Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
664results about How to "Prevent copying" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
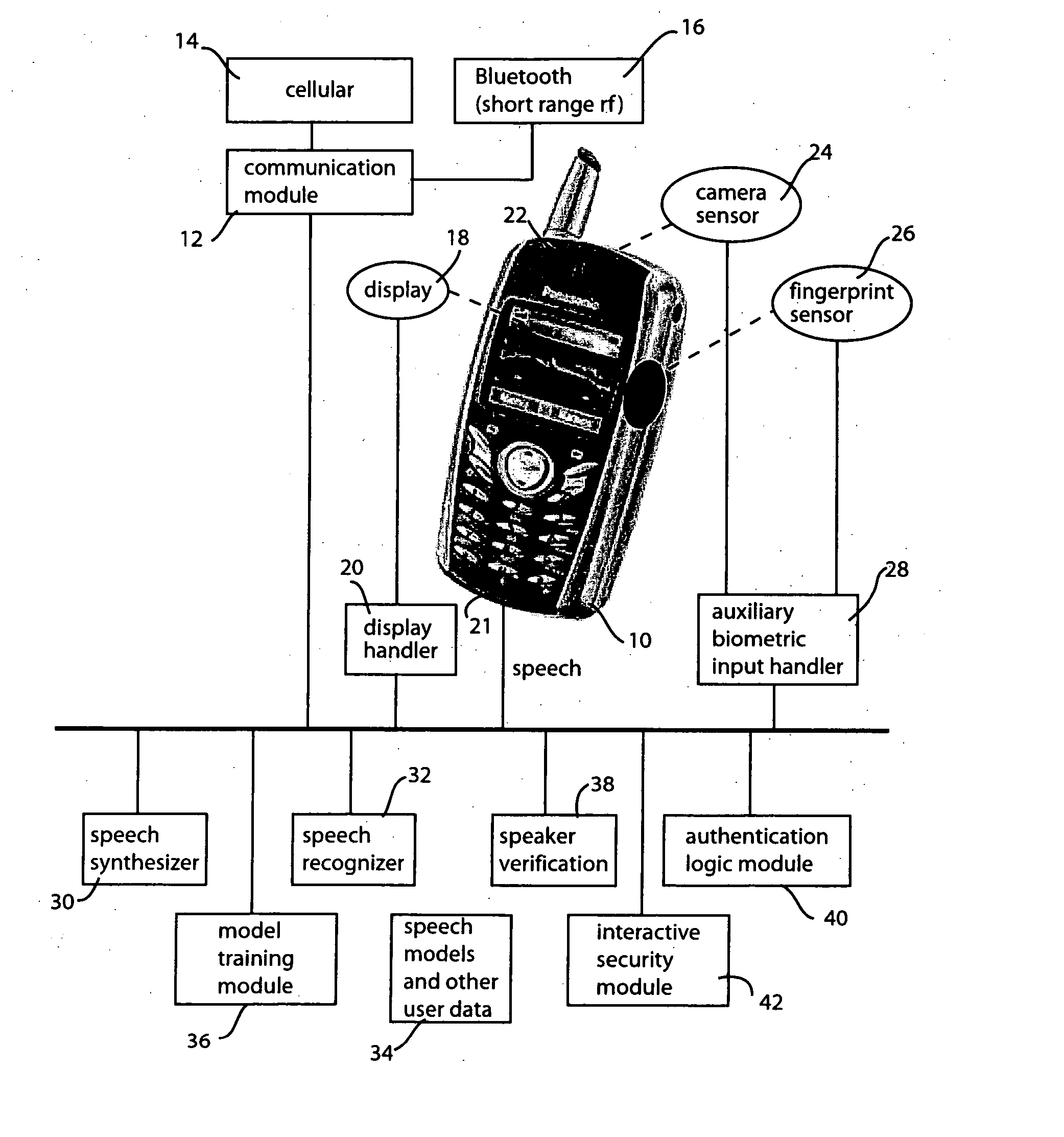
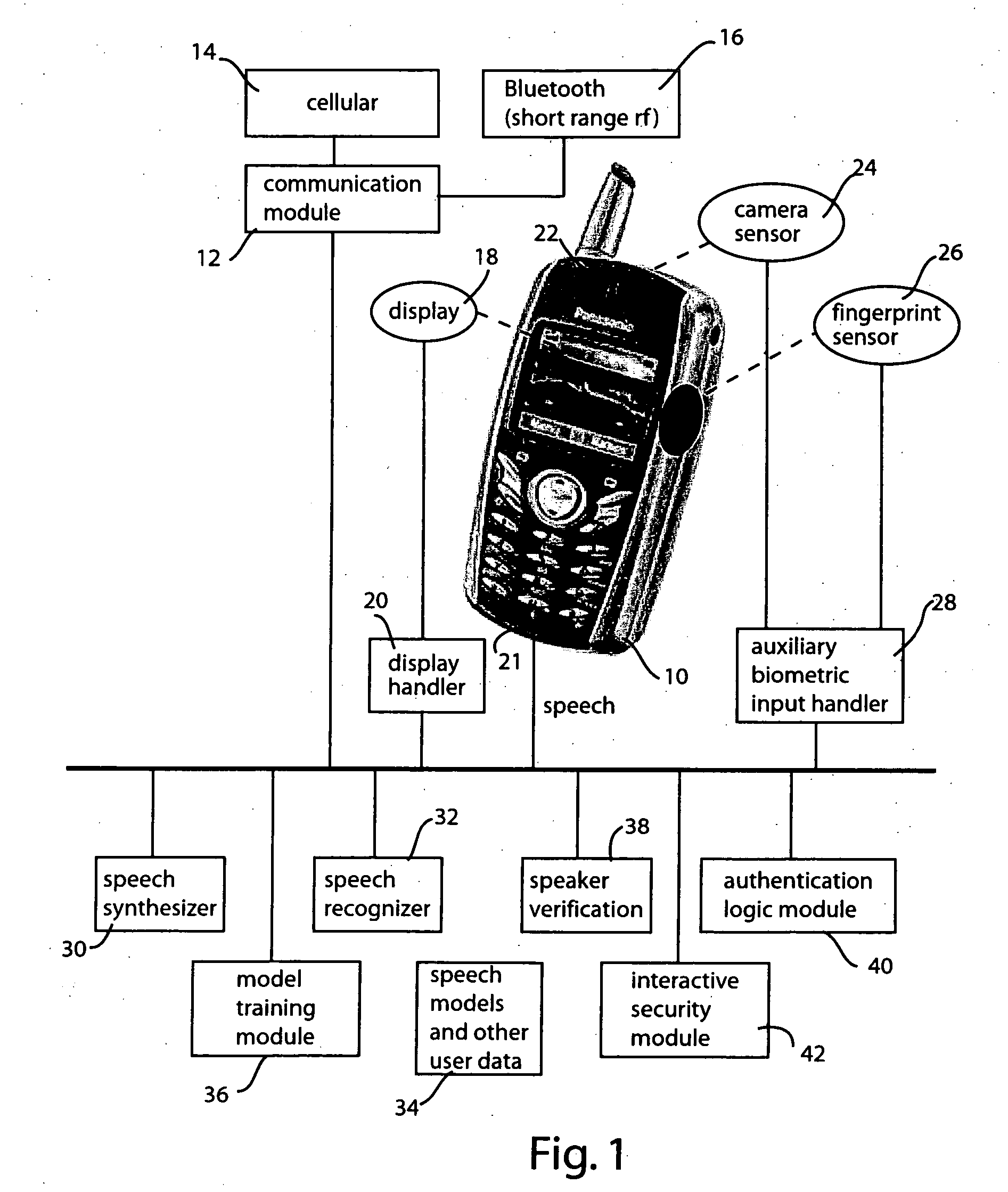
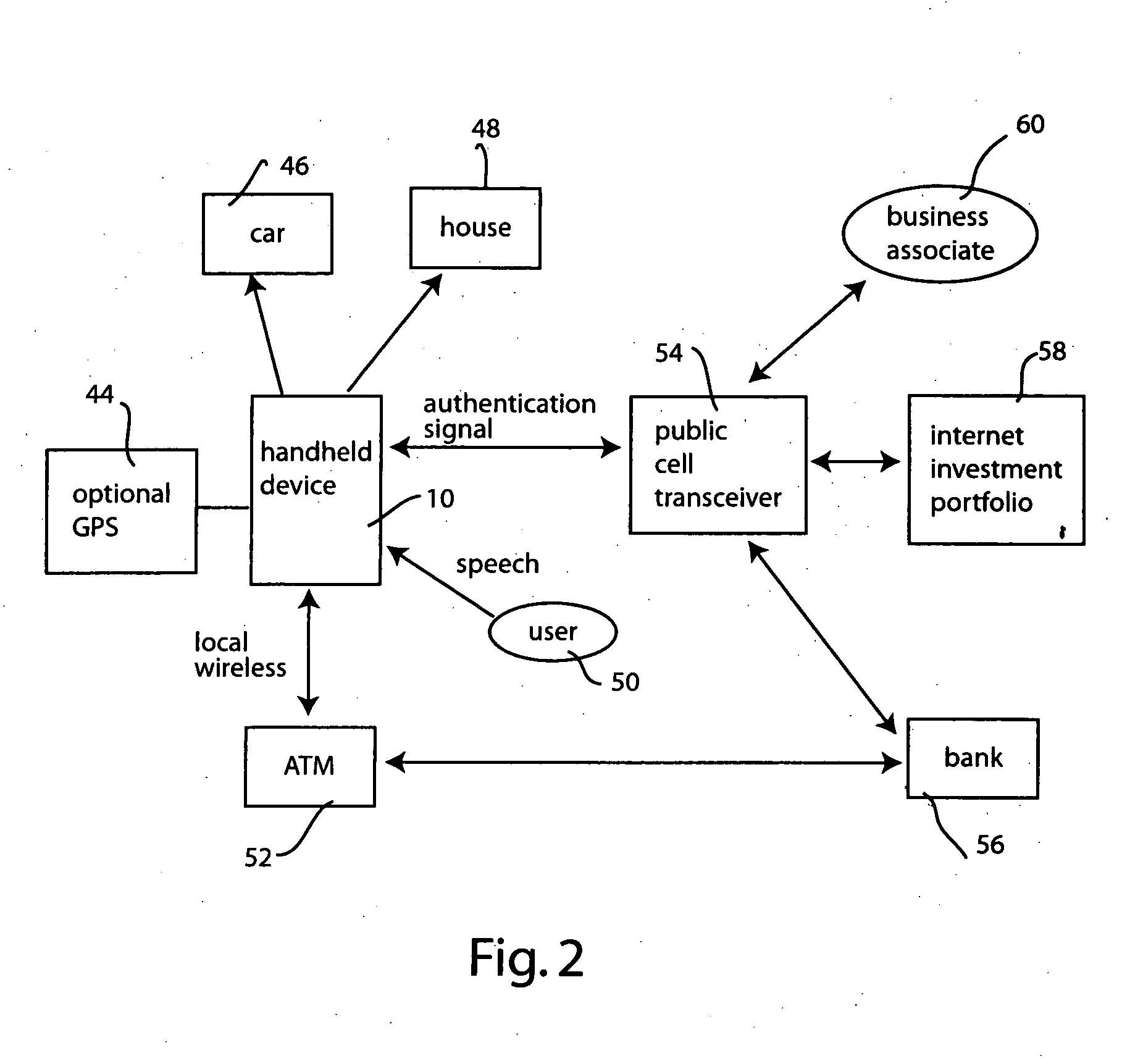
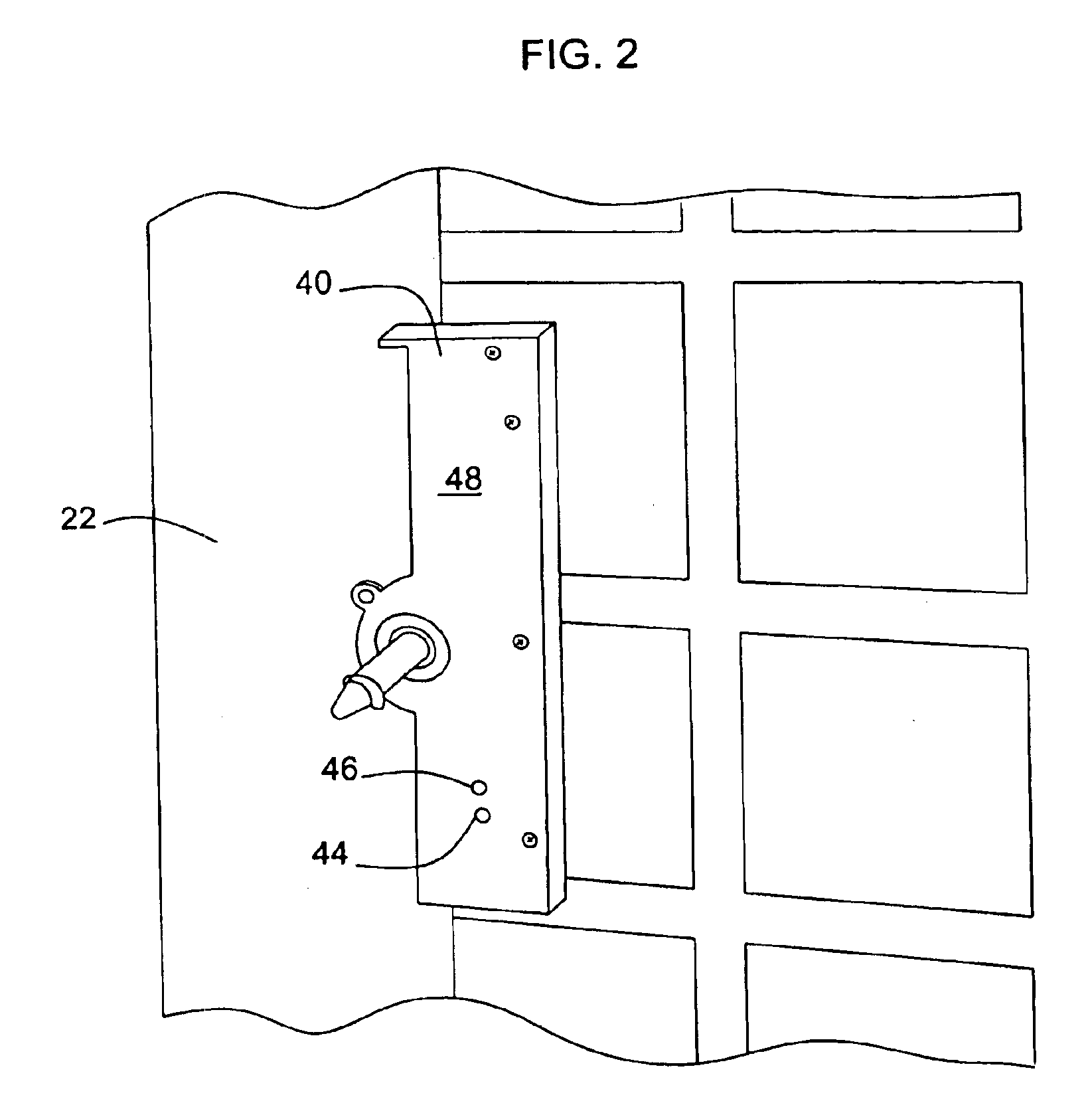
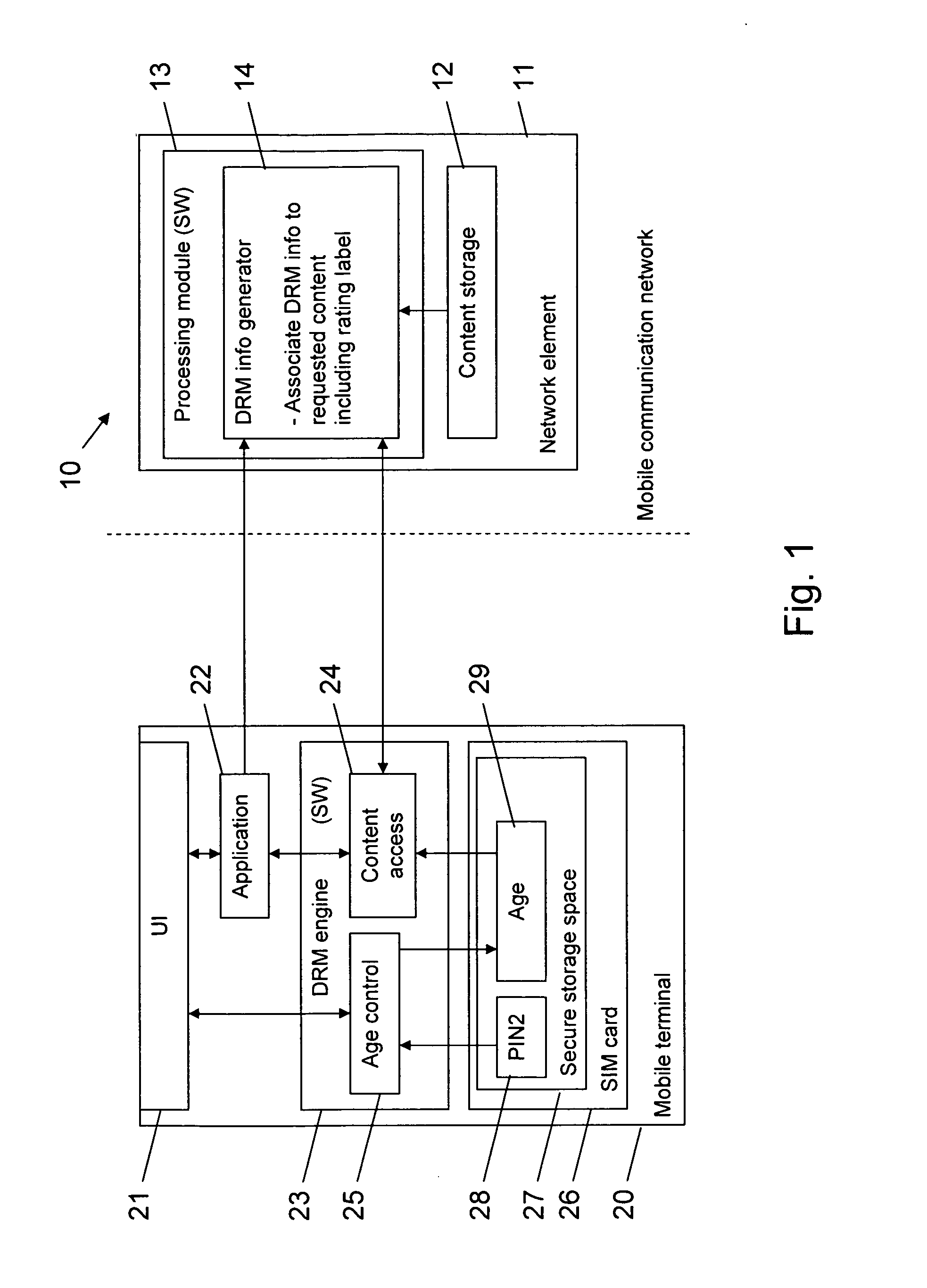
System and method for portable authentication
InactiveUS20050273626A1Copying be inhibitPrevent copyingUnauthorised/fraudulent call preventionDevices with voice recognitionSpeech patternsData memory
A portable device, such as a cellular telephone, engages the user in a challenge-response sequence that is based on recognition of the user's utterance and also upon verification of the user's speech patterns or voiceprint. The challenge-response protocol presents the user with an unexpected challenge word, which the user is then requested to respond to. The system maintains a secure data store of challenge words which it adapts and augments as the user makes use of the portable device. The portable device provides the user with a convenient, single access point through which he or she can authenticate with a variety of disparate secure devices ranging from door locks, ATM machines, financial institutions and third-party business associates.
Owner:PANASONIC CORP
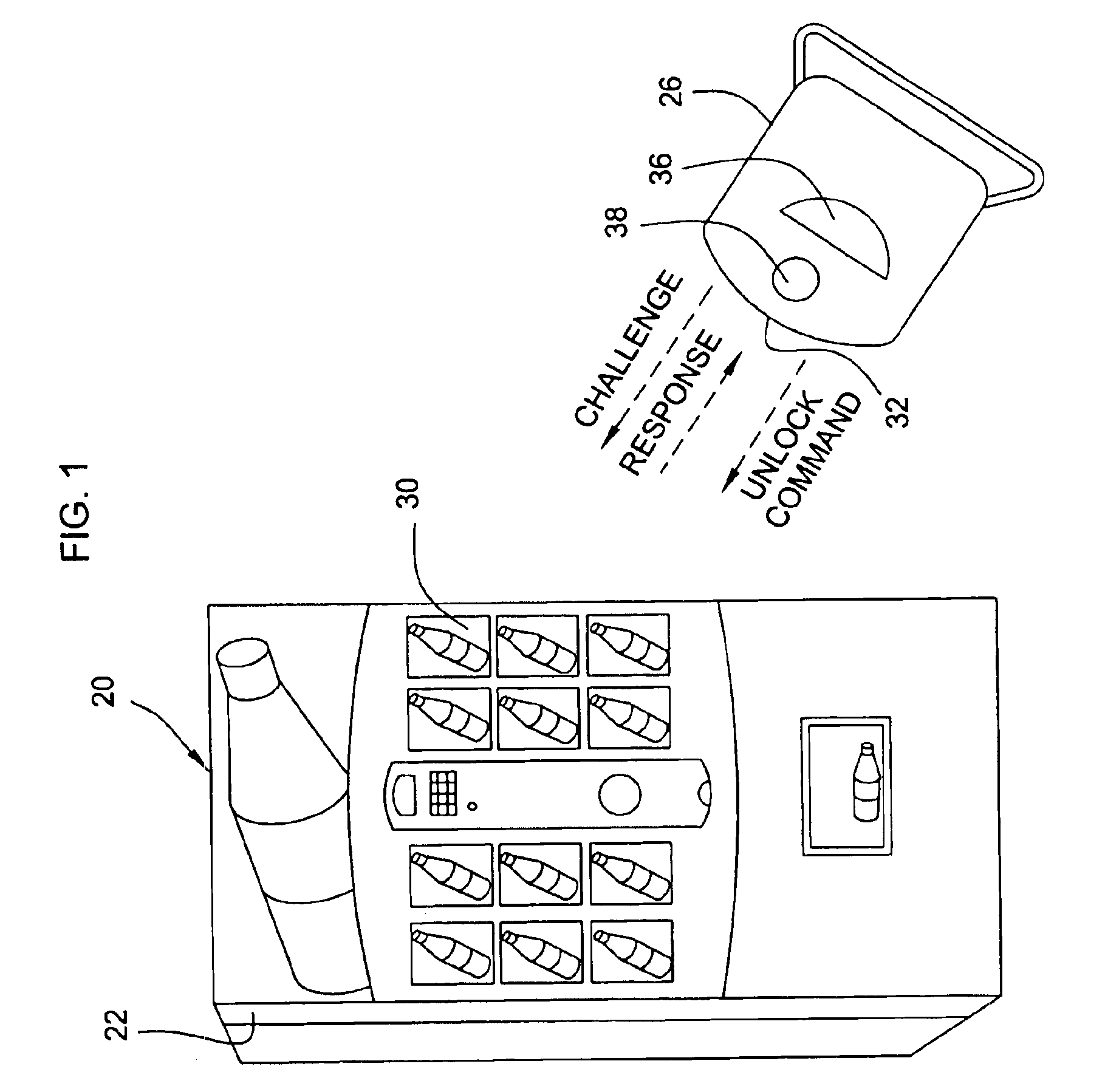
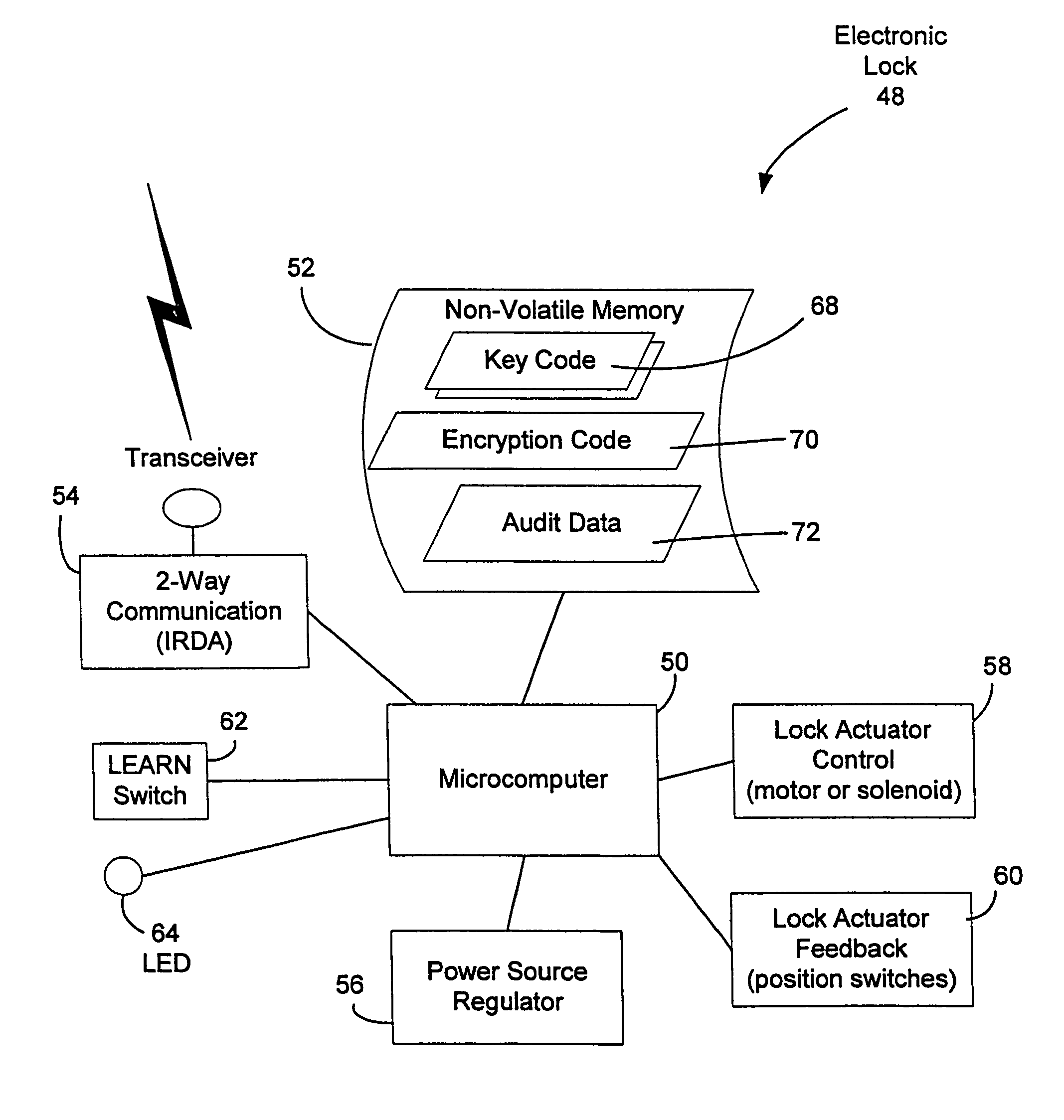
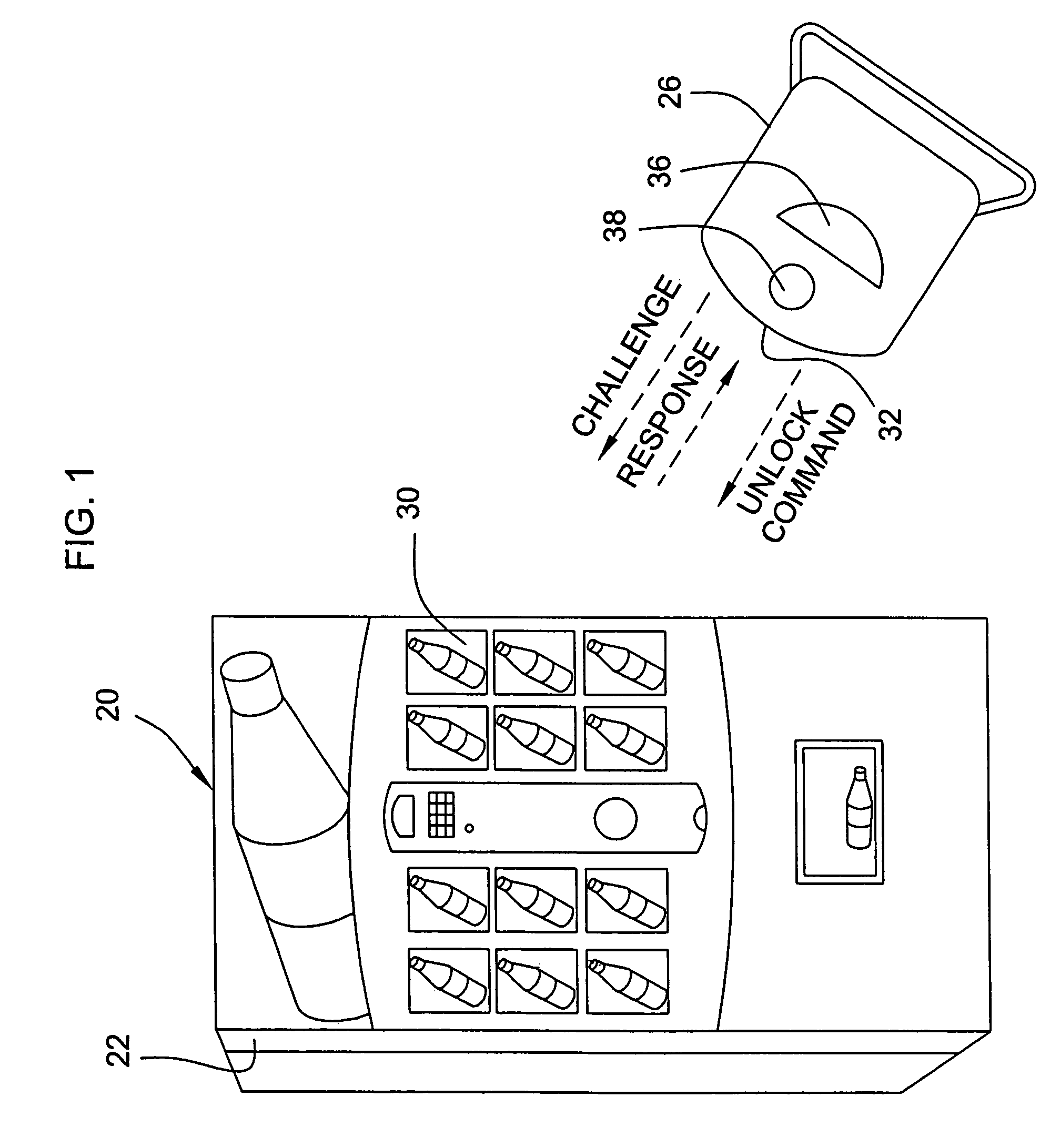
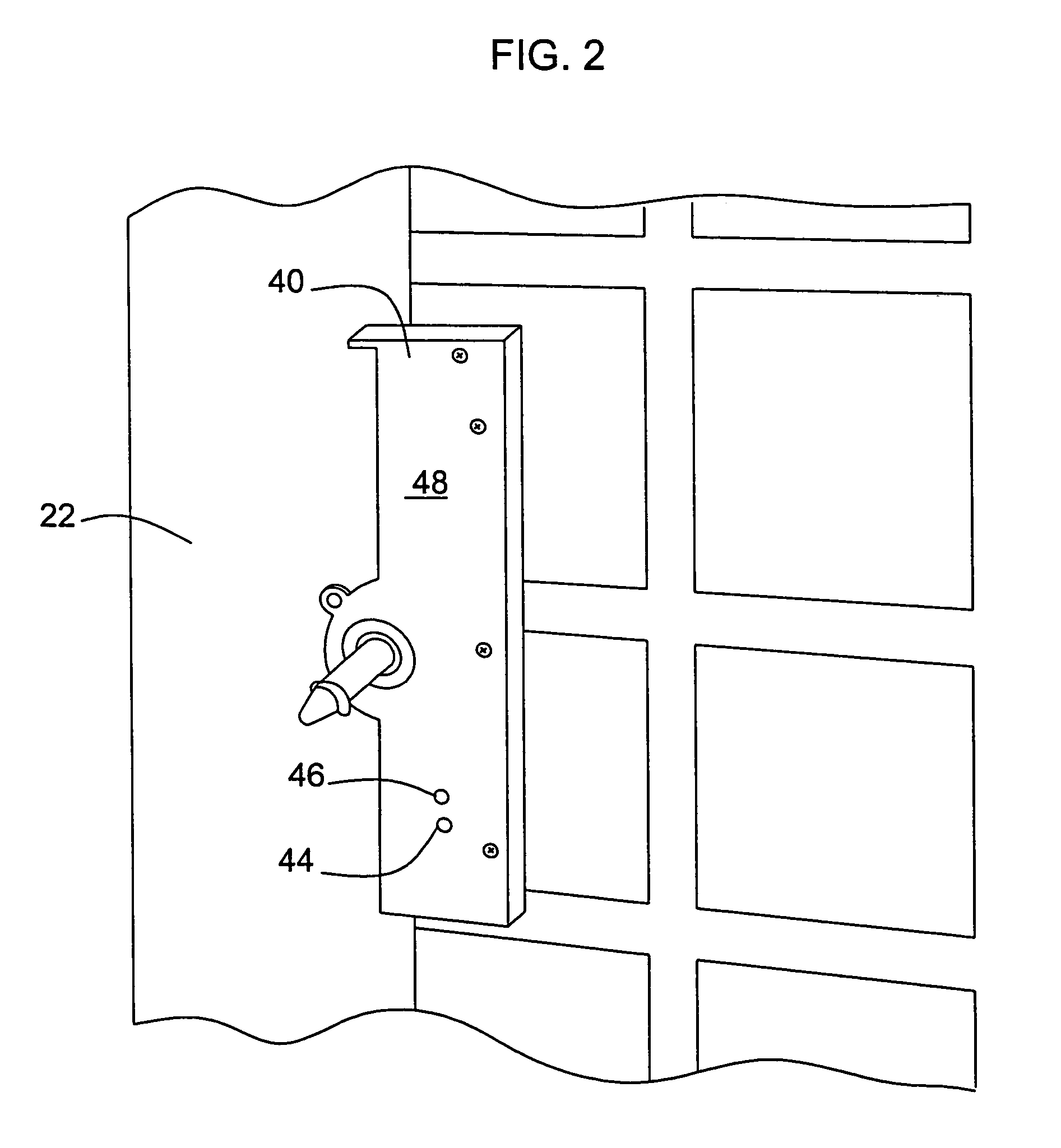
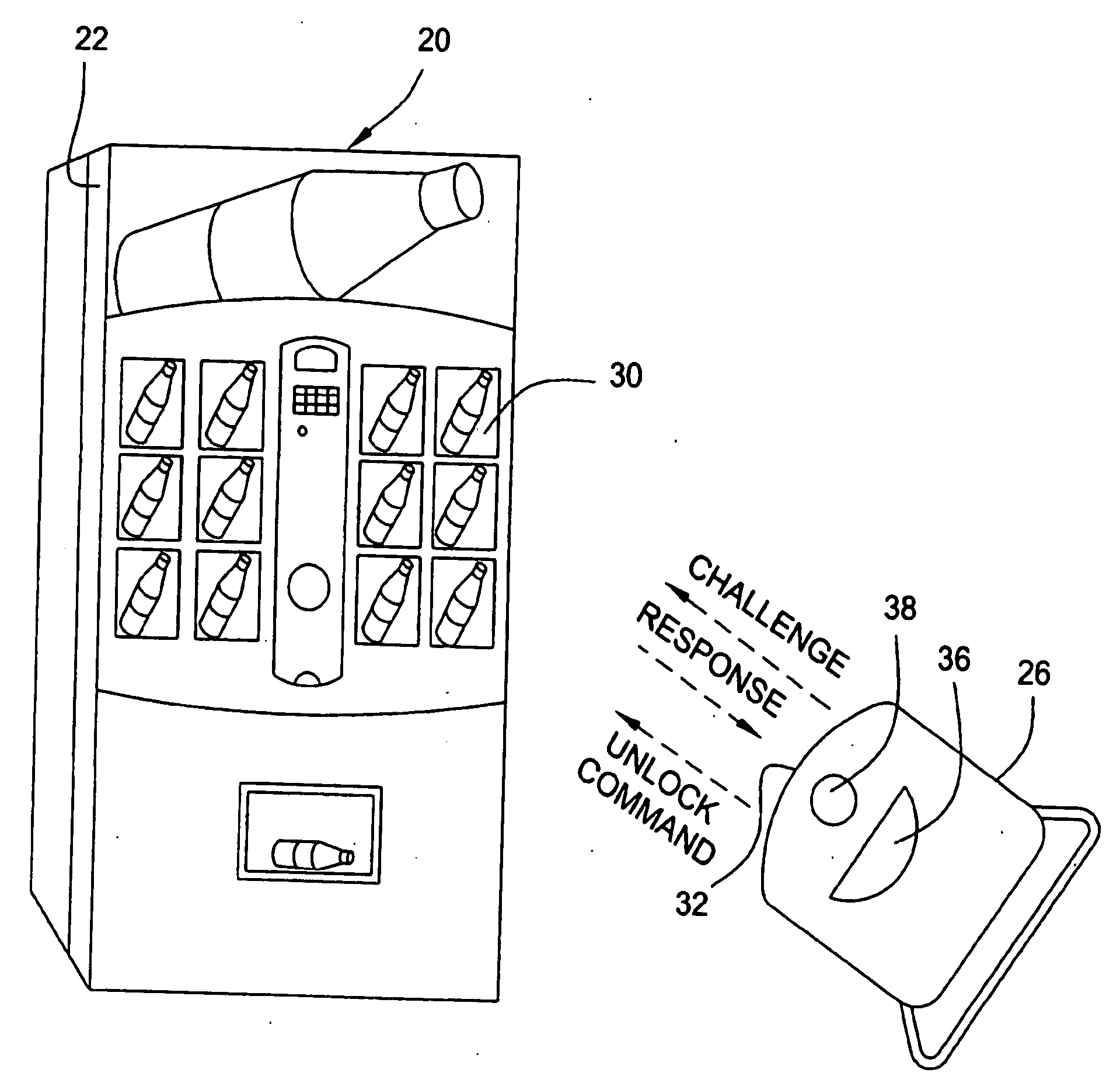
Vending machines with field-programmable locks
InactiveUS6900720B2Easily and inexpensively programmedImprove the level ofFrequency-division multiplex detailsDigital data processing detailsBiological activationHome based
Owner:MICRO ENHANCED TECH
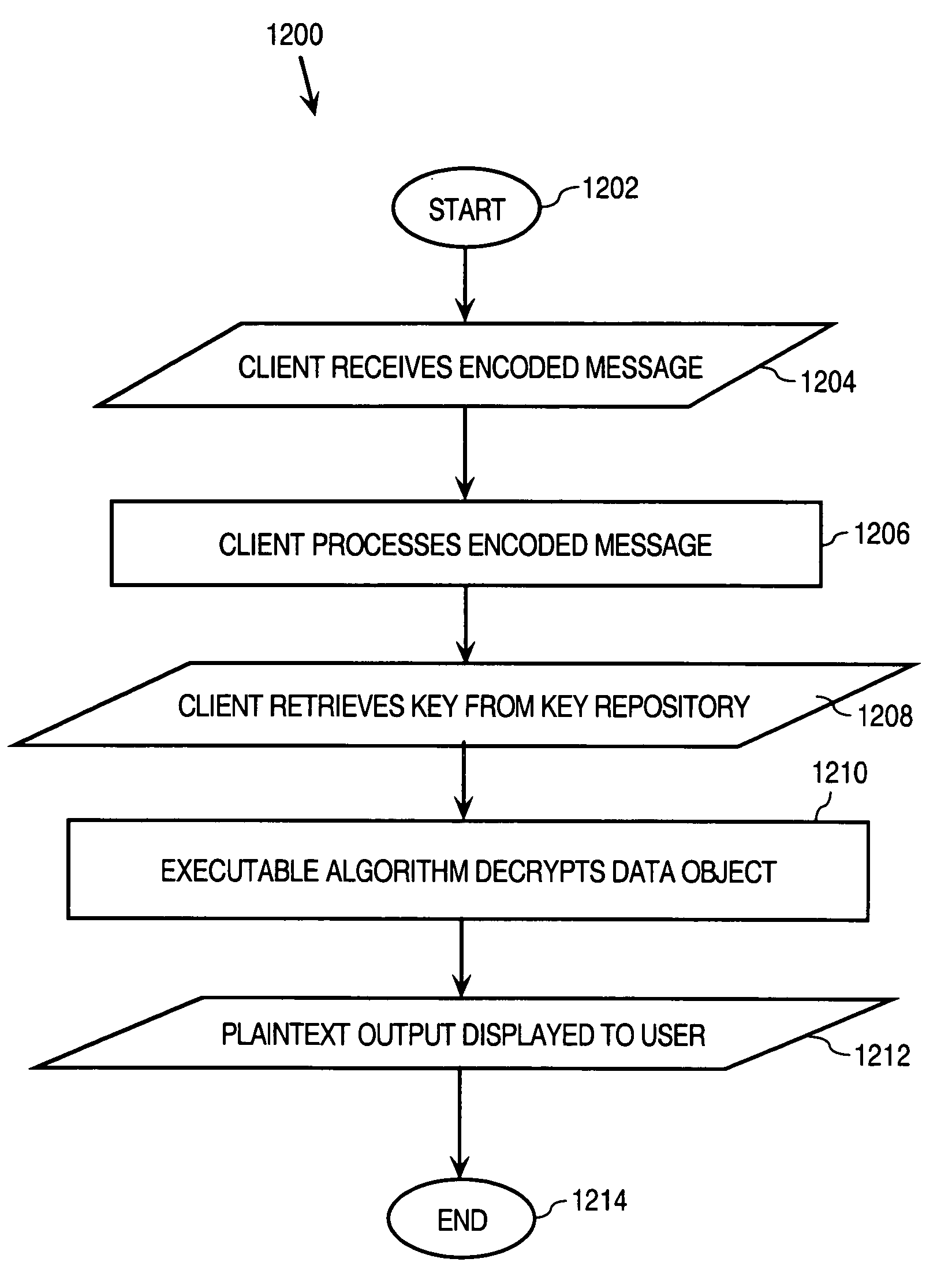
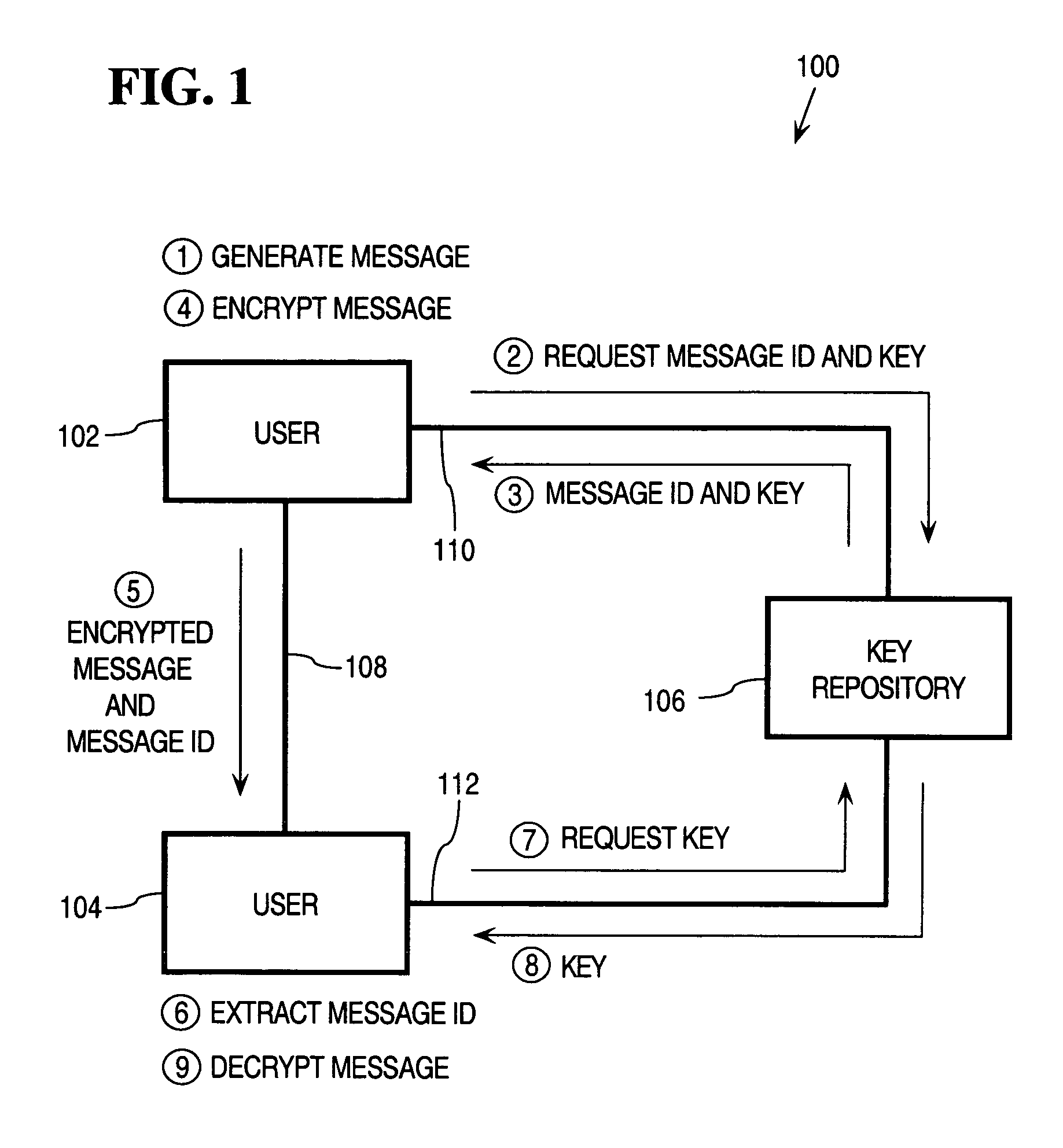
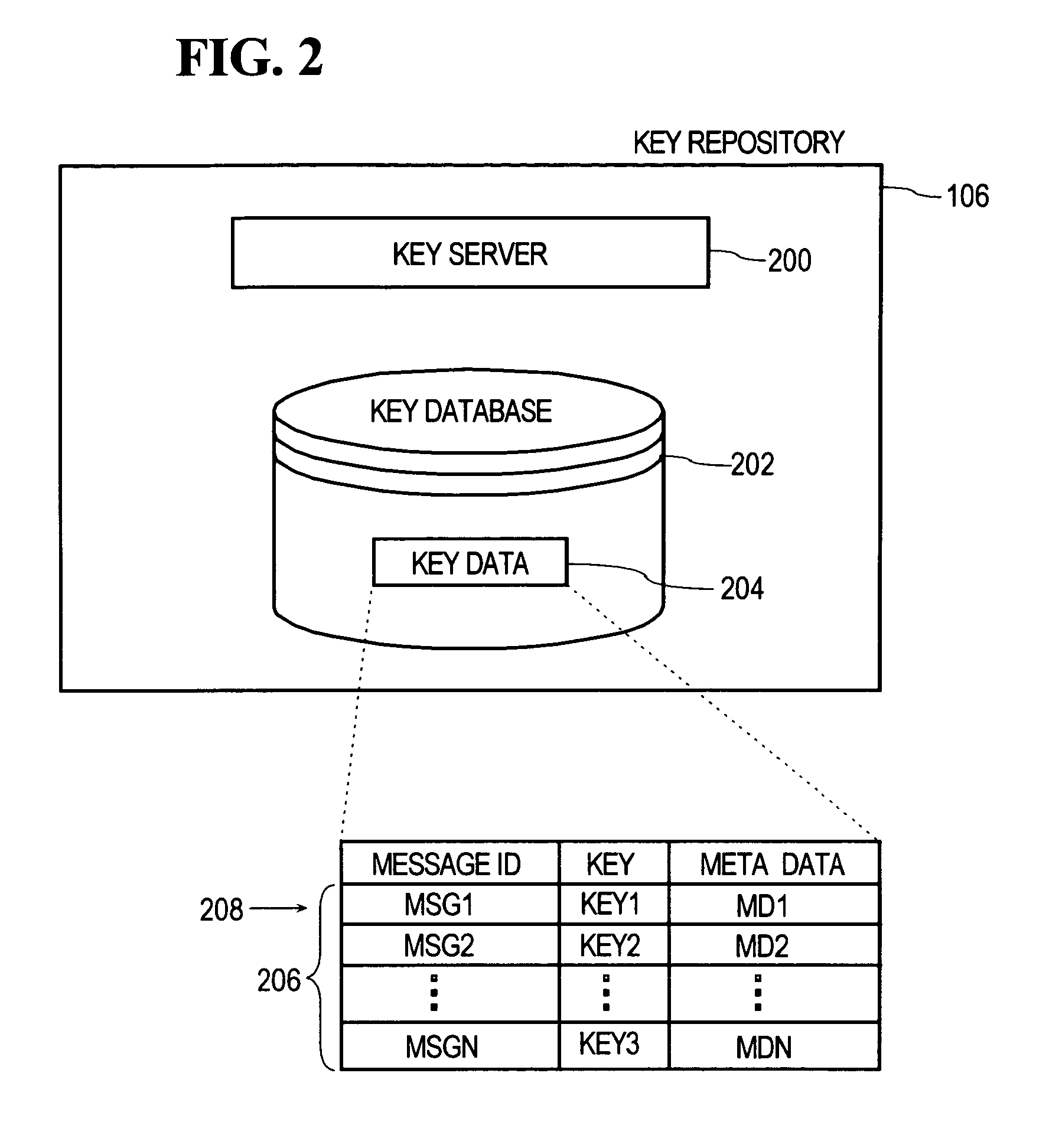
Dynamic encoding algorithms and inline message decryption
