Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
736 results about "Conditional access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
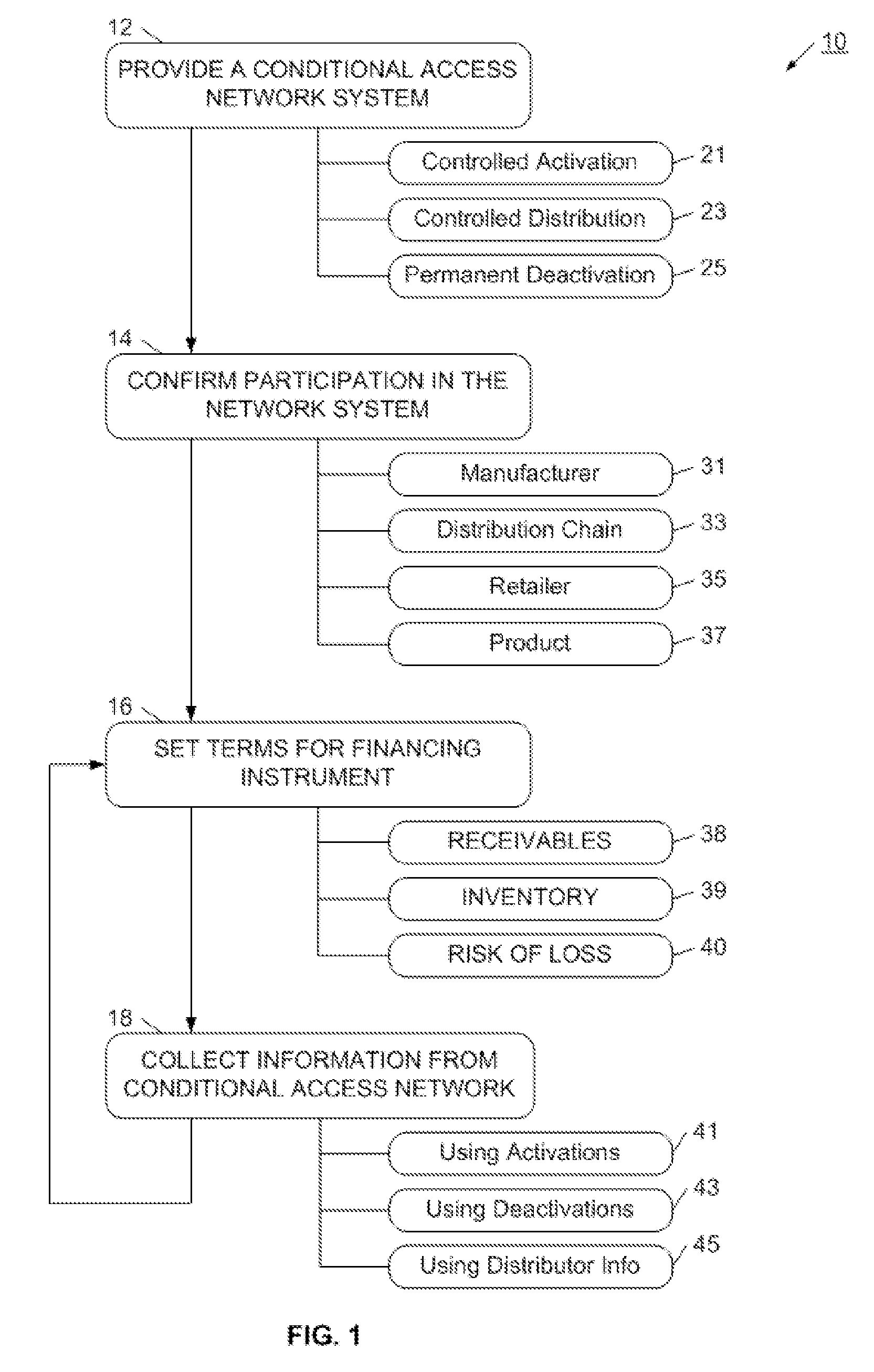
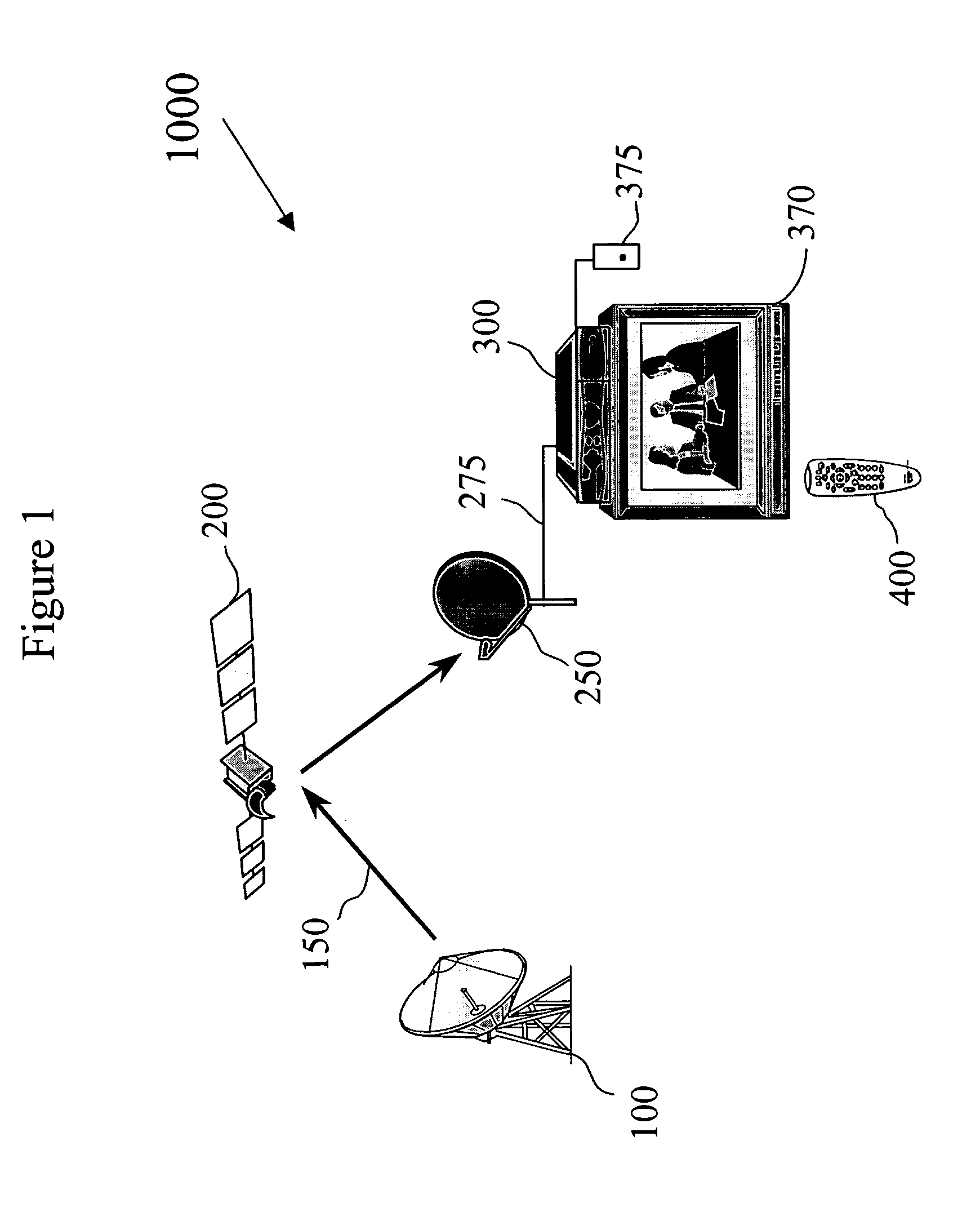
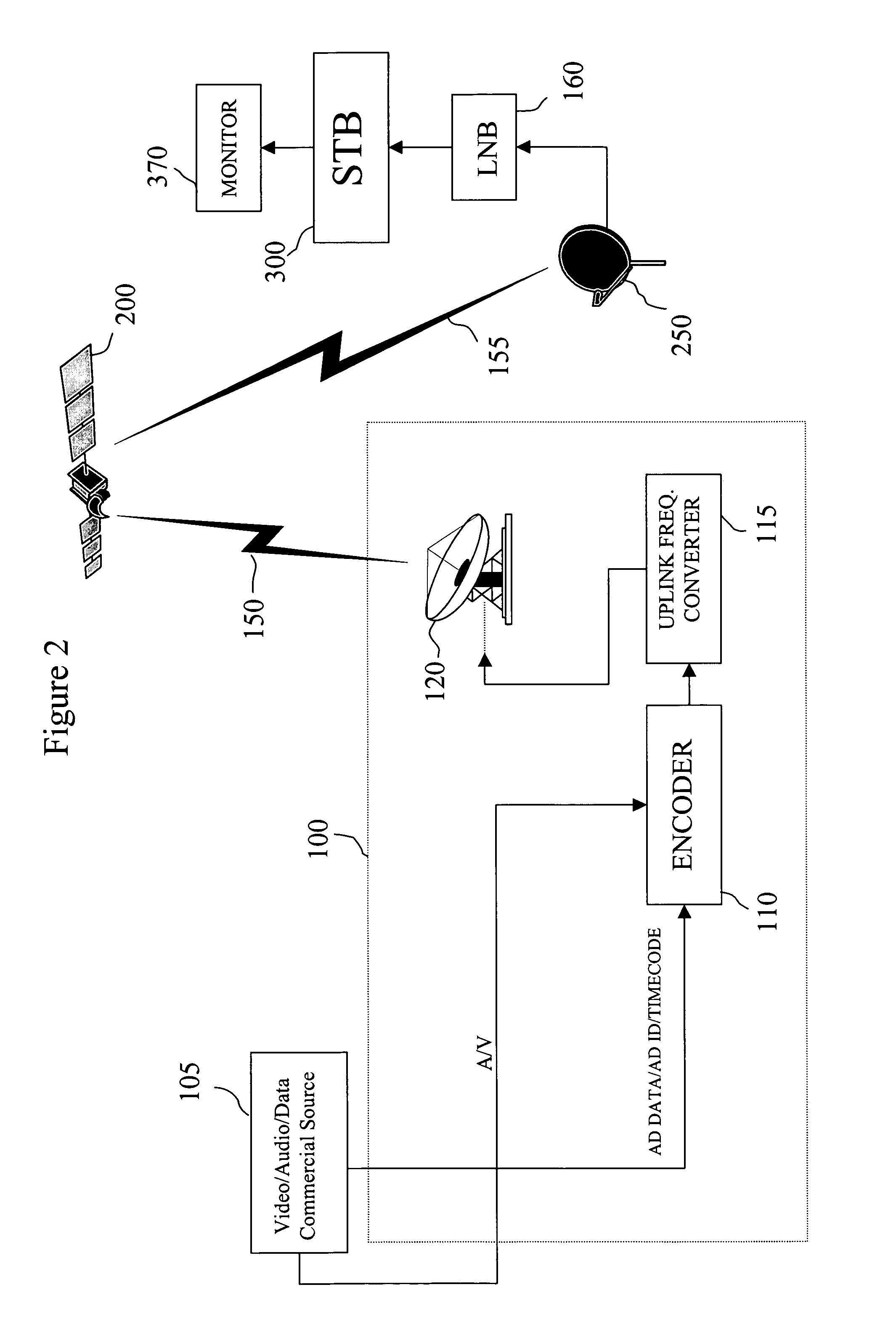
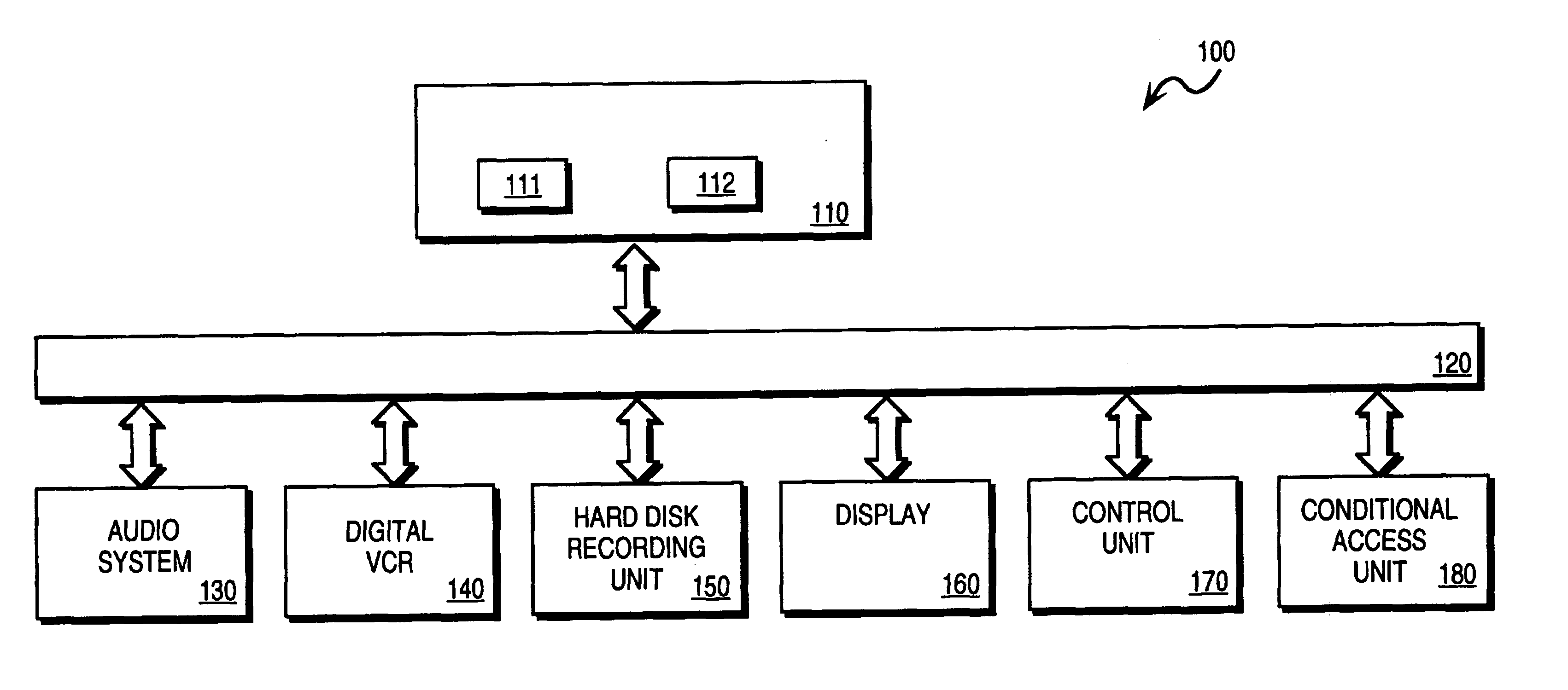
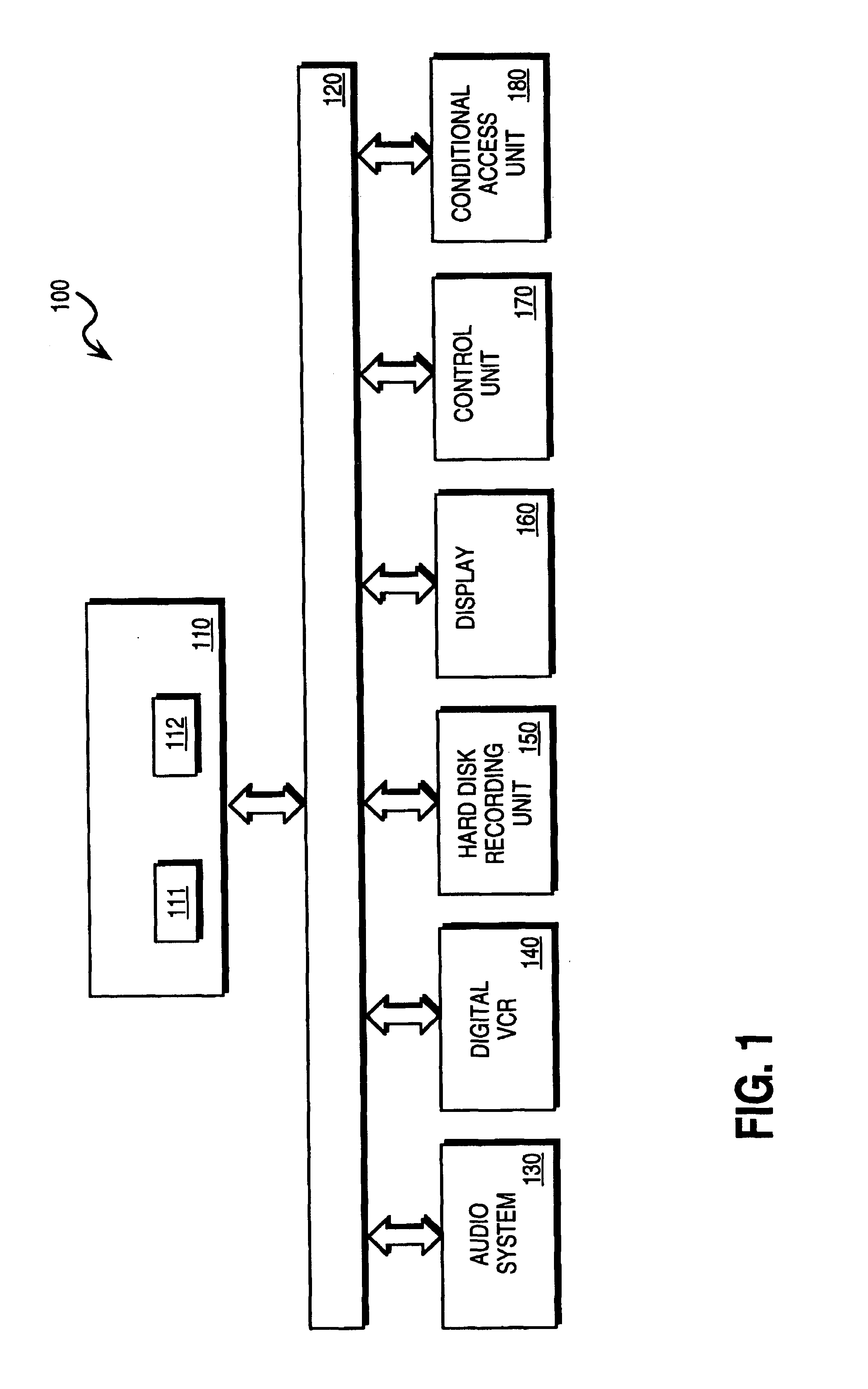
Conditional access (abbreviated CA) or conditional access system (abbreviated CAS) is the protection of content by requiring certain criteria to be met before granting access to the content. The term is commonly used in relation to digital television systems and to software.
