Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1778 results about "Application processor" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Processing data flows with a data flow processor
InactiveUS20110238855A1Increased complexityAvoid problemsMultiple digital computer combinationsPlatform integrity maintainanceData controlConfigfs
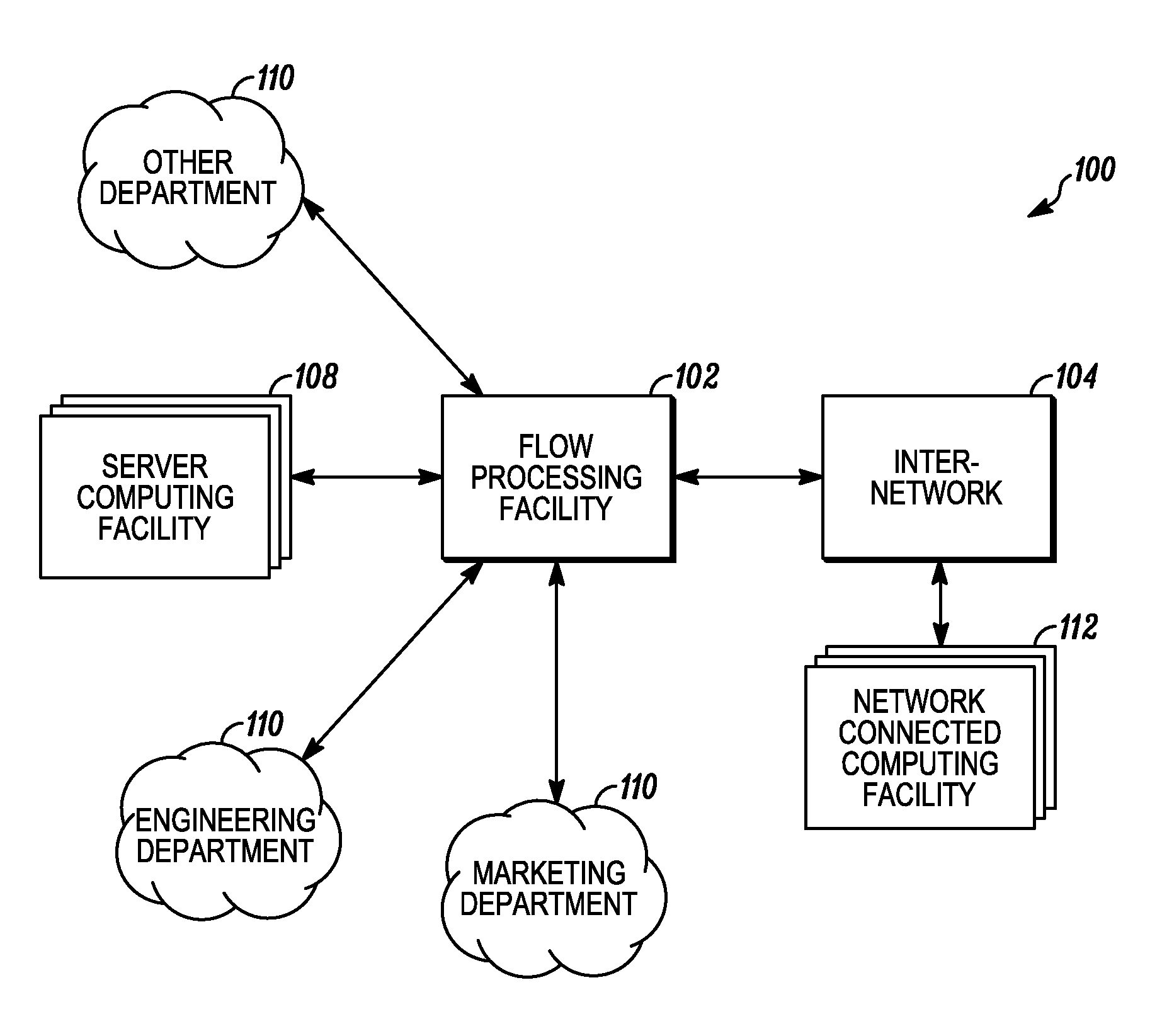
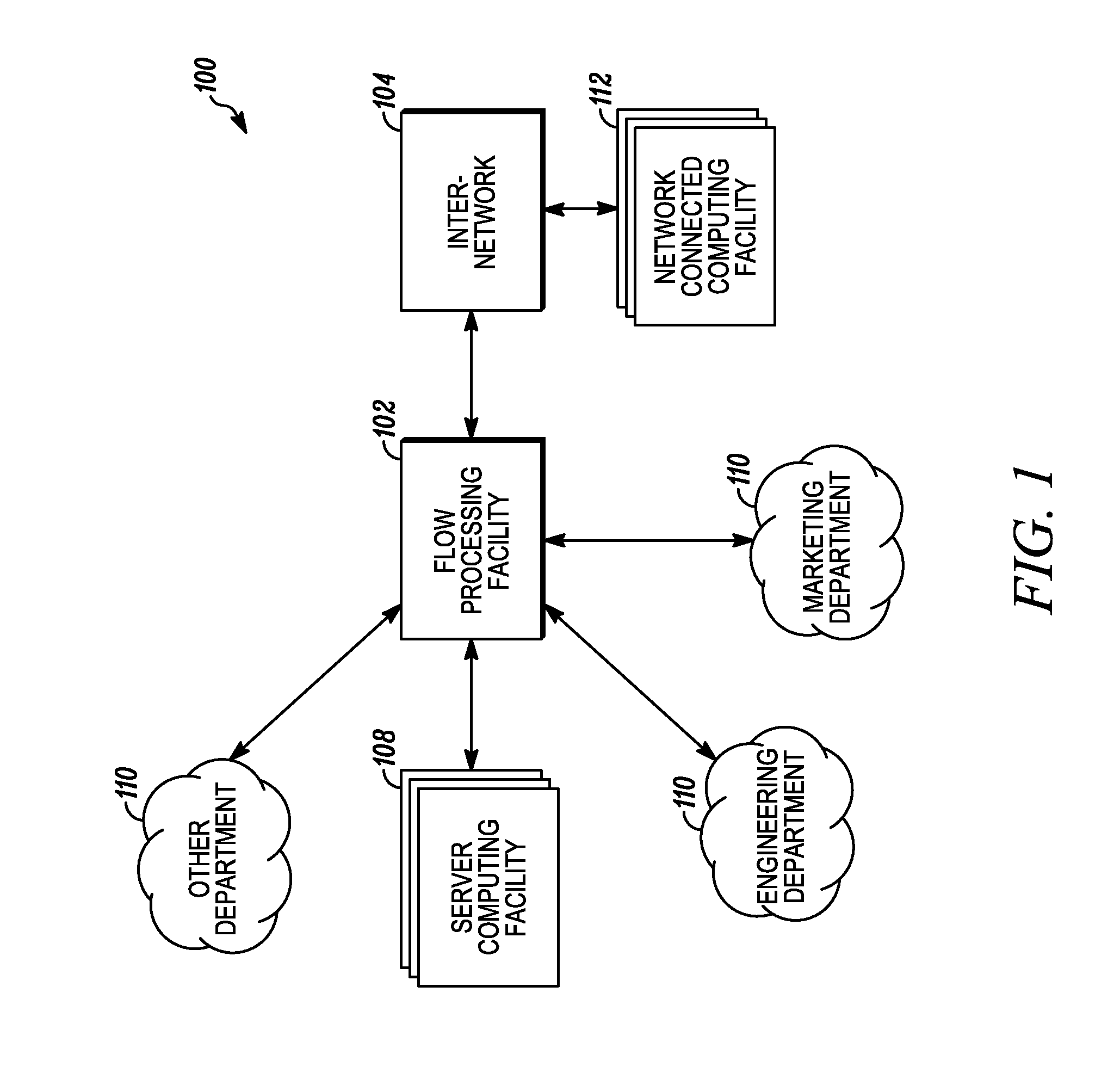
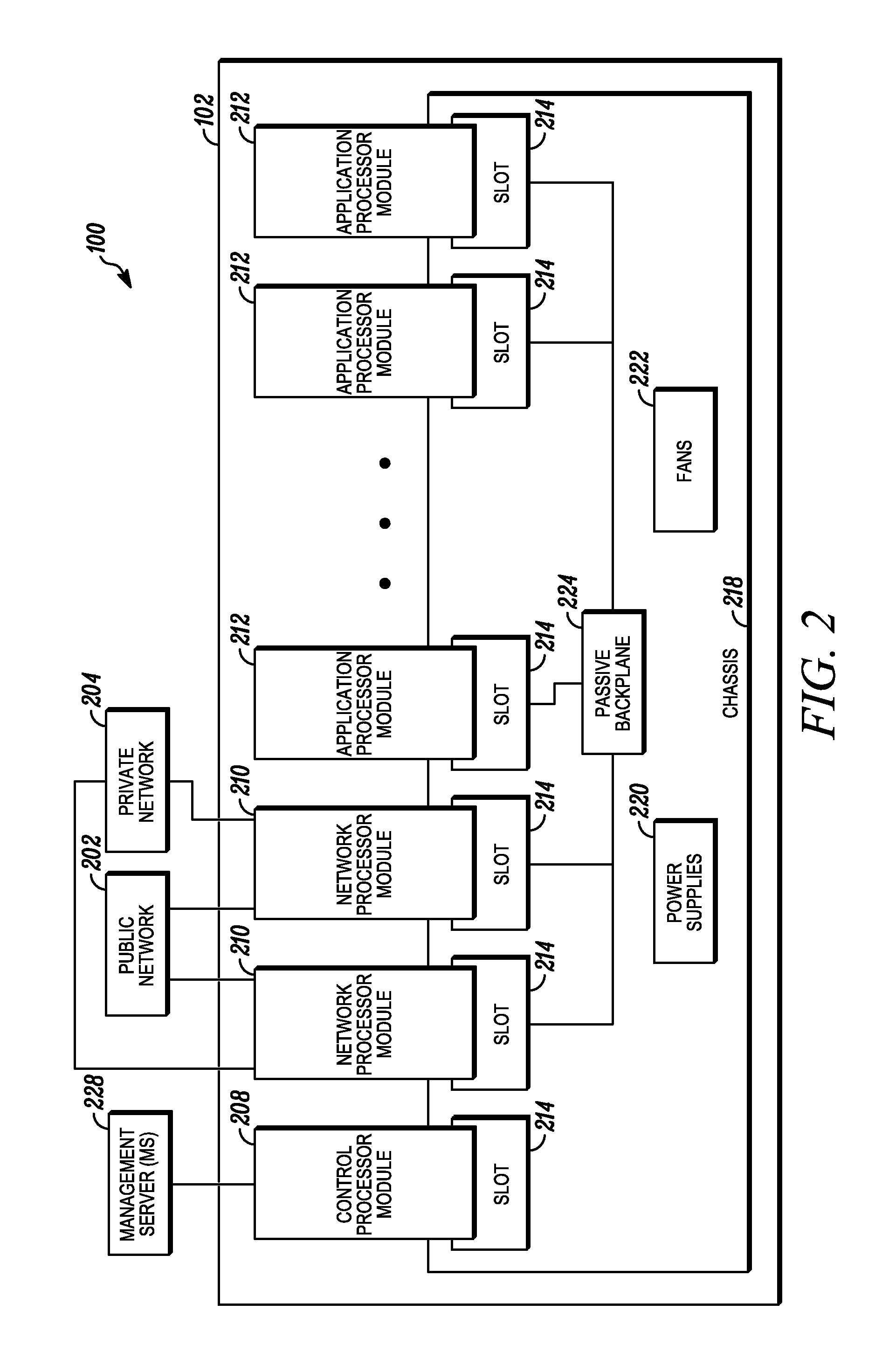
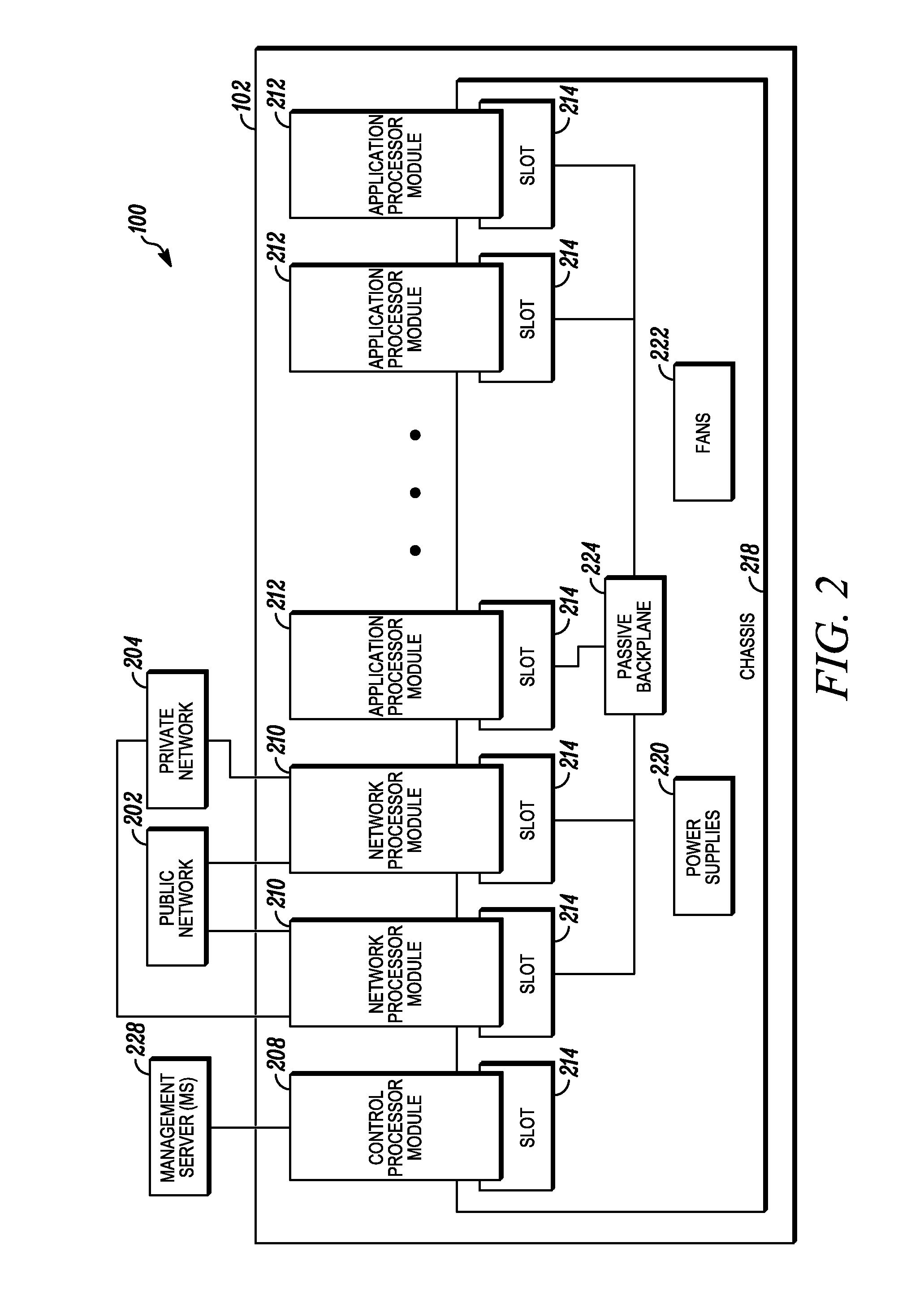
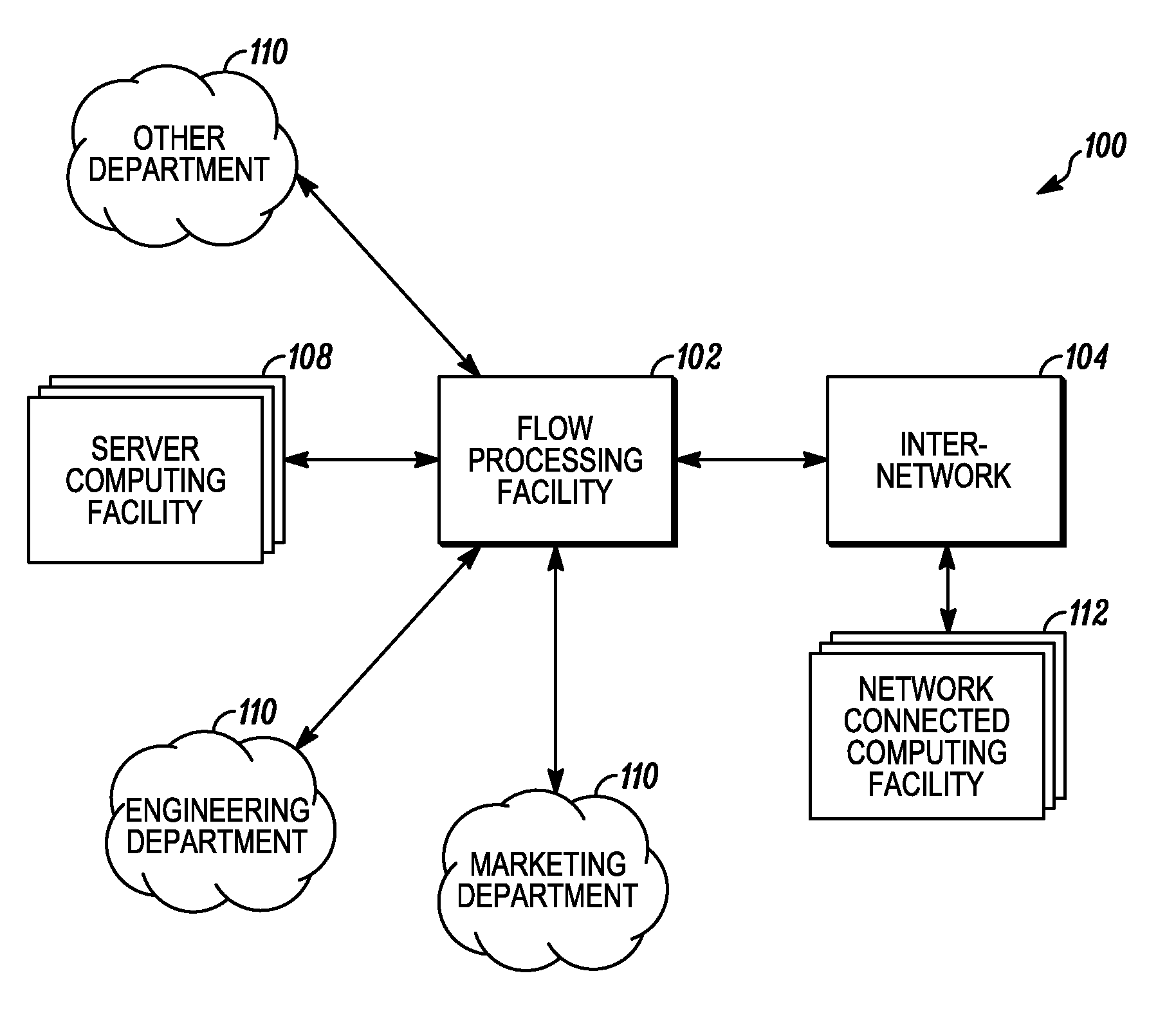
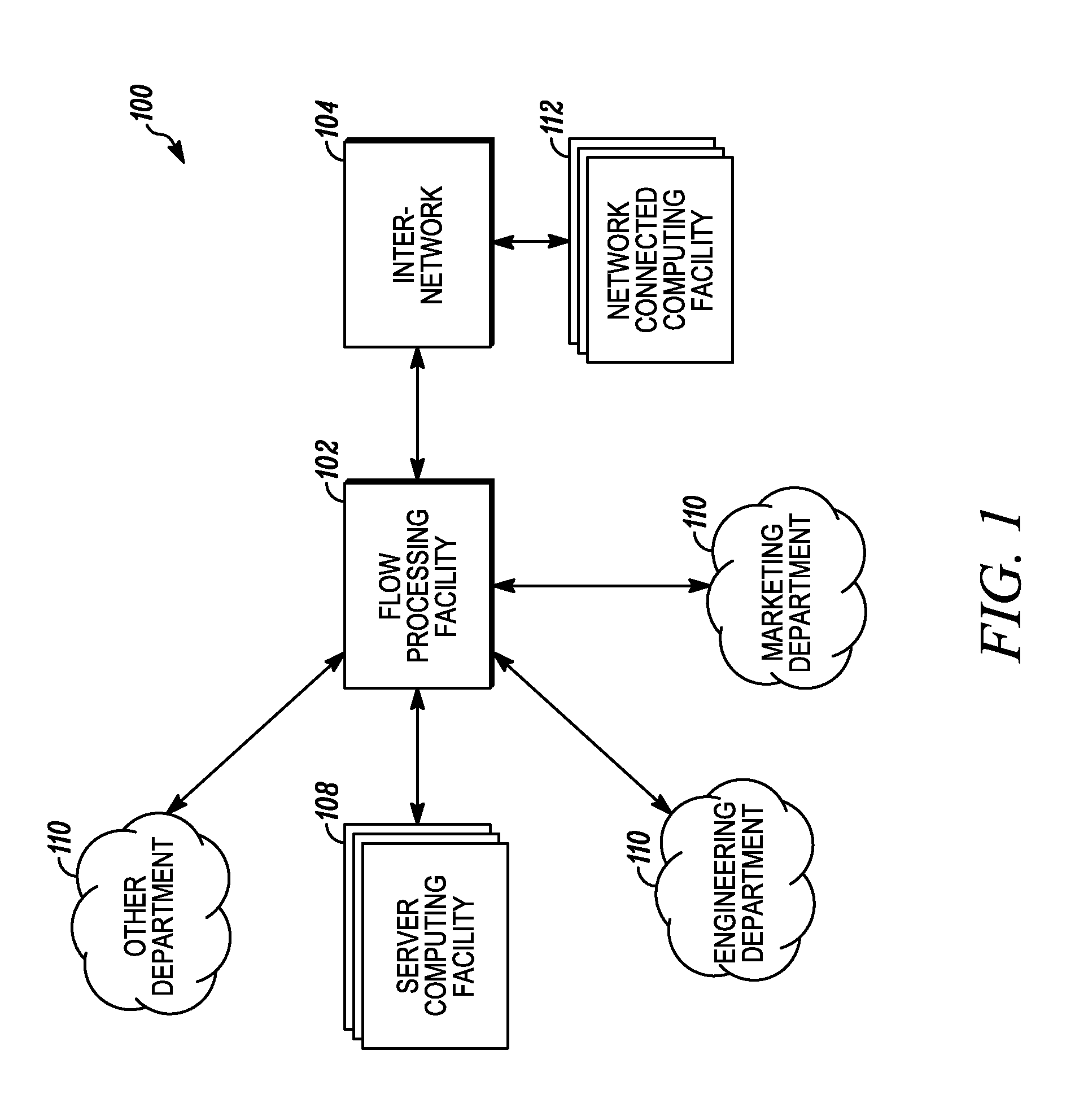
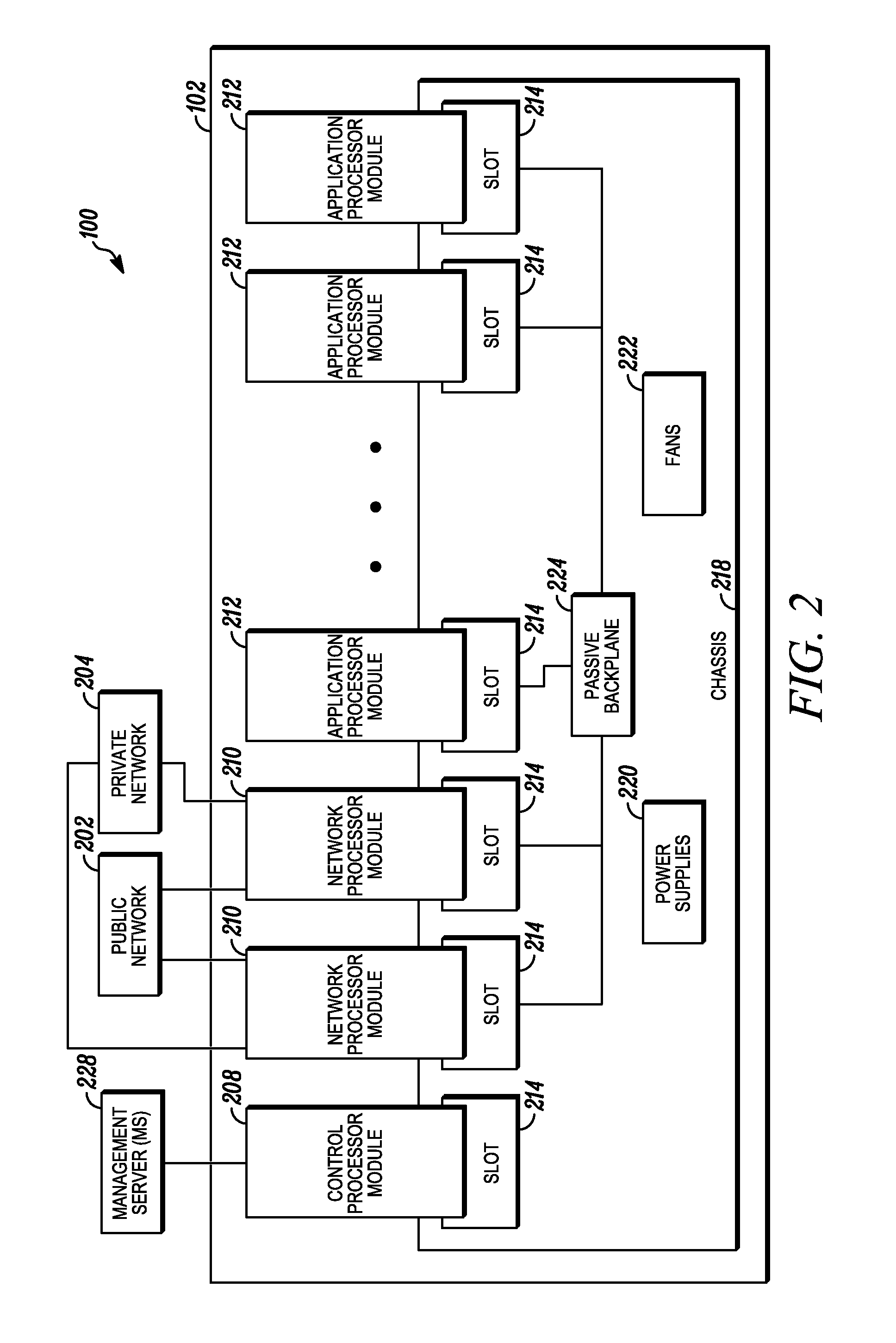
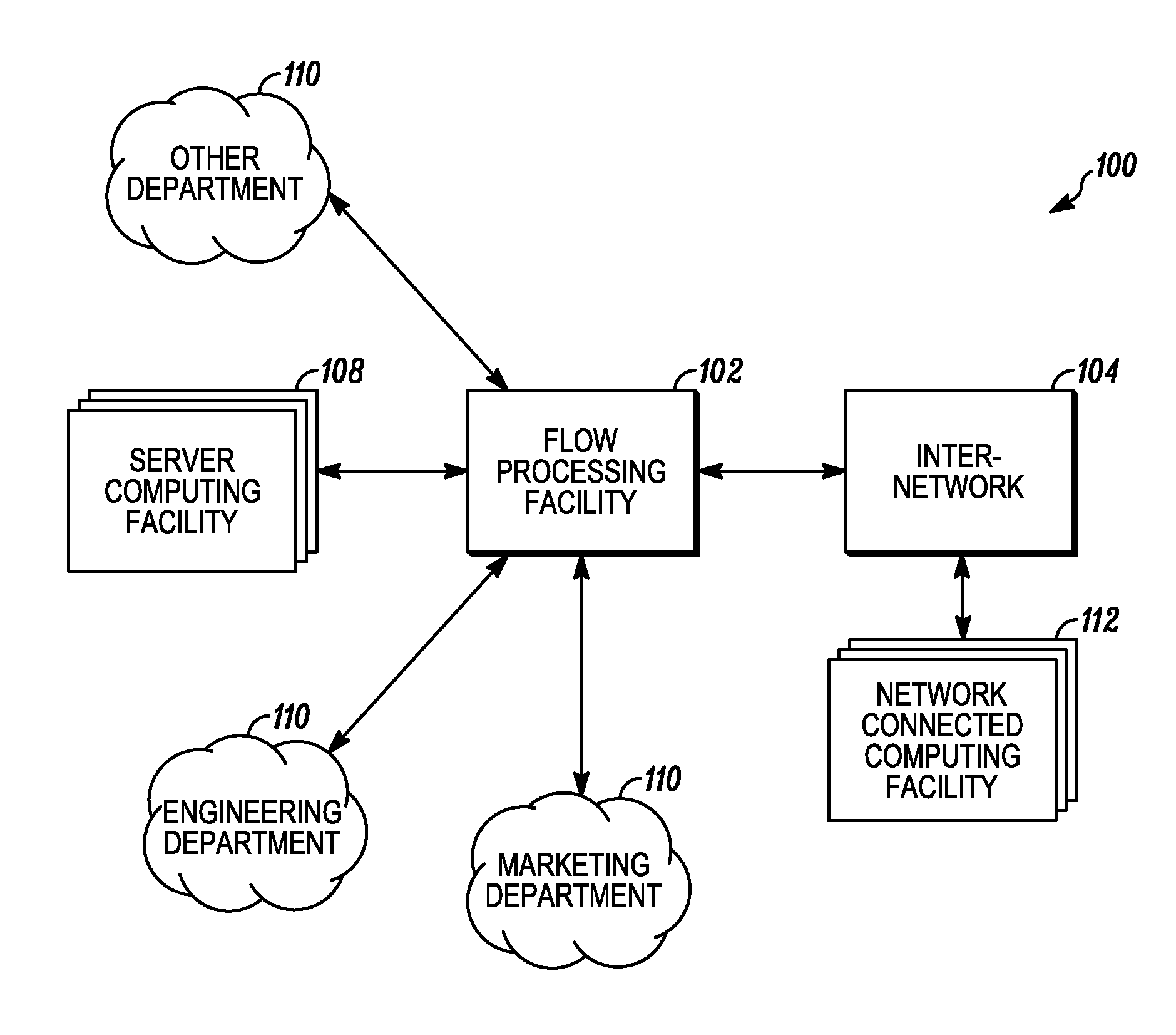
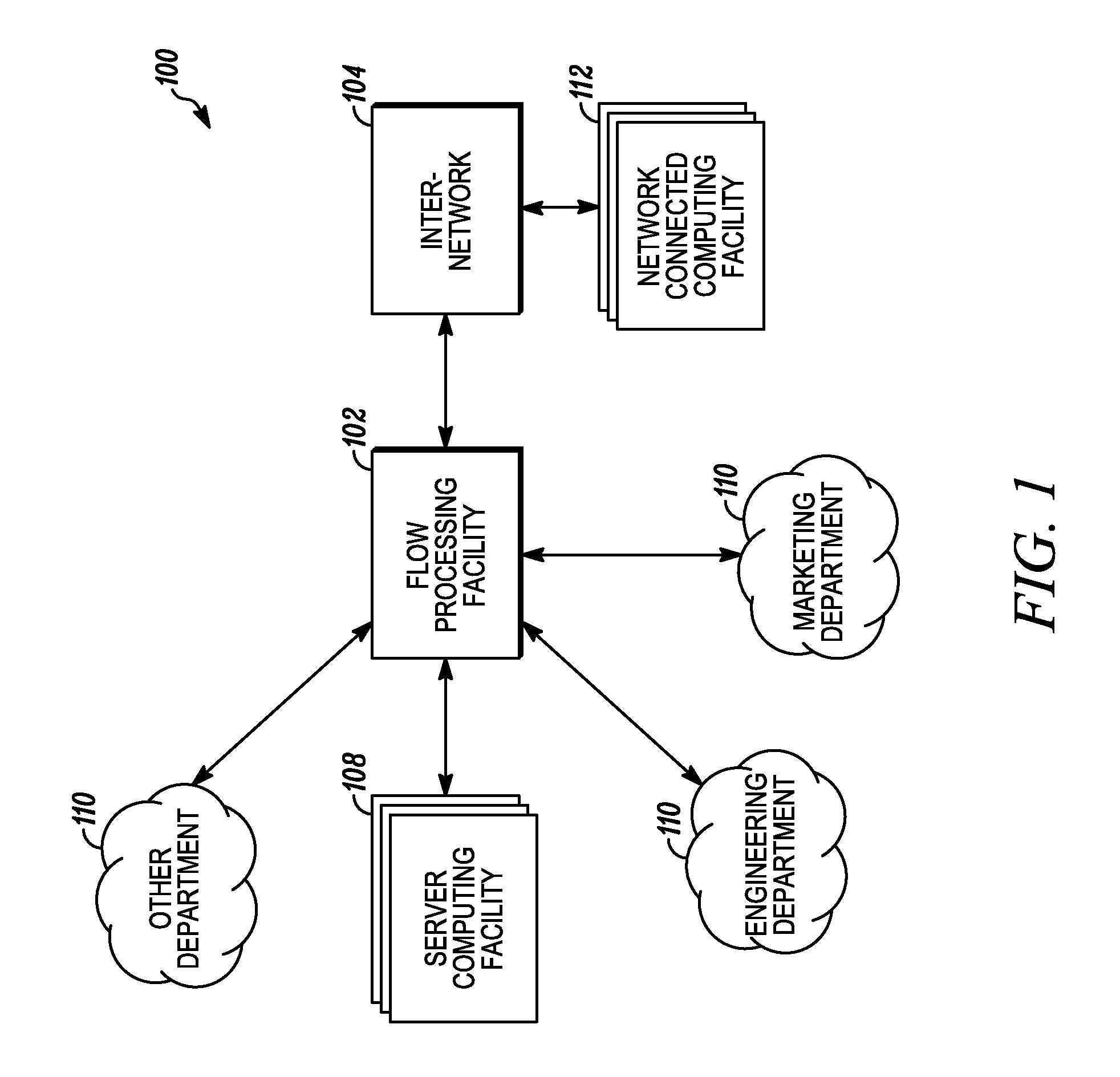
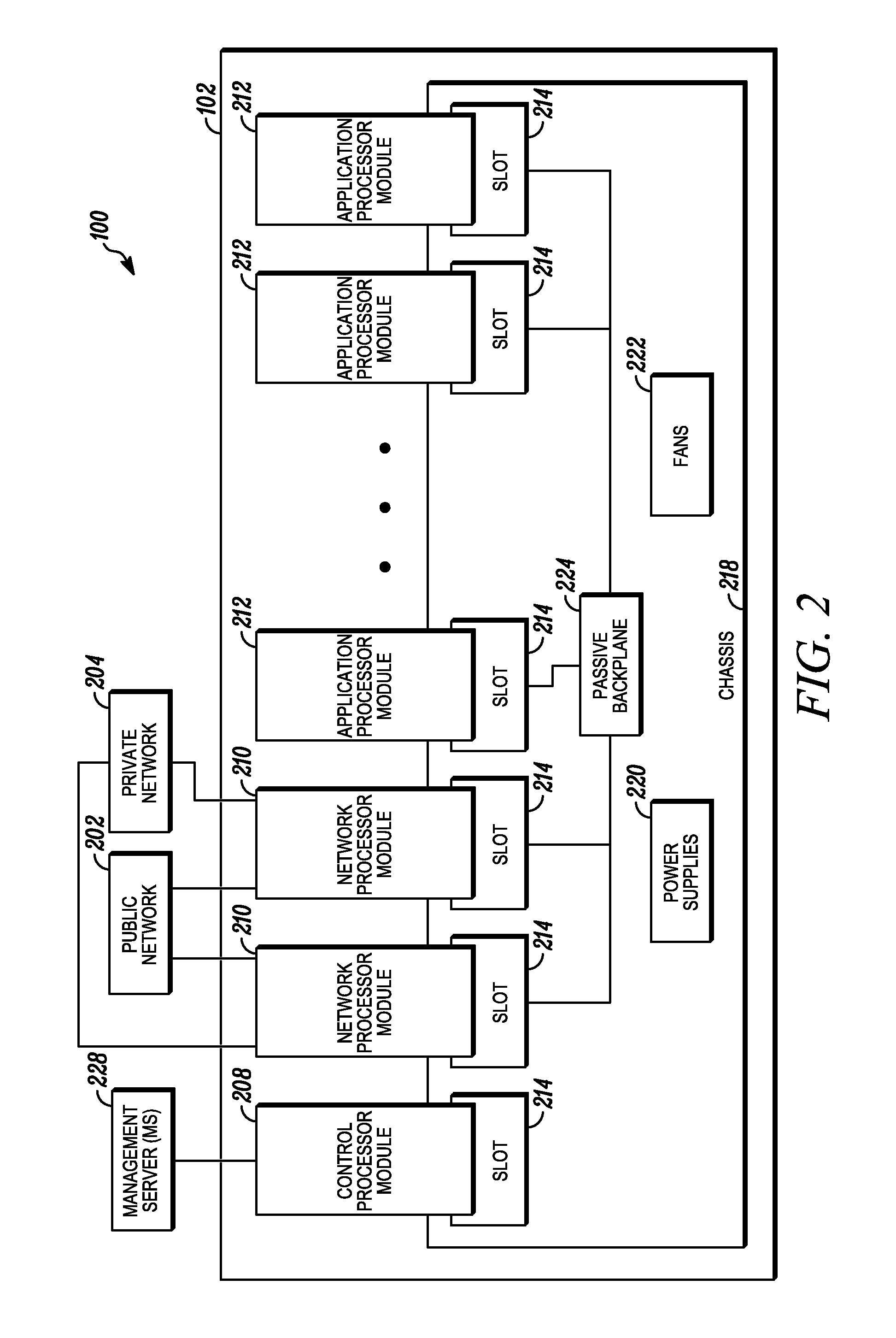
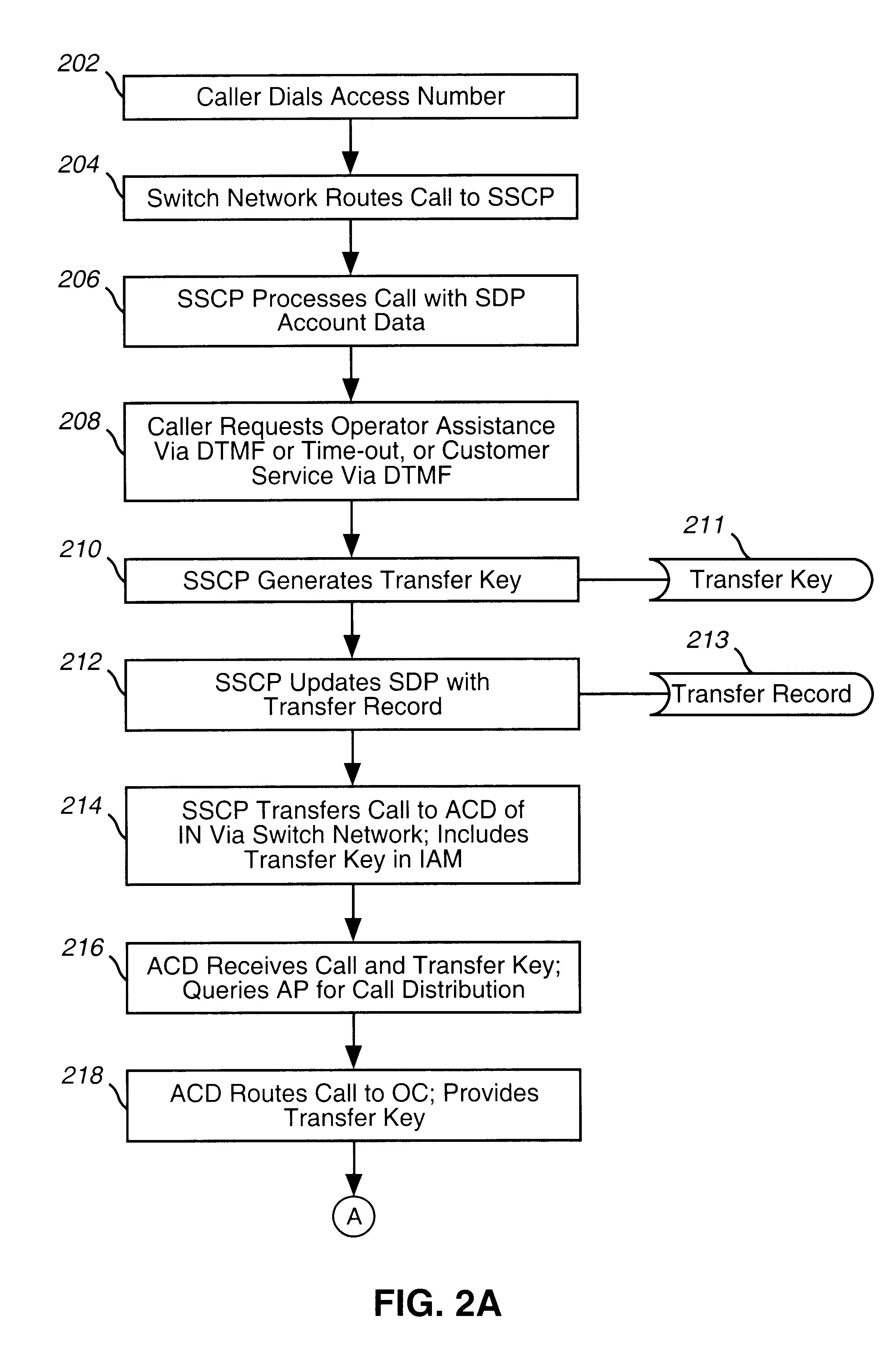
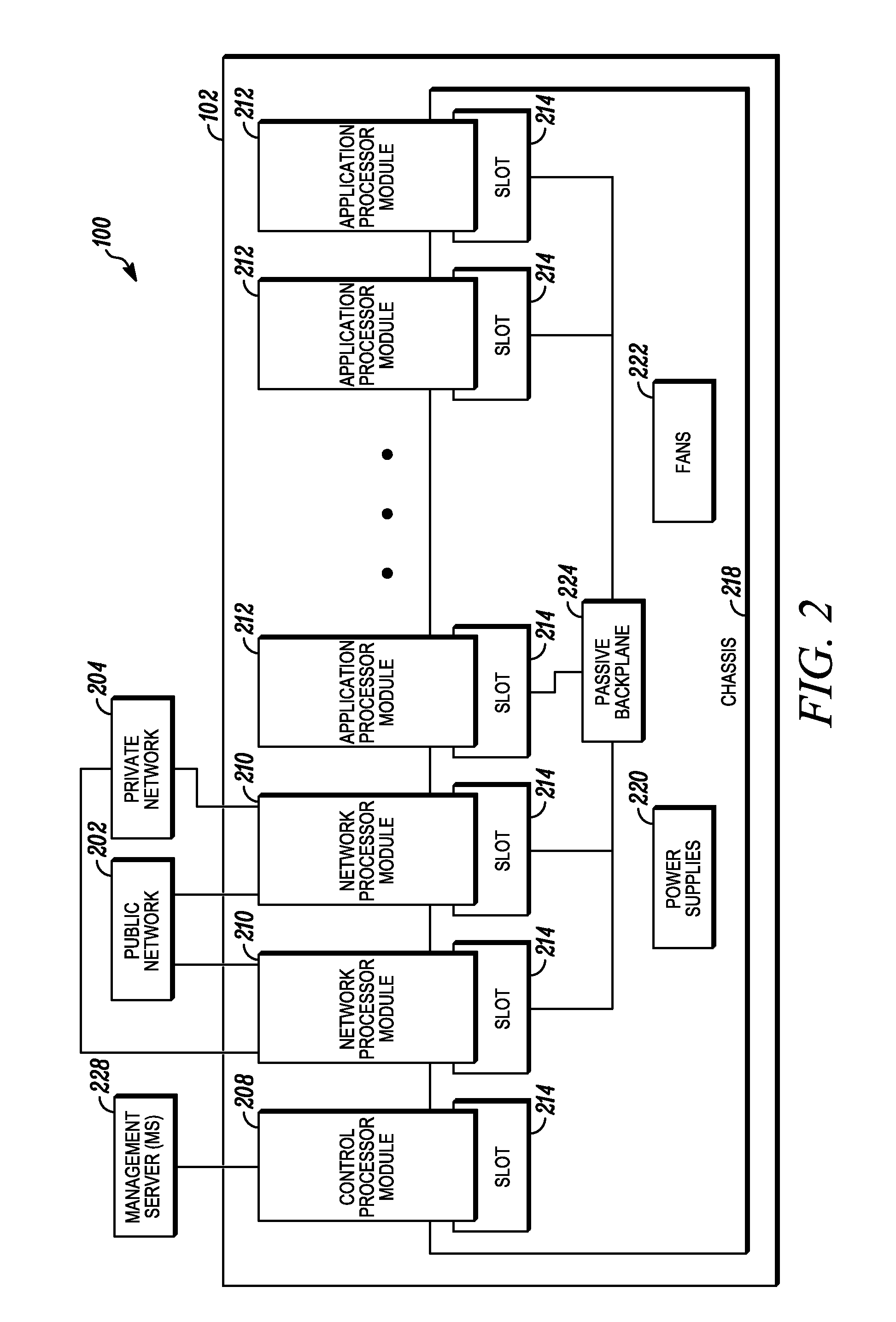
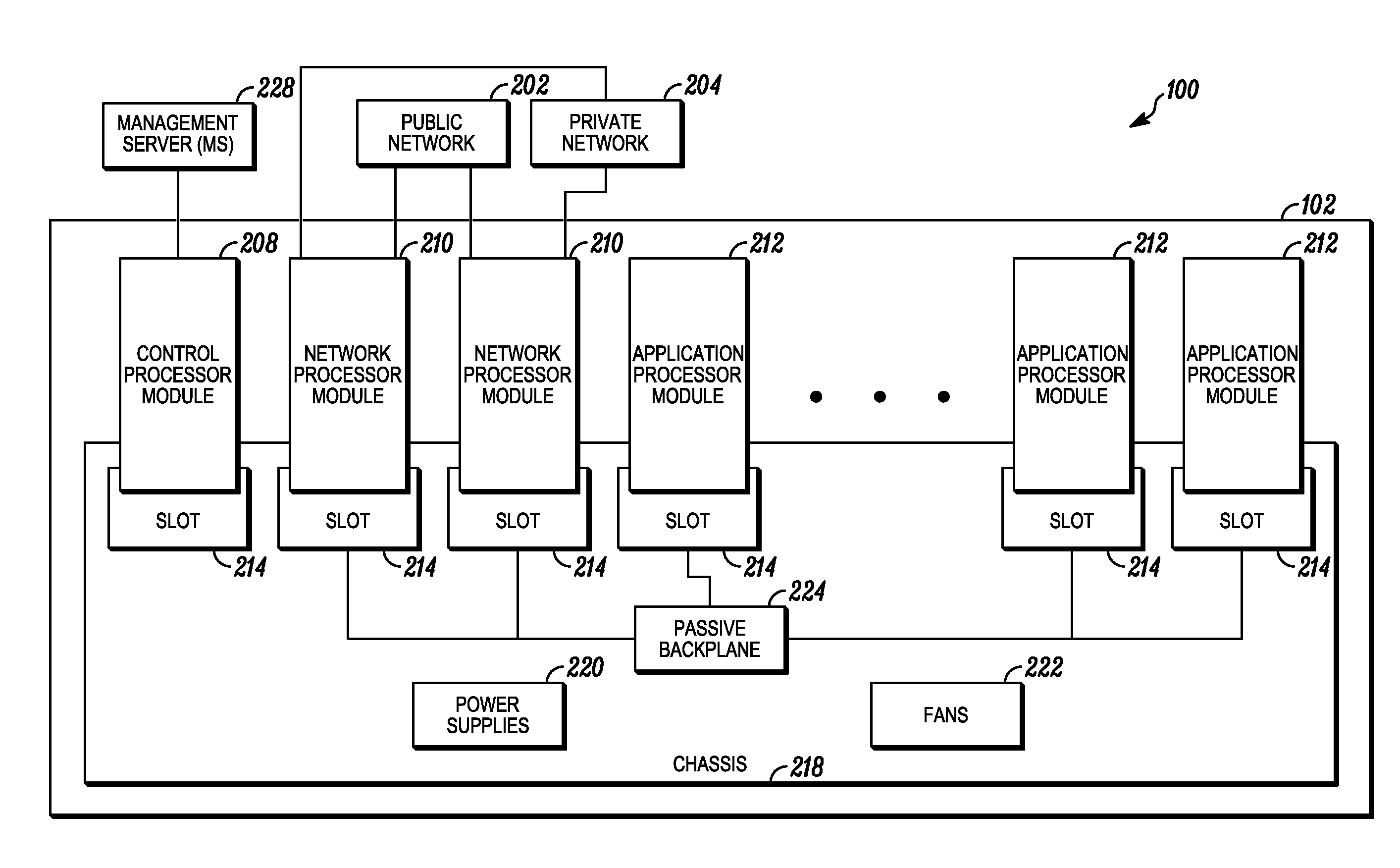
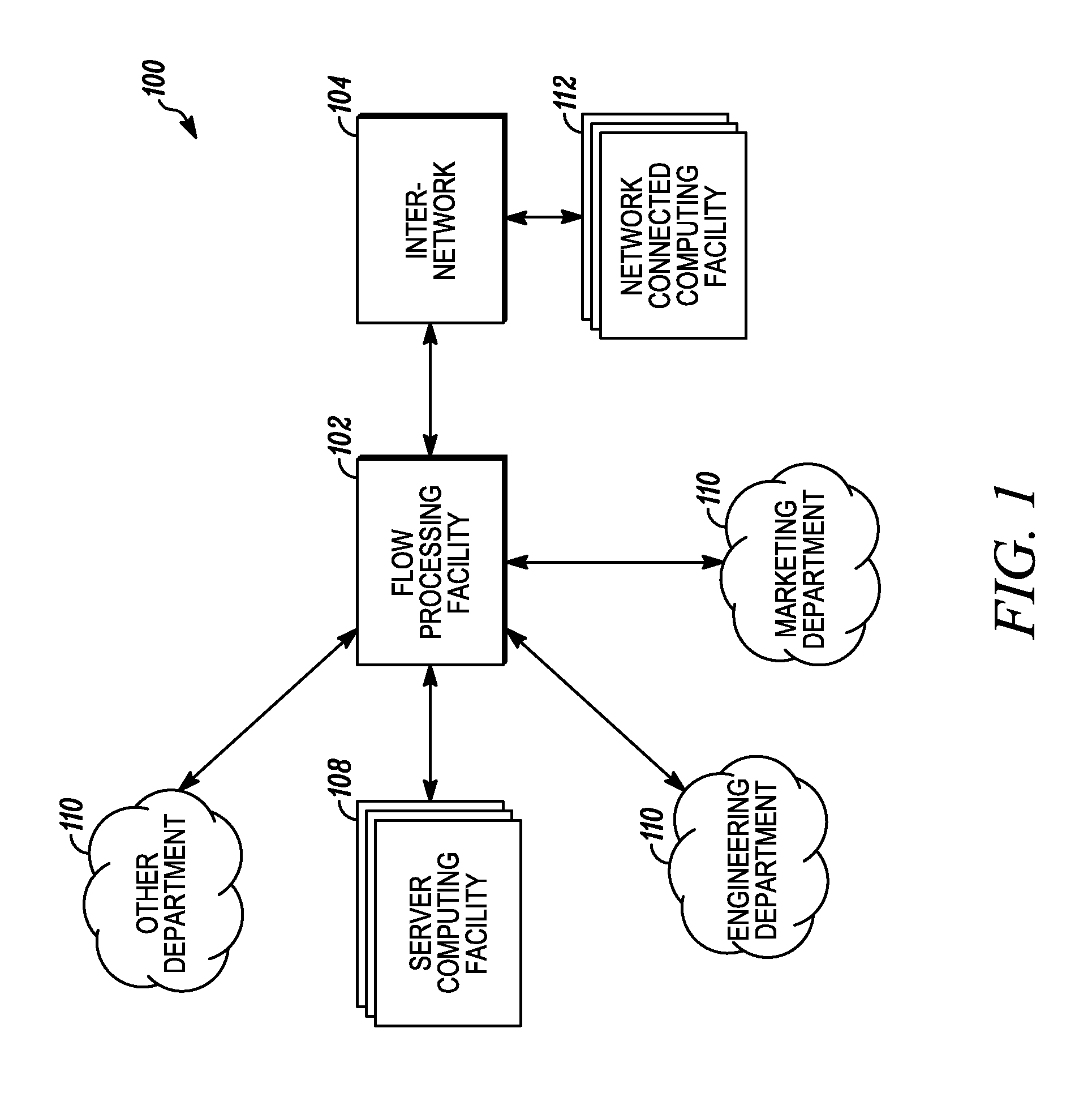
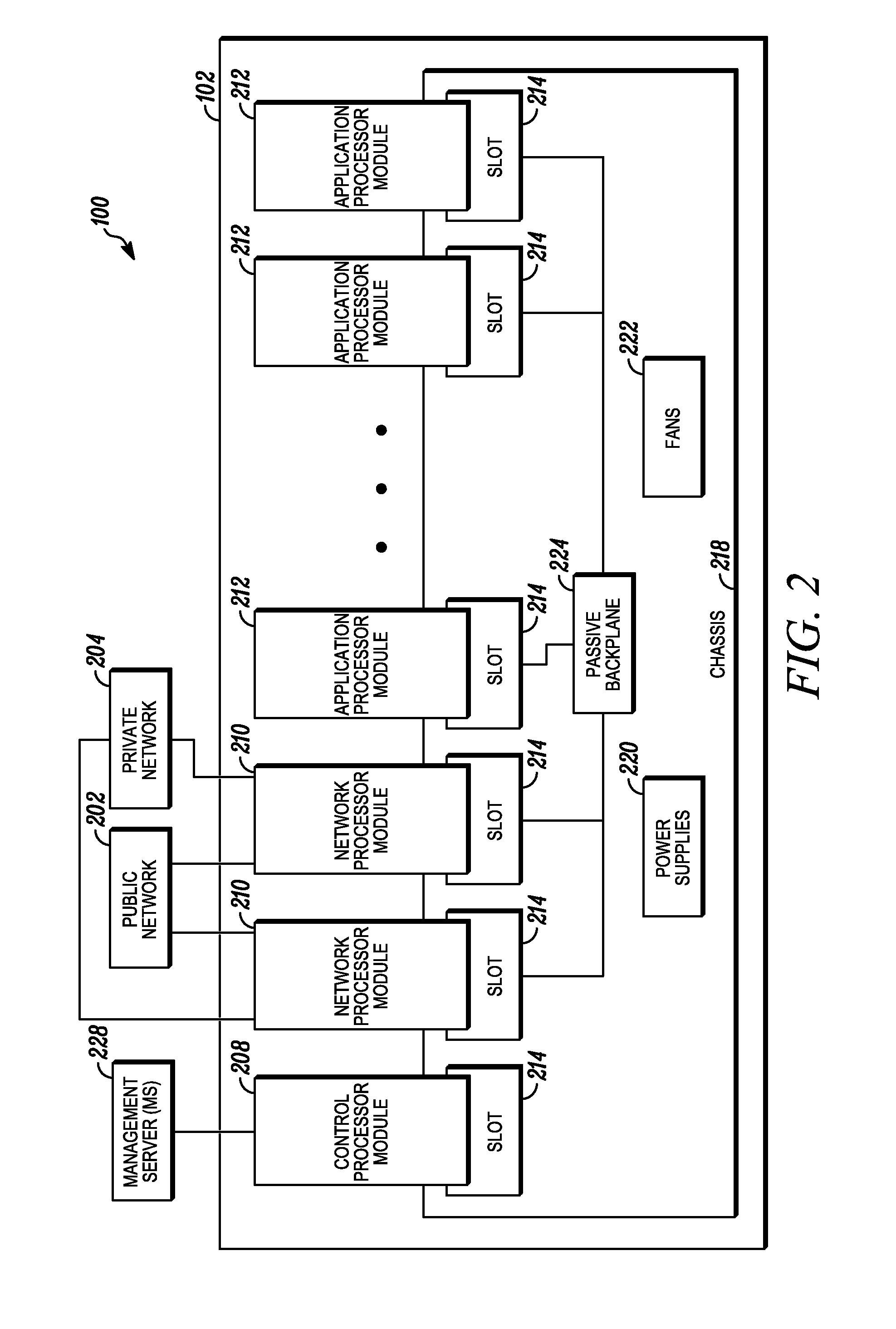
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:BLUE COAT SYSTEMS
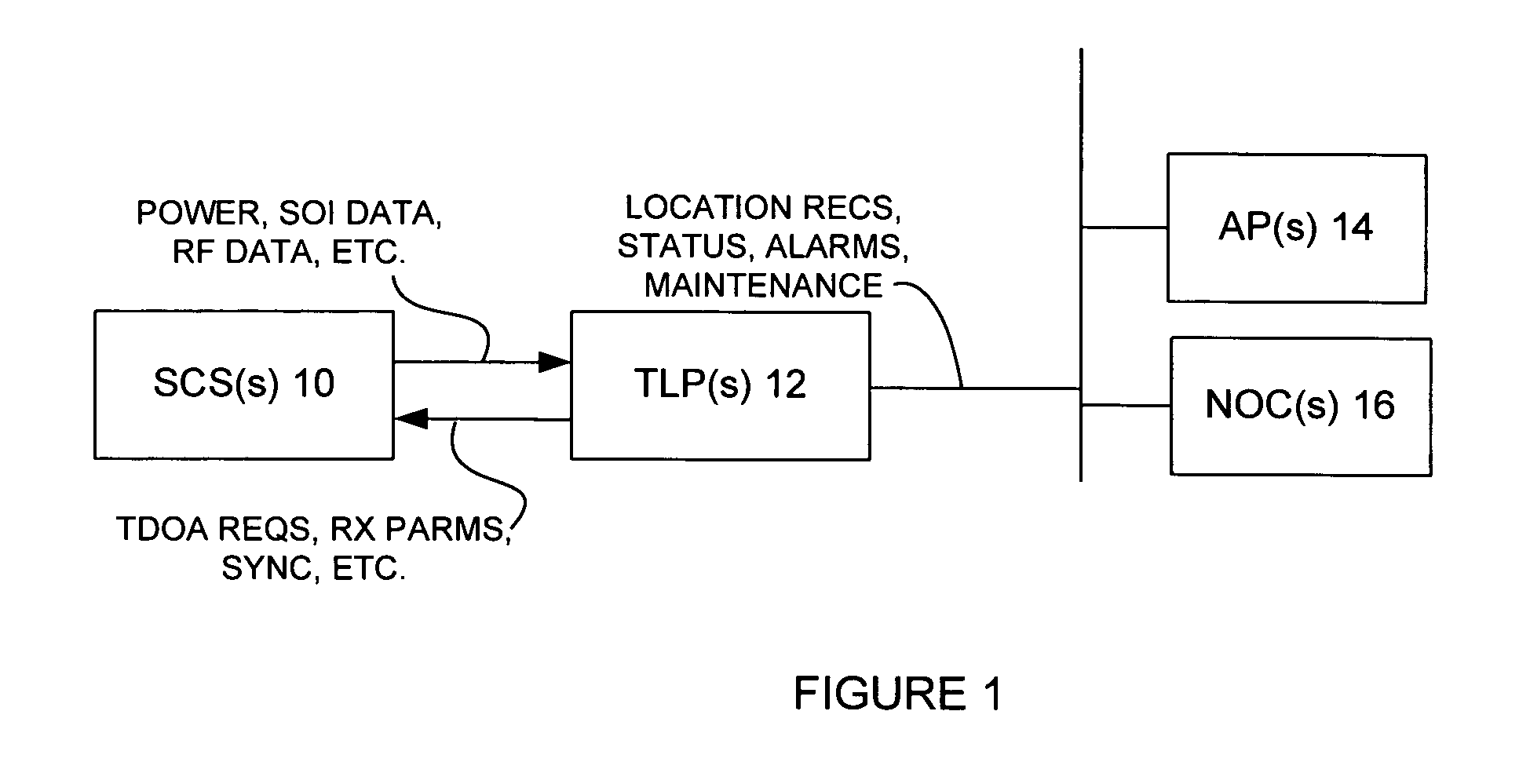
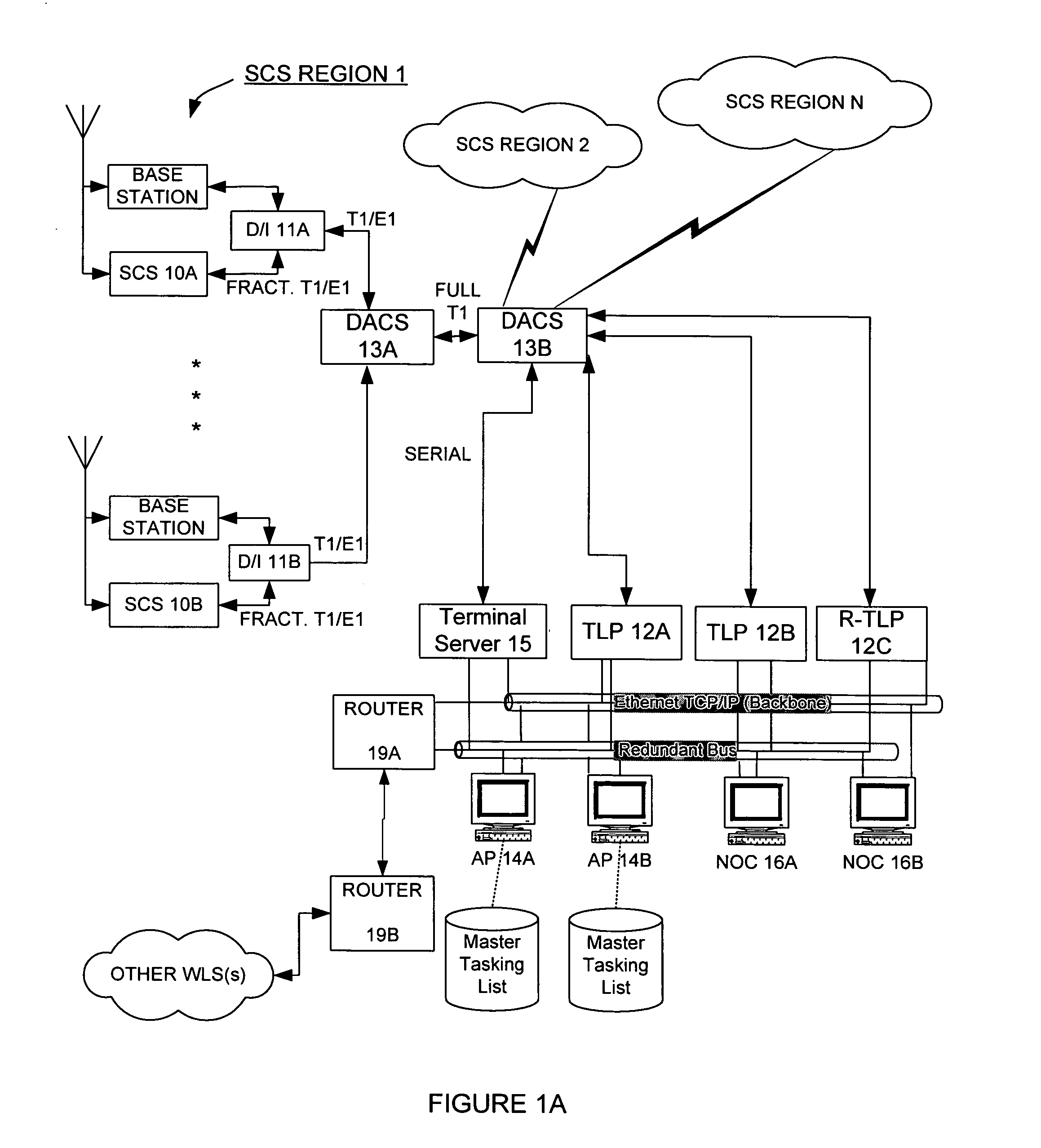
