Method for identification of equipment validity
A technology of legality authentication and equipment, applied in the field of information security, it can solve the problems of system paralysis, widespread data dissemination, and inability to modify rights, etc., to achieve the effect of authentication security and increase the difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
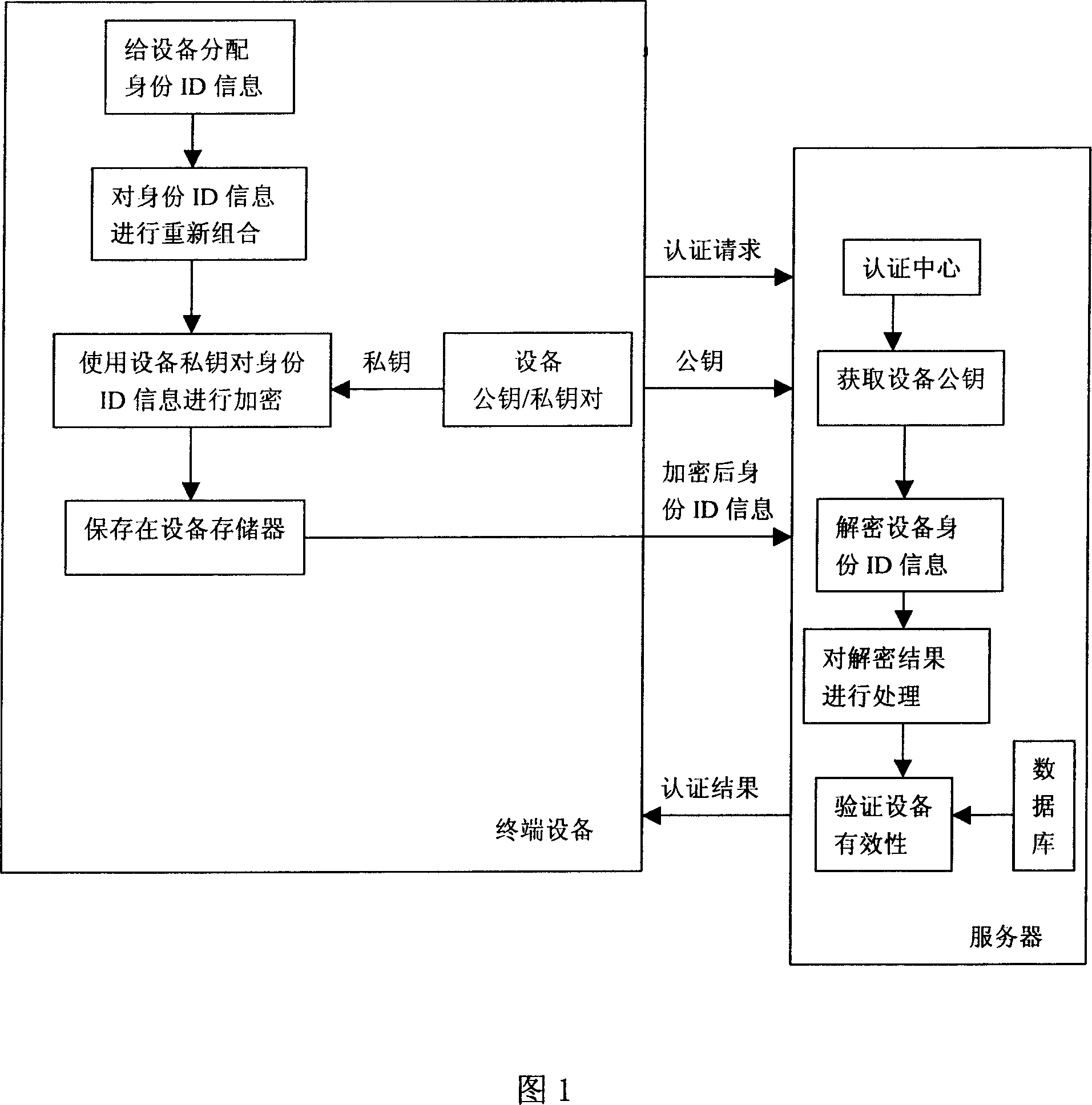
[0033] As shown in Figure 1, in order to prevent the information about the device from being falsified, the device legality authentication method that uses the device public key / private key to encrypt the device identity ID information includes the following steps:
[0034] The device side of the terminal:
[0035] 1) The device generates a public / private key pair and sends the public key to the server;
[0036] 2) The device re-encodes its original ID information to generate encoded ID information;
[0037] 3) The device encrypts the encoded ID information with the device private key to generate encrypted ID information and save it in the device memory.
[0038] Server side:
[0039] 1) The authentication center of the server receives the authentication request of the device;
[0040] 2) The server obtains the encrypted identity ID information stored in the device memory;
[0041] 3) The server decrypts the encrypted identity ID information with the device public key to o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com