InactiveUS7096355B1Prevent copyingKey distribution for secure communicationMultiple keys/algorithms usagePlaintextThird party
In general, data exchanged between users is protected using any of various encoding approaches. An example of encoding is encryption, but any kind of encoding may be used. The data used to encrypt the data exchanged between the users, referred to as a “key”, is maintained only in a key repository. Users must obtain a key from the key repository to either encode or decode, encrypt or decrypt data, after which the user's copy of the key is destroyed or otherwise rendered inoperable. A key management policy is employed to control access to the keys maintained by the key repository. Encoding algorithms may be dynamically changed over time. Users may negotiate different algorithms to be used with specific users or messages. Thus, different algorithms may be used between different sets of users depending upon what the member users of those sets negotiate among themselves. The frequency at which algorithms are changed may also be separately negotiated between users. The frequency may vary depending, for example, upon the perceived risk of intrusion by unauthorized third parties, the content of the messages being transmitted, or both. According to an inline message decryption approach, an encoded message is provided to a user in a form that enables the user's client to process the encoded message using conventional client tools and obtain the cleartext message. This eliminates the need for a user's client to be aware of the particular encoding algorithm used to encode the message. Various embodiments of the inline message decryption approach include: a) in-situ decryption; b) remote decryption; and c) data uploading. An approach is also provided for exchanging data between nodes in a network using sets of associated URLs.
Owner:CHECK POINT SOFTWARE TECH INC
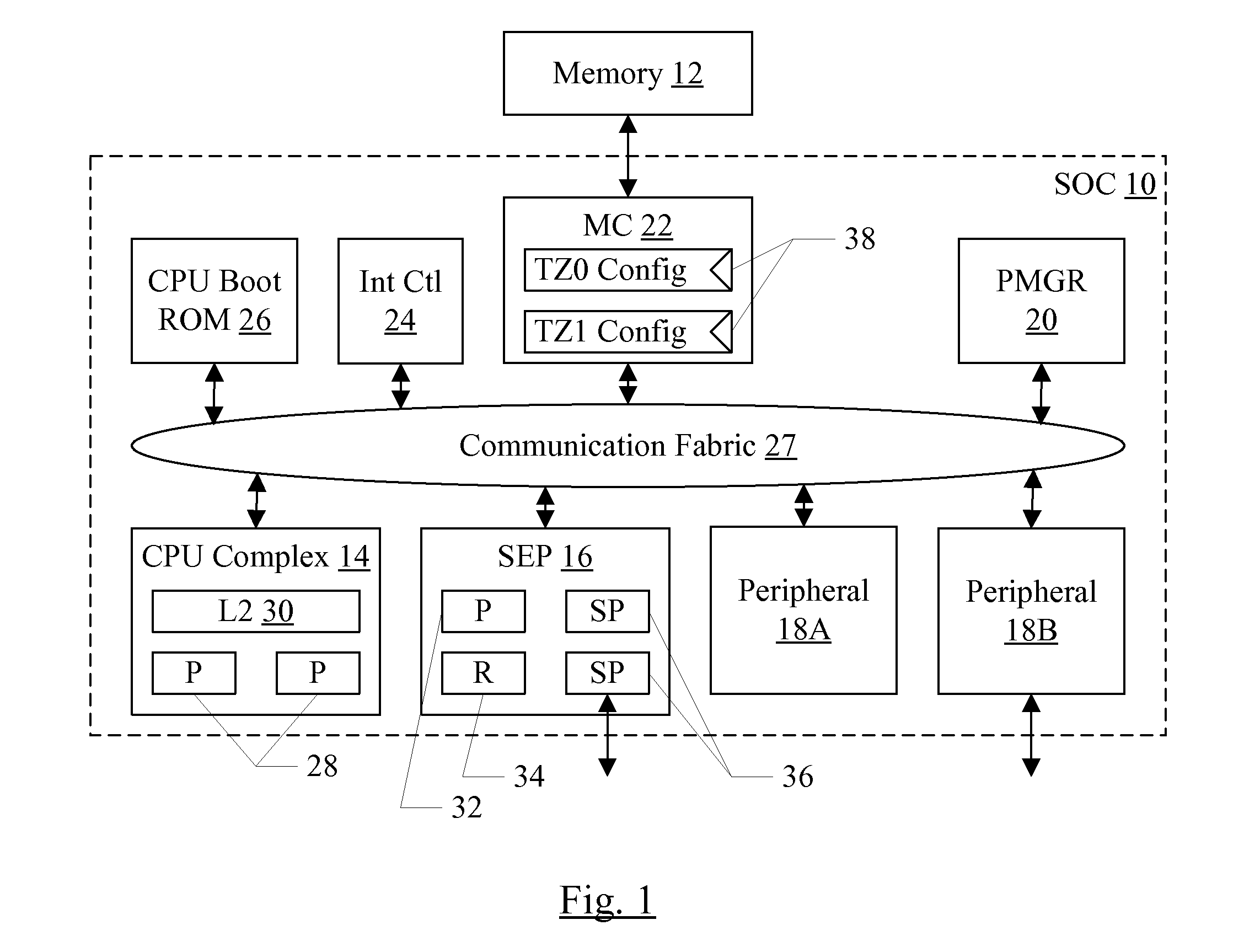
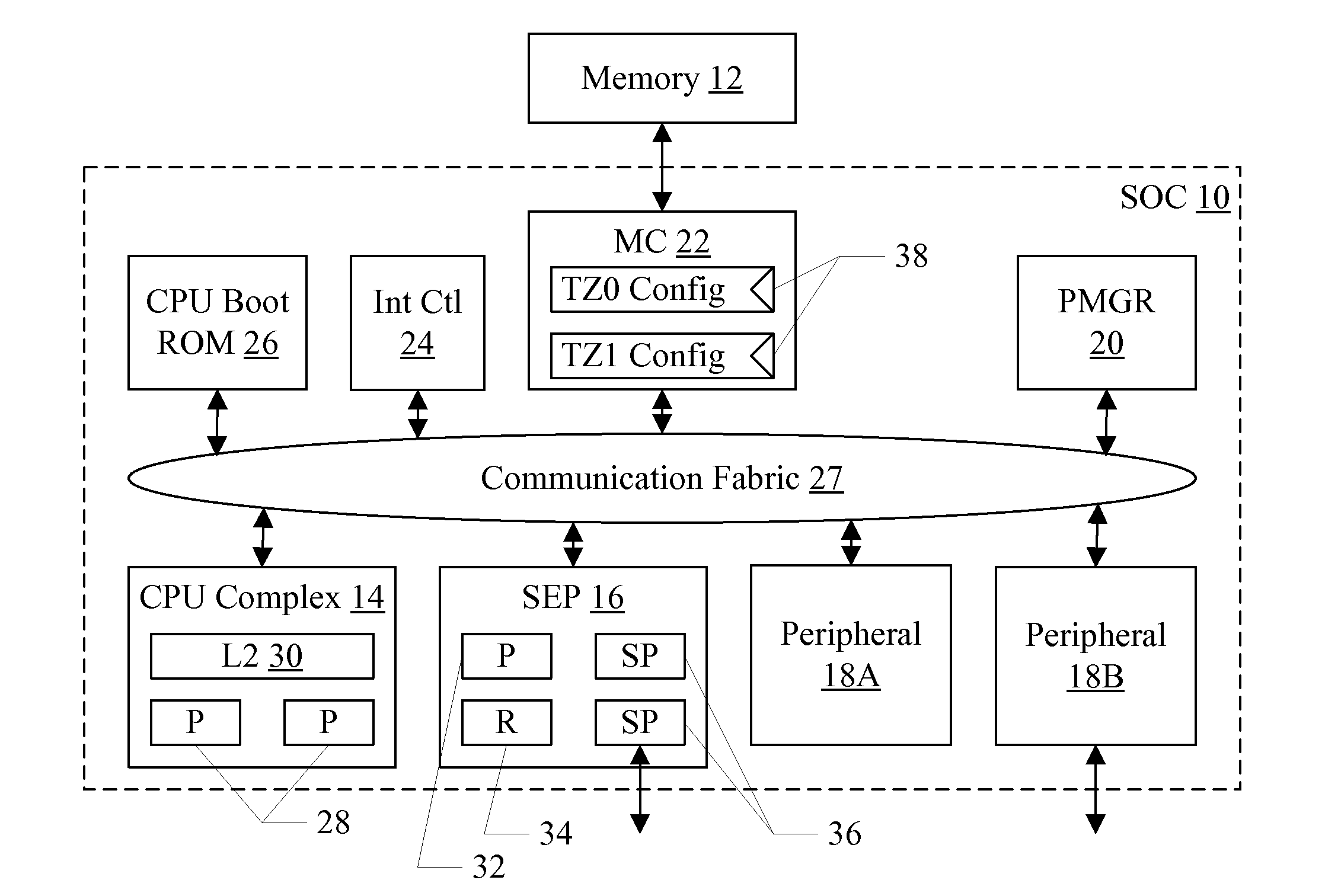