Applications processor including a database system, for use in a wireless location system
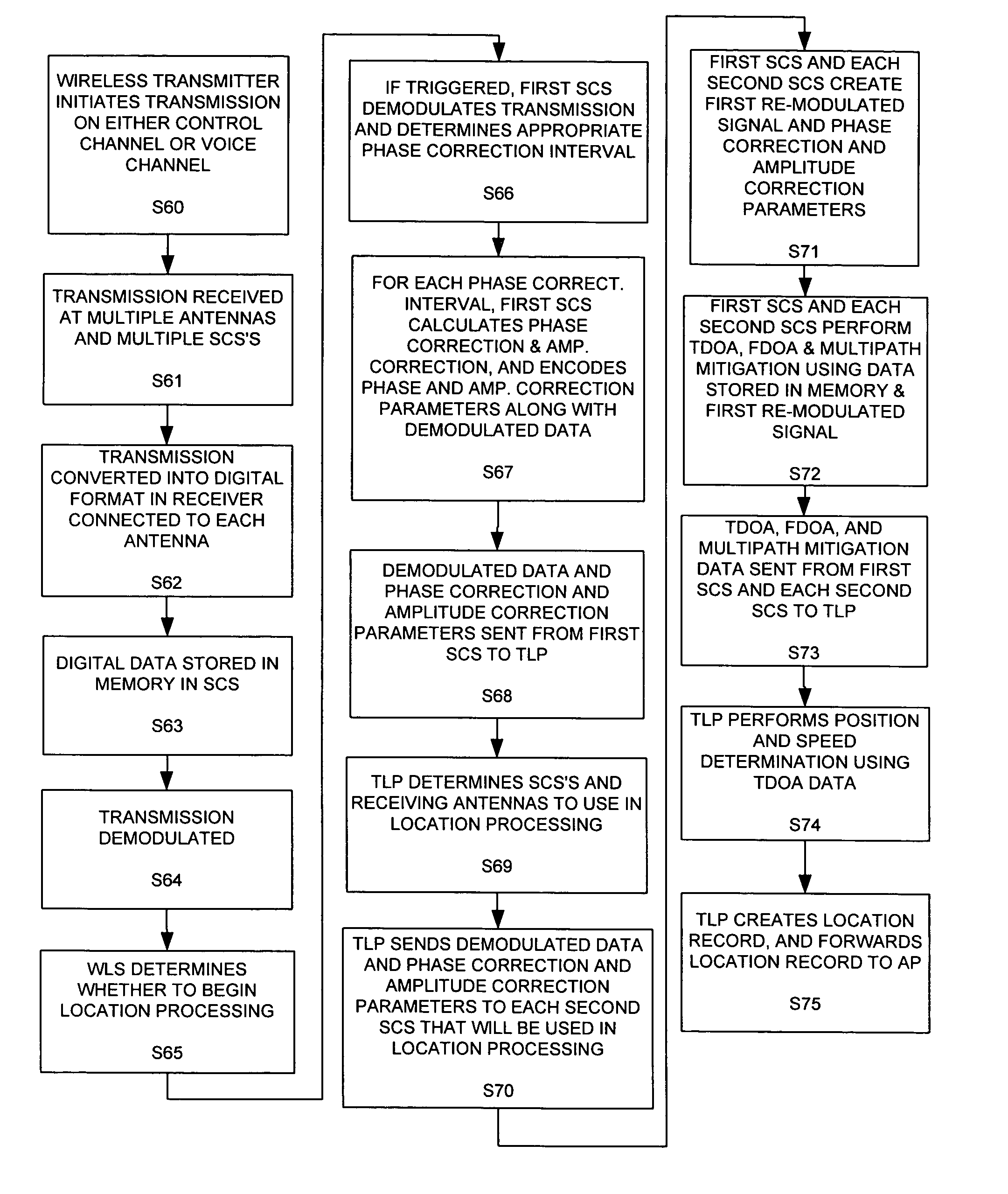
InactiveUS7271765B2Emergency connection handlingDirection finders using radio wavesComputer networkCollection system
An Applications Processor (14) including a centralized database system is used in a wireless location system (WLS). The APs 14 may be used to manage resources in the WLS, including signal collection systems (SCSs 10) and TDOA location processors (TLPs 12). Each AP 14 contains a database containing triggers for the WLS. The WLS can be programmed to locate only certain pre-determined types of transmissions. When a transmission of a pre-determined type occurs, then the WLS is triggered to begin location processing. Each AP 14 also contains applications interfaces that permit a variety of applications to securely access the WLS. These applications may access location records in real time or non-real time, create or delete certain types of triggers, or cause the WLS to take other actions. Each AP 14 is also capable of certain post-processing functions.
