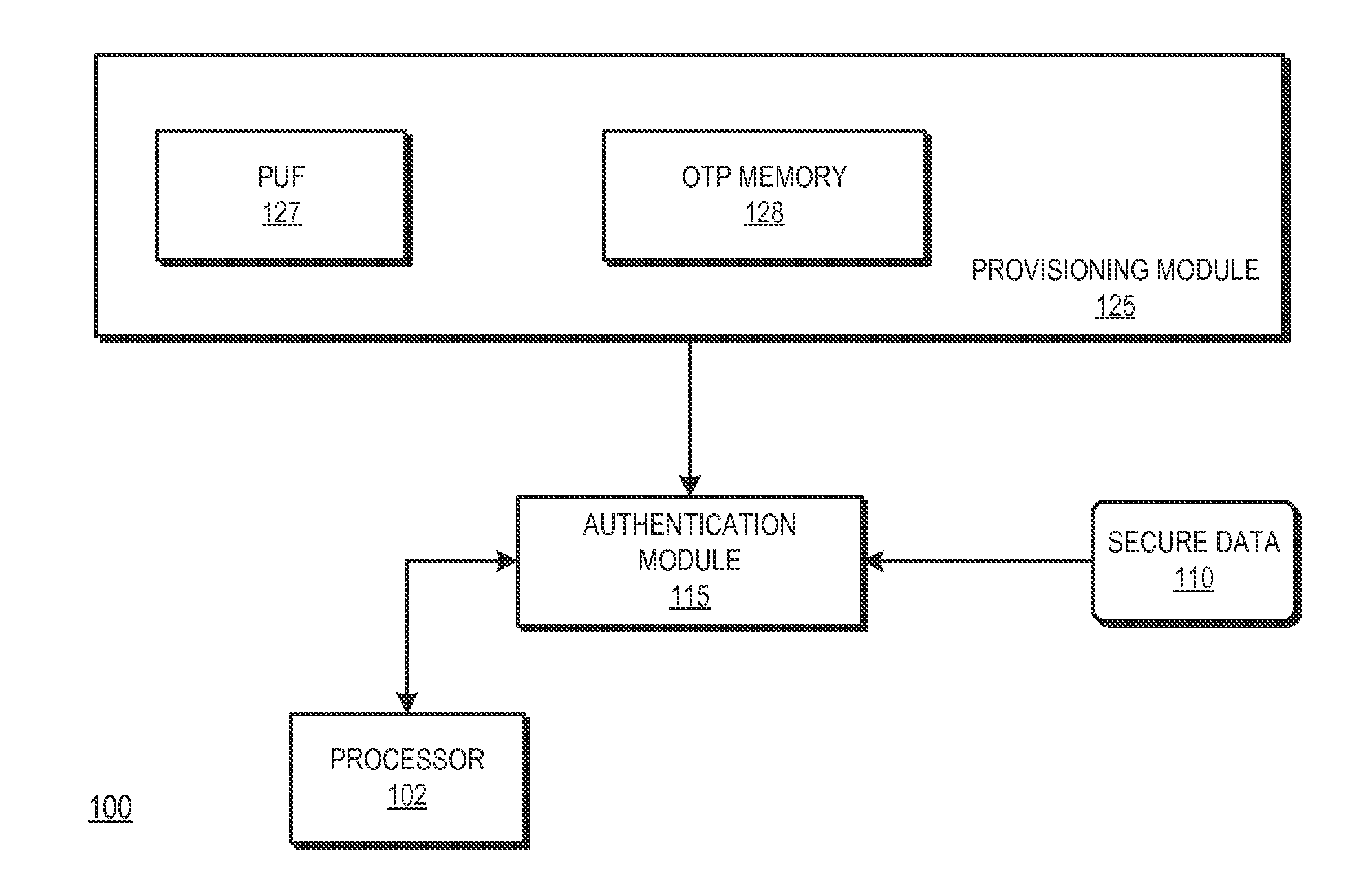
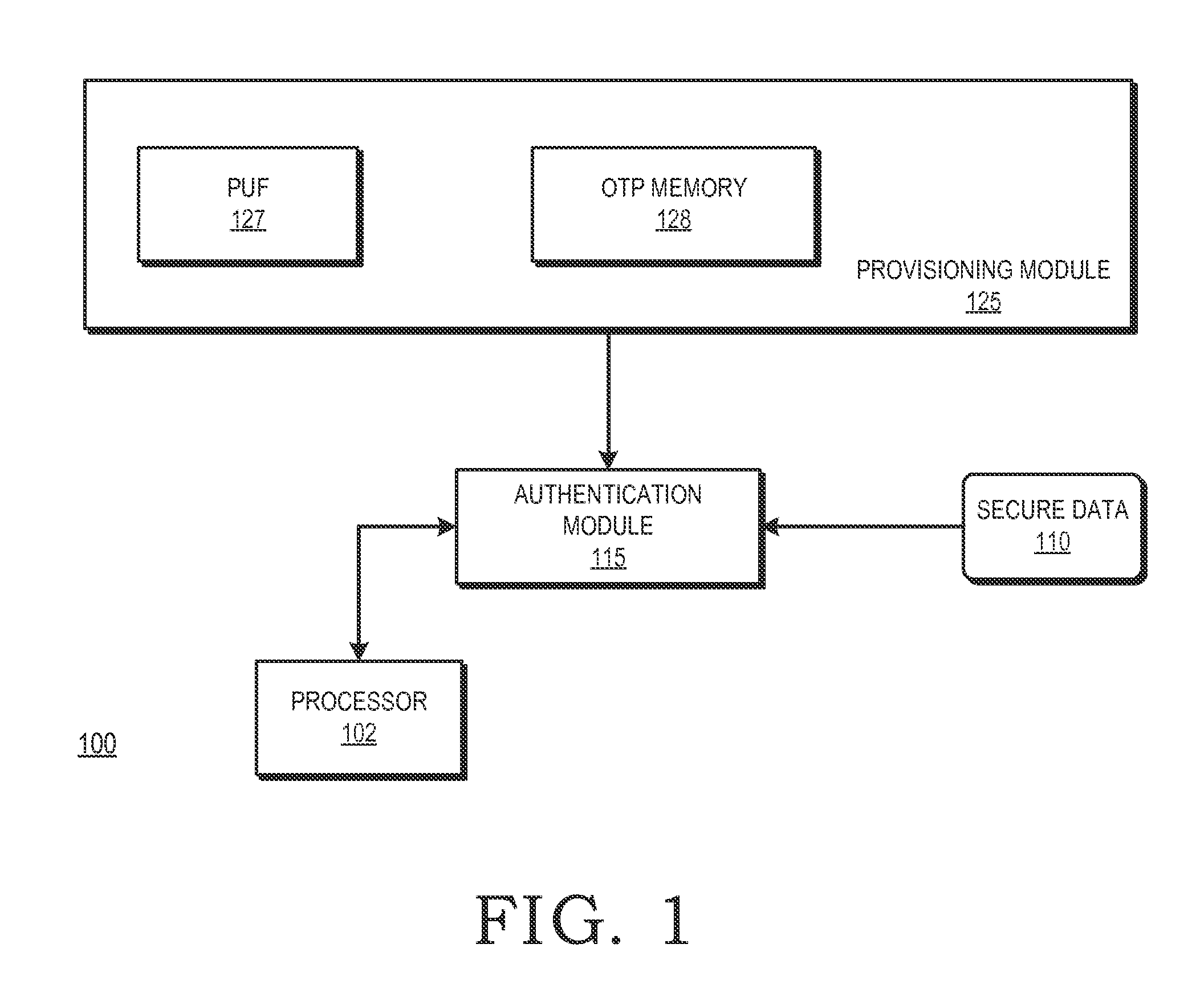
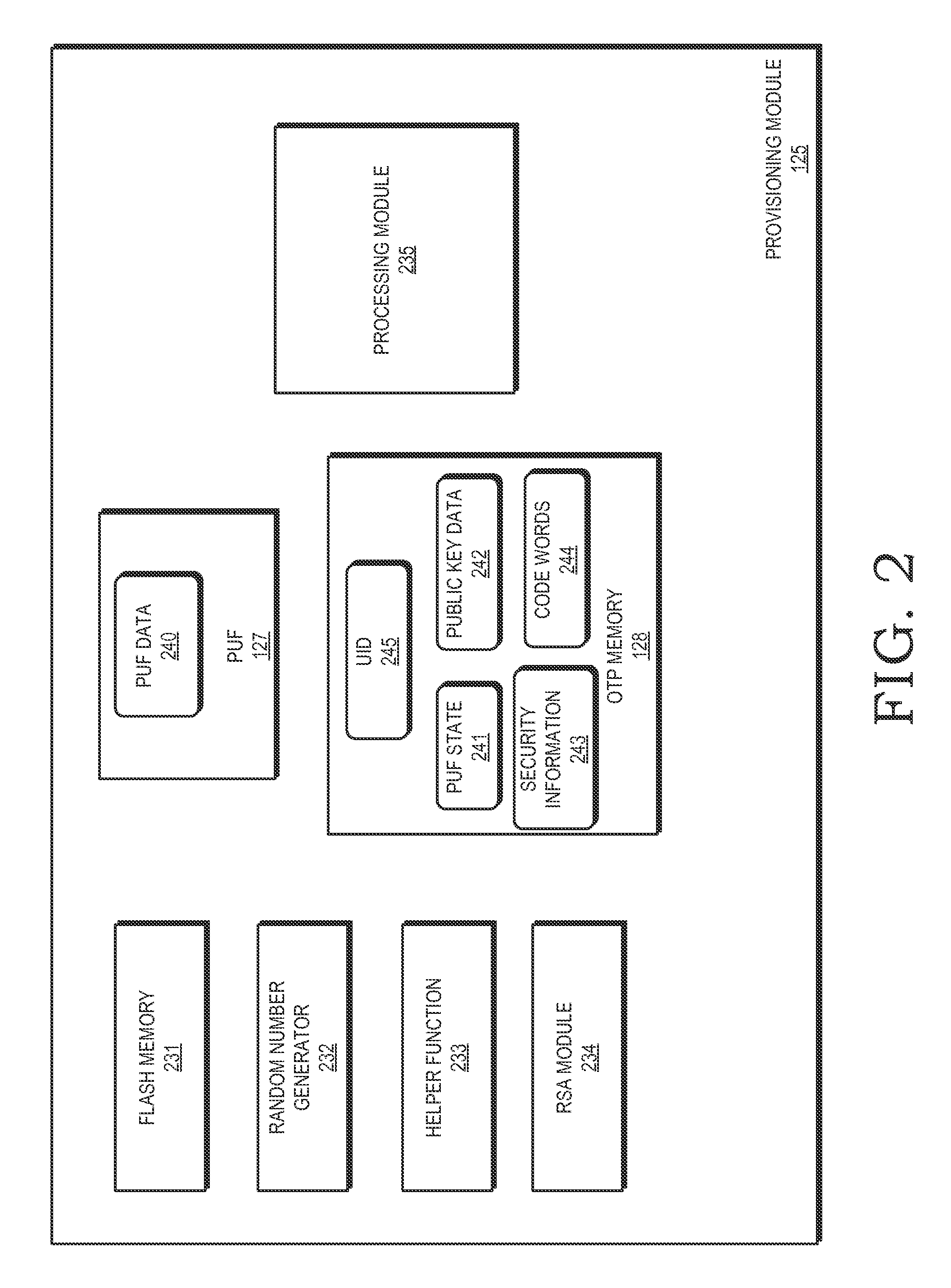
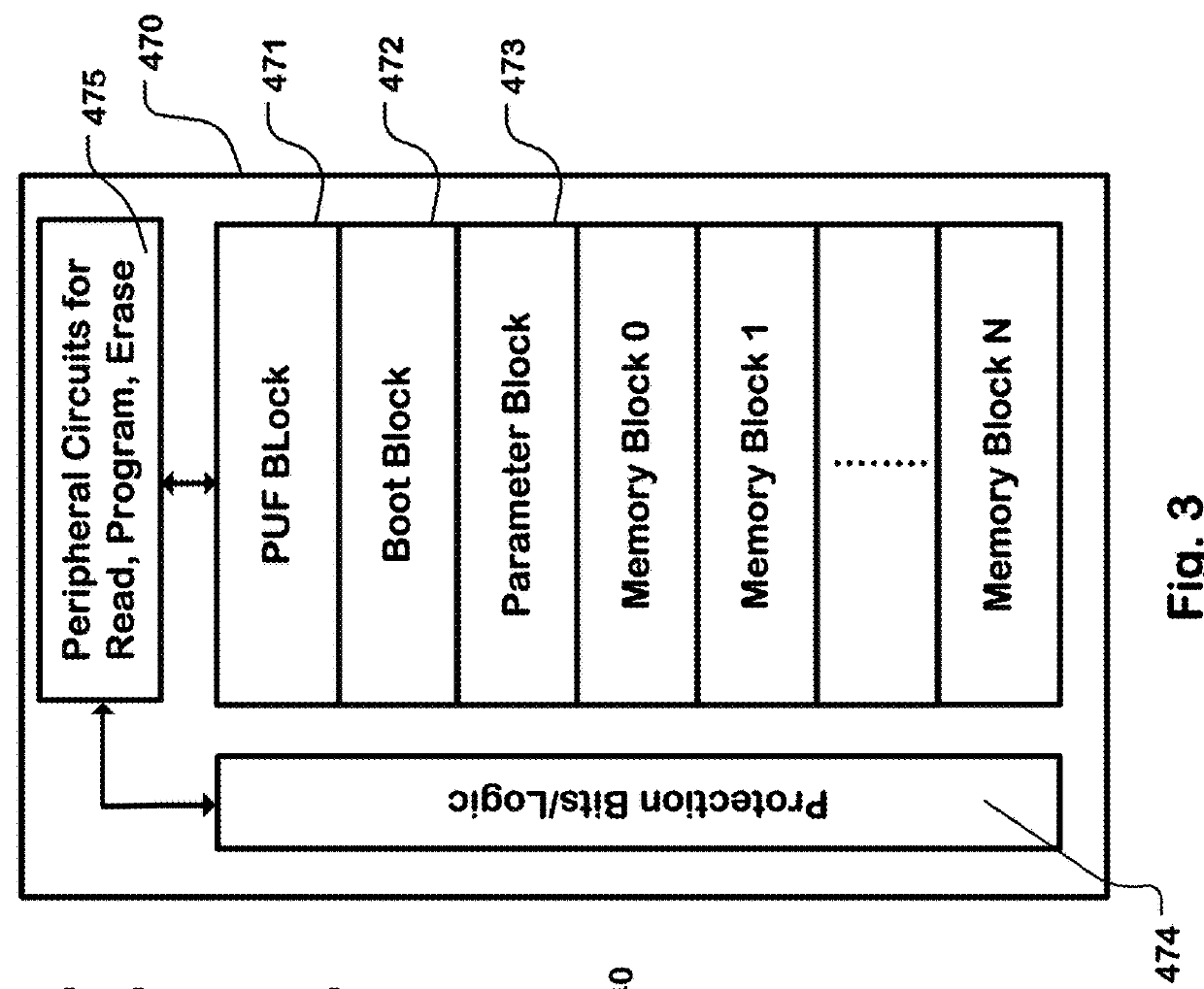
A one-time programmable (OTP) memory of an integrated circuit is provisioned based on identifier data generated by a physical unclonable function (PUF) of the integrated circuit. The identifier data is used as part of cryptographic operations to secure provisioning of security information at an OTP memory of at the integrated circuit. Because of the physical characteristics of the PUF and its incorporation in the integrated circuit, the identifier information is unique to the integrated circuit. Accordingly, the provisioned security information is also unique to the integrated circuit. The OTP memory can therefore be securely