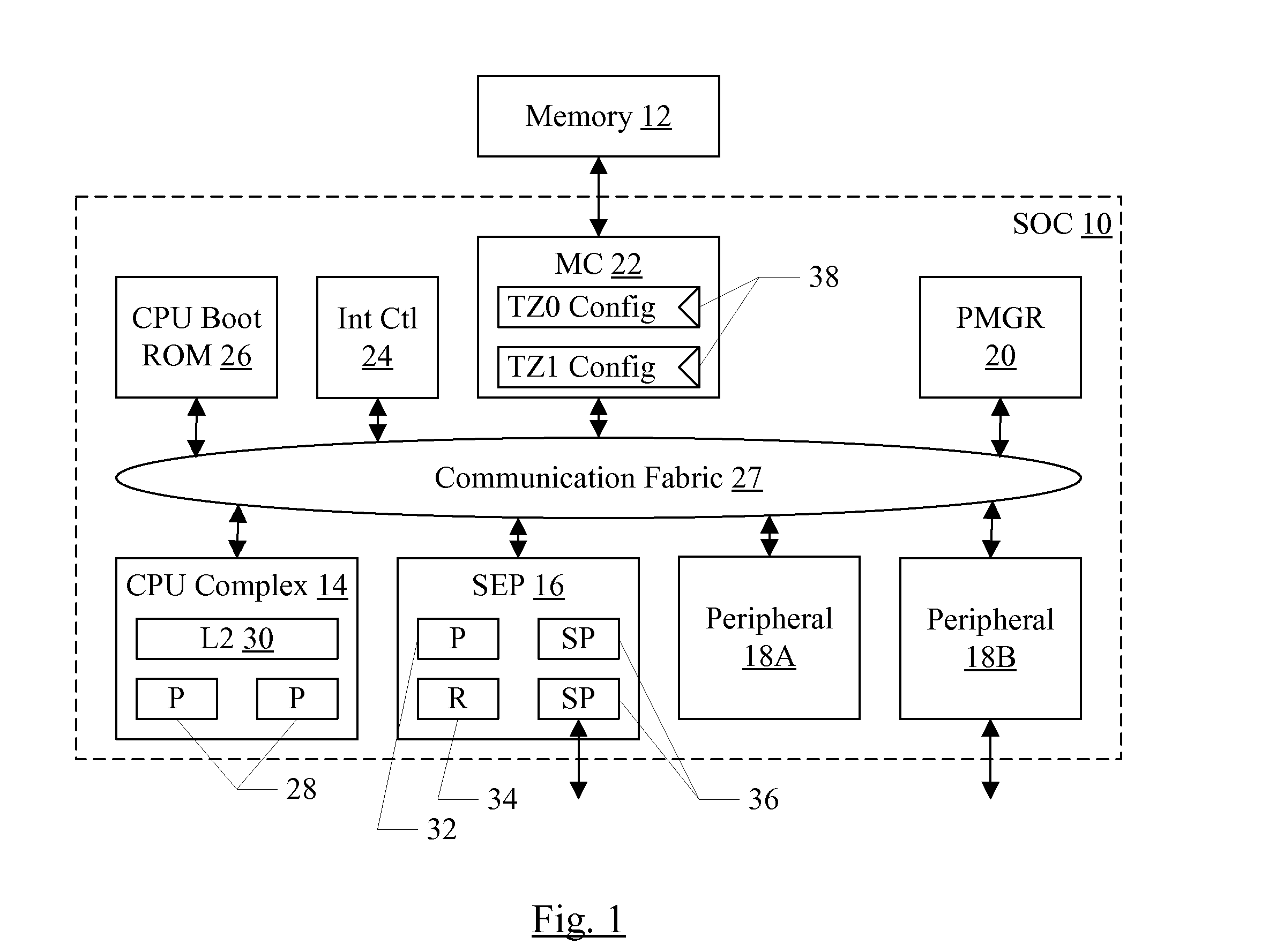
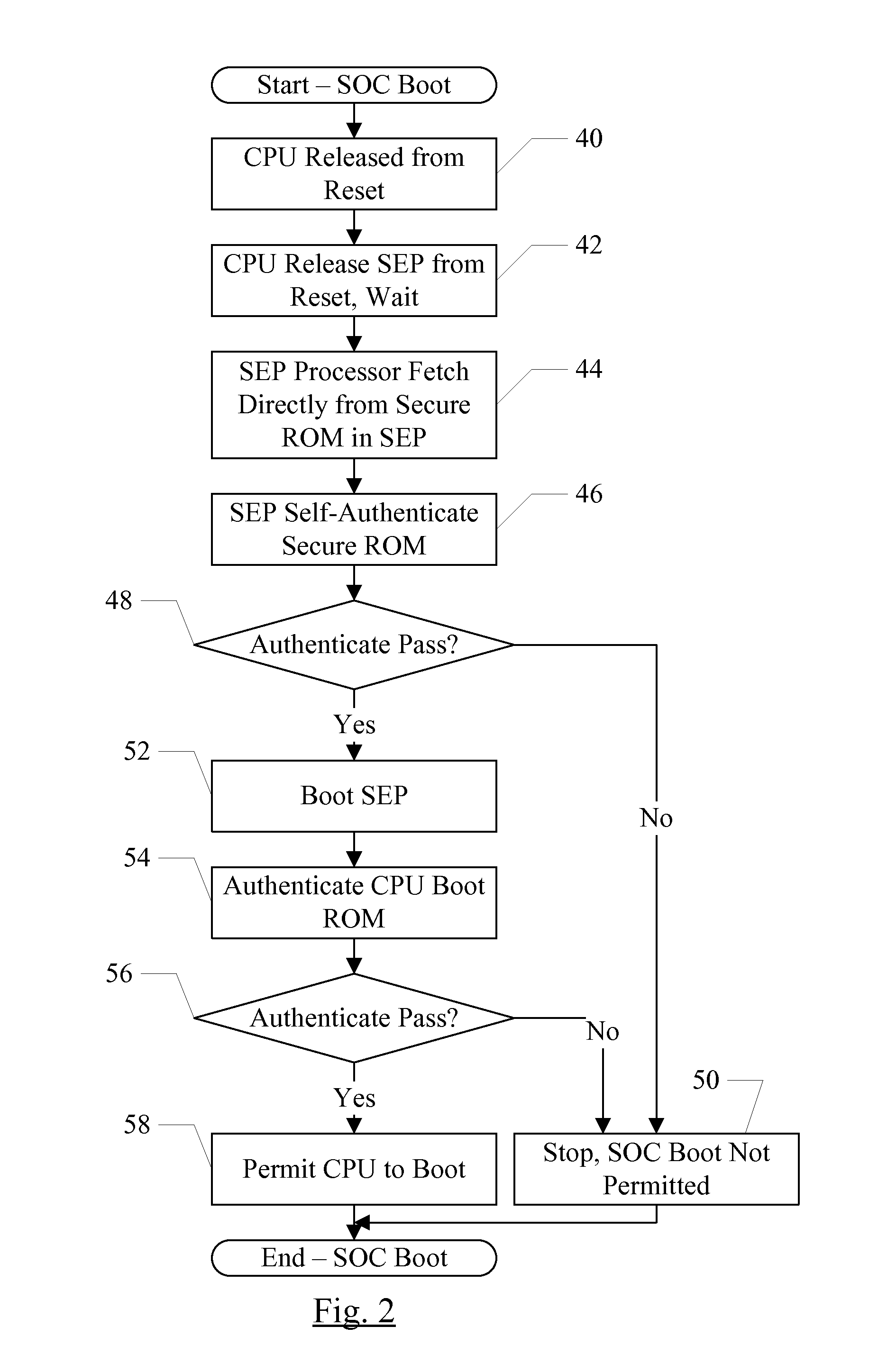
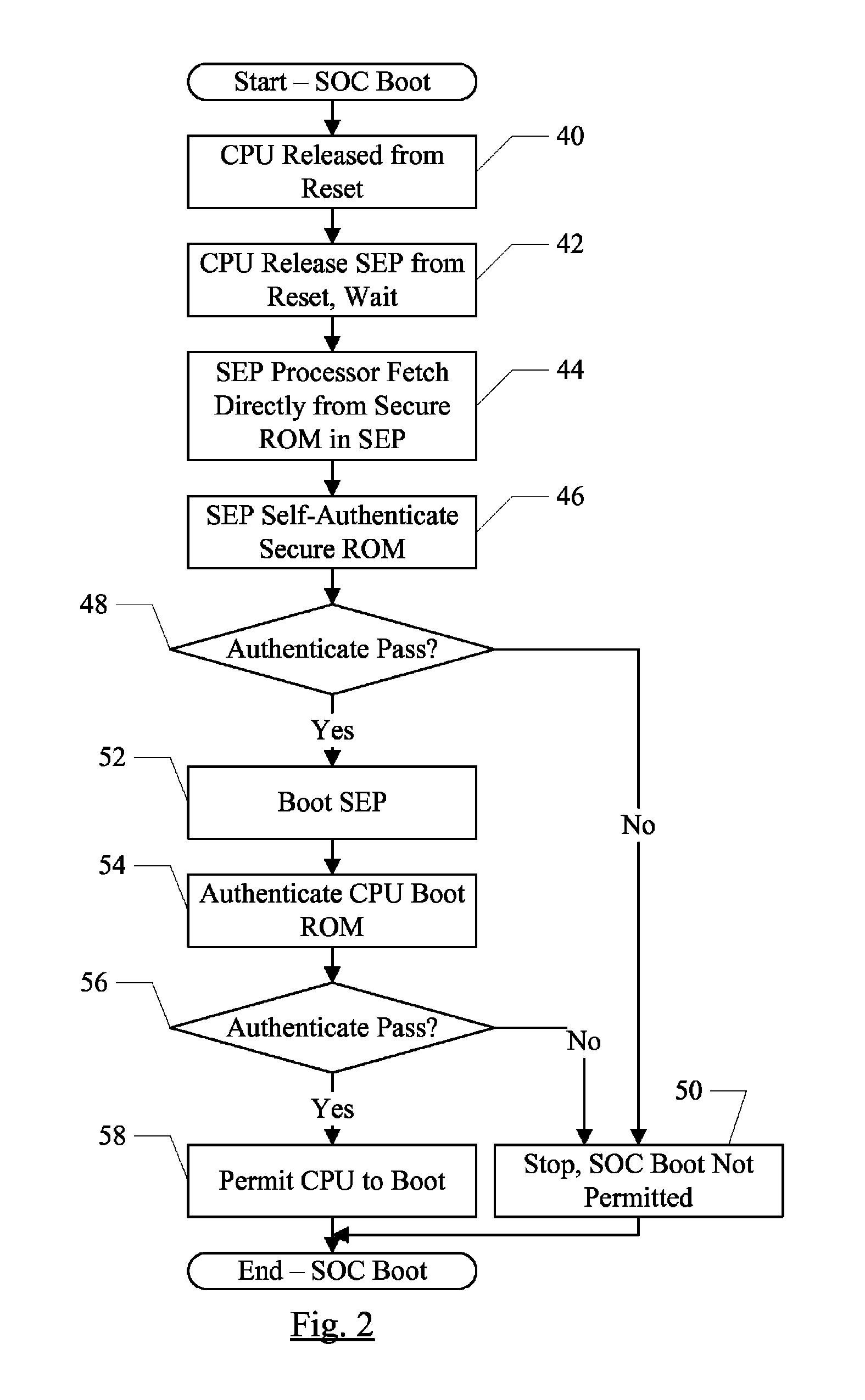
Security enclave processor for a system on a chip
ActiveUS8832465B2Prevent copyingMemory loss protectionUnauthorized memory use protectionApplication processorSystem on a chip
Owner:APPLE INC
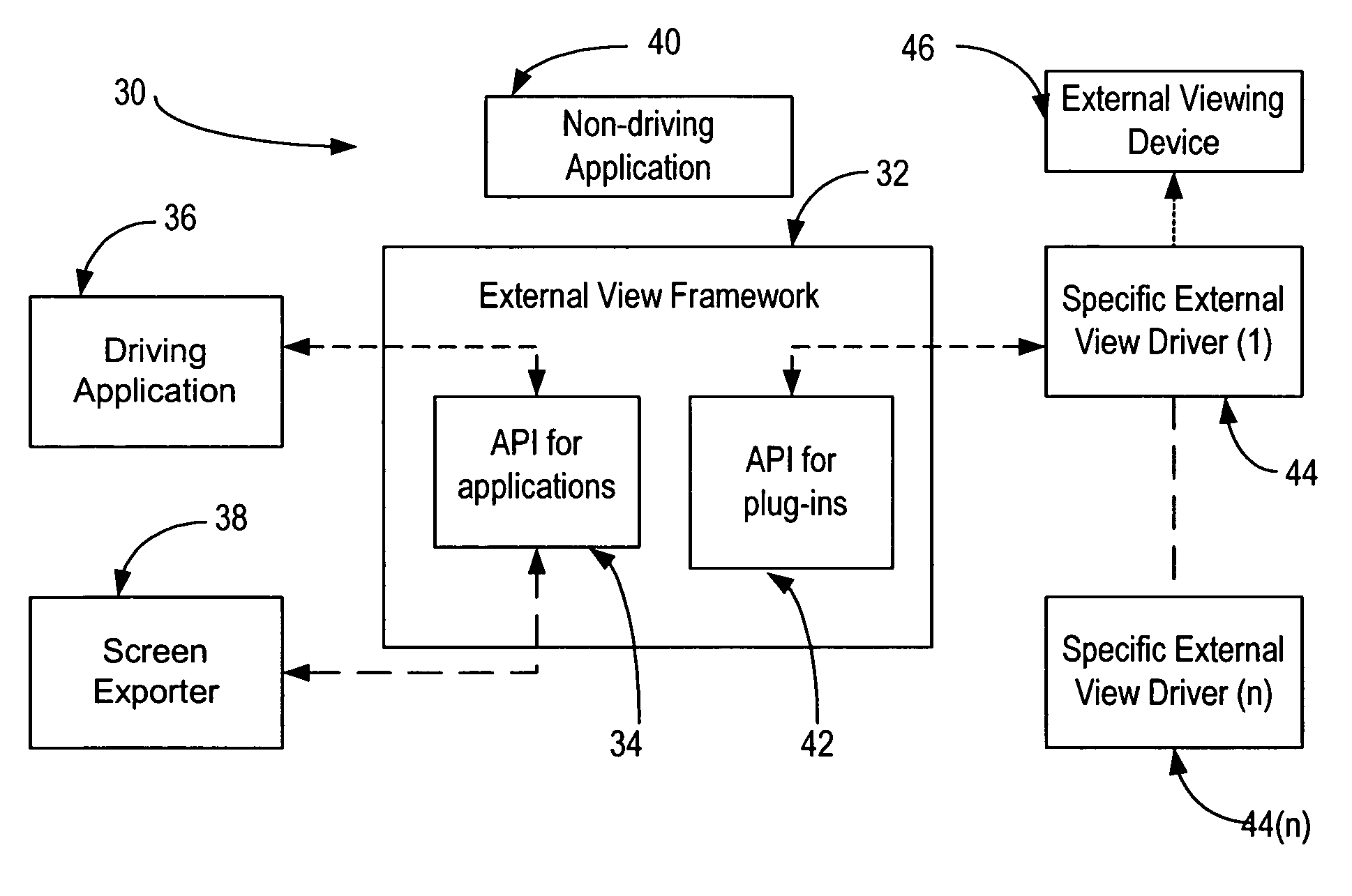
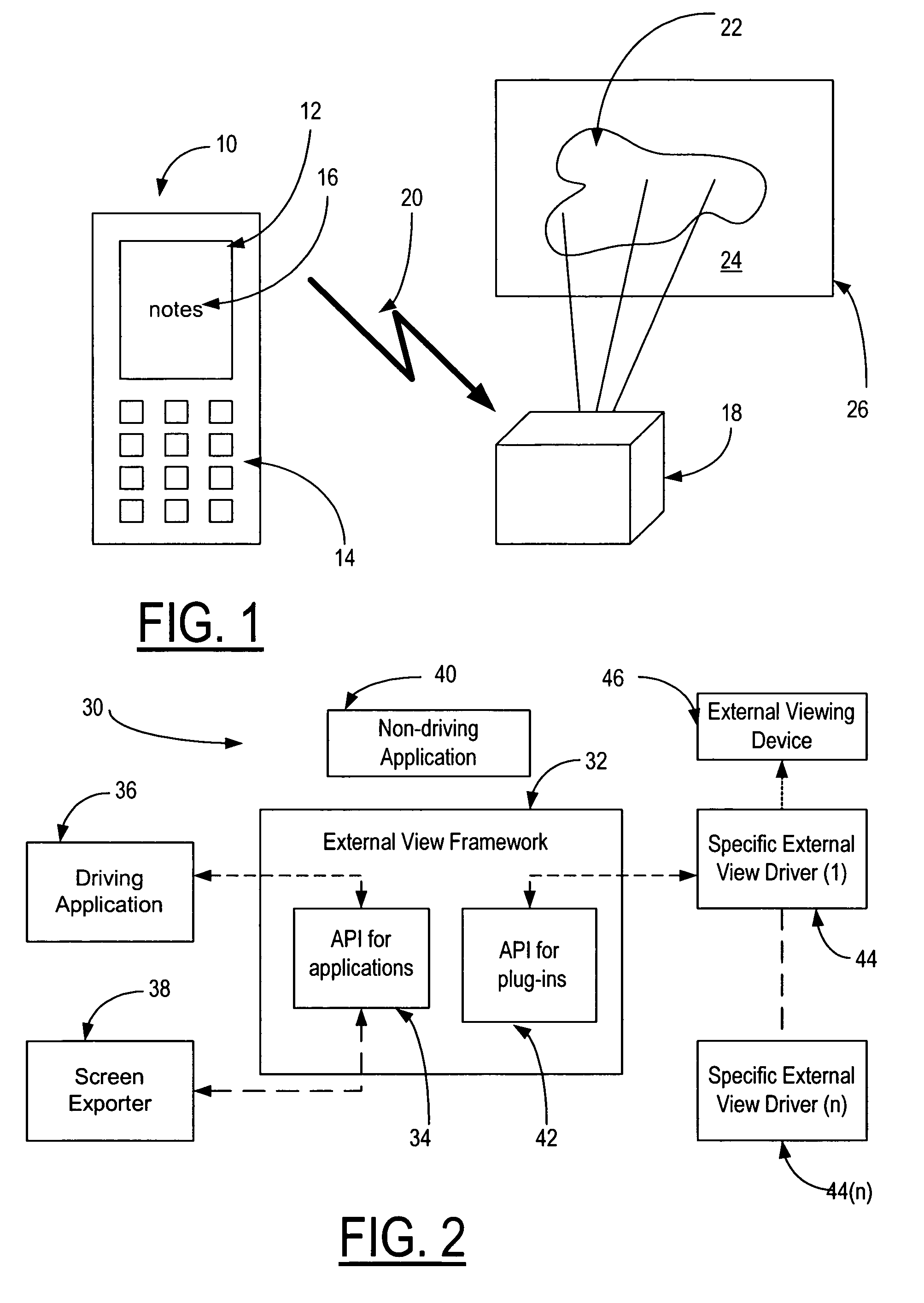
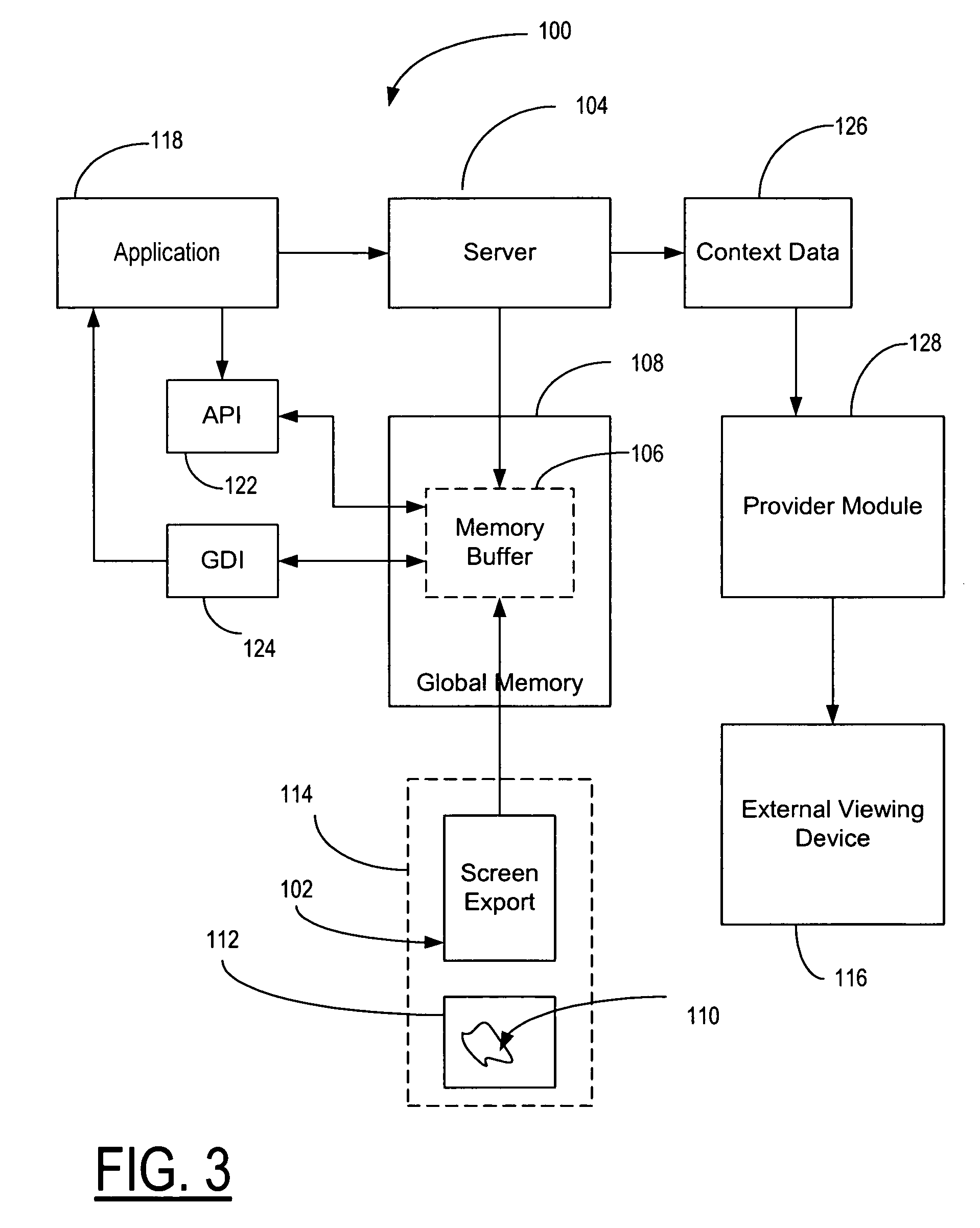
Method and apparatus for showing wireless mobile device data content on an external viewer
InactiveUS20060079214A1Prevent copyingSpecial service for subscribersSubstation equipmentImage resolutionDisplay device
A method, apparatus, system and computer program product are presented for showing a presentation created and running on a mobile device on an external display device wherein the information data content is transferred from the mobile device to the external display device independent of the characteristics, data format and screen resolution of the external display device.
Owner:RPX CORP
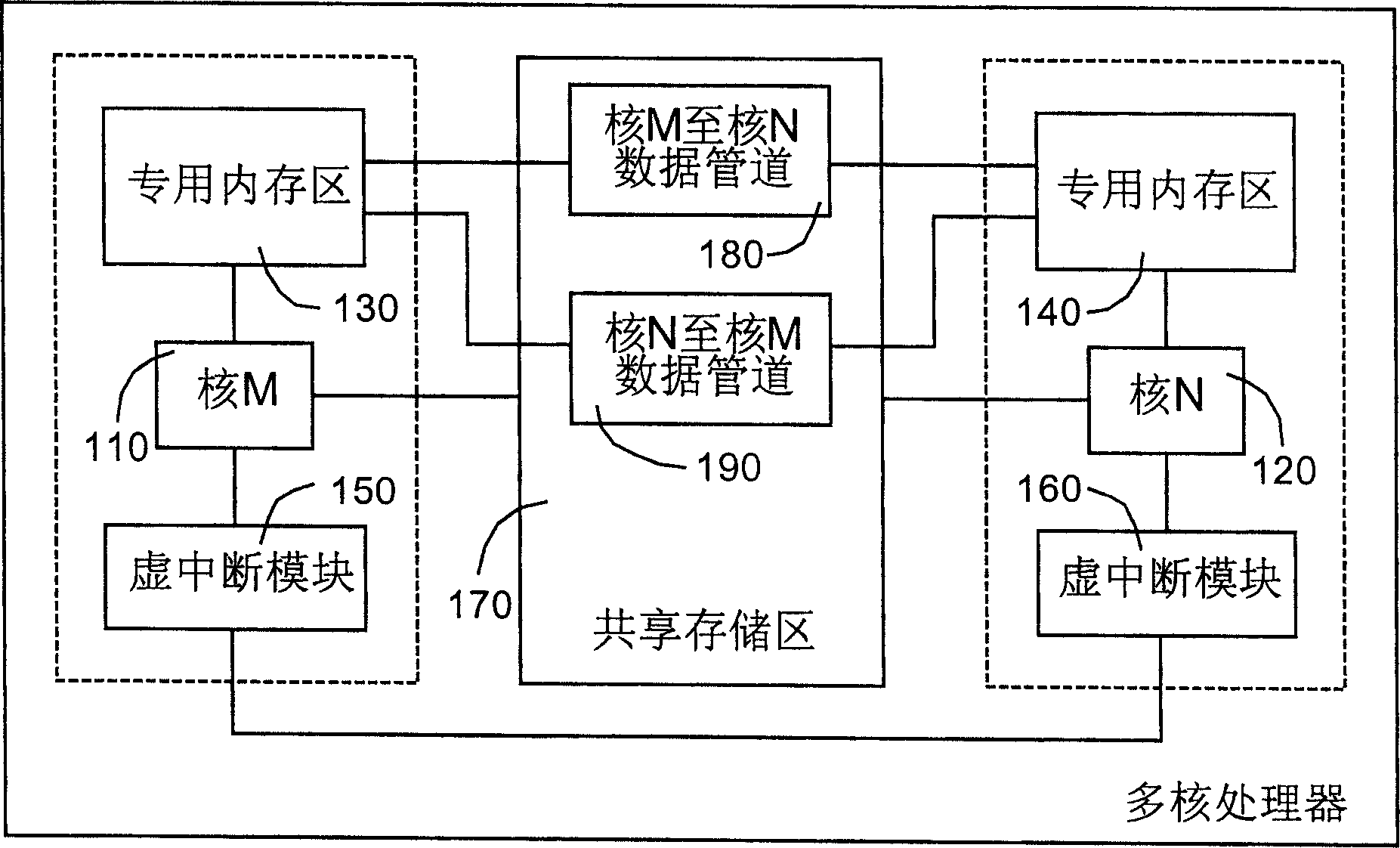
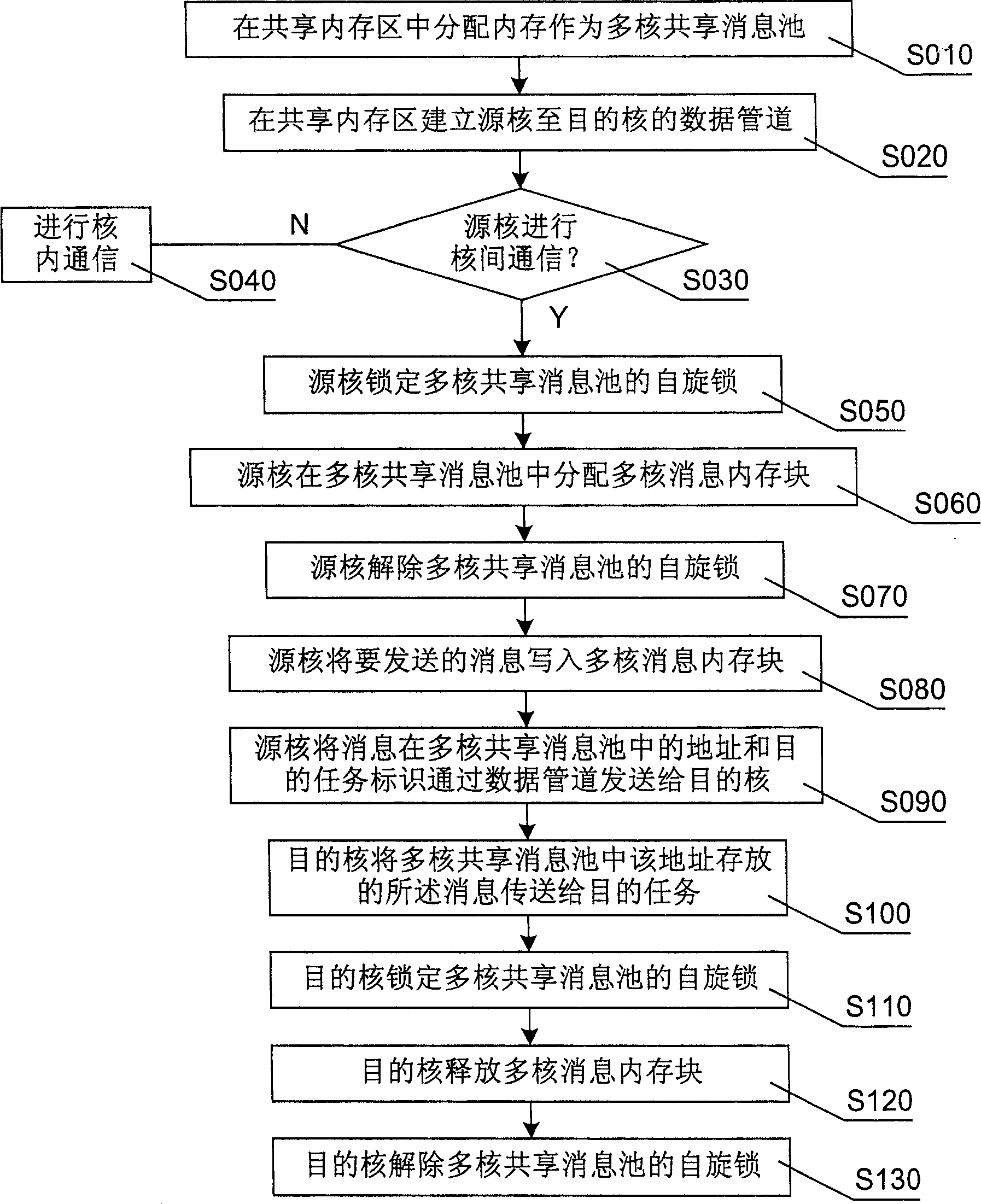
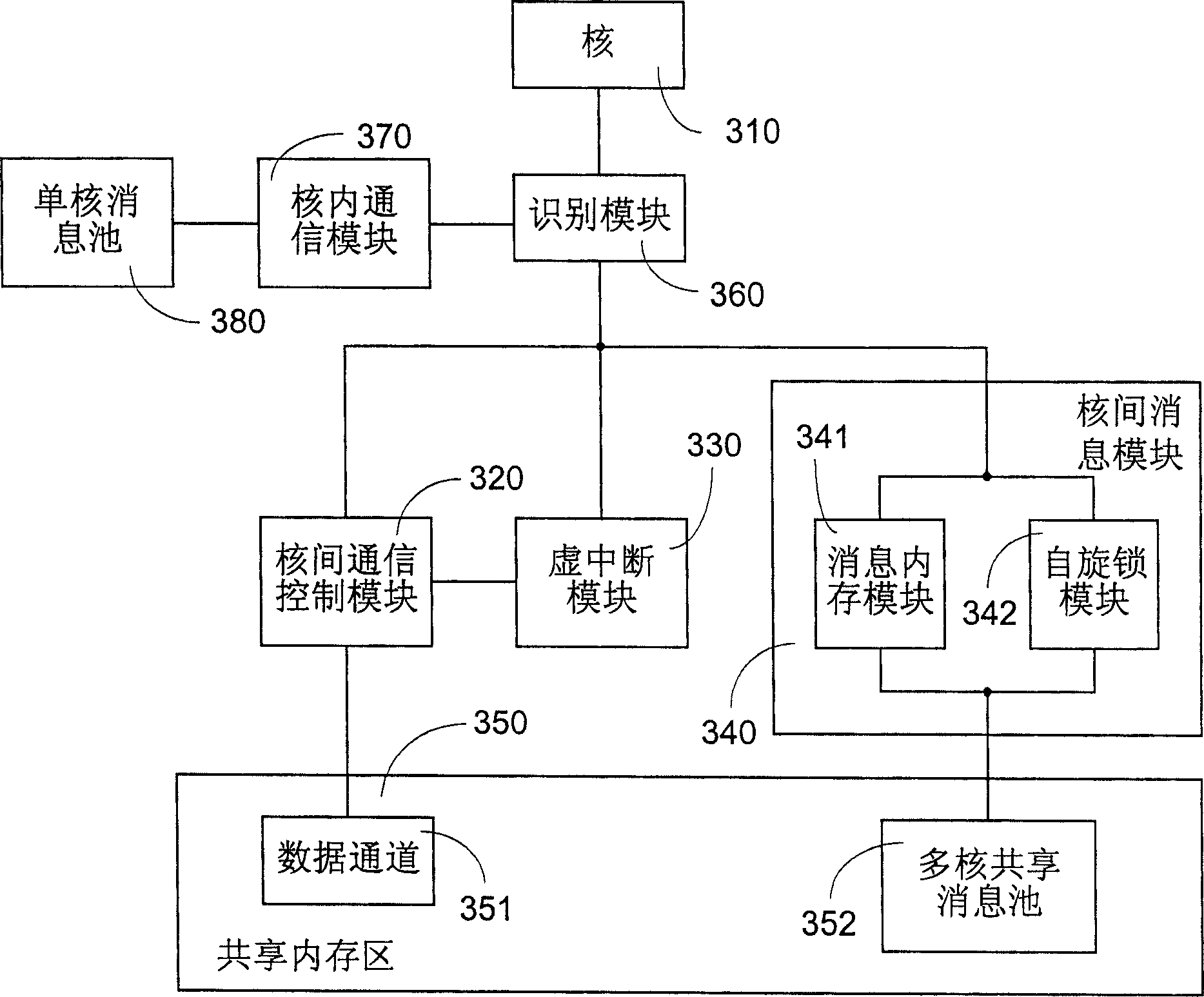
Inter core communication method and apparatus for multi-core processor in embedded real-time operating system
ActiveCN1904873APrevent copyingImprove efficiencyDigital computer detailsElectric digital data processingMessage queueDistributed memory
The invention discloses an inter-core communicating method of multi-core processor in embedded real time operation system. It includes following steps: distributing memory as multi-core information sharing pool; writing information the source core would send into the pool; sending the information to target core; target core sending the information storing in pool to target mission. The invention also discloses an inter-core communicating device. It improves the inter-core communicating efficiency and realizes the unification of inner core communication and inter-core communication.
