Information terminal appts. and identification system
An information terminal and authentication system technology, applied in the field of information terminal devices and authentication systems, can solve the problems of increased chances of being rejected, difficulty in obtaining identification results, etc., and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0054] The first embodiment is as followsfigure 1 shown.
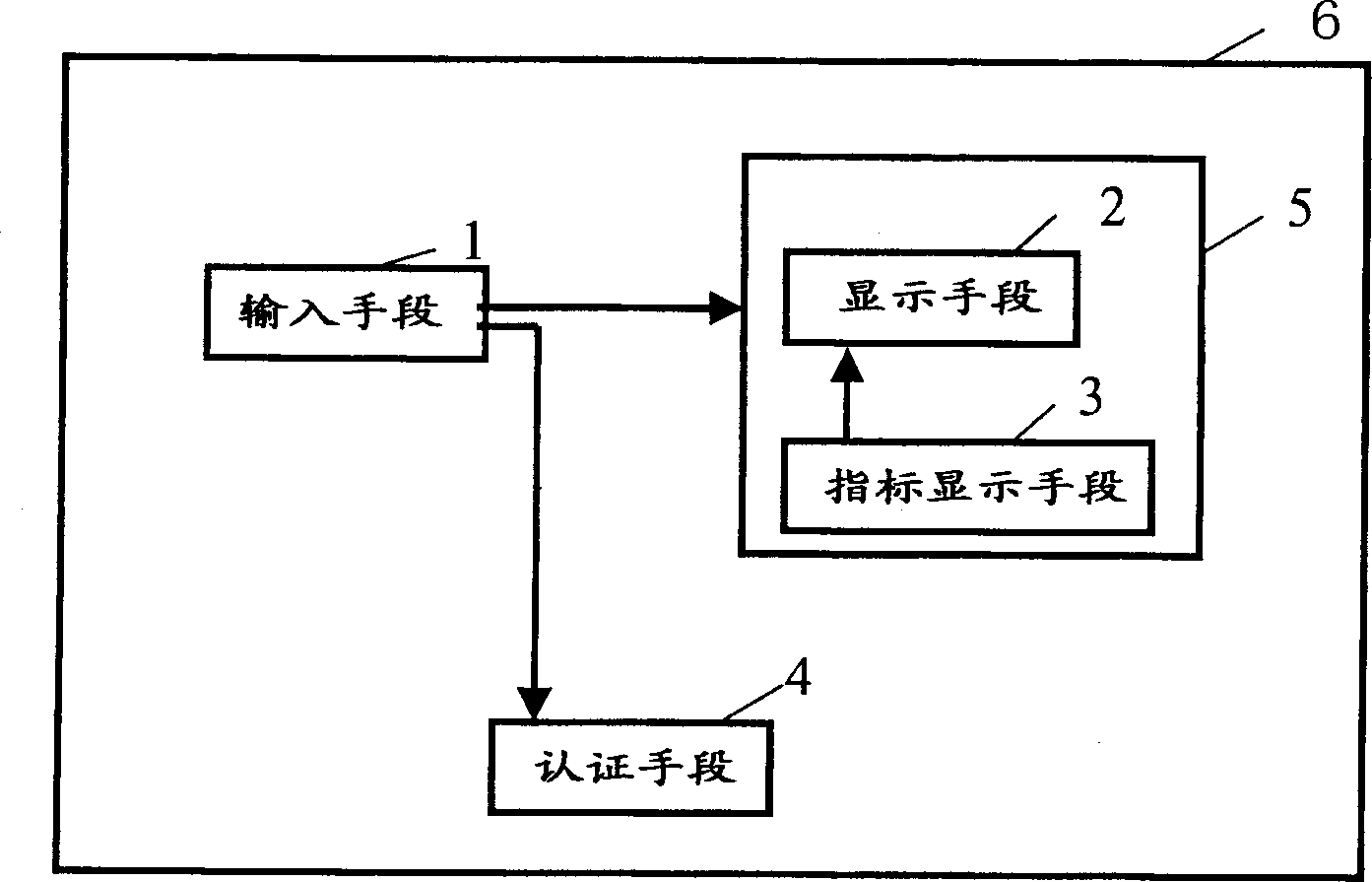
[0055] figure 1 It shows the functional structure diagram of the information terminal device 6 with an authentication function of this invention. figure 1 The information terminal device 6 with the authentication function is equipped with an input means for inputting human body information, a display means 2 for displaying the inputted human body information, an authentication means 4 for authenticating pre-registered users according to the inputted human body information, and has the ability to perform personal identification based on the human body information. The information terminal device 6 with the function of authentication, the display means 2 is equipped with the range index display means 3 for displaying the size and position of the human body information to be input, the rectangular range or the index of two points, etc. The human body information confirming means 5 constitutes.
[0056] The information t...
Embodiment 2
[0095] The configuration of Embodiment 2 of the present invention will be described.
[0096] The difference from the structure of the first embodiment is that the structure of the mobile phone 1002 is the same as that of the server 301 for registration, and the other structures are the same. Therefore, in Example 2 with reference to Figure 11 , FIG. 12 only explains the structure different from that of the first embodiment.