provisioned at later stages of the integrated circuit manufacturing and configuration process, such as after the integrated circuit has been packaged or attached to a printed circuit board.
Owner:VIXS SYSTEMS INC
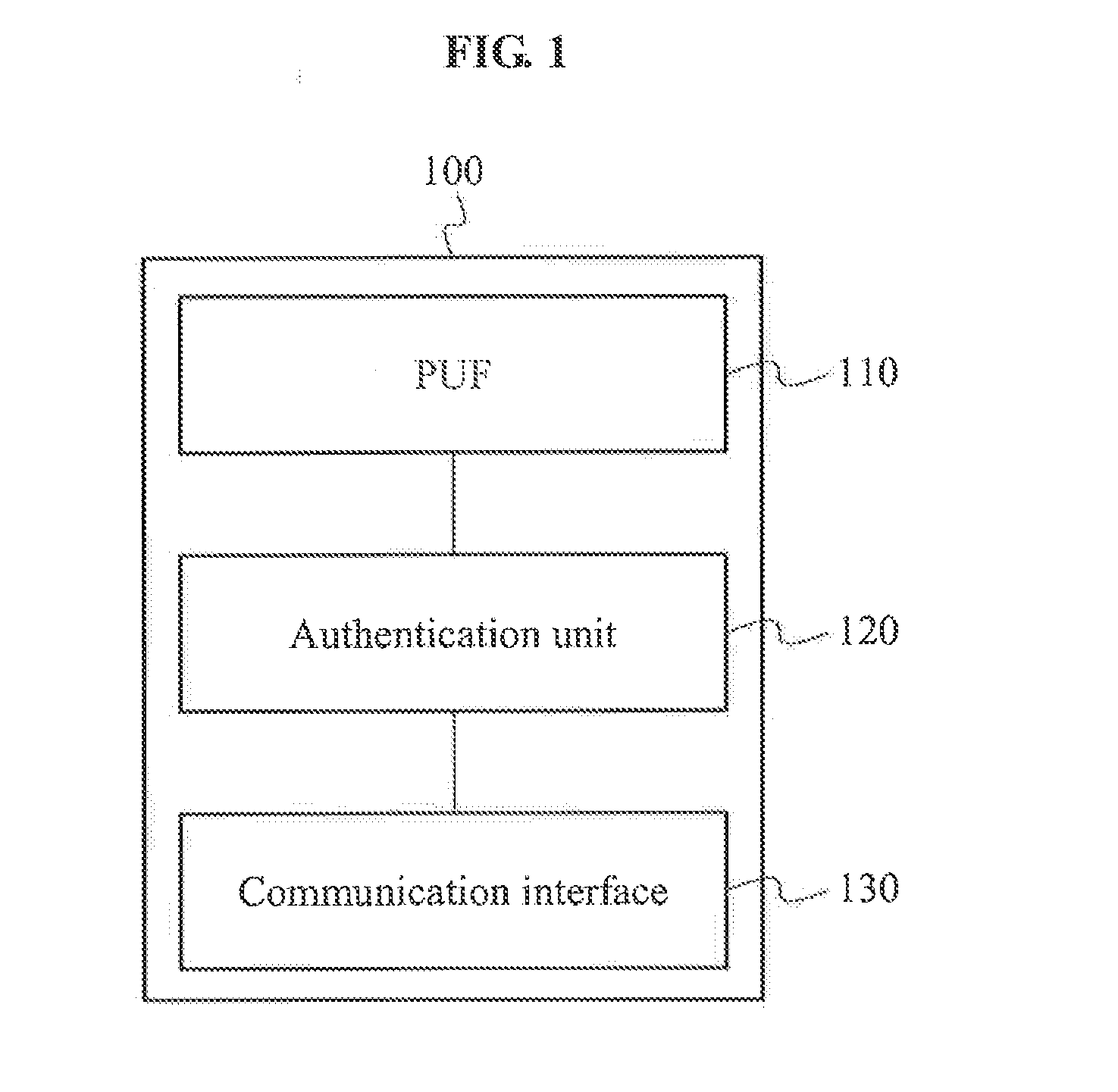
Secure authentication based on physically unclonable functions
ActiveUS20140279532A1FinanceDigital data processing detailsManufacturing variabilityCommunication interface
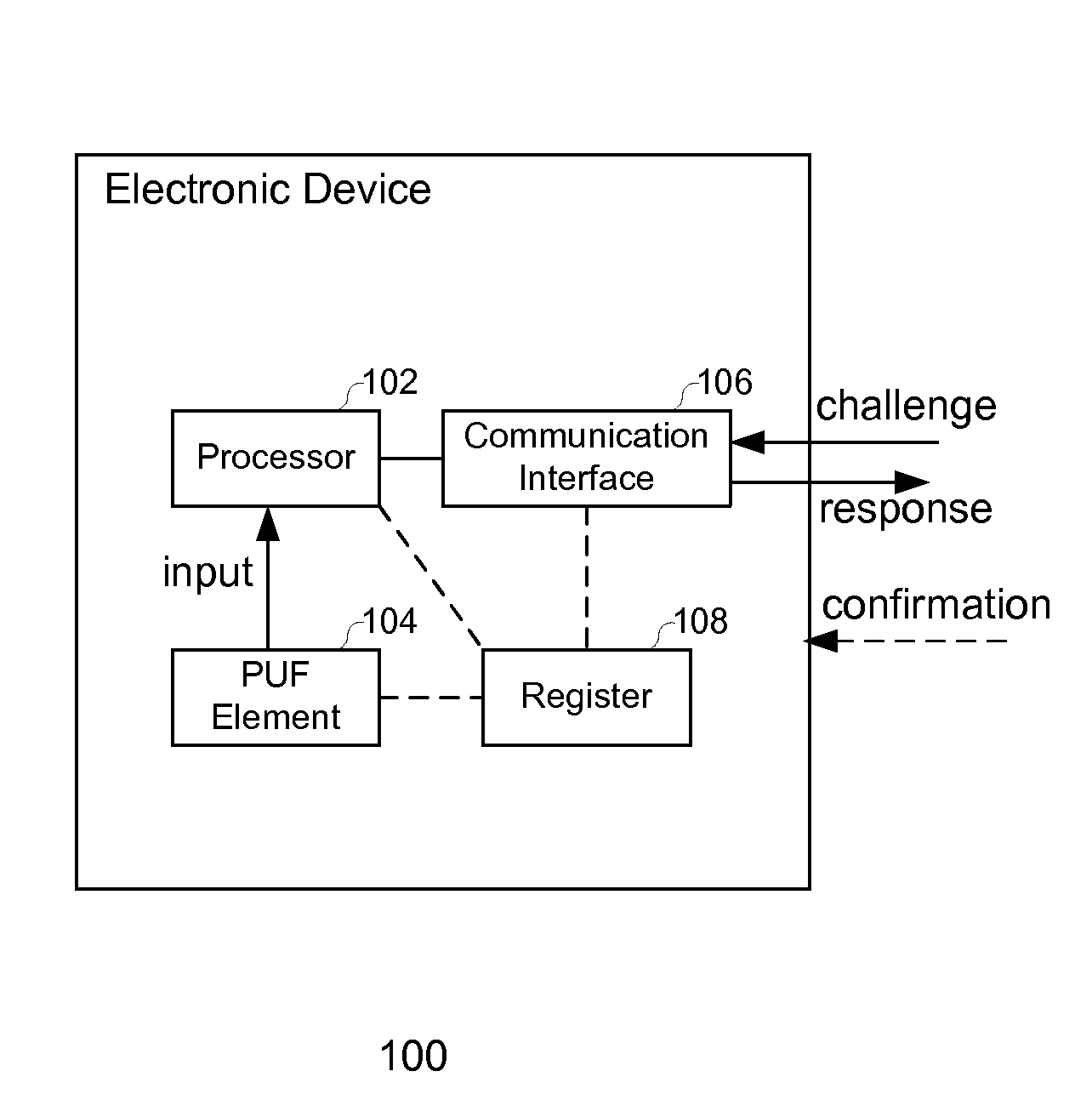
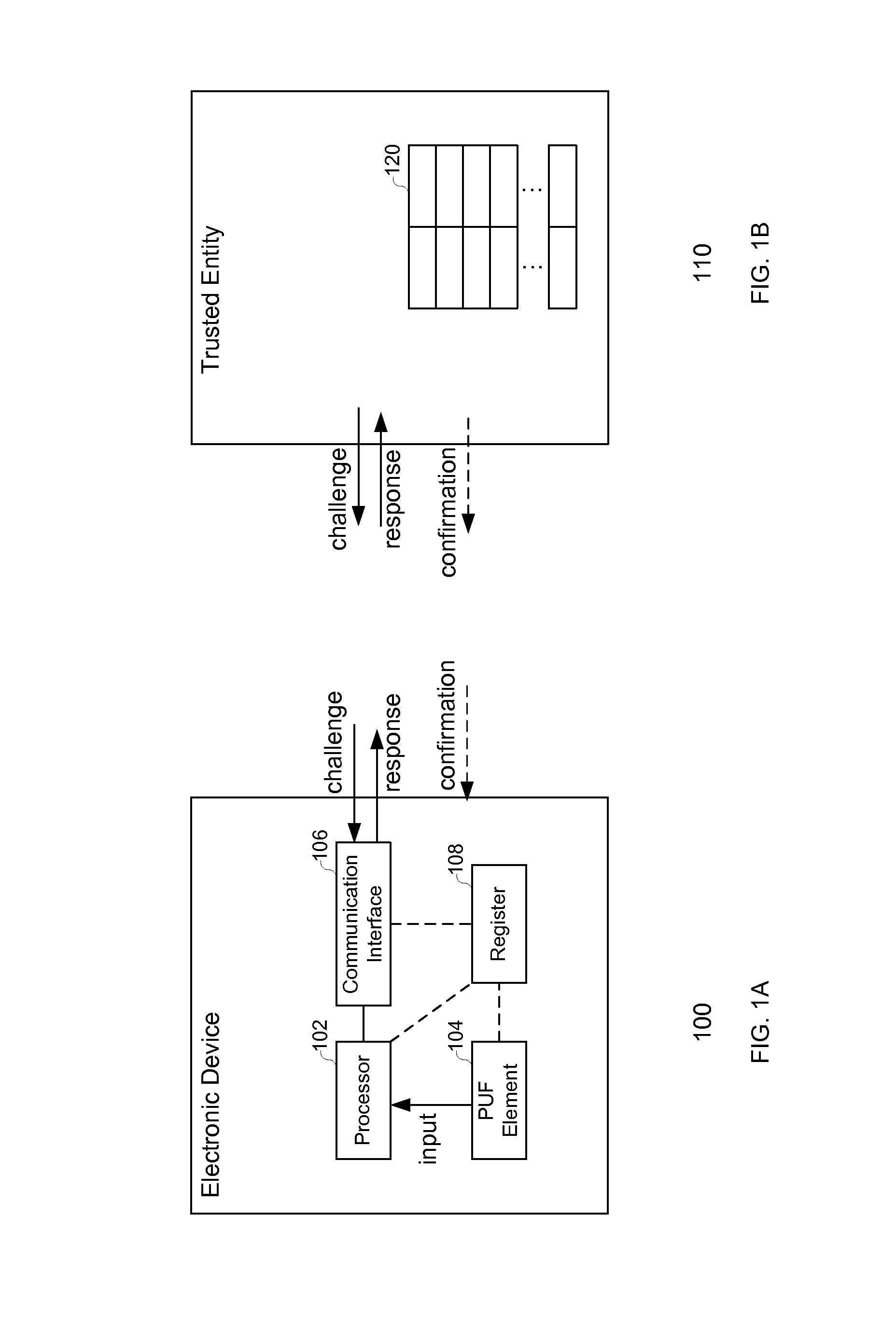
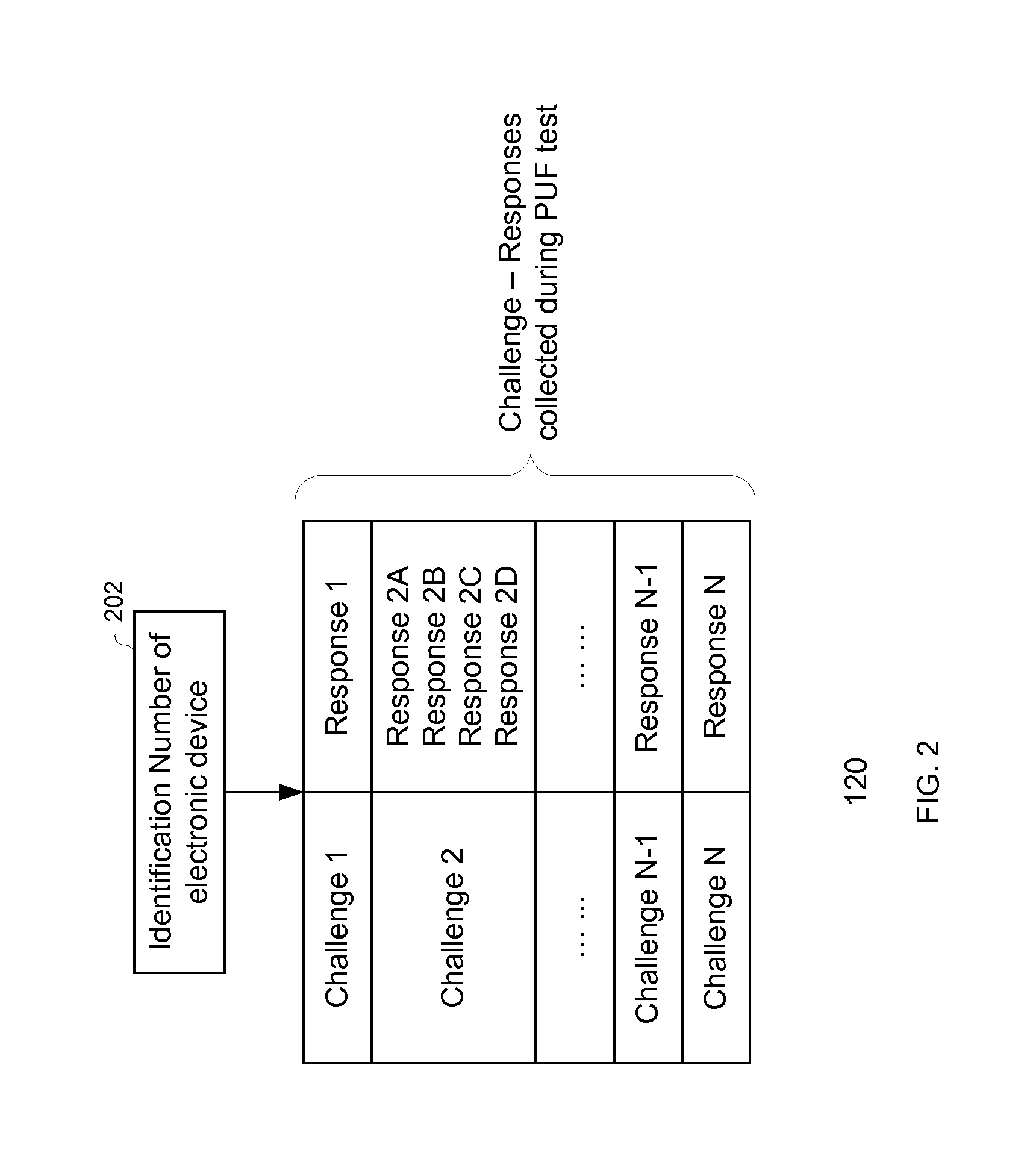
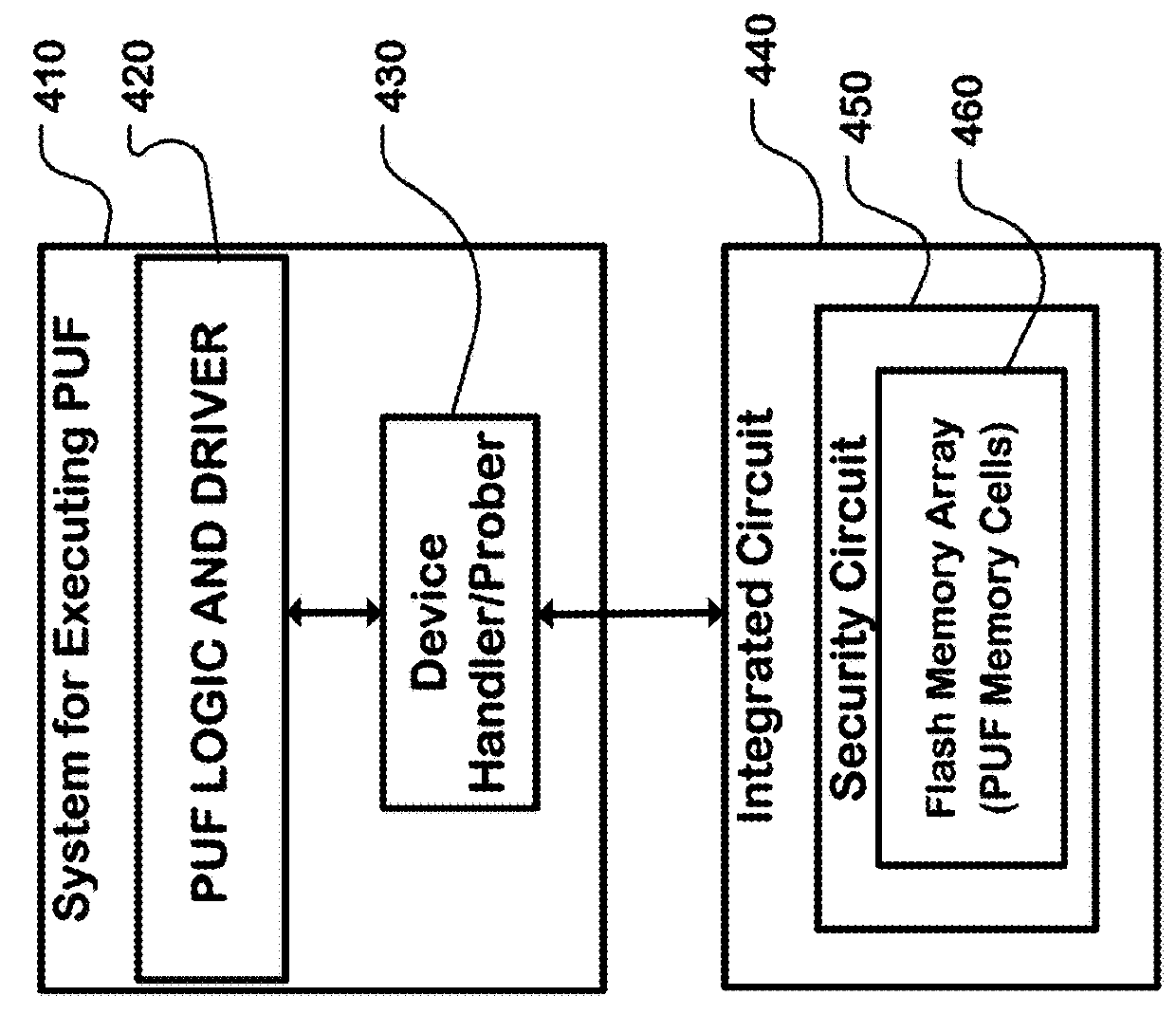
The invention relates to an electronic device, and more particularly, to systems, devices and methods of authenticating the electronic device using a challenge-response process that is based on a physically