Owner:DATANG MOBILE COMM EQUIP CO LTD
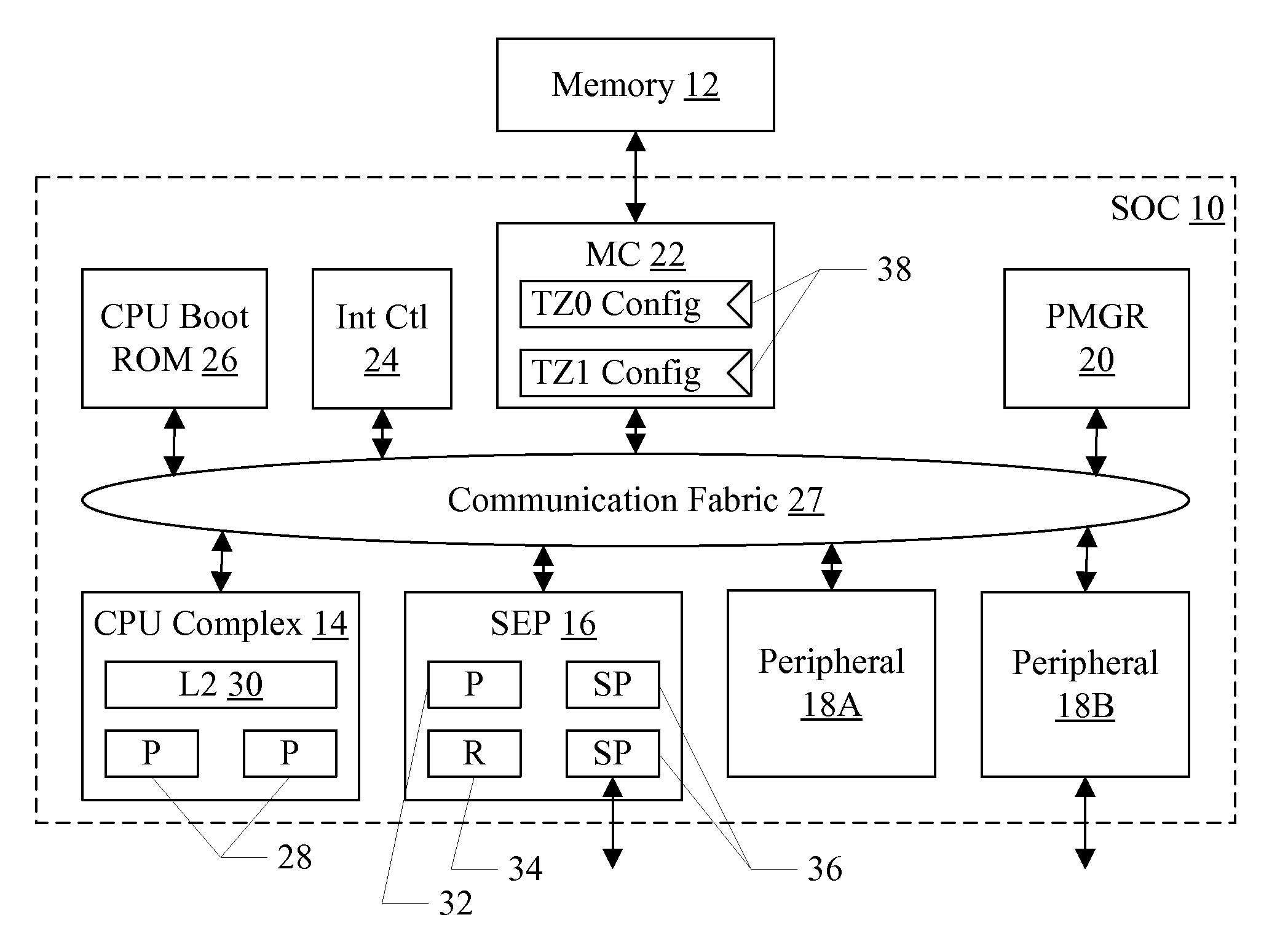
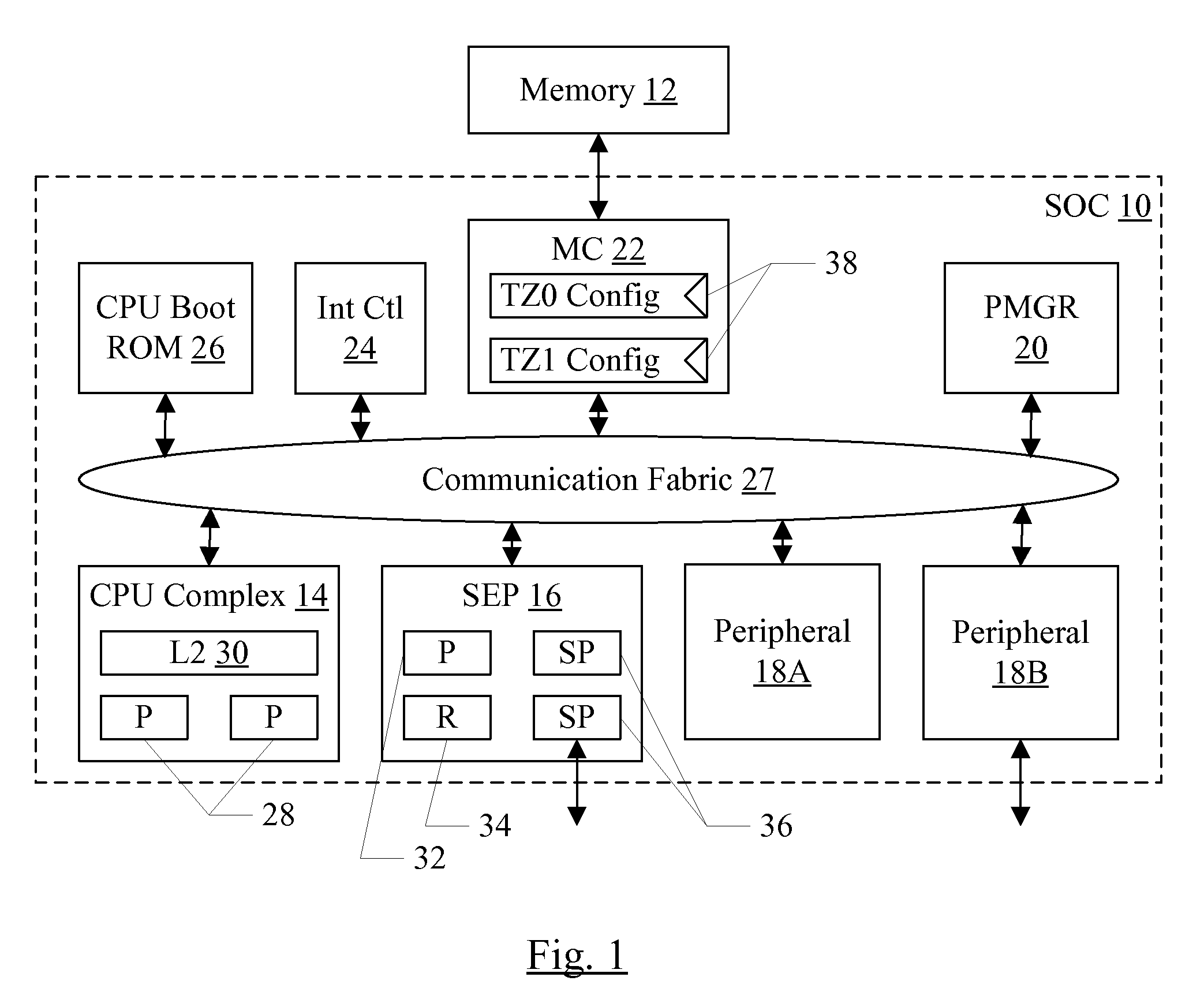
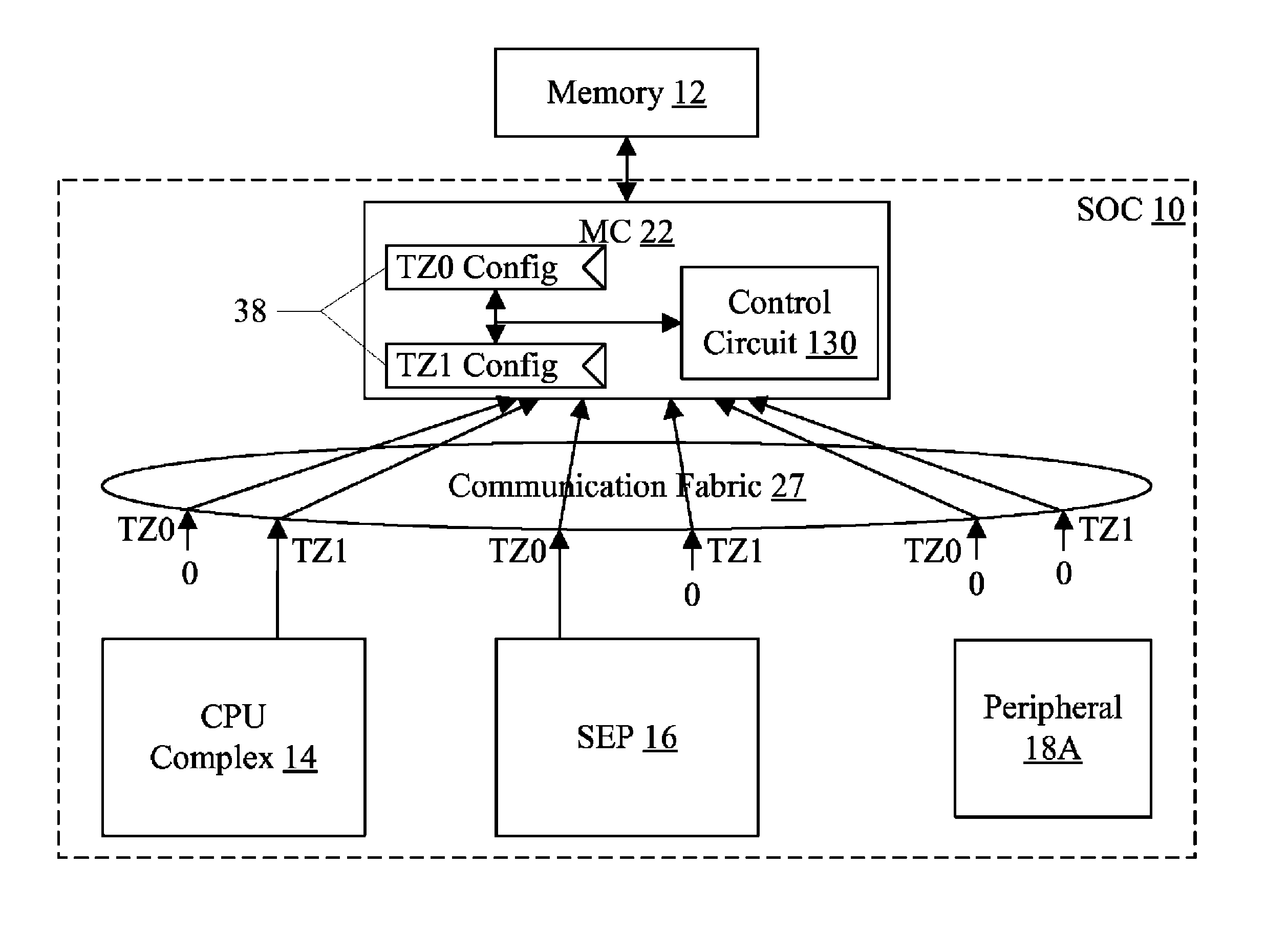
Trust Zone Support in System on a Chip Having Security Enclave Processor
ActiveUS20140089617A1Prevent copyingUnauthorized memory use protectionInternal/peripheral component protectionApplication processorSystem on a chip
An SOC implements a security enclave processor (SEP). The SEP may include a processor and one or more security peripherals. The SEP may be isolated from the rest of the SOC (e.g. one or more central processing units (CPUs) in the SOC, or application processors (APs) in the SOC). Access to the SEP may be strictly controlled by hardware. For example, a mechanism in which the CPUs / APs can only access a mailbox location in the SEP is described. The CPU / AP may write a message to the mailbox, which the SEP may read and respond to. The SEP may include one or more of the following in some embodiments: secure key management using wrapping keys, SEP control of boot and / or power management, and separate trust zones in memory.
Owner:APPLE INC
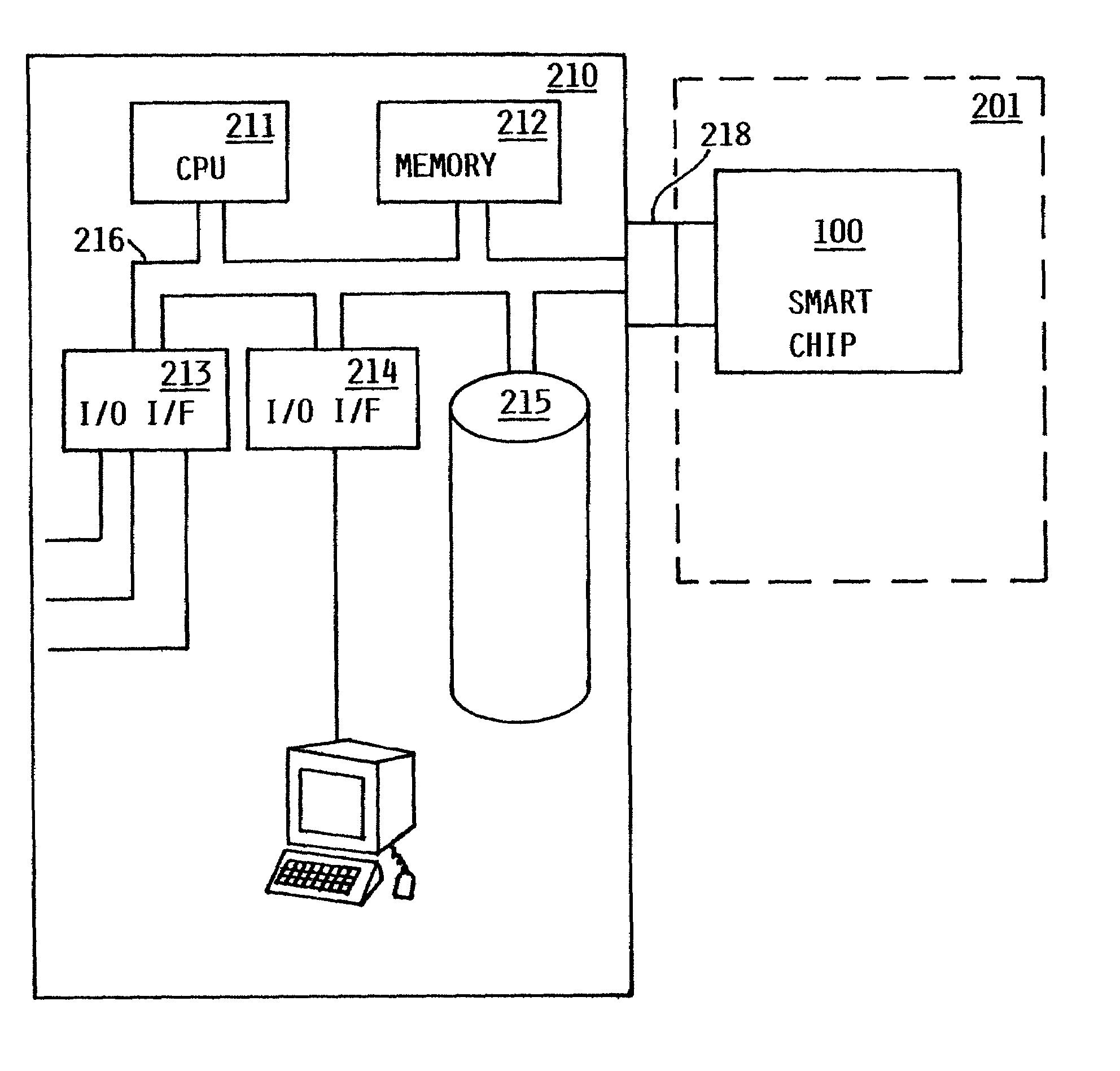
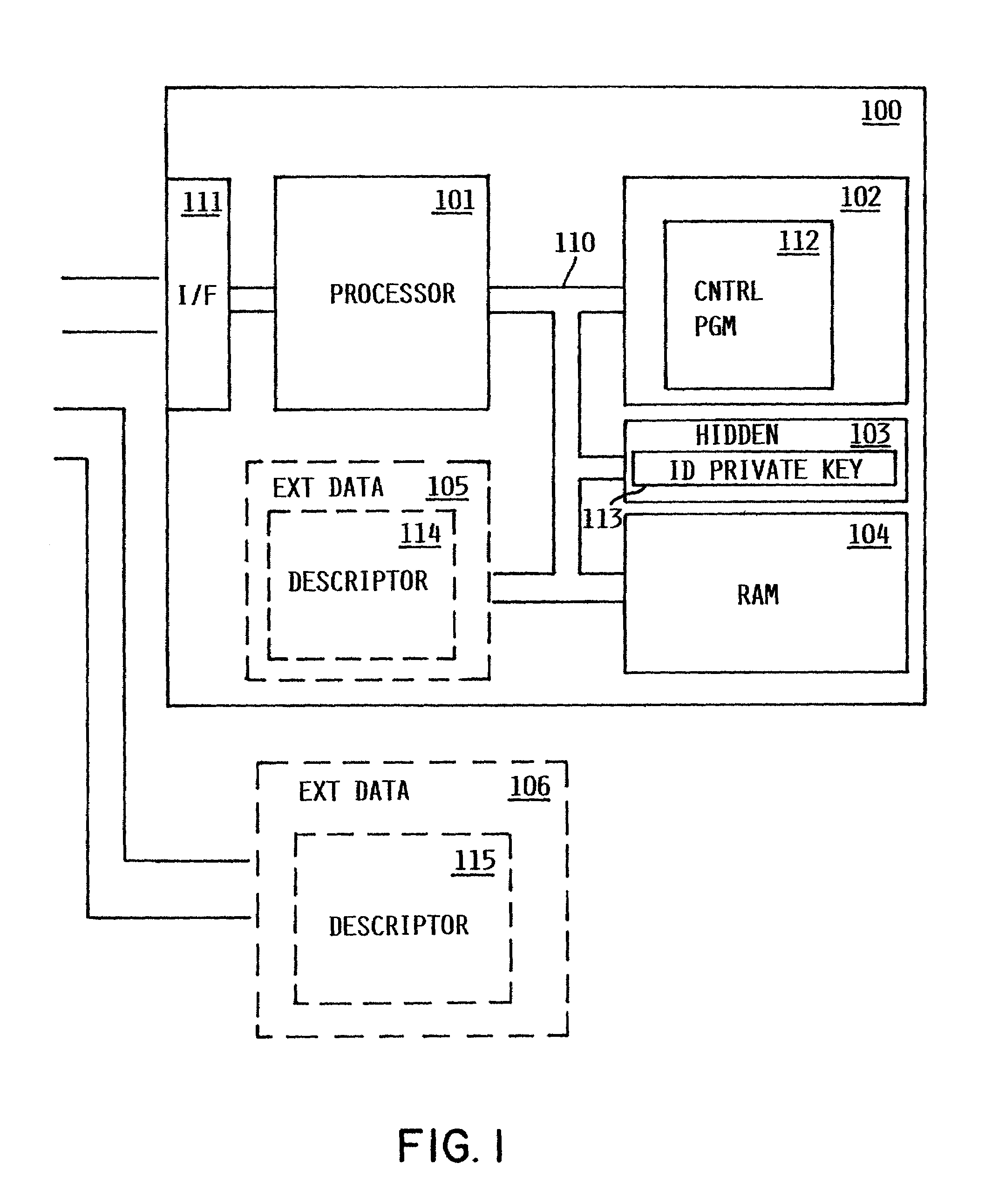
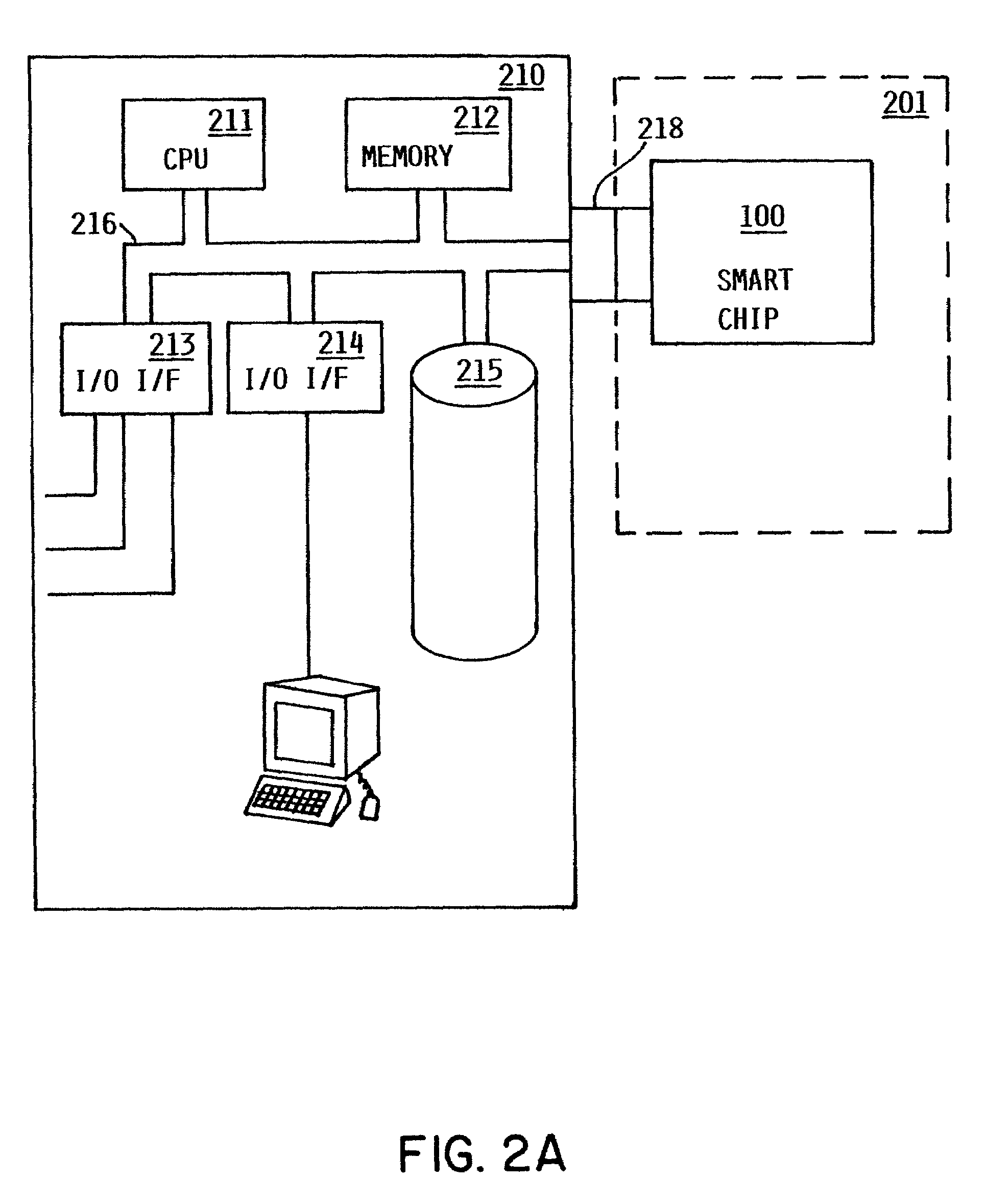
Method and apparatus for uniquely and authoritatively identifying tangible objects
InactiveUS7000115B2Alteration can be preventedEasy to readDigital data processing detailsUser identity/authority verificationDigital signatureTangible object
A smart chip protection system contains a unique public / private identity key pair and uses a separate public / private signature key pair. The identity private key is stored in permanent, secure storage such that it can not be read outside the chip. An issuing entity generates a descriptor containing the identity public key, attribute data, and a digital signature. The digital signature is generated by enciphering a derivation of the identity public key and the attribute data with the signature private key known only to the issuer. The authenticity of the descriptor data is verified by decrypting the signature with the signature public key using a known algorithm, and comparing the result to the derivation of the descriptor data. The identity of the object can be verified requesting the smart chip ro perform an encryption / decryption operation using its identity private key, and performing the complement using the public key.
Owner:IBM CORP
Vending machines with field-programmable locks
InactiveUS7821395B2Easy and inexpensiveReduce theft and fraudFrequency-division multiplex detailsDigital data processing detailsEngineeringHand held
A vending machine uses a field-programmable electronic lock that learns a key code from a corresponding electronic key, a hand-held program unit, or an external computing device via wireless communications. In one mode, the electronic lock has a learning process activation device that is accessible only when the door of the vending machine is in the open position. In another mode, the electronic lock is programmed in the field without first opening the vending machine. A program command and access control data including a new access code are transmitted wirelessly from a hand-held program unit or the like. Alternatively, an external computing device is used to program the electronic lock via long-range wireless communications, and an electronic key is then used to open the electronic lock to physically access the vending machine.
Owner:MICRO ENHANCED TECH
Security Enclave Processor for a System on a Chip
ActiveUS20140089682A1Prevent copyingUnauthorized memory use protectionHardware monitoringApplication processorSystem on a chip
An SOC implements a security enclave processor (SEP). The SEP may include a processor and one or more security peripherals. The SEP may be isolated from the rest of the SOC (e.g. one or more central processing units (CPUs) in the SOC, or application processors (APs) in the SOC). Access to the SEP may be strictly controlled by hardware. For example, a mechanism in which the CPUs / APs can only access a mailbox location in the SEP is described. The CPU / AP may write a message to the mailbox, which the SEP may read and respond to. The SEP may include one or more of the following in some embodiments: secure key management using wrapping keys, SEP control of boot and / or power management, and separate trust zones in memory.
Owner:APPLE INC
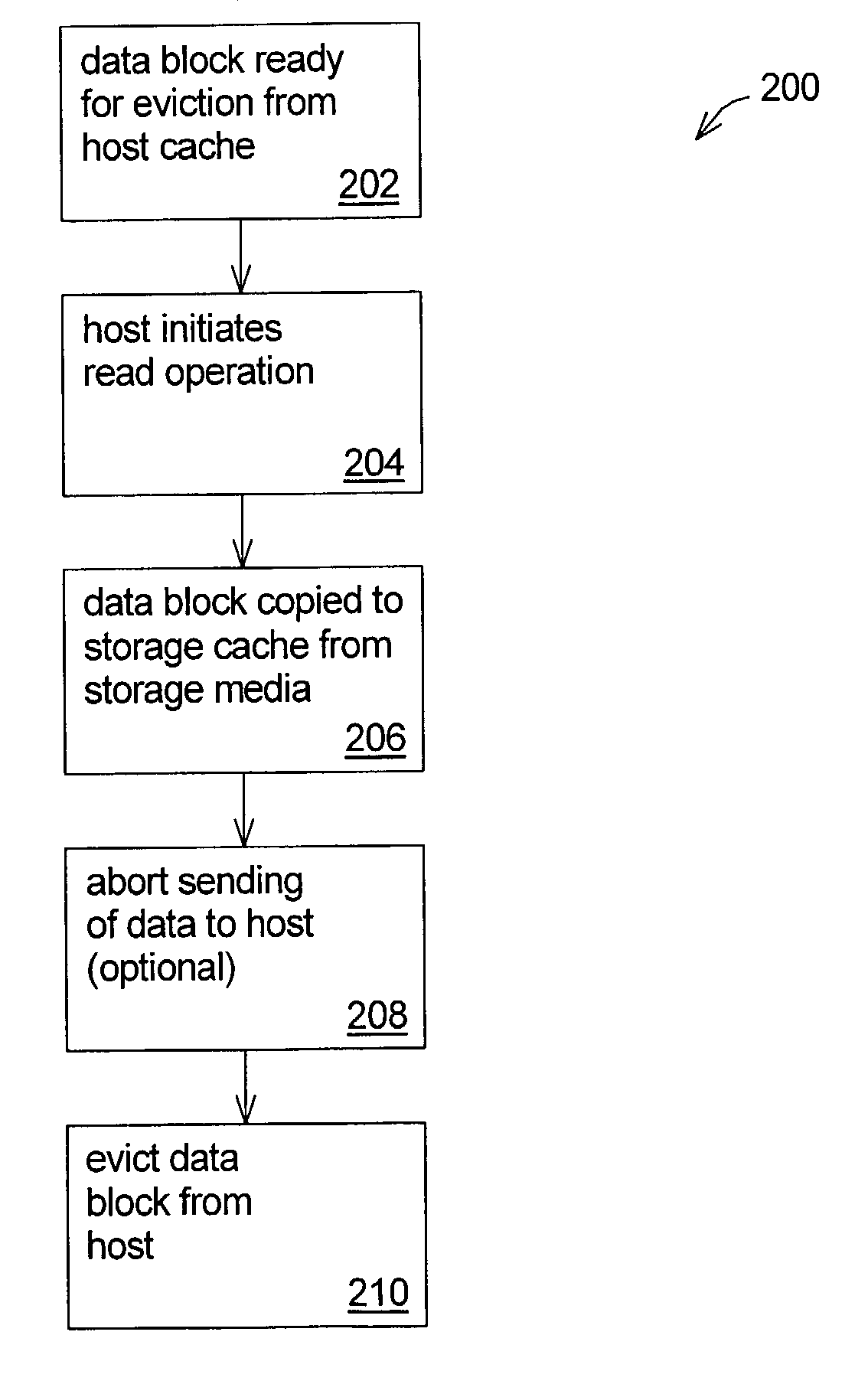
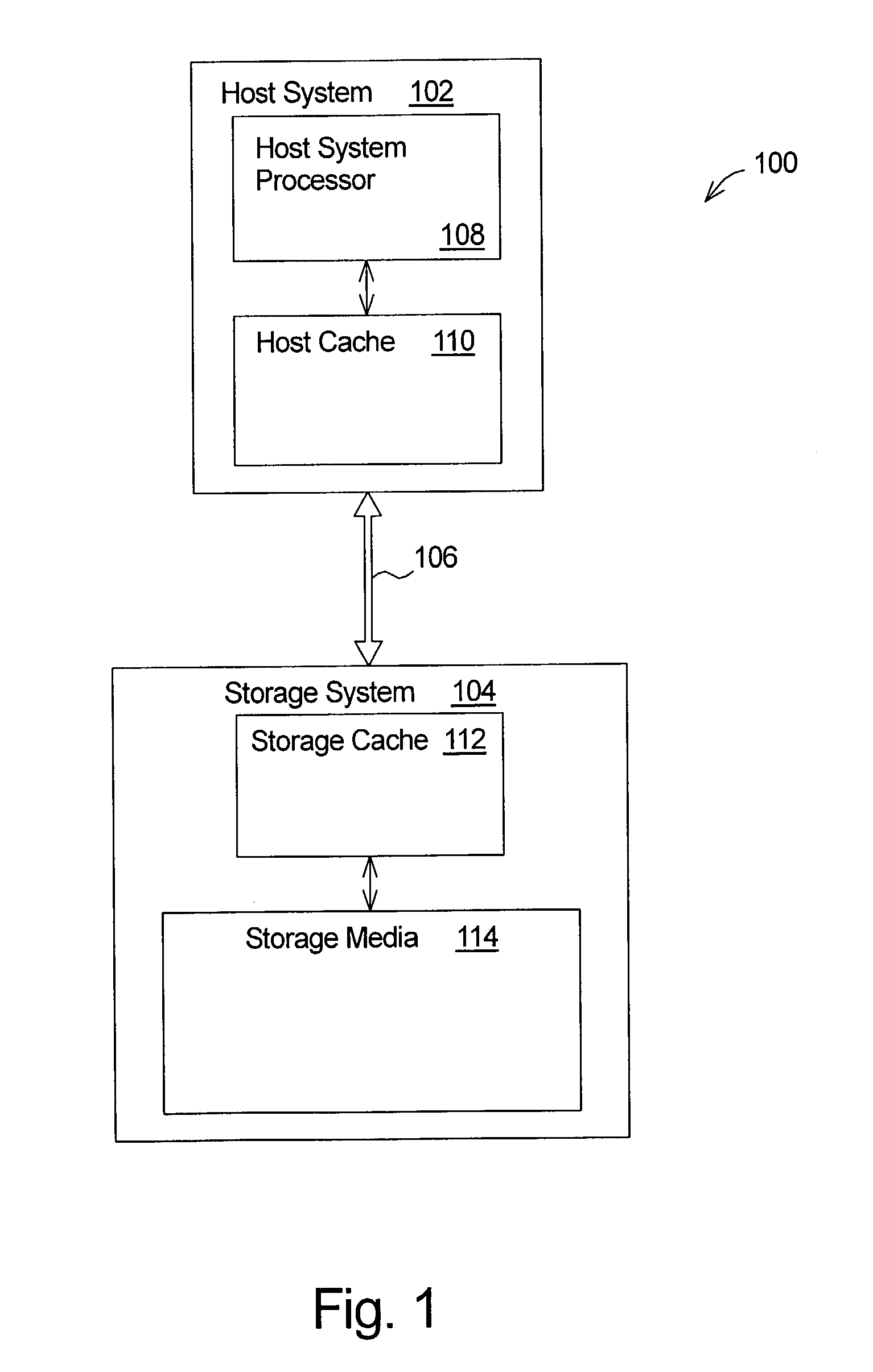
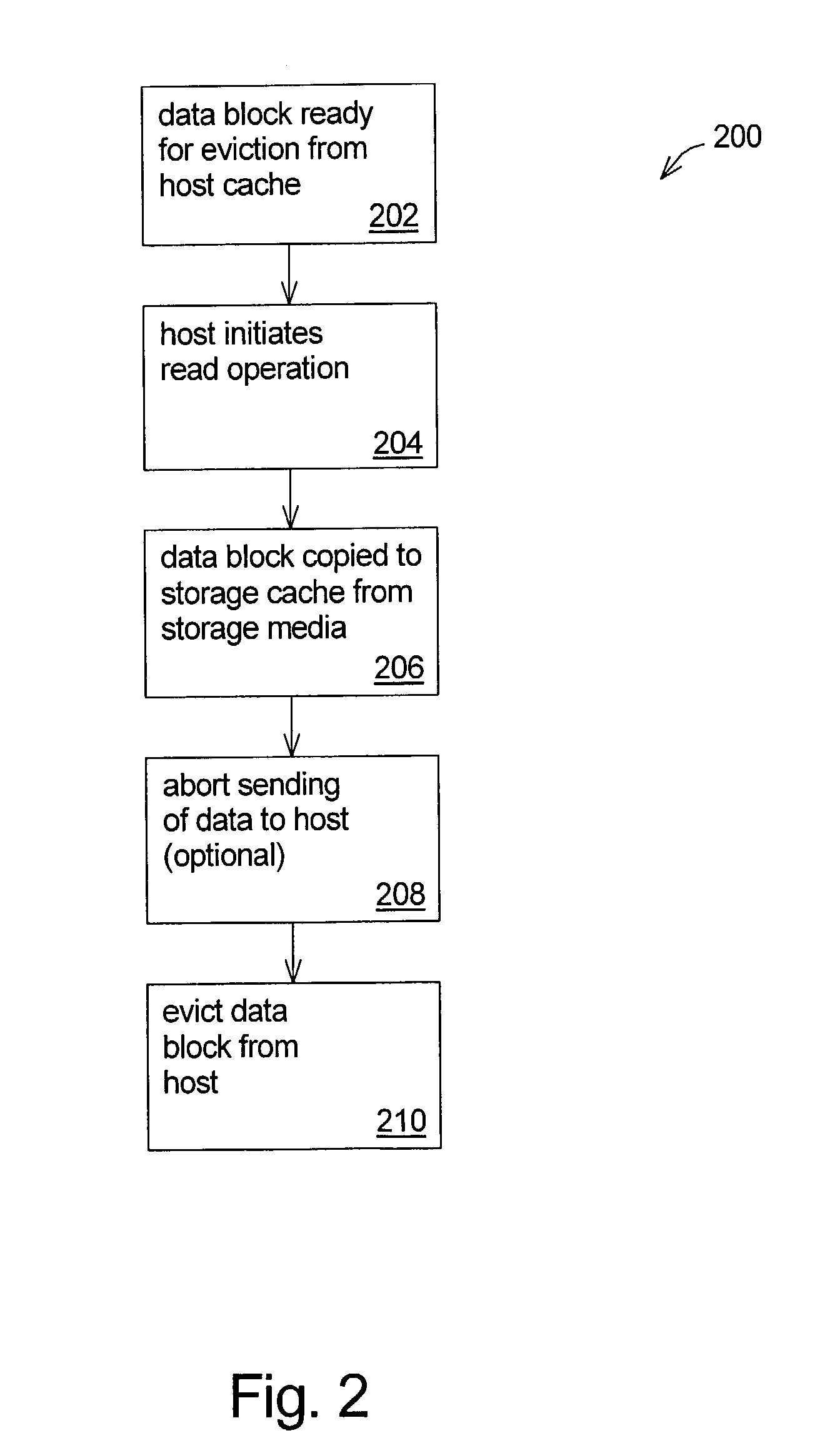
Techniques for cache memory management using read and write operations
InactiveUS7039765B1Prevent copyingMemory architecture accessing/allocationMemory systemsMass storageData storing
Techniques for cache memory management using read and write operations. A read or a write operation to a storage system is initiated for data that is held in a host system cache, but is ready to be evicted from the host system cache. In response to the read operation, the data stored in a mass-storage medium of the storage system is copied to the storage system cache memory in preparation for transfer to the host system. However, the read operation is initiated when the data is not presently needed by the host system. In response to the write operation, the data stored in the host system cache is copied to the storage system cache in preparation for transfer to the mass-storage medium. However, the write operation is initiated when the data is already stored in the mass-storage medium. Then, the data is evicted from the host system cache. This results in exclusivity in that the data becomes present in the storage system cache, but is no longer present in the host system cache.