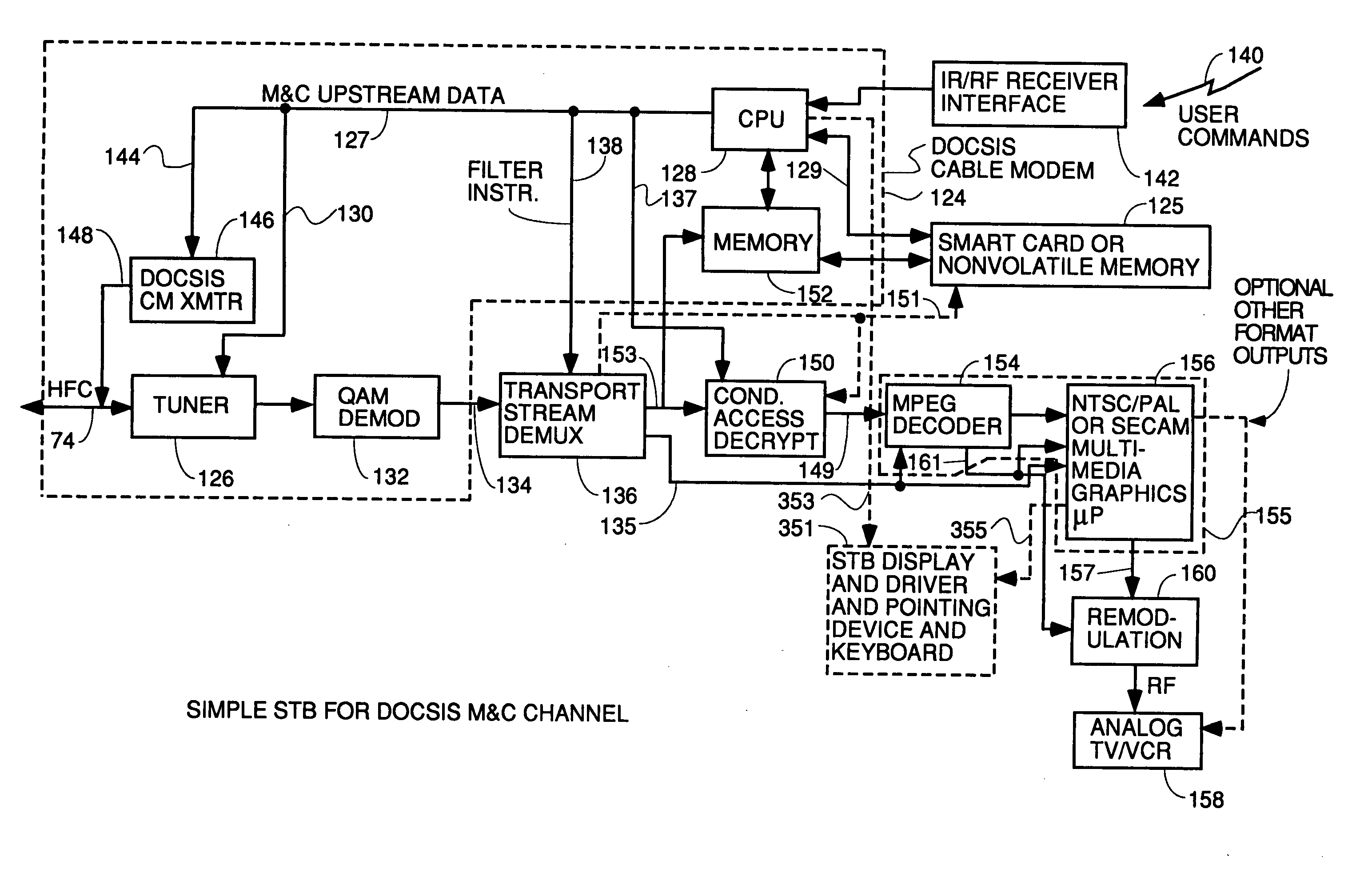
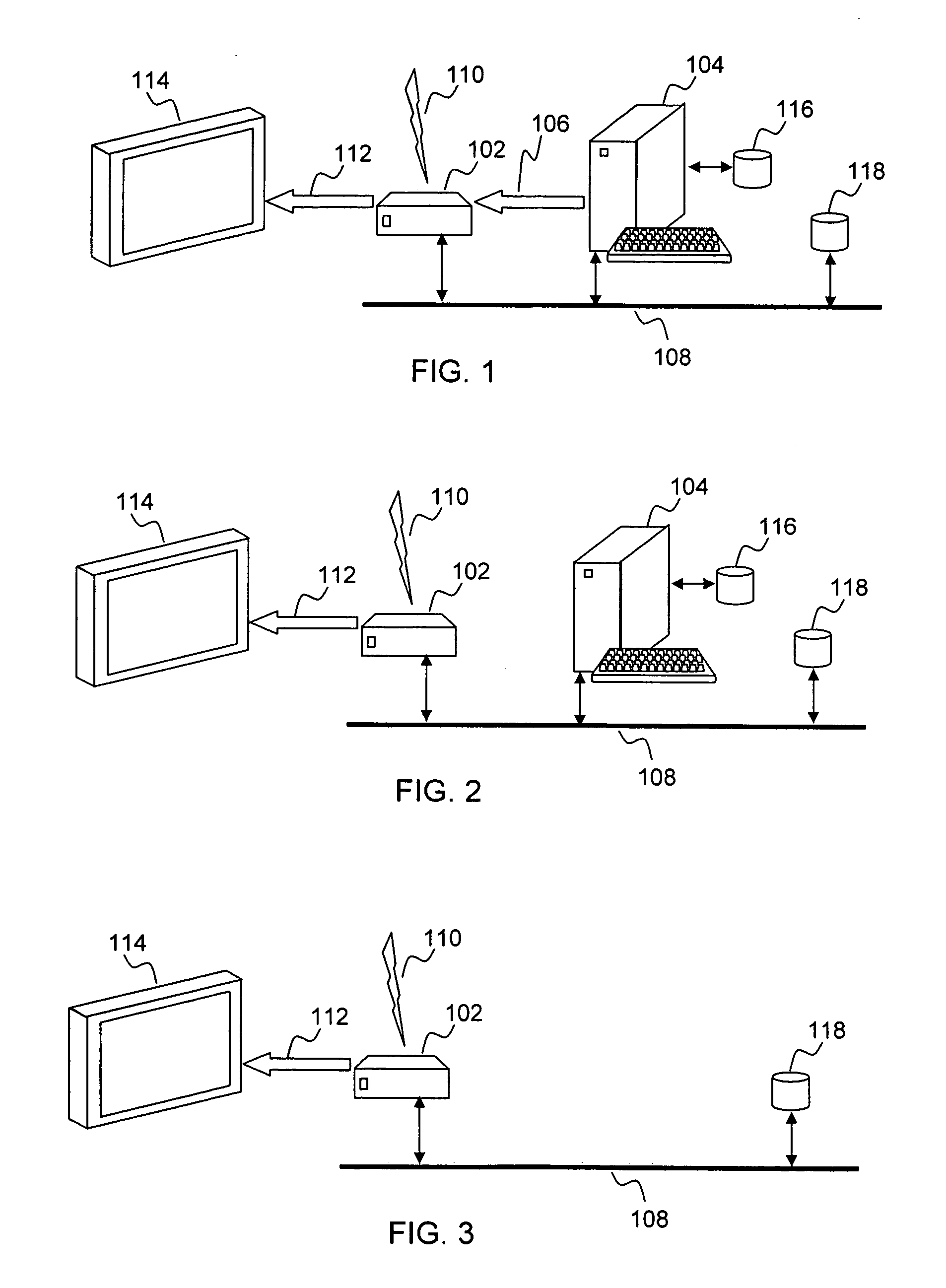
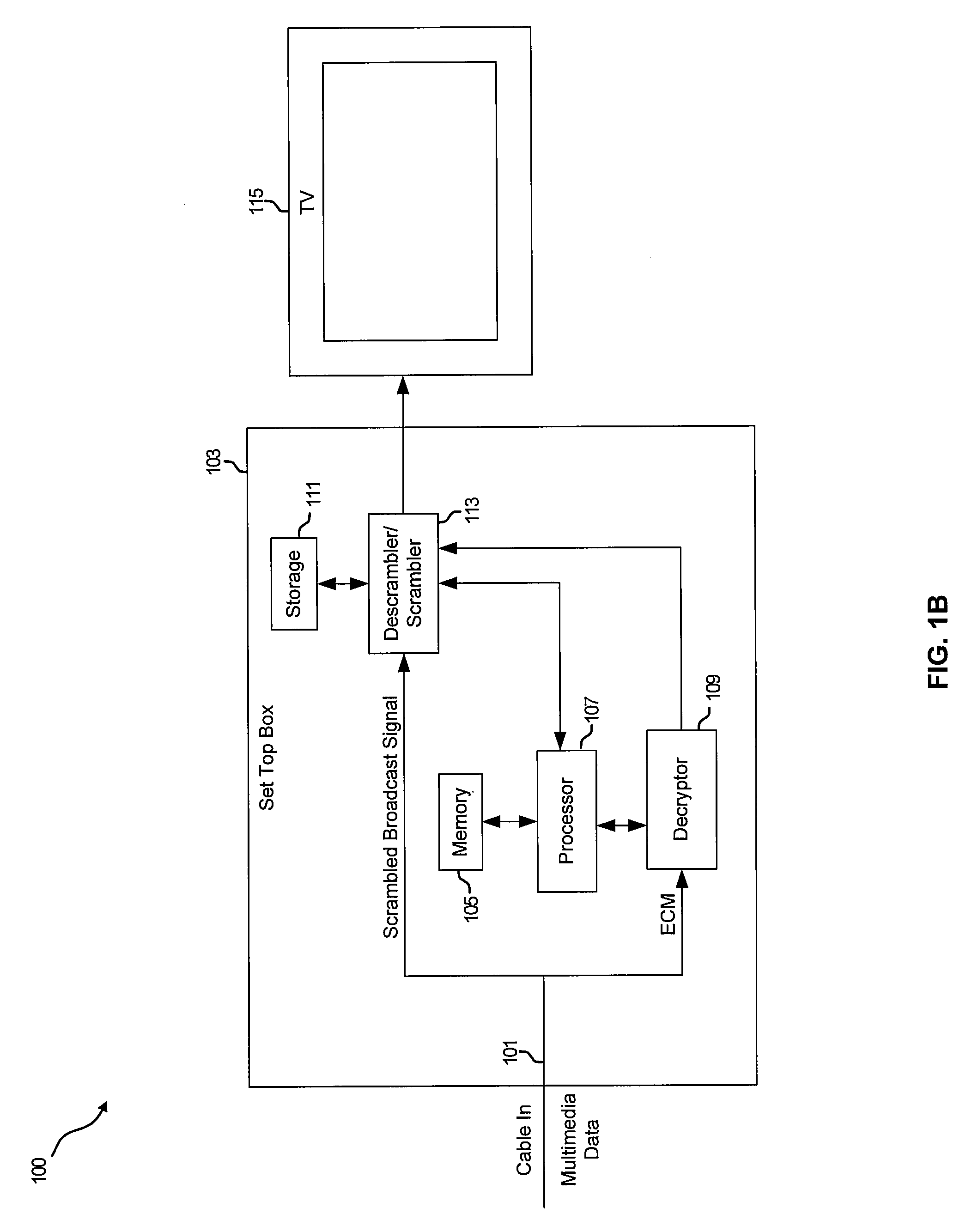
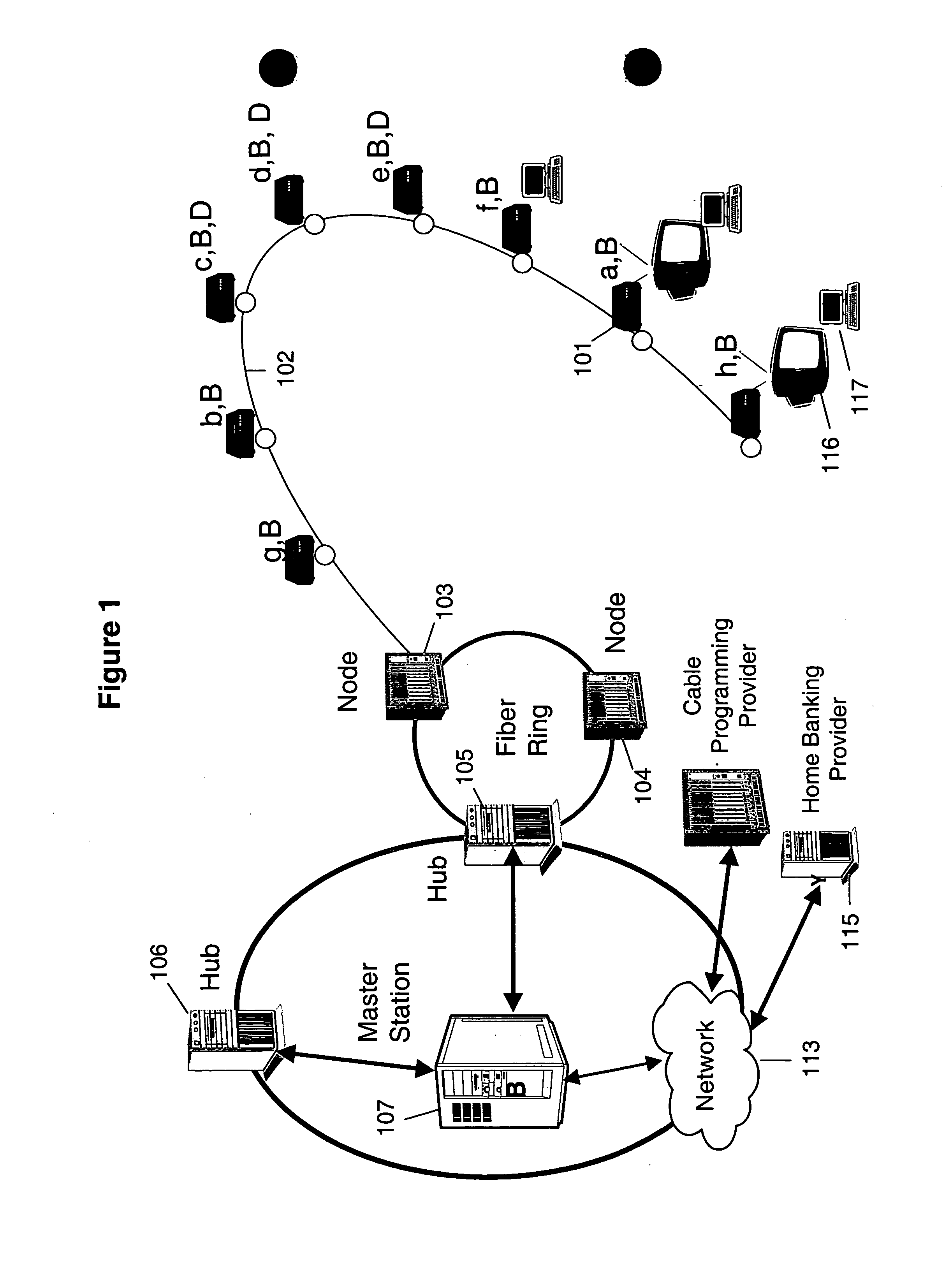
Thin DOCSIS in-band management for interactive HFC service delivery
InactiveUS20040181800A1Simple processLess-expensive to buildAnalogue secracy/subscription systemsTwo-way working systemsModem deviceConditional access
Circuitry and processes carried out thereby are disclosed for implementing simple single tuner set top box decoders which do not require a separate tuner for an out of band management and control channel. Removable smart card conditional access circuitry and replaceable modules having decoding circuitry for different compression schemes and encoding circuitry for different format television circuits is disclosed. An embodiment with a single tuner and a full DOCSIS compatible modem which can interface to personal computers, etc. is also disclosed to make the set top box a simple, inexpensive home gateway is also disclosed.
Owner:TERAYON COMM SYST
Secure integrated media center
InactiveUS20050125357A1Safe storageTelevision system detailsUnauthorized memory use protectionHard disc driveHigh definition tv
A set-top media system is disclosed which can be combined with an open architecture personal computer (PC) to provide a feature-rich secure integrated media center while meeting security rules of most major conditional access and content protection industry rules such as Cable Labs DFAST and PHILA agreements; and DTLA agreements for 5C-DTCP for IEEE1394, USB, and IP. The set-top media center and PC share common resources such as high definition display, remote control, hard disk drive, and other external unsecure storage devices. All media content is available seamlessly using a PC user interface, including controlled-content media such as high definition TV, within a PC desktop window. All controlled-content media is manipulated and managed within the set-top media system in a seamless manner. A novel mechanism is disclosed to allow controlled-content media to be stored on unsecure devices in encrypted form while overcoming the disk cloning attack problem for move operations.
Owner:SAADAT ABBAS SASAN +1
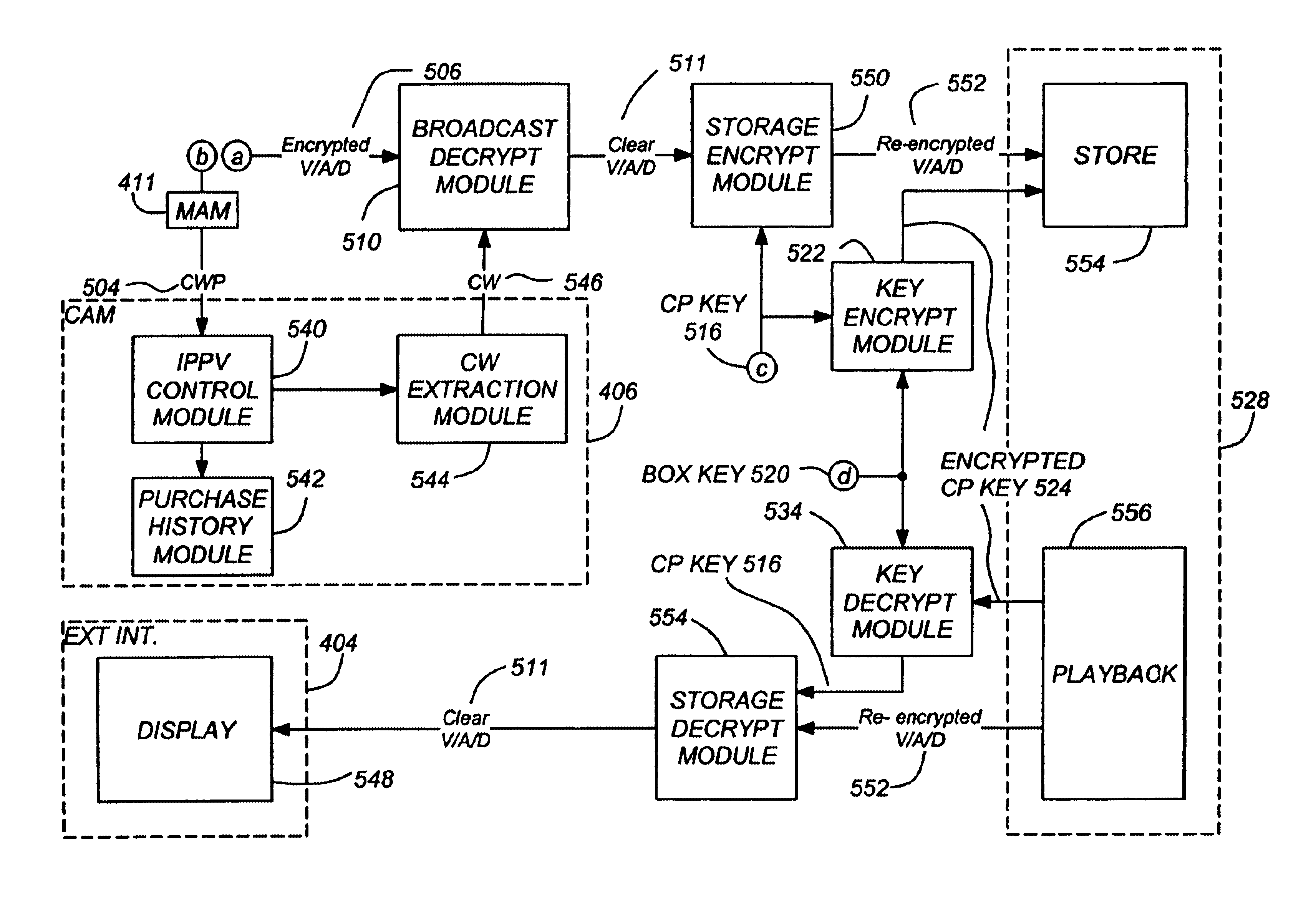
Video on demand pay per view services with unmodified conditional access functionality
InactiveUS6853728B1Eliminate concernsSafe storageBroadcast with distributionTelevision system detailsConditional accessVideo on demand
A system and method for storing and retrieving program material for subsequent replay is disclosed. The method comprises the steps of receiving access control information and the program material encrypted according to a first encryption key, the access control information including the first encryption key and control data; further encrypting the access control information and the encrypted program material according to a second encryption key; encrypting the second encryption key according to a third encryption key to produce a fourth encryption key; and storing the encrypted access control information and encrypted program material and the fourth encryption key.
