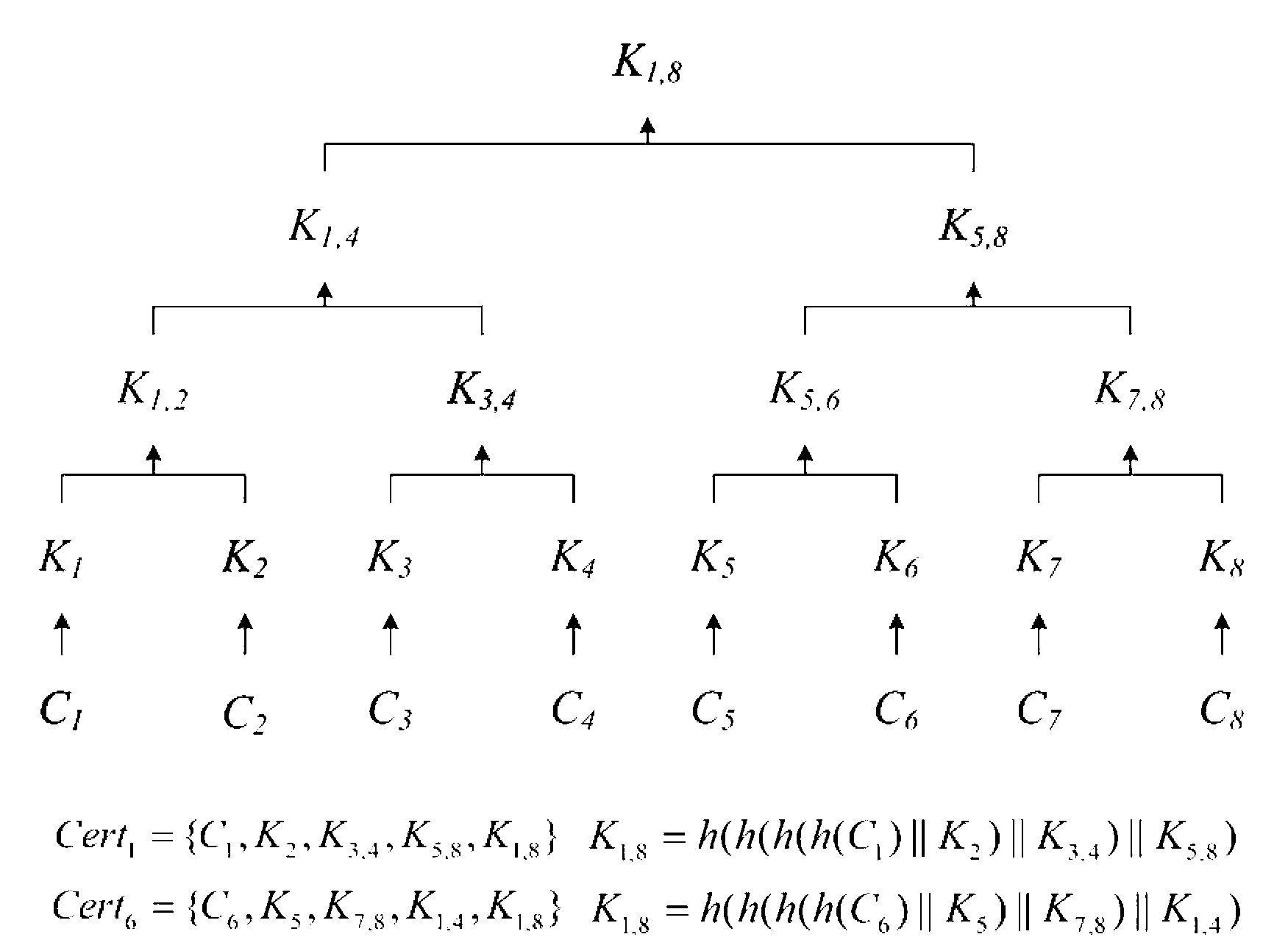Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
85results about How to "Authentication security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
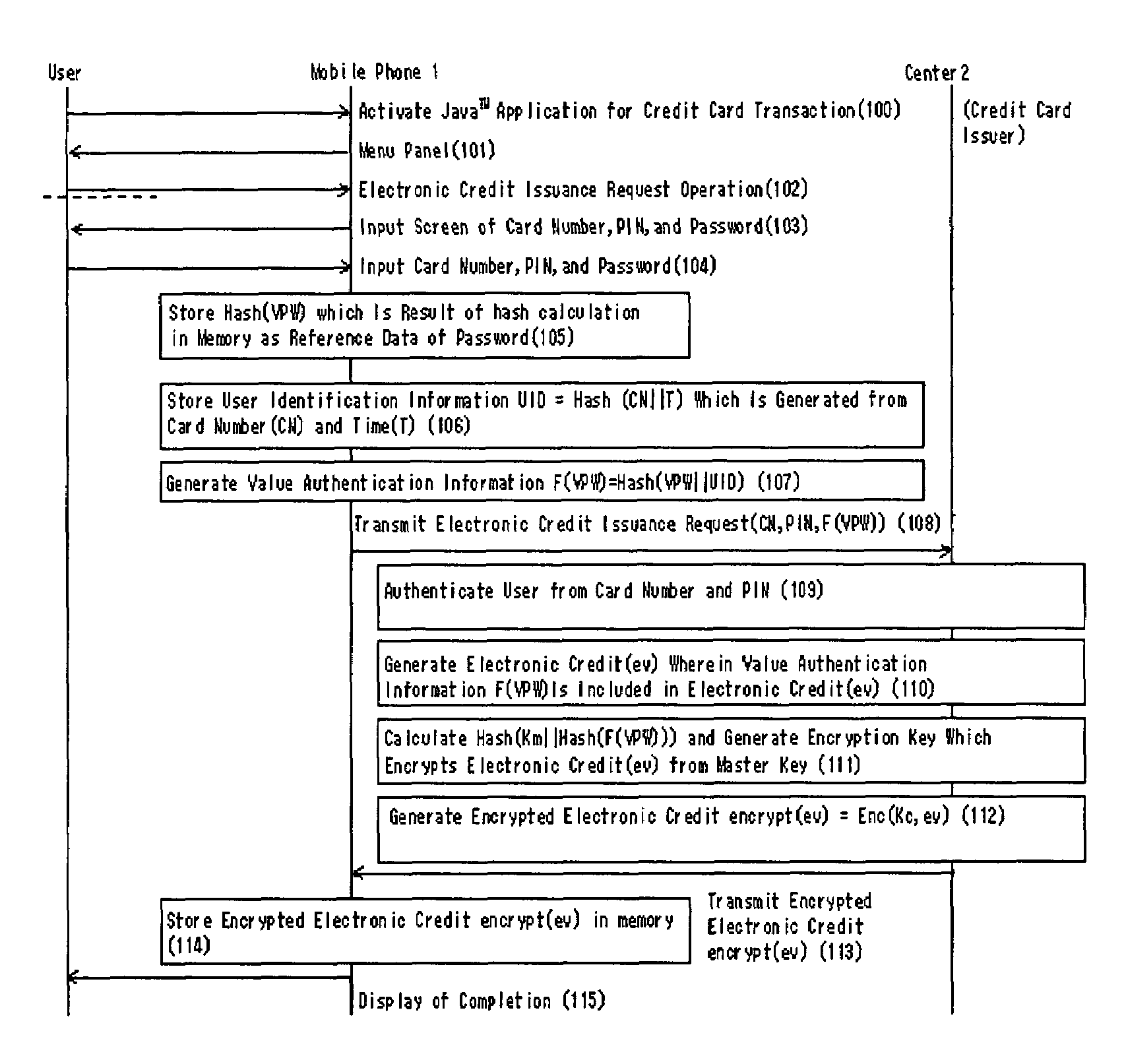
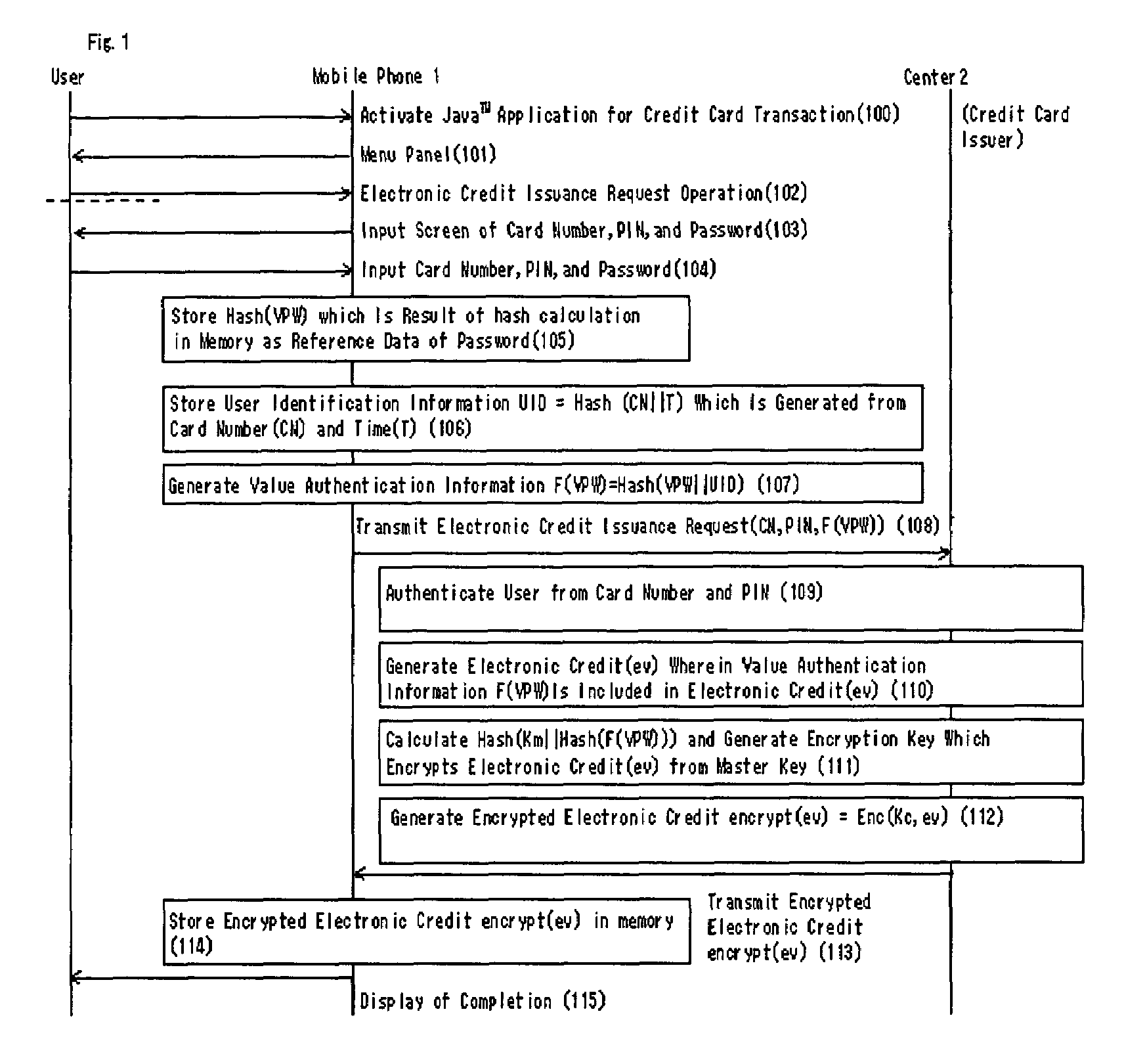
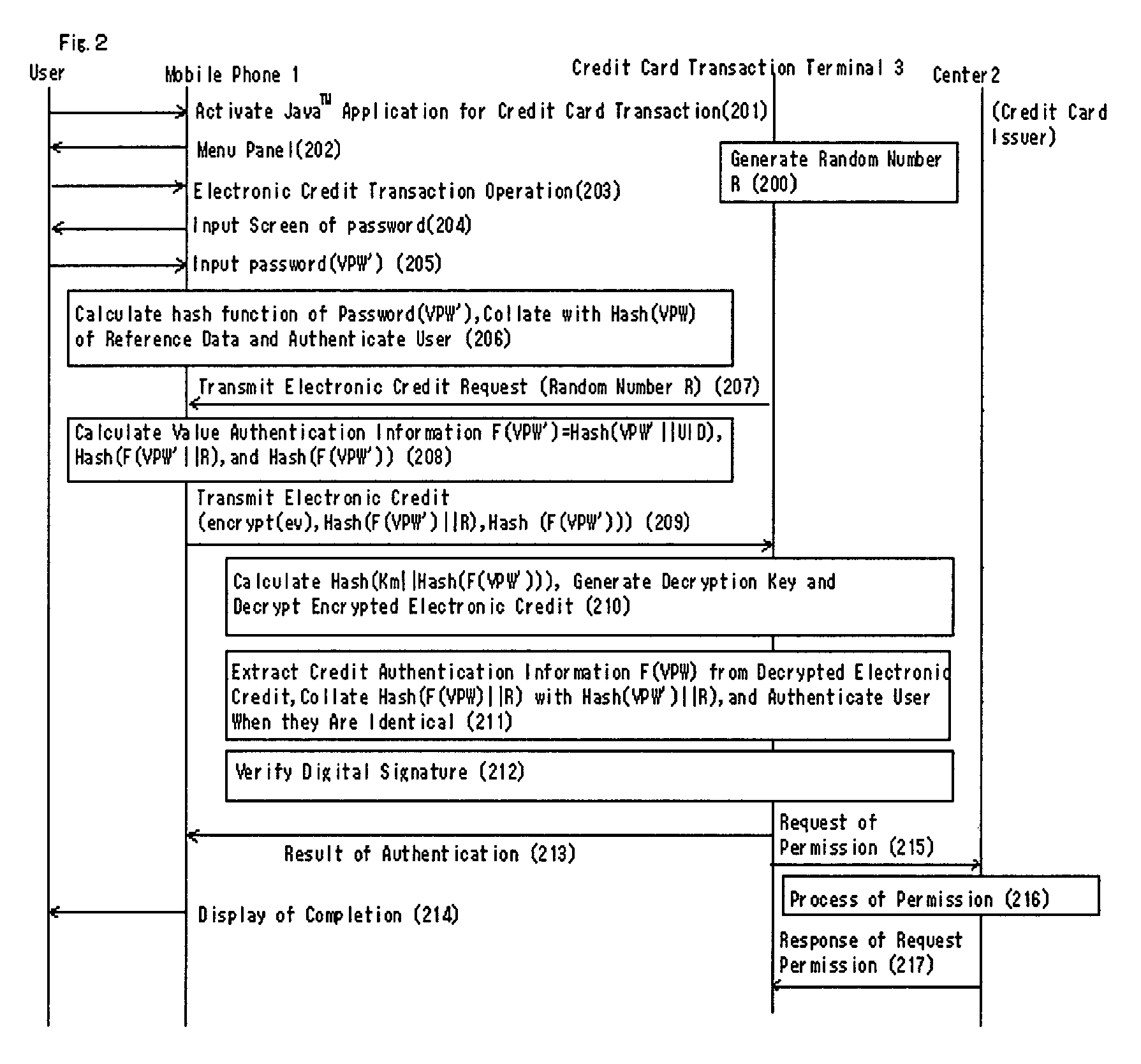
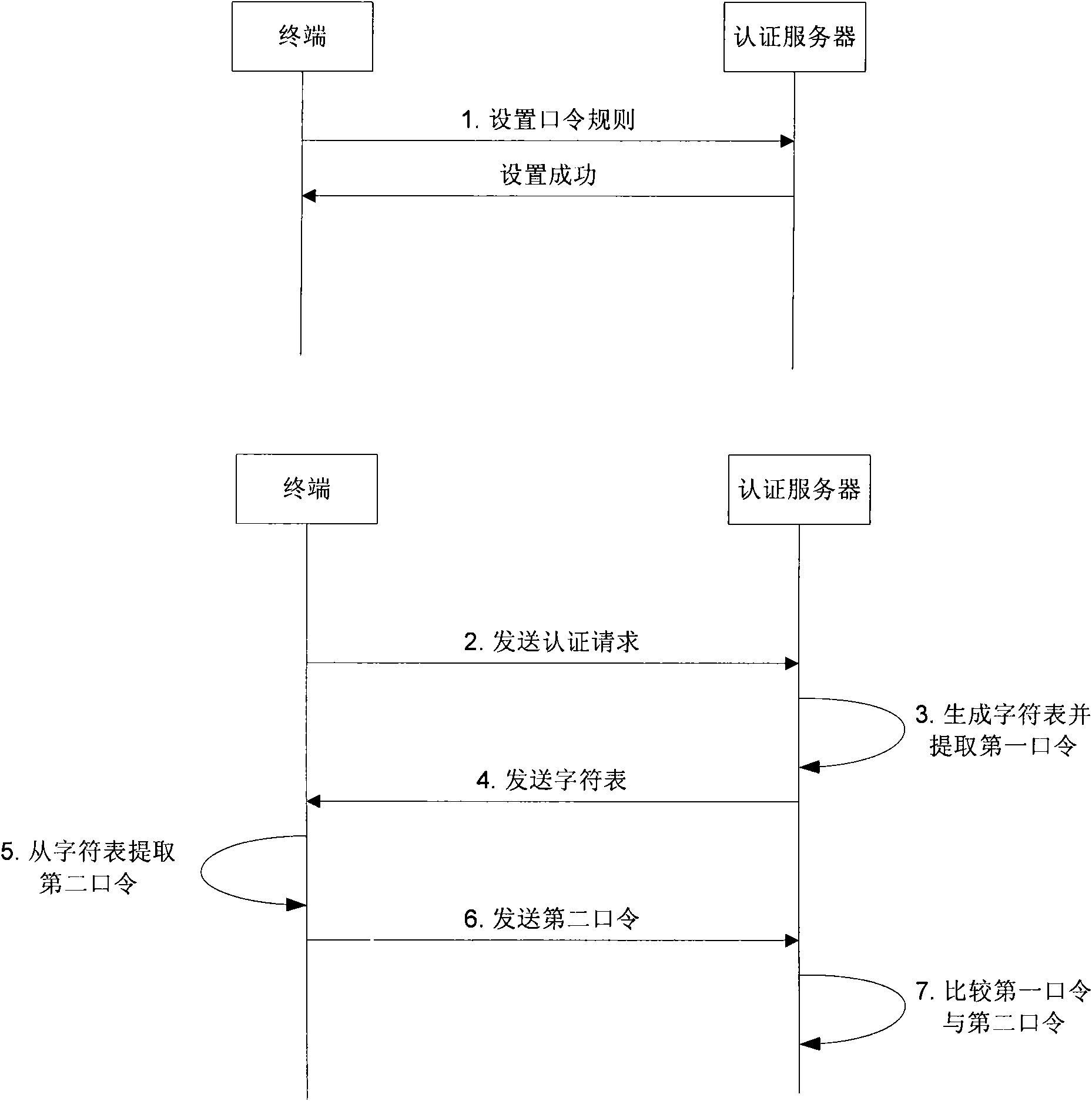
Authentication method, system and apparatus of an electronic value
ActiveUS7325132B2Improve securityAuthenticate the user safelyKey distribution for secure communicationUser identity/authority verificationUser inputUser authentication
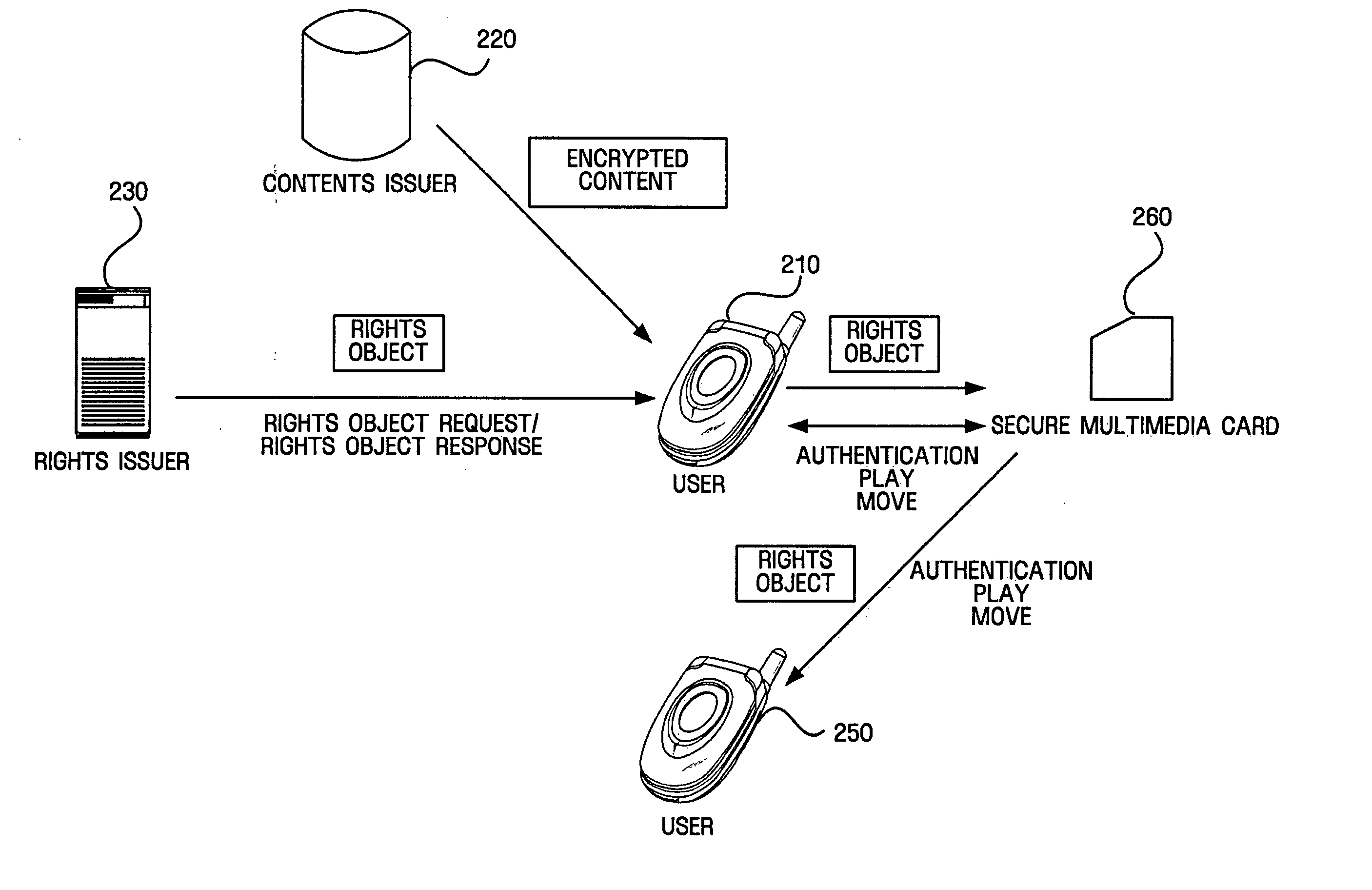
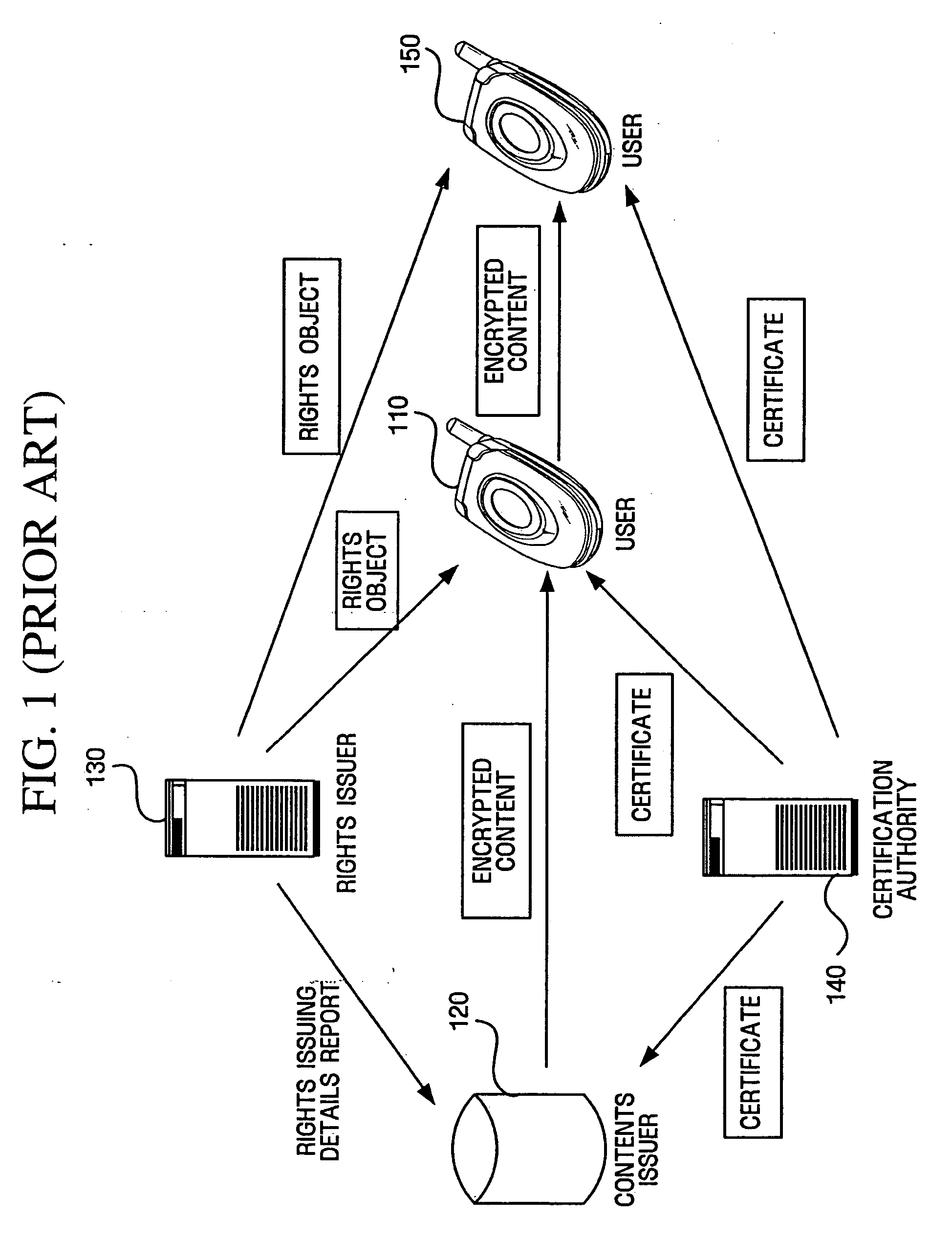
An authentication system providing a safety authentication process of electronic values with the use of mobile terminals which do not have a tamper-resistant function. The electronic value including encrypted value authentication information (F(VPW)), wherein an authentication information (VPW) corresponding to an electronic value specified by a user is acquired by the hash calculation, is stored in user's mobile terminal. In the user authentication process; authentication apparatus generates a random number R and transmits it to mobile terminal, mobile terminal generates value authentication information (F(VPW′)) from authentication information (VPW′) corresponding to electronic value input by user, further executes a hash calculation on data wherein value authentication information (F(VPW′)) and the random number R are concatenated, generates authentication information (F(VPW′)∥R), transmits it to the authentication apparatus with the electronic value, authentication apparatus decrypts the received electronic value, extracts the value authentication information (F(VPW)) from the electronic value, executes the hash calculation on data wherein value authentication information (F(VPW)) and the random number R are concatenated, generates the authentication information (F(VPW)∥R), and collates the received authentication information (F(VPW′)∥R) with the authentication information (F(VPW)∥R), so that the user is authenticated.