Owner:HEWLETT PACKARD DEV CO LP
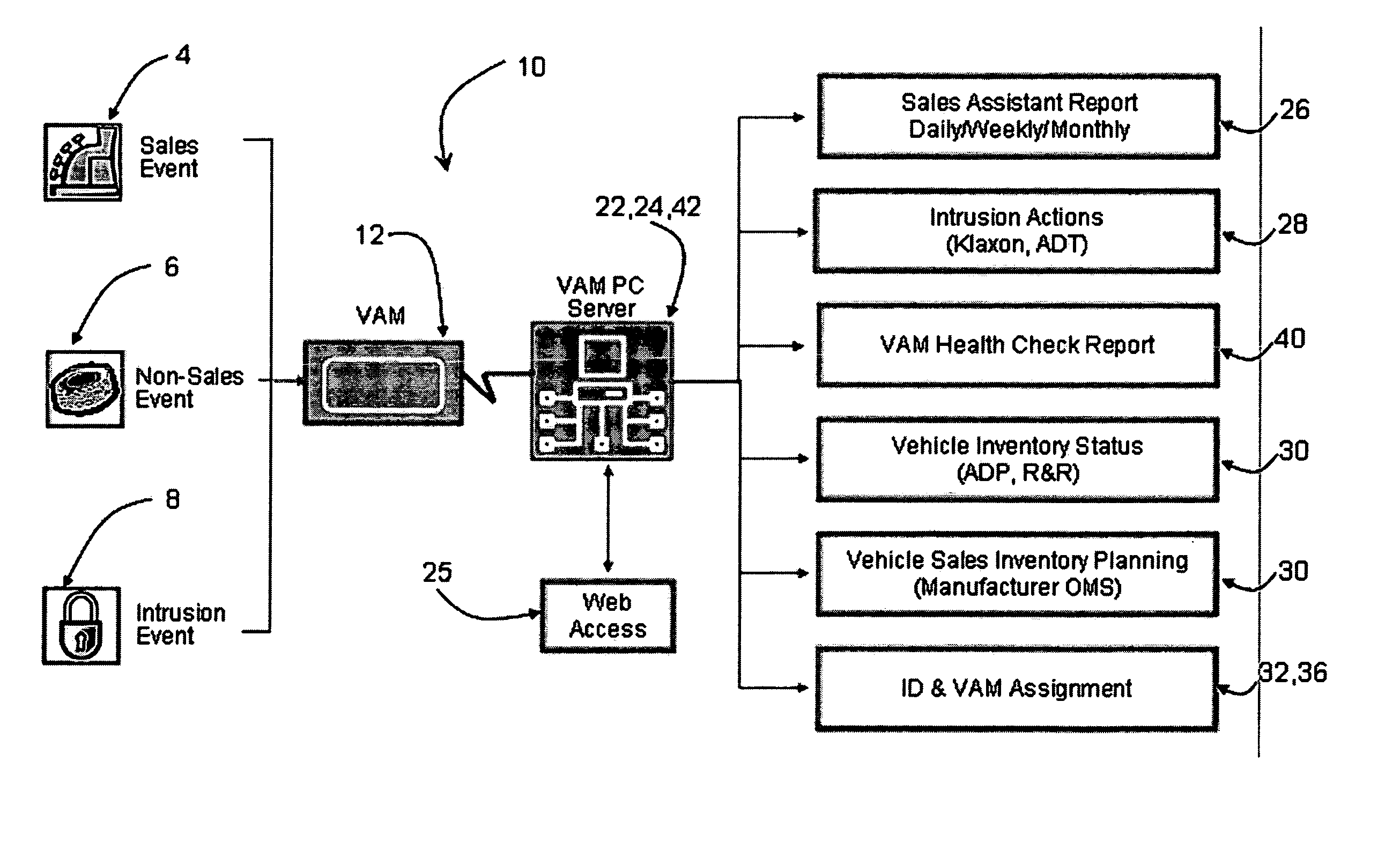
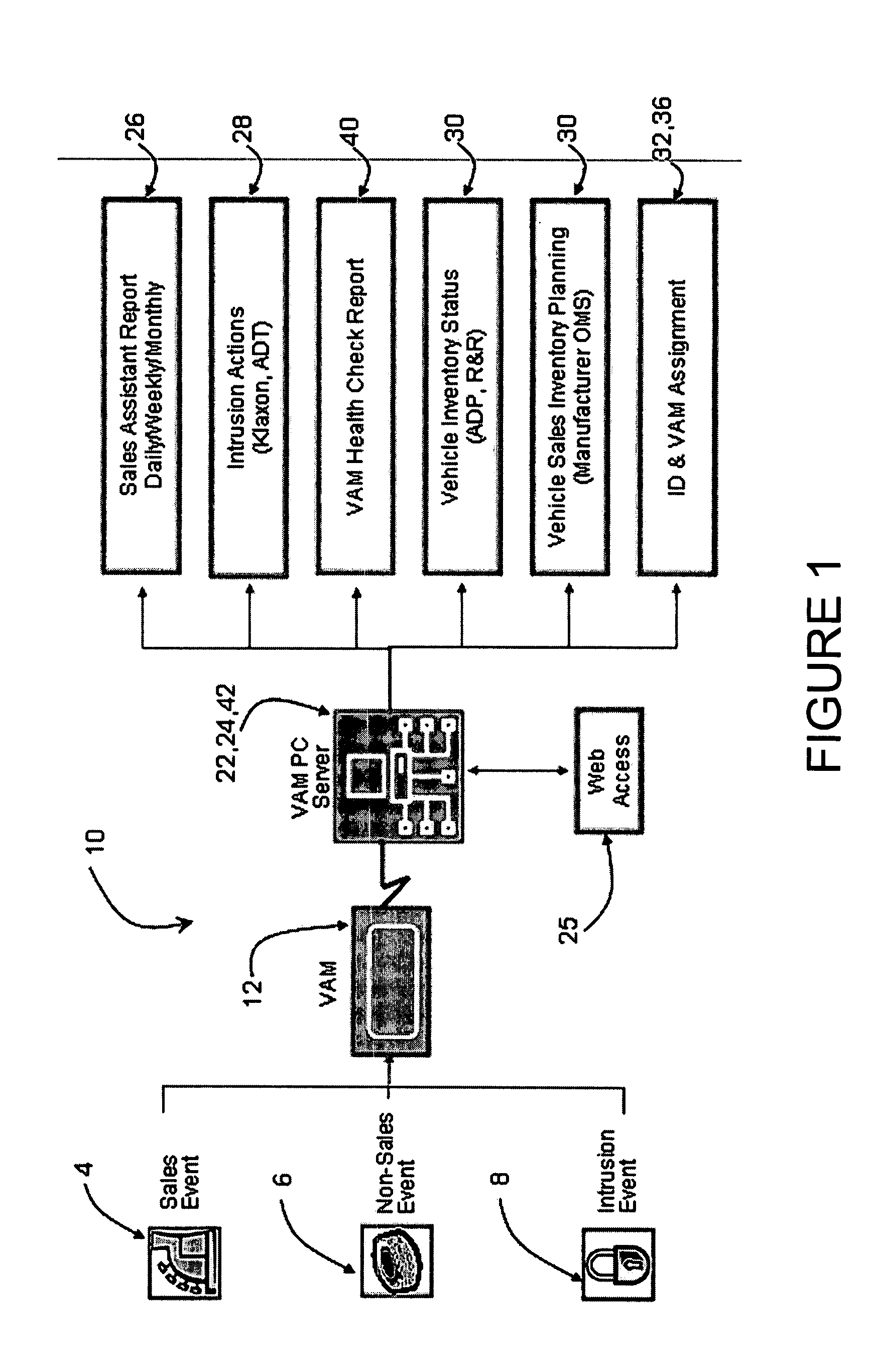
Vehicle activity module
ActiveUS20070273534A1Prevent copyingElectric signal transmission systemsDigital data processing detailsComputerized systemComputer module
Systems and methods are disclosed for maintaining security and data gathering for a number of vehicles. The systems include a vehicle activity module for each of the vehicles. The vehicle activity module has a wireless transmitter, a storage device, at least one sensor for receiving event information from identification devices, such as RFID cards, keypads, magnetic ID cards, and the like, a releasable key container, and a processor for accessing and analyzing information. The VAMs are wirelessly connected to a computer system. The VAMs control access to the keys, monitor information relating to access, and store and transmit information relating to sales events, non-sales events, and intrusion events. The VAMs are capable of autonomous operation, without the need to access the computer system to verify event information. The VAMs further include signal attenuating mechanisms to facilitate use of “smart keys.”
Owner:SENTRILOCK
Trust zone support in system on a chip having security enclave processor
ActiveUS8775757B2Prevent copyingUnauthorized memory use protectionInternal/peripheral component protectionApplication processorSystem on a chip
An SOC implements a security enclave processor (SEP). The SEP may include a processor and one or more security peripherals. The SEP may be isolated from the rest of the SOC (e.g. one or more central processing units (CPUs) in the SOC, or application processors (APs) in the SOC). Access to the SEP may be strictly controlled by hardware. For example, a mechanism in which the CPUs / APs can only access a mailbox location in the SEP is described. The CPU / AP may write a message to the mailbox, which the SEP may read and respond to. The SEP may include one or more of the following in some embodiments: secure key management using wrapping keys, SEP control of boot and / or power management, and separate trust zones in memory.
Owner:APPLE INC
Product anti-counterfeiting method and system based on electronic tag
InactiveCN102663591APrevent copyingCo-operative working arrangementsCommerceElectronic taggingAuthentication
The invention discloses a product anti-counterfeiting system and a product anti-counterfeiting method based on an electronic tag. The system comprises the electronic tag disposed on an anti-counterfeiting object and a verifying device. The system is characterized in that the electronic tag at least comprises a cipher processing unit which can carry out asymmetric cryptographic operation, and a memory module in which electronic tag identification information, an electronic tag authentication code, product information and a product authentication code are stored; the electronic tag holds at least one public key / private key cipher pair; and the verifying device verifies authenticity of the electronic tag through a challenge / response protocol based on an asymmetric cipher technology. The purpose of the invention is to provide an anti-counterfeiting method and an anti-counterfeiting system which enable manufacturers and consumers to verify product authenticity through communicating with the electronic tag disposed on the product.
Owner:樊俊锋 +1
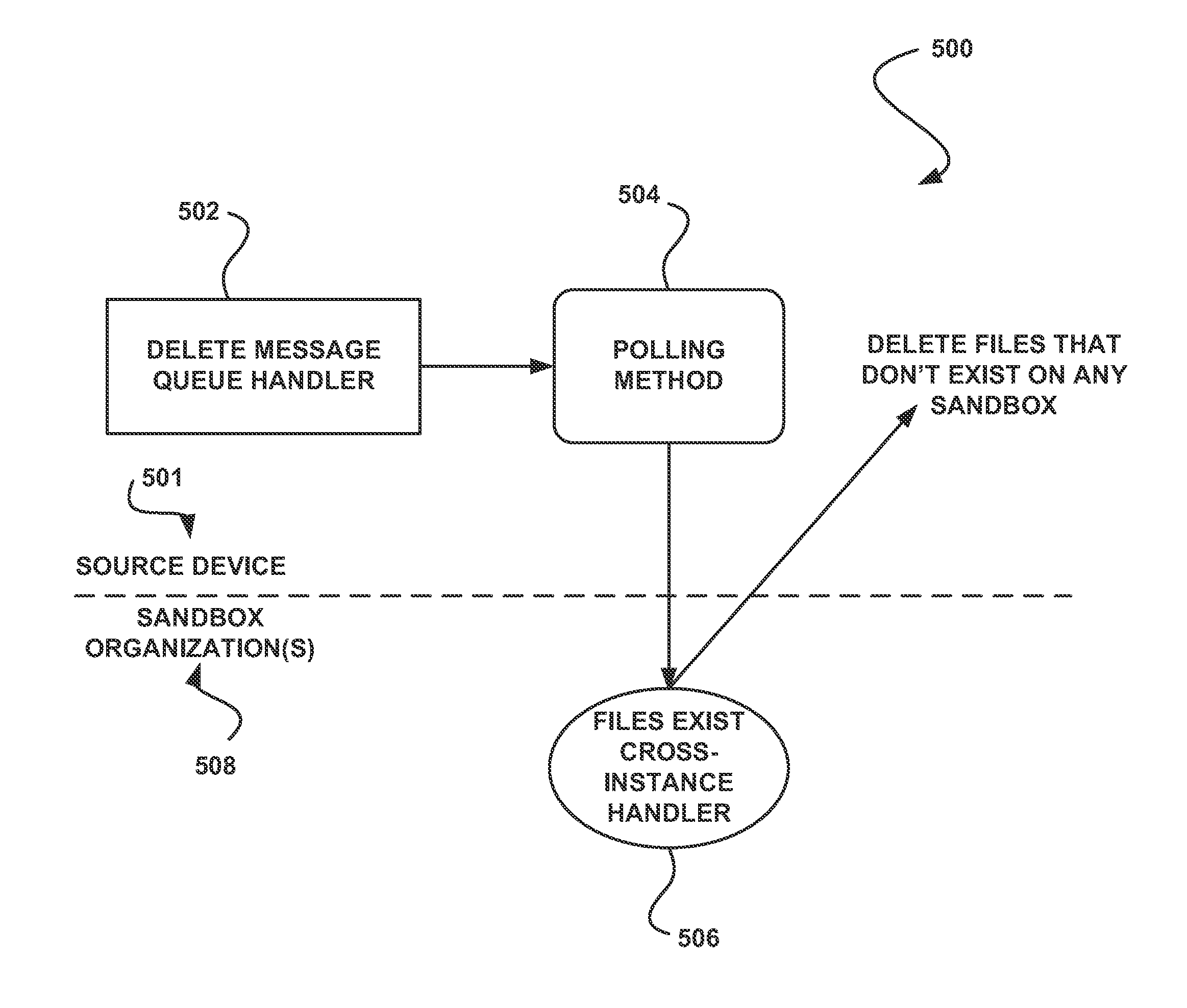
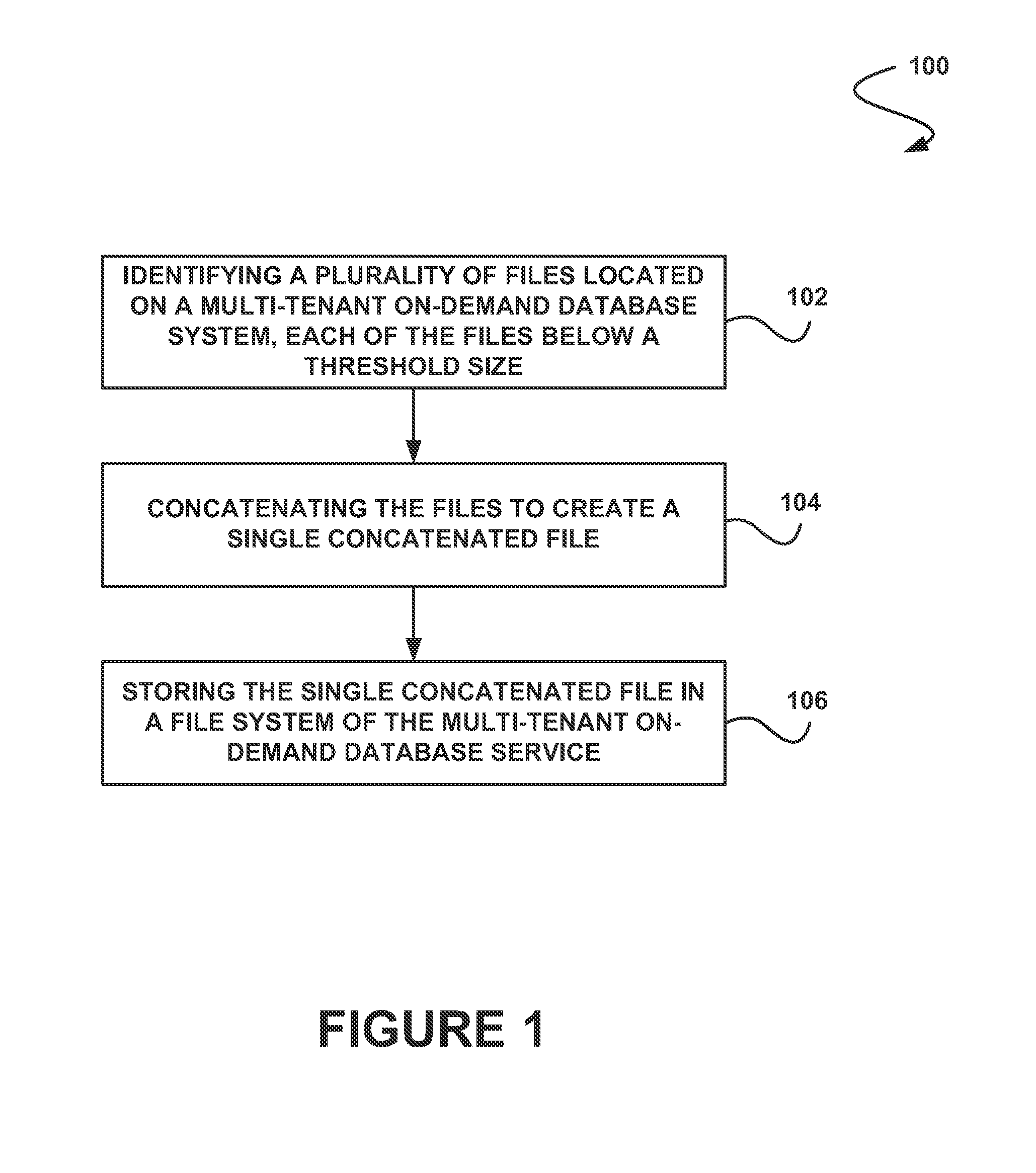
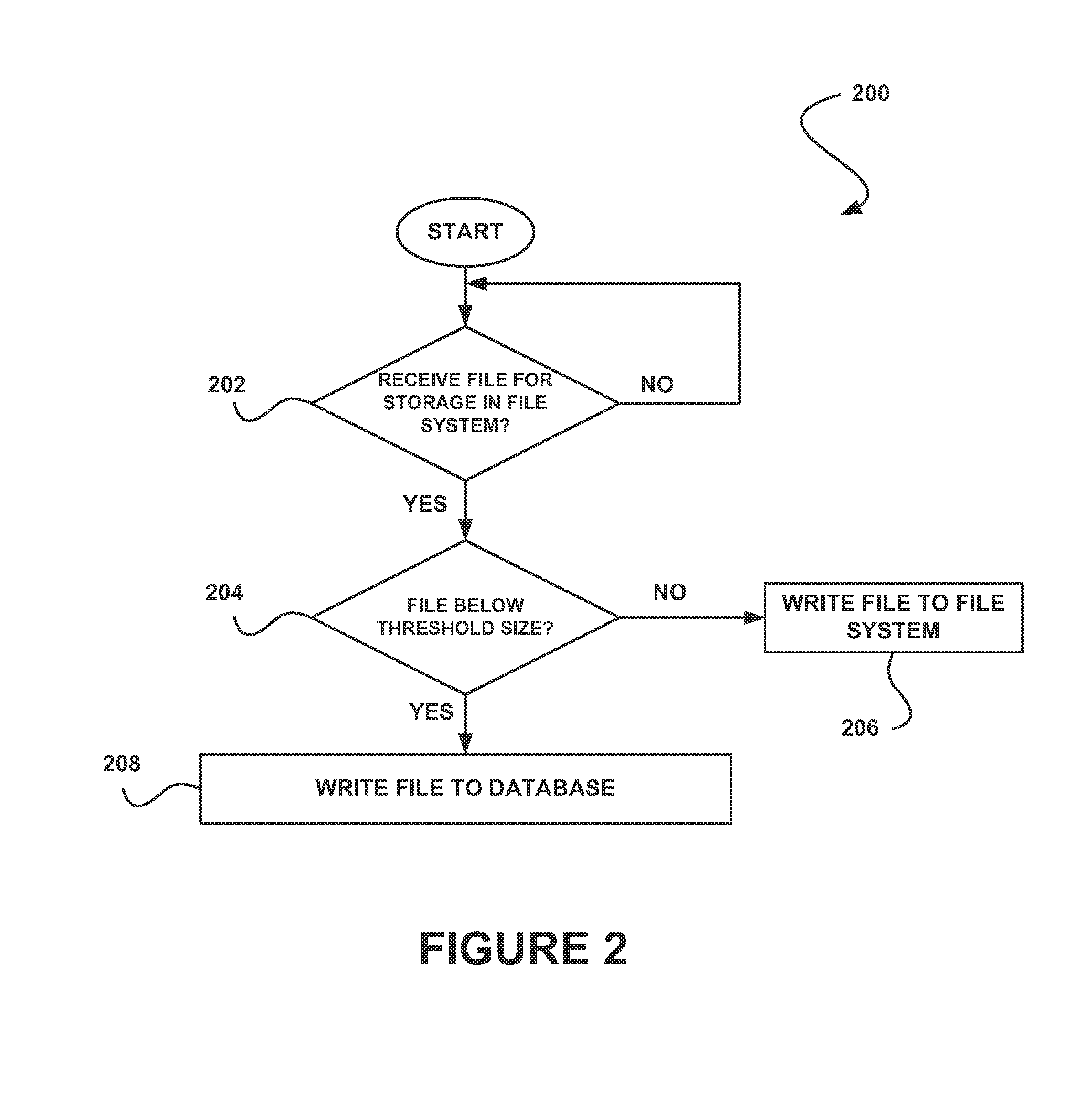
System, method and computer program product for storing file system content in a multi-tenant on-demand database system
ActiveUS20130246373A1Reduce in quantityPrevent copyingDigital data information retrievalDigital data processing detailsFile systemDatabase
In accordance with embodiments, there are provided mechanisms and methods for storing file system content in a multi-tenant on-demand database system. These mechanisms and methods for storing file system content in a multi-tenant on-demand database system can enable embodiments to reduce a number of files stored on a file system, avoid copying of all file system content to file system copies, etc.
Owner:SALESFORCE COM INC
Embedding, processing and detection of digital content, information and data
ActiveUS7660991B2Prevent copyingReduce processingTelevision system detailsUser identity/authority verificationProcessing typeData processing
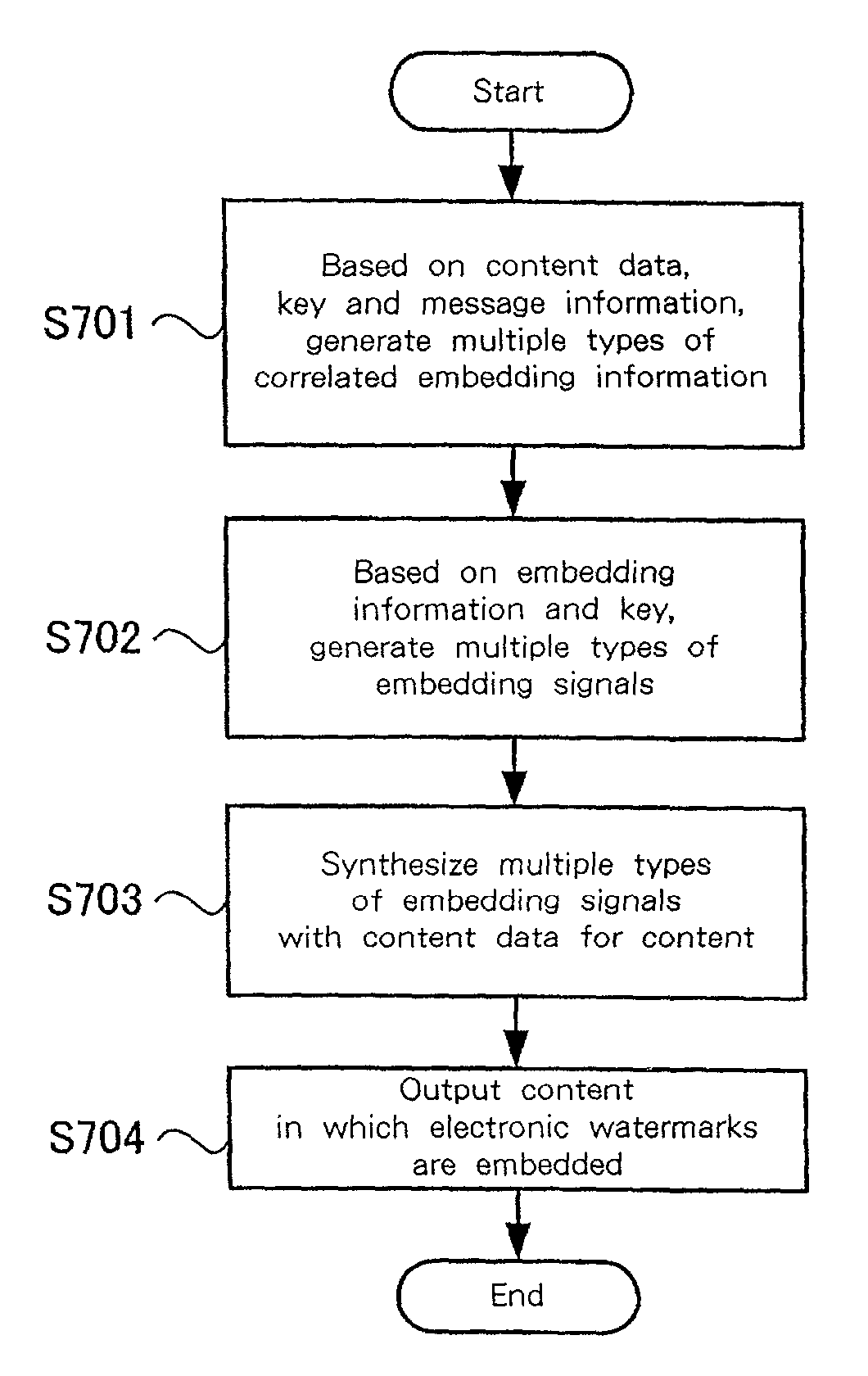
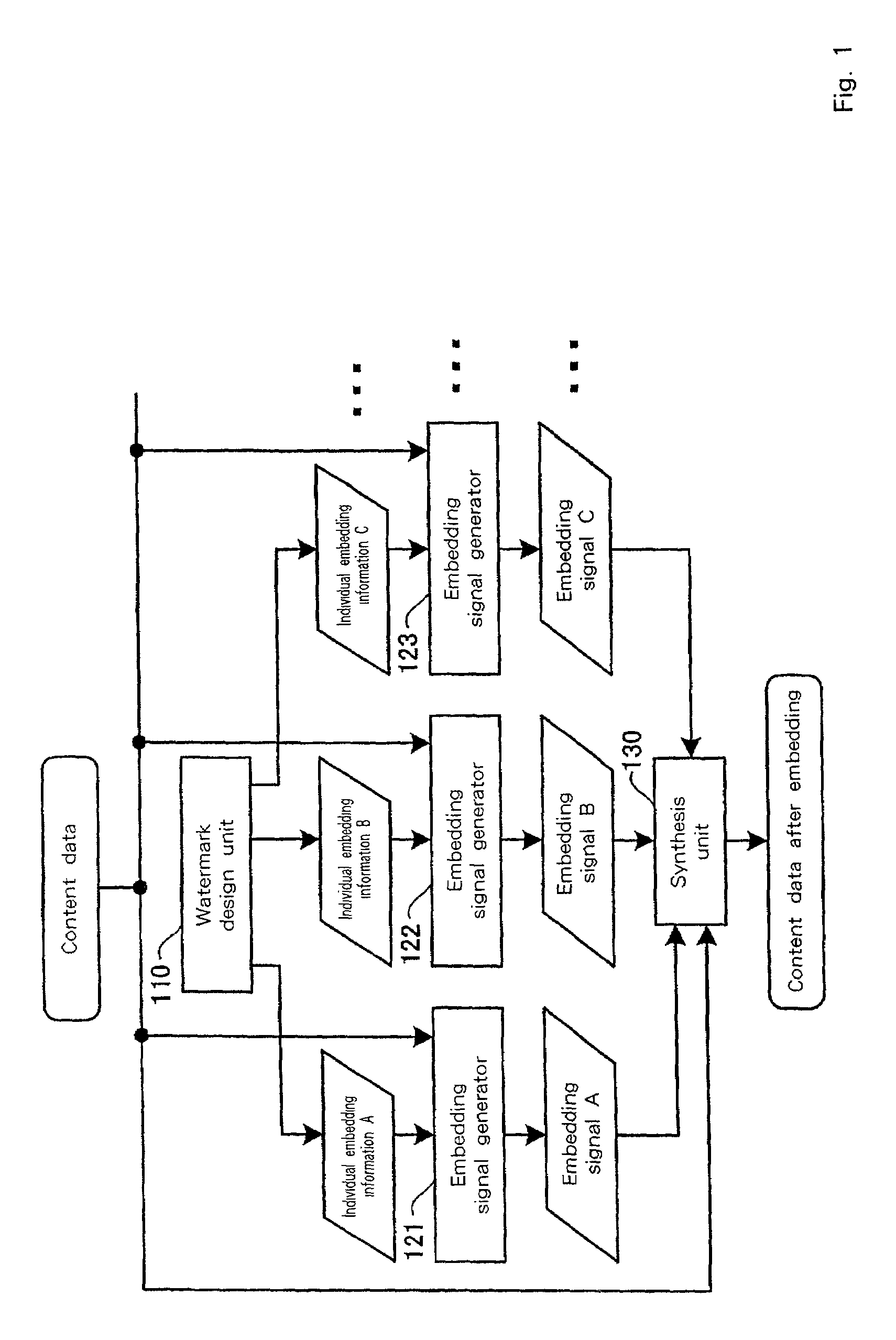
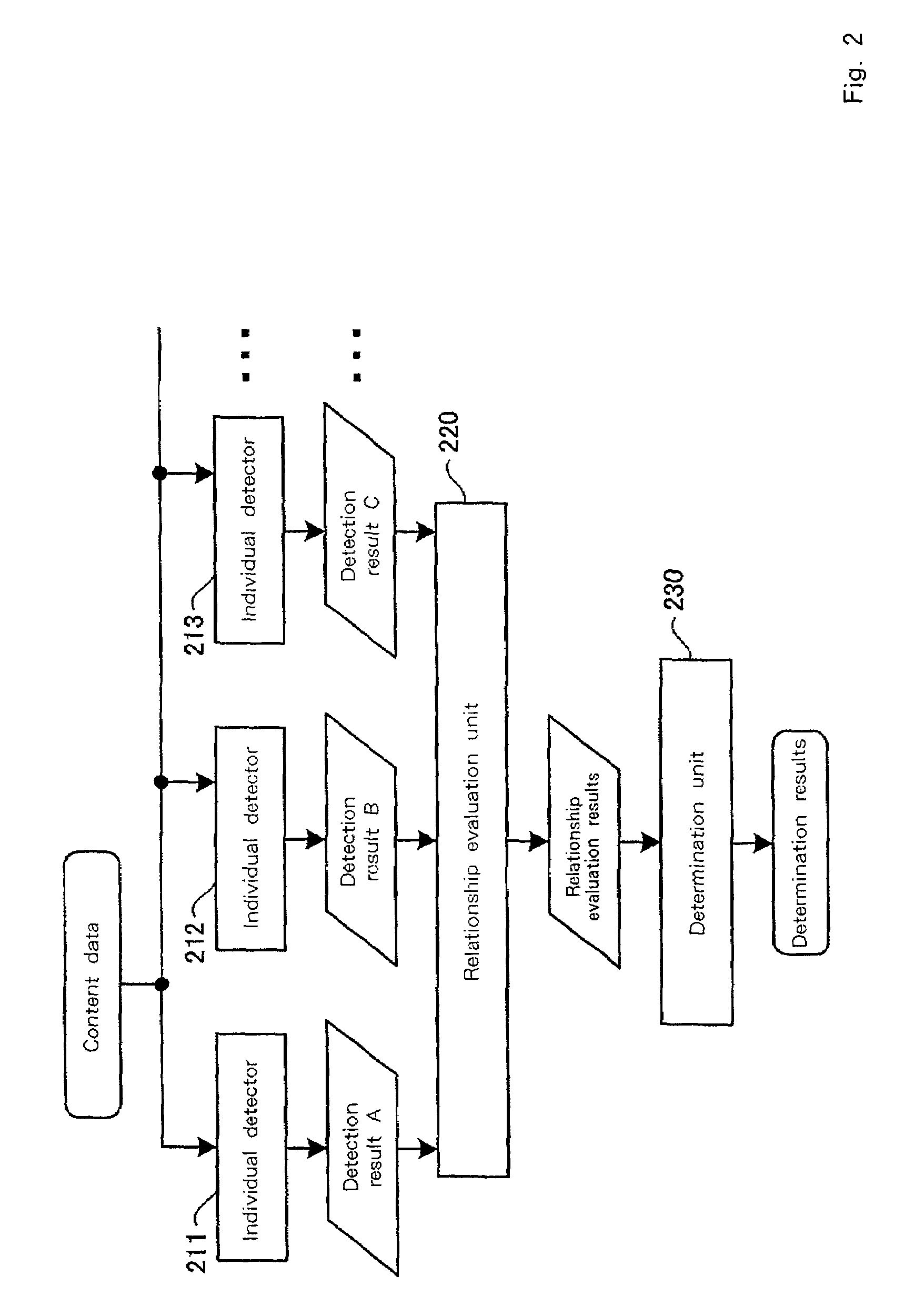
Enables identification and detection of processing and type of digital content, while using multiple electronic watermarks. One embodiment provides a data processing detection system having an embedding apparatus for adding a predetermined additional signal to digital content, including a watermark design unit and embedding signal generators for generating multiple types of additional signals, correlated with each other and of differing robustness from each other for the processing of the content data, and a synthesis unit for adding the multiple types of additional signals to the content data; and detection apparatus for detecting additional signals in the digital content, and for detecting the additional signals embedded by the embedding apparatus, including an individual detector for detecting in the content data multiple additional signals, and a determination unit for examining deterioration levels of the additional signals to determine the type of processing performed for the content data.