Owner:TRUE POSITION INC
Securing a network with data flow processing
InactiveUS20110214157A1Easy to detectPreventing data flowPlatform integrity maintainanceTransmissionData stream processingApplication software
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:CA TECH INC
Method and wi-fi device for setting communications mode
ActiveUS20130343251A1Extend battery lifeIncrease power consumptionPower managementTransmission systemsWi-FiMultiple input
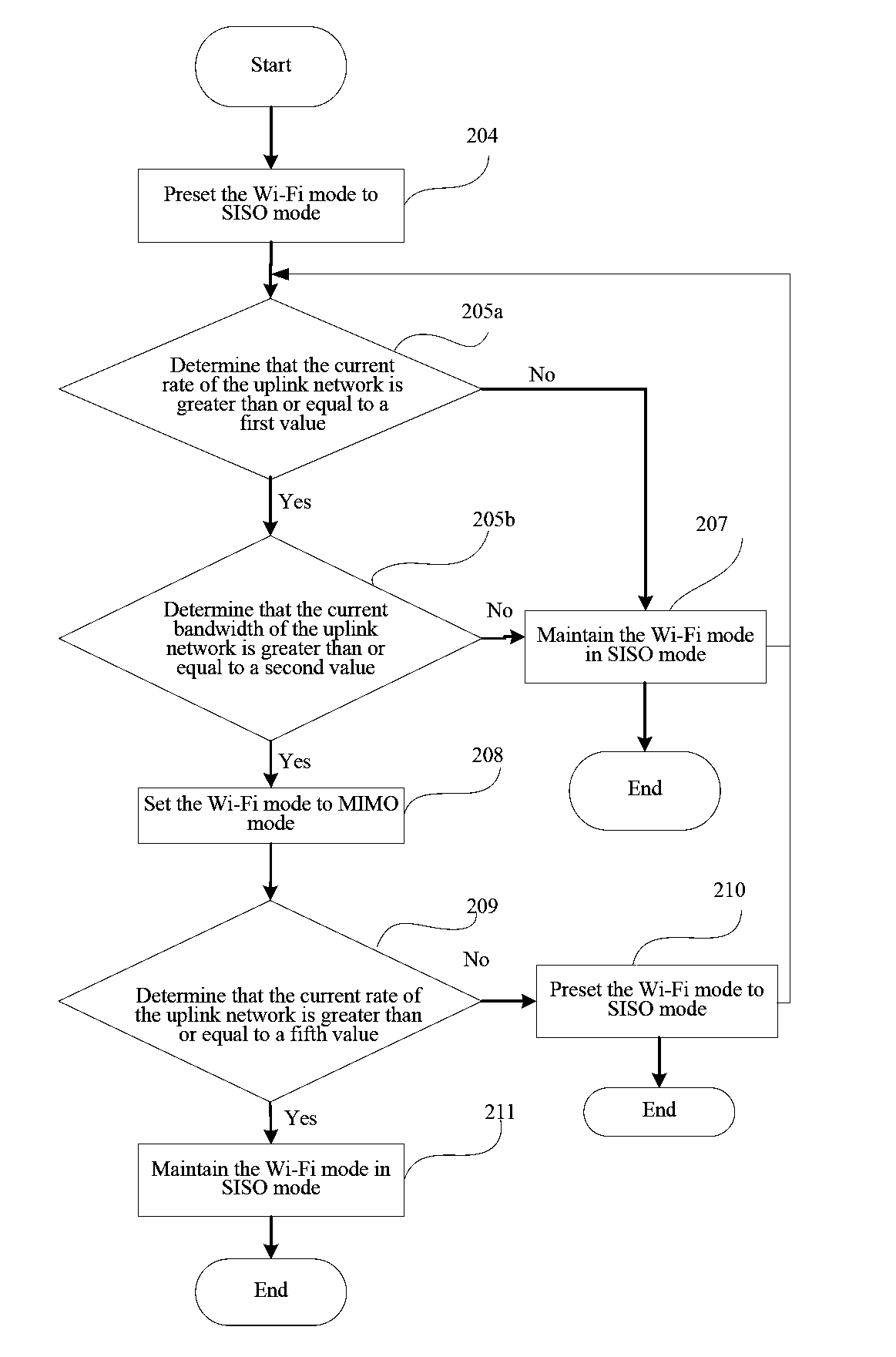
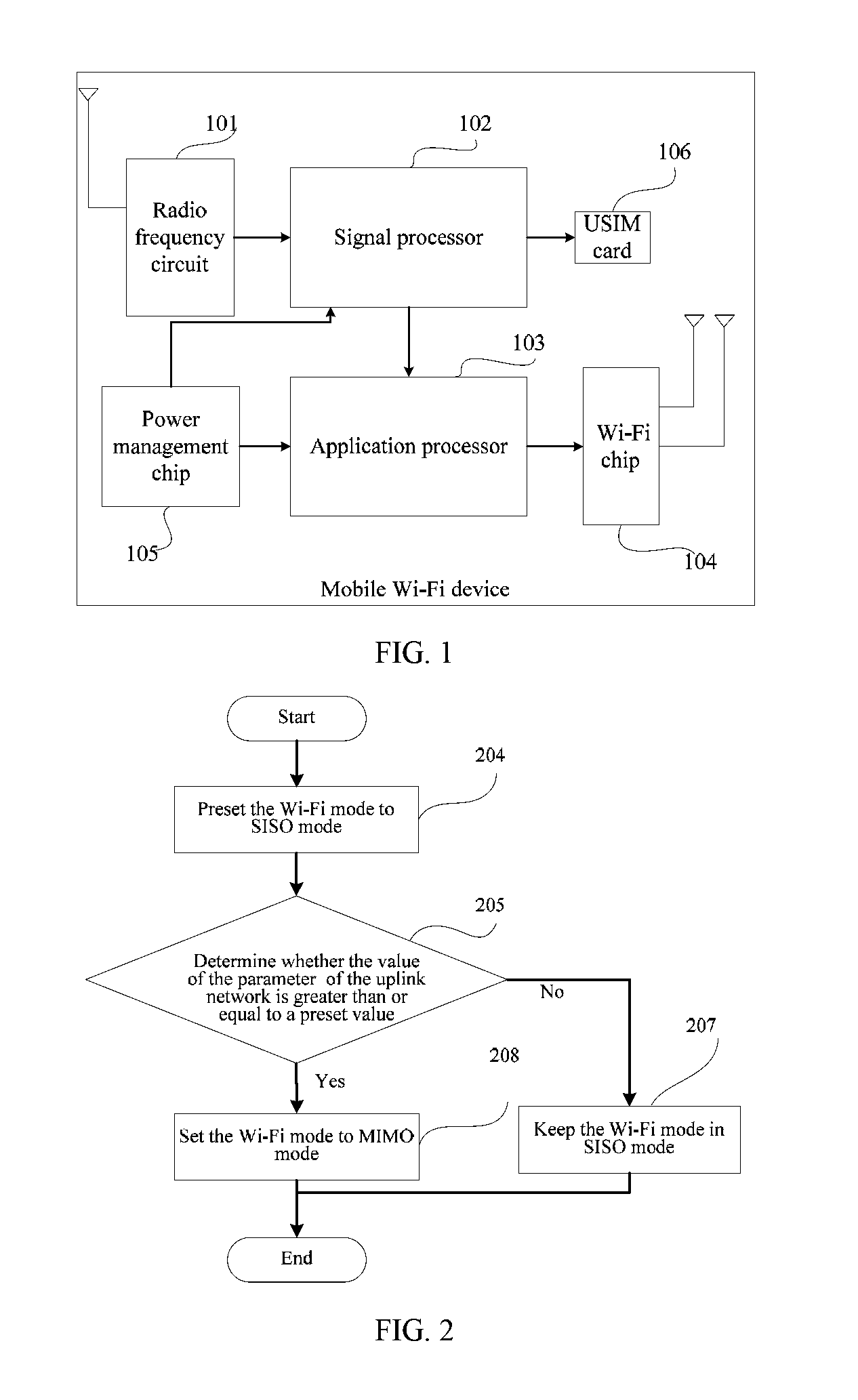
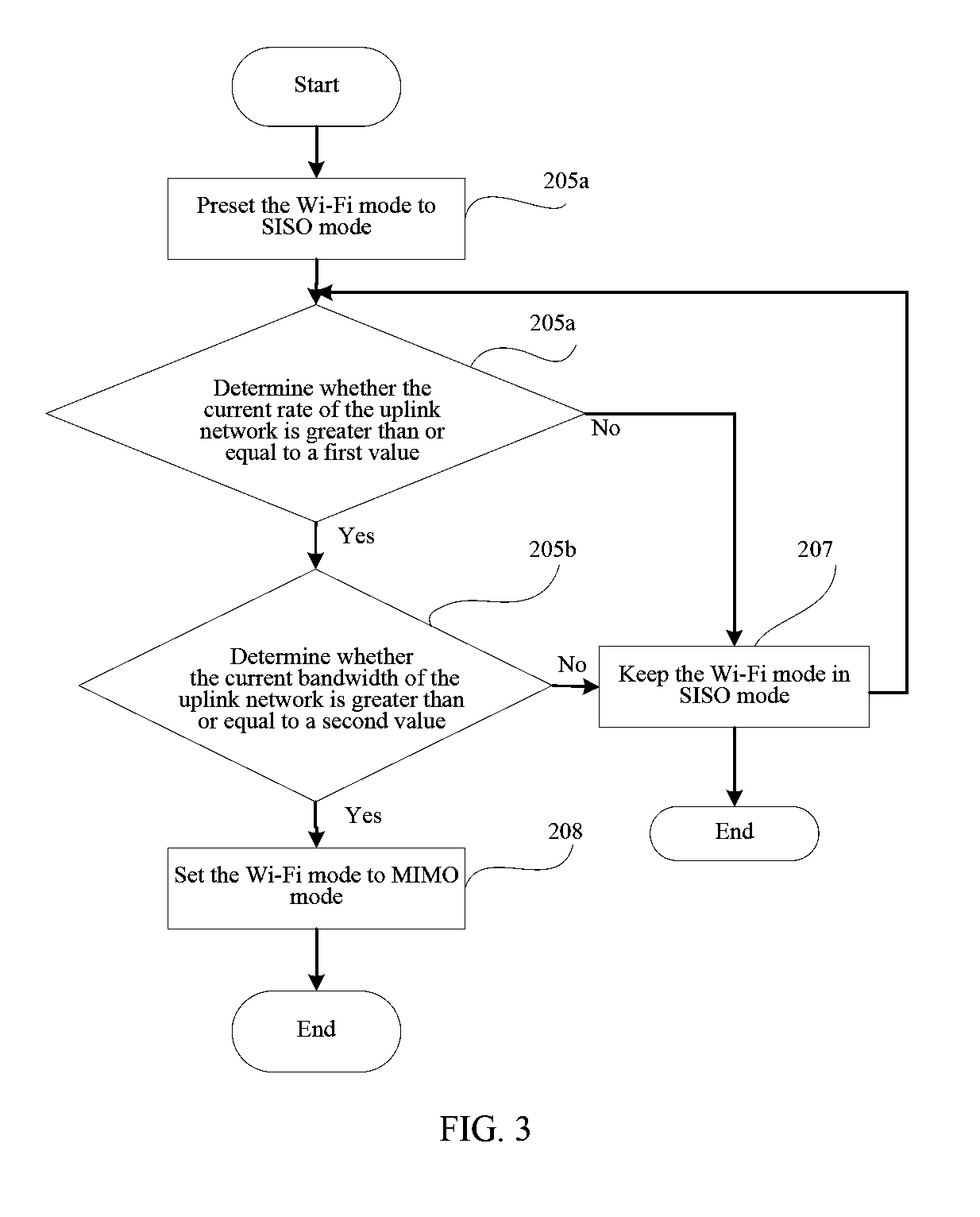
An embodiment of the present invention discloses a Wi-Fi device, including a radio frequency circuit, a signal processor, an application processor, and a Wi-Fi chip. The application processor is configured to preset the work mode of the Wi-Fi chip to a single input single output SISO mode, and is further configured to acquire a value of a parameter of an uplink wireless network, and when the value of the parameter of the uplink wireless network is determined to be greater than or equal to a preset value, set the work mode of the Wi-Fi chip to a multiple-input multiple-output MIMO mode. An embodiment of the present invention further discloses a method for setting a communications mode.
Owner:HUAWEI DEVICE CO LTD
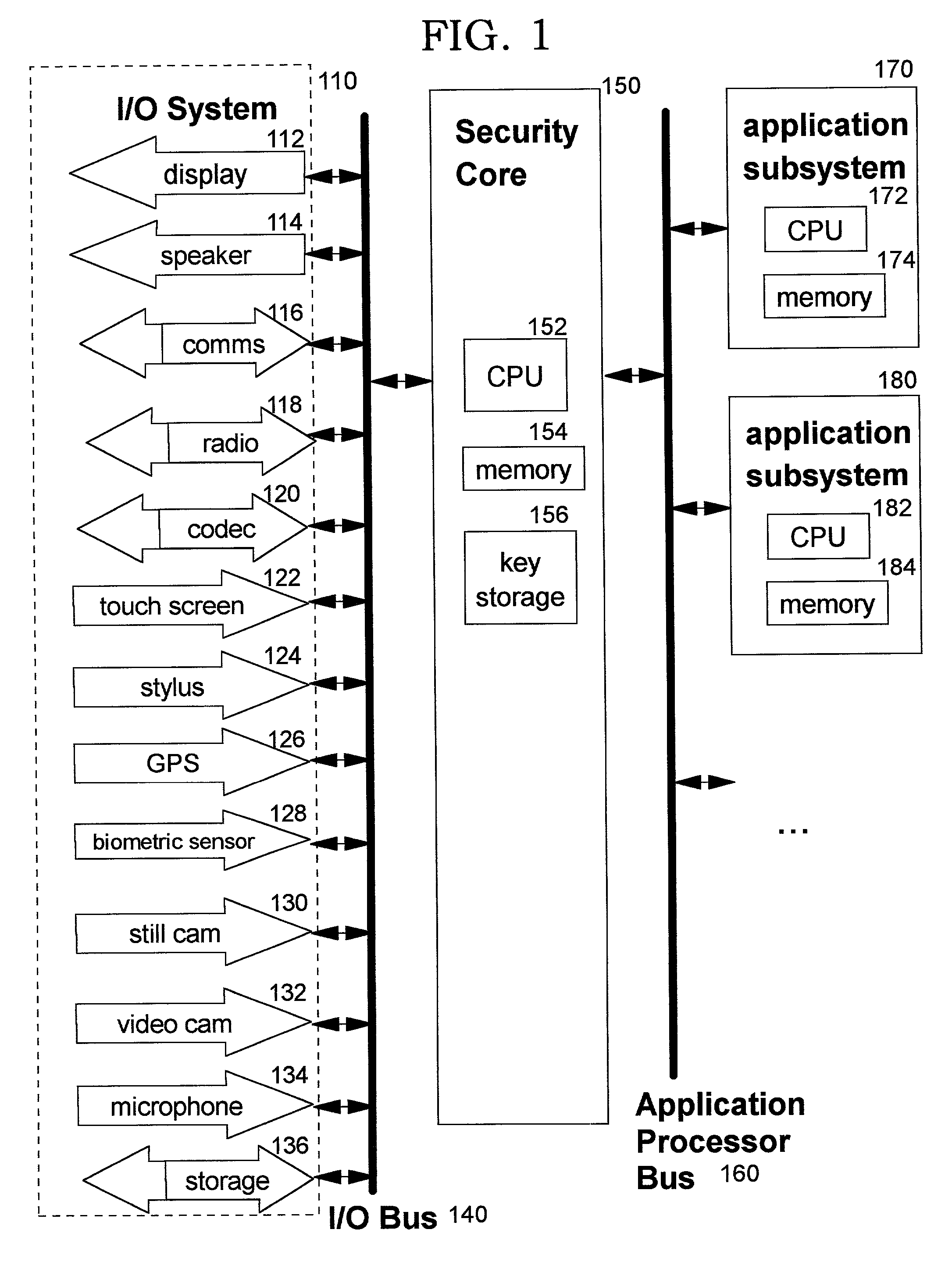
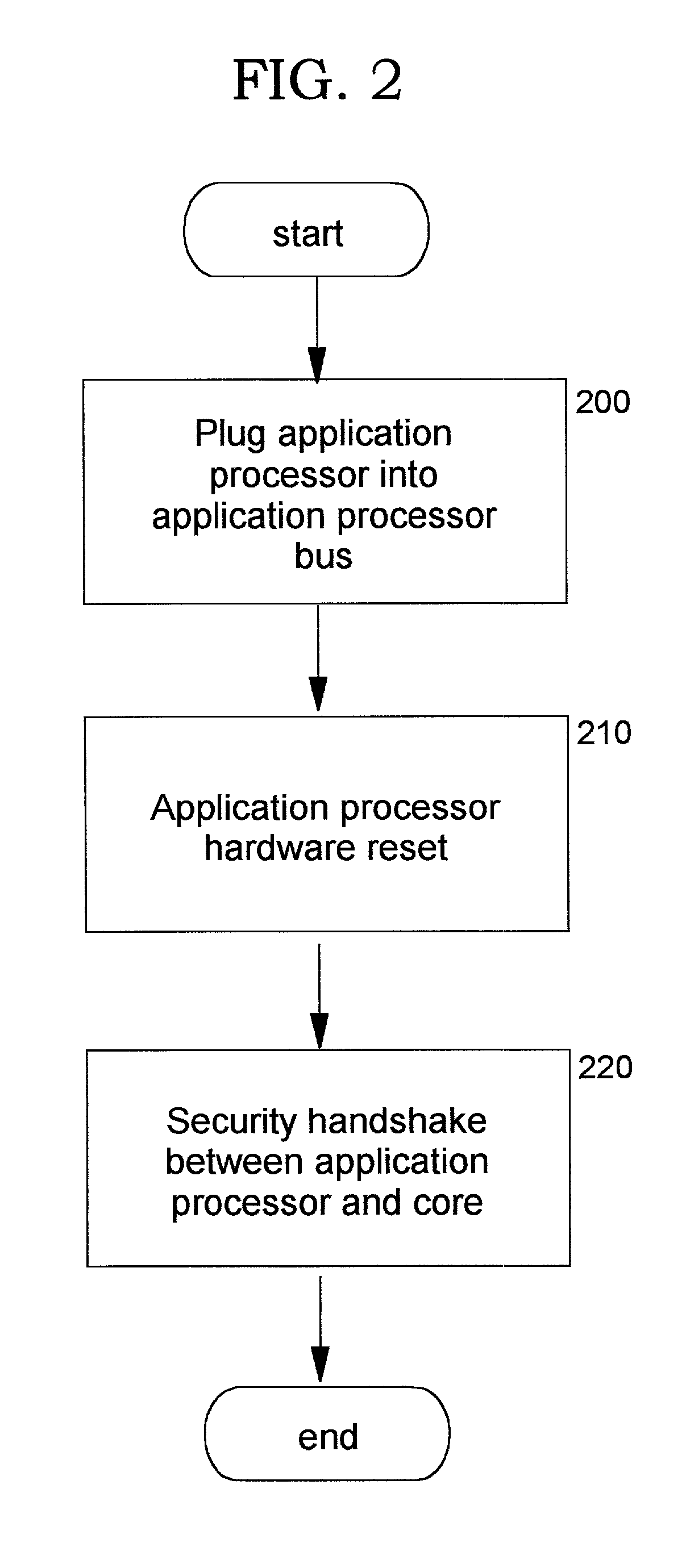
Secure integrated device with secure, dynamically-selectable capabilities
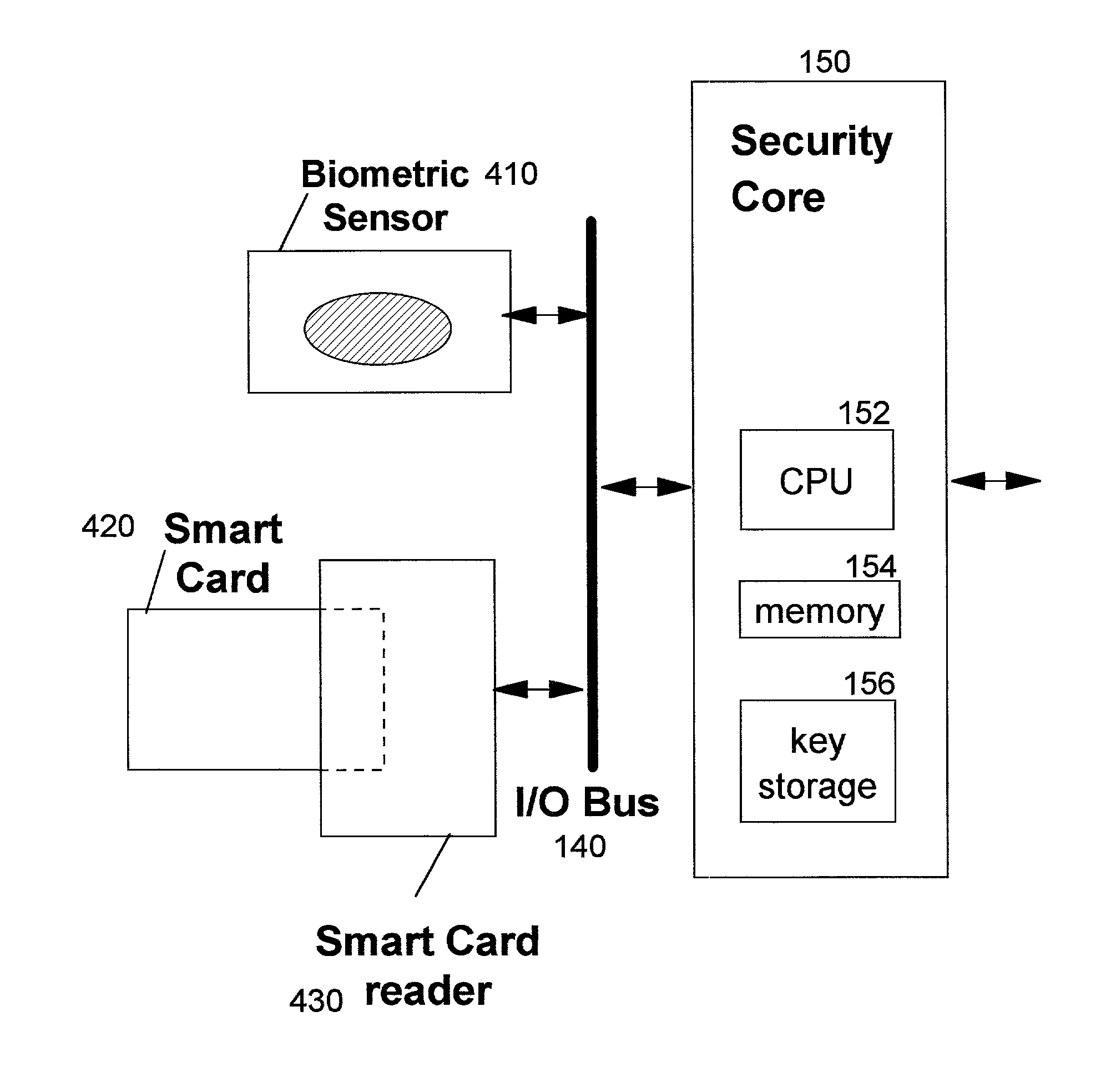
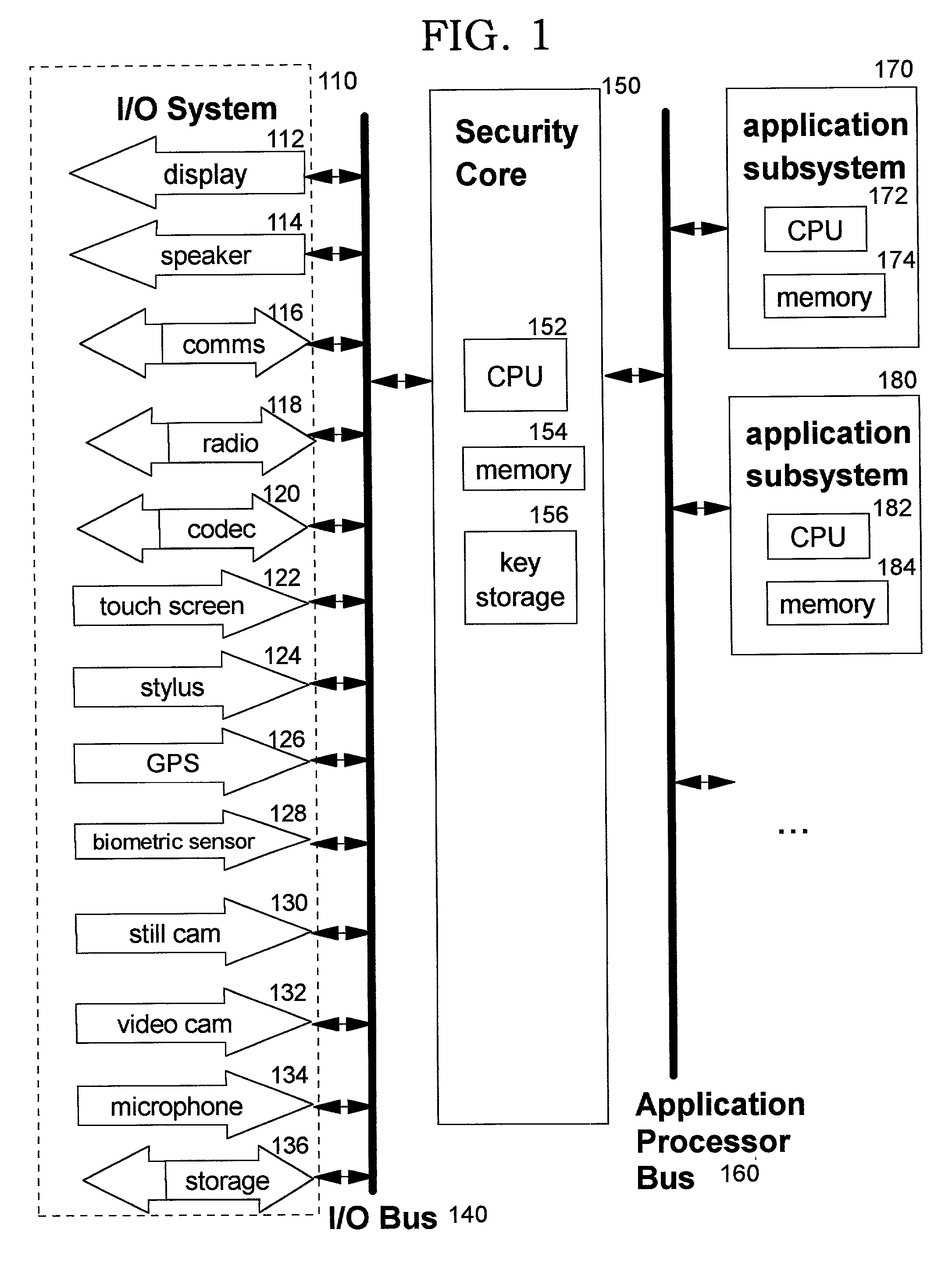
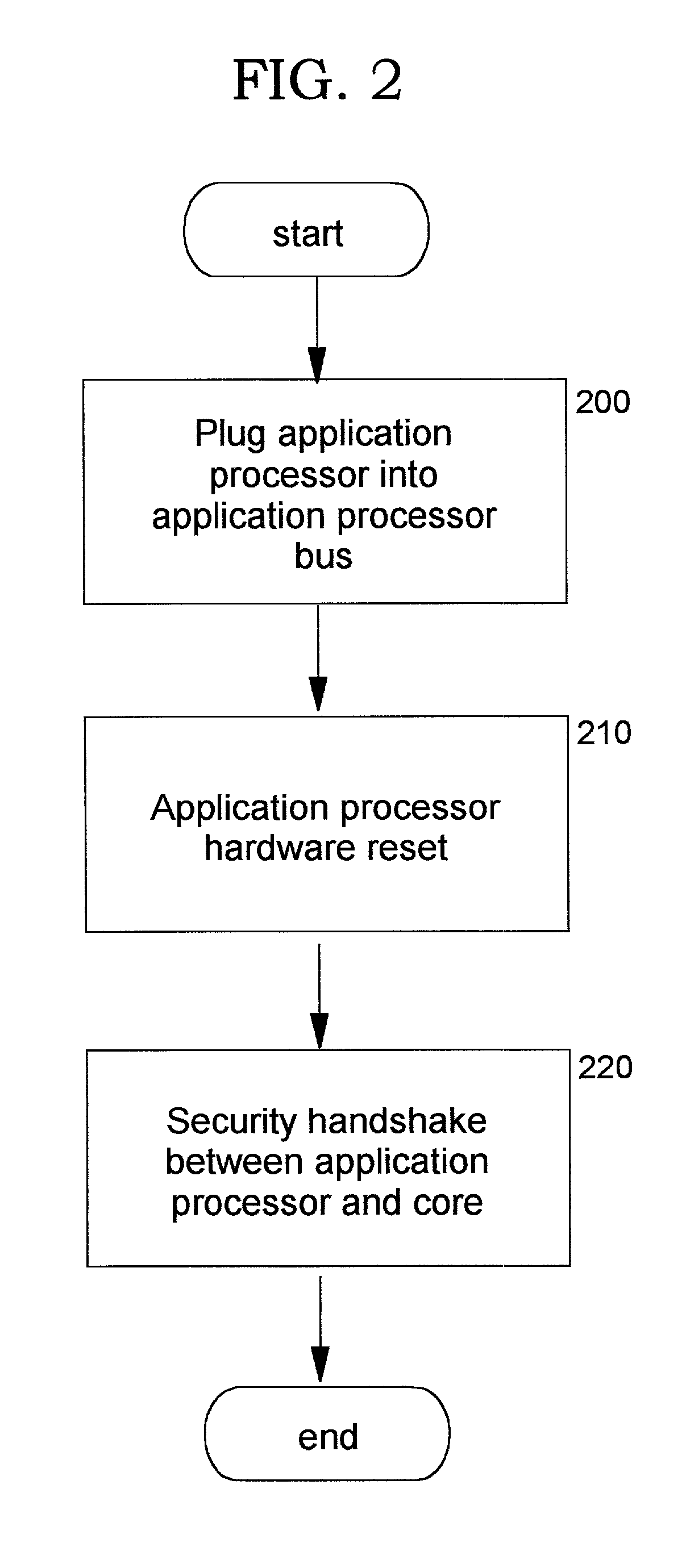
InactiveUS20030159044A1Improve securityUser identity/authority verificationDigital data protectionStructure of Management InformationOutput device
A method, system, computer program product, and method of doing business by providing a secure integrated device (such as a pervasive computing device) for which operating capabilities can be dynamically yet securely selected (including, but not limited to, pluggable connection of input / output devices and / or application processors that provide selected functions). Each input / output (I / O) device and application processor to be used is plugged in to a bus of a security core, and authenticates itself to the security core using public key infrastructure techniques, thereby creating a secure multi-function device. All of the multi-function device's input and output interactions with its environment necessarily traverse an I / O bus under the sole control of the security core. The only communication path between an application processor and the external environment (such as an I / O device) is through an application processor bus, which is likewise under control of the security core. Thus a user may dynamically yet securely select the capabilities of a multi-function device, and because each I / O device and application processor in use by that multi-function device is authenticated, the security of transactions or network services performed when using such devices is improved.