Owner:INTERTRUST TECH CORP
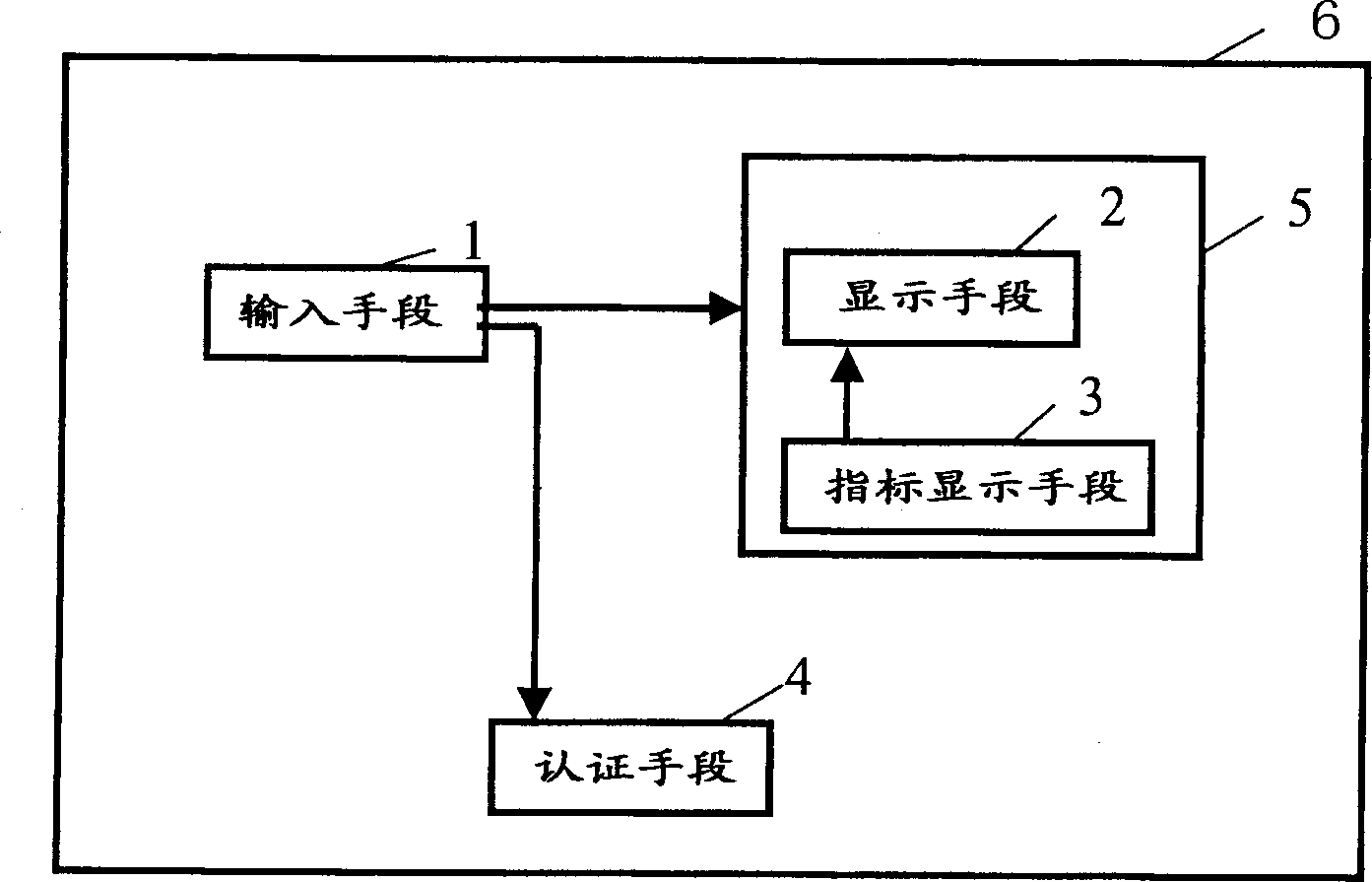
Information terminal appts. and identification system
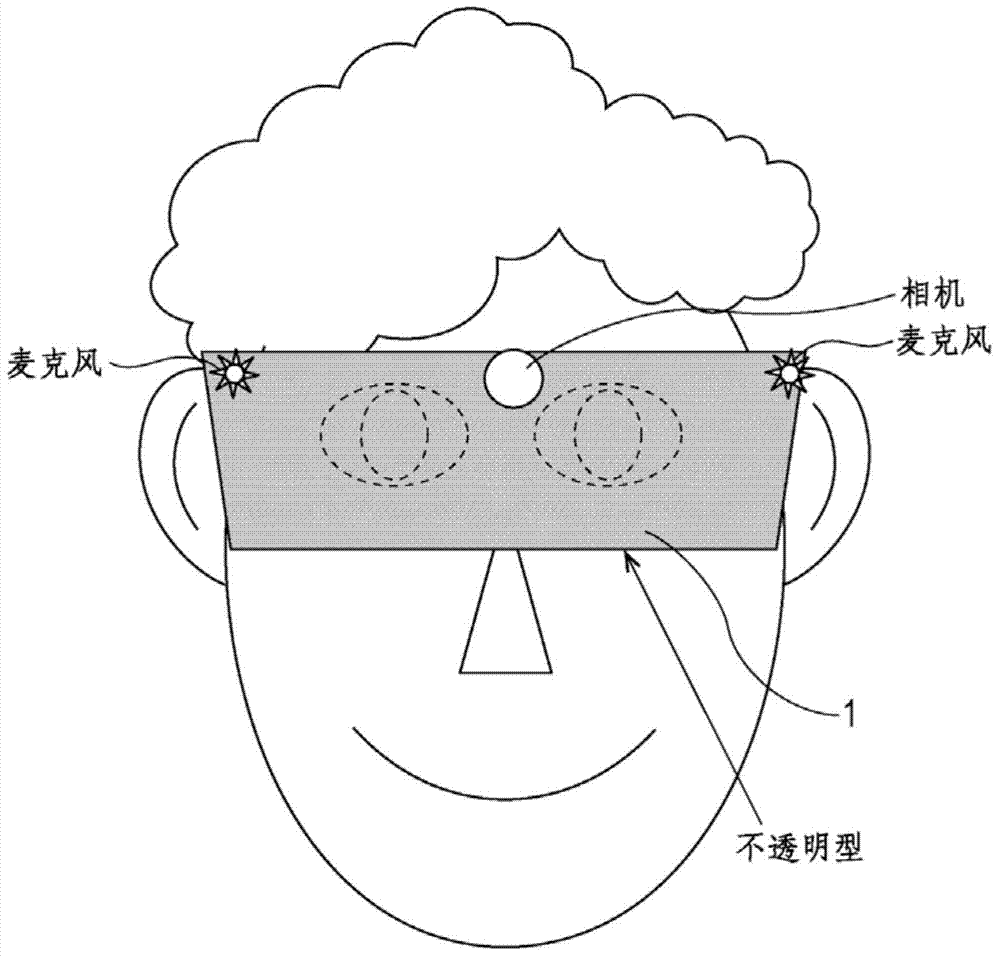
InactiveCN1369858AEnsure safetyAuthentication securityTelevision system detailsImage analysisHuman bodyAuthentication system
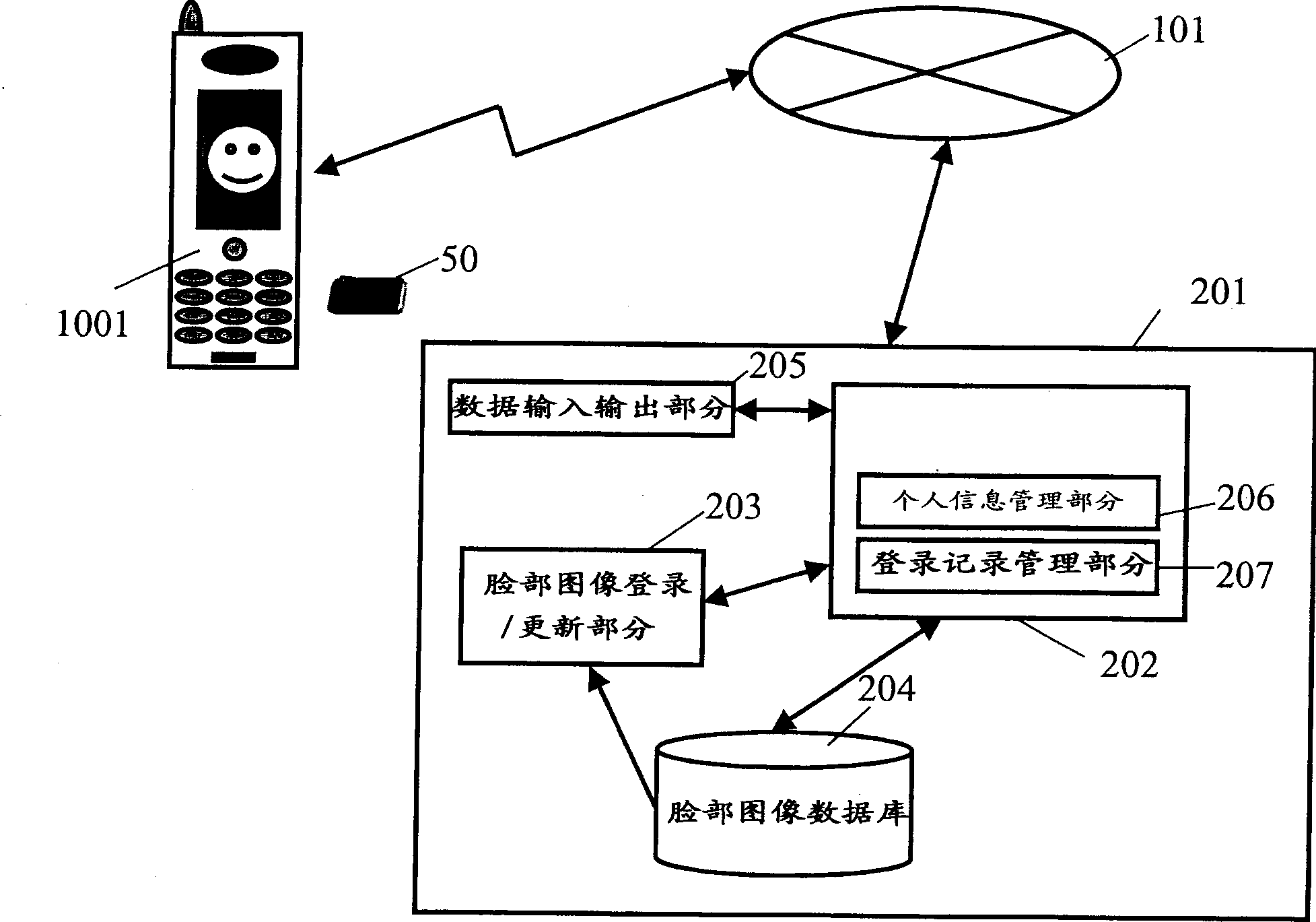
It includes input means for inputting the user's physical information, means for confirming the input human body information, and authentication means for authenticating pre-registered users based on the input human body information. The human body information specifying means includes display means and index display means for displaying an index for specifying a size, a range of a position, and the like of the input human body information. The index display means has a function for the user to confirm the status of the input human body information and a function for designating the size and position of the human body information when inputting the human body information.
Owner:PANASONIC CORP
Authentication between device and portable storage
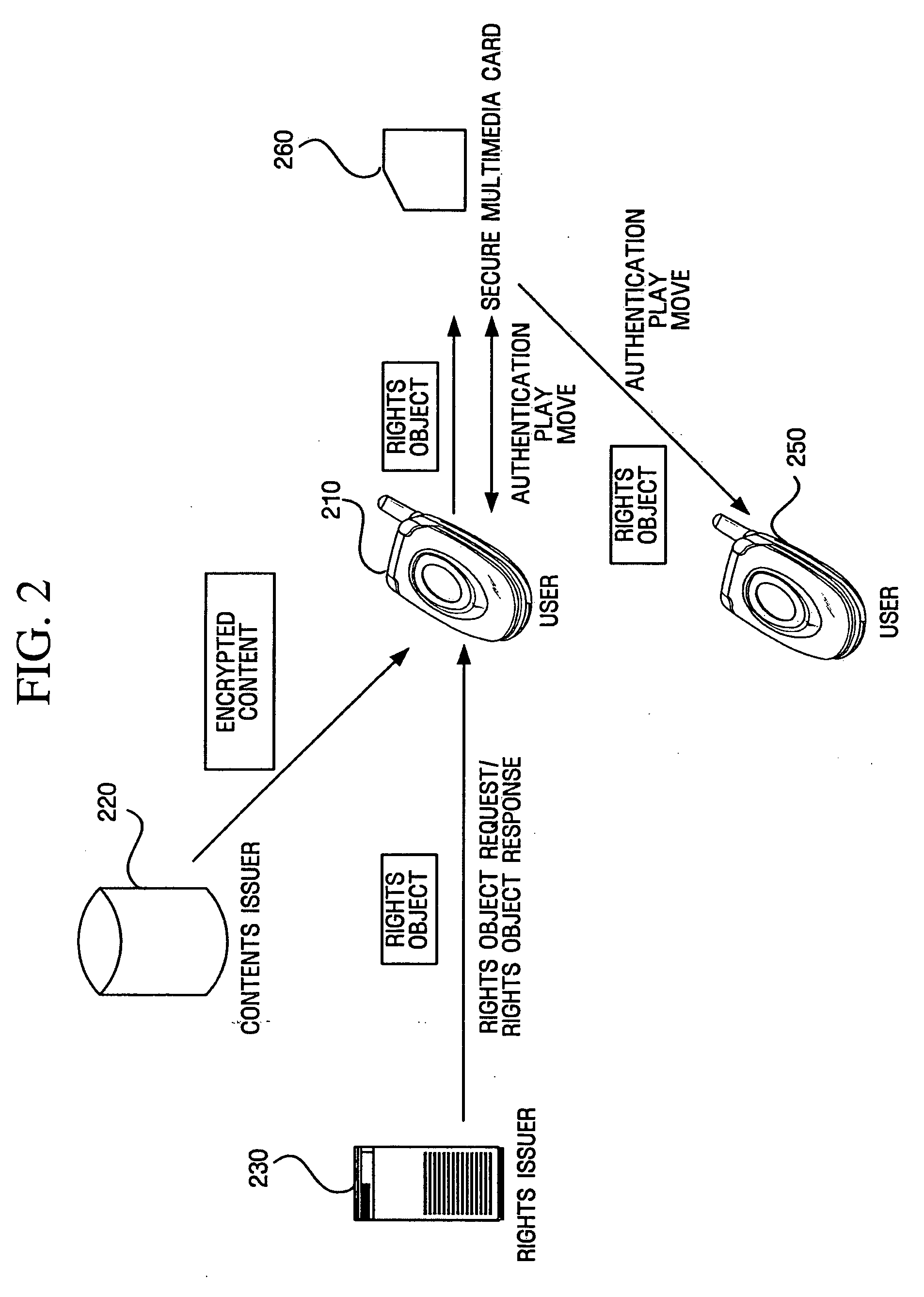
InactiveUS20050210279A1Authentication securityKey distribution for secure communicationPublic key for secure communicationComputer hardwareCryptographic nonce
For digital rights management (DRM), a method for performing authentication between a device and a portable storage, which is performed by the device, includes transmitting a first key to the portable storage, receiving a third key and a first encrypted random number obtained by encrypting a first random number using the first key from the portable storage and decrypting the first encrypted random number using a second key related with the first key, generating a second encrypted random number by encrypting a second random number using the third key and transmitting the second encrypted random number to the portable storage, and generating a session key using the first random number and the second random number. The technique guarantees secure authentication between the device and the portable storage for DRM.
Owner:SAMSUNG ELECTRONICS CO LTD
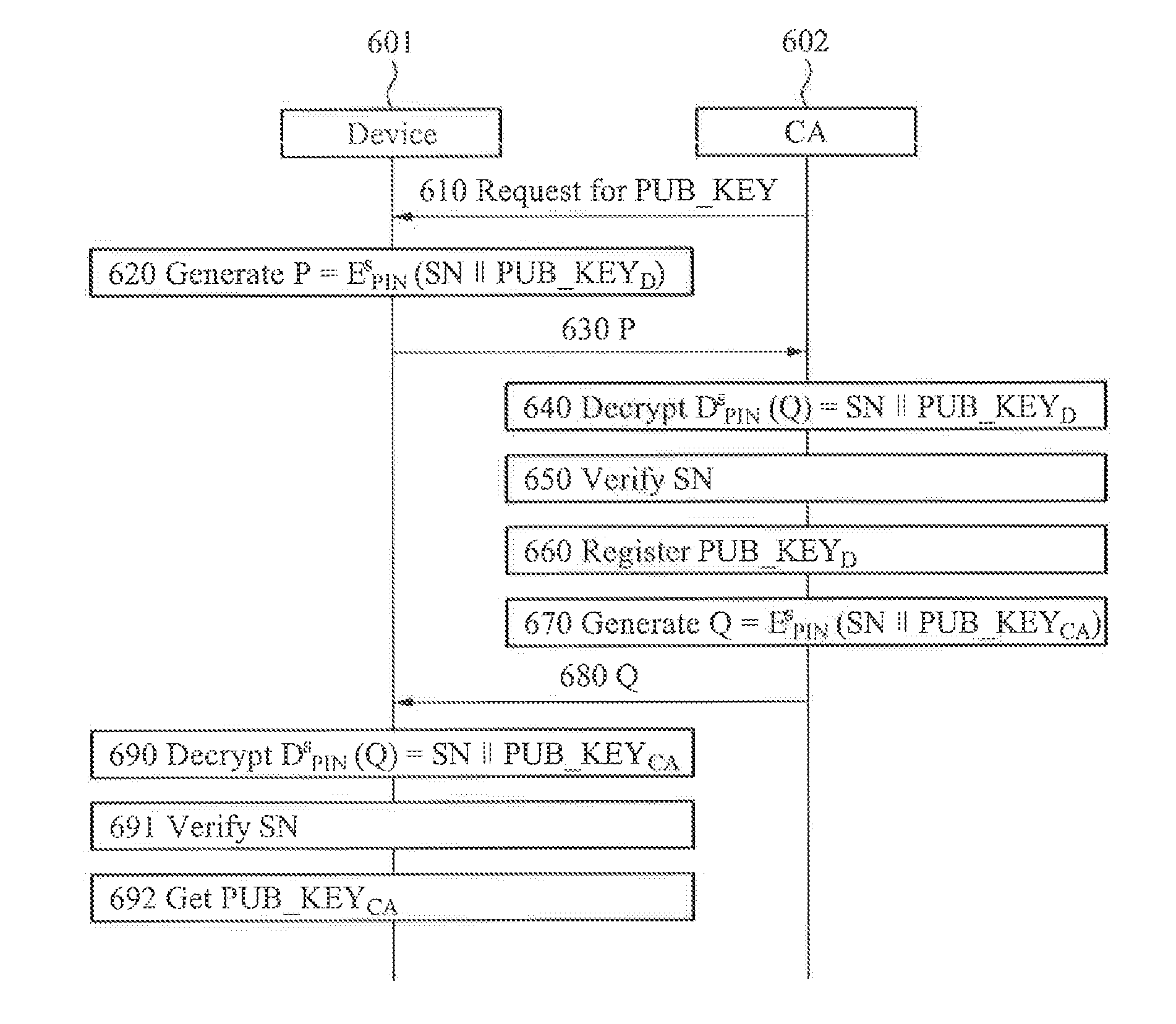
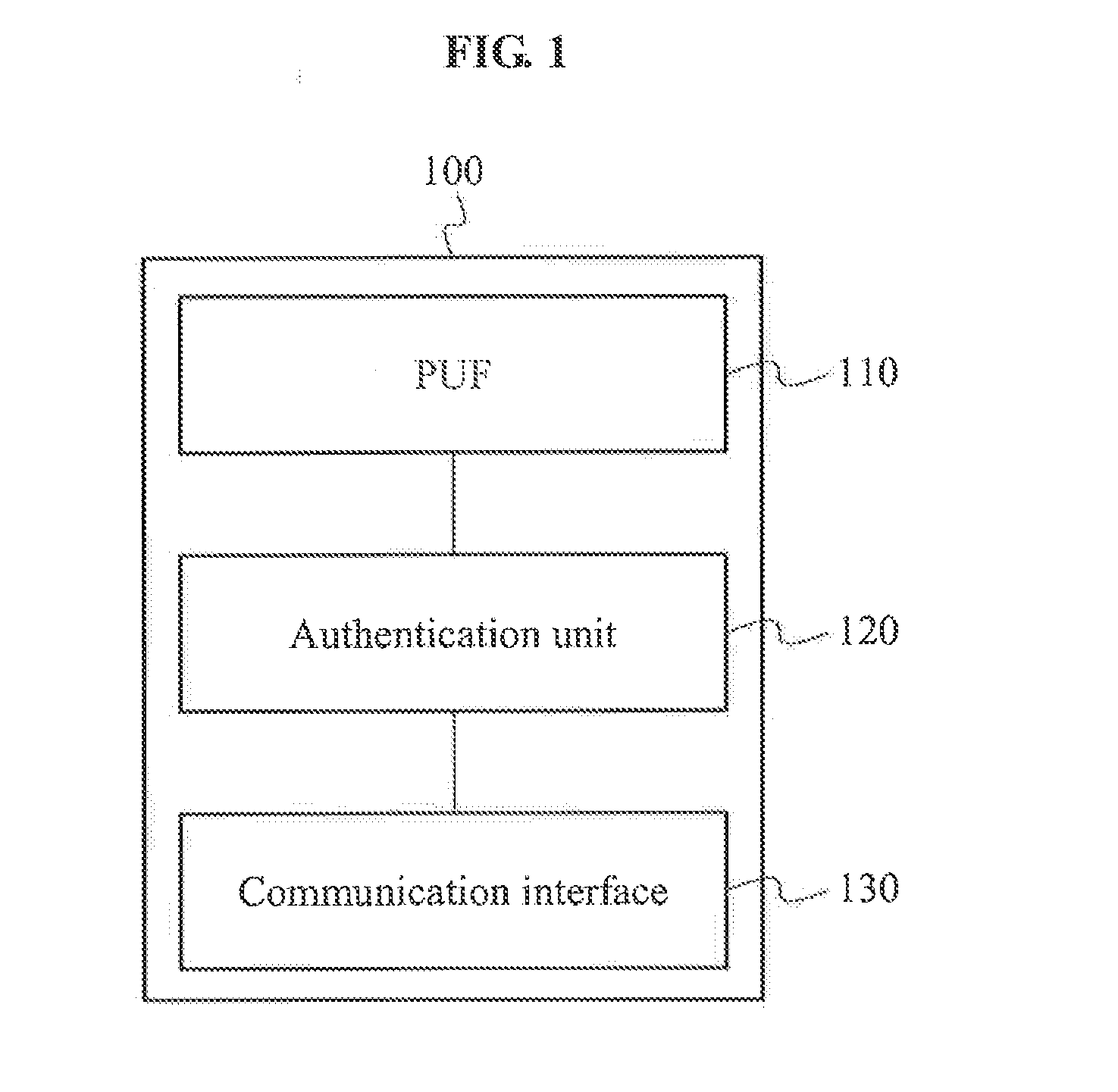
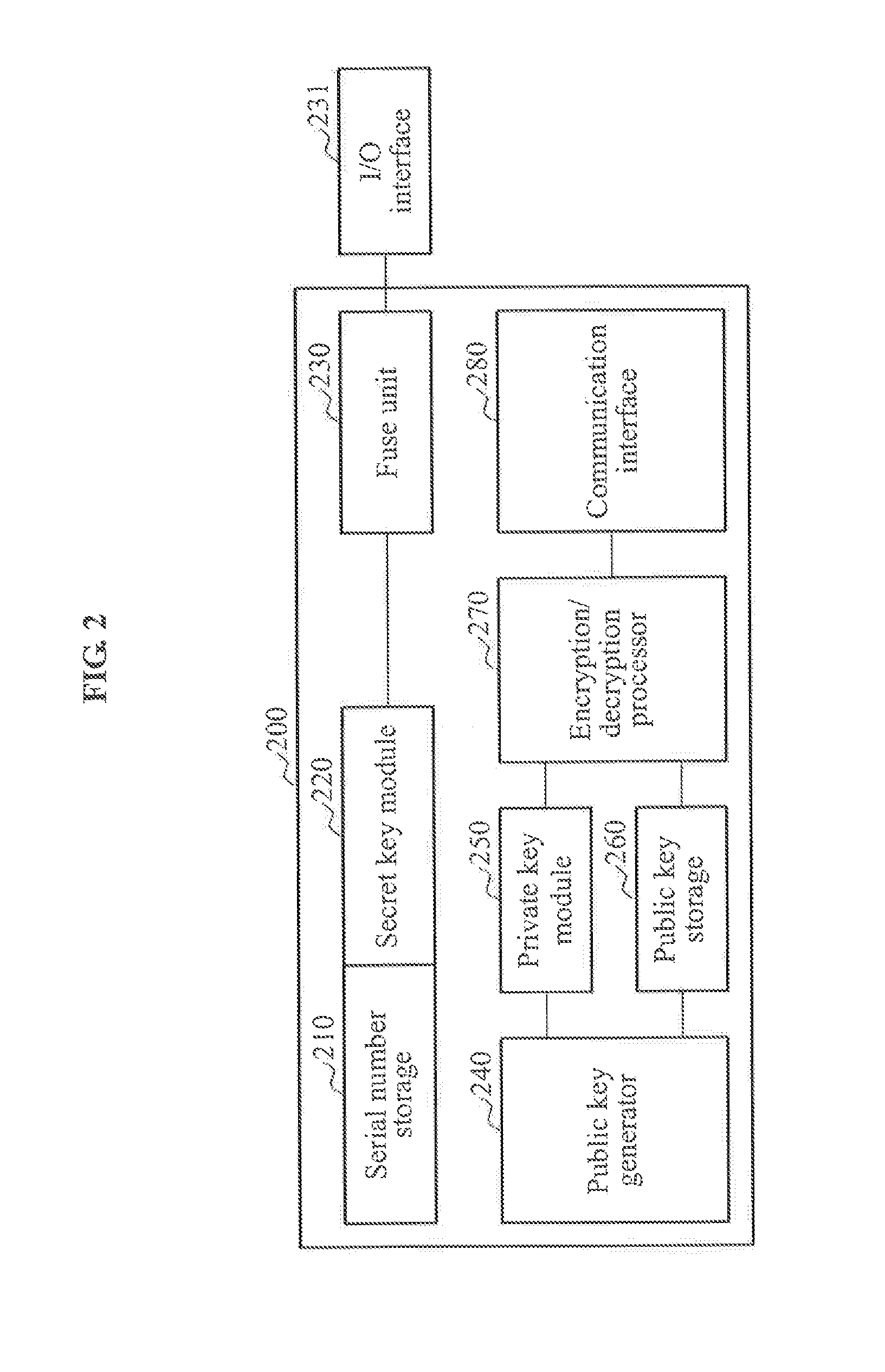
Apparatus and method for authentication between devices based on puf over machine-to-machine communications
ActiveUS20140310515A1Authentication securityGuaranteed reliabilityMultiple keys/algorithms usagePublic key for secure communicationPasswordSecret code
Terminal devices that perform machine-to-machine (M2M) communication may autonomously perform password authentication by autonomously generating a personal identity number (PIN) value, which is not exposed externally, using a physical unclonable function (PUF). A terminal apparatus that performs M2M communication may include a PUF embedded in the terminal apparatus to generate an authentication key for password authentication associated with the terminal apparatus, and an authentication unit to perform the password authentication associated with the terminal apparatus using the authentication key generated by the PUF.