[0097] The difference in the configuration of the mobile phone 1002 is that a speaker authentication section 23 for authentication using the speaker's voice is added. The speaker authentication part 23 uses the registered voice read out from the IC card 50 through the IC card reading interface 51 and the research result read out from the research completed function storage part 25 by the research completion function storage part 25 storing the result of the research registration voice. An authenticating section 24 for authenticating a speaker's voice ...
Embodiment 3
[0118] refer to Figure 17 The configuration of Embodiment 3 of the present invention will be described.
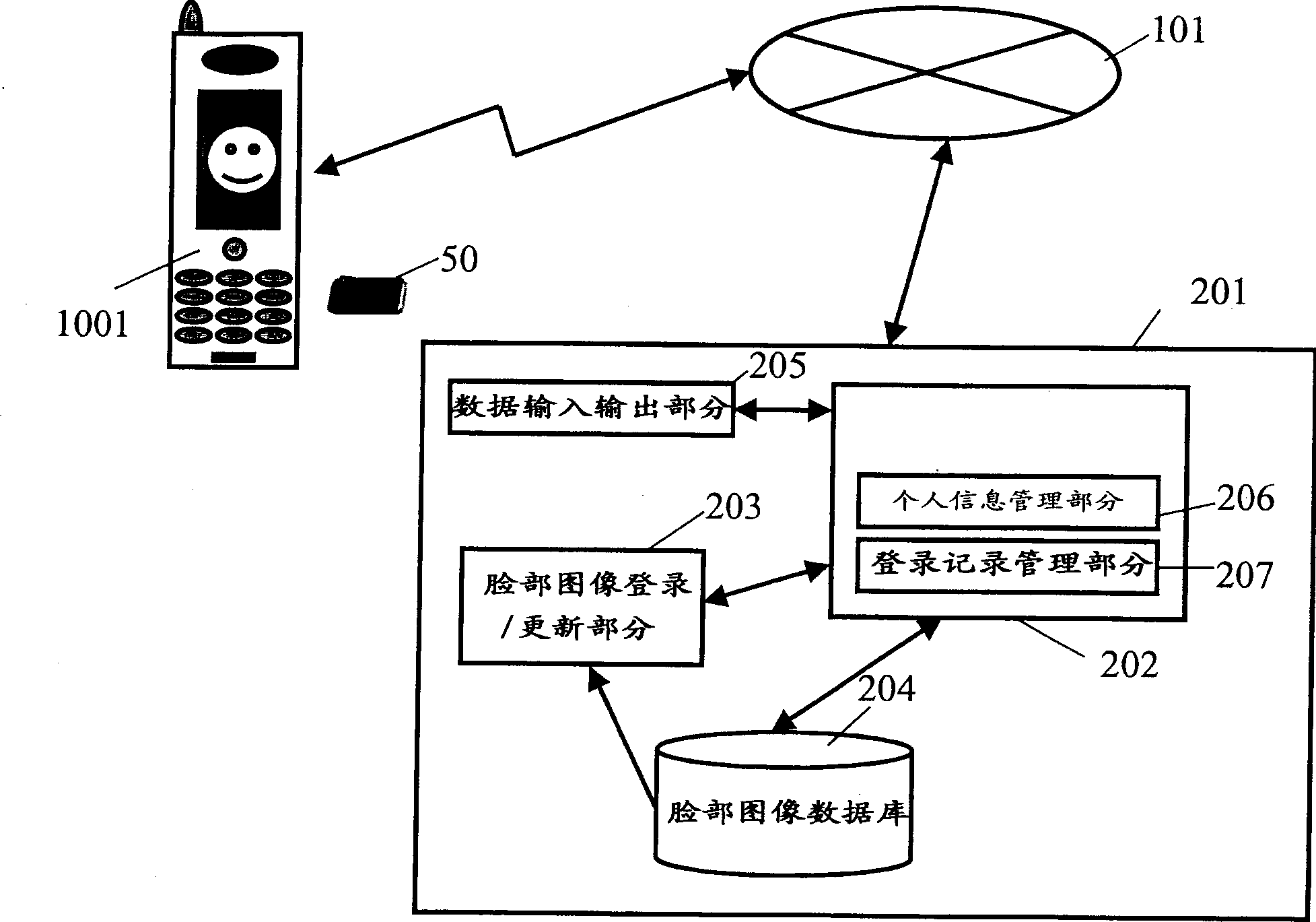
[0119] The difference from the configuration of Embodiment 1 is that an authentication function exists in the login / authentication server 401 .
[0120] exist Figure 17 In the structure, the mobile phone 1003 and the login / authentication server 401 are connected through the network. The login and authentication server 401 is composed of a system management section 402 that manages the entire login and authentication server 401, a login and authentication section 403 that conducts login research and authentication of facial images, and a facial image database 404 that stores facial images of users. The management part 402 is composed of a personal authentication support part 405 that implements facial image authentication manually, a personal information storage part 406 that includes the address, name, phone number, and login date of the logged-in user, and an authenti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com