Owner:DIRECTV LLC
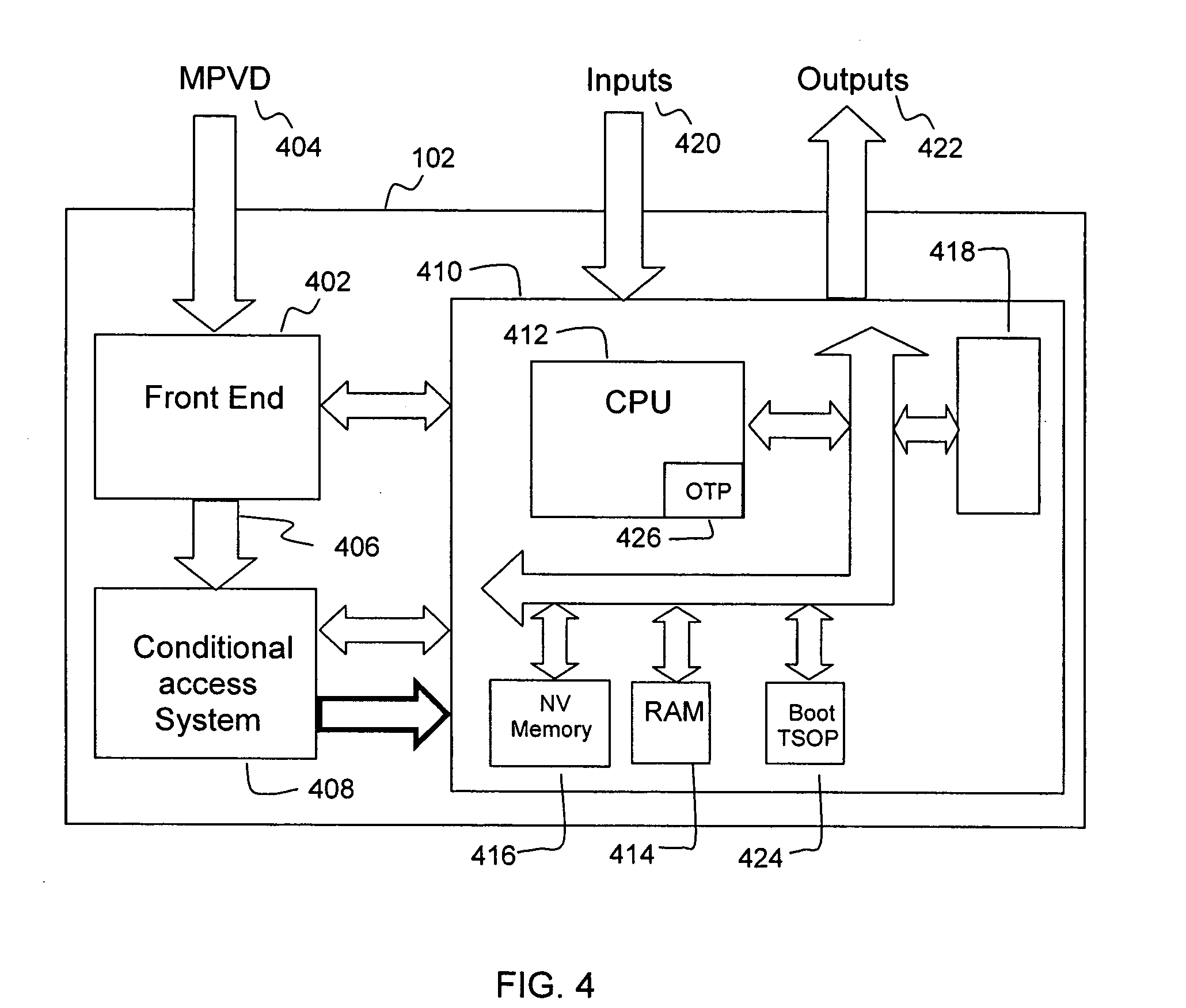
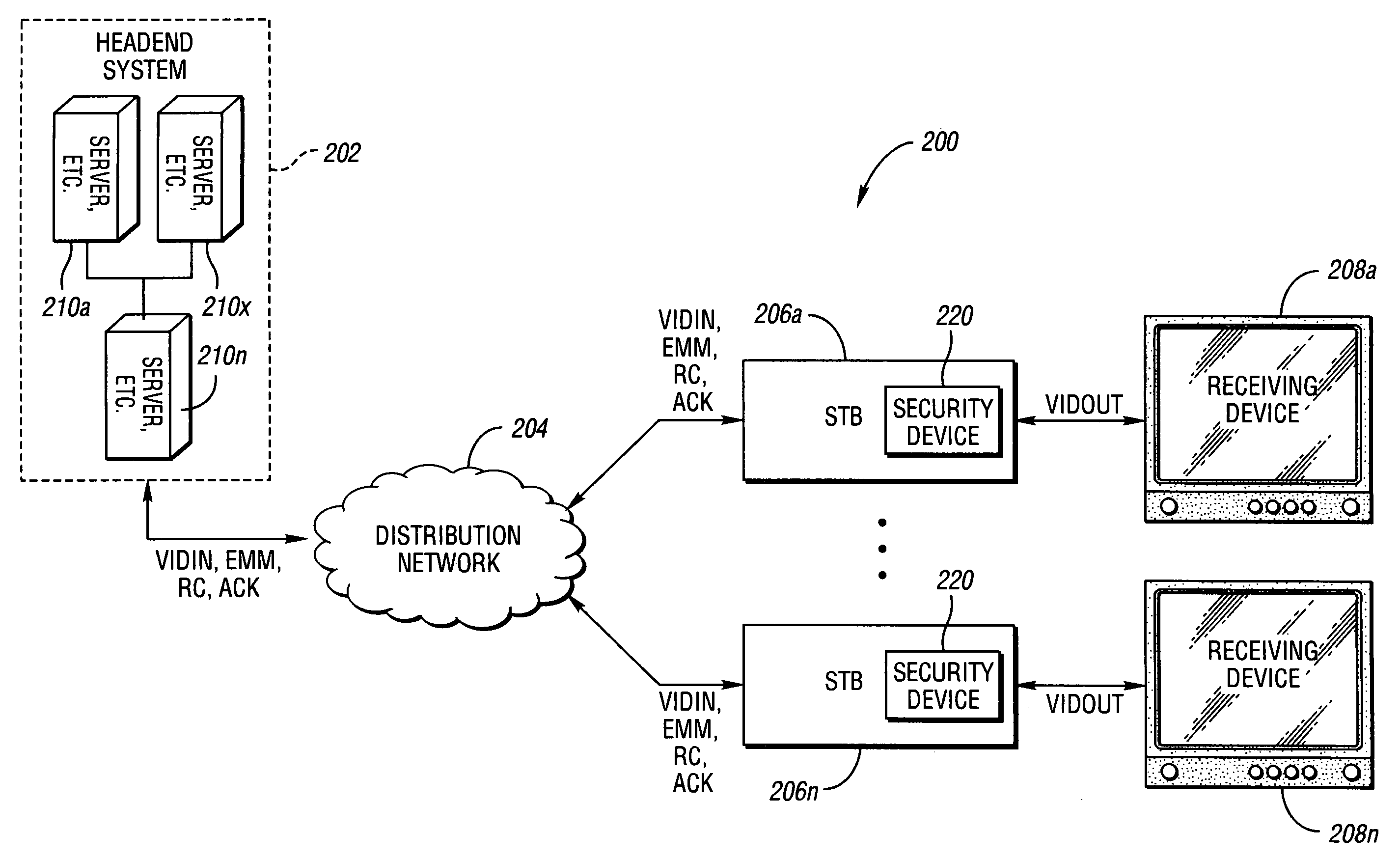
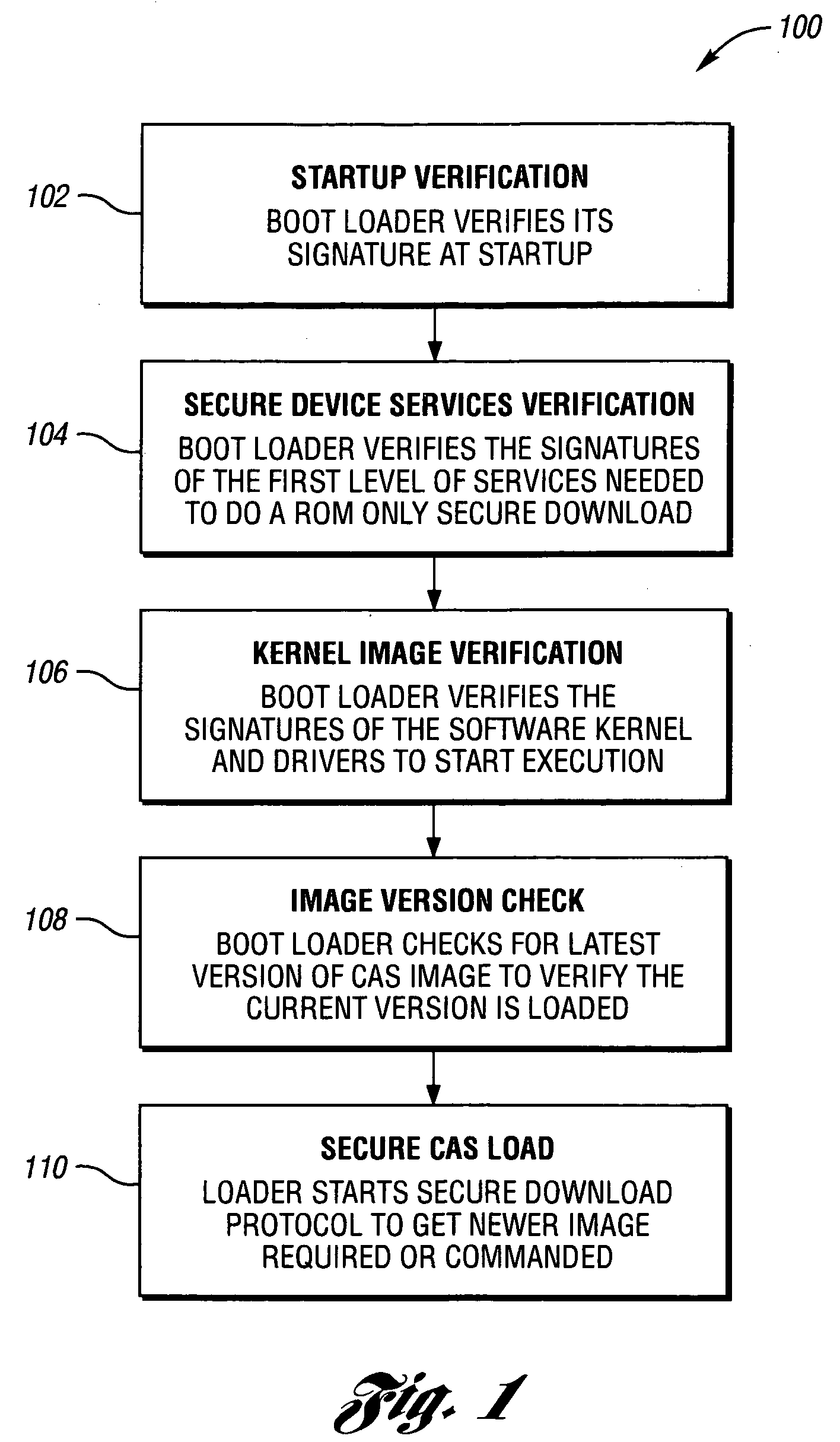
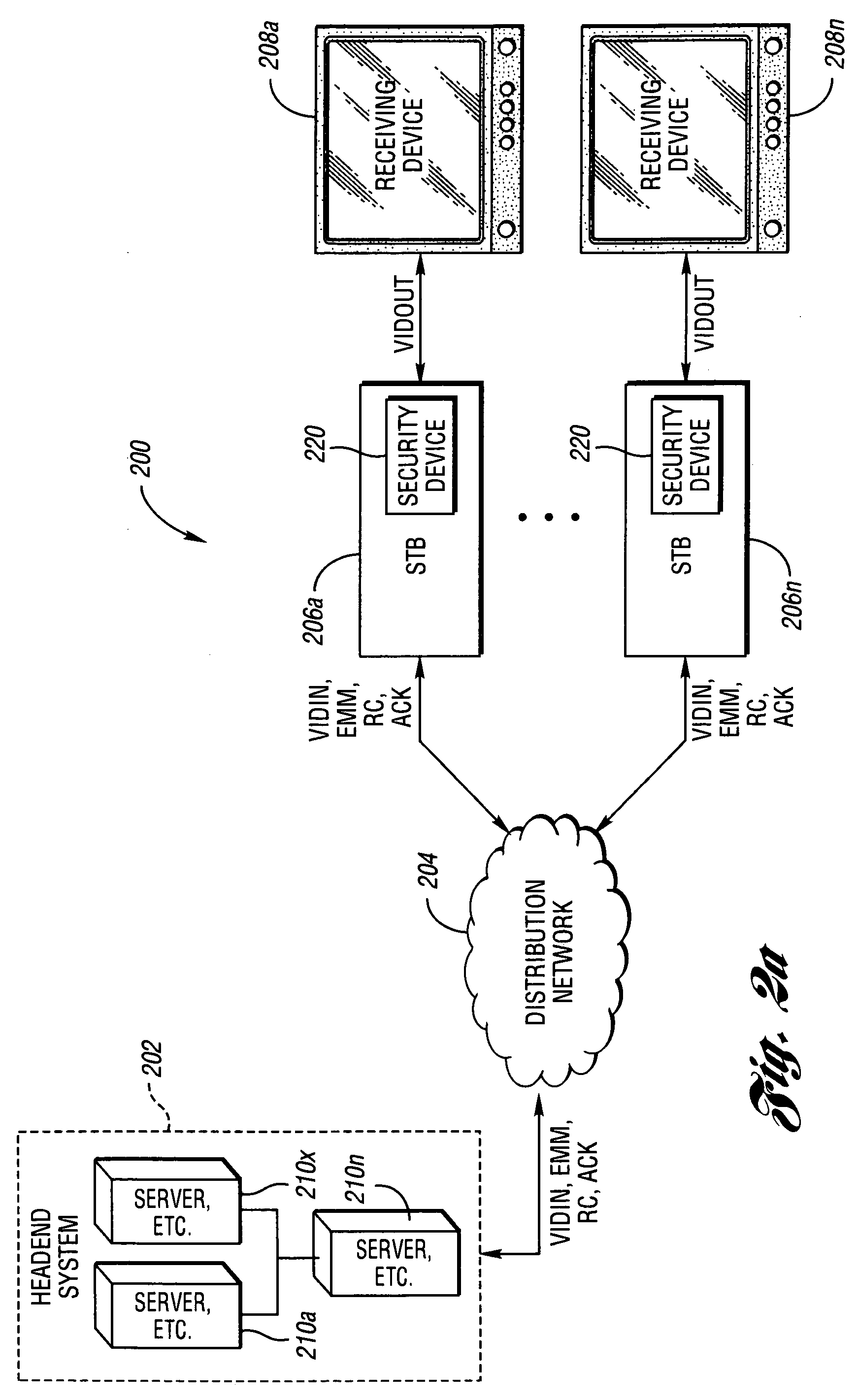
System and method for secure conditional access download and reconfiguration
ActiveUS20060137015A1Overcome deficienciesDigital data processing detailsUser identity/authority verificationSecurity softwareConditional access
A method of securely downloading at least one of conditional access software (CAS), Digital Rights Management software (DRMS), Trusted Domain Software (TDS), and Gaming Security Software (GSS) includes presenting a specialized entitlement management message (EMM) to initiate the download to a receiver security device using a supervisory logon key (SLK) split to logon with a second split contained inside the receiver security device, presenting a receiver digitally signed random challenge from the receiver security device to a sender security server to establish authentication of the receiver security device to the sender security server, and signing and returning the receiver random challenge from the sender security server to the receiver security device with a sender random challenge to establish authentication of the sender security server to the receiver security device.
Owner:COMCAST CABLE COMM LLC
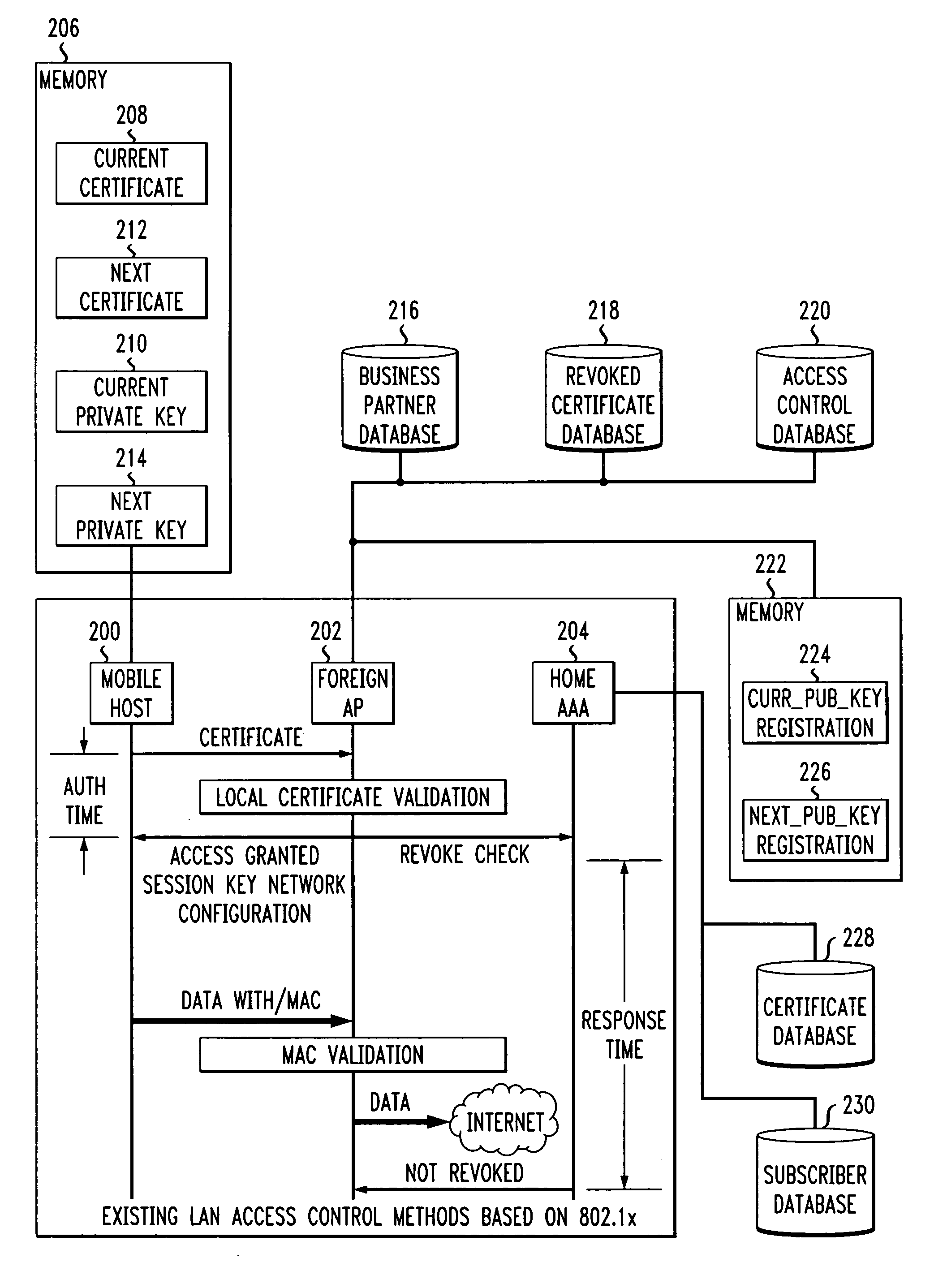
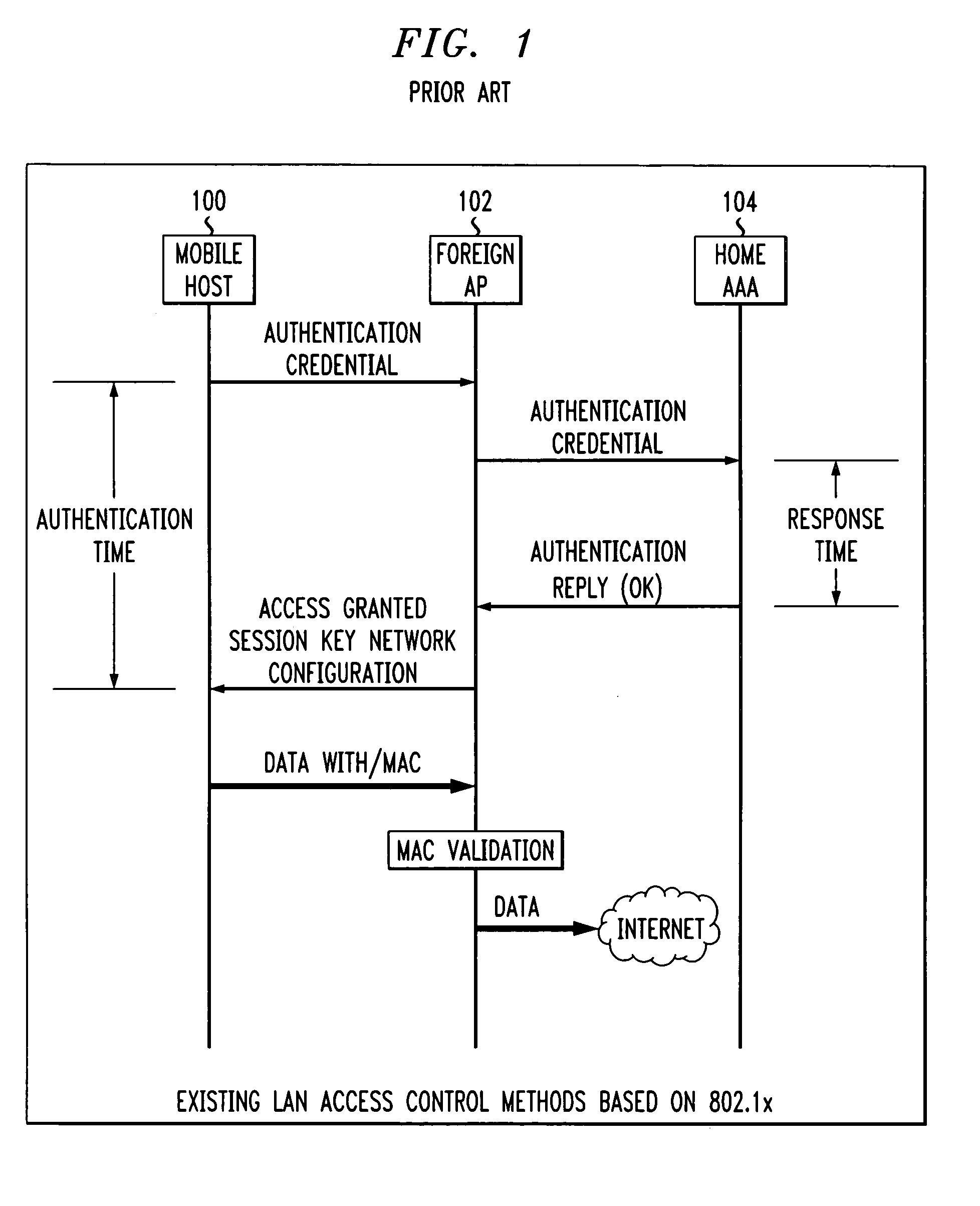
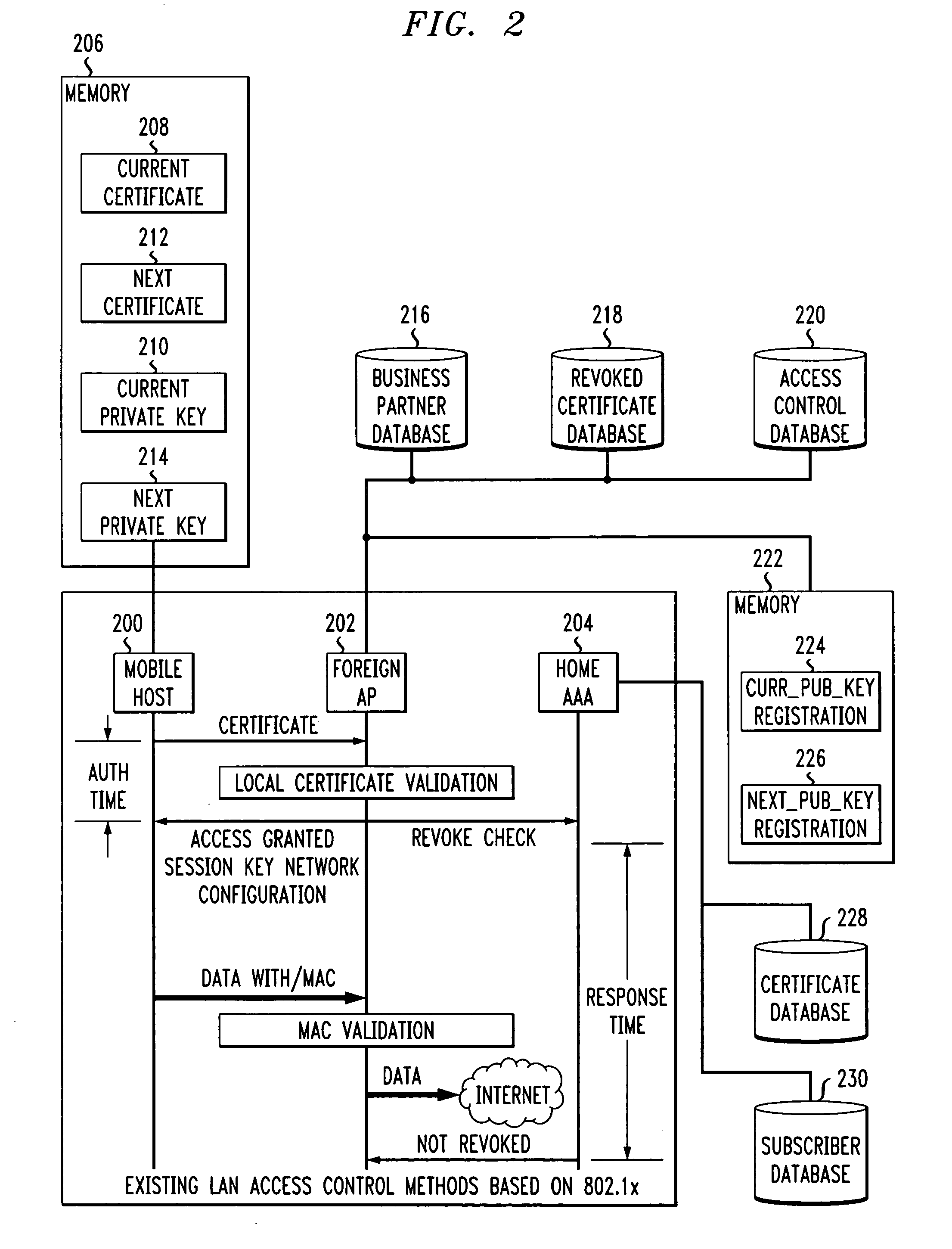
Fast authentication and access control system for mobile networking
InactiveUS6856800B1Easy to switchReduce certification timeUnauthorised/fraudulent call preventionEavesdropping prevention circuitsExpiration TimeWeb authentication
A fast authentication and access control method of authenticating a network access device to a communications network having an access point communicating with a remote authentication (home AAA) server for the network access device. The method includes the step of receiving an access request having an authentication credential from the network access device at the access point. The authentication credential includes a security certificate having a public key for the network access device and an expiration time. The security certificate is signed with a private key for the remote authentication server. The access point locally validates the authentication credential by accessing the public key of the remote authentication server from a local database, and checking the signature and expiration time of the security certificate. If the authentication credential is validated at the access point, the access point grants the network access device conditional access to the network by sending an access granted message to the network access device. The access granted message includes a session key encrypted with a public key for the network access device. The session key is stored in a database associated with the access point. The access point contacts the remote authentication server to check a revocation status of the security certificate for the network access device. If the access point receives a message from the remote authentication server that the authentication credential for the network access device has been revoked, it suspends network access for the network access device.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
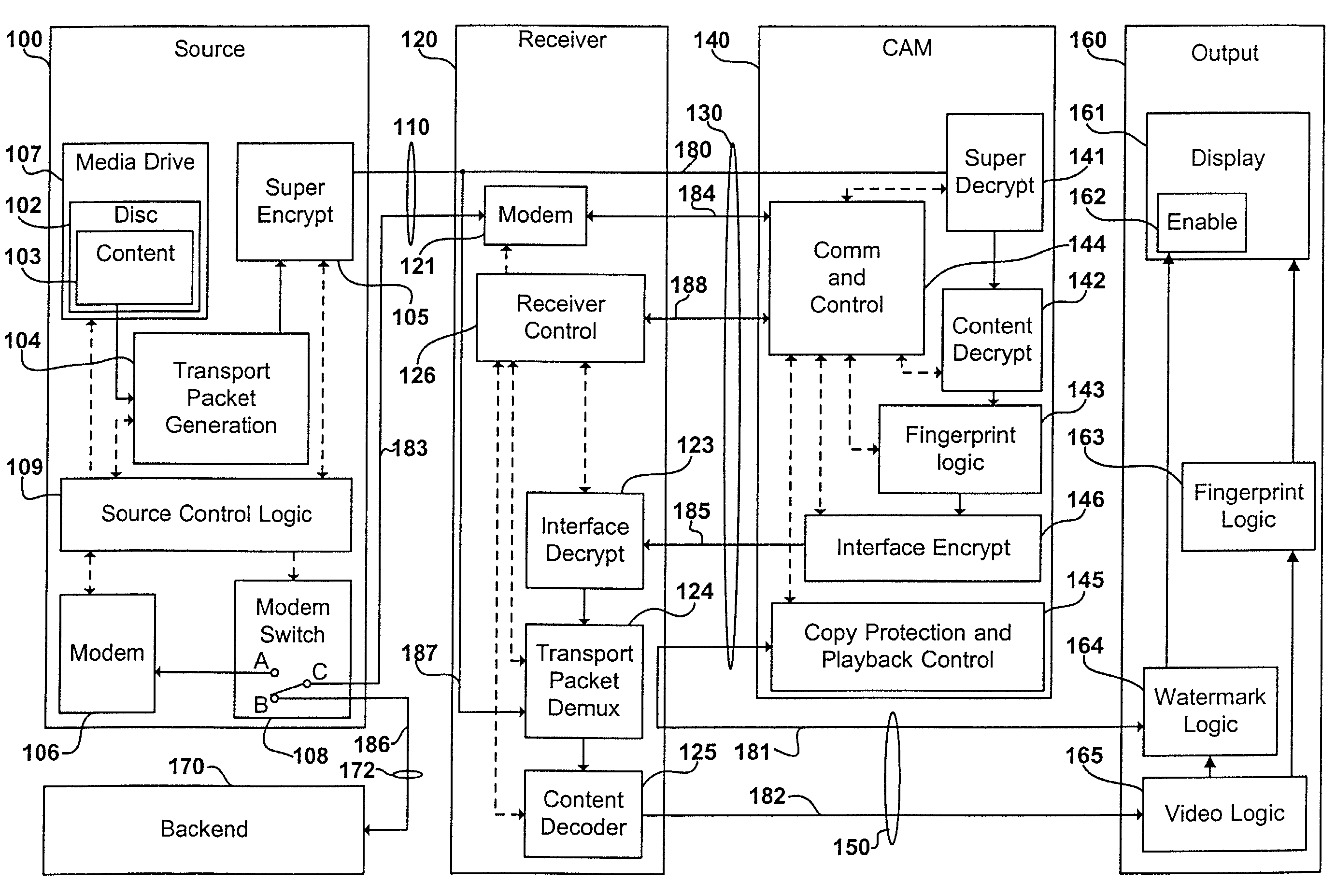
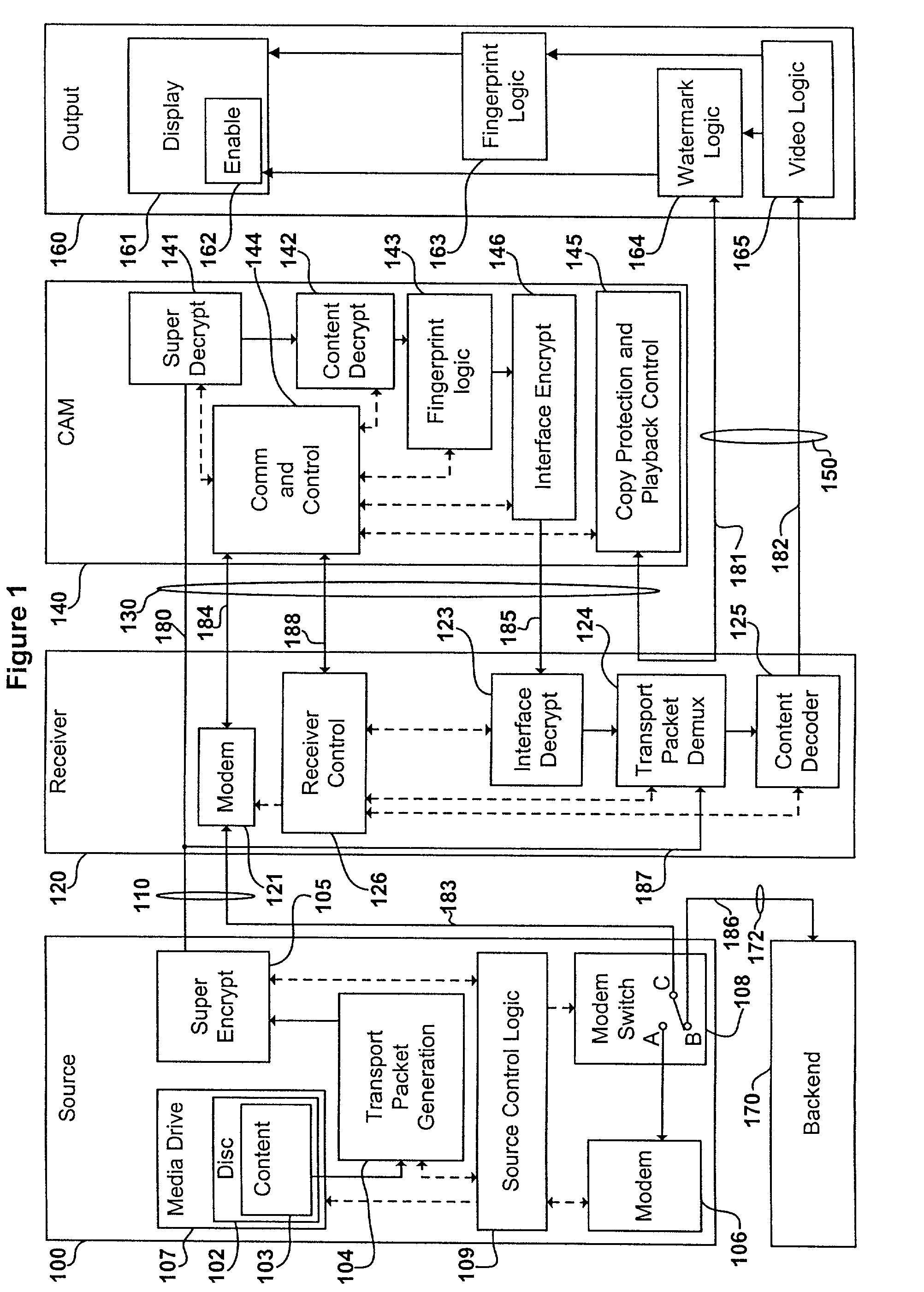
Digital content distribution system and method
InactiveUS7162642B2Prevent unauthorized accessObtaining unauthorized accessDigital data processing detailsUser identity/authority verificationContent distributionDigital content
A content distribution system and method which prevents unauthorized access to secured content such as movies and music. The apparatus includes a source, a receiver, an authorized security device such as a conditional access module (CAM) for decrypting authorized content, an output device for outputting content and a backend for managing accounts and system operations. One aspect of this invention provides a mechanism for providing secured content on a medium such as a DVD optical disc. These devices may verify that there is authorization to play the secured content, add watermarks to the secured content, convert the secured content to a displayable form and provide a means for preventing output of the secured content.