unclonable function (PUF). The electronic device comprises a PUF element, a processor and a communication interface. The PUF element generates an input signal based on at least one PUF that has unique physical features affected by manufacturing variability. A challenge-response database, comprising a plurality of challenges and a plurality of corresponding responses, is set forth by the processor based on the PUF-based input and further provided to a trusted entity. During the trusted transaction, the processor generates a response in response to a challenge sent by the trusted entity based on the PUF-based input, and thereby, the trusted entity authenticates the electronic device by comparing the response with the challenge-response database.
Owner:MAXIM INTEGRATED PROD INC
Physical unclonable function for security key
ActiveUS20180278418A1Increase entropyIncrease flexibility and reliabilityKey distribution for secure communicationPhysical unclonable functionComputer science
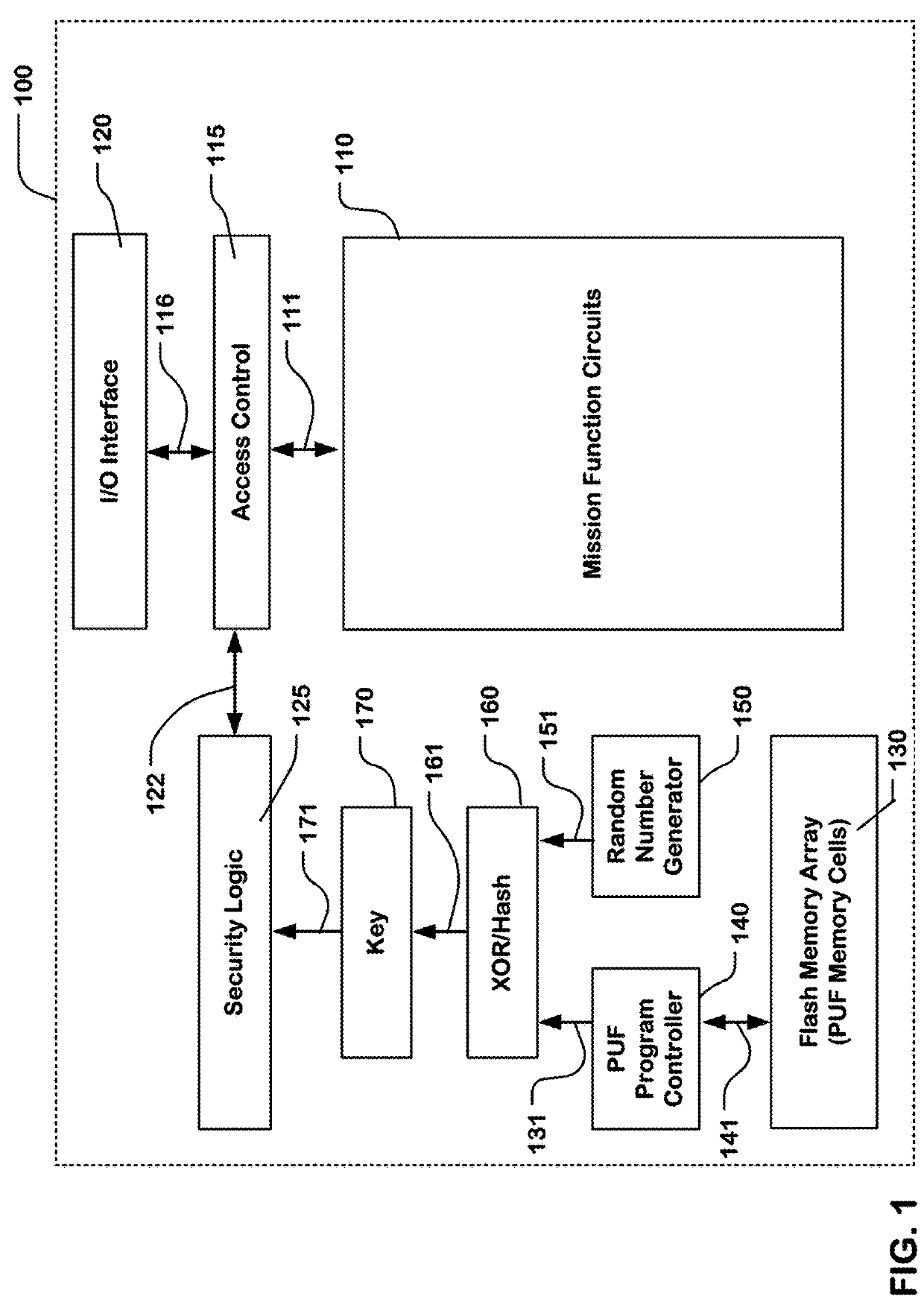
A system including a host and a guest device, where the guest device can be implemented on a single packaged integrated circuit or a multichip circuit and have logic to use a physical unclonable function to produce a security key. The device can include logic on the guest to provide the PUF key to the host in a secure manner. The physical unclonable function can use entropy derived from non-volatile memory cells to produce the initial key. Logic is described to disable changes to PUF data, and thereby freeze the key after it is stored in the set.