Owner:ICTK
Identity authentication system and method
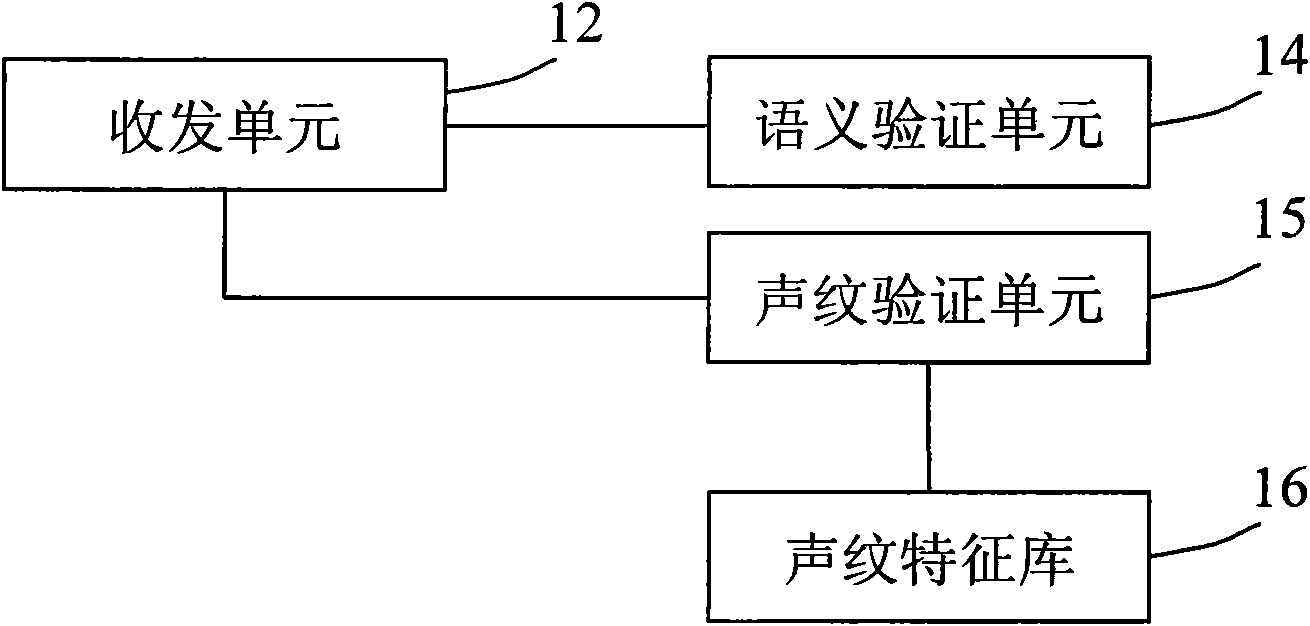
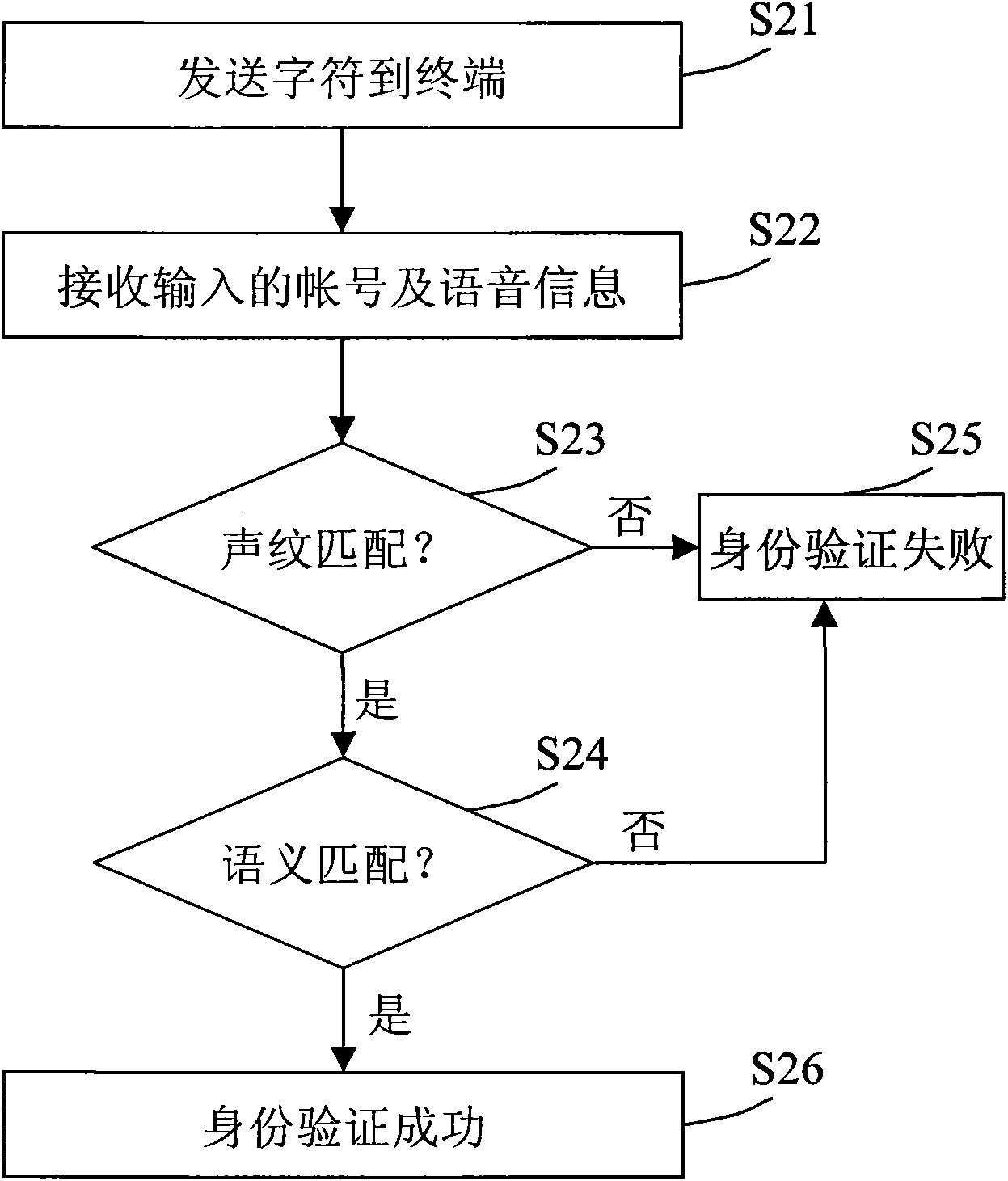
InactiveCN101685635AEasy to operateAuthentication securitySpeech analysisComputer terminalAuthentication system
The invention relates to an identity authentication system which comprises a voiceprint feature library, a receiving and sending unit, a semanteme authentication unit and a voiceprint authentication unit, wherein the voiceprint feature library is used for storing one or more voiceprint features, and each voiceprint feature corresponds to an account; the receiving and sending unit is used for sending one or more characters to terminals and receiving the input accounts and voice signals from the terminals; the semanteme authentication unit is used for confirming that the identity authenticationfails when the voice signals which are received by the receiving and sending unit are not matched with the pronunciations of the characters which are sent to the terminals; and the voiceprint authentication unit is used for confirming that the identity authentication fails when the voice signals which are received by the receiving and sending unit are not matched with the voiceprint features corresponding to the accounts in the voiceprint feature library. The invention also provides a corresponding method. By combining the voiceprint authentication with the semanteme authentication, the invention realizes safe identity authentication and is convenient for users to operate.
Owner:吕共欣
Wireless communication method and system for transmission authentication at the physical layer
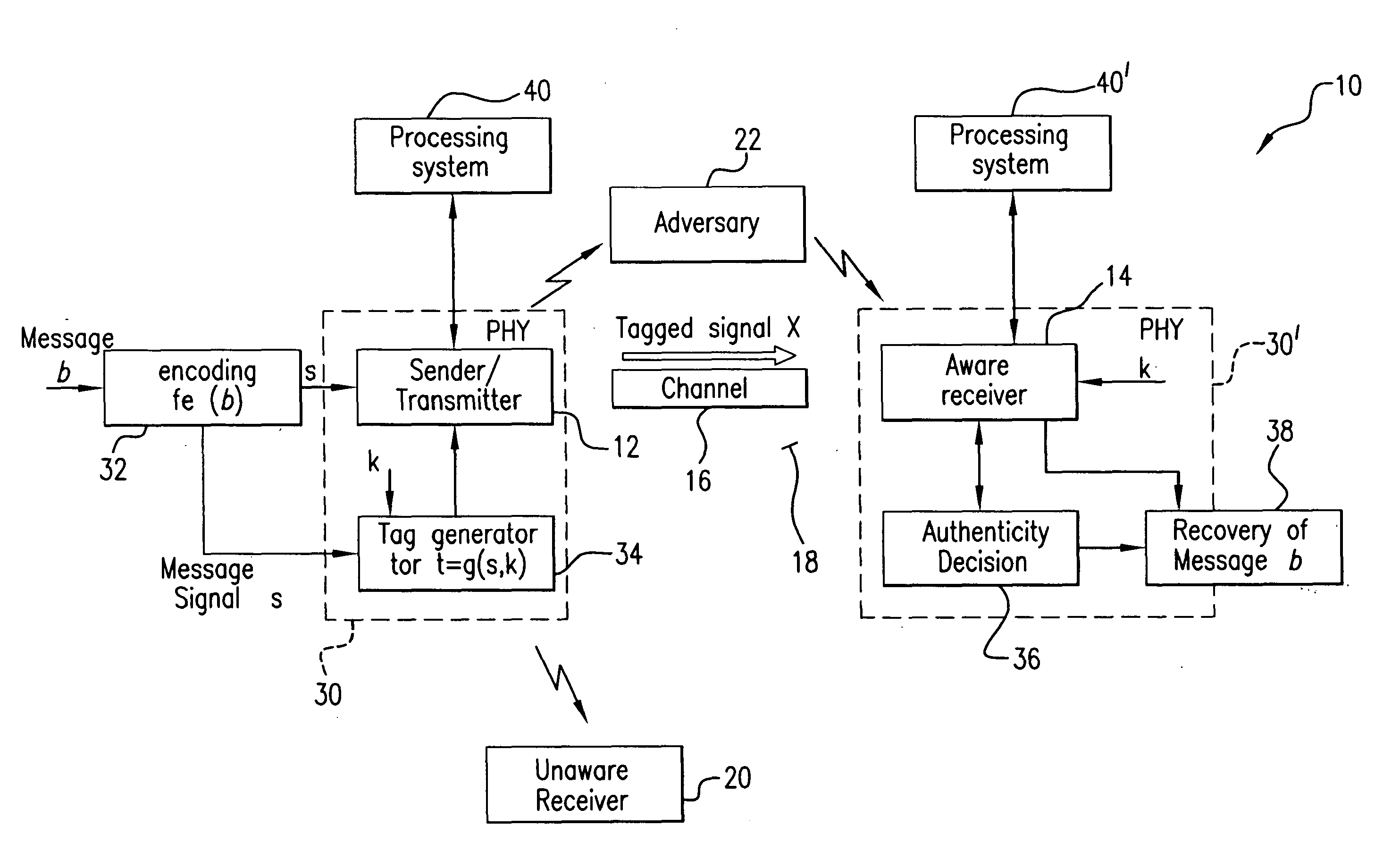
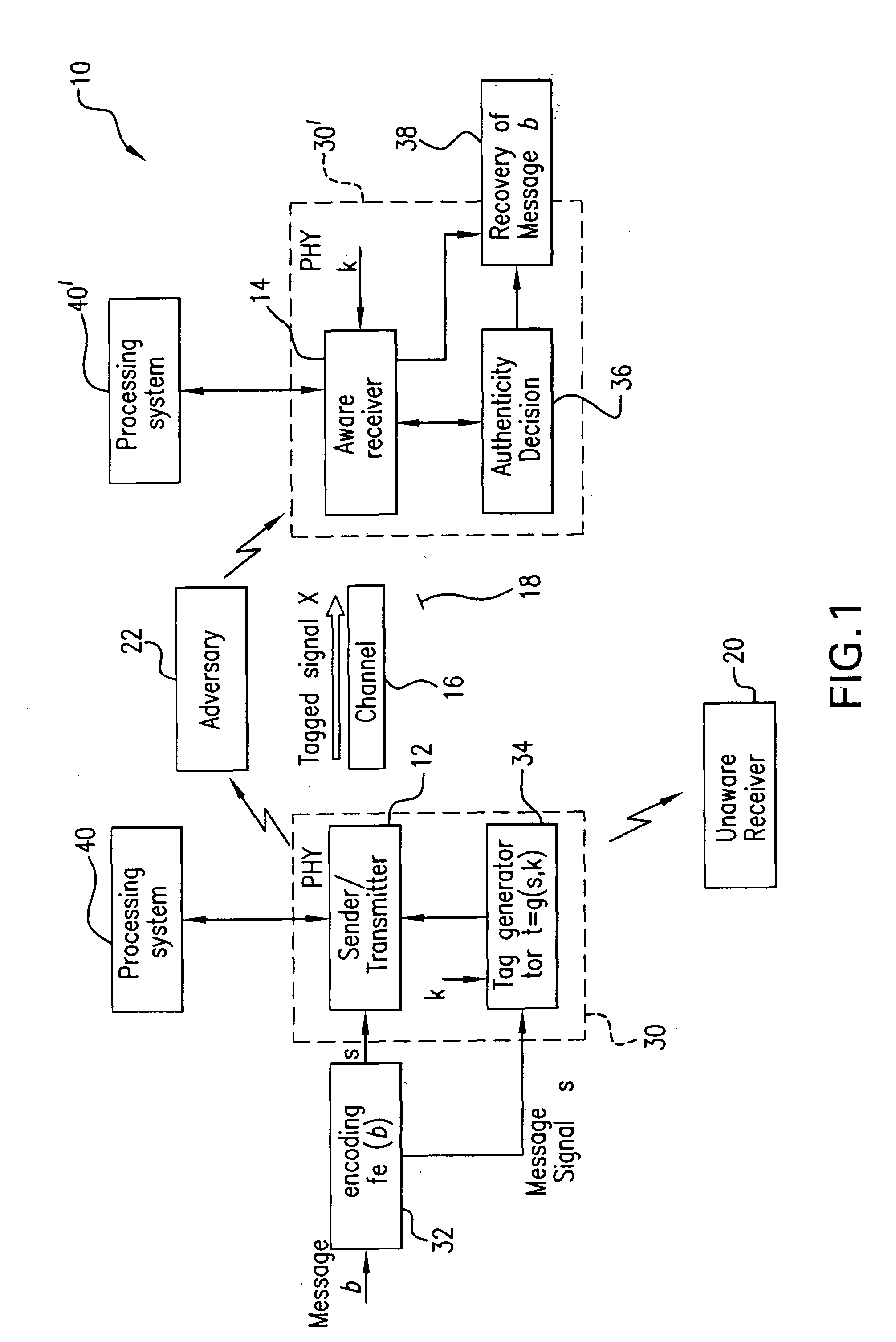
InactiveUS20100246825A1Improve anti-interference abilityAuthentication securityUser identity/authority verificationSecret communicationInterference (communication)Engineering
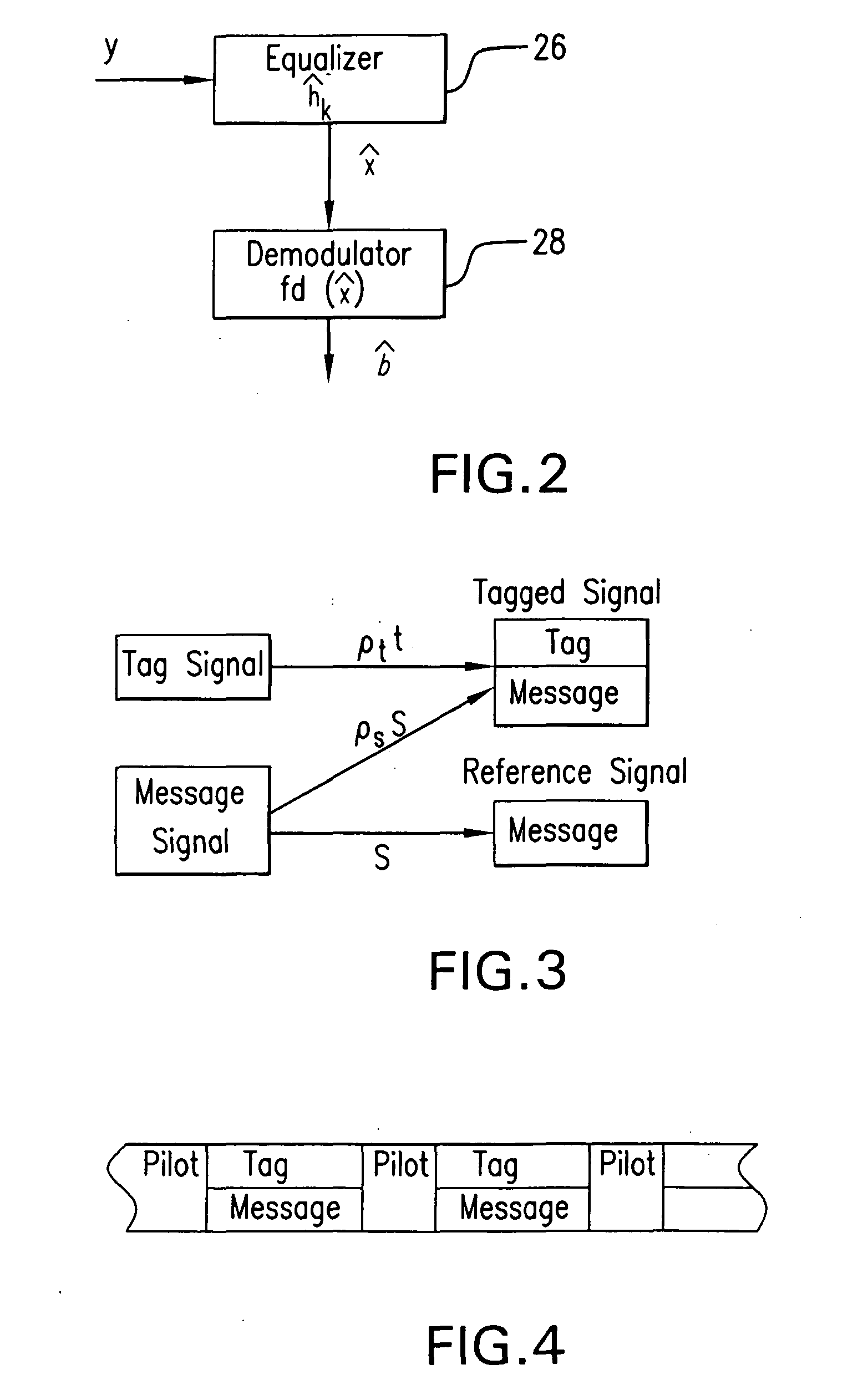
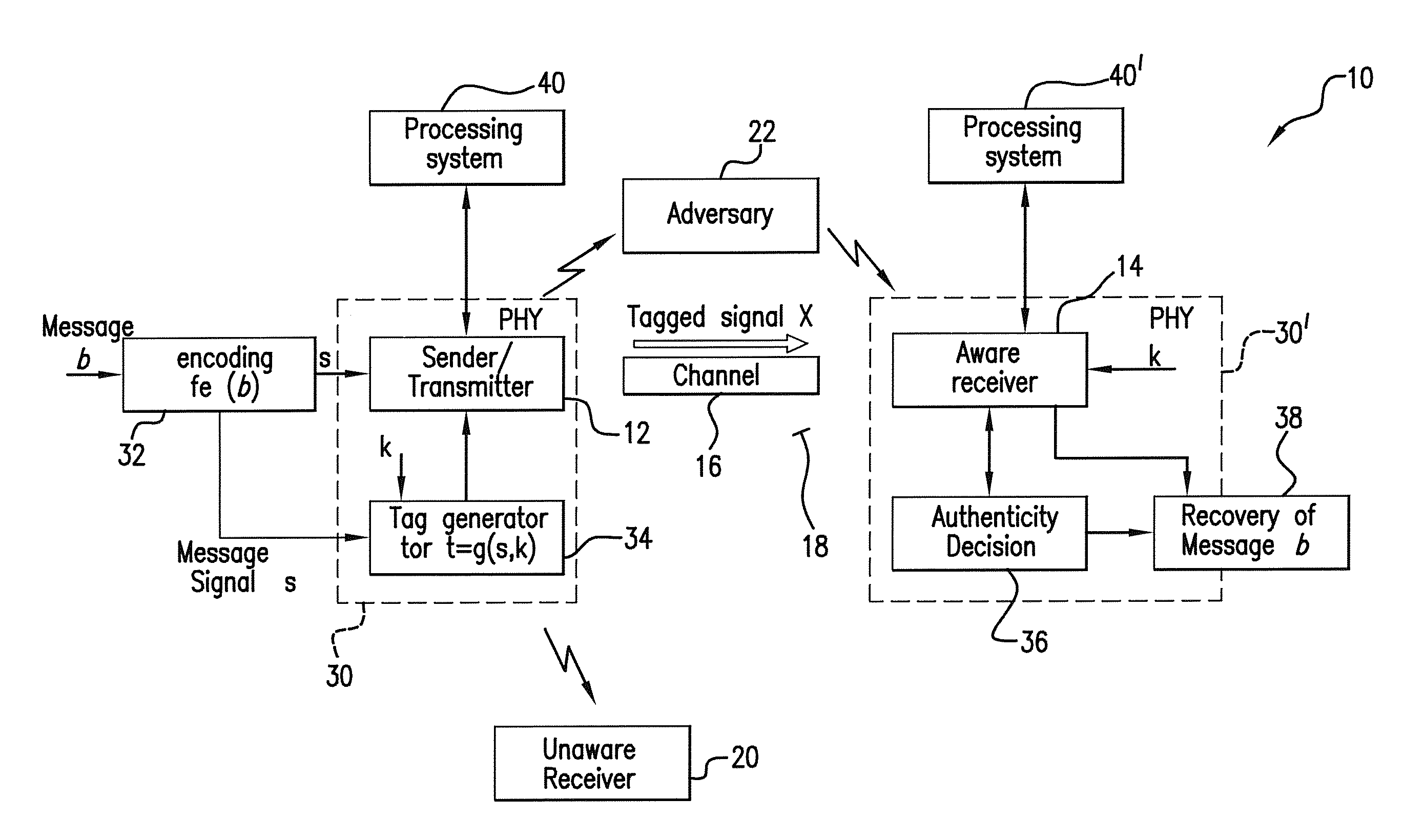
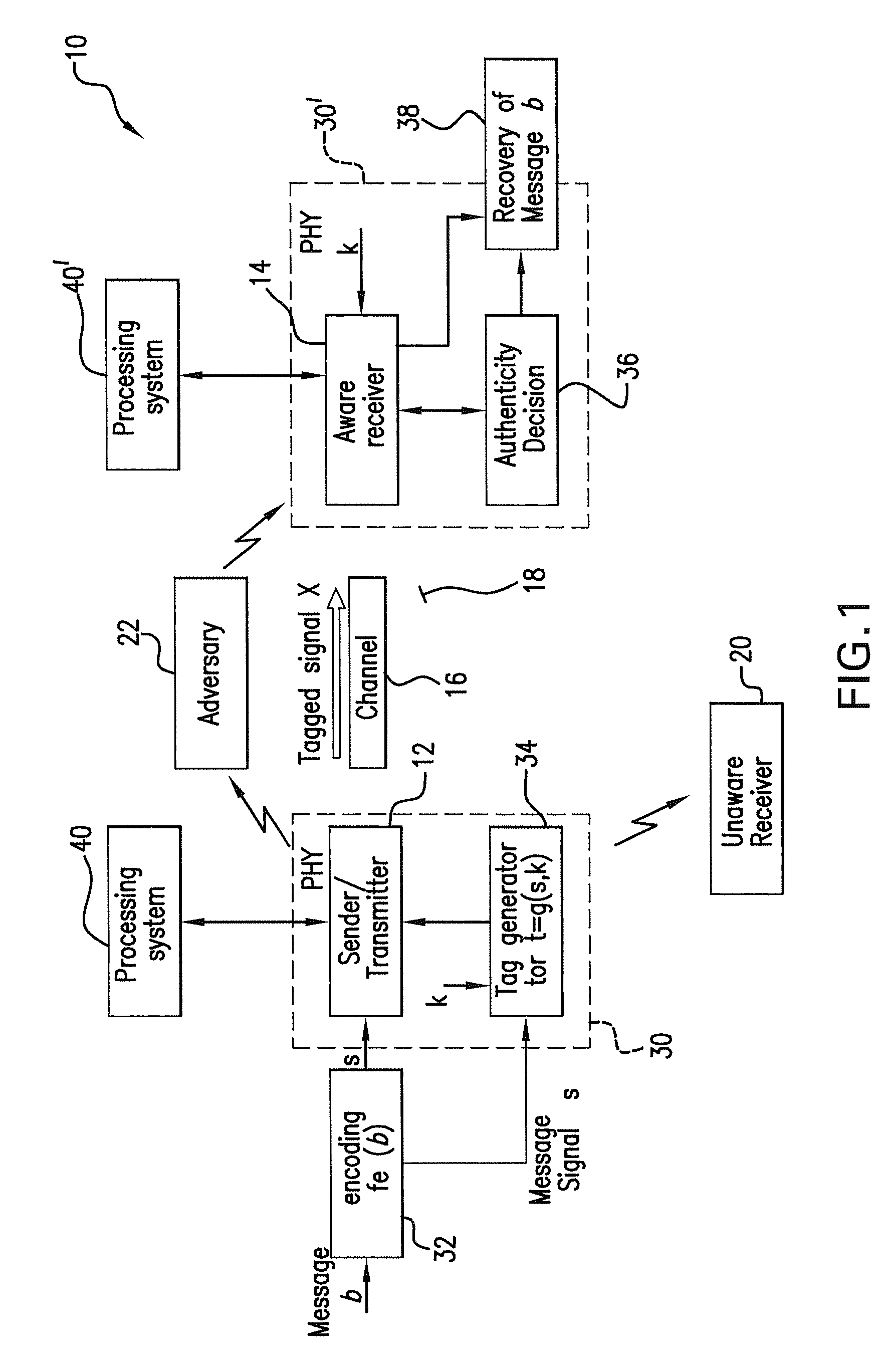
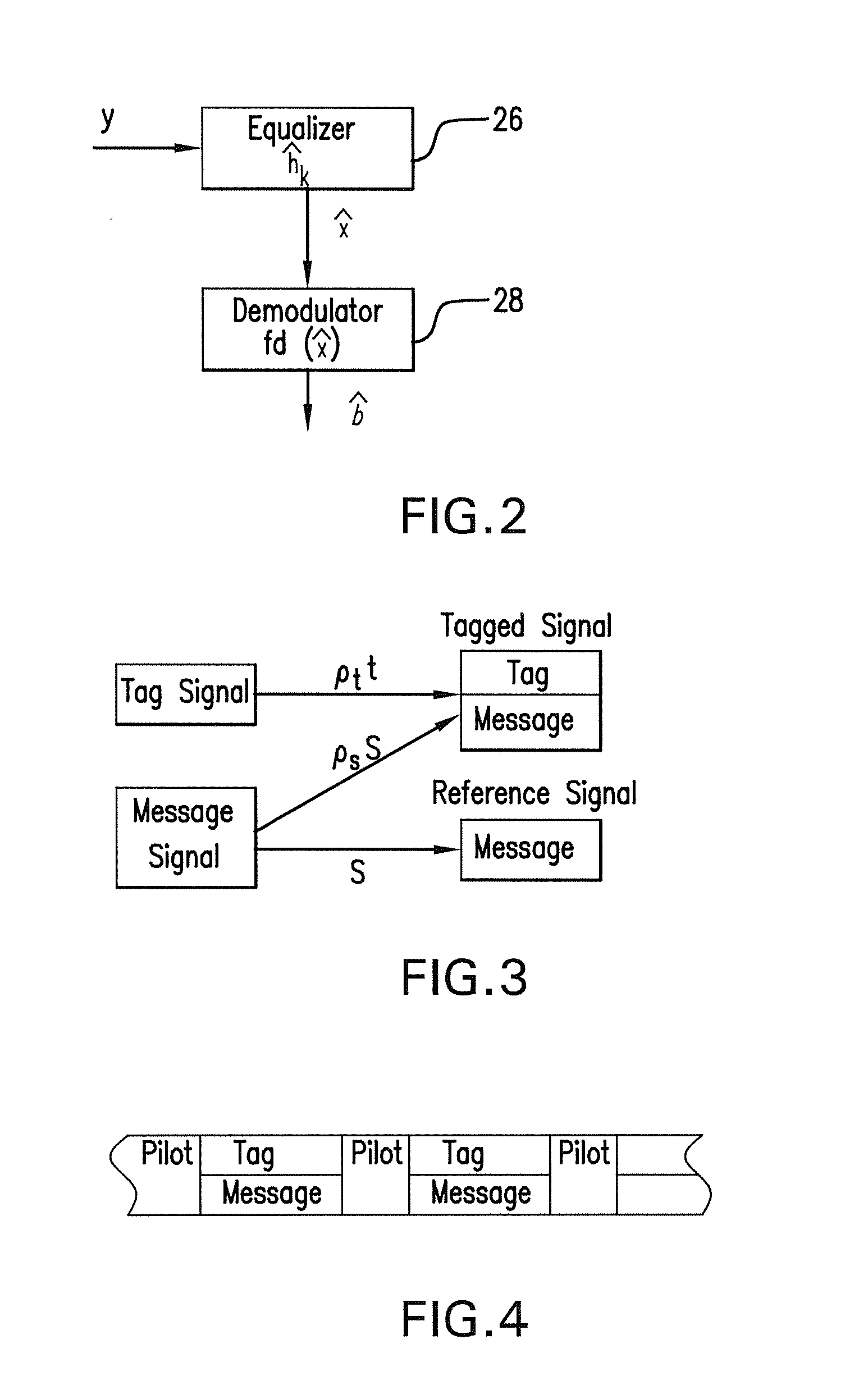
The subject authentication scheme encompasses a large family of authentication systems which may be built over existing transmission systems. By superimposing a carefully designed secret modulation on the waveforms, authentication is added to the signal without requiring additional bandwidth. The authentication information (tag signal) is sent concurrently with data (message signal). The authentication is designed to be stealthy to the uninformed user, robust to interference, and secure for identity verification. The tradeoffs between these three goals are identified and analyzed. The use of the authentication for channel estimation is also considered, and improved bit errors are demonstrated for time-varying channels. With a long enough authentication code word an authentication system is achieved with very slight data degradation. Additionally, by treating the authentication tag as a sequence of pilot symbols, the data recovery may be improved by the aware receiver.
Owner:ARMY US SEC THE THE +1
Wireless communication method and system for transmission authentication at the physical layer
ActiveUS20130163761A1Improve anti-interference abilitySafety verificationBroadcast specific applicationsSecret communicationTransfer systemPhysical layer