Owner:IBM CORP
Processing data flows with a data flow processor
InactiveUS20110213869A1Easy to detectPreventing data flowDigital computer detailsPlatform integrity maintainanceData stream processingApplication software
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:BLUE COAT SYSTEMS
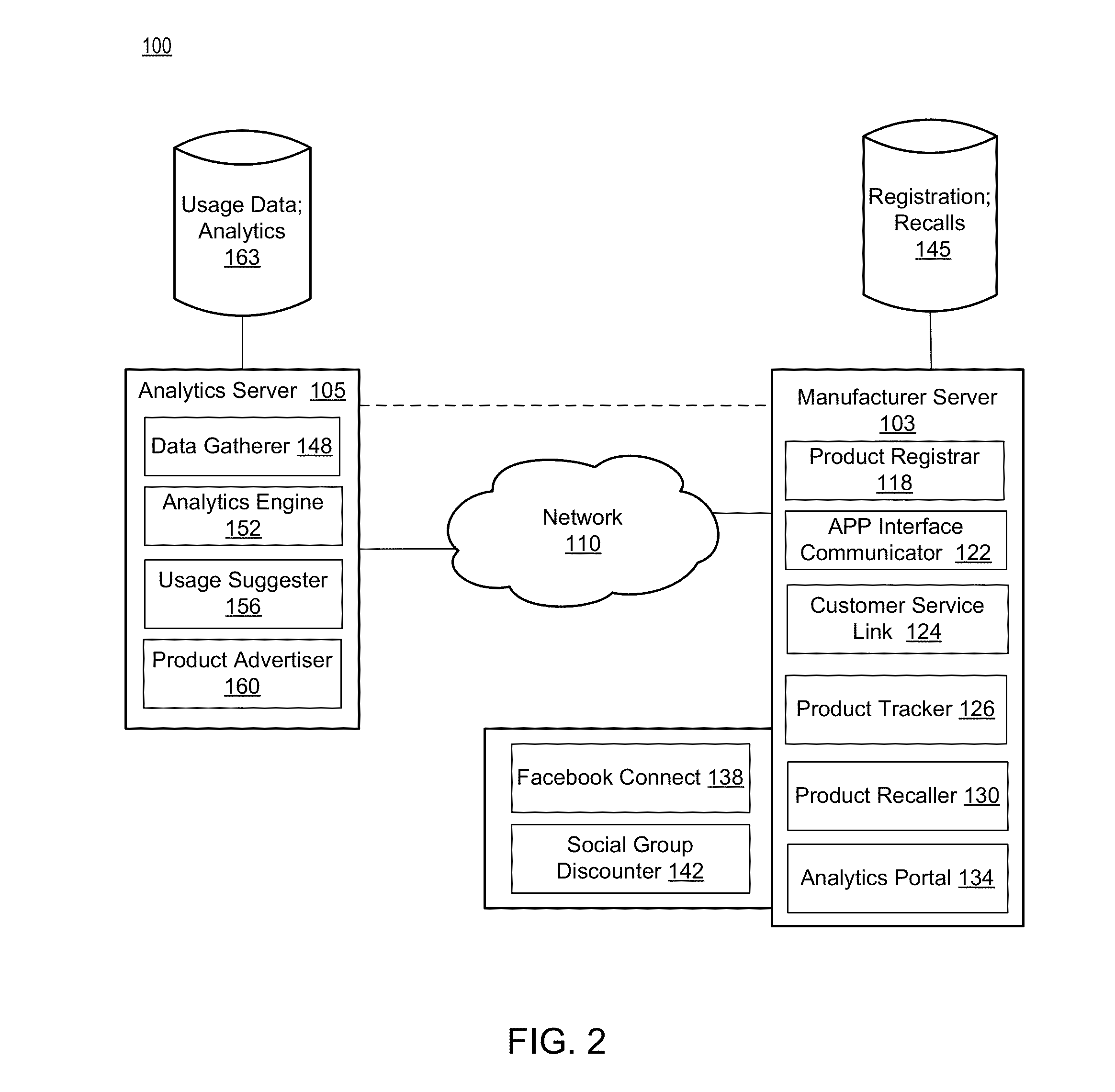
Product registration and tracking system
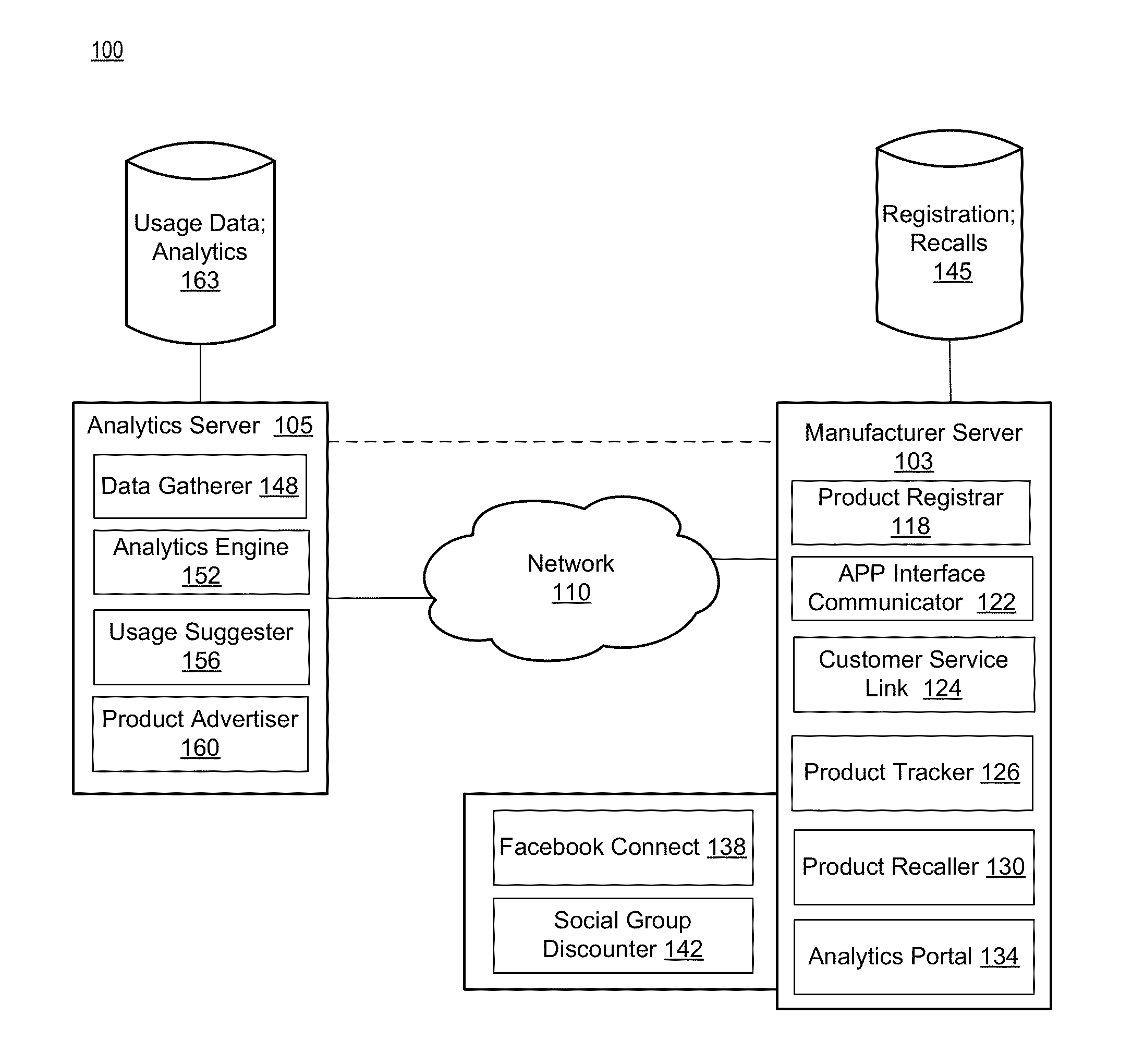
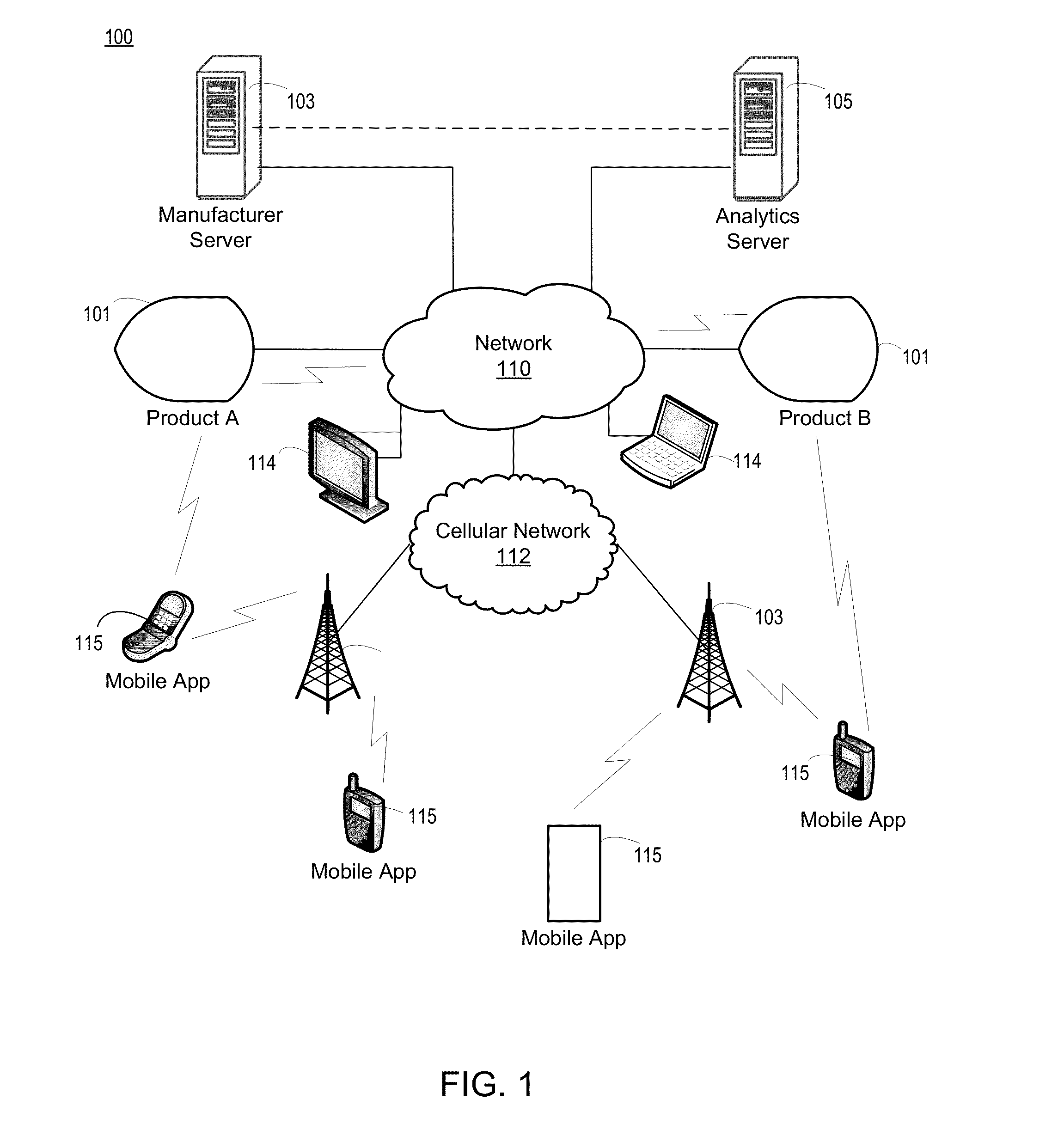
InactiveUS20130080251A1Convenient registrationCustomer relationshipMarketingApplication softwareComputer memory
A server for registration of products may include a processor and computer storage. The processor may be configured to receive, via a network, a communication from a product application executed on a computing device, the communication including a product identification (ID) associated with a product and an indication of registration of the product by a user of the product application. The processor may further be configured to register the product at least by storing, in the computer storage, the product ID and a relationship between the product and an identification of the user of the product application. The processor may further be configured to send a subsequent communication to the product application on the computing device based on the registration of the product.
Owner:ACCENTURE GLOBAL SERVICES LTD
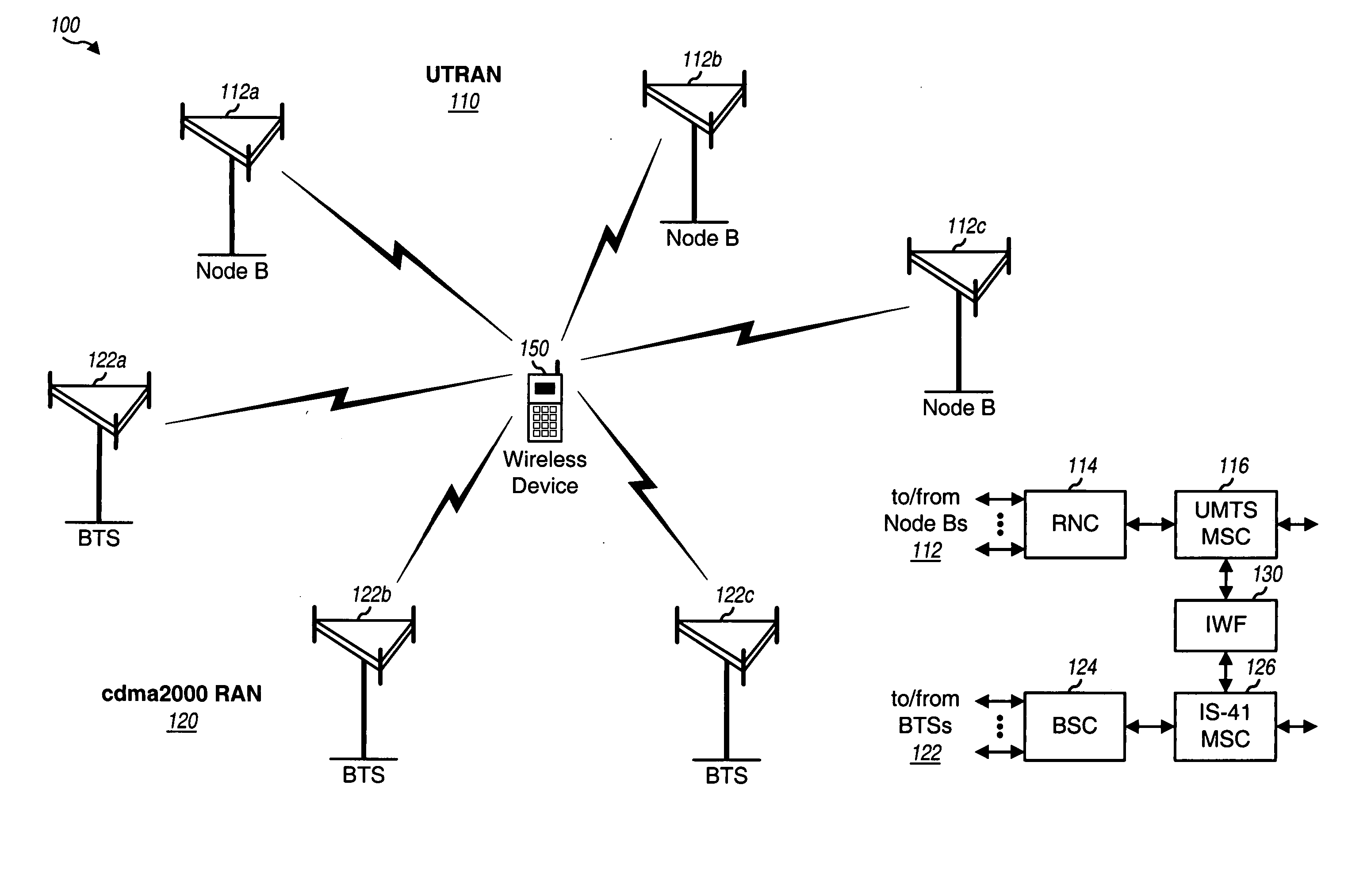
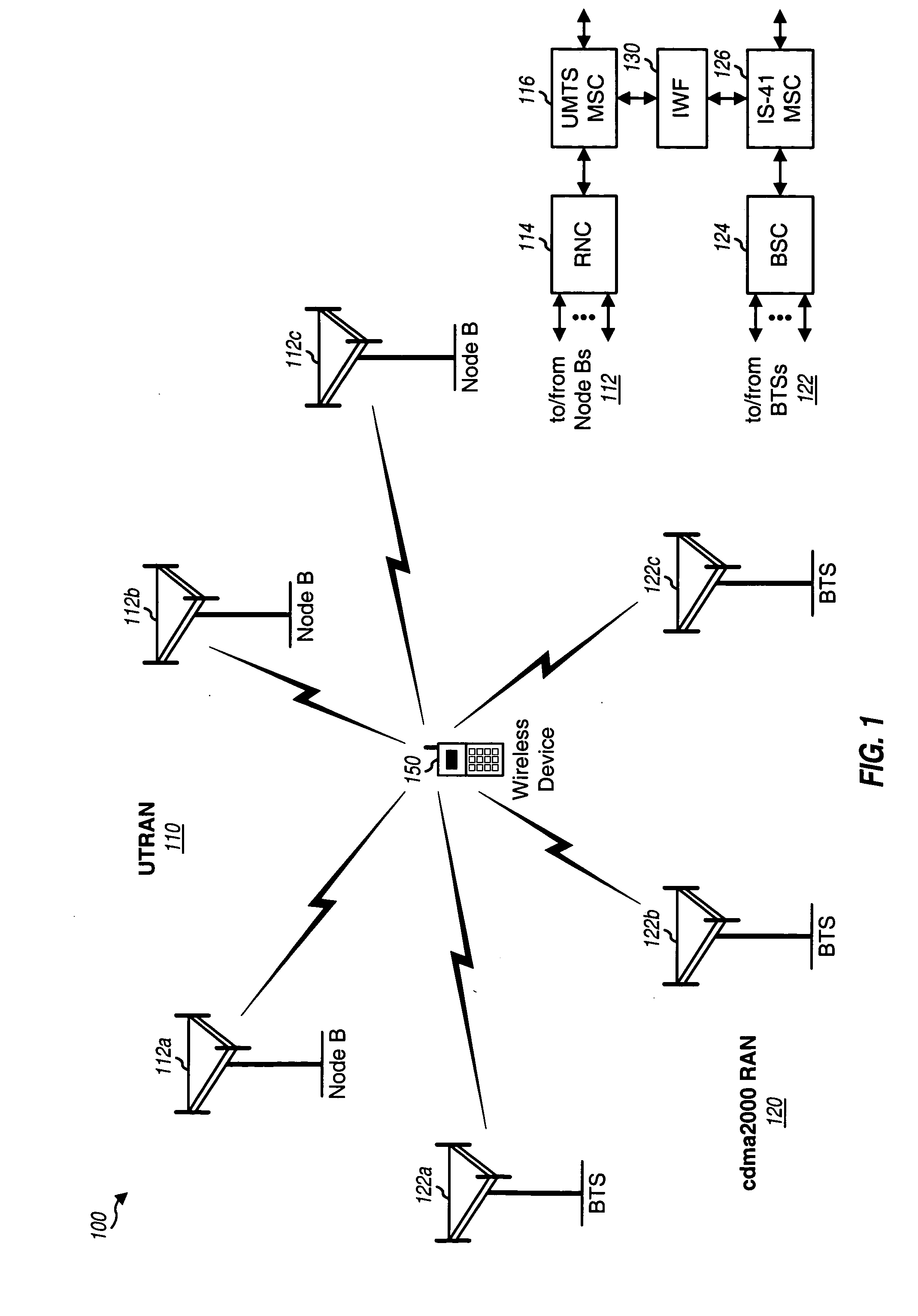
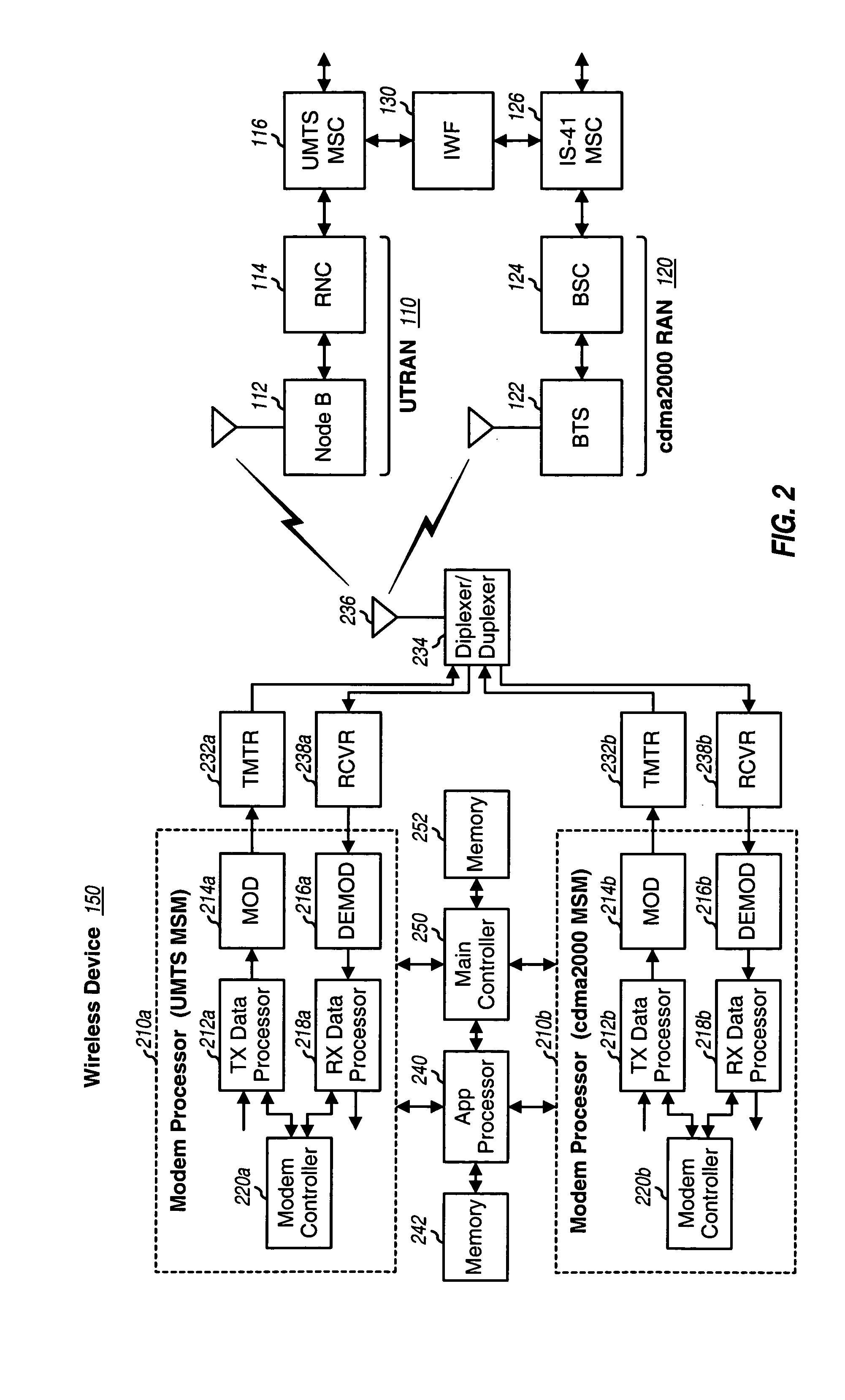
Inter-system handoff between wireless communication networks of different radio access technologies
Various schemes for performing inter-system handoff, e.g., from a UTRAN to a cdma2000 radio access network (RAN) are described. For a MAHHO scheme, the UTRAN uses measurements obtained by a multi-RAT device to determine suitable cdma2000 cell(s) for handover. The measurements are obtained by a candidate frequency search procedure, and the handover is accomplished by a handoff execution procedure. For a MDHHO scheme, the UTRAN relies on location information for the multi-RAT device to select suitable cdma2000 cell(s) for handover. For a CRHHO scheme, a new call is established on the cdma2000 RAN and the pending call on the UTRAN is released in a manner such that the handover appears seamless to the multi-RAT device. The multi-RAT device includes two modem processors that perform processing for the UTRAN and cdma2000 RAN and an application processor that controls the modem processors.
Owner:QUALCOMM INC
Database security via data flow processing
InactiveUS20110219035A1Easy to detectPreventing data flowDigital data information retrievalDigital data processing detailsComputer moduleData stream processing
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:BLUE COAT SYSTEMS
Secure integrated device with secure, dynamically-selectable capabilities
InactiveUS6968453B2Conveniently and economically providedEnsure safetyUser identity/authority verificationDigital data protectionStructure of Management InformationOutput device
A method, system, computer program product, and method of doing business by providing a secure integrated device (such as a pervasive computing device) for which operating capabilities can be dynamically yet securely selected (including, but not limited to, pluggable connection of input / output devices and / or application processors that provide selected functions). Each input / output (I / O) device and application processor to be used is plugged in to a bus of a security core, and authenticates itself to the security core using public key infrastructure techniques, thereby creating a secure multi-function device. All of the multi-function device's input and output interactions with its environment necessarily traverse an I / O bus under the sole control of the security core. The only communication path between an application processor and the external environment (such as an I / O device) is through an application processor bus, which is likewise under control of the security core. Thus a user may dynamically yet securely select the capabilities of a multi-function device, and because each I / O device and application processor in use by that multi-function device is authenticated, the security of transactions or network services performed when using such devices is improved.