Owner:GOOGLE LLC
Conditional access to digital rights management conversion
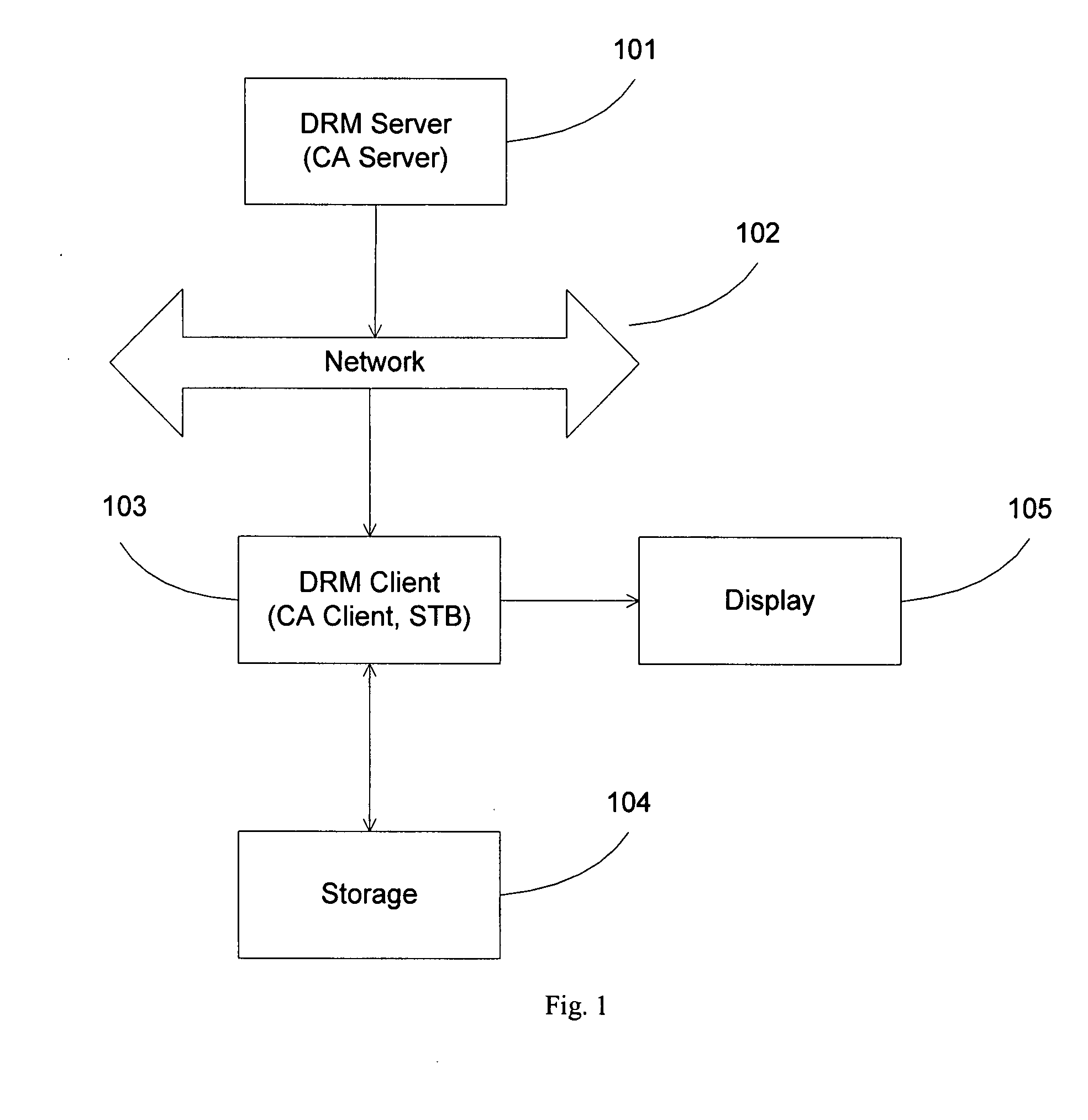
ActiveUS20050182931A1Drying solid materials with heatUser identity/authority verificationSecurity kernelDigital rights management system
The present invention provides for an interface between two seemingly incompatible and different content protection systems. Accordingly, protected content may be transferred between the respective security kernels of a conditional access (CA) and digital rights management (DRM) systems, while maintaining security of the content and any associated protection information. The transfer and consumption of protected content and the associated content protection information may be achieved by temporarily or permanently binding the respective security kernels of the CA and DRM systems, transcribing content protection information, and potentially transcribing the content.
Owner:MICROSOFT TECH LICENSING LLC
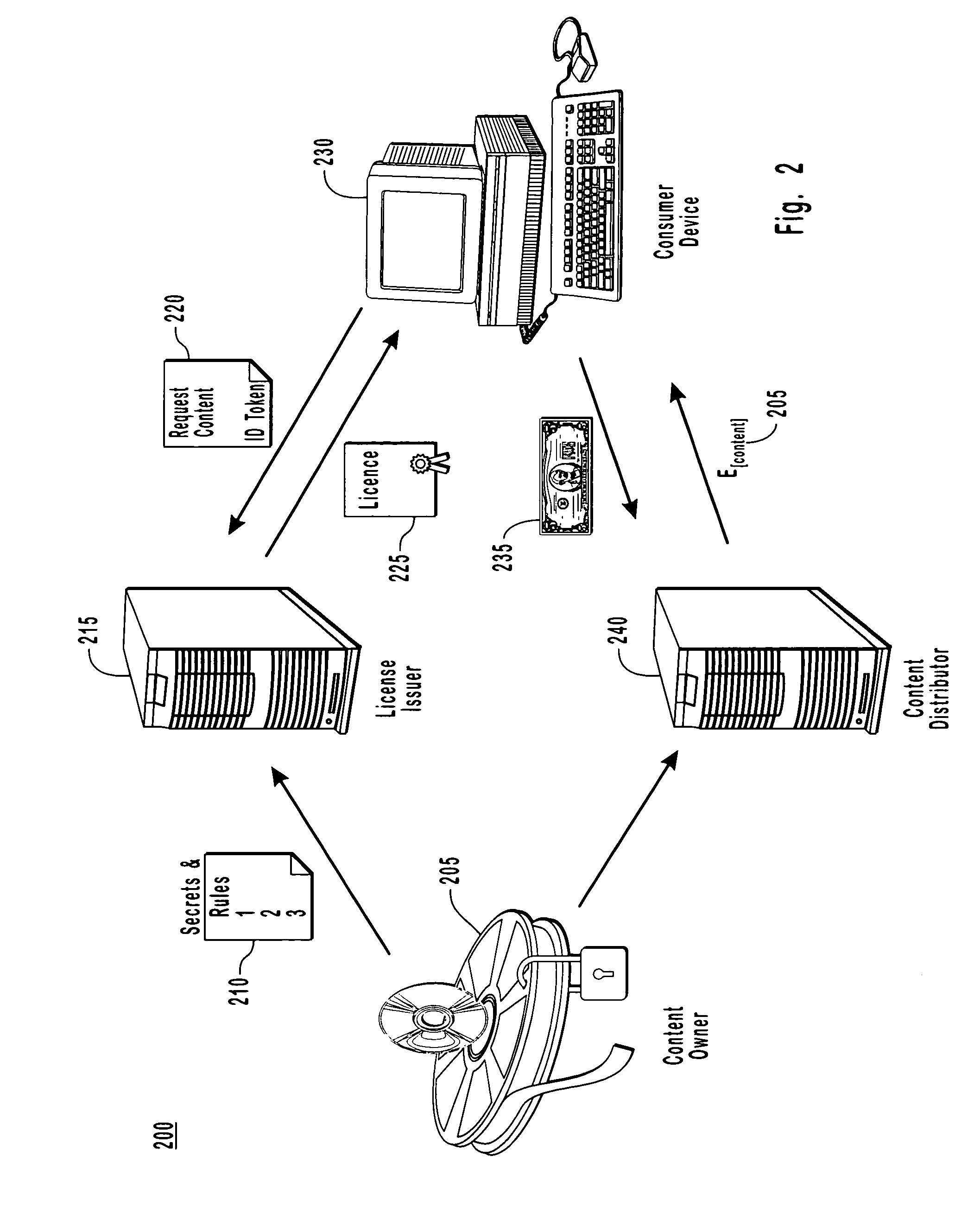
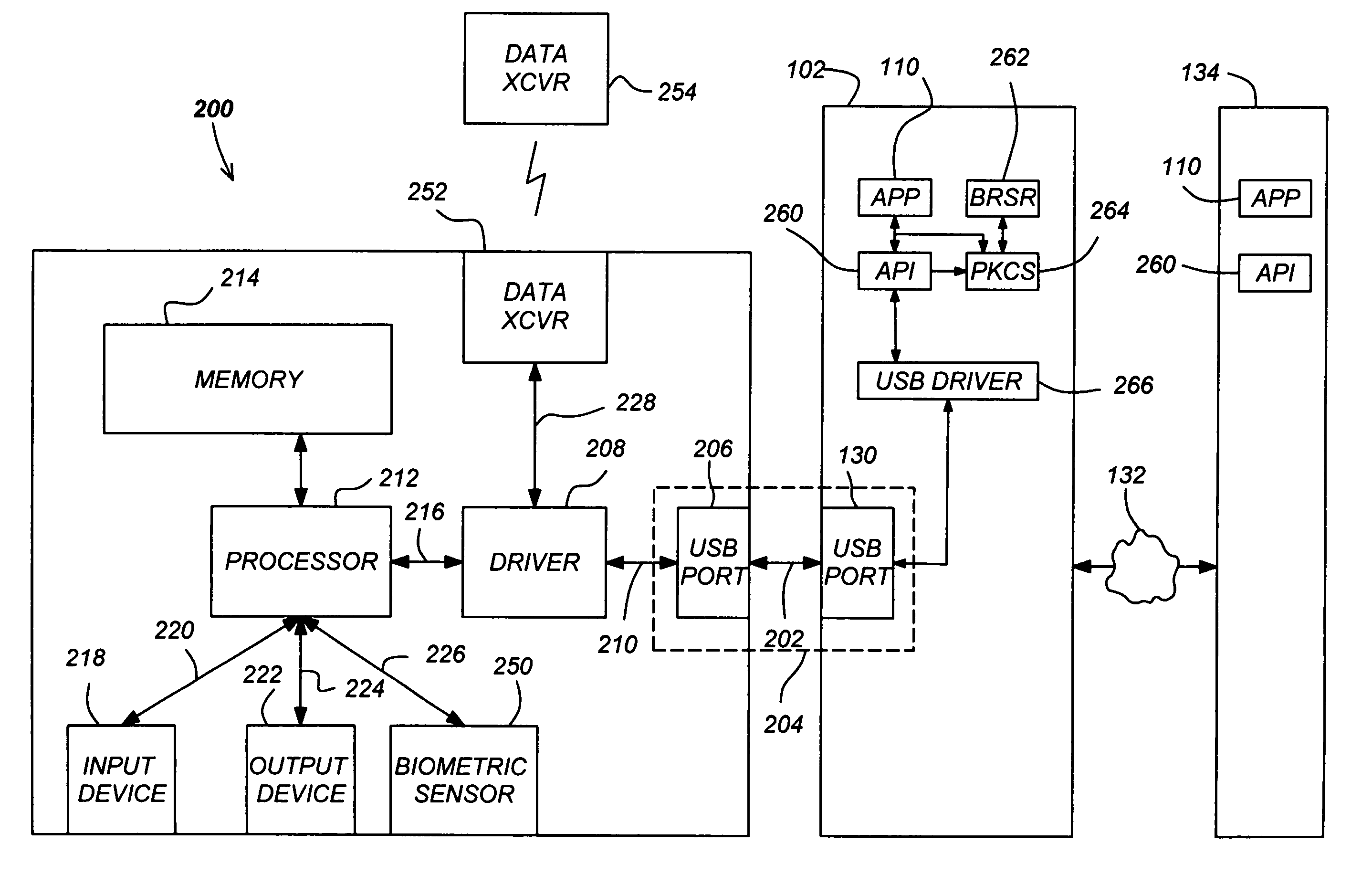
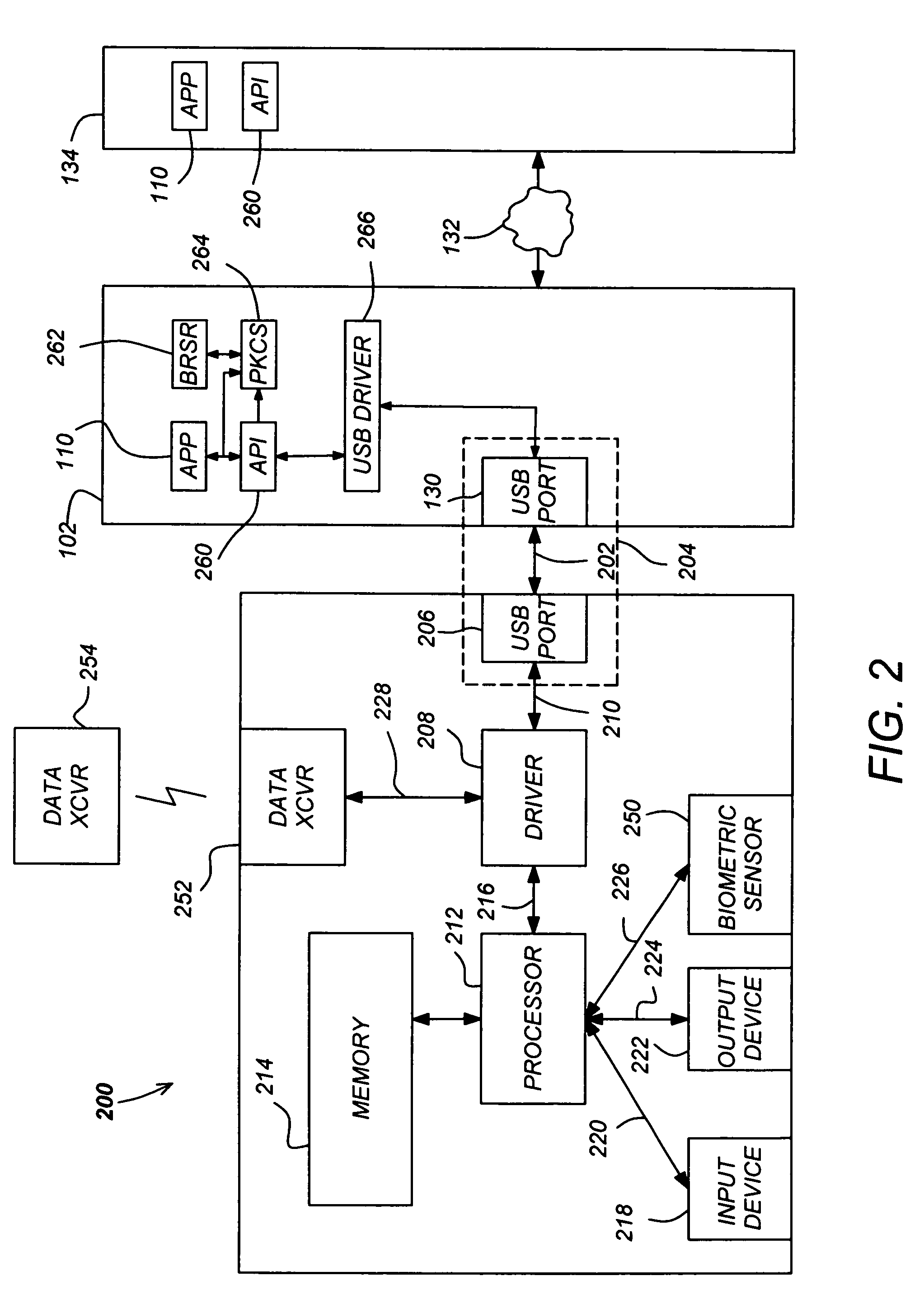
USB-compliant personal key with integral input and output devices
InactiveUS7272723B1Prevent copyingPrevent unauthorized useDigital data processing detailsUser identity/authority verificationUser inputConditional access
A compact, self-contained, personal key is disclosed. The personal key comprises a USB-compliant interface releaseably coupleable to a host processing device; a memory; and a processor. The processor provides the host processing device conditional access to data storable in the memory as well as the functionality required to manage files stored in the personal key and for performing computations based on the data in the files. In one embodiment, the personal key also comprises an integral user input device and an integral user output device. The input and output devices communicate with the processor by communication paths which are independent from the USB-compliant interface, and thus allow the user to communicate with the processor without manifesting any private information external to the personal key.