The subject authentication scheme encompasses a large family of authentication systems which may be built over existing transmission systems. By superimposing a carefully designed secret modulation on the waveforms, authentication is added to the signal without requiring additional bandwidth. The authentication information (tag signal) is sent concurrently with data (message signal). The authentication is designed to be stealthy to the uninformed user, robust to interference, and secure for identity verification. The tradeoffs between these three goals are identified and analyzed. The use of the authentication for channel estimation is also considered, and improved bit errors are demonstrated for time-varying channels. With a long enough authentication code word an authentication system is achieved with very slight data degradation. Additionally, by treating the authentication tag as a sequence of pilot symbols, the data recovery may be improved by the aware receiver.
Owner:US SEC THE ARMY THE +1
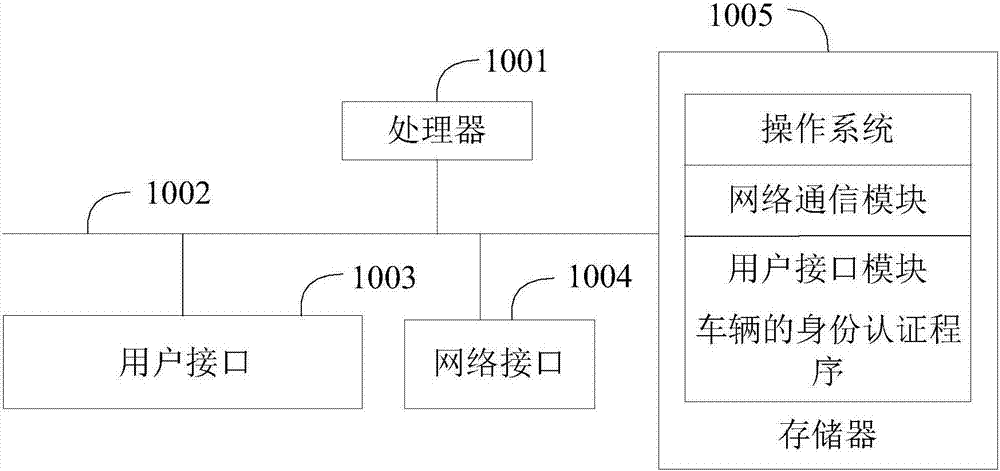
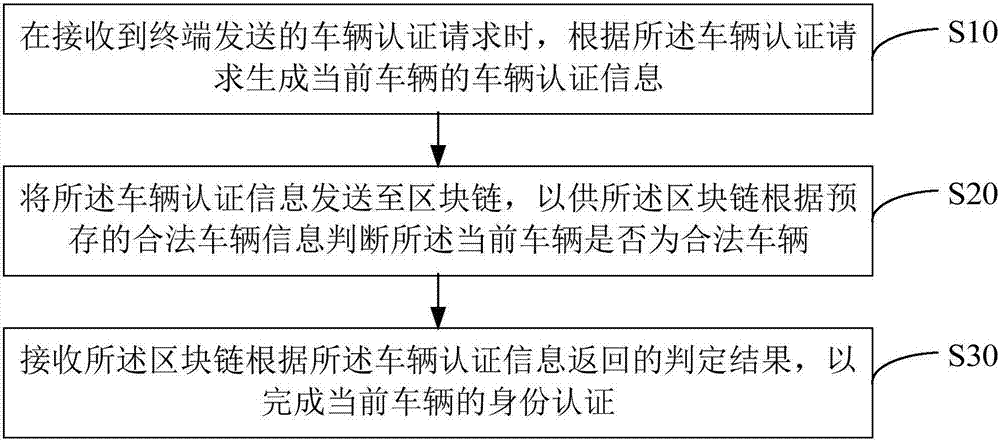
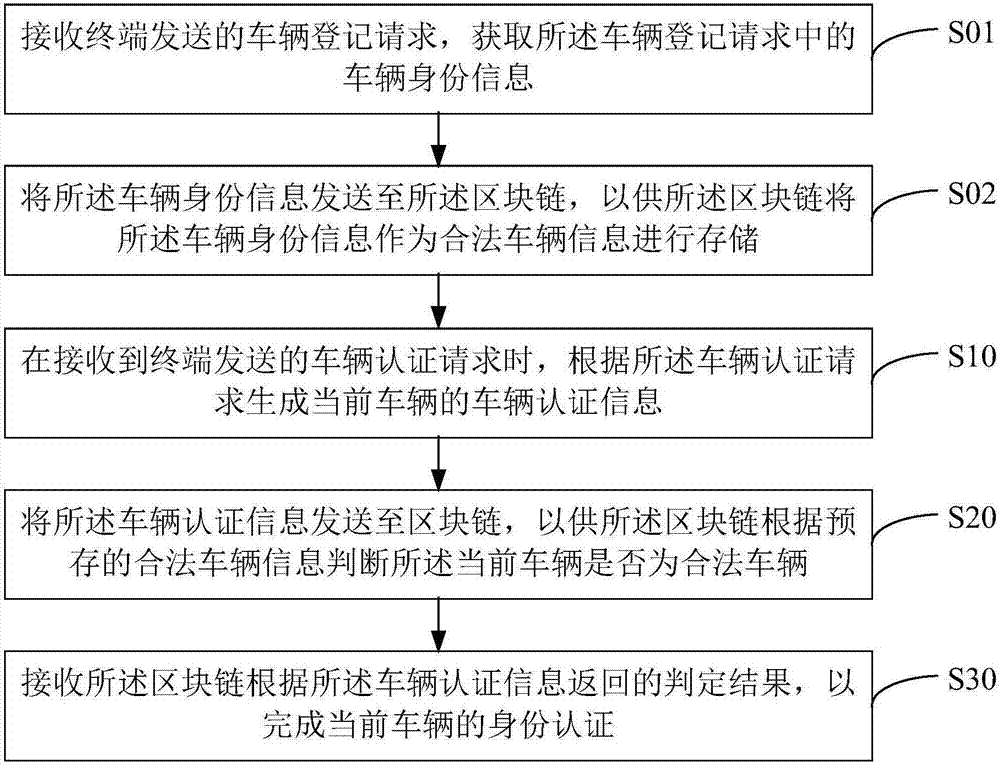
Vehicle identity authentication method and apparatus, and computer readable storage medium
InactiveCN107465673AAuthentication securityConvenient identity verificationRoad vehicles traffic controlTransmissionComputer terminalEmbedded system
The invention provides a vehicle identity authentication method and apparatus, and a computer readable storage medium. The vehicle identity authentication method comprises the following steps: when a vehicle authentication request sent by a terminal is received, generating vehicle authentication information of a current vehicle according to the vehicle authentication request; sending the vehicle authentication information to a block chain, so that the block chain judges whether the current vehicle is a legal vehicle according to pre-stored legal vehicle information; and receiving a judgment result returned by the block chain according to the vehicle authentication information so as to accomplish the identity authentication of the current vehicle. By adoption of the manner, the identity authentication of the vehicle can be accomplished securely and conveniently, the vehicle identity authentication precision is improved, the information sent by illegal vehicle is not received, thereby improving the anti-interference ability of the communication between the vehicles in the system, and the technical problem that the communication between the vehicles in the CACC is interfered easily is solved.
Owner:SHENZHEN ECHIEV AUTONOMOUS DRIVING TECH CO LTD
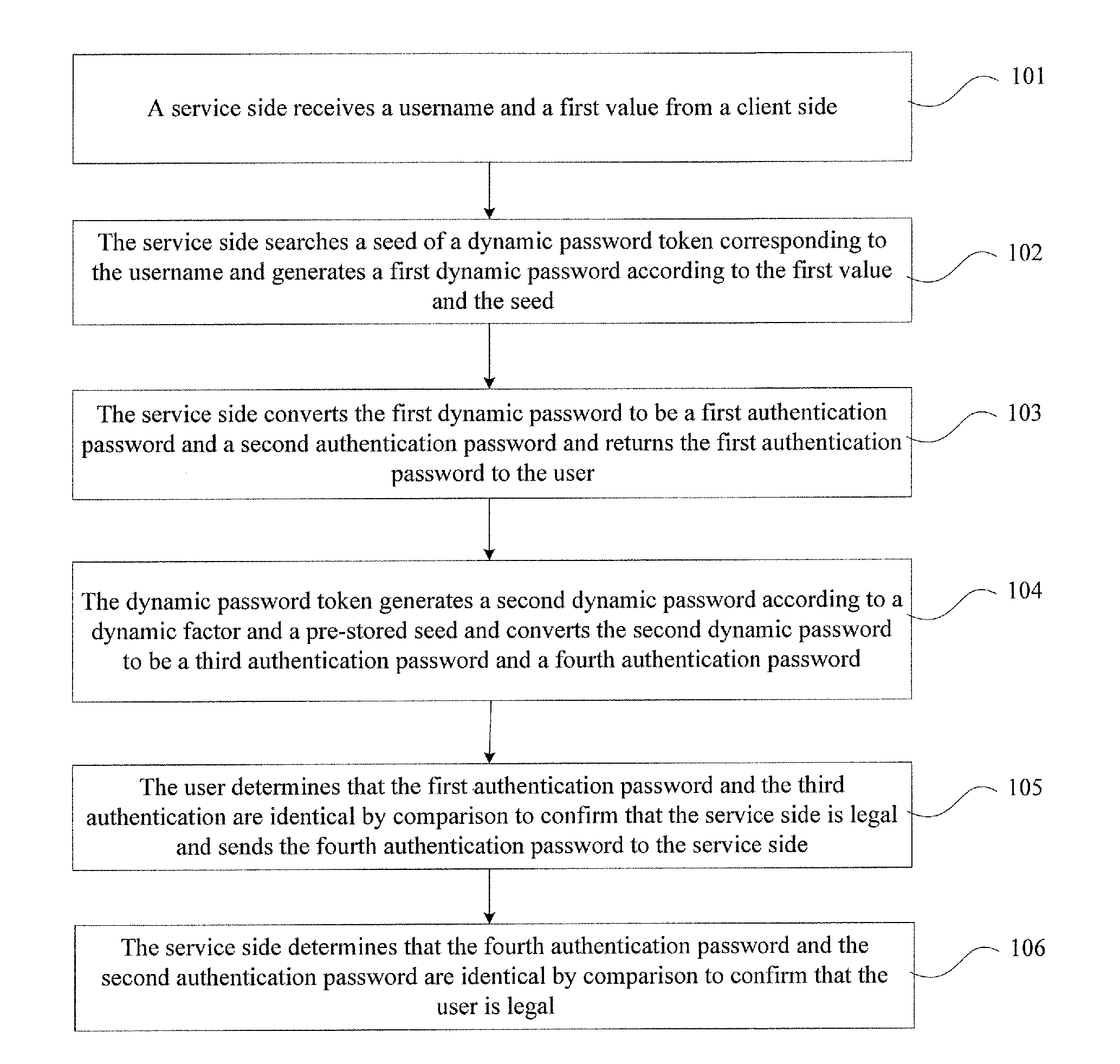
Authentication method, system, and device
ActiveUS20120137131A1Authentication securityAvoid illegal operationDigital data processing detailsUser identity/authority verificationPasswordClient-side
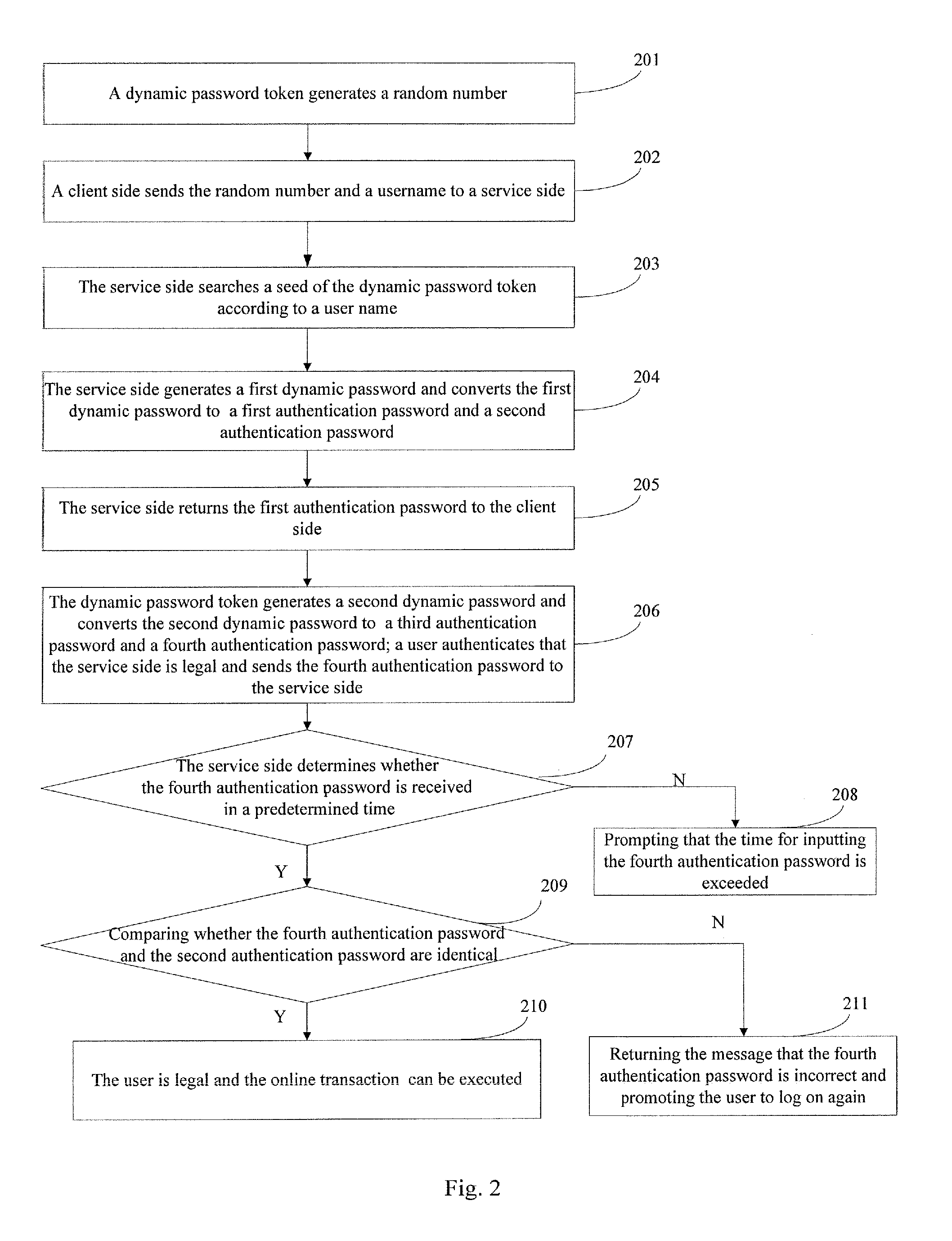
The present invention provides an authentication method, an authentication system, and an authentication device, which is in information security field. The method includes that a service side receives a username and a first value from a client side, searches a seed of a dynamic password token, and generates a first dynamic password according to the first value and the seed, converts the first dynamic password to the first authentication password and the second authentication password, and sends the first authentication password to the user; the dynamic password token generates a second dynamic password and sends the first authentication password to a user; the dynamic password token generates a second dynamic password and converts the second dynamic password to a third authentication password and a fourth authentication password; the user compares the first authentication password and the third authentication password to determine that they are identical, so as to confirm that the user is legal or the transaction is permissible. The invention prevents malicious attack and operation of illegal users, which improves the security of information and property of the users.