Owner:INT BUSINESS MASCH CORP
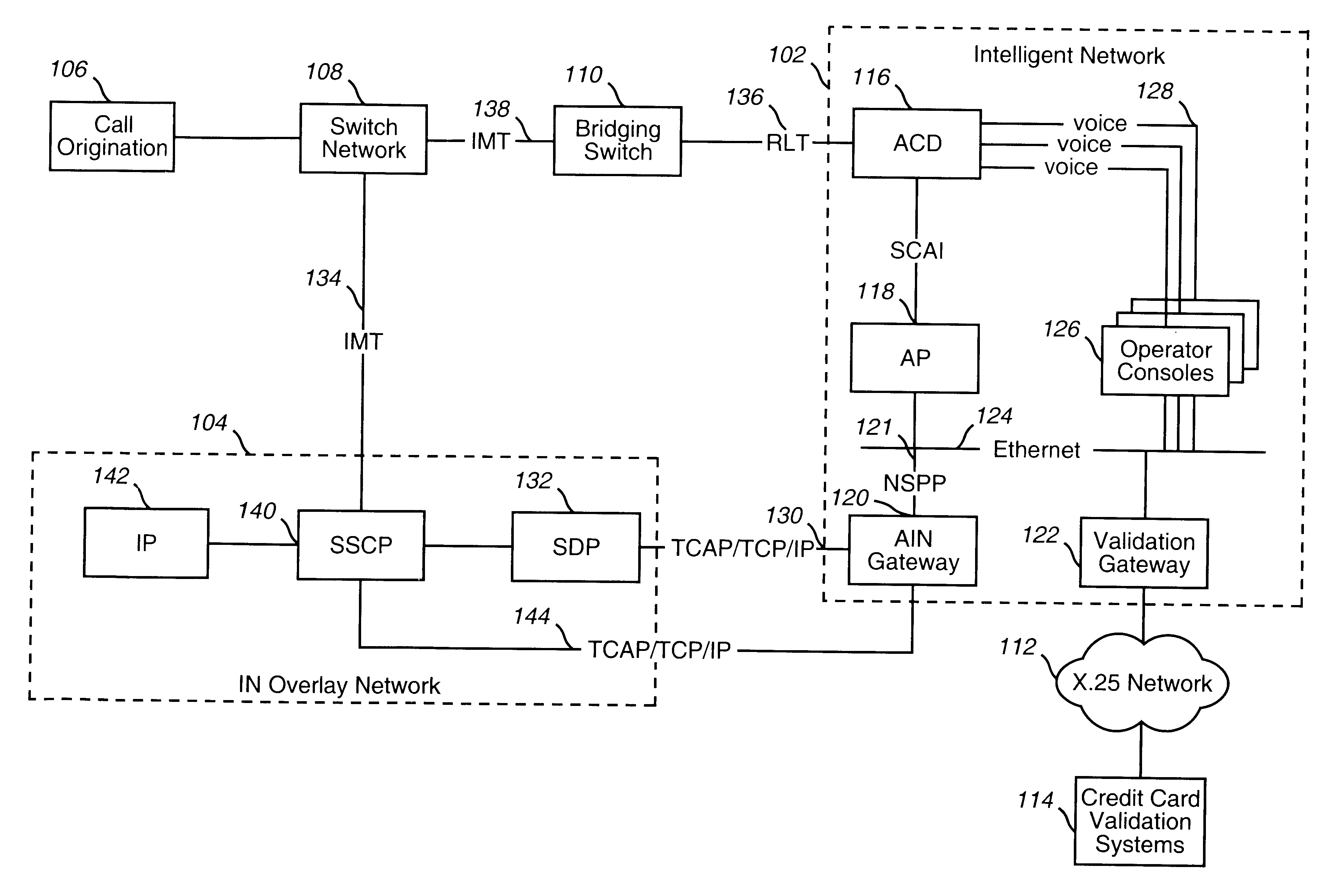
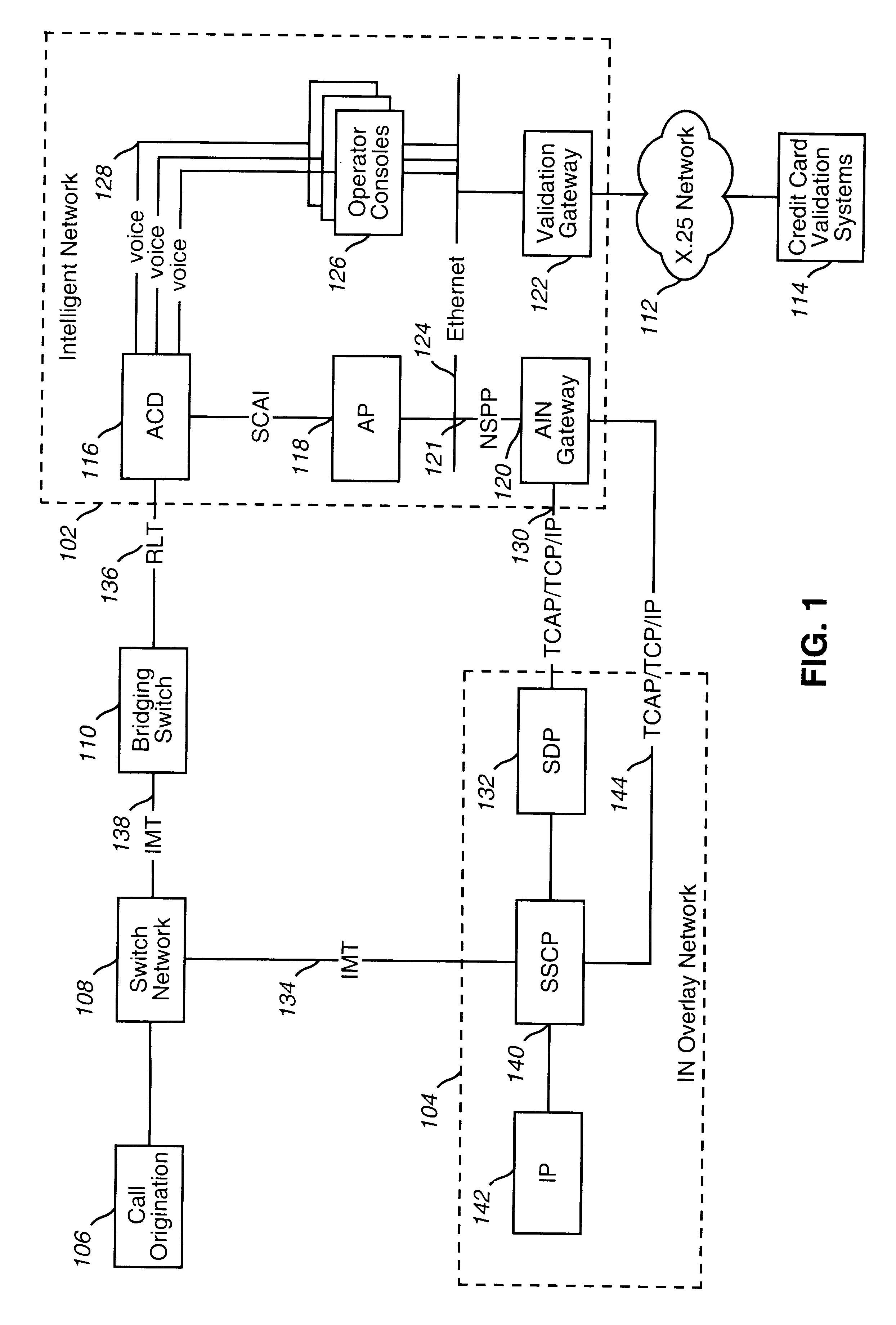
System and method for providing operator and customer services
InactiveUS6188761B1Augment automated serviceEfficiently assistComplete banking machinesInterconnection arrangementsCredit cardIntelligent Network
A system and method for providing operator and customer services for automated telecommunications services on an intelligent overlay network (104) is disclosed. Operator and customer services are provided by an intelligent network (102). The intelligent network (102) comprises an automated call distributor (116); an application processor (118); an advanced intelligent network gateway (AIN Gateway) (120); a validation gateway (122); and enhanced operator consoles (126). The AIN Gateway provides the intelligent network with an interface to the intelligent overlay network. This allows components within the intelligent network to communicate with components in the intelligent overlay network, and vice-versa. The validation gateway provides the intelligent network with an interface to credit card validation systems (114), and is used to apply charges to customer credit cards. Enhanced operator consoles provide for efficient and seamless integration of operator and customer services to automated services running on the intelligent overlay network. Such enhanced operator consoles are provided in the form of customized application programs that are executed by the operator consoles based on the context of calls that are transferred from the intelligent overlay network.
Owner:VERIZON PATENT & LICENSING INC
Processing data flows with a data flow processor
ActiveUS20110231510A1Easy to detectPreventing data flowDigital computer detailsPlatform integrity maintainanceData stream processingComputer module
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:CA TECH INC
Processing data flows with a data flow processor
InactiveUS20110231564A1Easy to detectPreventing data flowMultiple digital computer combinationsPlatform integrity maintainanceData stream processingComputer module
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:BLUE COAT SYSTEMS
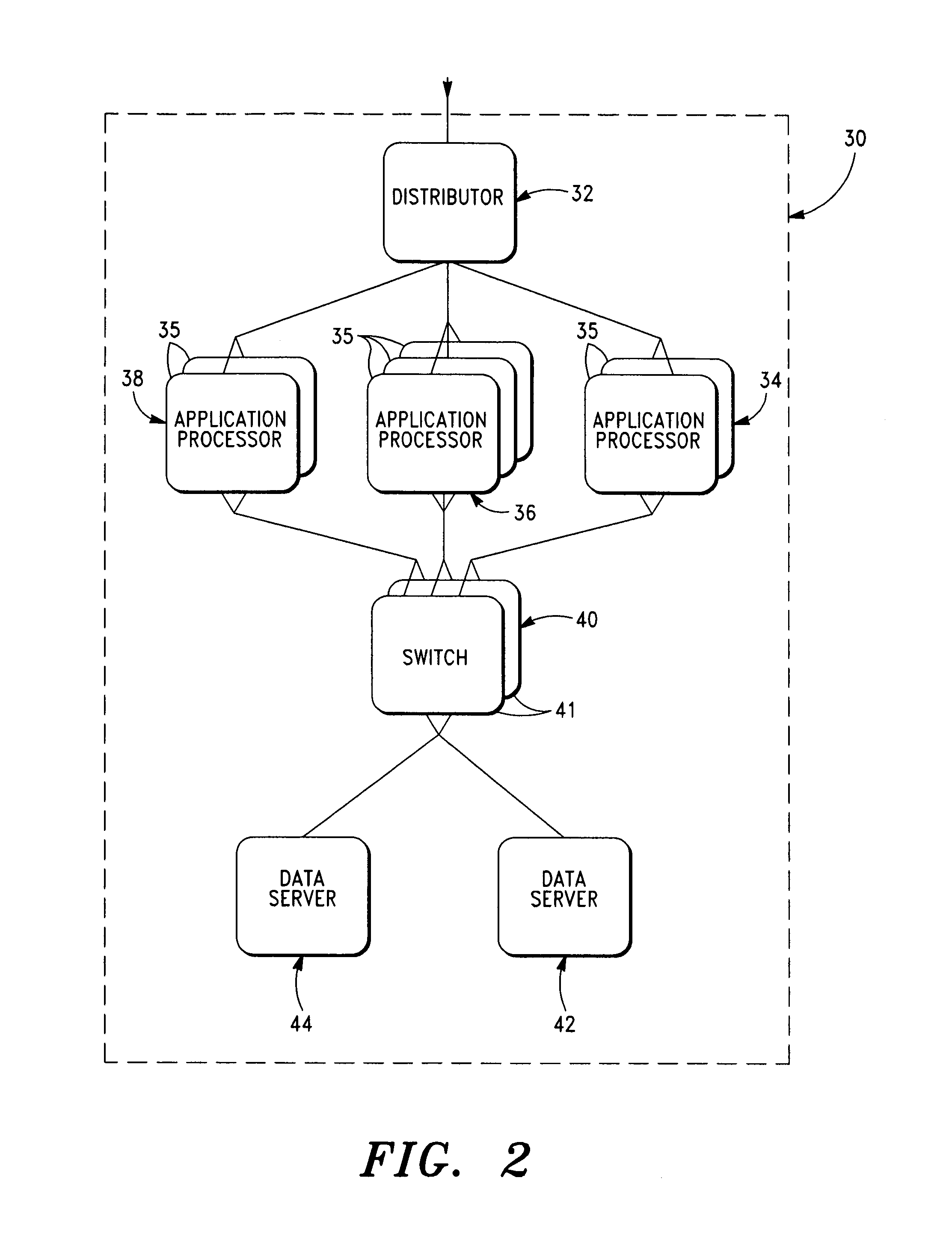
Survivable and scalable data system and method for computer networks
InactiveUS7047300B1Complete horizontalComplete vertical scalabilityMultiple digital computer combinationsTransmissionNetwork architectureData source
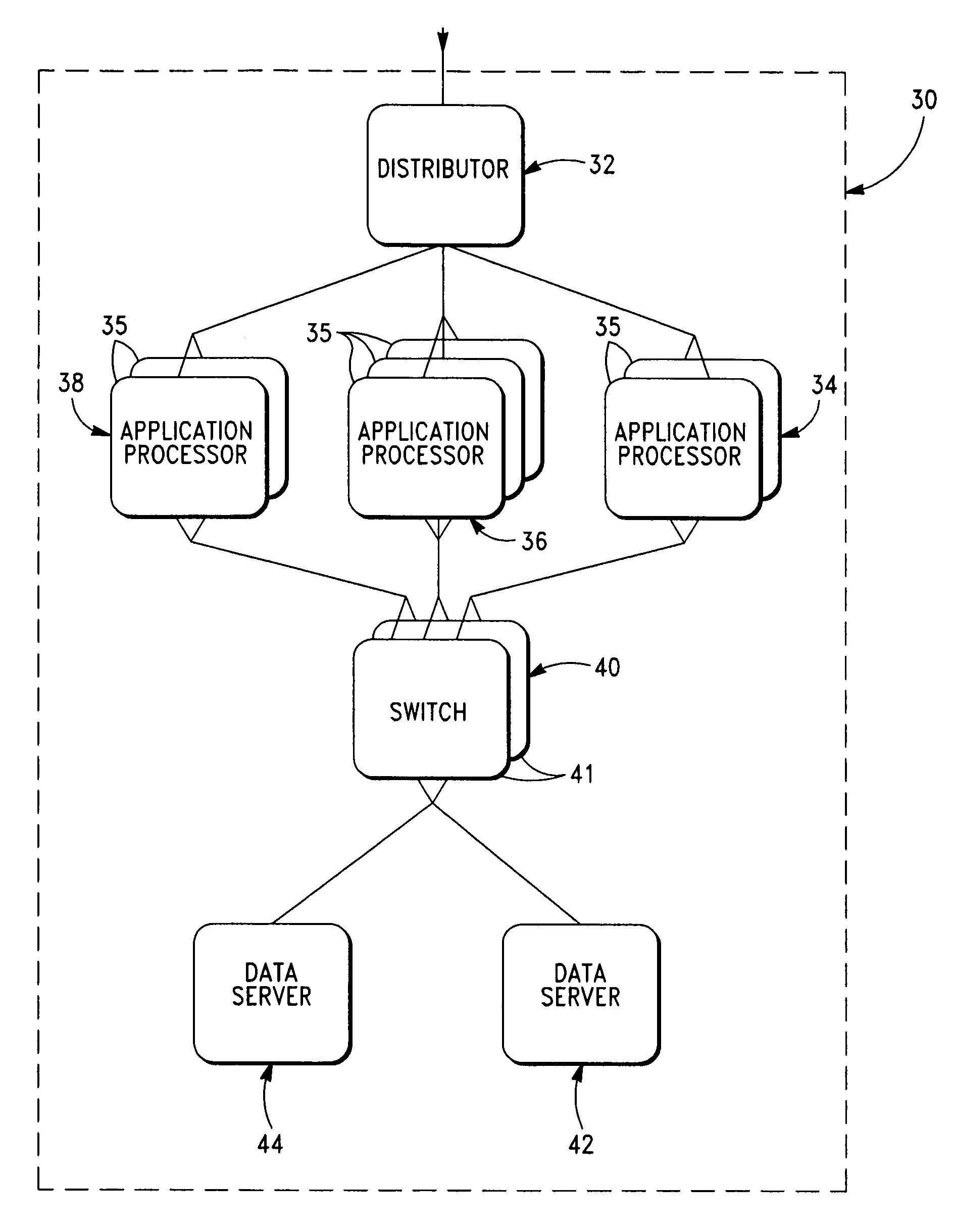
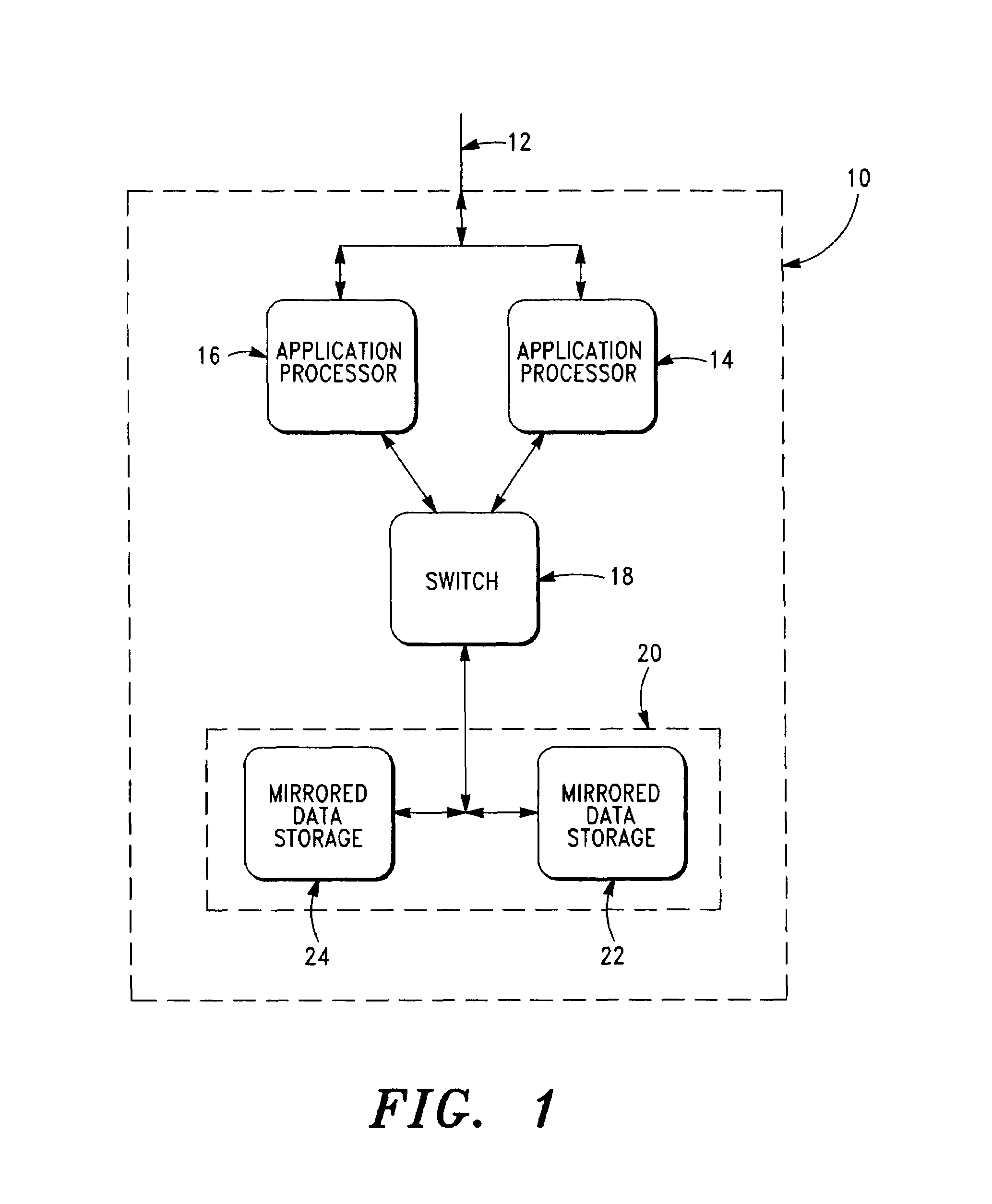
A fully scalable and survivable network architecture and method is disclosed. In particular, a system for providing network or intranet processing and stored data access and an associated method is provided. The system includes a plurality of sets of at least first and second application processors. Each of the first and second processors within a set apply substantially the same application. One or more switches operatively connect to at least the first and second processors and a plurality of data storage devices. The data stored in the data storage device is associated with the application and mirrored, and at least the first and second processors operate at substantially the same time to obtain data. Both sources of mirrored data are operational at the same time to output data.
Owner:SPRINT CORPORATION
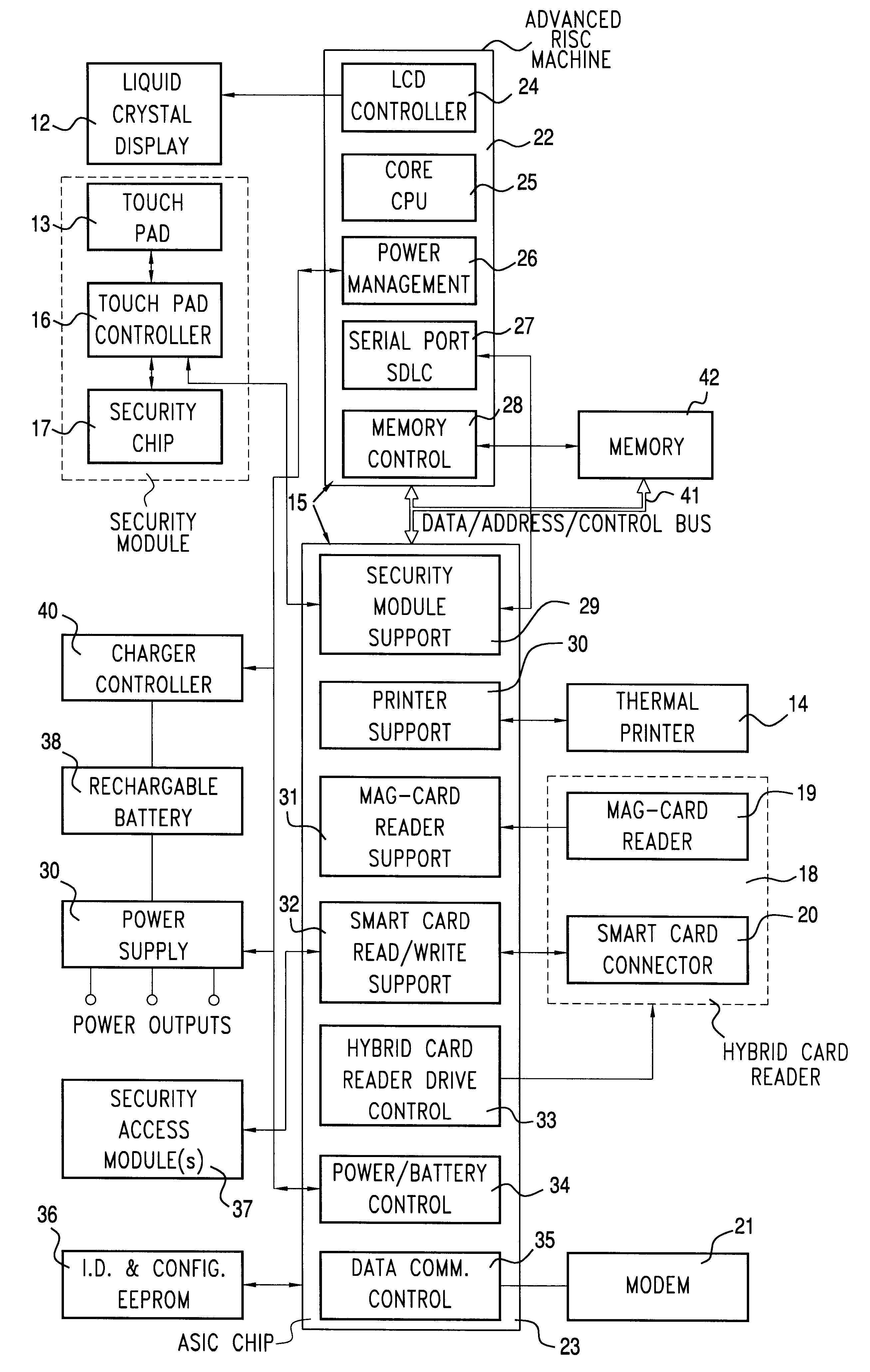
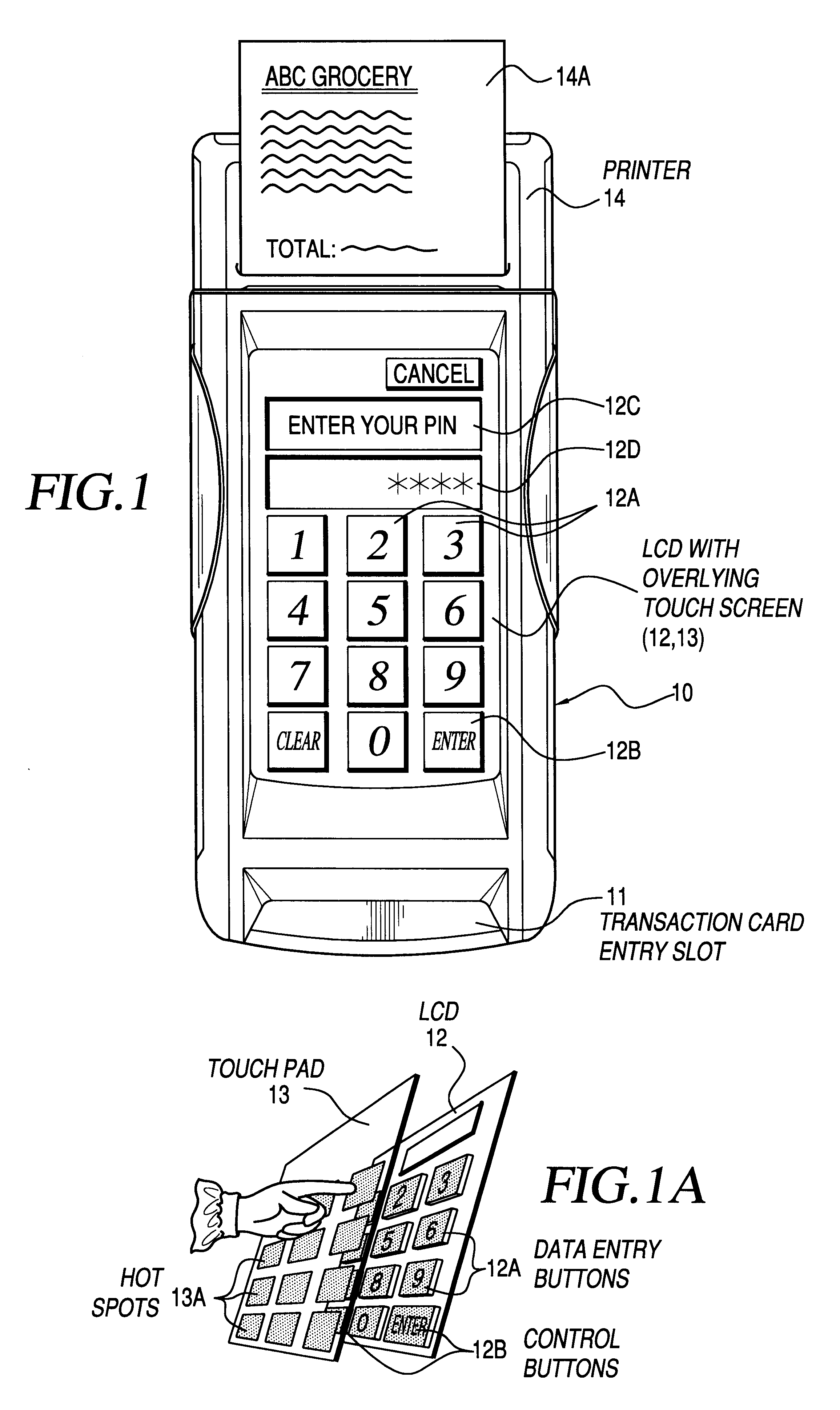
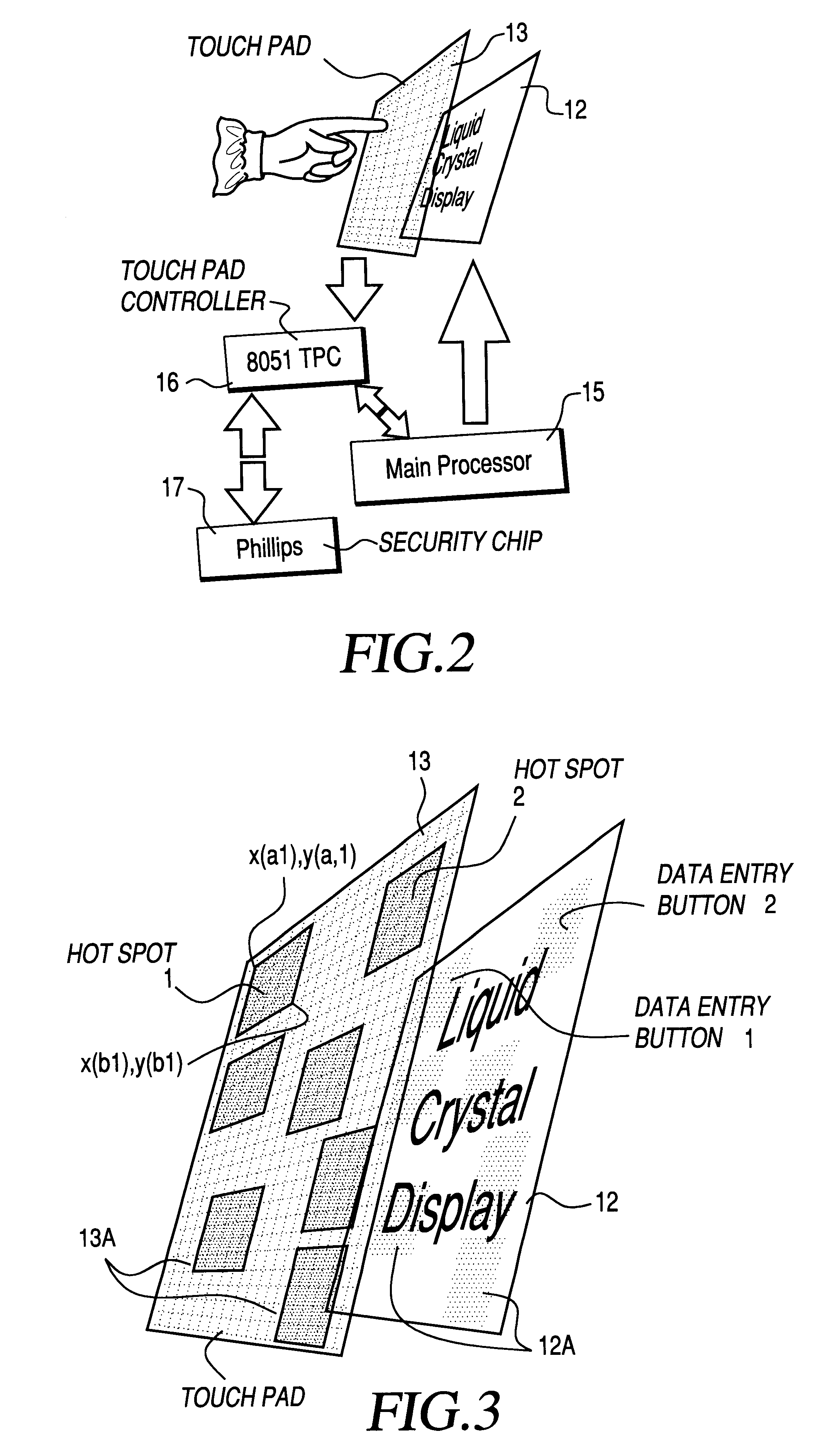
Method and apparatus for touch screen data entry
InactiveUS6630928B1Increase flexibilityEqual length code transmitterUser identity/authority verificationTouchpadHuman–computer interaction
Data entry apparatus comprising a display screen device, a touch pad mounted over the display screen device, and an application processor coupled to the touch pad and to the display screen device. The application processor has an application program processing module and a touch pad controller module. The application program processing module displays on the display screen a predefined data entry screen having a prearranged set of functional components and sends to the touch pad controller module a hot spot command defining a plurality of touch pad hot spots corresponding in area and location to the set of functional components. The touch pad controller module senses a touch event on the touch pad corresponding to one of the touch pad hot spots and sends to the application processor a touch event message identifying the touch pad hot spot corresponding to the touch event. PIN entry commands are issued by the application processor module and processed in the touch pad controller for secure PIN entry on the touch screen.