Owner:MACRONIX INT CO LTD
Systems and methods for stable physically unclonable functions
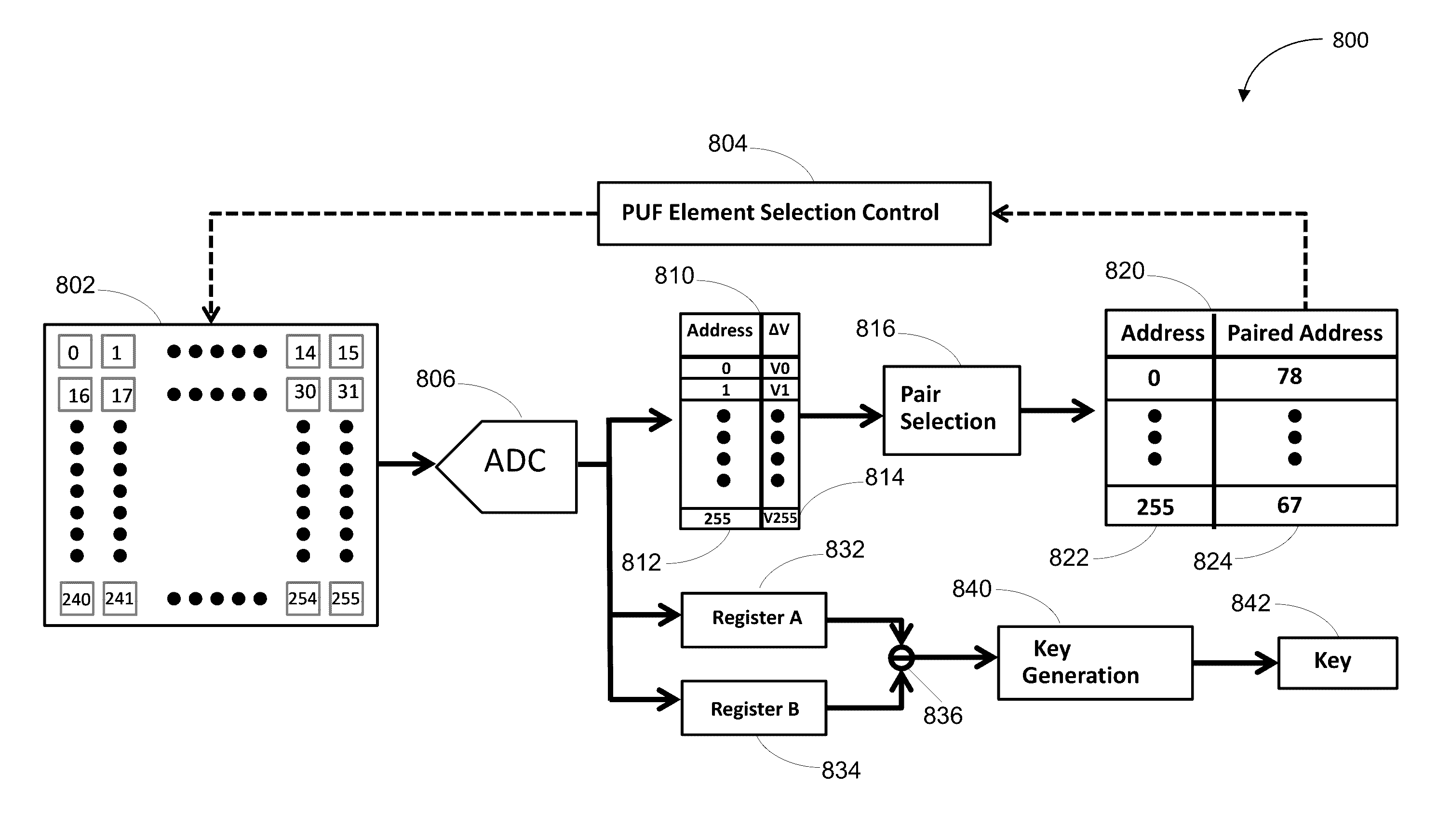
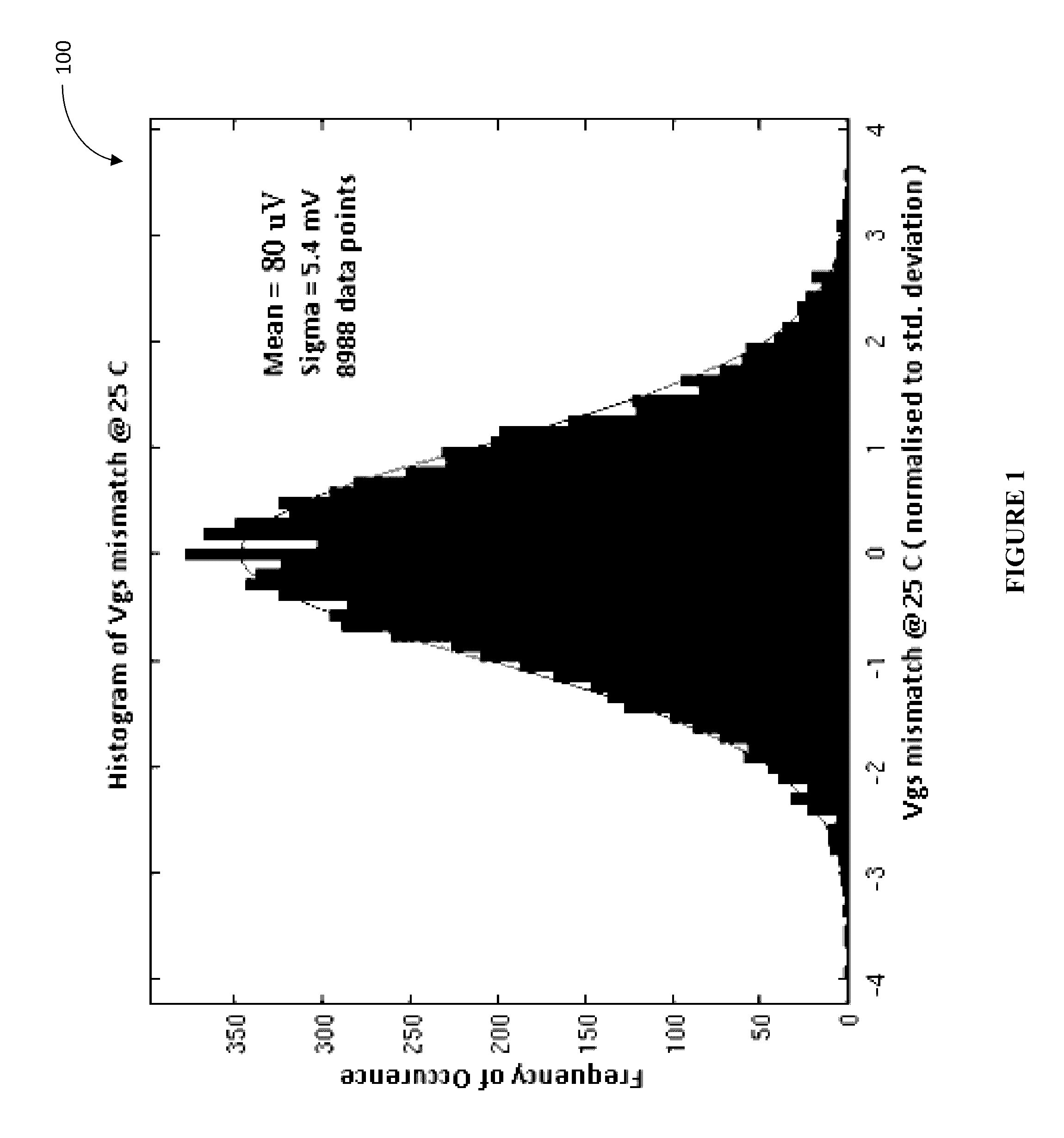
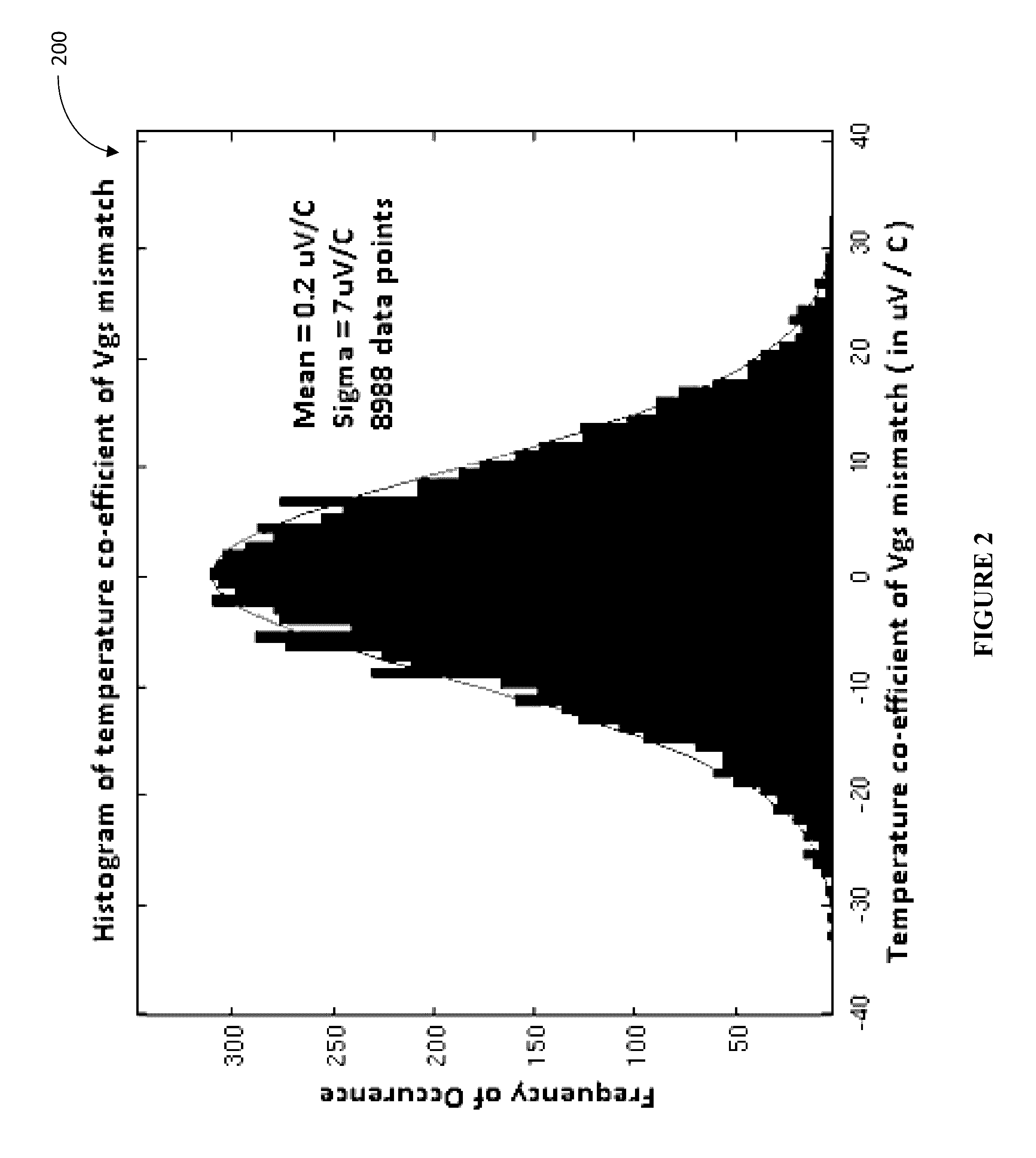
ActiveUS9485094B1Reduce PUF element sensitivityReduce utilizationKey distribution for secure communicationComputer hardwarePhysical unclonable function
Various embodiments of the invention allow to take advantage of the natural statistical variation of physical properties in a semiconductor device in order to create truly random, repeatable, and hard to detect cryptographic bits. In certain embodiments, this is accomplished by pairing mismatch values of PUF elements so as to ensure that PUF key bits generated thereform remain insensitive to environmental errors, without affecting the utilization rate of available PUF elements.
Owner:MAXIM INTEGRATED PROD INC
Physical unclonable function generation and management
ActiveUS20140327469A1Reliability increasing modificationsComputer hardwarePhysical unclonable function