Owner:TWITTER INC
Method and device for forwarding message
InactiveCN104796337APrevent copyingImprove forwarding speedData switching networksInternal memoryResource utilization
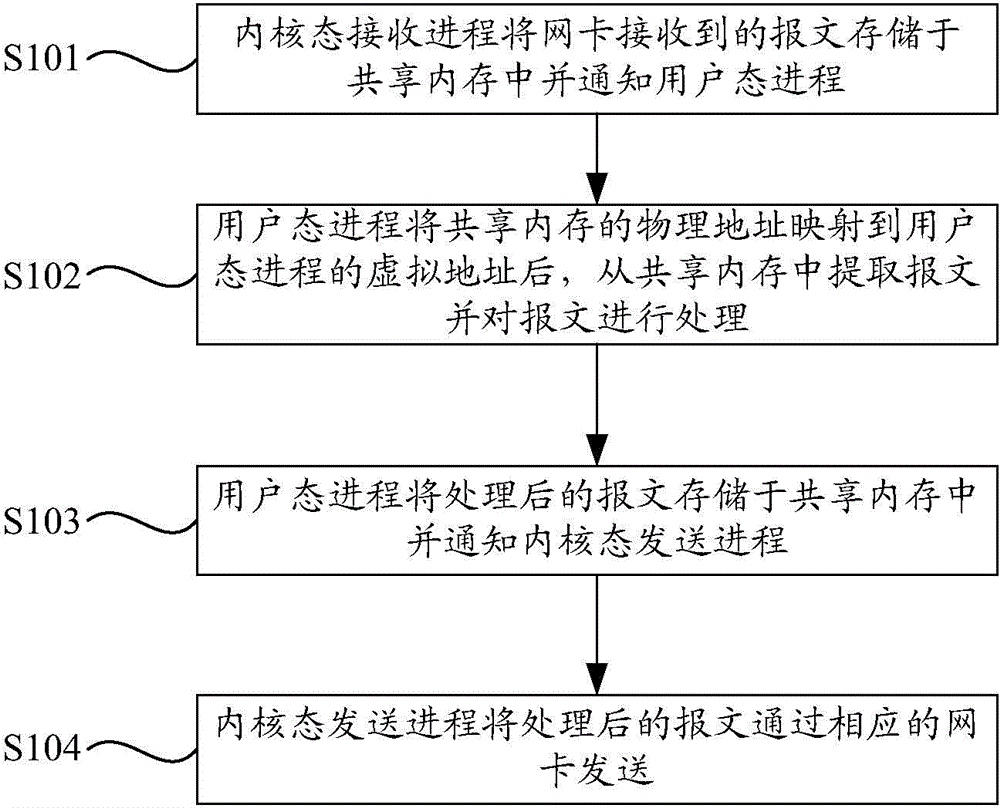
The invention discloses a method and device for forwarding a message. The method includes: a kernel-state receiving process stores the message received by a network card in a sharing internal memory and notifies a user-state process; the user-state process maps the physical address of the sharing internal memory to the virtual address of the user-state process and then extracts the message from the sharing internal memory and processes the message; the user-state process stores the processed message in the shearing internal memory and notifies a kernel-state transmitting process; the kernel-state transmitting process transmits the processed message through the corresponding network card. By the method, copying of the message from kernel space to application space is avoided, message forwarding speed is increased, and system resource utilization rate can be increased.
Owner:COMBA TELECOM SYST CHINA LTD +3
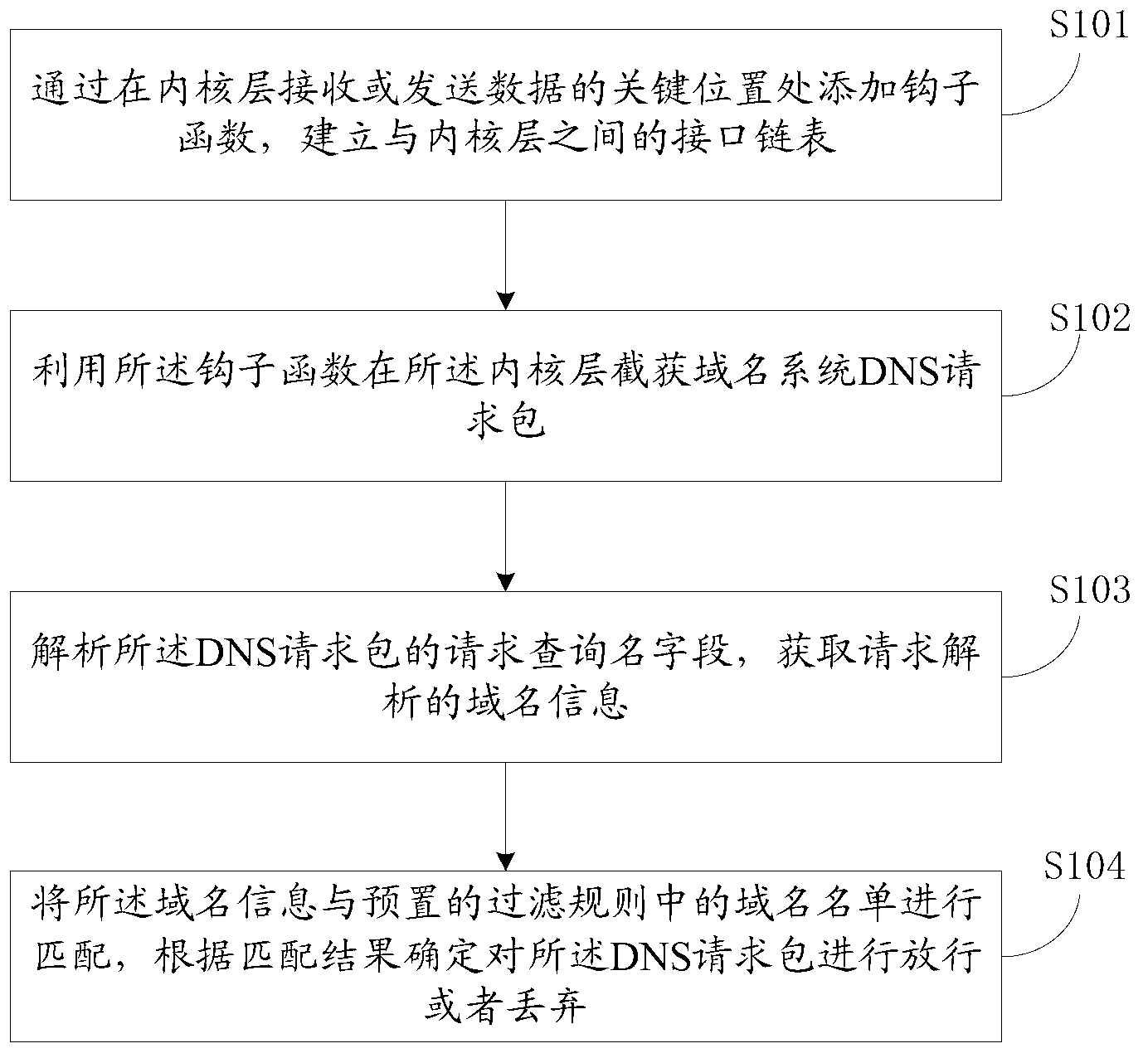
Method and device for network access control
The invention discloses a method and device for network access control. The method comprises the steps that a hook function is added to the key position, for receiving or sending data, of an kernel layer and an interface chain table between the hook function and the kernel layer is established; a DNS request packet is intercepted in the inner nuclear layer by the hook function; a requested inquiring name section of the DNS request packet is analyzed and domain name information requiring analysis is obtained; the domain name information is matched with a domain name list in a preset filtering rule and whether the DNS request packet is discharged or abandoned is determined according to a matching result. According to the method and device for network access control, DNS filtering can be achieved in a kernel mode.
Owner:BEIJING QIANXIN TECH
Digital authentication control method for access control system and access control system using the same
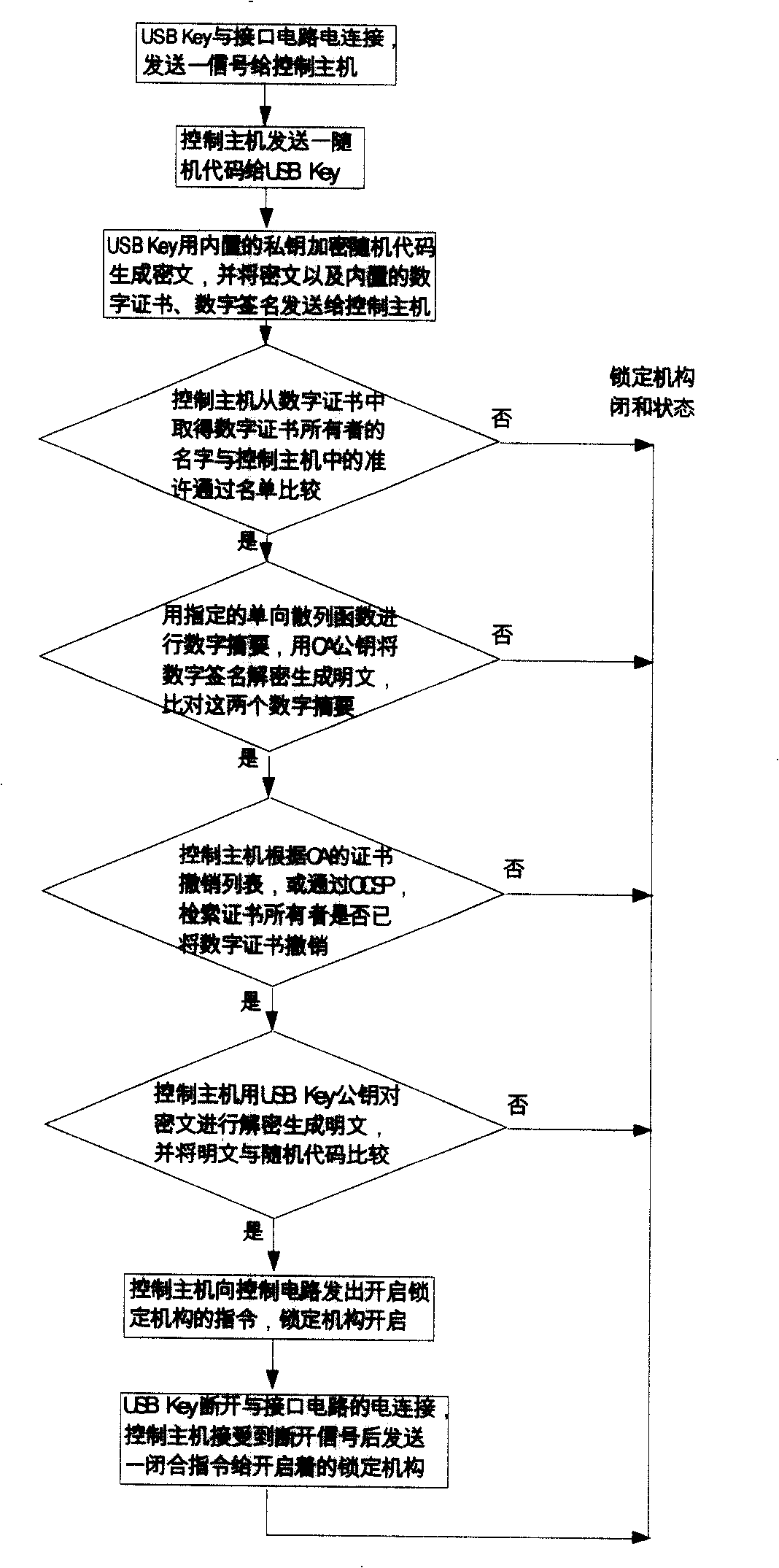
InactiveCN101246607AWill not leakImprove convenienceUser identity/authority verificationIndividual entry/exit registersElectricityCiphertext
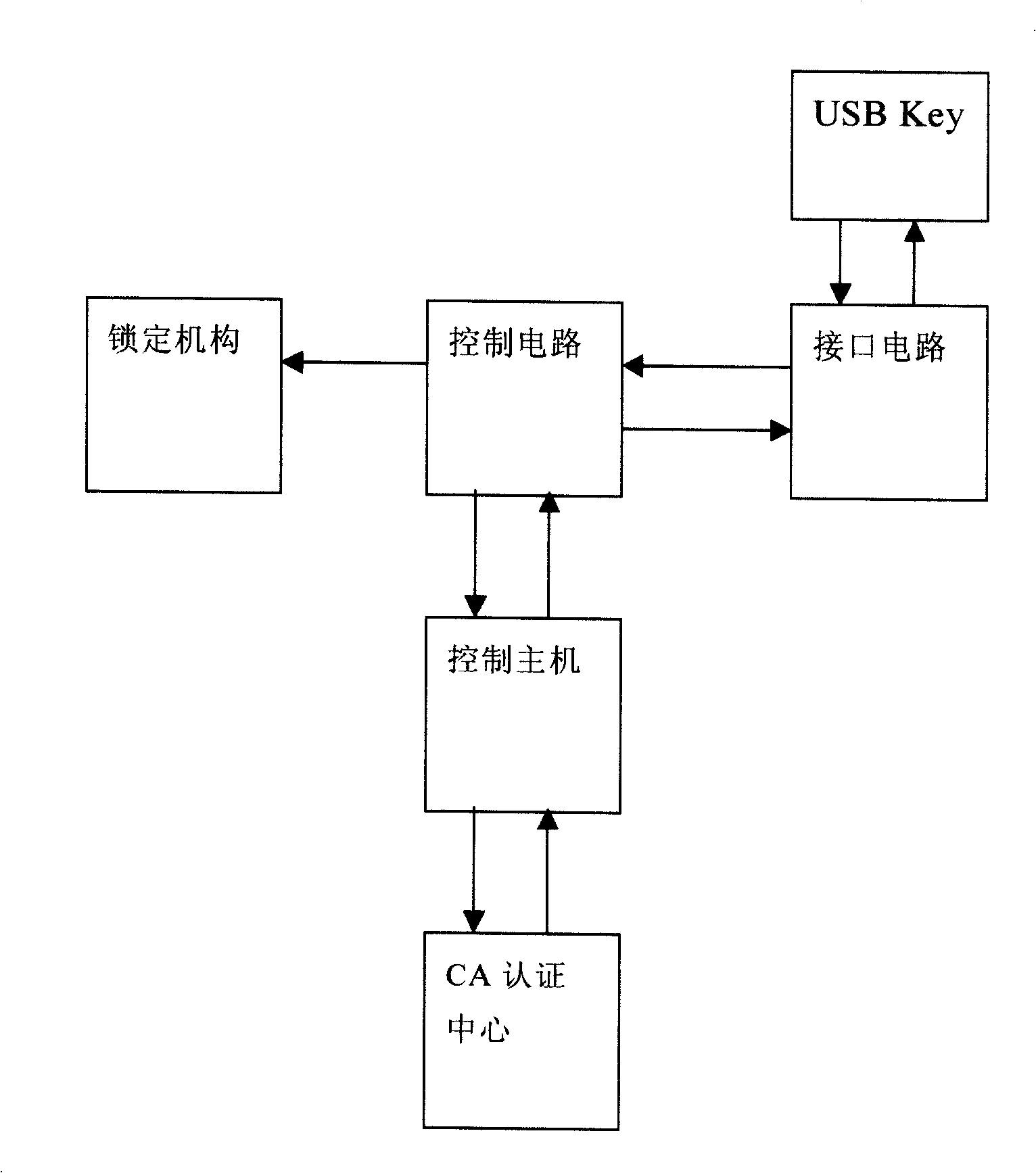
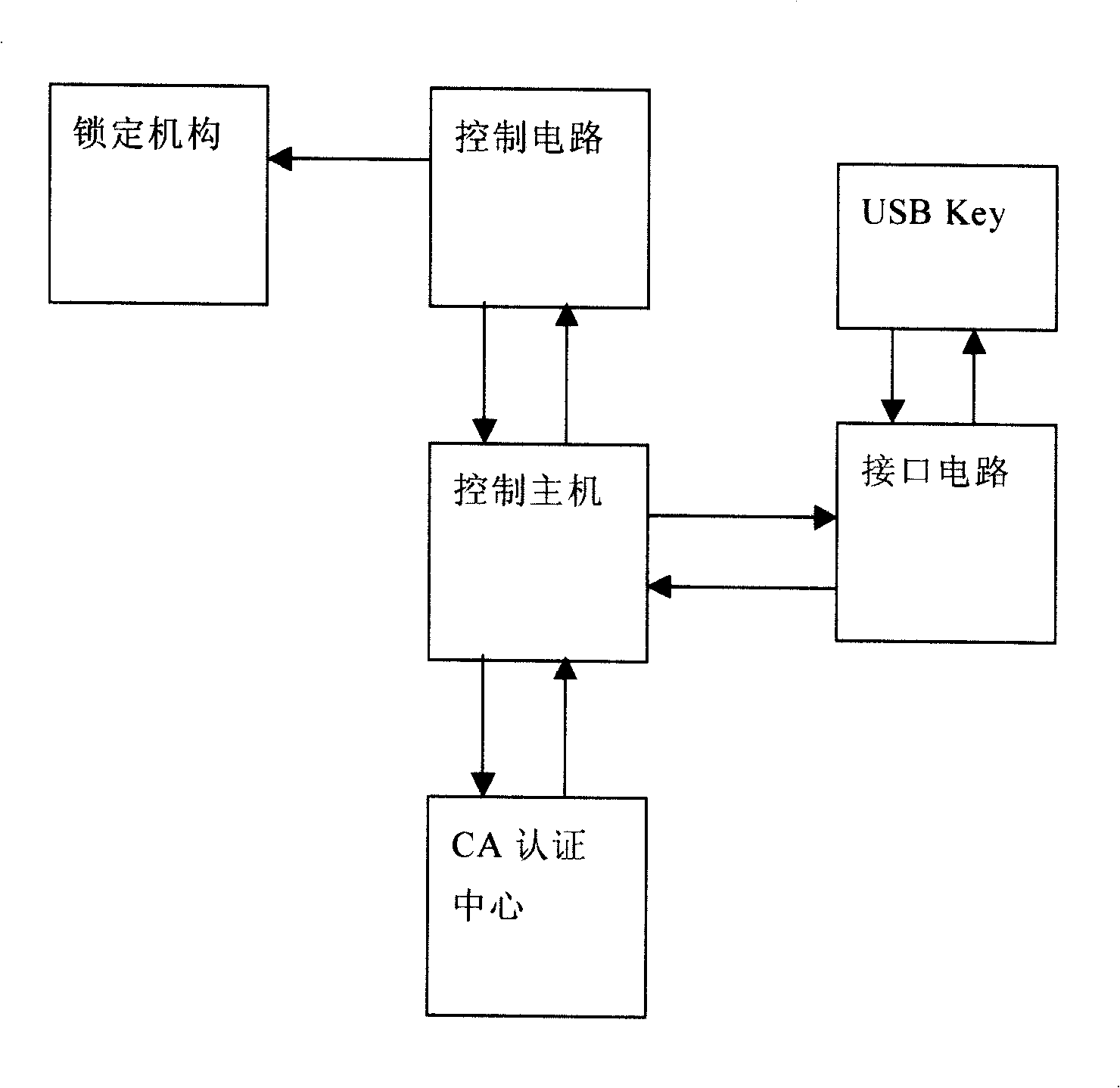
The present invention provides a digital certificate control method of access control system, the control master transmits a random code to USB Key when the USB Key is connected to the interface circuit, the USB Key uses inner key encryption to generate cryptograph and transmits to the control master, the control master USB Key of the digital certificate and decoding the received cryptograph to cleartext, the control master compares the cleartext with the random code, when the comparing result is identical, the indentity of USB Key holder is determined; the control master transmits opening command to open lock mechanism after determining legal identity and access permision of the holder, when USB Key breaks the connection with the interface circuit, the control master transmits closing command, the locking mechanism is closed. The invention also provides an access control system applying the above method, including an access control system, an inner key, a digital certificate and a USB Key of digital signature and a locking mechanism. The access control method and system of the invention has convenience, high security and high credibility.
Owner:陈年
Method and apparatus for performing electronic data file protection based on encrypted partition
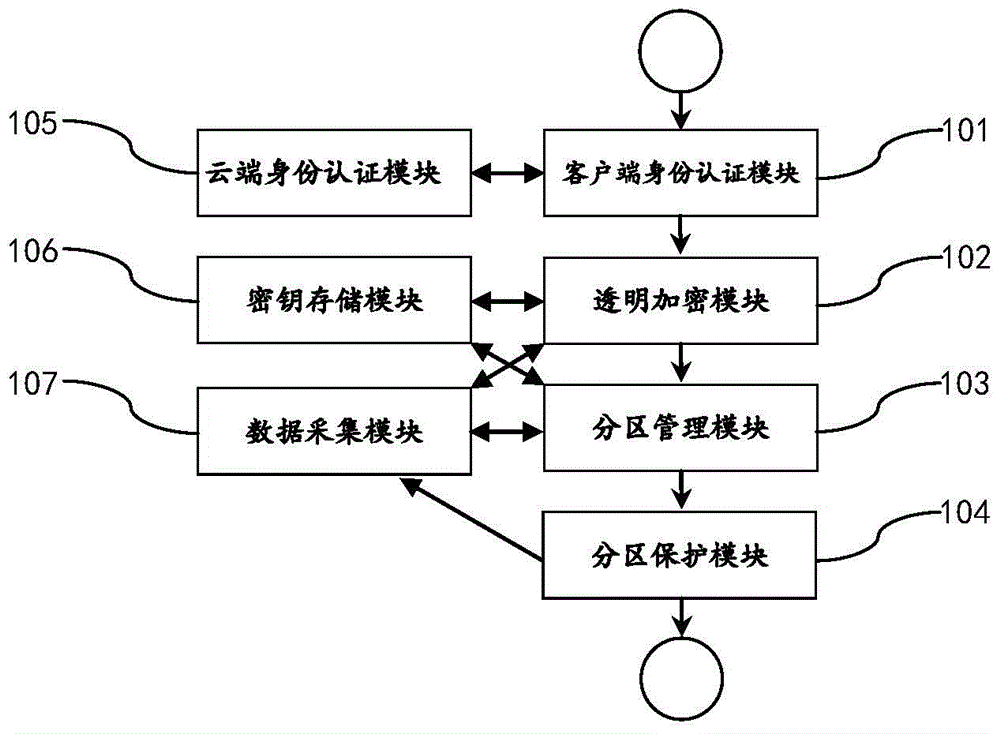
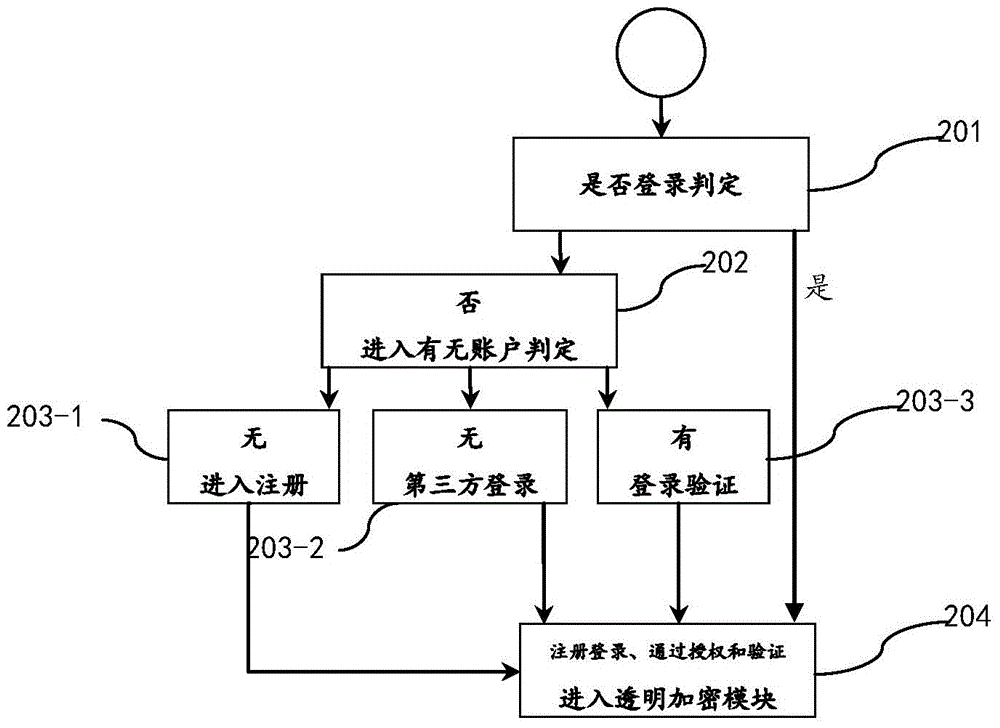
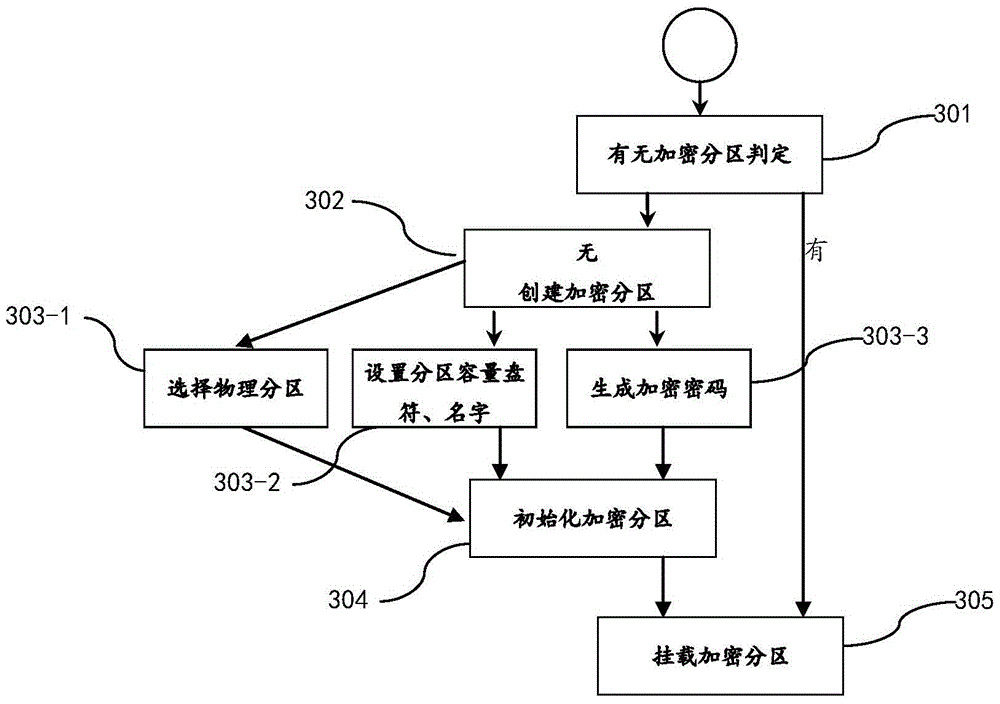
The present invention discloses a method and an apparatus for performing electronic data file protection based on an encrypted partition, and belongs to the field of electronic data file protection. The apparatus disclosed by the present invention adopts an overall design of ''a cloud server+a client''. The cloud server comprises a data acquisition module, a key storage module and a cloud identity authentication module. The client comprises a client identity authentication module, a transparent encryption module, a partition management module and a partition protection module. According to the method and apparatus disclosed by the present invention, ''a cloud server+a client'' dynamic authentication and transparent encryption / decryption are combined, so that files and folders can be effectively prevented from being freely accessed, duplicated or deleted by others, and the security of privacy data is ensured.