Owner:SAFENET
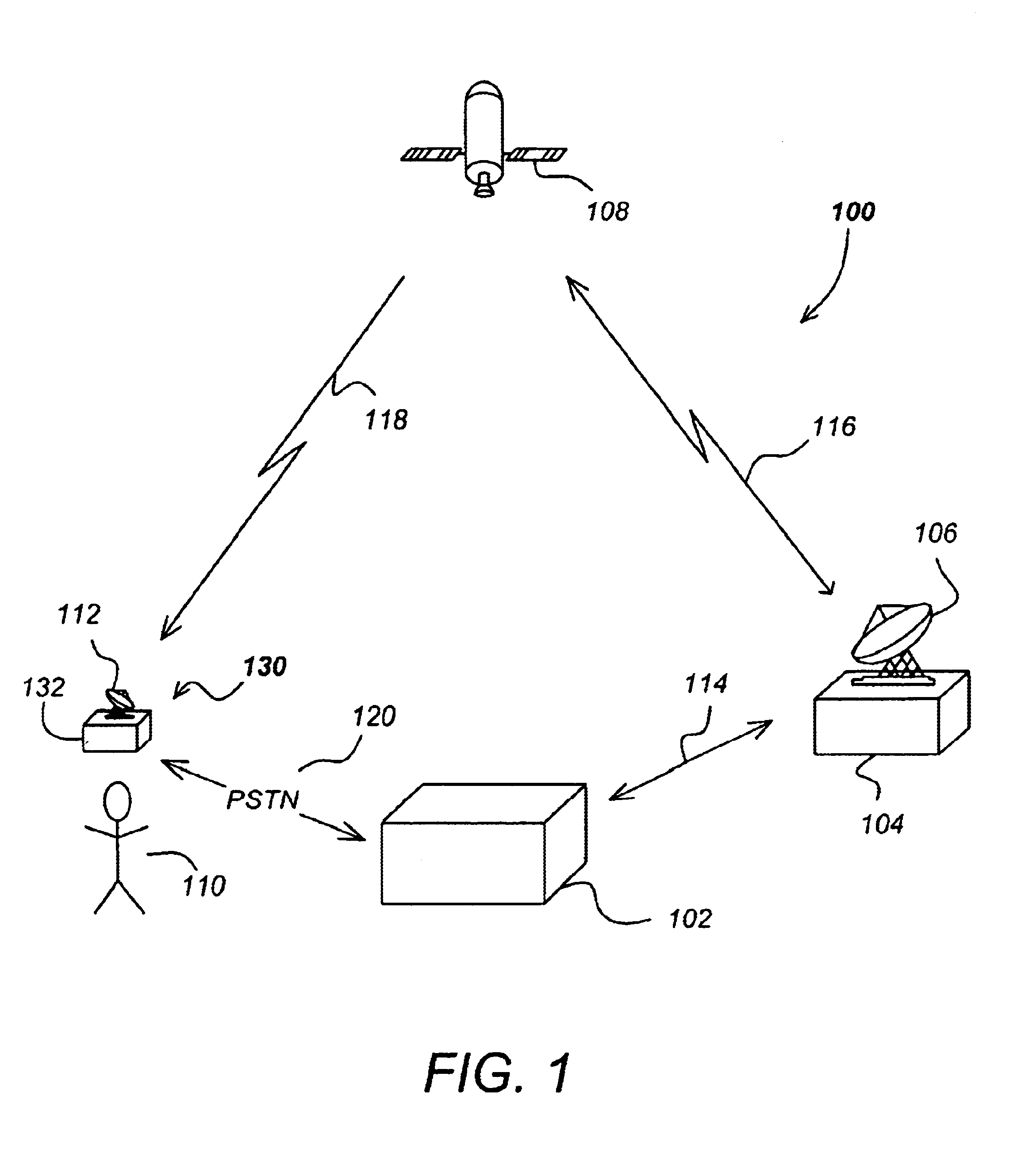
Conditional access method and device
InactiveUS6070796AInput/output for user-computer interactionAcutation objectsComputer hardwareAccess method
PCT No. PCT / FR96 / 01269 Sec. 371 Date Feb. 20, 1998 Sec. 102(e) Date Feb. 20, 1998 PCT Filed Aug. 8, 1996 PCT Pub. No. WO97 / 07448 PCT Pub. Date Feb. 27, 1997A conditional access device for use in connection with a host electronic equipment. The device includes a pointer peripheral containing one or more integrated circuit card coupler units. In addition, it also includes a device for acquiring personal information about a user. The personal information is locally compared with information stored in the integrated circuit card without passing through the host equipment.
Owner:SIRBU CORNEL
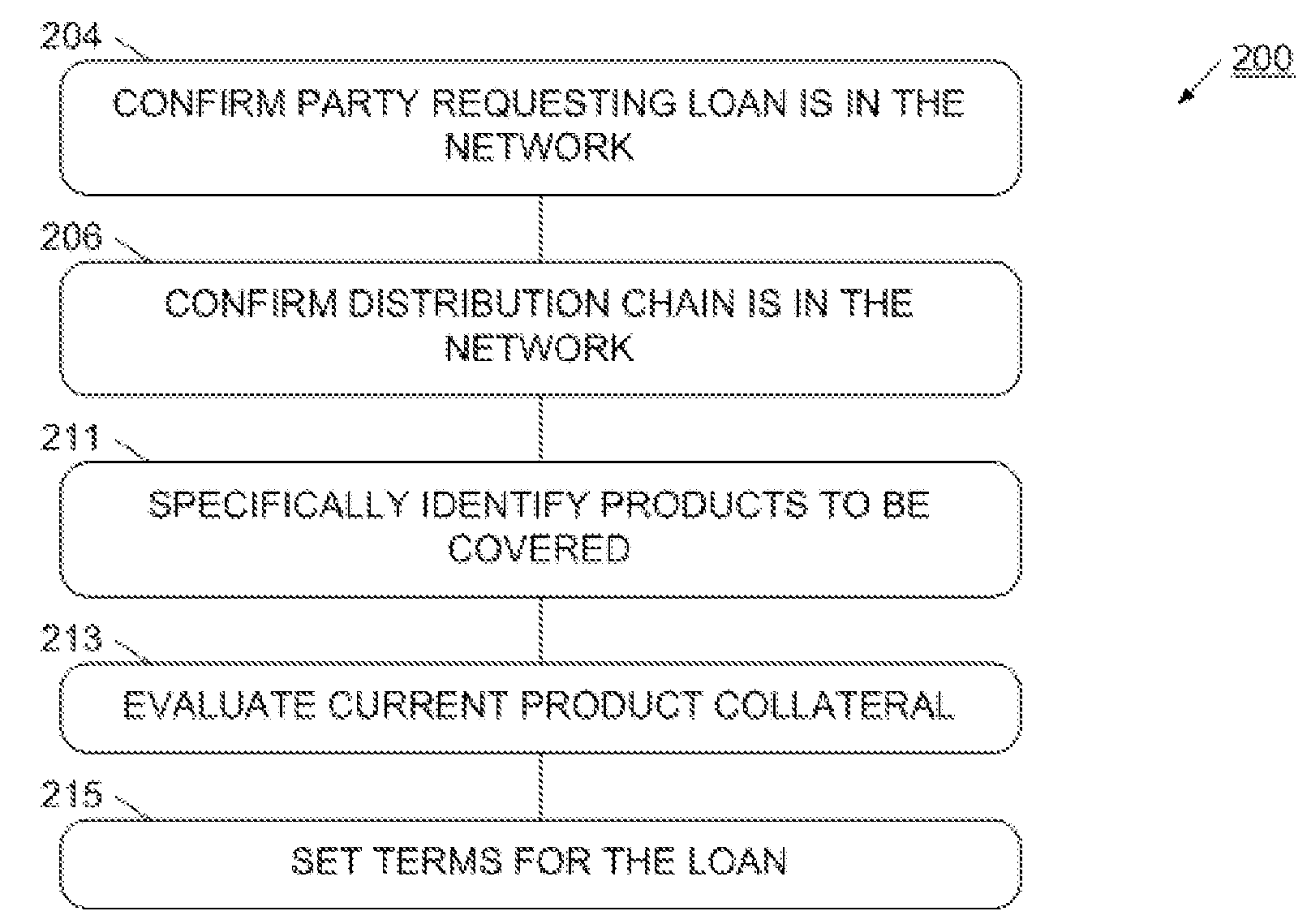
System and process for providing loans or other financing instruments
Automated financing products, services, and processes are enabled by the more complete, timely, and accurate information provided by a conditional access network. In one example, the financing product is an automated loan process. The automated loan process is able to receive timely product information, such as product status and location, and adapt loan terms, rate, or loan amount responsive to the information. For example, a loan may be adapted according to product activations, products that are deactivated, or according to which distributor is holding product. Information from the conditional access network may also be used to evaluate repayment terms. For example, the loan provider can use information from the conditional access network to confirm status of collateral, and accelerate the loan as appropriate. In this way, loan risk is reduced.
Owner:NXP BV
Generating a root key for decryption of a transmission key allowing secure communications
ActiveUS7725740B2Digital data processing detailsUnauthorized memory use protectionSecure communicationThird party
A method is used to restore the security of a secure assembly such as a chip card, after the contents of its second memory zone have been read by a third party. The method is for generating a security key implemented by a secure module comprising a central unit, a first conditional access memory zone and at least one second memory zone containing all or part of the user program. The method includes reading of all or part of the second memory zone, and generation of at least one root key based on all or part of the second zone data and on at least one item of secret information stored in the first memory zone.
Owner:NAGRAVISION SA
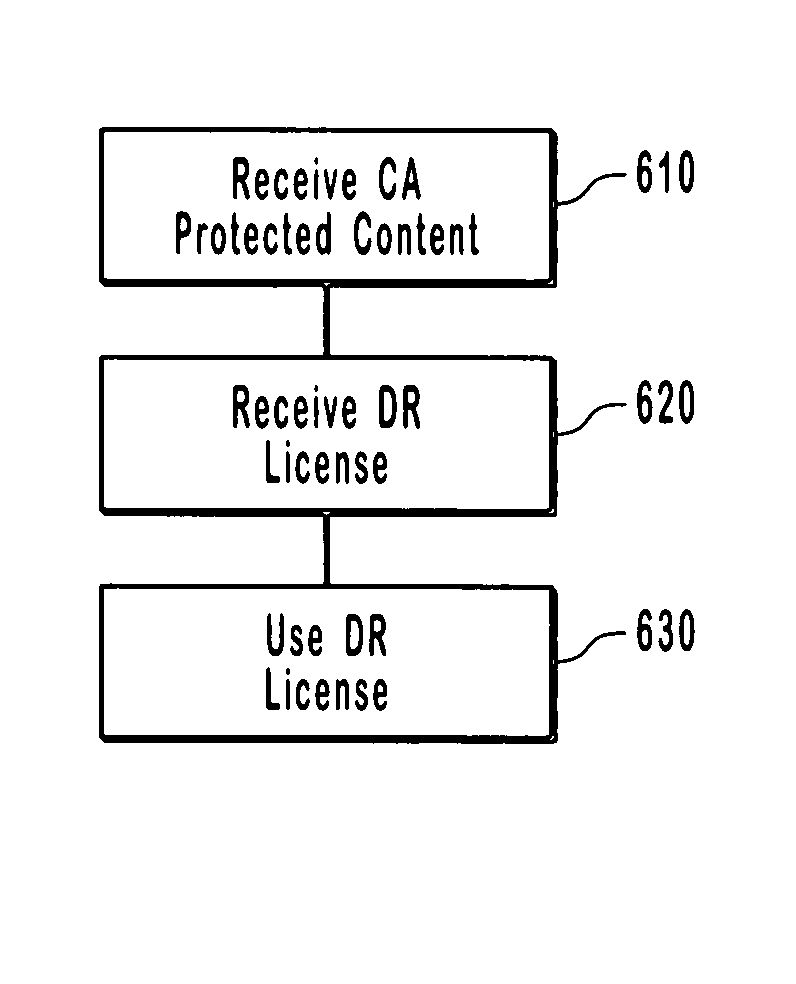
Systems and methods for conditional access and digital rights management
InactiveUS20070294170A1Simple deliverySecure and efficientTelevision system detailsProgram/content distribution protectionContent distributionDigital rights management system
Conditional access (CA) and digital rights management (DRM) in digital media delivery, processing, and storage systems. Methods and apparatuses are provided for managing digital rights under the protection of multiple CA and / or DRM systems. Some embodiments provide secure and robust methods for bridging multiple DRM systems in the digital media content distribution and playback systems. The present invention simplifies content delivery, conditional access, and digital rights management.
Owner:DIGITAL KEYSTONE
Systems and methods for conditional access and digital rights management
ActiveUS20090007240A1Simple deliveryDigital data processing detailsUser identity/authority verificationContent distributionConditional access
Conditional access (CA) and digital rights management (DRM) in digital media delivery, processing, and storage systems. Methods and apparatuses are provided for managing digital rights under the protection of multiple CA and / or DRM systems. Some embodiments provide secure and robust methods for bridging multiple DRM systems in the digital media content distribution and playback systems. The present invention simplifies content repurposing, after it has been bridged to a secondary DRM system, but still under the control of the original DRM system.
Owner:DIGITAL KEYSTONE
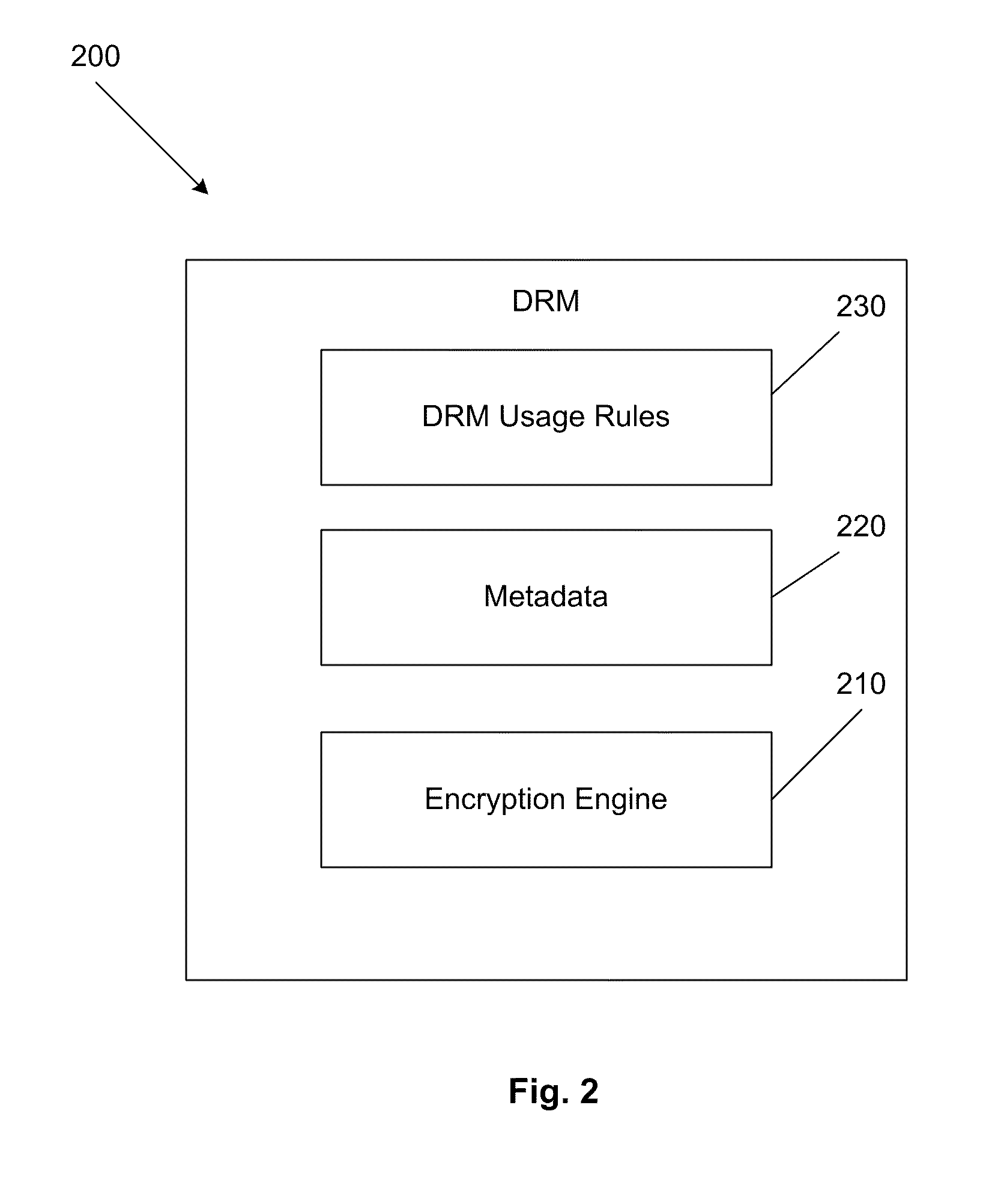
Content protection and digital rights management (DRM)
ActiveUS20100058485A1Digital data processing detailsAnalogue secracy/subscription systemsConditional accessDigital rights management
An end to end content protection system that includes enhanced digital rights management (DRM). The system provides content delivery to devices over a managed multimedia home network. The system includes a domain manager for receiving content, wherein the domain manager includes a cable card, conditional access component and a MSO security application and a managed client device, coupled to and registered with the domain manager, the managed client device running a security DRM application client, the managed client device communicates with the MSO security application in the domain manager, wherein the MSO security application of the domain manager and the security DRM application client of the managed client instantiate a preferred DRM as an overlay on top of any other content protection scheme.
Owner:COX COMMUNICATIONS
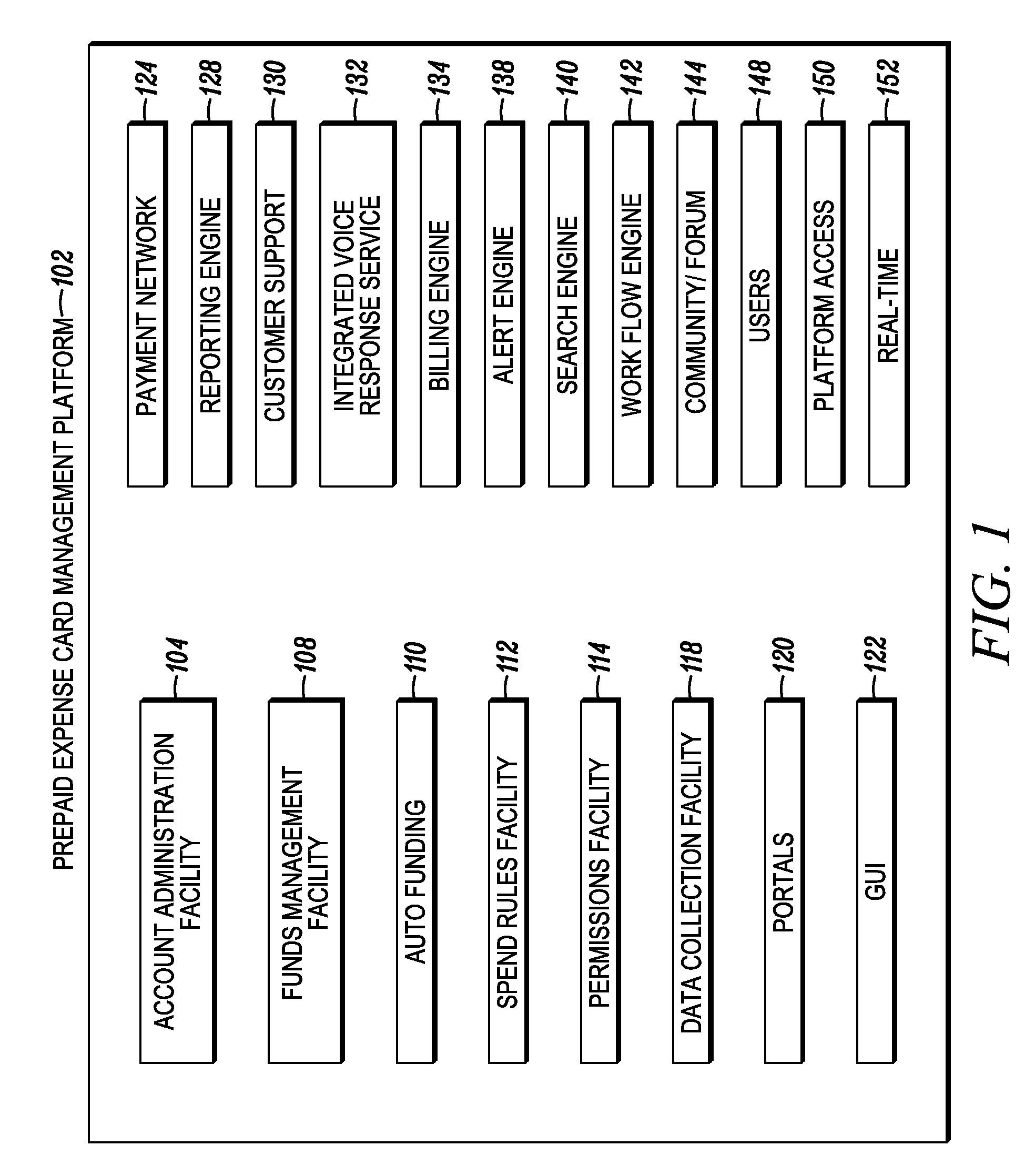
Prepaid expense card management platform
InactiveUS20090099965A1Increase spending controlReduce overhead timeFinancePre-payment schemesGraphical user interfaceConditional access
In embodiments of the present invention capabilities are described for a prepaid expense card management platform, where the management platform may be presented as a graphical user interface. The prepaid expense card management platform allows businesses to increase spending control and decrease overhead time associated with the administering of reimbursement expenditures. Controls enabled include funds allocation, funds transfer, user account administration, user access, spend rules, reports generation, usage profiles, conditional access, time usage restrictions, location usage restrictions, settlements processing, and alerts.
