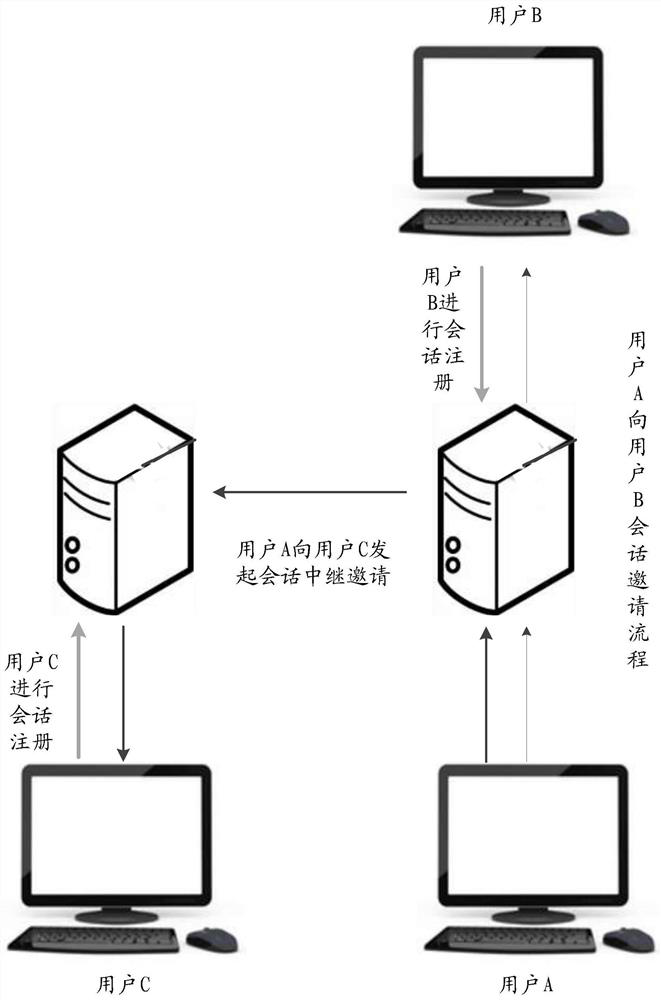
A kind of SIP user authentication method and device
A user authentication and user technology, applied in the field of network security, can solve problems such as low authentication efficiency, and achieve the effect of improving authentication efficiency and solving low authentication efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
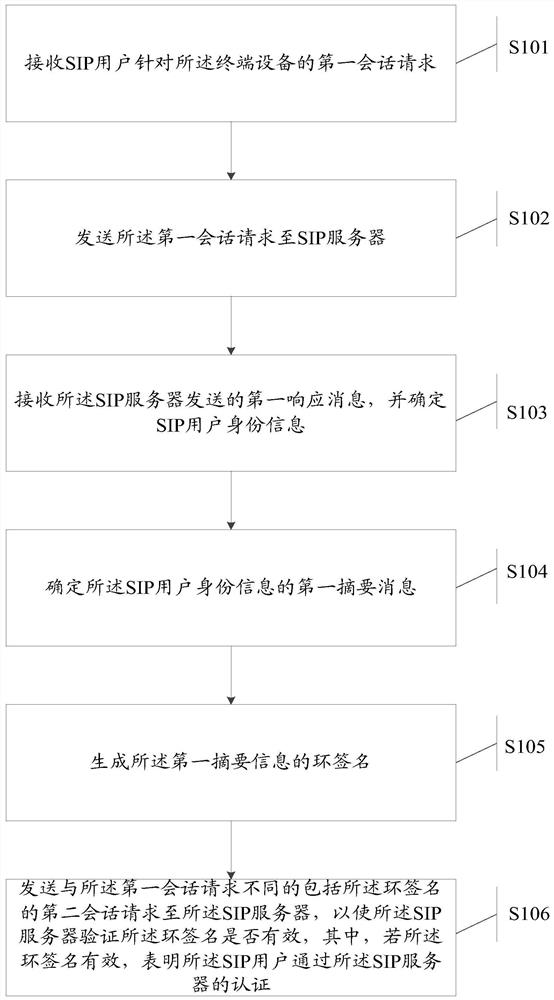
[0090] Please refer to figure 2 , Embodiment 1 of the present invention provides a session initiation protocol SIP user authentication method applied to a terminal device, including:
[0091] S101: Receive a first session request from a SIP user for the terminal device;
[0092] S102: Send the first session request to a SIP server;
[0093] S103: Receive the first response message sent by the SIP server, and determine the SIP user identity information;
[0094] S104: Determine the first summary message of the SIP user identity information;
[0095] S105: Generate a ring signature of the first digest message;
[0096] S106: Send a second session request including the ring signature different from the first session request to the SIP server, so that the SIP server can verify whether the ring signature is valid, wherein, if the ring signature is valid , indicating that the SIP user has passed the authentication of the SIP server.
[0097] In the specific implementation proc...
Embodiment 2
[0232] Based on the same inventive concept as Embodiment 1 of the present invention, please refer to Image 6 , the embodiment of the present invention also provides a session initiation protocol SIP user authentication device, which is applied to a terminal device, including:
[0233] The first receiving unit 10 is configured to receive a first session request from a SIP user for the terminal device;
[0234] A first sending unit 20, configured to send the first session request to a SIP server;
[0235] The second receiving unit 30 is configured to receive the first response message sent by the SIP server, and determine the SIP user identity information;
[0236] A determining unit 40, configured to determine the first summary message of the SIP user identity information;
[0237] A generating unit 50, configured to generate a ring signature of the first digest message;
[0238] The second sending unit 60 is configured to send a second session request including the ring si...
Embodiment 3
[0245] Based on the same inventive concept as Embodiment 1 of the present invention, please refer to Figure 7 , the embodiment of the present invention also provides a session initiation protocol SIP user authentication method applied to a SIP server, including:
[0246] S301: Receive a first session request sent by a SIP user for a terminal device;
[0247] S302: Send a first response message to the terminal device based on the first session request, so that the terminal device generates a ring signature of a first digest message of SIP user identity information;
[0248] S303: Receive a second session request sent by the terminal device that is different from the first session request and includes the ring signature, and verify whether the ring signature is valid, wherein if the ring signature is valid, it indicates that the SIP The user passes the authentication of the SIP server.
[0249] Steps S301 to S303 have been described in detail in Embodiment 1, and will not be ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com