Owner:HEWLETT PACKARD DEV CO LP
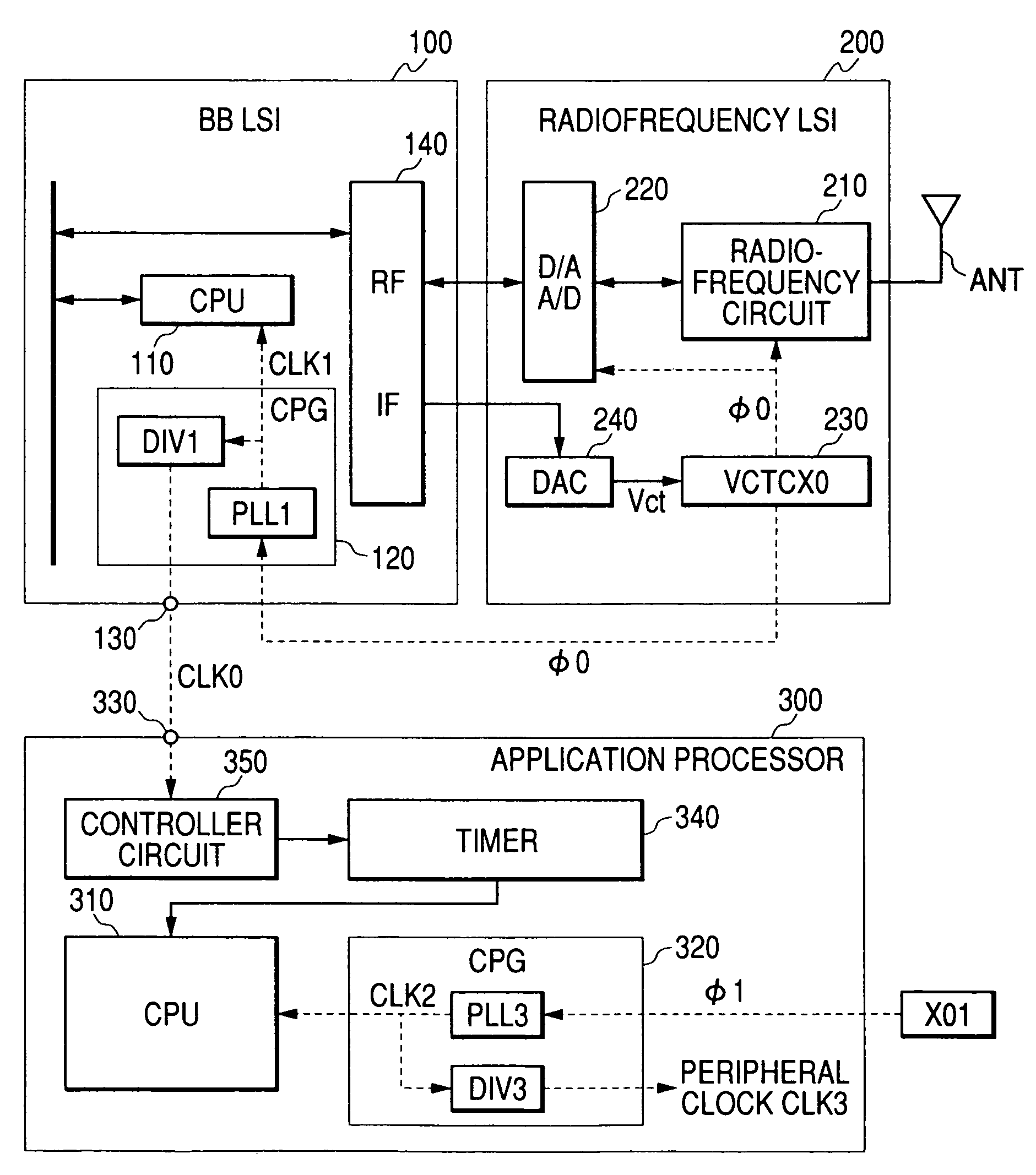
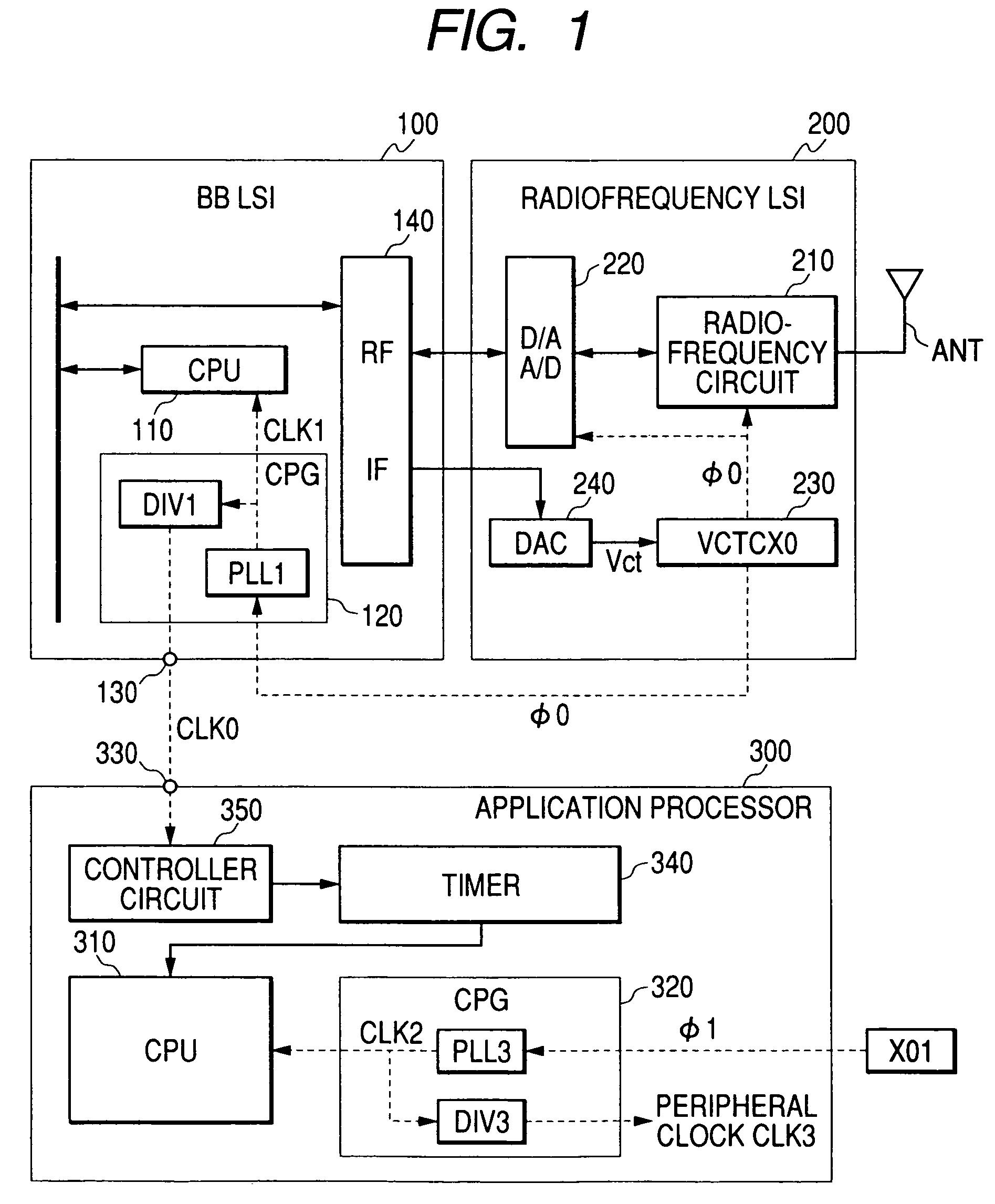
Radio communication semiconductor integrated circuit, data processing semiconductor integrated circuit and portable device
ActiveUS7444168B2Without lowering performanceAutomatic frequency control detailsData switching by path configurationEngineeringApplication processor
Owner:RENESAS ELECTRONICS CORP
Processing data flows with a data flow processor
ActiveUS9800608B2Increased complexityAvoid problemsMultiple digital computer combinationsPlatform integrity maintainanceData stream processingComputer module
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:CA TECH INC
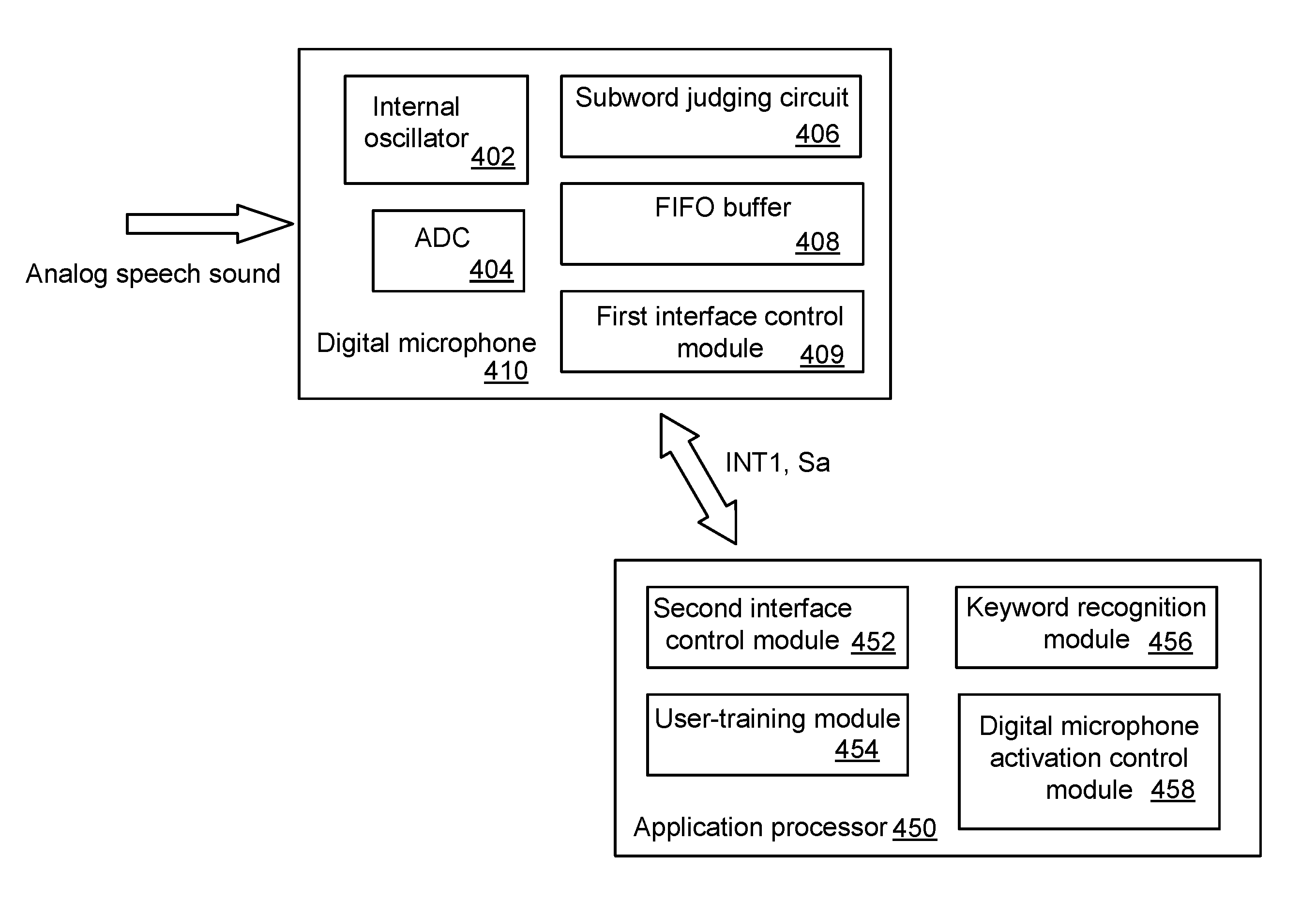
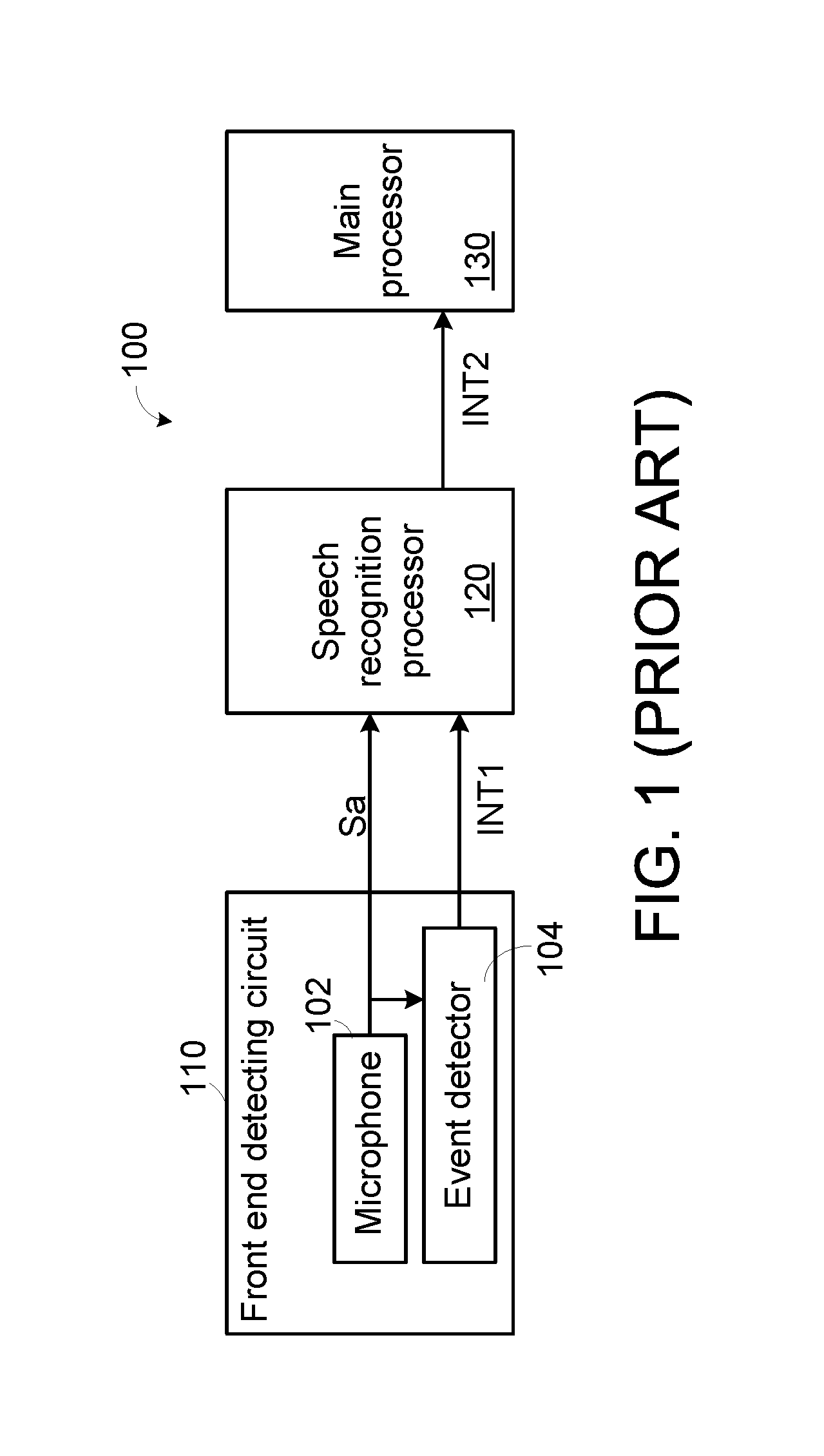
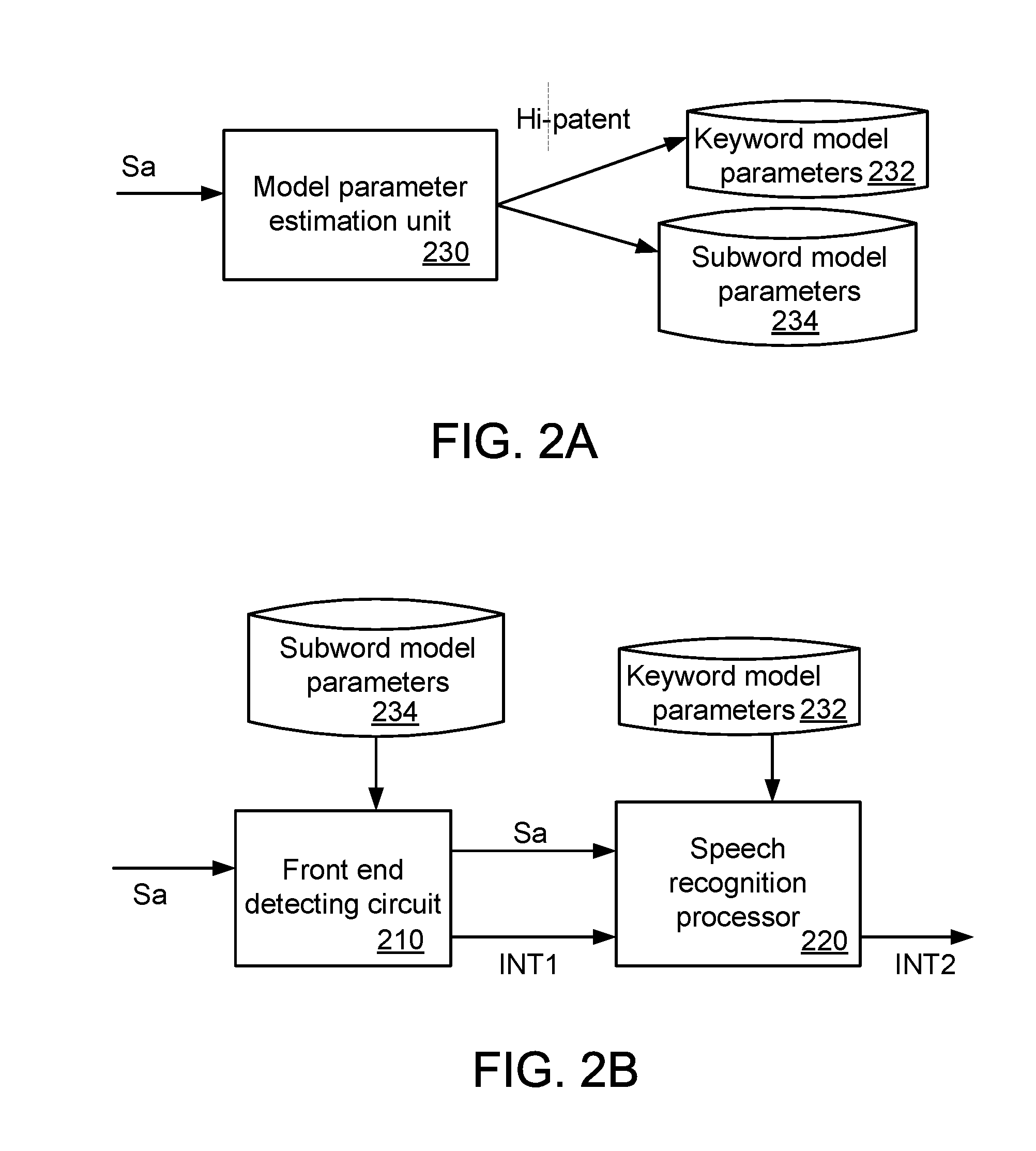
Voice wakeup detecting device with digital microphone and associated method
ActiveUS20160171976A1Accurate identificationPower managementSubstation equipmentSleep stateModel parameters
A voice wakeup detecting device for an electronic product includes a digital microphone and an application processor. The digital microphone has a function of judging whether a digital voice signal contains a subword according to subword model parameters. If the digital microphone confirms that the digital voice signal contains the subword, the digital microphone generates a first interrupt signal and outputs the digital voice signal. The application processor is enabled in response to the first interrupt signal. The application processor judges whether the digital voice signal contains a keyword according to keyword model parameters. If the application processor confirms that the digital voice signal contains the keyword, the electronic product is waked up from a sleep state to a normal working state under control of the application processor.
Owner:MEDIATEK INC
Performing enhanced background location scans to facilitate location-based geo-fencing
The disclosed embodiments facilitate location awareness in mobile computing devices while also reducing power consumption. A baseband processor performs background scanning of wireless networks, tracking the status of surrounding wireless networks while a primary application processor operates in a lower-power sleep state. Upon detecting a wireless network of interest, the baseband processor notifies (and wakes up) the application processor. The baseband processor can also be configured to track a subset of the wireless networks detected from previous scans to facilitate trajectory tracing.
Owner:APPLE INC
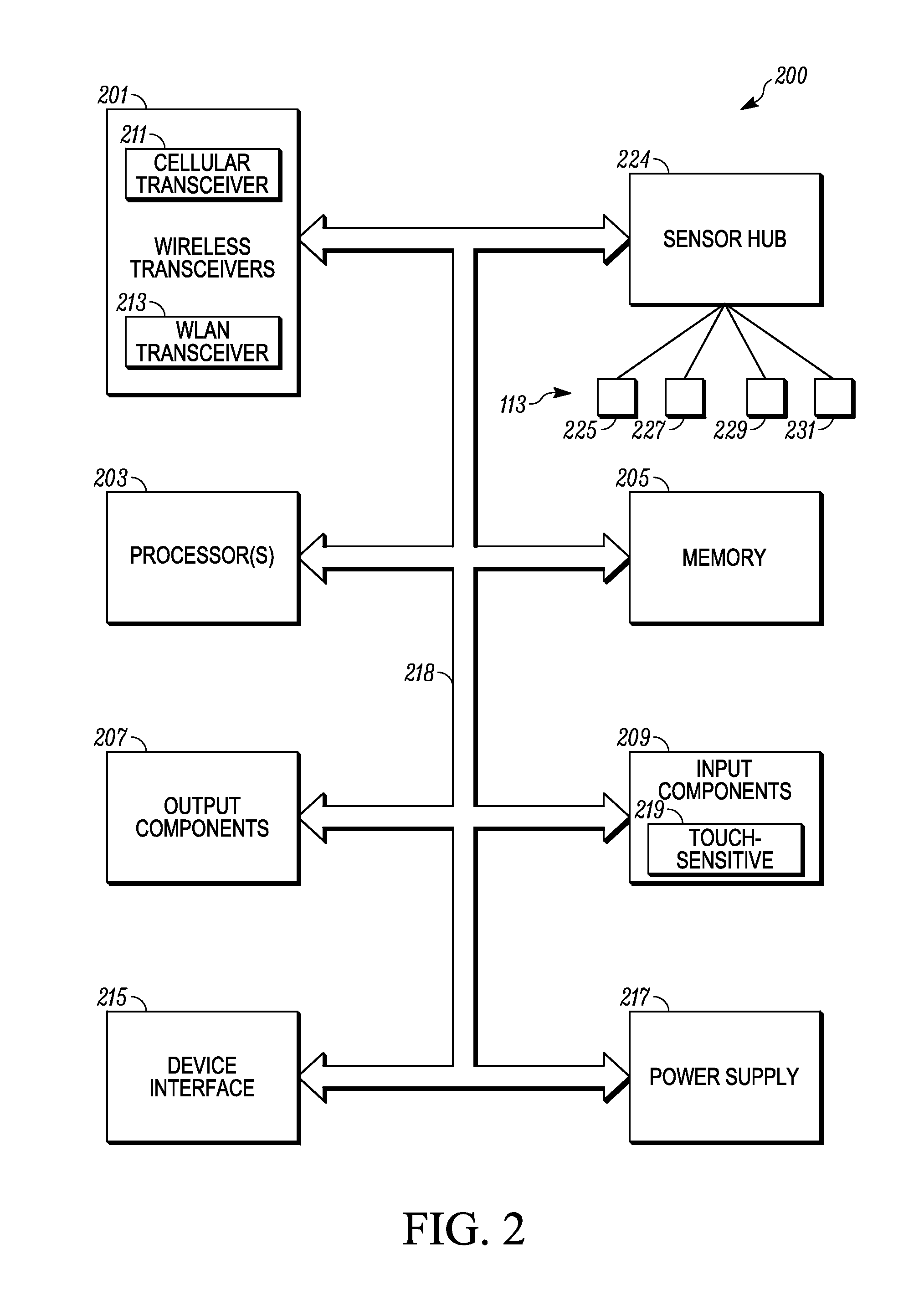
Electronic Device with Enhanced Method of Displaying Notifications
ActiveUS20140118272A1Input/output for user-computer interactionDigital data processing detailsDisplay deviceComputer science
There is disclosed an electronic device comprising a receiver, a display, an application processor and a sensor hub. The receiver is configured to receive notifications from a remote device. The display is configured to provide information including notifications. The application processor and the sensor hub are in communication with the display. The application processor is configured to provide instructions for displaying full screen information at the display during a non-sleep mode of the electronic device. The full screen information includes a first notification associated with information received by the electronic device during the non-sleep mode. The sensor hub is configured to provide instructions for displaying partial screen information at the display during a sleep mode of the electronic device. The partial screen information includes a second notification associated with information received by the electronic device during the sleep mode.
Owner:GOOGLE TECH HLDG LLC
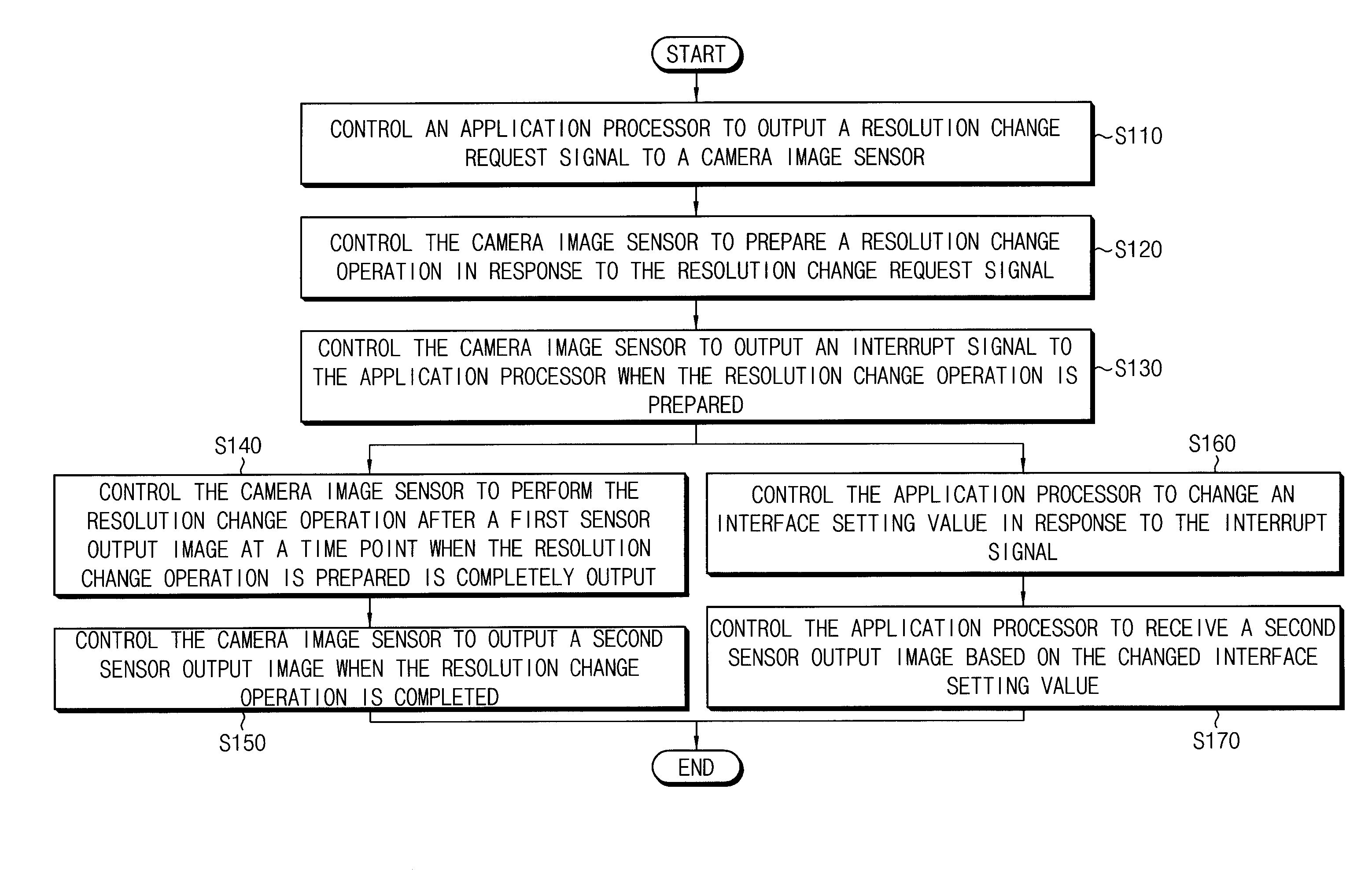
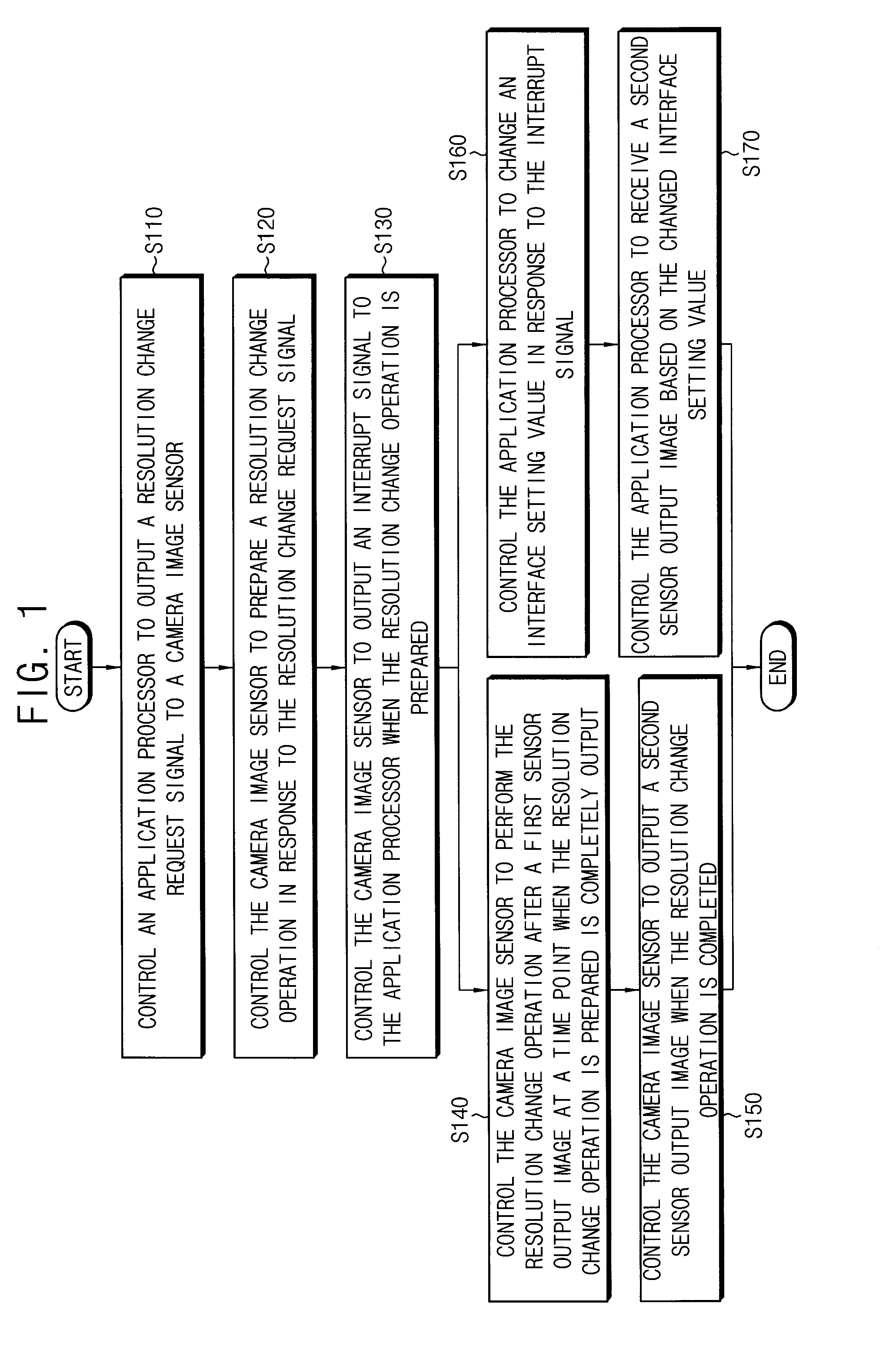
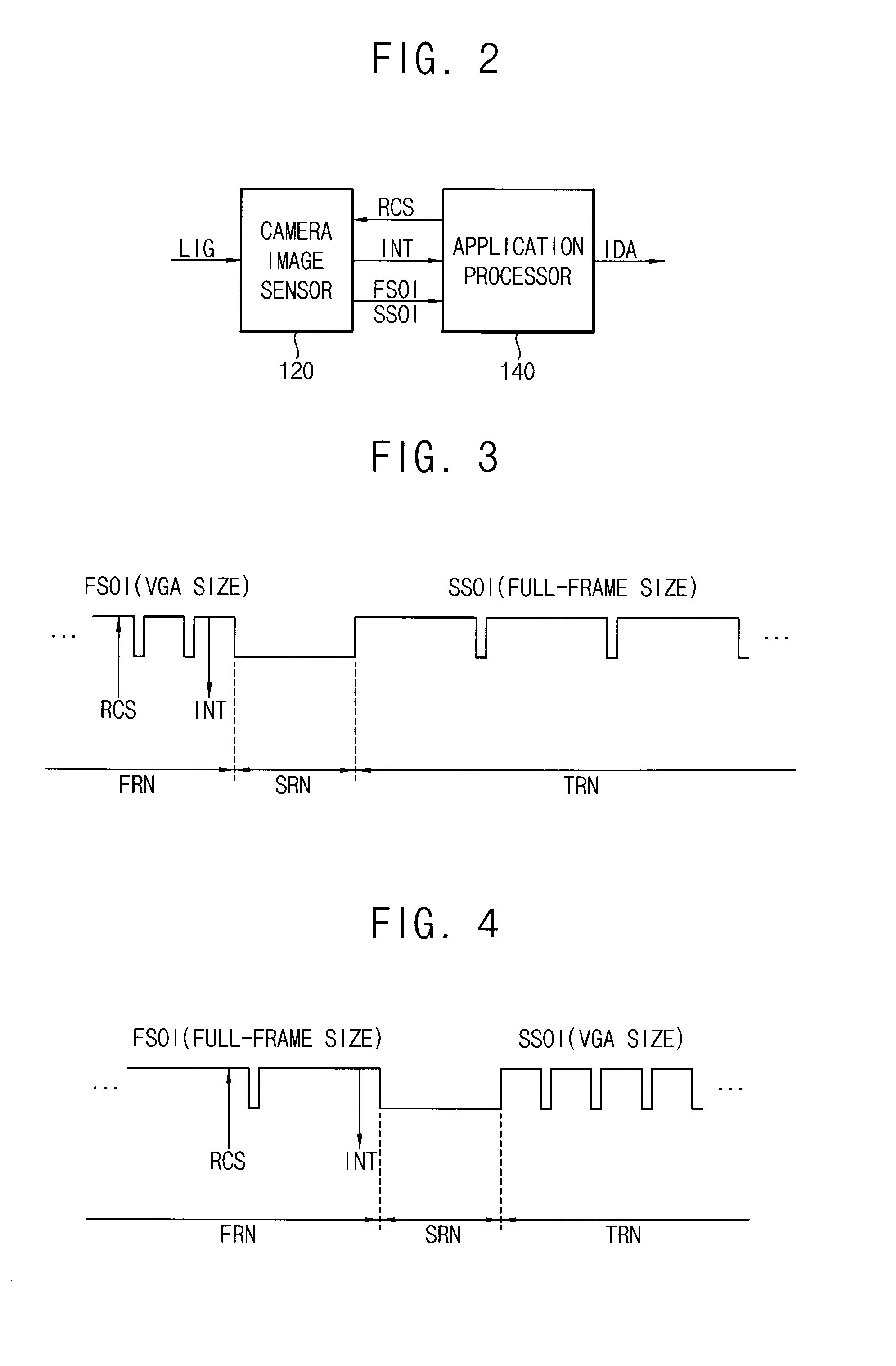
Method of changing an operation mode of a camera image sensor
InactiveUS20130201360A1Precise changeTelevision system detailsColor television detailsCamera imageImage resolution
By a method of changing an operation mode of a camera image sensor, an application processor outputs a resolution change request signal to the camera image sensor when an operation mode change signal is generated while the camera image sensor outputs a first sensor output image. The camera image sensor prepares a resolution change operation in response to the resolution change request signal, outputs an interrupt signal to the application processor when the resolution change operation is prepared, performs the resolution change operation after the first sensor output image is output, and outputs a second sensor output image when the resolution change operation is completed. The application processor changes an interface setting value in response to the interrupt signal, and receives the second sensor output image based on the changed interface setting value.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method of providing scalable computing between a portable computing device and a portable computing device docking station
ActiveUS20100250975A1Energy efficient ICTProgram control using stored programsScalable computingDocking station
A method of managing processor cores within a portable computing device (PCD) is disclosed and may include determining whether the PCD is docked with a PCD docking station when the PCD is powered on and energizing a first processor core when the PCD is not docked with the PCD docking station. The method may include determining an application processor requirement when an application is selected, determining whether the application processor requirement equals a two processor core condition, and energizing a second processor core when the application processor requirement equals the two processor core condition.