Owner:FEITIAN TECHNOLOGIES
Authentication system and authentication method
ActiveUS20150195280A1Authentication securityDetecting falsificationSynchronising transmission/receiving encryption devicesComputer terminalAuthentication system
Provided is an authentication system in which a client terminal that receives input of request information is connected to a server that executes a process with regard to the request information. The client terminal includes: a first authentication information generation unit that generates first authentication information based on information which is shared with the server; an encryption unit that generates encryption information; and a transmission unit that transmits the request information and encryption information to the server. The server includes: a reception unit that receives the request information and encryption information; a second authentication information generation unit that generates second authentication information; a decoding unit that generates reference information which is acquired by decoding the encryption information using the same common key method as in the client terminal while using the second authentication information as a key; and an authentication unit that compares the request information with the reference information.
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
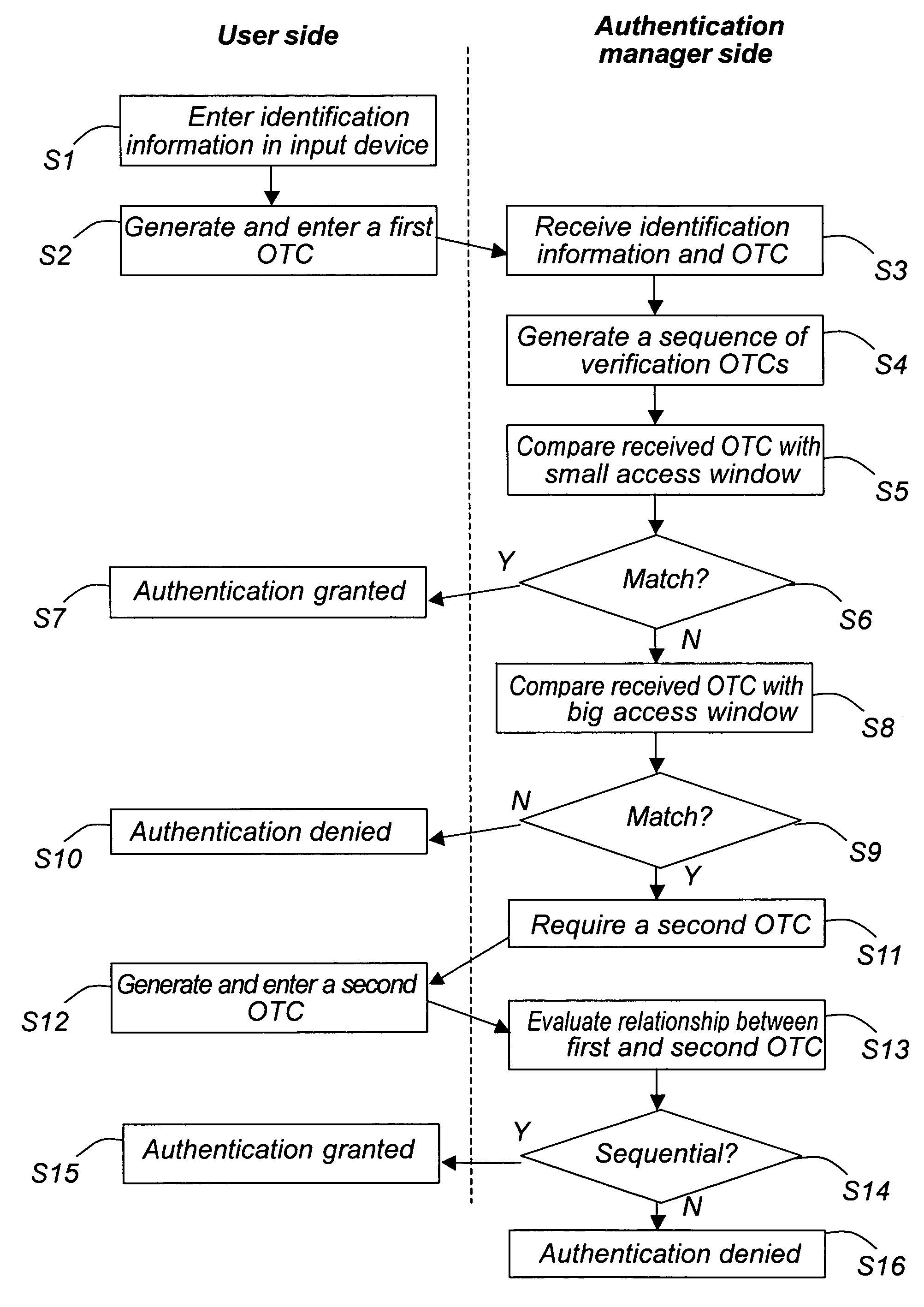
Method and system for user authentication in a digital communication system
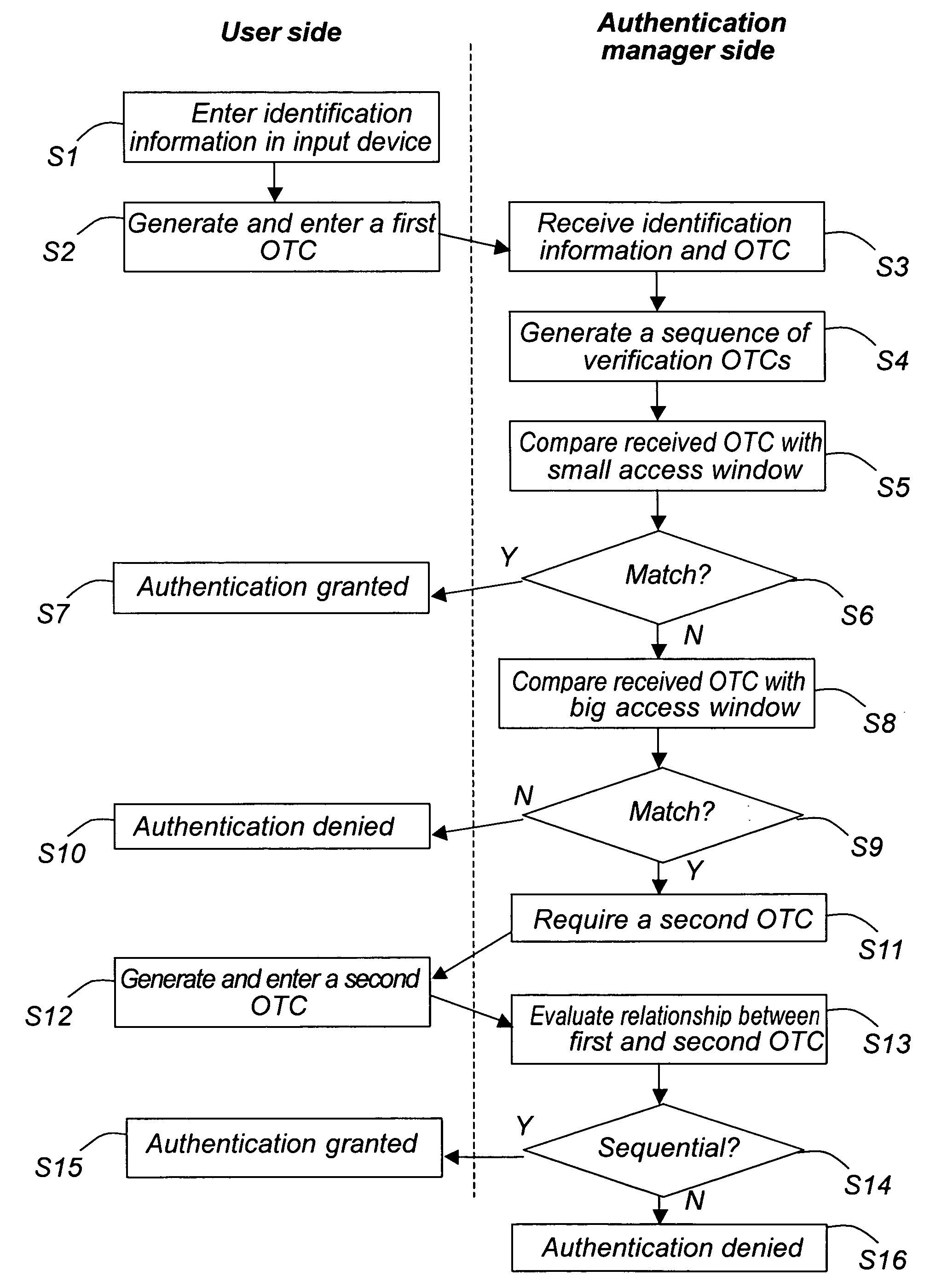
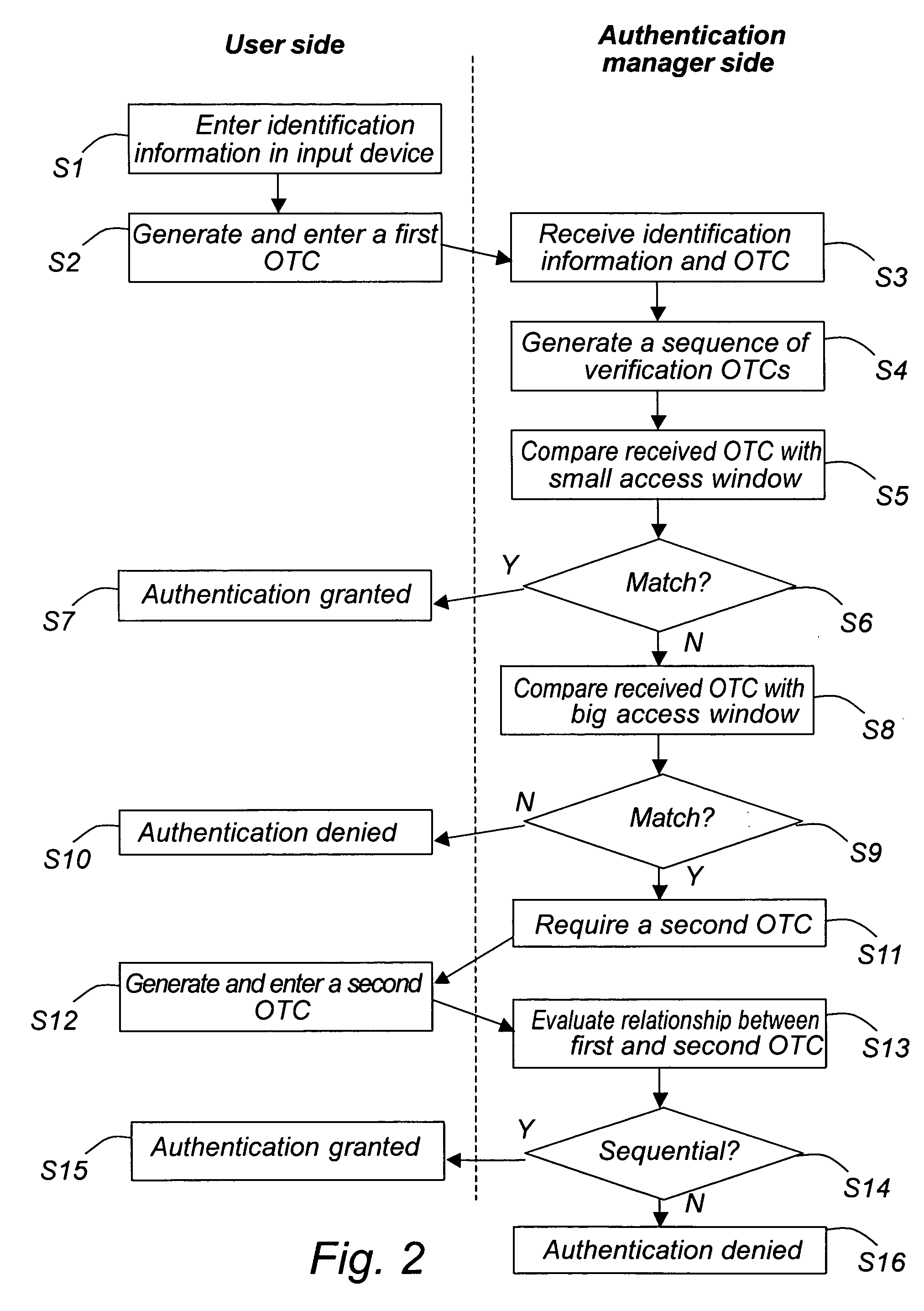
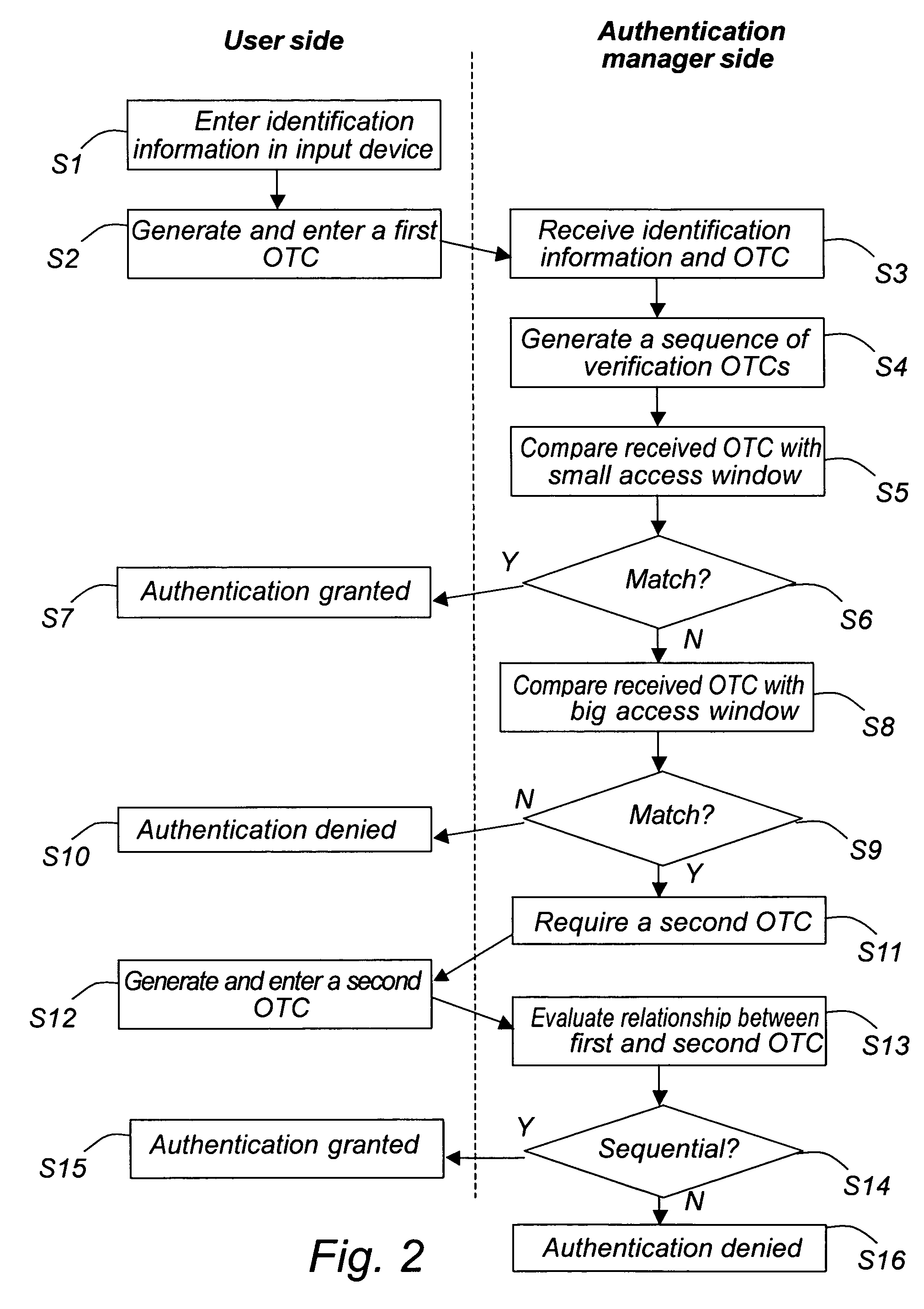
ActiveUS20050216744A1Easy to useMore secureSensing detailsDigital data processing detailsCommunications systemUser authentication
A method and a system for authentication and synchronization is disclosed. The user provides a first one time code (OTC) to the authentication manager. If this OTC is within a small access window, the user is directly authenticated and granted access to the system. If the provided OTC is outside the small window but within a big window, the authentication manager saves the first OTC, and a second OTC is required from the user. If the new, second OTC and the first OTC are in sequence, the end user will be authenticated, and admitted access to the system and the requested service.
Owner:TDS TODOS DATA SYST
Method for identification of equipment validity
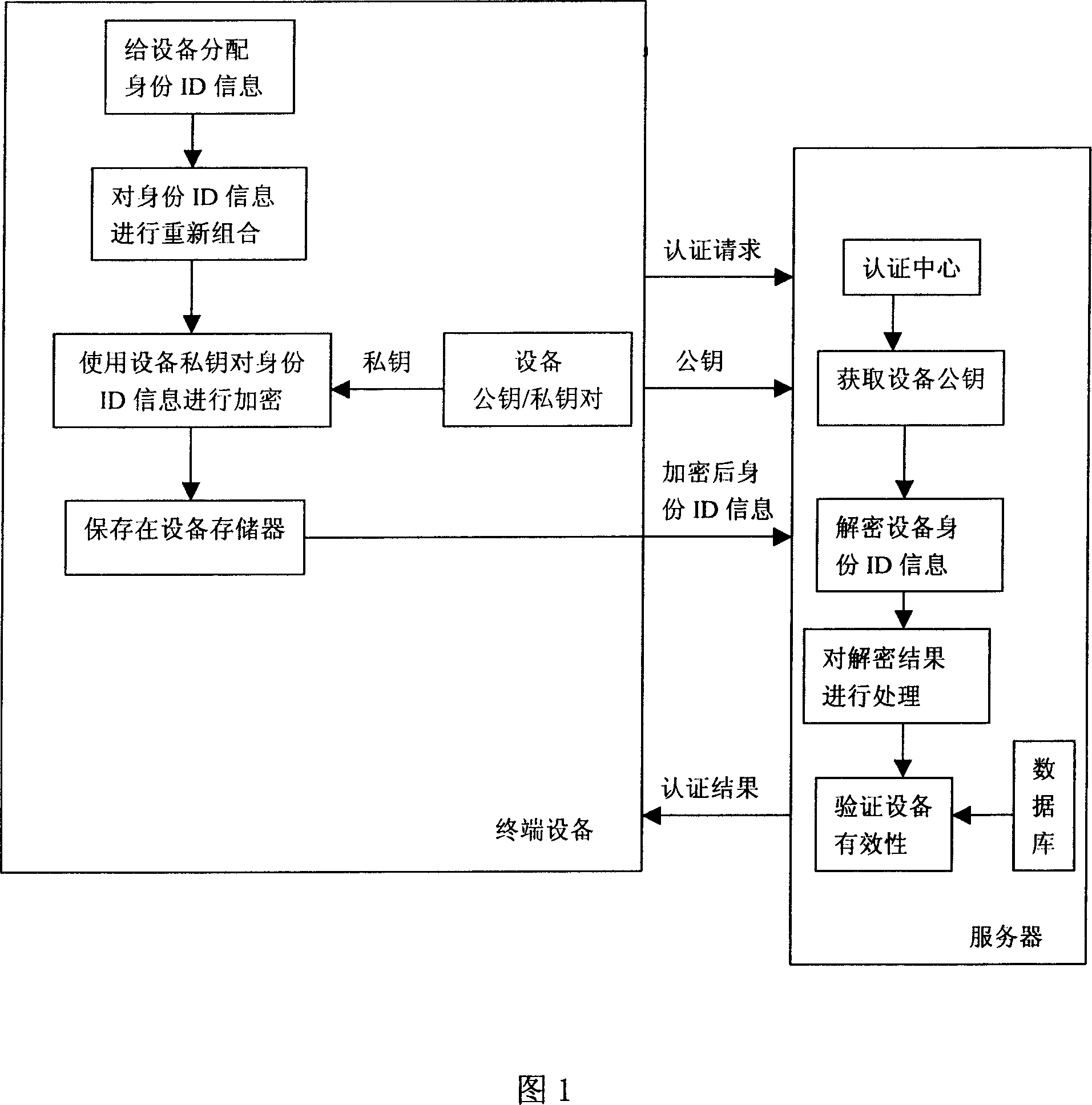
InactiveCN1925392AValid certificationIncrease the difficultyUser identity/authority verificationValidation methodsComputer science
This invention relates to digital copyright management system device legal identification or validation method and provides one device legal identification method, which comprises the following steps: a, device recodes original identification information to generate ID information; b, coding the ID information and then storing device memory; c, servo reading coded ID information to decode ID; d, servo restores codes identification; e, identifying servo ID information.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Electronic official document safety transmission method based on Web service
InactiveCN101321057AEnsure safety featuresSolve security issues such as confidentialityPublic key for secure communicationUser identity/authority verificationWeb serviceSOAP
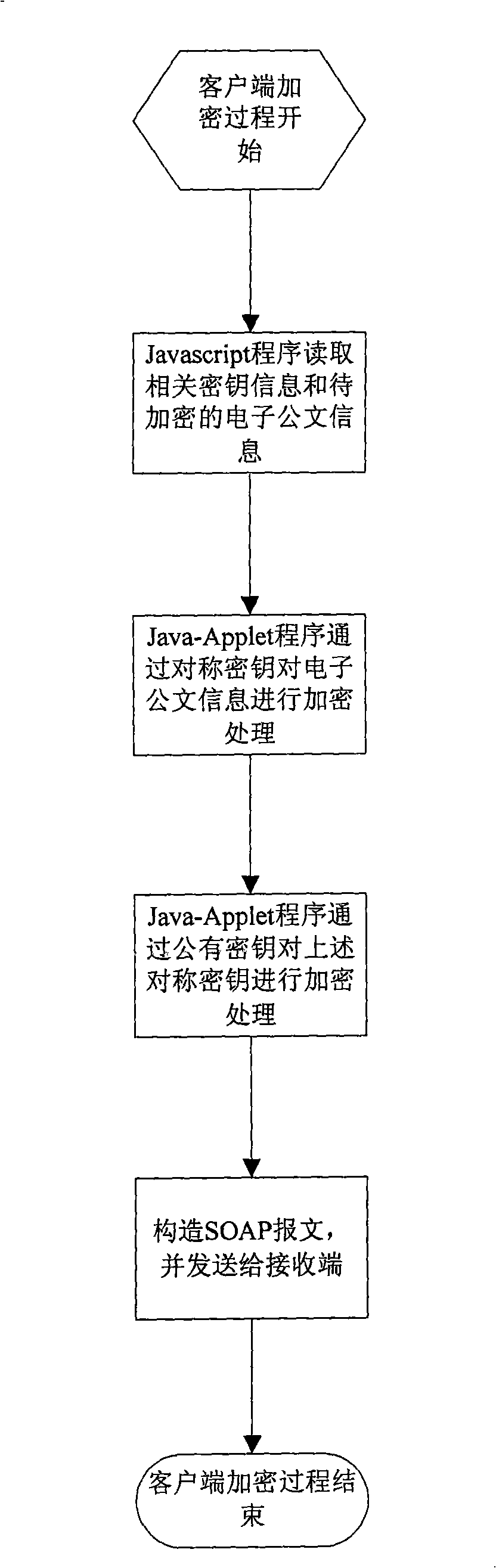
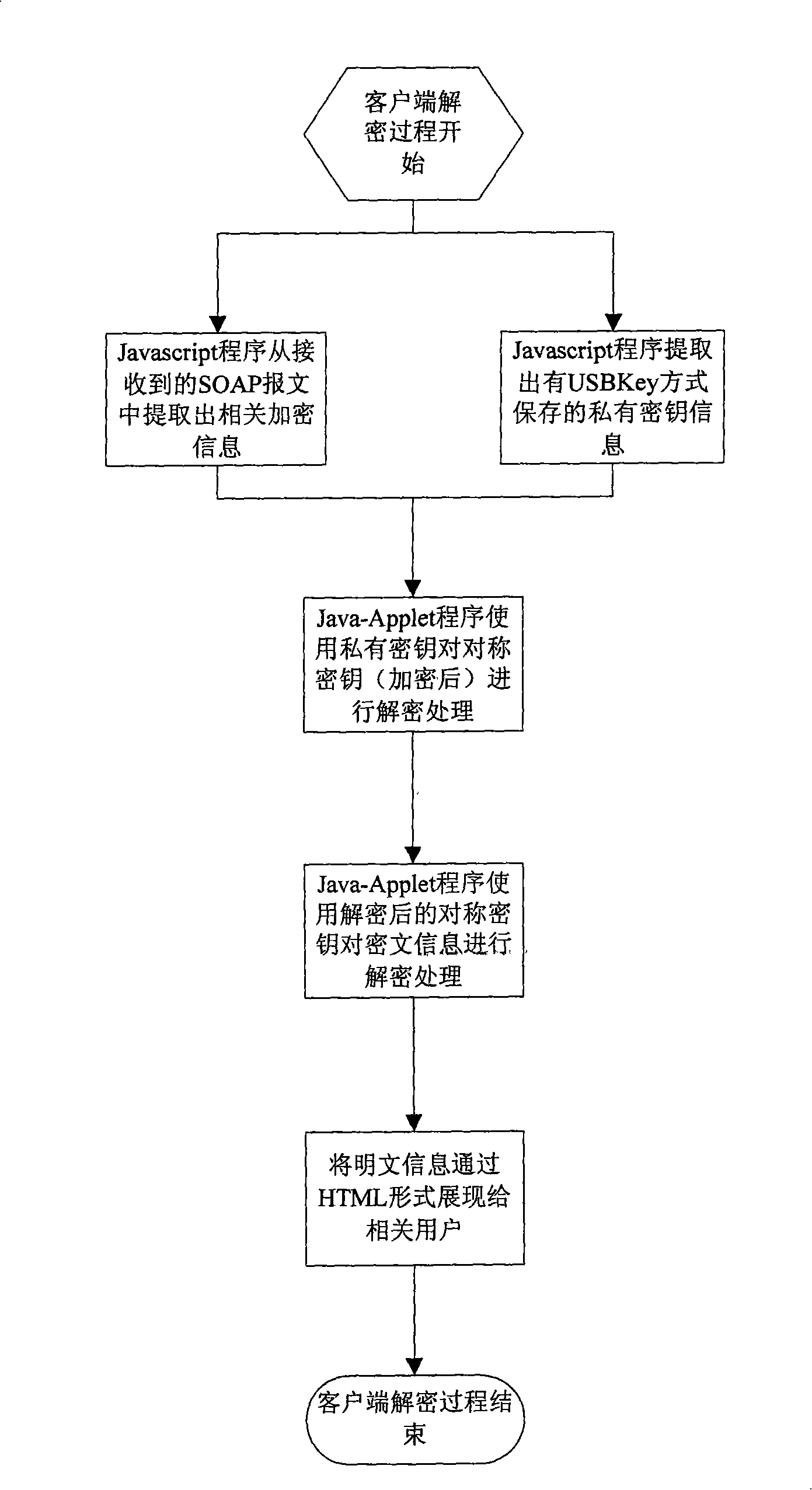
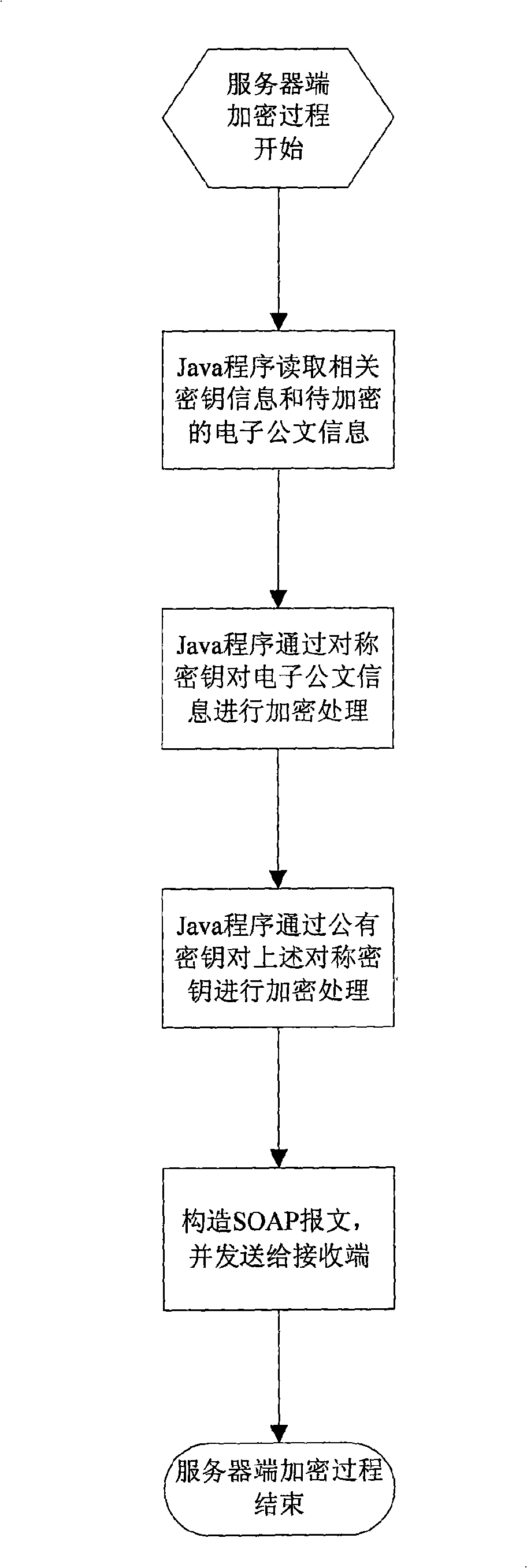
An electronic document secure transmission method based on the Web service is disclosed, comprising: encrypting by the client-end and reading the electronic document information and the related cipher key by the Javascript, performing the encryption by the Java-Applet program; finally constructing the SOAP information, transmitting to the receiver; decrypting the by the client-end, receiving the SOAP information by the Javascript and extracting the electronic document information and the encrypted information, then performing the decrypting process by the Java-Applet program, exhibiting to the user through the HTML form. The encryption of the server end is the same to that of the client-end, with the difference in that, the JAVA program is used in the encrypting process on the electronic document information, rather than the Java-Applet program; the server directly uses the Java program on the server to search the private cipher key information, rather than on the USBKey, and in the decrypting process, the server end uses the Java program to perform the decrypting process rather than the Java-Applet program. According to the invention, the transmission safety between the end to end transmission and the multipoint is ensured.