Methods, systems and devices related to authentication of chips using physical physical unclonable functions (PUFs) are disclosed. In accordance one such method, a test voltage is applied to a PUF system including a first subset of PUF elements that are arranged in series and a second subset of PUF elements that are arranged in series, where the first subset of PUF elements is arranged in parallel with respect to the second subset of PUF elements. In addition, the PUF system is measured to obtain at least one differential of states between the first subset of PUF elements and the second subset of PUF elements. Further, the method includes outputting an authentication sequence for the circuit that is based on the one or more differentials of states.
Owner:GLOBALFOUNDRIES US INC
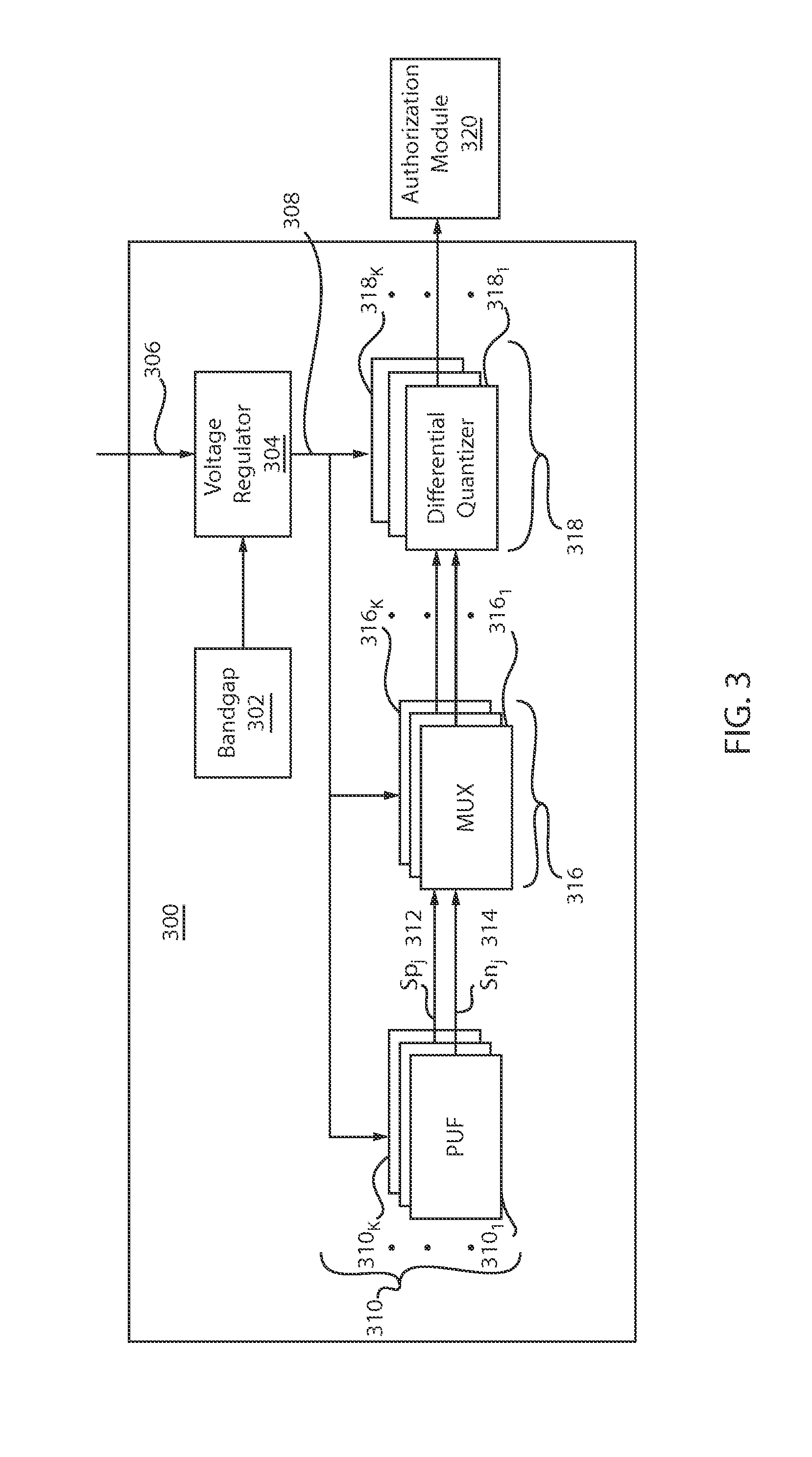
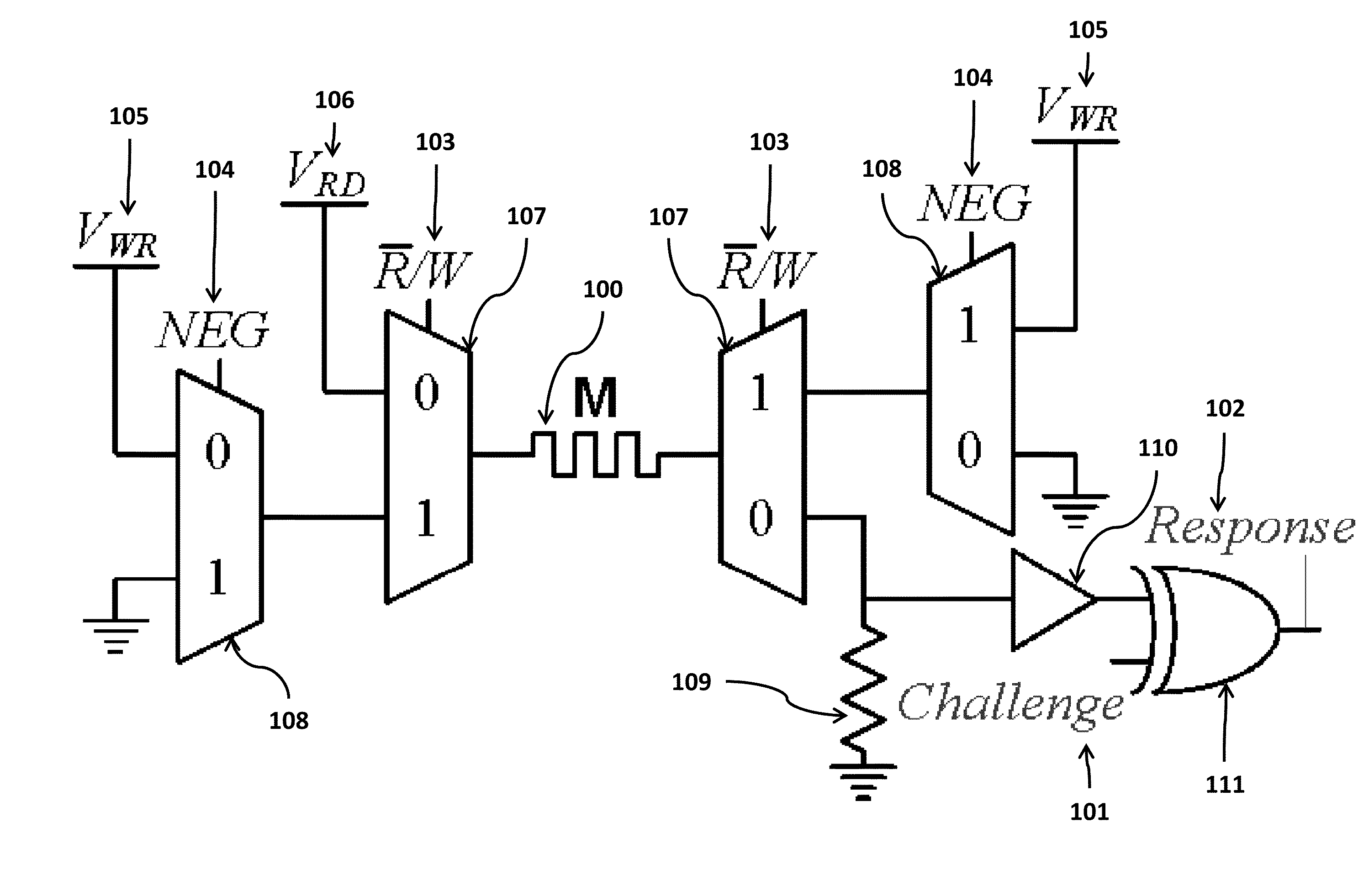
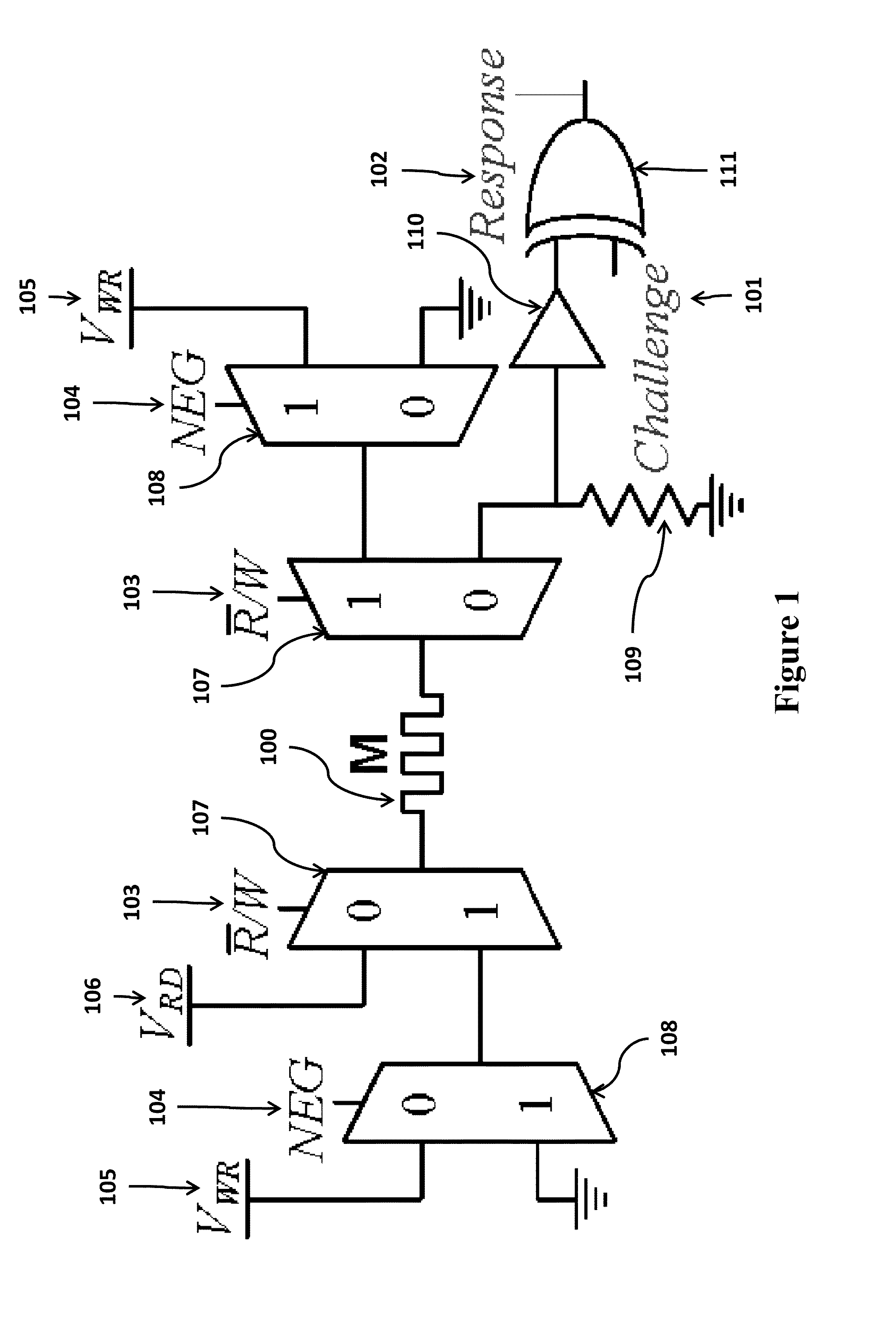
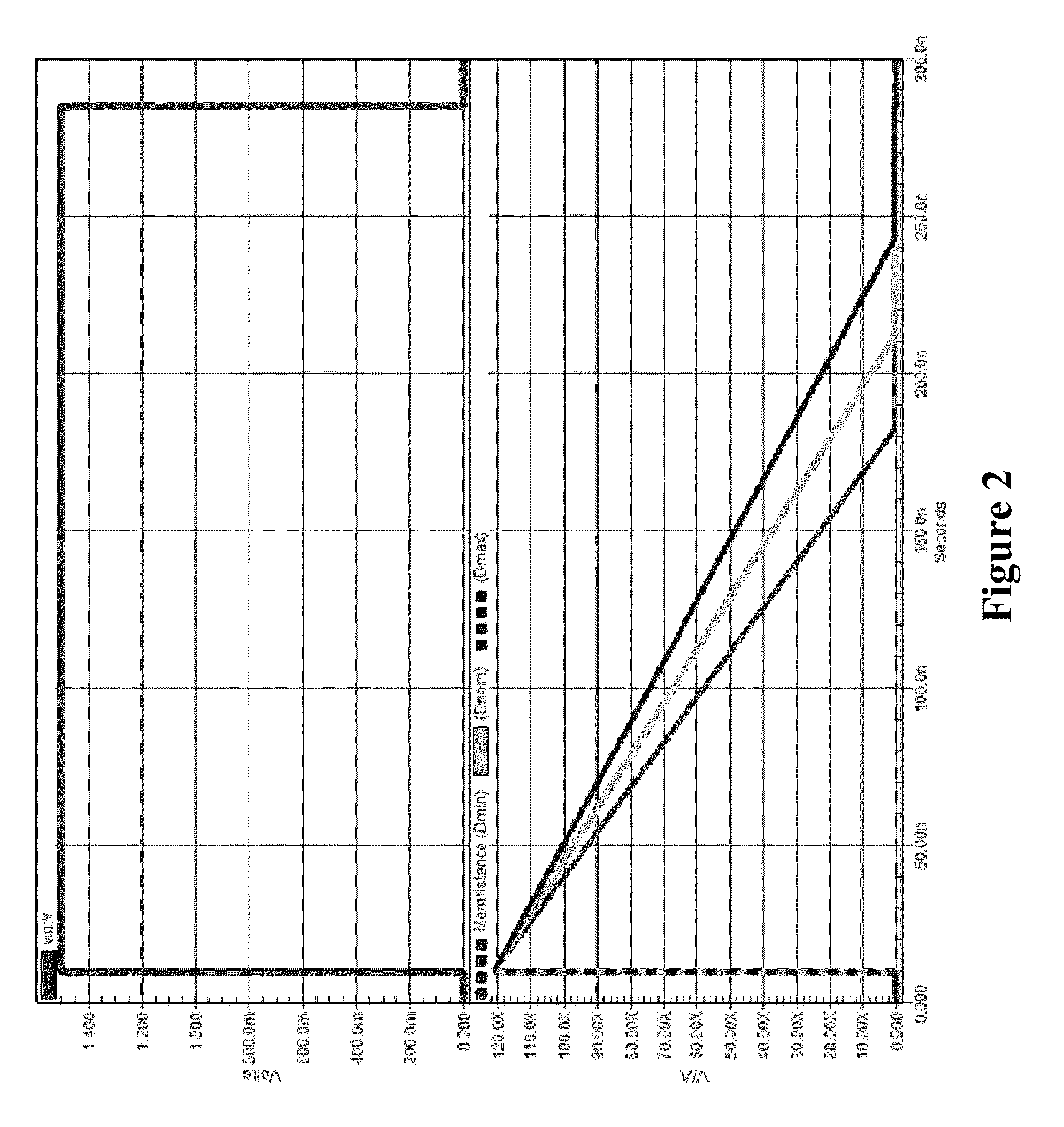
Write-Time Based Memristive Physical Unclonable Function
InactiveUS20140268994A1High resistance stateDigital storageInternal/peripheral component protectionHigh resistancePhysical unclonable function
A physical unclonable function (PUF) device consisting of a hybrid CMOS-memristor circuit that leverages variations in the required write-time of a memristor. Variations in the time required to write, or SET, a memristor from a high to low resistance state arise from variability in physical parameters such as the memristor thickness. When applying a SET voltage across the memristor for the nominal minimum SET time, variability leads to a situation where the memristor will actually SET to the low resistance state only 50% of the time. When the device does not SET it will remain in the high resistance state. Since the to resistance state of the memristor corresponds to reading either a logic 1 or logic 0 on the output of the circuit, the write-time based memristive PUF produces a digital signature directly corresponding to the fabrication process-induced physical variations of an integrated circuit.