Owner:QUALCOMM INC
Method and apparatus for transmitting/receiving a reference signal in a wireless communication system
ActiveUS20120176885A1Improve communication performanceTransmission path divisionMultiplex code allocationCommunications systemResource block
Disclosed are a method and apparatus for transmitting a reference signal. In a base station apparatus for transmitting a reference signal in a wireless communication system, a processor generates the same scrambling sequence for resource elements (REs) allocated to each layer for reference signal transmission, and spreads or covers Walsh codes such that scrambling sequences generated for the resource elements can be orthogonal to each other on a time axis, in order to generate a reference signal sequence. Here, the Walsh code spreading or covering by the processor is applied on a frequency axis on the basis of a plurality of resource blocks (RBs) or on the basis of a pair of resource blocks, such that mutually different sequences having mutually different sequence values can be mapped between resource blocks or between pairs of resource blocks. A transmission module transmits the reference signal, to which the thus-generated reference signal sequence is applied, to user equipment via each layer.
Owner:LG ELECTRONICS INC
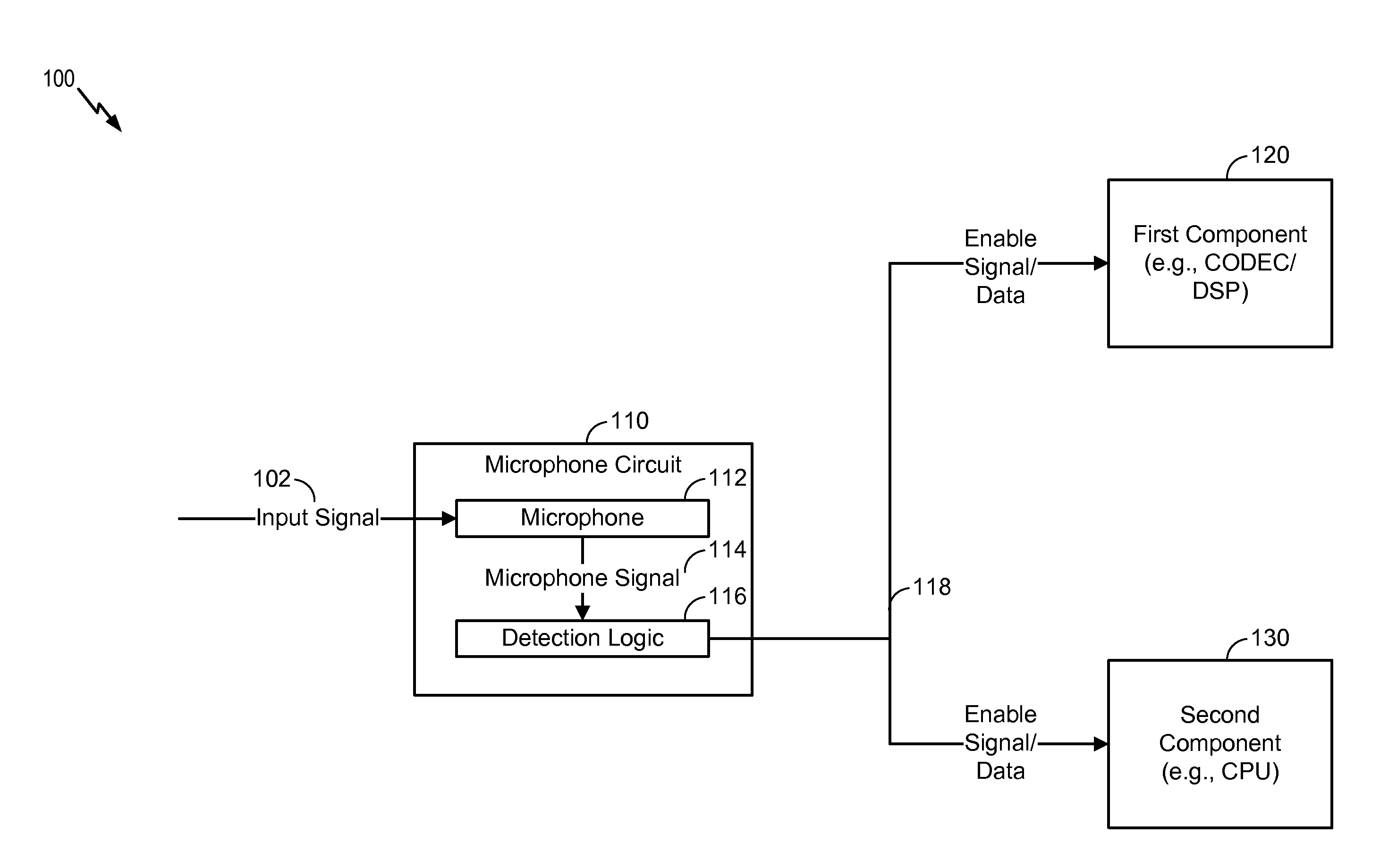
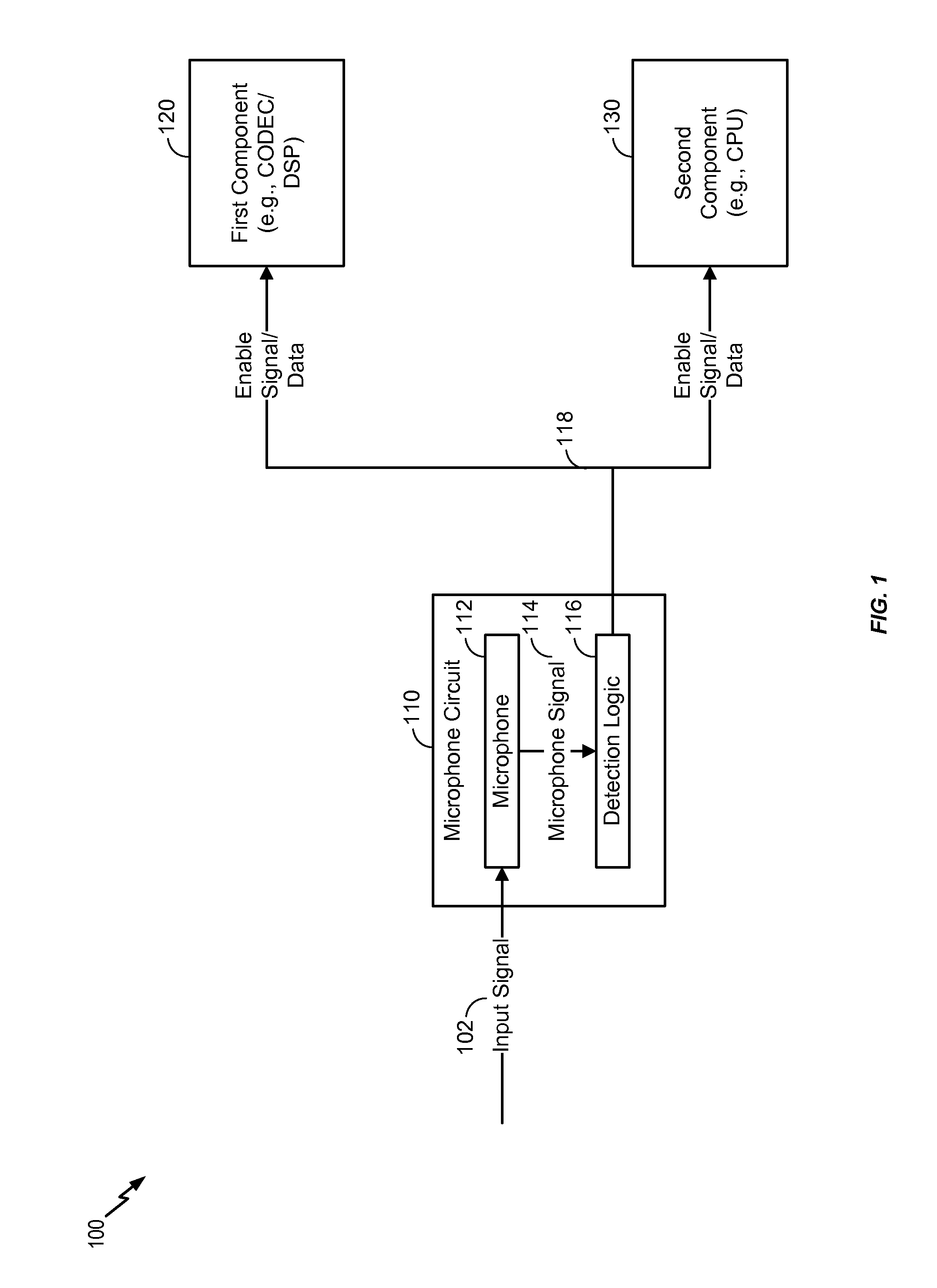
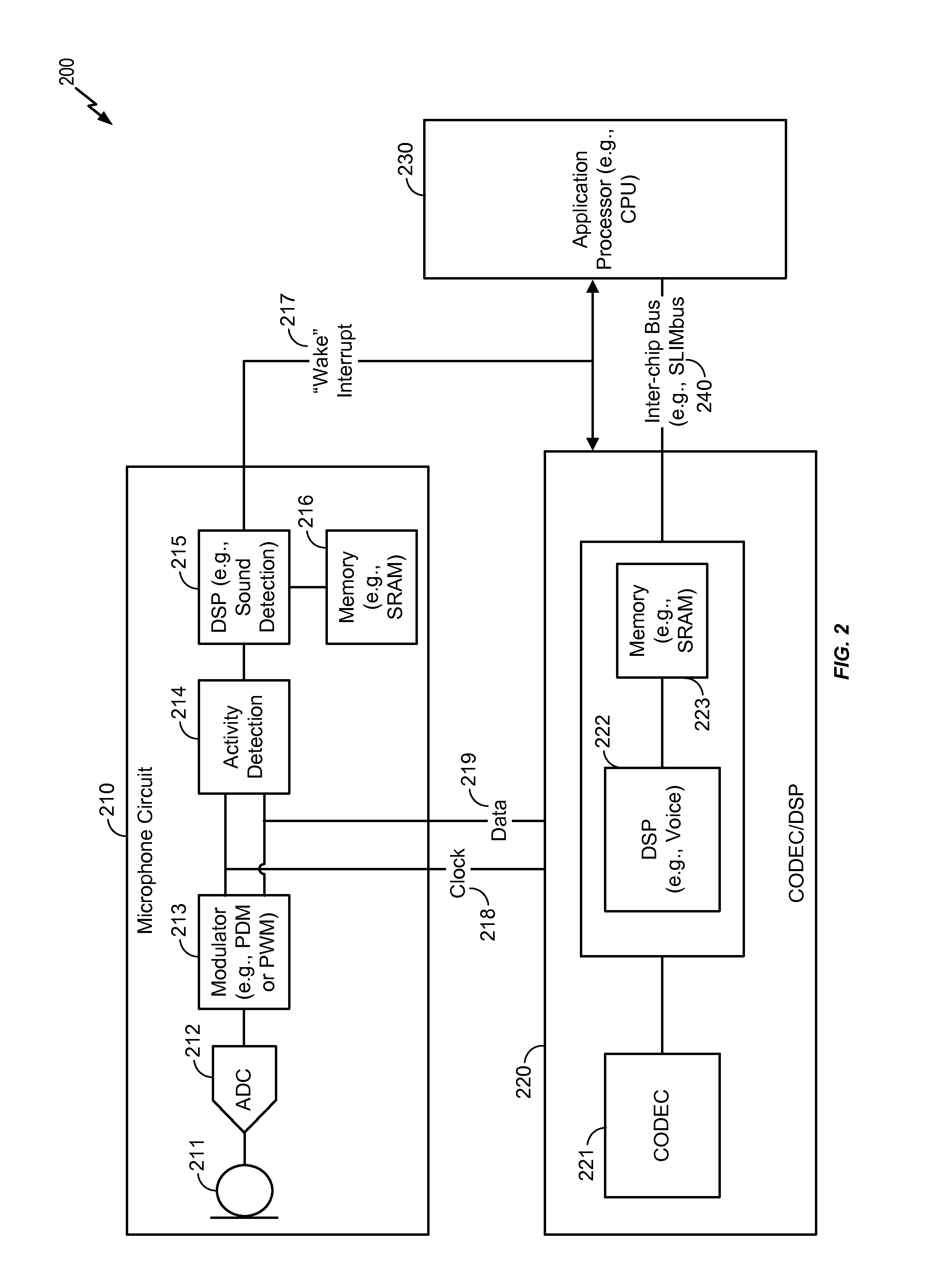
Selective enabling of a component by a microphone circuit
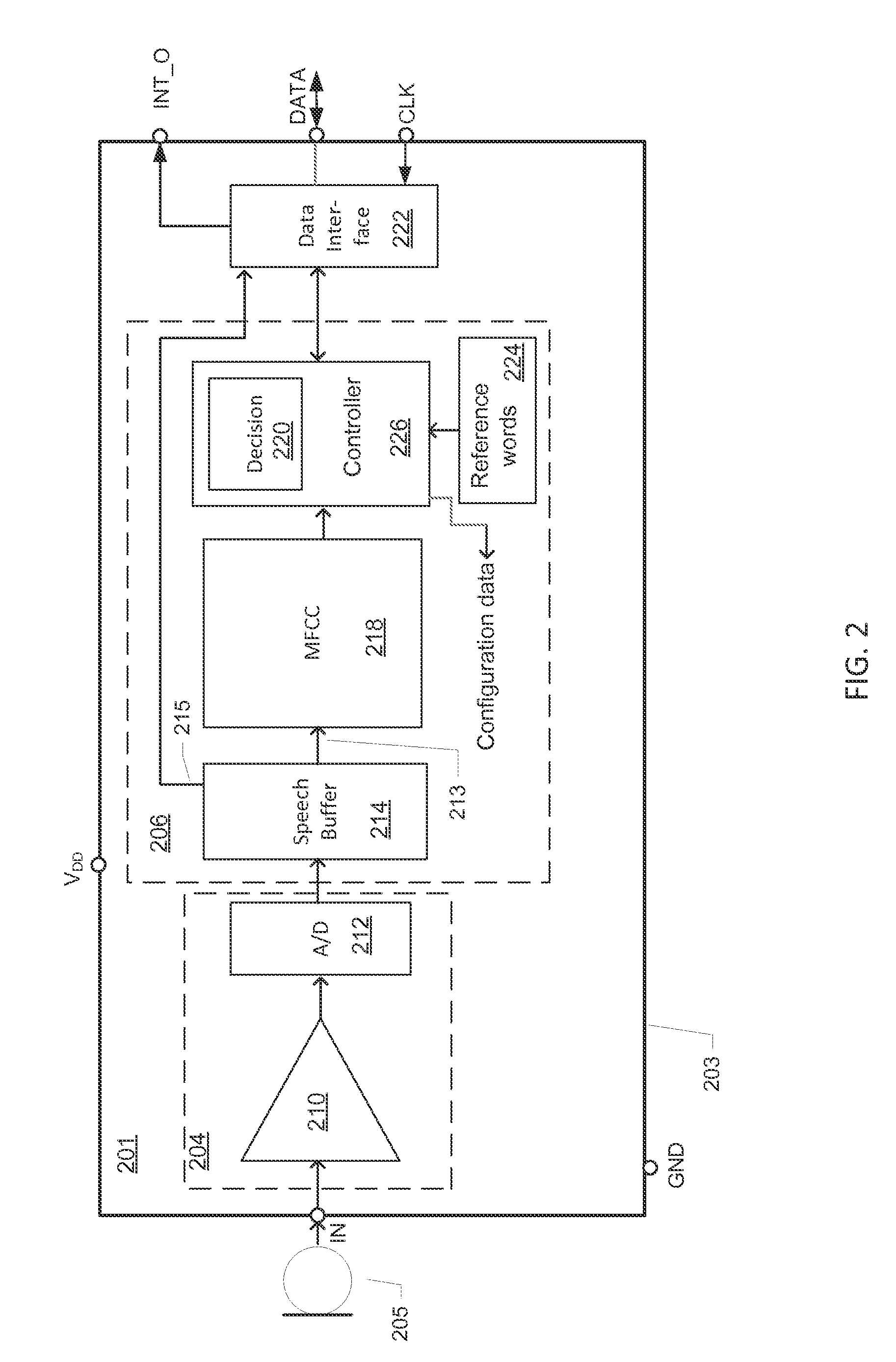
ActiveUS20160066113A1Reduce power consumptionDigital data processing detailsMouthpiece/microphone attachmentsSound detectionMicrophone signal
A microphone circuit includes a microphone configured to generate a microphone signal. The microphone circuit also includes a processor configured to perform sound detection based on the microphone signal and to determine whether to enable a component based on the sound detection. For example, the processor may be a digital signal processor (DSP) of the microphone circuit and the component may be external to the microphone circuit, such as a coder / decoder (CODEC), another DSP, and / or an application processor.
Owner:QUALCOMM INC
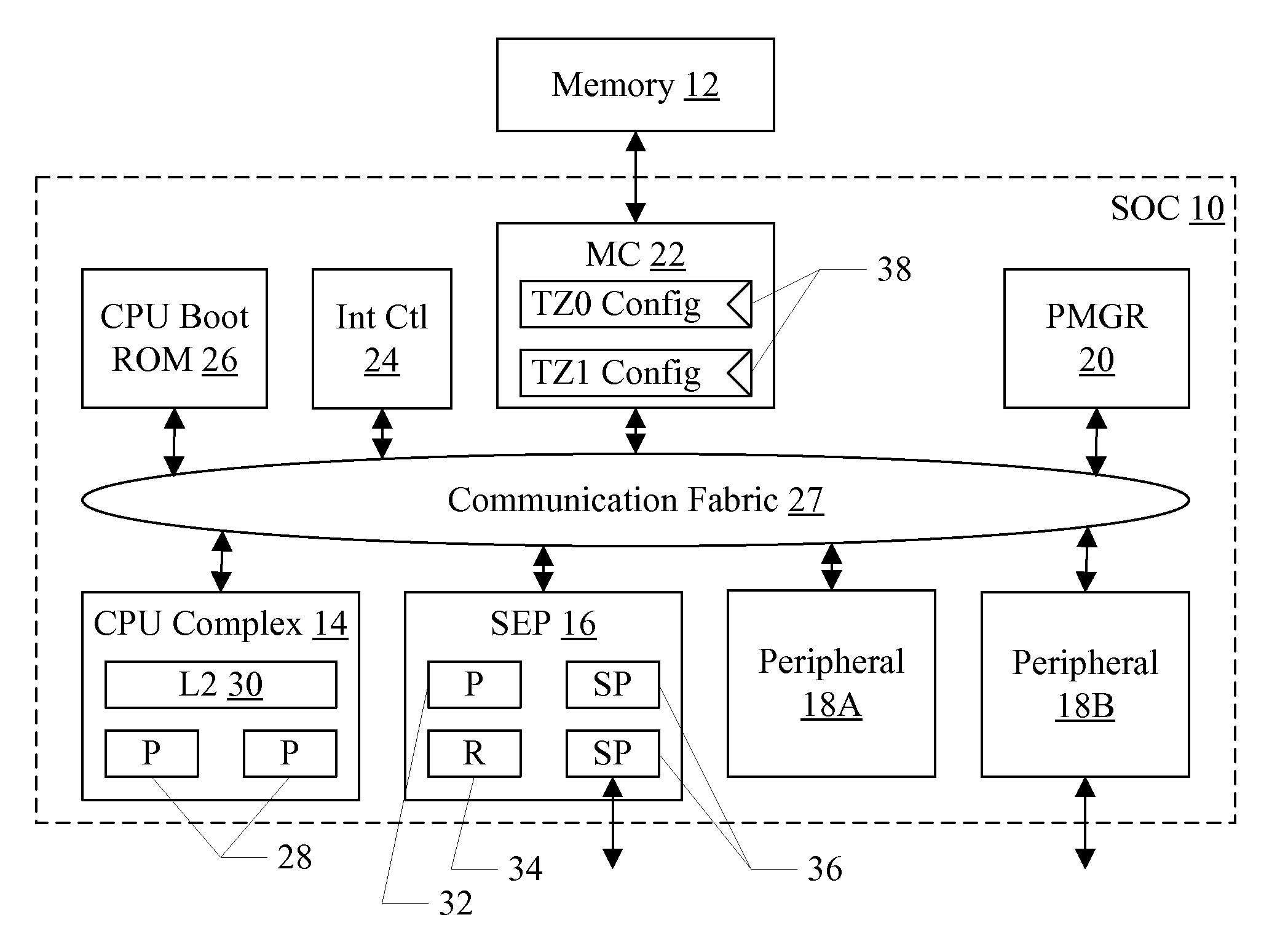
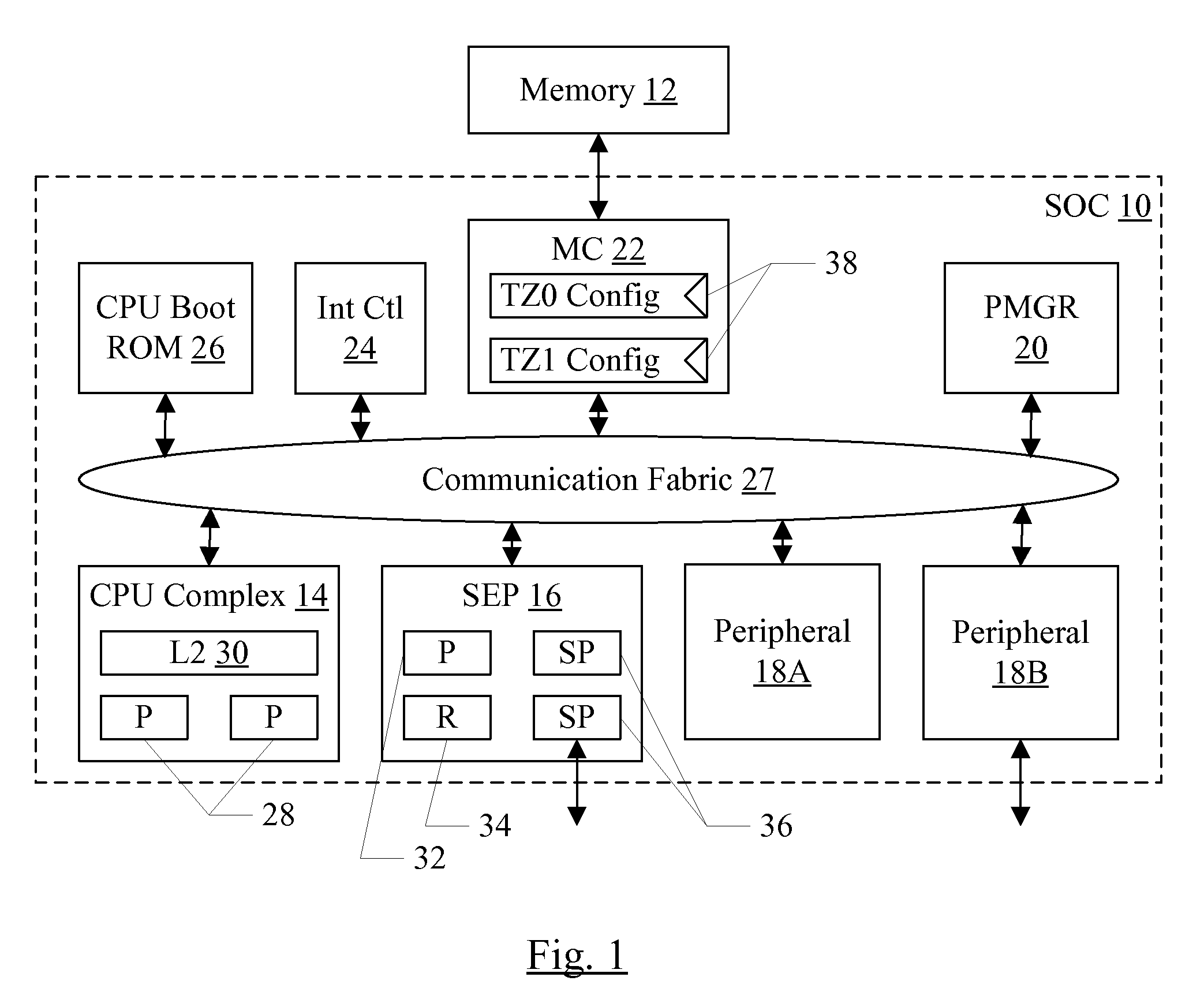
Security enclave processor for a system on a chip
ActiveUS8832465B2Prevent copyingMemory loss protectionUnauthorized memory use protectionApplication processorSystem on a chip
Owner:APPLE INC
Microphone circuit assembly and system with speech recognition
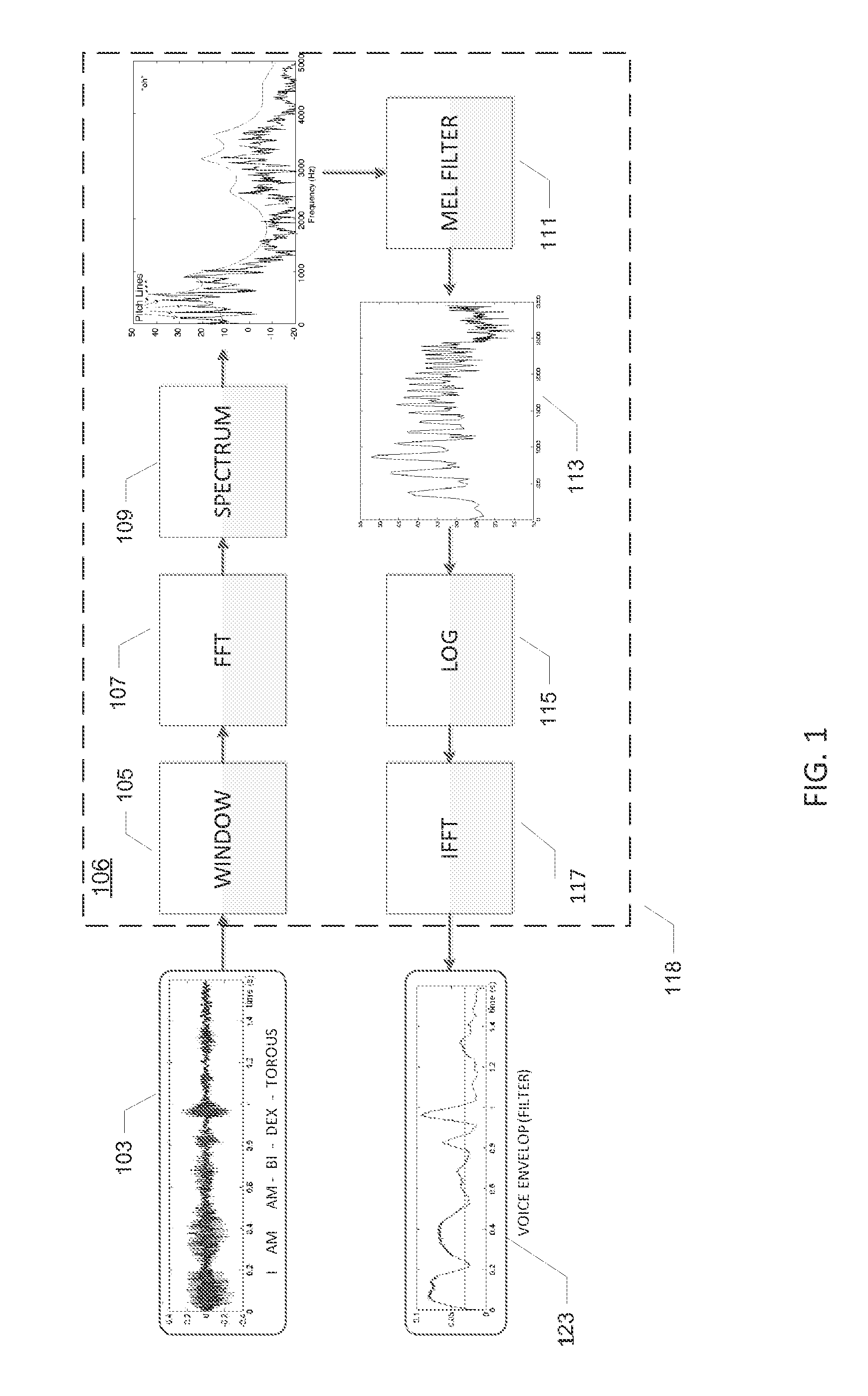
ActiveUS20140257813A1Reduce consumptionReduce loadHearing aids signal processingSpeech recognitionAnalog-to-digital converterApplication processor
A microphone circuit assembly for an external application processor, such as a programmable Digital Signal Processor, may include a microphone preamplifier and analog-to-digital converter to generate microphone signal samples at a first predetermined sample rate. A speech feature extractor is configured for receipt and processing of predetermined blocks of the microphone signal samples to extract speech feature vectors representing speech features of the microphone signal samples. The microphone circuit assembly may include a speech vocabulary comprising a target word or target phrase of human speech encoded as a set of target feature vectors and a decision circuit is configured to compare the speech feature vectors generated by the speech feature extractor with the target feature vectors to detect the target speech word or phrase.