Owner:BEIHANG UNIV
Vehicle-mounted network anonymous authentication system and method based on ring signature and vehicle communication platform
ActiveCN109802956ARealize communicationAuthentication securityUser identity/authority verificationCommunications securityRelevant information
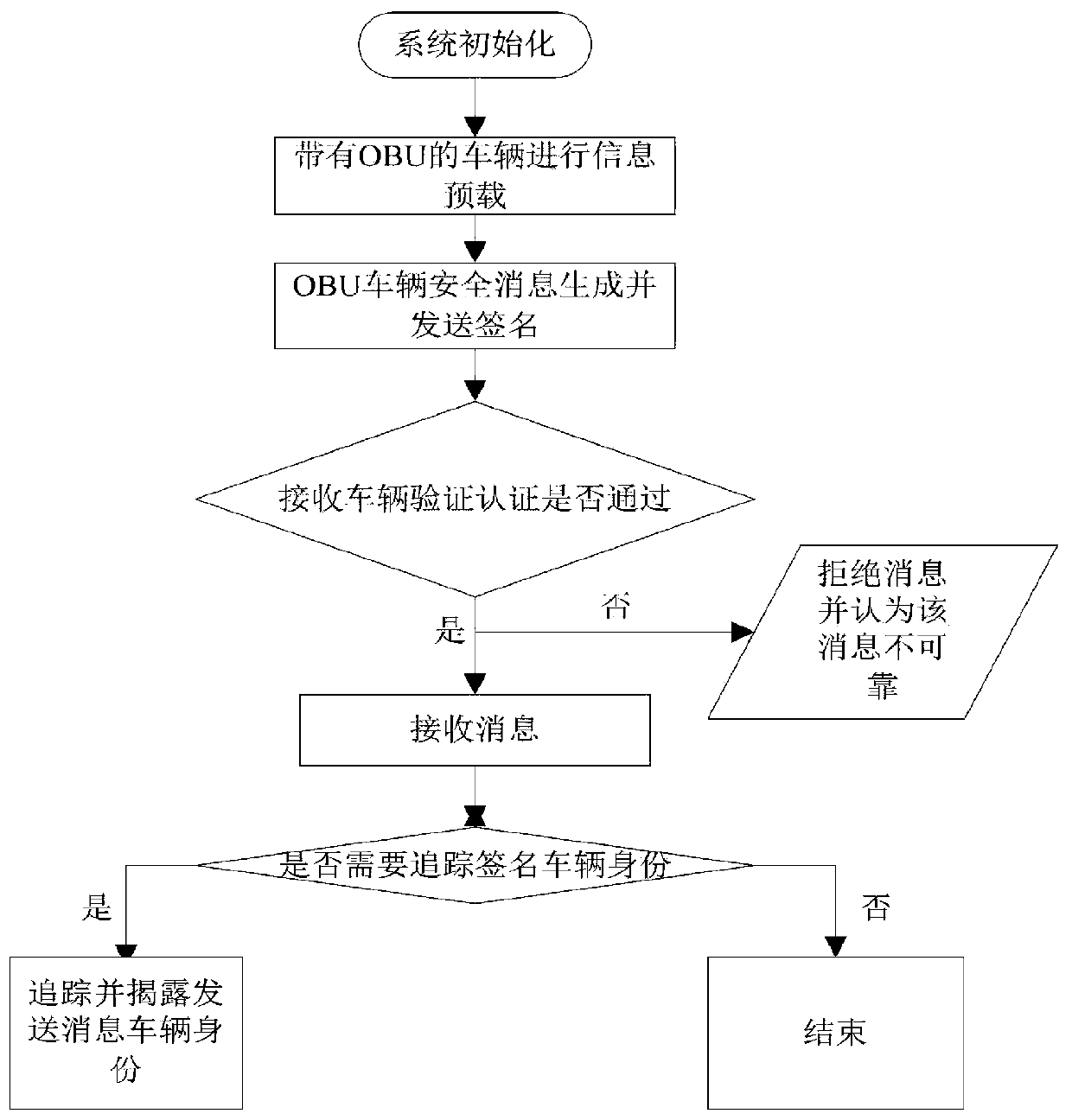
The invention belongs to the technical field of vehicle communication security, and discloses a vehicle-mounted network anonymous authentication system and method based on a ring signature, and a vehicle communication platform. The trust mechanism and the vehicle with the OBU are registered to generate a part of private keys; A vehicle of the OBU is registered and preloaded with public system parameters and corresponding public and private keys before being added into the vehicle-mounted ad hoc network. When the vehicle runs on a road, related state information is periodically broadcasted after safety certification; And when the signer finds that the signer anonymously leaks the false message or the behavior that the signer is damaged, the trust mechanism uncovers the real identity of thesender. According to the invention, the certificateless public key cryptosystem and the ring signature are combined to form the certificateless ring signature, so that anonymity and unforgeability aremet, and meanwhile, security authentication is met; A traceable algorithm is formed by adding related information to effectively solve the problem that when a signer anonymity leaks false messages orother destructive behaviors, identity tracking and revocation are carried out according to the received messages.
Owner:XIAN UNIV OF POSTS & TELECOMM
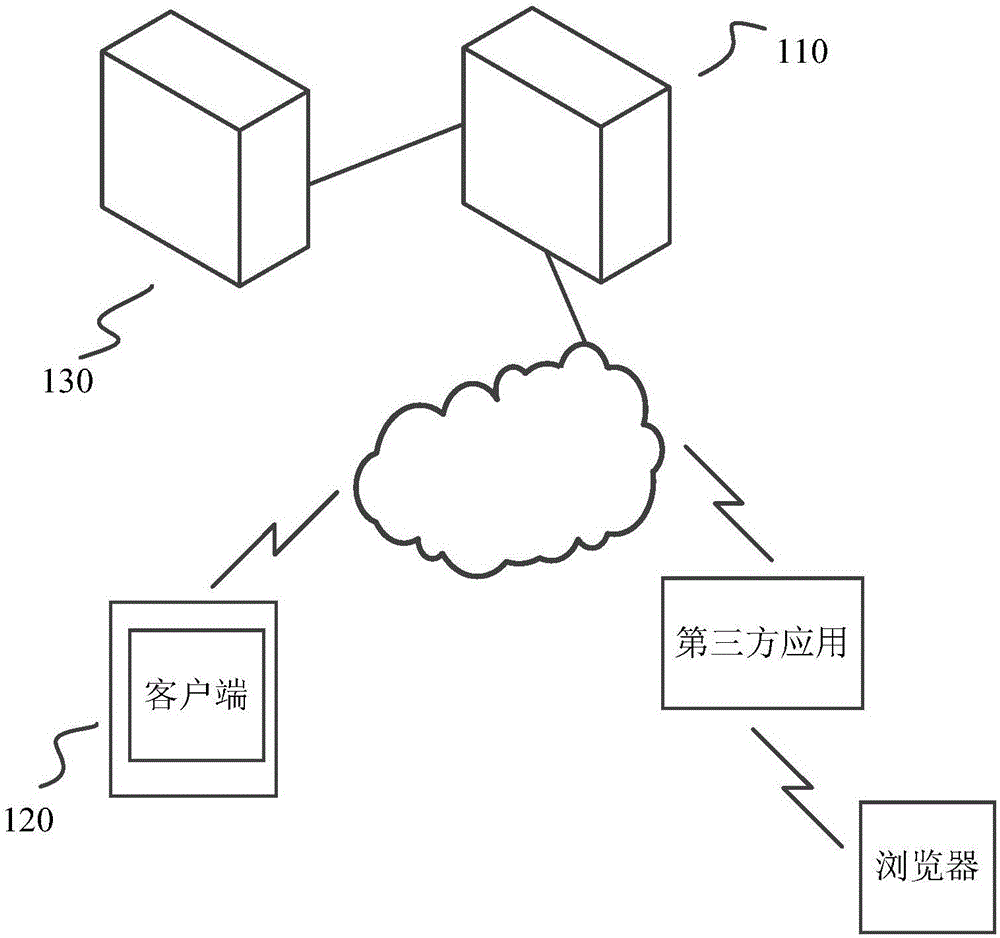
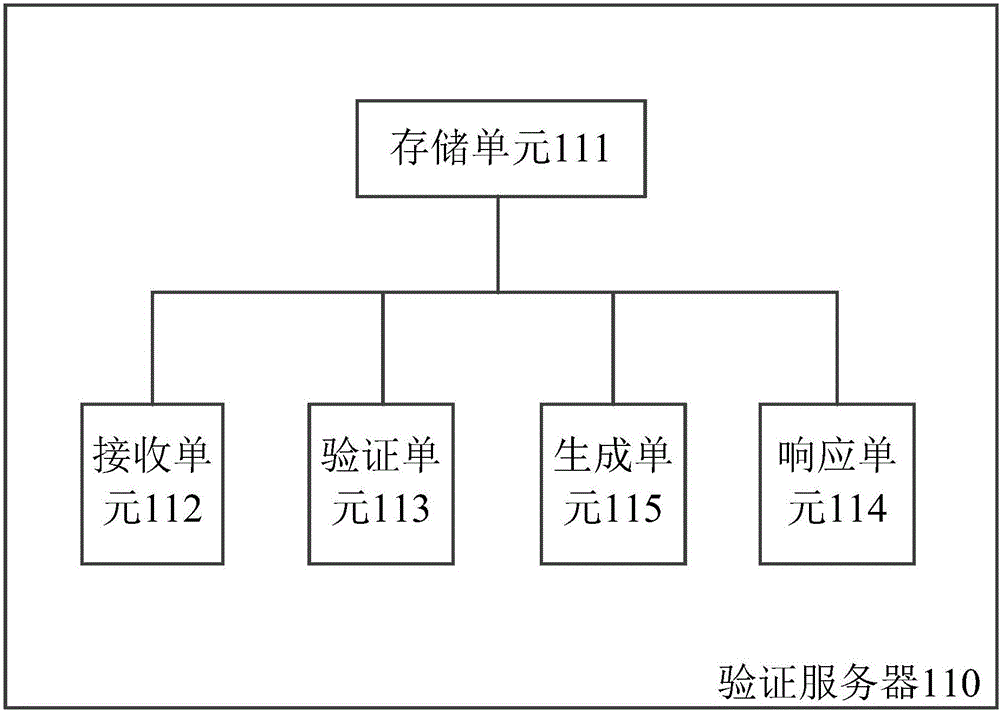
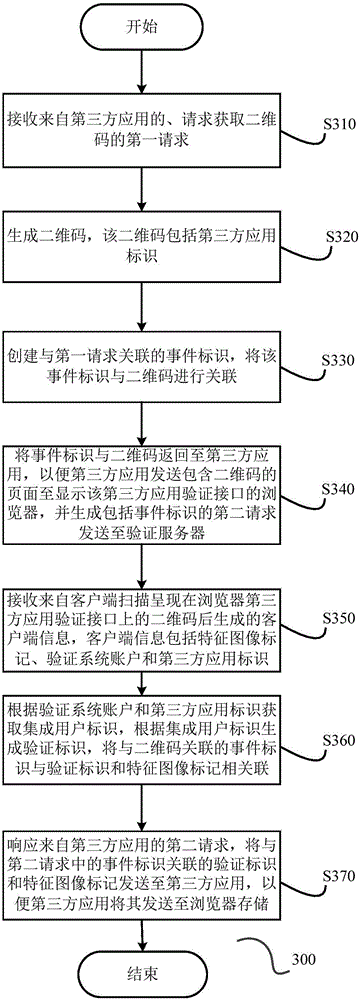
Feature image identification based verification method and system, and verification server
ActiveCN105162604AFast authenticationAuthentication securityUser identity/authority verificationCharacter and pattern recognitionThird partyValidation methods
The invention discloses a feature image identification based verification method, which is applicable to be used in a verification server in a feature image identification based verification system. The verification system is connected with a third party application integrating a verification interface of the verification system through a network, and also comprises a client side. The third party application permits a user to operate with a third party application account, the client side permits the user to operate with a verification system account, and the verification server stores an integrated user identification respectively associated with the third party application account and the verification system account. The method comprises receiving a feature image verification request from the third party application, wherein the feature image verification request comprises integrated user identification information and an image comprising the user characteristic; verifying the image and acquiring a verification result; and returning the verification result to the third party application, so as to enable the third party application to permit the user to operate with the third party application account corresponding to the integrated user identification. The invention also discloses a corresponding verification server and a verification system.
Owner:广州密码科技有限公司
Method of authentication of at least one user with respect to at least one electronic apparatus, and a device therefor
InactiveUS20150178489A1Secure authentication processEasy to operateDigital data processing detailsUnauthorized memory use protectionInternet privacyUser profile
A method of authentication of at least one user, by using a portable electronic authentication device, with respect to at least one electronic apparatus. The method includes establishing a communication between the authentication device and the electronic apparatus, detecting a movement performed by the user using the authentication device, comparing the detected movement with a stored user profile, and authenticating the user if the detected movement matches a stored user profile.
Owner:ORANGE SA (FR)
Armrest for Multiple Seating
ActiveUS20100295358A1Affect dispositionReduce riskSeating arrangementsAir-treatment apparatus arrangementsPhysical medicine and rehabilitationDual plane
An armrest for multiple seating has upper and lower support planes that overlap to permit respective use by neighbors. The upper armrest may be cut-away at the rear to accommodate the elbow of the user of the lower armrest. The dual plane armrest comprises an upper forearm support and a lower forearm support. The upper forearm support is disposed above the lower forearm support partially or completely. The configuration of the invention provides increased lateral space for neighbors without increasing lateral seat pitch.
Owner:LEE IN OK
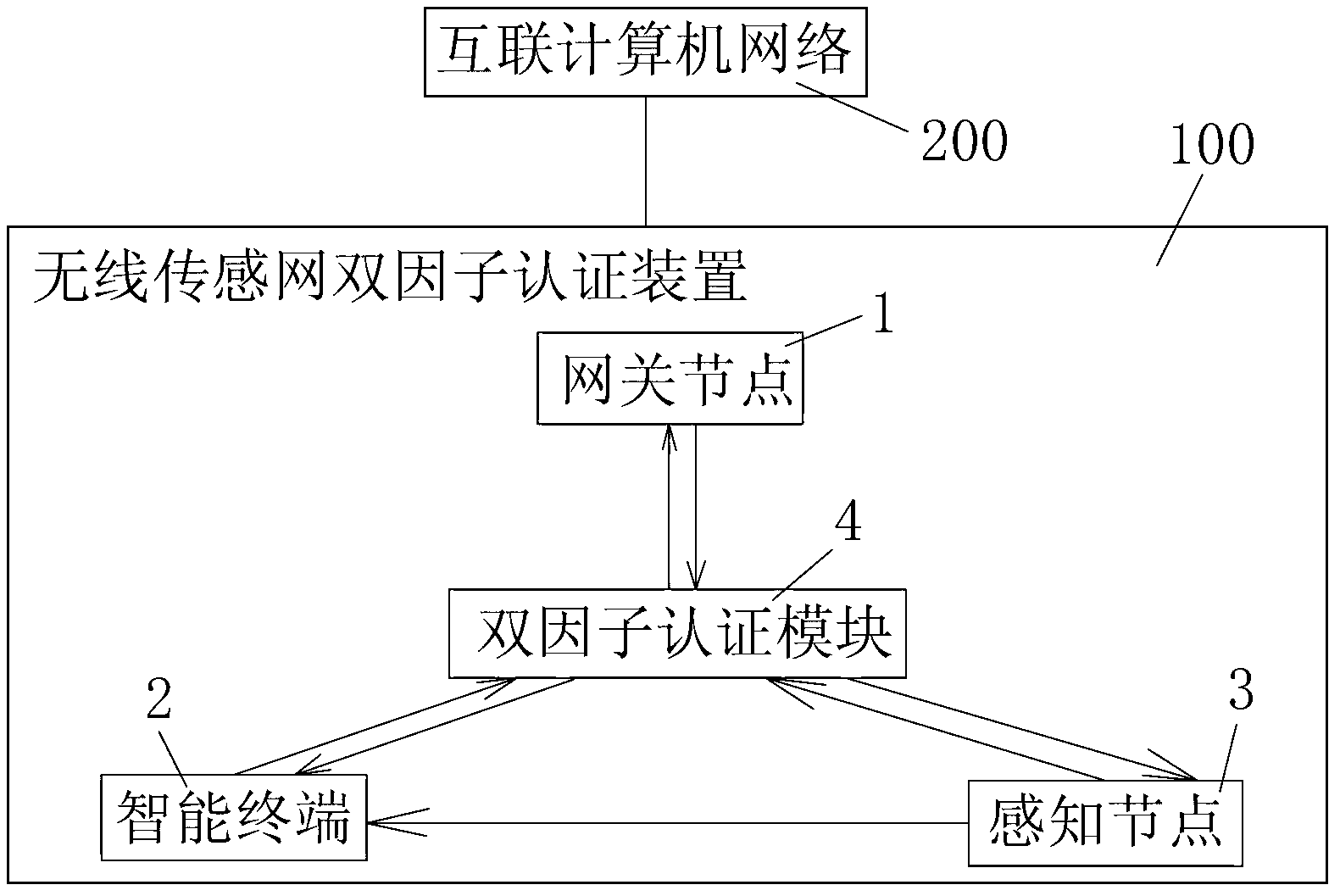
Two-factor authentication method and two-factor authentication device for wireless sensor network and network comprising two-factor authentication device
ActiveCN103313246AAuthentication securityThe certification process is reliableTransmissionSecurity arrangementPersonalizationInterconnection
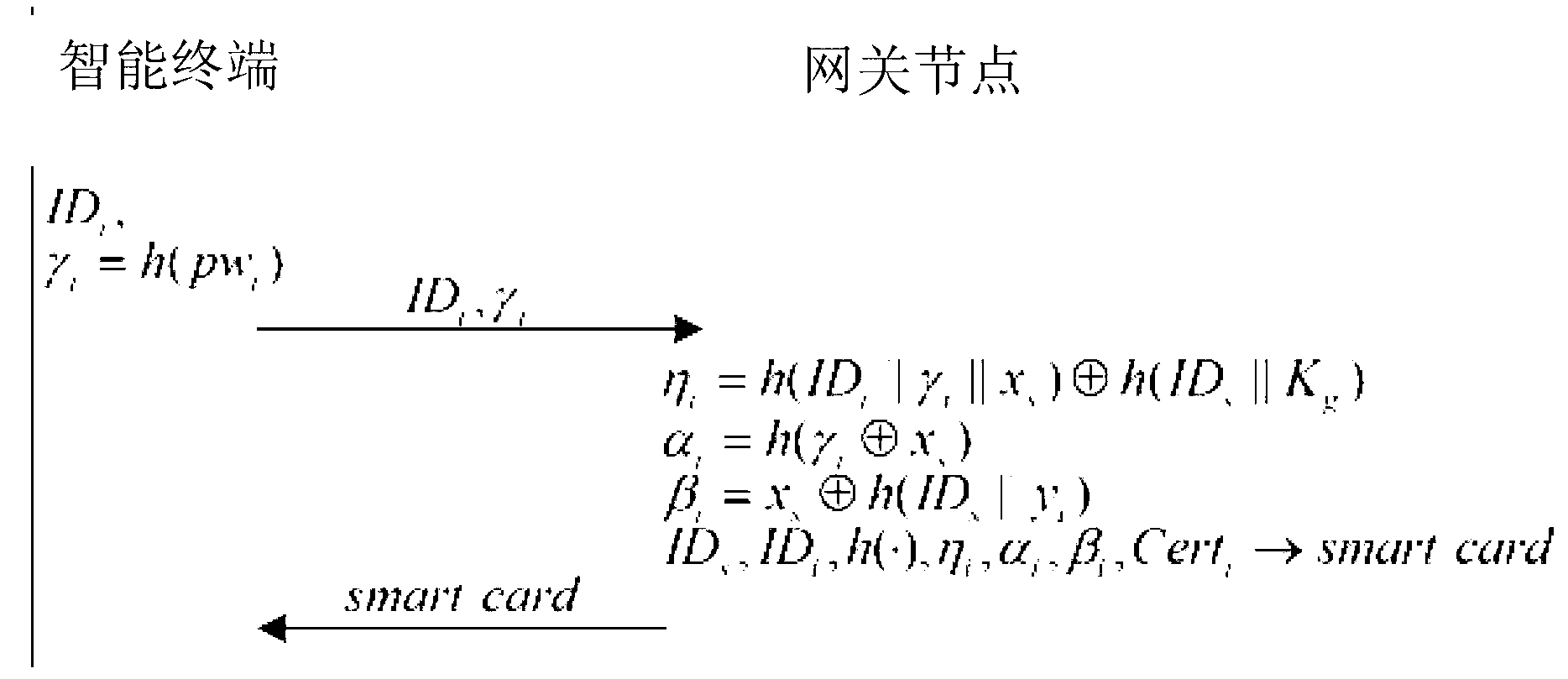
The invention discloses a two-factor authentication method and a two-factor authentication device for a wireless sensor network and a network comprising the two-factor authentication device. The two-factor authentication device comprises a gateway node, an intelligent terminal, a sensor node and a two-factor authentication module, and the gateway node, the intelligent terminal and the sensor node are communicated with each other. The Merkle hash tree based two-factor authentication method for the wireless sensor network is applied to the two-factor authentication module. The two-factor authentication method includes the steps of gateway pre-authentication: performing DoS (disk operating system)-attack resisting gateway pre-authentication on the basis of the Merkle hashtree; bidirectional authentication among gateway and sensor nodes: authenticating the sensor node by the gateway node after the sensor node finishes in authenticating an access request from the gateway node, wherein during bidirectional authentication, one-way hash is performed after connection with sensor node ID (identification) is established, so that personalized safety parameters for the sensor node are formed to resist attacks from gateway counterfeit and data counterfeit caused by leakage of the safety parameters. The invention further provides an interconnection computer network comprising the two-factor authentication device for the wireless sensor network.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI +1
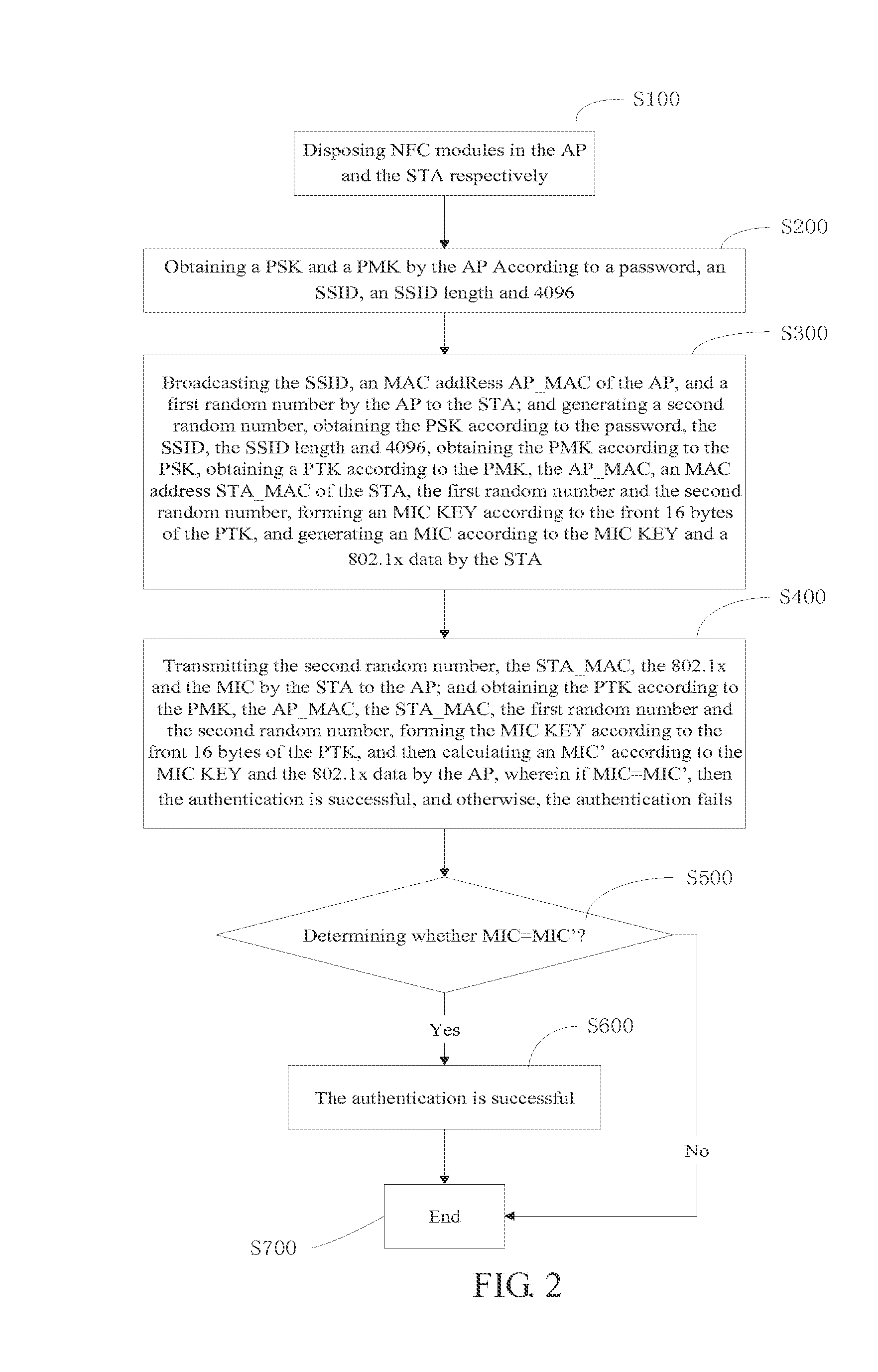
Method and system for securely accessing portable hotspot for intelligent mobile phones
ActiveUS20150065088A1Reliable communicationEliminate potential safety hazardsNear-field transmissionKey distribution for secure communicationSecurity authenticationData transmission
A method and a system for securely accessing a portable hotspot for intelligent mobile phones, comprises an intelligent mobile phone used as an AP and another intelligent mobile phone used as an STA. The AP comprises an AP NFC module and a first data transmission module; and the STA comprises an STA NFC module and a second data transmission module. The AP uses the NFC module to perform a WPA security authentication with the STA, and uses the first data transmission module to perform data encrypted transmission with the second data transmission module. In the method and the system of the present disclosure, the common WLAN authentication mechanism is not adopted, and the security authentication process between the AP and the STA is completed in the NFC manner instead.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
System and method for key exchange based on authentication information
ActiveCN106130716AValid certificationEffective attackKey distribution for secure communicationEncryption apparatus with shift registers/memoriesKey exchangeCiphertext
Disclosed are a system and method for key exchange based on user authentication information. The system for key exchange based on user authentication information includes a terminal configured to generate ciphertext corresponding to authentication information of a user of the terminal using a random number for the client and server identification information, and a server configured to decrypt the ciphertext received from the terminal using a private key for the server corresponding to the server identification information to restore the authentication information, authenticate the terminal using the restored authentication information, and generate a session key for the server corresponding to the authenticated terminal.