Owner:XLY SALVATIONDATA TECHNOLOGY INC
System and method for transferring message in ethernet based vehicle network
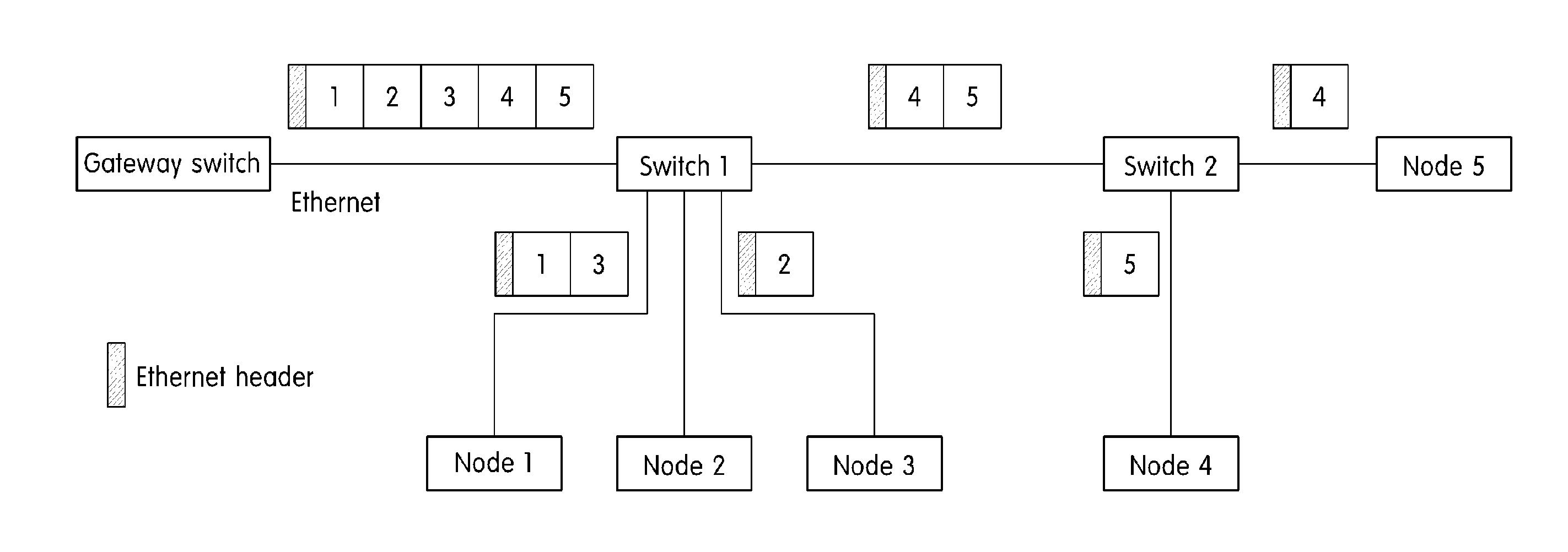
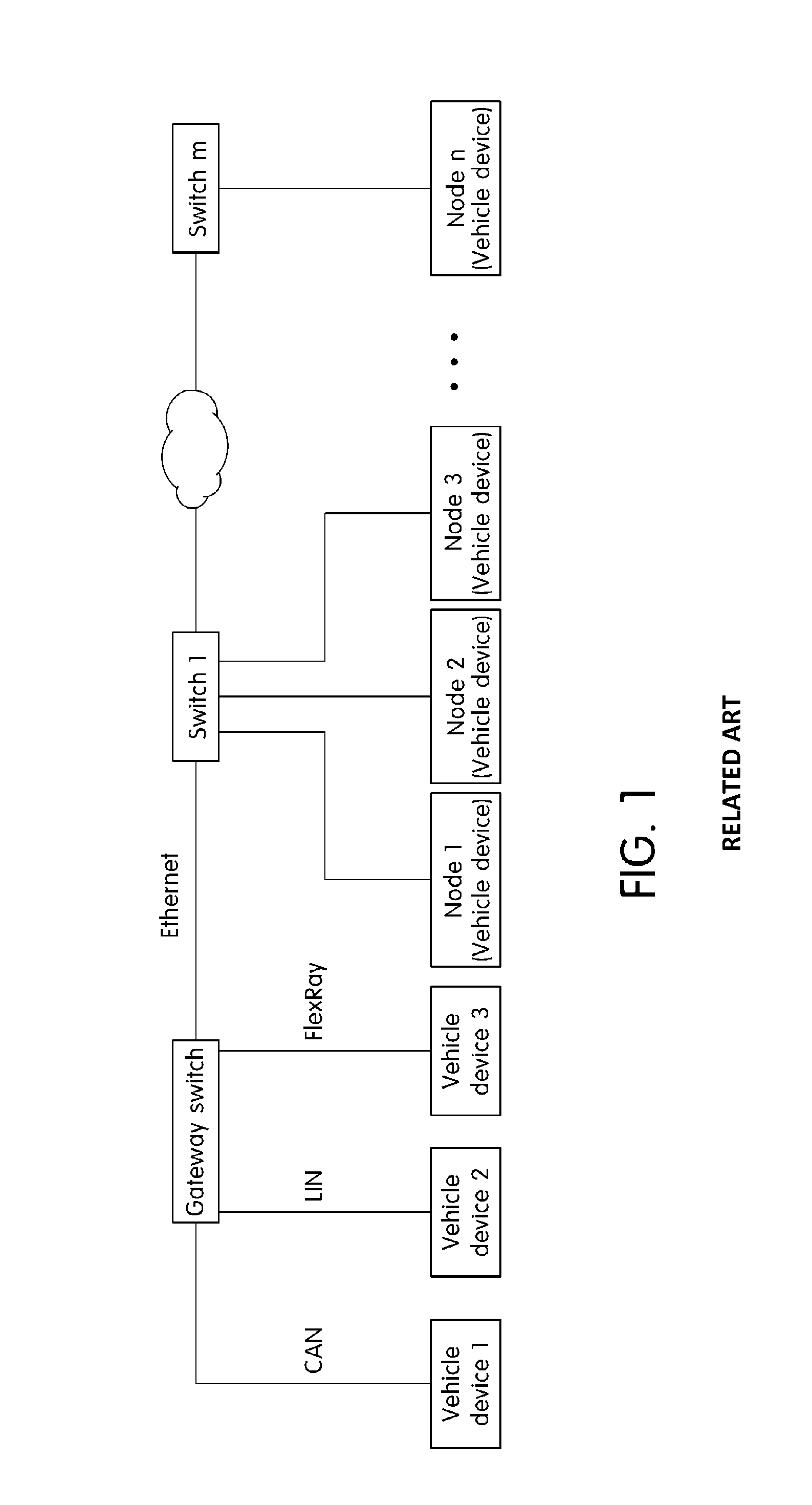
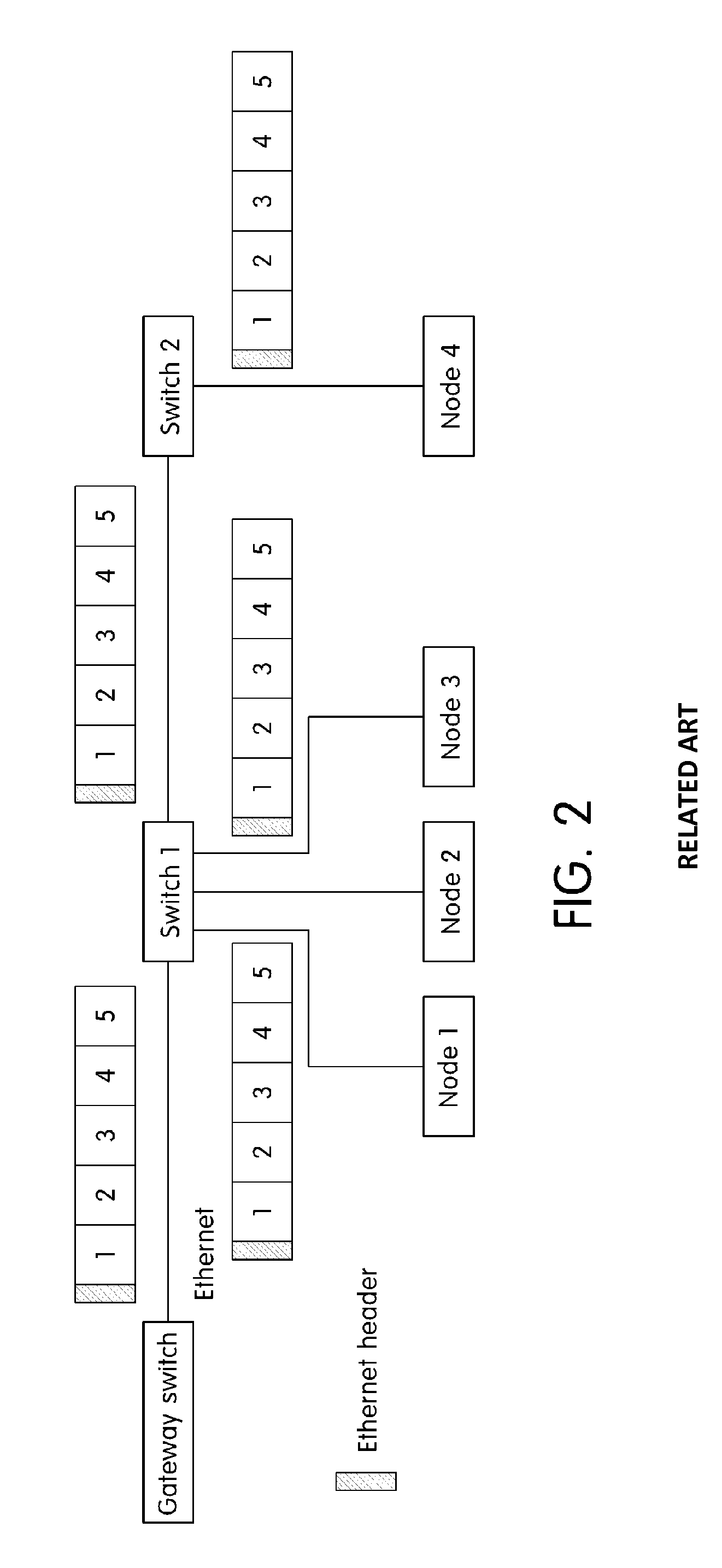
ActiveUS20150003456A1Transmit and receive messages more efficientlyWaste of bandwidthData switching by path configurationNetwork connectionsTransfer systemComputer science
An Ethernet based vehicle network message transferring system is provided that includes a gateway switch that connects the Ethernet to vehicle networks having different protocols and an Ethernet switch that switches Ethernet messages between the gateway switch and vehicle devices to transfer the Ethernet messages. The Ethernet switch includes a processing module that transfers the Ethernet messages received via the gateway switch in the different vehicle networks, a vehicle network process module that switches the messages transferred from the processing module, and a lookup table in which information necessary for switching the vehicle network process module is stored. The vehicle network process module analyzes an Ethernet message transferred via the processing module in the gateway switch to identify destinations of individual messages in the Ethernet message and divides the Ethernet message including information regarding the individual message according to destinations to transmit the divided Ethernet messages to vehicle devices of destinations.
Owner:HYUNDAI MOTOR CO LTD +2
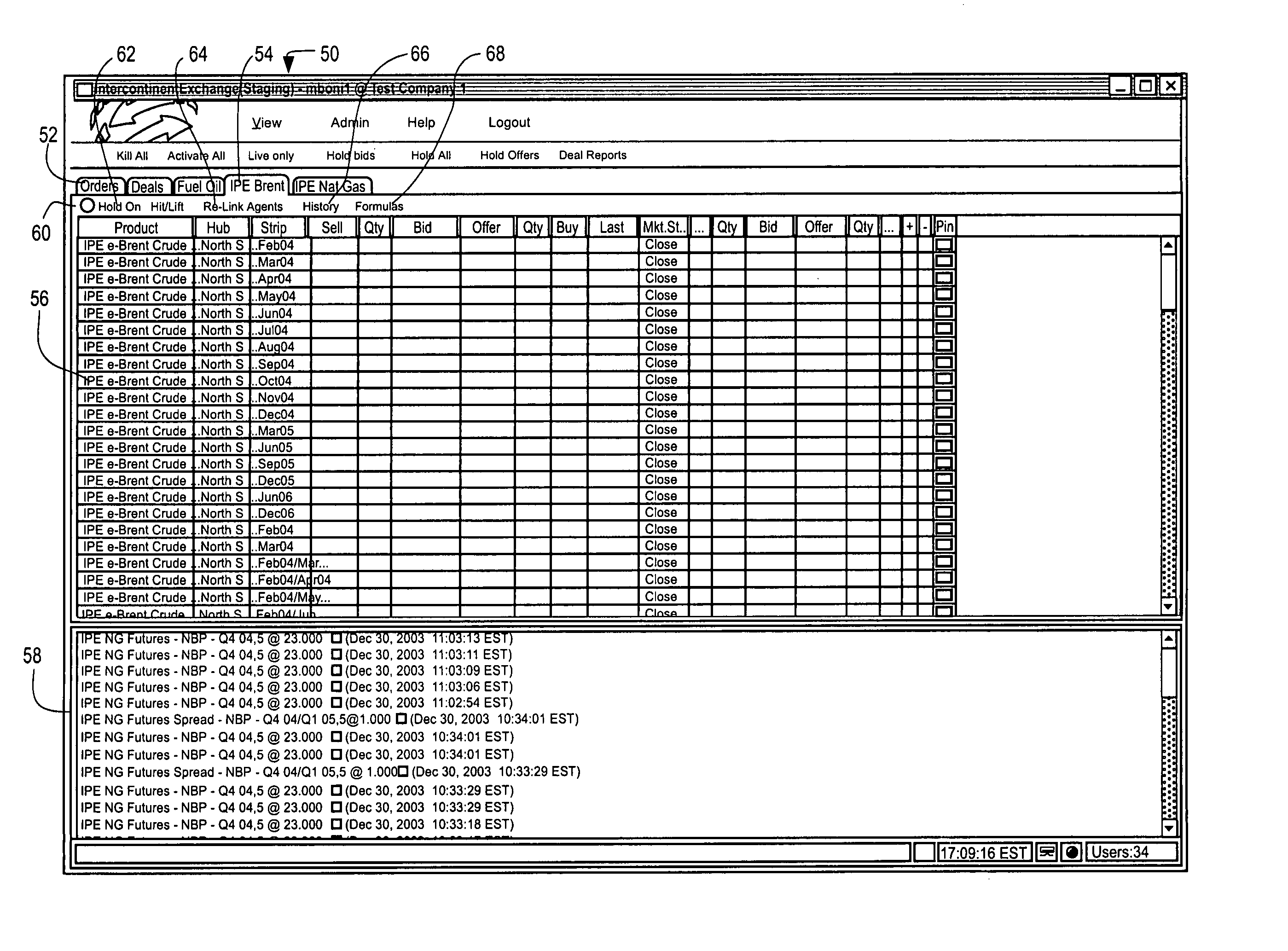
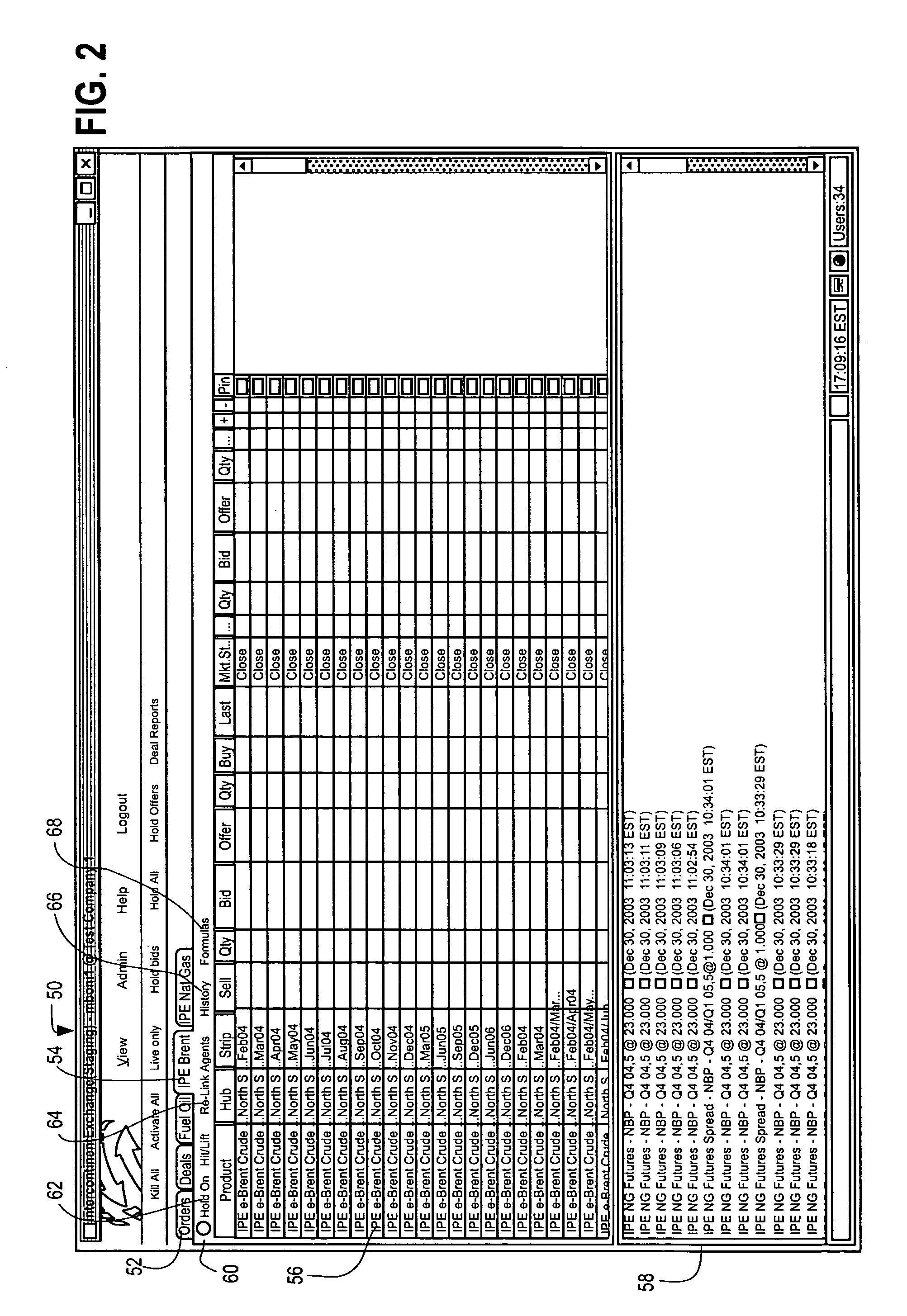
Electronic trading data integration and protection system
A trading system is disclosed which allows an exchange to protect market data from electronic reproduction by traders but allows the traders to use the market data (such as the last traded price, current resting bids and offers) to assist in making the trades. The system includes an exchange server having a database having market data relating to commodities traded over the exchange. A group of trader computers each having a display are coupled to the exchange server. The trader computers have a trader interface run on the computer allowing each trader to place and accept orders for commodities traded over the exchange. The trader interface is capable of receiving market data from the exchange server. An external data source such as an Excel spreadsheet is stored on the trader computer having at least one data field. A trader module is coupled to the trader interface and external data source. The trader module reads market data from the trader interface and the at least one data field of the external data source. The trader module displays the market data and the one data field on the display. The displayed data cannot be exported to the external data source but can be used to make trading decisions and manage orders.
Owner:INTERCONTINENTALEXCHANGE GROUP
Vending machines with field-programmable electronic locks
InactiveUS20070096867A1Easily and inexpensively programmedImprove the level ofElectric signal transmission systemsMultiple keys/algorithms usageService personnelBiological activation
A vending machine uses a field-programmable electronic lock that learns a key code from a corresponding electronic key. The electronic lock has a learning process activation device that is accessible when the door of the vending machine is in the open position. Using the learning process activation device, a service person activates the electronic lock to perform a key code learning operation, in which the electronic lock receives a key code transmitted from an electronic key and stores the key code in a non-volatile memory for future access control of the vending machine. Data encryption is employed in the communications between the key and the lock to ensure the security of the communications. A communication device installed in the vending machine for communicating with a home base computer allows the operation of the electronic lock to be remotely controlled for access control and auditing purposes.
Owner:DENISON WILLIAM D +2
System and method of utilizing a MAC address based unlocking key
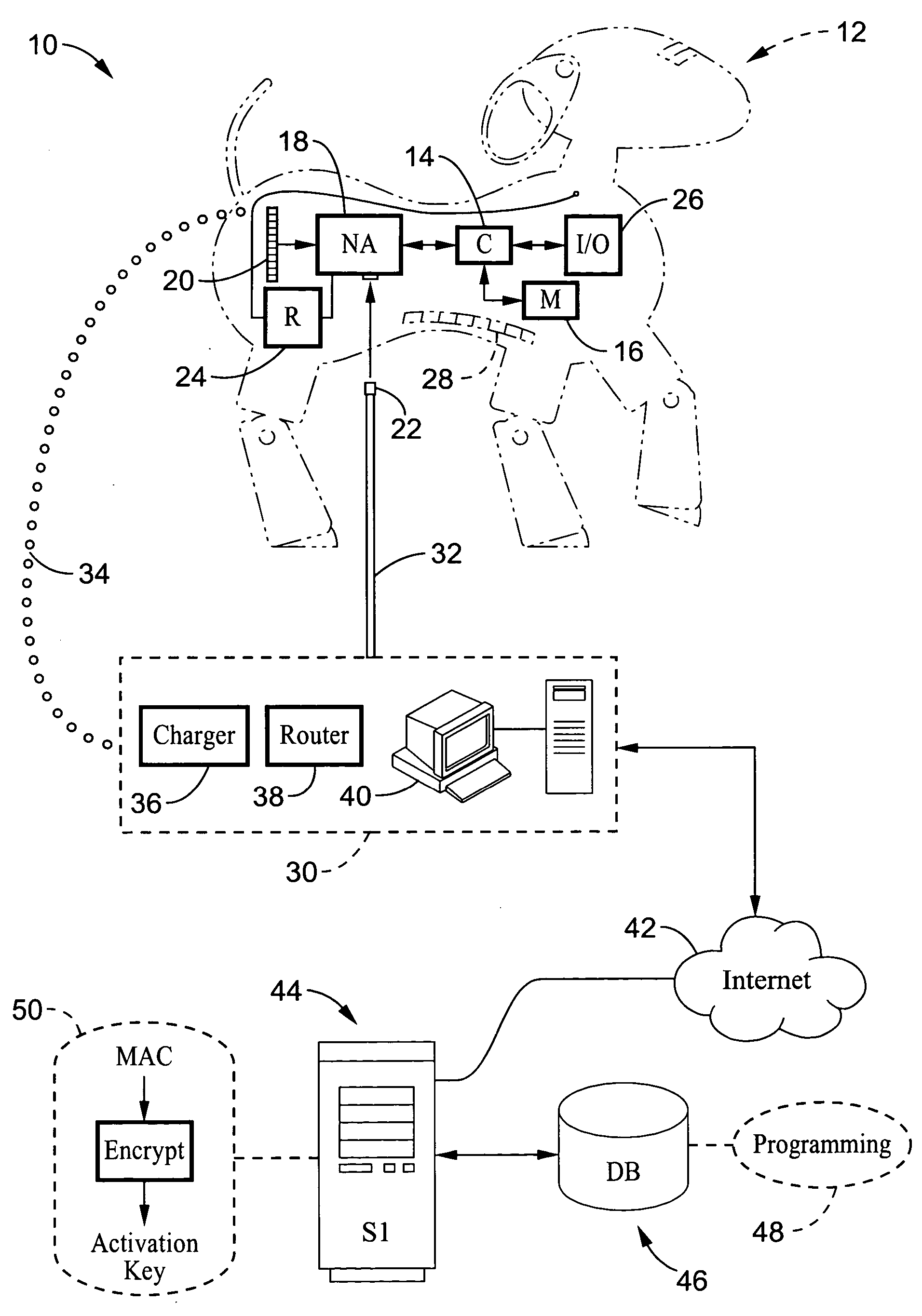
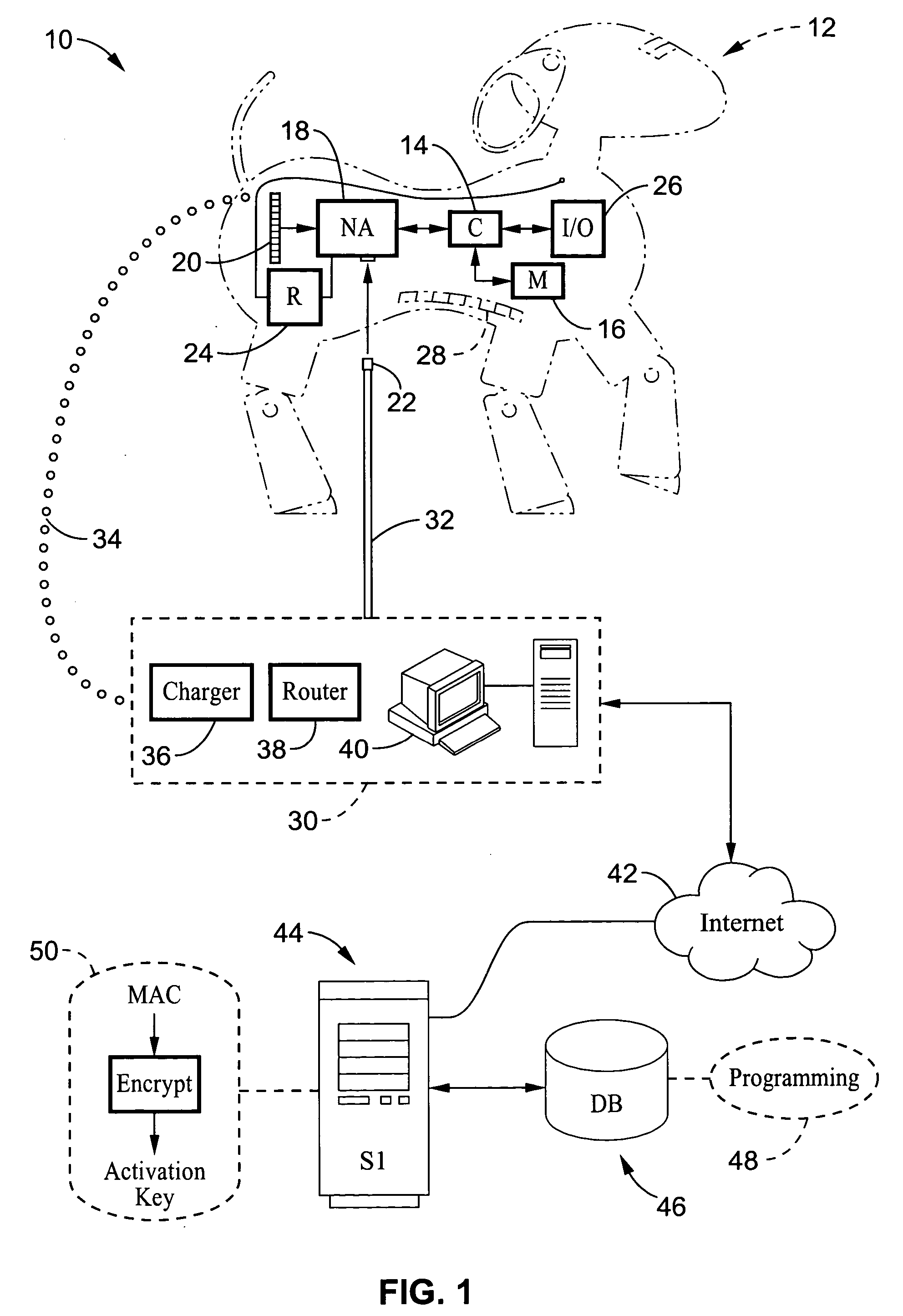
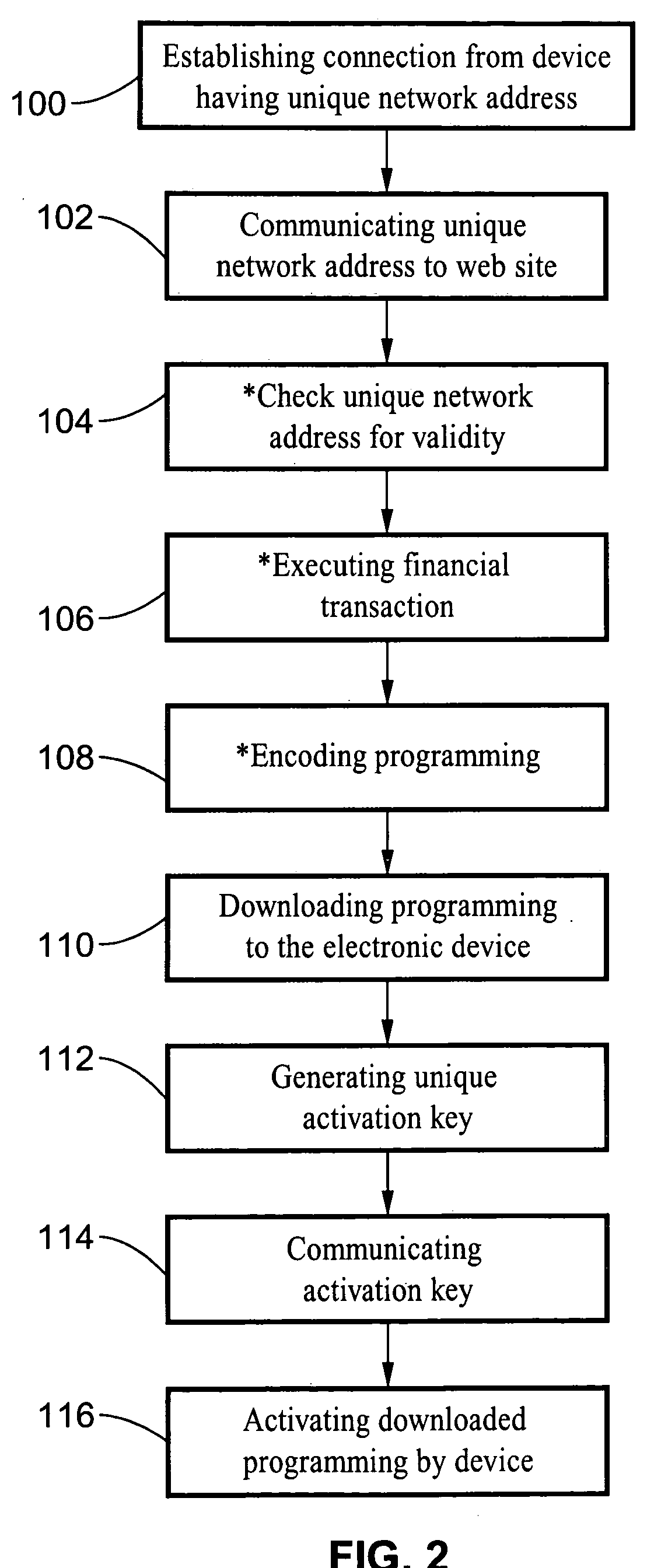
InactiveUS20060080464A1Inhibitory contentPrevent copyingComputer security arrangementsMultiple digital computer combinationsFinancial transactionNetwork address
A system and method are described for activating programming downloaded to electronic devices. The method involves the generation of an encrypted (or encoded) activation key which is produced in response to the network address (i.e. media access control (MAC) address) of the electronic device to which the download is directed. Programming can only be activated within the electronic device upon a match being detected between the activation key and the network address of the electronic device. Typically, the programming would be downloaded from a web site, such as from a manufacturer of the electronic device, in exchange for receipt of a payment preferably executed as an online financial transaction. The system and method prevent the copying of downloaded programs for a given electronic device for use by other users.