Owner:BY THE SEC OF THE AIR FORCE UNITED STATES OF AMERICA AS REPRESENTED
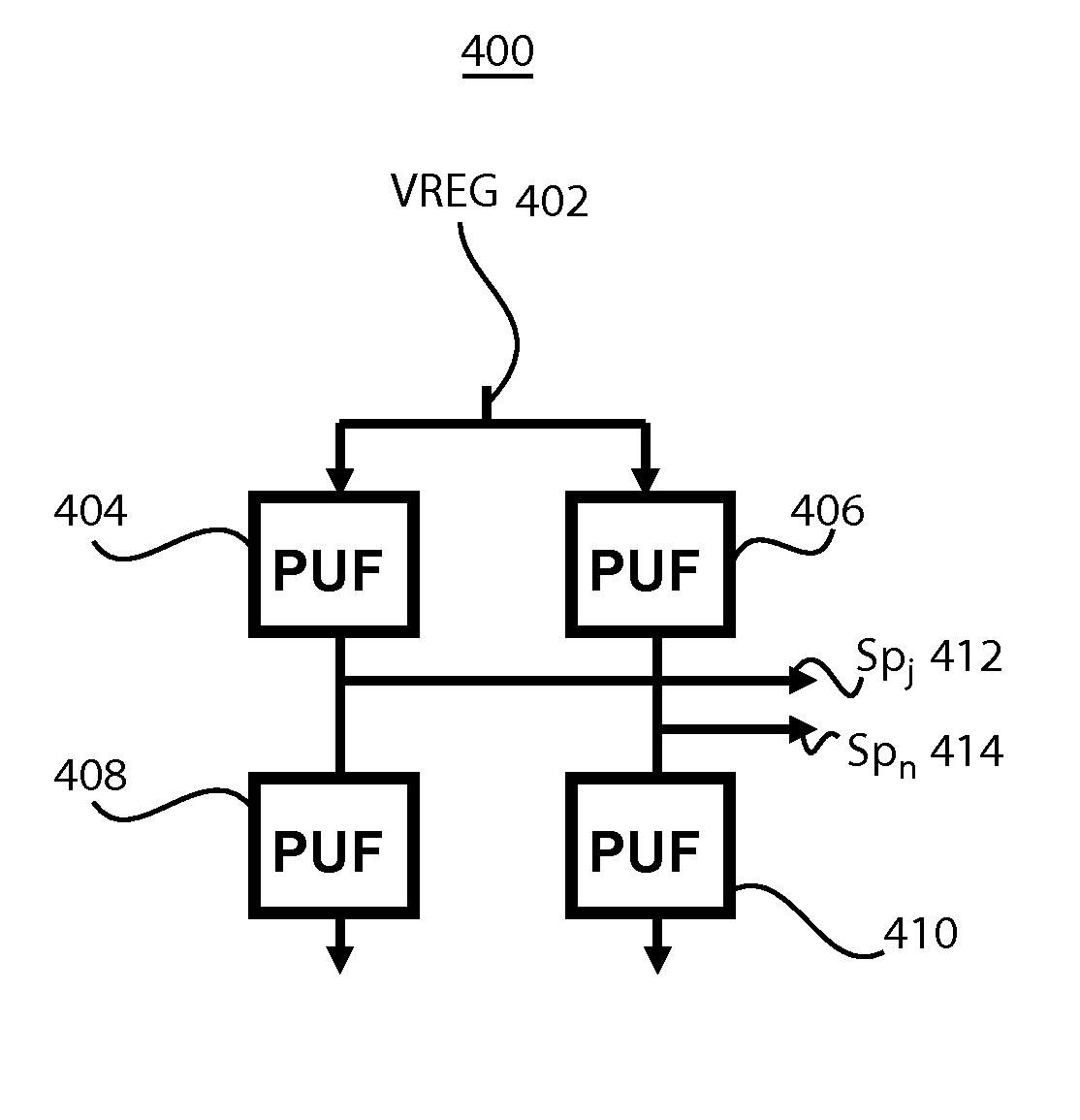
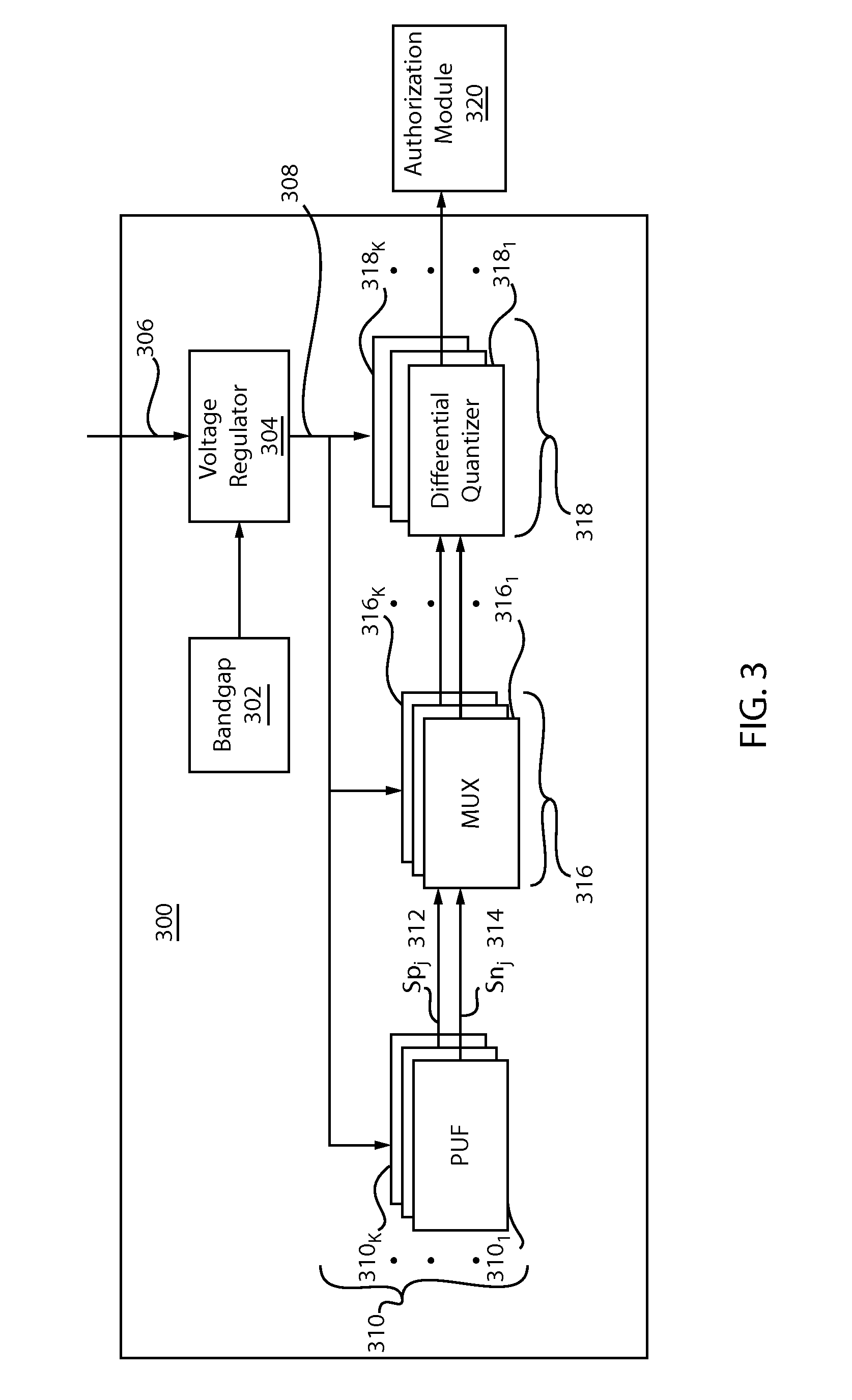
Physical unclonable function generation and management
Methods, systems and devices related to authentication of chips using physical physical unclonable functions (PUFs) are disclosed. In preferred systems, differentials of PUFs are employed to minimize sensitivity to temperature variations as well as other factors that affect the reliability of PUF states. In particular, a PUF system can include PUF elements arranged in series and in parallel with respect to each other to facilitate the measurement of the differentials and generation of a resulting bit sequence for purposes of authenticating the chip. Other embodiments are directed to determining and filtering reliable and unreliable states that can be employed to authenticate a chip.
Owner:GLOBALFOUNDRIES US INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com