Owner:ANALOG DEVICES INT UNLTD
Proxy-Based Push Service
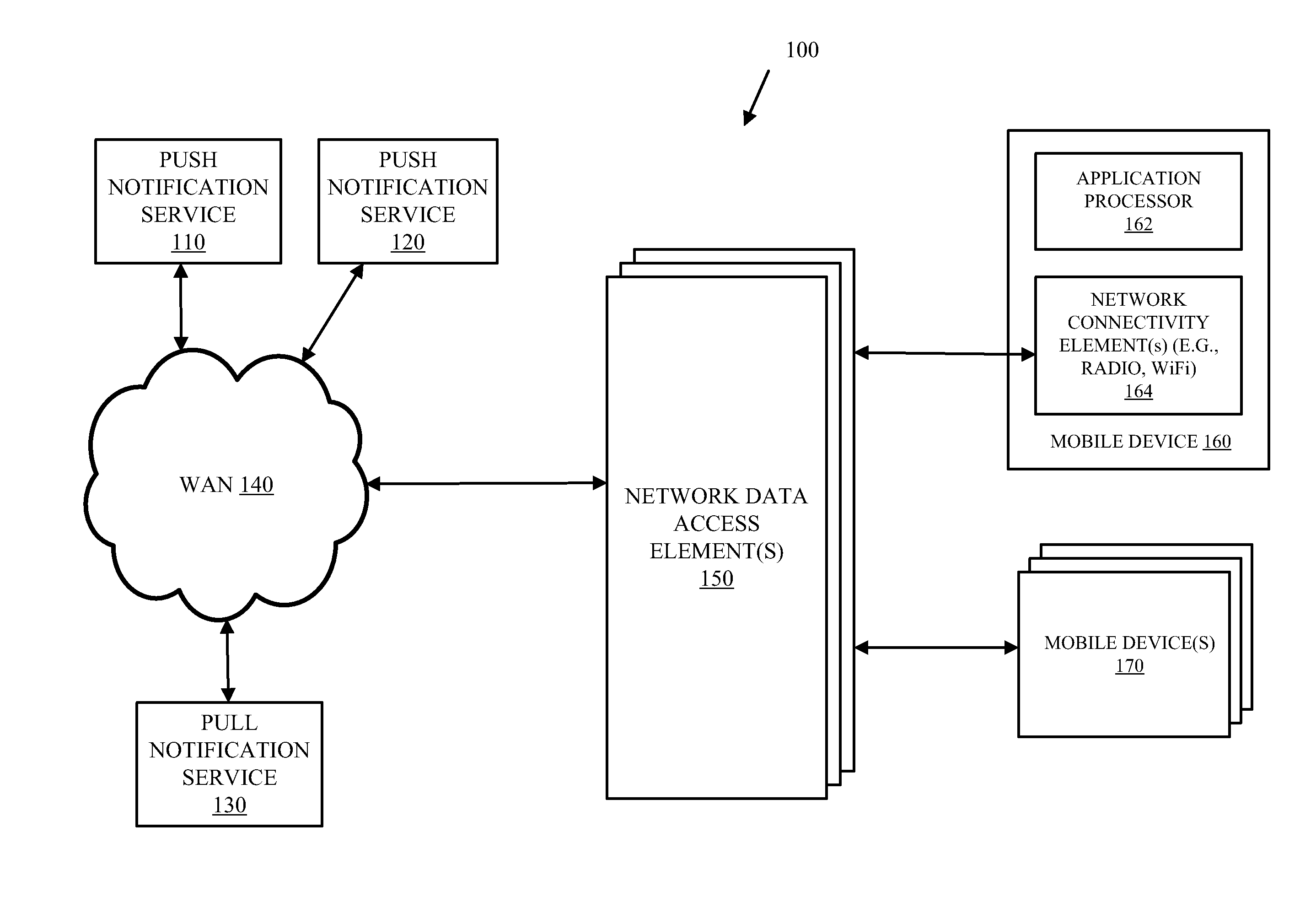
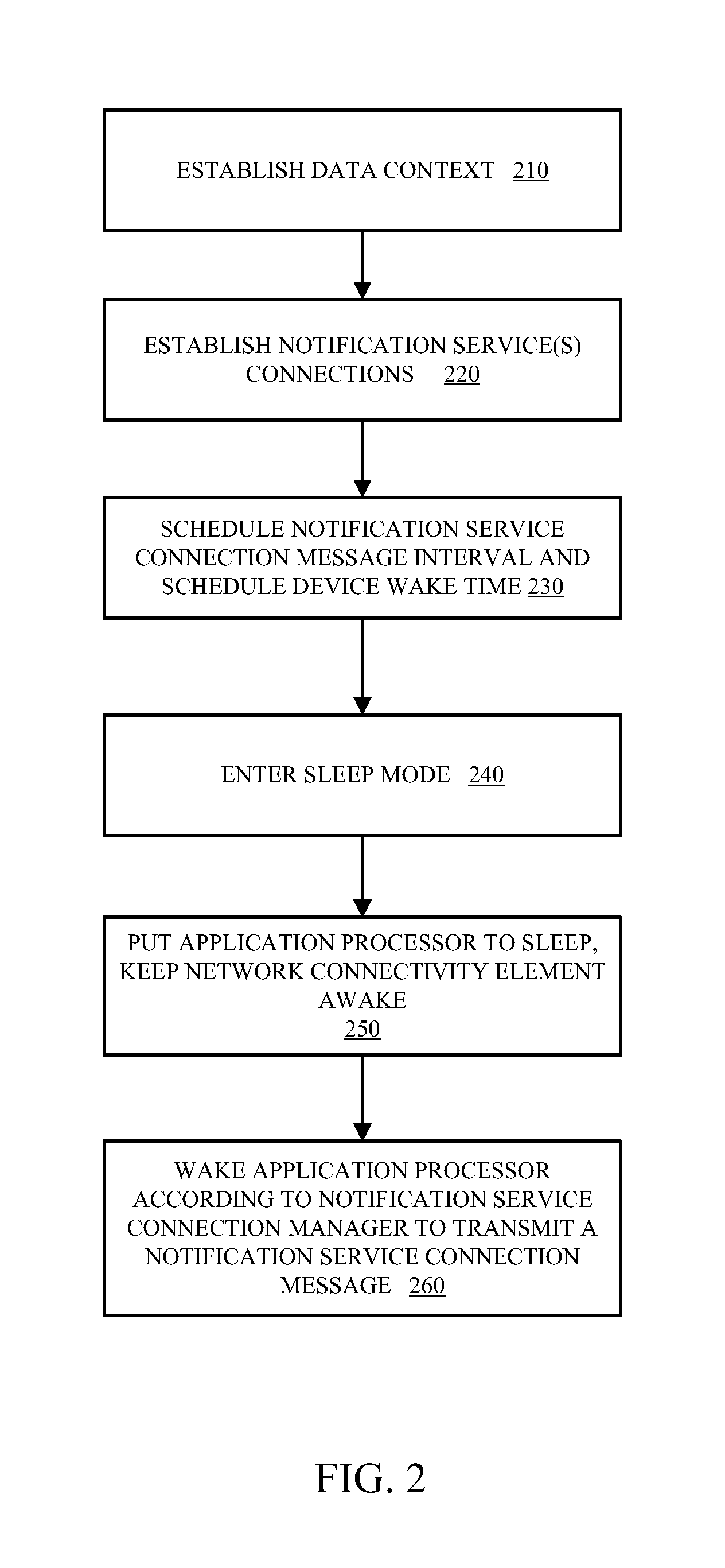
A method and apparatus to proxy notification service connections between a mobile client and a notification server. In one embodiment of the invention, a proxy receives a proxy setup request for the notification service from the mobile client. The proxy further establishes a notification connection with the notification server for the mobile client and maintains the notification connection without waking an application processor of the mobile client. The proxy receives a notification from the notification service and forwards the notification to the mobile client.
Owner:APPLE INC
Method of operating a WLAN mobile station
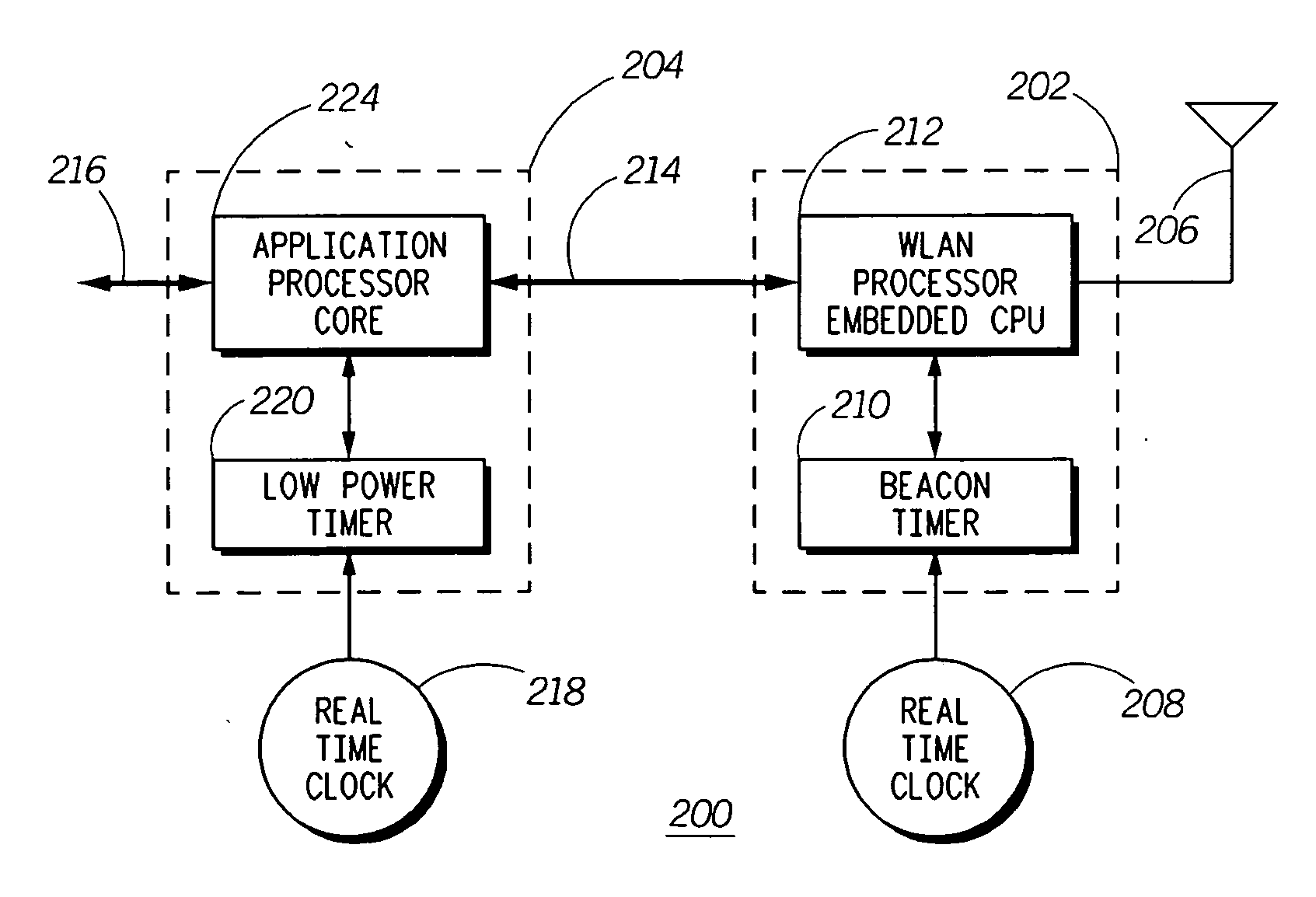
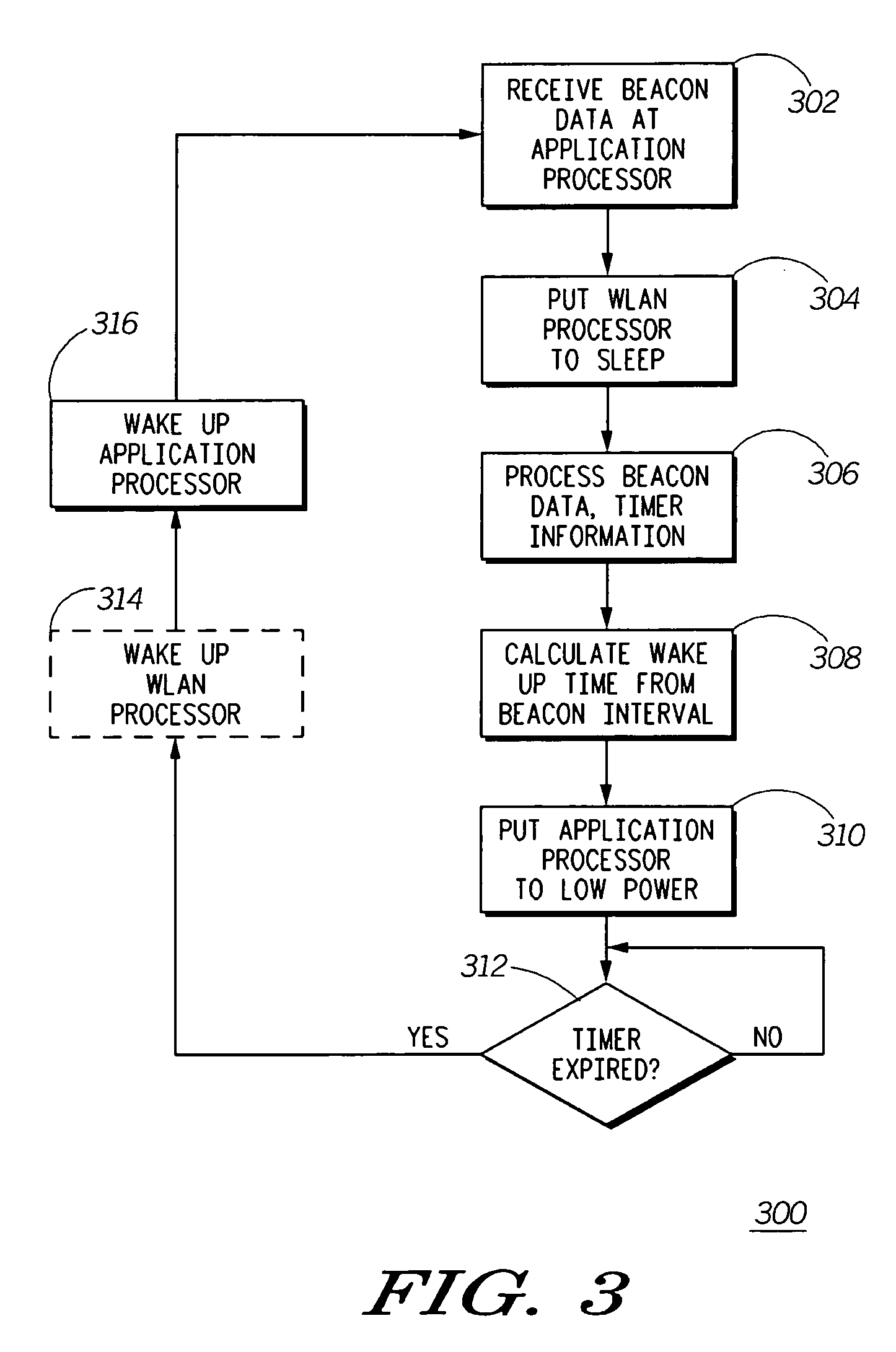
A wireless local area network (WLAN) mobile station (110, 112, 114) has an application processor core (204) and a WLAN processor (202). So as to conserve energy, when the two processors are not needed, they are both placed in a minimal power consumption mode. The WLAN processor operates a WLAN radio and receives beacon transmissions from an access point (120). Upon extracting the beacon data from a received beacon signal, the WLAN processor passes the beacon data to the application processor. To ensure receipt of the beacon data, the WLAN processor remains active until the application processor acknowledges receipt of the beacon data before transitioning back to a sleep mode. To prevent keeping the WLAN processor waiting longer than necessary, the application processor wakes up ahead of the beacon receipt time, in time to allow transition to an awake mode so that it is active by the time the WLAN processor passes the beacon data.
Owner:MOTOROLA INC
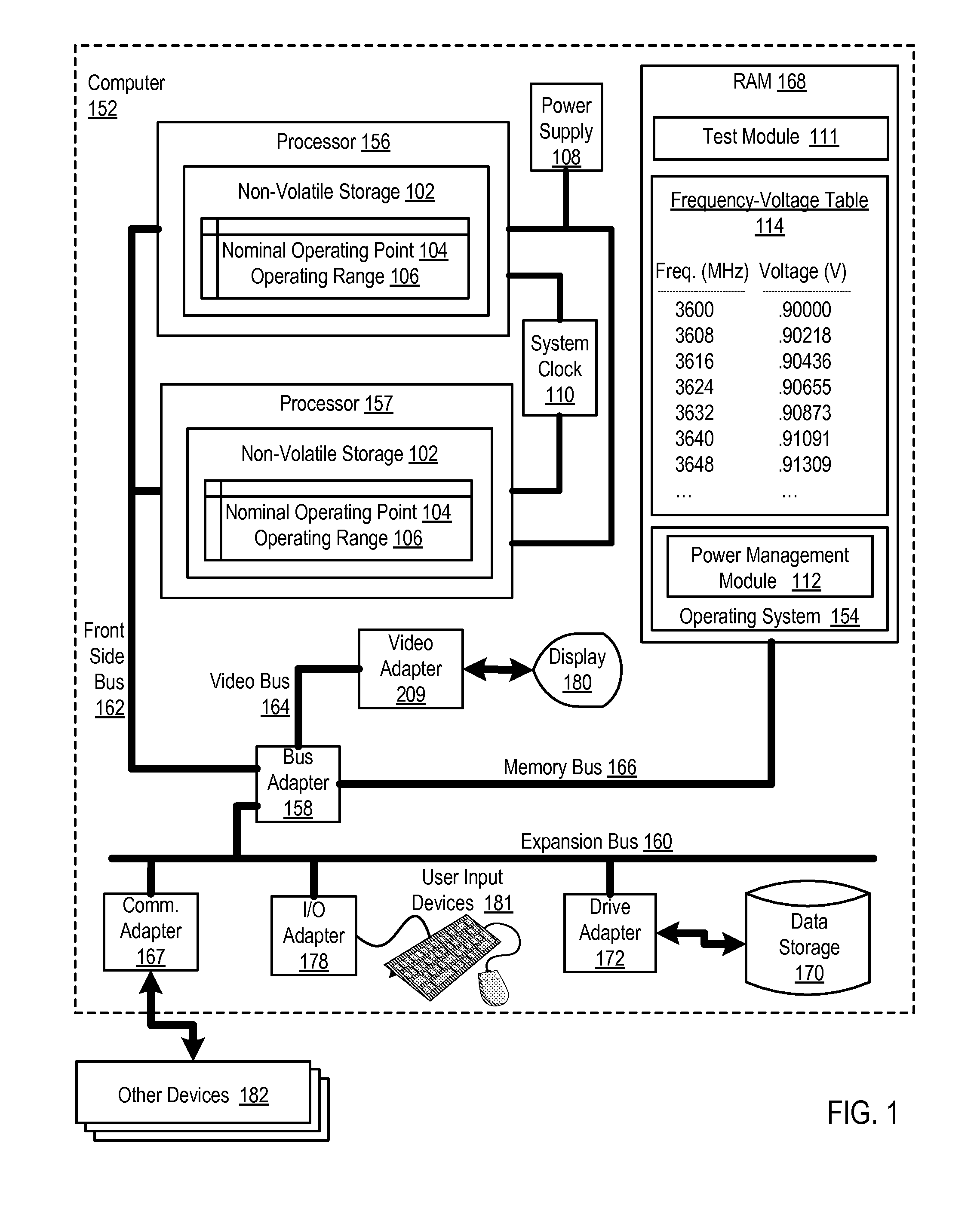
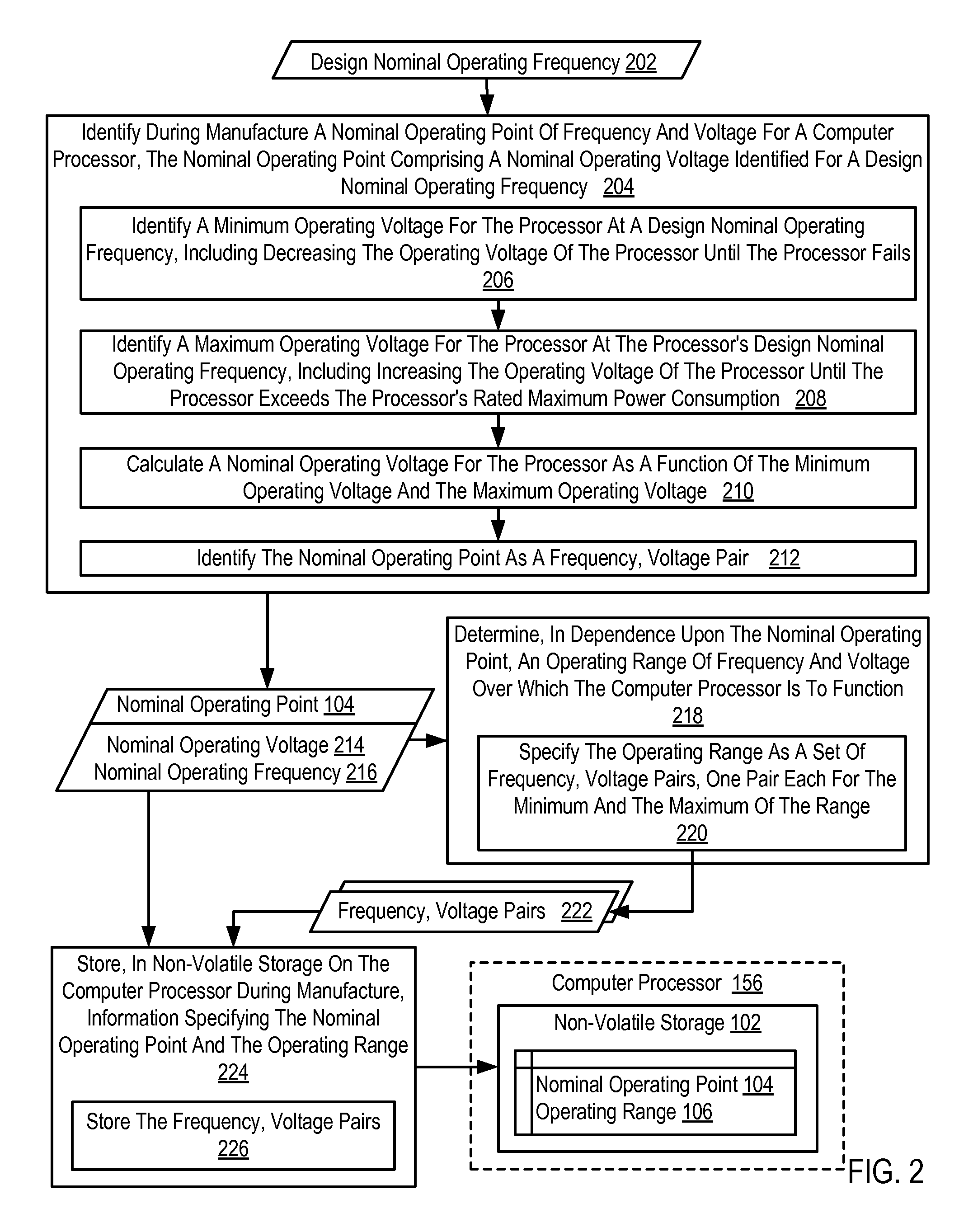
Dynamic Frequency And Voltage Scaling For A Computer Processor
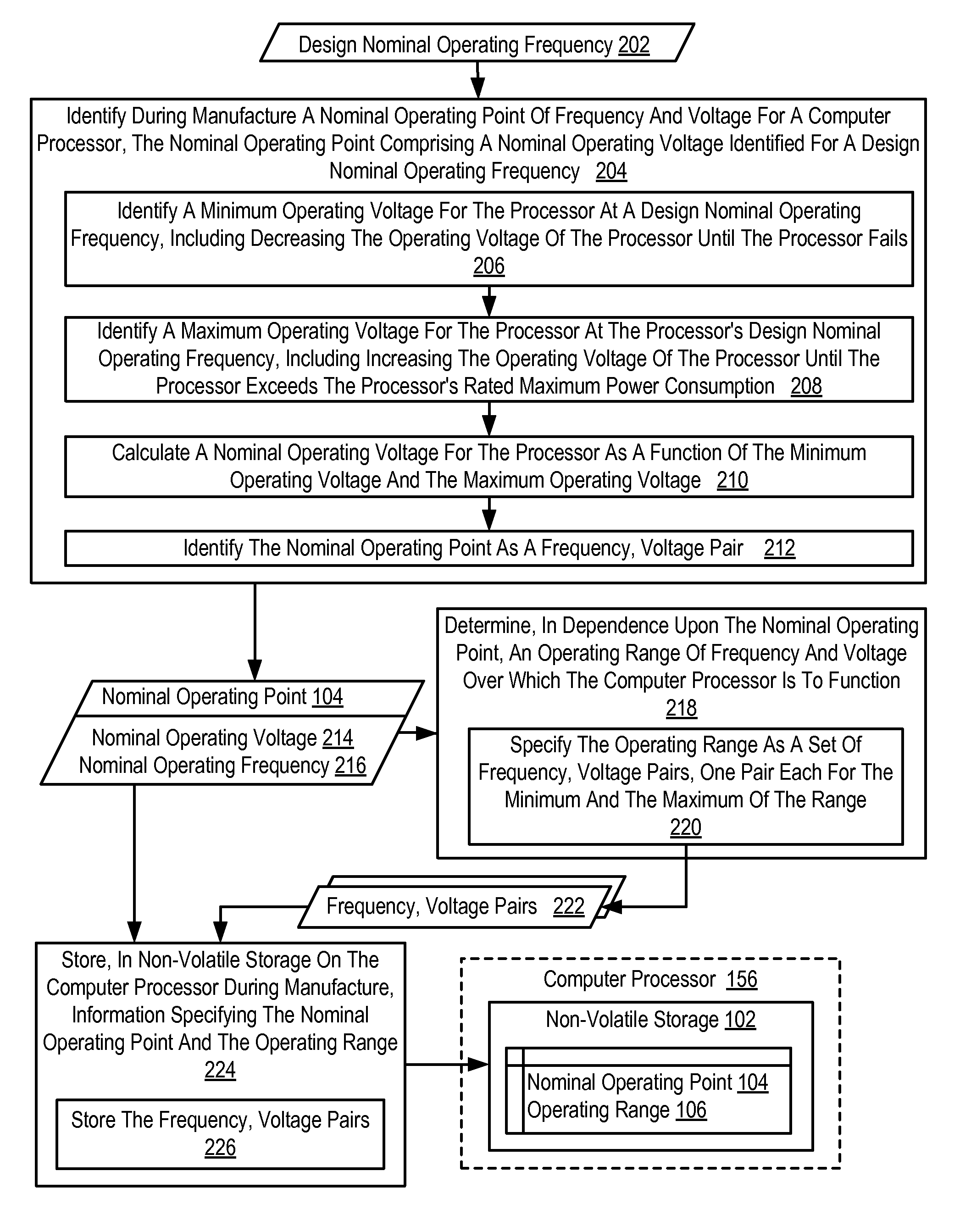
InactiveUS20100095137A1Energy efficient ICTVolume/mass flow measurementOperating pointVoltage regulation
Dynamic frequency and voltage scaling for a computer processor, including retrieving information specifying a nominal operating point of frequency and voltage and an operating range of frequency and voltage for the processor; creating, by the power management module dynamically at run time in dependence upon the retrieved information, a table of frequency, voltage pairs, each pair specifying an operating point of frequency and voltage for the processor, each pair disposed upon a line drawn in frequency-voltage space through the nominal operating point between the minimum operating point and the maximum operating point, the distance between each pair defined in dependence upon a minimum change in power supply voltage supported by the power supply; and selecting and applying, by the power management module from the table, an operating voltage and frequency for the processor in dependence upon current operating conditions of the processor.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com