Owner:SONY CORP +1
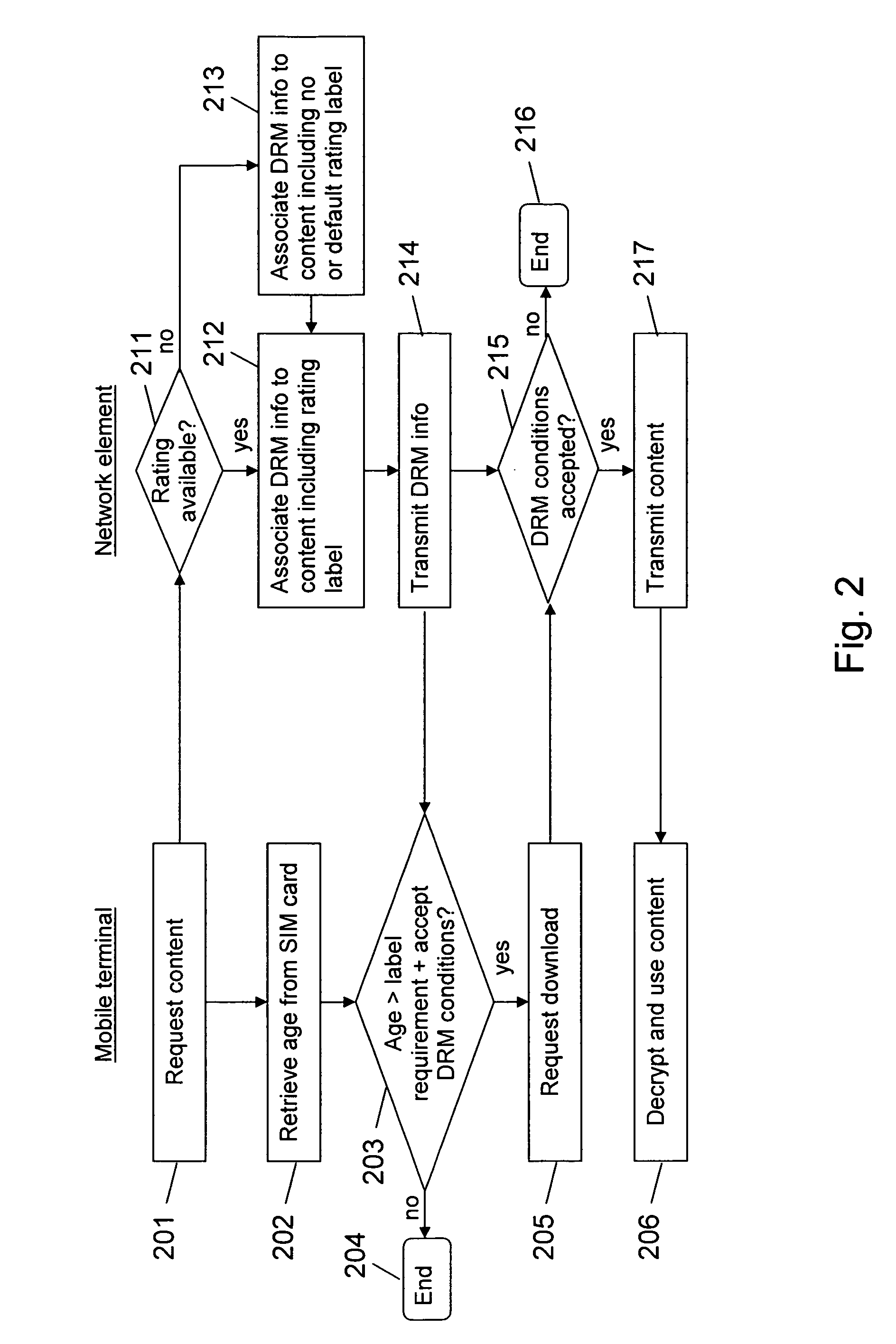
Content control
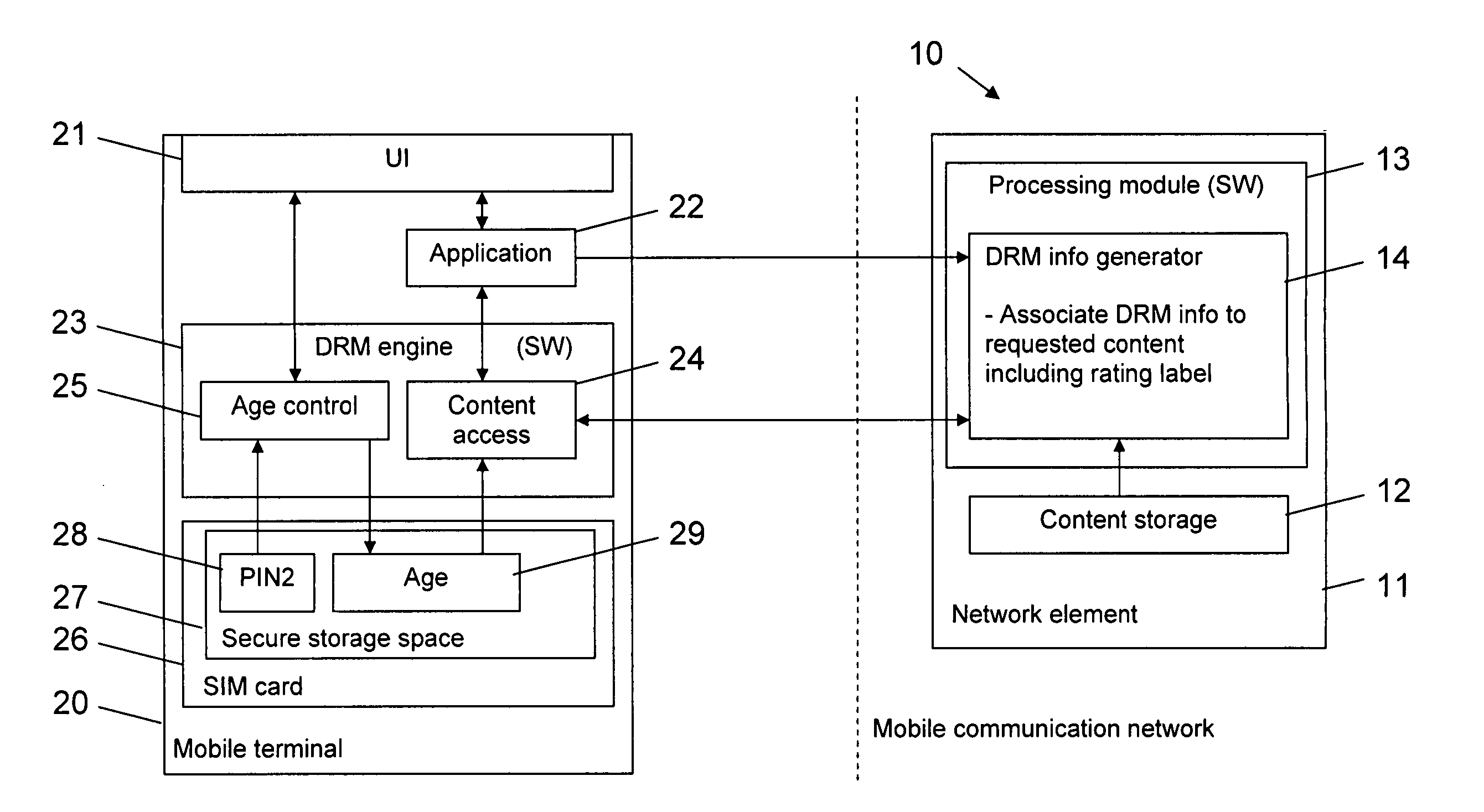
InactiveUS20060149727A1Consumes contentPrevent copyingProgram/content distribution protectionSpecial data processing applicationsUser deviceWorld Wide Web
The invention relates to content which can be accessed via a user device 20. In order to allow preventing users of a user device in an efficient and flexible way from consuming content to which they should not have access, a second device 26 stores an indication 29 of at least one attribute associated to a user, which is accessible by the user device 20. When an access to content is requested, the user device compares the available rating information with the available attribute indication, the user device 11 determines whether a user is allowed to access the requested content, and allows or prevents an access to the content accordingly.
Owner:NOKIA CORP
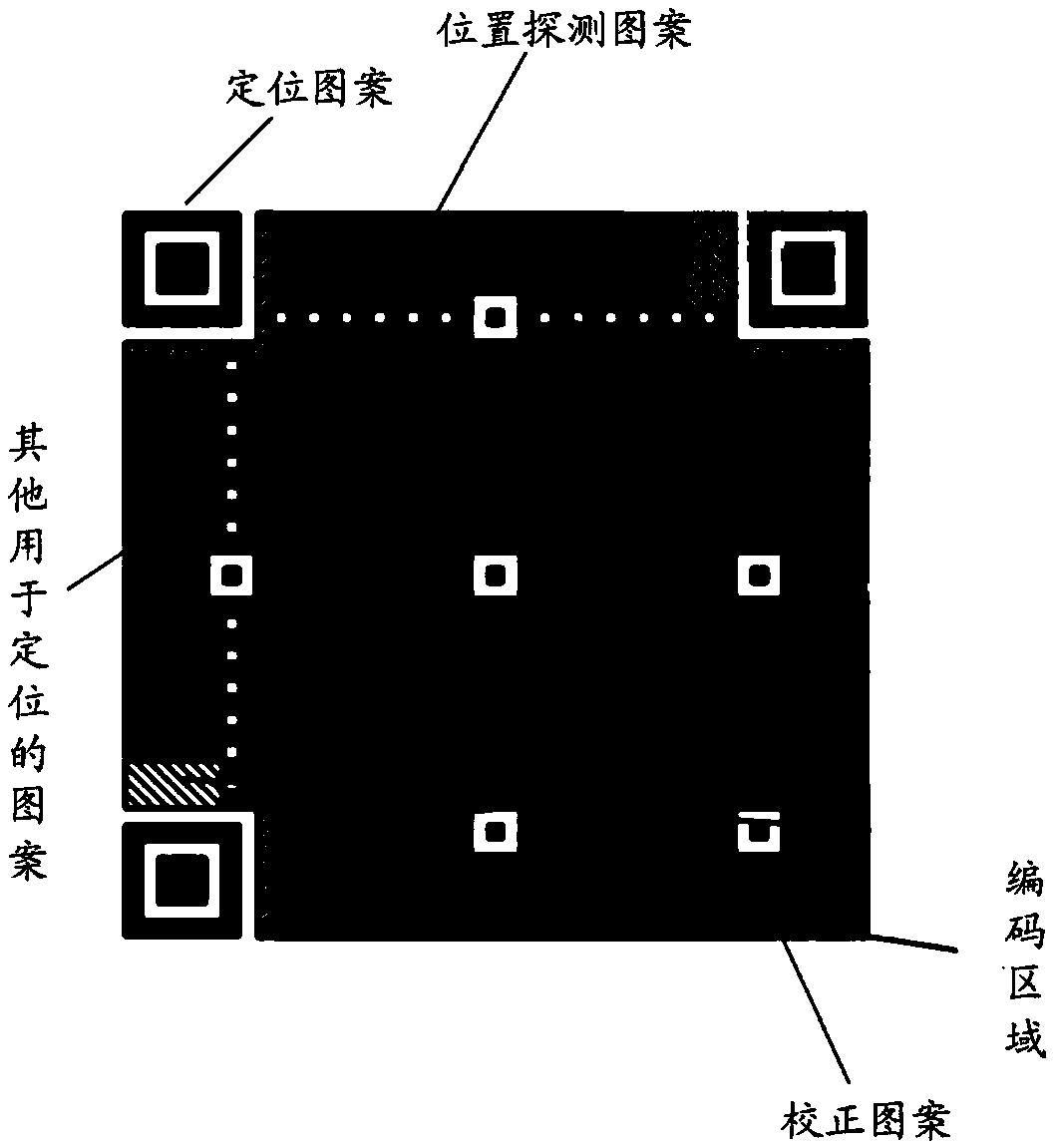
Two-dimensional code, encoding and identification method thereof and product with anti-counterfeiting function
ActiveCN108764420ARich Personalization FeaturesFlexible Personalization FeaturesRecord carriers used with machinesGraphicsDimensional modeling
Owner:CHINA BANKNOTE SECURITY PRINTING TECH RES INST CO LTD +1
Virtual machine system for input/output equipment virtualization outside virtual machine monitor
ActiveCN101976200AReduce the burden onImprove isolationTransmissionSoftware simulation/interpretation/emulationVirtualizationMemory sharing
The invention provides a virtual machine system for input / output equipment virtualization outside a virtual machine monitor. The virtual machine system comprises the virtual machine monitor; the virtual machine monitor is provided with a plurality of input / output virtual machines, and all I / O operations of clients and equipment sharing are processed by the input / output virtual machines; the plurality of input / output virtual machines are managed and dispatched by the virtual machine monitor; and an inter-domain communication mechanism and a memory sharing mechanism are formed between the input / output virtual machines and the virtual machine monitor. Functions of processing and sharing input and output are extracted from the virtual machine monitor based on a processor platform of hardware-aid virtualization technology, and processing, sharing and dispatching of the input and the output are performed in the prerogative client virtual machines running above the virtual machine monitor tofinish the I / O virtualization function so that better isolation and safety can be acquired and the burden of the virtual machine monitor can be reduced at the same time.
Owner:ZHEJIANG UNIV
Monitoring realization-based on-line examination system and method
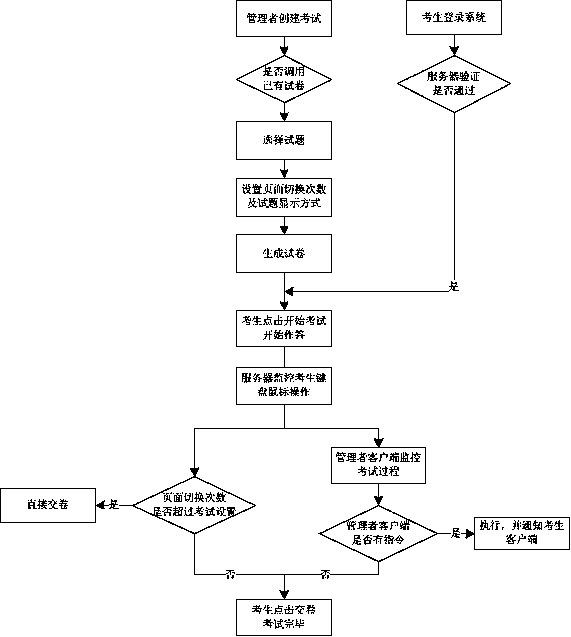
InactiveCN103514773AImprove effectivenessIncrease flexibilityTransmissionElectrical appliancesPaper basedComputer science
The invention discloses a monitoring realization-based on-line examination system and method. The system comprises an examinee user terminal, a manager user terminal, a server terminal, an examination question base, an examination paper generation module and an examination paper base. The examinee user terminal receives examinee logging information and an examinee answer sheet; the manager user terminal sets an examination requirement and carries out real-time monitoring on an examinee answering situation; the server terminal verifies the logging information of the examinee user terminal, responds to an instruction of the manager user terminal, shields responses of two hot keys: Ctrl+V and Ctrl+C, and records clicking situations of a keyboard and a mouse; the examination question base stores single questions of various examination questions; the examination paper base visits the examination question base to generate an examination paper or directly visits and invokes information in the examination paper base to generate an examination paper; and the examination paper base stores various examination papers generated by enterprises. With on-line examination services provided by the system, on the one hand, an examinee can take an examination any time any where; and on the other hand, a manager can monitor an examination process in real time. Therefore, cheating by the examinee can be prevented, thereby ensuring effectiveness as well as fairness and justice of the examination.
Owner:ZHENJIANG RETECH INFORMATION TECH
Software authentication method based on softdog
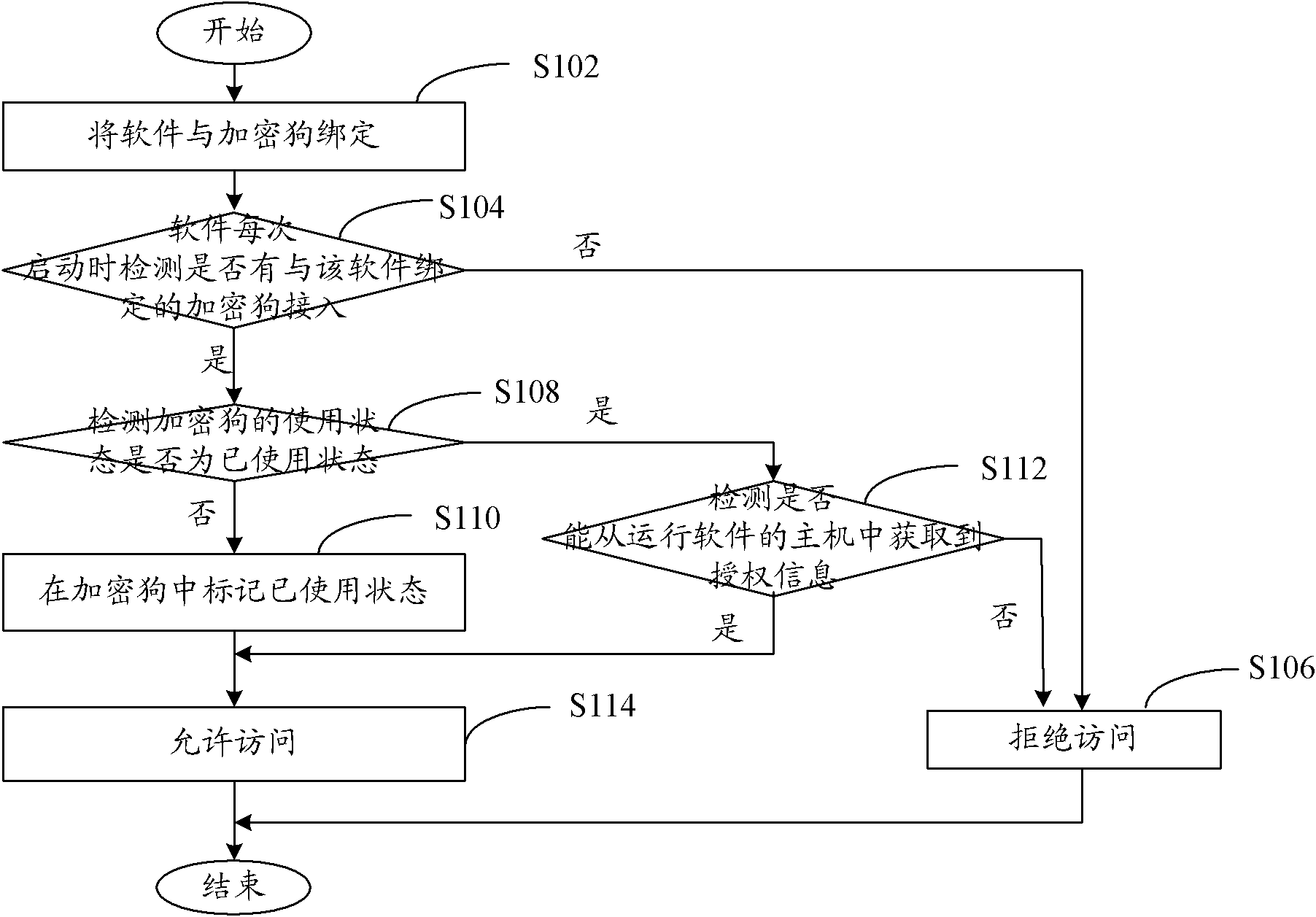
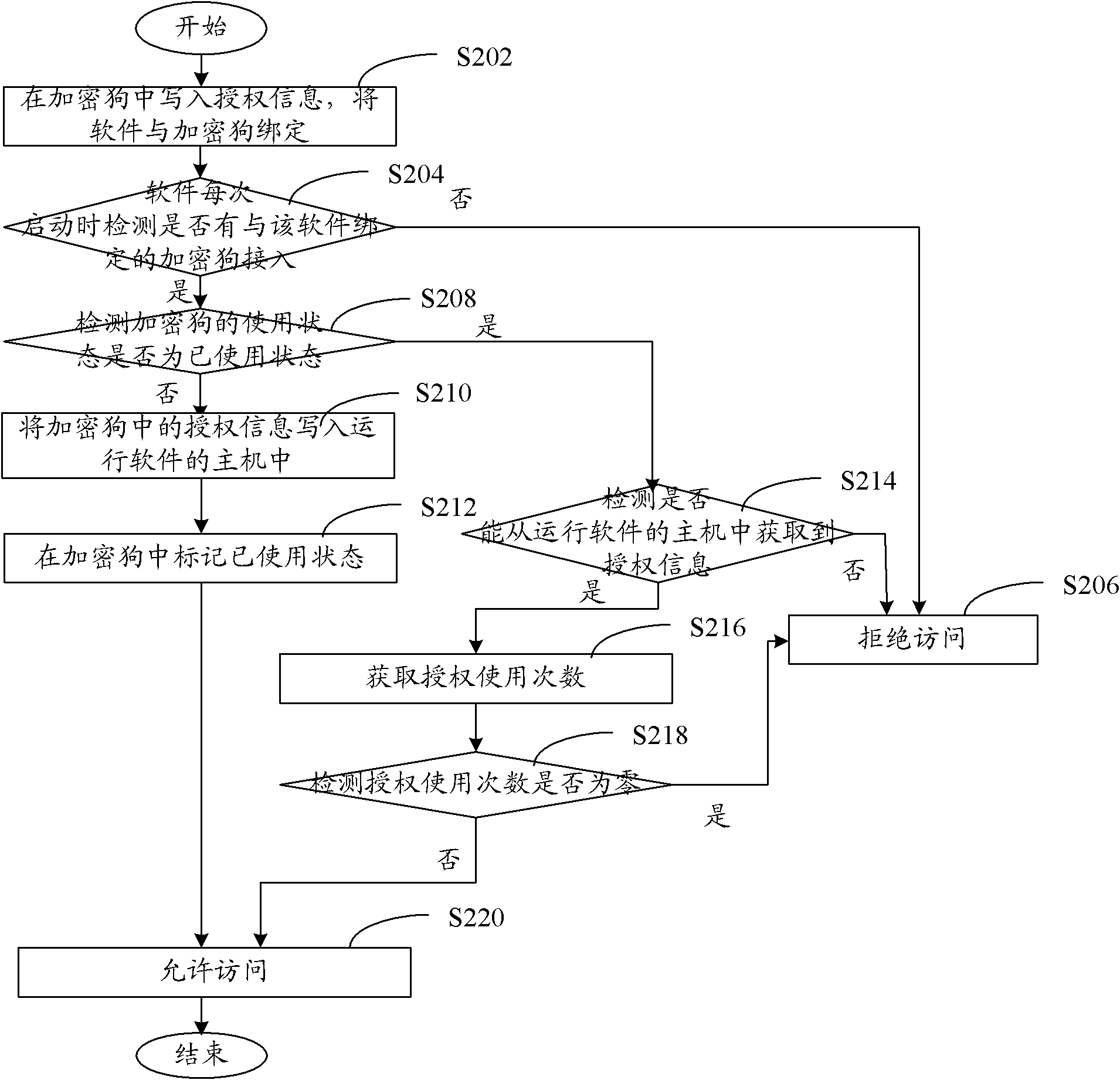
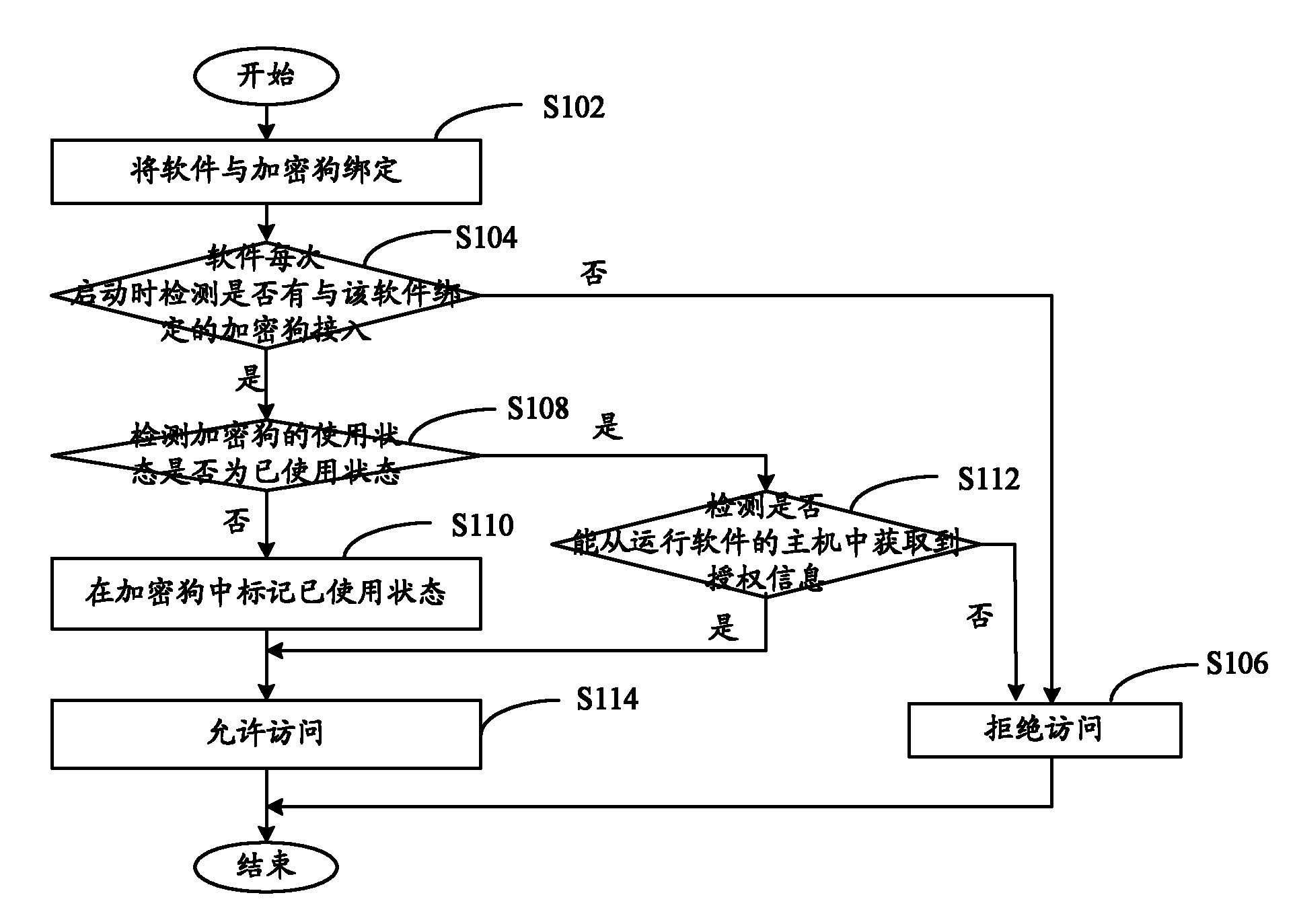
InactiveCN101996293AImprove securityPrevent copyingProgram/content distribution protectionCopy propagationAuthorization
The invention discloses a software authentication method based on a softdog, comprising the following steps: binding software and the softdog; detecting whether the softdog bound with the software is accessed or not when the software is started each time, if not, denying access, and if so, detecting whether the user mode of the softdog is a used mode or not, if the user mode of the softdog is not the used mode, marking the used state in the softdog and allowing access, if the user mode is a used mode, detecting whether an authorization message can be acquired from the host of operating software, if the authorization message can be acquired, allowing access, and otherwise denying access. By the invention, the fact that one softdog can be utilized on only one host can be ensured, thus effectively preventing the copy propagation behavior of a user possessing the softdog and protected documents, and improving the safety of software authentication.
Owner:SHENZHEN NETCOM ELECTRONICS CO LTD
Method and system for preventing the unauthorized copying of video content
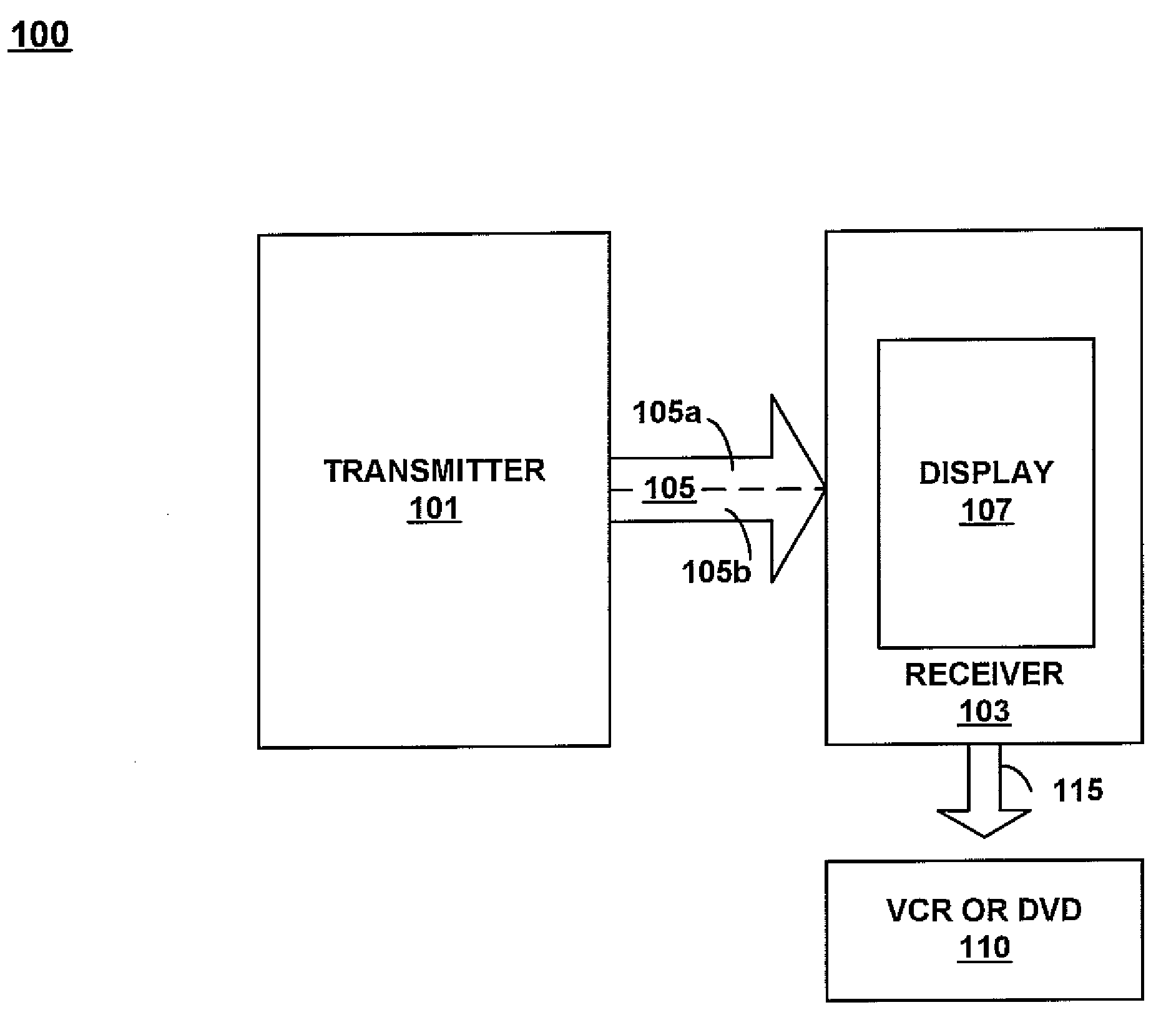
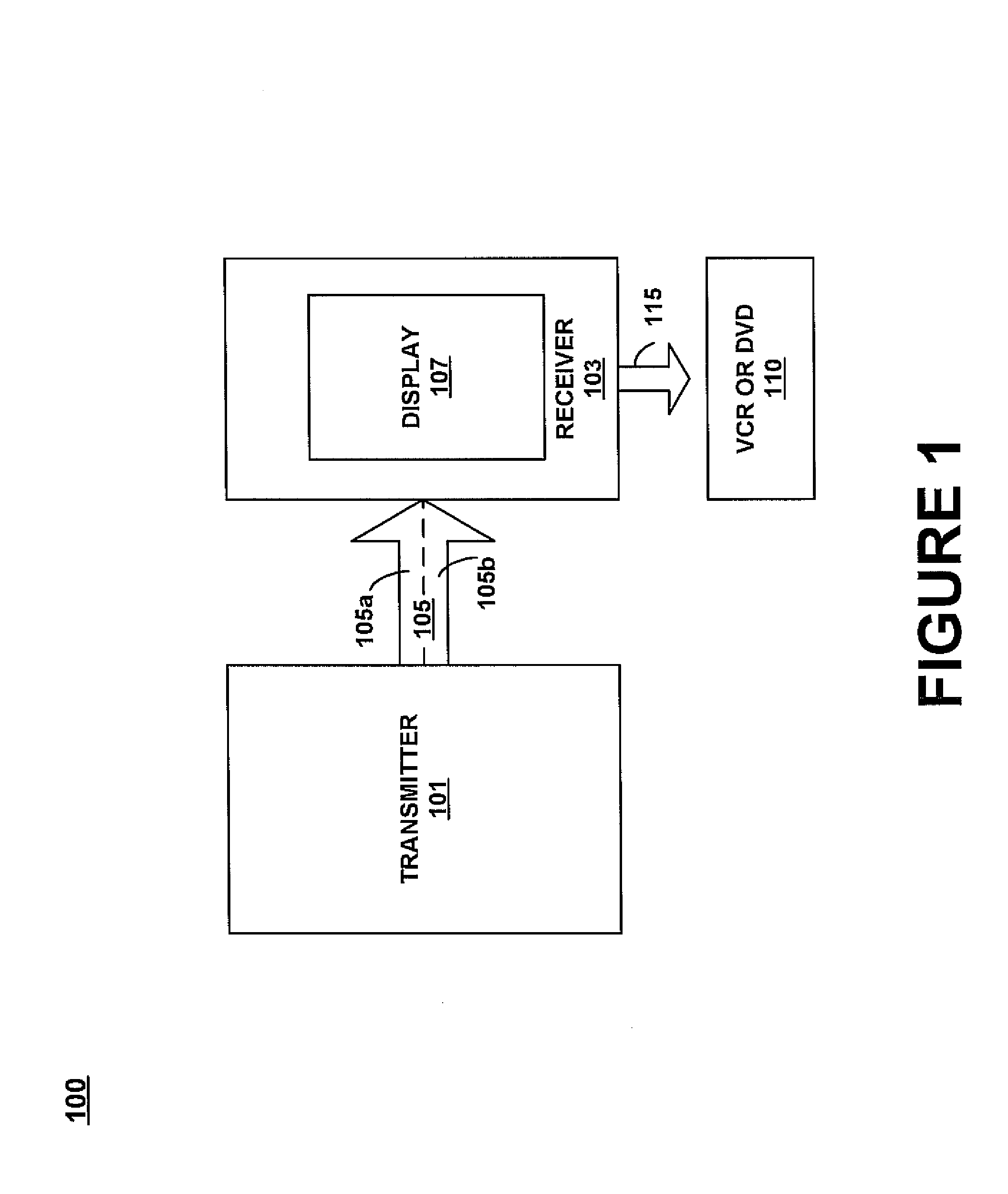
ActiveUS7382969B2Prevent copyingTelevision system detailsColor television signals processingDVD recorderDisplay device
A method for preventing the copying of useable video content is disclosed. The method includes identifying the video signal content of a video signal that is suitable to be extracted, extracting video content from the video signal to transmit to a receiver, and replacing the extracted video content with marred video content in the video signal. The method further includes placing the extracted video content in a user data channel of a program stream for transmission to a receiver. In addition, the method includes transmitting portions of the video signal that contains the marred video content in a first channel of the program stream, and transmitting the extracted video content in a second channel of the program stream to the receiver. The signals transmitted in the program stream are synchronized for presentation in the display of the receiver. Only the program stream components that contain the marred video content may be recorded by a VCR or DVD recorder and the marred video is unsuitable for piracy or rebroadcast.
Owner:RELIANCE ELECTRIC TECH +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com