Owner:PREPAID EXPENSE CARD SOLUTIONS
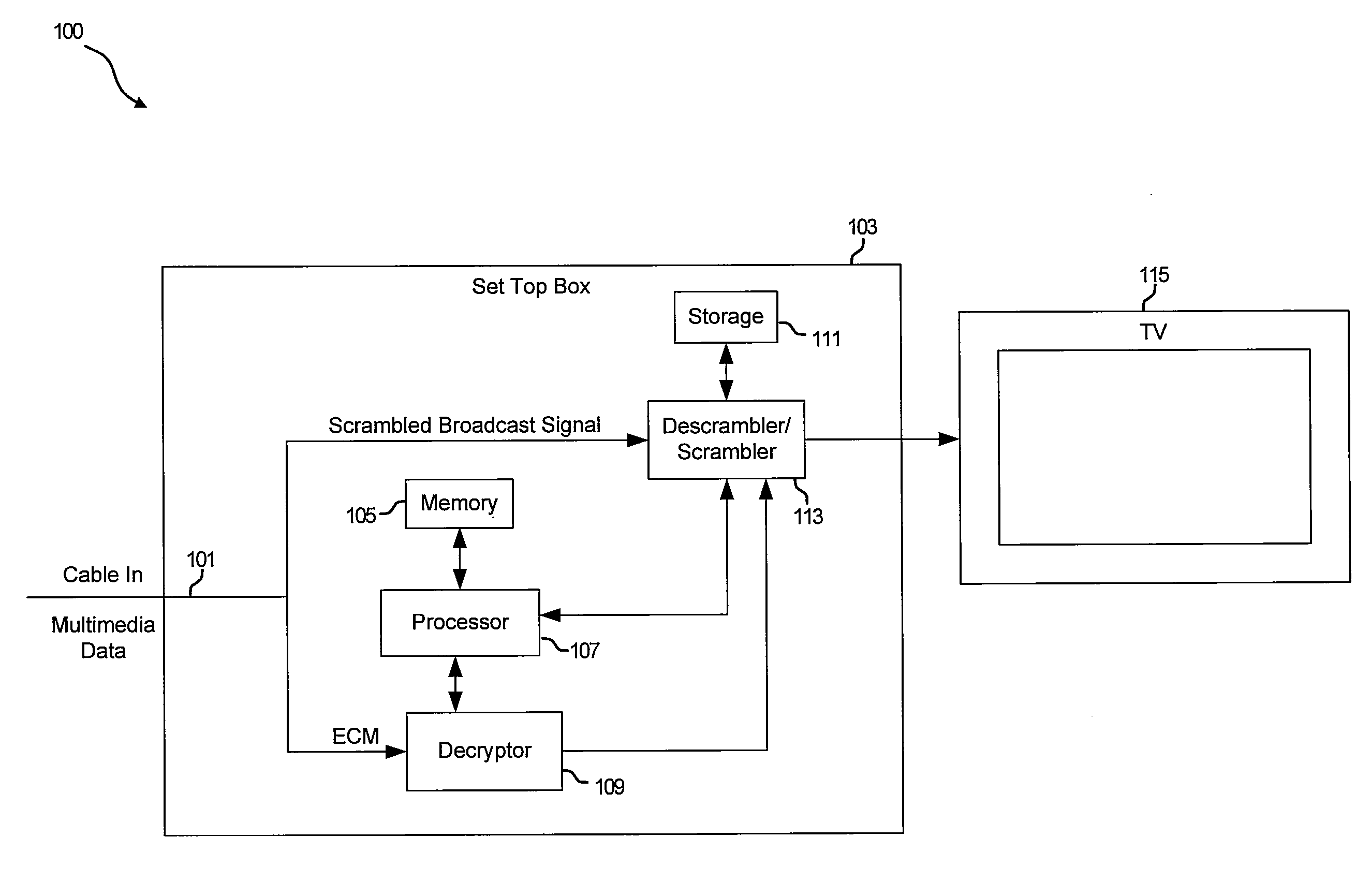
Method and apparatus for background caching of encrypted programming data for later playback
InactiveUS6961430B1Improve distributionTelevision system detailsColor television detailsDigital videoConditional access
A method and apparatus for enabling background caching of encrypted programming data on a storage medium for later playback in a digital video recorder (DVR) system. A set-top box (STB) equipped with a DVR searches a program guide for upcoming pay-per-view (PPV) events. When the PPV event begins, the STB tunes an appropriate transponder and begins receiving programming data packets containing audio, video, system time and conditional access data packets associated with the event, which are stored for playback on a storage medium. When the user turns the STB on and selects an option to playback a previously-recorded PPV event, the appropriate programming data is retrieved from the storage medium, and the STB recreates the original transmission timing of the data, to be displayed on a display device of the user.
Owner:HUGHES ELECTRONICS
Method for simulcrypting scrambled data to a plurality of conditional access devices
InactiveUS7039614B1Television system detailsData processing applicationsComputer hardwareConditional access
Owner:SONY CORP +1
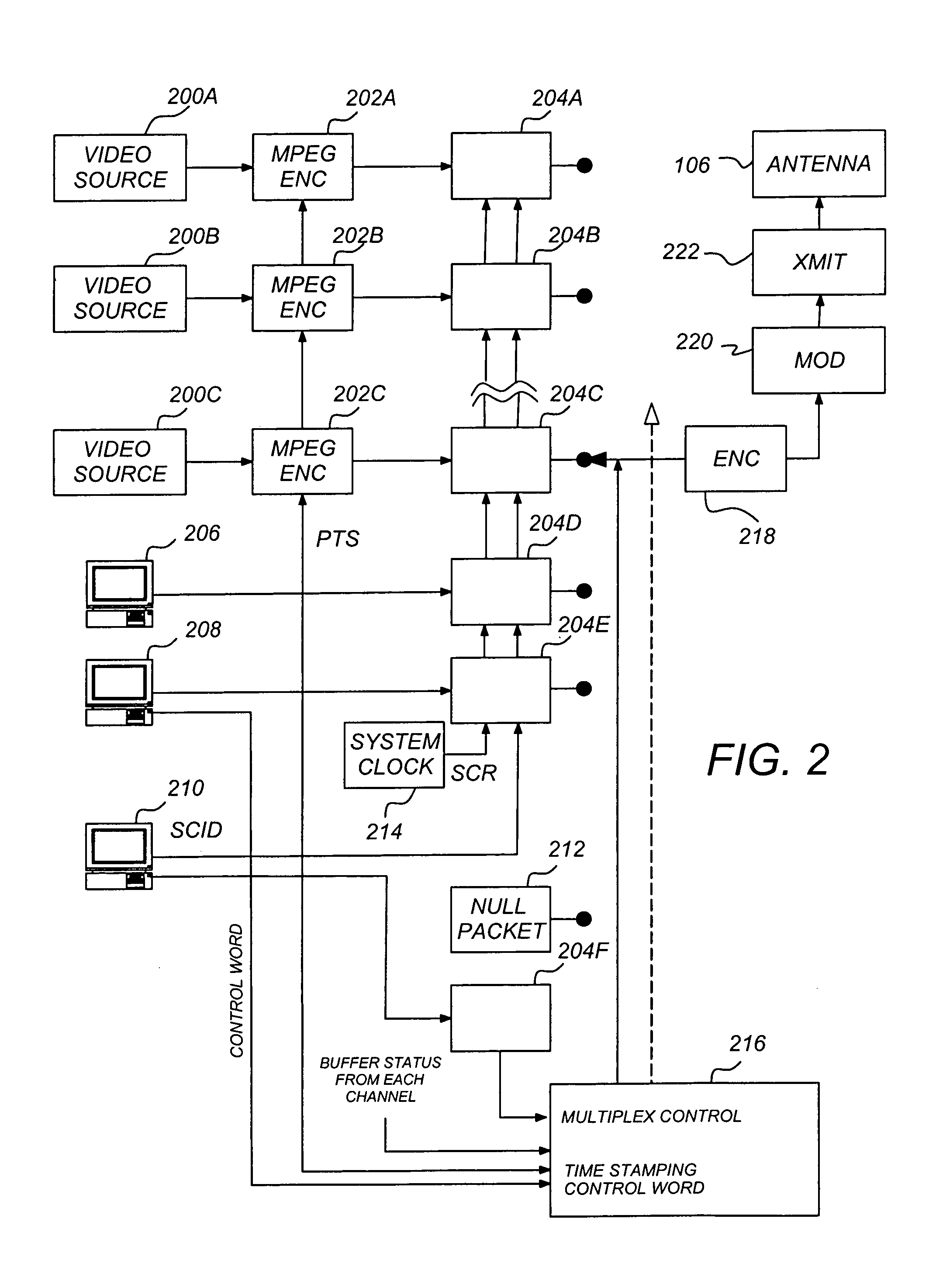
Digital television conditional access methods and apparatus for simultaneously handling multiple television programs
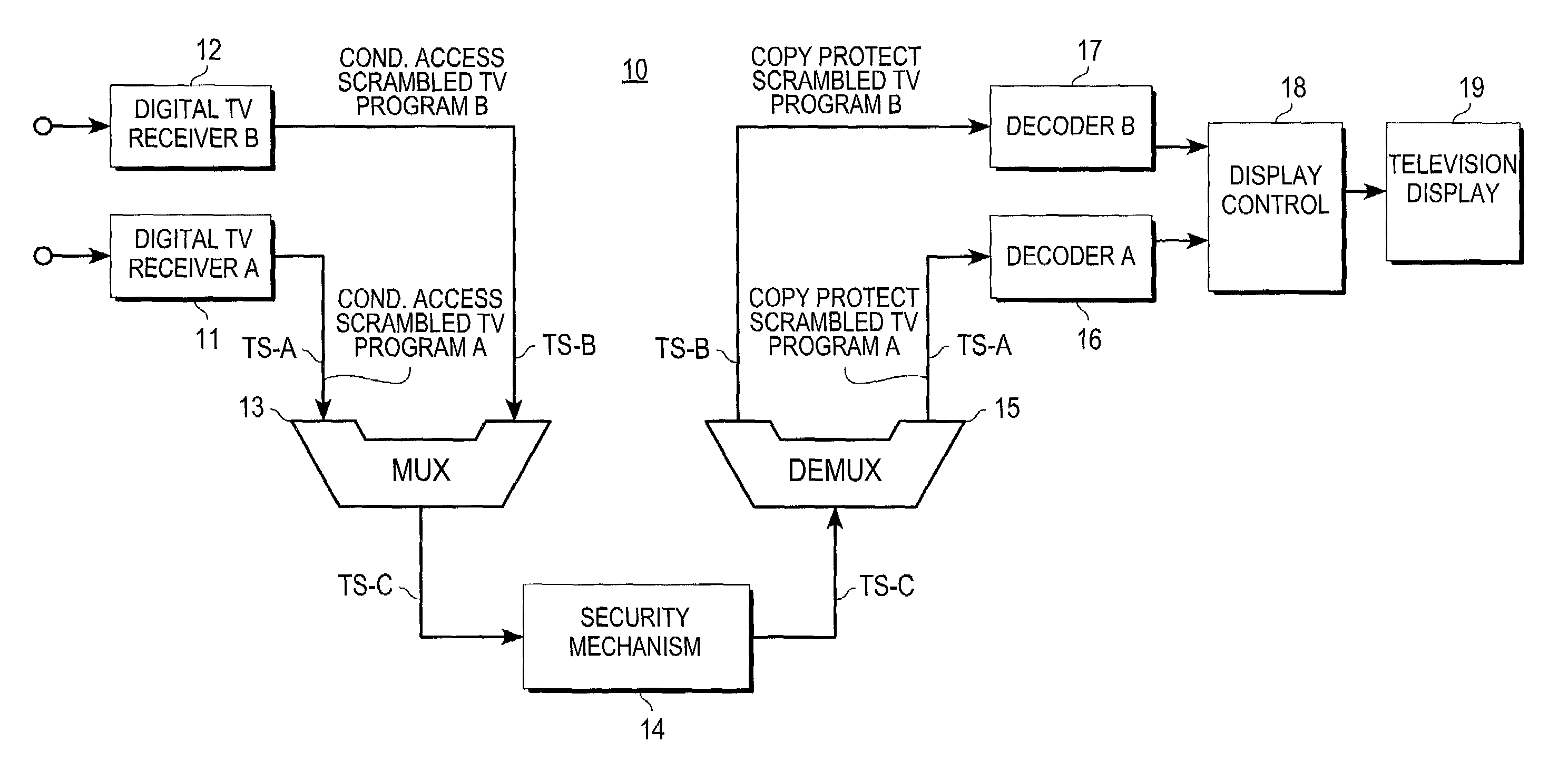
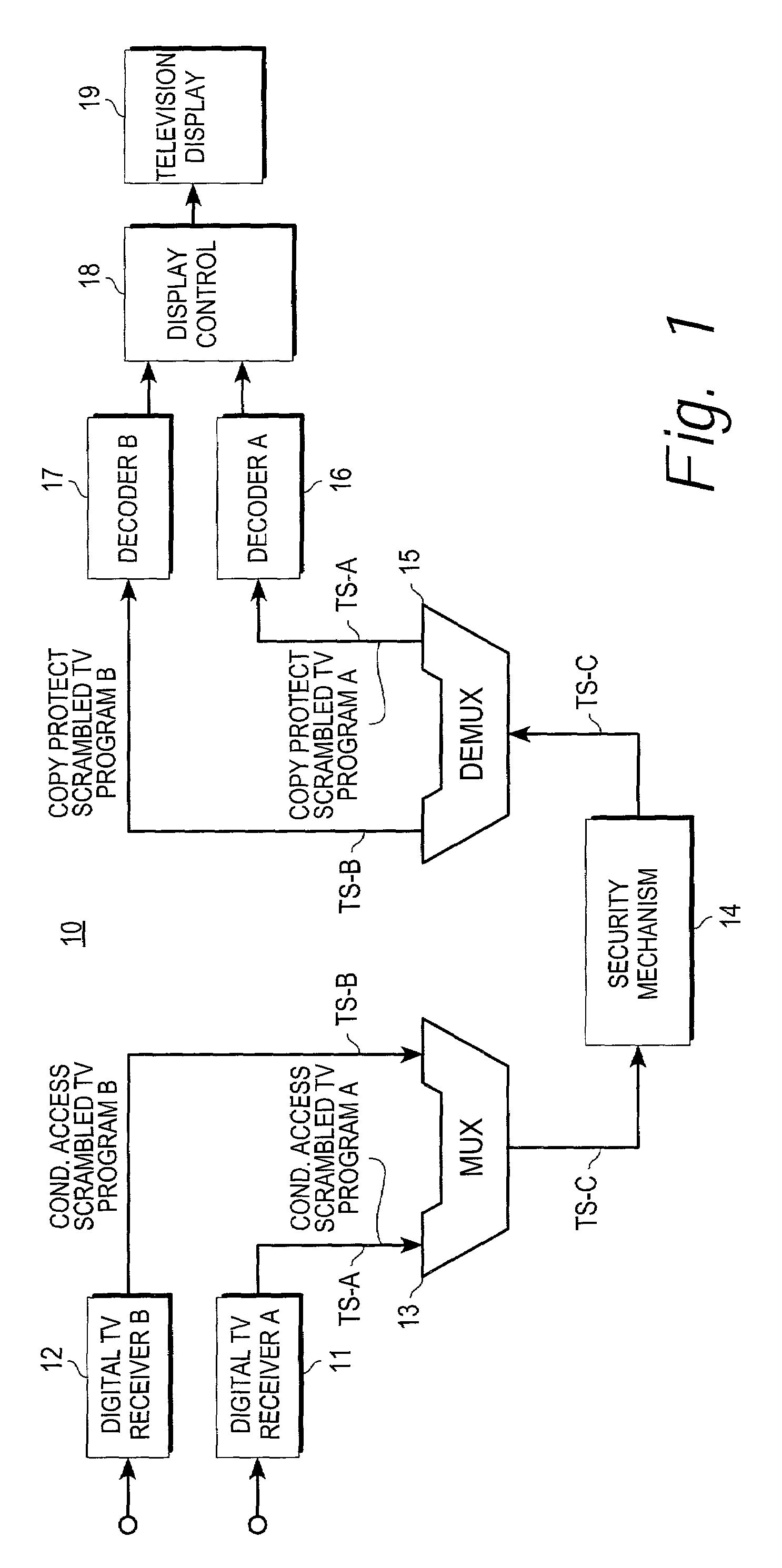
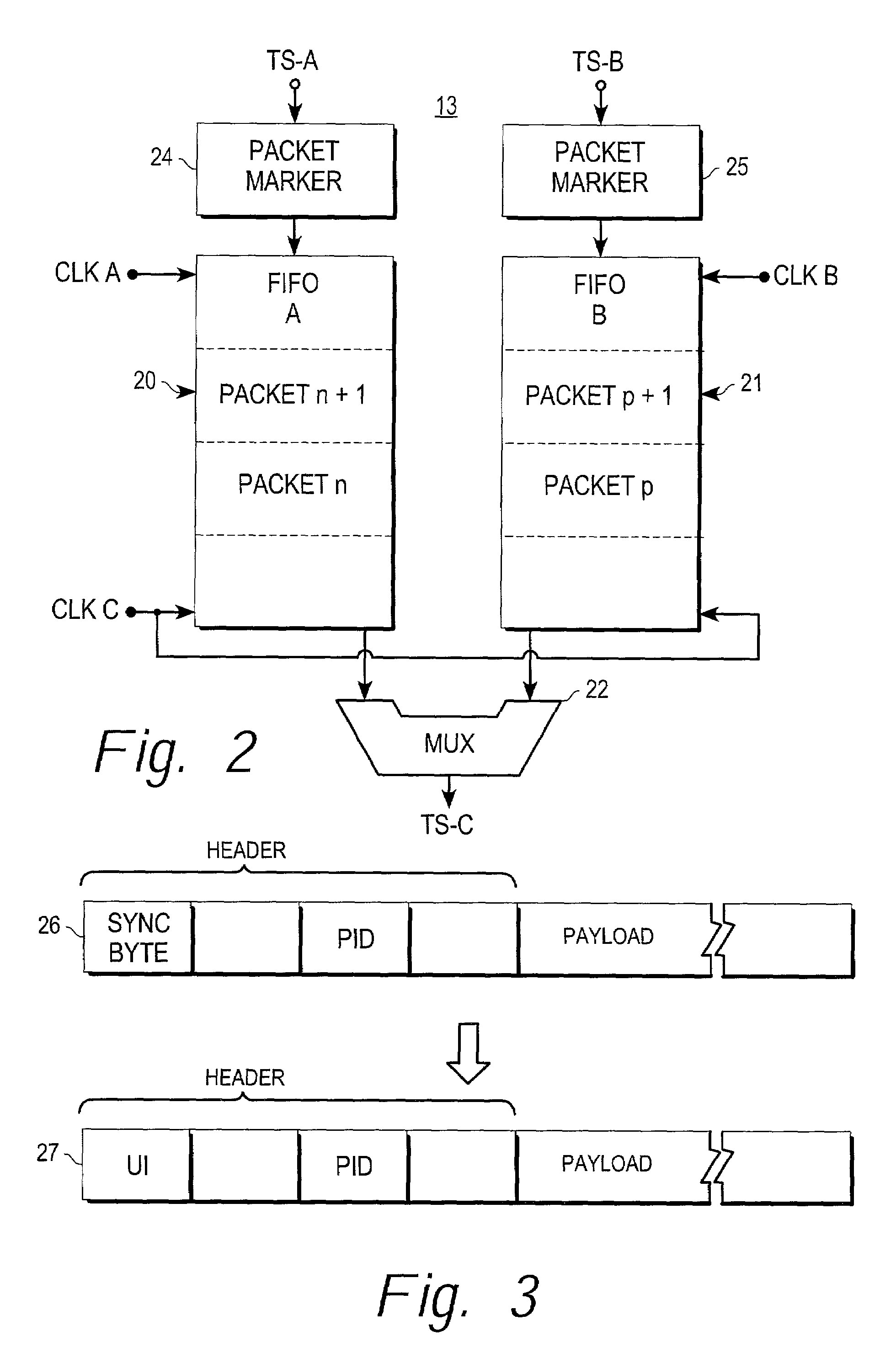
ActiveUS7508454B1Efficient and cost-effectiveTelevision system detailsPicture reproducers using cathode ray tubesMultiplexingAccess method
A digital television receiving system having a security mechanism which simultaneously handles two or more separate television program signals is described. The system includes a plurality of digital television receiver mechanisms for receiving a plurality of separate digital television program signal transport streams. The system also includes a multiplexer mechanism coupled to the digital television receiver mechanisms for tagging and multiplexing the received program signal transport streams into a single combined signal transport stream. The combined transport stream is supplied to a security mechanism which limits usable access to the combined stream to authorized users. The system further includes a demultiplexer mechanism for receiving an access-allowed combined transport stream from the security mechanism and demultiplexing the combined transport stream into separate transport streams corresponding to the separate transport streams received by the receiver mechanisms. The system also includes circuitry responsive to at least one of the demultiplexed transport streams for supplying image signals to a television display mechanism for producing television images.