Owner:SAMSUNG SDS CO LTD
Method and system for realizing mixed authentication
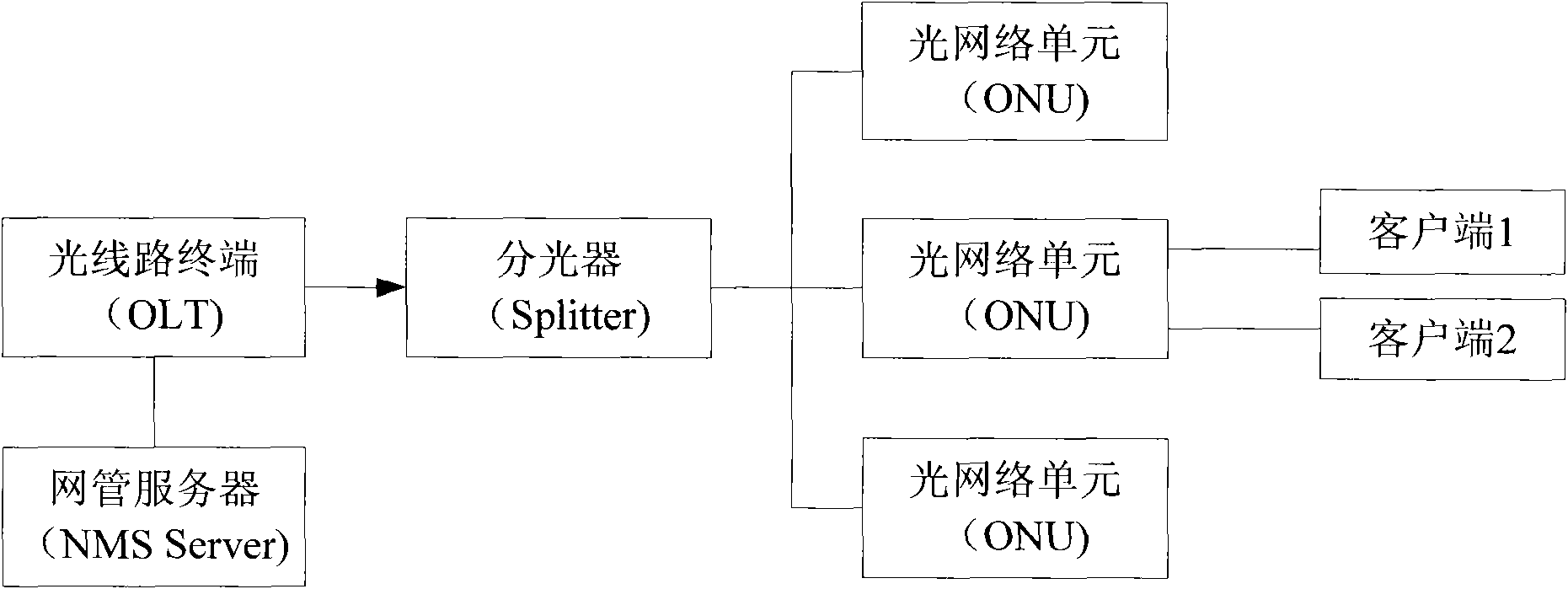
InactiveCN102170421AThe certification process is reliableAuthentication securityMultiplex system selection arrangementsData switching networksOptical network unitComputer science
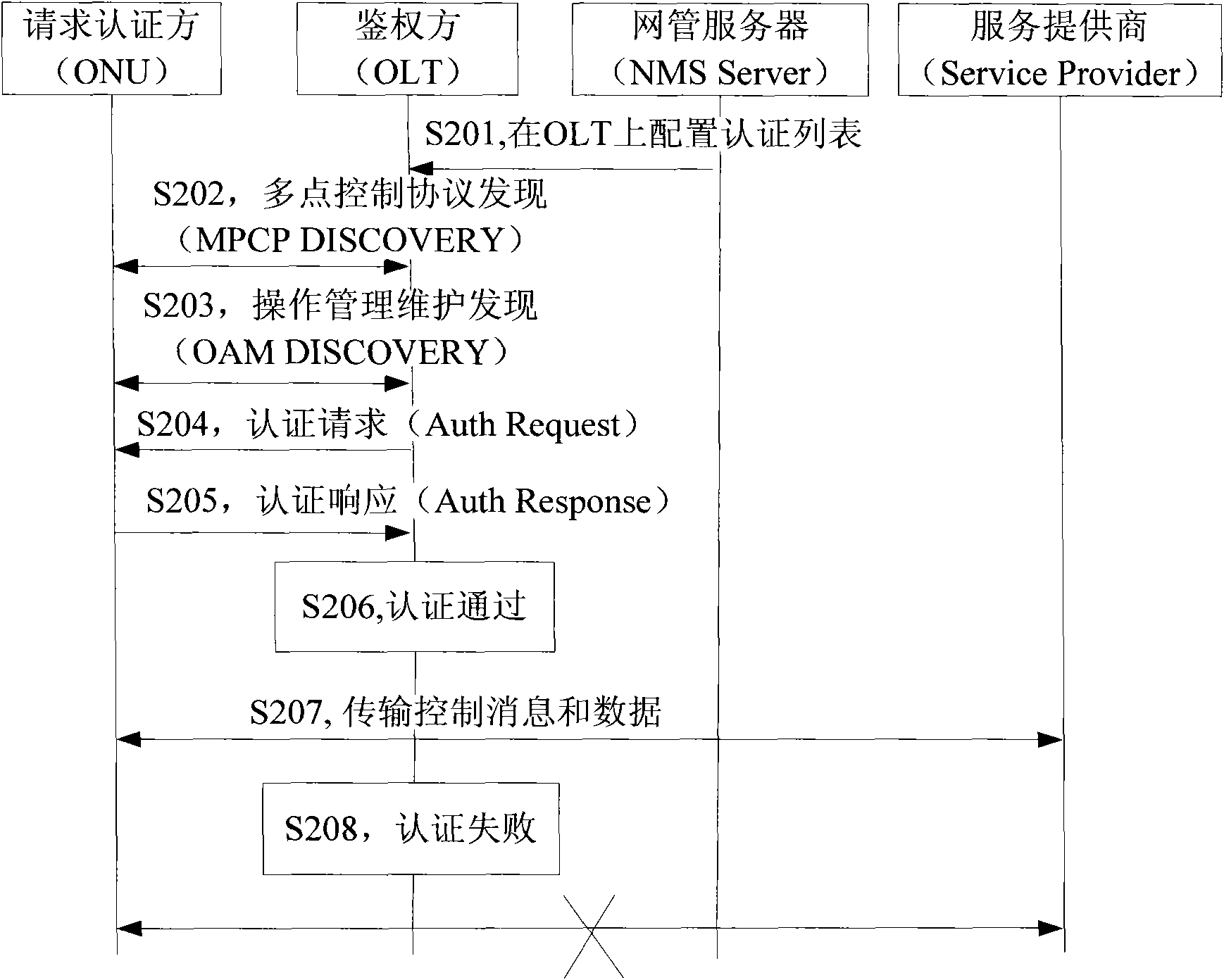
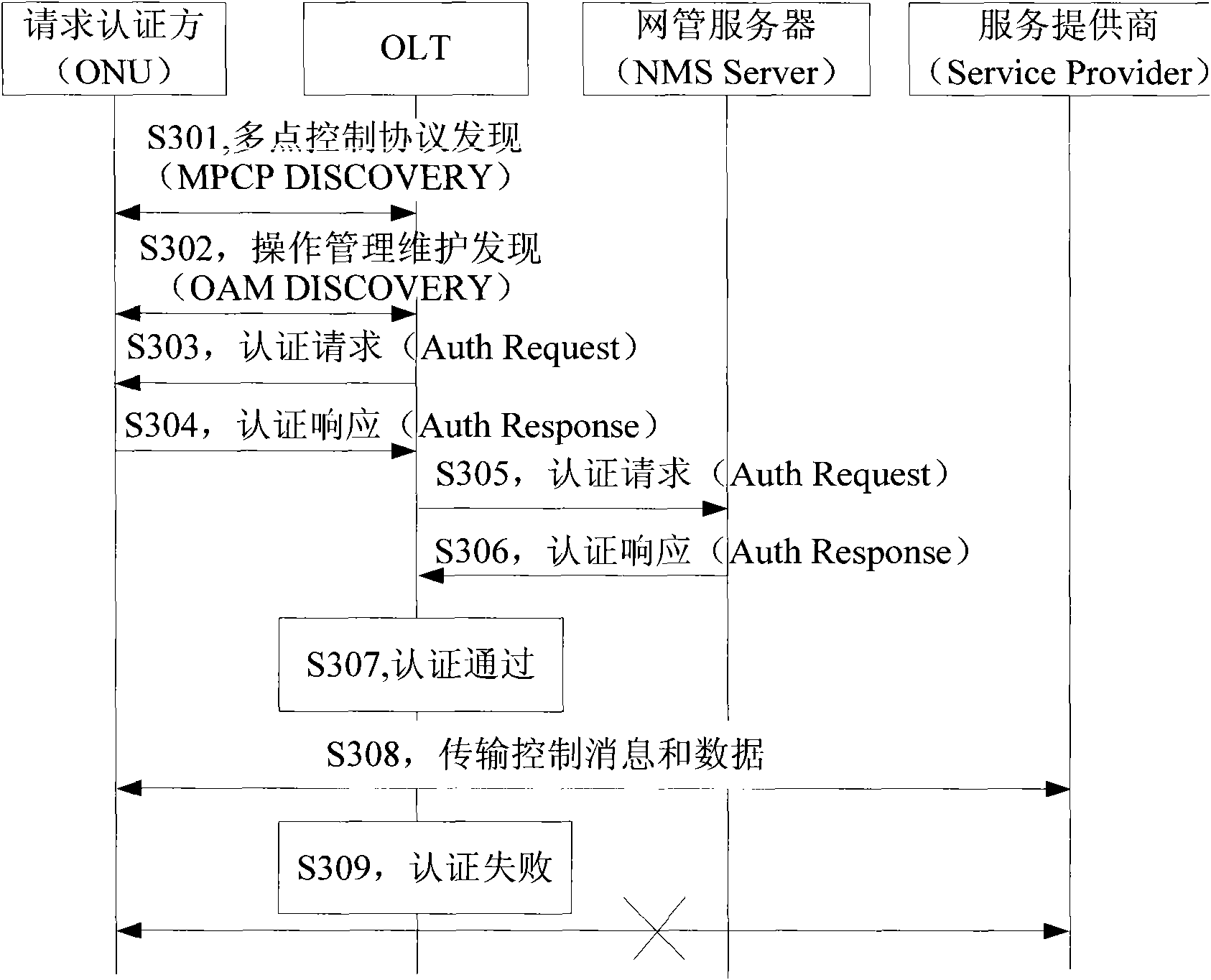
The invention provides a method for realizing mixed authentication. The method comprises the steps of obtaining a logic identifier and a physical identifier of an optical network unit; authenticating according to the logic identifier and the physical identifier; enabling the optical network unit to pass the authentication while the logic identifier and the physical identifier are legal; and otherwise, obtaining that the optical network unit fails to pass the authentication. The invention also provides a system for realizing the mixed authentication. By using the method and the system disclosed by the invention, the reliability and security of the ONU (Optical Network Unit) authentication process are improved.
Owner:ZTE CORP
Method and system for realizing user authentication through biological characteristic information
InactiveCN105868610AImprove reliabilityImprove securityDigital data authenticationTransmissionApplication serverPassword
The invention discloses a method and a system for realizing user authentication through biological characteristic information. The method comprises the following steps: a user initiates an authentication request on the basis of an application of biometric identification equipment; a security kernel of the biometric identification equipment acquires the biological characteristic information of the user on the basis of the authentication request, generates a corresponding user ID value according to the biological characteristic information and returns the user ID value to the application initiating the authentication request; the application sends the user ID value returned by the security kernel to an application server, and the application server finishes user authentication according to the user ID value. One novel internet user identity authentication method is provided, so that the user does not need a user name or a password, and the login effect of the user name and the password can be finished on different sets of equipment through simple operation.
Owner:LETV HLDG BEIJING CO LTD +1
Information processing device, information processing method, and computer program
InactiveCN103810409AAuthentication securityDigital data authenticationDigital output to display deviceInformation processingComputer graphics (images)
The invention discloses an information processing device, an information processing method, and a computer program. An information processing device includes a display that displays an input screen including a plurality of images, an image selecting section that selects at least one image within the input screen in accordance with an input operation from a user, and a controller that controls the information processing device on a basis of the image selected by the image selecting section. There is provided an information processing method including displaying an input screen including a plurality of images, selecting at least one image within the input screen in accordance with an input operation from a user, and controlling operation of an information processing device on a basis of the selected image. By using the device and the method, a risk of the inputted information being discovered by a third person who is behind or near the user can be prevented.
Owner:SONY CORP
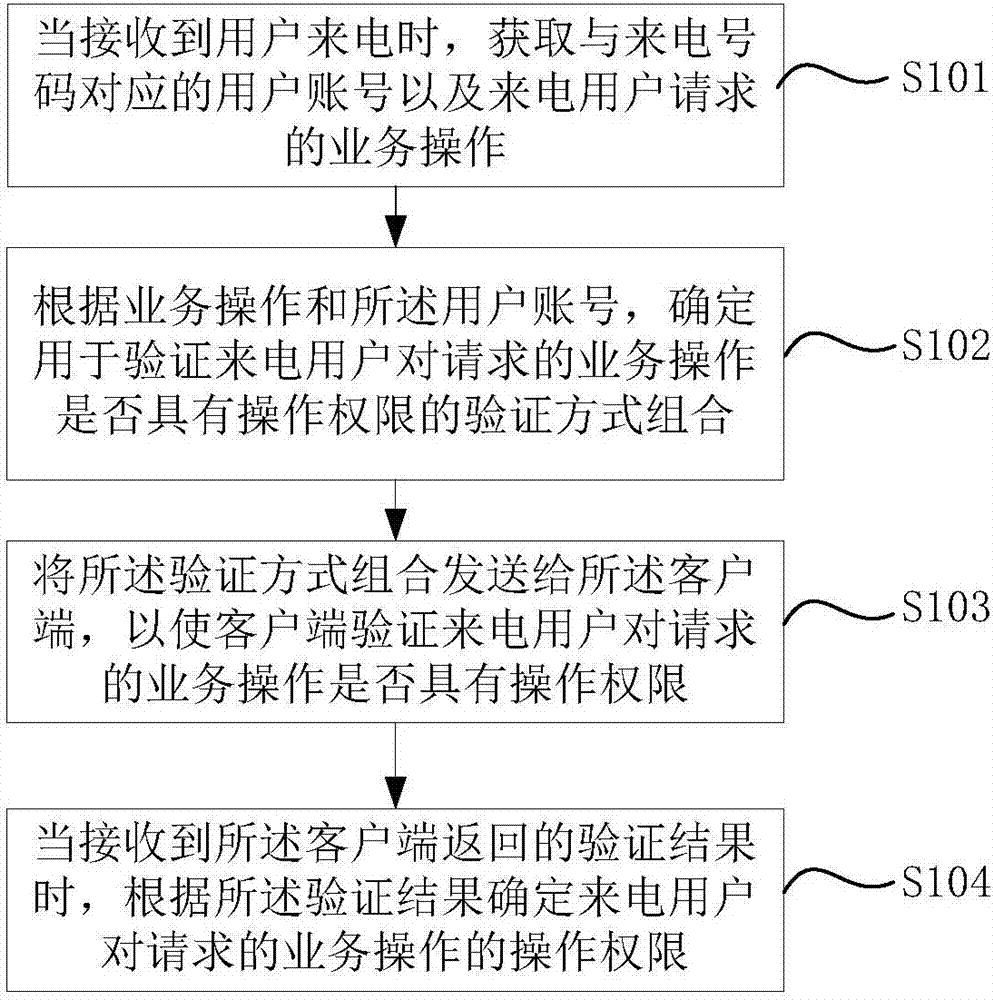
Identity authentication method and device
ActiveCN107231232AFast authenticationAuthentication securityUser identity/authority verificationSpecial service for subscribersStatus changedAuthentication
The embodiment of the invention provides an identity authentication method and device. The method comprises the steps that a user account corresponding to an incoming call number and a service operation requested by an incoming caller are acquired when the incoming call of a user is received; according to the service operation and the user account, an authentication mode combination used for verifying whether the incoming caller has an operational right for the requested service operation is determined; the authentication mode combination is sent to the client; and when an authentication result returned by the client is received, the incoming caller's operational right for the requested service operation is determines according to the authentication result. According to the method provided by the invention, in combination with the service operation requested by the incoming call user, an appropriate authentication method is selected; the identity of the incoming caller can be quickly verified through the interaction with the client used by the incoming call user; the whole identity authentication process is safe and fast; and long-term occupation of customer service resources can be effectively avoided.
Owner:ADVANCED NEW TECH CO LTD
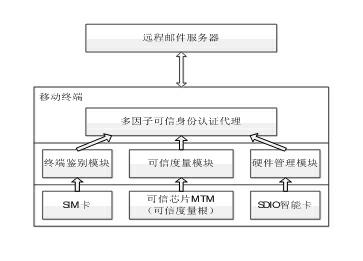
Mobile mailbox multi-factor trusted identity authentication method and system
InactiveCN102281510AImprove securityAuthentication securityMessaging/mailboxes/announcementsSecurity arrangementDigital inputHuman language
The invention discloses a multi-factor credible identity authenticating method. The method comprises the following steps that: a mobile terminal computes integrity measurement through a credible chip, collects information which is required by an integrity measurement report and comprises a personal credit registering system (PCRS) value and a standard meta language (SML) value, and encrypts the information by using an automated installation kit (AIK) private key in the credible chip to generate the integrity measurement report, wherein the PCRS value comprises a computed value for the integrity measurement of a mailbox system; verification information which comprises the integrity measurement report and mobile terminal authenticating information is signed by using an identity certificate in a security digital input and output (SDIO) intelligent card and the verification information is sent to a mailbox service platform; and the mailbox service platform verifies the authentication information of the mobile terminal, after successful verification, legality of the integrity measurement report which is received currently is detected by using prestored credibility verification information of the mailbox of the mobile terminal, and the mailbox system of a user terminal is activated after passing of the verification.