Owner:SMARDTV SA
Fast authentication and access control method for mobile networking
InactiveUS7174456B1Easy to switchReduce certification timeDigital data processing detailsUser identity/authority verificationExpiration TimeWeb authentication
A fast authentication and access control method of authenticating a network access device to a communications network having an access point communicating with a remote authentication (home AAA) server for the network access device. The method includes the step of receiving an access request having an authentication credential from the network access device at the access point. The authentication credential includes a security certificate having a public key for the network access device and an expiration time. The security certificate is signed with a private key for the remote authentication server. The access point locally validates the authentication credential by accessing the public key of the remote authentication server from a local database, and checking the signature and expiration time of the security certificate. If the authentication credential is validated at the access point, the access point grants the network access device conditional access to the network by sending an access granted message to the network access device. The access granted message includes a session key encrypted with a public key for the network access device. The session key is stored in a database associated with the access point. The access point contacts the remote authentication server to check a revocation status of the security certificate for the network access device. If the access point receives a message from the remote authentication server that the authentication credential for the network access device has been revoked, it suspends network access for the network access device.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
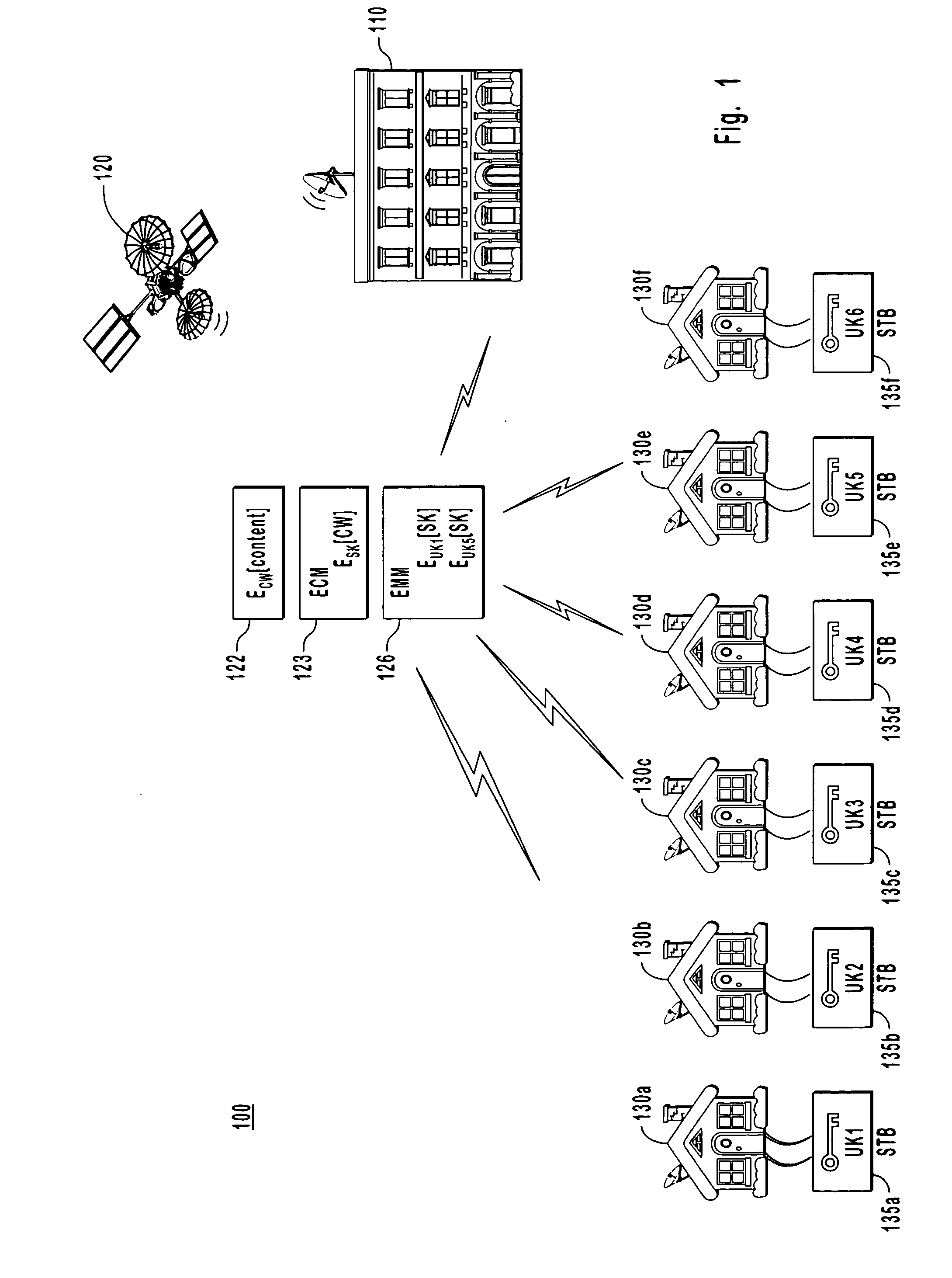
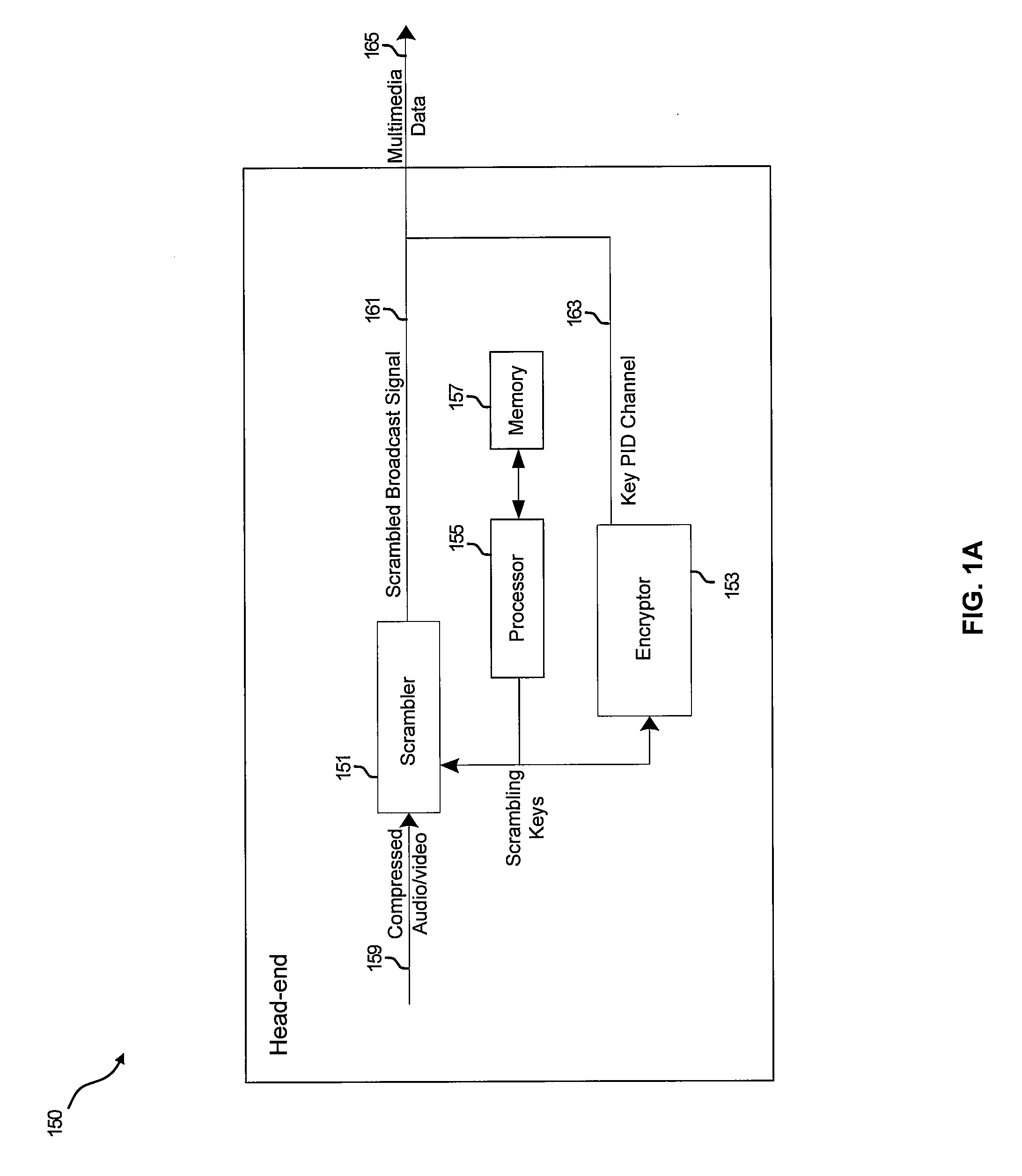
Method and system for a generic key packet for mpeg-2 transport scrambling
Methods and systems for a generic key packet for MPEG-2 transport scrambling and descrambling are disclosed and may comprise descrambling multiple package identifier channels in a transport stream utilizing a single generic key packet. The single generic key packet may comprise scrambling keys for each of the multiple package identifier channels, and may comprise scrambling keys for time intervals corresponding to two or more successive key change points. A key change point may be enabled to occur at the same time instant for each of the multiple package identifier channels, or may be enabled to occur at different time instants for one or more of the multiple package identifier channels. The scrambling / descrambling may comprise copy protection or conditional access descrambling. The generic key change packet may comprise information identifying a scrambling / descrambling algorithm, such as AES, DES and 3-DES, for example.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Conditional access method and apparatus of a receiver system for controlling digital TV program start time
ActiveUS20050198680A1Improve securityEasy to switchCircuit security detailsGHz frequency transmissionWork periodComputer hardware
A conditional access method and apparatus for use with a system for controlling of digital TV program start time. Subscriber access is authorized to digital program streams. Content are divided into a plurality of working periods. Each working period of the plurality of working periods is scrambled with a different working key. A working key of a given period is delivered ahead of the given period. The working key is synchronized with scrambling control bits in an header working keys are inserted into an entitlement control message (ECM) packet, and the ECM packet is encrypted using a service key. A time period is inserted into the ECM packet during which the service key is valid. A service key is inserted in an entitlement.
Owner:ARRIS ENTERPRISES LLC
System and method for secure conditional access download and reconfiguration
ActiveUS7383438B2Overcome deficienciesUser identity/authority verificationSecret communicationSecurity softwareConditional access
A method of securely downloading at least one of conditional access software (CAS), Digital Rights Management software (DRMS), Trusted Domain Software (TDS), and Gaming Security Software (GSS) includes presenting a specialized entitlement management message (EMM) to initiate the download to a receiver security device using a supervisory logon key (SLK) split to logon with a second split contained inside the receiver security device, presenting a receiver digitally signed random challenge from the receiver security device to a sender security server to establish authentication of the receiver security device to the sender security server, and signing and returning the receiver random challenge from the sender security server to the receiver security device with a sender random challenge to establish authentication of the sender security server to the receiver security device.
Owner:COMCAST CABLE COMM LLC
Methods, apparatus, and systems for providing media content over a communications network
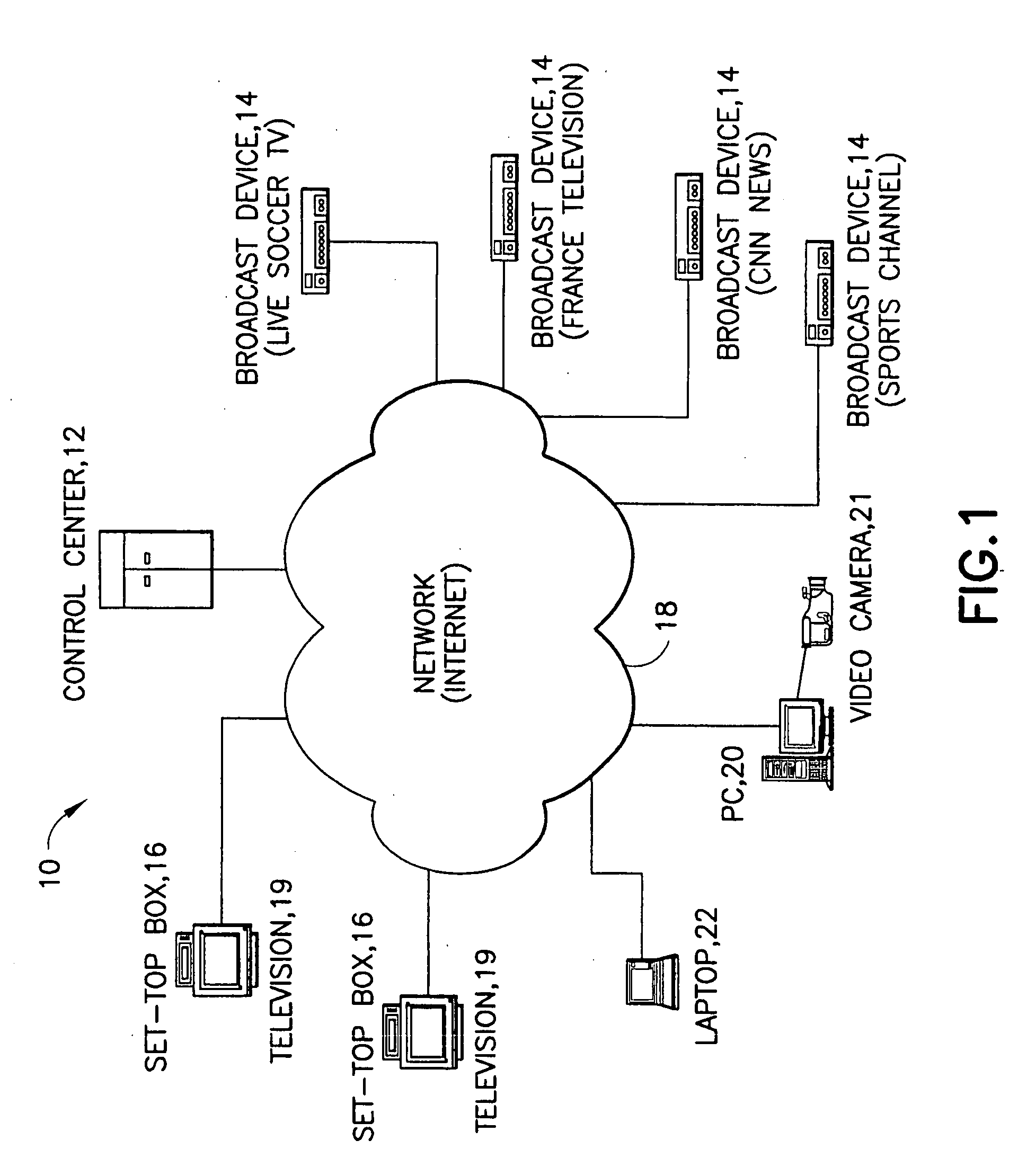
ActiveUS20070204321A1Solve insufficient bandwidthEfficient clusteringAnalogue secracy/subscription systemsSelective content distributionDigital dataConditional access
The present invention relates to broadcasting / multicasting of media content over a communication network using shared bandwidth available from peer-to-peer networking. The system of the present invention includes a plurality of broadcast devices, a plurality of receiving devices, a plurality of databases, and a control center. The control center is the central nerve of the network, and provides a number of services, including but not limited to channel control, ad insertion, conditional access, program guide services, and the like. The broadcast device converts media content, which can be television, radio, and other data, received from various content providers, into digital data packets, having a suitable format for transmission over the Internet. Each receiving device will request the relevant packets, decode the received packets, and display or present the media content contained in the packets via an associated device. Packets may be received directly from the broadcast devices or from peers (other receiving devices) on the network.
Owner:TVUNETWORKS
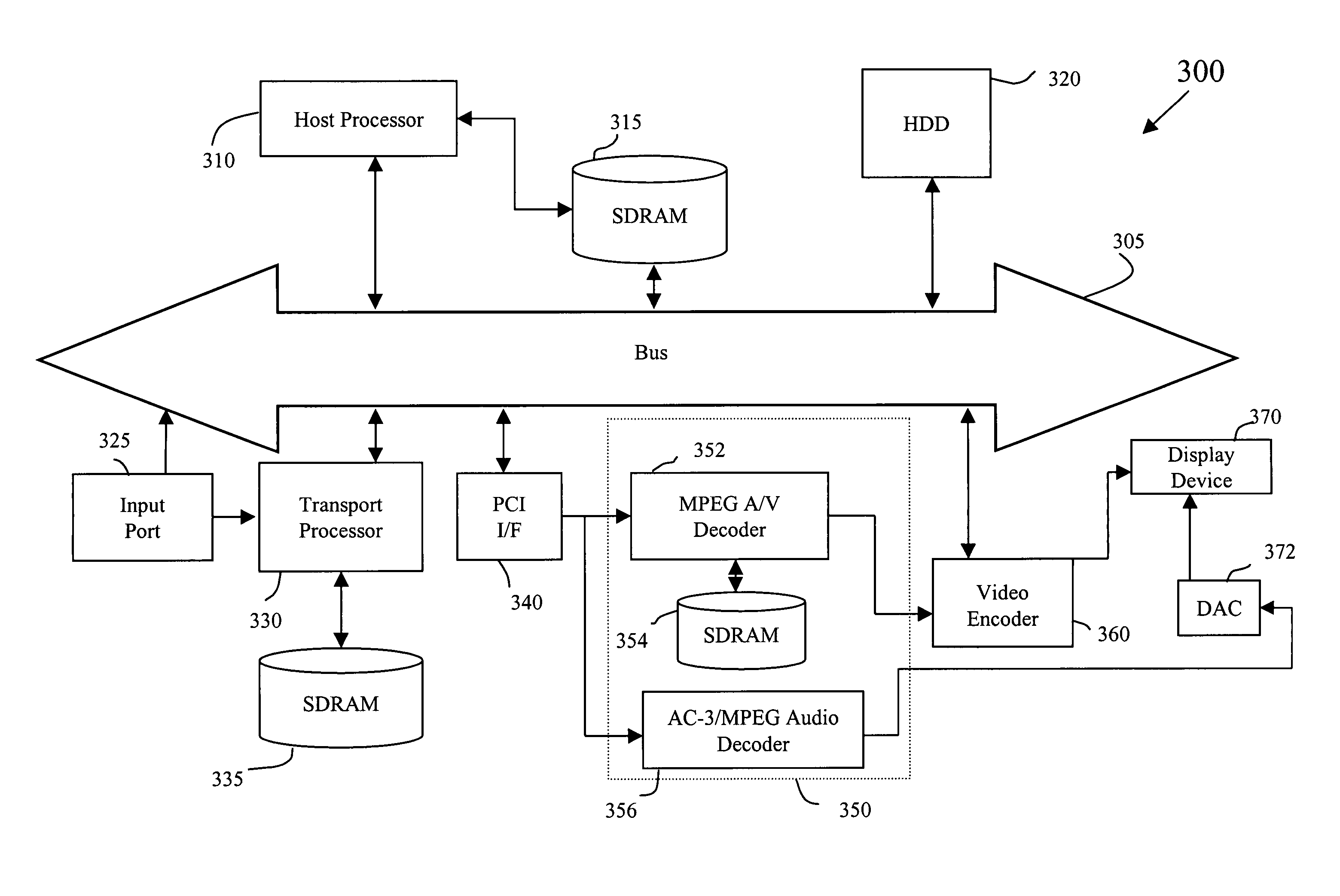
Apparatus for receiving cable TV broadcasting program, and multiplexer and de-multiplexer thereof
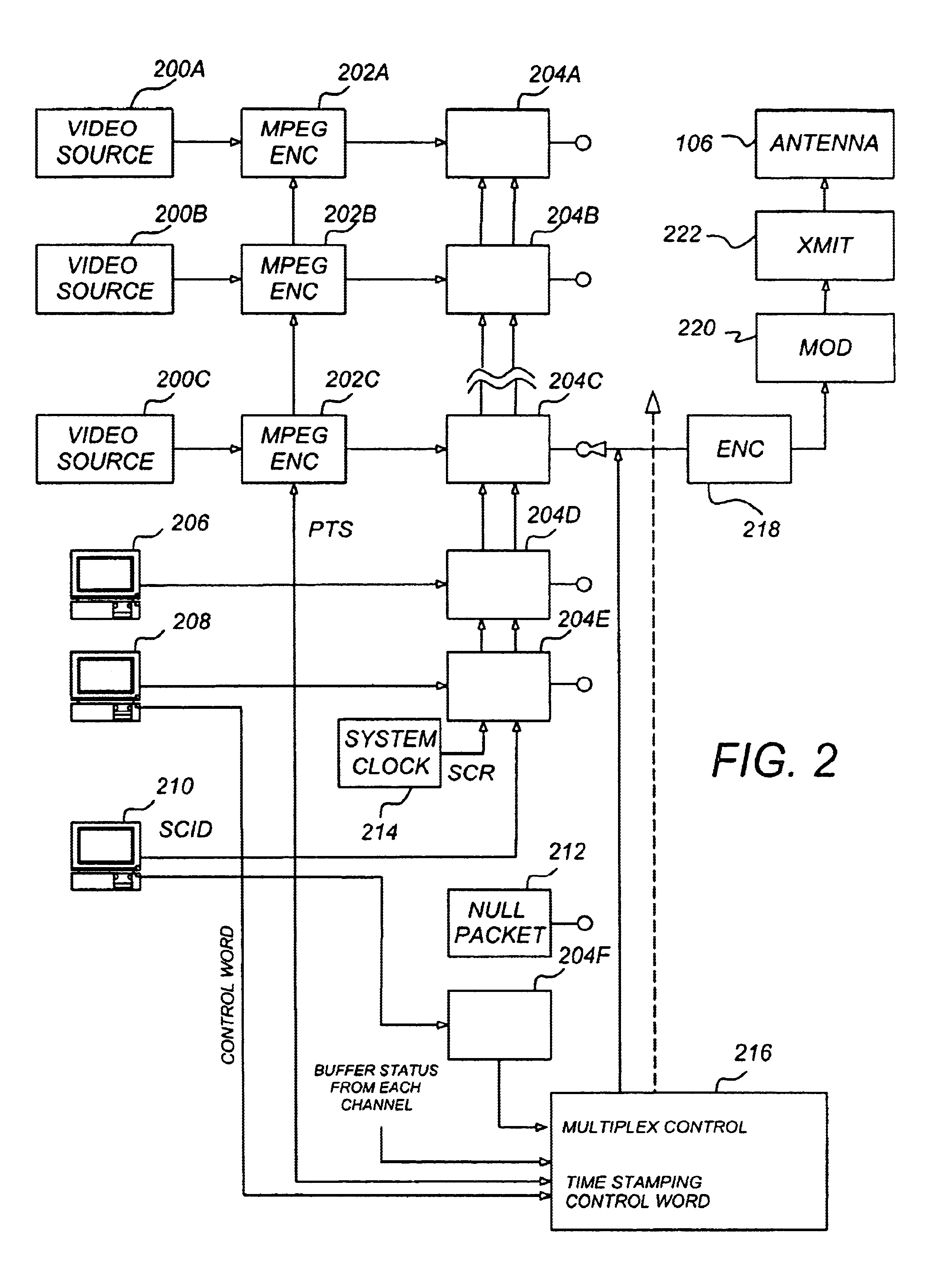
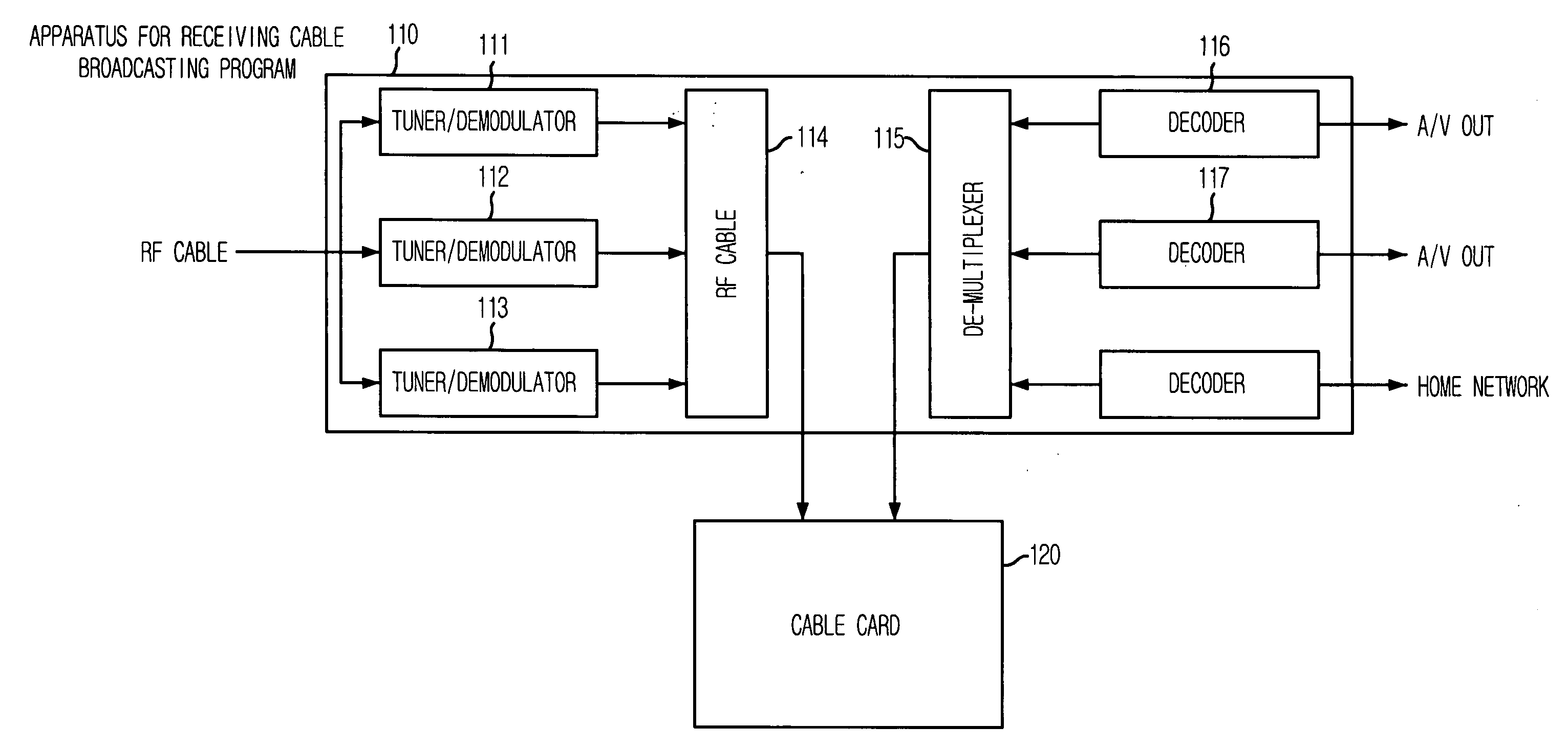
InactiveUS20070074256A1Reduce data volumeTime-division multiplexAnalogue secracy/subscription systemsProgram clock referenceMultiplexing
Provided are an apparatus for receiving cable broadcasting programs and a multiplexer and a de-multiplexer thereof for reducing data amount processed in a Cable CARD and for correcting synchronization of descrambled data stream. The apparatus includes: a multiplexing unit for filtering a broadcasting stream to select only programs selected by a viewer and multiplexing the selected programs; a conditional-access processing unit for receiving the multiplexed streams and processing the multiplexed streams for conditional access (descrambling); and a de-multiplexing unit for de-multiplexing the multi stream from the conditional-access processing unit and correcting a program clock reference (PCR).