Owner:上海和辰信息技术有限公司
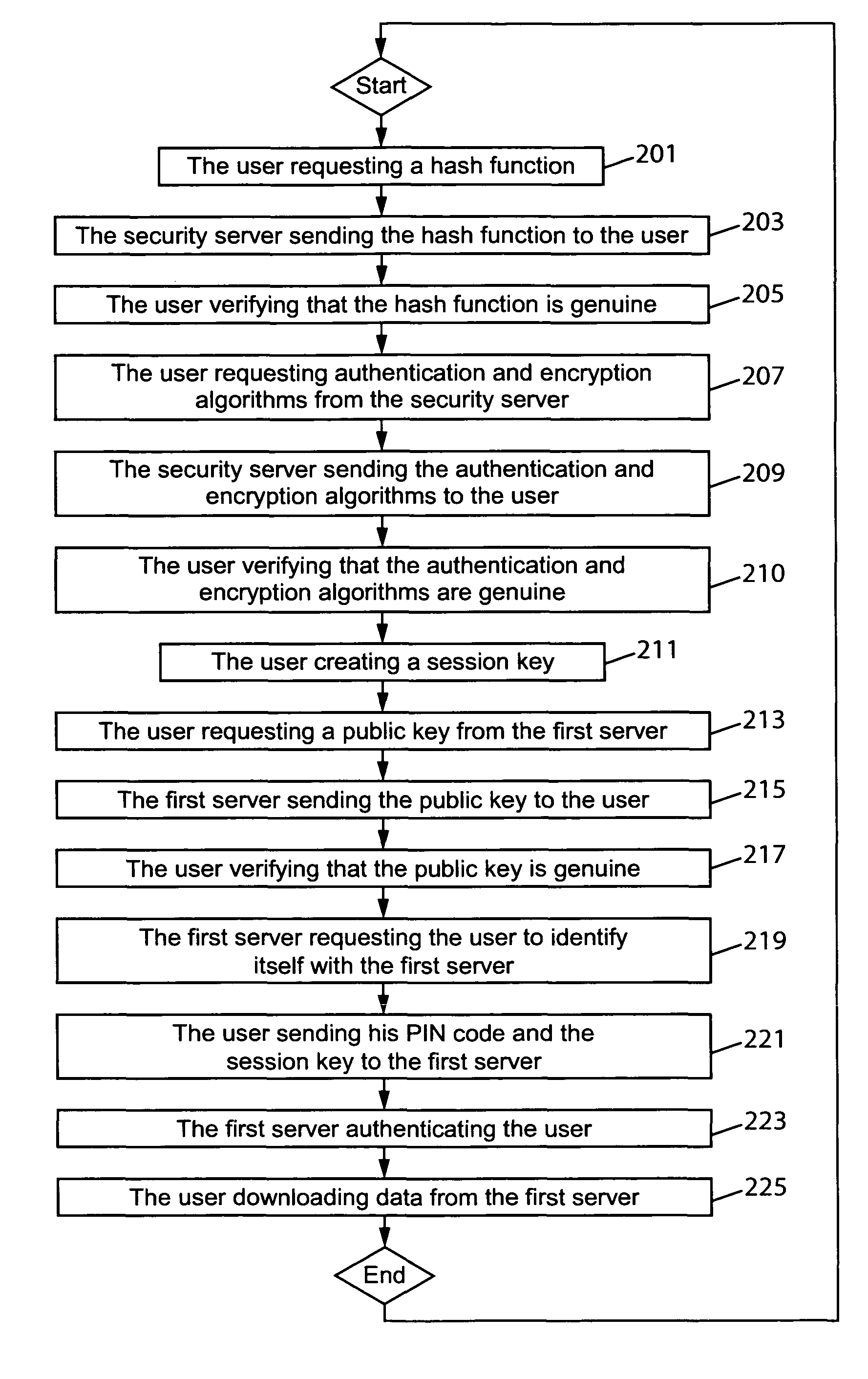
Establishing a secured communication session
ActiveUS8285989B2Authentication securityUser identity/authority verificationSecret communicationCommunications systemData Authentication Algorithm
The present invention relates to a method for establishing a secured communication session in a communication system between a user using an untrusted device and a server. According to the present invention the user first obtains an authentication algorithm and an encryption algorithm and then creates a session key. Next the user obtains a public key of the server and sends a personal identity number to the server for authentication by using the authentication algorithm, the personal identity number being encrypted by using the encryption algorithm and the public key of the server. The user also sends the session key to the server for encrypting purpose between the user and the server, the session key being encrypted by using the encryption algorithm and the public key of the server.
Owner:APPLE INC
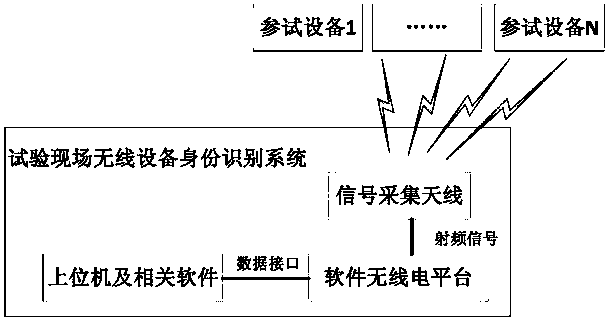
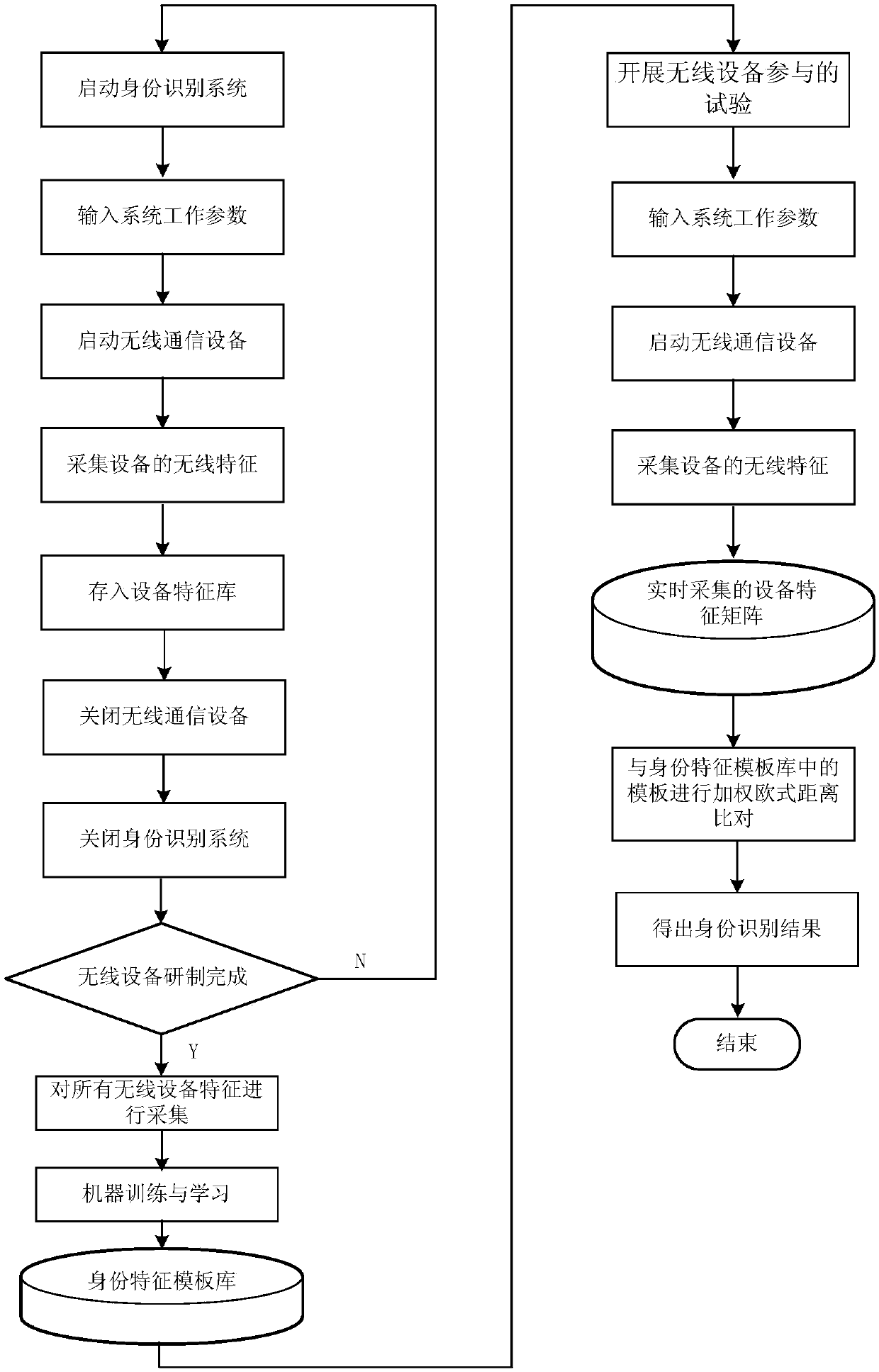
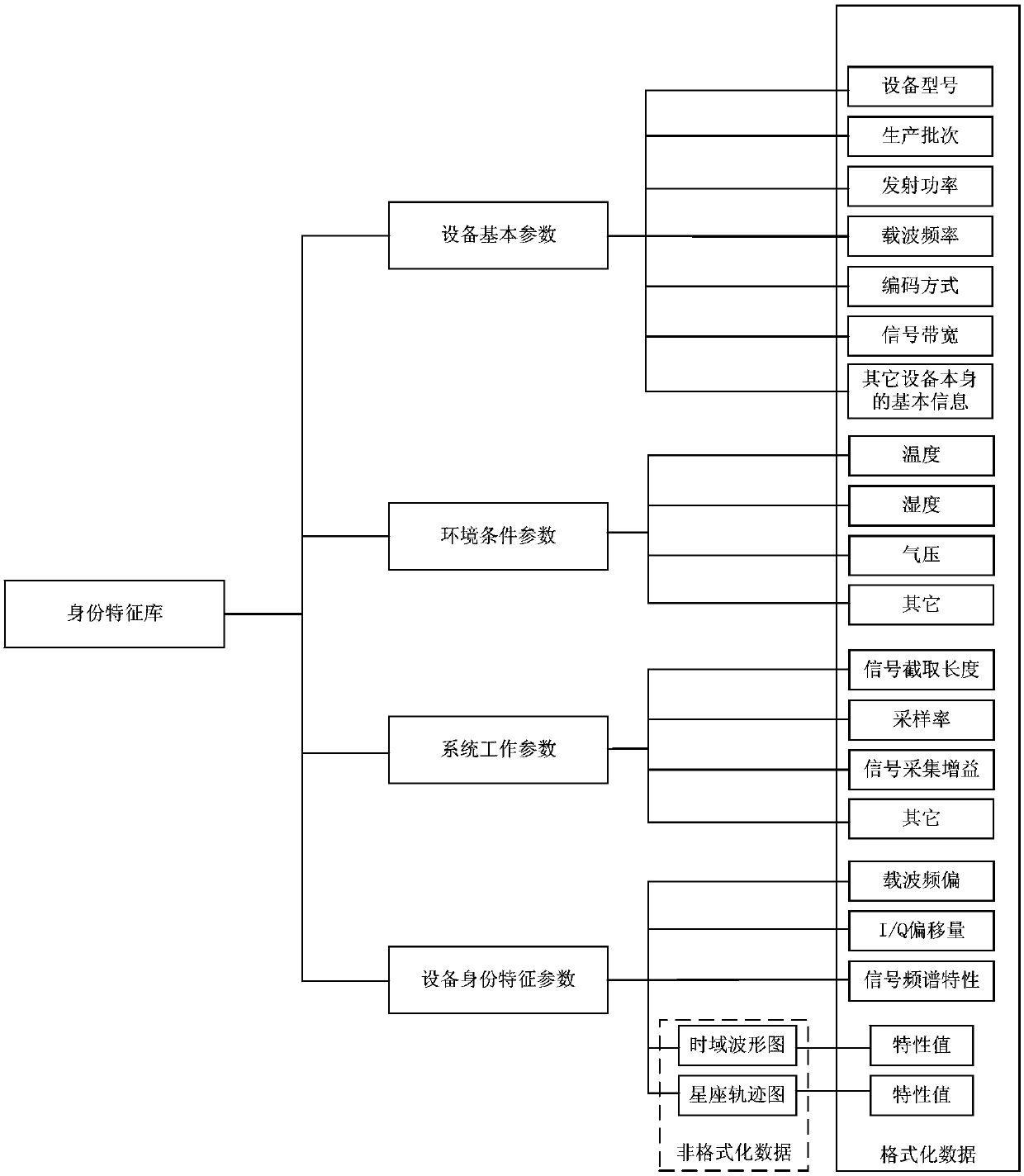
Test site wireless equipment identity recognition system and method
ActiveCN107944513AReduce workloadQuick recognitionCo-operative working arrangementsCharacter and pattern recognitionWireless transmissionIdentity recognition
The invention provides a test site wireless equipment identity recognition system and method. The test site wireless equipment identity recognition system comprises a signal acquisition antenna, a software radio platform, an upper computer and an identity management software system. The wireless fingerprint characteristics of the equipment are repetitively acquired for multiple times in the production link of the wireless equipment to form a sample database, and the wireless equipment fingerprint characteristics of the test equipment are acquired in real time in the test link of the wireless equipment to be compared with the characteristics in the sample database so as to obtain the identity information of the test equipment. Identity recognition and authentication can be rapidly and safely performed on the test wireless transmission electronic equipment in test so as to have great use value.
Owner:CHINA ACAD OF LAUNCH VEHICLE TECH
Method and system for user authentication in a digital communication system
ActiveUS7415615B2Easy to useMore secureSensing detailsDigital data processing detailsCommunications systemInternet privacy
A method and a system for authentication and synchronization is disclosed. The user provides a first one time code (OTC) to the authentication manager. If this OTC is within a small access window, the user is directly authenticated and granted access to the system. If the provided OTC is outside the small window but within a big window, the authentication manager saves the first OTC, and a second OTC is required from the user. If the new, second OTC and the first OTC are in sequence, the end user will be authenticated, and admitted access to the system and the requested service.
Owner:TDS TODOS DATA SYST
Method and system for on-line distributing authentication information
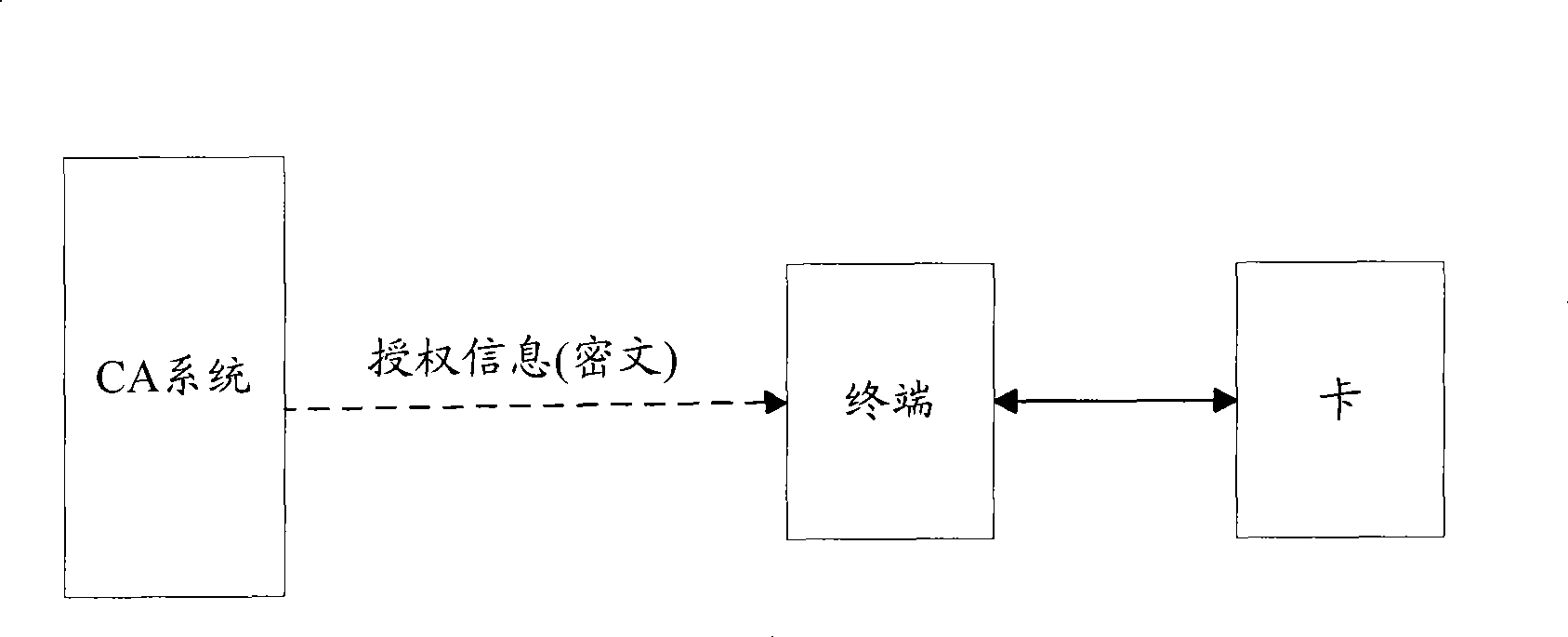
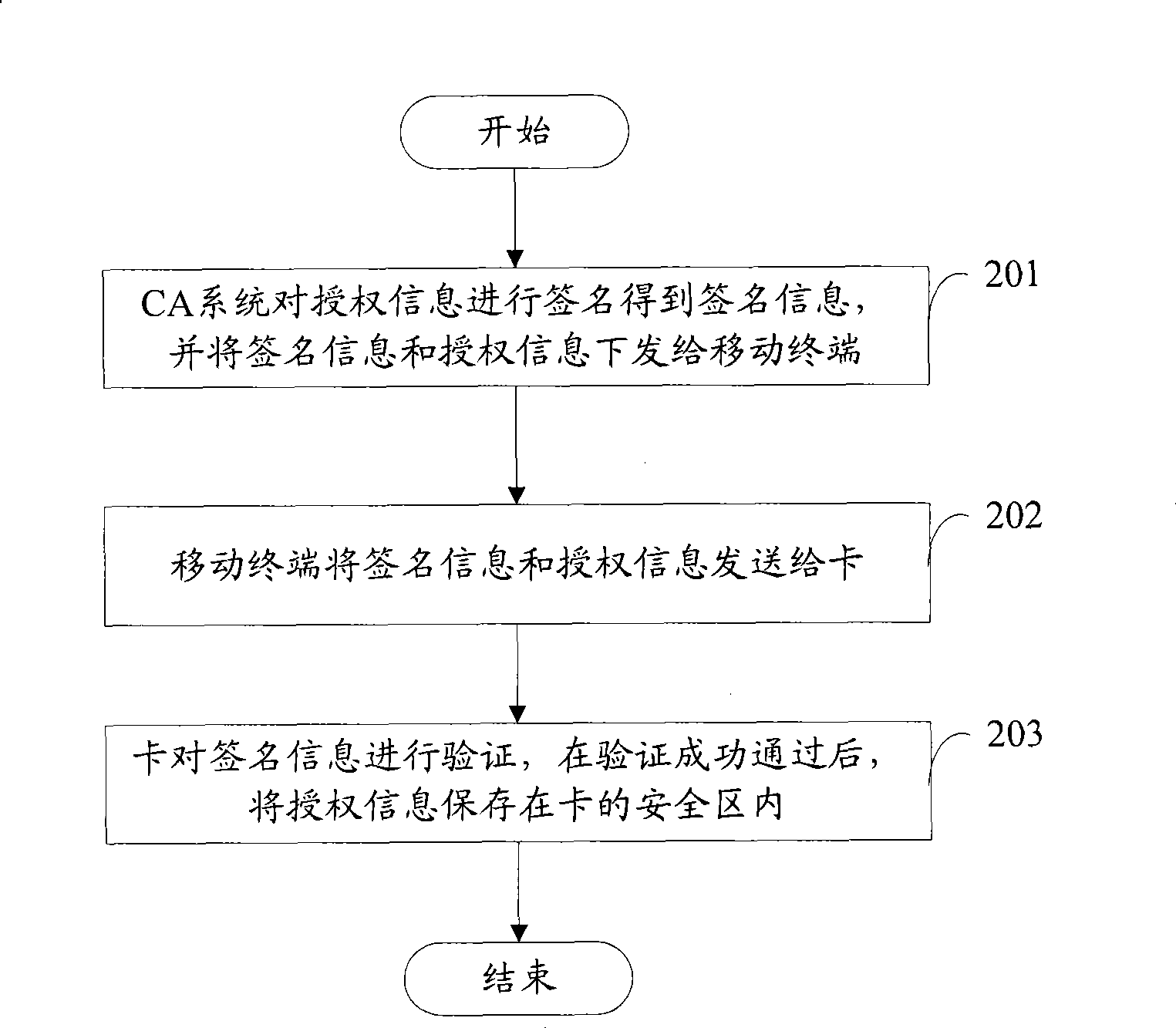
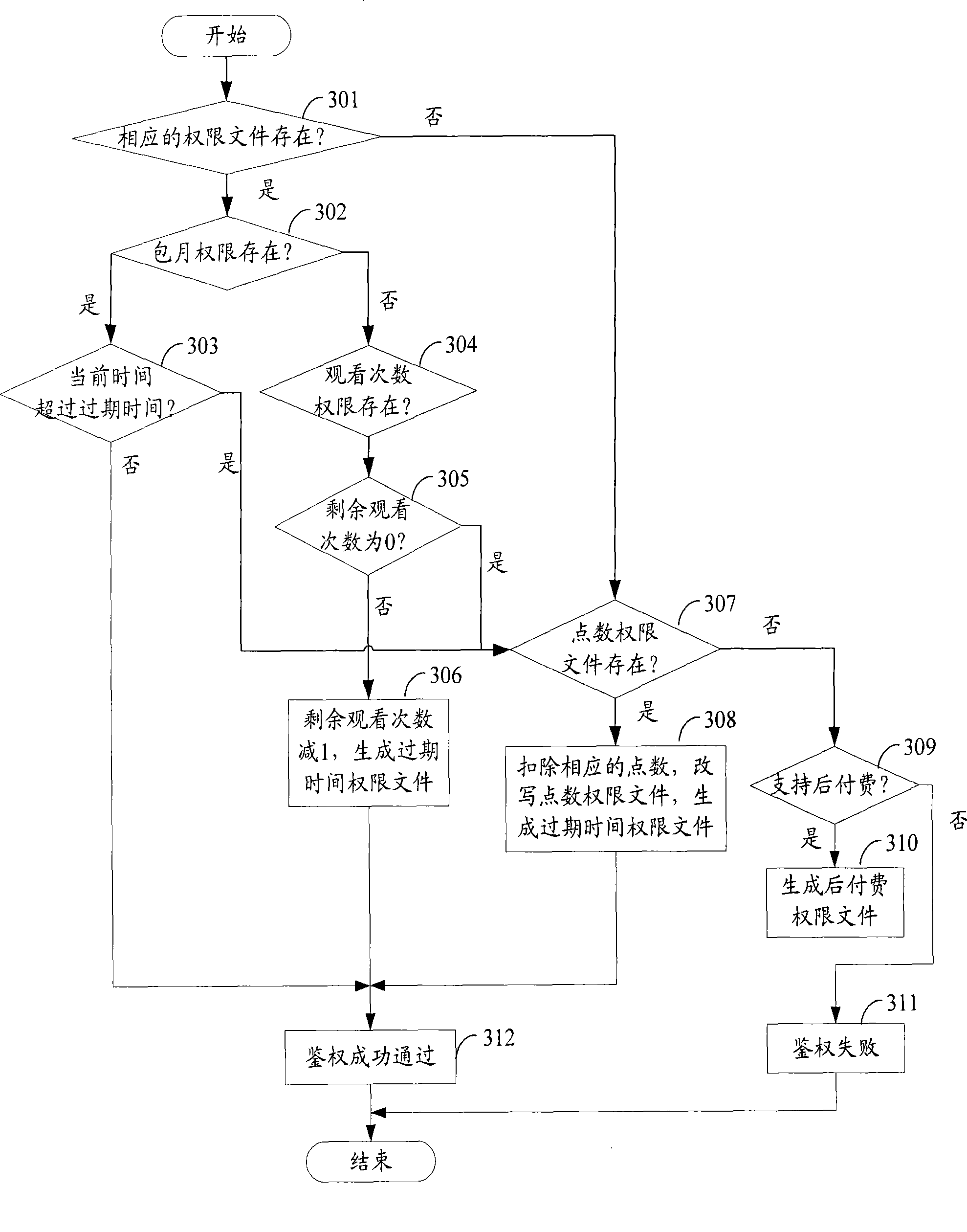
InactiveCN101420696AAuthentication IntegrityIntegrity guaranteedUser identity/authority verificationBroadcast-related systemsConditional accessAuthorization
The invention discloses a method used for online issuing authentication information; the method is used for issuing the authorization information to a condition accepting (CA) mobile terminal; the CA mobile terminal comprises a mobile terminal and a card which are connected with each other by an interface; the method comprises the steps as follows: firstly, the CA system signs the authorization information, gains the signature information of the authorization information, and issues the signature information and the authentication information to the mobile terminal; subsequently, the mobile terminal sends the signature information and the authentication information to the card; finally, the card verifies the signature information; if the verification is successful, the authentication information is memorized in the safety area of the card, thus ensuring the safety of the authentication information. The invention also discloses a system used for online issuing of the authorization information corresponding to the method. The method and the system can ensure the safety of the authorization, information, reduce the operation charges of the terminal side and the cost of the mobile terminal.
Owner:POTEVIO INFORMATION TECH
Authentication method
InactiveCN101640591ANot easy to forgetImprove securityUser identity/authority verificationComputer securityOne-time password
Owner:SIEMENS CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com