Owner:ELECTRONICS & TELECOMM RES INST
Data transport to mobile devices using a radio broadcast data channel
InactiveUS20050136884A1Broadcast specific applicationsBroadcast-related systemsRadio broadcastingBroadcast channels
The present invention relates to method and system for providing data services to mobile device (25) via a digital radio broadcast channel, wherein data is encrypted and forwarded to a digital radio broadcast domain based on a conditional access scheme. The additional access scheme is based on existing concepts of SIM / IMSI definition and algorithms. The invention enables initial message coverage for developing countries and extends rural message coverage for huge area countries, where little mobile coverage is provided.
Owner:NOKIA SOLUTIONS & NETWORKS OY
Method and system for encryption/decryption of scalable video bitstream for conditional access control based on multidimensional scalability in scalable video coding
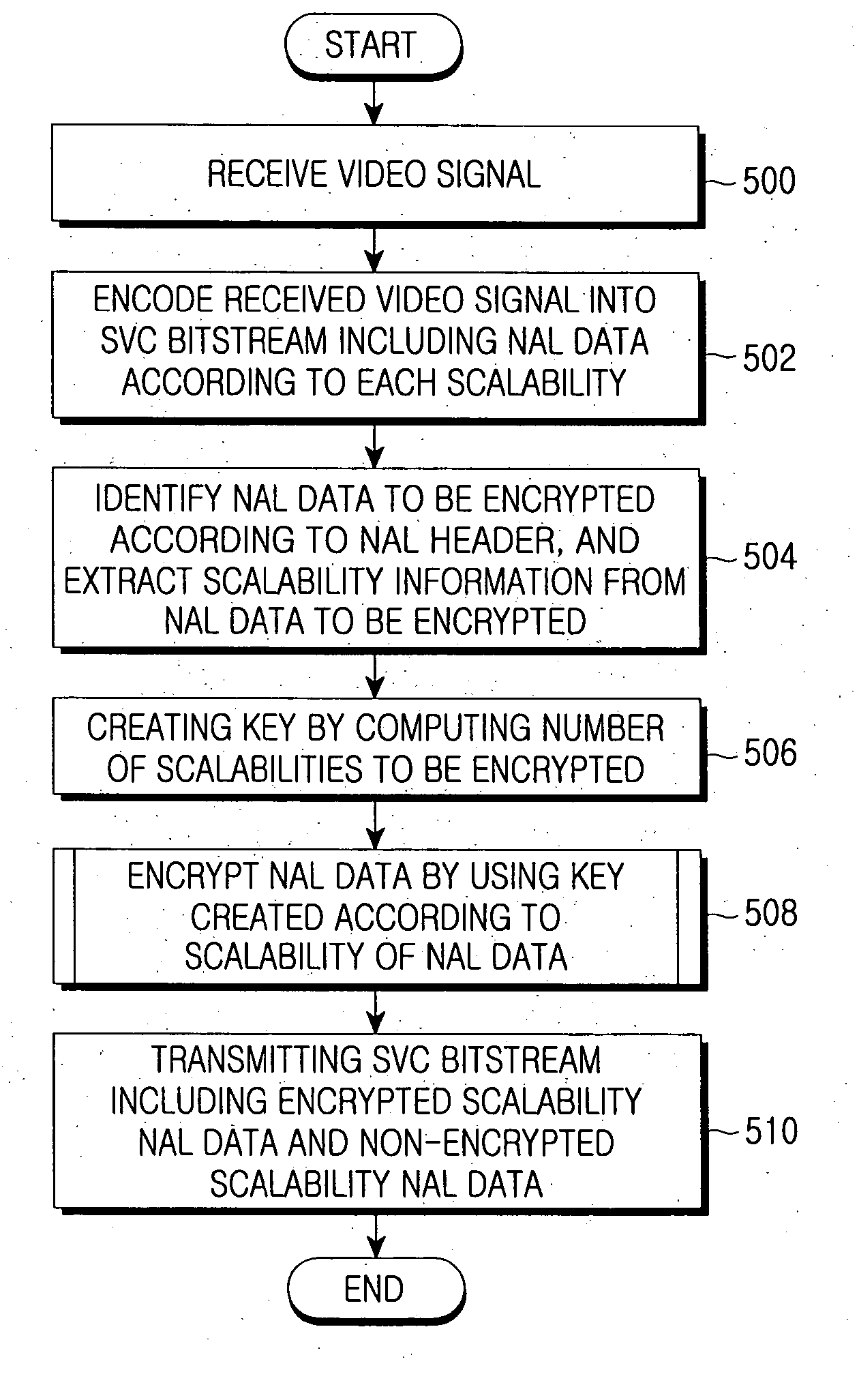
InactiveUS20070116277A1Easy to implementIncreased complexityPicture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningExtensibilityVideo bitstream
Disclosed is a system and method for encryption of a scalable video coding (SVC) bitstream, which is the next-generation coding technology. The encryption method encrypts Nation Adaptation Layer (NAL) data identified according to multidimensional scalability for space, time, and quality with respect to a bitstream created after an SVC encoding, thereby providing a multidimensional scalability function for space, time, and quality even after the encryption, so that the scalability is also maintained even in a bitstream extraction process after the encryption. According to such a scalable encryption method, a specific portion of an encrypted bitstream is removed in a bitstream extraction process, and user access to the bitstream is limited based on a combination of keys for accessing a specific scalability. Therefore, it is possible to protect scalable video content and to access the video content based on scalabilities.
Owner:SAMSUNG ELECTRONICS CO LTD +1
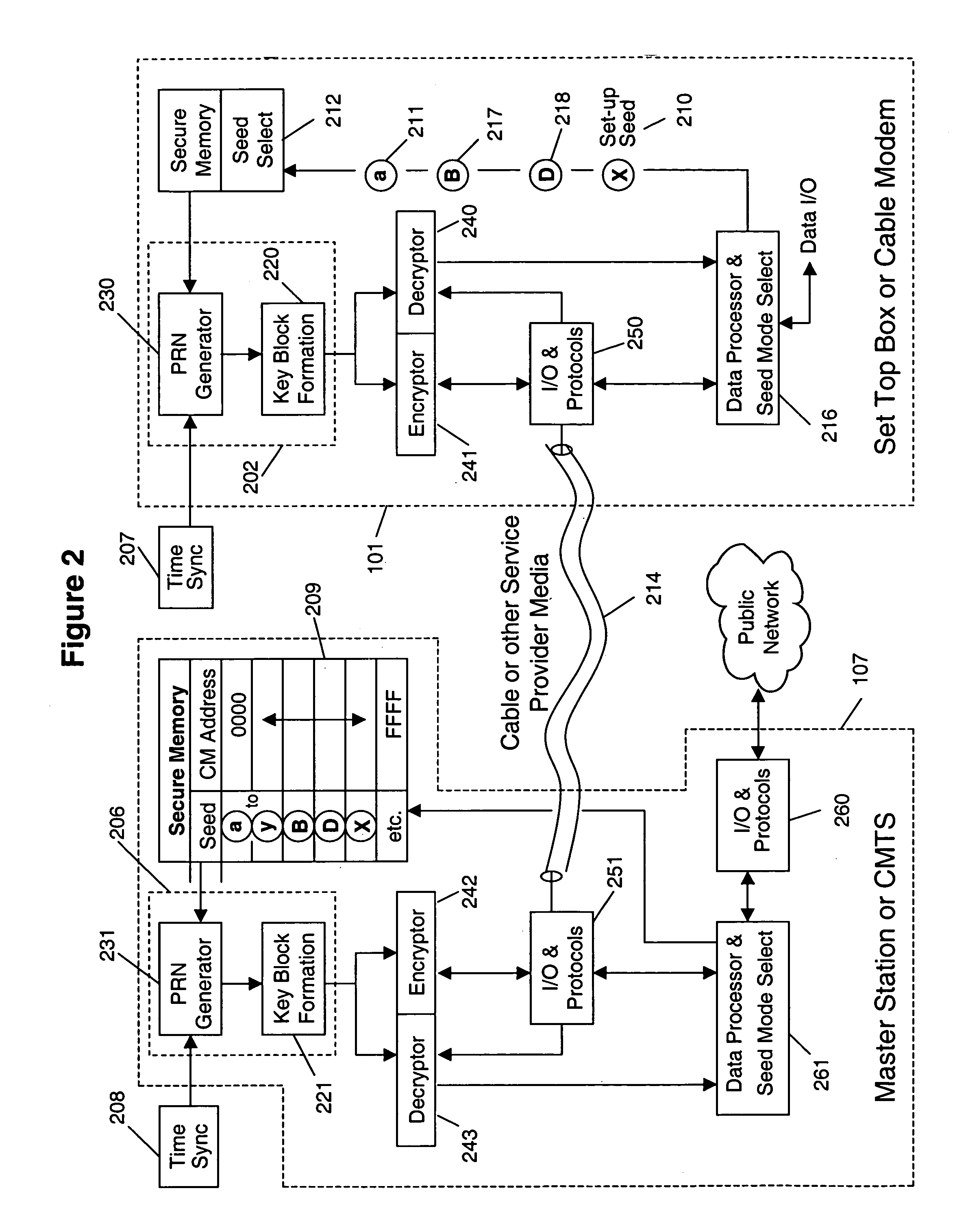
Cryptographic communications using in situ generated cryptographic keys for conditional access
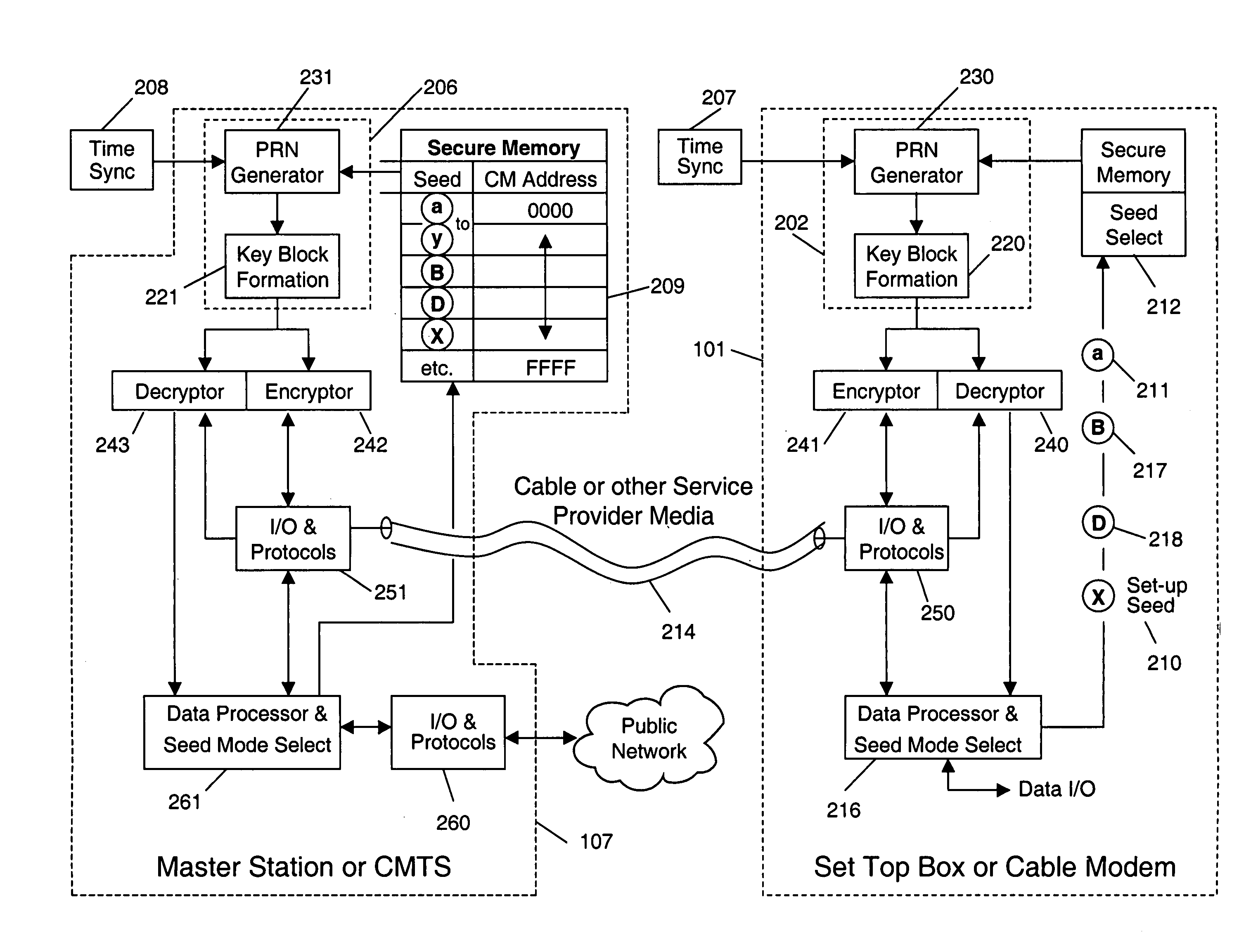
InactiveUS7149308B1Improve securityFacilitate communicationKey distribution for secure communicationComputer security arrangementsCryptographic key generationCommunication interface
A system and method for cryptographic communication among multiple users and a central service provider using in situ generated cryptographic keys. Each user communicates with the central service provider preferably using a user communication interface that includes an in situ key generator, which, after initialization with the user's own individual seed value, generates a unique cryptographic key. By distributing different user individual seeds unique to each user, each user's in situ key generator generates a unique set of keys. The central service provider also possesses an in situ key generator, and also preferably possesses a copy of all the individual seeds assigned to authorized users. The central service provider preferably communicates in a secure encrypted fashion with each user using cryptographic keys generated from that user's individual seed. Distribution of additional seed values common to more than one user, via encrypted communication using said unique individual cryptographic key generations, then permit secure conditional access to said users via signal encryption using key generations resulting from a seed value common to the intended group of users.
Owner:STEALTHKEY
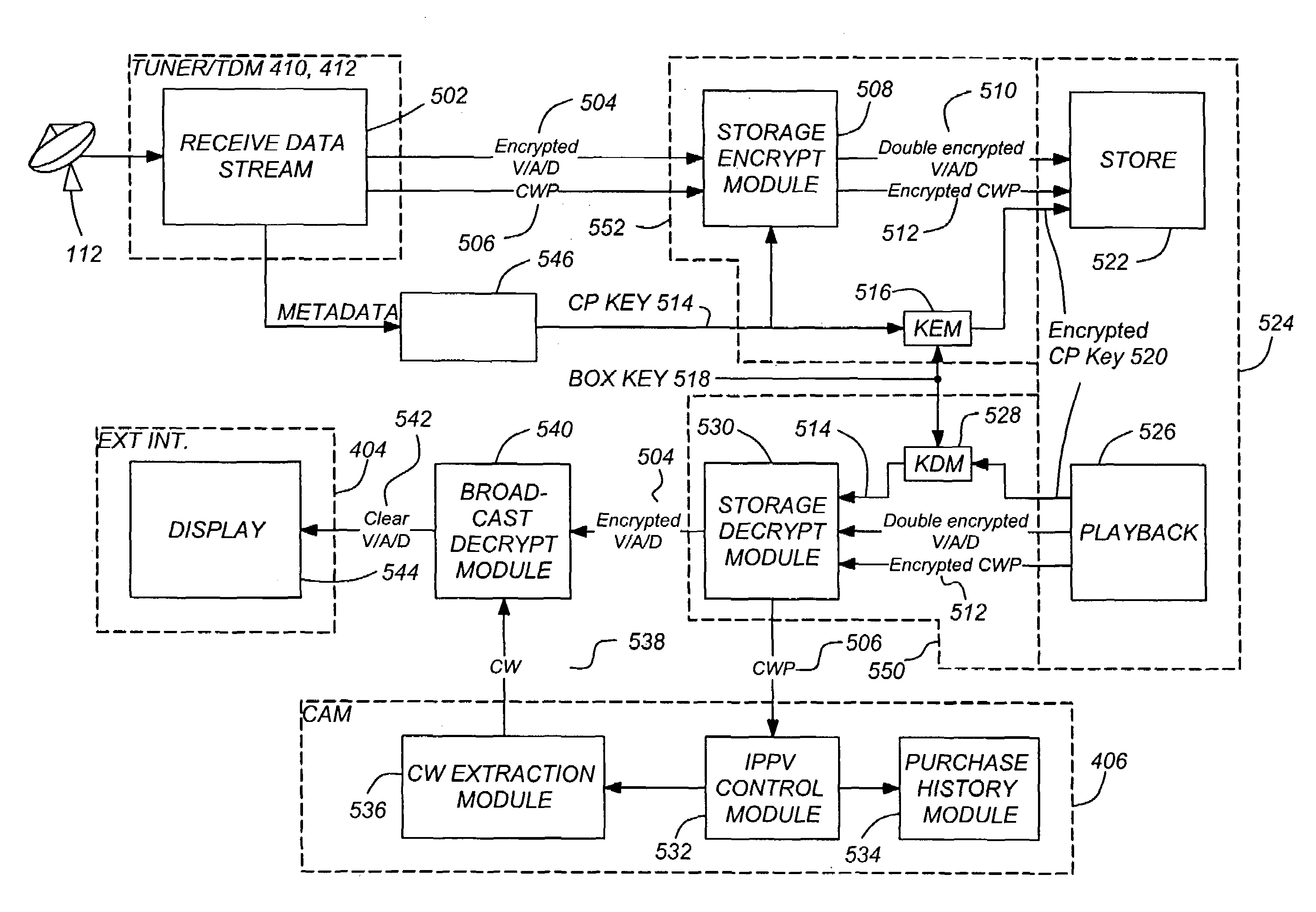
Super encrypted storage and retrieval of media programs in a hard-paired receiver and storage device
InactiveUS7203311B1Eliminate concernsChange is minimalTelevision system detailsKey distribution for secure communicationData streamConditional access
A method and apparatus for storing and retrieving program material for subsequent replay is disclosed. The apparatus comprises a tuner, for receiving a data stream comprising encrypted access control information and the program material encrypted according to a first encryption key, the access control information including the first encryption key; a first encryption module, communicatively coupled to the tuner and communicatively coupleable to a media storage device, for further encrypting the encrypted program material according to a second encryption key and for encrypting the second encryption key according to a third encryption key to produce a fourth encryption key; a first decryption module communicatively coupleable to the media storage device, for decrypting the fourth encryption key retrieved from the media storage device using the third encryption key to produce the second encryption key, and for decrypting the further encrypted program material retrieved from the media program device to produce the encrypted program material; a conditional access module communicatively coupled to the first decryption module, for decrypting the encrypted access control information to produce the first encryption key; and a second decryption module, for decrypting the program material using the first encryption key.
Owner:DIRECTV LLC
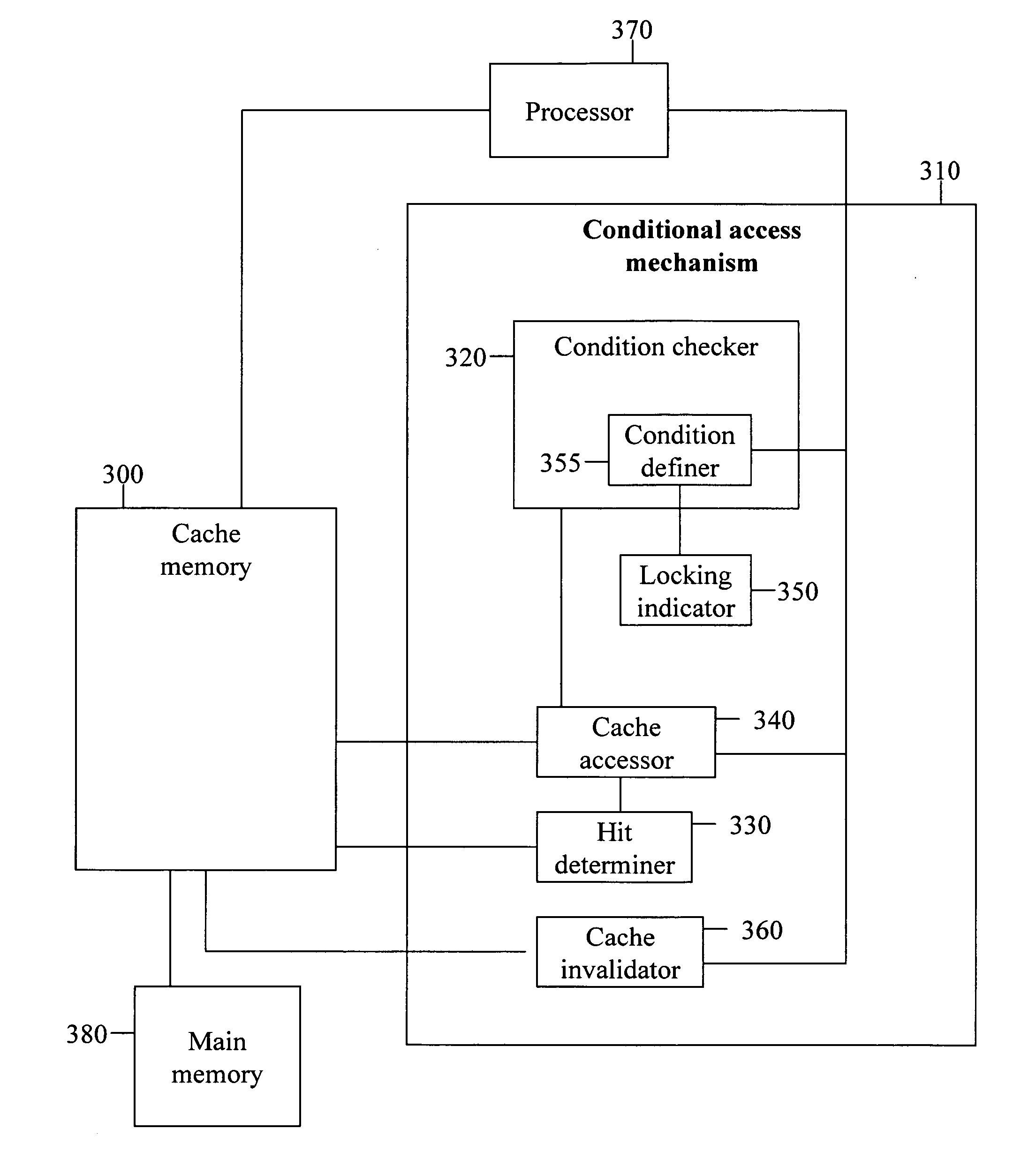
Conditionally accessible cache memory
A cache memory has a conditional access mechanism, operated by a locking condition. The conditional access mechanism uses the locking condition to implement conditional accessing of the cache memory.
Owner:ANALOG DEVICES INC
Providing alternative services based on receiver configuration and type of display device
InactiveUS20090150958A1Effective controlGood serviceAnalogue secracy/subscription systemsTwo-way working systemsTelevision systemUser device
The present invention provides a system for providing alternative services in a television system. In one implementation, a subscriber is provided an alternative service upon attempting to access an unauthorized service, thereby providing a framework for efficient control of conditional access and enhanced services. In addition, in one implementation, user device limitations or variations are handled conveniently through the same multi-purpose system for providing alternative services.
Owner:SYNAMEDIA LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com